Patents
Literature
215 results about "Localhost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
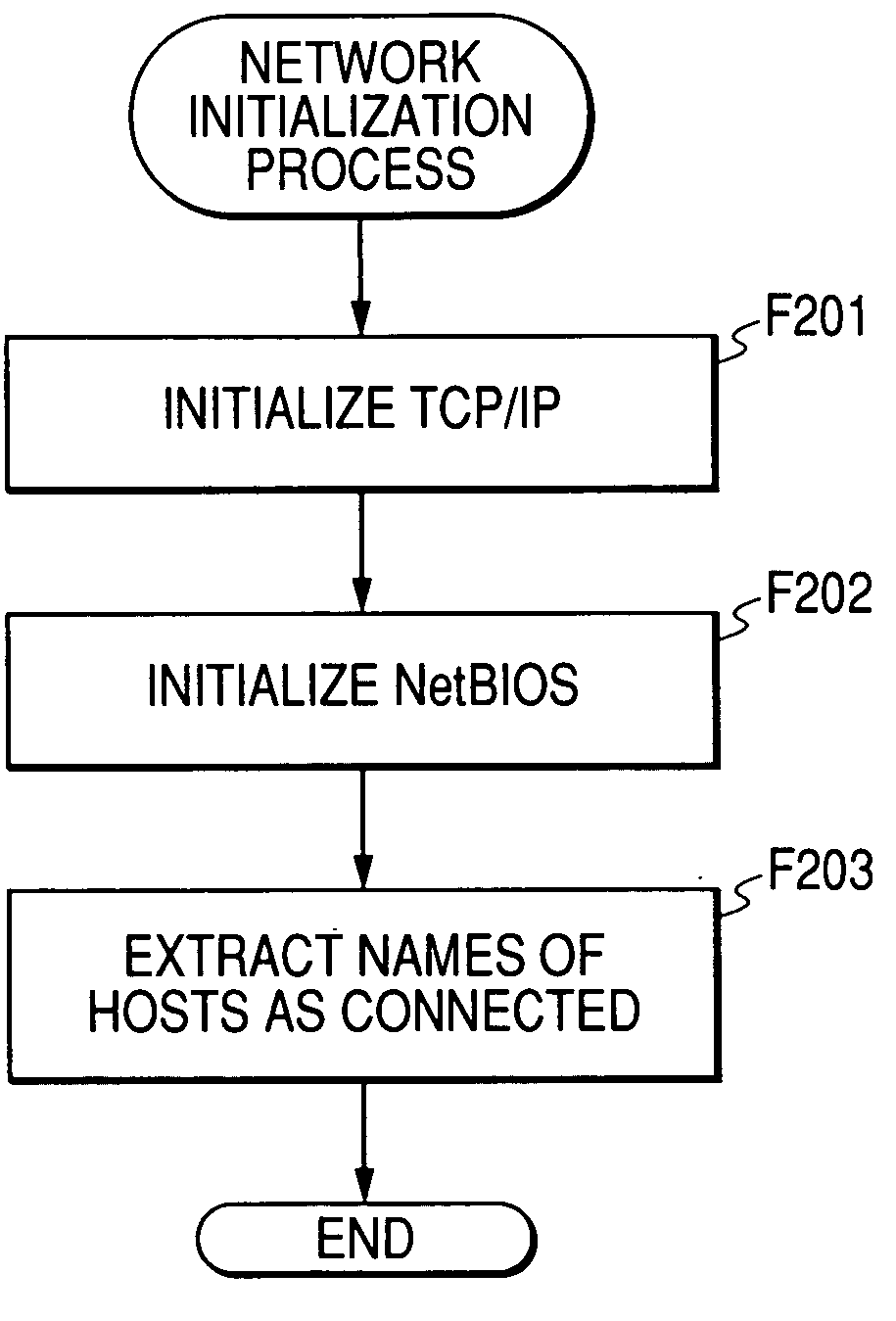
In computer networking, localhost is a hostname that means this computer. It is used to access the network services that are running on the host via the loopback network interface. Using the loopback interface bypasses any local network interface hardware.
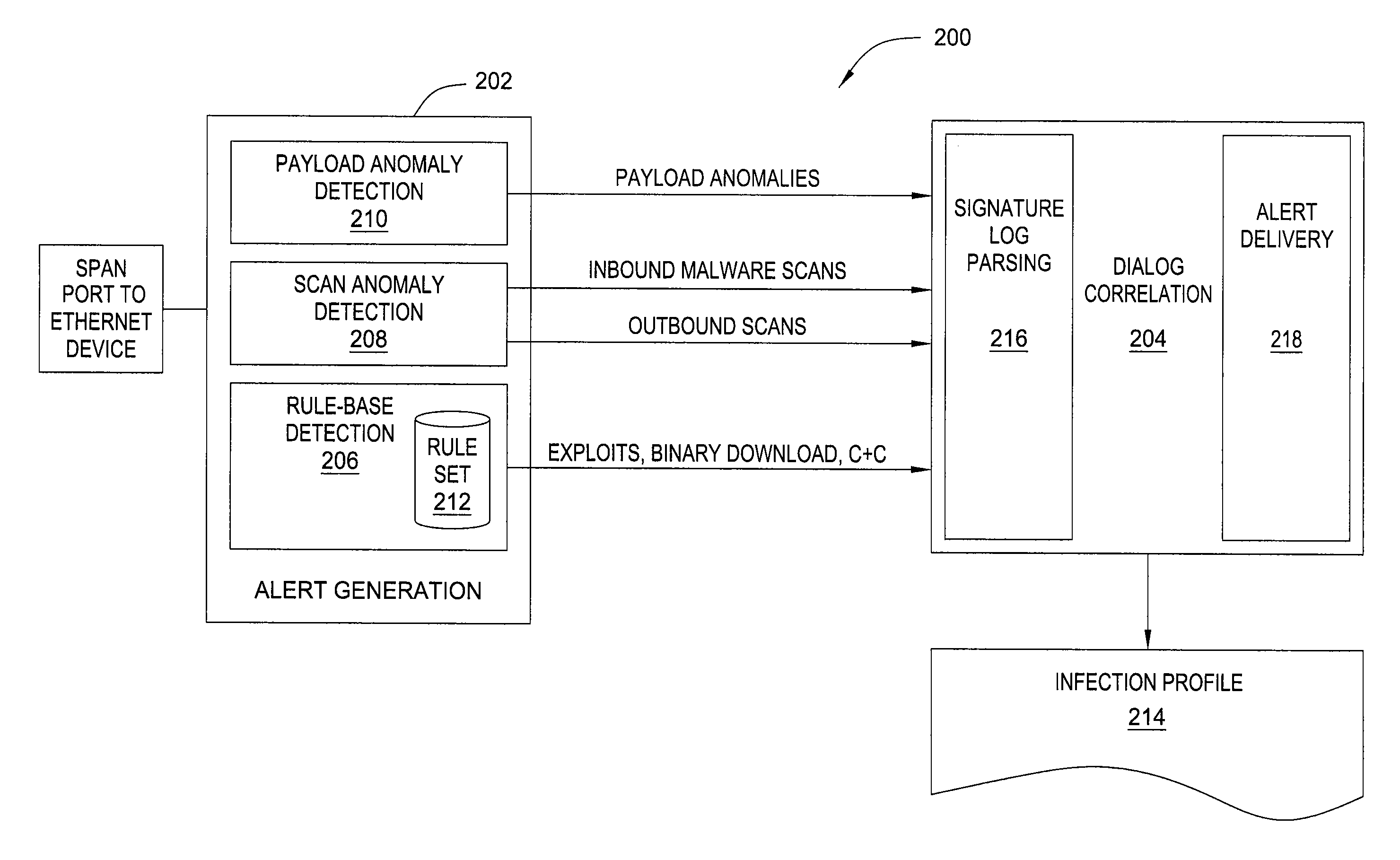
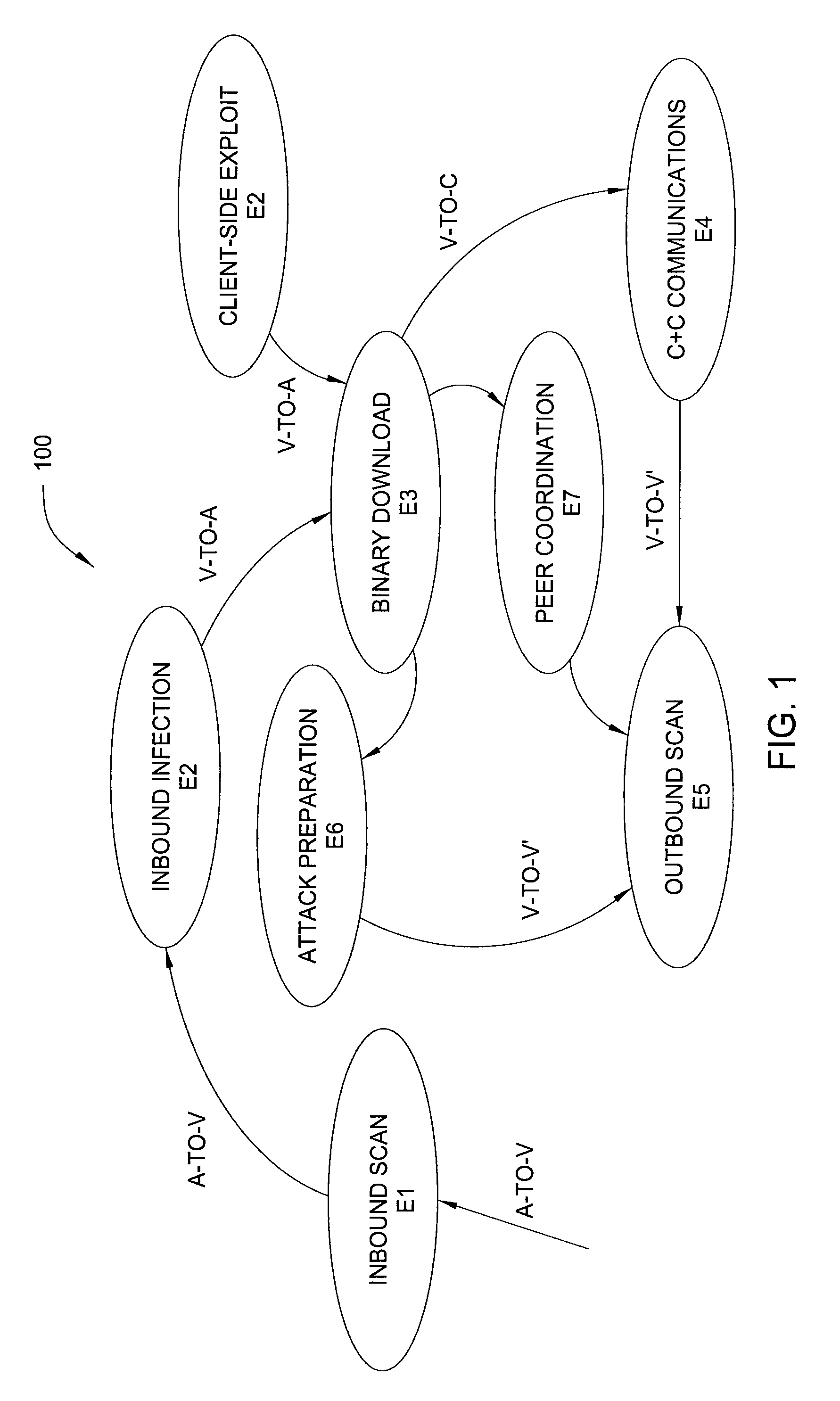
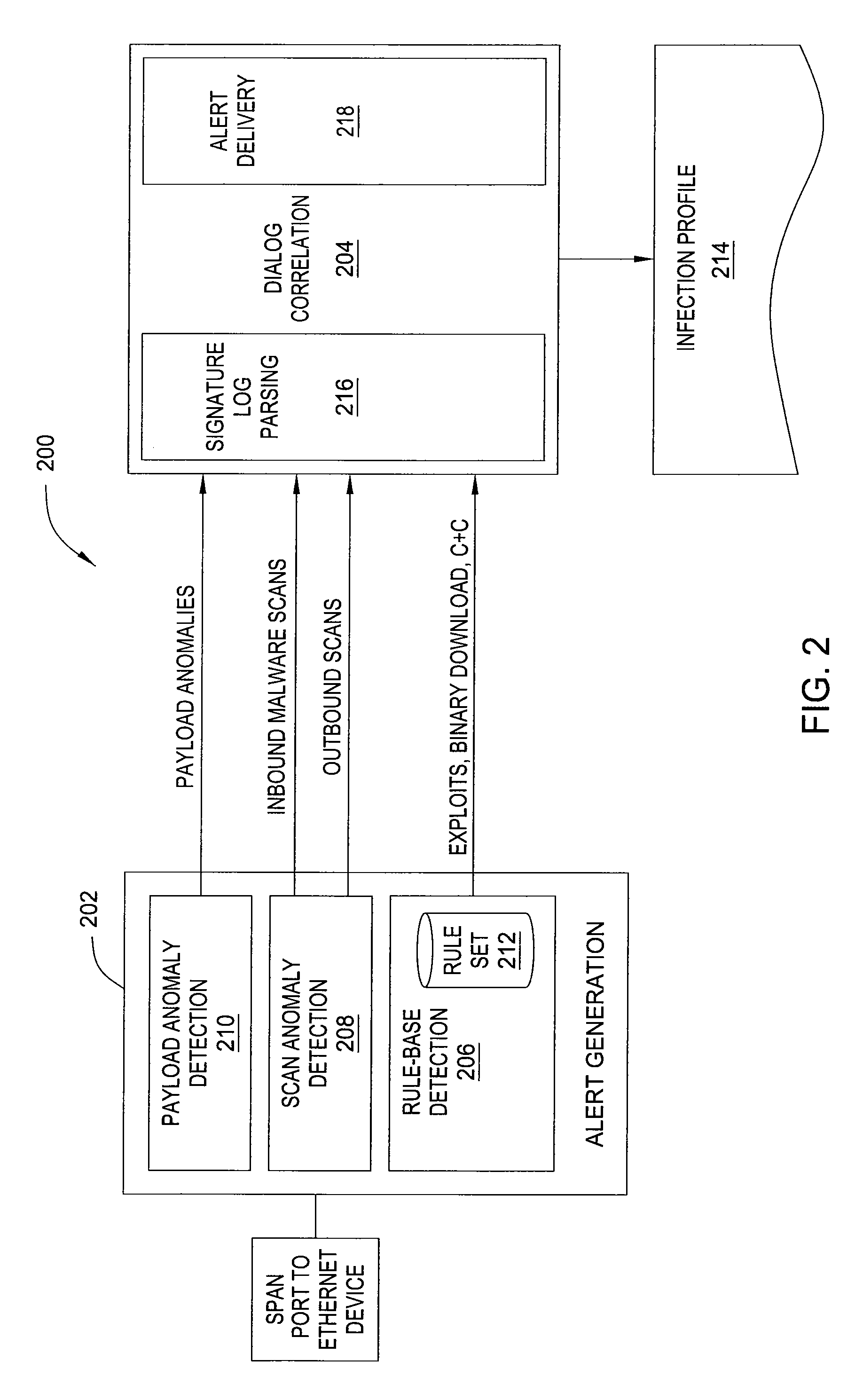
Method and apparatus for detecting malware infection
In one embodiment, the present invention is a method and apparatus for detecting malware infection. One embodiment of a method for detecting a malware infection at a local host in a network, includes monitoring communications between the local host and one or more entities external to the network, generating a dialog warning if the communications include a transaction indicative of a malware infection, declaring a malware infection if, within a predefined period of time, the dialog warnings includes at least one dialog warning indicating a transaction initiated at the local host and at least one dialog warning indicating an additional transaction indicative of a malware infection, and outputting an infection profile for the local host.
Owner:SRI INTERNATIONAL
Method And Apparatus For Trusted Federated Identity
InactiveUS20120072979A1Well formedDigital data processing detailsUser identity/authority verificationTrusted ComputingFederated identity
A trusted computing environment, such as a smartcard, UICC, Java card, global platform, or the like may be used as a local host trust center and a proxy for a single-sign on (SSO) provider. This may be referred to as a local SSO provider (OP). This may be done, for example, to keep authentication traffic local and to prevent over the air communications, which may burden an operator network. To establish the OP proxy in the trusted environment, the trusted environment may bind to the SSO provider in a number of ways. For example, the SSO provider may interoperate with UICC-based UE authentication or GBA. In this way, user equipment may leverage the trusted environment in order to provide increased security and reduce over the air communications and authentication burden on the OP or operator network.
Owner:INTERDIGITAL PATENT HLDG INC
Determining address of closest edge server
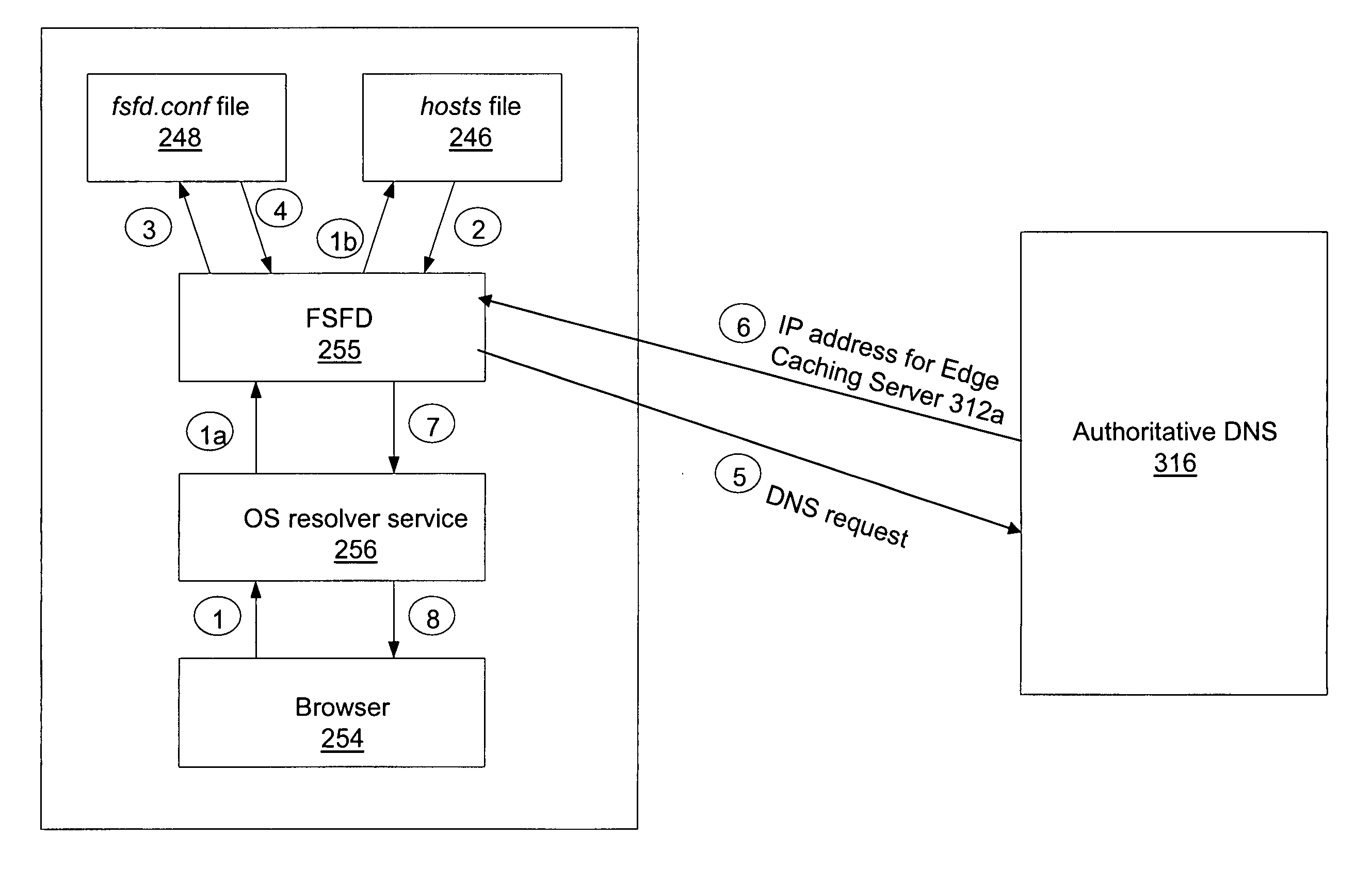
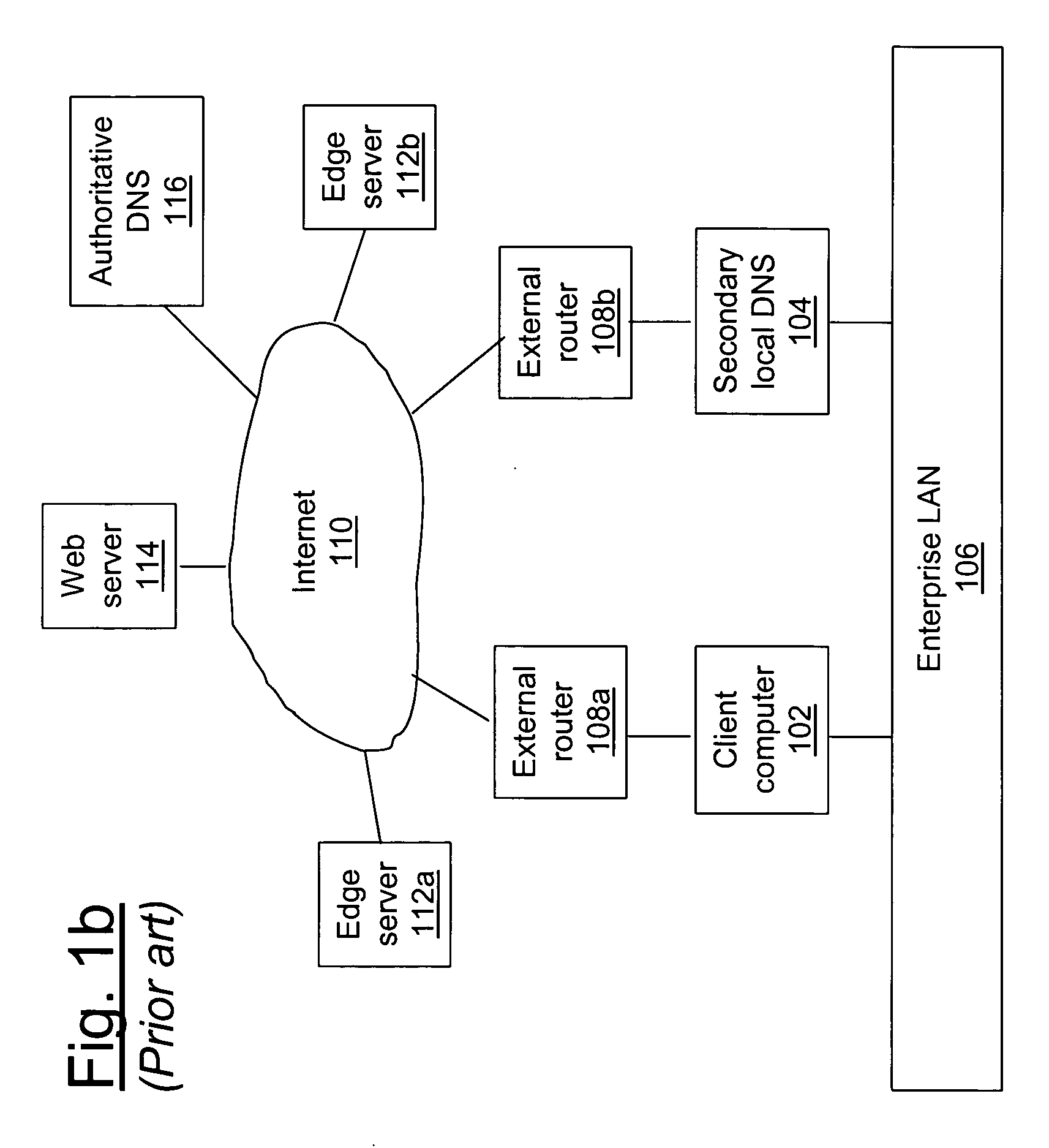
A method and system is presented for bypassing a local Domain Name Server (DNS) when using edge caching servers. Domain names of frequently used business applications that are known to rely upon edge servers, together with the corresponding authoritative DNSs, are listed in both local hosts file and user defined FSFD local configuration file fsfd.conf. When the client computer's browser attempts to resolve a domain name, a File System Filtering Driver (FSFD) in the client computer intercepts the browser's request. If the domain name which is being resolved is found in a local FSFD configuration file fsfd.conf, then the FSFD initiates a DNS request directly to the appropriate authoritative DNS whose IP address gets extracted from the fsfd.conf record, thus bypassing the local DNS. The authoritative DNS returns the IP address for an edge caching server that is topographically proximate to the client computer's browser.
Owner:LINKEDIN
Context-sensitive copy and paste block
InactiveUS20170154188A1Digital data protectionProgram/content distribution protectionData miningAutomatic processing
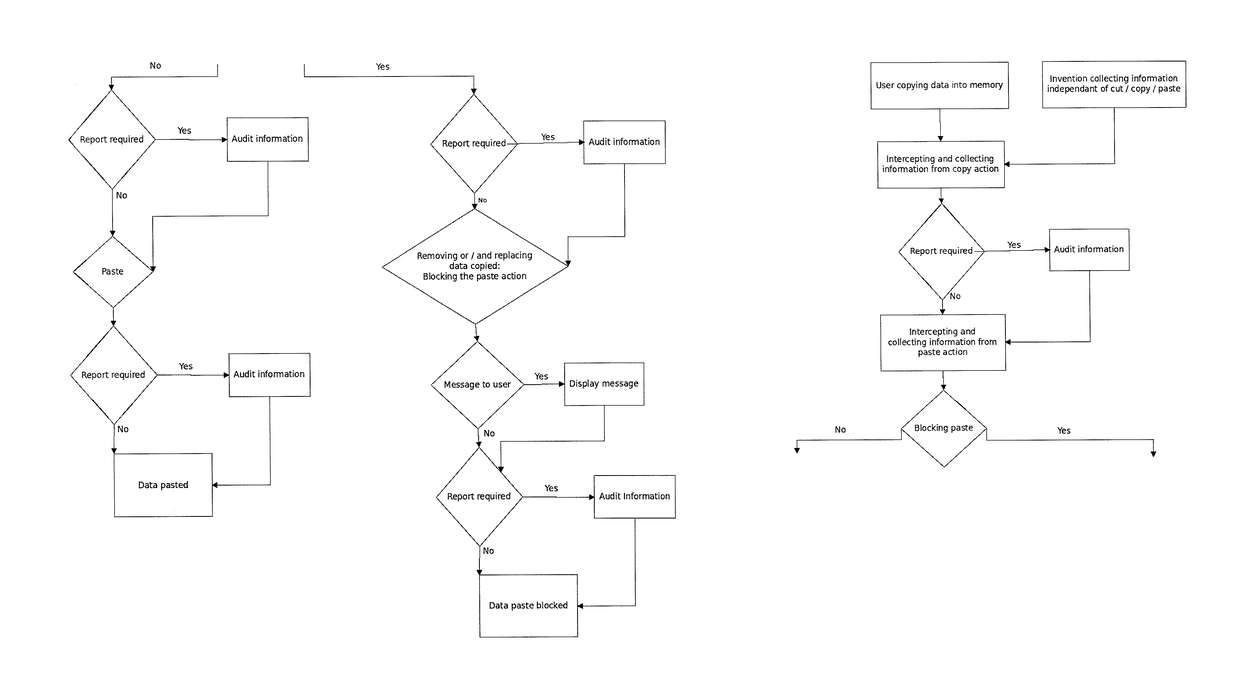
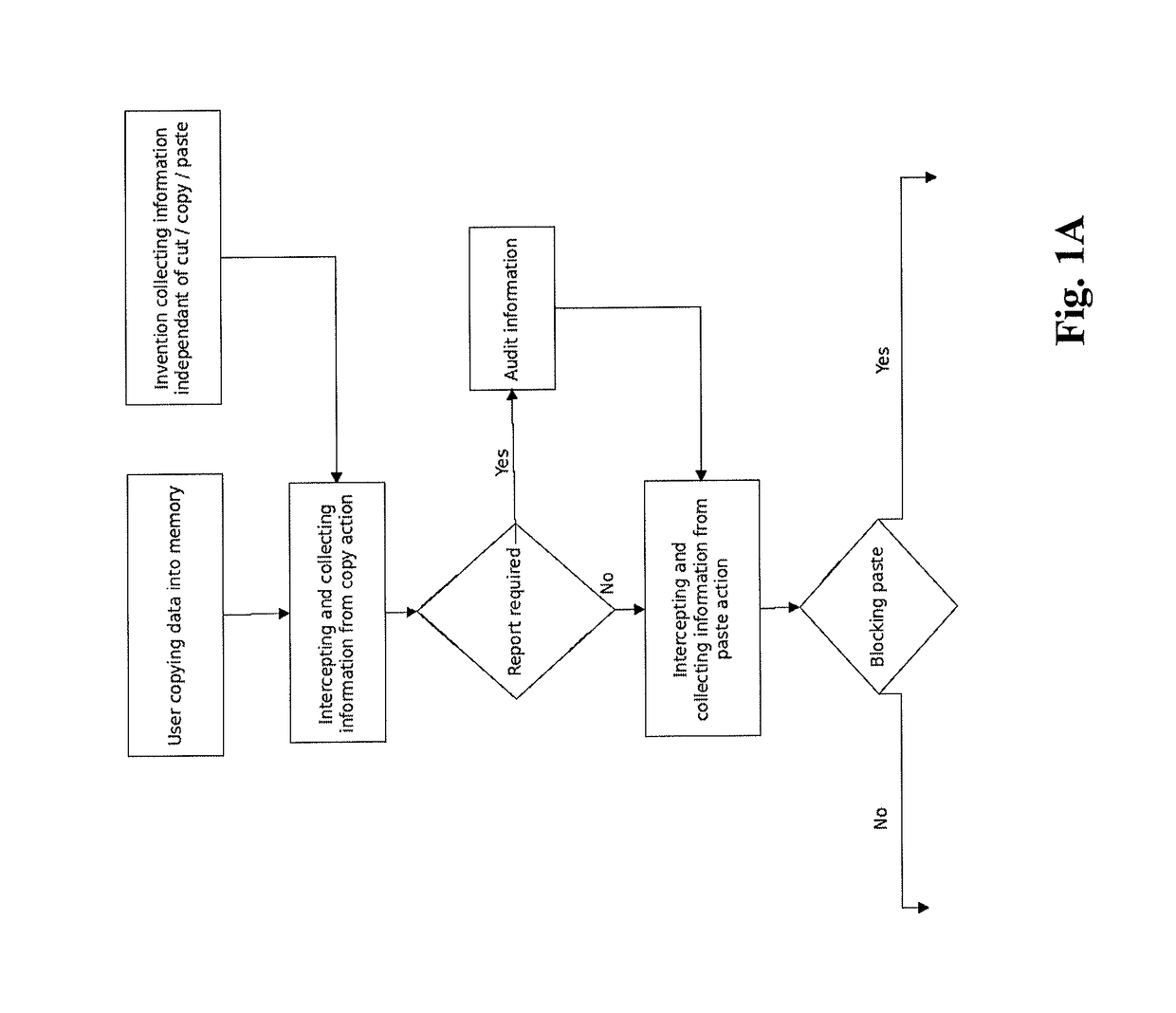
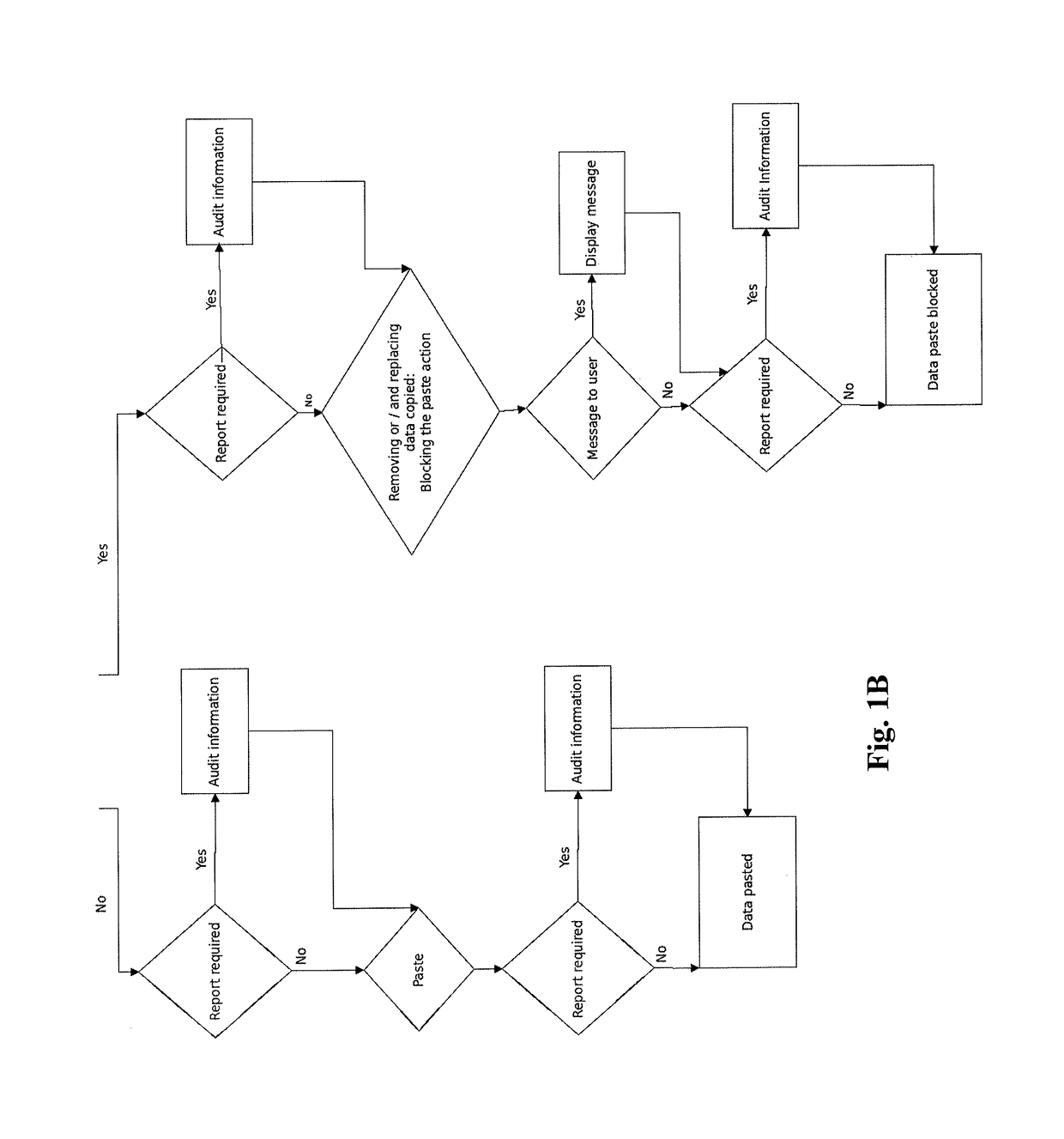
A cut / copy action controller includes a command detector detects a cut / copy action in response to a user command; a rule applicability determiner determines, based on the source and / or destination, whether the cut / copy action satisfies a rule controlling the user action; and blocks the cut / copy action and / or the paste action in accordance with the rules. A report of the copy action may be transmitted to a log. The cut / copy action may automatically store content to an automated processor storage location such as a clipboard of a local host. A rule generator may generate a rule such that when the recurrence information indicates low recurrence of the information associated then the rule yields the blocking of the copy action.
