Patents
Literature
272results about How to "Exposure was also limited" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
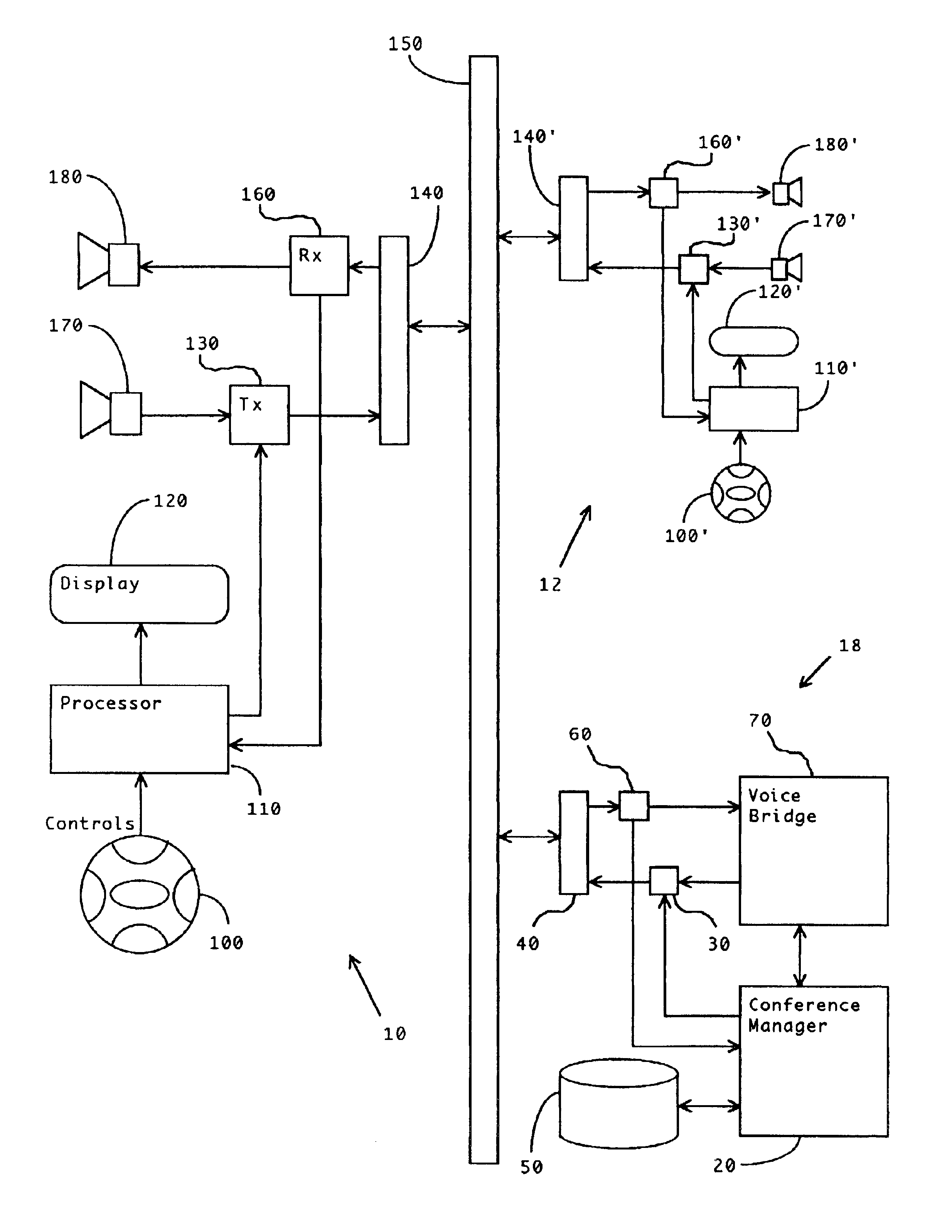
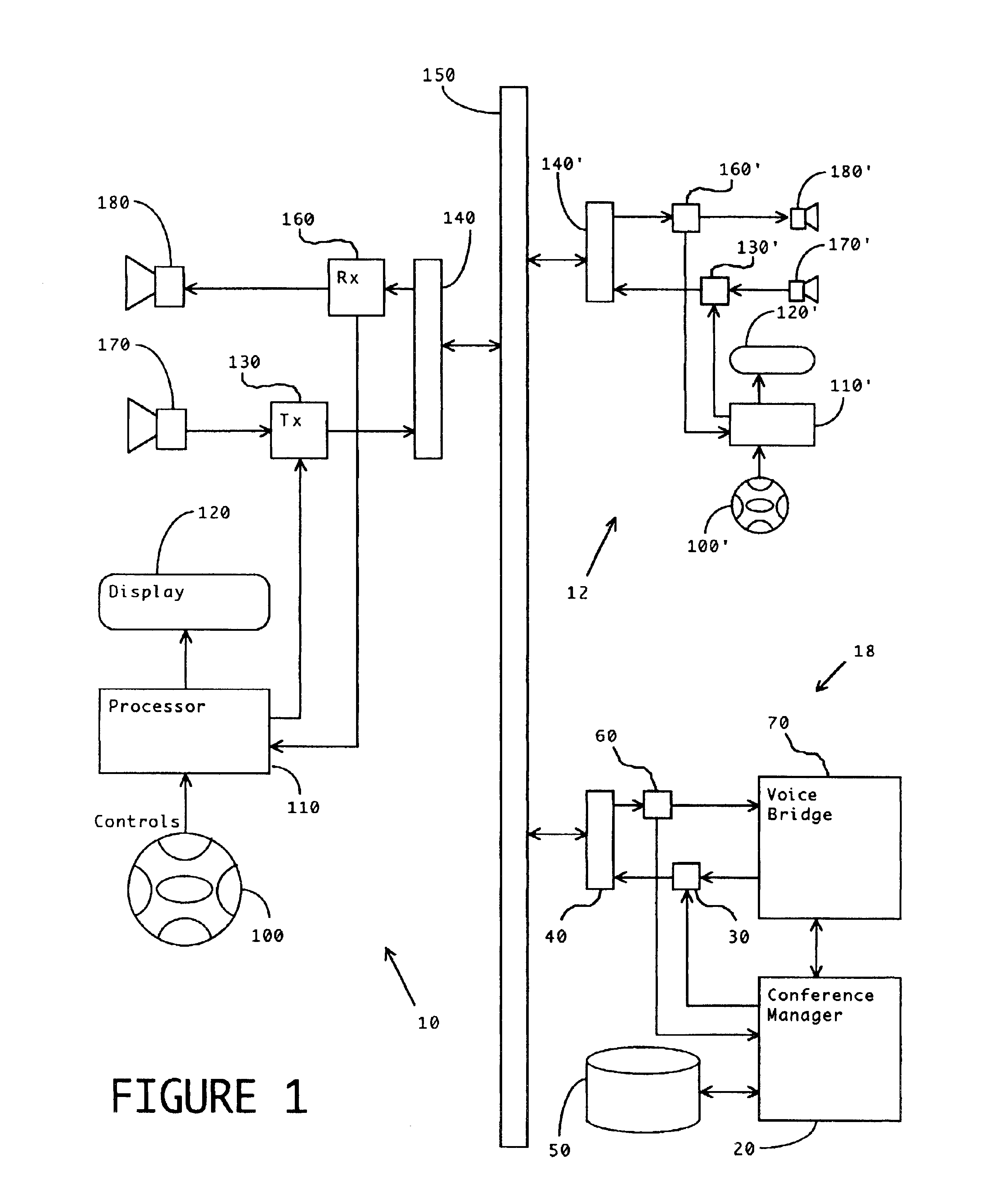
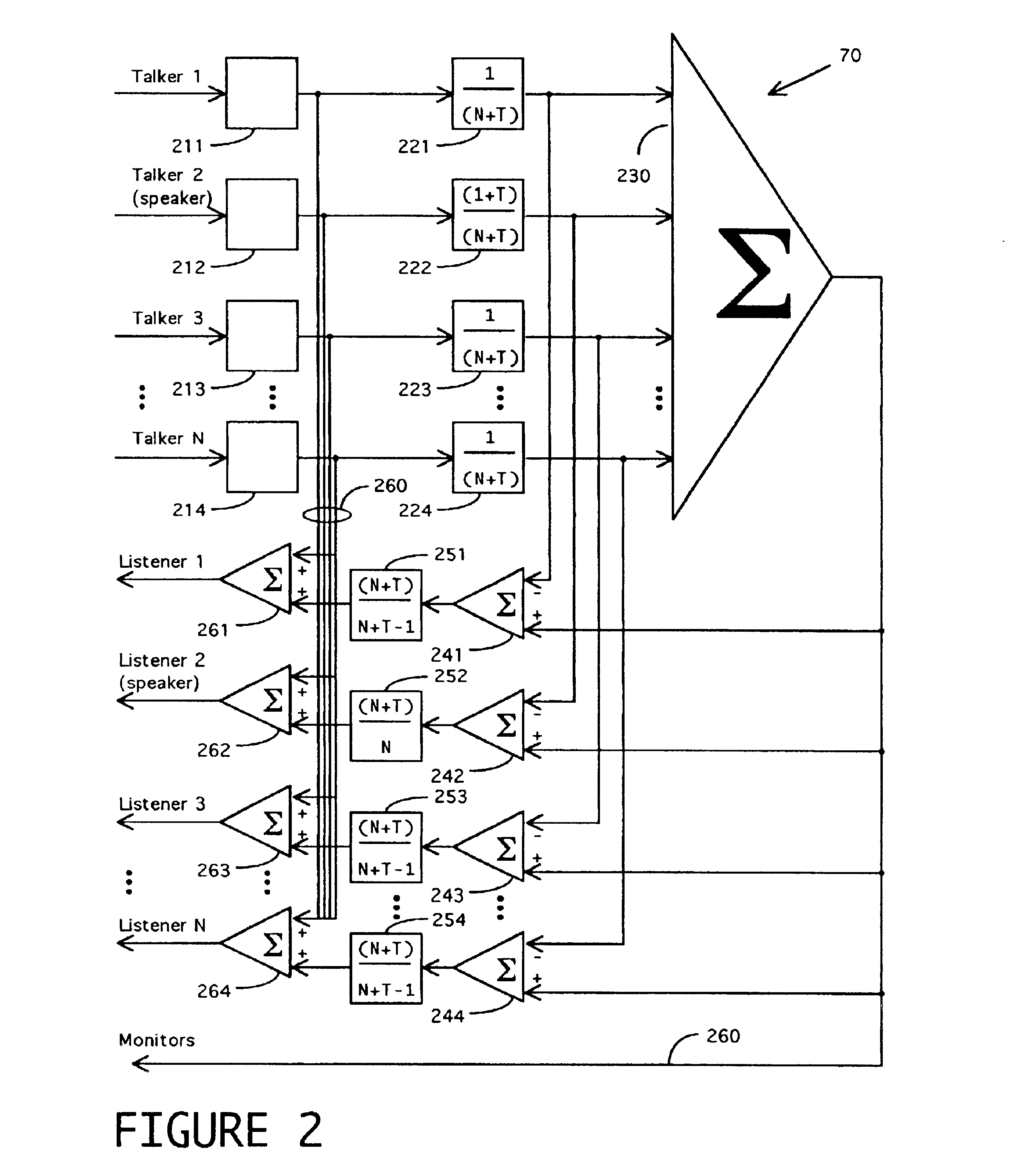
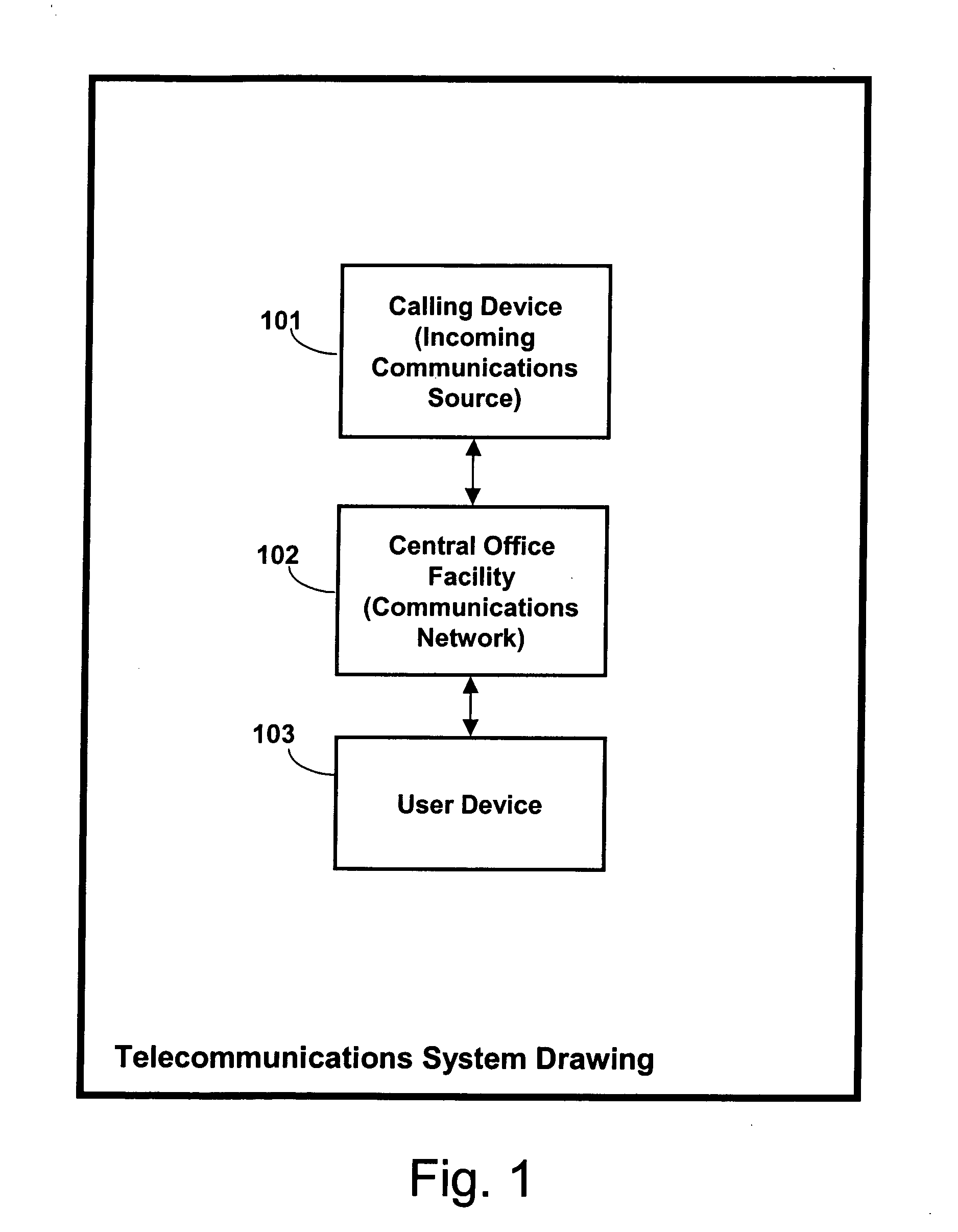
Method and apparatus for improved conference call management
InactiveUS6839417B2Exposure was also limitedIncrease exposureSpecial service for subscribersWireless networksOrganizational controlWorkstation
A method and apparatus are disclosed to allow individuals to initiate, join, manage, and participant in a conference call. Members of a community can meet and collaborate over telephones, especially cellular telephones, or computer workstations, in a way that is freeform or prescribed, automatic or moderated, spontaneous or scheduled, unassisted, and selectably anonymous. The invention provides broadly customizable degrees of collective and individual organizational control, and provides social safeguards to minimize disruptions by unruly participants.
Owner:BUFFALO PATENTS LLC
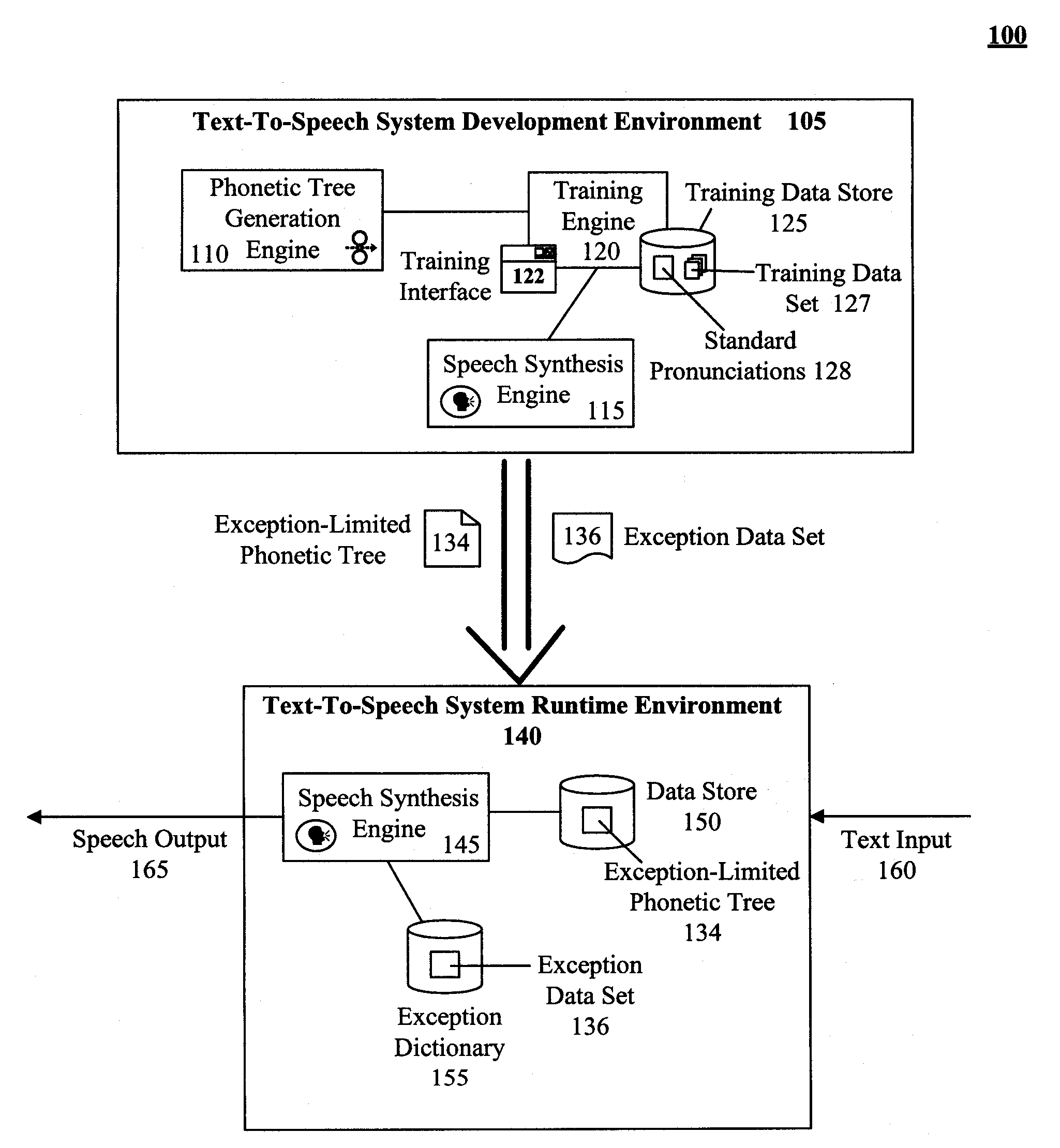
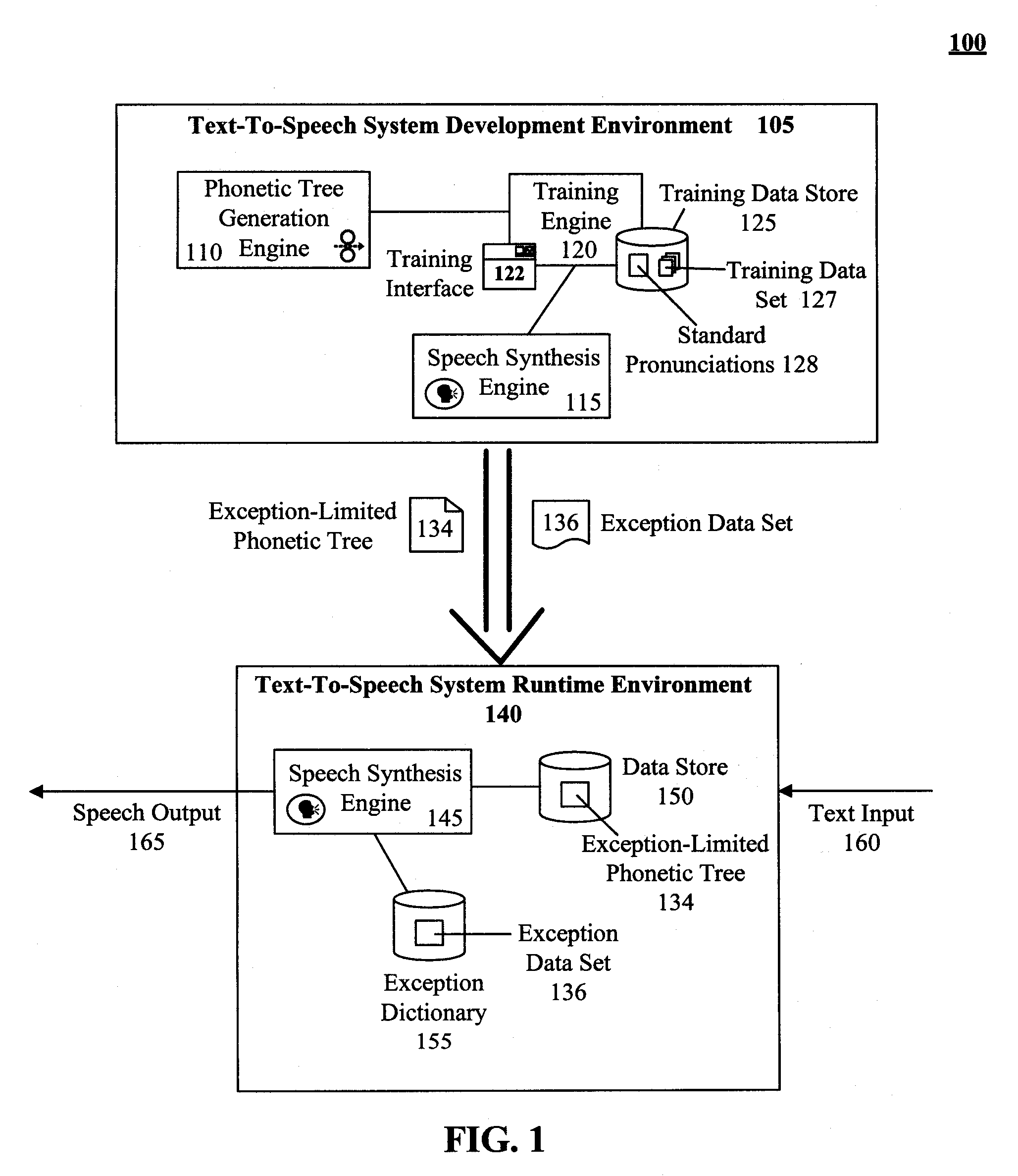
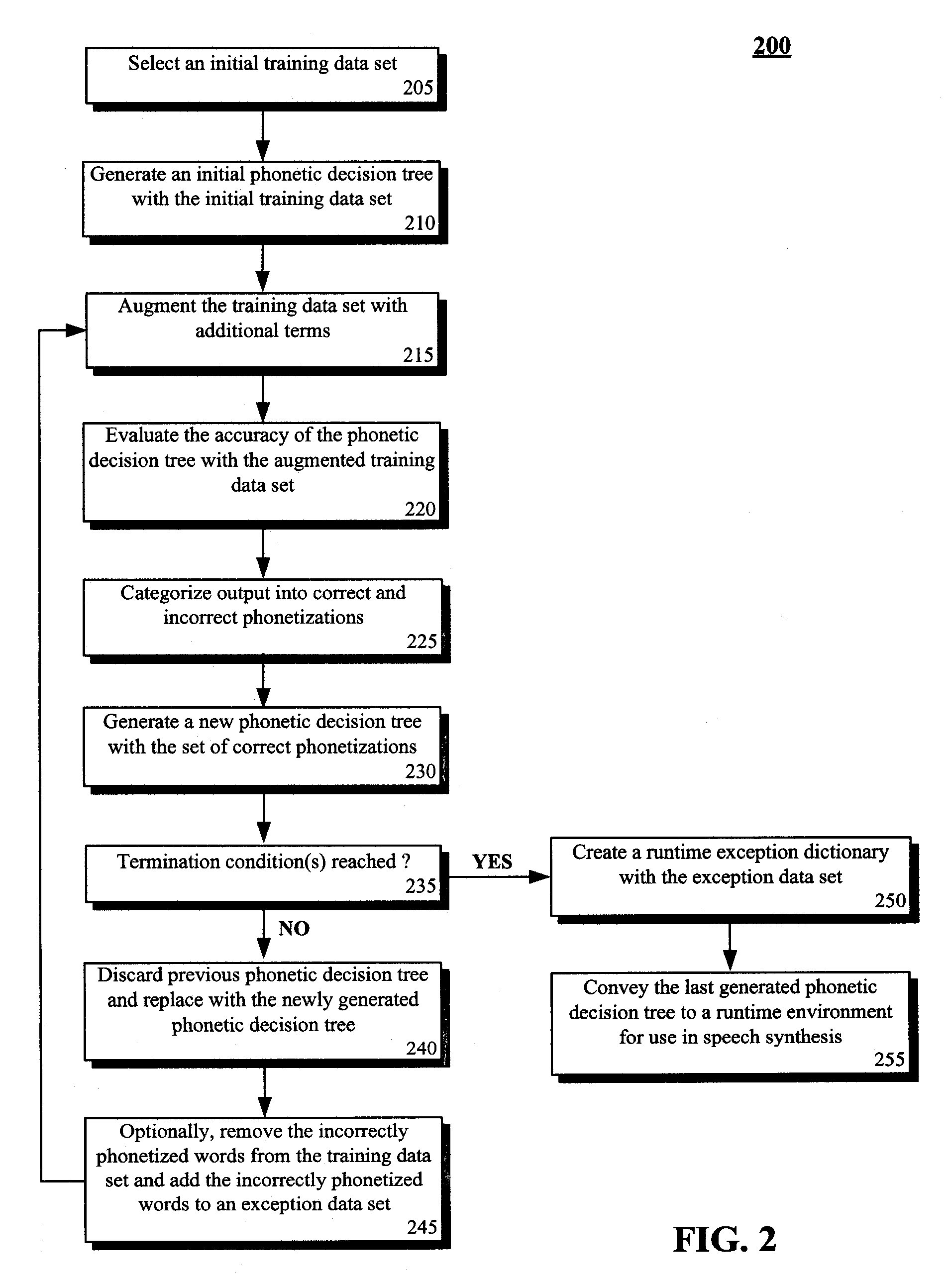
Technique for training a phonetic decision tree with limited phonetic exceptional terms
ActiveUS20080319753A1Exposure was also limitedSpeech recognitionSpeech synthesisTheoretical computer scienceSpeech sound
The present invention discloses a method for training an exception-limited phonetic decision tree. An initial subset of data can be selected and used for creating an initial phonetic decision tree. Additional terms can then be incorporated into the subset. The enlarged subset can be used to evaluate the phonetic decision tree with the results being categorized as either correctly or incorrectly phonetized. An exception-limited phonetic tree can be generated from the set of correctly phonetized terms. If the termination conditions for the method have been determined to be unsatisfactorily met, then steps of the method can be repeated.
Owner:CERENCE OPERATING CO
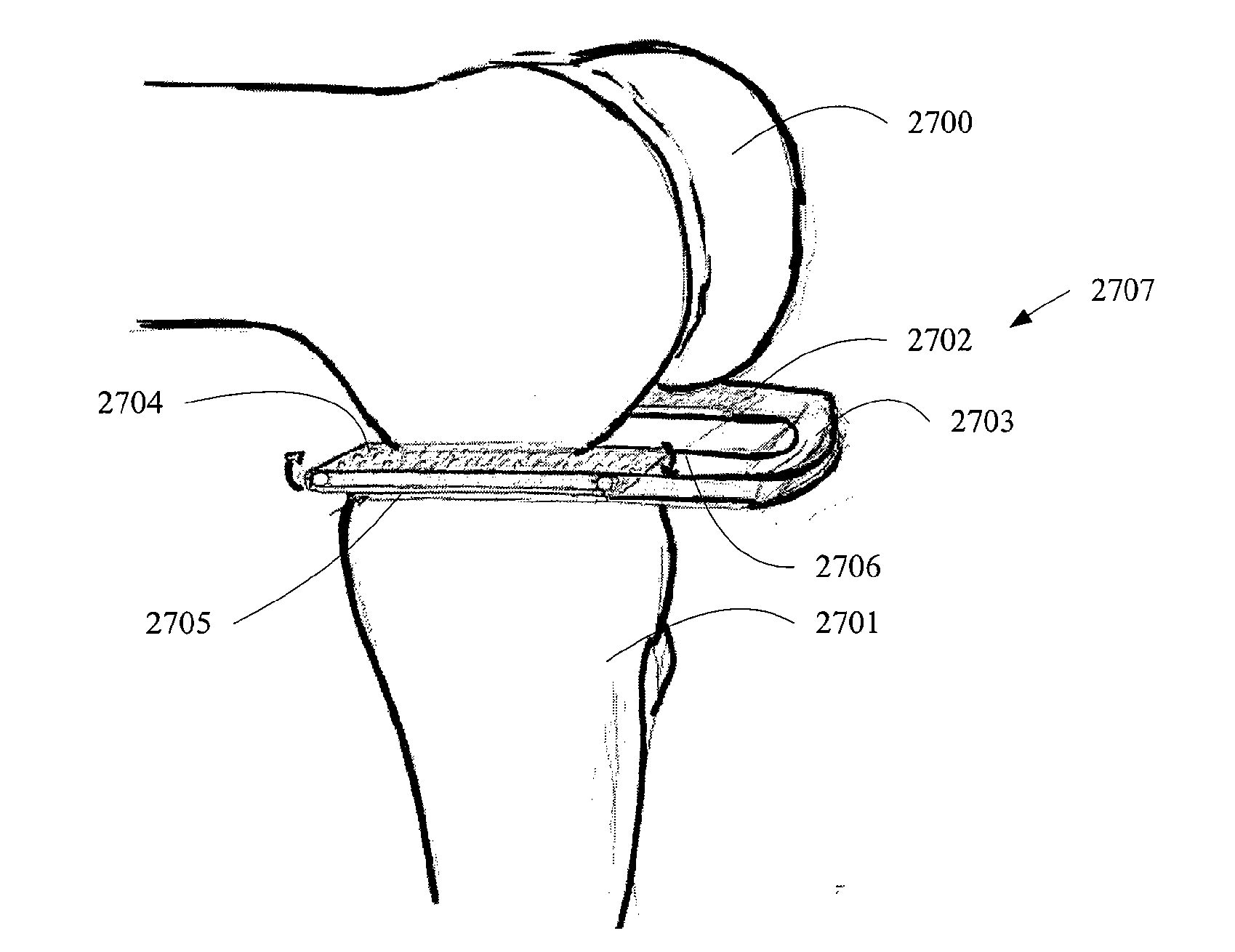
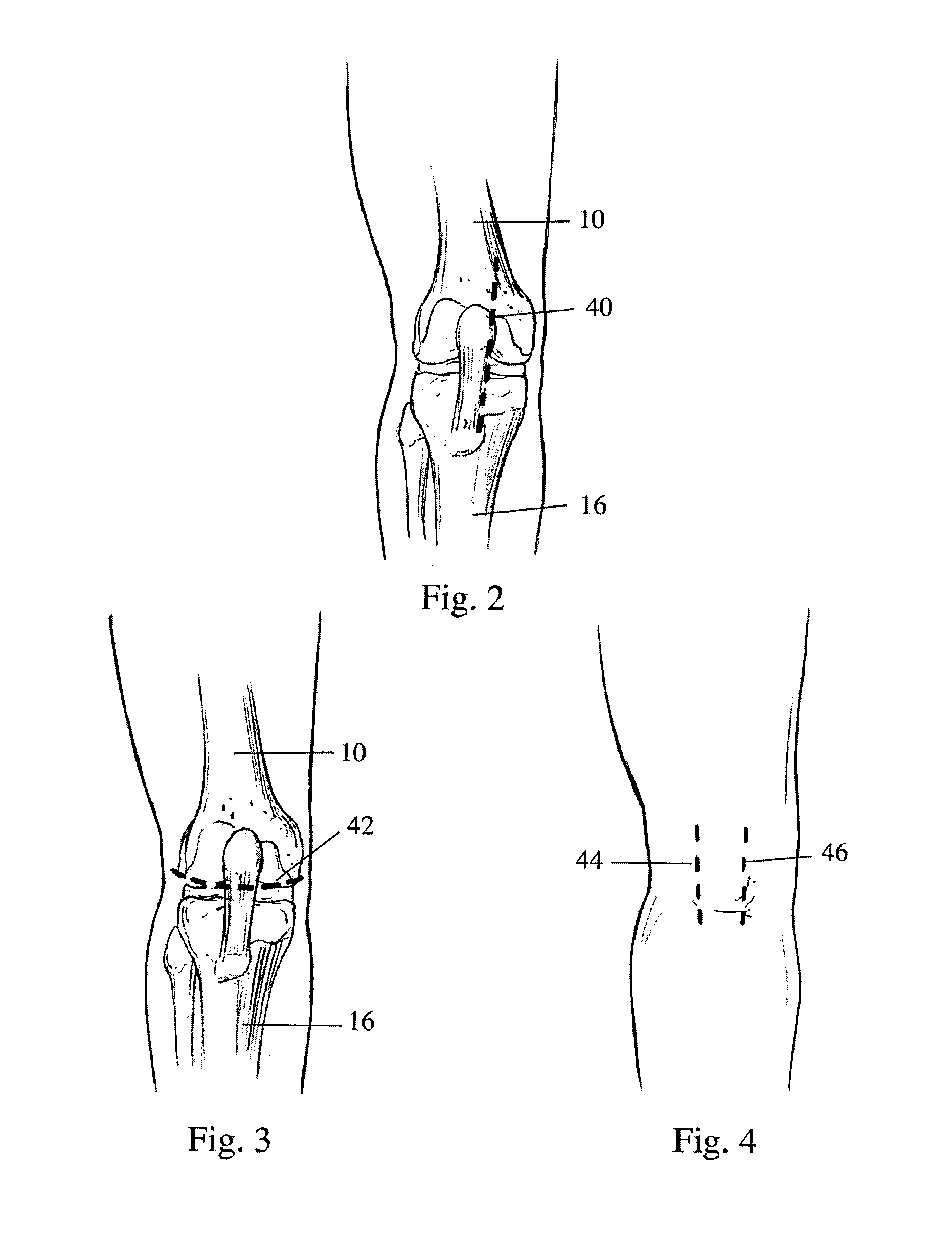
Apparatus and method for sculpting the surface of a joint
InactiveUS20100145343A1Exposure was also limitedDiagnosticsNon-surgical orthopedic devicesBones jointsGear wheel
Methods and devices for sculpting bones, particularly in preparation for implanting prosthetic devices to replace articulating bone joint surfaces. Improved bone removal devices including burr mills driven by gears and loop drives are provided. Reciprocating cutters and belt cutters are also provided. Some devices have either integral or removable expandable portions to vary the force and bone resection depth. Devices can have irrigation ports and plenums to remove bone fragments. Some cutters are dual cutters, adapted to remove bone in two or more regions, such as the knee joint, simultaneously.
