System and method for automatically analyzing, detecting and classifying malicious program behavior
An automatic analysis and malicious program technology, applied in the field of automatic analysis of malicious program dynamic behavior, can solve the problems of difficulty in feature code extraction, difficult to deal with packing, behavior abstraction and unclear detection and classification methods, etc., to improve the detection rate and classification. The effect of accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be described in detail below in conjunction with specific embodiments.
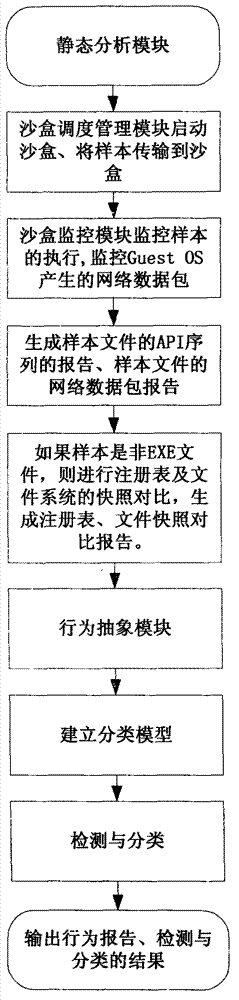
[0030] refer to figure 1 , step 1, the static analysis module first statically analyzes the structure of the executable sample file to obtain the compiler version of the sample, build time, multi-language information, section information of the PE file, import table of the PE file, whether the PE file is packed And packing type, etc., the static analysis module will obtain information related to malicious programs, combined with the dynamic analysis information of malicious programs obtained by the sandbox monitoring module, to provide richer data for the classification of the final integrated classification algorithm.
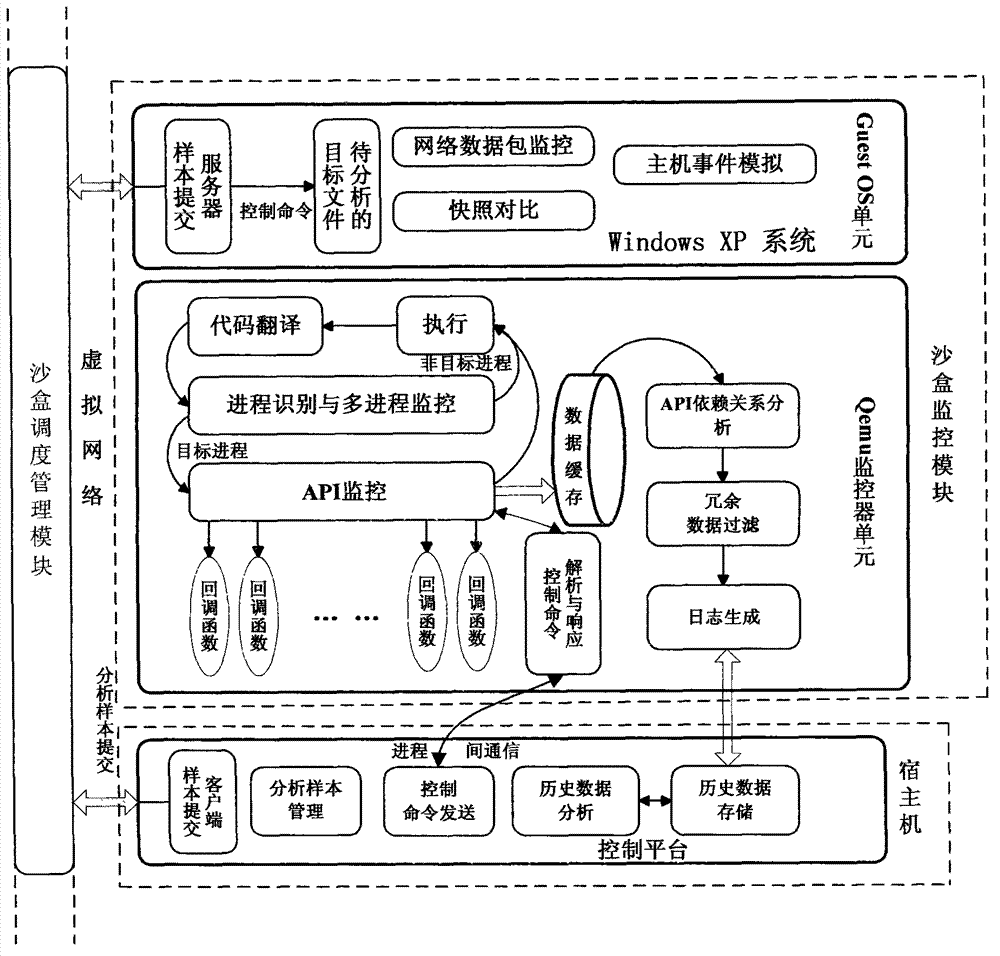
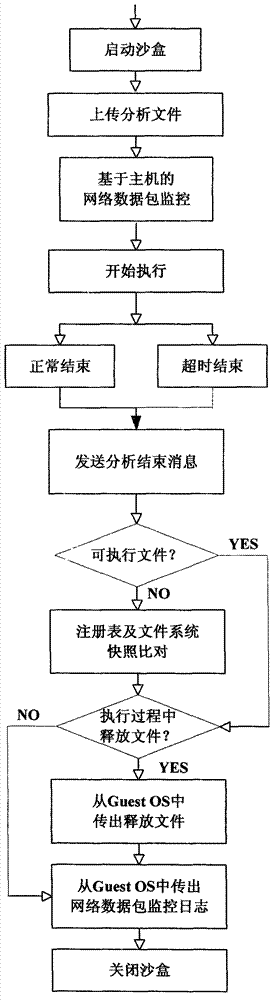
[0031] Step 2, after the static analysis is completed, the sample file will enter the dynamic analysis automation process. The dynamic analysis process of sample files will be automatically managed by the sandbox scheduling management module. The sandbo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com