Owner:SECUDE AG
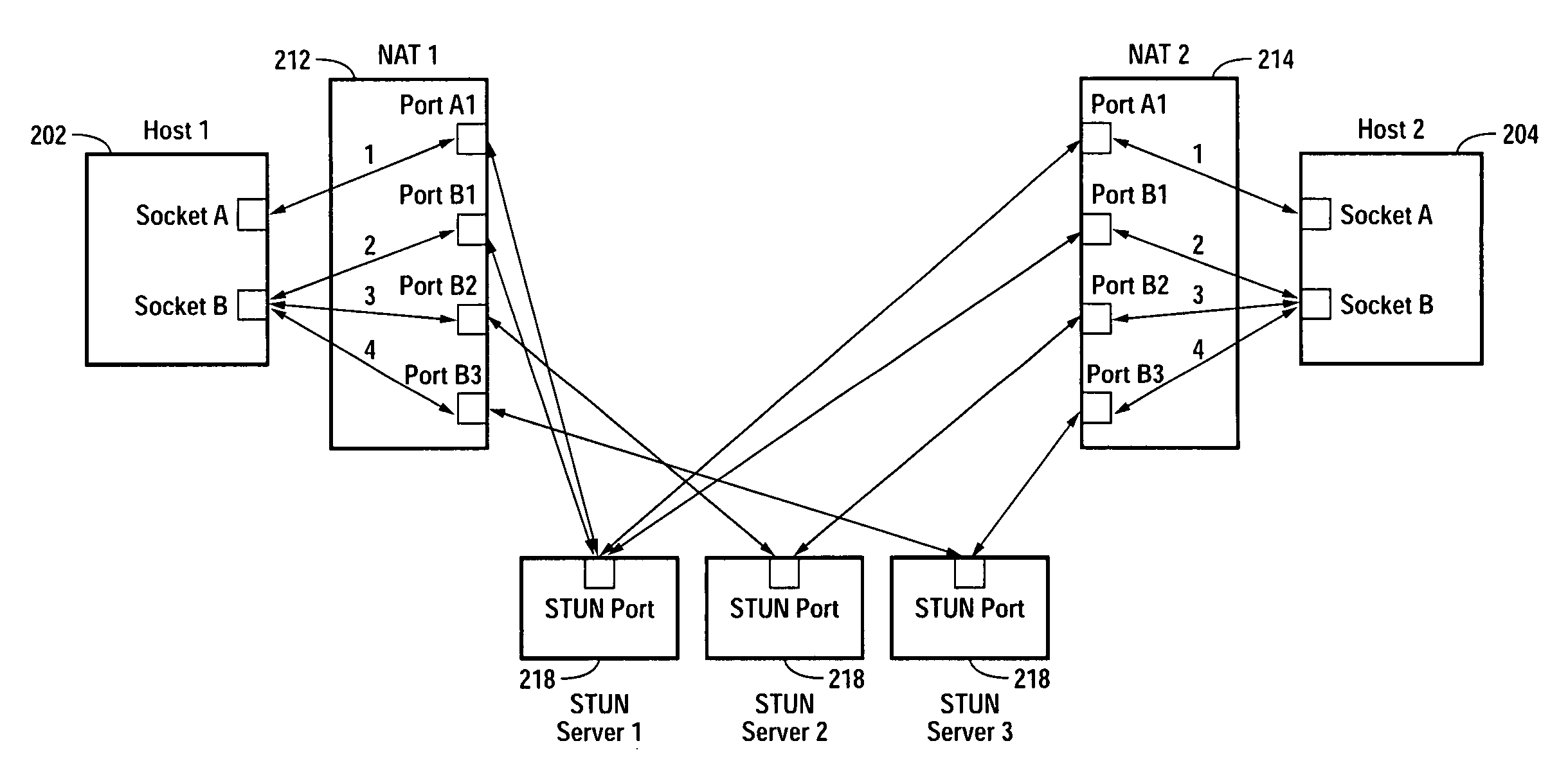
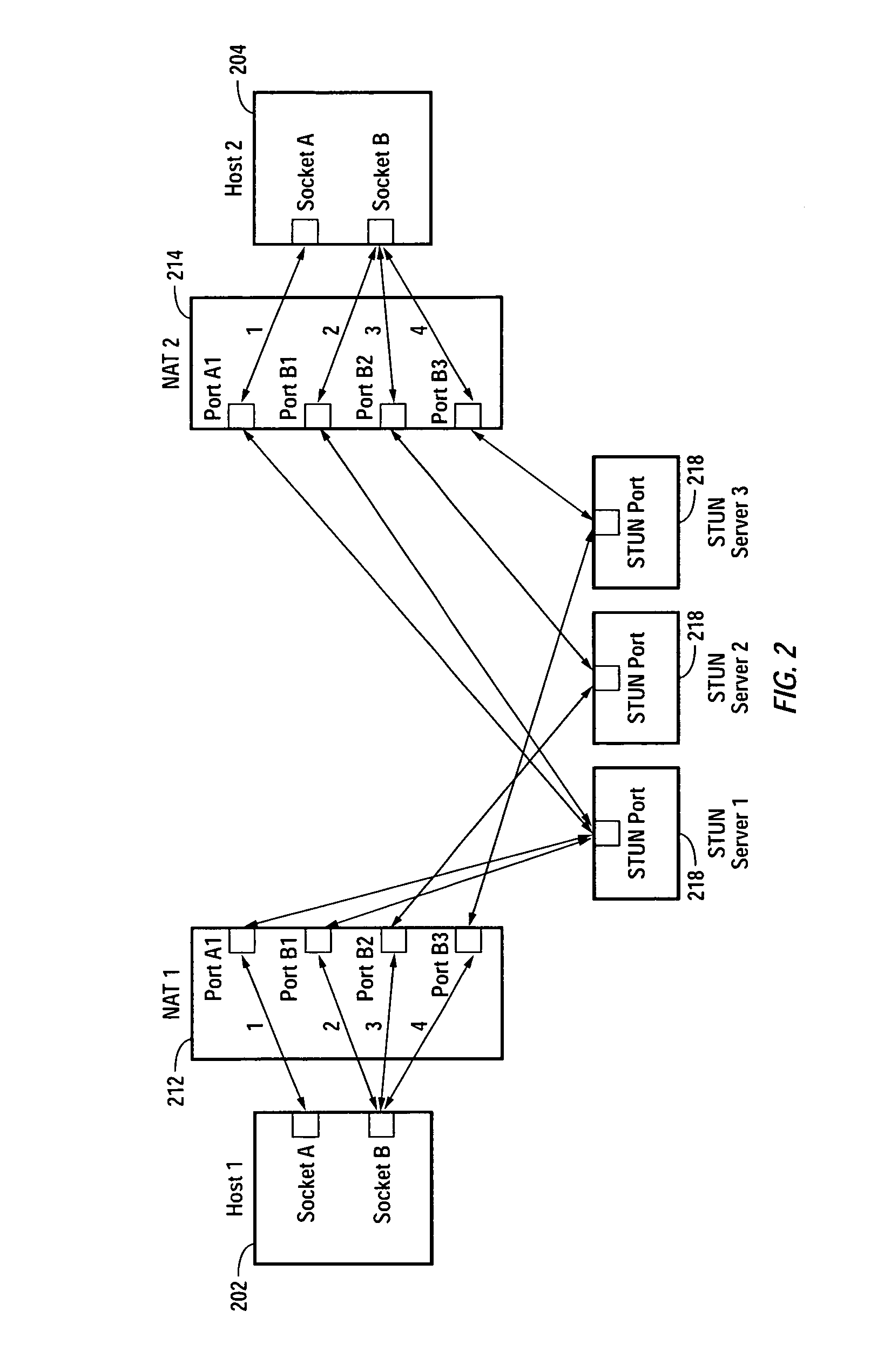
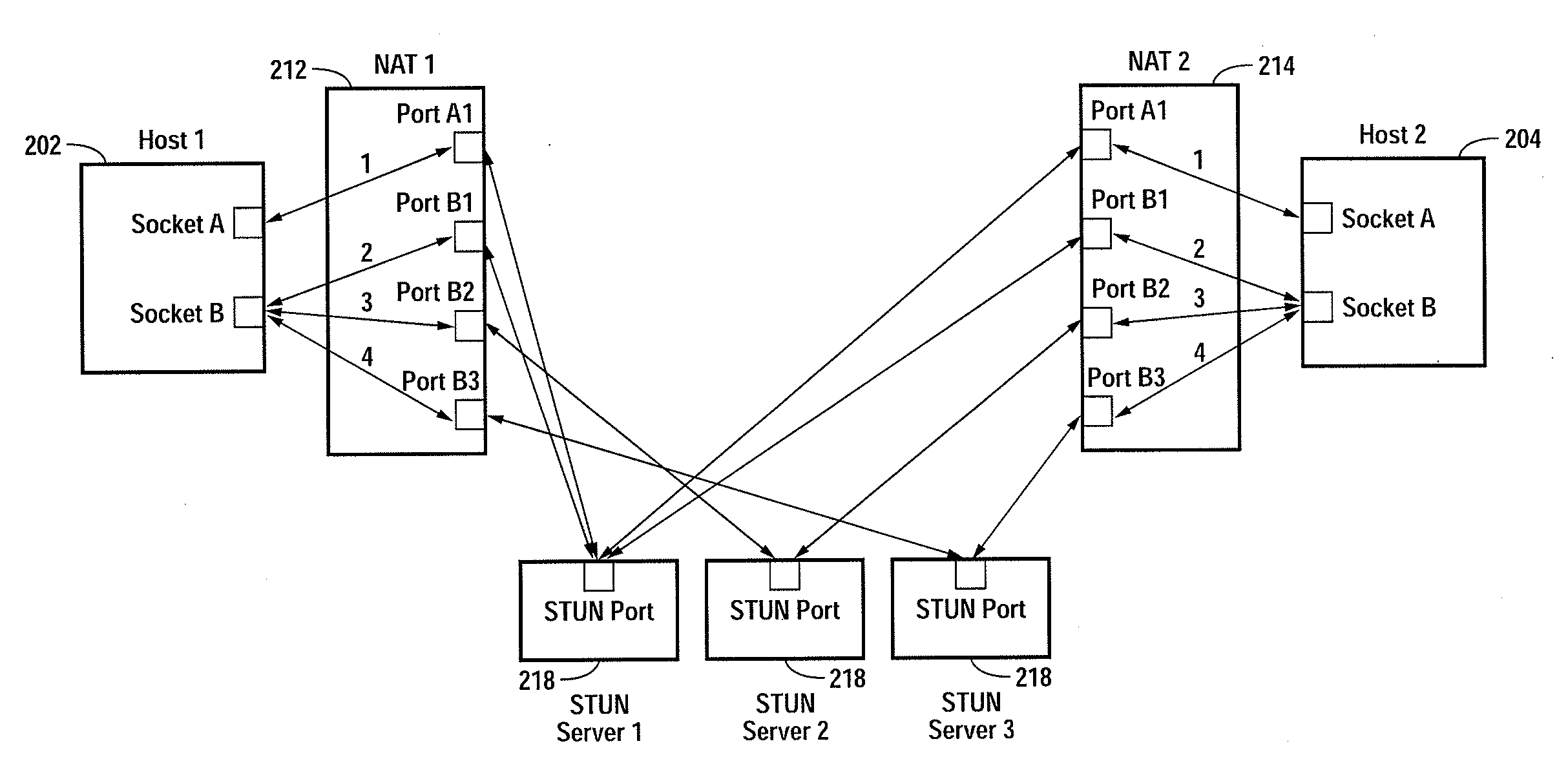
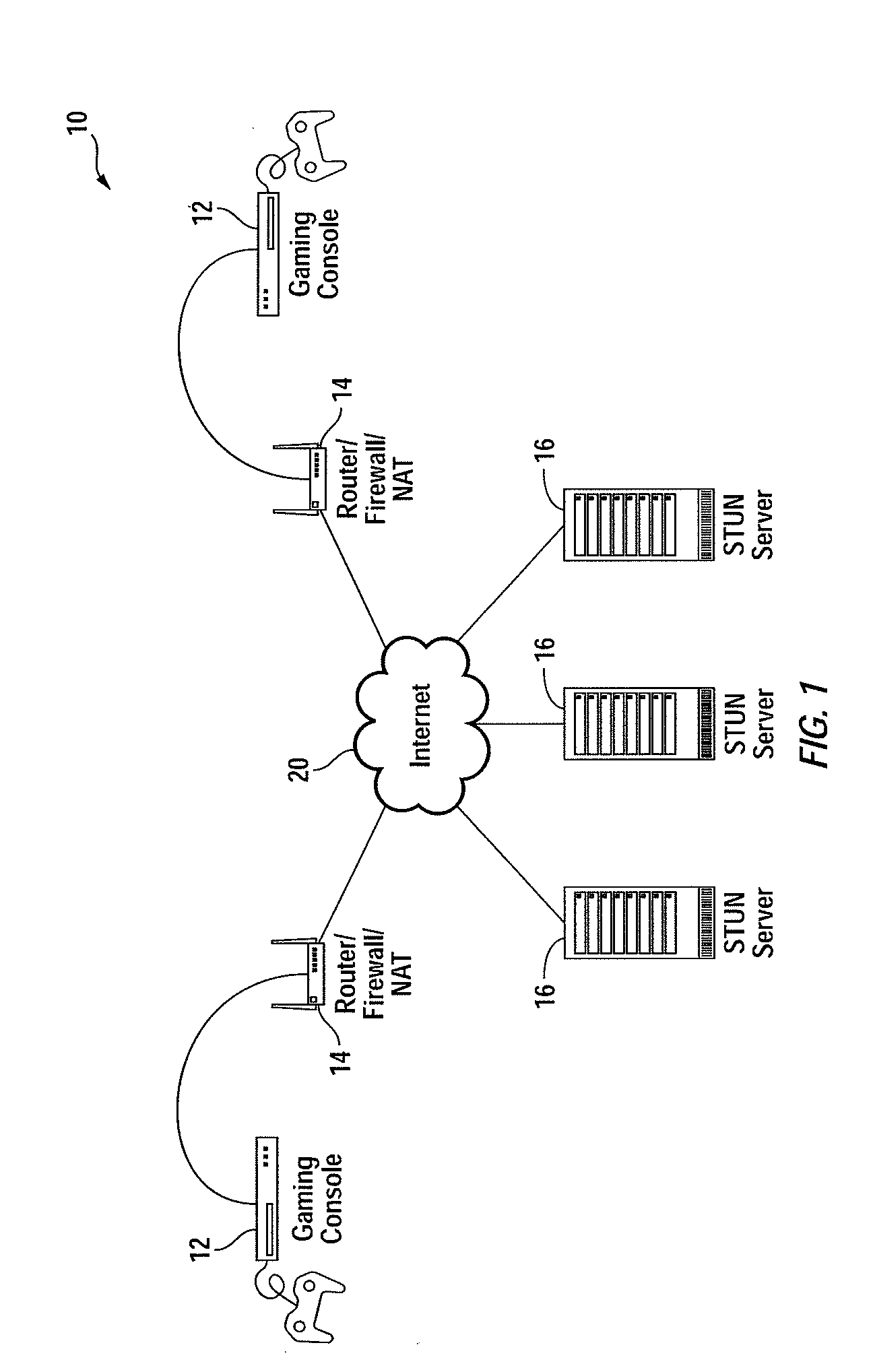
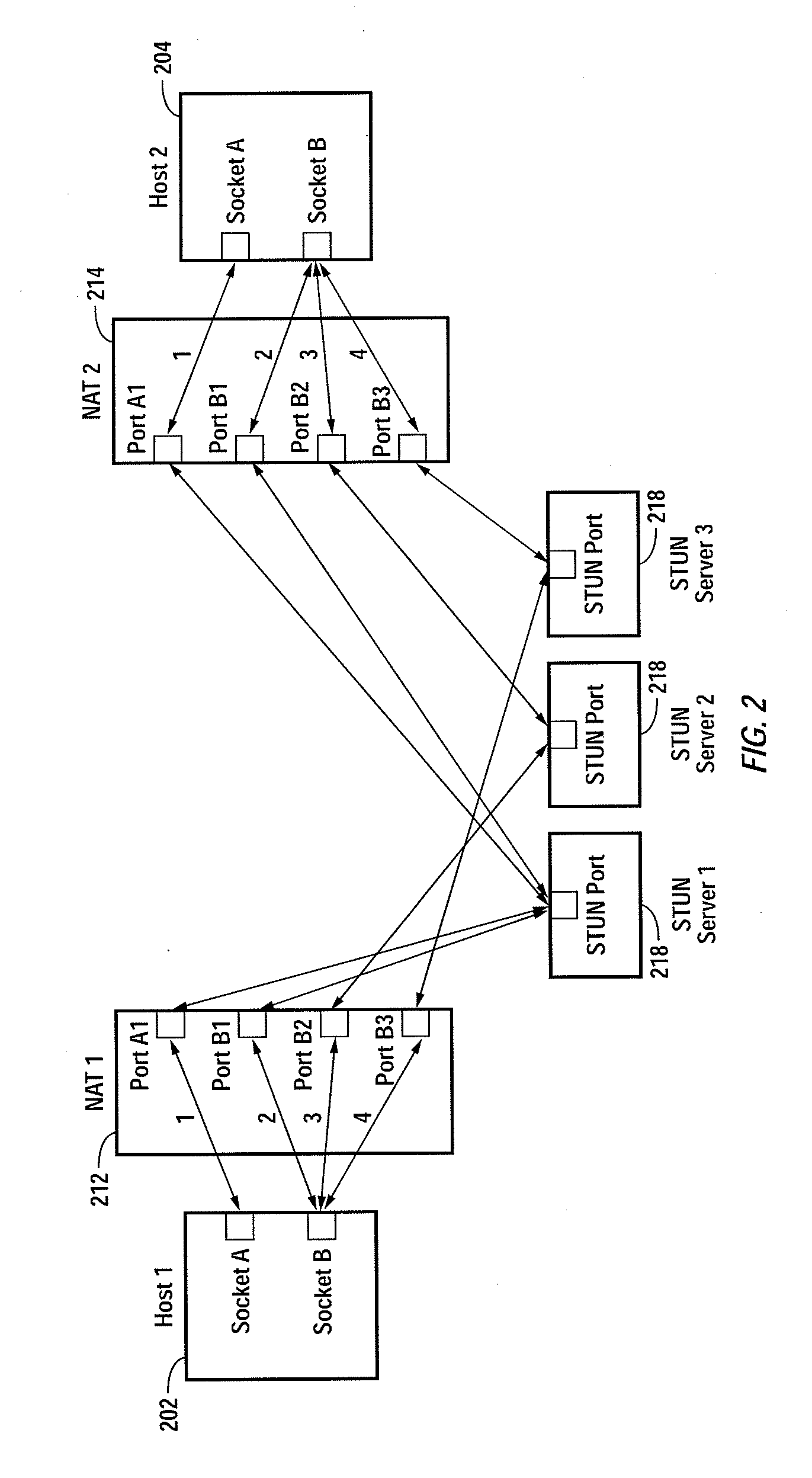
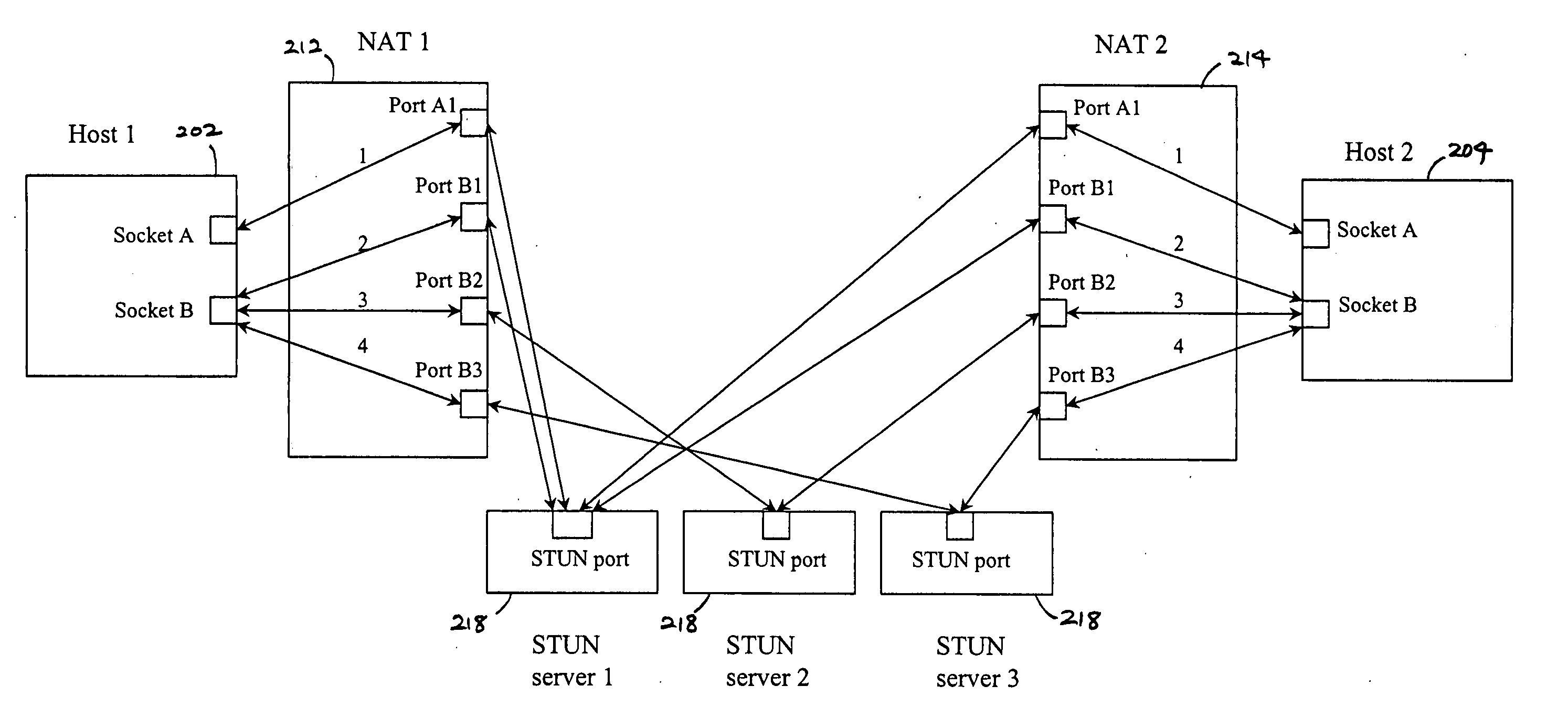
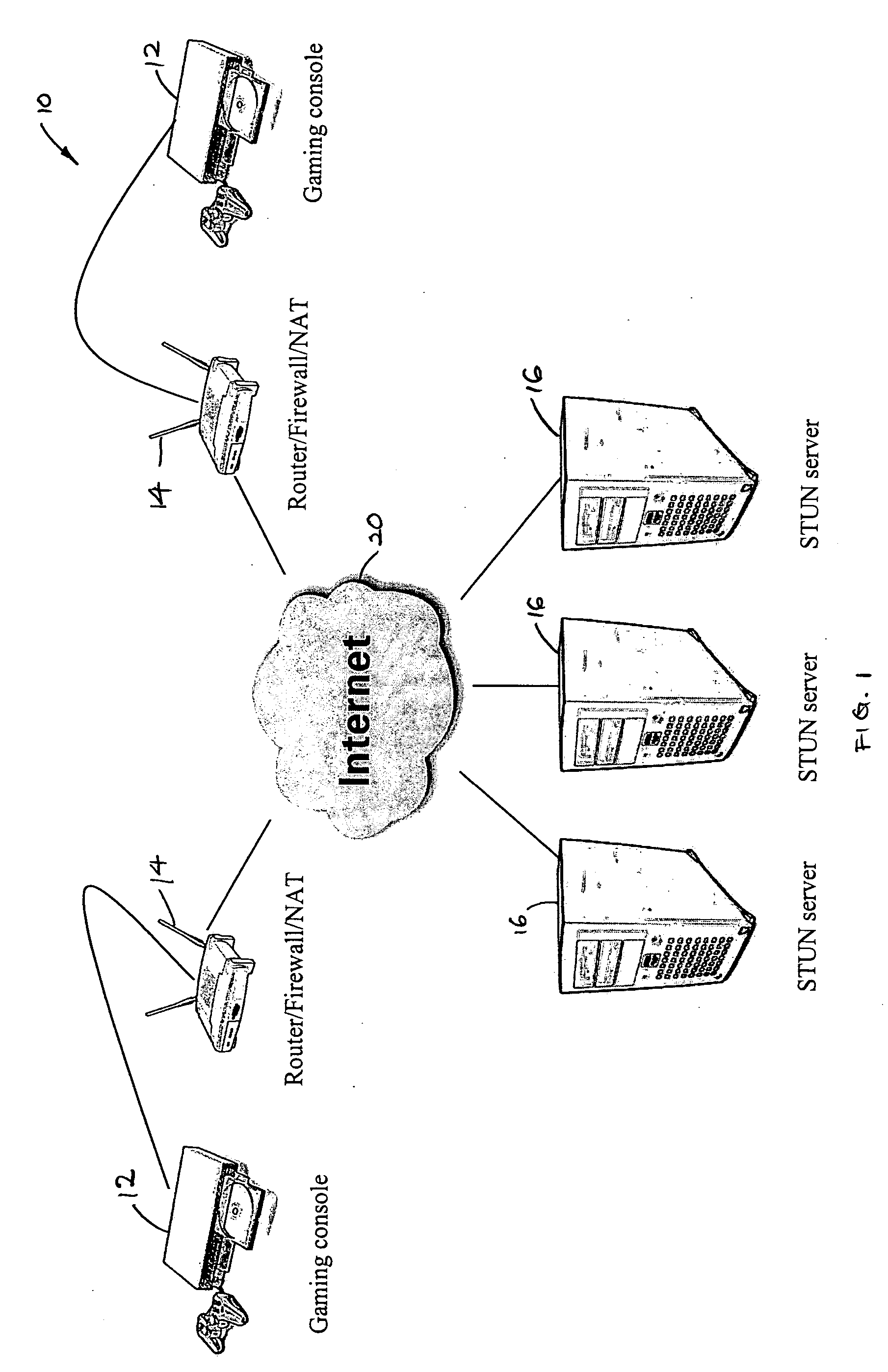
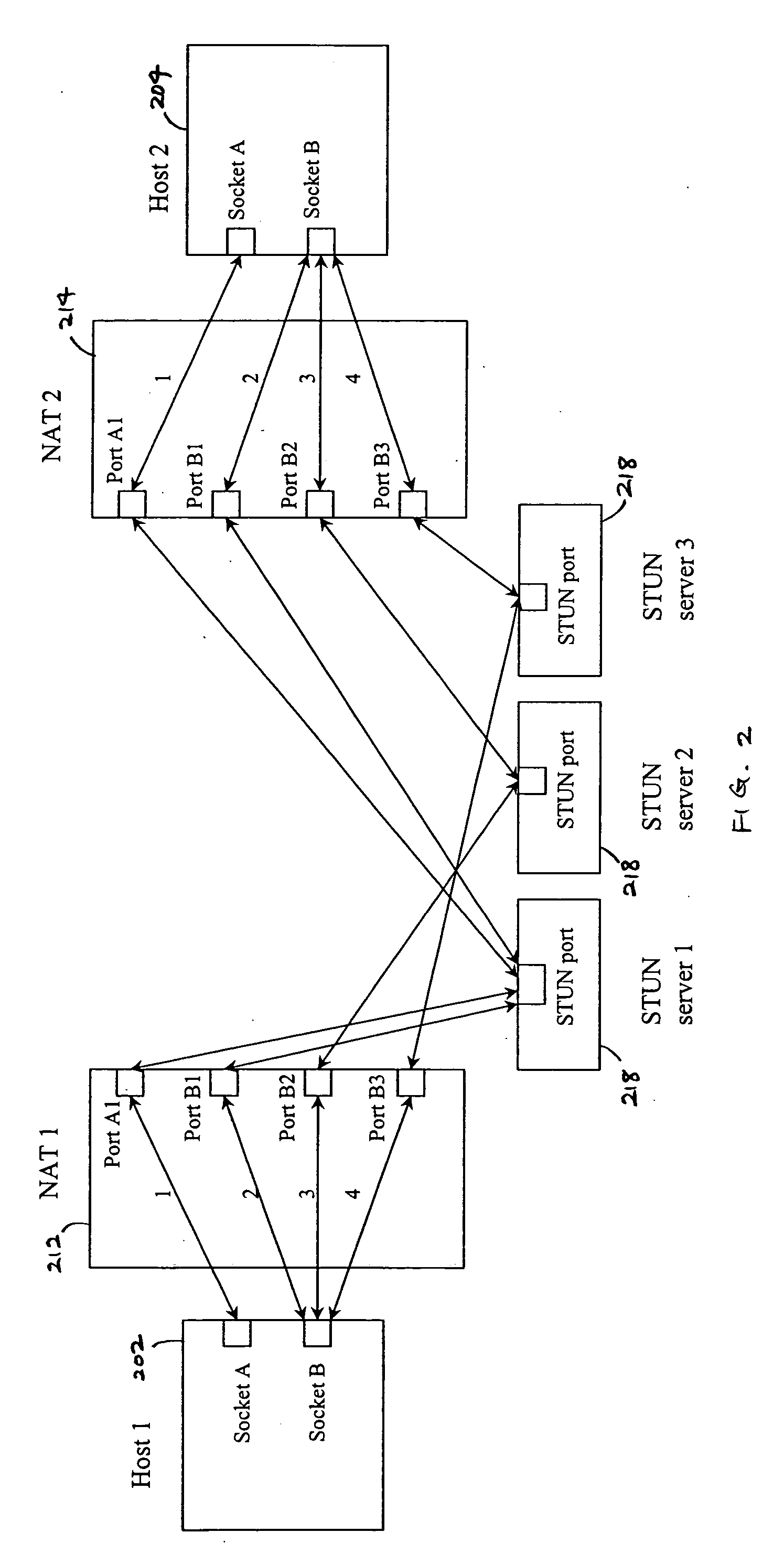
Multiplayer peer-to-peer connection across firewalls and network address translators using a single local port on the local host
Embodiments of the invention achieve a very high success rate in multilayer peer-to-peer connection across firewalls and network address translators (NATs) using a single port on the local host. In one embodiment, a system of providing peer-to-peer connection comprises a plurality of host devices disposed behind corresponding NATs; and a plurality of STUN servers. Each host device includes a first socket bound to a first private port and a second socket bound to a second private port. Each host device sends a first STUN packet through the first socket to a first STUN server and a second group of STUN packets through the second socket to the STUN servers via public ports of the corresponding NAT. The STUN servers identify the public port numbers of the public ports. Each host device is configured to calculate a predicted public port number of the corresponding NAT for the second socket, based on the public port numbers of the public ports for the first socket and the second socket, the predicted public port number to be used for peer-to-peer connection between the second socket of the host device and other host devices.
