Patents
Literature
1539 results about "Database access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
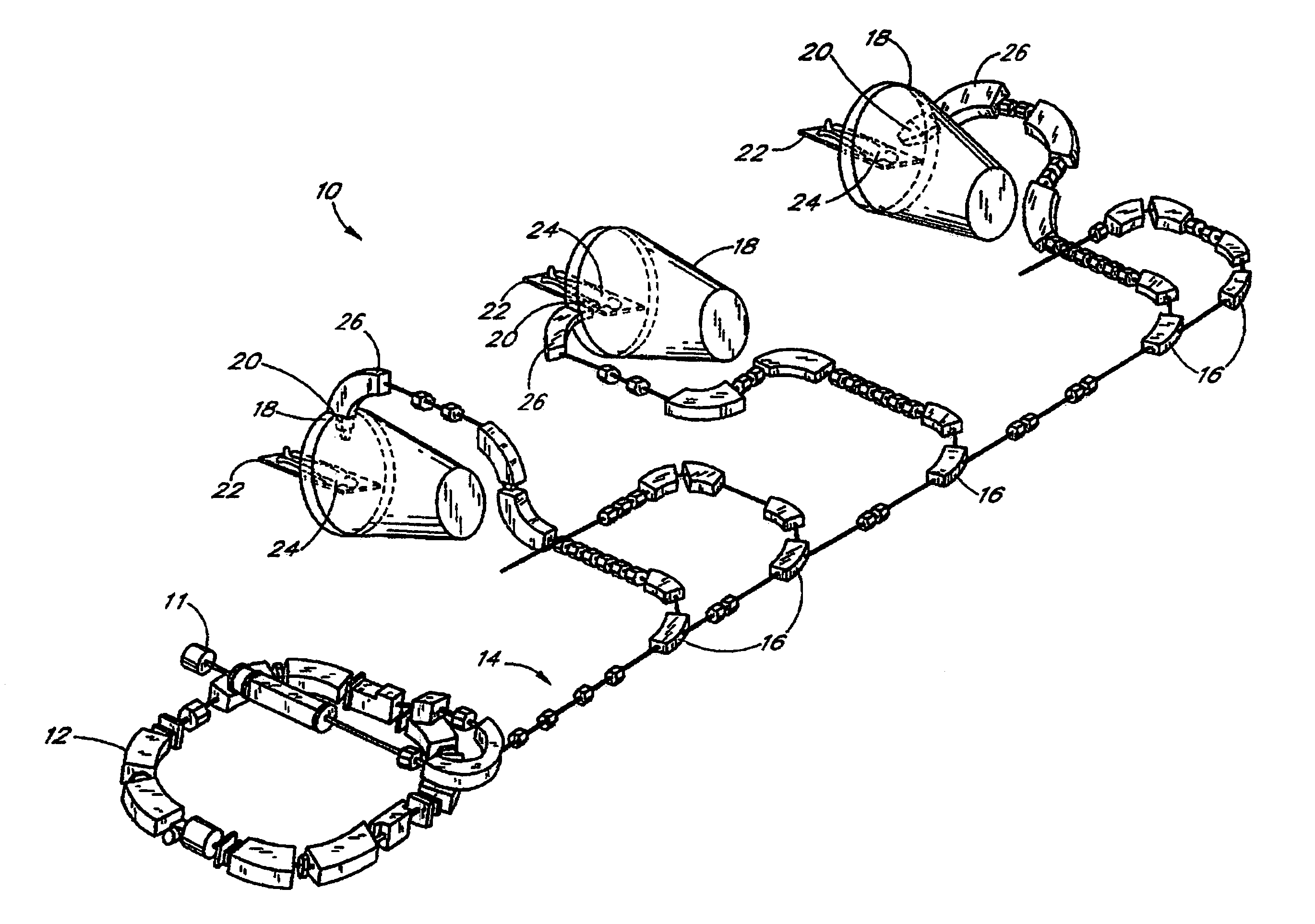
Database access system
ActiveUS7181438B1Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
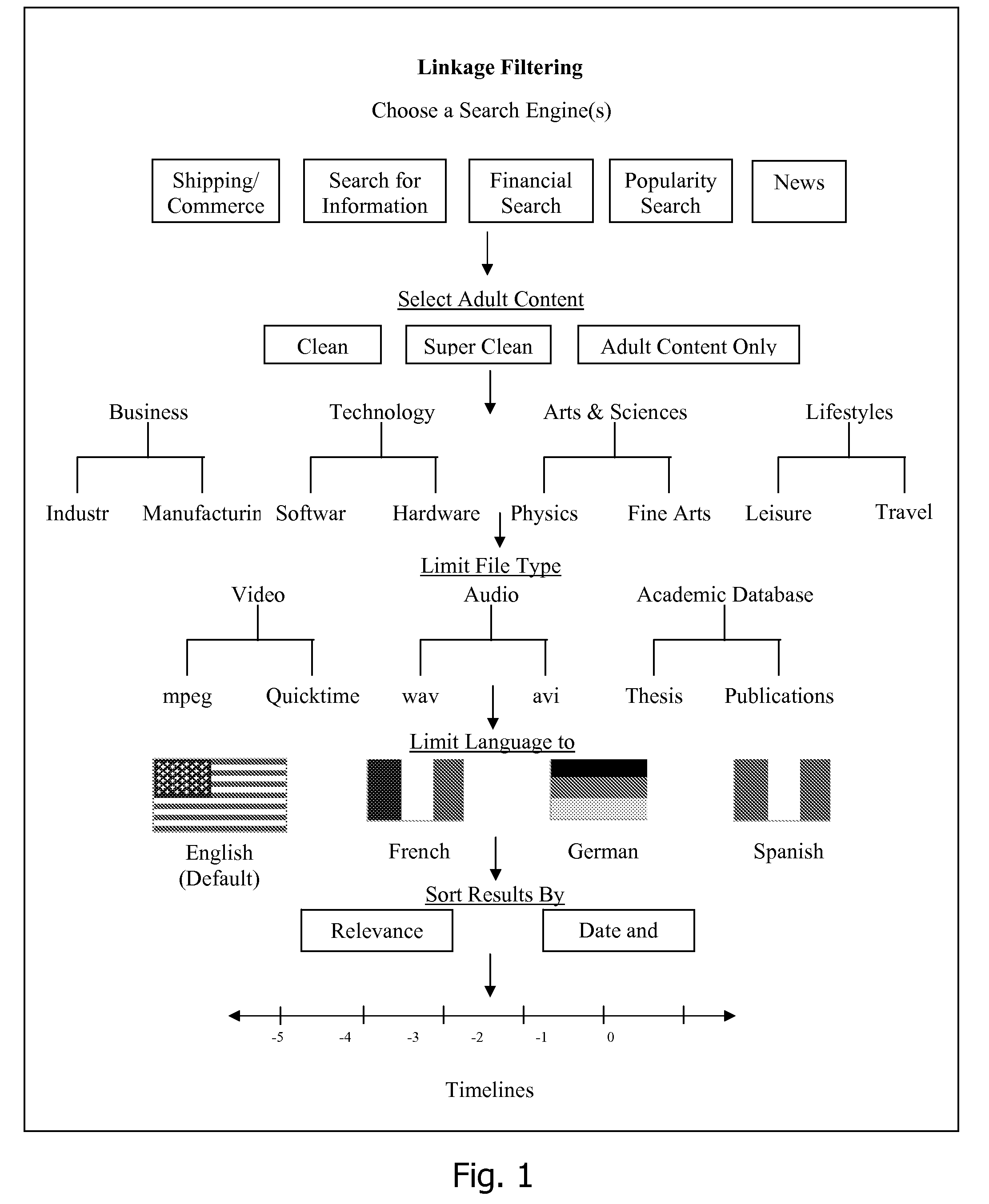
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
Database access system
InactiveUS20070156677A1Increased formationGood user interfaceDigital data information retrievalAdvertisementsPersonal detailsAnonymity
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
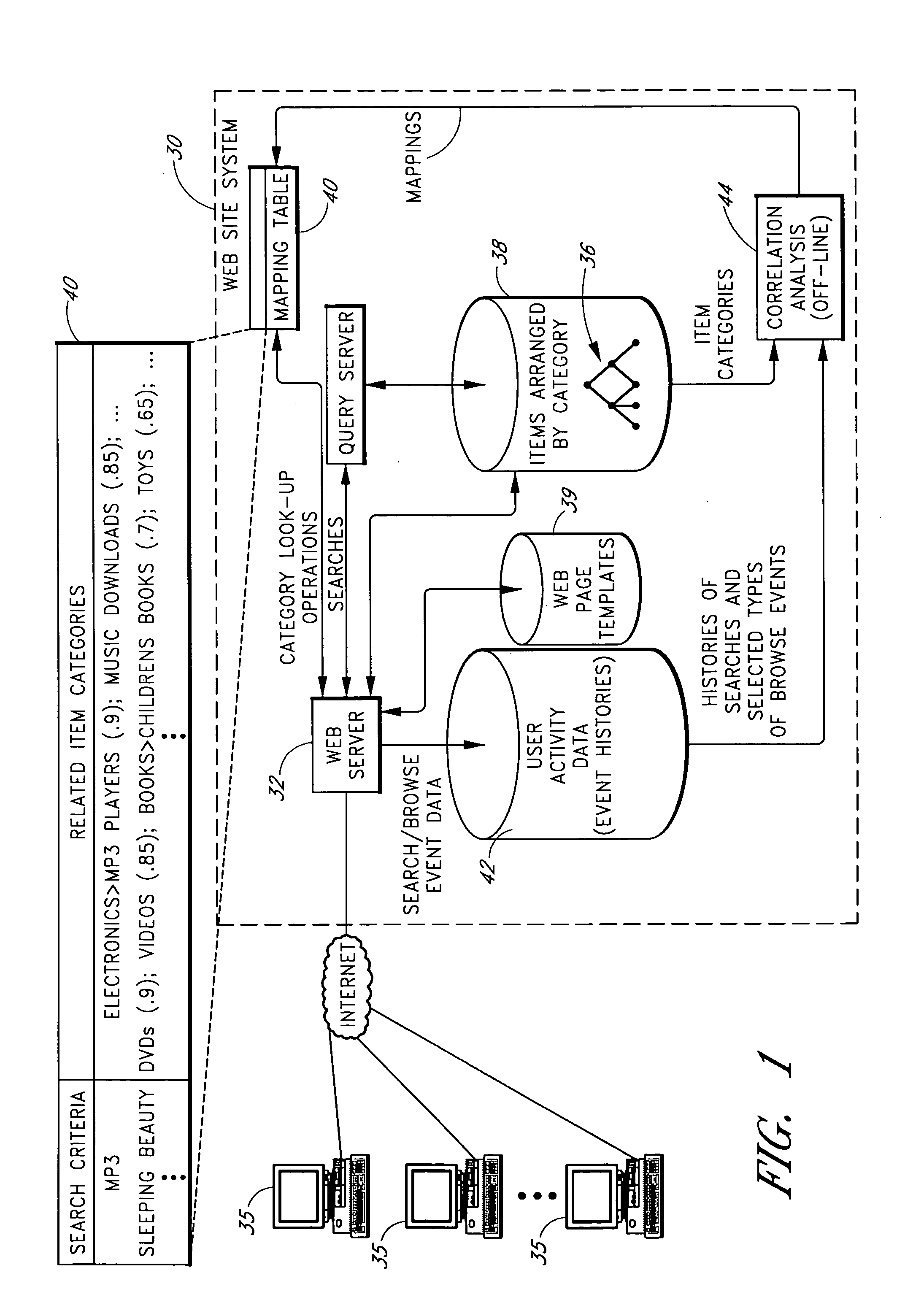
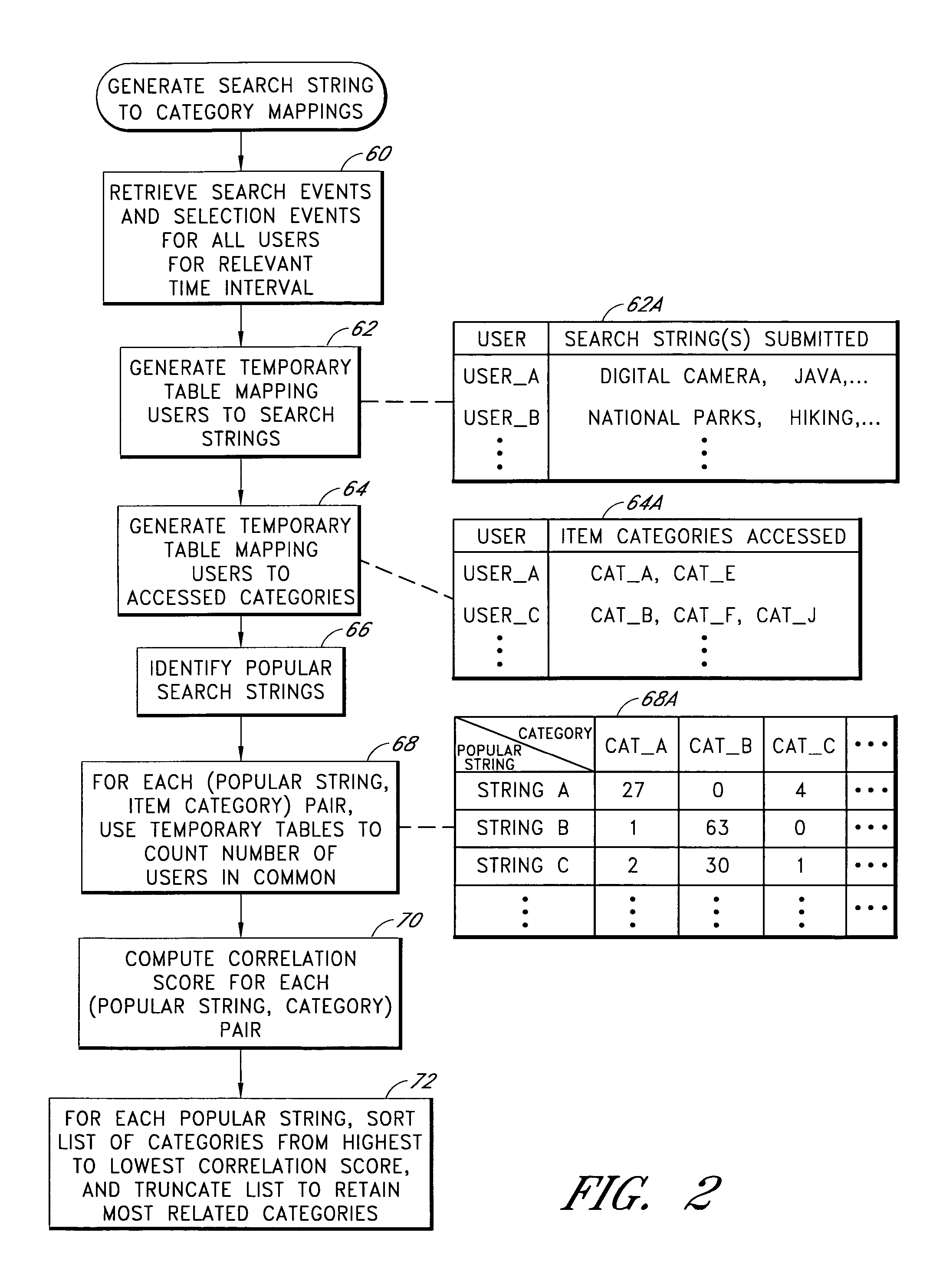
Automated detection of associations between search criteria and item categories based on collective analysis of user activity data
A web site or other database access system provides access to a database in which items are arranged within item categories, such as browse categories of a hierarchical browse tree. Actions of users of the system are monitored and recorded to generate user activity data reflective of searches, item selection actions, and possibly other types of actions. A correlation analysis component collectively analyses the user activity to automatically identify associations between specific search criteria, such as specific search strings, and specific item categories. The results of the analysis are stored in a mapping table that is used to suggest specific item categories on search results pages.
Owner:AMAZON TECH INC
Structure independent searching in disparate databases
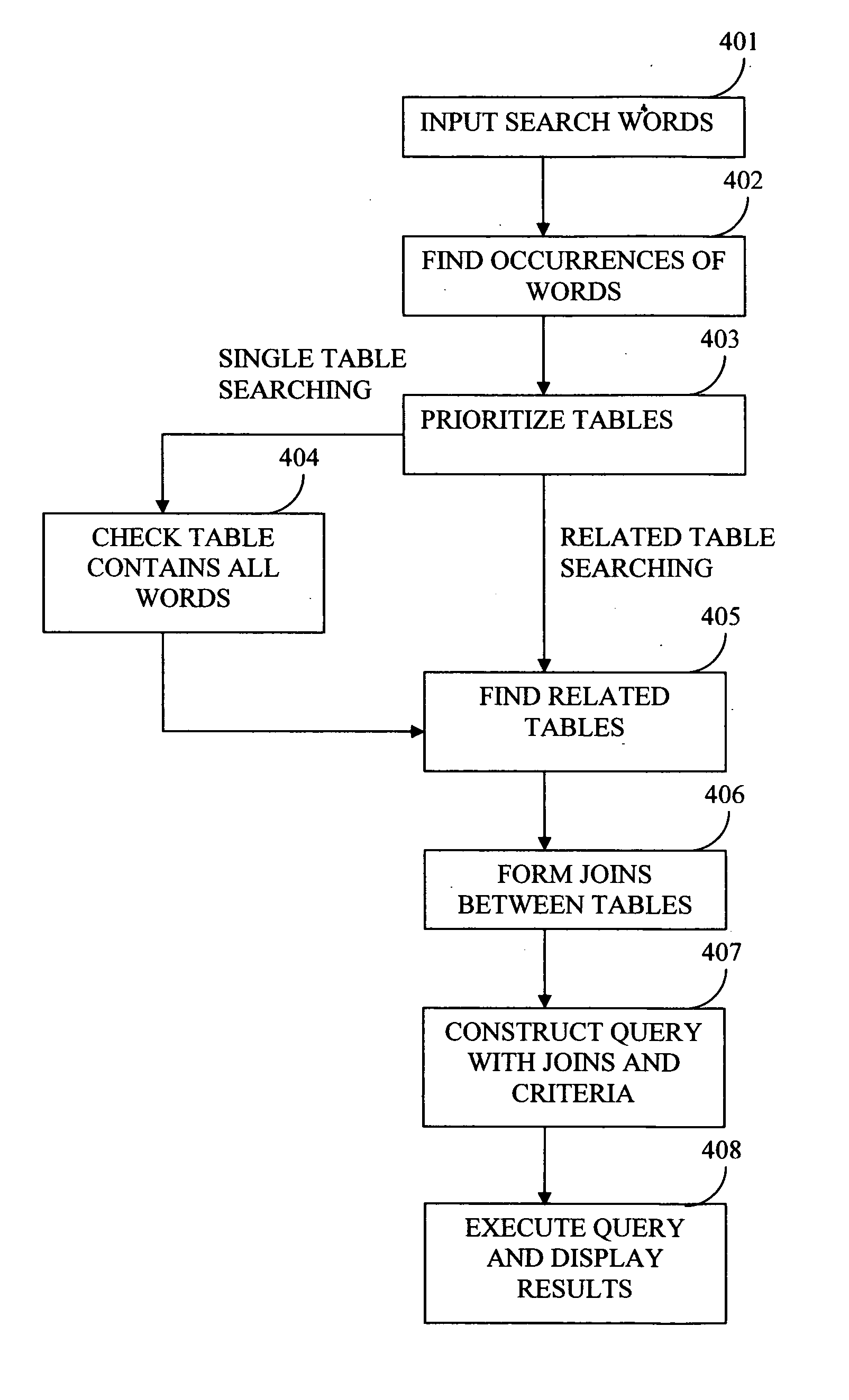
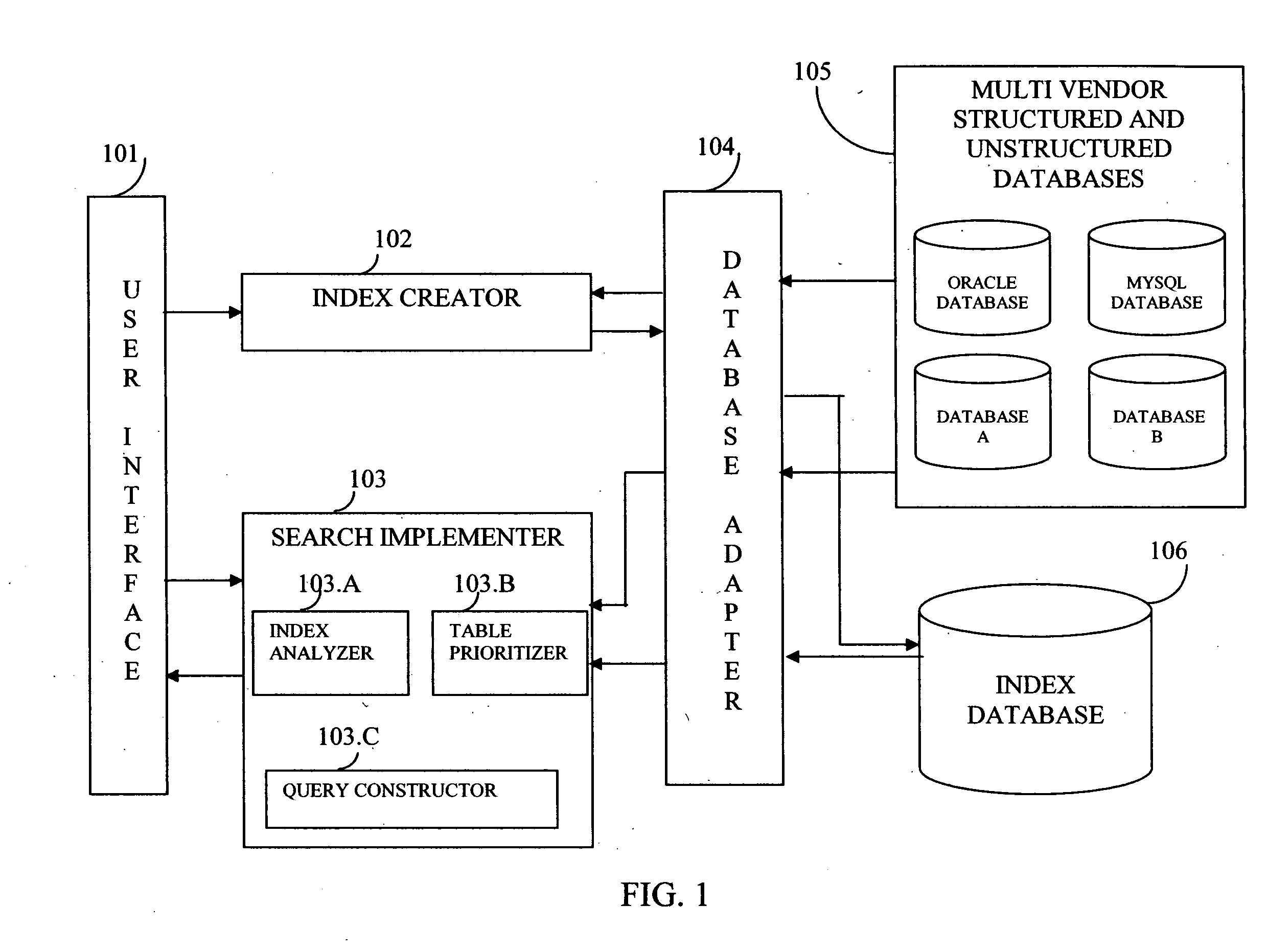
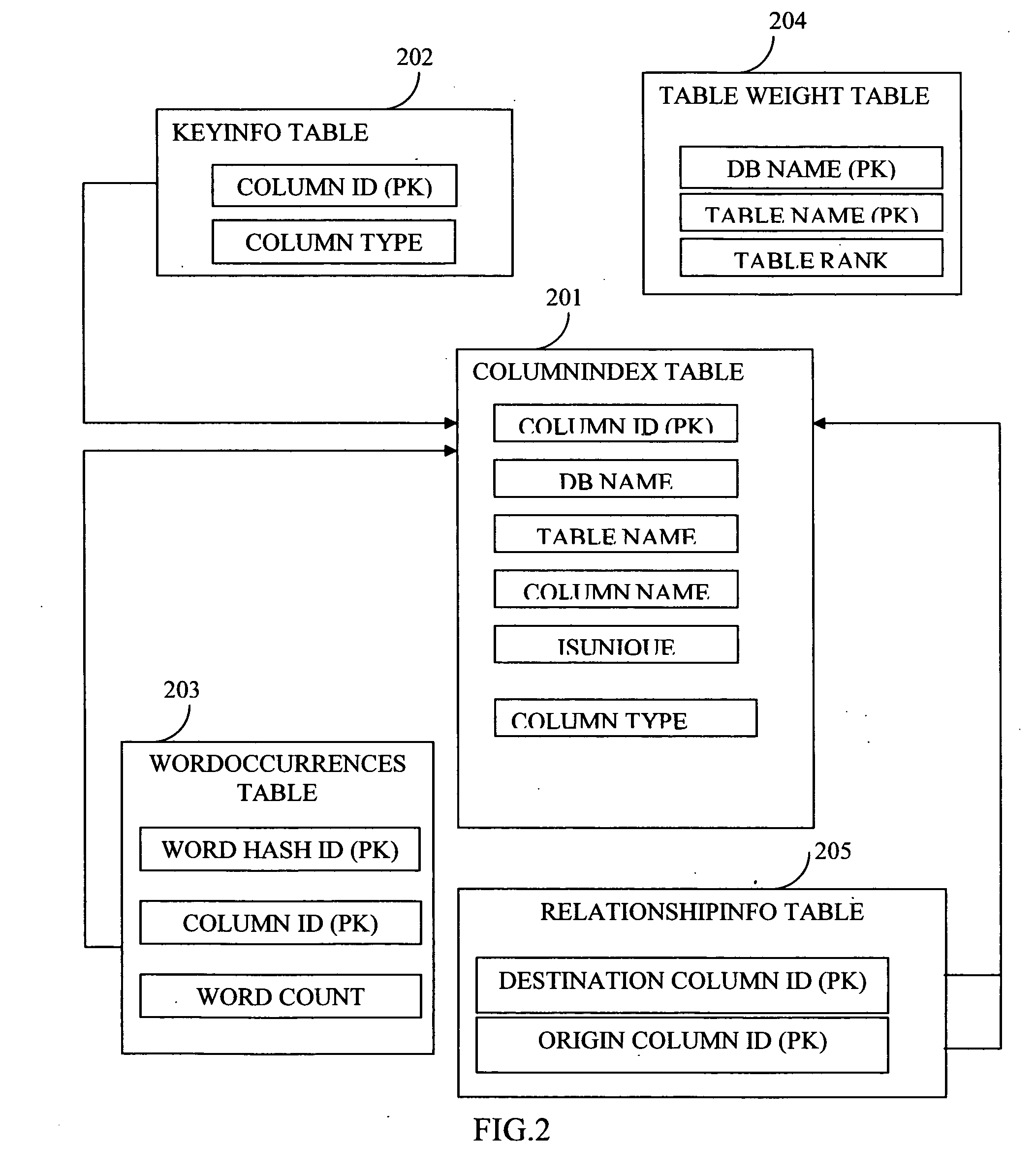
InactiveUS20060074881A1Resolve differencesDatabase management systemsOther databases indexingSearch wordsDatabase access
This invention allows keyword searches in both structured and unstructured databases, and across multiple databases of different vendors. An index database is created comprising word occurrences and table relationship information. In the case of unstructured databases with no predetermined schema, the relationship between different tables is derived through propagative n-level indexing and data is then populated in index tables. A database adapter enables indexing and searching across multi-vendor databases, which resolves discrepancies across different database access methodologies. Given a set of keyword inputs, the rows containing the search words and all the related rows are searched using word occurrences and relationship information.
Owner:ADVENTNET
Interactive virtual thematic environment
InactiveUS7373377B2Multiple digital computer combinationsImage data processing detailsTime informationInteractive software
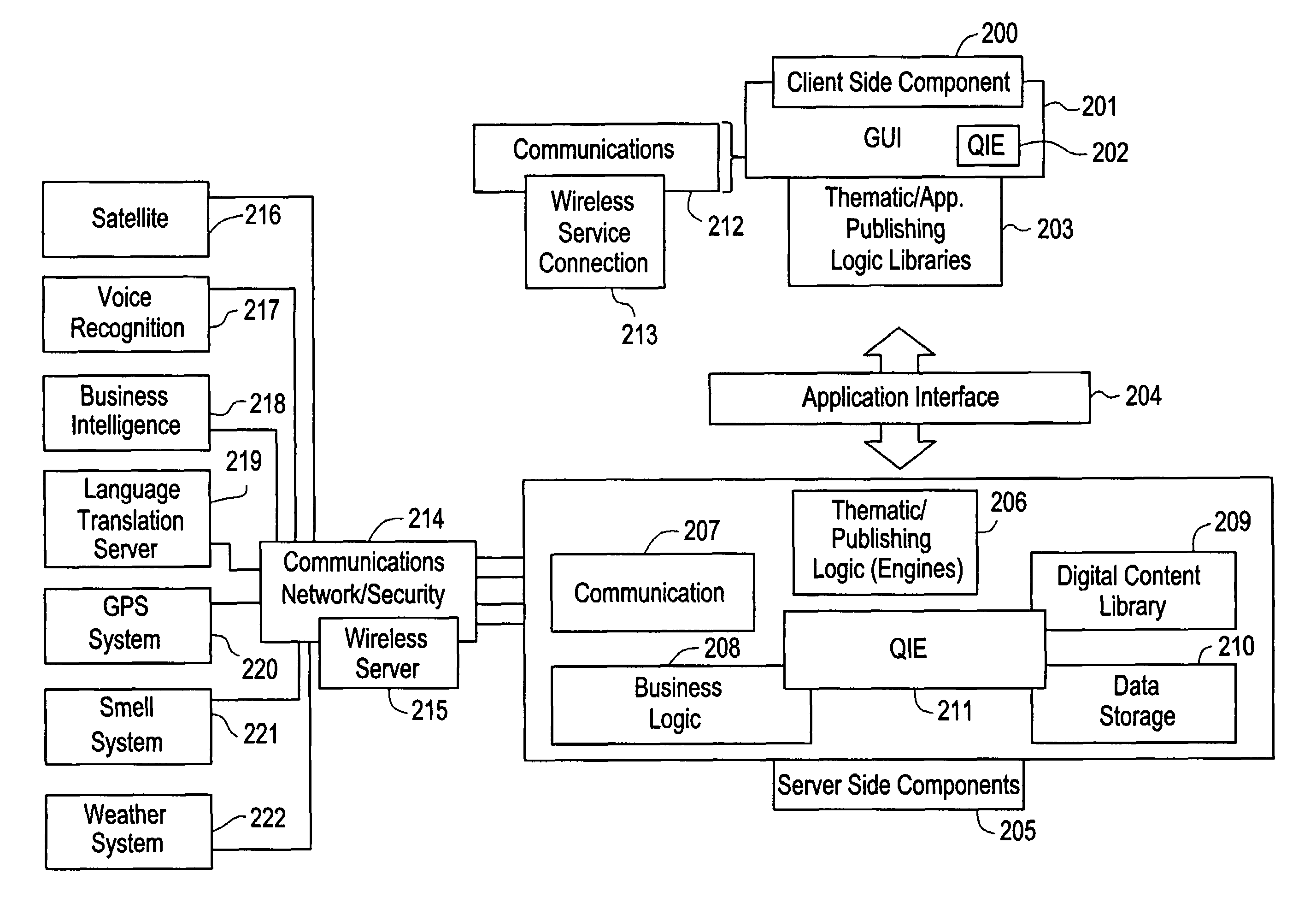
The present invention is directed to a method of integrating information, including real-time information, into a virtual thematic environment using a computer system, including accessing the stored information from a database or downloading the real-time information from a source external to the thematic environment; inserting the real-time information into the thematic environment; and displaying the information to a user within the thematic environment. In one embodiment, the computer system is connected to a holographic projection system such that the images from the thematic environment can be projected as holographic projections. The computer system includes an interactive software application platform having at least one thematic / publishing logic module which contains thematic environment rules; at least one digital content library module which provides content management on the thematic environment; and at least one quantum imaging environment (QIE) module which interprets content such that the content is manipulated and accessed by any device.
