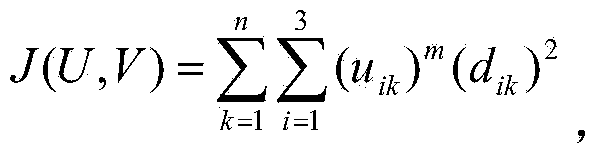Patents
Literature
998 results about "Classification rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Given a population whose members each belong to one of a number of different sets or classes, a classification rule or classifier is a procedure by which the elements of the population set are each predicted to belong to one of the classes. A perfect classification is one for which every element in the population is assigned to the class it really belongs to. An imperfect classification is one in which some errors appear, and then statistical analysis must be applied to analyse the classification.
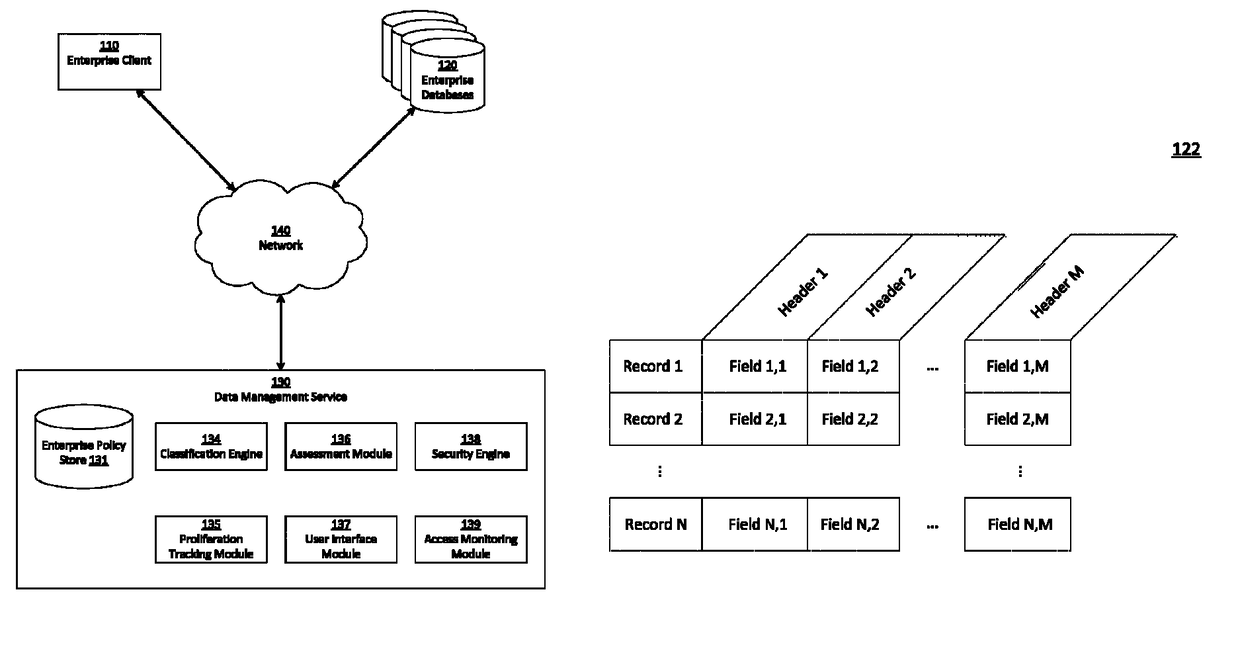
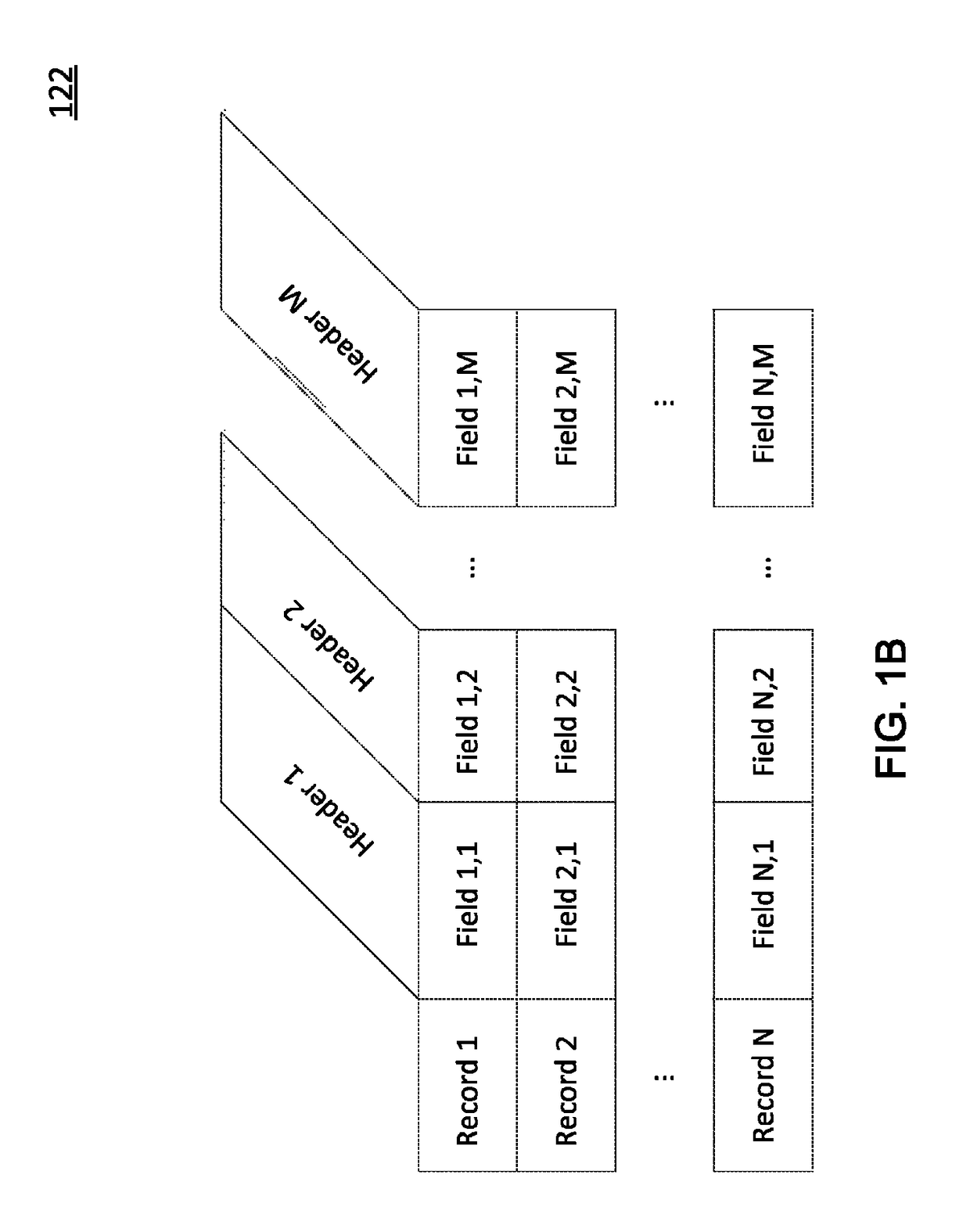
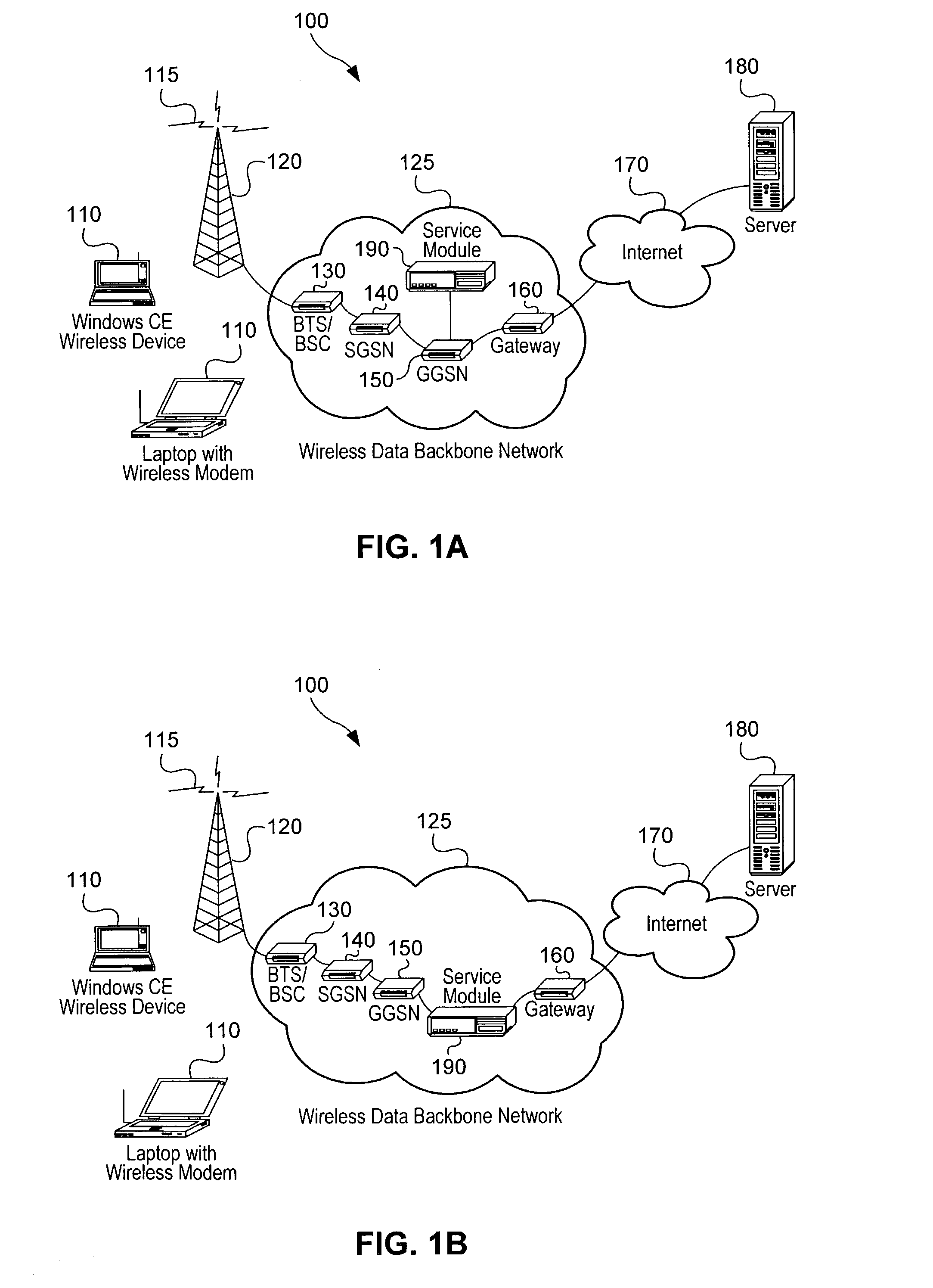
Identifying and securing sensitive data at its source
ActiveUS9785795B2Reduce processRelational databasesDigital data protectionData managementClassification rule
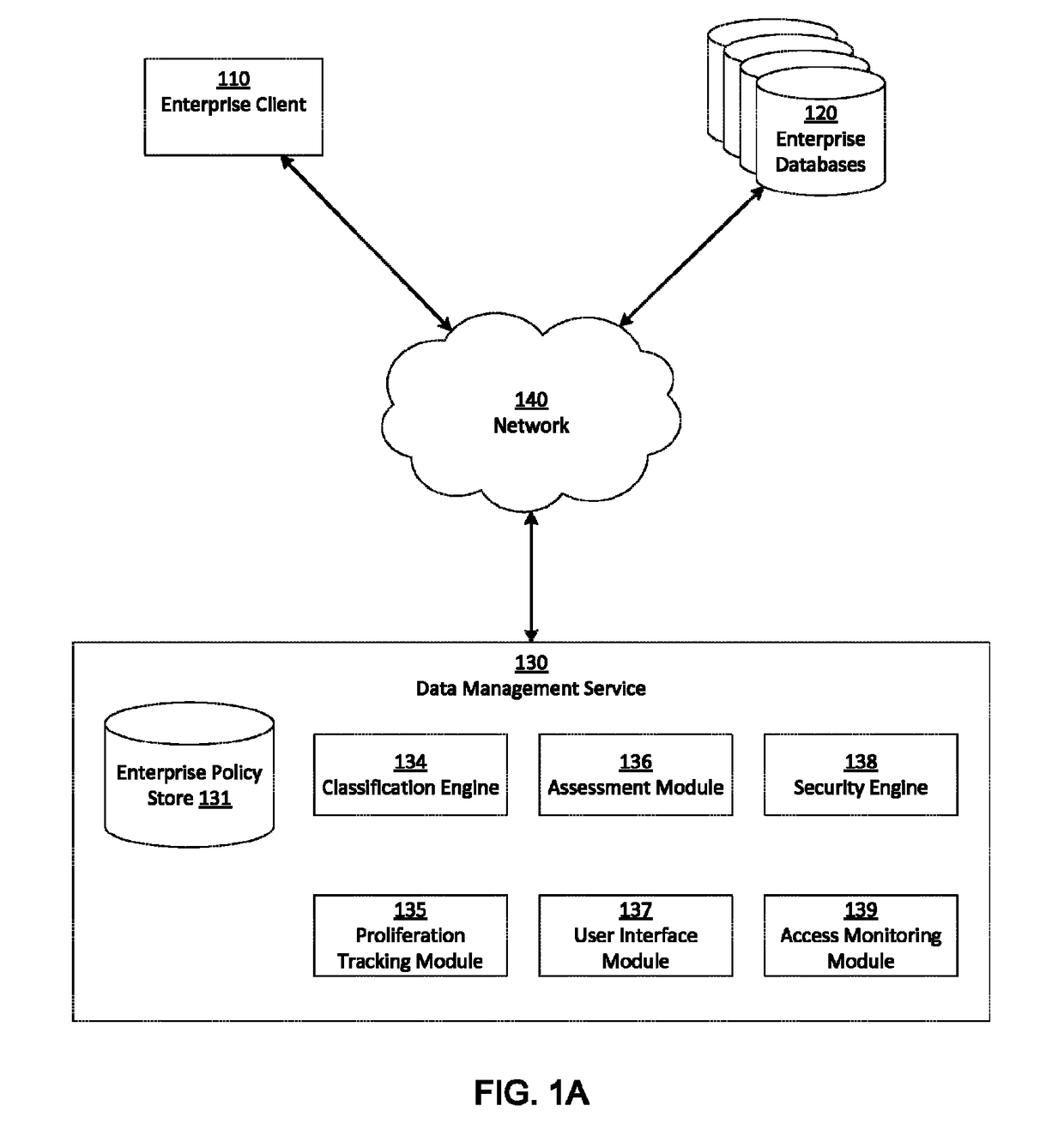
A data management service identifies sensitive data stored on enterprise databases according to record classification rules that classify a data record as having a sensitive data type if the data record includes fields matching at least one of the record classification rules. The data management service determines assessment scores for enterprise databases according to sensitive data records and protection policies on the enterprise databases. The data management service provides an interface that groups enterprise databases having common attributes or common sensitive data types and indicates aggregated assessment scores for the groups of enterprise databases. Through the interface with the grouped enterprise databases, an administrator apply protection policies to enterprise databases. To apply the protection policy, the data management service applies the protection policy to a source database from which dependent enterprise databases access the sensitive database.
Owner:INFORMATICA CORP
Fault diagnostics and prognostics based on distance fault classifiers
InactiveUS7188482B2Easy to interpret, calibrate and implementMaximize distanceAir-treating devicesSpace heating and ventilationOnline algorithmAir filter
The present invention is directed to a mathematical approach to detect faults by reconciling known data driven techniques with a physical understanding of the HVAC system and providing a direct linkage between model parameters and physical system quantities to arrive at classification rules that are easy to interpret, calibrate and implement. The fault modes of interest are low system refrigerant charge and air filter plugging. System data from standard sensors is analyzed under no-fault and full-fault conditions. The data is screened to uncover patterns though which the faults of interest manifest in sensor data and the patterns are analyzed and combined with available physical system information to develop an underlying principle that links failures to measured sensor responses. These principles are then translated into online algorithms for failure detection.
