Patents
Literature
3077 results about "Status changed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Under immigration laws, a change of status allows a non-citizen alien to live permanently in the United States. The person will have their temporary residence status changed into lawful permanent resident status. This will grant them other civil rights as well. This is process is also known as "adjustment of status.".
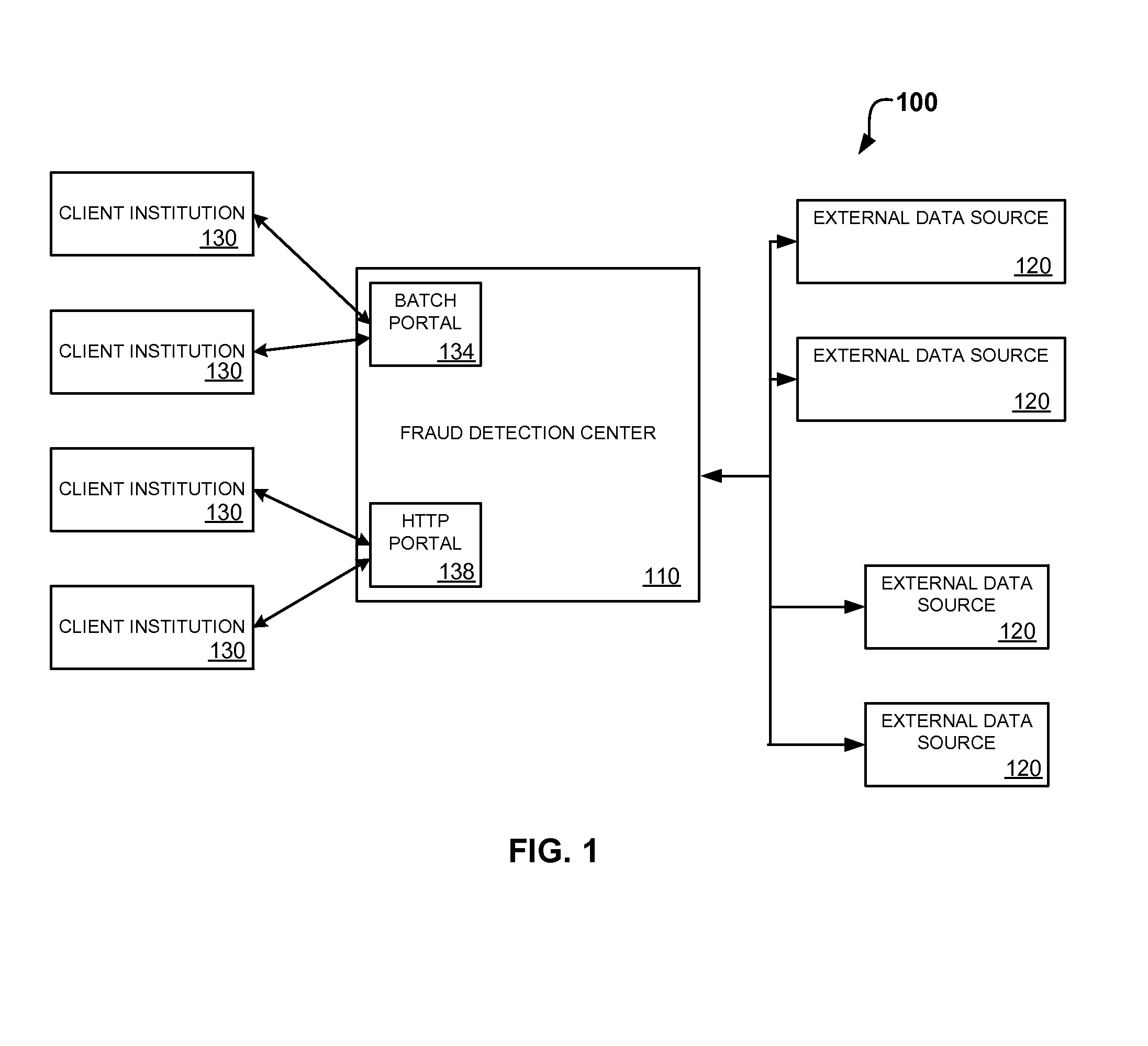
Dispensing digital objects to an electronic wallet
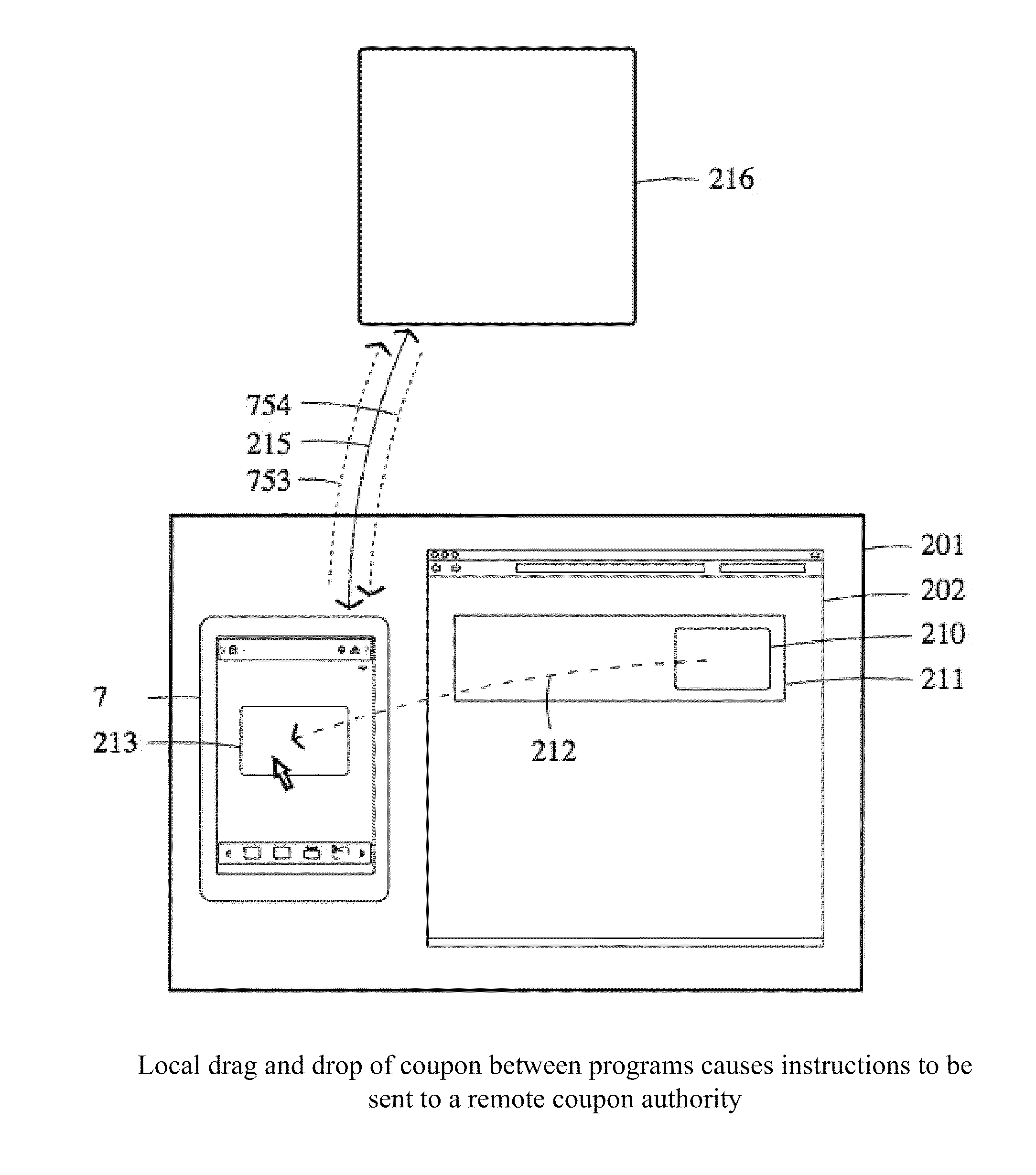
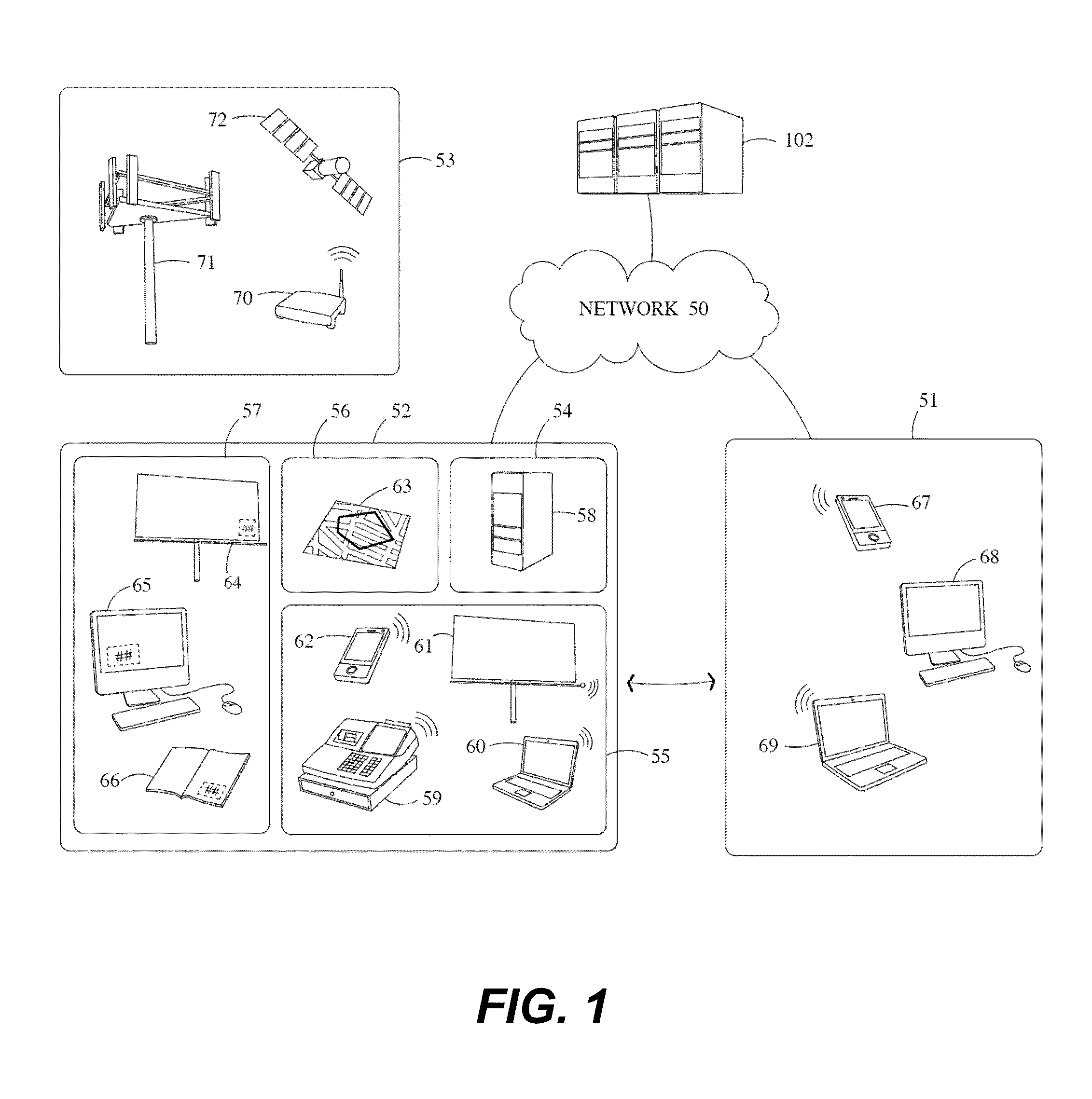
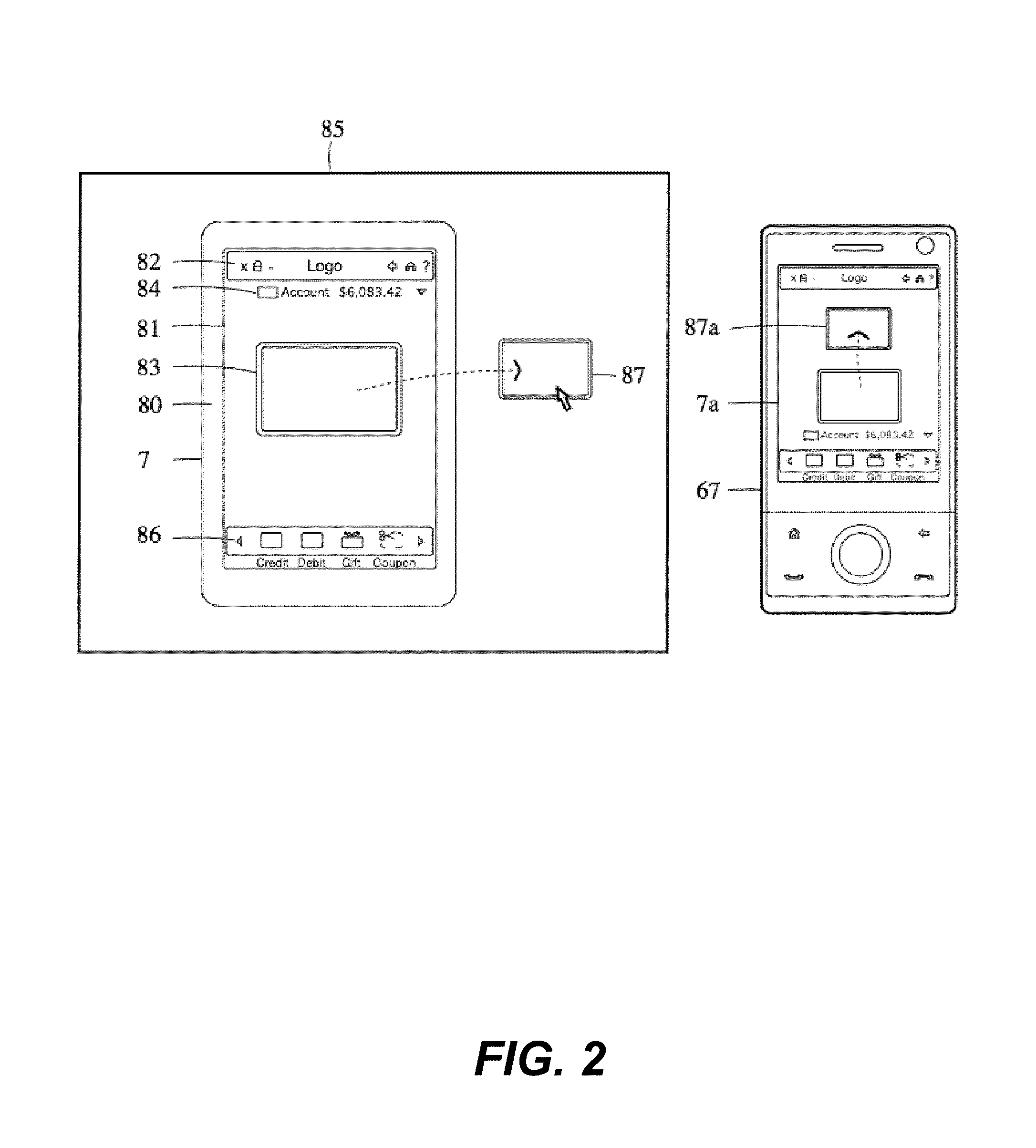
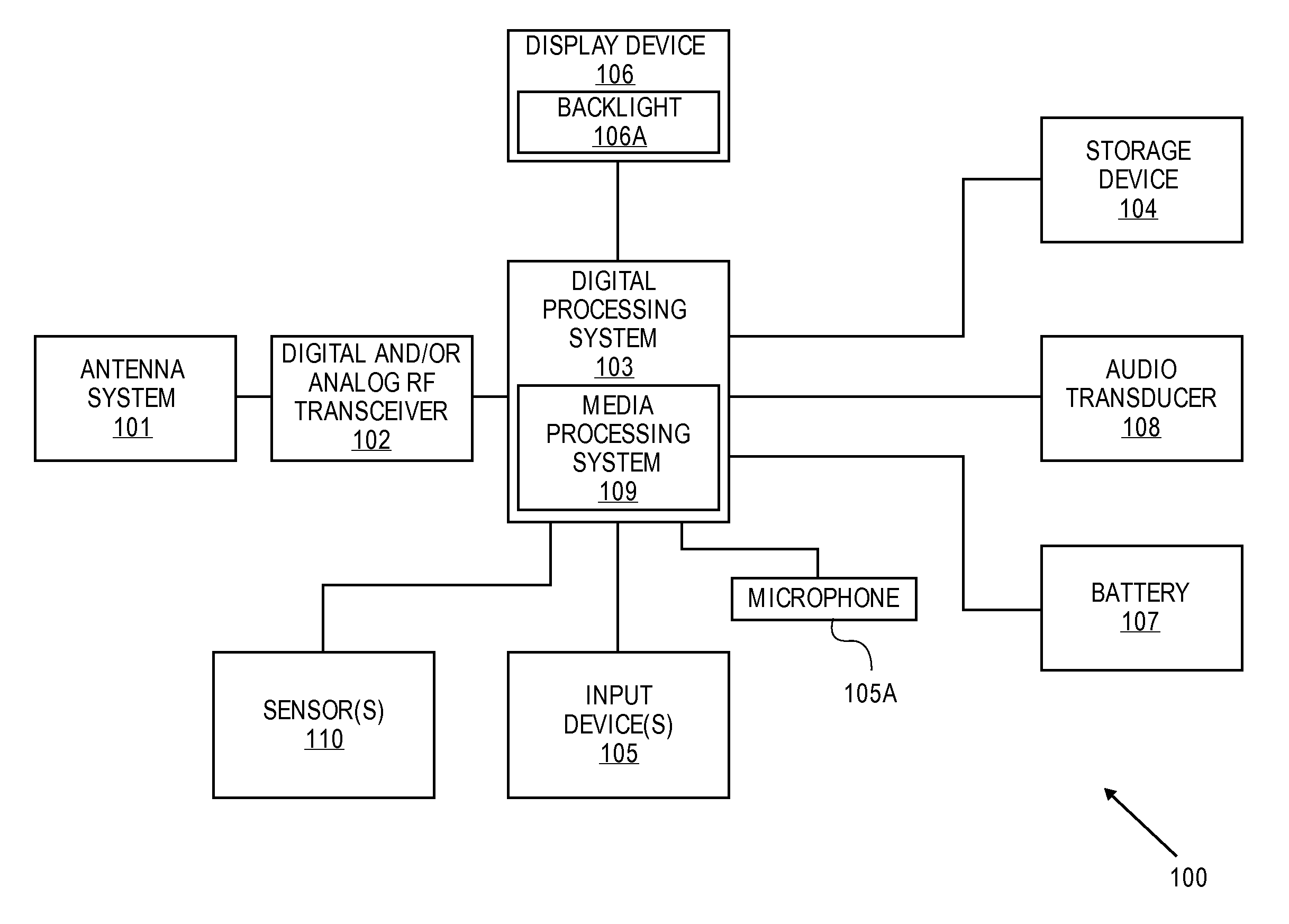
A configuration system and method is disclosed that includes a unified and integrated configuration that is composed of a payment system, an advertising system, and an identity management system such that the unified system has all of the benefits of the individual systems as well as several additional synergistic benefits. Also described are specific configurations including the system's access point architecture, visual wallet simulator user interface, security architecture, coupon handling as well as the system's structure and means for delivering them as targeted advertising, business card handling, membership card handling for the purposes of login management, receipt handling, and the editors and grammars provided for customizing the different types of objects in the system as well as the creation of new custom objects with custom behaviors. The configurations are operable on-line as well as through physical presence transactions.
Owner:GOOGLE LLC
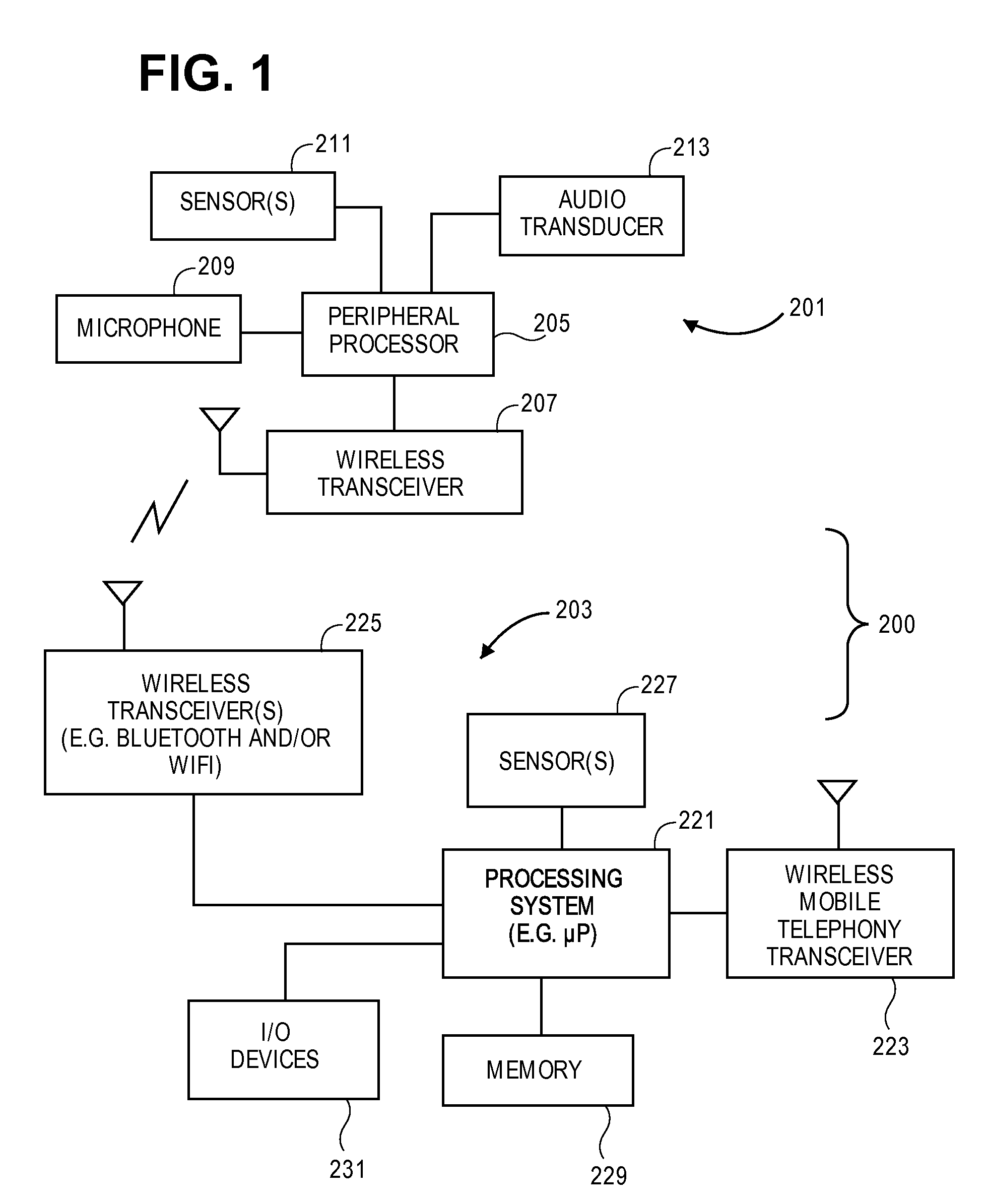
Dynamic routing of audio among multiple audio devices
ActiveUS20090003620A1Devices with sensorDevices with wireless LAN interfaceHuman–computer interactionAdaptive routing
A routing screen is presented on an electronic device by a user interface application in response to receiving a notification that an external audio device is connected to the electronic device. The routing screen displays representations of an internal audio device and the external audio device. In one aspect, the representations are buttons. In another aspect, the representations are entries in a list. If a user selects one of representations, the user interface application causes the audio signals to be routed to the audio device represented by the selection. An application control screen having a set of objects that represent functions for an audio application may also be displayed. One of the objects on the application control screen is modified in response status changes in the external audio device. A user may select this object to access the routing screen when the external audio device is connected.
Owner:APPLE INC
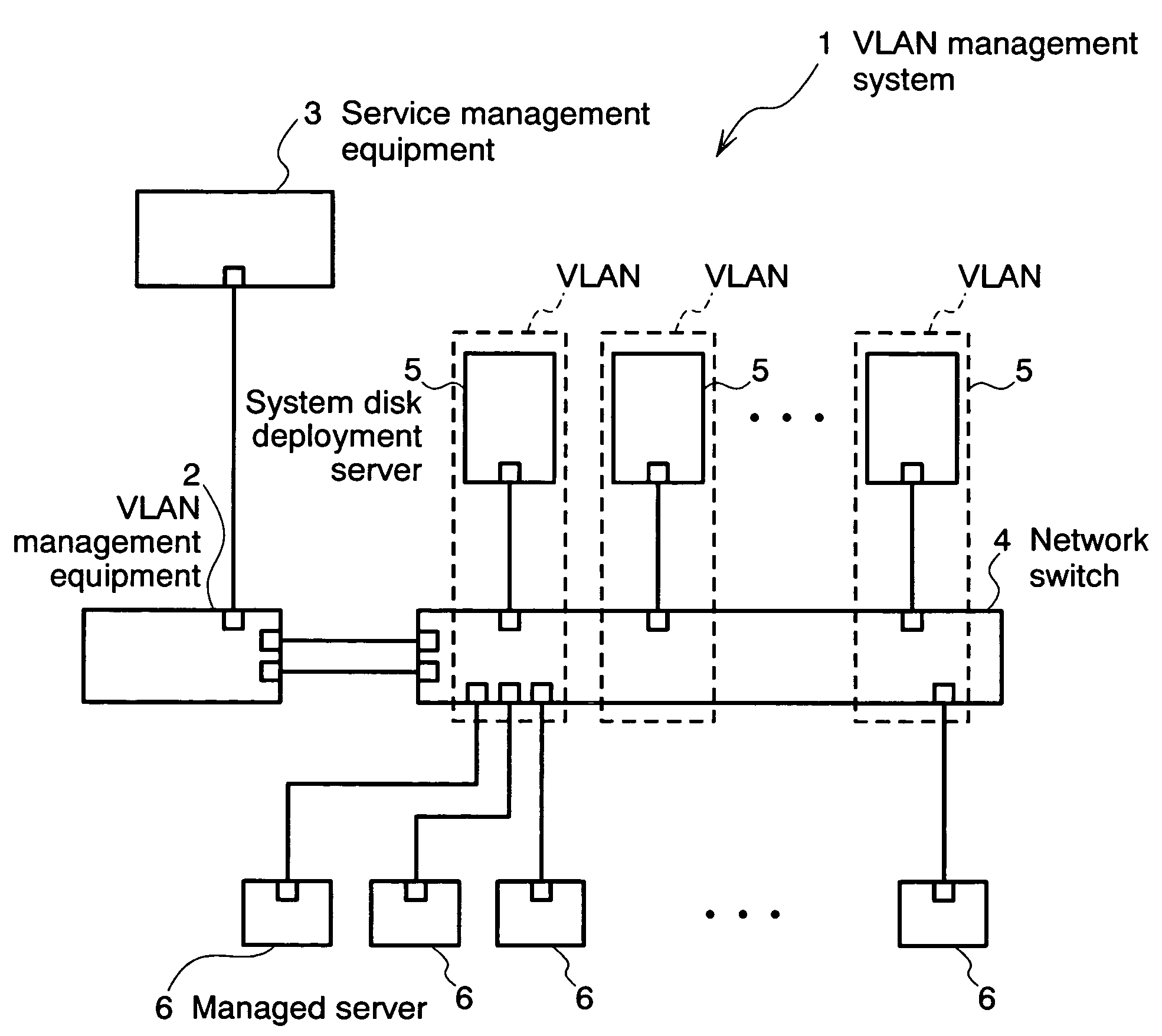
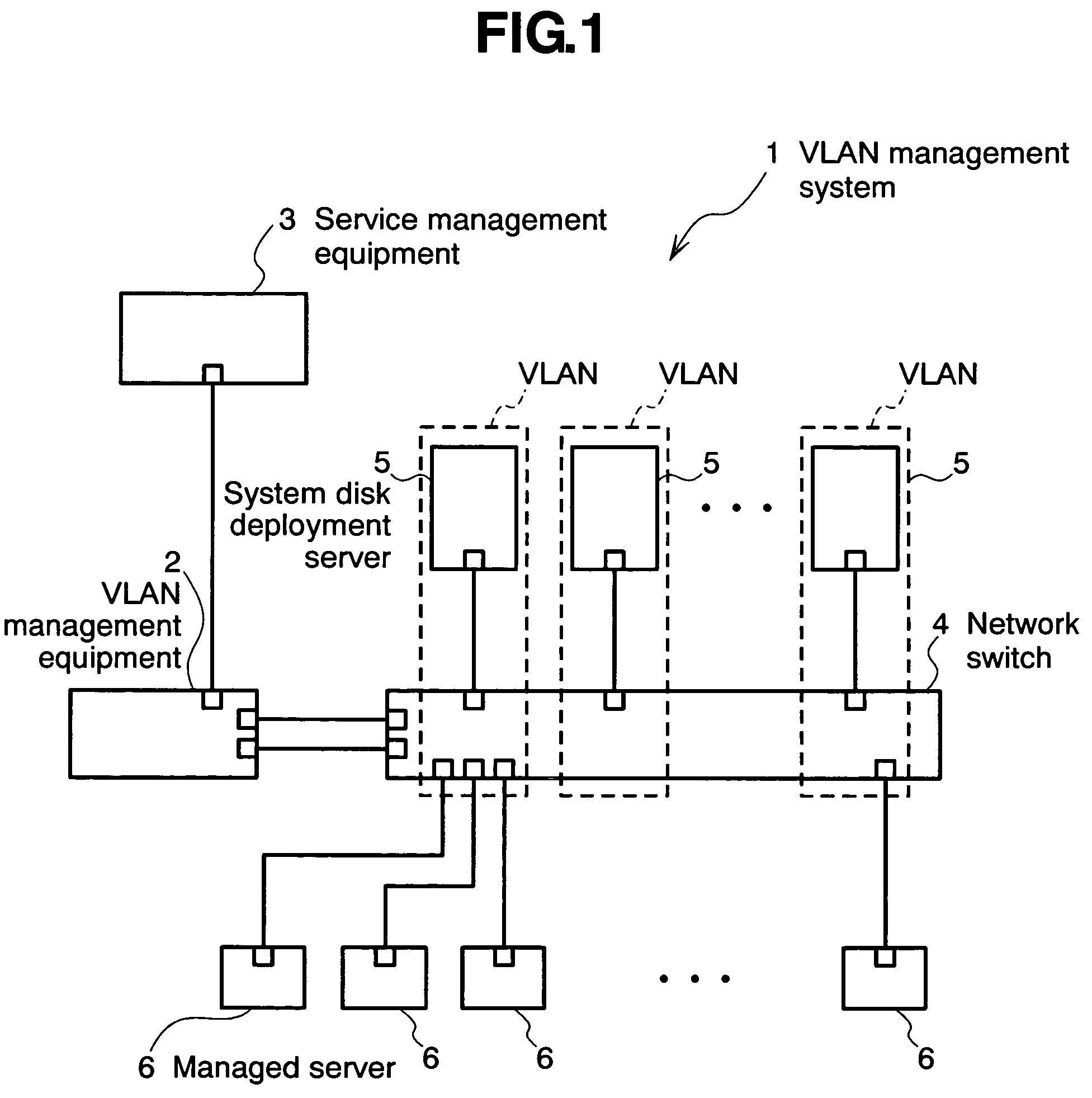
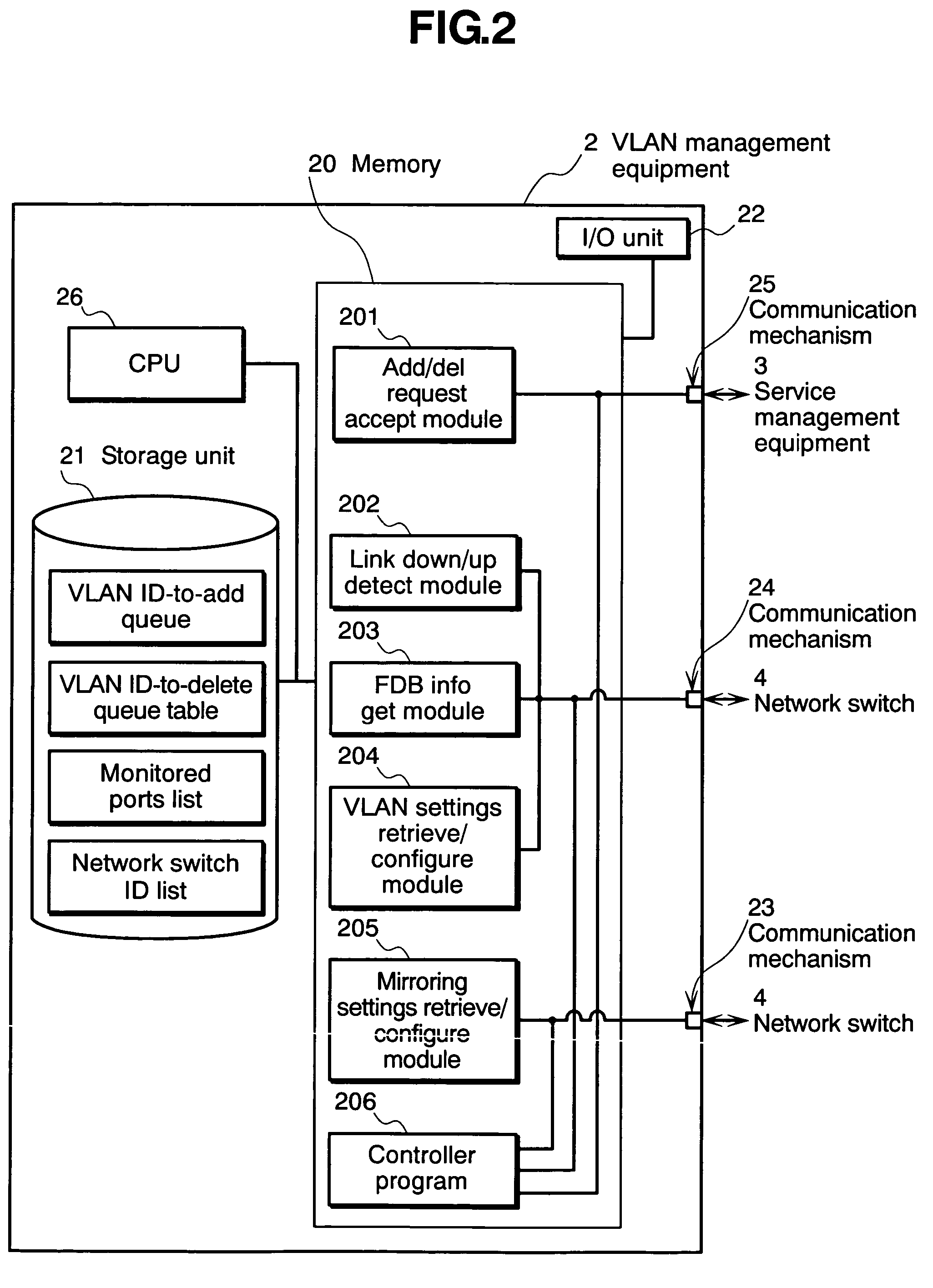
Virtual network management method, virtual network management program, virtual network management system, and virtual network means
InactiveUS7649851B2Lighten the taskDigital computer detailsData switching by path configurationManagement information baseNetwork management
The invention relates to a network management method wherein: a service management equipment holds the mapping of services and virtual networks as management information; a managed server sends an advice to a VLAN management equipment when its status changes; and the VLAN management equipment receives the advice and refers to the information contained in the advice to thereby identify the managed server and the connection port of a network switch, and configures a virtual network belonging to the identified port of the network switch. The method alleviates the task of reconfiguration associated with the adding or deleting of servers.