Owner:QUANTUM IMAGING LLC
Method and system for granting access to personal information
InactiveUS20070130101A1Modified easily and seamlesslyOvercome disadvantagesDigital data processing detailsSpecial data processing applicationsWeb siteThird party
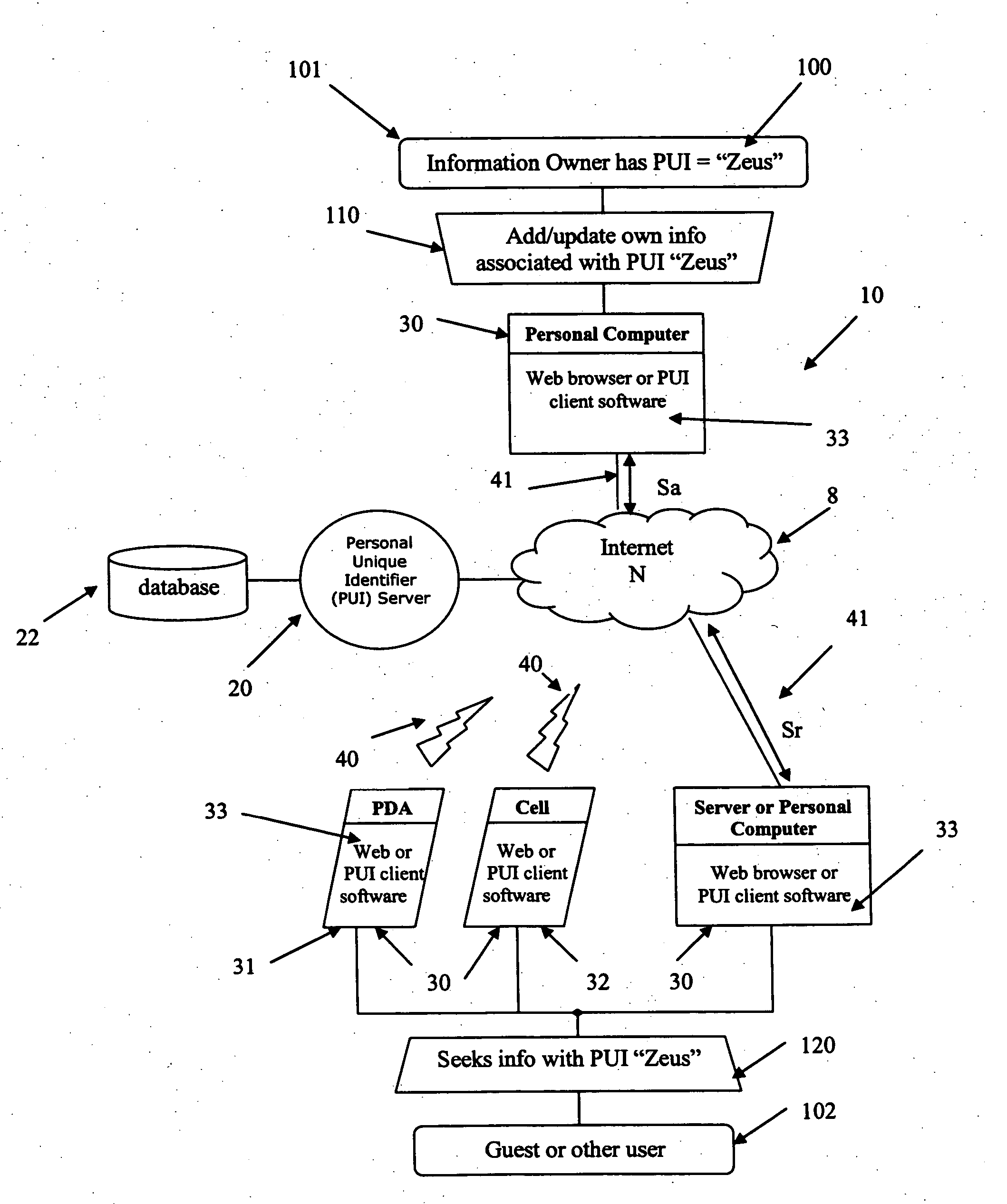
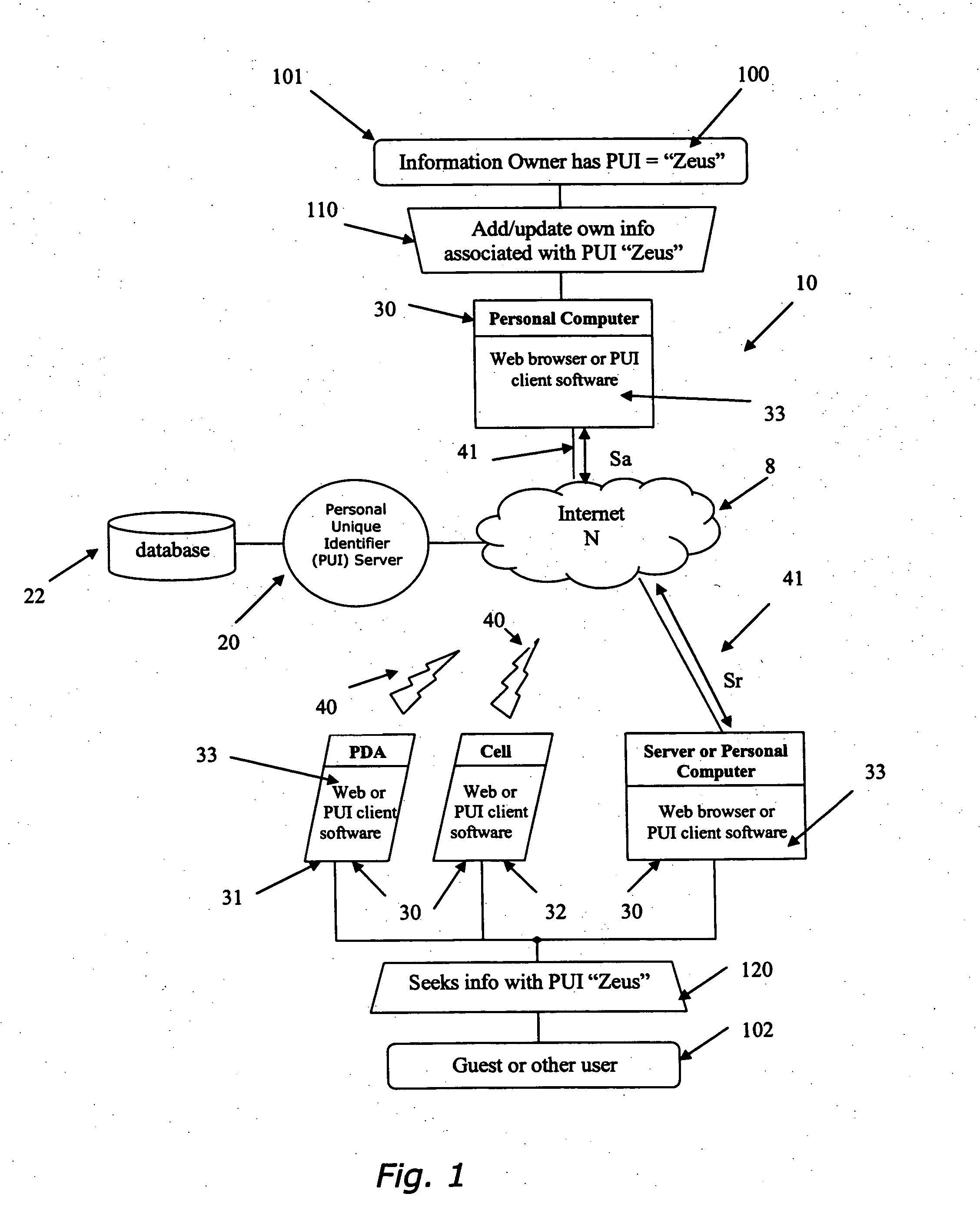
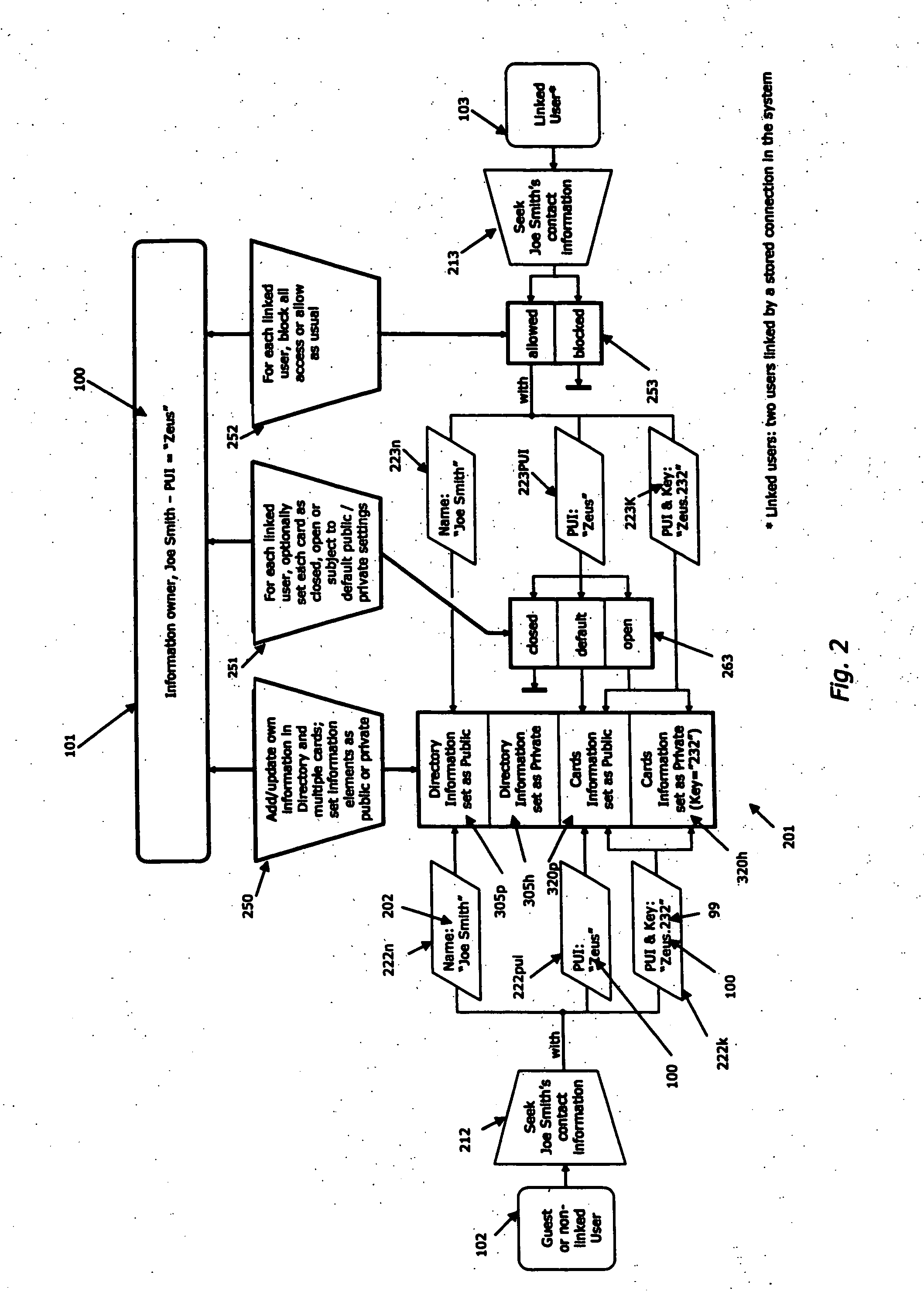
A system and method to permit users to have personal unique identifiers associated with personal information stored on a database accessed by an identity server is disclosed. The identity server is connected to one or more networks including the Internet. Users can distribute the personal unique identifier to third parties who can then obtain the personal information by accessing the server through the network. The users may modify the information stored in the database, which can then assist third parties in obtaining the modified information by inputting the personal unique identifier, or permitting client software to do so automatically on their behalf, in turn making updates to that information for the third party. This can be done over a large period of time such that third parties can easily access personal information of the user even if that information changes. The third parties may also be organizations or corporations with extensive customer lists that wish to update their client contact information with minimum interference to the customers and at minimal costs to the organization. Furthermore, users can use the personal unique identifier to populate electronic forms, such as web forms, provided on web sites hosted by organization or corporation, for the convenience of the organization or corporation and the use. The personal information of the user may also be organized in different cards having a variety of reveal and hidden status levels permitting access to additional information if a key, comprising an alphanumeric code, is entered together with the unique identifier.
Owner:ANDERSON TERRY PAUL +1
System, program product, and methods to enhance media content management
ActiveUS8250051B2Efficient managementEasy to integrateDigital data processing detailsApparatus for meter-controlled dispensingContent managementDatabase access
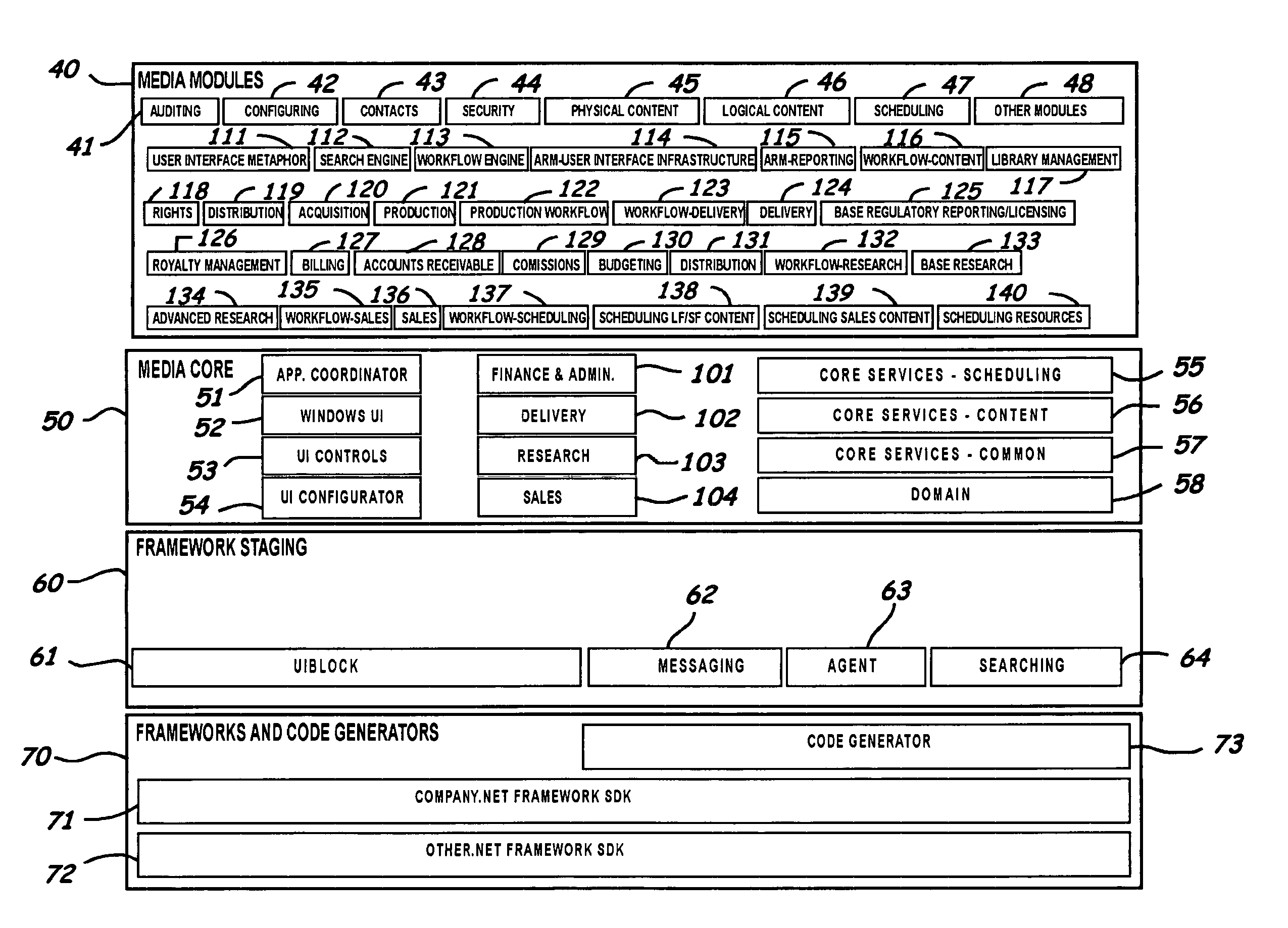
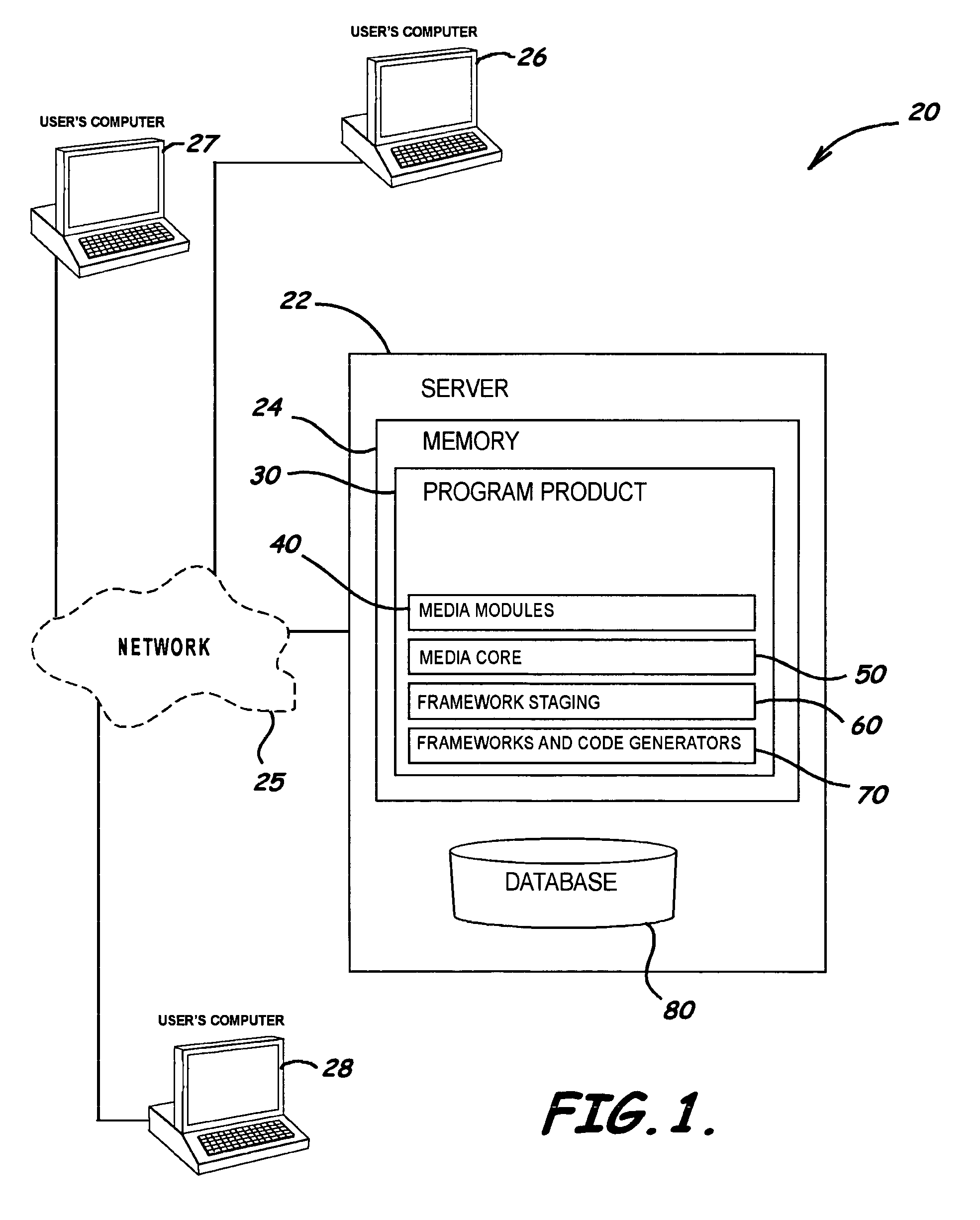
Embodiments of systems, program products, and methods to enhance and more effectively manage media content are provided. An embodiment of a method, for example, can include analyzing a user assigned role to allow access to specific data in a database in response to the user assigned role, capturing and storing metadata from multiple sources accessible by a plurality of different types of users, and tracking access to and changes in data in a database in response to user database access to thereby form transaction activity trails describing access and changed data to enhance digital file management and allow a plurality of media content management services to be performed.
Owner:HBC SOLUTIONS
Identifying and securing sensitive data at its source
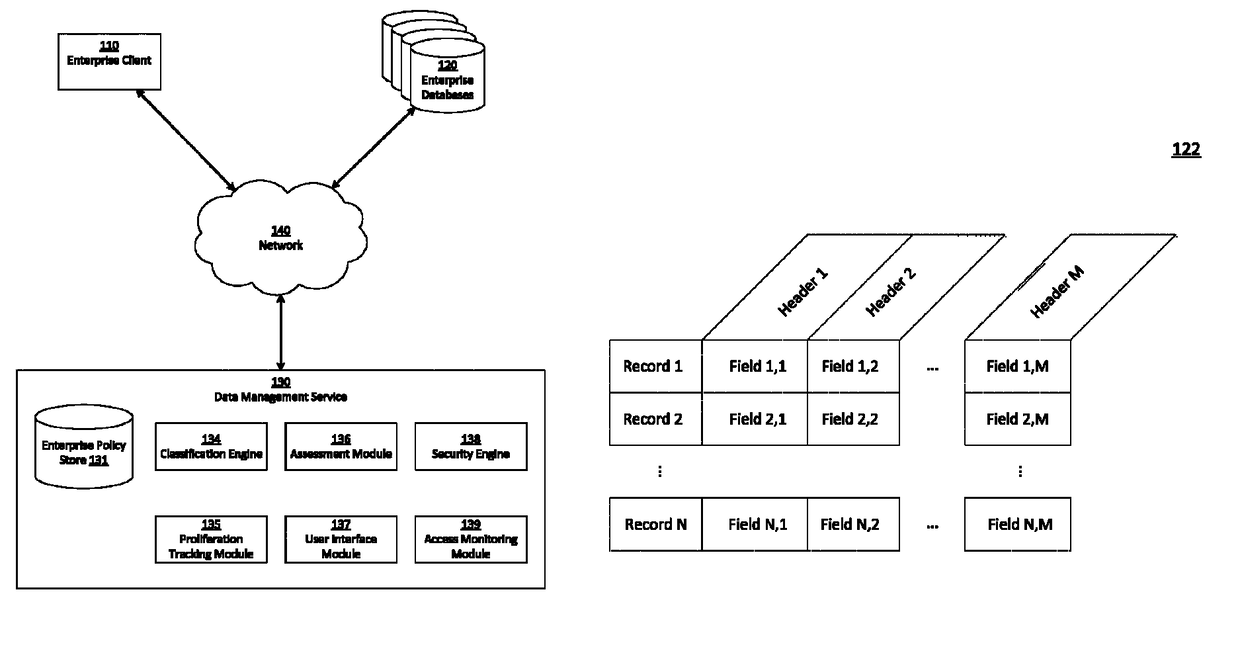
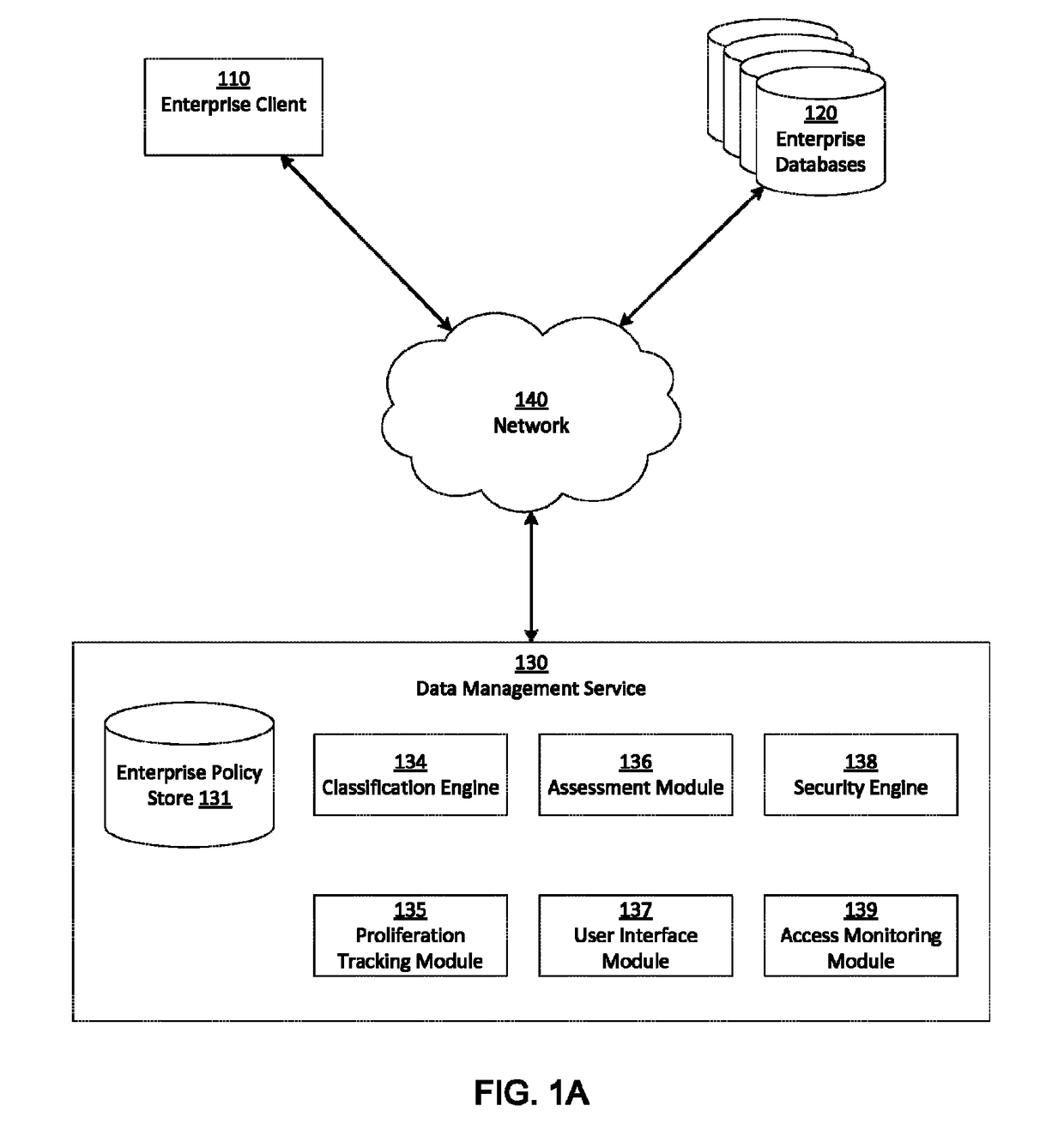
ActiveUS9785795B2Reduce processRelational databasesDigital data protectionData managementClassification rule
A data management service identifies sensitive data stored on enterprise databases according to record classification rules that classify a data record as having a sensitive data type if the data record includes fields matching at least one of the record classification rules. The data management service determines assessment scores for enterprise databases according to sensitive data records and protection policies on the enterprise databases. The data management service provides an interface that groups enterprise databases having common attributes or common sensitive data types and indicates aggregated assessment scores for the groups of enterprise databases. Through the interface with the grouped enterprise databases, an administrator apply protection policies to enterprise databases. To apply the protection policy, the data management service applies the protection policy to a source database from which dependent enterprise databases access the sensitive database.
Owner:INFORMATICA CORP
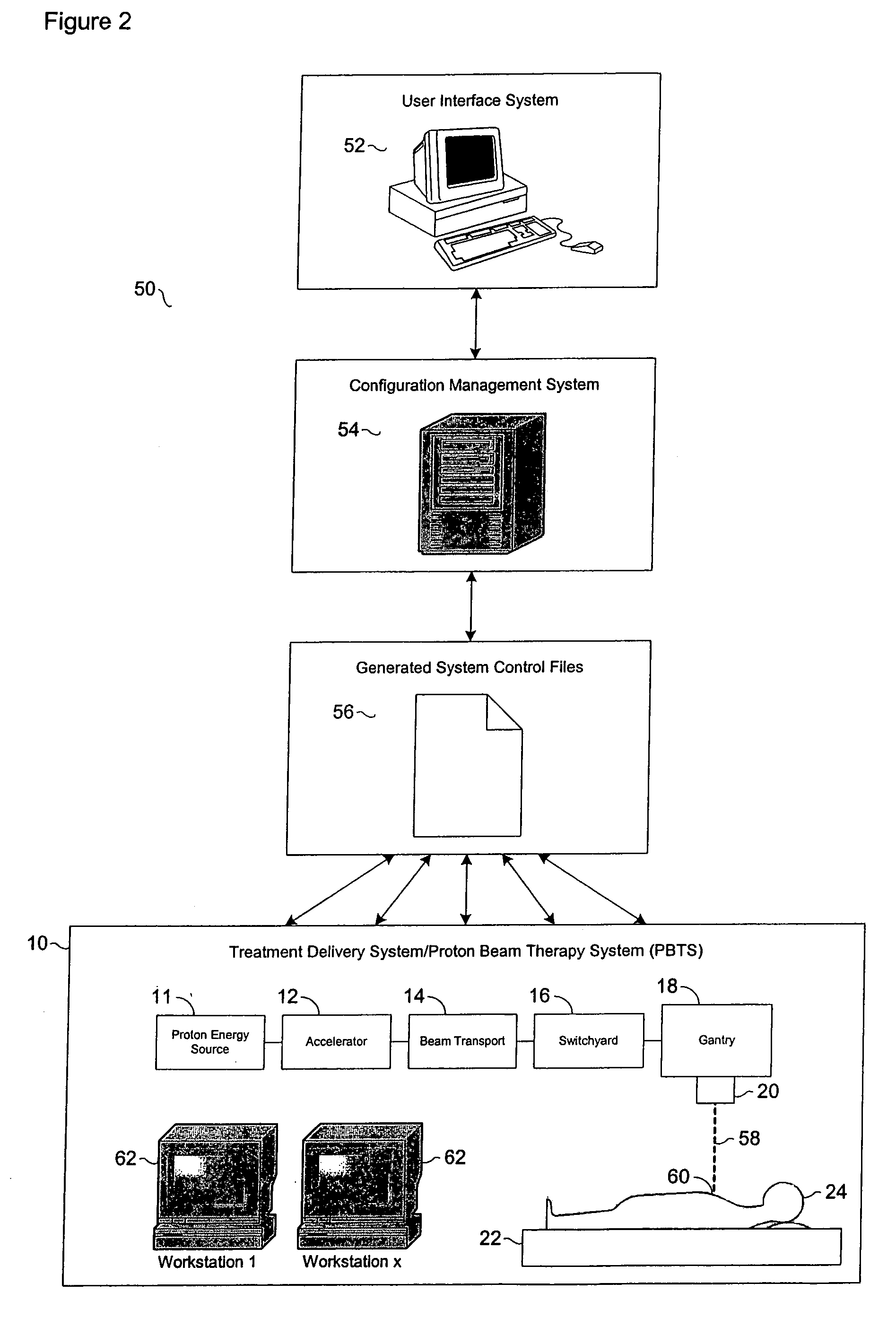
Configuration management and retrieval system for proton beam therapy system
InactiveUS7084410B2Reduce generationEasy accessNuclear monitoringDigital computer detailsOperation modeSingle point of failure
In a complex, multi-processor software controlled system, such as proton beam therapy system (PBTS), it may be important to provide treatment configurable parameters that are easily modified by an authorized user to prepare the software controlled systems for various modes of operation. This particular invention relates to a configuration management system for the PBTS that utilizes a database to maintain data and configuration parameters and also to generate and distribute system control files that can be used by the PBTS for treatment delivery. The use of system control files reduces the adverse effects of single point failures in the database by allowing the PBTS to function independently from the database. The PBTS accesses the data, parameters, and control settings from the database through the system control files, which insures that the data and configuration parameters are accessible when and if single point failures occur with respect to the database.