Owner:CARRIER CORP
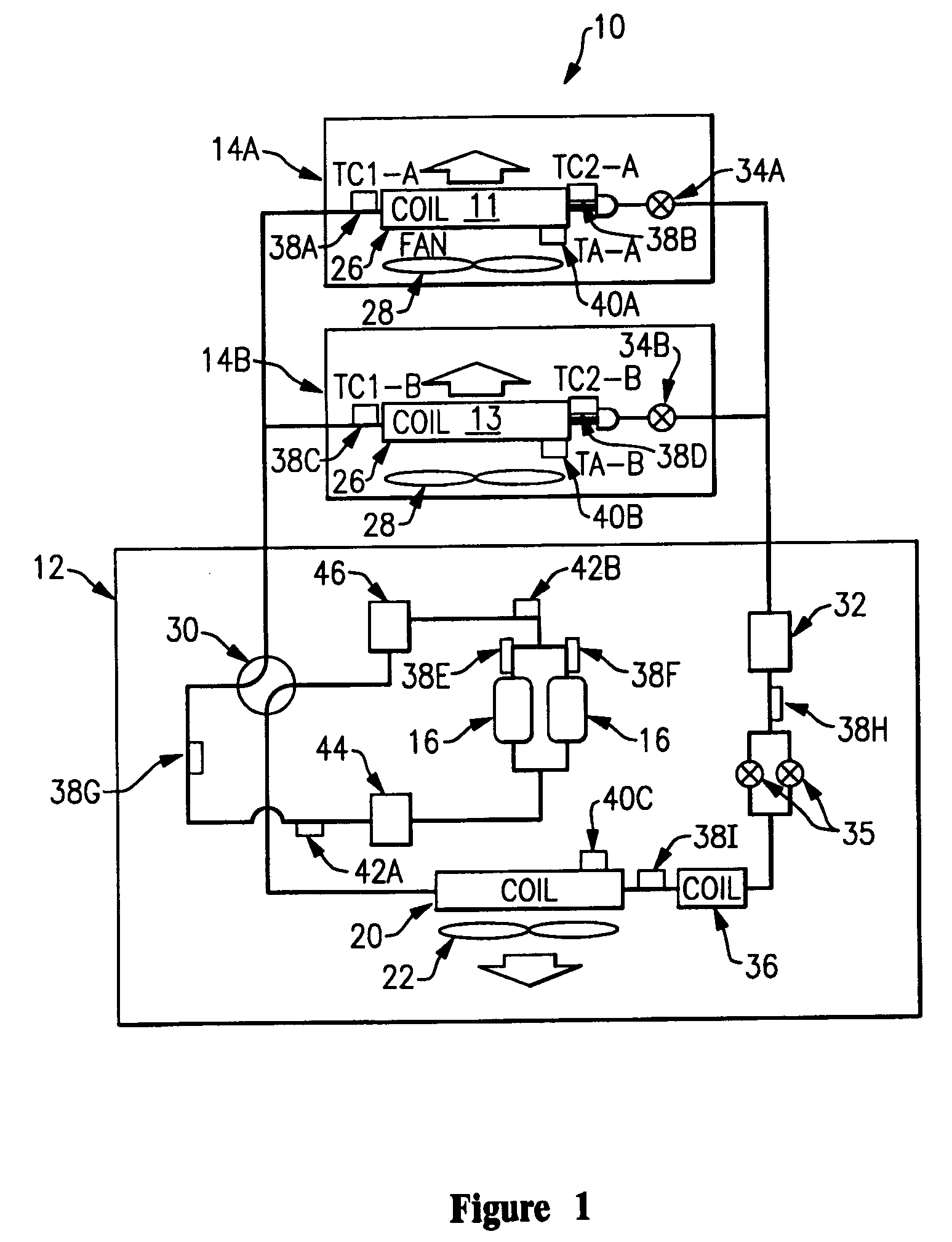
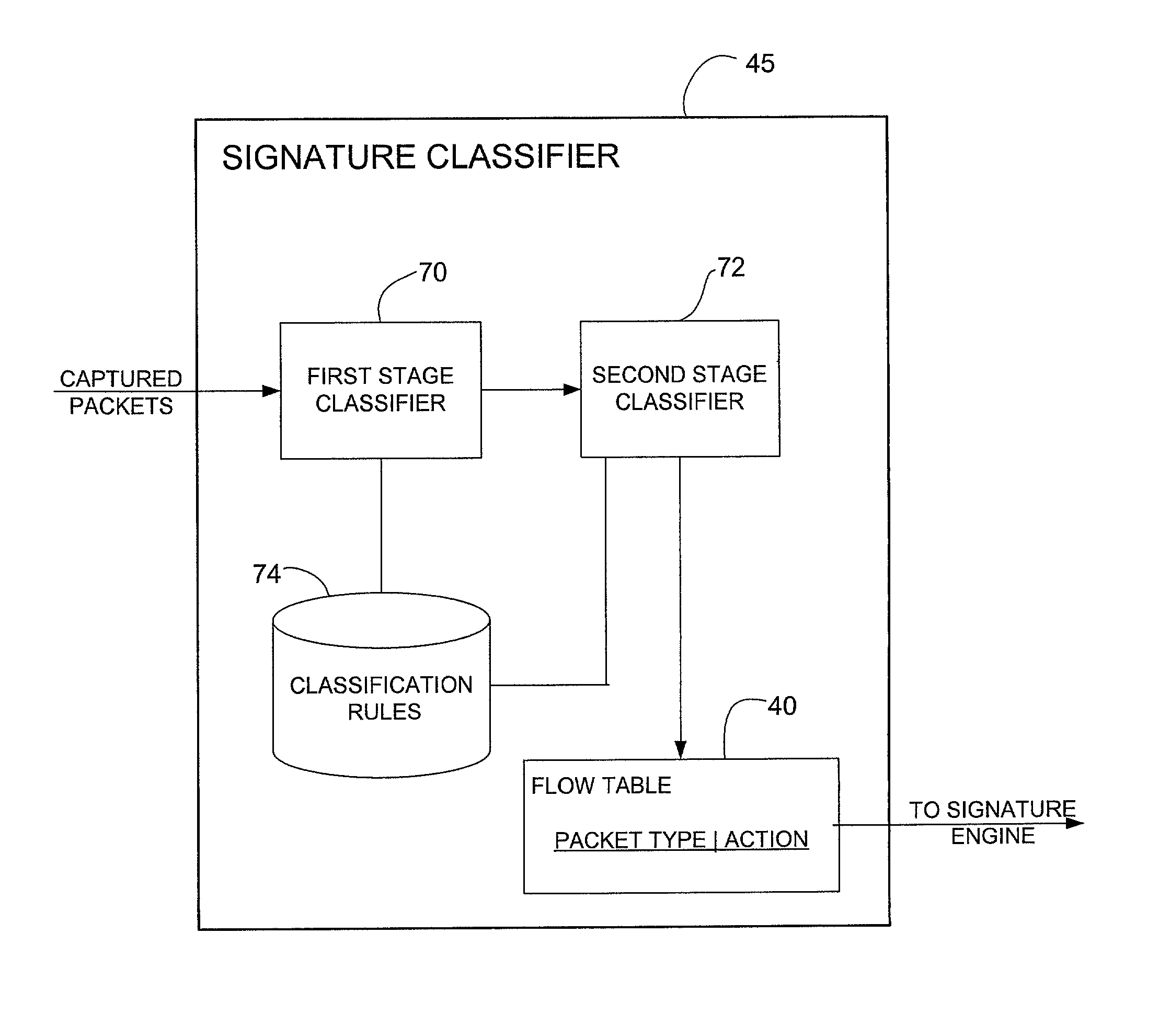
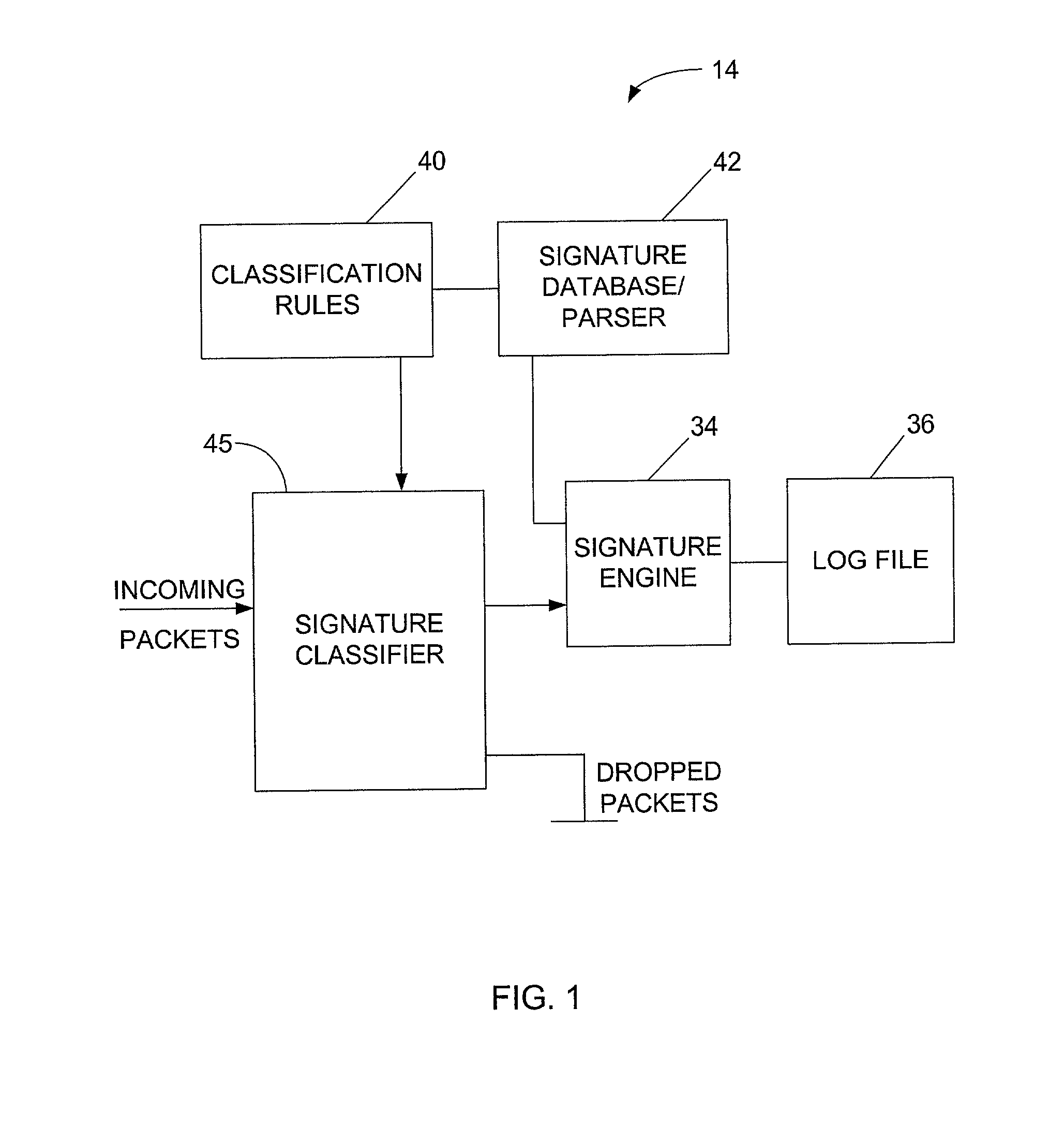
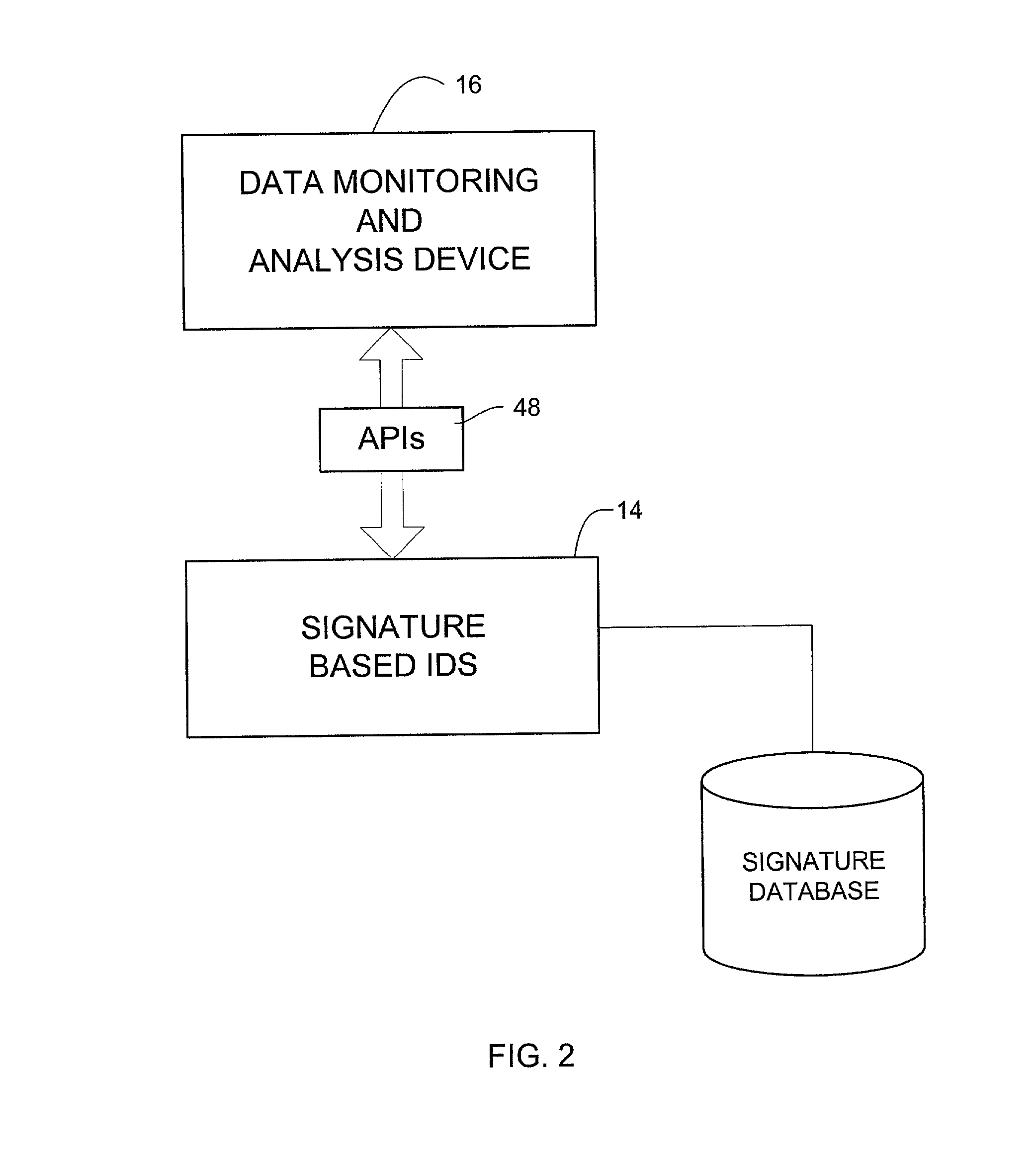
Signature based network intrusion detection system and method
Owner:MCAFEE LLC
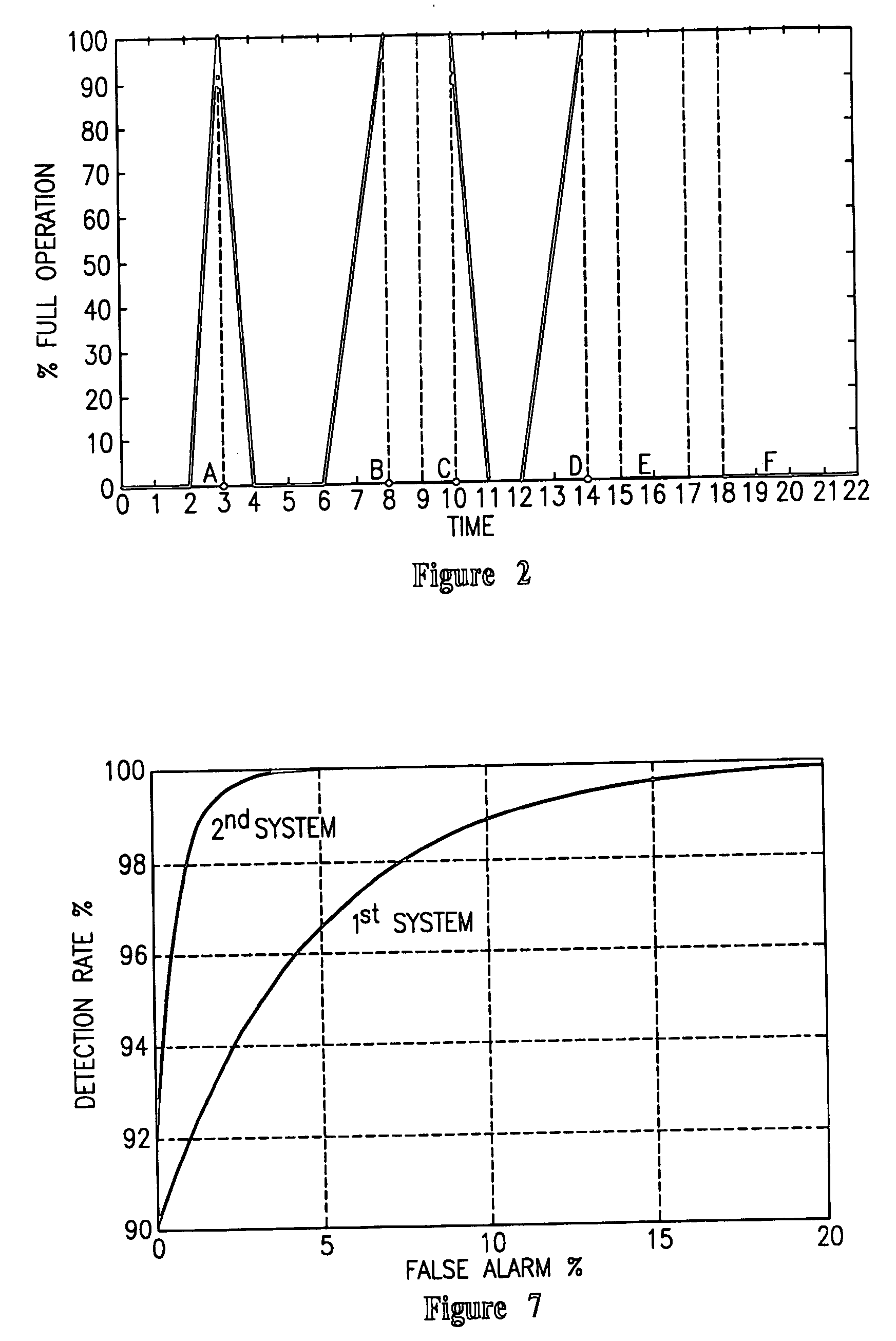
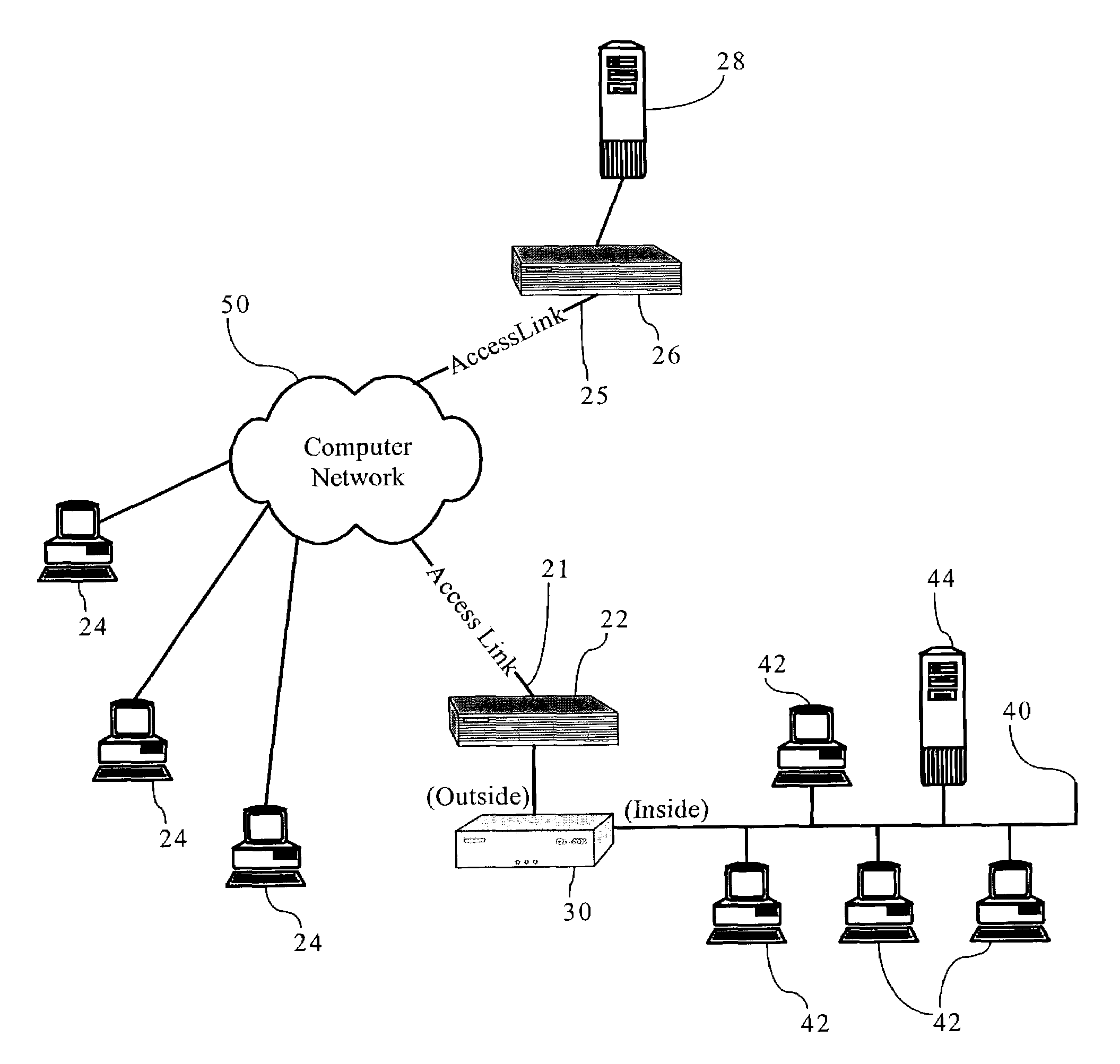
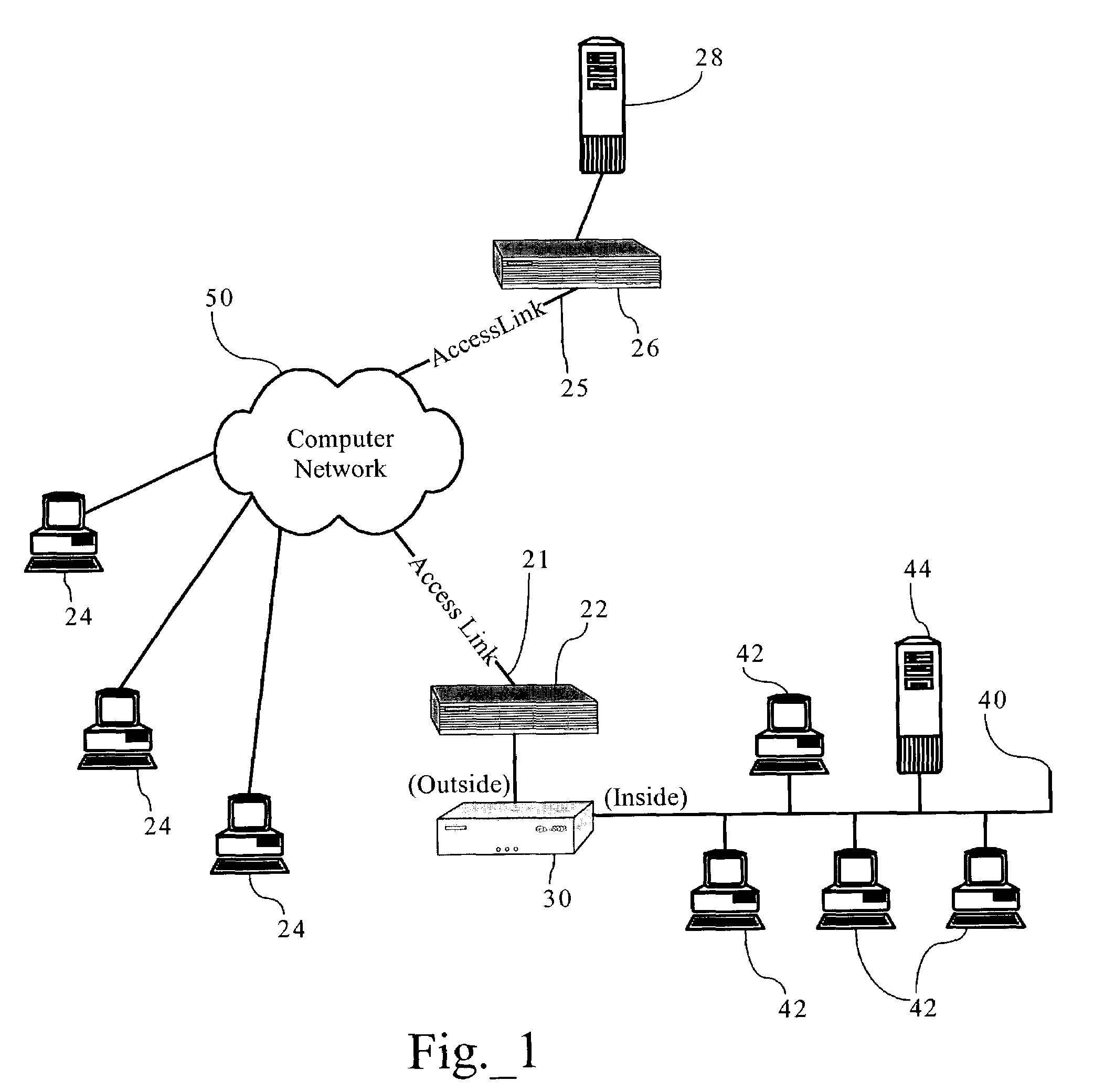
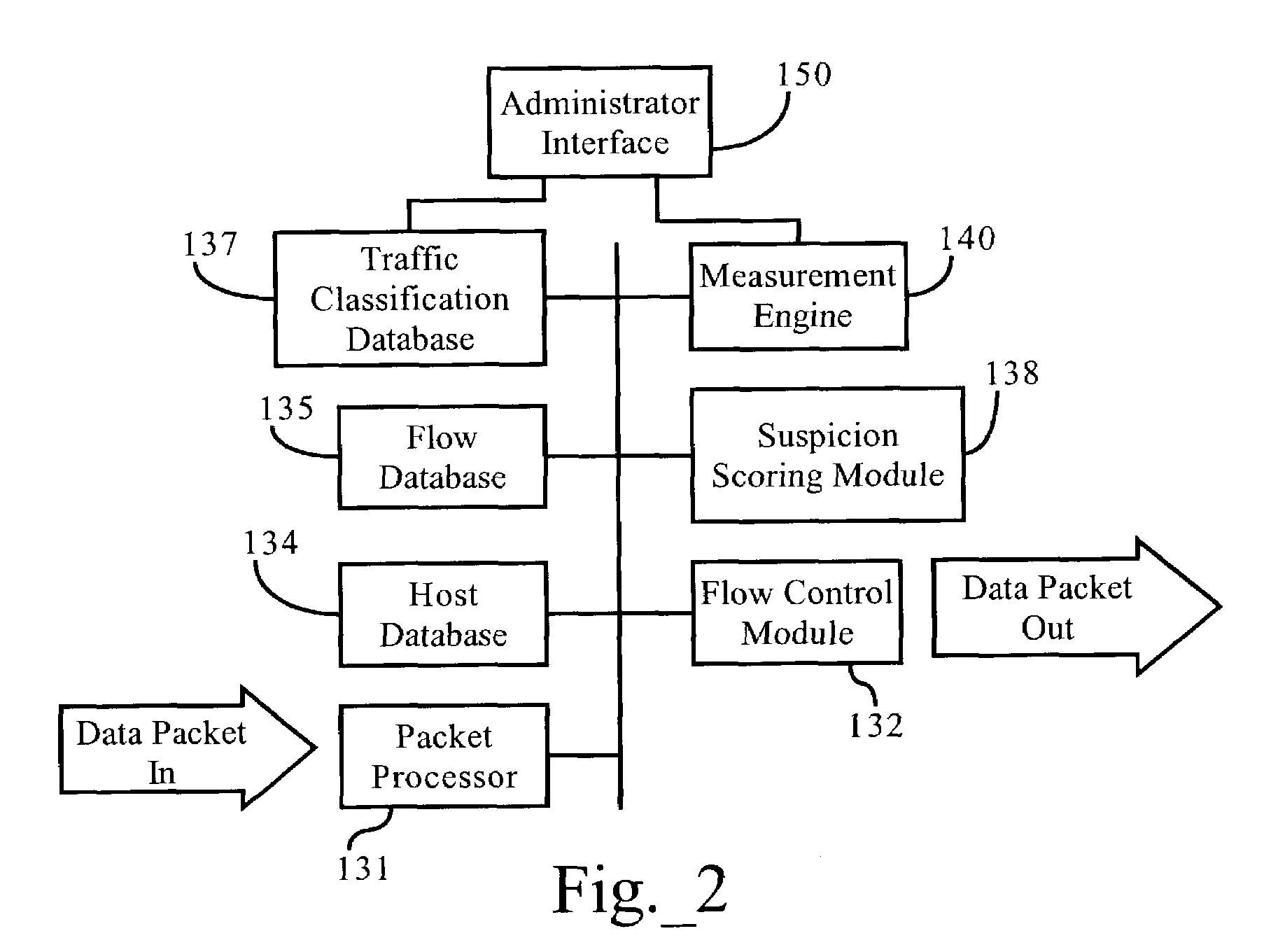
Methods, apparatuses, and systems allowing for bandwidth management schemes responsive to utilization characteristics associated with individual users
ActiveUS7296288B1Digital data processing detailsUnauthorized memory use protectionHTTP tunnelData stream
Methods, apparatuses and systems allowing for bandwidth management schemes responsive to utilization characteristics associated with individual users. In one embodiment, the present invention allows network administrators to penalize users who carry out specific questionable or suspicious activities, such as the use of proxy tunnels to disguise the true nature of the data flows in order to evade classification and control by bandwidth management devices. In one embodiment, each individual user may be accorded an initial suspicion score. Each time the user is associated with a questionable or suspicious activity (for example, detecting the set up of a connection to an outside HTTP tunnel, or peer-to-peer application flow), his or her suspicion score is downgraded. Data flows corresponding to users with sufficiently low suspicion scores, in one embodiment, can be treated in a different manner from data flows associated with other users. For example, different or more rigorous classification rules and policies can be applied to the data flows associated with suspicious users.
Owner:CA TECH INC
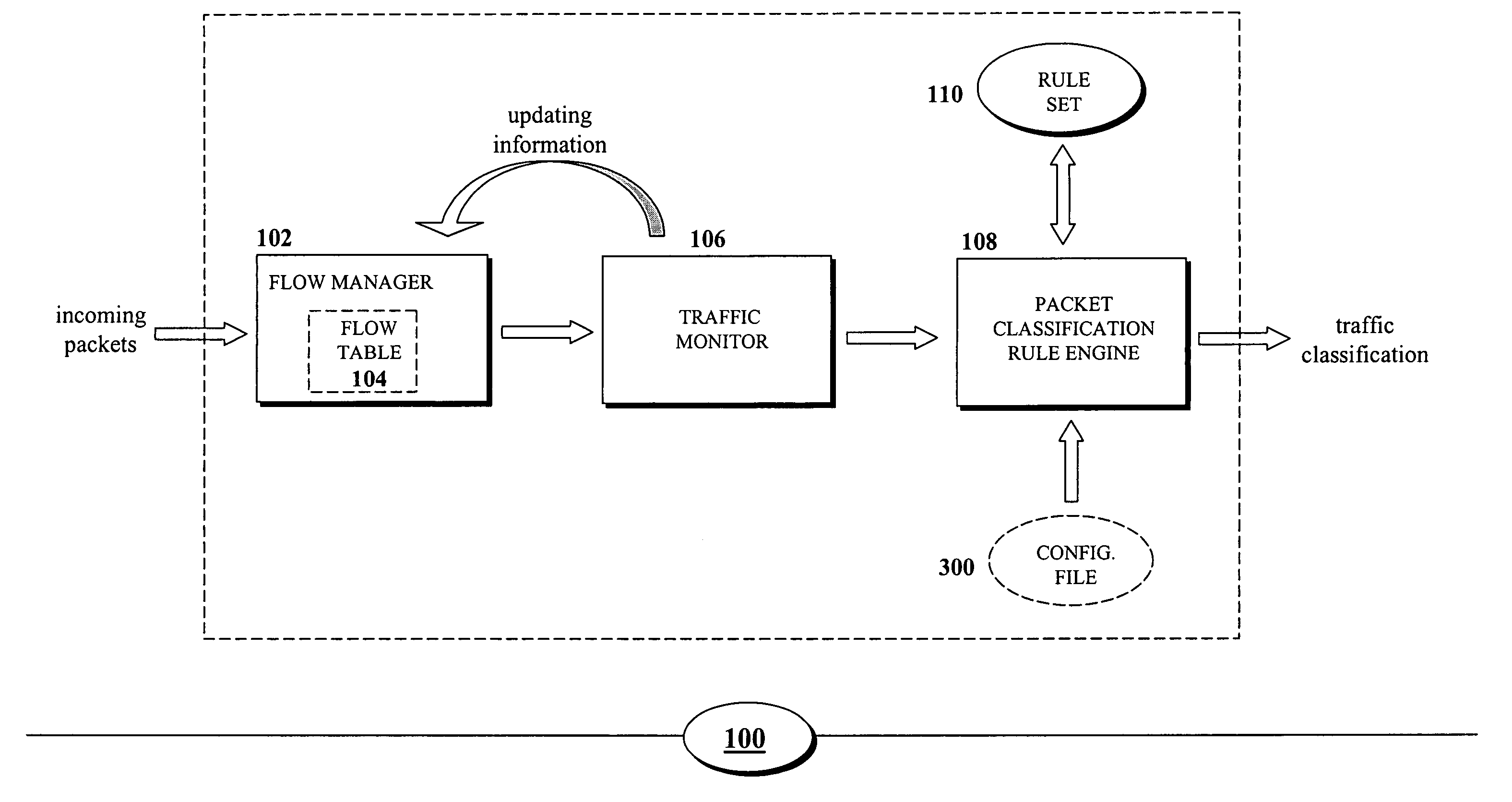
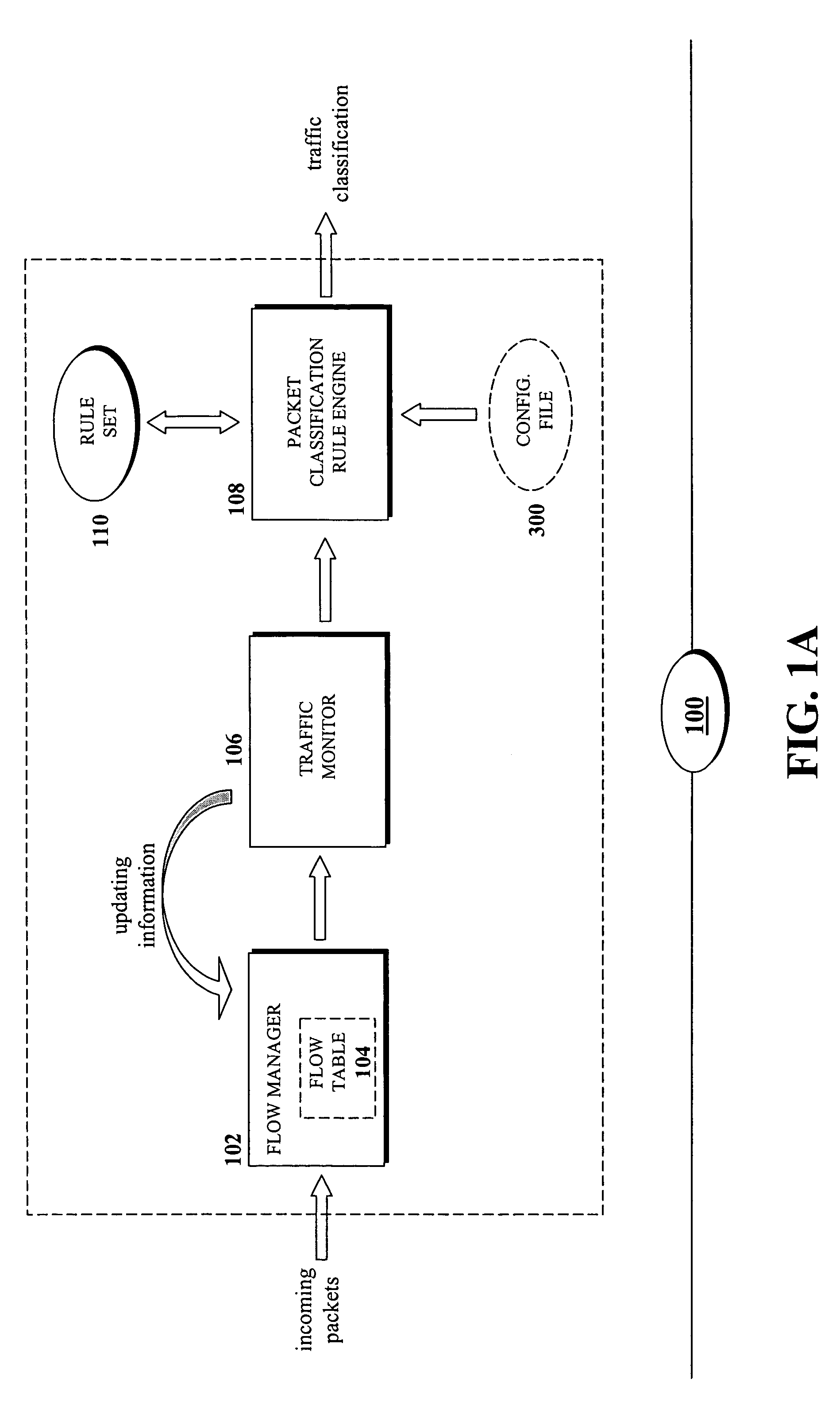
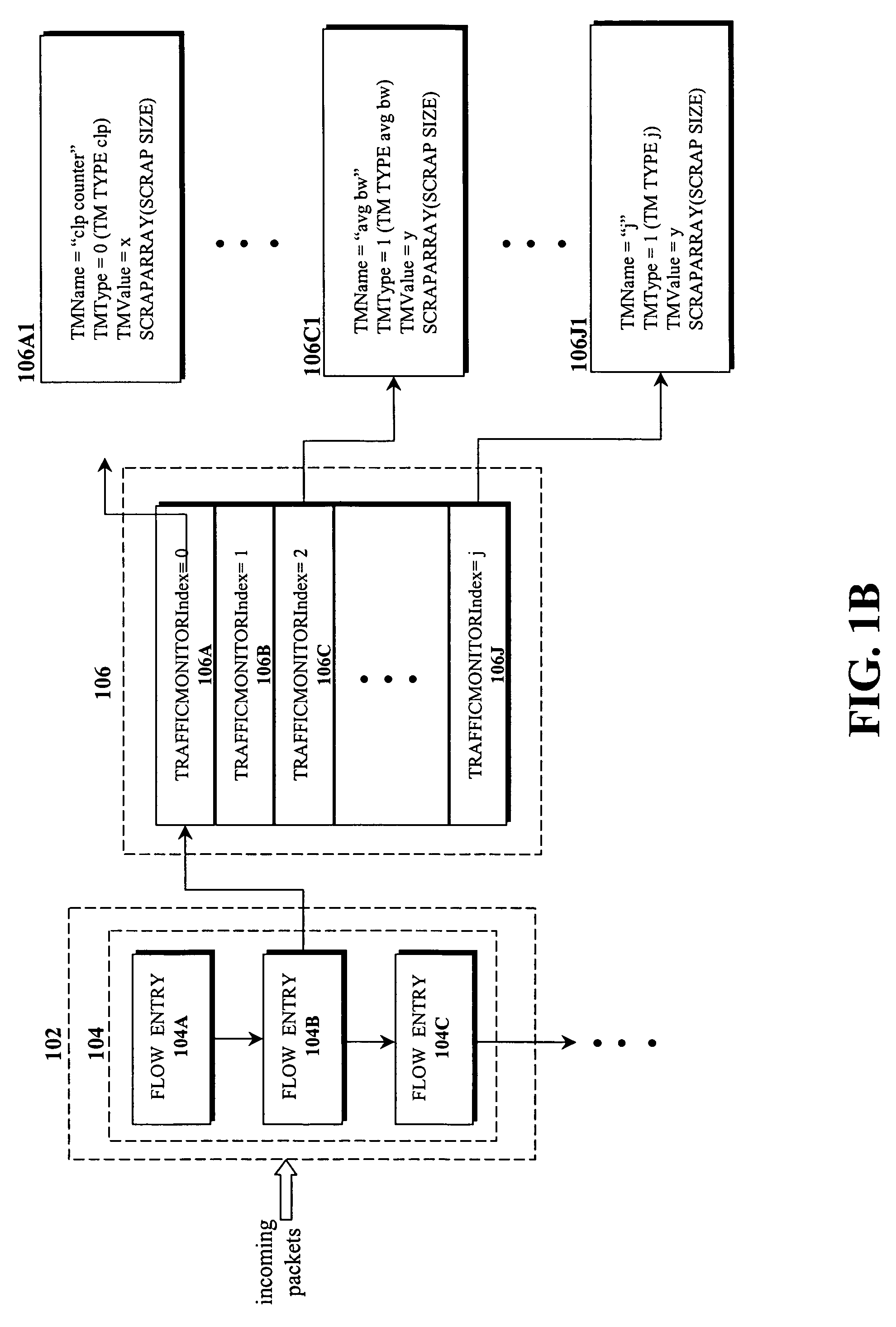
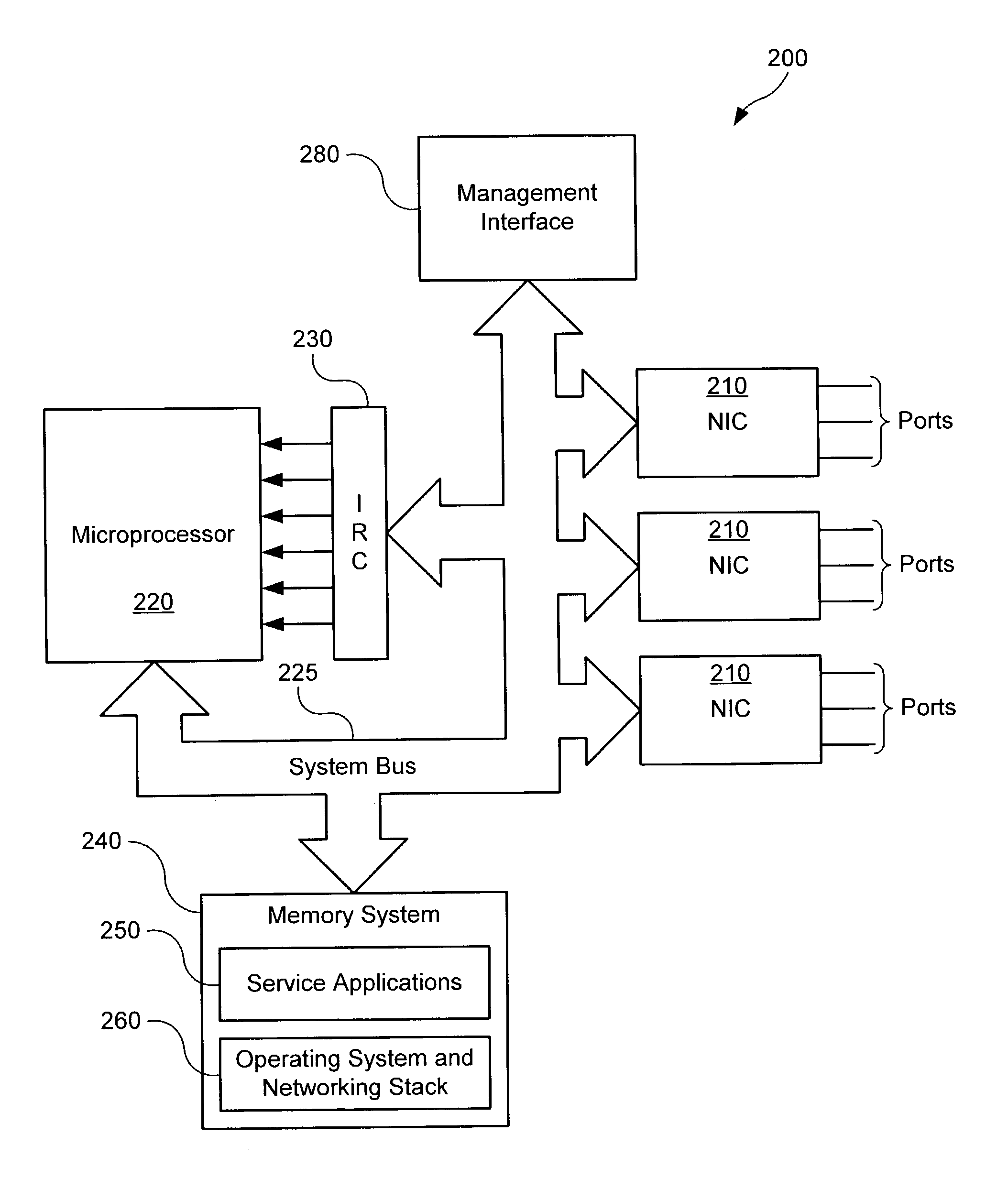
Configurable rule-engine for layer-7 and traffic characteristic-based classification
A system and method for data flow classification based on a configurable rule-engine, is presented herein. In accordance with an embodiment of the invention, the system includes a data flow managing mechanism configured to identify, track, and manage the data flows and a rule set, which includes a plurality of rules for comparing information contained within data flow with pre-specified values. The system also includes a configurable classification rule engine for classifying the data flows into one of a plurality of traffic classes based on results of the comparisons. The configurable classification rule engine is configured via a configuration file that specifies and allows for the modification and reconfiguration of the pre-specified values and information regarding the data flows, the rule set, and the traffic classes.
