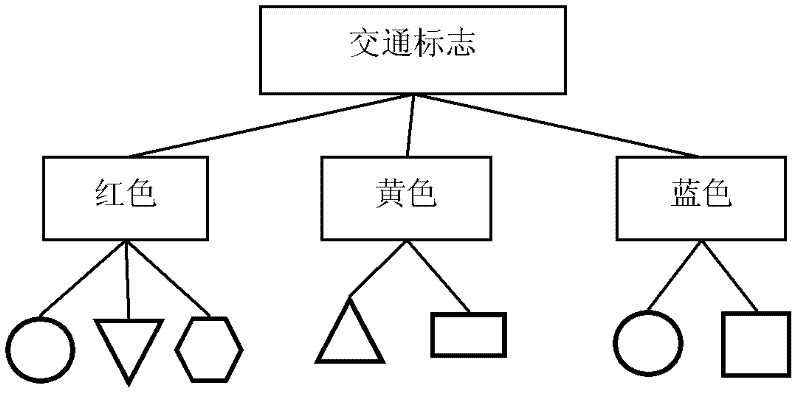
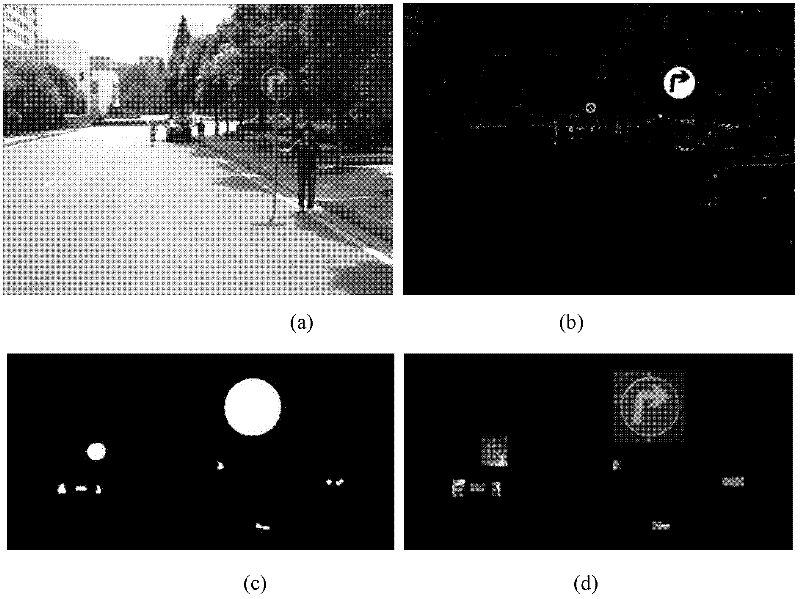
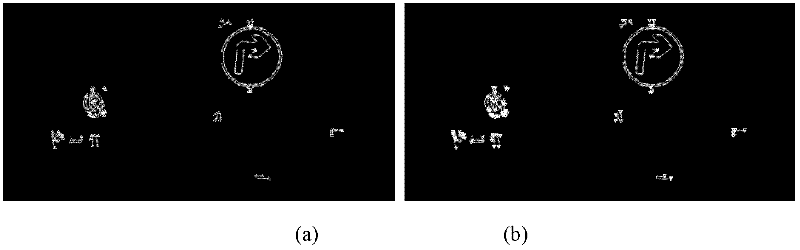
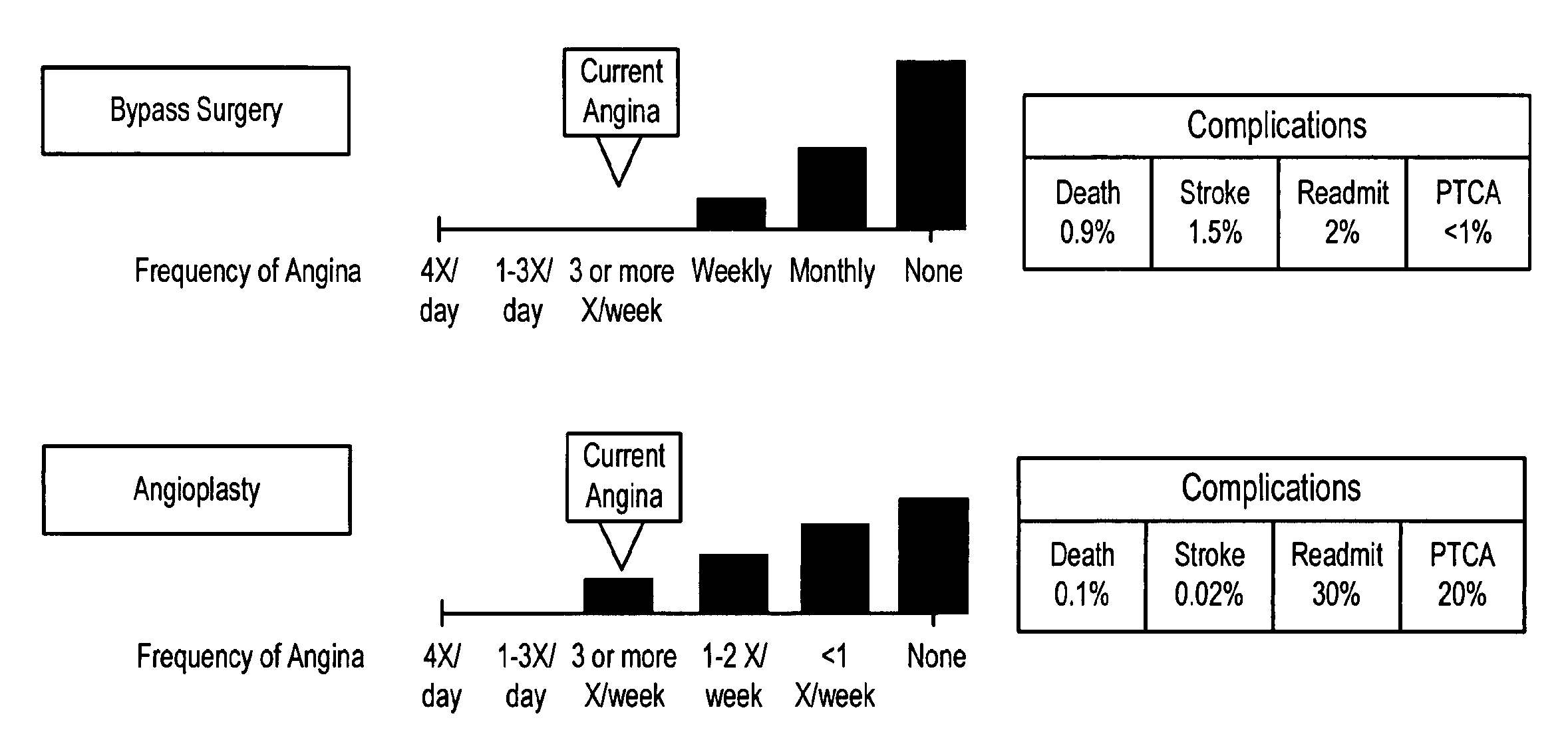
Patents
Literature
3188results about How to "Reduce redundancy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
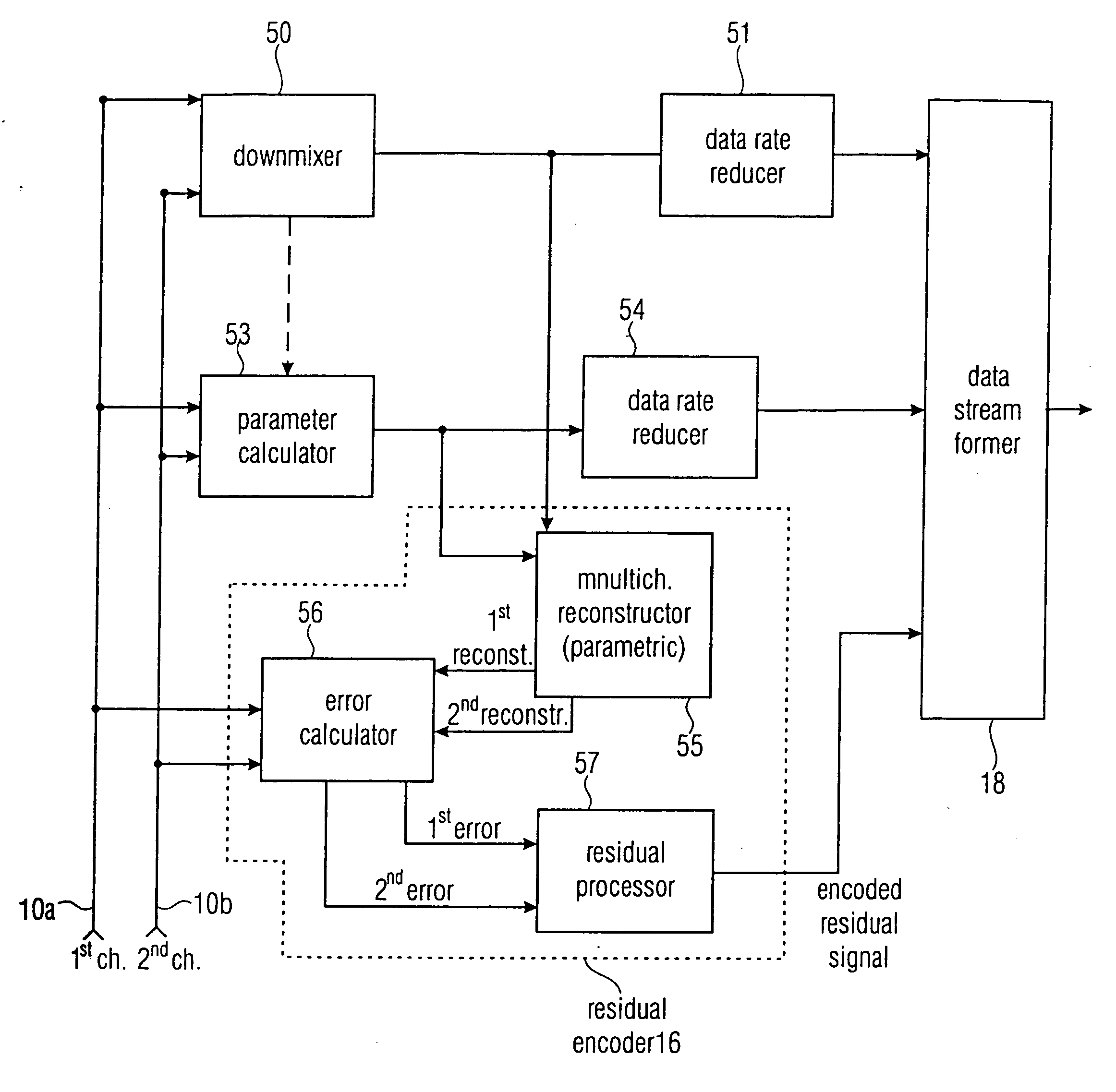
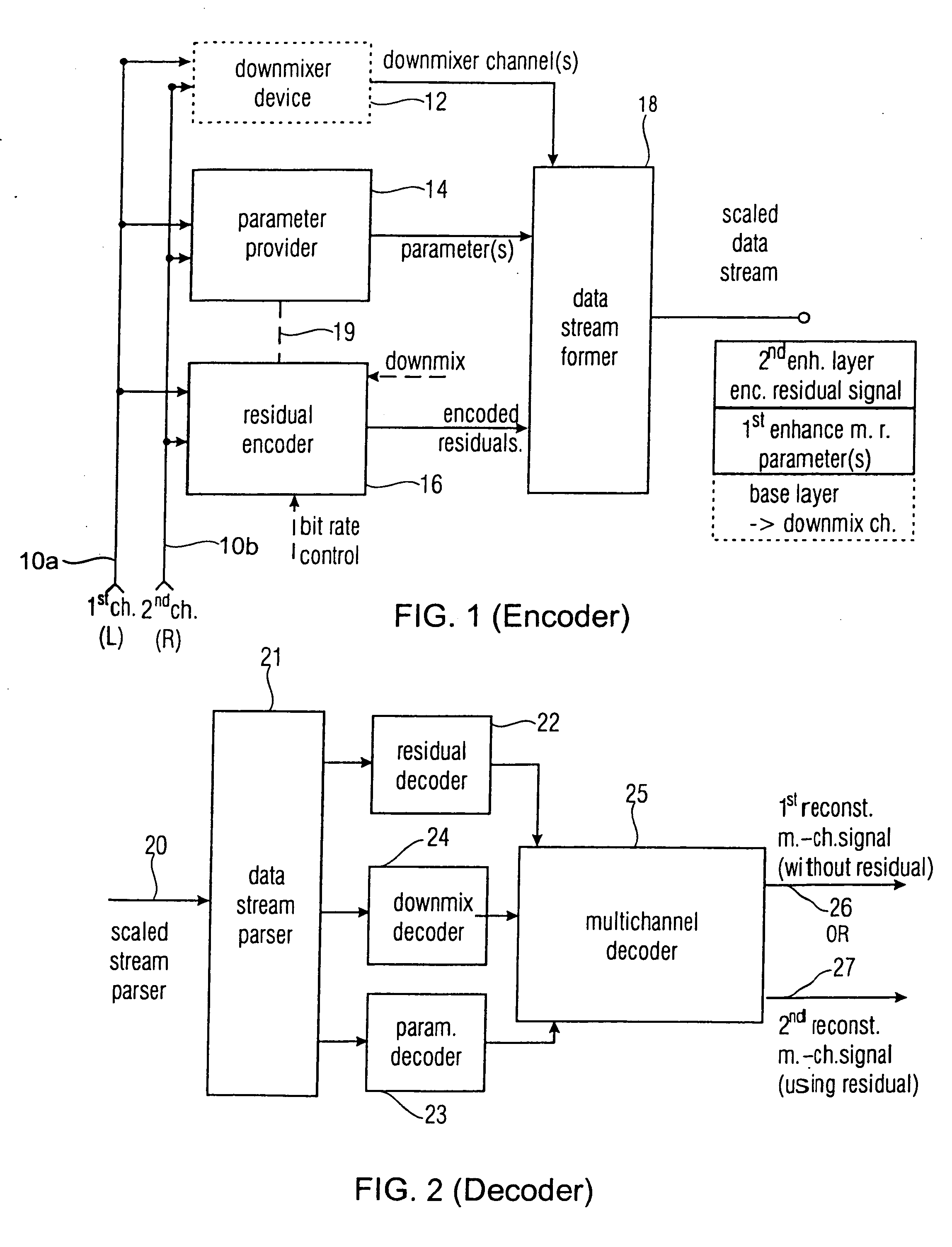
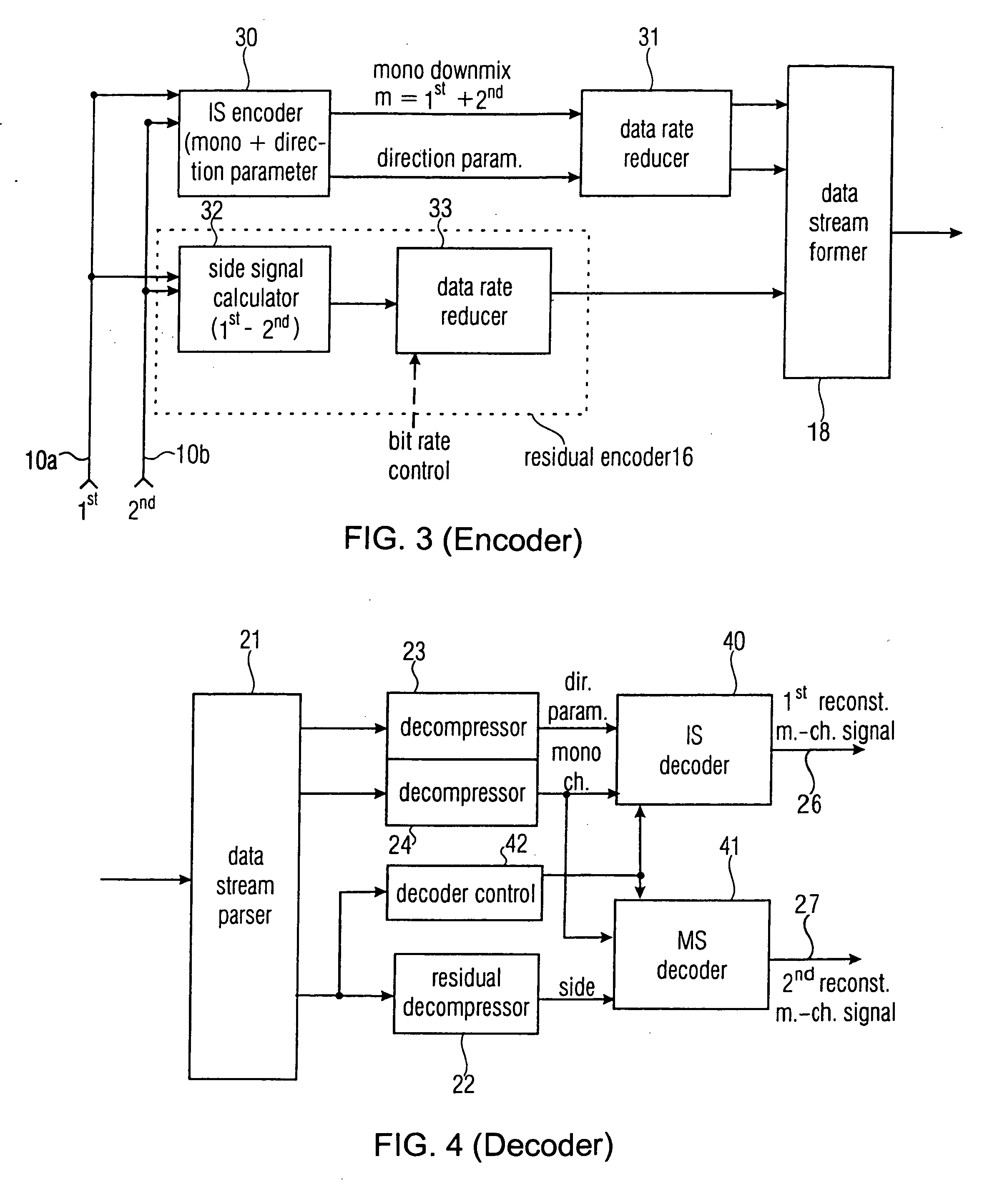
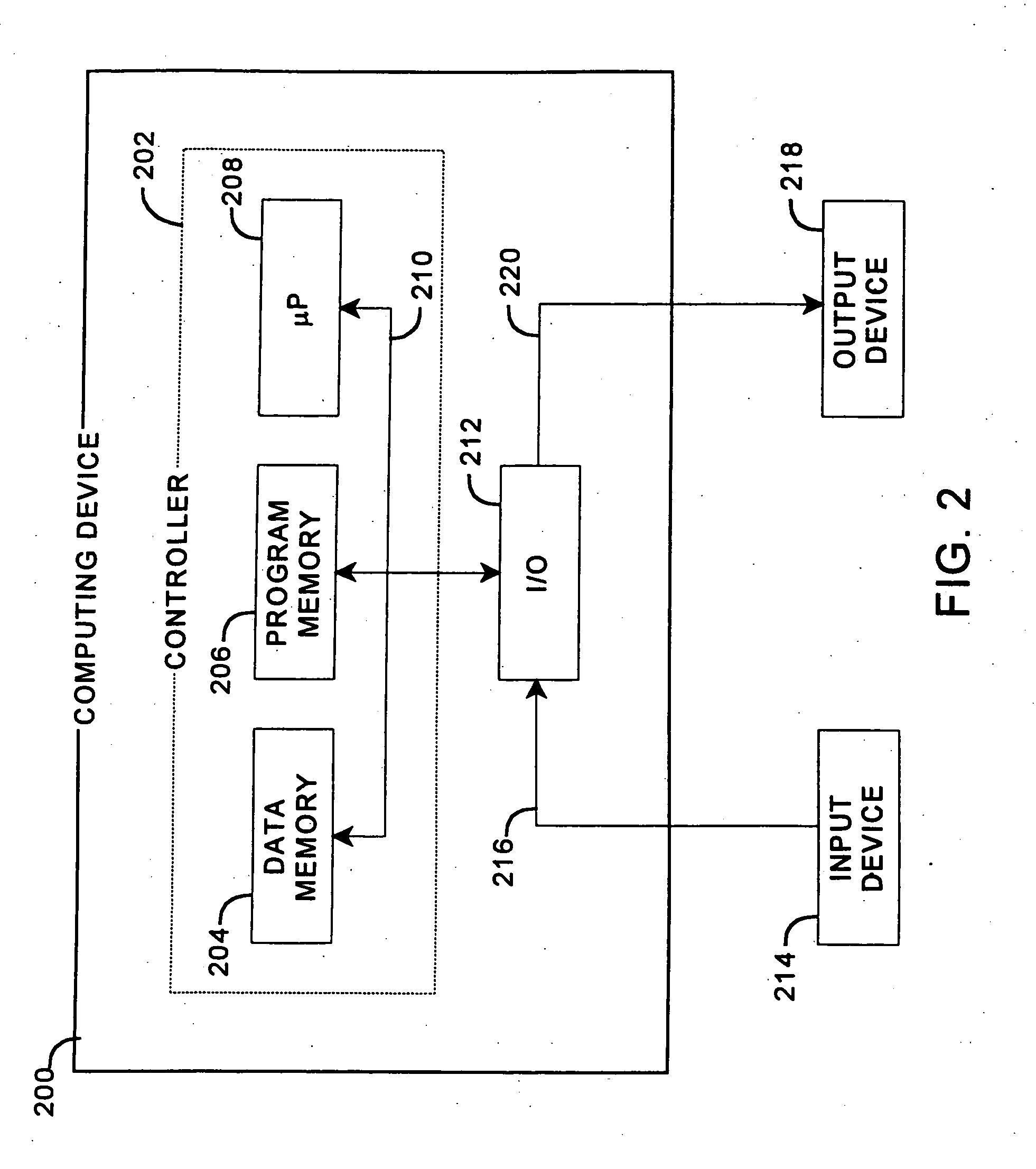
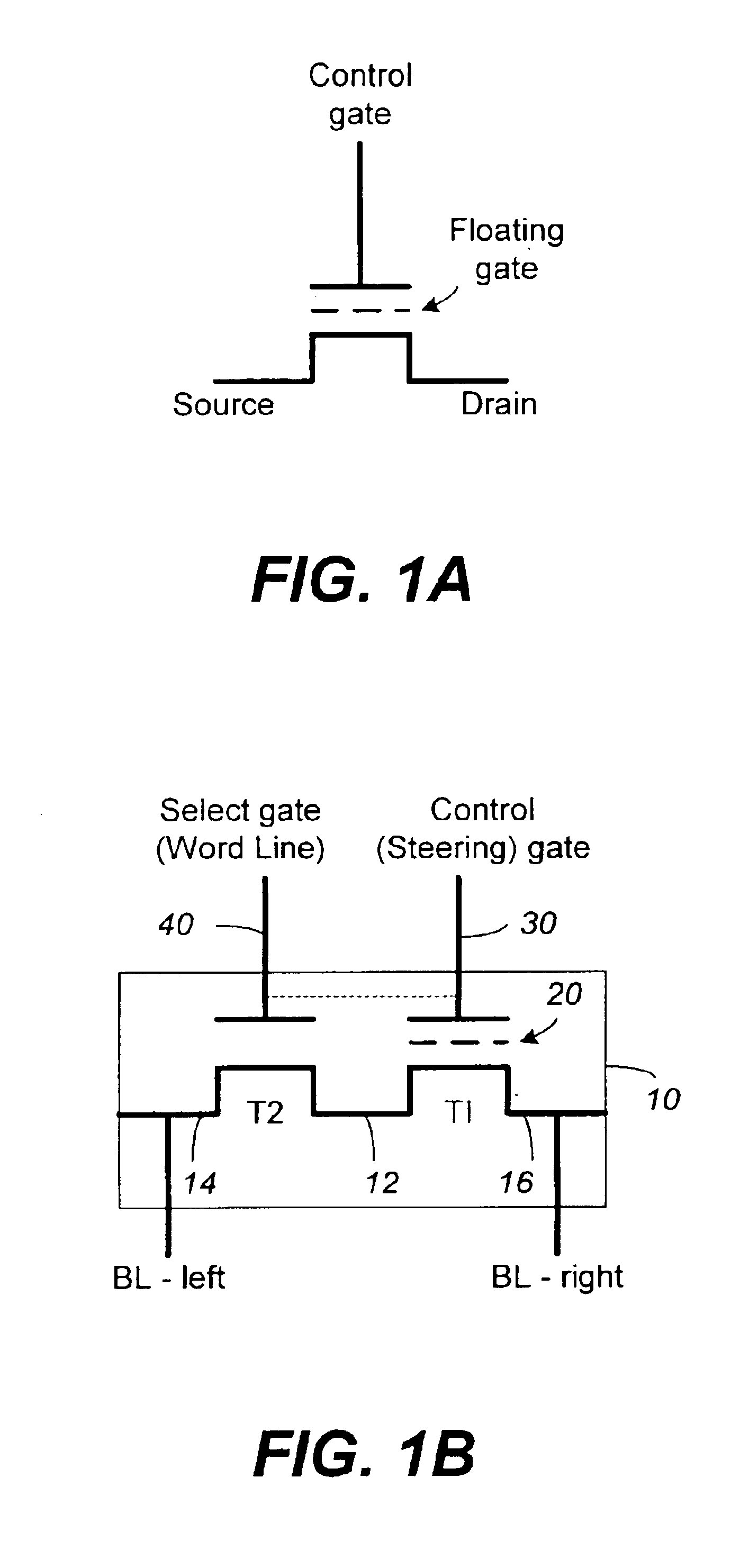
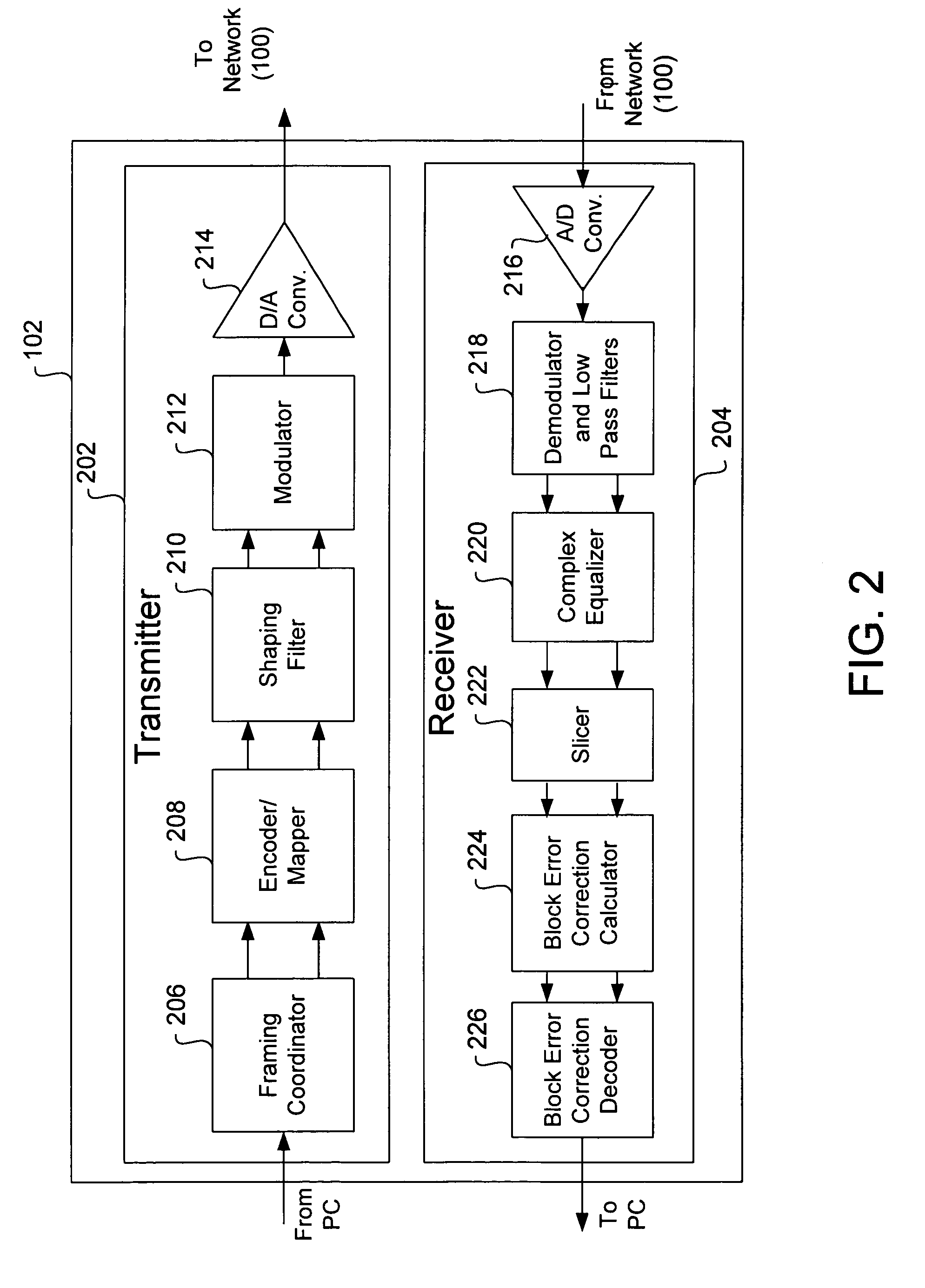
Near-transparent or transparent multi-channel encoder/decoder scheme
ActiveUS20060190247A1Quality improvementReduce bitrateError preventionFrequency-division multiplex detailsChannel decoderComputer science
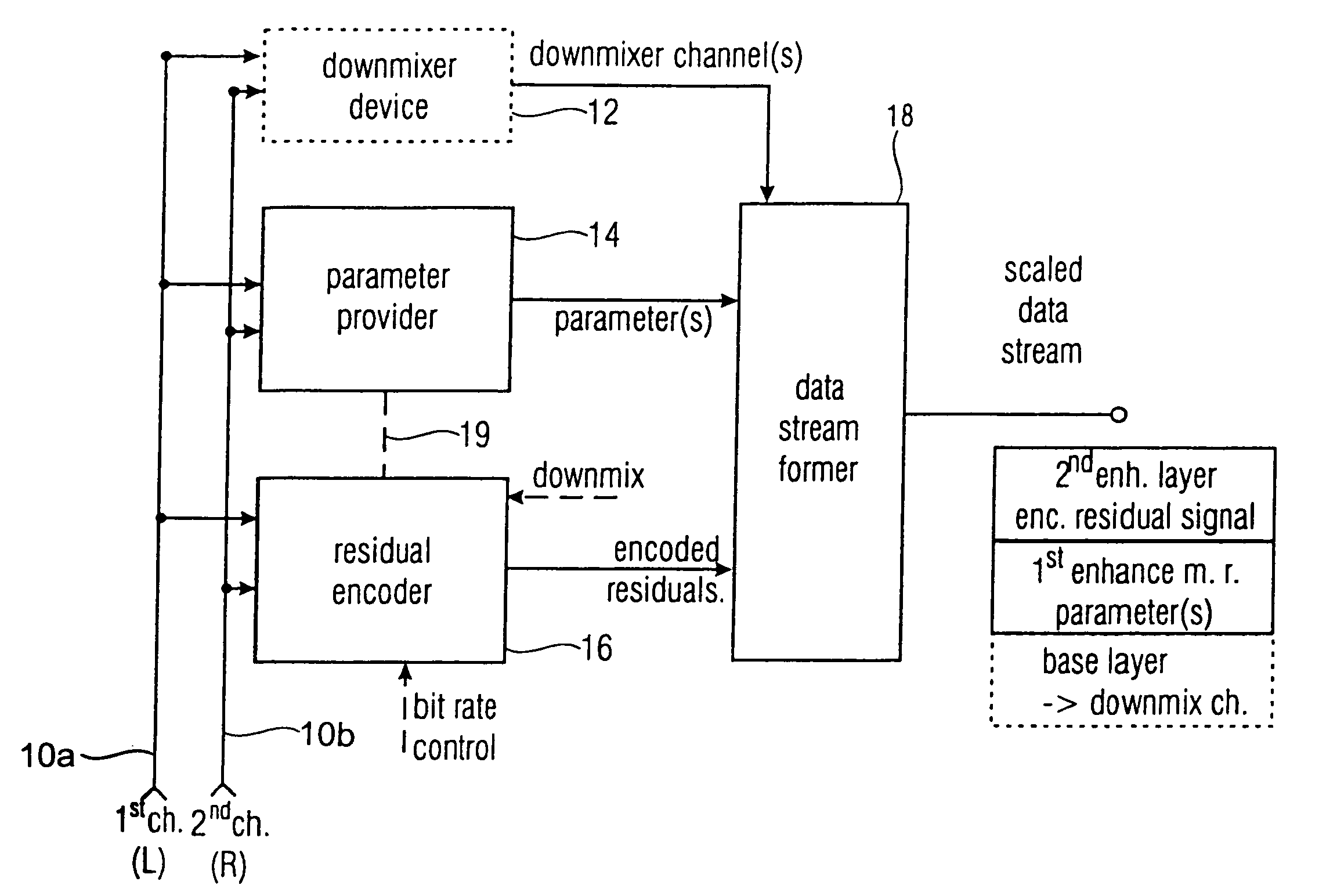
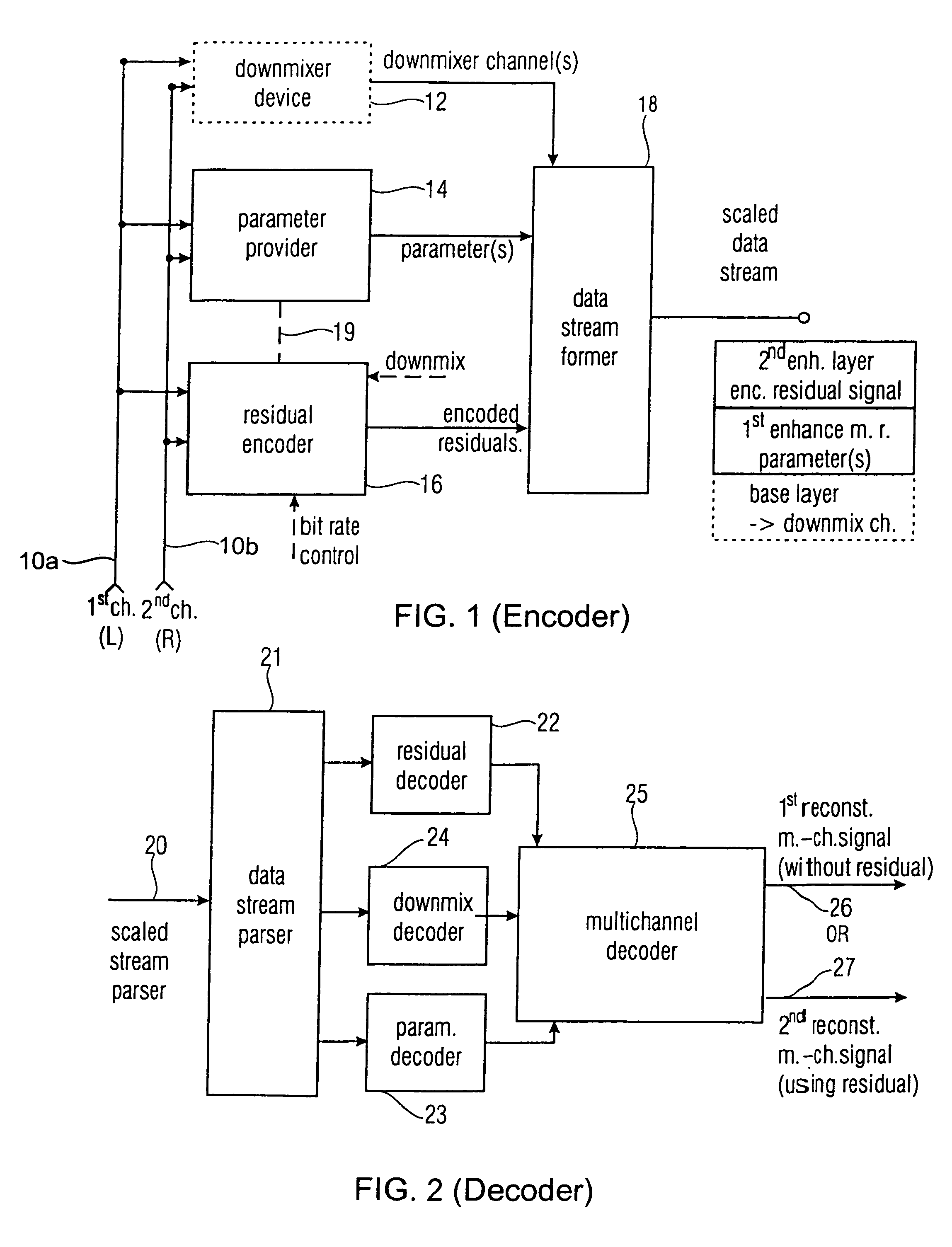
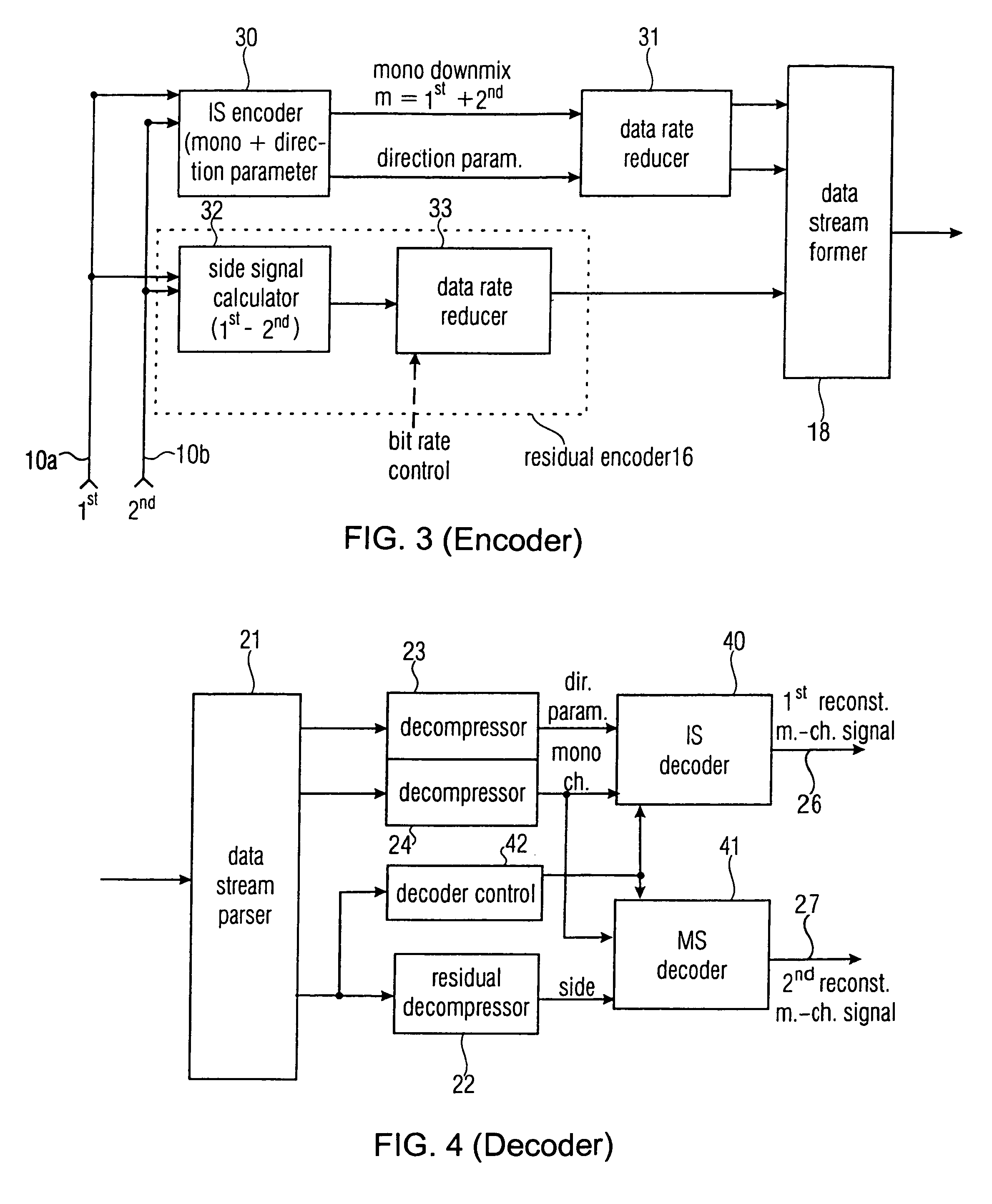
A multi-channel encoder / decoder scheme additionally preferably generates a waveform-type residual signal. This residual signal is transmitted together with one or more multi-channel parameters to a decoder. In contrast to a purely parametric multi-channel decoder, the enhanced decoder generates a multi-channel output signal having an improved output quality because of the additional residual signal.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
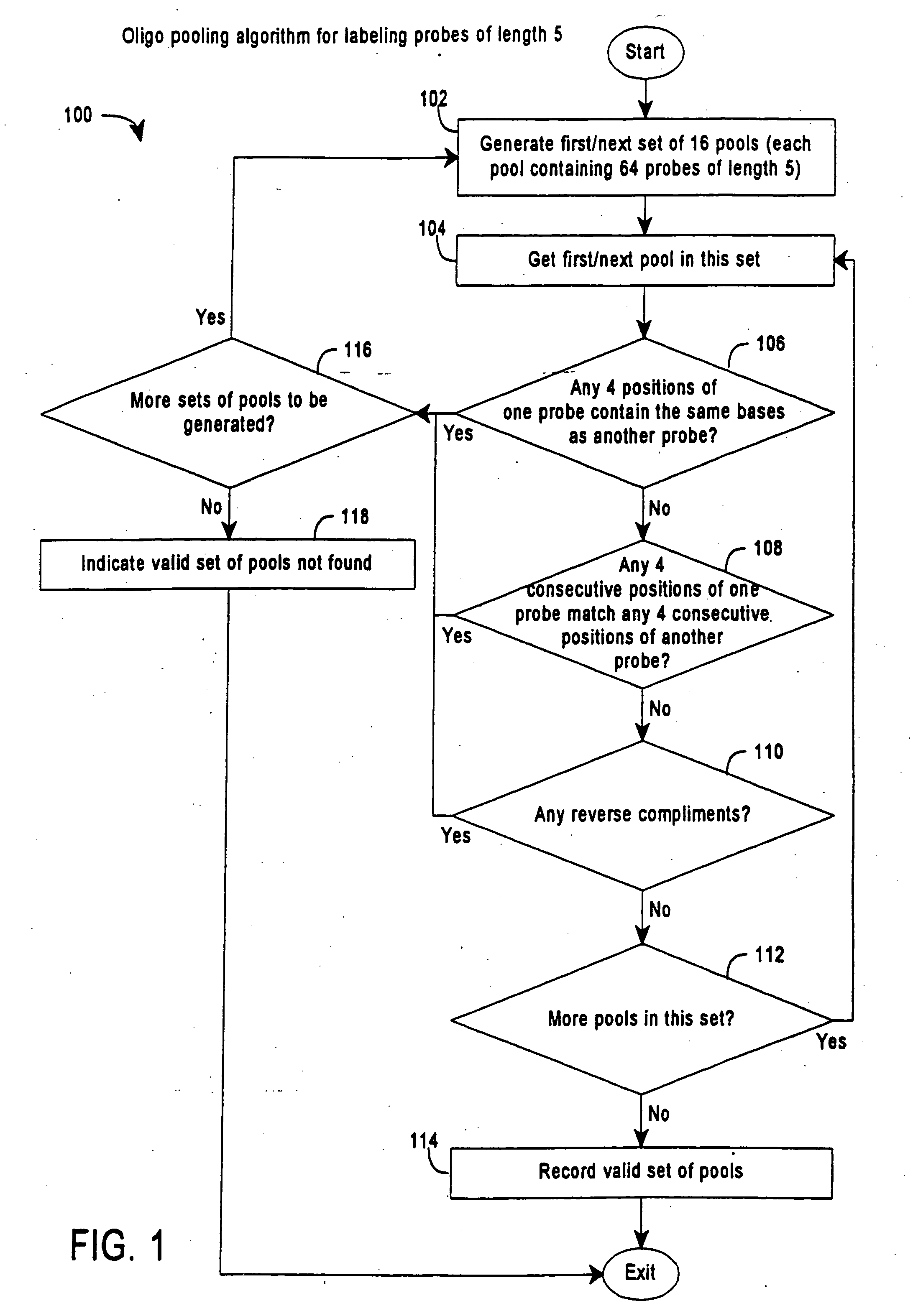
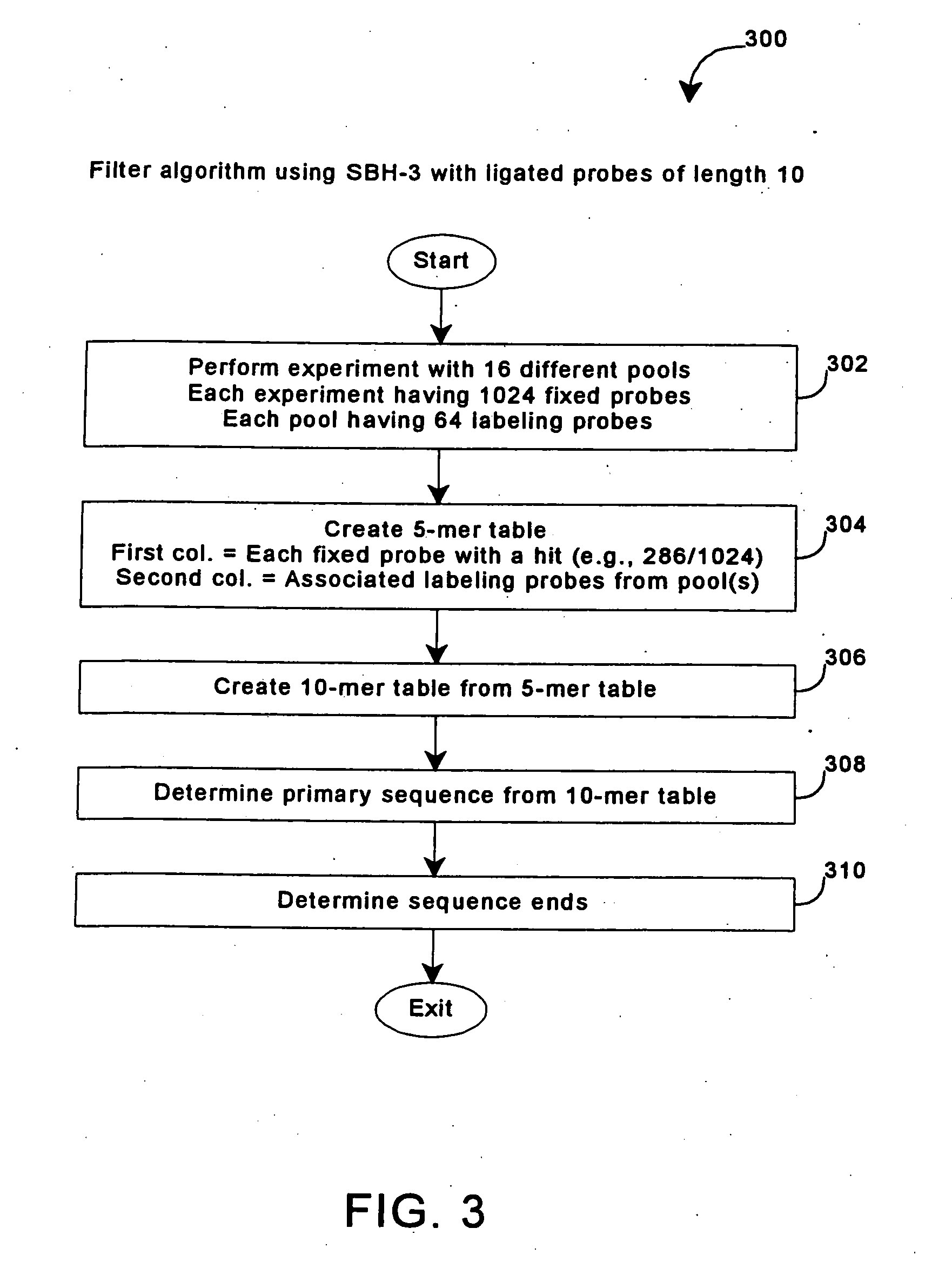
Enhanced sequencing by hybridization using pools of probes
InactiveUS20050191656A1Enhances SBH methodReduce redundancySugar derivativesMicrobiological testing/measurementNucleic acid sequencingNucleic acid sequence
The invention provides methods for sequencing by hybridization (SBH) using pools of probes that allow greater efficiency in conducting SBH by reducing the number of separate measurements of hybridization signals required to identify each particular nucleotide in a target nucleic acid sequence. The invention also provides pools and sets of pools of probes, as well as methods of generating pools of probes.
Owner:COMPLETE GENOMICS INC
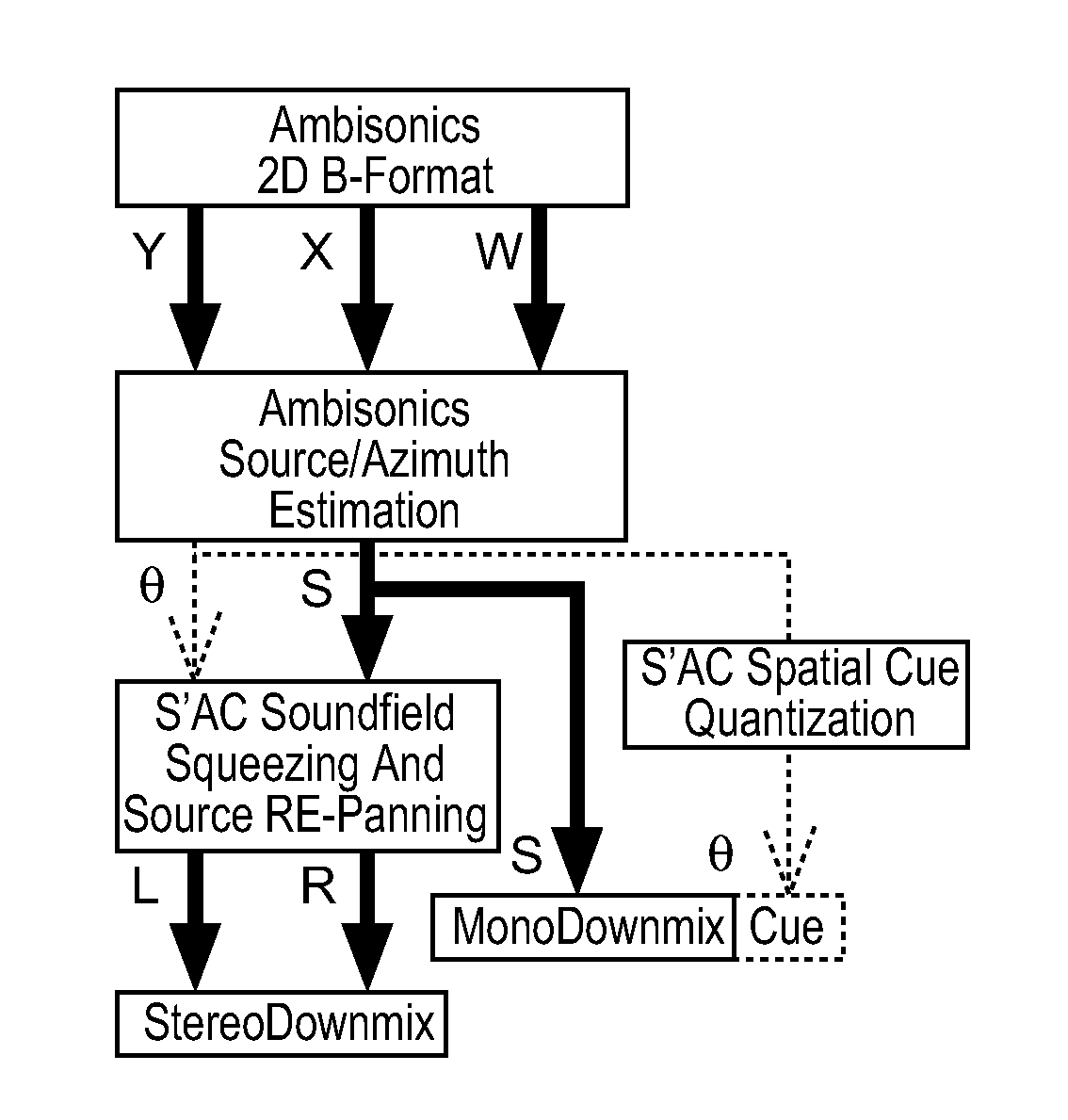
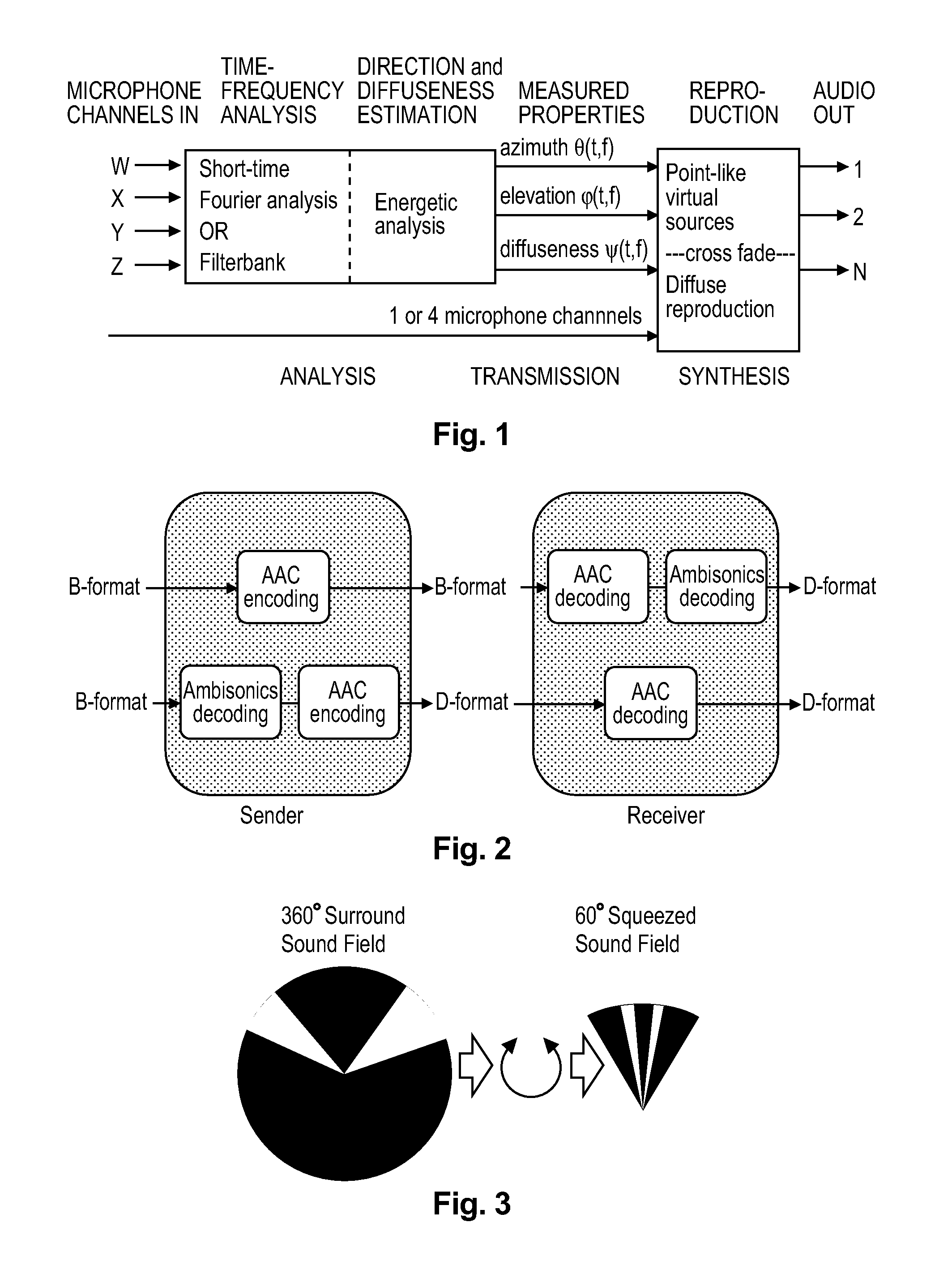