Owner:CAYENNE MEDICAL INC
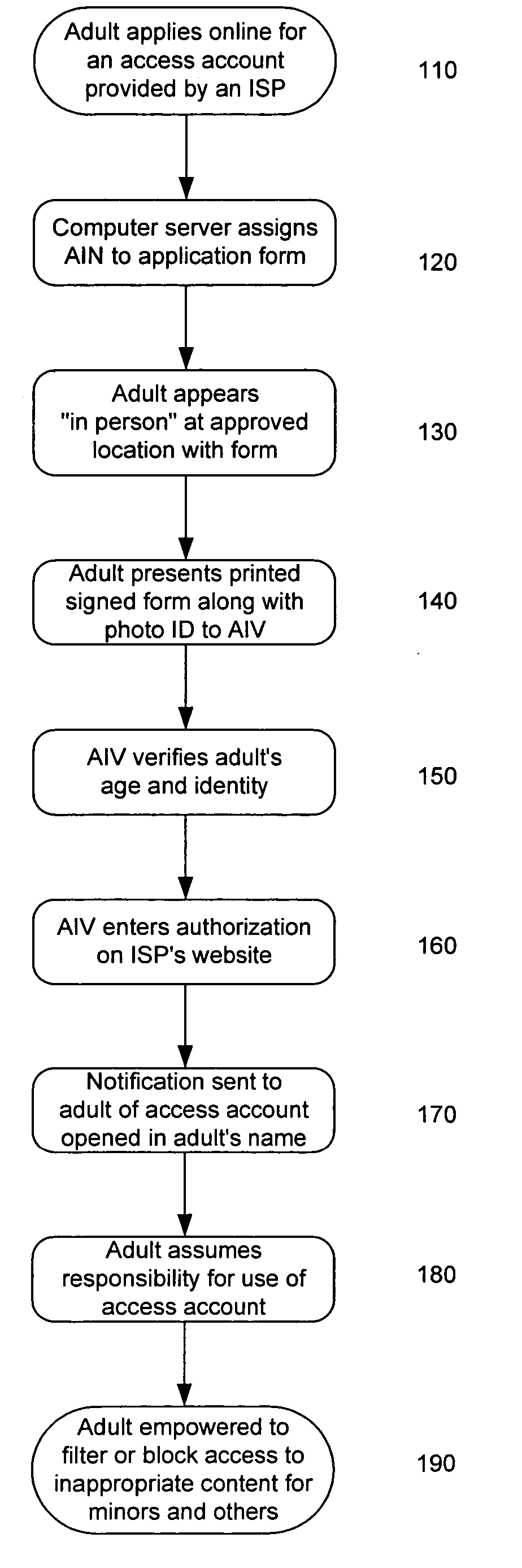
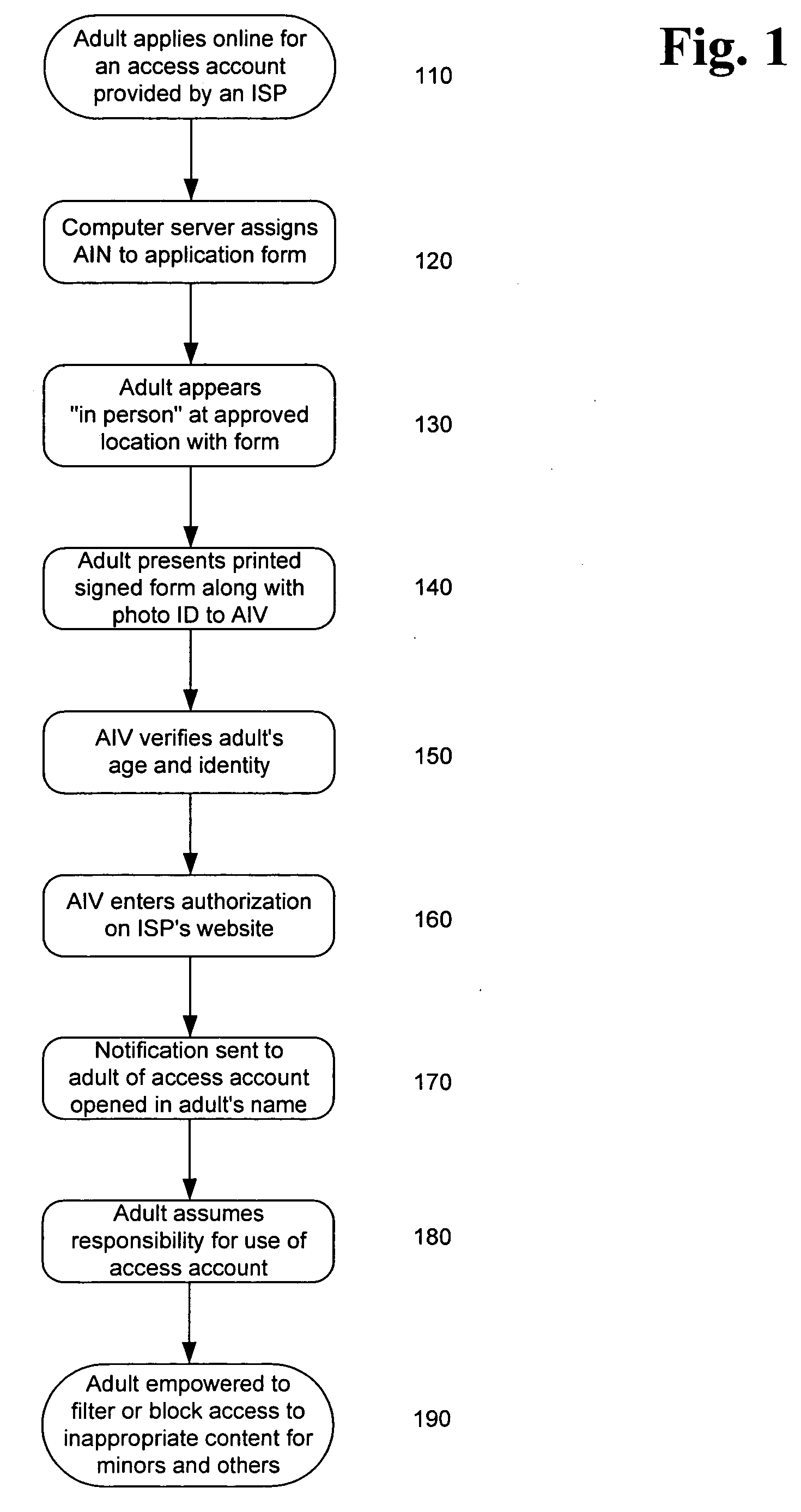
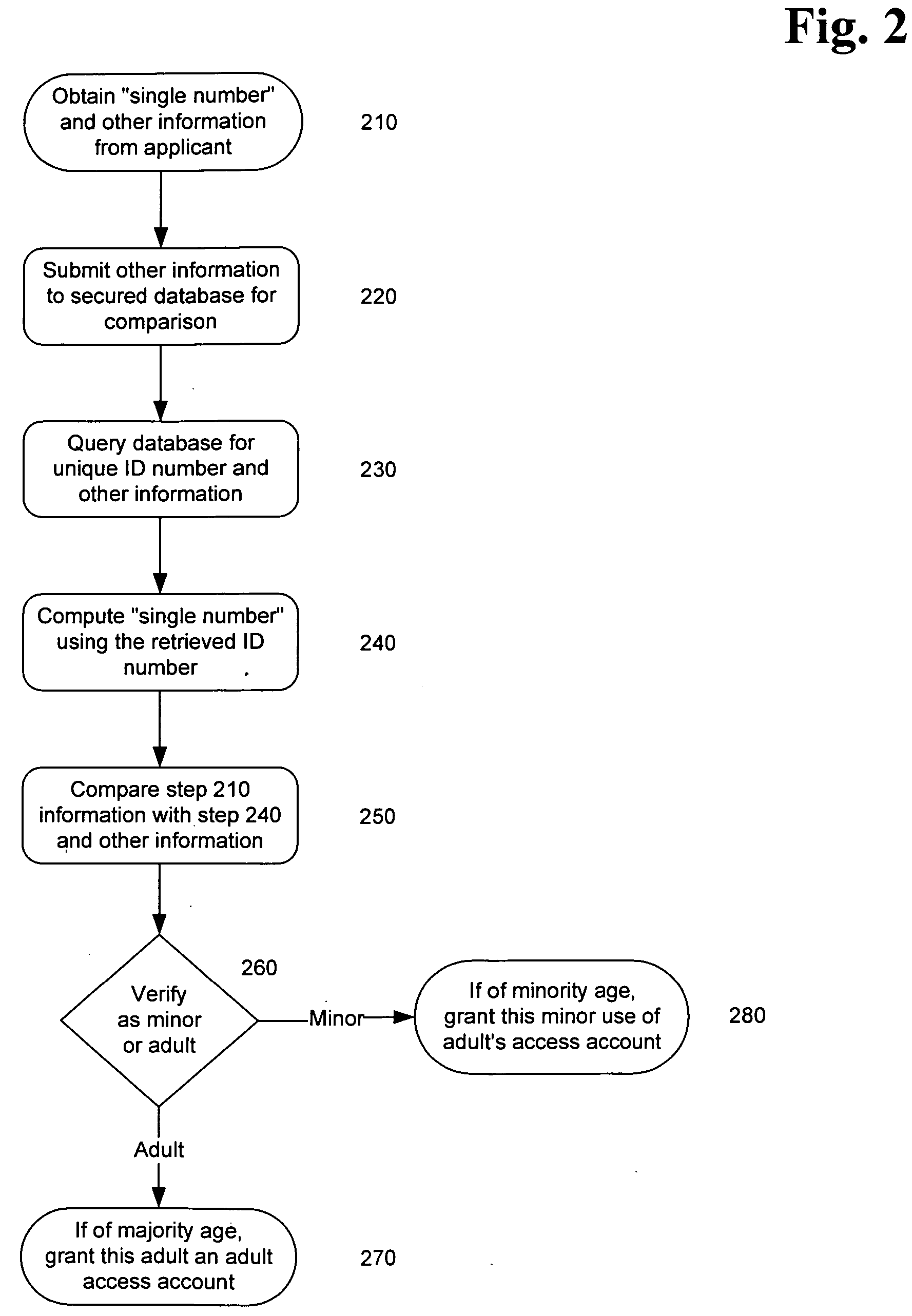
System and method for verifying the age and identity of individuals and limiting their access to appropriate material
InactiveUS20060173792A1Exposure was also limitedPayment architectureSecret communicationLimited accessInternet privacy
Limiting access to the Internet, eCommerce websites, accounts and / or other venues, for example, by providing an Internet access account, and / or other access account, to an “in person” and / or “single number” age verified and identified “adult” who assumes responsibility for use of such account and viewing of appropriate material via such account by “in person” age verified and identified individuals, while being empowered by control of a “single access account” that filters inappropriate material based on (1) user profiles created by age verified and identified adults and stored on provider's “access server” and / or (2) “mandatory” provider imposed filtering.
Owner:GLASS PAUL H
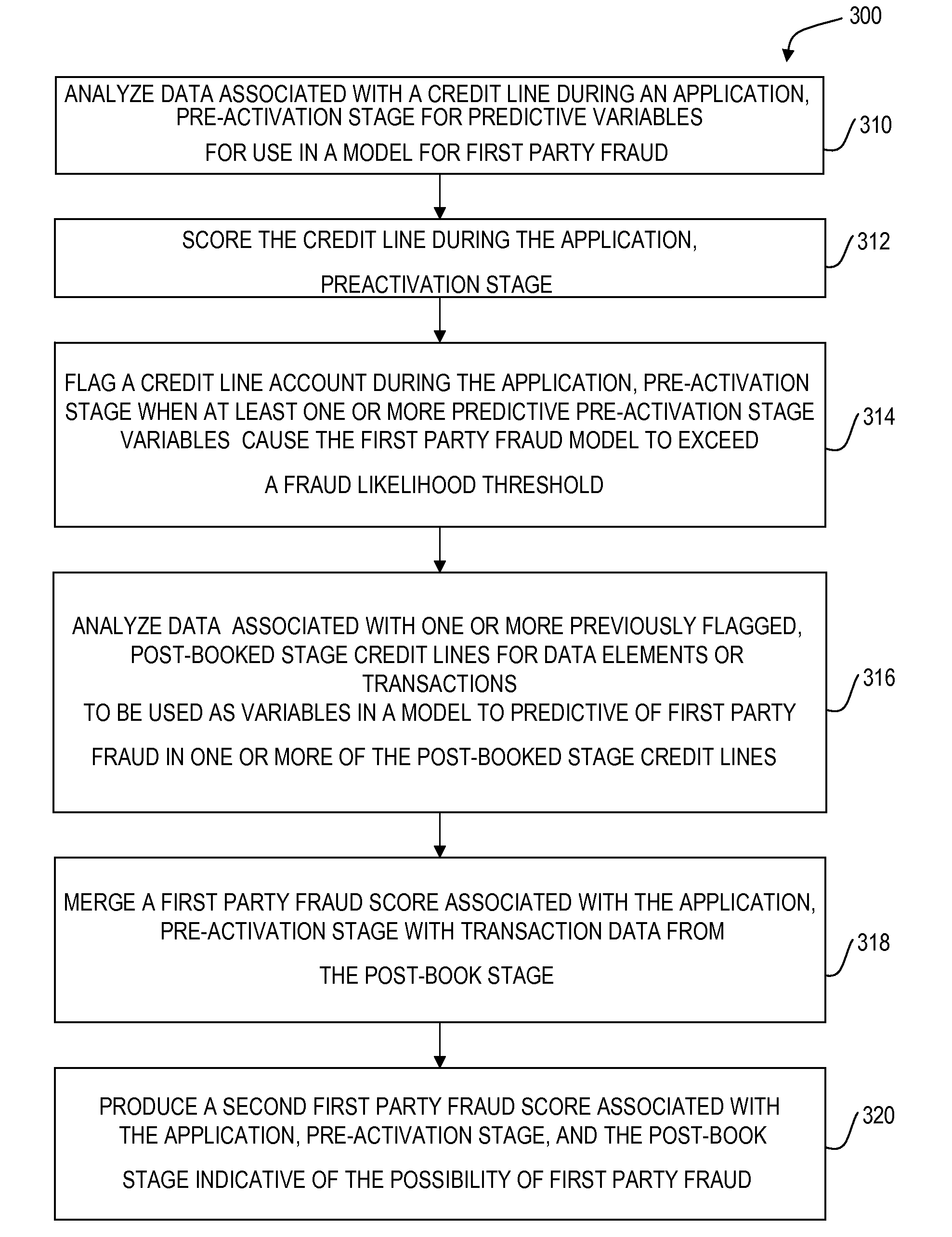
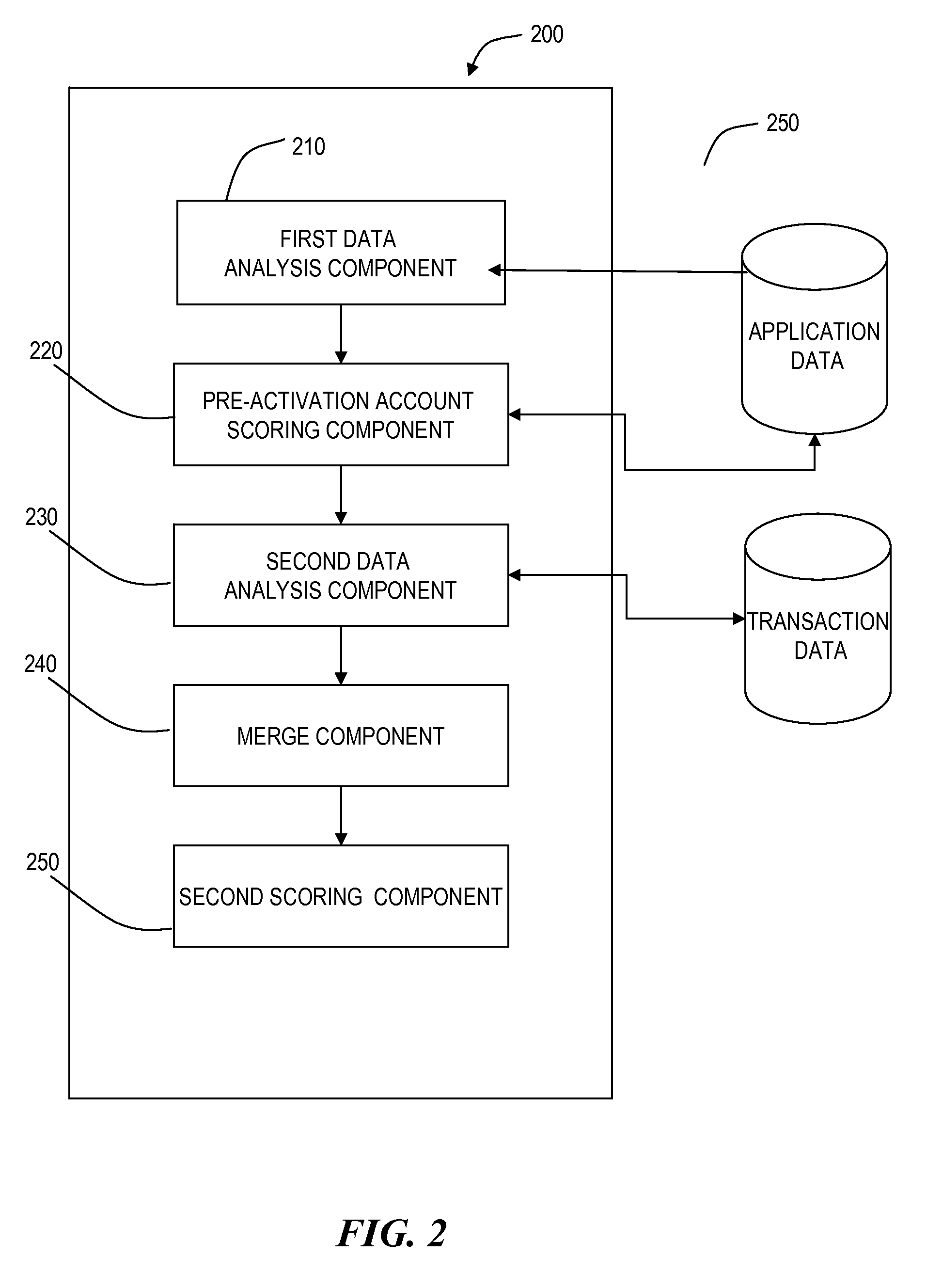
Detecting first party fraud abuse
InactiveUS20090222308A1Exposure was also limitedLittle recourseComplete banking machinesFinanceAlgorithmPredictive value
A computerized method includes analyzing data associated with a credit line during an origination stage for predictive variables for use in a model for first party fraud, and flagging an account during the origination stage when at least one or more predictive origination stage variables cause a model score to exceed a pre-defined fraud likelihood threshold. The computerized method also includes analyzing data associated with one or more previously flagged, post-booked stage credit lines for data elements or transactions to be used as variables in a model to predictive of first party fraud at the customer-level or in one or more of the post-booked stage credit lines.
Owner:FAIR ISAAC & CO INC
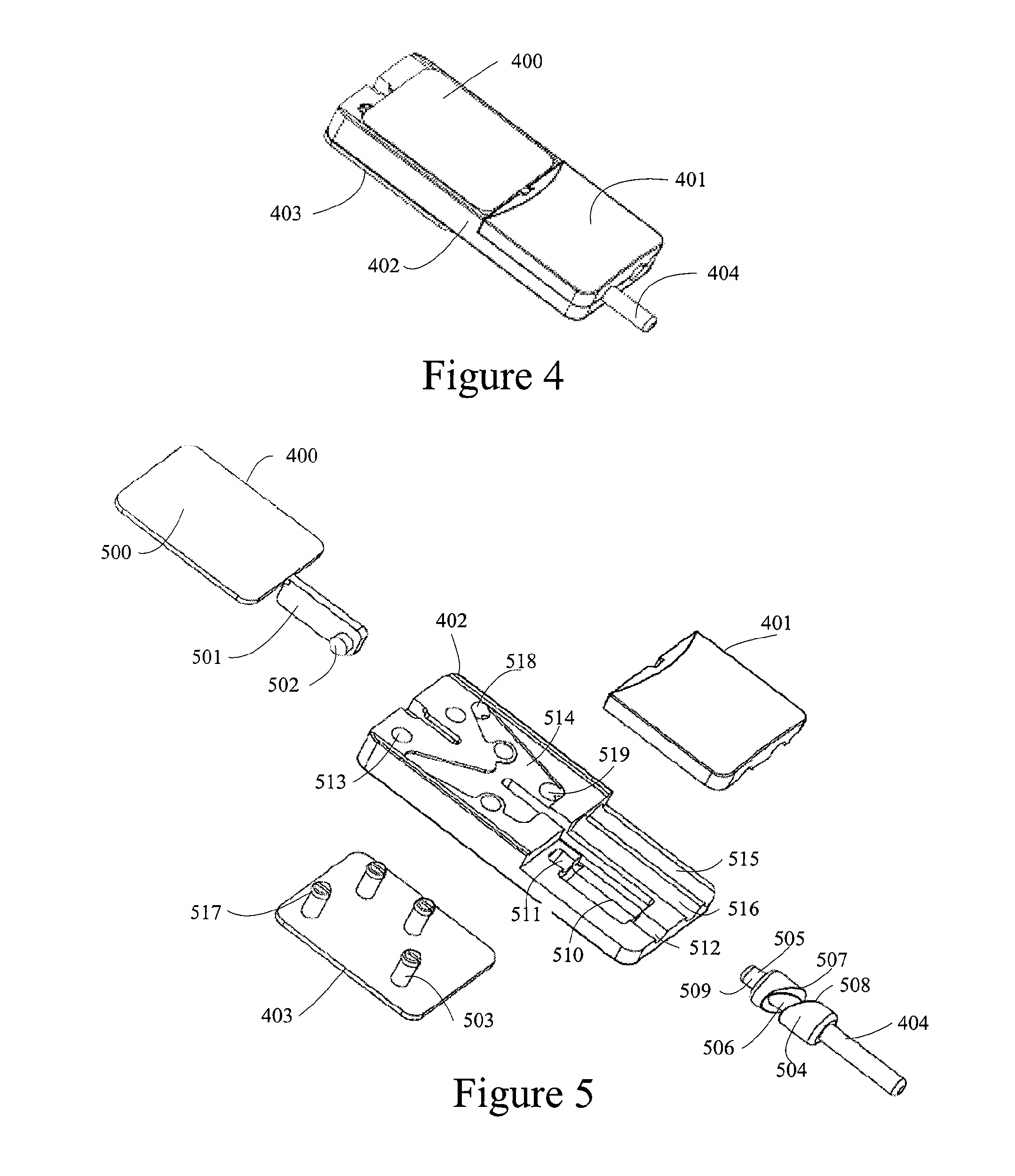
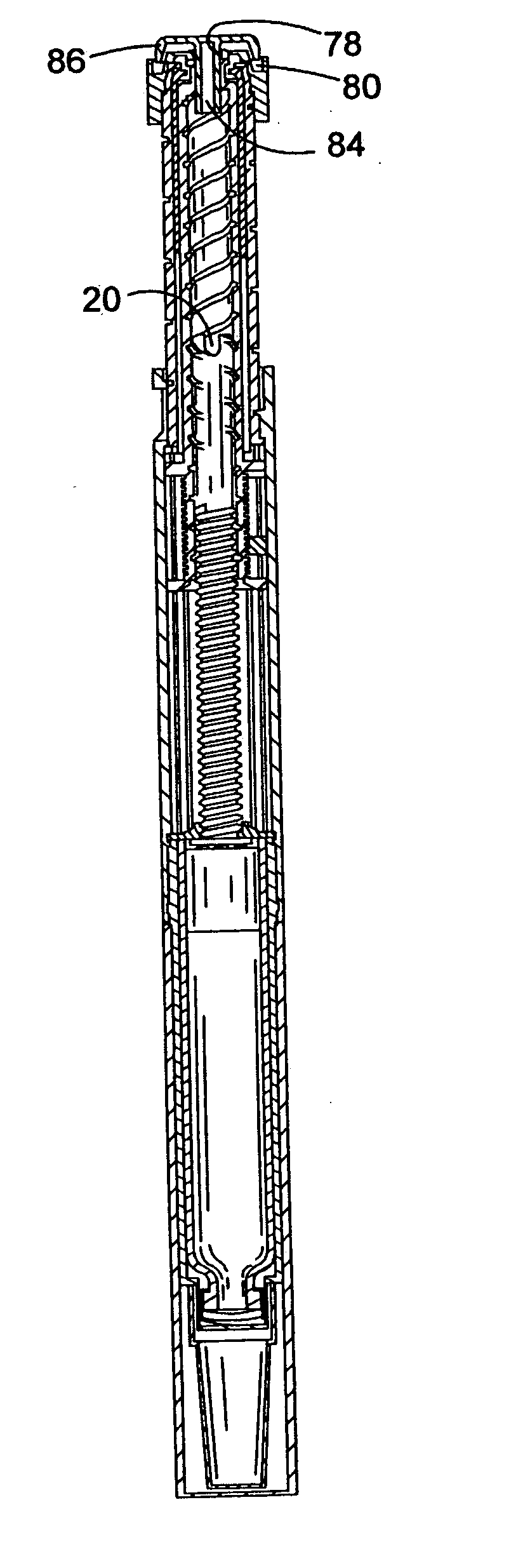
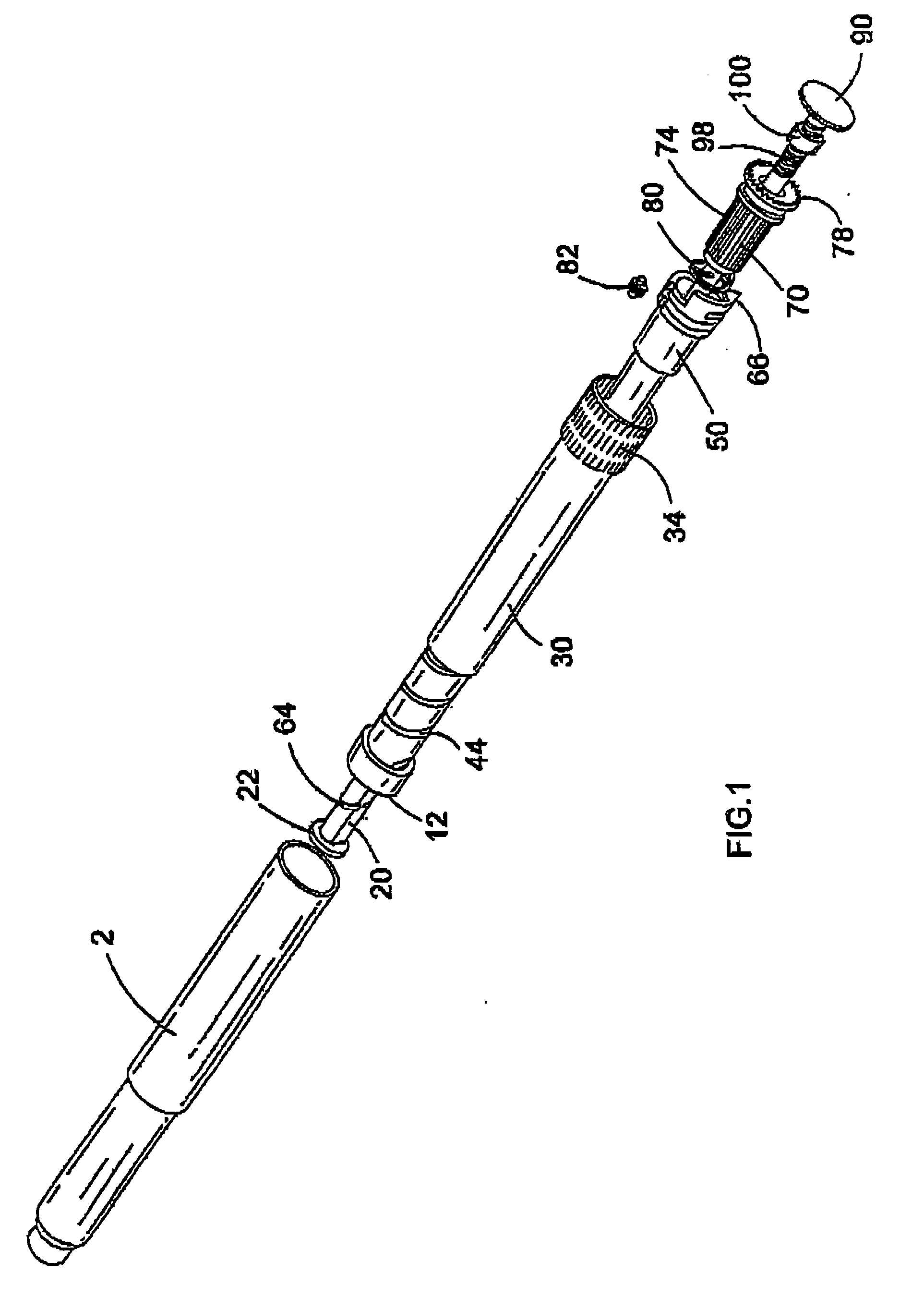
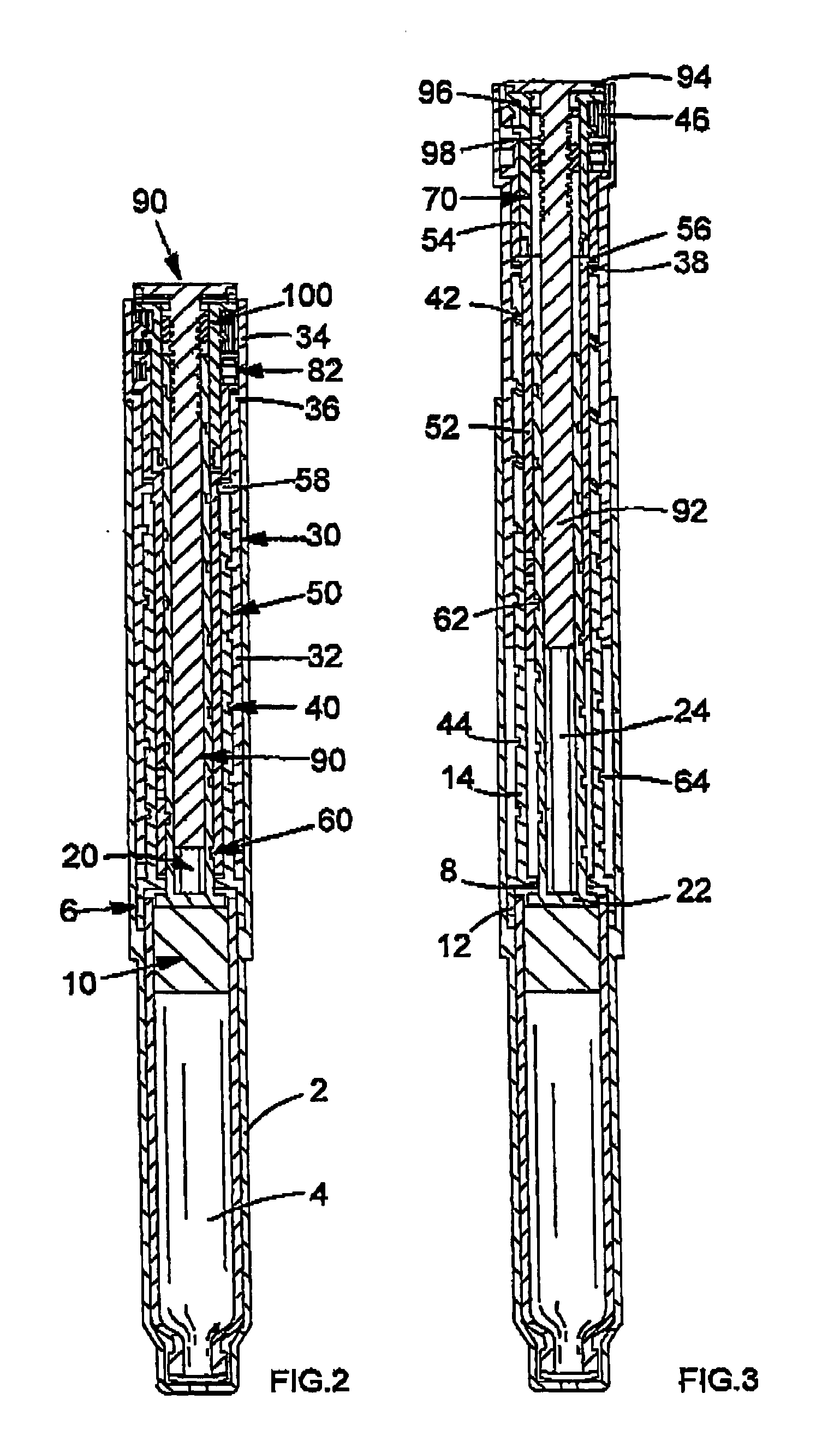
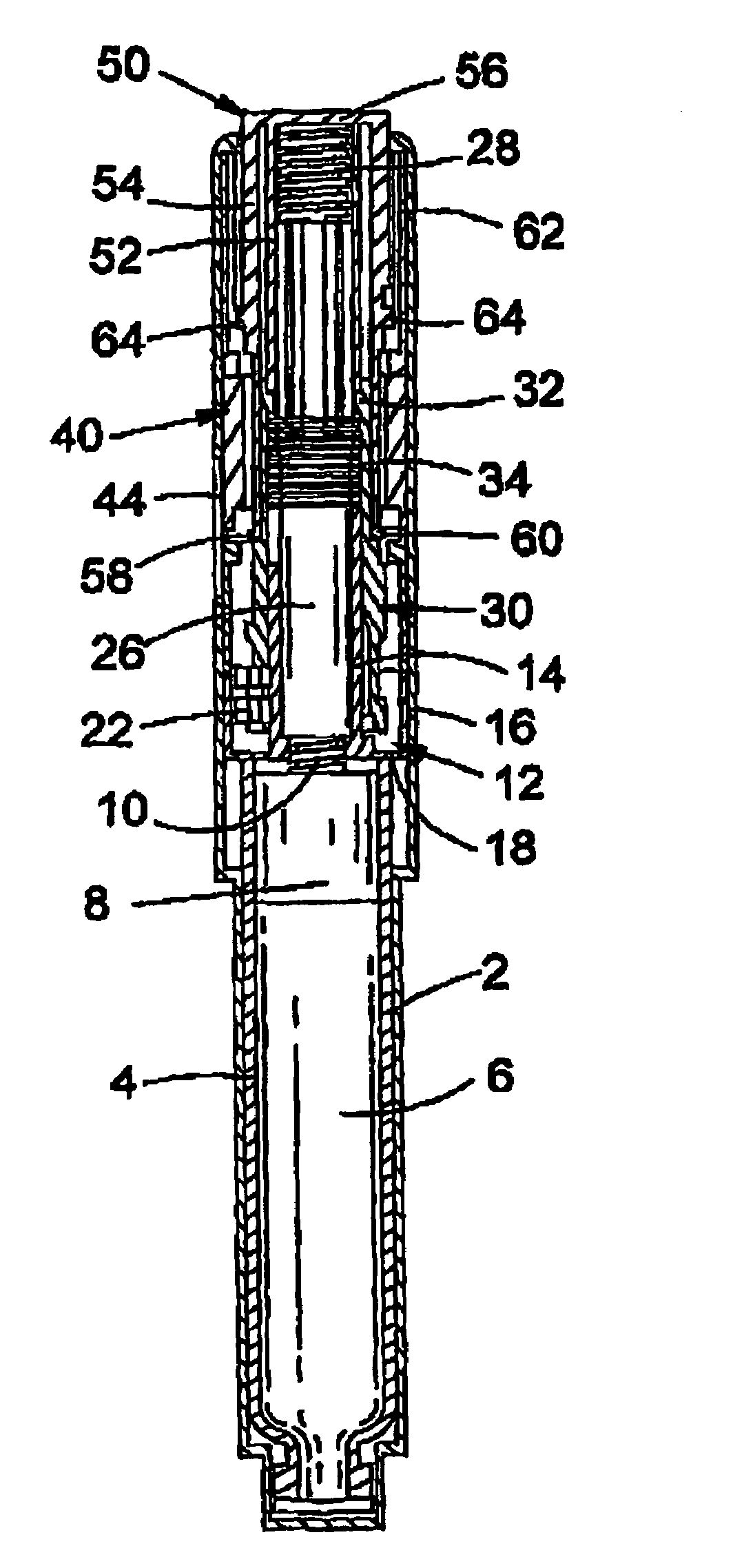