Owner:LOGITECH EURO SA
Multiplayer Peer-to-Peer Connection Across Firewalls and Network Address Translators Using a Single Local Port on the Local Host
Owner:LOGITECH EURO SA
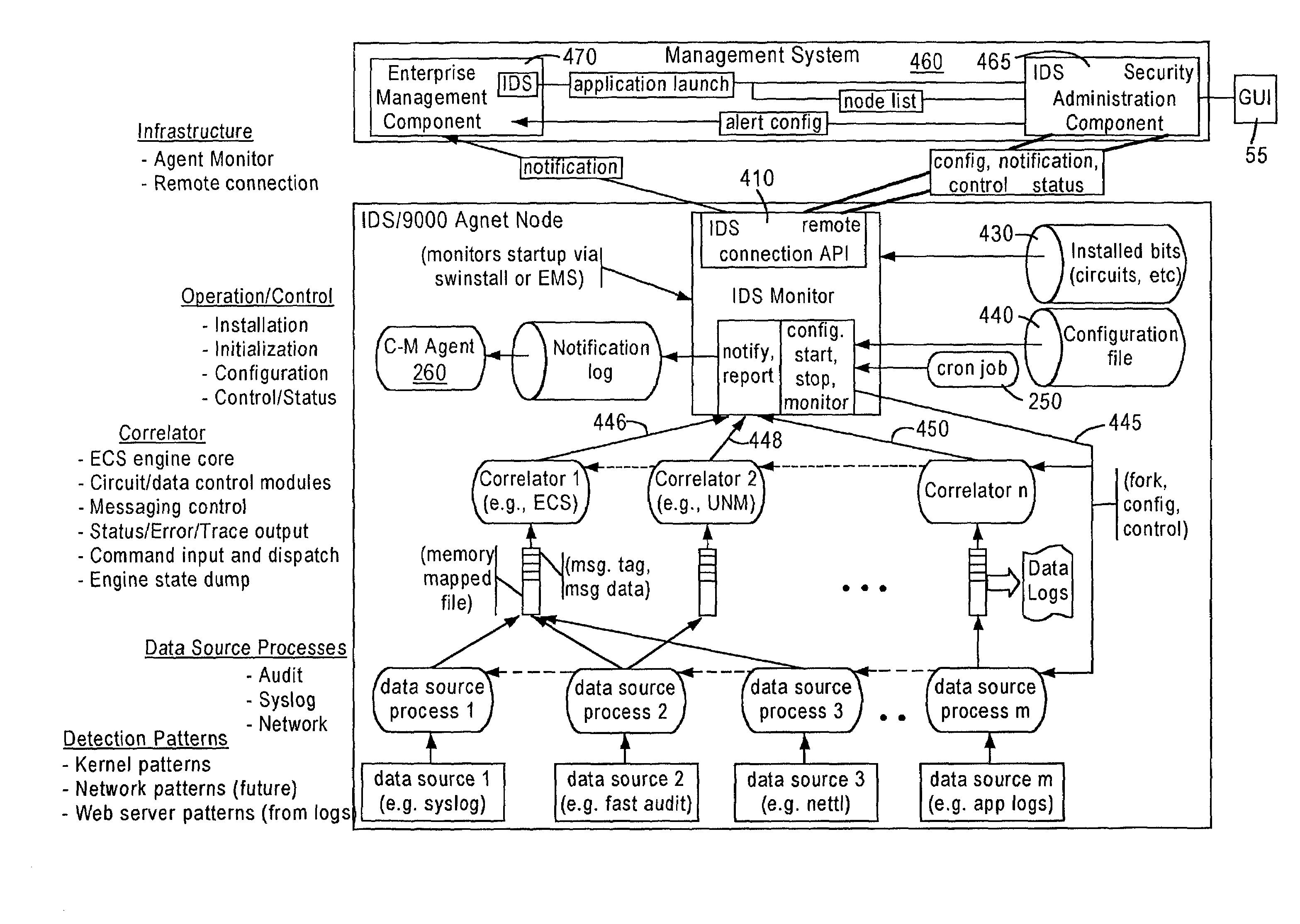
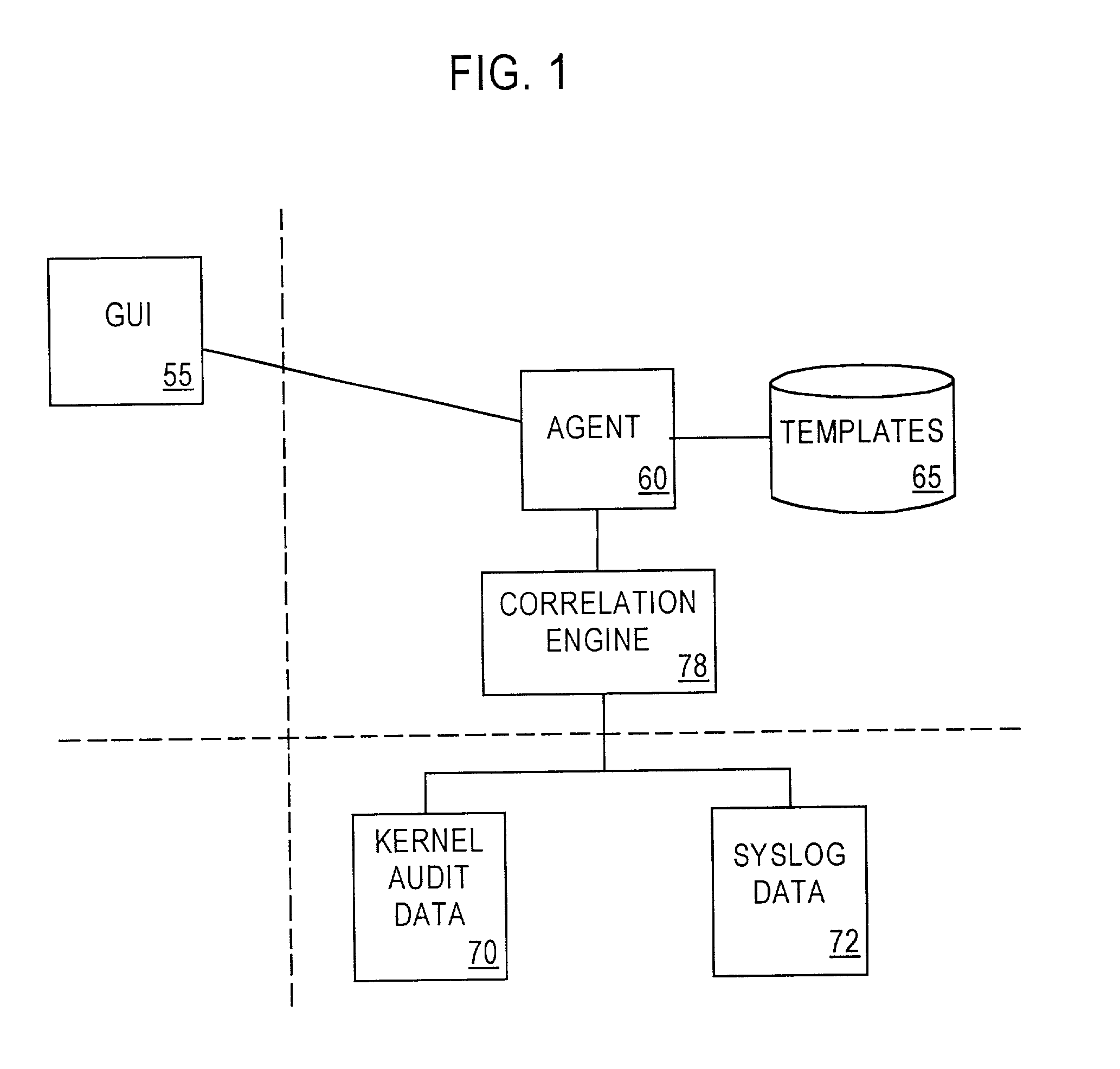
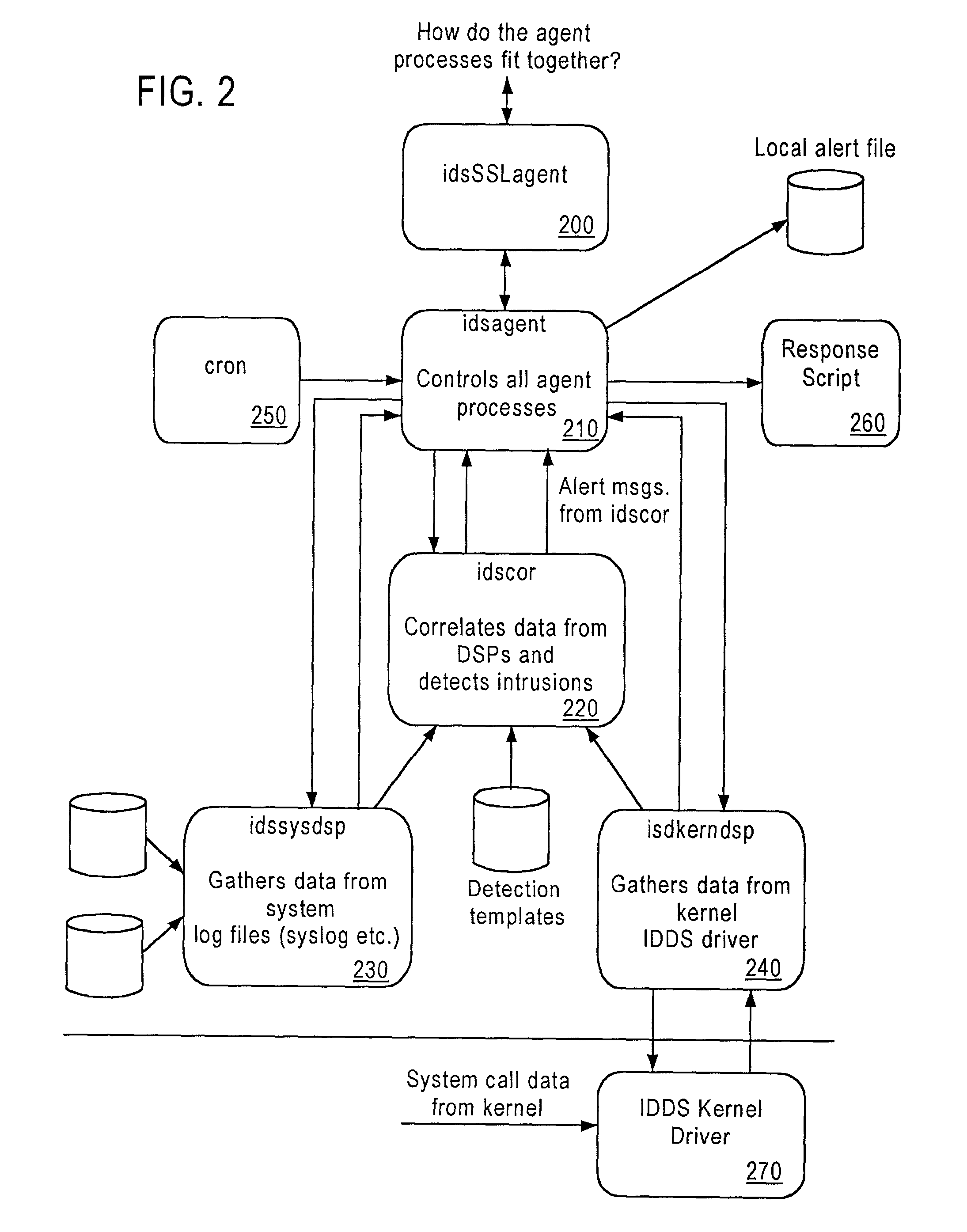
Computer architecture for an intrusion detection system
InactiveUS7007301B2Provide protectionAccurate measurementData processing applicationsMemory loss protectionOperational systemCritical system
The present application is directed to a host-based IDS on an HP-UX intrusion detection system that enhances local host-level security within the network. It should be understood that the present invention is also usable on, for example, Eglinux, solaris, aix windows 2000 operating systems. It does this by automatically monitoring each configured host system within the network for possible signs of unwanted and potentially damaging intrusions. If successful, such intrusions could lead to the loss of availability of key systems or could compromise system integrity.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Multiplayer peer-to-peer connection across firewalls and network address translators using a single local port on the local host
Embodiments of the invention achieve a very high success rate in multilayer peer-to-peer connection across firewalls and network address translators (NATs) using a single port on the local host. In one embodiment, a system of providing peer-to-peer connection comprises a plurality of host devices disposed behind corresponding NATs; and a plurality of STUN servers. Each host device includes a first socket bound to a first private port and a second socket bound to a second private port. Each host device sends a first STUN packet through the first socket to a first STUN server and a second group of STUN packets through the second socket to the STUN servers via public ports of the corresponding NAT. The STUN servers identify the public port numbers of the public ports. Each host device is configured to calculate a predicted public port number of the corresponding NAT for the second socket, based on the public port numbers of the public ports for the first socket and the second socket, the predicted public port number to be used for peer-to-peer connection between the second socket of the host device and other host devices.
Owner:LOGITECH EURO SA
Parallel I/O network file server architecture
InactiveUS20020083111A1Digital data information retrievalMultiple digital computer combinationsMass storageVirtual file system
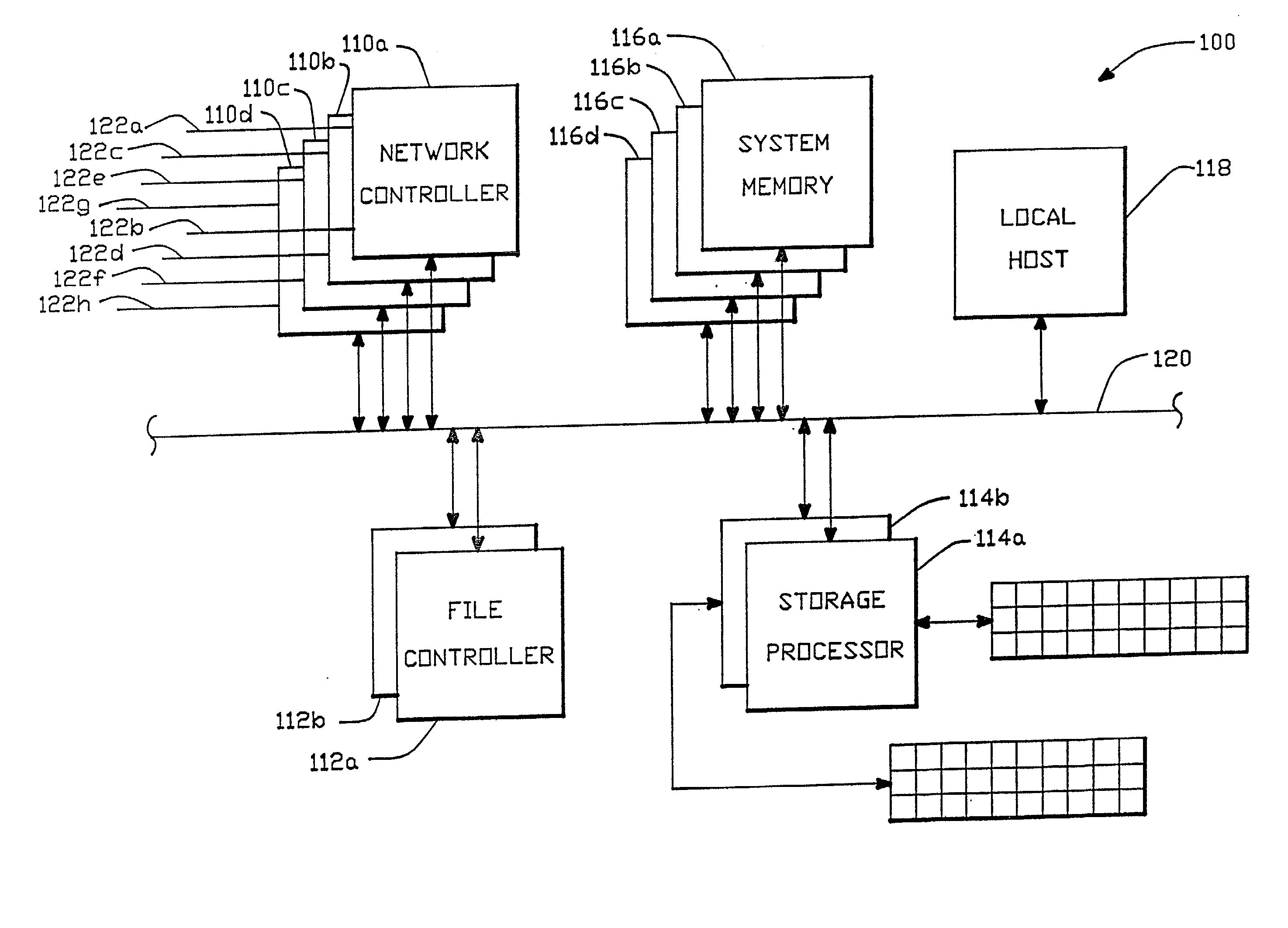
A file server architecture is disclosed, comprising as separate processors, a network controller unit, a file controller unit and a storage processor unit. These units incorporate their own processors, and operate in parallel with a local Unix host processor. All networks are connected to the network controller unit, which performs all protocol processing up through the NFS layer. The virtual file system is implemented in the file control unit, and the storage processor provides high-speed multiplexed access to an array of mass storage devices. The file controller unit control file information caching through its own local cache buffer, and controls disk data caching through a large system memory which is accessible on a bus by any of the processors.
Owner:AUSPEX SYST
Routing device
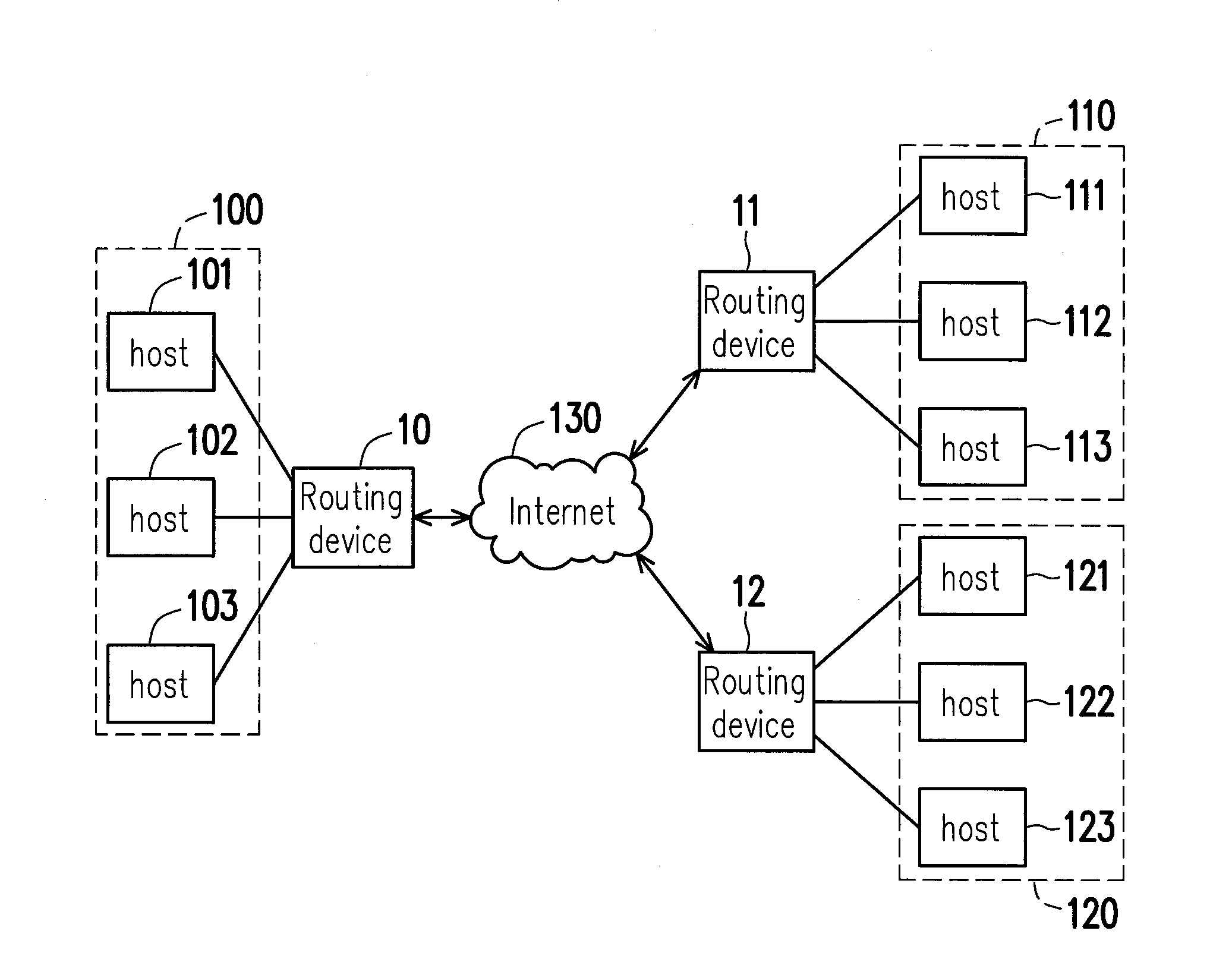
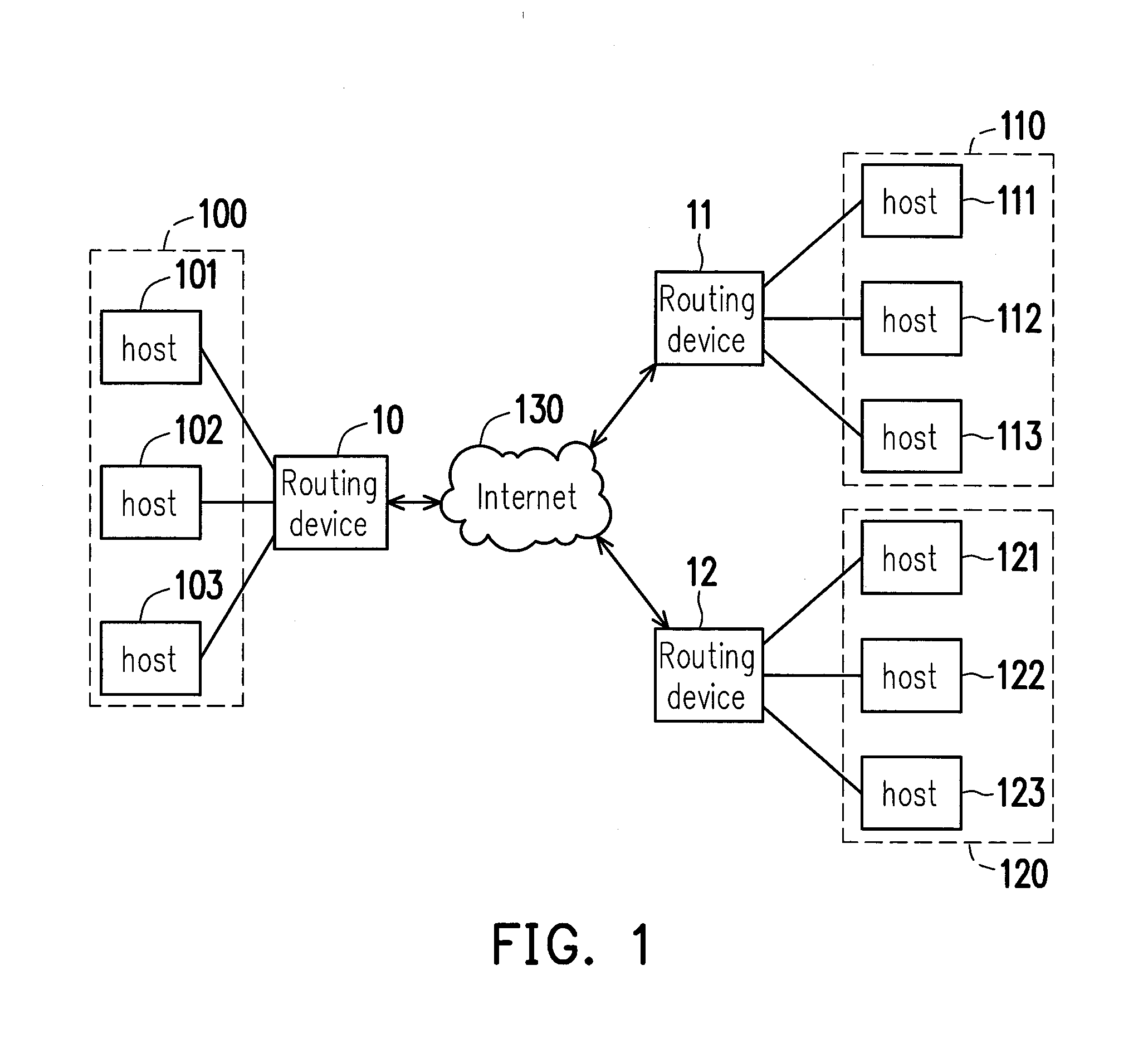
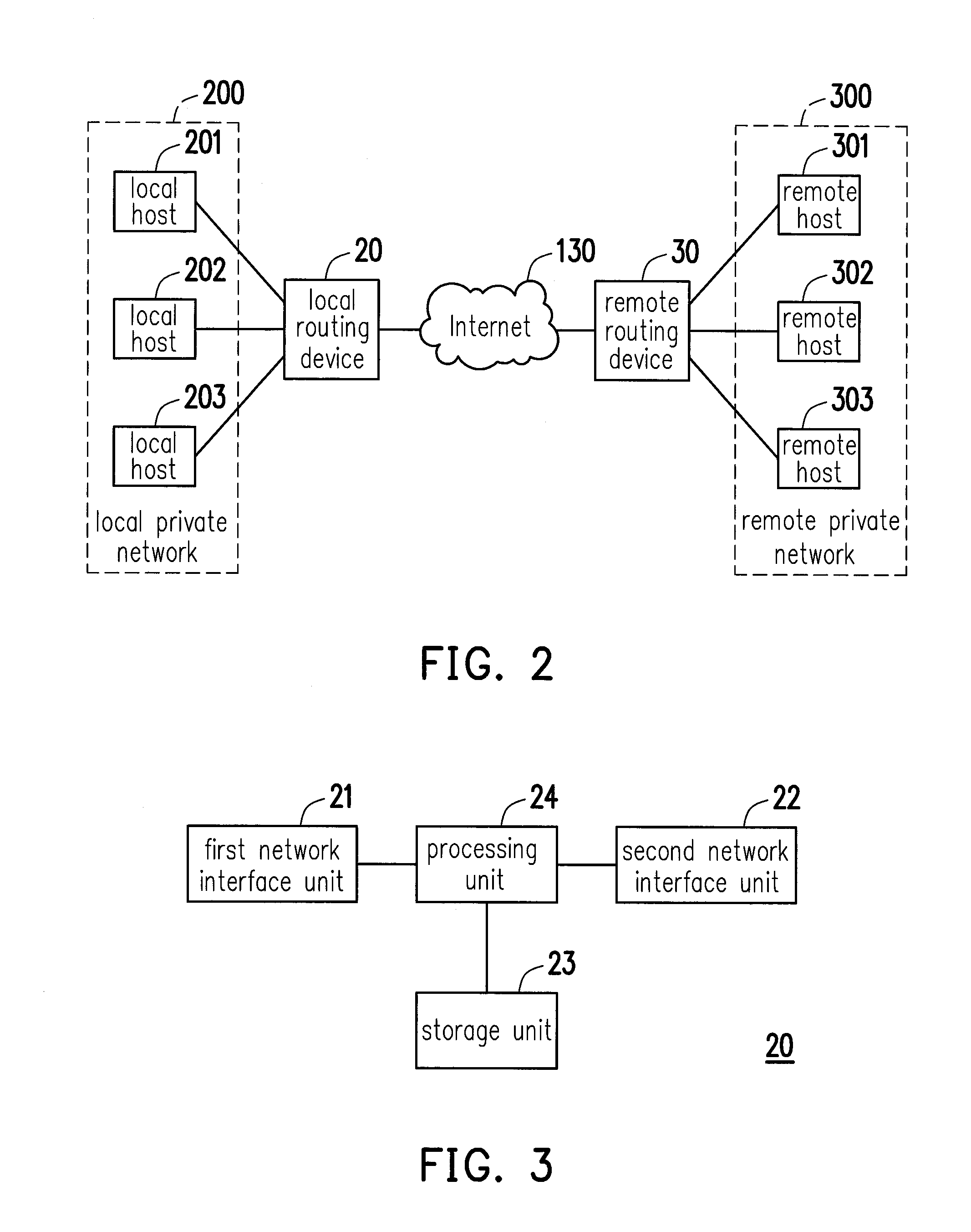
A routing device is provided, the routing device includes a first network interface unit, a second network interface unit and a processing unit. The first network interface unit connects the routing device to a local private network. The second network interface unit connects the routing device to the Internet. The processing unit assigns a virtual subnet to a remote routing device for a remote host in a remote private network to obtain a virtual Internet protocol (IP) address according to the virtual subnet. The processing unit receives a network packet from a local host in the local private network through the first network interface unit, and encapsulates the network packet according to a public IP address of the remote routing device to generate an alternative packet. Then, the processing unit delivers the alternative packet to the Internet through the second network interface unit.
