Patents
Literature
67 results about "Federated identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
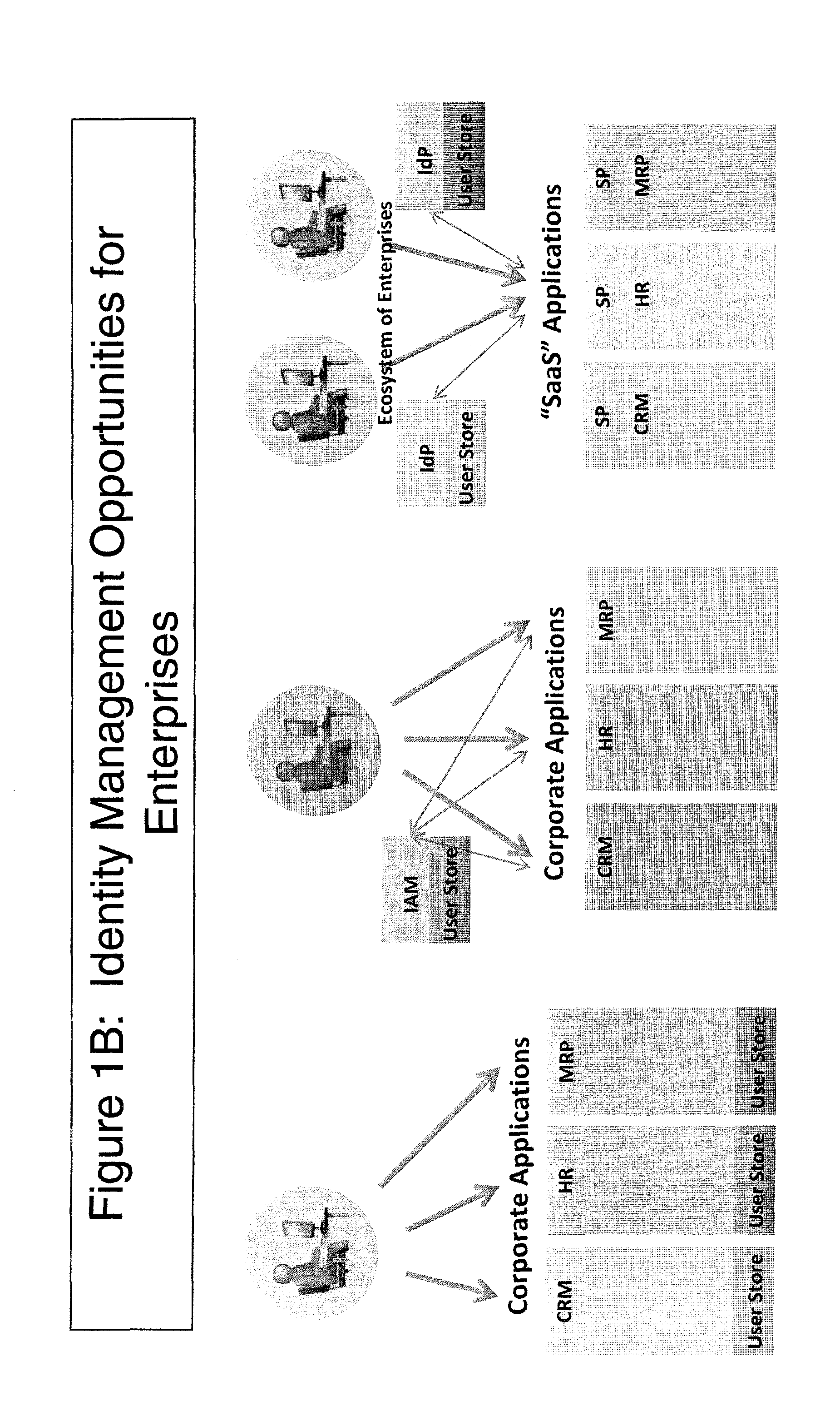
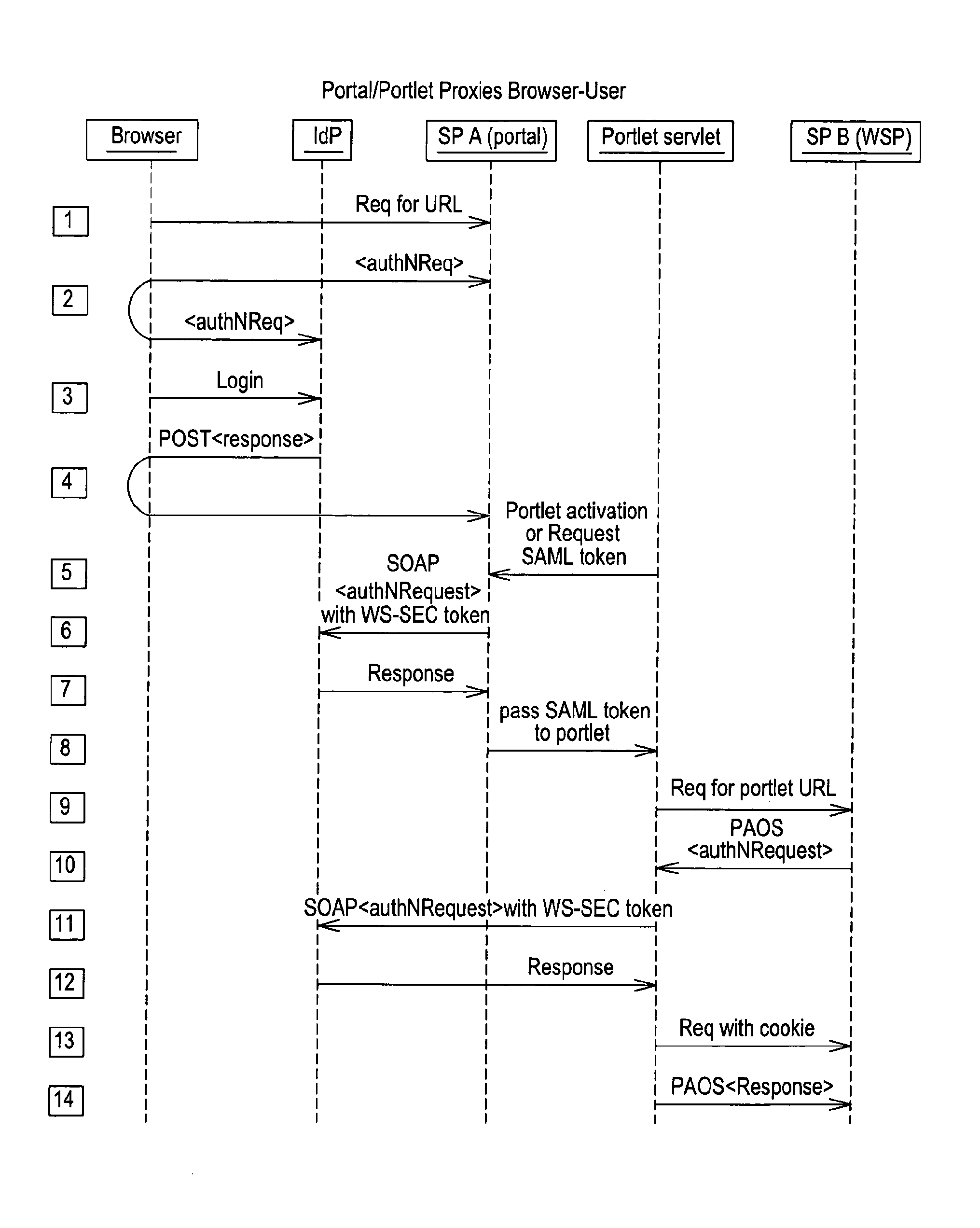
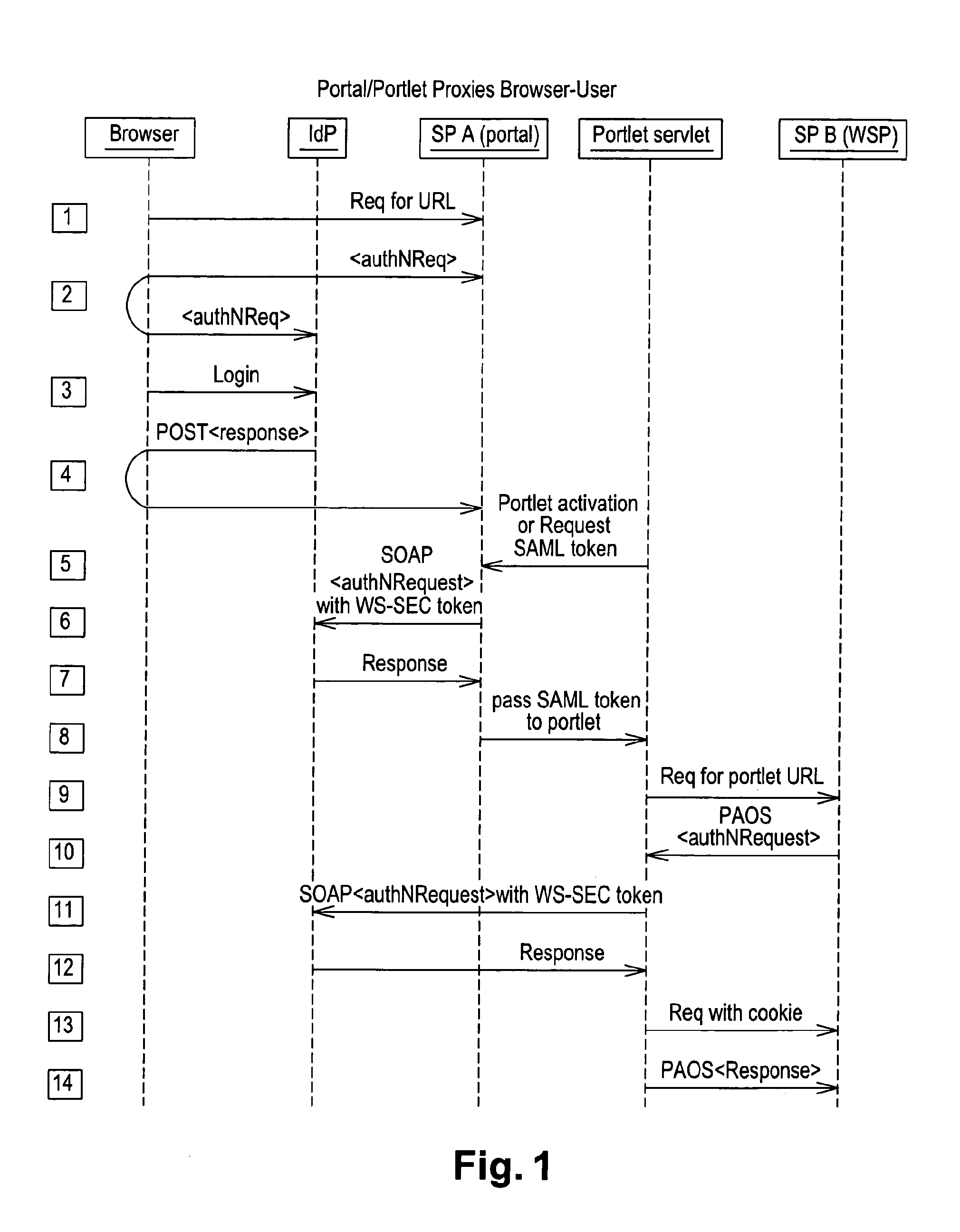
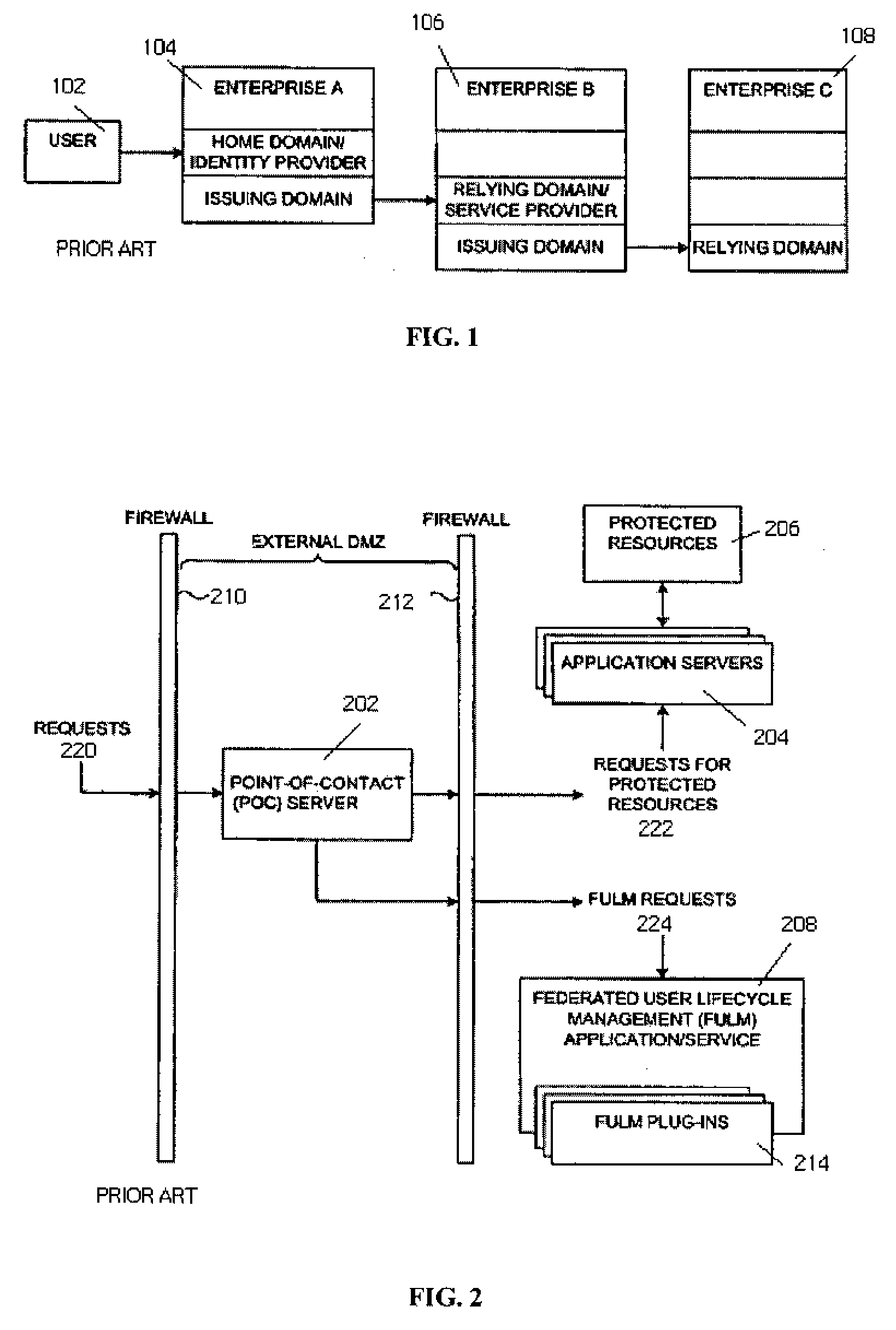
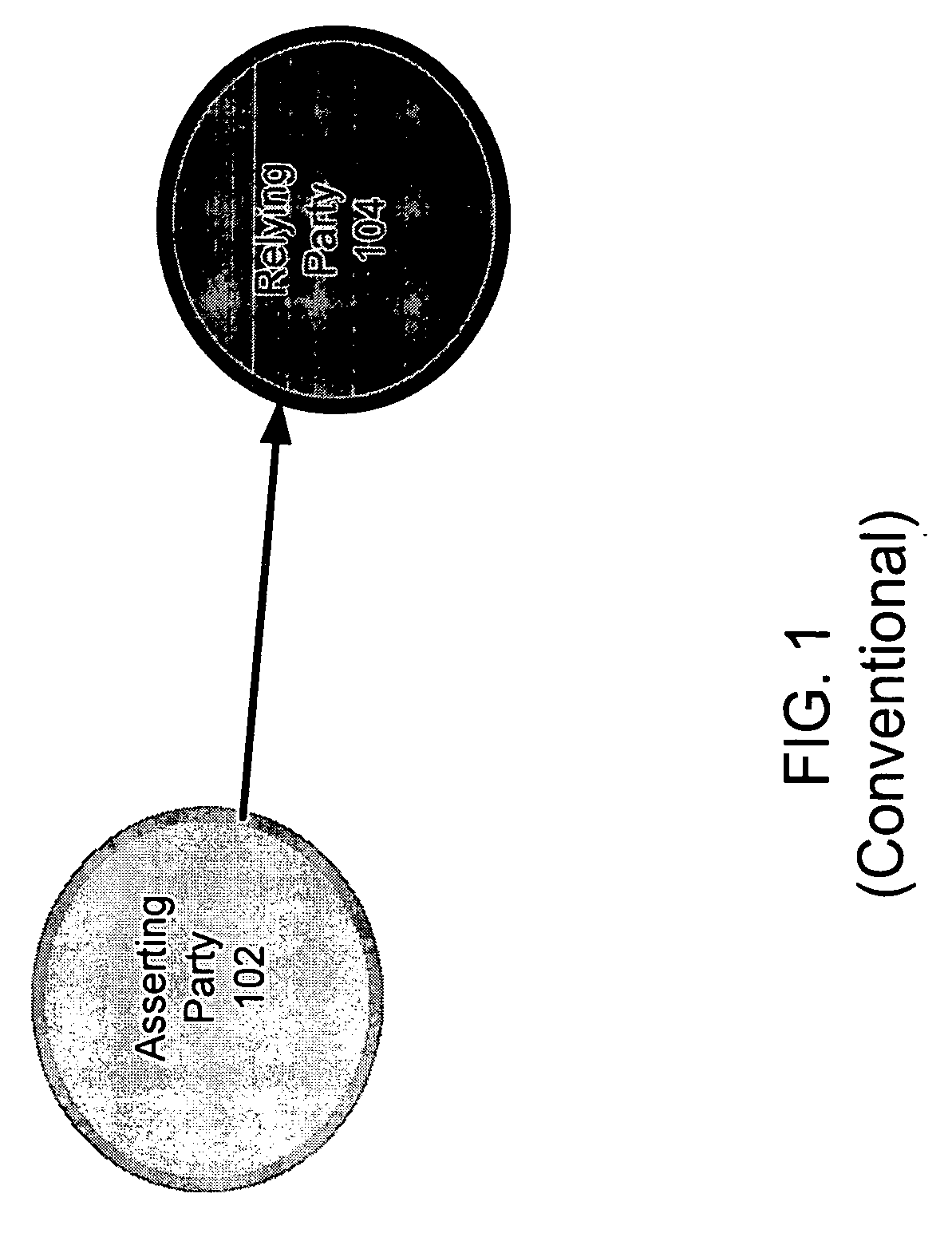
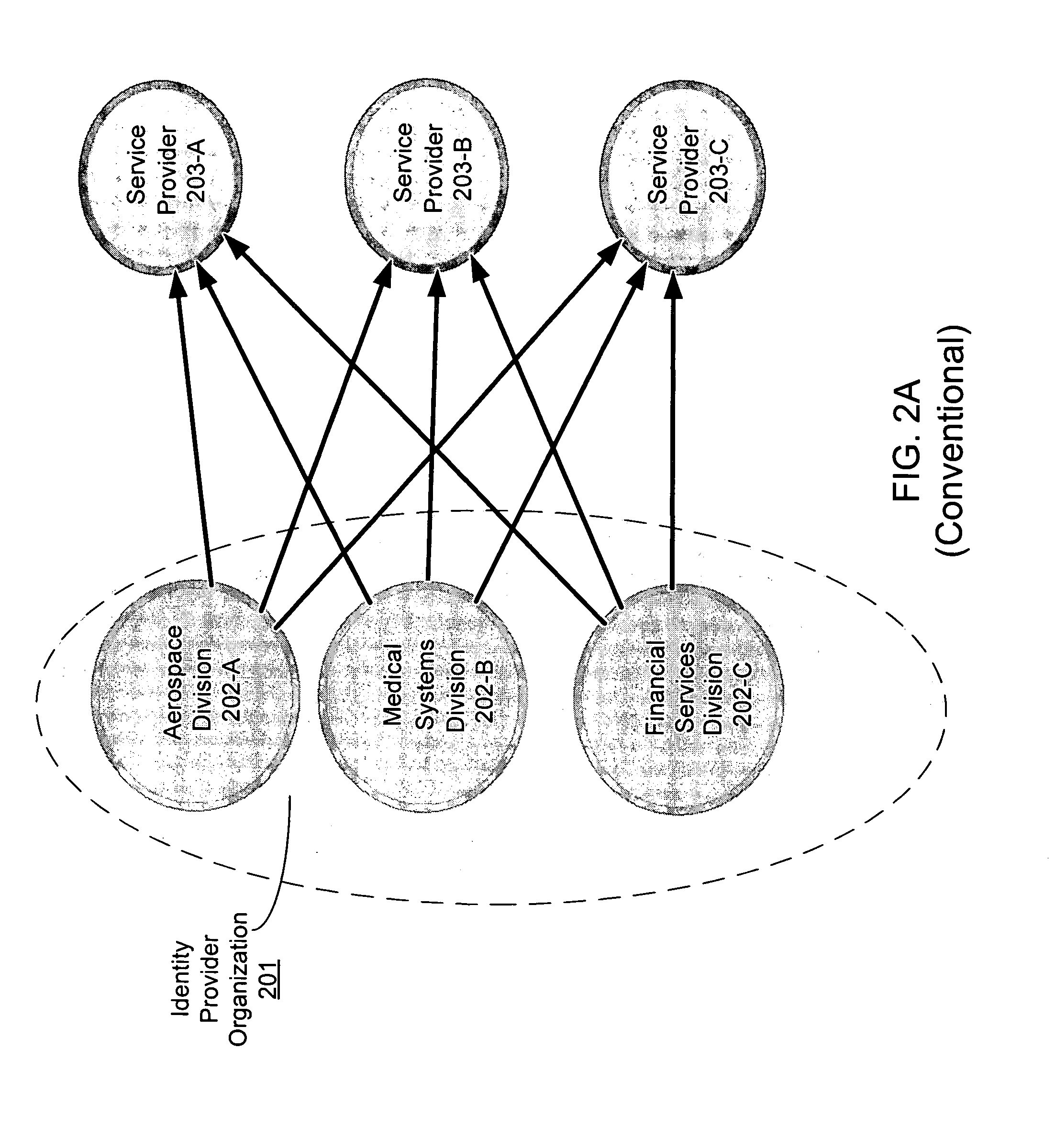
A federated identity in information technology is the means of linking a person's electronic identity and attributes, stored across multiple distinct identity management systems. Federated identity is related to single sign-on (SSO), in which a user's single authentication ticket, or token, is trusted across multiple IT systems or even organizations. SSO is a subset of federated identity management, as it relates only to authentication and is understood on the level of technical interoperability and it would not be possible without some sort of federation.
