Patents
Literature
6794results about "Other databases querying" patented technology
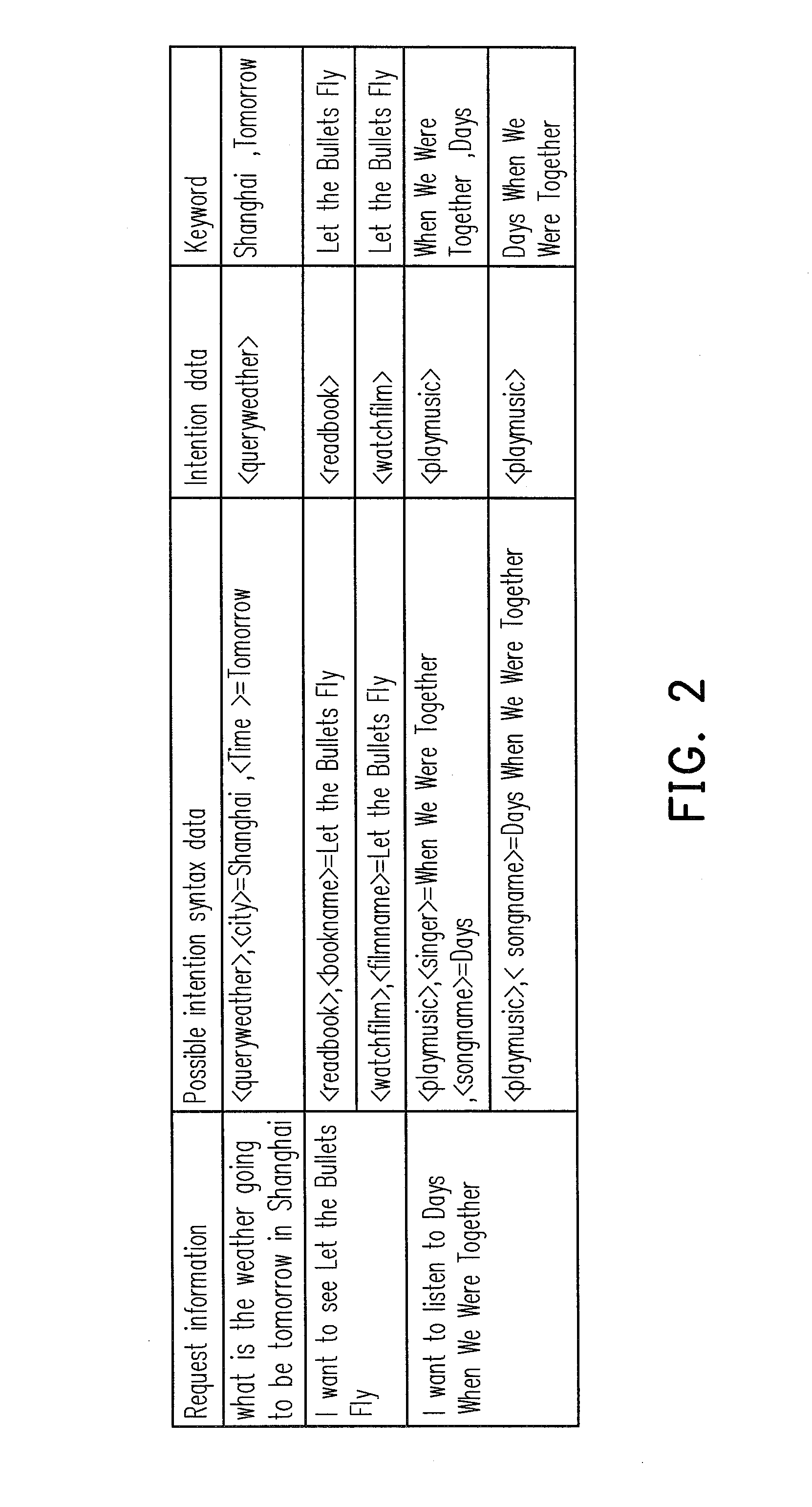
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
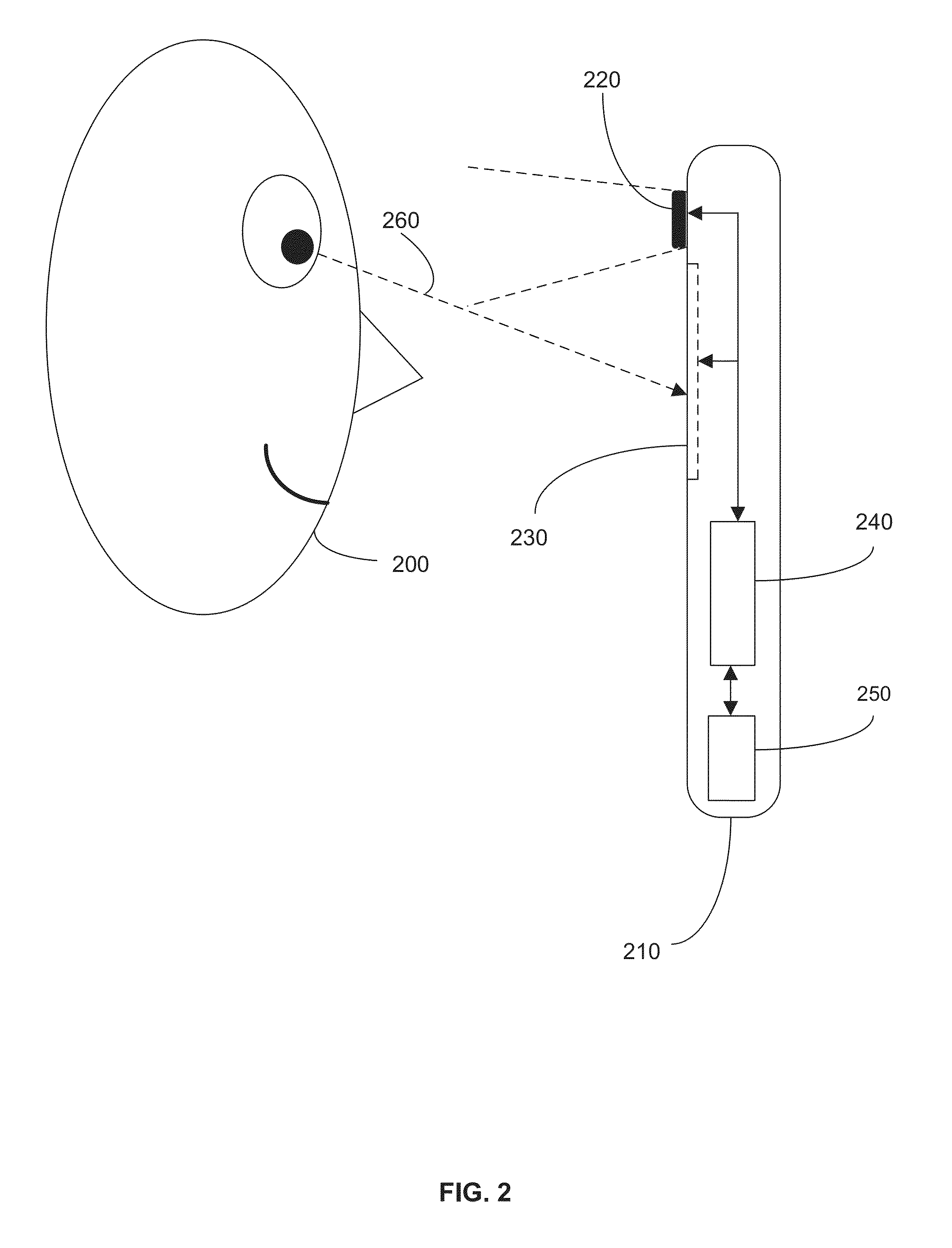
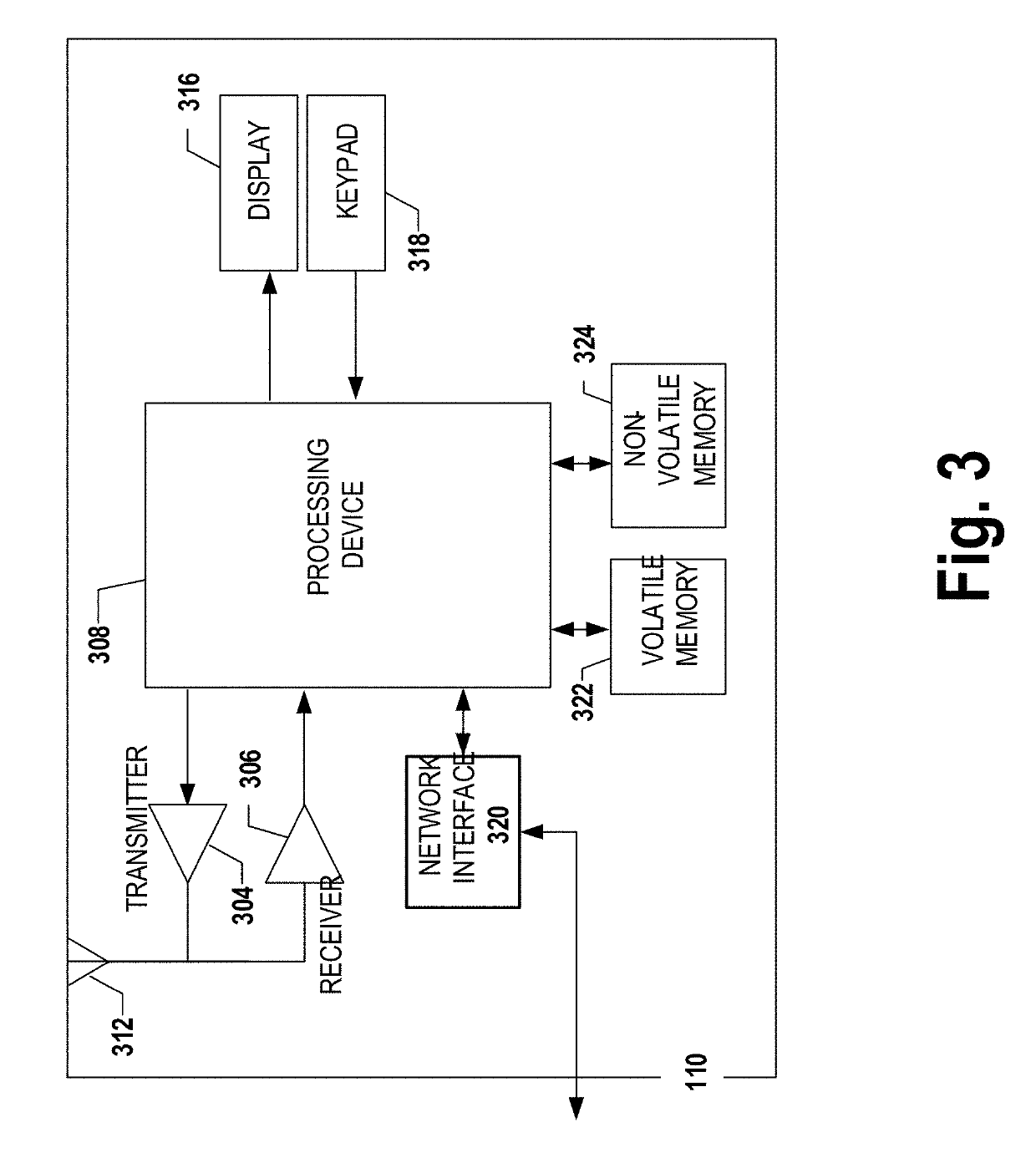
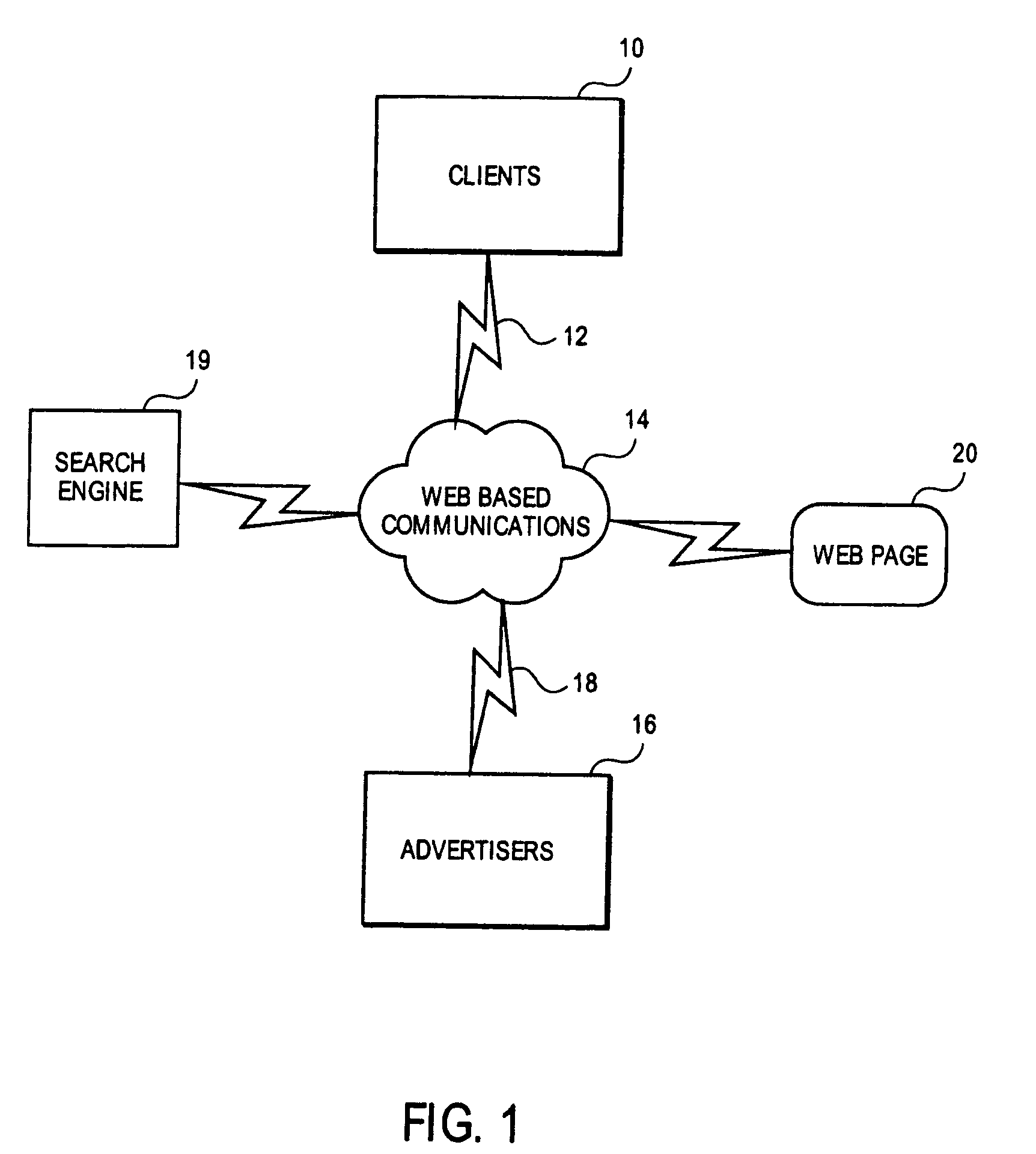
Method and device for monitoring and analyzing signals
A method and system for monitoring and analyzing at least one signal are disclosed. An abstract of at least one reference signal is generated and stored in a reference database. An abstract of a query signal to be analyzed is then generated so that the abstract of the query signal can be compared to the abstracts stored in the reference database for a match. The method and system may optionally be used to record information about the query signals, the number of matches recorded, and other useful information about the query signals. Moreover, the method by which abstracts are generated can be programmable based upon selectable criteria. The system can also be programmed with error control software so as to avoid the re-occurrence of a query signal that matches more than one signal stored in the reference database.
