Patents
Literature
6902results about "Other databases indexing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
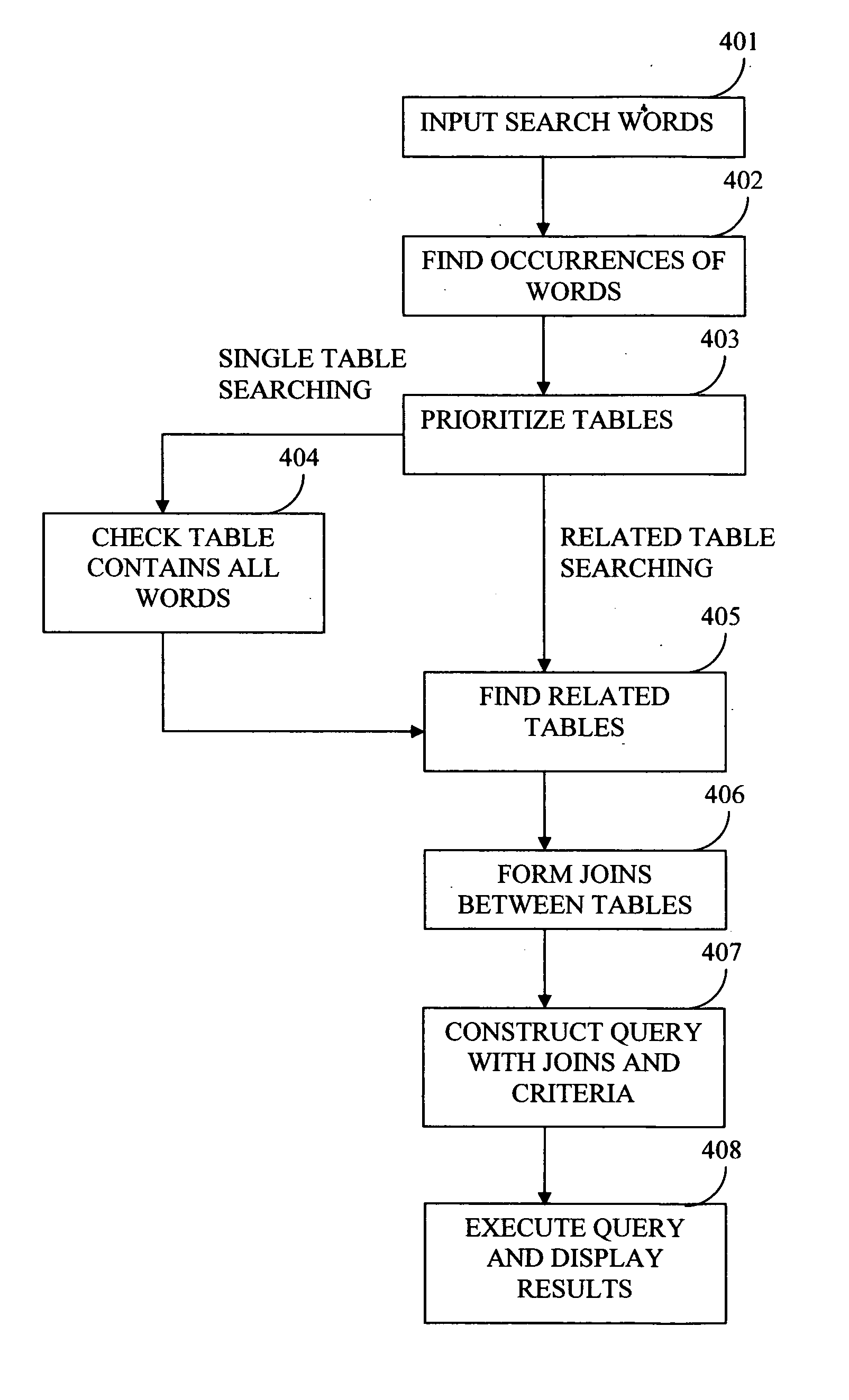
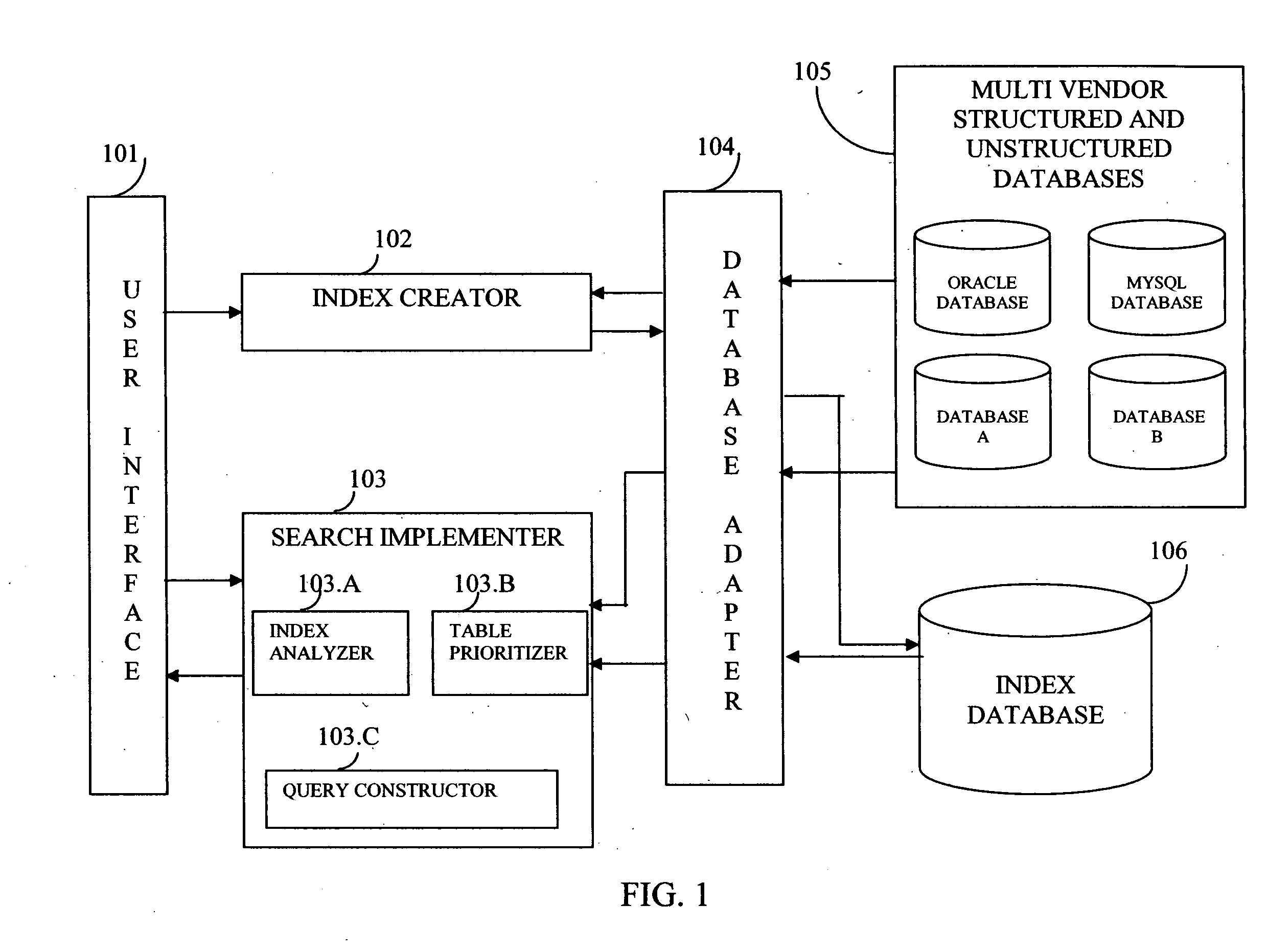
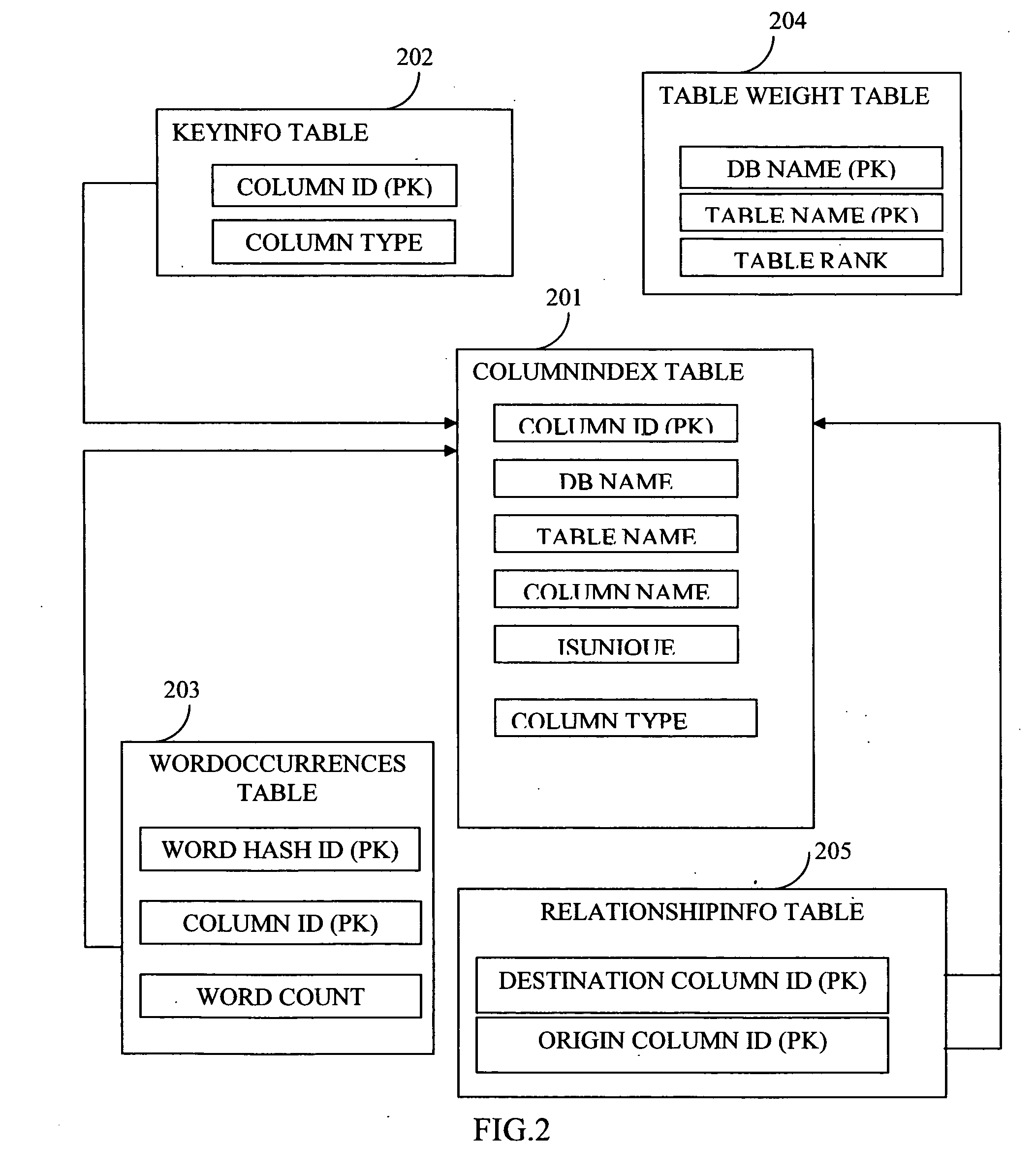
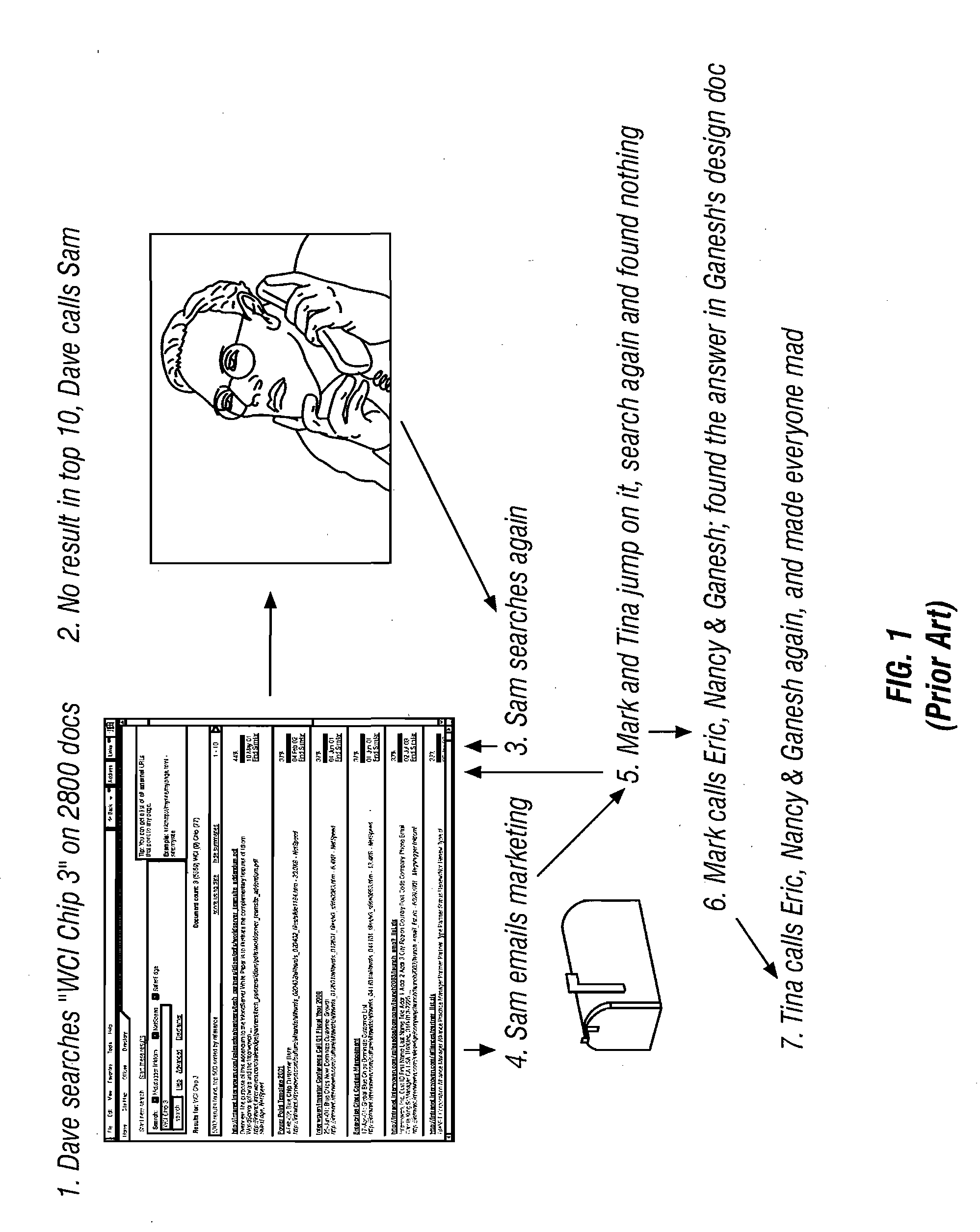
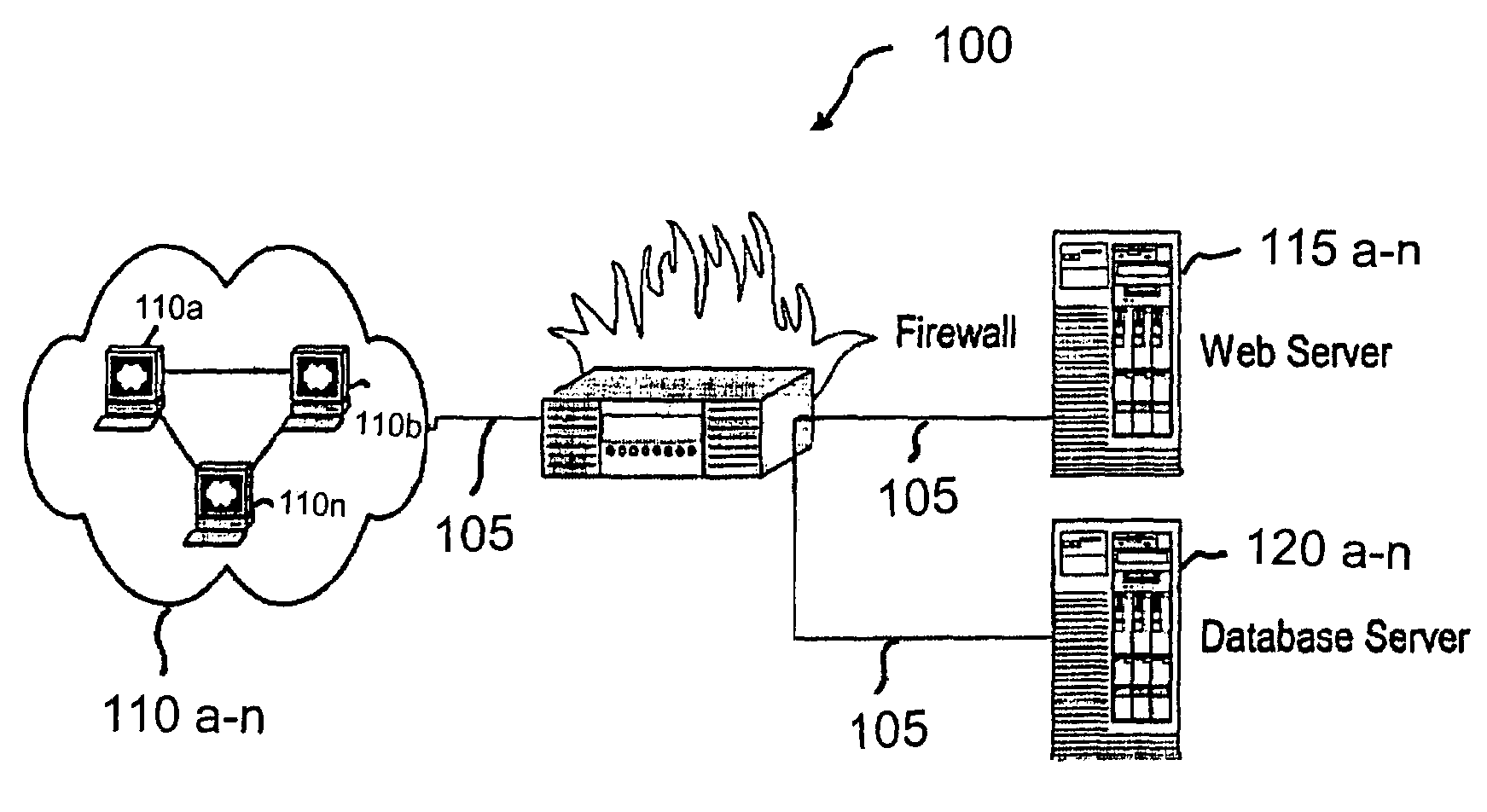
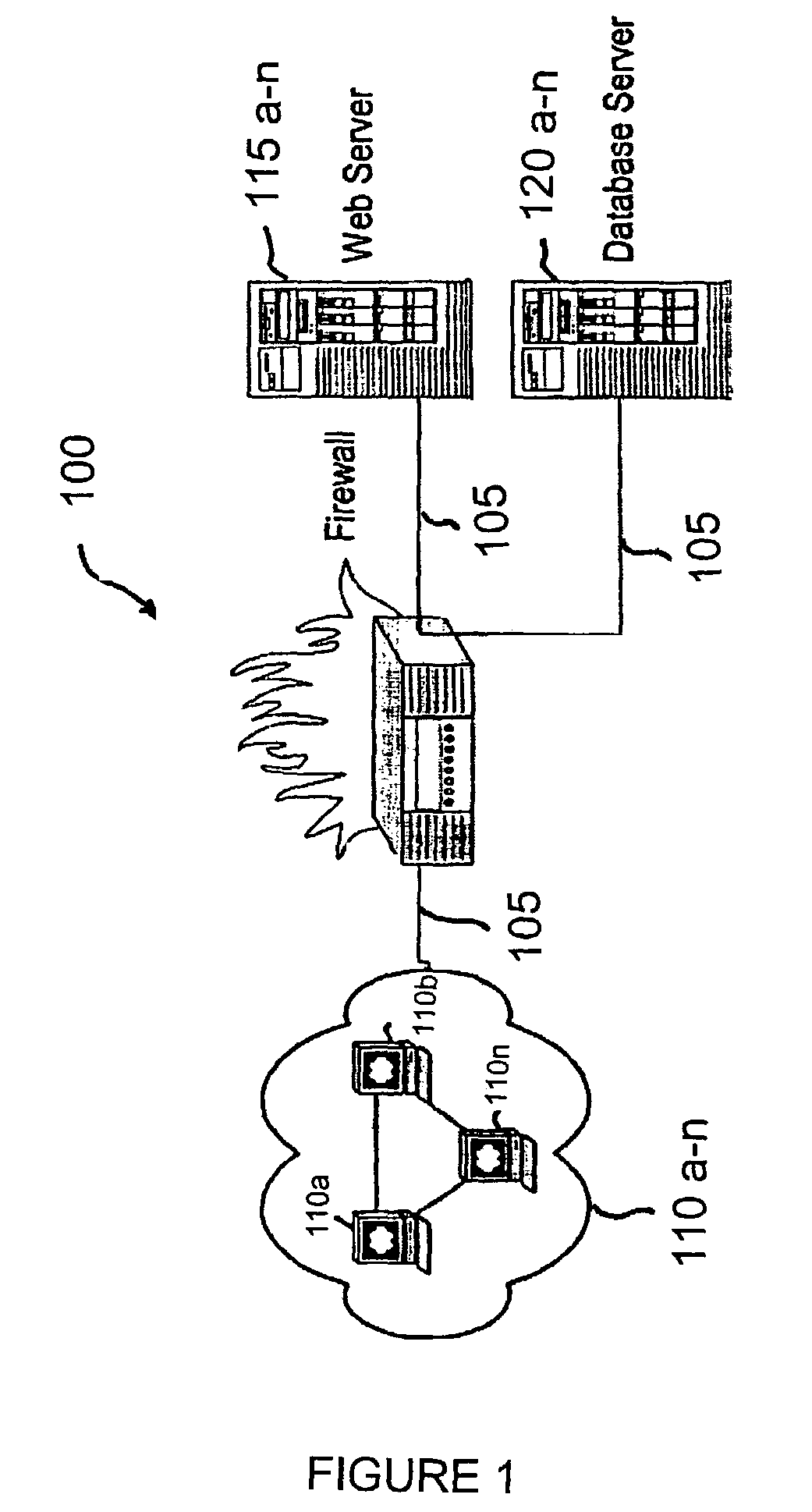
Structure independent searching in disparate databases
InactiveUS20060074881A1Resolve differencesDatabase management systemsOther databases indexingSearch wordsDatabase access
This invention allows keyword searches in both structured and unstructured databases, and across multiple databases of different vendors. An index database is created comprising word occurrences and table relationship information. In the case of unstructured databases with no predetermined schema, the relationship between different tables is derived through propagative n-level indexing and data is then populated in index tables. A database adapter enables indexing and searching across multi-vendor databases, which resolves discrepancies across different database access methodologies. Given a set of keyword inputs, the rows containing the search words and all the related rows are searched using word occurrences and relationship information.
Owner:ADVENTNET
Method and apparatus for identifying, extracting, capturing, and leveraging expertise and knowledge
InactiveUS20060200556A1Economical to useMinimal effortDigital computer detailsOther databases indexingWork patternMarine navigation
The invention comprises a set of complementary techniques that dramatically improve enterprise search and navigation results. The core of the invention is an expertise or knowledge index, called UseRank that tracks the behavior of website visitors. The expertise-index is designed to focus on the four key discoveries of enterprise attributes: Subject Authority, Work Patterns, Content Freshness, and Group Know-how. The invention produces useful, timely, cross-application, expertise-based search and navigation results. In contrast, traditional Information Retrieval technologies such as inverted index, NLP, or taxonomy tackle the same problem with an opposite set of attributes than what the enterprise needs: Content Population, Word Patterns, Content Existence, and Statistical Trends. Overall, the invention emcompasses Baynote Search—a enhancement over existing IR searches, Baynote Guide—a set of community-driven navigations, and Baynote Insights—aggregated views of visitor interests and trends and content gaps.
Owner:MONETATE INC
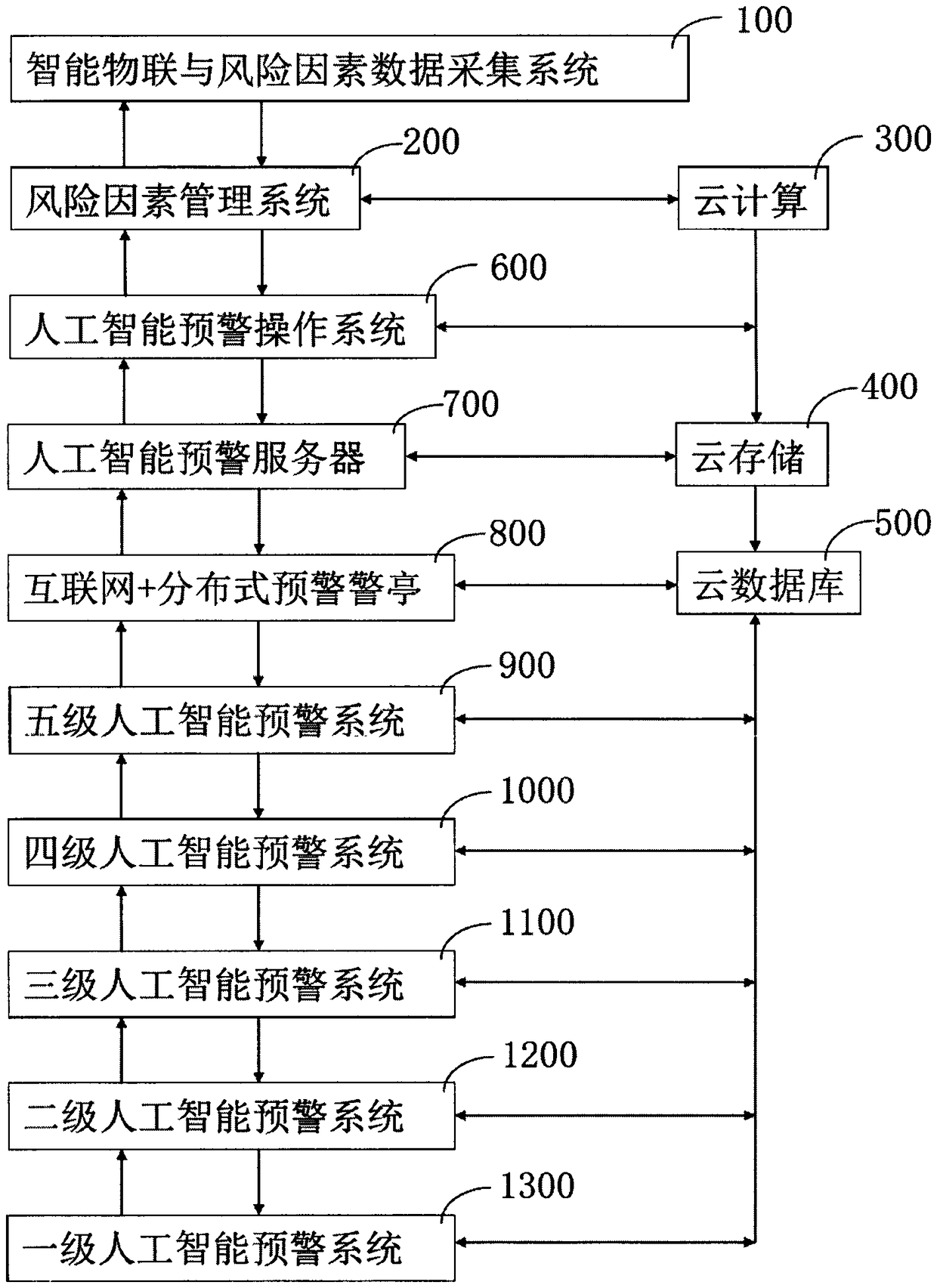
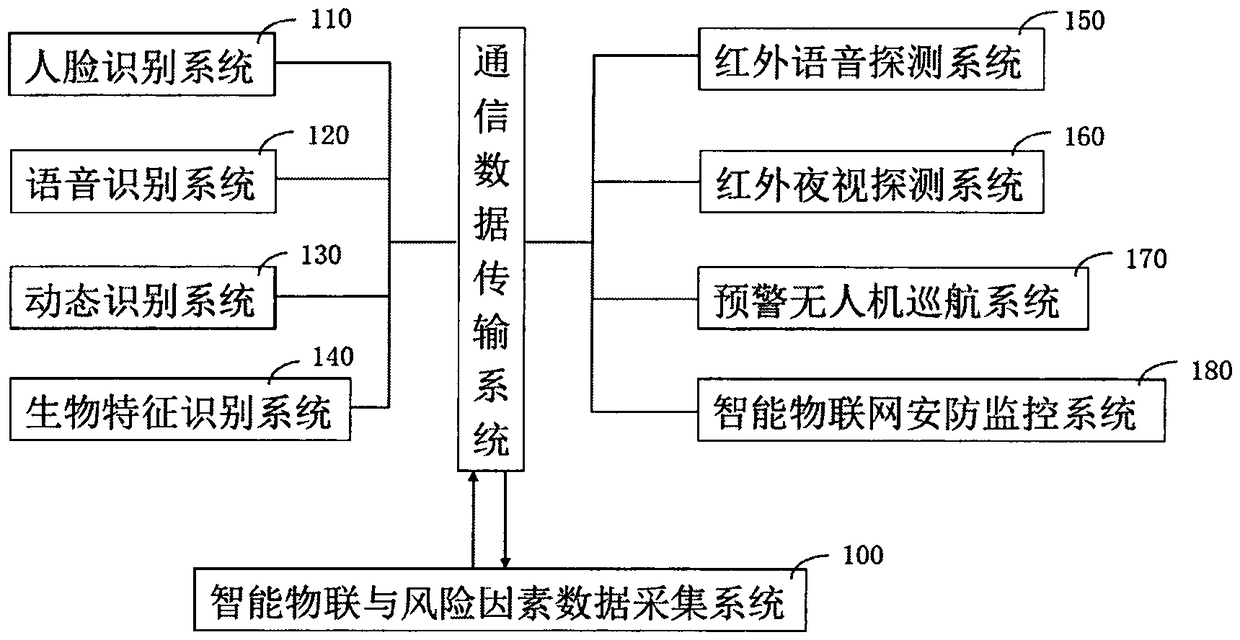
Artificial intelligence early warning system
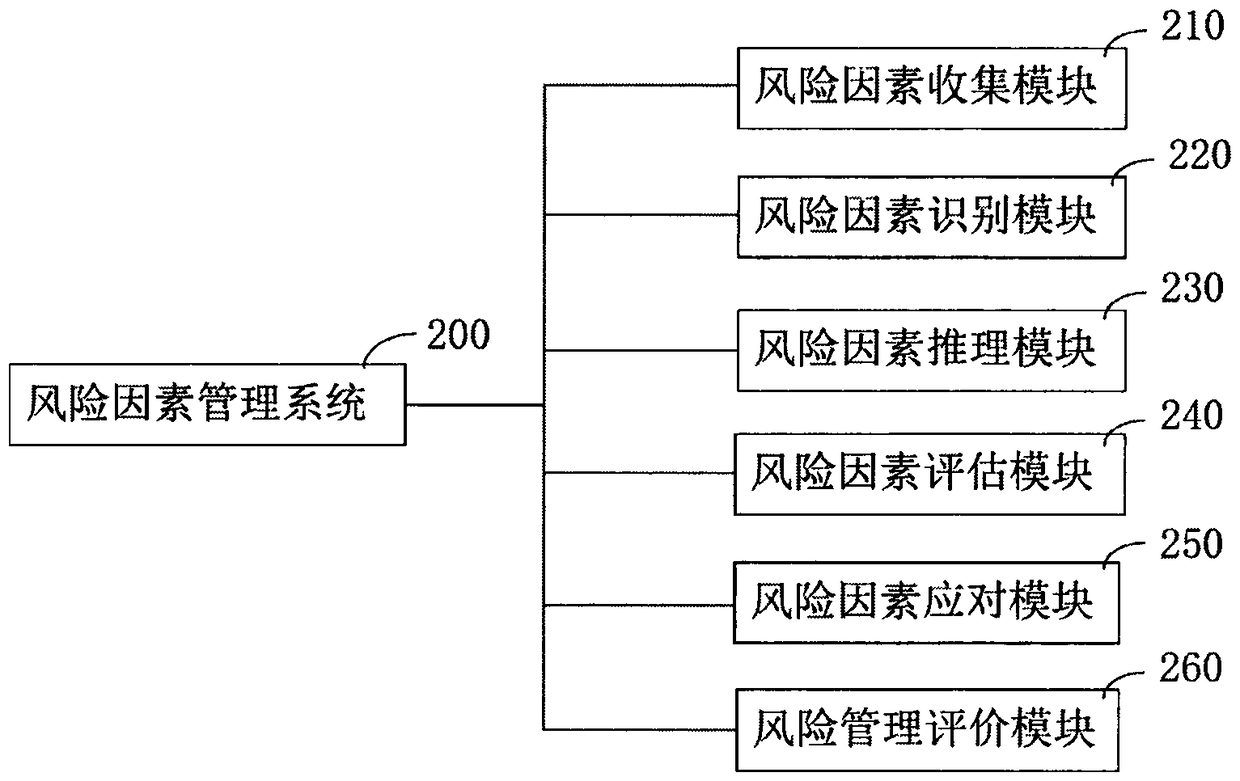
ActiveCN109447048APrevent overpassSemantic analysisOther databases indexingThree levelInformation resource
The invention relates to an artificial intelligence early warning system. The system comprises an intelligent Internet of Things and risk factor data acquisition system (100), and a risk factor management system (200), a cloud computing device (300), a cloud storage device (400), a cloud database (500), and an artificial intelligence early warning operation system (600), an artificial intelligenceearly warning server (700), an internet + distributed early warning police booth (800), a five-level artificial intelligence early warning system (900), a four-level artificial intelligence early warning system (1000), a three-level artificial intelligence early warning system (1100), a two-level artificial intelligence early warning system (1200) and a one-level artificial intelligence early warning system (1300). The artificial intelligence early warning system of the present invention collects, compares, analyzes, deduces, evaluates the risk factors, and carries out the cloud computing, cloud storage, graded alarming and prevention and control, so that all-weather 24-hour monitoring on monitoring points around the police box is achieved, a user can share information, the utilization rate of information resources is increased, and the safety guarantee is increased for maintaining the stability of the borderlands.
