Patents
Literature
160 results about "Java Card" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
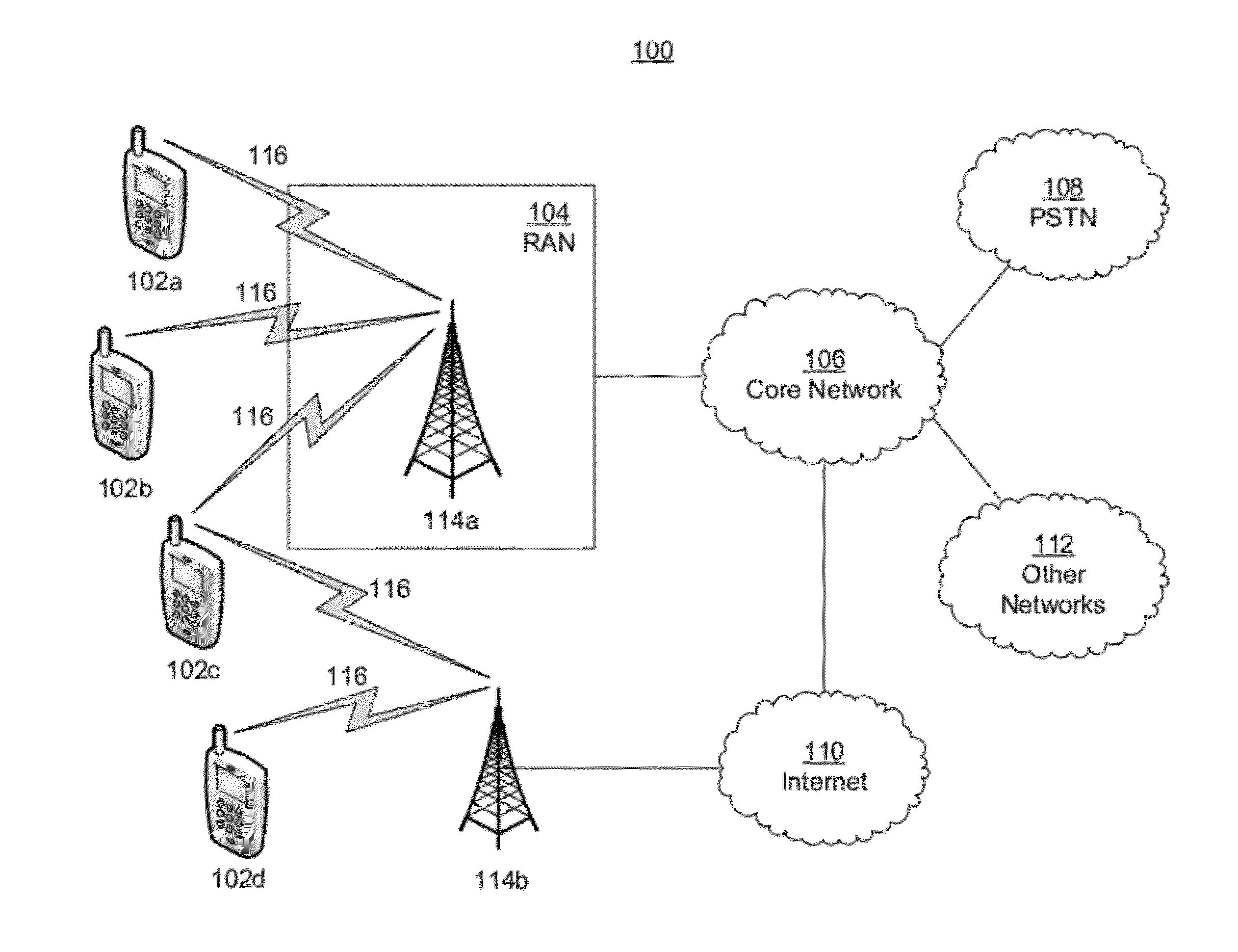
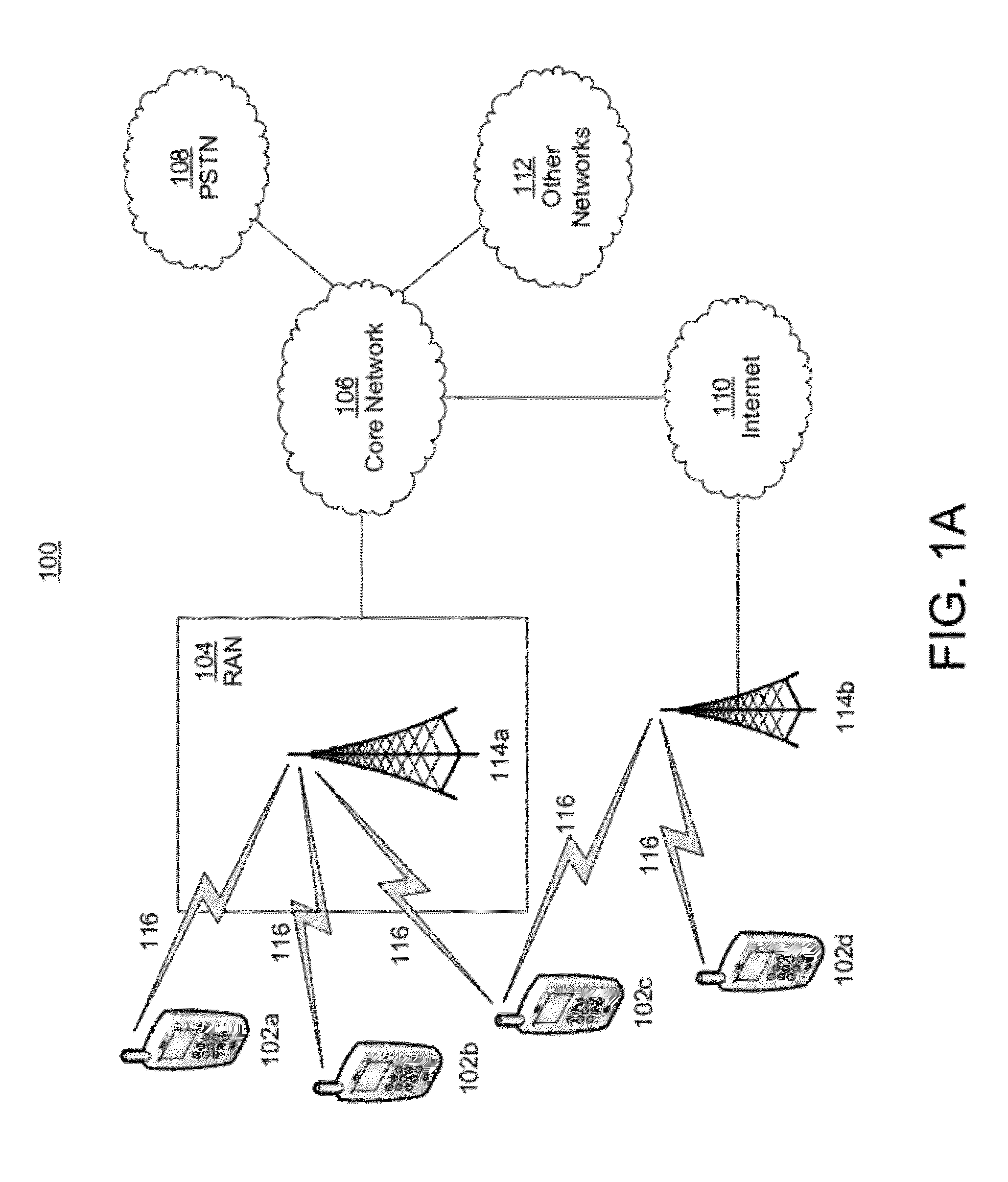
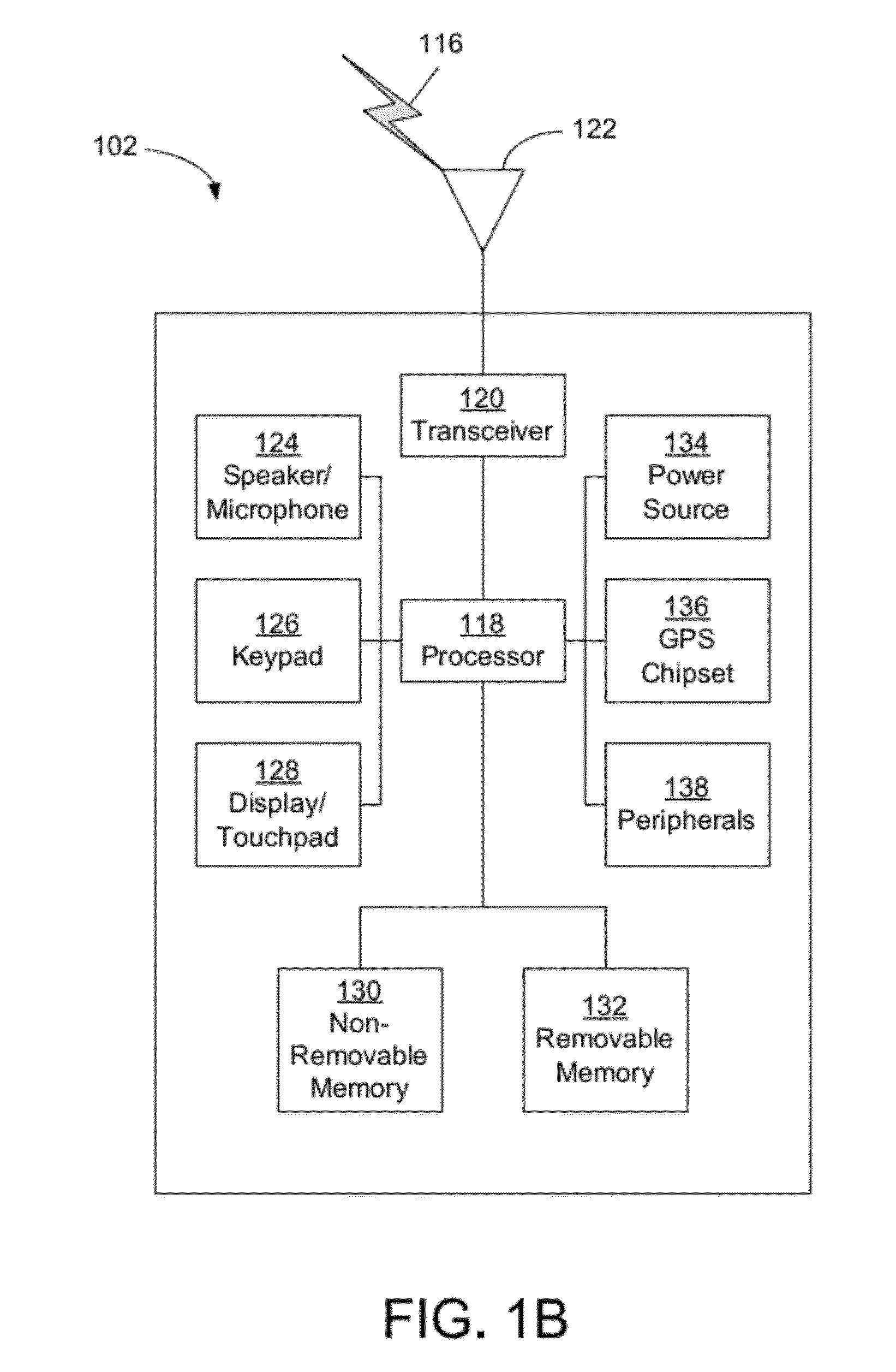
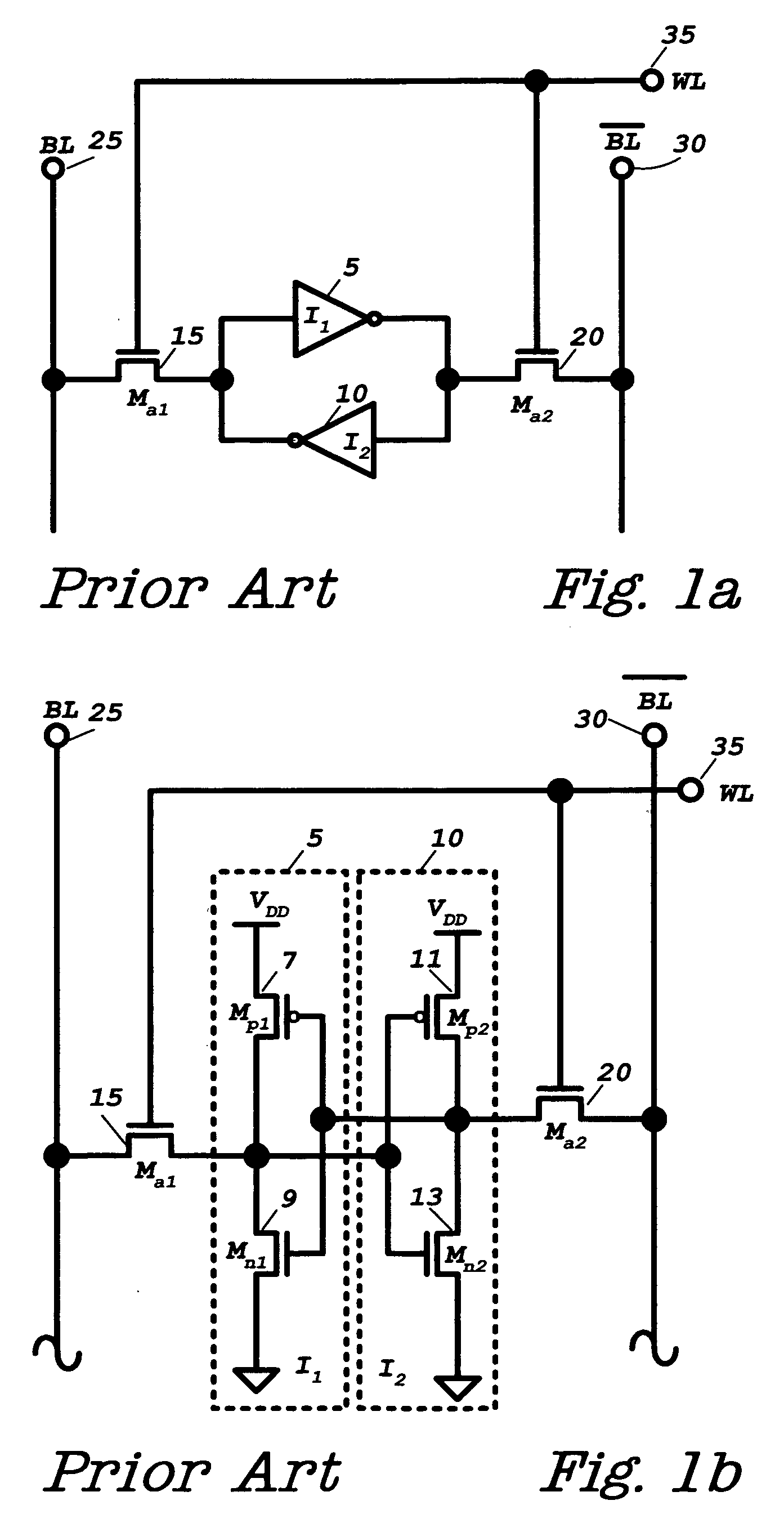
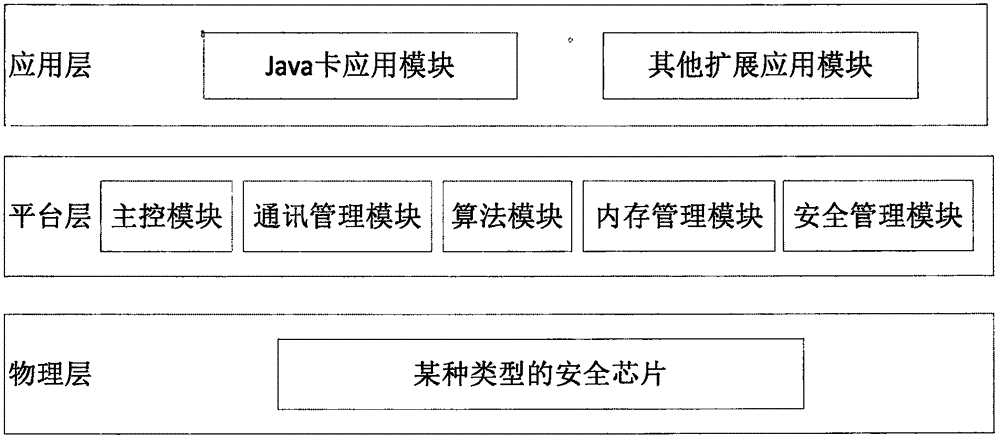
Java Card refers to a software technology that allows Java-based applications (applets) to be run securely on smart cards and similar small memory footprint devices. Java Card is the tiniest of Java platforms targeted for embedded devices. Java Card gives the user the ability to program the devices and make them application specific. It is widely used in SIM cards (used in GSM mobile phones) and ATM cards. The first Java Card was introduced in 1996 by Schlumberger's card division which later merged with Gemplus to form Gemalto. Java Card products are based on the Java Card Platform specifications developed by Sun Microsystems (later a subsidiary of Oracle Corporation). Many Java card products also rely on the GlobalPlatform specifications for the secure management of applications on the card (download, installation, personalization, deletion).
Method And Apparatus For Trusted Federated Identity
InactiveUS20120072979A1Well formedDigital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
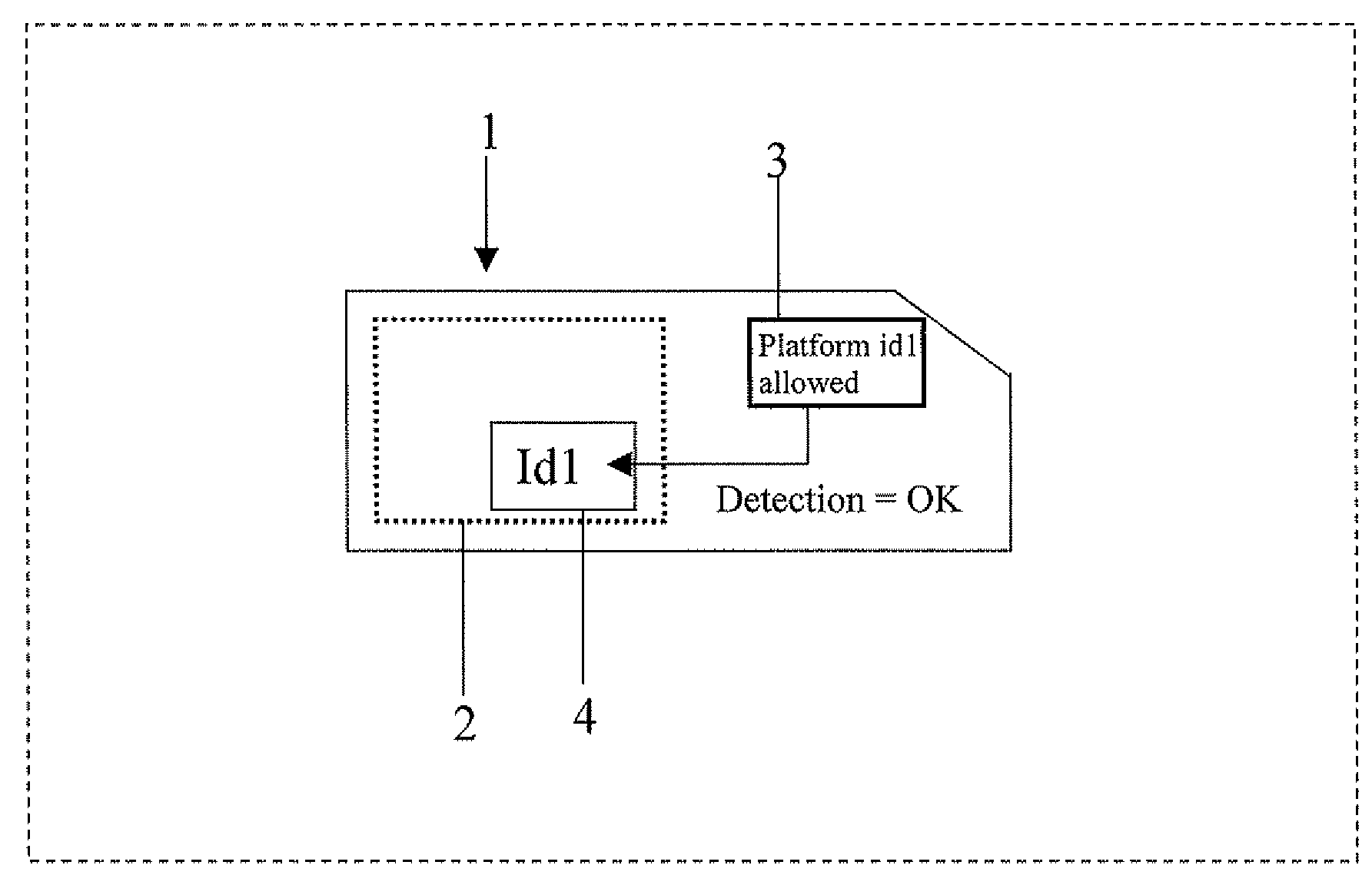
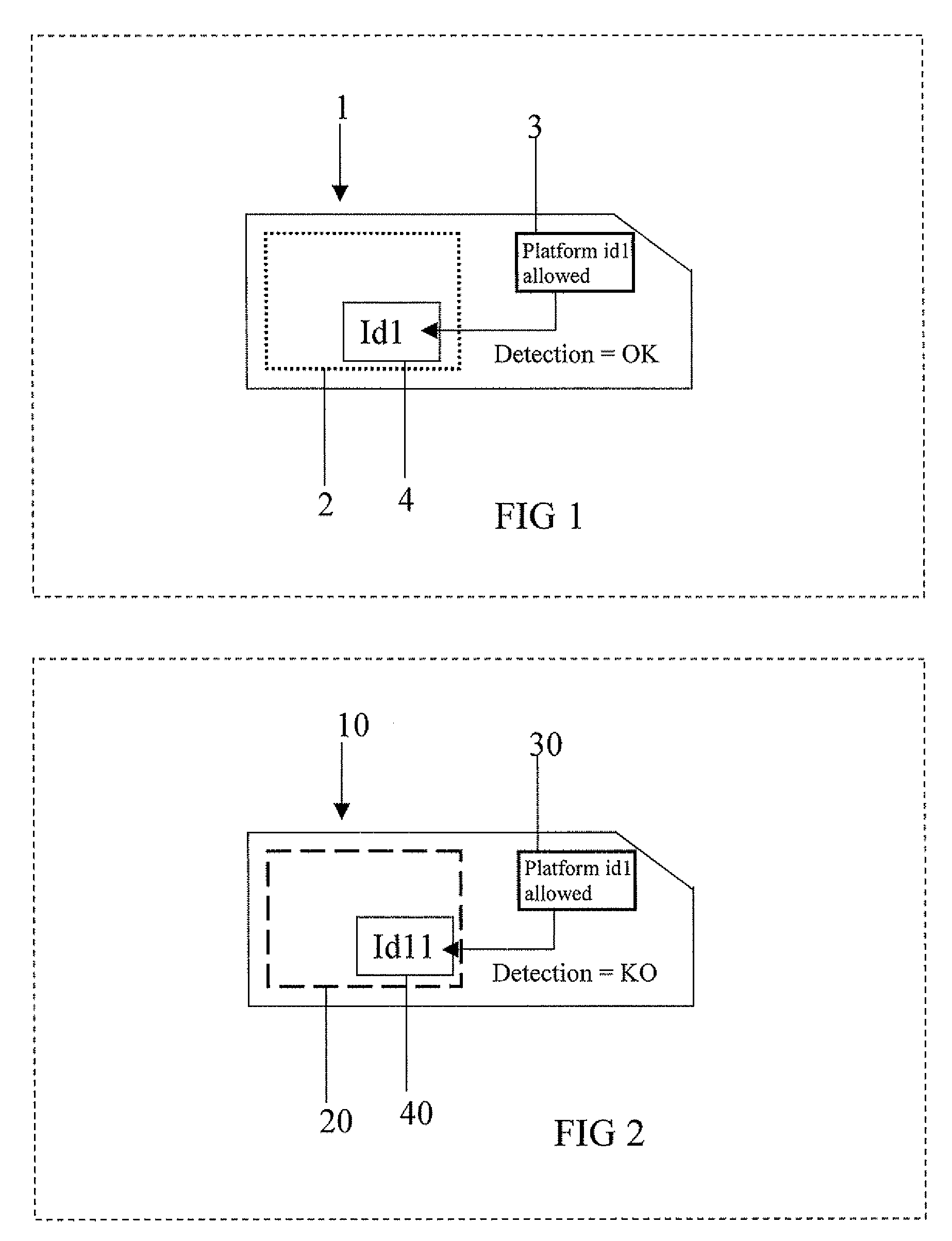
Method for controlling the execution of an applet for an IC card
ActiveUS20080288699A1Preventing executionAvoid business lossInternal/peripheral component protectionComponent plug-in assemblagesOperating systemJava Card
A method for controlling the execution of an applet for an IC Card including a java card platform, includes a phase for downloading the applet inside the IC Card, a phase for executing the applet through the java card platform and a phase for storing an identification platform number inside a memory portion of the IC Card. The phase for executing the applet has a first step for detecting the identification platform number to perform the phase for executing the applet with or without restrictions, respectively if the identification platform number is not or is detected by the step for detecting. The applet is a java card applet or a SIM toolkit applet.