Owner:WISTARIA TRADING INC
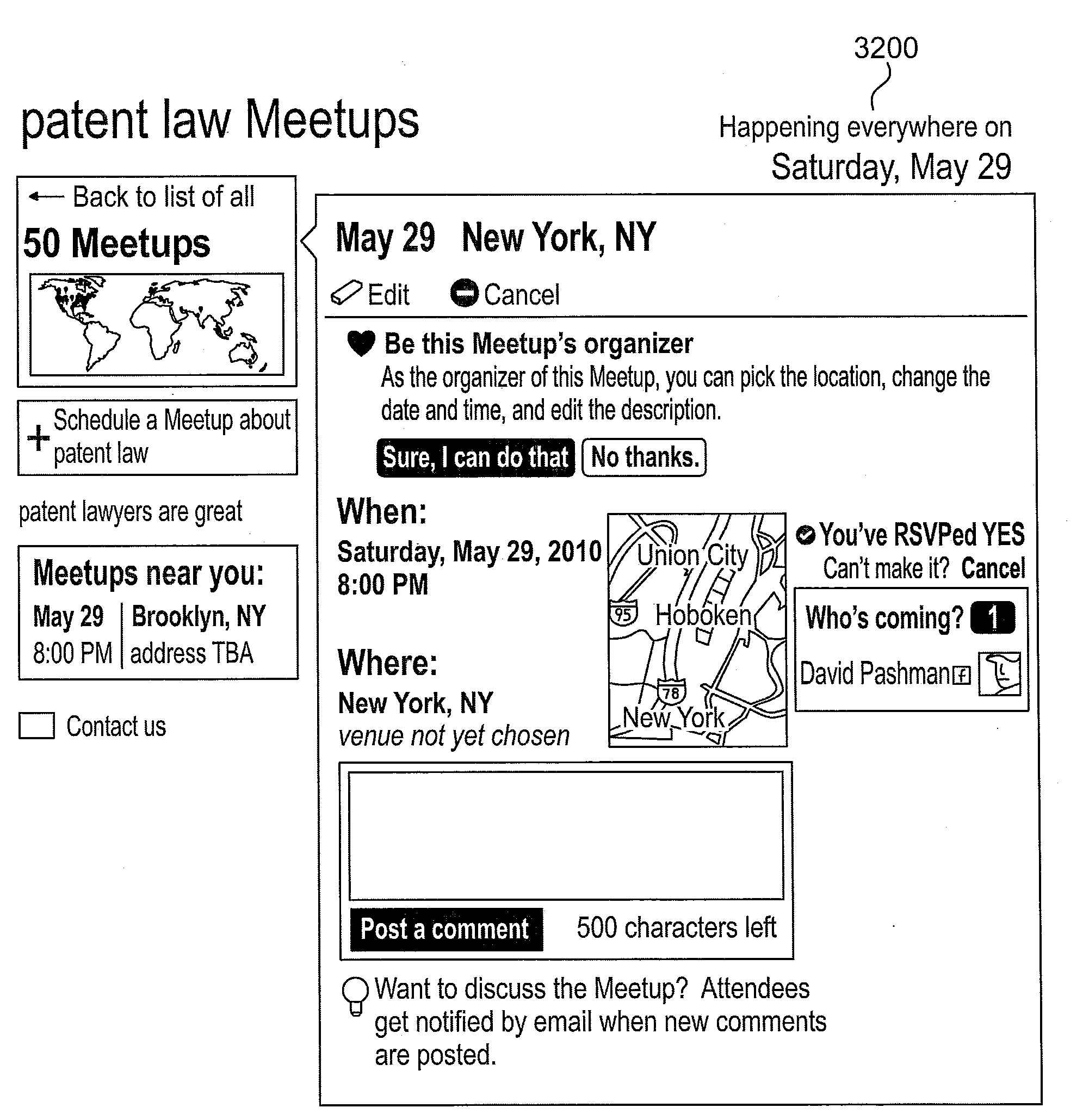
Web-Based Interactive Meeting Facility with Recommendations to Users
ActiveUS20110289433A1Overcome problemsServices signallingOffice automationComputer scienceSubject specific
A computer implemented method for providing recommendations for an in-person meeting group, the method comprising: collecting user information, wherein the user information provides information related to topical interests and location information for at least one of a plurality of users; comparing the user information with a topical listing of in-person meeting groups in the same geographical region as the at least one user, wherein the in-person meeting group is formed and maintained through a web-based meeting facility; and providing an in-person meeting group recommendation to the at least one user based on the comparison.
Owner:MEETUP
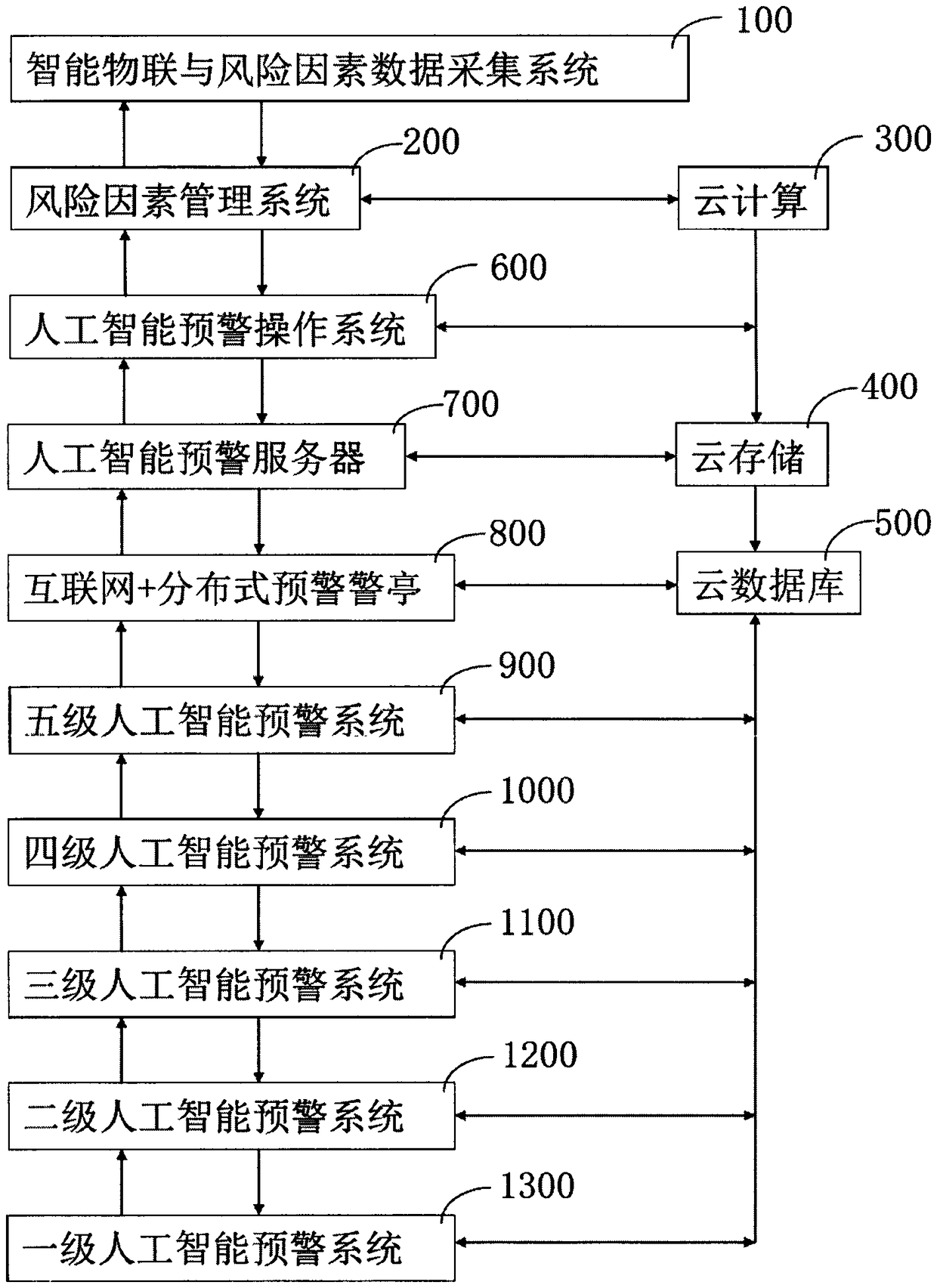
Artificial intelligence early warning system
ActiveCN109447048APrevent overpassSemantic analysisOther databases indexingThree levelInformation resource
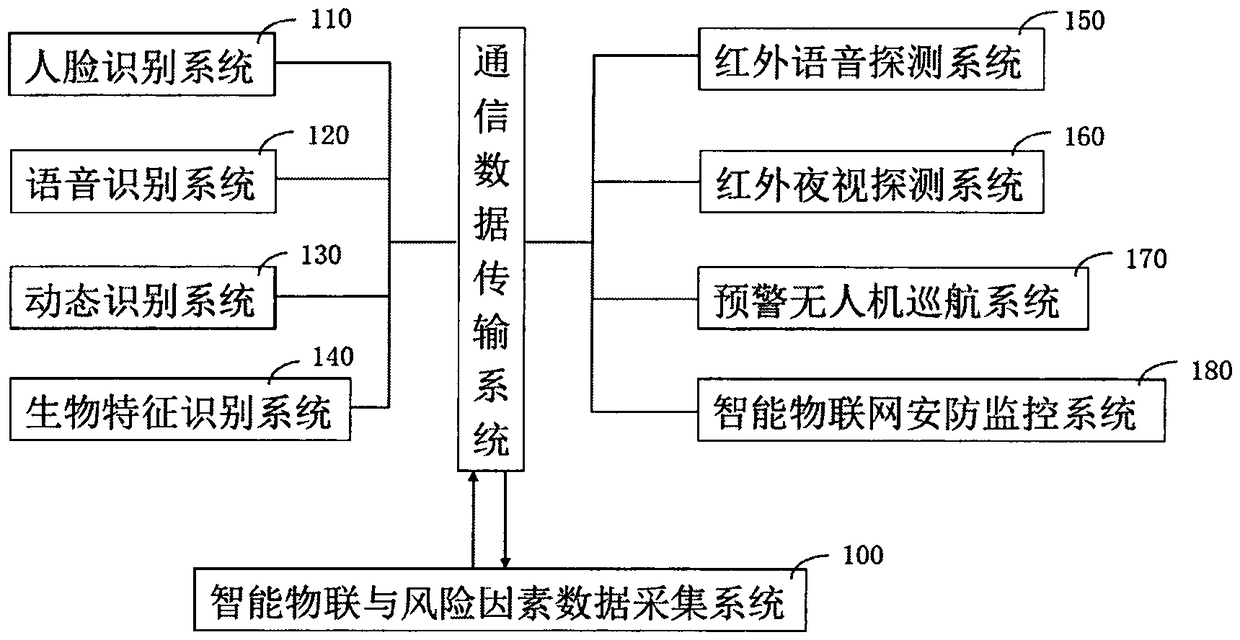
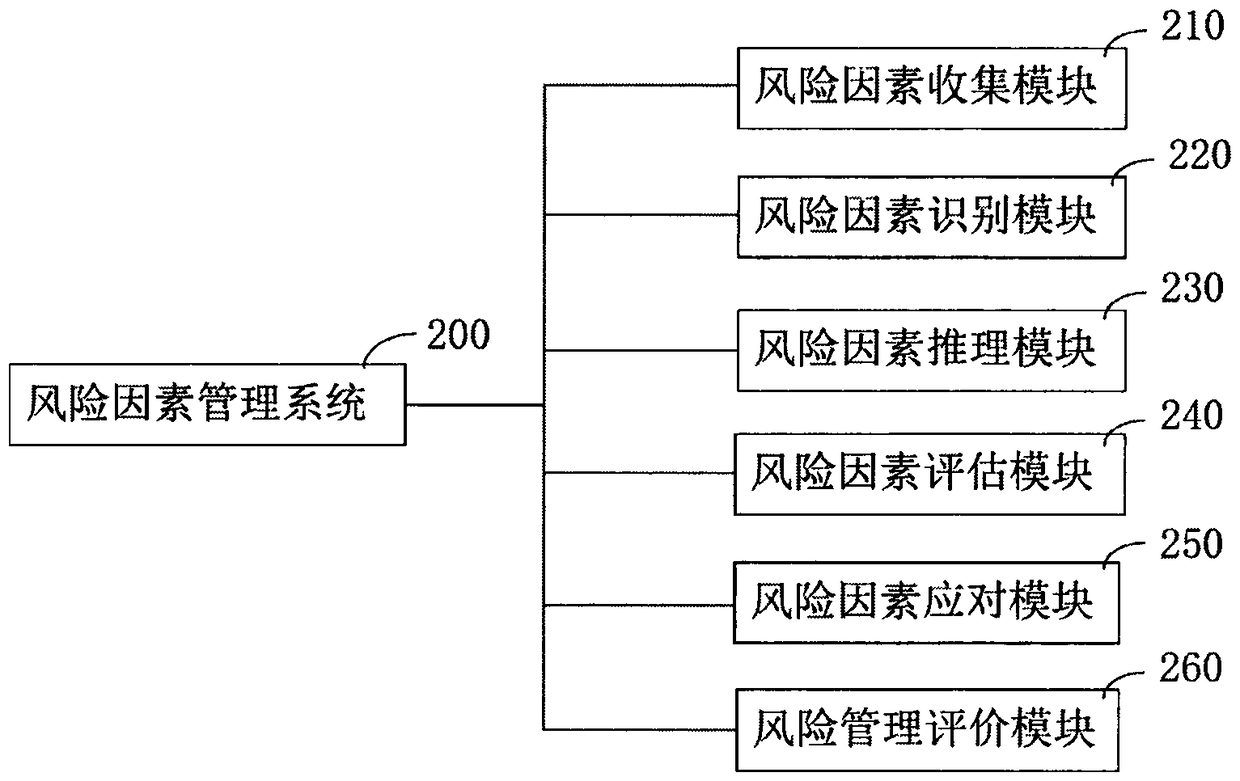
The invention relates to an artificial intelligence early warning system. The system comprises an intelligent Internet of Things and risk factor data acquisition system (100), and a risk factor management system (200), a cloud computing device (300), a cloud storage device (400), a cloud database (500), and an artificial intelligence early warning operation system (600), an artificial intelligenceearly warning server (700), an internet + distributed early warning police booth (800), a five-level artificial intelligence early warning system (900), a four-level artificial intelligence early warning system (1000), a three-level artificial intelligence early warning system (1100), a two-level artificial intelligence early warning system (1200) and a one-level artificial intelligence early warning system (1300). The artificial intelligence early warning system of the present invention collects, compares, analyzes, deduces, evaluates the risk factors, and carries out the cloud computing, cloud storage, graded alarming and prevention and control, so that all-weather 24-hour monitoring on monitoring points around the police box is achieved, a user can share information, the utilization rate of information resources is increased, and the safety guarantee is increased for maintaining the stability of the borderlands.