Owner:苏州闪驰数控系统集成有限公司
Relationship collaboration system
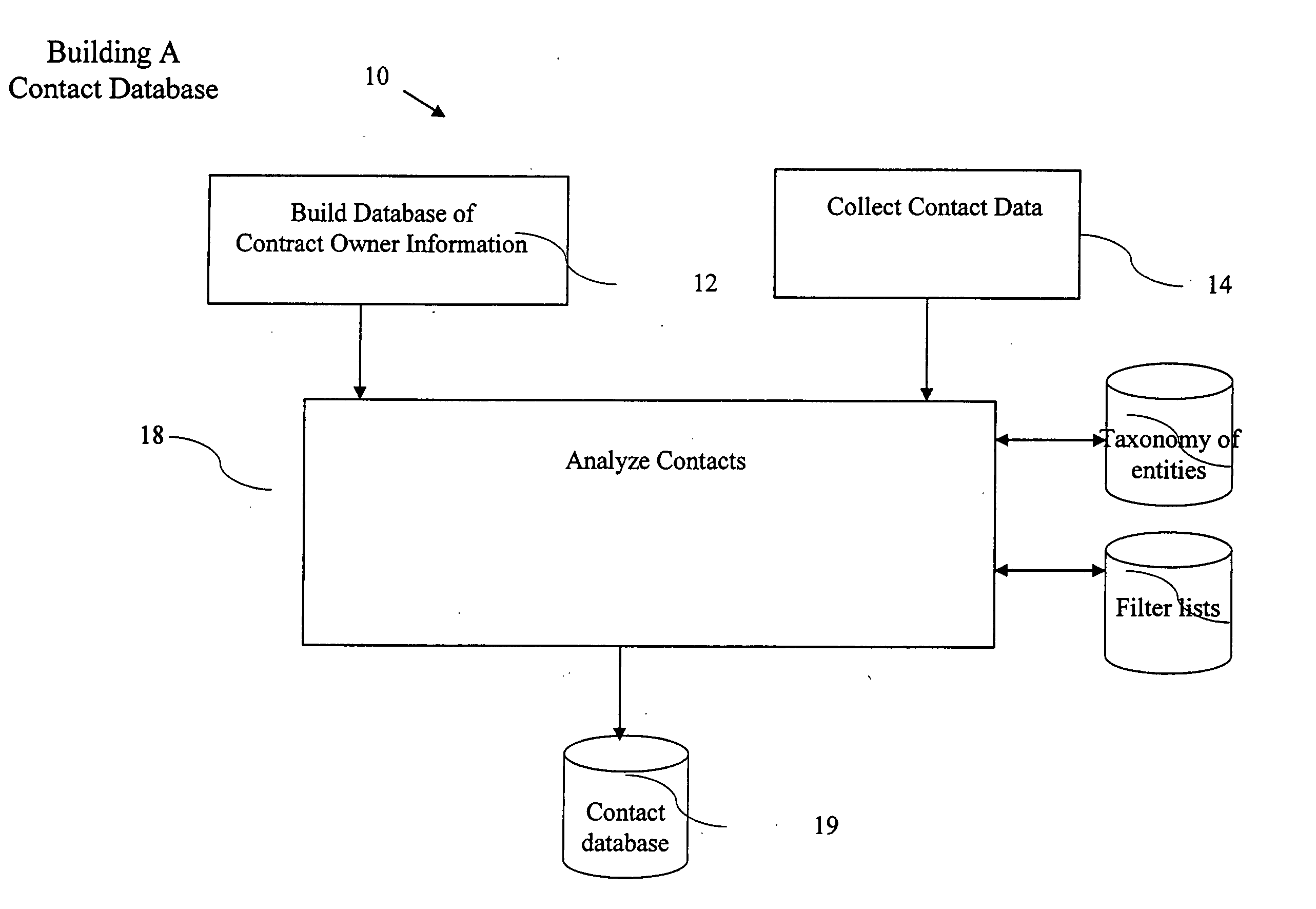
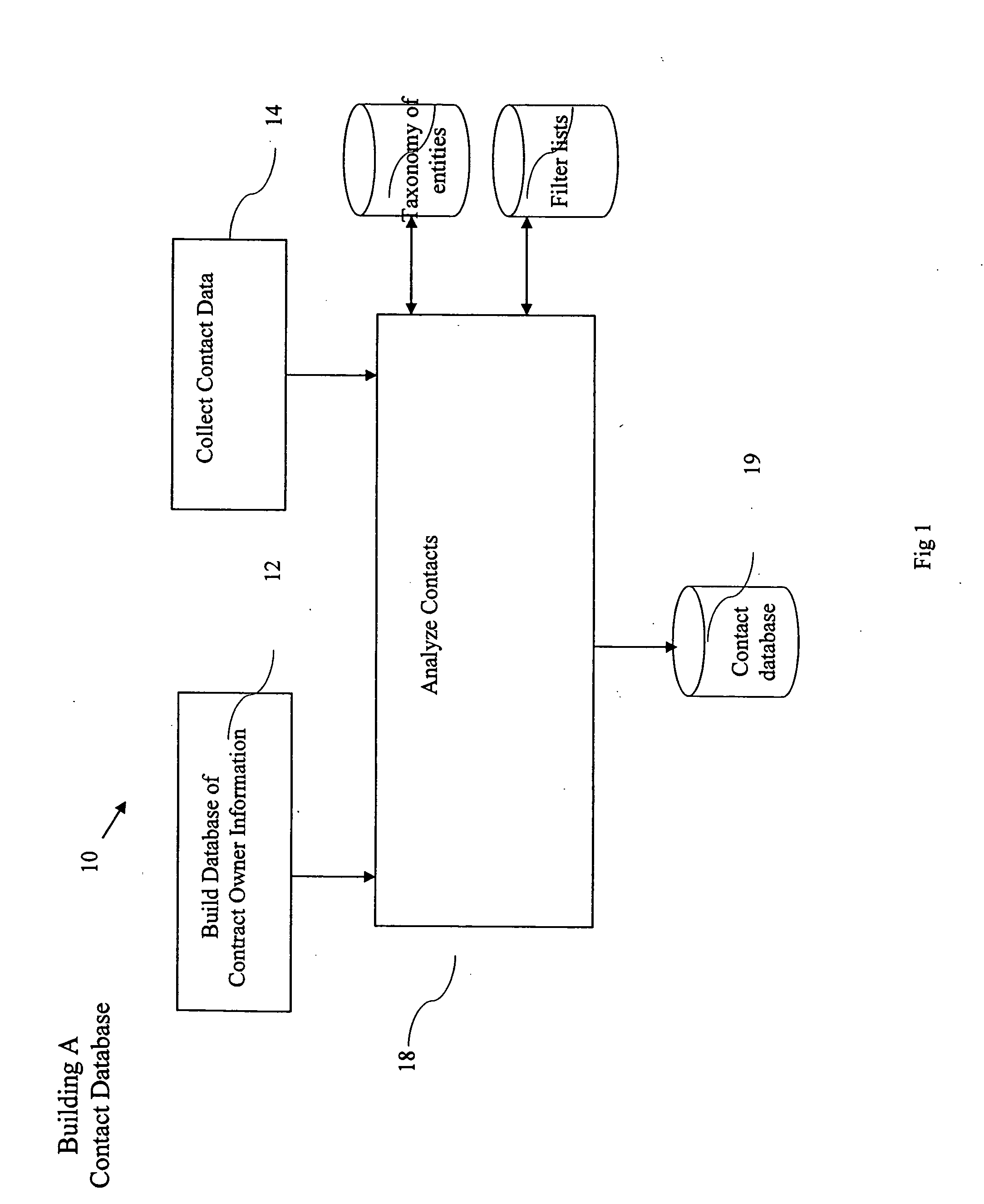
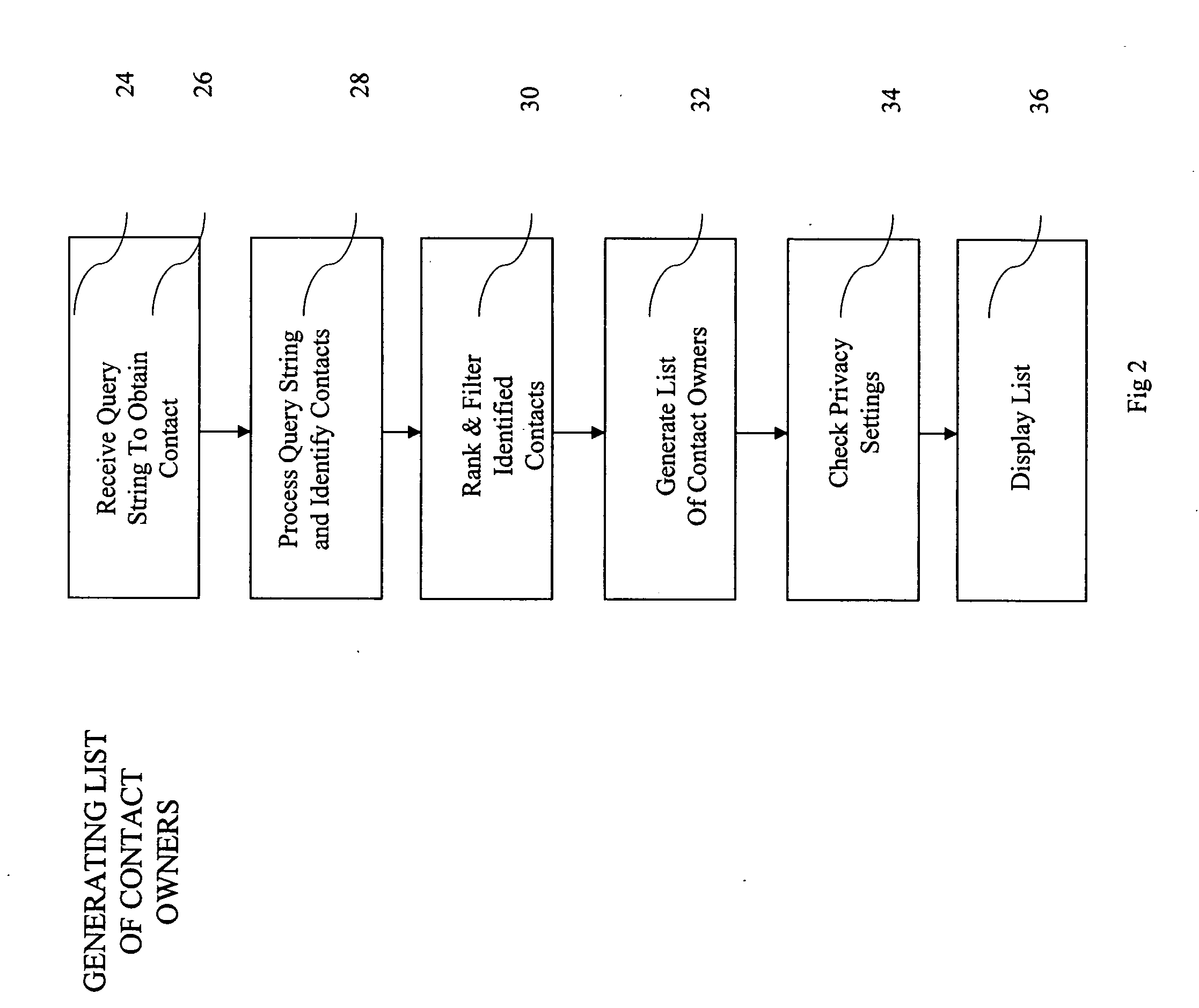
ActiveUS20050065980A1Improve identityData processing applicationsWeb data indexingDomain nameEmail address
A computer implemented method of processing data containing information about relationships between contacts and a community of contact owners, comprises: collecting data including contact information, contact owner information and one or more values related to strength of a relationship between the contact and the contact owner; evaluating the strength of the relationship based on the one or more values; and storing the collected data and evaluated strength in a computer database. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include a domain name field; and setting the domain name field as a key field; whereby a record for an entity is found by reference to a domain name. A method of keying a database, comprises: building a database of records, each containing information about an entity, and each of which include an email address field; and setting the email address field as a key field; whereby a record for an entity is found by reference to an email address. A method of keying a database, comprising: building a database of records, each containing information about an entity, and each of which includes a field holding an identifier uniquely associated with an entity by a convention of computer networking; and setting the field holding the identifier as a key field; whereby a record for an entity is found by reference to an identifier. A method of sharing relationship information, comprising: maintaining a database of relationship information records; selecting contact information according to a selection criterion; and returning selected relationship information also complying with restrictions set in a set of hierarchical privacy policies.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
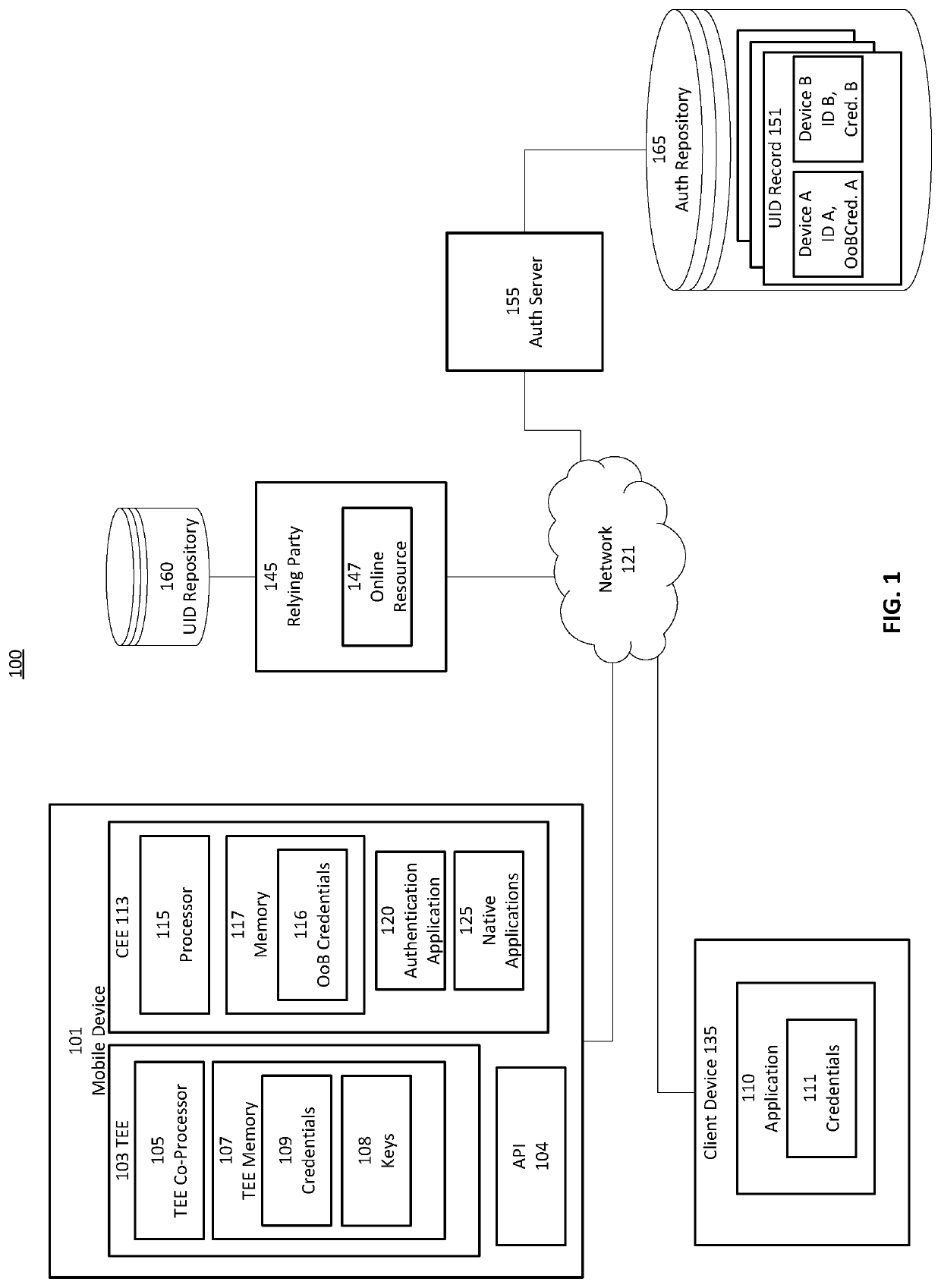
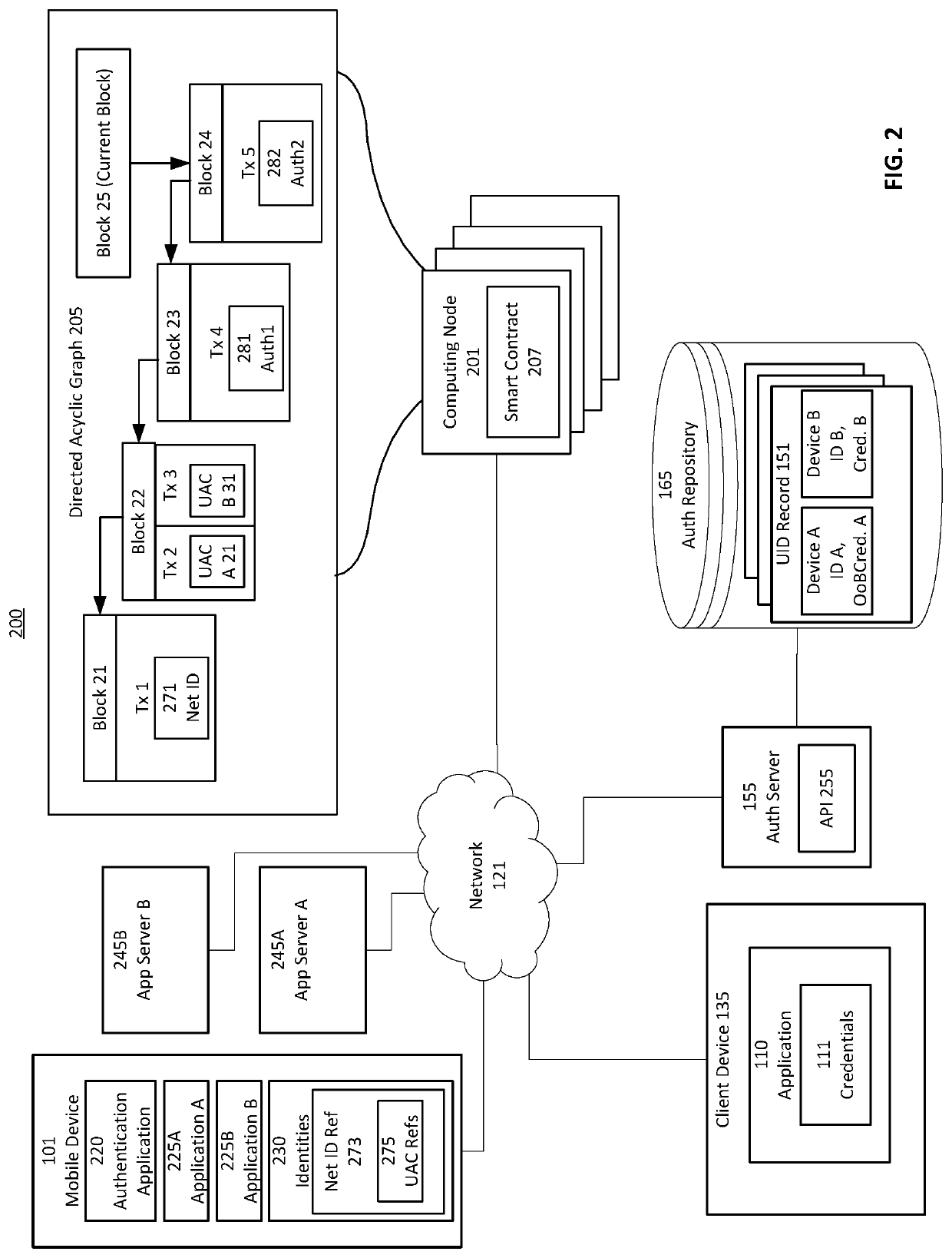
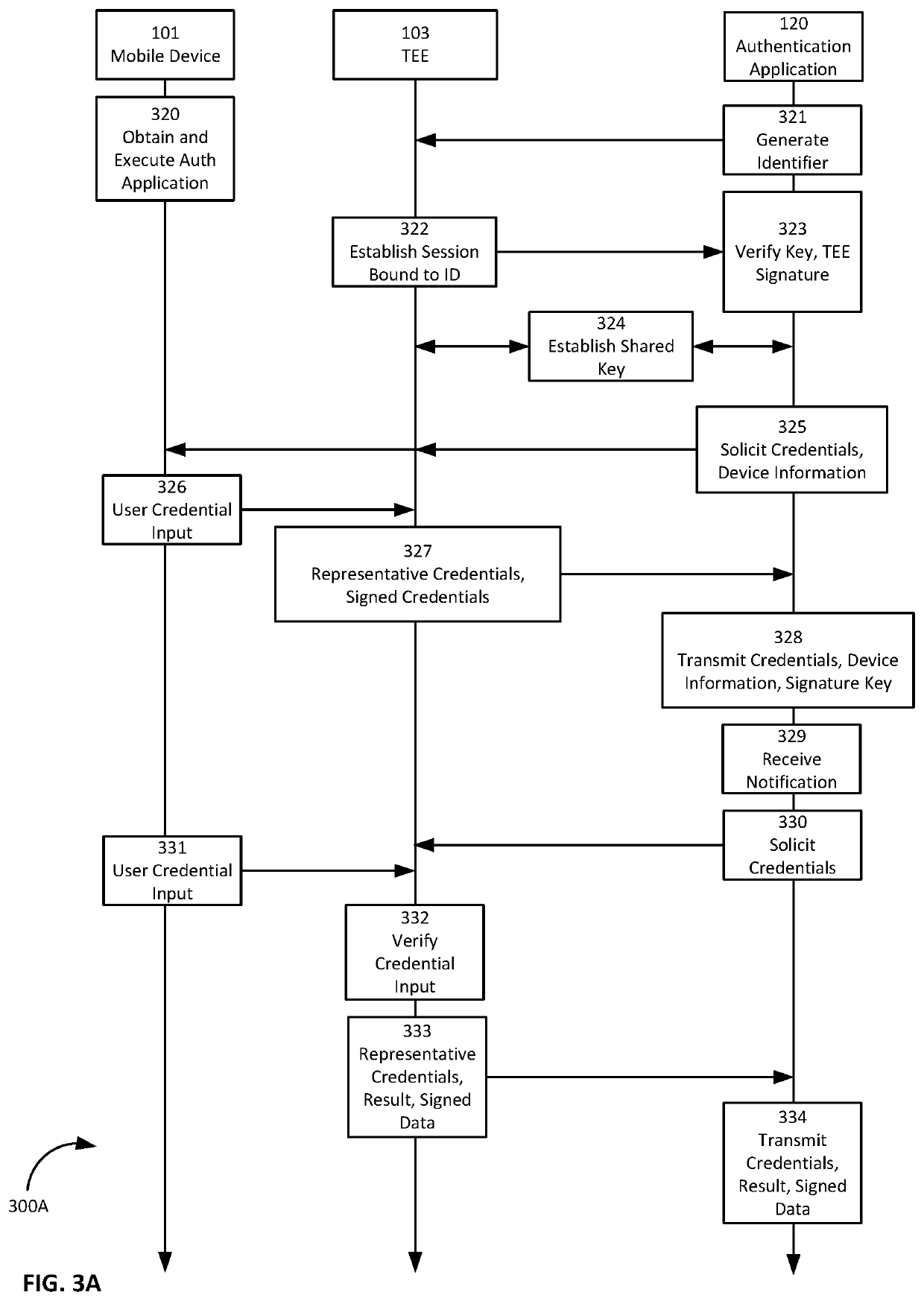
Federated identity management with decentralized computing platforms
ActiveUS20200067907A1Key distribution for secure communicationDigital data protectionInternet privacyEngineering
Provided is a process that establishes user identities within a decentralized data store, like a blockchain. A user's mobile device may establish credential values within a trusted execution environment of the mobile device. Representations of those credentials may be generated on the mobile device and transmitted for storage in association with an identity of the user established on the blockchain. Similarly, one or more key-pairs may be generated or otherwise used by the mobile device for signatures and signature verification. Private keys may remain resident on the device (or known and input by the user) while corresponding public keys may be stored in associated with the user identity on the blockchain. A private key is used to sign representations of credentials and other values as a proof of knowledge of the private key and credential values for authentication of the user to the user identity on the blockchain.
Owner:HYPR CORP
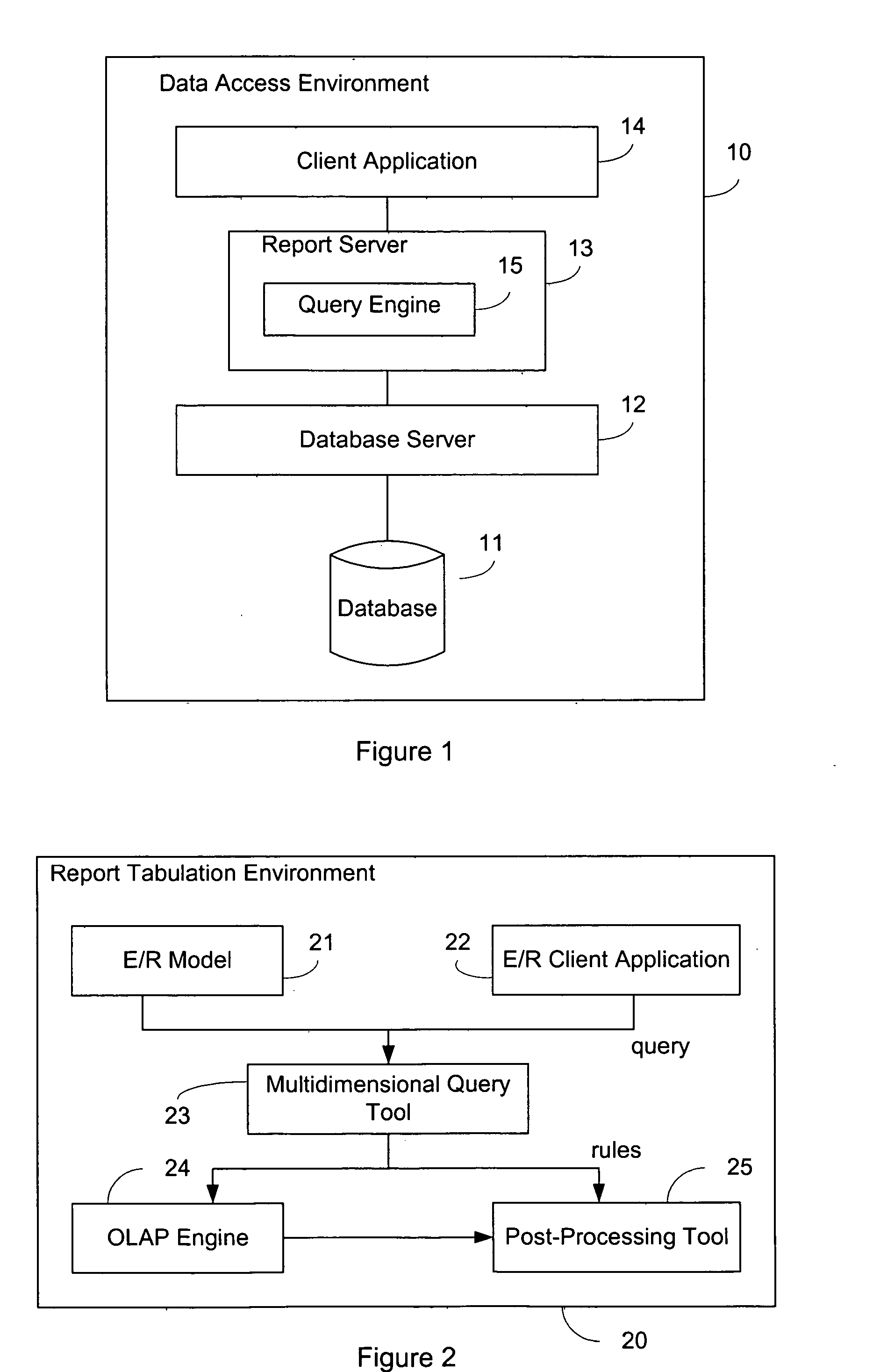
System and method of multidimensional query results processing
A multidimensional query results processing system for translating output of an execution of a multidimensional query into a data result set that reflects the semantics of an entity / relationship schema report specification is provided. The system comprises a result set description generation module for producing a result set description that reflects the semantics of the report specification, a tabular row generation module for converting the results of the single multi-dimensional query into a collection of rows of data, a tabular summary level calculation module for calculating a summarization level of a row a data, a tabular header row generation module for producing a header row to include in the row of data, and a cross-tabulated result generation module for converting the results of the single multi-dimensional query into a result set that matches the semantics of the report specification.