Owner:STMICROELECTRONICS INT NV
Method and apparatus for trusted federated identity
InactiveUS8533803B2Digital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
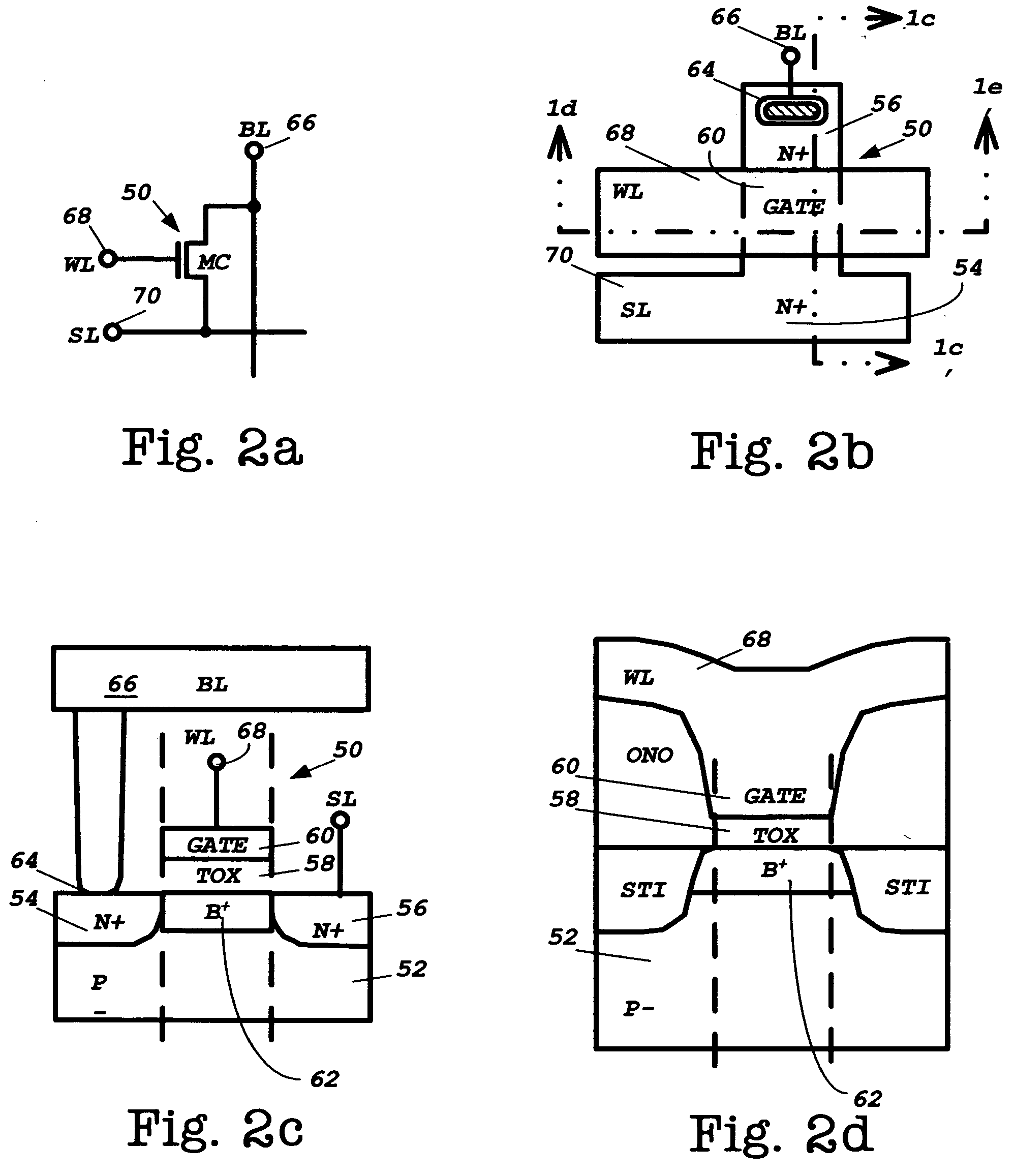
Combo memory design and technology for multiple-function java card, sim-card, bio-passport and bio-id card applications
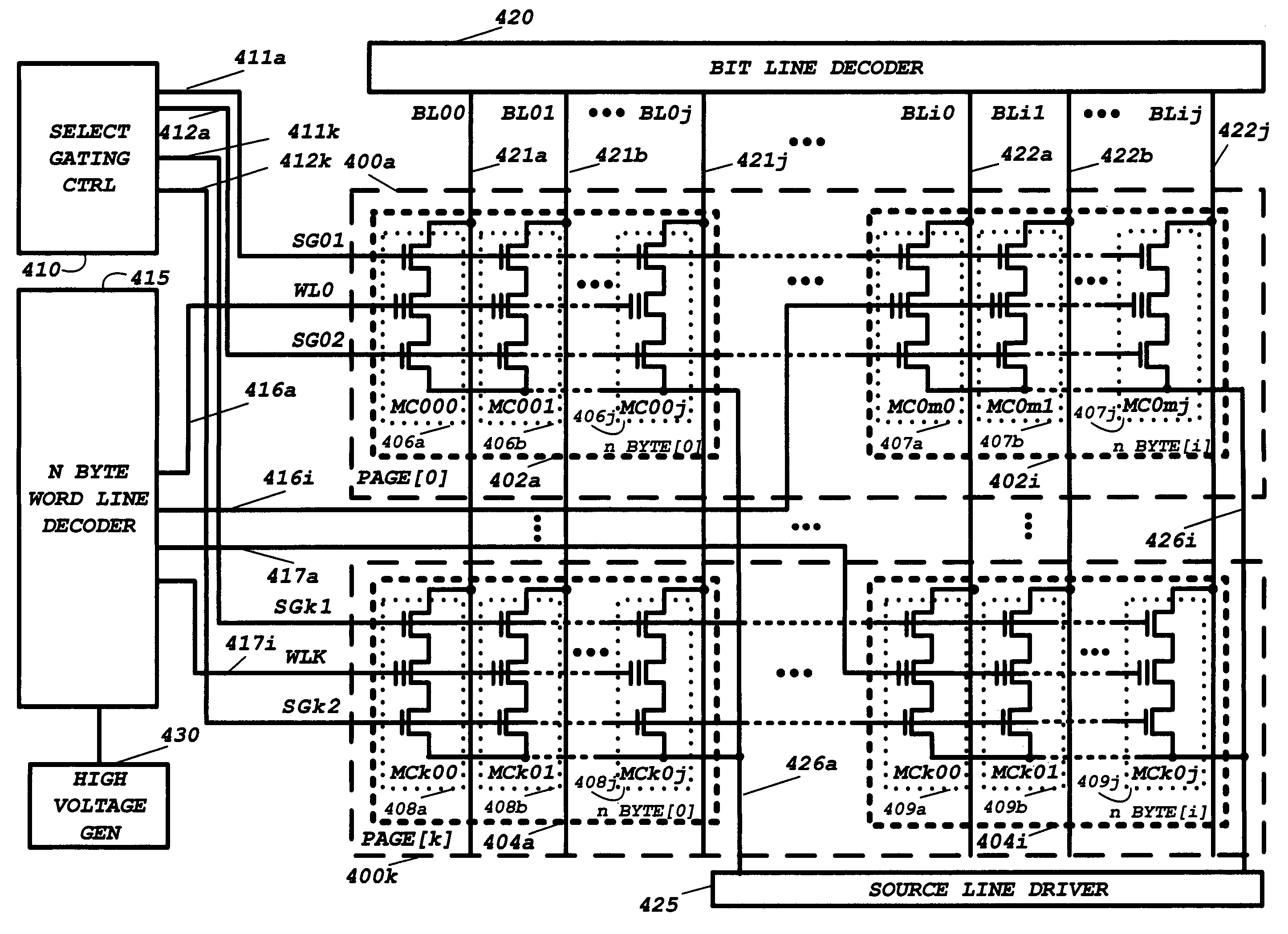
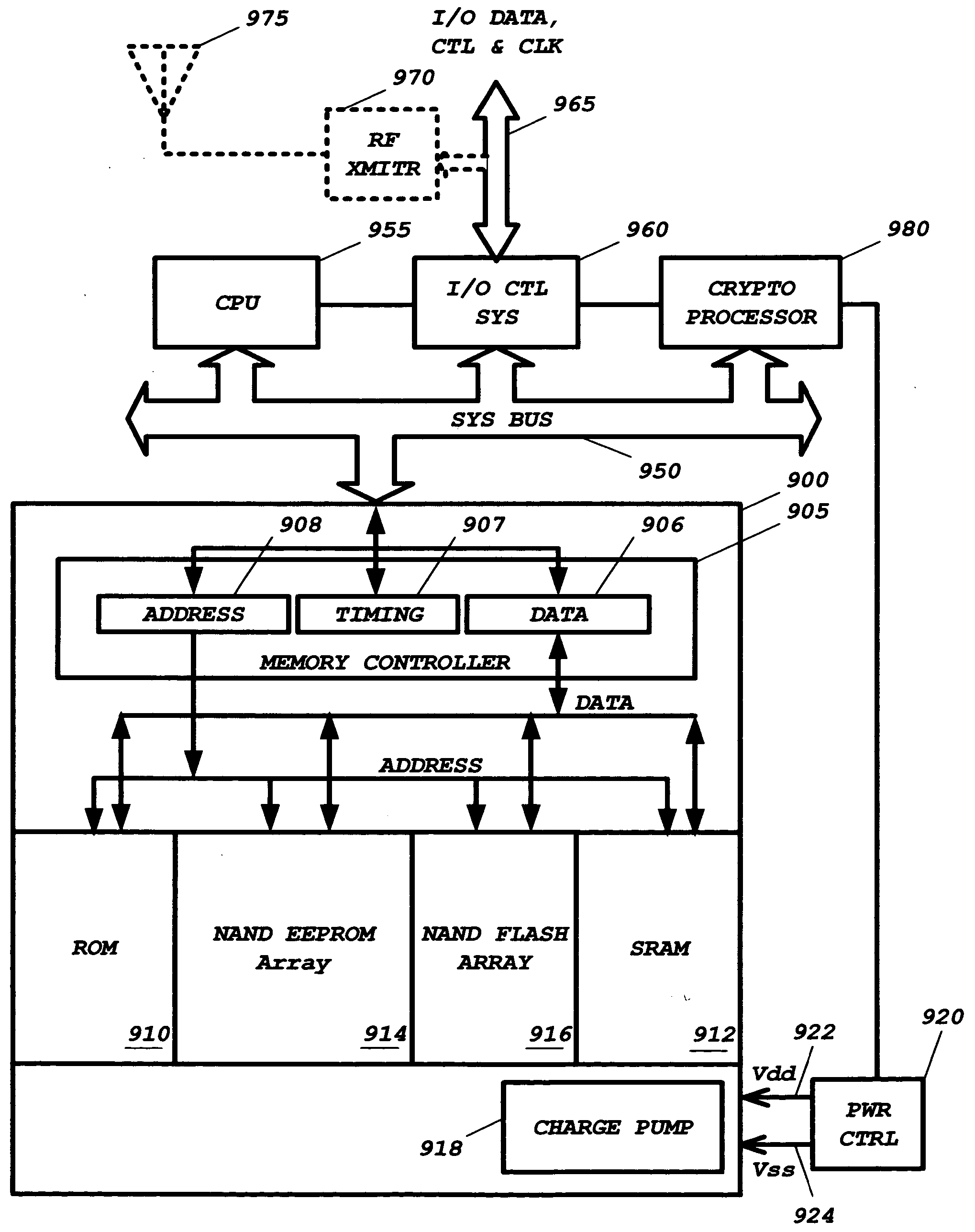
A combination volatile and nonvolatile memory integrated circuit has at least one volatile memory array placed on the substrate and multiple nonvolatile memory arrays. The volatile and nonvolatile memory arrays have address space associated with each other such that each array may be addressed with common addressing signals. The combination volatile and nonvolatile memory integrated circuit further has a memory control circuit in communication with external circuitry to receive address, command, and data signals. The memory control circuit interprets the address, command, and data signals, and for transfer to the volatile memory array and the nonvolatile memory arrays for reading, writing, programming, and erasing the volatile and nonvolatile memory arrays. The volatile memory array is may be a SRAM, a pseudo SRAM, or a DRAM. Any of the nonvolatile memory arrays maybe masked programmed ROM arrays, NAND configured flash memory NAND configured EEPROM.
Owner:CALLAHAN CELLULAR L L C
Novel combo memory design and technology for multiple-function java card, sim-card, bio-passport and bio-id card applications
A combination volatile and nonvolatile memory integrated circuit has at least one volatile memory array placed on the substrate and multiple nonvolatile memory arrays. The volatile and nonvolatile memory arrays have address space associated with each other such that each array may be addressed with common addressing signals. The combination volatile and nonvolatile memory integrated circuit further has a memory control circuit in communication with external circuitry to receive address, command, and data signals. The memory control circuit interprets the address, command, and data signals, and for transfer to the volatile memory array and the nonvolatile memory arrays for reading, writing, programming, and erasing the volatile and nonvolatile memory arrays. The volatile memory array is may be a SRAM, a pseudo SRAM, or a DRAM. Any of the nonvolatile memory arrays maybe masked programmed ROM arrays, NAND configured flash memory NAND configured EEPROM.
Owner:CALLAHAN CELLULAR L L C
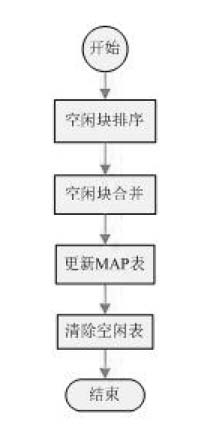
Java card system and space distribution processing method thereof
ActiveCN102521145AImprove access speedRealize distributionMemory adressing/allocation/relocationFragment processingElectricity
The invention provides a Java card system, which comprises an electrically erasable and programmable read-only memory space. The invention further provides a memory space distribution processing method of the Java card system, which includes a space distribution method, a trash recycling method and a stacked fragment processing method. The Java card system and the space distribution processing method thereof can efficiently achieve system space distribution, and lead application programs supplying to providers to be distributed in a continuous electrically erasable and programmable read-only memory (EEPROM) so as to increase access speed of application entities. By means of the trash recycling method, space in the Java card system occupied by trashes is tidied efficiently, a limited memory space of a Java card is led to be reasonably used, and sufficient space is provided for downloading of the application programs.
Owner:EASTCOMPEACE TECH
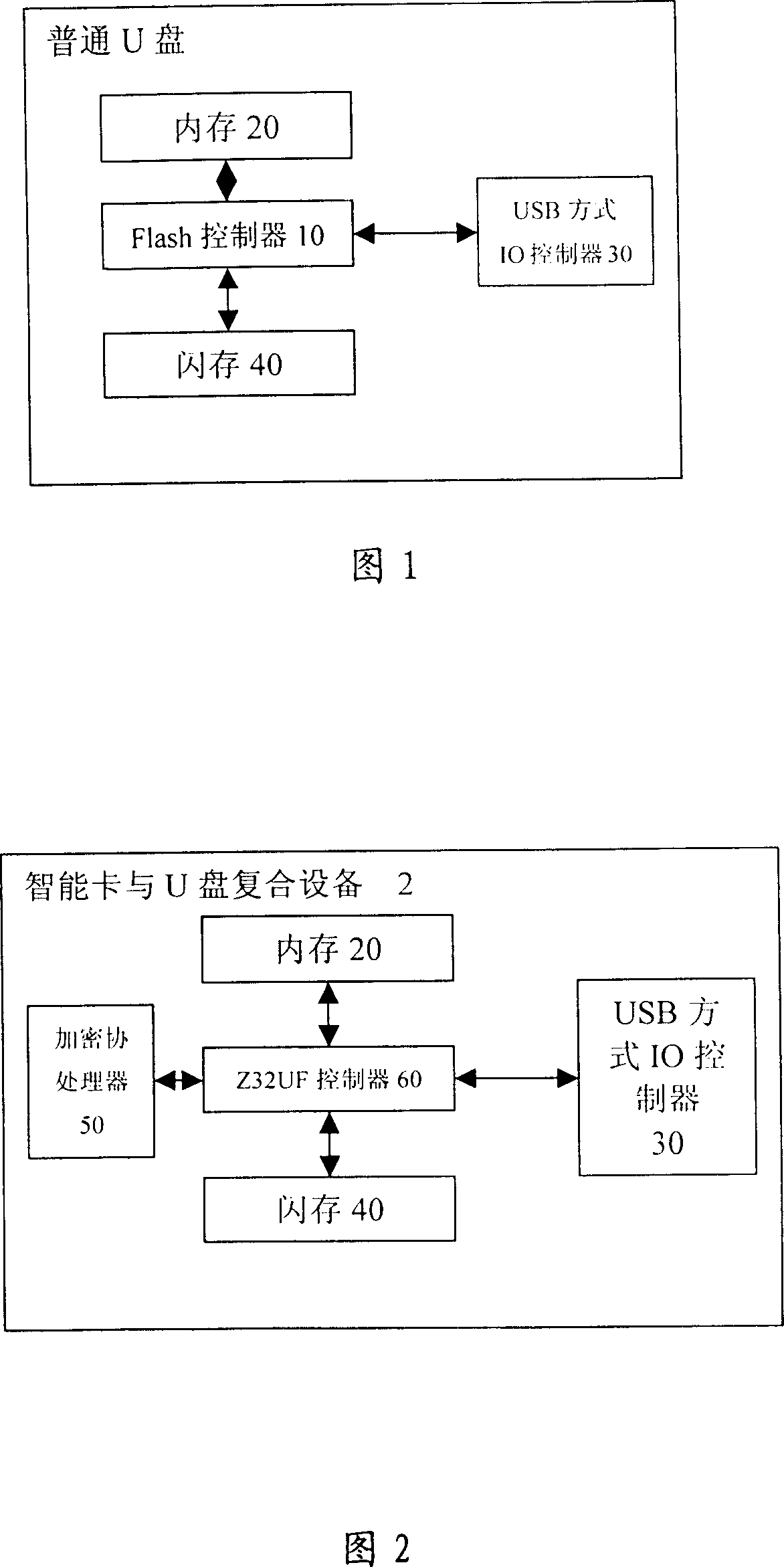
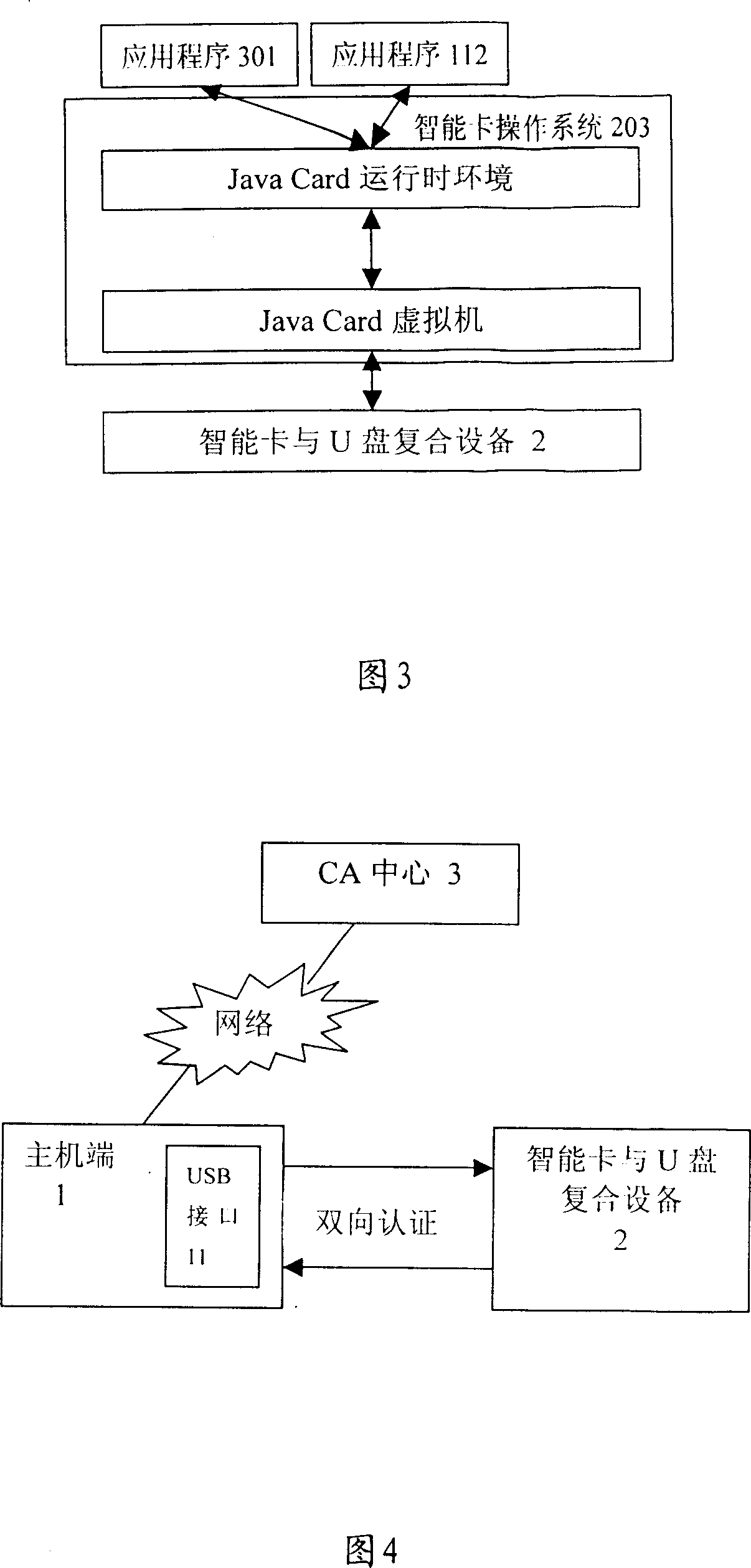
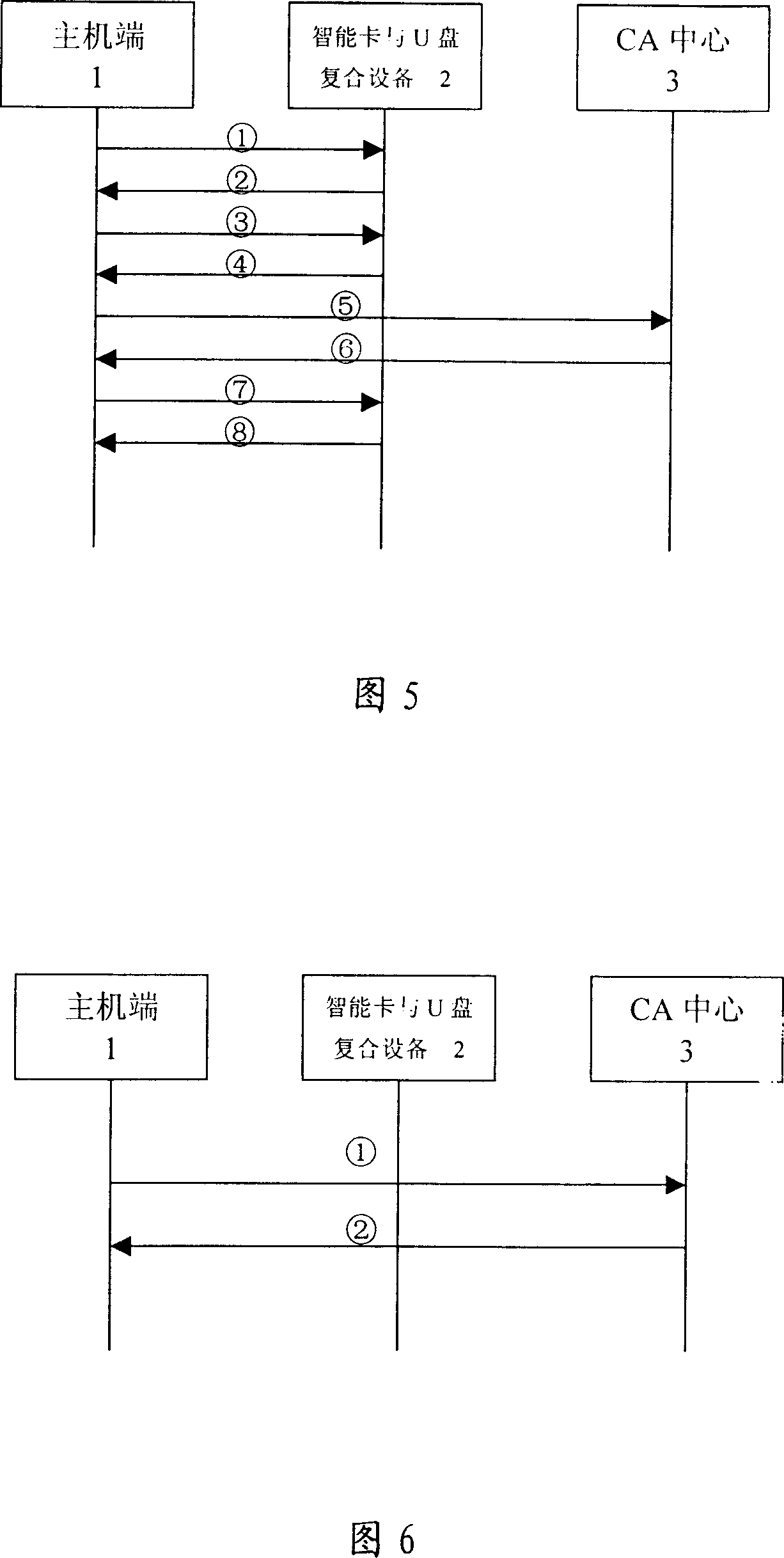
Intelligent card and U disk compound device and its access security improvement method based on bidirectional authentication mechanism
InactiveCN101009556AImprove confidentialityHigh utility valueSecuring communicationOperational systemSmart card
The invention discloses an intelligence card, U disc complex equipment and method to improve the access security based on the bidirectional identification mechanism. The operation system 203 of intelligence card which is worked following the technical specifications of Java Card is mounted in intelligence card and U disc complex equipment, and the application program 301 which is used to control the read-write of flask disc and application program 112 which is used to complete the identification are run in the operation system 203 of intelligence card. The bidirectional identification based on the digital certificate is realized by three steps: (1)the generation and load of equipment certificate of intelligence card and U disc complex equipment, (2)the certificate of host computer is generated, (3)the bidirectional identification is realized between the host computers, intelligence card and U disc complex equipment. The access of ordinal U disc is not controlled any more. The bidirectional identification mechanism which is realized by the digital certificate can confirm the identity of intelligence card and U disc complex equipment, and it has perfect secrecy, and can satisfy the requirement of security for the special department.