Owner:RPX CLEARINGHOUSE
Systems and methods for providing differentiated services within a network communication system
ActiveUS7031314B2Lower performance requirementsEfficient managementData switching by path configurationNetwork connectionsDifferentiated servicesCommunications system
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to one of a plurality of service applications that may supported by the service module. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. The service application may then perform application-specific process of the data communicated between the client and server. In order to increase processing efficiency associated with classifying the connection between the client and the server, the service module stores classification rules in a plurality of hashing tables, with hash conflicts arranged as an m-ary tree structure. This arrangement enables the service module to efficiently search for classification rules and resolve hash conflicts without imposing a significant processing penalty.
Owner:OPTIMORPHIX INC
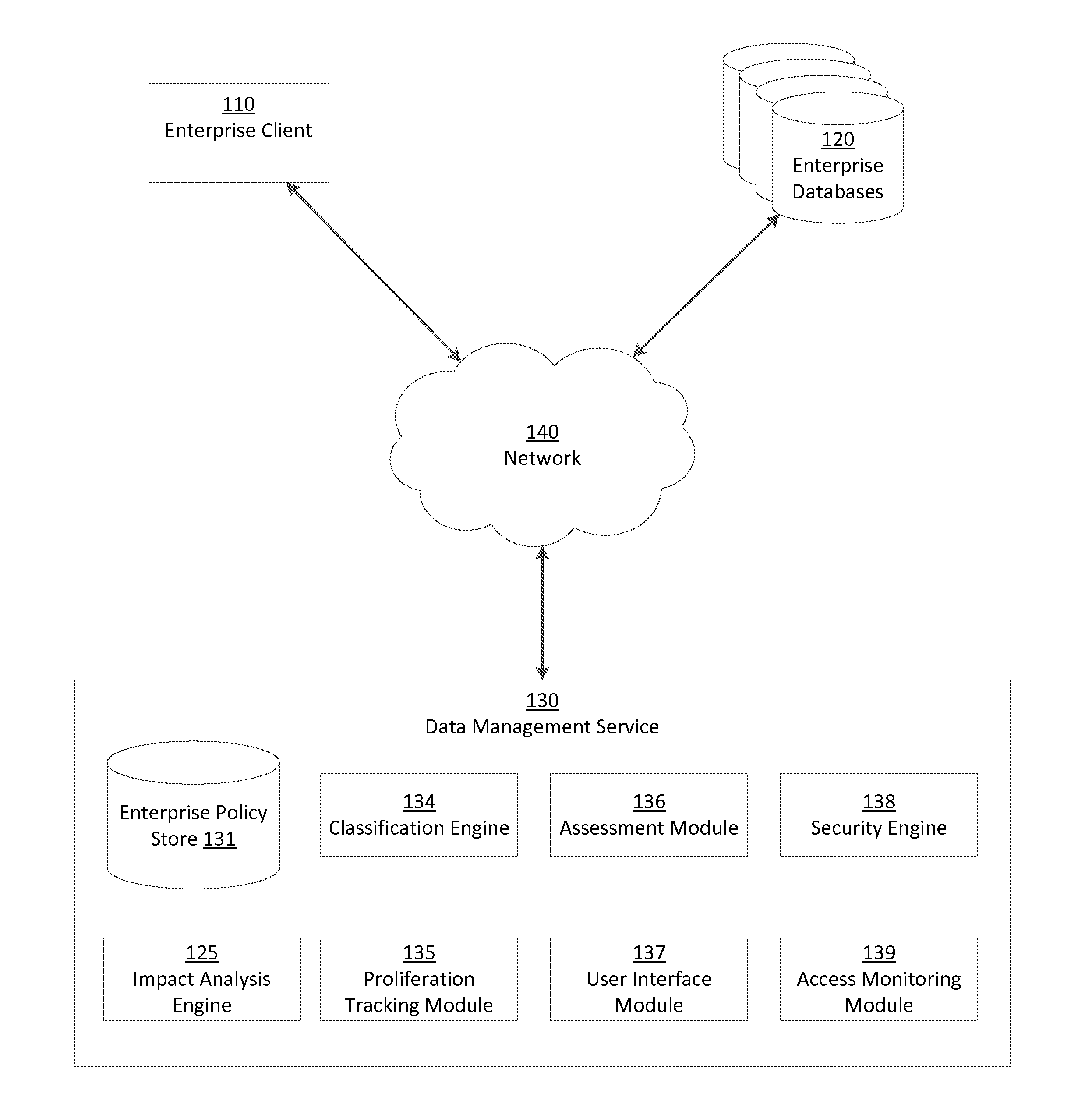
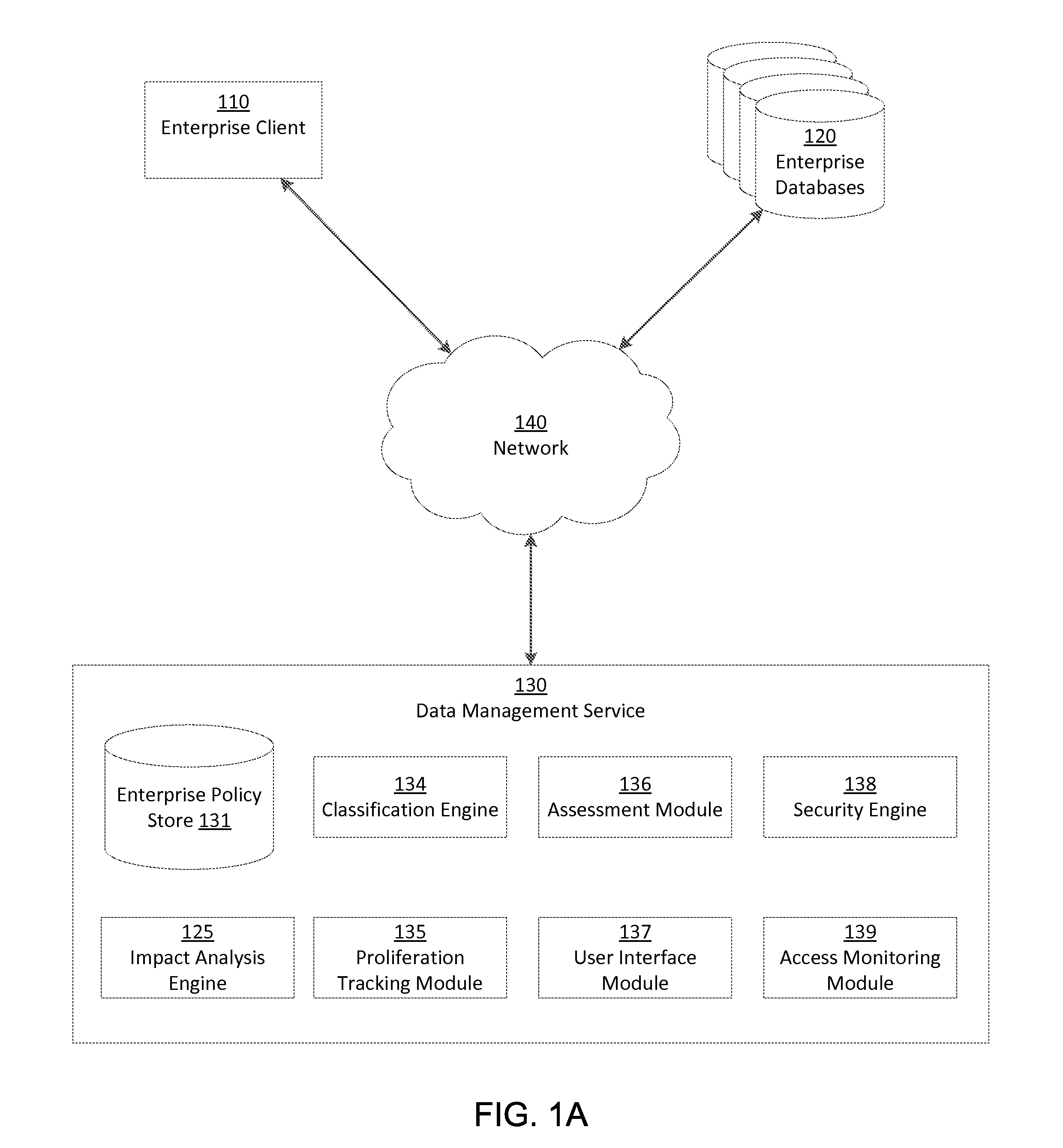
Assessment type-variable enterprise security impact analysis
ActiveUS20150326601A1Easy to identifyReduce processDigital data information retrievalMemory loss protectionClassification ruleData records
A data management service identifies sensitive data stored on enterprise databases according to record classification rules that classify a data record as having a sensitive data type if the data record includes fields matching at least one of the record classification rules. Methods and systems rely on a set of impact factors each having a set of set of value bands representing a range for the impact factor and a corresponding value (between 0 and 1). The factors, ranges, and values all are customizable for an organization. Impact scoring calculations take into account each of the impact factors, and each is weighted to represent a specific risk perception or assessment type. A similar impact scoring is applied to data quality using volume of data as a key attribute of the quality.
Owner:INFORMATICA CORP
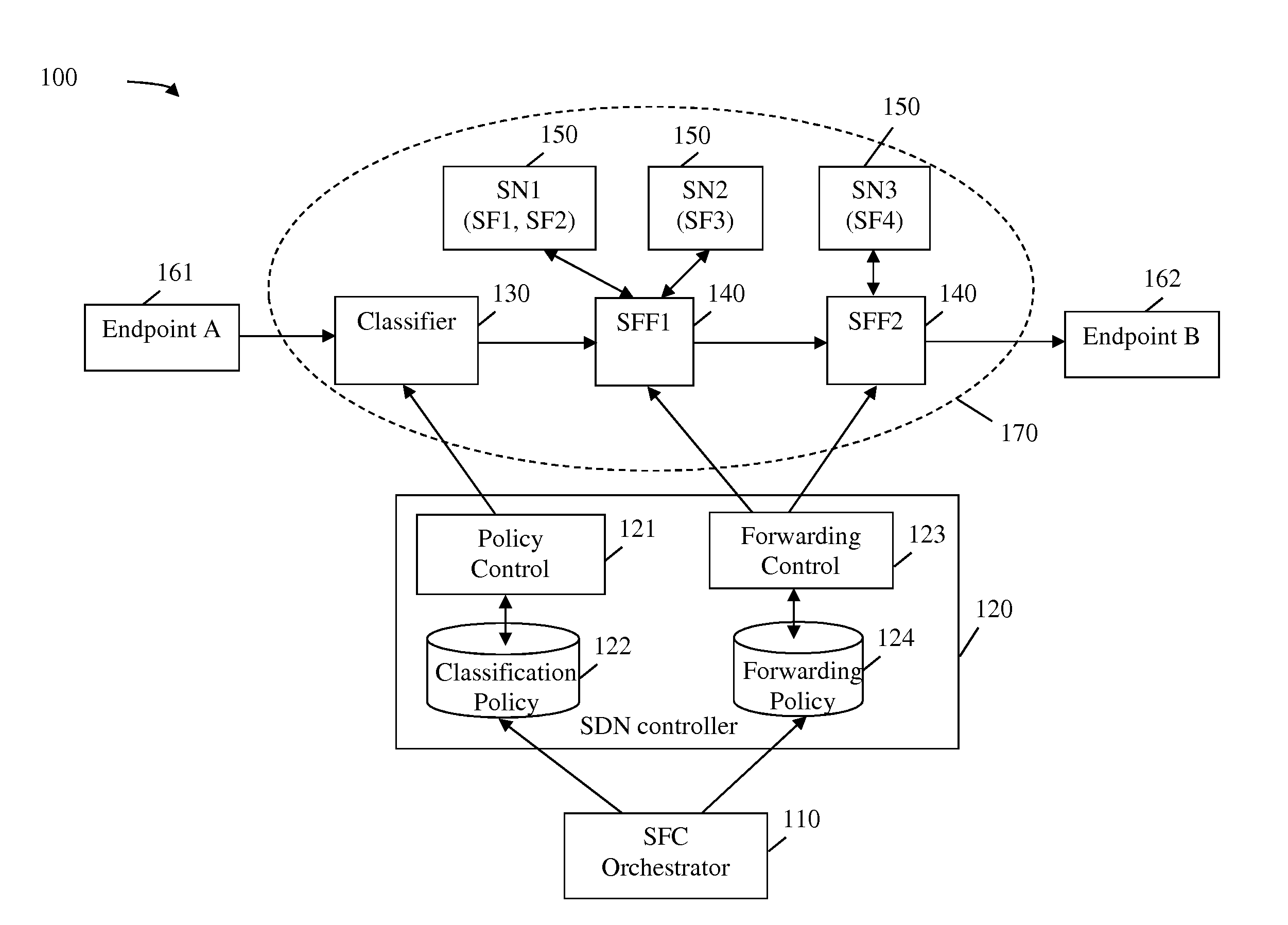
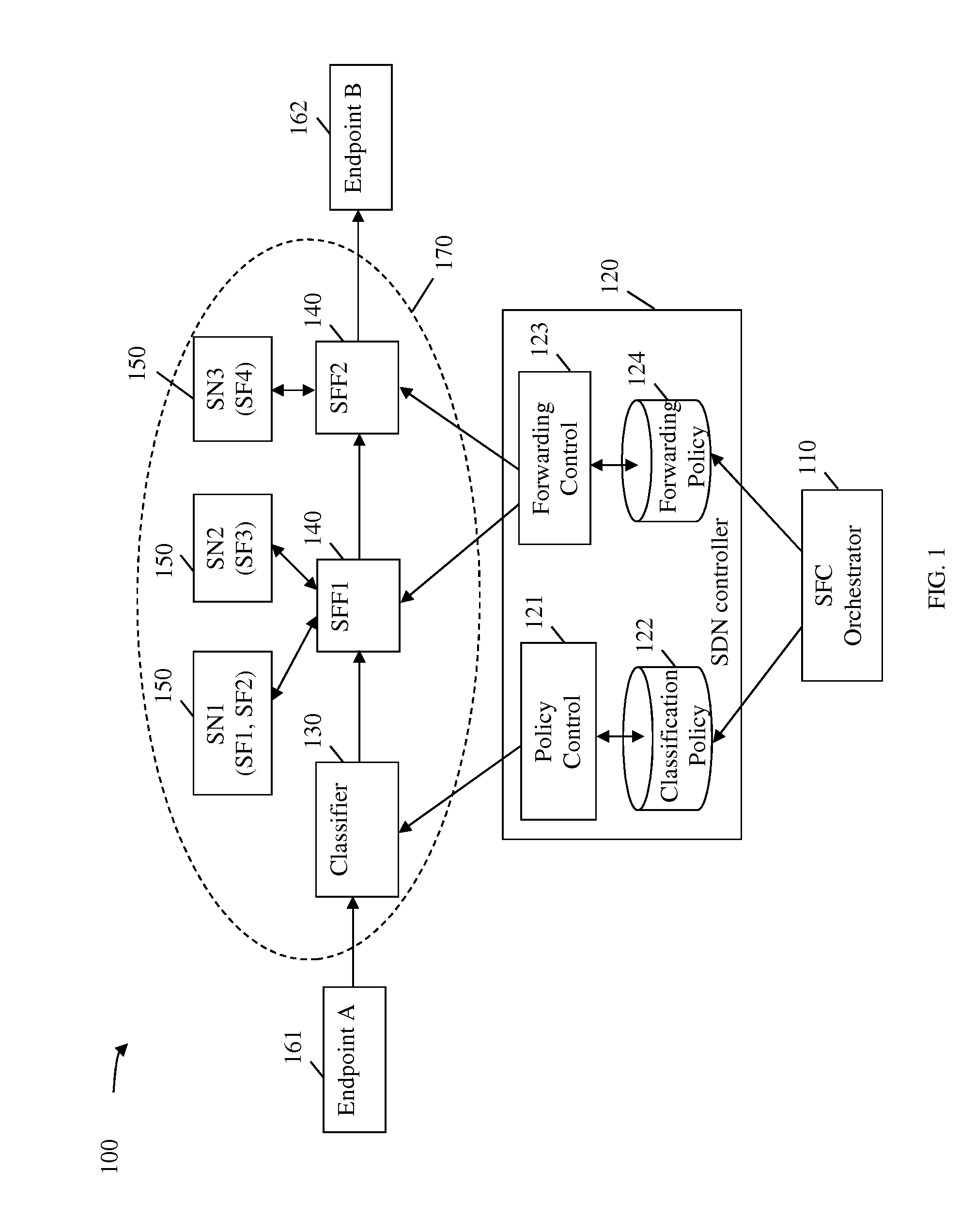
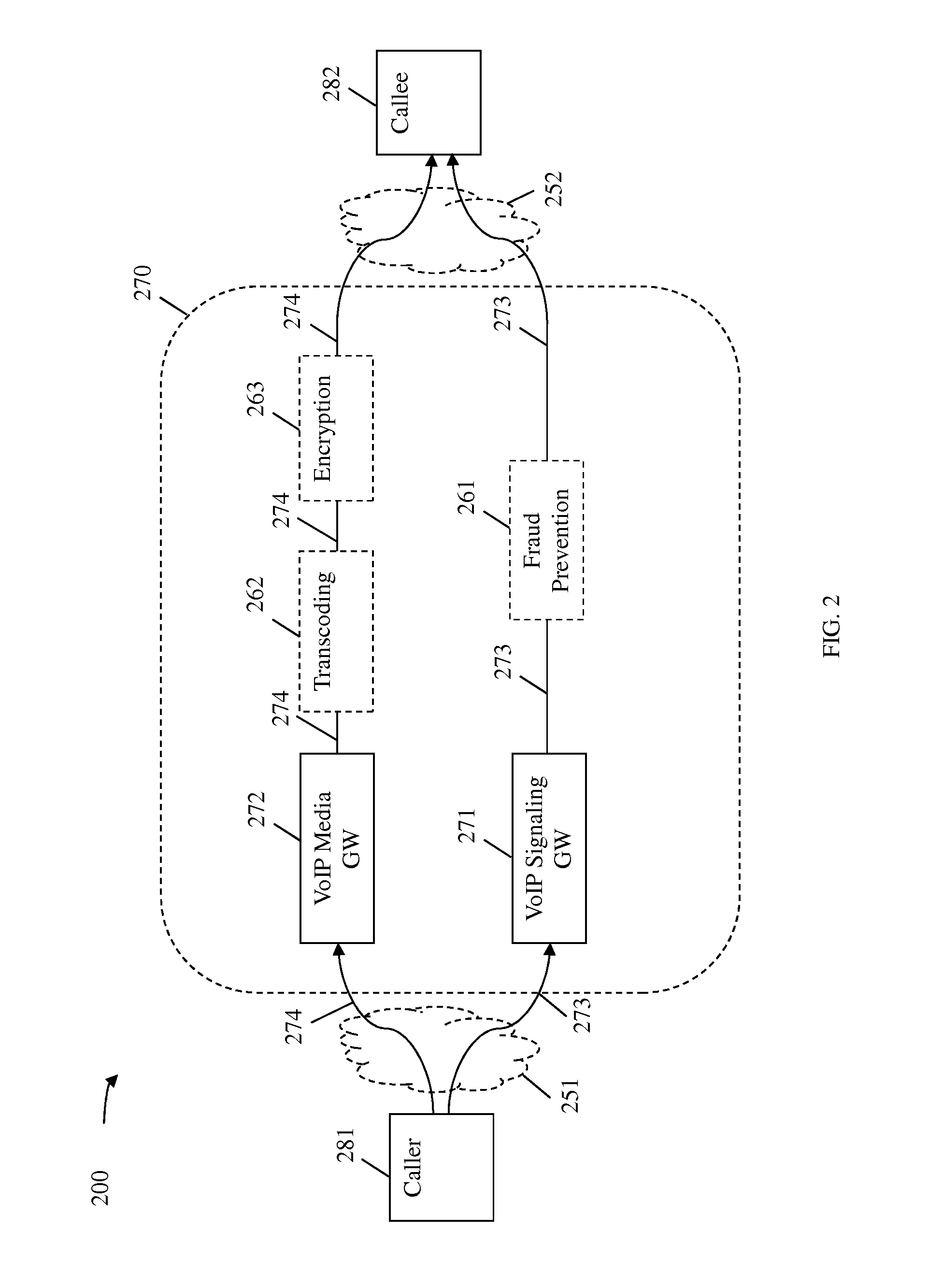
Exchanging Application Metadata for Application Context Aware Service Insertion in Service Function Chain
A method implemented by a network element (NE), comprising receiving a classification message comprising a classification rule for identifying a service function chain (SFC) in a network, wherein the SFC comprises an ordered set of service functions (SFs) that provides services to an application, and a dynamic application-specific contextual data associated with an operation of the application, receiving a first of a plurality of application data packets, determining that the first of the application data packets matches the classification rule, generating a first SFC packet by adding the dynamic application-specific contextual data to the first of the application data packets according to the classification rule to enable communication of the dynamic application-specific contextual data to at least one of the SFs in the SFC, and sending the first SFC packet towards a next NE according to an SF path in the network associated with the SFC.
Owner:FUTUREWEI TECH INC
Proxy architecture for providing quality of service(QoS) reservations
ActiveUS20050198261A1Minimizing software upgradeDigital computer detailsData switching networksQuality of serviceClassification rule
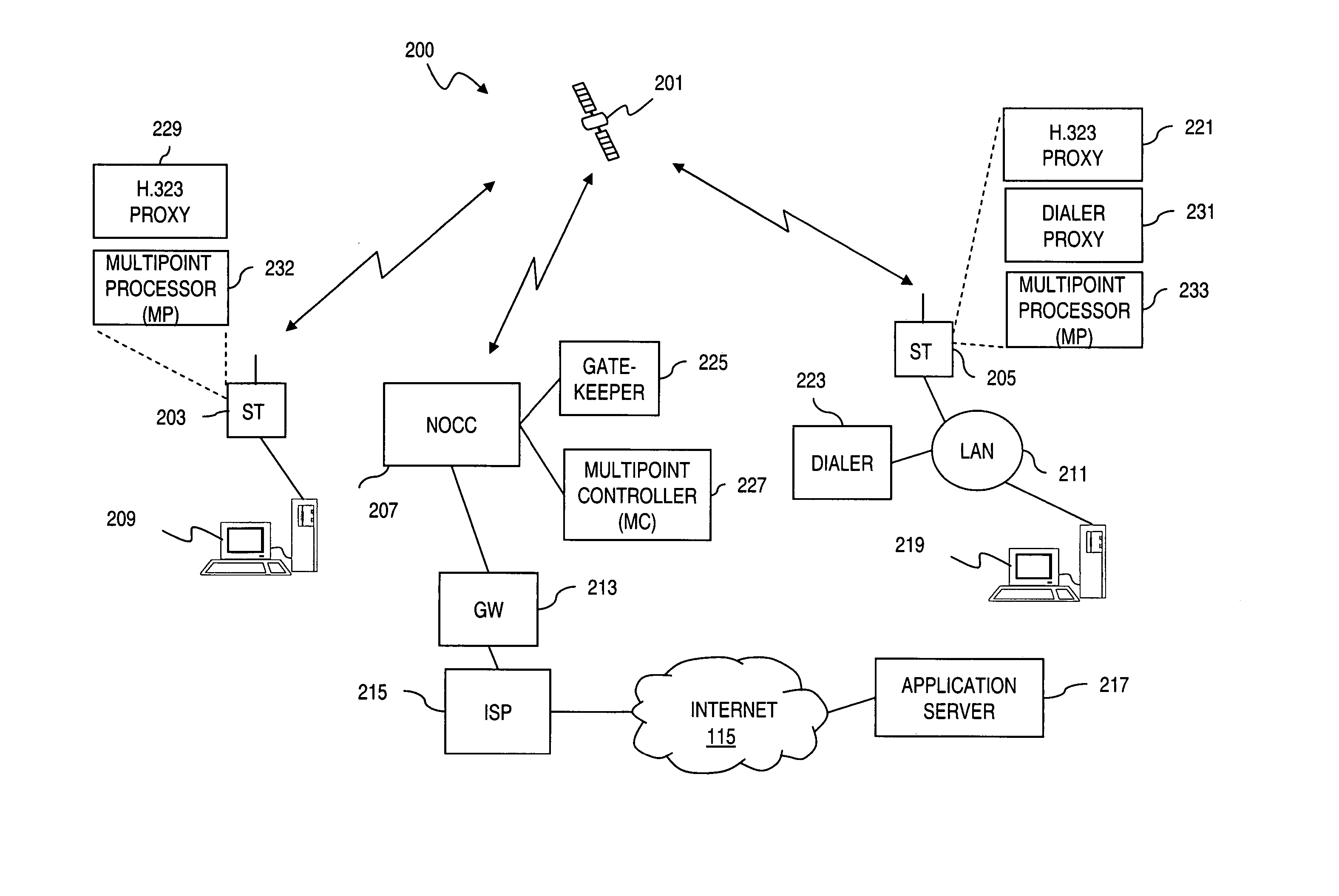
An approach is provided for providing quality of service reservations in a packet-based radio communication network is disclosed. Connection information including connection rate is extracted from a dataflow from an application requesting connection-oriented service. A request message is sent to a proxy for establishing a connection based on the connection information over the network, wherein the proxy configures a classification rule based on flow criteria from the request message and accordingly initiates establishment of the connection over the network to a destination terminal. A confirmation that the connection can be established is selectively received according to the connection information, wherein the dataflow satisfying the flow criteria from the application is transported over the established connection to the destination terminal. This approach as particular applicability to shared capacity systems, such as a satellite communication system.
Owner:HUGHES NETWORK SYST
System and method for mitigating denial of service attacks on communication appliances
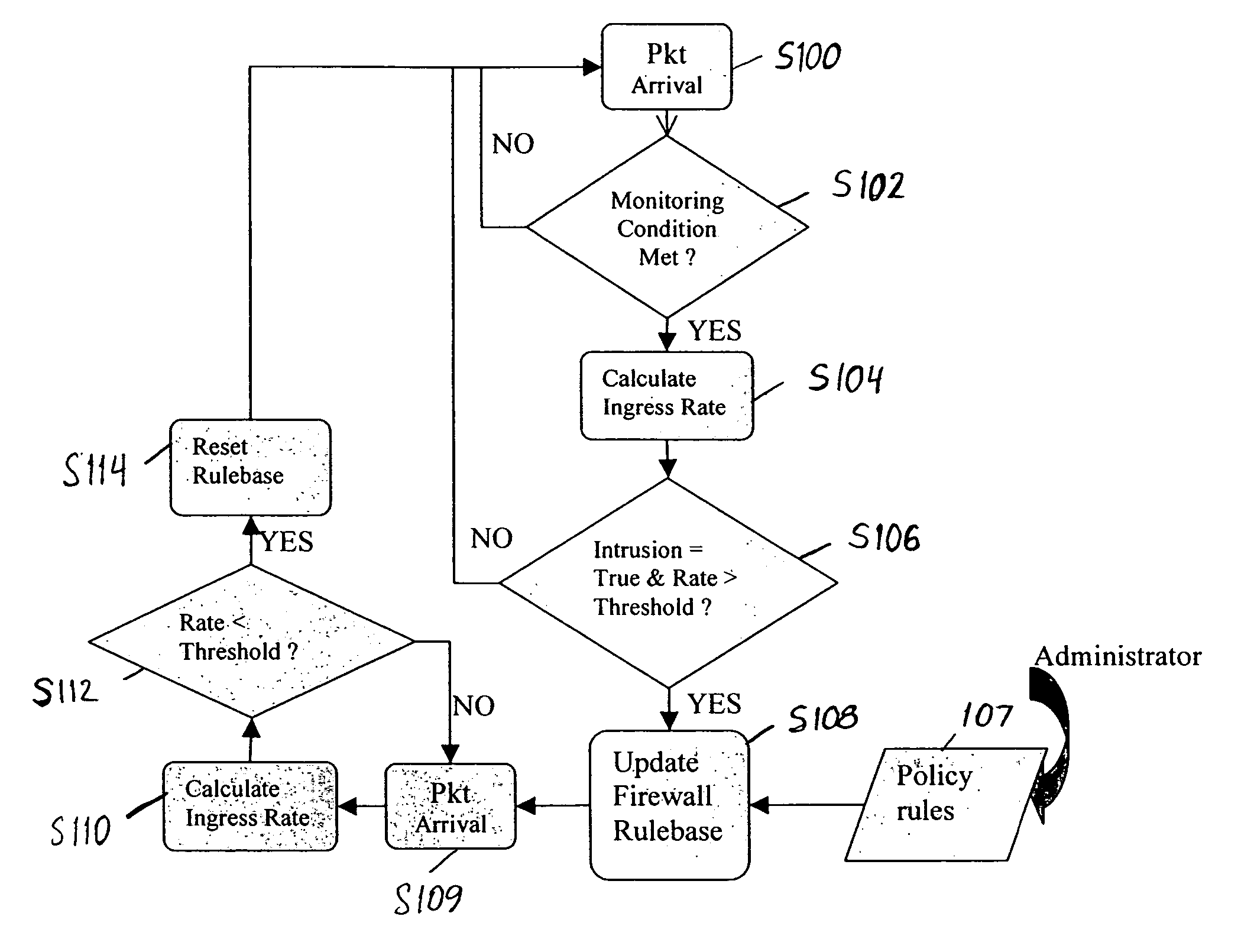
InactiveUS20060288411A1Preventing and limiting effect Denial-of-ServiceMemory loss protectionData taking preventionData packClassification rule
A method for preventing or limiting the effects of Denial-of-Service attacks in a communication appliance having a packet-classification rule base which allows all legitimate packets to be forwarded to the communication appliance includes monitoring incoming packets to the communication appliance to determine whether conditions indicating a Denial-of-Service attack are present. If a Denial-of-Service attack is present, a rule base subset of the packet-classification rule base is selected from a plurality of rule base subsets based on a current one of a plurality of operating states of the communication appliance.