Owner:IBM CORP
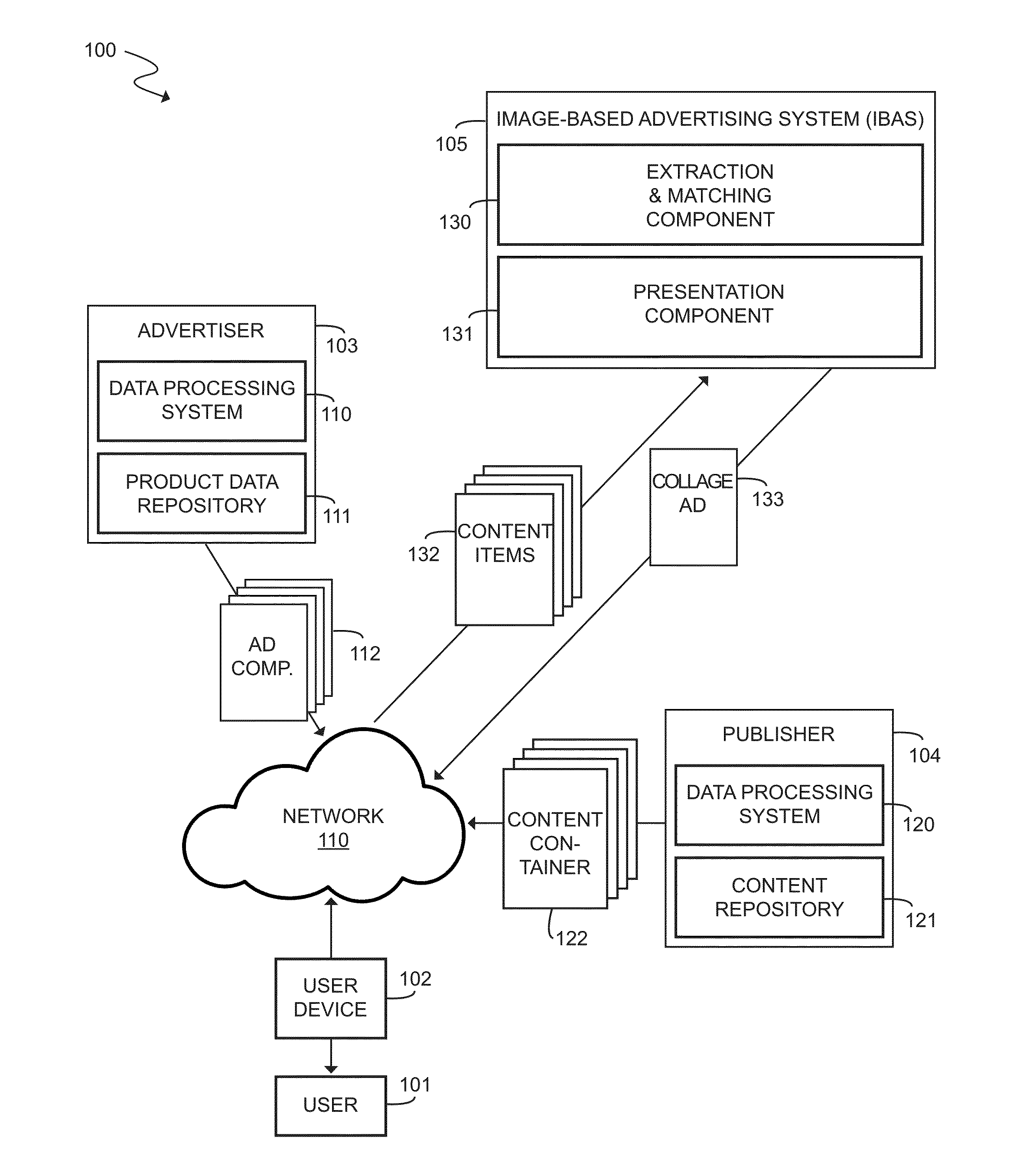
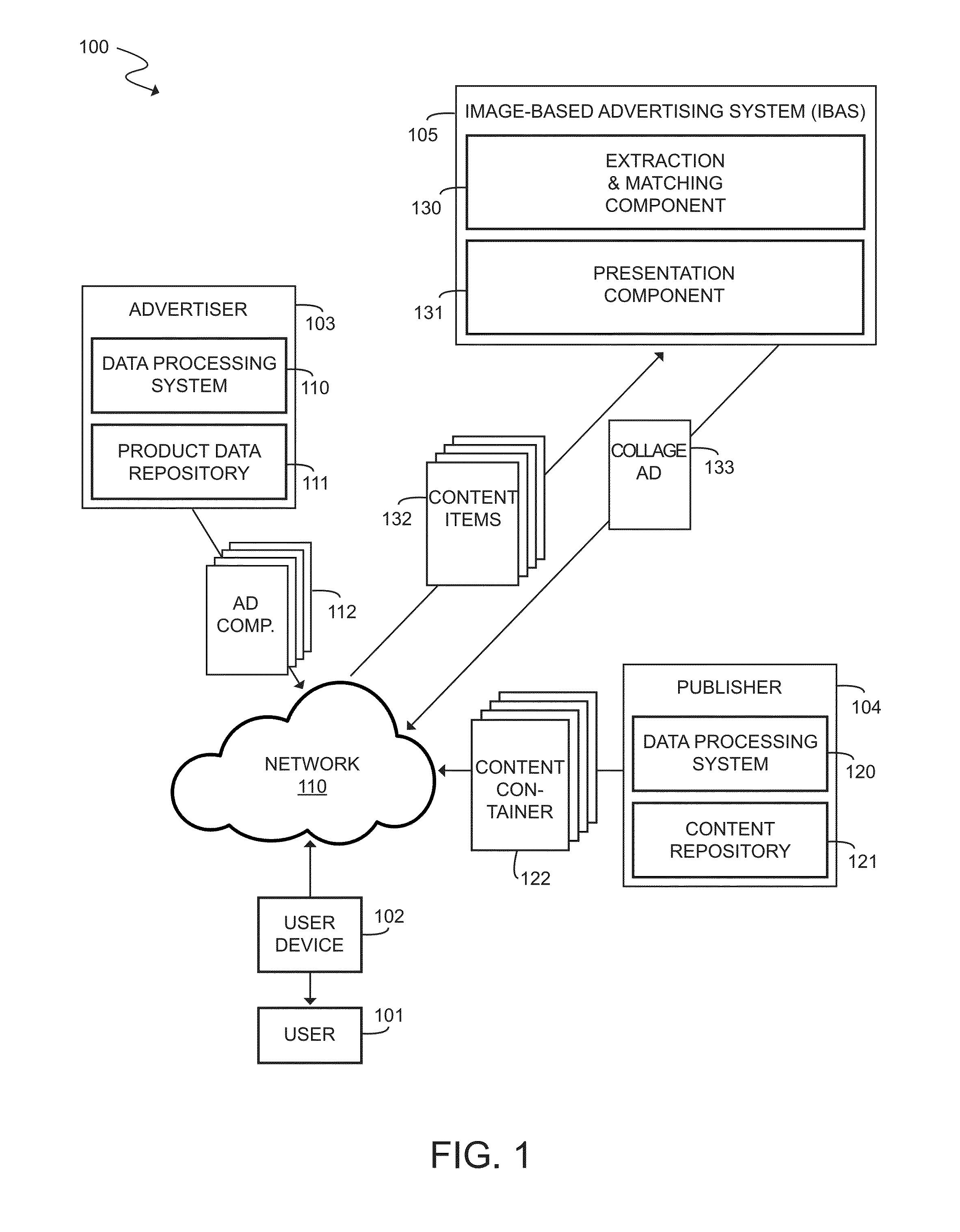
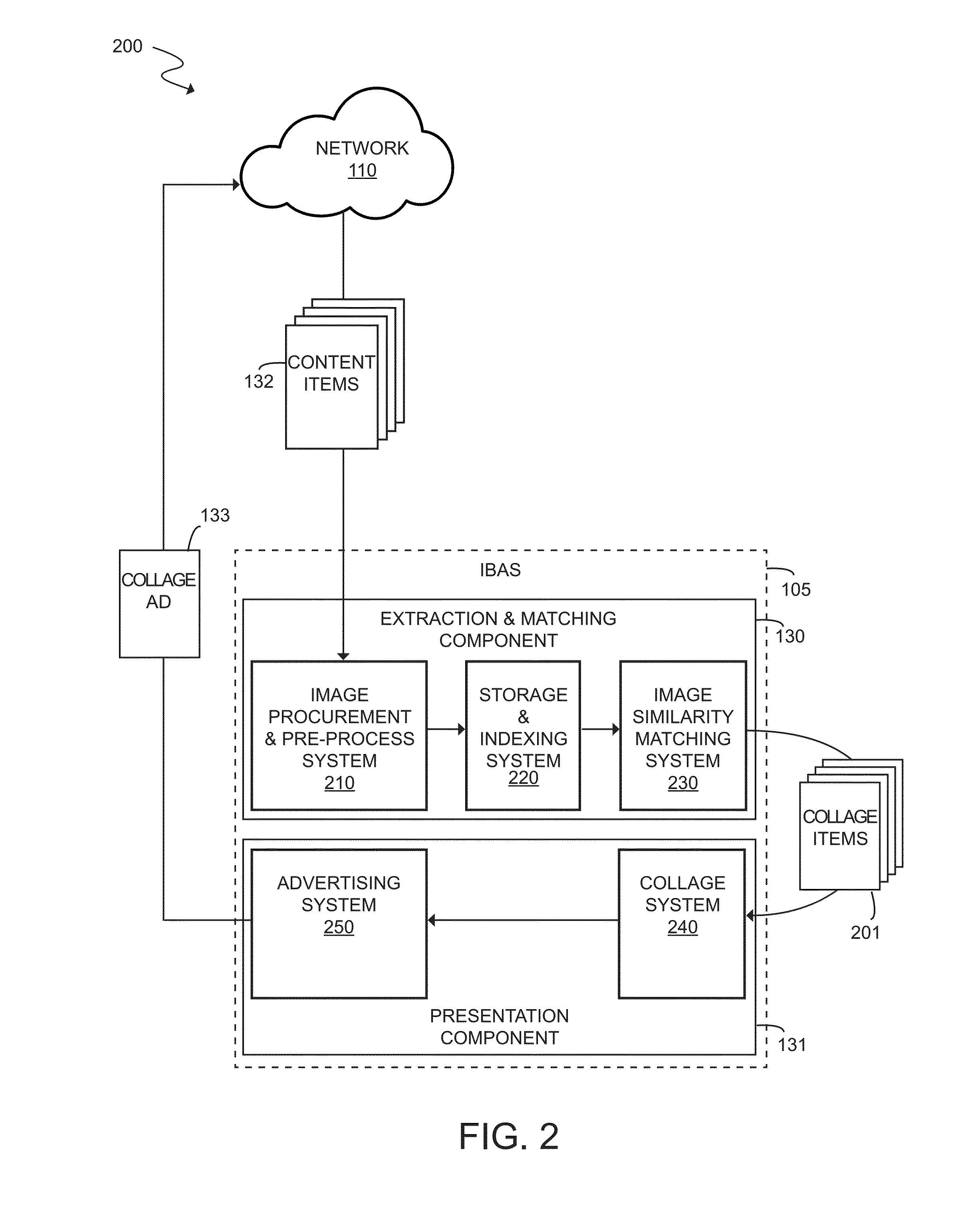
Pictollage: Image-Based Contextual Advertising Through Programmatically Composed Collages
InactiveUS20150178786A1Well formedAdvertisementsOther databases indexingComputer graphics (images)Visual perception
A system and method for creating and serving image-based contextual advertising through programmatically composed image collages, including the procurement, indexing and matching of query images, the procurement, indexing and matching of web images and the transferring of indexed and matched data from those web images to the query images, the procurement, indexing and matching of product images to be used as collage ad components, the matching and selection of one or more decorative template elements and one or more structural templates, the programmatic combining of the product images and the templates and template elements into a collage and the distribution of this collage for display to a user as a collage ad, based at least in part on the visual data extracted and indexed from the query image.
Owner:CLAESSENS CATHARINA A J
Method and apparatus for suggesting/disambiguation query terms based upon usage patterns observed
InactiveUS20070150466A1Minimal effortImprove the usefulnessOther databases indexingSpecial data processing applicationsWeb siteWork pattern
The invention comprises a set of complementary techniques that dramatically improve enterprise search and navigation results. The core of the invention is an expertise or knowledge index, called UseRank that tracks the behavior of website visitors. The expertise-index is designed to focus on the four key discoveries of enterprise attributes: Subject Authority, Work Patterns, Content Freshness, and Group Know-how. The invention produces useful, timely, cross-application, expertise-based search and navigation results. In contrast, traditional Information Retrieval technologies such as inverted index, NLP, or taxonomy tackle the same problem with an opposite set of attributes than what the enterprise needs: Content Population, Word Patterns, Content Existence, and Statistical Trends. Overall, the invention emcompasses Baynote Search—a enhancement over existing IR searches, Baynote Guide —a set of community-driven navigations, and Baynote Insights—aggregated views of visitor interests and trends and content gaps.
Owner:MONETATE INC
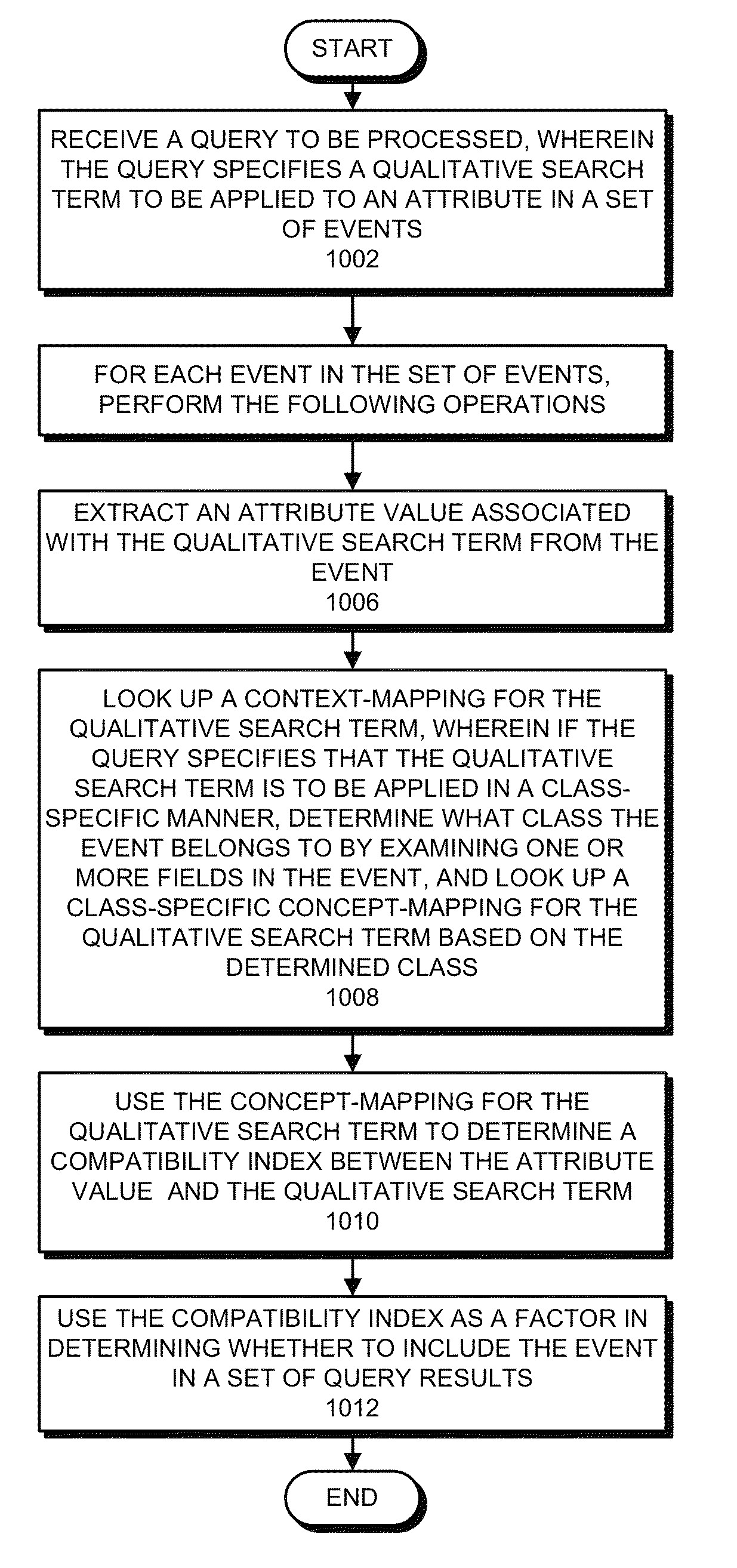
Facilitating execution of conceptual queries containing qualitative search terms
The disclosed embodiments relate to a system that facilitates performing searches based on qualitative search terms. During operation, the system receives a query that applies a qualitative search term to an attribute of data items in a set of data items. While executing the query, the system processes each data item in the set of data items by extracting an attribute value from the data item and then using a concept-mapping to determine a compatibility index for the attribute value, wherein the concept-mapping associates each attribute value with a numerical compatibility index that indicates a compatibility between the attribute value and the qualitative search term. Finally, the system uses the compatibility index as a factor in determining whether to include the data item in a set of query results.
Owner:SPLUNK INC
Method and apparatus for using ternary and binary content-addressable memory stages to classify packets
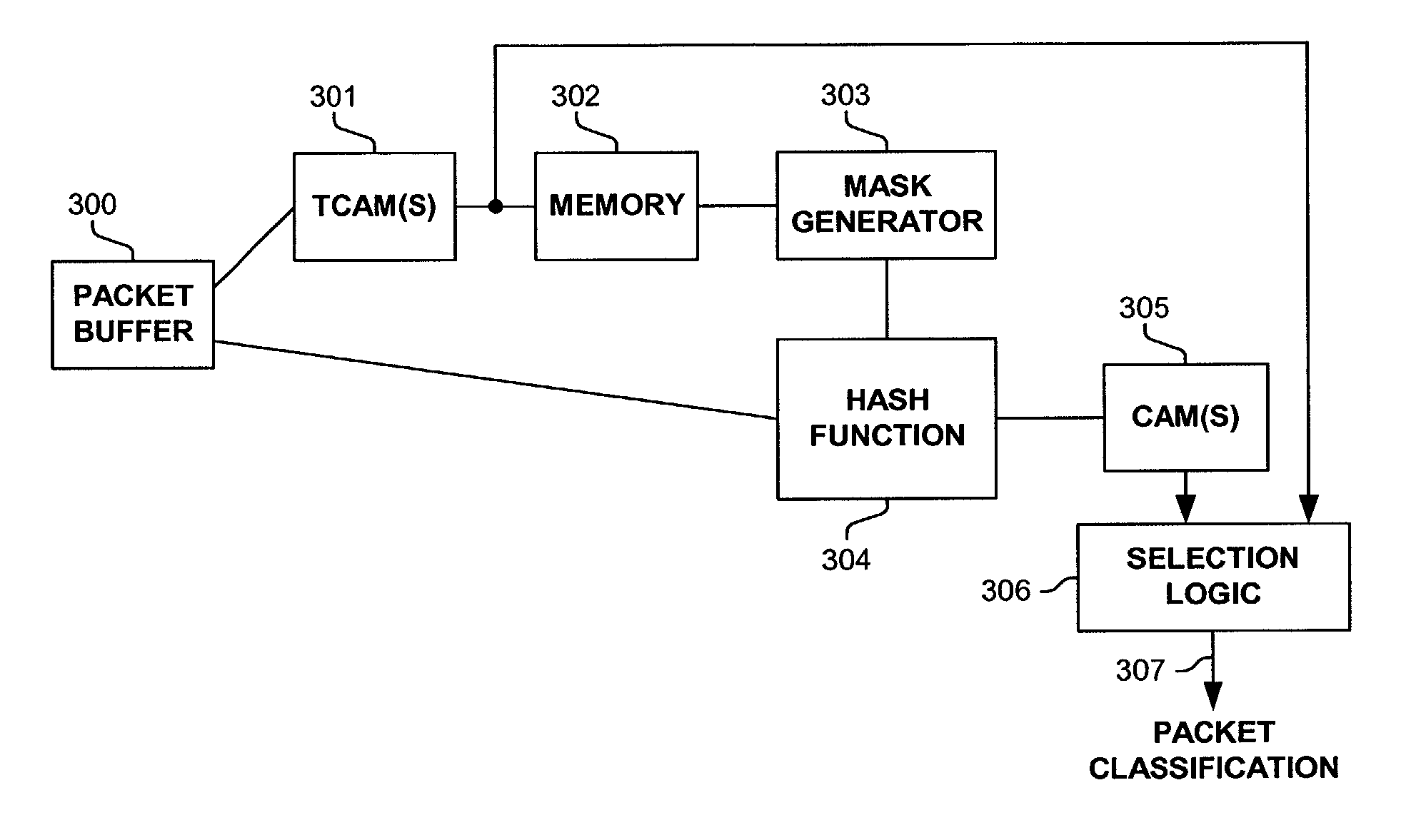
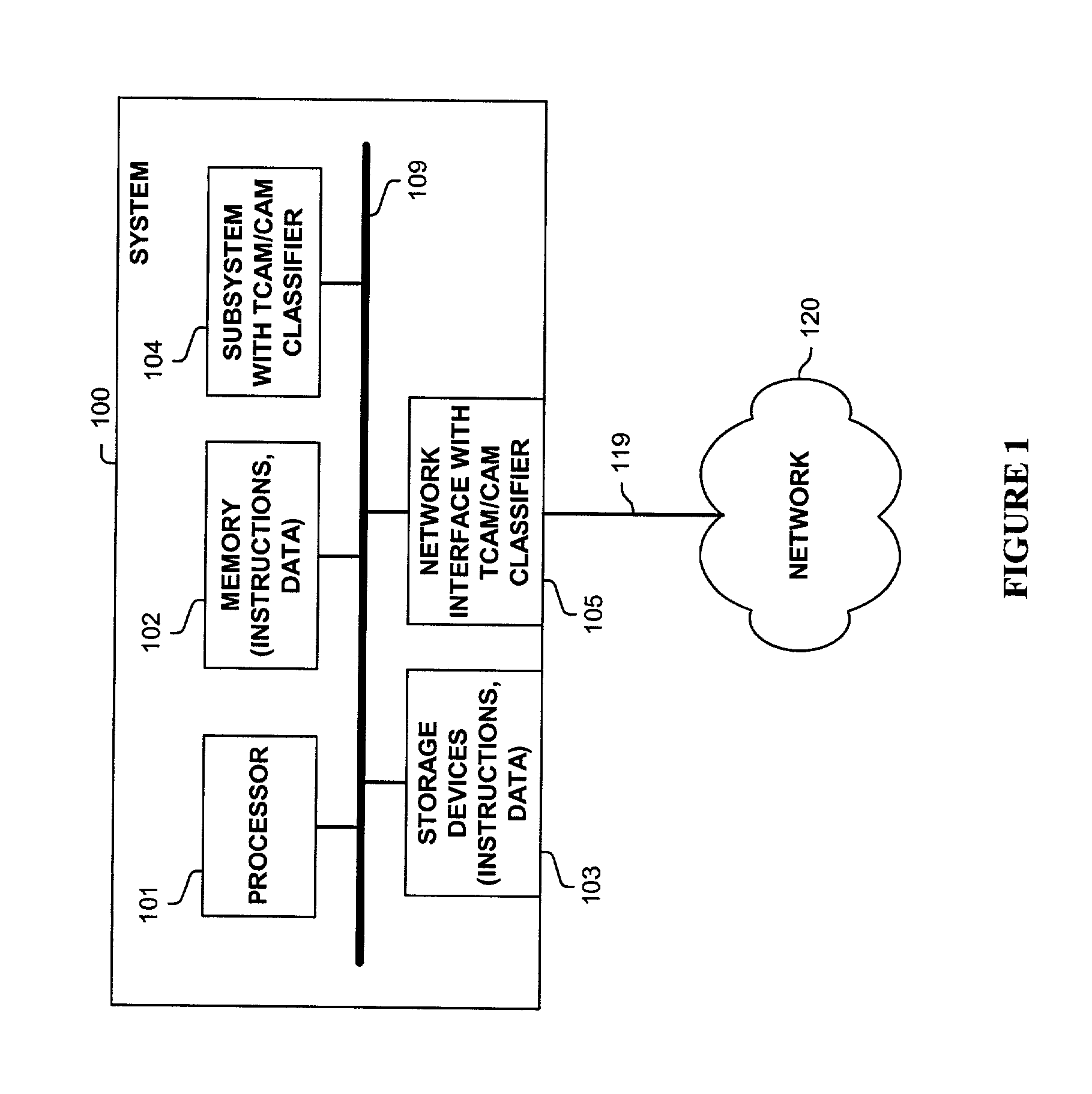
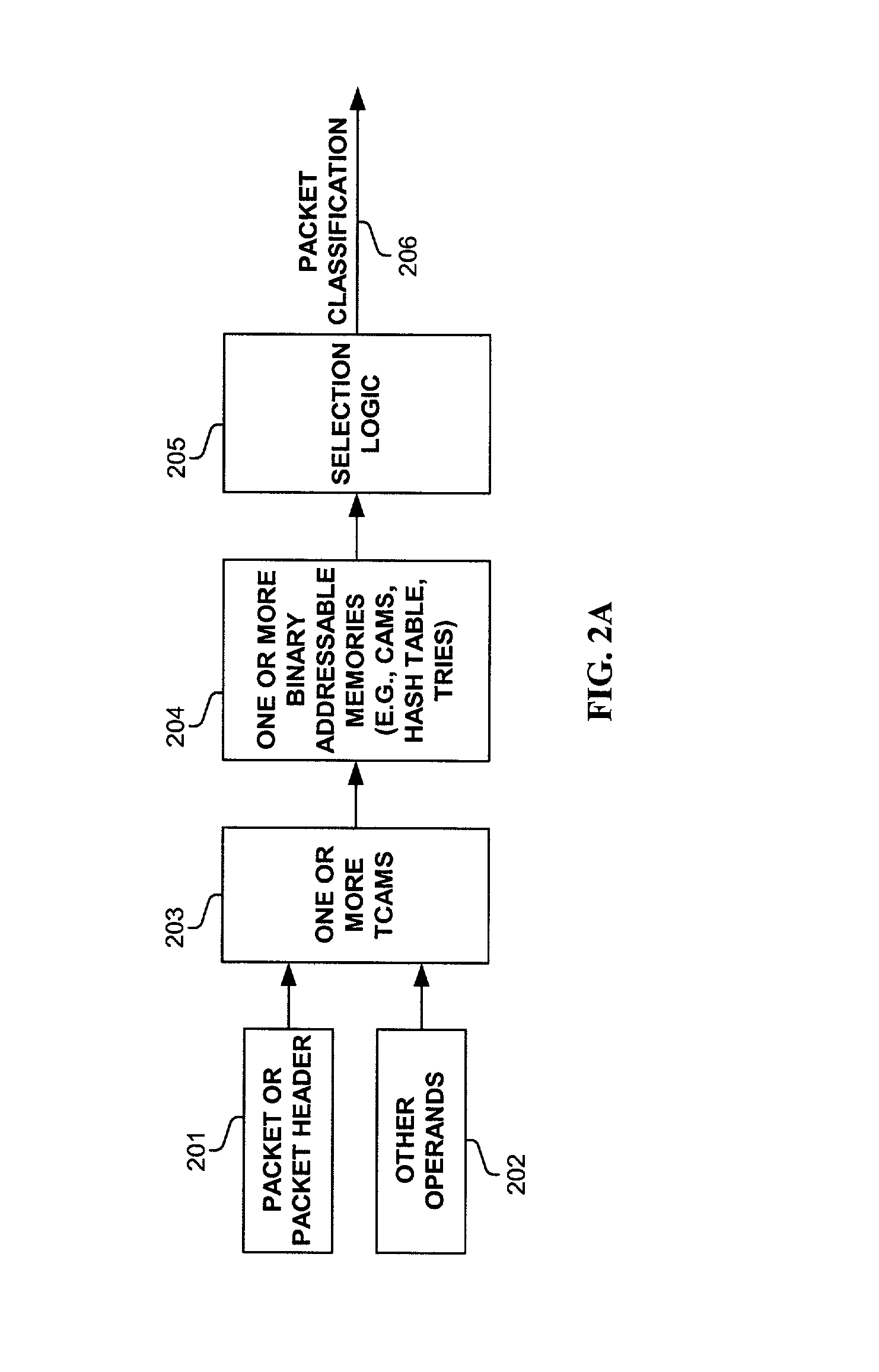
InactiveUS7002965B1Data processing applicationsDigital computer detailsQuality of serviceVirtual LAN
Methods and apparatus are disclosed herein for classifying packets using ternary and binary content-addressable memory stages to classify packets. One such system uses a stage of one or more TCAMS followed by a second stage one or more CAMS (or alternatively some other binary associative memories such as hash tables or TRIEs) to classify a packet. One exemplary system includes TCAMs for handling input and output classification and a forwarding CAM to classify packets for Internet Protocol (IP) forwarding decisions on a flow label. This input and output classification may include, but is not limited to routing, access control lists (ACLs), quality of service (QoS), network address translation (NAT), encryption, etc. These IP forwarding decisions may include, but are not limited to IP source and destination addresses, protocol type, flags and layer 4 source and destination ports, a virtual local area network (VLAN) id and / or other fields.