Owner:中国信息安全产品测评认证中心 +1
Method for performing read-write operation on programmable read-only memory with cache by JAVA card
ActiveCN102063384AImprove performanceMemory adressing/allocation/relocationRecord carriers used with machinesProgrammable read-only memoryRandom access memory
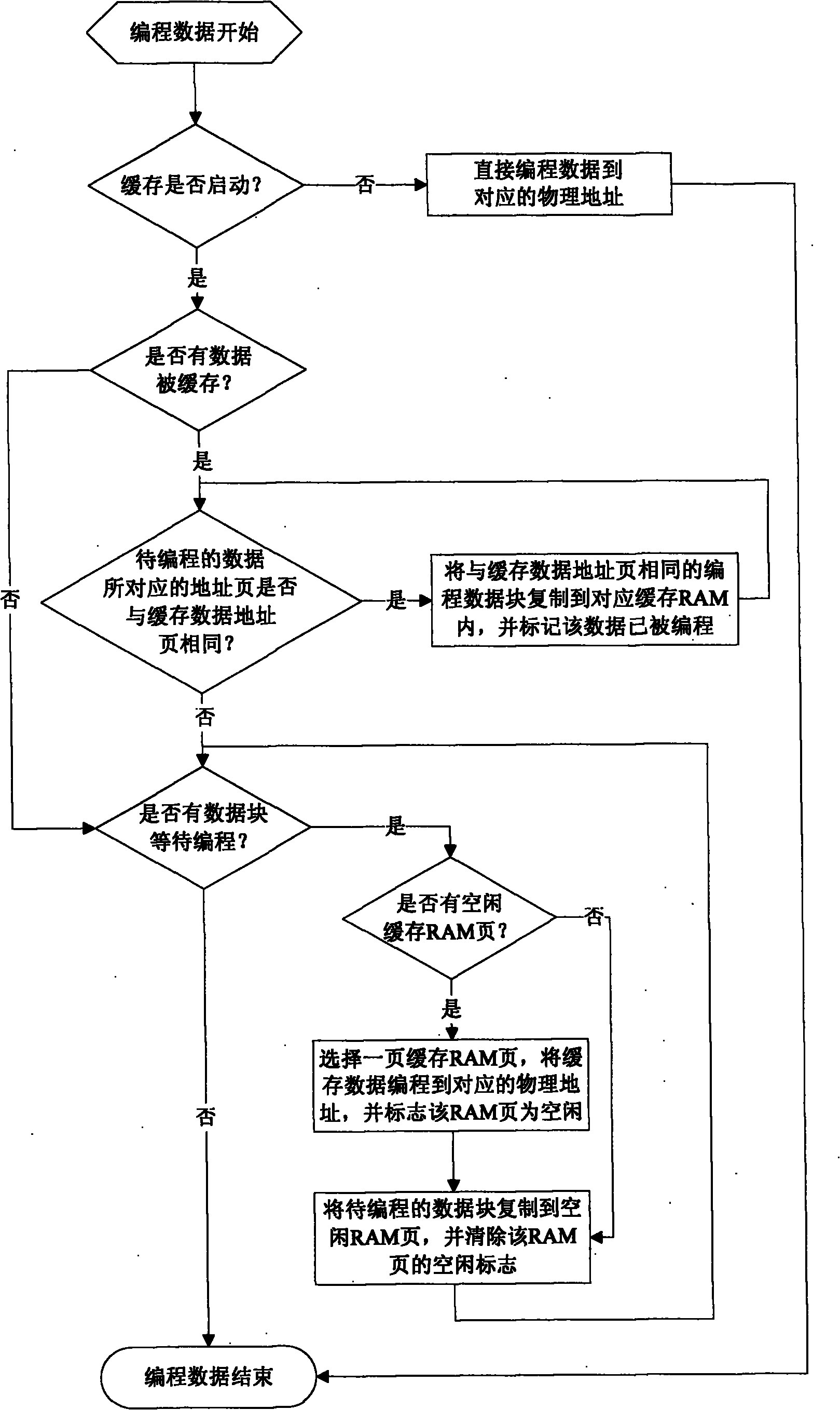
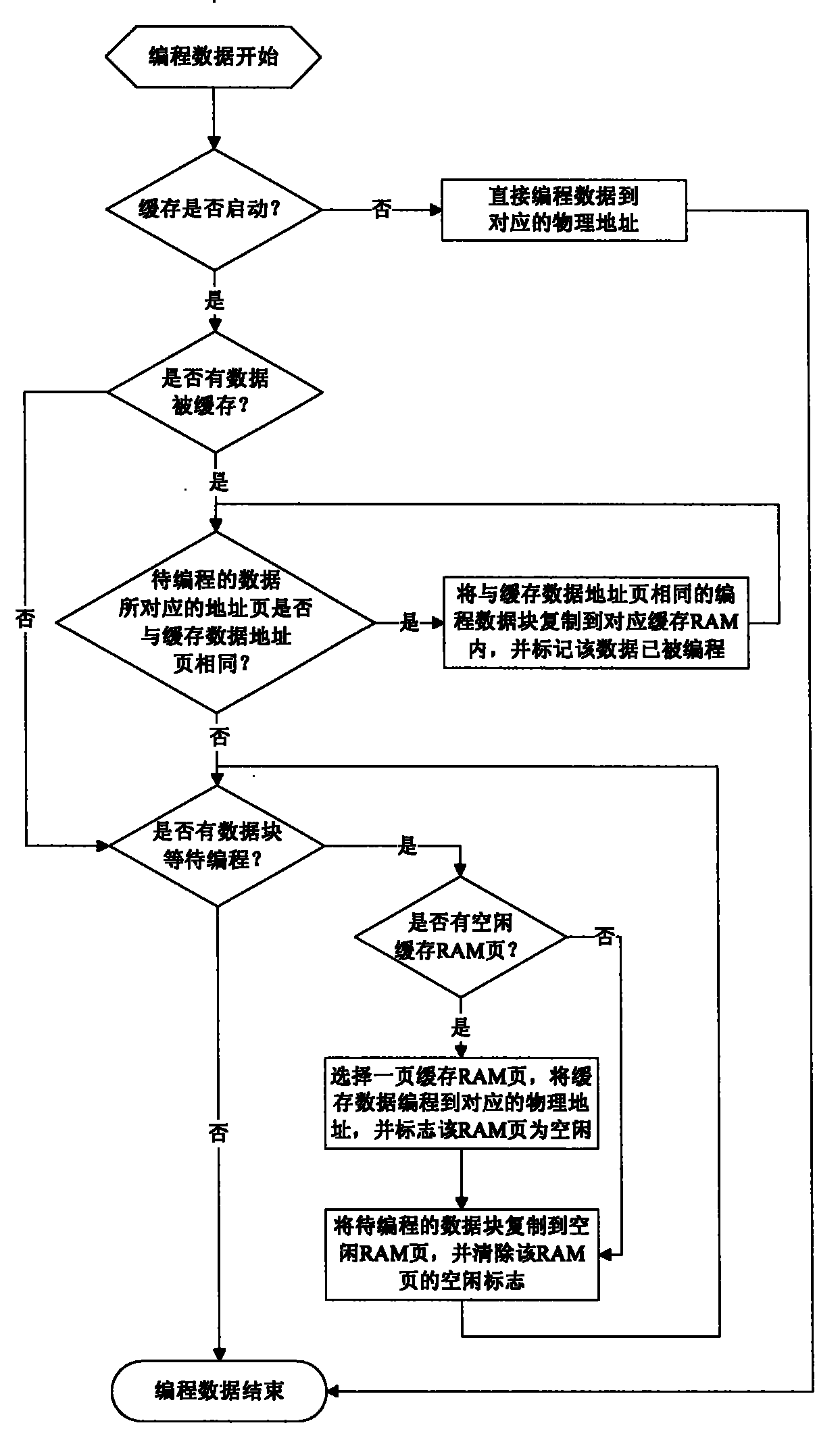
The invention discloses a method for performing read-write operation on a programmable read-only memory (EEPROM / FLASH ROM) with cache by a JAVA card. The technical scheme is that: a JAVA card operating system distributes an RAM (random access memory) space several times larger than the page size for caching the dynamic data of the EEPROM / FLASH according to the page size of the EEPROM / FLASH. When the EEPROM / FLASH is programmed, the data is not written immediately, and the data to be written is cached in the cache RAM. The cache data is written into the EEPROM / FLASH only when an operating system refreshes a new cache RAM. When the operating system reads data, the data, if cached, is read from the cache RAM. Through the data caching method, the programming times of the EEPROM / FLASH can be reduced, and thus the card operation speed is improved and the service life of the card is prolonged.
Owner:HENGBAO
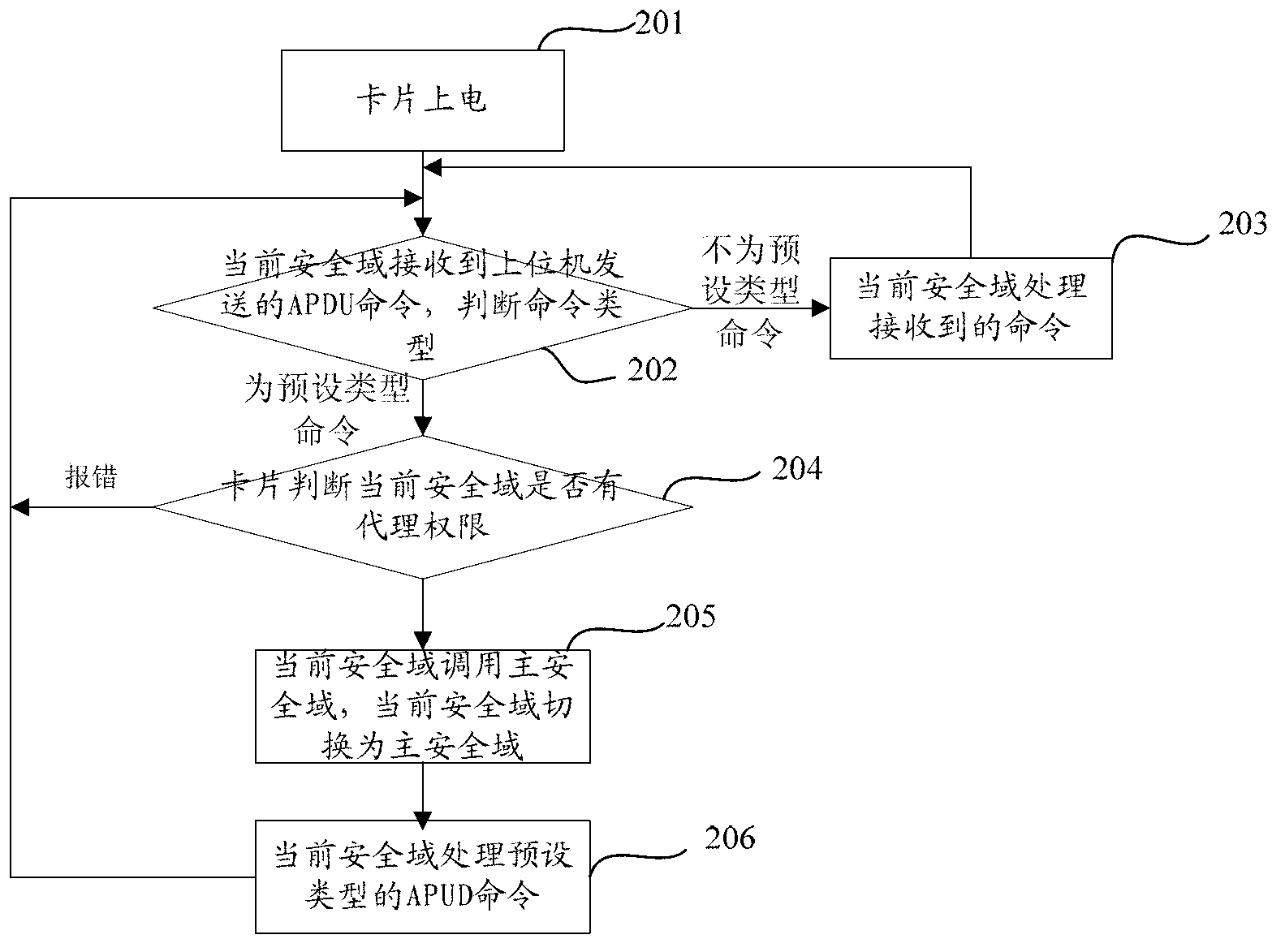
Realization method for security domain on java card
ActiveCN102801705AFlexible Management InterfaceImprove securityUser identity/authority verificationPersonalizationData validation
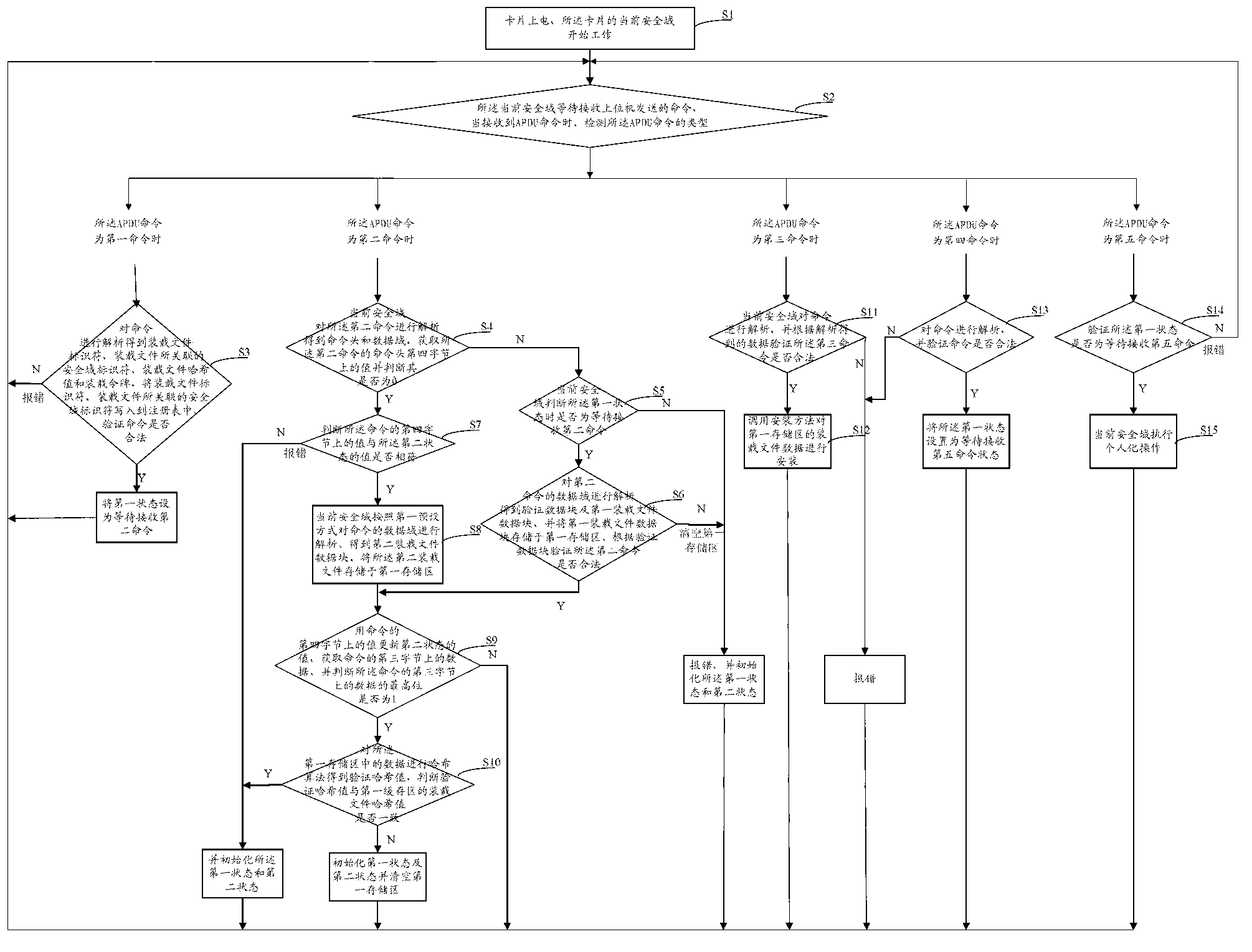
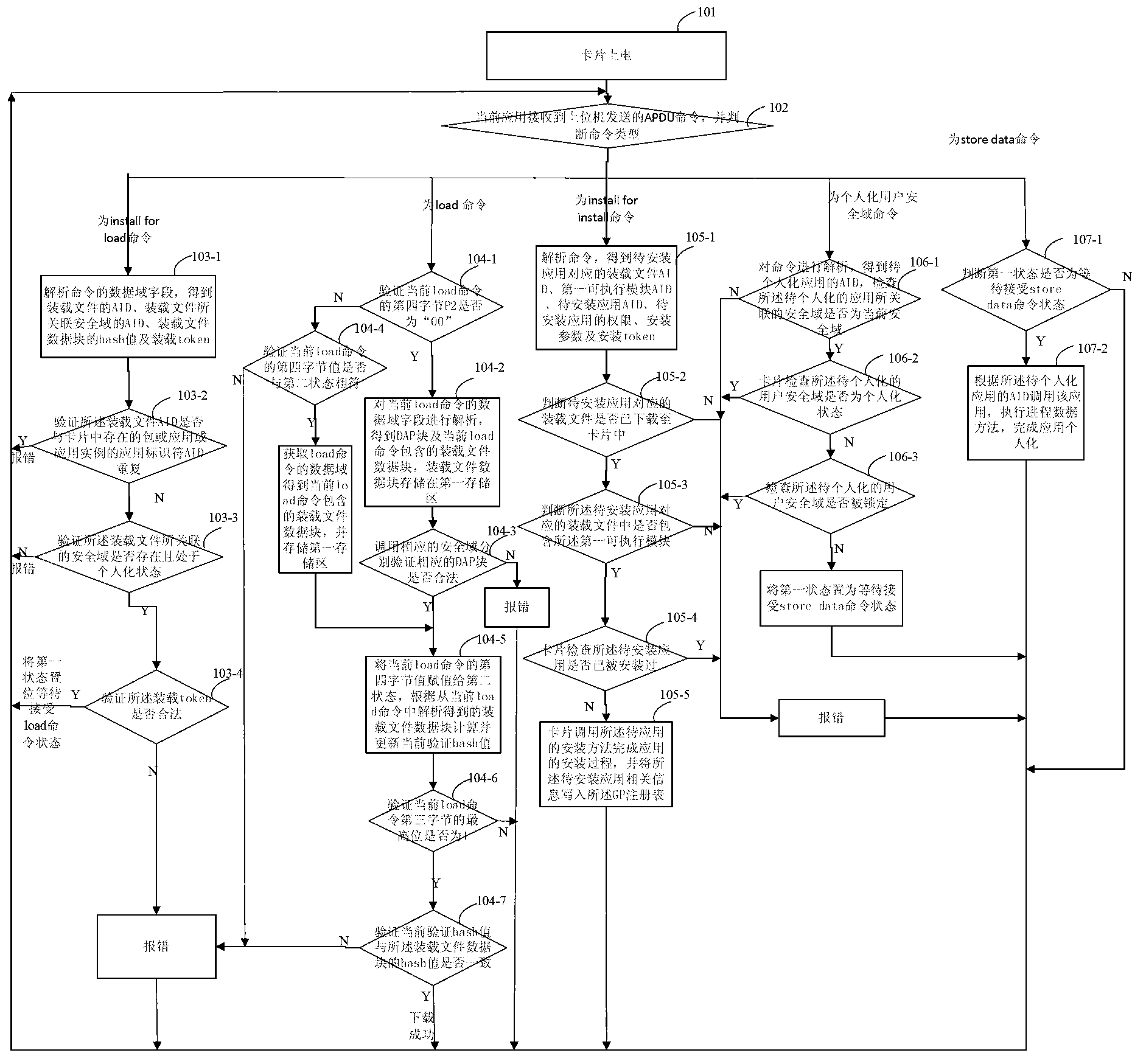
The invention discloses a realization method for a security domain on a java card, and relates to the field of smart cards. The method comprises the following steps of: receiving and resolving a first command by using a current security domain to obtain application related information, and setting a first state into waiting for the reception of a second command; receiving and resolving the second command to obtain a loaded file data block, storing the loaded file data block into a first memory area, verifying whether the second command is legal or not, continuing the method if the second command is legal, otherwise reporting an error; receiving and resolving a third command, verifying whether the third command is legal or not according to resolved data, and if the third command is legal, calling an installation method, and installing application according to the data of the first memory area; receiving and resolving a fourth command, judging whether the fourth command is legal or not, and if the fourth command is legal, setting the first state into waiting for the reception of a fifth command; and receiving the fifth command, and executing application personalization operation. By using the scheme, the security of application downloading, installation and personalization processes of the card is ensured.
Owner:FEITIAN TECHNOLOGIES
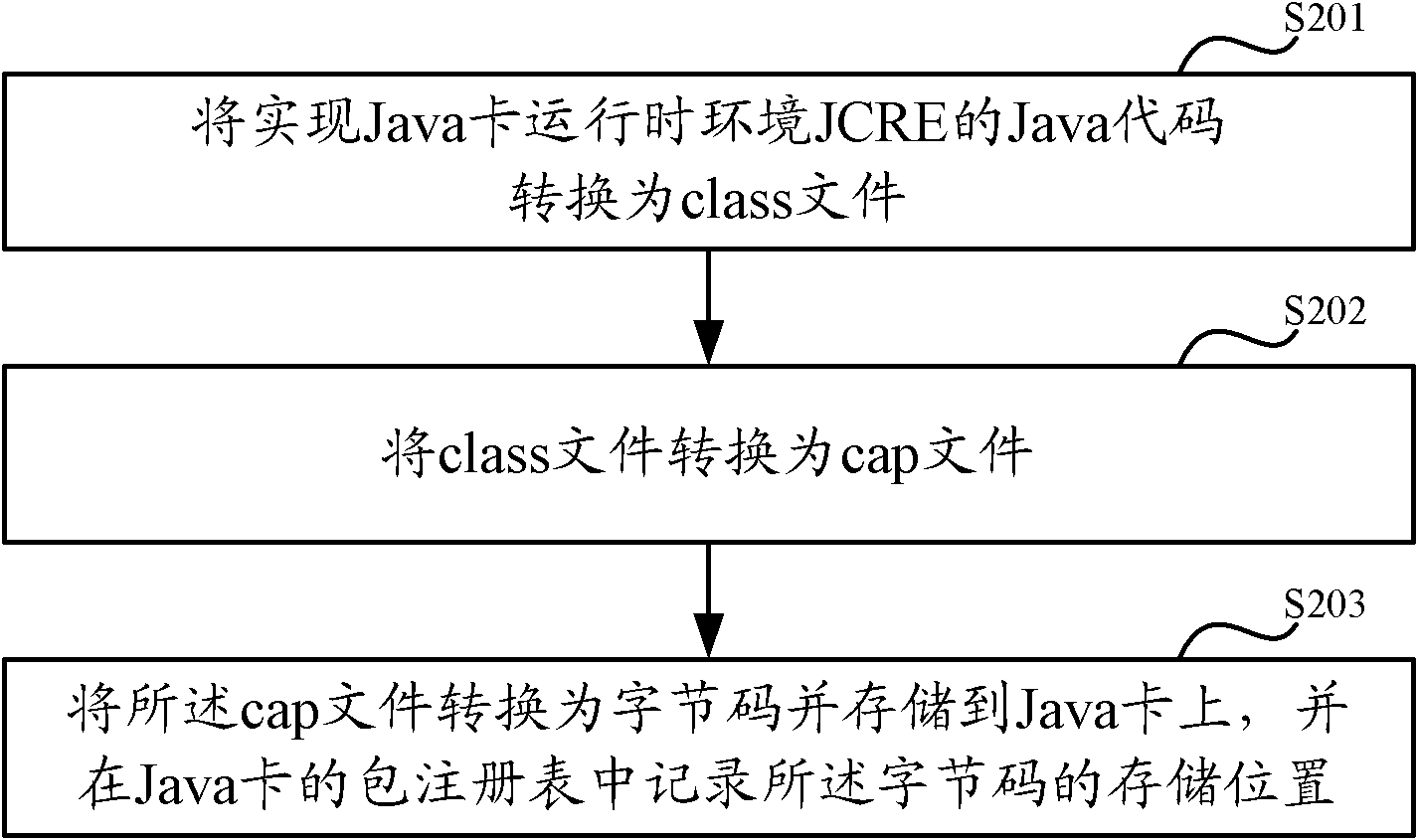
Method and system for storing bytecode of JCRE (Java card run time environment)
InactiveCN102023885AAchieve mutual independenceProgram controlRecord carriers used with machinesApplication softwareRunning time
The invention discloses a method and system for storing a bytecode of a JCRE (Java card run time environment). The method comprises: converting a Java code used for realizing the JCRE into a class file; converting the class file into a cap file; converting the cap file into a bytecode and storing the bytecode into the Java card; and recording the storage position of the bytecode in a package registry. By the invention, because the Java code of the JCRE is stored according to the loading process of an application program, in the loading process, with the Java card of the JCRE and a COS code are not required to be compiled together, only the Java code of the JCRE is modified, and the COS code is not required to be modified, therefore mutual independence of the Java code of the JCRE and a COS in the bottom layer is achieved.