Owner:LOMA LINDA UNIV MEDICAL CENT
Database access system
InactiveUS7801896B2Increased formationGood user interfaceDigital data information retrievalAdvertisementsAnonymityPopulation statistics
An improved human user computer interface system, wherein a user characteristic or set of characteristics, such as demographic profile or societal “role”, is employed to define a scope or domain of operation. The operation itself may be a database search, to interactively define a taxonomic context for the operation, a business negotiation, or other activity. After retrieval of results, a scoring or ranking may be applied according to user define criteria, which are, for example, commensurate with the relevance to the context, but may be, for example, by date, source, or other secondary criteria. A user profile is preferably stored in a computer accessible form, and may be used to provide a history of use, persistent customization, collaborative filtering and demographic information for the user. Advantageously, user privacy and anonymity is maintained by physical and algorithmic controls over access to the personal profiles, and releasing only aggregate data without personally identifying information or of small groups.
Owner:RELATIVITY DISPLAY LLC
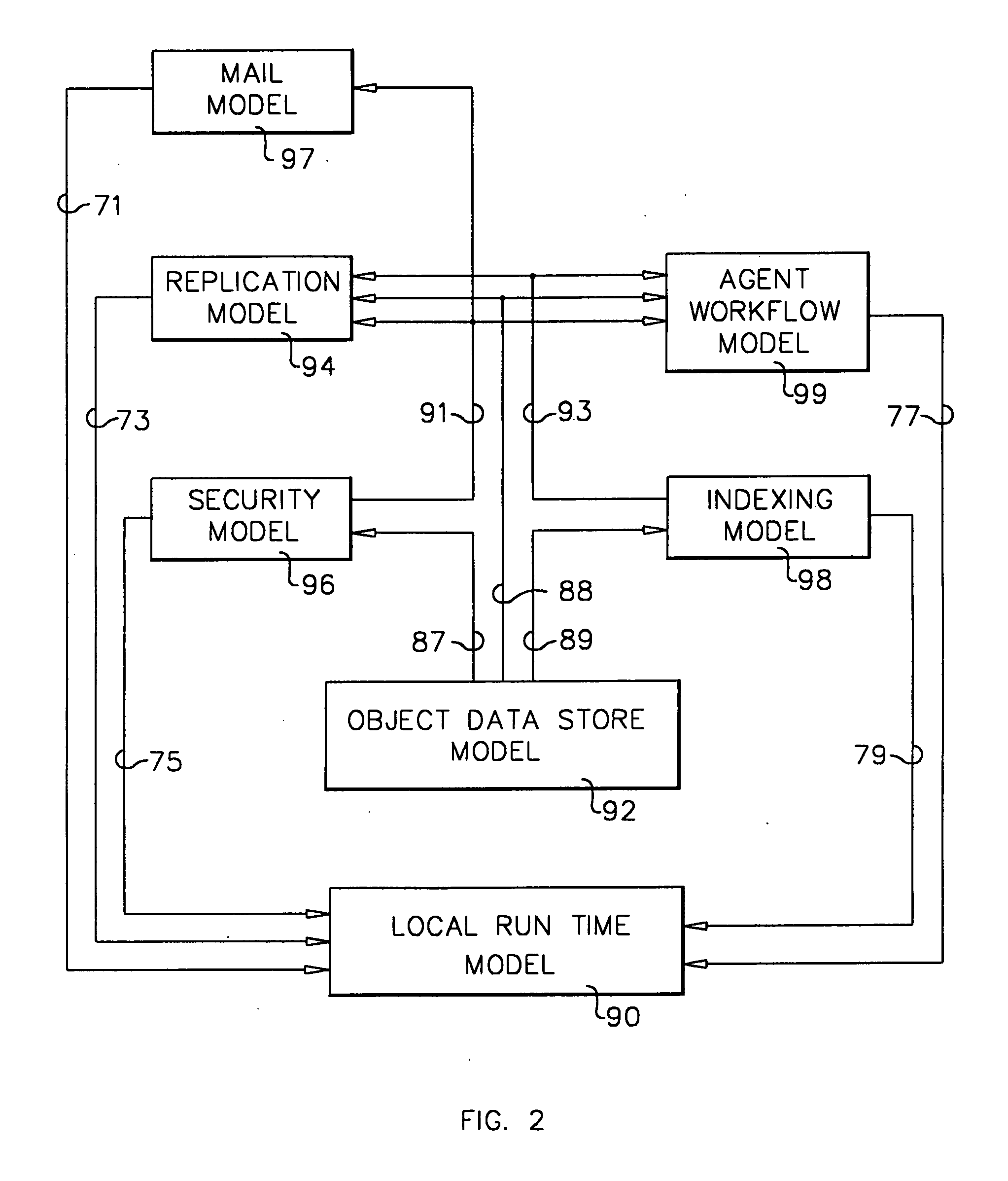
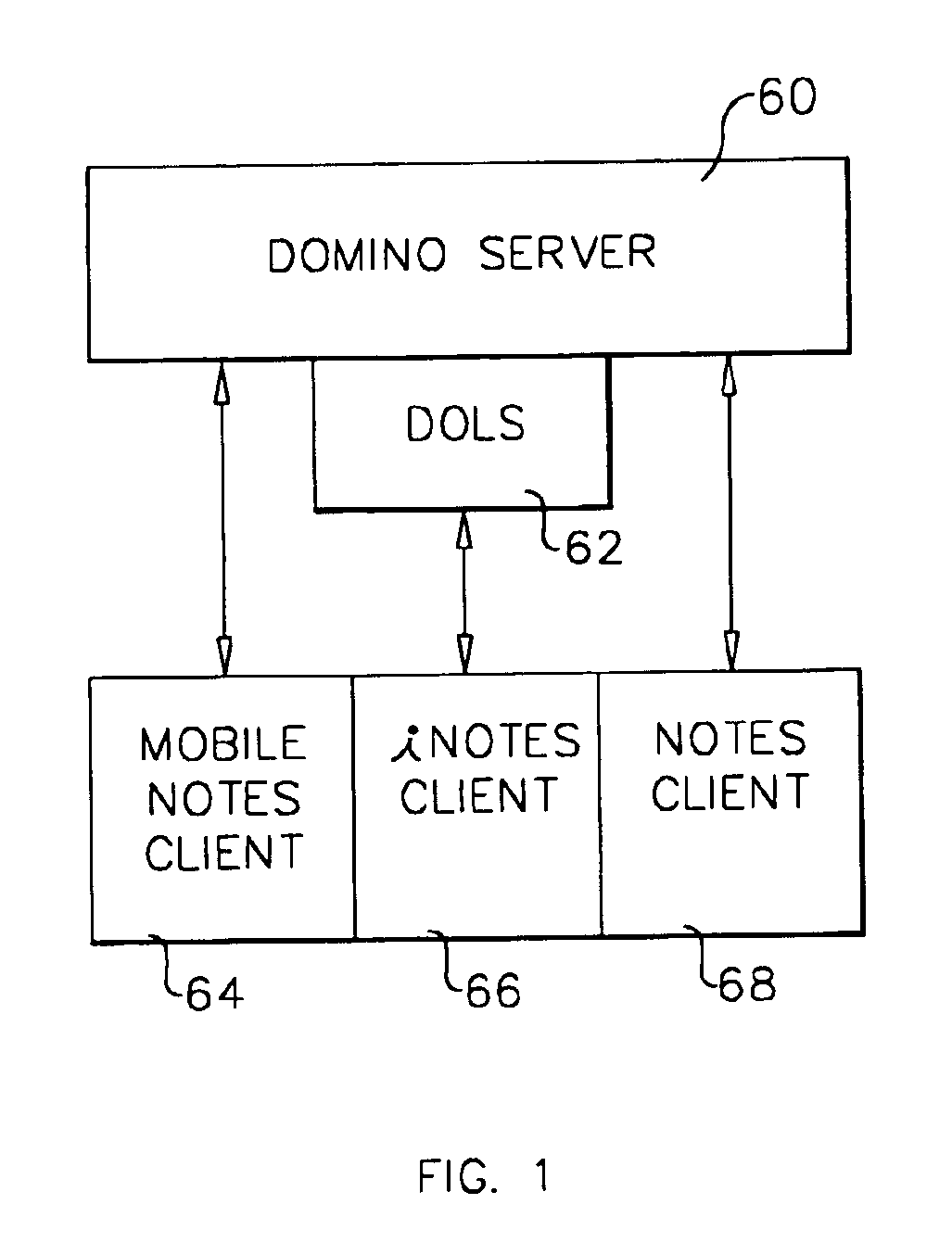
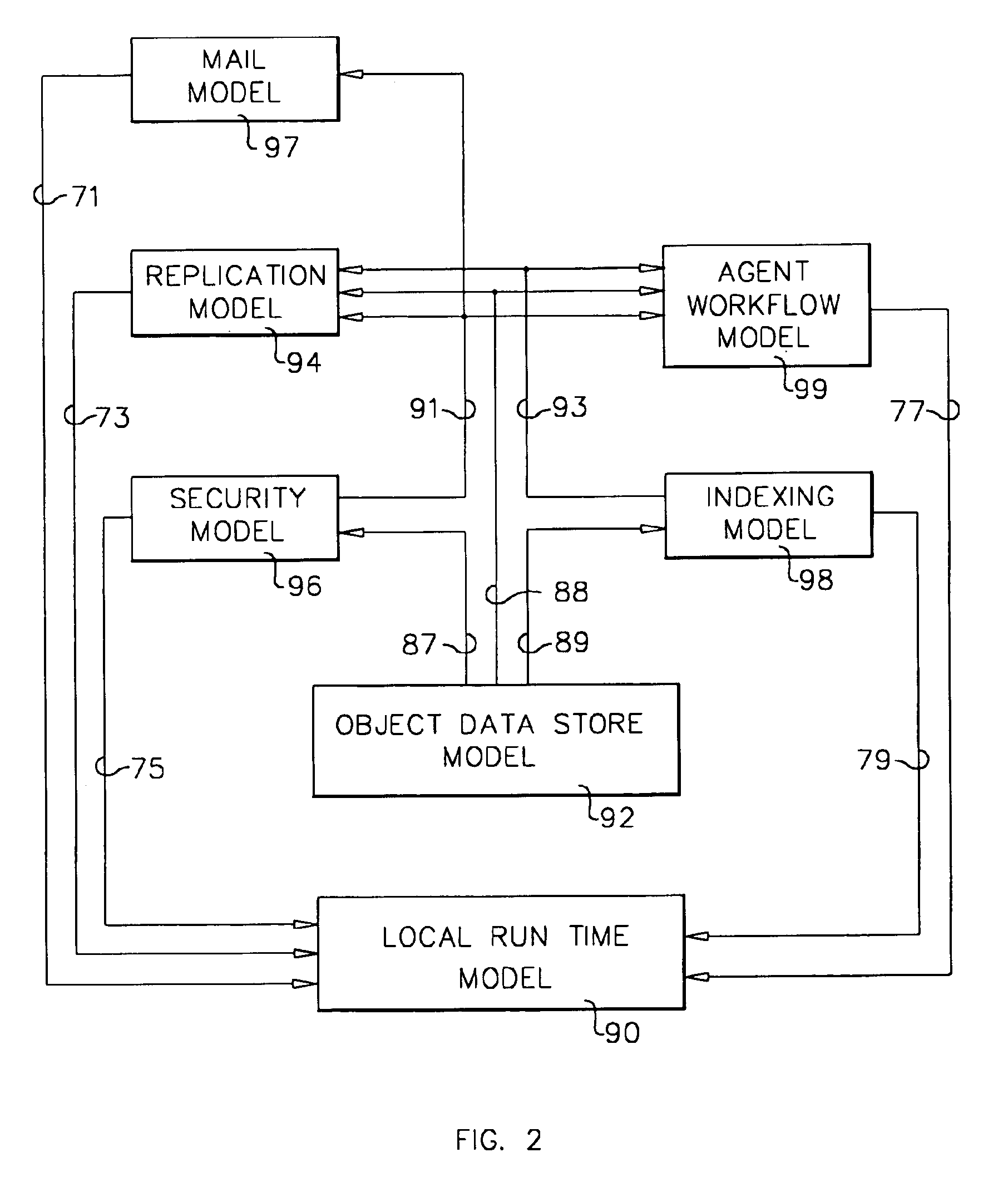
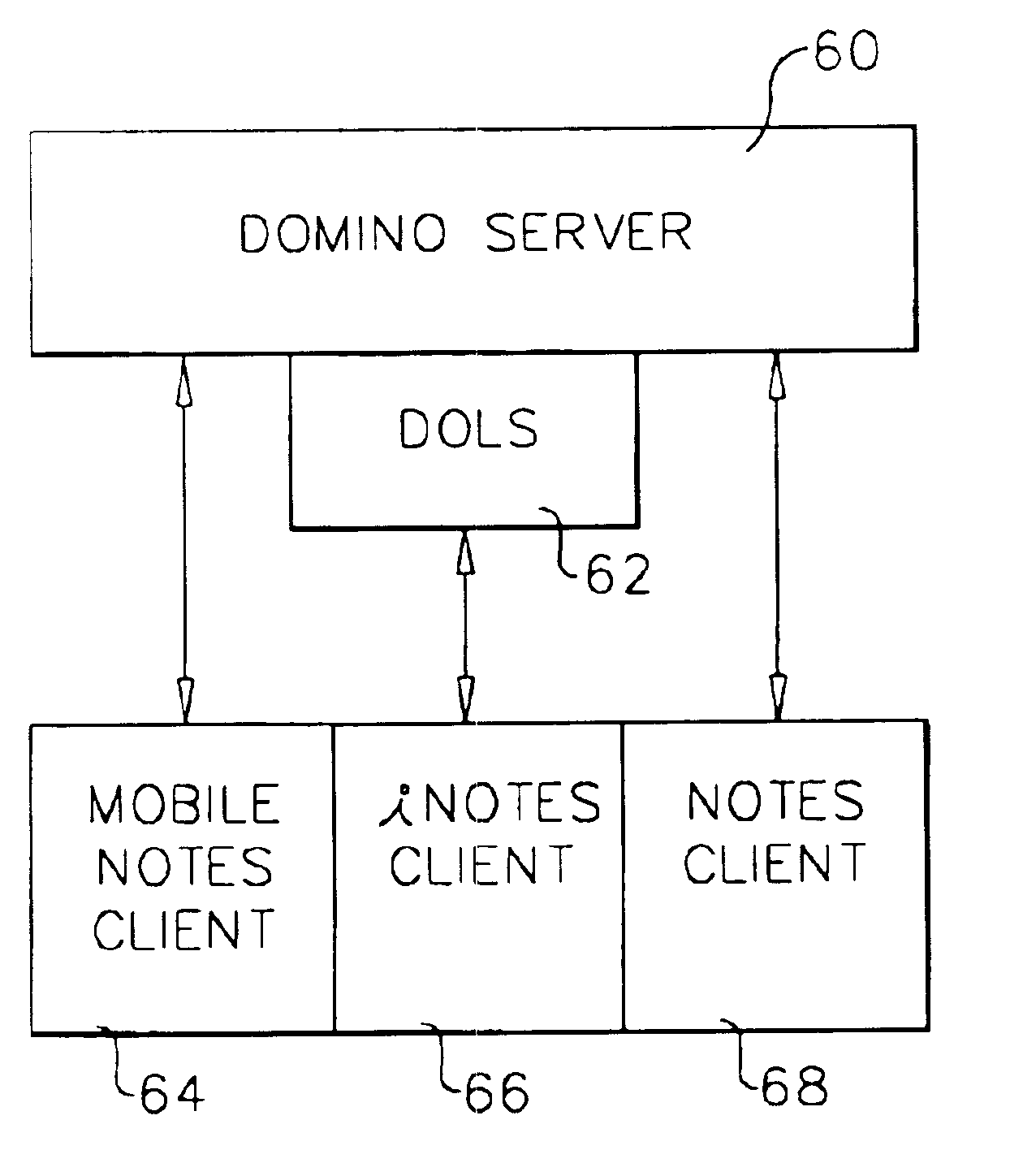
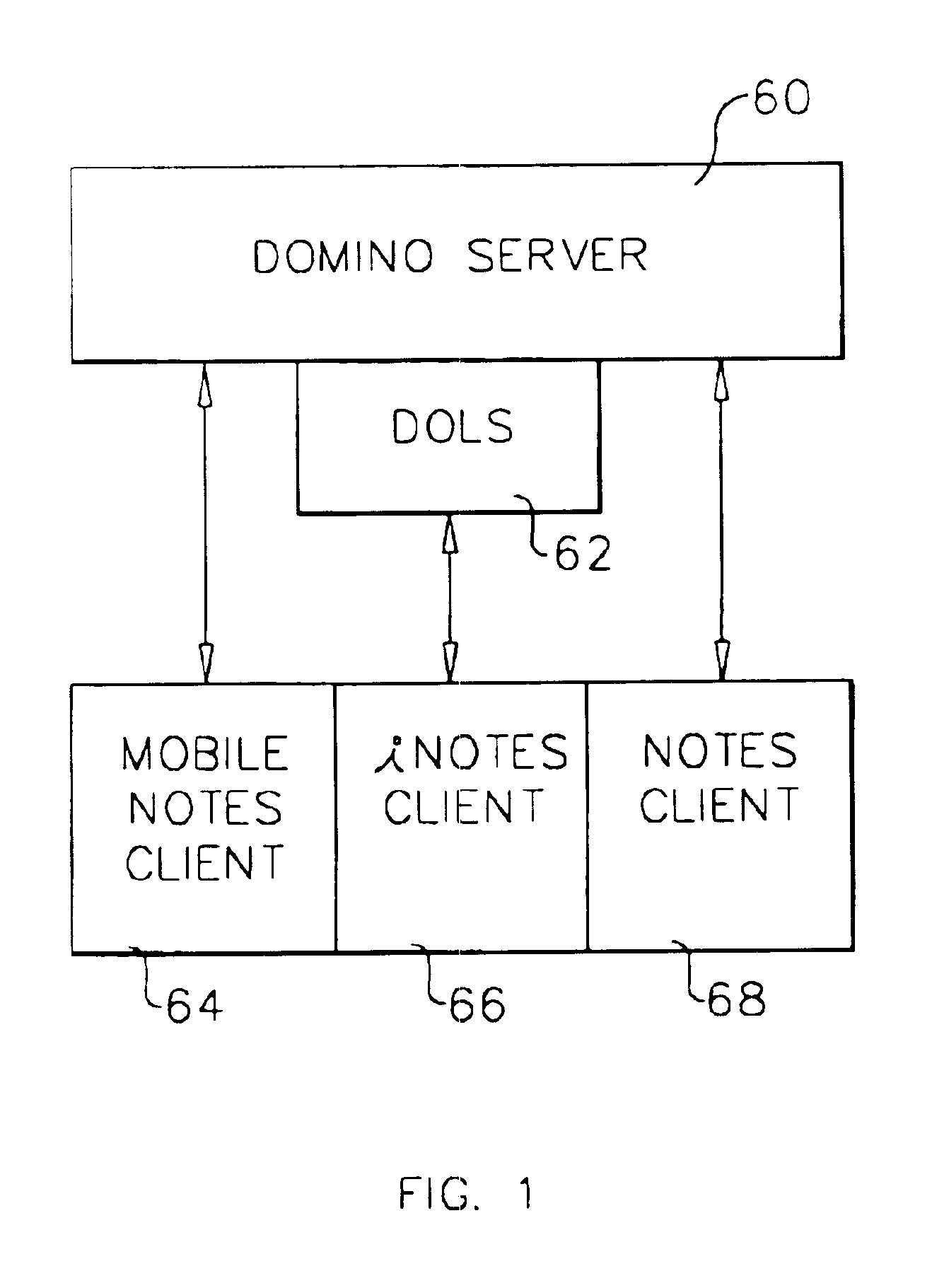
System and method for developing and administering web applications and services from a workflow, enterprise, and mail-enabled web application server and platform
ActiveUS20040201604A1Digital computer detailsOffice automationDocumentation procedurePartial application
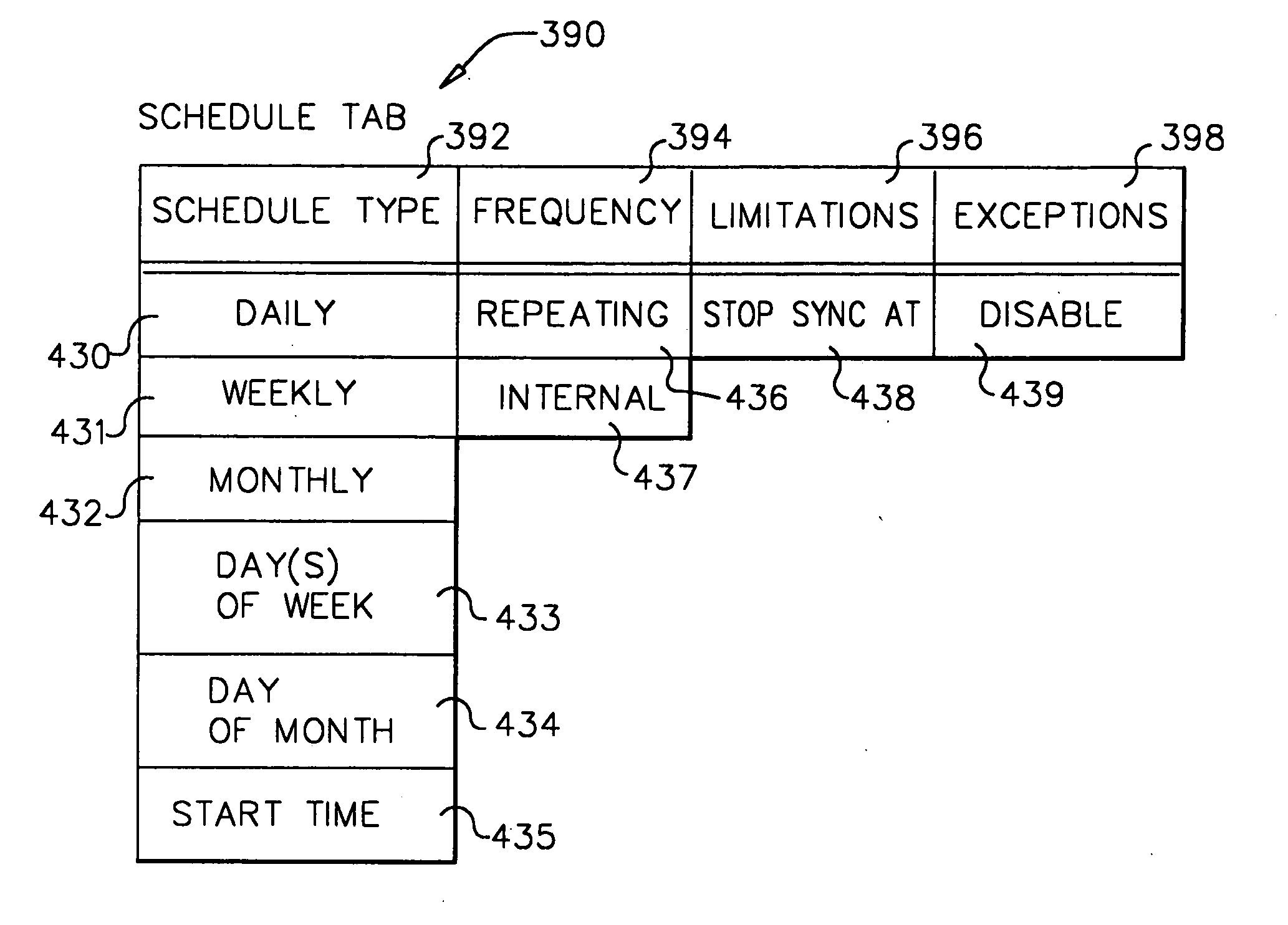
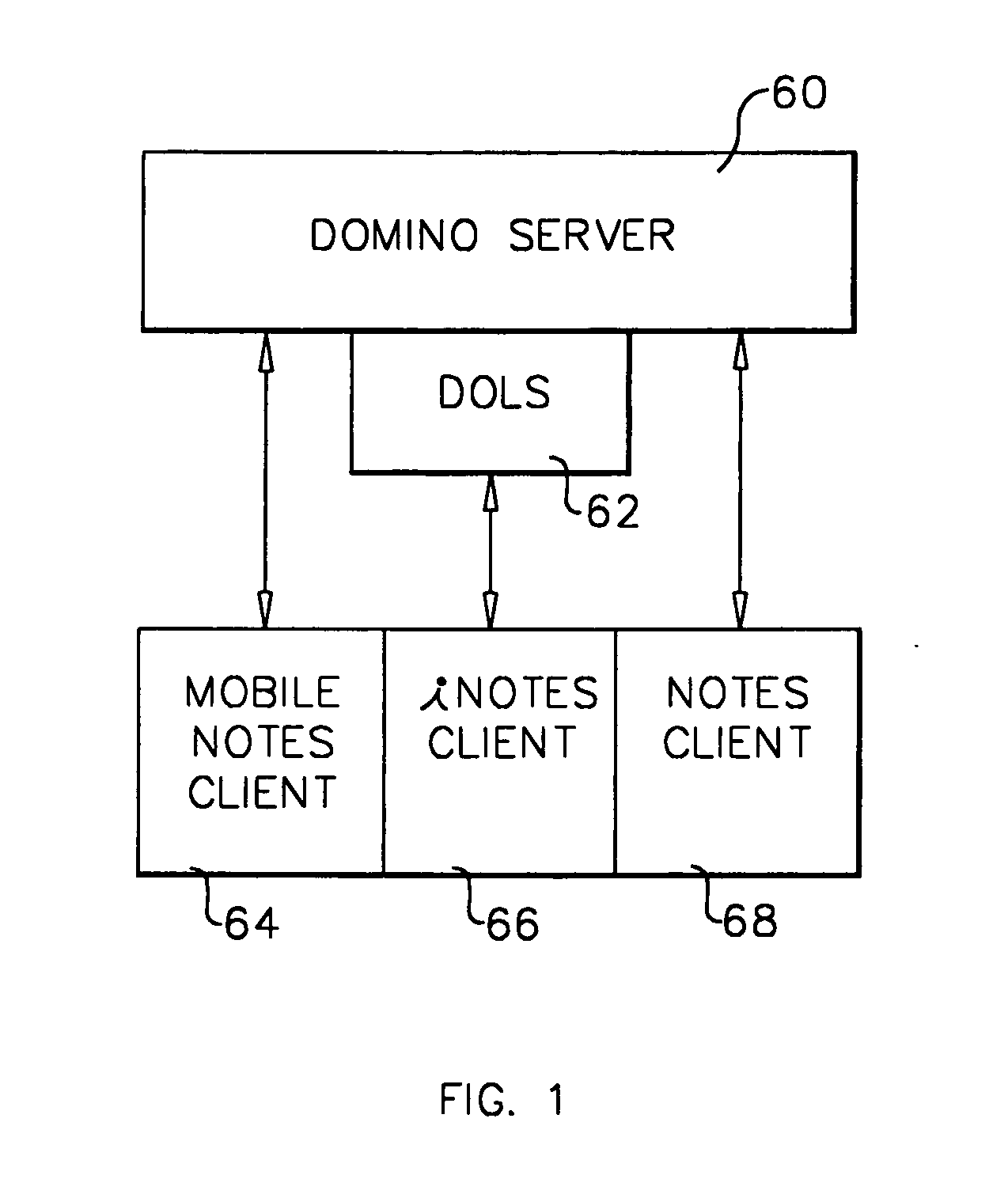
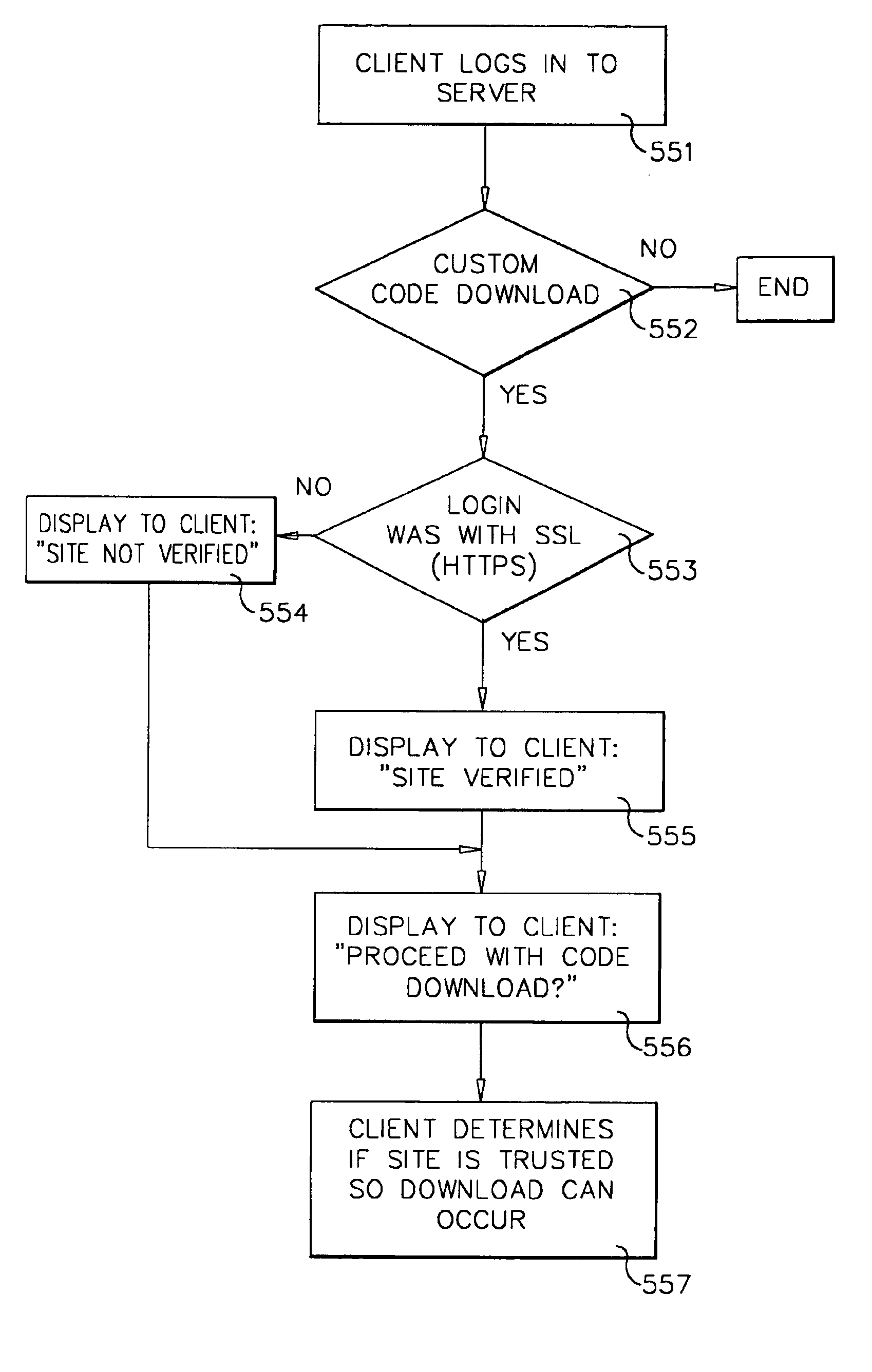
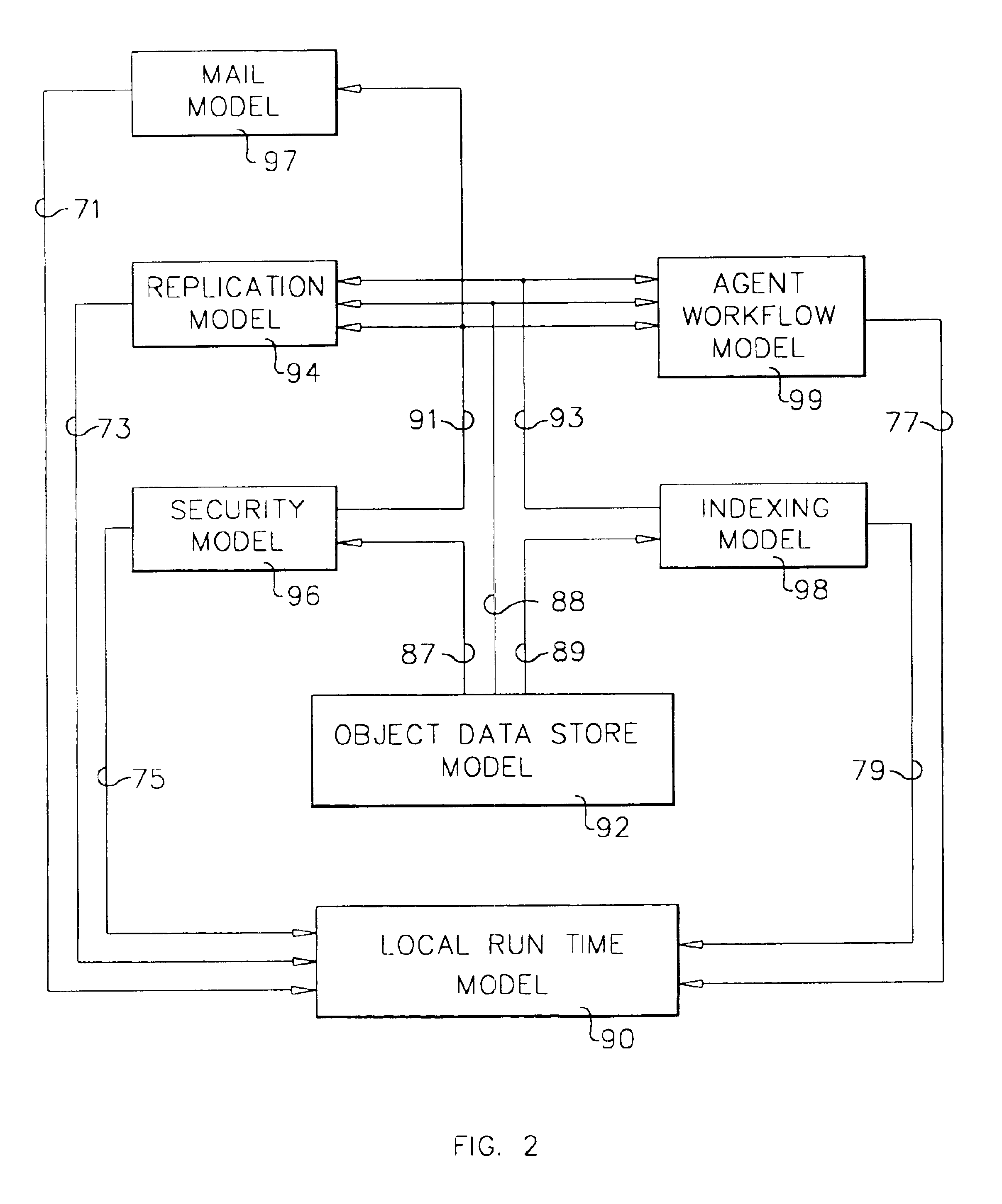
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and. remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:HCL TECH LTD
System and method for a web based trust model governing delivery of services and programs
InactiveUS6854016B1Broaden applicationDigital data processing detailsMultiple digital computer combinationsPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino Offline Services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:TREND MICRO INC
Method, system, and computer program product for managing database servers and service
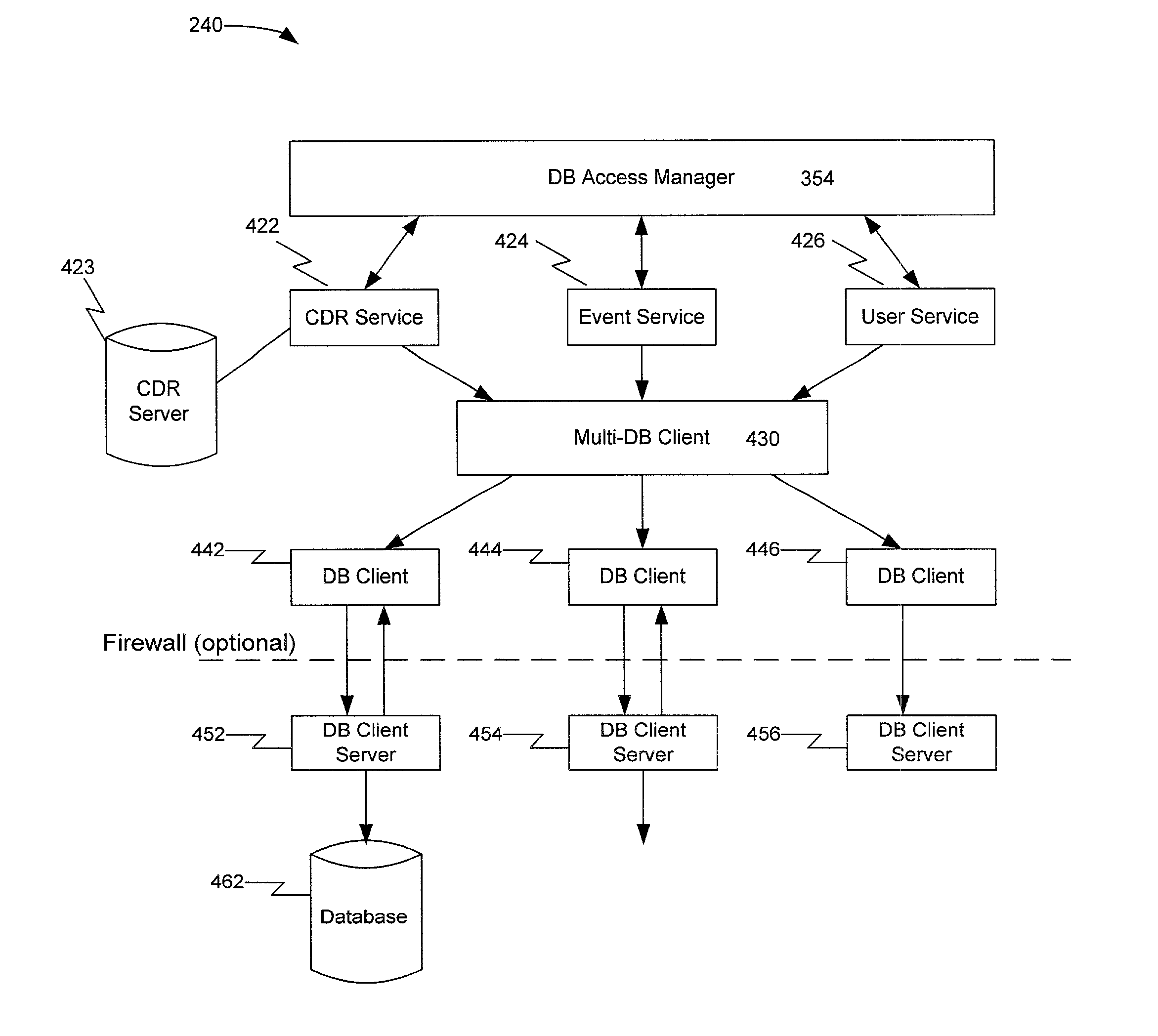
InactiveUS7123608B1Interconnection arrangementsDigital data processing detailsDatabase serverComputer module
A system, method, and computer program product for managing database servers and services is disclosed, which expands the capabilities of existing systems by providing better scalability and security. A database management system includes databases consisting of database clients and servers that handle the storing of information, a multi-database client that manages database servers, service modules which allow other systems to access the database servers, and a database access manager that manages requests from the service modules. A database access manager facilitates and coordinates interaction between the service modules and the multi-database client. Service modules provide interfaces from which other external or internal systems can access the managed databases. Requests can be sent between systems and the database access manager via the service modules. Two present and representative implementations of service modules are: user management and call detail record (CDR) collection. The user management service module allows systems to access user account information stored in the databases. The CDR collection service module inserts details for each call made on the network.