Owner:AVAYA INC
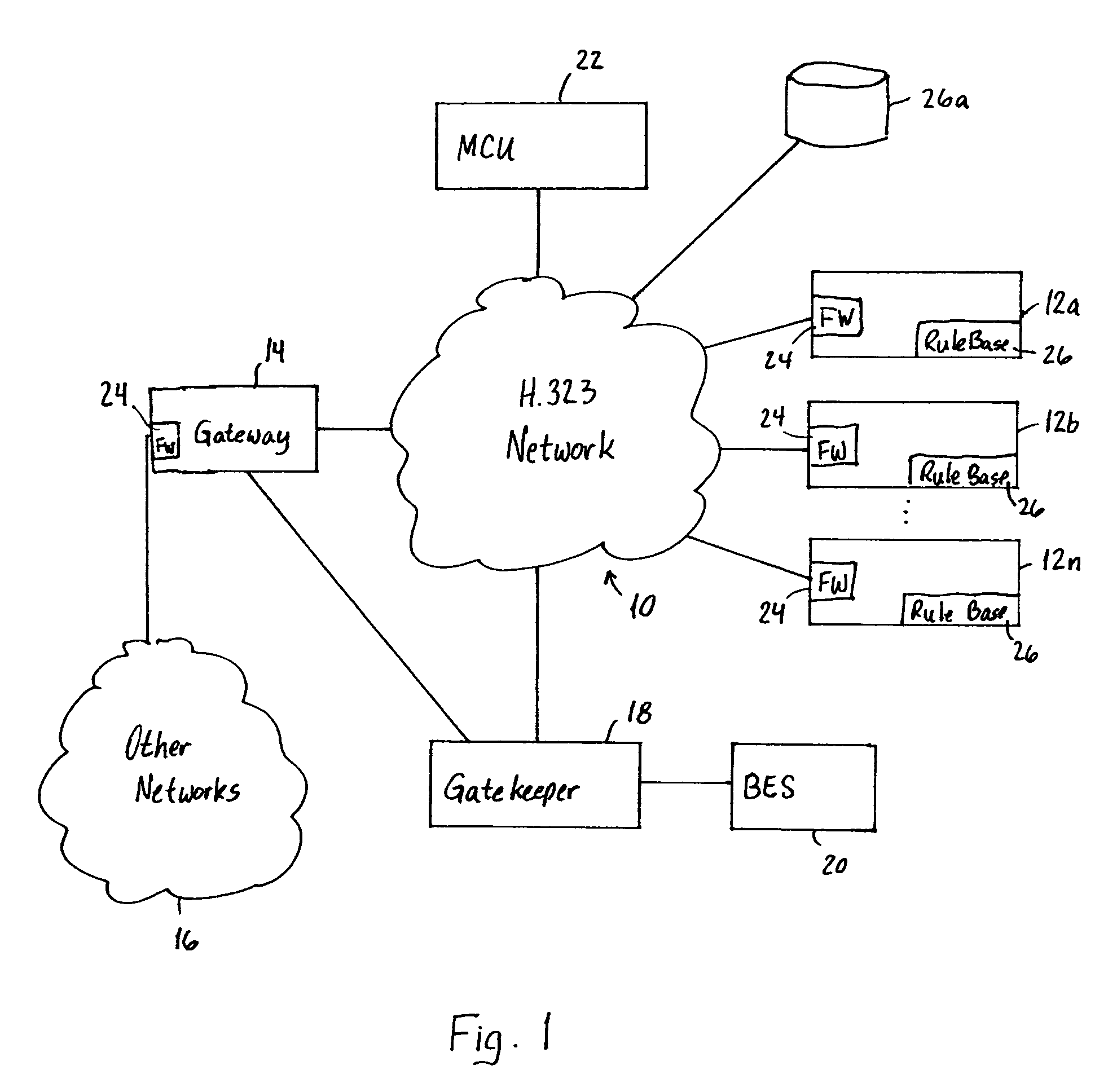
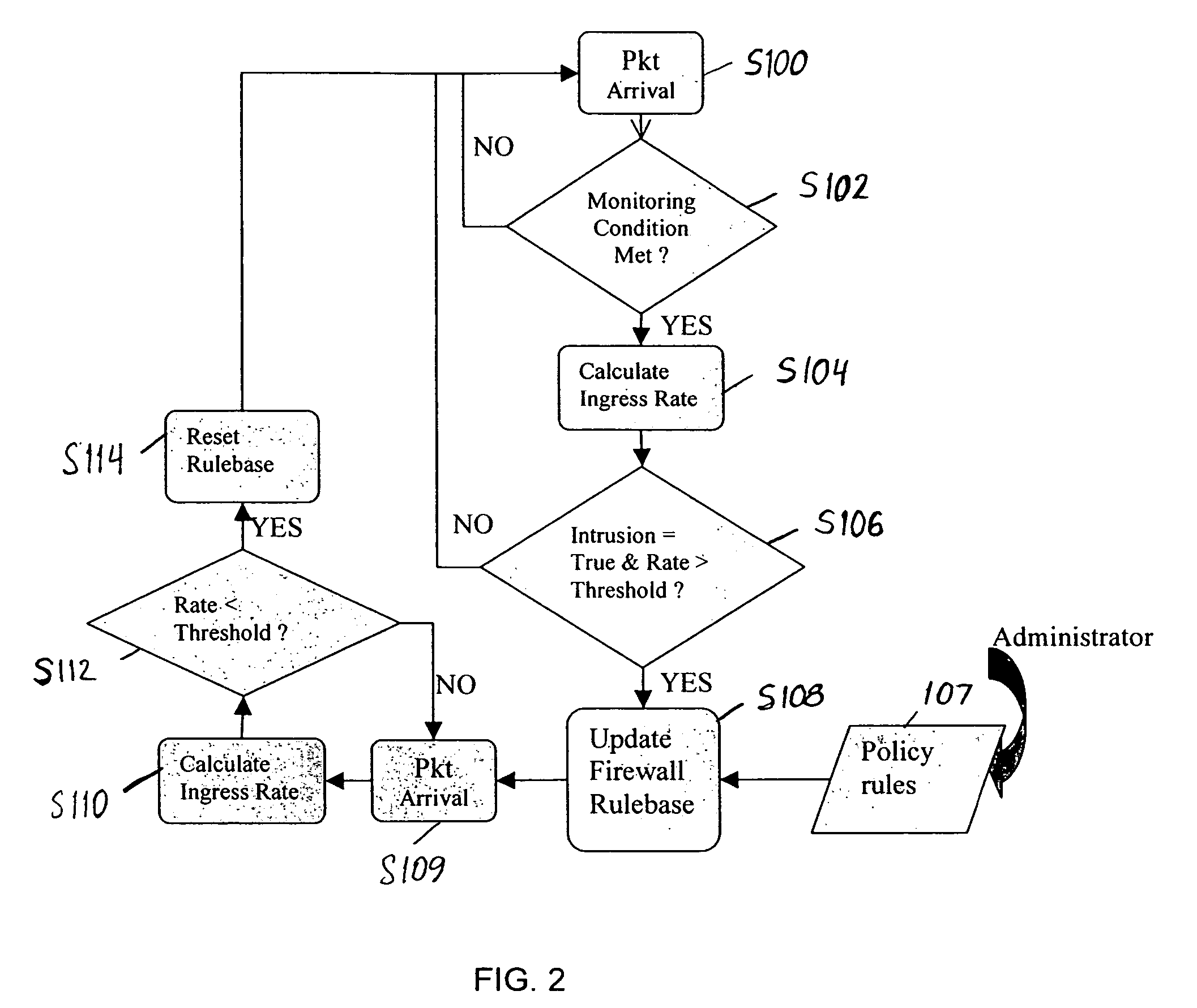
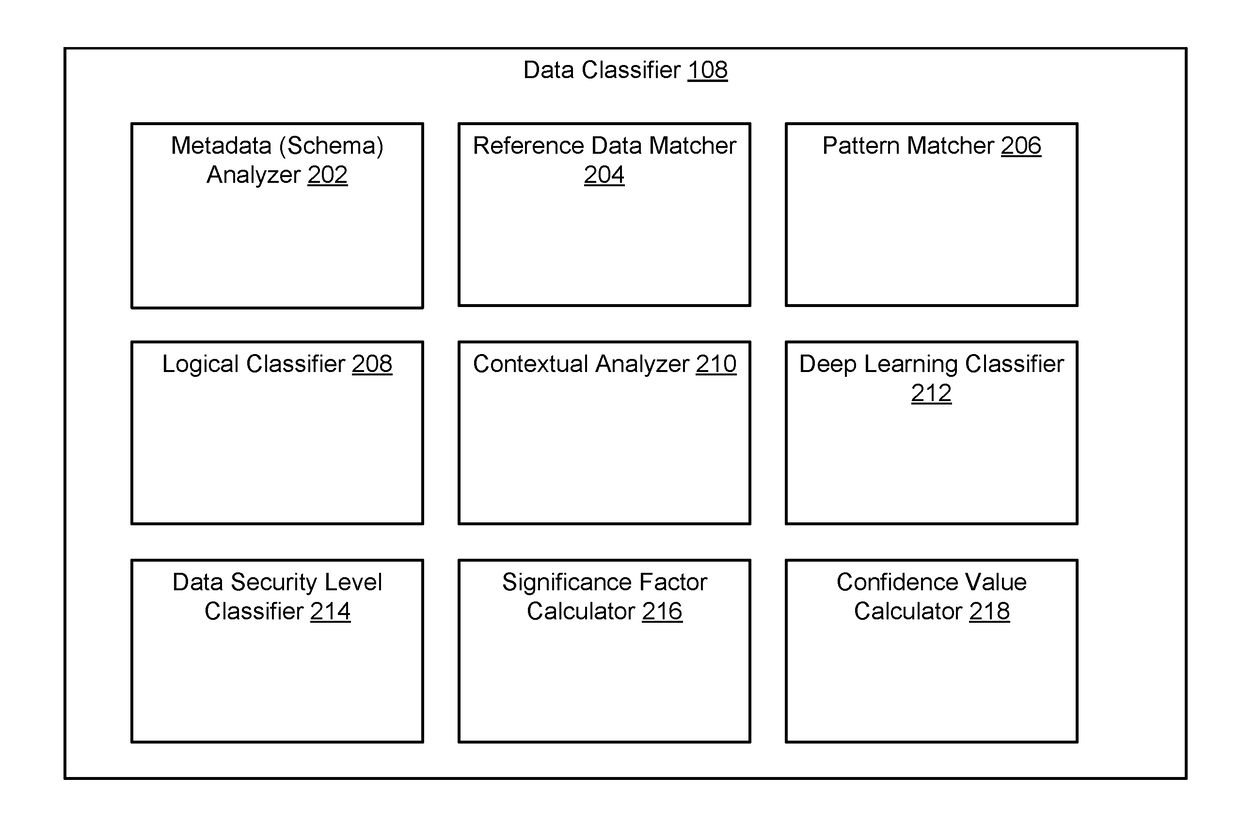
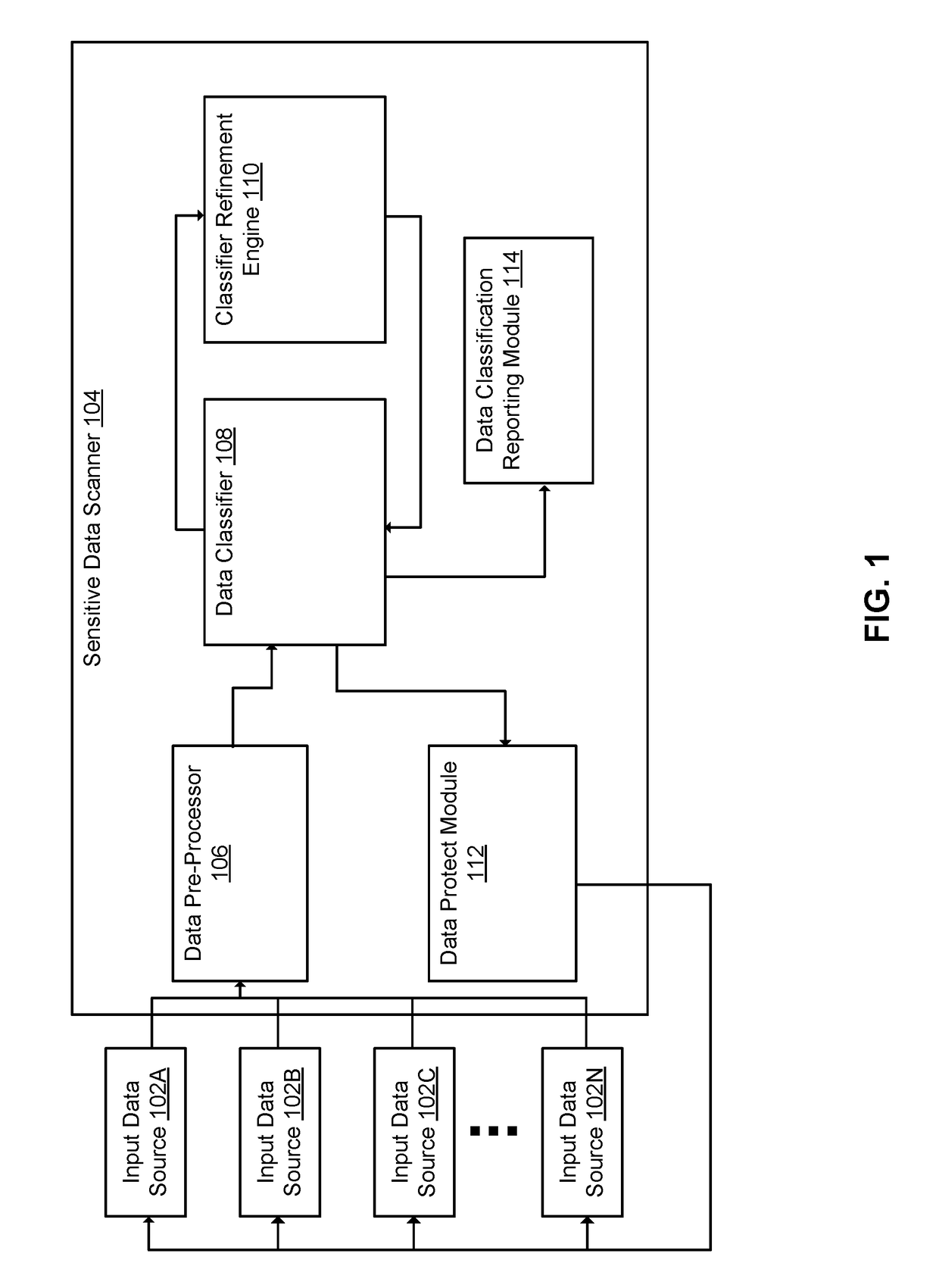
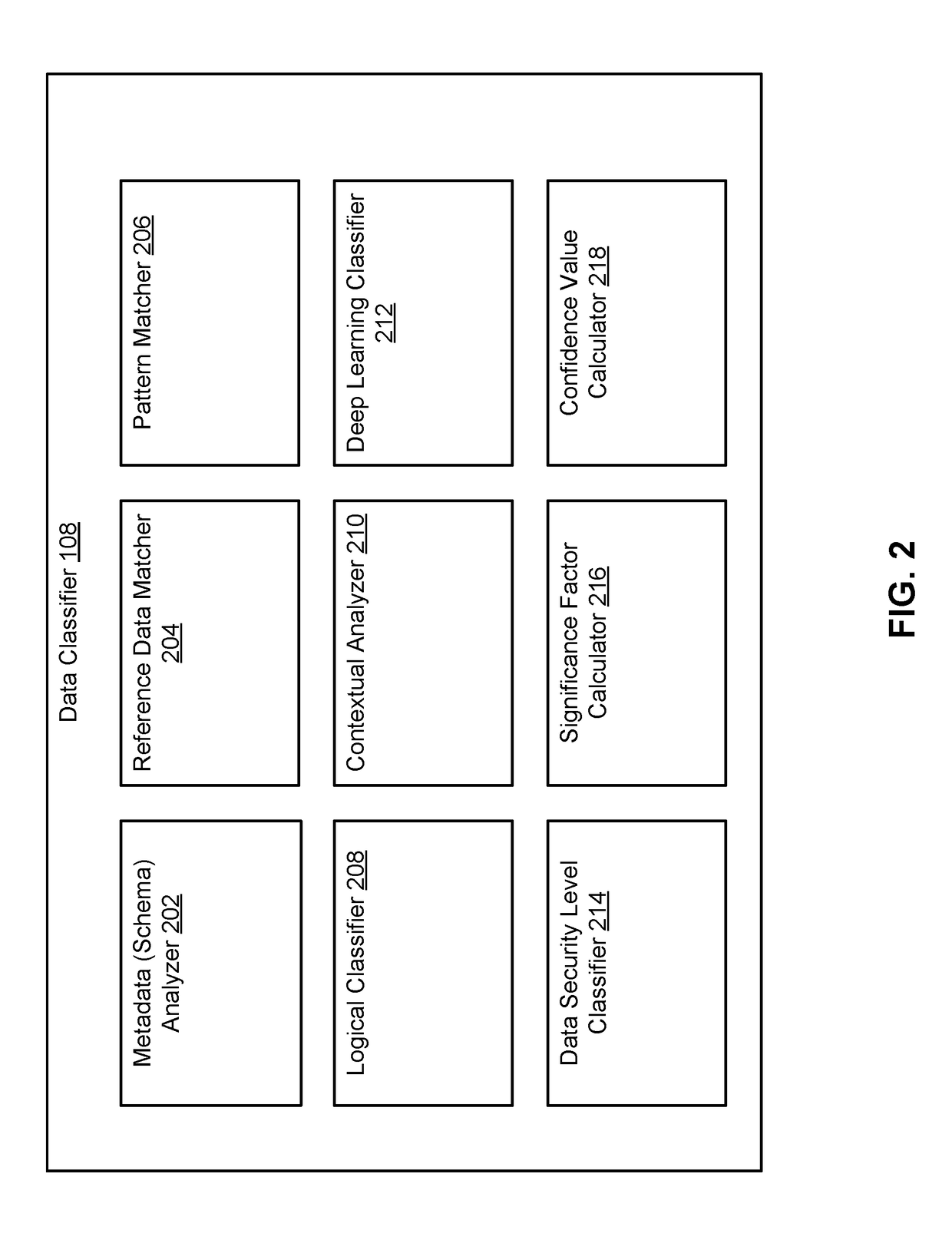
Sensitive Data Classification
A gateway device includes a network interface connected to data sources, and computer instructions, that when executed cause a processor to access data portions from the data sources. The processor accesses classification rules, which are configured to classify a data portion of the plurality of data portions as sensitive data in response to the data portion satisfying the rule. Each rule is associated with a significance factor representative of an accuracy of the classification rule. The processor applies each of the set of classification rules to a data portion to obtain an output of whether the data is sensitive data. The output are weighed by significance factors to produce a set of weighted outputs. The processor determines if the data portion is sensitive data by aggregating the set of weighted outputs, and presents the determination in a user interface. Security operations may also be performed on the data portion.
Owner:PROTEGRITY CORP
Terminal application program classifying method and terminal
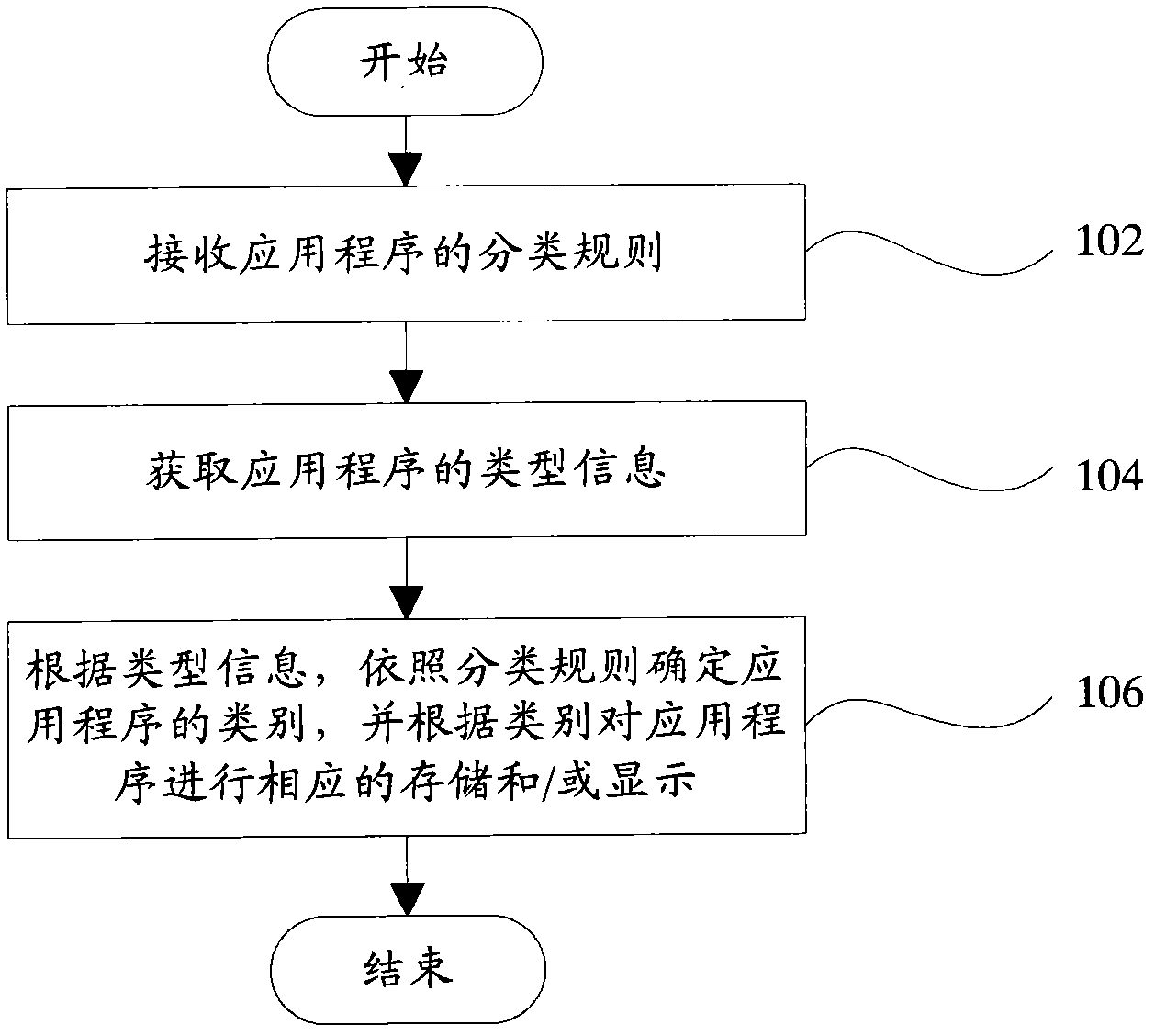
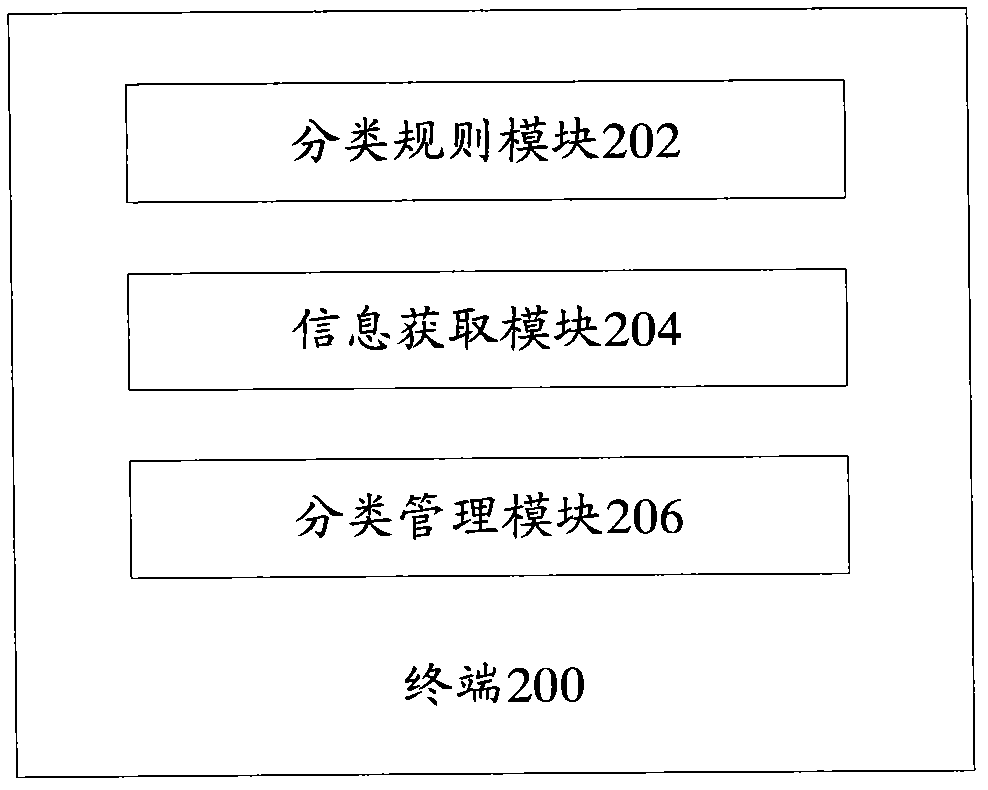
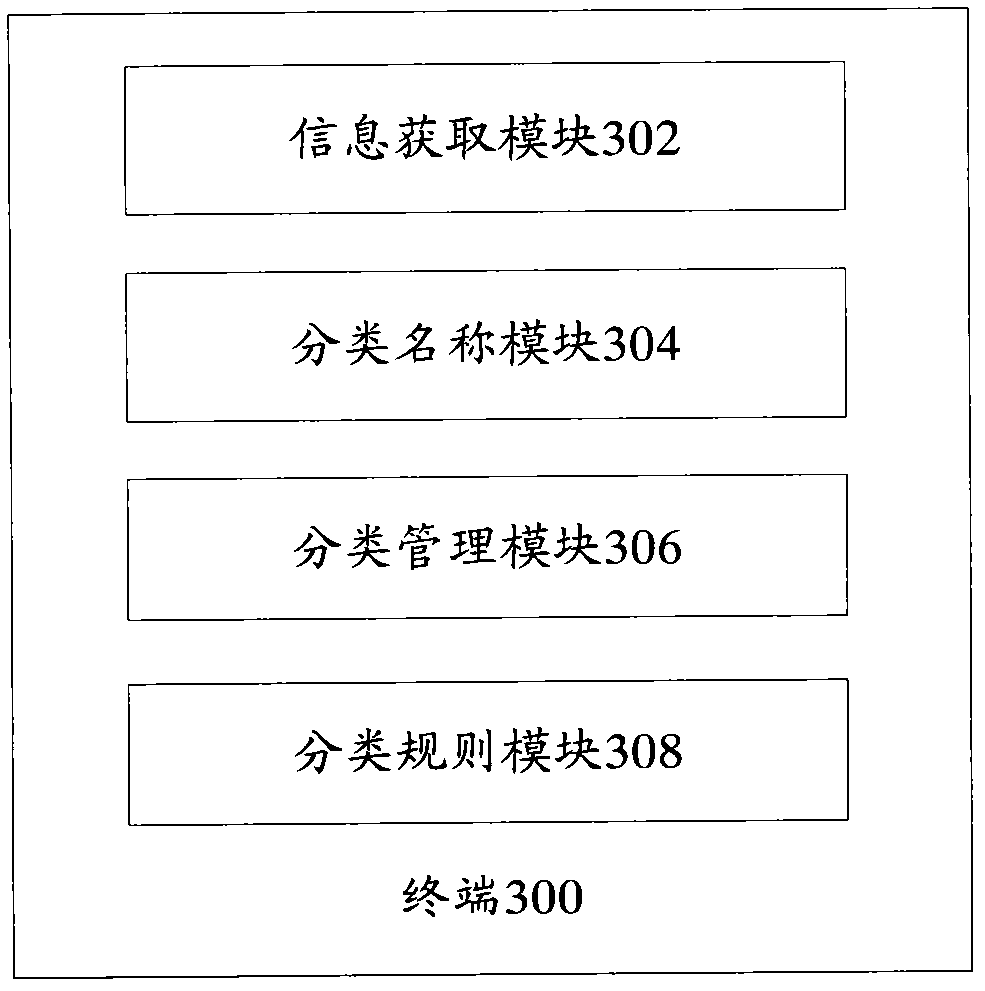
ActiveCN102135992ANo manual operation requiredSpecial data processing applicationsComputer terminalClassification rule
The invention provides a terminal application program classifying method. The method comprises the following steps: 102, receiving a classification rule of an application program; 104, acquiring type information of the application program; and 106, determining the type of the application program according to the type information and the classification rule, and storing and / or displaying the application program according to the type. The invention provides a terminal as well. By the method and the terminal, automatic classification of the application program can be realized without manual operation of users.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
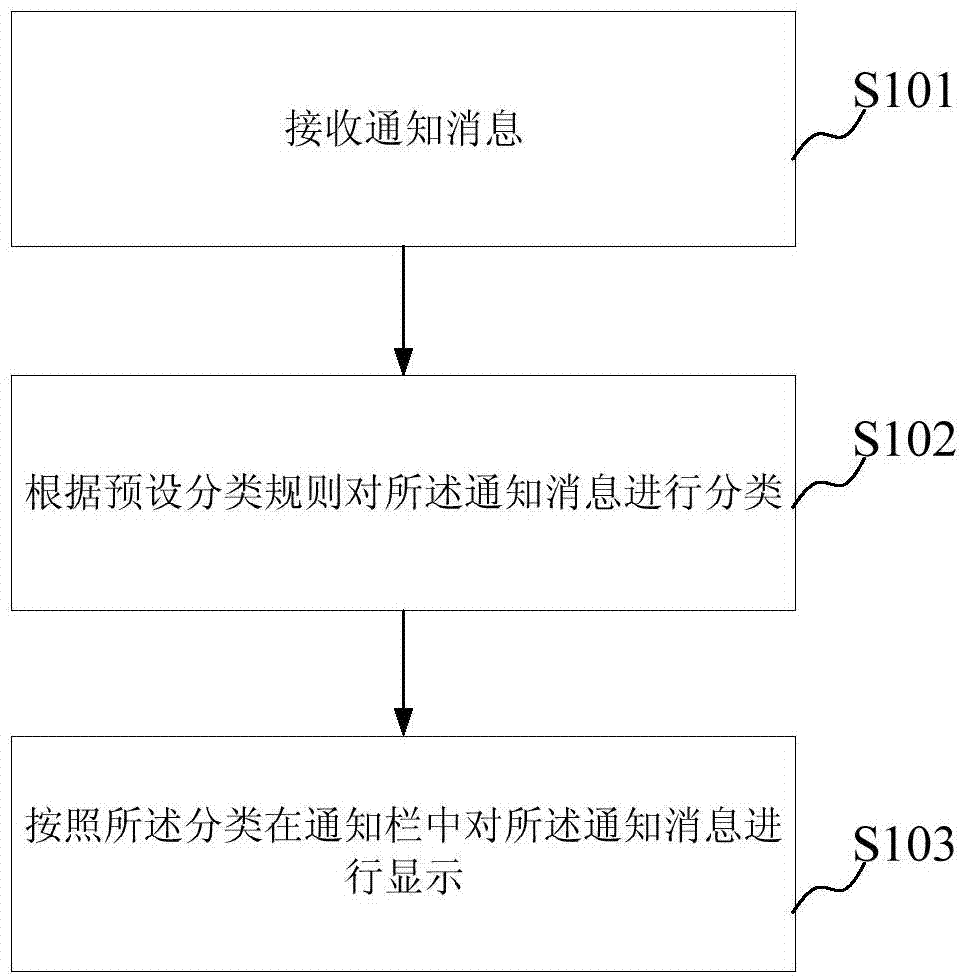
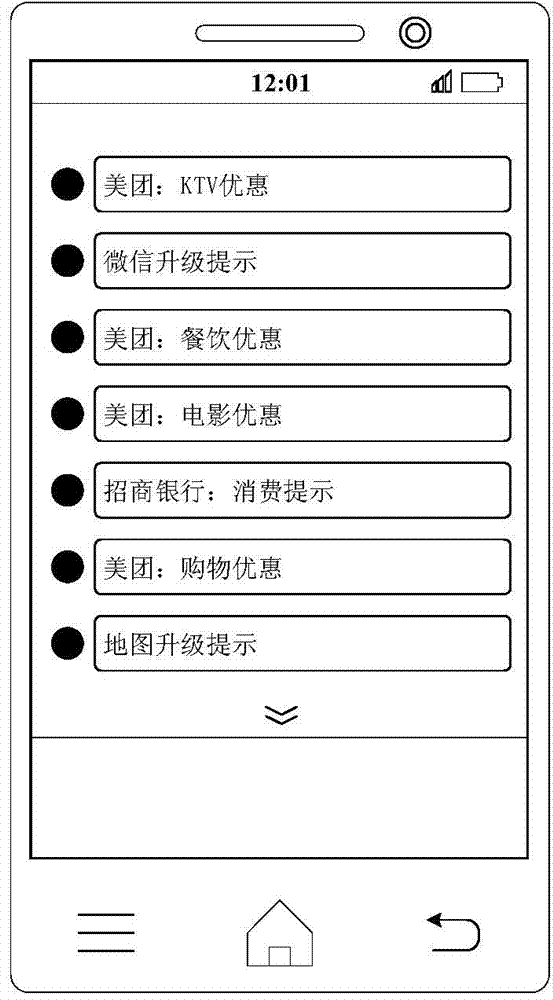
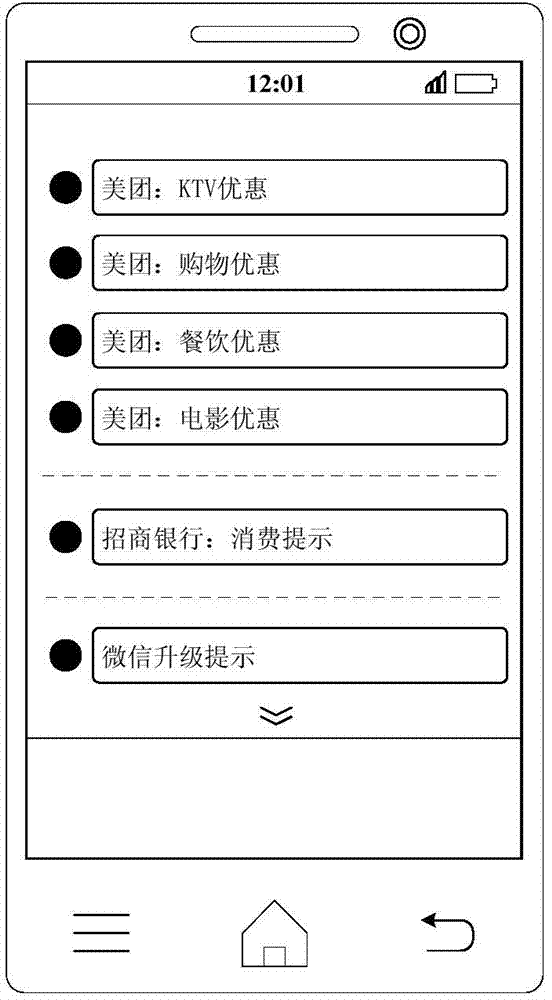
Method and device for displaying notification messages
ActiveCN104506715AImprove operational efficiencyImprove reading speedSubstation equipmentTerminal equipmentComputer terminal
The disclosed embodiment provides a method and a device for displaying notification messages, which are applied to terminal equipment. The method comprises the following steps: receiving the notification messages; classifying the notification messages according to the preset classification rule; displaying the notification messages in notification bars according to the classification. In the method provided by the embodiment, the terminal equipment such as a mobile phone can classify the notification messages according to the preset classification rule after receiving the notification message of a system or each APP (application); for example, the notification messages with the same source are classified into the same class, and then the notification messages are displayed in the notification bars according to the classification, thus an interface of each notification bar is concise and not disordered; a user can rapidly find out concerned message; the reading speed of the user is improved; the operation efficiency of the terminal equipment is improved; the user experience is also optimized.