Owner:苏州闪驰数控系统集成有限公司
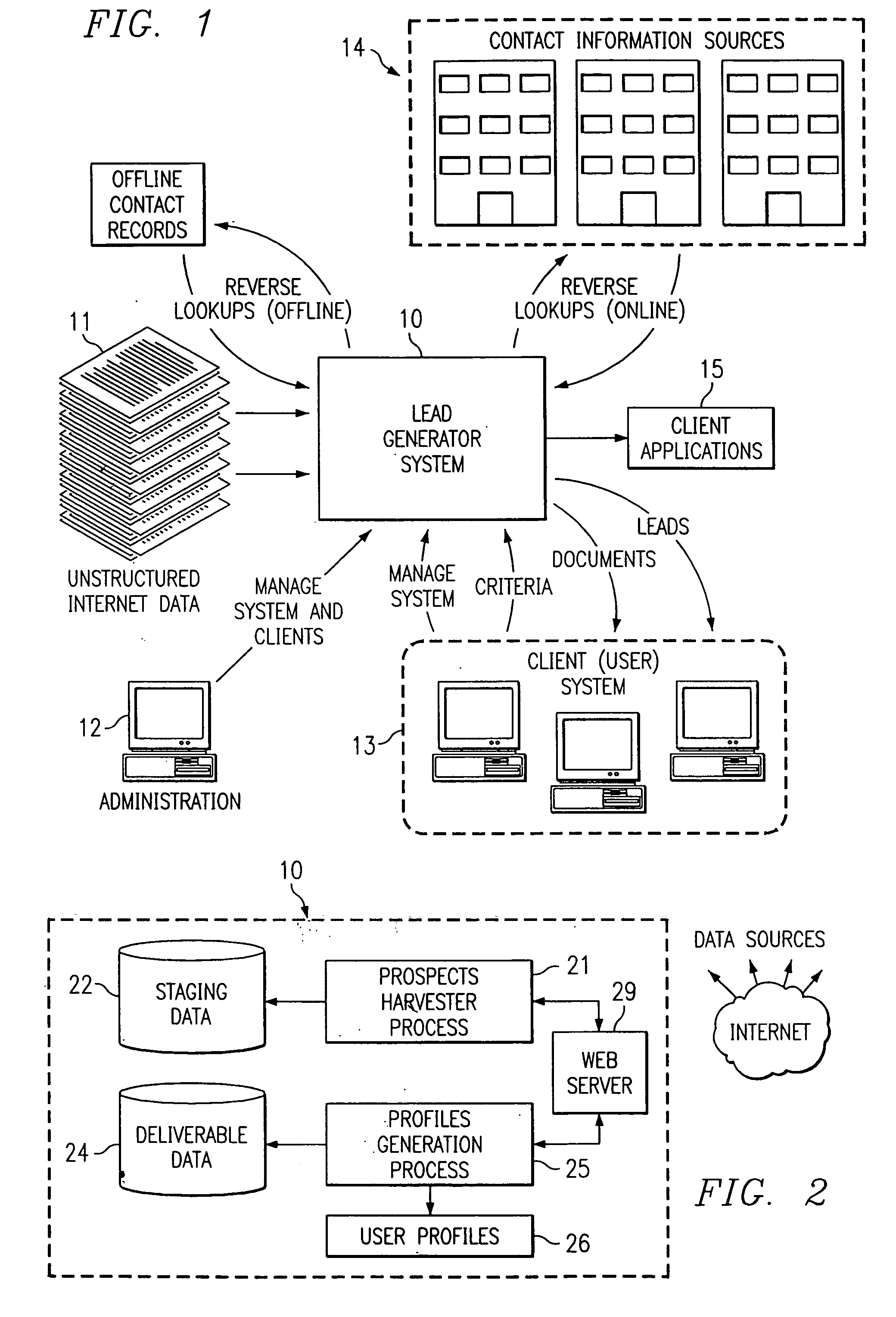
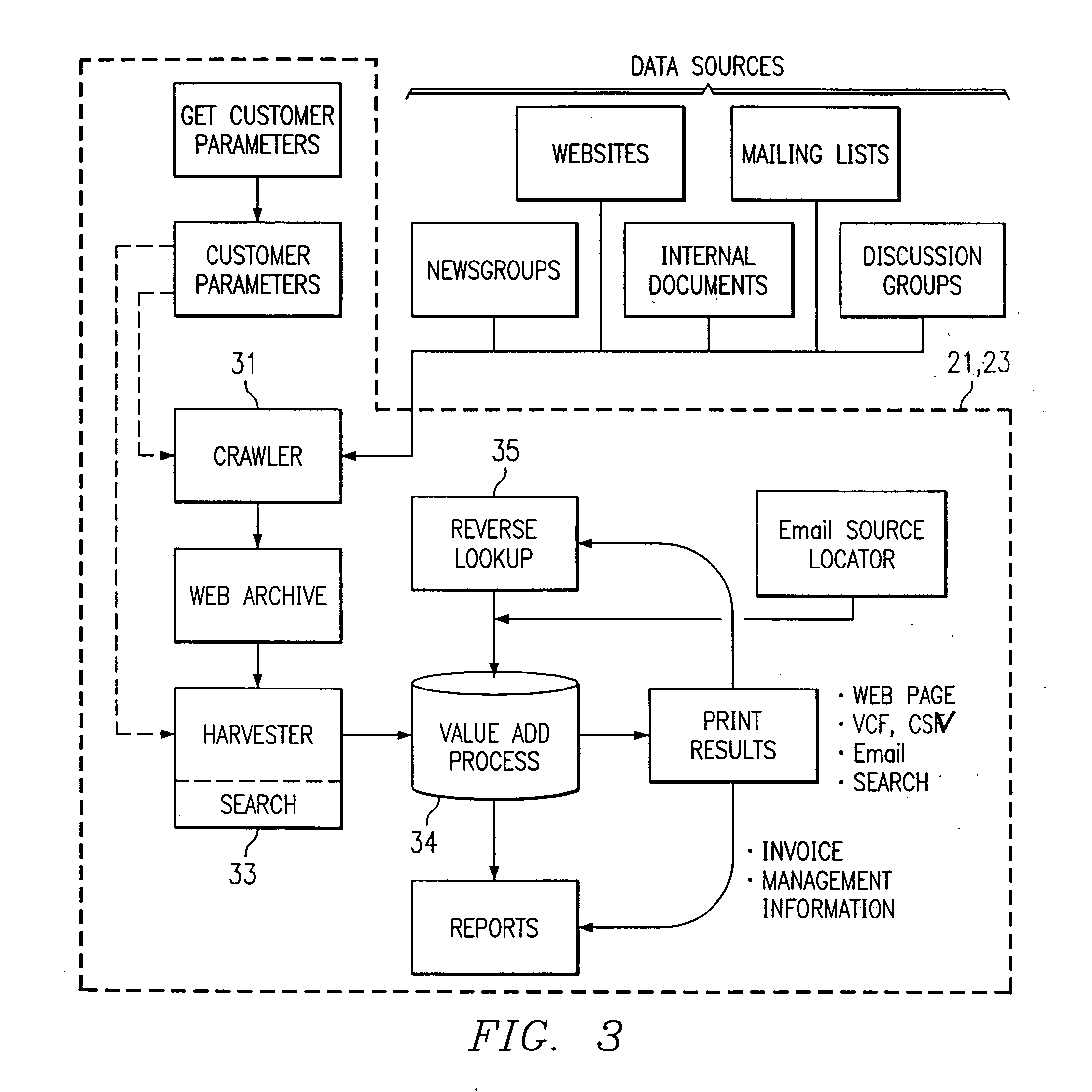
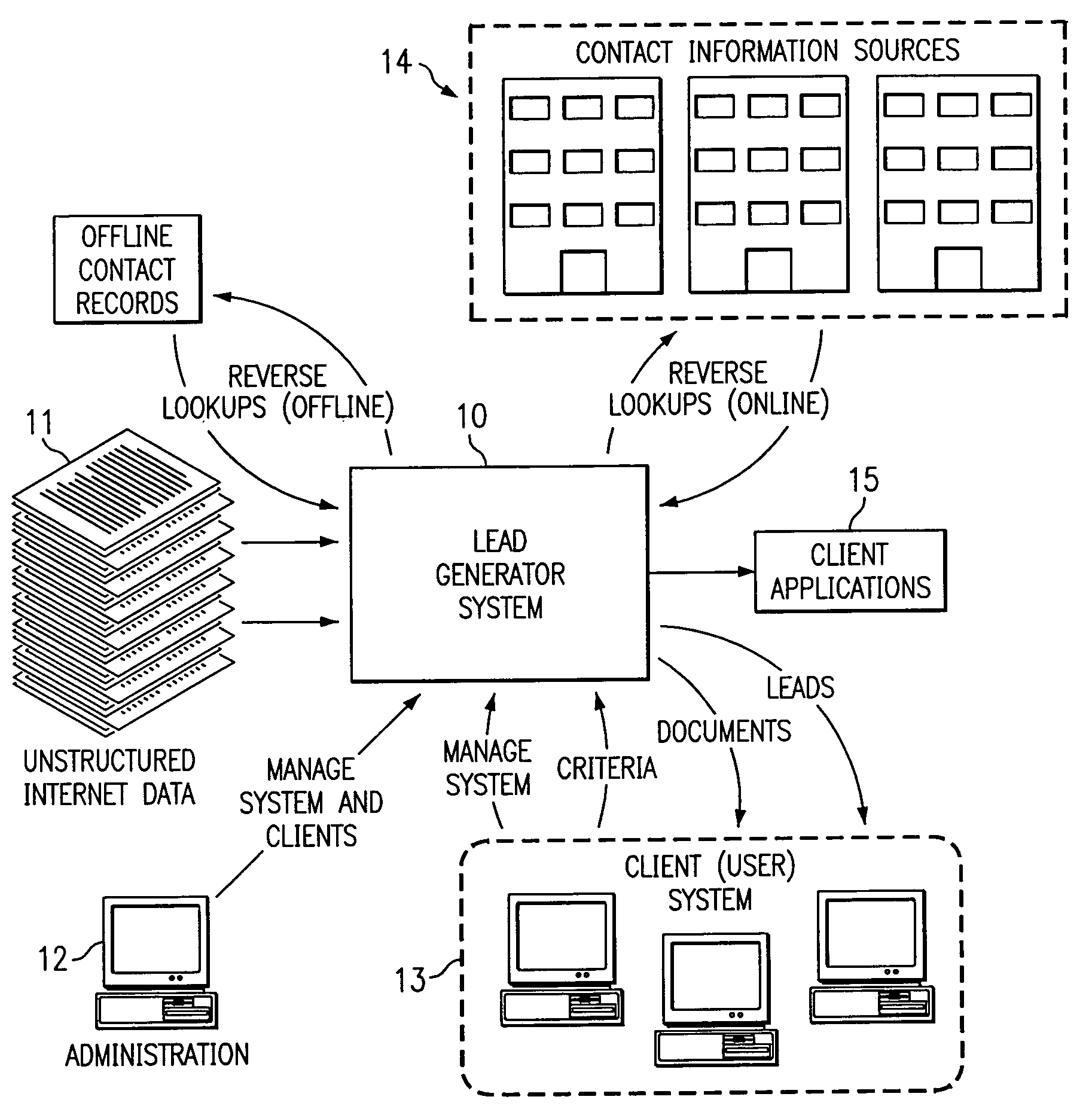
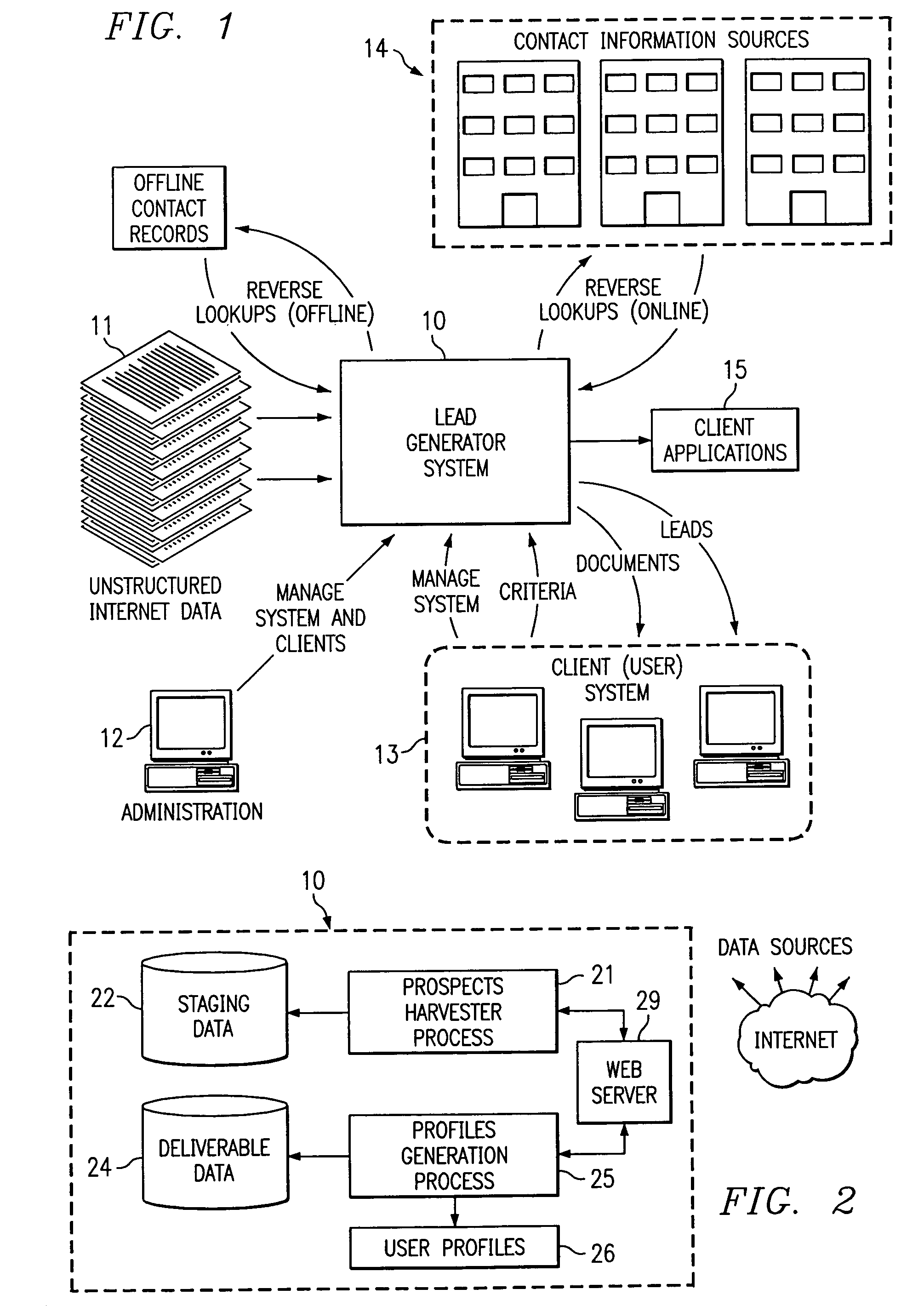
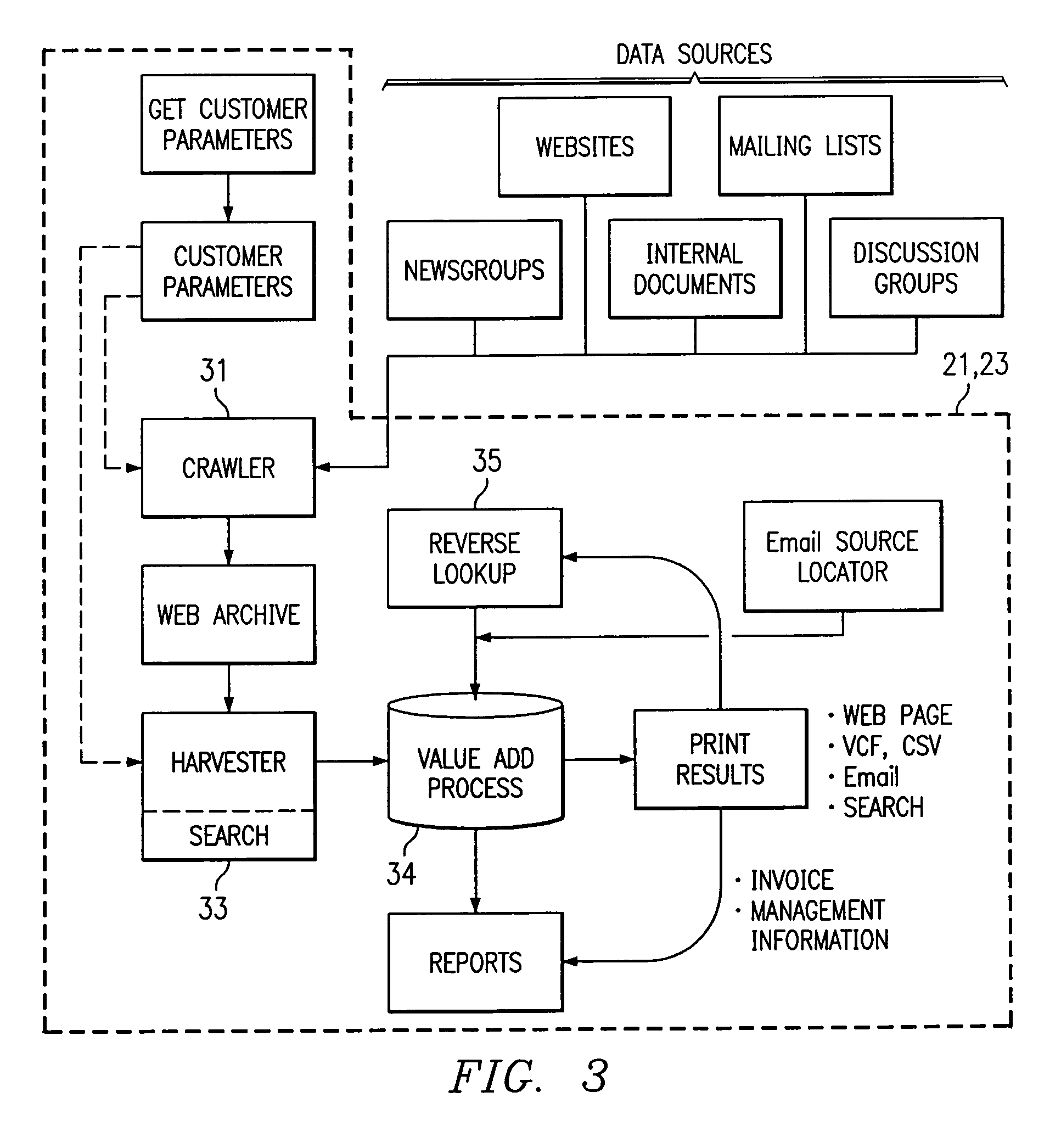
Text mining system for web-based business intelligence
A text mining system for collecting business intelligence about a client, as well as for identifying prospective customers of the client, for use in a lead generation system accessible by the client via the Internet. The text mining system has various components, including a data acquisition process that extracts textual data from various Internet sources, a database for storing the extracted data, a text mining server that executes query-based searches of the database, and an output repository. A web server provides client access to the repository, and to the mining server.
Owner:ALTO DYNAMICS LLC
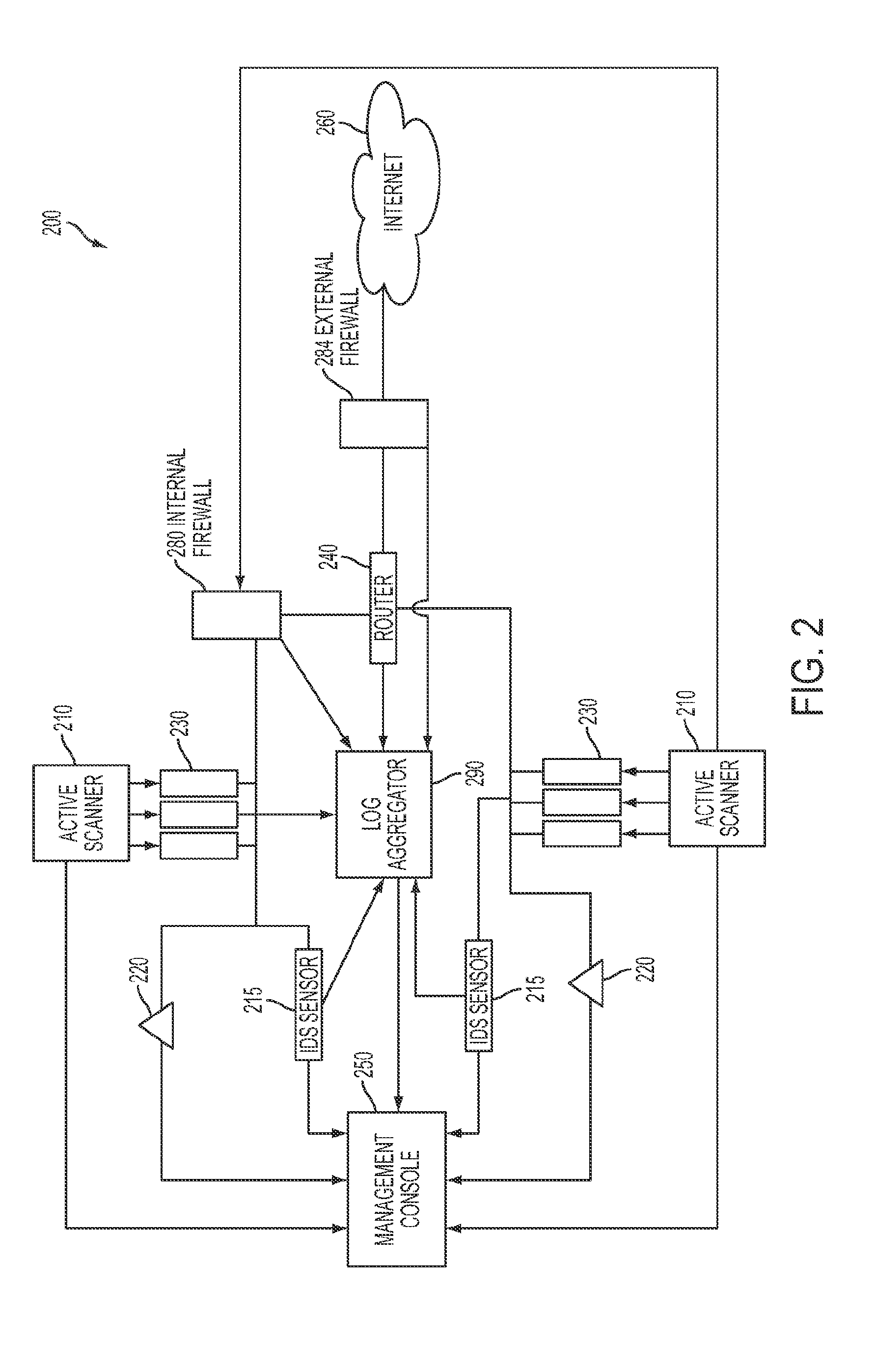
System and method for strategic Anti-malware monitoring
ActiveUS20140013434A1Mitigate and manage governanceMitigate and manage and riskMemory loss protectionError detection/correctionAnti virusFile system
The system and method described herein may leverage active network scanning and passive network monitoring to provide strategic anti-malware monitoring in a network. In particular, the system and method described herein may remotely connect to managed hosts in a network to compute hashes or other signatures associated with processes running thereon and suspicious files hosted thereon, wherein the hashes may communicated to a cloud