Owner:CHEMTRON RES
Dynamic object-driven database manipulation and mapping system having a simple global interface and an optional multiple user need only caching system with disable and notify features
The present invention provides enhanced database access and performance when correlating or translating one database to another database or to an object programming application. The system and method of enhanced database access and performance of the invention provides a simplified high-level wrapper interface for global coordination of multiple software components and ease of use. Performance is also enhanced by utilizing an optional enhanced multiple user data caching system. The multiple user caching system of the invention provides a process of obtaining data from a data source, creating accessible data in the random access memory of at least one computer system the first time such data is read by a user wherein the data source corresponding to the cache is accessible to at least two users. Thus, the present invention is directed to dynamic mapping of databases to selected objects and a system and method for providing a multiple user caching system in such an environment or system.
Owner:THOUGHT
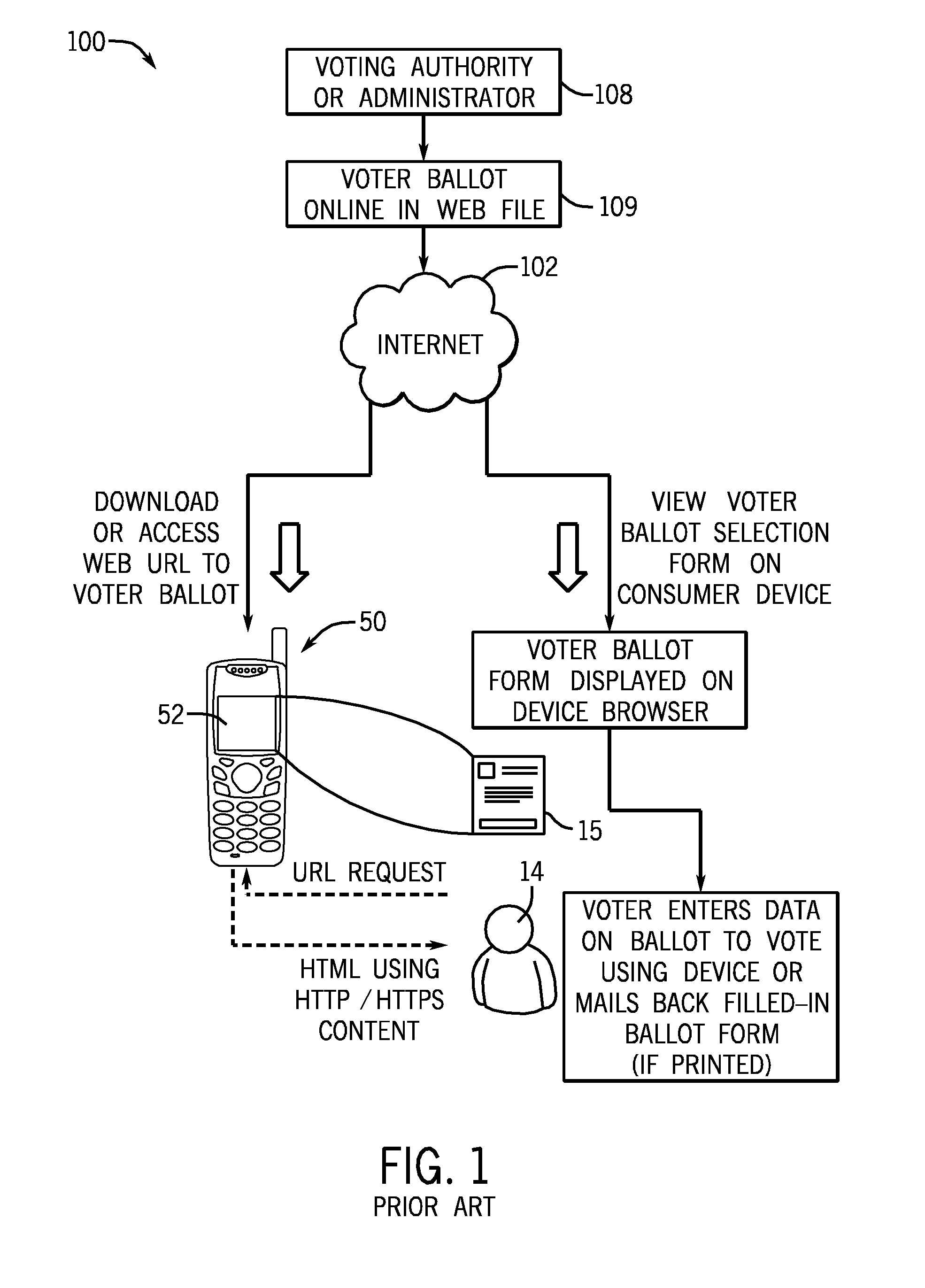
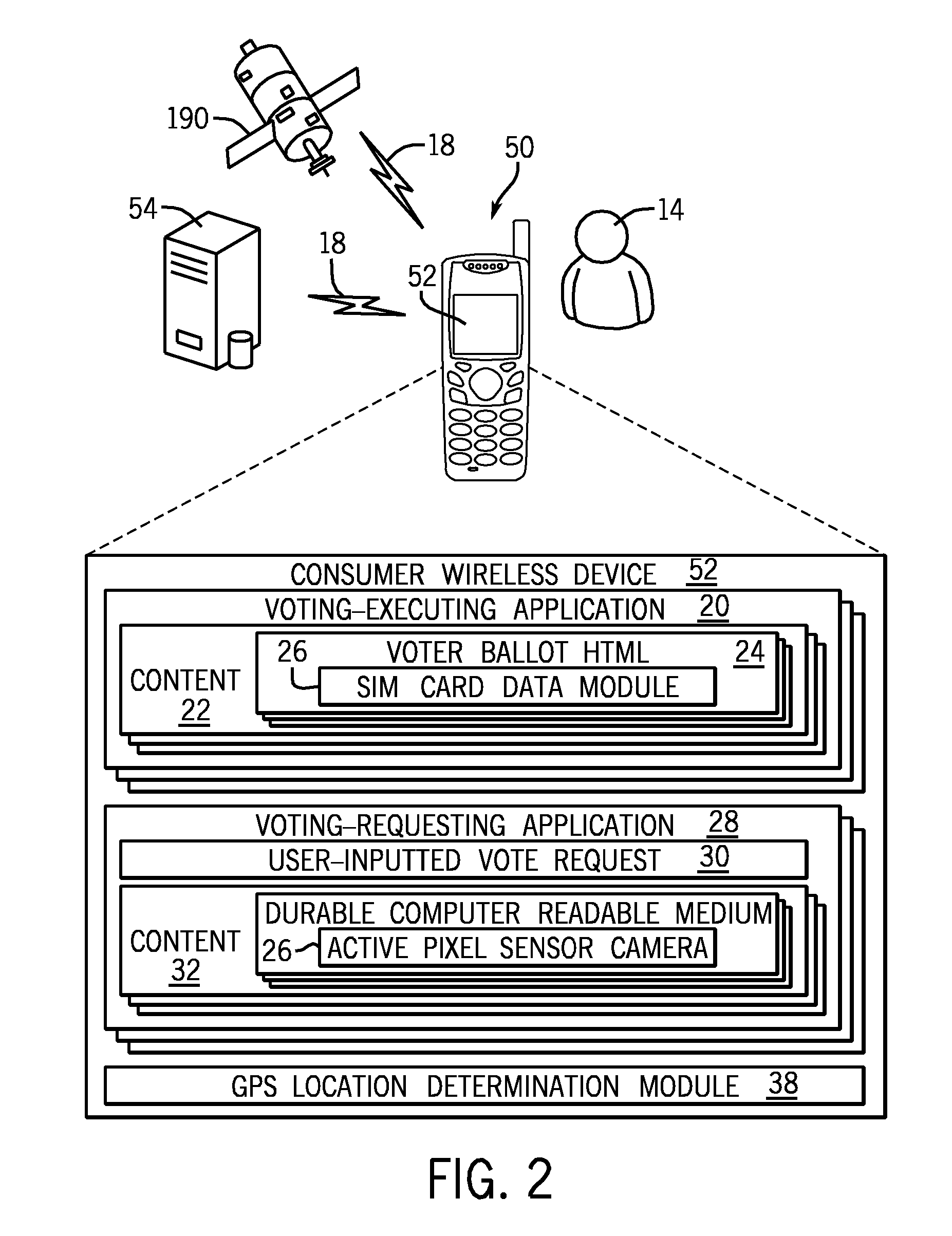
GPS location authentication method for mobile voting
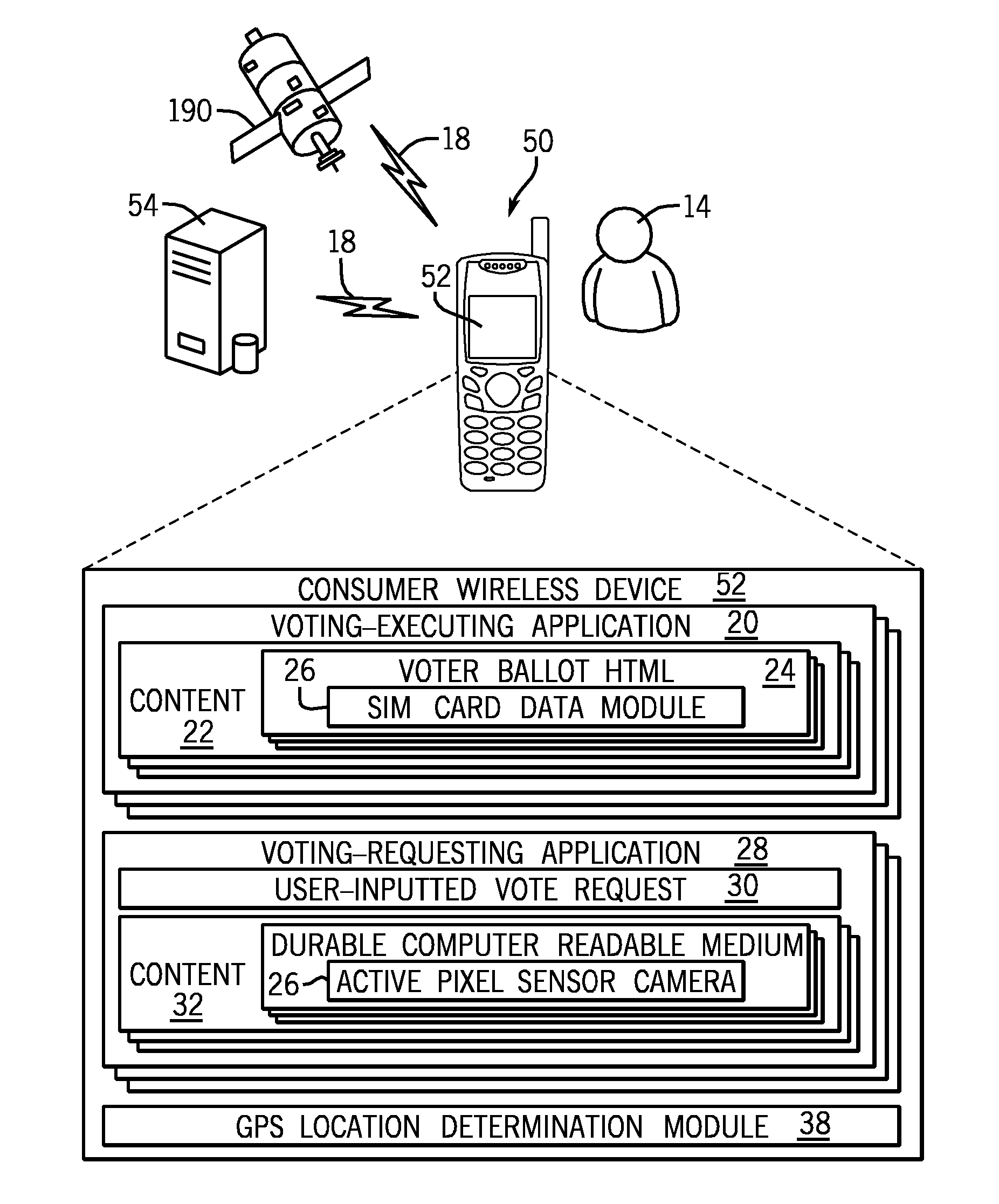
ActiveUS20110053559A1Voting apparatusUnauthorised/fraudulent call preventionInternet privacyEngineering
A system and method for authenticating votes received from a voter's mobile device comprising a computer programmed with a set of computer-readable instructions and a database accessed by mobile device reading a durable computer readable medium stored in a computer server, the database comprising a registered voter and a geographical location for the registered voter's postal mail delivery address, means to receive a vote in an election over a wireless carrier network, means to determine the geographical location of a device which transmitted the vote over the wireless network comprising cell tower triangulation, and means to reject the vote if the geographical location of the device which transmitted the vote is not within a predetermined distance from the geographical location for the registered voter stored in the database.
Owner:RPX CORP
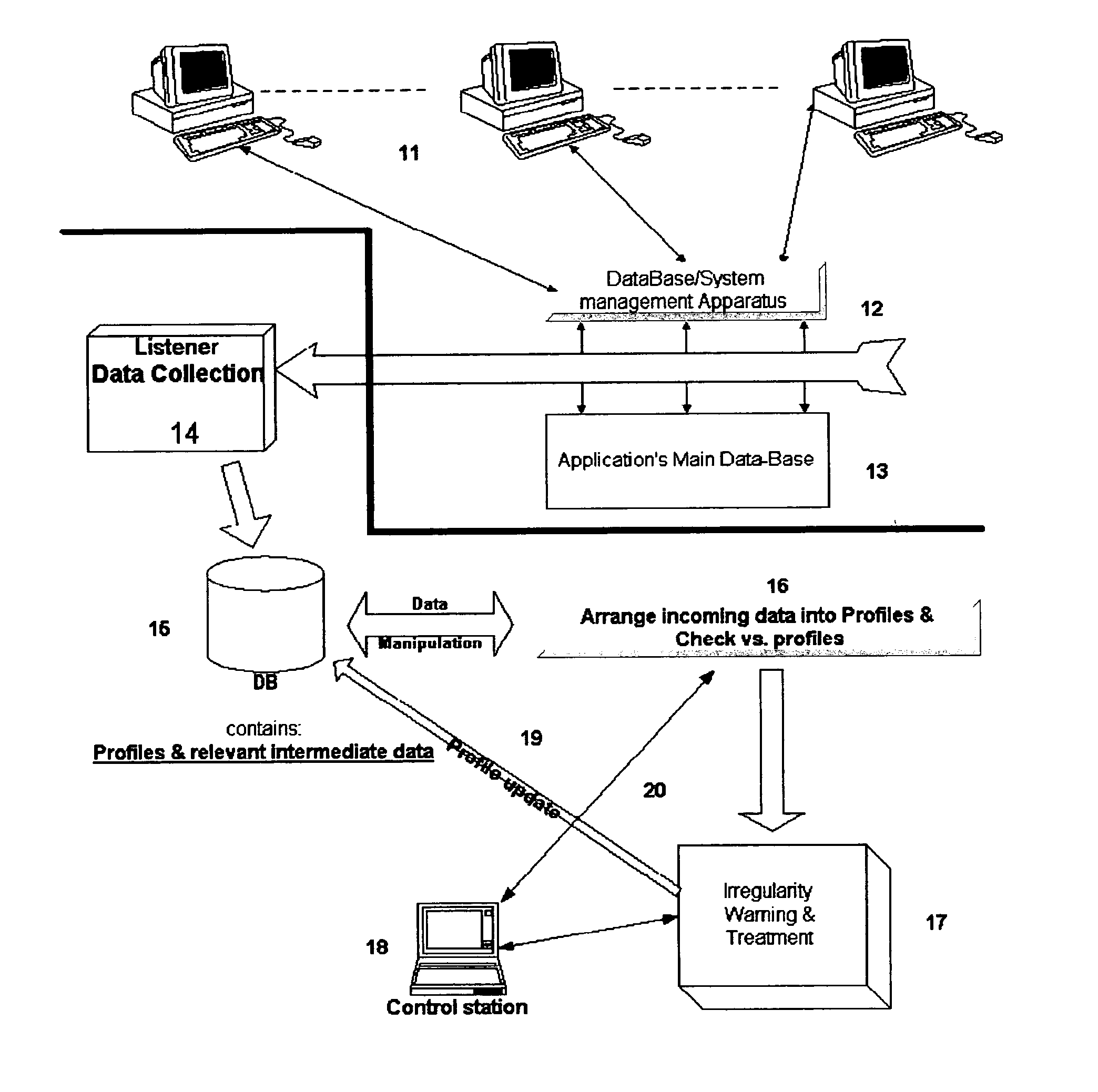
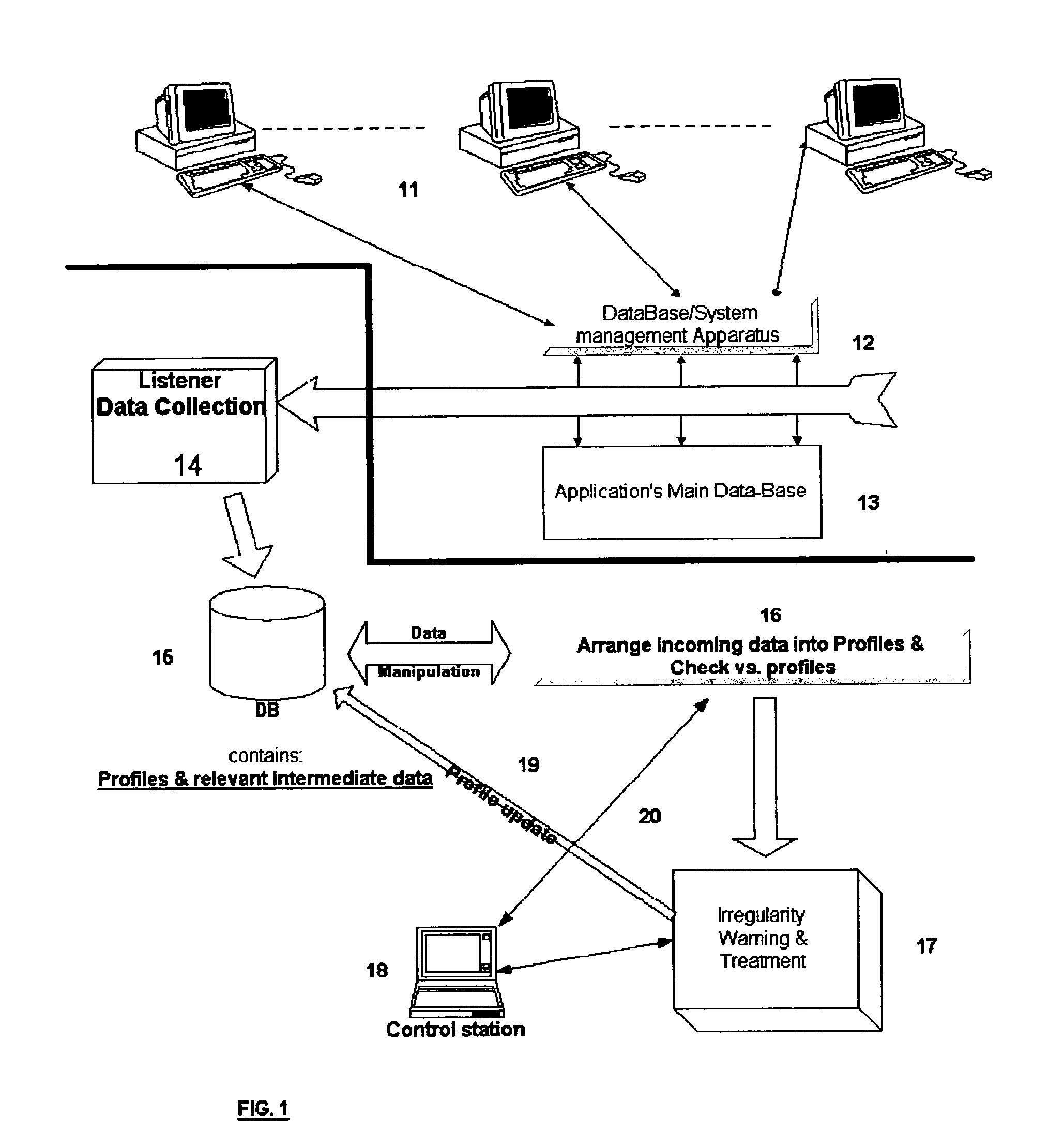
Detection of misuse or abuse of data by authorized access to database
InactiveUS20050086529A1Raise the possibilityEasy to detectDigital data processing detailsHardware monitoringConfigfsData content
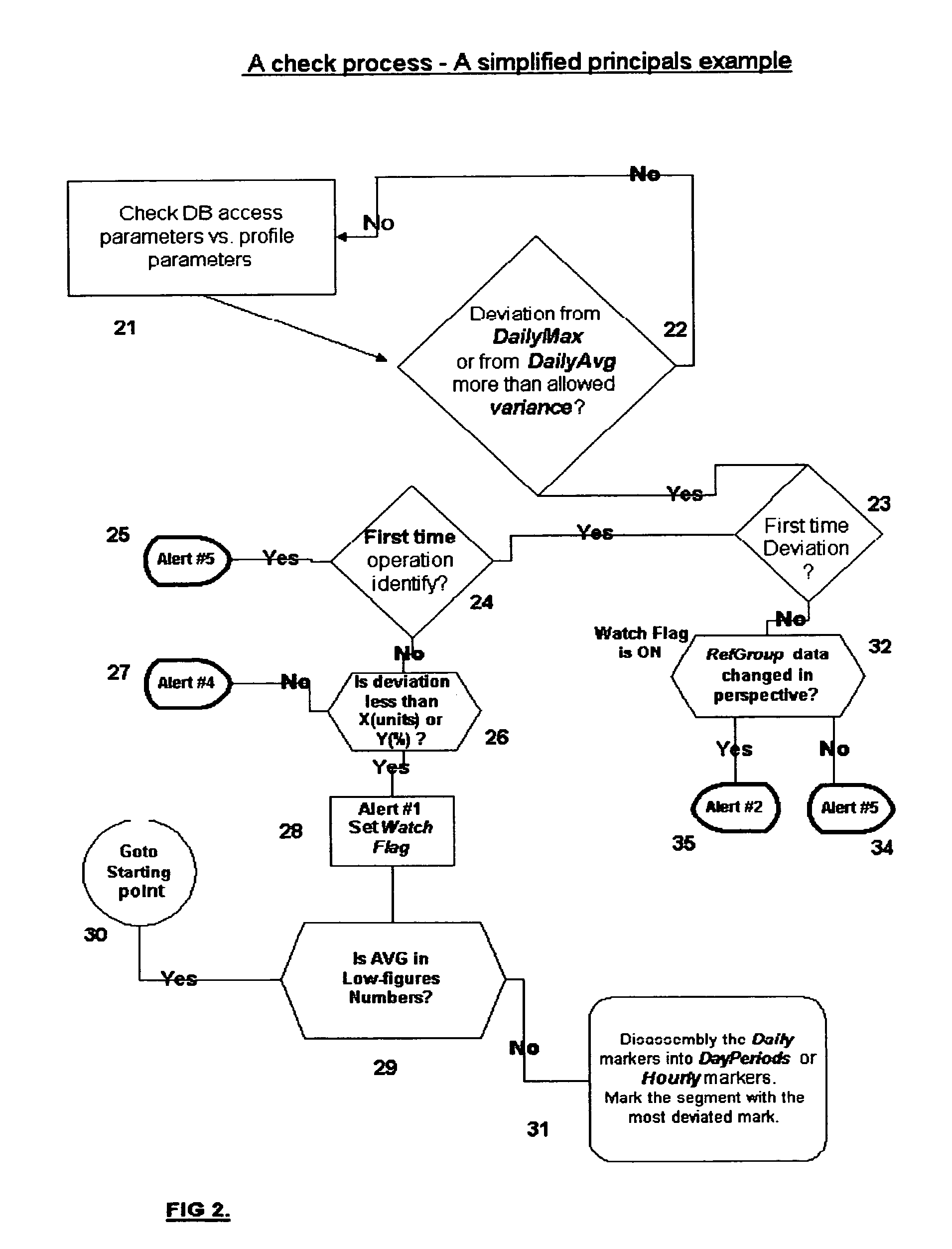
The present invention relates to a system for detecting misuse and / or abuse of data related to database done by a user with authorized access to a data system and its database. User behavior is monitored as to its nature of database access, analyzed to create, and compare to, a specific profile. No understanding for the meaning of data content is needed. Each deviation from normal pattern, stored in the profile, is checked in various parameters and ranked, reporting to a system owner.