Owner:HITACHI LTD
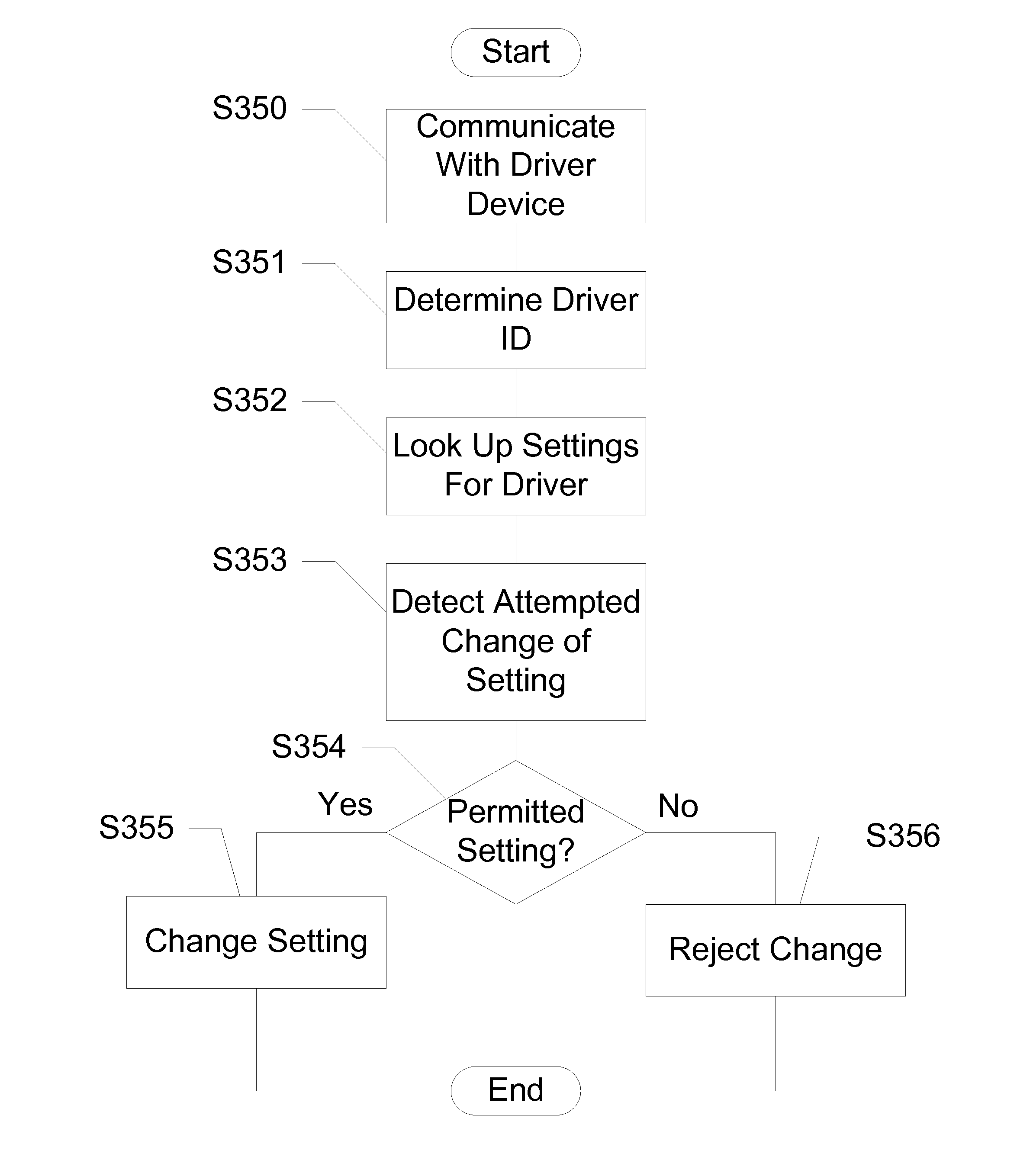
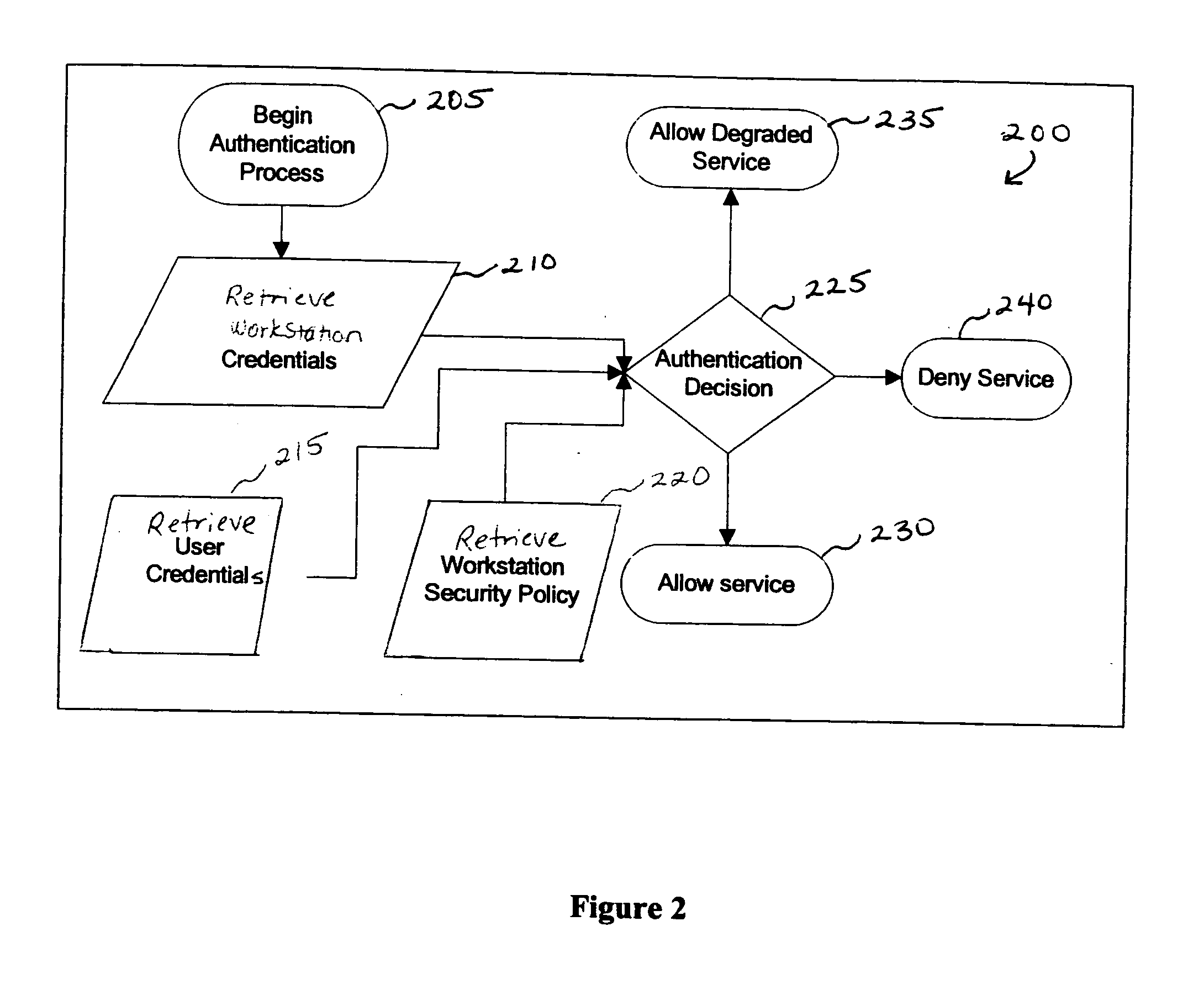
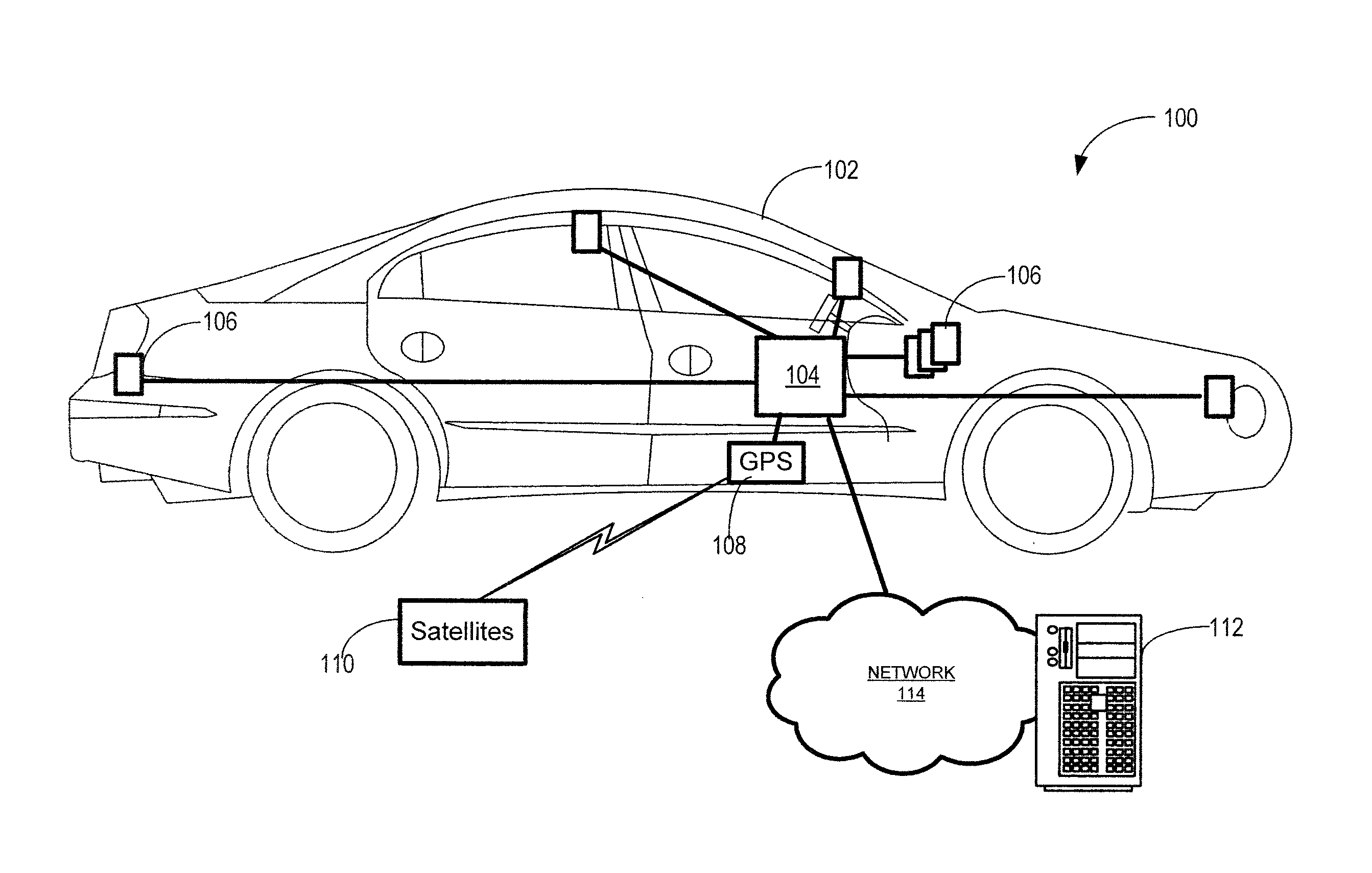
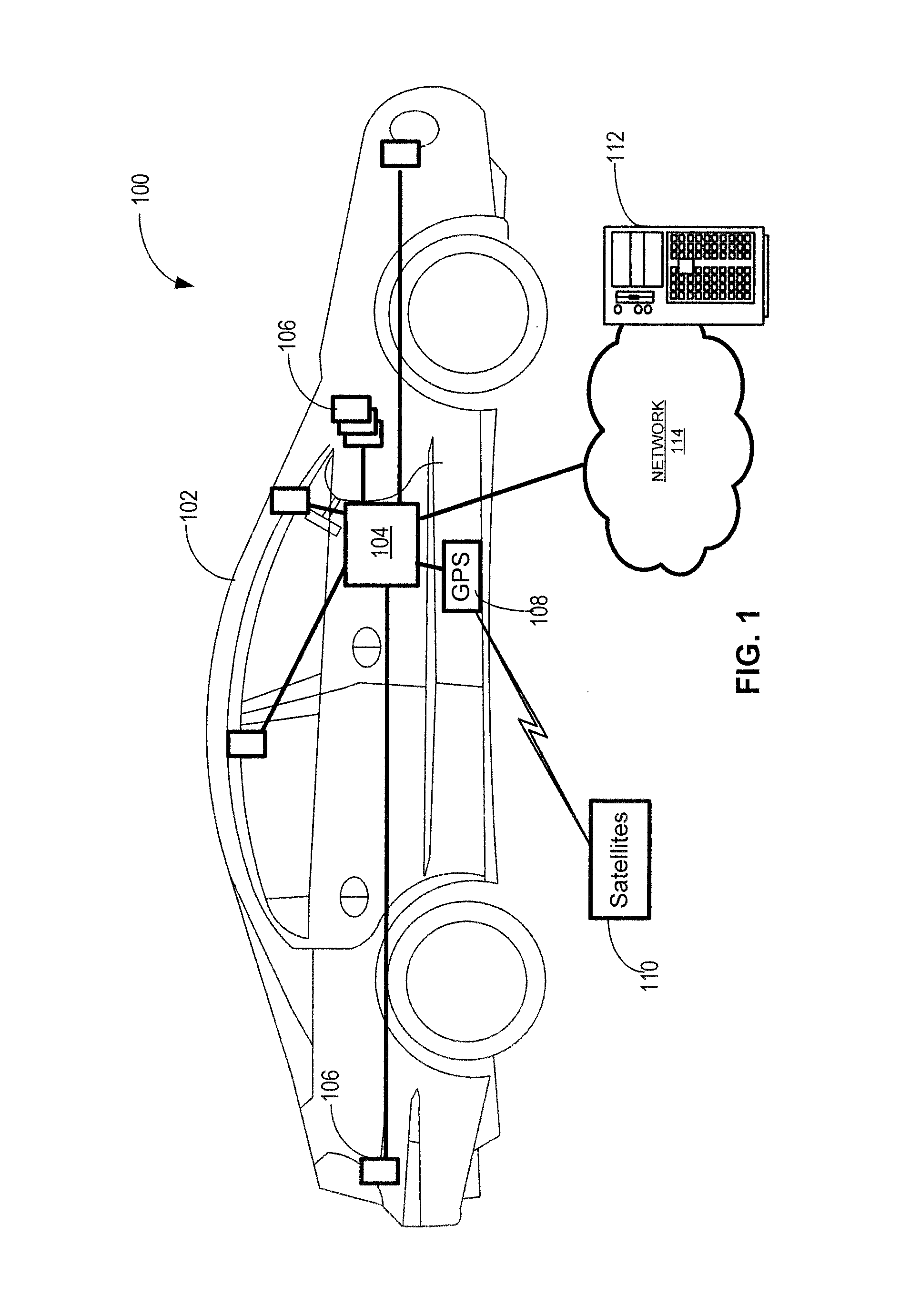
Devices, Systems and Methods for Controlling Permitted Settings on a Vehicle
ActiveUS20110137520A1Limiting distractionNetwork traffic/resource managementAnalogue computers for trafficDistractionDriver/operator
Devices, systems, and methods are disclosed for altering permitted settings of a vehicle according to a driver identified through short range wireless communication. The vehicle captures a unique identifier from a wireless communication device of the driver of the vehicle. This unique identifier is used to reference a database to determine the identity of the driver as well as settings for the driver created by a controlling authority. The controlling authority may be, for instance, a parent or employer of the driver. The settings may limit certain devices within the vehicle and / or the vehicle itself. Speed control settings, radio settings, wireless communication device settings, and various other settings are all possible to limit distractions to the driver. Further, the settings may be influenced by the number or identities of passengers within the vehicle.
Owner:HYUNDAI MOTOR CO LTD +1
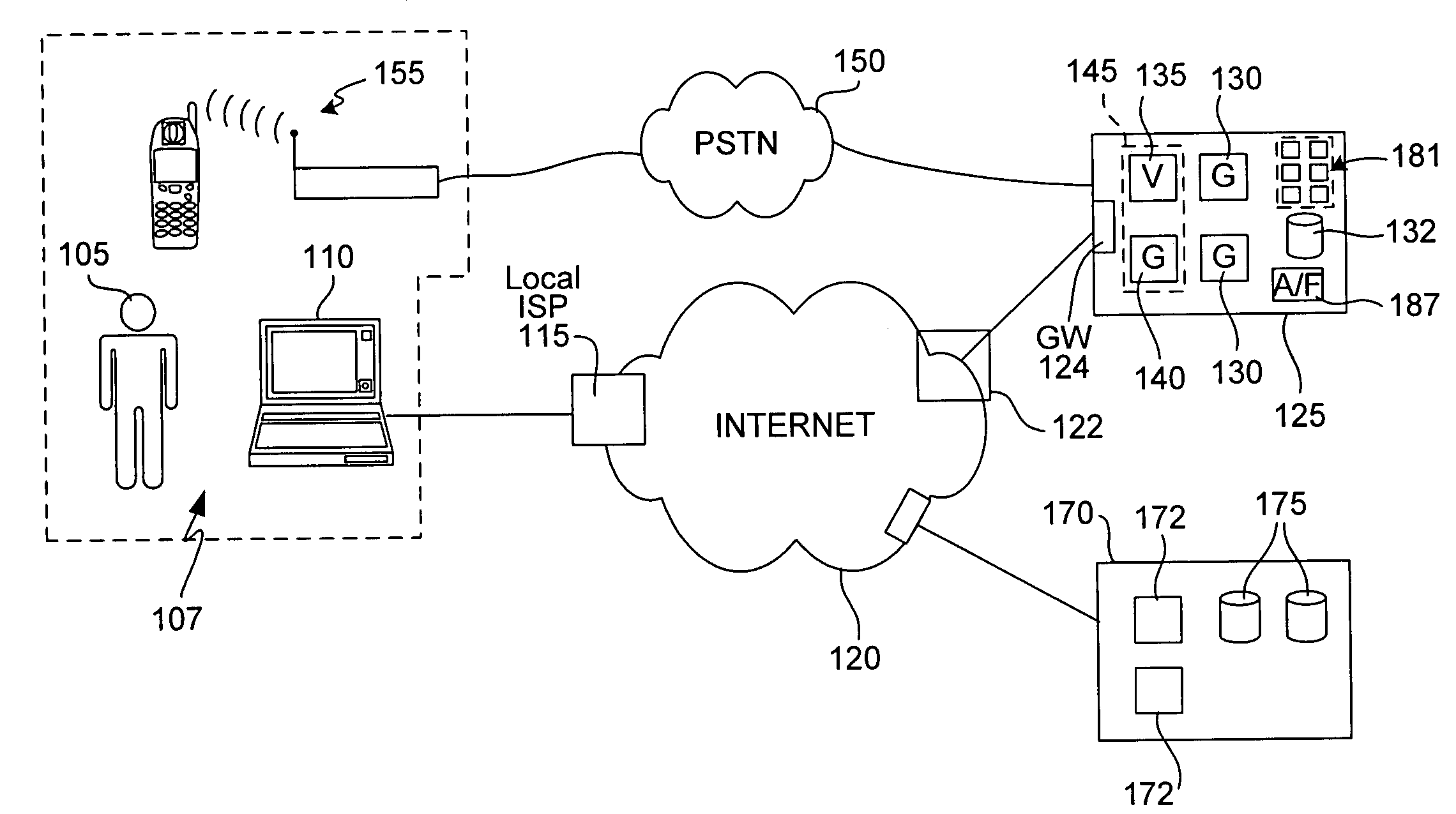
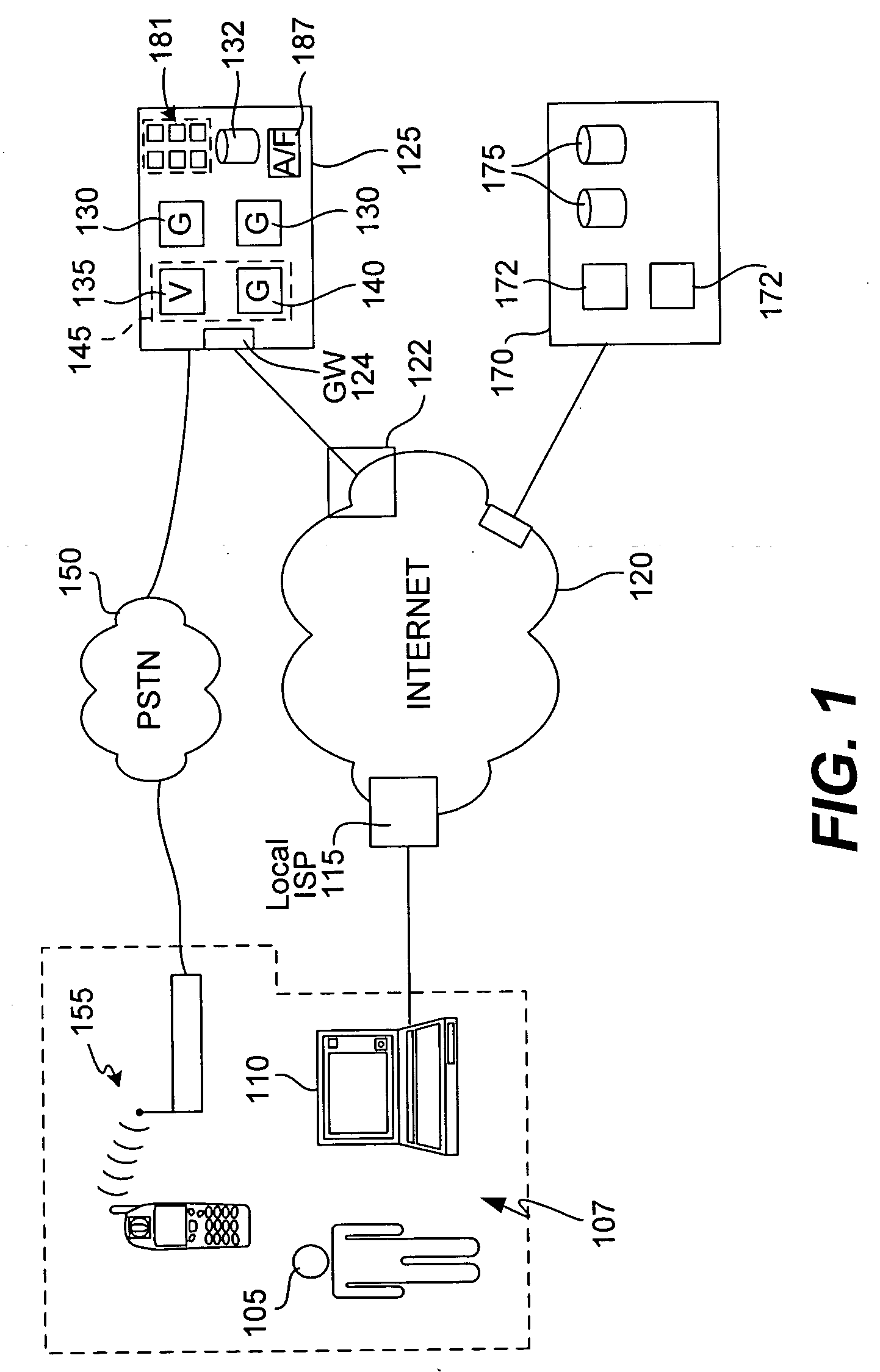
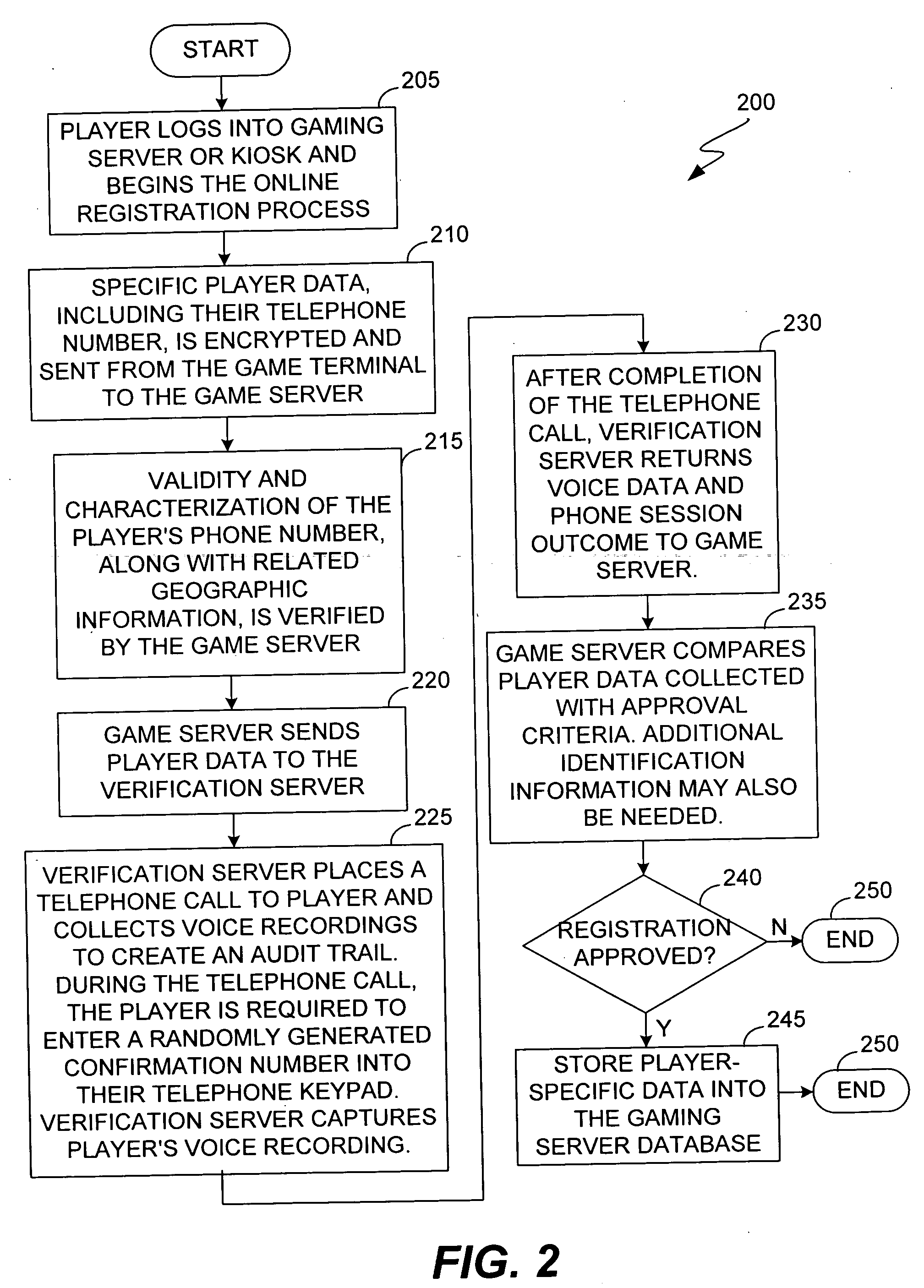
Location and user identification for online gaming
ActiveUS20060095790A1Digital data processing detailsComputer security arrangementsUser inputTelephone network
The present invention provides methods and devices for determining the location, identity and age of a user who desires to initiate a gaming session from an uncontrolled environment such as a home, a gaming kiosk or a hotel room. In some implementations, the user's location is determined in part by reference to a database of land telephone lines and corresponding addresses. The location may be verified by reference to a location determined by other methods, e.g., by determining the location of an Internet service provider's network device that is near a user's host device. In other implementations, the user's location is determined by information provided by a cellular telephone network. The user may be asked to input a confirmation number and / or make an oral response during a telephone call to a telephone number associated with the uncontrolled environment. These the oral response may be analyzed to verify the user's identity. The user may also be prompted to make statements verifying his or her identity, age, a maximum amount available for wagering or other statements, which are preferably recorded and stored.
Owner:IGT
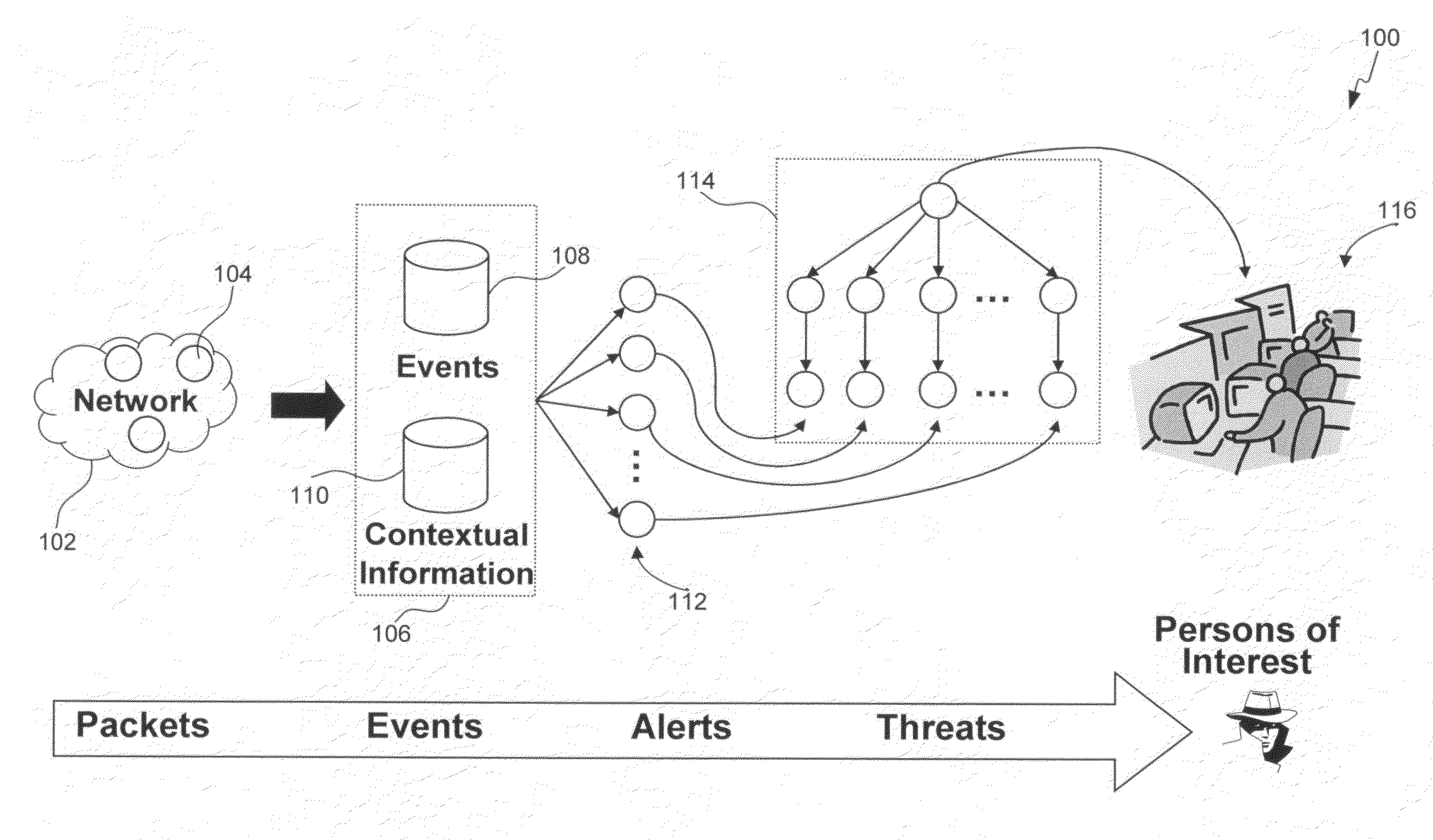
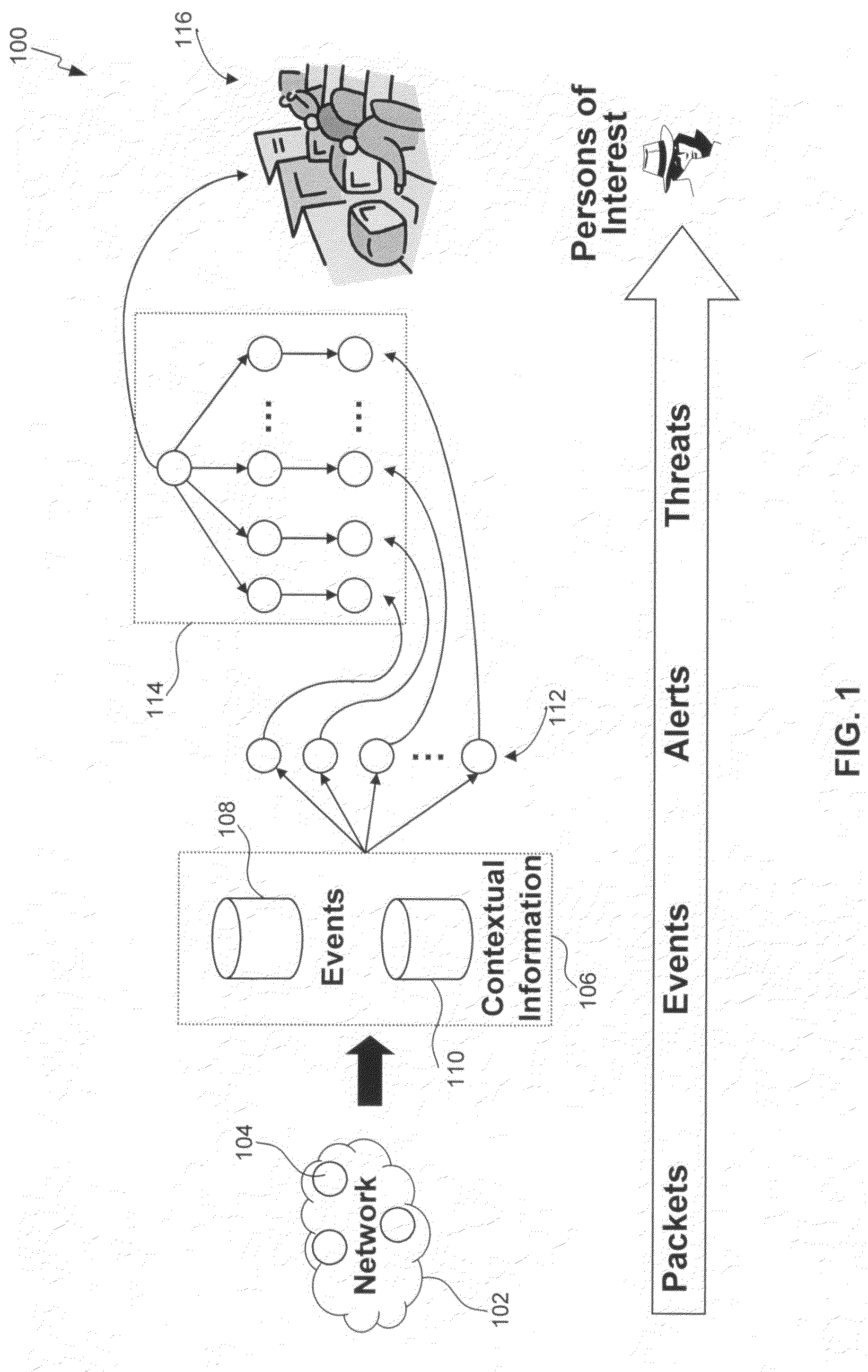
Insider threat detection
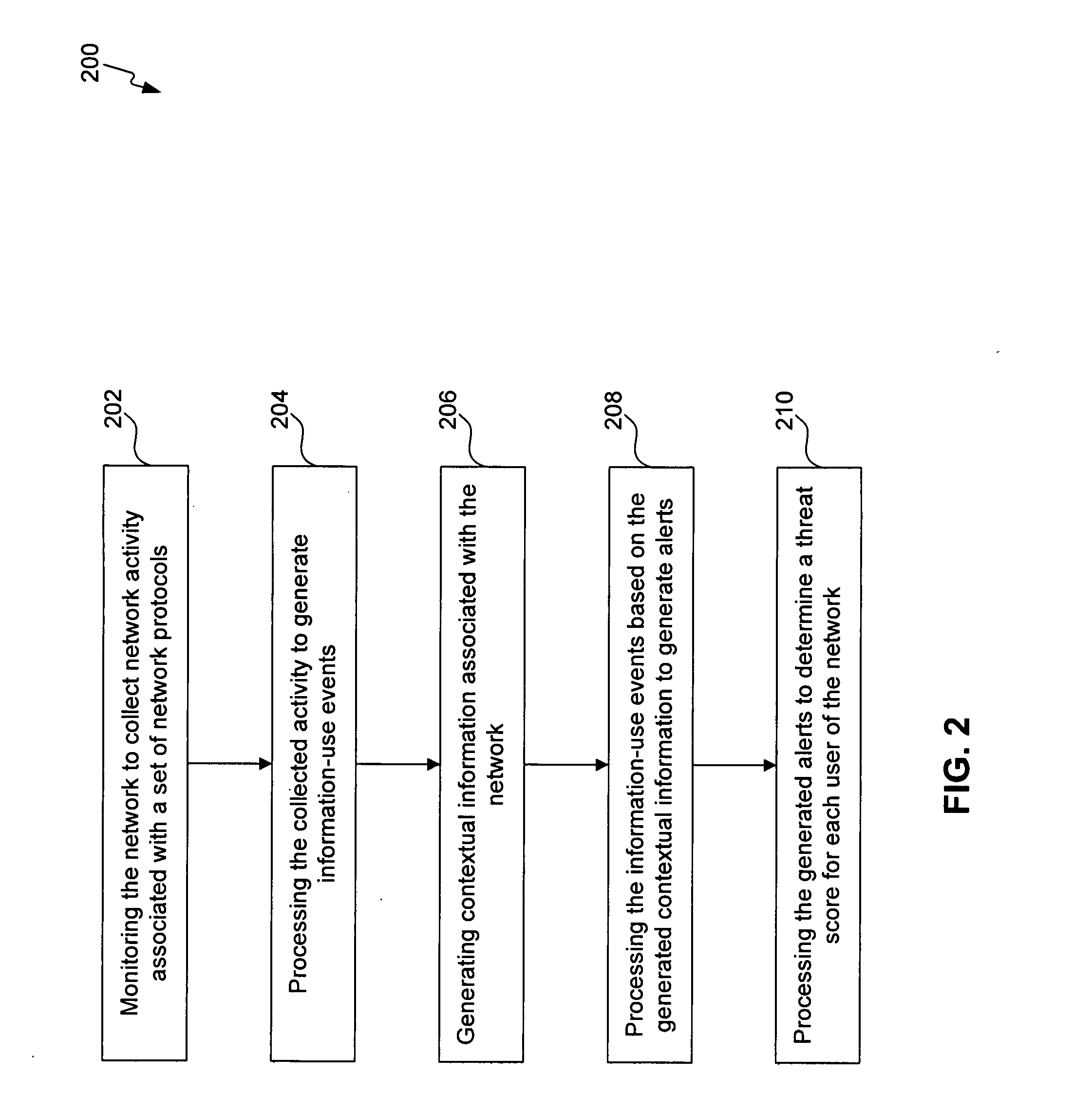
Methods, systems, and computer program products for insider threat detection are provided. Embodiments detect insiders who act on documents and / or files to which they have access but whose activity is inappropriate or uncharacteristic of them based on their identity, past activity, and / or organizational context. Embodiments work by monitoring the network to detect network activity associated with a set of network protocols; processing the detected activity to generate information-use events; generating contextual information associated with users of the network; and processing the information-use events based on the generated contextual information to generate alerts and threat scores for users of the network. Embodiments provide several information-misuse detectors that are used to examine generated information-use events in view of collected contextual information to detect volumetric anomalies, suspicious and / or evasive behavior. Embodiments provide a user threat ranking system and a user interface to examine user threat scores and analyze user activity.