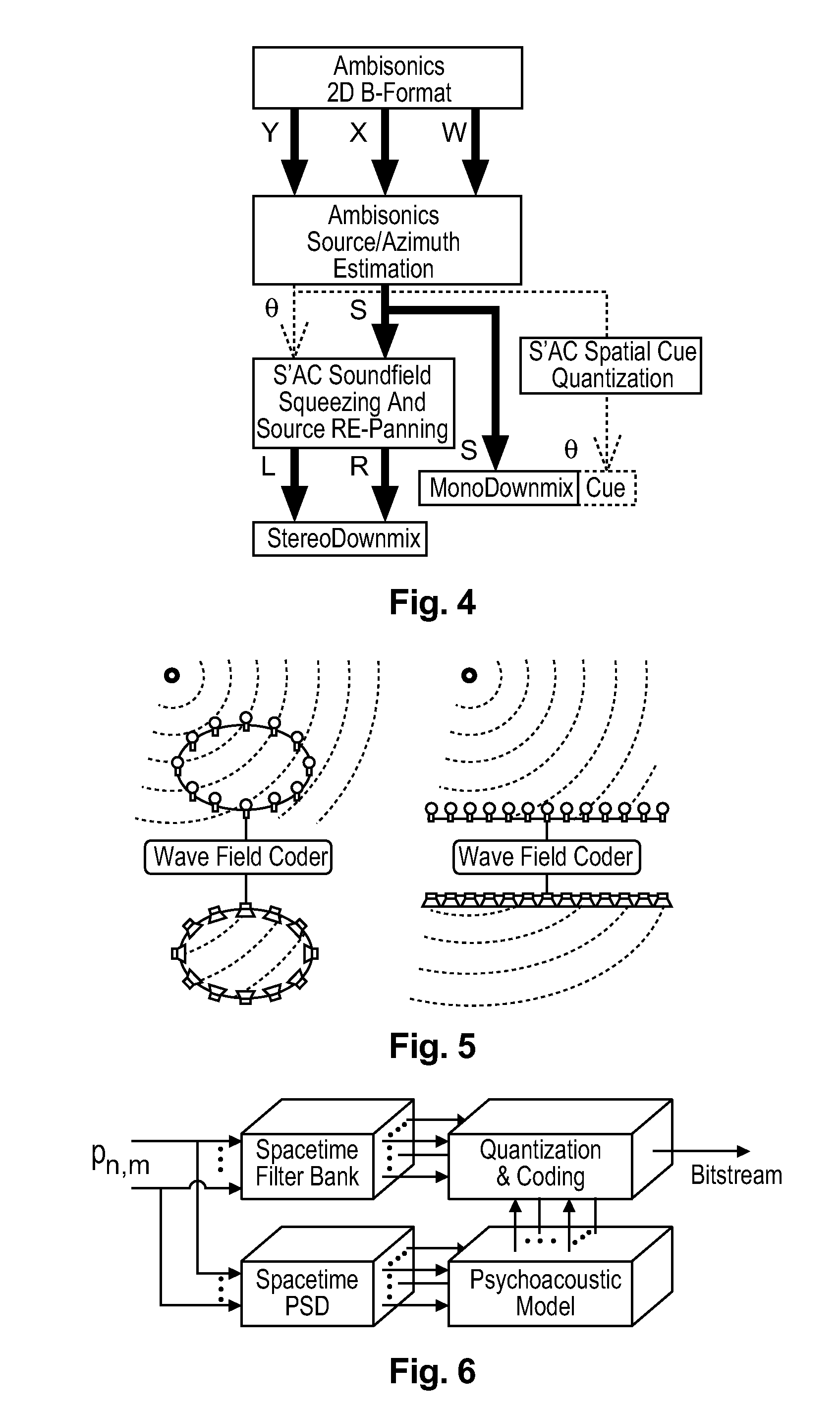
Method and apparatus for encoding and decoding successive frames of an ambisonics representation of a 2- or 3-dimensional sound field
ActiveUS20120155653A1Easy accessThe result is reasonableBroadcast information characterisationSpeech analysisTime domainData rate
Representations of spatial audio scenes using higher-order Ambisonics HOA technology typically require a large number of coefficients per time instant. This data rate is too high for most practical applications that require real-time transmission of audio signals. According to the invention, the compression is carried out in spatial domain instead of HOA domain. The (N+1)2 input HOA coefficients are transformed into (N+1)2 equivalent signals in spatial domain, and the resulting (N+1)2 time-domain signals are input to a bank of parallel perceptual codecs. At decoder side, the individual spatial-domain signals are decoded, and the spatial-domain coefficients are transformed back into HOA domain in order to recover the original HOA representation.
Owner:DOLBY LAB LICENSING CORP
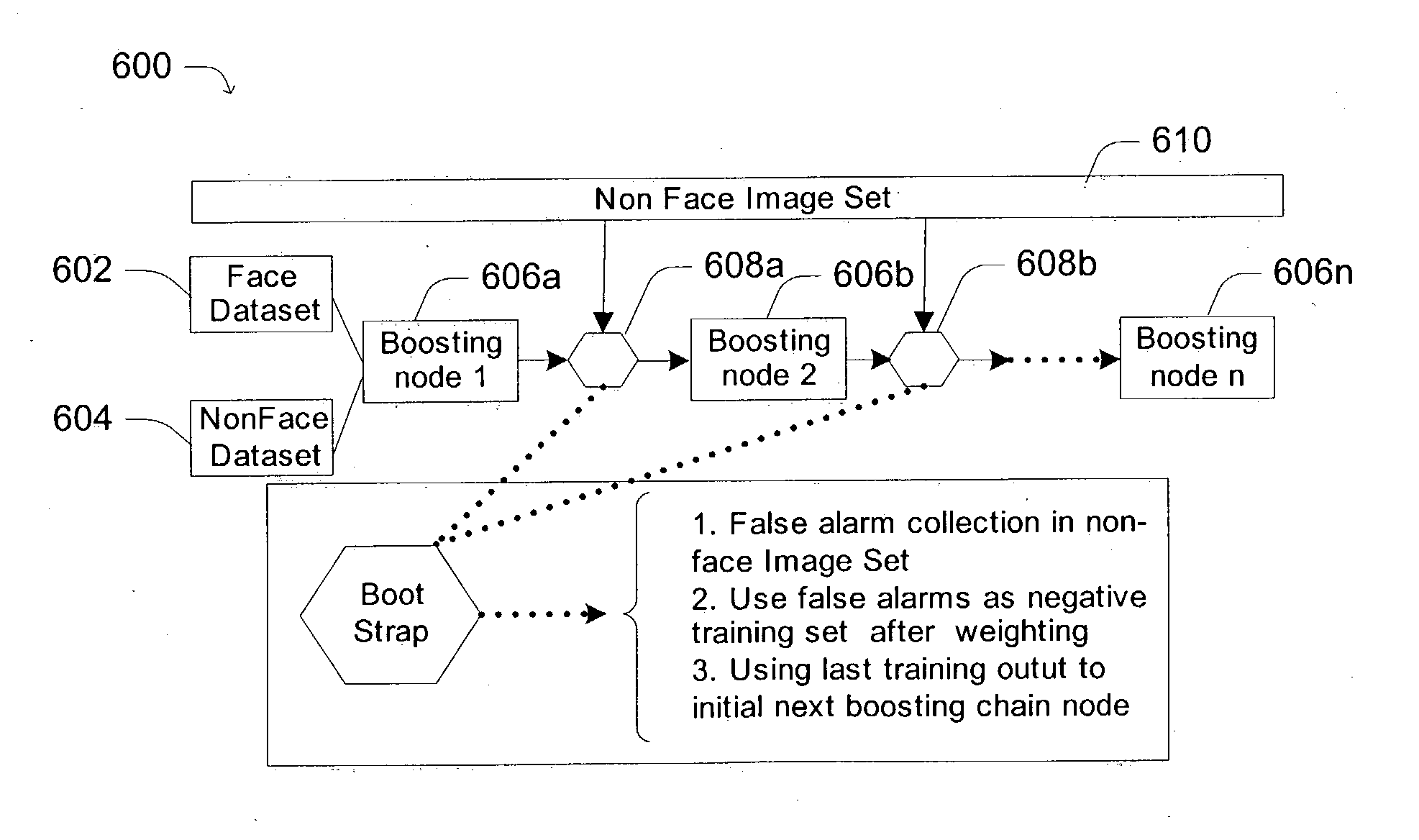
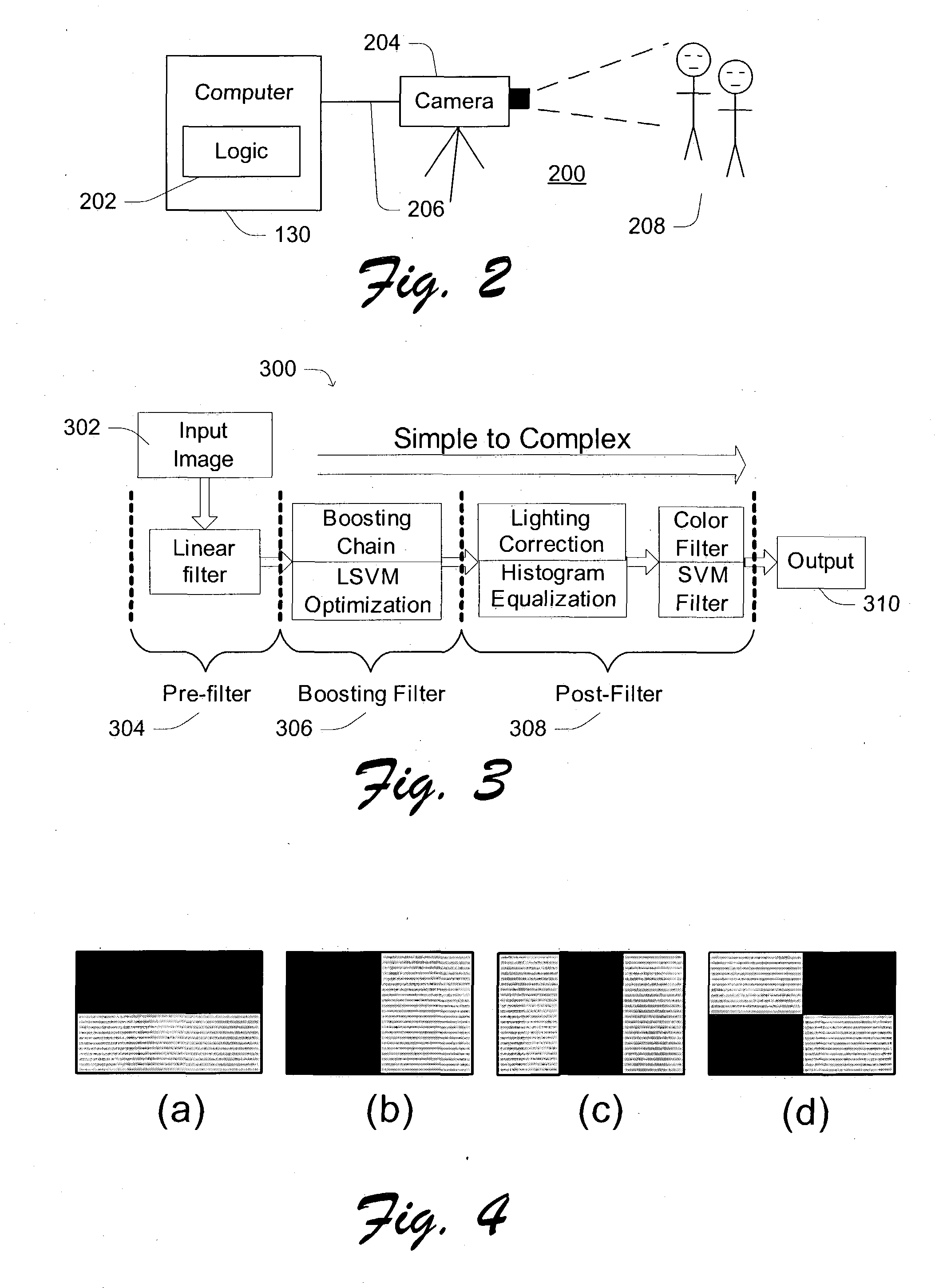
Robust multi-view face detection methods and apparatuses
ActiveUS20050013479A1Easy to detectImprove efficiencyCharacter and pattern recognitionPattern recognitionFace detection
Face detection techniques are provided that use a multiple-stage face detection algorithm. An exemplary three-stage algorithm includes a first stage that applies linear-filtering to enhance detection performance by removing many non-face-like portions within an image, a second stage that uses a boosting chain that is adopted to combine boosting classifiers within a hierarchy “chain” structure, and a third stage that performs post-filtering using image pre-processing, SVM-filtering and color-filtering to refine the final face detection prediction. In certain further implementations, the face detection techniques include a two-level hierarchy in-plane pose estimator to provide a rapid multi-view face detector that further improves the accuracy and robustness of face detection.