Owner:IDOT COMP
System for automated, mid-session, user-directed, device-to-device session transfer system
InactiveUS7191233B2Multiple digital computer combinationsSecuring communicationDiagnostic Radiology ModalityPager
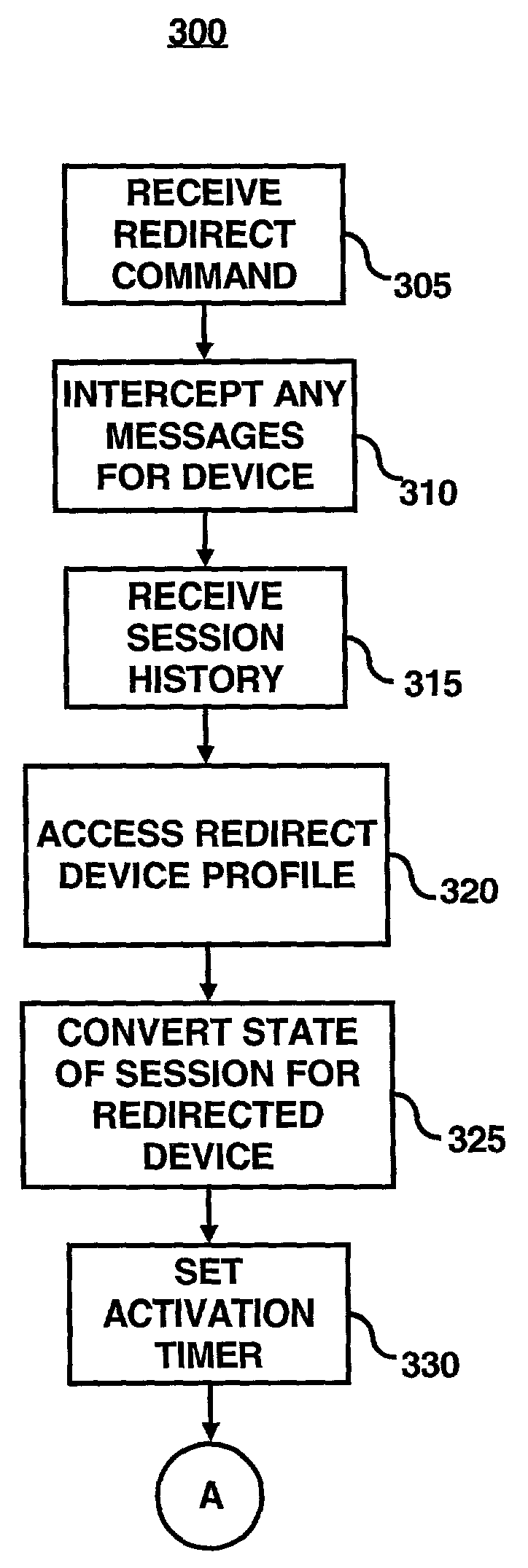
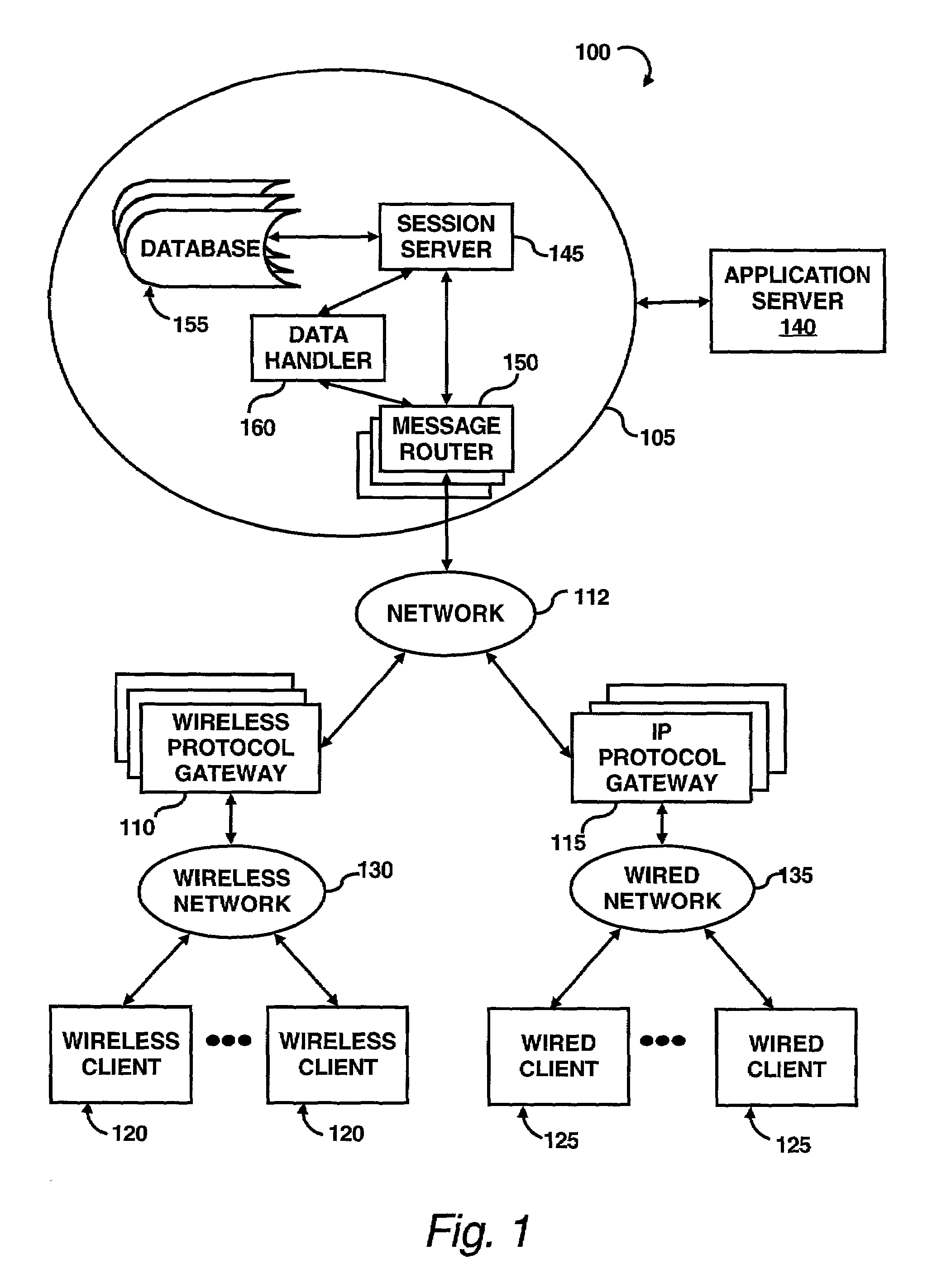
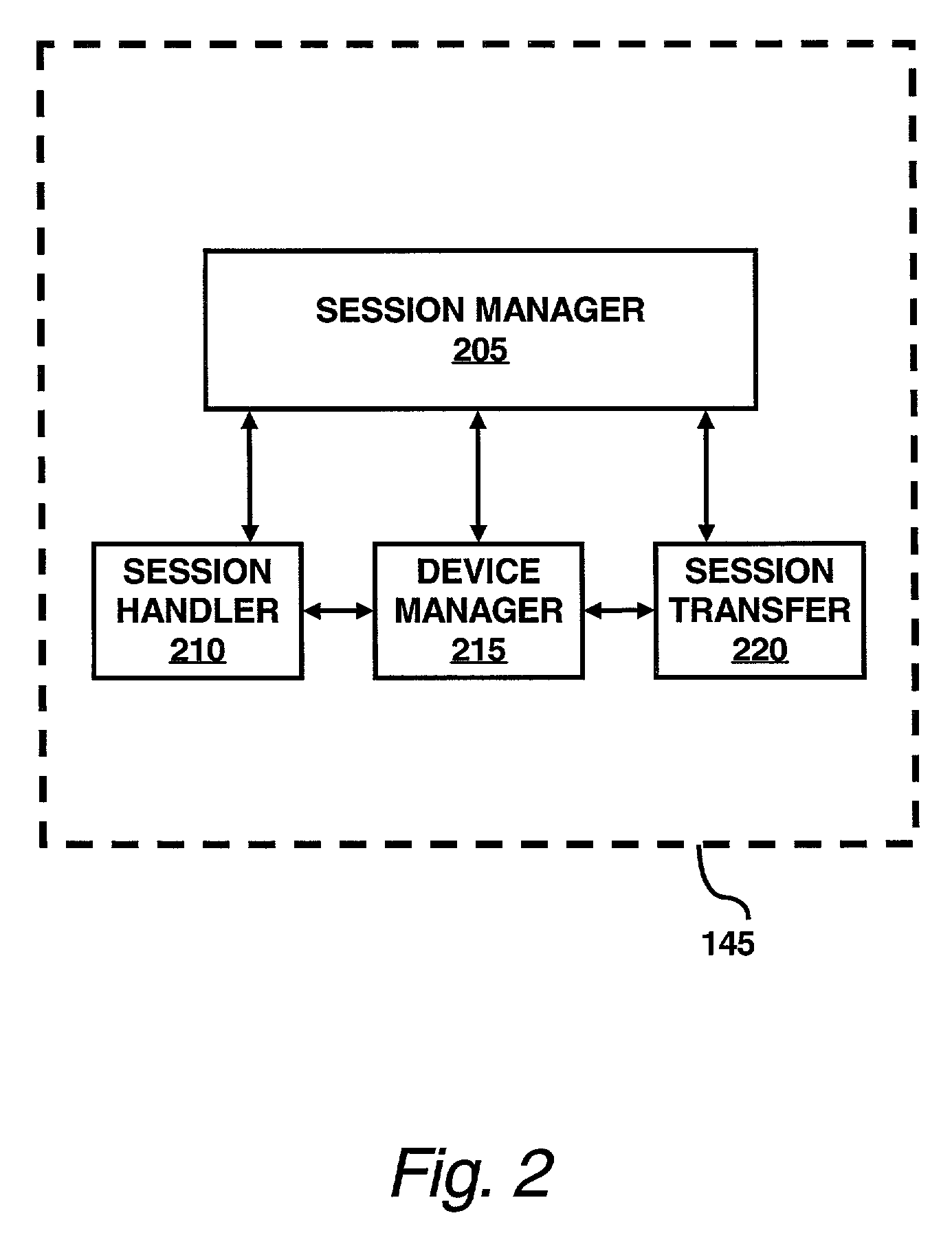
A session transfer module of a session server provides the capability to a user to direct a transfer of an on-going session from one device to another device while maintaining the session. The session transfer module is invoked by a user in a way consistent with the user interface of the client application, including by a graphical user command, a command line prompt, or a voice command. The client provides a selection of possible devices that may receive the redirected session. The session transfer module receives the selected device with the session redirect command over a communication network. The communication network may be wired (e.g., public switched telephone network (“PSTN”), Internet, etc.,) a wireless network (e.g., digital telephone network, pager network, etc.,) or a combination of the wired and wireless networks. The session transfer module may be configured to discontinue the session with the current device and to block any subsequent messages of the transferring session from reaching the device. The session transfer module may be further configured to access a device profile from a device profile database to convert the blocked messages into a format compatible to the format and / or modality of the redirected device. The session transfer module may be further configured to push the session to the redirected device in response to an activation (e.g., log-on) of the redirected device by the user. Alternatively, the session transfer module may be further configured to push the session back to the device in response to a time-out in the activation of the redirected device.
Owner:CRFD RES
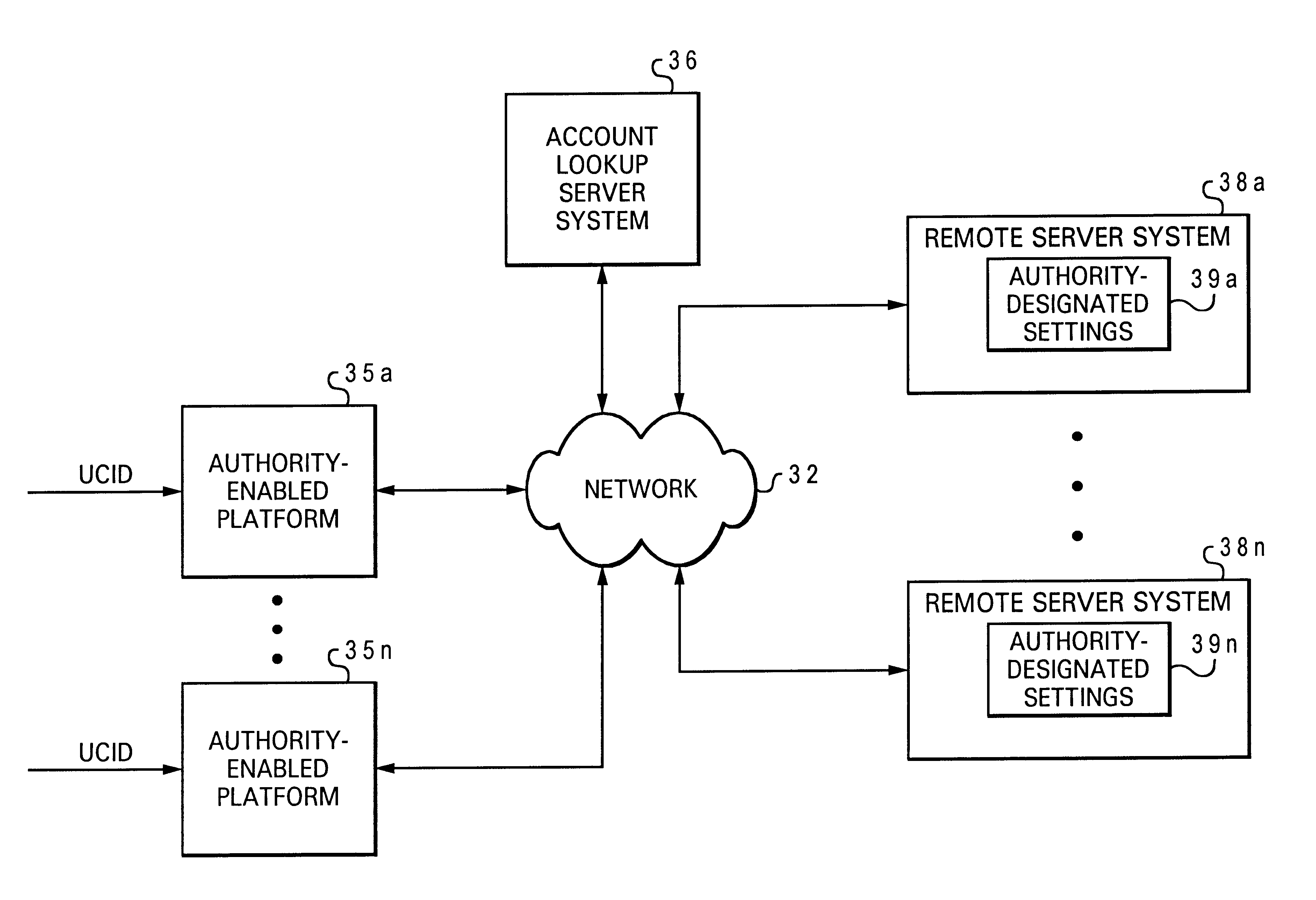
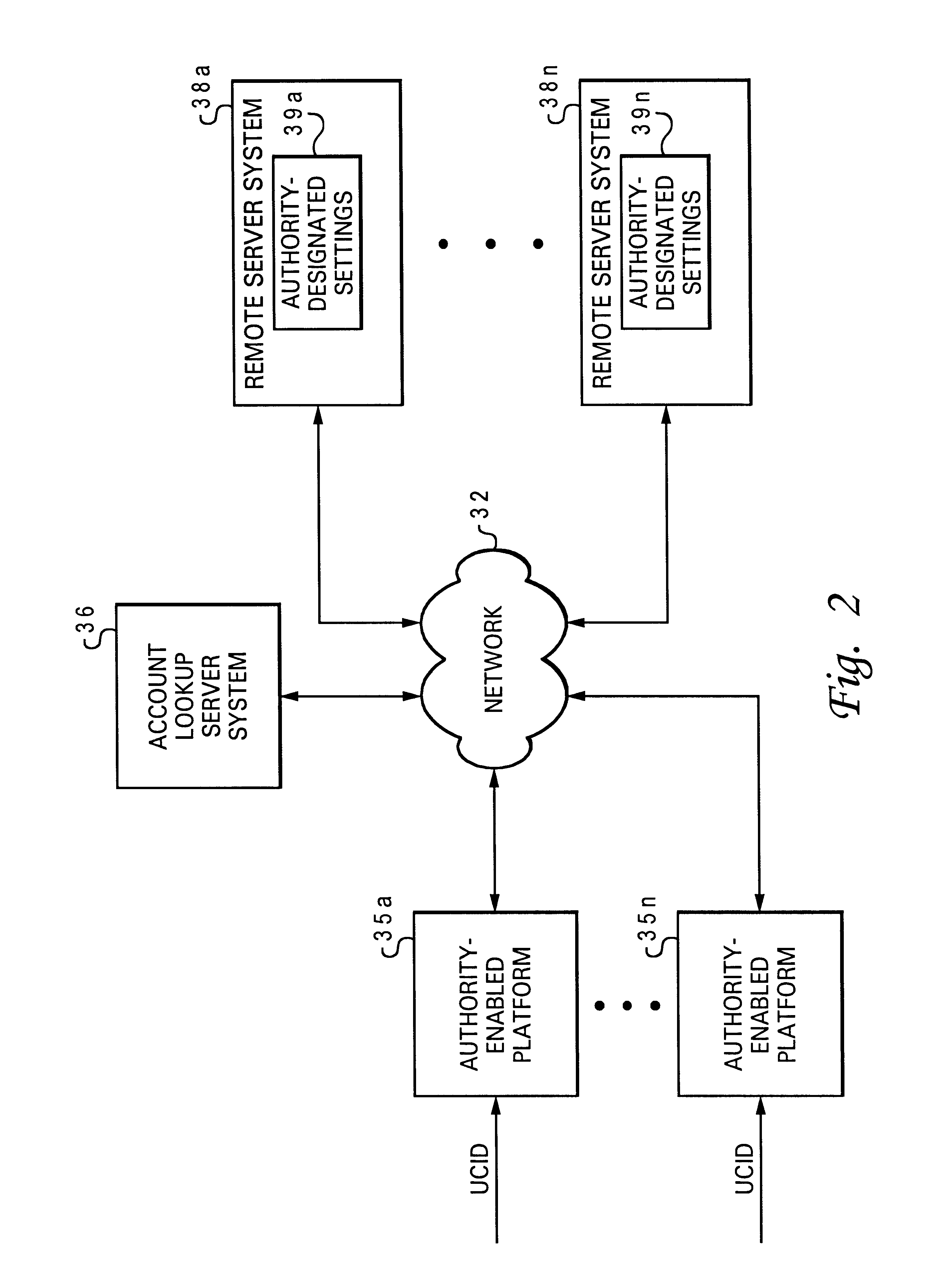
Monitoring and managing user access to content via a universally accessible database
InactiveUS6658415B1Data processing applicationsComputer security arrangementsUniversal IdentifierDatabase
In accordance with the present invention, multiple authority-designated settings are accessed at an authority-enabled system via a network from a universally accessible database according to a particular universal identifier associated with a particular user. The particular user is only allowed access to a selection of multiple of types of content from the authority-enabled system that are enabled according to the authority-designated settings received at the authority-enabled system, such that an authority-enabled system enforces an authority-designated access policy for a particular user received via a universally accessible database.
Owner:IBM CORP
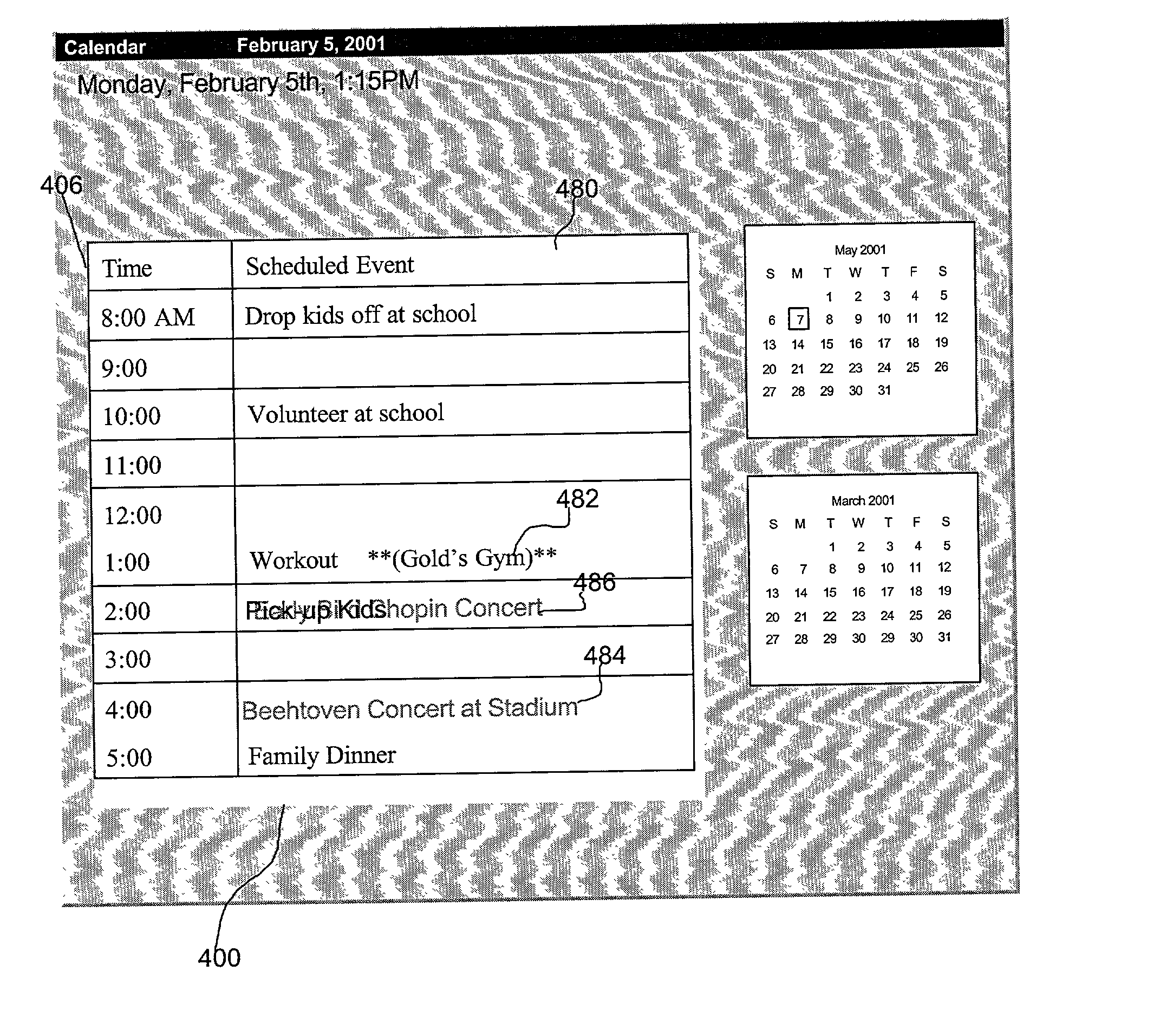
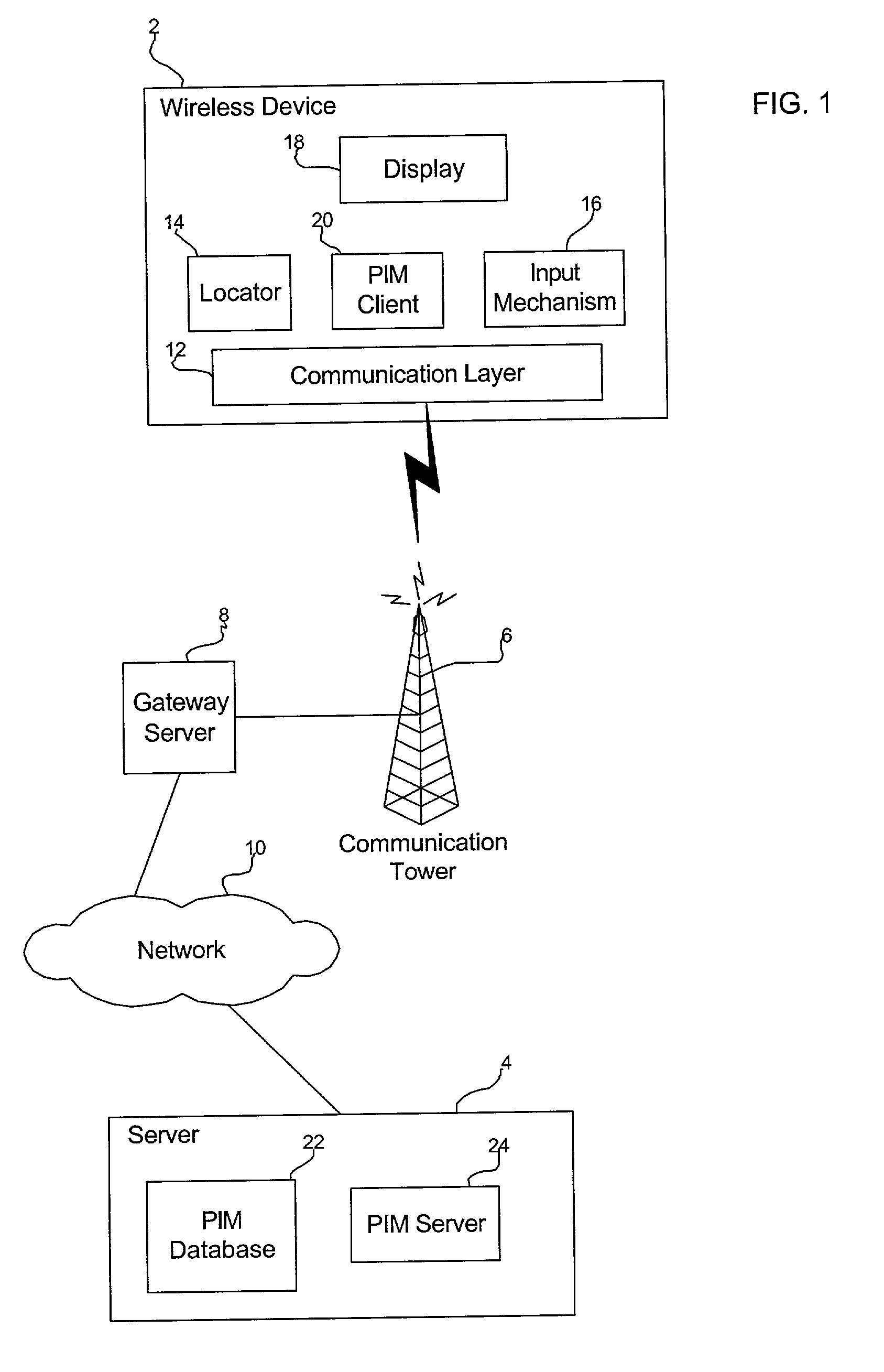
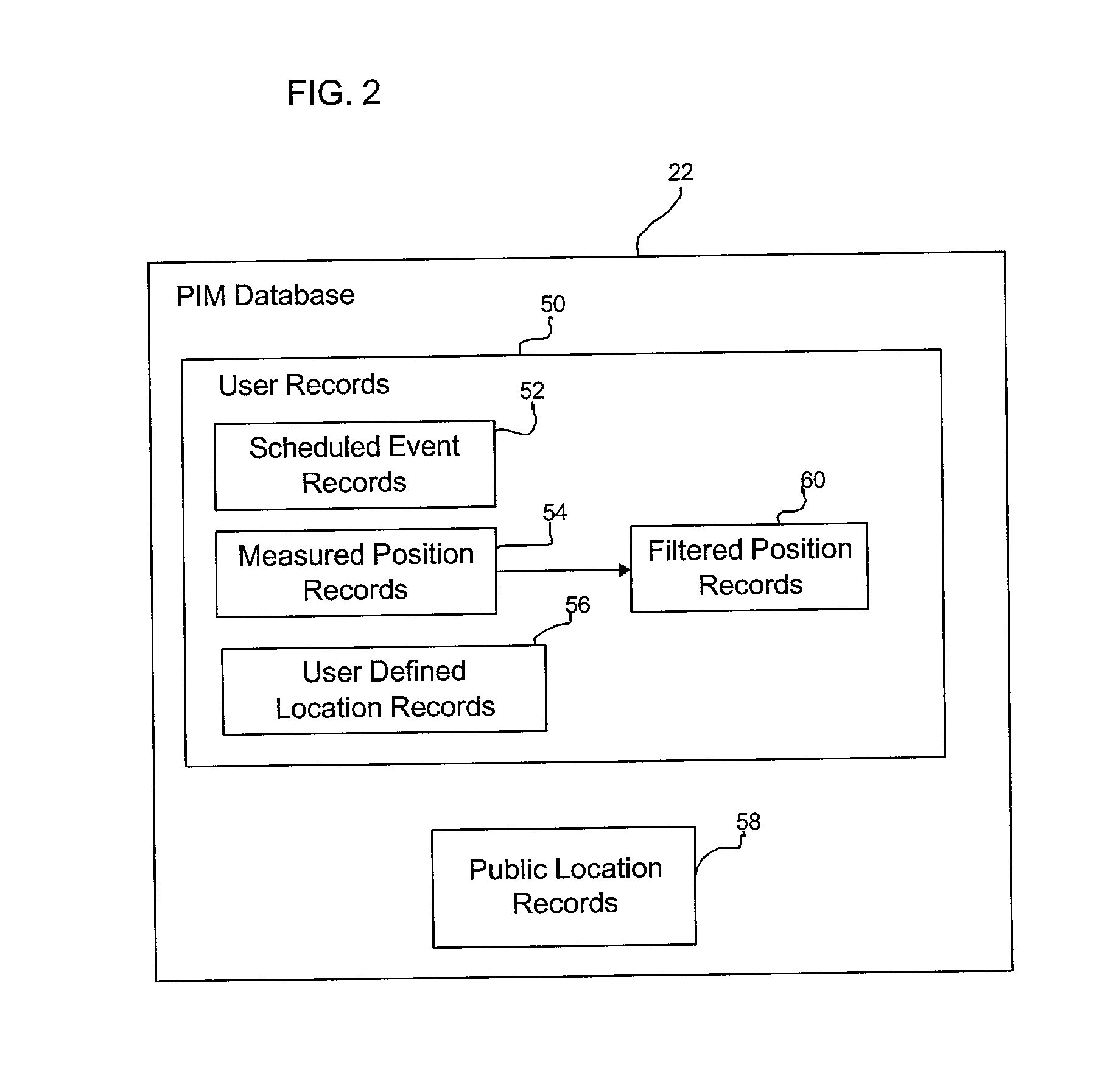
Method, system, and program for accessing calendar information for shadowed users from a database
InactiveUS20020196280A1Information can be usedSubstation equipmentOffice automationPersonal information managerDatabase access
Provided is a method, system, and program for accessing calendar information of users in a database for presentation by a personal information manager. Scheduled event records for users are maintained within the database. Further maintained in the database is information on a current location of wireless devices of users in the database, wherein one user is associated with each wireless device. Scheduled event records and the current location of a wireless device for a shadowed user are provided from the database to a device operated by a shadower user in the database.