Owner:MITRE SPORTS INT LTD
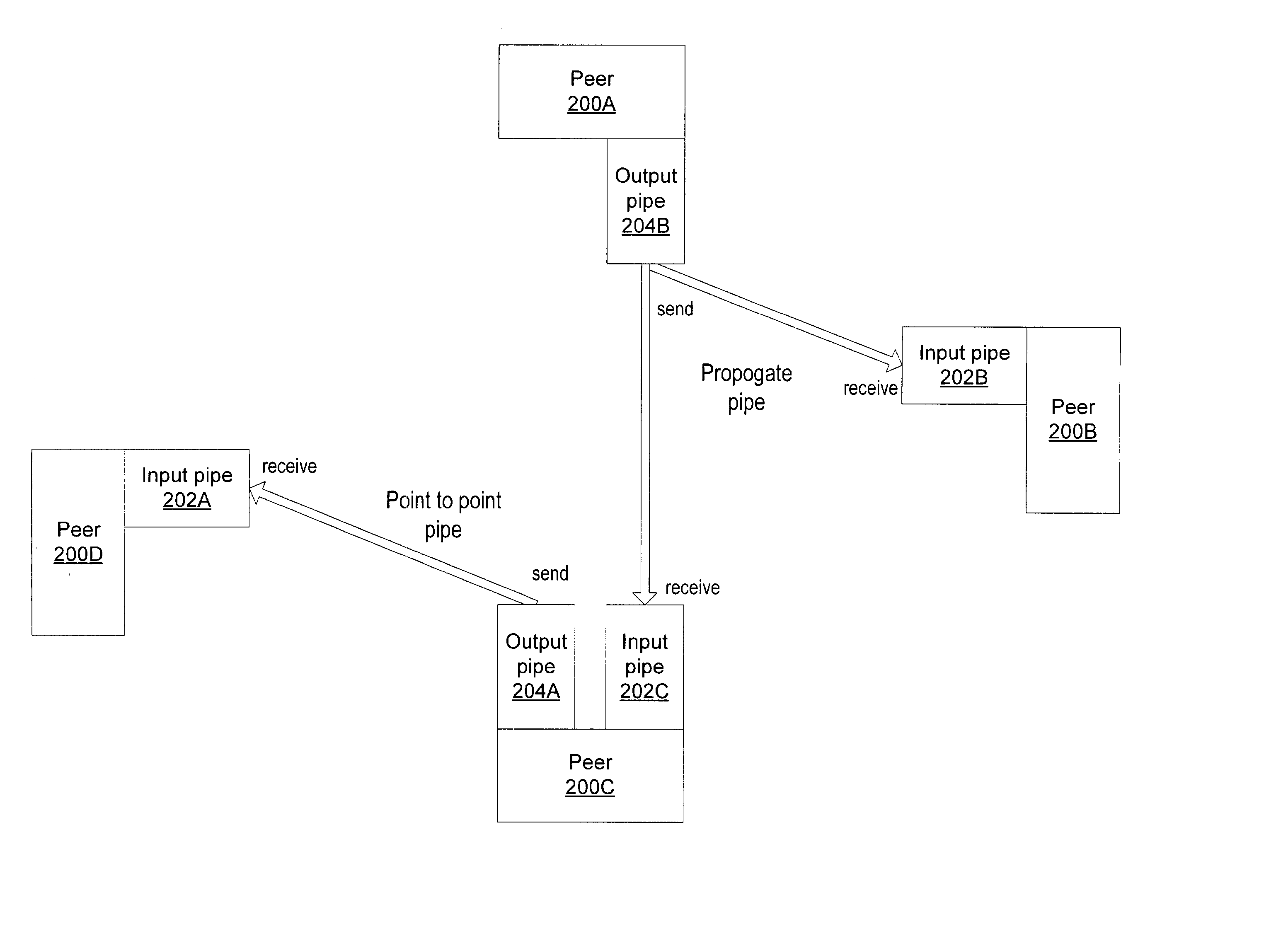
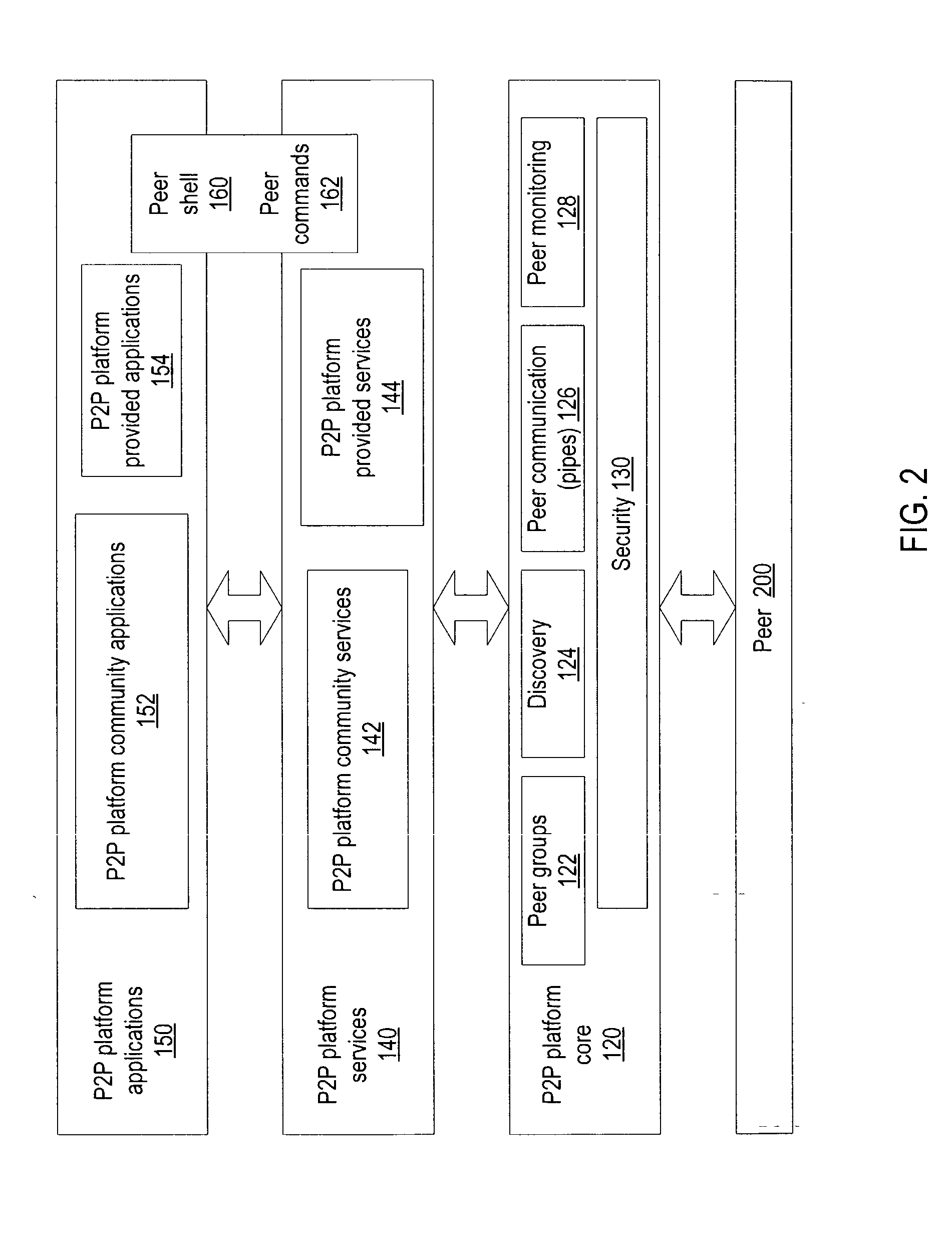
Peer-to-peer presence detection
ActiveUS20030041141A1Multiprogramming arrangementsMultiple digital computer combinationsPeer-to-peerStatus changed
Embodiments of a decentralized mechanism for detecting the presence of entities in a peer-to-peer network. In one embodiment, using pipes, a peer may uniquely and independently generate an identity for a peer-to-peer network entity. The identity may be used to probe the peer-to-peer network for presence of instances of the corresponding entity on other peers regardless of which peer the identity was generated on and without using a central identity repository or presence system. In one embodiment, net crawling may be used to map identities and resolve the locations of instances of the corresponding entities. An entity may move anywhere on the network, and the decentralized mechanism for detecting entity presence may be used to locate the instance(s) of the entity.
Owner:ORACLE INT CORP
Investigative identity data search algorithm
InactiveUS8935266B2AdaptableGood flexibilityDigital data information retrievalDigital data processing detailsData miningUser interface
An identity search algorithm for identifying a plurality of identity data such as personal names and entity names that might exist in a table or file containing a large number of identity data in an investigative environment. The algorithm is intended to identify person and entities in the shortest time possible with an overly inclusive results. The core algorithm is used in an environment with a growing number of names in the table, and implemented with a web-based user interface, it can dramatically improve identity-searching efficiency and increase the chance to generate useful leads in typical discovery and investigation.
Owner:WU JIANQING
Virtual clustering and load balancing servers
ActiveUS20050160133A1Resource allocationMultiple digital computer combinationsLoad SheddingIntelligent Network
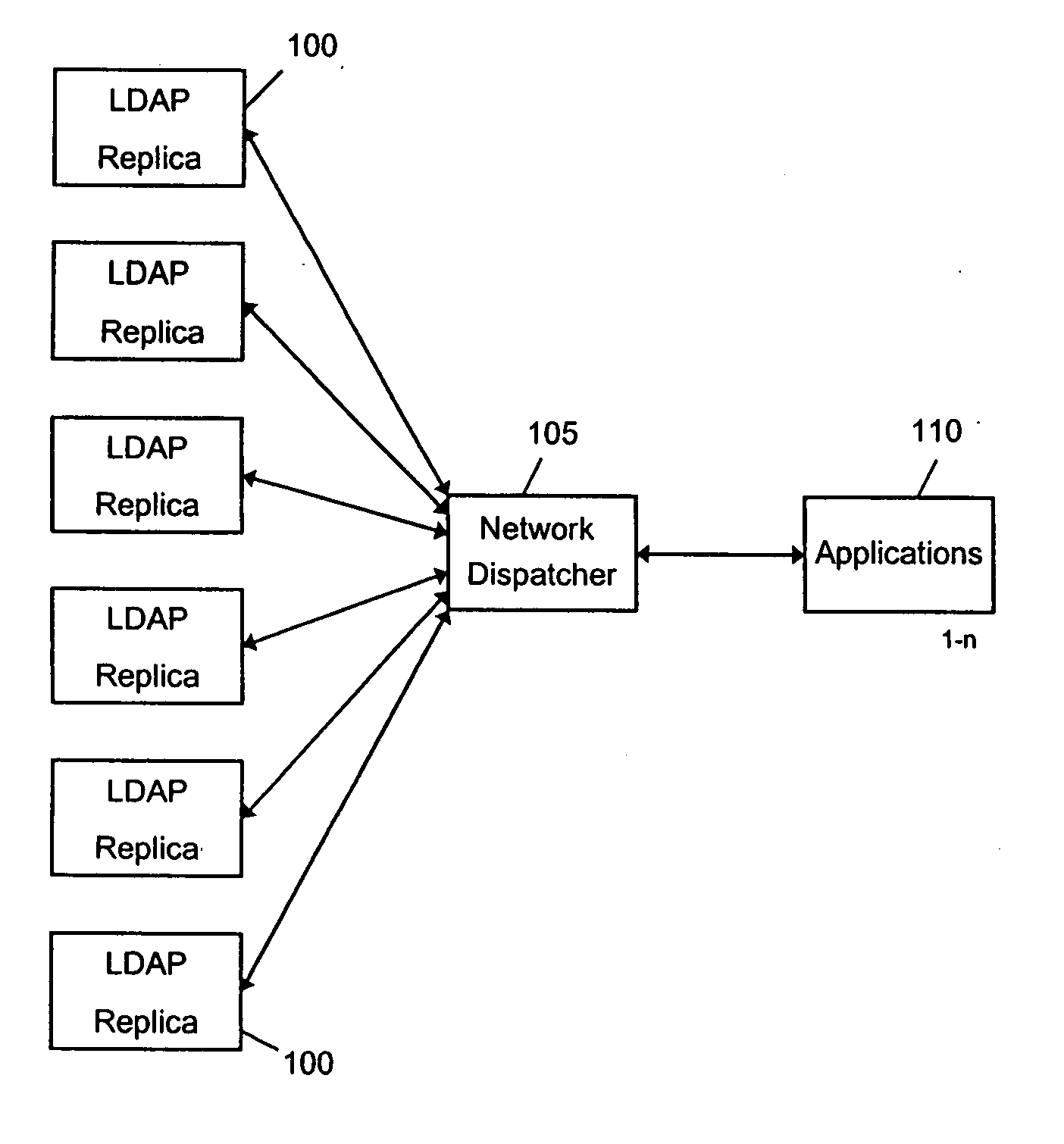
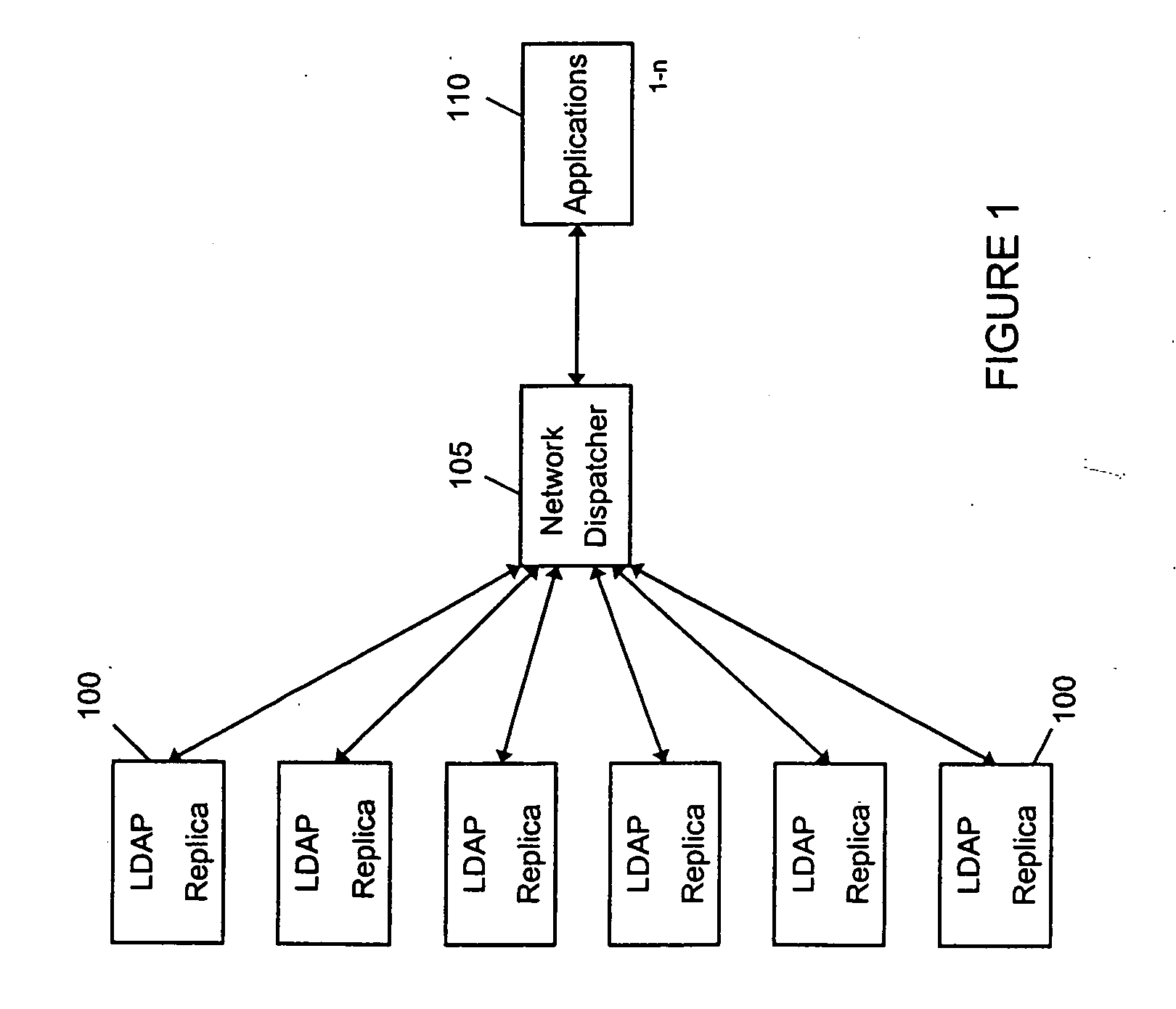
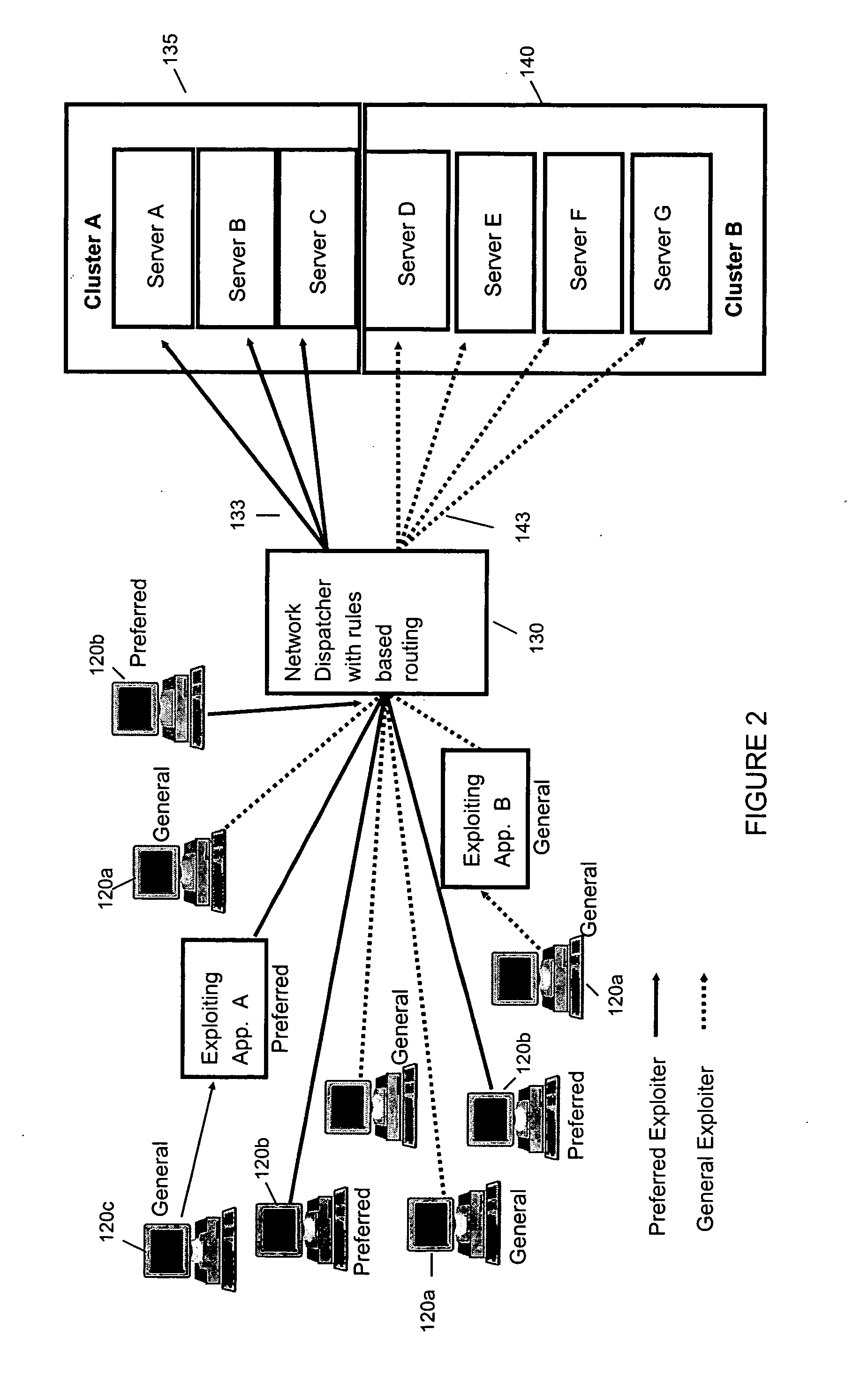
A method and system is provided intelligent network dispatchers that are capable of routing requests to one or more servers (e.g., LDAP servers) based on the requested application or the identity of the requester. The servers may be grouped into virtual clusters so that a particular cluster may service requests associated with a particular application or based on a type of customer (e.g., preferred or general customer) in order to grade levels of service. Also, a system resource monitor may provide continual monitoring of servers in virtual clusters to determine when one or more servers are overburdened or under burdened based on statistical performance data. As a servers performance changes, the system resource monitor may advise the intelligent network dispatcher causing a change in the rate of requests to the overburdened / under burdened server. The server may be temporarily removed from the virtual cluster until performance levels normalize. Further, servers may be re-assigned to other virtual clusters on demand to provide increased capacity to a virtual cluster.
Owner:TWITTER INC
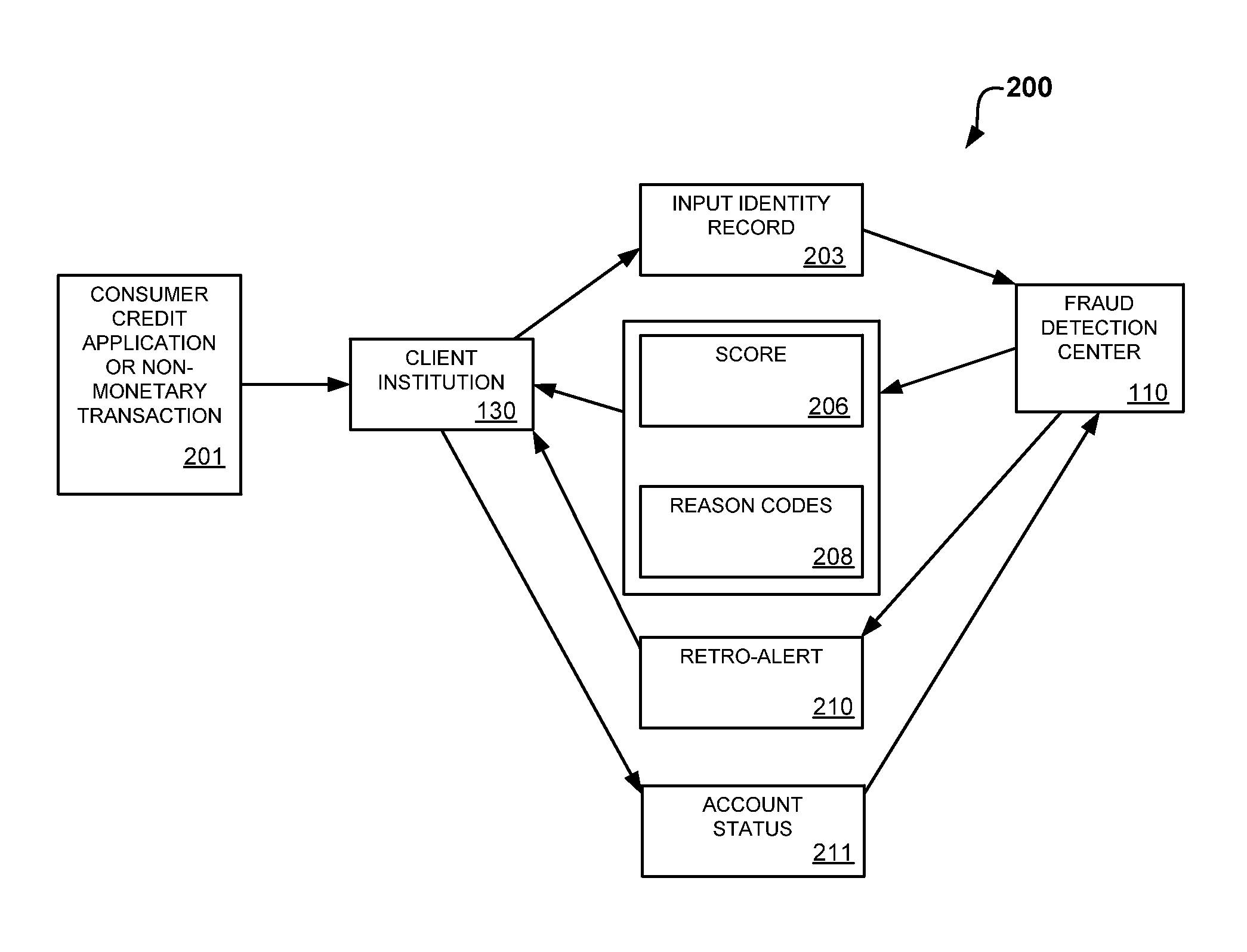
System and method for credit scoring using an identity network connectivity
A technique is provided for determining credit ratings without the need for traditional credit bureau data. In at least one embodiment of the invention, a method comprises the steps of providing a network of linked identity records, each identity record comprising identity related information; receiving an identity record comprising identity related information of the entity; linking the received identity record with at least one of the identity records in the network of linked identity records, quantifying a plurality of linked identity records related to the entity; and generating a credit rating for the entity based on the quantified identity records. Application of the invention is particularly useful for individuals with less than a few years credit behavior recorded on a credit bureau, such as immigrants or young people with limited traditional historical information (“thin file”) and individuals with no traditional historical information (“no hit”).
Owner:LEXISNEXIS RISK SOLUTIONS FL
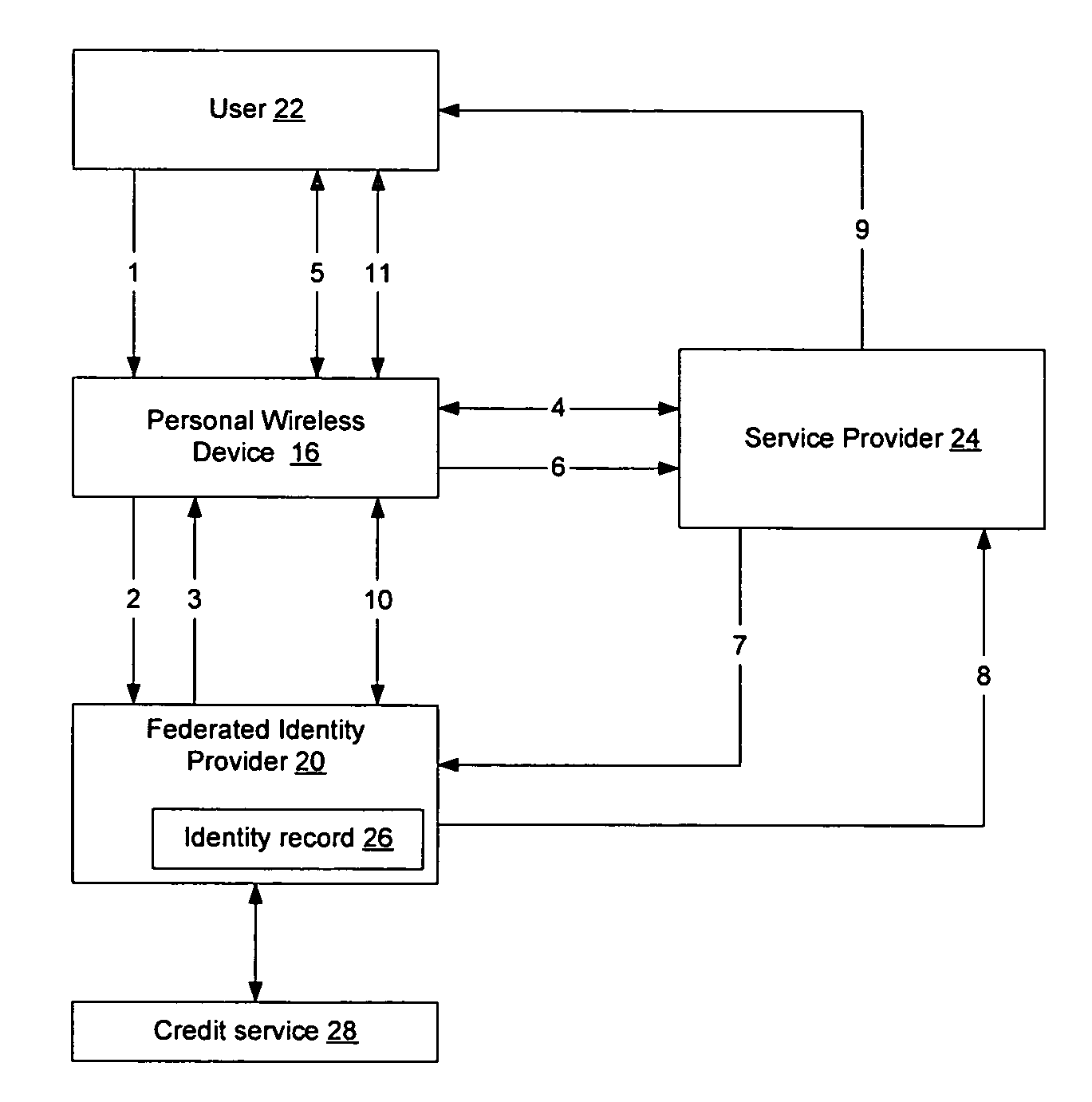
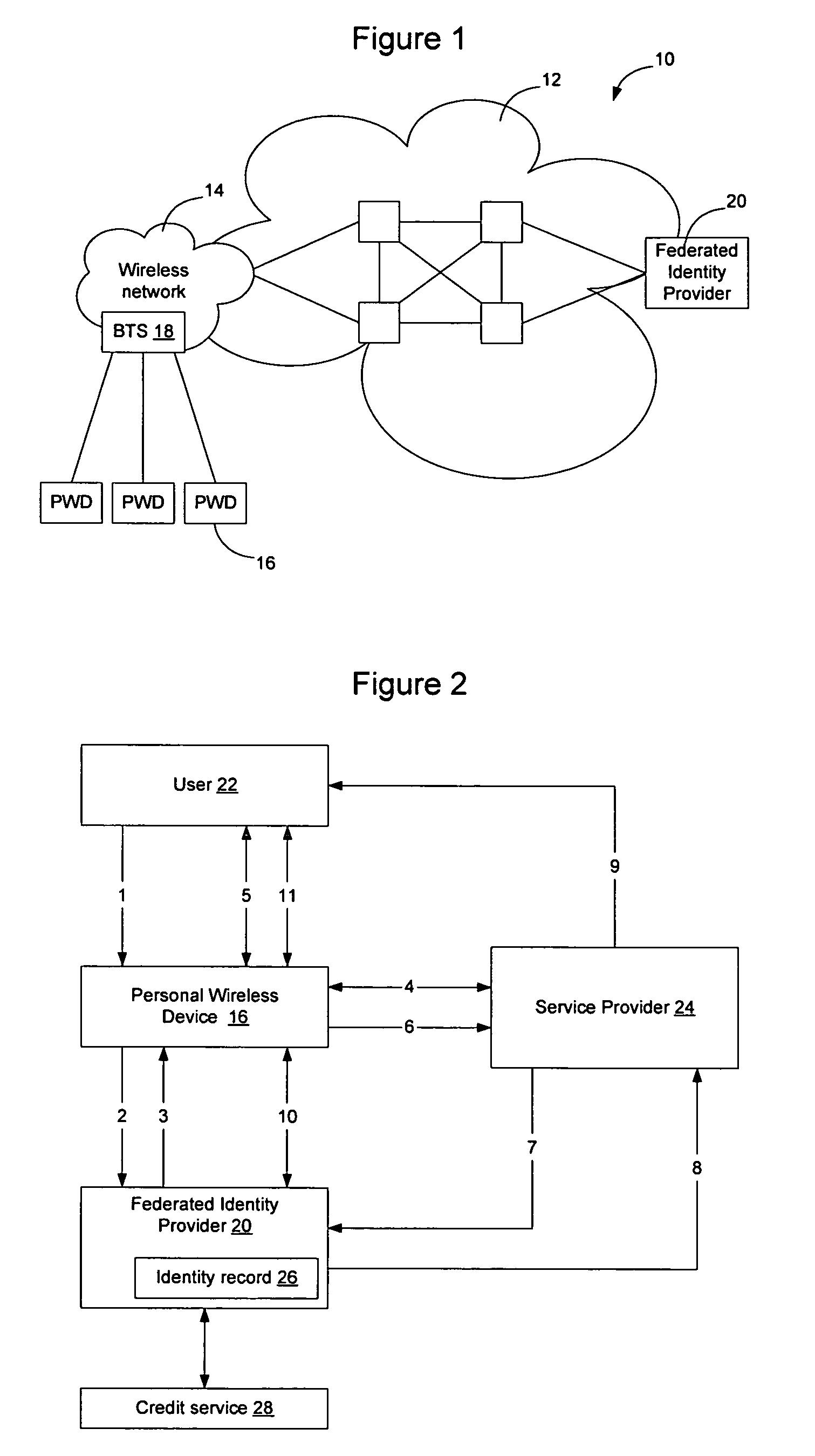
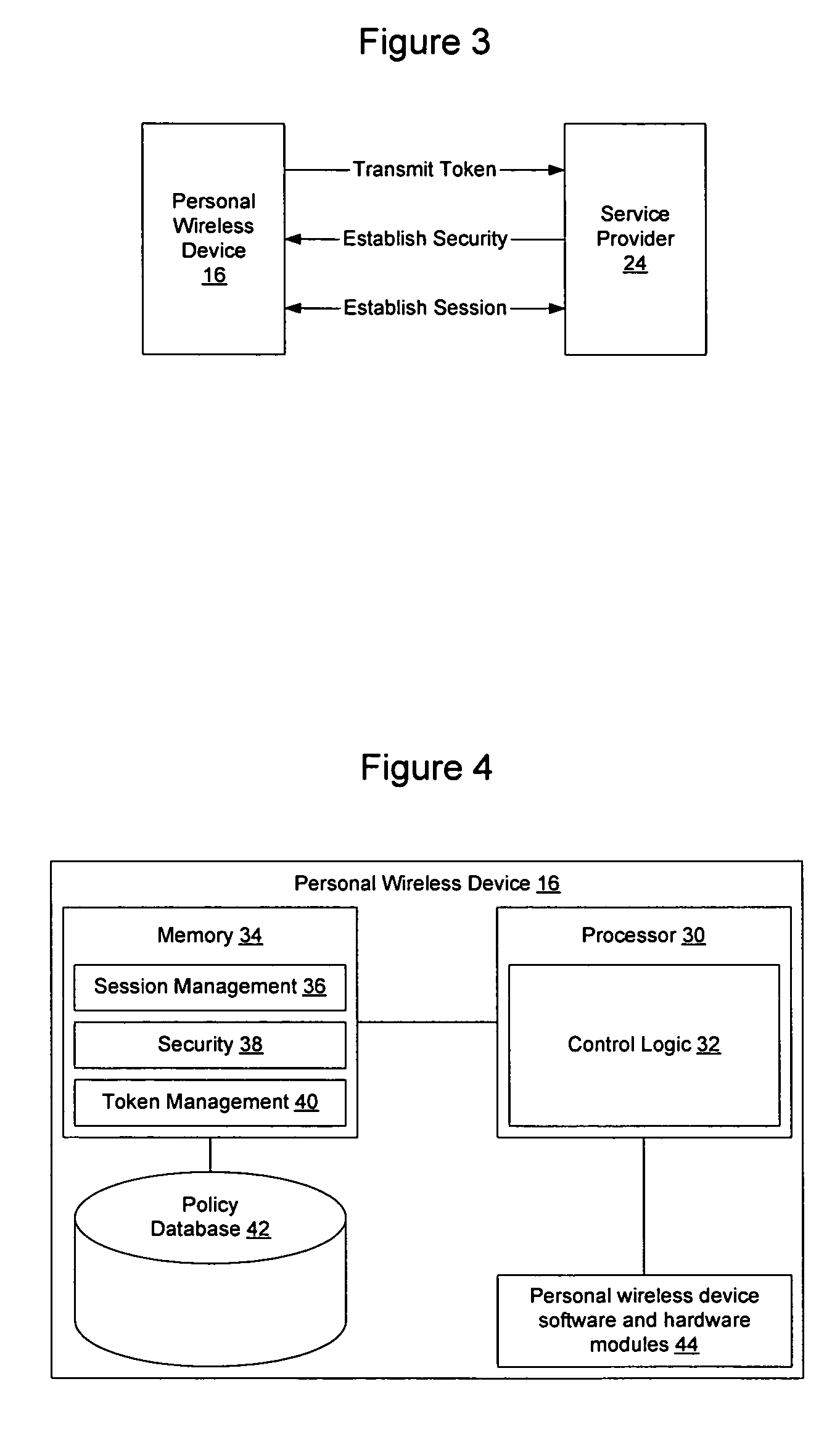
Method and apparatus for establishing a federated identity using a personal wireless device
ActiveUS8522039B2User identity/authority verificationDigital data authenticationCryptographic protocolBluetooth
A federated identity, established through possession of a single sign-on token, will allow a personal wireless device (PWD) to be used in a commercial environment to purchase goods or services, access a building, access a telephone, wireless, or computer network, or in numerous other instances. The token may be obtained by the user authenticating with the PWD and the PWD authenticating with the network. When the PWD comes within range of a service provider, a session is established using a short range wireless protocol, such as Bluetooth or infrared. The session is secured using a security protocol such as SSL, and the service provider authenticates its identity to the PWD. Policy may be implemented regarding transmission of the token to the service provider. Upon receipt of the token, the service provider will validate the token with the federated identity provider, obtain identifying information, and complete the transaction.