database that aggregates all known virus or malware signatures that various anti-virus vendors have catalogued to detect malware infections without requiring the hosts to have a local or resident anti-virus agent. Furthermore, running processes and file system activity may be monitored in the network to further detect malware infections. Additionally, the network scanning and network monitoring may be used to detect hosts that may potentially be participating in an active botnet or hosting botnet content and audit anti-virus strategies deployed in the network.
Owner:TENABLE INC
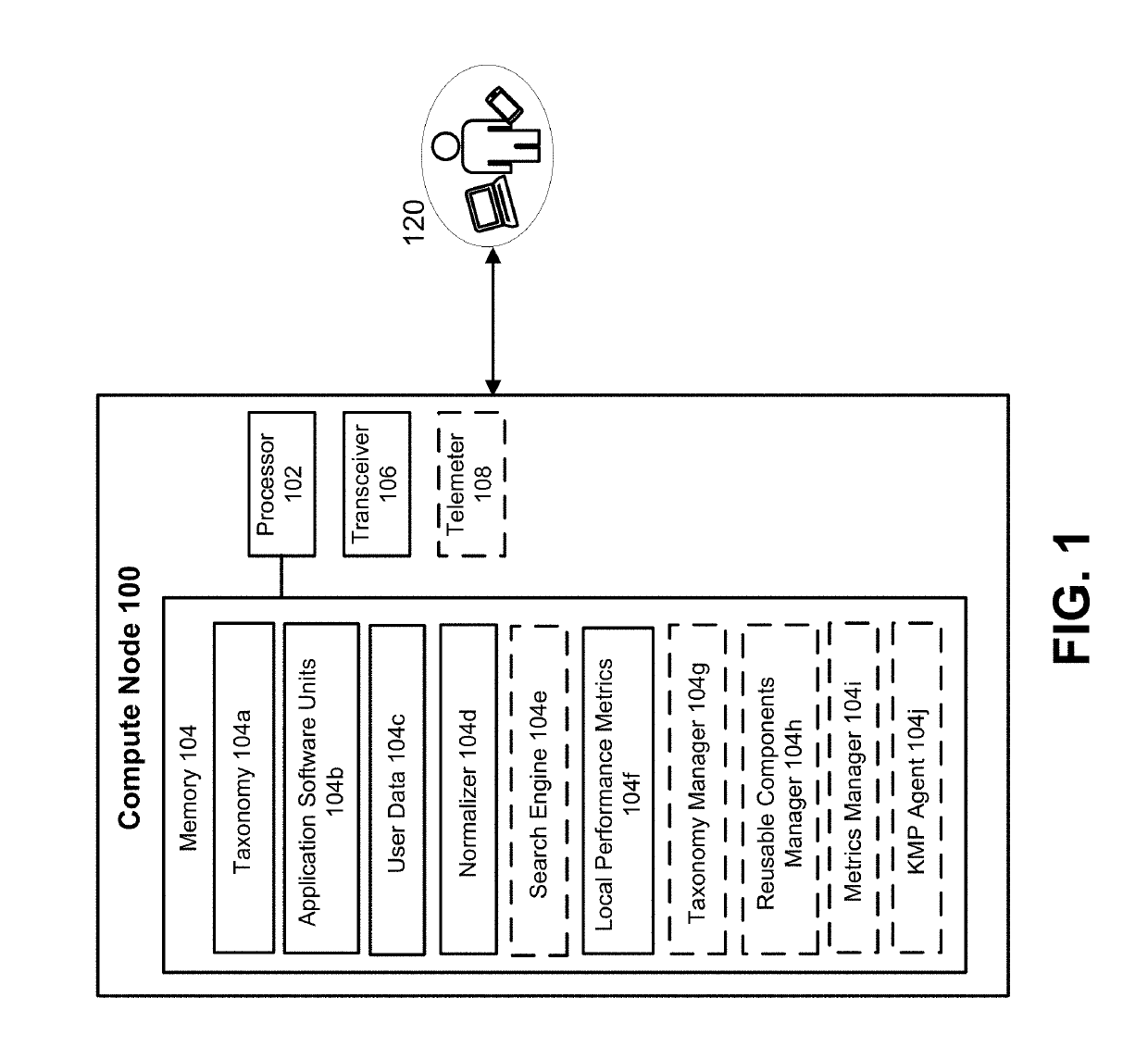
Active adaptation of networked compute devices using vetted reusable software components
ActiveUS20190171438A1Other databases queryingKnowledge representationReusable softwareParallel computing
A method includes receiving a text description of a system capability request, and converting the text description into a normalized description of the system capability request. A repository is then queried, based on the normalized description and using a search algorithm, to identify multiple candidate application software units (ASUs). The candidate ASUs are displayed to a user for selection. The user-selected ASU is then deployed, either locally or to at least one remote compute device, in response to receiving the user selection. Deployment can include the user-selected candidate ASU being integrated into a local or remote software package, thus defining a modified software package that is configured to provide the system capability.