Owner:ZHIGU HLDG
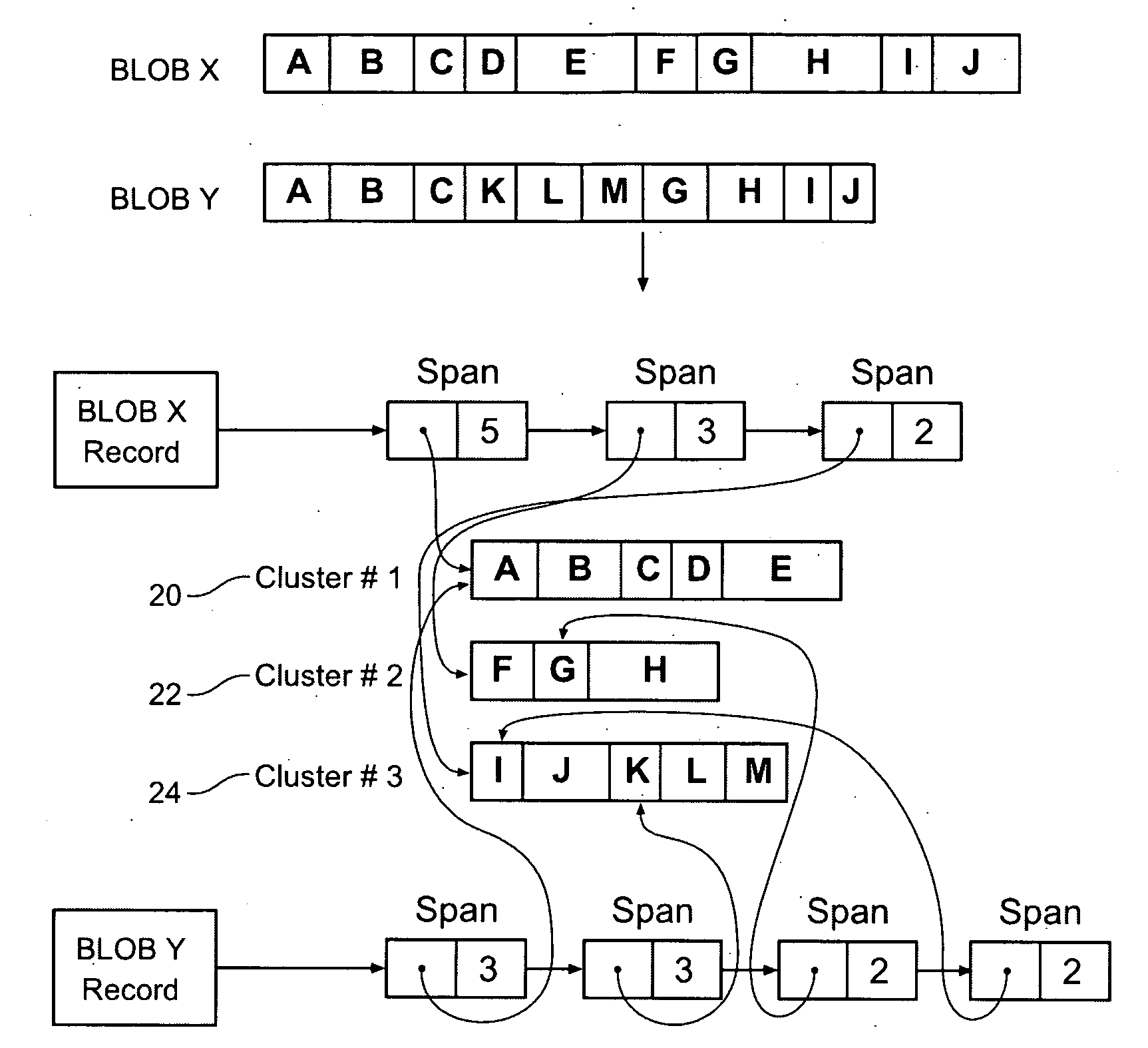
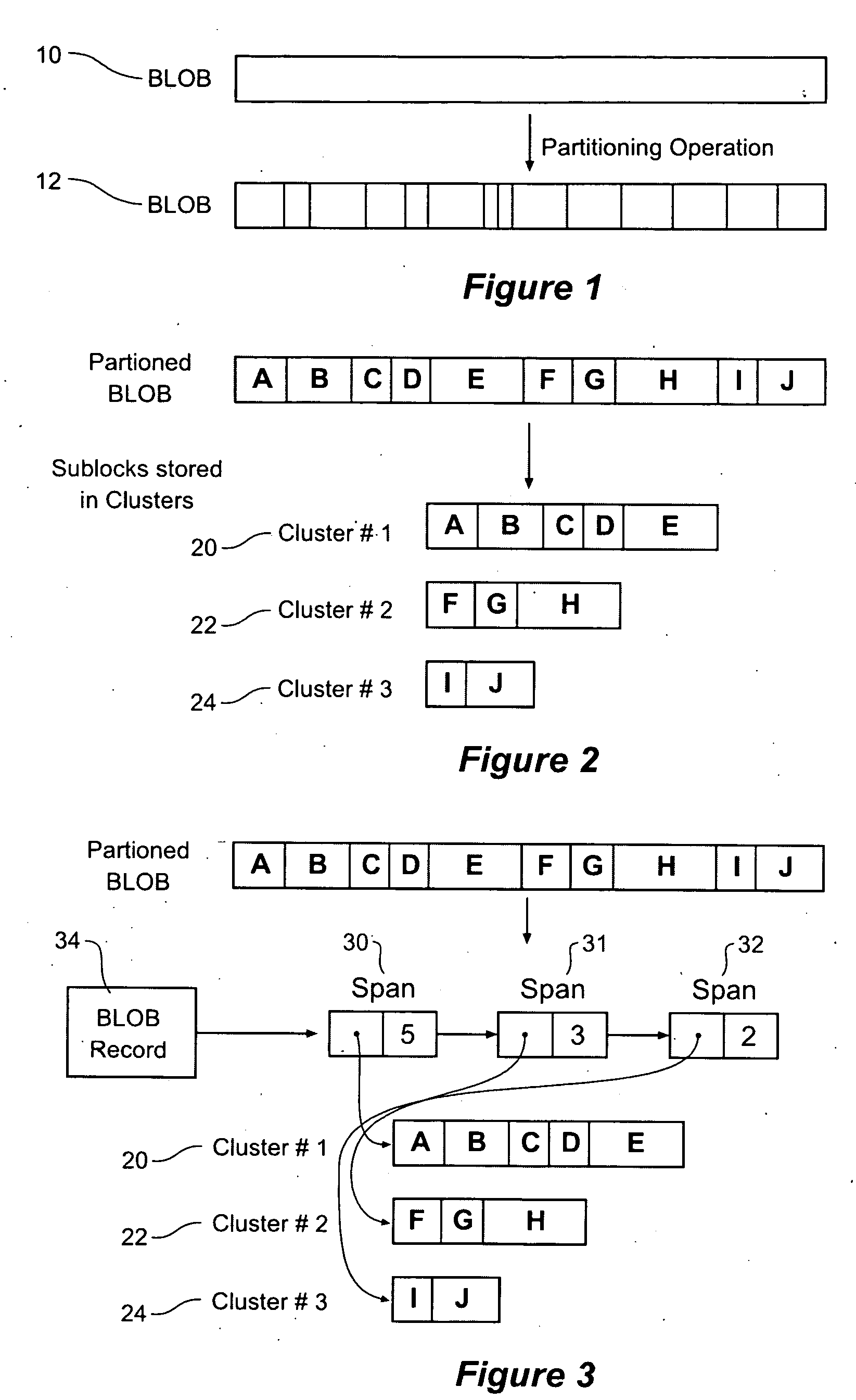
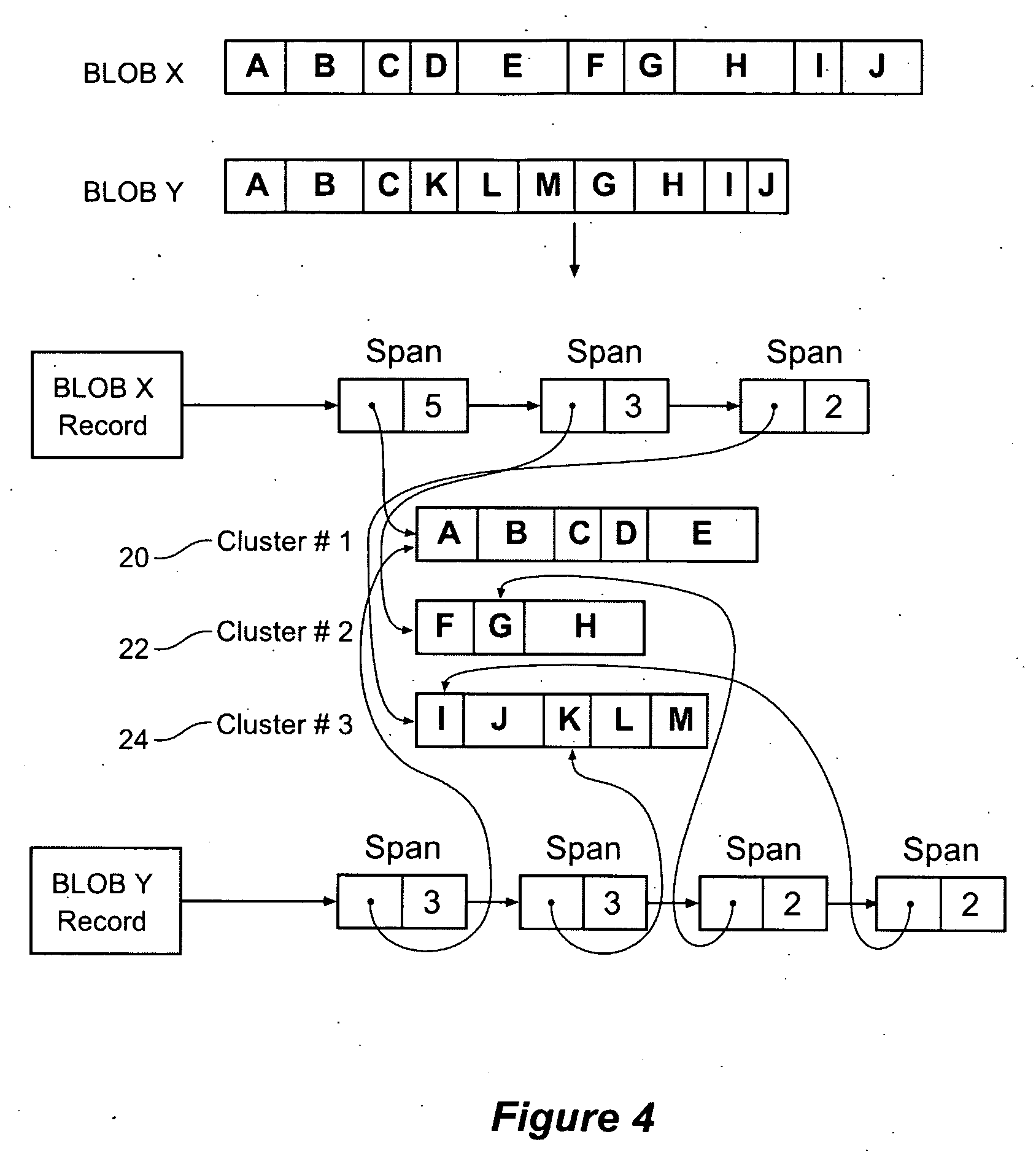
Method and apparatus for storing data with reduced redundancy using data clusters
InactiveUS20060282457A1Improve efficiencyReduce redundancyDigital data information retrievalData processing applicationsData miningBinary large object
Method and apparatus for storing data in a reduced redundancy form. Binary Large Objects (BLOBs) are partitioned into subblocks according to a partitioning method, and the subblocks are stored in subblock clusters. Each BLOB is represented as a list of spans of subblocks which identifies a contiguous sequence of subblocks within a cluster. Storage redundancy can be reduced because the spans of two different BLOBs can refer to the same subblocks. An index may be used to map subblock hashes to subblock cluster numbers.
Owner:QUANTUM CORP
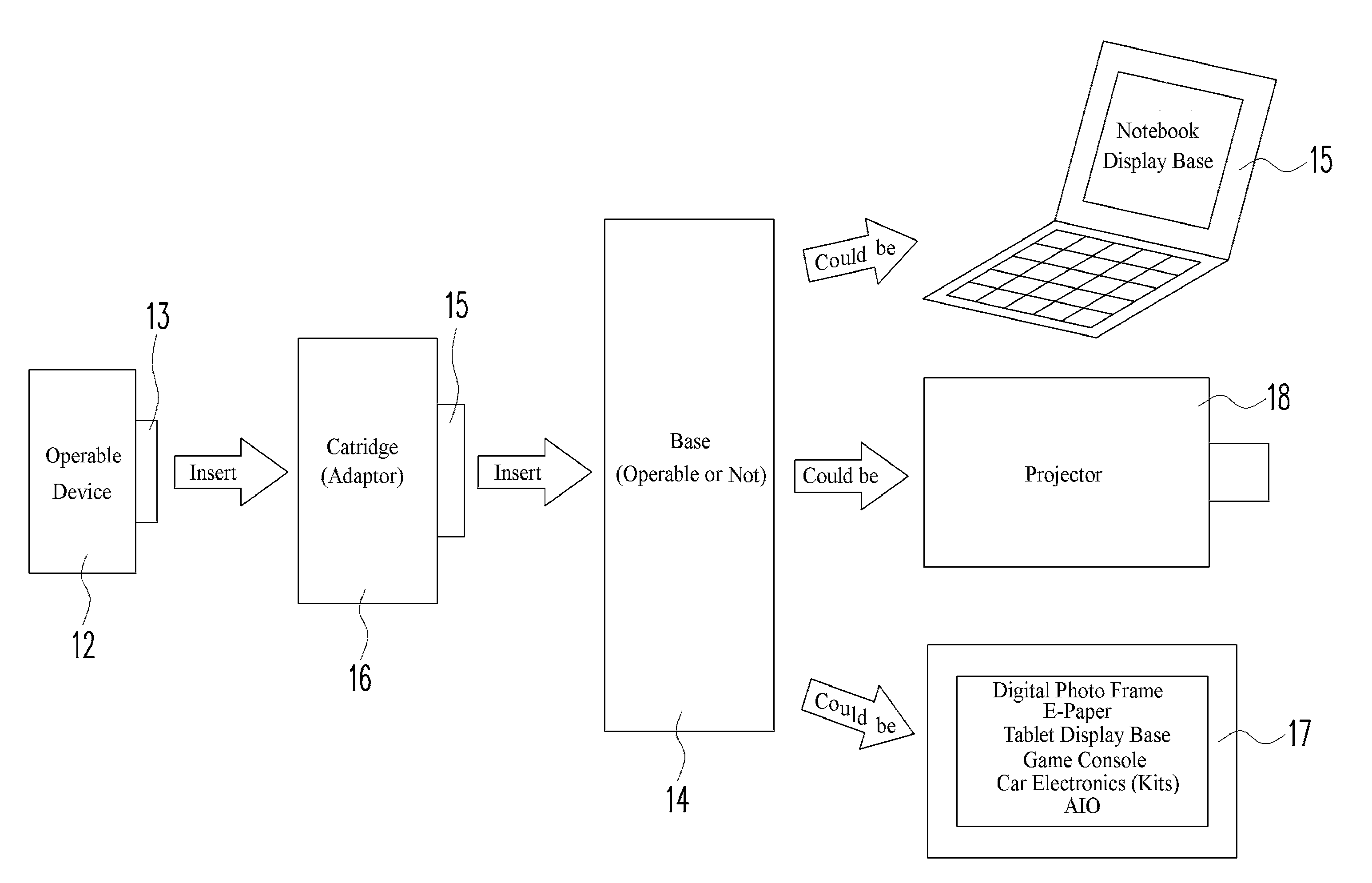
Modular system having expandable form factor
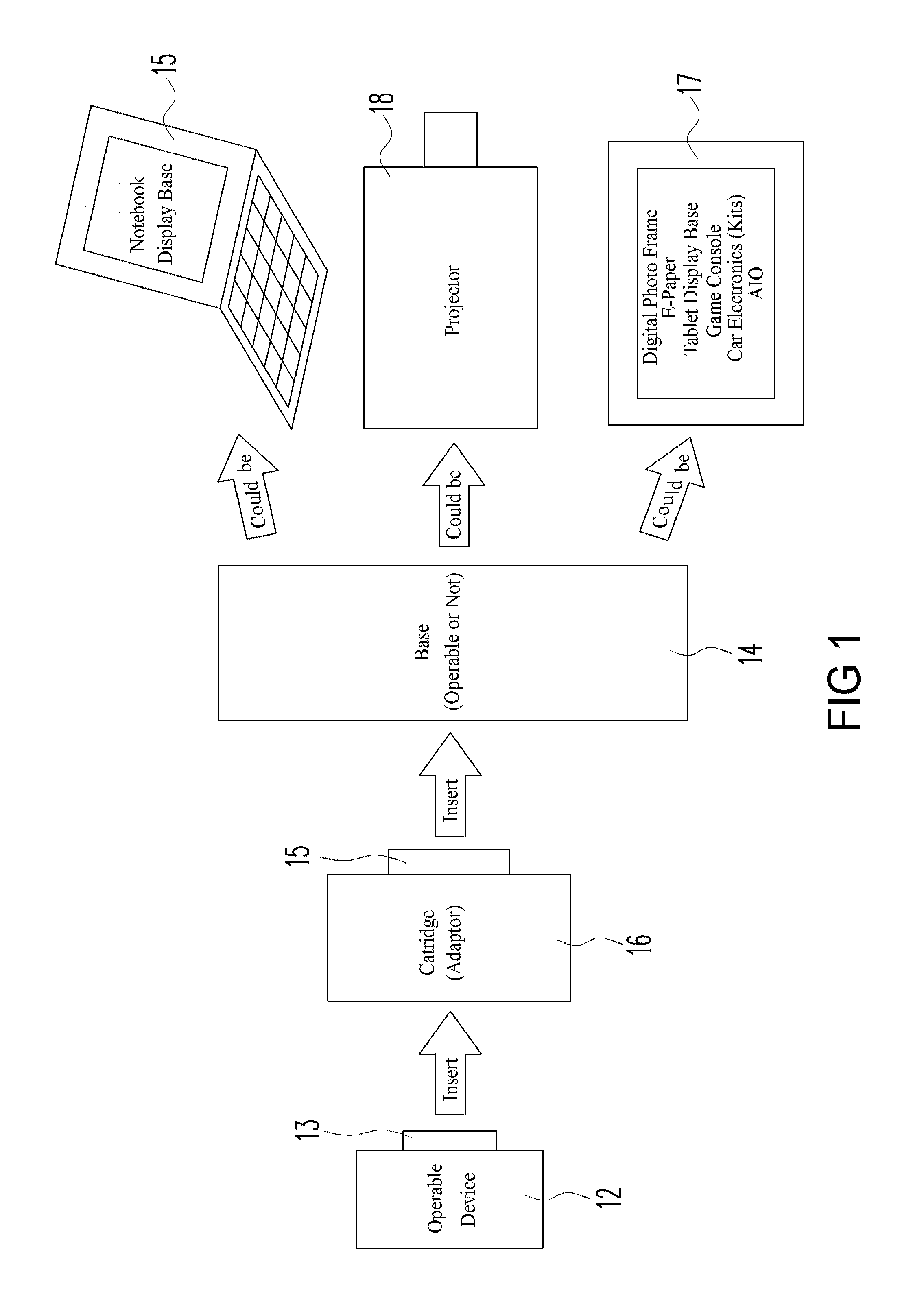
ActiveUS20120087078A1Reduce redundancyImprove operabilityBatteries circuit arrangementsPower supply for data processingModularityEmbedded system
A modular system of devices, in which a (master) device can be combined with one or more of other (slave) devices to transform to functional electronic devices having expanded functionalities and features in different form factors and / or platforms. The master device is docked to the slave device via a data / electrical interface, to transform the master device to the larger form factor of the slave device, with the master device maintaining control of the slave device, substantially based on the operating system installed in the master device, with access to the data, application programs, functionalities and features embodied in the master device. An intermediate removable physical interface adaptor (or docking adaptor) is provided to facilitate docking compatibility of the master device to the slave device. An enhanced charging and power management scheme is provided to optimize power management for the master device and the slave device.
Owner:COMPAL ELECTRONICS INC
Highly compact non-volatile memory and method thereof
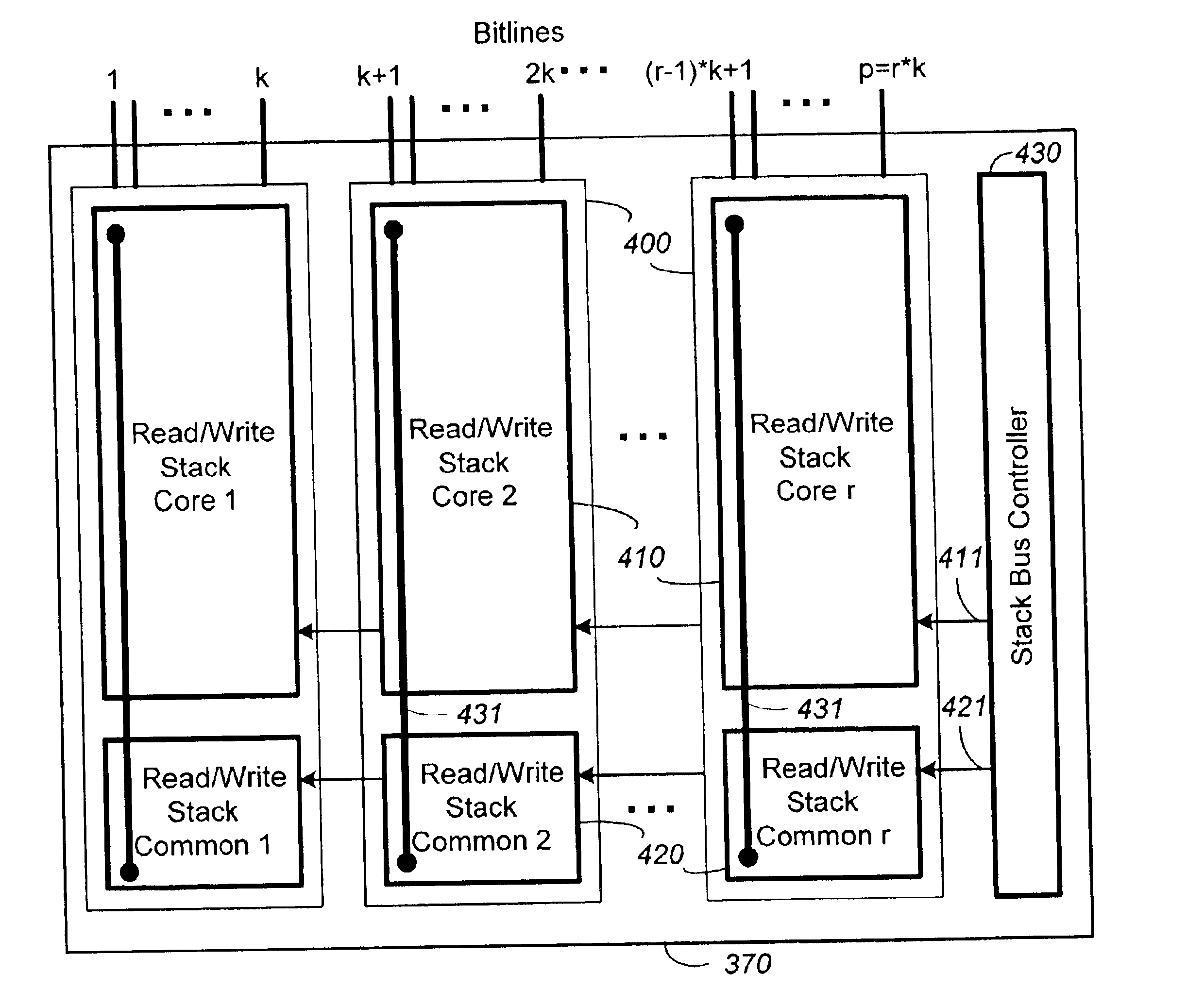
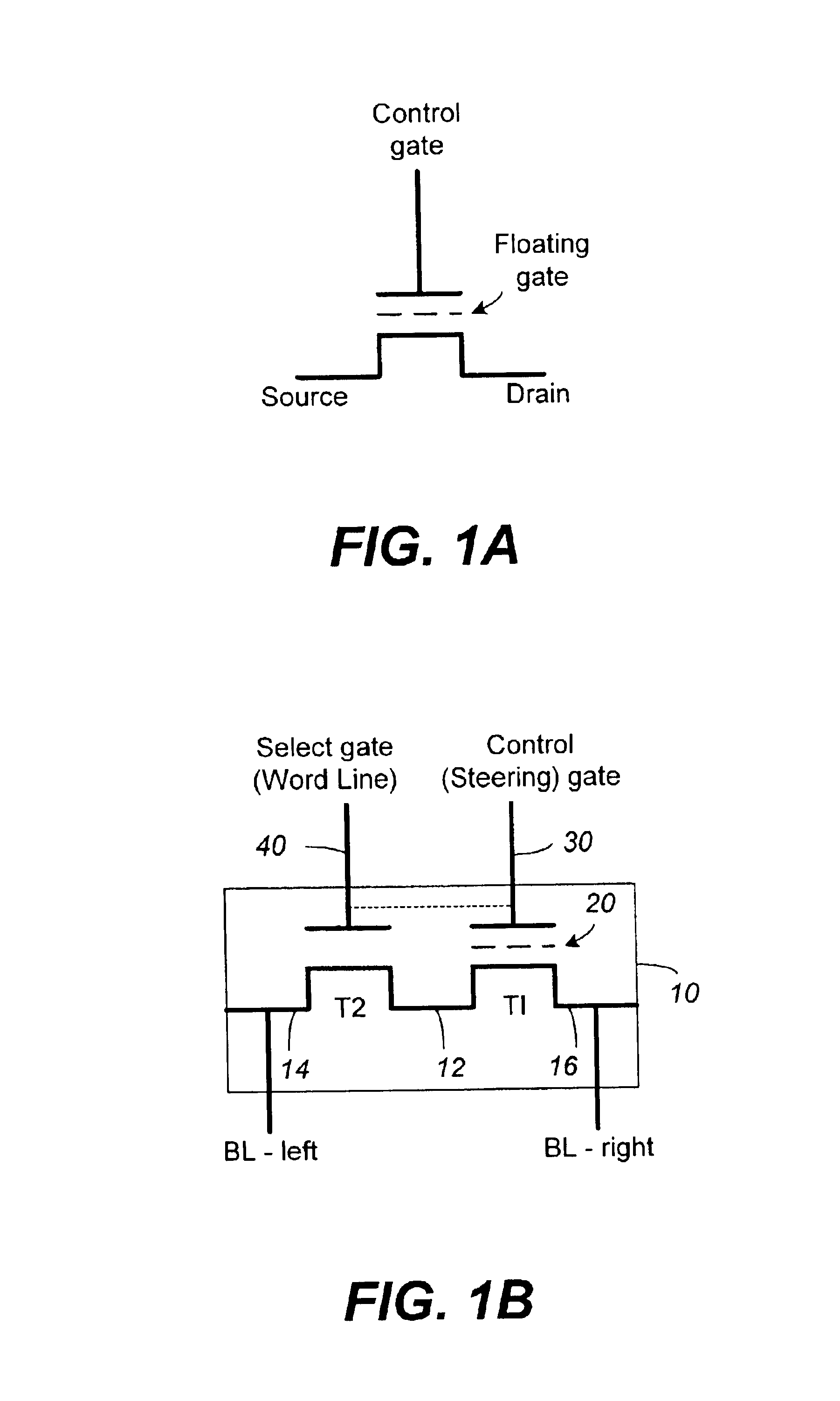
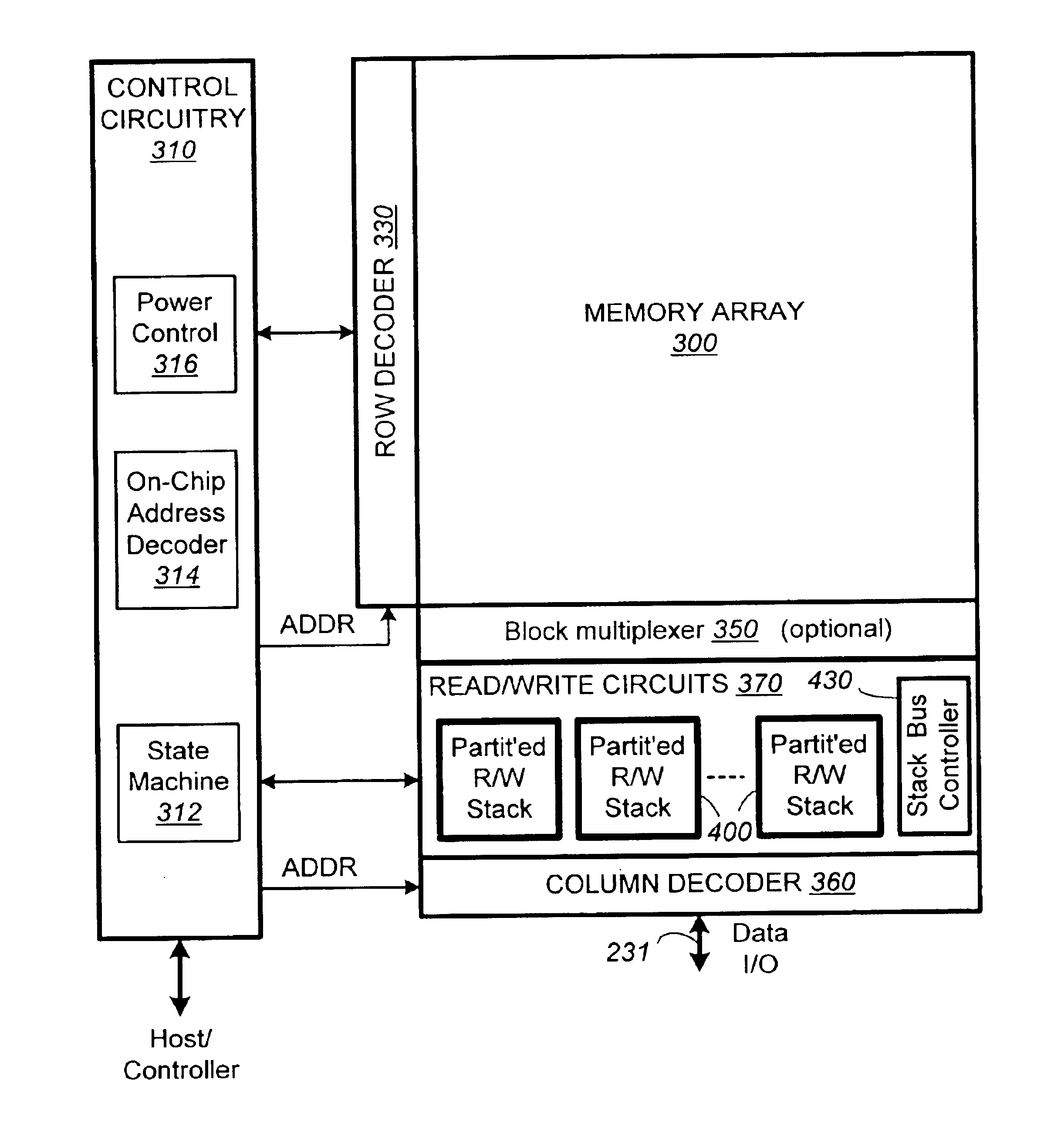
InactiveUS6983428B2Improve performanceReduce redundancyRead-only memoriesDigital storageComputer architectureNon-volatile memory
A non-volatile memory device capable of reading and writing a large number of memory cells with multiple read / write circuits in parallel has an architecture that reduces redundancy in the multiple read / write circuits to a minimum. The multiple read / write circuits are organized into a bank of similar stacks of components. In one aspect, each stack of components has individual components factorizing out their common subcomponents that do not require parallel usage and sharing them as a common component serially. Other aspects, include serial bus communication between the different components, compact I / O enabled data latches associated with the multiple read / write circuits, and an architecture that allows reading and programming of a contiguous row of memory cells or a segment thereof. The various aspects combined to achieve high performance, high accuracy and high compactness.
