Realization method for security domain on java card
An implementation method and security domain technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve problems such as low security and cardholder interests cannot be guaranteed, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
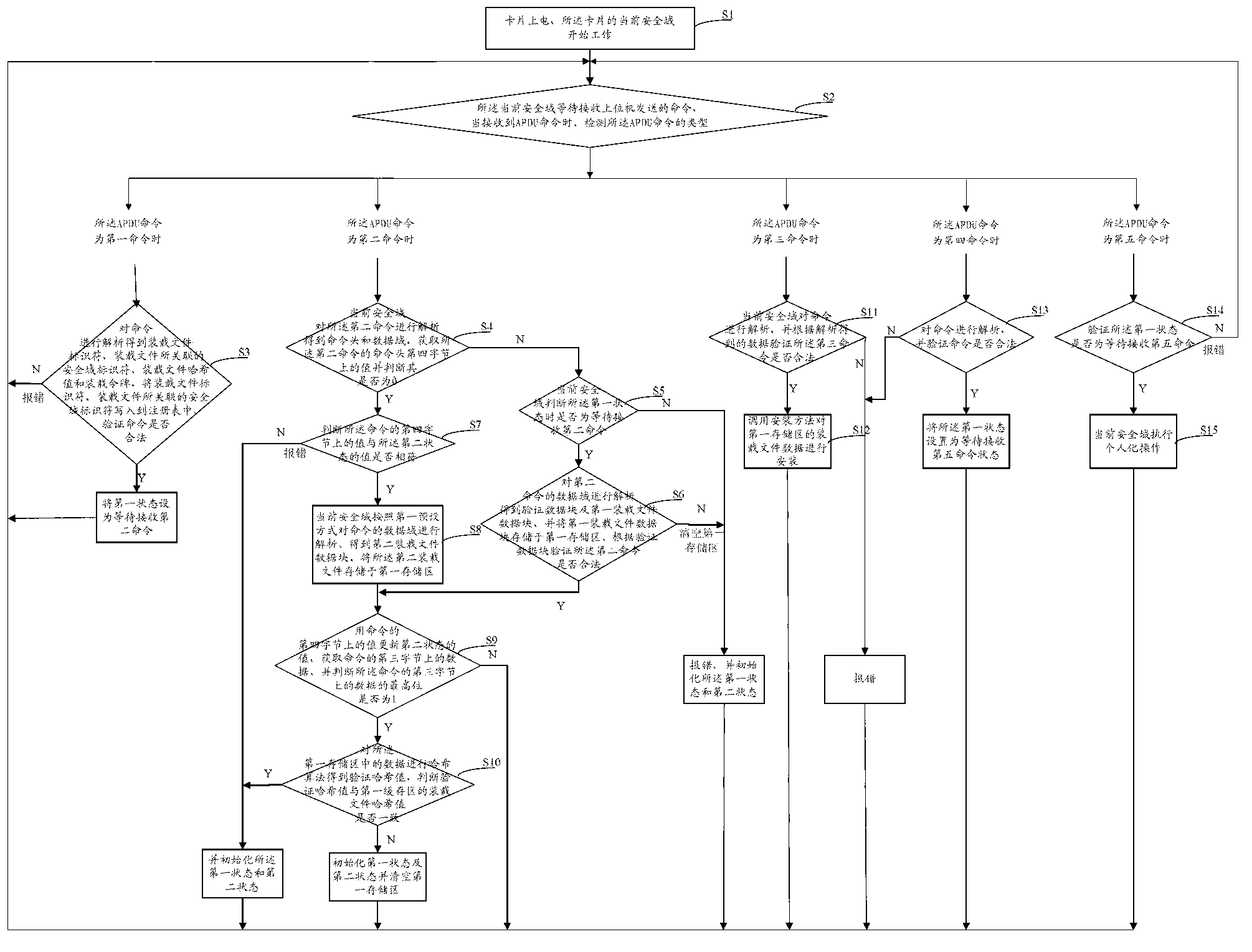
[0050] S1: The card is powered on, and the current security domain of the card starts to work;
[0051] S2: The current security domain is waiting to receive the command sent by the host computer. When receiving the APDU command, detect the type of the APDU command. If it is the first command, execute S3; if it is the second command, execute S4- S10; if it is the third command, execute S11-S12; if it is the fourth command, execute S13; if it is the fifth command, execute S14-S15; if it is other APDU commands, operate according to the APDU command ;
[0052] In this embodiment, the first command is an install for load command, the second command is a load command, the third command is an install for install command, the fourth command is an install for personalization command, and the fifth command is a store data Order.