Owner:CISCO TECH INC
Method of storing and retrieving miniaturized data
InactiveUS7185018B2Data processing applicationsDigital data processing detailsMiniaturizationDatabase
Owner:ZENTRONIX
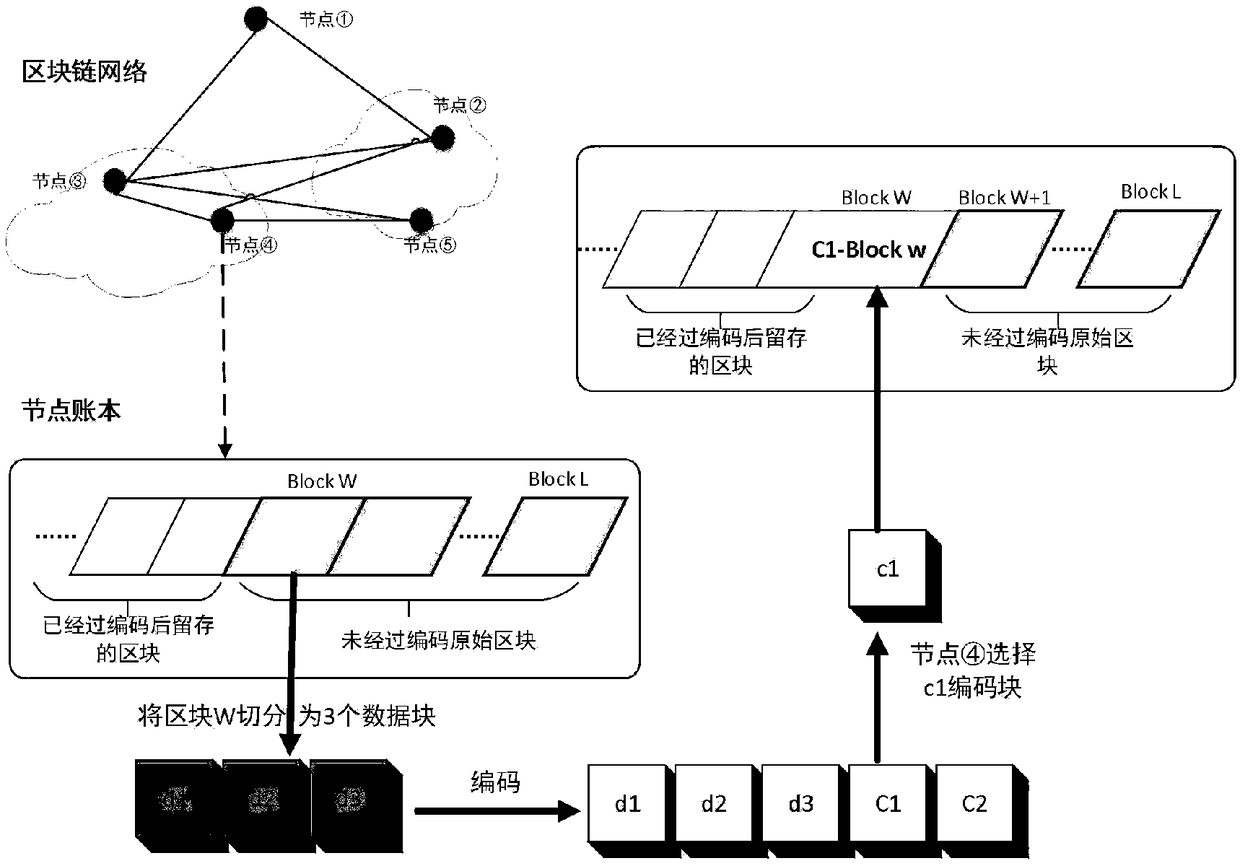
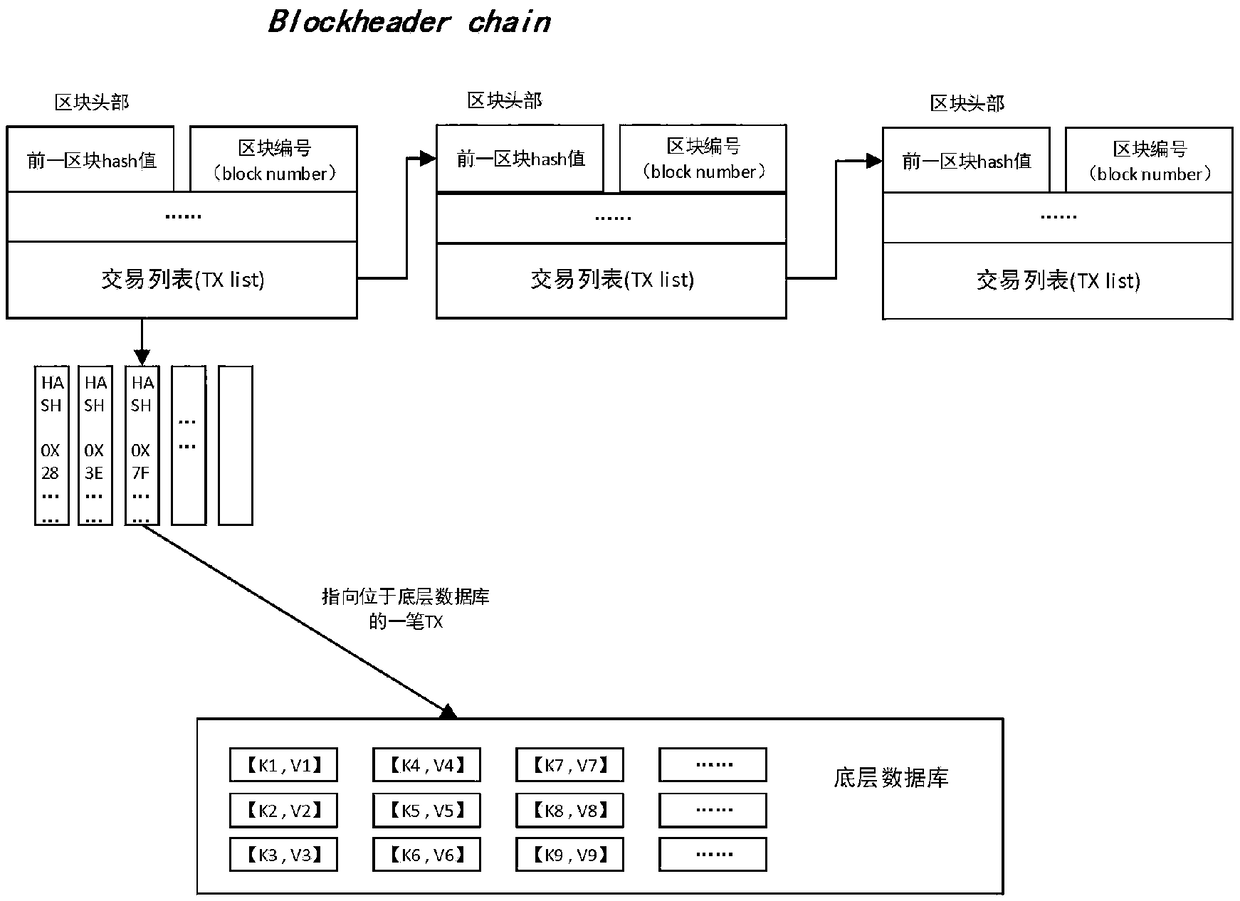
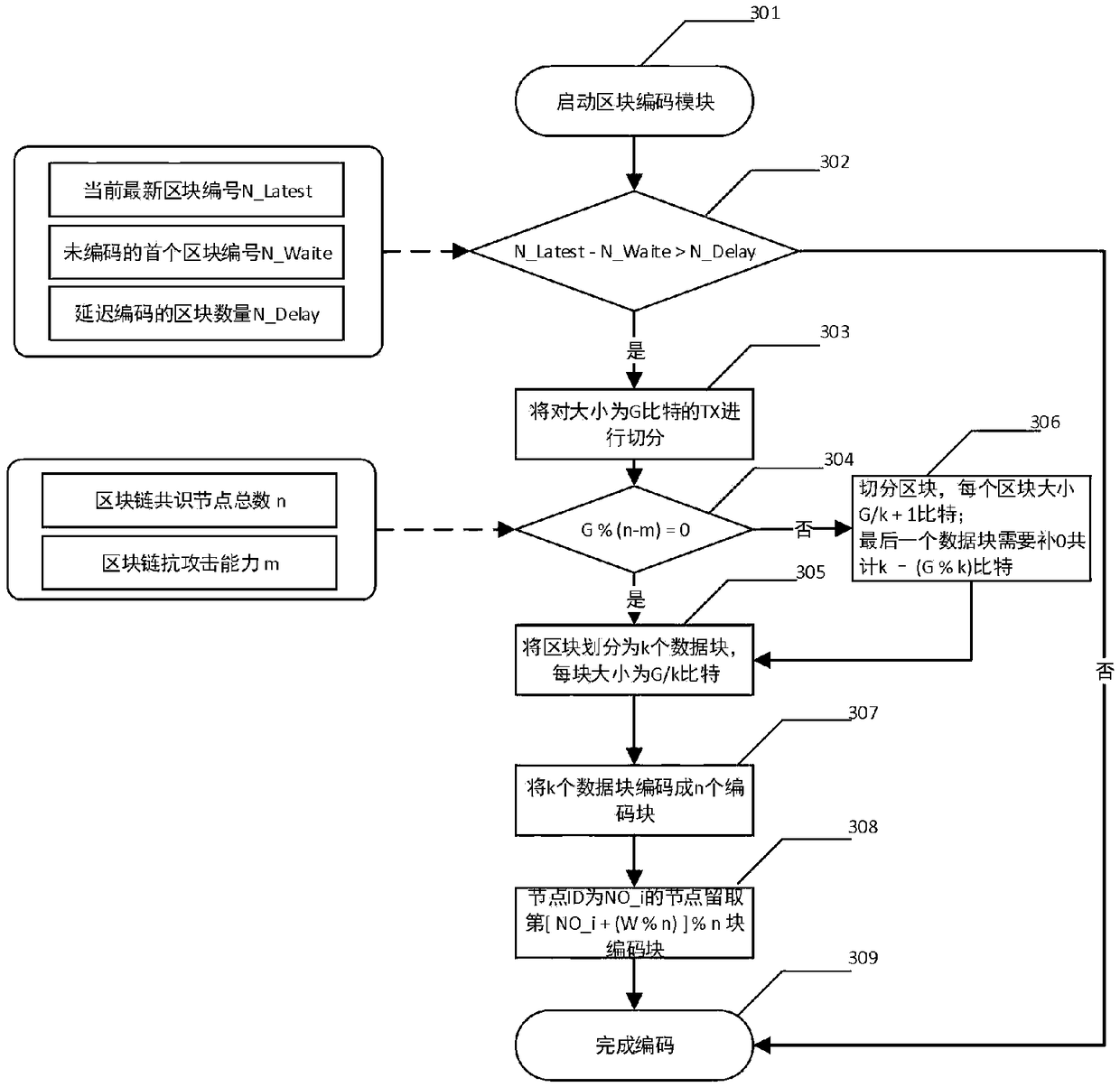
Block chain account book distributed storage technology based on erasure code
InactiveCN109359223AReduce redundancyReduce demandOther databases indexingTransmissionCoding blockComputer architecture
The invention relates to a block chain account book distributed storage technology based on erasure code, and belongs to the block chain technology field. The technology comprises the following steps:a) the block delay coding strategy allows to delay the coding of a certain number of new blocks to meet the synchronization requirements of other block chain consensus nodes for blocks; B) accordingto the set block coding algorithm, the blocks satisfying the coding condition are cut into k data blocks, each data block having a size of about 1 / k of the original block, and further the cut k datablocks are encoded into n (n) k encoded blocks by the erasure coding technology; (c) each block chain node reserves a part of that coding block, and finally the whole block chain network store the coding blocks decentrally; D) when the original block needs to be recovered from the encoded block, the current node collects the remaining encoded block corresponding to the block from the remaining nodes, and then recovers the original block according to the corresponding decoding algorithm. The method reduces the requirement of the block chain for storage resources and improves the utilization rate of storage space.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
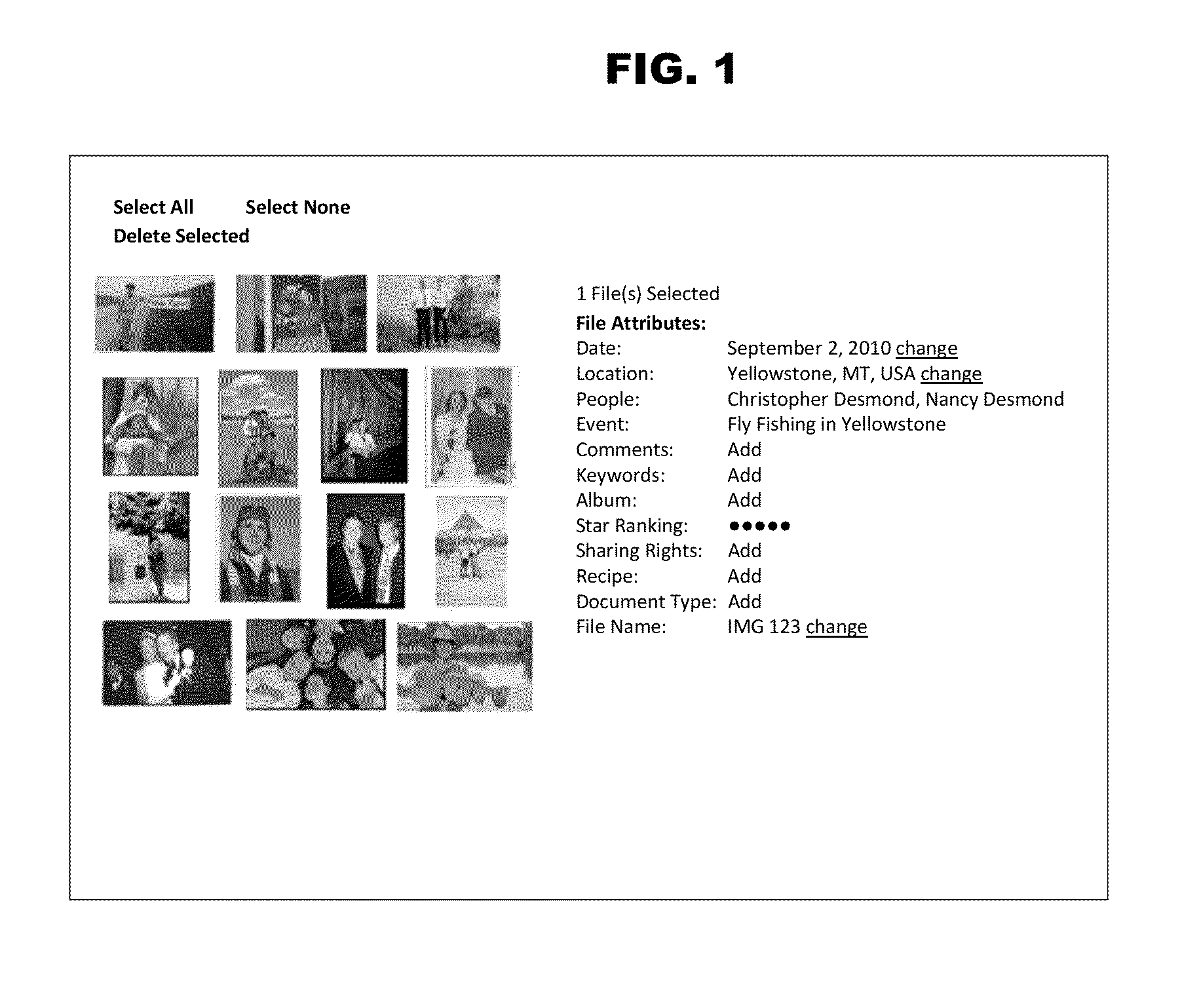
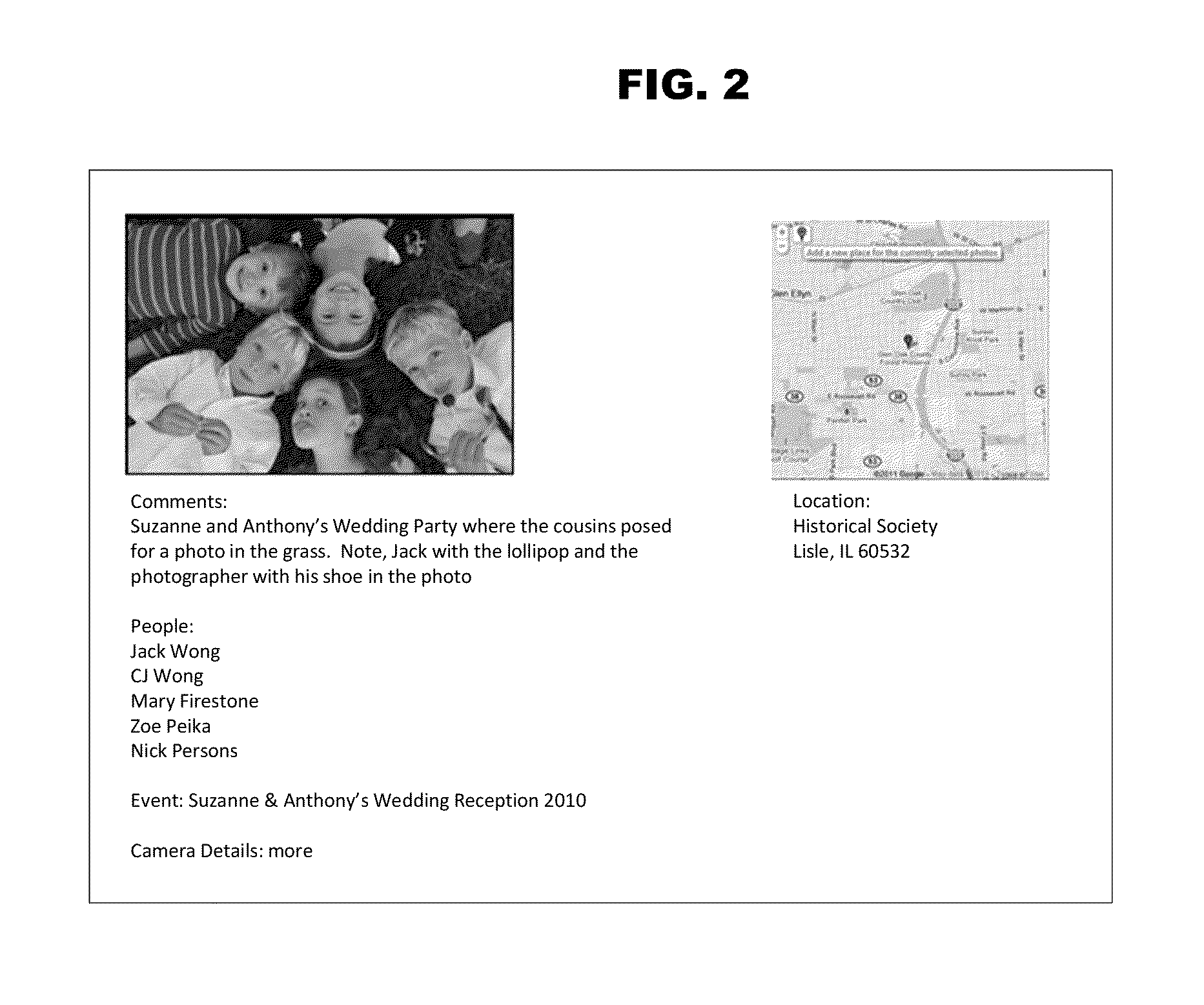
Method and apparatus for managing digital files
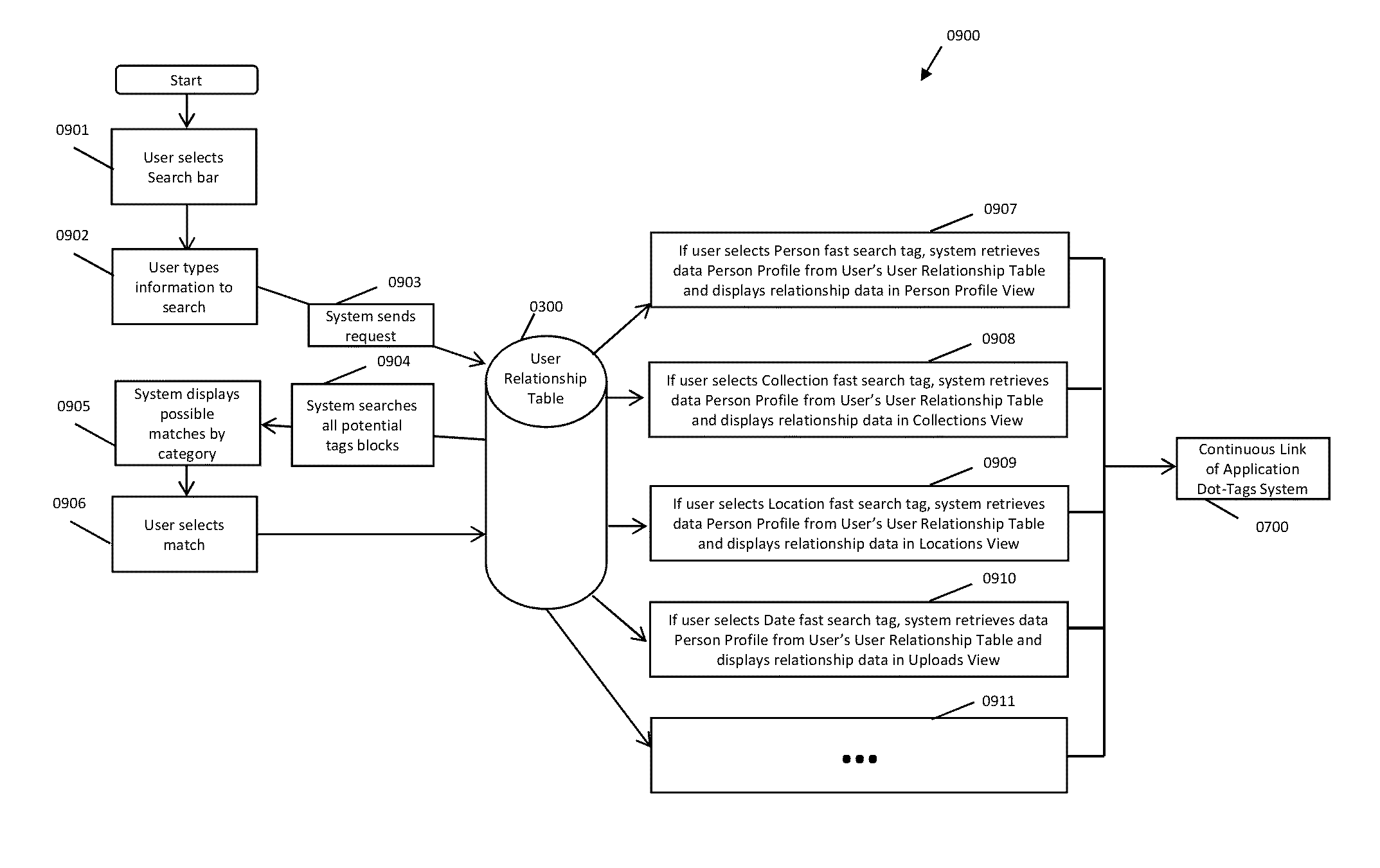
ActiveUS20140181089A1Save a lot of timeSignificant informationDigital data processing detailsStill image data indexingDisplay deviceEngineering
A computer-implemented method of associating digital tags with digital files comprises storing a plurality of digital files having embedded therein content data and metadata including tags; receiving, via a user interface device of a client device, a first tag label containing alphanumeric text created and inputted by a user of the client device; modifying, using a controller device, a selected first one of the tags of the metadata in a first of the digital files to include the first tag label; receiving, via the user interface device or another user interface device, an instruction to search for all of the digital files having at least the first tag label; responsive to receiving the instruction, automatically searching for all of the digital files having at least the first tag label; and displaying, on a video display device associated with the client device, a first indication of the first tag label.
Owner:MEMORYWEB
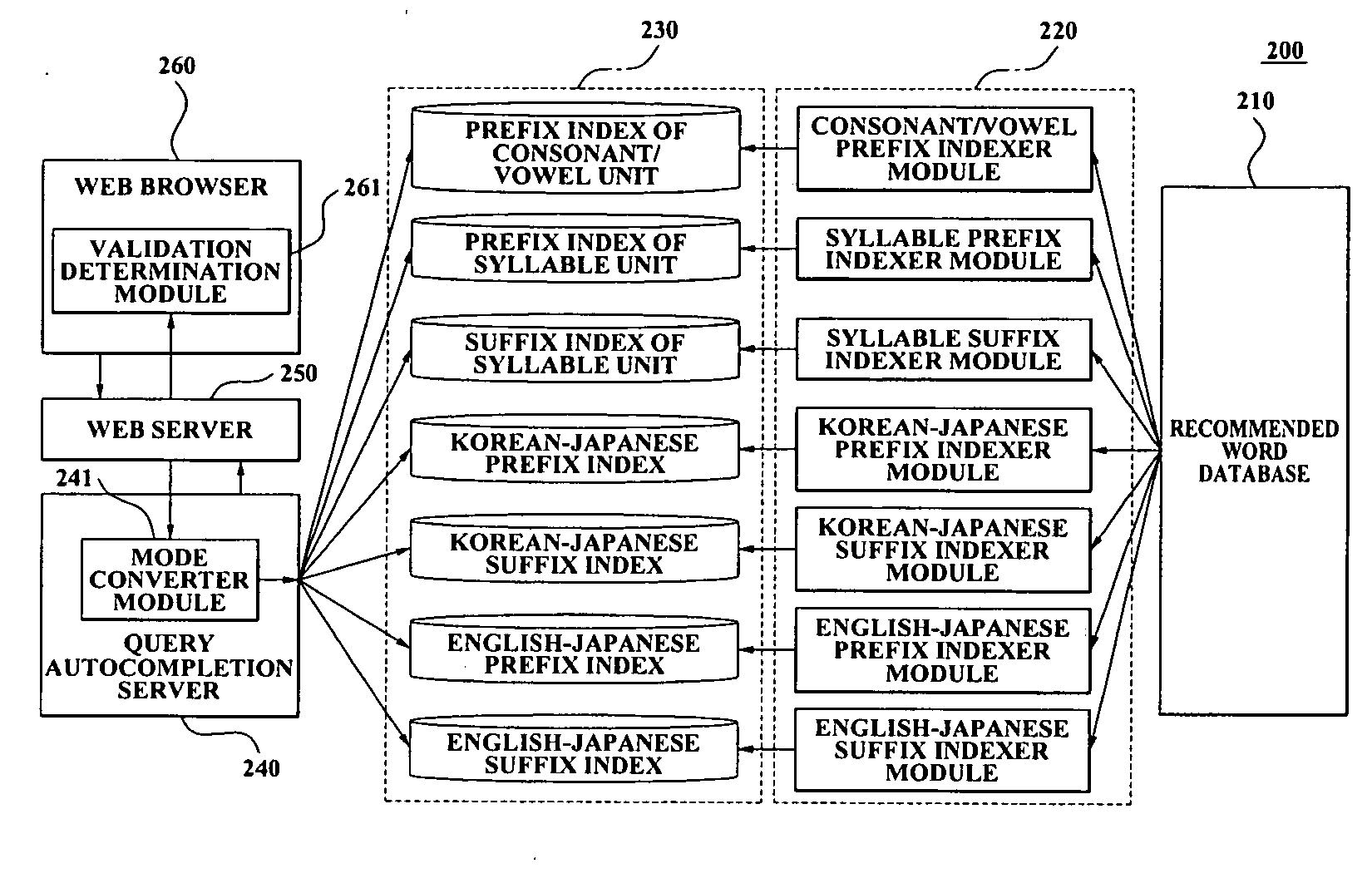
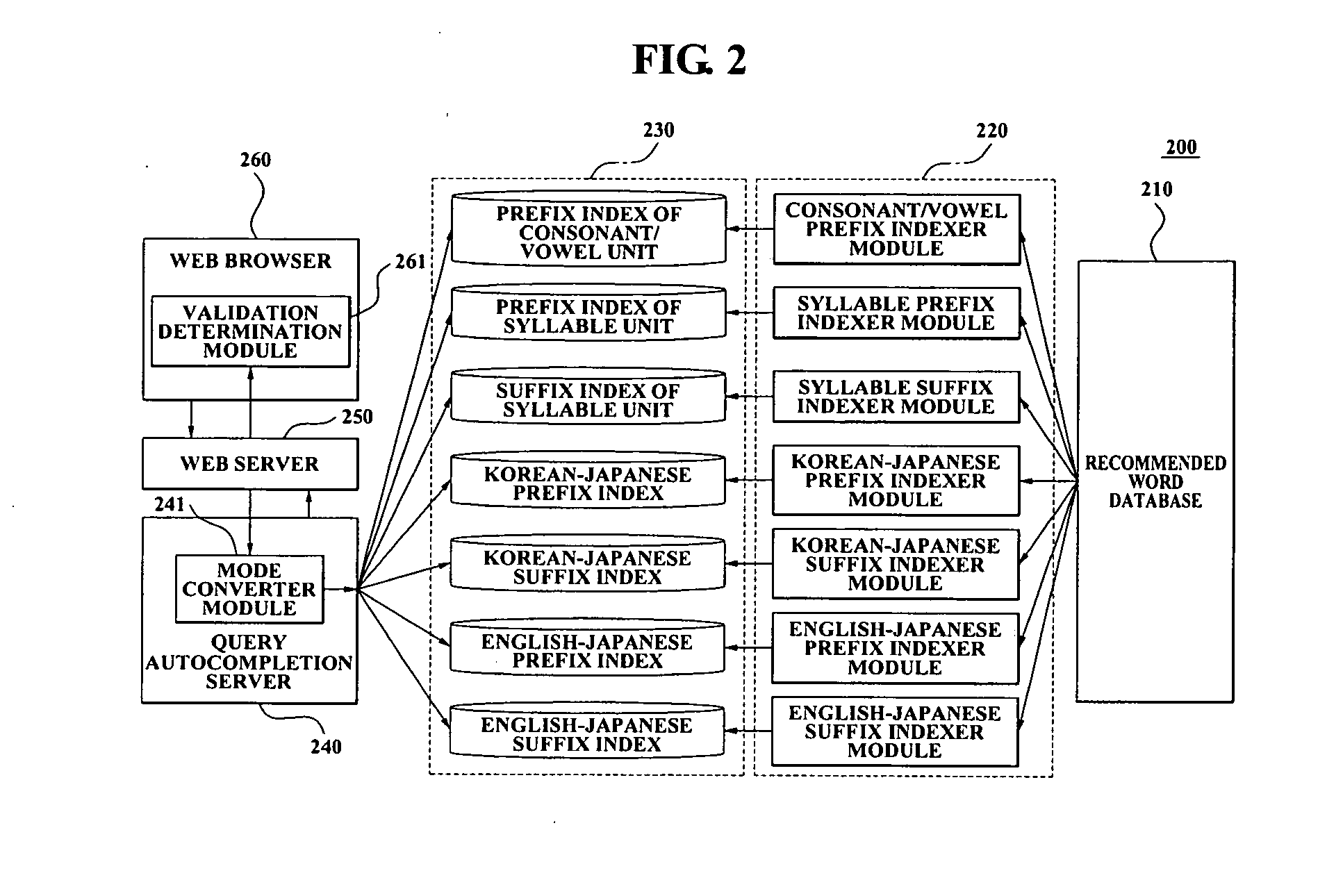
System and method of providing autocomplete recommended word which interoperate with plurality of languages
ActiveUS20070100890A1Avoid mistakesEnter exactlyNatural language translationOther databases indexingWeb browserWord list
A system and method of providing an autocomplete recommended word, which classify a recommended word list according to indexes of various languages, store the recommended word list for each index, extract a corresponding autocomplete recommended word according to a user query and a setting mode which is received from a user's web browser, provide the user with the corresponding autocomplete recommended word, and thereby may propose a suitable recommended word according to the user query.