Owner:INNOVATIVE MEMORY SYST INC
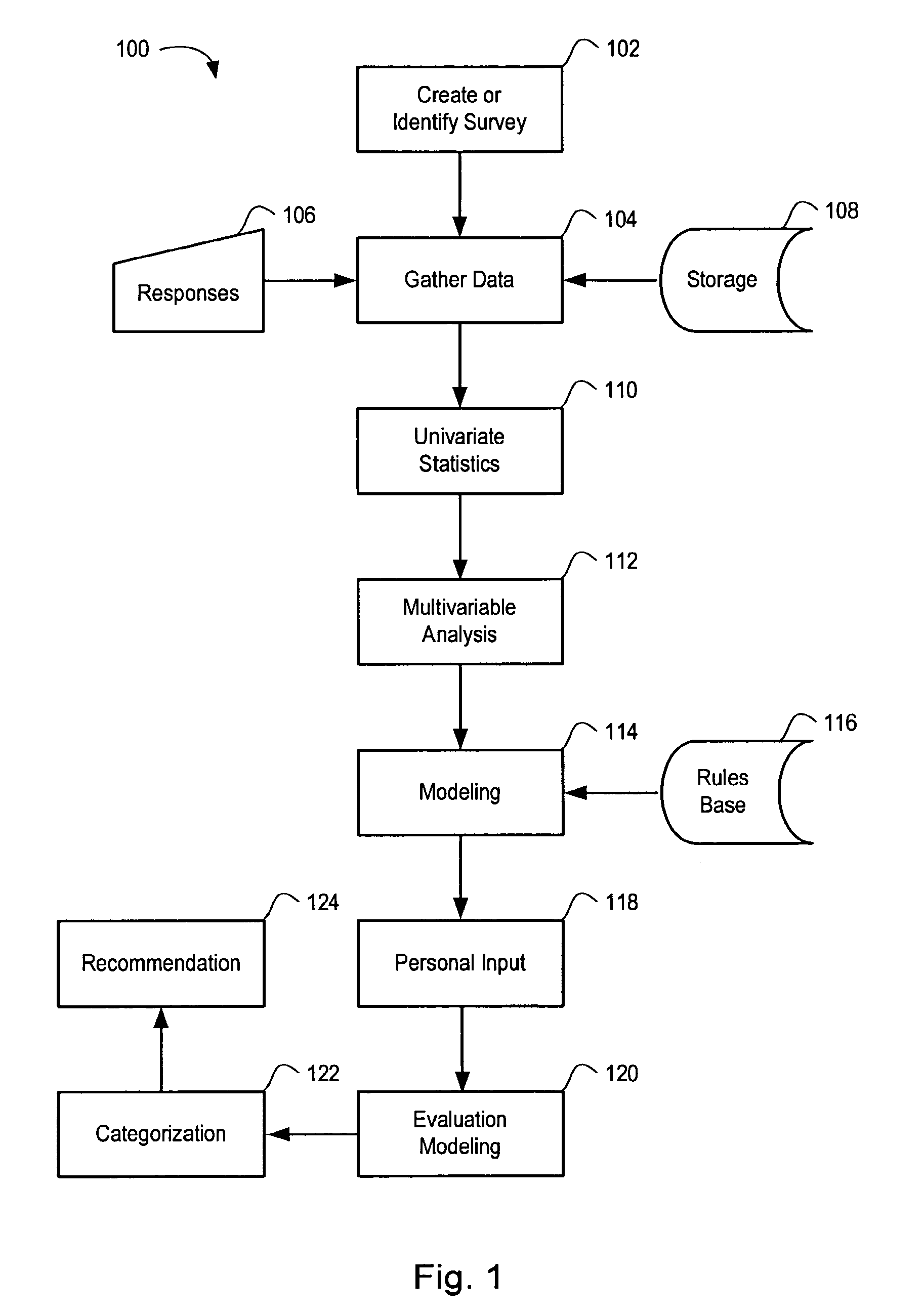
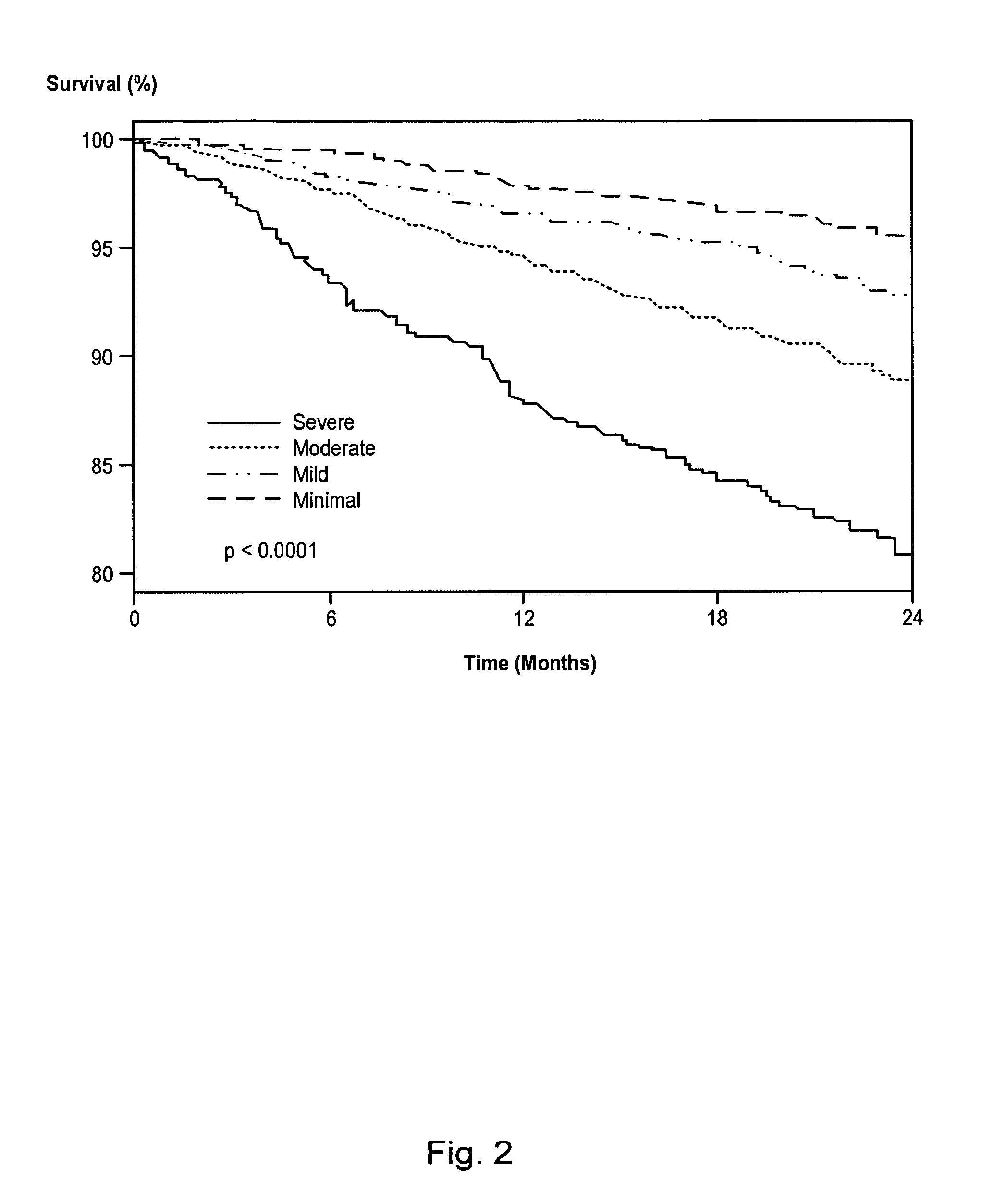
Systems and methods for risk stratification of patient populations
ActiveUS20050203773A1Disseminate reduced redundancy requestsReduce redundancyAnalogue computers for chemical processesComputer-assisted medical data acquisitionProgram instructionHealth risk
A statistical processing system includes a server operably configured with program instructions implementing a plurality of statistical models to at least one of (a) predict a health outcome based on questionnaire responses, (b) assist a patient's choice of therapeutic modality based on questionnaire responses, and (c) assess a health risk or status based on questionnaire responses. Also provided is a research agency communicating with the server and contracted to provide the statistical models using a visual interface communicated by the server. The server is configured to analyze requests received from users relating to a plurality of said statistical models to reduce redundancy in requests for patient data.
Owner:TERUMO MEDICAL CORP
Method for Coding RGB Color Space Signal
InactiveUS20080298694A1Reduce redundancyIncrease the compression ratioColor television with pulse code modulationCharacter and pattern recognitionPattern recognitionYcbcr color space
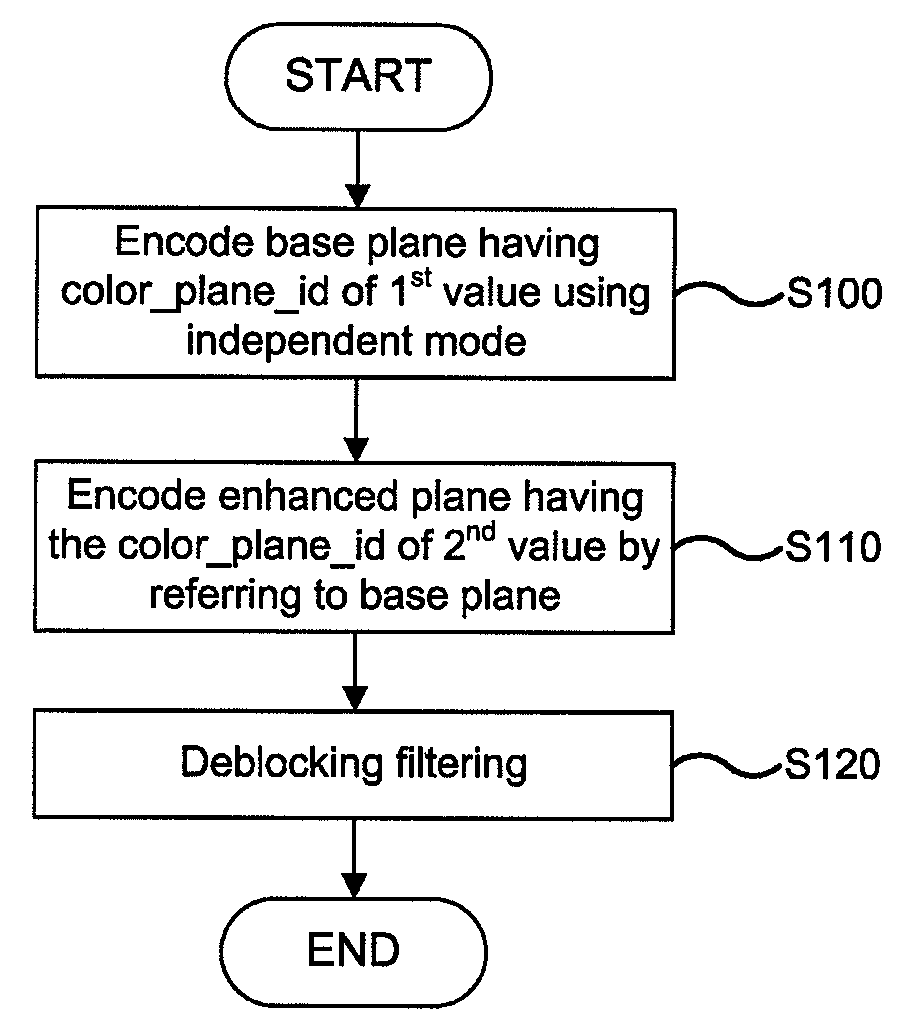
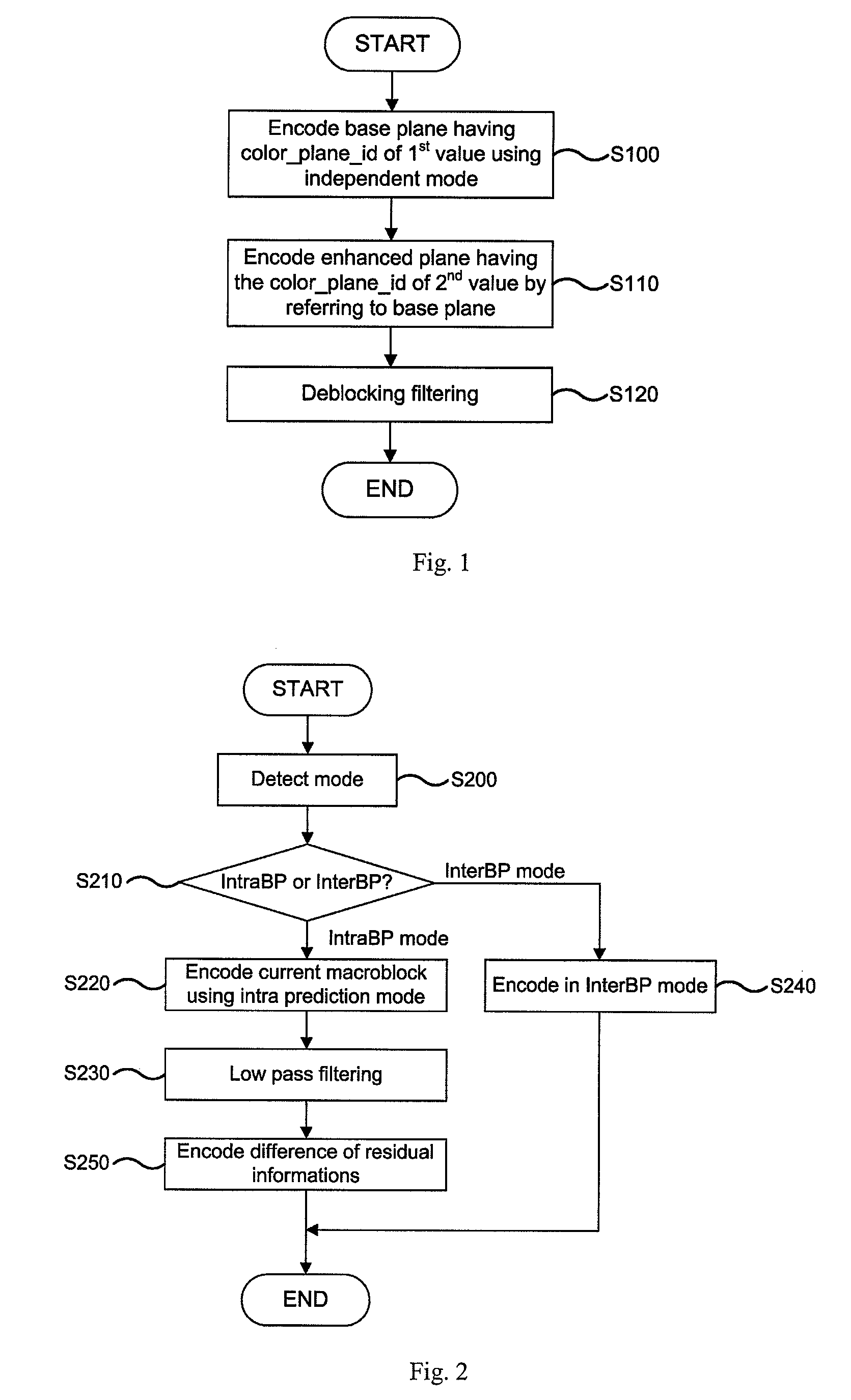
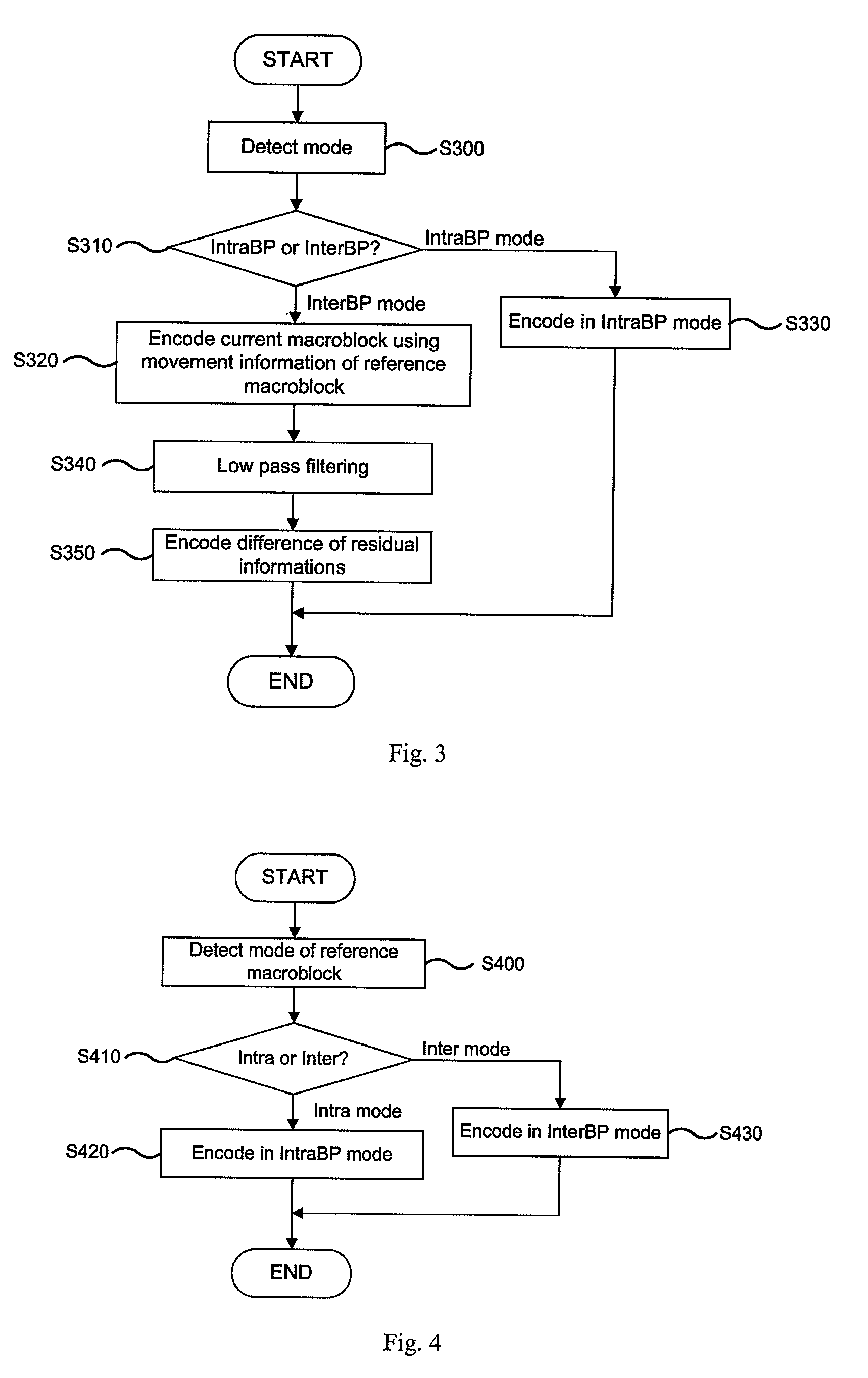
A method for coding an RGB color space signal is disclosed. In accordance with the method, a base plane is encoded using an independent mode, and an enhanced plane is encoded by referring to the base plane without converting the RGB color space signal into YCbCr color space signal to reduce a redundancy between RGB planes and improve a compression ratio of an image.
Owner:KOREA ELECTRONICS TECH INST
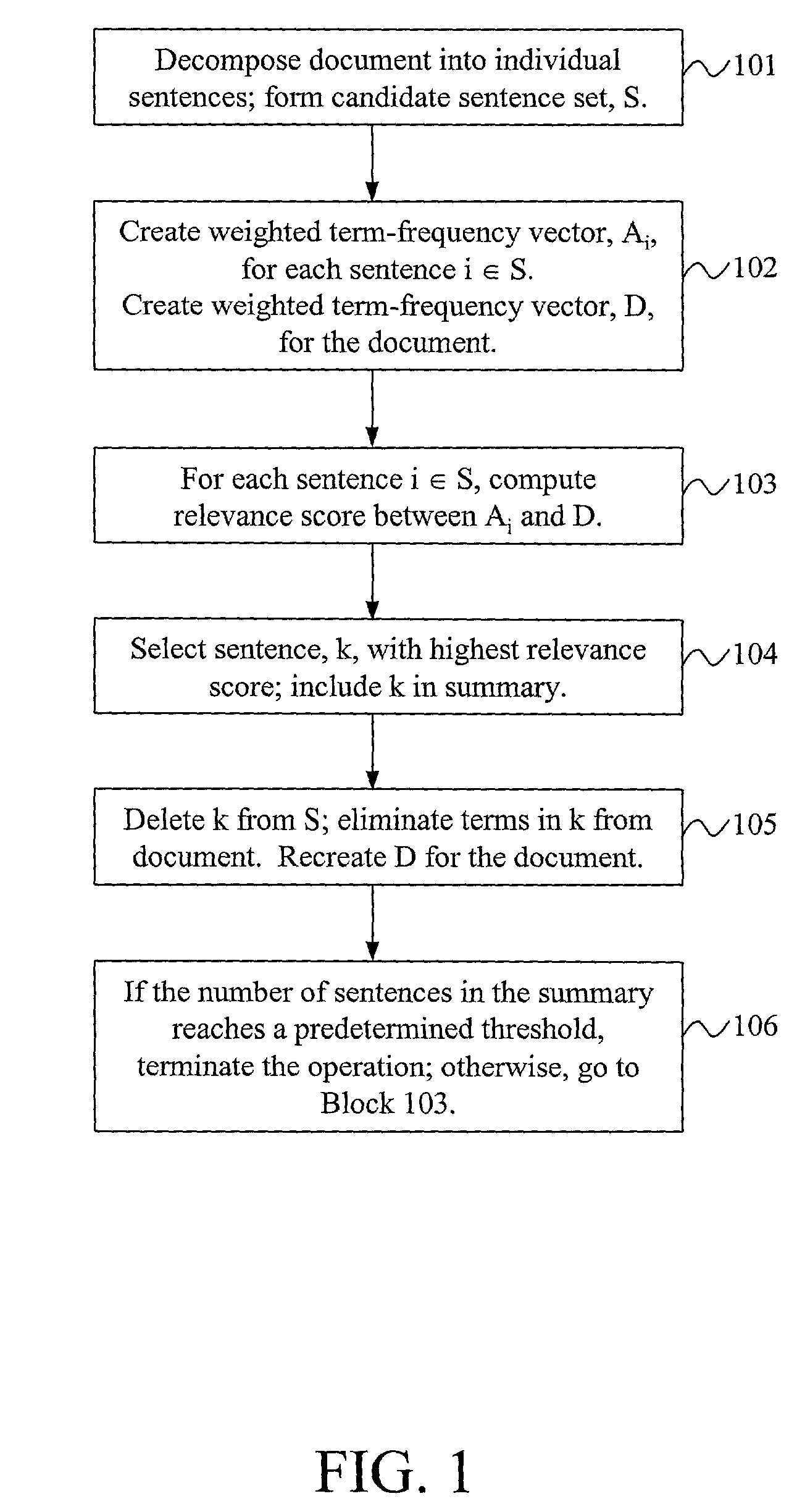
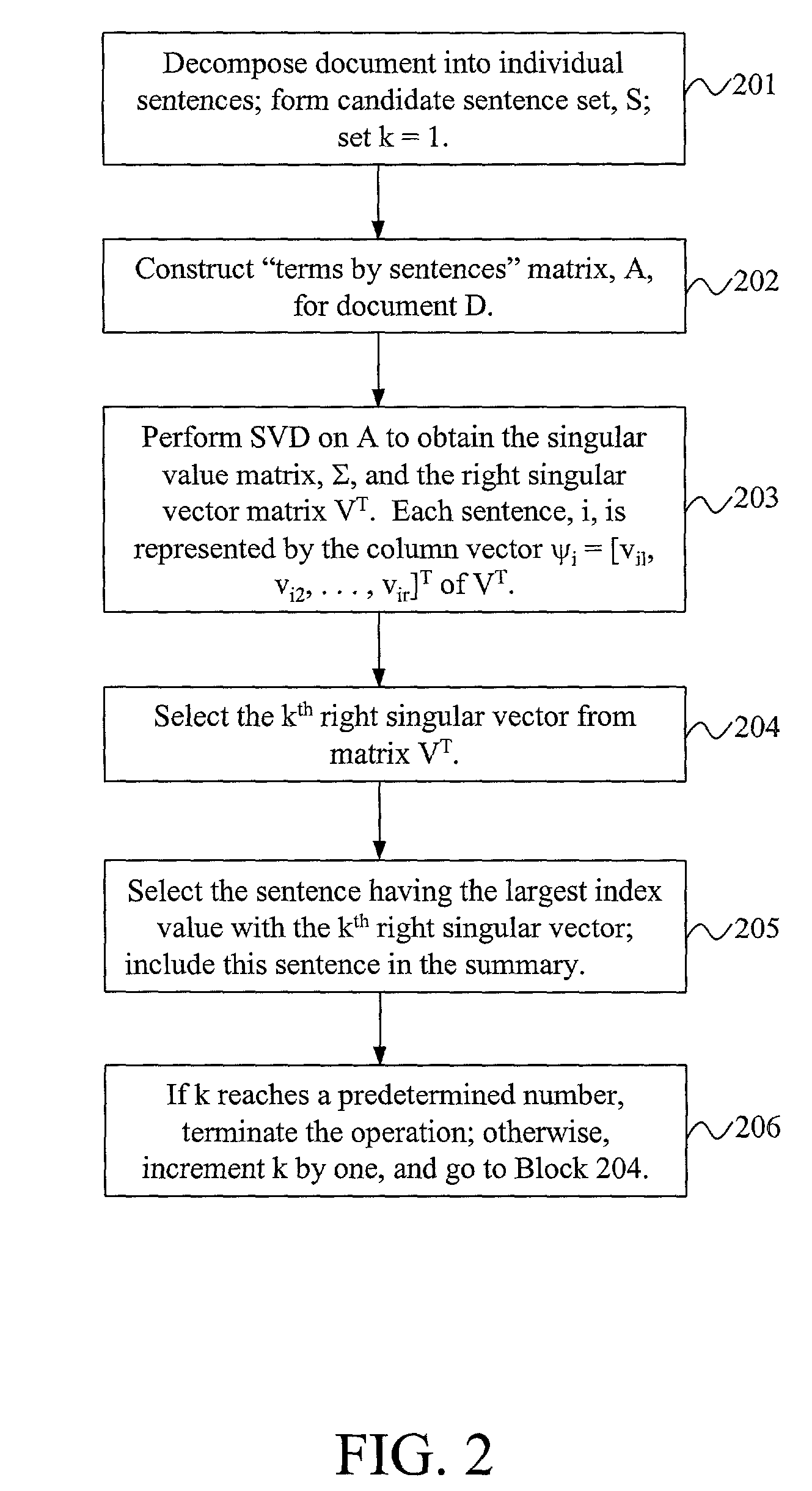
Test summarization using relevance measures and latent semantic analysis
InactiveUS7607083B2Wide coverageReduce redundancyFinanceReservationsSingular value decompositionDocument preparation
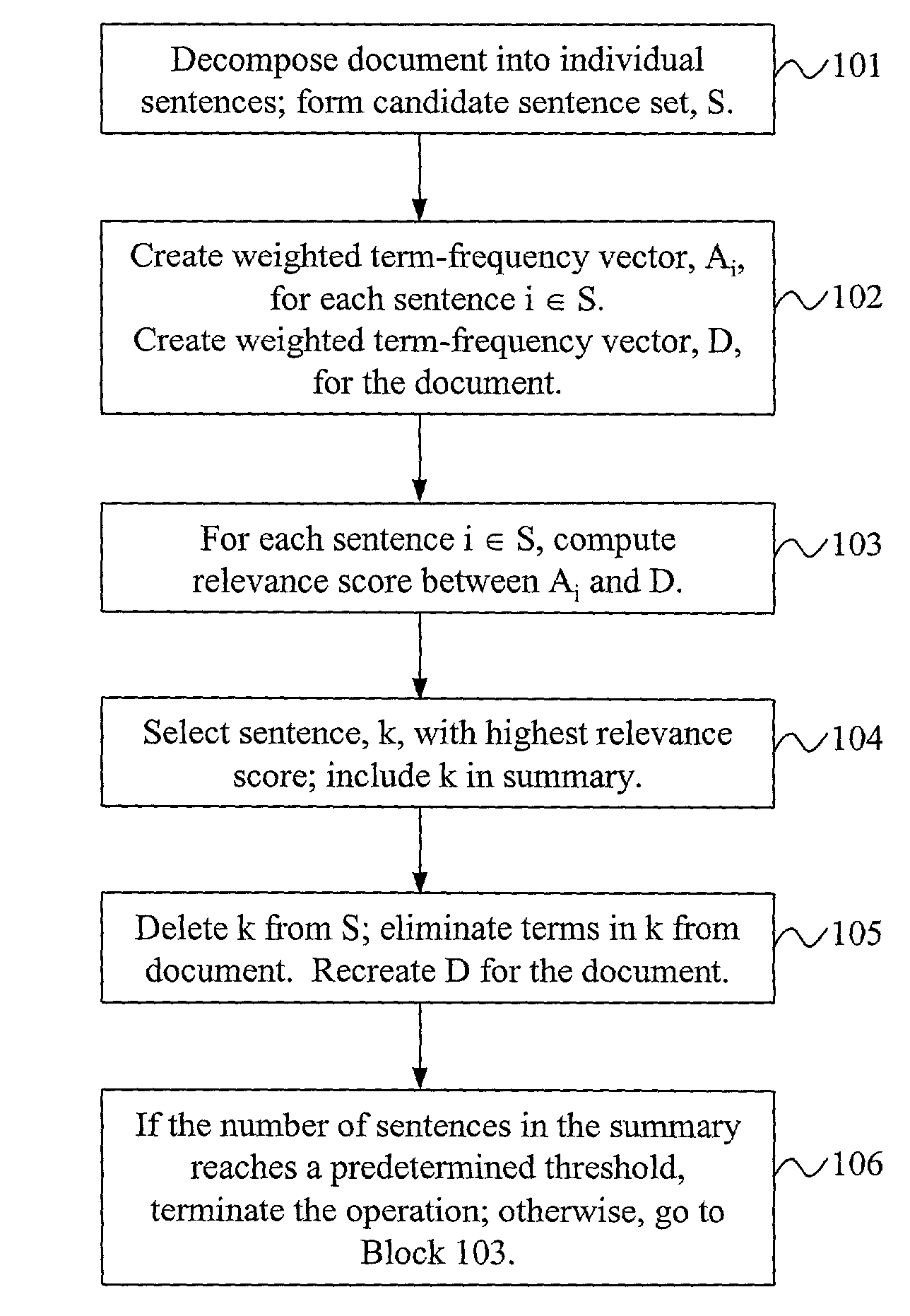
Text summarizers using relevance measurement technologies and latent semantic analysis techniques provide accurate and useful summarization of the contents of text documents. Generic text summaries may be produced by ranking and extracting sentences from original documents; broad coverage of document content and decreased redundancy may simultaneously be achieved by constructing summaries from sentences that are highly ranked and different from each other. In one embodiment, conventional Information Retrieval (IR) technologies may be applied in a unique way to perform the summarization; relevance measurement, sentence selection, and term elimination may be repeated in successive iterations. In another embodiment, a singular value decomposition technique may be applied to a terms-by-sentences matrix such that all the sentences from the document may be projected into the singular vector space; a text summarizer may then select sentences having the largest index values with the most important singular vectors as part of the text summary.
Owner:NEC CORP
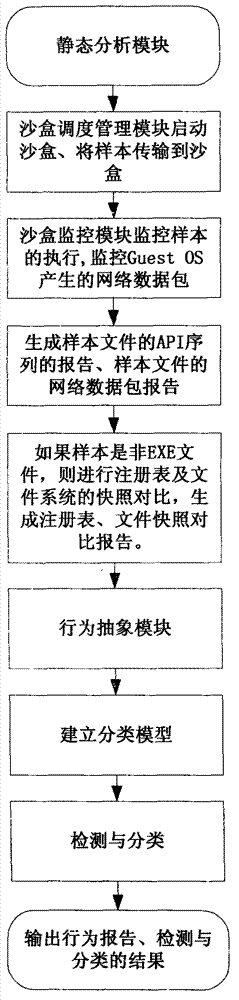
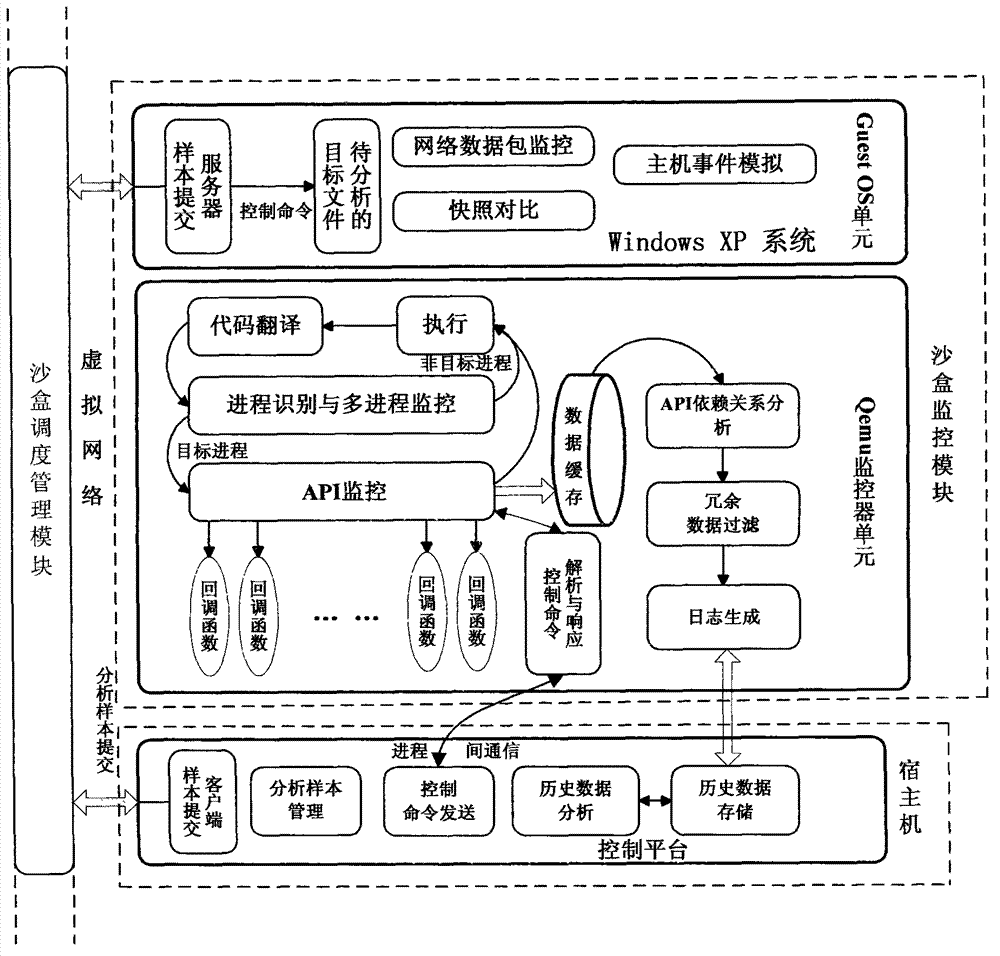
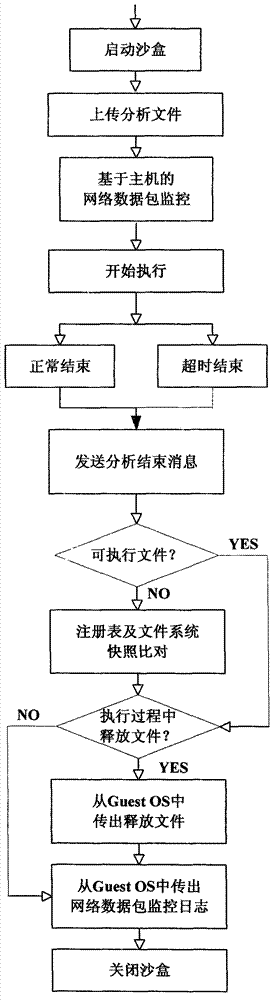
System and method for automatically analyzing, detecting and classifying malicious program behavior
ActiveCN102930210ACause damageOvercome shortcomings such as inability to perform adequatelyPlatform integrity maintainanceSpecial data processing applicationsDomain nameNetwork behavior
The invention discloses a system and a method for automatically analyzing, detecting and classifying a malicious program behavior. The system comprises a static analysis module, a sandbox dispatching management module, a sandbox monitoring module, a behavior abstraction module and a detection and classification module. Compared with the prior art, the system has the advantages that 1, the system is based on a behavior monitoring technology in an instruction set simulation environment; and 2, a virtual Internet is established in a sandbox through means of environment configuration, server program modification and the like, and a common network service is simulated, so that operations such as domain name server (DNS) resolution, http access, file download, Email login and mailing initiated by a malicious program can be successfully executed, the malicious program is inveigled to generate a malicious network behavior, the network behaviors are prevented from damaging a host machine and a real network, and the defects that the malicious program network behavior cannot be fully expressed during dynamic behavior analysis of a malicious program and the like are overcome.