[0053] S3: The current security domain parses the first command to obtain the command header and data field, and parses the data field of the first command...
Embodiment 2
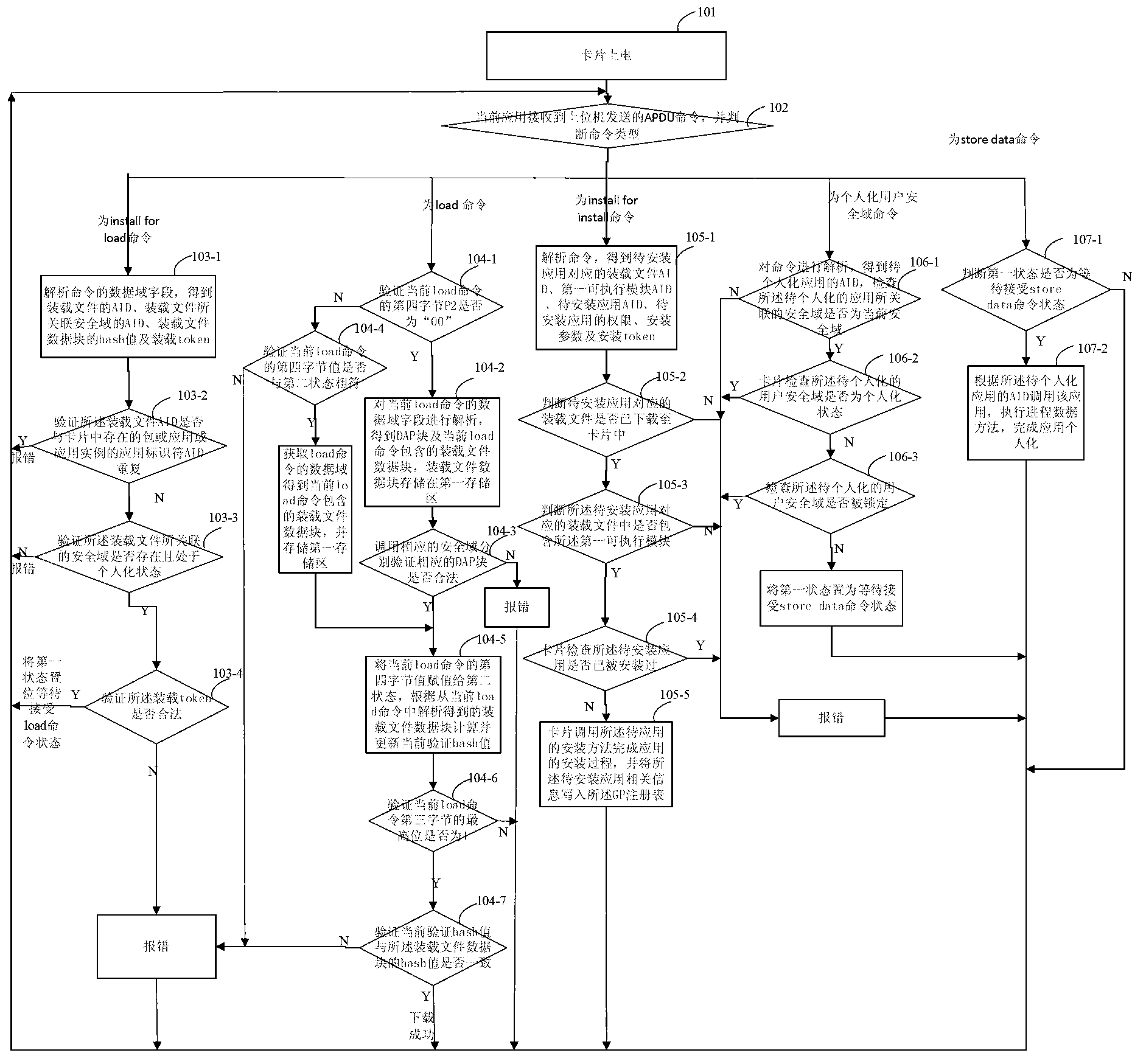
[0067] Embodiment 2 of the present invention provides a method for implementing a security domain on a java card. The method takes the main security domain receiving the install for load command, load command, install for install command, install for personalization command and store data command as an example, The specific process is as follows:
[0068] Step 101: Power on the card;
[0069] Step 102: The current security domain of the card receives the APDU command sent by the host computer, and judges the command type;
[0070] The current security domain can be the main security domain or the user security domain; it can be the default security domain application after the card is powered on or the security domain application selected by the select command. In particular, the default application after the card is powered on is When the non-secure domain application or the application selected by the select command is a non-secure domain application, before this step, the ...