System and method for indexing, correlating, managing, referencing and syndicating identities and relationships across systems
ActiveUS20100274815A1Rich and more detailed and more completeRaise the possibilityDigital data information retrievalDigital data processing detailsThird partyFederated identity
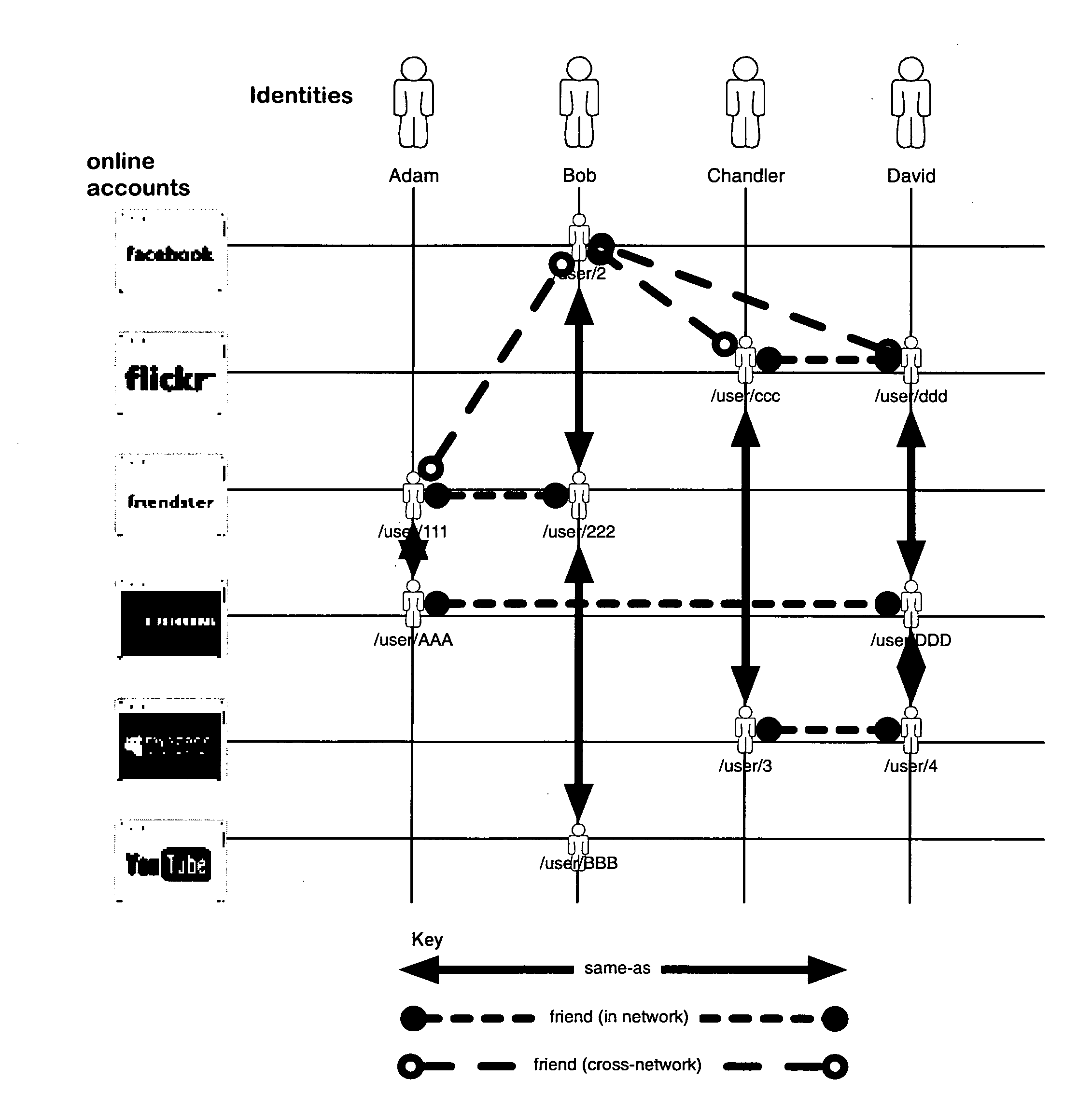
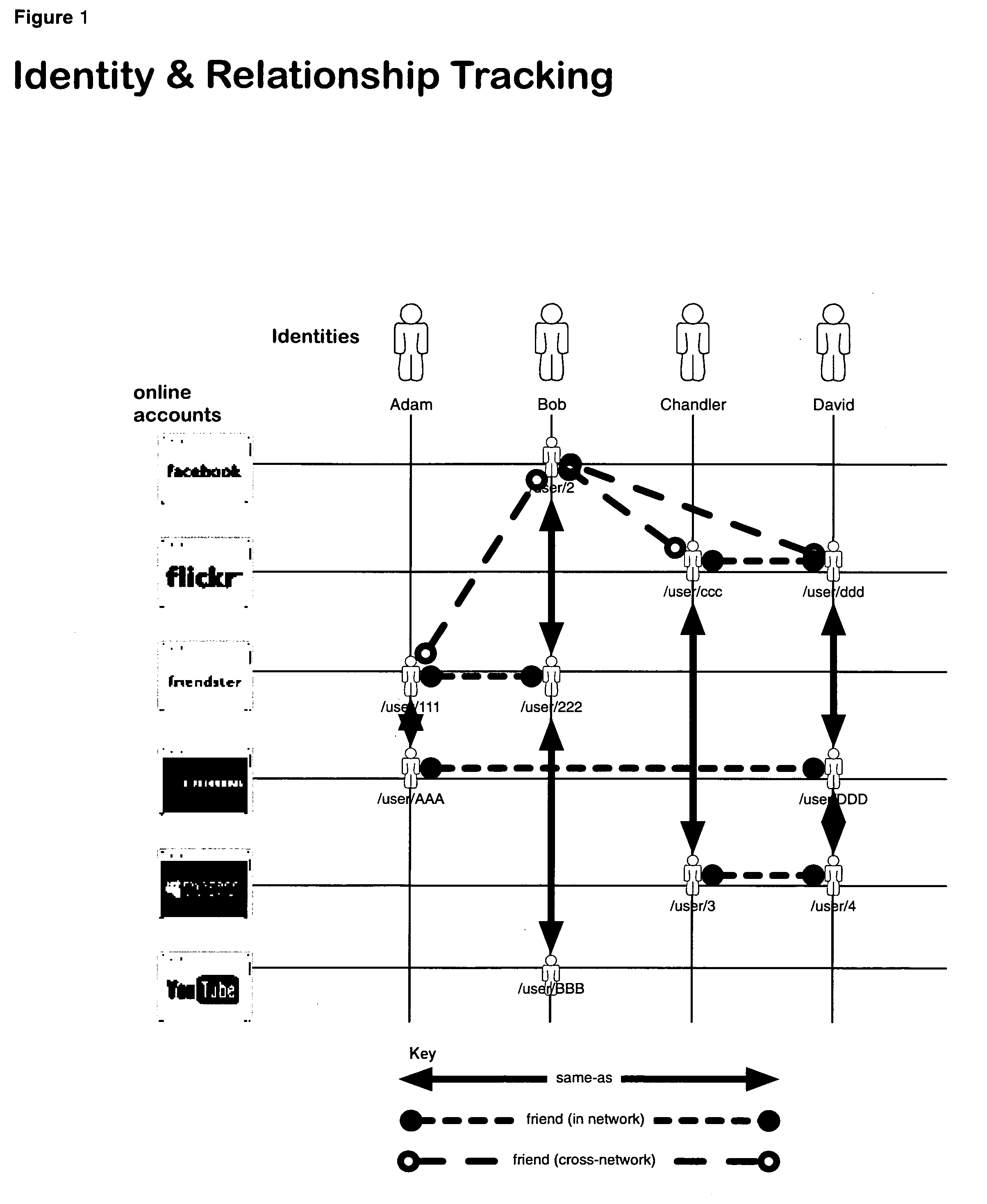
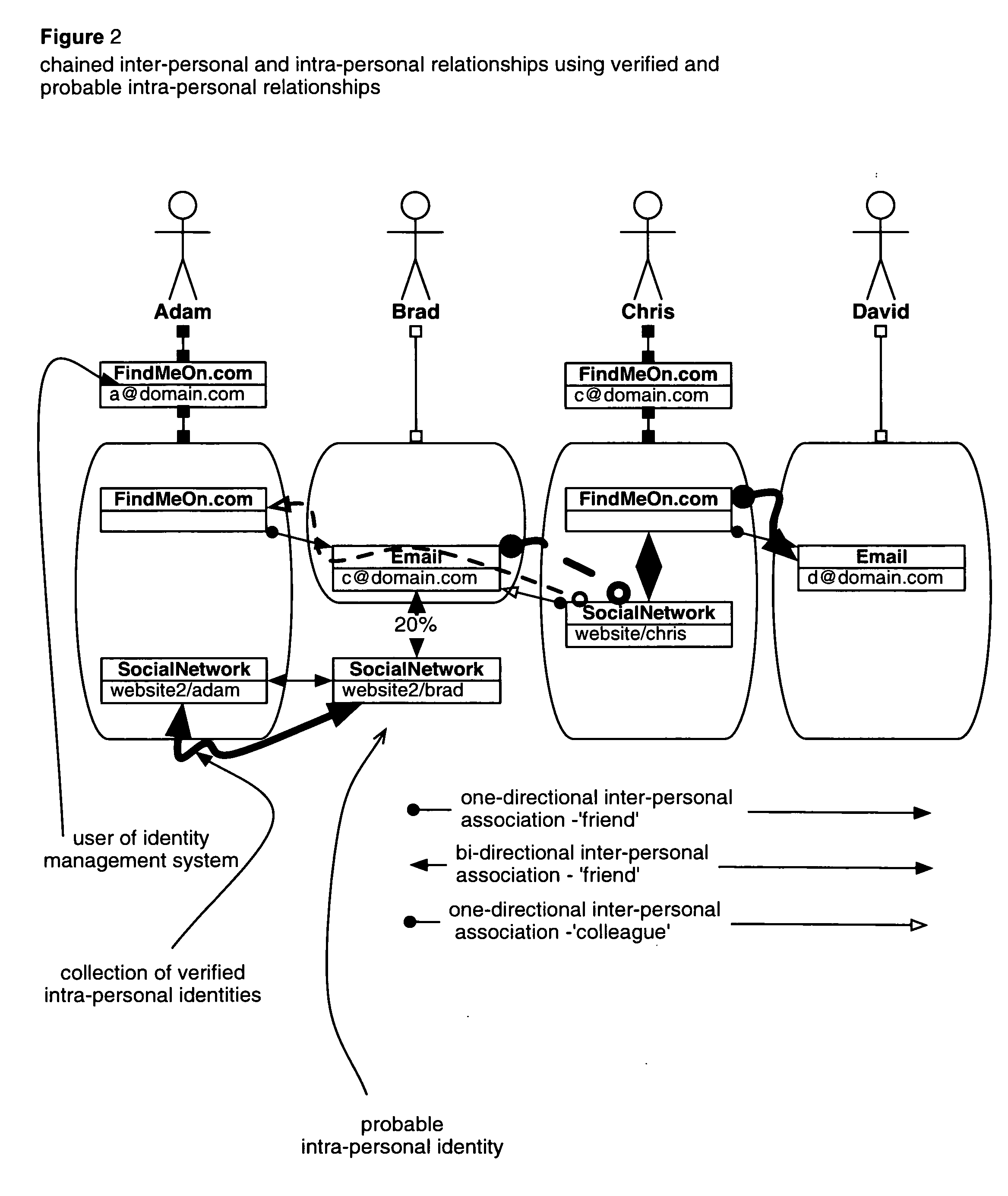
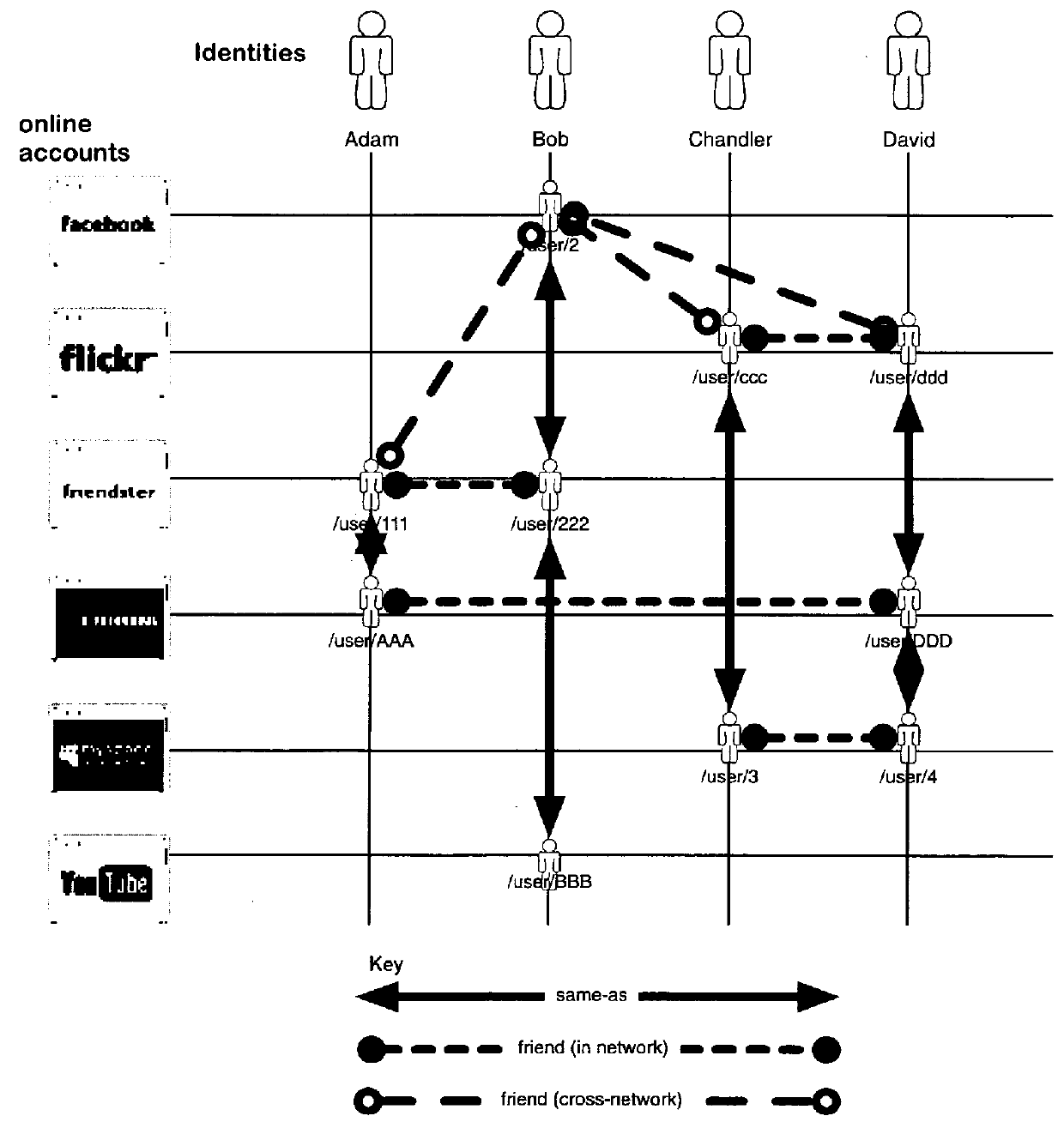
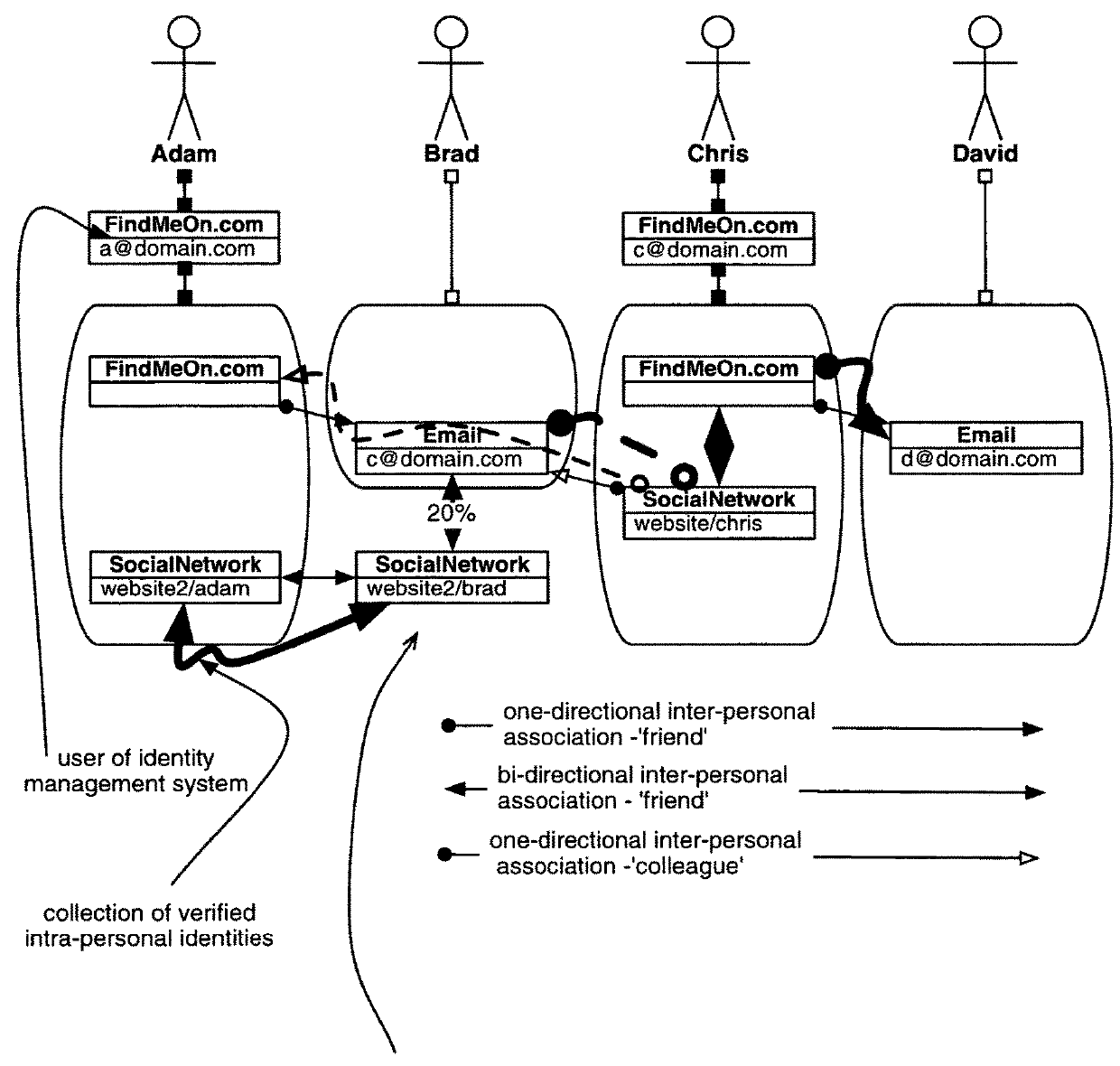
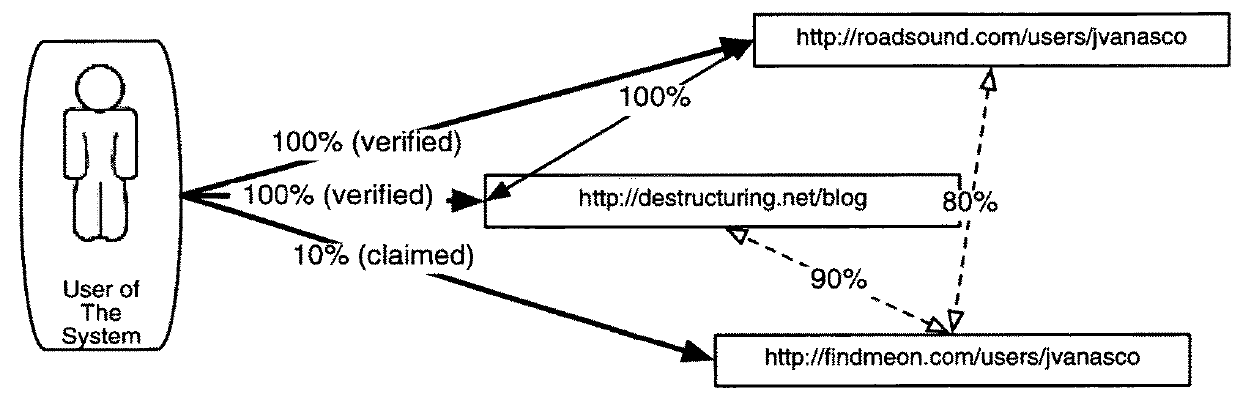
A networking database containing a plurality of records for different identities in which identities are connected to one another by defined or interpreted Inter-Personal and Intra-Personal relationships. Individuals using the system may define, group and categorize specific identities and relationships; the system may also define, categorize and group both identities and relationships belonging to individuals registered with the system and unregistered users through computational analysis. Identities and relationships may be discovered by the system via an opt-in user-provided mechanism, via a third-party providing information, or through the system's own discovery. Identity and Relationship data can then be used to customize content.
Owner:VANASCO JONATHAN BRIAN
System and method for discovery enrichment in an intelligent workload management system
InactiveUS20110126275A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationVirtualizationService-oriented architecture
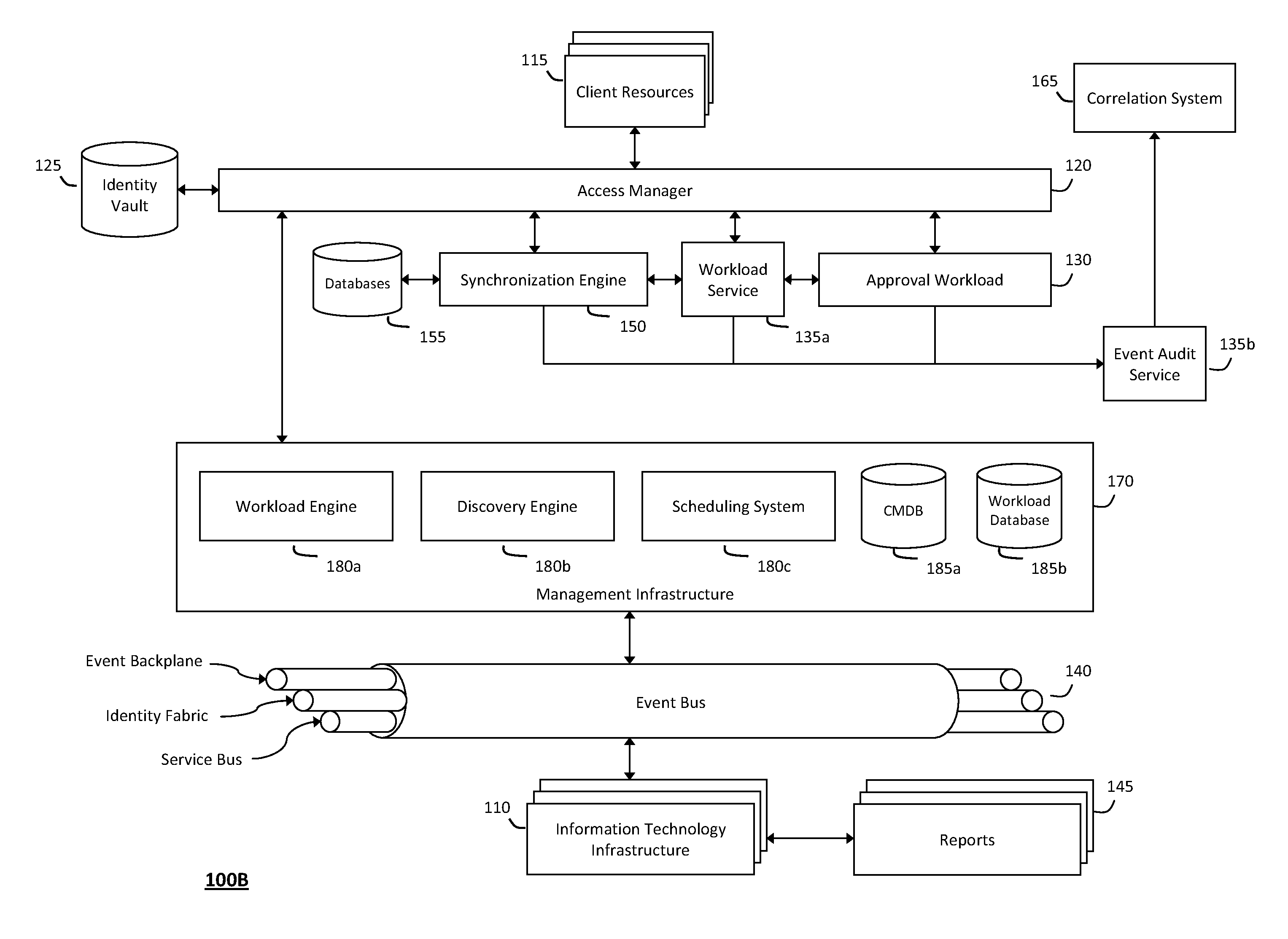
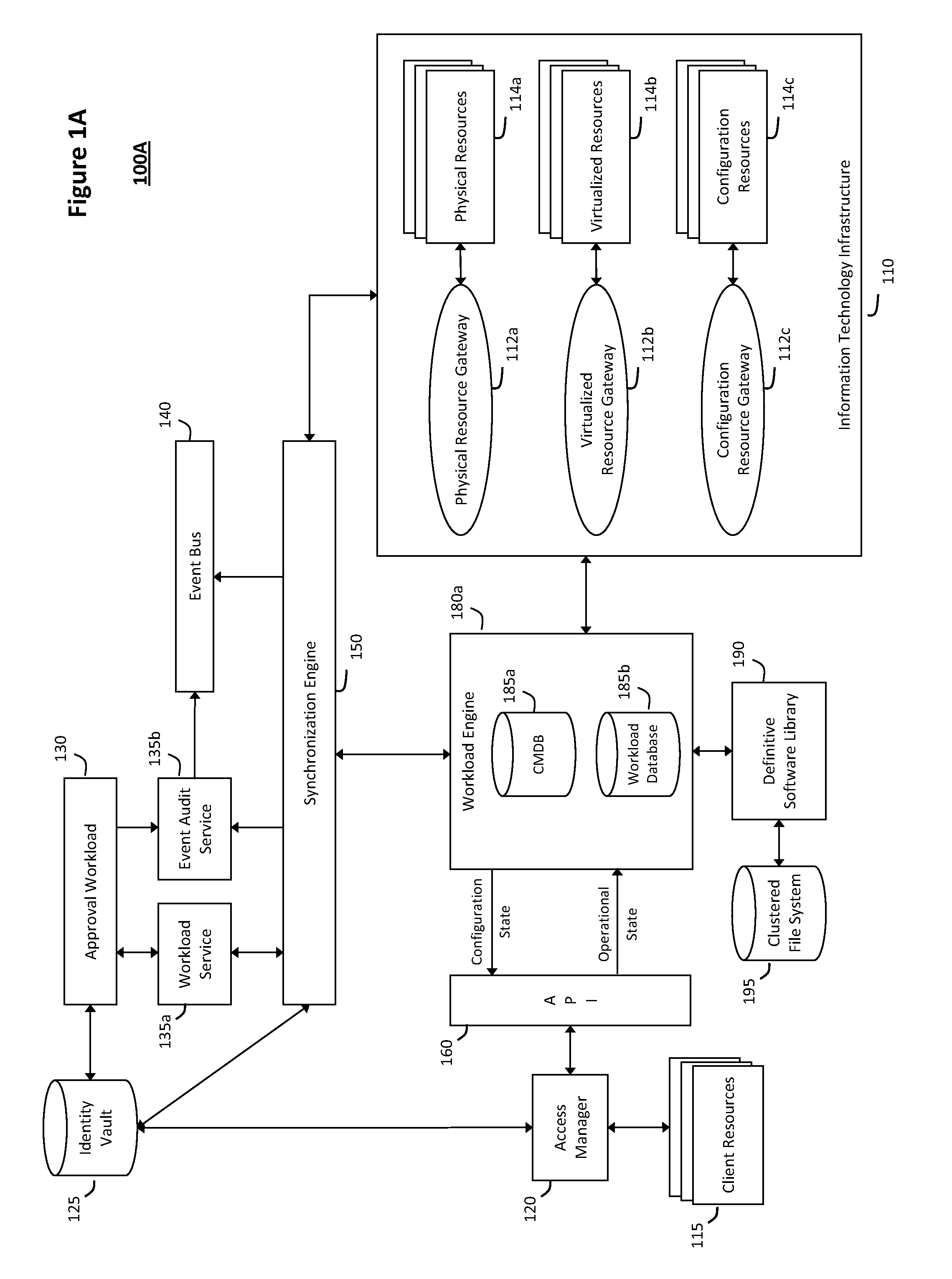
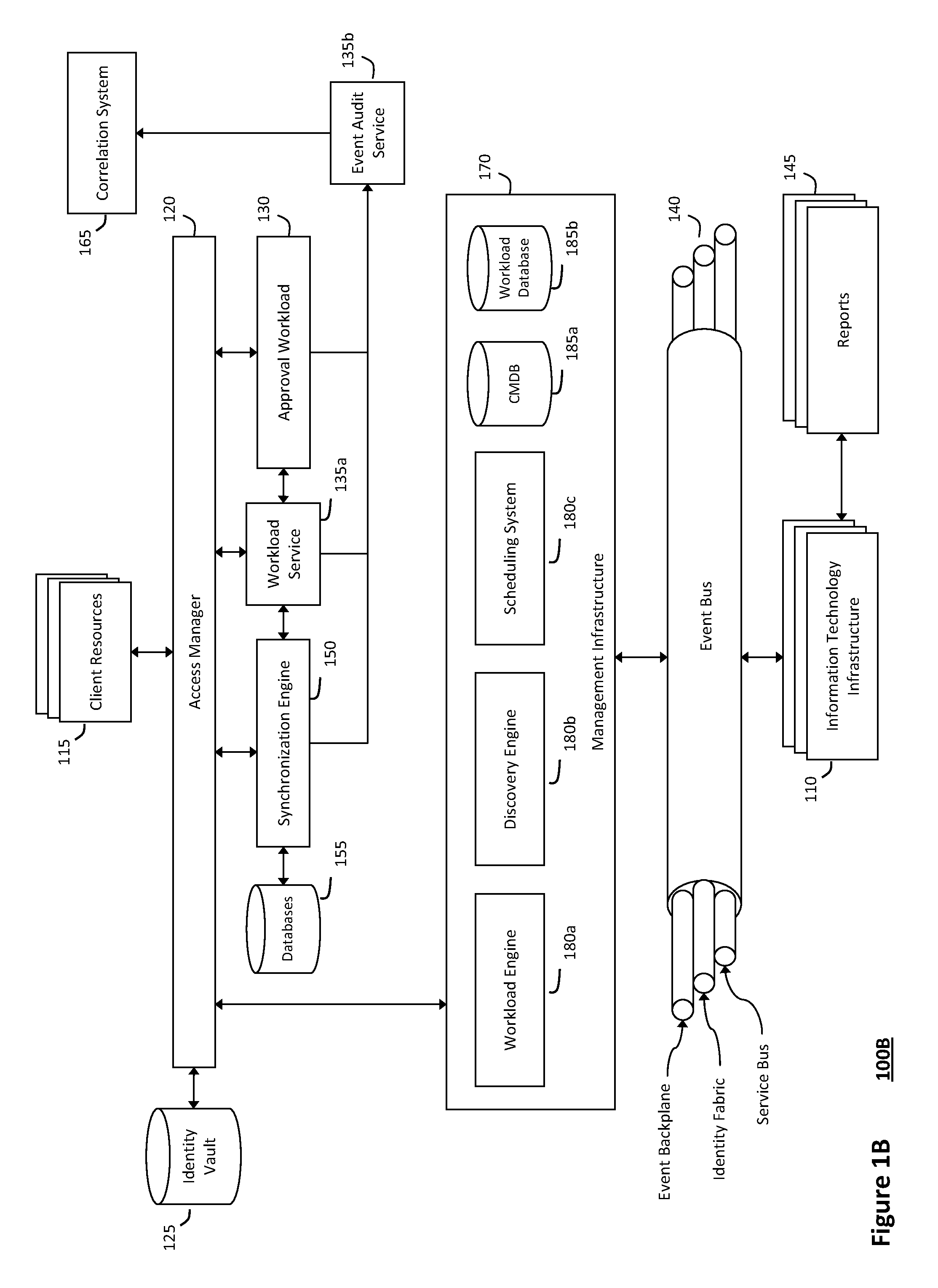
The system and method described herein for discovery enrichment in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing identities and access credentials, which may provide information that can enrich discovery of physical and virtual infrastructure resources. For example, a discovery engine may reference federated identity information stored in an identity vault and enrich a discovered infrastructure model with the federated identity information. Thus, the model may generally include information describing physical and virtualized resources in the infrastructure, applications and services running in the infrastructure, and information derived from the federated identity information that describes dependencies between the physical resources, the virtualized resources, the applications, and the services.