Owner:JIANGSU JINLING TECH GRP CORP
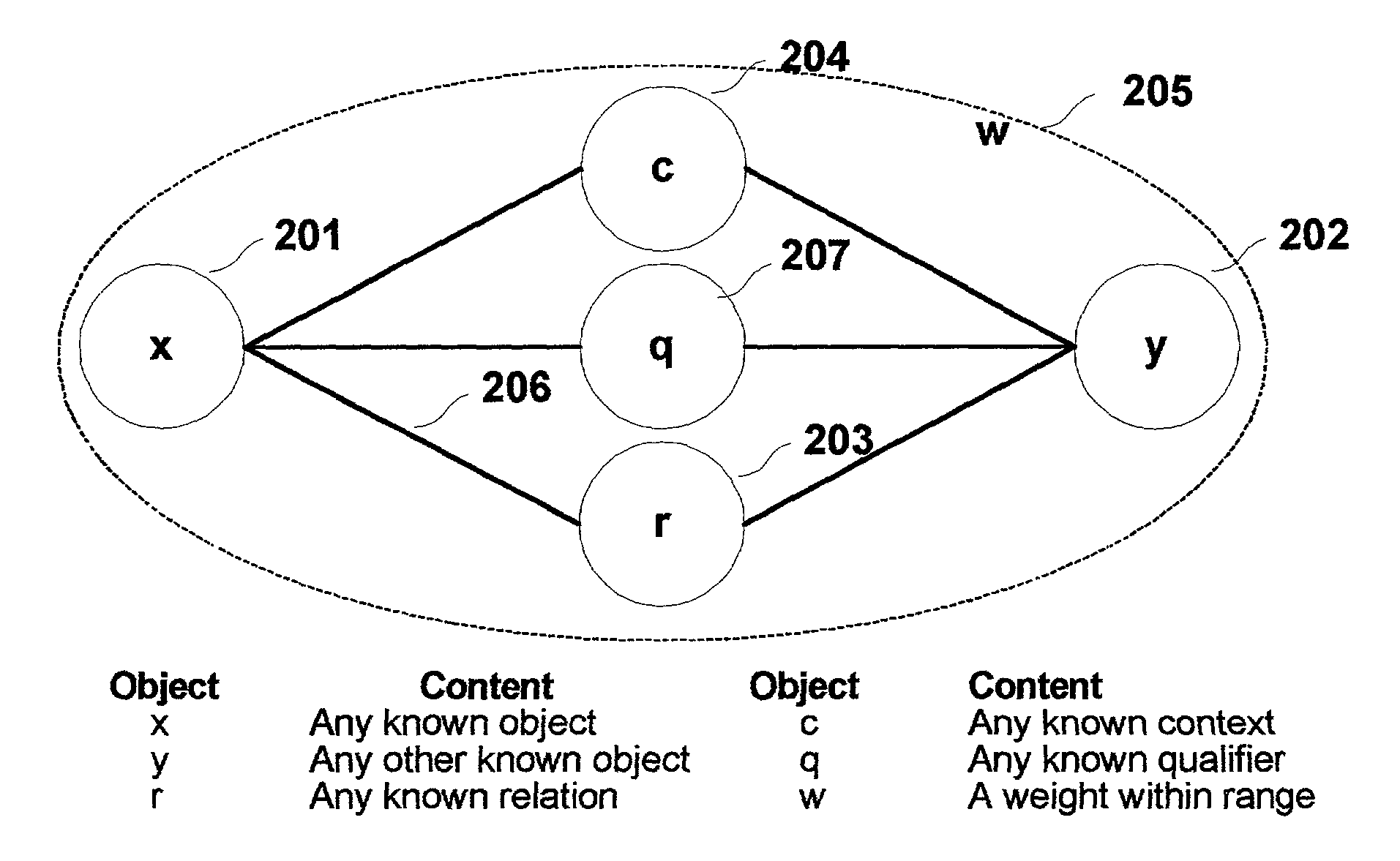
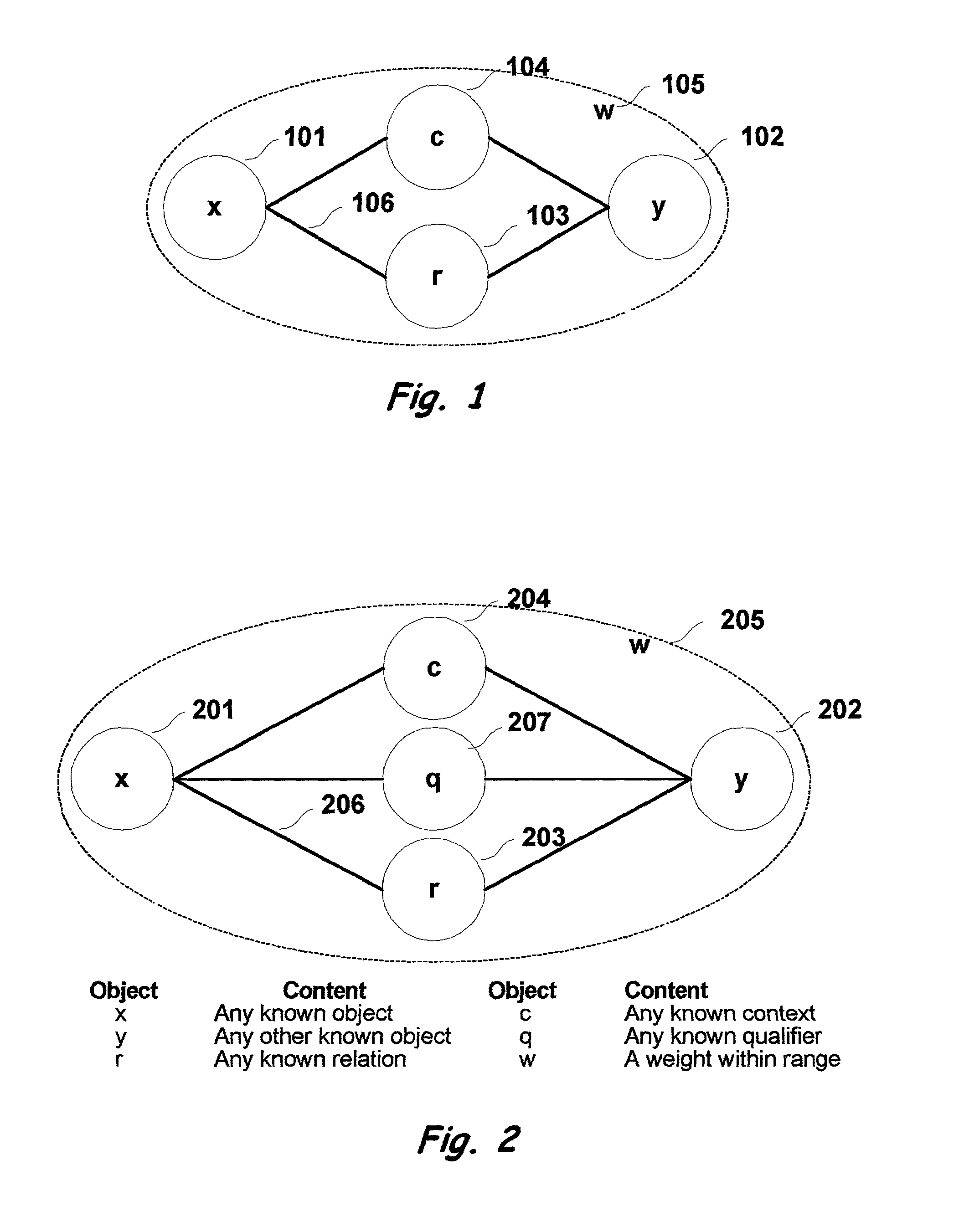
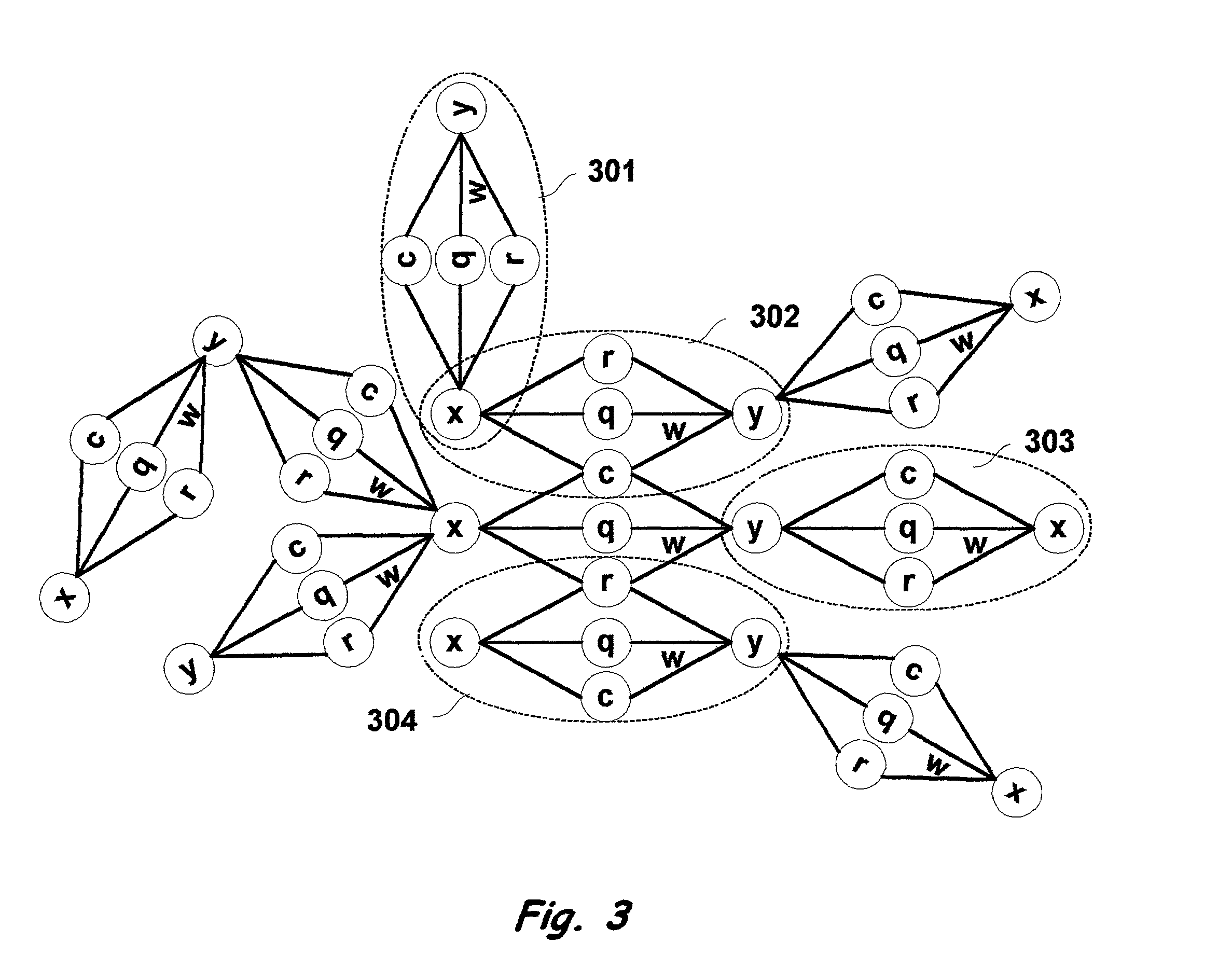
Multi-dimensional method and apparatus for automated language interpretation
InactiveUS7403890B2Sufficient massImprove abilitiesSemantic analysisChaos modelsShort-term memoryMulti dimensional
A method and apparatus for natural language interpretation are described. The invention includes a schema and apparatus for storing, in digital, analog, or other machine-readable format, a network of propositions formed of a plurality of text and / or non-text objects, and the steps of retrieving a string of input text, and locating all associated propositions in the network for each word in the input string. Embodiments of the invention also include optimization steps for locating said propositions, and specialized structures for storing them in a ready access storage area simulating human short-term memory. The schema and steps may also include structures and processes for obtaining and adjusting the weights of said propositions to determine posterior probabilities representing the intended meaning. Embodiments of the invention also include an apparatus designed to apply an automated interpretation algorithm to automated voice response systems and portable knowledge appliance devices.
Owner:KNOWLEDGENETICA CORP
Method for recognizing road traffic sign for unmanned vehicle
InactiveCN102542260AFast extractionFast matchingDetection of traffic movementCharacter and pattern recognitionClassification methodsNear neighbor
The invention discloses a method for recognizing a road traffic sign for an unmanned vehicle, comprising the following steps of: (1) changing the RGB (Red, Green and Blue) pixel value of an image to strengthen a traffic sign feature color region, and cutting the image by using a threshold; (2) carrying out edge detection and connection on a gray level image to reconstruct an interested region; (3) extracting a labeled graph of the interested region as a shape feature of the interested region, classifying the shape of the region by using a nearest neighbor classification method, and removing a non-traffic sign region; and (4) graying and normalizing the image of the interested region of the traffic sign, carrying out dual-tree complex wavelet transform on the image to form a feature vector of the image, reducing the dimension of the feature vector by using a two-dimension independent component analysis method, and sending the feature vector into a support vector machine of a radial basis function to judge the type of the traffic sign of the interested region. By using the method, various types of traffic signs in a running environment of the unmanned vehicle can be stably and efficiently detected and recognized.
Owner:CENT SOUTH UNIV
Systems and methods for risk stratification of patient populations
ActiveUS7853456B2Disseminate reduced redundancy requestsReduce redundancyAnalogue computers for chemical processesComputer-assisted medical data acquisitionHealth riskProgram instruction
A statistical processing system includes a server operably configured with program instructions implementing a plurality of statistical models to at least one of (a) predict a health outcome based on questionnaire responses, (b) assist a patient's choice of therapeutic modality based on questionnaire responses, and (c) assess a health risk or status based on questionnaire responses. Also provided is a research agency communicating with the server and contracted to provide the statistical models using a visual interface communicated by the server. The server is configured to analyze requests received from users relating to a plurality of said statistical models to reduce redundancy in requests for patient data.
Owner:TERUMO MEDICAL CORP
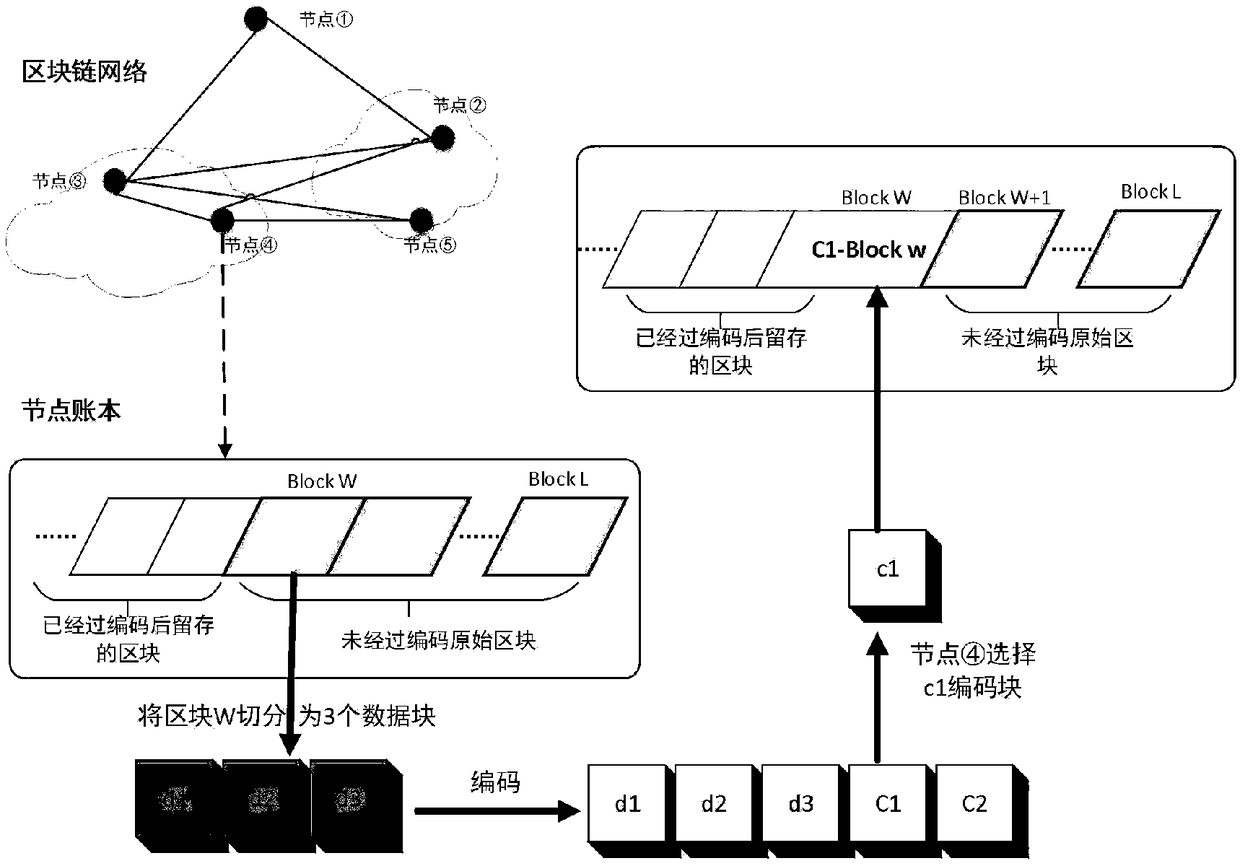
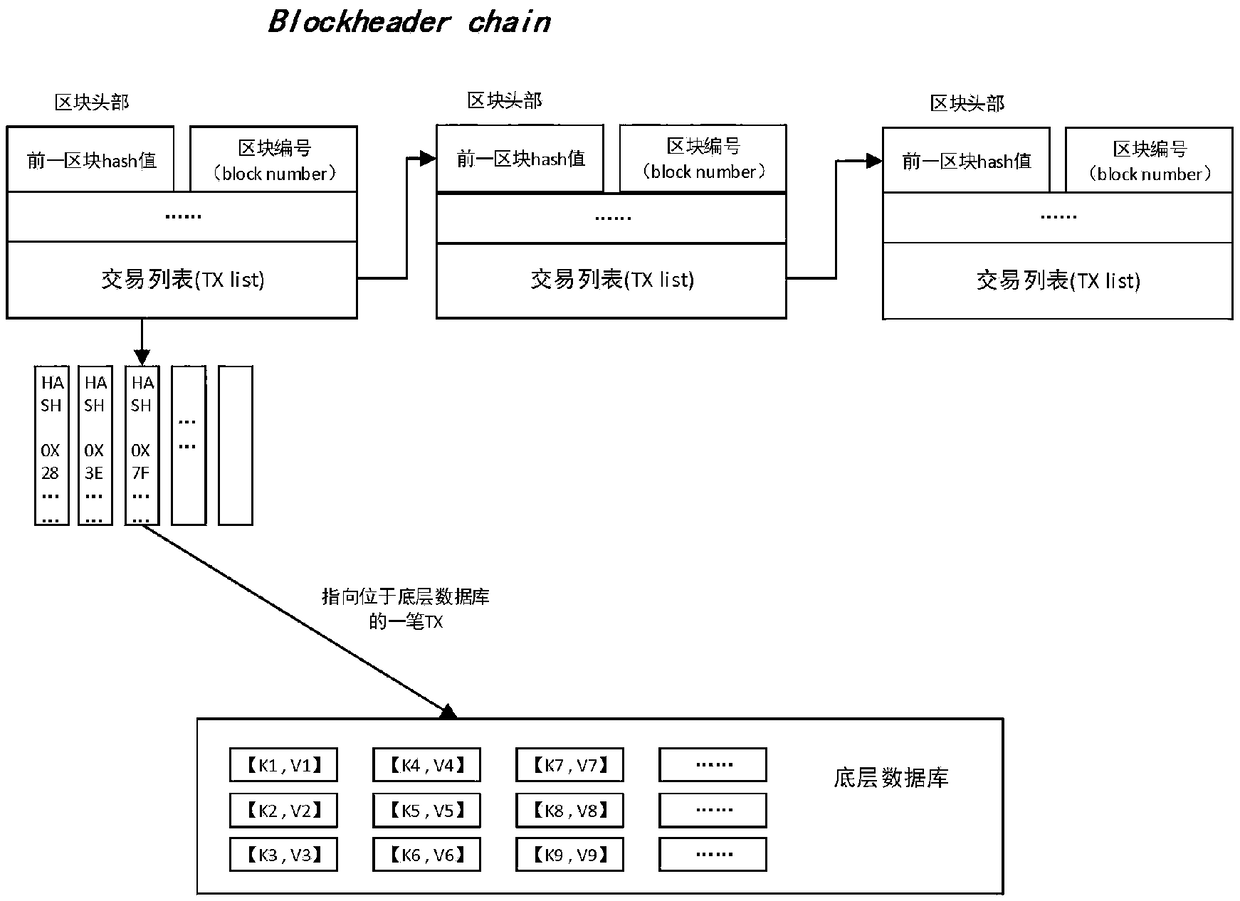
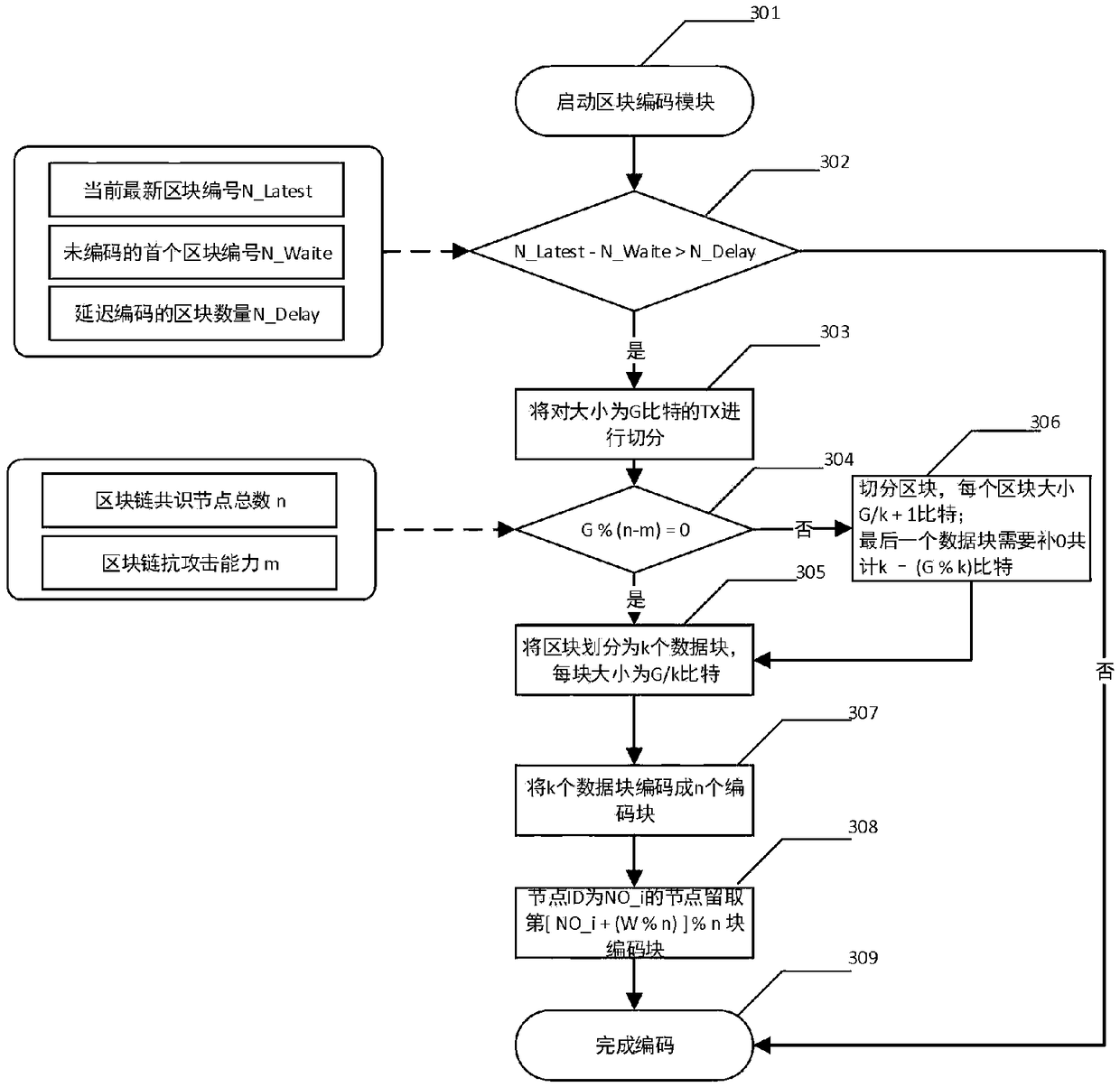
Block chain account book distributed storage technology based on erasure code
InactiveCN109359223AReduce redundancyReduce demandOther databases indexingTransmissionCoding blockComputer architecture
The invention relates to a block chain account book distributed storage technology based on erasure code, and belongs to the block chain technology field. The technology comprises the following steps:a) the block delay coding strategy allows to delay the coding of a certain number of new blocks to meet the synchronization requirements of other block chain consensus nodes for blocks; B) accordingto the set block coding algorithm, the blocks satisfying the coding condition are cut into k data blocks, each data block having a size of about 1 / k of the original block, and further the cut k datablocks are encoded into n (n) k encoded blocks by the erasure coding technology; (c) each block chain node reserves a part of that coding block, and finally the whole block chain network store the coding blocks decentrally; D) when the original block needs to be recovered from the encoded block, the current node collects the remaining encoded block corresponding to the block from the remaining nodes, and then recovers the original block according to the corresponding decoding algorithm. The method reduces the requirement of the block chain for storage resources and improves the utilization rate of storage space.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
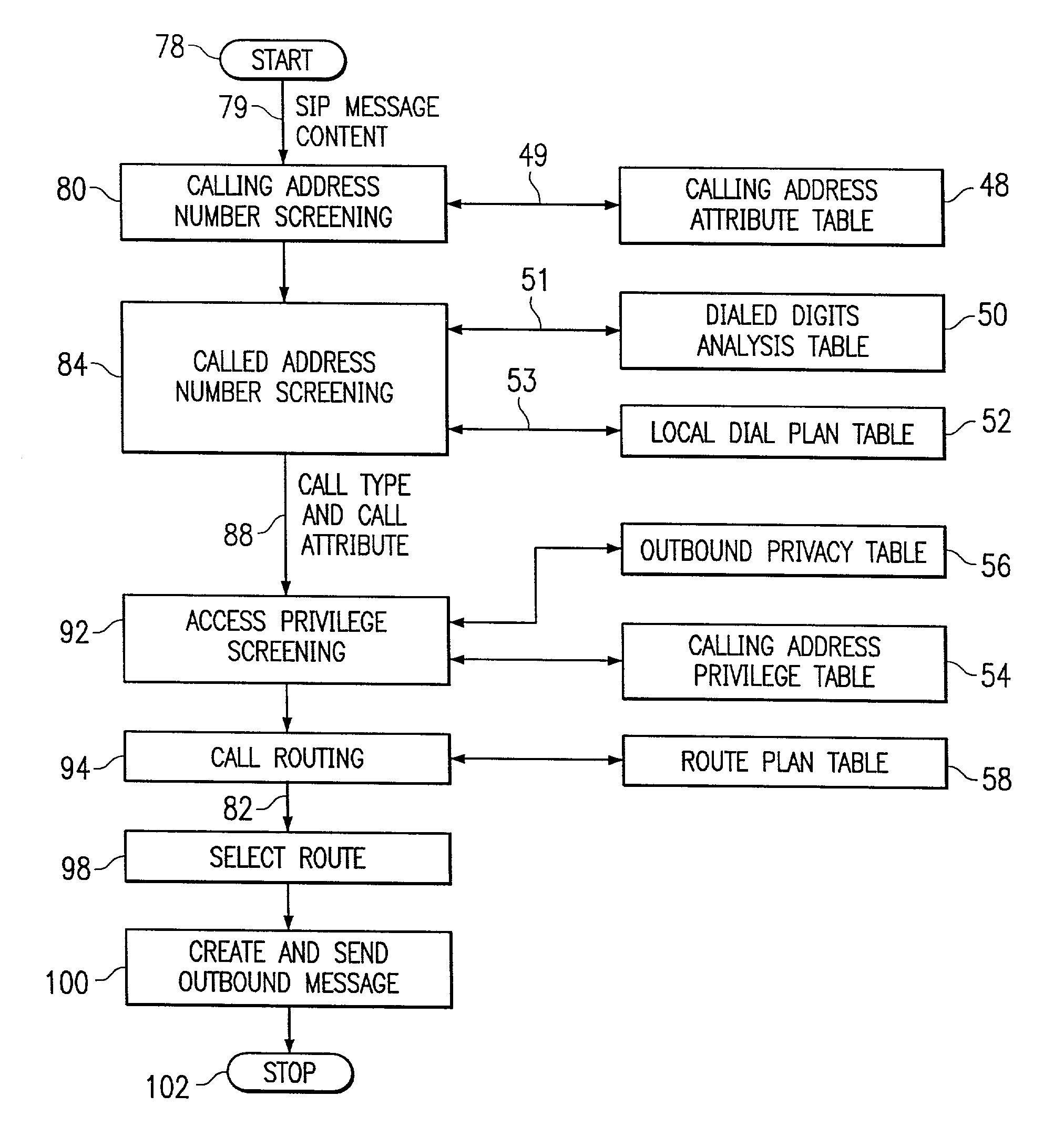
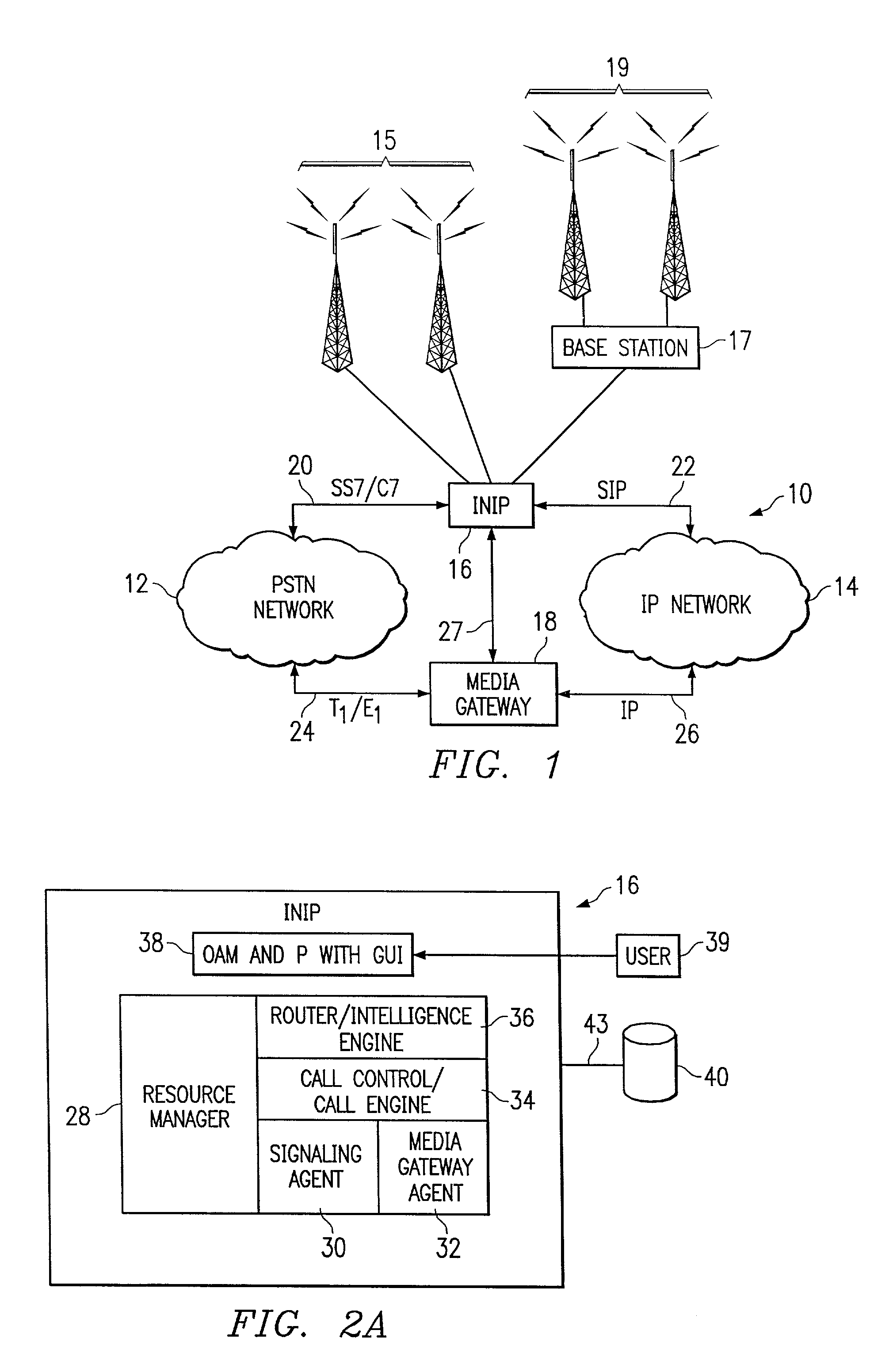
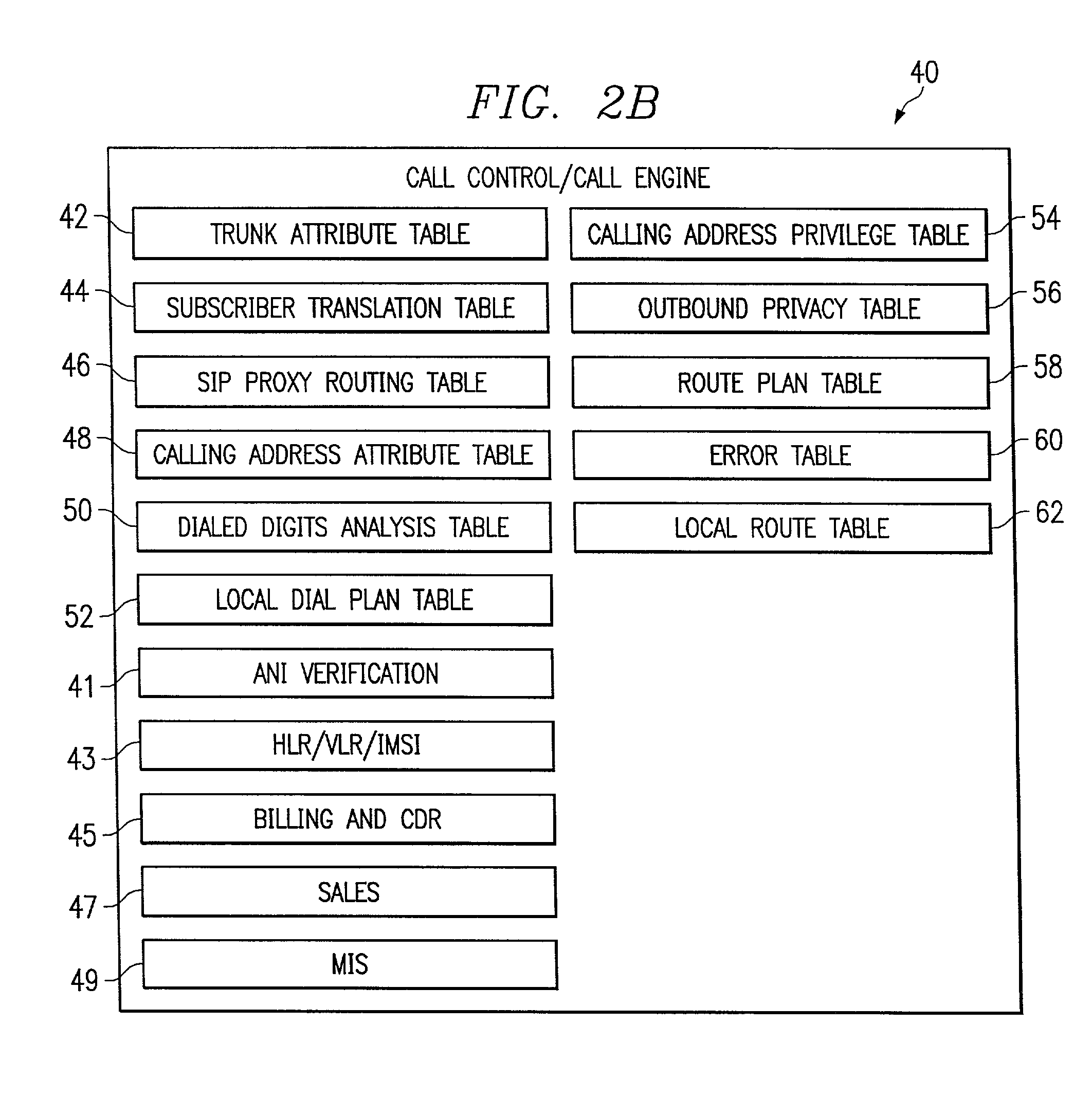
Intelligence engine
InactiveUS6961334B1Reduce redundancyImprove usabilitySpecial service for subscribersGraded-service arrangementsControl layerTelecommunications network
One aspect of the invention is an intelligence engine. The intelligence engine includes a distributor layer operable to communicate with at least one call agent in a telecommunications network. The call agent may receive state-driven information associated with a call between an originator and a termination point. The intelligence engine also includes a telephony management layer. The telephony management layer is operable to receive a plurality of stateless requests from the distributor layer, access a database entry associated with the requests, spawn at least one request to obtain information associated with the originator and the termination point if necessary to route the call, and send the information to the call agent to route the call. In a particular embodiment, the intelligence engine further includes a facility management command and control layer. The facility management command and control layer is operable to receive an indicator signal associated with the call from the network. The call is controlled by the call agent. The facility management command and control layer is also operable to access a database entry associated with the call agent in response to the indicator signal and to reassign control of the call from the call agent to a second call agent.