Owner:BEIJING WATCH DATA SYST
Method and apparatus for trusted federated identity
InactiveCN102783115AUser identity/authority verificationDigital data authenticationInternet privacyTrusted Computing
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
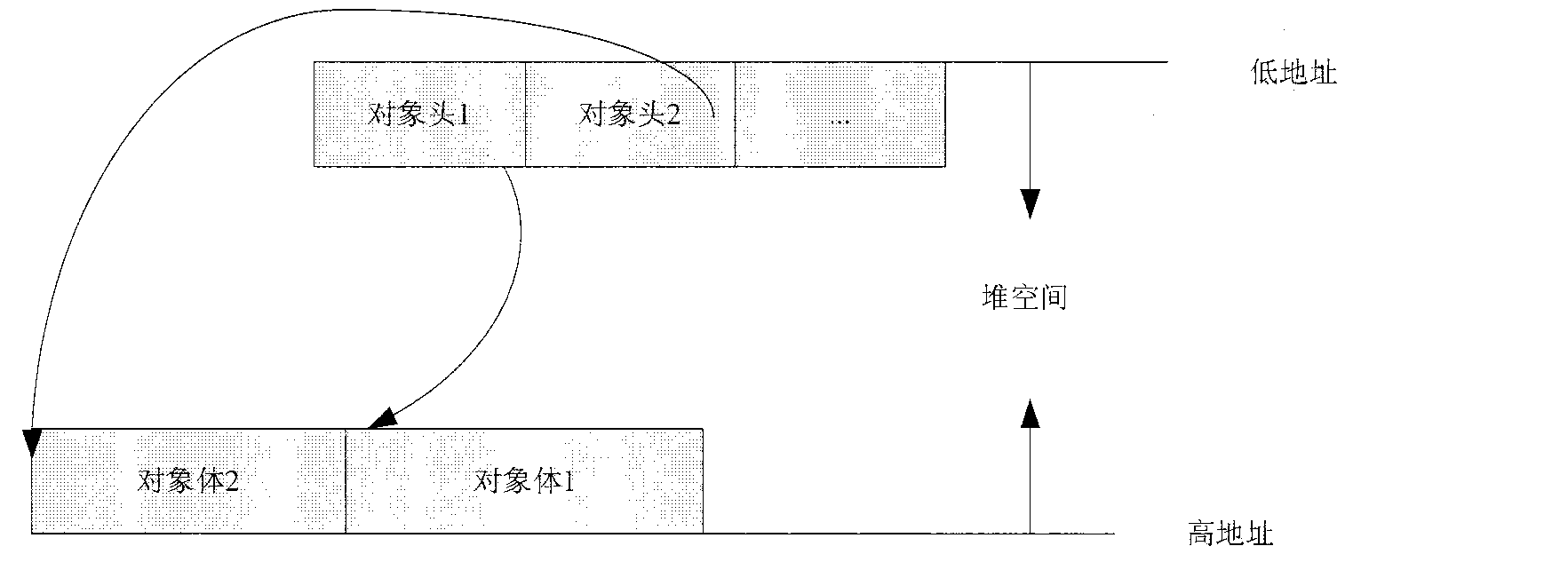
JAVA card object management method
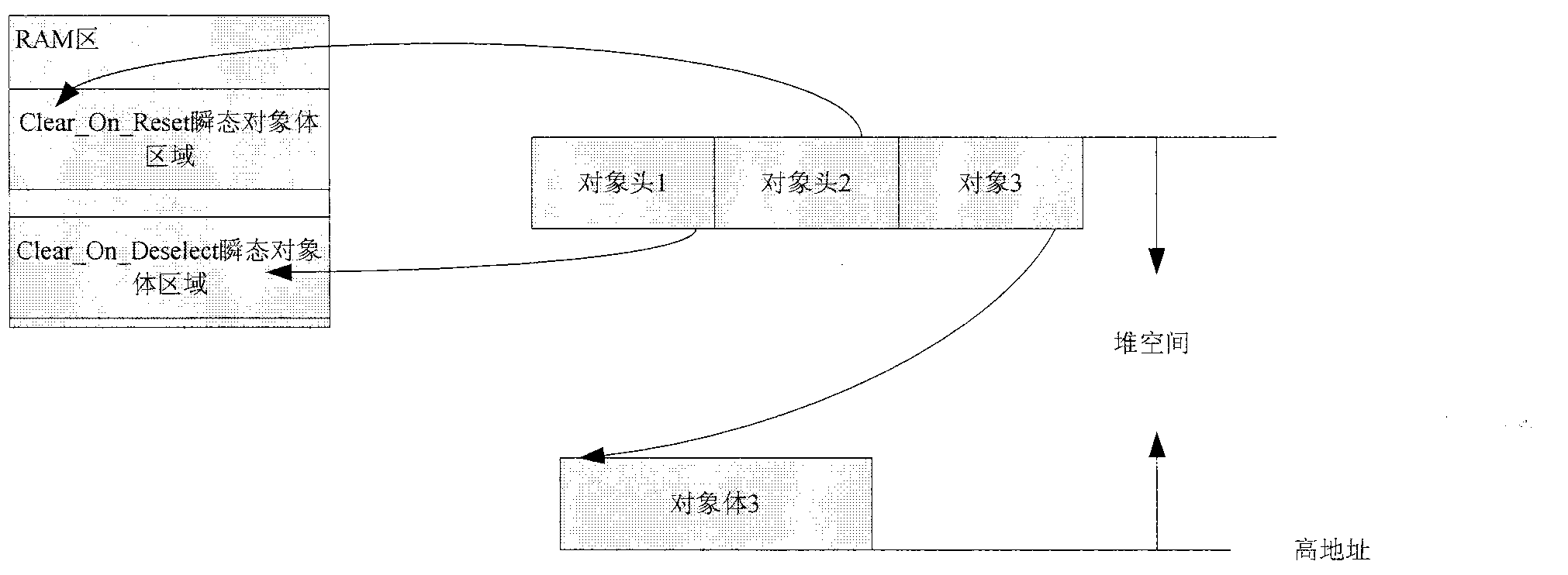
InactiveCN102799660AHeap space savingSave spaceSpecial data processing applicationsJavaSoftware engineering
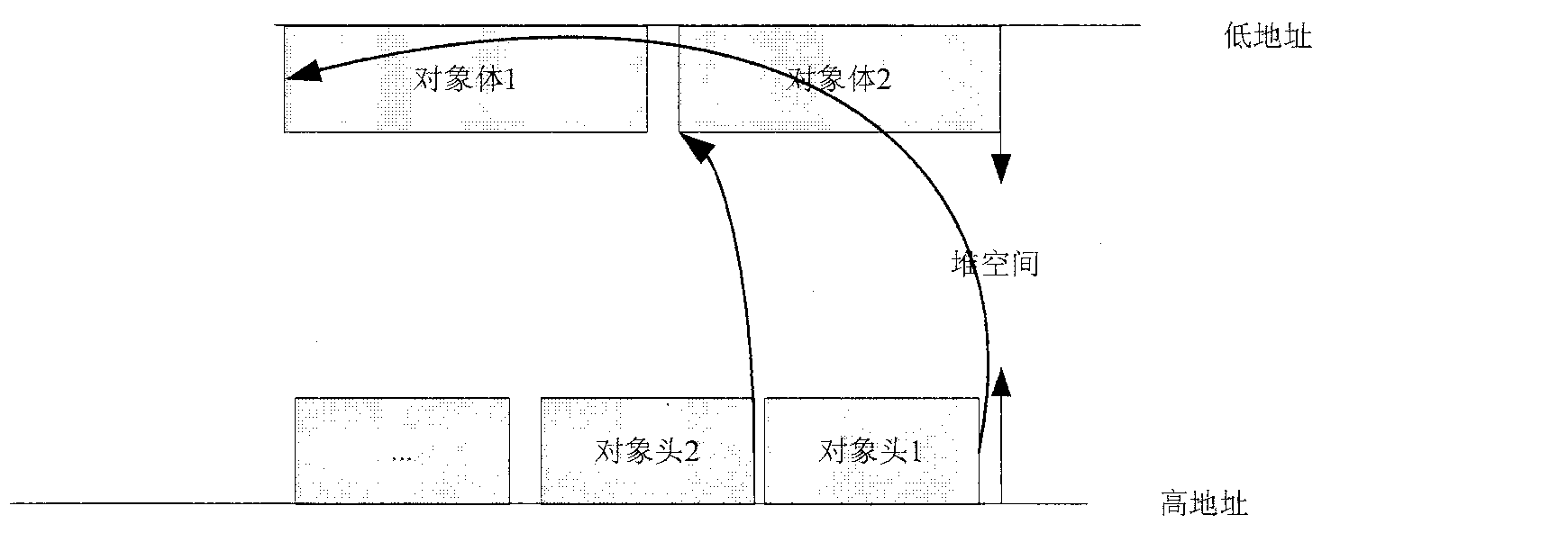
The invention relates to a JAVA card object management method, comprising the following content: a JAVA card object is jointly composed of an object head and an object body, and the object head and the object body are stored in a stack in a separated manner; the object heads of all the types fixedly occupy eight bytes, and the object body occupies a storage space in different sizes according to concrete content of an object; and certain page blocks are allocated in advance to be taken as a space for the object heads according to the design requirements of a JAVA card. The JAVA card object management method disclosed by the invention improves object creating and access efficiency and is beneficial to more reasonable application to limited storage space of a JAVA intelligent card.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Remote card issuing method of mobile phone payment card based on JAVA card
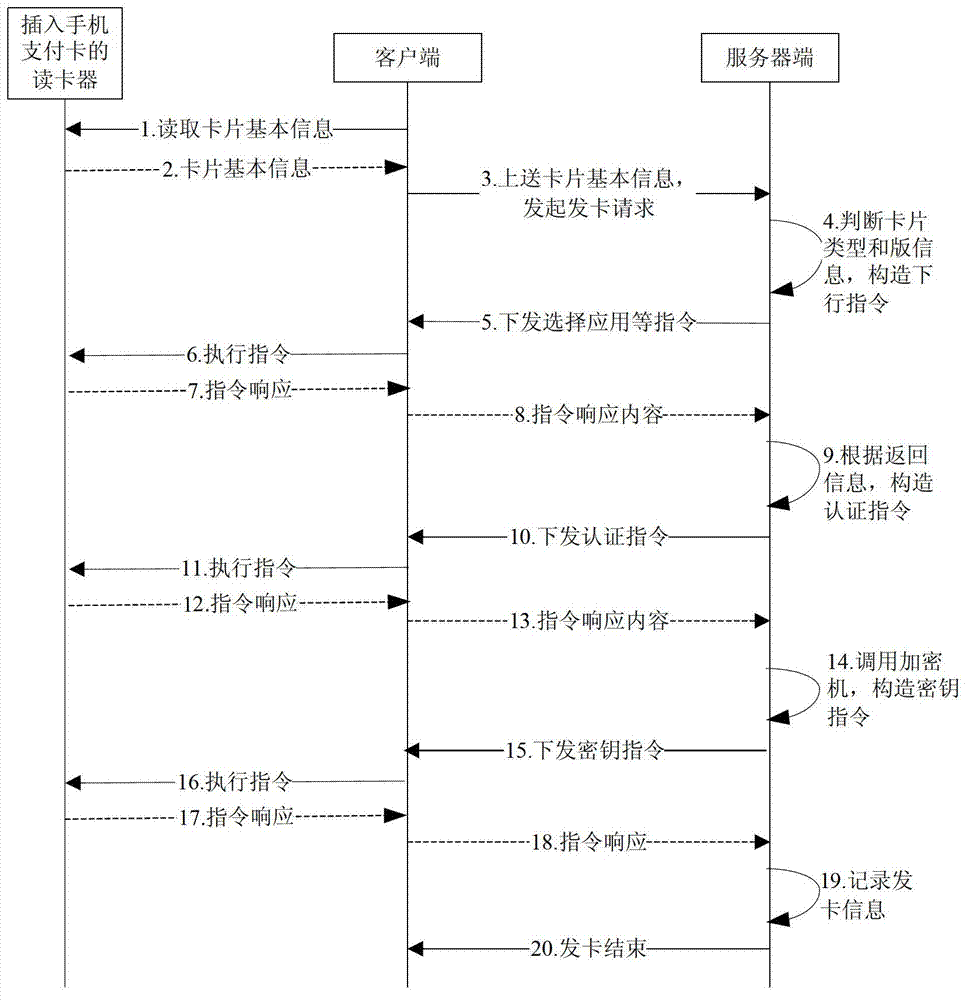
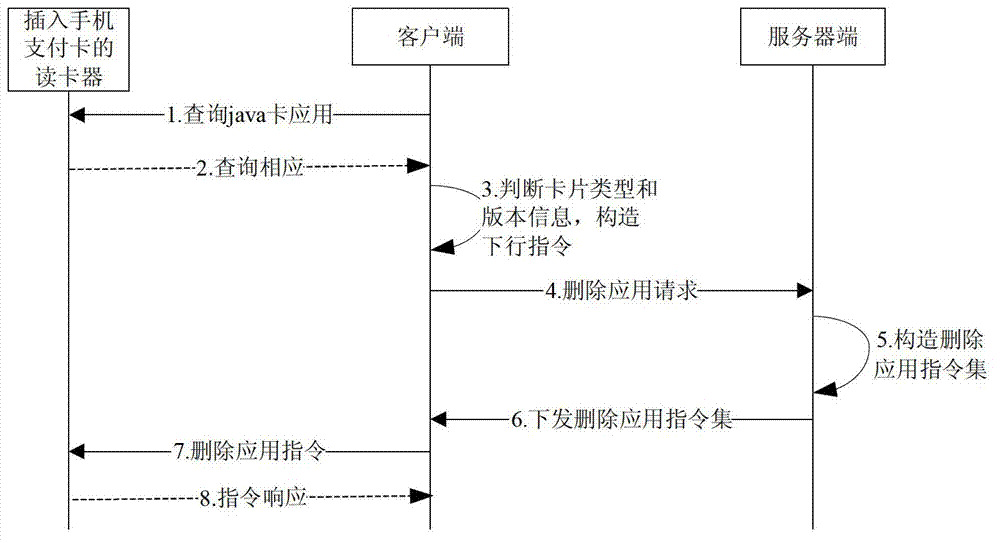
ActiveCN102902553AFast card issuanceSafety managementProgram loading/initiatingTransmissionUser needsComputer hardware
The invention provides a remote card issuing method of a mobile phone payment card based on a JAVA card, which comprises the following steps of: firstly inquiring card applications installed on the mobile phone payment card to obtain the opened card applications and the card applications which are not opened; and then, selecting the card applications needing to be opened according to the user needs, sending basic information of the mobile phone payment card to a server side, carrying out external authentication on the card applications needing to be opened, and updating a secret key of the mobile phone payment card after the external authentication succeeds. According to the remote card issuing method provided by the invention, remote card issuing can be simultaneously carried out on multiple mobile phone payment cards through the server side, and the card issuing speed is rapid; and by storing the secret key through an encryption equipment, the secret key is safer and more convenient to manage; the card applications can be deleted or newly added and can be freely combined according to the user needs, and the card issuing process and the user application process are also recorded and managed through the server end, thus avoiding errors in the using process.
Owner:中电福富信息科技有限公司
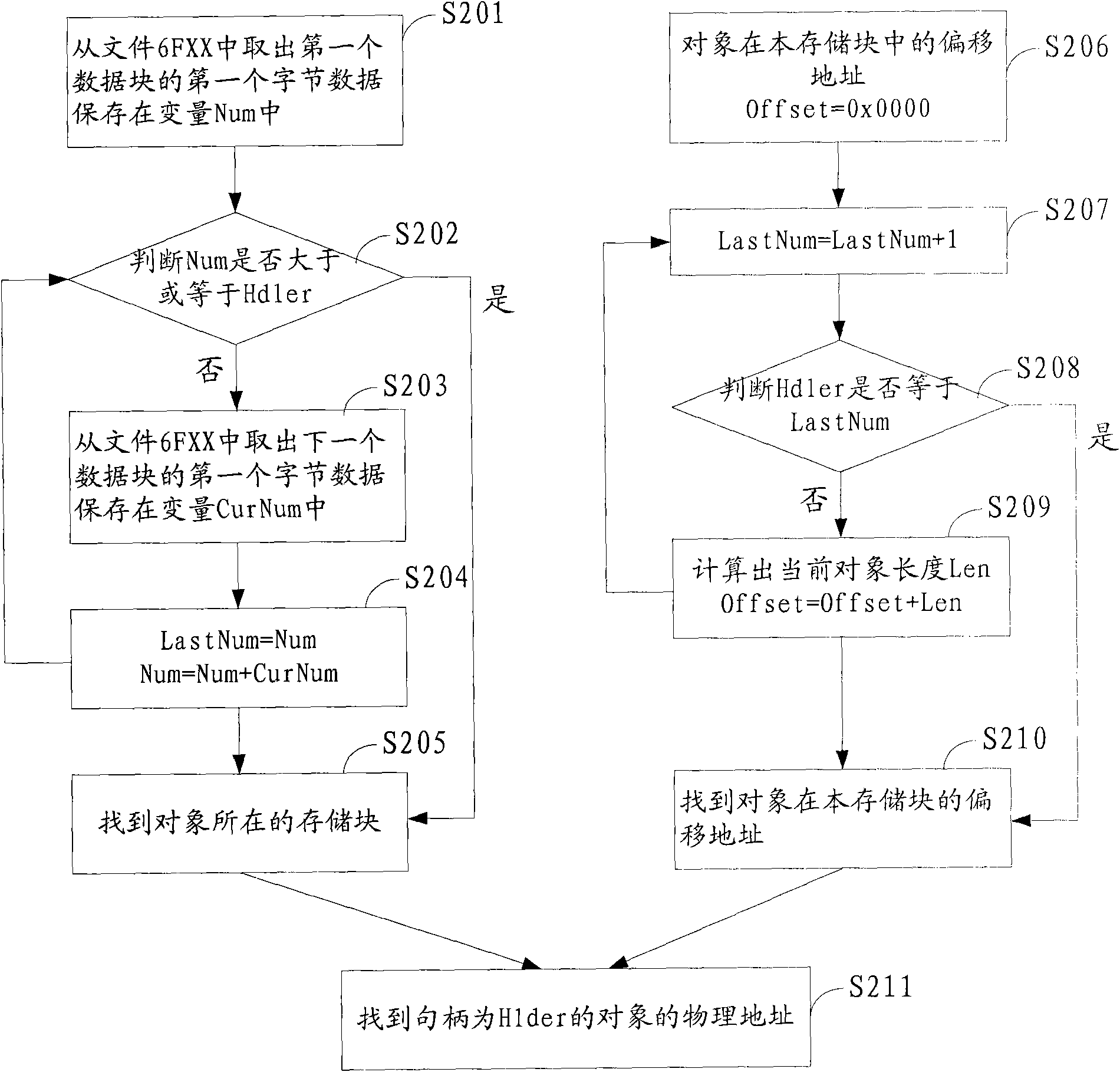
JAVA card object management method and JAVA card
InactiveCN101777061AEfficient managementRecord carriers used with machinesSpecial data processing applicationsSmart cardApplication software
The embodiment of the invention provides a JAVA card object management method and a JAVA card, relating to intelligent card field. Limit object management capacity of JAVA card can be utilized to manage great amount of objects efficiently. The solution scheme is as follows: creating objects in memory chunks in a JAVA card memory area in sequence according to the sequence in which an application program applies for objects, wherein, the JAVA card memory area is composed of a plurality of memory chunks, each memory chunk corresponds to a memory chunk number; allocating absolute handles for the objects in sequence according to the creation sequence of the objects, wherein, the absolute handles are the creation sequence number of the objects. Another scheme is as follows: determining the memory chunk in which the object to be searched is located according to the absolute handle of the object to be searched; and determining the object to be searched in the memory chunk according to the absolute handle of the object to be searched.
Owner:BEIJING WATCH DATA SYST
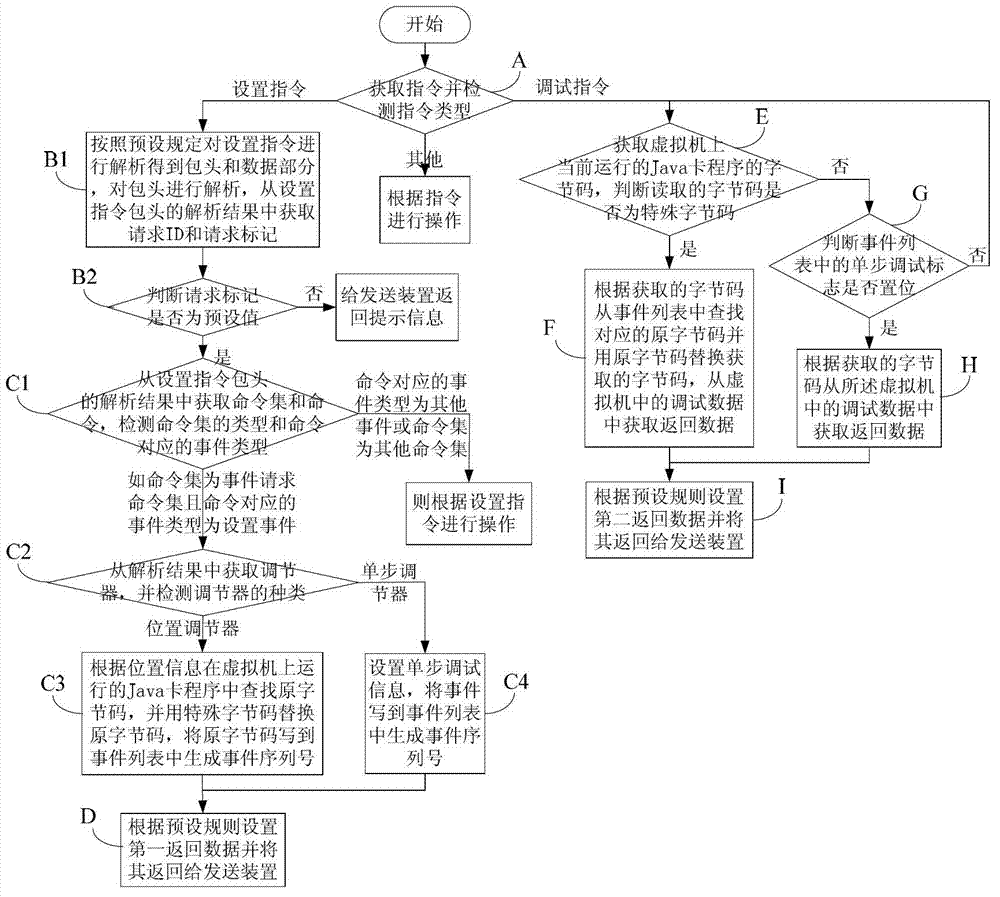
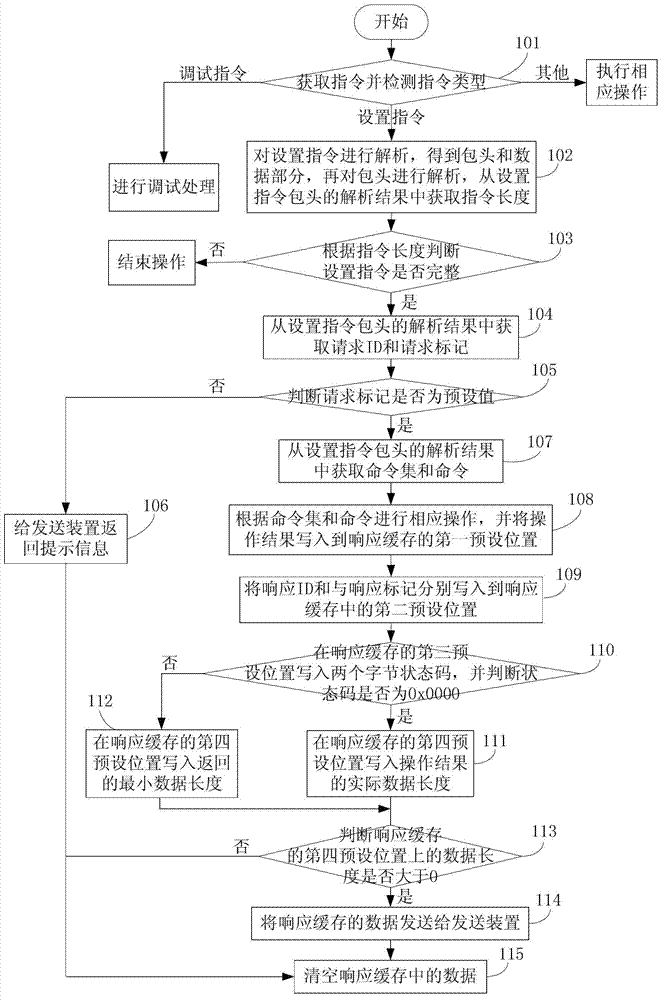
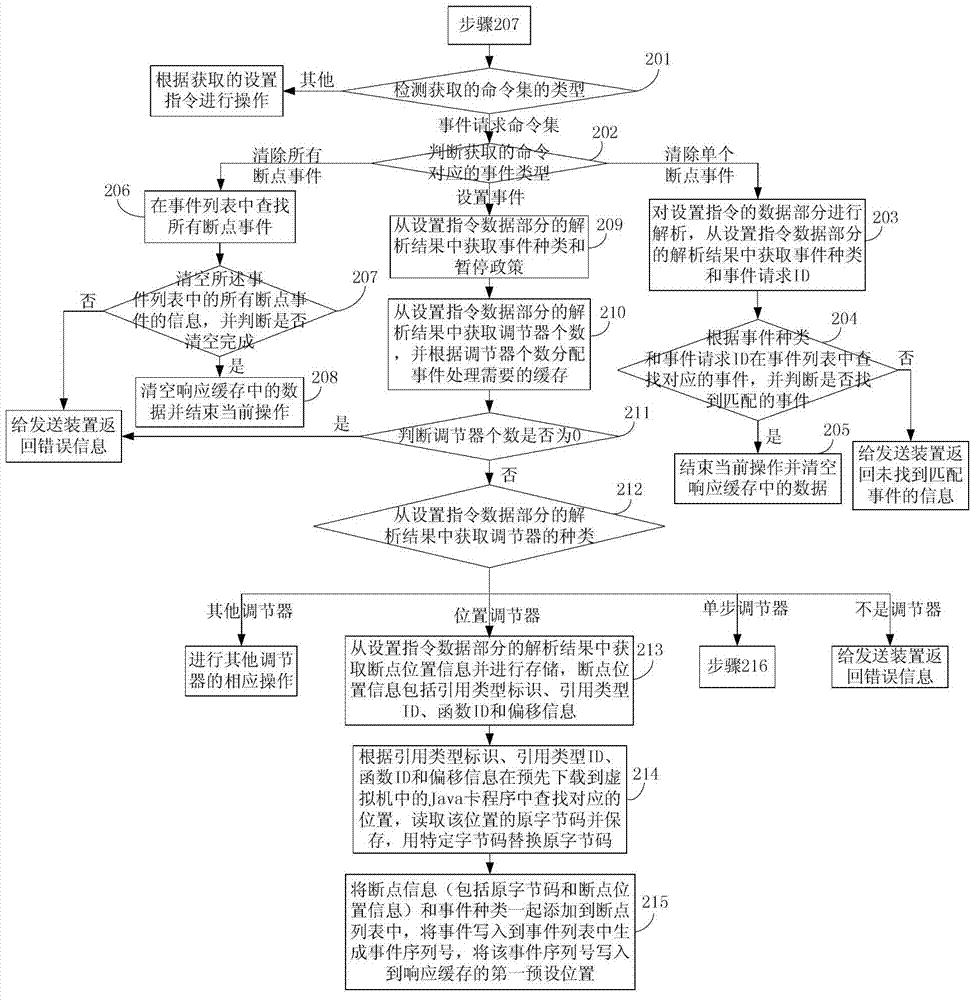
Method for processing Java card debugging information
The invention discloses a method for processing Java card debugging information. The method comprises the following steps of: acquiring an instruction, detecting the type of the instruction, if the instruction is an unprocessed setting instruction and an adjuster is a position adjuster, replacing original byte codes corresponding to position information in a Java card program running on a virtual machine by using special bytes, and writing the original byte codes into an event list to generate an event serial number; if the adjuster is a single-step adjuster, setting single-step debugging information, and writing an event into the event list to generate an event serial number; if the instruction is a debugging instruction, acquiring byte codes of the current Java card program running on the virtual machine, and judging whether the byte codes are special byte codes; and if the byte codes are special byte codes, searching the corresponding original byte codes from the event list, replacing the special byte codes with the original byte codes to obtain returned data, otherwise, when the setting of a single-step debugging mark in the event list is judged, acquiring the returned data according to the byte codes. The method is convenient to use and is capable of monitoring and checking the debugging process of a virtual machine in real time.
