Sensitive Data Classification
a sensitive data and classification technology, applied in the field of data protection, can solve the problems of inability to scale the tedious process of manually discovering sensitive data in electronic systems, the inability of data growth and distribution to compete with the pace of data growth and distribution, and the difficulty of an admin to keep track of where such data is being stored in a system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example machine
Architecture
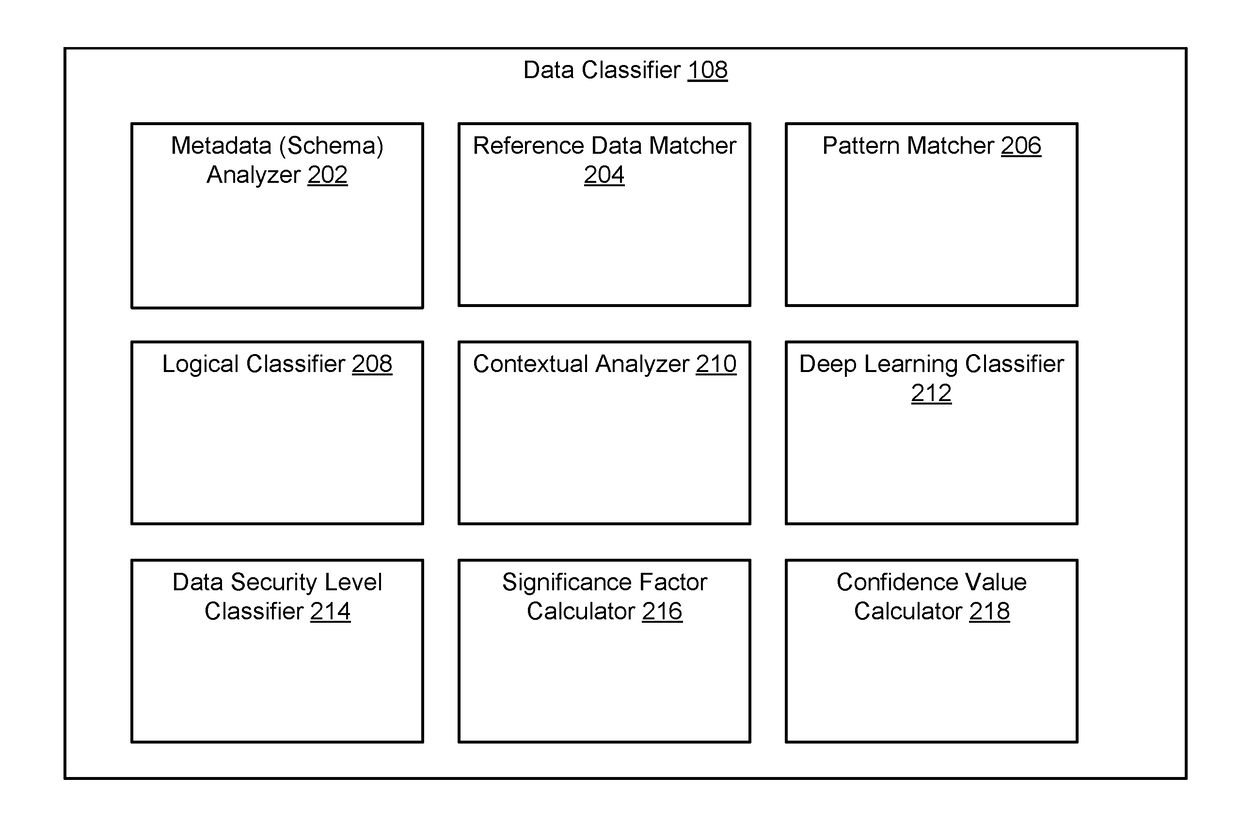