Owner:RIBBON COMM OPERATING CO INC
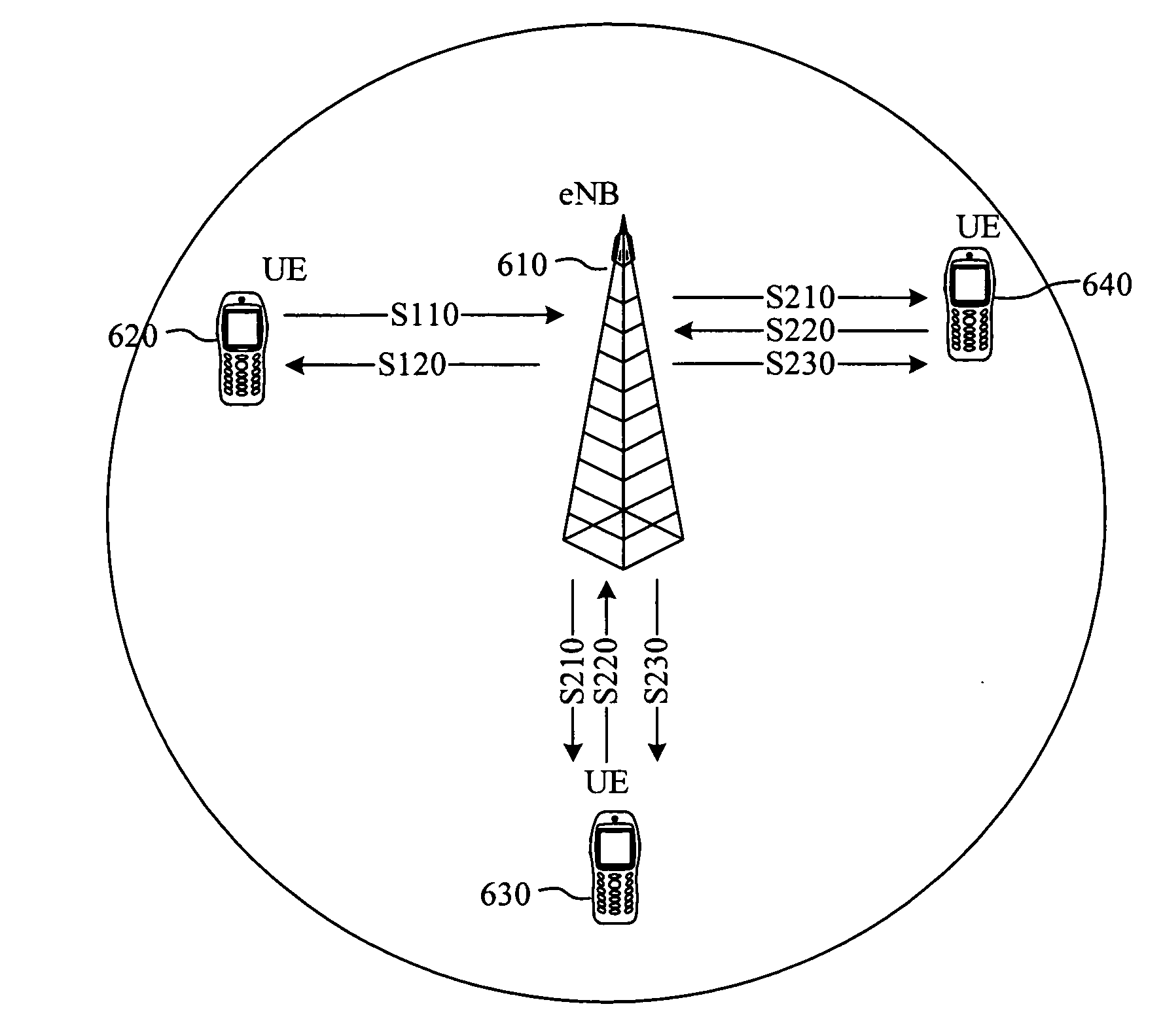
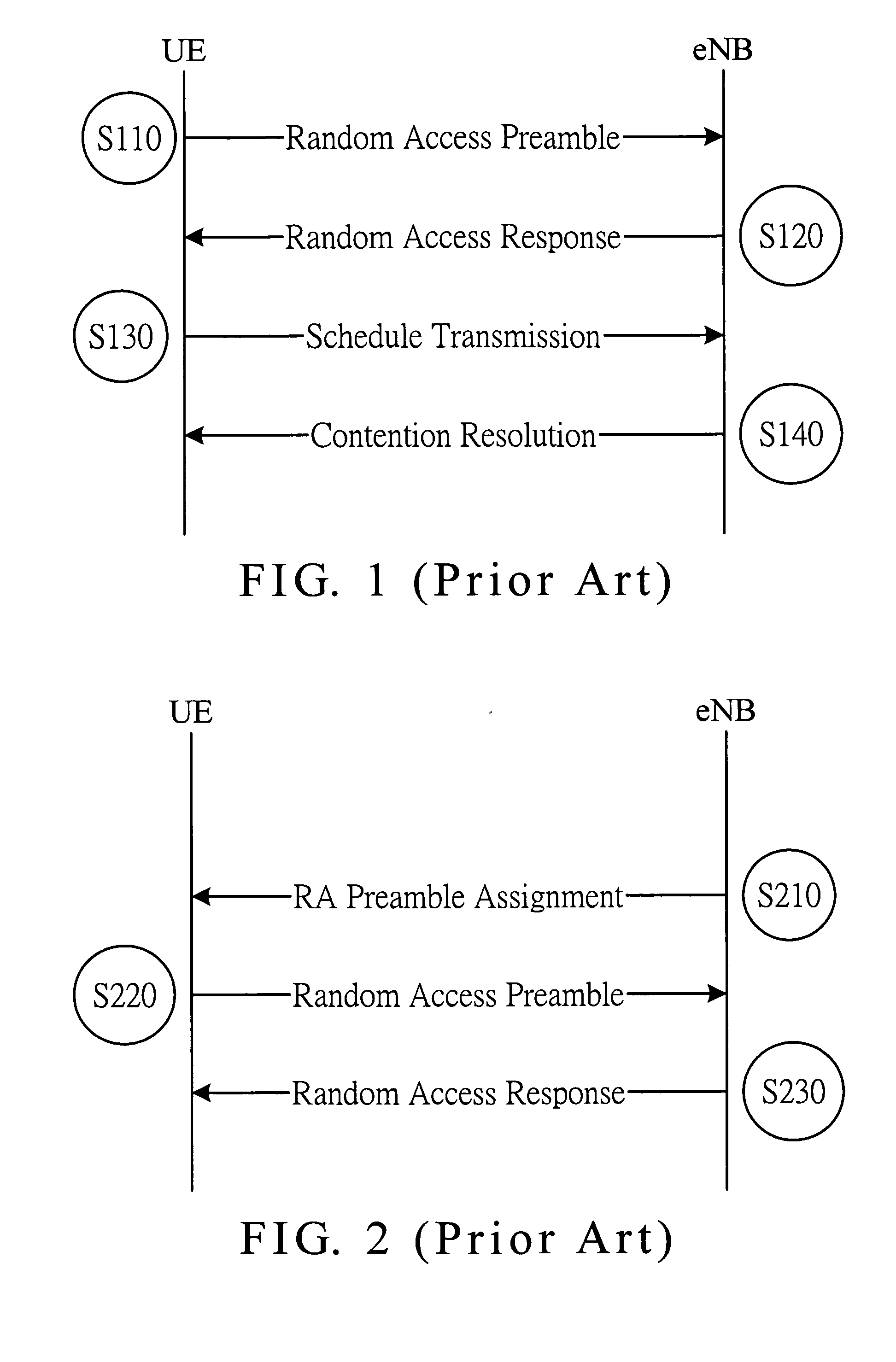
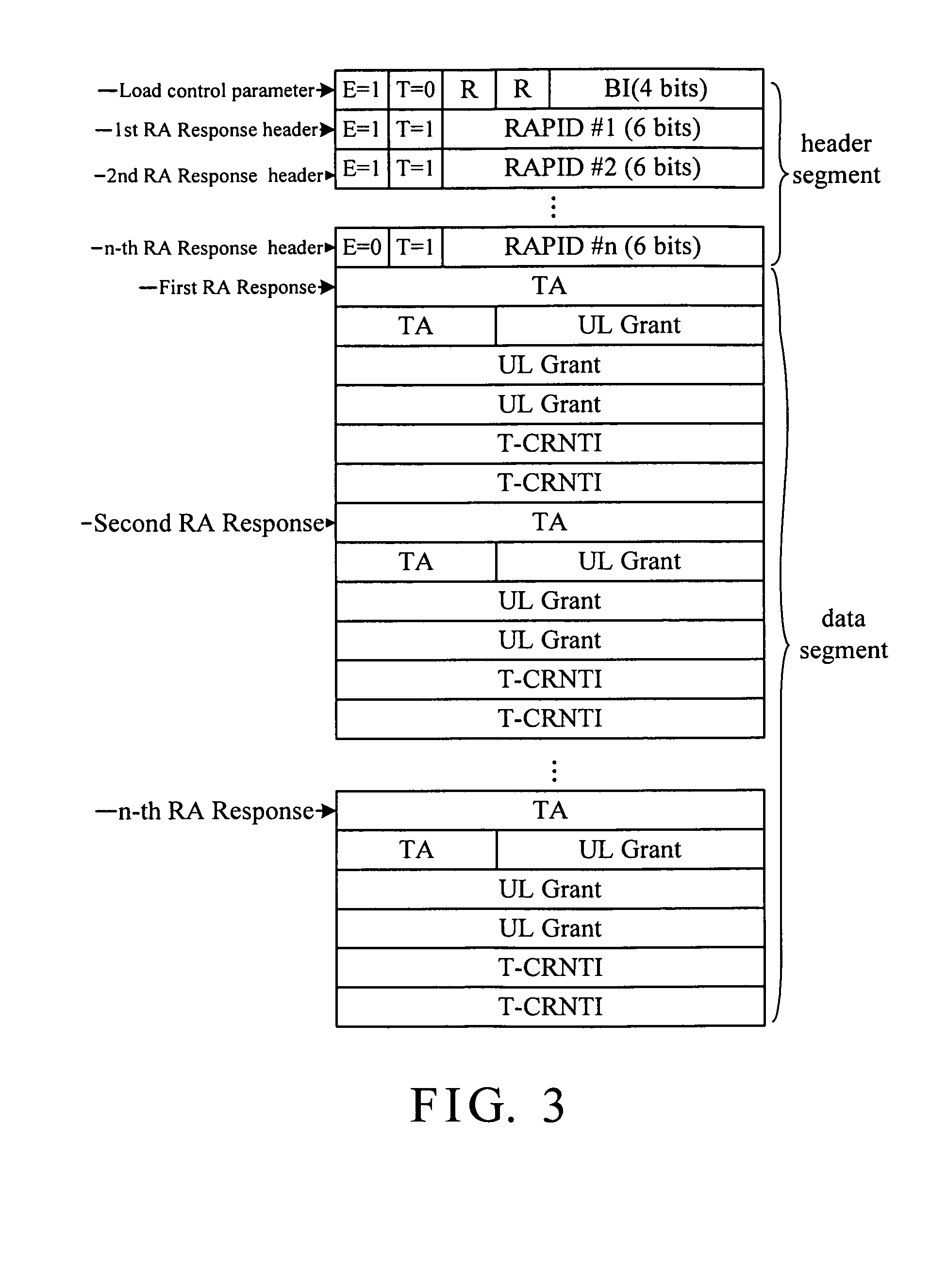
Frame format for random access response of wireless communication transmission
InactiveUS20090175253A1Reduce redundancyReduce numberWireless commuication servicesWireless communication systemsVariable length
A frame format for random access response of wireless communication transmission is provided. The frame format comprises a header segment and a variable length data segment. The header segment includes one or more random access response subheader and 0 to N load control subheader. The variable length data segment including one or more random access response data payload corresponding to the one or more random access response subheader. The one or more random access response subheader includes a status indication field to represent a last random access response subheader, a load control subheader, a random access response data payload with a T-CRNTI field, or a random access response data payload without a T-CRNTI field.
Owner:SUNPLUS MMOBILE
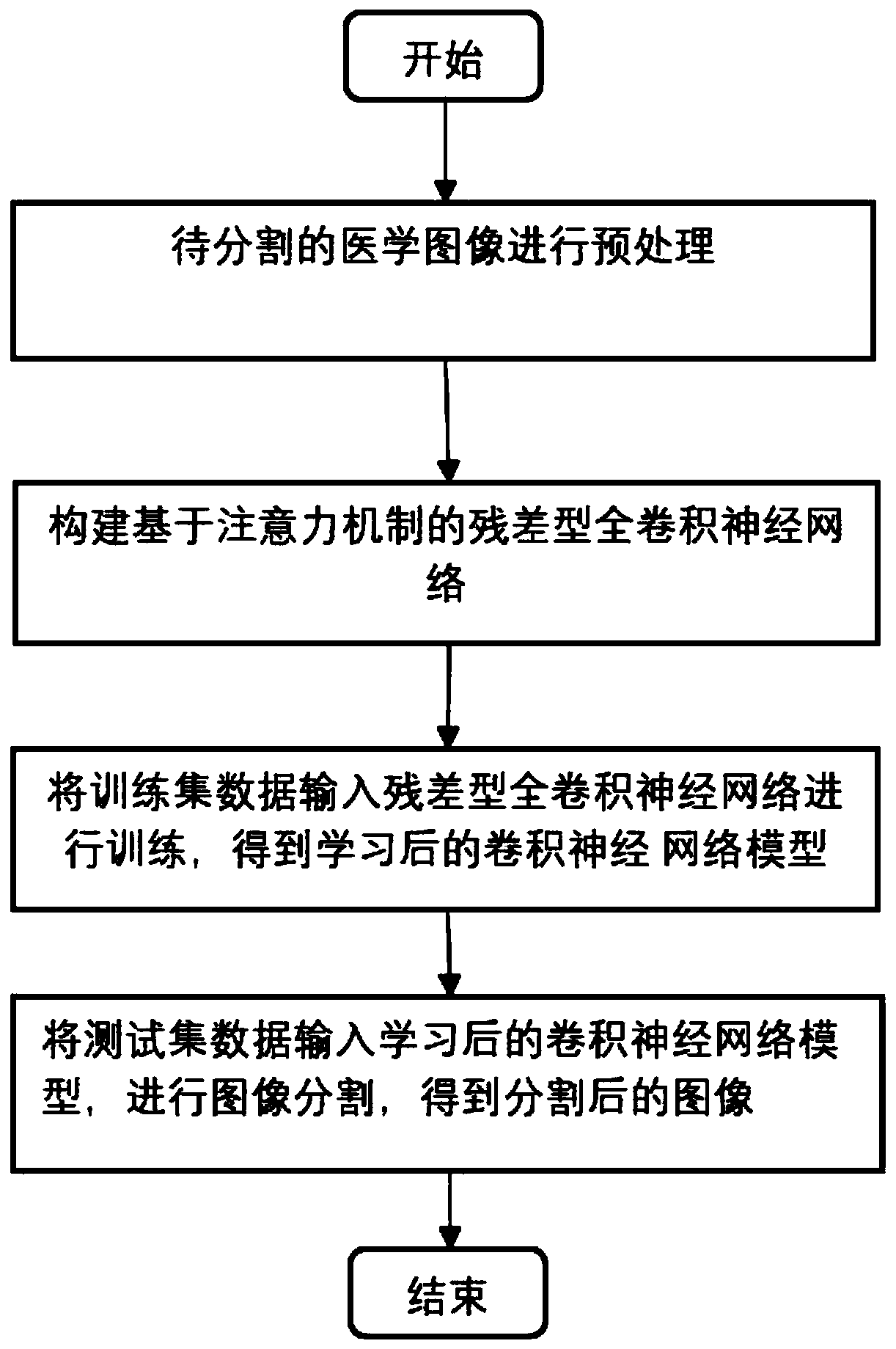
Medical image segmentation method of residual full convolutional neural network based on attention mechanism
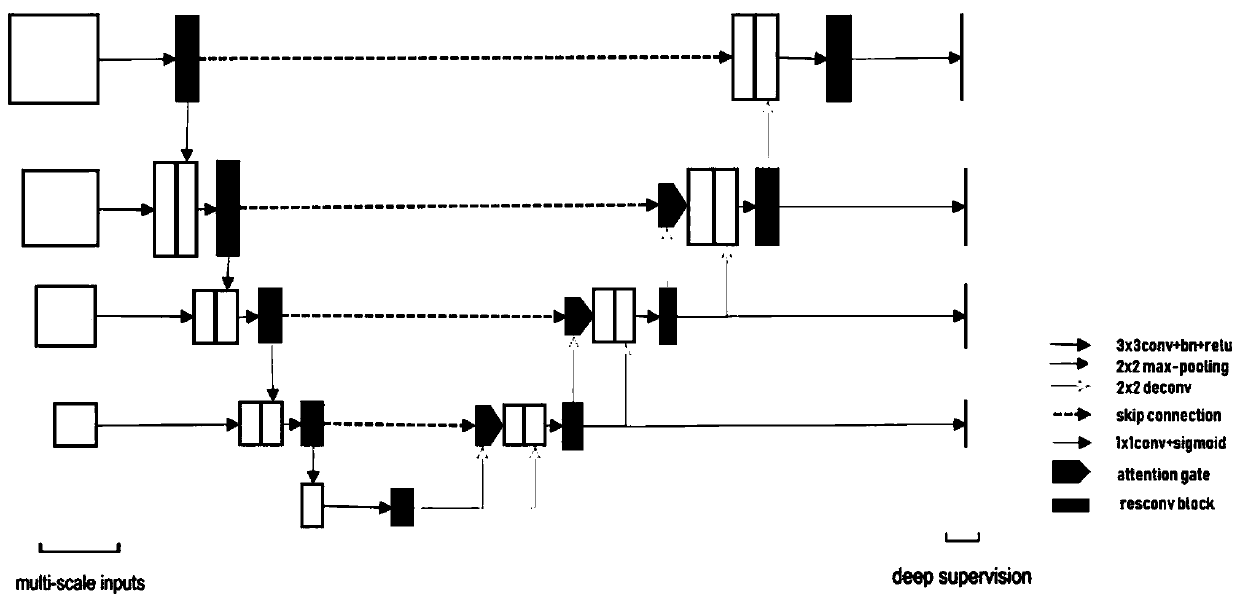
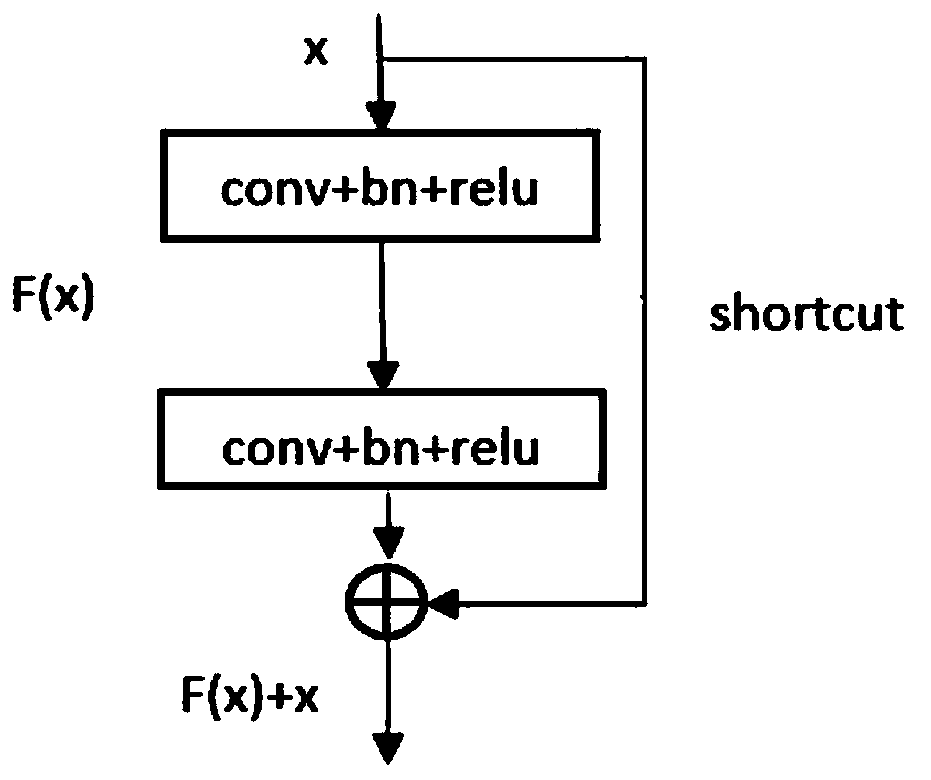
ActiveCN110189334ASolve the problem of lack of spatial features of imagesReduce redundancyImage enhancementImage analysisImage segmentationImaging Feature
The invention provides a medical image segmentation method of a residual full convolutional neural network based on an attention mechanism. The medical image segmentation method comprises the steps: preprocessing a to-be-segmented medical image; constructing a residual full convolutional neural network based on the attention mechanism, wherein the residual full convolutional neural network comprises a feature map contraction network, an attention network and a feature map expansion network group; inputting the training set data into a residual error type full convolutional neural network for training to obtain a learned convolutional neural network model; and inputting the test set data into the learned convolutional neural network model, and performing image segmentation to obtain segmented images. According to the medical image segmentation method, an attention network is utilized to effectively transmit image features extracted from a feature map contraction network to a feature mapexpansion network; and the problem of lack of image spatial features in an image deconvolution process is solved while the attention network can also inhibit image regions irrelevant to a segmentation target in a low-layer feature image, so that the redundancy of the image is reduced, and meanwhile, the accuracy of image segmentation is also improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
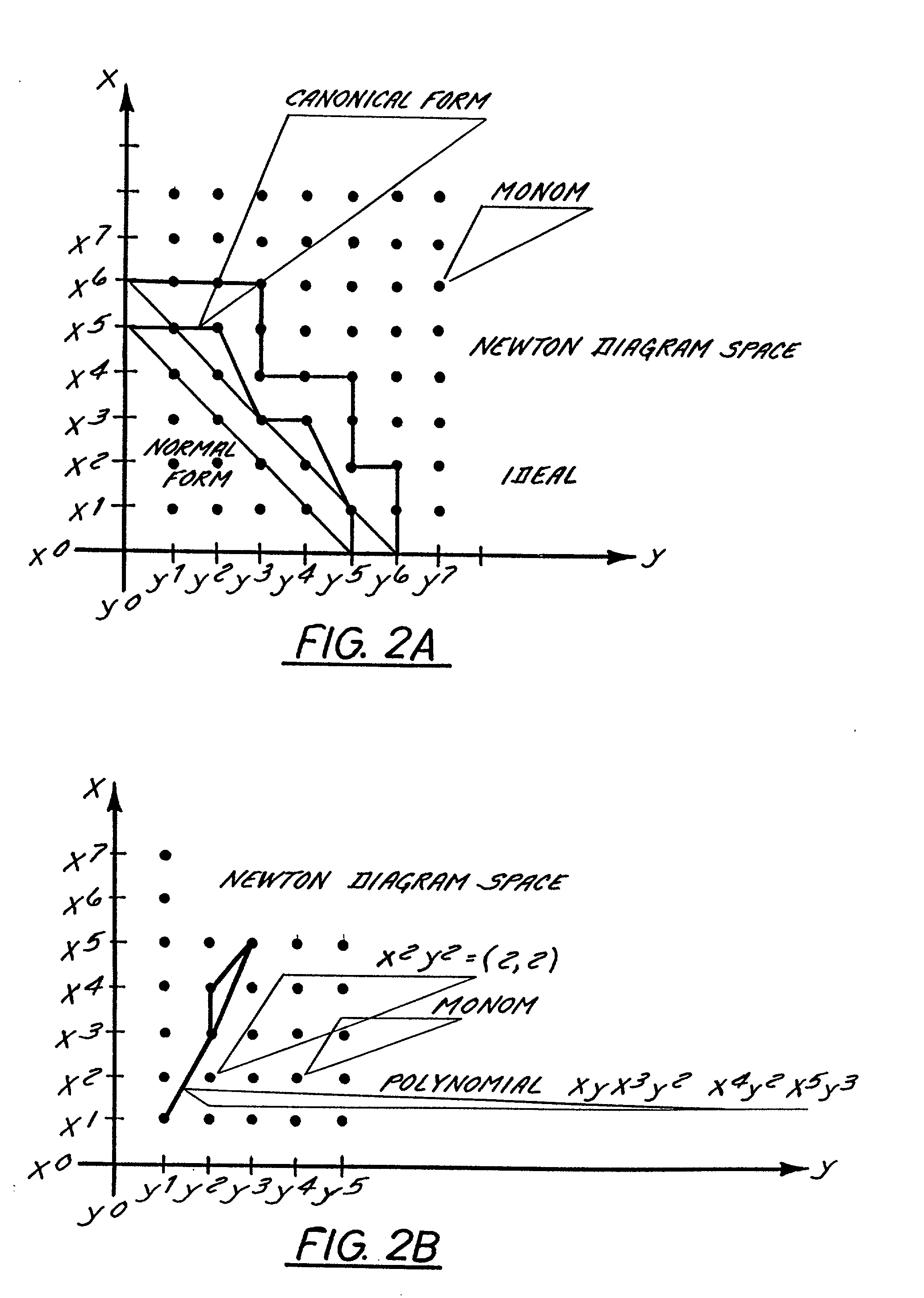
Method of isomorphic singular manifold projection still/video imagery compression
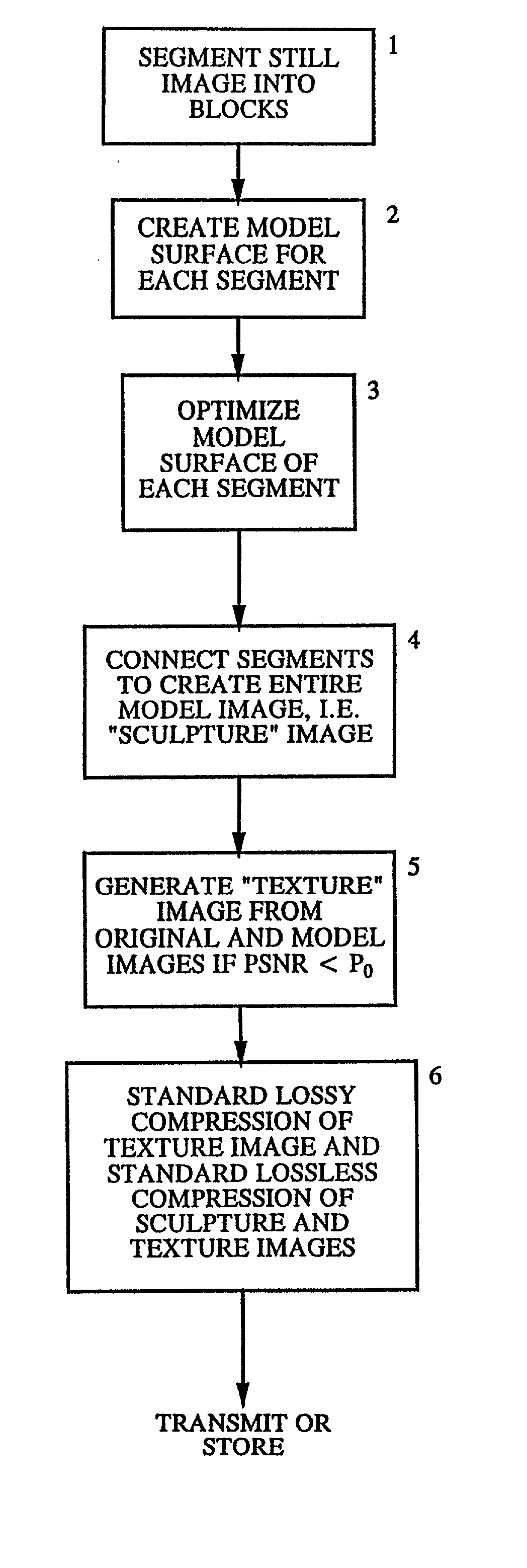
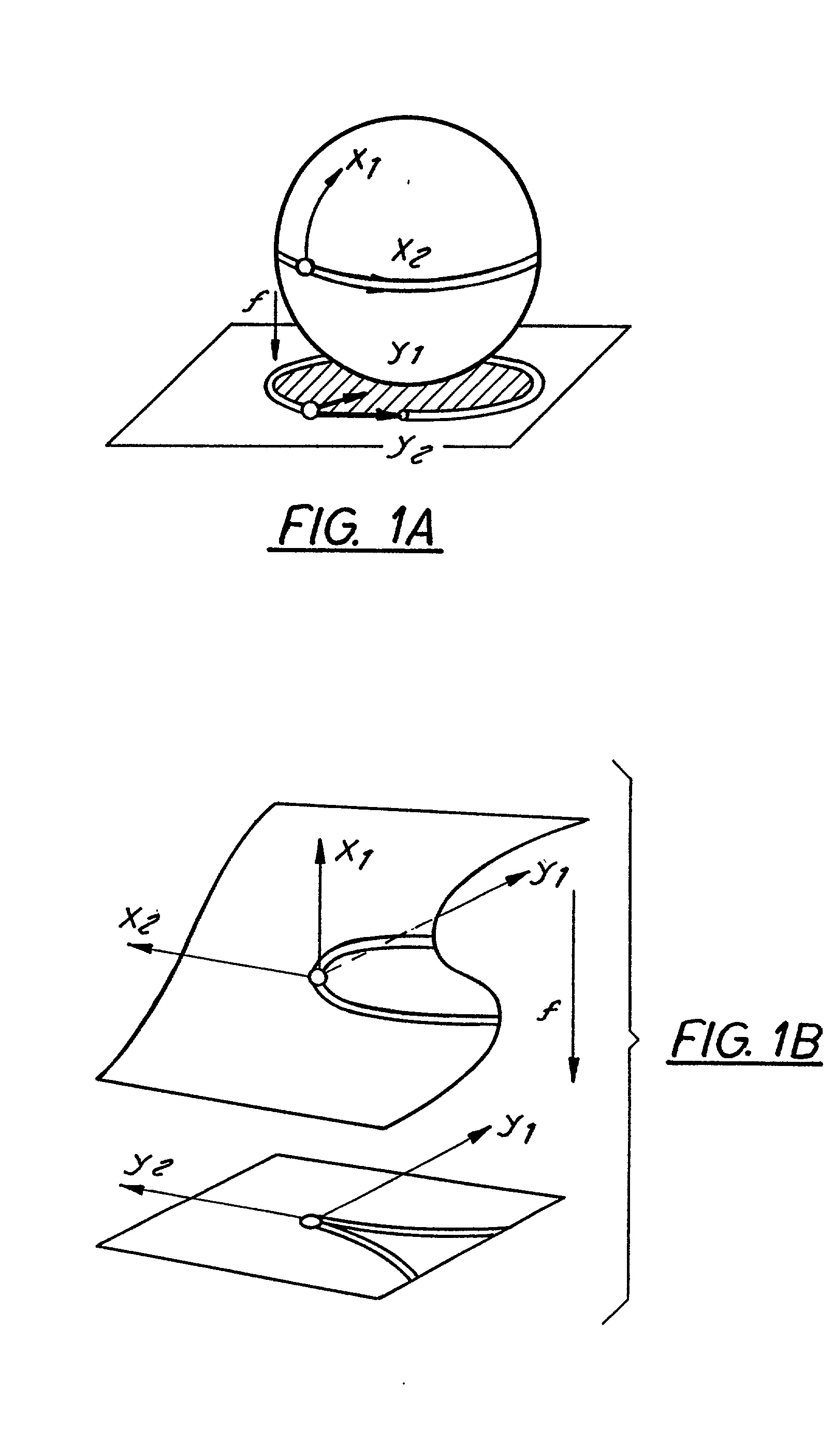
InactiveUS20020176624A1Reduction procedureReduce redundancyCharacter and pattern recognitionImage codingPattern recognitionImage compression
Methods and apparatuses for still image compression, video compression and automatic target recognition are disclosed. The method of still image compression uses isomorphic singular manifold projection whereby surfaces of objects having singular manifold representations are represented by best match canonical polynomials to arrive at a model representation. The model representation is compared with the original representation to arrive at a difference. If the difference exceeds a predetermined threshold, the difference data are saved and compressed using standard lossy compression. The coefficients from the best match polynomial together with the difference data, if any, are then compressed using lossless compression. The method of motion estimation for enhanced video compression sends I frames on an "as-needed" basis, based on comparing the error between segments of a current frame and a predicted frame. If the error exceeds a predetermined threshold, which can be based on program content, the next frame sent will be an I frame. The method of automatic target recognition (ATR) including tracking, zooming, and image enhancement, uses isomorphic singular manifold projection to separate texture and sculpture portions of an image. Soft ATR is then used on the sculptured portion and hard ATR is used on the texture portion.