Owner:MICRO FOCUS SOFTWARE INC
Method And Apparatus For Trusted Federated Identity
InactiveUS20120072979A1Well formedDigital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
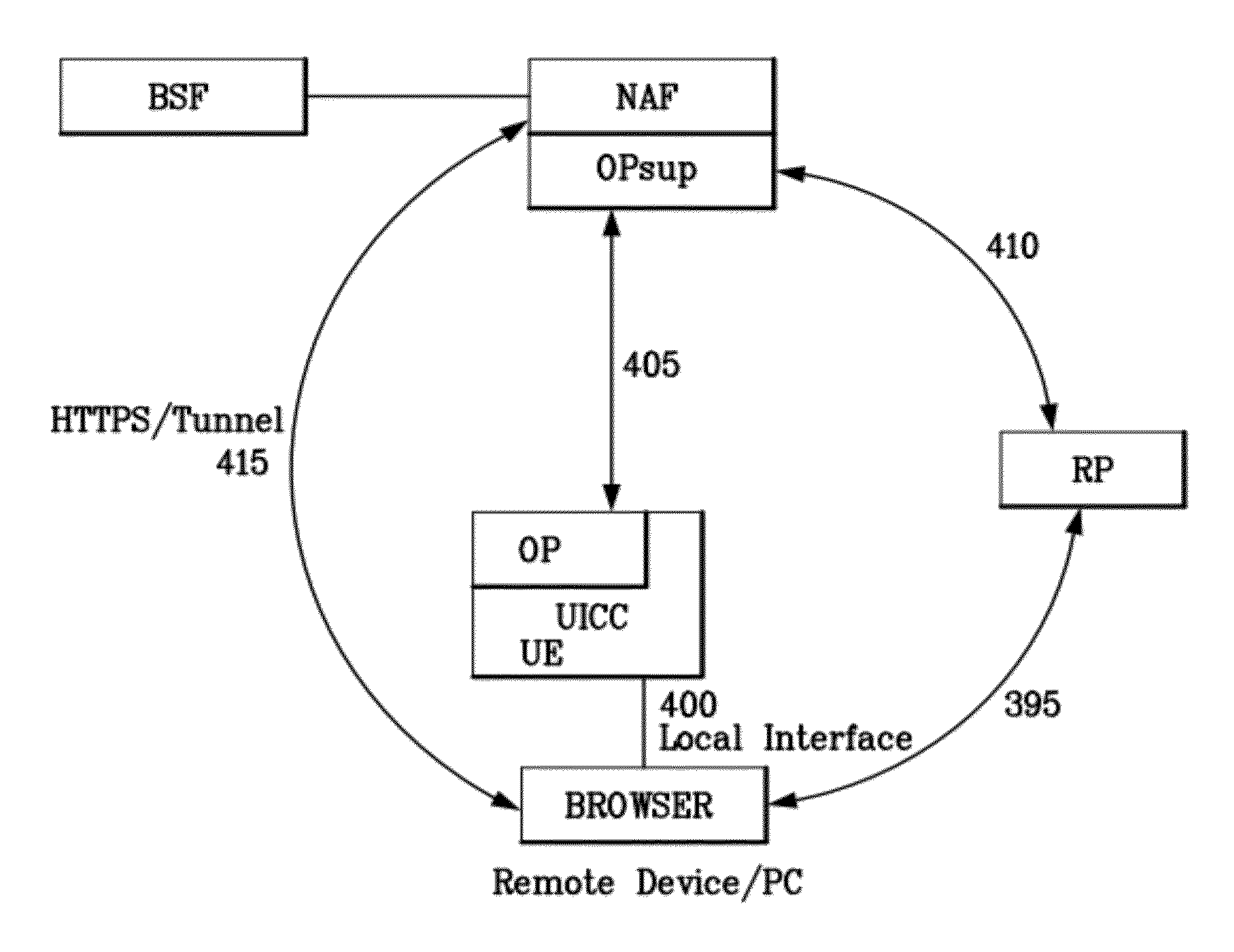
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
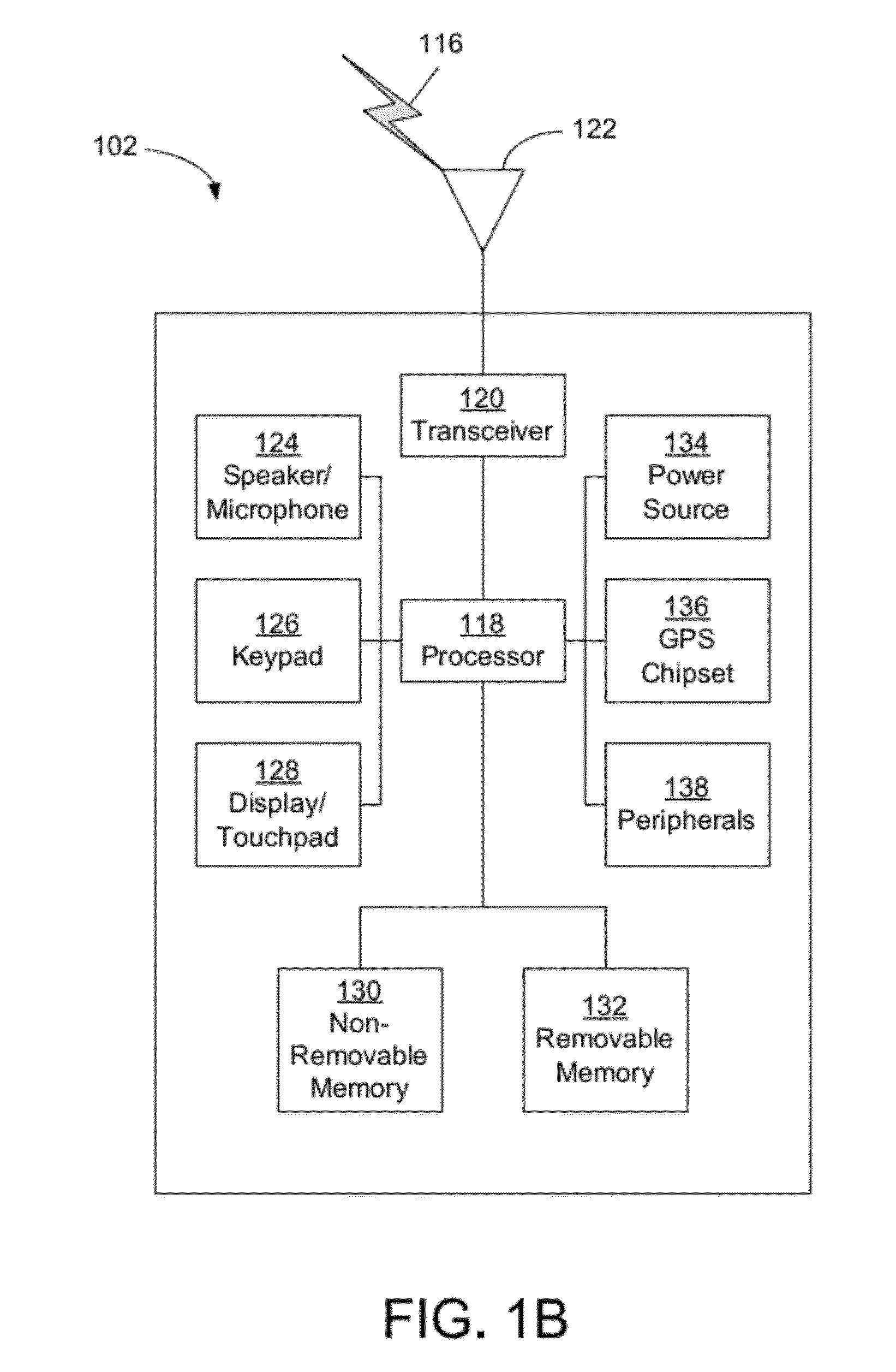
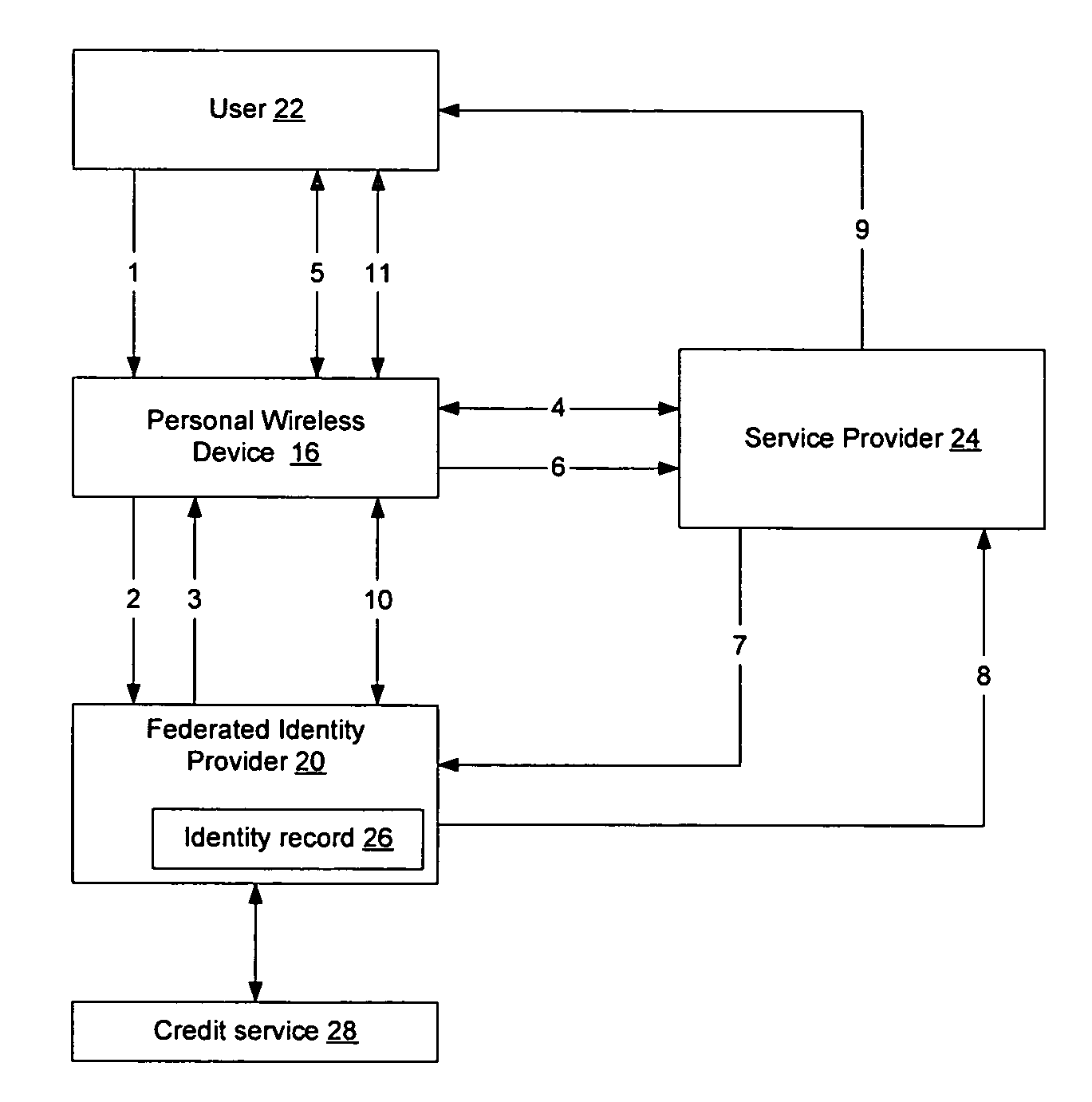
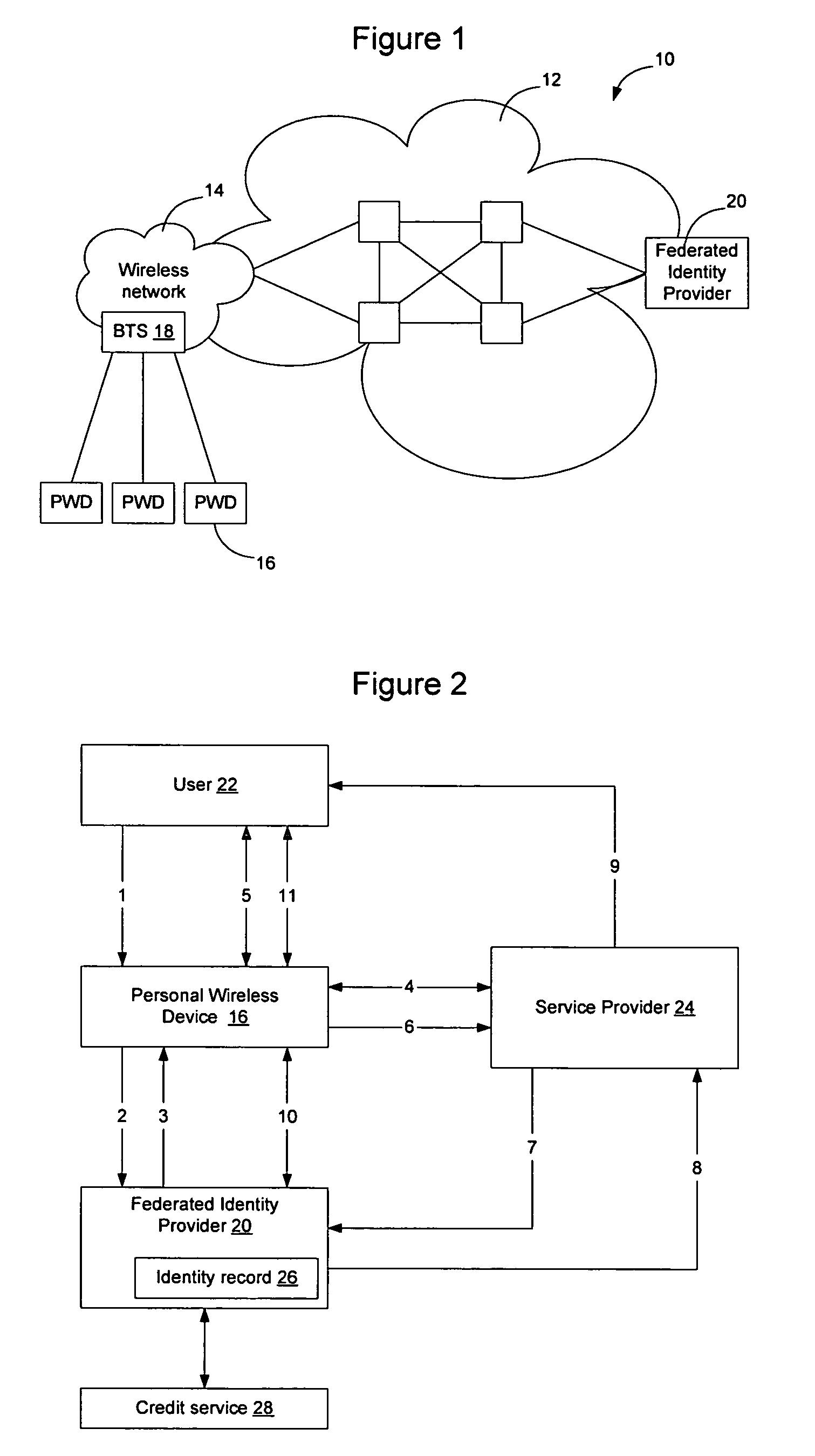
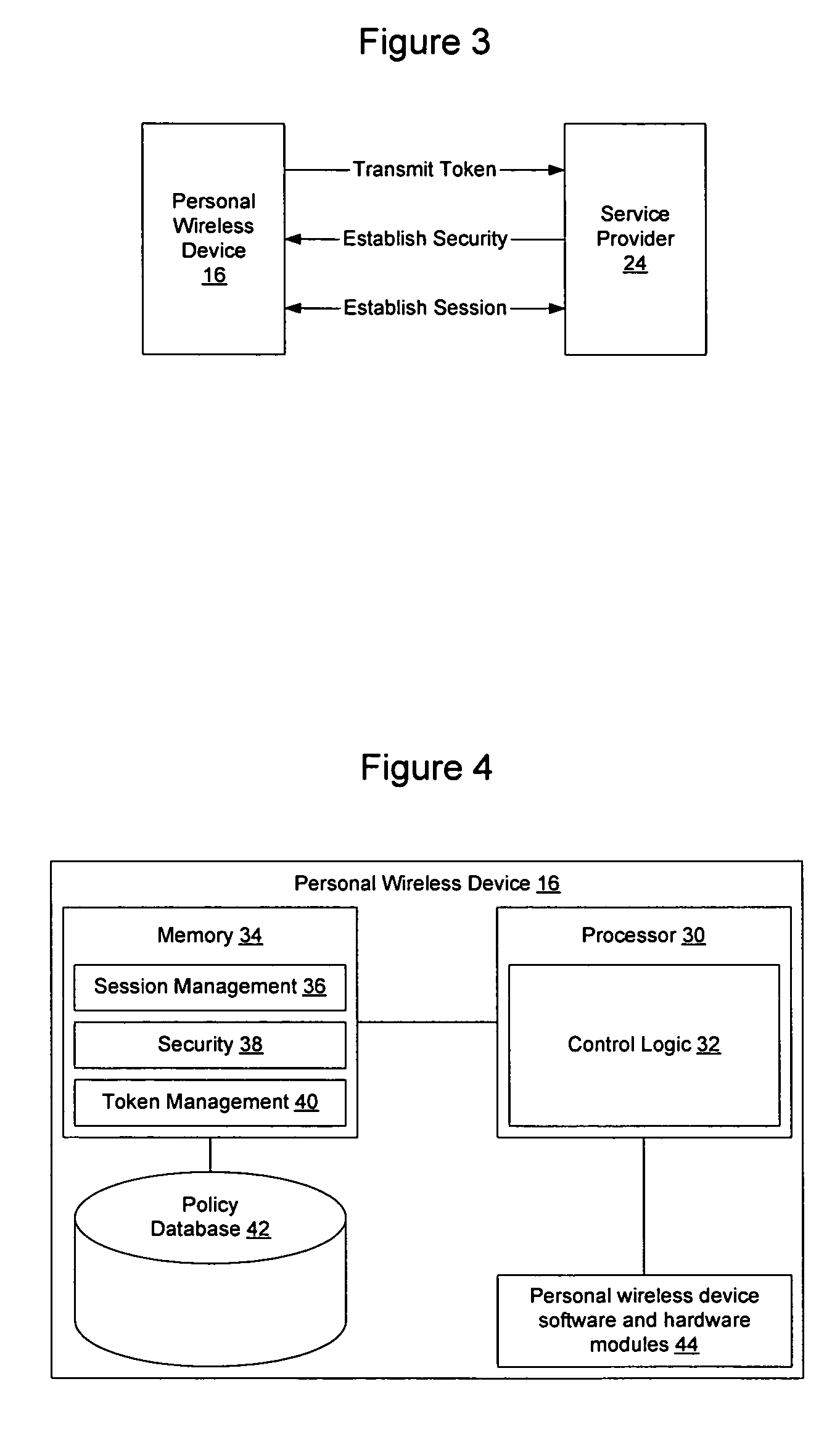
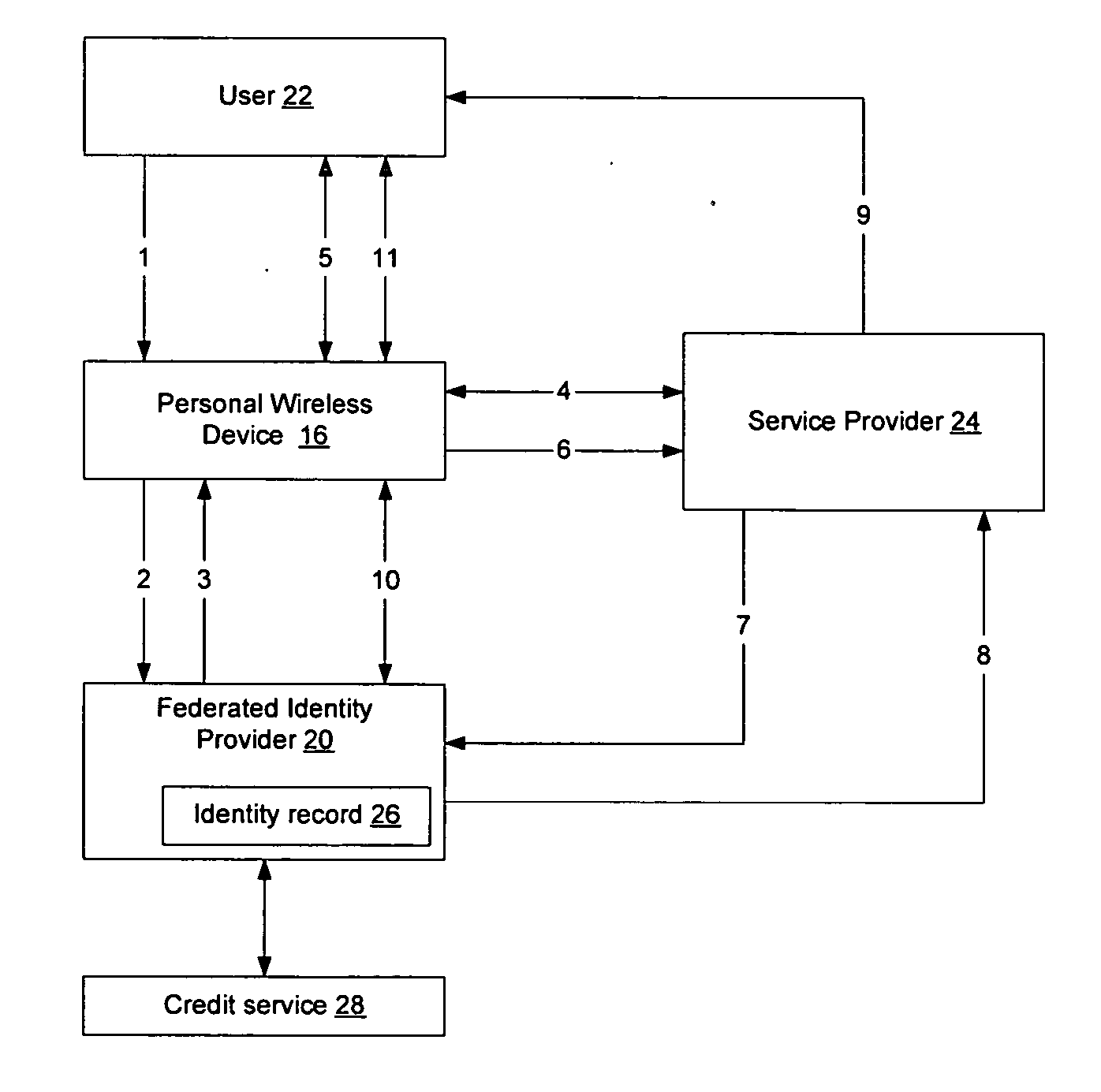
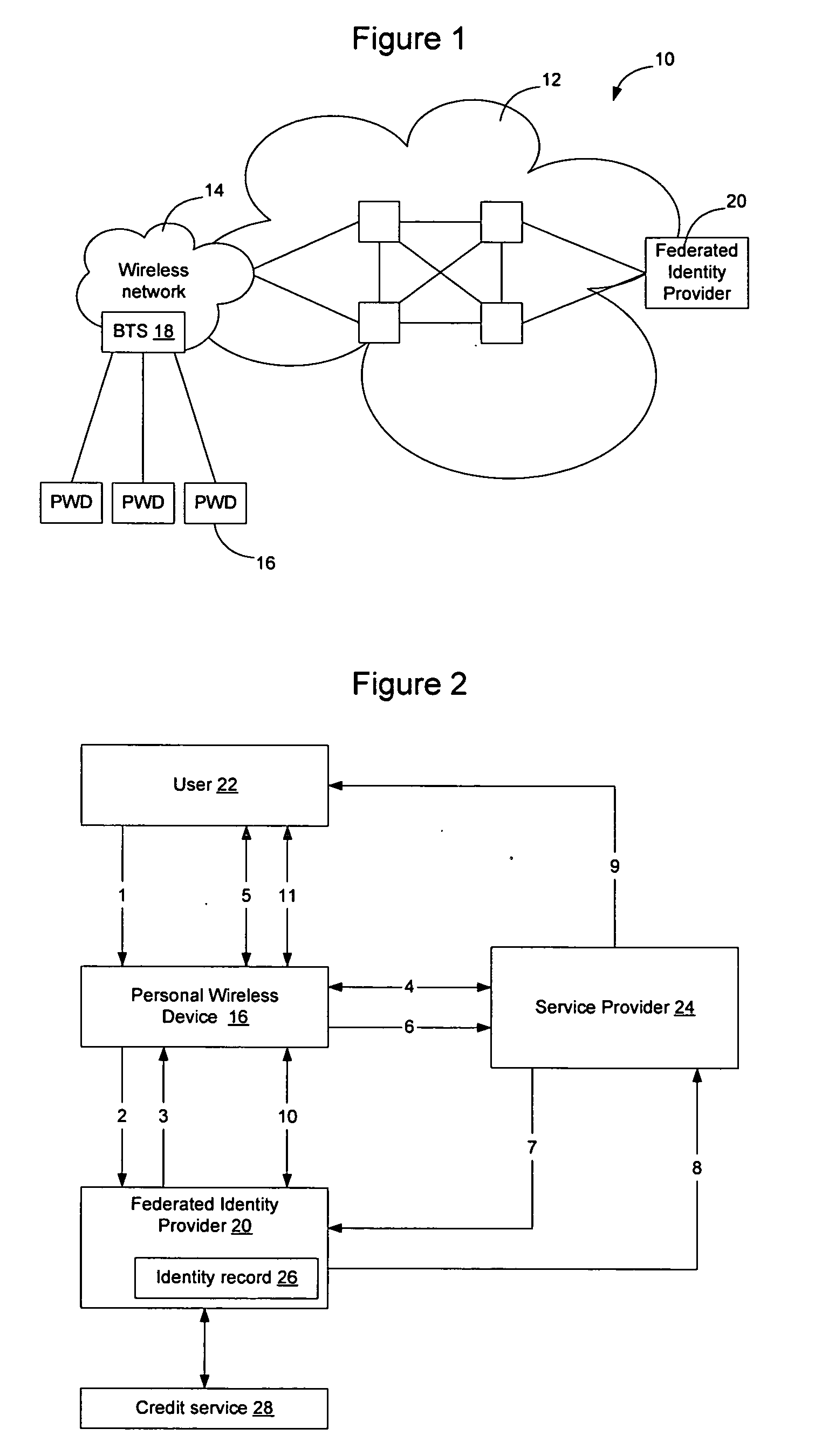
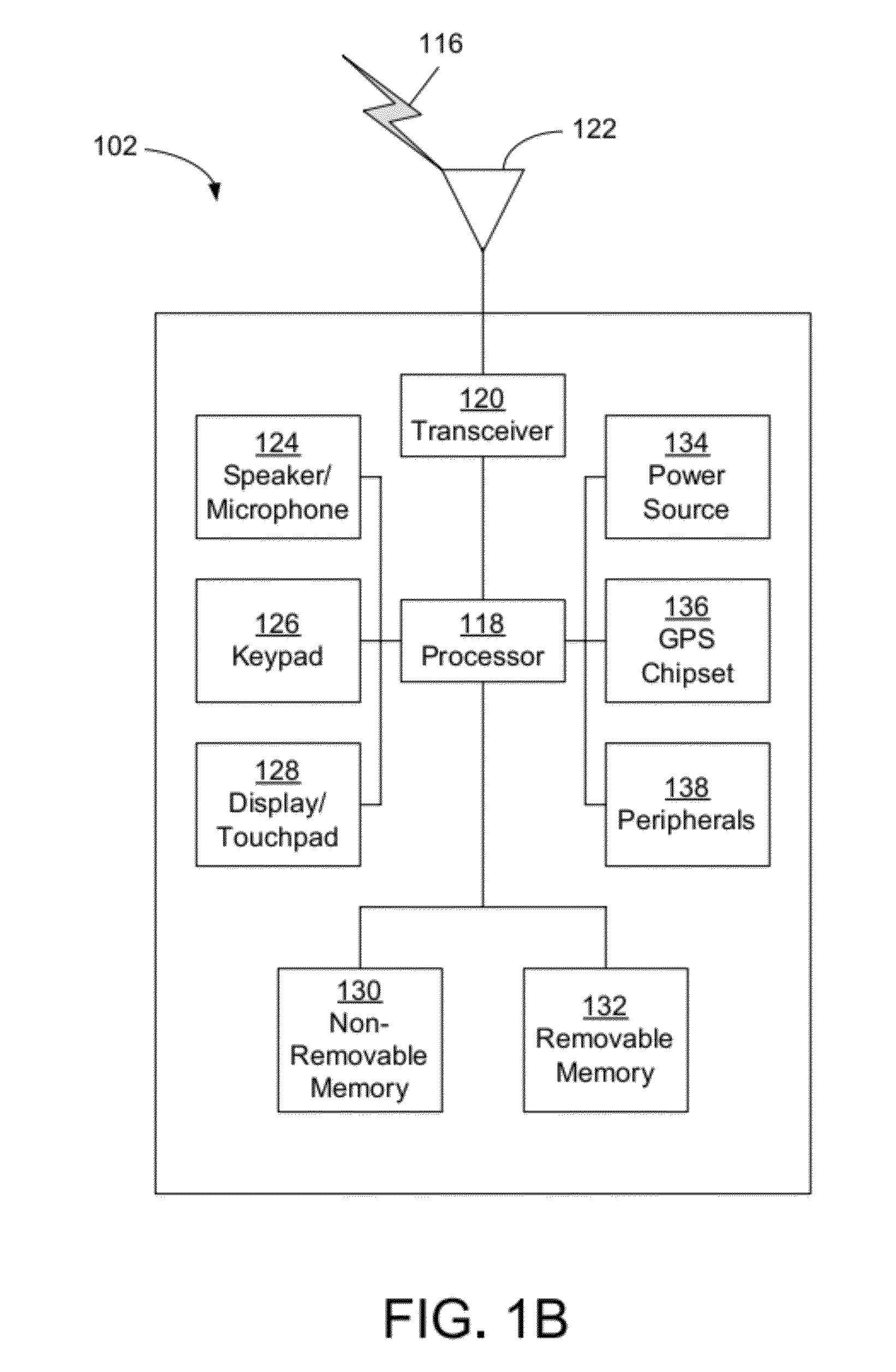
Method and apparatus for establishing a federated identity using a personal wireless device
ActiveUS8522039B2User identity/authority verificationDigital data authenticationCryptographic protocolBluetooth
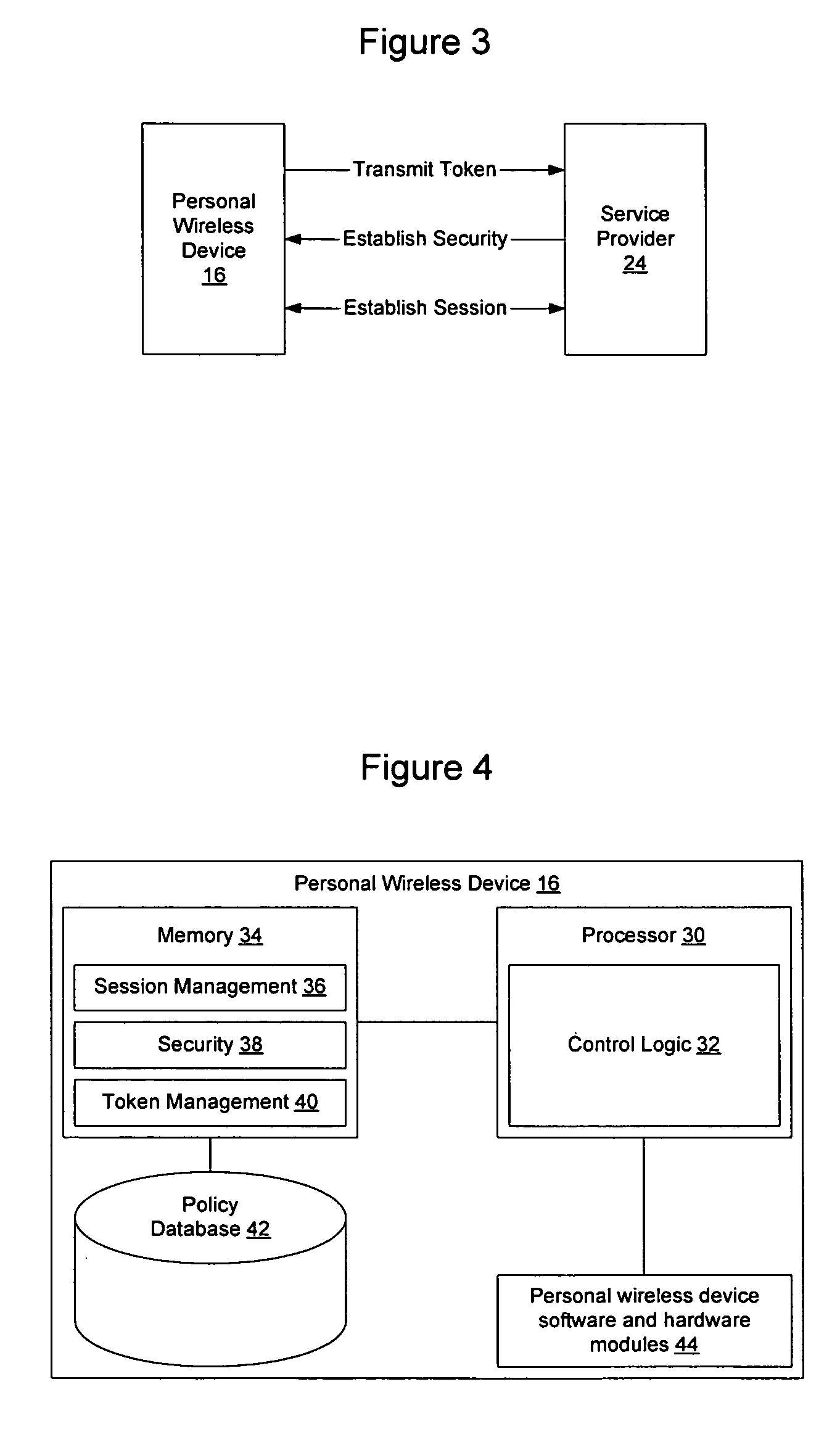
A federated identity, established through possession of a single sign-on token, will allow a personal wireless device (PWD) to be used in a commercial environment to purchase goods or services, access a building, access a telephone, wireless, or computer network, or in numerous other instances. The token may be obtained by the user authenticating with the PWD and the PWD authenticating with the network. When the PWD comes within range of a service provider, a session is established using a short range wireless protocol, such as Bluetooth or infrared. The session is secured using a security protocol such as SSL, and the service provider authenticates its identity to the PWD. Policy may be implemented regarding transmission of the token to the service provider. Upon receipt of the token, the service provider will validate the token with the federated identity provider, obtain identifying information, and complete the transaction.