Owner:APPLE INC
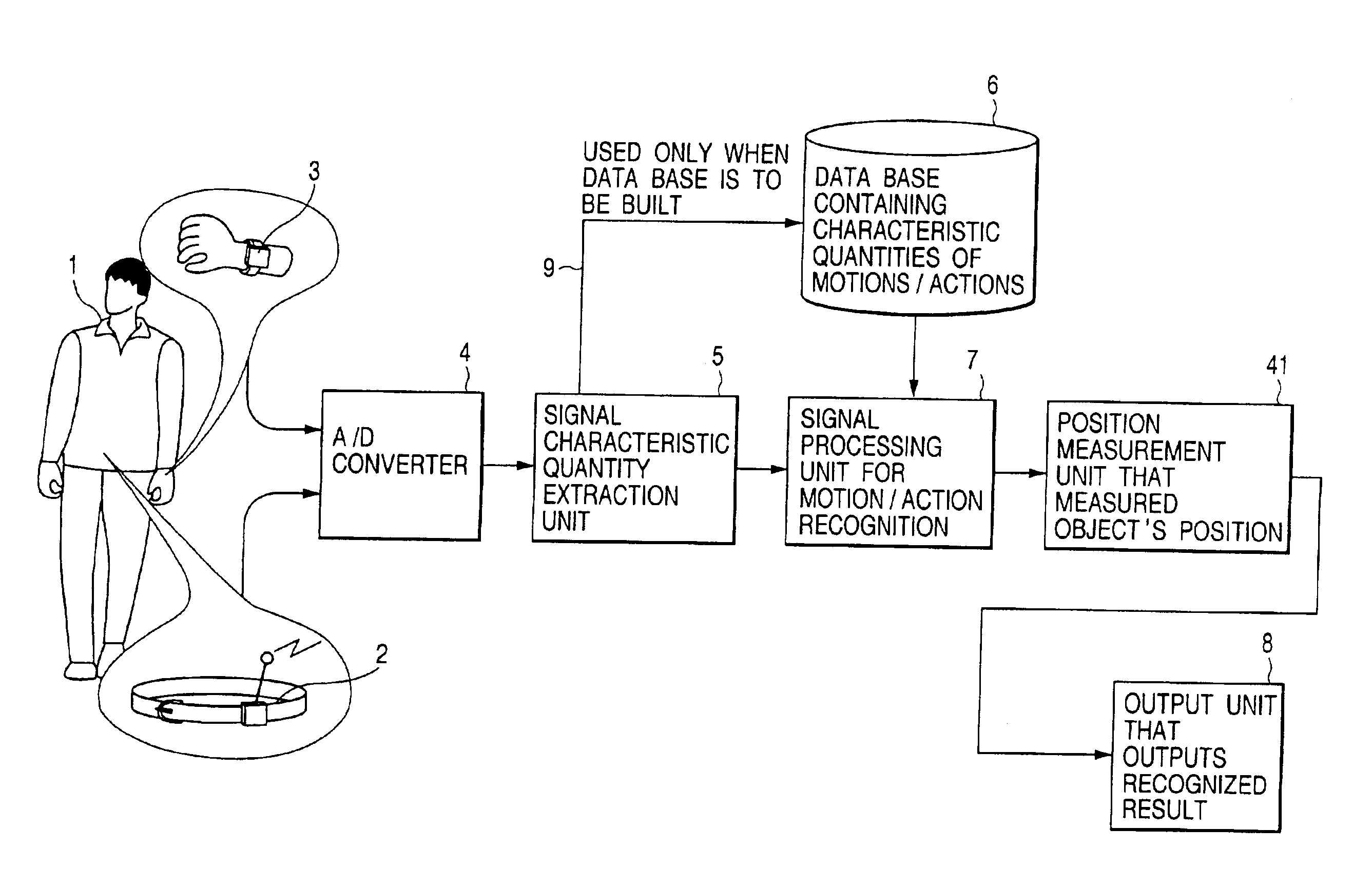
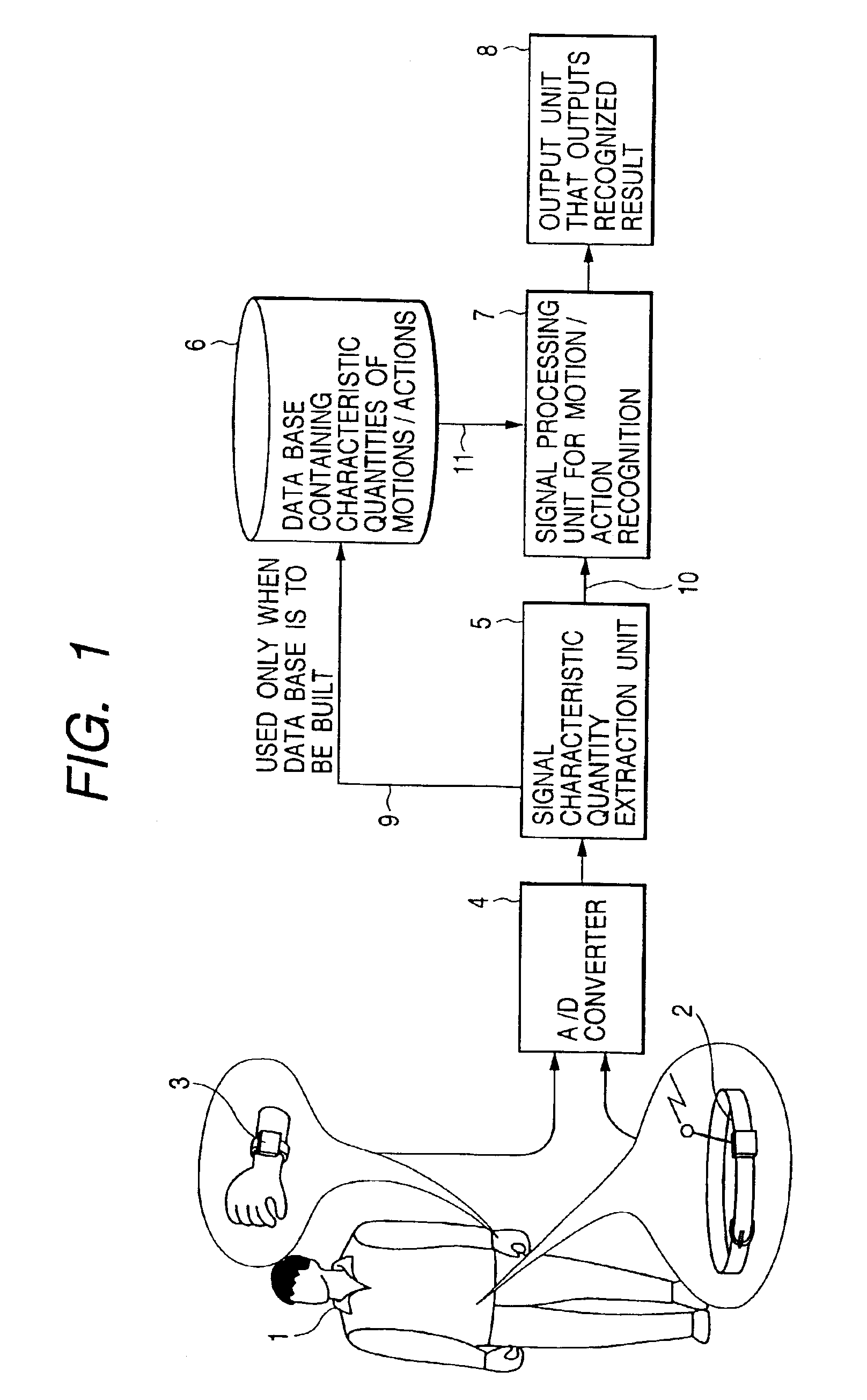
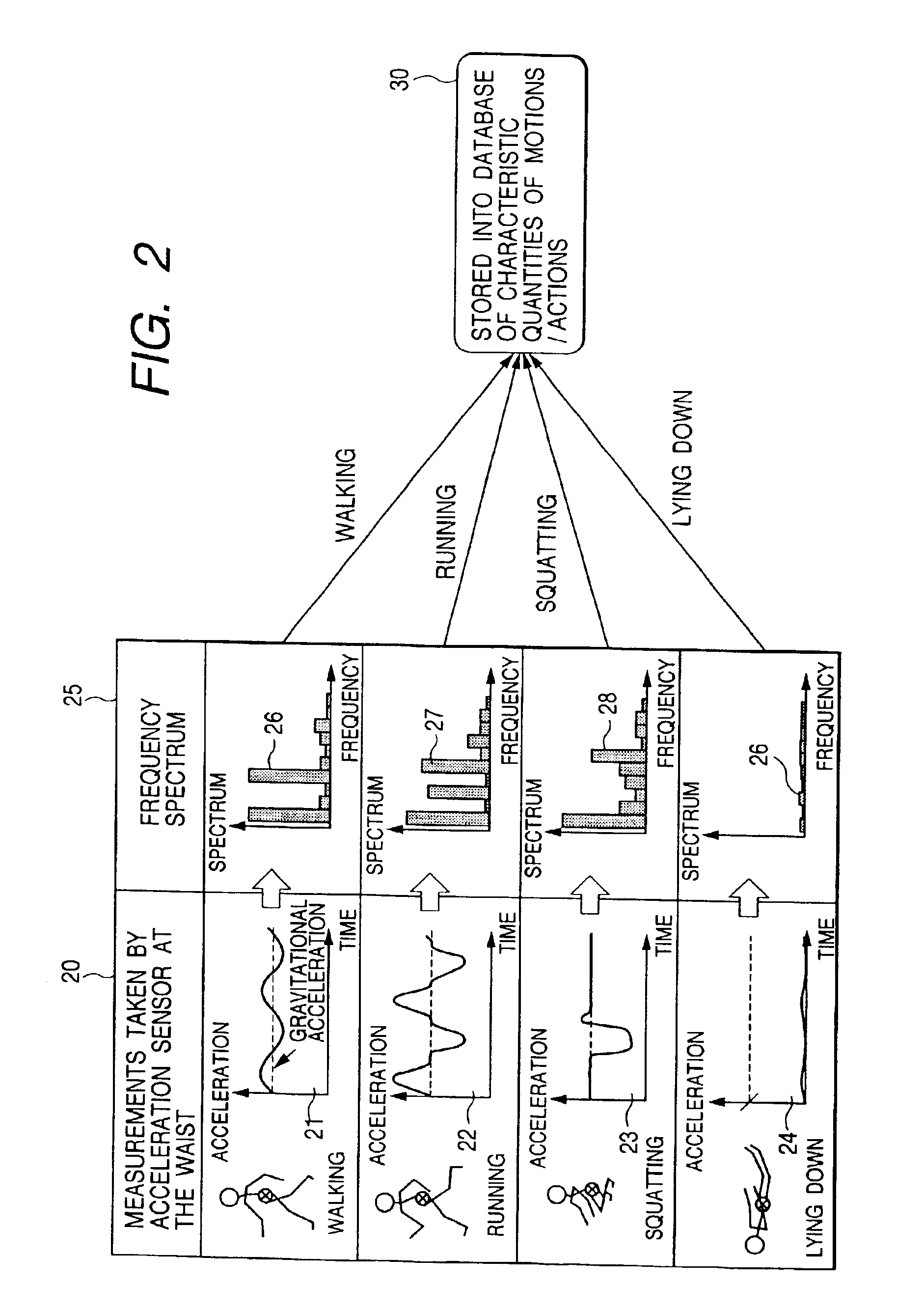
Method, apparatus and system for recognizing actions
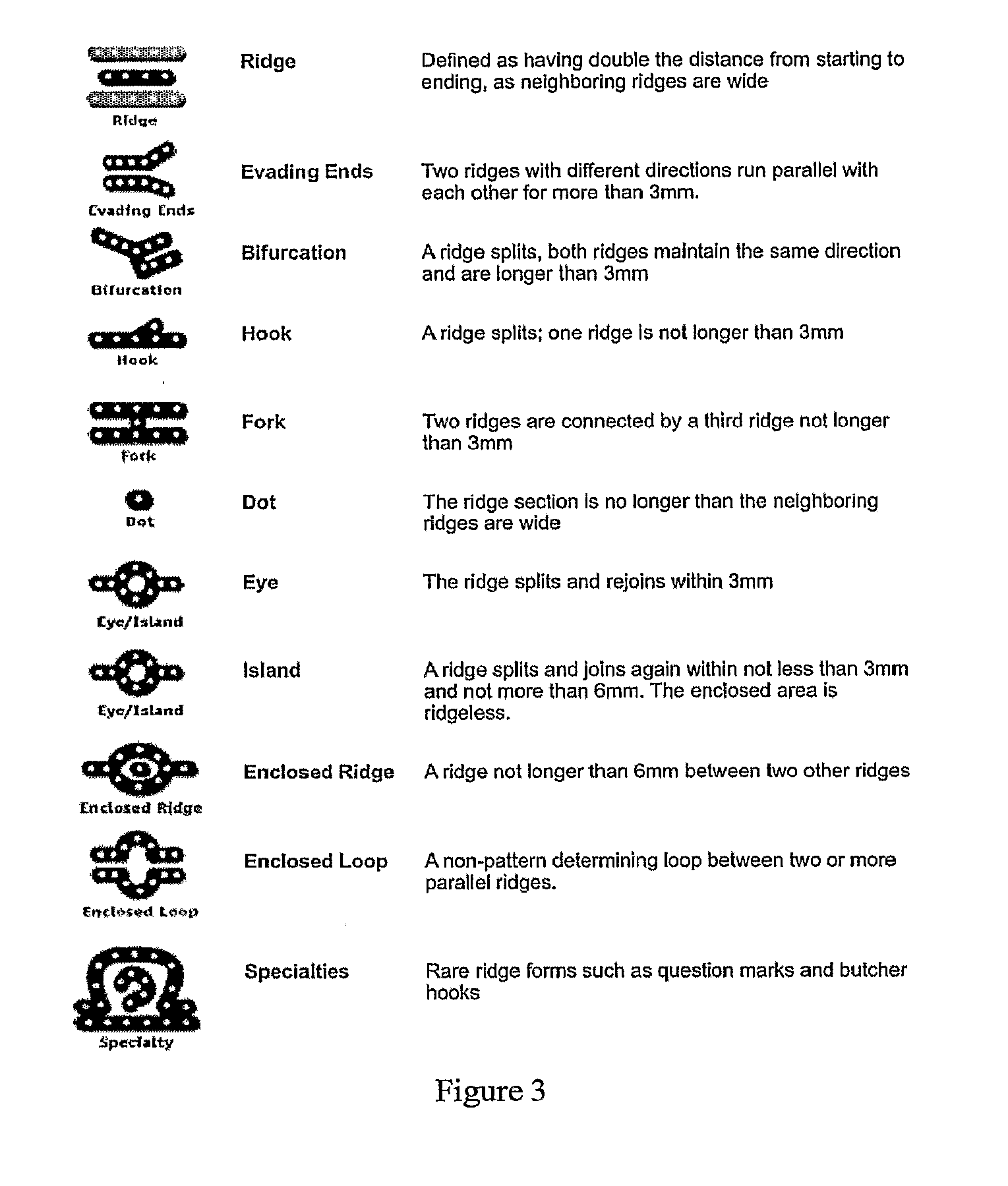
InactiveUS6941239B2More precisionFreedom of movementInput/output for user-computer interactionGymnastic exercisingPhysical medicine and rehabilitationState variation
An object of the present invention is to provide a method, an apparatus and a system for automatically recognizing motions and actions of moving objects such as humans, animals and machines.Measuring instruments are attached to an object under observation. The instruments measure a status change entailing the object's motion or action and to issue a signal denoting the measurements. A characteristic quantity extraction unit extracts a characteristic quantity from the measurement signal received which represents the motion or action currently performed by the object under observation. A signal processing unit for motion / action recognition correlates the extracted characteristic quantity with reference data in a database containing previously acquired characteristic quantities of motions and actions. The motion or action represented by the characteristic quantity with the highest degree of correlation is recognized and output.
Owner:APPLE INC
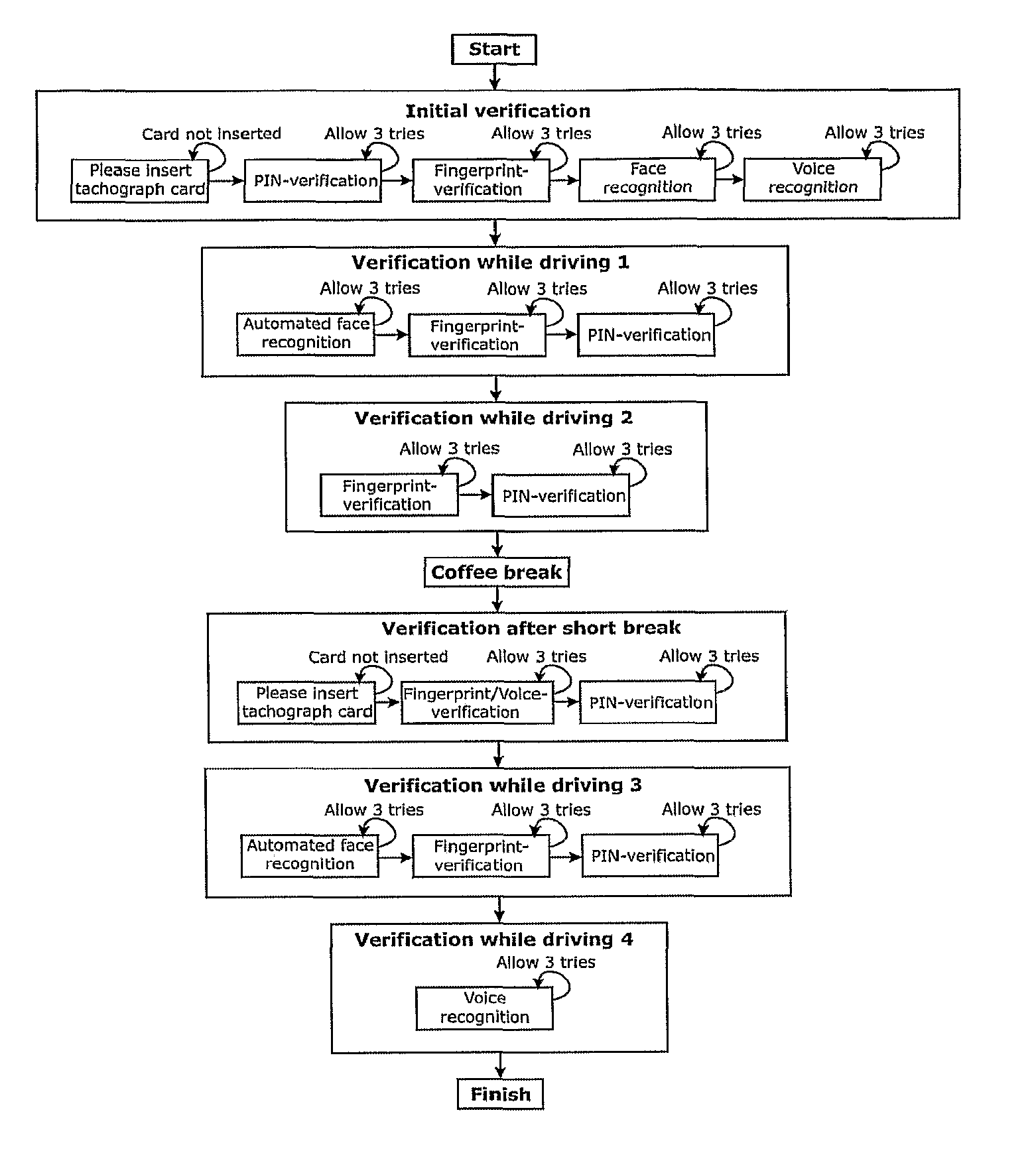
Method for performing driver identity verification
InactiveUS8344849B2Improve security levelElectric signal transmission systemsImage analysisRemedial actionEngineering
Method for assuring that the operator of a vehicle is an authorized driver, the method including utilizing an onboard, multi-mode driver identification system to ascertain whether an operator is an authorized driver. A first driver identification procedure is performed on a present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle. A second driver identification procedure is performed on the present operator of the vehicle and determining whether the present operator is an authorized or unauthorized driver of the vehicle, wherein the first and second driver identification procedures are performed with a time interval therebetween, the time interval being dependent upon the nature of the work being performed by the operator. A remedial measure is exercised to avert potentially negative impact when the present operator of the vehicle is determined to be an unauthorized driver based upon at least one of the performed identification procedures.
Owner:VOLVO TECH
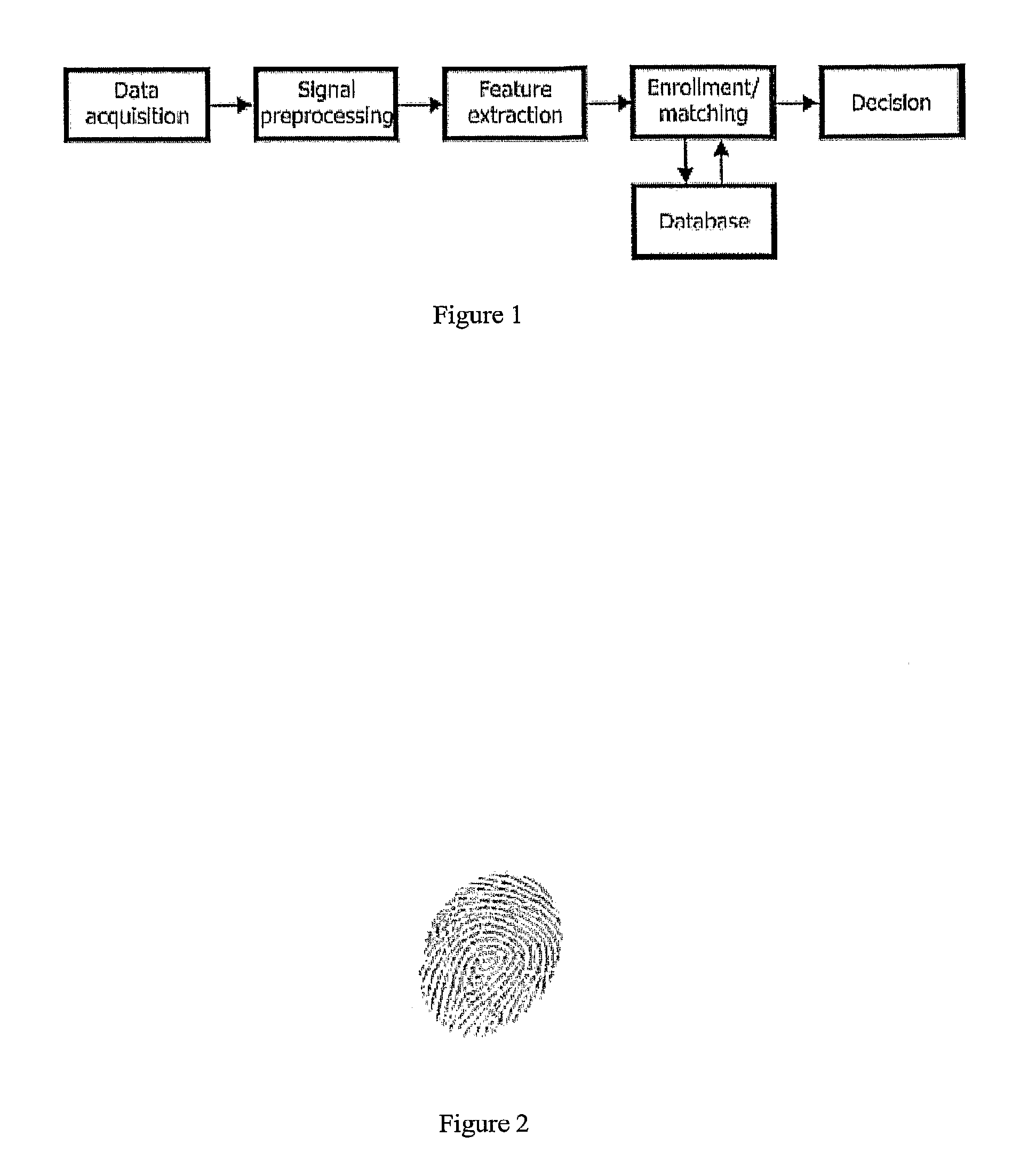
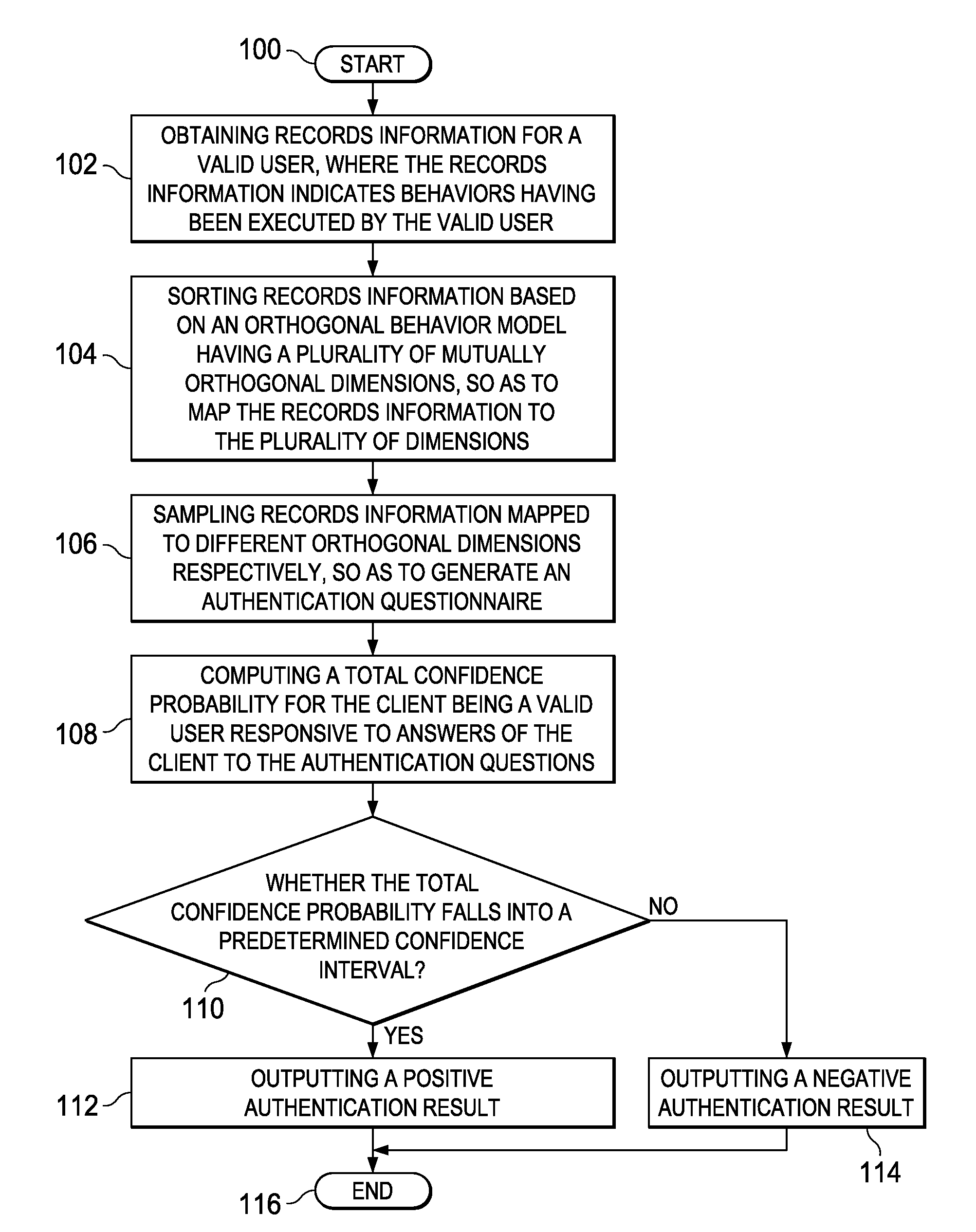
Authentication method and apparatus
InactiveUS8495718B2More reliableMore securityDigital data processing detailsAnalogue secracy/subscription systemsConfidence intervalCausality
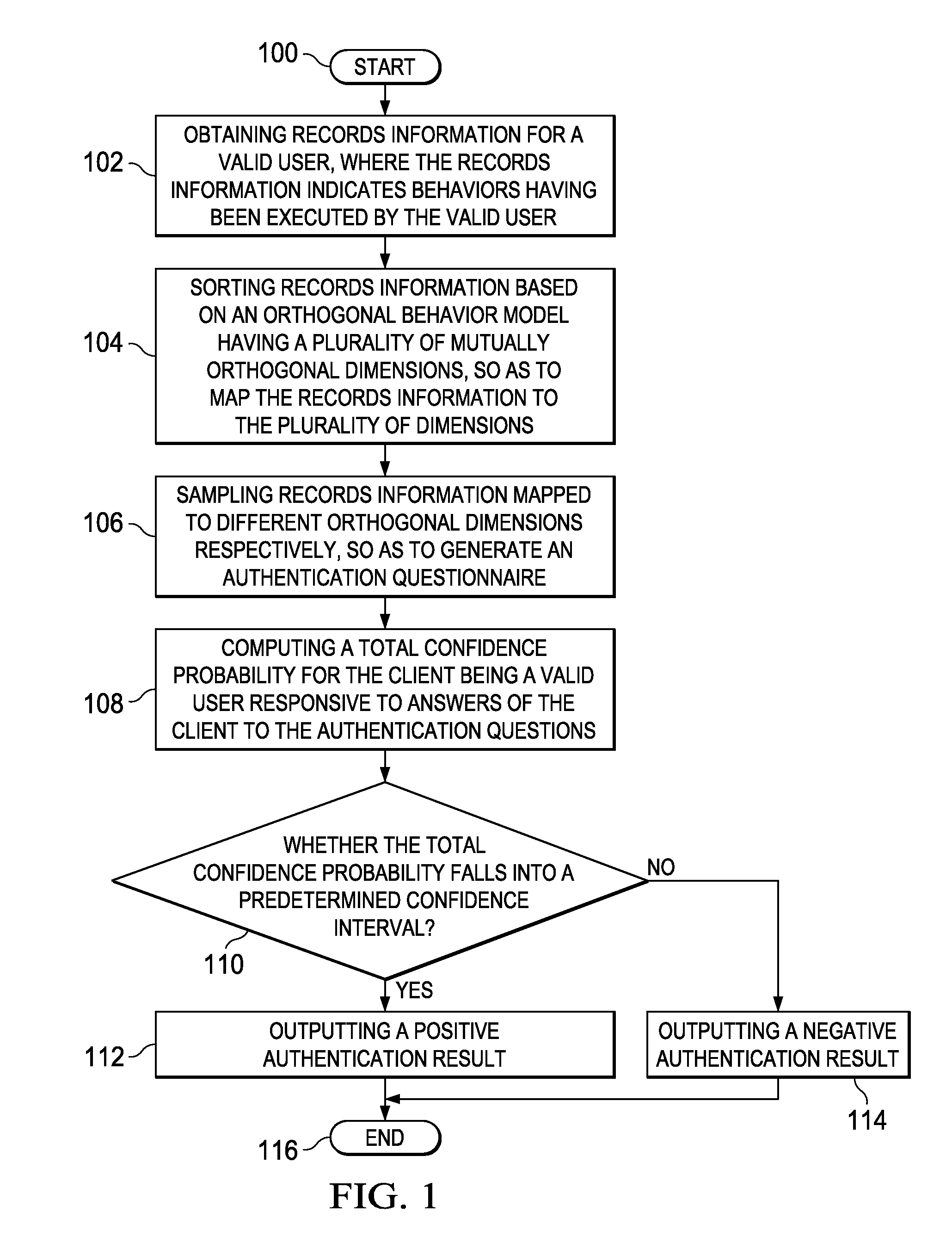
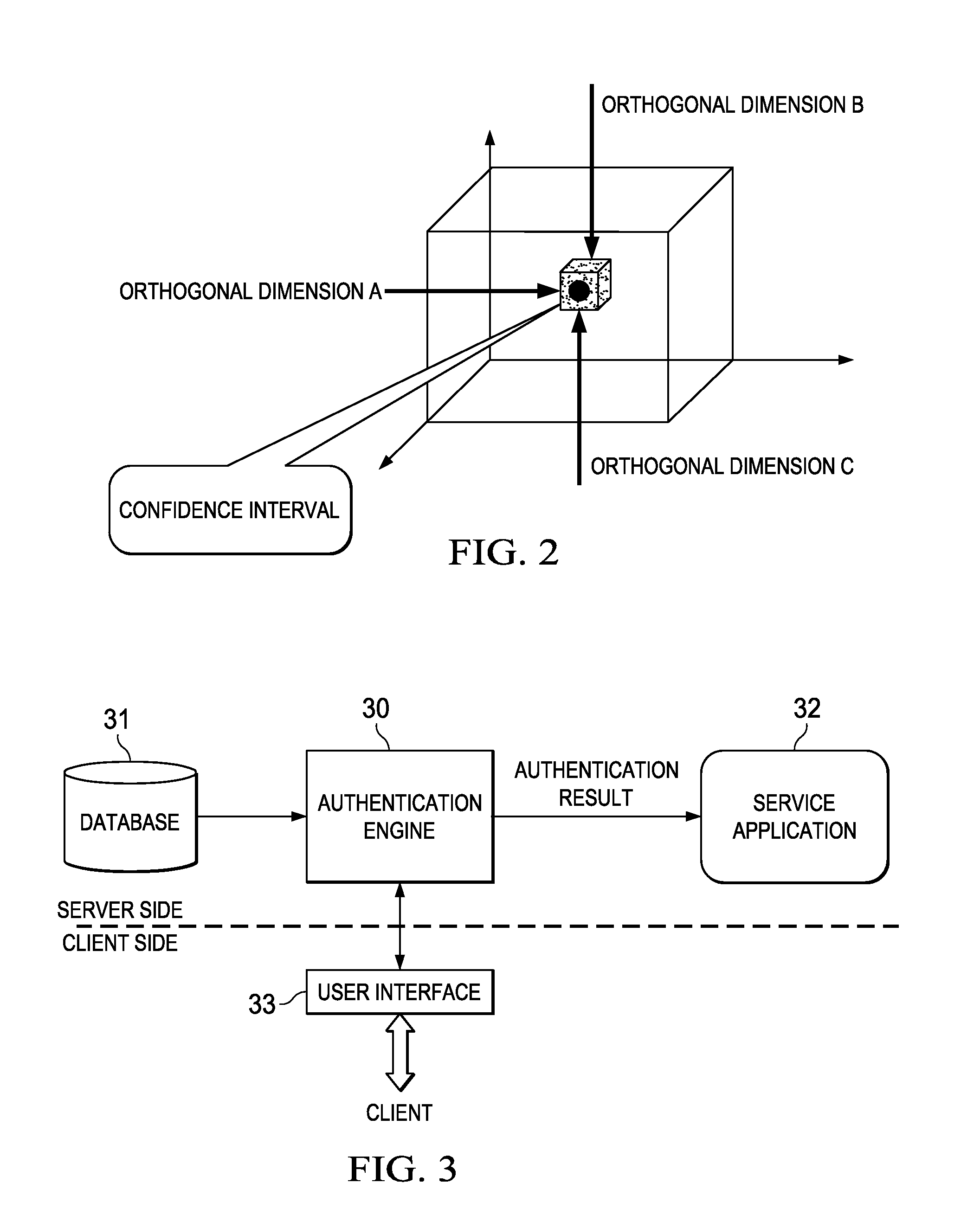
An identity authentication method is provided. The method comprises obtaining records information of a valid user, where the records information indicates behaviors having been executed by the valid user; mapping, based on an orthogonal behavior model having multiple mutually orthogonal dimensions, records information to the multiple dimensions, wherein behaviors indicated by records information mapped to different dimensions do not overlap therebetween and have no logical cause and effect relationship; sampling records information mapped to different dimensions, respectively, so as to generate an authentication questionnaire including a plurality of authentication questions; computing, responsive to answers of a client to the authentication questionnaire, a total confidence P for the client being a valid user; outputting a positive authentication result, responsive to the total confidence probability P falling into a confidence interval; and outputting a negative authentication result, responsive to the total confidence probability P failing to fall into a confidence interval. The present invention further provides a corresponding identity authentication apparatus.