Embodiment 3
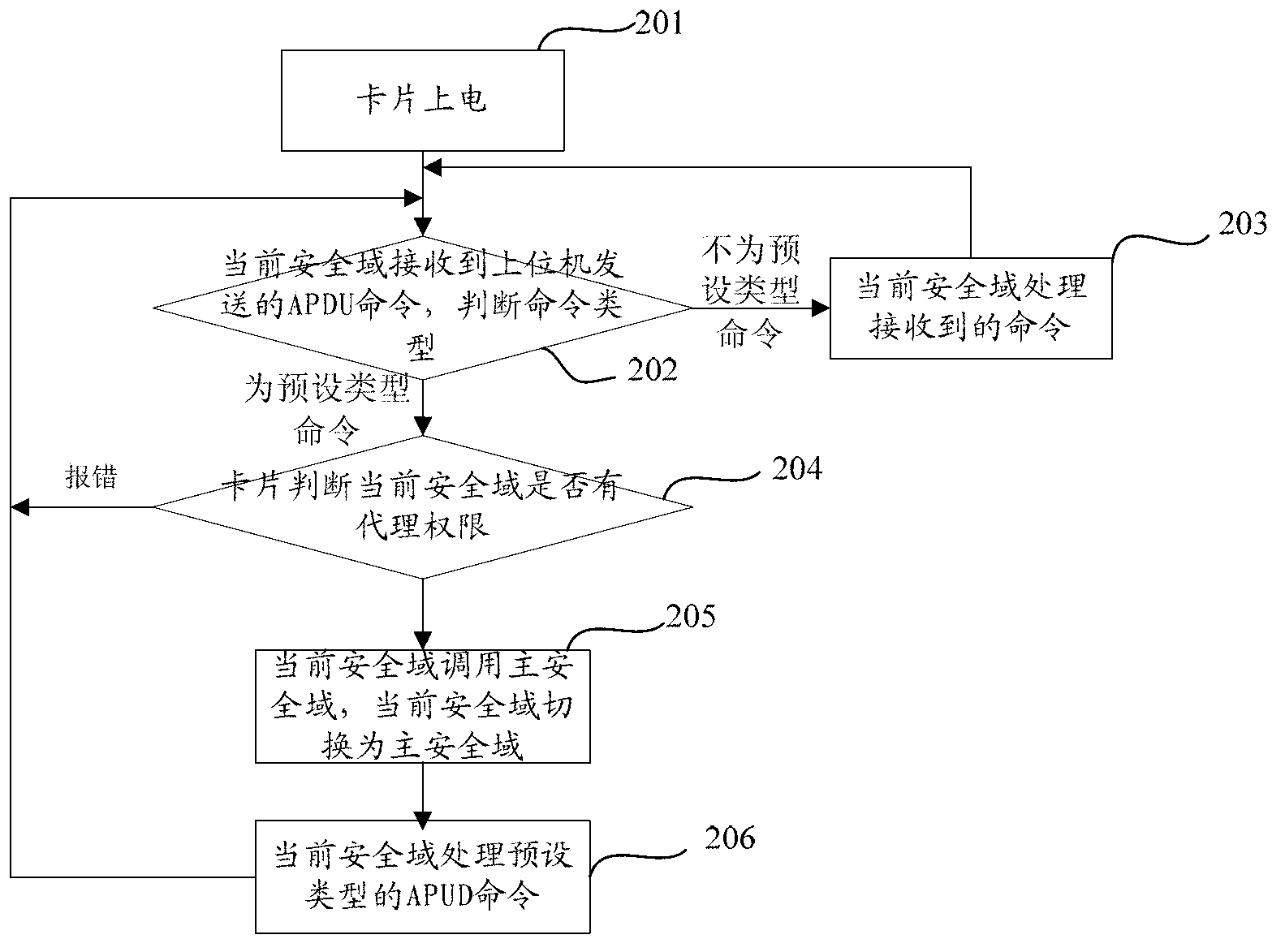
[0133] Embodiment 3 of the present invention provides yet another implementation method of the security domain on the java card. The method takes the user security domain receiving the install for load command, load command, install for install command, install for personalization command and store data command as an example , the method is as follows:
[0134] Step 201: power on the card;
[0135] Step 202: The current security domain in the card receives the APDU command sent by the host computer, and judges the command type. If the command type is a preset type command, execute steps 204-206, otherwise execute step 203;
[0136] Preferably, the current security domain is the user security domain, and before this step, the step of selecting the user security domain as the current security domain by the card receiving a select command sent by the host computer may also be included. In this embodiment, the preset type commands include an install for load command and an instal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com