Owner:XIAOMI INC
Proxy architecture for providing quality of service(QoS) reservations
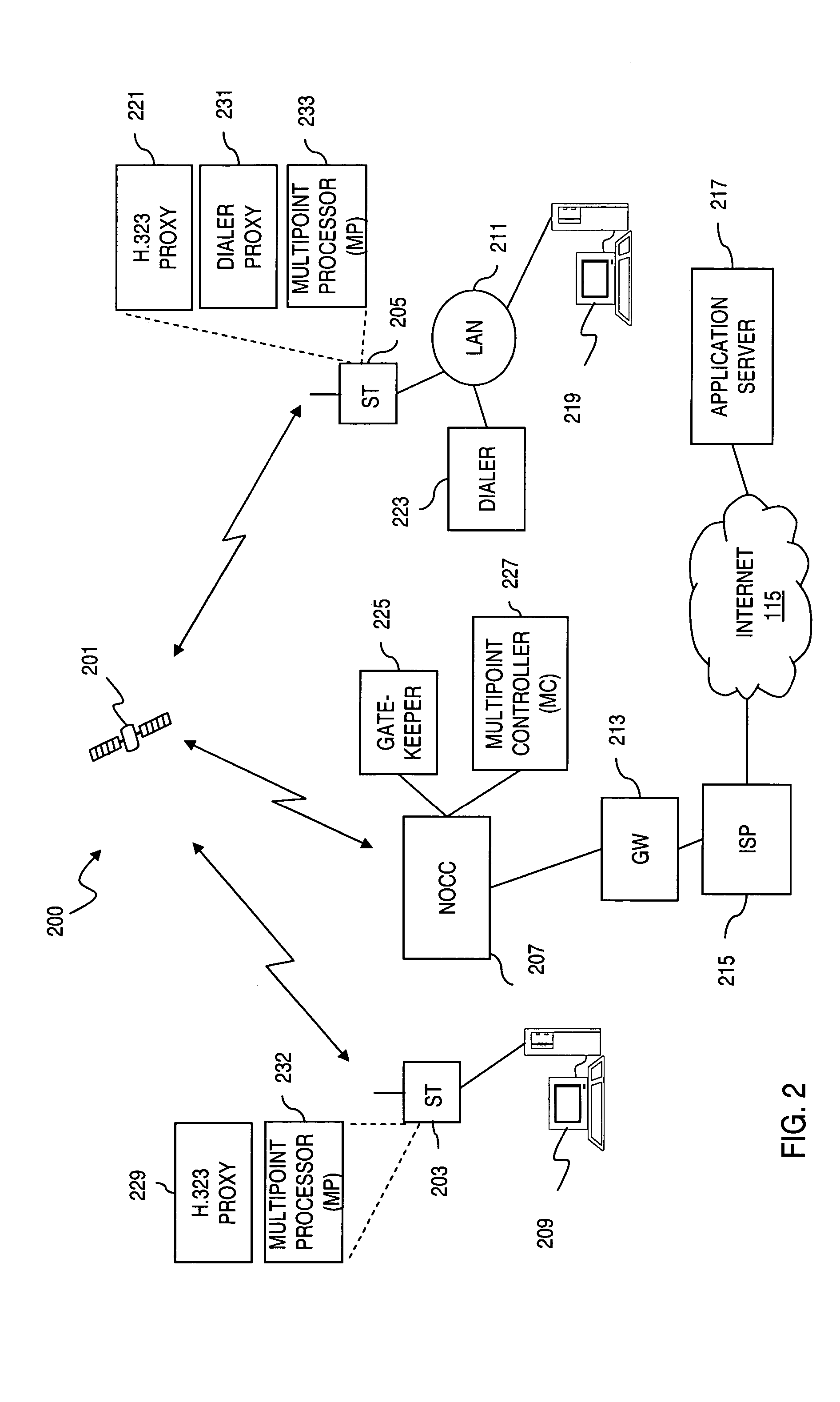
ActiveUS7353279B2Minimizing software upgradeMultiple digital computer combinationsGenerating/distributing signalsQuality of serviceClassification rule
An approach is provided for providing quality of service reservations in a packet-based radio communication network is disclosed. Connection information including connection rate is extracted from a dataflow from an application requesting connection-oriented service. A request message is sent to a proxy for establishing a connection based on the connection information over the network, wherein the proxy configures a classification rule based on flow criteria from the request message and accordingly initiates establishment of the connection over the network to a destination terminal. A confirmation that the connection can be established is selectively received according to the connection information, wherein the dataflow satisfying the flow criteria from the application is transported over the established connection to the destination terminal. This approach as particular applicability to shared capacity systems, such as a satellite communication system.
Owner:HUGHES NETWORK SYST
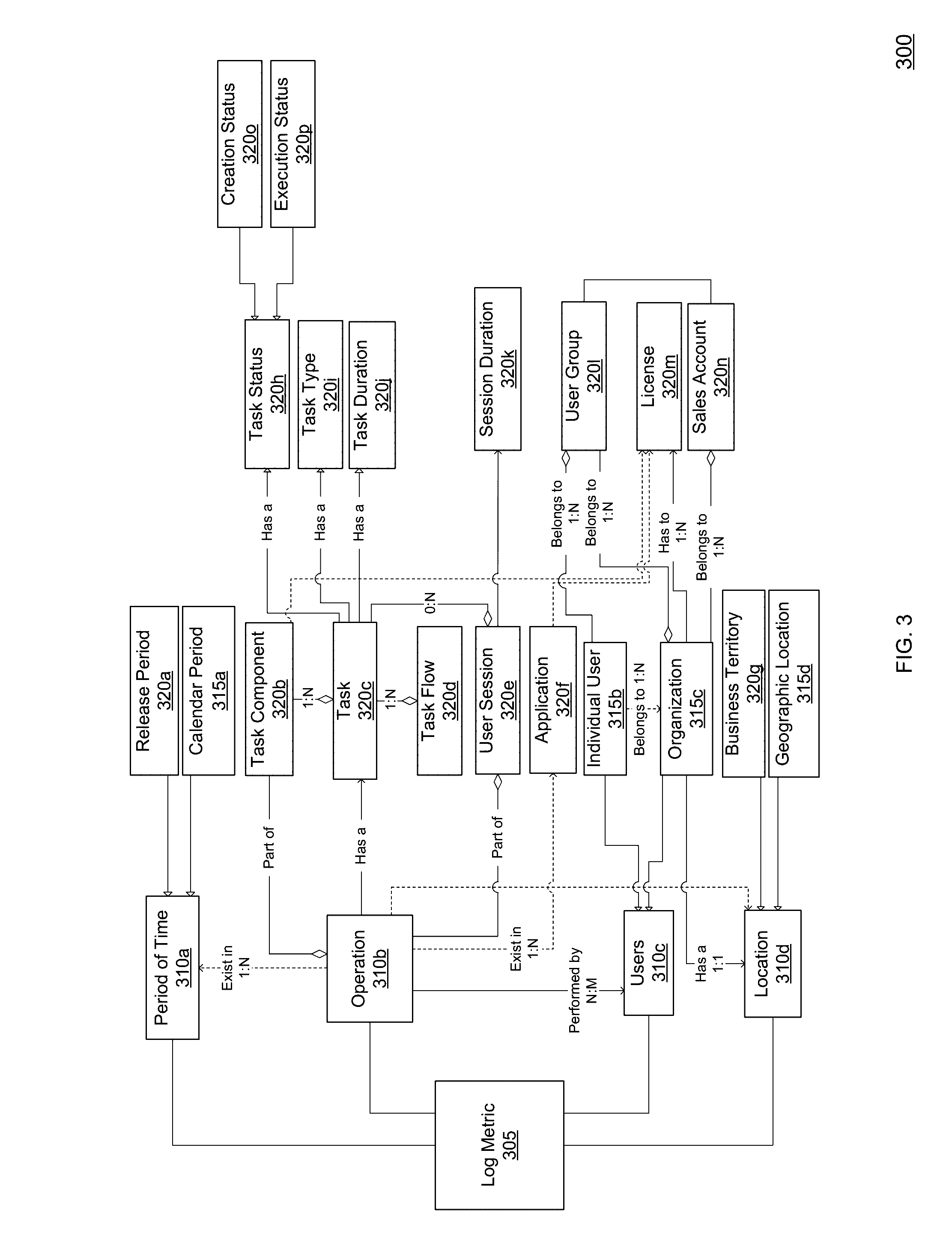
Metric Recommendations in an Event Log Analytics Environment
ActiveUS20160335260A1Flexible and extendibleFlexible and recommendationDigital data information retrievalSpecial data processing applicationsDecision takingClassification rule
A system and method are disclosed for providing metric recommendations by a cloud event log analytics system. The log analytics system includes a user interface which allows users to view metric recommendations, view, modify, annotate, delete, or create log metrics. In a first embodiment, centroid vectors are created from metadata associated with user access of log metrics. The centroid vectors are compared to metrics vectors created from log metrics and the results are ranked and provided to users as metric recommendations. In a second embodiment, classification rules are inferred for metric matrix tables containing metadata about log metric usage. Classification rules are assigned to a decision tree used to calculate composite probabilities of interest of log metrics. A recommendation matrix incorporate the composite probabilities of interest to predict the degree of interest an analytics user may have in a log metric for a given role.
Owner:INFORMATICA CORP
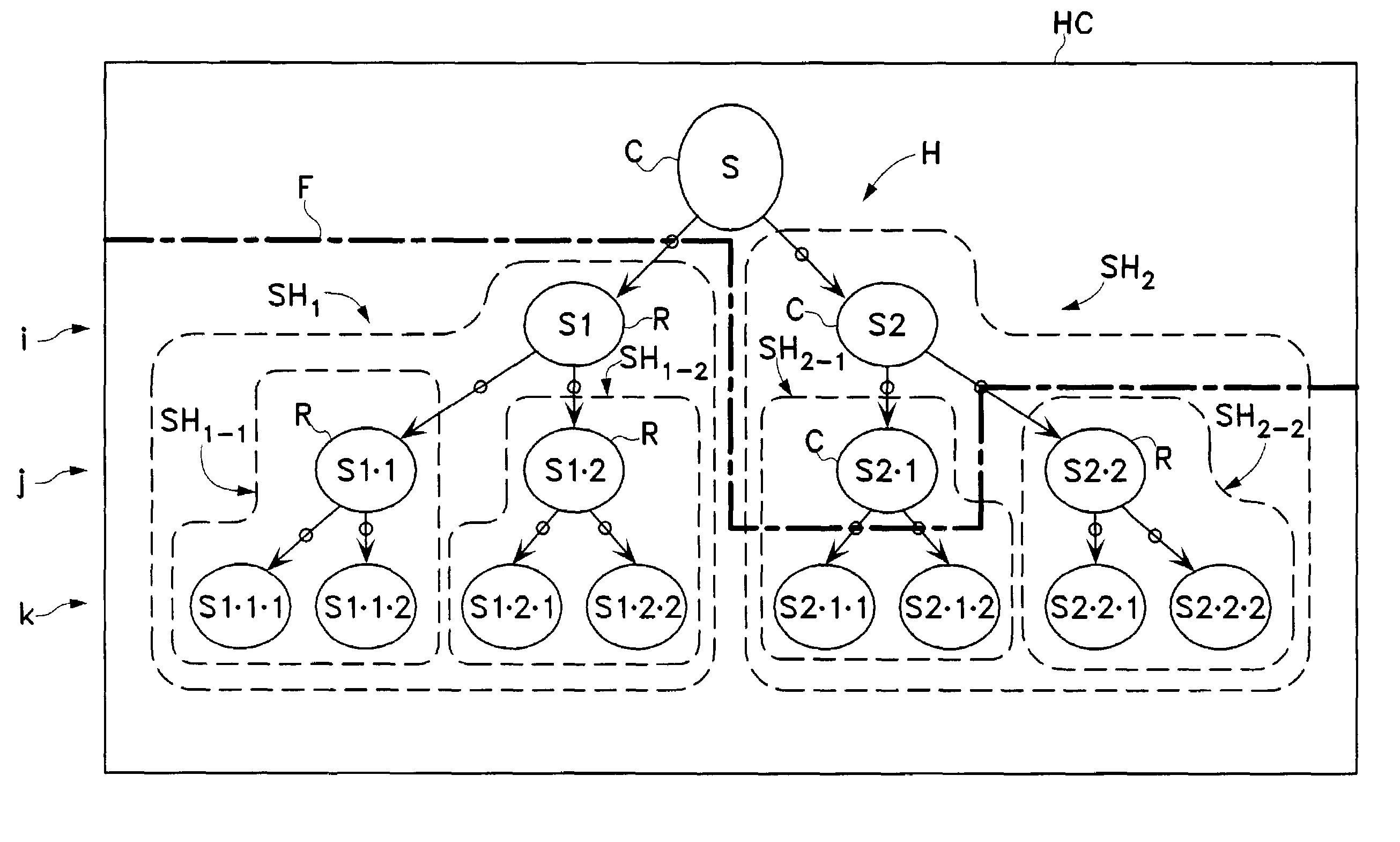
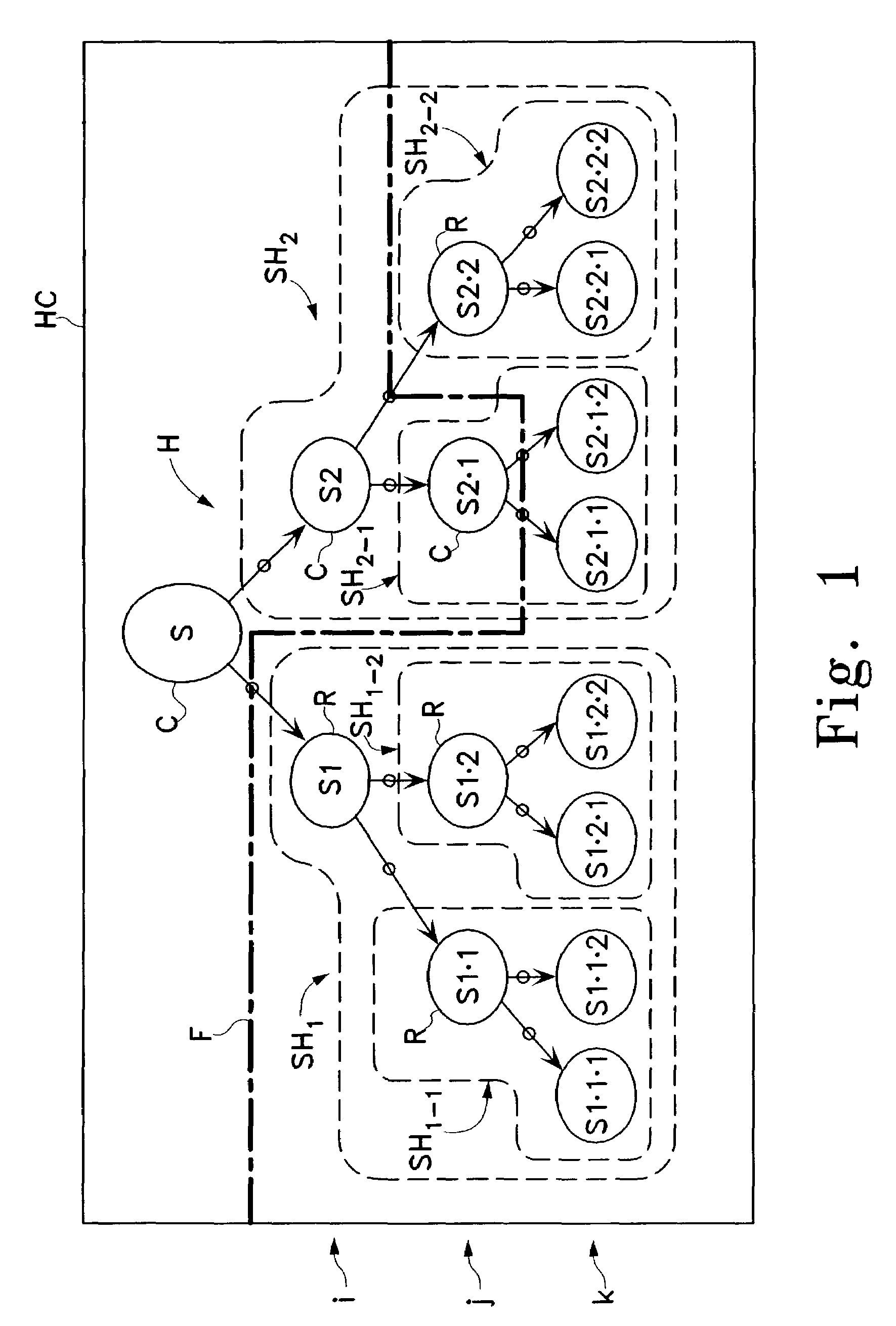
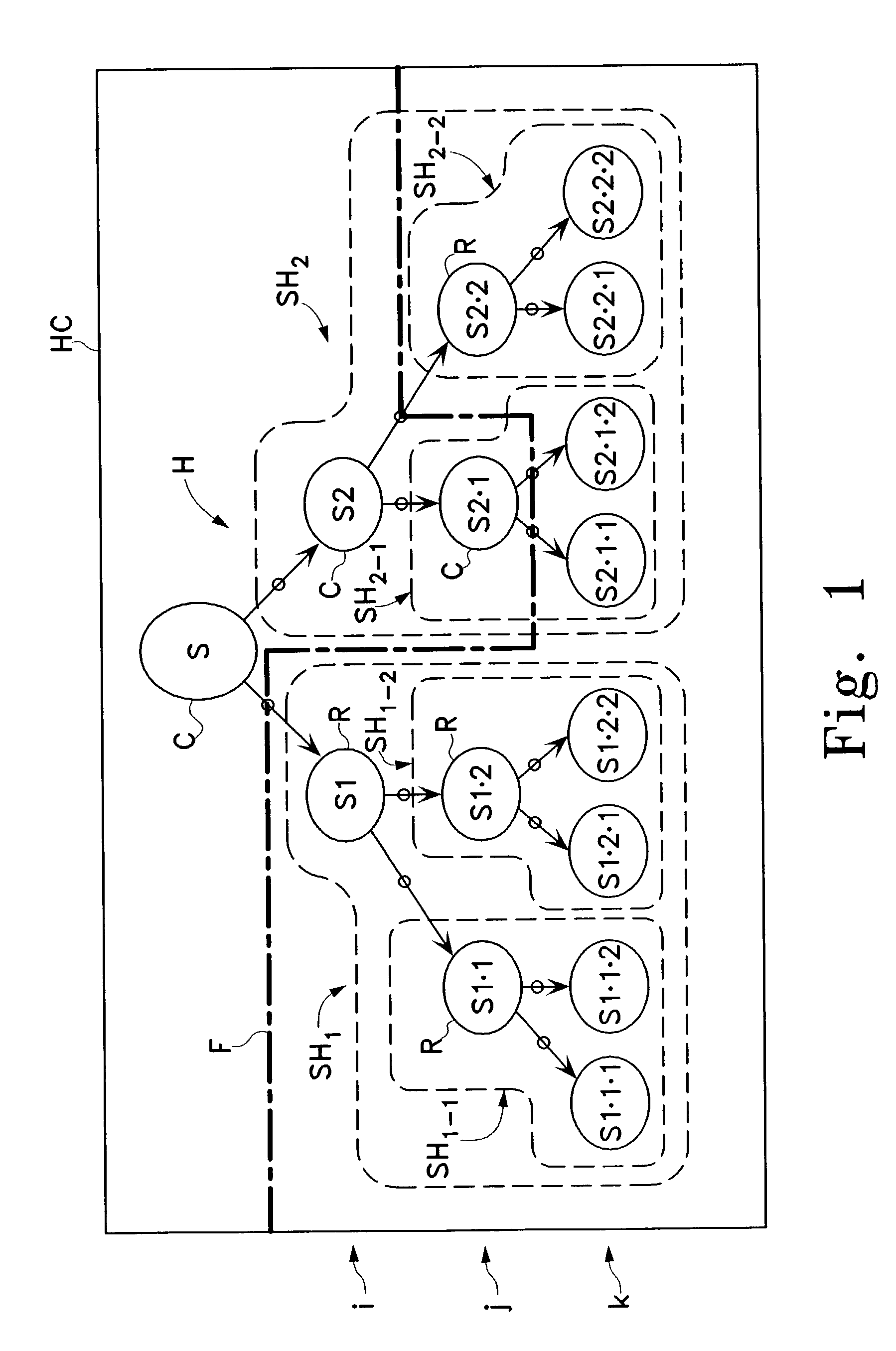
Hierarchical categorization method and system with automatic local selection of classifiers
InactiveUS7349917B2Sufficient dataSufficient performanceData processing applicationsDigital data processing detailsClassification ruleLocal selection
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
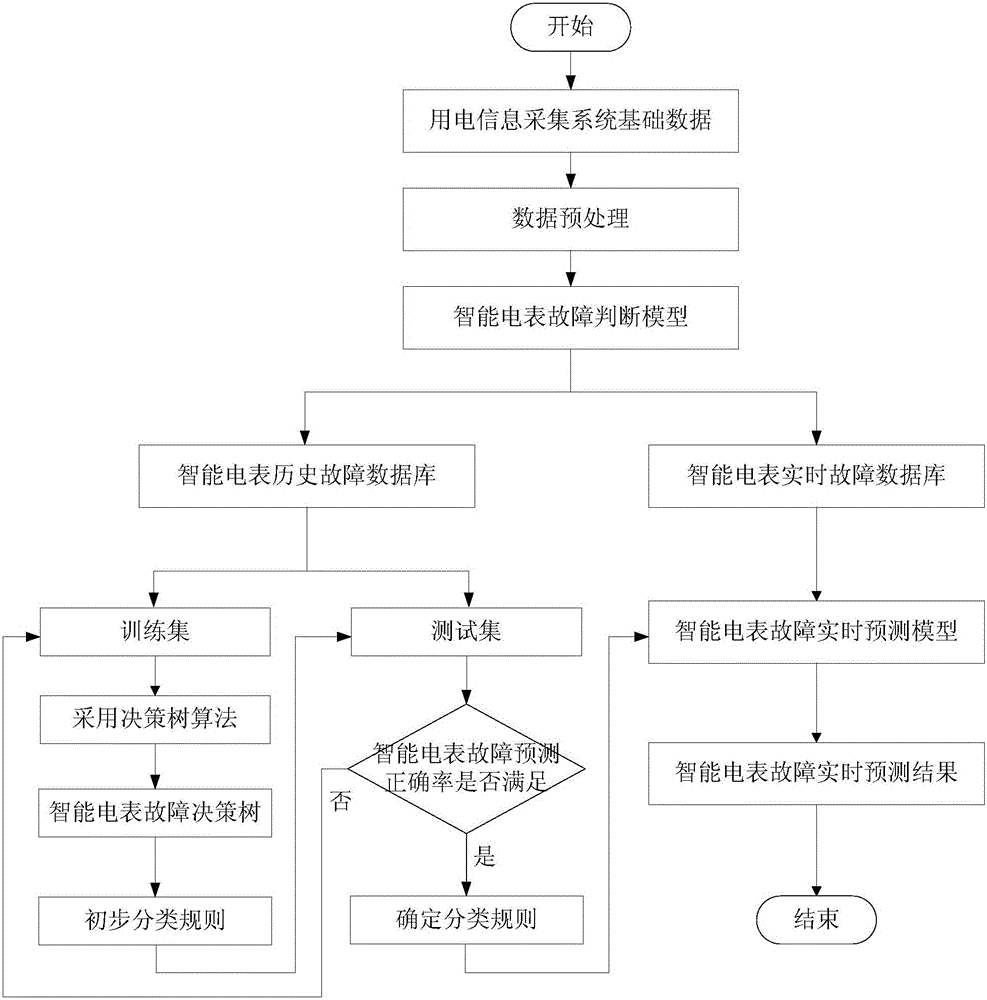
Intelligent ammeter fault real time prediction method based on decision-making tree
Provided is an intelligent ammeter fault real time prediction method based on a decision-making tree, comprising the steps of: 1, pre-processing intelligent ammeter data of an electricity information acquisition system; 2, according to an intelligent ammeter fault determination model, screening the fault data of intelligent ammeters in the electricity information acquisition system and sending the fault data into an intelligent ammeter fault database; 3, dividing the historic data in the intelligent ammeter fault database into a training set and a test set, employing a decision-making tree algorithm to perform data excavation on the training set, and forming an intelligent ammeter fault decision-making tree and a preliminary classification rule; 4, through the data of the test set, performing accuracy assessment on the preliminary classification rule, determining the preliminary classification rule if the accuracy meets requirements, or else returning to the training set for training again; 5, generating an intelligent ammeter fault real time prediction model according to a finally determined classification rule; and 6, linking an intelligent ammeter real time fault database to the intelligent ammeter fault real time prediction model for real time prediction to obtain intelligent ammeter fault real time prediction results.