Owner:ARCHEMY INC
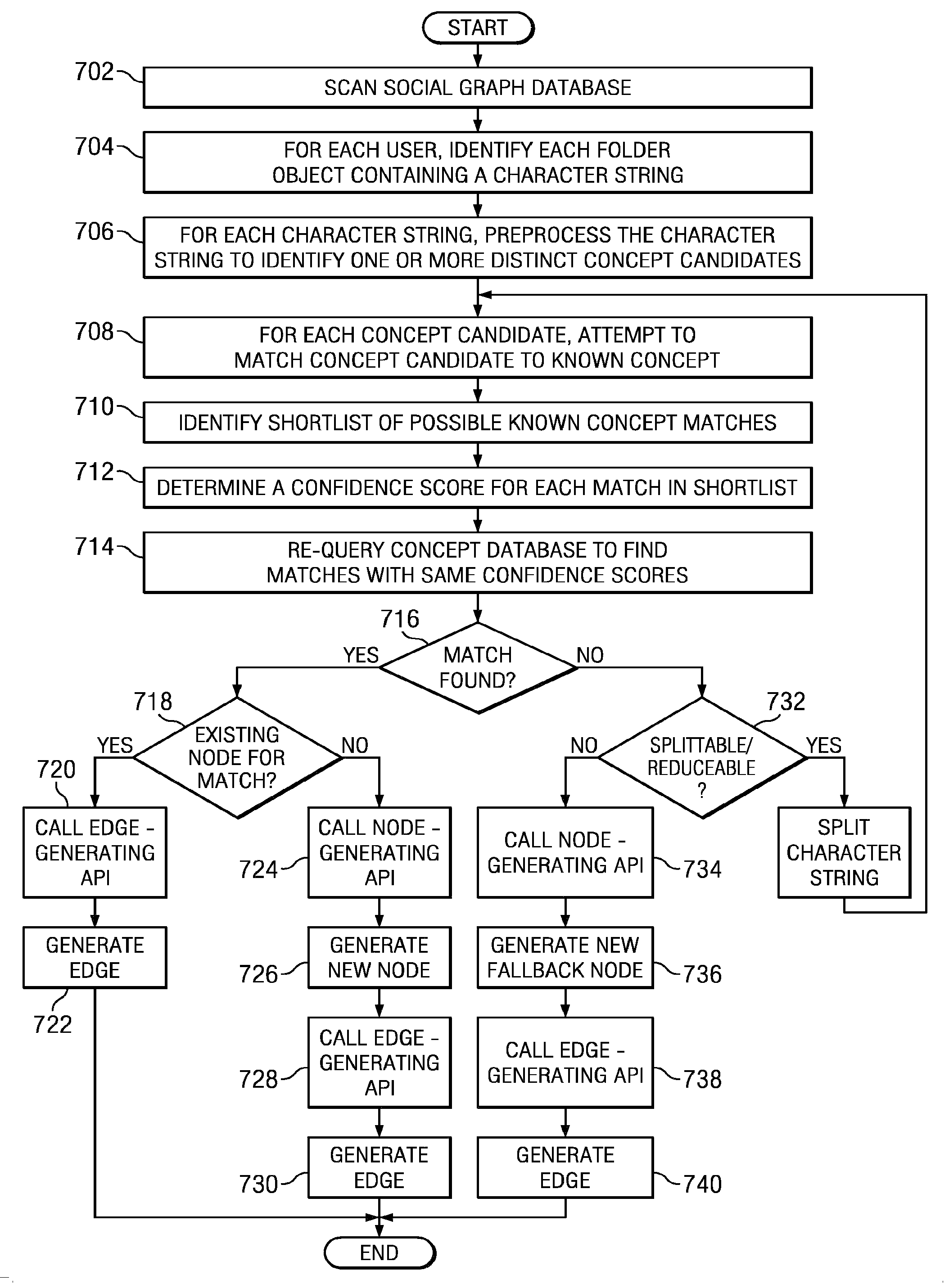
Automatically Generating Nodes and Edges in an Integrated Social Graph
In one embodiment, a method includes maintaining a data store of nodes and edges and for each of one or more users: scanning items of content associated with the corresponding user node; identifying a candidate item of content; searching for matches between the candidate item of content and existing nodes; determining whether or not a match between the candidate item of content and an existing node exists; and when it is determined that at least one match exists, generating an edge from the user node to the existing node for which the best match is determined; and when it is determined that no match exists, generating a new node based on the candidate item of content, and generating an edge from the user node to the new node.
Owner:META PLATFORMS INC
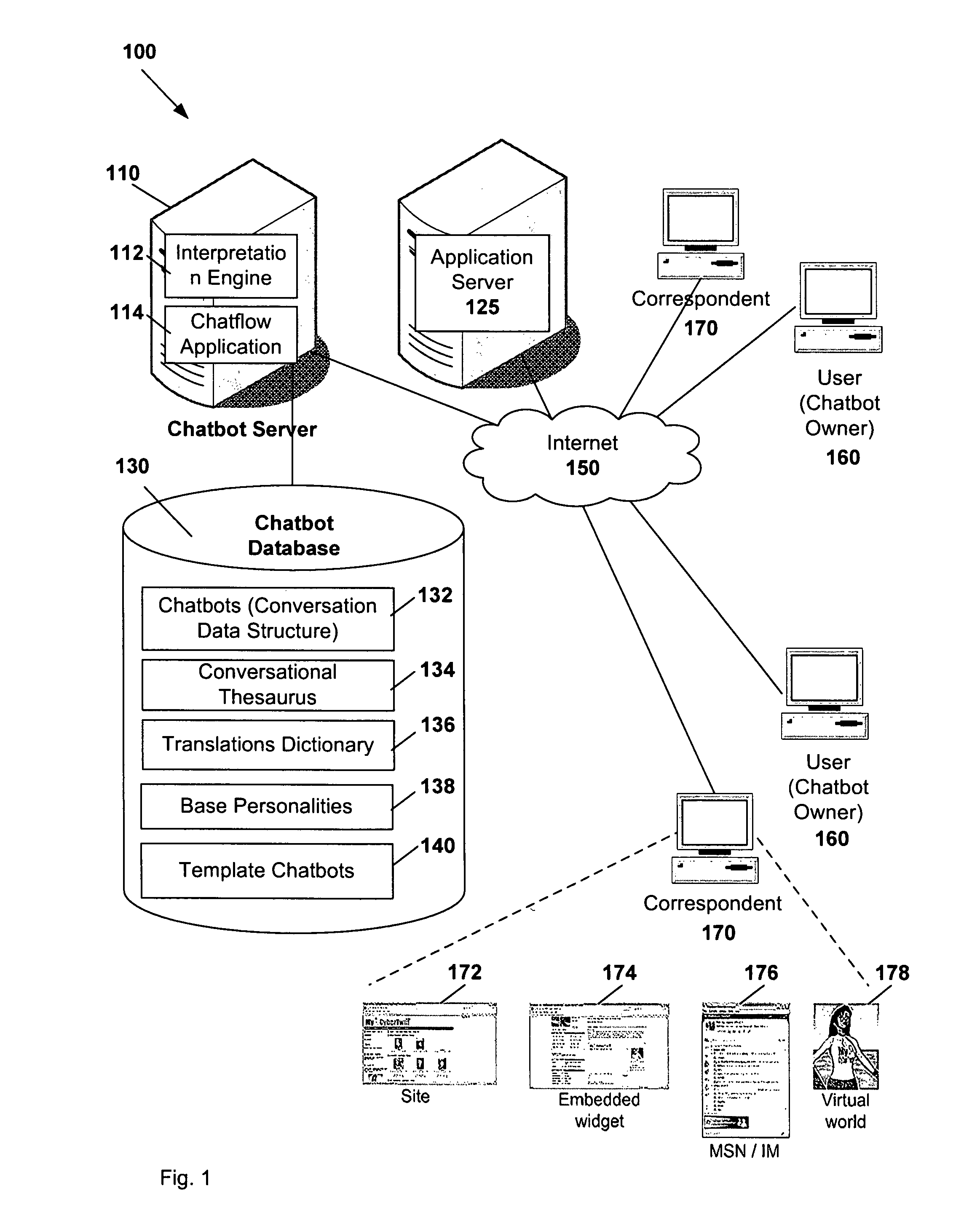
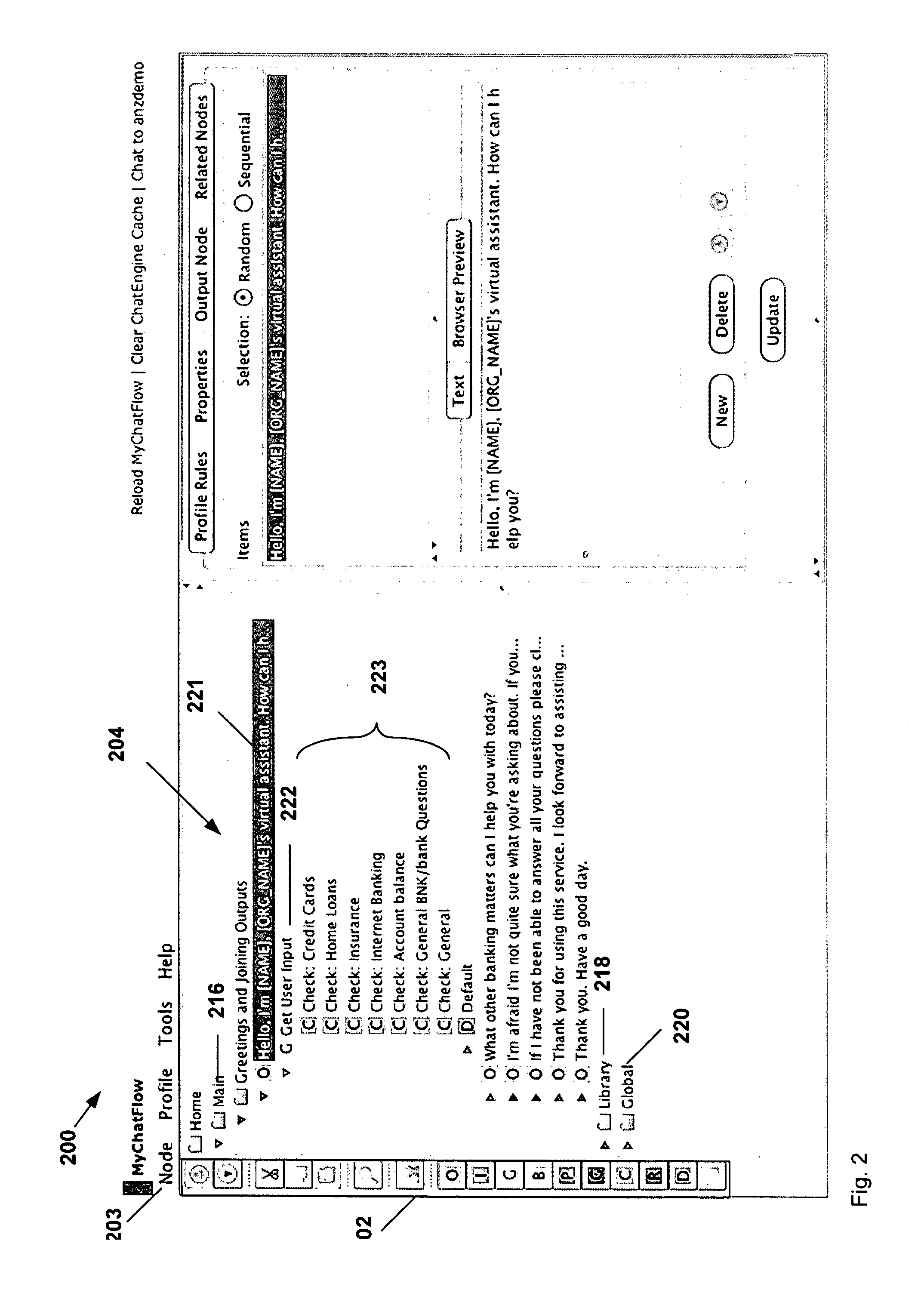
Chatbots
ActiveUS8630961B2Better conversationCreated rapidly and easilyNatural language data processingArtificial lifeNODALComputer network
Owner:SERVICENOW INC
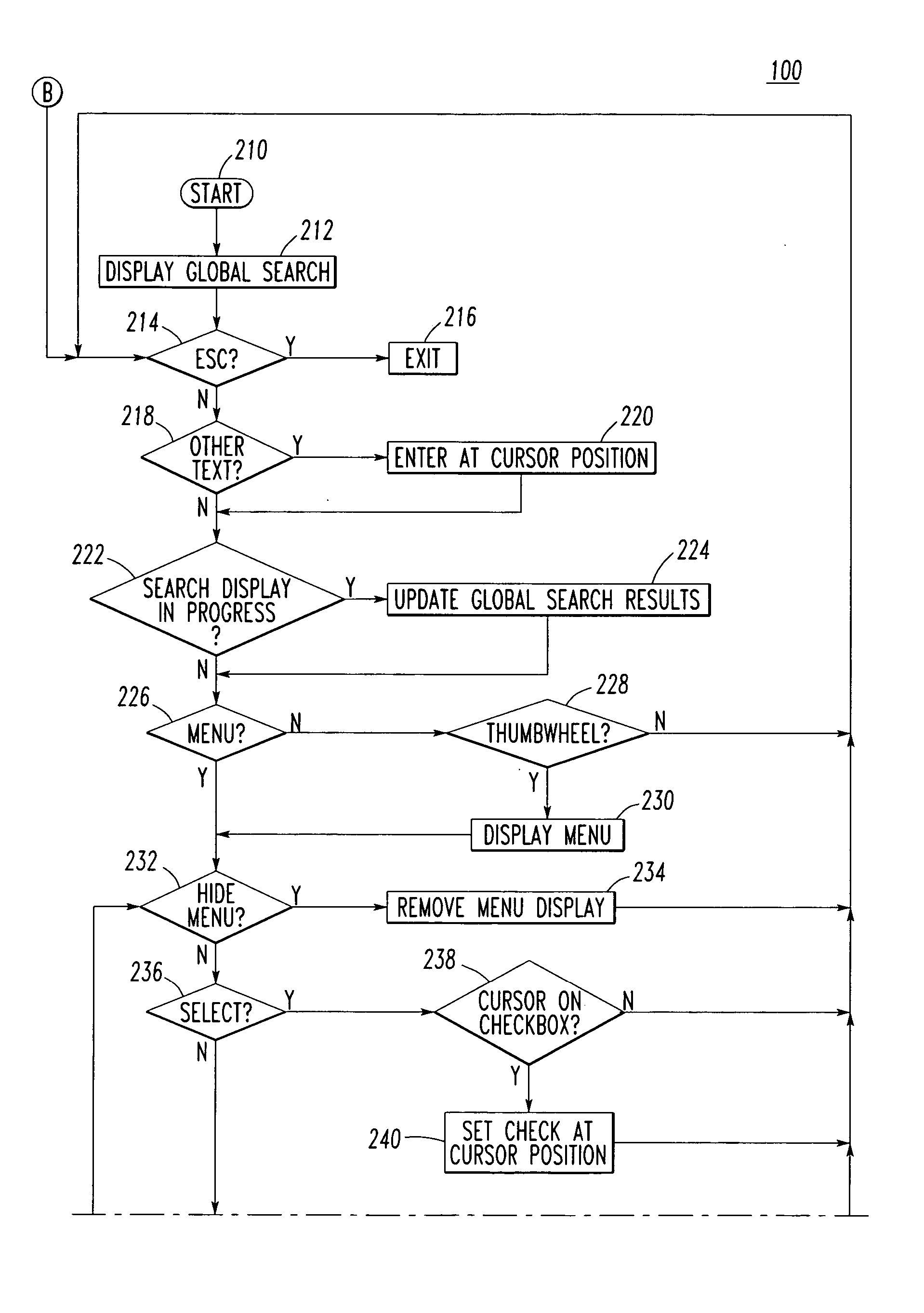
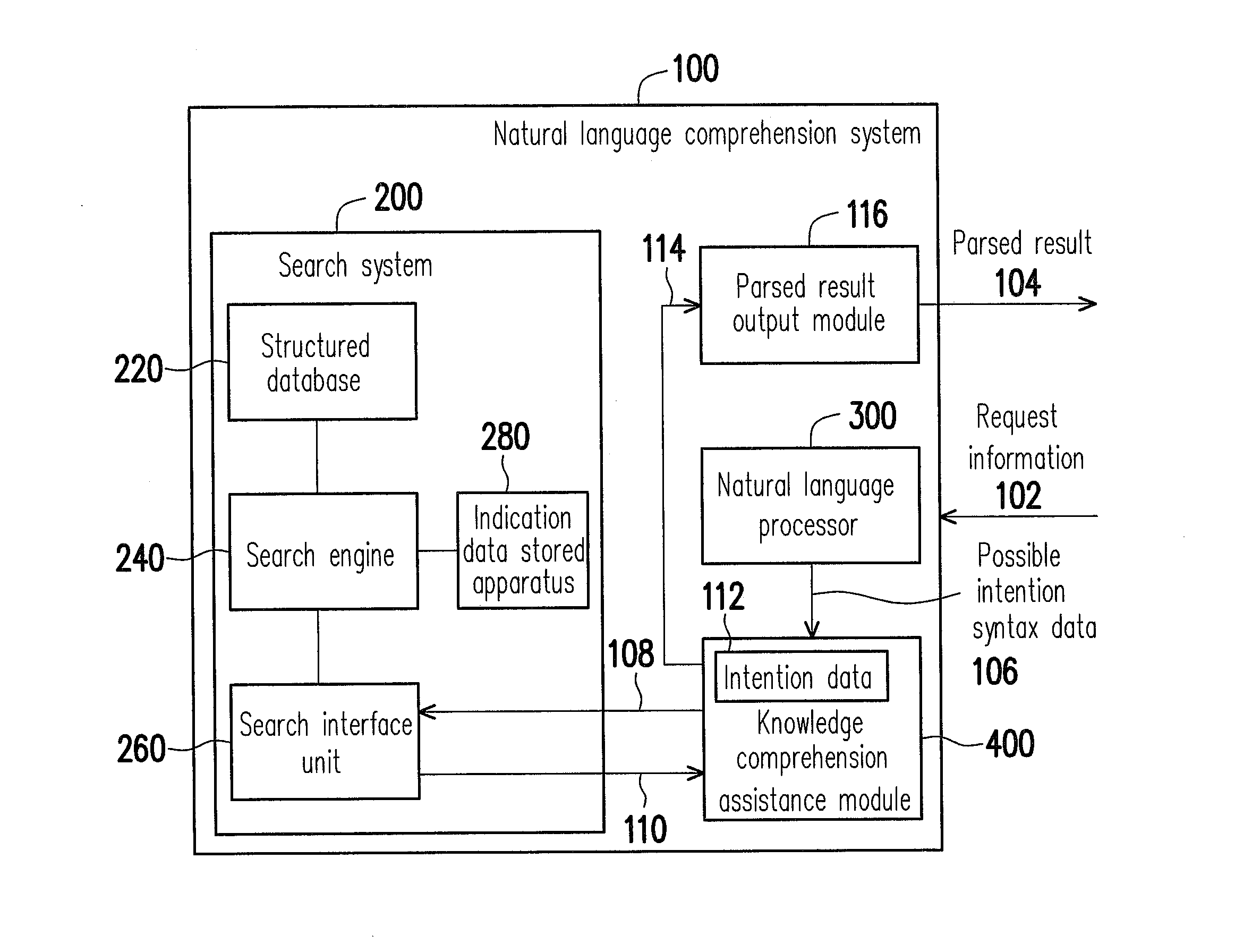
Method and device for monitoring and analyzing signals
InactiveUS7660700B2Data processing applicationsDigital data processing detailsReference databaseControl software
A method and system for monitoring and analyzing at least one signal are disclosed. An abstract of at least one reference signal is generated and stored in a reference database. An abstract of a query signal to be analyzed is then generated so that the abstract of the query signal can be compared to the abstracts stored in the reference database for a match. The method and system may optionally be used to record information about the query signals, the number of matches recorded, and other useful information about the query signals. Moreover, the method by which abstracts are generated can be programmable based upon selectable criteria. The system can also be programmed with error control software so as to avoid the re-occurrence of a query signal that matches more than one signal stored in the reference database.
