System and method for optimizing byte codes for JAVA card
An optimization method and bytecode technology, applied in the field of smart cards, can solve problems such as unrealizable, limiting the execution speed of smart card dual-core JAVA cards, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
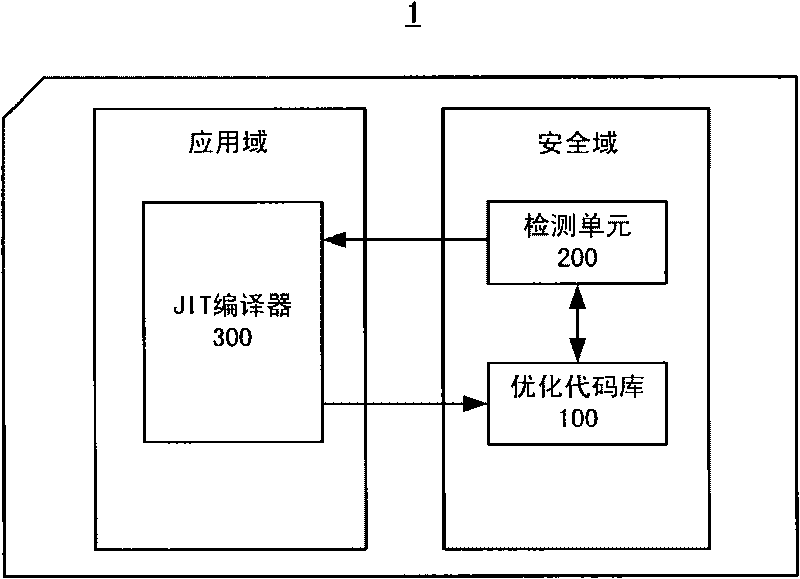
[0026] figure 1 A block diagram of a bytecode optimization system according to Embodiment 1 of the present invention is shown. Such as figure 1 As shown, the bytecode optimization system 1 includes an optimized code library 100, a detection unit 200 and a JIT compiler 300 located in the JAVA card application domain.
[0027] The optimized code repository 100 stores optimized codes of bytecode sequences of secure domain applications. The optimized codes stored in the optimized code library 100 also include those optimized codes obtained by running standard test programs and simulating byte code sequences of actual running conditions, which are pre-stored before the JAVA card leaves the factory.
[0028] When the application program is installed or used in the security domain, the detection unit 200 detects whether there is a corresponding optimized code in the bytecode sequence of the application program in the optimization code library 100, and there is no corresponding opti...
Embodiment 2
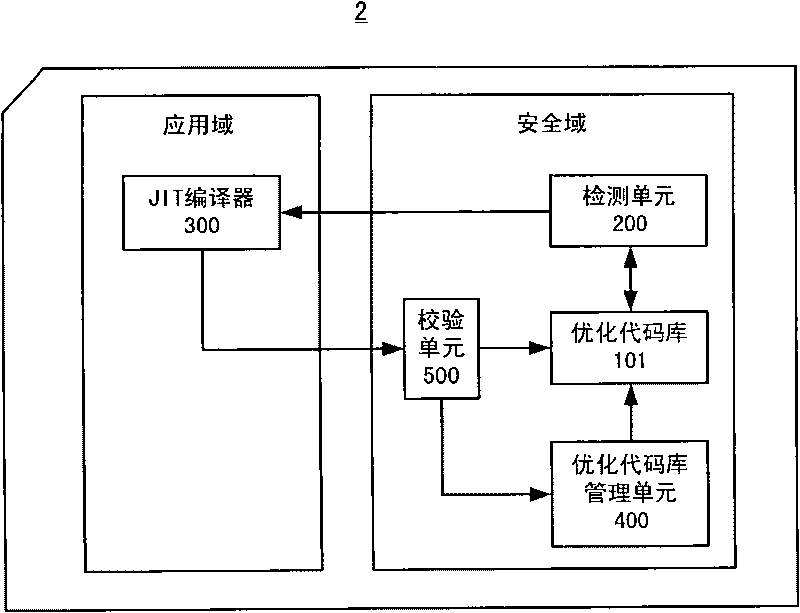
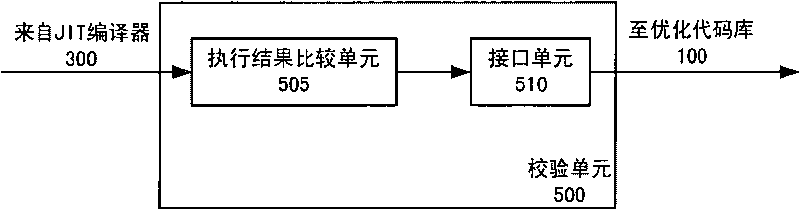
[0031] figure 2 A block diagram of a bytecode optimization system according to Embodiment 2 of the present invention is shown. Such as figure 2 As shown, the bytecode optimization system 2 includes an optimized code library 101 , a detection unit 200 , a JIT compiler 300 , an optimized code library management unit 400 and a verification unit 500 . exist figure 2 in, with figure 1 Similar elements have been given the same reference numerals and their details will not be repeated below.
[0032] as reference figure 1 Like the optimized code library 100 described, in this embodiment, the optimized code library 101 also stores optimized codes of bytecode sequences of applications in the security domain. In addition, the optimized code library 101 also stores the storage time and usage times of each optimized code, so as to make statistics about which optimized codes are most frequently used and which optimized codes are least used. For example, for the optimized code A st...
Embodiment 3
[0044] Figure 4 A block diagram of a bytecode optimization system according to Embodiment 3 of the present invention is shown. Such as Figure 4 As shown, the bytecode optimization system 3 includes an optimized code library 100 , a detection unit 200 , a JIT compiler 300 and a security level judgment unit 600 . exist Figure 4 in, with figure 1 Similar elements have been given the same reference numerals and their details will not be repeated below.
[0045] From a security point of view, it is unsafe for the detection unit 200 to transmit all bytecode sequences of the security domain application program to the JIT compiler 300 in the application domain for optimization. In fact, there are different security levels among bytecode sequences of applications. For bytecode sequences that are closely related to security, such as bytecode sequences that implement encryption and decryption functions, the security level is naturally much higher. For this Part of the bytecode se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com