Owner:国网新疆电力有限公司营销服务中心 +1
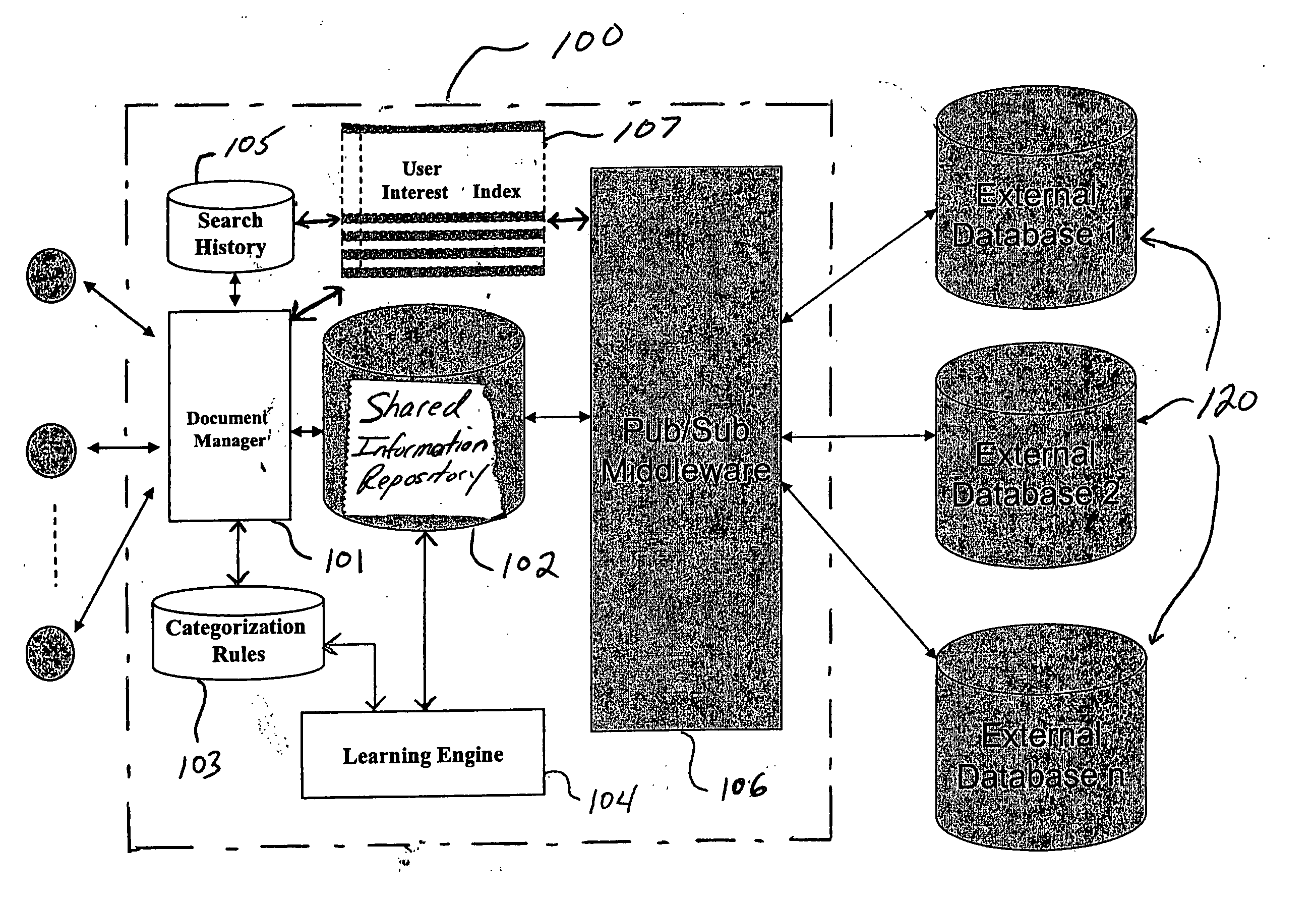
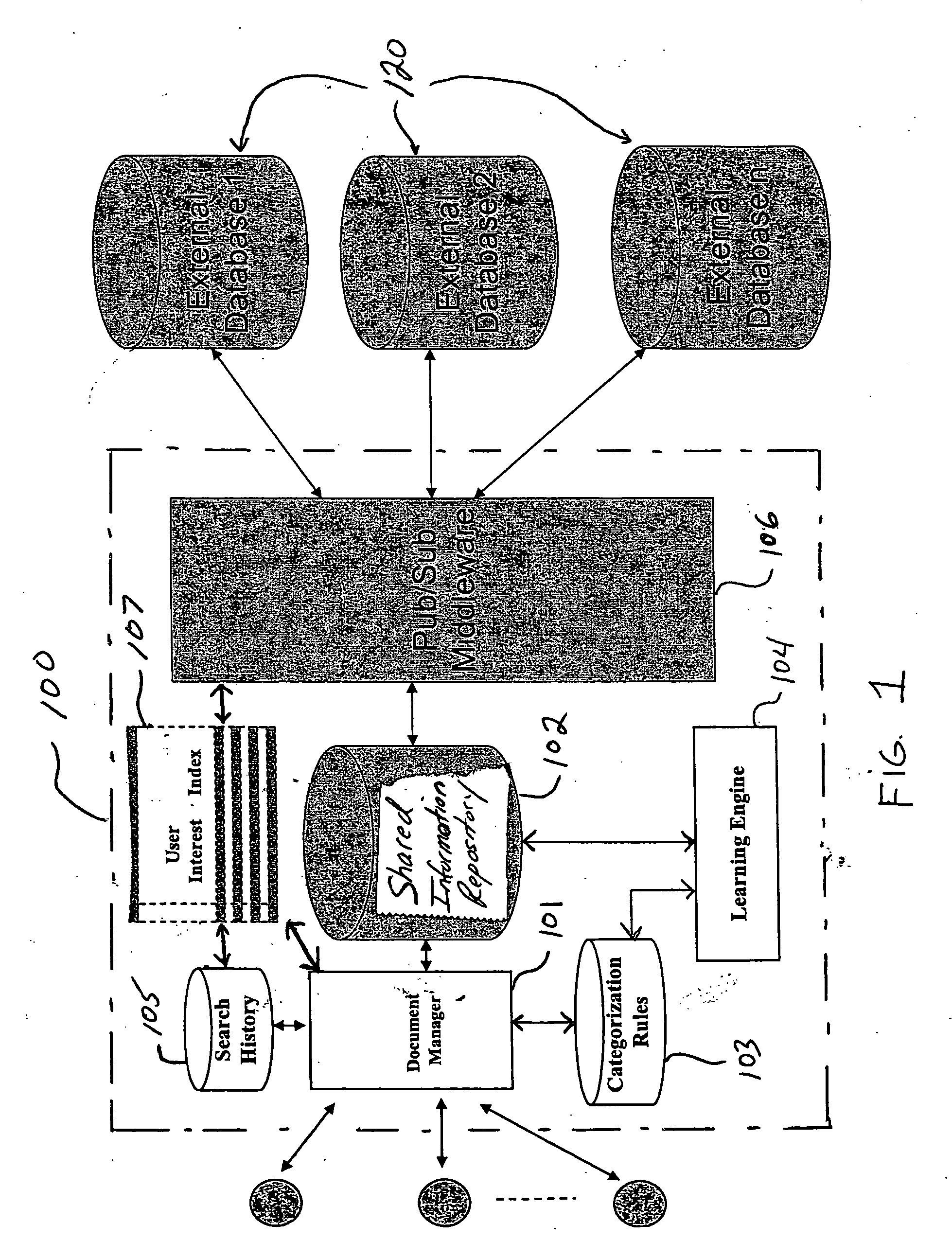
Systems and methods for building and implementing ontology-based information resources
ActiveUS20070043742A1Digital data processing detailsSpeech analysisInformation resourceSemi automatic
Systems and methods are provided for building and implementing ontology-based information resources. More specifically, multi-user collaborative, semi-automatic systems and methods are provided for constructing ontology-based information resources that are shared by a community of users, wherein ontology categories evolve over time based on categorization rules that are specified by the community of users as well as categorization rules that are automatically learned from knowledge obtained as a result of multi-user interactions and categorization decisions.
Owner:IBM CORP
Electrical power system short-term load forecasting method based on big data technology
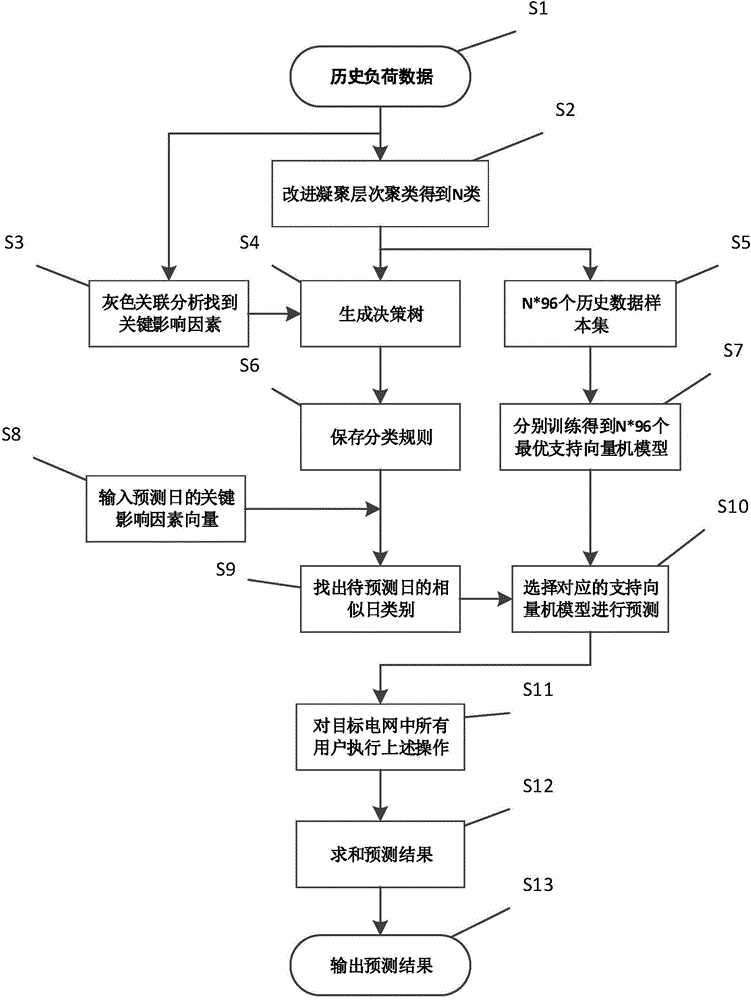
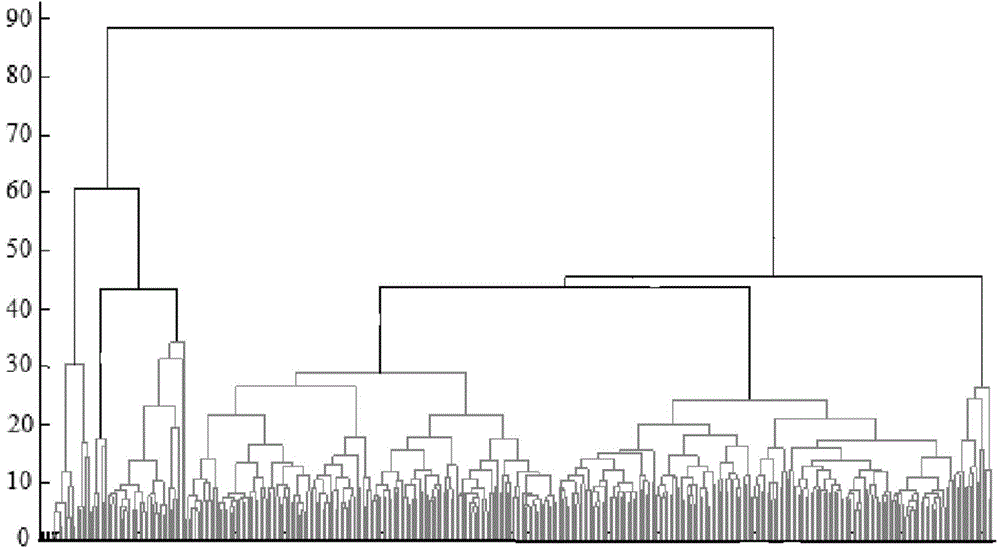
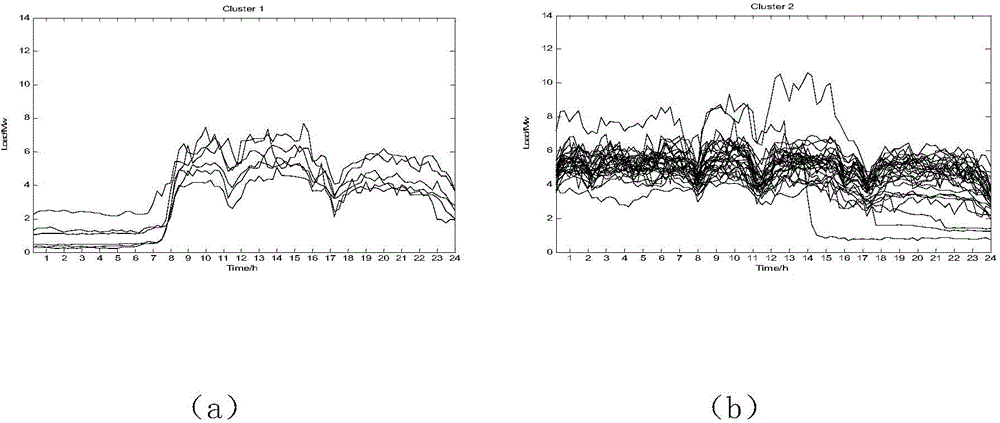
ActiveCN104881706AImprove securityImprove stabilityForecastingUtilization behaviorLoad following power plant
The present invention provides a electrical power system short-term load forecasting method based on a big data technology. The user-level load forecasting is realized by utilizing a data mining technology, and user-level loads are accumulated to form a system load. The electrical power system short-term load forecasting method comprises the steps of: conducting load curve clustering analysis, and classifying load curves with similar shape features into a class; determining key influence factors, and achieving the purposes of reducing classifying rules and simplifying a forecasting model; establishing classifying rules, and adopting a CART decision tree algorithm to obtain condensation level clustering analysis results; classifying days to be forecast; training the forecasting model and forecasting, and selecting a corresponding support vector machine model to complete the forecasting according to the obtained classification results of the days to be forecast; and completing the step of calculating the system load on a Hadoop big data calculating platform. The electrical power system short-term load forecasting method based on the big data technology studies a user-level load forecasting framework, discovers electricity utilization behavior rules of a user by utilizing the data mining technology, and increases the precision of load forecasting.
Owner:TIANJIN HONGYUAN HUINENG TECH
Rear-end collision pre-warning method based on driver types
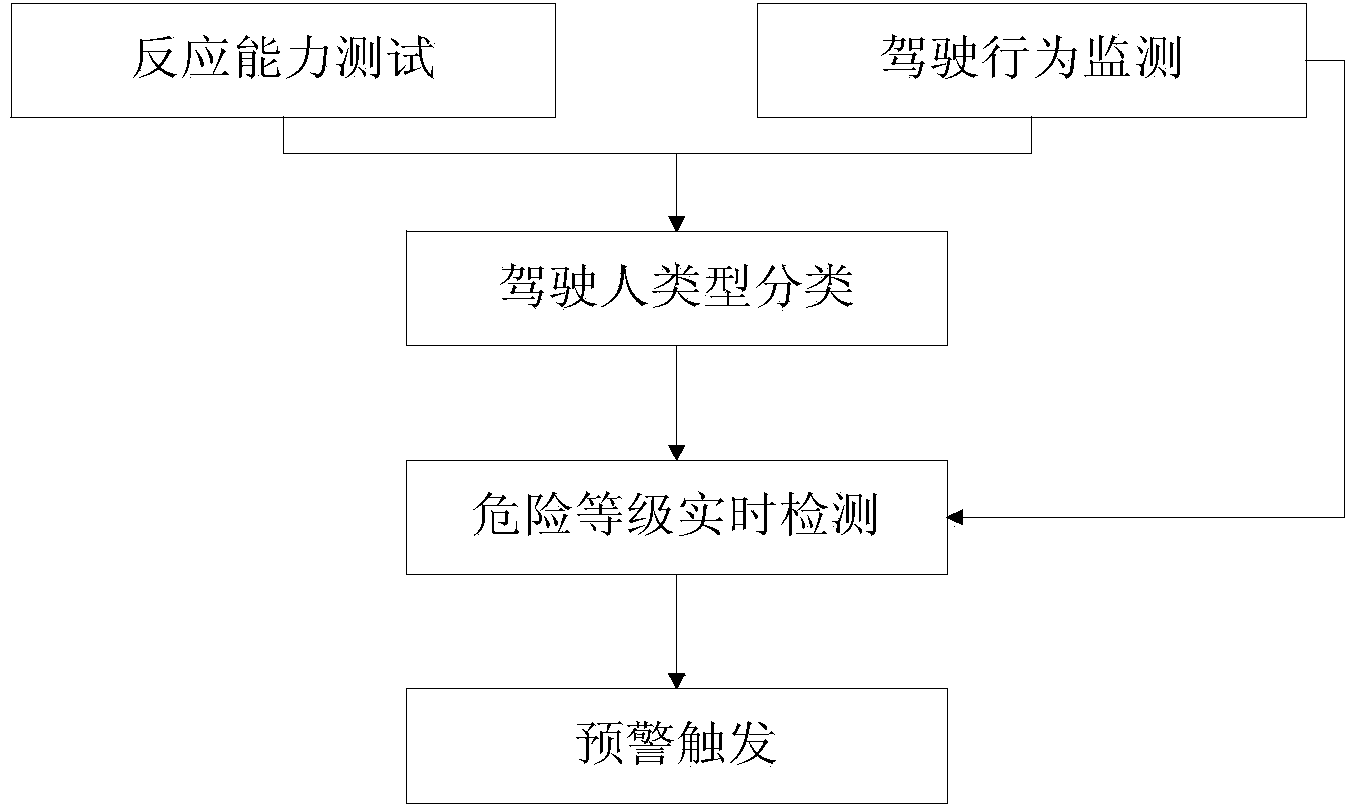
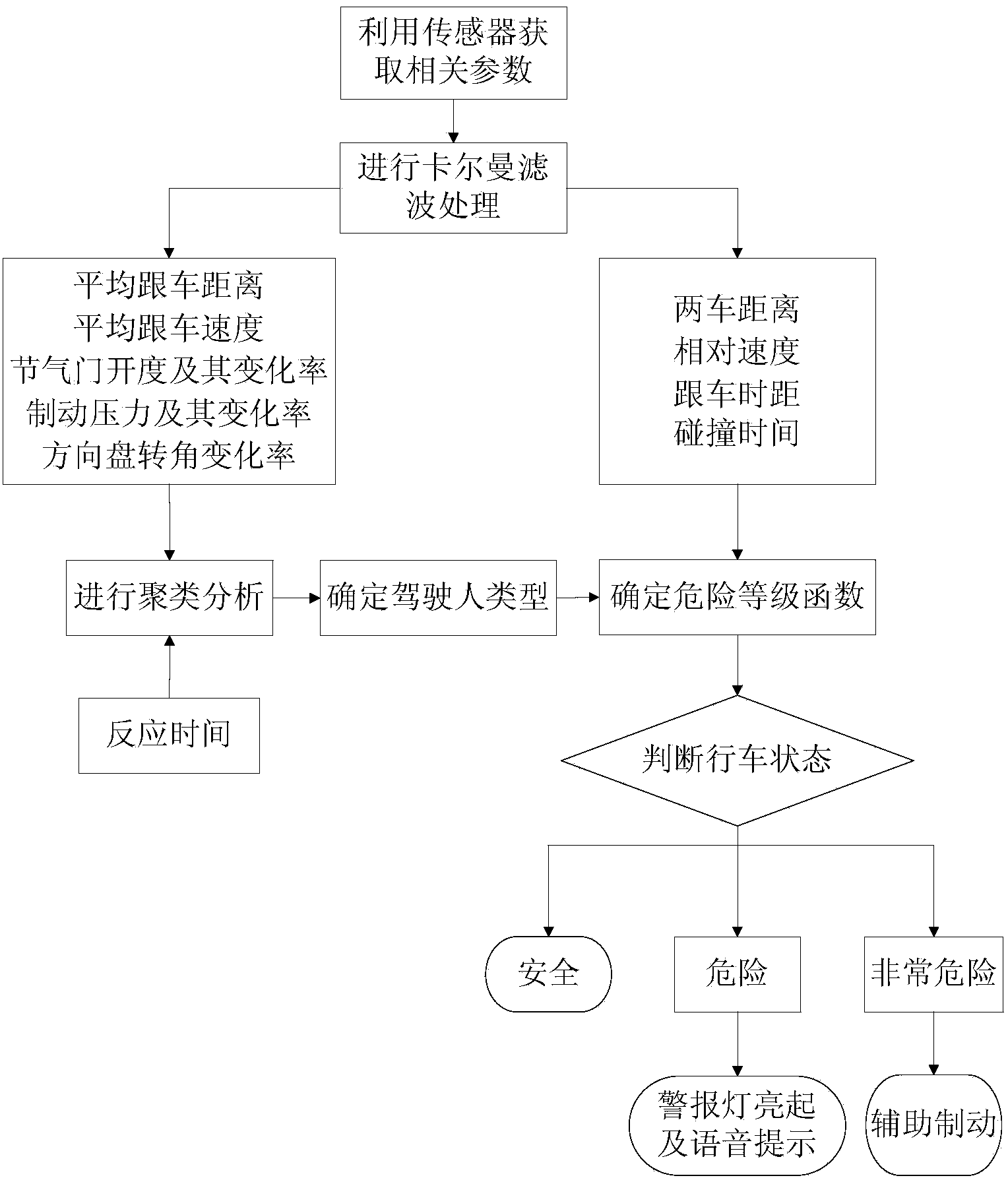
InactiveCN103531042AAvoid the impact of rear-end warningImprove detection accuracyDetection of traffic movementAnti-collision systemsRear-end collisionReaction time test
The invention discloses a rear-end collision pre-warning method based on driver types, and aims to solve the problem that the pre-warning accuracy is reduced due to no consideration of driving habits of different types of drivers in the prior art. The rear-end collision pre-warning method comprises the steps as follows: 1, an emergency reaction ability test: reaction time of a tested driver is tested by a reaction time tester; 2, driving behavior monitoring: corresponding sensors are respectively utilized to acquire operation parameters of the tested driver, a distance between the tested vehicle and a vehicle ahead and a relative speed; 3, classification of driver types: according to emergency reaction ability test data and driving behavior monitoring data of the tested driver, an unsupervised cluster analysis method is adopted to determine the driver type on the basis of a preset reaction capacity classification rule and a driving style membership grade function; 4, real-time danger level detection: a danger level judgment equation suitable for the driver type of the tested driver is selected to judge current driving danger level of the tested vehicle; and 5, pre-warning triggering.
Owner:JILIN UNIV
Hierarchical categorization method and system with automatic local selection of classifiers
InactiveUS20040064464A1Solve the lack of training dataSufficient performanceData processing applicationsDigital data processing detailsClassification ruleLocal selection
The present invention relates generally to the classification of items into categories, and more generally, to the automatic selection of different classifiers at different places within a hierarchy of categories. An exemplary hierarchical categorization method uses a hybrid of different classification technologies, with training-data based machine-learning classifiers preferably being used in those portions of the hierarchy above a dynamically defined boundary in which adequate training data is available, and with a-priori classification rules not requiring any such training-data being used below that boundary, thereby providing a novel hybrid categorization technology that is capable of leveraging the strengths of its components. In particular, it enables the use of human-authored rules in those finely divided portions towards the bottom of the hierarchy involving relatively close decisions for which it is not practical to create in advance sufficient training data to ensure accurate classification by known machine-learning algorithms, while still facilitating eventual change-over within the hierarchy to machine learning algorithms as sufficient training data becomes available to ensure acceptable performance in a particular sub-portion of the hierarchy.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
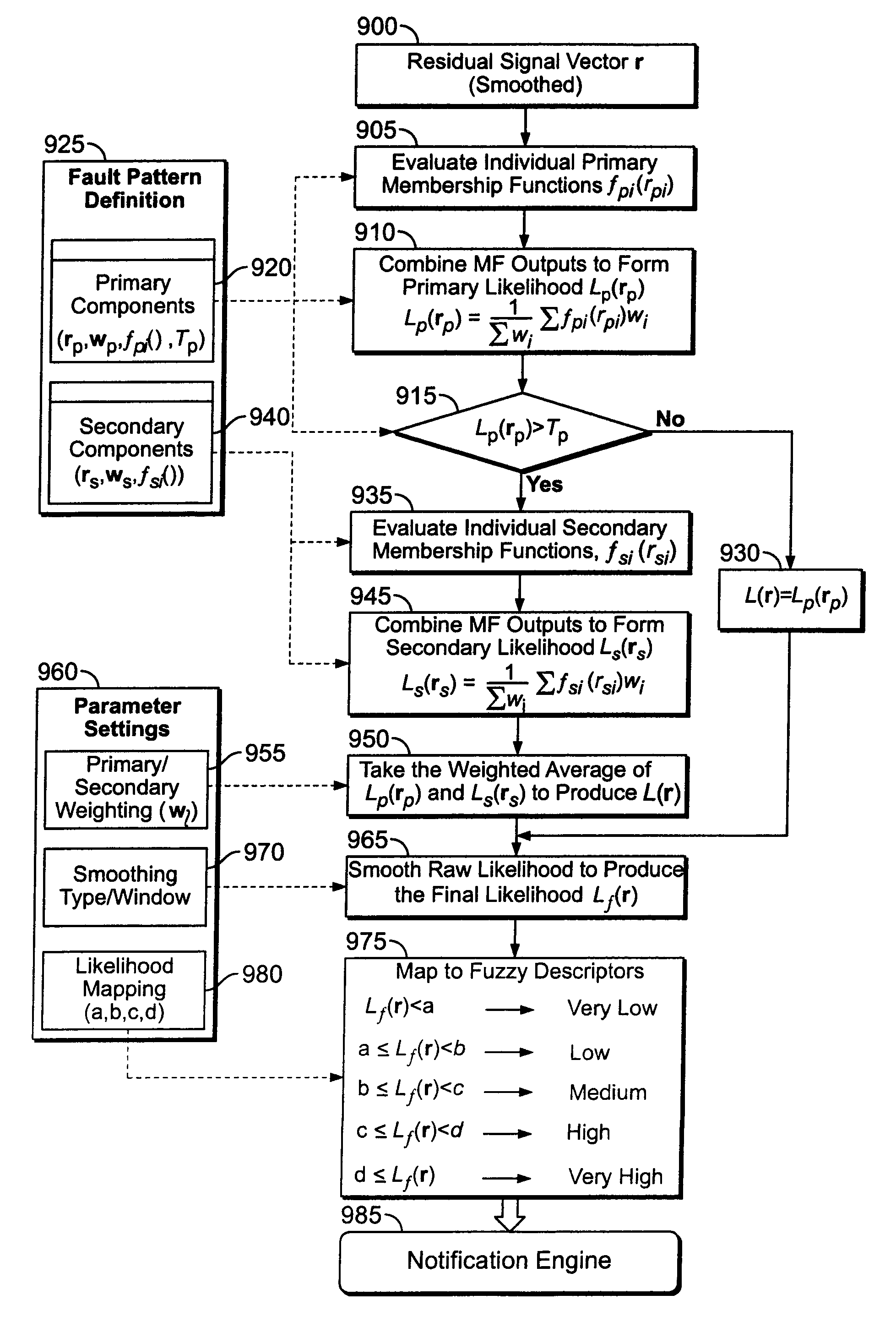
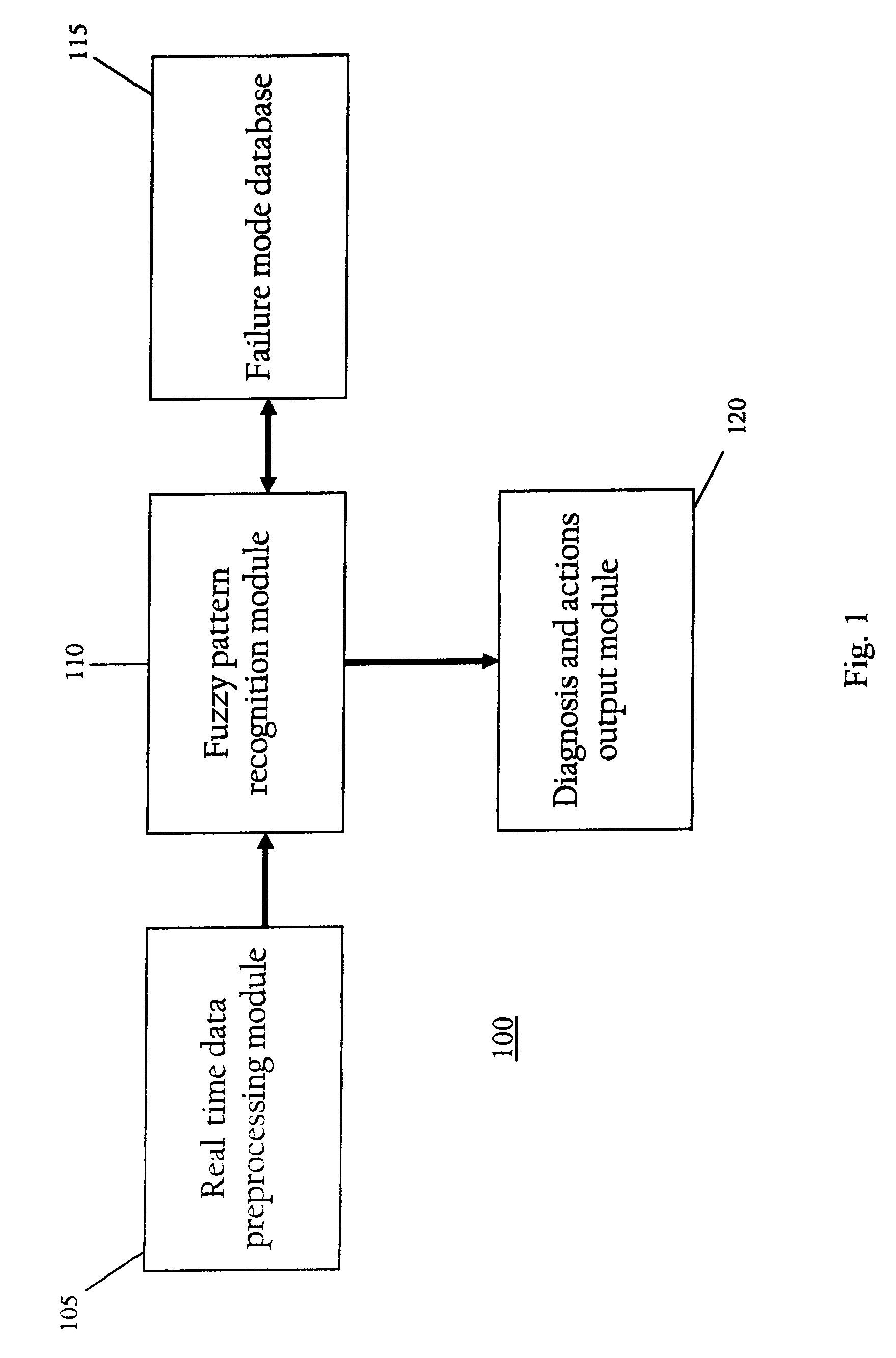
Fuzzy classification approach to fault pattern matching
ActiveUS7941701B2Error detection/correctionTesting/monitoring control systemsPattern matchingMonitoring system
A method and apparatus are provided for diagnosing faults in a monitored system. Estimates of parameter data are generated from the system with reference parameter data characteristic of known behavior of the system. The generated estimates of the parameter data are compared with measured parameter data. A residual is determined for each of the parameters based on a relationship between the estimates of the parameter data and the measured parameter data. A fuzzy classification rule is implemented to determine a likelihood that a predetermined fault exists by using residuals for parameters used to indicate the existence of the predetermined fault.