Owner:WISTARIA TRADING INC
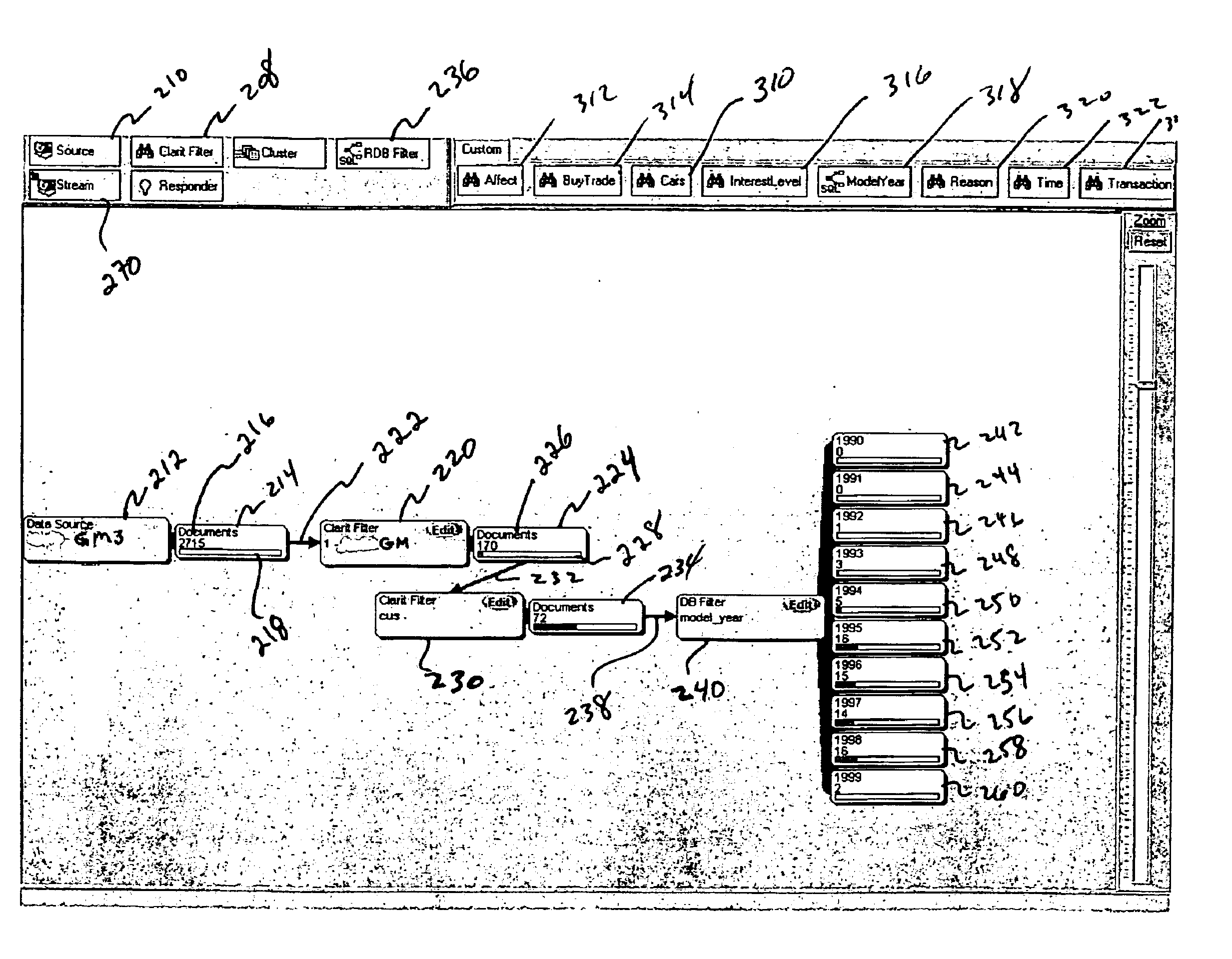
Method and apparatus for information mining and filtering
InactiveUS6915308B1Data processing applicationsDigital data processing detailsInformation analysisData stream
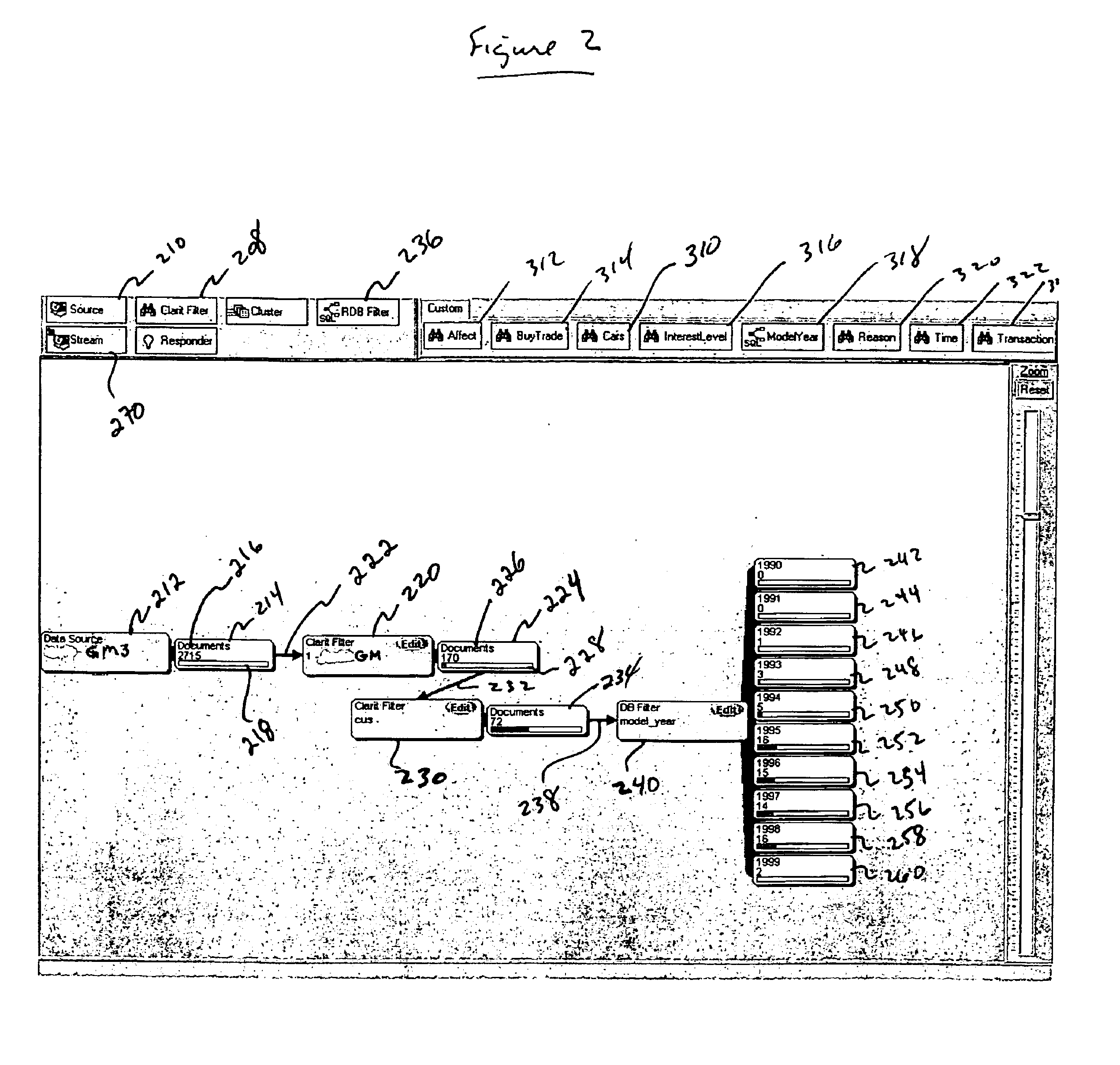
The present invention combines a data processing structure with a graphical user interface (GUI) to create an information analysis tool wherein multiple functions are combined in a network to extract information from multiple data sources. The functional network is created, and graphically represented to the user, by linking individual operations together. The combination of individual operations is not limited by the input or output characteristic of any single operation. The form of the input to or output from a by individual operation, whether from a database or from another operation, is the same. That is, both the input to and the output from an analysis function is a list of document identifiers and corresponding document characteristics. Because the form of the input and output from each operation is the same, arbitrary combinations into of operations may be created. Moreover, functional networks of individual operations can then be used for database retrieval as well as to filter data streams. Furthermore, the user is able to create a visual representation of the structure forming a functional network which may be dynamically updated as new data is added or functions switched in or out. Because, inter alia, the network structure dynamically responds to information as it is presented to the network, the visual representation of the network conveniently provides the user with information concerning the characteristics of the database or stream of data that are substantially unavailable through conventional search, filtering, or clustering techniques alone.