Owner:APPLE INC
System and method for indexing, correlating, managing, referencing and syndicating identities and relationships across systems
ActiveUS10007895B2Raise the possibilityDigital data information retrievalDigital data processing detailsThird partyFederated identity
A networking database containing a plurality of records for different identities in which identities are connected to one another by defined or interpreted Inter-Personal and Intra-Personal relationships. Individuals using the system may define, group and categorize specific identities and relationships; the system may also define, categorize and group both identities and relationships belonging to individuals registered with the system and unregistered users through computational analysis. Identities and relationships may be discovered by the system via an opt-in user-provided mechanism, via a third-party providing information, or through the system's own discovery. Identity and Relationship data can then be used to customize content.
Owner:VANASCO JONATHAN BRIAN
Method and Apparatus for Multi-Domain Identity Interoperability and certification
ActiveUS20090089625A1Memory loss protectionDigital data processing detailsInternet privacyFederated identity
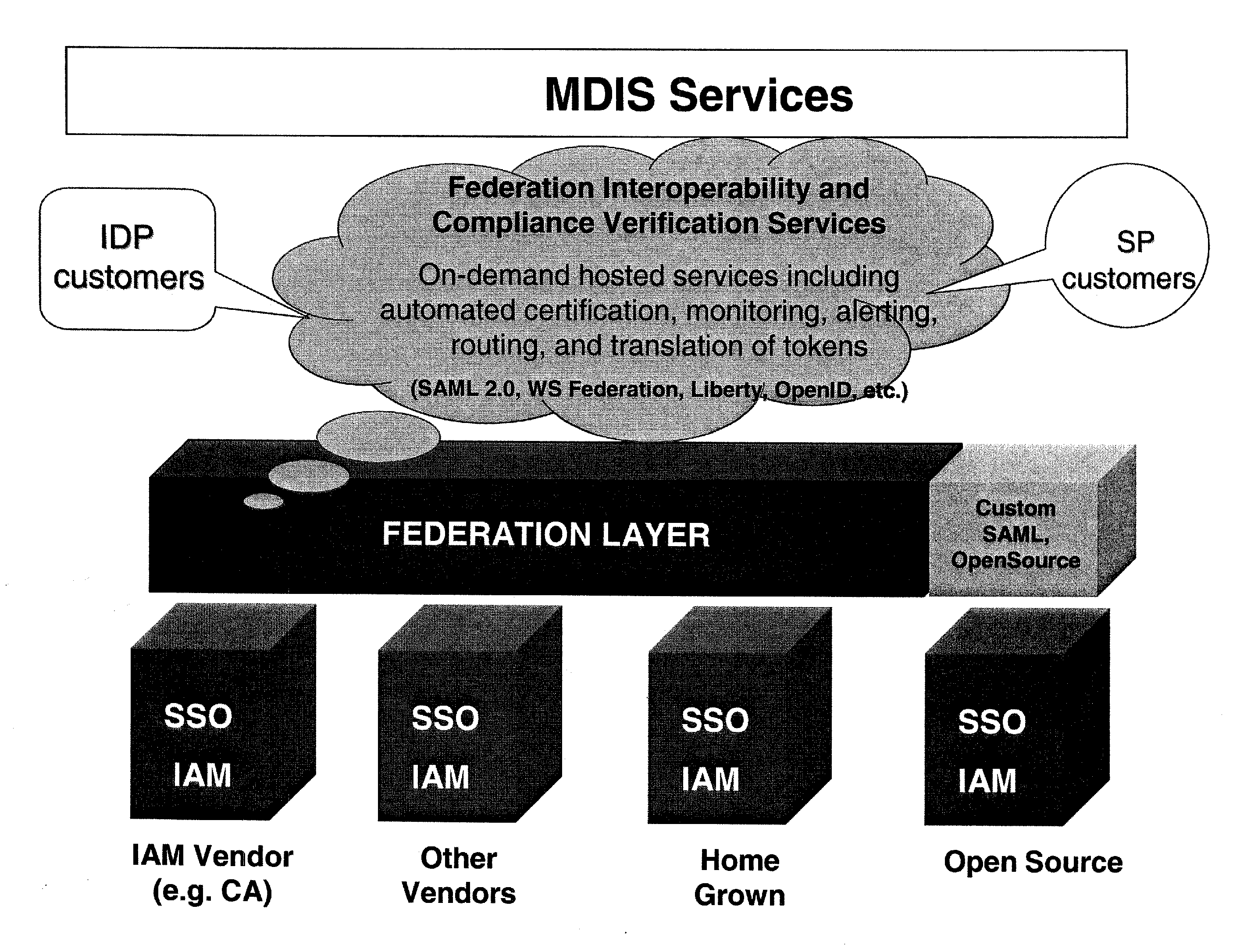
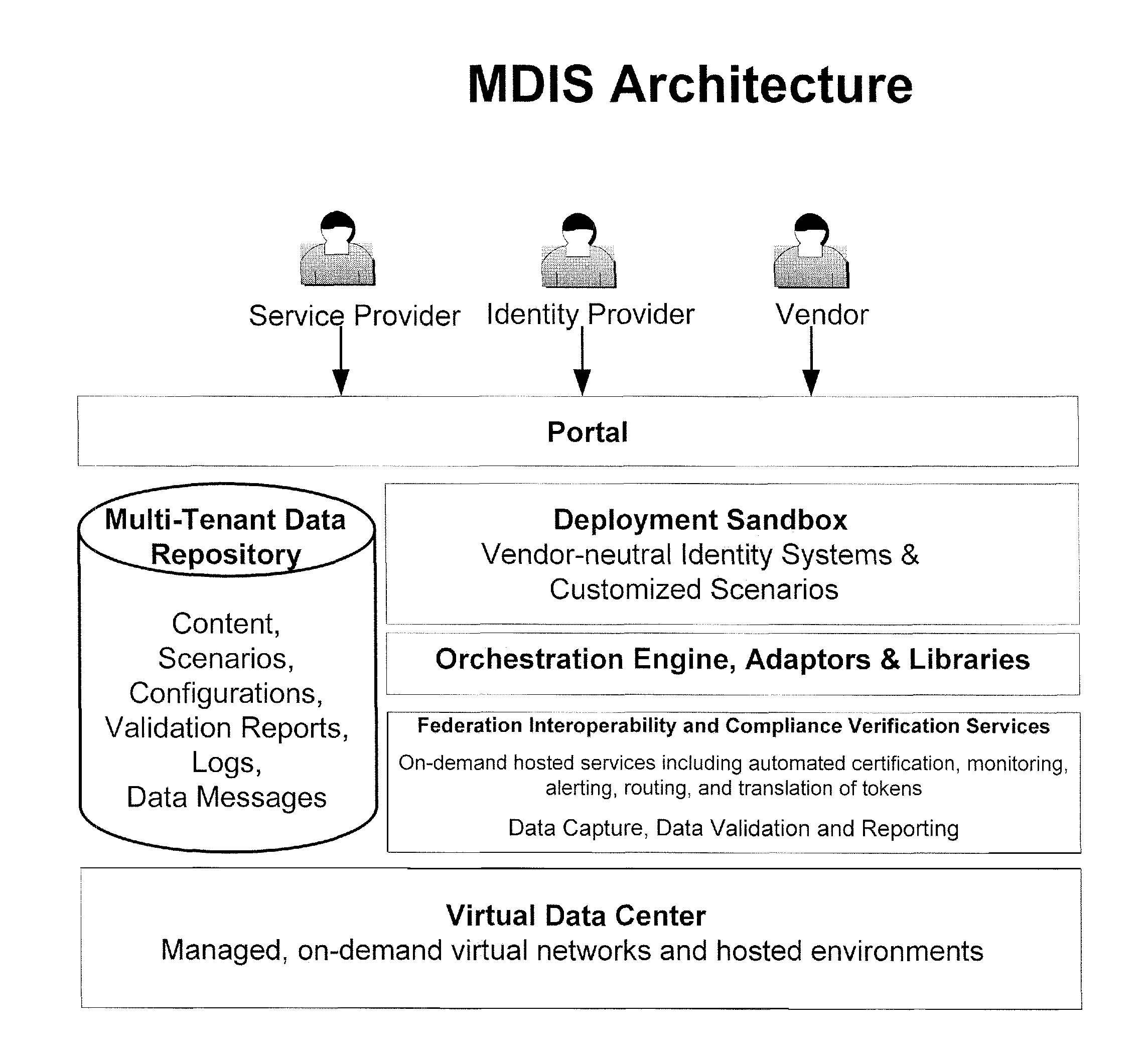
A method and apparatus to provide identity management deployment interoperability and compliance verification. In one embodiment, the system also provides on-demand services including automated certification, monitoring, alerting, routing, and translation of tokens for federated identity related interactions between multi-domain identity management systems is provided.
Owner:FUGEN SOLUTIONS
Method and apparatus for establishing a federated identity using a personal wireless device
A federated identity, established through possession of a single sign-on token, will allow a personal wireless device (PWD) to be used in a commercial environment to purchase goods or services, access a building, access a telephone, wireless, or computer network, or in numerous other instances. The token may be obtained by the user authenticating with the PWD and the PWD authenticating with the network. When the PWD comes within range of a service provider, a session is established using a short range wireless protocol, such as Bluetooth or infrared. The session is secured using a security protocol such as SSL, and the service provider authenticates its identity to the PWD. Policy may be implemented regarding transmission of the token to the service provider. Upon receipt of the token, the service provider will validate the token with the federated identity provider, obtain identifying information, and complete the transaction.
Owner:APPLE INC
Proxy-based profile management to deliver personalized services
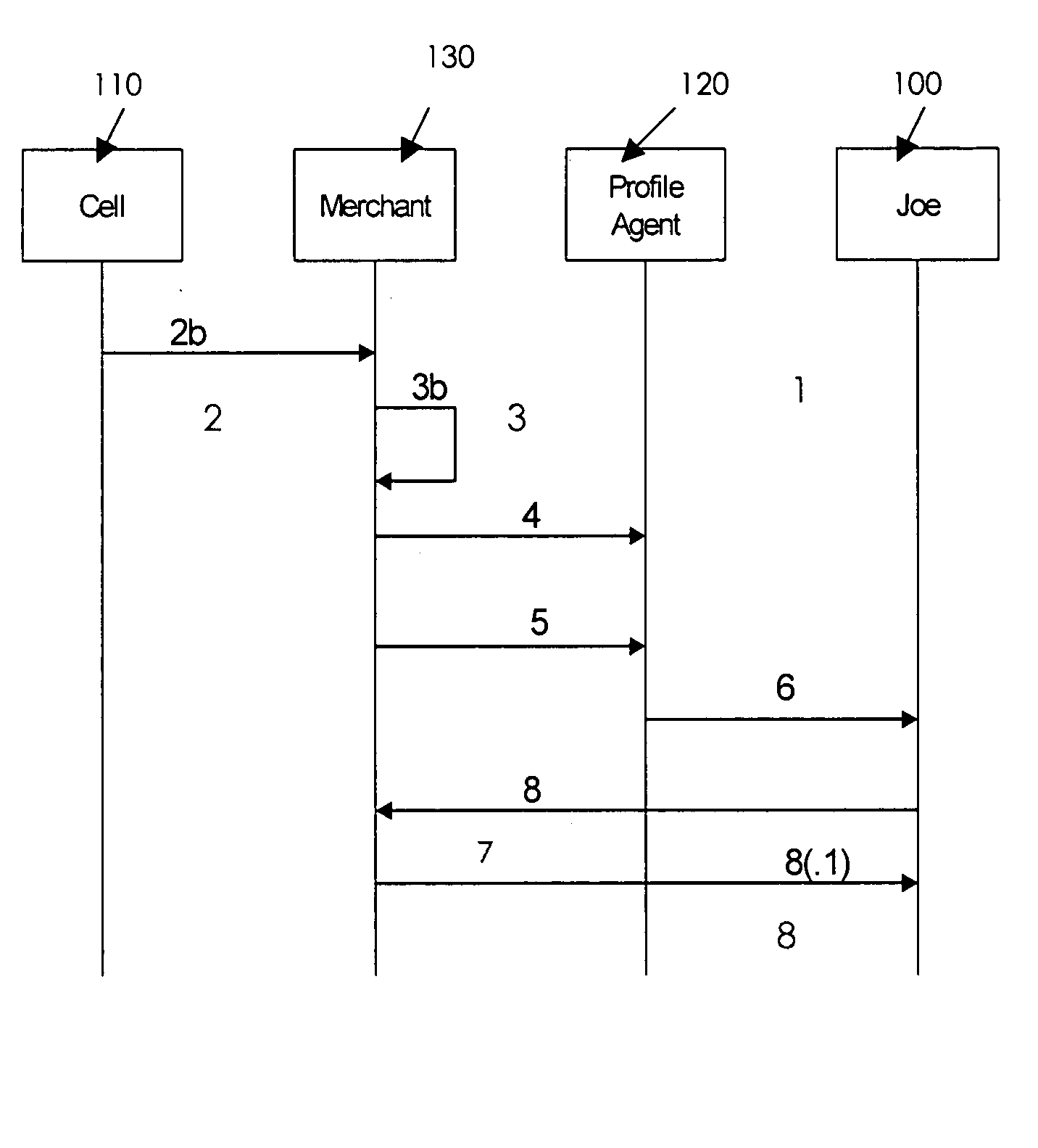
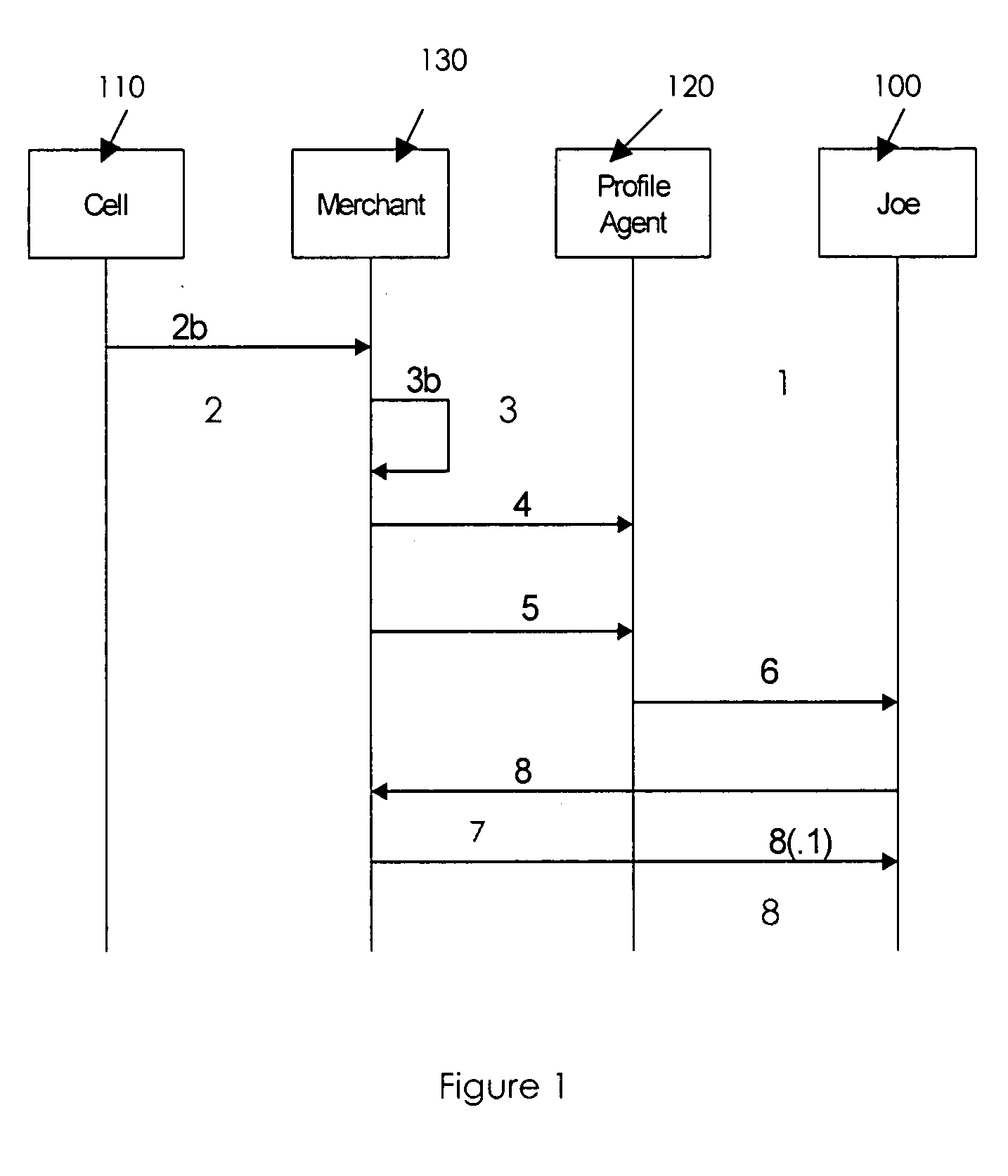
A third-party profile service based on a proxy server model is described, where a user's profile service resides at a URL, in contrast to a profile service that requires federation identity. A profile service is provided that augments location-based services offered by service providers targeting mobile users via, for example, wireless and Wifi Networks. Additional personalization is driven by identity / profile services. Participants in the scenario are not required to share an identity or profile (i.e., static federation is not required). The user establishes a single profile with a trusted provider, hands-off solicitations to a profile agent that operates on behalf of the user to apply policies and preferences. The agent also provides privacy and anonymity (opaqueness).
Owner:AT&T INTPROP I L P
Federated authentication of client computers in networked data communications services callable by applications
InactiveUS20150074407A1Key distribution for secure communicationUser identity/authority verificationClient-sideData treatment
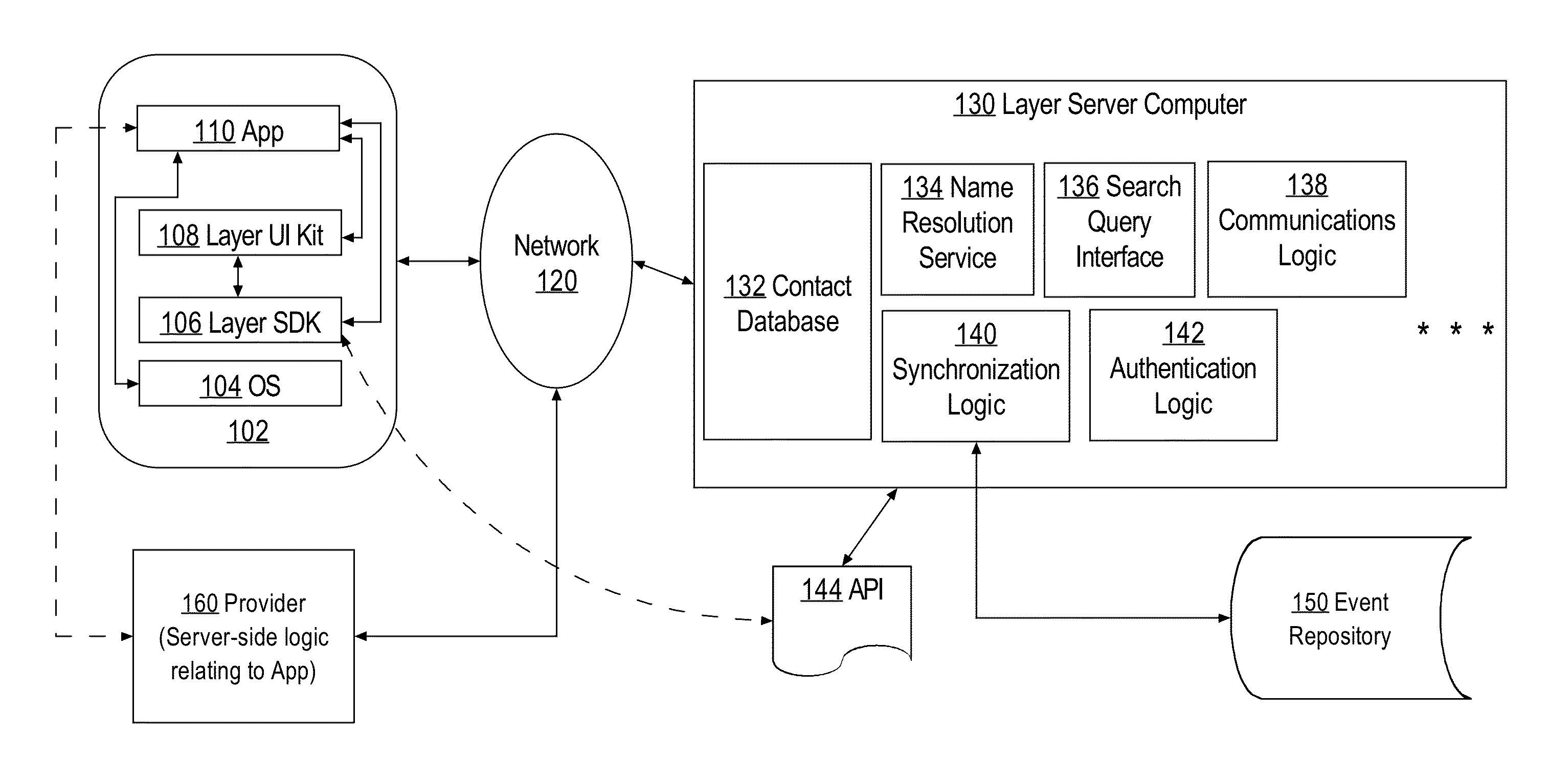
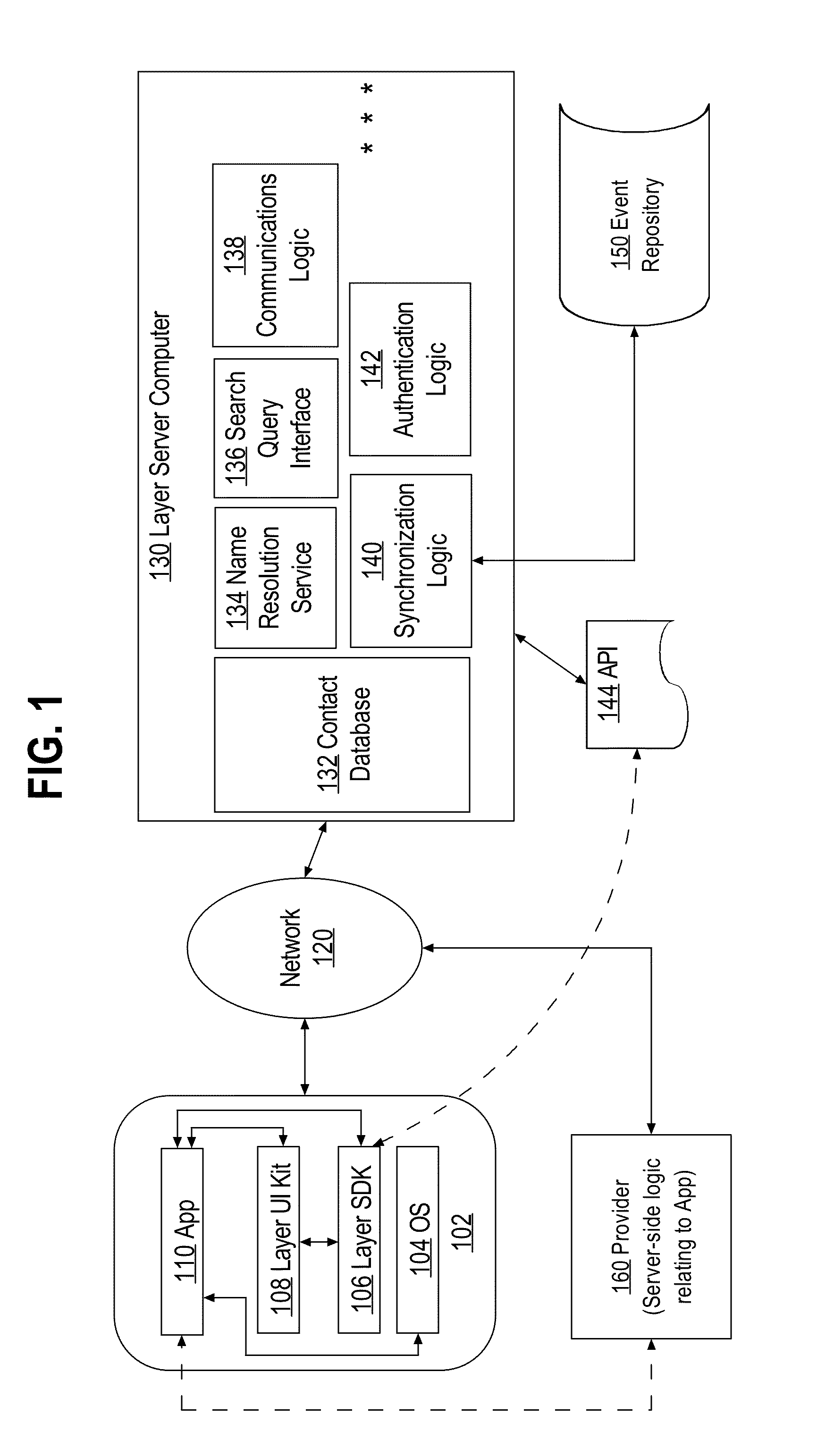
A data processing method providing improved and efficient authentication of client computers by server computers, the method comprising: using authentication logic of a server computer, establishing a secure socket connection with a client computer; receiving, from the client computer, a request to use a communications service that is implemented at the server computer, and in response to the request, determining that the client computer is unauthenticated; providing a nonce value to the client computer; receiving from the client computer an encrypted identity token that includes the nonce and a user identifier, wherein the identity token has been encrypted using a provider computer and an encryption key of the provider computer, wherein the encryption key is known at the server computer; validating the identity token and obtaining the user identifier therein; creating and storing a session token that is uniquely associated with the client computer and that includes a session identifier, the user identifier, and a binding to the secure socket connection.