Owner:IBM CORP
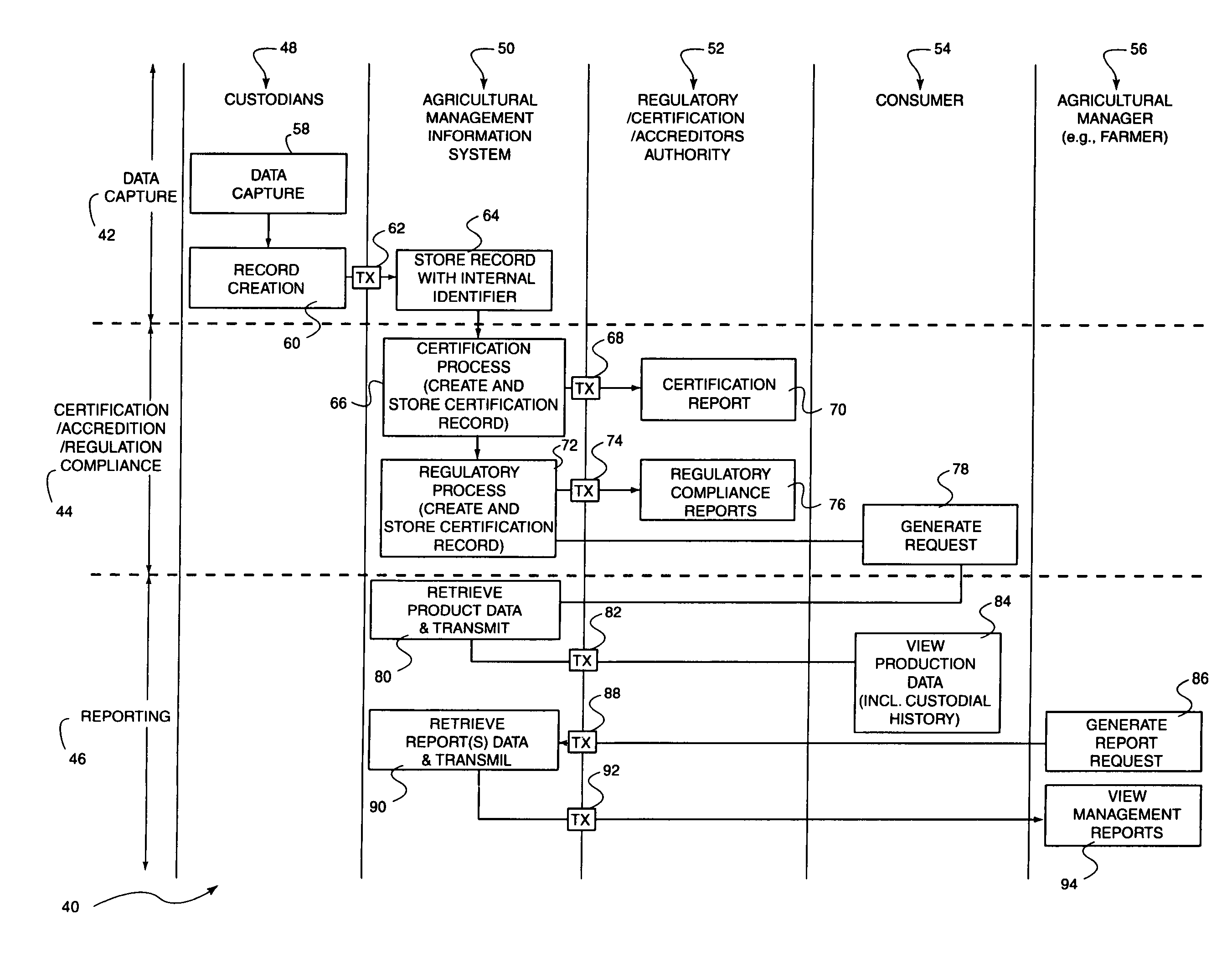
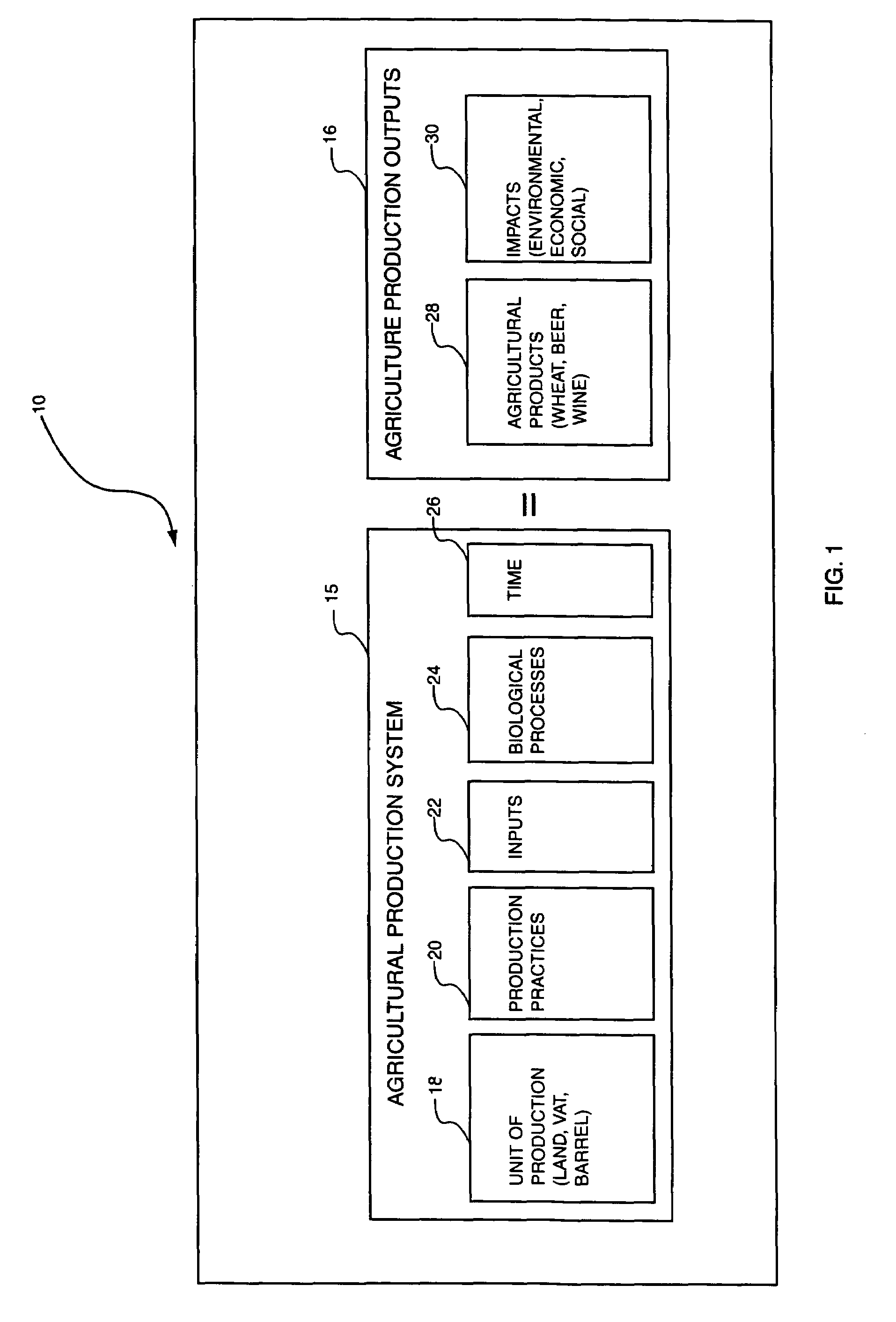
Method and system to communicate agricultural product information to a consumer
InactiveUS7440901B1Digital data processing detailsCustomer communicationsThe InternetProduct Identifier
A method to communicate agricultural product information to a user includes receiving, at a management information system, a request for agricultural product information. The request includes an agricultural product identifier. An agricultural product record, identified utilizing the agricultural product identifier, is then accessed and retrieved from a database at the management information system. The agricultural product record includes agricultural product data collected on the chain of custody of the agricultural product. The agricultural product data, as contained within the record, is then communicated to a user responsive to the request. The communication of the request, and the response, may be performed via the Internet as web-based communications.
Owner:SUREHARVEST SERVICES LLC
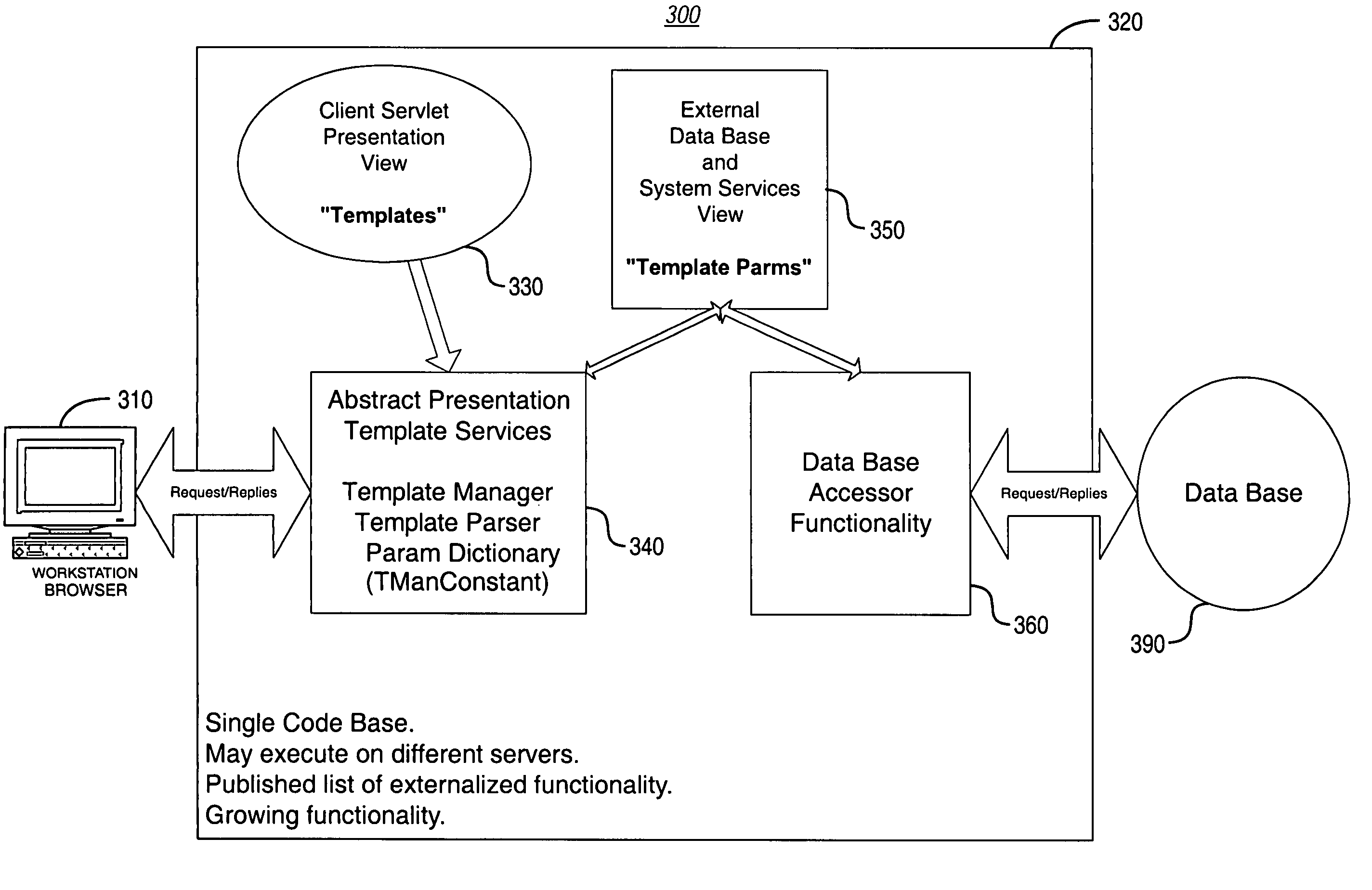
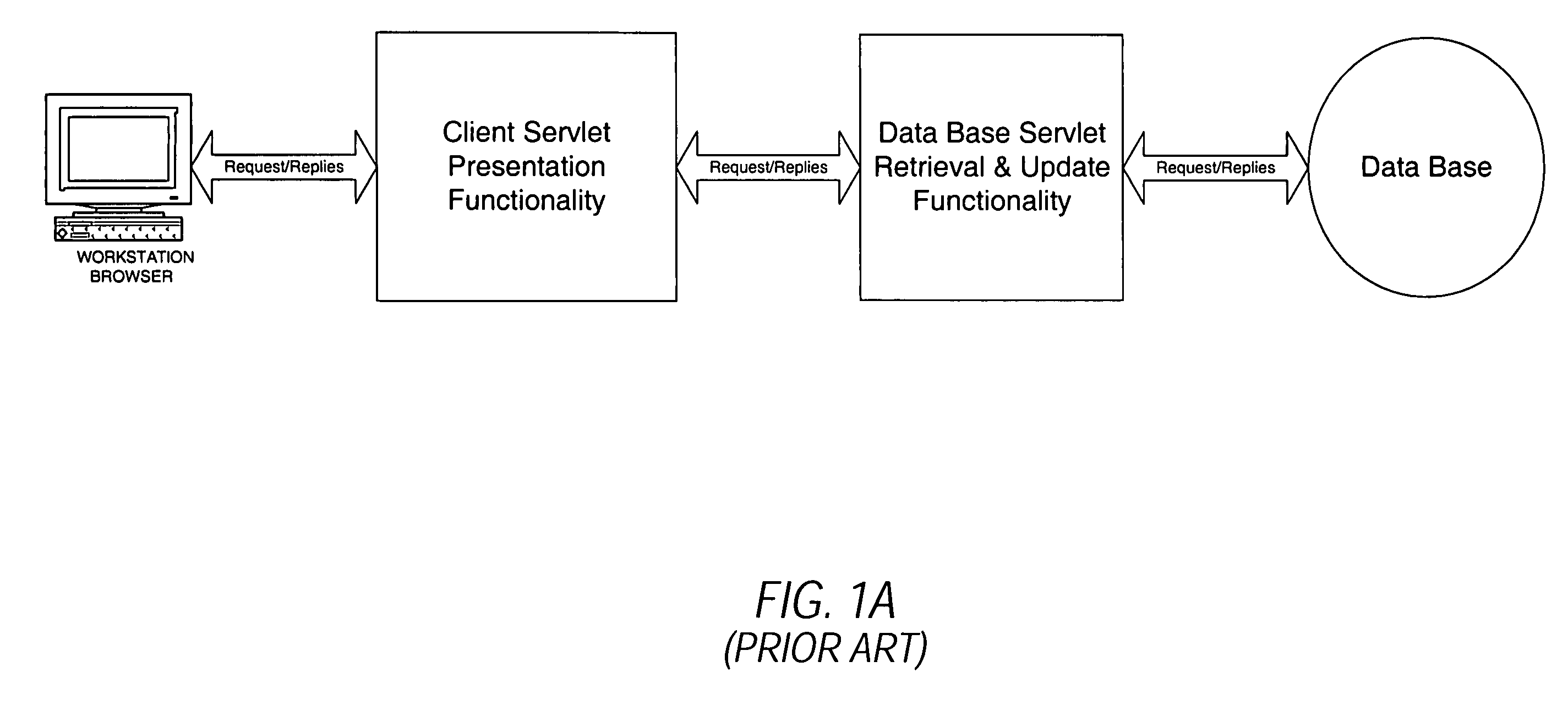
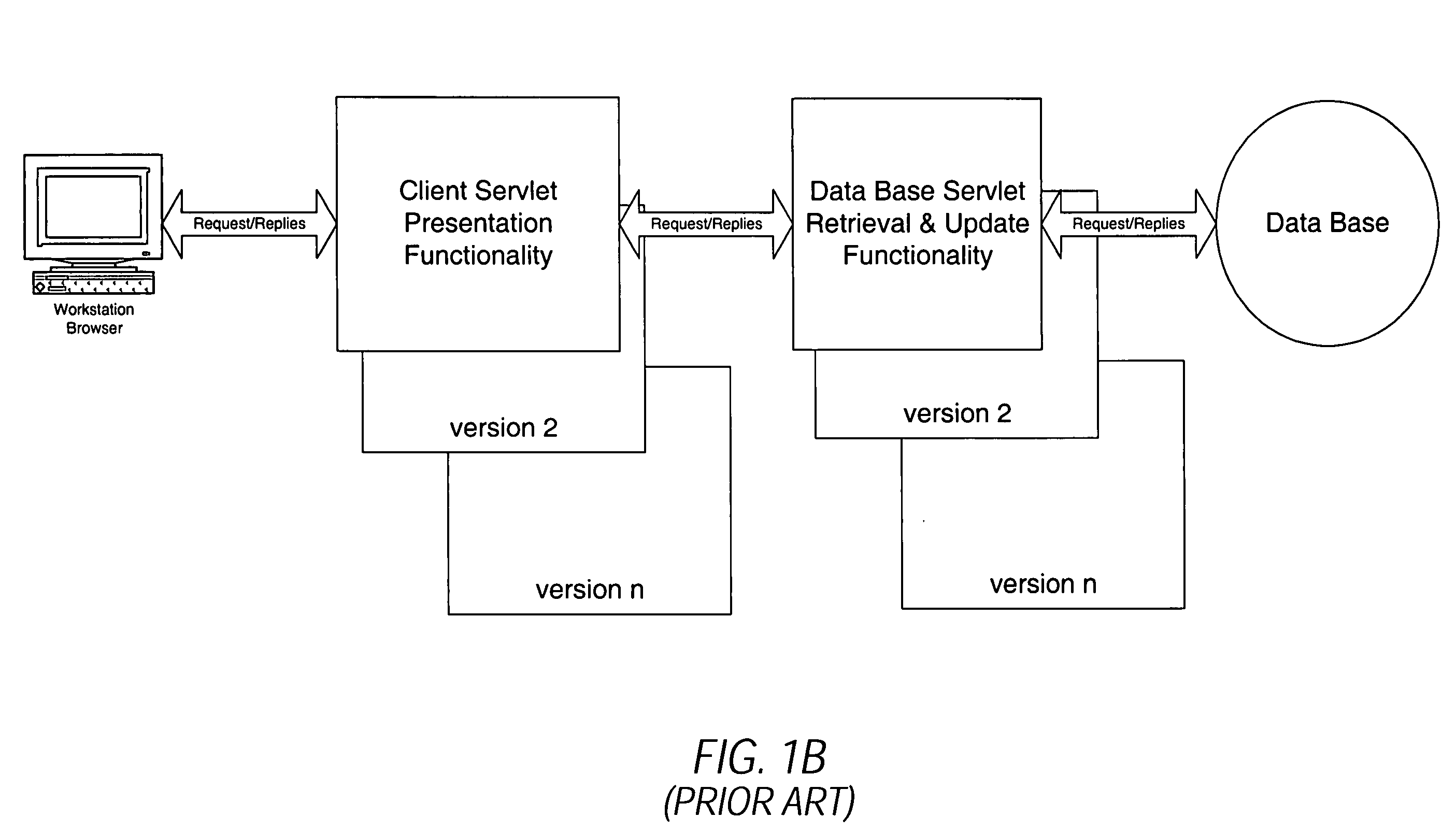
System and methodology for dynamic application environment employing runtime execution templates
InactiveUS7111231B1Digital data information retrievalSpecial data processing applicationsThe InternetApplication software
A dynamic application environment or system is described that includes a client, a run-time system, and a back-end database. The client comprises a workstation or desktop PC running browser software, such as Microsoft Internet Explorer or Netscape Navigator. The back-end database comprises a back-end (e.g., server-based) database system, such as an SQL-based database system. The run-time system includes a collection or repository module for storing “presentation templates,” a Template Services Module or engine, a Template Parameters Module, and a Database Accessor Module. The presentation templates are employed for presentation of the application to the user interface (at the client). At application run-time, the templates are provided to the Template Services Module, which includes a Template Manager and a Template Parser. These provide generic processing of the templates, which may be assembled to complete a finished product (i.e., run-time application). For instance, the Template Services Module knows how to load and parse a template and then look up its parameters, regardless of the application-specific details (e.g., user interface implementation) embodied by the template. In use, the system is deployed with presentation templates that represent the various client views of the target application, for the various platforms that the application is deployed to. In this manner, when new functionality needs to be added to the system, it may simply be added by expanding the run-time library portion of the system.
Owner:INTELLISYNC CORP
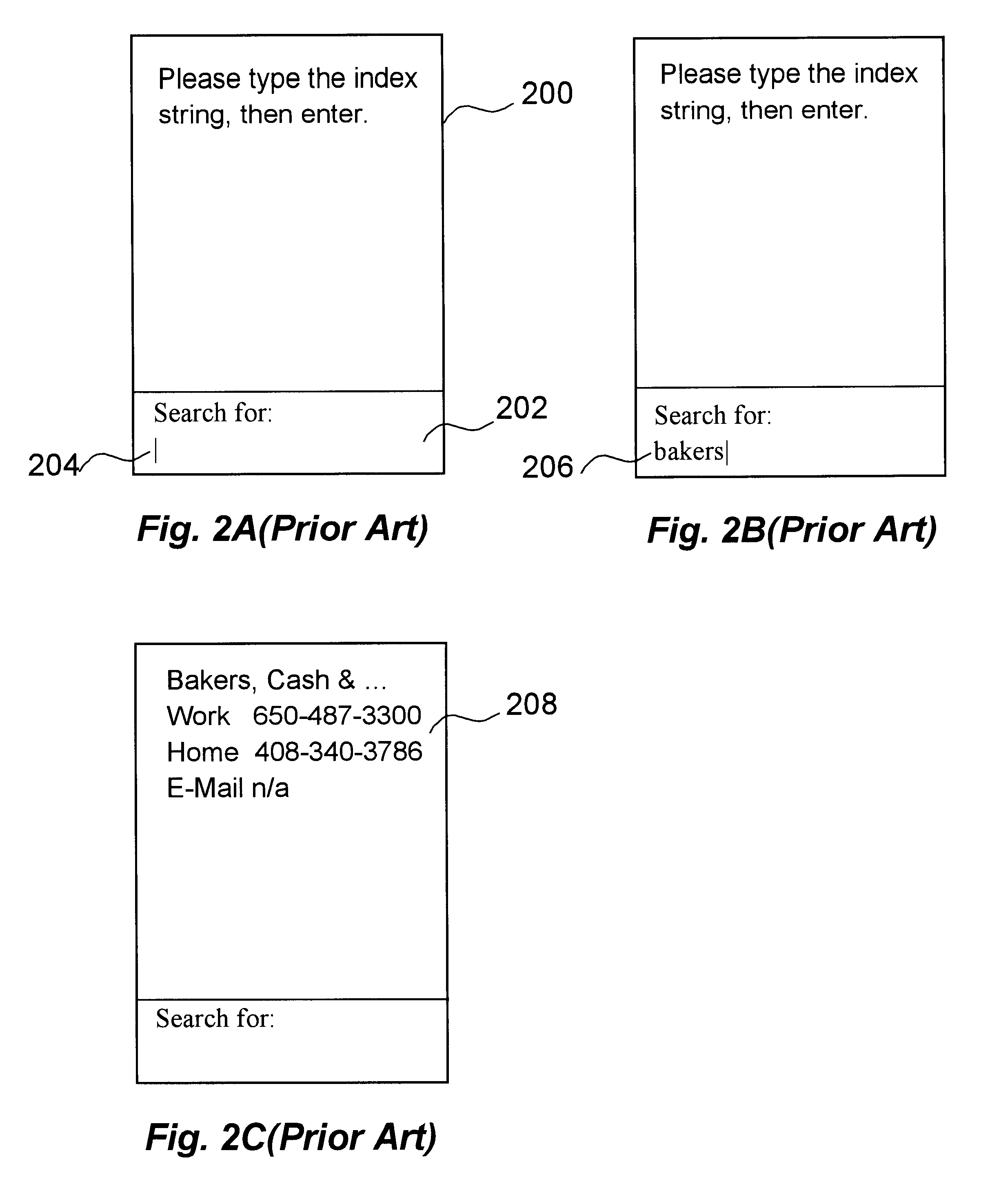
Scrolling method and apparatus for zoom display
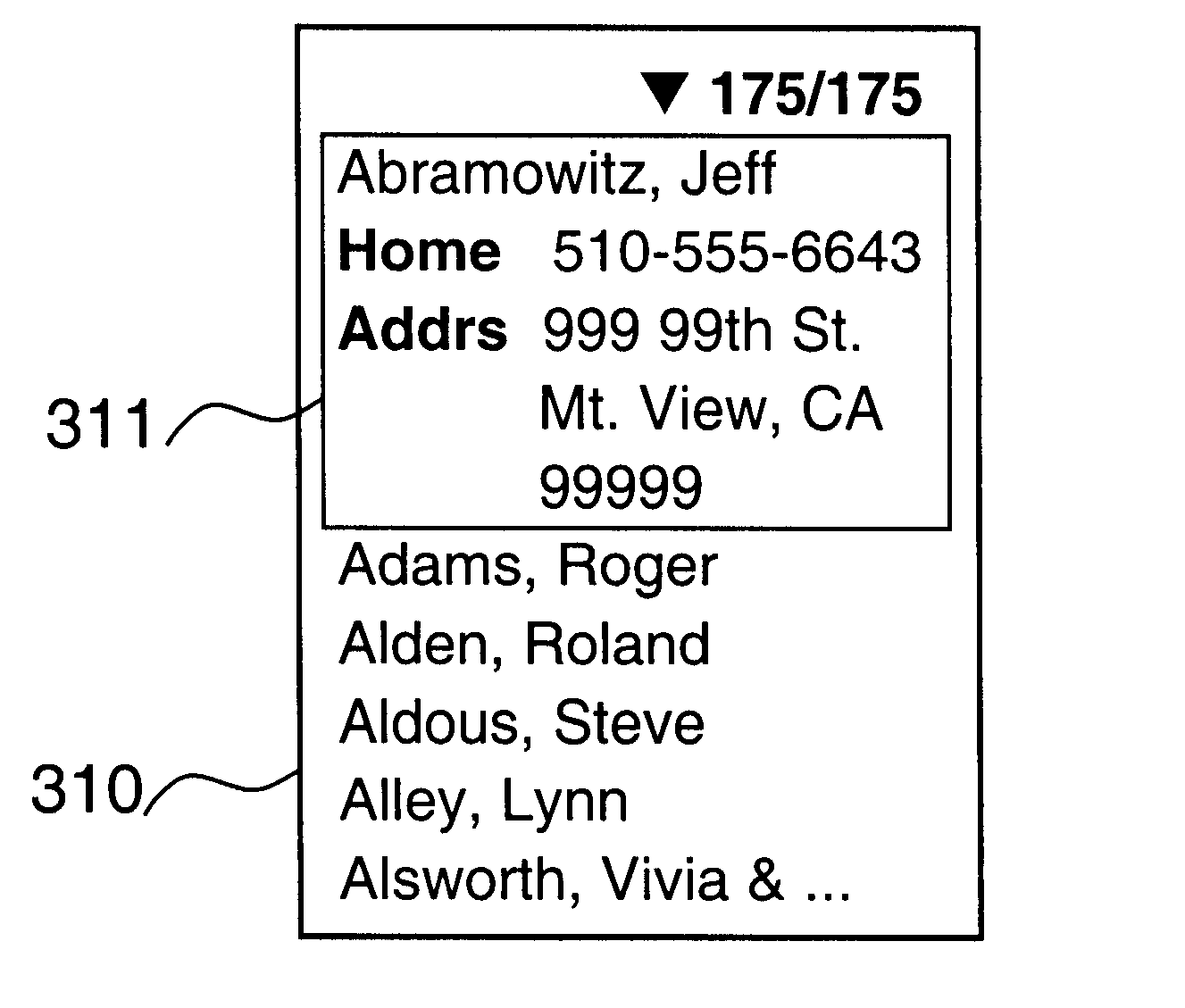
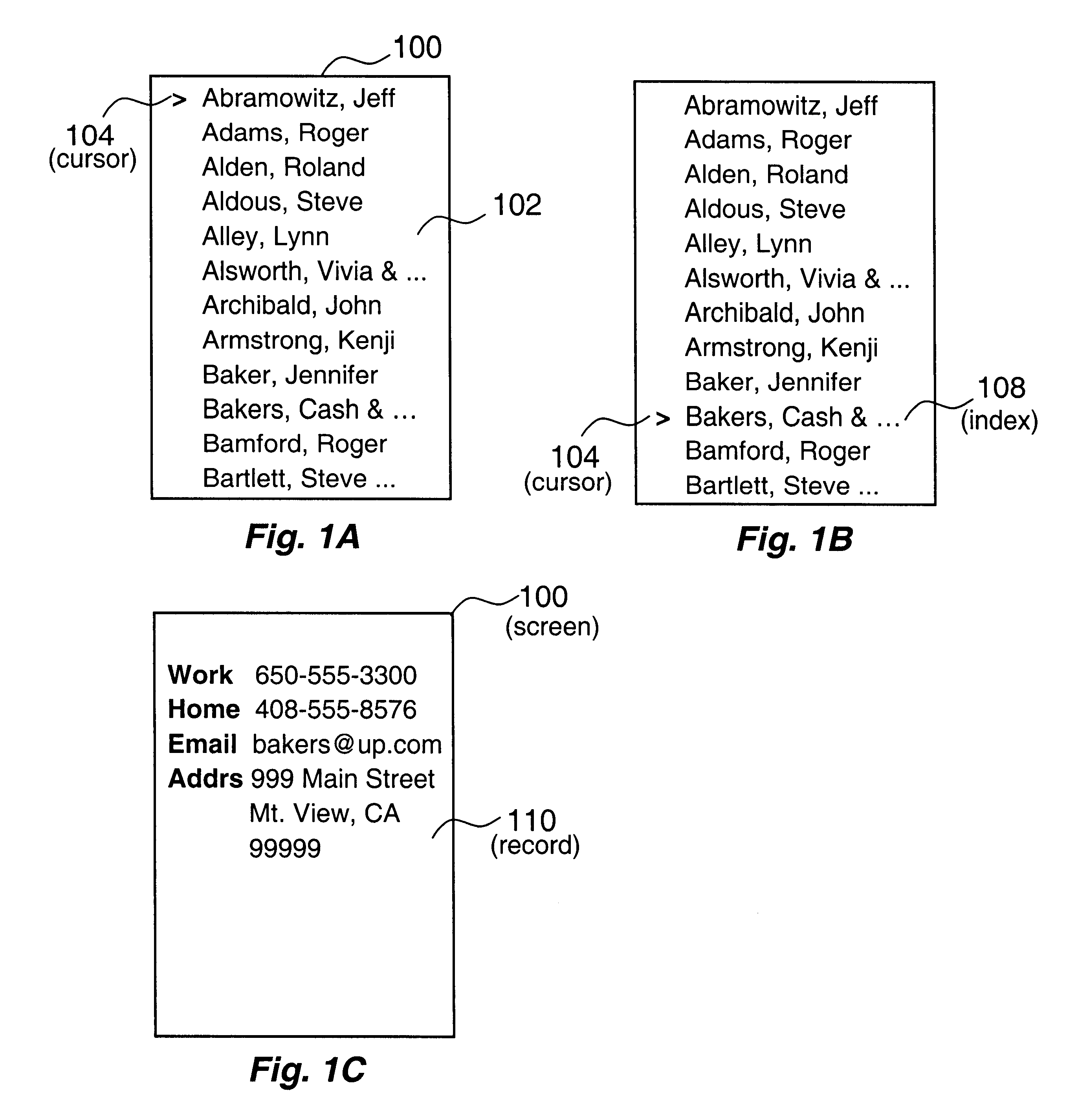
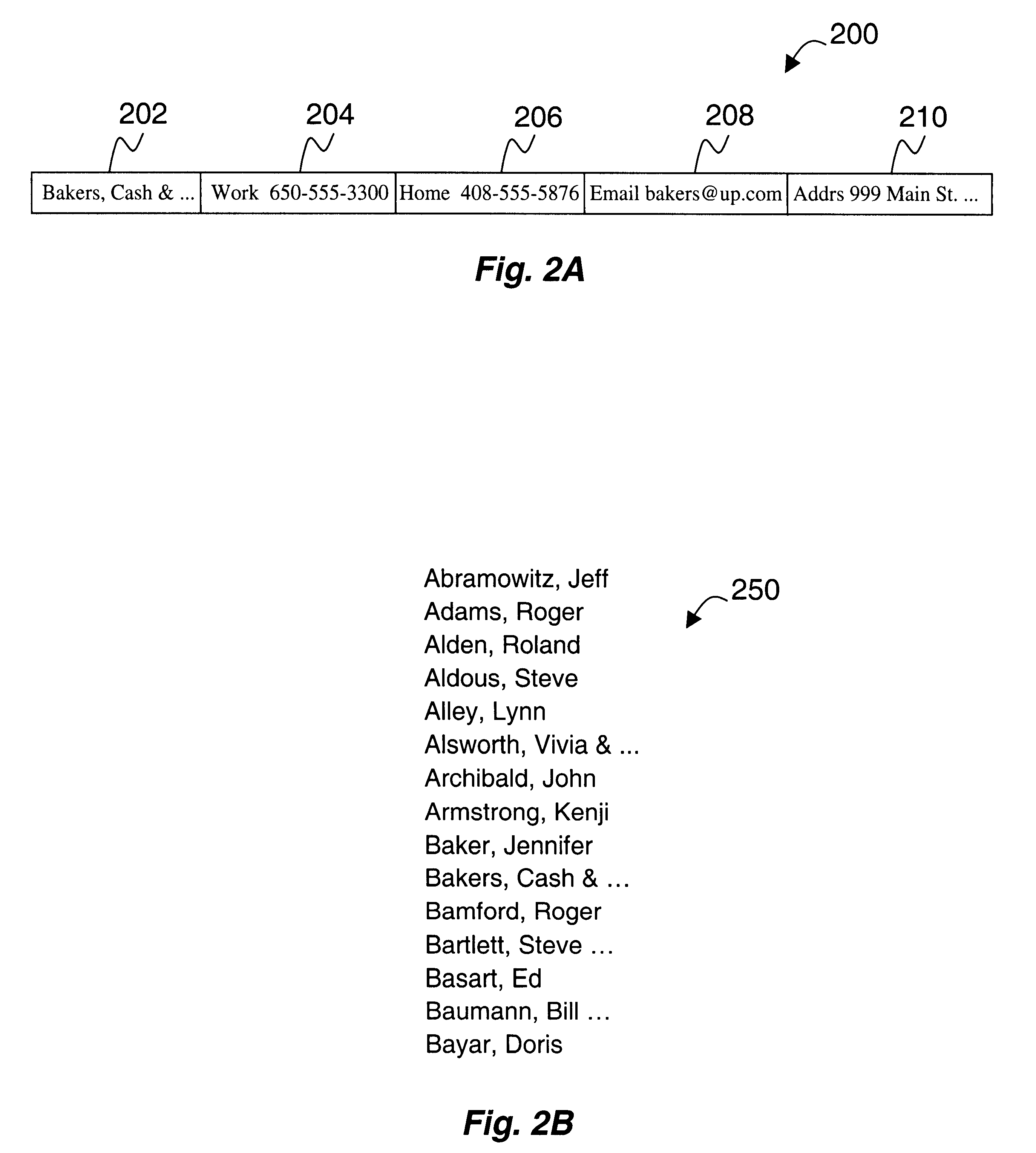
According to one aspect of the disclosed system, a user supplies character-based queries to retrieve and display a record from a structured database. For every character the user enters, a progressively reduced list of indexes that start with the entered characters is displayed. When a desired index identifying the record is among those indexes being displayed, the user may cease the character entry and scroll a zoom window upon the desired index to explore the record. According to another aspect of the disclosed system, the zoom window maintains a display of an index and at least one field of a record. Consequently, the user can access and display pertinent information of a certain record from a database quickly and efficiently with less keystrokes.