Owner:FEITIAN TECHNOLOGIES
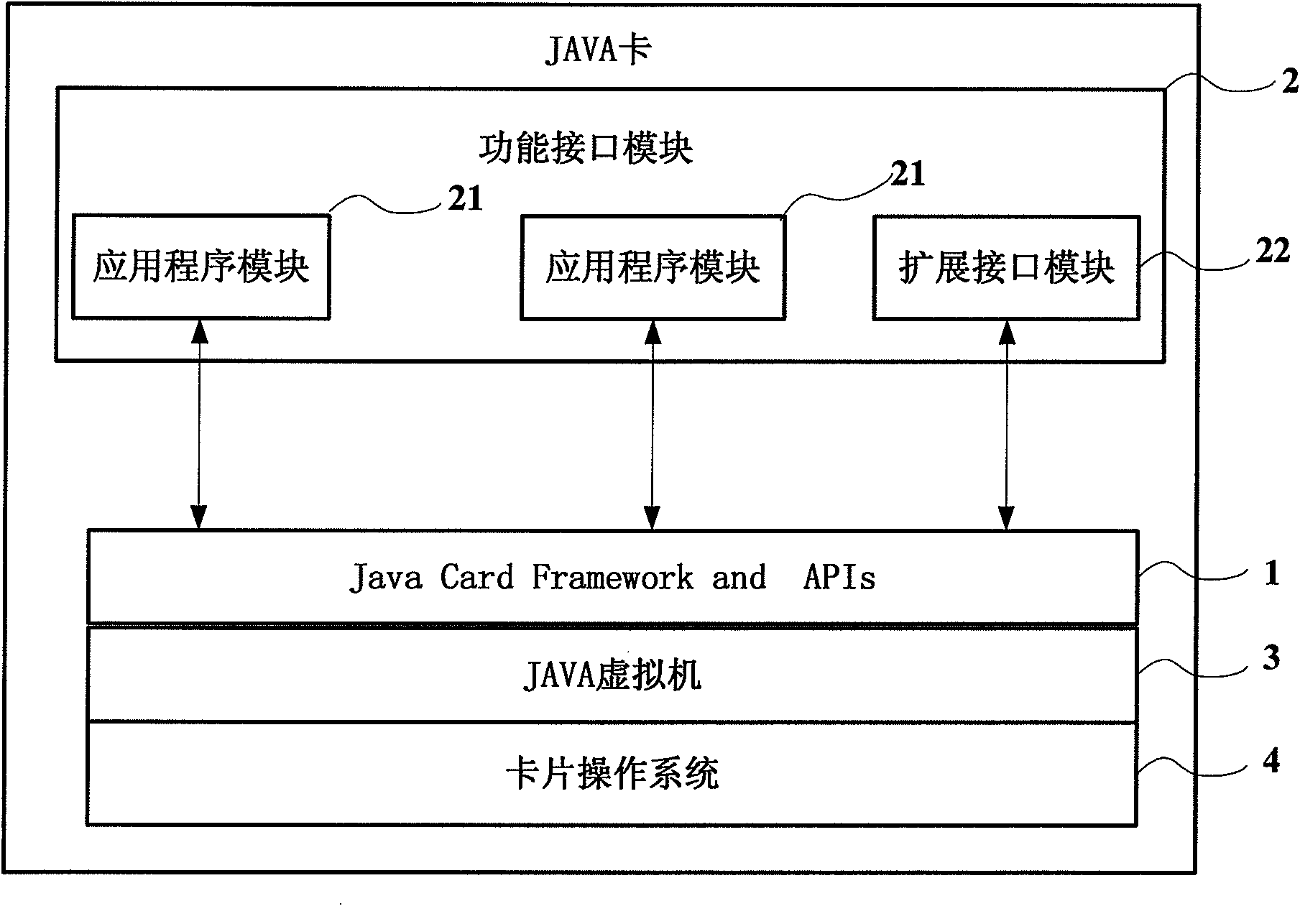
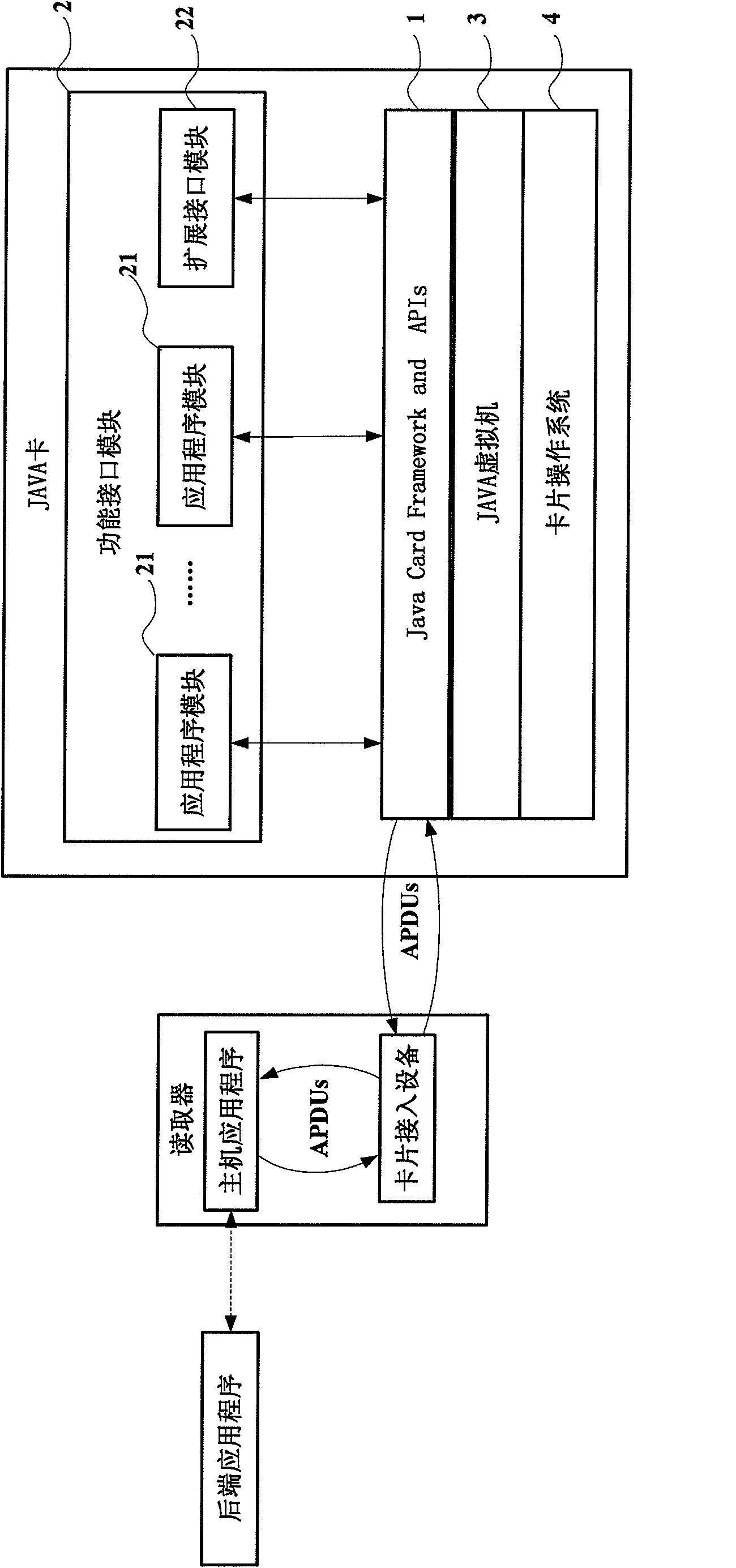
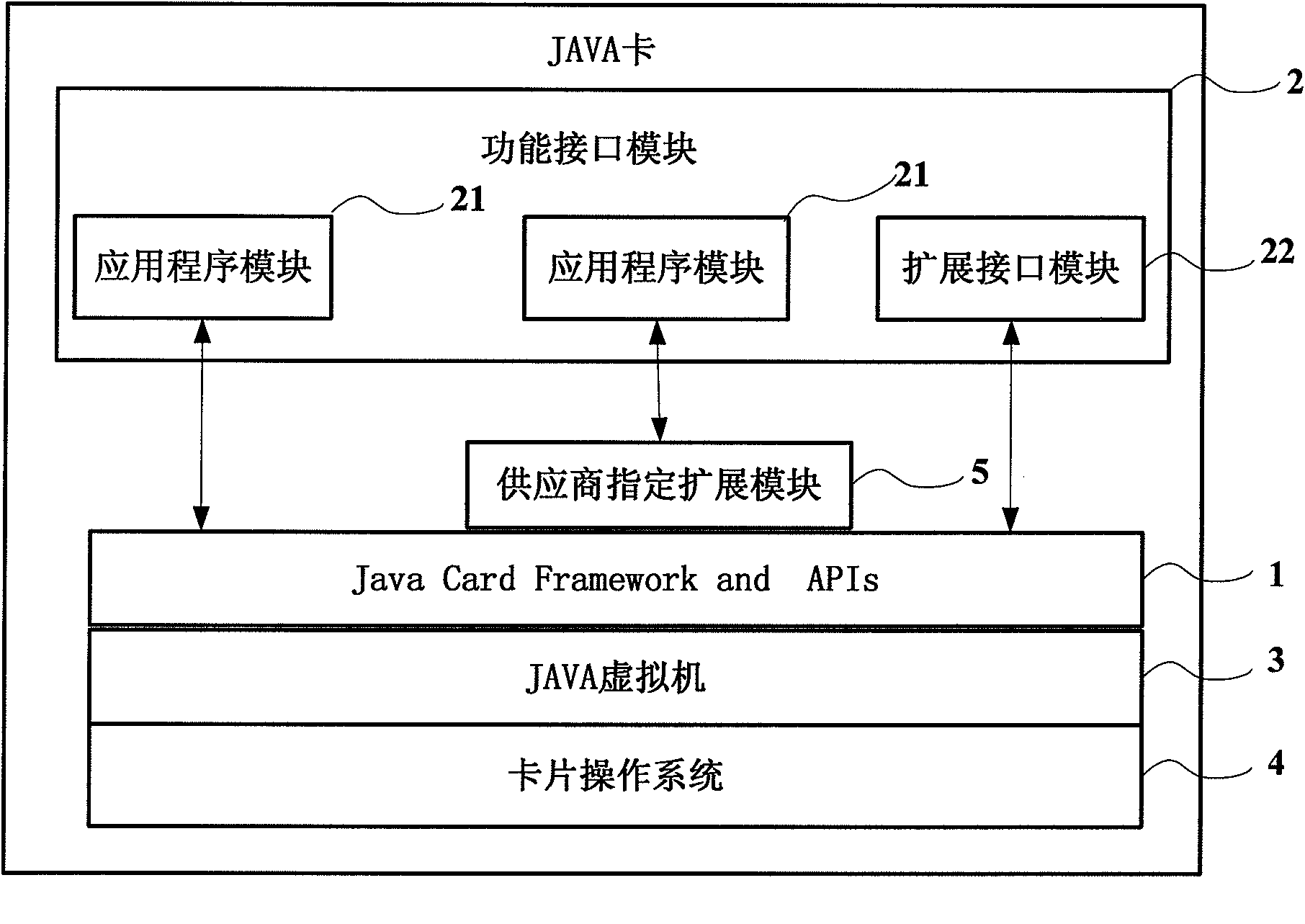
JAVA card
InactiveCN101986740ASpecific program execution arrangementsNetwork data managementOperational systemComputer module
The invention discloses a JAVA card, which aims to develop application of products with different functions on a USIM (universal subscriber identity module) smart card by utilizing a JAVACARD technology. The JAVA card comprises Java Card Framework and APIs, a functional interface module, a JAVA virtual machine and a card operation system, wherein the Java Card Framework and APIs is used for receiving APDU (application protocol data unit) transmitted by card access equipment and forwarding the APDU to the functional interface module; the functional interface module is connected with the Java Card Framework and APIs, and processes an APDU command to ensure that the processing result returns an APDU response through the Java Card Framework and APIs; the JAVA virtual machine is used to realize the uniformity of card interfaces and uniformity of programming language, including different technologies of various card suppliers on the card bottom; and the card operation system is responsible for processing of the lower layer.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +1
Smart card and method for integrating multiple telecom applications on same
InactiveCN102054173AConsider speedConsider execution efficiencyCharacter and pattern recognitionRecord carriers used with machinesSmart cardJava Card
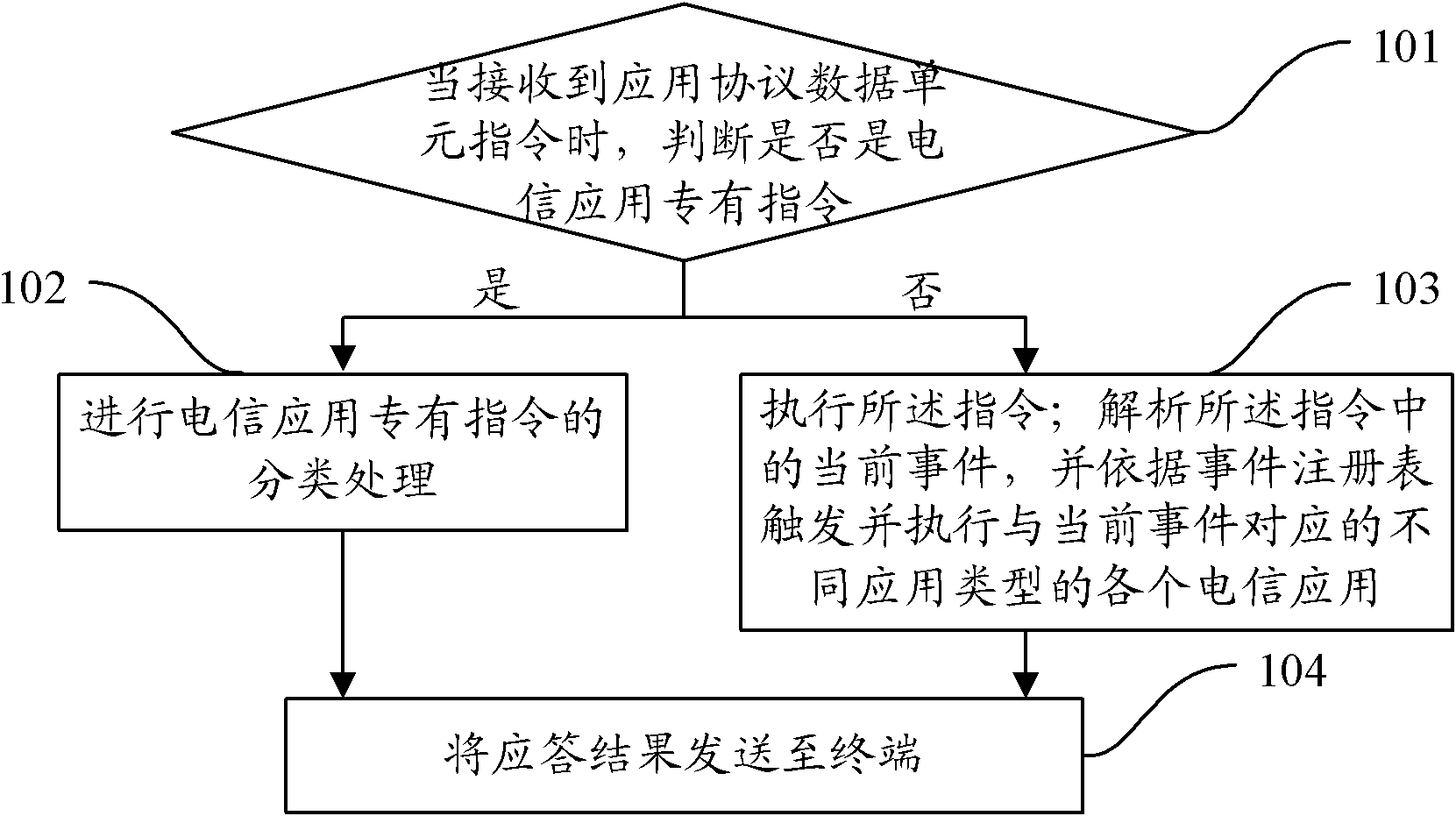
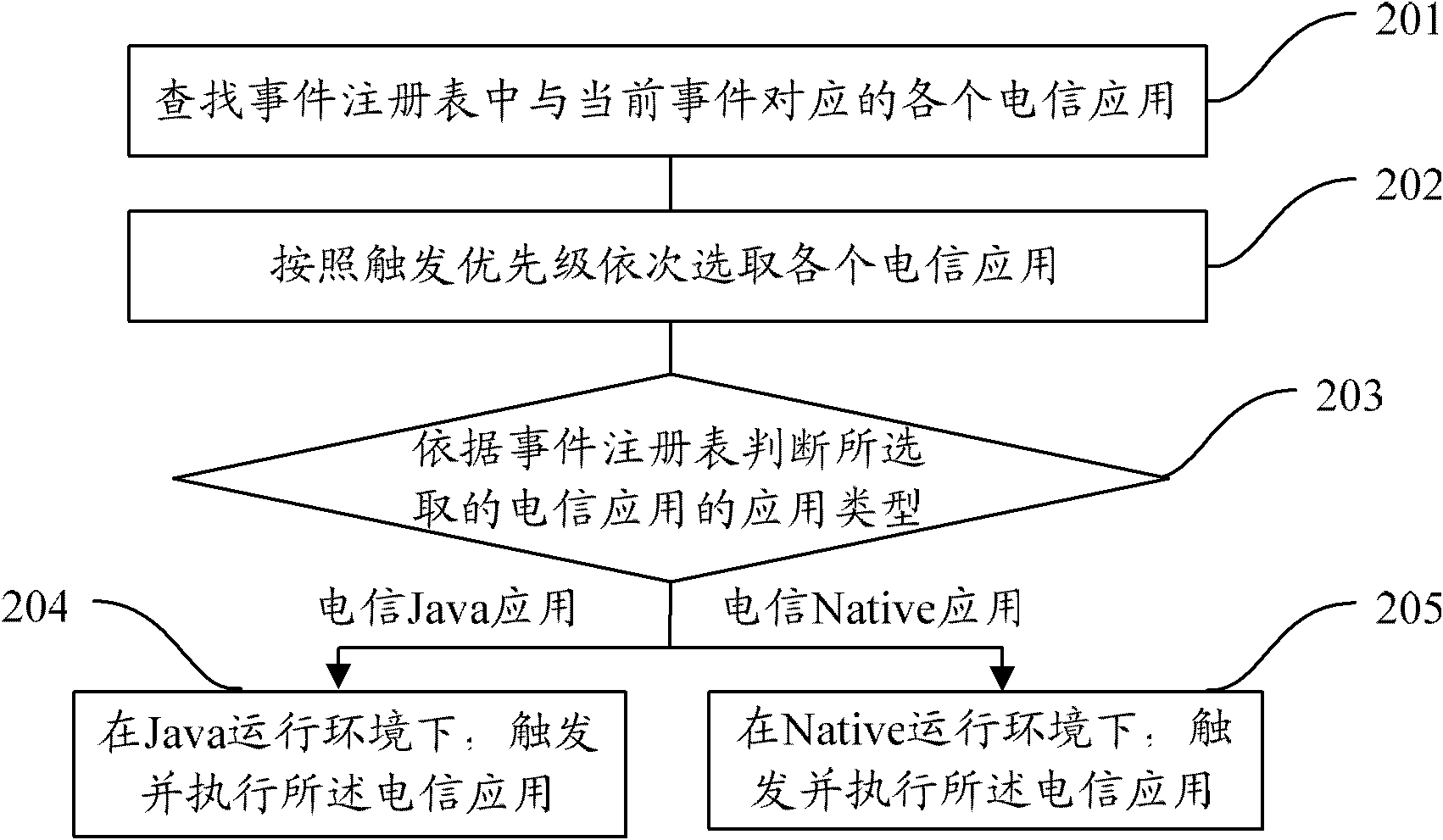
The invention provides a smart card and a method for integrating multiple telecom applications on the same. The method comprises the following steps: when receiving application protocol data unit (APDU) instructions, judging whether the APDU instructions are the instructions special for telecom applications; if so, classifying the instructions special for telecom applications; if not, executing the instructions; and analyzing the current events in the instructions and triggering and executing various types of telecom applications corresponding to the current events according to an event registry. By adopting the smart card and the method, the advantages of both the Native card and the Java card can be considered, thus ensuring the executing speed of the smart card and simultaneously realizing addition and deletion of applications.
