A method of protecting computer data security
A data security and computer technology, applied in the computer field, can solve problems such as hidden dangers of computer information security, easy intrusion by hackers, and loss of people, and achieve the effect of solving information security protection problems, easy to popularize, and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The technical solution of this patent will be further described in detail below in conjunction with specific embodiments.
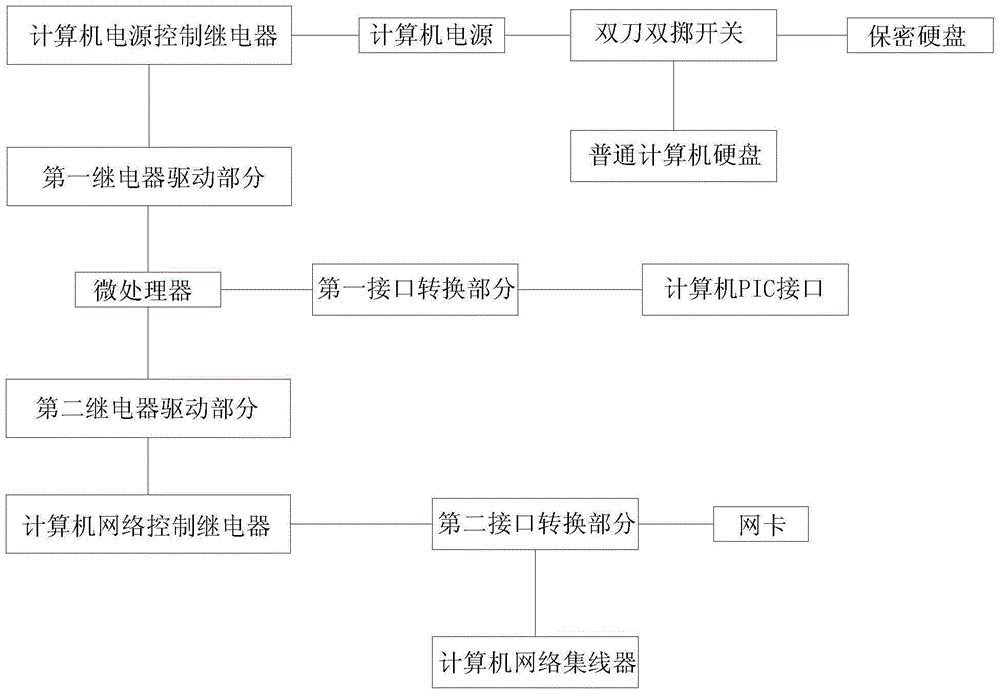
[0016] Please refer to Figure 1, a method for protecting computer data security, including a microprocessor, a relay drive part, a computer power control relay, a computer network control relay, a computer power supply, a double-pole double-throw switch, a computer hard disk, an interface conversion part, and a network card and a computer network hub, the relay driving part includes a first relay driving part and a second relay driving part, the computer hard disk includes a security hard disk and an ordinary computer hard disk, and the interface conversion part includes a first interface conversion part and a second interface conversion part , the output end of the microprocessor is respectively connected to the input end of the first relay driving part, the input end of the second relay driving part and the input end of the first interface convers...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com