Owner:SMARTSIGNAL CORP
Method and module for extracting and interpreting information of remote-sensing image
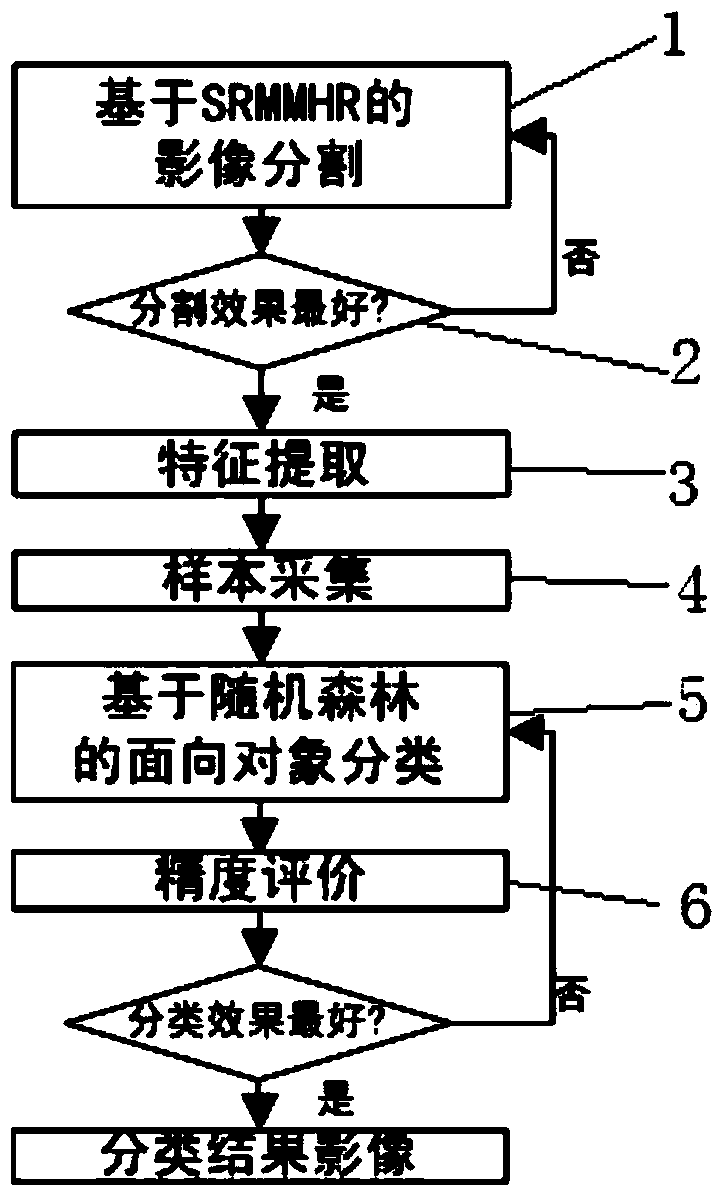
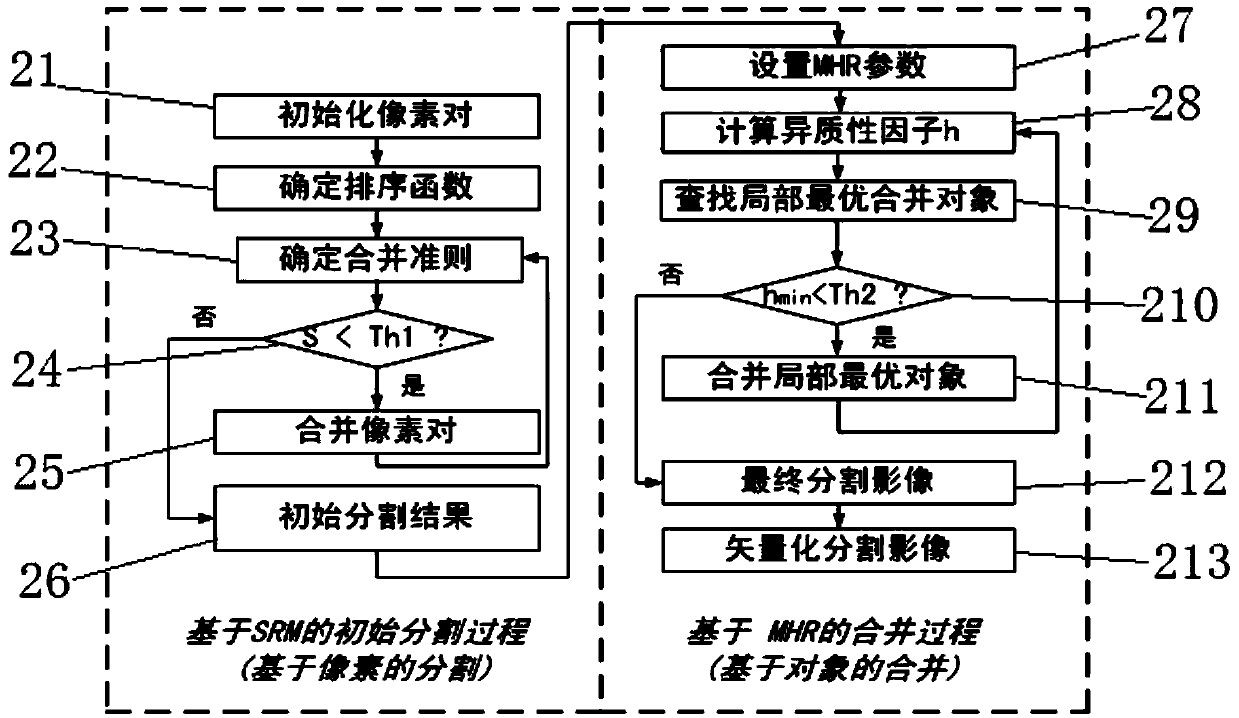
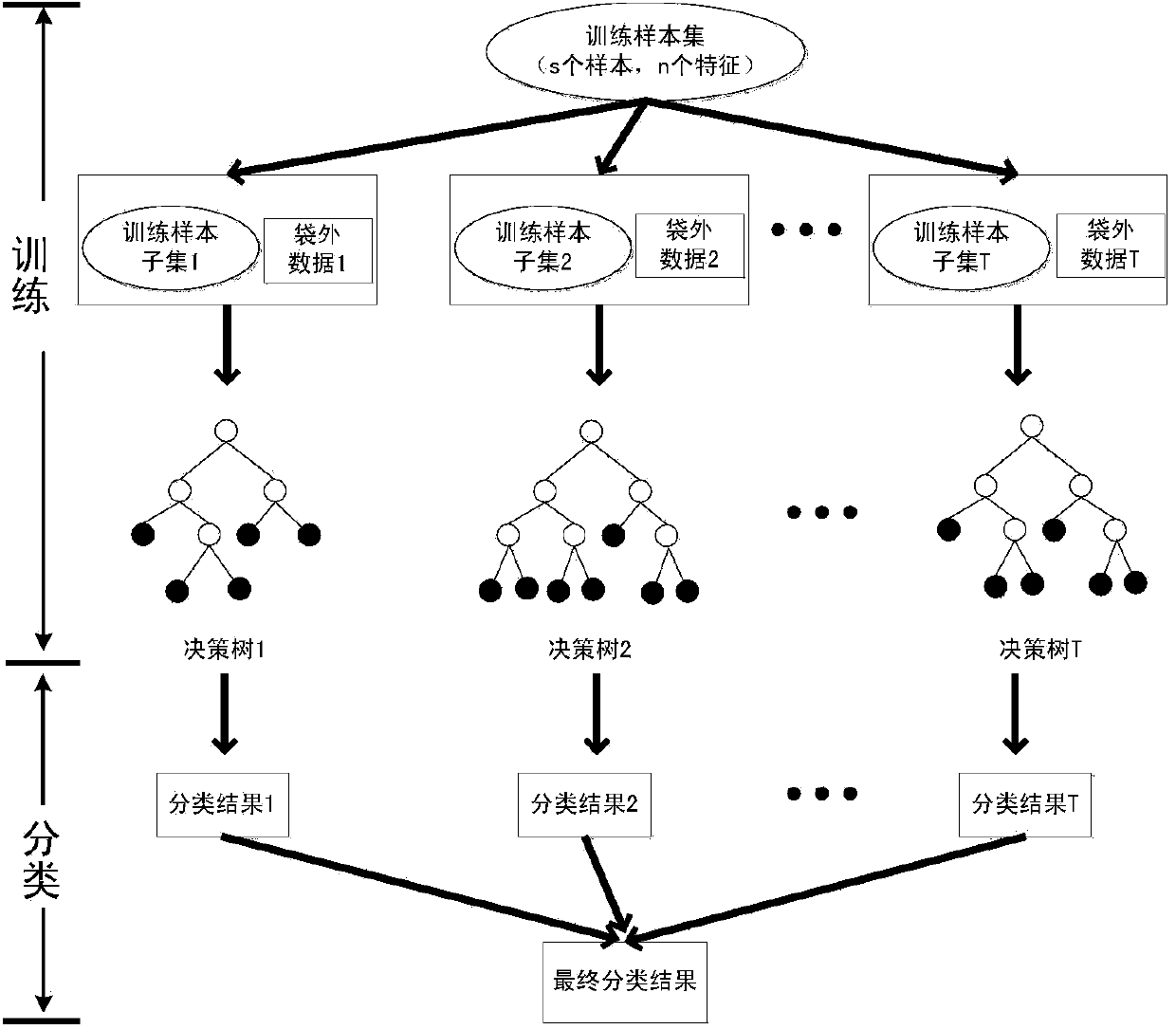
InactiveCN103500344AEffective segmentationHigh precisionCharacter and pattern recognitionObject basedClassification rule
The invention discloses a method and module for extracting and interpreting information of a remote-sensing image, and provides a geographical element object based automatic interpreting method based on SRMMHR and random forest. The module extracts and interprets the information of the remote-sensing image by the adoption of the method. The method and module for extracting and interpreting the information of the remote-sensing image can achieve effective segmentation of the remote-sensing image, automatic optimization of characteristics, and automatic establishment of a classification rule set; a means which is little in manual intervention, high in degree of automation and high in interpreting precision is provided for extracting and interpreting the information of the remote-sensing image.
Owner:CHINESE ACAD OF SURVEYING & MAPPING
Semi-supervised data integration model for named entity classification
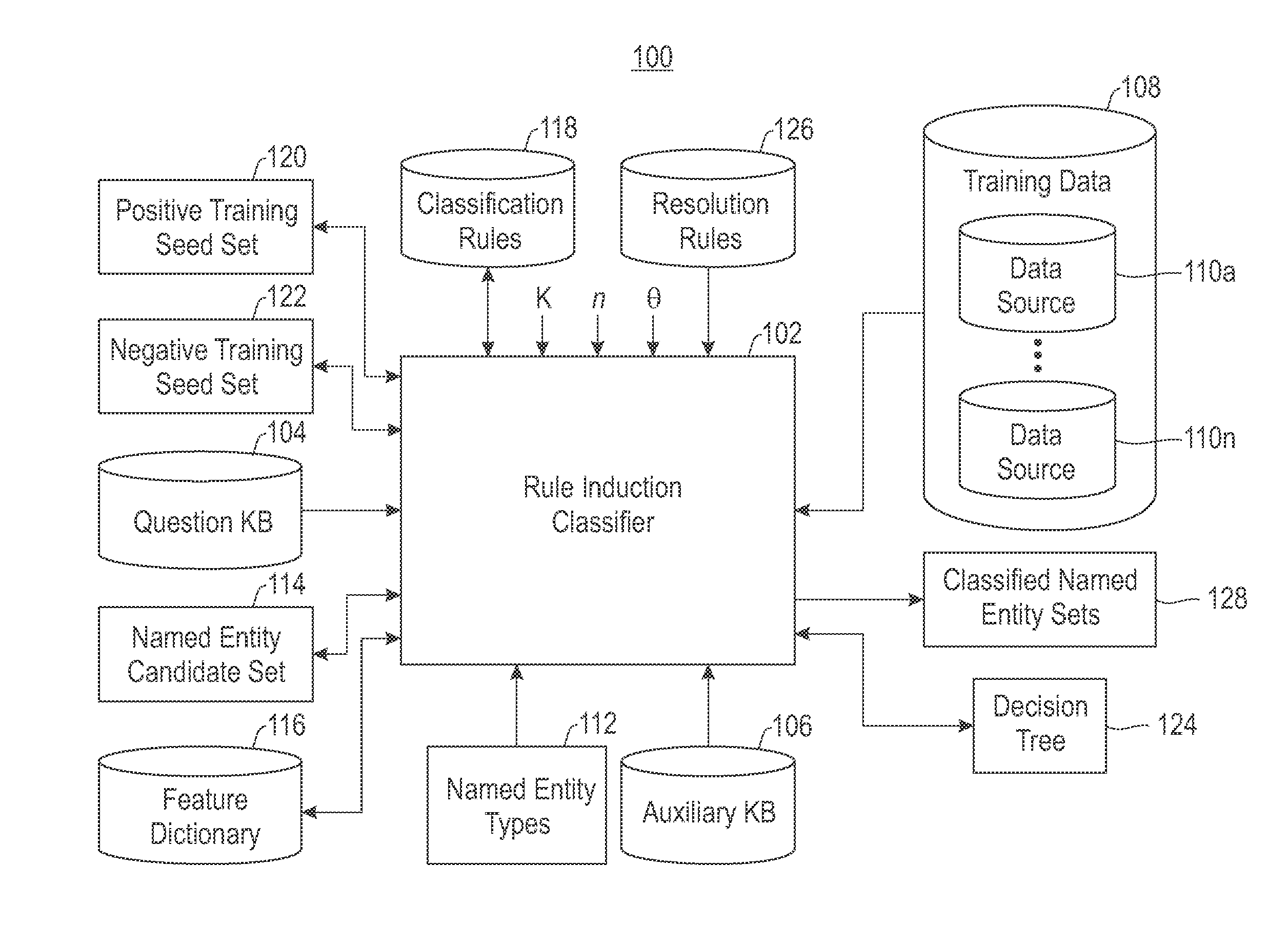
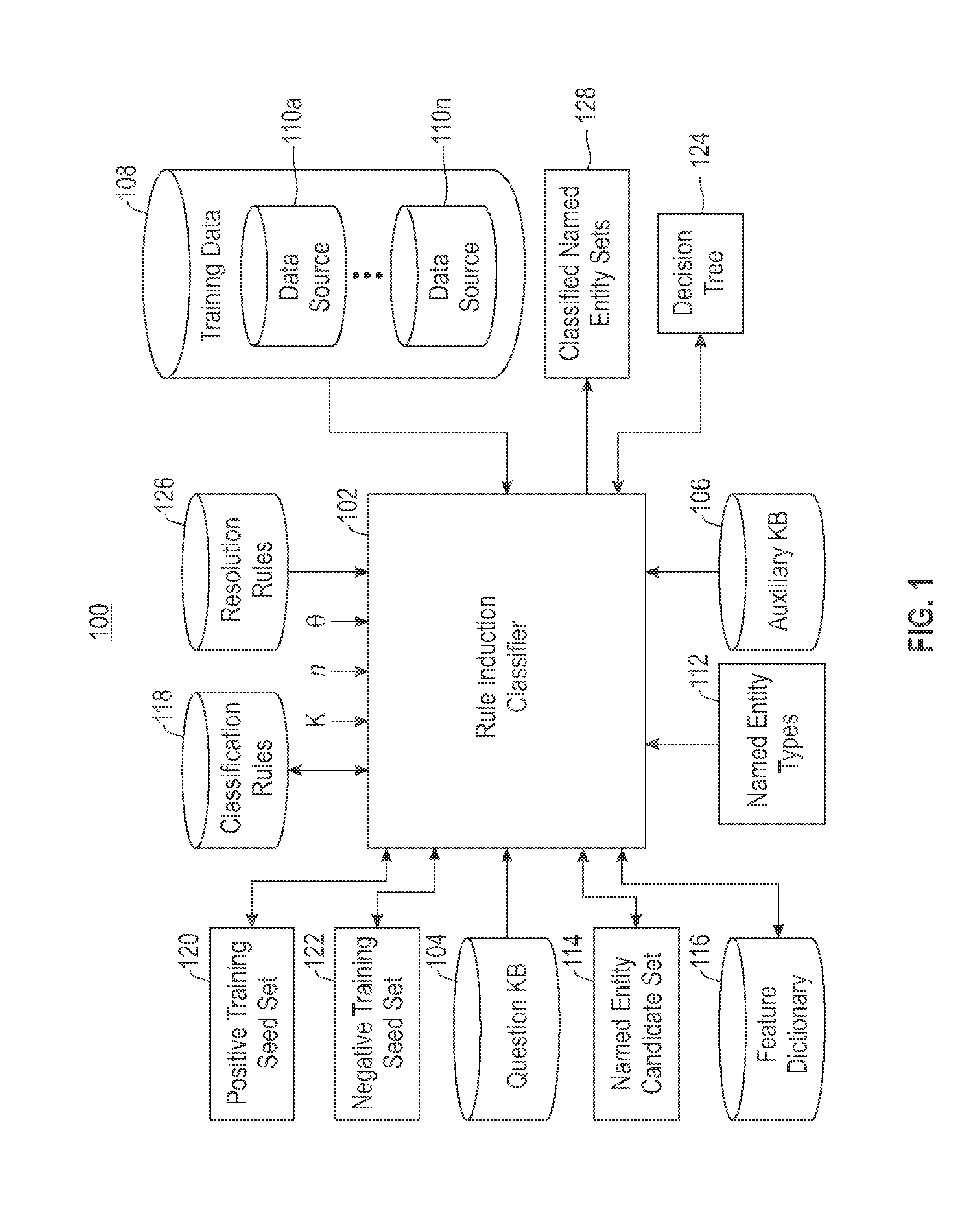
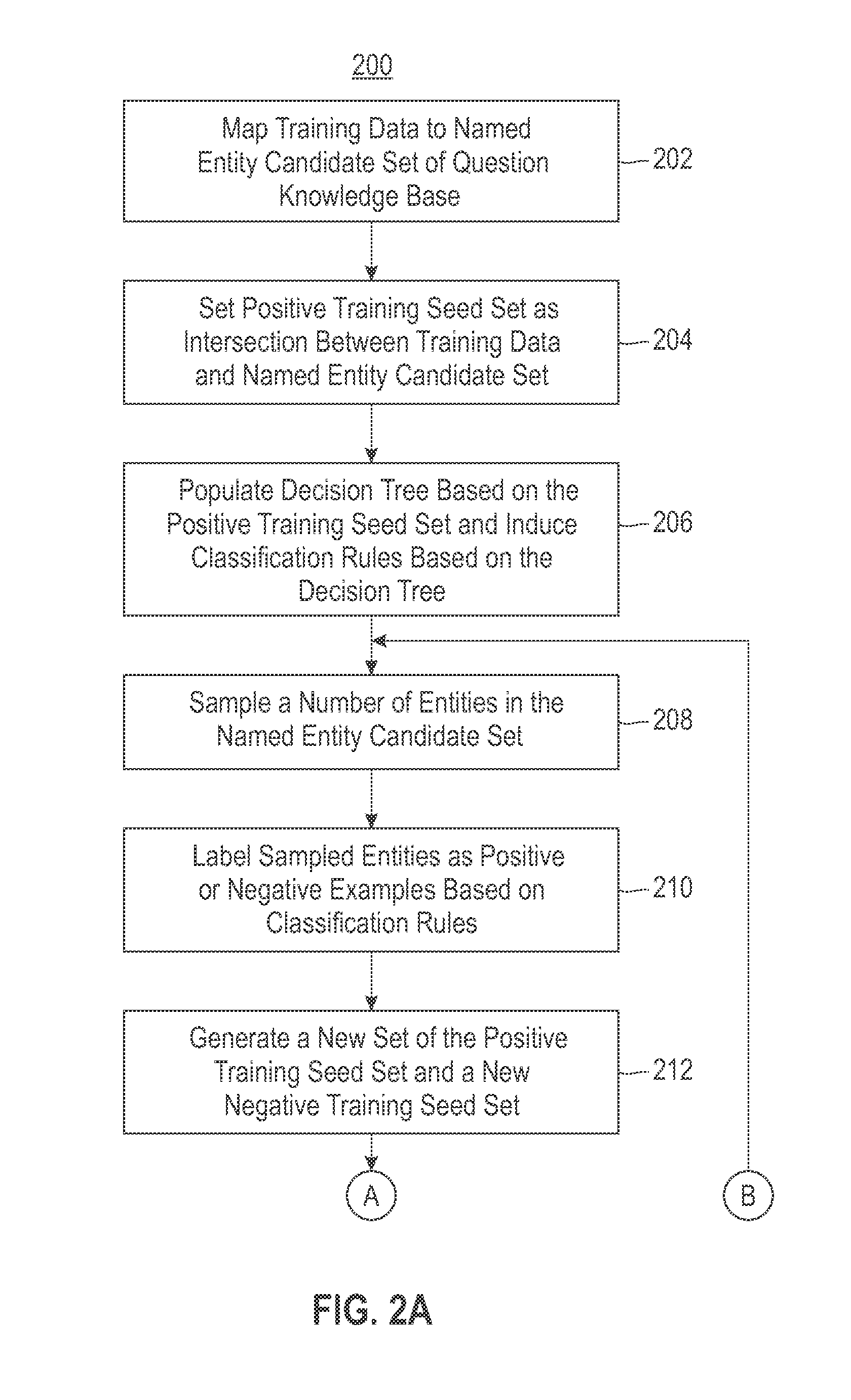
ActiveUS20140172754A1Digital computer detailsMachine learningInformation repositoryClassification rule
According to one embodiment, a semi-supervised data integration model for named entity classification from a first repository of entity information in view of an auxiliary repository of classification assistance data is provided. Training data are compared to named entity candidates taken from the first repository to form a positive training seed set. A decision tree is populated and classification rules are created for classifying the named entity candidates. A number of entities are sampled from the named entity candidates. The sampled entities are labeled as positive examples and / or negative examples. The positive training seed set is updated to include identified commonality between the positive examples and the auxiliary repository. A negative training seed set is updated to include negative examples which lack commonality with the auxiliary repository. In view of both the updated positive and negative training seed sets, the decision tree and the classification rules are updated.
Owner:IBM CORP
Method and system for dynamic allocation of resources in a cellular network
One example method is provided for dynamic allocation of air interface resources in a cellular network comprising at least three wireless cells located within a geographical proximity of each other, the method comprising determining, by a central managing entity, one or more classification rules for classifying each of said plurality of mobile devices according to the one or more classification rules; providing, by the central management entity, to a group of base stations associated with the at least three cells, information that comprises: information that relates to the determined one or more classification rules; information that relates to semi-static allocation of blocks of air interface resources adapted for use by one or more specific members of the group of base stations.