Owner:GEMTEK TECH CO LTD
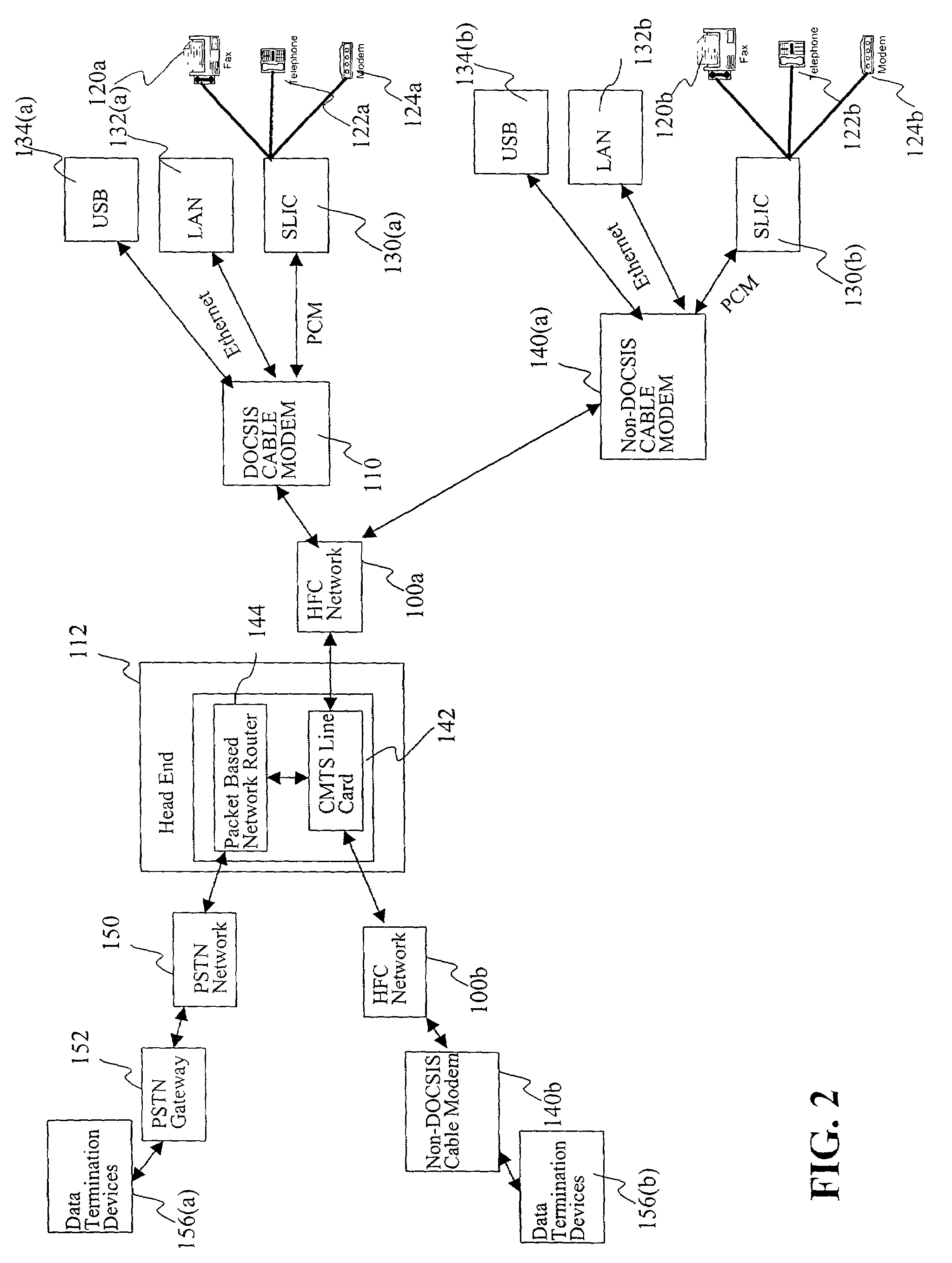
Method for opening a proprietary MAC protocol in a non-DOCSIS modem compatibly with a DOCSIS modem
InactiveUS7164690B2Broadband local area networksTime-division multiplexCommunications systemProtocol processing
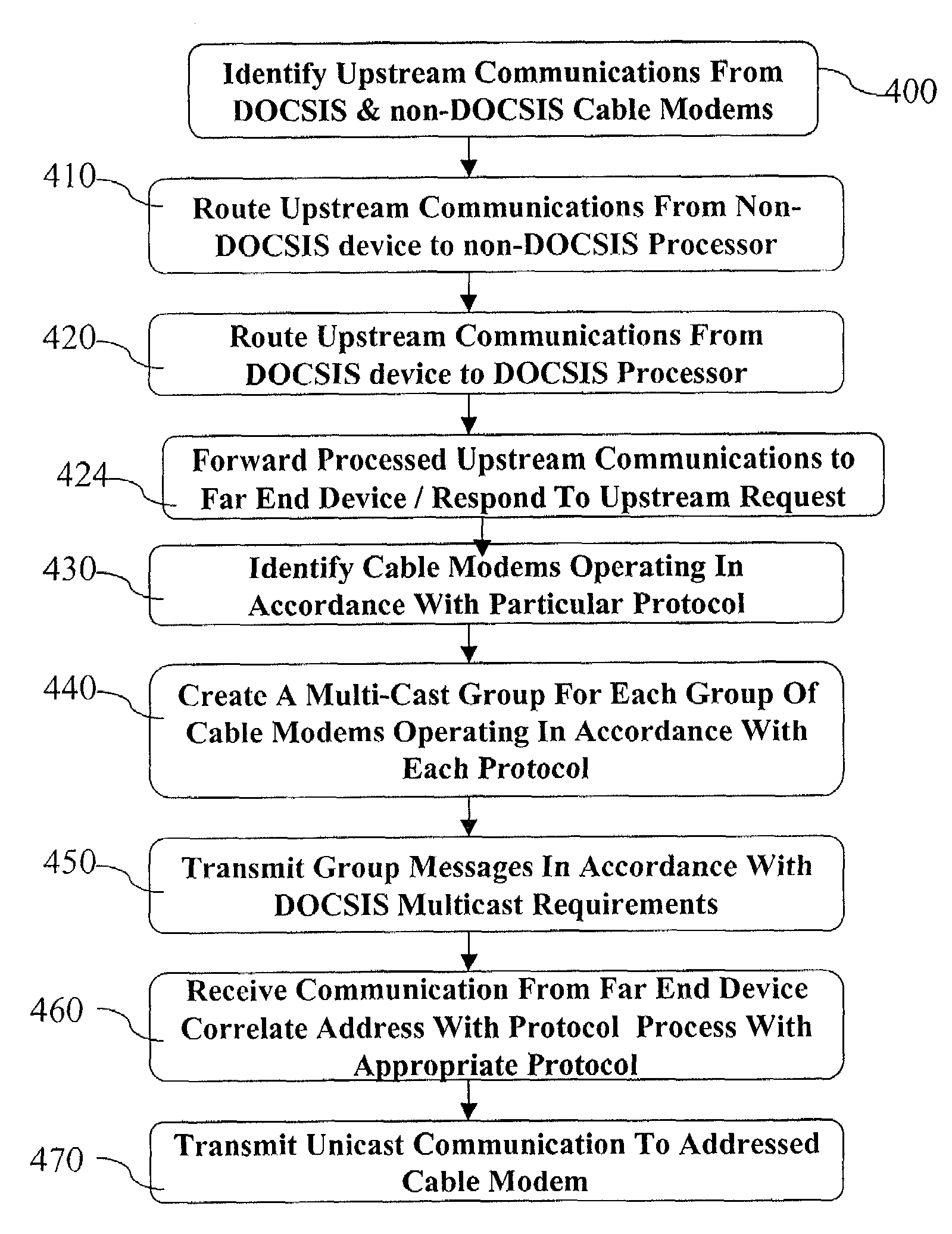
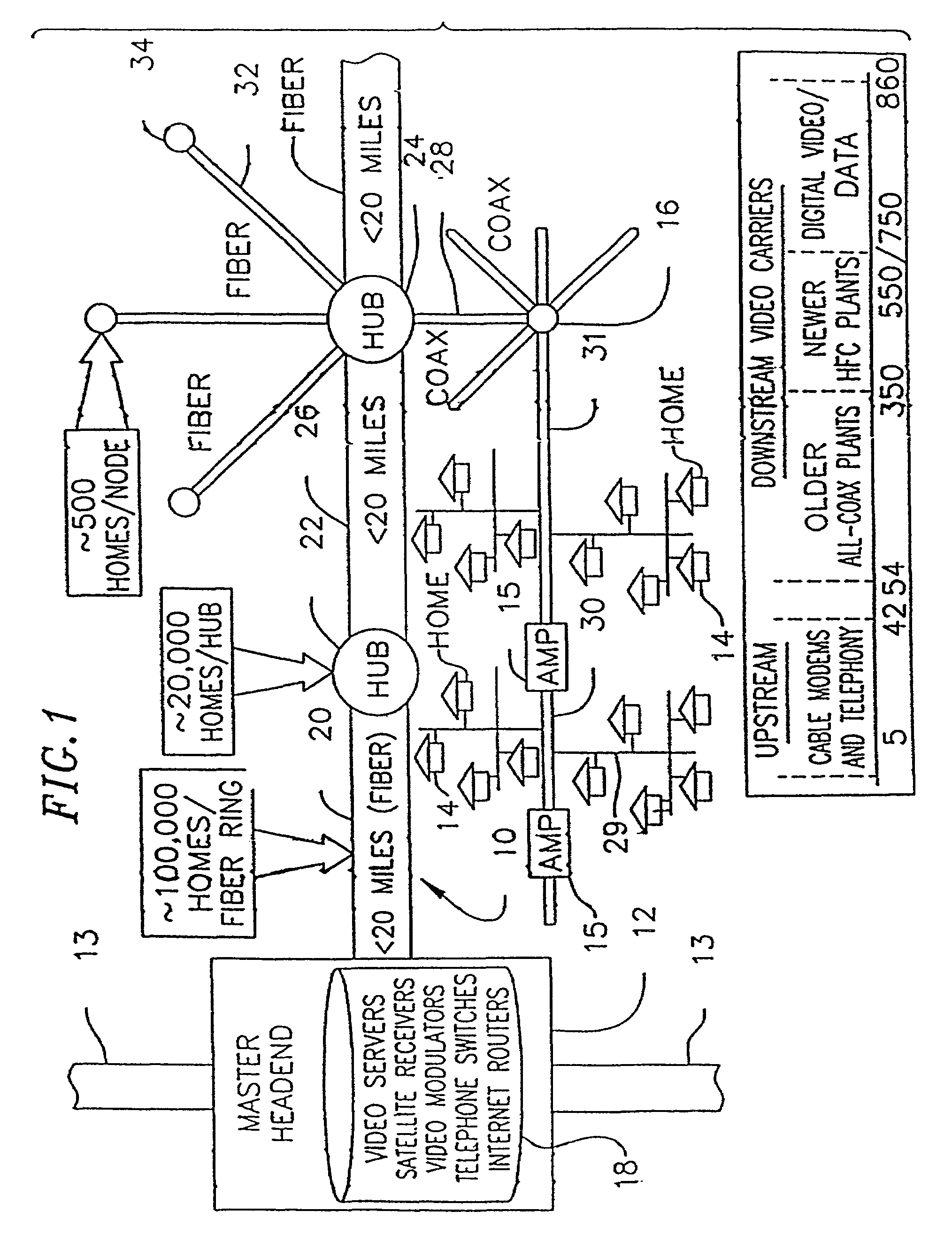
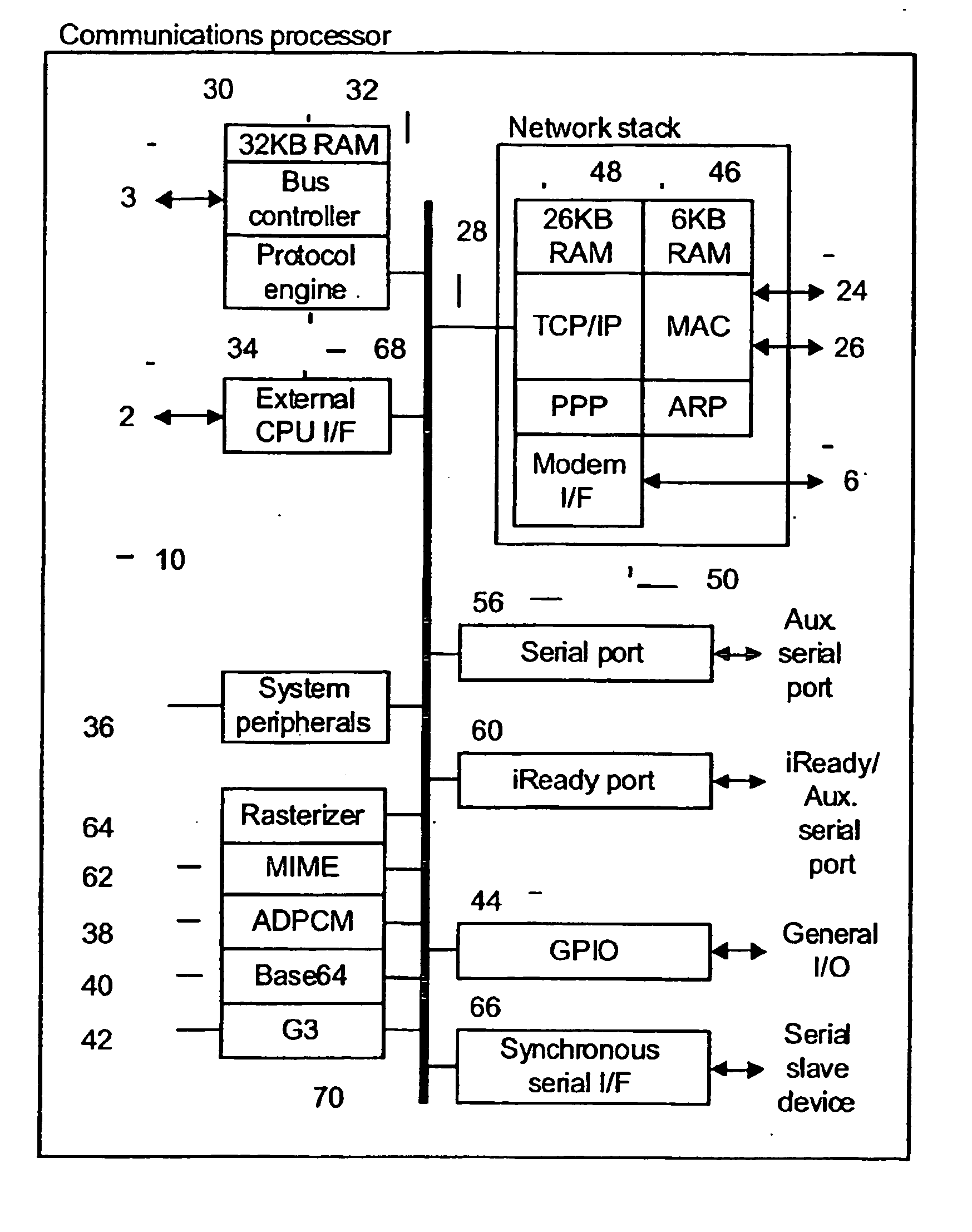
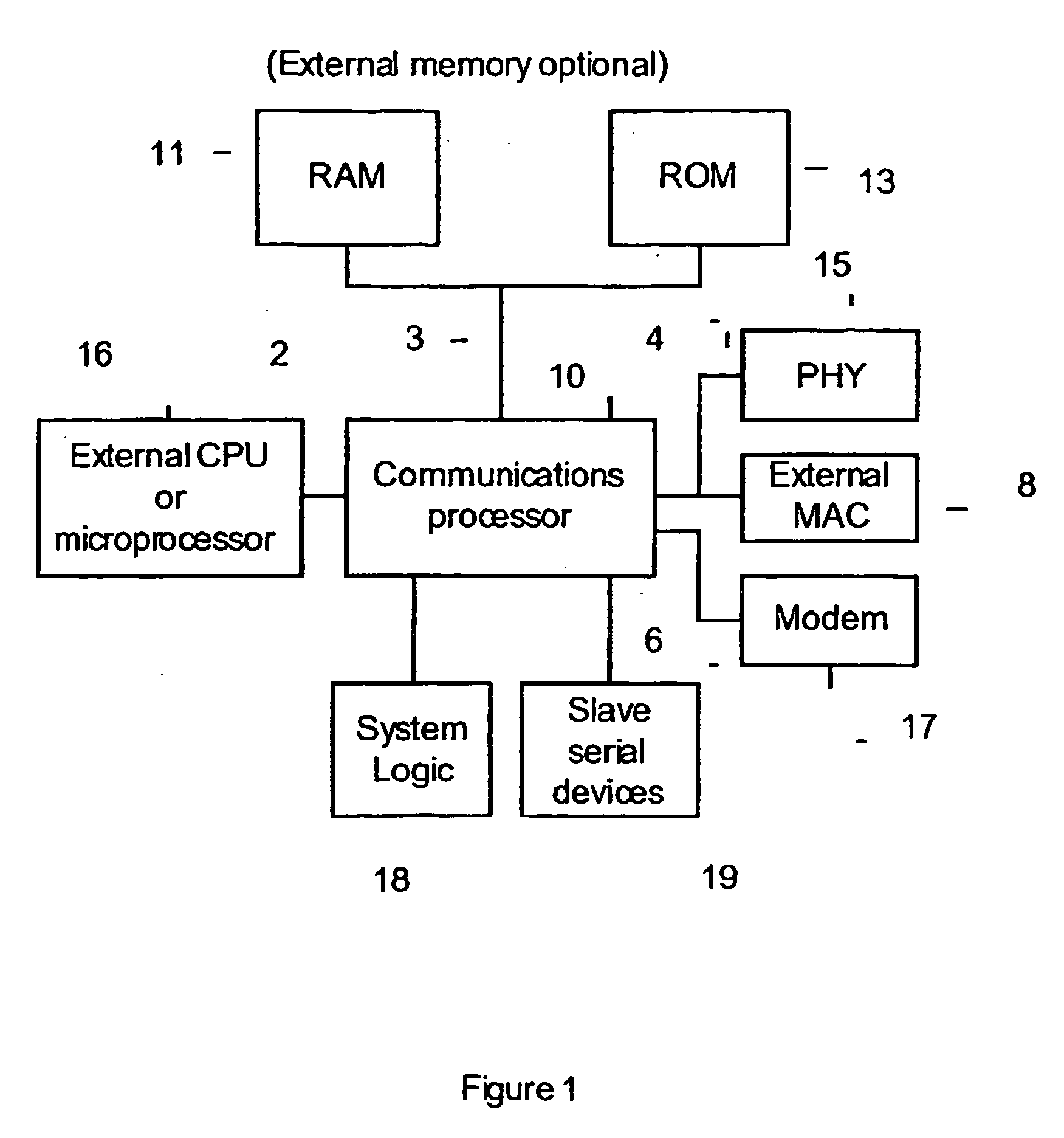
A two way communication system is adapted for compatible inter-operation of a plurality of devices operating in accordance with a plurality of protocols. The communication system includes a first group of one or more remote devices that interface with a local host in accordance with a first protocol and a second group of one or more remote devices that interface wit the local host in accordance with a second protocol. The local host includes a protocol processor that identifies transmissions from the first and second groups of remote devices and routes transmissions from the first group of remote devices to a first processor operating in accordance with the first protocol and also routes transmissions from the second group of remote devices to a second processor operating in accordance with the second protocol.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
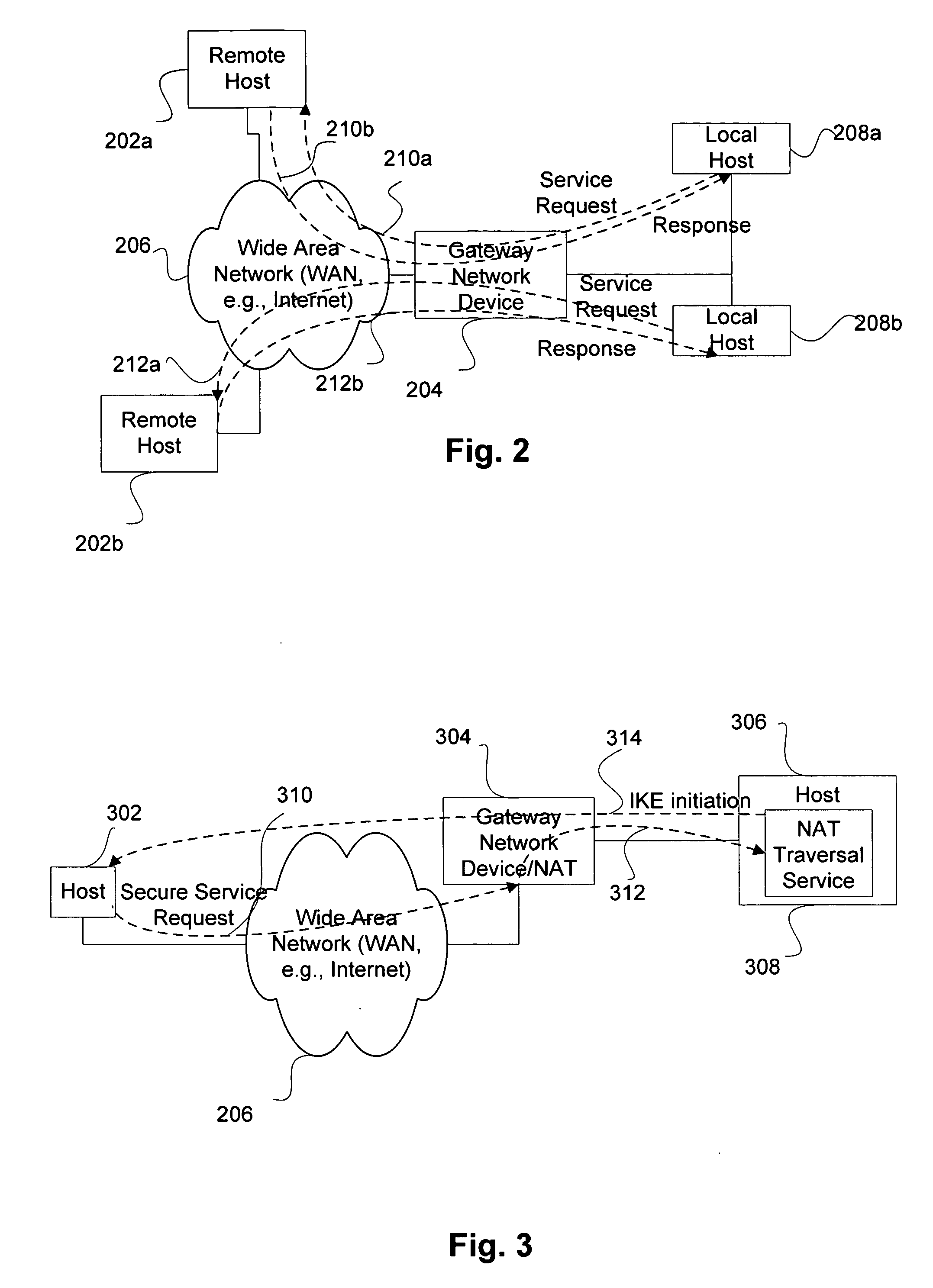
Service for NAT traversal using IPSEC
Disclosed are methods and apparatus for methods and apparatus for facilitating a secure connection between a first and a second node in a computer network where one or both of the nodes may or may not reside behind a network address translation (NAT) enabled gateway. Embodiments of the present invention provide a seamless integration by providing a uniform solution for establishing secure connections, such as IPSEC, between two nodes irrespective of whether they are behind a NAT-enabled gateway or not. In general, a gateway is operable to receive a request from a remote host for a secure connection to a local host that within the home network of the gateway. The gateway then forwards this received request to a NAT traversal service. The NAT traversal service receives the request and then automatically sends an initiation message to set up a secure session, e.g., performing authentication and exchanging keys. In a specific aspect, the setup data utilizes an IKE (Internet Key Exchange) initiation message that is sent to the originator of the request via the gateway. Upon receipt of this initiation message, the gateway is then able to set up a two way connection to allow other setup data to flow between the remote and local hosts to complete the setup session and then secure data to flow between the remote and local hosts in a secure communication session, such as in IPSec or VPN session.
Owner:CISCO TECH INC
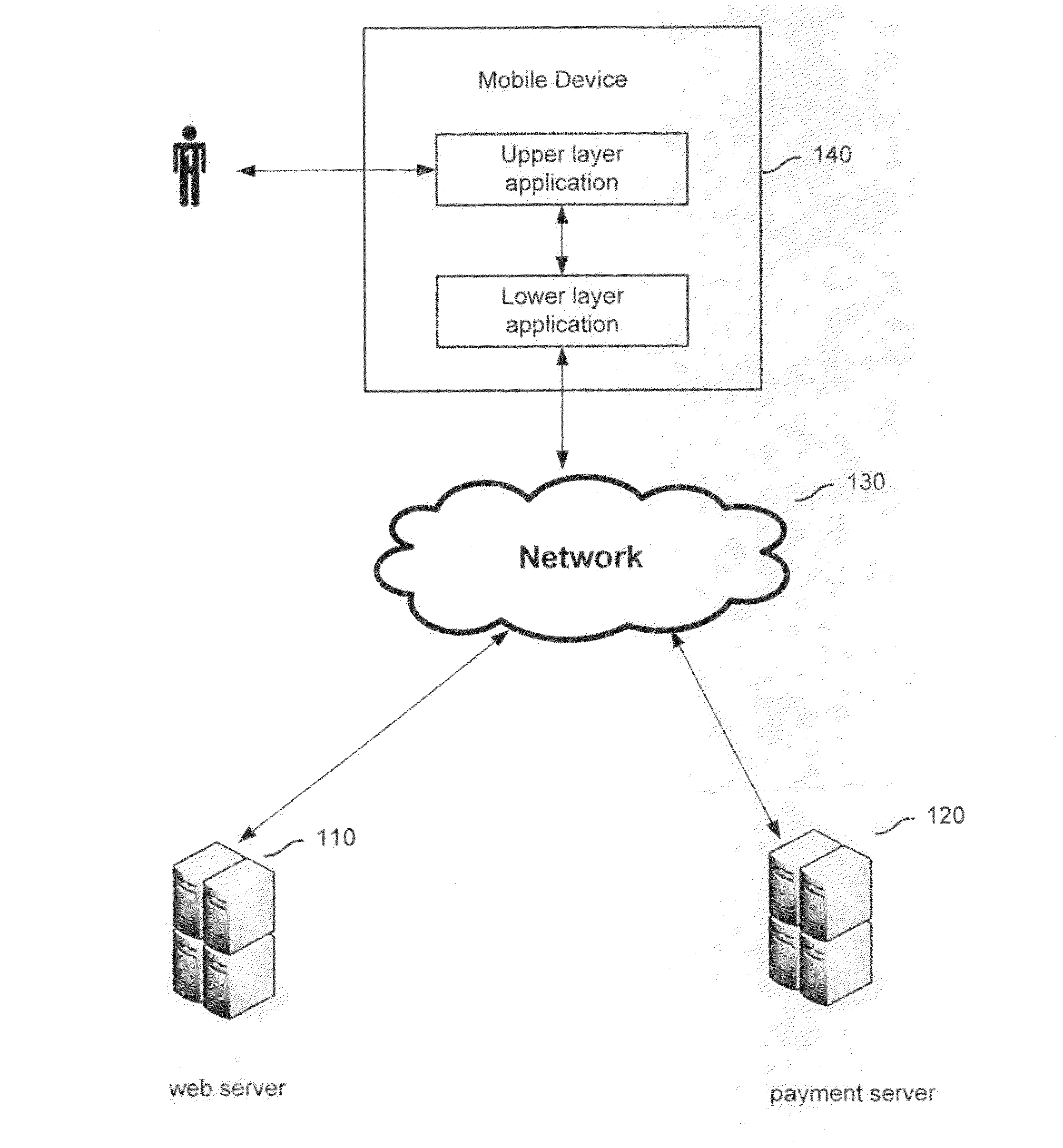
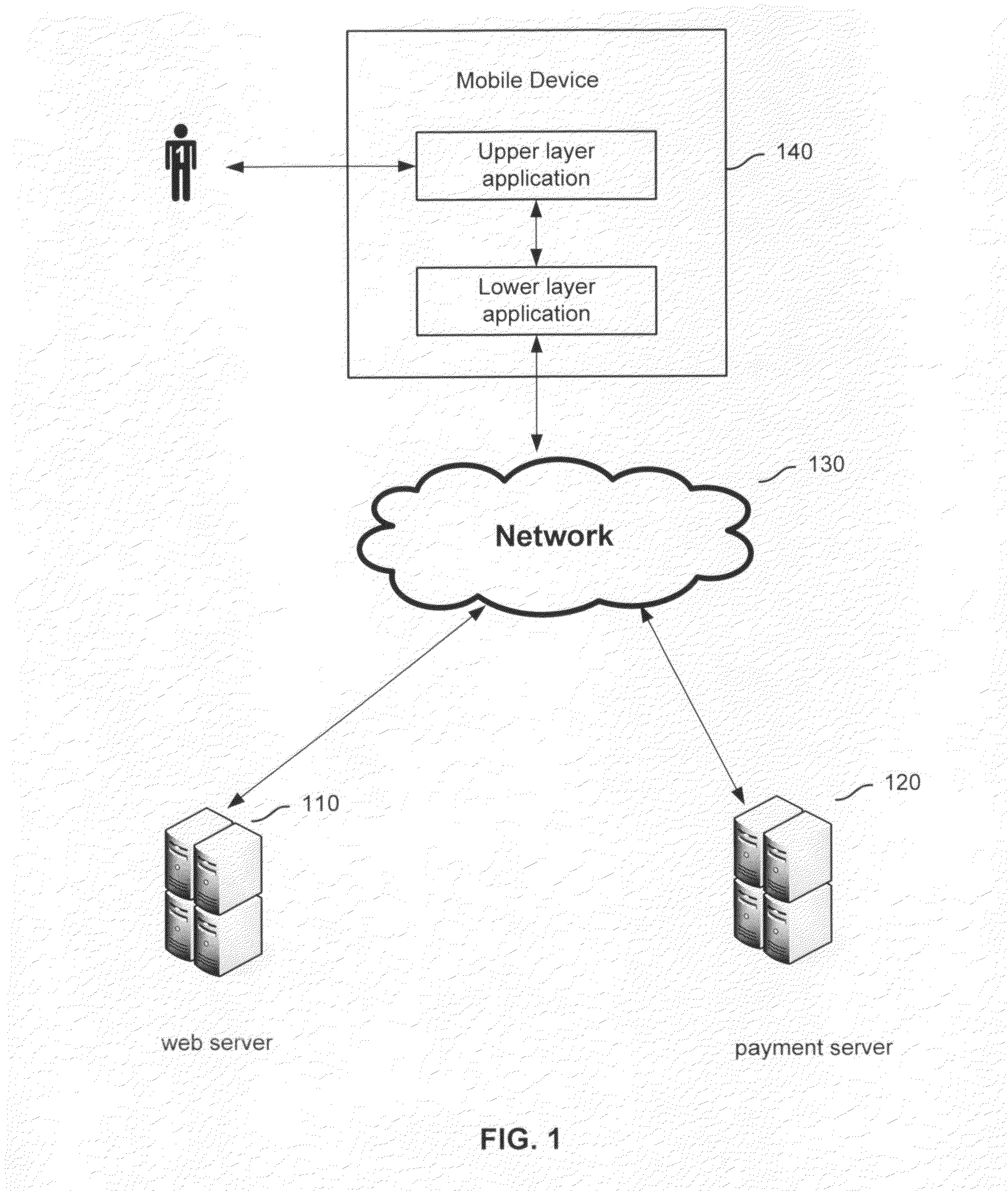
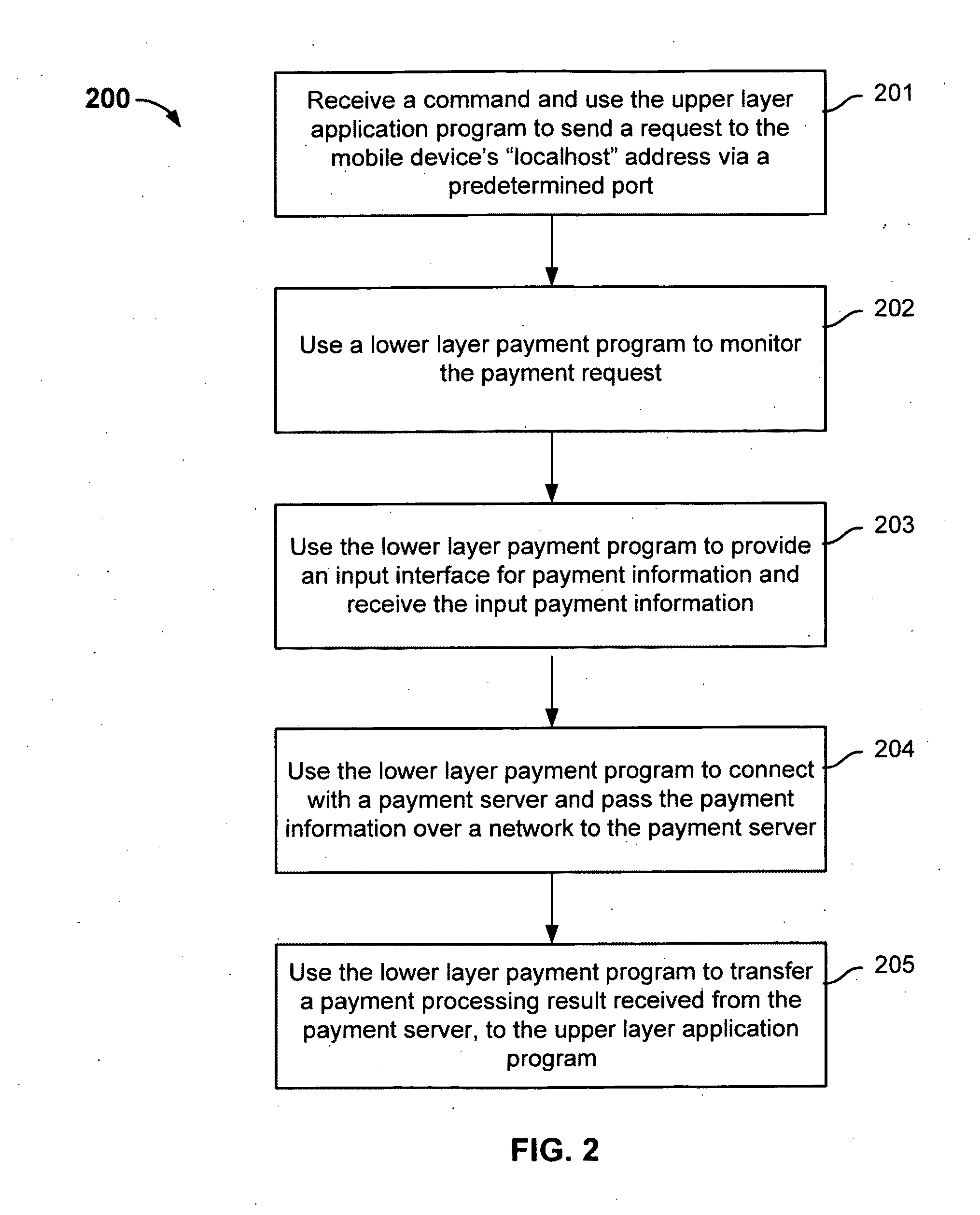
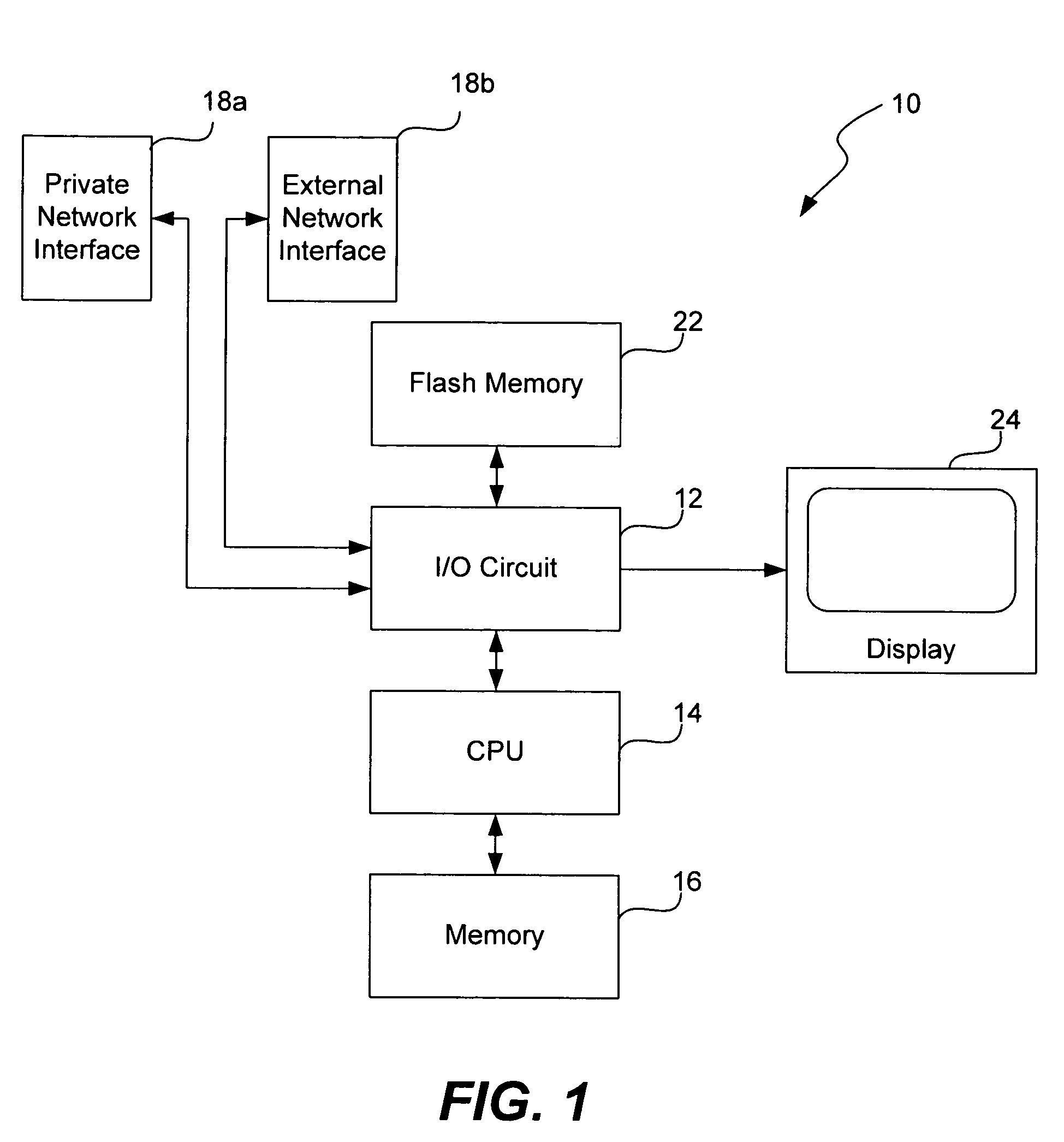
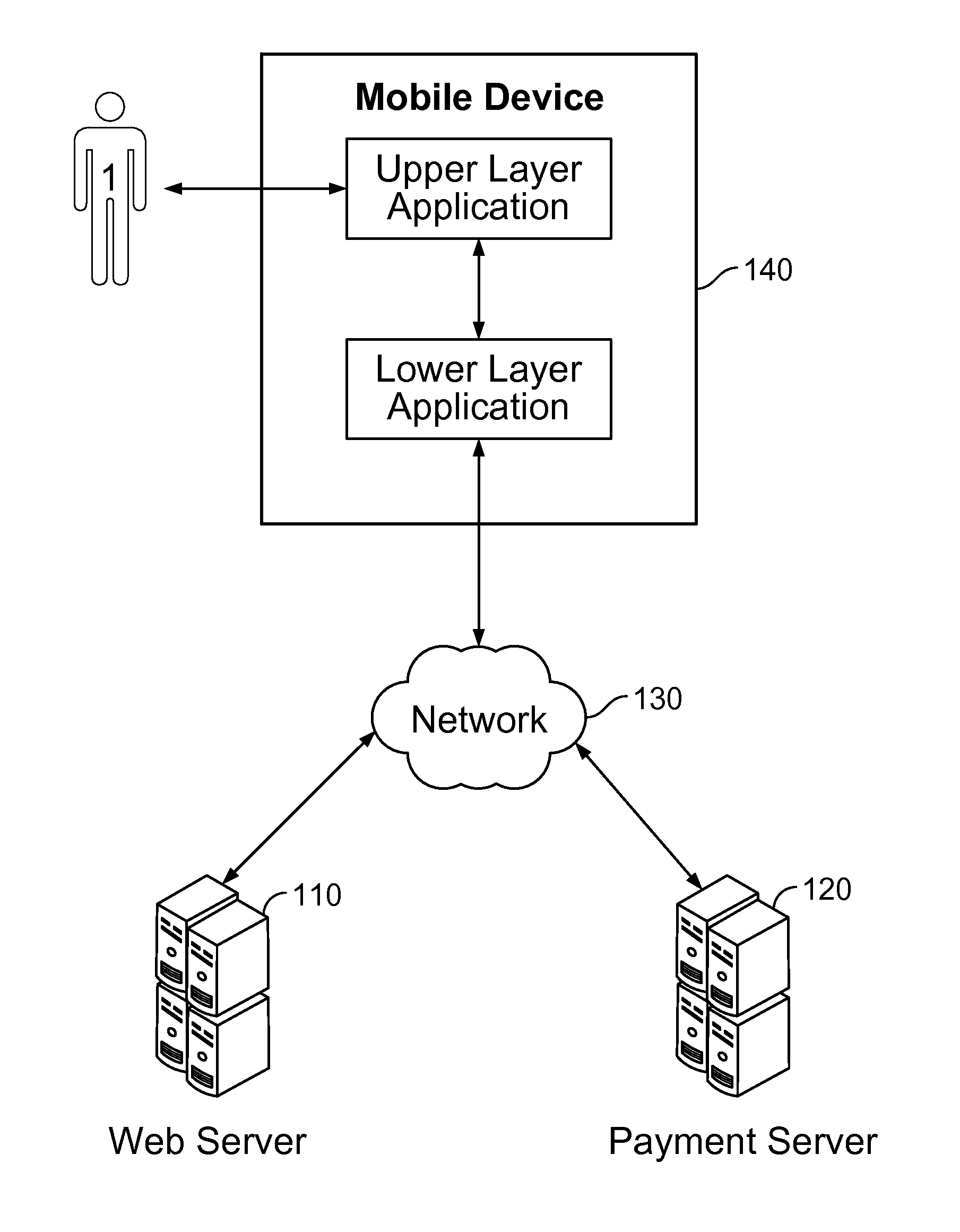
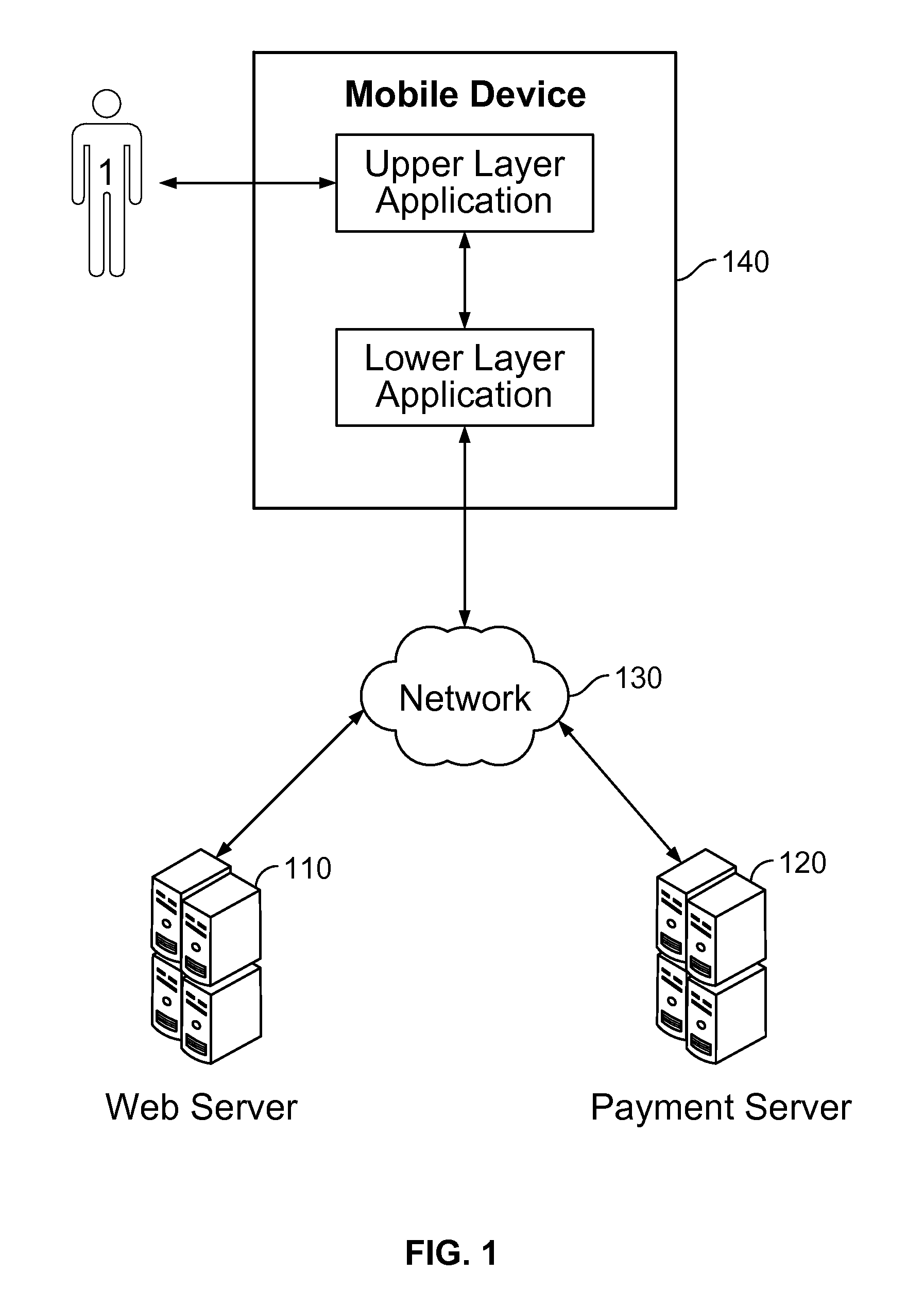
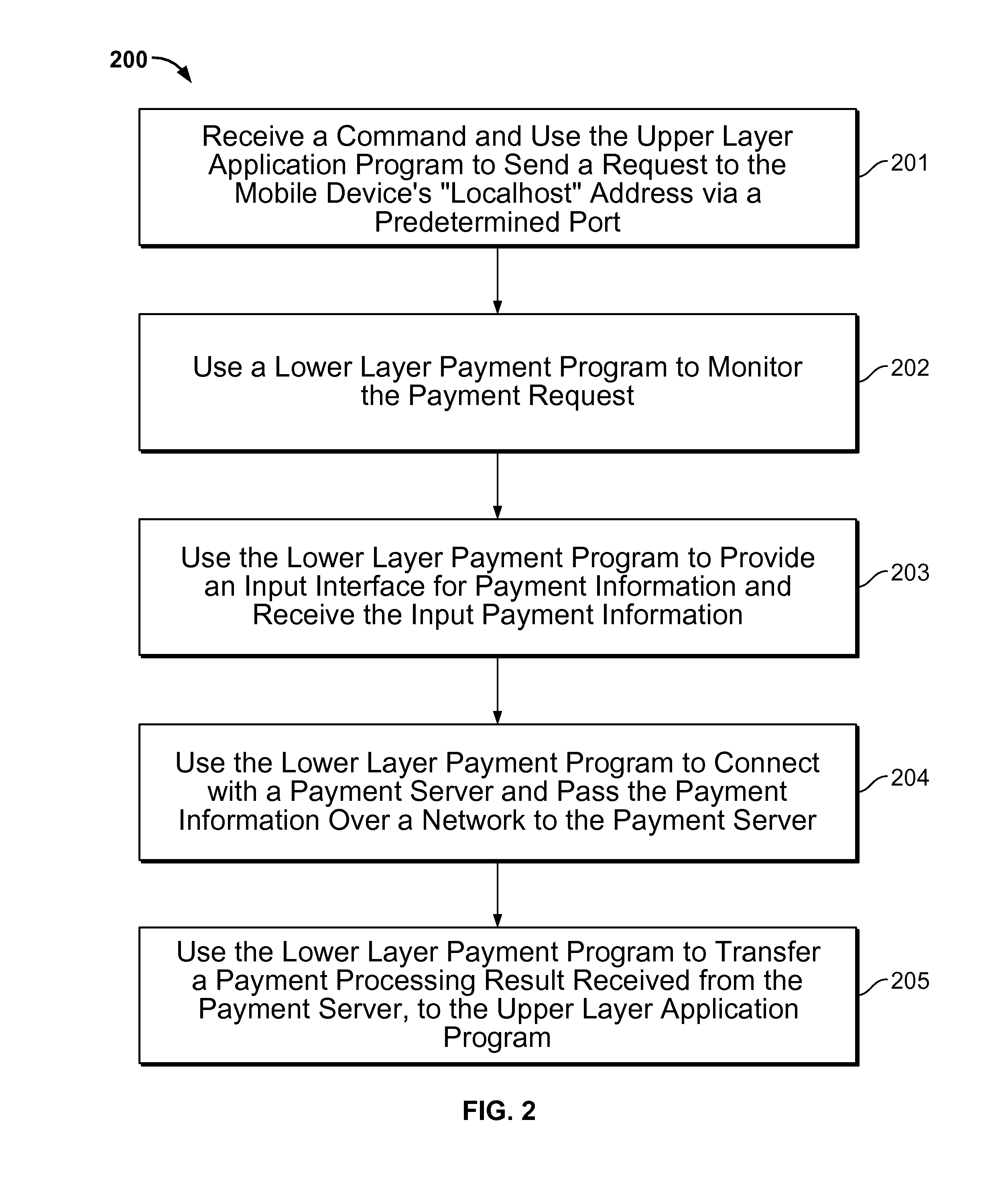
Method and system for payment through mobile devices
Processing payment through a mobile device includes: receiving a command; using an upper layer application program on the mobile device to generate a payment request based on the command and send the payment request to localhost address of the mobile device via a predetermined port; using a lower layer payment program on the mobile device to monitor the payment request sent from the localhost address of the mobile device via the predetermined port; in response to the payment request, using the lower layer payment program to provide an input interface for payment information in and receive the input payment information; using the lower layer payment program to connect with a payment server and pass the payment information over a network to the payment server; and using the lower layer payment program to transfer a payment processing result received from the payment server, to the upper layer application program.