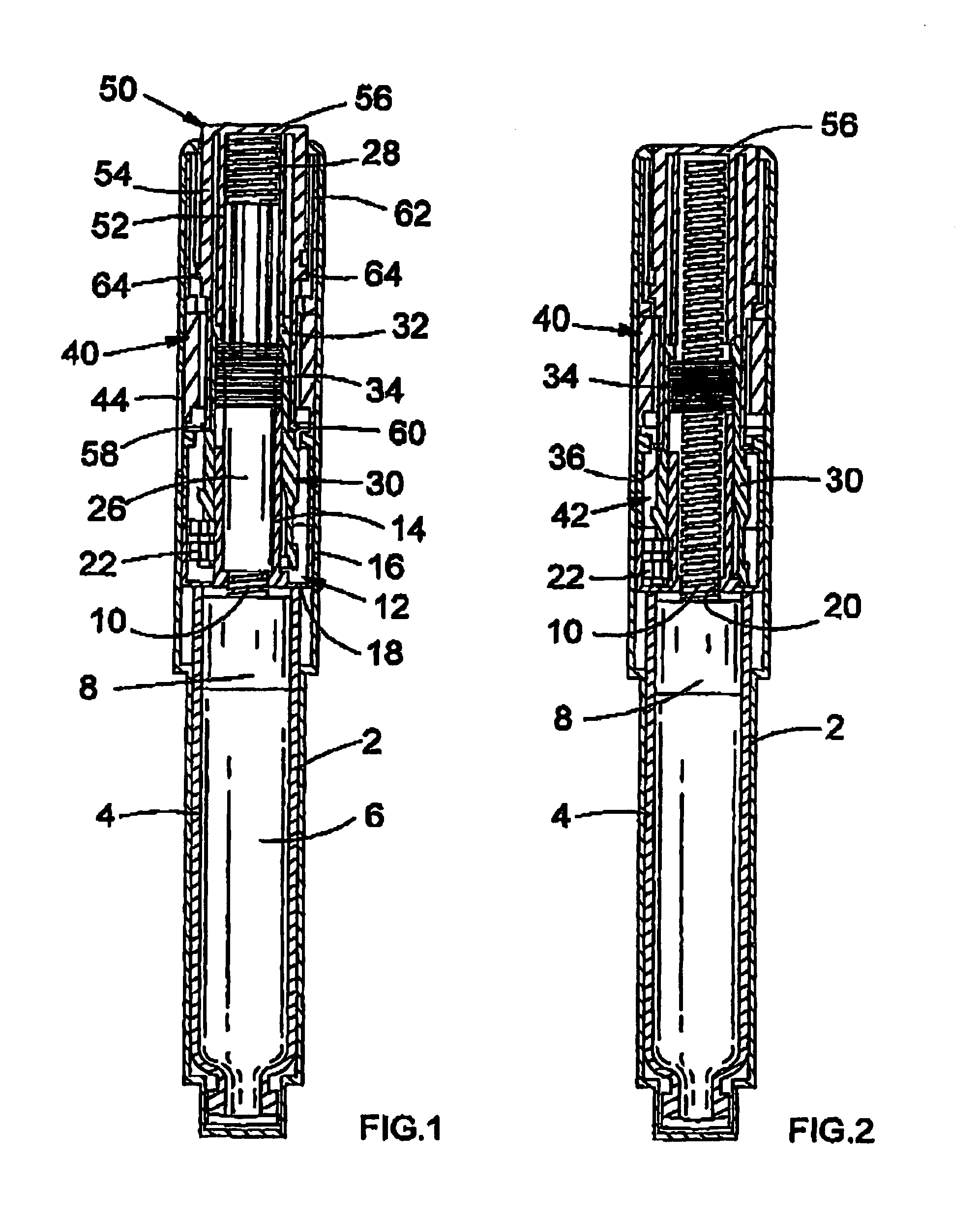
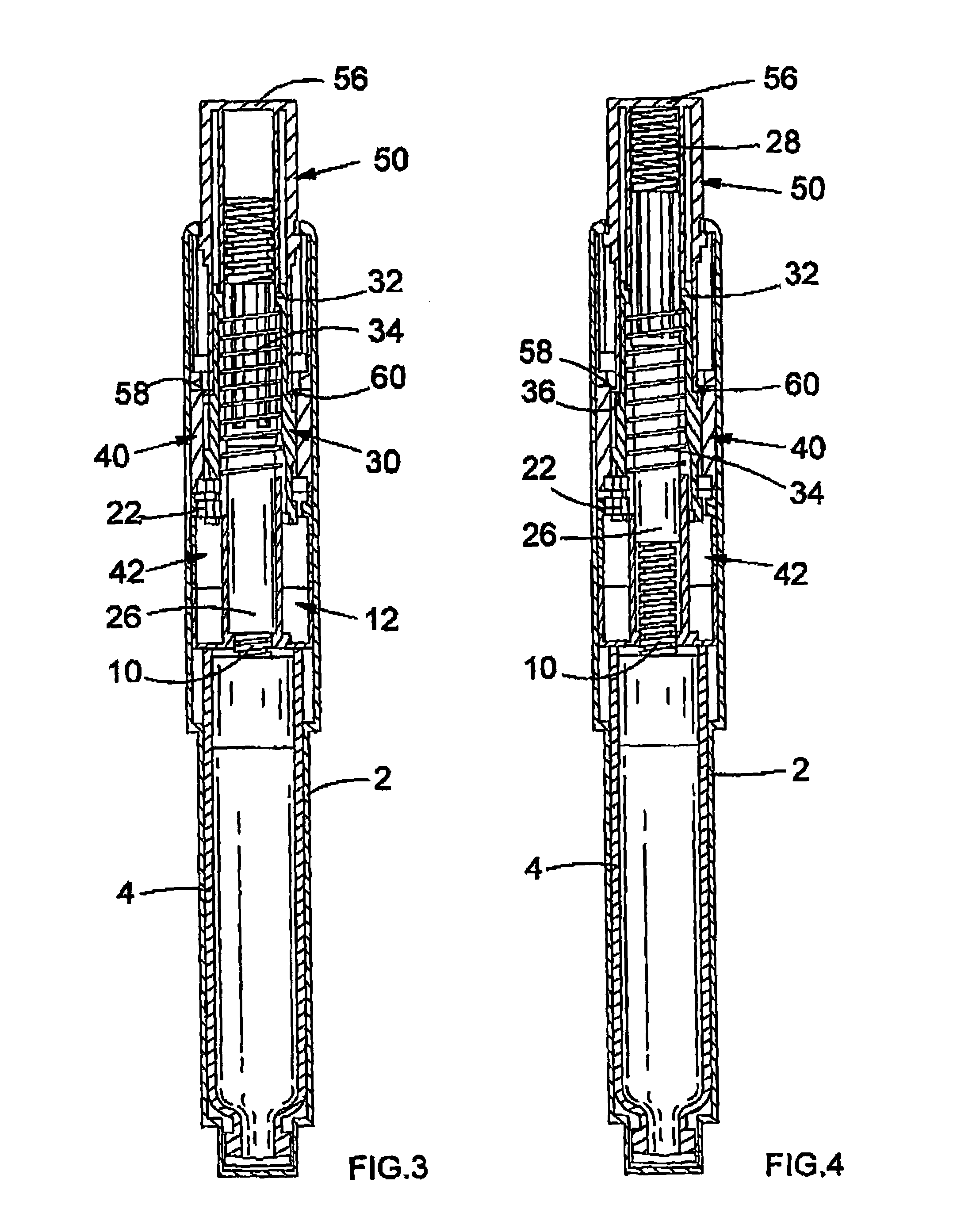
Drive mechanisms suitable for use in drug delivery devices
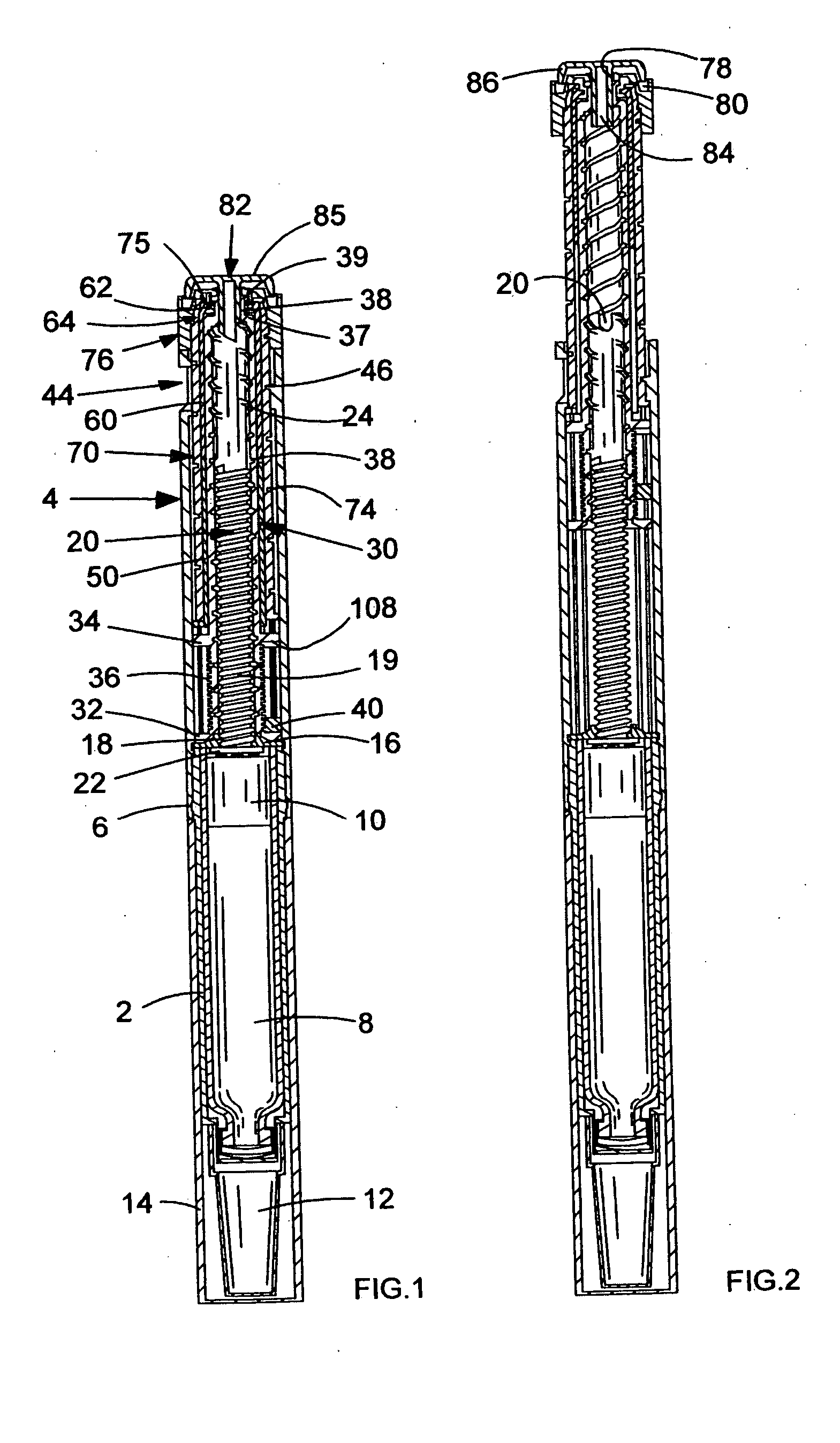
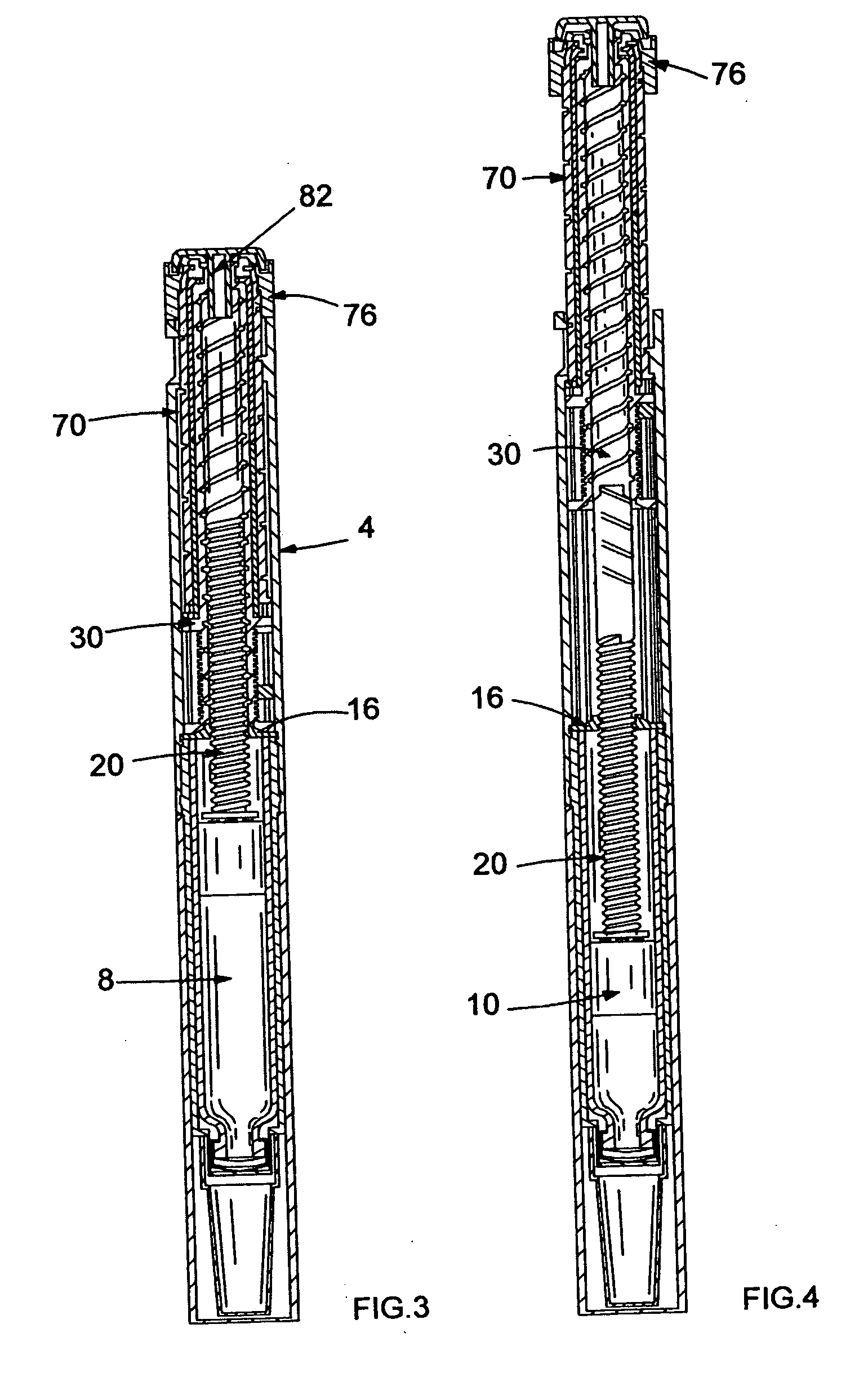
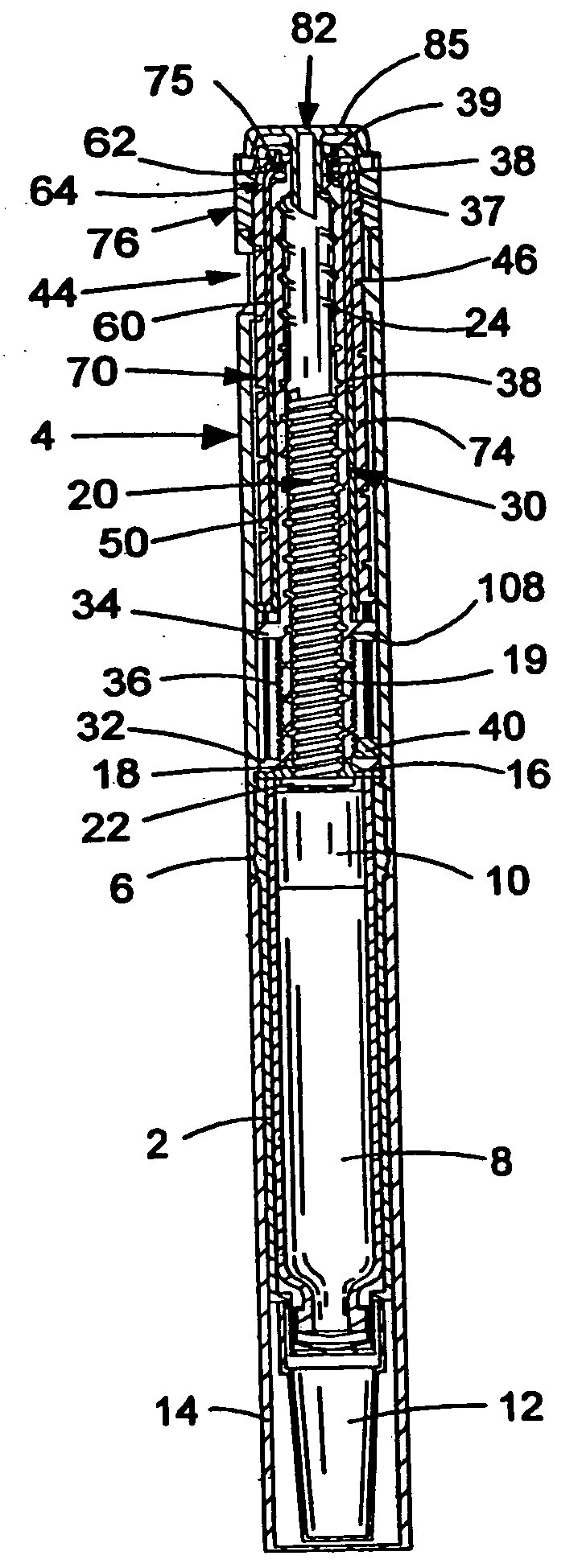
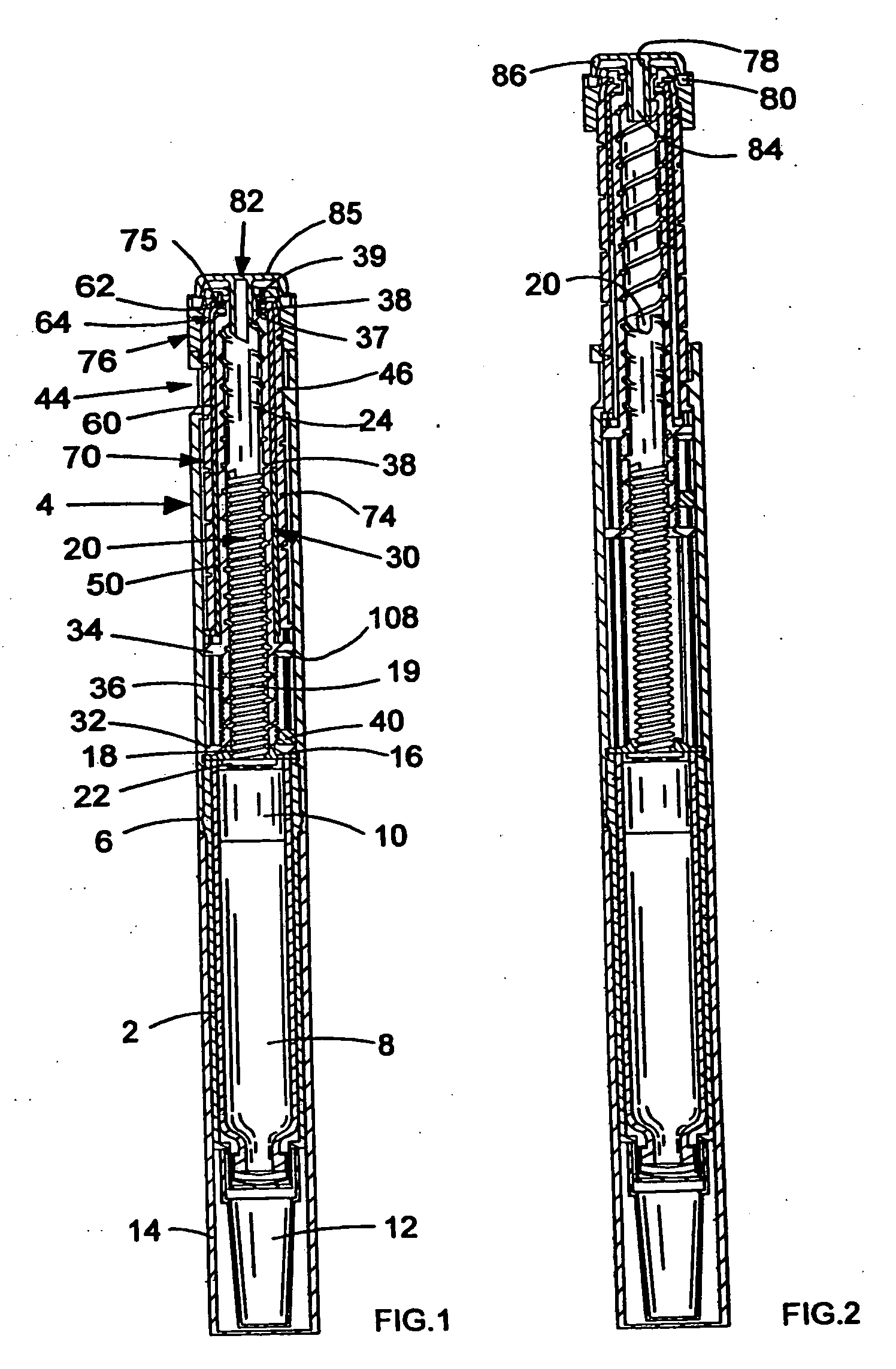
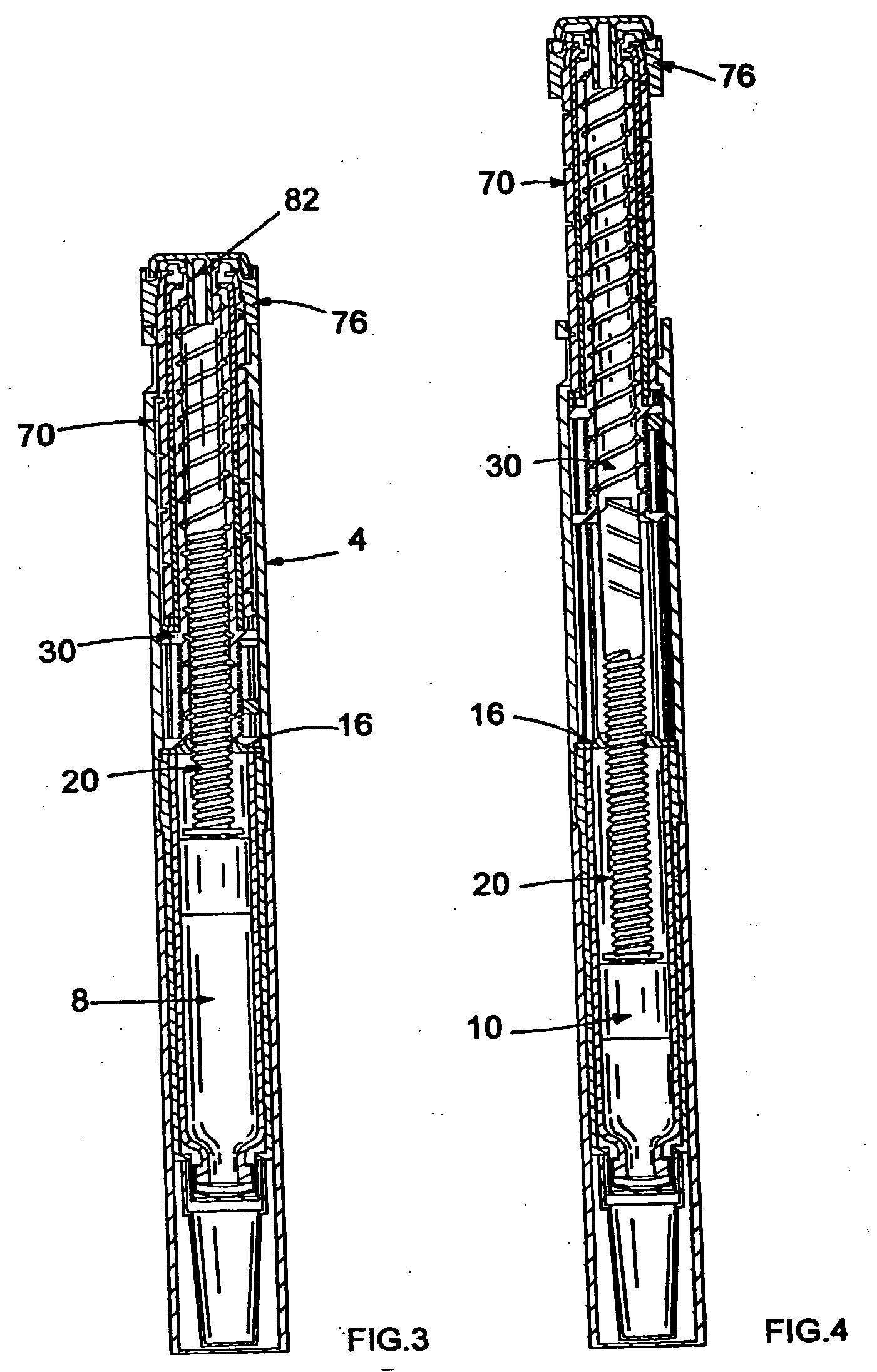
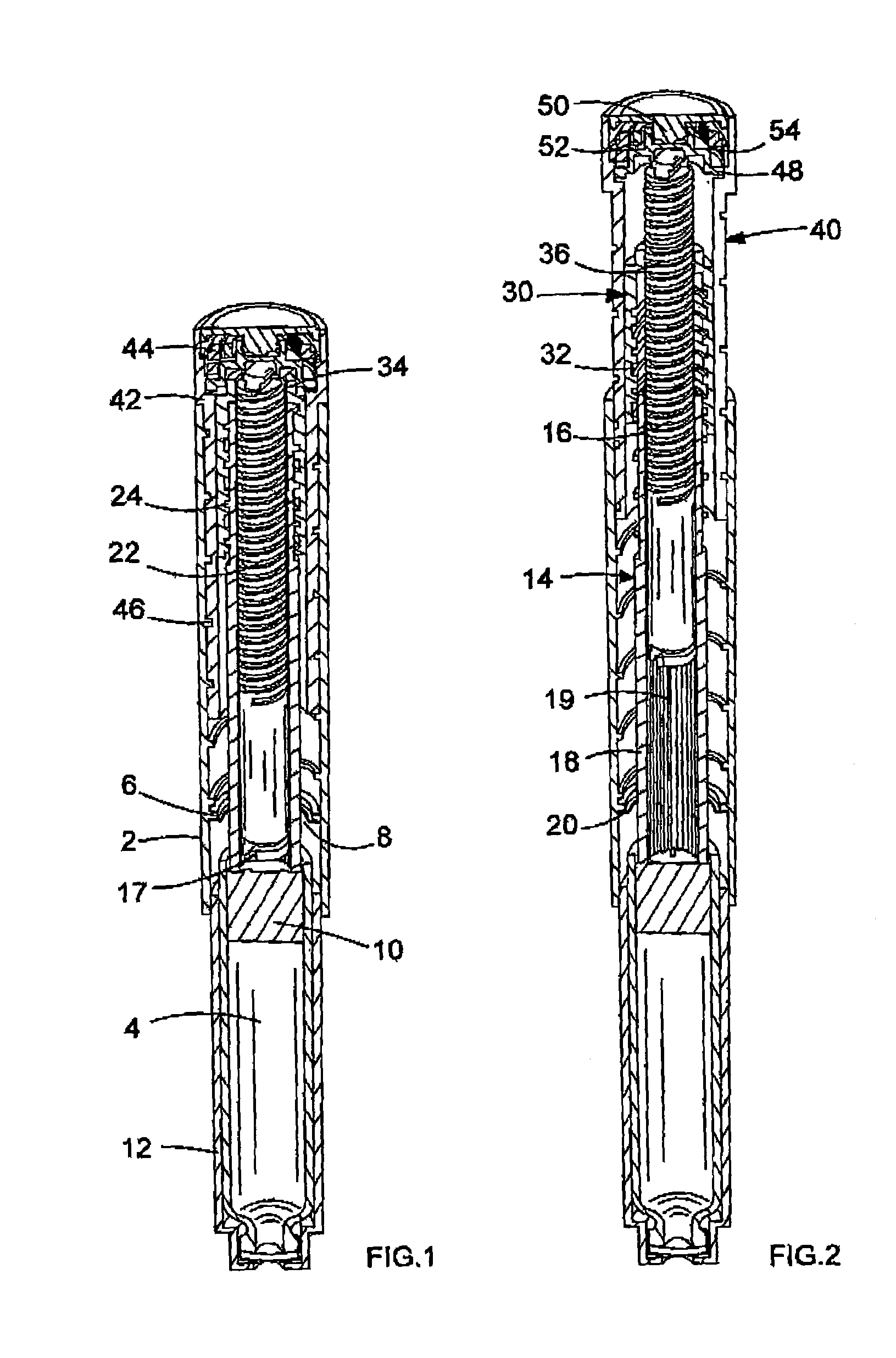
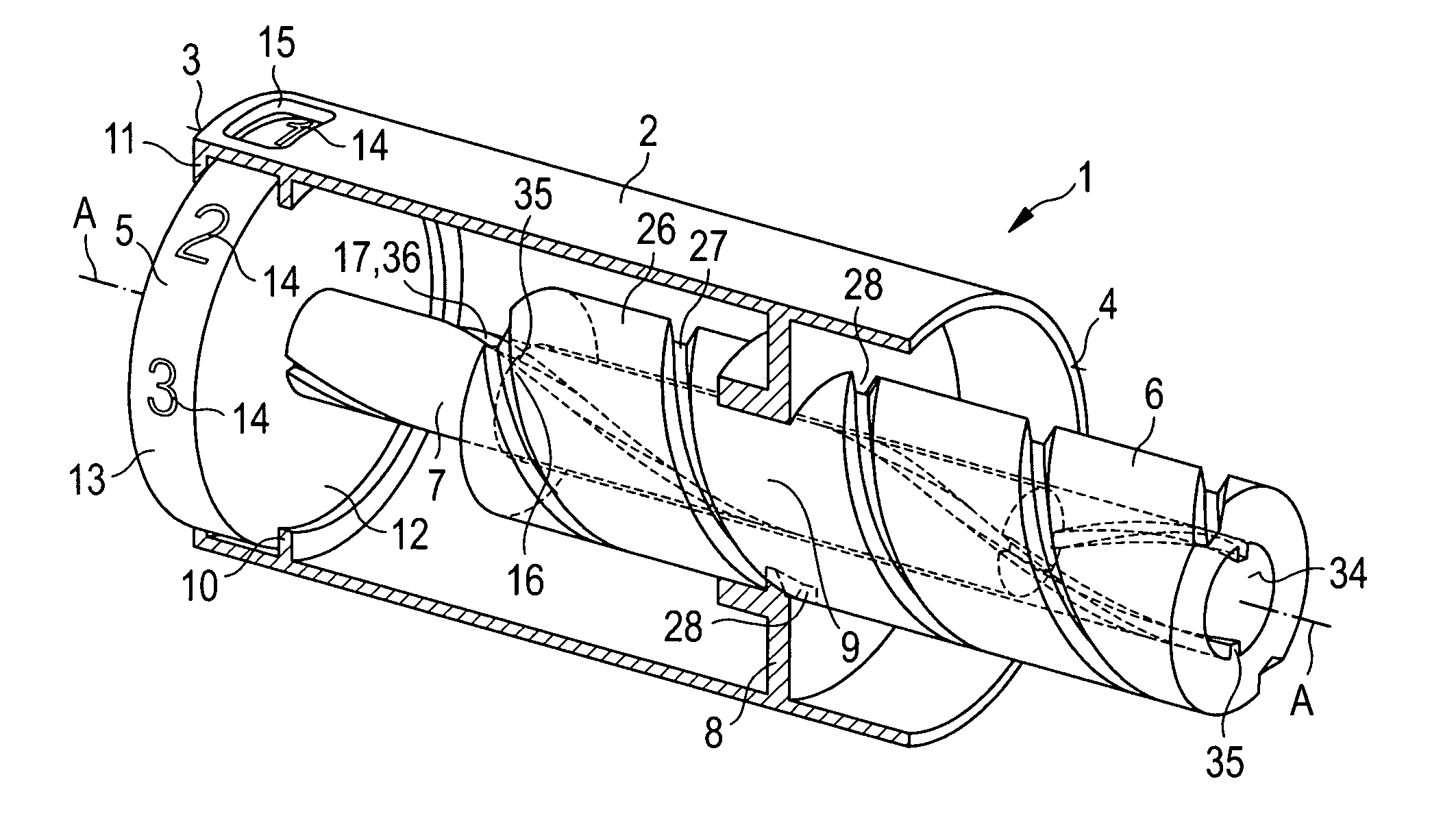
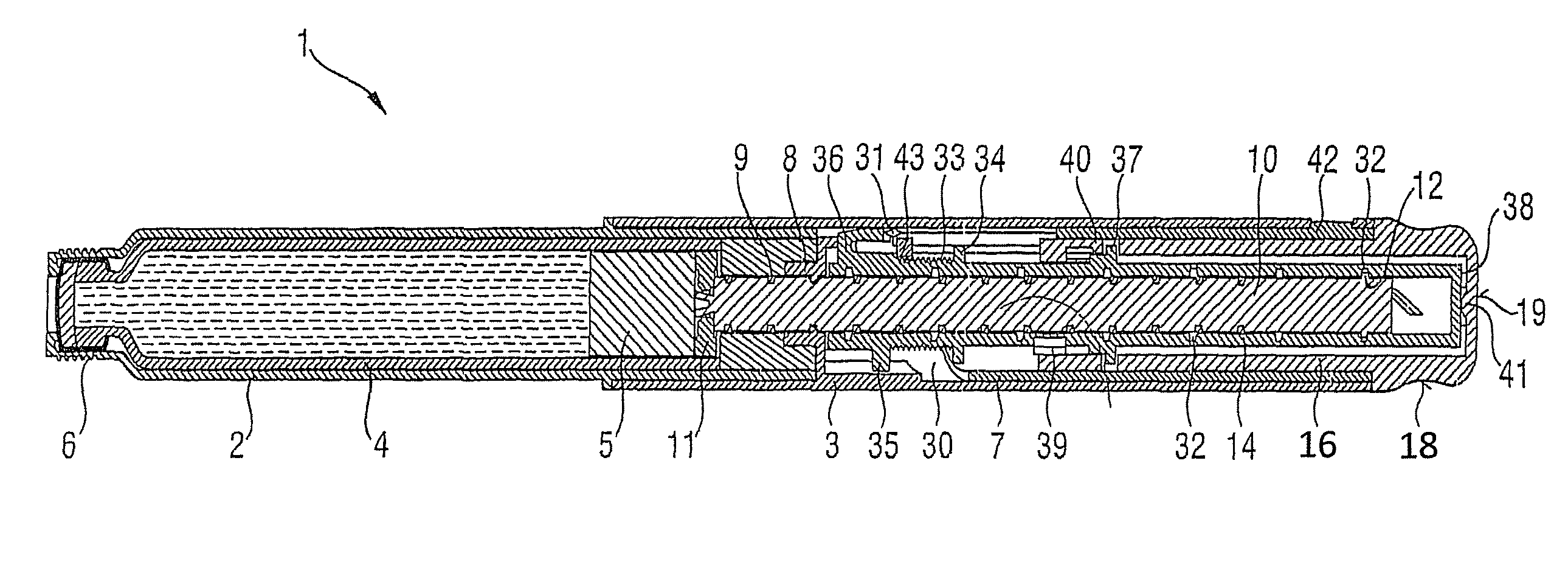
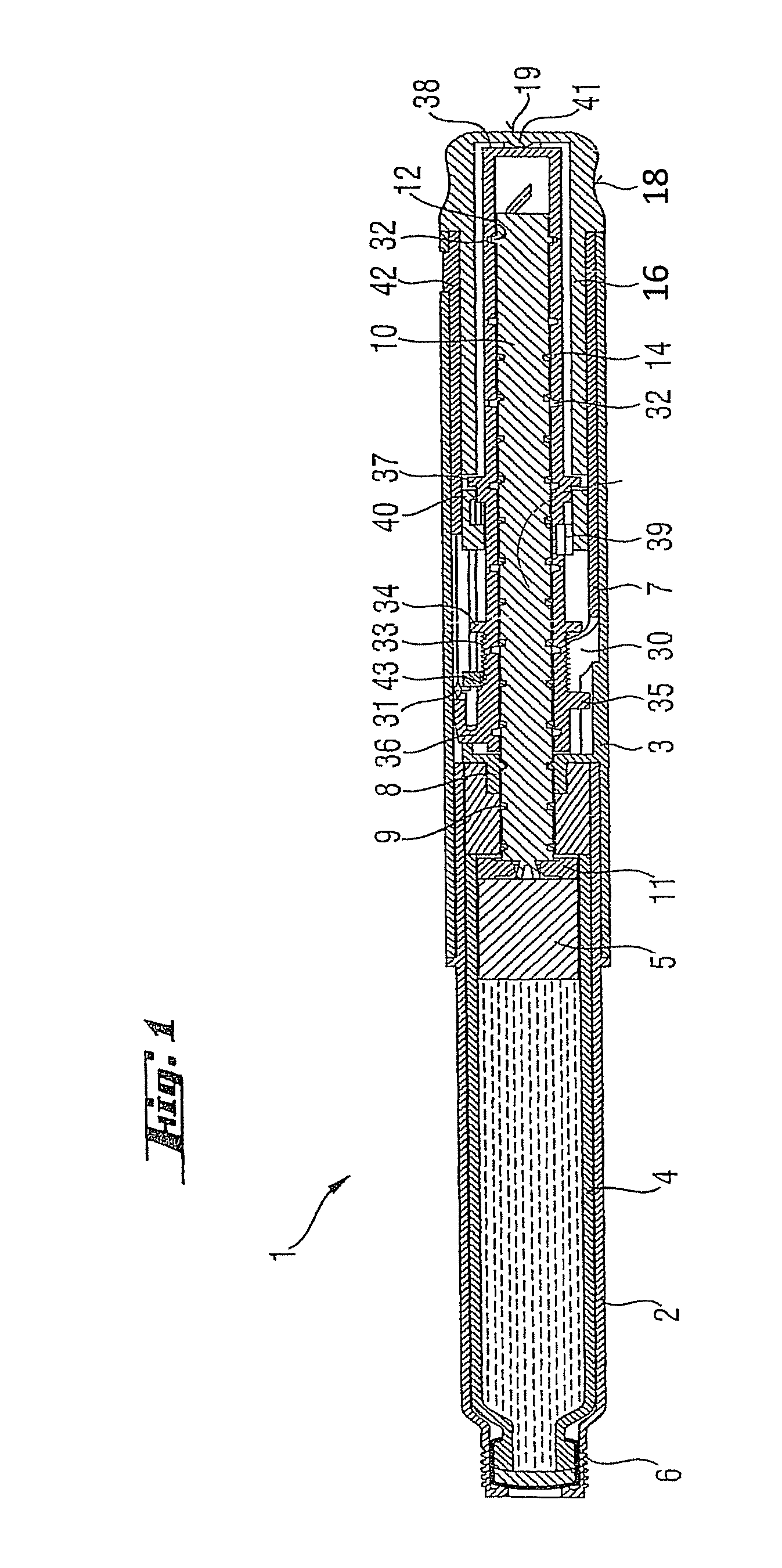
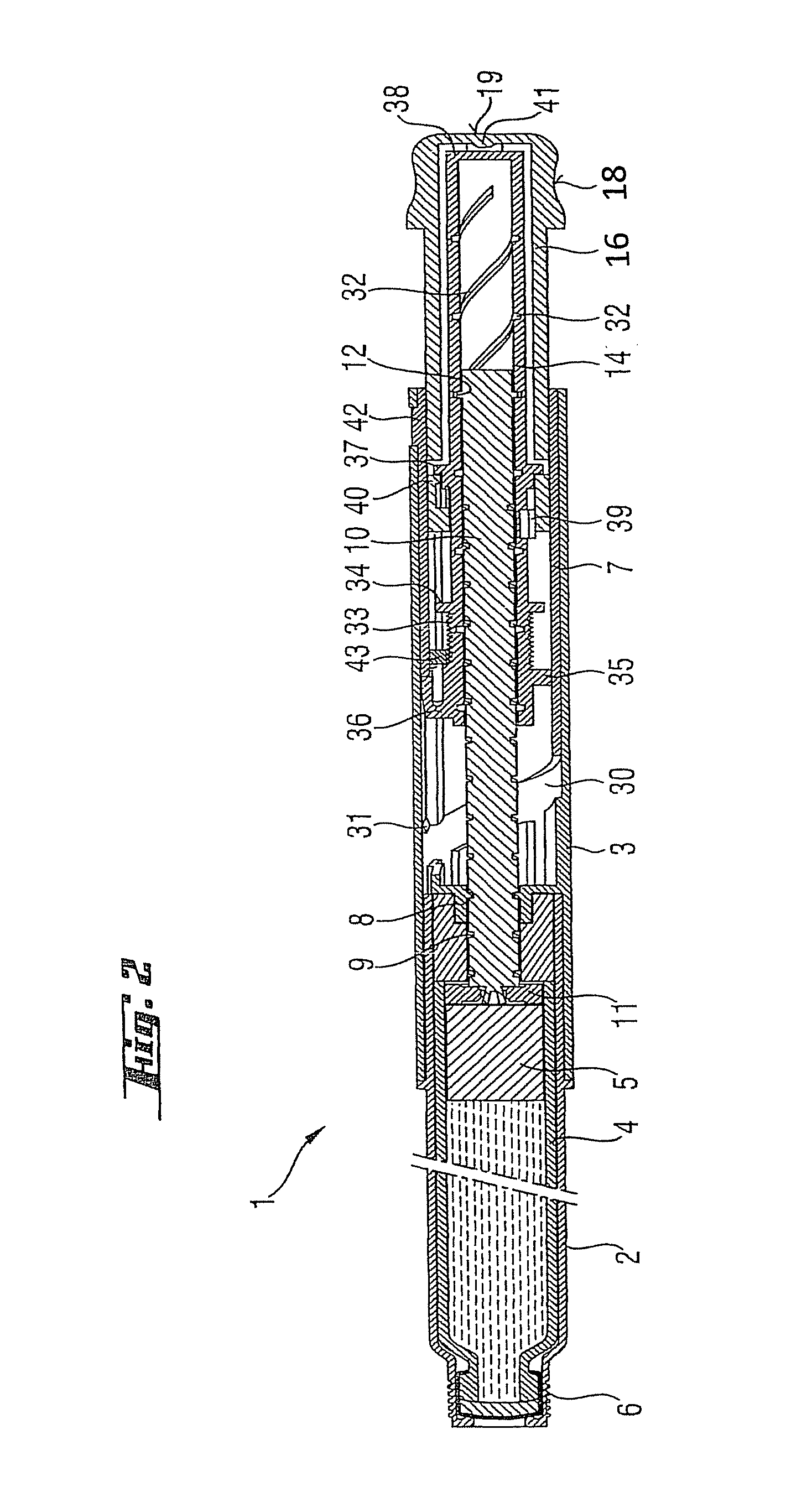
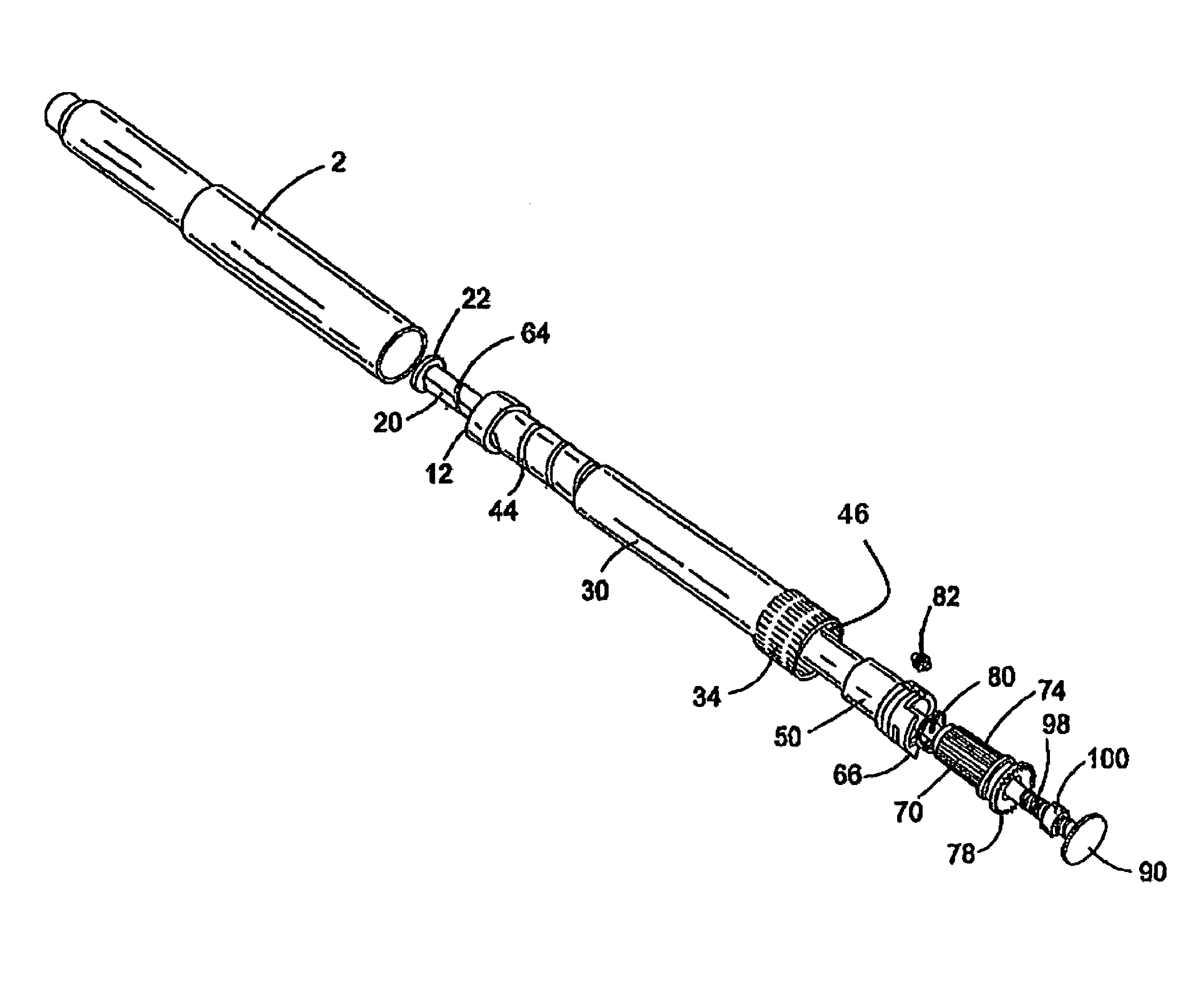
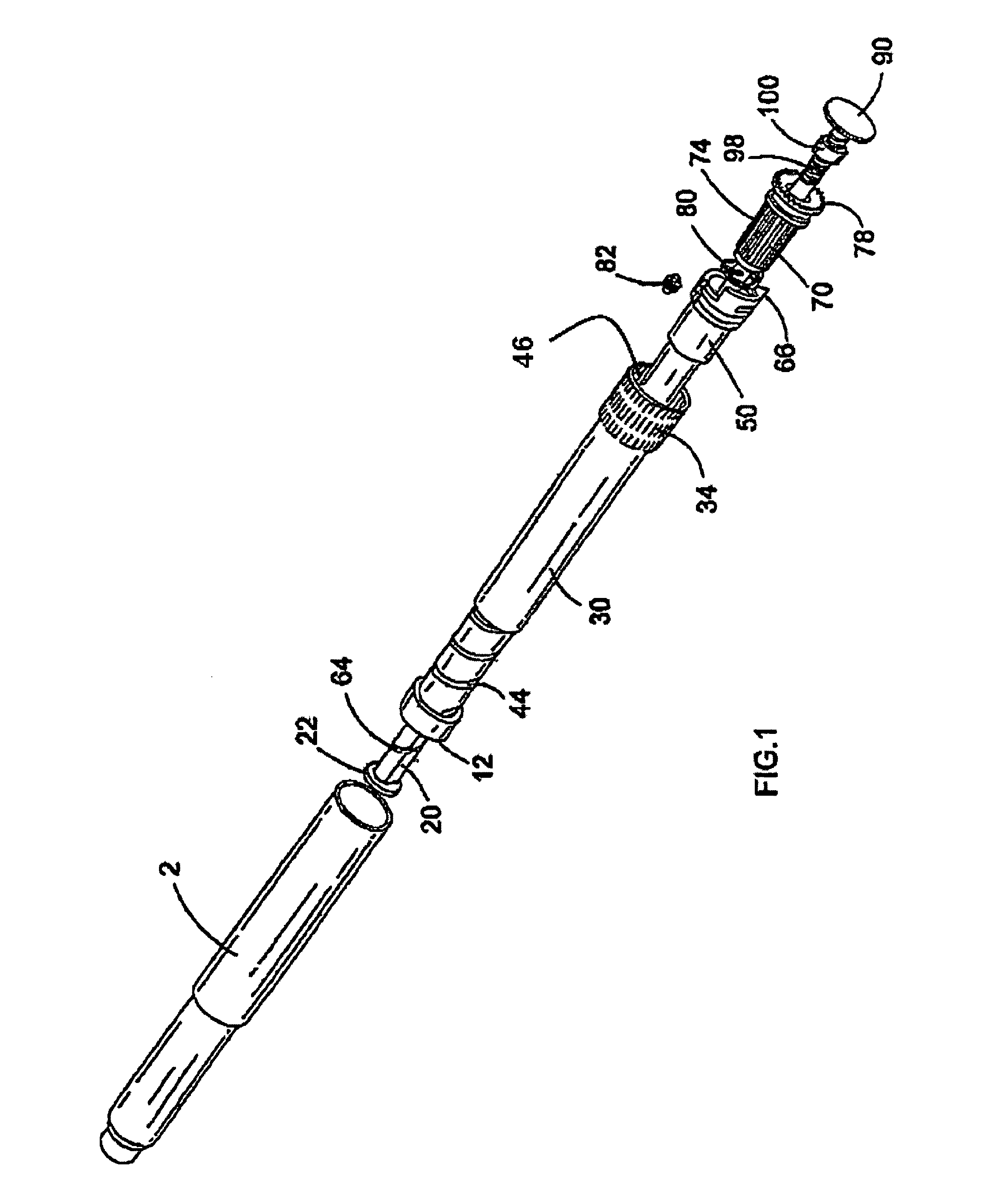
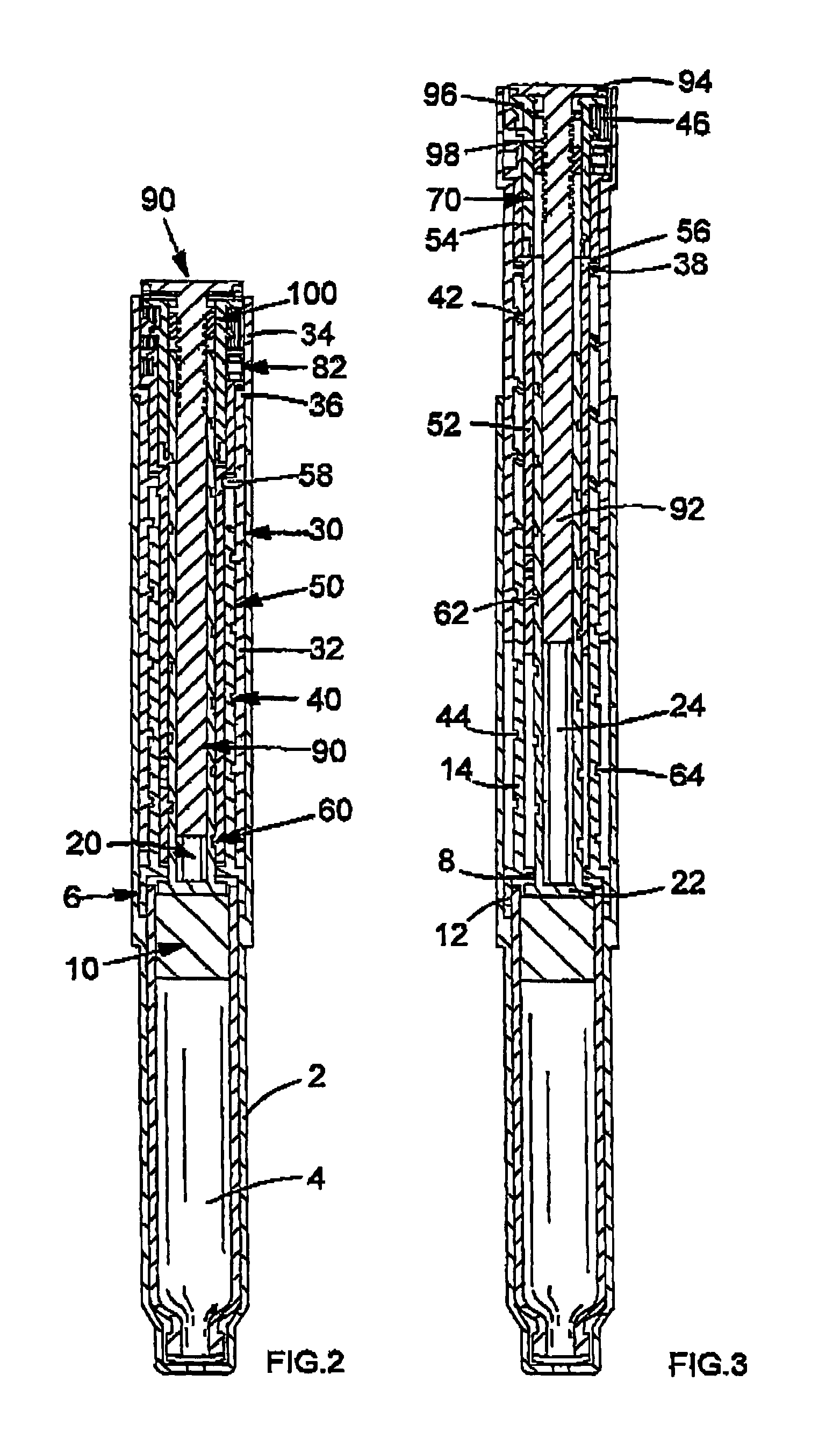
InactiveUS20050033244A1Safe and correct and comfortable handlingExposure was also limitedAmpoule syringesMedical devicesBiomedical engineeringClutch
A drive mechanism suitable for use in drug delivery devices is disclosed. The drive mechanism may be used with injector-type drug delivery devices, such as those permitting a user to set the delivery dose. The drive mechanism may include a housing, a dose dial sleeve, and a drive sleeve. A clutch is configured to permit rotation of the drive sleeve and the dose dial sleeve with respect to the housing when the dose dial sleeve and drive sleeve are coupled through the clutch. Conversely, when the dose dial sleeve and drive sleeve are in a de-coupled state, rotation of the dose dial sleeve with respect to the housing is permitted and rotation of the drive sleeve with respect to the housing is prevented. In the de-coupled state, axial movement of the drive sleeve transfers force in a longitudinal direction for actuation of a drug delivery device.
Owner:SANOFI AVENTIS DEUT GMBH
Drive mechanisms suitable for use in drug delivery devices
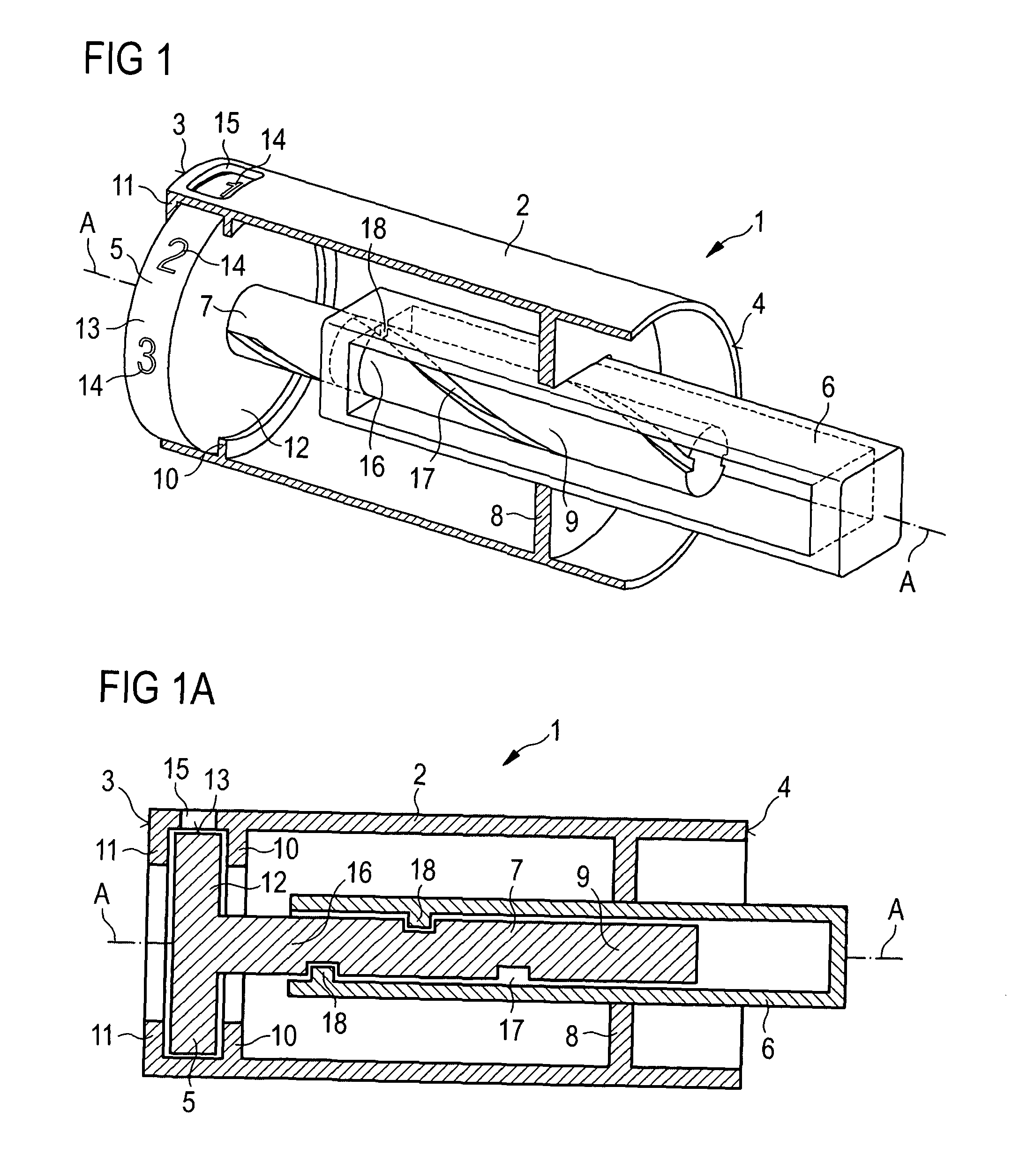
ActiveUS20070093761A1Safe and correct and comfortable handlingExposure was also limitedAmpoule syringesMedical devicesBiomedical engineeringClutch