Owner:LAYER INC
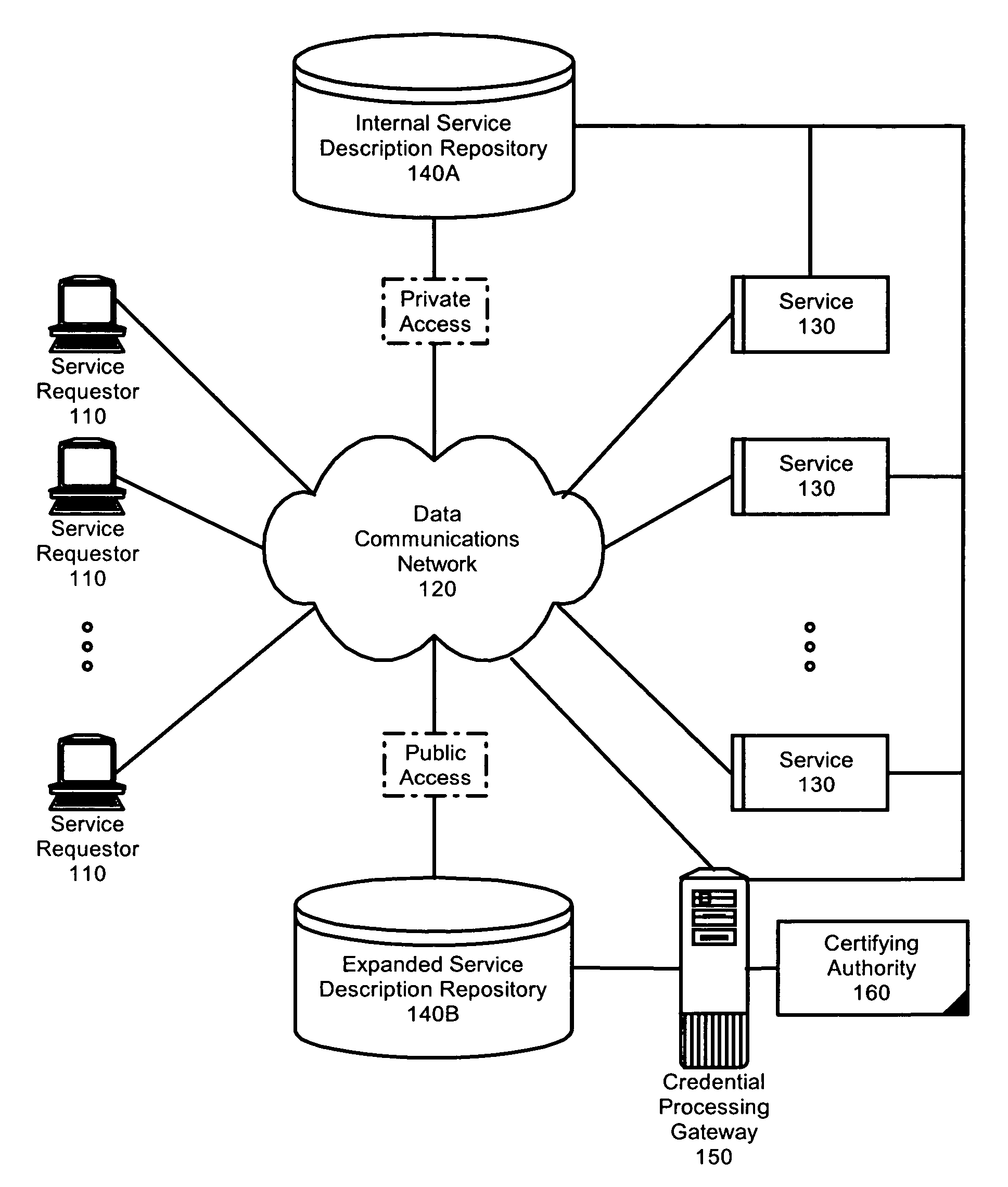
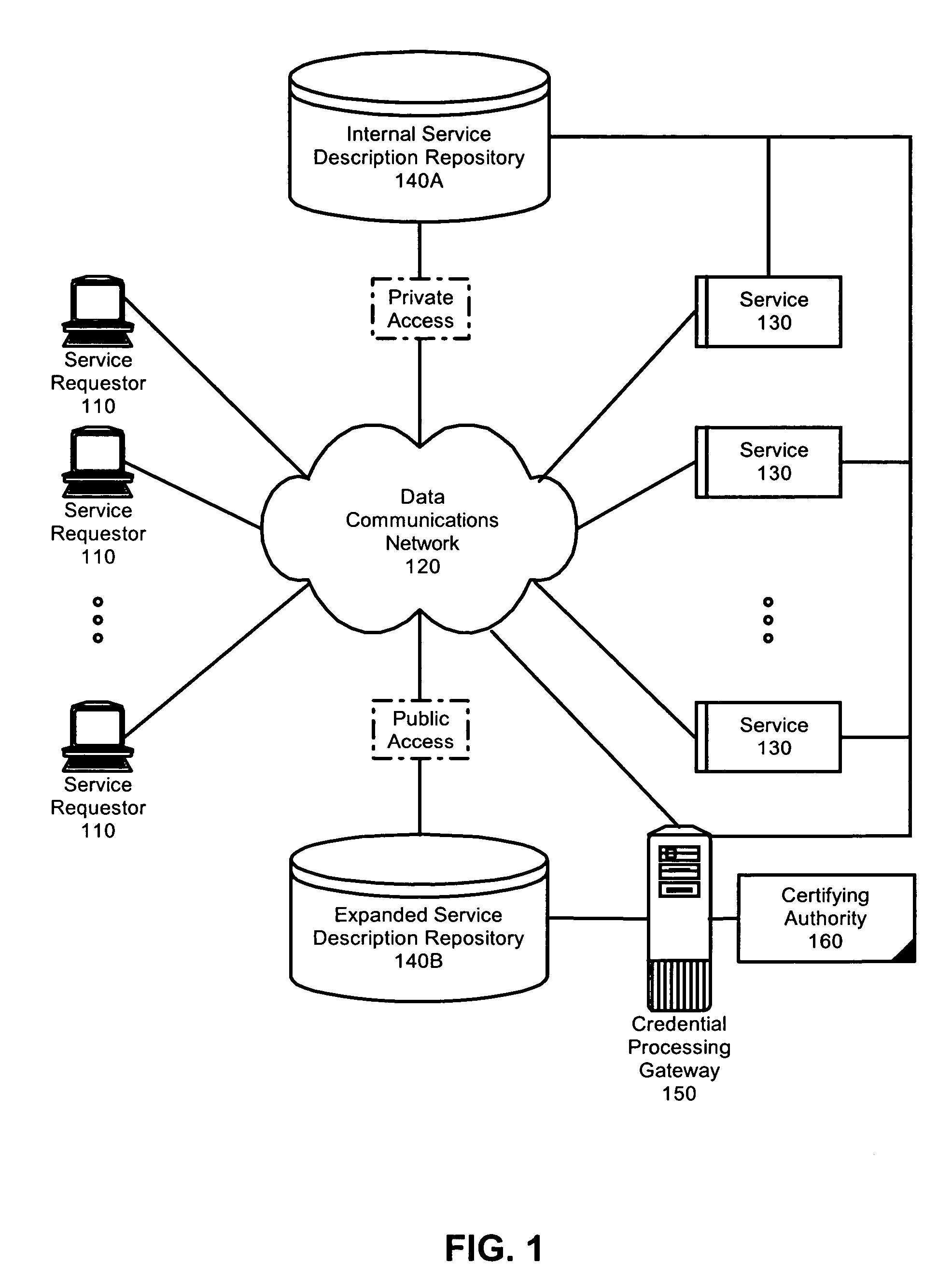
Federated identity brokering
InactiveUS20060021010A1Make up for deficienciesDigital data processing detailsUser identity/authority verificationTrusted authorityFederated identity
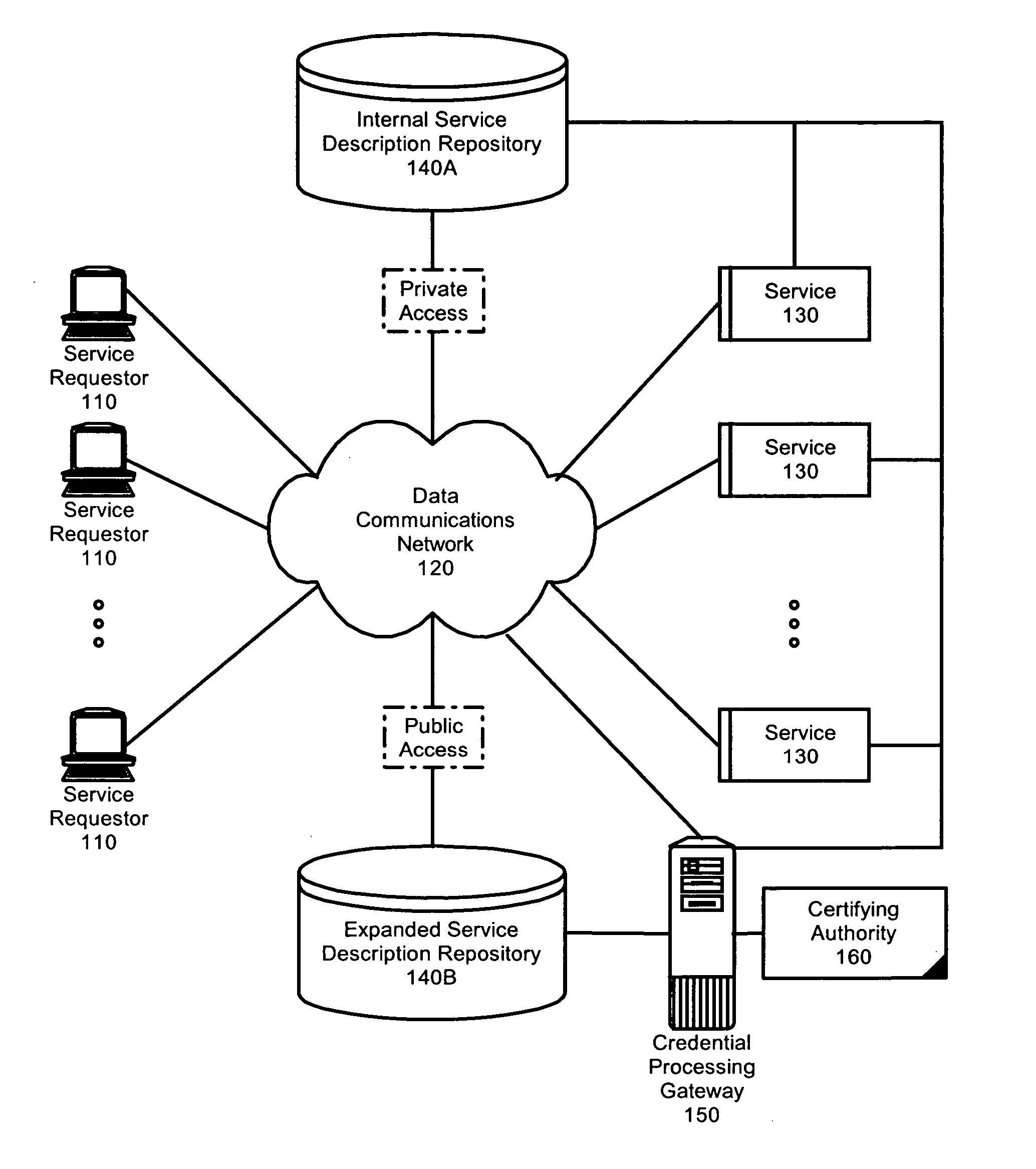
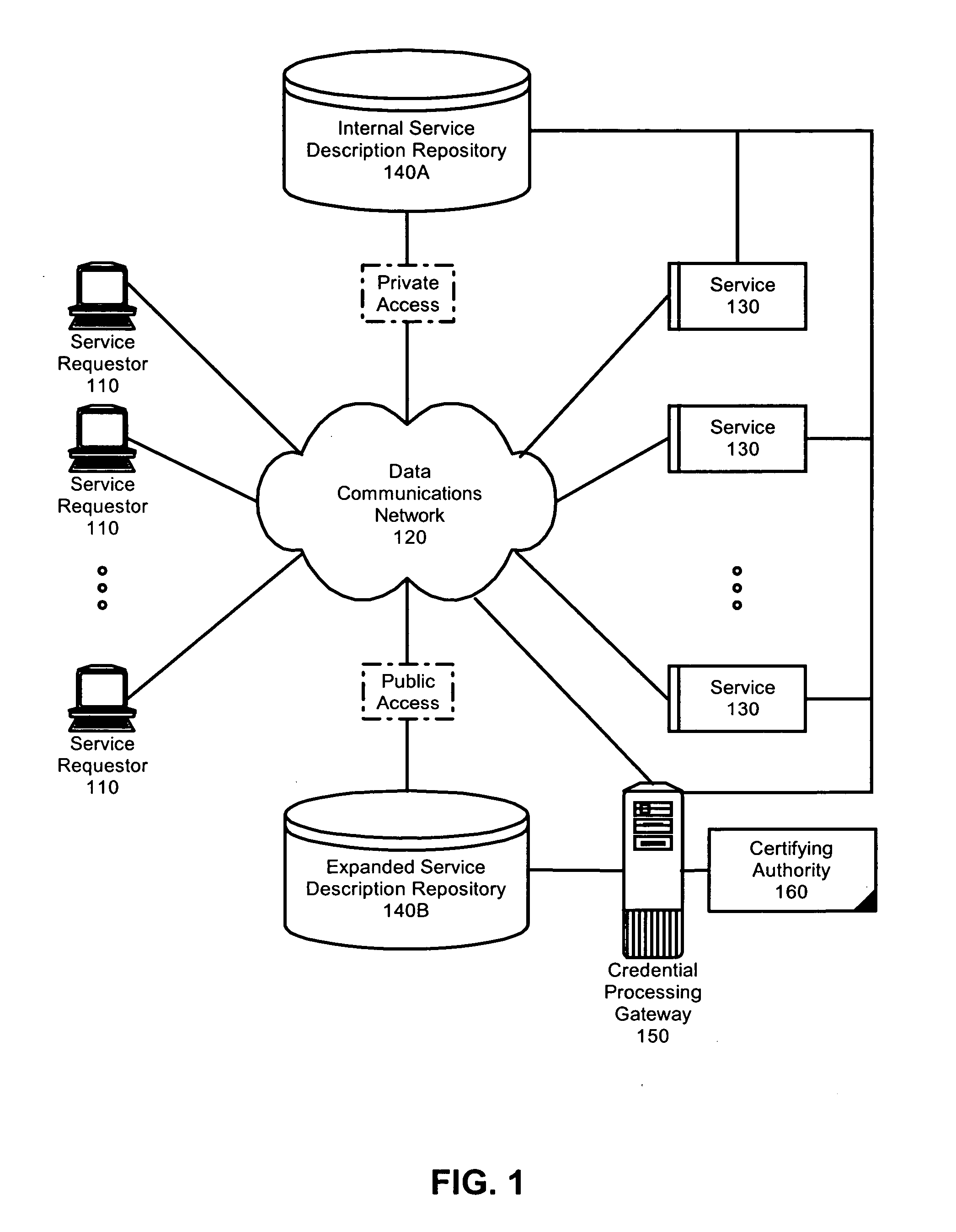
A method, system and apparatus for federated identity brokering. In accordance with the present invention, a credential processing gateway can be disposed between one or more logical services and one or more service requesting clients in a computer communications network. Acting as a proxy and a trusted authority to the logical services, the credential processing gateway can map the credentials of the service requesting clients to the certification requirements of the logical services. In this way, the credential processing gateway can act as a federated identity broker in providing identity certification services for a multitude of different service requesting clients without requiring the logical services to include a pre-configuration for specifically processing the credentials of particular service requesting clients.
Owner:IBM CORP
Access control for federated identities
ActiveUS7444519B2Digital data processing detailsMultiple digital computer combinationsThird partyData access control
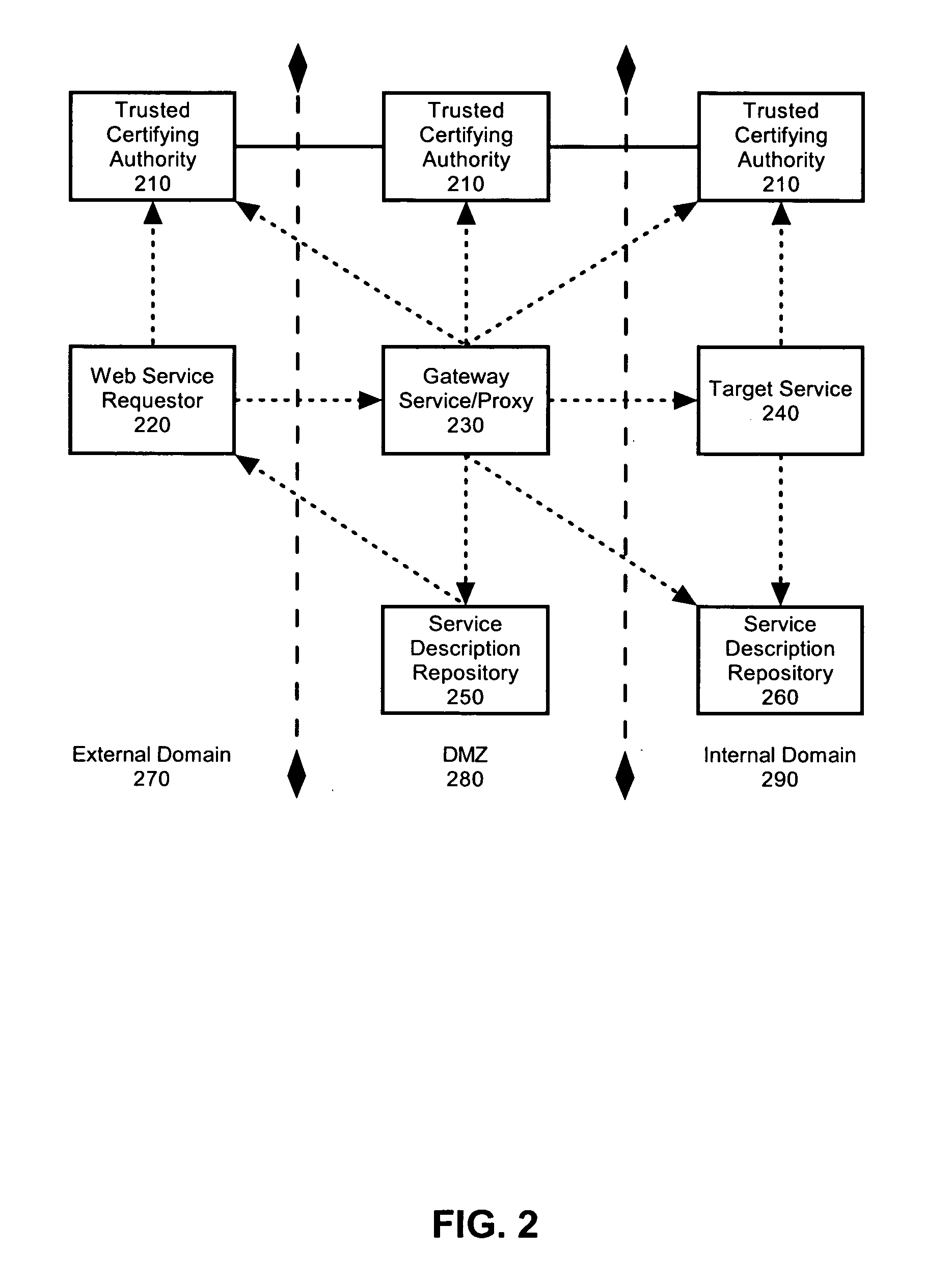
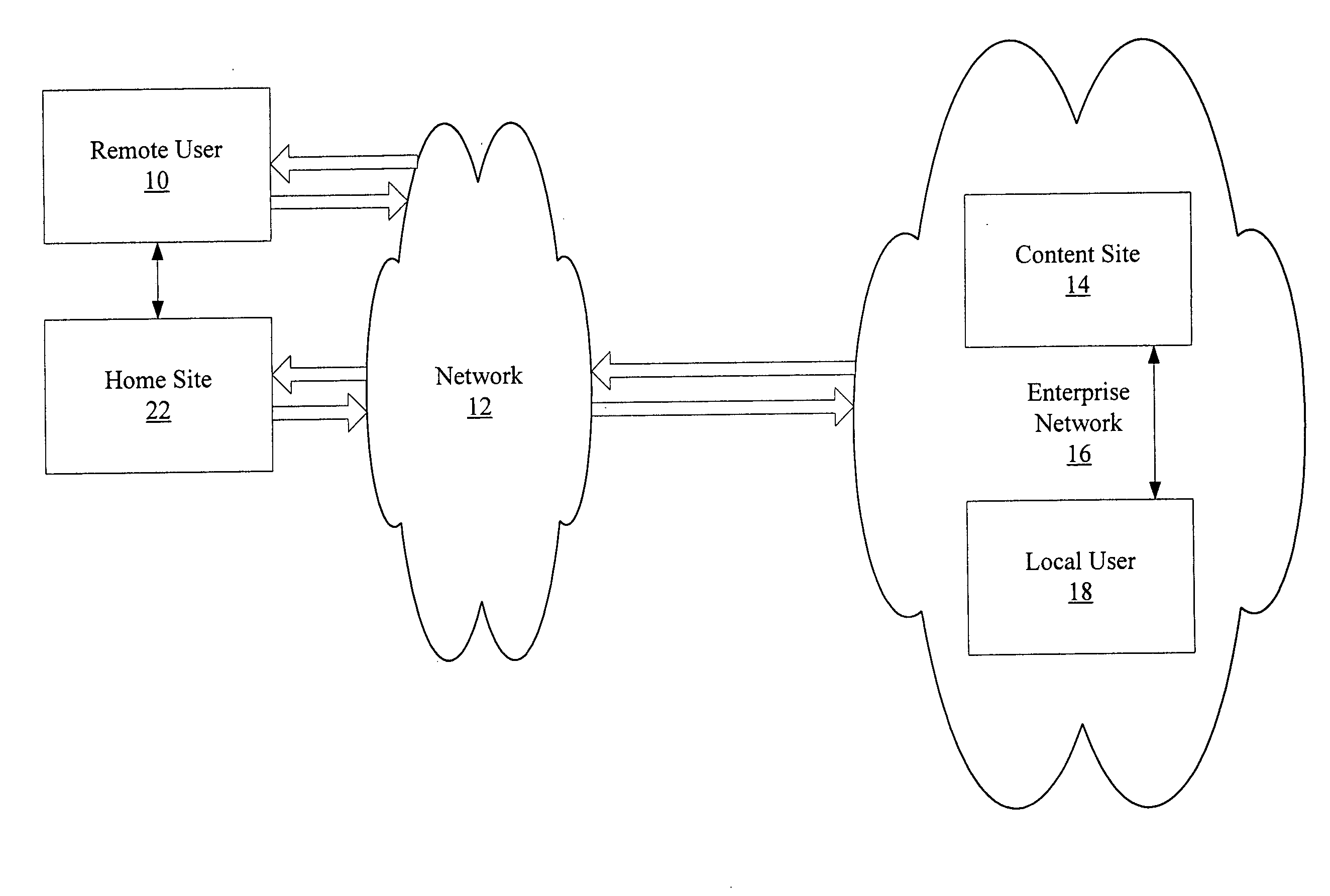
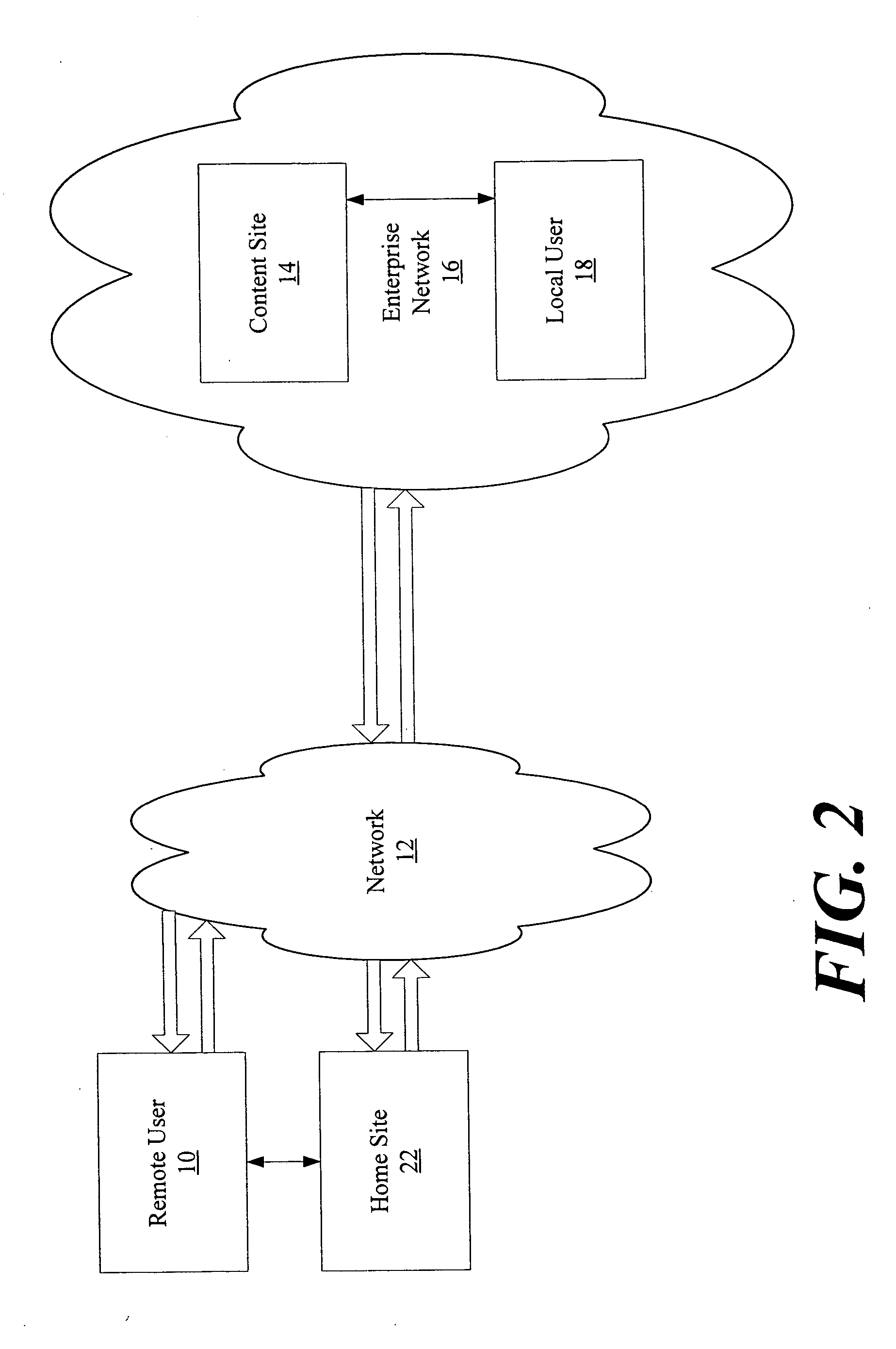
An authentication process in a network environment provides a remote user with secured access to an enterprise network based on recognition of a third-party security token. The method includes authenticating the user against a plurality of third-party security tokens, wherein the third-party security tokens originate from a range of different partner home sites. The remote user, prior to obtaining secured access to the enterprise network, is not known to the enterprise network, and does not need to be associated with any security tokens previously originating from the enterprise network. The enterprise network is provided with the ability to rely upon third-party security tokens to authenticate the remote user.
Owner:GOOGLE LLC
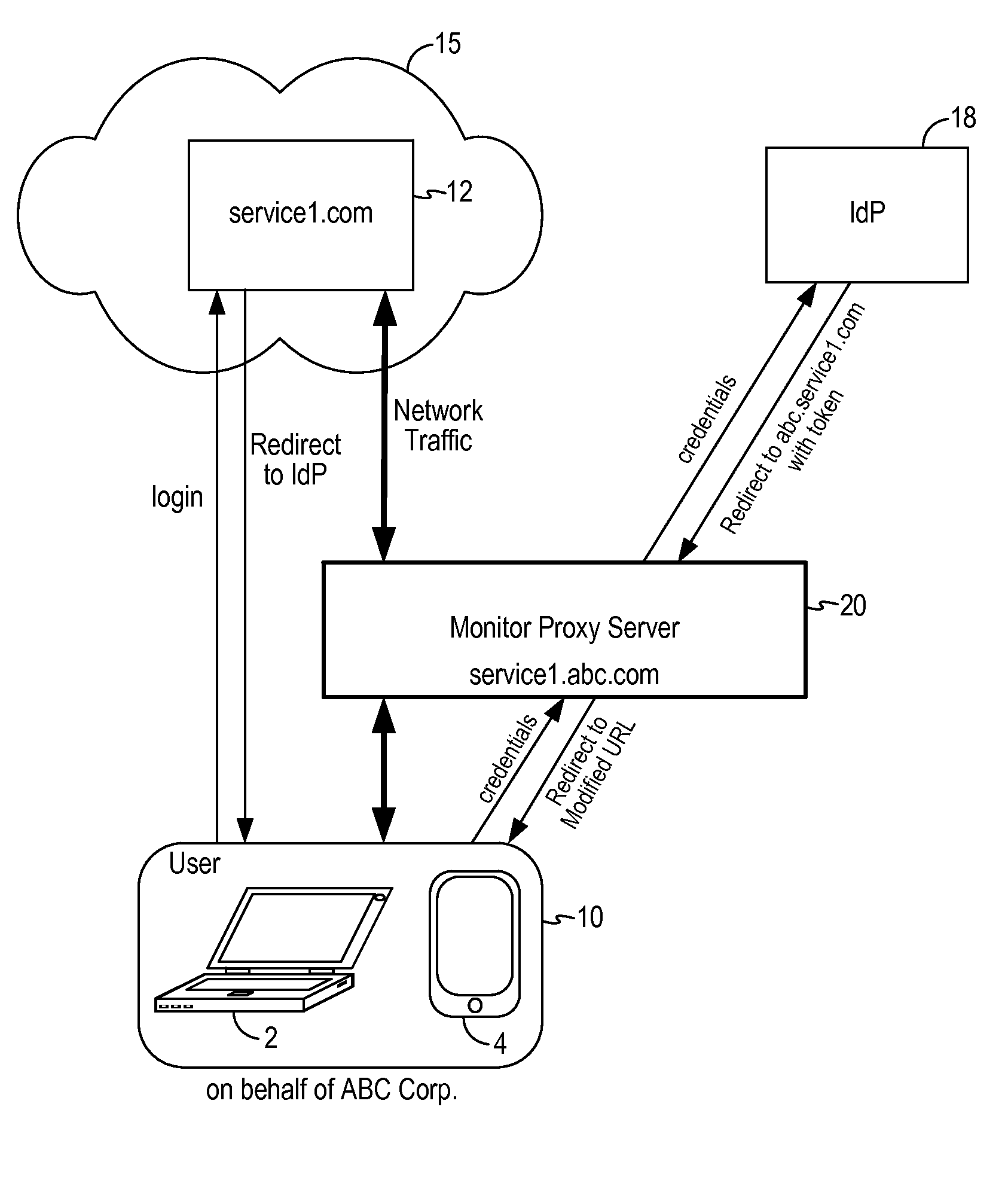
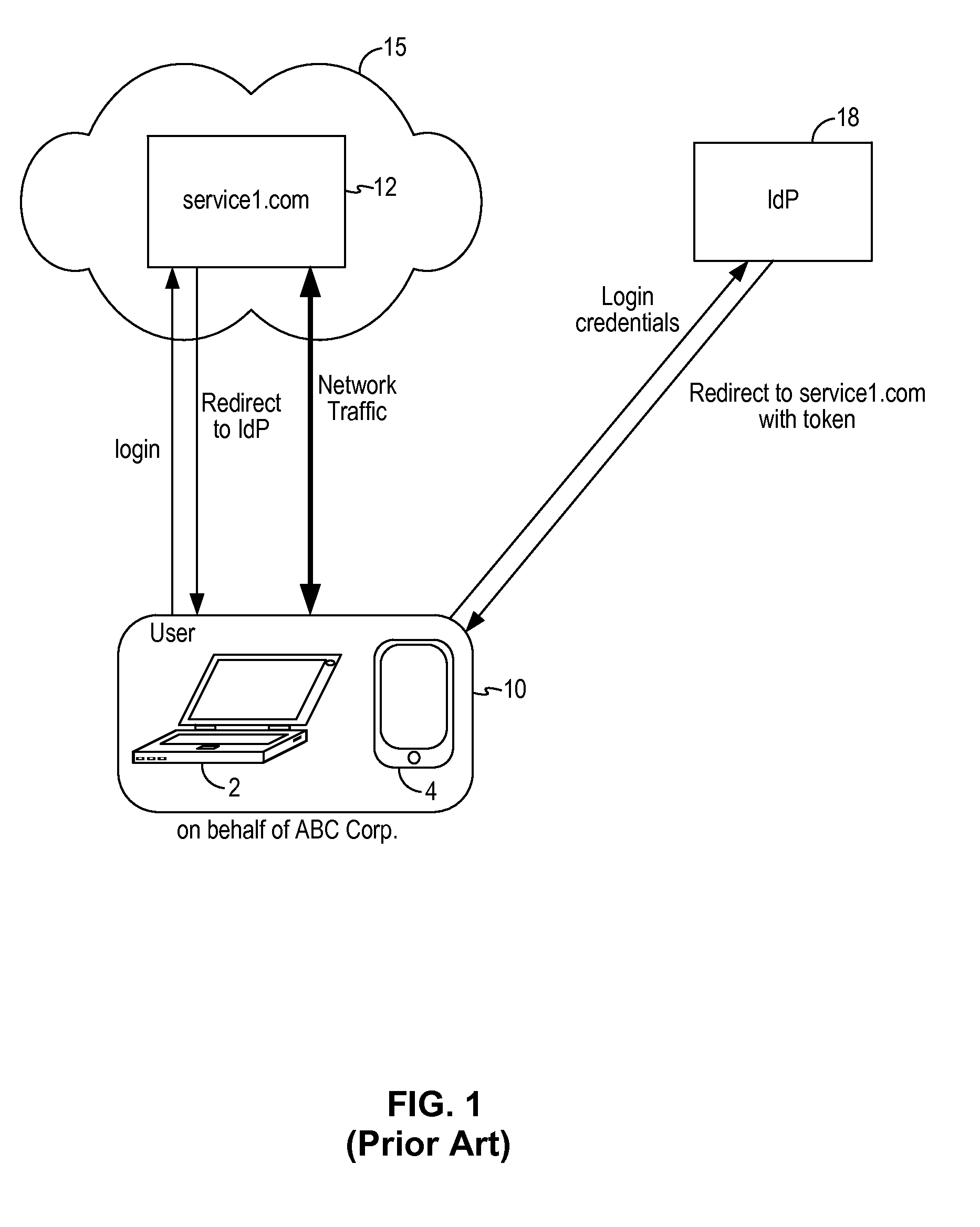
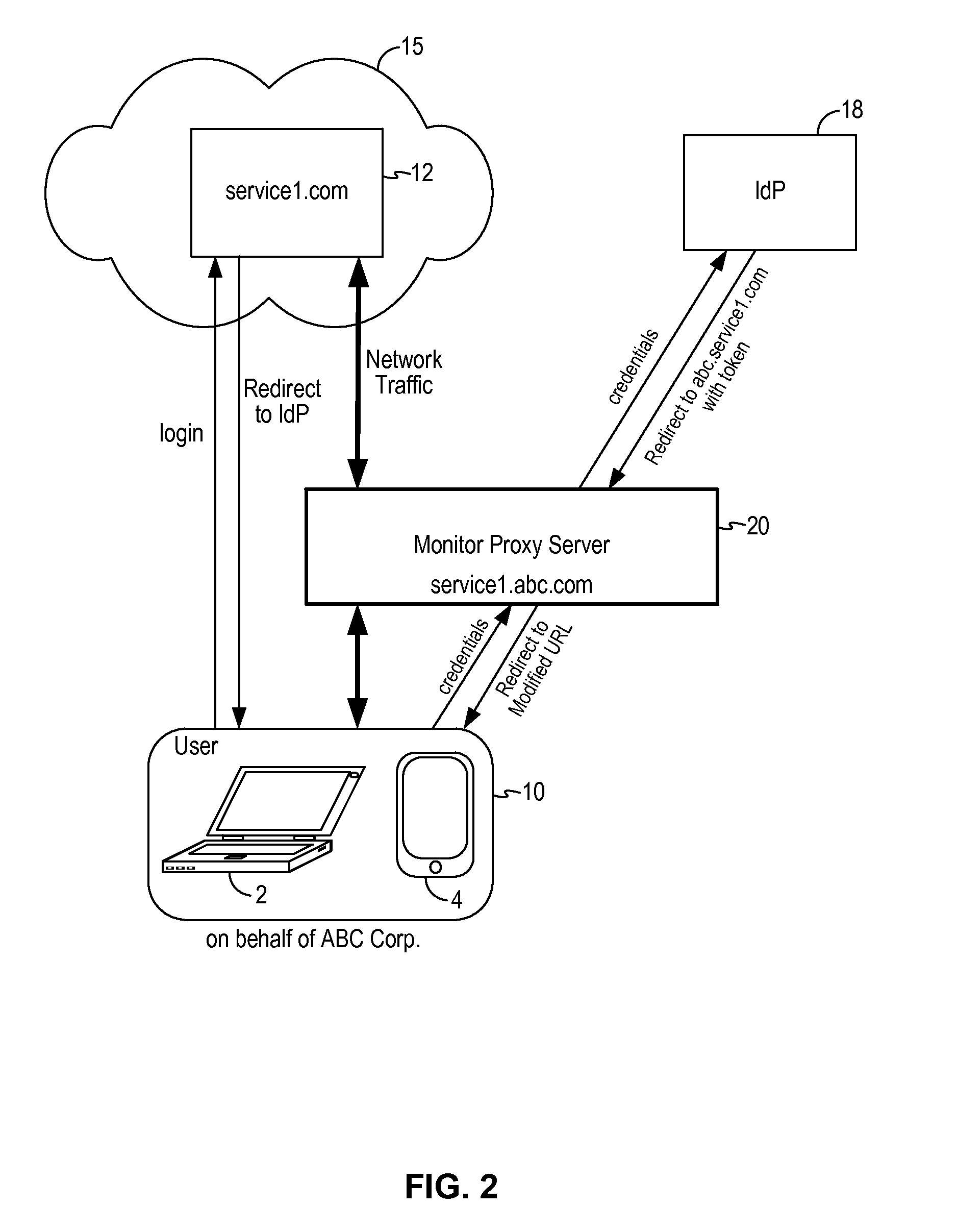
Network traffic monitoring system and method to redirect network traffic through a network intermediary
ActiveUS9137131B1Digital computer detailsData switching networksMonitoring systemNetwork communication
A network traffic monitoring system for redirecting network traffic between a client device and a cloud service includes a monitor proxy server configured as a network intermediary between the client device and a federated identity provider and between the client device and the cloud service. The monitor proxy server is configured to receive a redirect response generated by the federated identity provider upon user authentication. The monitor proxy server is configured to rewrite the redirect web address to the web address of the monitor proxy server. The monitor proxy server is further configured to rewrite a response web address in network communications between the cloud service and the client device to the web address of the monitor proxy server. As a result, network traffic between the cloud service and the client device is routed through the monitor proxy server after user authentication by the federated identity provider.