Owner:ADVANCED NEW TECH CO LTD
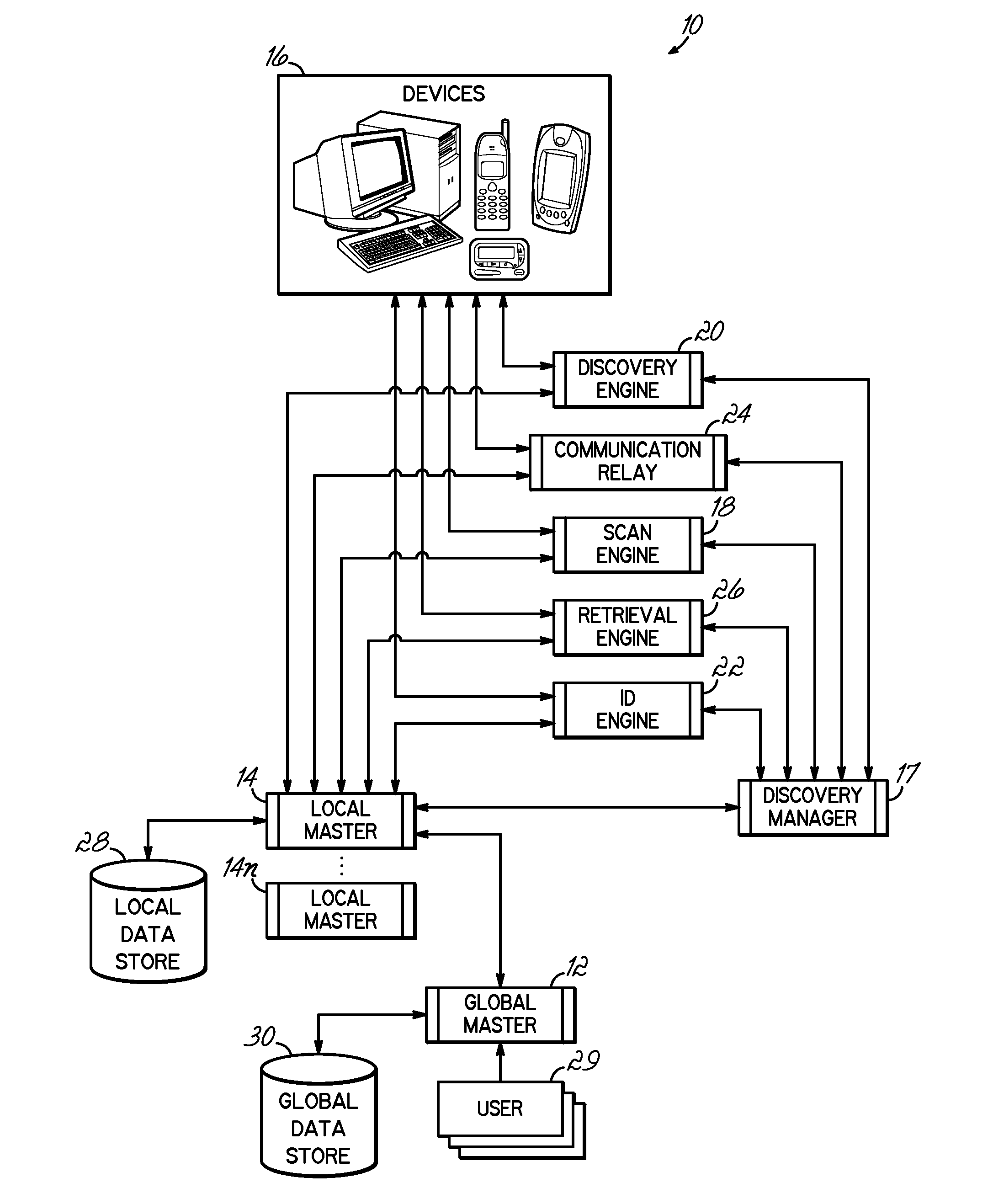
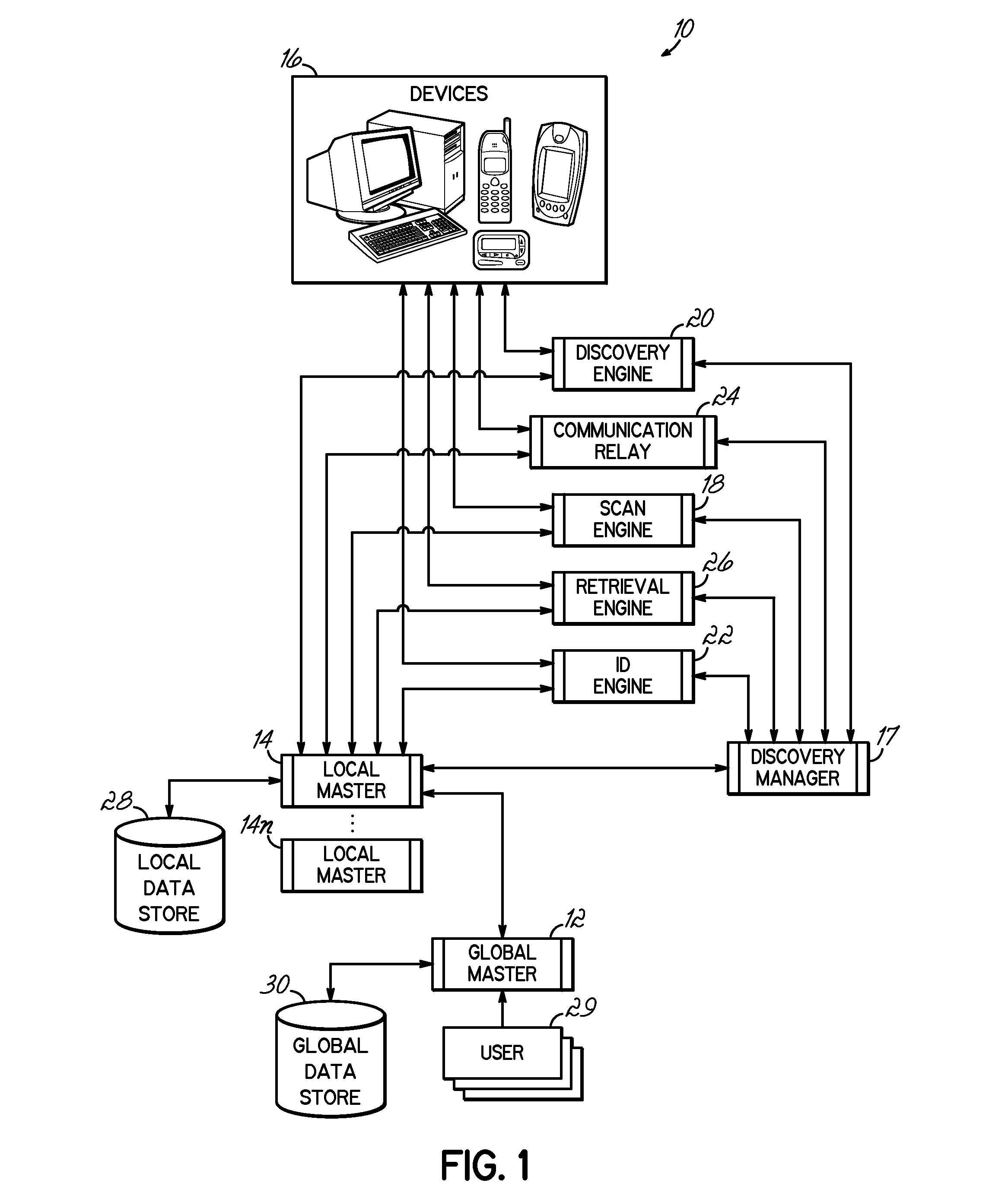
Network device inventory system
ActiveUS20080049644A1Improve system integrityQuick updateError preventionTransmission systemsLocalhostReal-time computing
A network device identification process and system where a centralized global master is coupled to multiple local masters that locally retain a portion of the data from the global master, and that coordinate the dynamic performance of discovery and identification processes within the domains assigned to those local masters. The processes identify and validate devices on the network.
Owner:WALMART APOLLO LLC
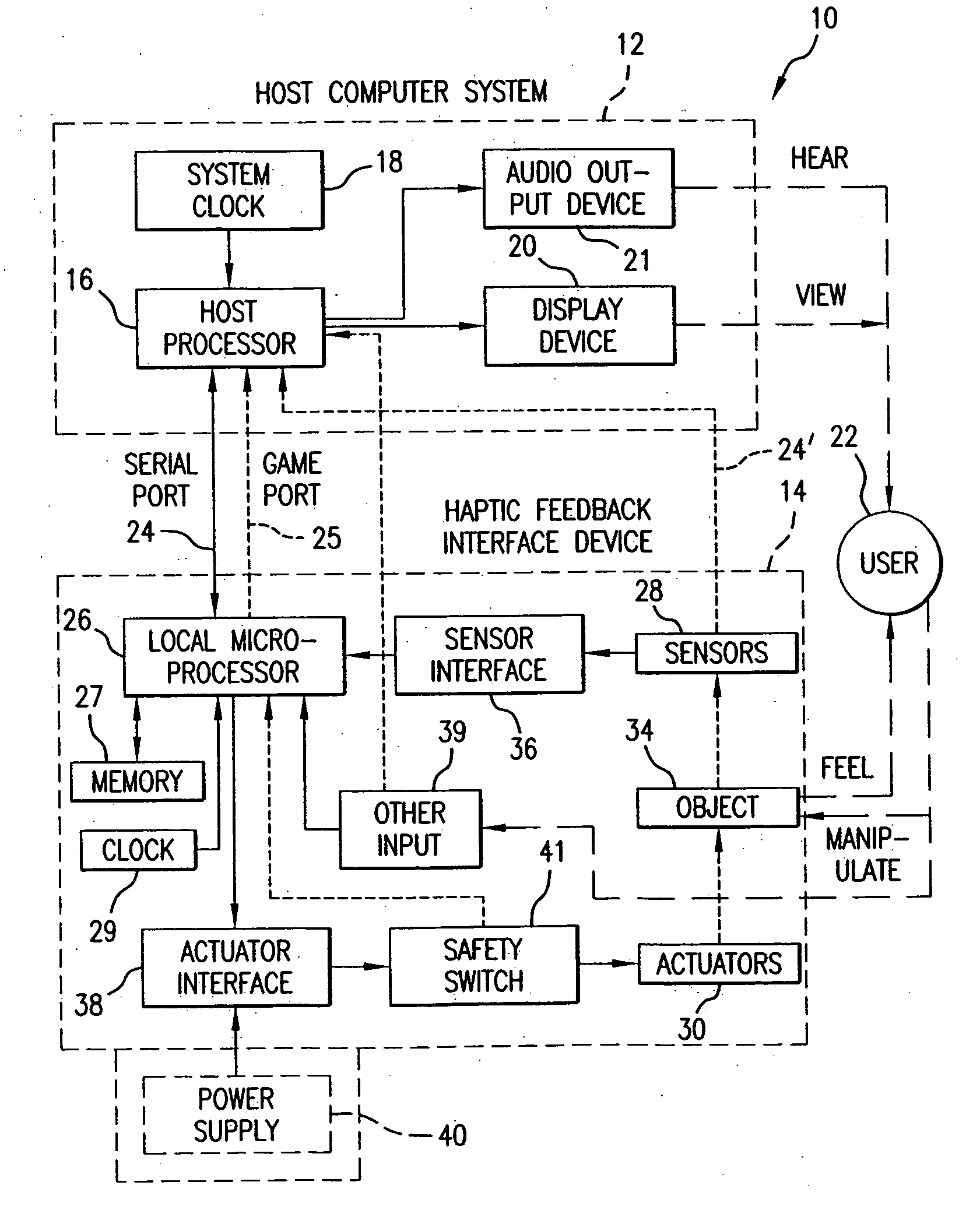
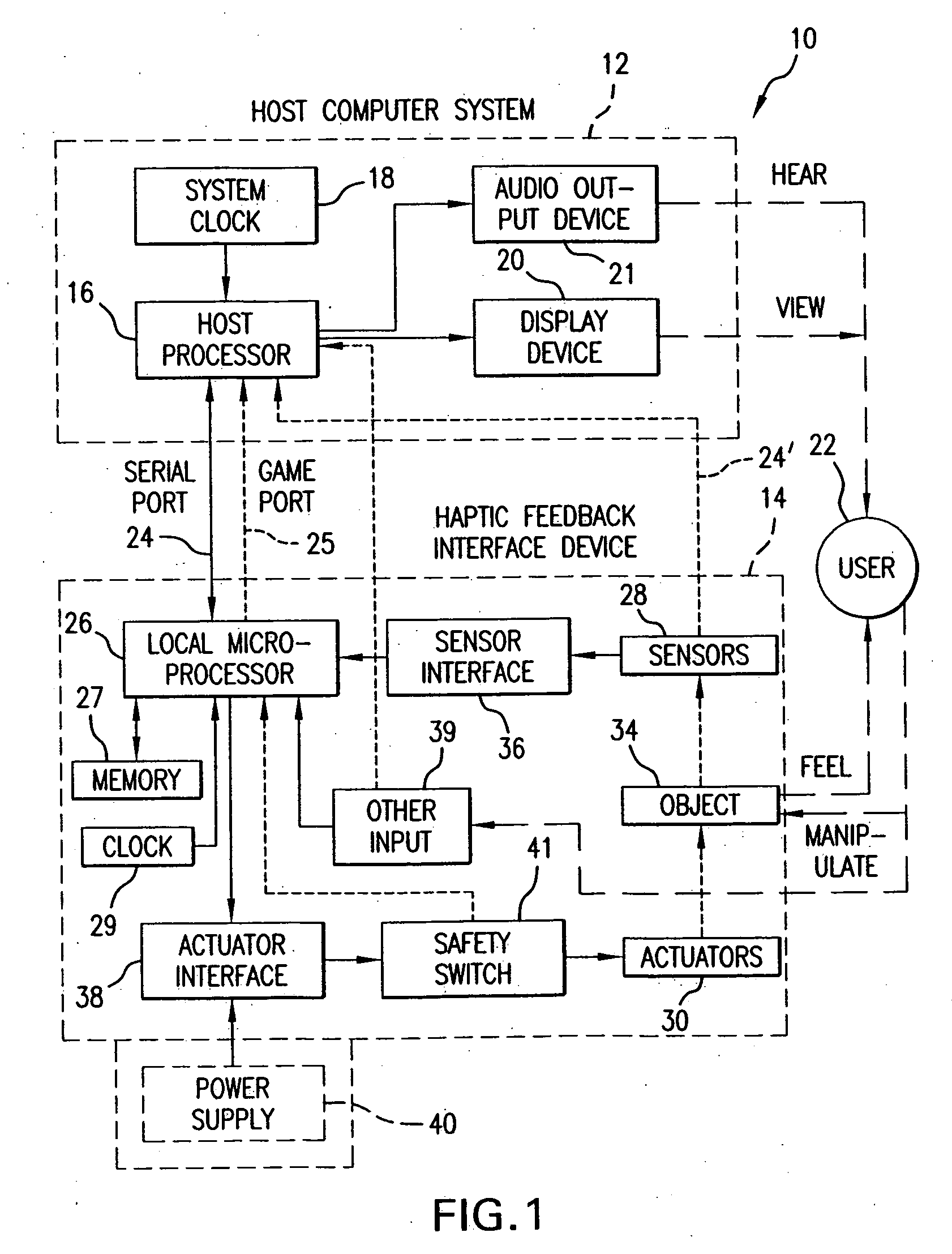
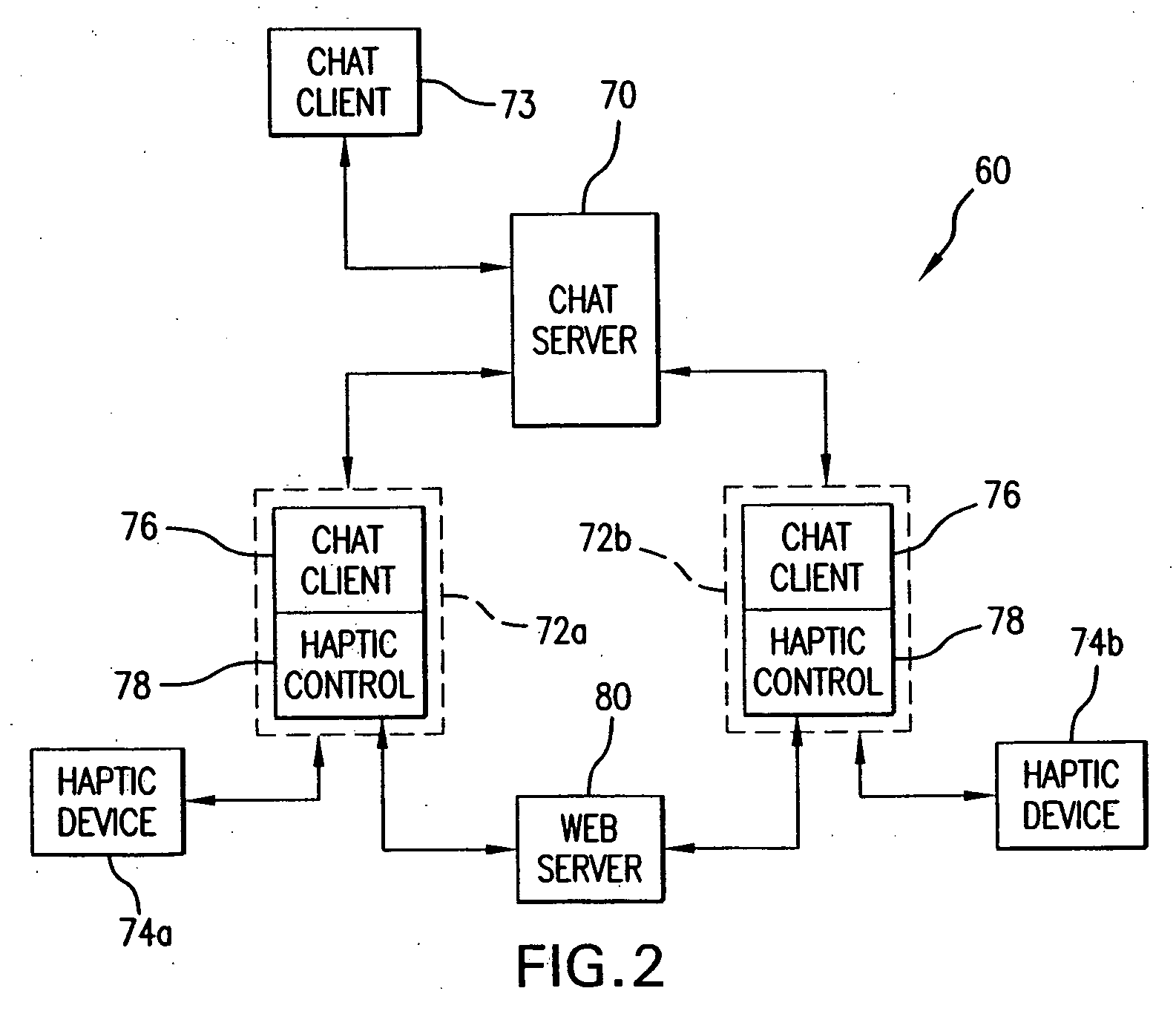
Chat interface with haptic feedback functionality
InactiveUS20070033259A1Enhancements to chat messagesInput/output for user-computer interactionMultiple digital computer combinationsDisplay deviceRemote computer
Owner:IMMERSION CORPORATION
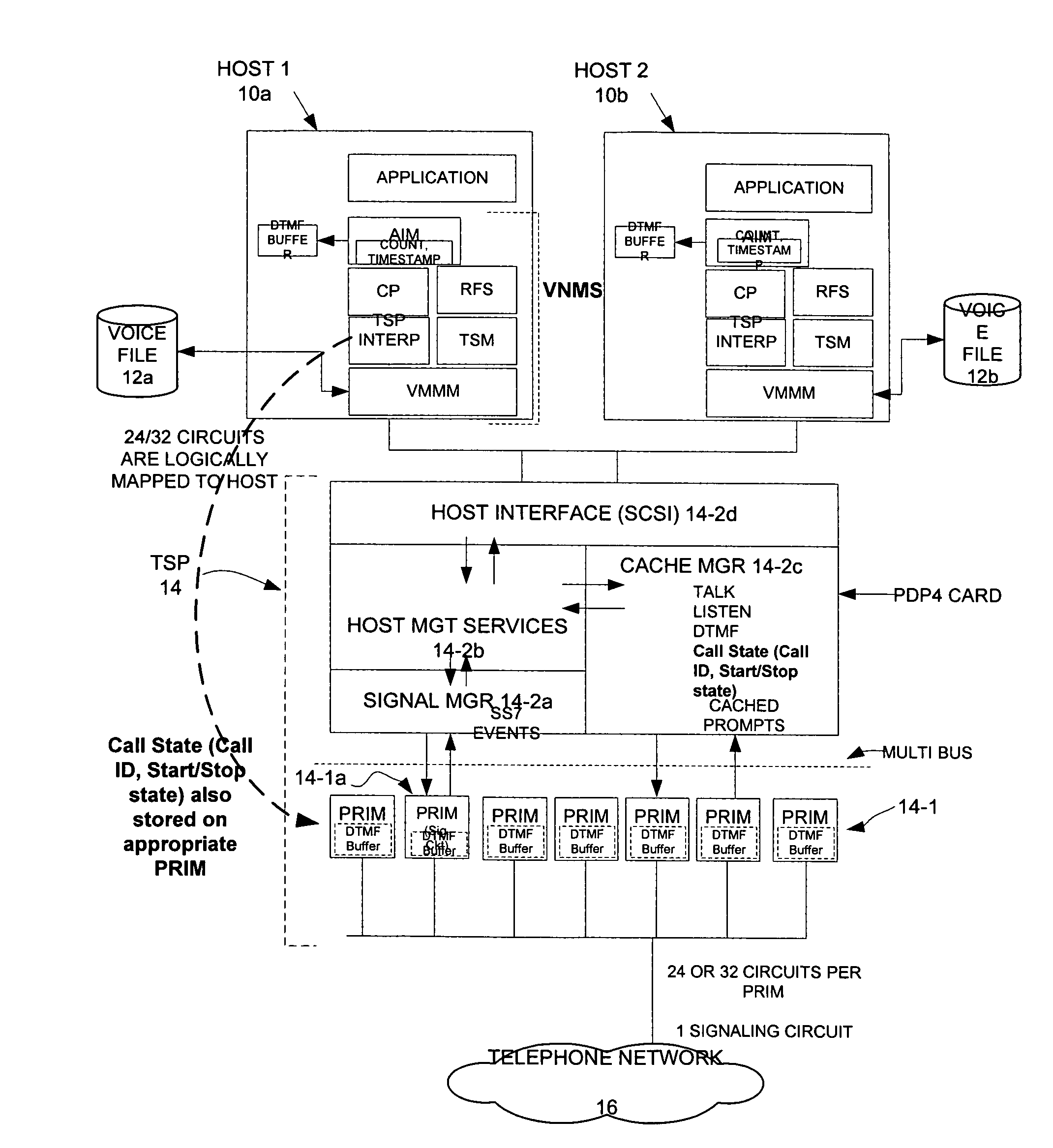
Distributed network applications platform architecture
ActiveUS7095828B1Data switching by path configurationSubstation equipmentTelephone networkDistributed computing
A system and methods that allow local access of data residing and processed on remote messaging system computers is provided. In an illustrative implementation, a plurality of messaging systems having host computers coupled to network interface units (NIUs) act as messaging system nodes (MS Nodes). The NIUs of each of the MS Nodes are interconnected to form a wide area network (WAN) such that data may be freely communicated between the MS Nodes. An exemplary messaging system architecture comprises a host computer interconnected to a NW that, itself, is interconnected to telephone networks and to external computer networks. NIUs support a number of interfaces that allow the communication of data between the NIU and the host, and between the NIU and the external telephone and computer networks. In the distributed messaging system, a call originating from a local MS Node requesting data that resides on a remote messaging system may be transferred to the remote MS Node that has the requested data. The call is processed such that a local NIU accepts the call and communicates the call to a local host. The local host processes the call and determines that the data being requested resides on a remote host. The call is then passed back to the local NIU and transferred to the appropriate NIU using the WAN for processing by the appropriate remote host having the requested data.
Owner:UNISYS CORP
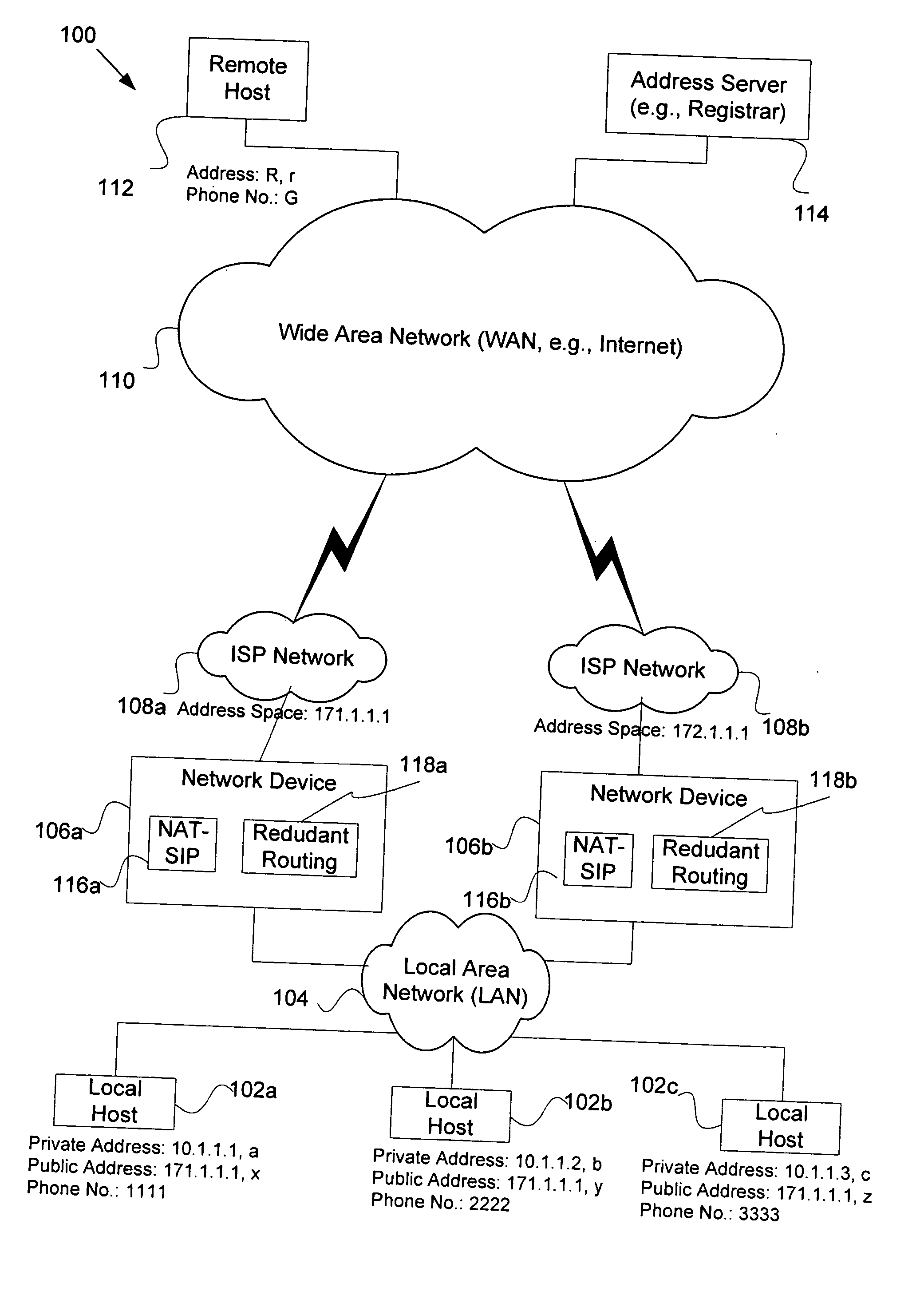
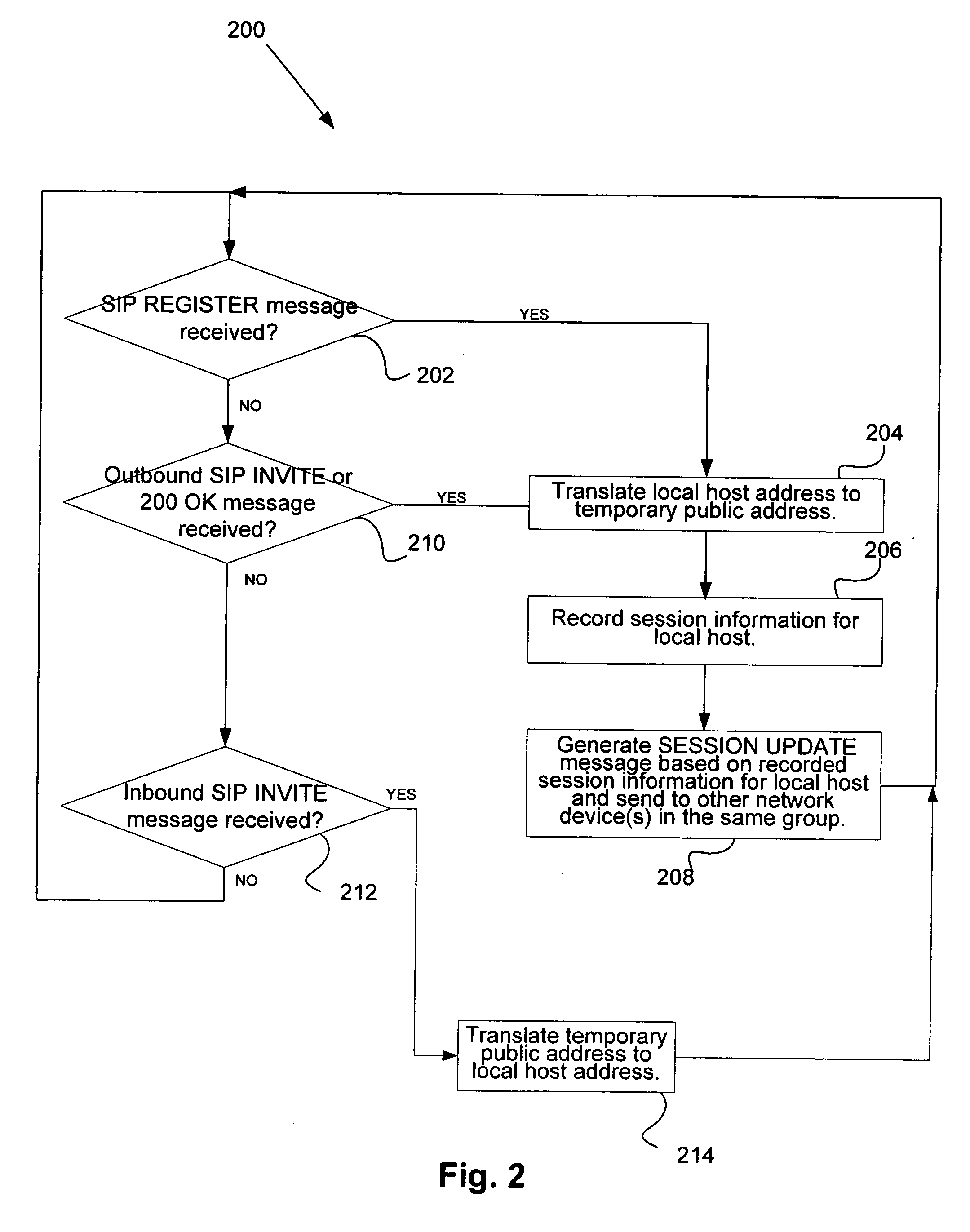
Mechanisms for providing connectivity in NAT redundant/fail-over scenarios in unshared address-space
InactiveUS20070019540A1Error preventionFrequency-division multiplex detailsFailoverNetwork address translation
Disclosed are methods and apparatus for facilitating reliable session based communication with a local host via a subnet of redundant network devices that also implement network address translation (NAT) or the like. In general, embodiments of the present invention include mechanisms for reestablishing access to a local host after the local host's active network device has failed and been replaced by a new active network device with an address space that differs from the failed network device. In this invention, the network devices associated with the same local host also implement NAT, or the like. In brief, for each of its associated local hosts, the new active network device causes an address server to be updated with a new public address that is assigned from its address space to the local host. This update allows other remote hosts access to the local hosts by obtaining the updated address information from the address server. Communication sessions that were established prior to the failing active network device may also be retained by the new active network device. In this aspect, for each ongoing particular session between a remote host and a local host of the new active network device, the new active network device updates the remote host with a new public address assigned to local host for use in the particular session.