A drive mechanism suitable for use in drug delivery devices is disclosed. The drive mechanism may be used with injector-type drug delivery devices, such as those permitting a user to set the delivery dose. The drive mechanism may include a housing, a dose dial sleeve, and a drive sleeve. A clutch is configured to permit rotation of the drive sleeve and the dose dial sleeve with respect to the housing when the dose dial sleeve and drive sleeve are coupled through the clutch. Conversely, when the dose dial sleeve and drive sleeve are in a de-coupled state, rotation of the dose dial sleeve with respect to the housing is permitted and rotation of the drive sleeve with respect to the housing is prevented. In the de-coupled state, axial movement of the drive sleeve transfers force in a longitudinal direction for actuation of a drug delivery device.
Owner:SANOFI AVENTIS DEUT GMBH
Biochip electroporator and its use in multi-site, single-cell electroporation
InactiveUS20090163140A1Exposure was also limitedMeet growth needsTransmission systemsSubstation equipmentEmbedded systemEngineering
A remote access and control system for remotely controlling a wide variety of devices using an application installed in a cell phone in conjunction with a control module in communication with the cell phone and the device(s). A portal-based access and control system is also disclosed.
Owner:PACKHAM DONALD L +3
System and method for the pretreatment of the endplates of an intervertebral disc
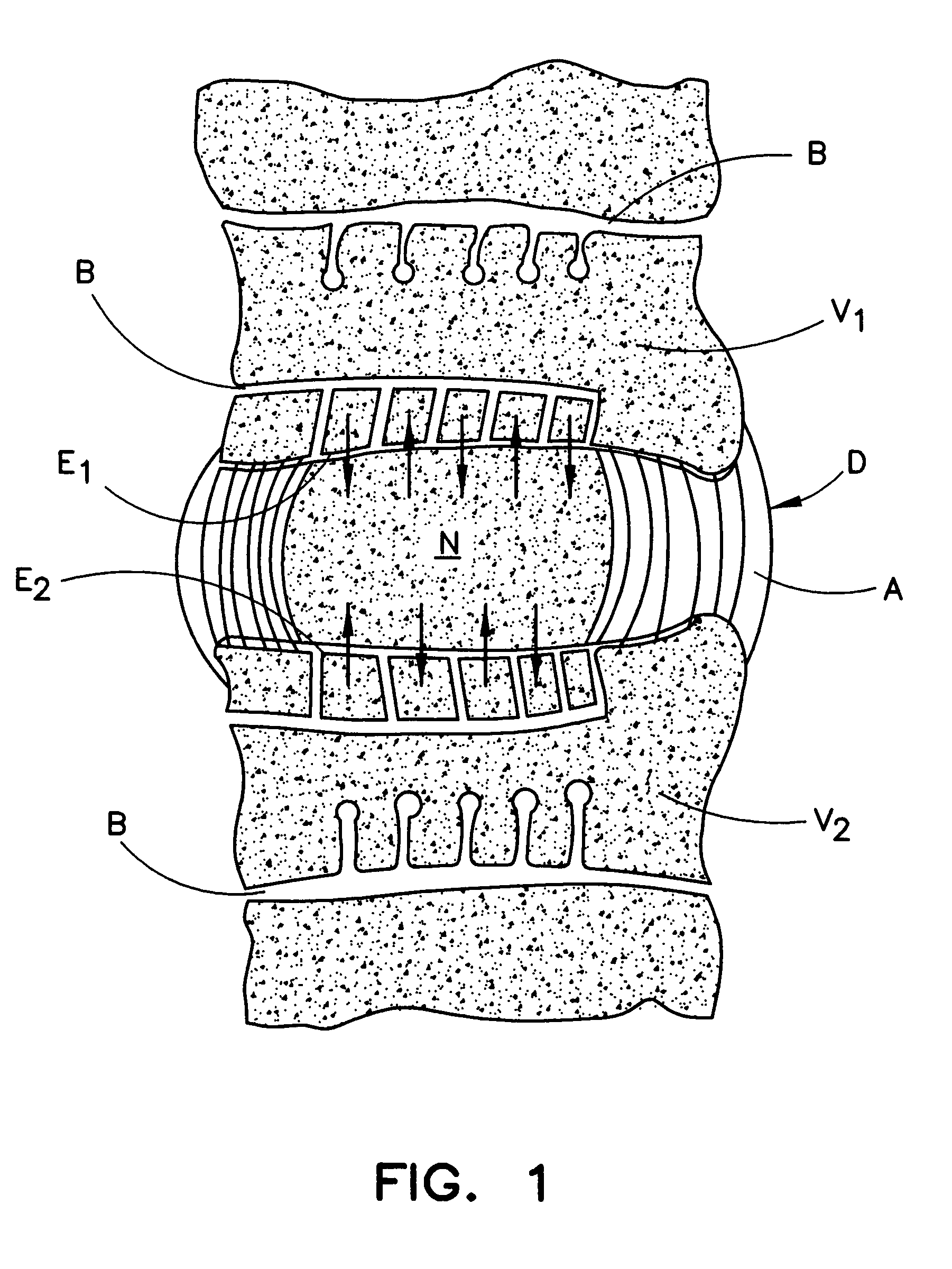
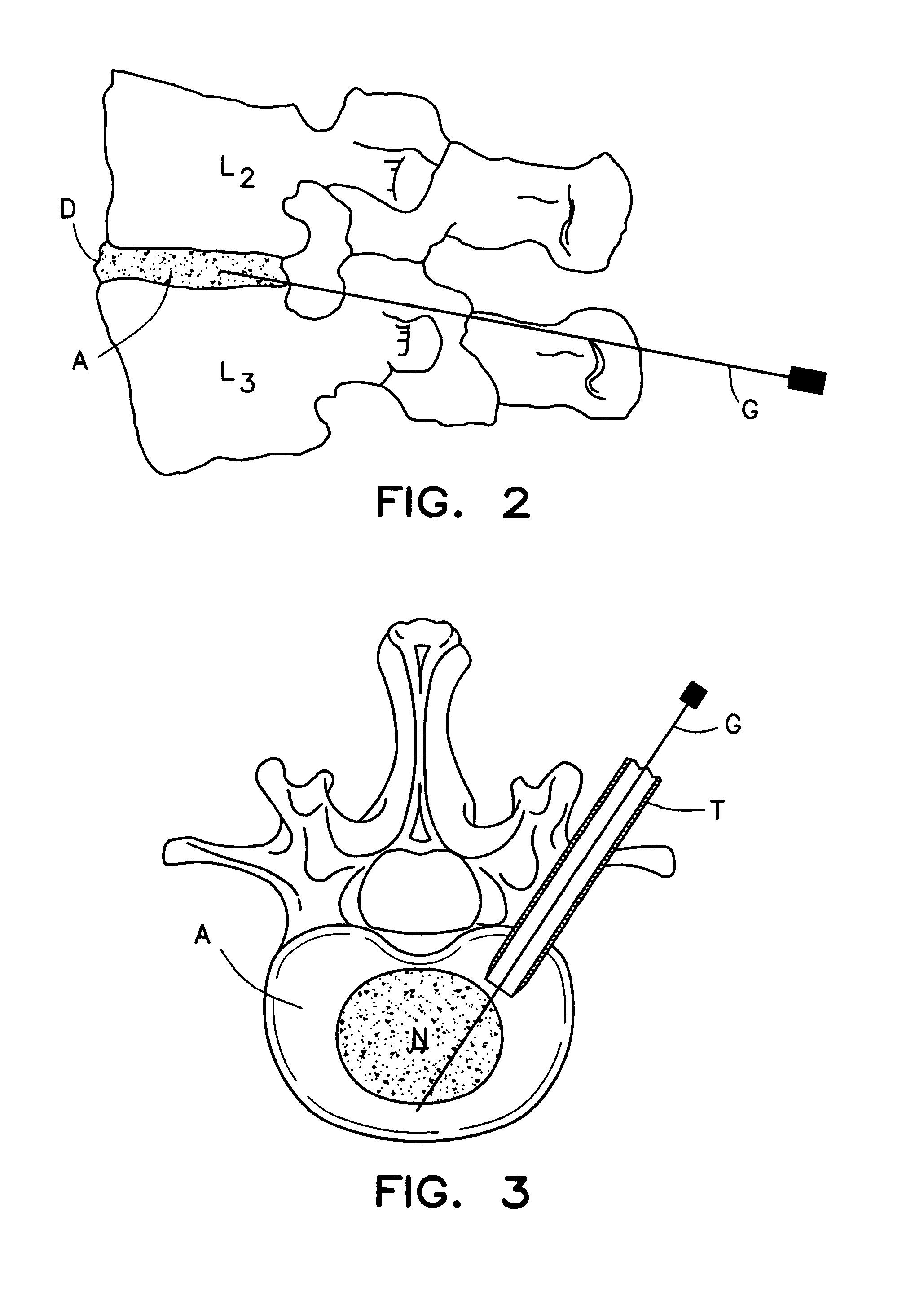
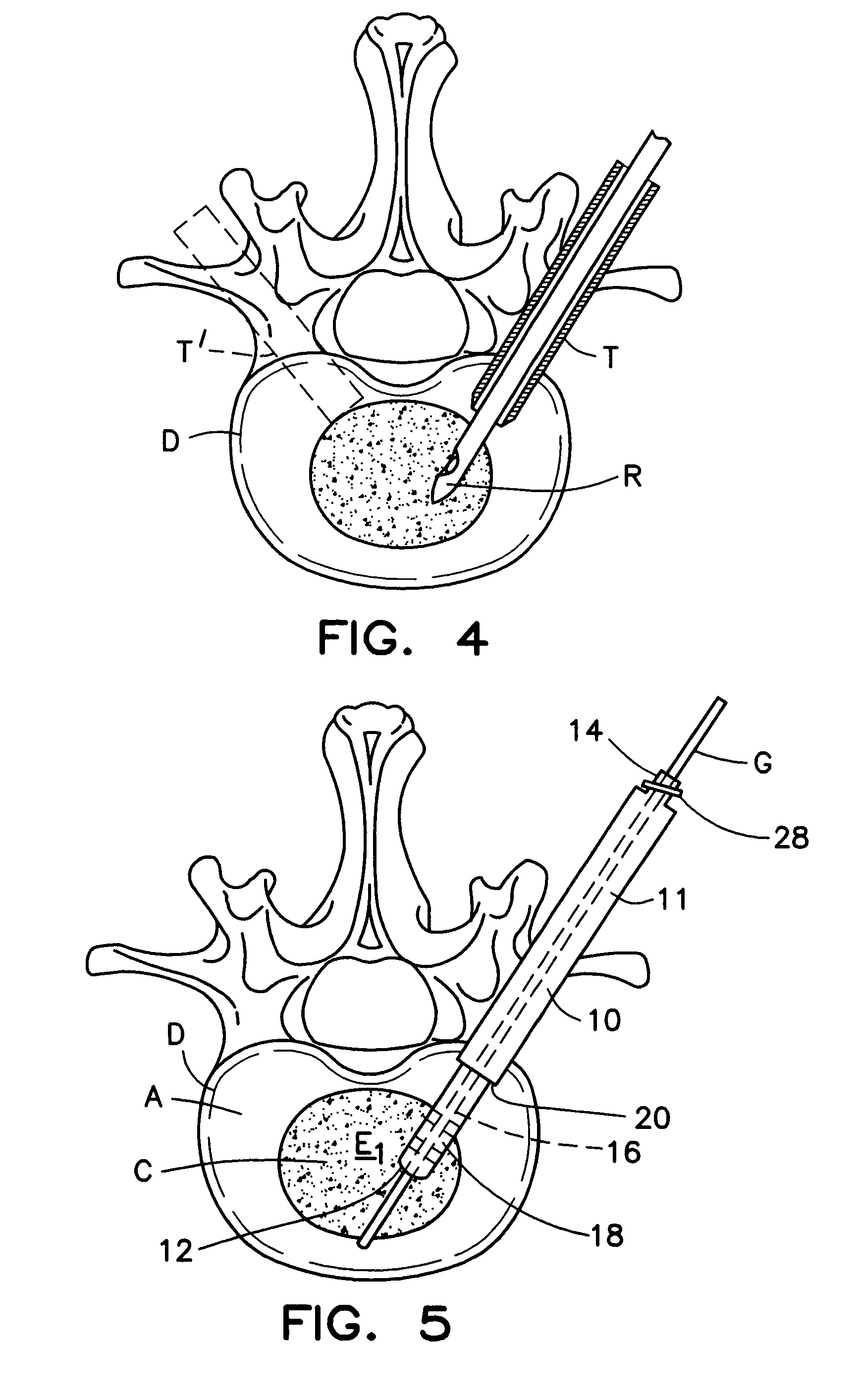
InactiveUS20050130929A1Avoid contactImprove cell migration characteristicOrganic active ingredientsBiocideCompact discLamina terminalis
A method for the pre-treatment of an intervertebral disc prior to the introduction of a disc prosthesis or implant includes removing at least a portion of the nucleus pulposus of the intervertebral disc to expose at least a portion of the endplate of an adjacent vertebra to the disc. A fluent treatment material is then injected into the disc space to come into contact with the portion of the endplate. The fluent treatment material is operable to prepare the portion of the endplate to accommodate a disc prosthesis, implant or graft subsequently introduced into the disc space. Different fluent treatment materials are provided that depend upon the condition of the vertebral endplates.