Owner:BEIJING WATCH DATA SYST
Java card system rubbish recovering method
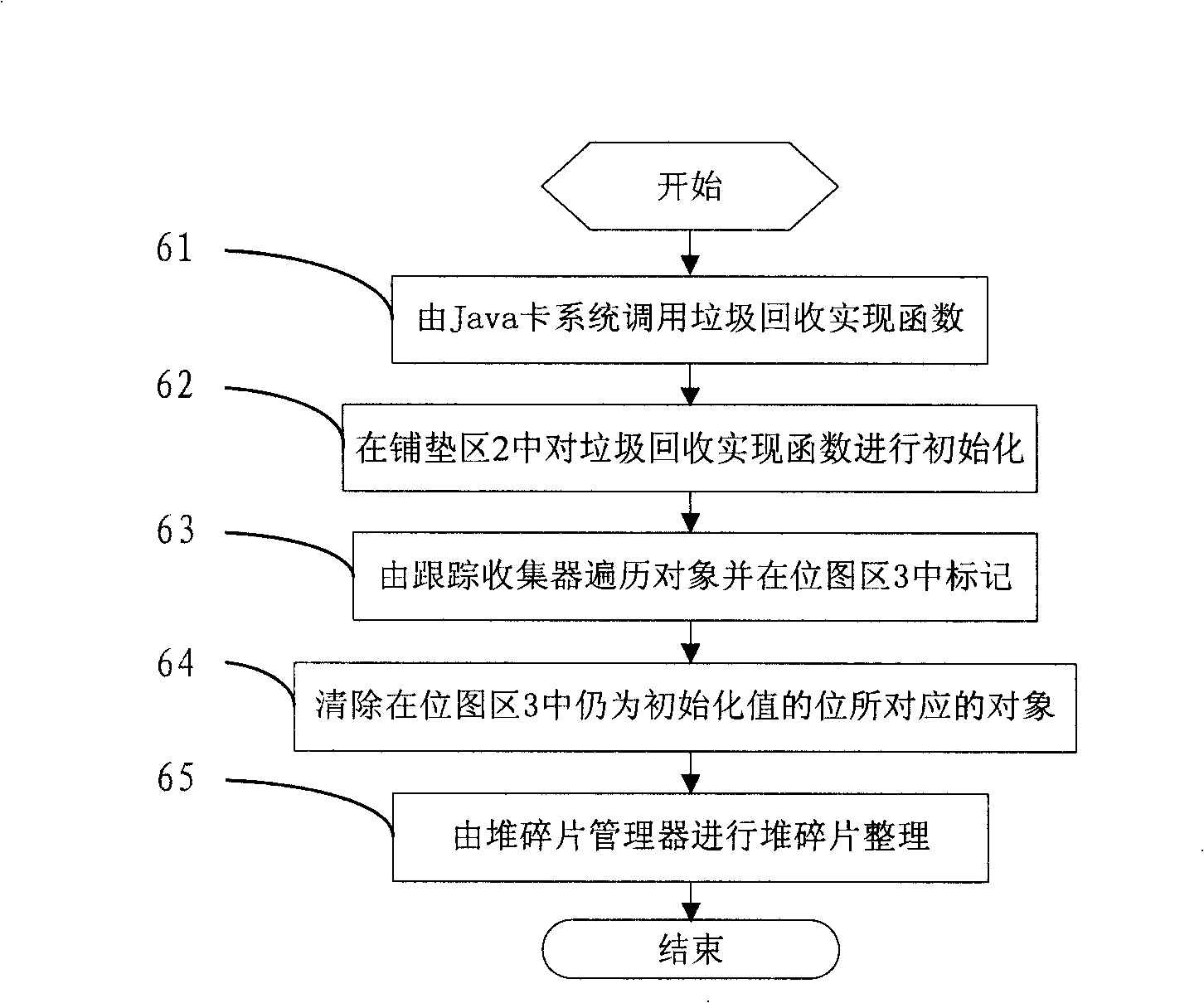
ActiveCN101246440AThe recovery method is simpleResource allocationRadio/inductive link selection arrangementsRecovery methodComputer hardware
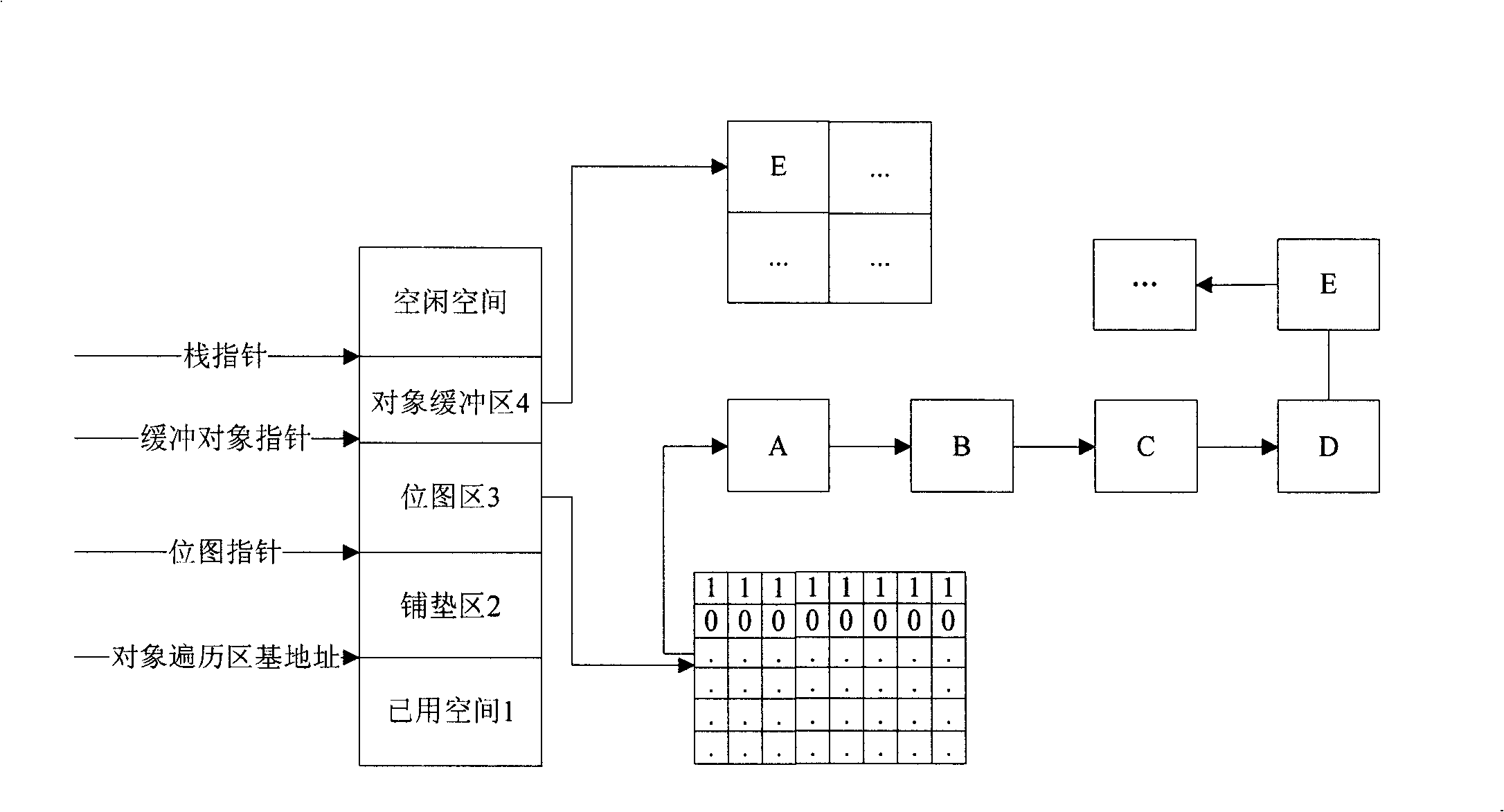
The invention relates to Java card system rubbish recovery method comprising the following steps: 1) invoking rubbish reclamation realization function by Java card system,2) initializing the rubbish reclamation realization function in place mat zone, 3) traversing and marking objects in the bitmap by the trace gatherer, 4) clearing the objects corresponded by initialized value's bite in bitmap zone. The Java card system rubbish recovery method efficiently cleans up the space occupied by the Java card system (that is the objects which can not arrive in objects ergodic process) to make more reasonably utilize the limit memory space and to provide more sufficient space for download of application programs.
Owner:EASTCOMPEACE TECH
System and method for optimizing byte codes for JAVA card
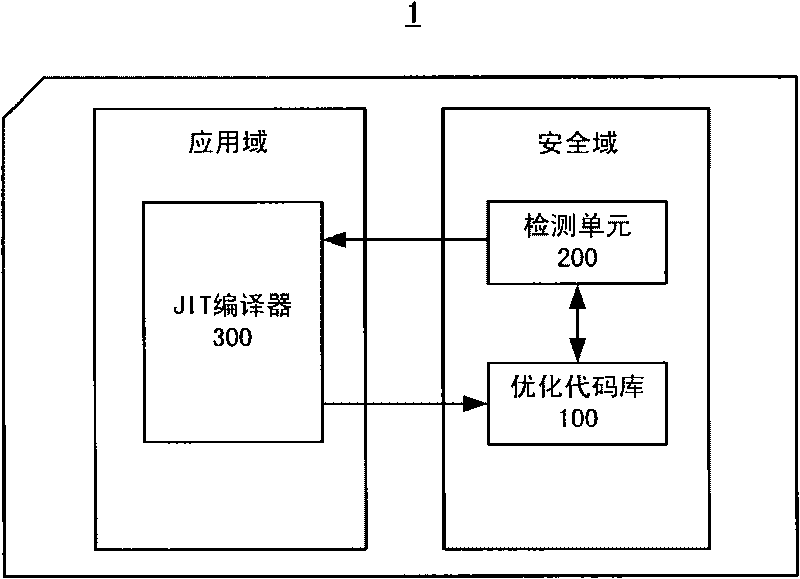
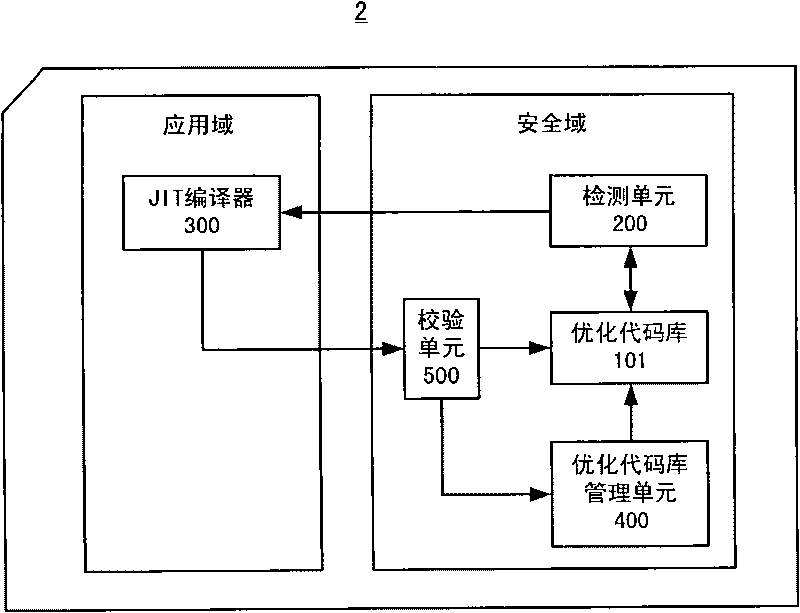
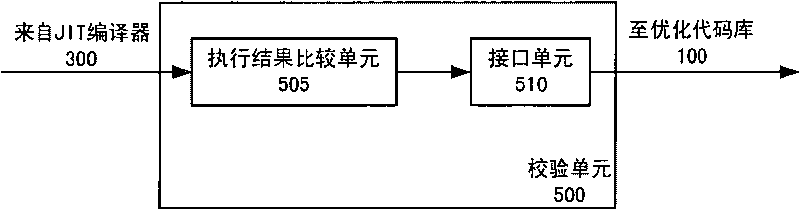
InactiveCN101739280AAchieve optimizationHigh speedProgram controlRecord carriers used with machinesSecurity domainApplication software
The invention relates to a system and a method for optimizing byte codes for a JAVA card, wherein the JAVA card comprises an application domain and a security domain. The method for optimizing the byte codes for the JAVA card comprises the steps of: detecting whether a byte code sequence of an application program in the security domain has an optimized code or not; when a detection result is negative, transmitting the byte code sequence to the application domain; in the application domain, compiling the received byte code sequence into a local code of the security domain to serve as the optimized code; and storing the optimized code in the security domain. The system and the method can realize the optimization of the byte codes in the security domain of the JAVA card and increase the speed of program execution of the JAVA card.
Owner:爱思开电讯投资(中国)有限公司
Cap file for the personalization of a JAVA application
InactiveUS20100077392A1Meet the requirementsAcutation objectsPayment architecturePersonalizationApplication software
A personalization method of one application capable of being executed on a Java card contains the successive steps of:generating a package containing mandatory components corresponding to the application, and a custom component corresponding to information required to personalize the application;loading the package onto a Java card;installing the application from the loaded package, the application being personalized according to the information as soon as the application is in the Installed state, i.e. at the end of the completion of the step of installing.
Owner:CASSIS INT PTE
JAVA card object calling method and apparatus
ActiveCN105045597AImprove securityMathematical modelsSoftware engineeringSmart cardApplication software
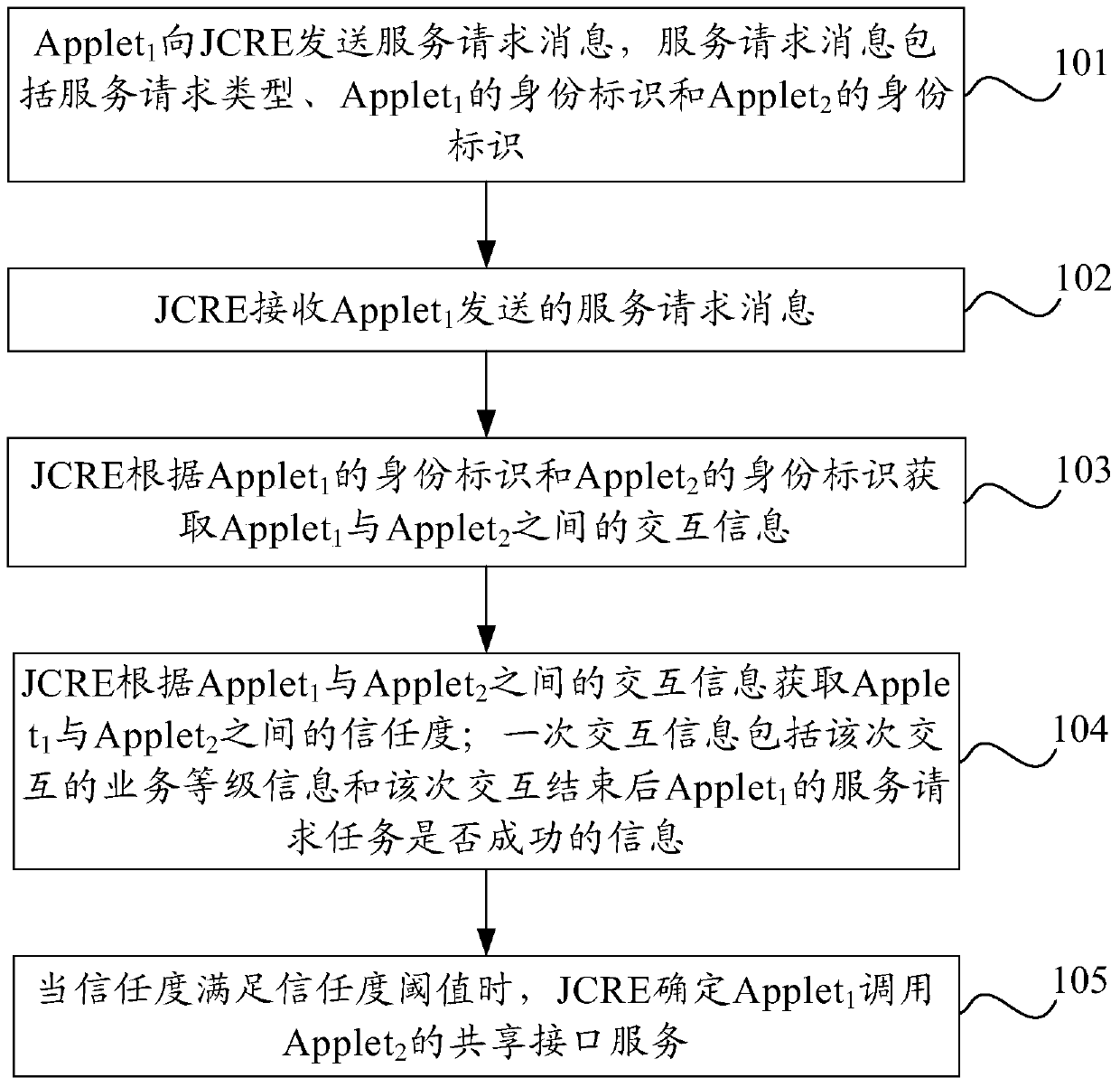
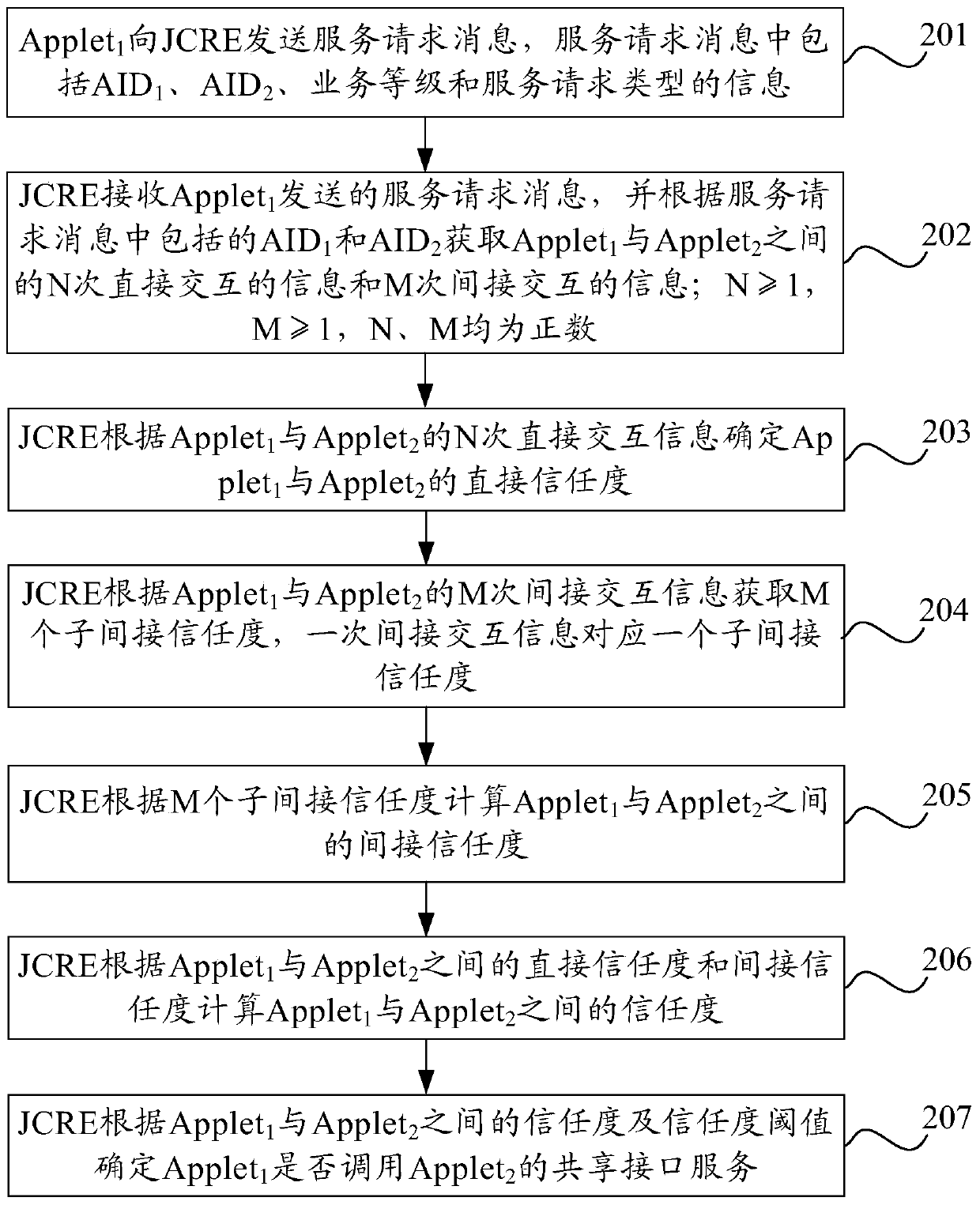
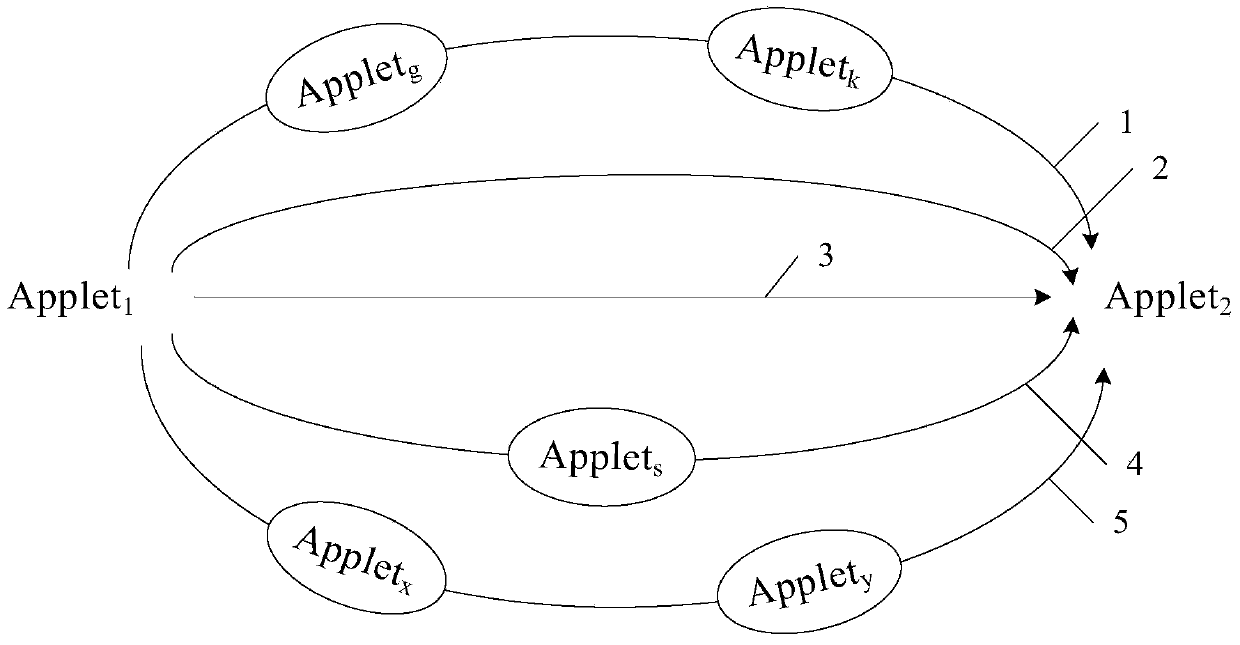
Embodiments of the present invention disclose a JAVA card object calling method and apparatus, relate to the smart card field, and are used to improve security of interaction between Applets in a JAVA card. The method comprises: receiving, by a JCRE, a service request message sent by an application program Applet1; acquiring, by the JCRE, interaction information between the Applet1 and an Applet2 according to an identity of the Applet1 and an identity of the Applet2; acquiring, by the JCRE, credibility between the Applet1 and the Applet2 according to interaction information between the Applet1 and the Applet2, wherein one interaction information comprises service level information of the interaction and information about whether a service request task of the Applet1 succeeds after the interaction; and when the credibility meets a credibility threshold, determining, by the JCRE, that the Applet1 calls a shared interface service of the Applet2.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Object processing method and device of Java card and Java card
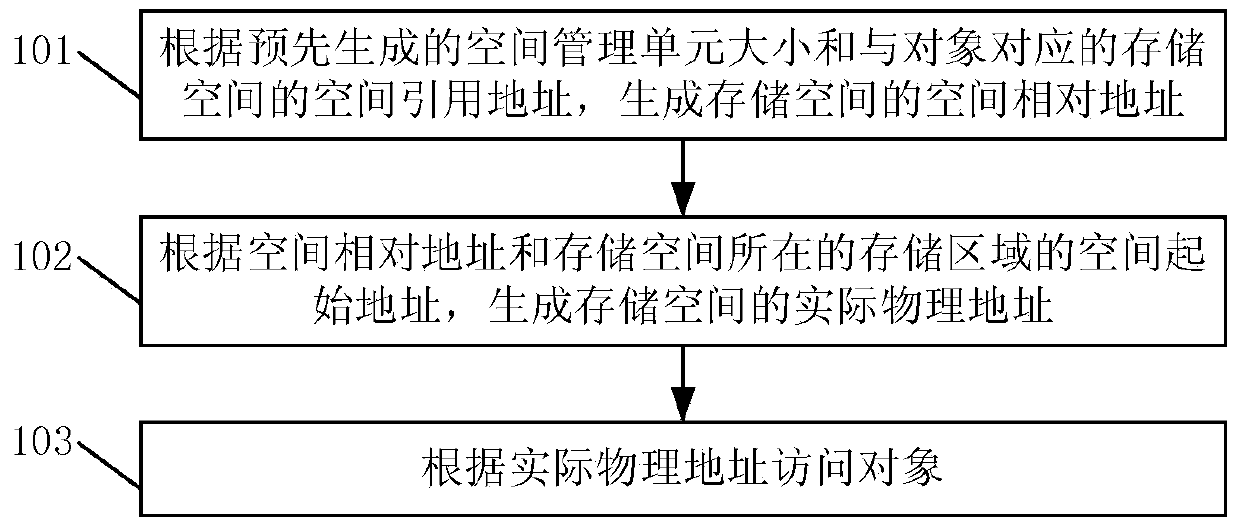
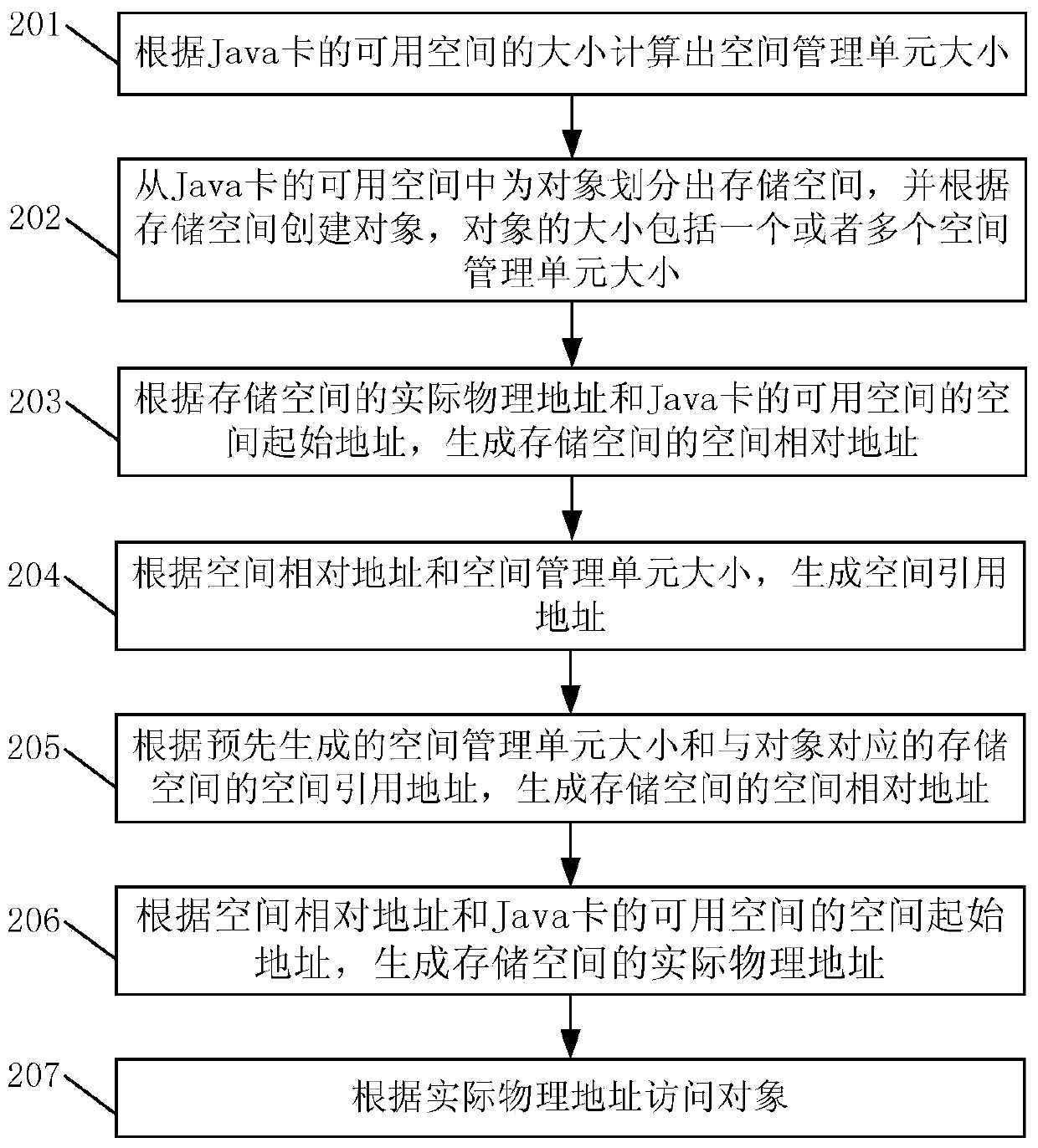
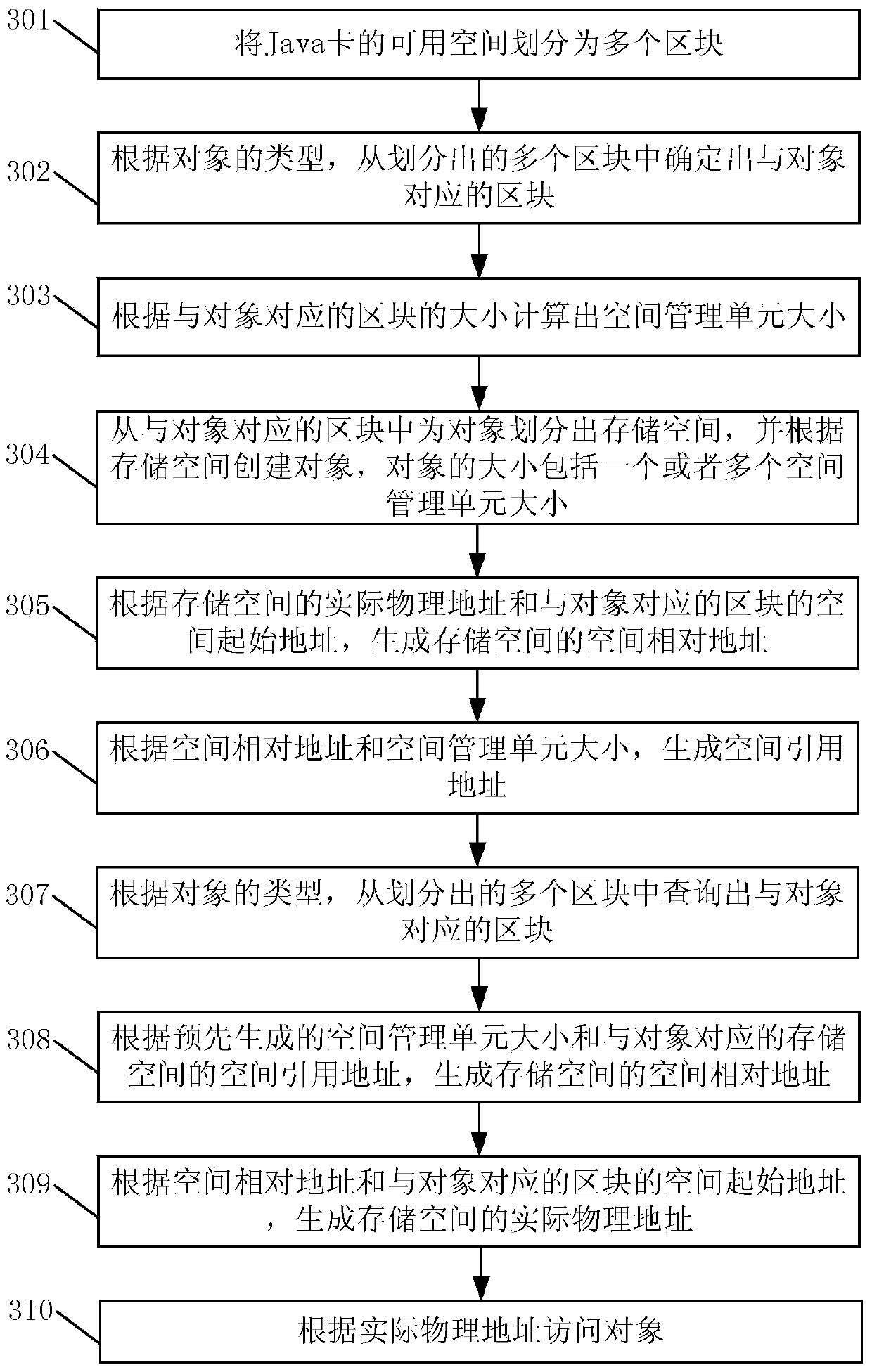
InactiveCN103778067ARun fastIncrease available spaceMemory adressing/allocation/relocationPhysical addressSpace management
The invention discloses an object processing method and device of a Java card, and the Java card. The method comprises the following steps: generating the space relative address of a storage space according to the size of a space management unit generated in advance and the space quote address of the storage space, which corresponds to an object; generating the actual physical address of the storage space according to the space relative address and the space start address of a storage area where the storage space is positioned; accessing the object according to the actual physical address. In the process of obtaining the actual physical address, an object list is not required to be looked up, so that the object processing process is simplified, the object processing speed is increased, thereby increasing the operation speed of the Java card greatly; as the object list is not required to be set up, the space occupied by the object list in the Java card is saved, thereby expanding the available space in the Java card.