Owner:CISCO TECH INC
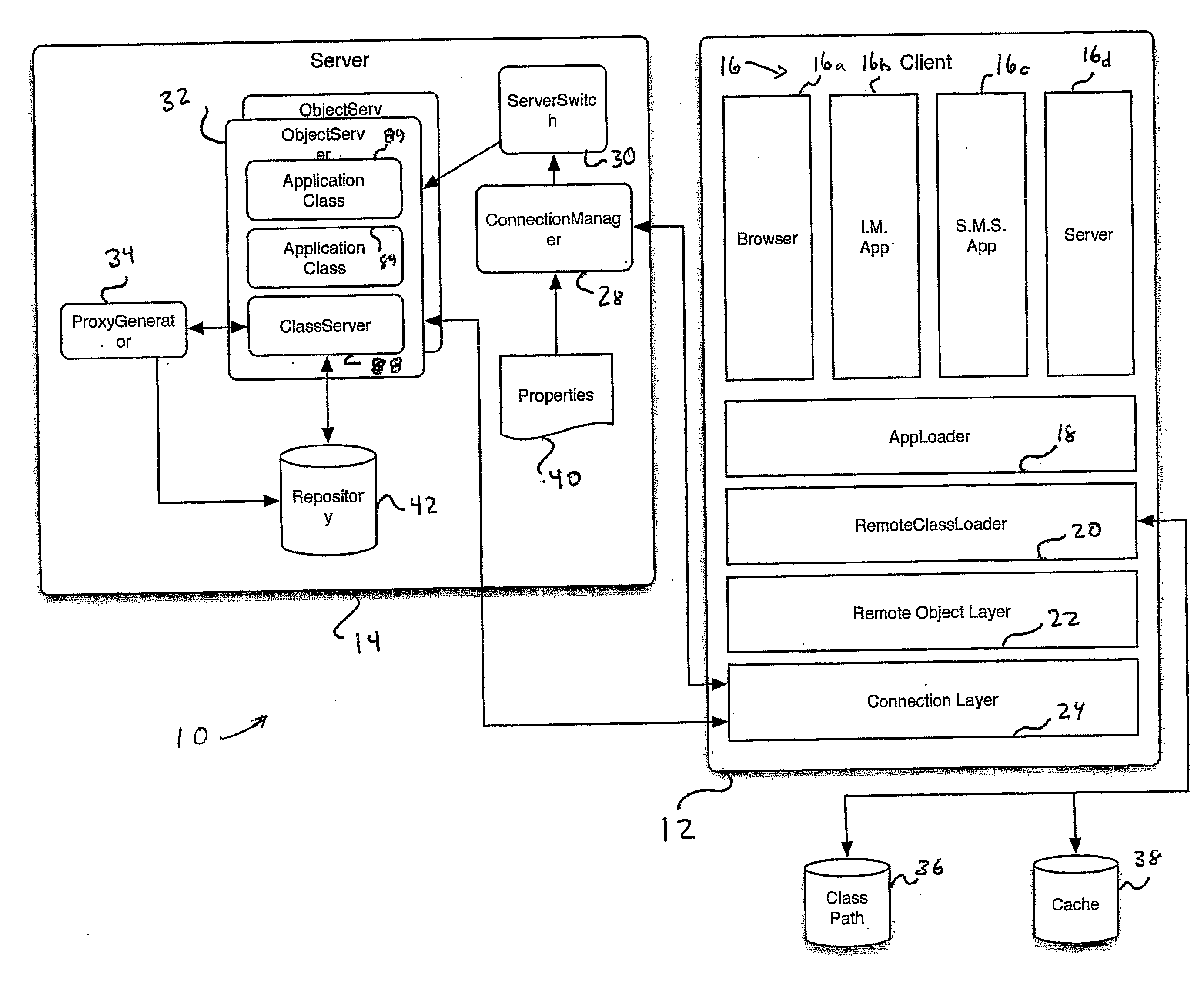
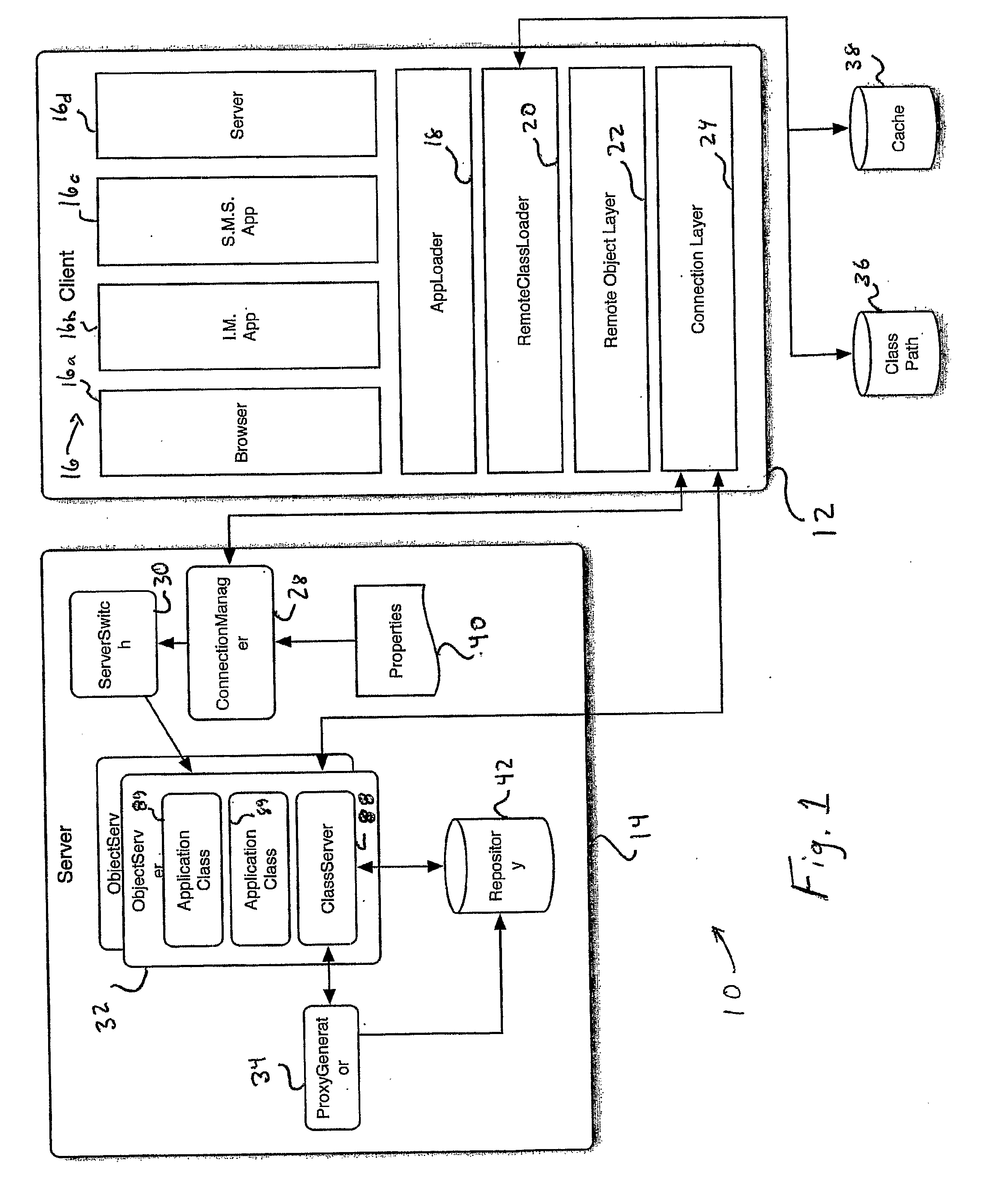
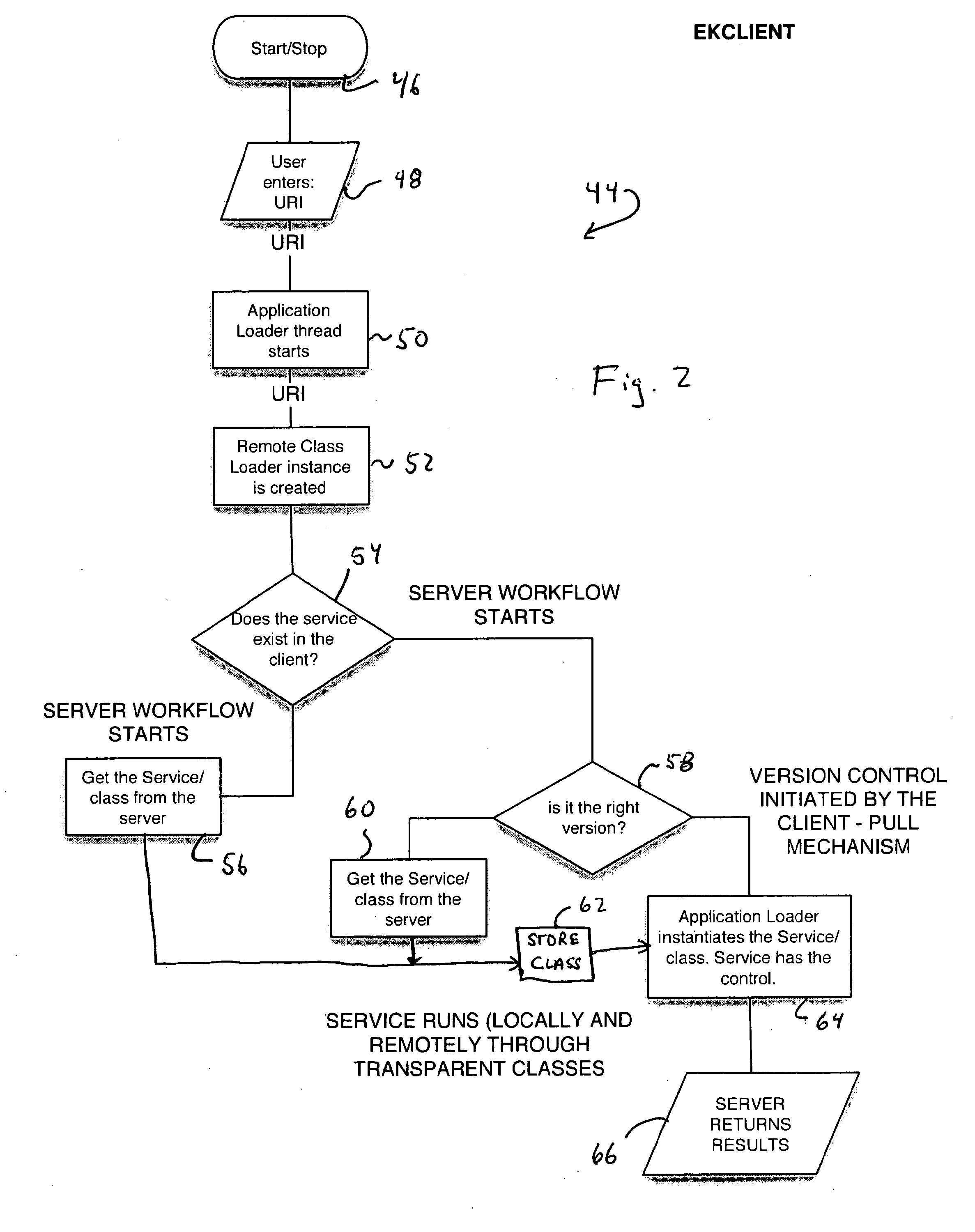
Distributed Virtual Machine Architecture
InactiveUS20090094316A1Increase in sizeImprove convenienceInterprogram communicationMultiple digital computer combinationsClient-sideApplication software
A distributed virtual machine architecture includes a virtual machine client (16) and a virtual machine server (32). The virtual machine client provides a platform upon which an application may be run on a host device (12). The virtual machine server may appear anywhere within the network to which the host of the virtual machine client is connected (14). When the application request a class, the virtual machine client determines such class exists on the local host (12) or a client proxy exist for the class. If neither exists, the virtual machine client connects to the virtual machine server to send a request for the class. If a proxy does exist, a proxy is returned to the virtual machine client. However, if a proxy does not exist, the virtual machine server dynamically generates the proxy (34) to be returned to the virtual machine client.
Owner:DOTFX
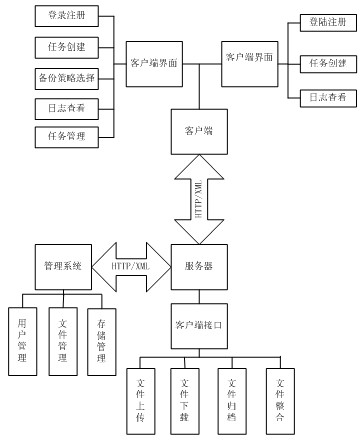
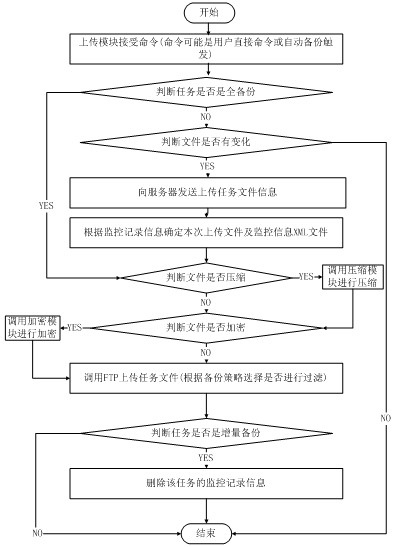
File online backup method
InactiveCN102169453AImplement selective backupImplement multi-tasking backup modeRedundant operation error correctionEngineeringDirectory
The invention relates to a file online backup method. The traditional backup method is complex in operation and has low backup efficiency. The method disclosed by the invention comprises a file backup stage and a file recovery stage, wherein during backup, a user file is partitioned by a backup agent, and the sub-block data are sent to a storage server through a network. During recovery, the backup agent downloads the original backup data to the specified directory of a local host from the storage sever through the network. By the method, the backup is selected according to the type of the file, selective backup of the file of the specific type is realized, a multi-task backup mode is realized at the same time, and multiple folders can be independently backed up.
Owner:HANGZHOU DIANZI UNIV
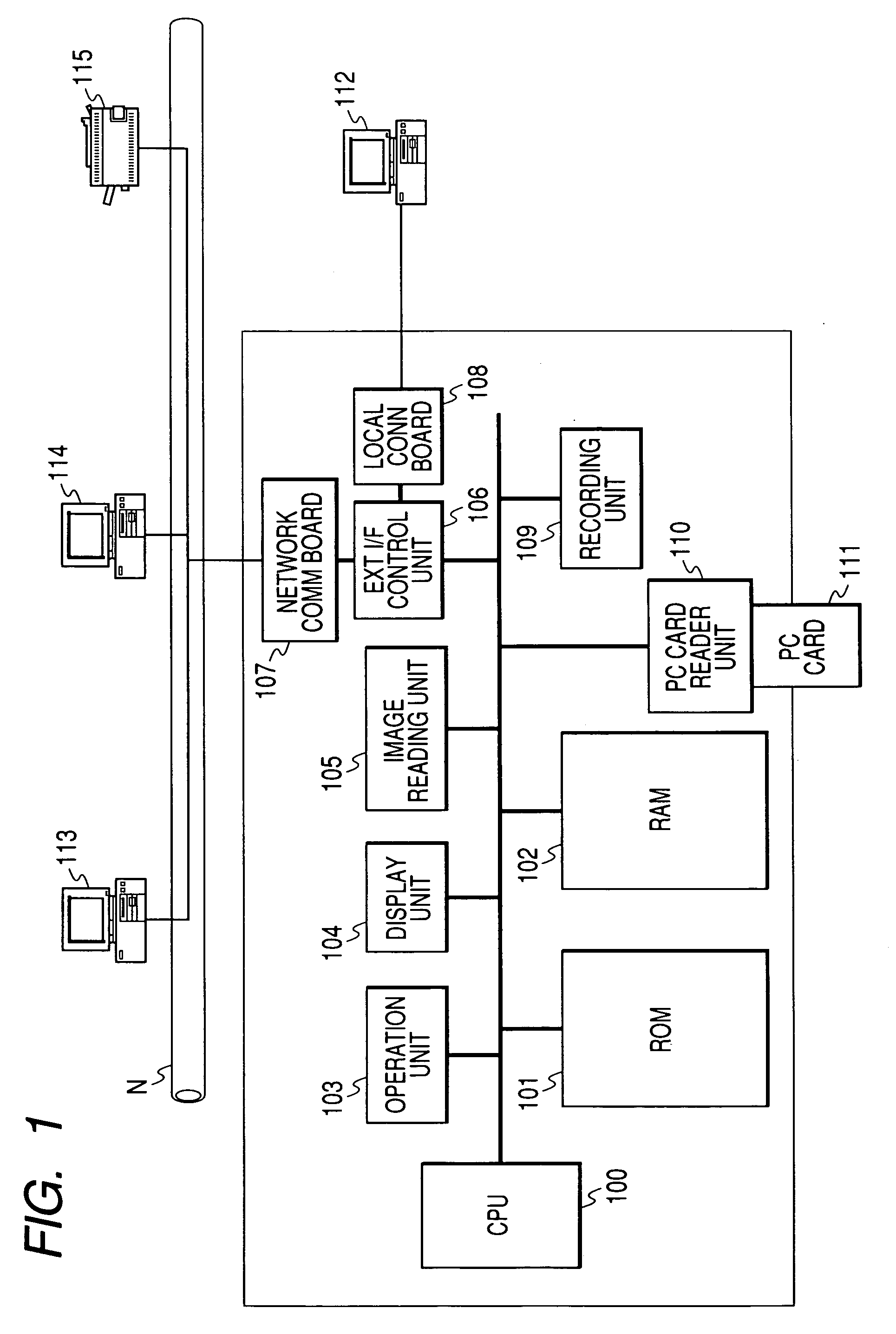
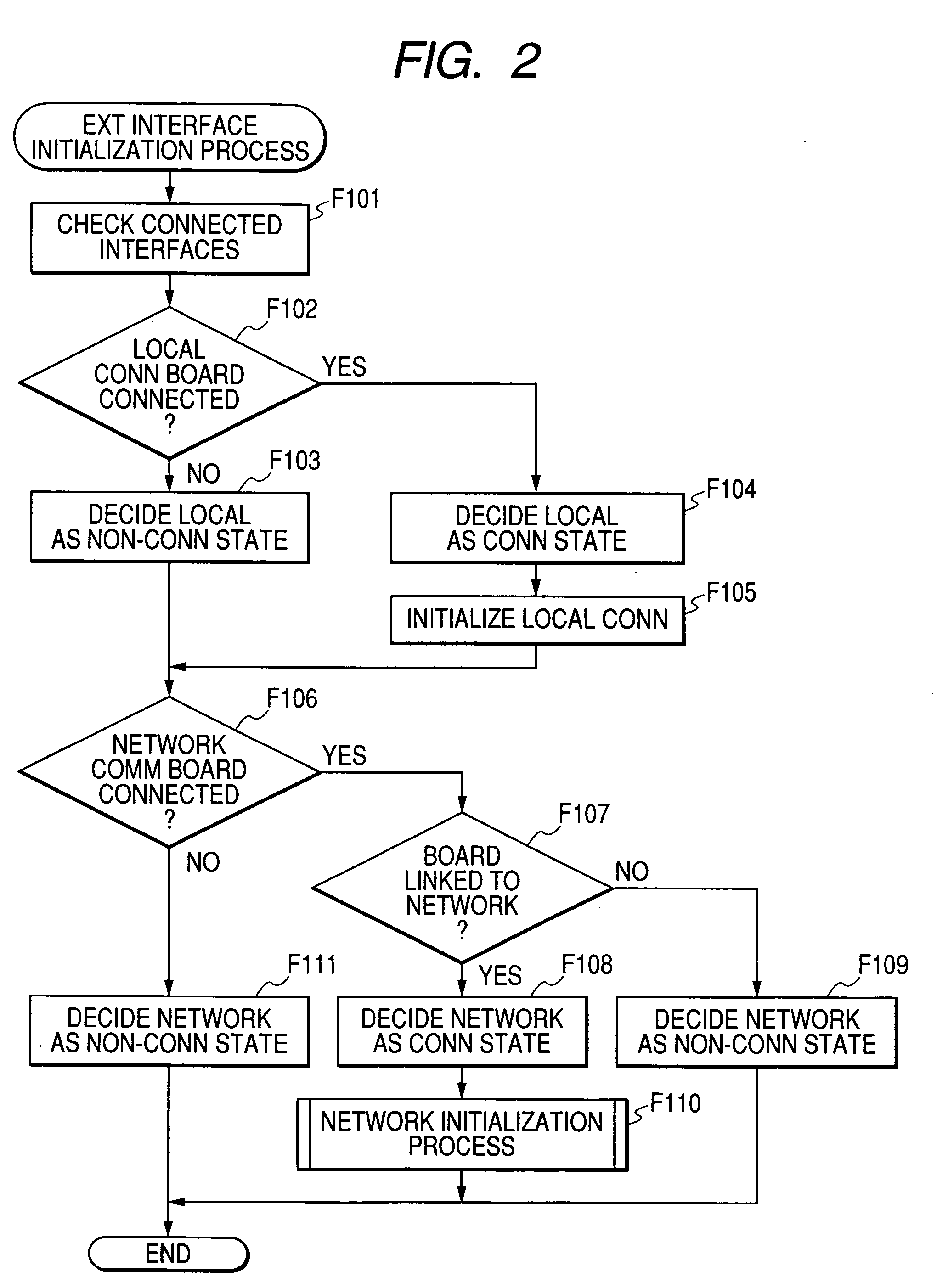
Image processing apparatus, control method for image processing apparatus and control program for image processing apparatus
InactiveUS20060026673A1Digital data processing detailsUser identity/authority verificationImaging processingCard reader
When an unregistered PC card 111 not having an access level registration is mounted in a PC card reader part 110, a user interface requesting an access level setting to the user is executed through an operation unit 103 or a display part 104 (or a local host 112). Also when a PC card 111, having registration as to whether or not to transmit the mounting and on a destination of notice of the mounting, is mounted in the PC card reader part 110, a PC card mounting notice message is transmitted to a destination according to such registered information. With this configuration, there is provided an access control comprehensively usable to the PC cards of various types, capable of activating an access control user interface at the PC card mounting and transmitting a PC card mounting to host / user.
Owner:CANON KK
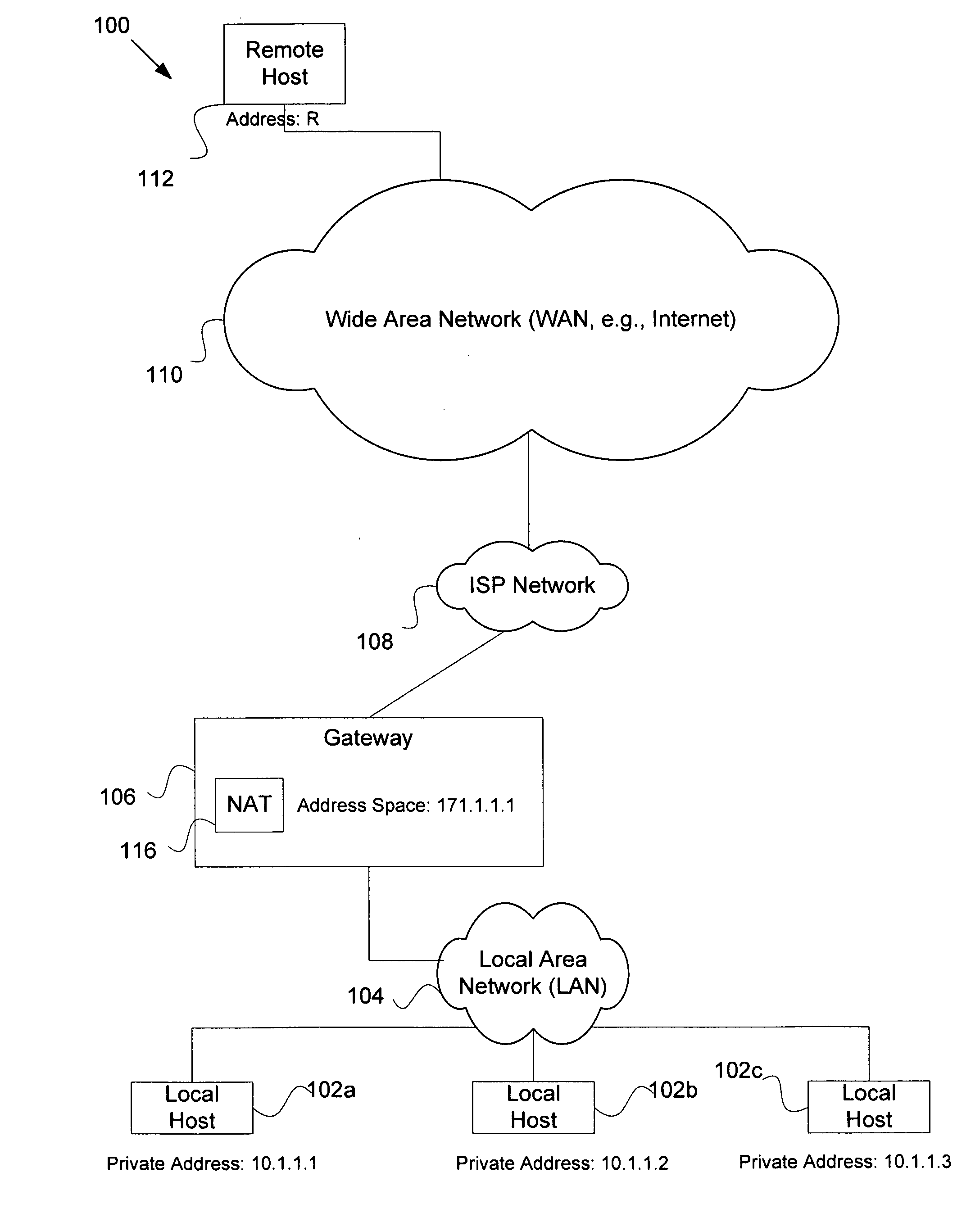
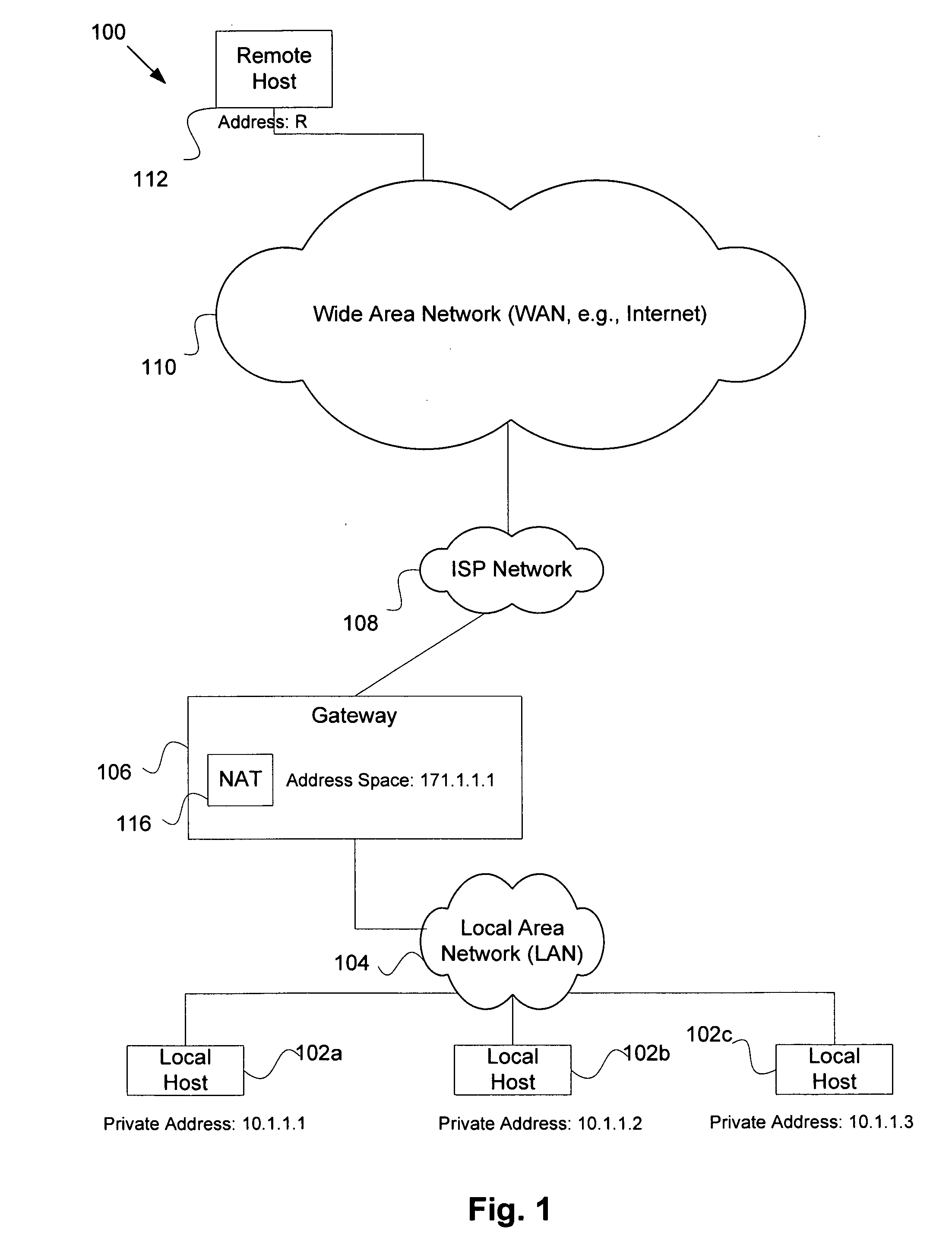
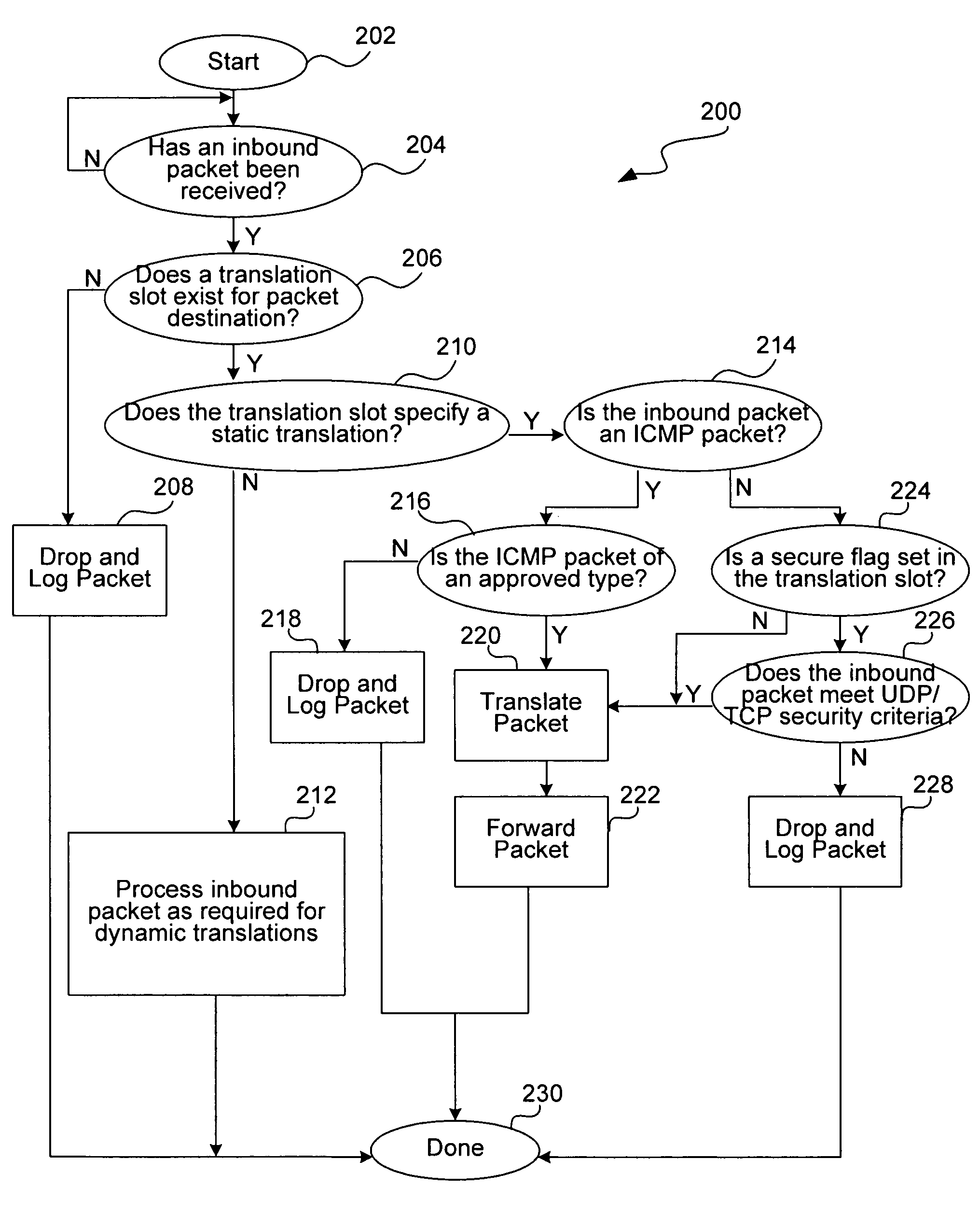
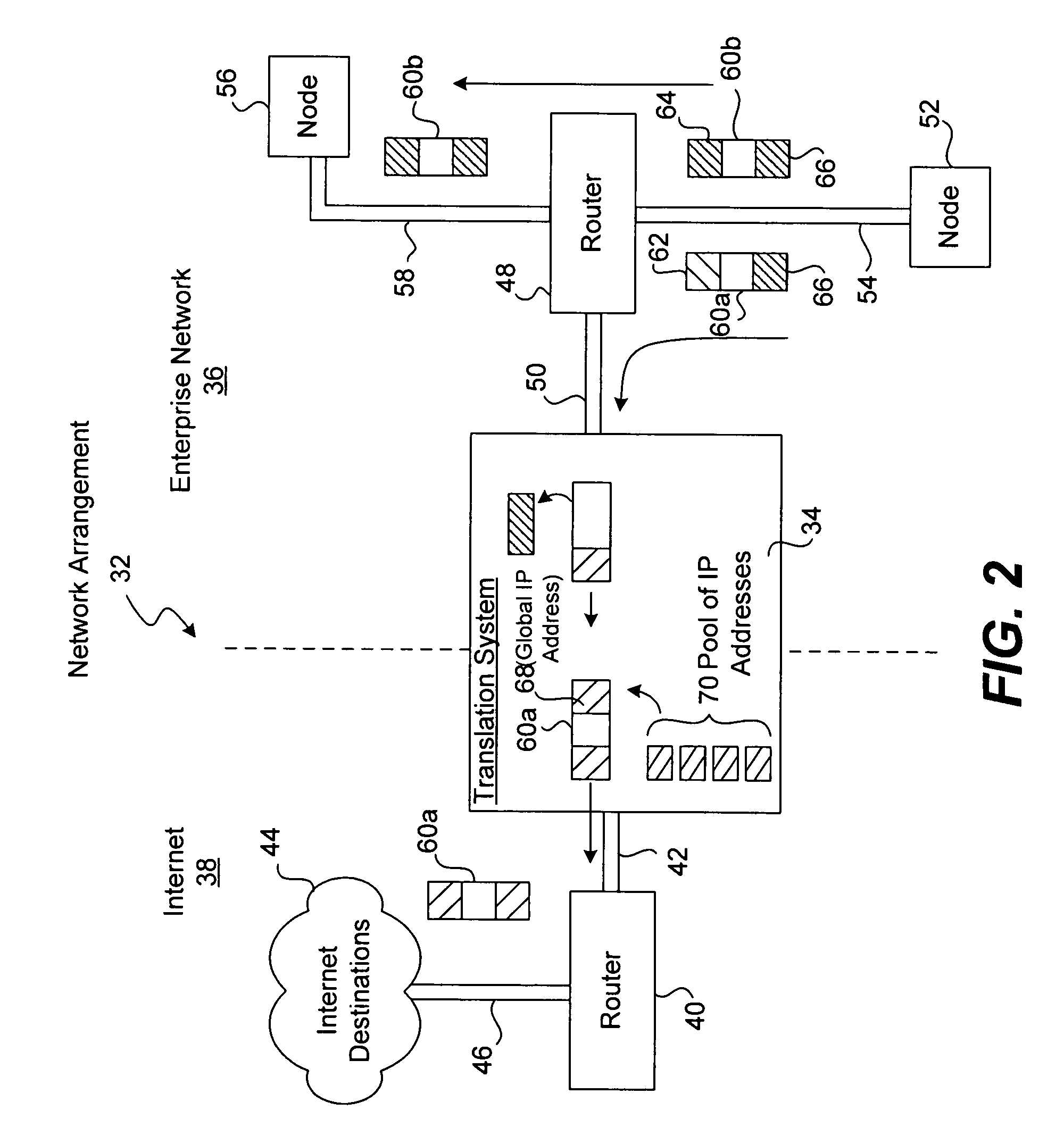
Security system for network address translation systems
InactiveUS7583668B1Data switching by path configurationMultiple digital computer combinationsIp addressThe Internet
A system and method are disclosed for providing perform network address translation of network layer addresses of packets exchanged between nodes on a local network and nodes outside the local network. This allows local hosts in an enterprise network to share global IP addresses from a limited pool of such addresses available to the enterprise. The translation may be accomplished by replacing the source address in headers on packets destined for the Internet and by replacing destination address in headers on packets entering the local enterprise network from the Internet. Packets arriving from the Internet are screened by an adaptive security algorithm. According to this algorithm, packets are dropped and logged unless they are deemed nonthreatening.