Owner:SKYHIGH SECURITY LLC
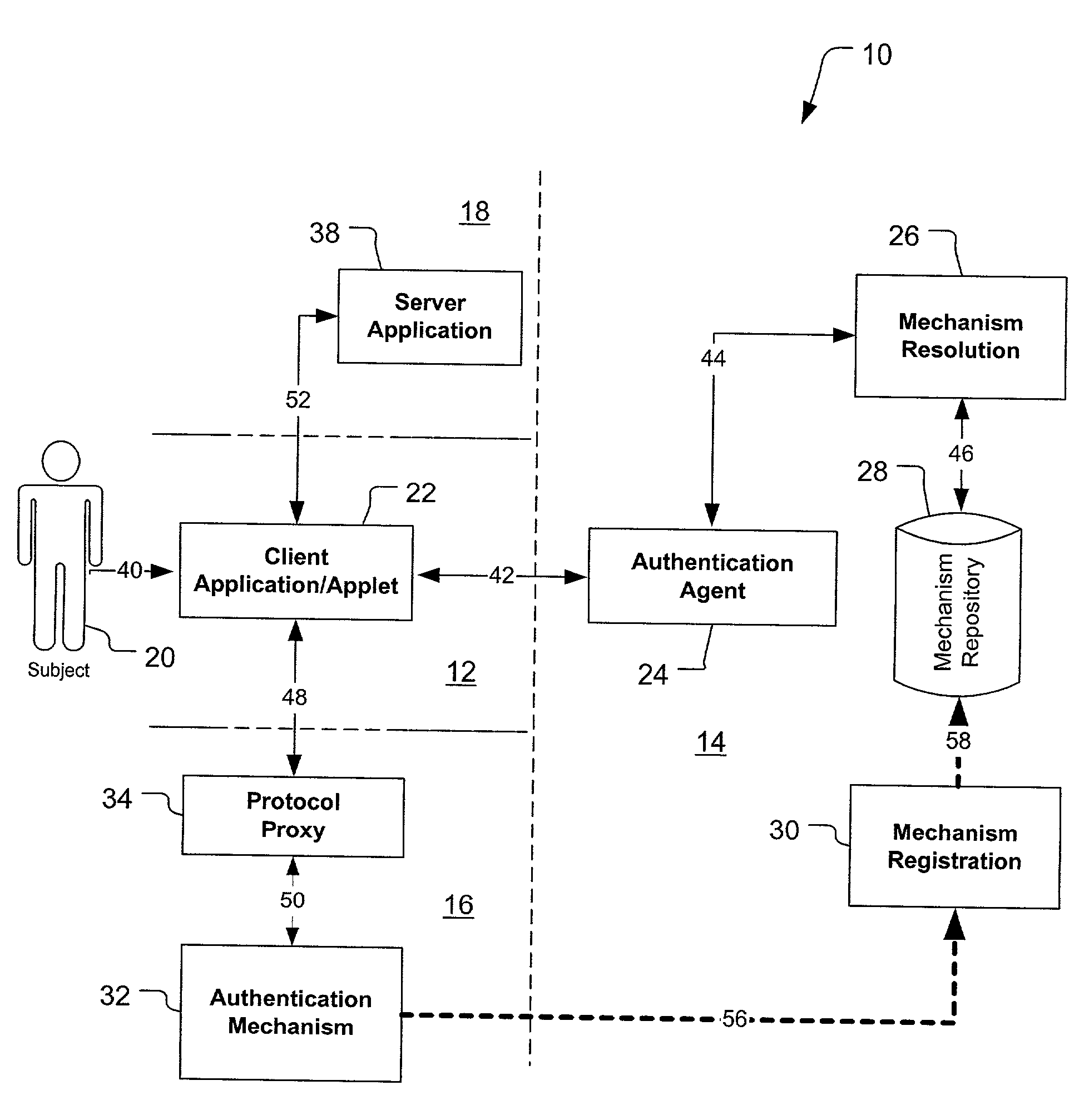
Federated authentication service
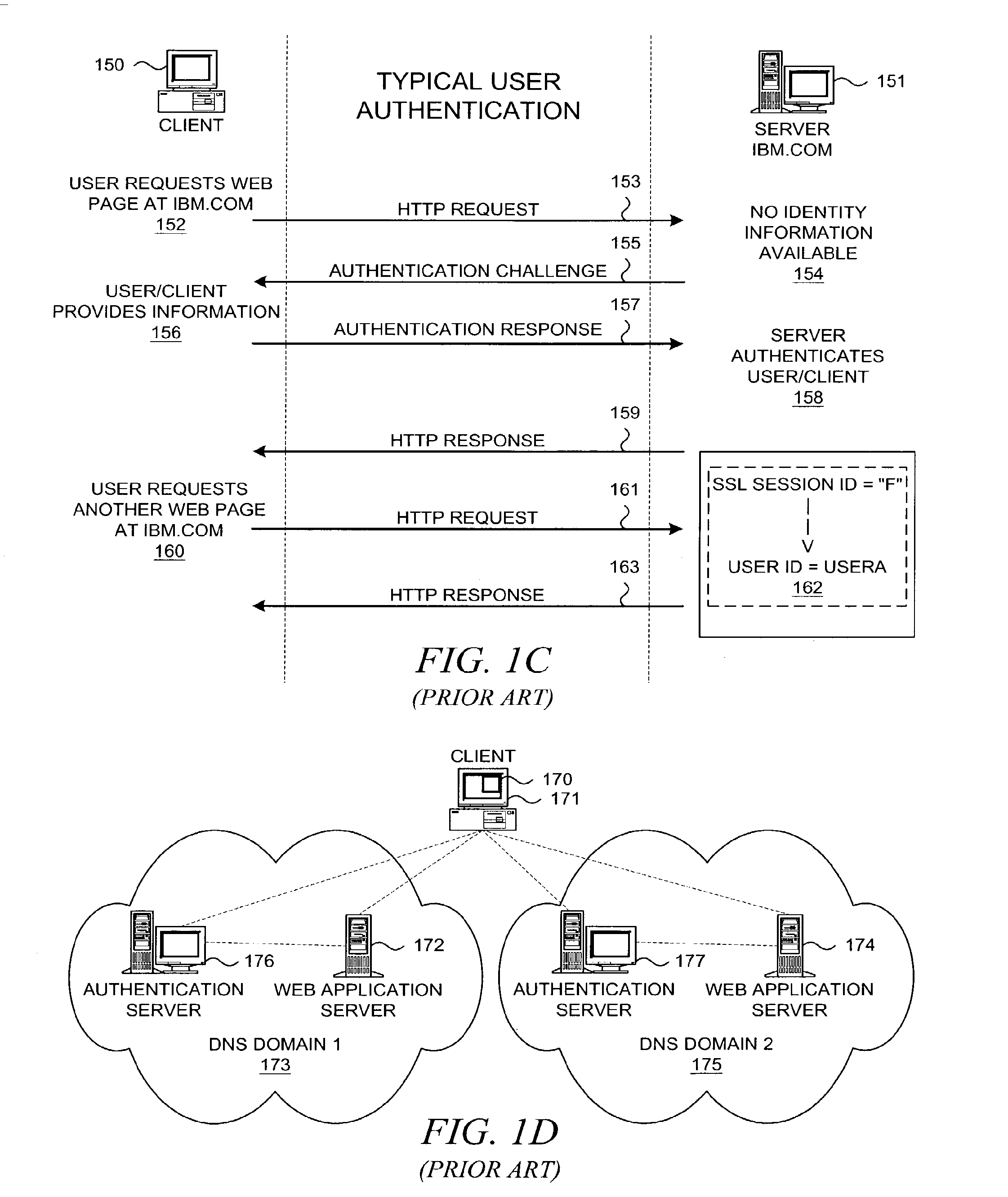
InactiveUS20030046391A1Effectively abstractingEasy to manageUser identity/authority verificationMultiple digital computer combinationsInternet Authentication ServiceFederated identity
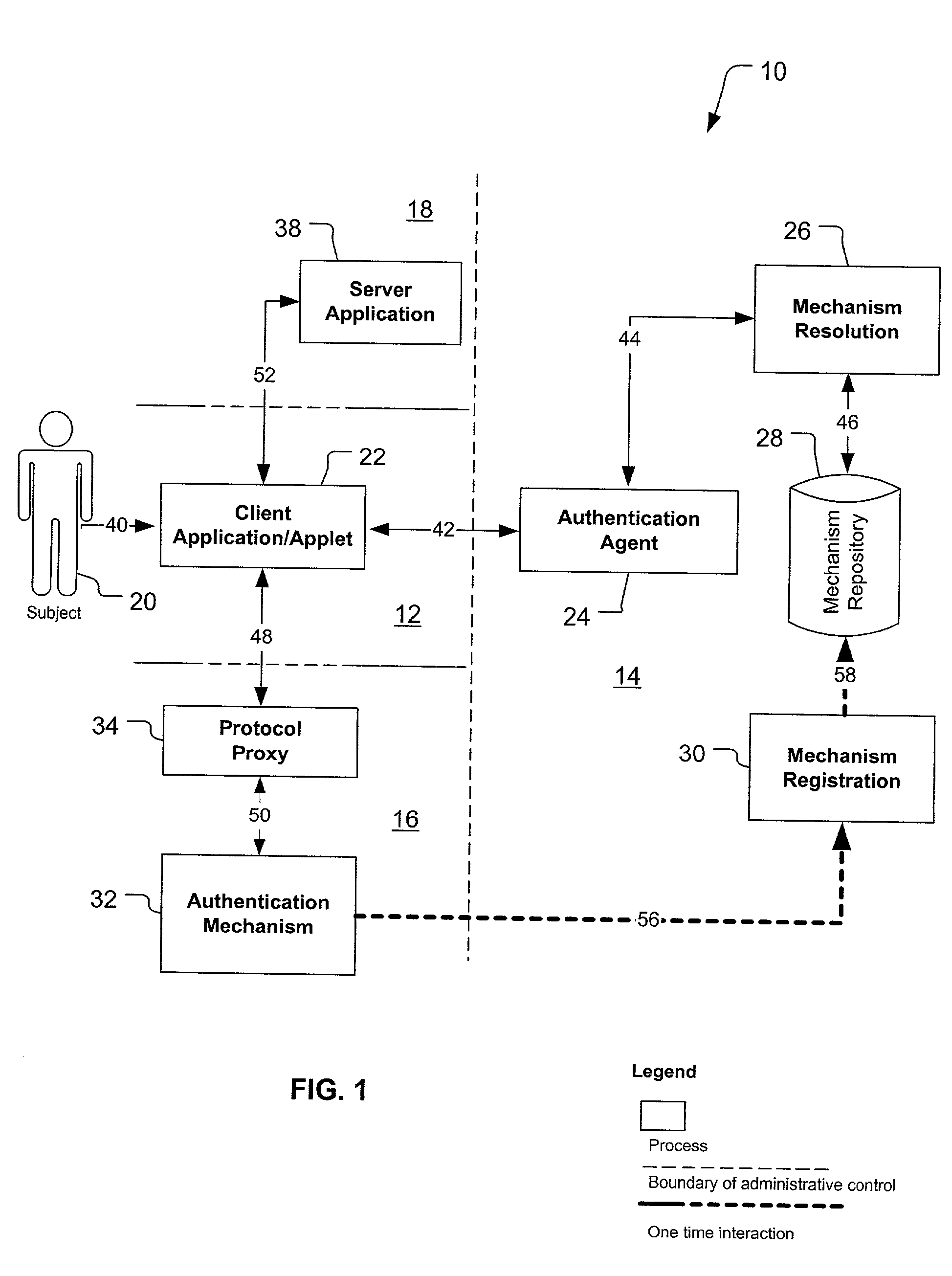
A federated authentication service technology (10) for authenticating a subject (20) residing in a subject domain (12) on a network to a server application (38) residing in a server domain (18), wherein an authentication mechanism (32) residing in an authentication domain (16) affects the service provided by the server application (38). A client (22), which may be integrated non-human instances of the subject (20), authenticates the subject (20) and a protocol proxy (34) mediates with the authentication mechanism (32) to obtain a name assertion which the client can use to access the server application (38). When multiple authentication mechanisms (32) are available, an optional agent (24), mechanism resolution process (26) and mechanism repository (28), all residing in an agent domain (14), may be used to resolve to one suitable authentication mechanism (32).
Owner:PROOFPOINT INC
Method and apparatus for trusted federated identity
InactiveUS8533803B2Digital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
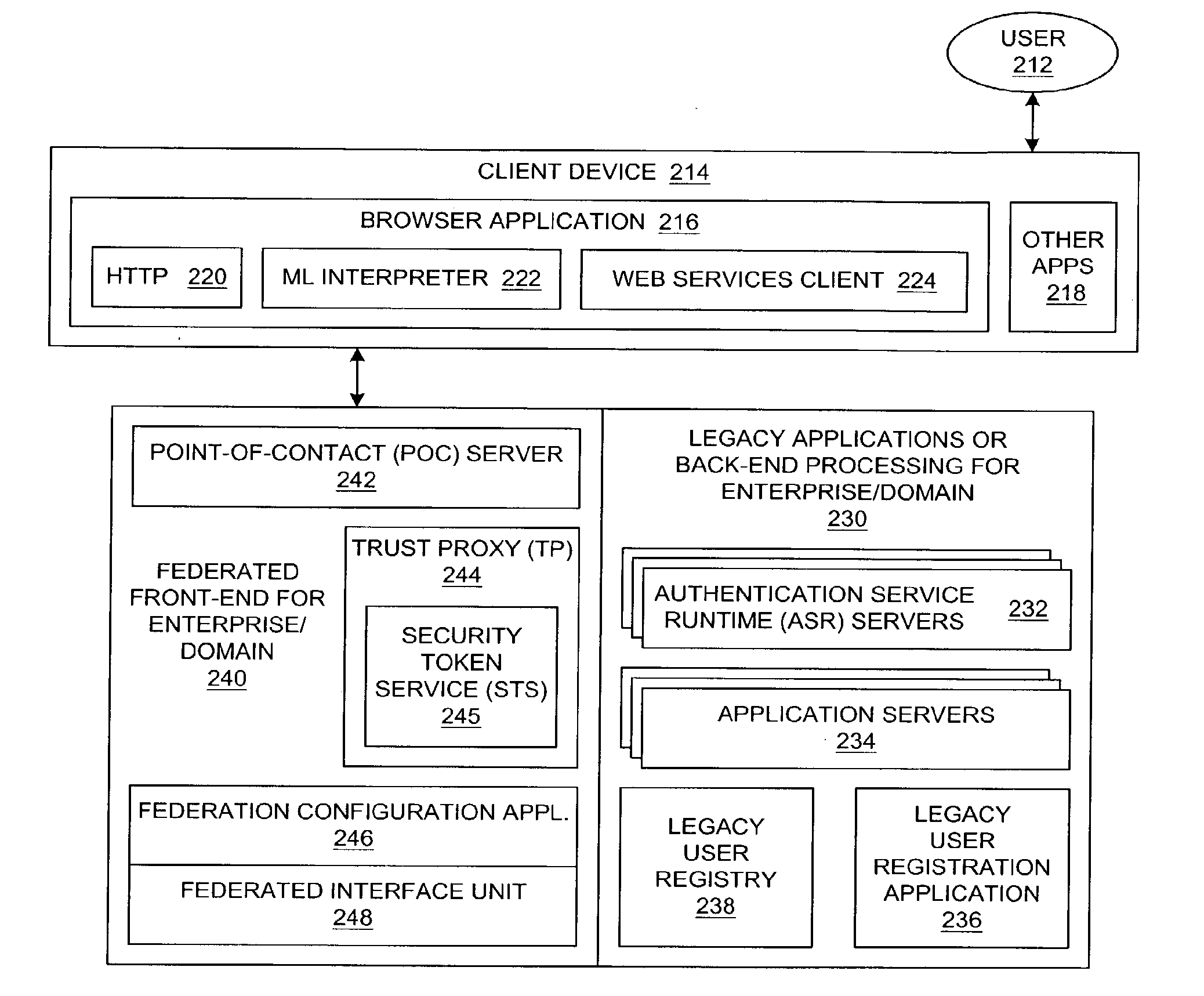
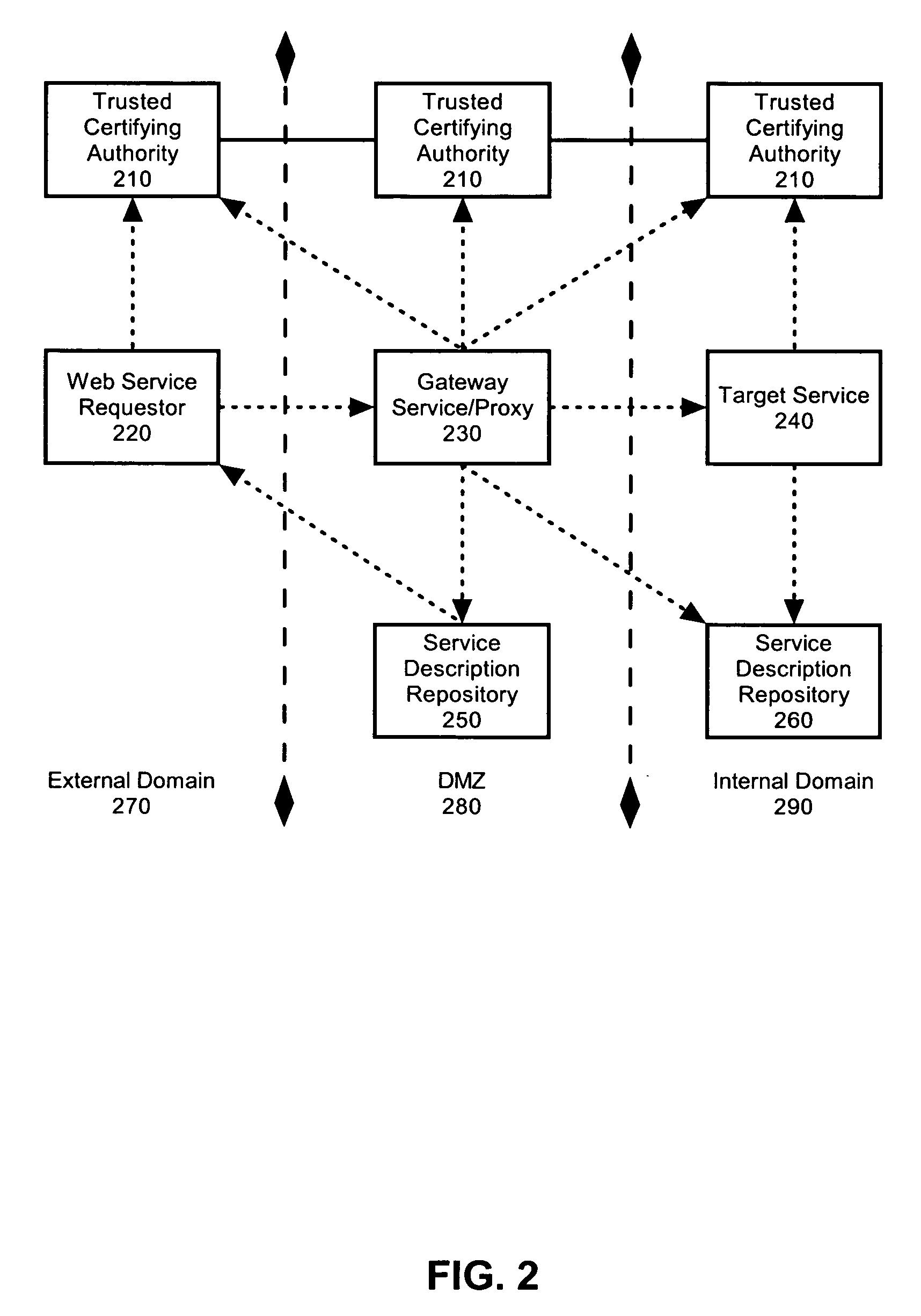
Method and system for native authentication protocols in a heterogeneous federated environment
InactiveUS20070234417A1User identity/authority verificationMultiple digital computer combinationsInternet privacyTrust relationship
A method is presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions.
Owner:IBM CORP
Access control for federated identities
ActiveUS20050188212A1Digital data processing detailsMultiple digital computer combinationsThird partyFederated identity
An authentication process in a network environment provides a remote user with secured access to an enterprise network based on recognition of a third-party security token. The method includes authenticating the user against a plurality of third-party security tokens, wherein the third-party security tokens originate from a range of different partner home sites. The remote user, prior to obtaining secured access to the enterprise network, is not known to the enterprise network, and does not need to be associated with any security tokens previously originating from the enterprise network. The enterprise network is provided with the ability to rely upon third-party security tokens to authenticate the remote user.