Owner:NHN CORP
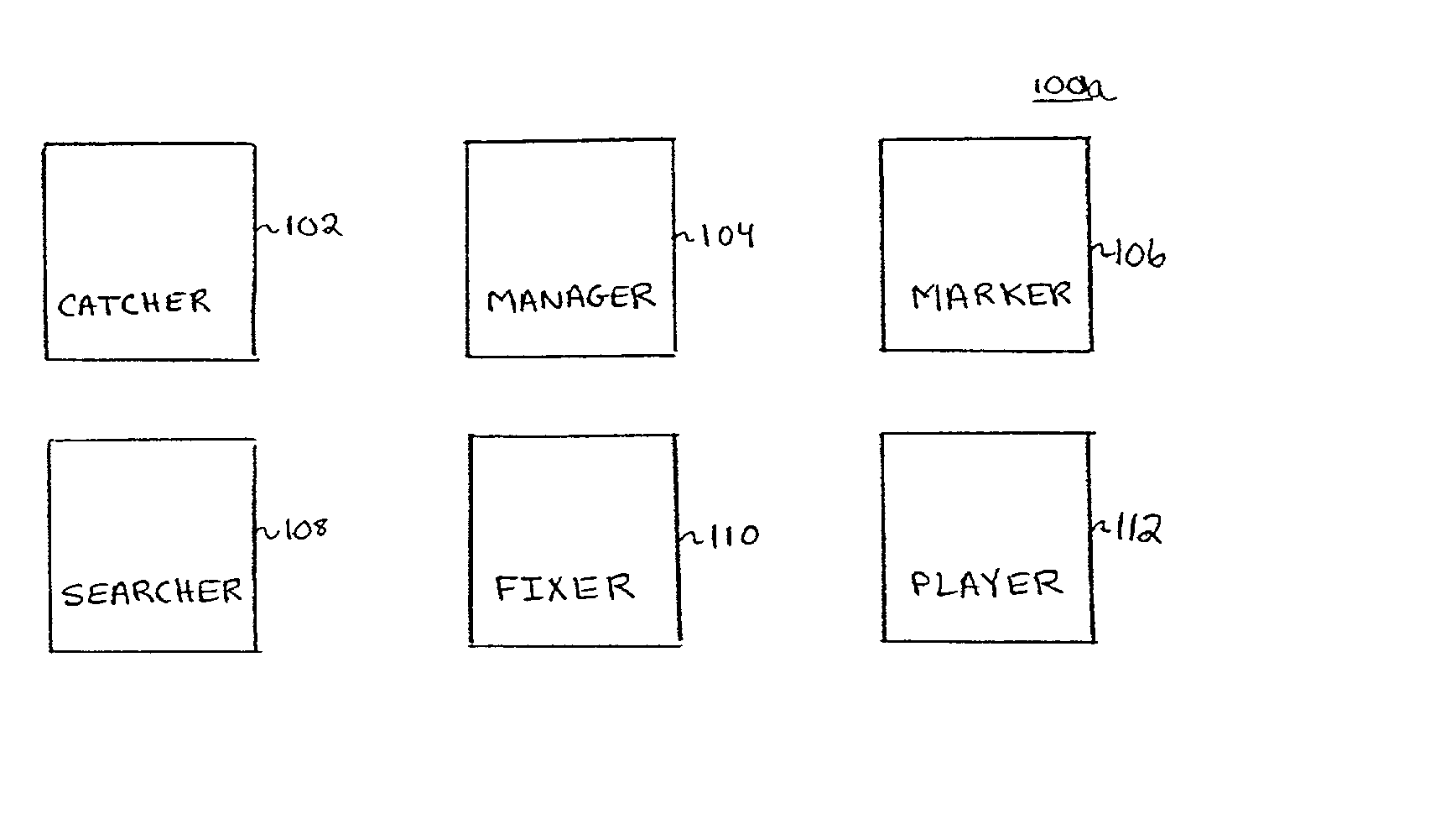
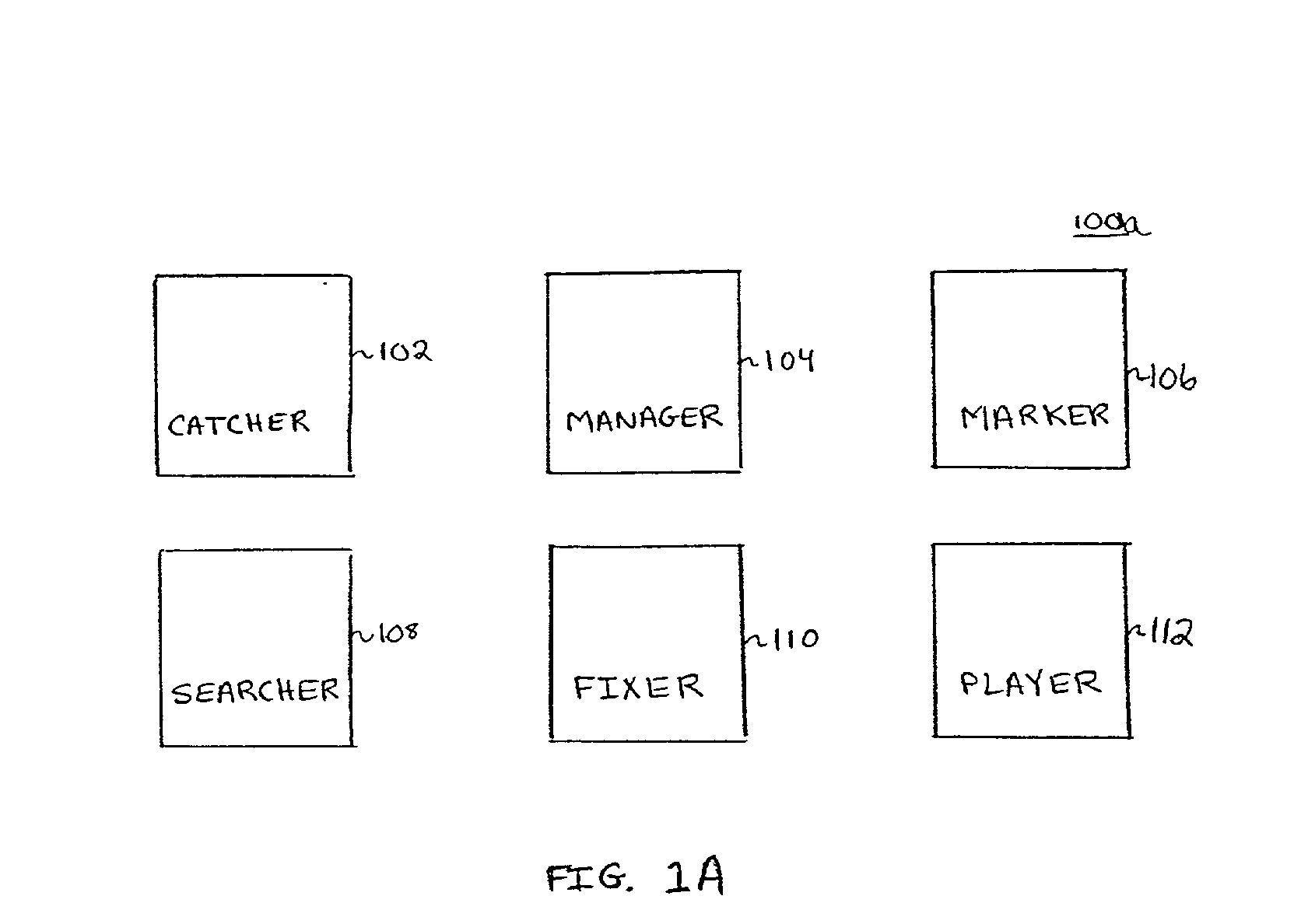
System, method and computer program product for catching, marking, managing and searching content
InactiveUS20020107829A1Digital data processing detailsOther databases indexingDrag and dropWorld Wide Web
A system, method and computer program product for organizing can include catching, marking, managing, searching, fixing and playing content. The catcher can include registering the content in a database. The catcher can assign the content to an album. The marking method can include marking content including managing a hierarchy of tag and subtag attributes, creating a new tag attribute; changing a hierarchical relationship of one tag attribute and subtag attributes of the one tag attribute; deleting an undesired tag attribute; renaming a misnamed tag attribute, or displaying the hierarchy of tag and sub-tag attributes as a tag tree list. The method can further include associating any of the tag attributes with any of the content. Associating can be done by dragging and dropping tags from the tag tree list to content records or the catcher. The method can further include searching the content by one or more search tag attributes. The manager can also be used to mark and organize the content in albums.
Owner:NET ALBUM NET
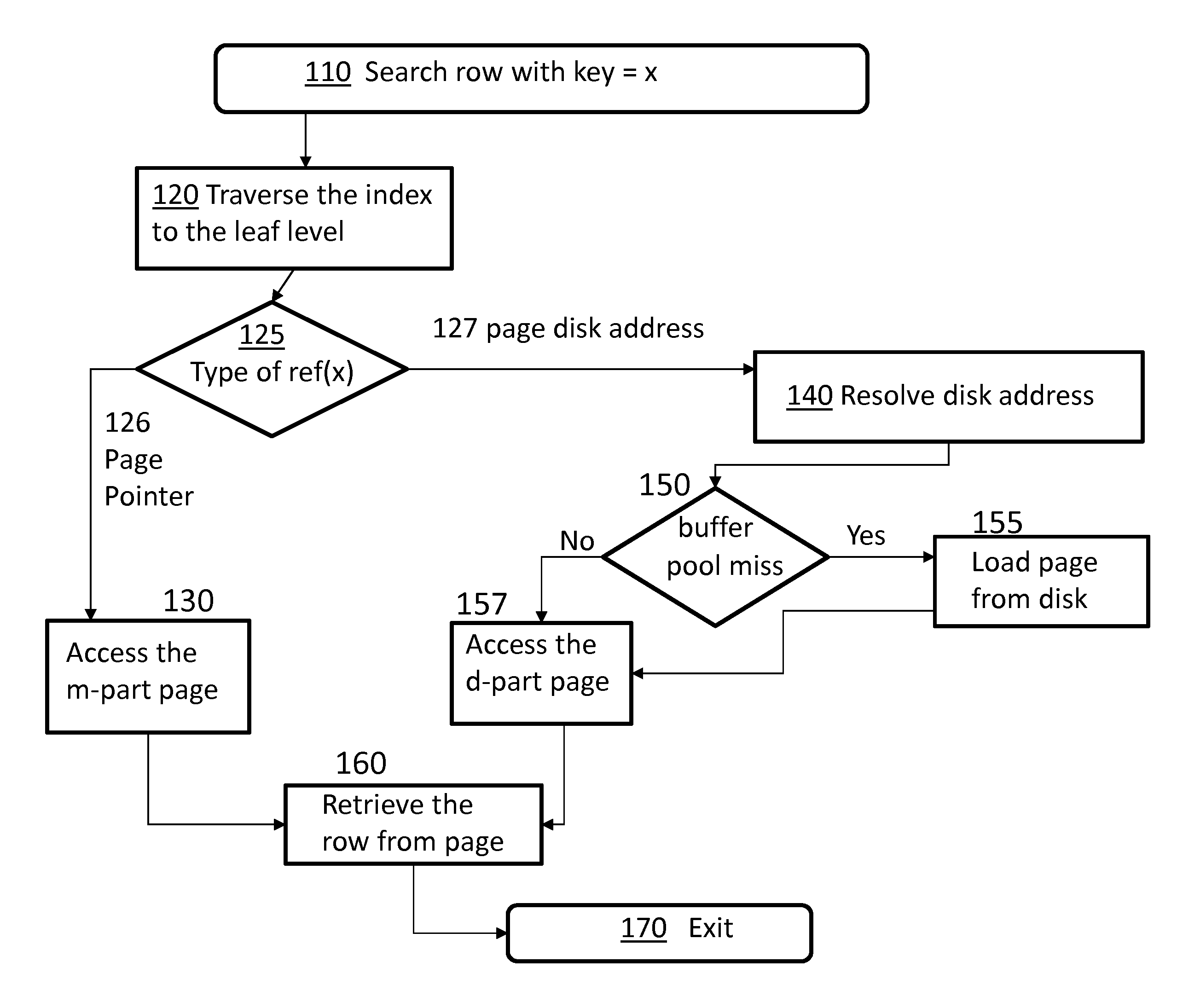
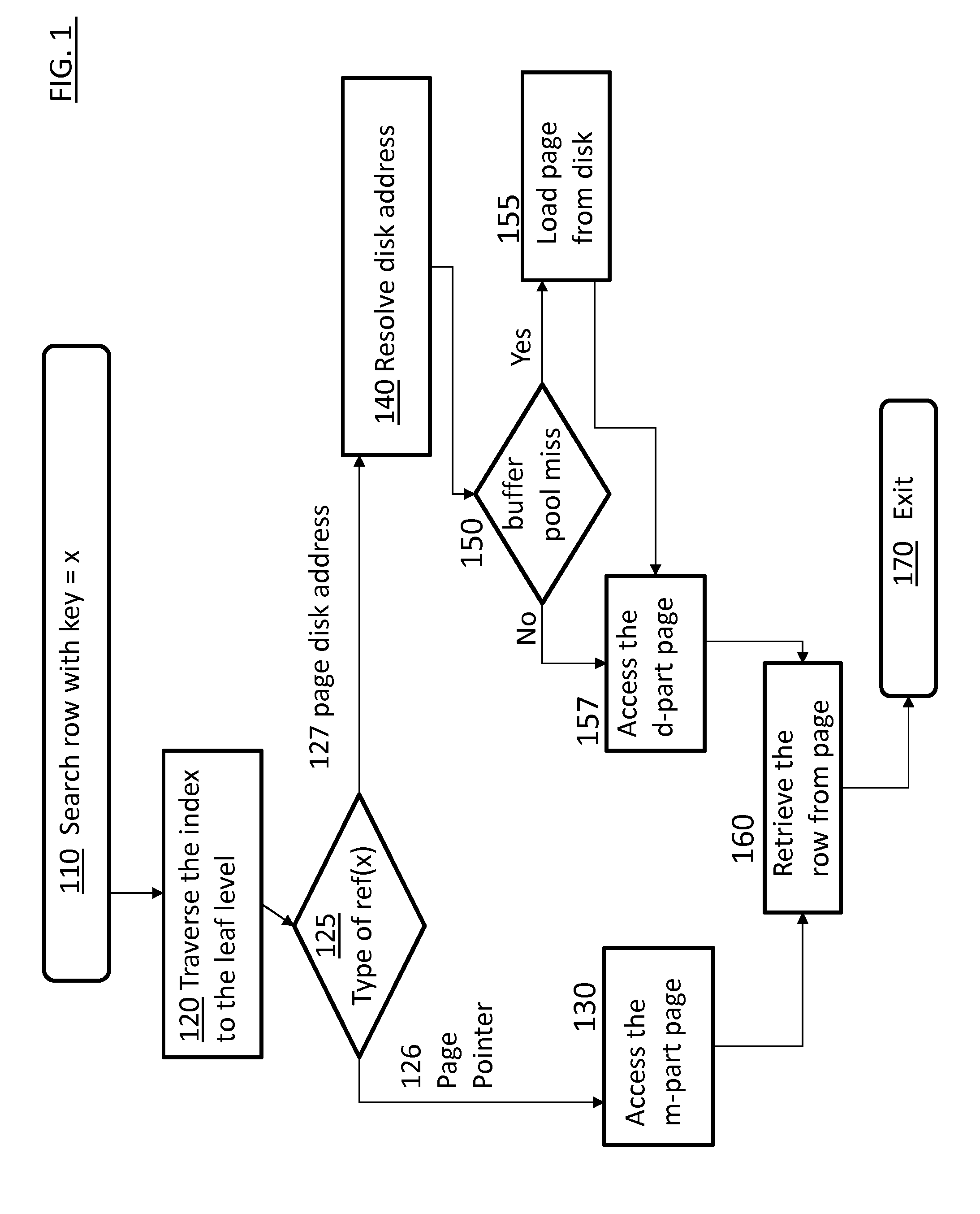
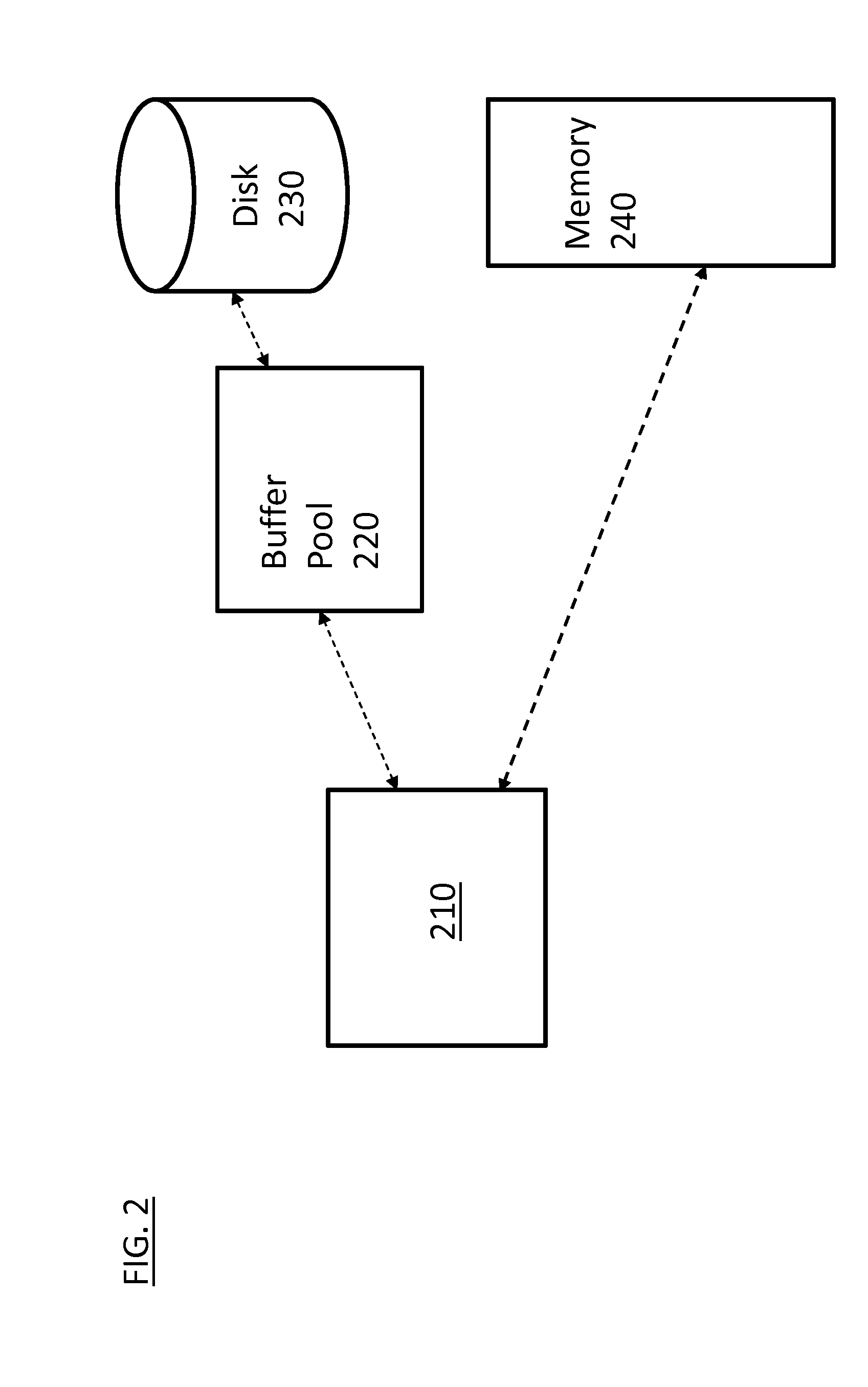
Hybrid table implementation by using buffer pool as permanent in-memory storage for memory-resident data
InactiveUS20140136510A1Digital data processing detailsOther databases indexingData retrievalData management
Embodiments relate to a method, system, and computer program product for data management. An aspect includes a search index that is created for a database. The search index has a reference value of a first or a second type associating data to a storage location in a first memory or a second memory respectively. Responsive to a data retrieval request, data is accessed using the reference value from the first or the second memory. If there is a data migration between the first and second memory storage, the reference values are then recalculated and altered in the search index accordingly.
Owner:IBM CORP
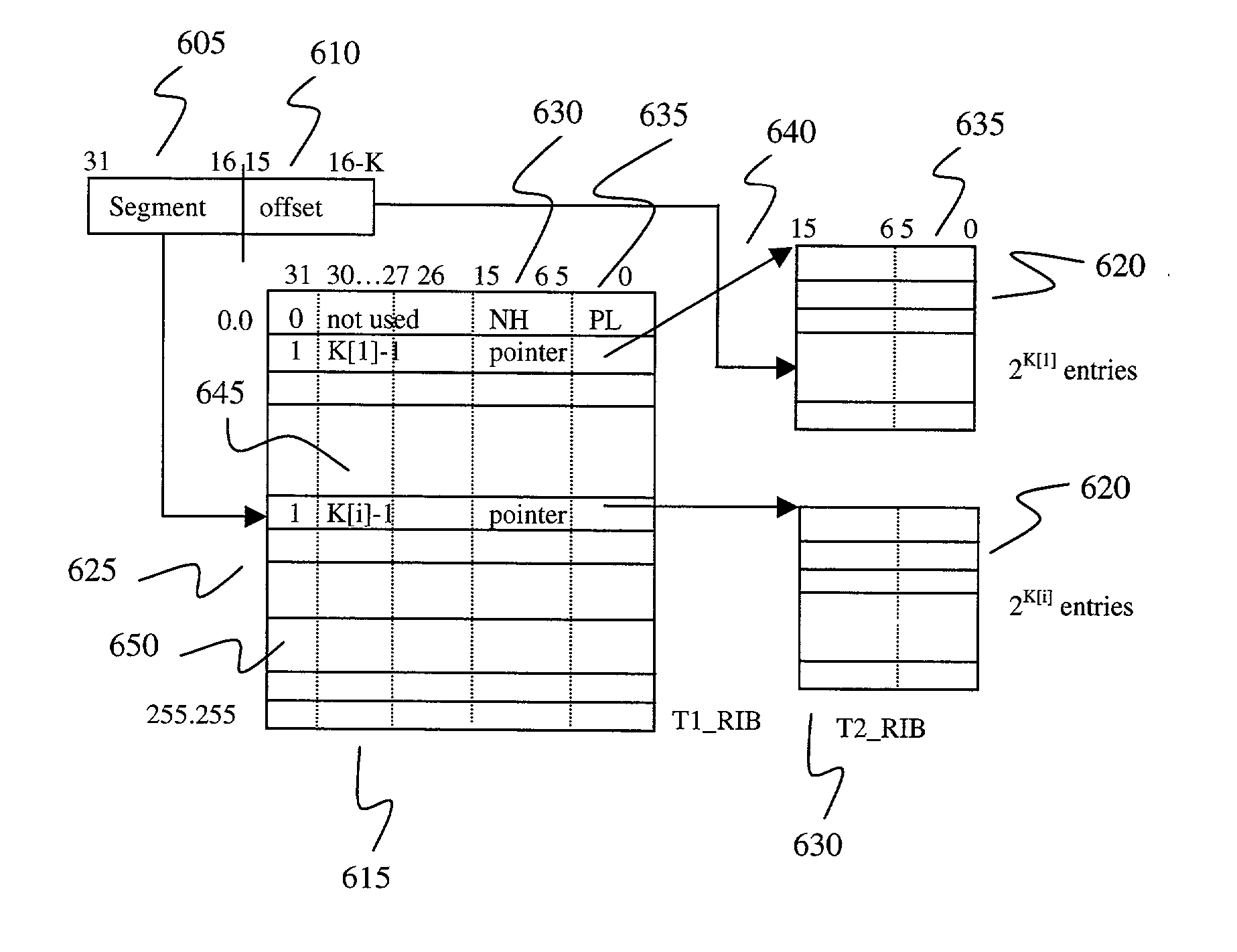
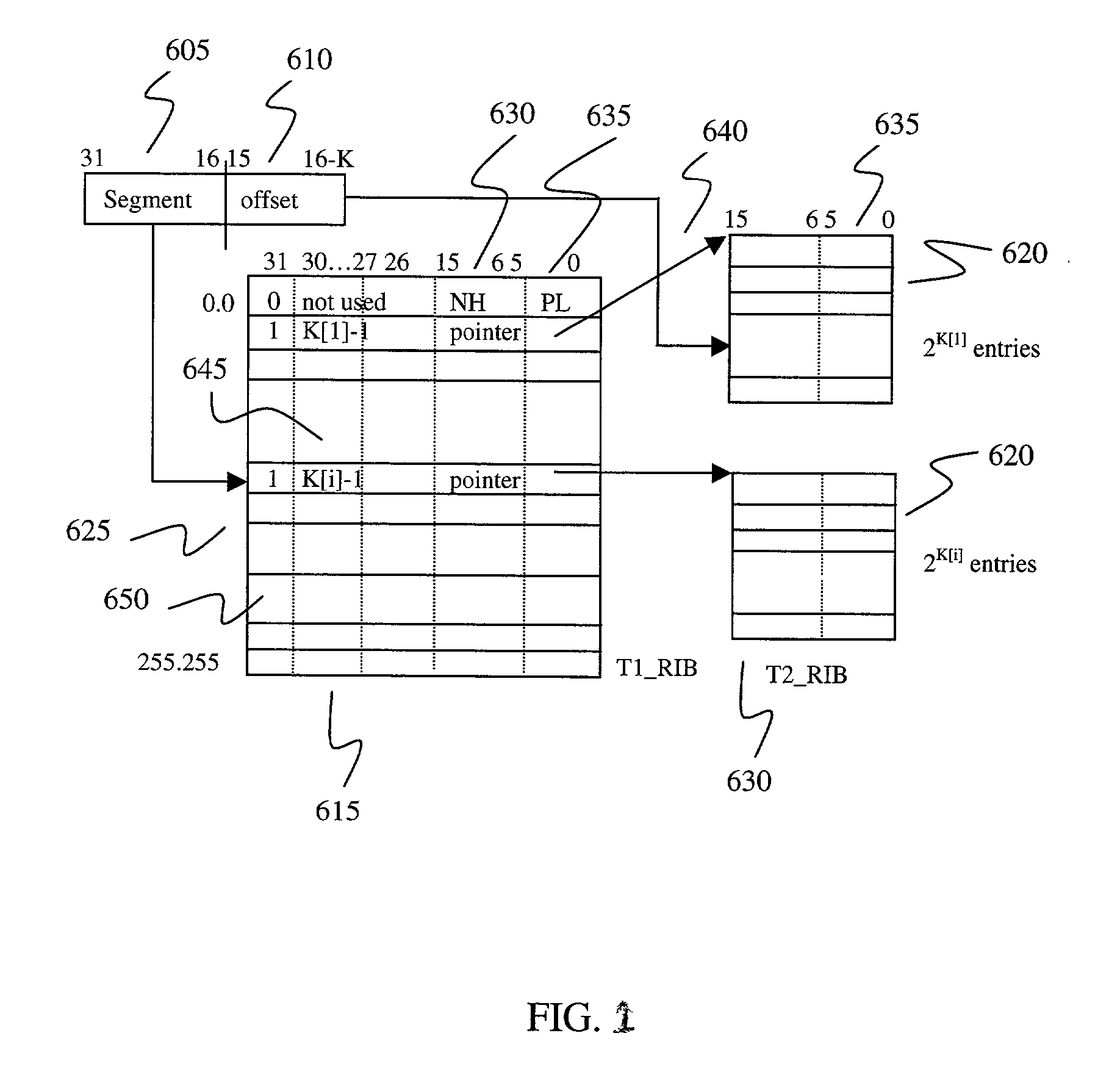
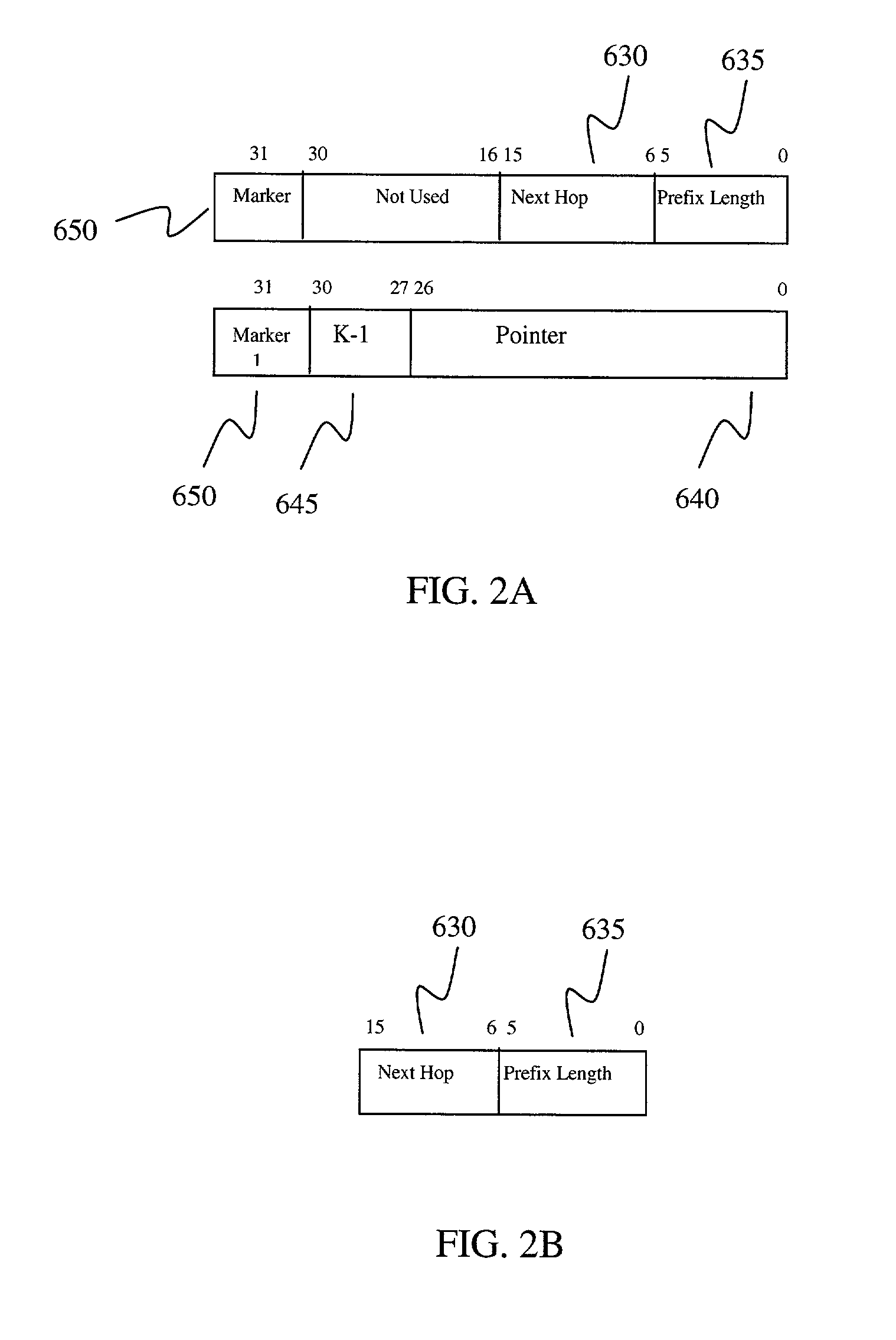
Fast IP route lookup with 16/K and 16/Kc compressed data structures
InactiveUS20020172203A1Data switching by path configurationOther databases indexingPresent dayArray data structure
An advanced data structure allows lookup based upon the most significant 16 bits and the following variable number of K bits of the IP destination address. This 16 / K scheme requires less than 2 MB memory to store the whole routing tables of present day backbone routers. A 16 / Kc version utilizes bitmaps to compress the table to less than 0.5 MB. For the 16 / K data structure each route lookup requires at most 2 memory accesses while the 16 / Kc requires at most 3 memory accesses. By configuring the processor properly and developing a few customized instructions to accelerate route lookup, one can achieve 85 million lookups per second (MLPS) in the typical case with the processor running at 200 MHz. Further, the lookup method can be implemented using pipelining techniques to perform three lookups for three incoming packets simultaneously. Using such techniques, 100 MLPS performance can be achieved.