Owner:JUSTSYST EVANS RES
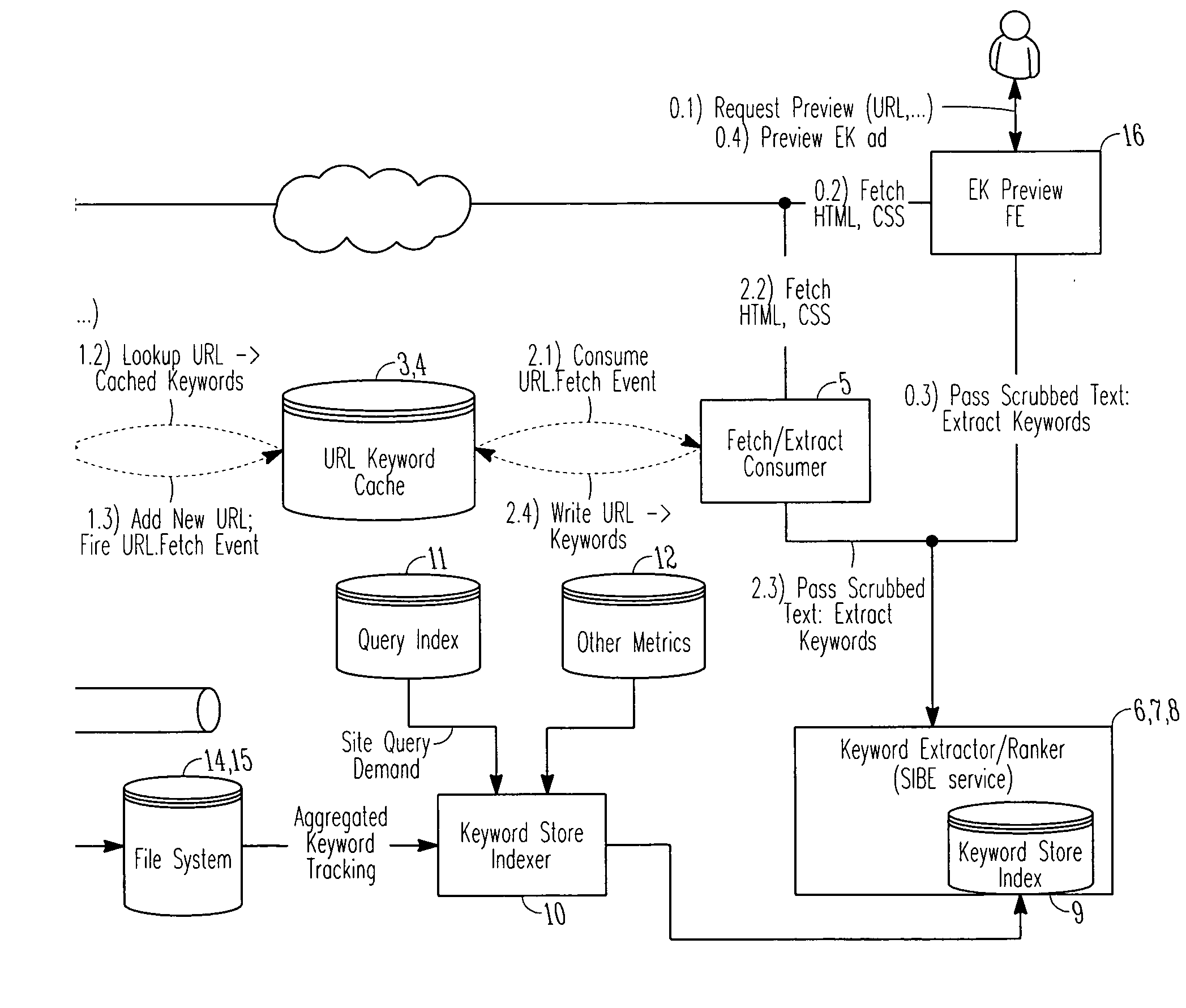
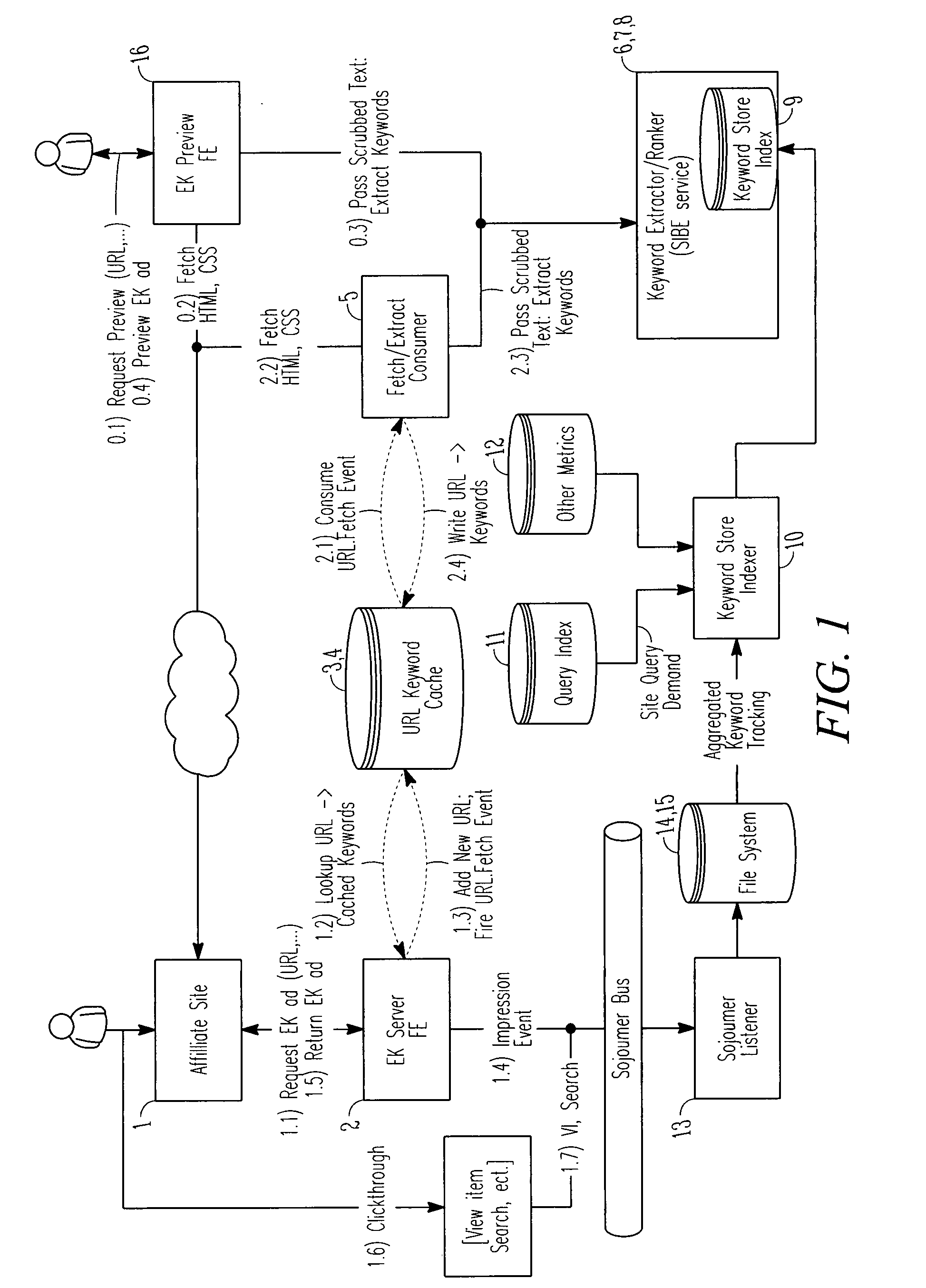
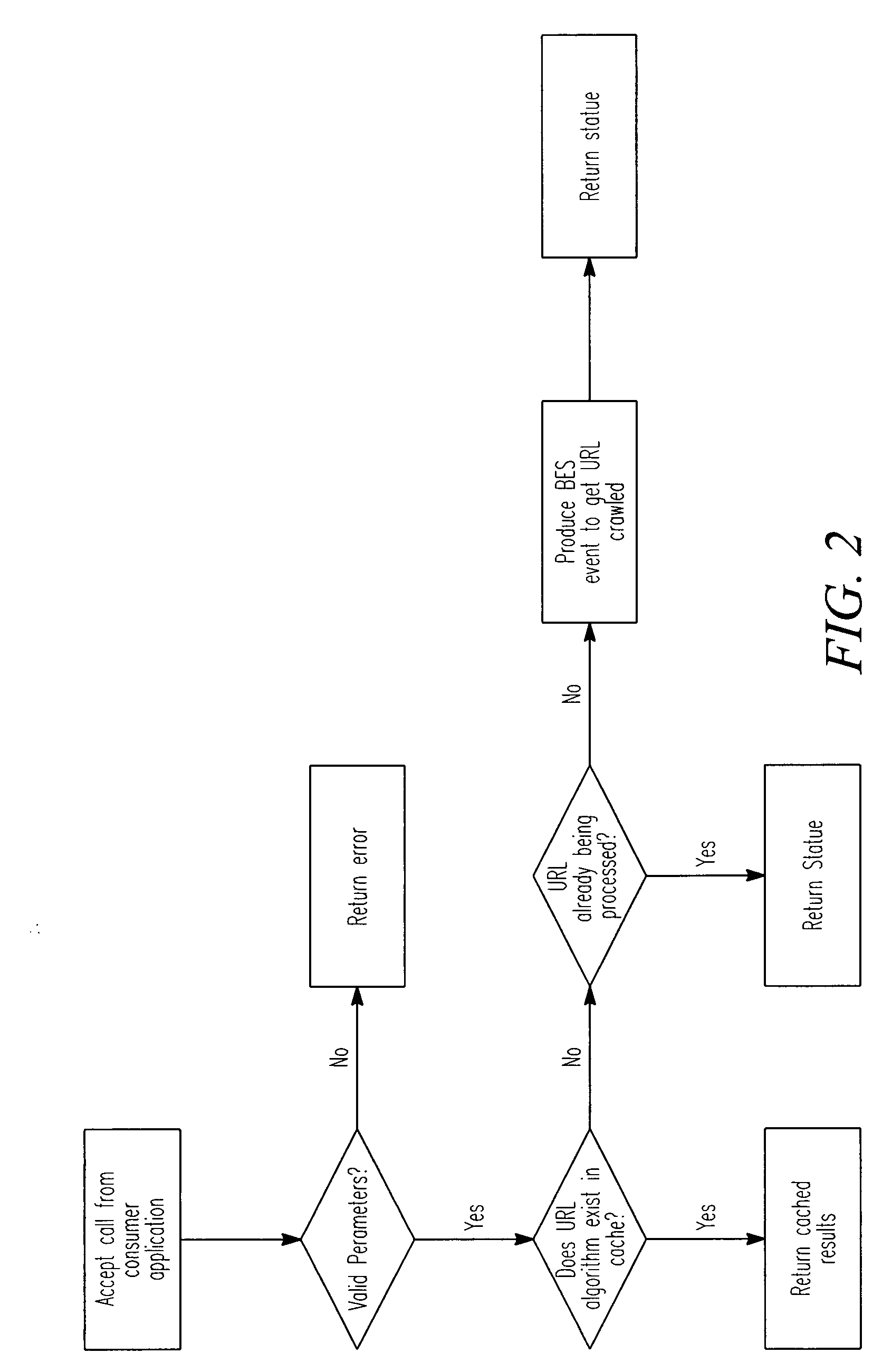
System and method for keyword extraction
ActiveUS20070288514A1More interfaceData amountWeb data indexingDigital data processing detailsWeb pageKeyword extraction
A computer-implemented system and method for keyword extraction are disclosed. The system in an example embodiment includes a keyword extraction component to extract relevant keywords from content of a web page, to identify items relevant to the extracted keywords, and to rank the relevant items.
Owner:EBAY INC
Method of searching for personal information management (PIM) information and handheld electronic device employing the same
ActiveUS20060047644A1Speed of search is optimizedOptimized for speedOther databases queryingSpecial data processing applicationsPersonal information managementElectronic equipment
A method of searching for Personal Information Management information of a handheld electronic device includes accepting input of one or more search criteria, such as text search criteria and / or name search criteria; accepting input of a representation of a plurality of different databases or applications of the handheld electronic device including Personal Information Management information to be searched; and conducting a search of the different databases or applications based upon the one or more search criteria and the representation of different databases or applications. The method determines one or more search results from the search and displays those search results.
Owner:MALIKIE INNOVATIONS LTD
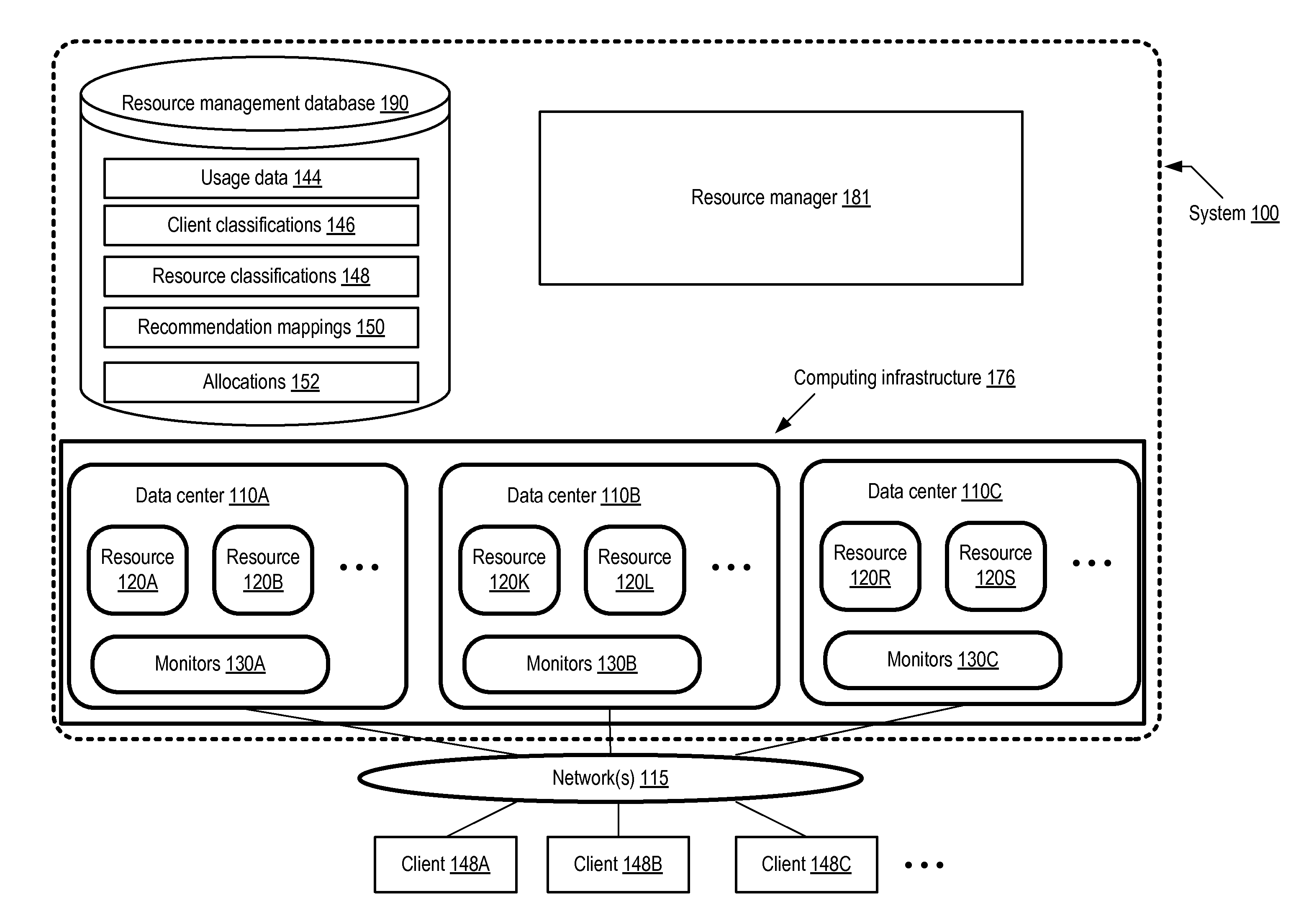
Client Classification-Based Dynamic Allocation of Computing Infrastructure Resources
Methods and apparatus for classification-based dynamic allocation of computing resources are described. A method comprises determining usage data sources corresponding to one or more clients of a computing infrastructure, and assigning values to client classification categories associated with a particular client based on metrics obtained from the particular client's usage data sources. The method includes generating a recommendation mapping between values of the client classification categories, and one or more resources of the infrastructure, based at least in part on resource classification information. The method further includes allocating at least a portion of the one or more resources to the particular client based at least in part on the recommendation mapping.