Owner:INT BUSINESS MASCH CORP
Monitoring system and method for patient care
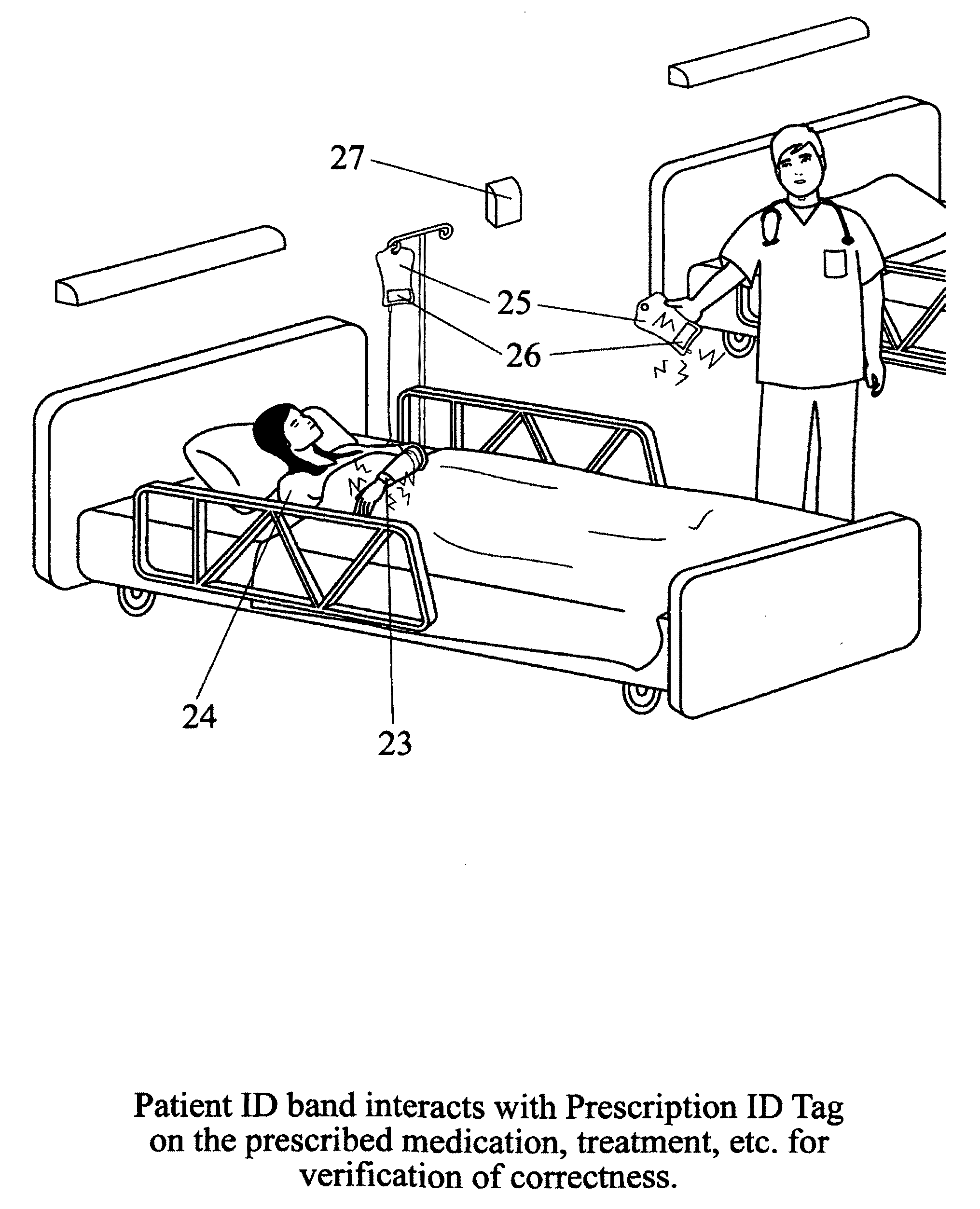
A patient care monitoring system and method employ active RFID devices integrated with digital processing, memory and timing circuitry for patient identification, care giver identification and for identification of each prescribed treatment, procedure, medication and general and / or special care action. At the point-of-care, each care action identity device will match directly with the targeted patient identity device or issue an error warning to prevent mistakes. The patient identity device will also interact with an associated sensor network to proactively prompt care givers to provide general care actions, such as altering a patient's laying position, changing bed pan / clothing / bed sheet, etc. for invalid patients. Also the patient identity tag will furnish periodic records of every care action, mistakes, remedies, care givers' identities and time and date for a central processor of a healthcare facility to monitor the quality of patient care. Such record can also be potentially accessed via the Internet by the responsible regulatory agencies, accreditation associations, insurance firms and even patients' families to ensure patient care is meeting the standards as well as medical billing accuracy.
Owner:HUANG CHING CHING +4
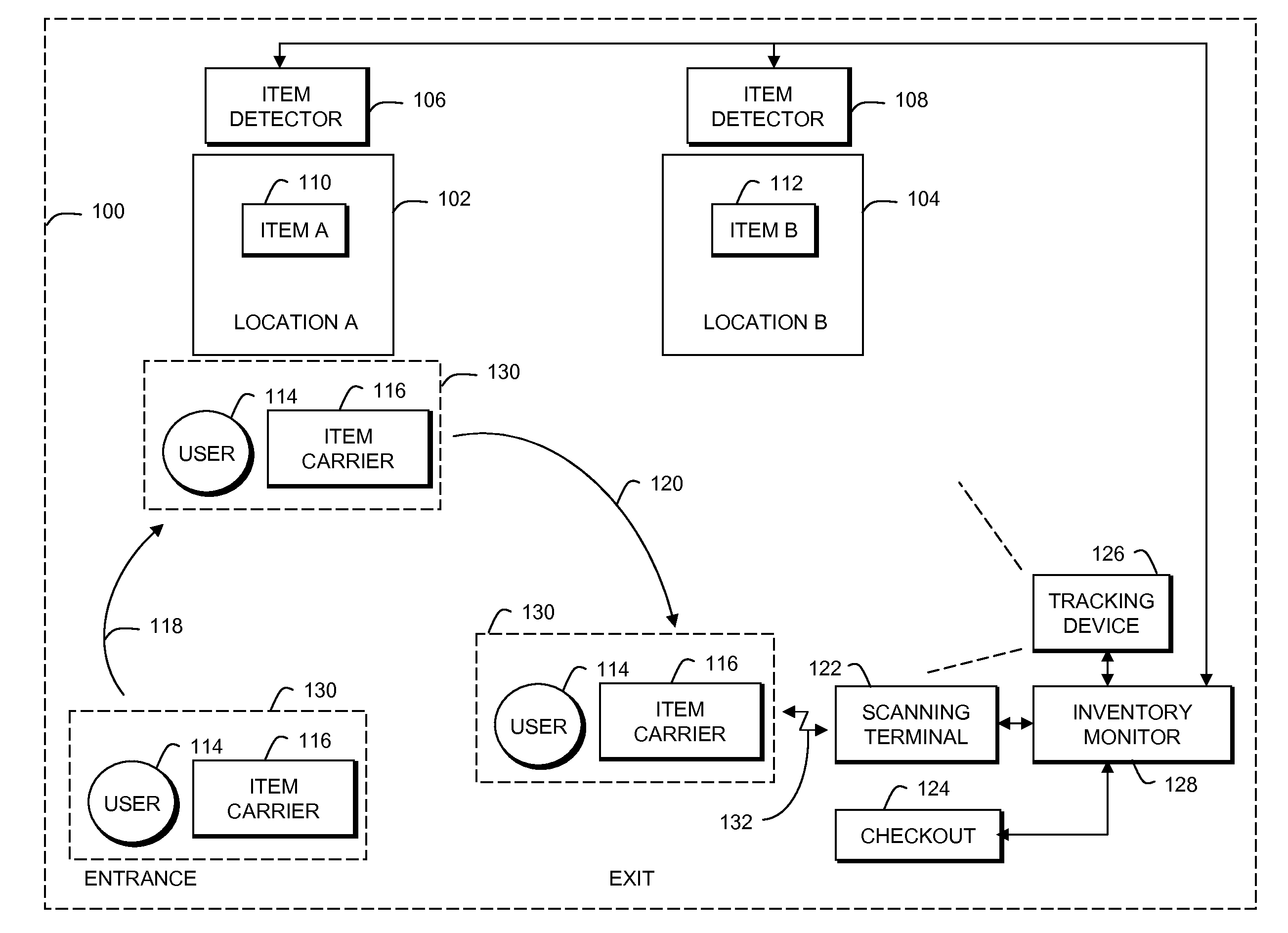
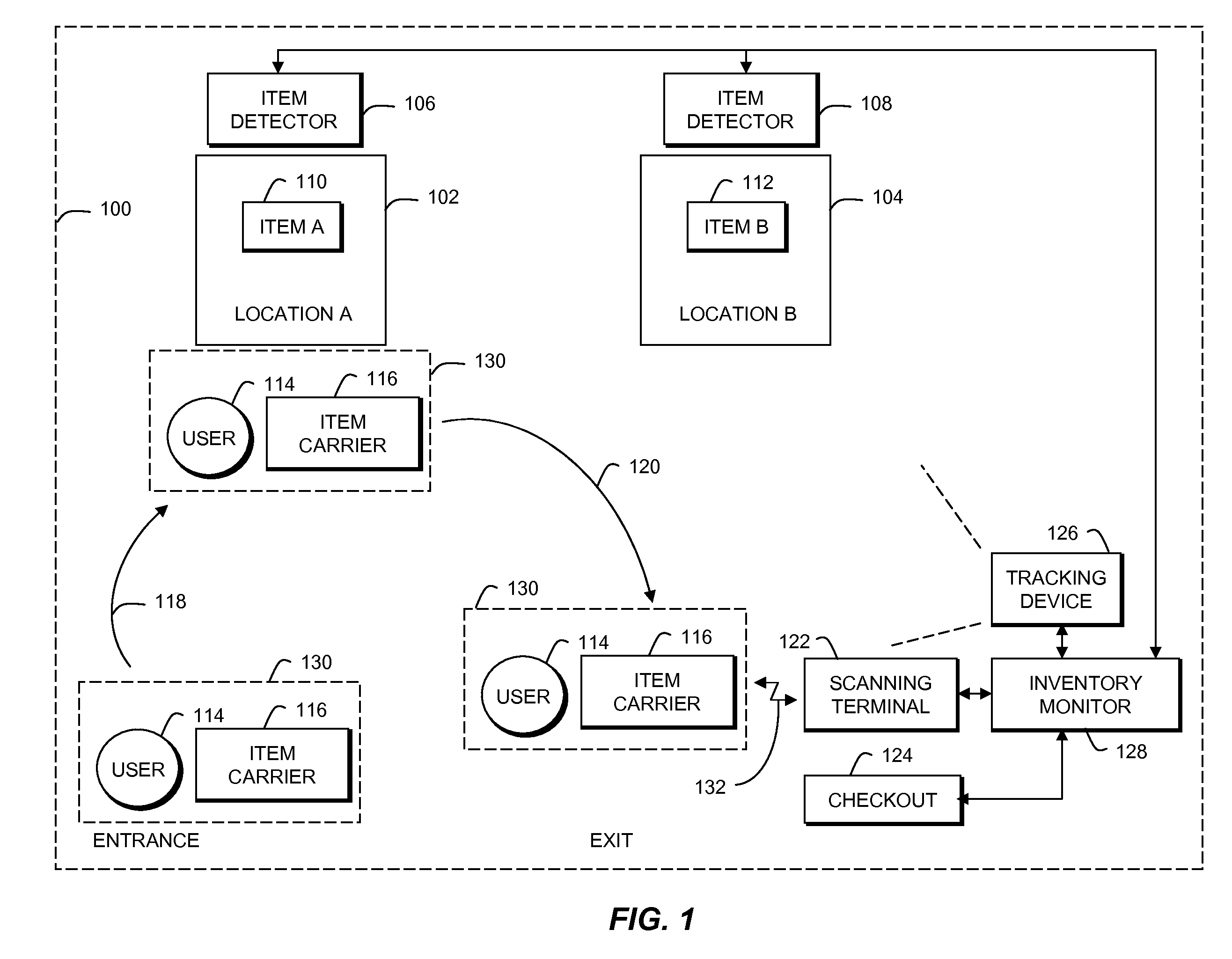
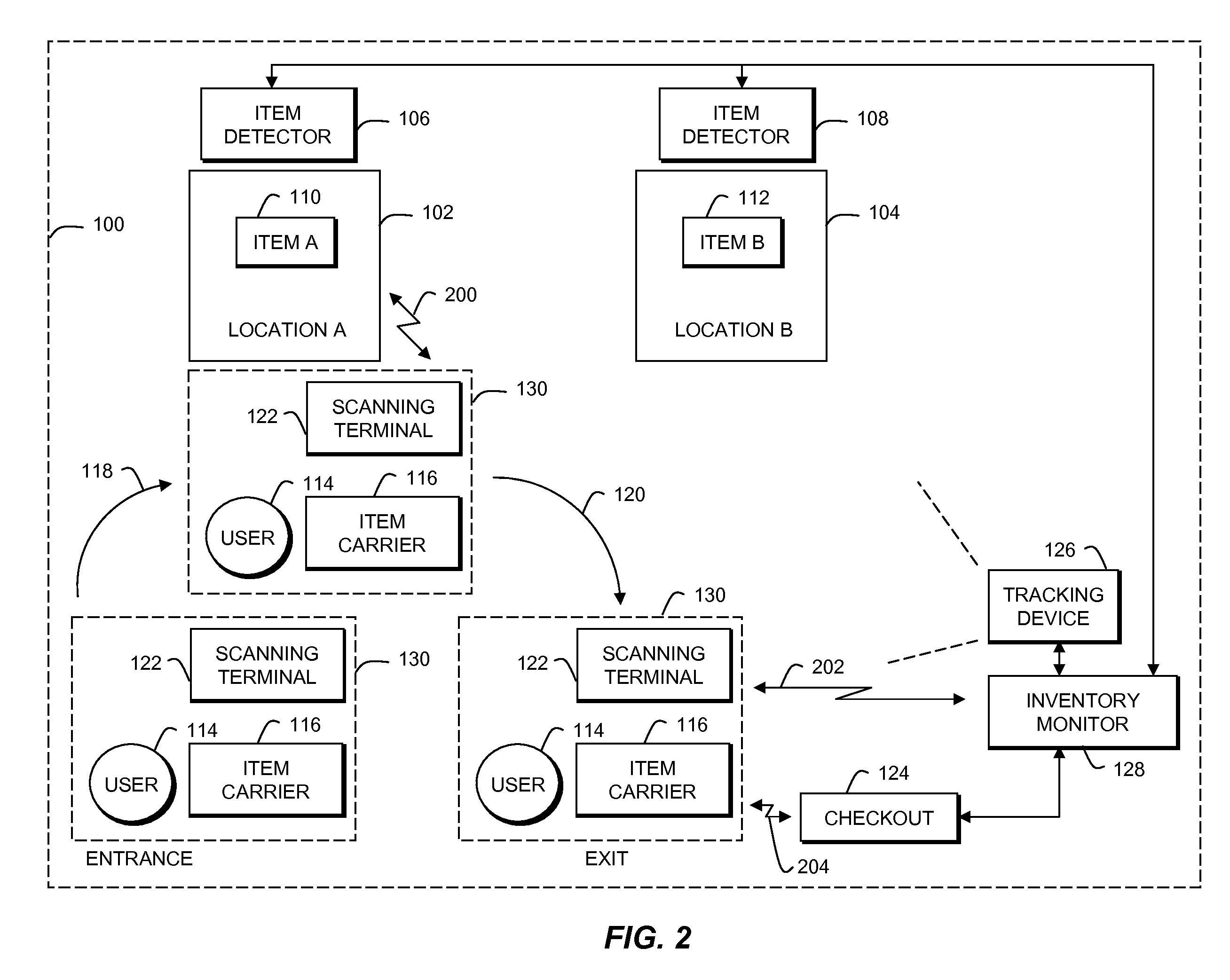
Inventory monitoring using complementary modes for item identification
A technique for inventory monitoring using complementary modes for item identification includes; storing items in known locations within a defined area; tracking a user in the defined area; detecting that the user has removed an item from its known storage location; ascertaining a first identity of the item using first means; scanning the item to obtain a second identity of the item using second means different than the first means; correlating the results from detecting, ascertaining and scanning to determine if there is a discrepancy, and providing an alert if there is a discrepancy. If there is no discrepancy, checkout can proceed.
Owner:SYMBOL TECH INC
Enhanced Subscriber Authentication Using Location Tracking
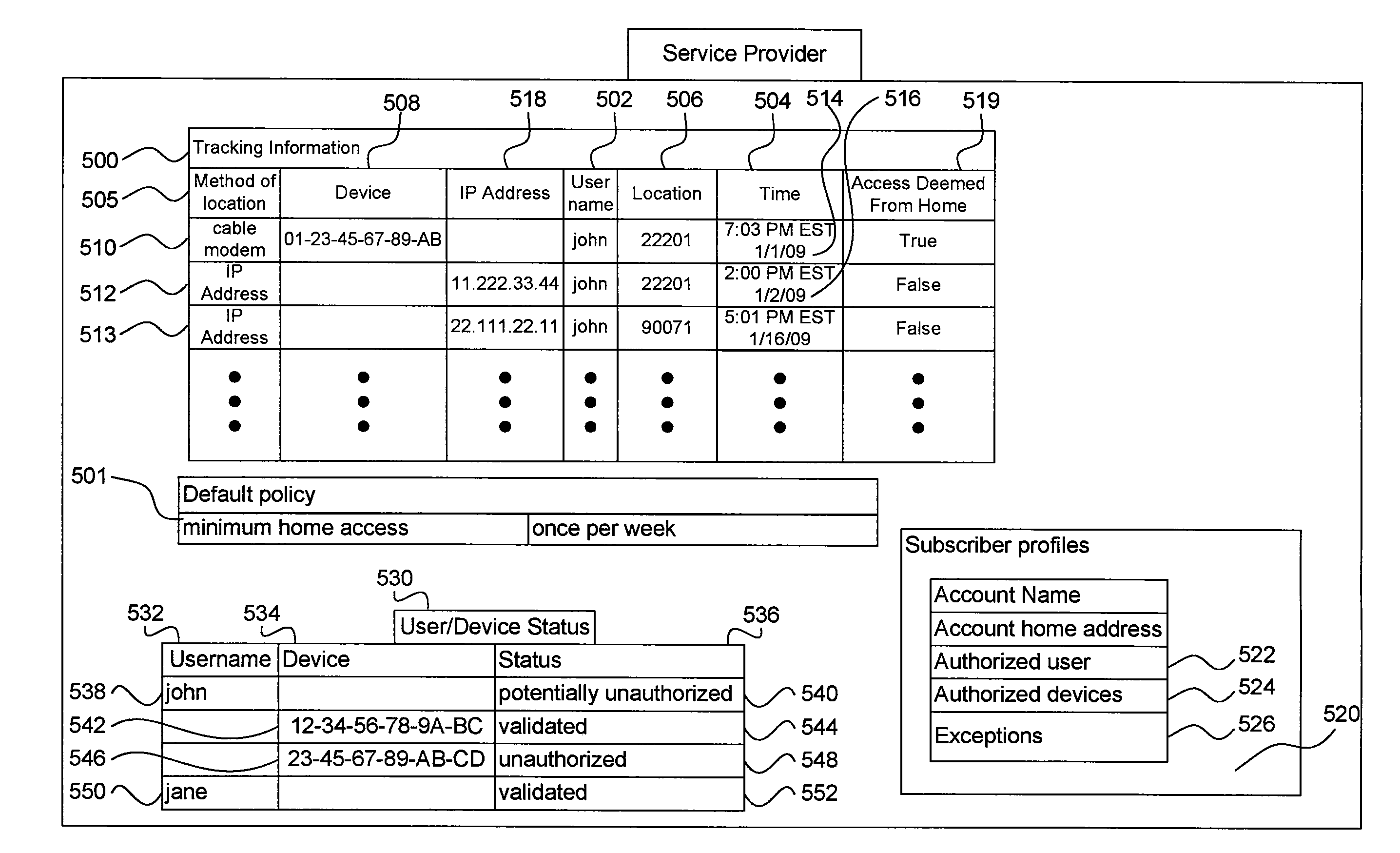
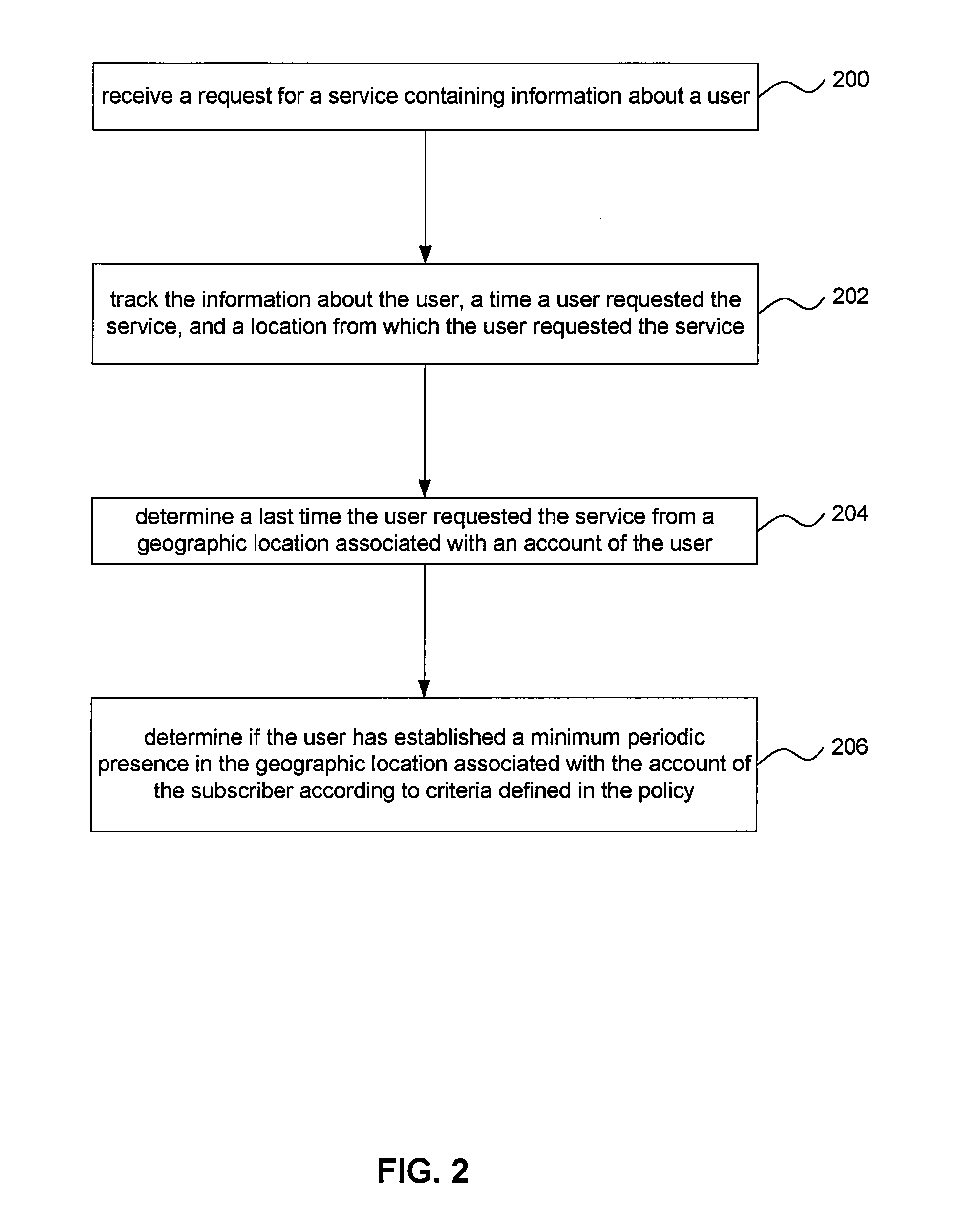
ActiveUS20110167440A1Avoid obscuring purposeUnauthorised/fraudulent call preventionEavesdropping prevention circuitsLocation trackingTerms of service
Tracking and analysis of the location of user and device access to telecommunications services may be used to validate that a given user or device is part of an authorized subscriber household and is therefore properly accessing those services in accordance with the terms of service. A service provider may determine, based on previously collected data and user information collected while a user accesses a service, whether the user's pattern of access establishes a required pattern of access determined by the service provider, such as access on a minimum periodic basis from the home of an authorized subscriber.
Owner:CSC HLDG
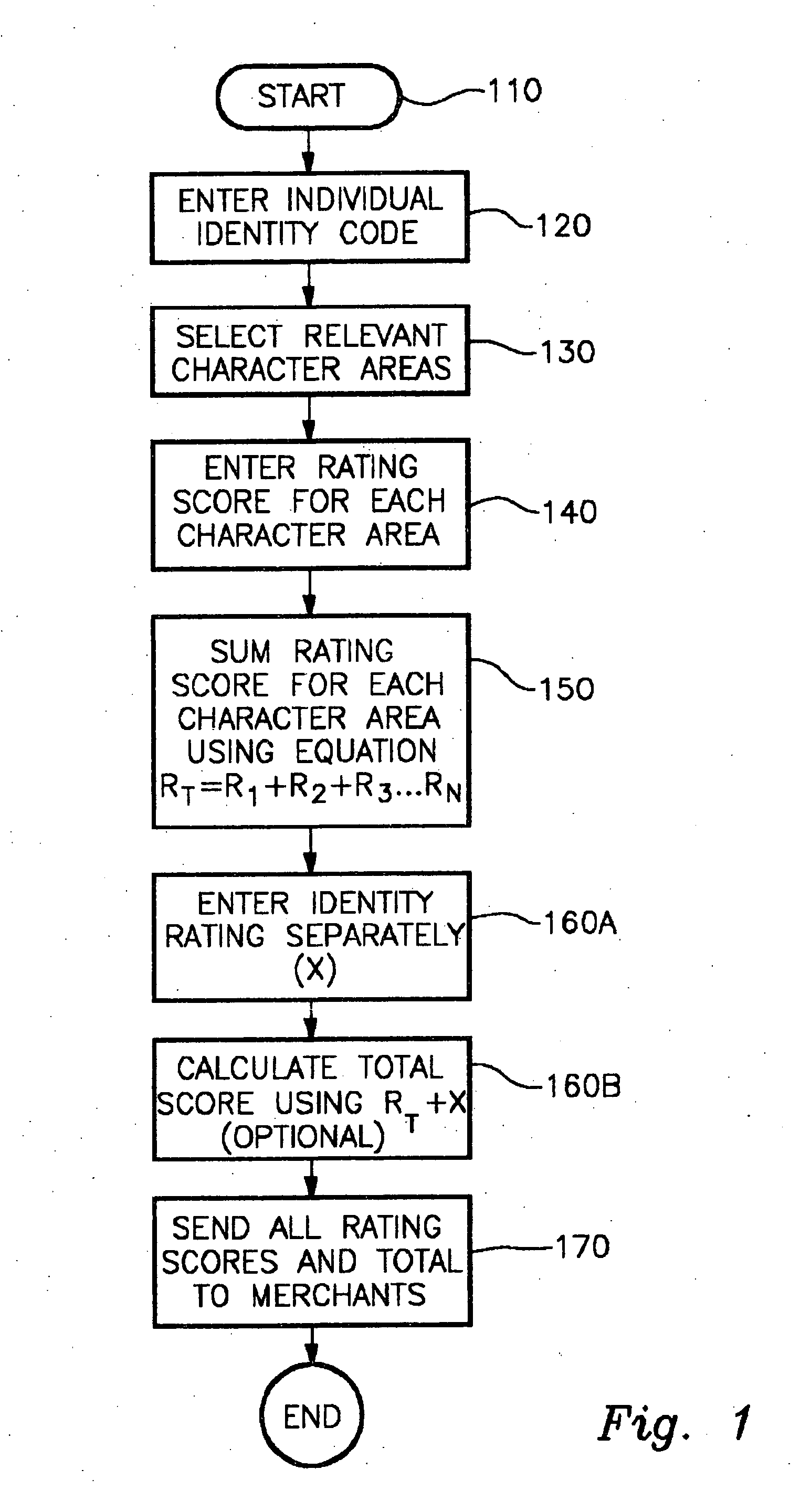
Integrated verification system
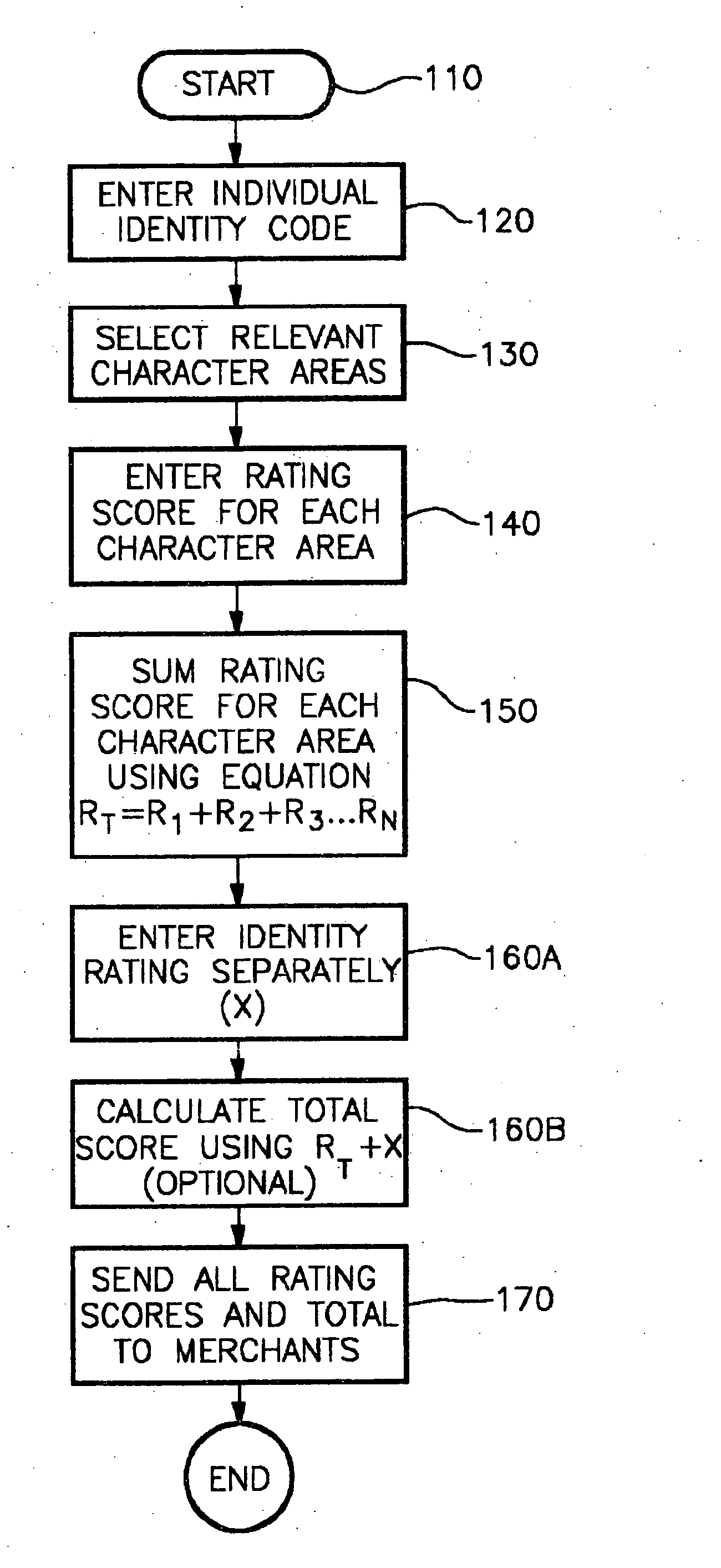
InactiveUS20050027983A1Avoid lostHigh identity scoreUser identity/authority verificationDigital data authenticationDigital signatureVerification system
The subject invention comprises a process and means for an integrated and standardized verification rating of individuals seeking credit or access, or for sending a digital signature for access purposes including means comprising of a scaled rating for an individual's identity, along with potential other individual attributes that will be rated in order to apprise a merchant or other entity of the authenticity of the individual seeking credit or permit access to an entity or sending a digital signature.
Owner:KLAWON KEVIN T
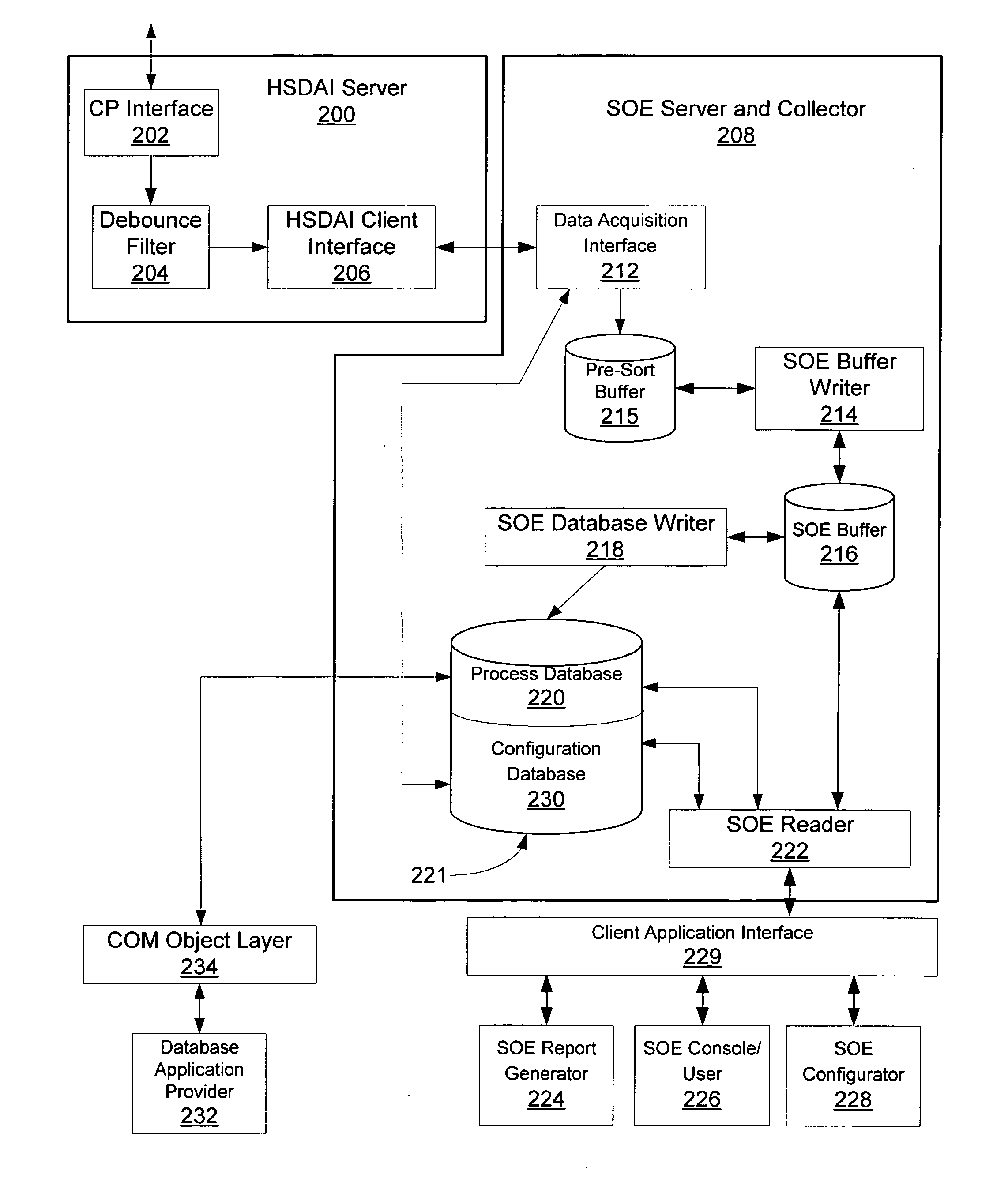
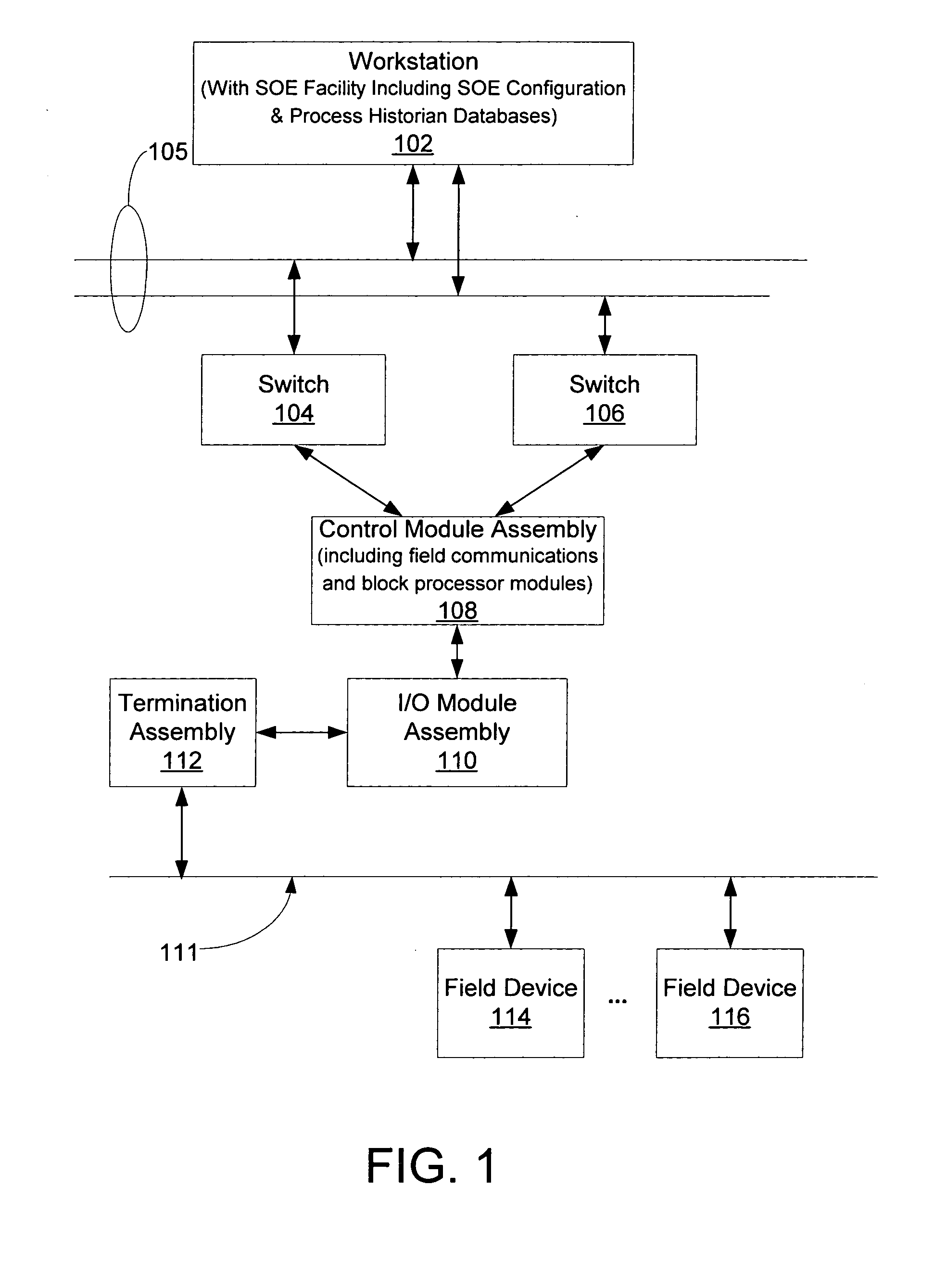
Sequence of events recorder facility for an industrial process control environment
ActiveUS20070244571A1Facilitate carrying out recited stepProgramme controlComputer controlDigital dataProcess control network
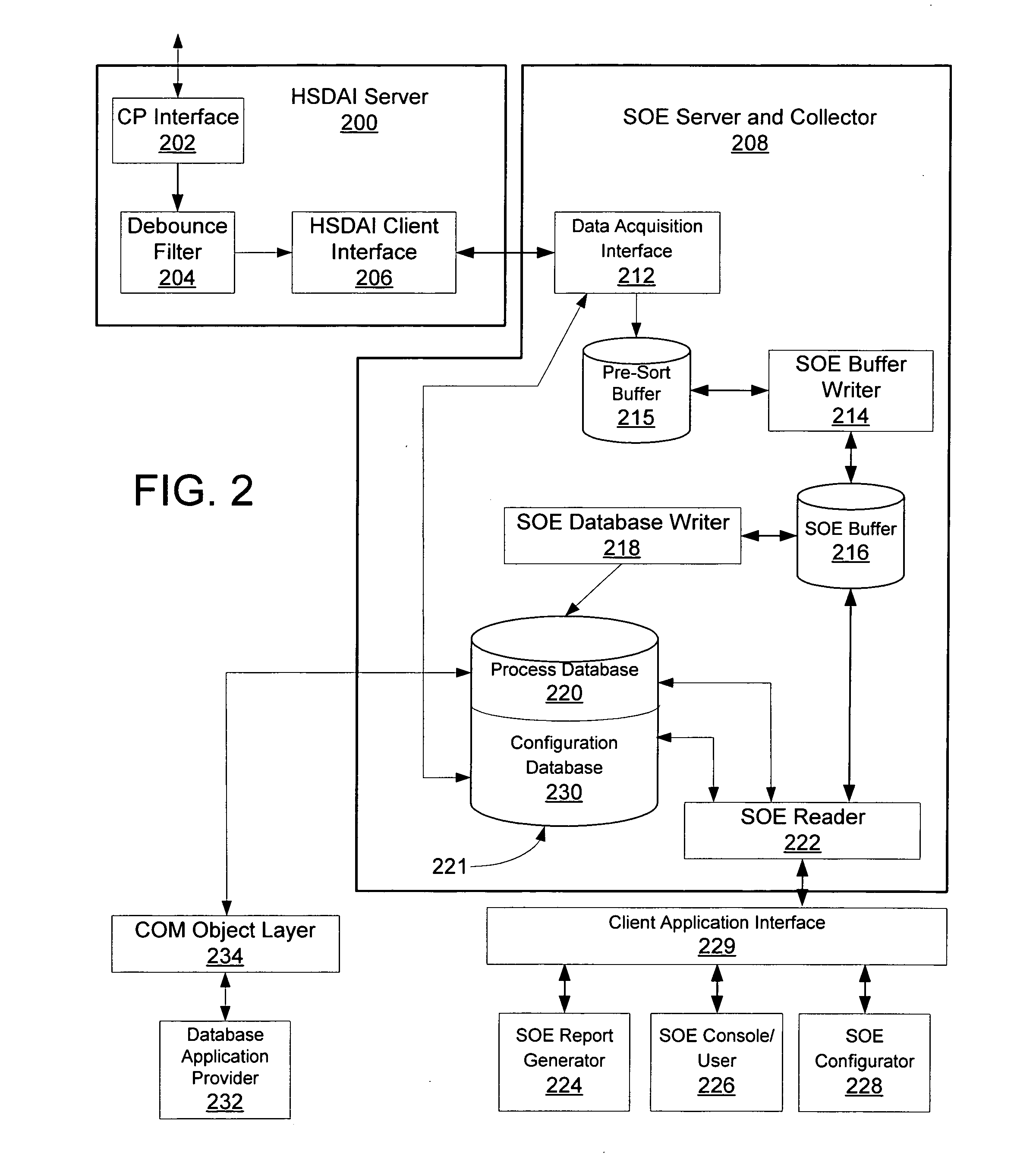
A sequence of events (SOE) recorder facility in a process control network environment is described herein. The SOE recorder facility is hosted by a networked node that receives digital signal status change (event) data from a networked controller. The sequence of events recorder facility receives a configured set of digital data signals from the controller, temporarily buffers the events in chronological order according to timestamps assigned to the events by their sources (e.g., fieldbus modules). The data is thereafter copied / removed from the buffer and provided to multiple destinations including: a process database that maintains an archival copy of the received event data for rendering event reports, and an SOE client user interface for rendering event logs to printers and / or graphical user interface displays.