Owner:GOLDPAC GRP LTD
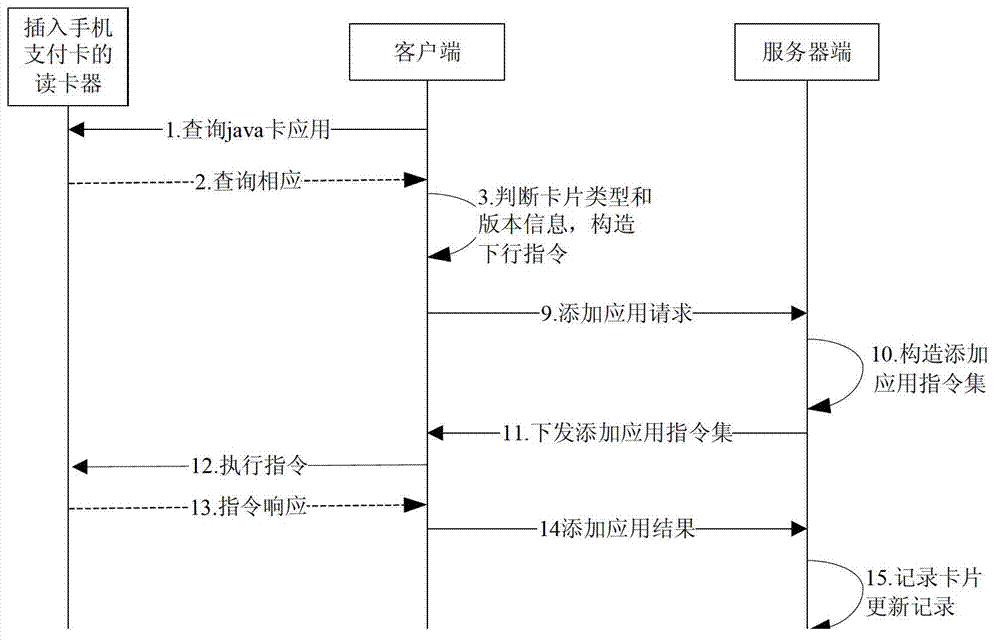
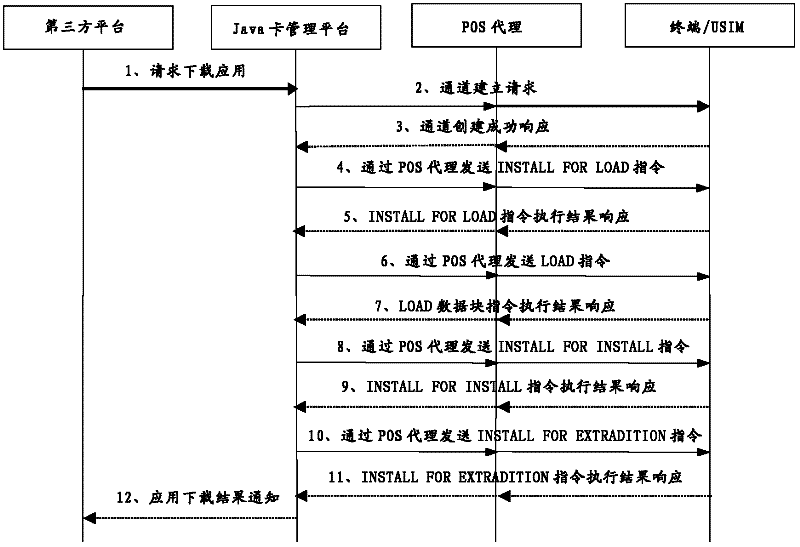
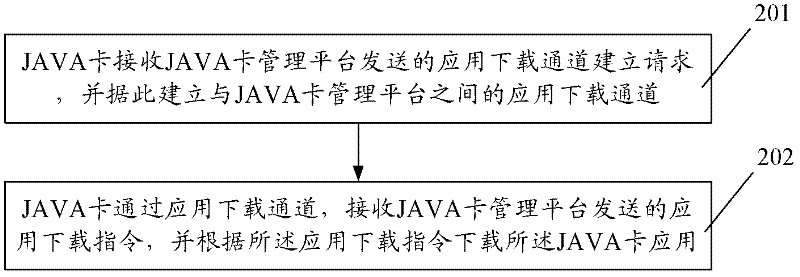
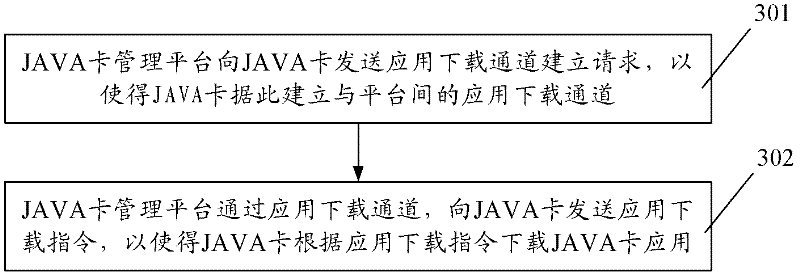
Method, device and system for downloading Java card application
The invention provides a method, device and system for downloading a Java card application. The method comprises the following steps of: receiving an application download channel establishment request transmitted by a Java card management platform, and establishing an application download channel with the Java card management platform according to the application download channel establishment request; and receiving an application download instruction transmitted by the Java card management platform through the application download channel, and downloading the Java card application according to the application download instruction. In the method, device and system for downloading the Java card application, a related instruction of application download, transmitted by the Java card management platform, is directly received through a Java card, and the Java card application download is performed in an OTA (Over-the-Air) mode according to the instruction; and compared with the prior art, the invention has the advantage of capability of opening the application without going to business networks with POS (Point Of Sale), so that the generalization efficiency of the new Java card application is greatly increased.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
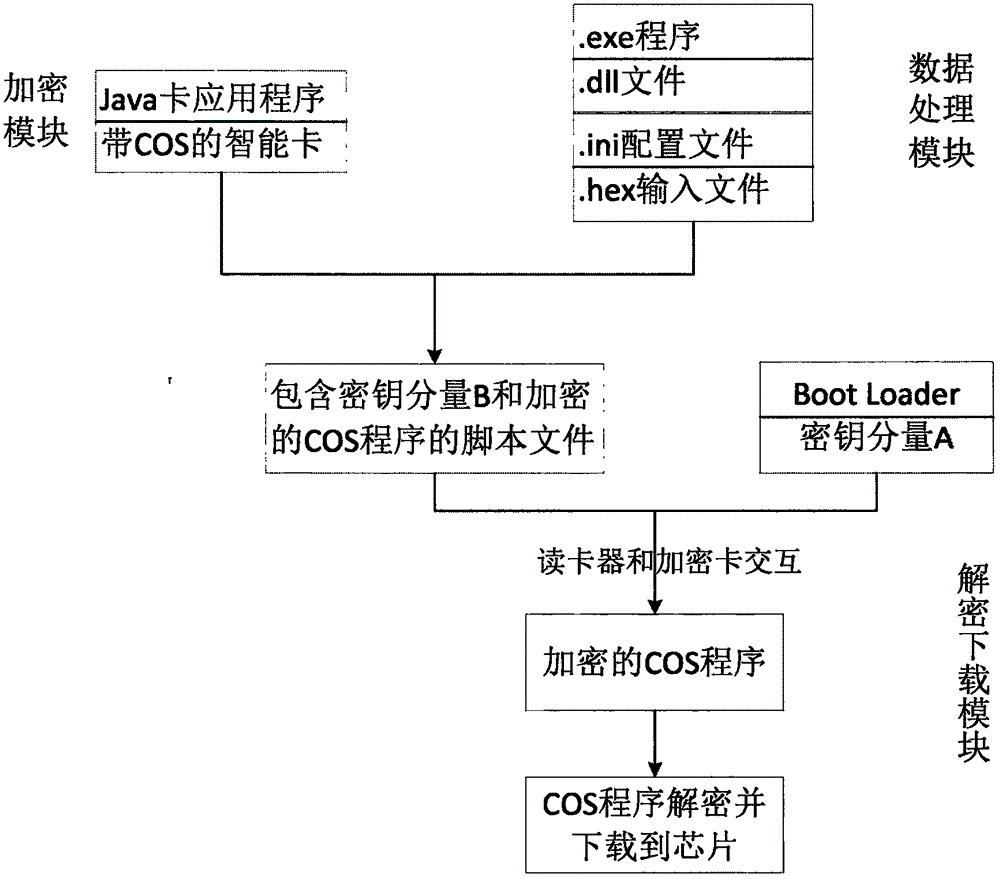
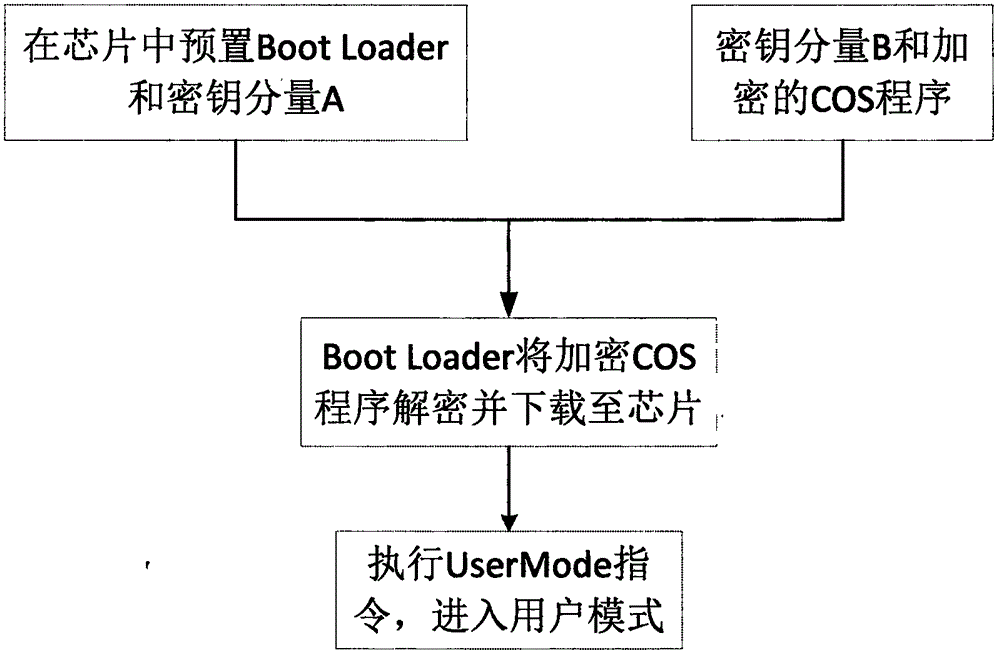
Intelligent card COS encrypting and downloading system
ActiveCN106056017AImprove securityPrevent leakageSensing by electromagnetic radiationPlaintextSmart card
An intelligent card COS encrypting and downloading system disclosed by the present invention comprises an encryption module, a data processing module, a decrypting and downloading module. The encryption module embodies a COS encryption card and is a Java card application which is developed based on a Java card platform and has an encryption function, and programs in the data processing module are responsible for analyzing a configuration file to obtain scripts containing a secret key component B, then analyzing an HEX file to obtain a COS program of the plaintext, and finally obtaining a script file containing the secret key component B and an encrypted COS program by the interaction of a card reader and the encryption card. In the decrypting and downloading module, a Boot Loader preset in a chip utilizes a secret key component A and the secret key component B in the scripts to generate a secret key needed by the decryption, and in the chip, the encrypted COS program is decrypted and downloaded to the chip. The above three modules perform the respective functions, thereby realizing an encryption function of the encryption card to the COS program and a decrypting and downloading function of the COS program.
Owner:星汉智能科技股份有限公司
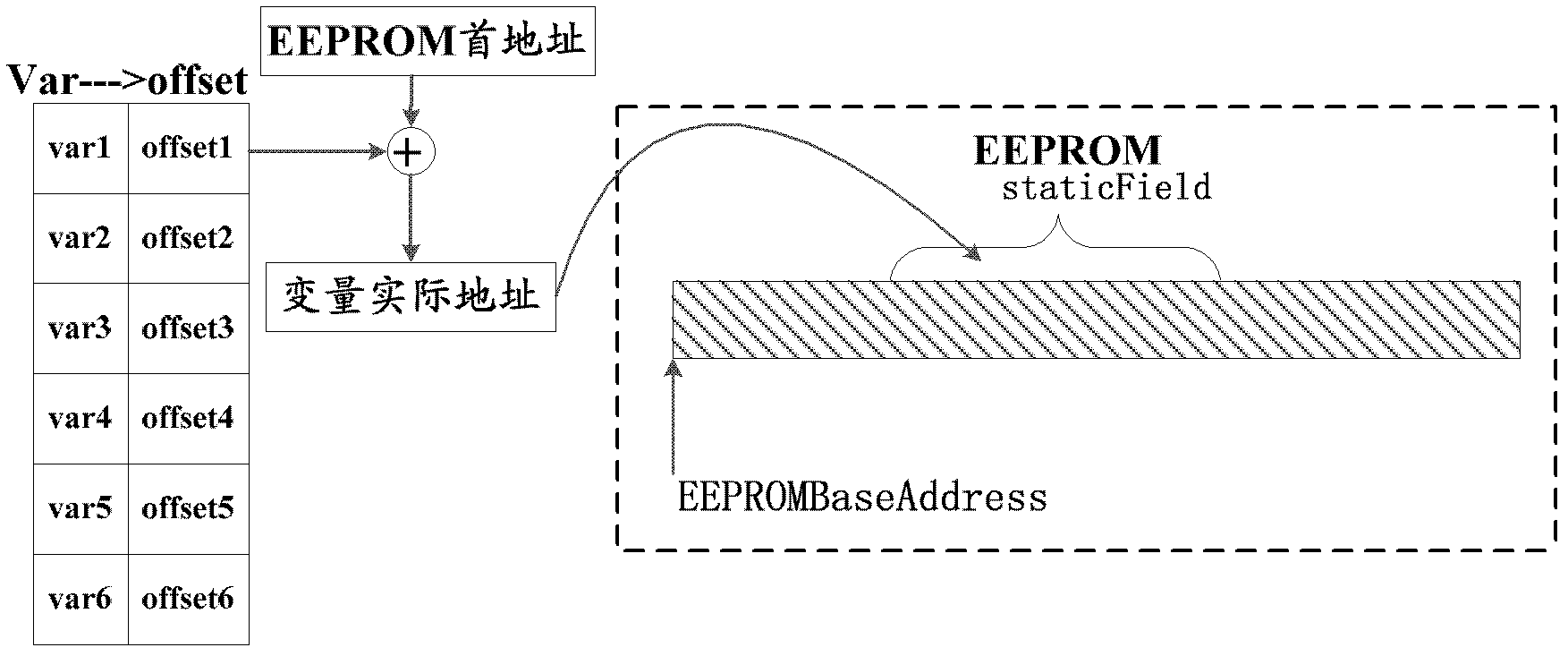
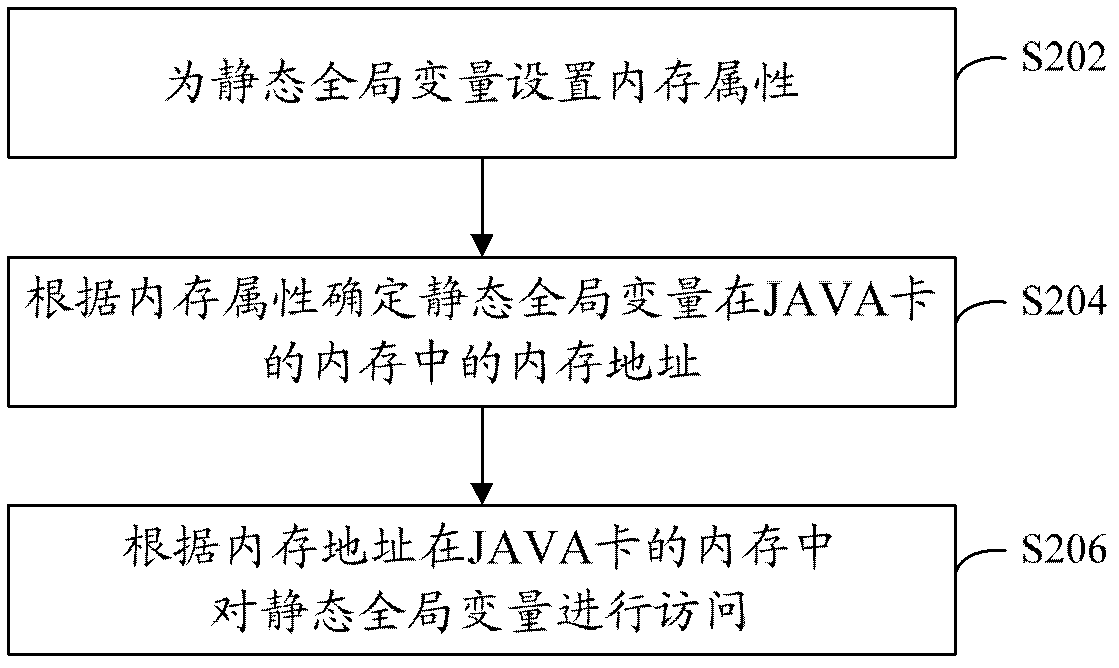
Method and device for data processing of JAVA card
ActiveCN102591787AClear handlingRealize processingMemory adressing/allocation/relocationMemory addressProgrammable read-only memory
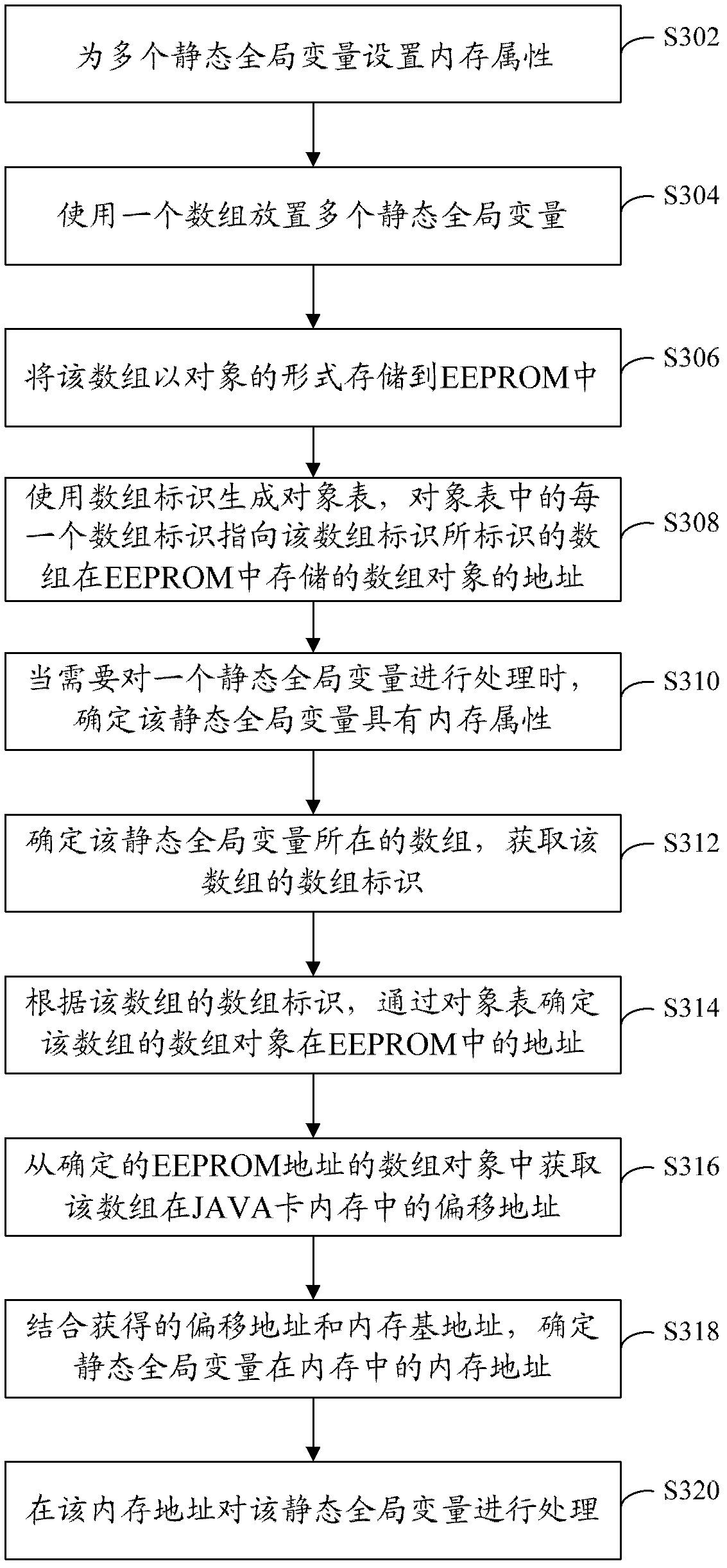
The invention provides a method and a device for data processing of a JAVA card. The method for data processing of the JAVA card is used for accessing to static global variables in a memory and includes: setting the memory attribute for the static global variable to indicate processing of the static global variable in the memory of the JAVA card corresponding to the processing of the memory attribute; determining a memory address of the static global variable in the memory of the JAVA card according to the memory attribute; and accessing to the static global variable in the memory of the JAVA card according to the memory address. By means of the method and the device for data processing of the JAVA card, time consumption and low efficiency caused by repeatedly accessing to an EEPROM (electrically erasable programmable read-only memory) can be avoided, and JAVA card development and JAVA program execution efficiency can be improved.