Owner:GOOGLE LLC
Automating trust establishment and trust management for identity federation
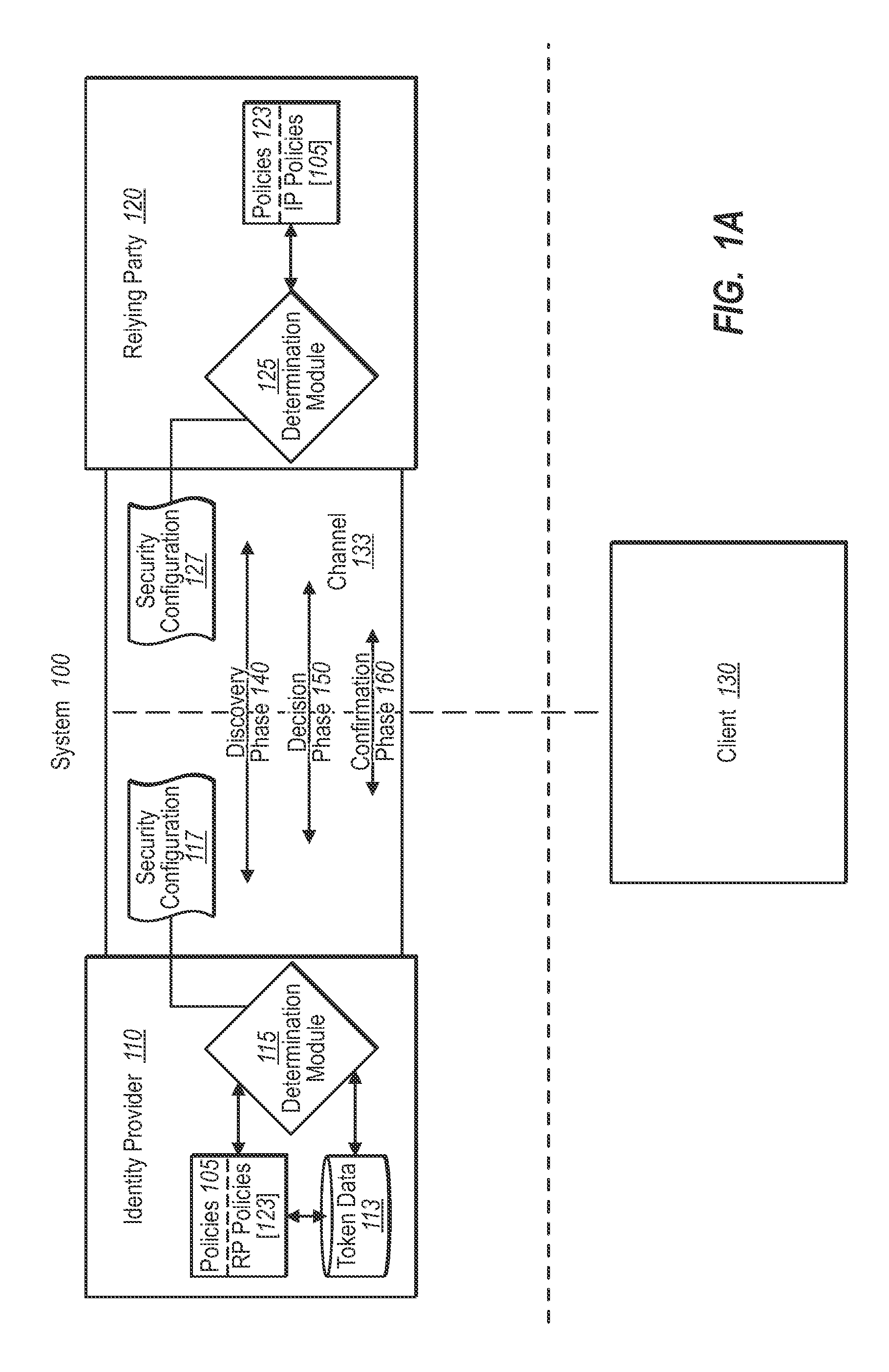
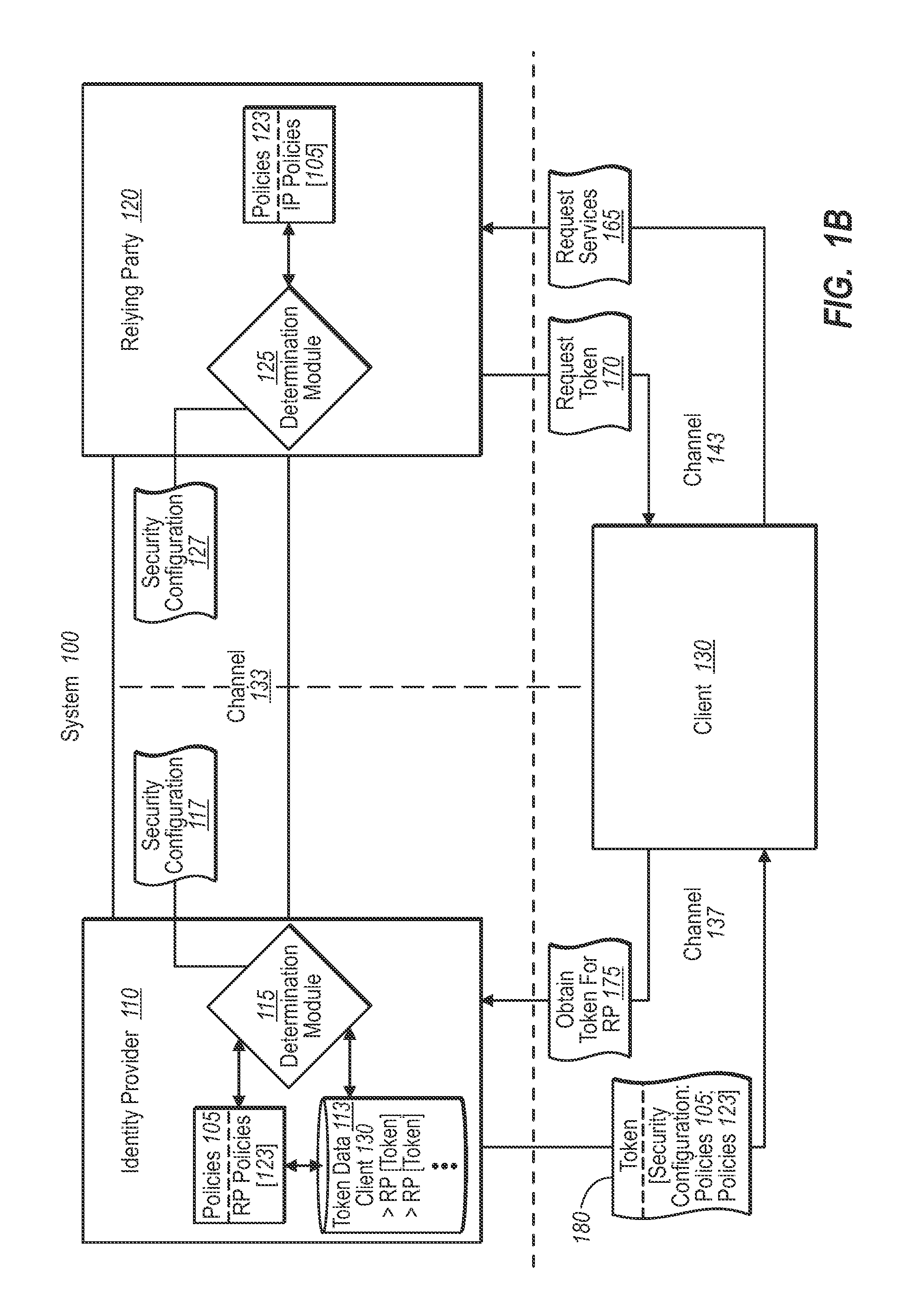
InactiveUS20090307744A1Computer security arrangementsTransmissionTrust relationshipIdentity provider
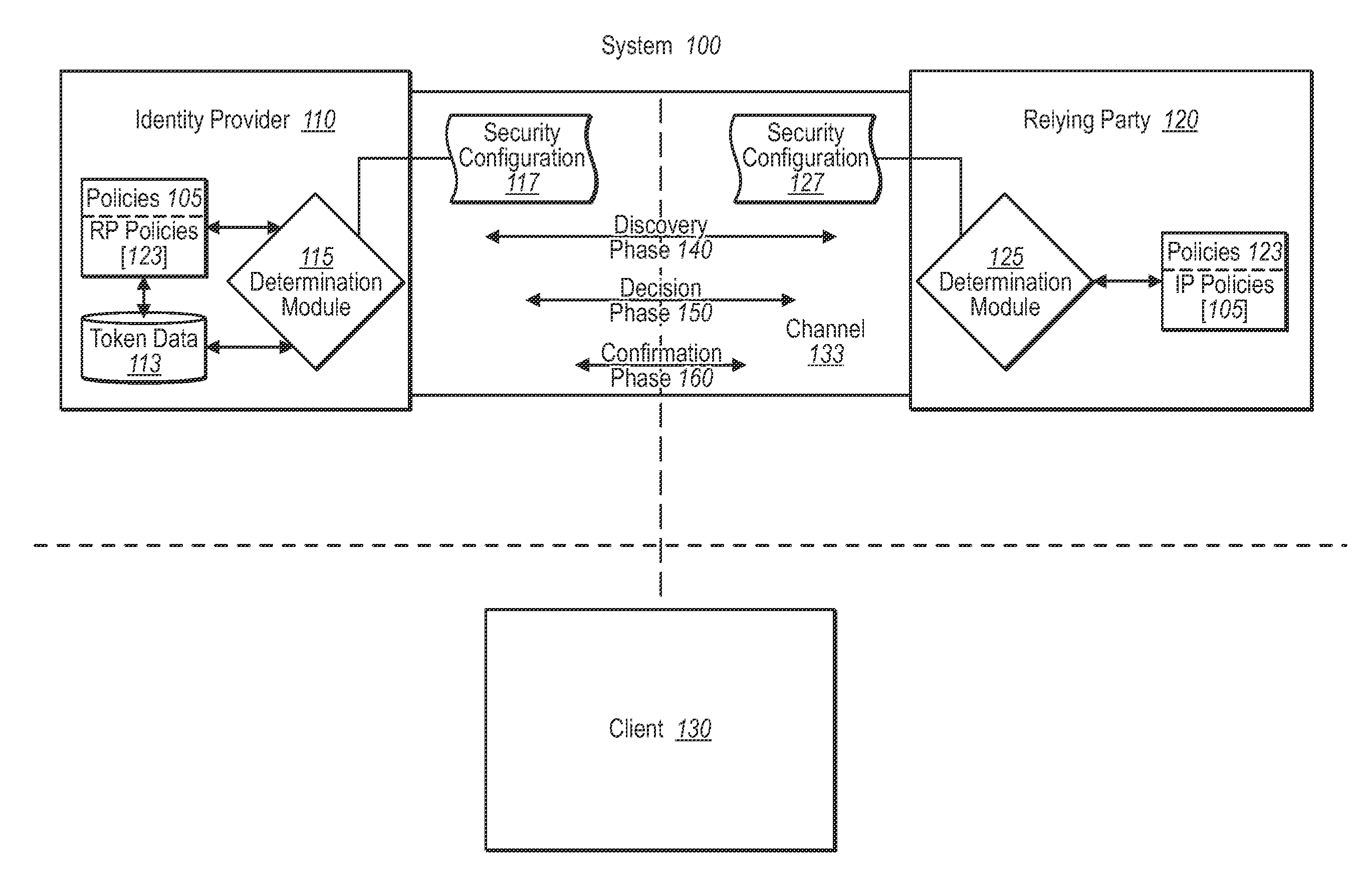
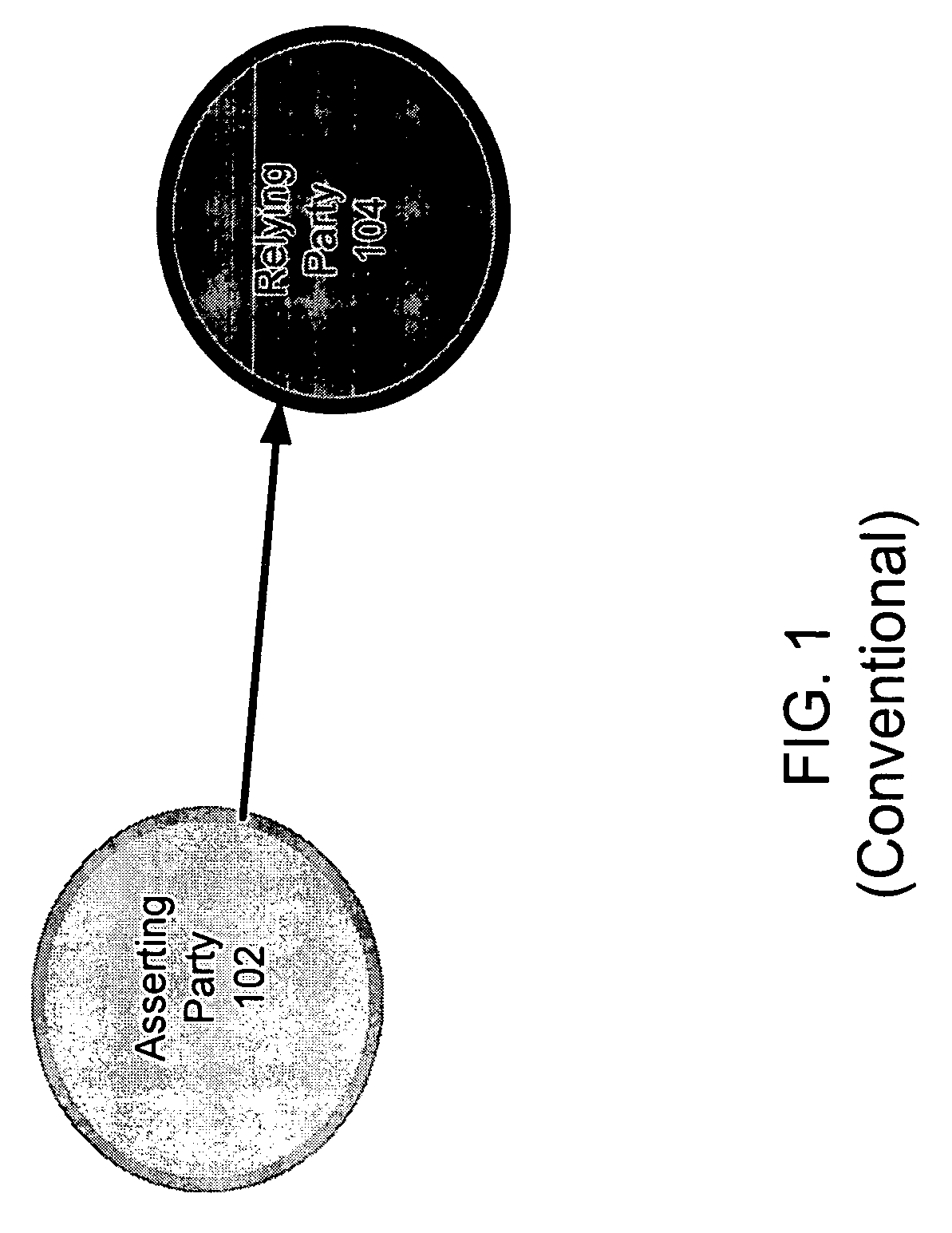
A federated identity verification system includes an identity provider that provides security tokens ultimately to one or more relying parties for access by the client to services at a relying party. Specifically, the relying party can validate the security token from an identity provider (whether directly or via a client) when verifying that the received security token conforms to security configuration data previously exchanged with the identity provider. To establish the trust relationship, the identity provider and one or more relying parties exchange security configuration information through an agreed-to communication channel. The security configuration information indicates the settings that the other party needs to use for establishing, maintaining, and / or monitoring the trust relationship. The communication channel allows both parties to flexibly and continually synchronize changes to security configurations, and thus maintain, change, or end the trust relationship automatically, as desired.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for multi-domain identity interoperability and compliance verification
ActiveUS8434129B2Memory loss protectionDigital data processing detailsInternet privacyFederated identity
Owner:FUGEN SOLUTIONS
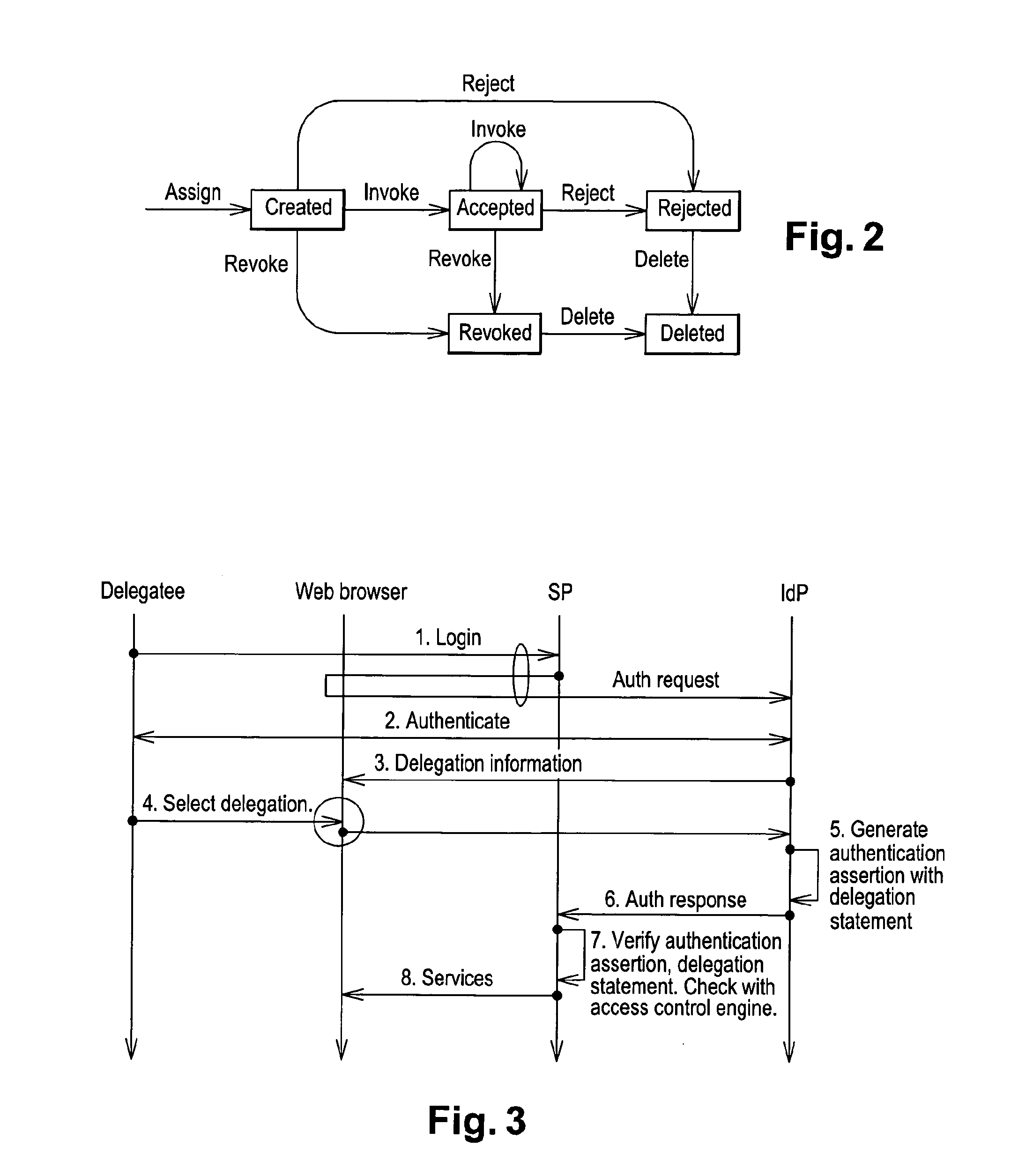
User to user delegation service in a federated identity management environment
ActiveUS20140020051A1User identity/authority verificationDigital data protectionComputer networkIdentity provider
Method for providing user-to-user delegation service in federated identity environment, characterized in that it comprises a delegation or assignment step wherein a delegator specifies said delegation at an identity provider for delegating a privilege or task to a delegatee to be performed at a service provider.
Owner:THALES DIS FRANCE SA
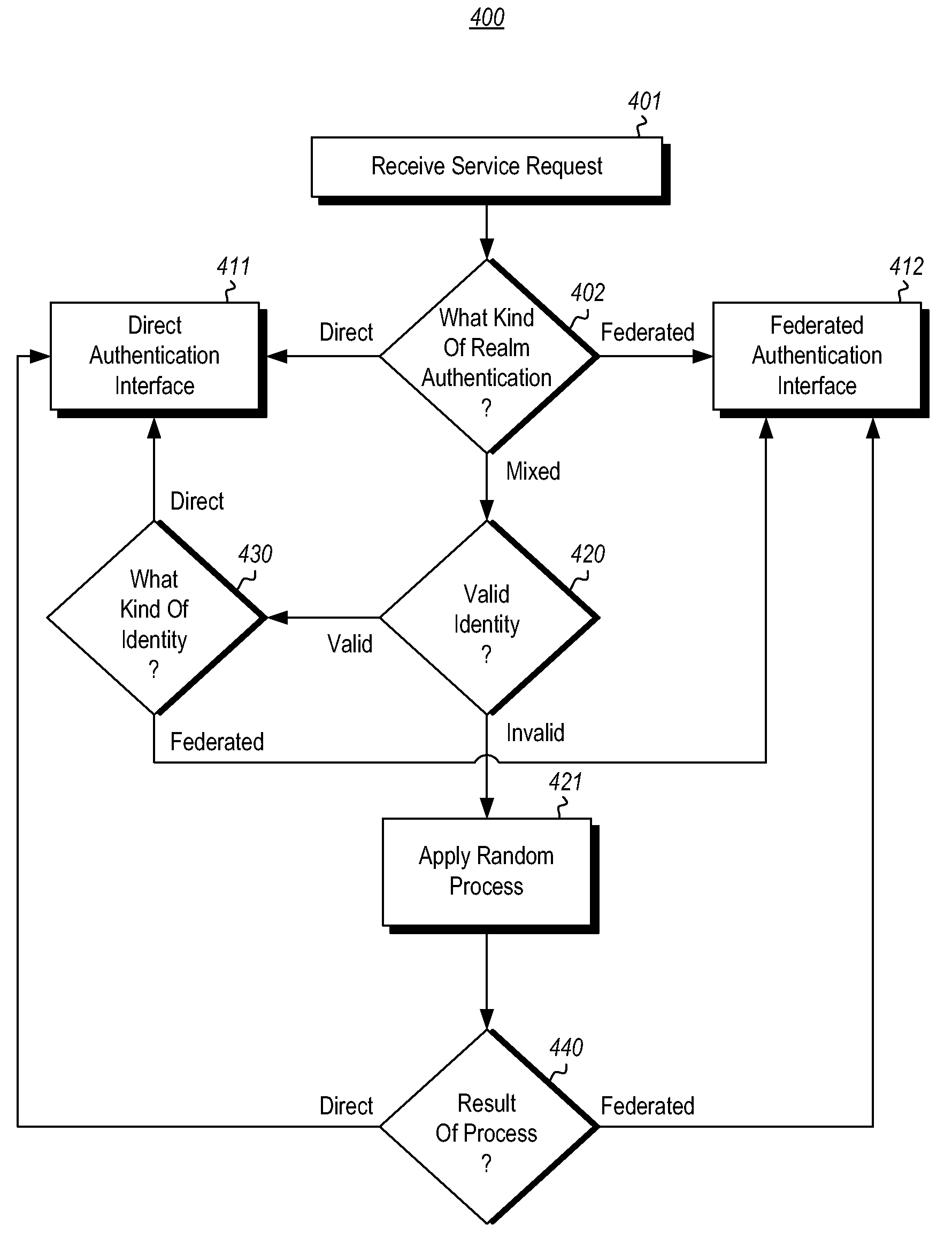
Home realm discovery in mixed-mode federated realms
InactiveUS20130117826A1Well formedDigital data processing detailsUser identity/authority verificationInternet privacyFederated identity
The authentication of identities within a realm in which some identities are authenticated using direct authentication, and some identities are authenticated using federated authentication. Requests for service from valid identities in the realm that are to be authenticated by direct authentication are responded to with a direct authentication interface. Requests for service from valid identities in the realm that are to be authenticated by federated authentication are responded to with a federated authentication interface. Requests for service from invalid identities are responded to pseudo-randomly with either the direct authentication interface or the federated authentication interface.
Owner:MICROSOFT TECH LICENSING LLC
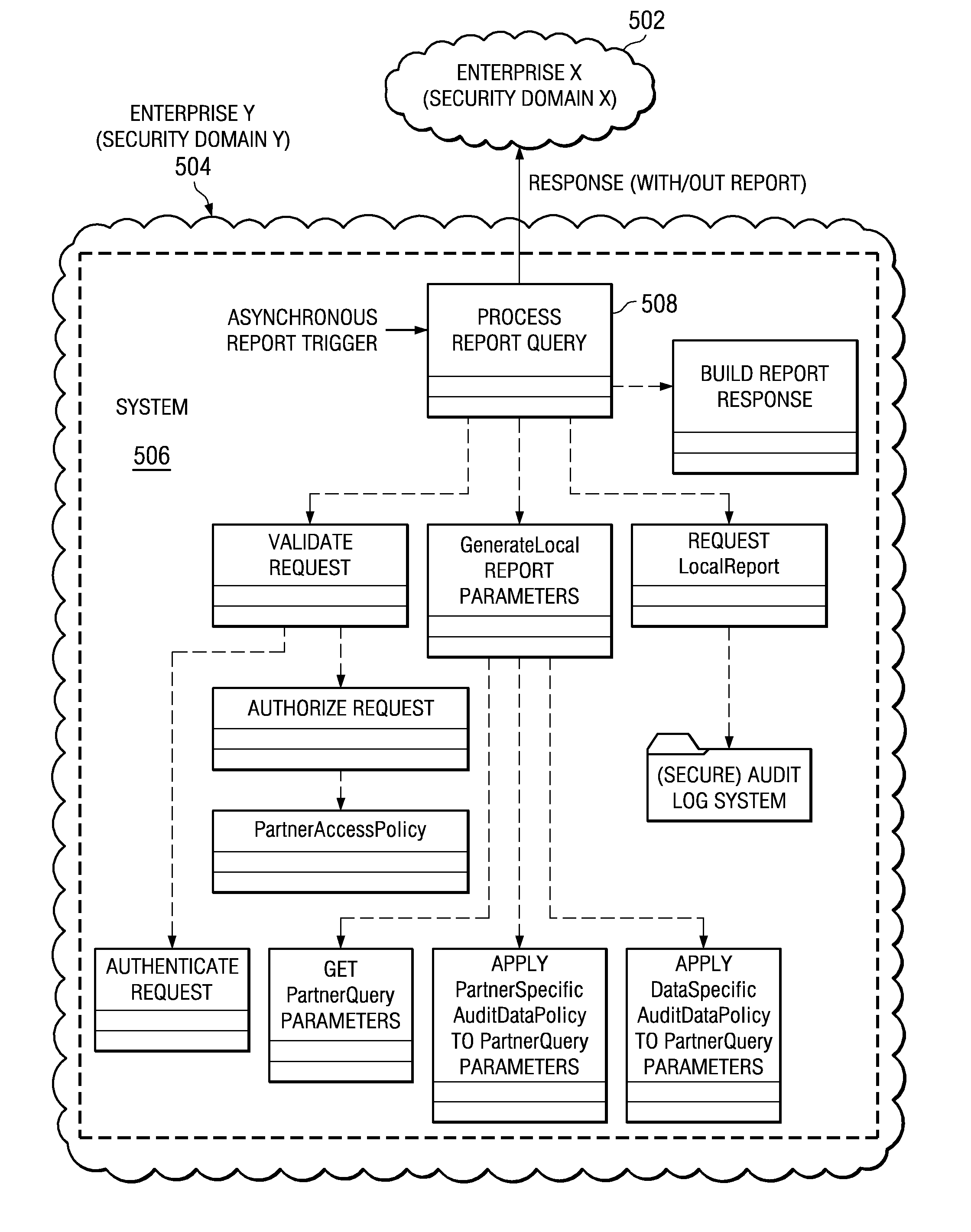
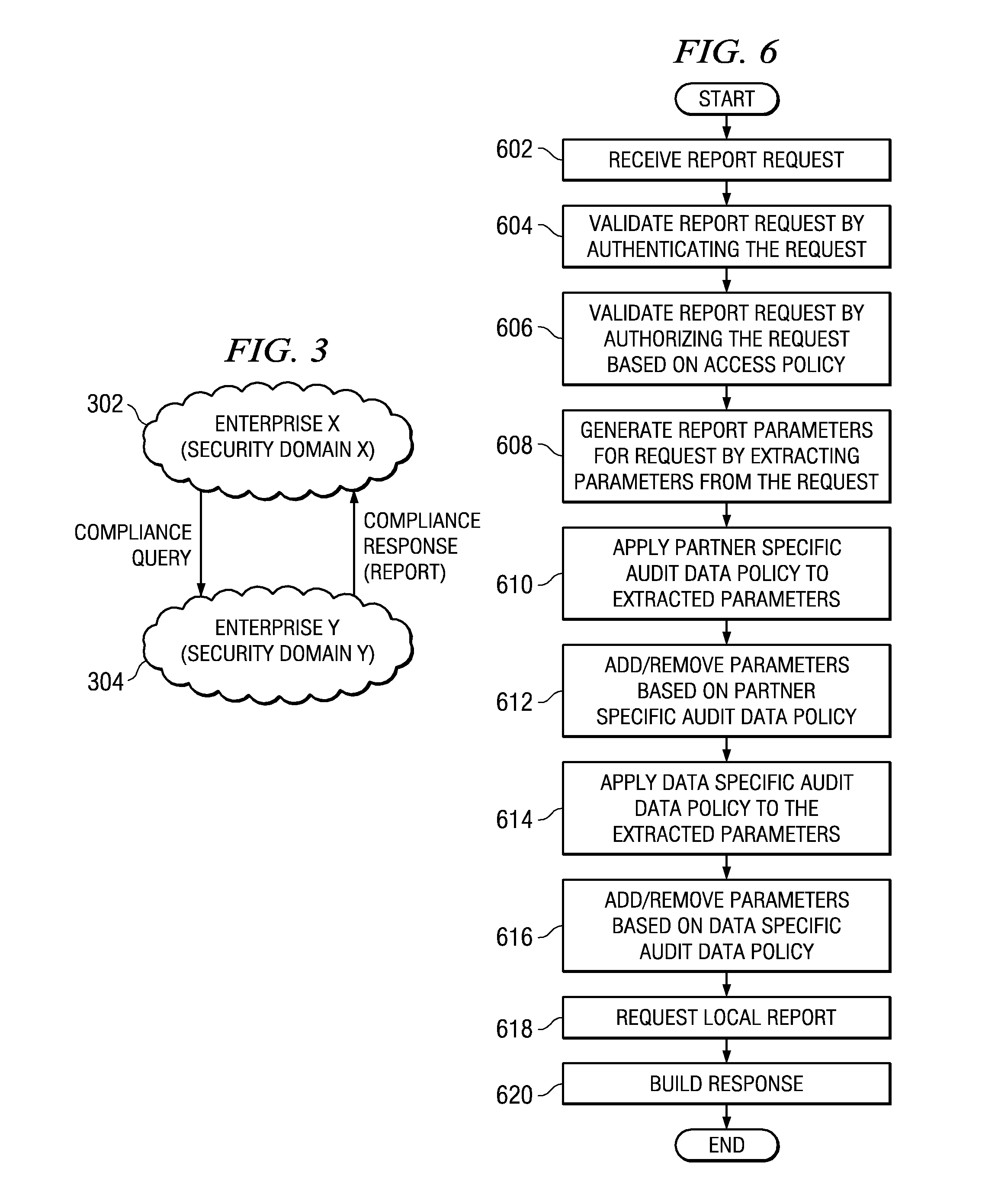
Secure audit log access for federation compliance
ActiveUS20080168567A1Digital data processing detailsAnalogue secracy/subscription systemsData processing systemLimited access
A computer implemented method, data processing system, and computer program product for allowing limited access to a federation partner's audit logs in a secure, controlled manner, for the purposes of compliance demonstration. A request for audit data is received by a partner in the federated environment. The partner validates the request and requests a local report using local parameters against a local audit log store. The partner then builds a response based on the local report.