Owner:GOOGLE LLC
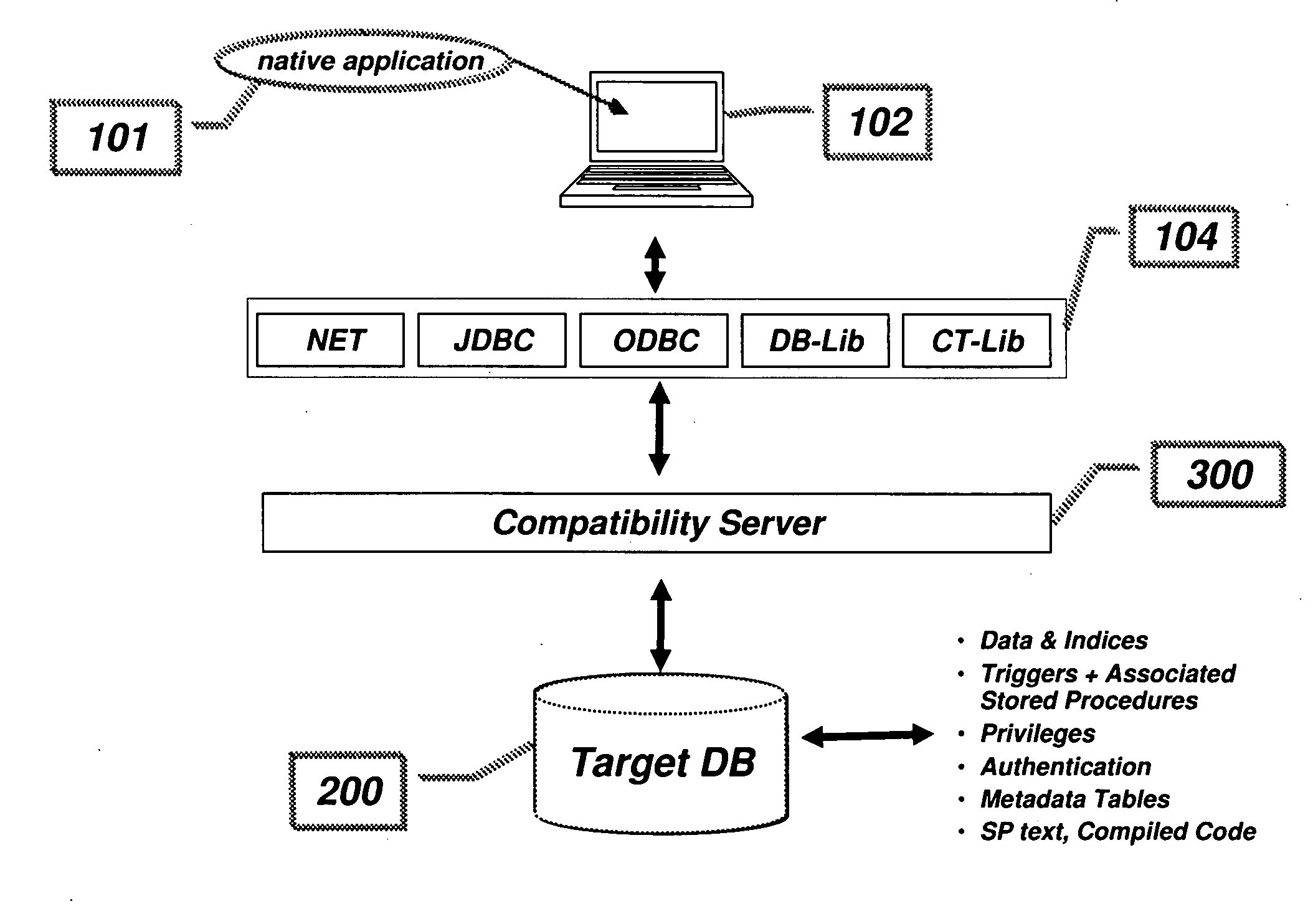
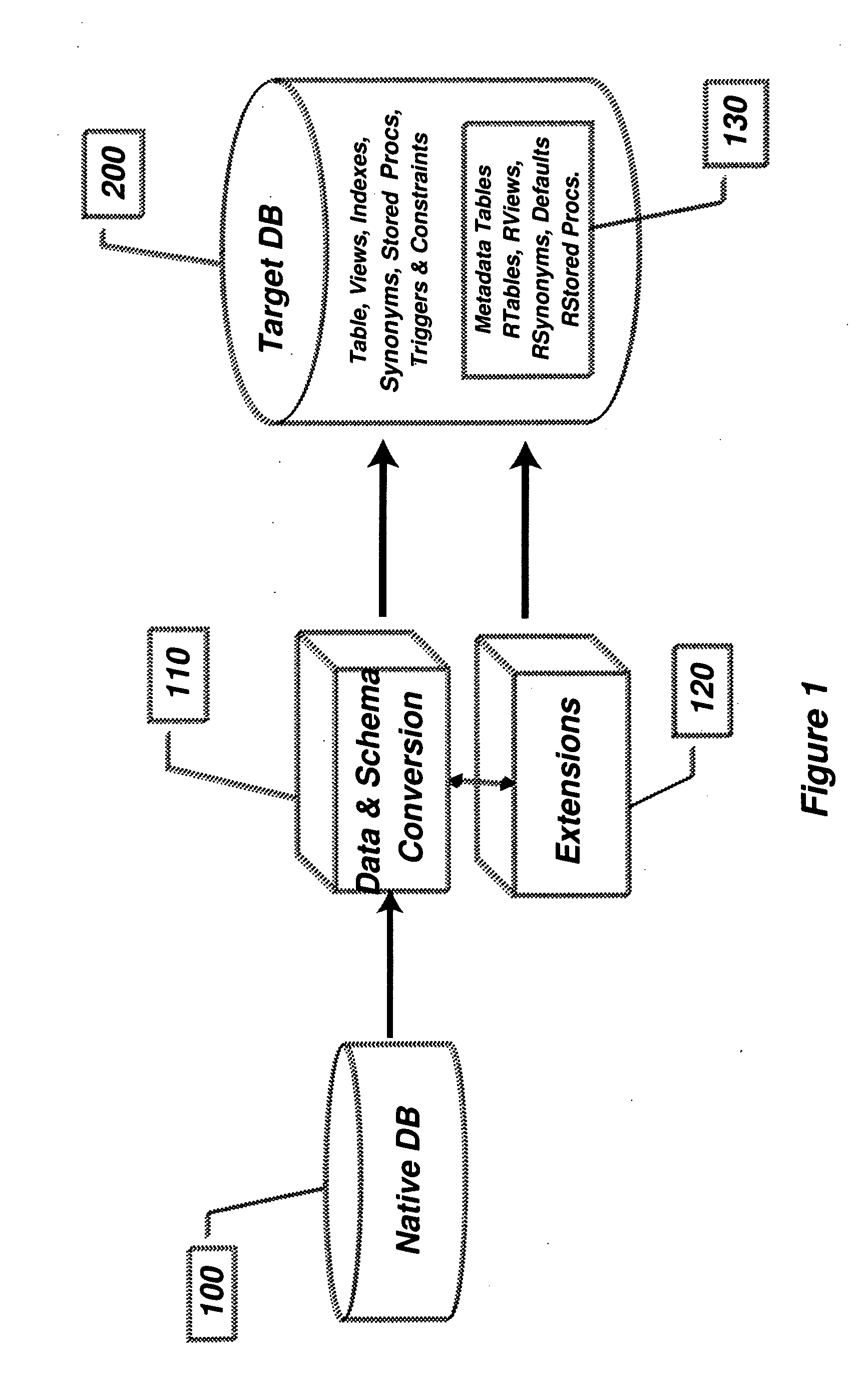
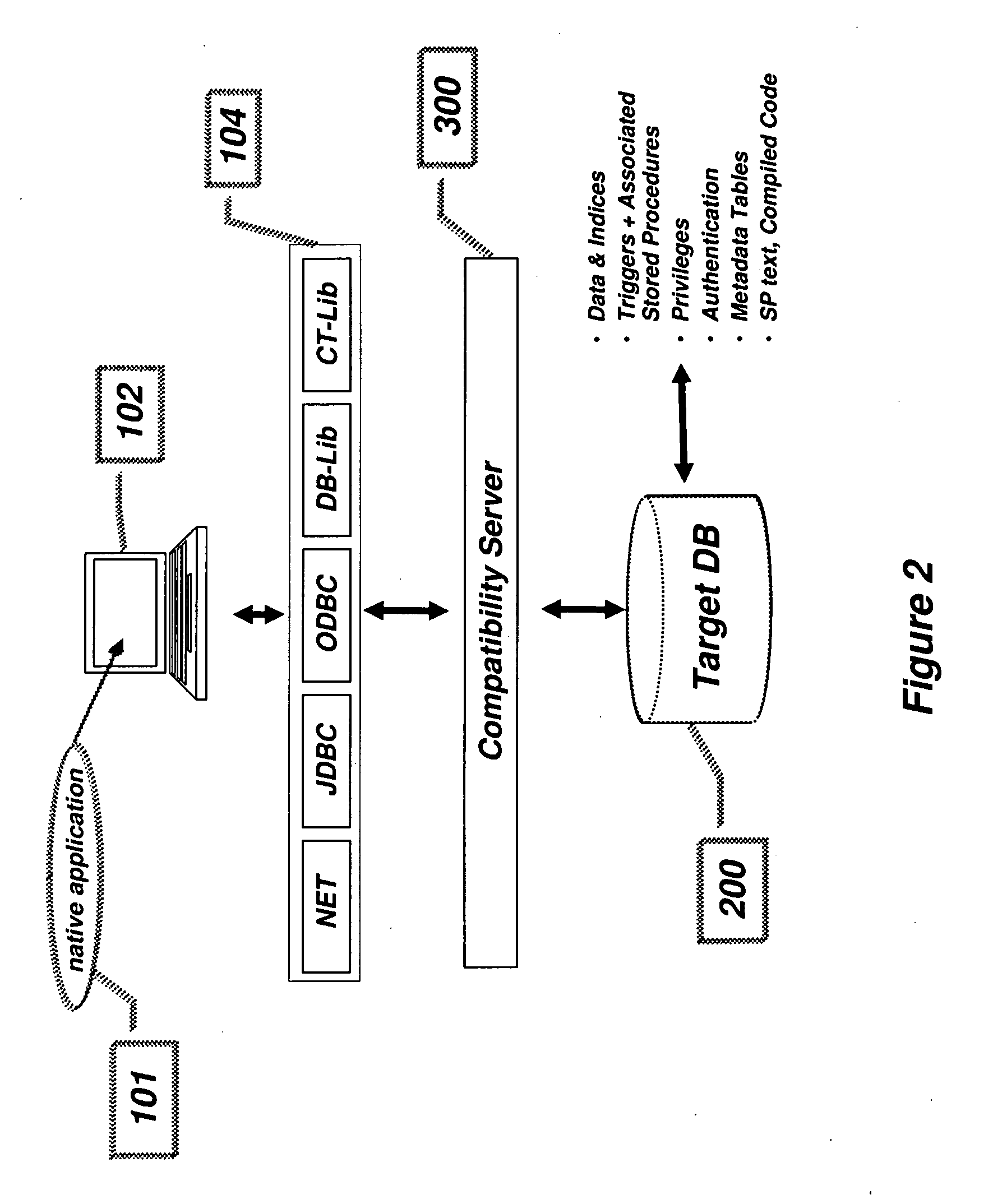
Compatibility Server for Database Rehosting
InactiveUS20100094838A1Digital data information retrievalDigital data processing detailsApplication programming interfaceDatabase application
A system and method describing a compatibility server for rehosting database applications written for a specific vendor's database on the database of a second vendor, without the need of rewriting the application to take into account differences in the application programming interfaces between the first vendor's database and the second vendor's database. Requests for access to the database are translated from one format to another at execution time. The server is also capable of translating error messages, data types and data formatting from the format used by the second database to that expected when making requests to the first database. Stored procedures defined in the first database are migrated to the second database as text blocks, and are translated at execution time into a high level programming language, compiled and executed against the second database. All information necessary for the mapping of schema, data, data types, error and status messages and data formatting, as well as information necessary to execute stored procedures, is stored in a plurality of metadata tables in the second database, which are created during a migration phase prior to executing the application.
Owner:ANTS SOFTWARE
Method and apparatus for displaying a record from a structured database with minimum keystrokes
An improved query input technique is disclosed in which a user supplies a few character-based queries and is able to retrieve and display at least as portion of a record from a structured database. For every character the user enters, a progressively reduced list of indexes that start with the entered characters is displayed. When a desired index identifying the record is among those indexes being displayed, the user may cease the character entry and scroll a zoom window upon the desired index to explore the full record. Various visual feedback indicators can also be displayed for the benefit of the user. Consequently, the user can access and display pertinent information of a certain record from a database quickly and efficiently with a reduced number keystrokes.
Owner:GOOGLE LLC
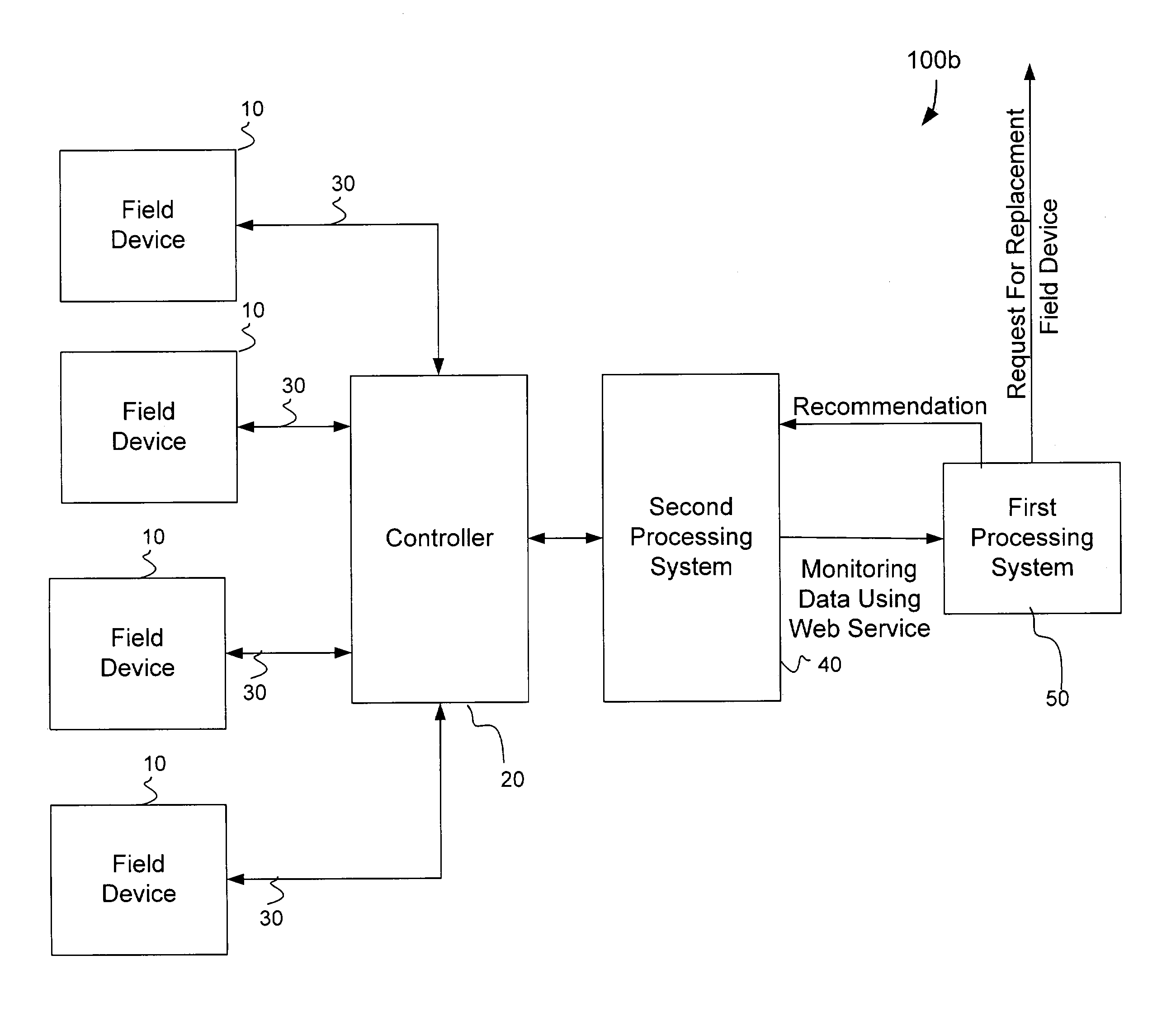
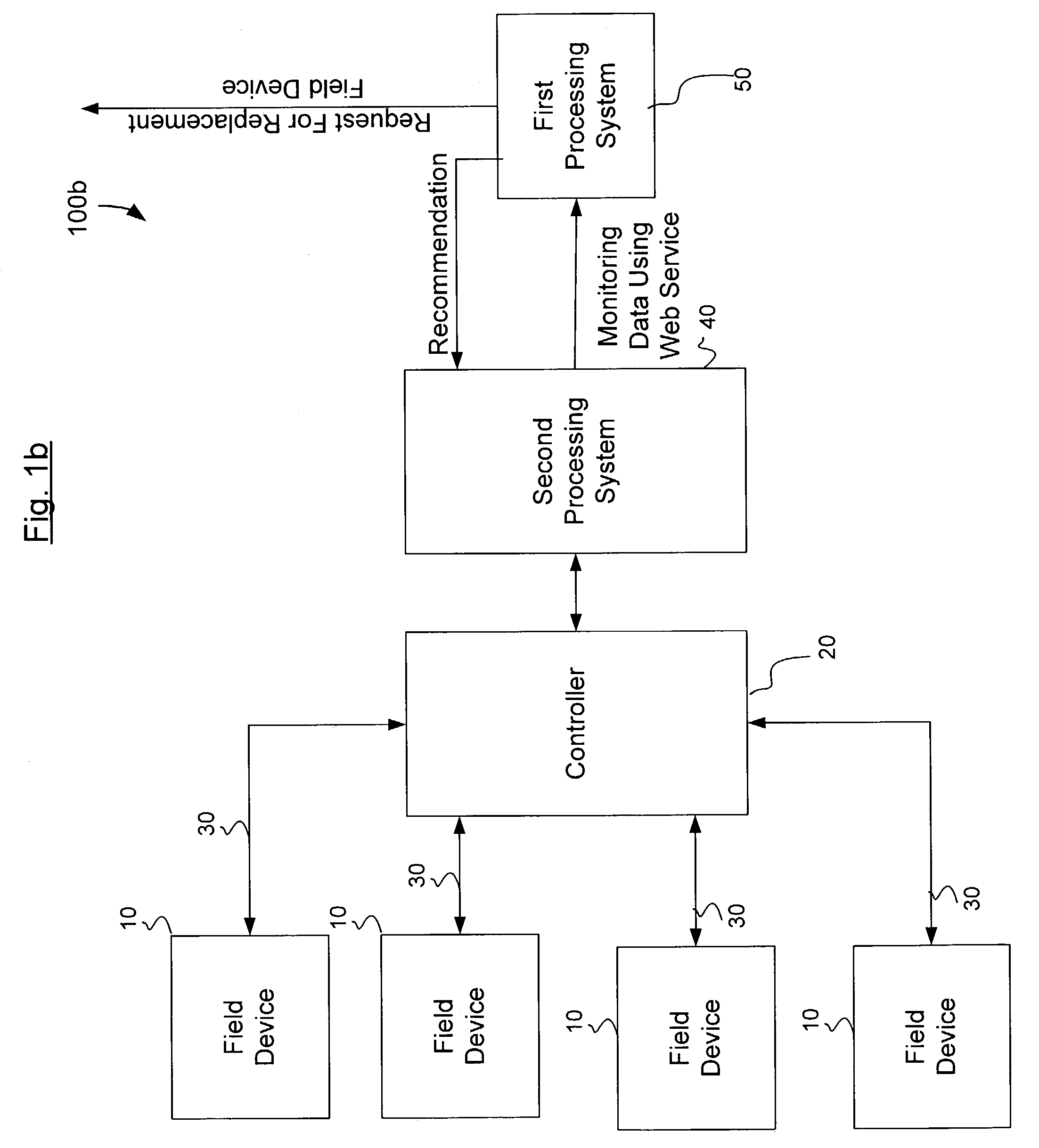
Arrangements and methods for monitoring processes and devices using a web service
An arrangement, storage medium, and method are provided for accessing monitoring data from a storage arrangement of a processing system using a Web Service, in which the monitoring data is associated with a field device. For example, the monitoring data may be in an Extensible Markup Language (“XML”) format, and a Simple Object Access Protocol can be used to access a particular portion of the monitoring data from the database. Moreover, based on the monitoring data, the field device can be replaced before problems arise therewith.