Owner:SPINEWAVE
Drive mechanisms suitable for use in drug delivery devices
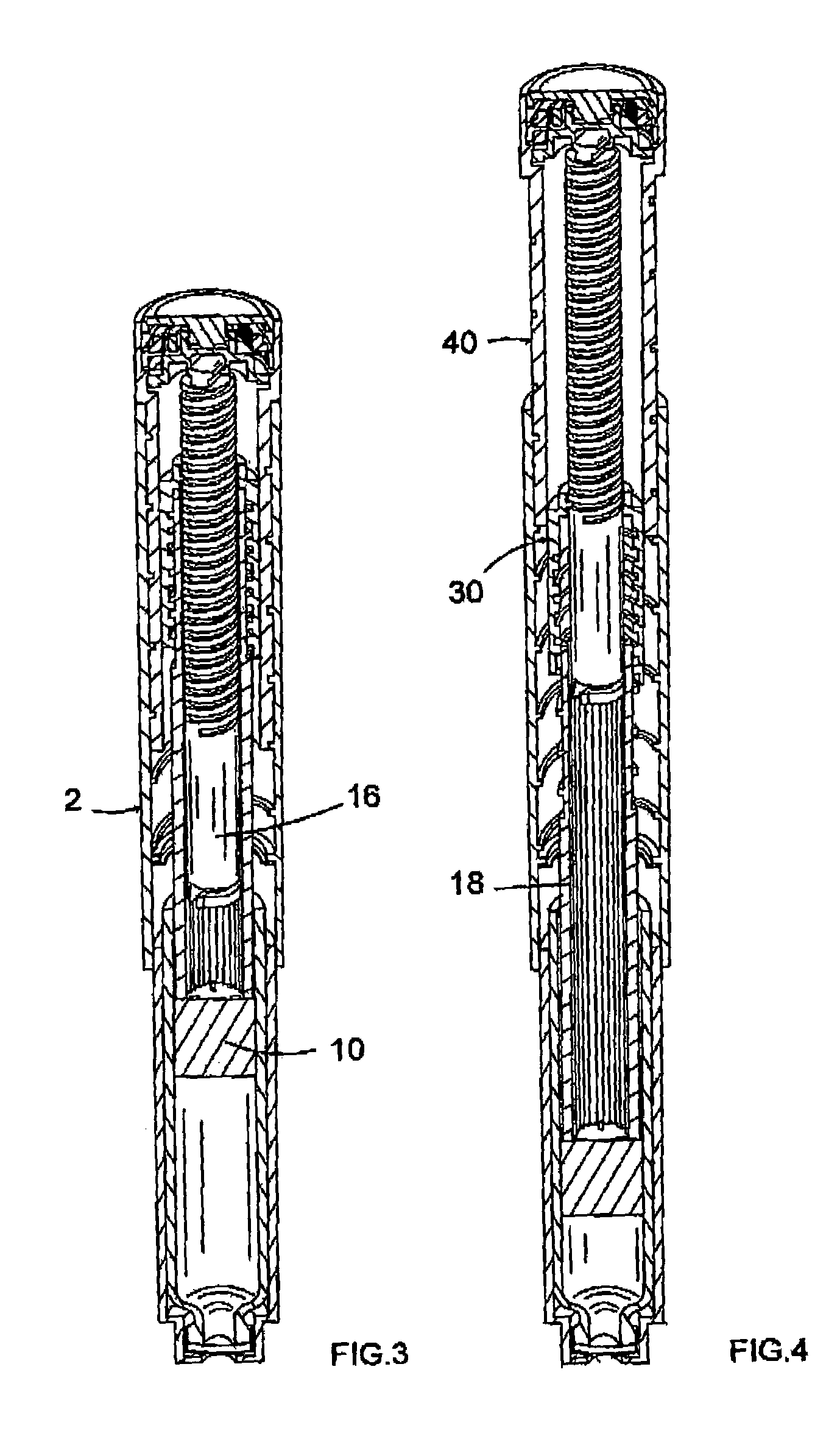
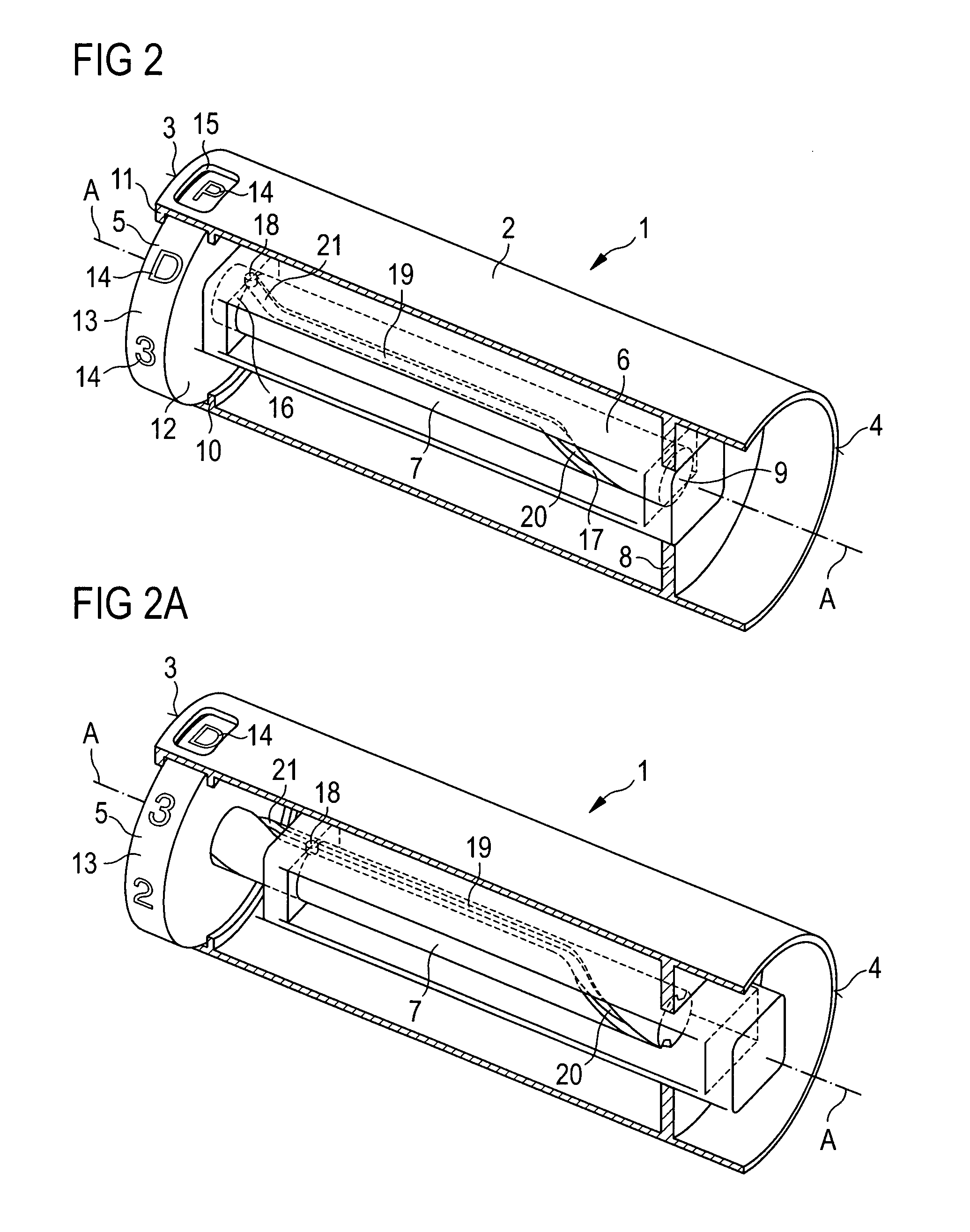
ActiveUS7094221B2Safe and correct and comfortable handlingExposure was also limitedInfusion syringesMedical devicesScrew threadPiston rod
A drive mechanism suitable for use in drug delivery devices is disclosed. The drive mechanism may be used with injector-type drug delivery devices, such as those permitting a user to set the delivery dose. The drive mechanism may include a housing, a dose dial sleeve having a helical thread of a first lead, and a two-part piston rod. The two-part piston rod may include an outer part having a helical thread of a second lead and an inner part having a helical thread of a third lead. In such an embodiment, the first lead of the thread of the dose dial sleeve may be equal to the sum of the second lead of the thread of the outer part of the piston rod and the third lead of the thread of the inner part of the piston rod.
Owner:SANOFI AVENTIS DEUT GMBH
Apparatus for mixing and dispensing components
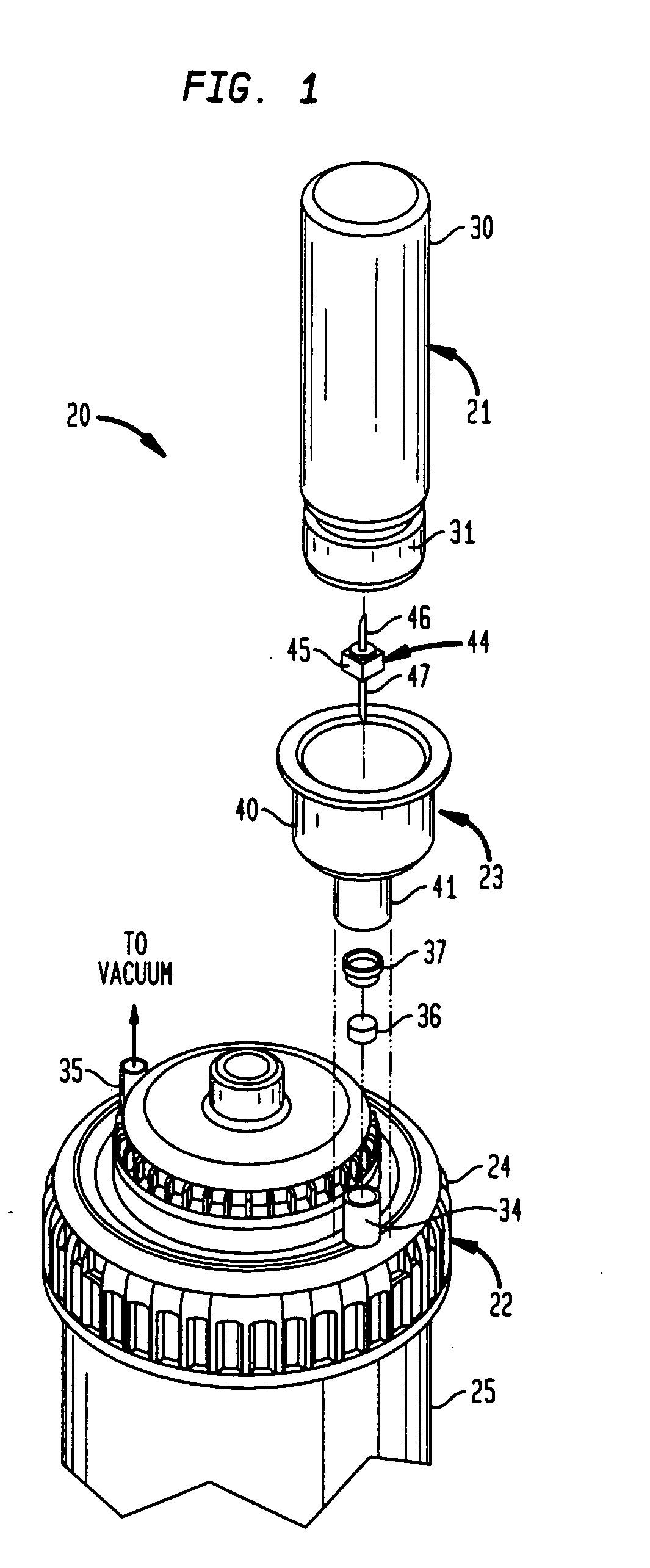
InactiveUS20040196735A1Exposure was also limitedReduce in quantitySurgical furnitureRotary stirring mixersEngineeringBone cement
Apparatus and methods for mixing and dispensing components. The methods and apparatus of the invention are particularly advantageous to manually mix the components of radiopaque bone cement and inject the resulting radiopaque bone cement into skeletal structures. The manually actuated apparatus of the invention comprises: (1) a sealed mixing chamber for mixing components; (2) a dispensing chamber isolated from the sealed mixing chamber; (3) a controllable portal to open a flow path between the sealed mixing chamber and the dispensing chamber so that the dispensing chamber can receive the mixed components after they are mixed; and (4) a drive mechanism associated with the dispensing chamber to force the mixed contents from the dispensing chamber.
Owner:GLOBUS MEDICAL INC
Apparatus and method for monitoring tissue vitality parameters
Apparatus for monitoring a plurality of tissue viability parameters of a tissue layer element, in which two different illumination sources are used via a common illumination element in contact with the tissue. One illumination source is used for monitoring blood flow rate and optionally flavoprotein concentration, and collection fibers are provided to receive the appropriate radiation from the tissue. The other illuminating radiation is used for monitoring any one of and preferably all of NADH, blood volume and blood oxygenation state of the tissue element, and collection fibers are provided to receive the appropriate radiation from the tissue. In one embodiment, the wavelengths of the two illumination sources are similar, and common collection fibers for the two illuminating radiations are used. In another embodiment, the respective collection fibers are distanced from the illumination point at different distances correlated to the ratio of the first and second illuminating wavelengths.
Owner:CRITISENSE
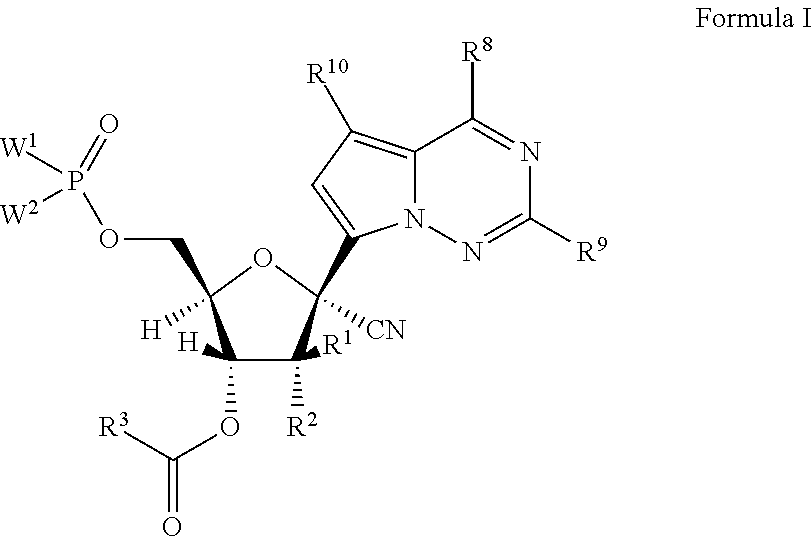
1'-substituted-carba-nucleoside prodrugs for antiviral treatment
ActiveUS20120020921A1Exposure was also limitedEfficient extractionSaccharide with heterocyclic radicalsBiocidePhosphateSugar
Provided are prodrugs of pyrrolo[1,2-f][1,2,4]triazin-7-yl nucleoside phosphates wherein the 1′ position of the nucleoside sugar is substituted with CN. The compounds, compositions, and methods provided are useful for the treatment Hepatitis C infections.
Owner:GILEAD SCI INC
Drive mechanisms suitable for use in drug delivery devices
InactiveUS20050004529A1Safe and correct and comfortable handlingExposure was also limitedAmpoule syringesIntravenous devicesEngineeringScrew thread
A drive mechanism for use in a drug delivery device comprising an epicyclic gearbox. This drive mechanism includes a housing having a helical thread; a piston rod having a non-circular cross section and an external helical thread; a dose dial sleeve, which is threadedly engaged with the housing and being rotatable with respect to the housing; and a drive sleeve, located between the housing and the piston rod, which is threadedly engaged with the piston rod.
Owner:SANOFI AVENTIS DEUT GMBH
Bicompartmental implants and method of use
InactiveUS7520901B2Facilitate proper alignment and orientationRestores individual patient joint kinematicsJoint implantsFemoral headsAnatomical structuresArticular surfaces
The present invention provides a method and device for restoring individual patient joint kinematics using minimally invasive surgical procedures. The instrumentation of the invention sculpts the articular surface of a first bone that normally articulates in a predetermined manner with a second bone. The instrumentation includes a bone sculpting tool and a mount for attaching the tool to the second bone. The implant system is comprised of implants that provide intraoperative surgical options for articular constraint and facilitate proper alignment and orientation of the joint to restore kinematics as defined by the individual patient anatomy.
Owner:CAYENNE MEDICAL INC
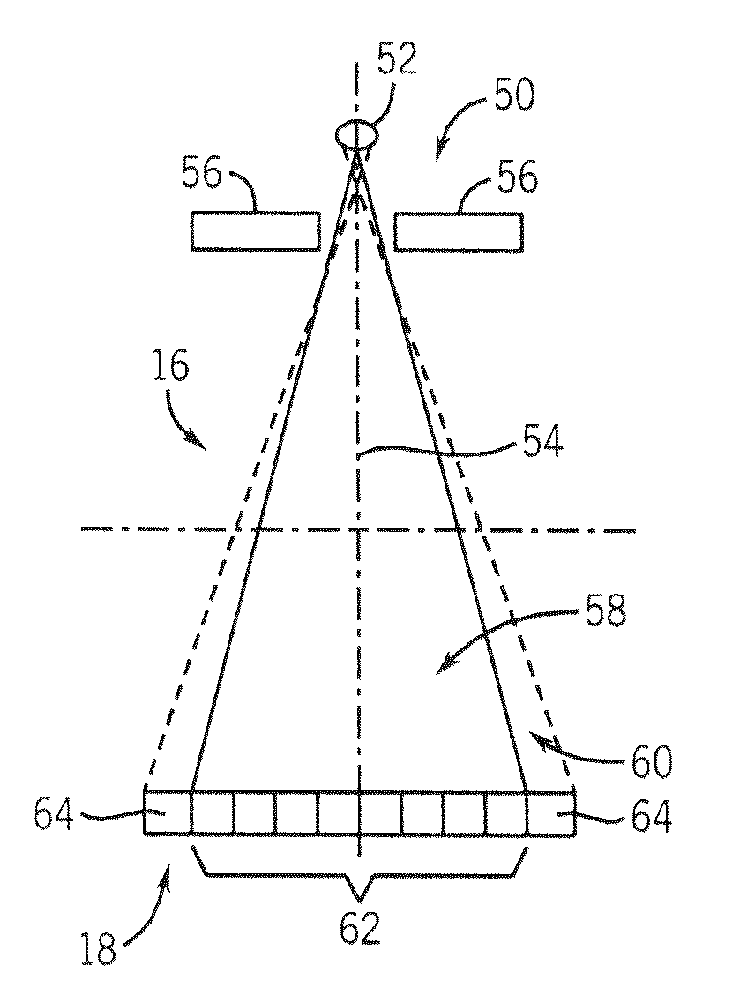
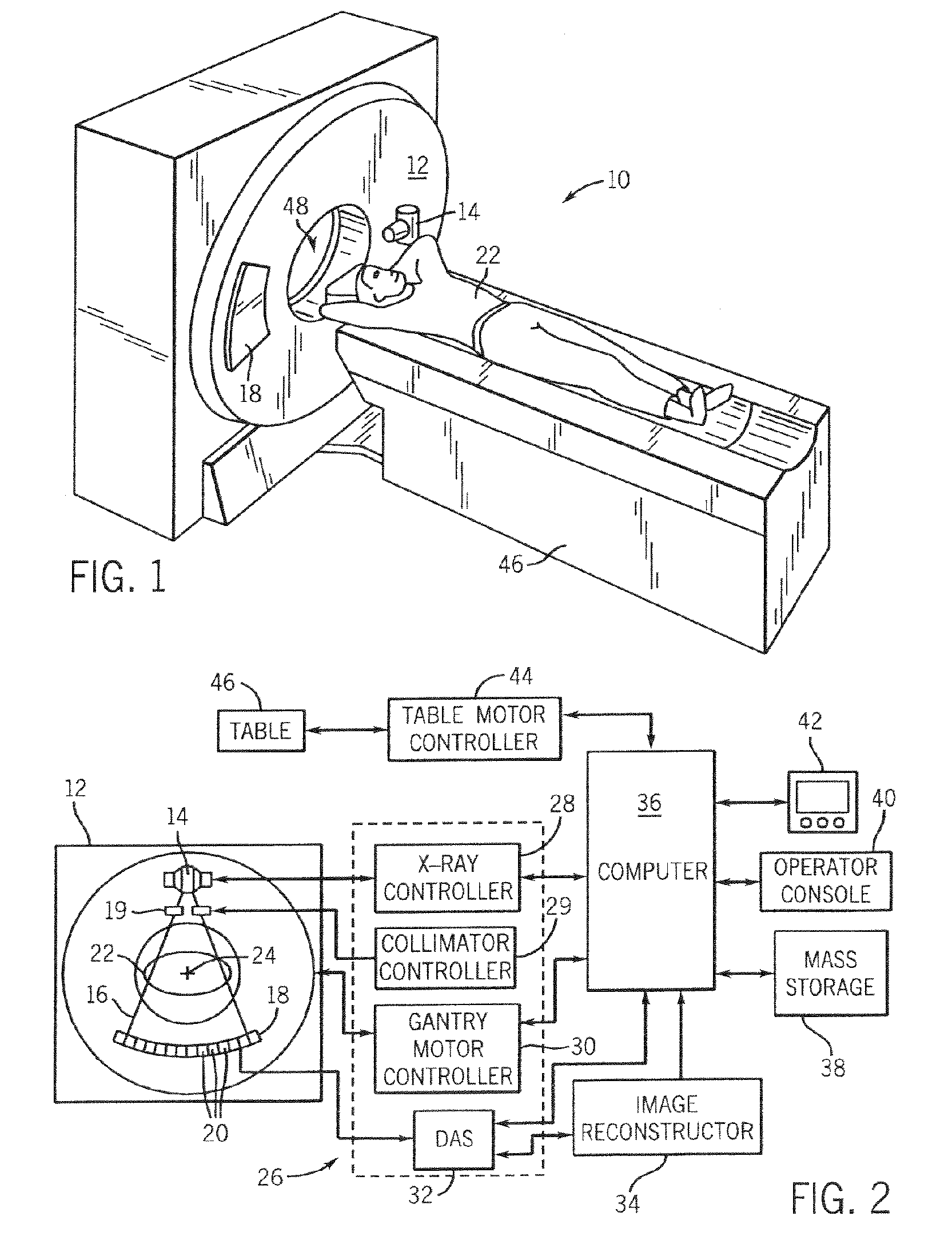
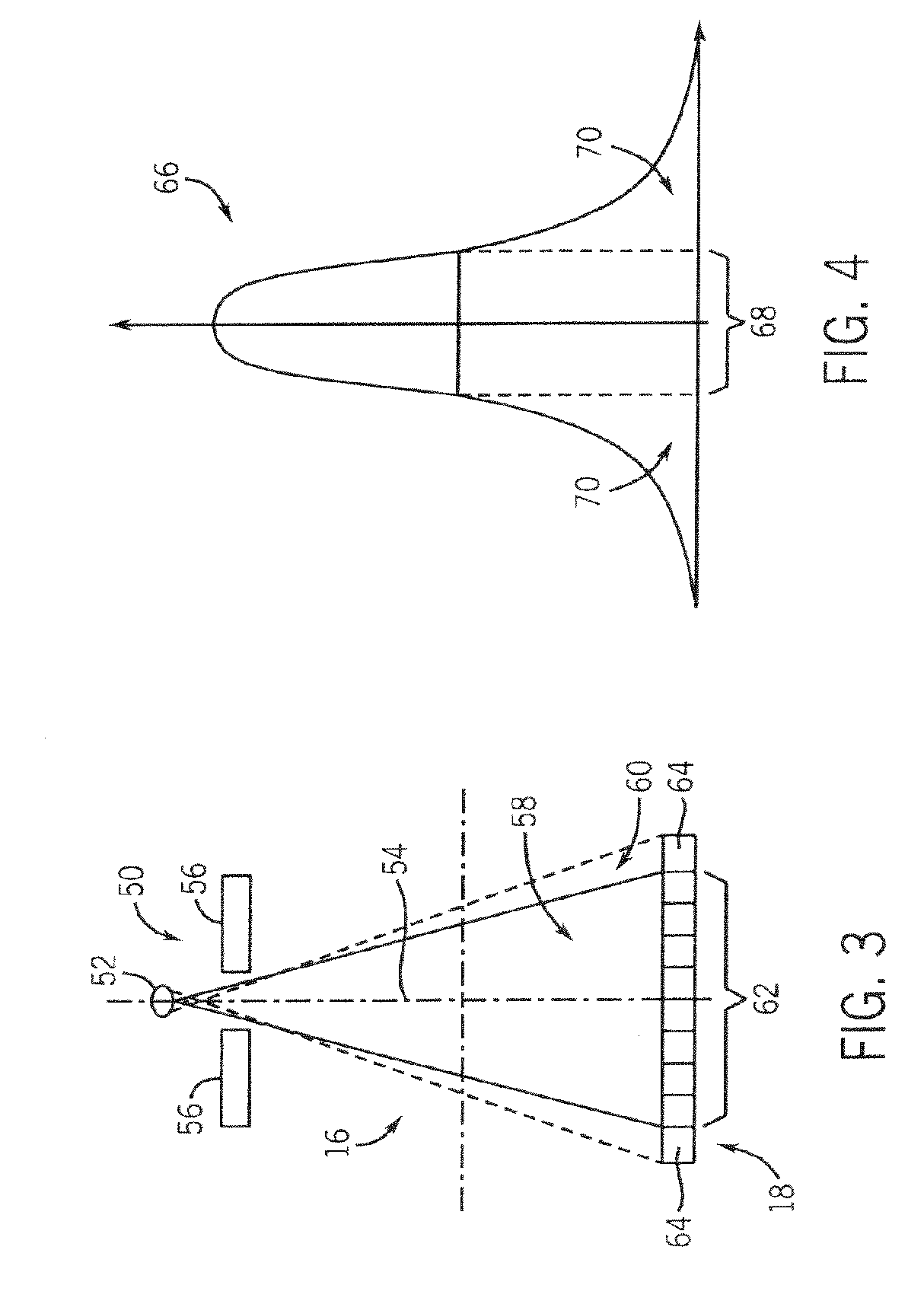
Apparatus for acquisition of CT data with penumbra attenuation calibration
InactiveUS7260171B1Detection sacrificedQuality sacrificedMaterial analysis using wave/particle radiationHandling using diaphragms/collimetersUltrasound attenuationScout Scan
The present invention is a directed method and apparatus for collimating a radiation beam such that the full intensity of the radiation beam does not impinge detectors of a radiation detector assembly that are particularly susceptible to saturation or over-ranging. This collimation can be dynamically adjusted on a per view basis using empirical or scout scan data.
Owner:GENERAL ELECTRIC CO
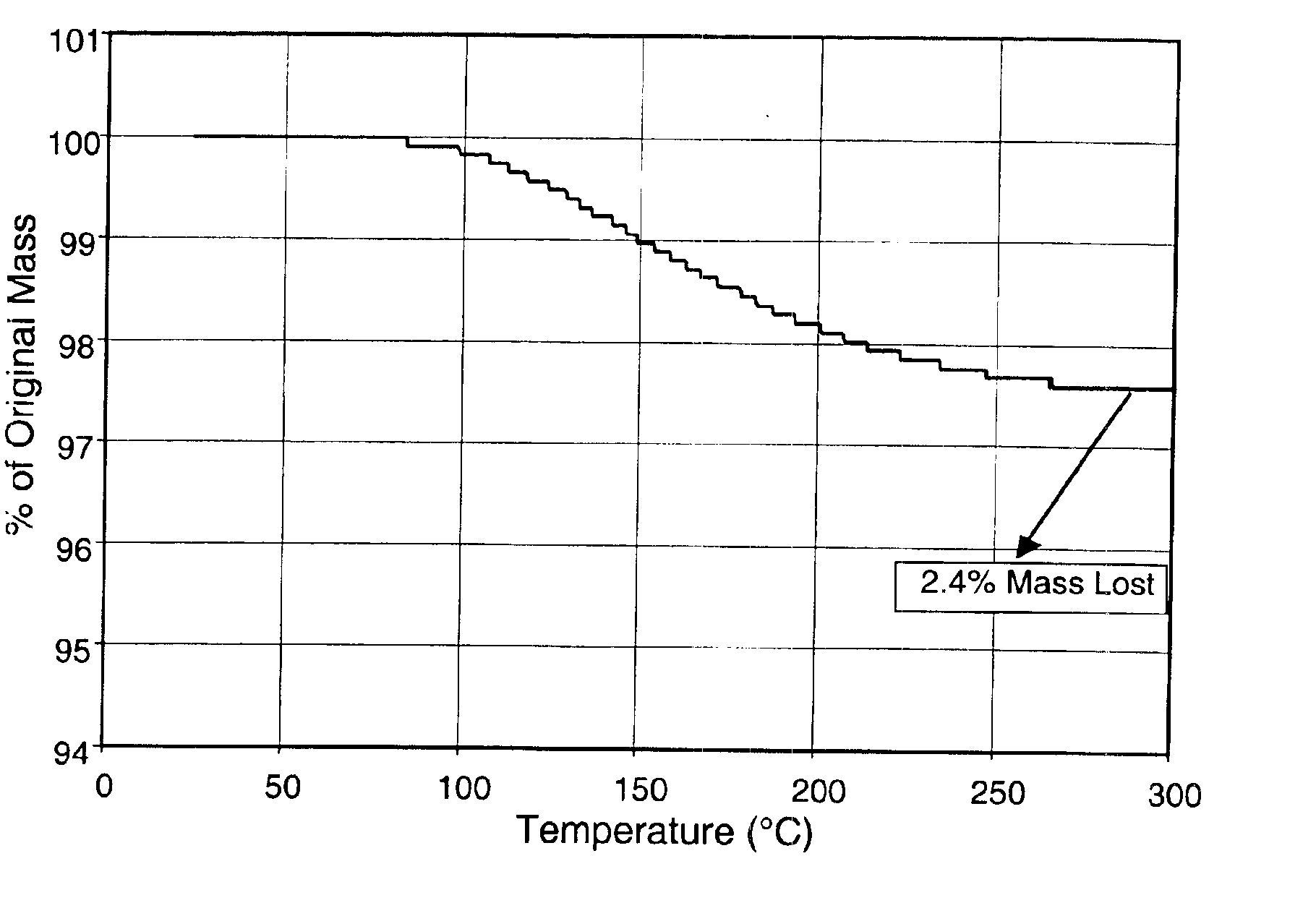
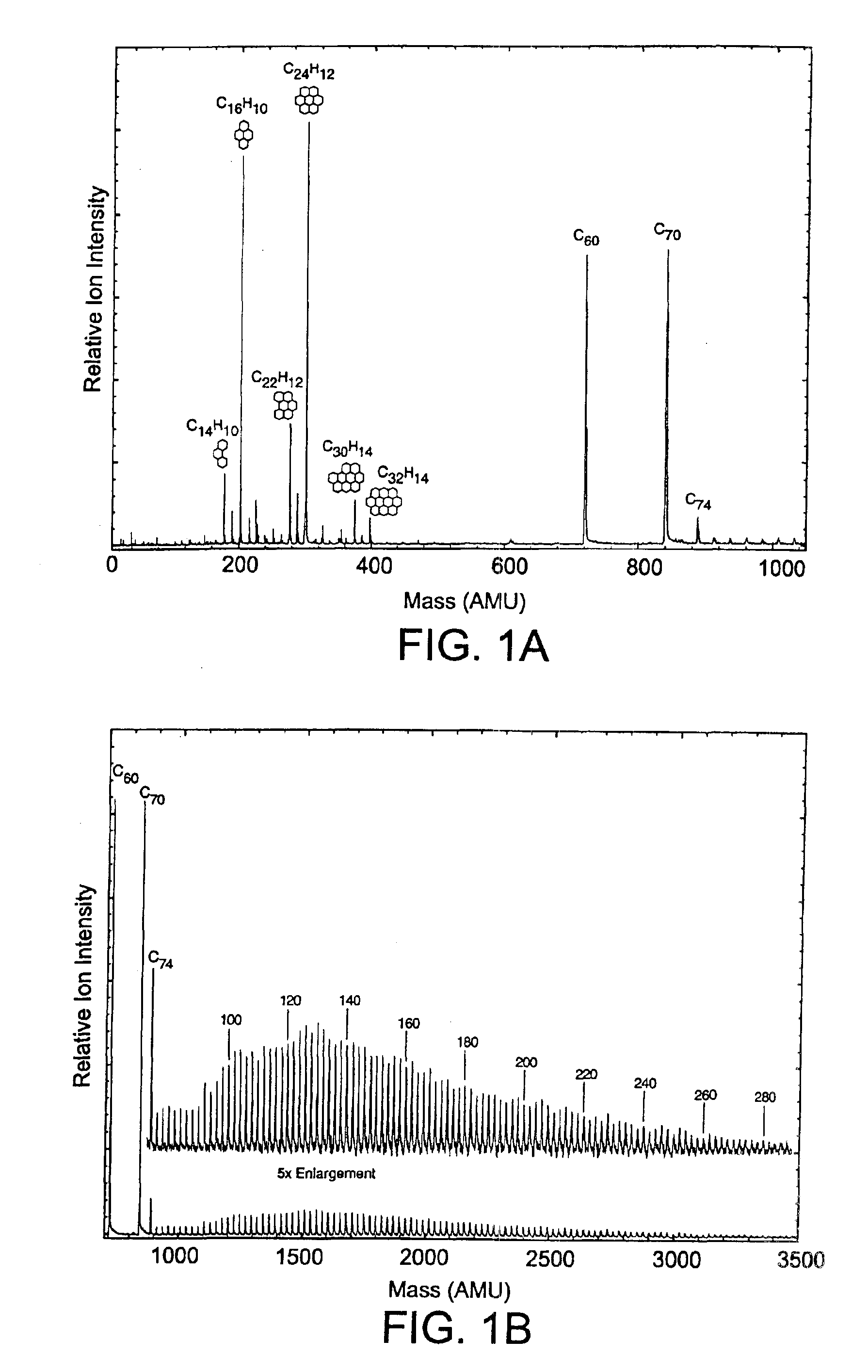
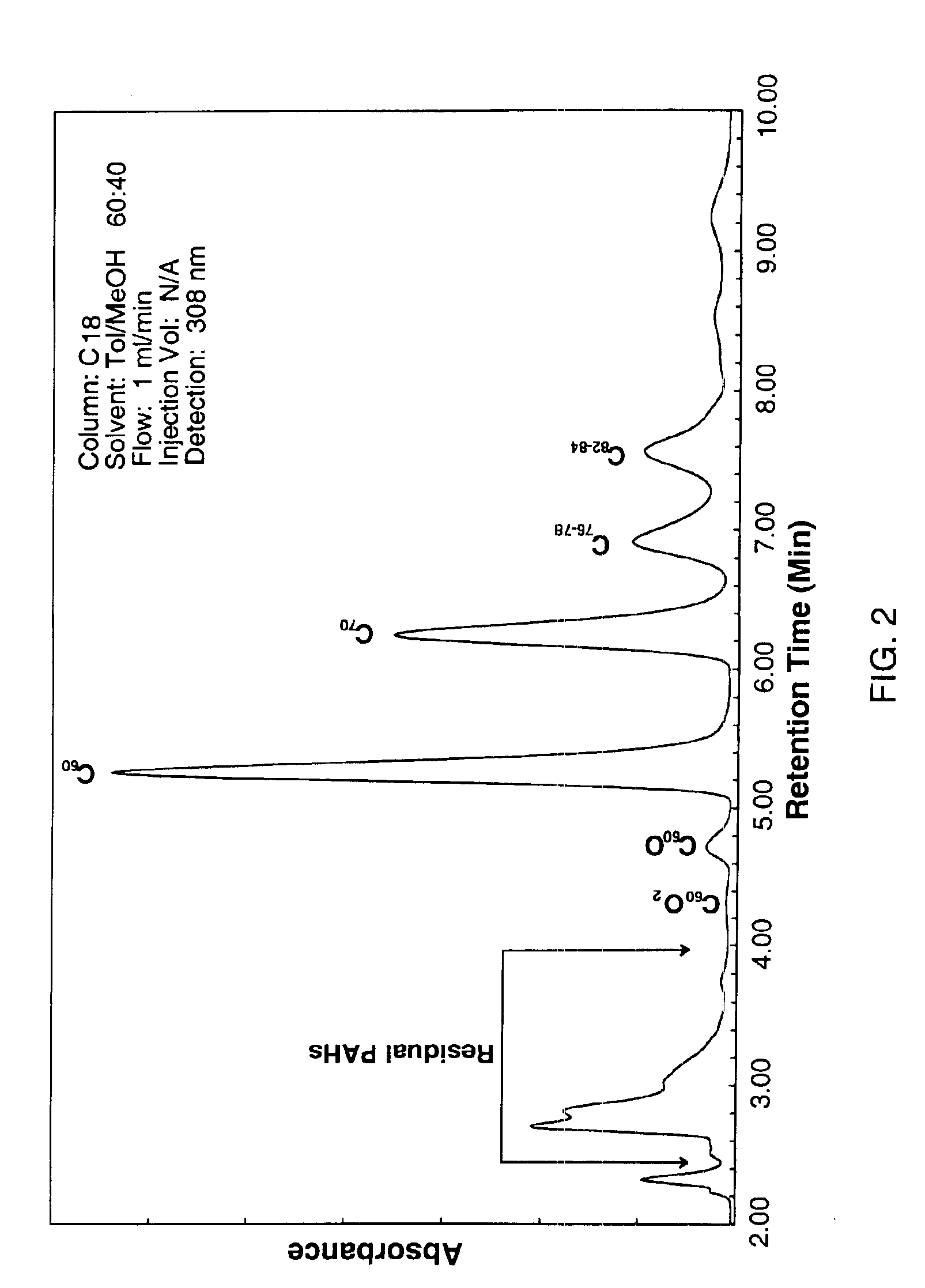
Process for the removal of impurities from combustion fullerenes
InactiveUS6923915B2Without incurring undo costEfficient removalMaterial nanotechnologyFullerenesO-XylenePurification methods
The invention generally relates to purification of carbon nanomaterials, particularly fullerenes, by removal of PAHs and other hydrocarbon impurities. The inventive process involves extracting a sample containing carbon nanomaterials with a solvent in which the PAHs are substantially soluble but in which the carbon nanomaterials are not substantially soluble. The sample can be repeatedly or continuously extracted with one or more solvents to remove a greater amount of impurities. Preferred solvents include ethanol, diethyl ether, and acetone. The invention also provides a process for efficiently separating solvent extractable fullerenes from samples containing fullerenes and PAHs wherein the sample is extracted with a solvent in which both fullerenes and PAHs are substantially soluble and the sample extract then undergoes selective extraction to remove PAHs. Suitable solvents in which both fullerenes and PAHs are soluble include o-xylene, toluene, and o-dichlorobenzene. The purification process is capable of treating quantities of combustion soot in excess of one kilogram and can produce fullerenes or fullerenic soot of suitable purity for many applications.
