Network device inventory system
a network device and inventory system technology, applied in the field of distributed computer systems, can solve the problems of increased loss of connectivity, network damage and compromise of confidential data, and large networks without efficient knowing that all the devices on the network are functioning properly, so as to improve system integrity, reduce processing and memory requirements, and improve the effect of system integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
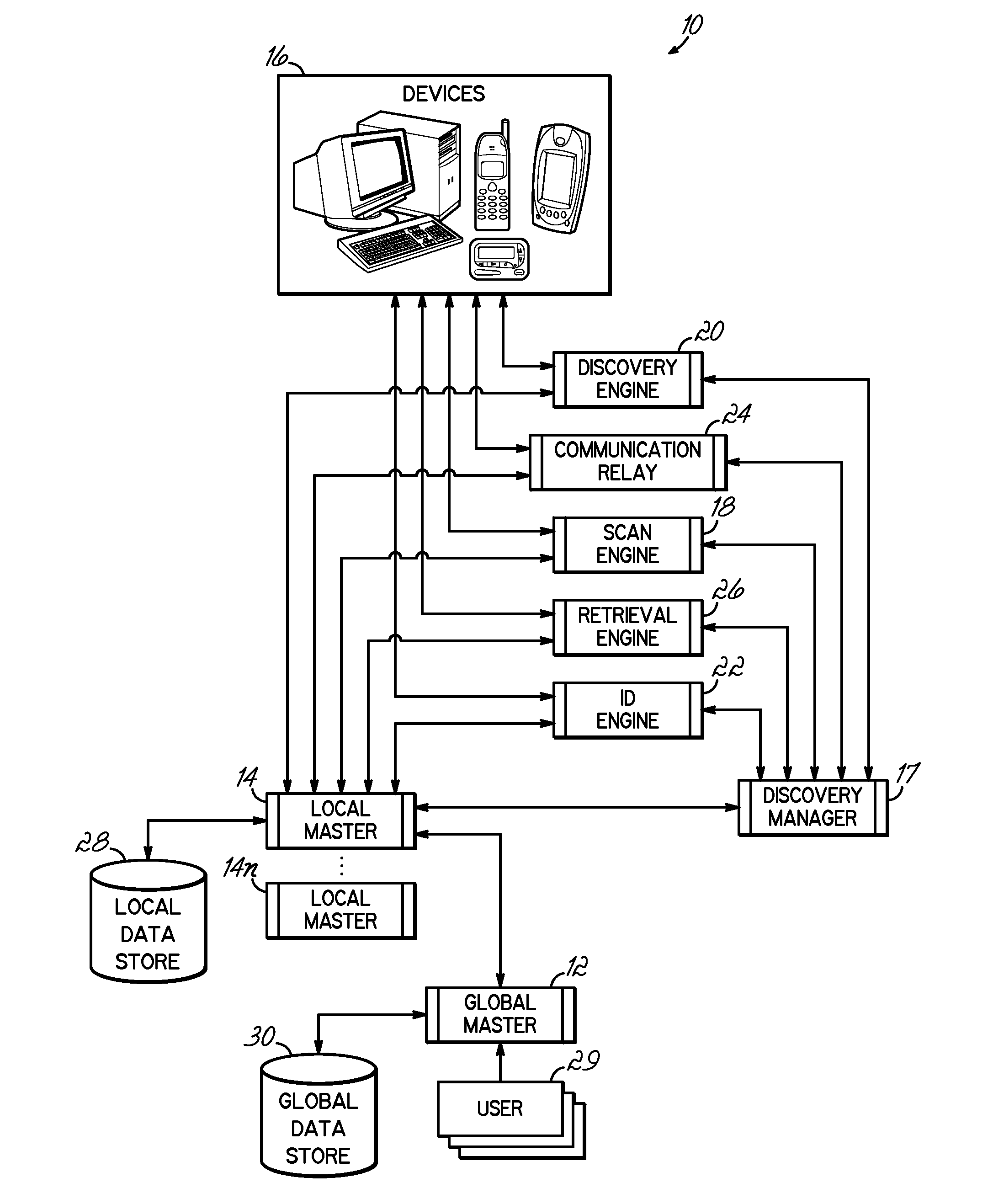