Owner:TESILICA
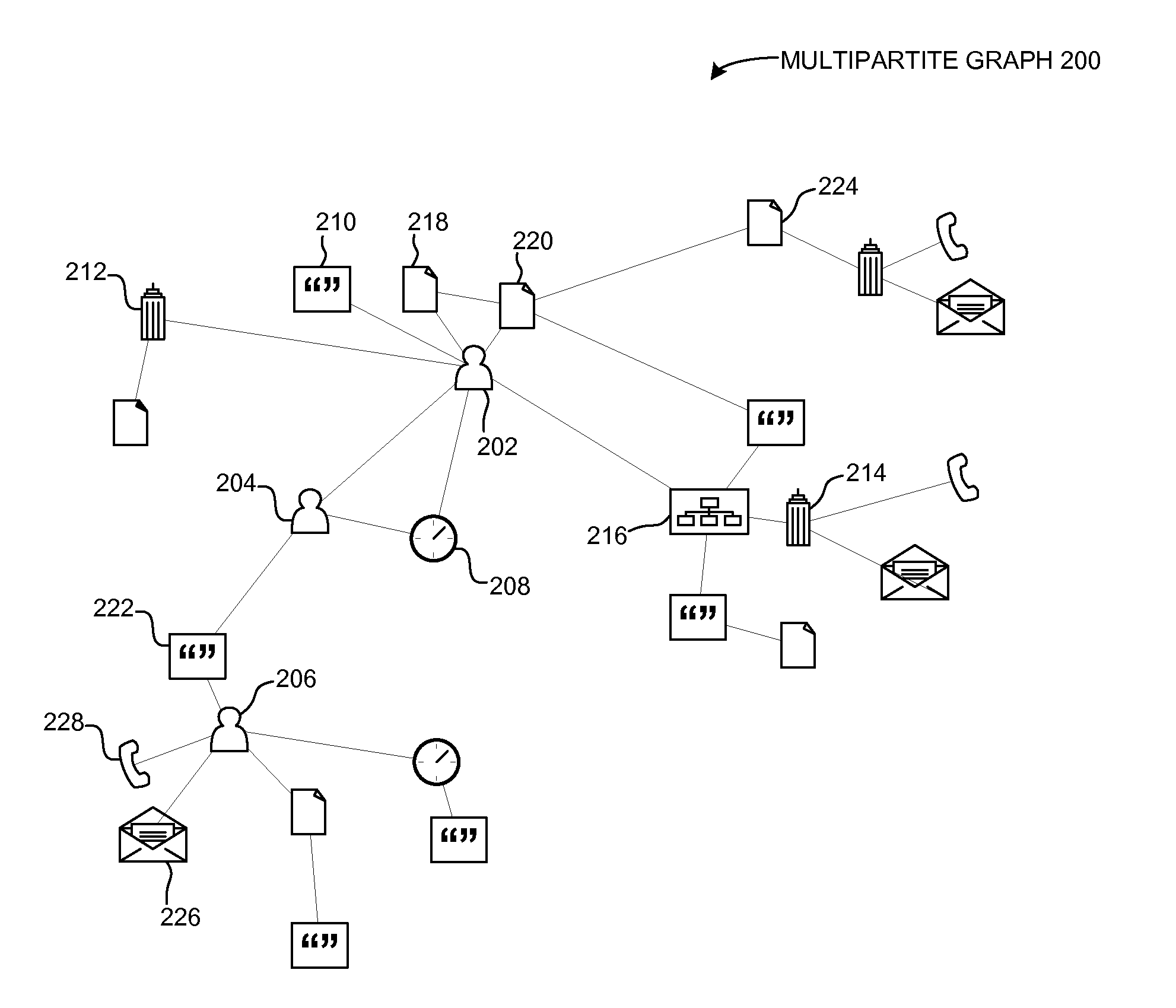
Generating a relationship visualization for nonhomogeneous entities
ActiveUS20130155068A1Drawing from basic elementsNatural language data processingDocumentationDocument management system
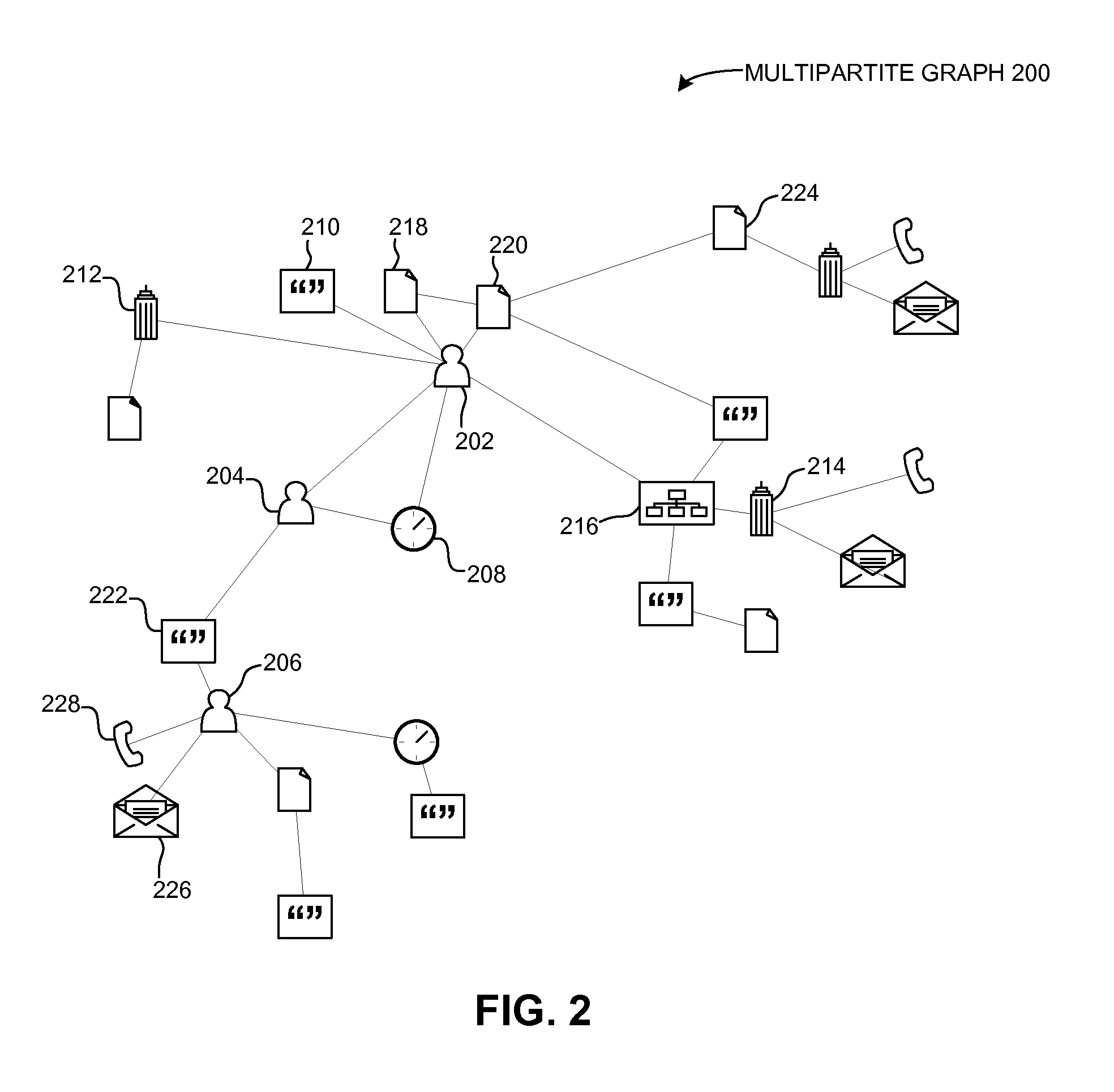
A relationship visualization system displays contextual information for a relationship between two entities of a document management system, such as for a user and a document. The system can receive a request for a relationship visualization from a user, such that the request indicates the user and a document. Then, the system determines, from a multipartite graph, a set of relationship paths coupling entity nodes corresponding to the user and the document. A relationship path can include one or more entity nodes indicating contextual information for the relationship between the user and the document. Then, the system selects a first group of entity nodes from the set of relationship paths to represent the relationship between the user and the document. The system then provides a relationship visualization that displays contextual information from the first group of entity nodes to illustrate the relationship between the user and the document.
Owner:XEROX CORP
Decentralized database optimizations
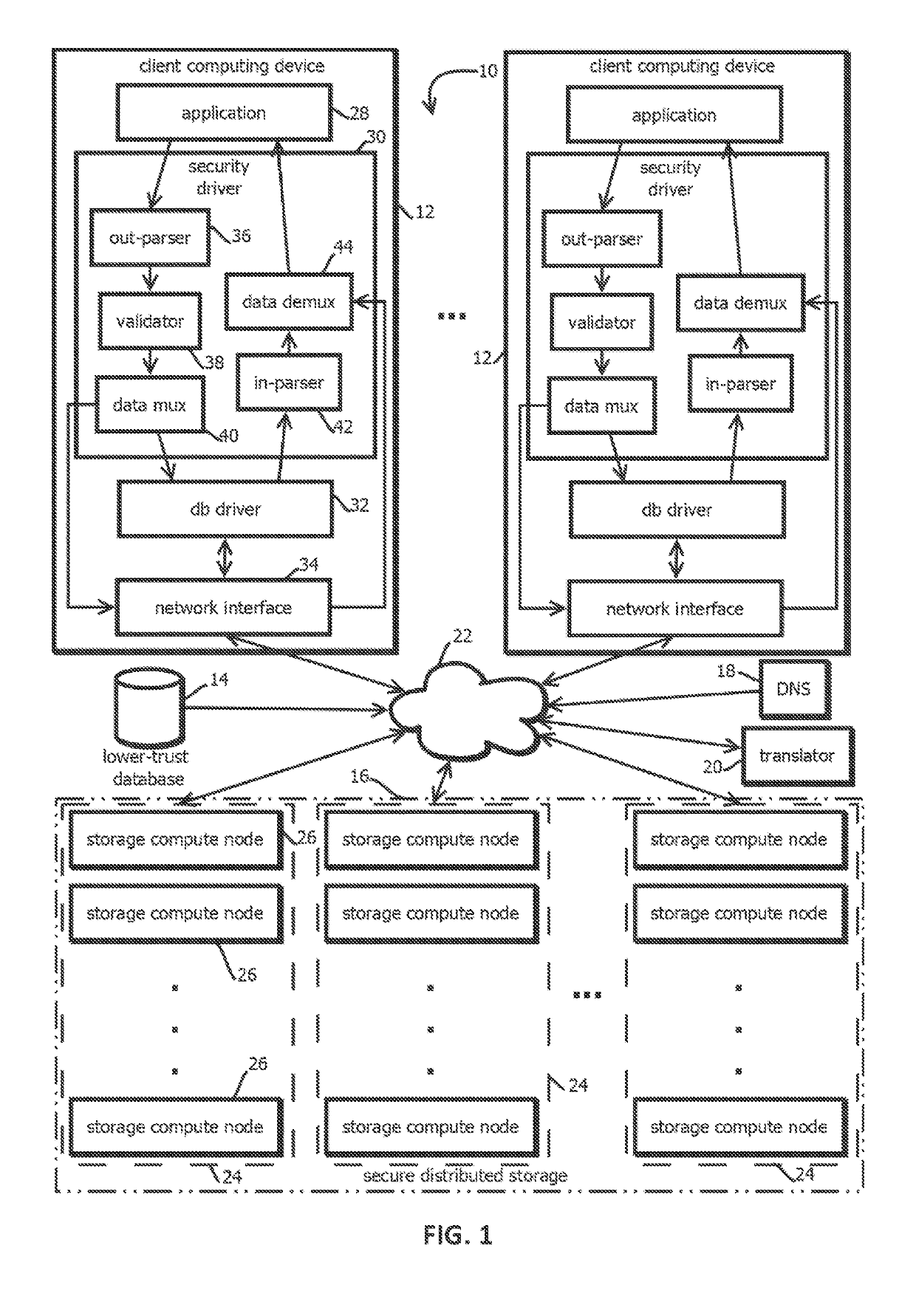
ActiveUS20190288850A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationRelational databaseData storing
Techniques for managing data stored within a database, such as a decentralized database are provided. Some techniques involve managing some data within a lower-trust database and some other data within a higher-trust database. A higher-trust database may be a decentralize database including a blockchain. A lower-trust database may store references to data within the blockchain, and optionally other data in association with those references. Disclosed techniques include WHERE clause query handling in databases with reference values, replacement of distinct data in a relational database with a distinct reference to that data, number line storing for secure indexing, APIs for databases, and consensus operations for private blockchain networks.
Owner:ALTR SOLUTIONS INC
Data query method and system and storage medium
InactiveUS20150213134A1High cost of deploymentPoor service performanceWeb data indexingDigital data processing detailsData providerClient-side
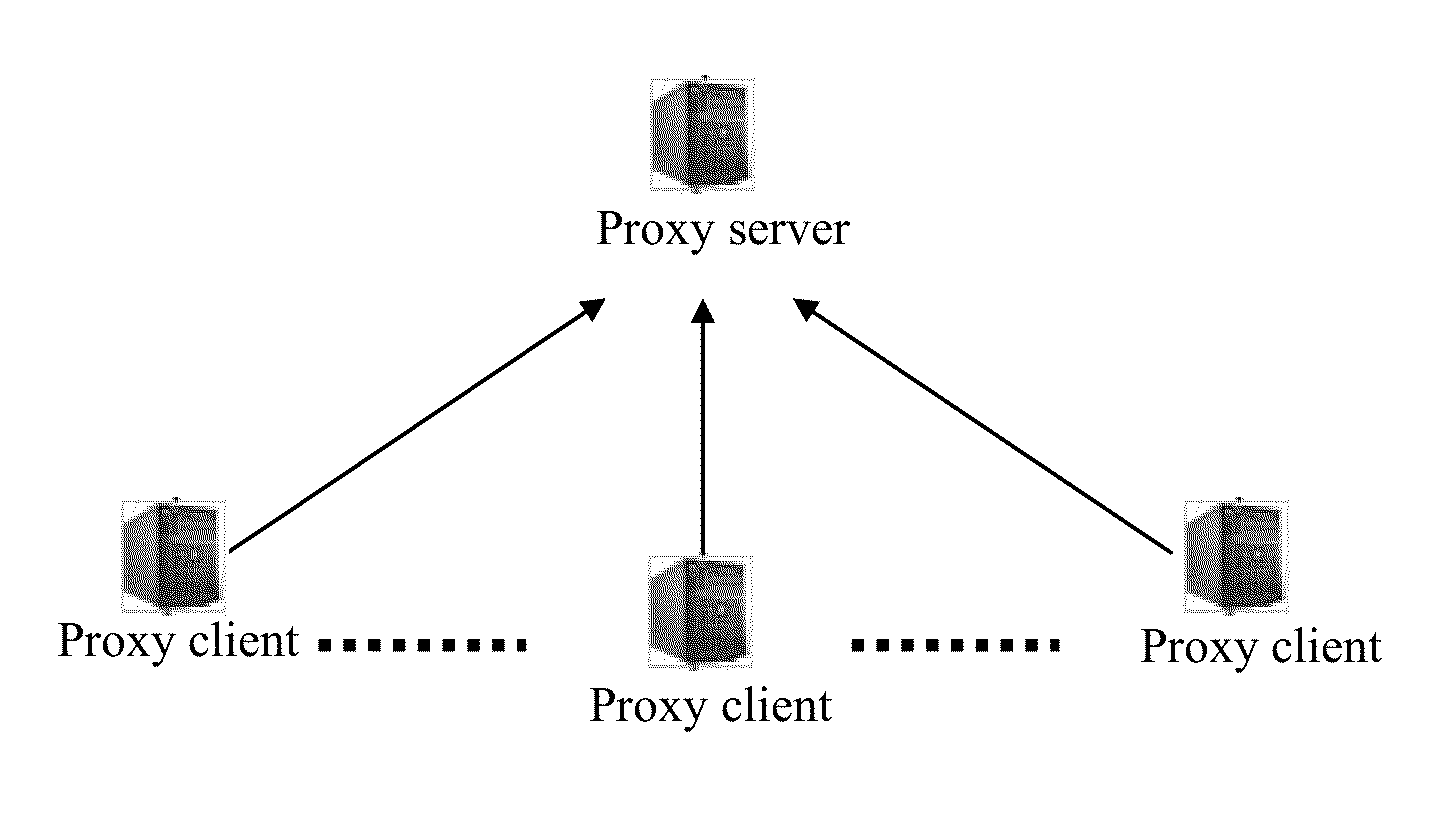
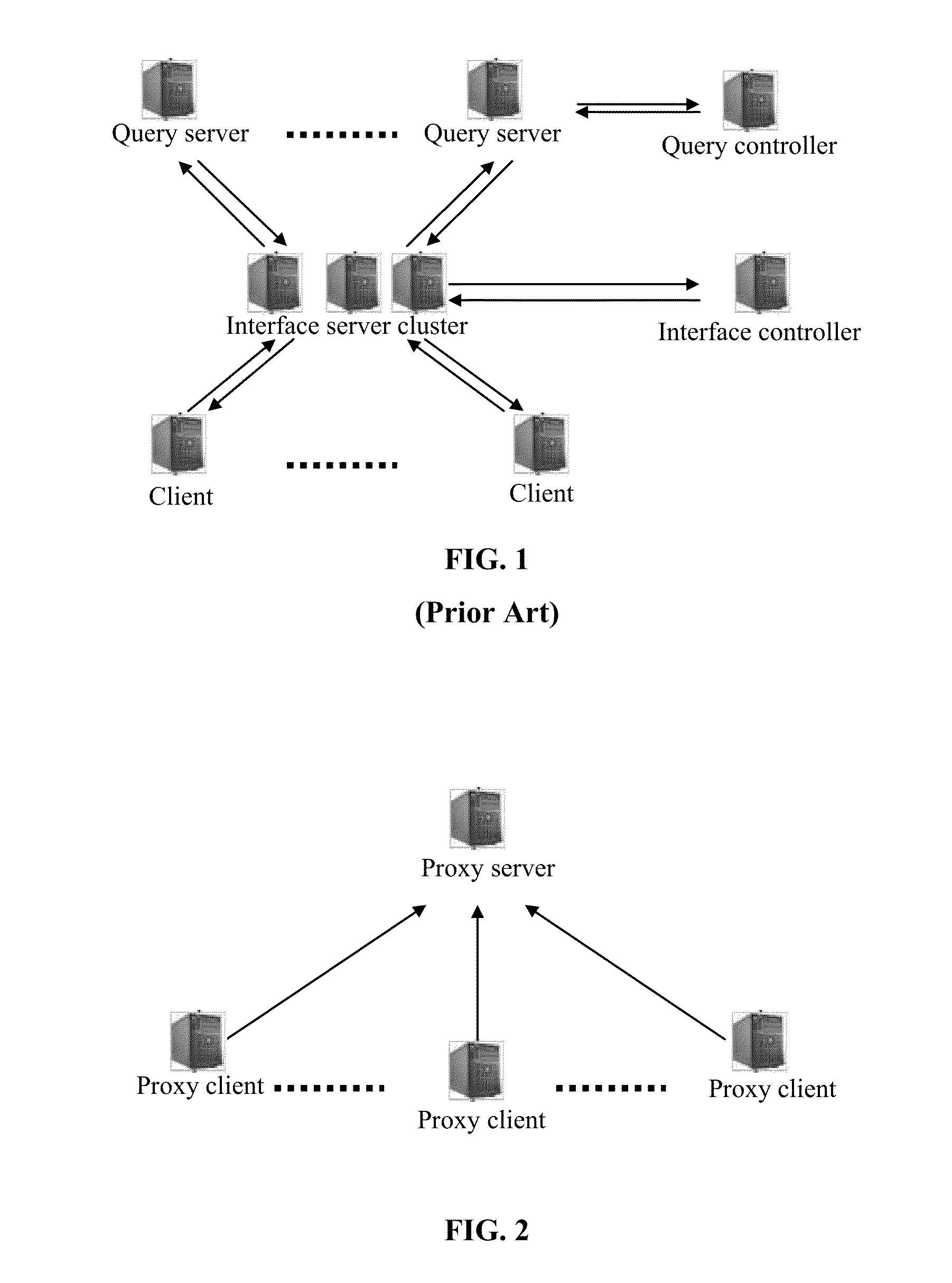
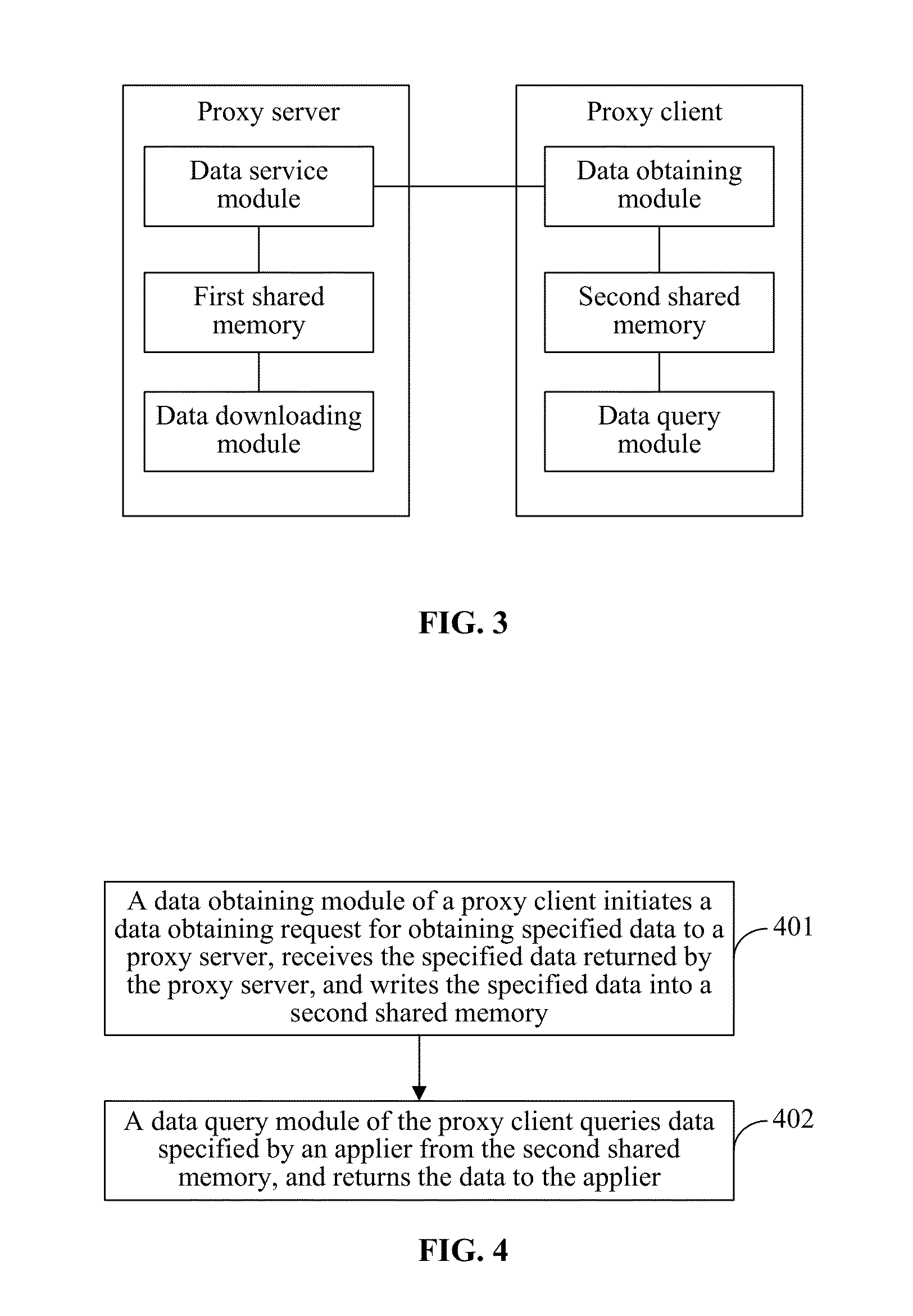
The present disclosure discloses a data query system, method, and storage medium. The data query system includes a proxy server and at least one proxy client. The proxy server is disposed on a server that serves as a data provider, and is configured to provide the proxy client with a data delivery service. The proxy client is disposed on a client that serves as a data user, and is configured to obtain data from the proxy server and save the data and provide a data query service. The proxy client thus includes a data obtaining module, a data query module, and a second shared memory. Accordingly, the present disclosure further discloses a data query method. The present disclosure has a simple structure, achieves fast data update, requires a low deployment cost, saves bandwidth resources, and achieves excellent service performance.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Hierarchical storage management using dynamic tables of contents and sets of tables of contents
InactiveUS20080294611A1Overcomes shortcomingData processing applicationsDigital data processing detailsMemory hierarchyStorage management
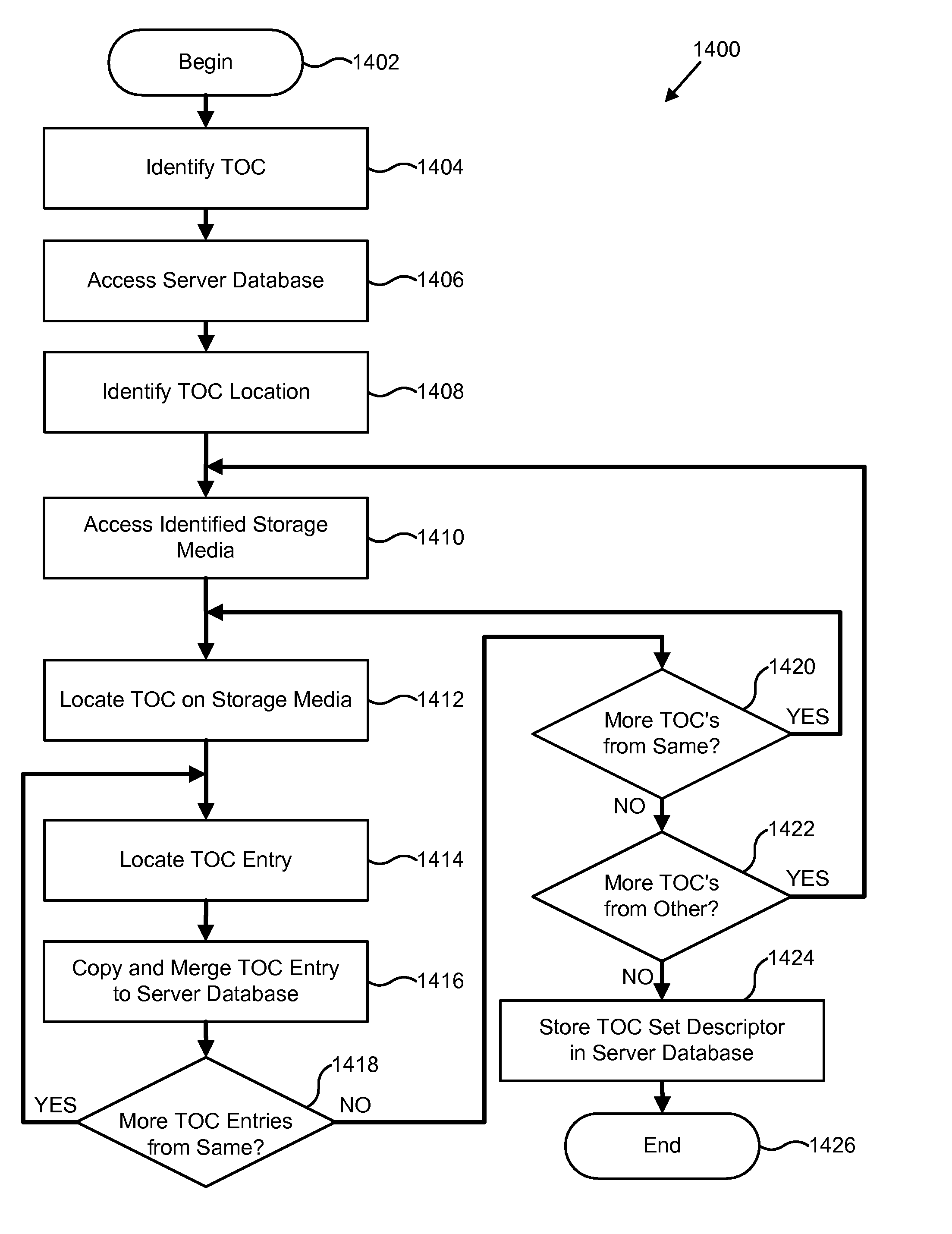
A system, apparatus, and process creates a table of contents (TOC), including one or more table of contents (TOC) entries, to manage data in a hierarchical storage management system. Each TOC entry contains metadata describing the contents and attributes of a data object within an image, which is an aggregation of multiple data objects into a single object for storage management purposes. The TOC is stored in a storage hierarchy, such as magnetic disk, for fast access of and efficient operation on the aggregated TOC entries. The system, apparatus, and process also provide for aggregating the TOC entries from one or more TOCs into a TOC set in the storage management server database. The TOC set may be manipulated and queried in order to find a particular data object or image referenced by a TOC entry. The TOC entries, TOCs, and TOC sets may be dynamically managed by the hierarchical data storage management system through implementation of a set of policy management constructs that define appropriate creation, retention, and movement of the objects within the database and storage hierarchy.
Owner:IBM CORP
Methods and systems for structuring event data in a database for location and retrieval
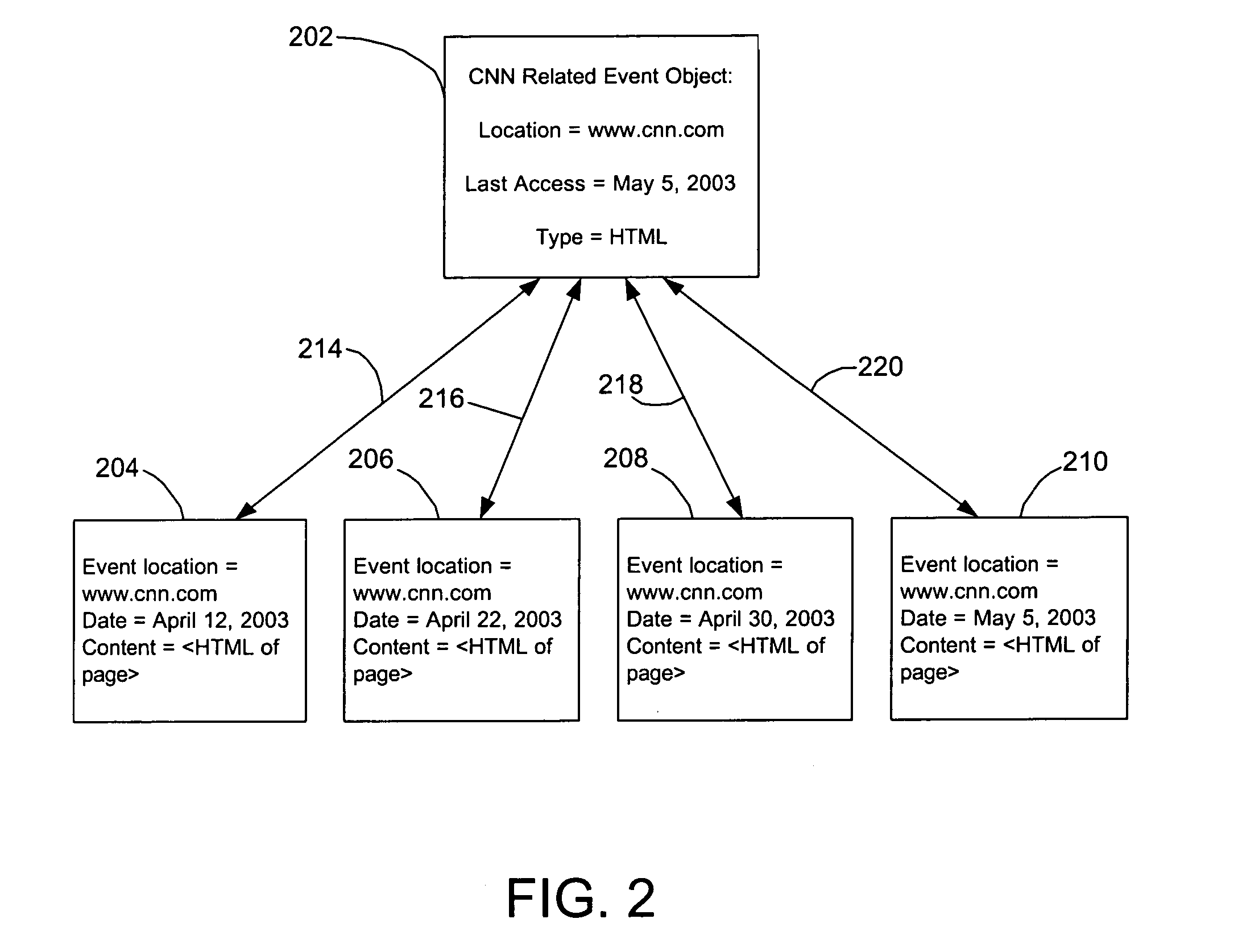
InactiveUS20050223027A1Digital data processing detailsOther databases retrievalEvent objectData mining
Methods and systems are provided for configuring event data representing activity within a computer, which allows that article to be more readily accessed by a search engine. In one embodiment, an event associated with an article is captured, wherein the event comprises event data, the event is indexed, a related event object is created related to the event, wherein the related event object comprises a set of one or more related events, and the related event object is associated with the one or more related events.