Owner:FRONTIER CARBON CORP
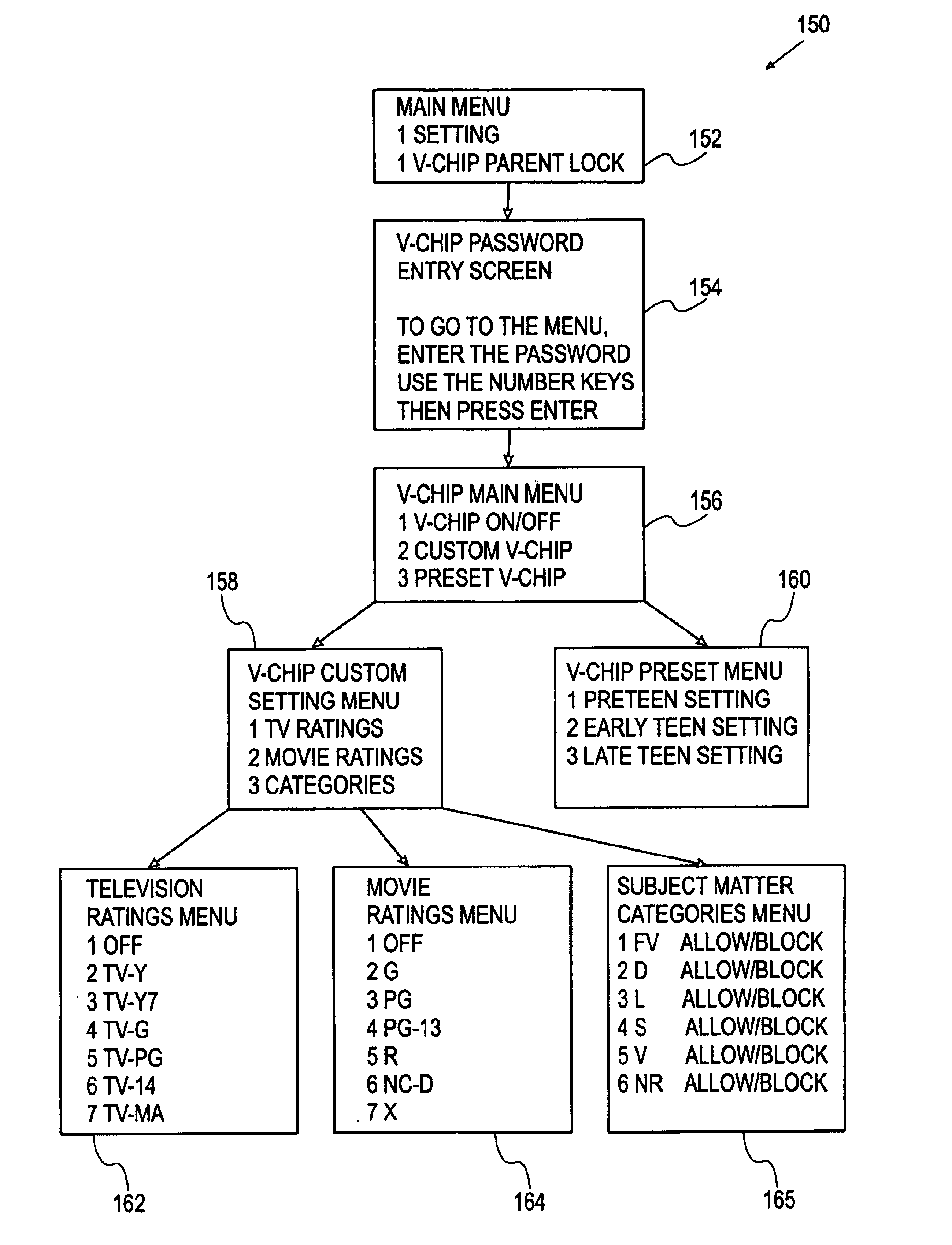
"V-chip" preset criteria
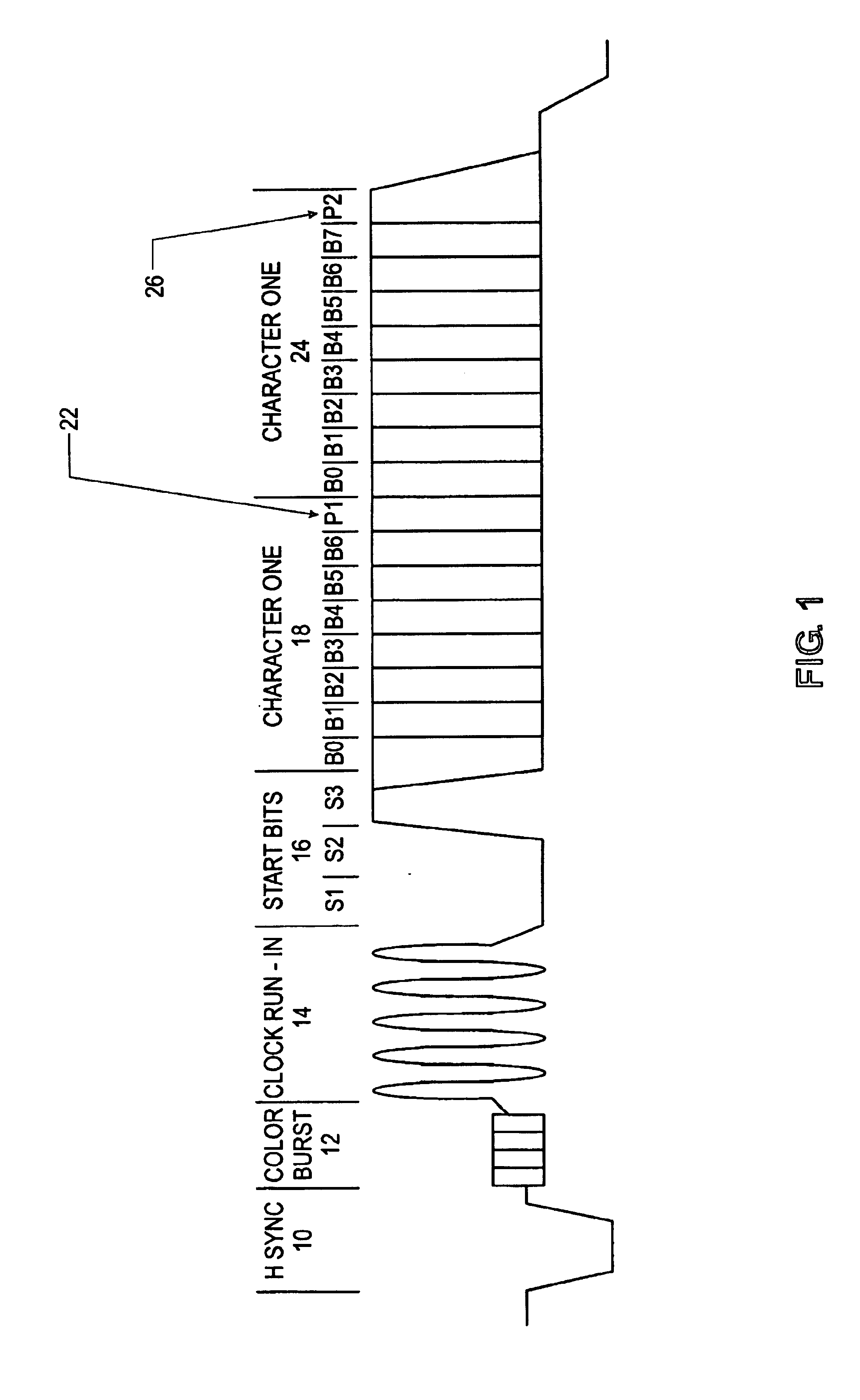
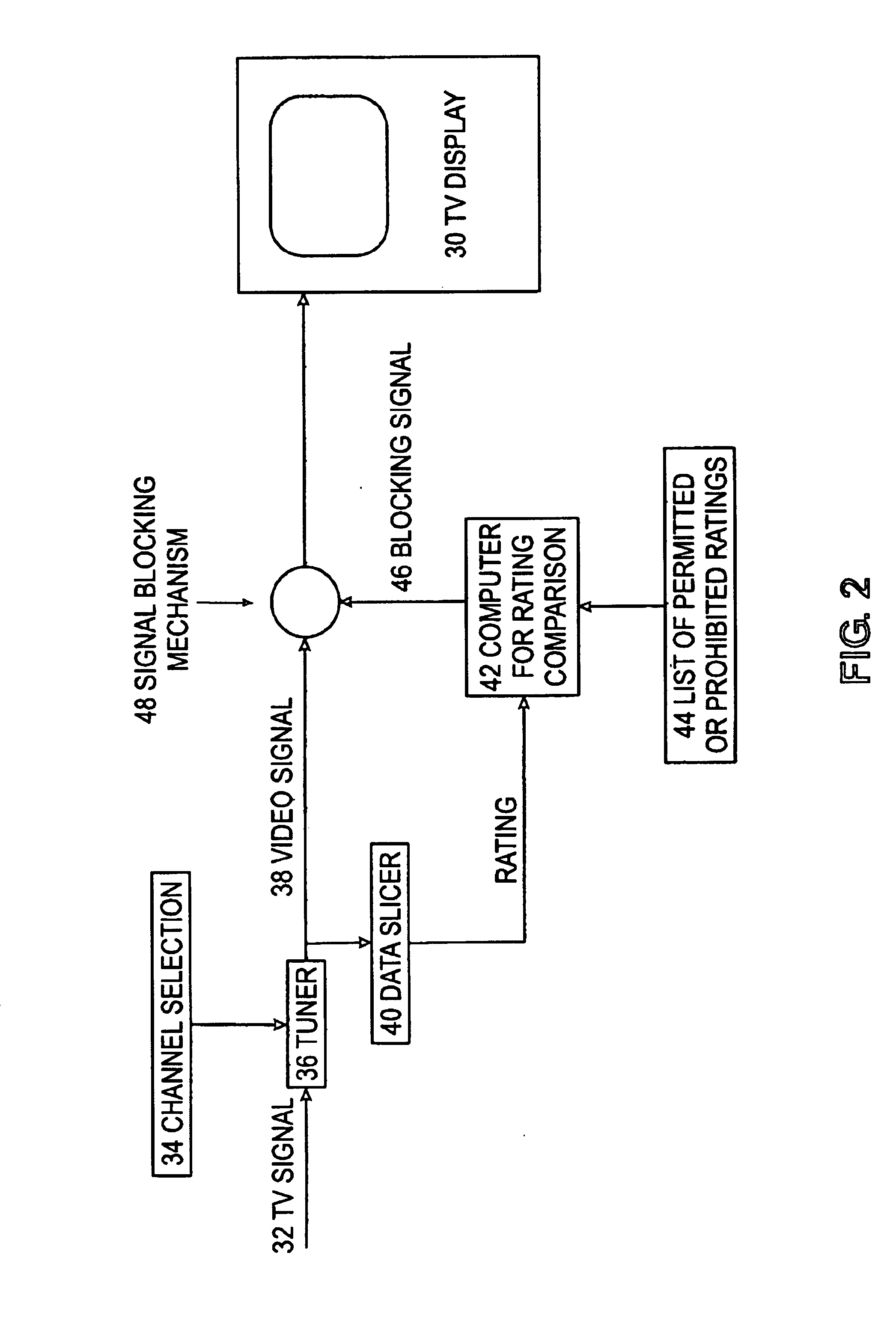
InactiveUS6944876B1Exposure was also limitedChoose simpleTelevision system detailsAnalogue secracy/subscription systemsTelevision systemOutput device
Systems, methods and apparatus are provided for allowing a user to supervise personal exposure to a program exhibited by a consumer electronics device, such as a television system. The consumer electronics device includes “V-chip” circuitry that analyzes a signal and either blocks or passes the signal based on certain content-based criteria. In this connection, a user can program the “V-chip” circuitry with the preset content-based criteria in the form of preset content-based specification sets, which are stored in the consumer electronics device by the manufacturer. The preset content-based specification sets specify either allowable or objectionable content within a program signal received by the consumer electronics device. The “V-chip” circuitry receives a content-based indicator set, which is indicative of the actual content of the program signal. One of the preset content-based specification sets is conveniently selected by a user. The “V-chip” circuitry then compares the content-based indicator set with the selected preset content-based specification set when the program signal is received by the consumer electronics device. Based on this comparison, the “V-chip” circuitry either passes the signal to an output device for transformation of the signal into the program, or blocks the signal from being sent to the output device.
Owner:MITSUBISHI ELECTRIC US
System and method for a business payment connection
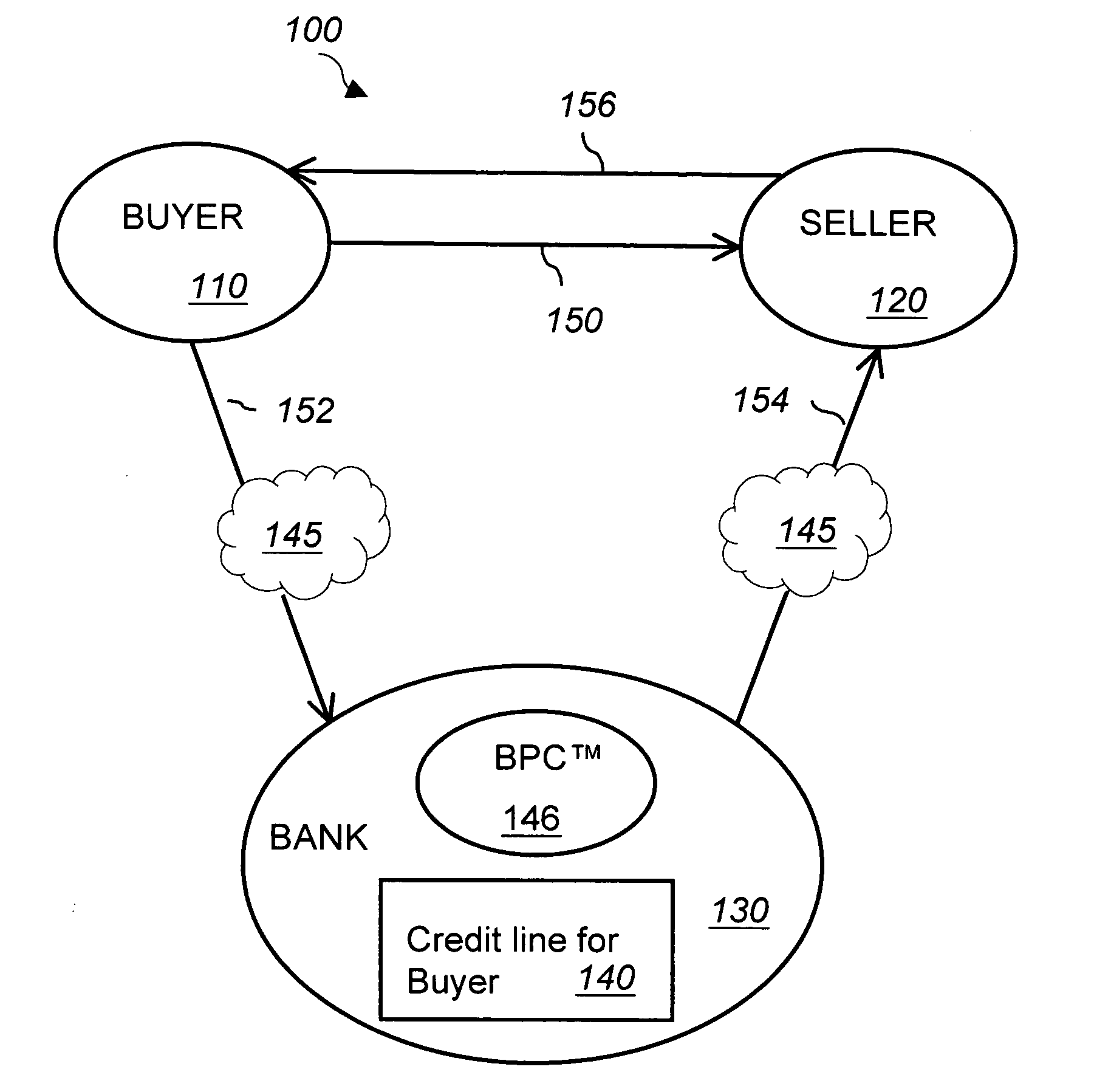
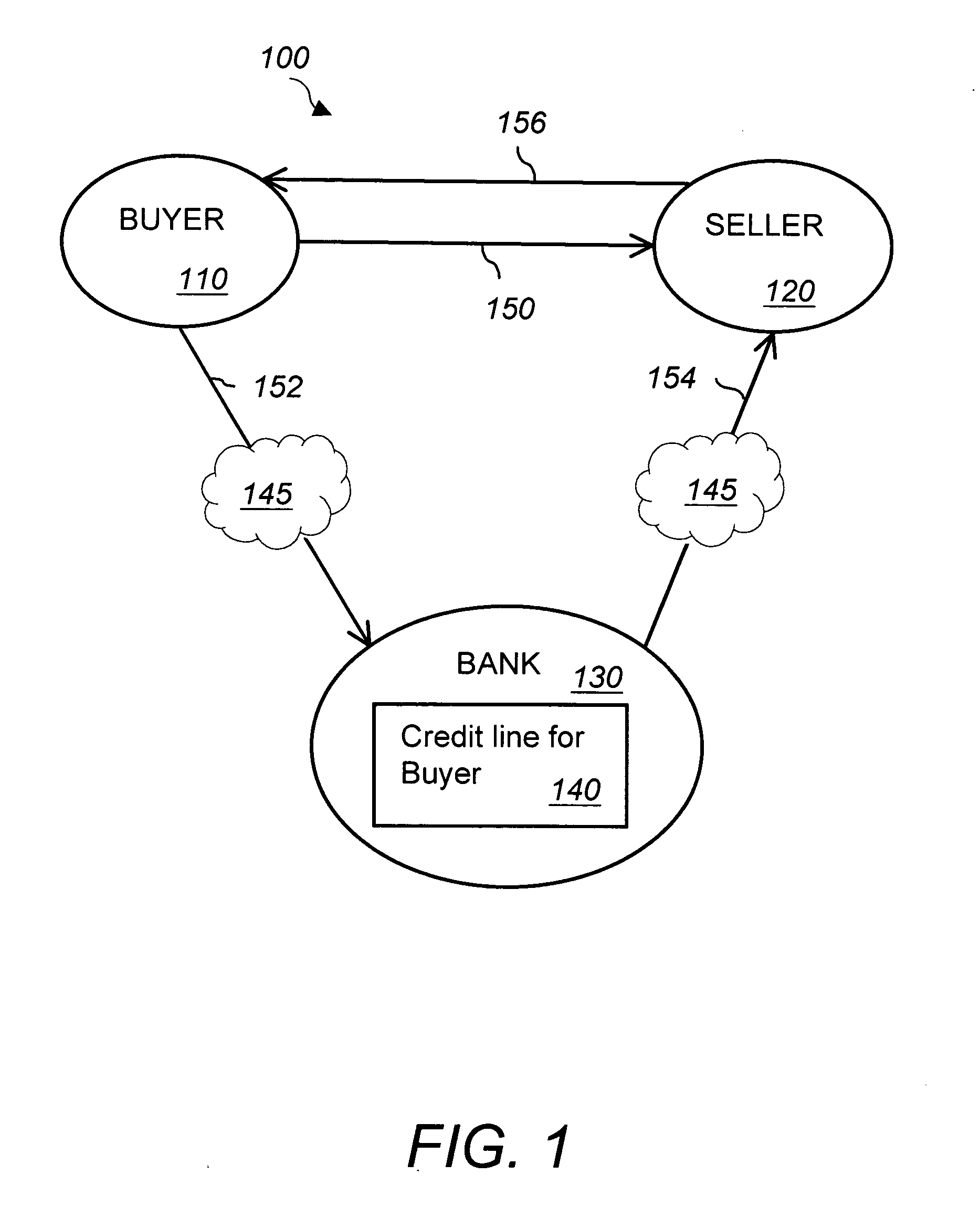
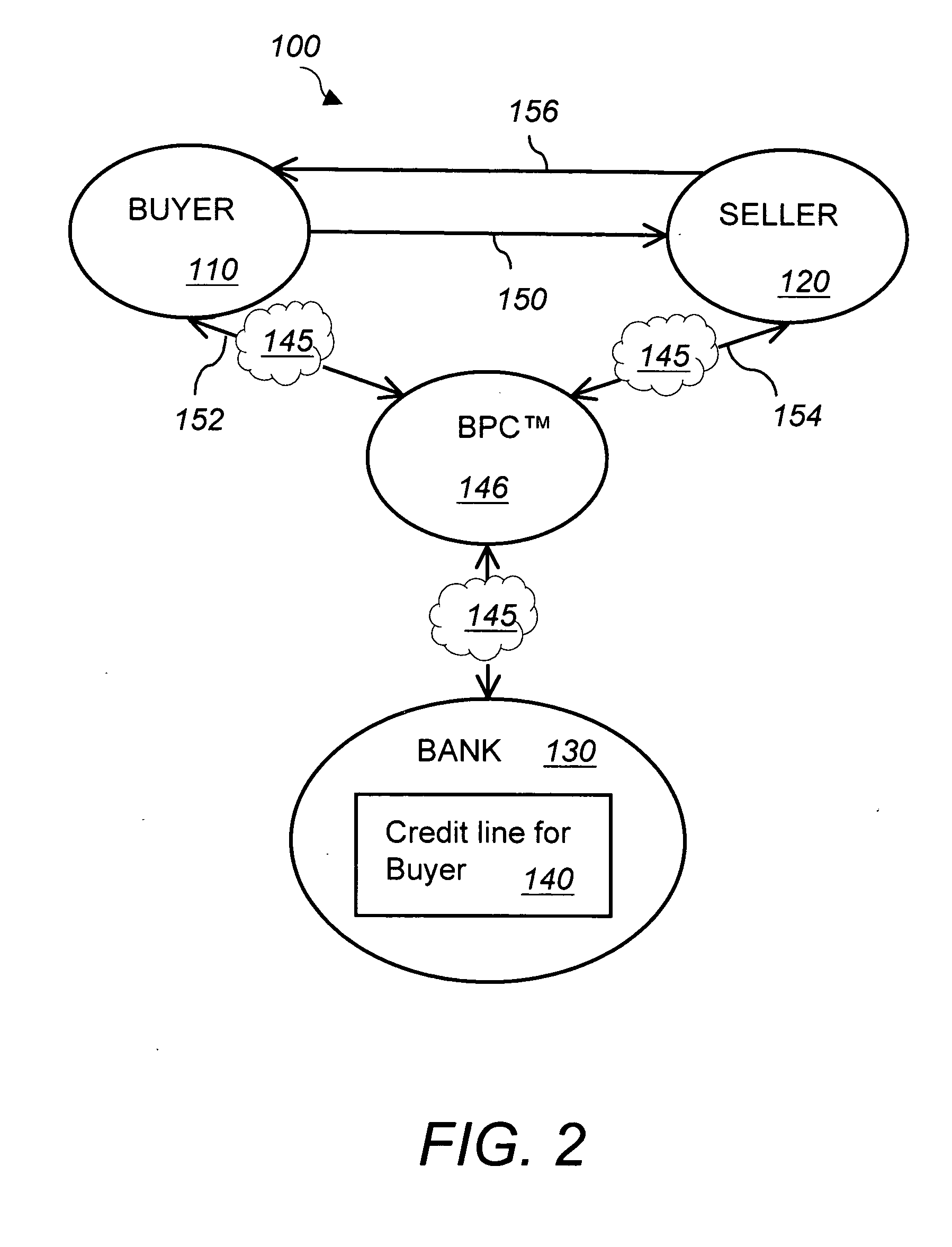
InactiveUS20050027654A1Improve developmentExposure was also limitedFinancePayment architectureNetwork connectionInvoice
An online business payment method that provides credit and cash flow management for at least one seller of products or services, at least one buyer of the products or services, and a financial institution via a business payment system accessible via a network connection. The method includes first establishing a credit line for the buyer by the financial institution. Next, placing a purchase order for a product or service by the buyer to the seller and entering a purchase order number into the business payment system. Next, accepting the purchase order by the seller and providing the product or service to the buyer. Next, sending an invoice by the seller to the buyer and entering the invoice into the business payment system against the purchase order number. Next, approving the invoice by the buyer, entering the approval into the business payment system and notifying the financial institution of the approved invoice by the business payment system. Finally, approving payment of the approved invoice by the financial institution and paying the invoice by transferring money from the buyer's credit line to an account of the seller. The seller sets a payment term for the invoice and pays a seller's fee to the financial institution upon receipt of the invoice payment. The seller's fee depends upon the invoice payment term. The buyer pays interest to the financial institution when the invoice payment term is not met. Access to the online business payment system is secure and selective access permissions are defined for each member.
Owner:ADRIAN ALEXANDRA J
Drill bits with reduced exposure of cutters
InactiveUS6935441B2Easy to implementTorque is limitedEarth drilling toolsDrill bitsEngineeringCompressive strength
A rotary drag bit and method for drilling subterranean formations, including a bit body being provided with at least one cutter thereon exhibiting reduced, or limited, exposure to the formation, so as to control the depth-of-cut of the at least one cutter, so as to control the volume of formation material cut per bit rotation, as well as to control the amount of torque experienced by the bit and an optionally associated bottomhole assembly regardless of the effective weight-on-bit are all disclosed. The exterior of the bit preferably includes a plurality of blade structures carrying at least one such cutter thereon and including a sufficient amount of bearing surface area to contact the formation so as to generally distribute an additional weight applied to the bit against the bottom of the borehole without exceeding the compressive strength of the formation rock.
Owner:BAKER HUGHES INC
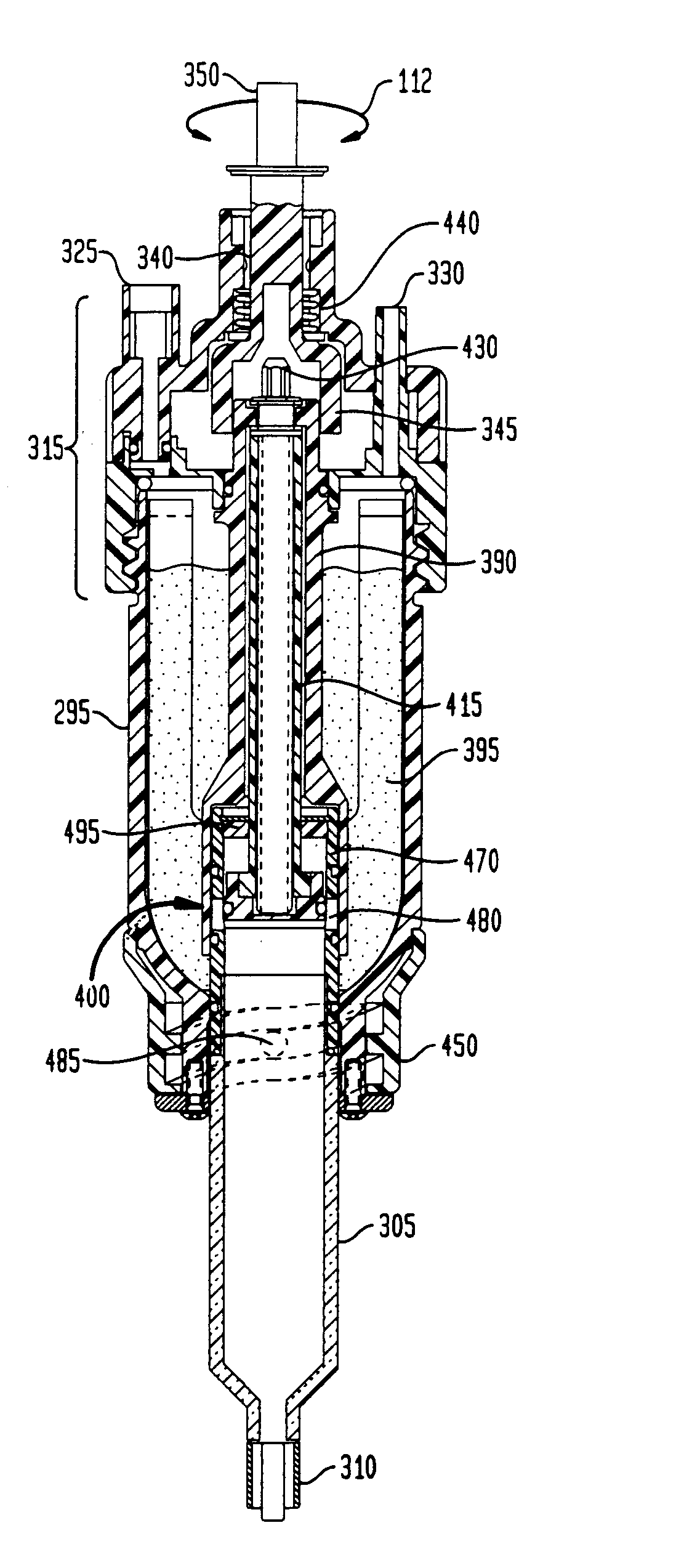
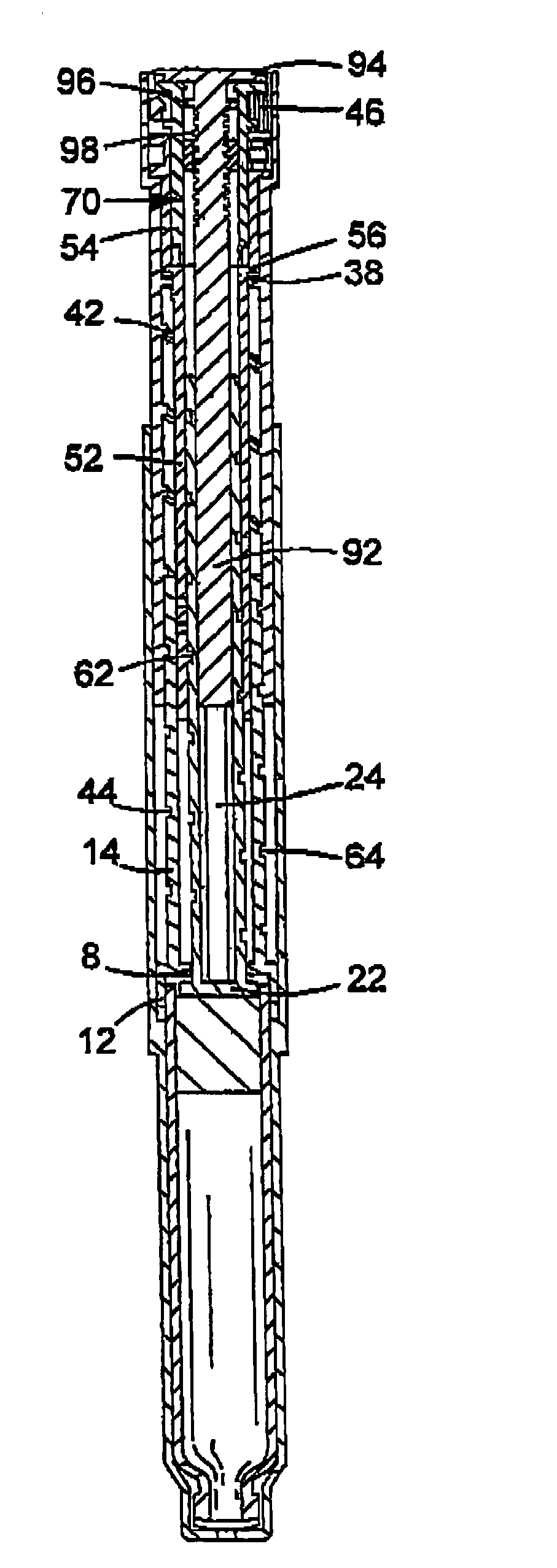
Drive assembly suitable for use in a drug delivery device and drug delivery device
ActiveUS20120010575A1Easy to implementConducive to compact designInfusion syringesIntravenous devicesDrug deliveryEngineering
A drive assembly for use in a drug delivery device is proposed, the drive assembly comprising: a housing having a proximal end and a distal end; an axis extending between the proximal end and the distal end; at least one drive member; a piston rod adapted to be driven along the axis by the drive member; an indicator adapted to provide positional information about a position of the piston rod relative to the proximal end, wherein the indicator and the piston rod are configured to convert a movement of the piston rod with respect to the housing into a rotational movement of the indicator. Additionally, a drug delivery device comprising the drive assembly is provided for.