Owner:PHYSICAL OPTICS CORP
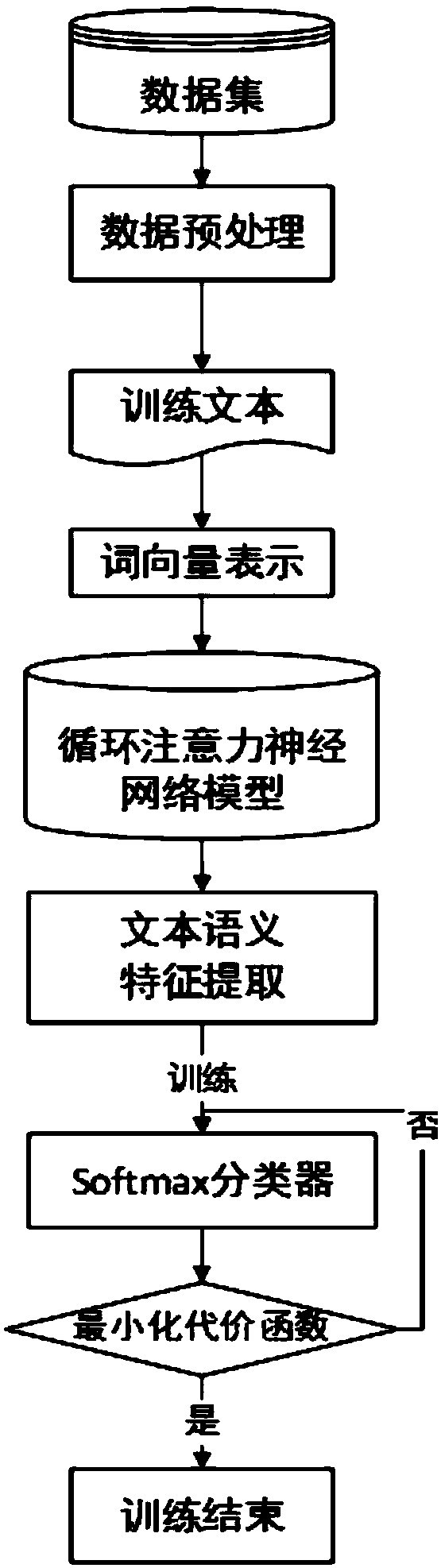
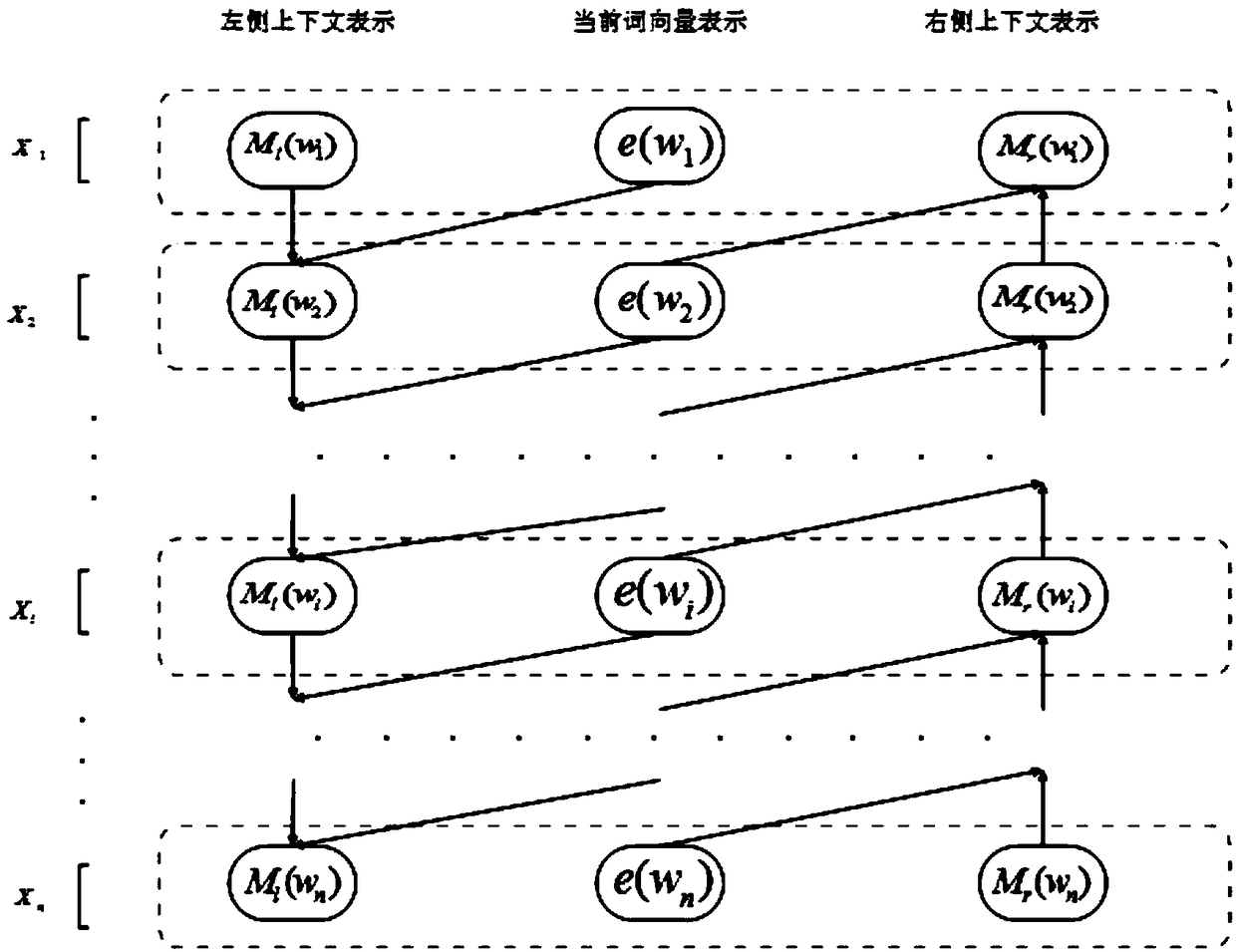
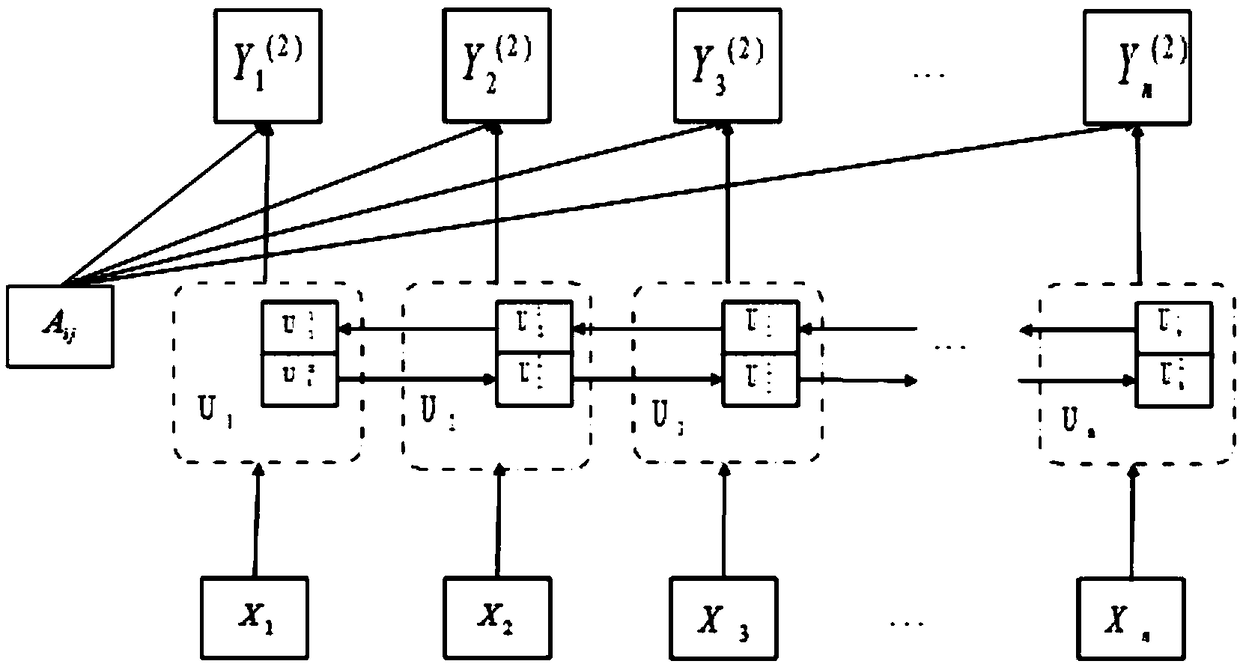
A text classification method based on a bidirectional cyclic attention neural network
ActiveCN109472024AImprove accuracyImprove performanceSemantic analysisNeural architecturesFeature vectorText categorization
The invention discloses a text classification method based on a bidirectional cyclic attention neural network, and belongs to the technical field of learning and natural language processing. The method comprises the following steps: step 1, preprocessing data; Step 2, according to the preprocessed data, generating and training a word vector of each word through a Word2vec method; Step 3, performing text semantic feature extraction on the word vector according to the word vector, fusing an attention mechanism and a bidirectional recurrent neural network, calculating the overall weight of each word, and converting the weight into an output value Y (4) of a model; And step 4, taking the feature vector Y (4) as the input of a softmax classifier according to the feature vector Y (4), and carrying out classification identification. According to the method, the attention mechanism is fused in the text feature learning model, the effect of keywords can be effectively highlighted, the performance of the model is greatly improved, and the text classification accuracy is further improved.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY
Near-transparent or transparent multi-channel encoder/decoder scheme
ActiveUS7573912B2Quality improvementReduce bitrateError preventionFrequency-division multiplex detailsWave shapeComputer science
A multi-channel encoder / decoder scheme additionally preferably generates a waveform-type residual signal. This residual signal is transmitted together with one or more multi-channel parameters to a decoder. In contrast to a purely parametric multi-channel decoder, the enhanced decoder generates a multi-channel output signal having an improved output quality because of the additional residual signal.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Highly compact non-volatile memory and method therefor with internal serial buses
InactiveUS6891753B2Improve performanceReduce redundancyRead-only memoriesDigital storageBus masteringComputer science
A non-volatile memory device capable of reading and writing a large number of memory cells with multiple read / write circuits in parallel has an architecture that reduces redundancy in the multiple read / write circuits to a minimum. The multiple read / write circuits are organized into a bank of similar stacks of components. Redundant circuits among each stack are factored out. In one aspect, a serial bus allows communication between components in each stack, thereby reducing the number of connections in a stack to a minimum. A bus controller sends control and timing signals to control the operation of the components and their interactions through the serial bus. In a preferred embodiment, the bus transactions of corresponding components in all the similar stacks are controlled simultaneously.
Owner:INNOVATIVE MEMORY SYST INC
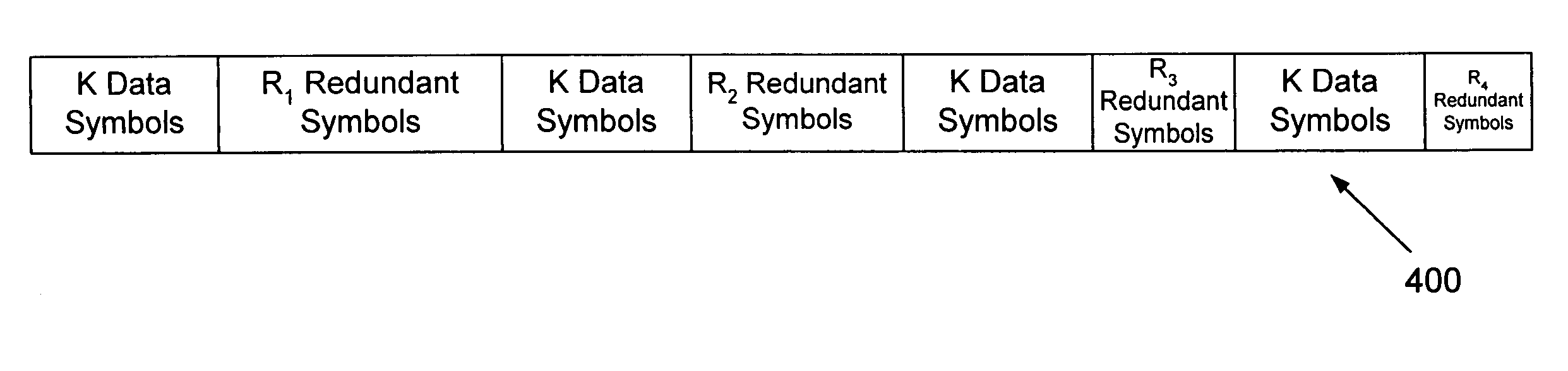
System and method for block error correction in packet-based digital communications
InactiveUS6965636B1Avoid mistakesReduce redundancyError prevention/detection by using return channelError detection/correctionTime scheduleSignal-to-noise ratio (imaging)
A system and method for efficiently correcting block errors in packet-based digital communications are provided whereby the ratio of redundant symbols / message symbols over the length of a data packet decreases in order to more efficiently use available bandwidth. The reduction of this ratio, and subsequently the change in a corresponding framing schedule, may be determined through negotiations between the transmitting device and the receiving devices. Each receiving device calculates a redundancy requirement based on signal-to-noise ratio samples. This requirement is returned to the transmitting device in the form of a schedule request. The transmitting device determines if a new framing schedule is needed based on the schedule request, and communicates this new framing schedule to the receiving device. Once the receiving device acknowledges receipt of the new schedule, the transmitting device switches to the new framing schedule for future data packet transmissions.
Owner:ARRIS SOLUTIONS
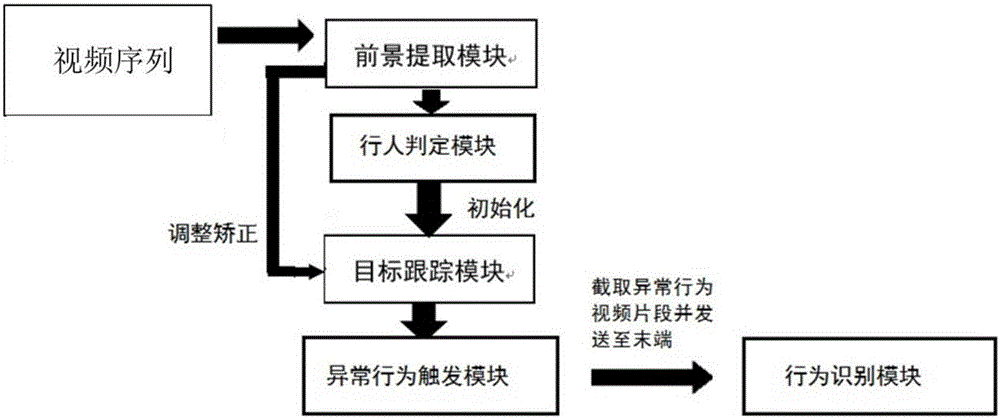
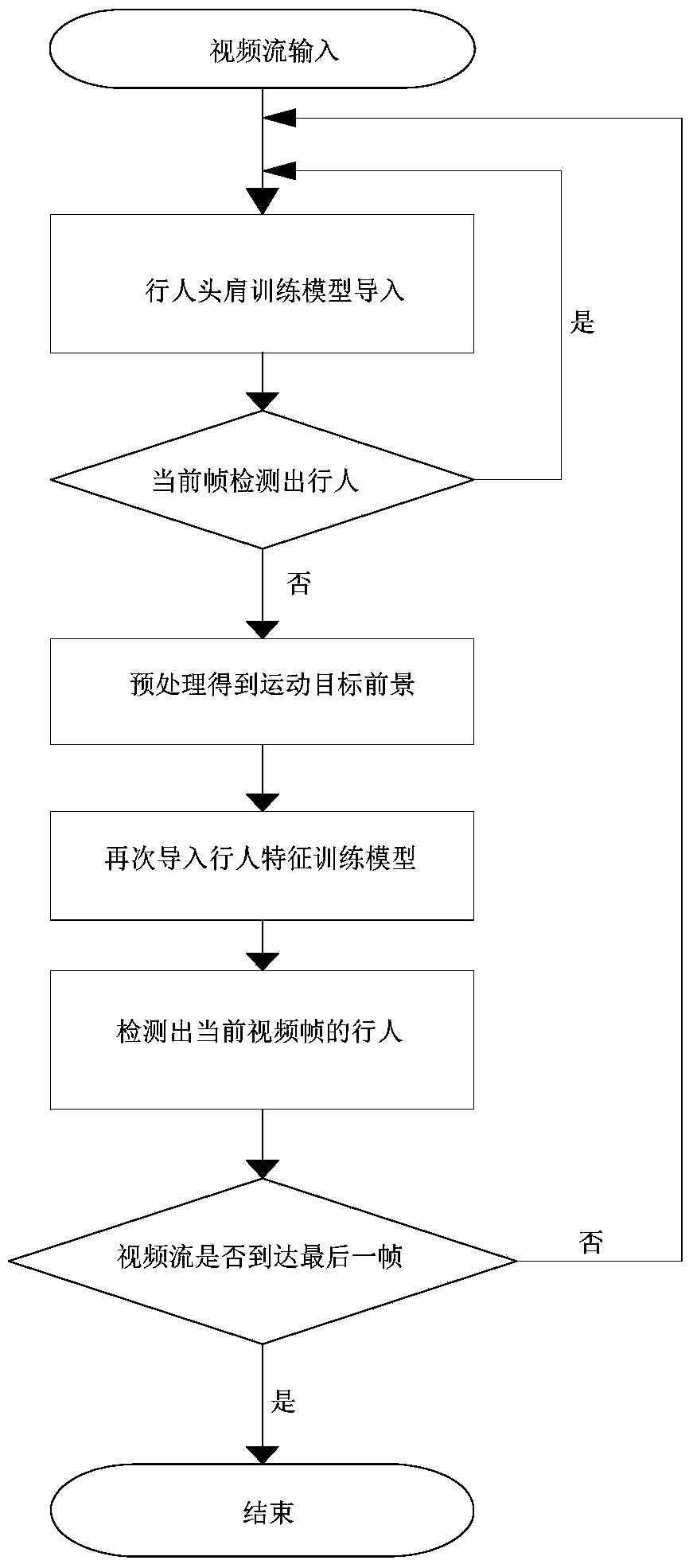
Method for identifying abnormal motion in video and system thereof
InactiveCN106571014AEliminate the effects ofImprove accuracyCharacter and pattern recognitionAlarmsPattern recognitionVideo sequence
The invention discloses a method for identifying abnormal motion in a video. The method comprises the steps that an area of which the pixels have certain change is extracted from a video sequence through a foreground extraction module; a movement target detected by the foreground extraction module is judged through a pedestrian judgment module, and a rectangular box judged to be a pedestrian is kept and transmitted to a target tracking module; each identified target in the scene is continuously tracked in a multi-target way through the target tracking module; the posture of each target tracked by the target tracking module within each frame of time is judged through an abnormal behavior trigger module and behavior analysis is performed on the abnormal behavior; and the abnormal behavior is processed and computed into a video segment through a behavior identification module, and the abnormal behavior is alarmed and the behavior type of the abnormal behavior is identified. The invention also discloses a system for identifying the abnormal motion in the video. The problem that abnormal behavior (falling down) detection of massive video data cannot be performed in real time can be solved and the detection accuracy can be greatly enhanced.
Owner:SHANGHAI VSI INTELLIGENT TECH
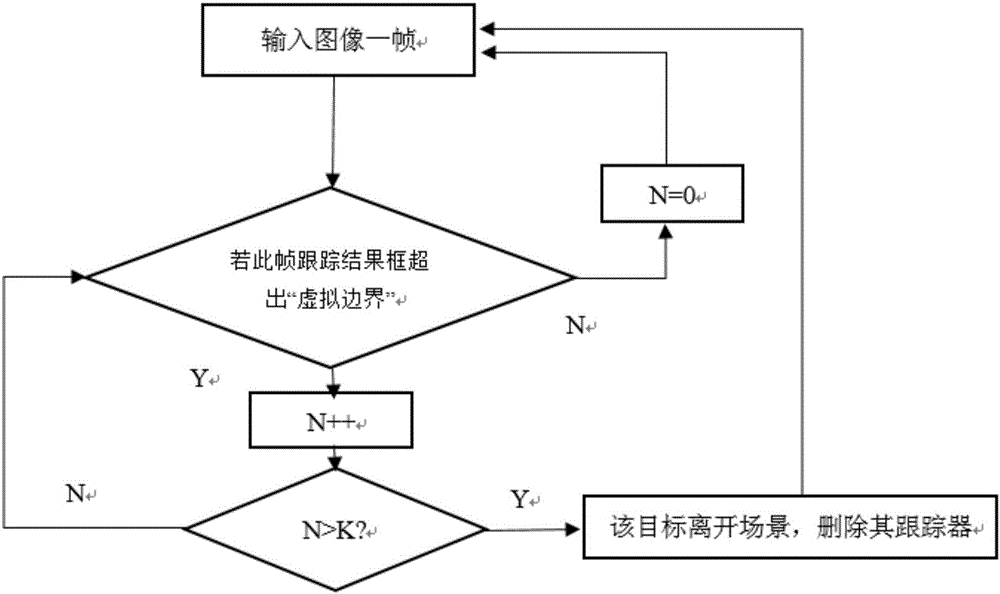
Multi-target tracking system based on deep learning and implementation method
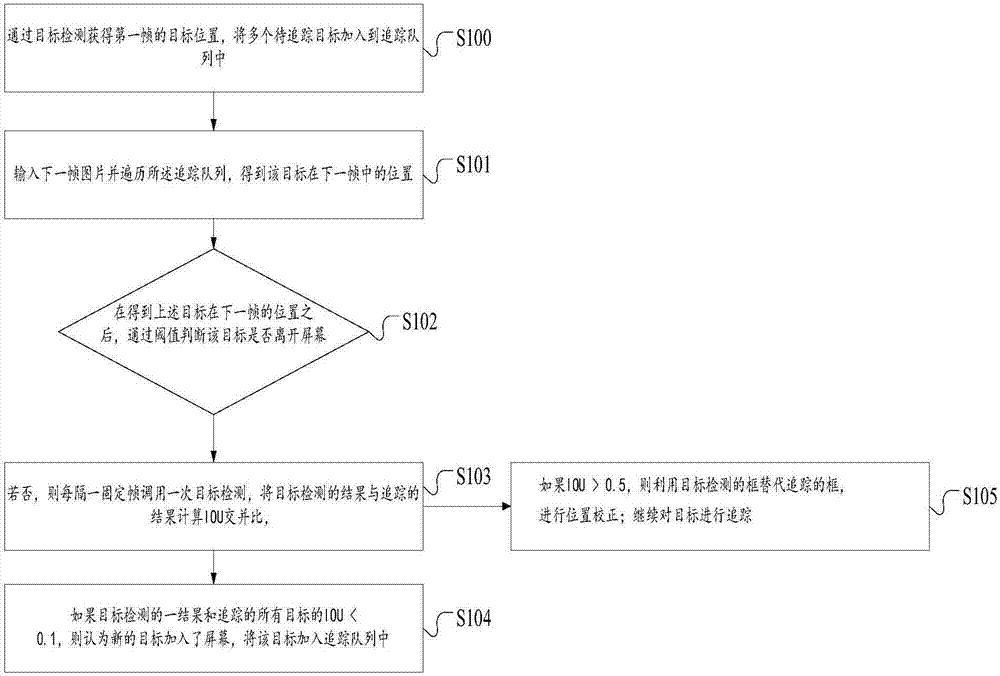
InactiveCN106875425AReduce redundancyHigh speedImage enhancementImage analysisFixed frameMulti target tracking
The invention relates to a multi-target tracking system based on deep learning and an implementation method. The method comprises the following steps: getting the target position of a first frame through target detection, and adding multiple to-be-tracked targets to a tracking queue; inputting a next frame of image and traversing the tracking queue to get the position of the target in the next frame; after getting the position of the target in the next frame, judging whether the target is off the screen based on thresholds; if the target is not off the screen, invoking target detection every other fixed frame, and calculating the IOU (intersection over union) of the target detection result and the tracking result; if IOU<0.1, judging that a new target is added to the screen, and adding the target to the tracking queue; if IOU>0.5, replacing the tracking box with the target detection box to correct the position; and continuing target tracking. By carefully designing the network structure and improving the training method, under the condition of high tracking precision, the tracking speed is increased significantly, network redundancy is reduced, and the size of the model is reduced.
Owner:北京飞搜科技有限公司
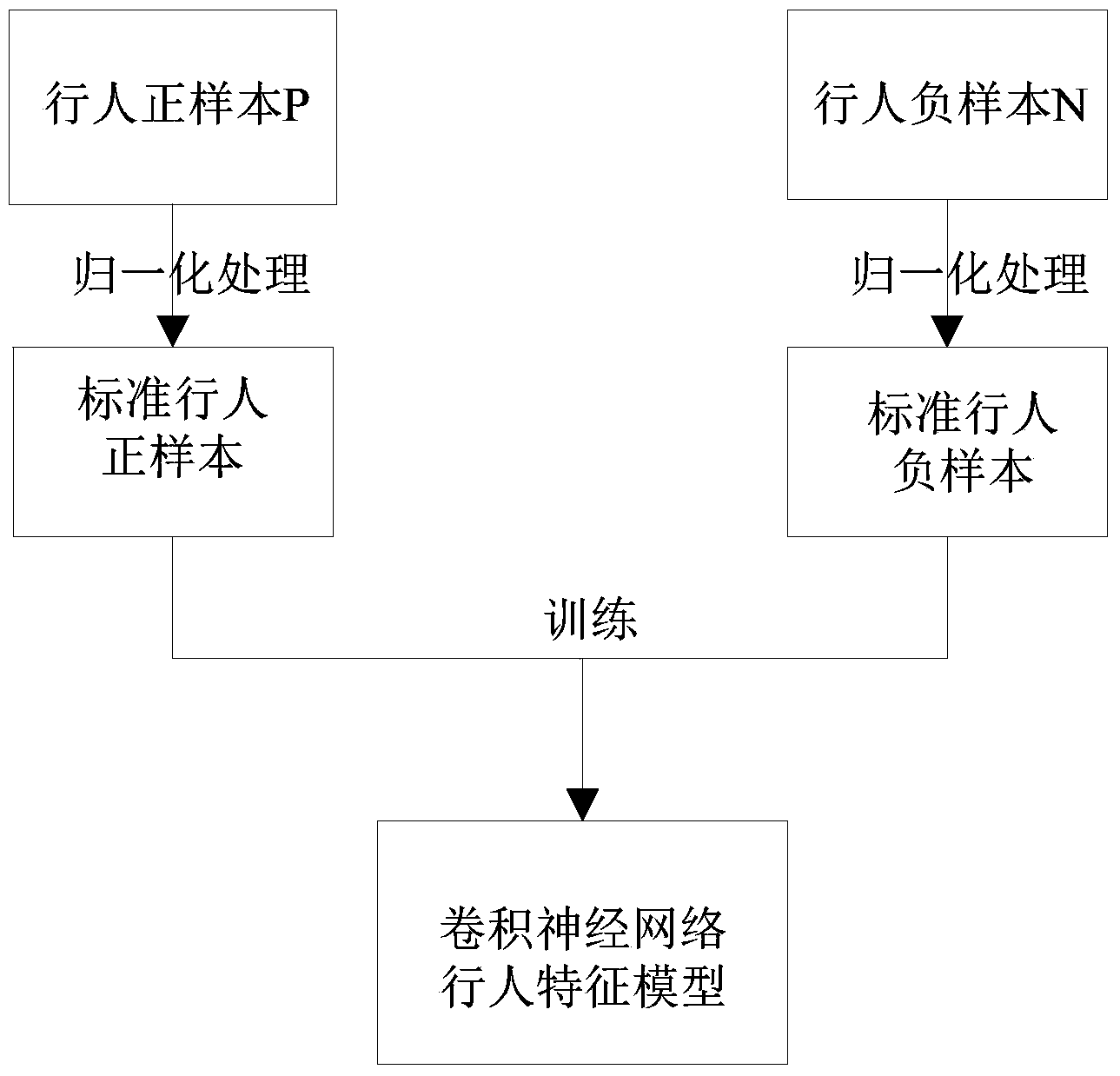
Pedestrian detection method
InactiveCN104166861AGuaranteed accuracyReduce redundancyCharacter and pattern recognitionPositive sampleData file
Provided is a pedestrian detection method. The pedestrian detection method comprises the following steps that a pedestrian positive sample set and a pedestrian negative sample set needed for training a convolutional neural network are prepared; the sample sets are preprocessed and normalized to conform to a unified standard, and a data file is generated; the structure of the convolutional neural network is designed, training is carried out, and a weight connection matrix is obtained during convergence of the network; self-adaptive background modeling is carried out on videos, information of moving objects in each frame is obtained, coarse selection is carried out on detected moving object regions at first, the regions with height to width ratios unsatisfying requirements are excluded, and candidate regions are generated; each candidate region is input into the convolutional neural network, and whether pedestrians exist is judged.