Owner:CISCO TECH INC
Method and system for payment through mobile devices
Processing payment through a mobile device includes: receiving a command; using an upper layer application program executing on the mobile device to generate a payment request based on the command and send the payment request to be processed by a lower layer payment program, using the lower layer payment program executing on the mobile device to monitor the payment request sent from the localhost address of the mobile device via the predetermined port; in response to the payment request, using the lower layer payment program to provide an input interface for payment information in and receive the input payment information; using the lower layer payment program to connect with a payment server and pass the payment information over a network to the payment server; and using the lower layer payment program to transfer a payment processing result received from the payment server, to the upper layer application program.
Owner:ADVANCED NEW TECH CO LTD
Encapsulation protocol for linking storage area networks over a packet-based network
InactiveUS6965934B1Eliminates and reduces disadvantageMultiple digital computer combinationsTransmissionFiberSCSI
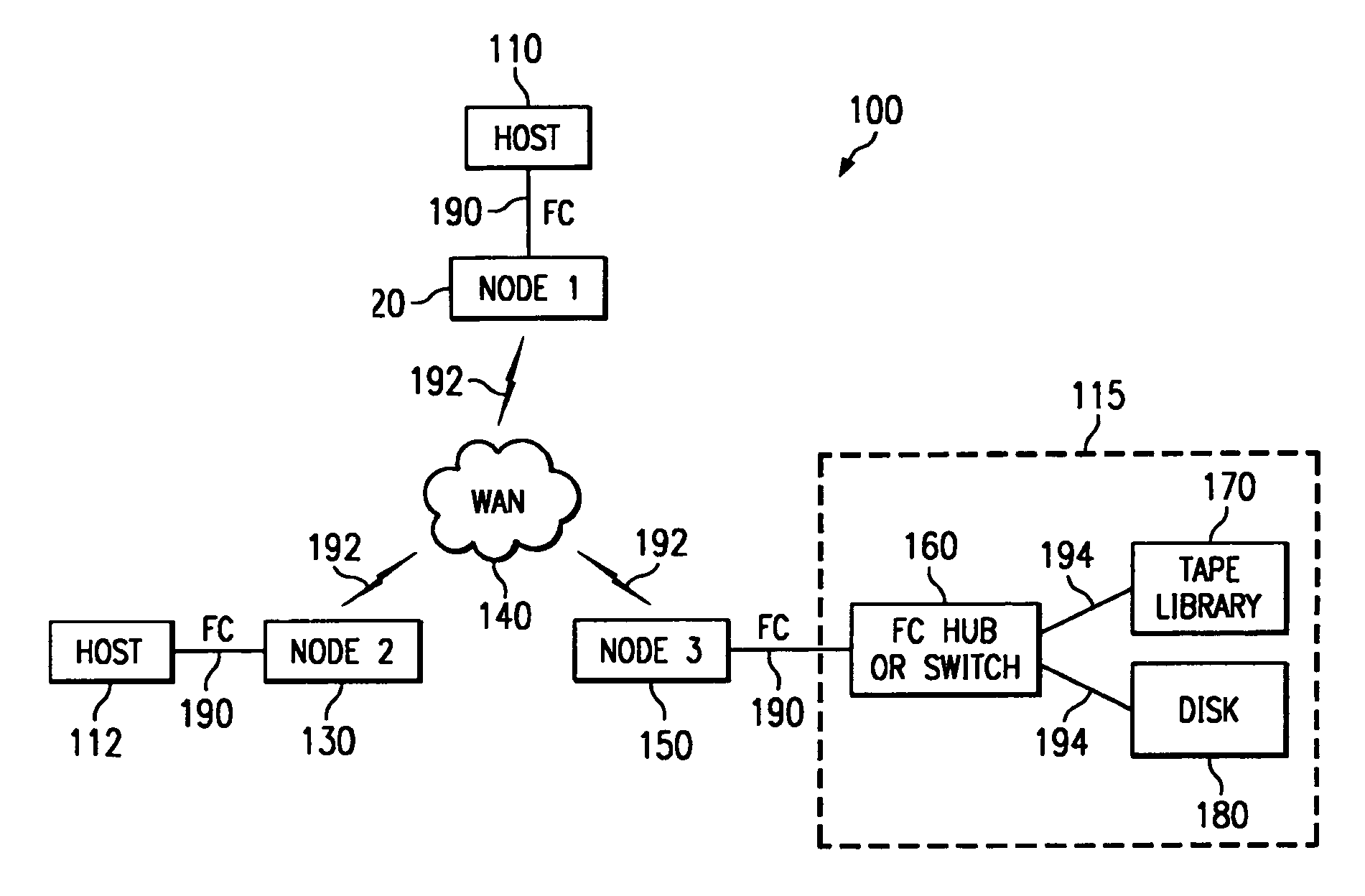
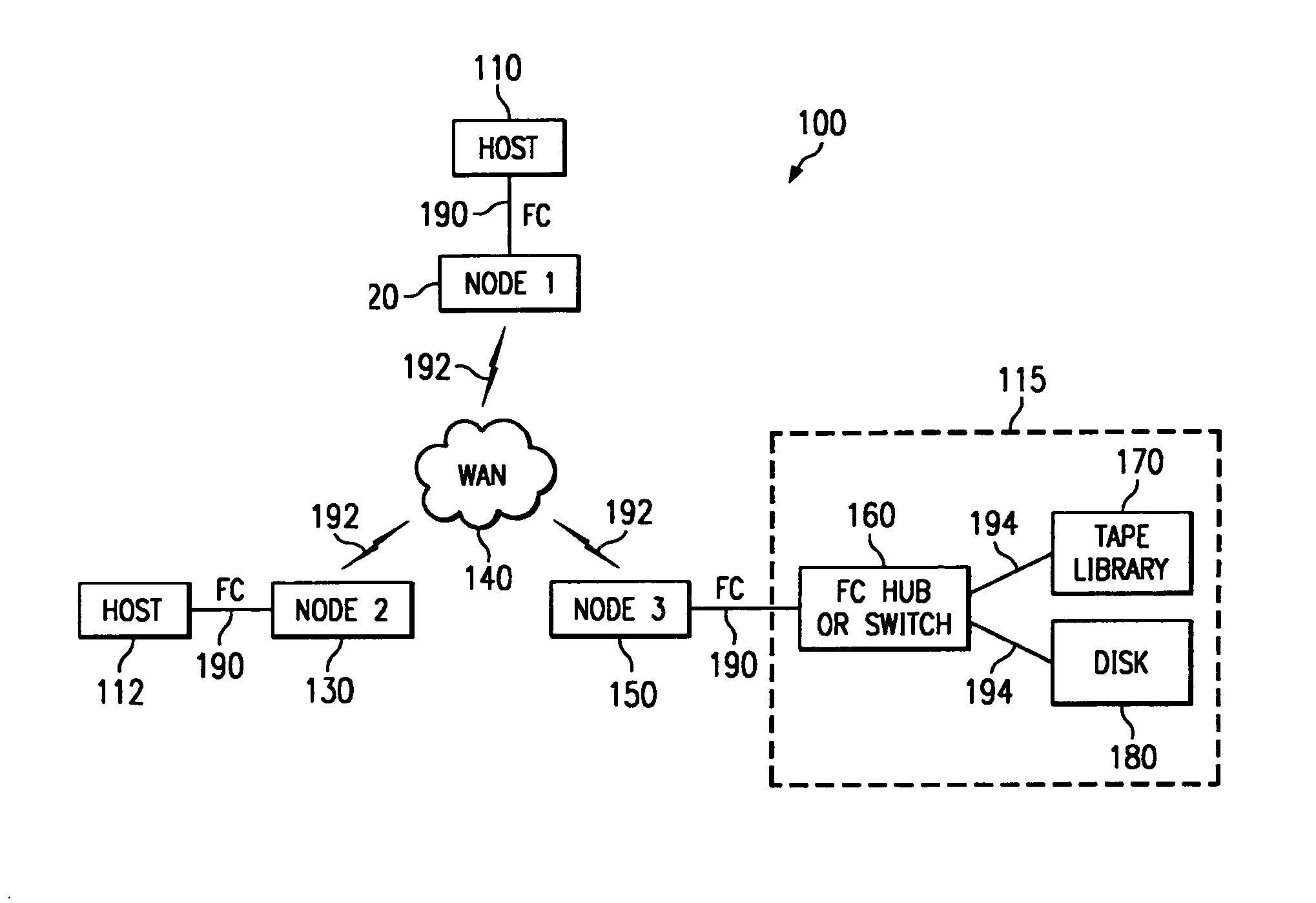
A method and system are disclosed for encapsulating SCSI protocol for data transmission between two or more nodes across a packet-based network. The method of the present invention includes the steps of, at each node in the network, identifying all other available nodes on the network, and the remote devices attached to those nodes; representing one or more of the attached remote devices such that they are made available to the node's local hosts; encapsulating the I / O phases between one or more local hosts and one or more of the remote devices; and repeating the encapsulating step for subsequent I / Os between one or more hosts and one or more devices. The step of encapsulating I / O phases between a local host and a remote device can further comprise encapsulating task management functions, error recovery functions and normal I / O processing functions. Each node can be a Fibre Channel-to-SCSI router.
Owner:CF DB EZ +1
Method of mutually authenticating between software mobility device and local host and a method of forming input/output (i/o) channel
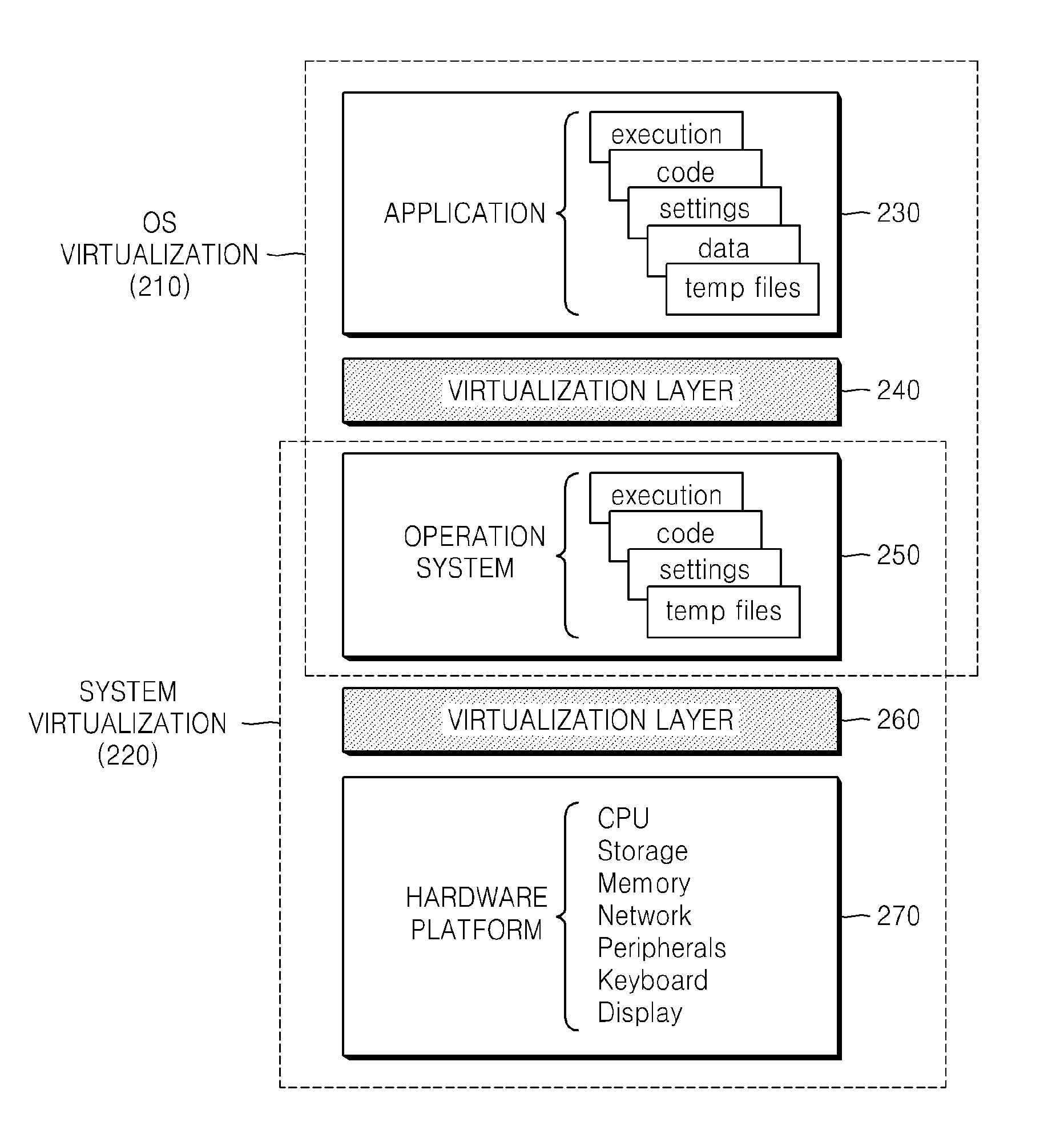
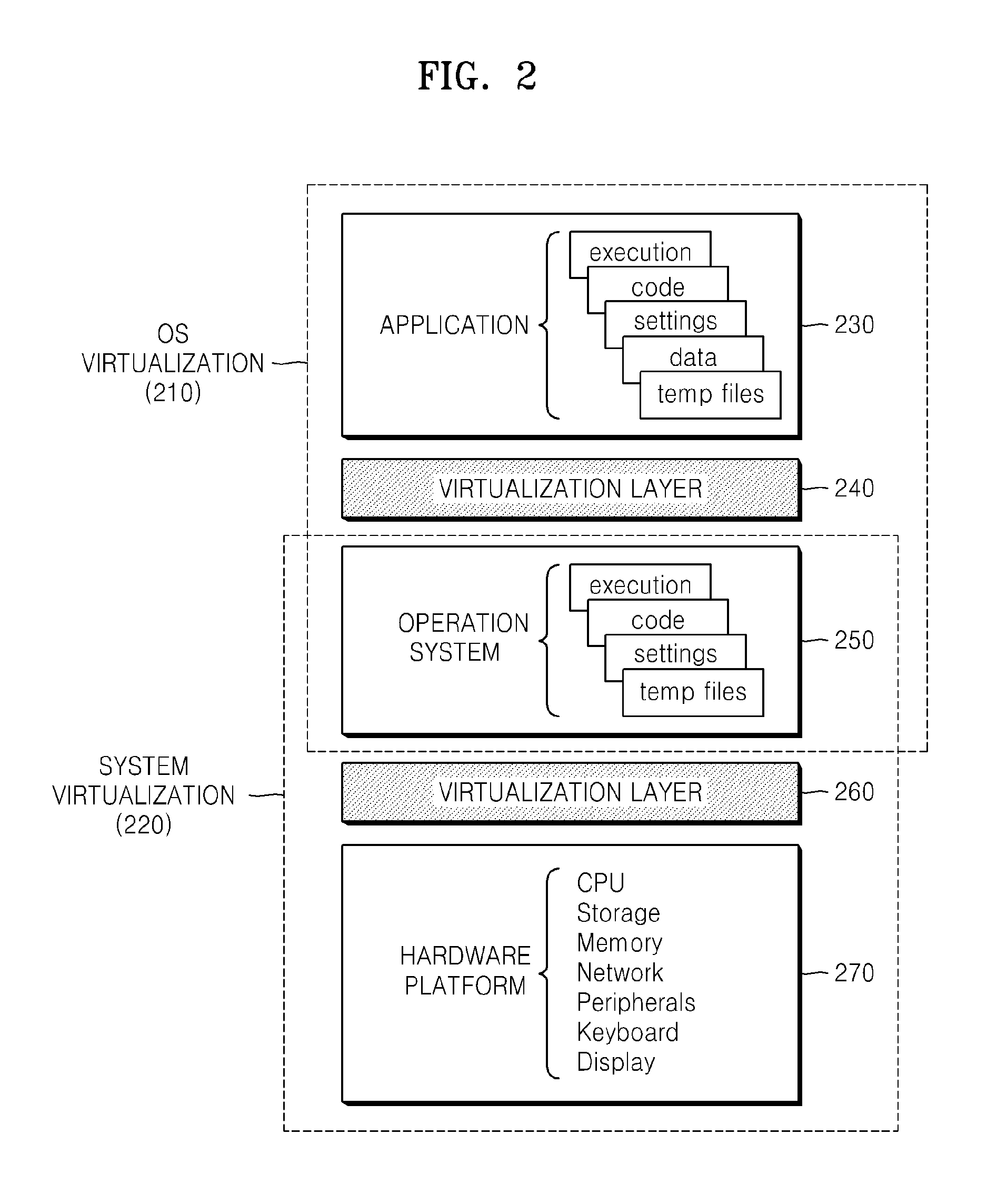
InactiveUS20090055918A1Ensure safetyDigital data processing detailsAnalogue secracy/subscription systemsComputer hardwareVirtualization
A method of mutually authenticating between a local host and a software mobility device including an operating system virtualization layer, and a method of forming an input / output (I / O) channel. The method of authenticating a local host in the software mobility device includes requesting a certificate from the local host in which an integrity value of the local host is stored, and receiving the certificate from the local host; receiving an integrity value measured in the local host and comparing the measured integrity value with the integrity value included in the certificate to verify the local host; and when the local host is verified, encrypting a security profile of the software mobility device and transmitting the encrypted security profile to the local host so as to provide secure communication between the local host and the software mobility device.
Owner:SAMSUNG ELECTRONICS CO LTD
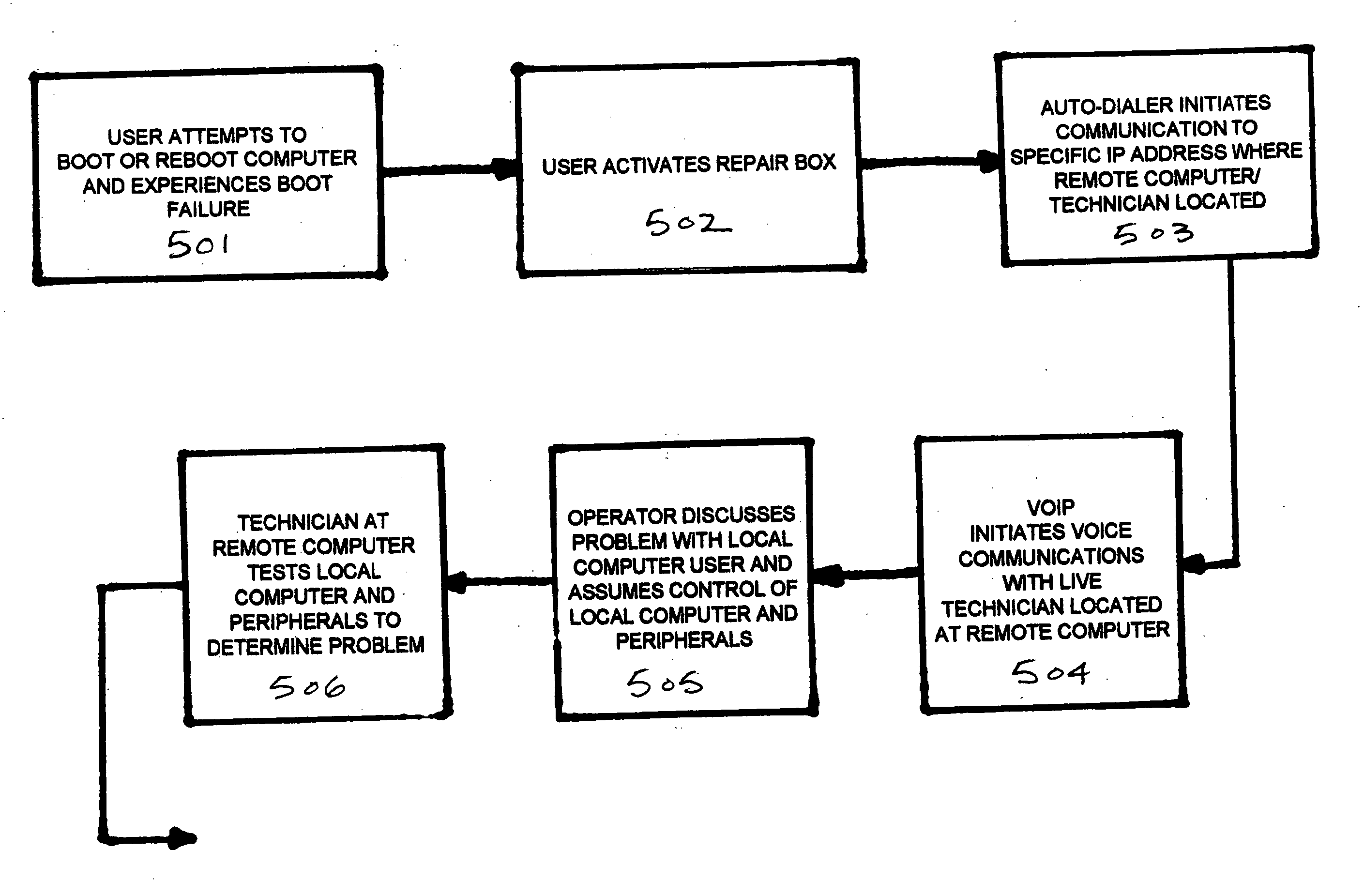
Maintenance device for remotely accessing and repairing failed computer systems
InactiveUS20060271773A1Detecting faulty hardware by remote testDigital computer detailsEngineeringRemote computer
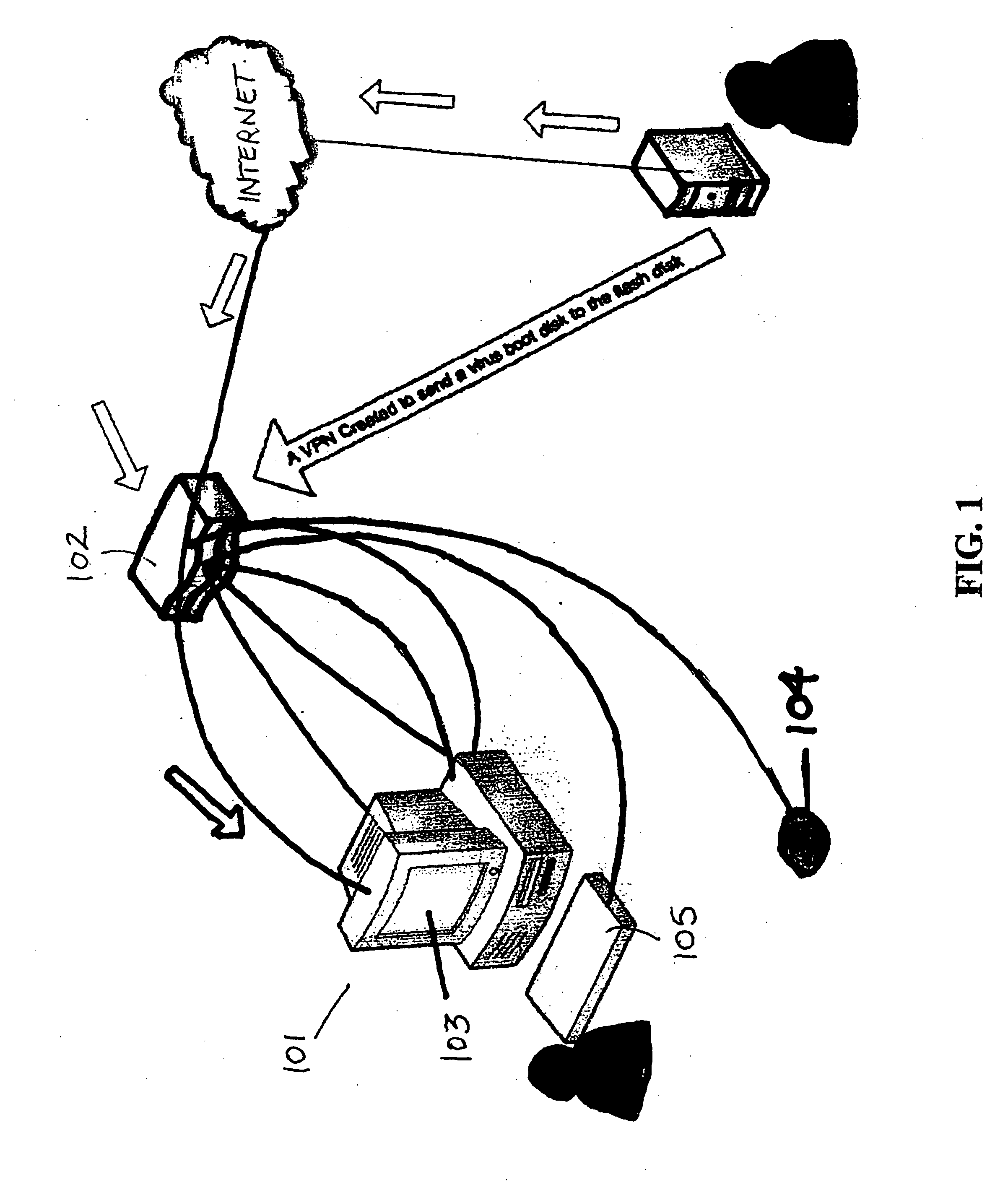
A software and hardware driven CRASH REPAIR BOX allows a local computer to be diagnosed and repaired from a remote computer location. The CRASH REPAIR BOX is particularly useful in situations where the local host computer has failed to properly BOOT. Using a memory and memory controller, software for a particular user platform, such as WINDOWS XP™ or WINDOWS 2000™, will be loaded from the remote computer into the CRASH REPAIR BOX and stored in the memory. The BIOS in the local host computer is then reconfigured to BOOT from the memory in the CRASH REPAIR BOX. Thus, utilizing the platform software stored in the memory of the CRASH REPAIR BOX, the local host computer will be able to properly and fully BOOT. Once the local host computer is able to fully BOOT from the software stored in the memory, further diagnostics and repairs can then be conducted.
Owner:INCHARGE TECH
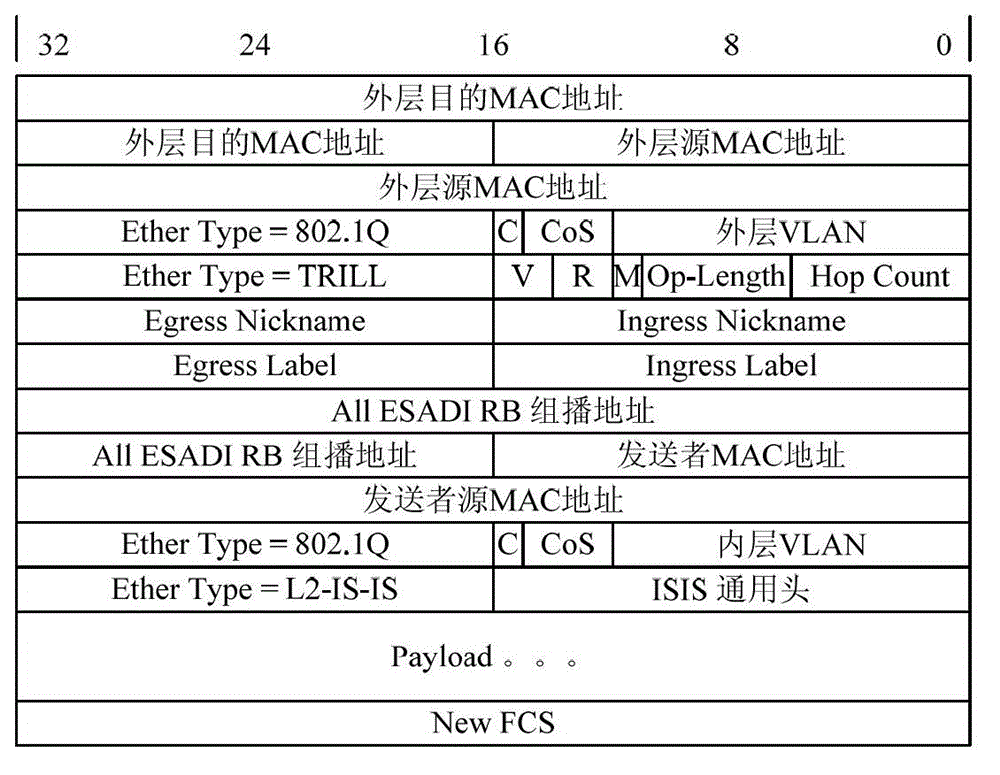
Packet forwarding method in TRILL (transparent interconnection of lots of links) network and routing bridge
ActiveCN102868614AReduce lookupAvoid wasting timeData switching networksInterconnectionMedia access control
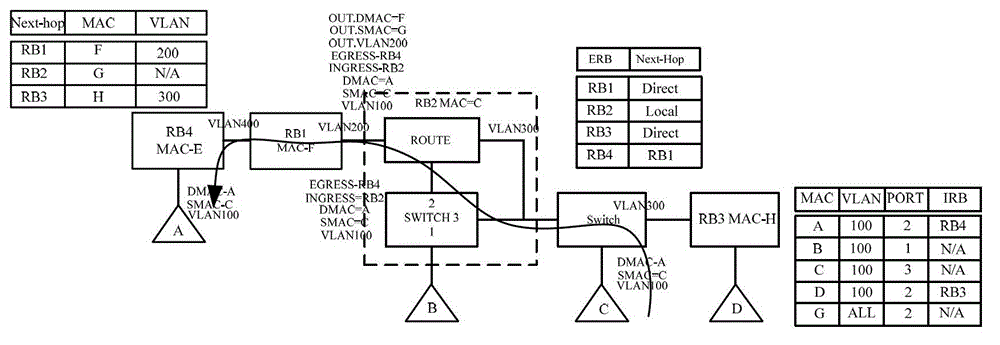
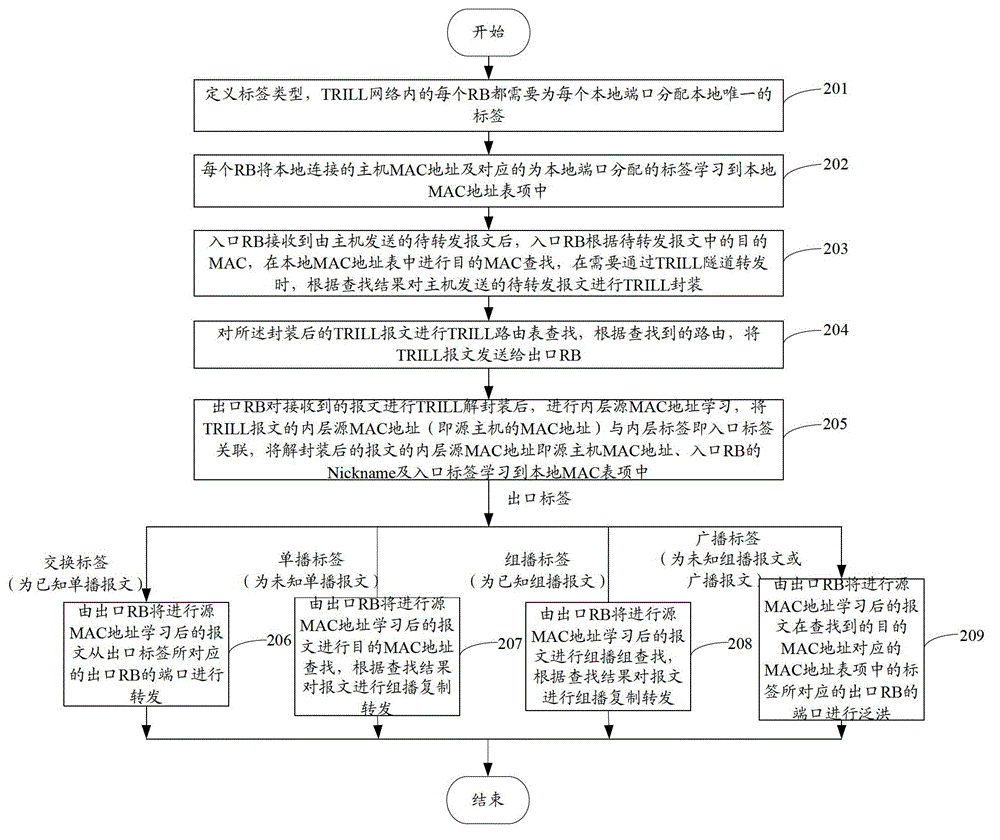
The invention discloses a packet forwarding method in a TRILL (transparent interconnection of lots of links) network and a router bridge. Both an entrance RB (router bridge) and an exit RB distribute local unique labels for local ports, and an MAC (media access control) address of a local host and the labels distributed for the local ports are learnt into local MAC address table entries; an MAC address table entry corresponding to a target MAC address of a packet to be forwarded from the local host is searched by the entrance RB in a local MAC address table, TRILL encapsulation including the entrance RB, the entrance label, the exit RB and the exit label is performed for the packet to be forwarded according to search results, and the encapsulated TRILL packet is sent to the exit RB; TRILL decapsulation is performed by the exit RB for the TRILL packet, an inner layer source MAC address is learnt, the inner layer source MAC address, the entrance RB and the entrance label are learnt to the local MAC address table entries, and the decapsulated packet is forwarded according to the exit label. By adopting the method and the routing bridge, the packet forwarding based on the labels can be realized, the search of the MAC address table can be reduced, and the complexity of packet forwarding can also be reduced.