Owner:SANOFI AVENTIS DEUTSCHLAND GMBH
Compressed composition comprising magnesium salt
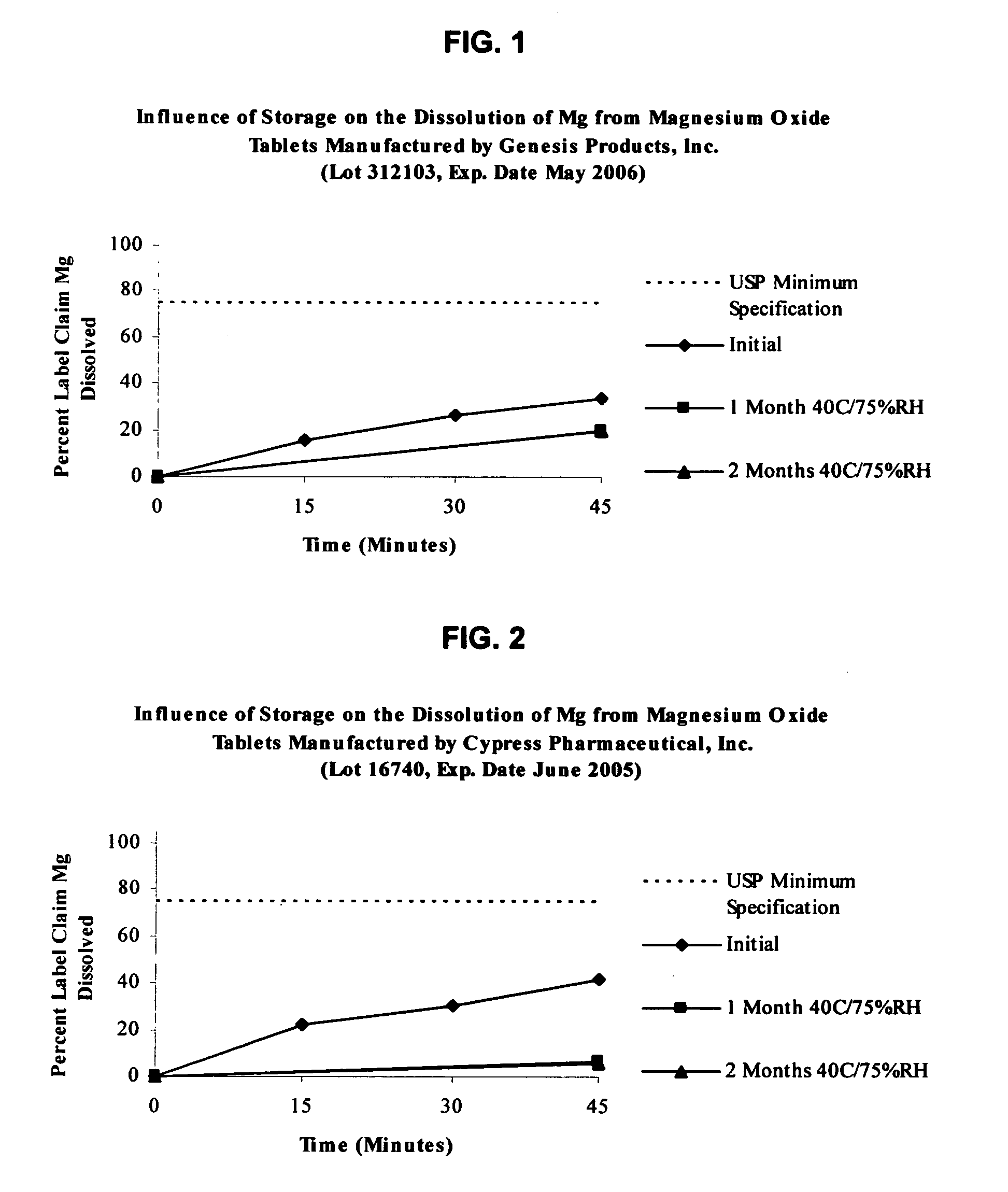
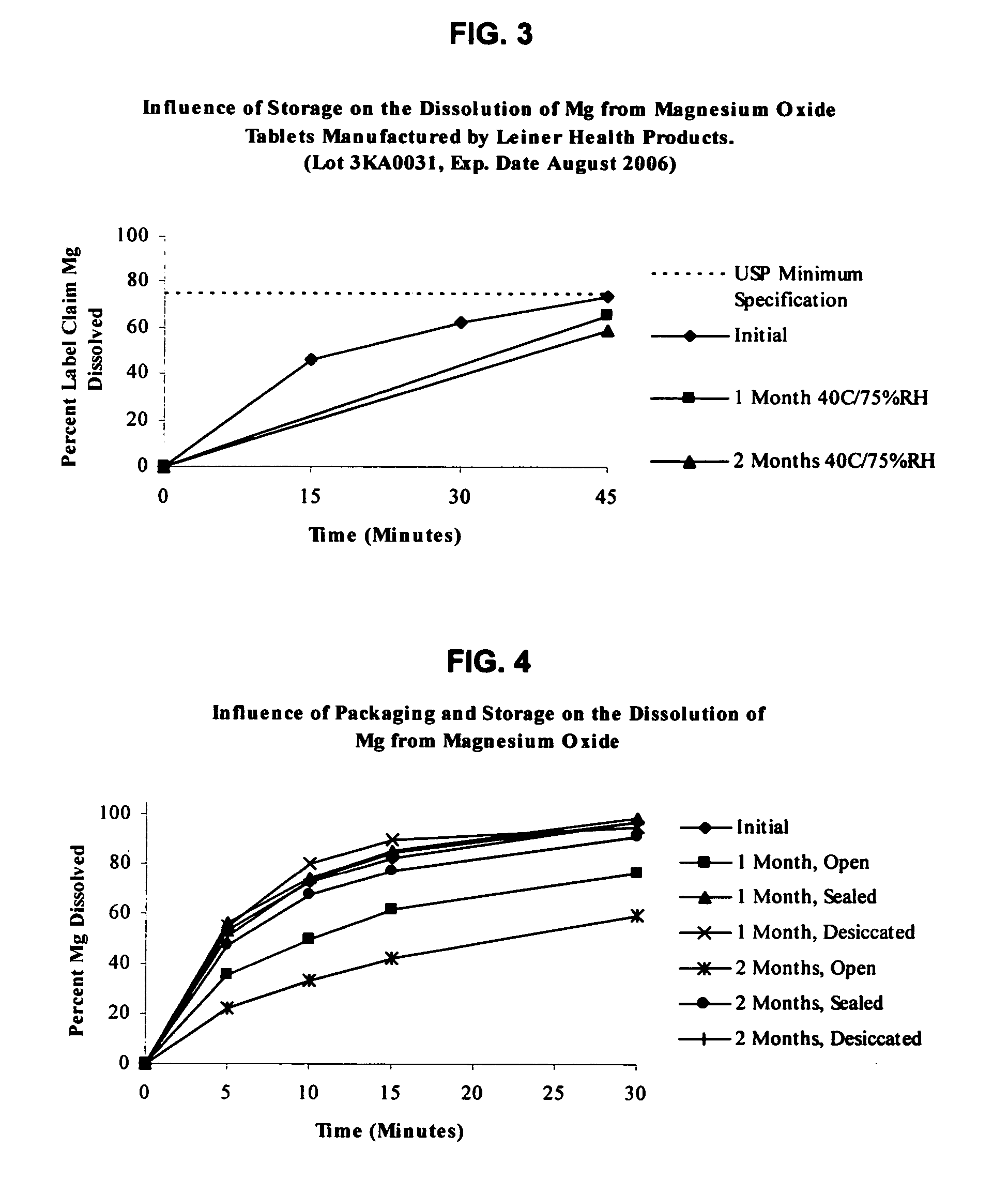
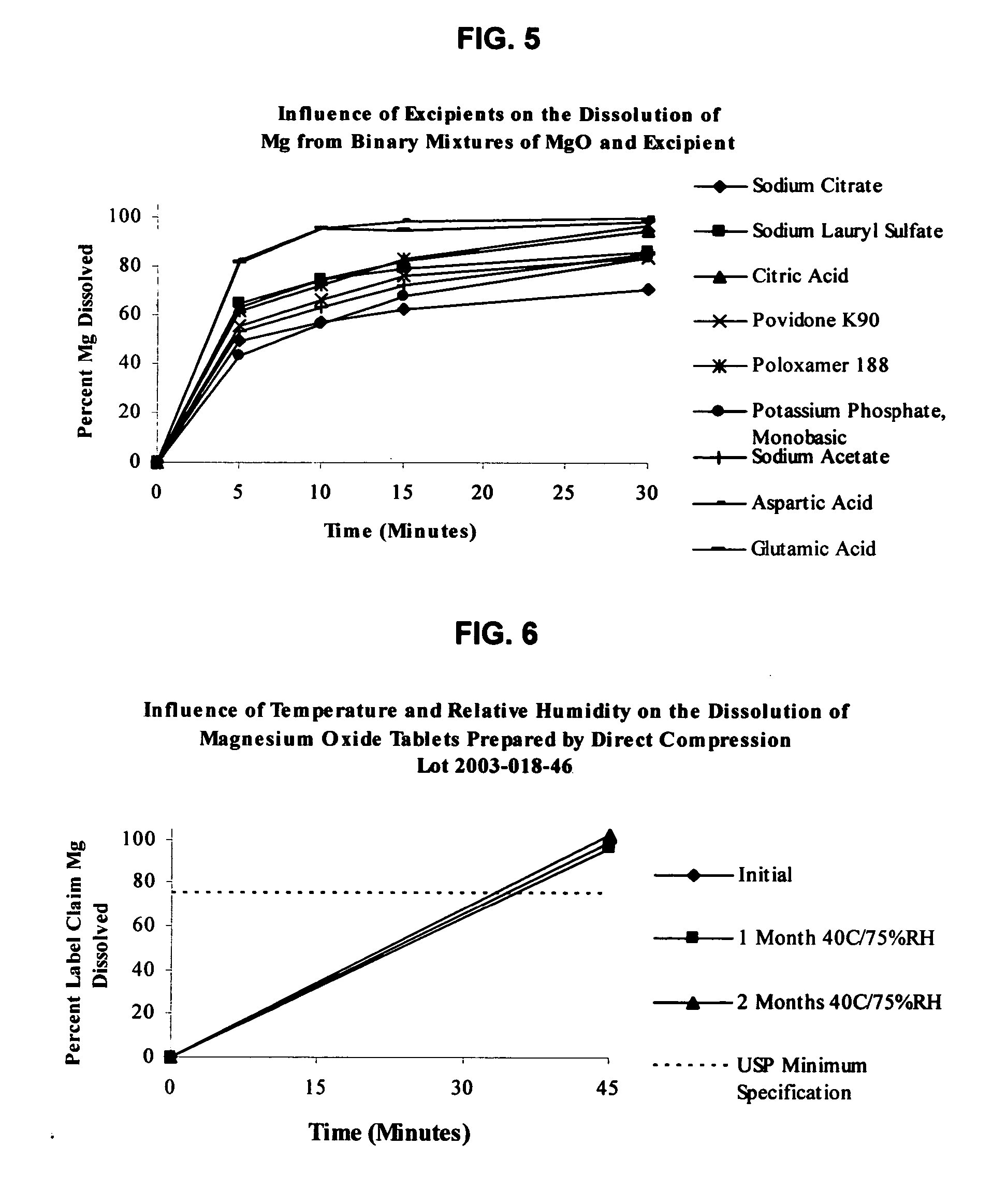
InactiveUS20050220865A1Stable dissolution profileDisintegrates quicklyBiocidePill deliveryInorganic saltsCellulose
An oral solid compress composition comprising a magnesium salt is provided. The composition provides a rapid dissolution of the magnesium salt, wherein not less than 75% of the magnesium salt dissolves within 45 minutes after placement in hydrochloric acid (0.1 N, 900 mL) as per USP Method <711>. In a particular embodiment, the magnesium salt is an inorganic salt such as MgO, Mg(OH)2, MgCl2, and others. The composition can be prepared by dry granulation, direct compression or another suitable process. The composition provides a substantially stable dissolution profile for the magnesium salt so that the dissolution profile changes only minimally even after an extended period of storage under pharmaceutically acceptable conditions when packaged in a sealed container-enclosure system. The solid composition may also exclude a cellulose-based composition. The compressed composition can be prepared and stored under anhydrous conditions.
Owner:BLAINE PHARMA
Apparatus and Method for Sculpting the Surface of a Joint
InactiveUS20070260253A1Eliminate needImprove balanceEndoscopic cutting instrumentsSurgical sawsProsthesisSacroiliac joint
Methods and devices for sculpting bones, particularly in preparation for implanting prosthetic devices to replace articulating bone joint surfaces. Improved bone removal devices including burr mills driven by gears and loop drives are provided. Reciprocating cutters and belt cutters are also provided. Some devices have either integral or removable expandable portions to vary the force and bone resection depth. Devices can have irrigation ports and plenums to remove bone fragments. Some cutters are dual cutters, adapted to remove bone in two or more regions, such as the knee joint, simultaneously.
Owner:CAYENNE MEDICAL INC
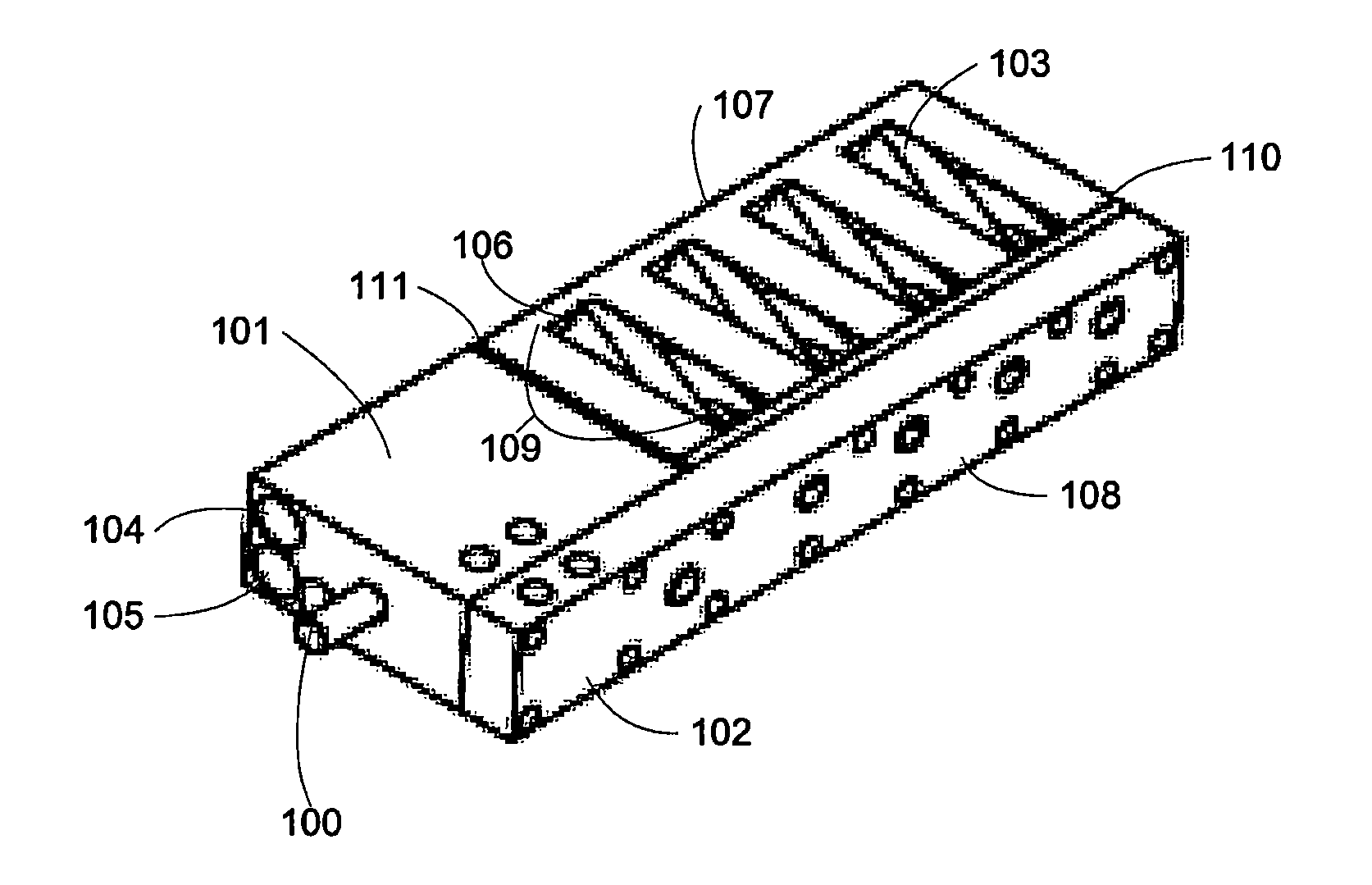
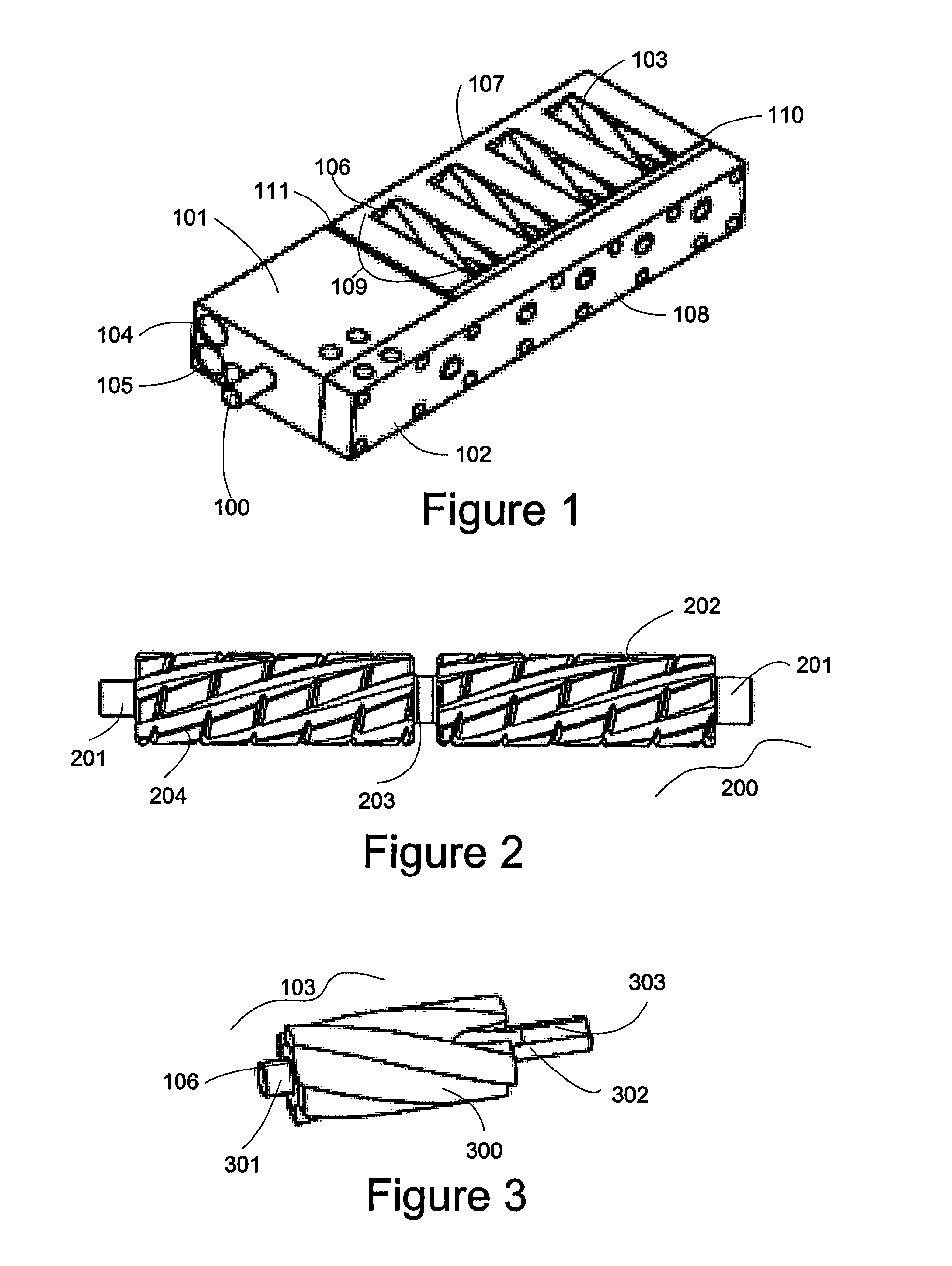
Dose dial and drive mechanisms suitable for use in drug delivery devices
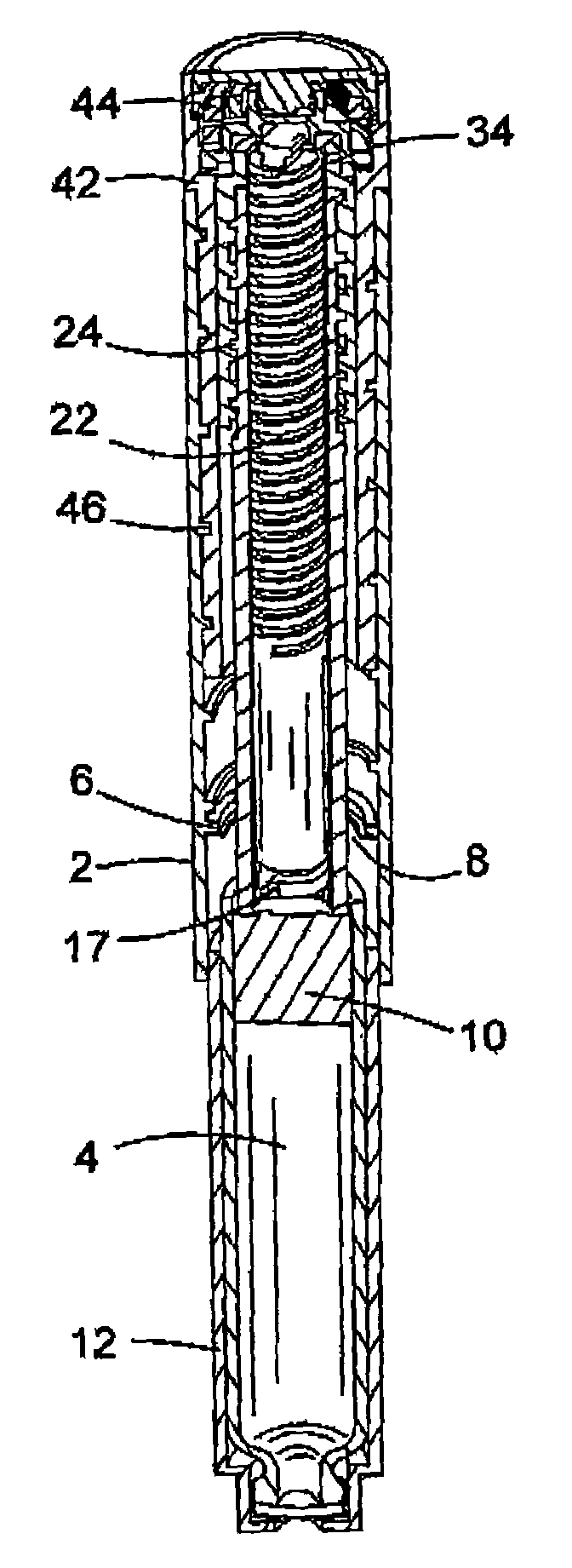
ActiveUS7090662B2Safe and correct and comfortable handlingExposure was also limitedAmpoule syringesIntravenous devicesDisplay deviceEngineering
A dose dial and drive mechanism for use in a drug delivery device having a housing, a dose dial sleeve, a piston rod, a drive sleeve threadedly connected to the piston rod, a reset sleeve, which is located between the drive sleeve and the housing, and a dose display. When the dose dial sleeve travels towards the second end of the housing the reset sleeve is carried with the dose dial sleeve towards the second end of the housing resetting the dose display to a zero position and when the dose dial sleeve and / or the reset sleeve travels towards the first end of the housing, the dose dial sleeve and / or reset sleeve engage(s) with the drive sleeve thus advancing both the drive sleeve and the piston rod towards the first end of the housing.
Owner:SANOFI AVENTIS DEUT GMBH
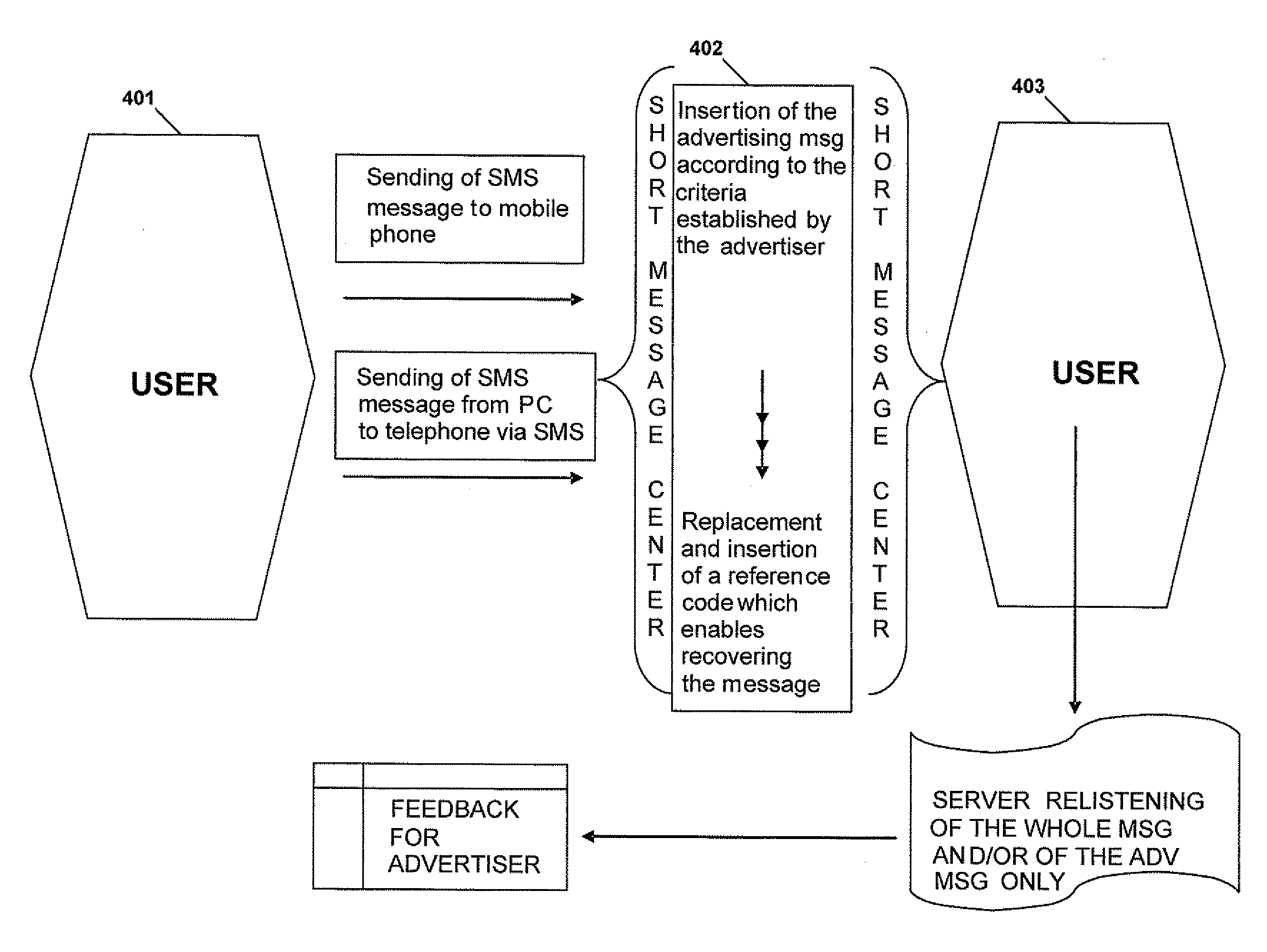
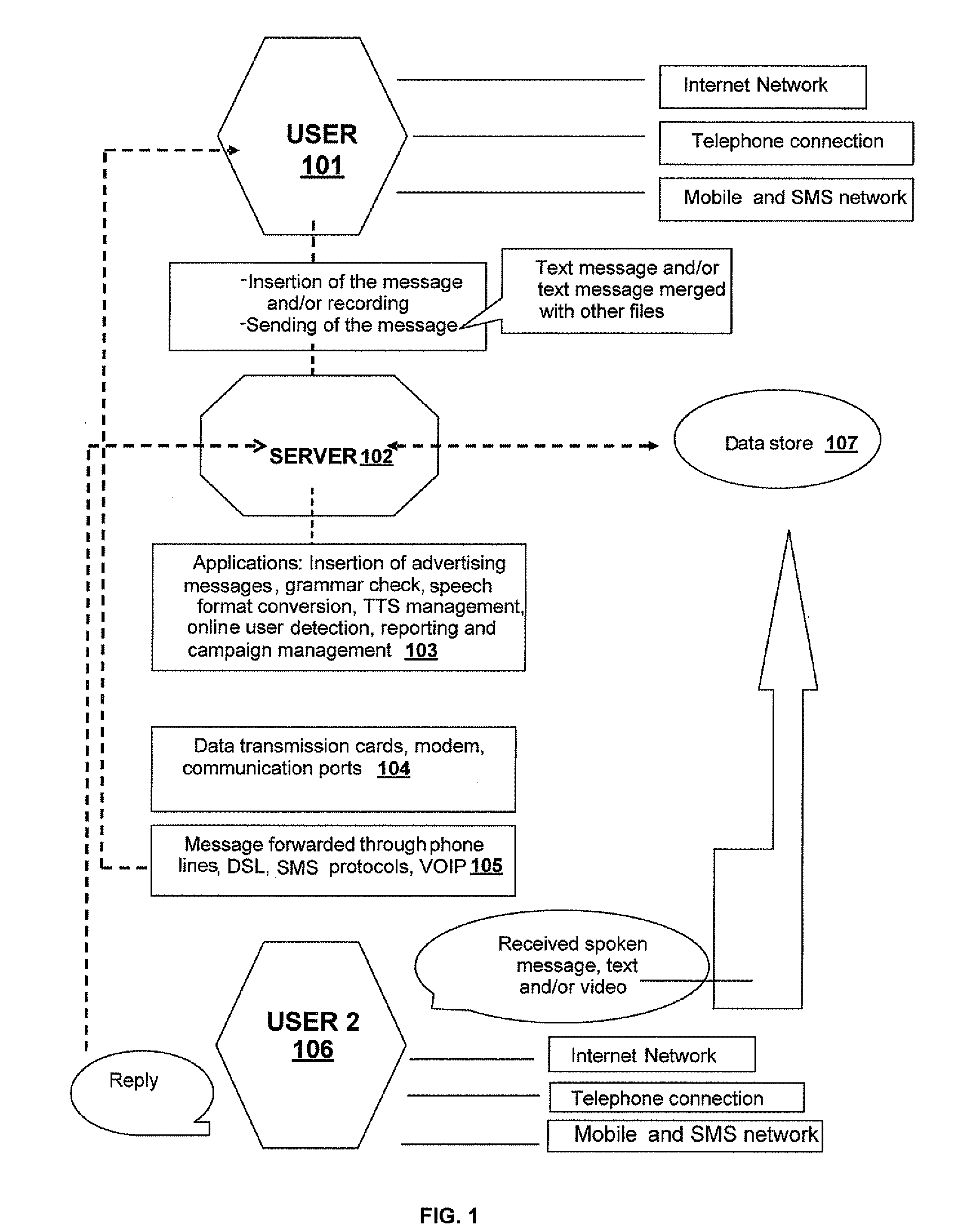
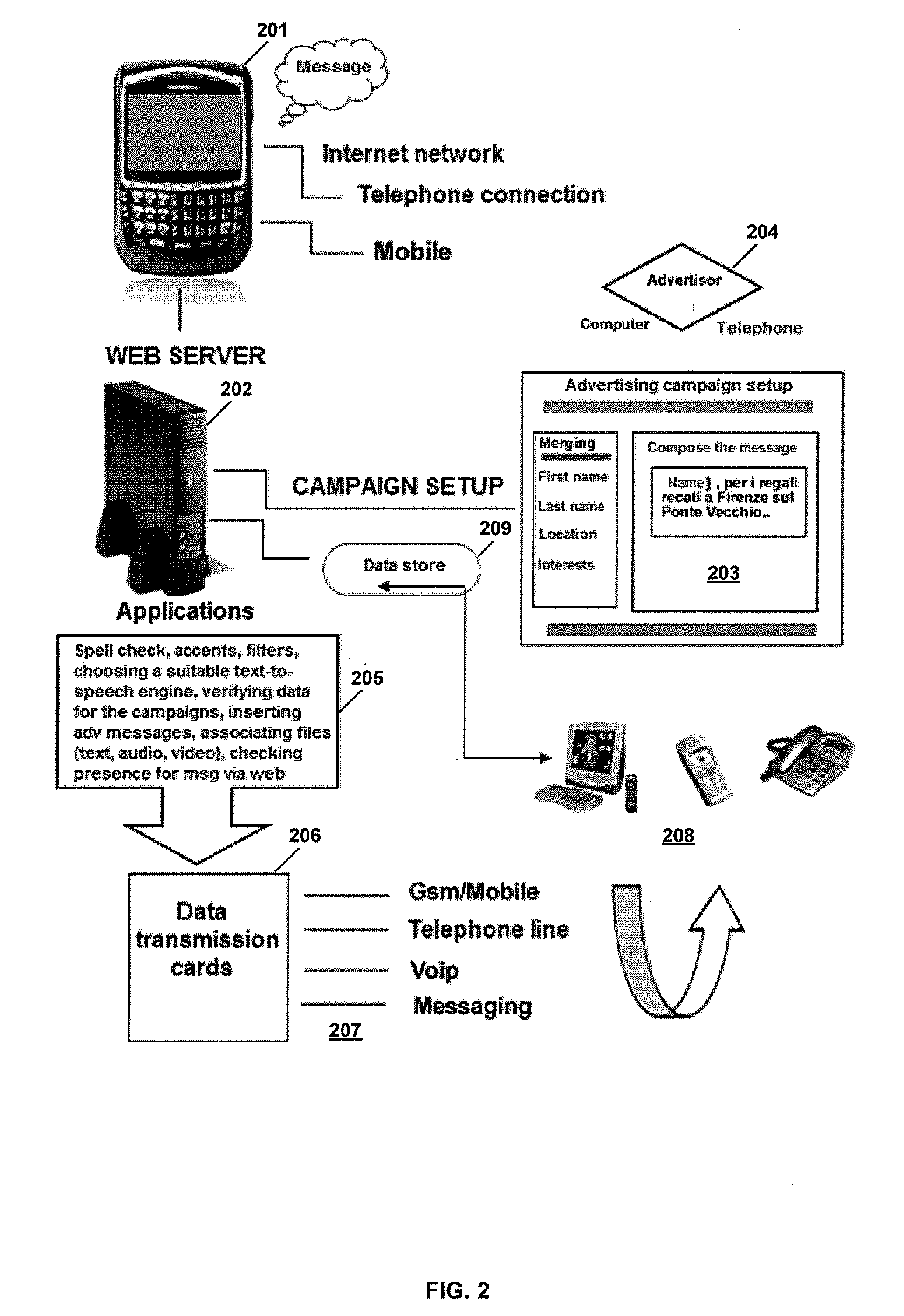
System to generate and set up an advertising campaign based on the insertion of advertising messages within an exchange of messages, and method to operate said system
A method is provided that includes receiving message data at a server from a first remote device. The message data is associated with a message and the message includes text of one or more words, one or more characters, one or more symbols, or any combination thereof. The method also includes determining an intended recipient of the message and parsing the message data to identify text that matches criteria associated with an advertisement campaign. Further, the method includes composing an advertisement based on characteristics of the intended recipient and based on the text that matches the criteria associated with the advertisement campaign. Additionally, the method includes creating an audio file based on the message data and the advertisement and sending the audio file from the server to a second remote device, the second remote device associated with the intended recipient.