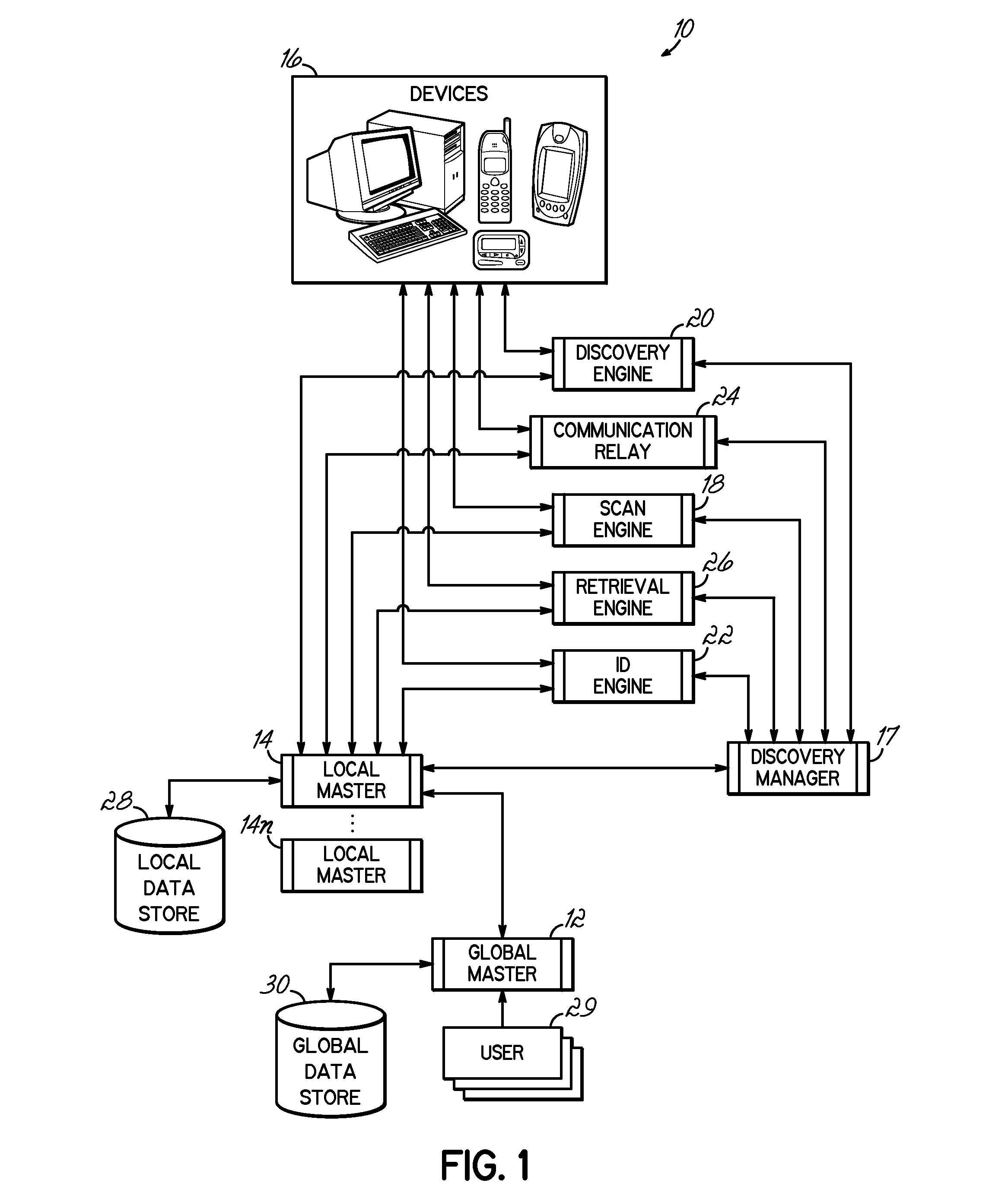
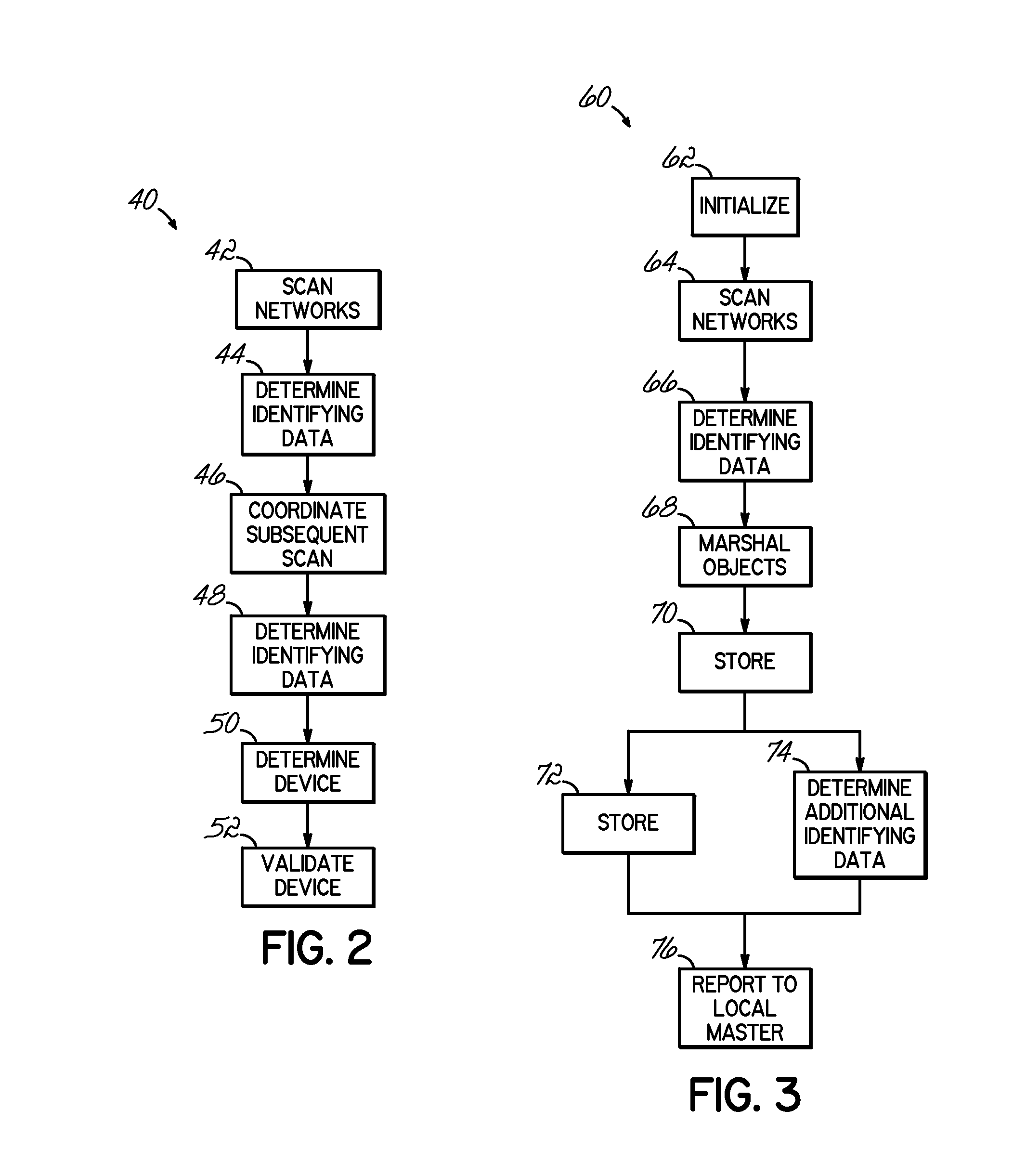
[0023]An embodiment consistent with the invention identifies and validates network devices by actively crawling through networks to collect identifying data. The identifying data comprises information indicative of a particular device or network, e.g., “hints” comprising the type of port, traffic, protocol and / or operating system used by a device. Other identifying data may include a serial number or previously assigned identifier associated with the device. The embodiment correlates the determined identifying data to stored device information. In this manner, the identifying data may be matched in order to categorize a device as being either known or unknown. Unknown devices may then be evaluated to determine if they should be approved and cataloged, or disabled from the network.
[0024]To accomplish this network device validation, the embodiment shown in FIG. 1 relies on a distributed network inventory system 10 configured to identify, classify and / or validate network devices 16. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com