Owner:SCHNEIDER ELECTRIC SYST USA INC
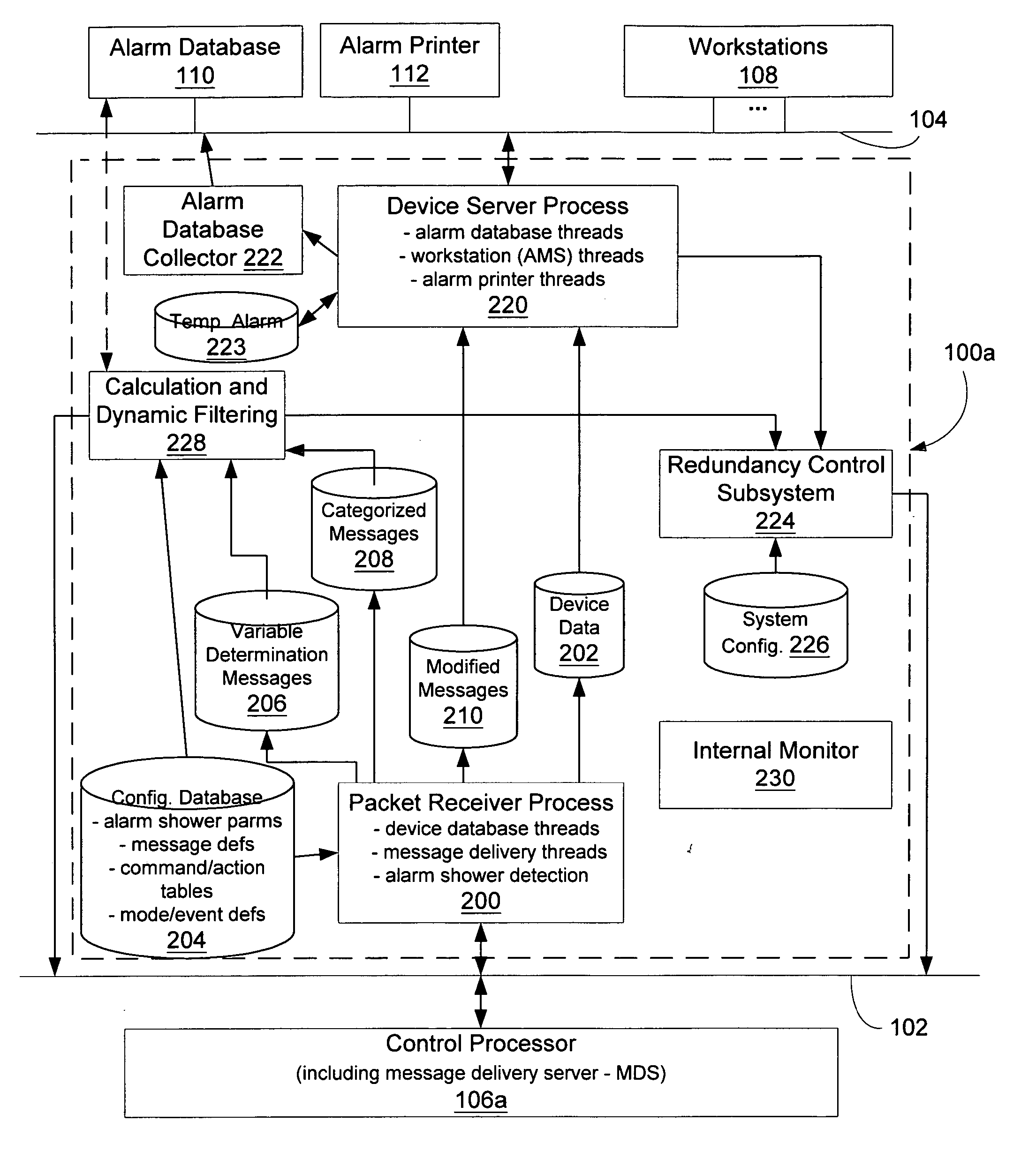
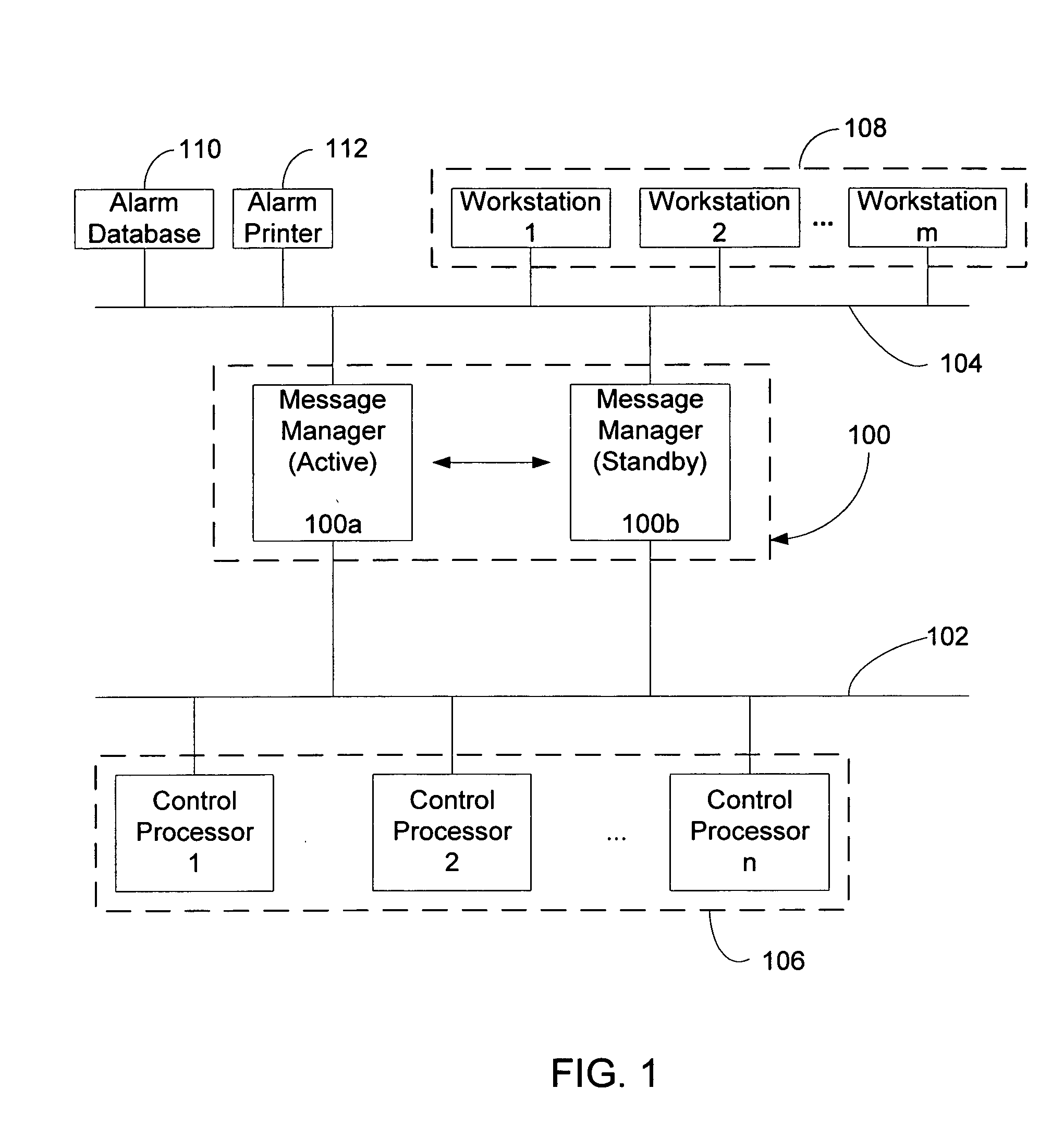
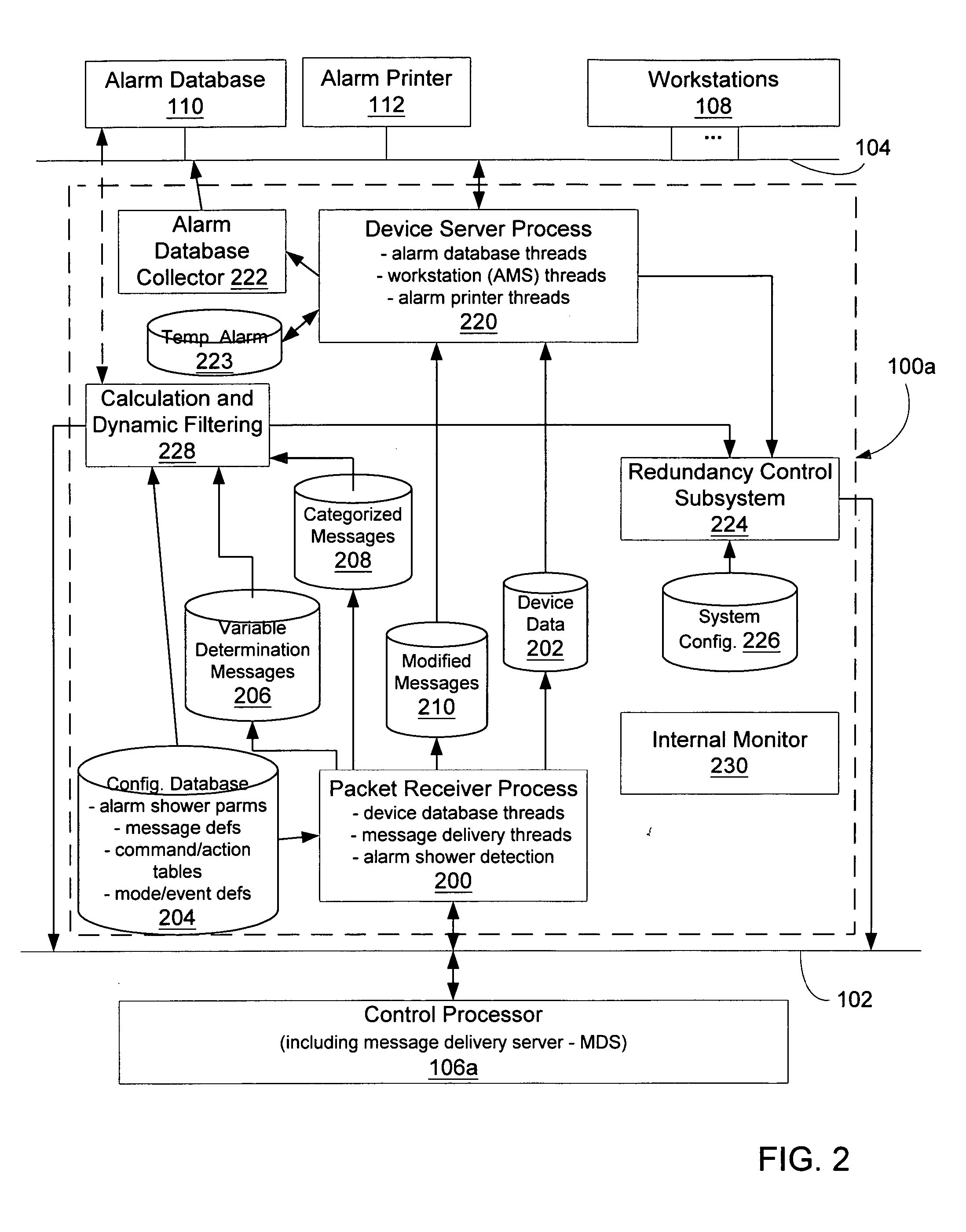
Message management facility for an industrial process control environment
InactiveUS20060168013A1Easy to implementProgramme controlTesting/monitoring control systemsAlarm messageProcess control network
A message management facility is described herein that is hosted by a networked node, in a process control network environment, that is separate from a control processor. The message management facility routes a stream of messages received from the control processor to a set of destinations on a supervisory network. By interposing the message management facility on a node that is interposed, in a message steam, between alarm message sources (control processors) and alarm message sinks (workstations, printers, historians), a number of additional functions can be implemented to carry out a number of advanced functions. Examples of such functions include: table-based routing of a single alarm to a number of destinations on an application network, suppressing alarm showers by applying a criterion to received messages when shower conditions have been sensed, invoking commands based upon a configured category assigned to particular identified messages prior to delivery of the message to its final destination, and invoking actions in response to event / mode status changes (including re-prioritizing alarms).
Owner:INVENSYS SYST INC
System and method for verifying the age and identity of individuals and limiting their access to appropriate material
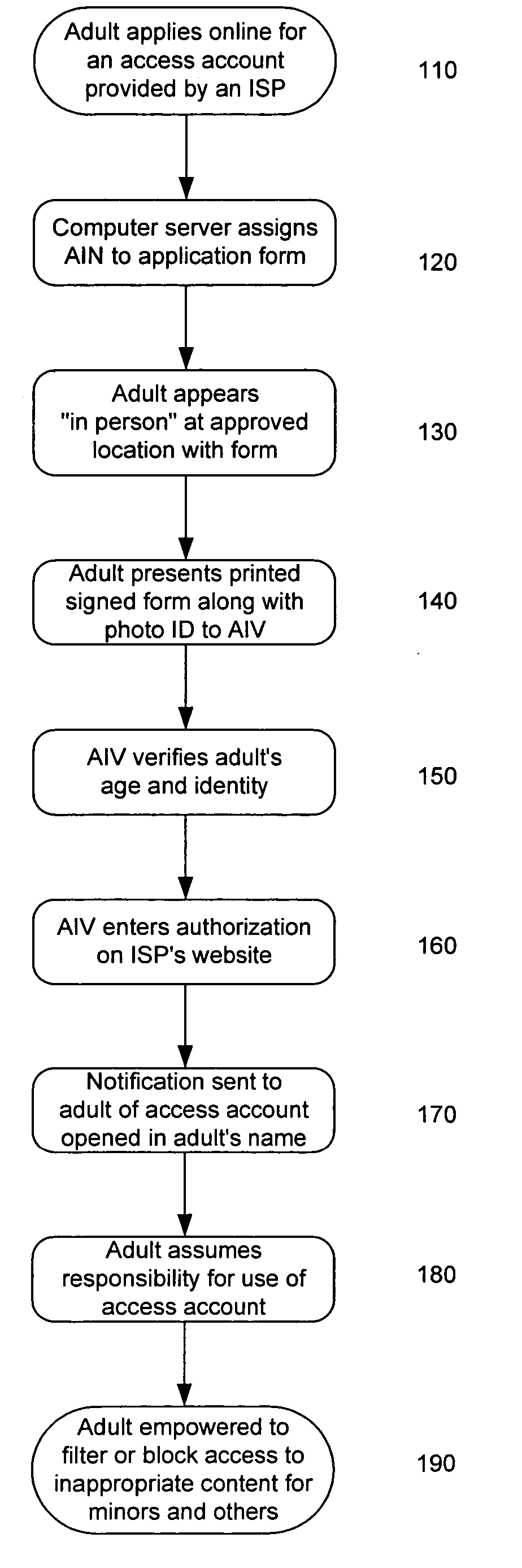
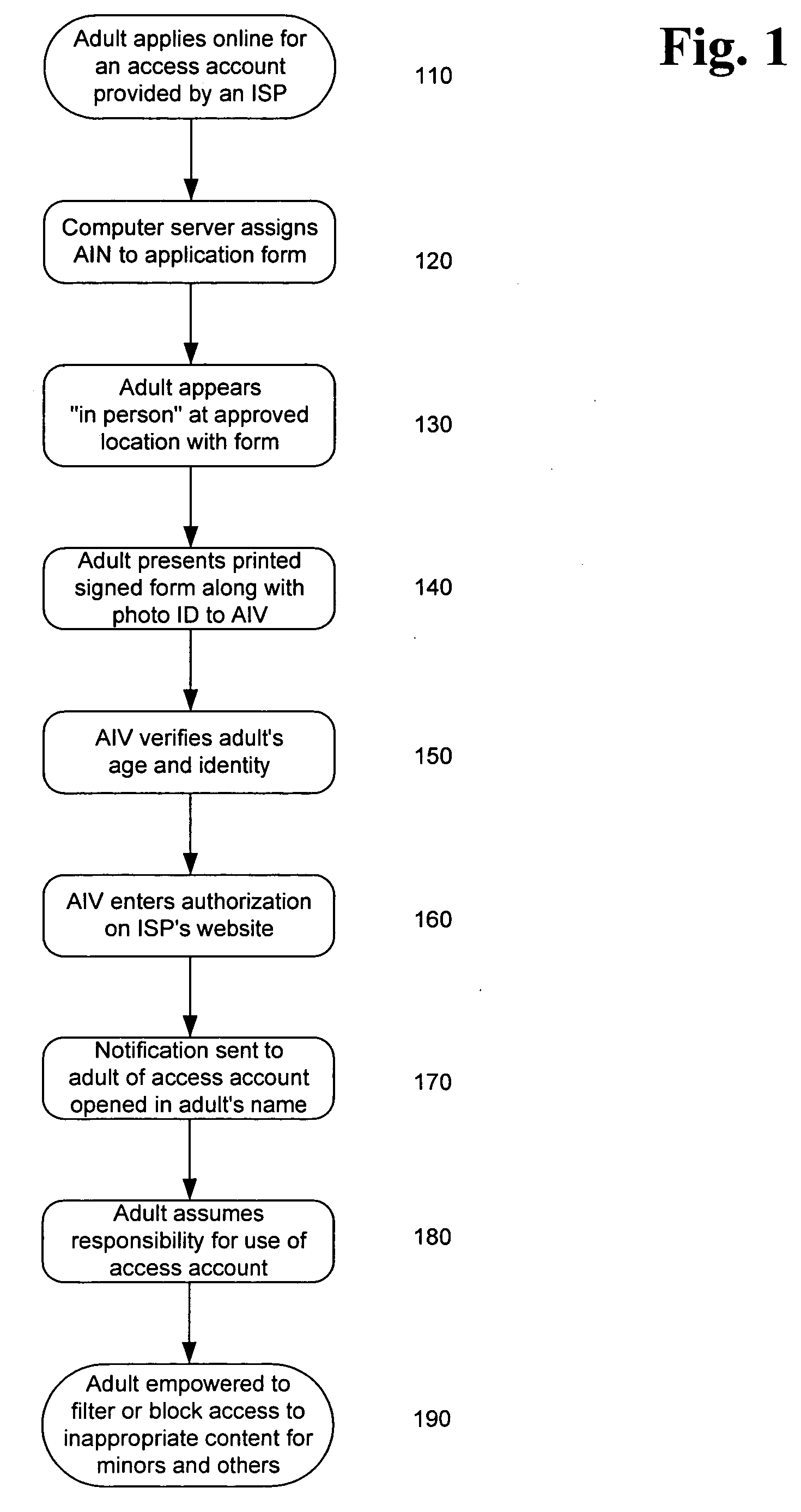
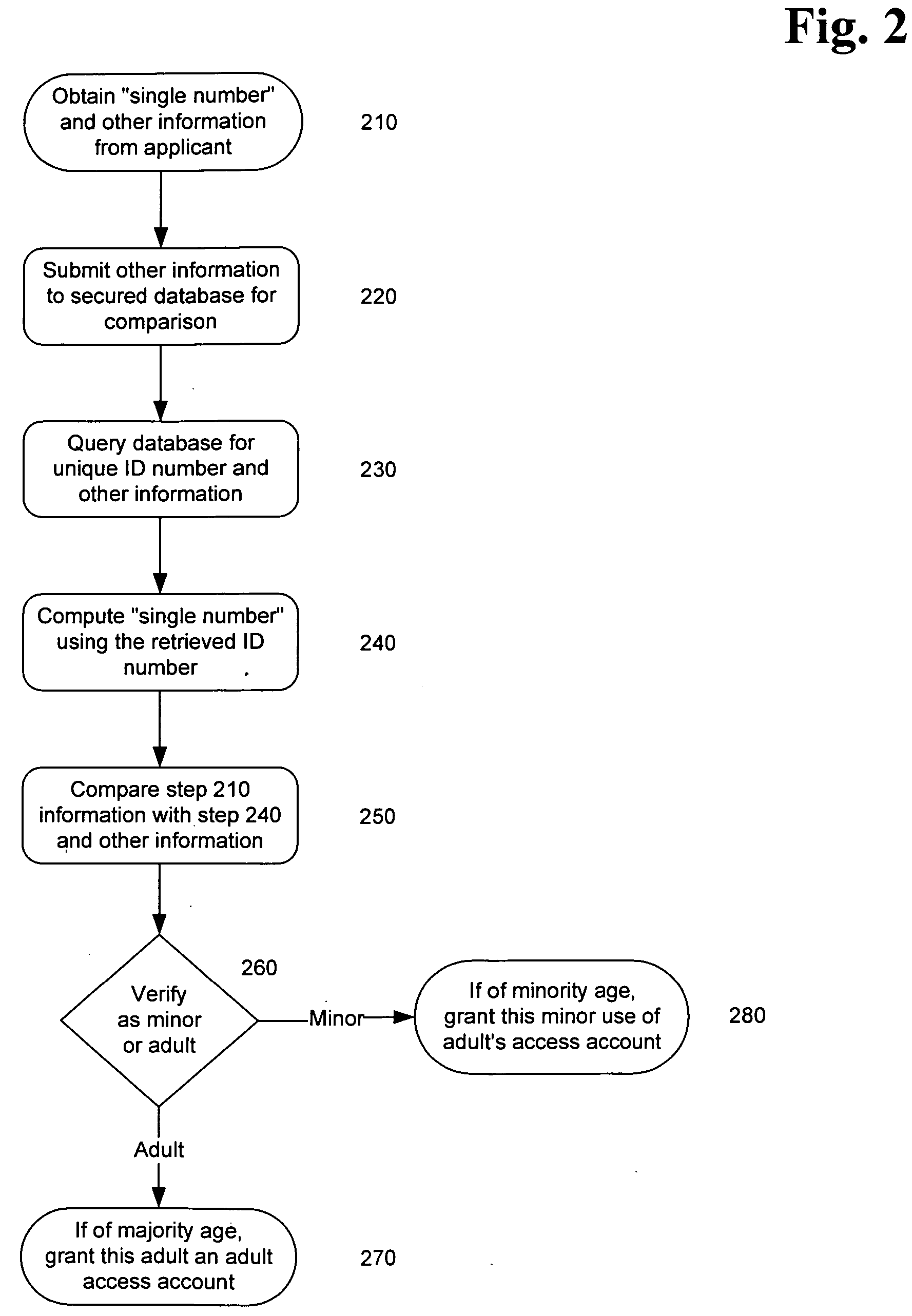
InactiveUS20060173792A1Exposure was also limitedPayment architectureSecret communicationLimited accessInternet privacy
Limiting access to the Internet, eCommerce websites, accounts and / or other venues, for example, by providing an Internet access account, and / or other access account, to an “in person” and / or “single number” age verified and identified “adult” who assumes responsibility for use of such account and viewing of appropriate material via such account by “in person” age verified and identified individuals, while being empowered by control of a “single access account” that filters inappropriate material based on (1) user profiles created by age verified and identified adults and stored on provider's “access server” and / or (2) “mandatory” provider imposed filtering.
Owner:GLASS PAUL H
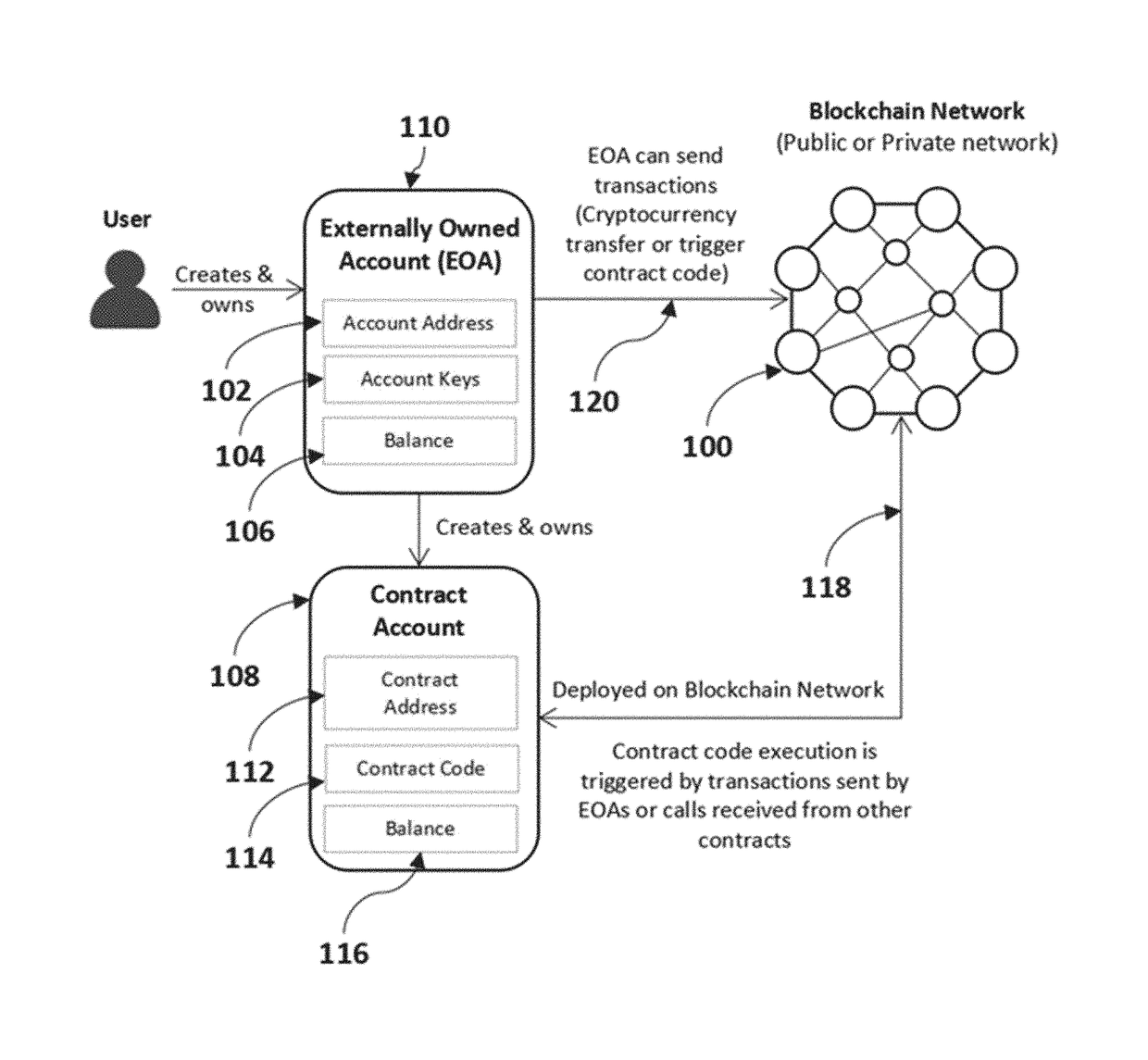
Method and system for blockchain-based combined identity, ownership, integrity and custody management
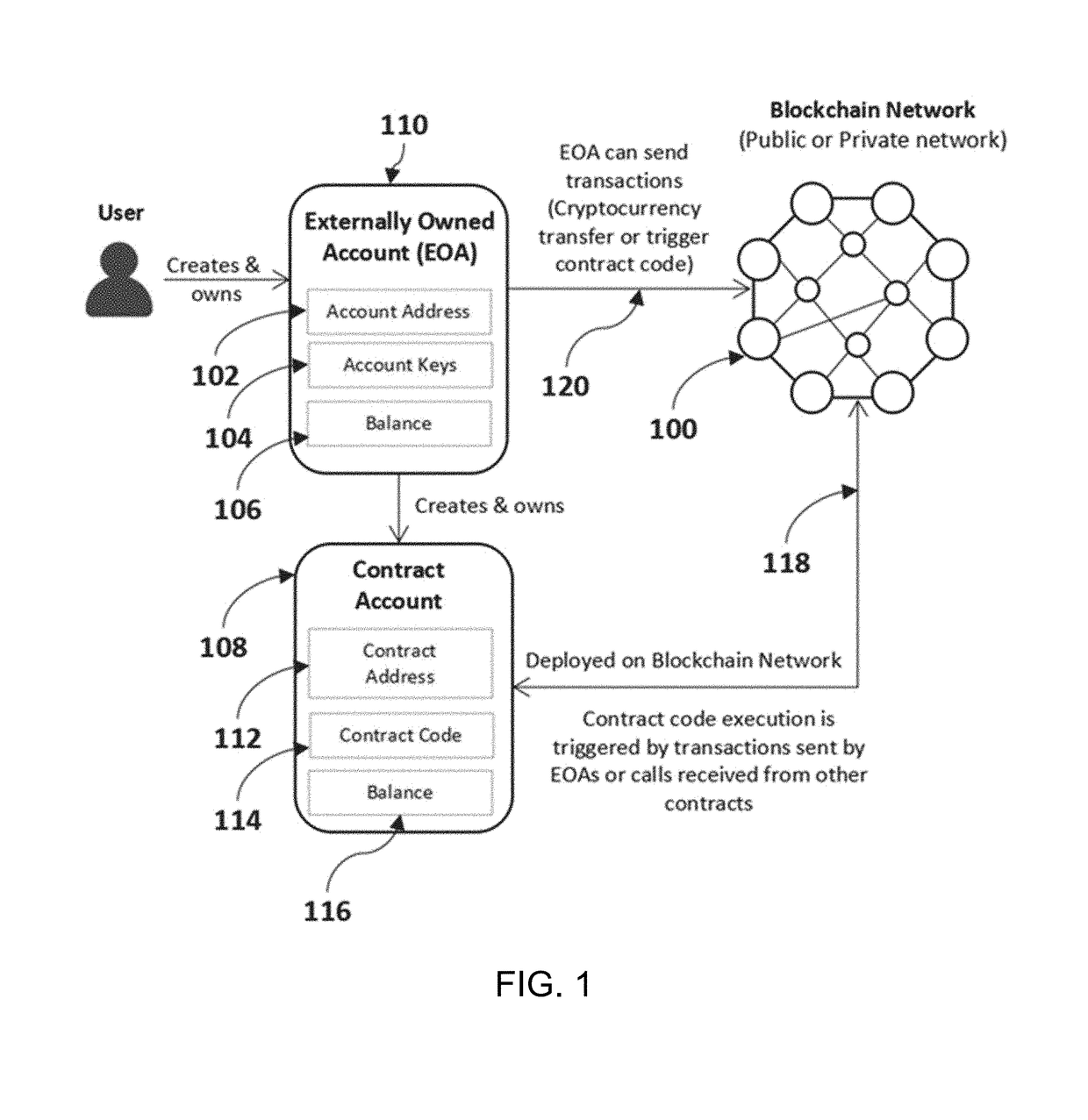
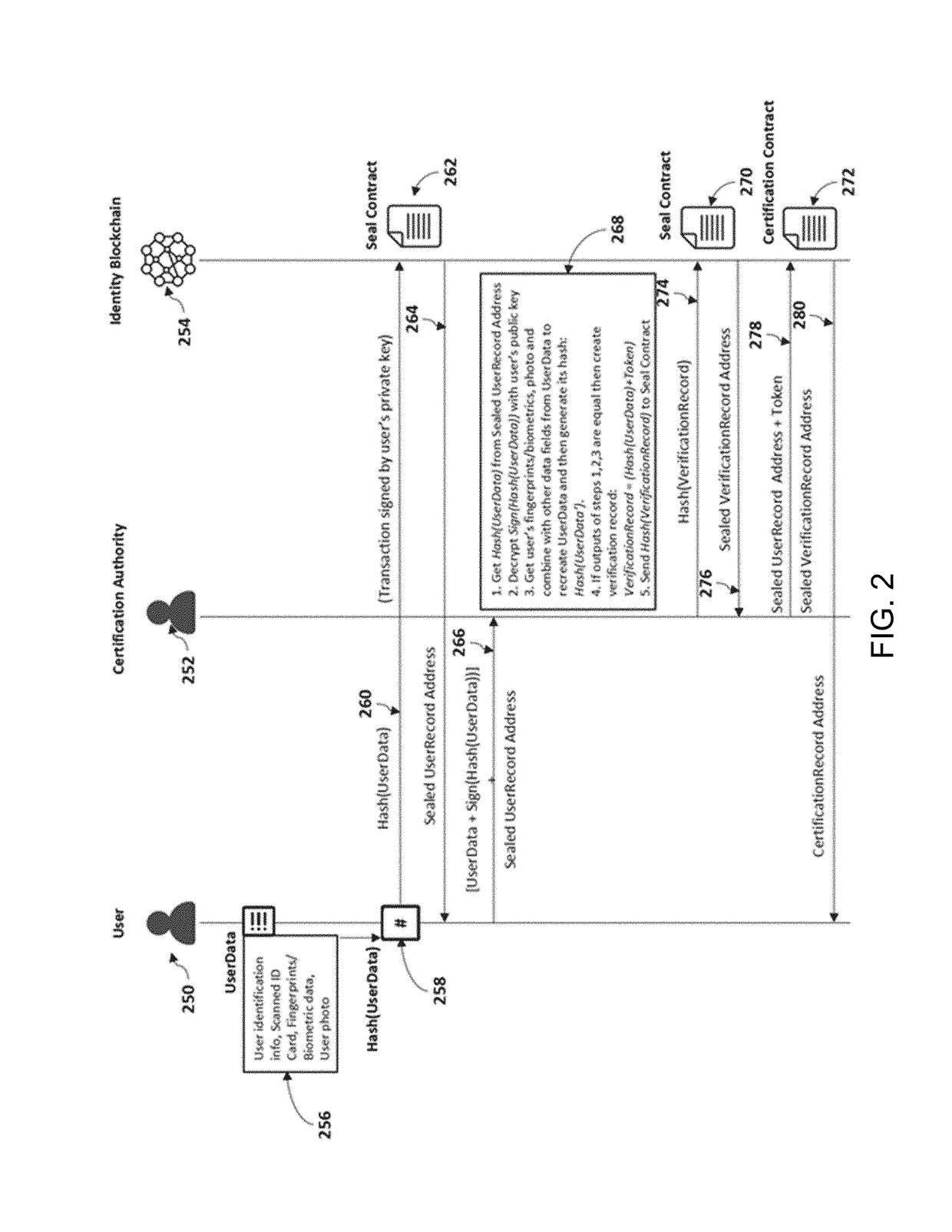
A method of issuing blockchain-based digital certificates comprising receiving from a user hashed user identification information and object information, recording to a digital certificate smart contract deployed at a digital certificate smart contract address on a blockchain network the hashed user identification information and object information and a timestamp of when the hashed user identification information and the object information were received, defined as a received timestamp, signing the digital certificate smart contract with an issuer signature, performing a user identity verification process to confirm a user identity, upon confirming the user identity, generating a combination certificate configured to be shared by the user to verify the user's ownership of an object associated with the object information, and sending the combination certificate to the user.