Owner:BRAINTEXTER
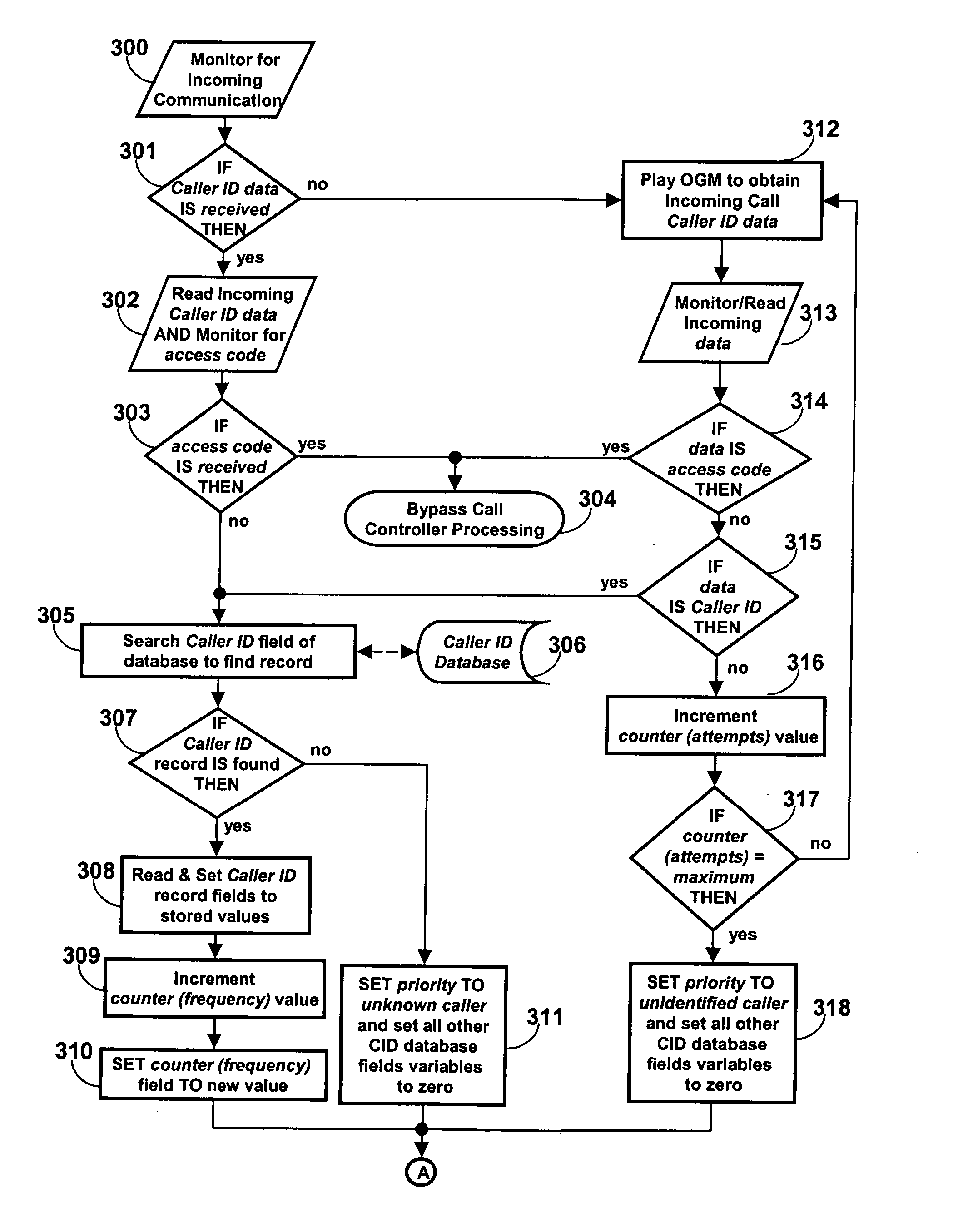
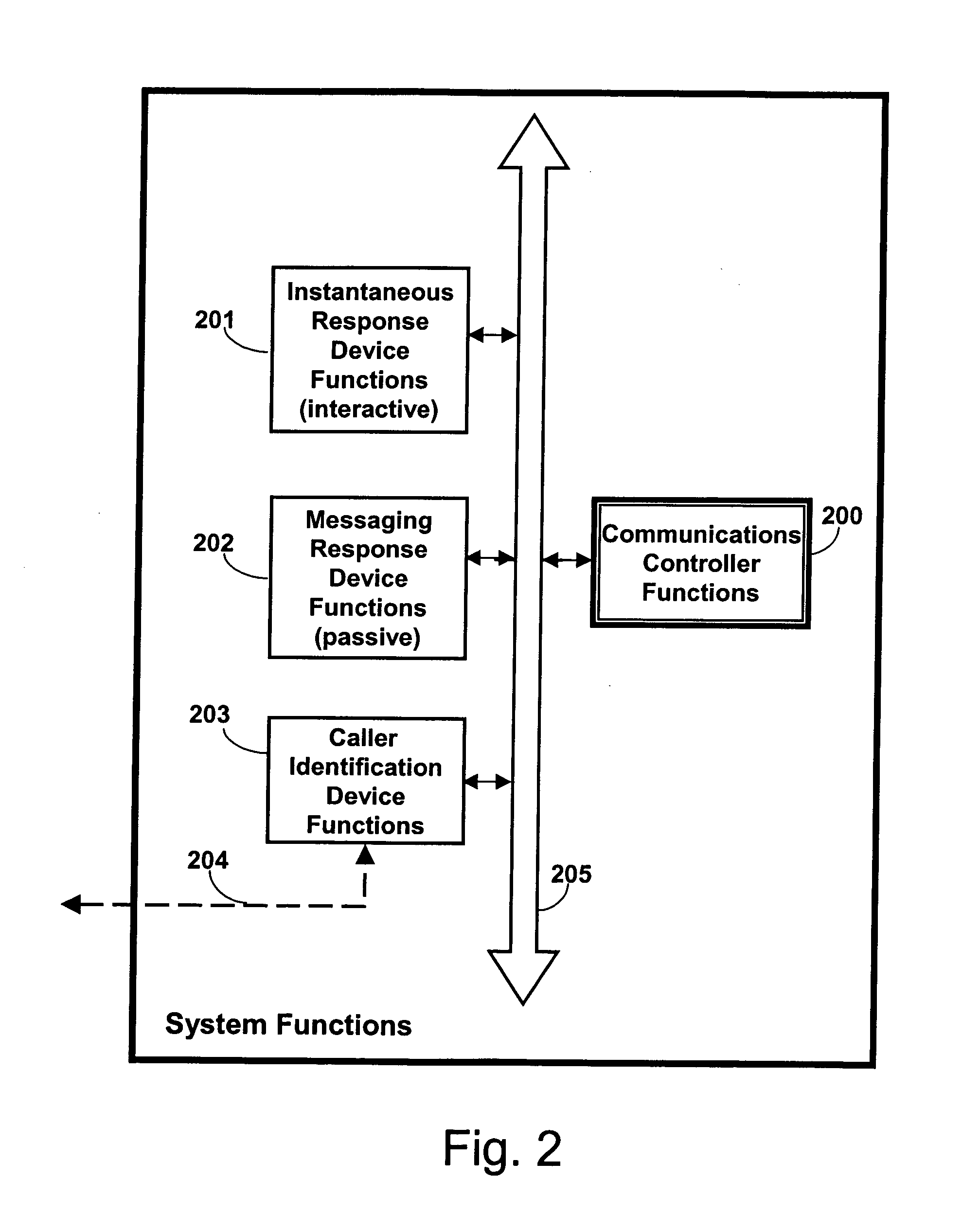
Communications control method and apparatus
InactiveUS20060094404A1Exposure was also limitedSpecial service for subscribersPower supply for data processingBehavioral modelingCommunication control
A communications controller is provided for empowering the user of a communications device, such as a telephone or other device, to assume control over incoming communications. This communications controller is based on artificial intelligence and behavior modeling techniques. Each communication is identified by unique identification information associated with an incoming communication. The user selects one of a plurality of different priority rating levels for a particular communication. The user also selects or infers block time intervals for each priority to indicate times during which incoming communication is not desired. Dynamic communications control is achieved by also determining the mood of the user or mode of the device. Undesirable communications will be “blocked”. For example, when that particular caller places a call to the user, the user's communication controller determines the caller's identification information and recalls the priority and corresponding blocking time interval for that particular caller. The user's mood or the mode of the communications device is determined. The call is accordingly passed to the communication device or blocked.
Owner:BURGESS SHELIA JEAN
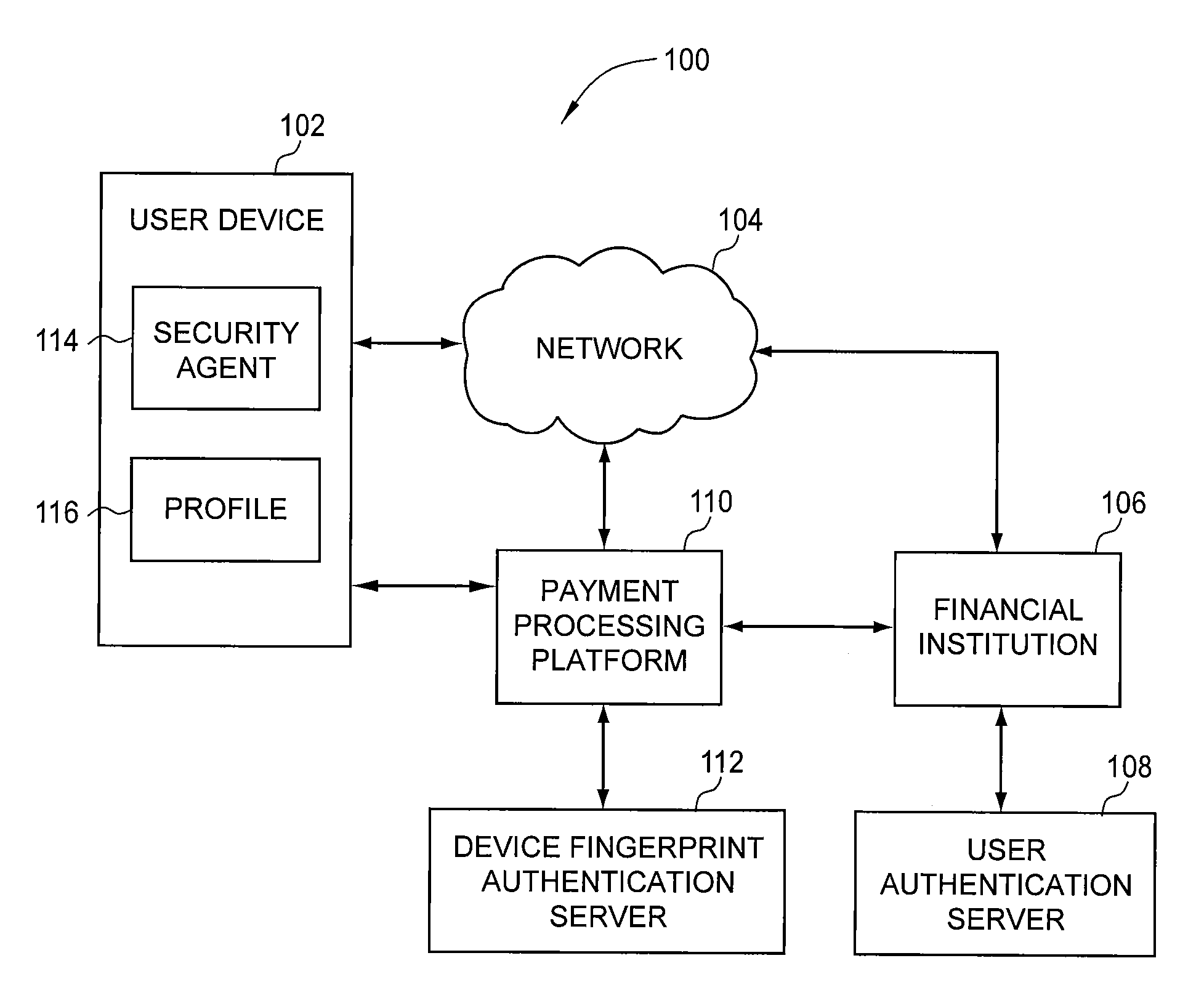
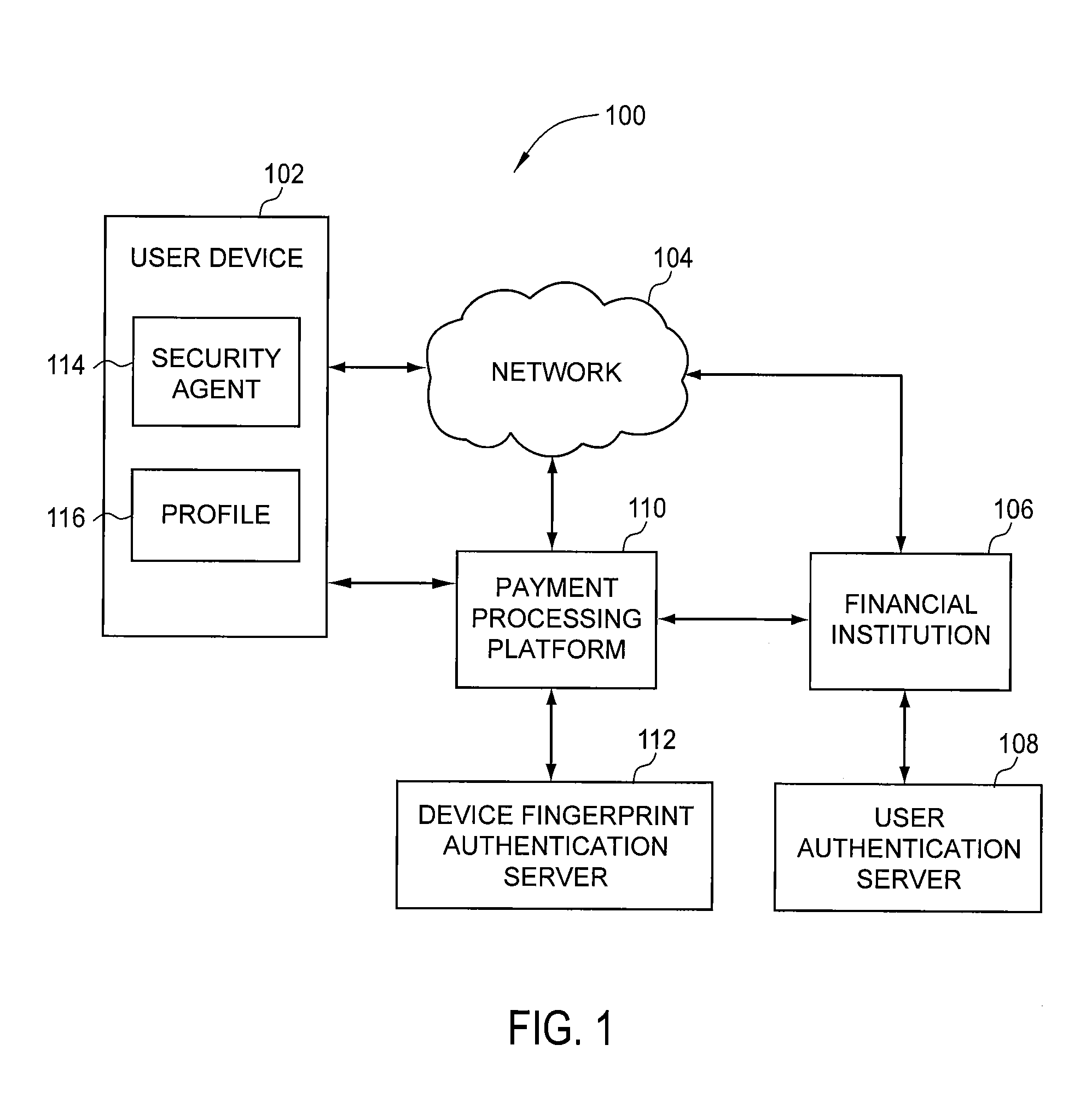
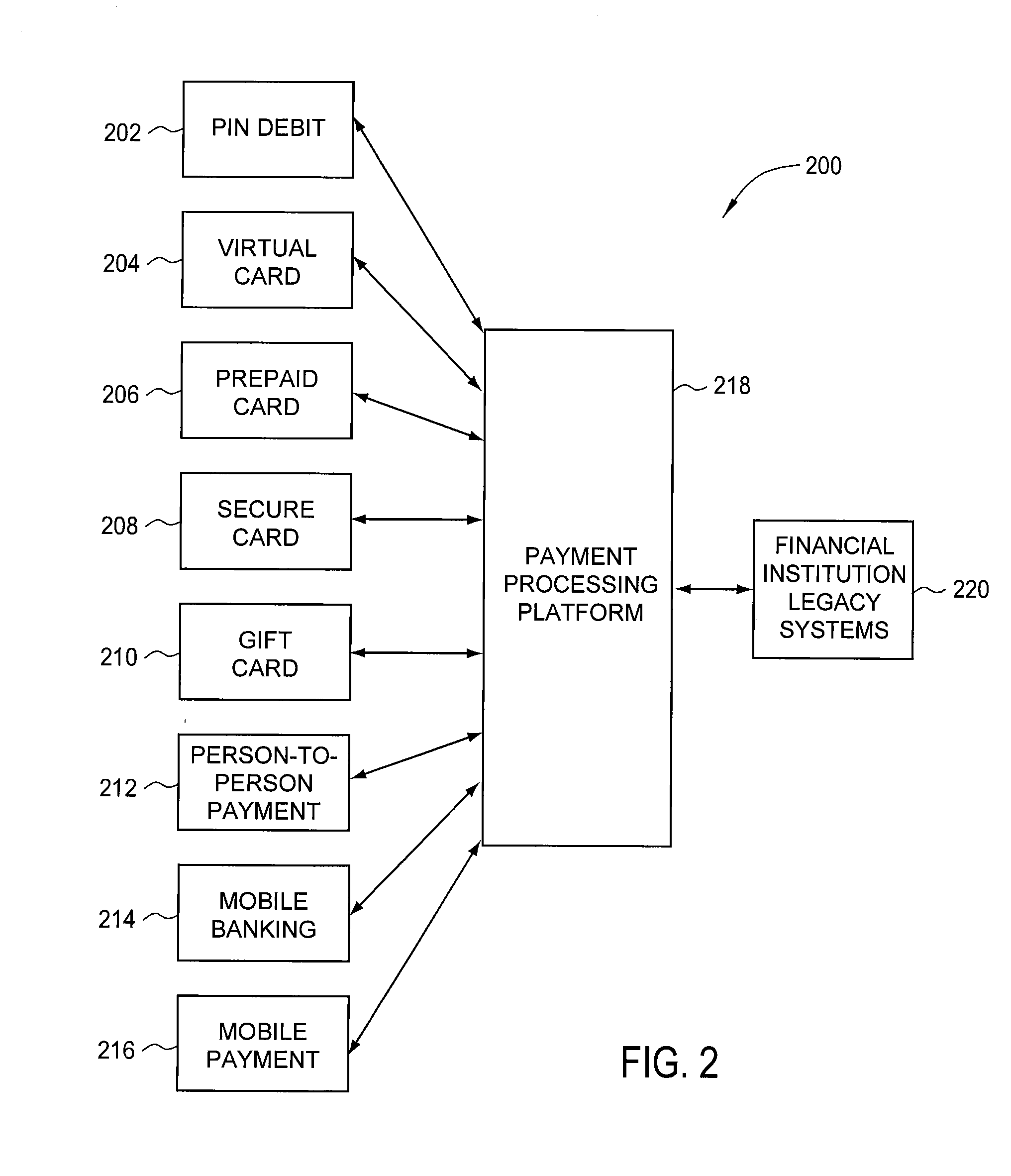
Payment Processing Platform
InactiveUS20090281951A1Reduce expensesExposure was also limitedSecret communicationPayment circuitsPayment transactionIdentity theft
A method for generating a child product that is linked to a core account. A payment processing platform receives a user selection of control parameters that define use restrictions for the child product and the core account that provides financial backing for the child product. The child product is generated and may be used for payment transactions within the use restrictions defined by the control parameters. The child product is delivered to a recipient as a physical card or as a virtual card or both as a physical card and a virtual card. Advantageously, the financial institution needs to modify its legacy payment processing infrastructure minimally in order to process payment transactions made using the child product. From a user perspective, child products protect consumers from fraud or identity theft and limit a customer's exposure when child products are lost or stolen.
Owner:VERIENT
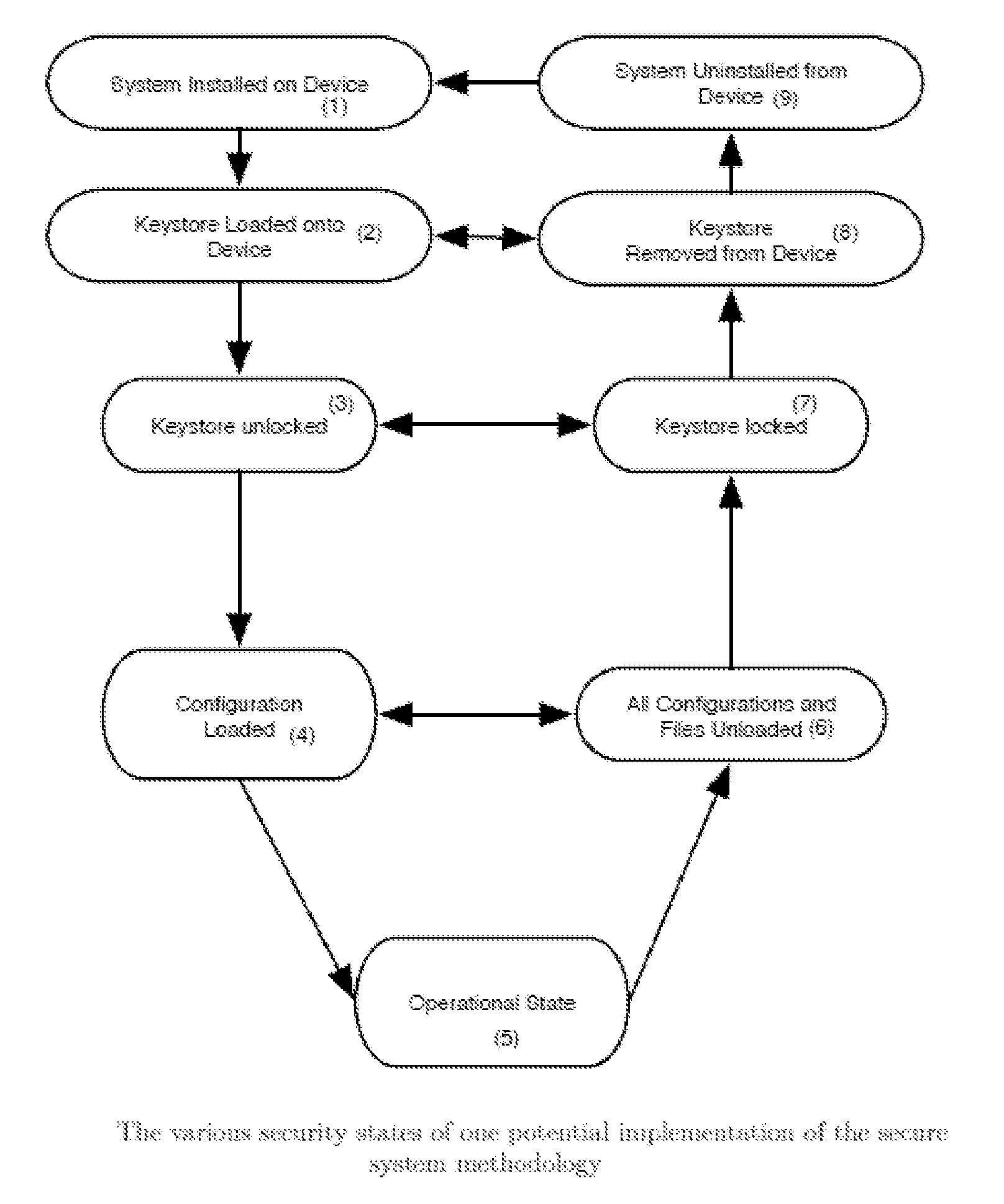
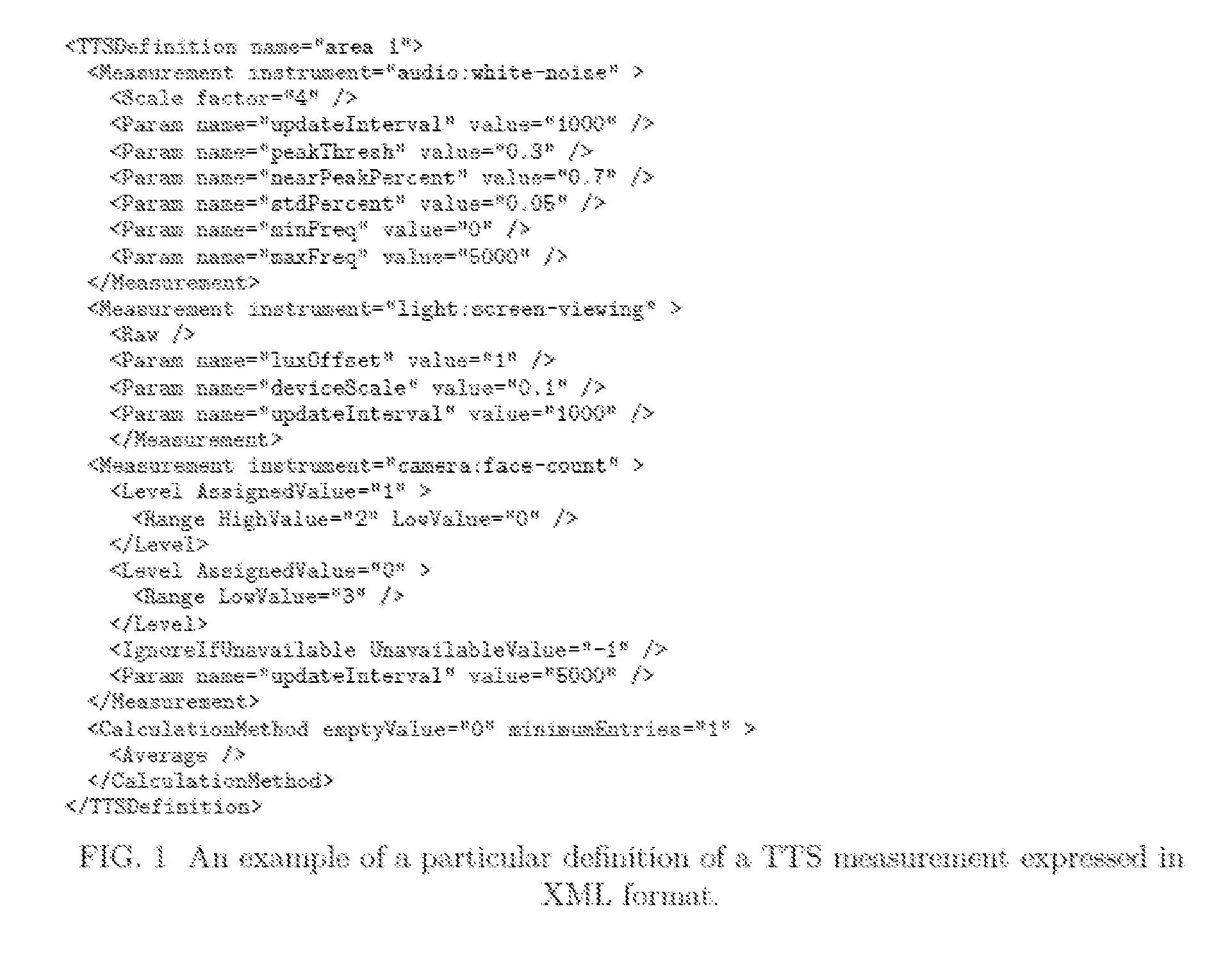
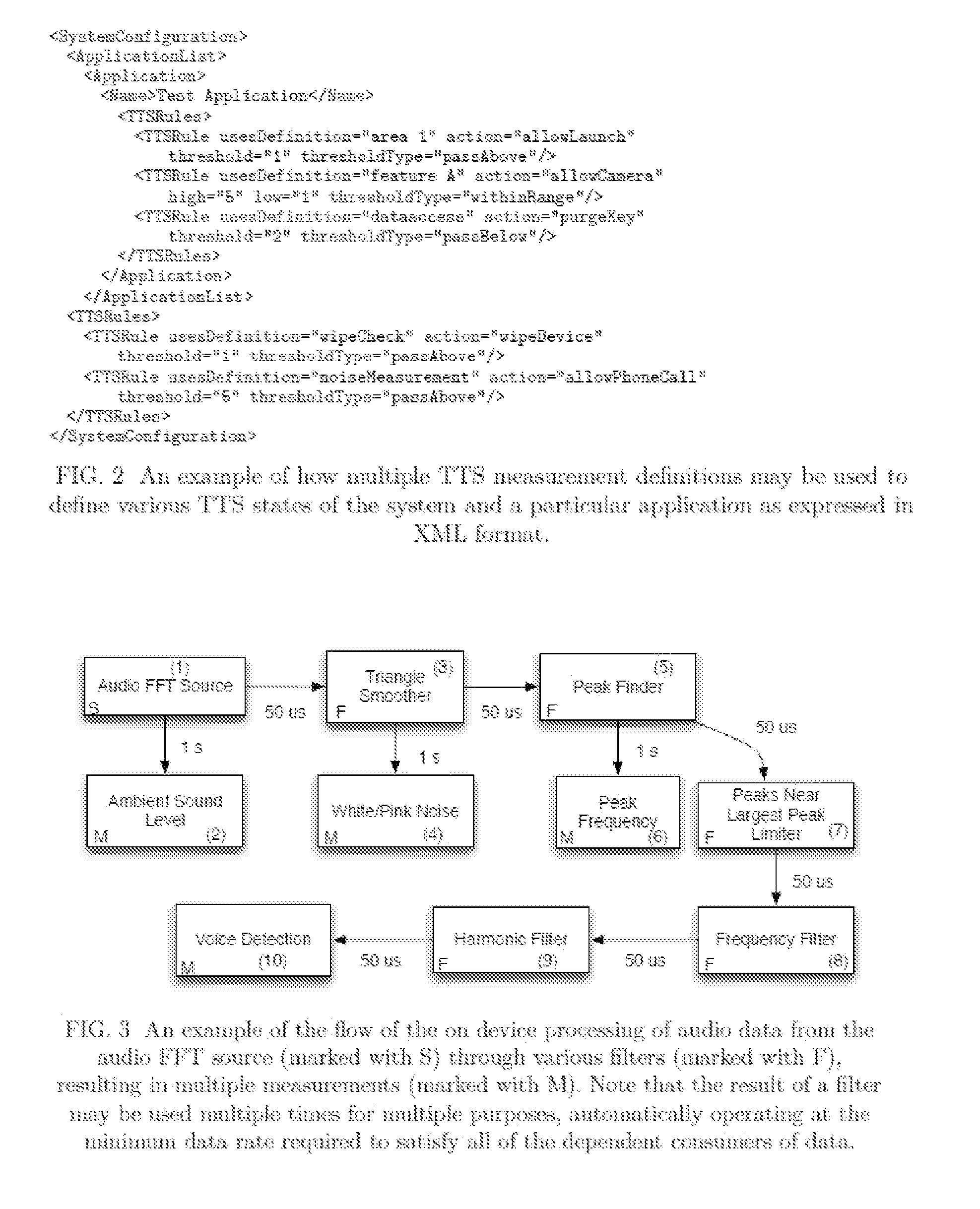
Methods of dynamically securing electronic devices and other communications through environmental and system measurements leveraging tailored trustworthy spaces
ActiveUS20150121506A1Exposure be also limitedWithout the risk of the receiving device compromising the security of the sending systemDigital data processing detailsUnauthorized memory use protectionData transmissionSafe system
This invention is for a system capable of securing one or more fixed or mobile computing device and connected system. Each device is configured to change its operating posture by allowing, limiting, or disallowing access to applications, application features, devices features, data, and other information based on the current Tailored Trustworthy Space (TTS) definitions and rules which provided for various situationally dependent scenarios. Multiple TTS may be defined for a given deployment, each of which specifies one or more sensors and algorithms for combining sensor data from the device, other connected devices, and / or other data sources from which the current TTS is identified. The device further achieves security by loading digital credentials through a unidirectional multidimensional physical representation process which allows for the device to obtain said credentials without the risk of compromising the credential issuing system through the data transfer process. This secure system methodology may be used to create a Mobile Secure Compartmentalized Information Facility (M-SCIF), among other applications.
Owner:INTERNET INFRASTRUCTURE SERVICES
Drive mechanisms suitable for use in drug delivery devices
ActiveUS8226631B2Prevent rotationSafe and correct and comfortable handlingJet injection syringesMedical devicesPharmaceutical SubstancesBiomedical engineering
The present invention relates to drive mechanisms suitable for use in drug delivery devices, in particular pen-type injectors, wherein a number of pre-set doses of medicinal product can be administered. In particular, the present invention relates to such drug delivery devices where a user may activate the drug delivery device.
Owner:SANOFI AVENTIS DEUT GMBH
Drive mechanisms suitable for use in drug delivery devices
InactiveUS7918832B2Safe and correct and comfortable handlingExposure was also limitedAmpoule syringesIntravenous devicesEngineeringScrew thread
Owner:SANOFI AVENTIS DEUT GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com