Owner:CISCO TECH INC
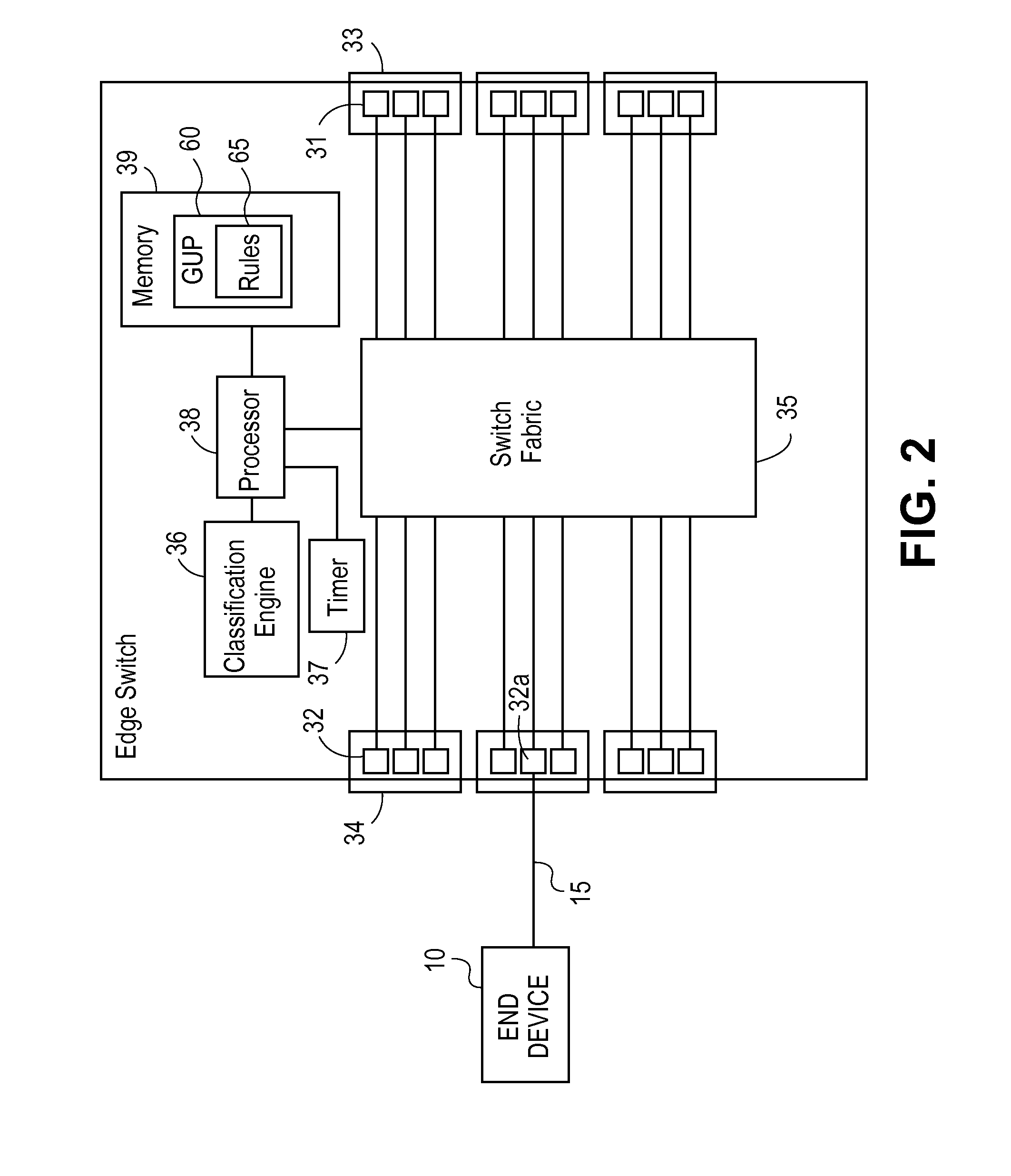
Dynamic Network Service Association and On Demand Service Provisioning
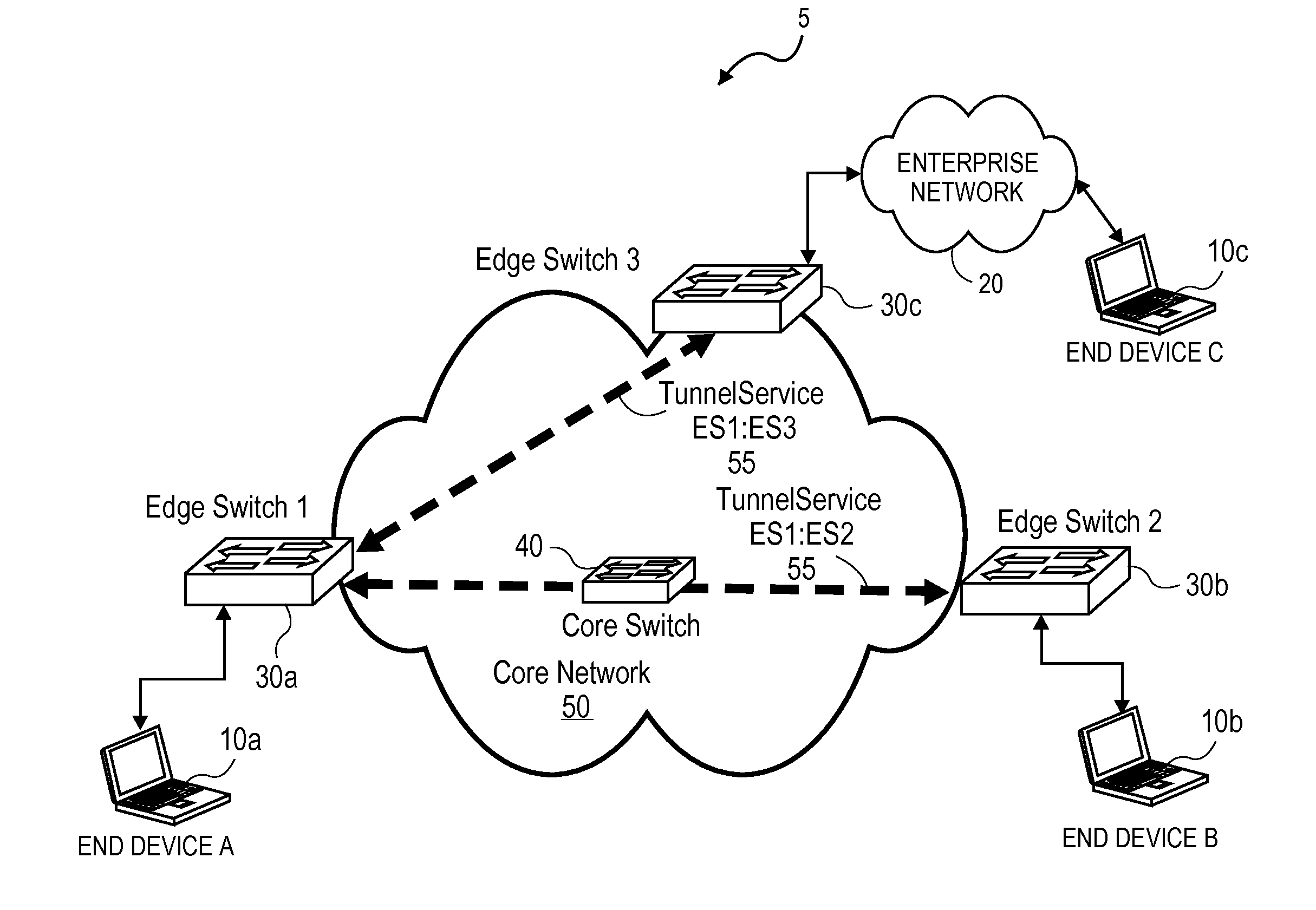
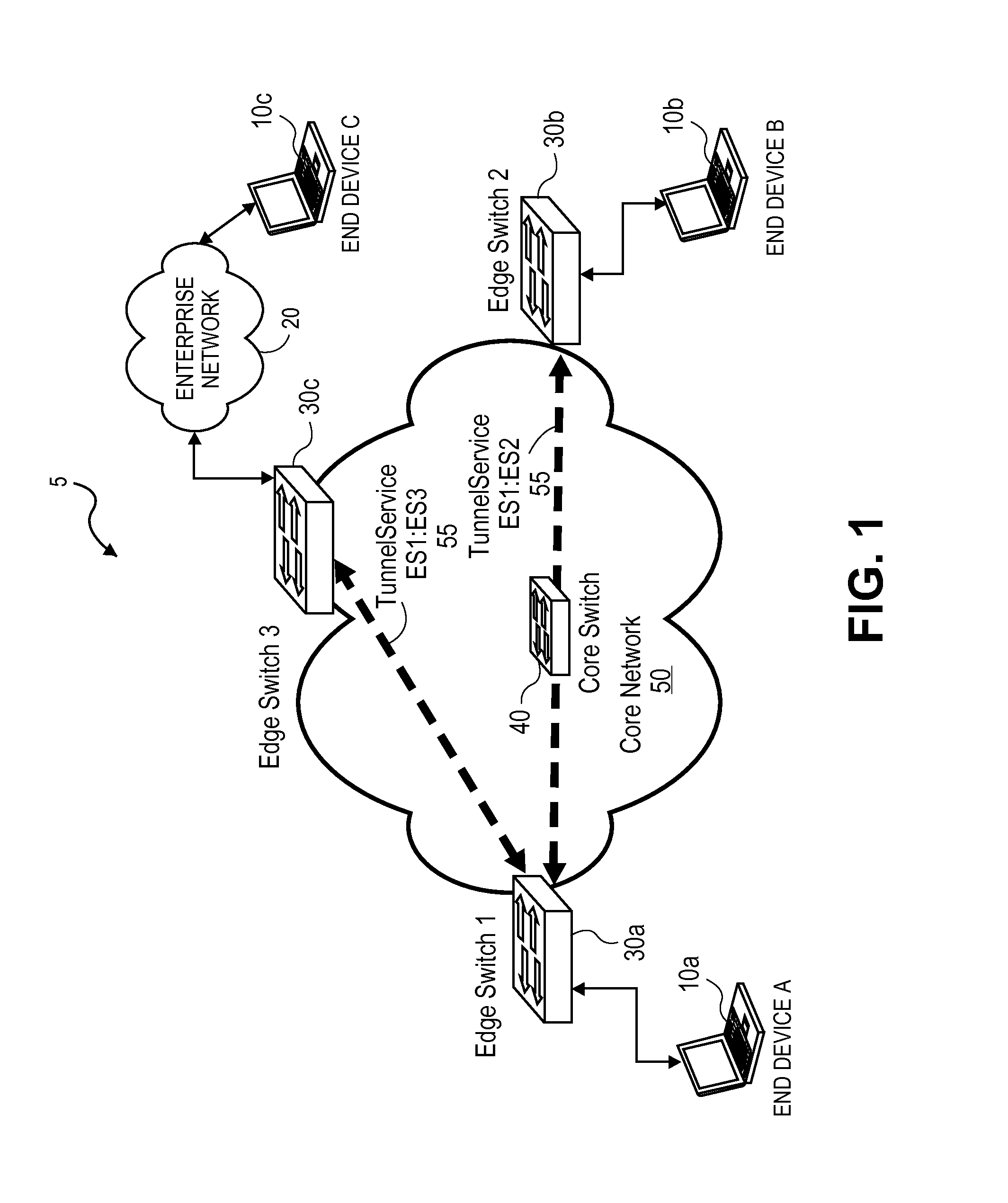
An edge switch enables service provisioning and dynamic service association for end devices coupled to the edge switch. The edge switch maintains a generic user profile that includes classification rules for classifying incoming traffic from the end devices to Virtual Local Area Network (VLAN) VLAN tunnel services. Upon detecting incoming traffic on an access port of the edge switch, the edge switch accesses the generic user profile to determine whether the incoming traffic matches one of the classification rules, and if so, automatically associates the incoming traffic with a VLAN tunnel service indicated by the matching classification rule to provide tunnel-based connectivity to remote end devices associated with the VLAN tunnel service.
Owner:RPX CORP
System and Method For Labeling and Identifying Lymph Nodes In Medical Images
A method for assigning a lymph node in a medical image with an anatomical name, the method including: identifying landmarks in a medical image; computing features relative to the landmarks given a location of a lymph node in the medical image; and assigning an anatomical name to the location of the lymph node by using a classifier that compares the computed features with classification rules.
Owner:SIEMENS HEALTHCARE GMBH +1
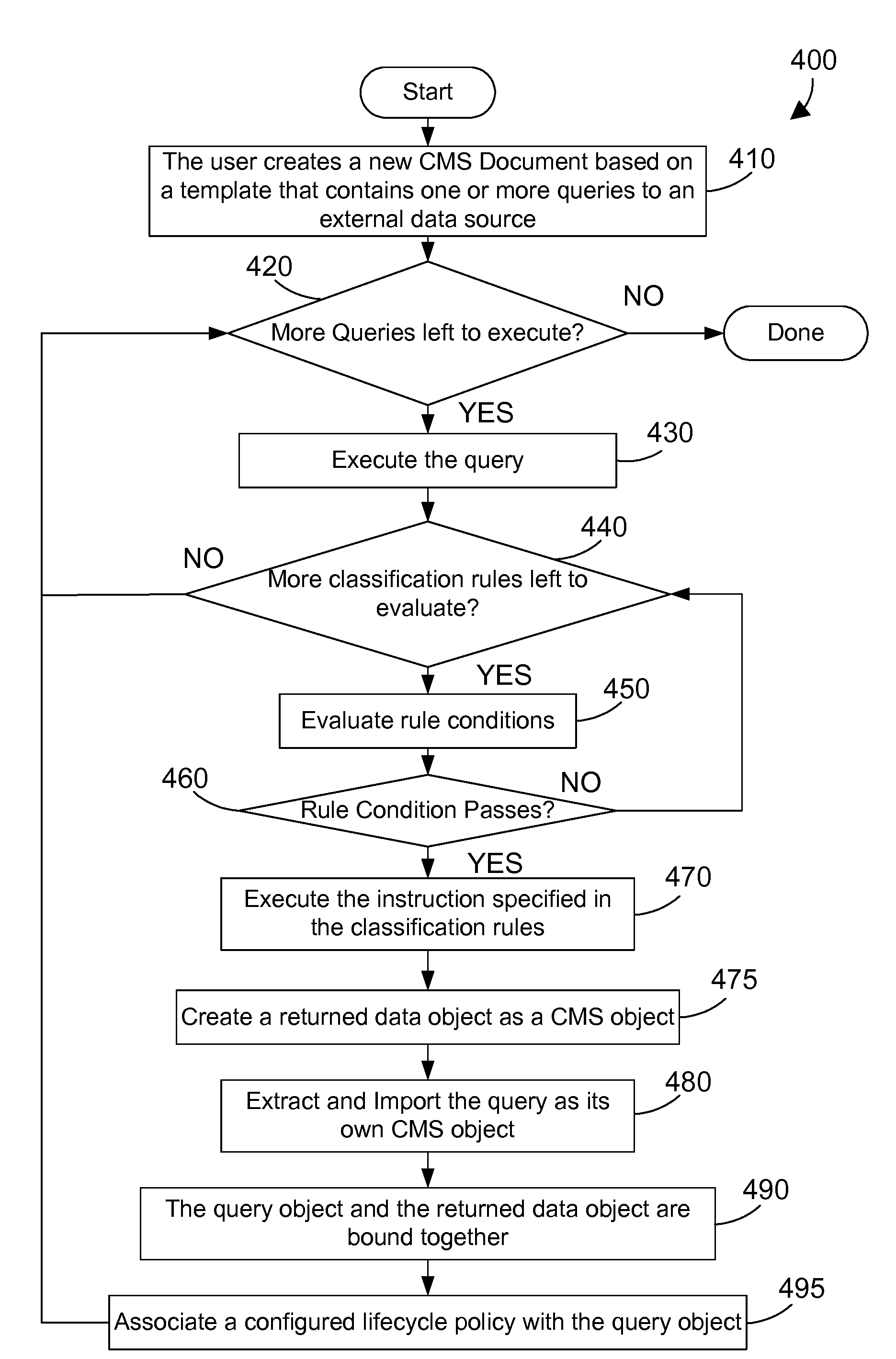
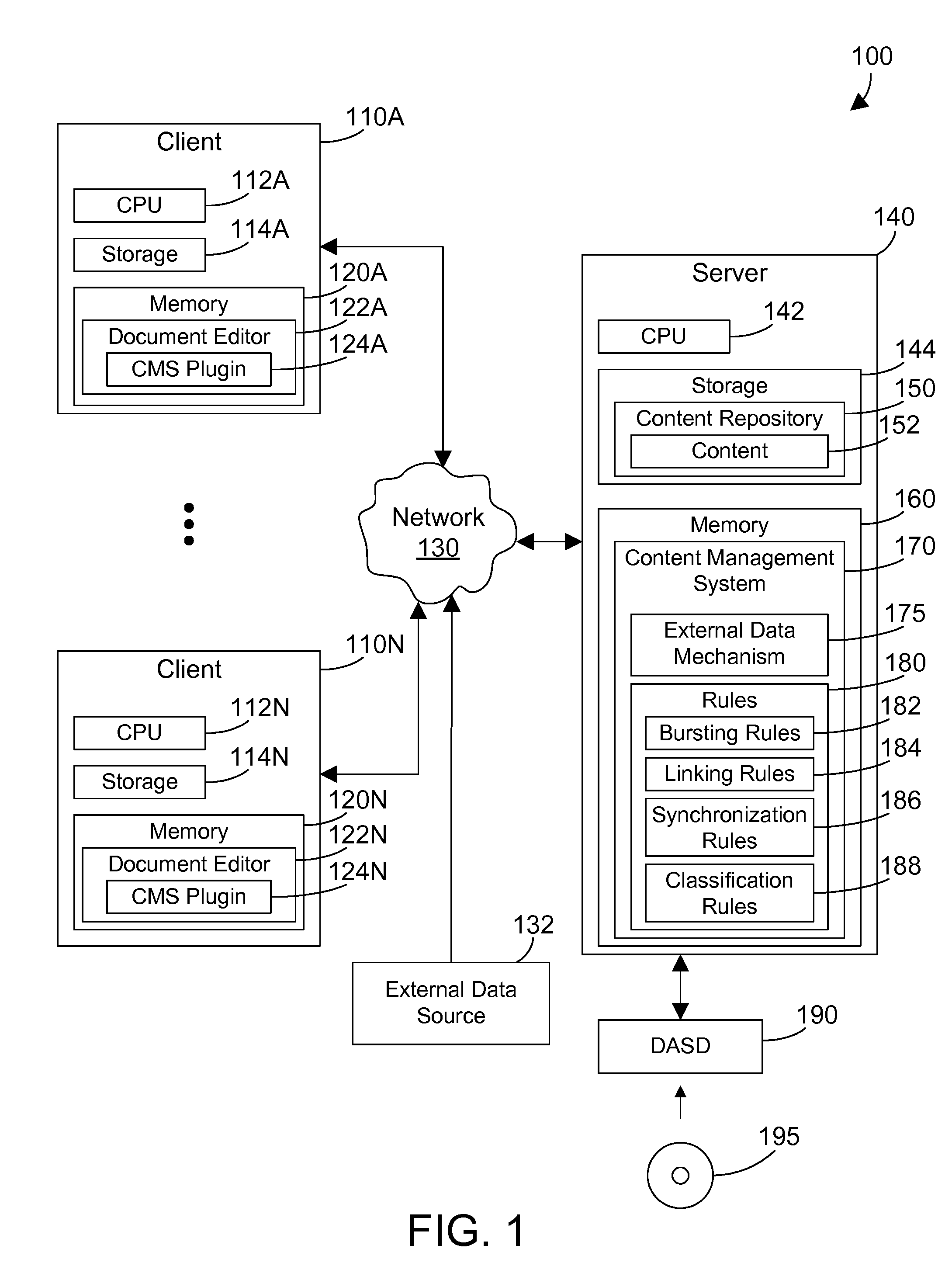
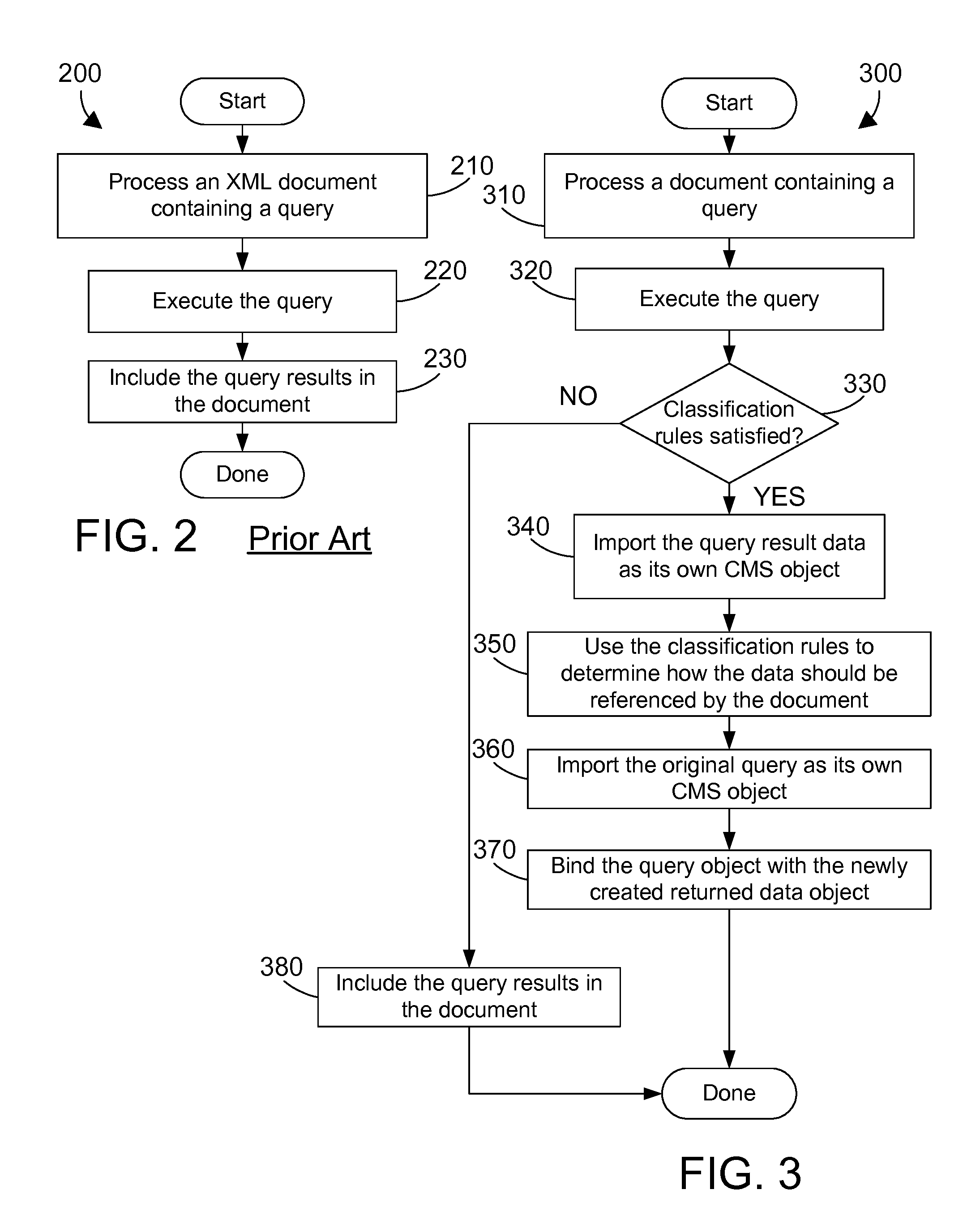
Content management system that retrieves data from an external data source and creates one or more objects in the repository
InactiveUS20090018999A1Digital data processing detailsObject oriented databasesFormal relationshipsExternal data
A content management system (CMS) provides a way to include data from an external source as an object in the repository managed by the CMS. The CMS includes an external data mechanism that processes a document with a query to a data source external to the repository. The external data mechanism executes the query, and creates one or more objects in the repository according to the type of data returned as defined by classification rules. Each object containing data returned from the query is linked to that query via a formal relationship in the CMS. When an object that has a formal relationship with a query is checked out of the repository, the query corresponding to the object may be executed, and the data returned from the query may be stored in the object. In the alternative, the data may be used directly if a corresponding lifecycle policy indicates the corresponding query should not be executed.
Owner:IBM CORP
Apparatus and method for classifying multi-dimensional biological data
InactiveUS20070026406A1Reduce loss valueMicrobiological testing/measurementBiostatisticsAlgorithmClassification rule
Apparatus and method for classifying multi-dimensional biological data are described. In some embodiments, a methodology for deriving a linear classification rule can be used for predicting a biological activity or a biological state. Advantageously, the methodology described herein facilitates obtaining robust and sparse classifiers that account for uncertainty involved in real-world experiments and improve computational efficiency and ease of interpretation of results.
Owner:US DEPT OF HEALTH & HUMAN SERVICES
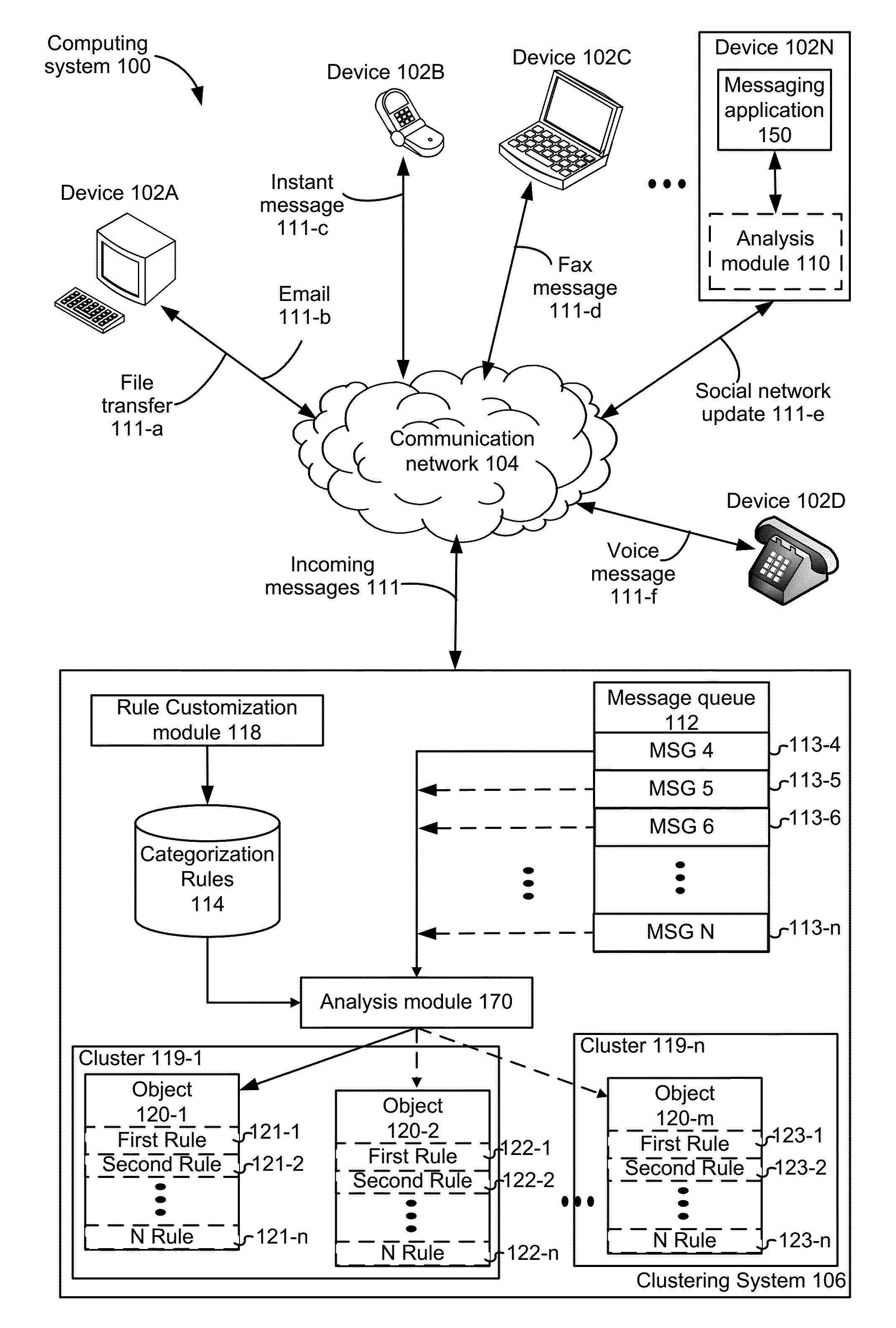
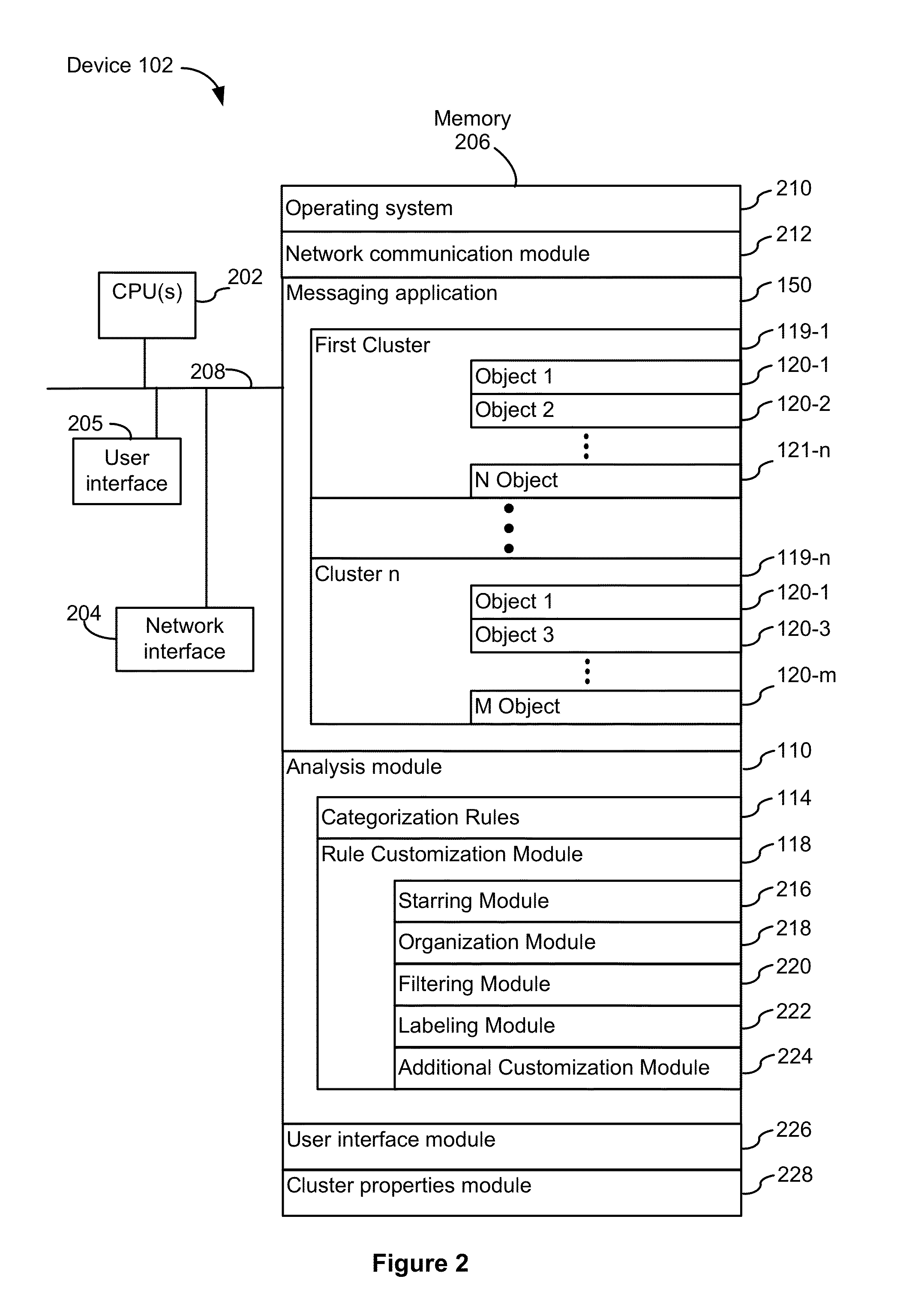
Systems and methods for message categorization management
InactiveUS20150186494A1Less cumbersomeMetadata text retrievalDigital data processing detailsDrag and dropFiltering rules
Systems and methods for categorizing objects in accordance with one or more user categorization actions are disclosed. In some embodiments, the occurrence of one or more categorization actions is detected for a first object in a list of objects in a messaging application. Categorization actions include starring the object, dragging and dropping an object from one cluster to another, adding a new cluster label, and providing filtering rules for an object. Then a set of properties for the first object is updated in accordance with the one or more categorization actions. The updated set of properties for the first object is compared to one or more categorization rules. For instance, an exemplary categorization rule is that a starred message is to be displayed in a primary cluster. Then information for displaying the first object in the list of objects in accordance with the one or more categorization rules is prepared.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com