Owner:MADISETTI VIJAY K
Method and apparatus for network assessment and authentication
InactiveUS20060272011A1Prevent overly frequent reassessmentImprove securityDigital data processing detailsUser identity/authority verificationWorkstationNetwork service
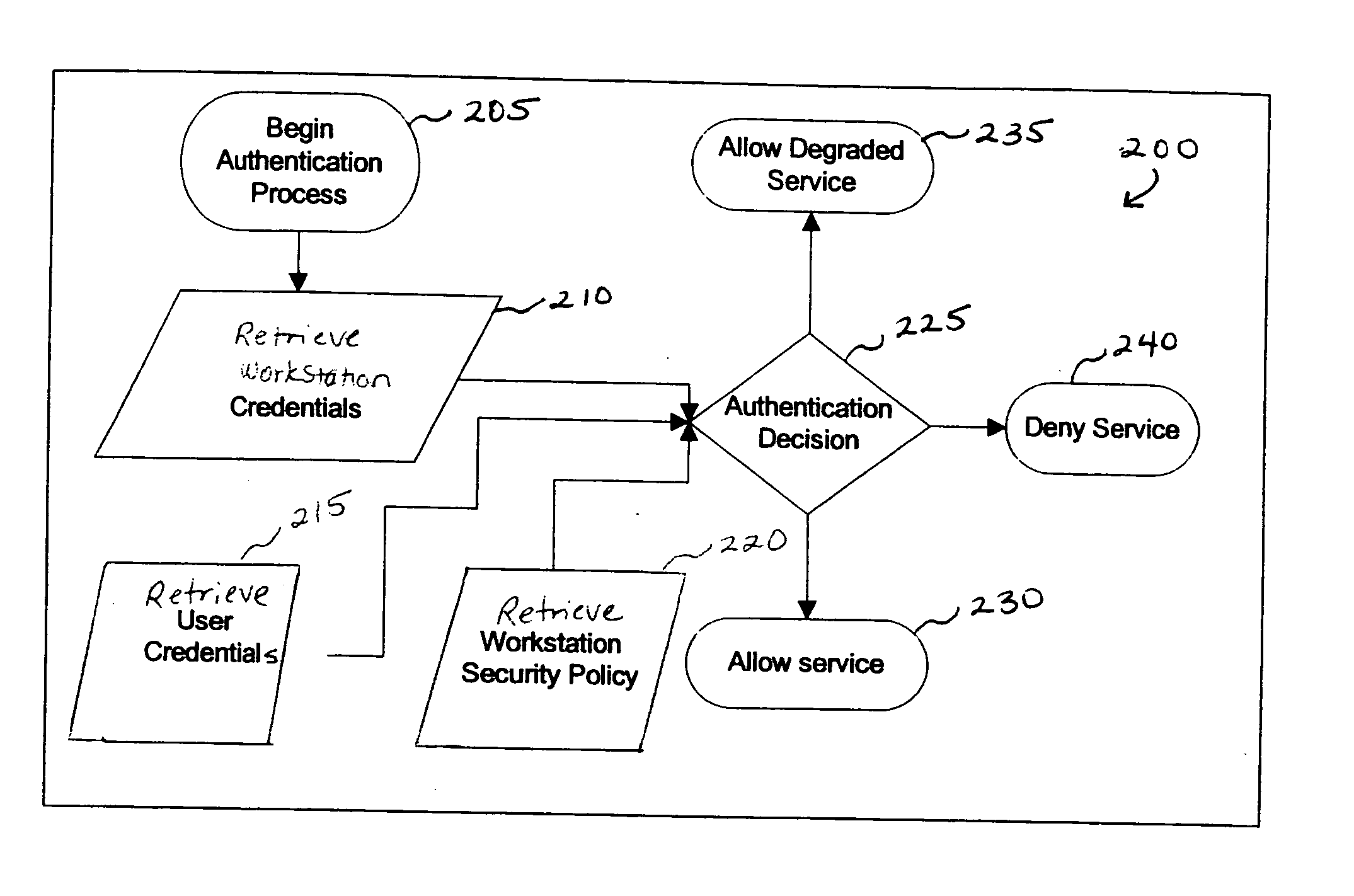
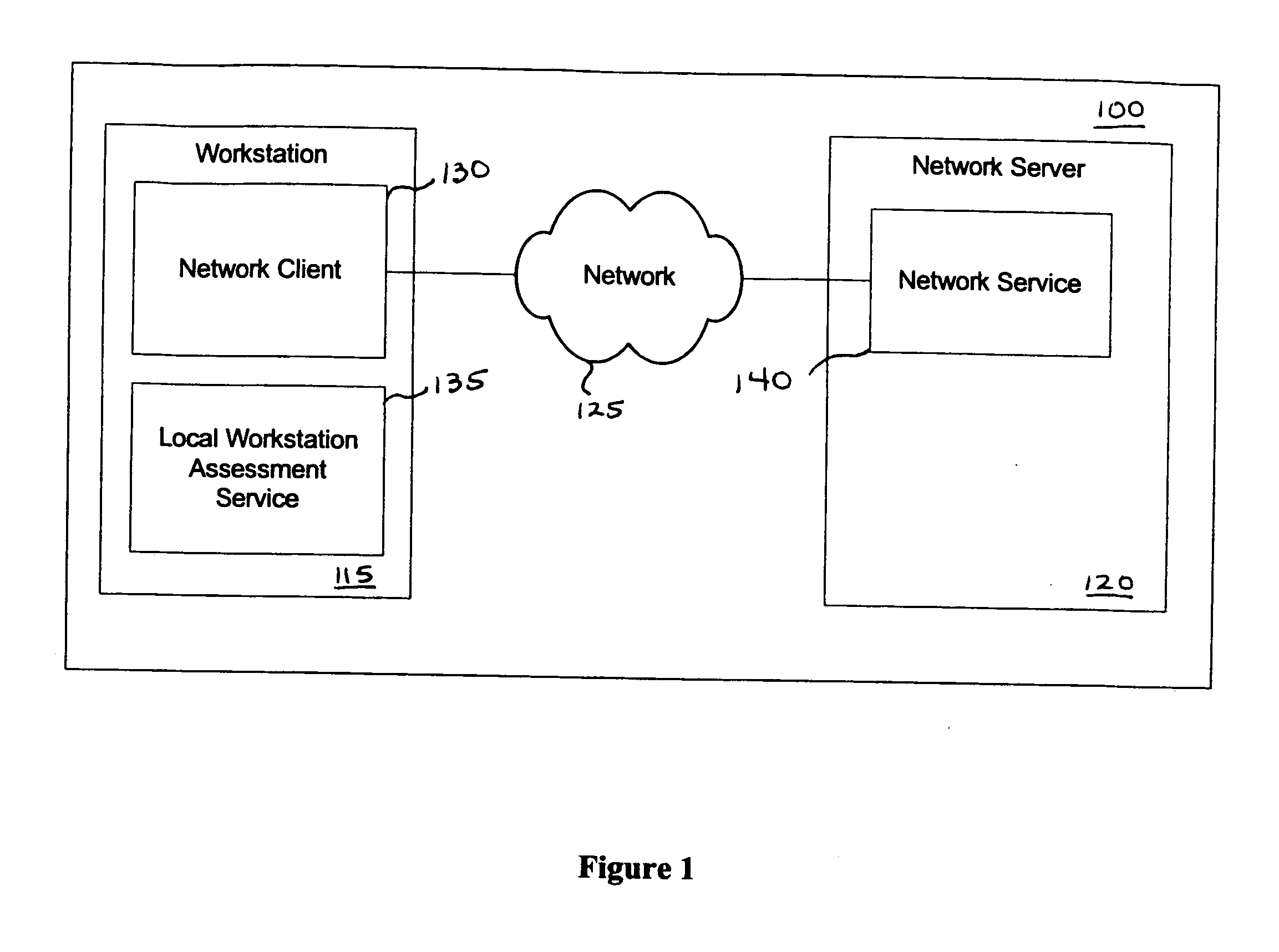
Providing a user with assurance that a networked computer is secure, typically before completion of the log-in operation. This can be accomplished by extending the local log-in process to perform a host assessment of the workstation prior to requesting the user's credentials. If the assessment finds a vulnerability, the log-in process can inform the user that the machine is or may be compromised, or repair the vulnerability, prior to completion of the log-in operation. By performing vulnerability assessment at the level of the workstation, a network server is able to determine whether the workstation is a “trusted” platform from which to accept authentication requests. If the vulnerability assessment shows that the workstation is compromised, or if the possibility of remote compromise is high, the network server can elect to fail the authentication on the grounds that the workstation cannot be trusted. Optionally, a vulnerability assessment tool may be able to repair the vulnerability of the workstation, and then allow the authentication to proceed.
Owner:IBM CORP
Driver log generation
A system for determining a driver log entry comprises a processor and a memory. The processor is configured to determine a log start time. The processor is configured to determine a driver identity after the log start time. The processor is configured to determine whether a change to the driver identity has occurred based at least in part on a sensor data. In the event that the driver identity has changed, the processor is configured to determine a log stop time and determine a driver log entry using the log start time, the driver identity, and the log stop time.
Owner:DRIVECAM
Designs, interfaces, and policies for systems that enhance communication and minimize disruption by encoding preferences and situations
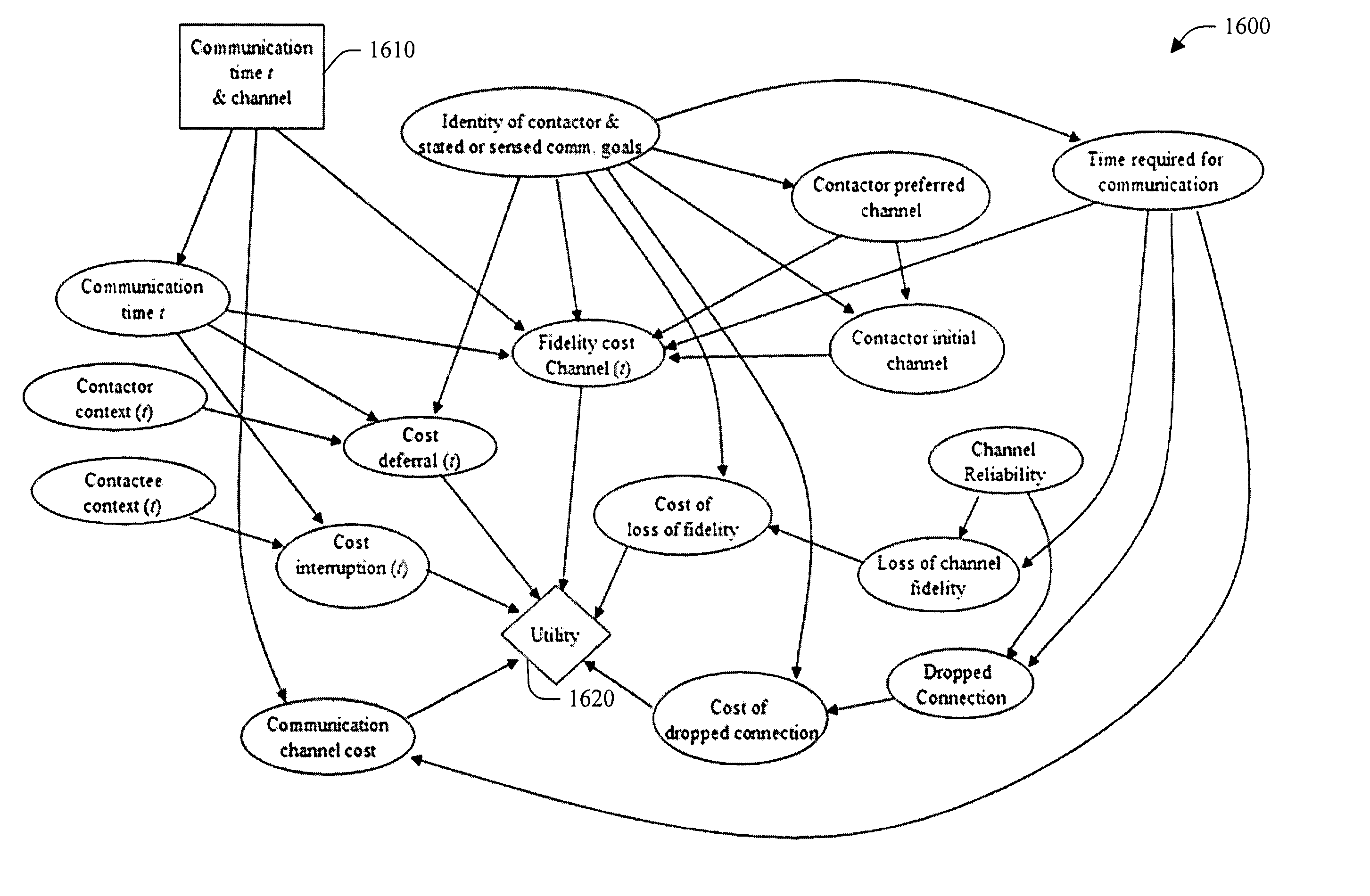
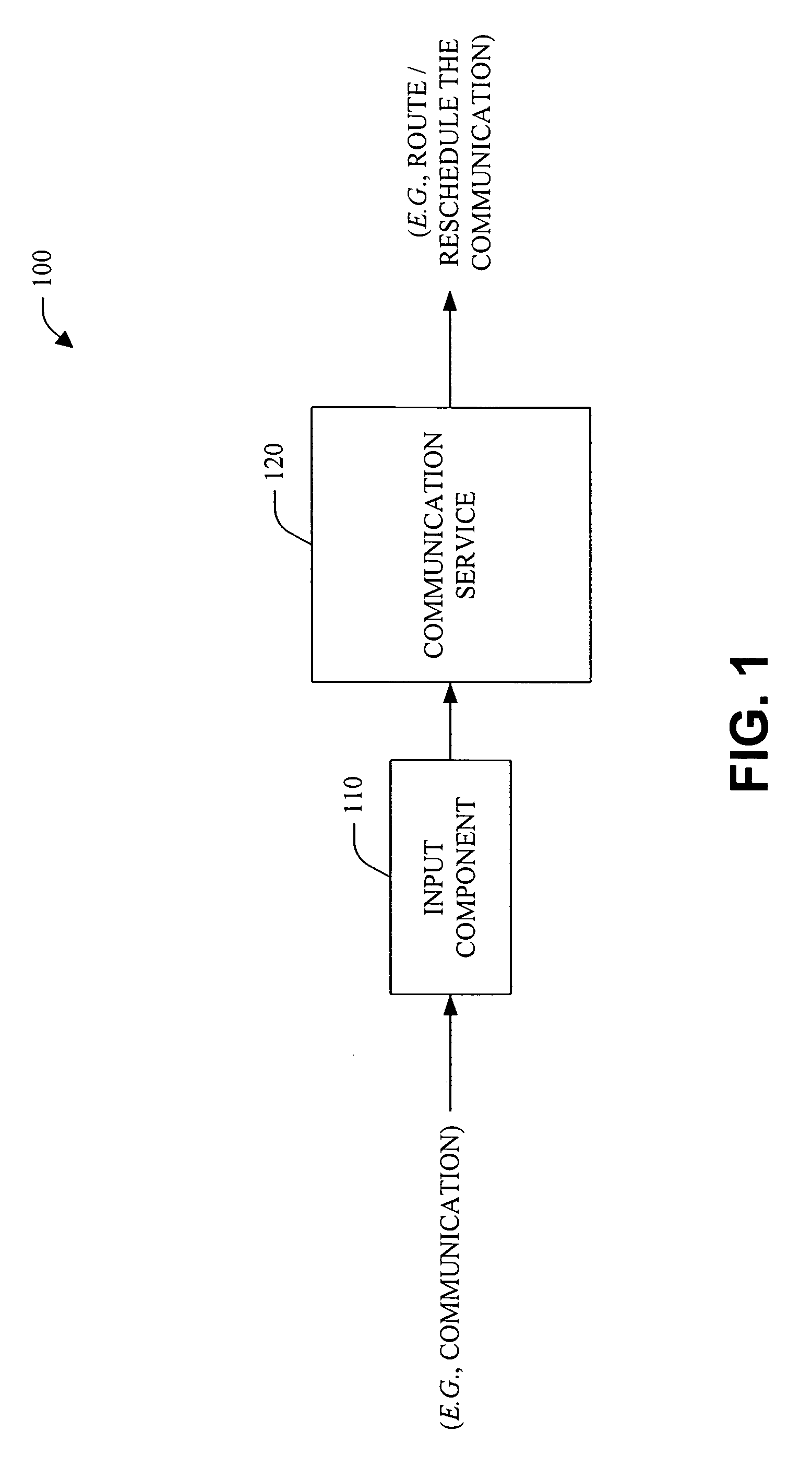
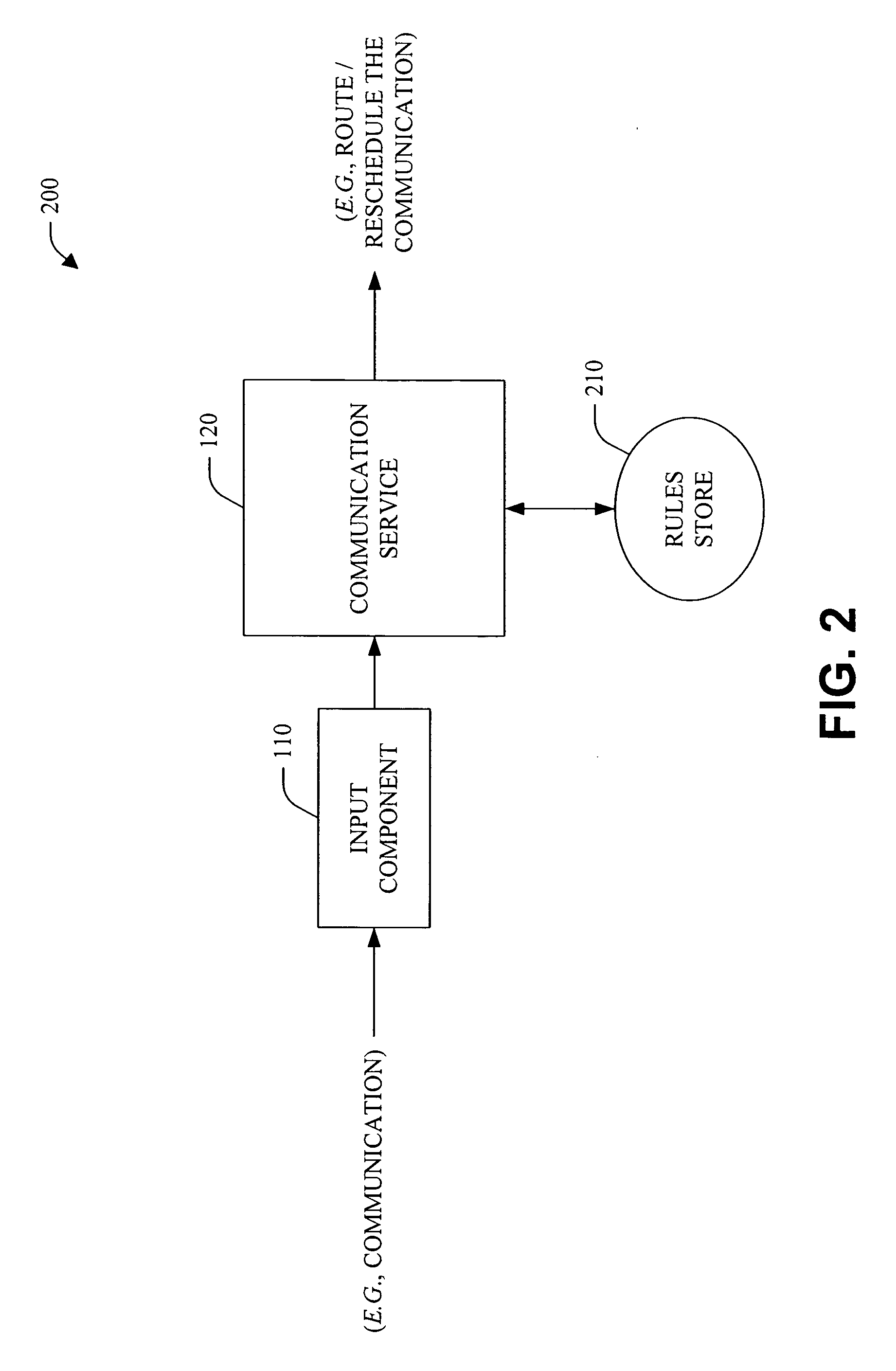
InactiveUS20050084082A1Enhance interpersonal communicationValue maximizationSpecial service for subscribersDigital computer detailsCost benefitStatus changed
The present invention relates to utilizing identity and context-sensitive decision-making for handling communications, including, channel selection, routing, and rescheduling operations. The systems and methods provide a service that allows users to assess preferences regarding real-time call handling and performs dynamic decision-making about the best timing and channel for interpersonal communication. This service can be based on various cost-benefit analyses (e.g., basic and extended) that consider cost of interruption and preferences of contactors and contactees to guide communications, and / or on decision-making under uncertainty. Statistical models that are learned from data are joined with user preferences to generate expected costs of interruption for office activity and over time, based on a user's activities, locations, calendar information and preference assessments. In addition, statistical forecasting provides presence and availability predictions. The foregoing can provide an enhanced interpersonal communication system that can maximize the value and minimize the cost of communication among people.
Owner:MICROSOFT TECH LICENSING LLC
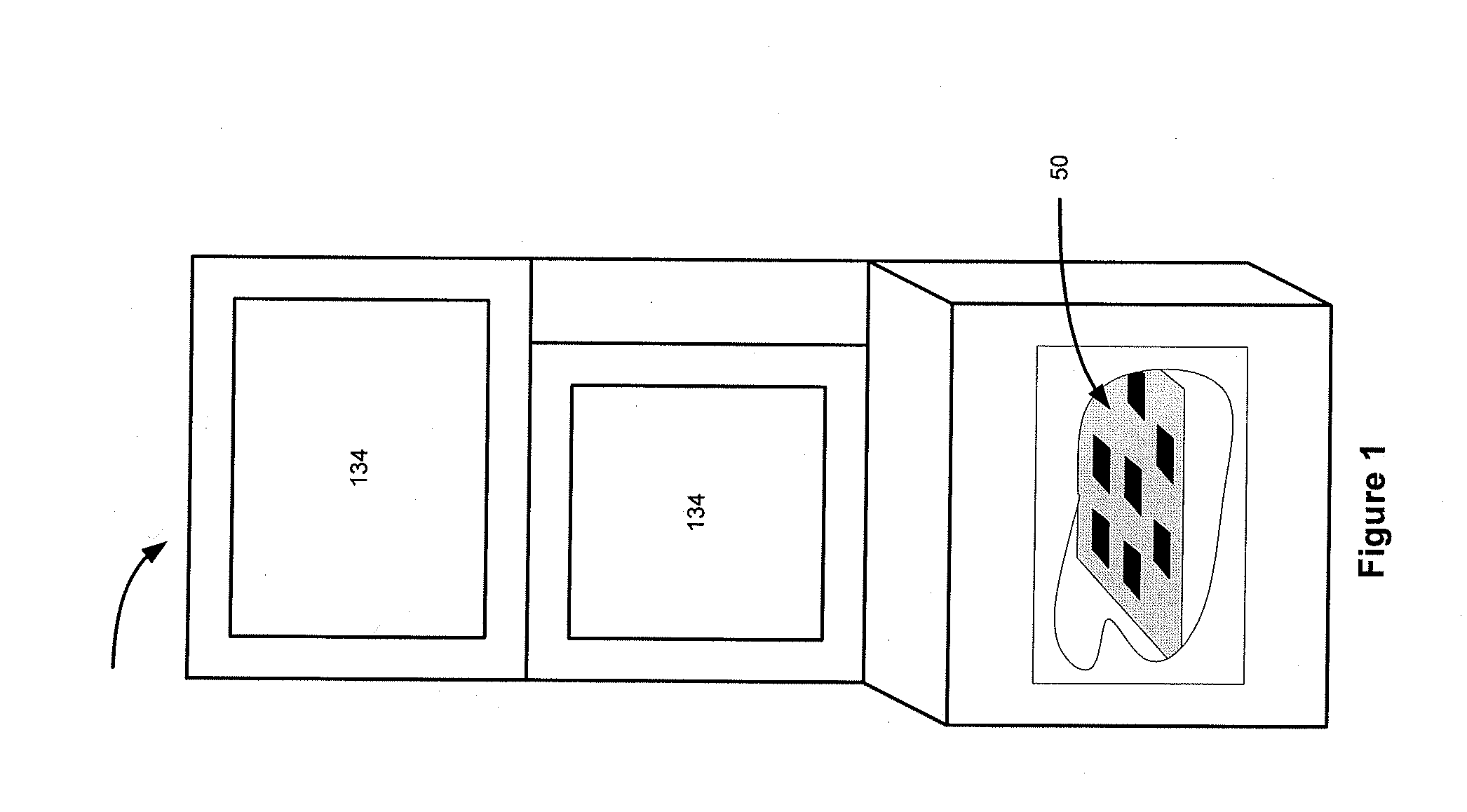
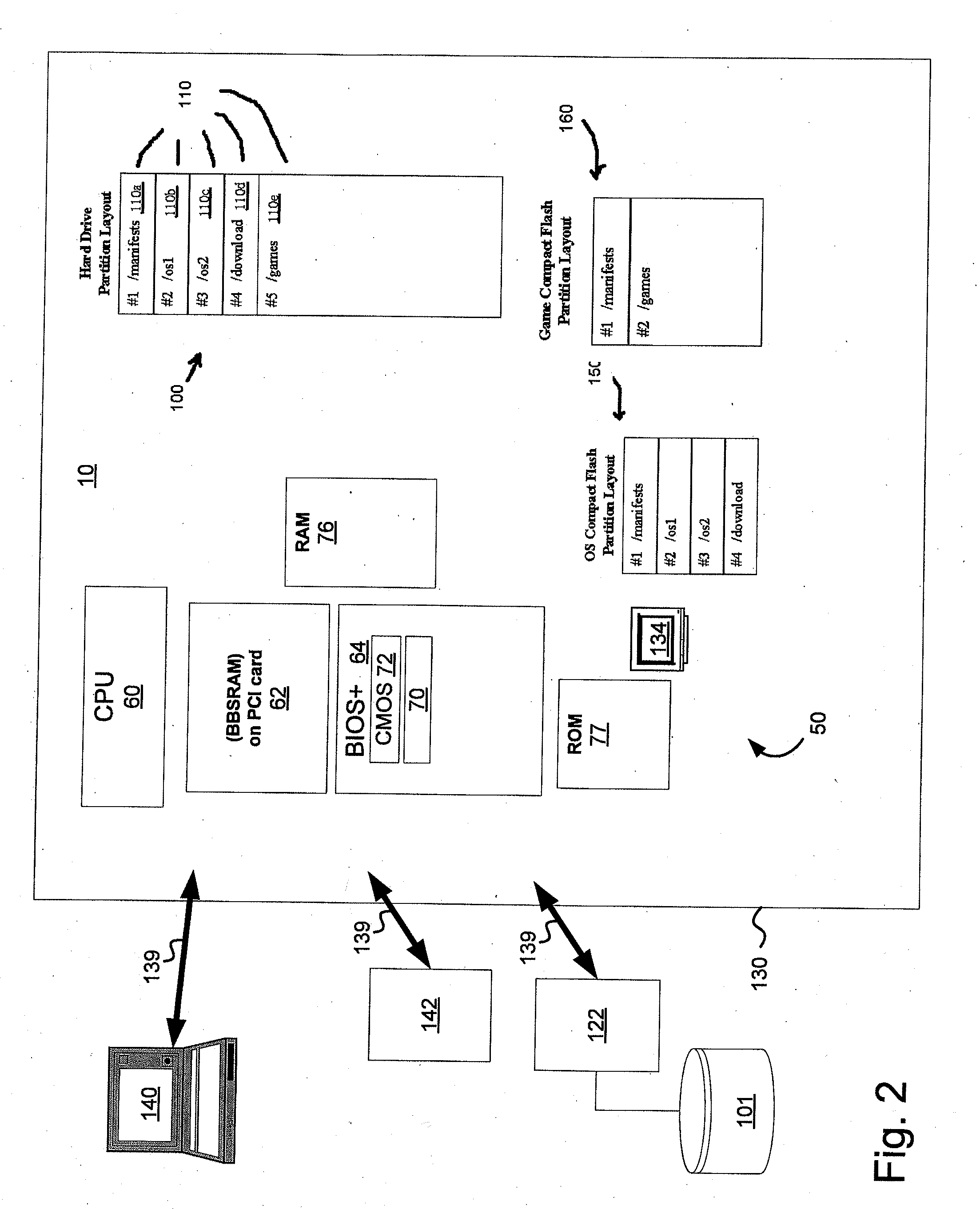
Data Integrity and Non-Repudiation
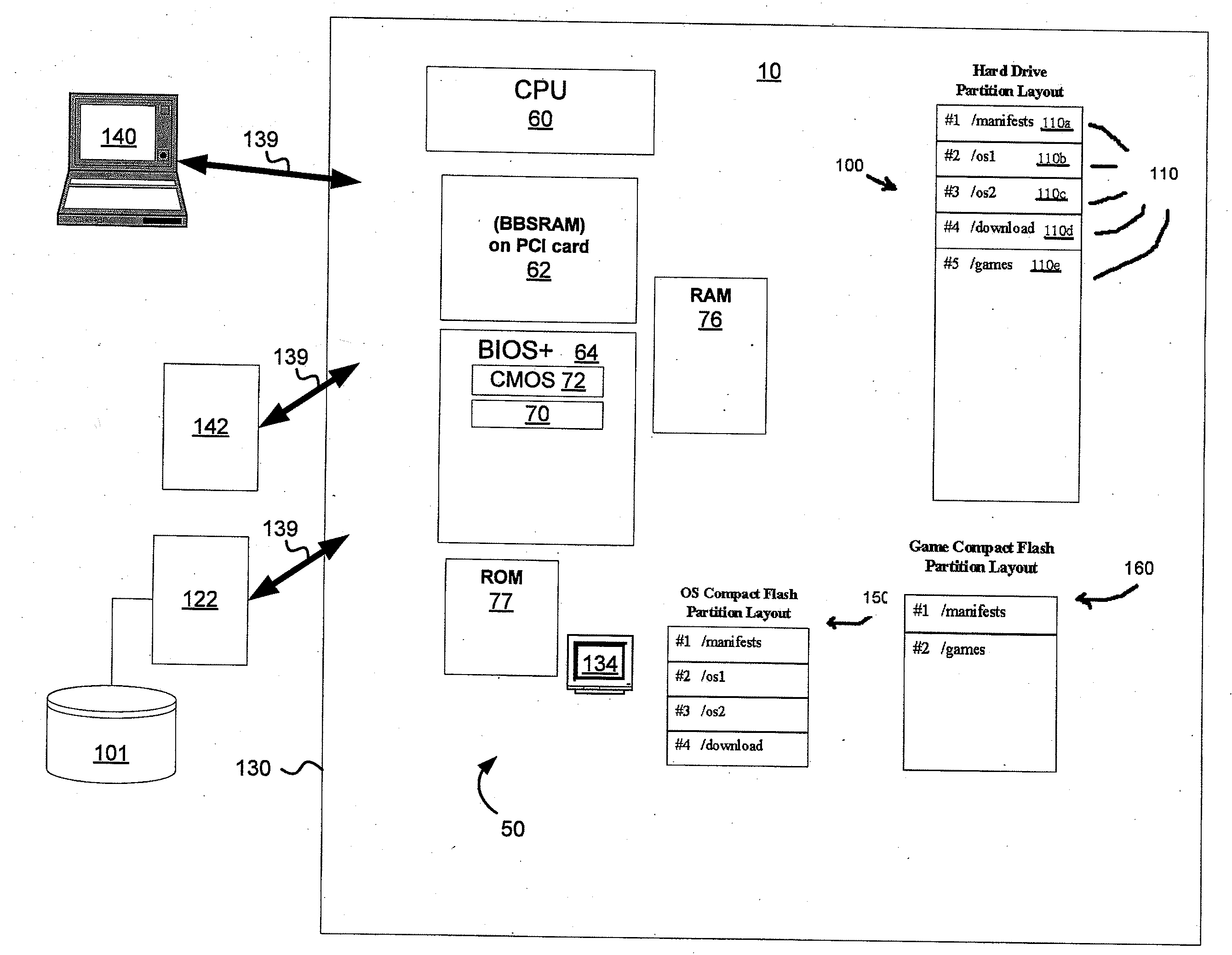
ActiveUS20080045342A1Reduce boot timeImprove loading timeUnauthorized memory use protectionHardware monitoringComputer hardwareData integrity
Disclosed is a system and method that uses digital signature technology to authenticate the contents of one or more manifests located on a storage device. Each manifest contains a list of file records, where each record contains the name of a file stored on the storage device, and a signature value derived from the contents of the file. At boot time, the gaming machine first authenticates the contents of the manifest and then authenticates the contents of the files using the signature value stored in the manifest. Files are verified using the signature, as they are needed, during the boot up of the operating system and throughout normal operation. This method reduces the boot time of the gaming machine and eliminates the need to check digital signatures for each individual file or over the entire contents of a non-secure media. Similarly, a method of adding authentication ability to legacy software components without necessarily altering the legacy software components is disclosed. Introduction of a stronger authentication algorithm, or when a private key has been compromised would normally require the software component to be re-built to support the new algorithm or private / public key pair; however, a method is disclosed where algorithms and key pairs may be changed and applied to legacy software without having to re-built, re-test, re-sign, or re-submit the component to regulatory agencies for approval. Also disclosed is a system and method of establishing a trusted environment containing a gaming operating system and associated authentication module, file system drivers, and / or network drivers that may be used to in the process of authenticating contents of one or more manifests located on a storage device.