Owner:IBM CORP
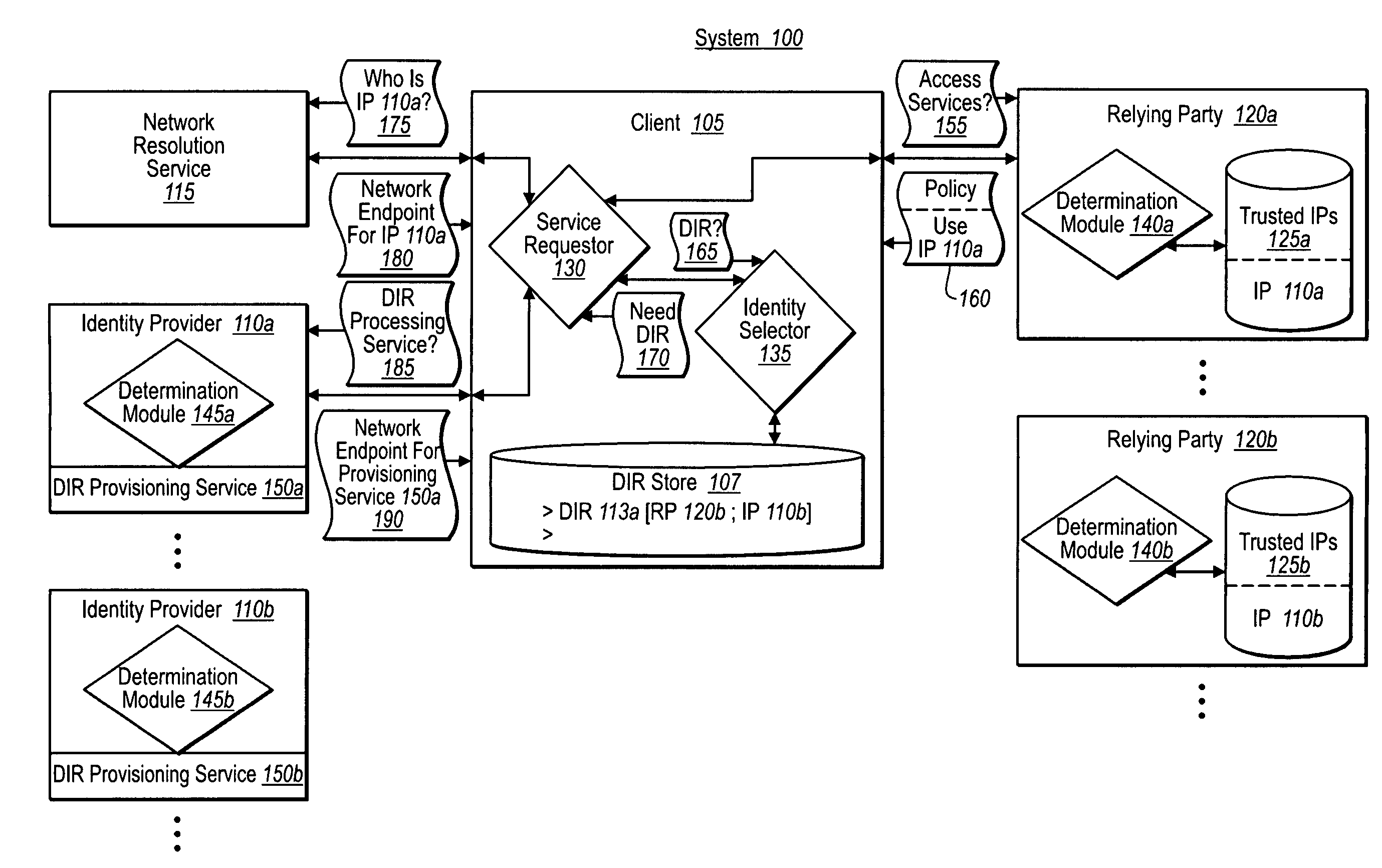
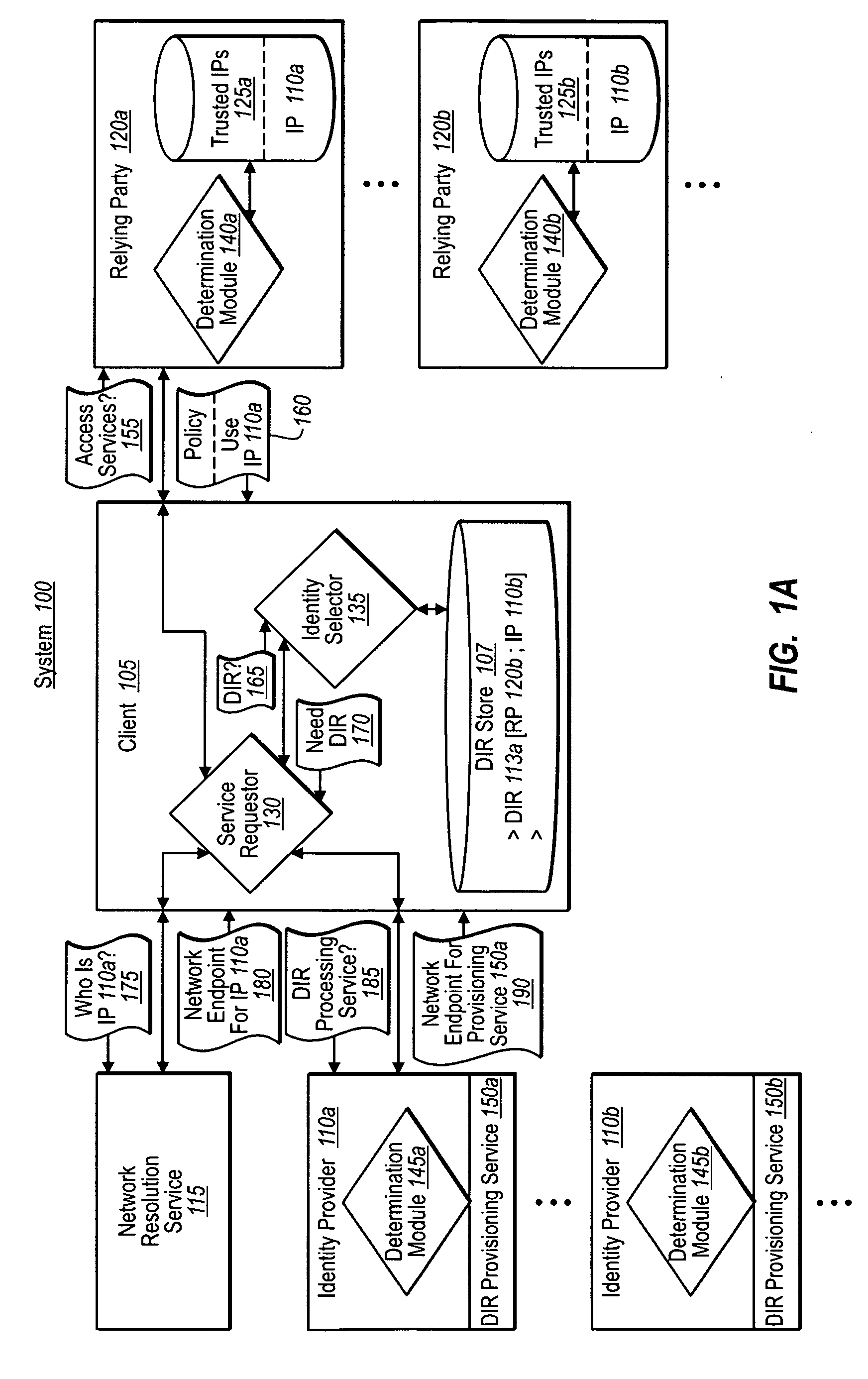
Obtaining digital identities or tokens through independent endpoint resolution
ActiveUS20090320095A1Digital data processing detailsMultiple digital computer combinationsDigital identityDomain name
A federated identity provisioning system includes relying parties, identity providers, and clients that obtain tokens from identity providers for access to a relying party's services. When a client contacts a new relying party, the relying party provides information that the client can independently resolve and evaluate for trustworthiness. For example, the relying party provides a generic domain name address. The client can then resolve the domain name address over various, authenticated steps to identity an endpoint for a digital identity provisioning service. The client can further interact with and authenticate the provisioning service (e.g., requiring digital signatures) to establish a trust relationship. Once determining that the client / user trusts the provisioning service, the client / user can then provide information to obtain a digital identity representation. The client can then use the digital identity representation with the corresponding identity provider to obtain one or more tokens that the relying party can validate.
Owner:MICROSOFT TECH LICENSING LLC
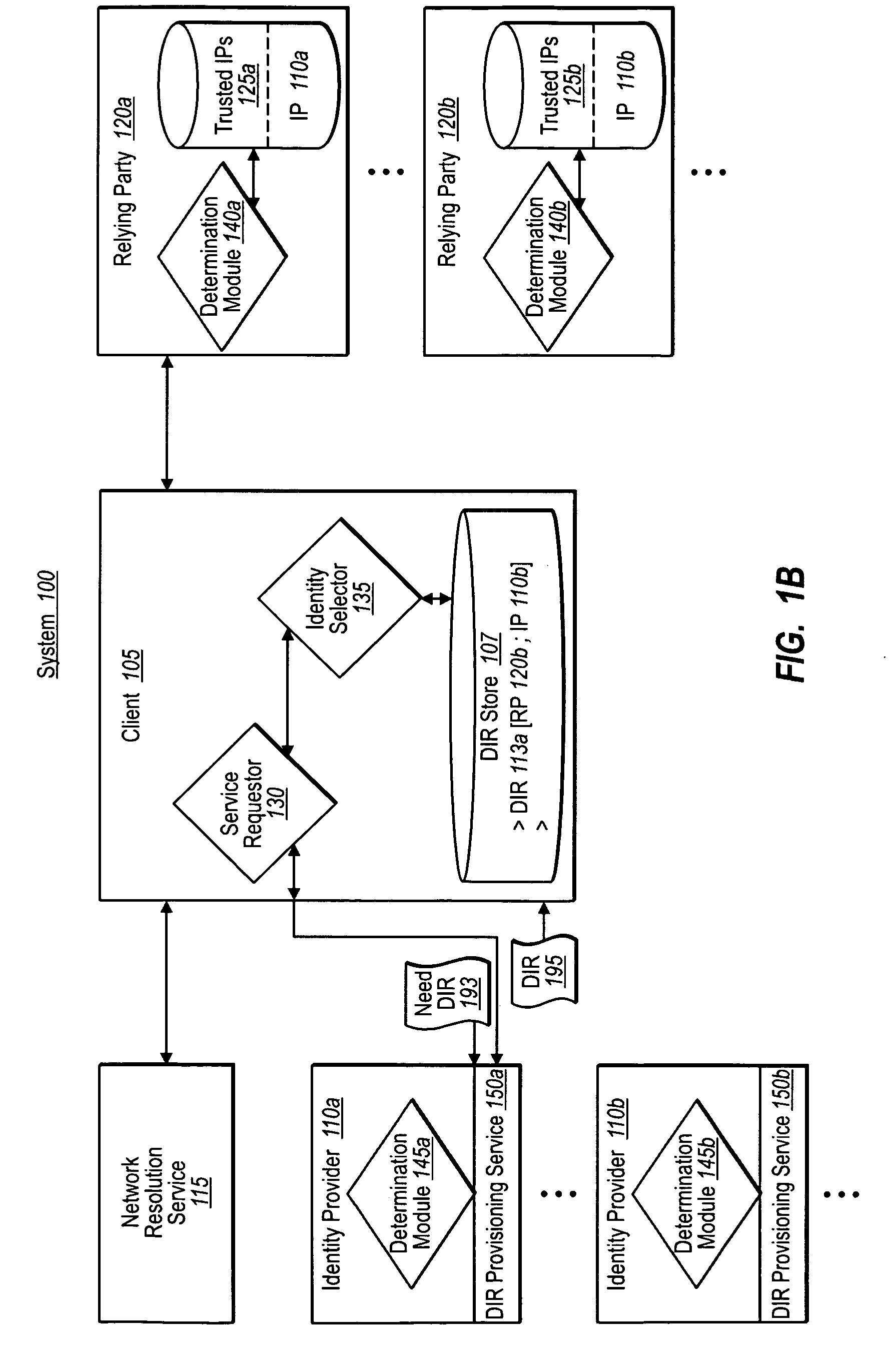
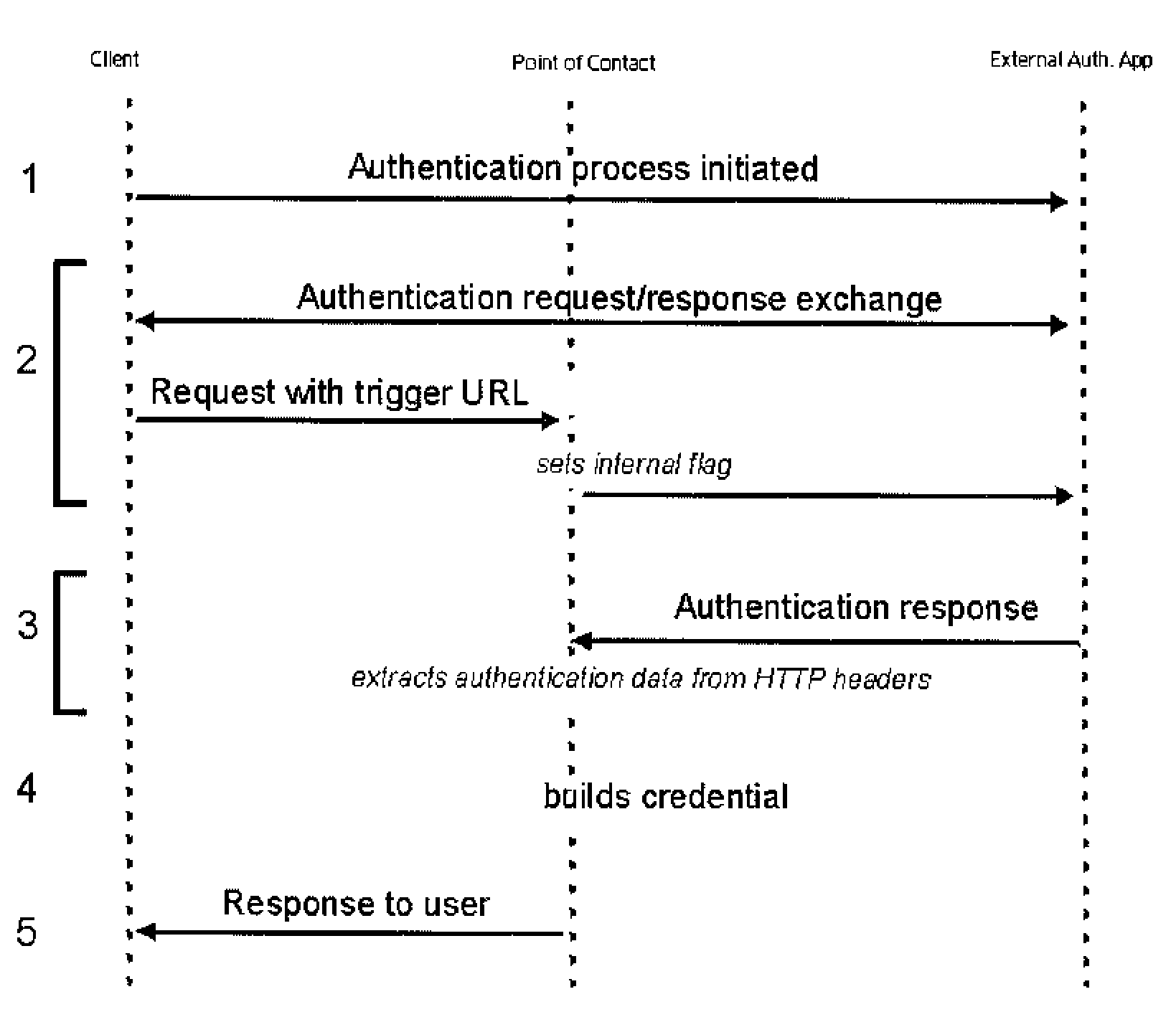
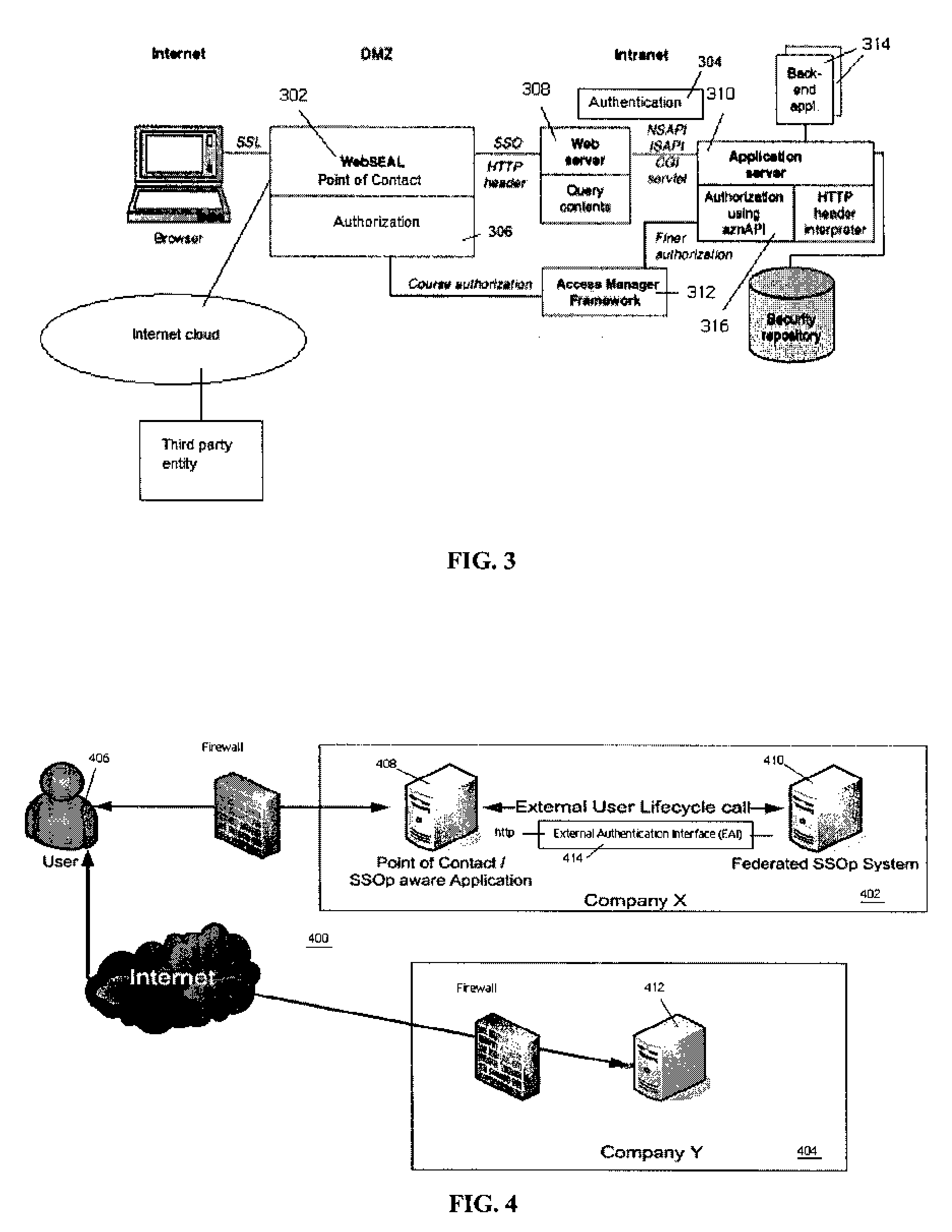
External user lifecycle management for federated environments
InactiveUS20080271121A1Digital data processing detailsUser identity/authority verificationThird partyInternet privacy
The present invention provides a generic technique that externalizes the management of a user session, particularly in the context of a federated environment. The invention obviates any requirement to design and implement special software (or any requirement to modify a previously installed plug-in) to enable third party SSOp-aware applications to manage the lifecycle of a user session. In an illustrative embodiment, the user session lifecycle is managed externally through an external authentication interface (EAI) that has been extended to enable any POC (or SSOp-aware application) to interface to a federated identity provider component using a simple HTTP transport mechanism. In the inventive approach, HTTP request and response headers carry the information that is used by the POC to initiate and later destroy a user session, and such information is provided by a federated entity without requiring use of a special authentication API.
Owner:IBM CORP
Home realm discovery in mixed-mode federated realms
InactiveUS8601554B2Digital data processing detailsUser identity/authority verificationFederated identityAuthentication
The authentication of identities within a realm in which some identities are authenticated using direct authentication, and some identities are authenticated using federated authentication. Requests for service from valid identities in the realm that are to be authenticated by direct authentication are responded to with a direct authentication interface. Requests for service from valid identities in the realm that are to be authenticated by federated authentication are responded to with a federated authentication interface. Requests for service from invalid identities are responded to pseudo-randomly with either the direct authentication interface or the federated authentication interface.
Owner:MICROSOFT TECH LICENSING LLC
Router for managing trust relationships
InactiveUS20080016195A1Digital data processing detailsUnauthorized memory use protectionComputer networkIdentity provider
One embodiment relates to a method of managing trust relationships between federated identity and service providers. An assertion of a user identity is received from an identity provider via a first federation protocol, wherein a destination service provider is indicated with the assertion. Permission of the user identity to access the destination service provider is verified. If permission is verified, the user identity is asserted to the destination service provider via a second federation protocol. Other embodiments and features are also disclosed.
Owner:MICRO FOCUS LLC
Configuring identity federation configuration
InactiveUS20130160105A1Reduce the amount requiredEnsure consistencyDigital data processing detailsMultiple digital computer combinationsFederated identityComputing systems
A method and apparatus for configuring identity federation configuration. The method includes: acquiring a set of identity federation configuration properties of a first computing system and a set of identity federation configuration properties of a second computing system; identifying one or more pairs of associated properties in the first and the second sets, where the pairs of associated properties include one property from each set of identity federation configuration; displaying, properties that need to be configured manually from the each sets of identity federation configuration properties, where the properties that need to be configured manually do not include the property in any pair of associated properties for which the value can be derived from the value of another property in the pair; automatically assigning a property that can be derived from the value of another property; and providing each computing systems with each set of identity federation properties.
Owner:IBM CORP
Method and Computer Program Product for Implementing an Identity Control System
InactiveUS20160283473A1Text database indexingSpecial data processing applicationsObfuscationControl system
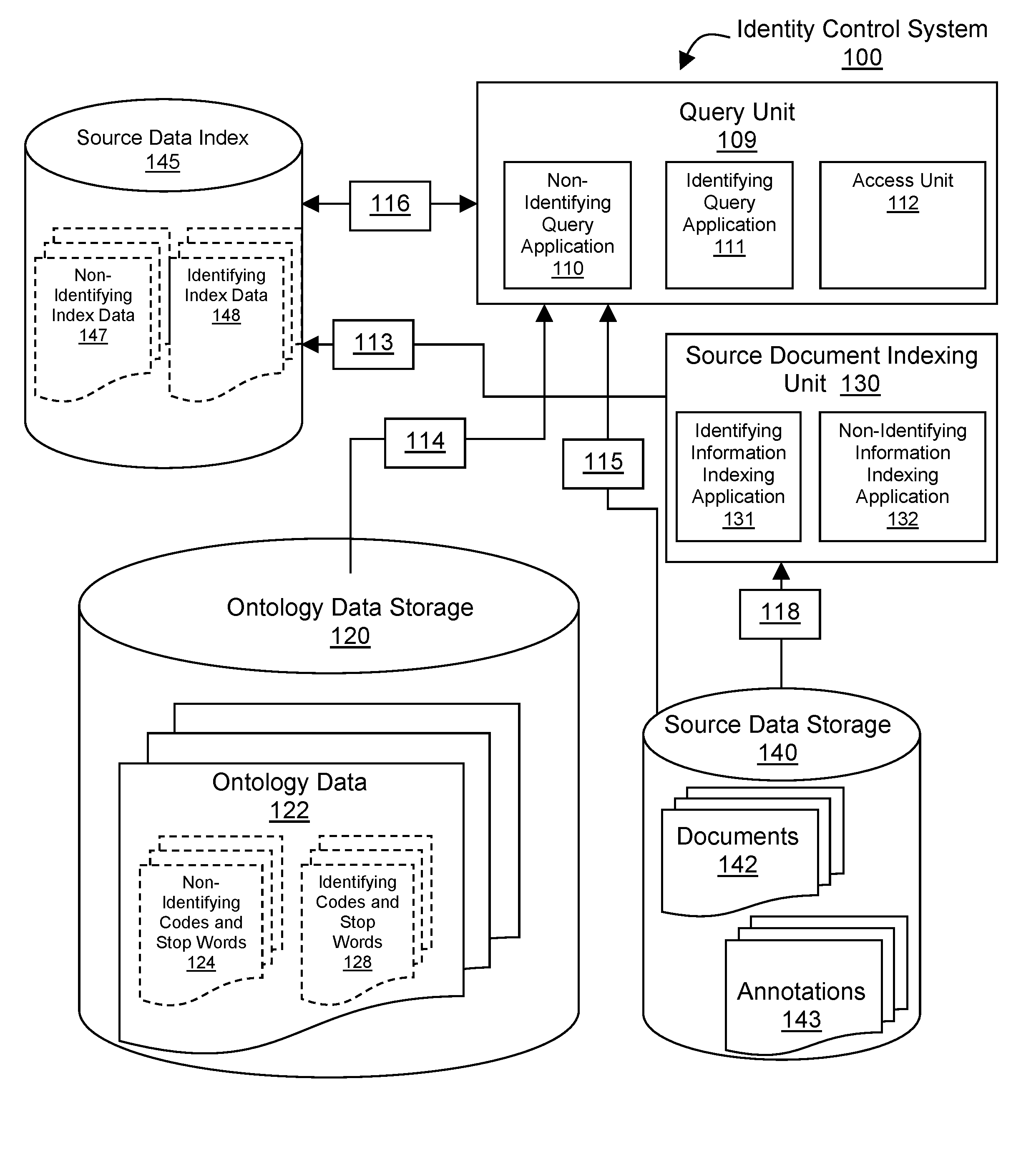
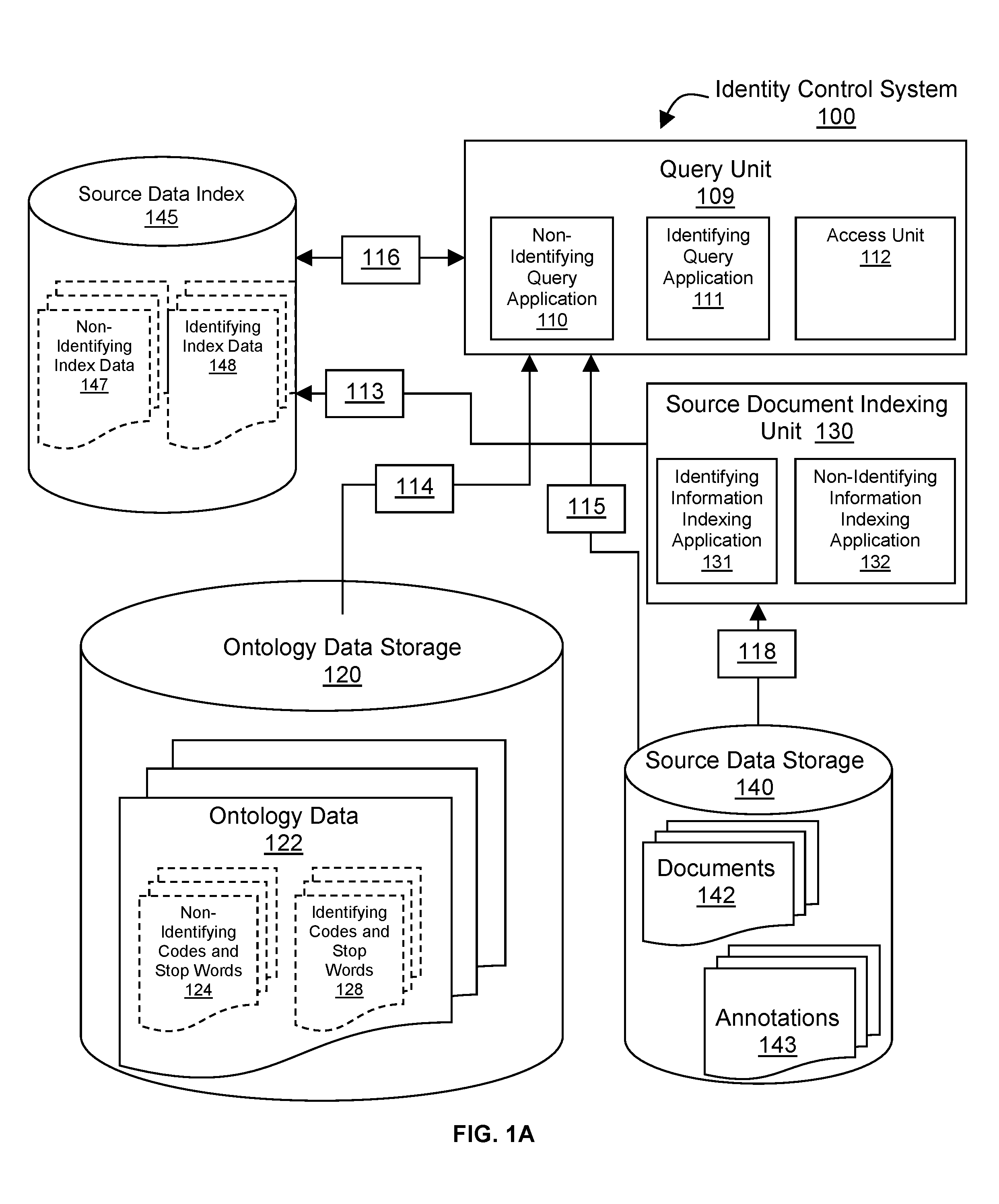
Method and computer program products for implementing an identity control system are disclosed. Documents are abstracted by mapping non-identifying words in the documents to non-identifying concepts that are designated by codes, which codes are linked to non-identifying descriptions and may optionally non-identifying values. Similarly, identifying words in the documents are abstracted by mapping identifying and / or potentially identifying words in the documents to identifying concepts that are designated by codes, which codes are themselves non-identifying and have non-identifying descriptions and may optionally have values, which values may be identifying or may be obfuscations of the identifying information. Non-identifying codes and optional values, the words that are mapped to those codes and stop-words are indexed as non-identifying index data. Identifying codes and optional values, and the words that are mapped to those codes are indexed as identifying index data. An access unit controls the authentication, authorization and access to the query, analysis and retrieval methods that operate on the non-identifying and identifying indexes in such a manner as to provide only the type, level, format and duration of identifying information to which the end-user is authorized. Storage and access control of documents along with their codes and indexes may be local or federated, and is under the control of the identifying information owners and / or their authorized agents who may grant access to end-users within a local or federated set of identity control systems.
Owner:GNOETICS +1
Federated identity brokering
InactiveUS7581248B2Digital data processing detailsUnauthorized memory use protectionTrusted authorityFederated identity
A method, system and apparatus for federated identity brokering. In accordance with the present invention, a credential processing gateway can be disposed between one or more logical services and one or more service requesting clients in a computer communications network. Acting as a proxy and a trusted authority to the logical services, the credential processing gateway can map the credentials of the service requesting clients to the certification requirements of the logical services. In this way, the credential processing gateway can act as a federated identity broker in providing identity certification services for a multitude of different service requesting clients without requiring the logical services to include a pre-configuration for specifically processing the credentials of particular service requesting clients.
Owner:INT BUSINESS MASCH CORP
Router for managing trust relationships
InactiveUS7926089B2Digital data processing detailsUnauthorized memory use protectionComputer networkIdentity provider
One embodiment relates to a method of managing trust relationships between federated identity and service providers. An assertion of a user identity is received from an identity provider via a first federation protocol, wherein a destination service provider is indicated with the assertion. Permission of the user identity to access the destination service provider is verified. If permission is verified, the user identity is asserted to the destination service provider via a second federation protocol. Other embodiments and features are also disclosed.
Owner:MICRO FOCUS LLC
Method and apparatus for trusted federated identity
InactiveCN102783115AUser identity/authority verificationDigital data authenticationInternet privacyTrusted Computing
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com