Owner:SMAR RES CORP
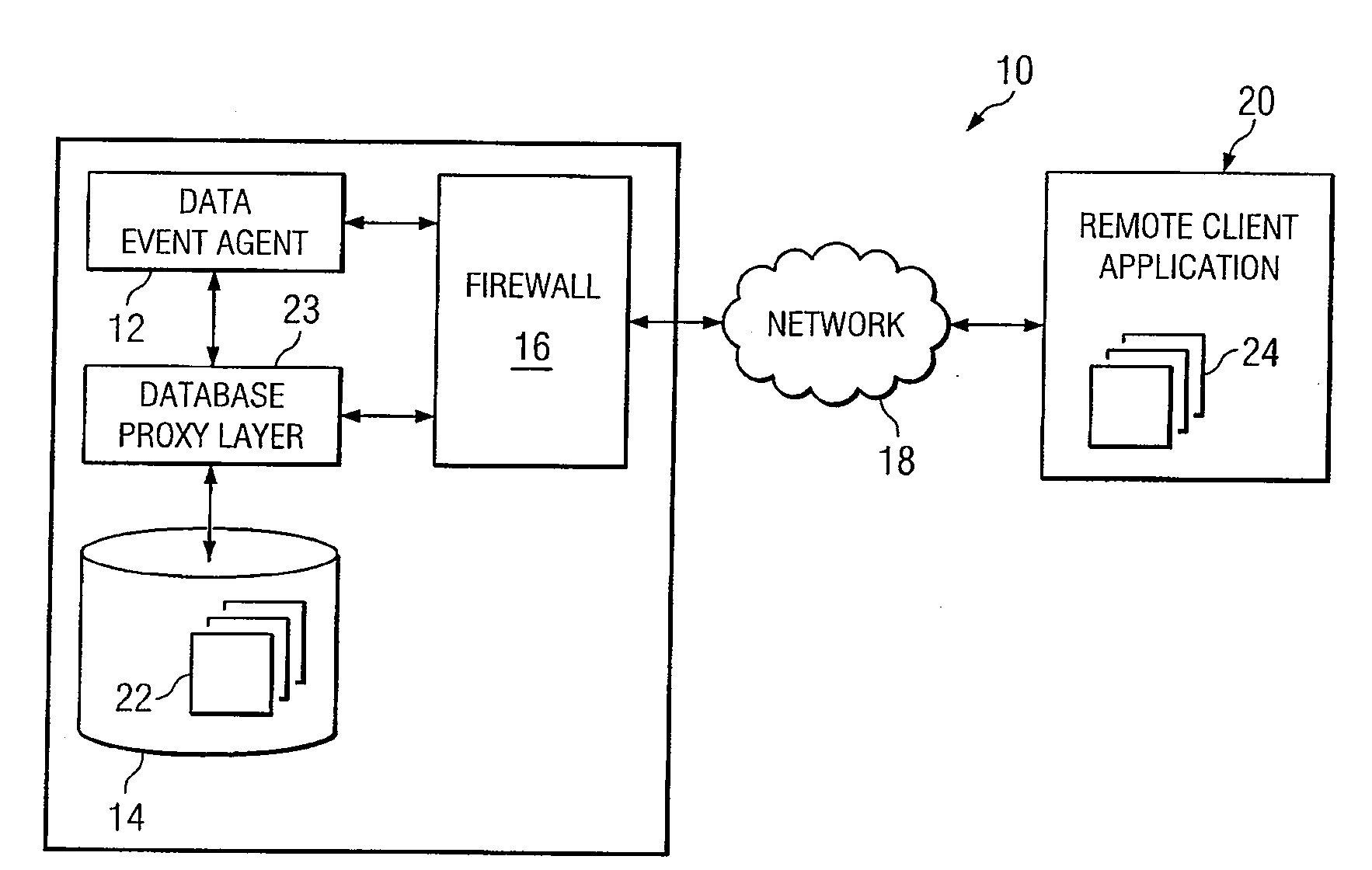
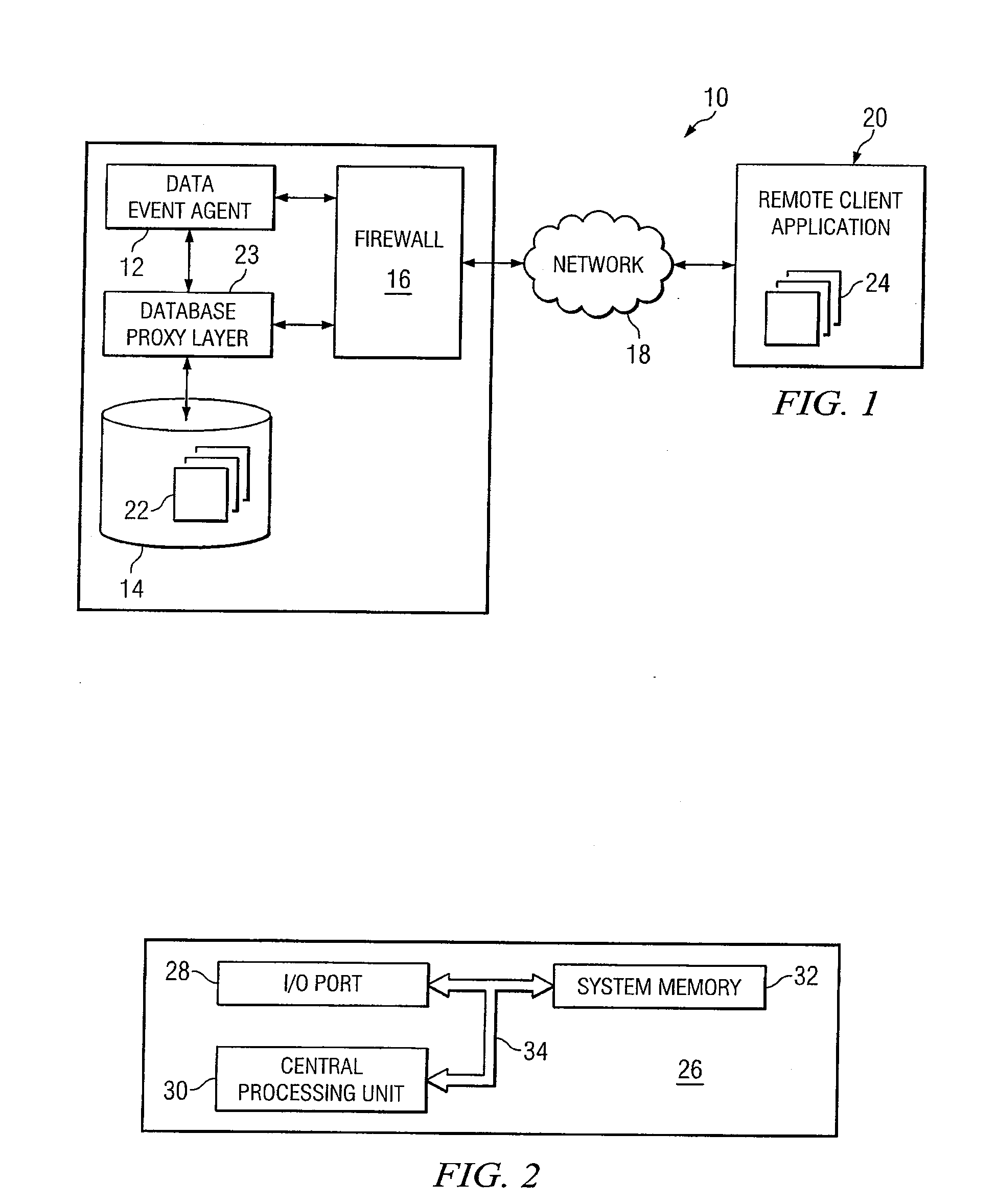
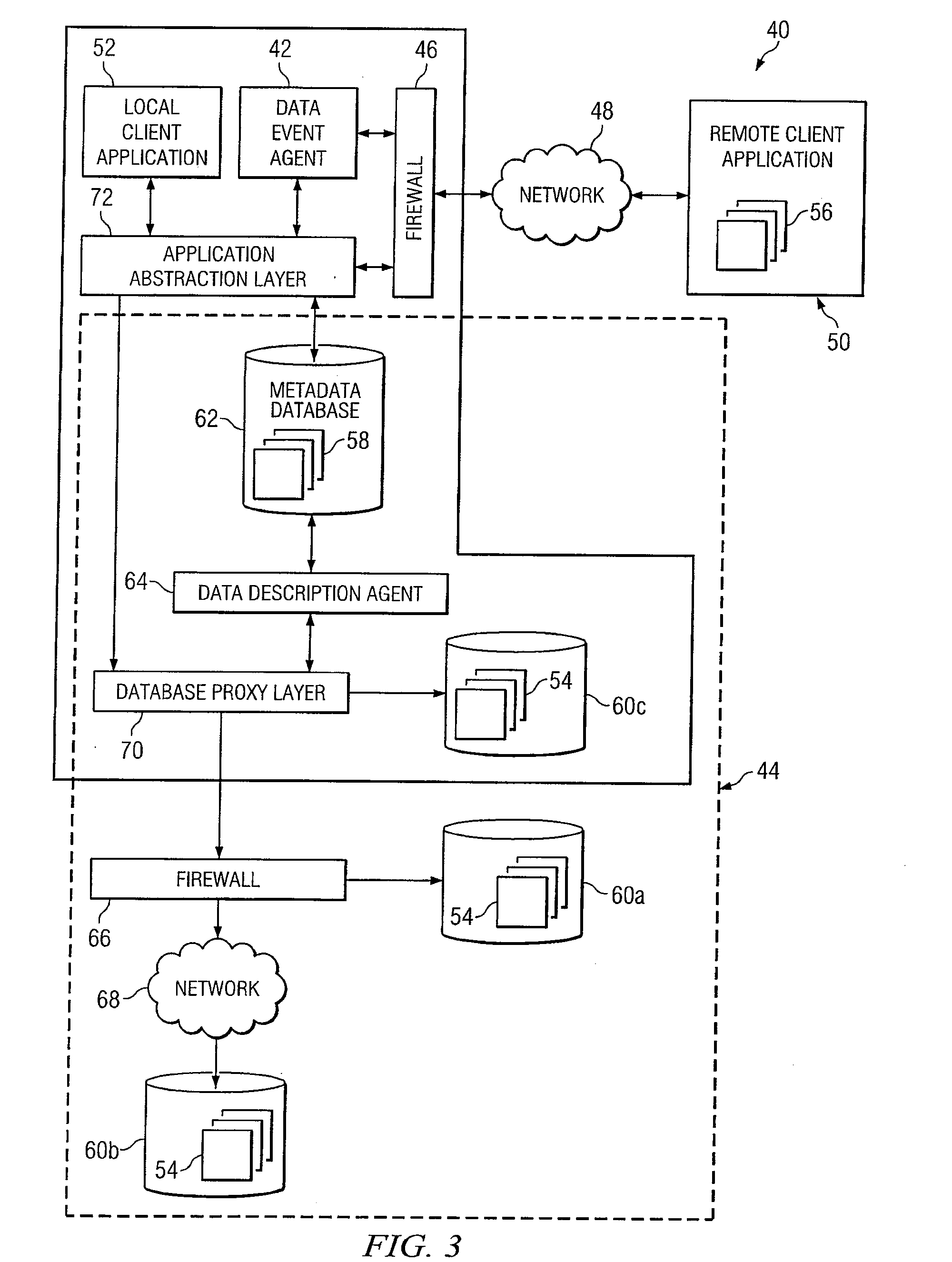
System and Method for Providing Remote Access to Events From A Database Access System
ActiveUS20080016146A1Digital data information retrievalDigital data processing detailsClient-sideApplication software
In one embodiment, a database access system includes a remote client application, a database having a plurality of data records, and a data event agent. The database has a plurality of data records and is coupled to the data event agent. The data event agent is remotely coupled to the remote client application through a firewall and operable to receive a query from the remote client application. In response to receipt of the query, the data event agent stores the query in memory in order to continually filter additions and modifications to data records against the one or more filter criteria included in the query. In the event that a data record matches the query, the data event agent transmits the data record to the remote client application.
Owner:RAYTHEON CO
System and method for managing concurrent scheduled or on-demand replication of subscriptions
InactiveUS6845383B1Broaden applicationDigital data authenticationOffice automationPartial applicationApplication software
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:IBM CORP
Distributed data storage system and method
InactiveUS20030187853A1Maximum system efficiencyImprove efficiencyOffice automationSpecial data processing applicationsMass storageSoftware distribution
A distributed data storage system and method comprising a highly integrated mass storage controller system permitting distributed management and control of data storage is disclosed. The present invention in some preferred embodiments permits mass storage media to be made available on a network in a fashion to permit global access, while automatically handling many high-level file access and data integrity / security / control functions normally associated with a host operating system. This integration and redistribution of functionality permits spatial diversification of data resources, automatic mirroring of data, fault isolation, data security, and a plethora of other control functions to be integrated into the mass storage device. This integration permits peer-to-peer communication between mass storage devices to both unburden the host data consumers but also isolate the data management functions from the data presentation functions normally associated with host systems. Exemplary embodiments of the present invention as applied to specific preferred system contexts include but are not limited to distributed data storage in a networked environment, brokered data access metering, database access / control, data backup, journaling, checkpointing, and automated software distribution.
Owner:HENSLEY ROY AUSTIN +1
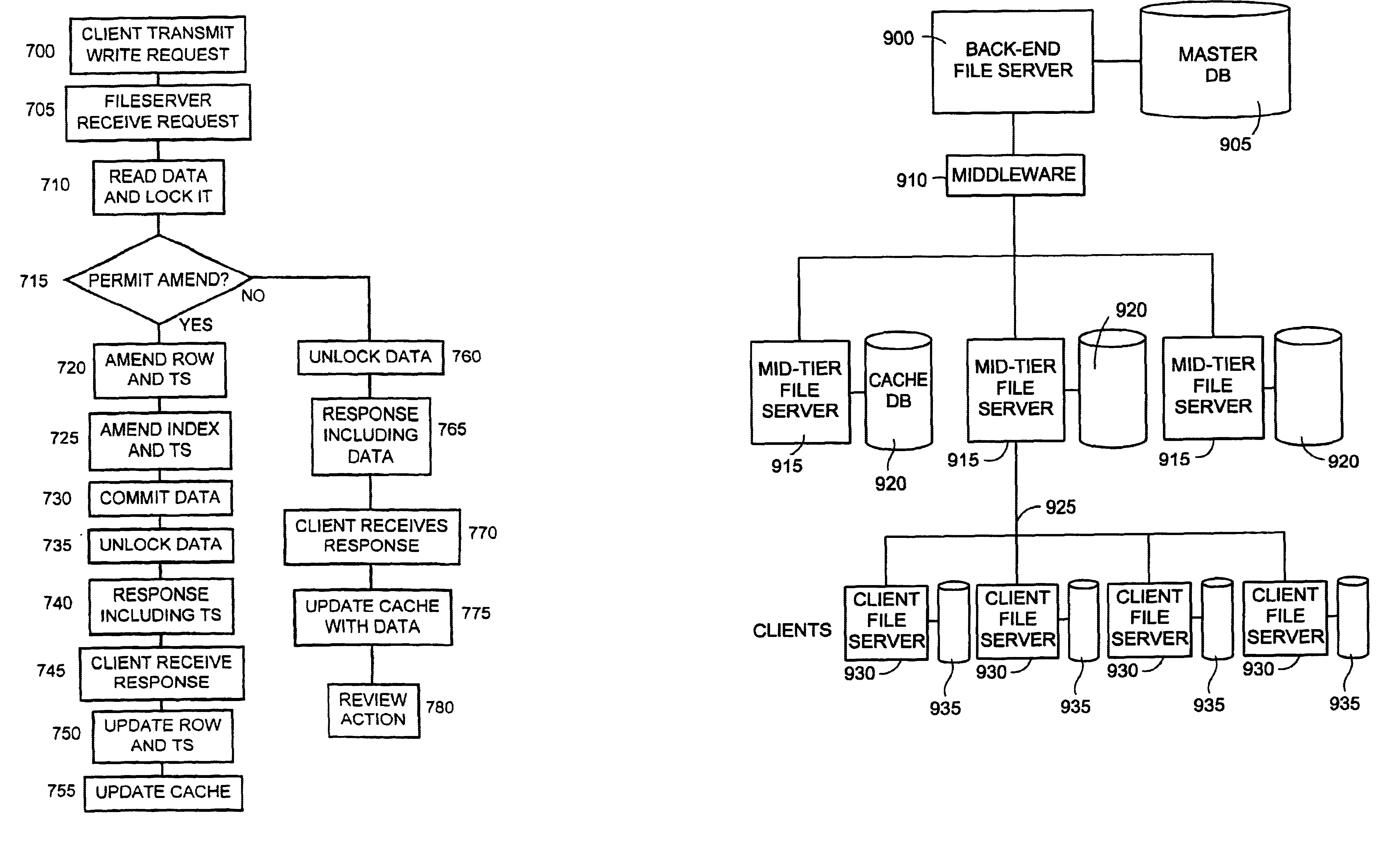
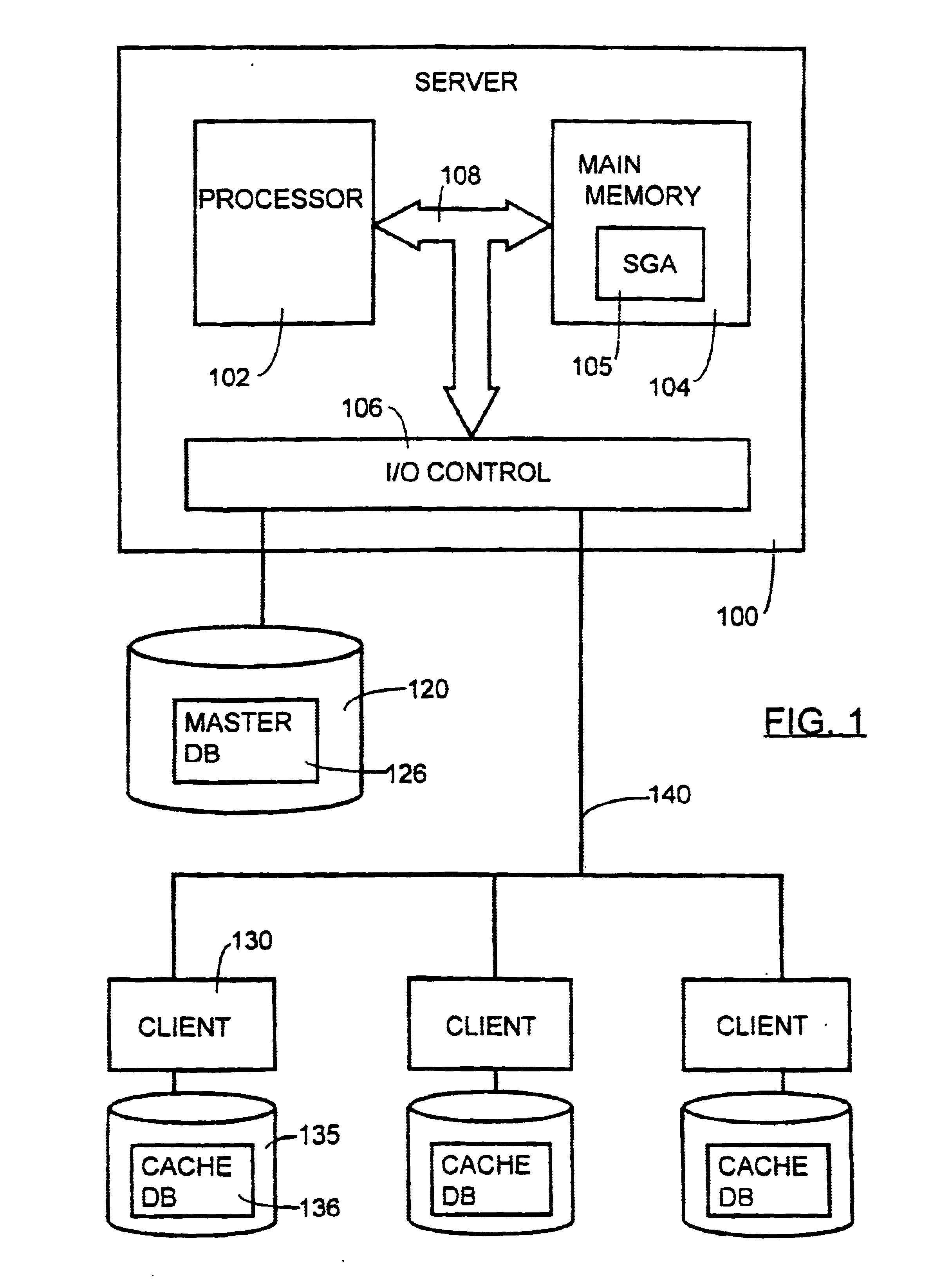
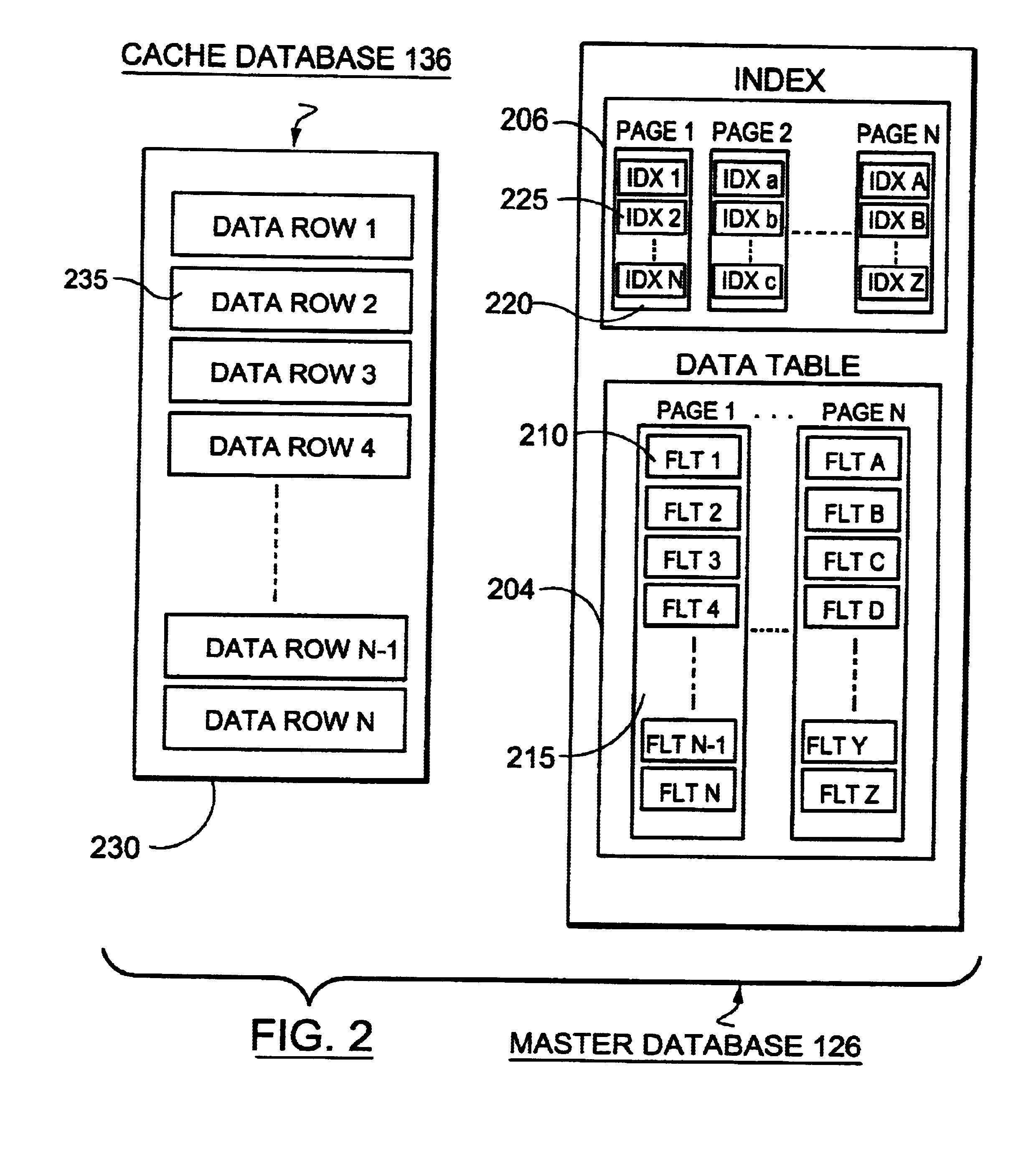
Database access
InactiveUS6934717B1Data processing applicationsSpecial data processing applicationsClient-sideFile server
In a client / server computer environment having a fileserver running a mater database and clients supporting cache databases, inconsistent data write accesses are prevented by using a data locking technique, which locks data during the course of an up-date transaction requested by one client. This prevents access to the same data by another client. Data consistency is checked prior to the write access, by comparing a time stamp associated with a respective cache database entry and a time stamp associated with the index to the corresponding data entry in the master database. Time stamp equivalence obviates the need to access the master database or to transfer data across the client / server communications network.
Owner:BRITISH TELECOMM PLC
Method for diagnosing and prescribing a regimen of therapy for human health risk
InactiveUS20050260610A1Data processing applicationsMicrobiological testing/measurementHuman DNA sequencingRegimen
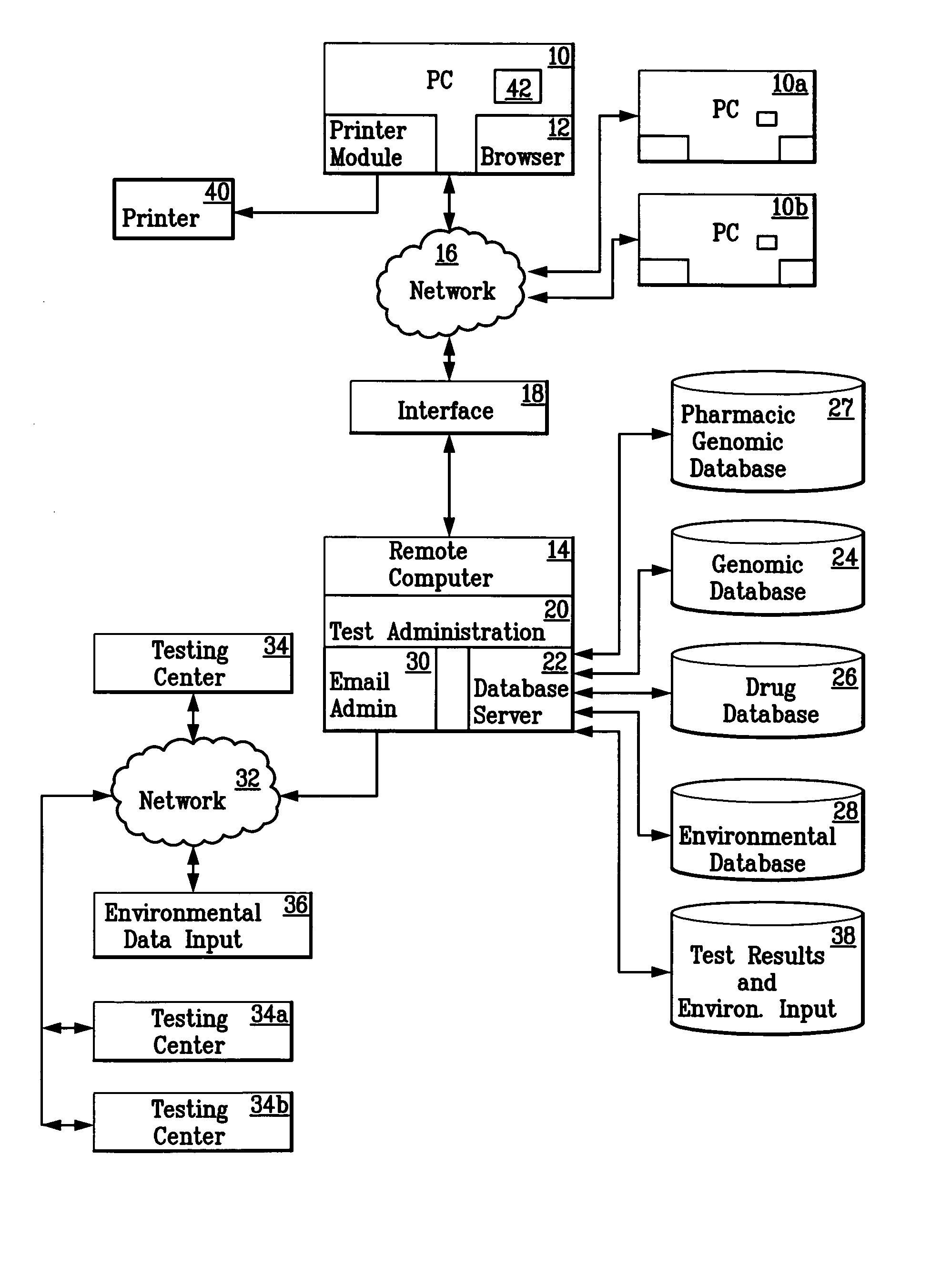
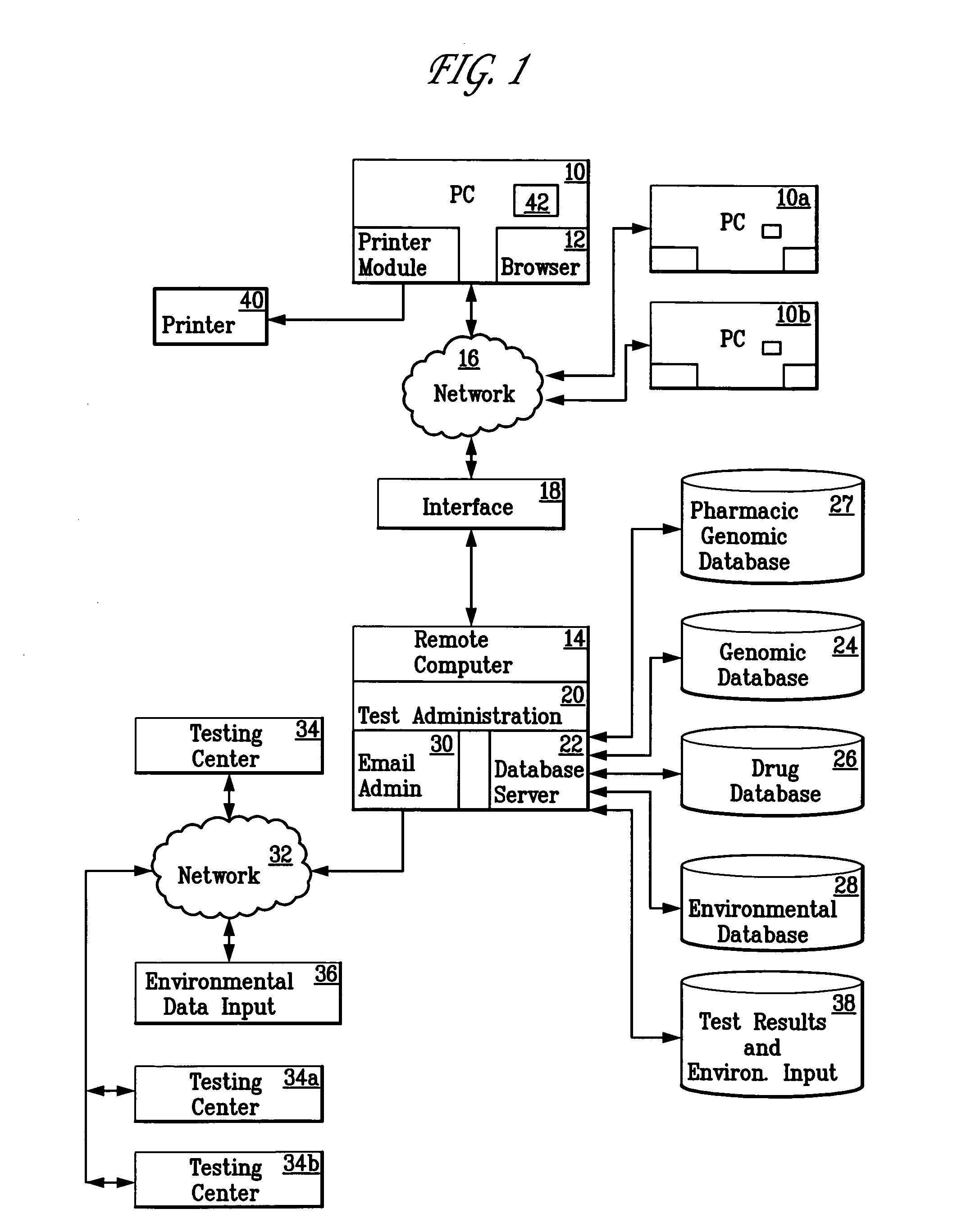
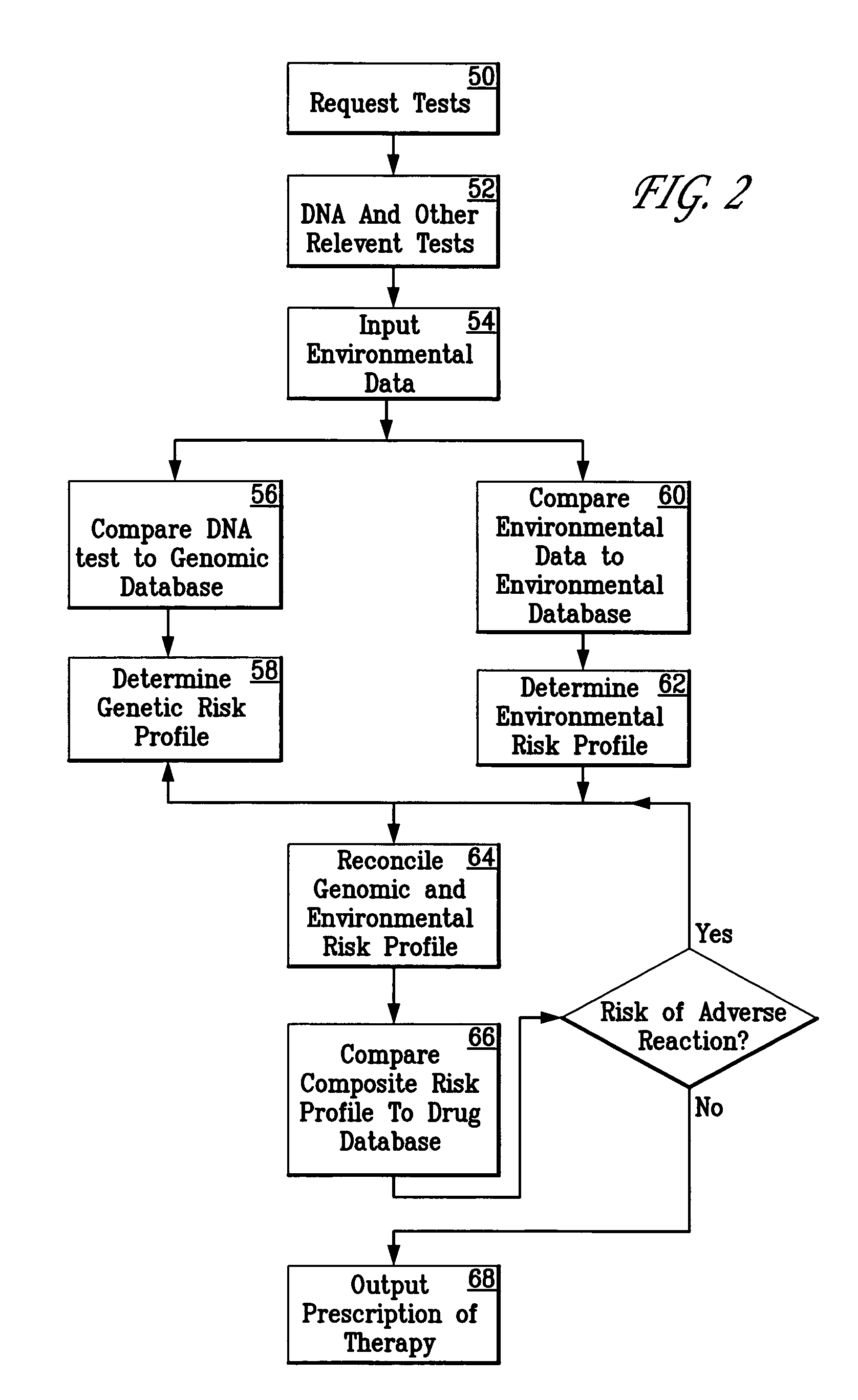
A patient is diagnosed and a regimen of treatment is prescribed in a system which tests the patients, receives test results from a patient, including DNA test results. A database of human genome data correlating human health disorder with DNA genetic tests is accessed. A database of environmental factors which correlate known human health disorders with environmental conditions is accessed. Risk factors including genetic risk and environmental risk are developed, and from these, a composite risk factor is developed. This is used to access a database of prescribed drug therapy.
Owner:KLIMANJARO PARTNERSHIP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com