Owner:LNW GAMING INC
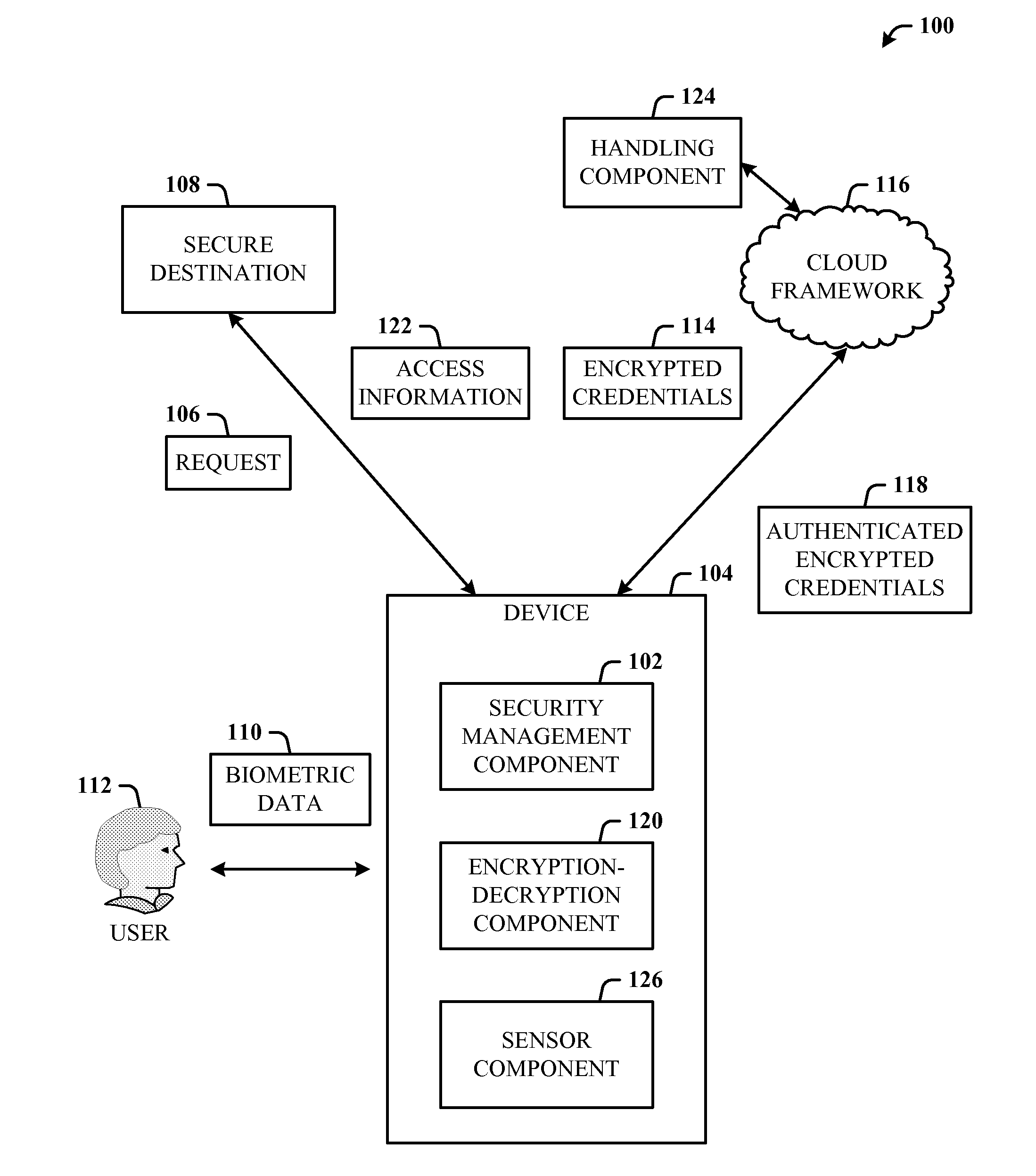
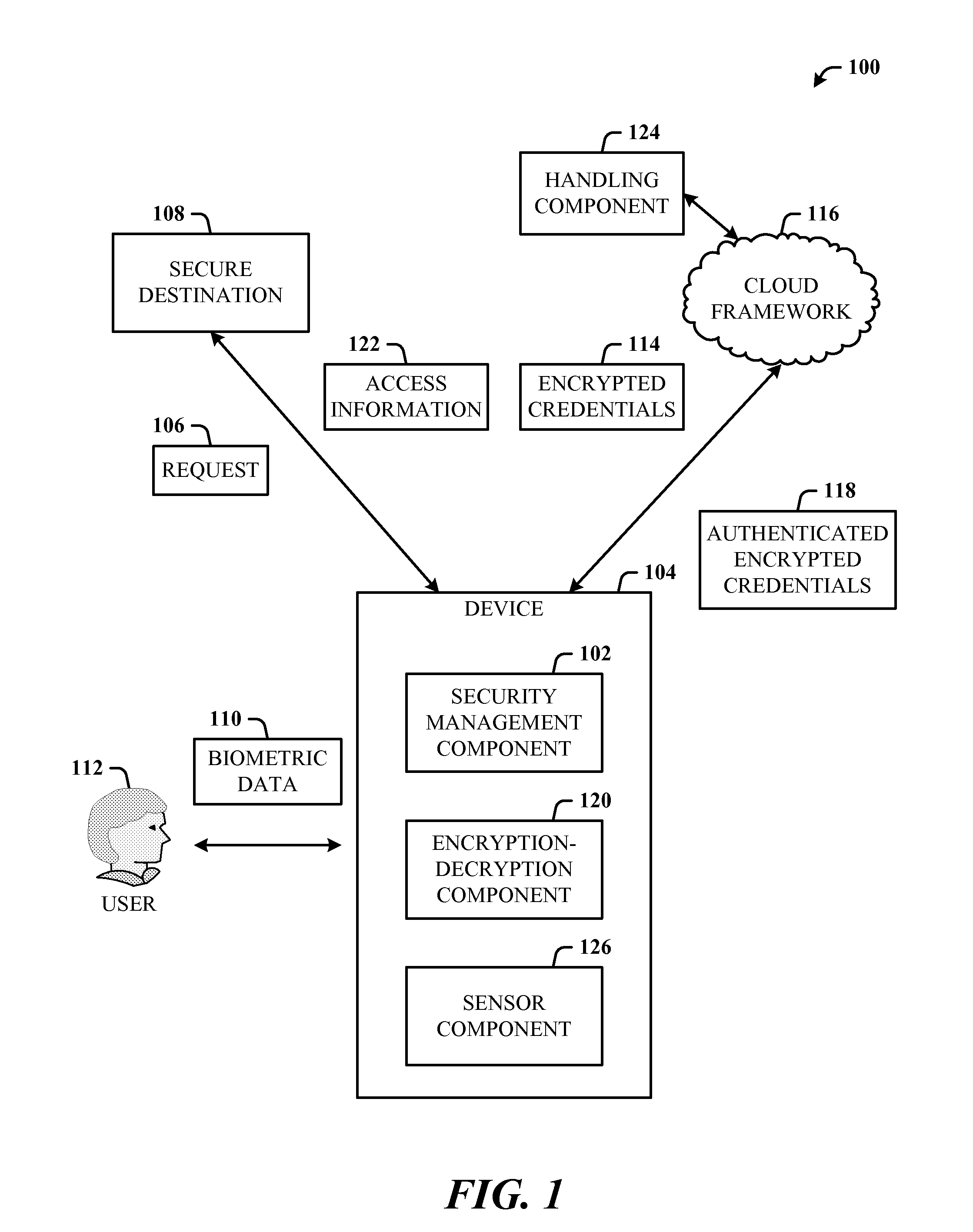
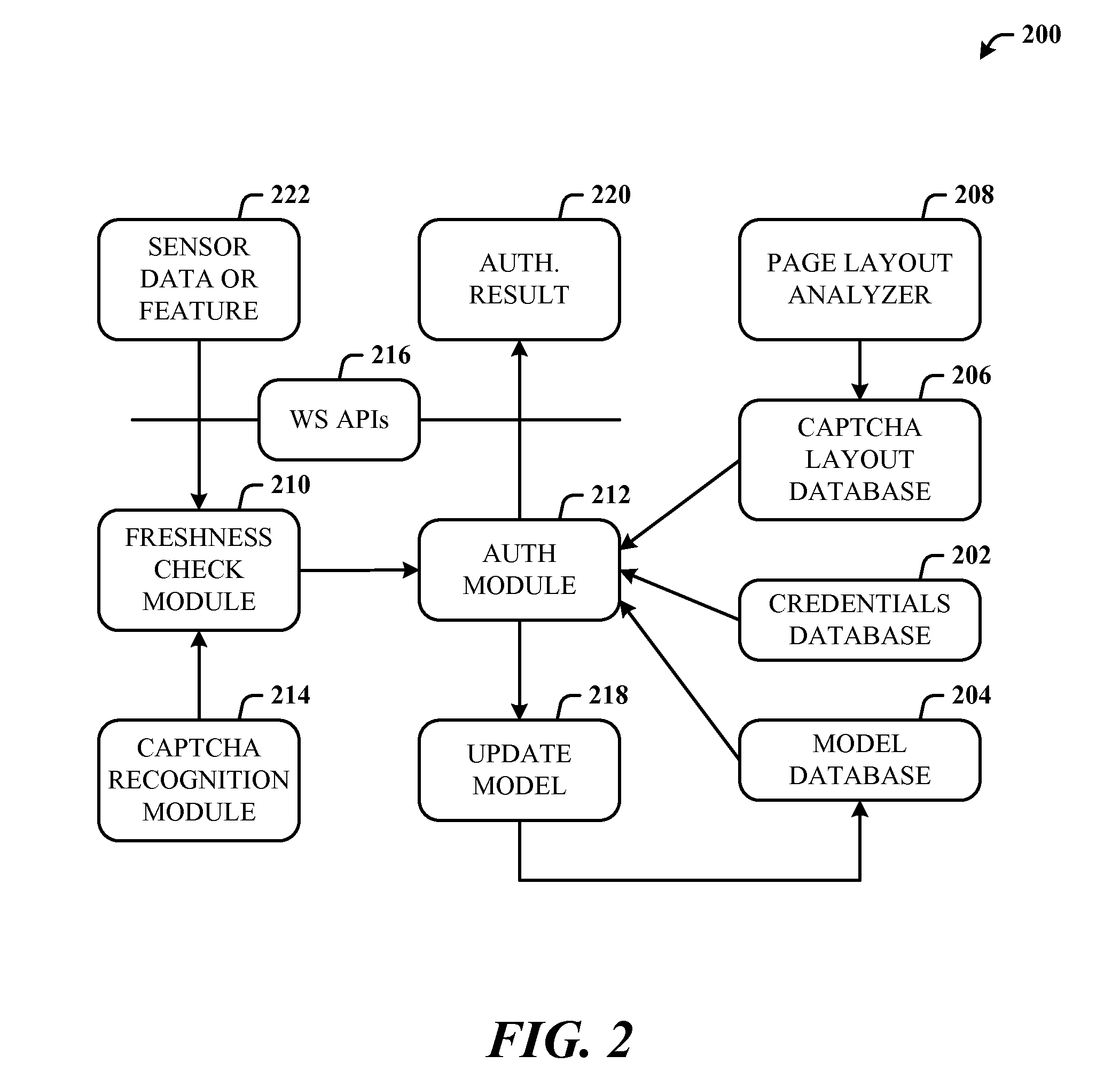
Usable security of online password management with sensor-based authentication
ActiveUS20120297190A1Improve usabilityAuthentication is convenientUser identity/authority verificationDigital data authenticationCryptographic protocolUsability
A multi-party security protocol that incorporates biometric-based authentication and withstands attacks against any single party (e.g., mobile phone, cloud, or the user). The protocol involves the function split between mobile and cloud and the mechanisms to chain-hold the secrets. A key generation mechanisms binds secrets to a specific device or URL (uniform resource locator) by adding salt to a master credential. An inline CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) handling mechanism uses the same sensor modality as the authentication process, which not only improves the usability, but also facilitates the authentication process. This architecture further enhances existing overall system security (e.g., handling untrusted or compromised cloud service, phone being lost, impersonation, etc.) and also improves the usability by automatically handling the CAPTCHA.
Owner:MICROSOFT TECH LICENSING LLC
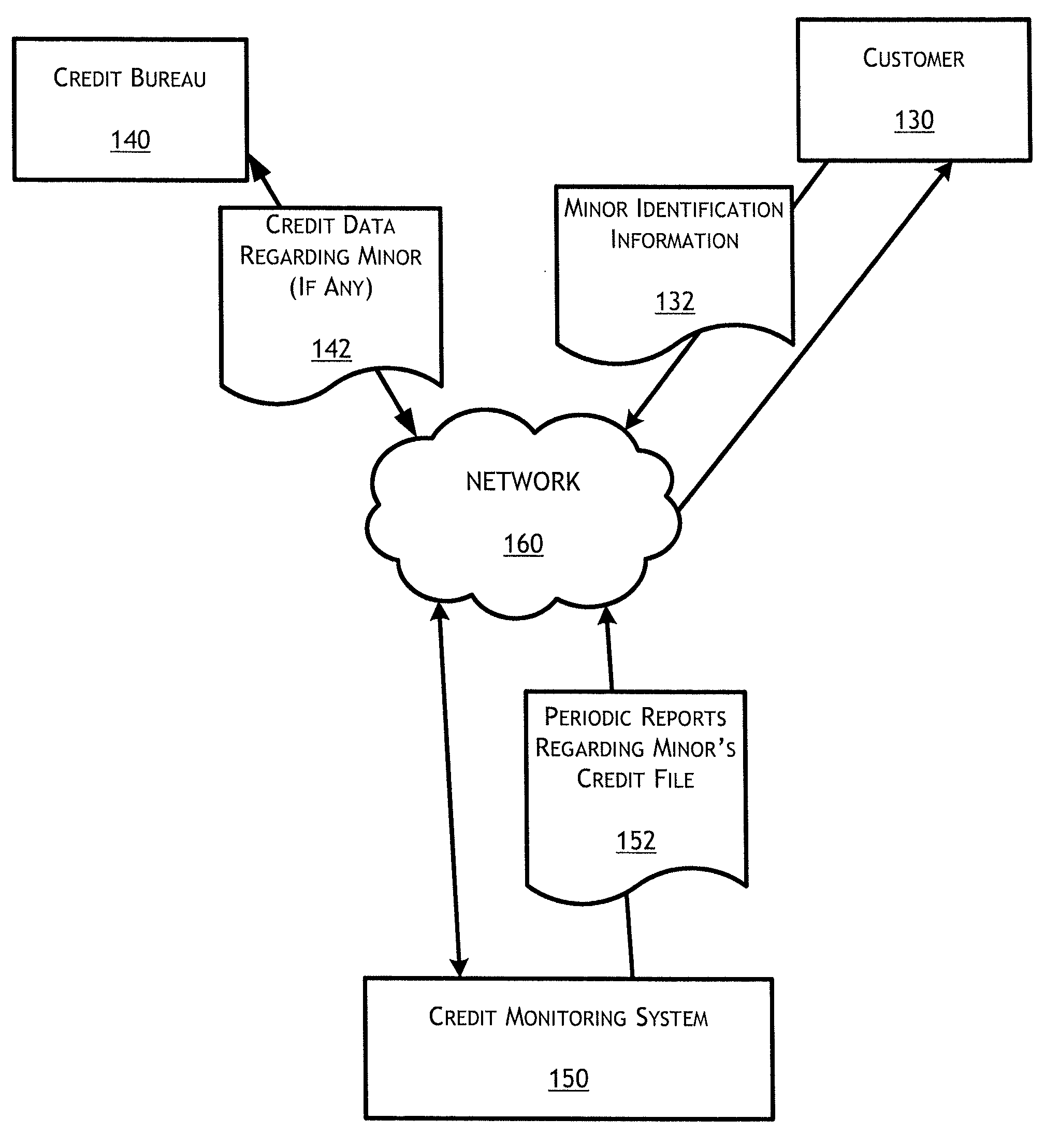
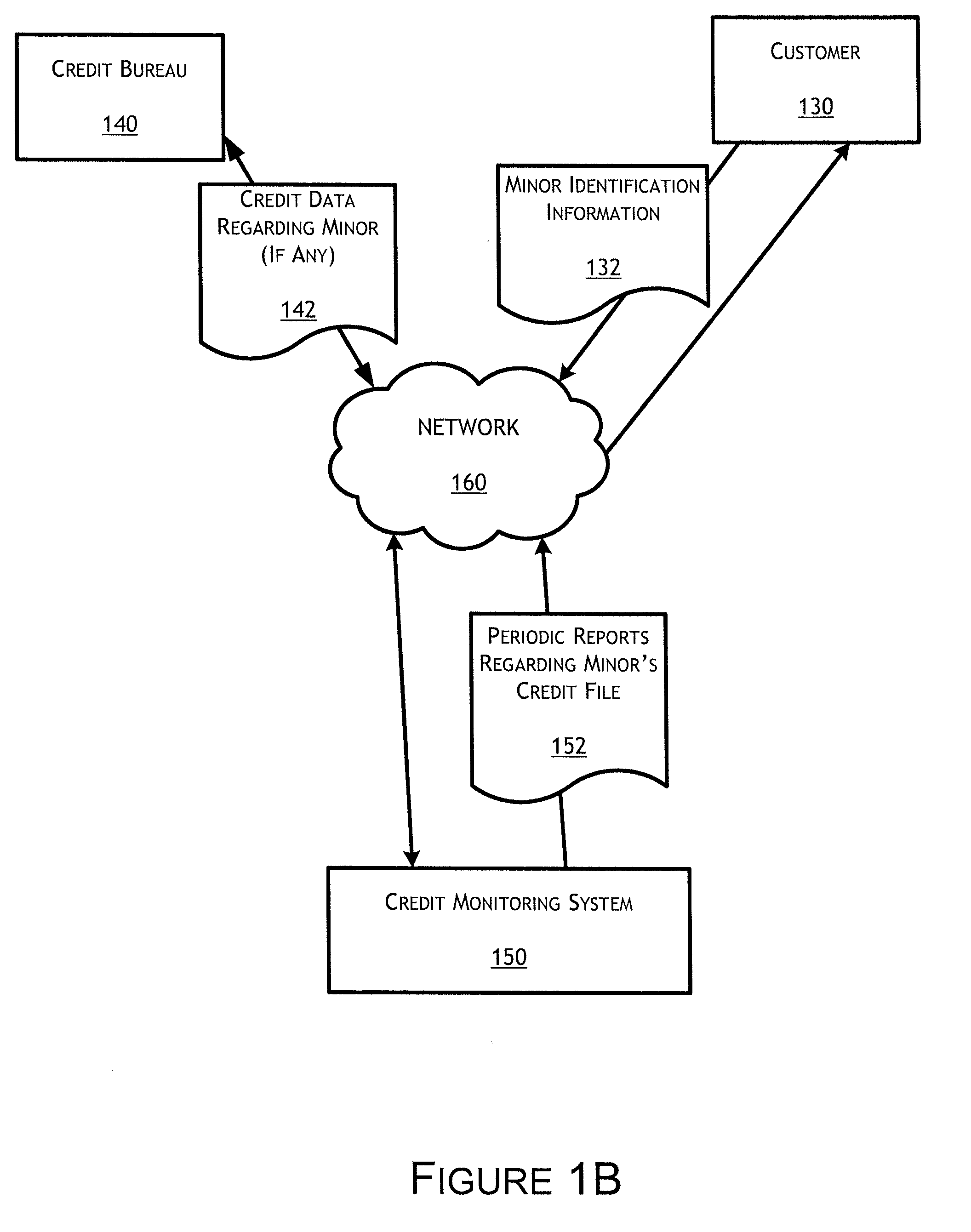
Child identity monitor
ActiveUS7975299B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMonitoring systemData mining
Owner:CONSUMERINFO COM
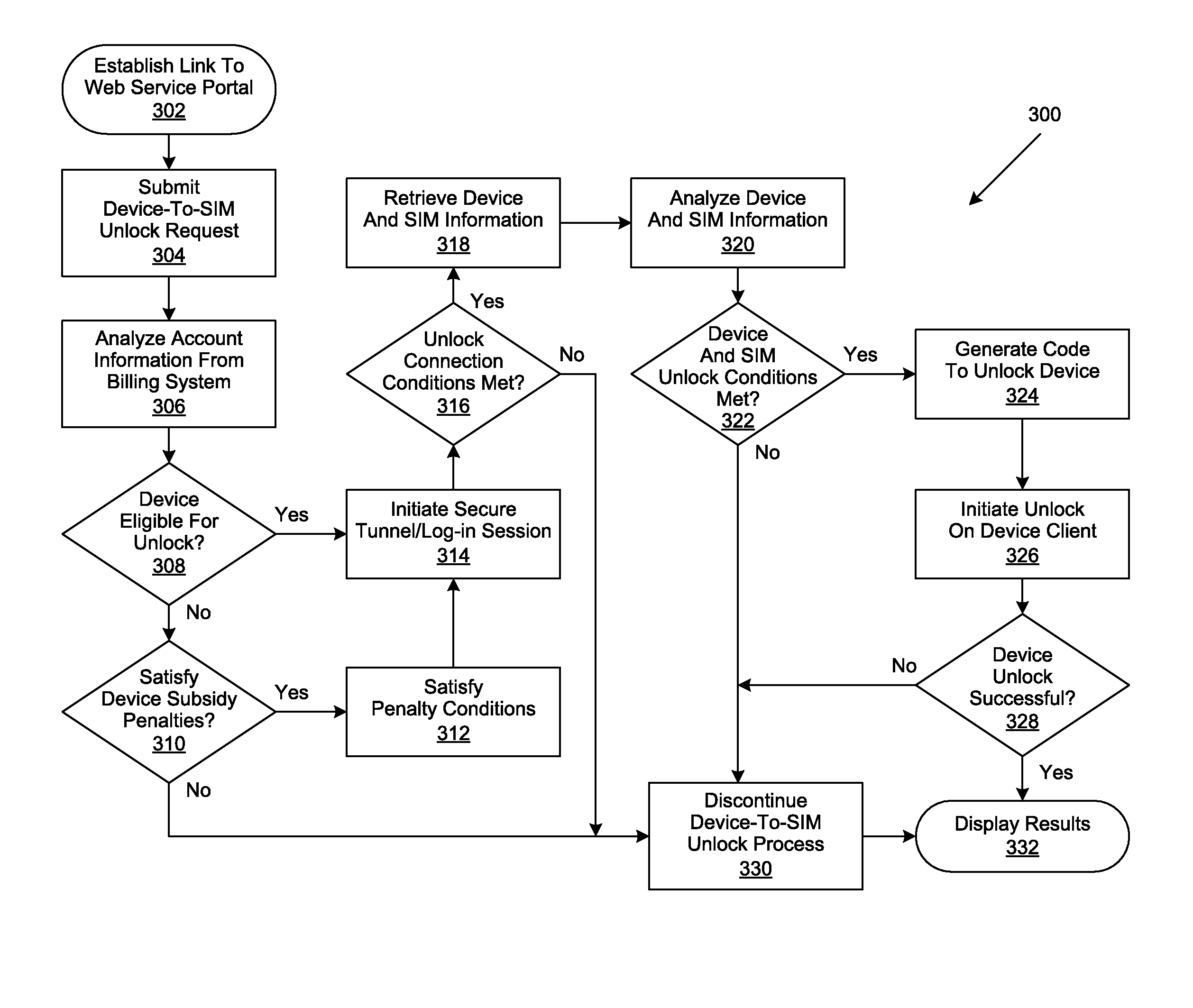
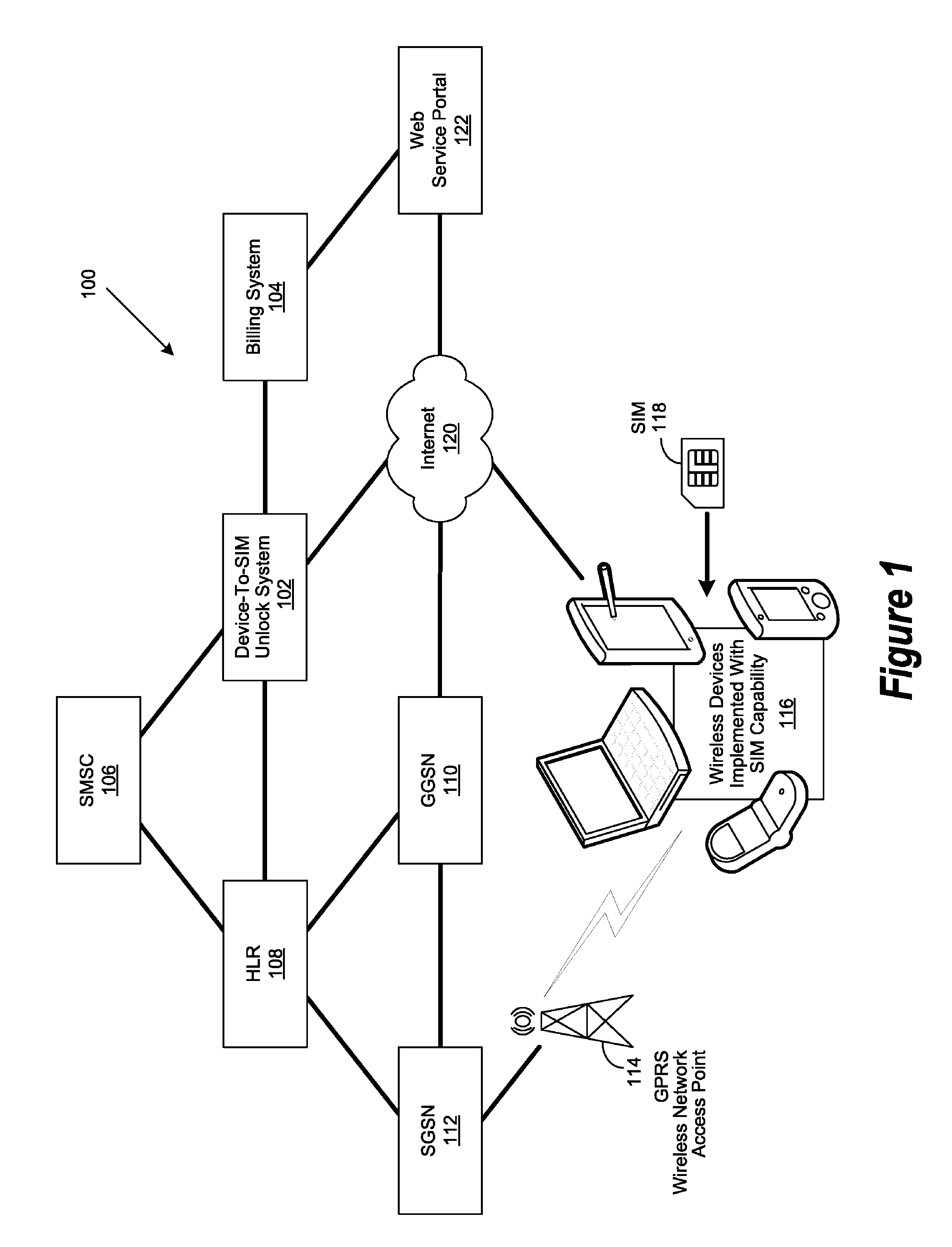
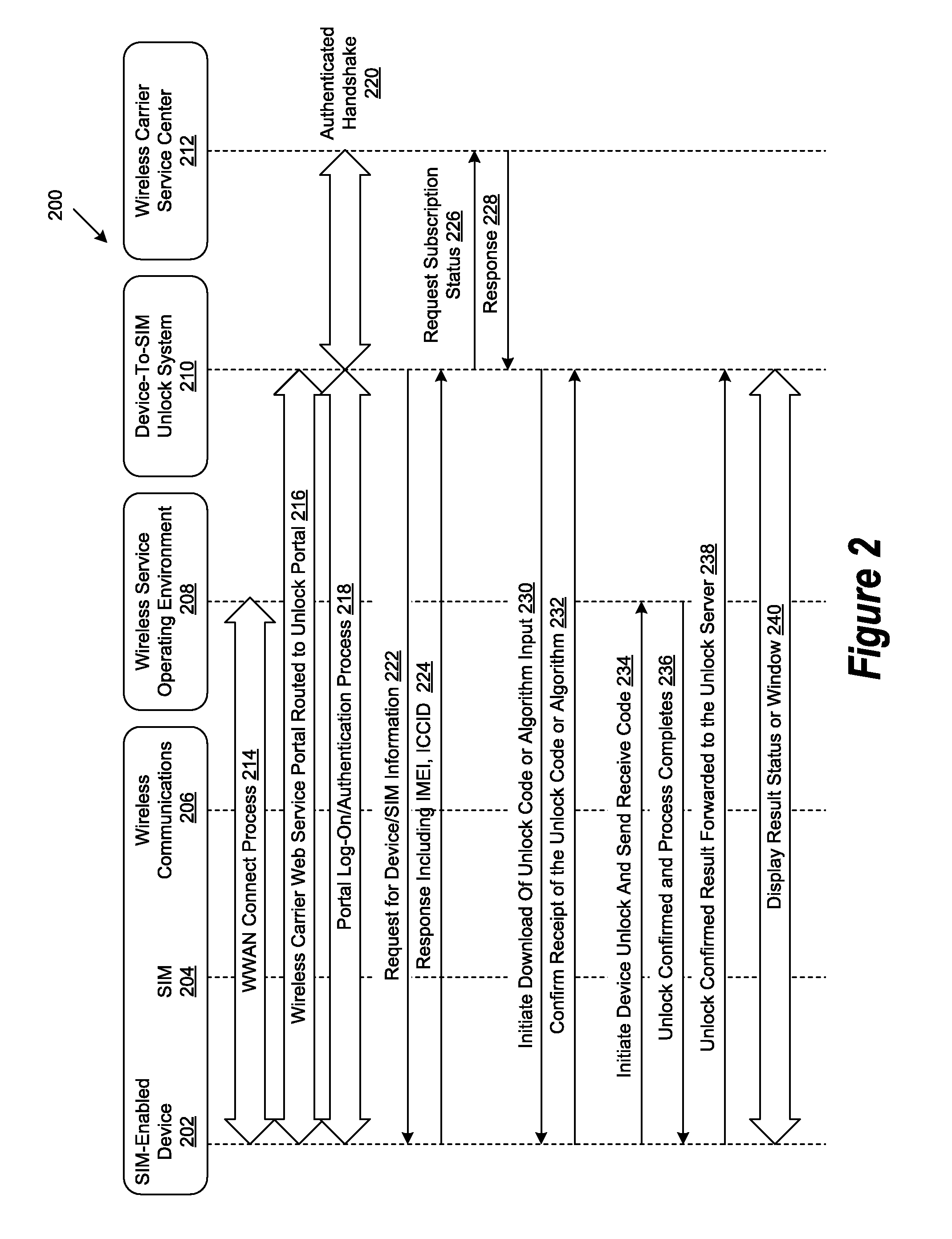
Subscriber identity module unlocking service portal
ActiveUS8050705B2Less carrier-specificGood refreshingMultiplex system selection arrangementsSpecial service for subscribersSIM lockPayment
Owner:DELL PROD LP
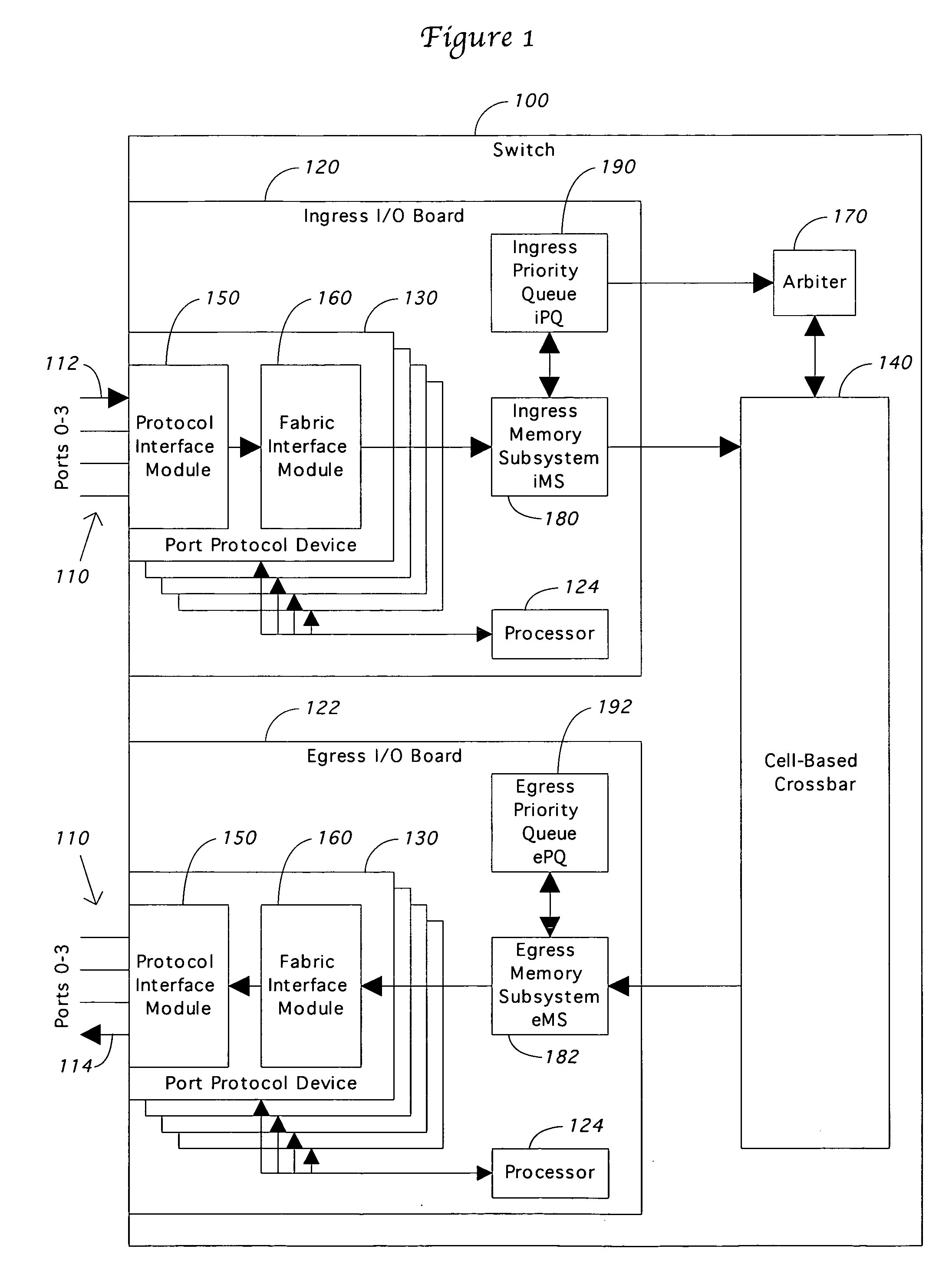
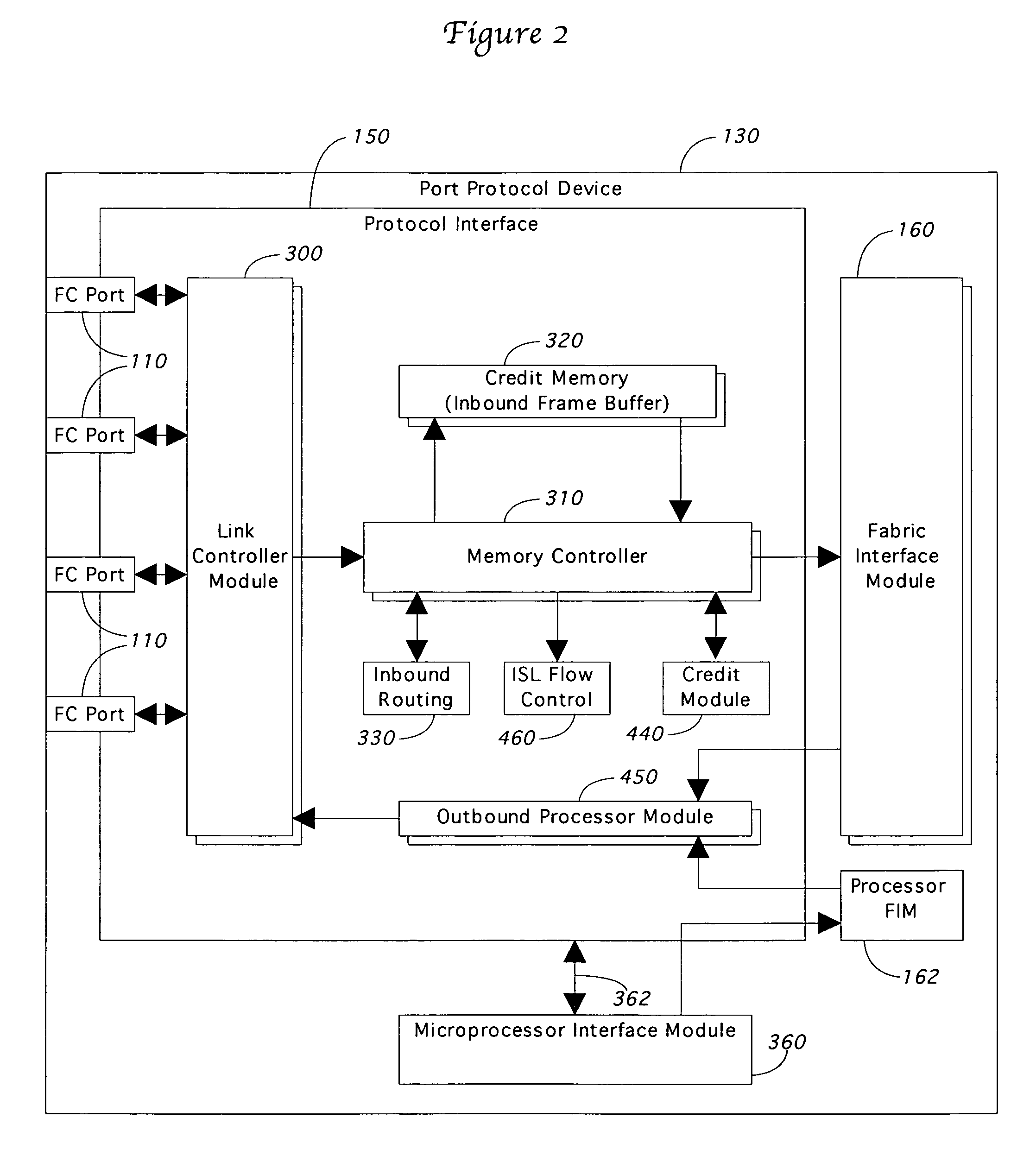
Port congestion notification in a switch
A congestion notification mechanism provides a congestion status for all destinations in a switch at each ingress port. Data is stored in a memory subsystem queue associated with the destination port at the ingress side of the crossbar. A cell credit manager tracks the amount of data in this memory subsystem for each destination. If the count for any destination exceeds a threshold, the credit manager sends an XOFF signal to the XOFF masks. A lookup table in the XOFF masks maintains the status for every switch destination based on the XOFF signals. An XON history register receives the XOFF signals to allow queuing procedures that do not allow a status change to XON during certain states. Flow control signals directly from the memory subsystem are allowed to flow to each XOFF mask, where they are combined with the lookup table status to provide a congestion status for every destination.
Owner:MCDATA SERVICES CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com