Owner:GOOGLE LLC
System and method of managing indexation of flash memory
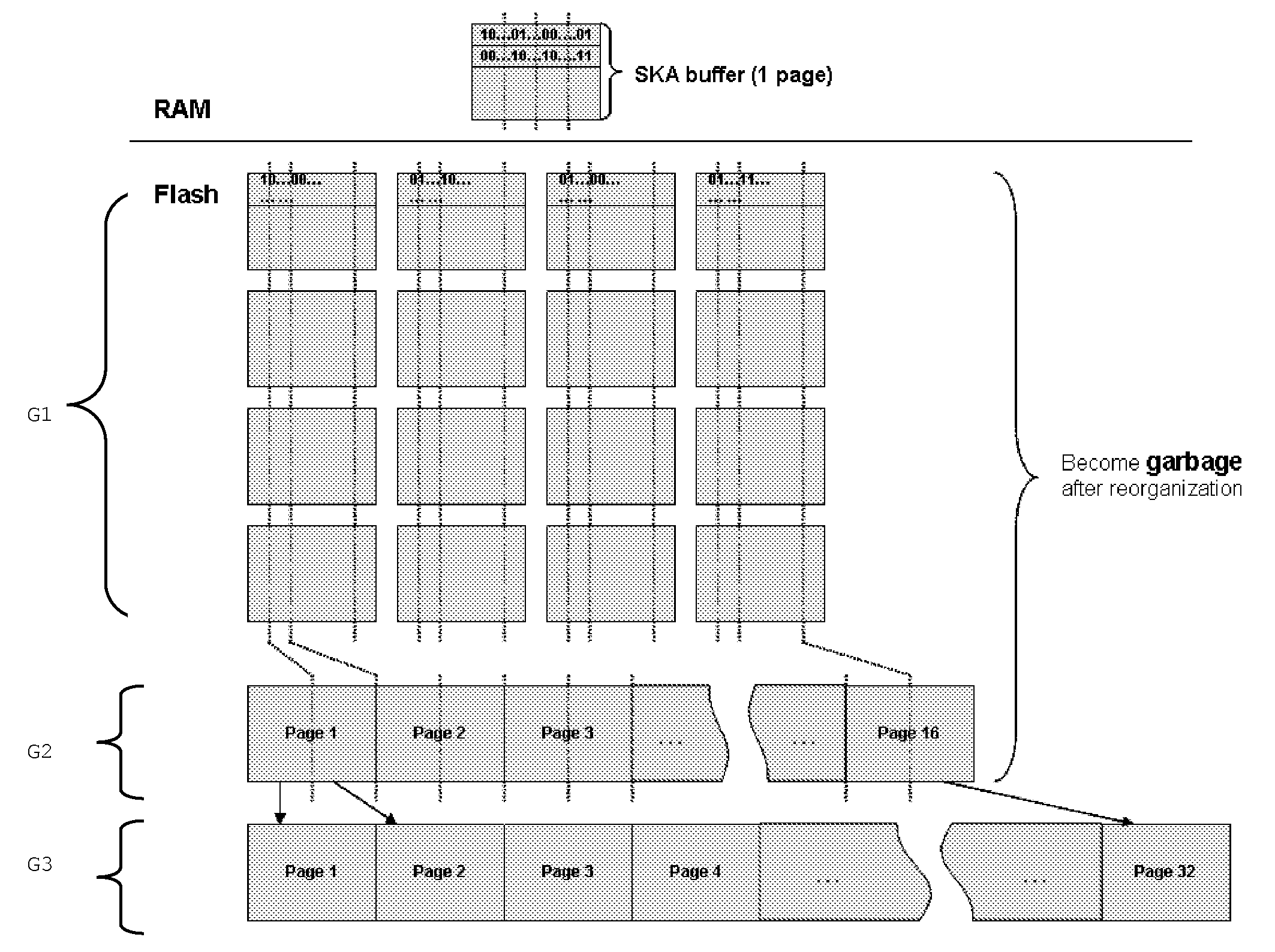
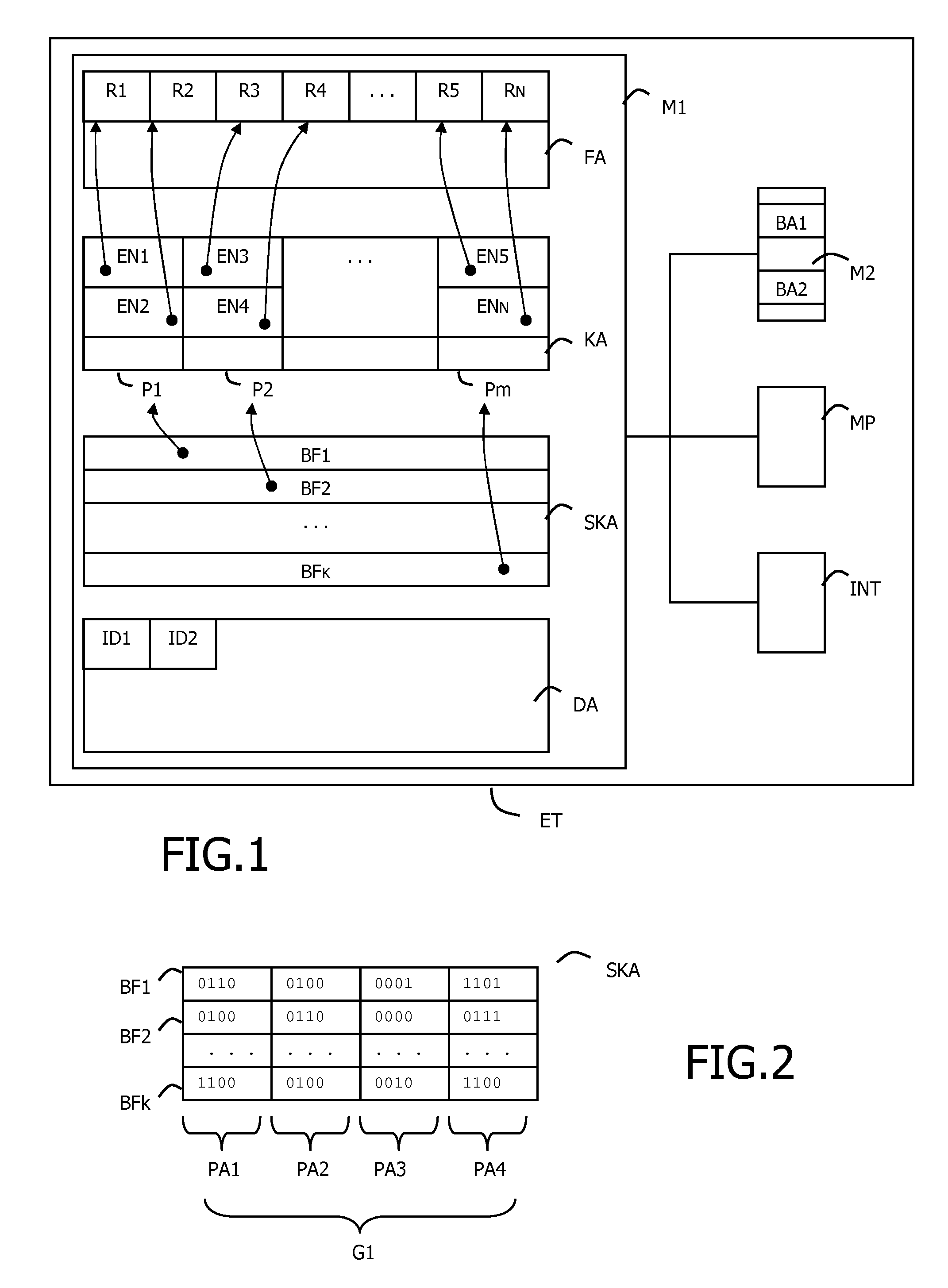
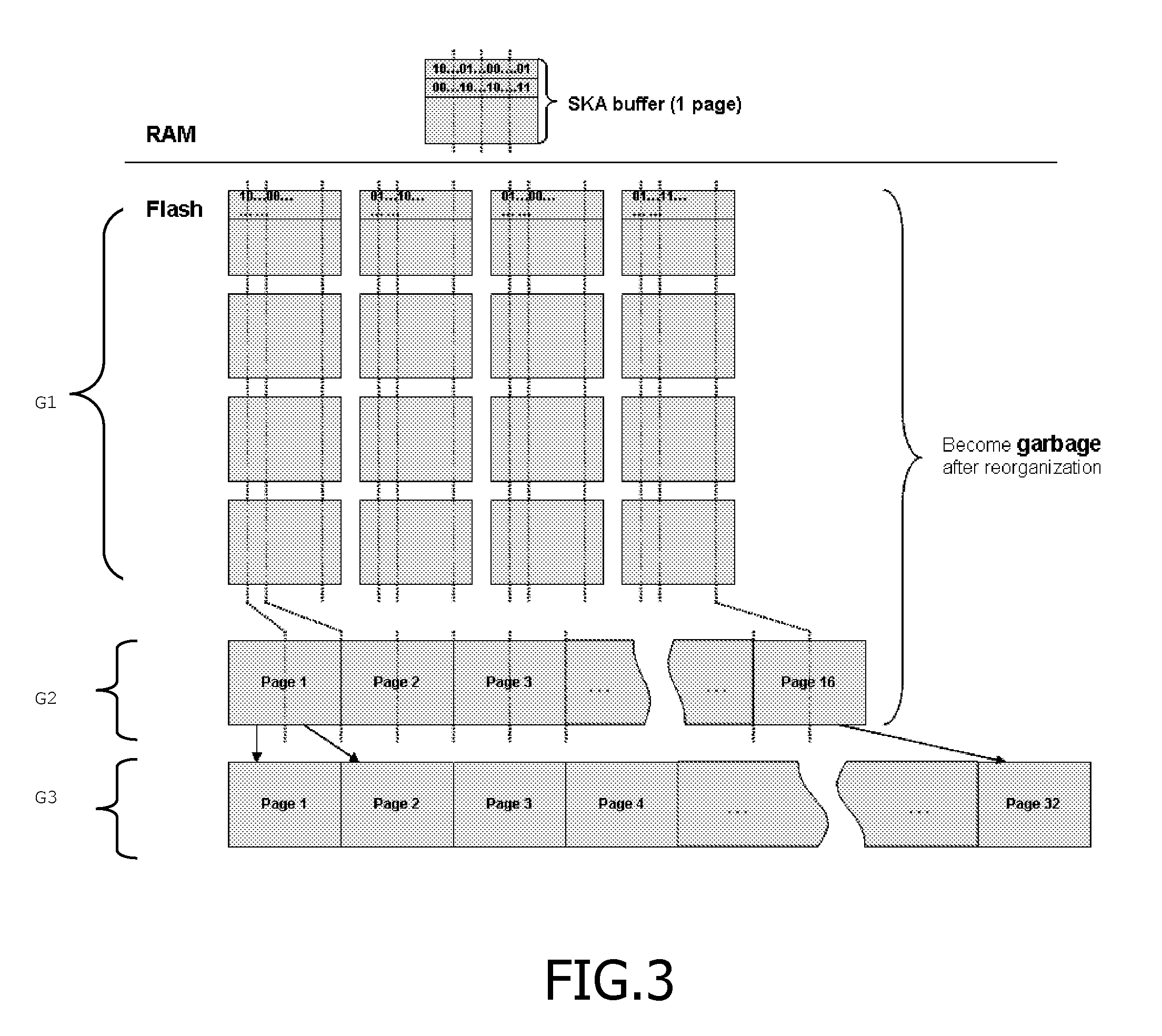
InactiveUS20100199027A1Minimizing RAM consumptionReduce consumptionMemory adressing/allocation/relocationOther databases indexingHash functionIndexation
The invention is a system of managing indexation of memory. Said system has a microprocessor, and a flash memory. Said flash memory has an indexed area comprising indexed items, and an index that is structured in a plurality of index areas comprising a plurality of entries. Said flash memory comprises an index summary comprising a plurality of elements. Each index summary element is linked to an index area of said index. Each index summary element is built from all entries belonging to said linked index area and is built using k hash functions, with 1≦k.
Owner:GEMPLU
Generating search database based on sensor measurements
InactiveUS20150106403A1Digital data processing detailsObject oriented databasesMobile deviceData mining
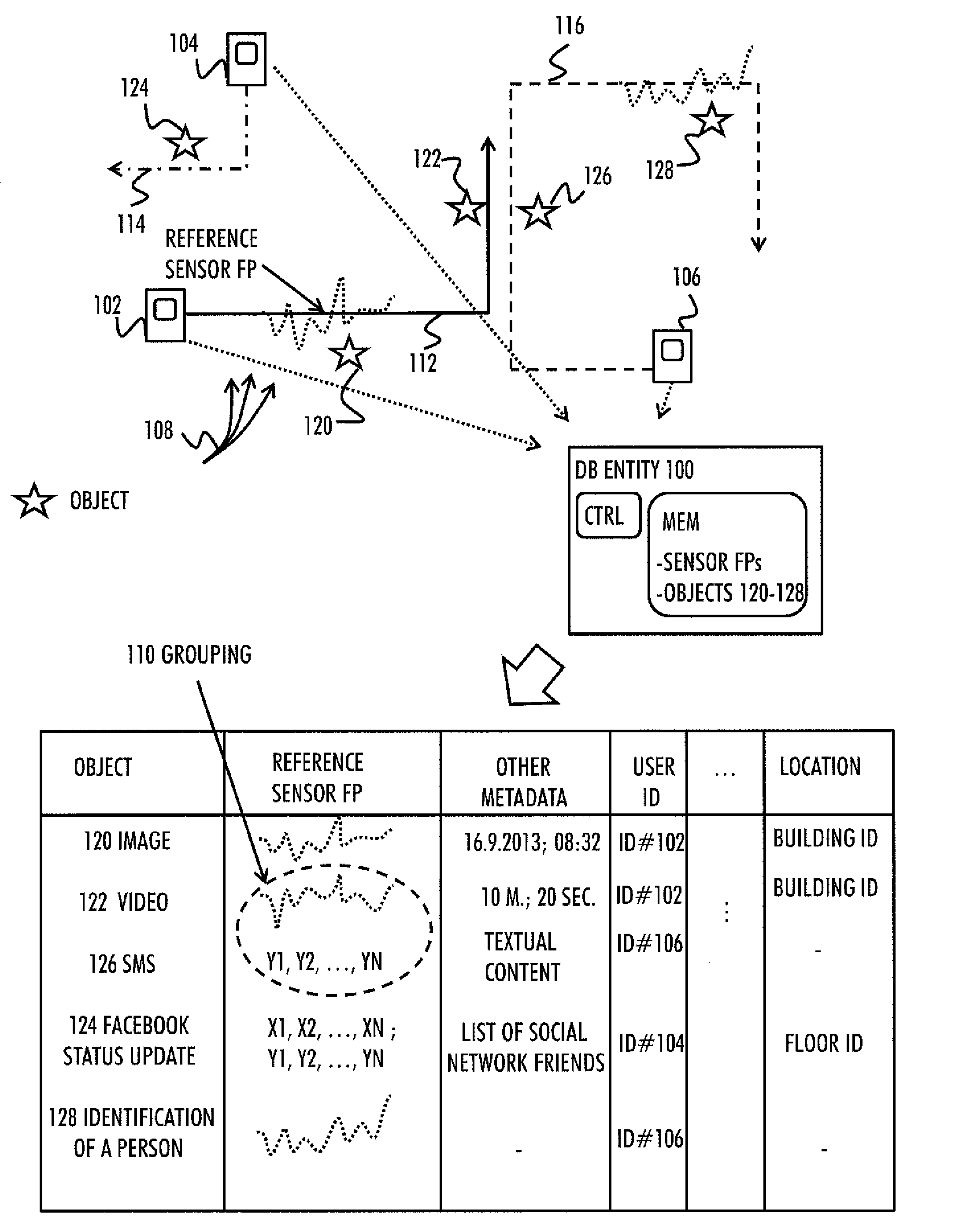
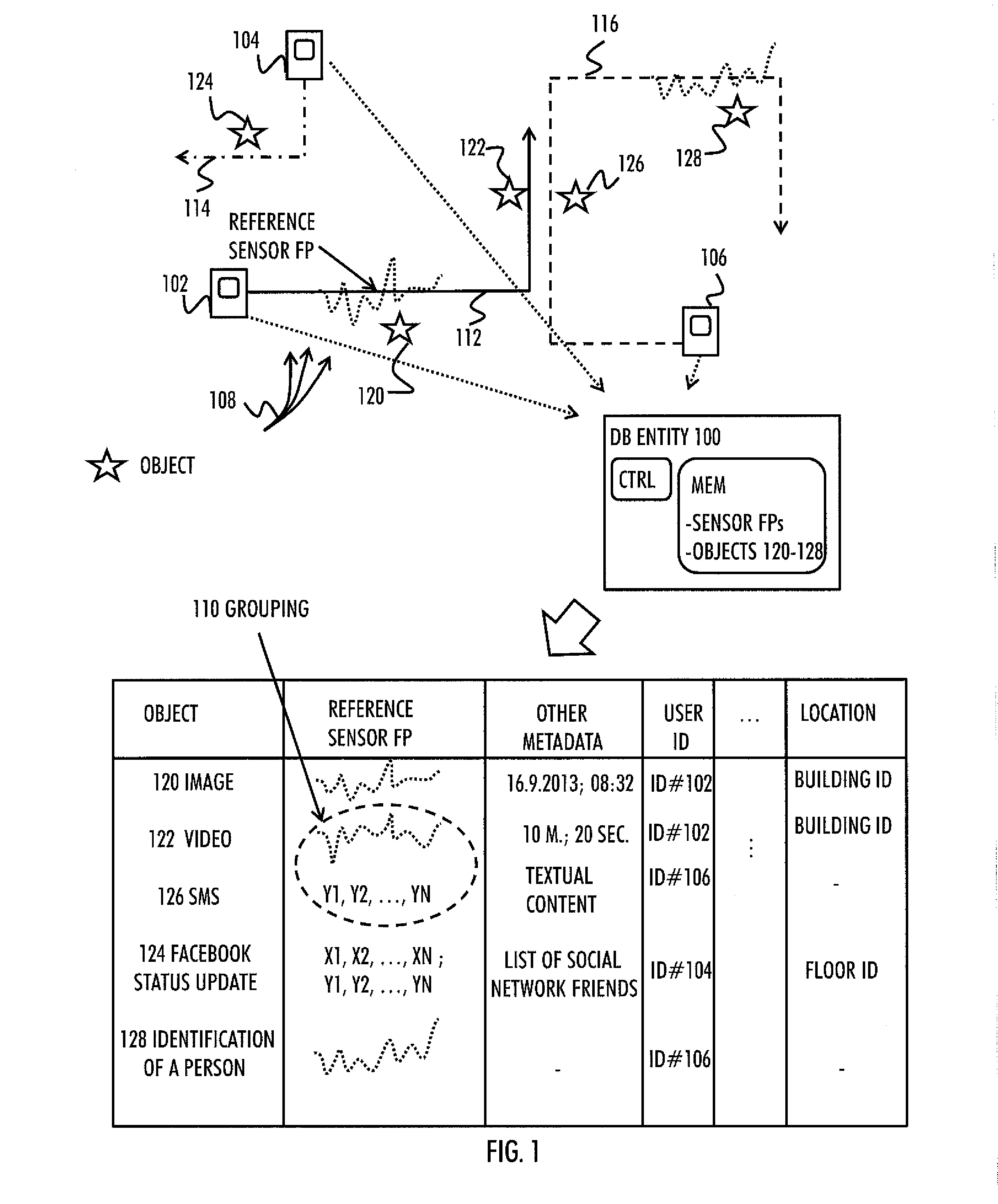
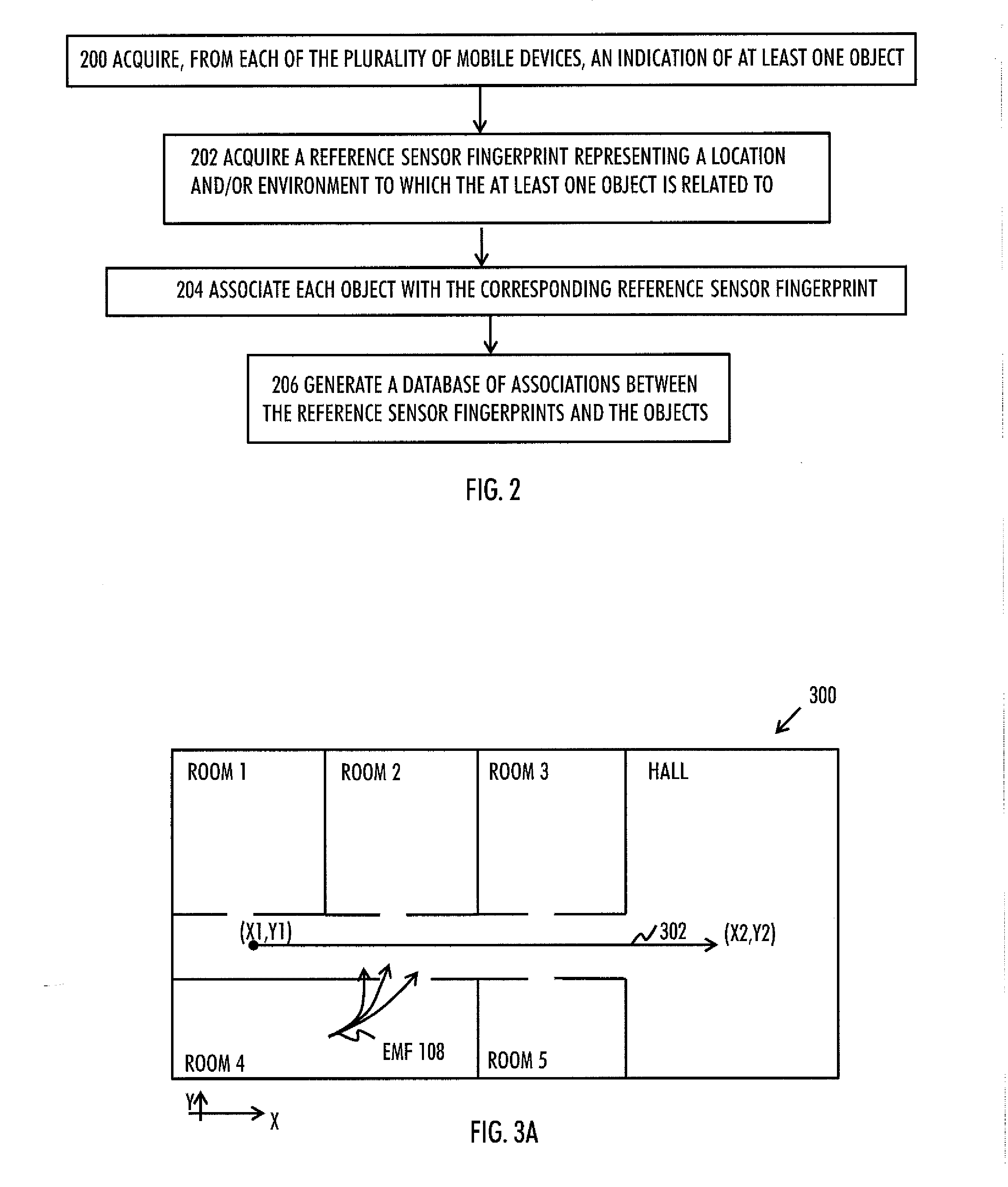
There is provided a database entity for generating a search database, comprising: at least one processor and at least one memory including a computer program code, wherein the at least one memory and the computer program code are configured, with the at least one processor, to cause the database entity at least to: acquire, from each of the plurality of mobile devices, an indication of at least one object; acquire a reference sensor, fingerprint representing a context to which the at least one object is related to; associate each object with the corresponding reference sensor fingerprint; and generate a database of associations between the reference sensor fingerprints and the objects.
Owner:INDOORATLAS
System and method for investigating large amounts of data
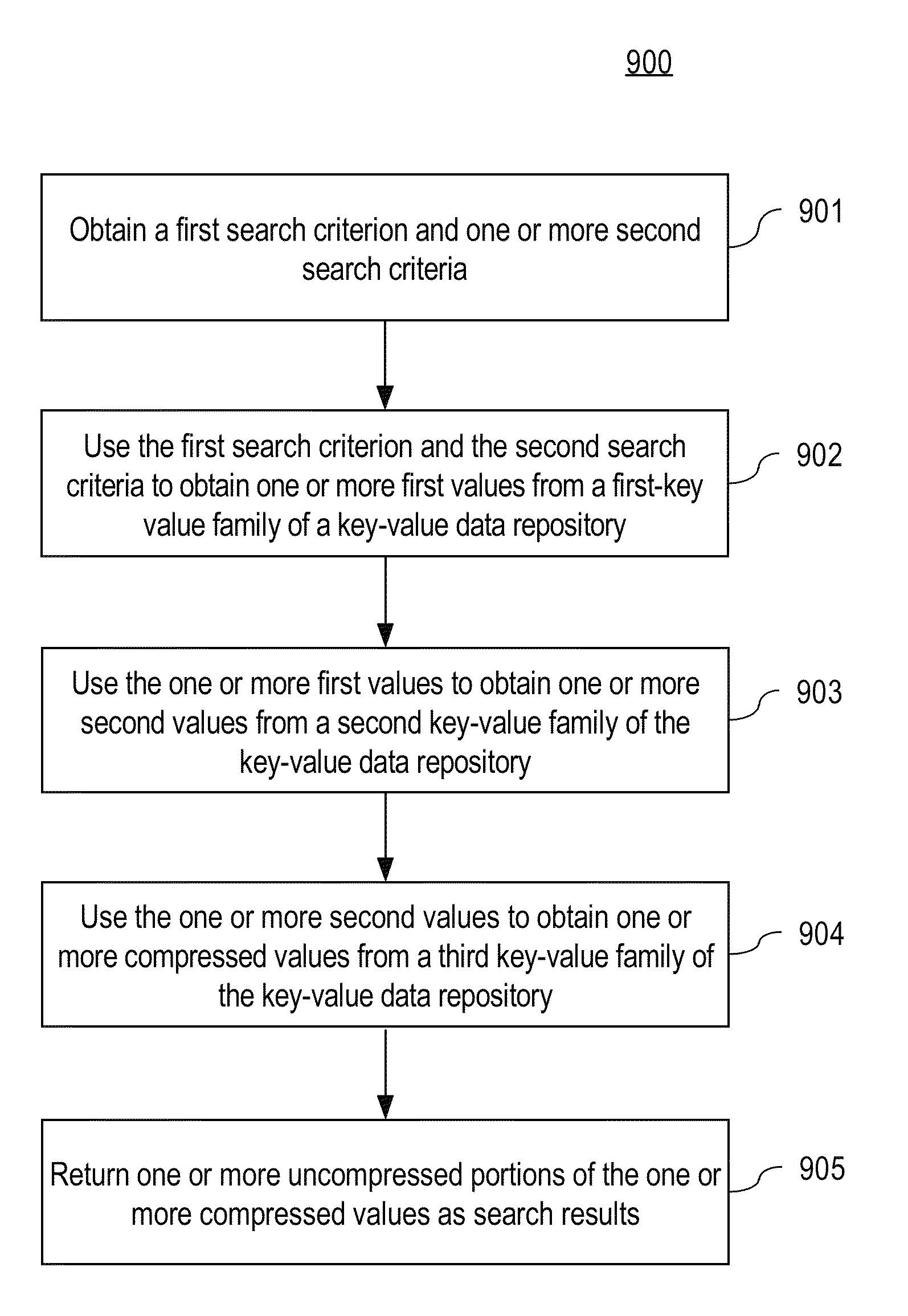
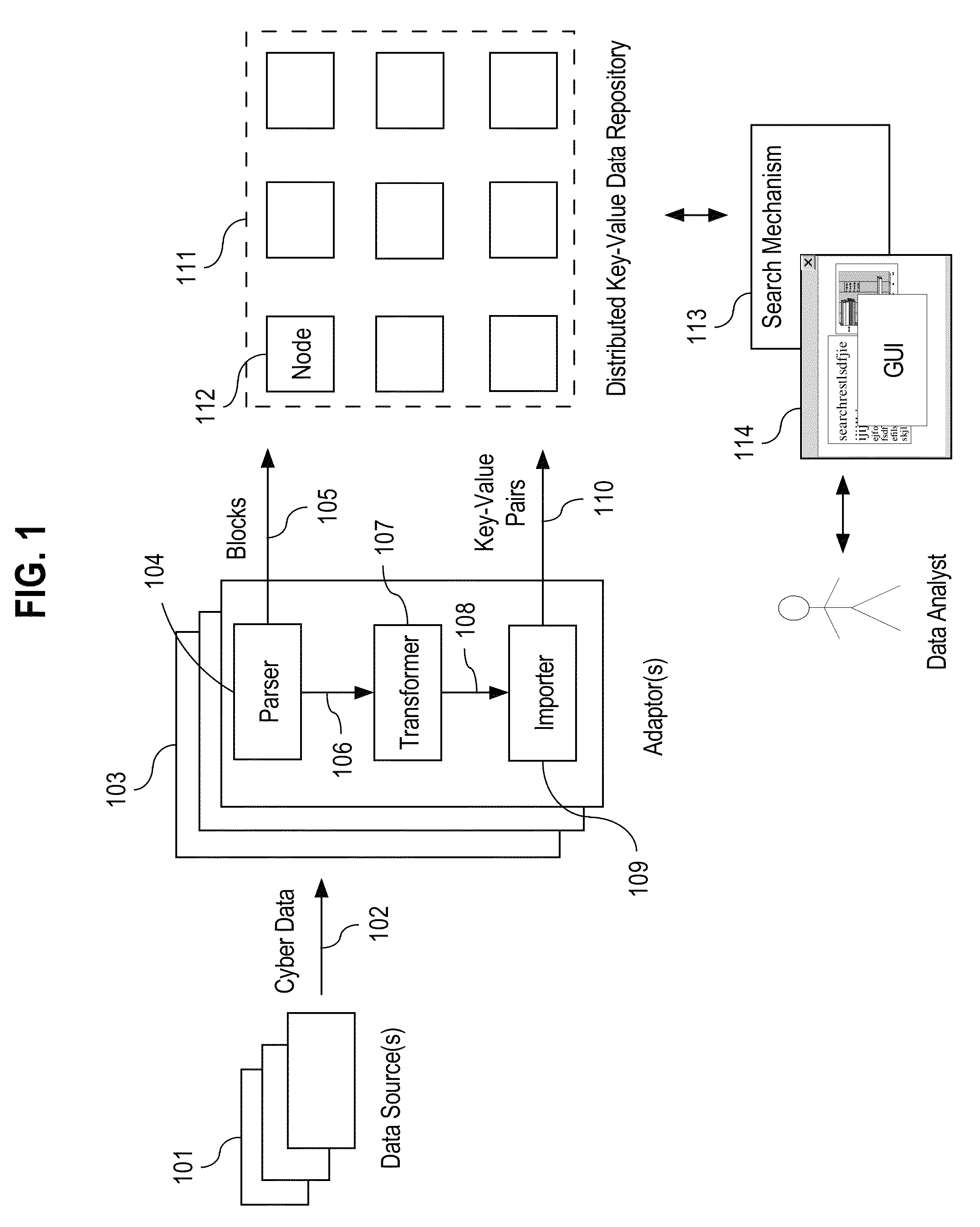
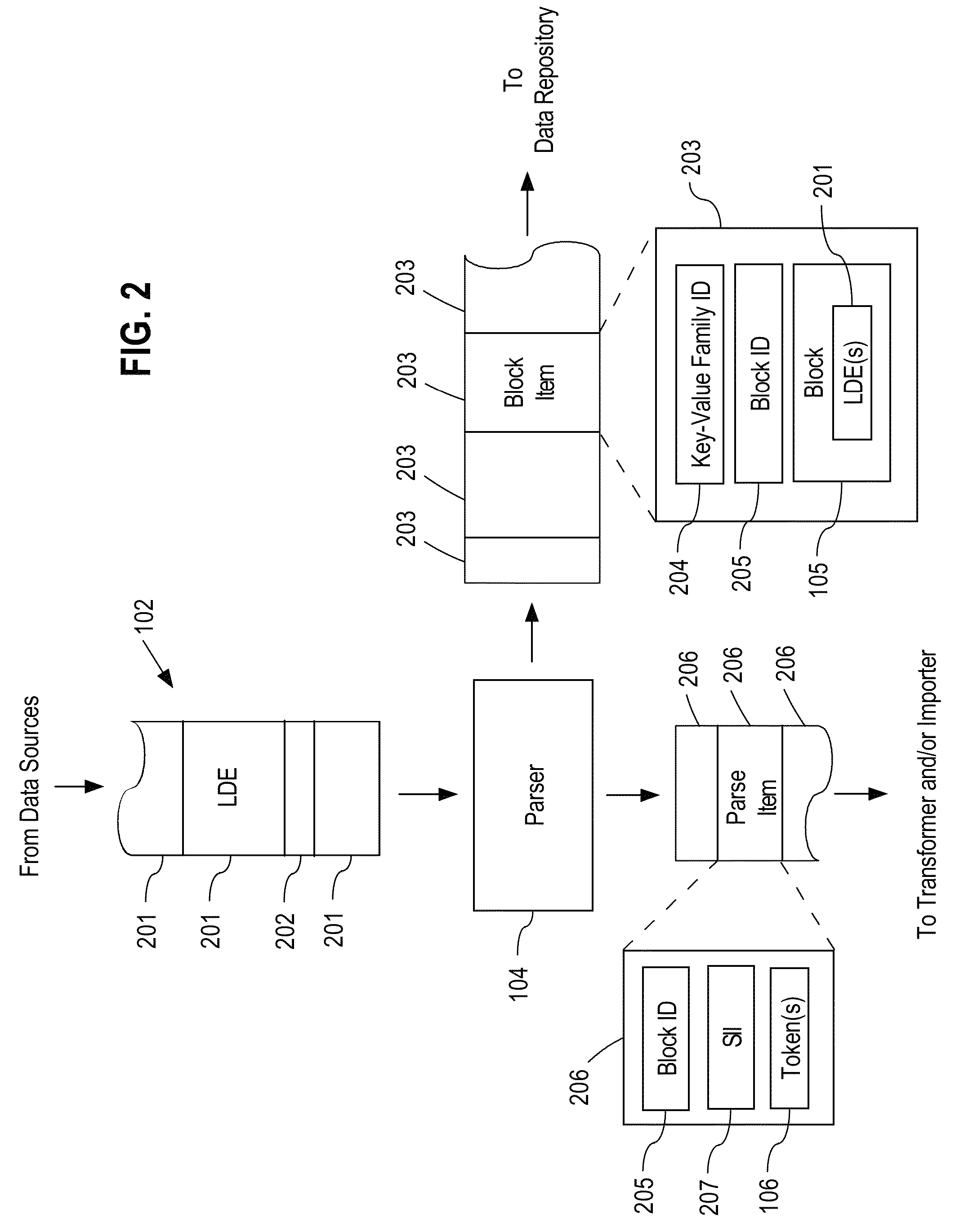
A data analysis system is proposed for providing fine-grained low latency access to high volume input data from possibly multiple heterogeneous input data sources. The input data is parsed, optionally transformed, indexed, and stored in a horizontally-scalable key-value data repository where it may be accessed using low latency searches. The input data may be compressed into blocks before being stored to minimize storage requirements. The results of searches present input data in its original form. The input data may include access logs, call data records (CDRs), e-mail messages, etc. The system allows a data analyst to efficiently identify information of interest in a very large dynamic data set up to multiple petabytes in size. Once information of interest has been identified, that subset of the large data set can be imported into a dedicated or specialized data analysis system for an additional in-depth investigation and contextual analysis.