Owner:XINHUASAN INFORMATION TECH CO LTD
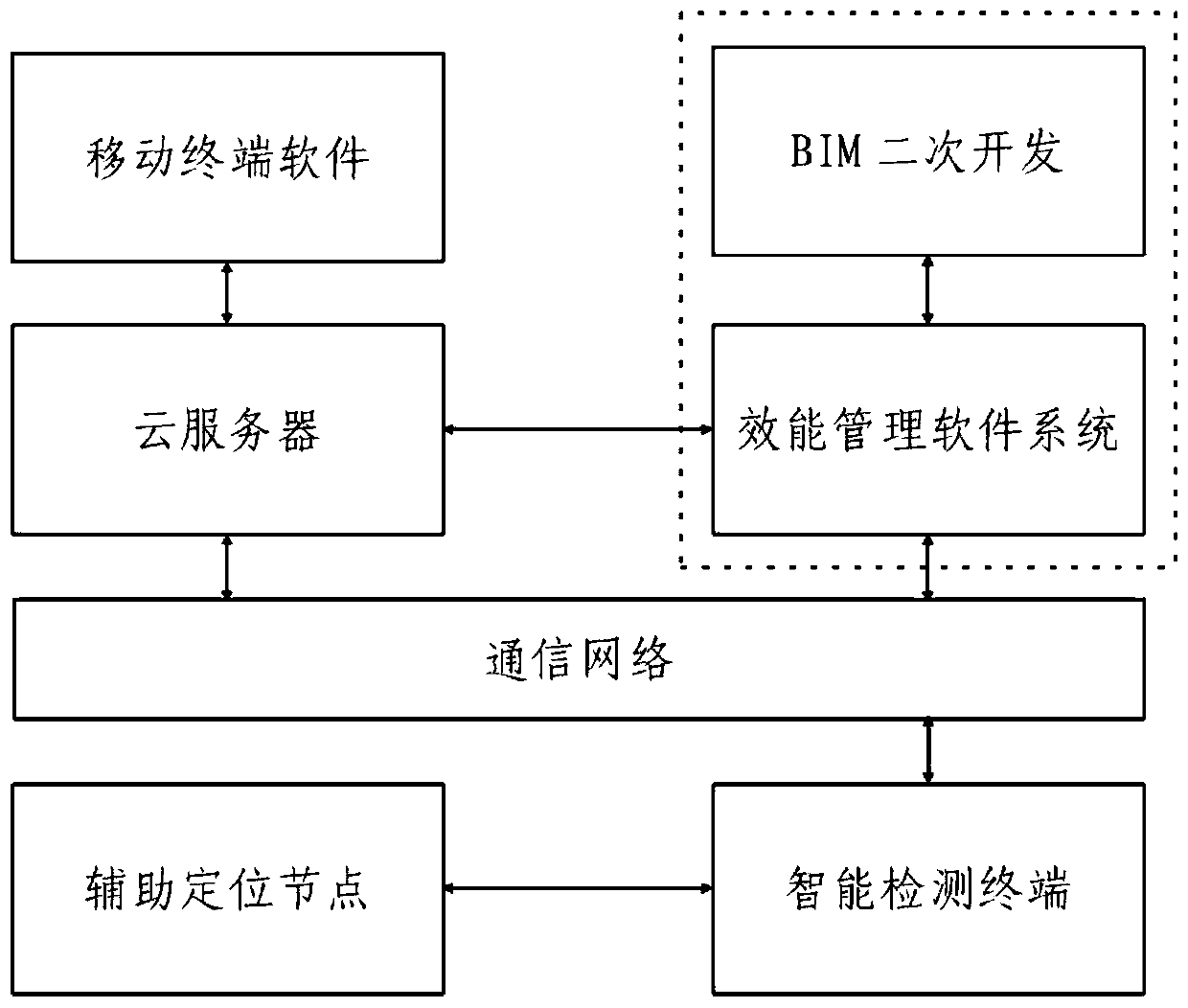
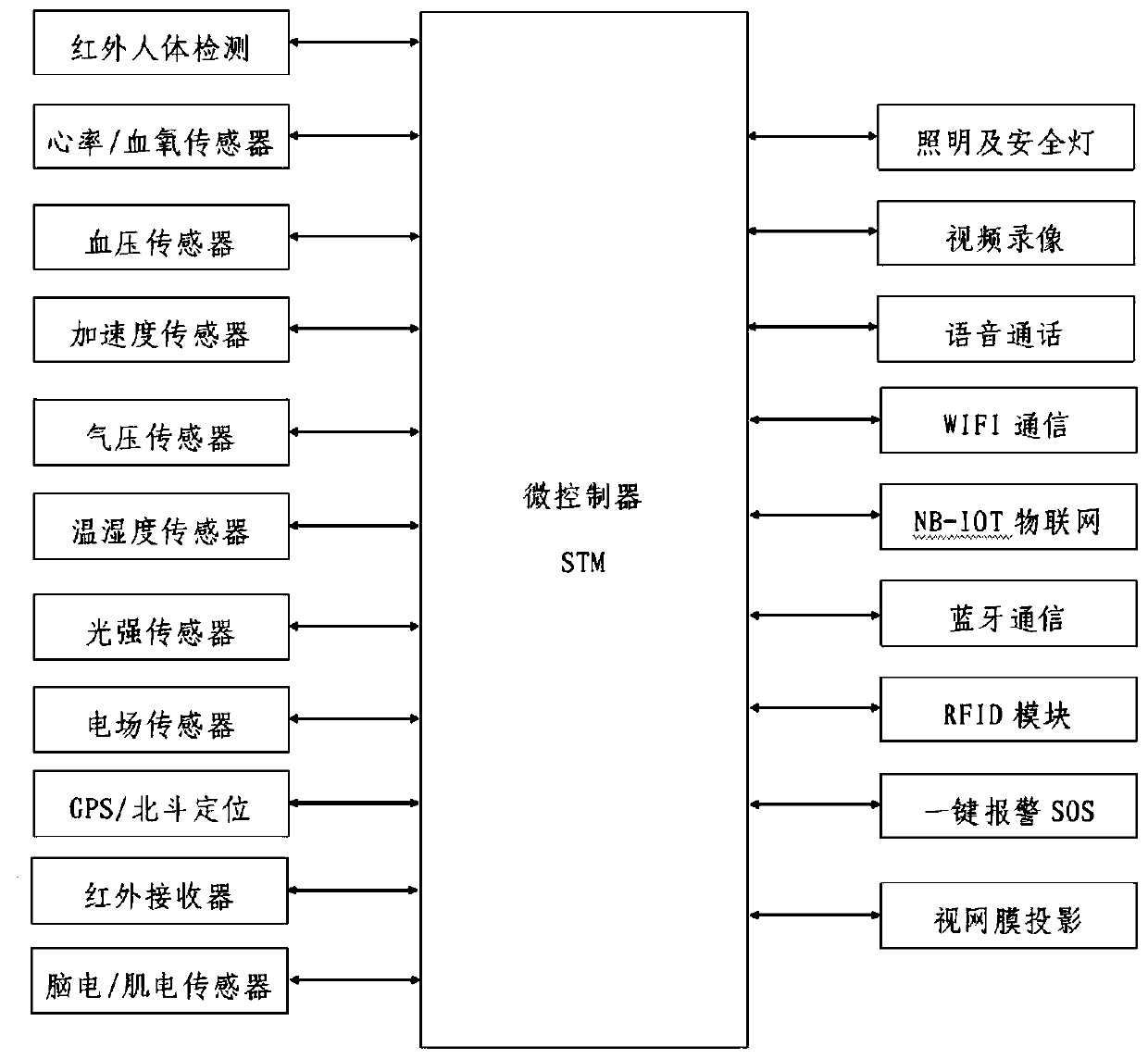
Building construction site personnel efficiency management system and method
PendingCN109767144ALow costNo electromagnetic interferenceResourcesReal time analysisMathematical model
The invention discloses a building construction site personnel efficiency management system and method. The system comprises an intelligent detection terminal worn by a constructor and a local host, Wherein the intelligent detection terminal is used for acquiring physiological status data, environmental status data and on-site construction process of a constructor and uploading the acquired data to the local host; The method has the beneficial effects that the method is used; wherein the intelligent detection terminal is worn on a person; Authentication of constructor identity, Whether safe wear, Physiological indicators such as heart rate and respiration, Activity position and other information, uploading the data to a cloud server and a local computer host; The method comprises the following steps: establishing a mathematical model, analyzing whether a person correctly wears a safety helmet, is in a correct construction position, and has an accident in the body, finally analyzing thelabor state in real time, timely giving an information warning if the conditions of long-time sabotage, illegal operation, border crossing and the like exist, and automatically commanding a field manager to give intervention by a system if the conditions are not corrected.
Owner:孔祥明
XML based scripting framework, and methods of providing automated interactions with remote systems
InactiveUS20060265469A1Multiple digital computer combinationsTransmissionRemote systemRemote computer
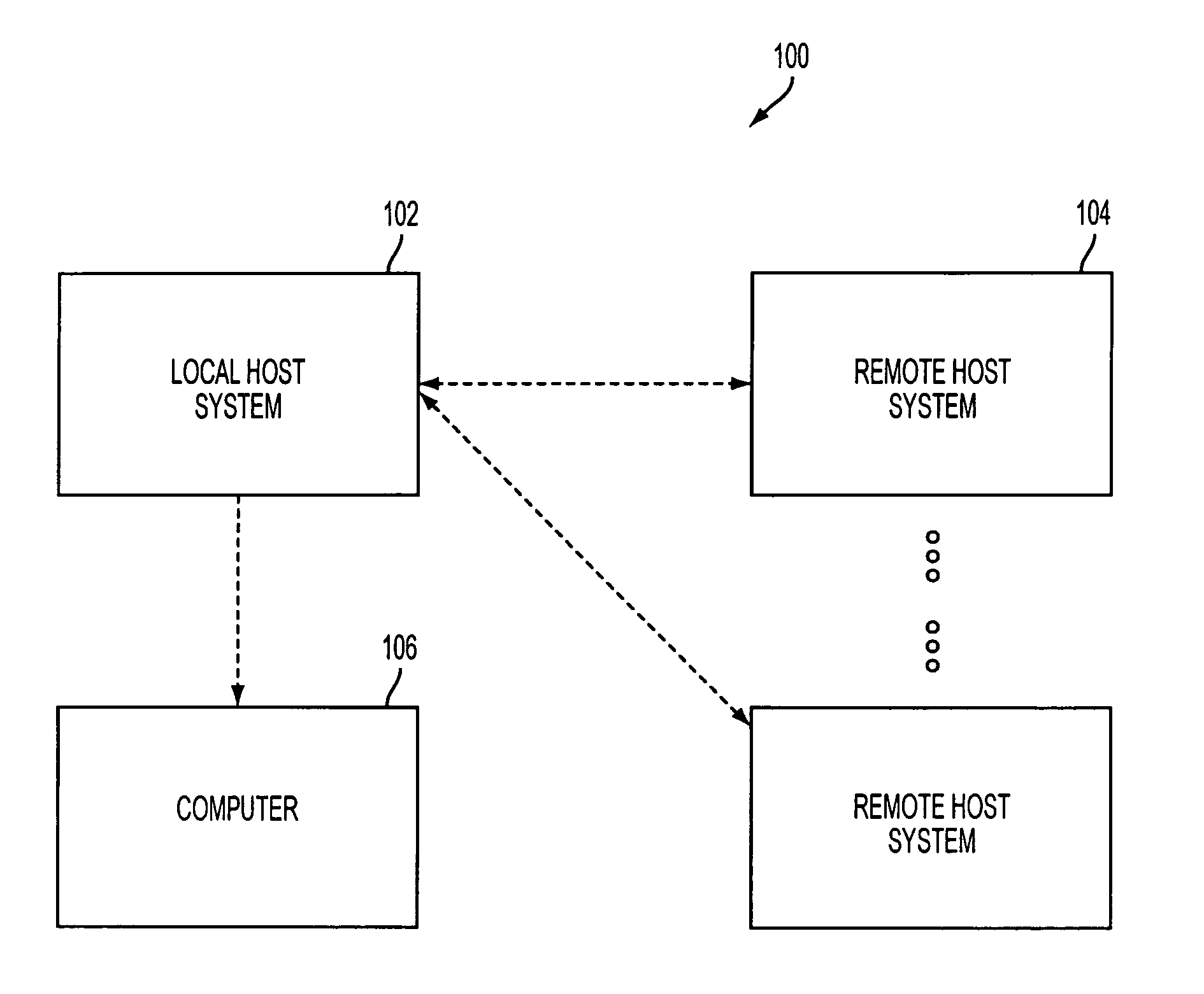
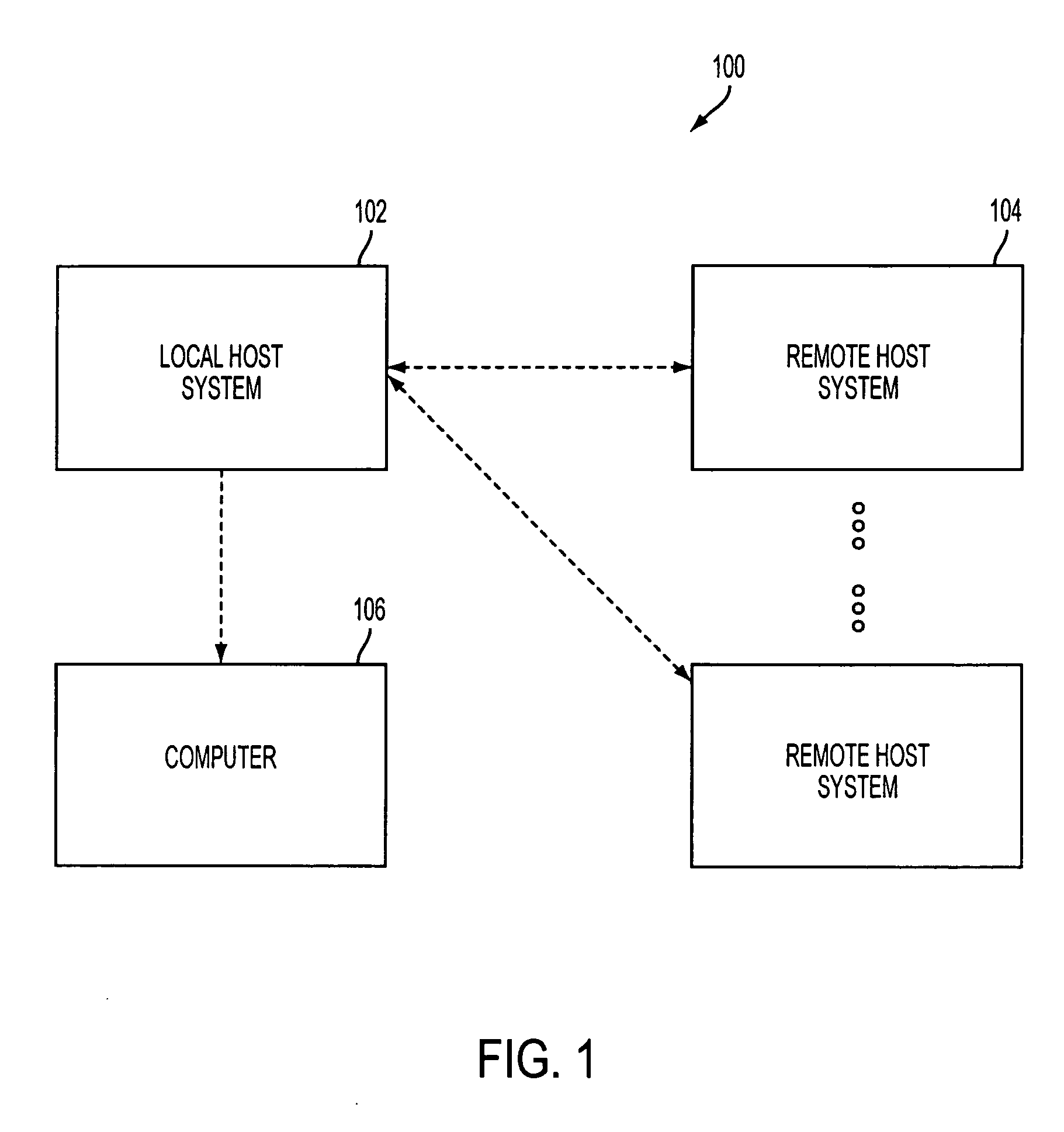
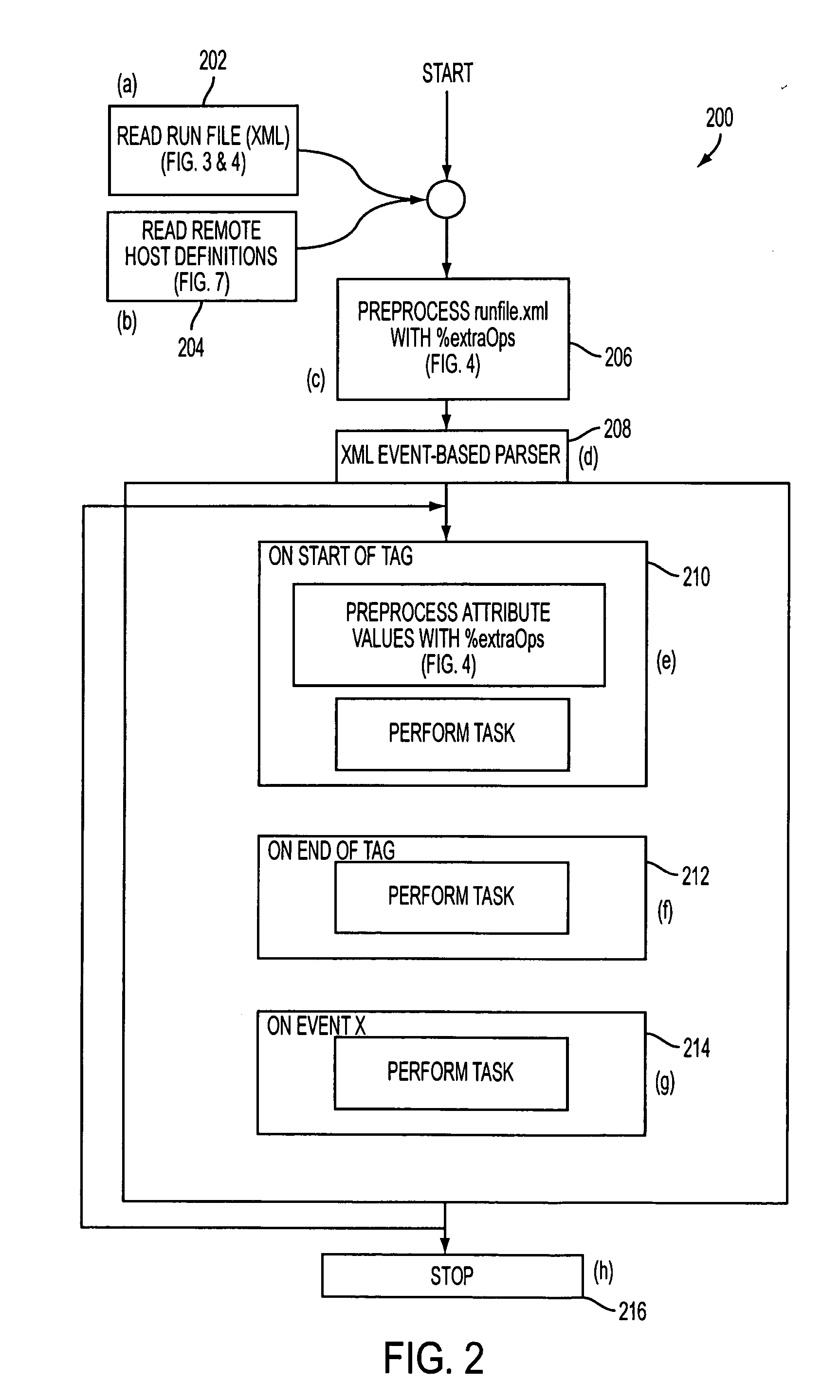
A method of creating an XML based framework to perform automated forecasting includes sending a file from a local host computer to a remote computer, receiving a file at the local host computer from the remote computer, installing the received file on the local host computer, and executing commands on the local host computer and the remote computer. Executing a command on the remote computer includes reading a run file and a host definition file. A framework for interacting between the local host computer and the remote computer is determined based on types of XML tags, the XML tags including at least one of a start of a tag, end of a tag, and text between the start of a tag and the end of a tag. Computer program products for creating an XML based framework to perform automated forecasting are also described.
Owner:UNITED STATES OF AMERICA
Clock synchronizing method over fault-tolerant Ethernet
ActiveUS7200158B2Compensation delayTime-division multiplexData switching by path configurationTransceiverMedia access controller
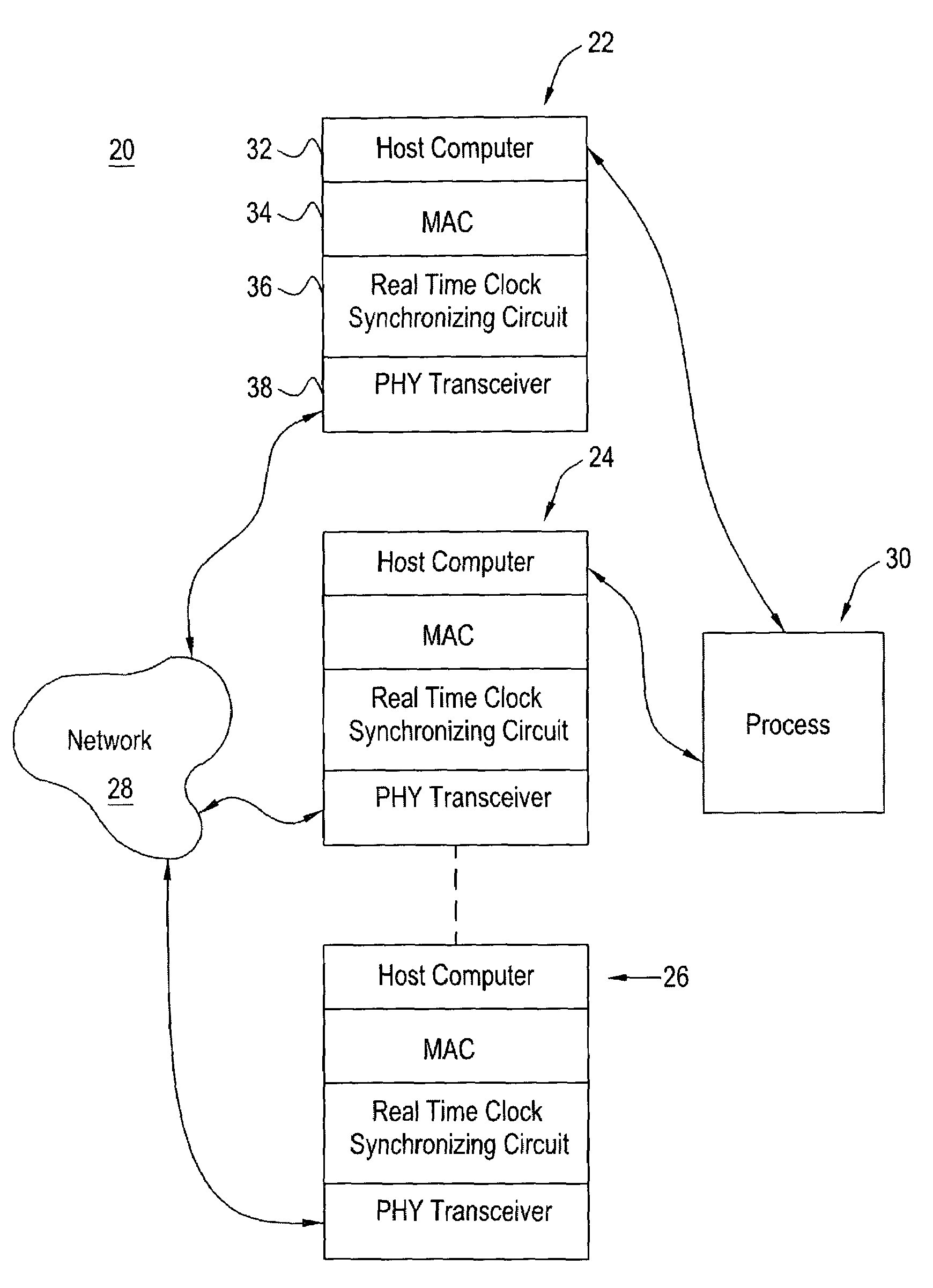
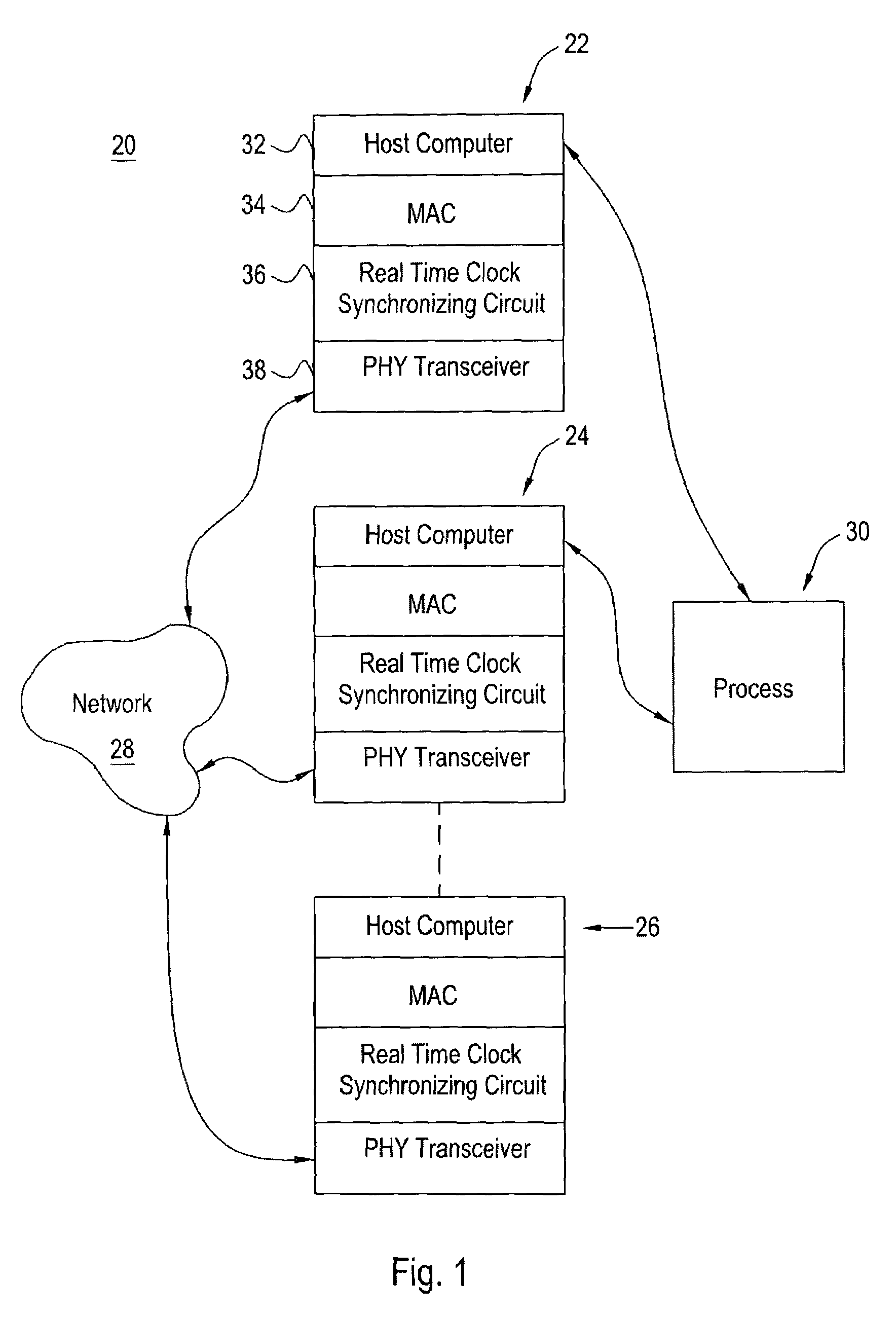
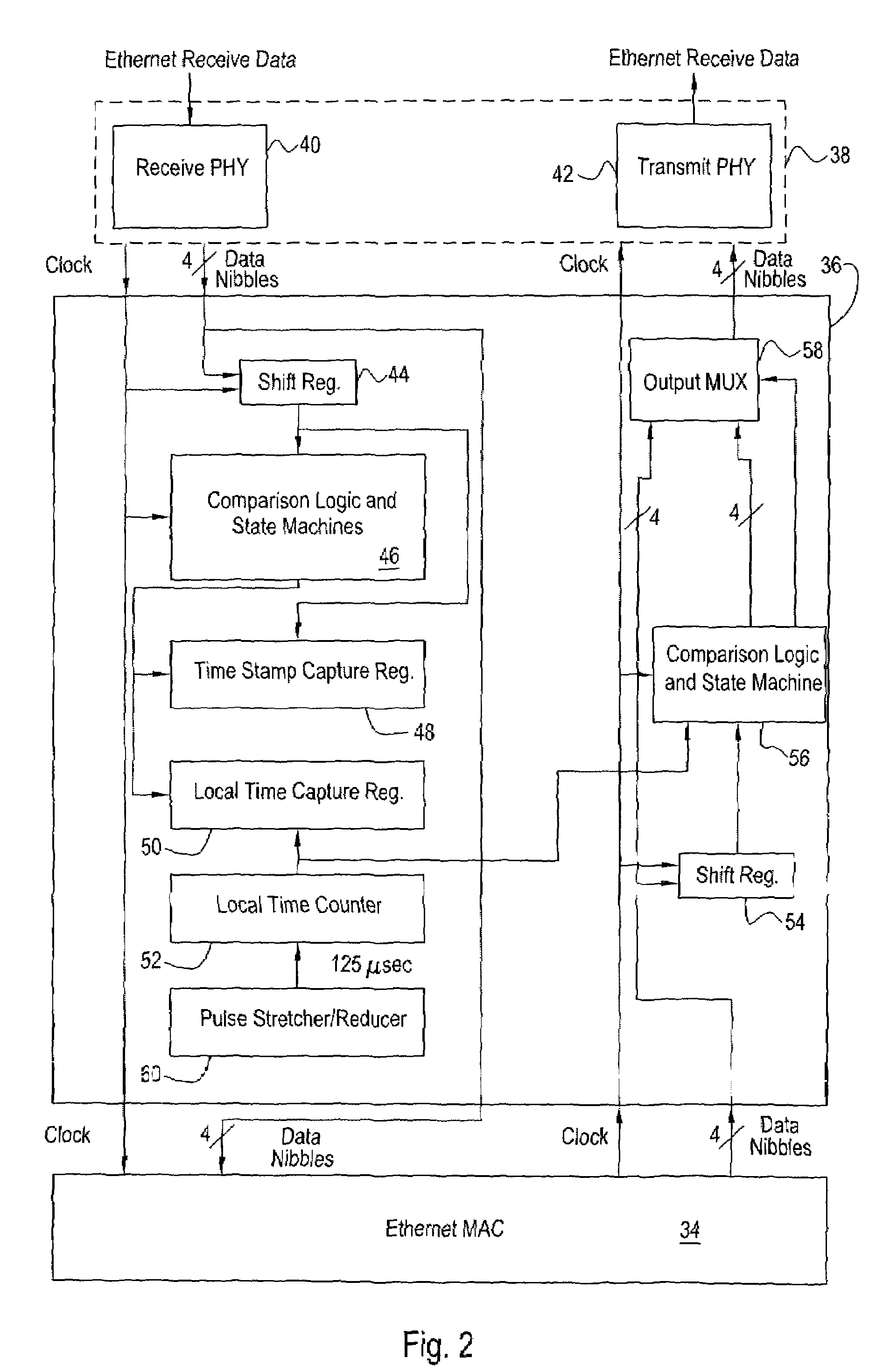
A device that recognizes the time synchronization packet and substitutes a real-time value from the master internal counter into the proper place in a data packet is placed between an Ethernet Media Access Controller (MAC) and a Physical Interface Transceiver (PHY). A second device monitors the packet passing from the MAC to the PHY and determines when it is a time synchronization packet from the time master. Upon recognition of the proper packet, the second device simultaneously captures the master's time value and captures the value of a local real-time clock. The result of these captures are presented to the local host computer which controls the time base clock that increments the local real-time clock to either speed up or slow down this local clock, thereby synchronizing the local clock to the time master clock. The offset and skew of the local clock to the master clock is reduced to only the network latency plus variability due to network congestion.
Owner:HONEYWELL INT INC
Offload system, method, and computer program product for processing network communications associated with a plurality of ports
ActiveUS20070064724A1Easy to integrateEasy to manufactureTime-division multiplexMultiple digital computer combinationsTransport layerNetwork communication
An offload system, method, and computer program product are provided for handling transport layer processing of a connection between a local host and a remote host via at least one network. A network interface associated with the local host is utilized for such purpose. A plurality of ports allow communication between the local host and the at least one network. The communications corresponding with the connection are monitored and the connection is associated with at least one port. At least one of the ports receiving the communications corresponding with the connection are identified.
Owner:NVIDIA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com