Owner:BEIJING WATCH DATA SYST
Method for initializing java card and java card
ActiveCN102521094AImplement initializationShorten initialization timeFunctional testingSensing record carriersJava CardNon-volatile memory
The invention discloses a method for initializing a java card and the java card. The method comprises the following steps: the java card is electrified, receives commands, judges the received commands and executes different operations aiming at different commands; if the received commands are commands of a first APDU (Application Protocol Data Unit), the java card judges whether the value of a lifecycle flag bit is a preset value or not; if the value of the lifecycle flag bit is not the preset value, the java card returns error codes; otherwise, the java card acquires the data of an operating environment from the commands of the first APDU and writes the data of the operating environment into a non-volatile memory (NVM) of the java card. According to the method for initializing the java card and the java card, the data of the operating environment are written into the NVM of the java card through the commands of the APDU, so that the time for initializing the java card can be reduced, and the production efficiency of java cards is increased.
Owner:FEITIAN TECHNOLOGIES
Method and device for garbage collection in java card
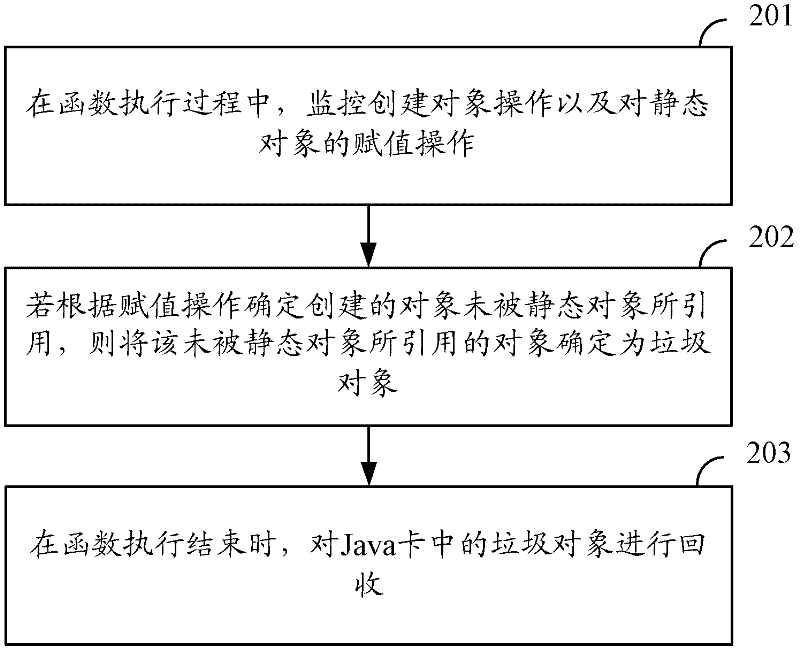
ActiveCN102270134AAvoid questions that take up too much timeImprove timelinessProgram synchronisationSpecific program execution arrangementsState of artValue assignment
The invention discloses a method and device for recycling garbage in a Java card, which are used for actively recycling garbage in the Java card in a partial step garbage recycling manner, so that the garbage is recycled in multiple small time slices, the problem that the one-step recycling of all garbage in the Java card occupies too much time in the prior art is solved, and the efficiency for recycling the garbage in the Java card is increased. The method comprises the following steps of: in a function executing process, monitoring object creating operation and value assignment operation for static objects, confirming objects which are not quoted by the static objects as garbage objects if the created objects are confirmed as objects which are not quoted by the static objects according to the value assignment operation, and recycling the garbage objects in the Java card when function execution is over. The invention further discloses a device for recycling garbage in a Java card.
Owner:BEIJING WATCH DATA SYST
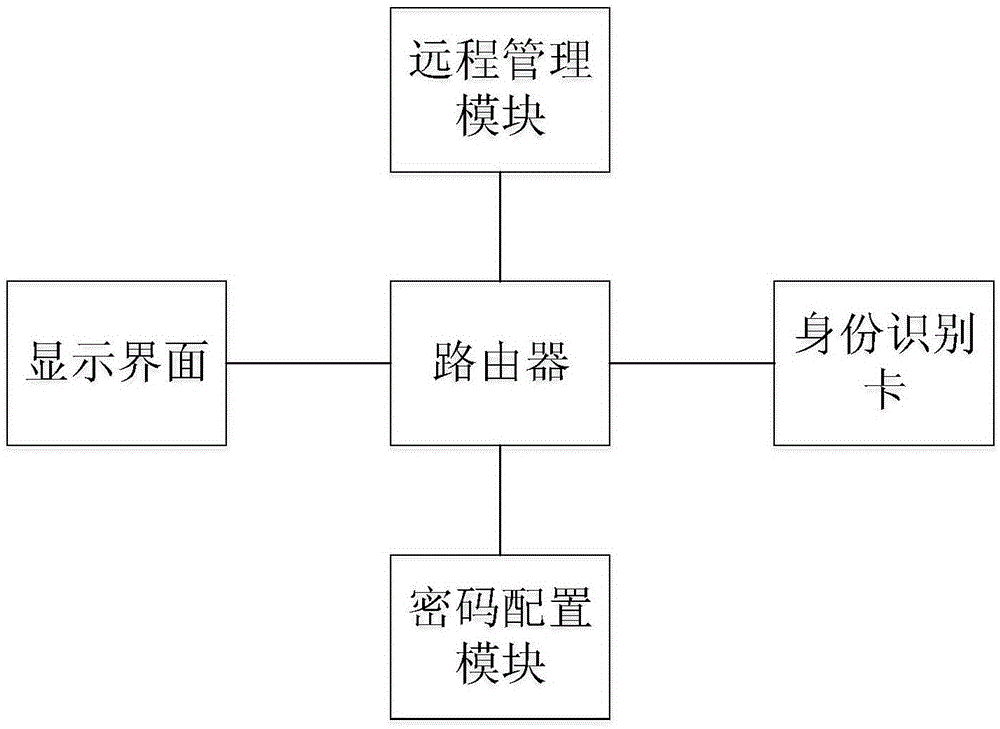
Router
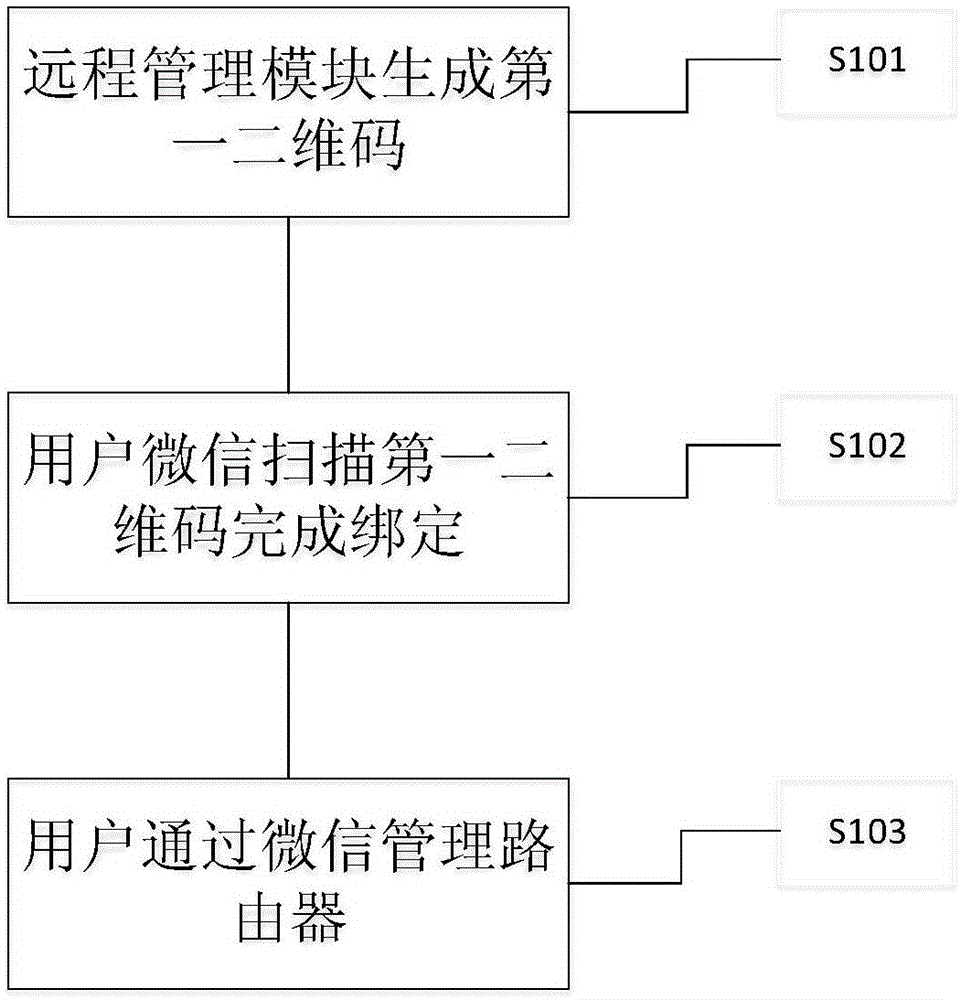
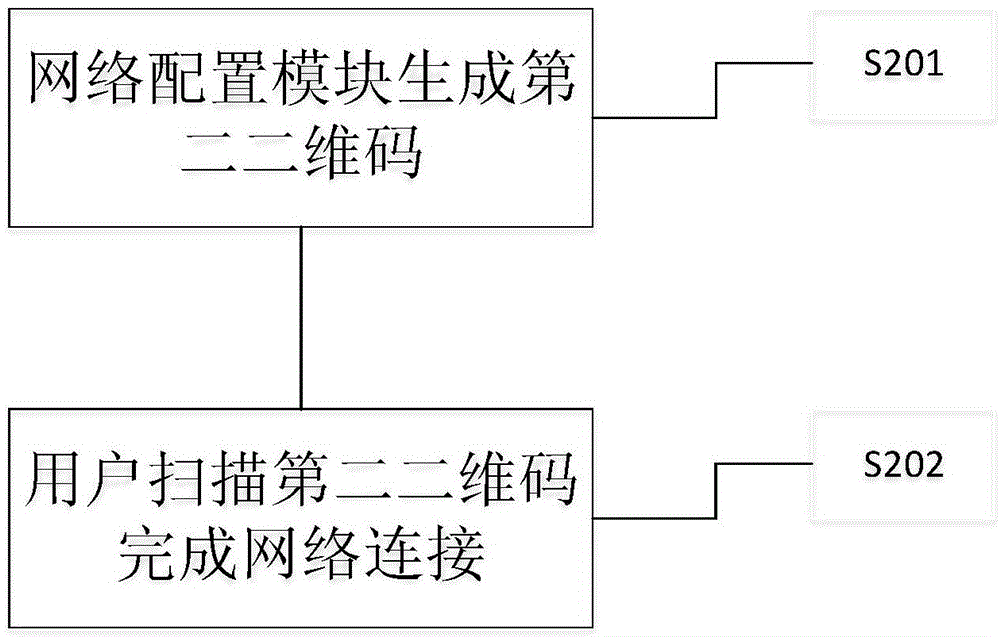
The invention discloses an intelligent router. The router is provided with an identification card, a display interface, a password configuration module and a remote management module; and the password configuration module is used to generate a random network password. Through the router, the trouble of user configuration is omitted firstly, a user does not need to know complex router configuration any longer, and account information provided by a service provider is stored in an encrypted java card so that the account information can be obtained by a stranger difficultly, and safety of the user's account information is guaranteed. An Internet password is generated by one click, so the router enables surrounding people to be not capable of using free network without permission of an owner, and user's Internet experience is guaranteed. Secondly, people having some router configuration knowledge can directly manage the router through wechat and are free of a trouble that a monitoring interface needs to be opened every time. Connection is automatically performed when a two-dimension code is scanned, and then a trouble that the password needs to be input every time when a guest visit a person at home is omitted.
Owner:北京博思汇众科技有限公司
Authorizing and descrambling method and apparatus in CAS of mobile multimedia broadcast
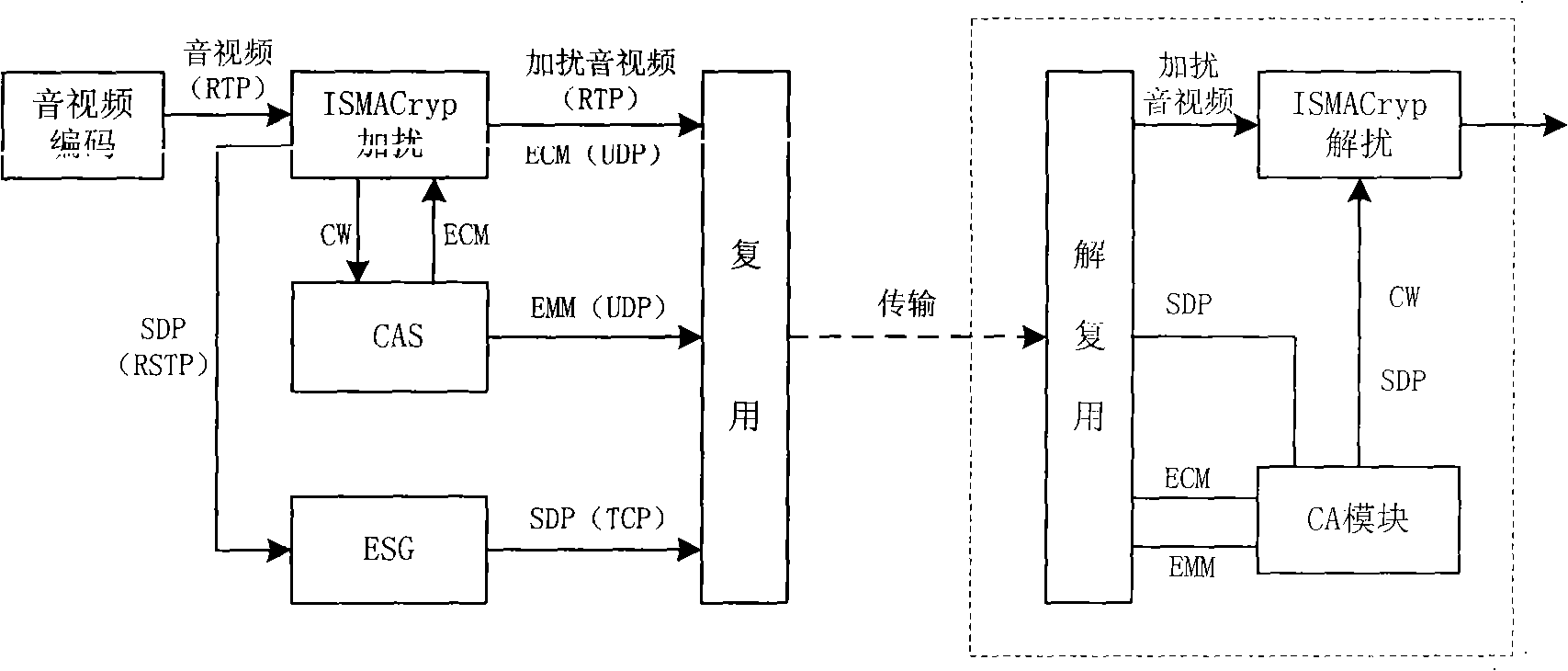
ActiveCN101291419AEasy for manufacturers to industrializeLower the thresholdAnalogue secracy/subscription systemsOperational systemData stream
The invention discloses an authorizing-descrambling method used in digital multimedia broadcasting CAS. An SD / TF smart card is applied to the authorizing-descrambling method, and an operating system of the SD / TF smart card adopts Java Card platform technology. The method separates machines from cards, and has low cost as well as high safety. The invention also provides a device for realizing the method. The device comprises a terminal and the SD / TF smart card, wherein the terminal comprises a universal interface driver module; the SD / TF smart card comprises a distribution module, a filter module, an encryption-decryption-authorization control module and a descrambling module; a data stream orderly passes the universal interface driver module, the distribution module, the filter module, the encryption-decryption-authorization control module and the descrambling module; a descrambled data stream orderly passes the distribution module and the universal interface driver module and then returns to the terminal.
Owner:武汉国广天喻信息技术有限公司
JAVA CARD based backup and recovery method for data in application
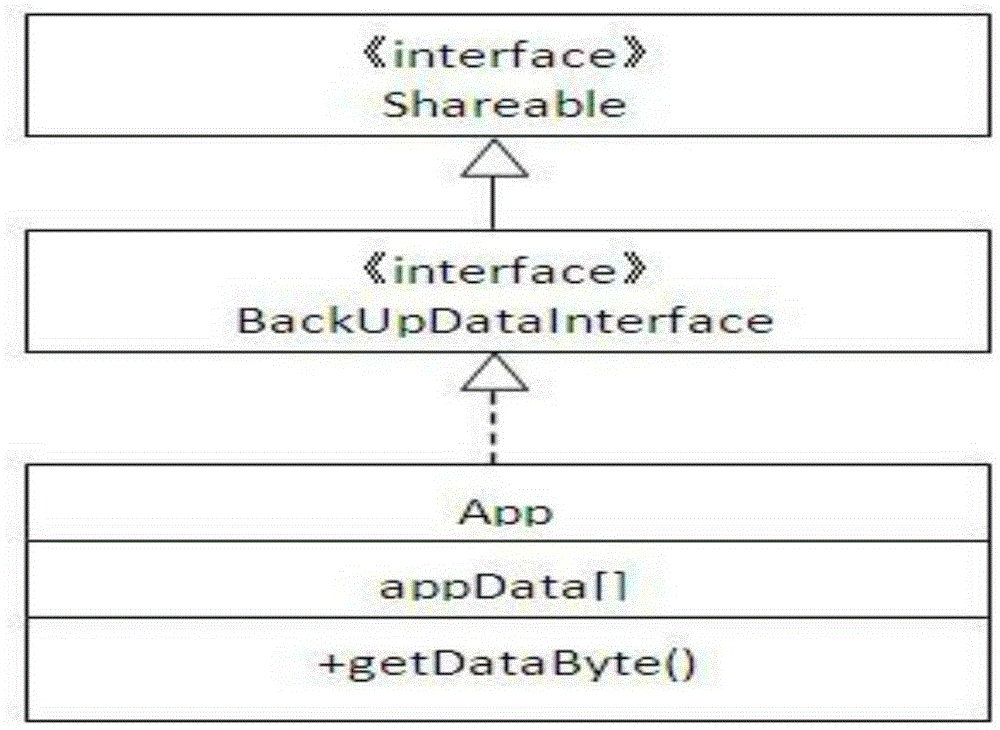
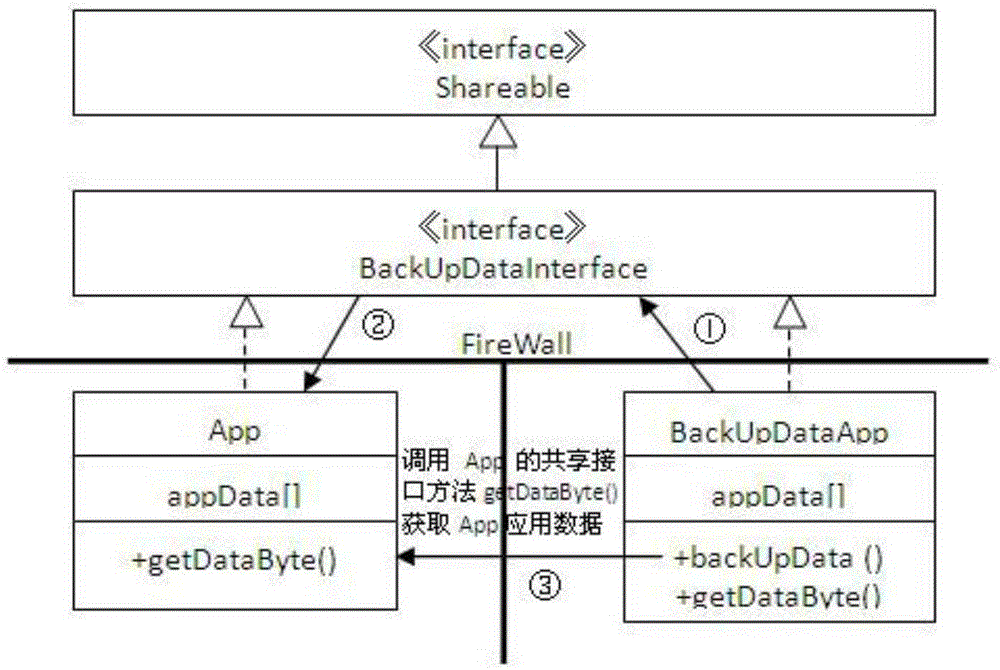
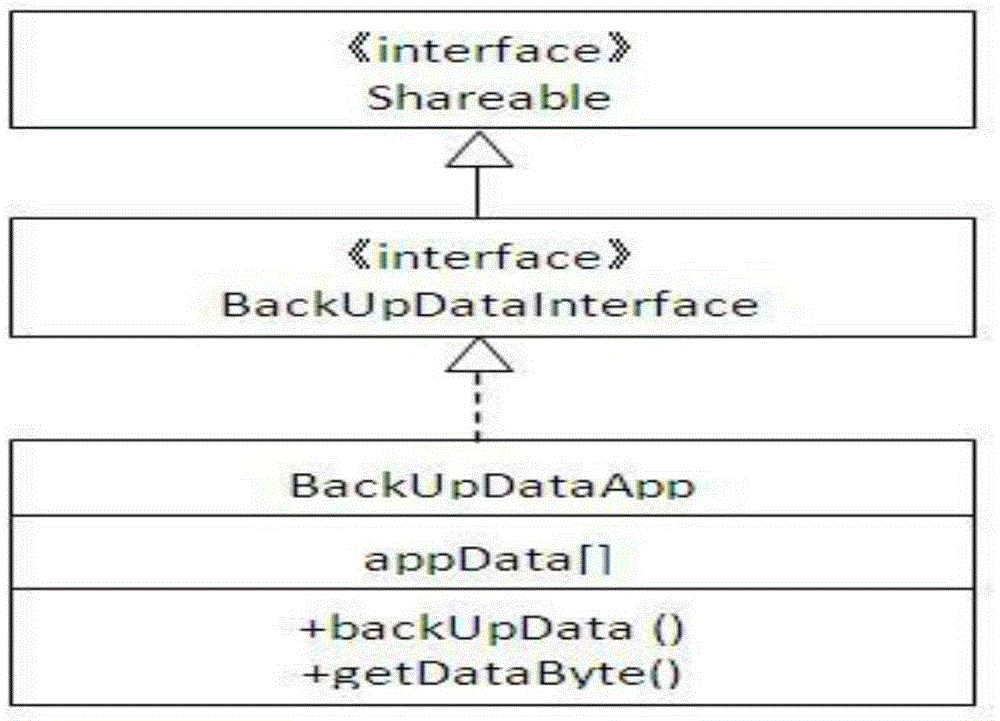
InactiveCN105302666AEfficient use ofImprove securityRedundant operation error correctionRecovery methodJava Card
The invention provides a JAVA CARD based backup and recovery method for data in an application. The method comprises: developing a BackUpDataApp; obtaining data in an App by utilizing the BackUpDataApp, and performing backup on the data; deleting an App package, writing the data into a new App package, and installing a new App; and obtaining the data backed up in the BackUpDataApp by utilizing the new App, and writing the data into a corresponding region of the new App, so that the data in the App of the JAVA CARD is recovered. According to the method, the data in the App are efficiently and securely backed up and recovered.
Owner:EASTCOMPEACE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com