Owner:PALANTIR TECHNOLOGIES
Intent-based analytics
In performing network analysis, a declarative specification of a collector element and a declarative specification of a processing element are received. The declarative specification of the collector element specifies a dynamically updating query associated with networking components of a computer network. The processing element dynamically processes dynamically updated results of the dynamically updating query. At least the collector element and the processing element are executed. An indication of a detected anomaly is provided based at least in part on a result of the execution of the collector element and the processing element.
Owner:APSTRA INC
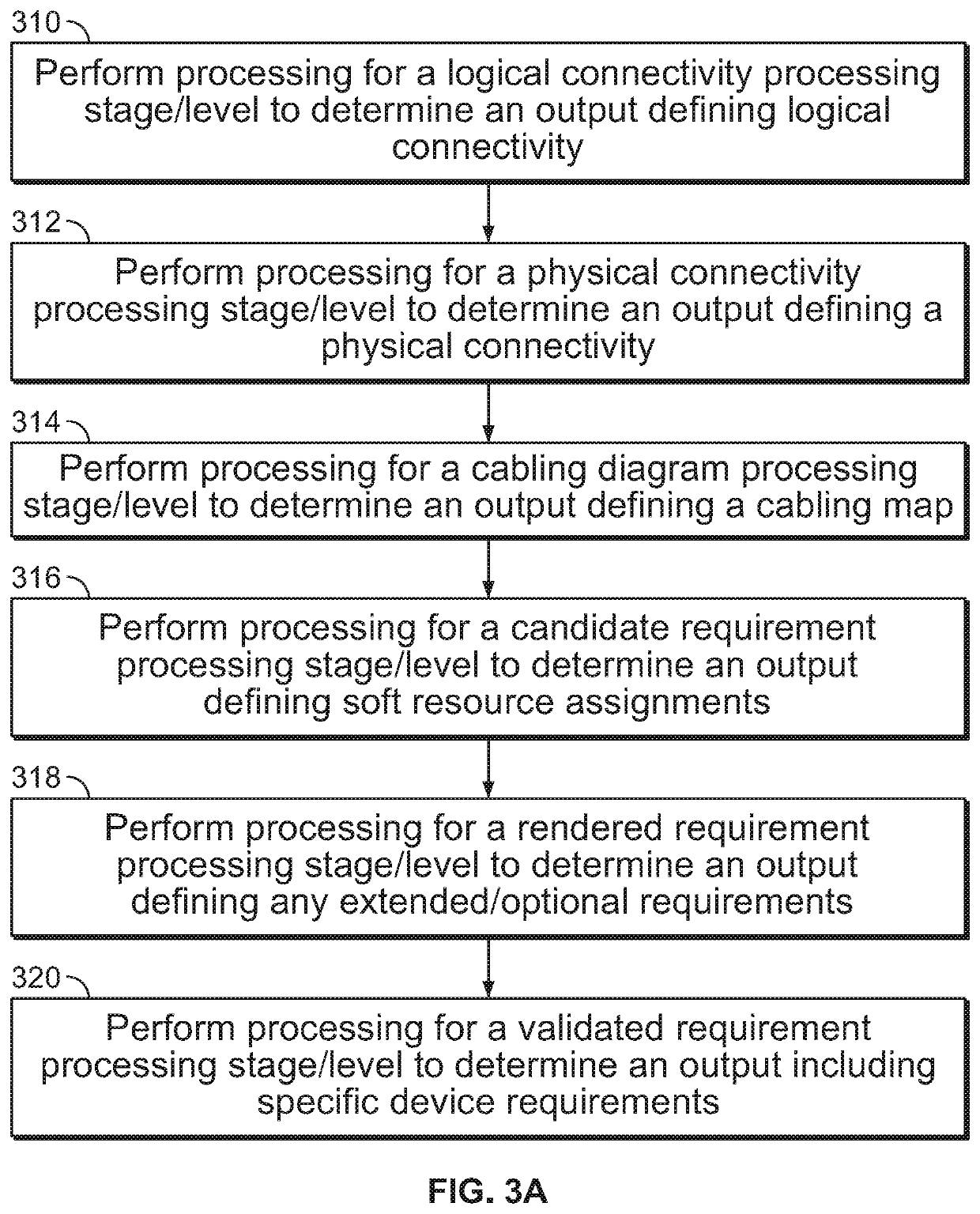
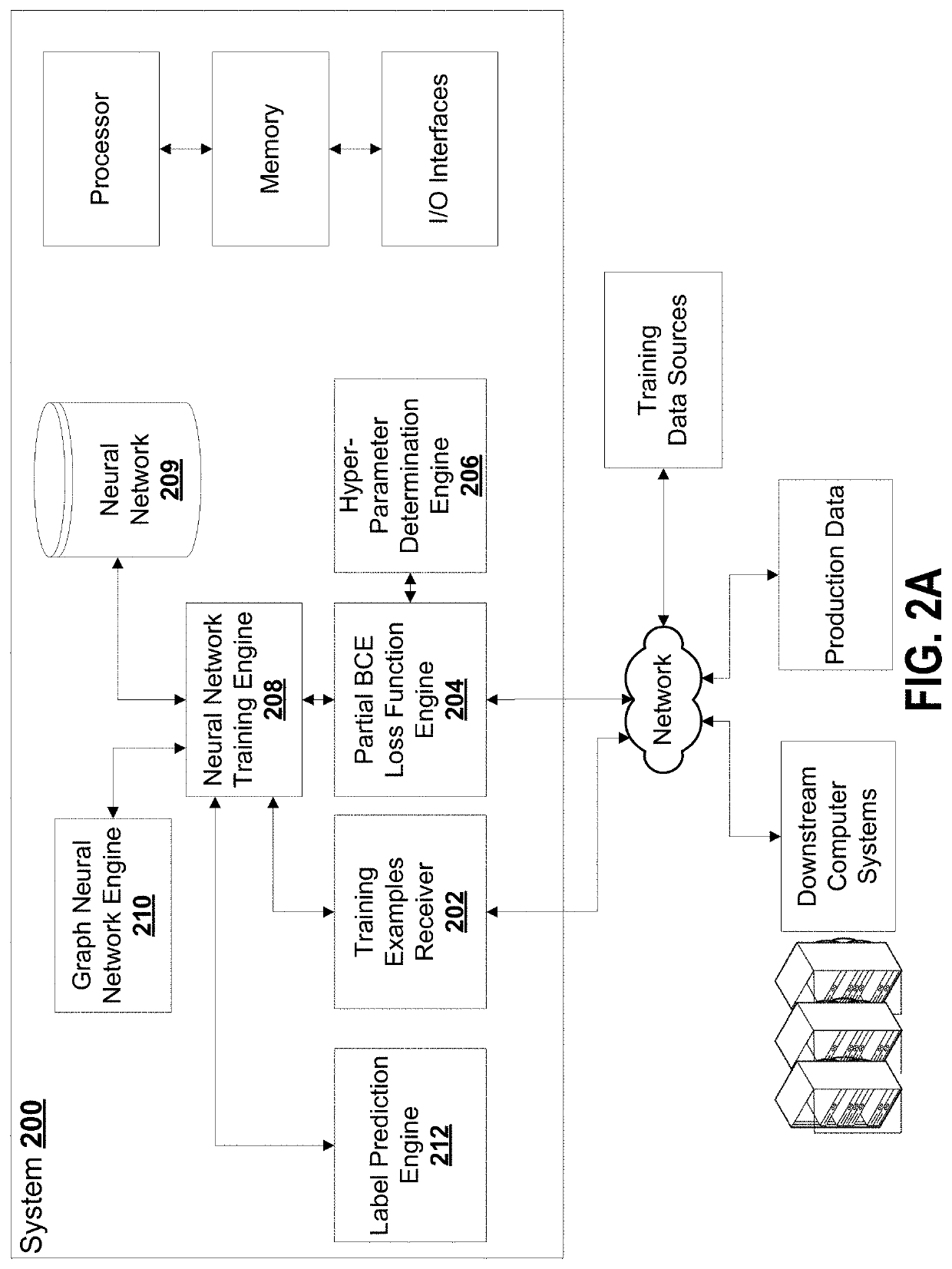
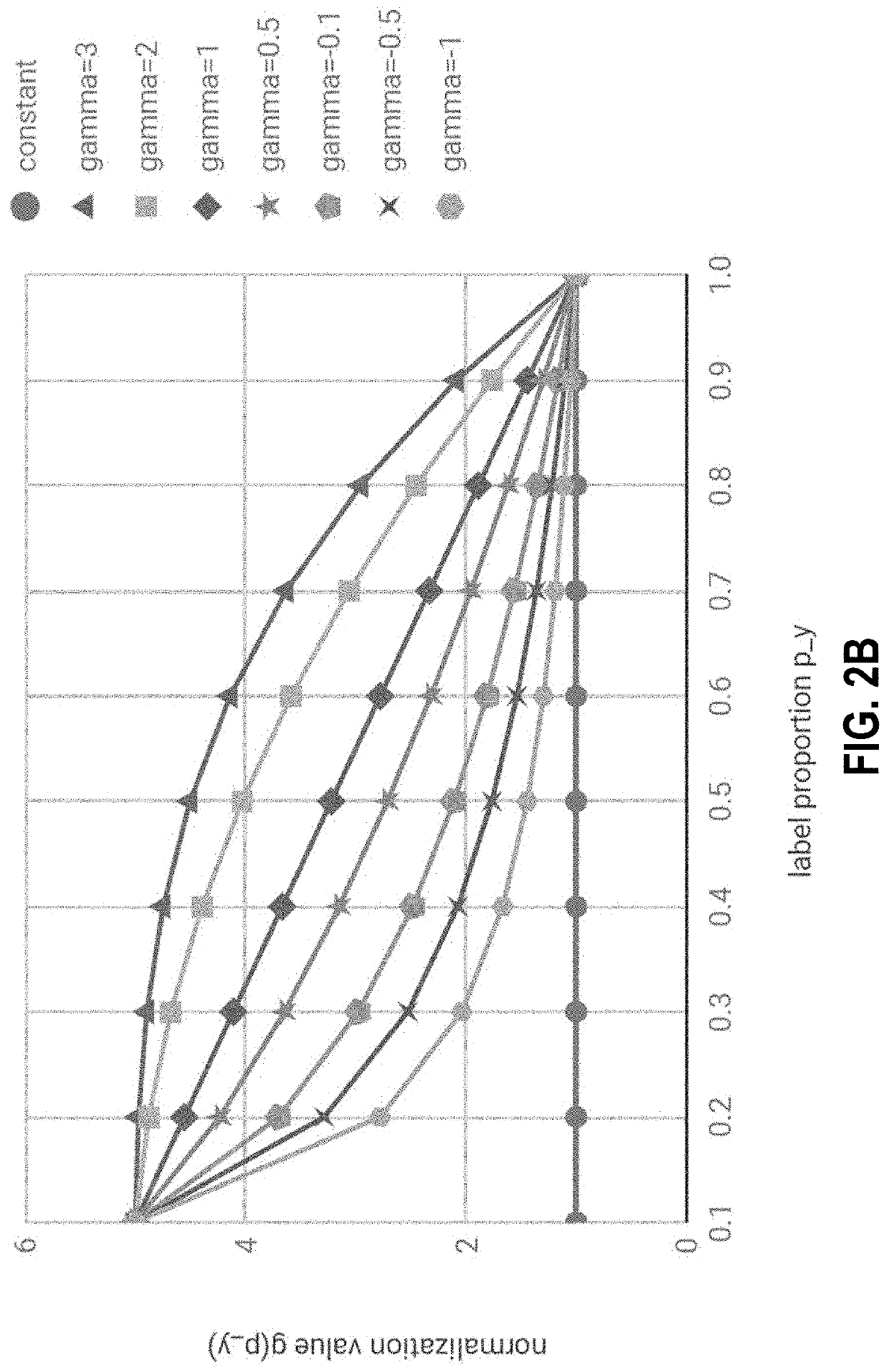
System and method for a convolutional neural network for multi-label classification with partial annotations
PendingUS20200160177A1Low costAvoid disadvantagesOther databases indexingMachine learningMulti-label classificationGraph neural networks
Effectively training machine learning systems with incomplete / partial labels is a practical, technical problem that solutions described herein attempt to overcome. In particular, an approach to modify loss functions on a proportionality basis is noted in some embodiments. In other embodiments, a graph neural network is provided to help identify correlations / causations as between categories. In another set of embodiments, a prediction approach is described to, based on originally provided labels, predict labels for unlabelled training samples such that the proportion of labelled labels relative to all labels is increased.
Owner:ROYAL BANK OF CANADA
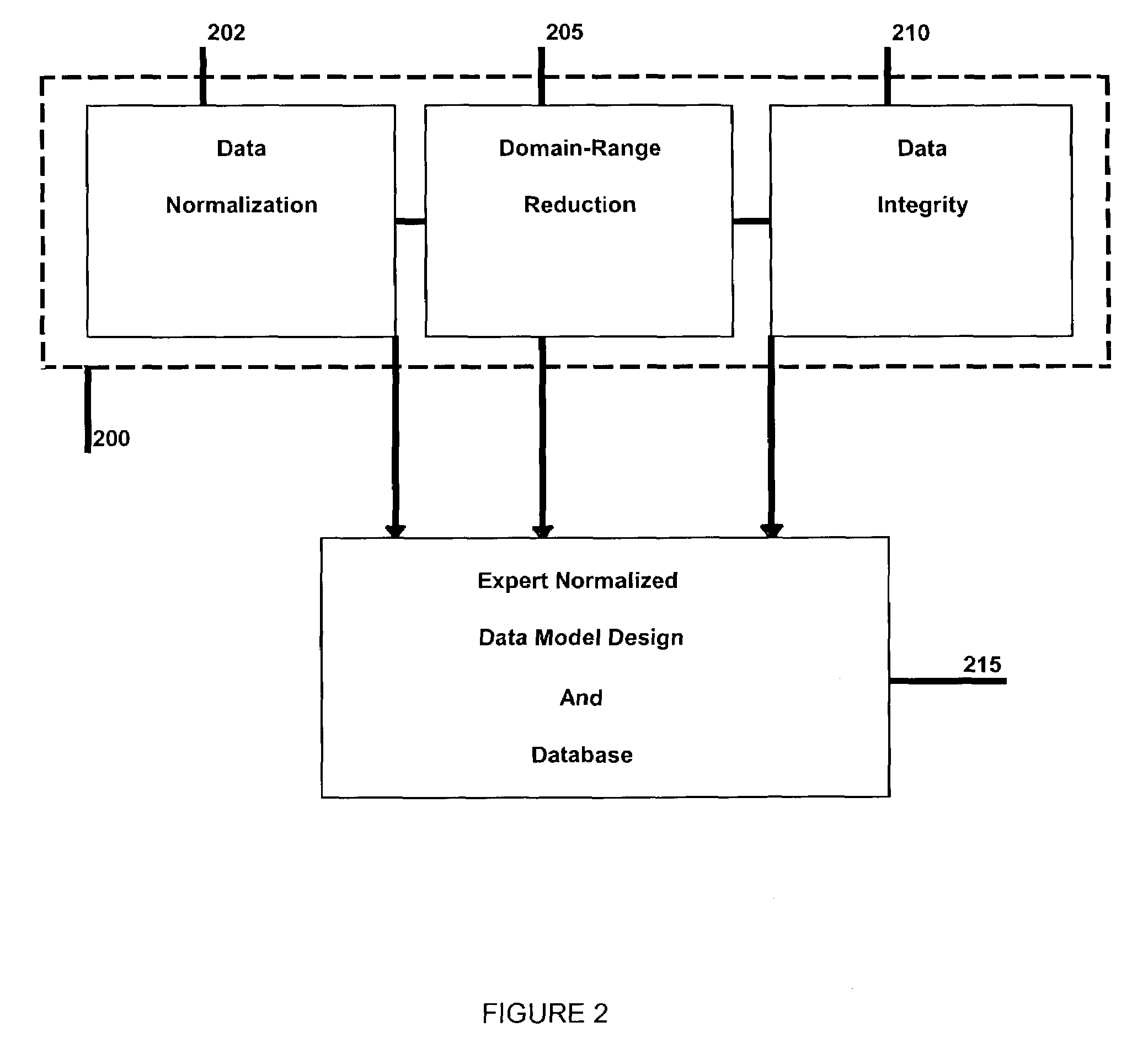
Data entry, cross reference database and search systems and methods thereof
ActiveUS7225197B2Improve data integritySpeed efficientData processing applicationsDigital data processing detailsData integrityData field
A method and system unifying existing data of a target industry from existing sources of the data by designing a data model by applying varying data integrity methods to define characteristics, features and / or functions of items in the target industry as data elements, electronically reading, parsing and transforming data from existing electronic data sources of the target industry to input to the data model, designing user interfaces to the data model, the user interfaces corresponding to user segments of the target industry, and dynamically maintaining normalization of the data model according to the varying data integrity methods during any type of access to the data model by the user segments. A data entry access to the data model comprises dynamically constructing search indexes, each search index defined as a unique data field and a text searchable concatenation of other fields' data in any given data table of the data model.
Owner:ELECDECOM
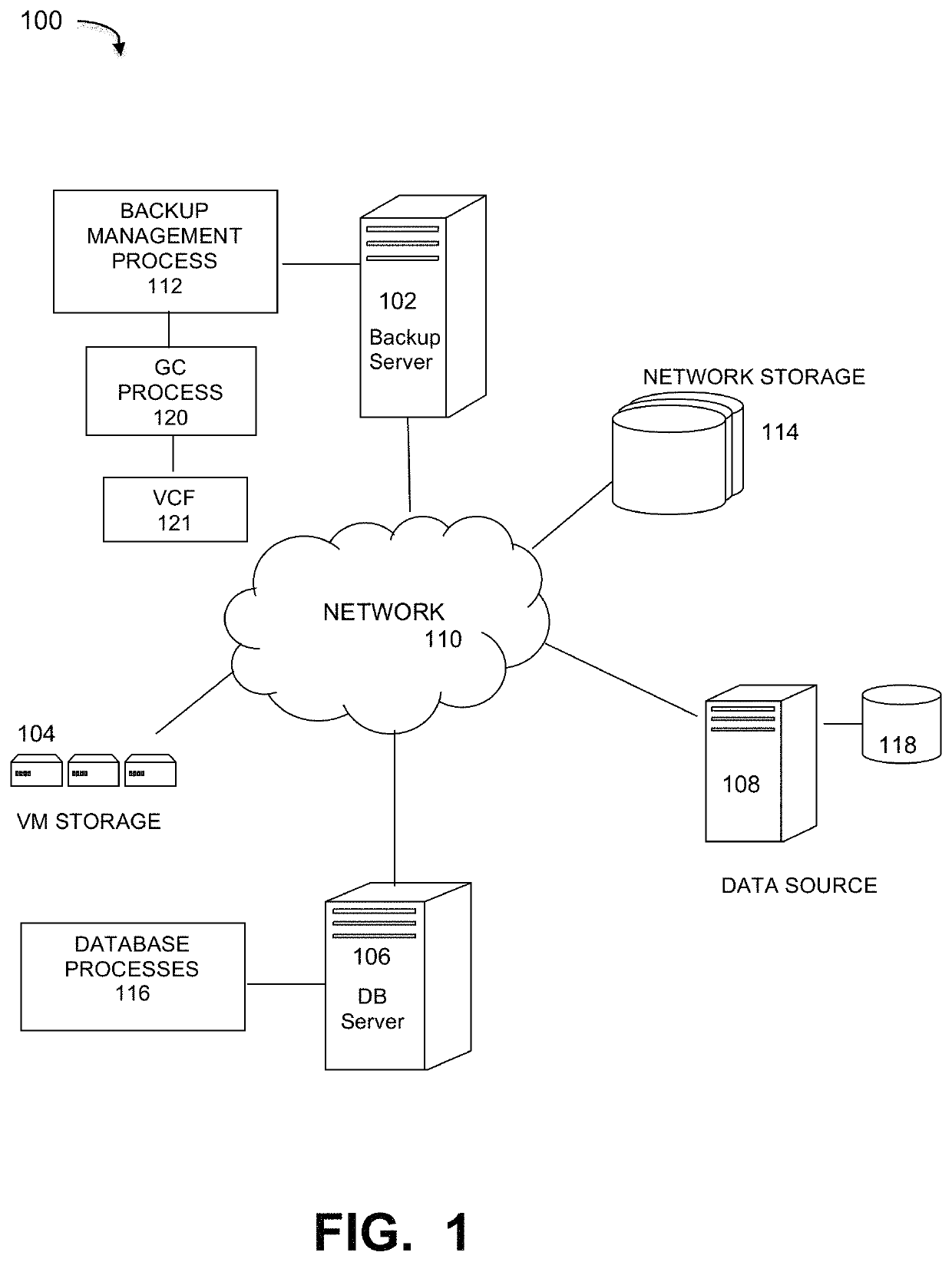
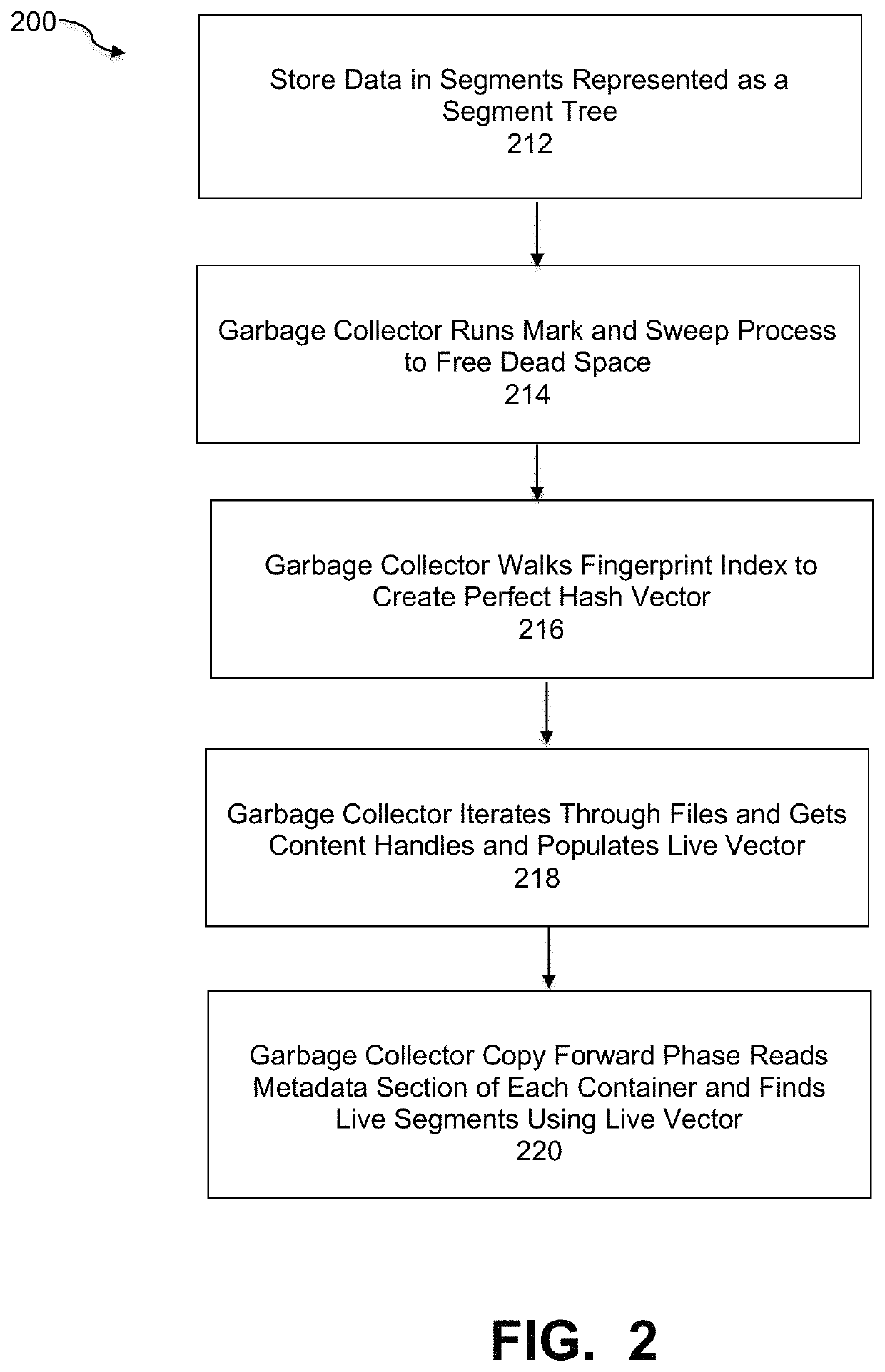
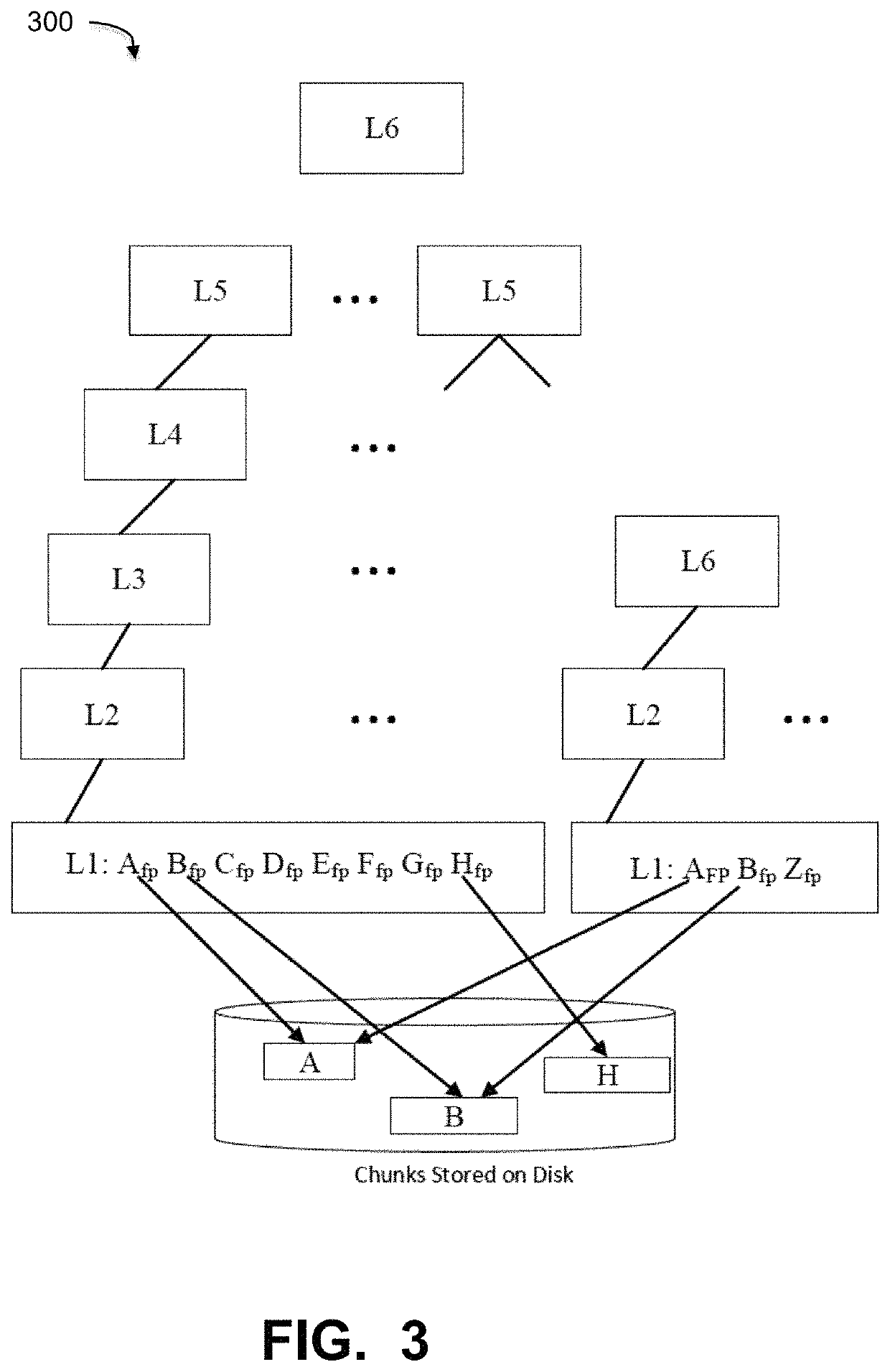
Virtual copy forward method and system for garbage collection in cloud computing networks
ActiveUS10795812B1Memory architecture accessing/allocationMemory adressing/allocation/relocationData packRefuse collection
A garbage collection (GC) process within a deduplication backup network comprising a GC component identifying metadata stored in file system (FS) segments, storing the metadata in a metadata container locally on the server as well as on cloud storage, and reading the locally stored metadata container through the GC process to obtain metadata of the FS containers and determine live data regions of the FS containers, wherein the metadata contains fingerprints of all segments of the file system containers; and a copy forward component forwarding the live data regions to new containers written both locally on the server and on the cloud storage, writing live portions of the metadata container to a new metadata container written both locally on the server and on the cloud storage, and deleting dead compression regions from the cloud storage and deleting the original metadata container from local storage and the cloud storage.
Owner:EMC IP HLDG CO LLC
Method of storing and retrieving miniaturised data
InactiveUS20070030186A1Digital data processing detailsCode conversionMiniaturizationComputer science
Owner:ZENTRONIX
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com