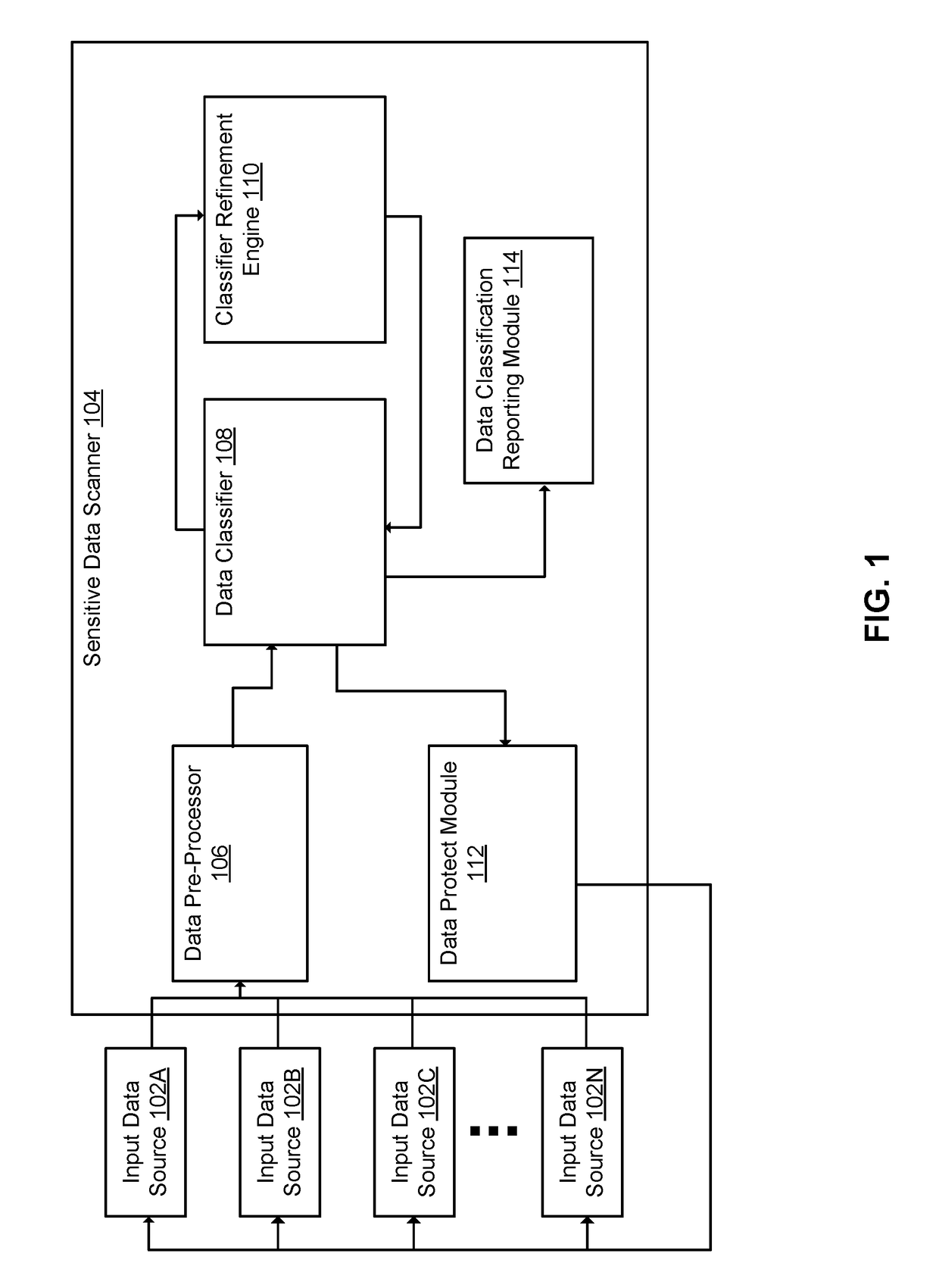
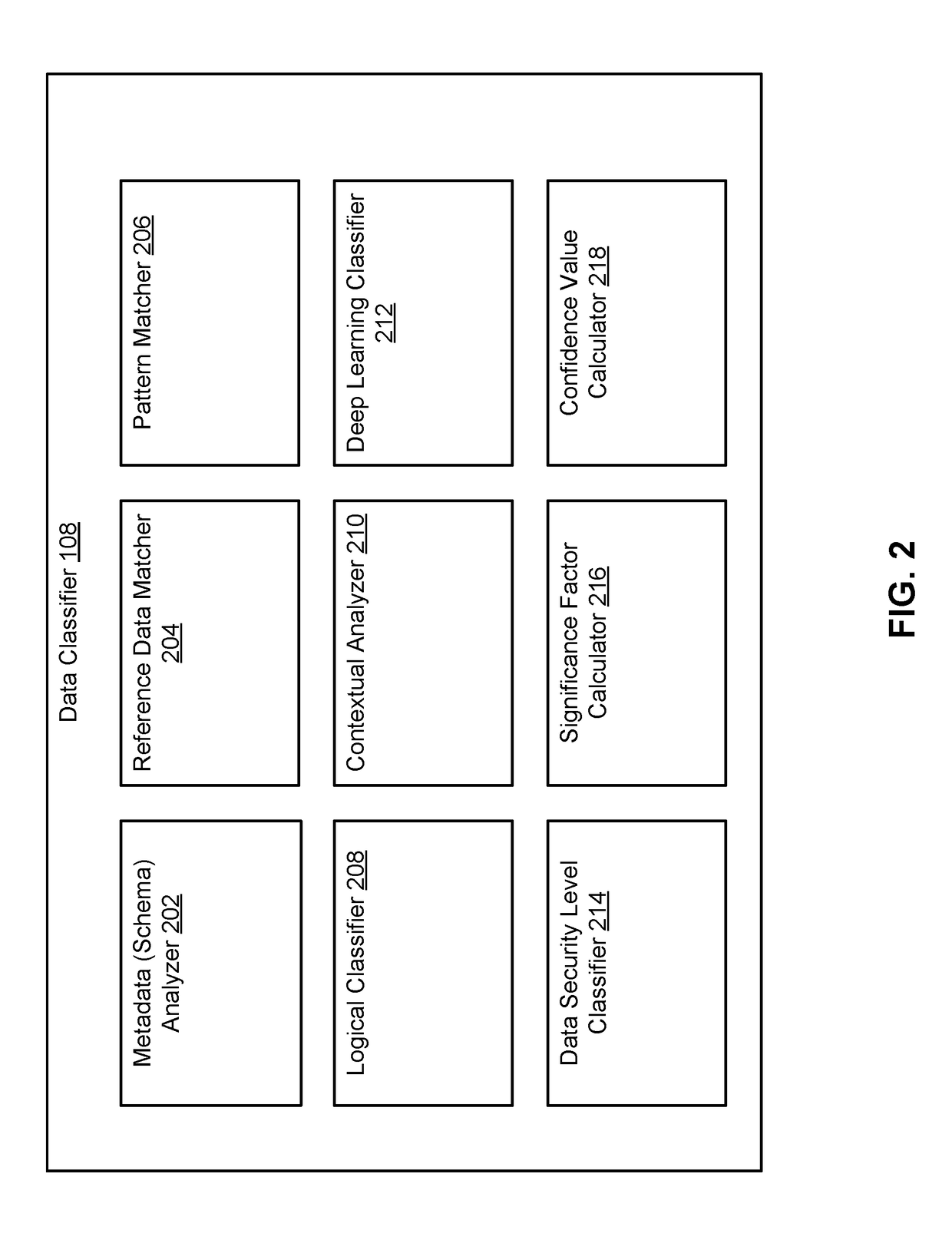
[0110]FIG. 13 is a block diagram illustrating components of an example machine able to read instructions from a machine-readable medium and execute them in one or more processors (or controllers), according to an embodiment. Portions, or all, of the example machine described in FIG. 13 can be used with the components described above with reference to FIGS. 1-3. For example, the example machine may be used to execute the data classifier 108.
[0111]In FIG. 13 there is a diagrammatic representation of a machine in the example form of a computer system 1300. The computer system 1300 can be used to execute instructions 1324 (e.g., program code or software) for causing the machine to perform any one or more of the methodologies (or processes) described herein. In alternative embodiments, the machine operates as a standalone device or a connected (e.g., networked) device that connects to other machines. In a networked deployment, the machine may operate in the capacity of a serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com