Owner:成都六活科技有限责任公司
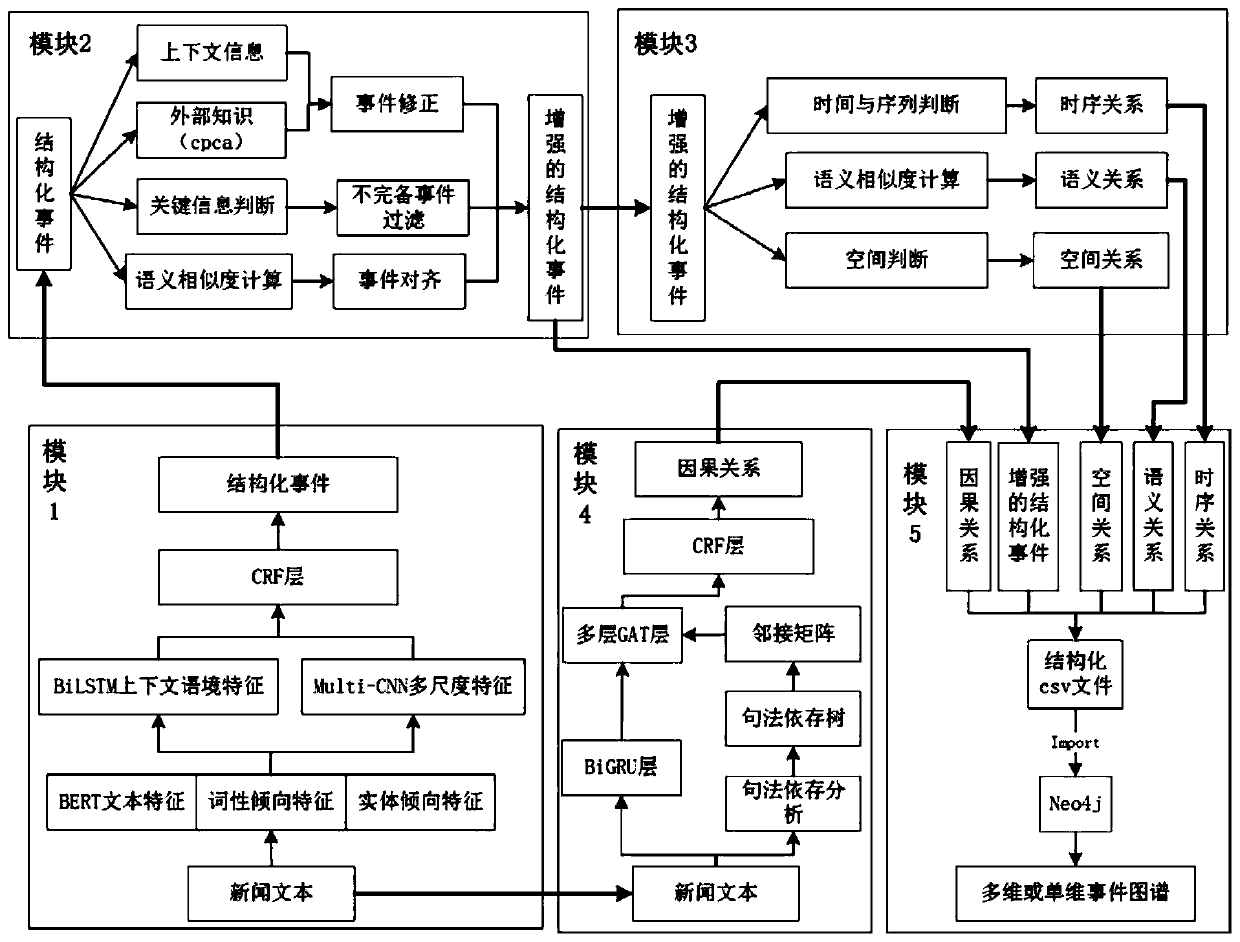
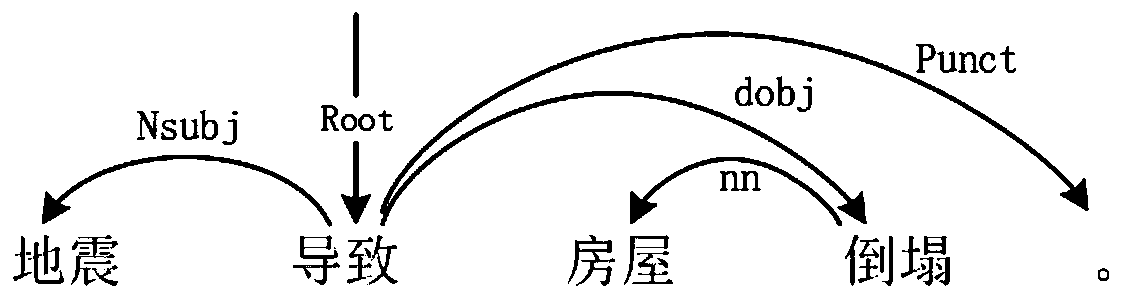
Event atlas construction system and method based on multi-dimensional feature fusion and dependency syntax
ActiveCN111581396AOvercoming the defects of the impact of the buildImprove the extraction effectSemantic analysisNeural architecturesEvent graphEngineering
The invention discloses an event atlas construction system and method based on multi-dimensional feature fusion and dependency syntax. The event graph construction method based on multi-dimensional feature fusion and dependency syntax is realized through joint learning of event extraction, event correction and alignment based on multi-dimensional feature fusion, relationship extraction based on enhanced structured events, causal relationship extraction based on dependency syntax and graph attention network and an event graph generation module. According to the event graph construction method and device, the event graph is constructed through the quintuple information of the enhanced structured events and the relations between the events in four dimensions, and the defects that in the priorart, event representation is simple and depends on an NLP tool, the event relation is single, and the influence of the relations between the events on event graph construction is not considered at the same time are overcome. According to the event atlas construction method provided by the invention, the relationships among the events in four dimensions can be randomly combined according to different downstream tasks, and the structural characteristics of the event atlas are learned to be associated with potential knowledge, so that downstream application is assisted.
Owner:XI AN JIAOTONG UNIV
Data disaster tolerance system suitable for WAN
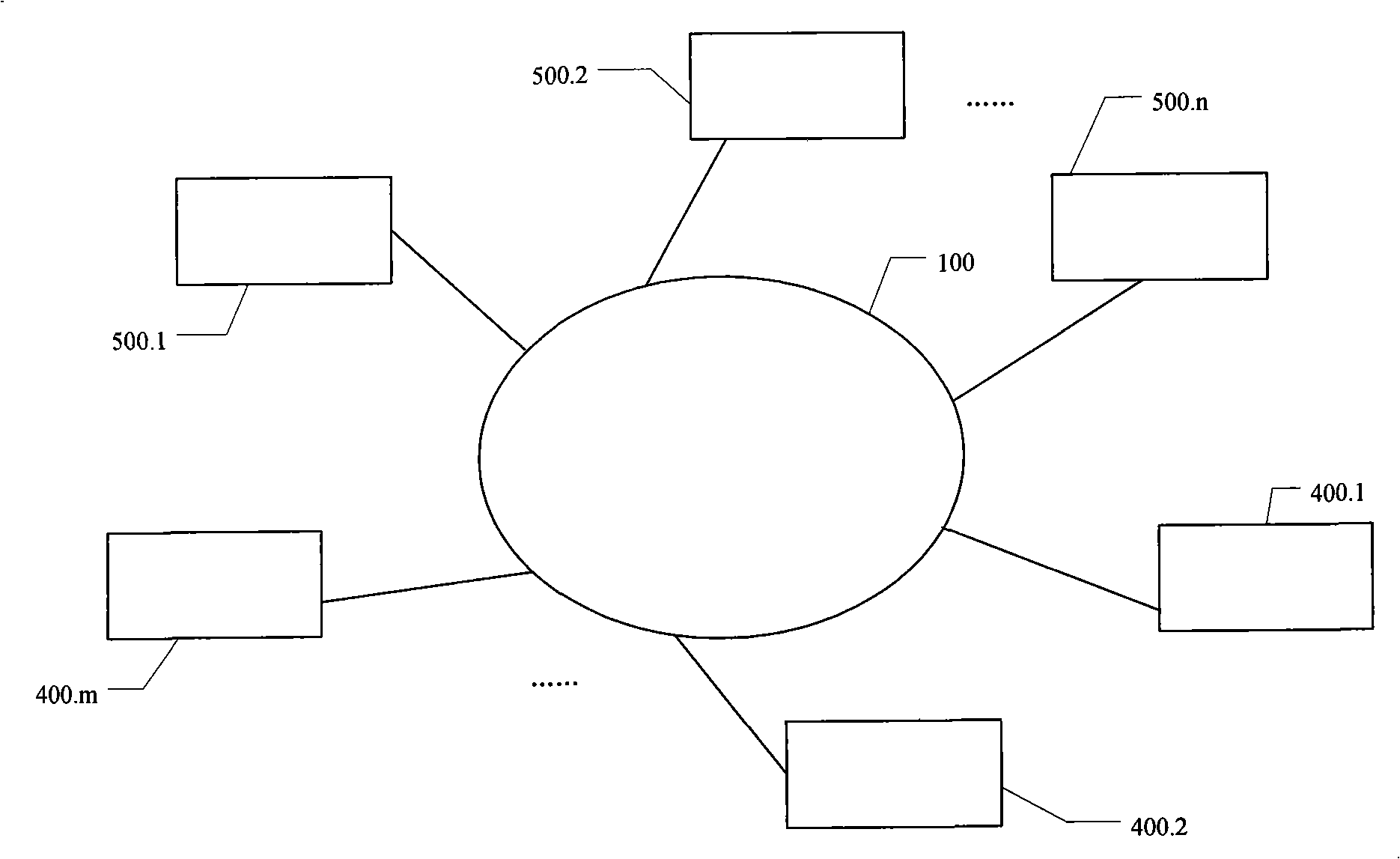
InactiveCN101316274ATo achieve the purpose of disaster recoveryReduce data volumeTransmissionRedundant operation error correctionComputer moduleGeolocation
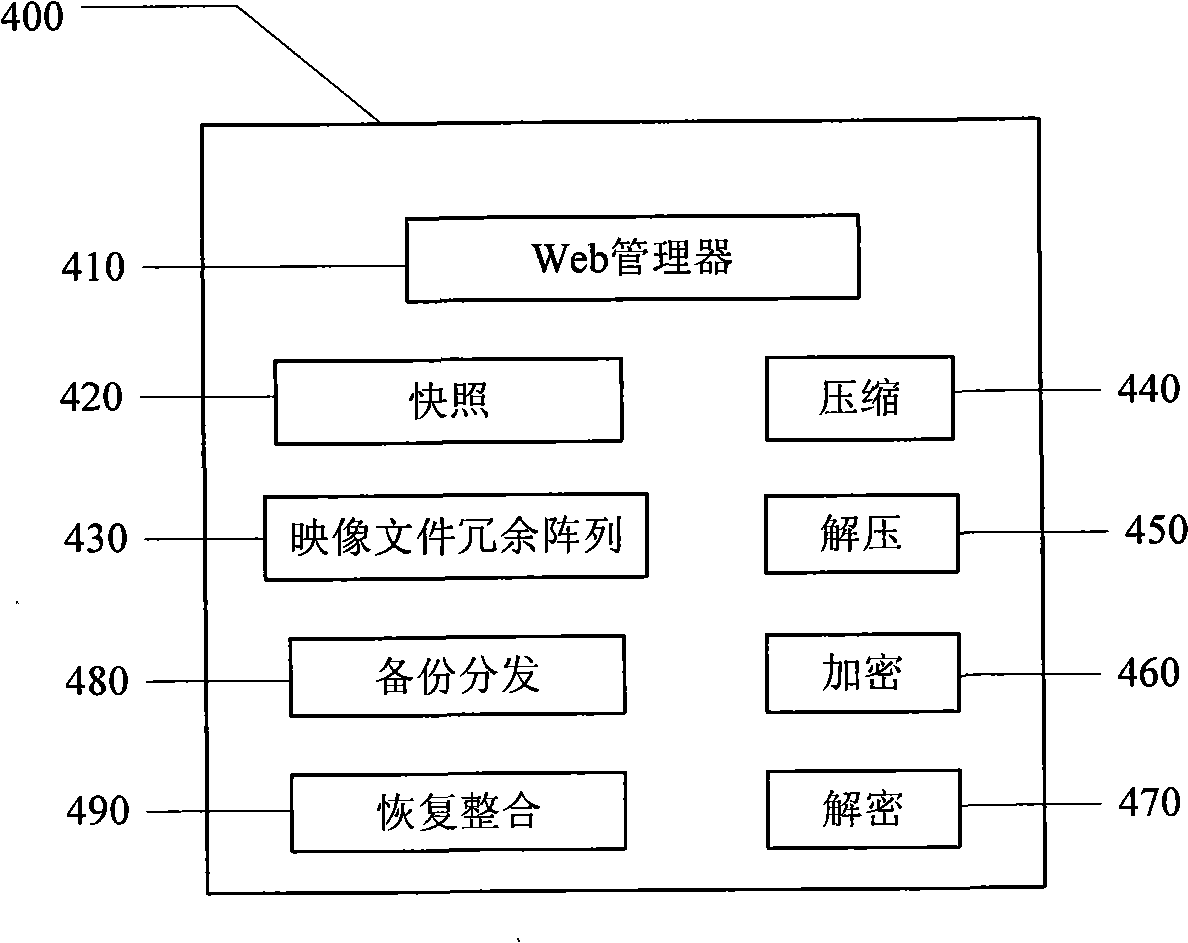
The invention discloses a data disaster tolerant system which is applicable to a wide area network, pertains to the technical filed of computer information storage and solves the problem that the current data disaster tolerant system does not take the effect of data transmission links and the need of lots of redundant data storage space in the wide area network into consideration. The system of the invention comprises M local storage clients connected to the wide area network and N storage servers in different geographical positions; every local storage client consists of a web manager, a snap module, a mapping file redundant array module, a compression module, a decompression module, an encryption module, a decryption module, a backup distribution module and a recovery and integration module; the storage server consists of a failure detection module, a distributed arbitration module, a recovery module, a distributed copy service module, a backup and recovery service module. The system of the invention combines disaster tolerant coding and copying, reduces the amount of redundant data and effectively utilizes storage space. Meanwhile, data to be transmitted is compressed and encrypted, thus improving the safety and reliability of data on network transmission, effectively utilizing network bandwidth and reaching excellent disaster tolerant effect.
Owner:HUAZHONG UNIV OF SCI & TECH
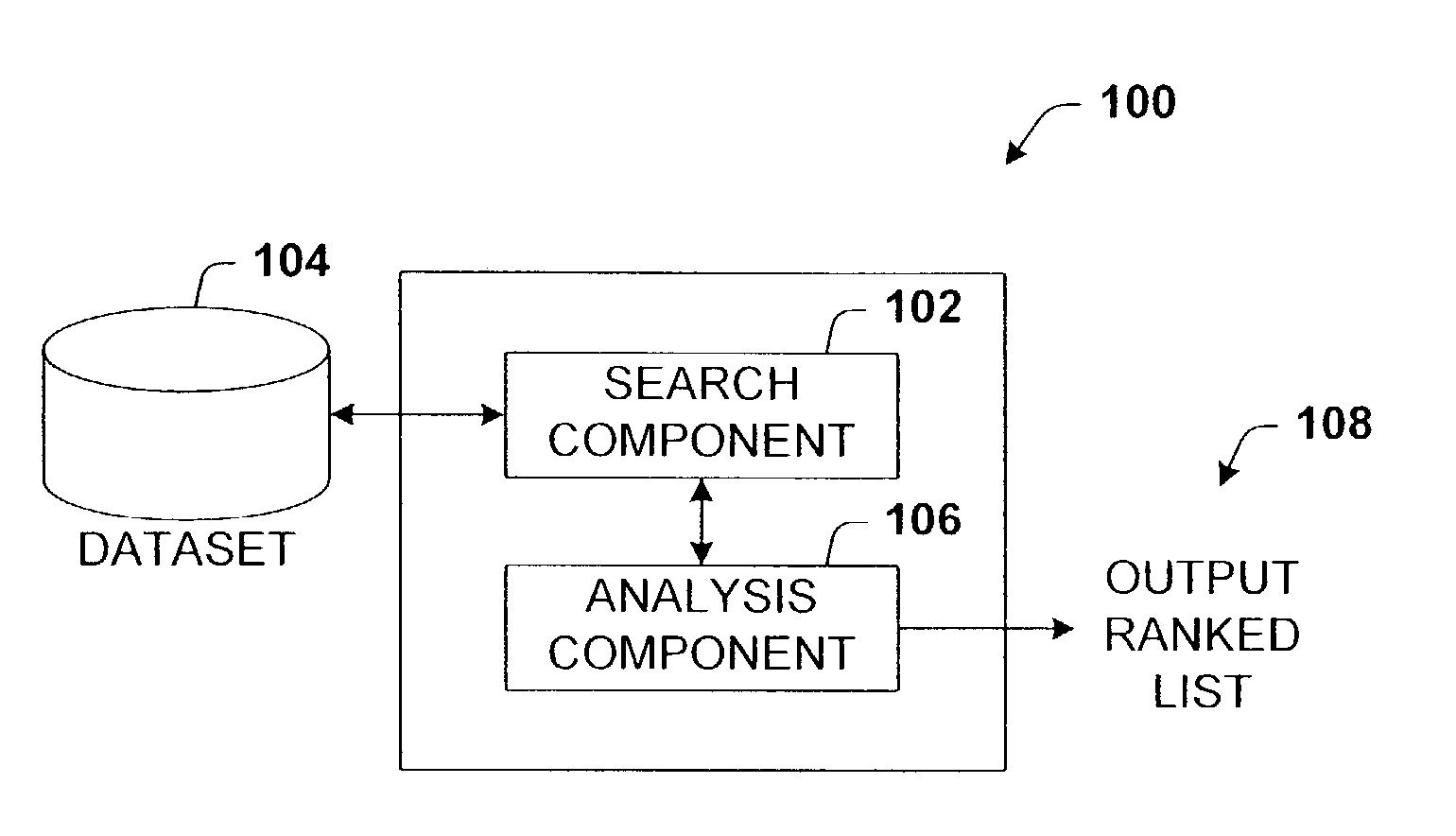
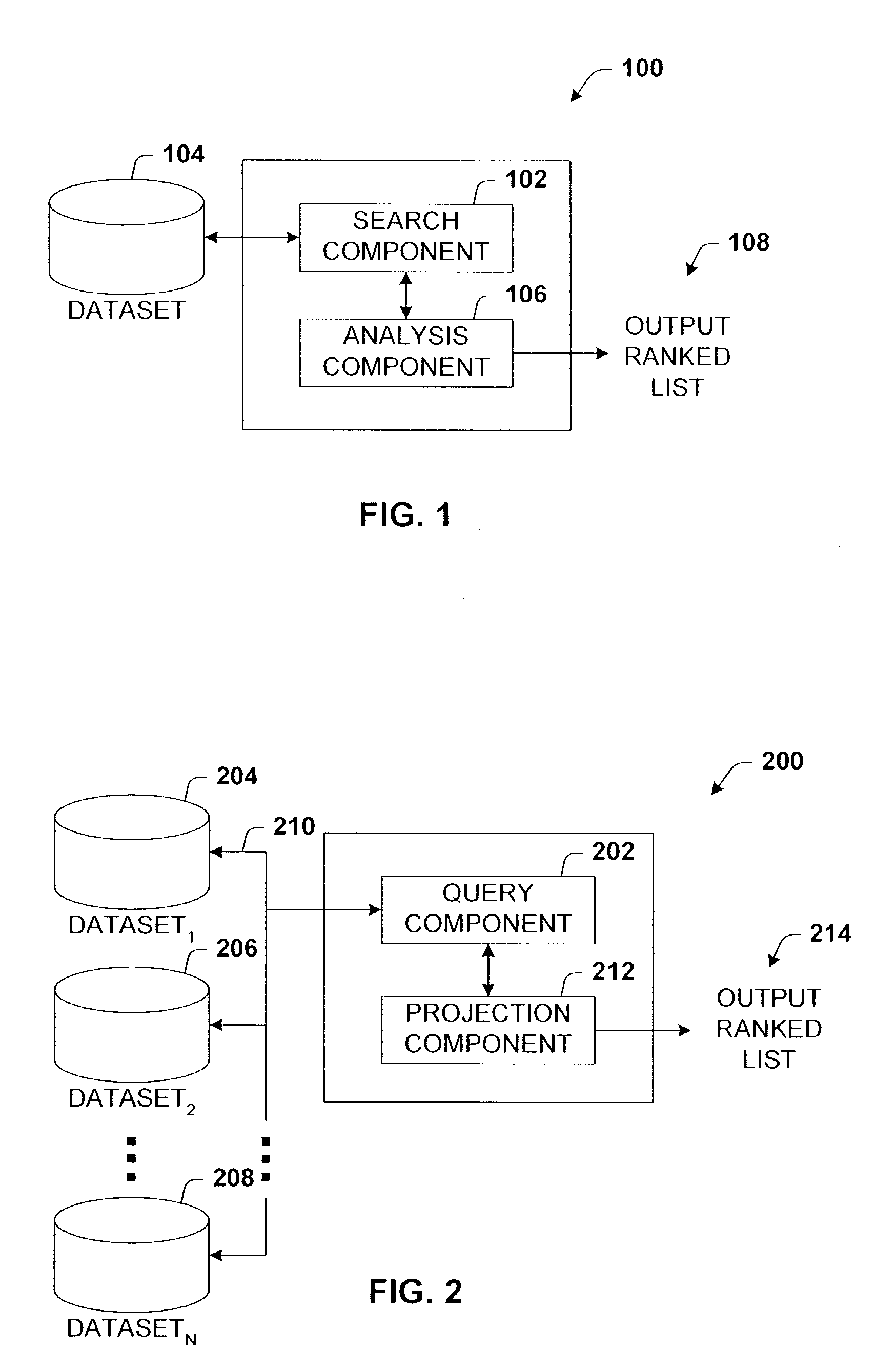
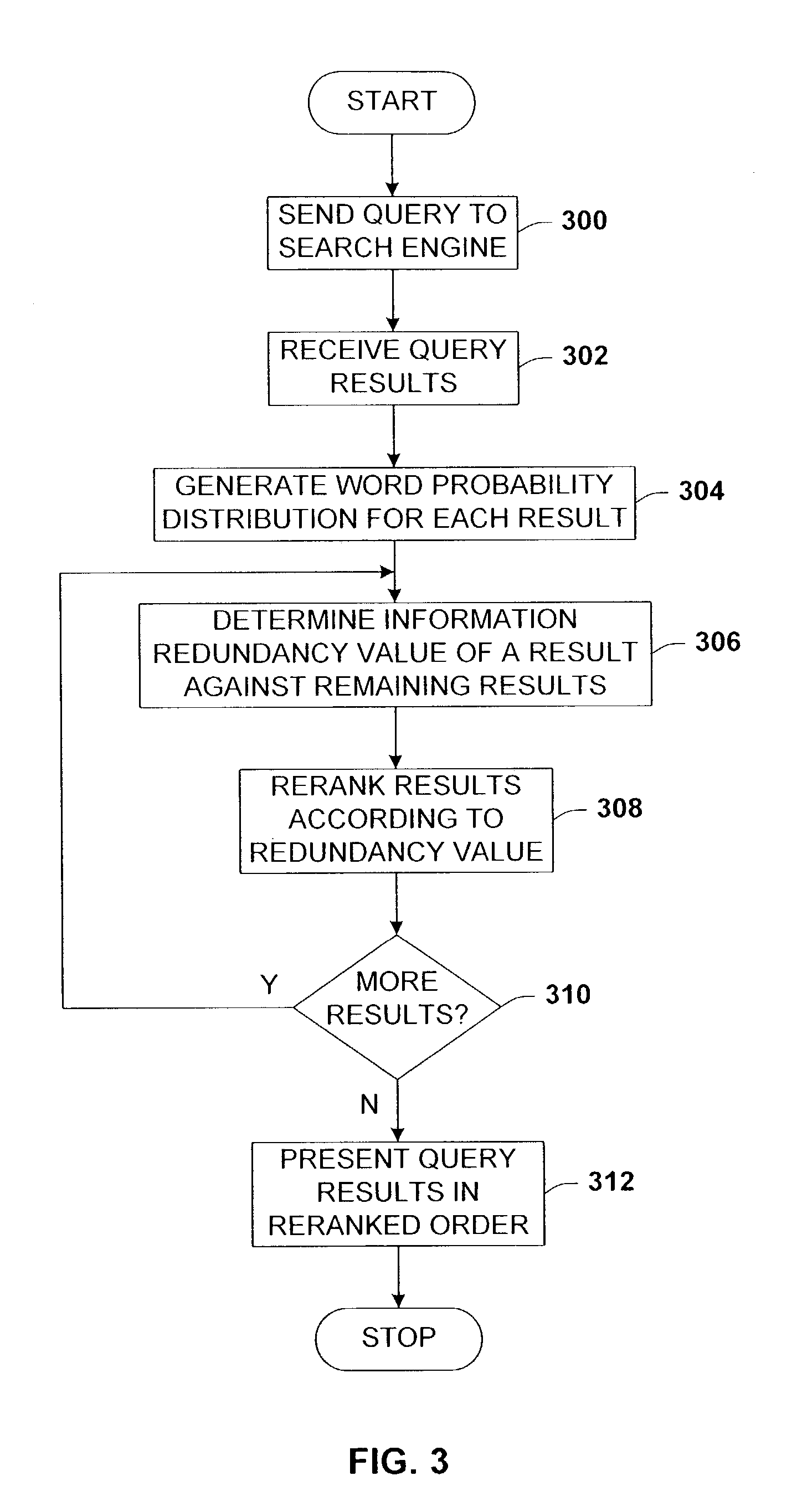
Utilizing information redundancy to improve text searches
InactiveUS7051014B2Reduce in quantityHigh information redundancyData processing applicationsDigital data information retrievalData sourceDocumentation
Architecture for improving text searches using information redundancy. A search component is coupled with an analysis component to rerank documents returned in a search according to a redundancy values. Each returned document is used to develop a corresponding word probability distribution that is further used to rerank the returned documents according to the associated redundancy values. In another aspect thereof, the query component is coupled with a projection component to project answer redundancy from one document search to another. This includes obtaining the benefit of considerable answer redundancy from a second data source by projecting the success of the search of the second data source against a first data source.
Owner:MICROSOFT TECH LICENSING LLC
Entropy coding method and decoding method based on text
InactiveCN1980395AReduce redundancyHigh compressibilityTelevision systemsDigital video signal modificationDecoding methodsNonzero coefficients
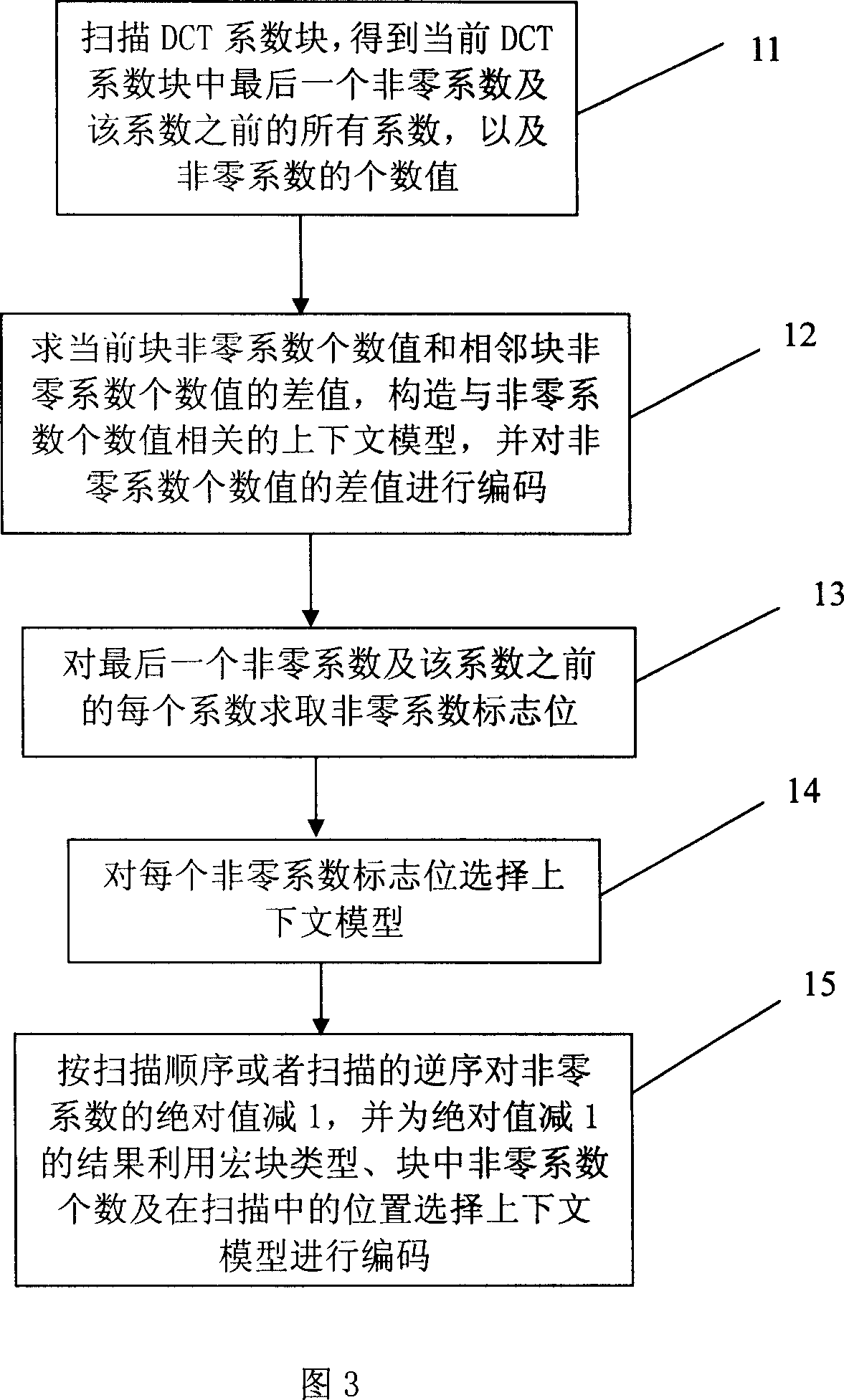
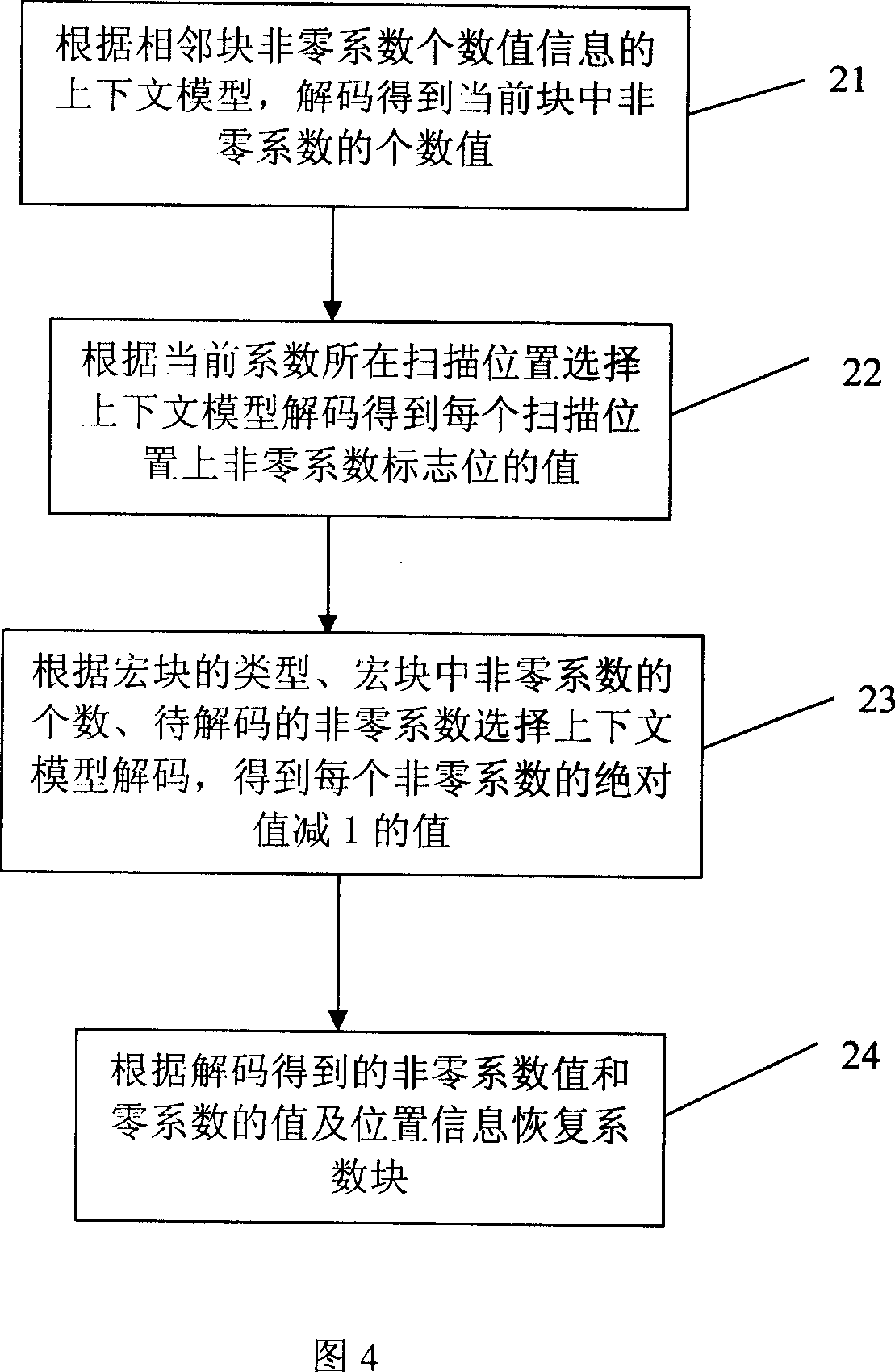
The method includes following steps: scanning DCT coefficient blocks according to sequence so as to obtain last one nonzero coefficient (NC) and the coefficient in front of the last one NC in coefficient block, and number value of NC; based on the number value of NC to calculate difference value between number value of NC in this block and number value of NC in adjacent block, and constructing context model for number value of NC; calculating flag bit of NC for last one NC and coefficients before the last one NC; selecting context model to encode flag bit of NC; subtracting 1 from absolute value of NC according to scanning sequence or scanning inverted sequence; and selecting context model to encode number value of NC, and its position in the scan etc; encoding sign bit. The invention also discloses corresponding decoding method.
Owner:联合信源数字音视频技术(北京)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com