Owner:ADOBE SYST INC
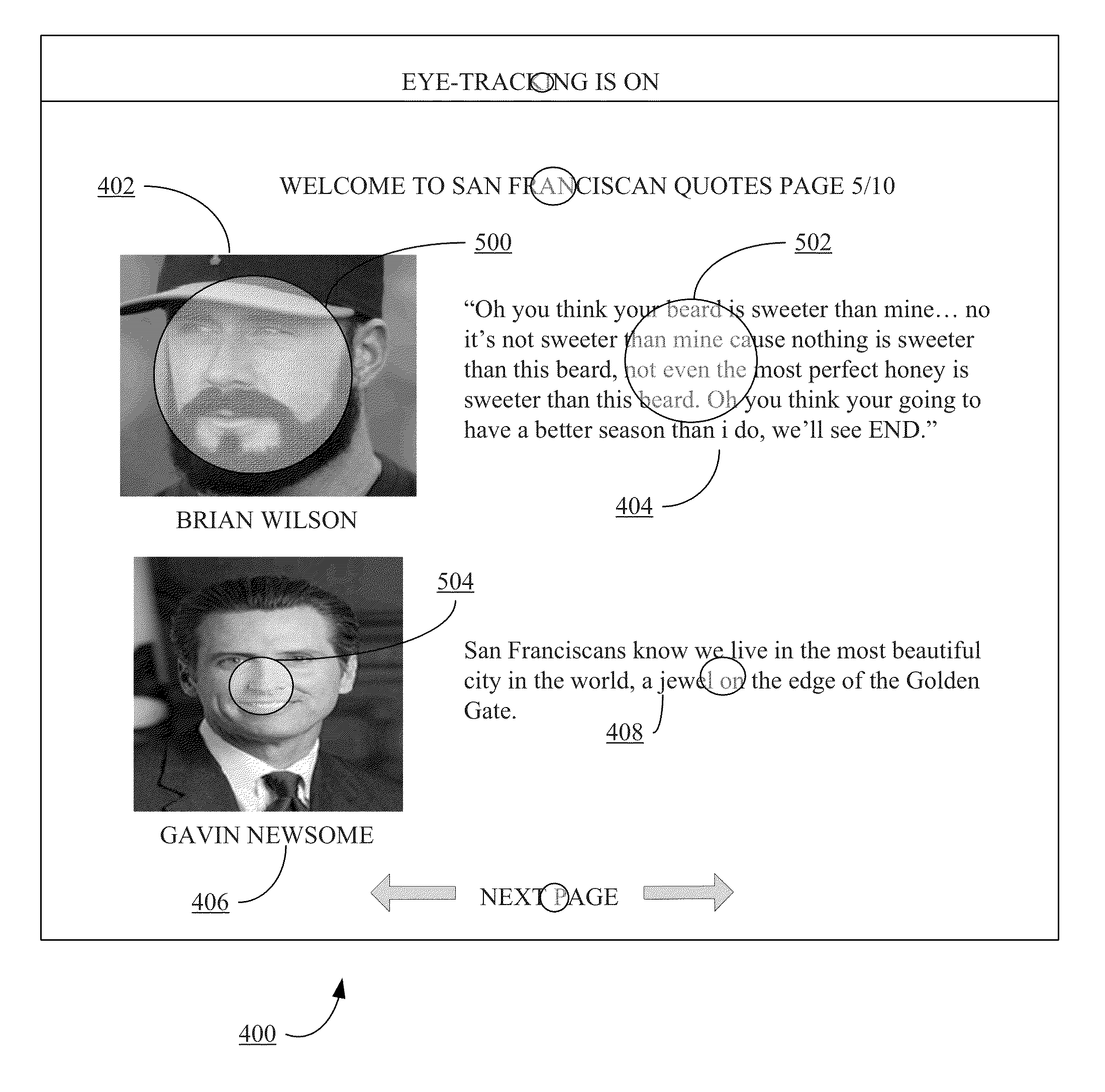
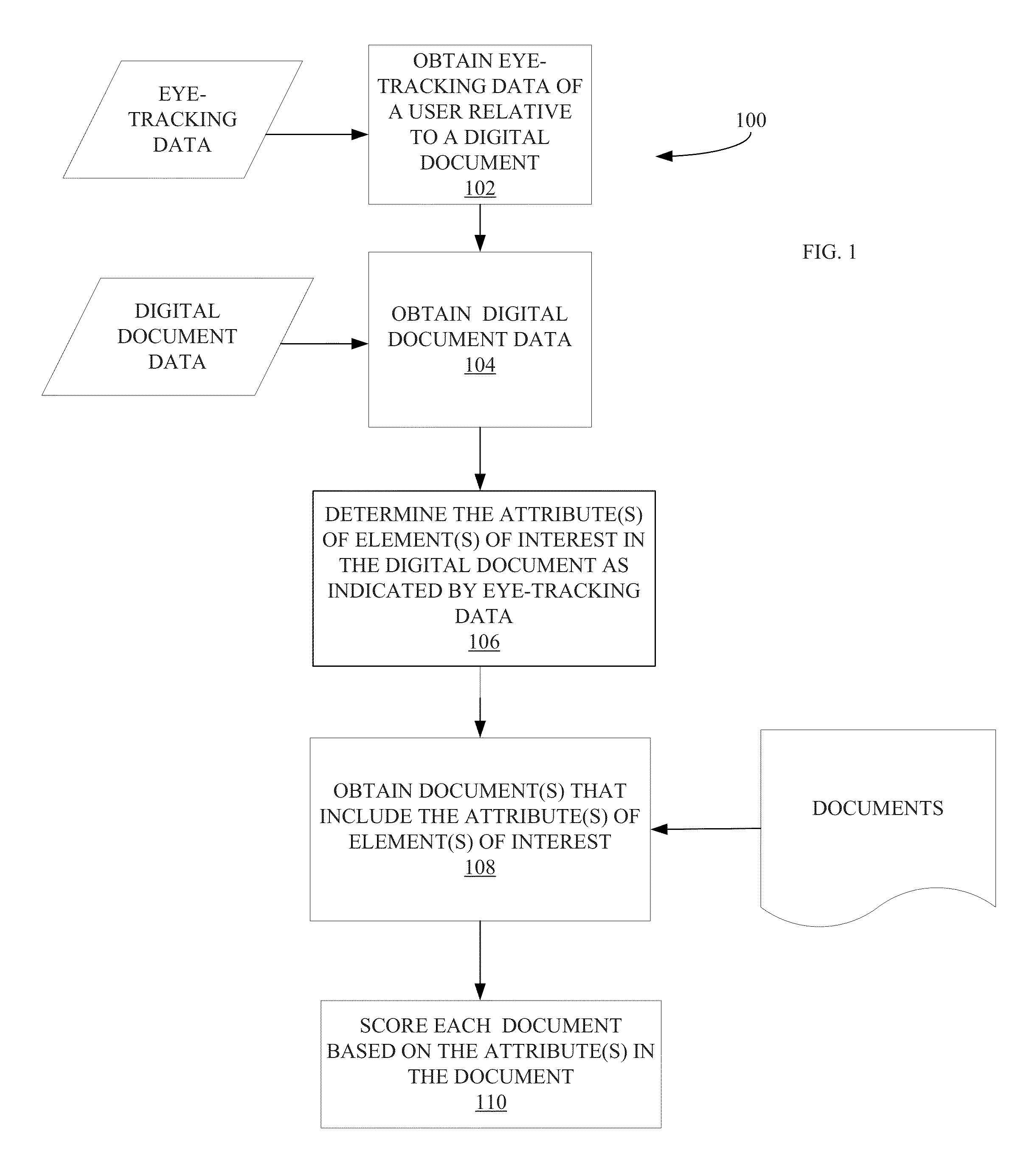
Method and system of scoring documents based on attributes obtained from a digital document by eye-tracking data analysis
ActiveUS20130054622A1Web data indexingDigital data processing detailsDocument preparationDocumentation
In one exemplary embodiment, a set of attributes derived from an element of a first digital document is obtained. The element is identified from eye-tracking data of a user viewing the digital document. A search query of a database comprising at least one query term is received. A set of documents in the database is identified according to the search query. An attribute score is determined for each document. The set of documents are sorted according to the attribute score. Optionally, a commonality between the query term and at least one member of the set of attributes may be determined. The search query may be generated by the user. The database may be a hypermedia database.
Owner:BUCKYBALL MOBILE
Web-based system and method for archiving and searching participant-based internet text sources for customer lead data
A text mining system for collecting business intelligence about a client, as well as for identifying prospective customers of the client, for use in a lead generation system accessible by the client via the Internet. The text mining system has various components, including a data acquisition process that extracts textual data from various Internet sources, a database for storing the extracted data, a text mining server that executes query-based searches of the database, and an output repository. A web server provides client access to the repository, and to the mining server.
Owner:ALTO DYNAMICS LLC
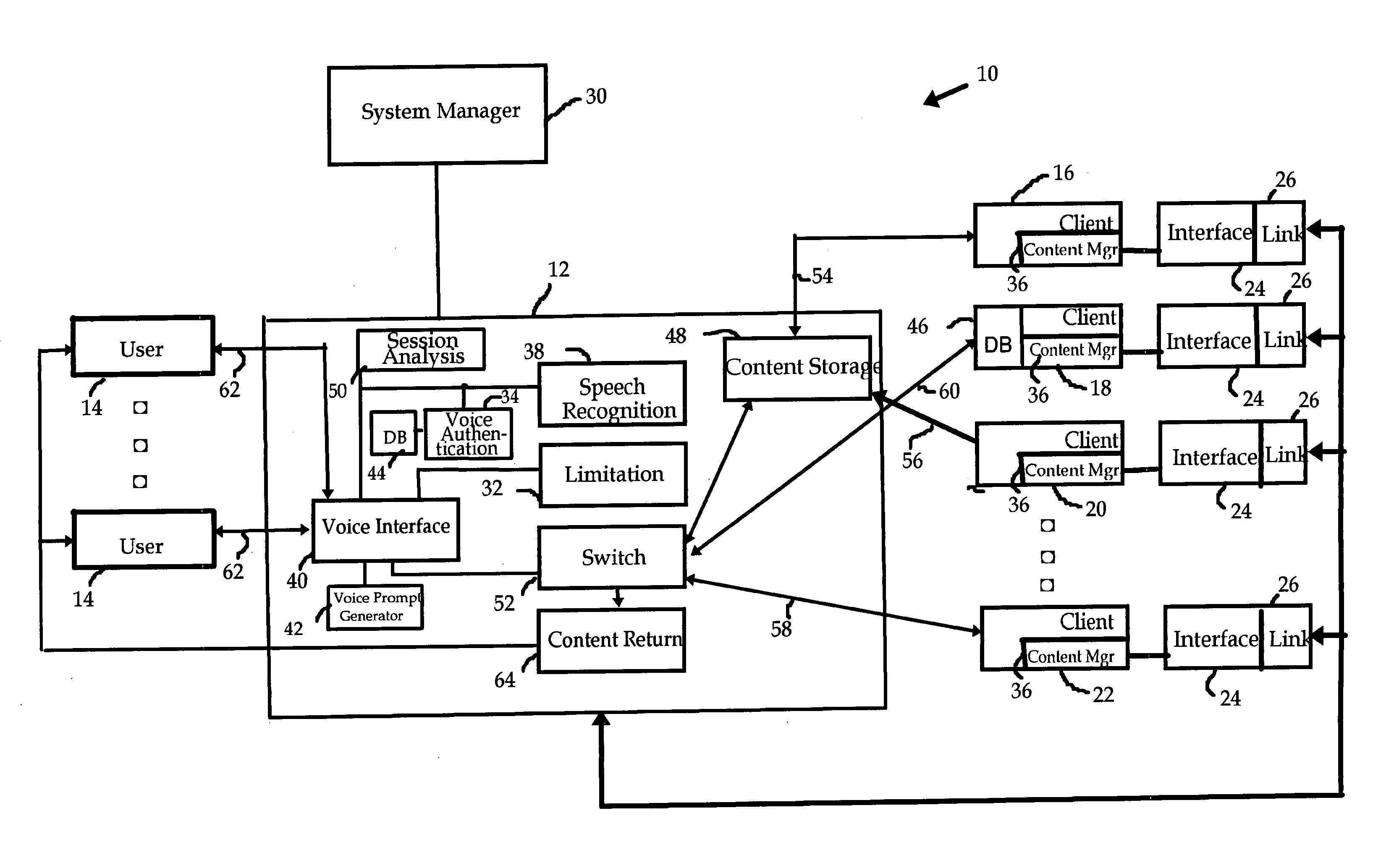
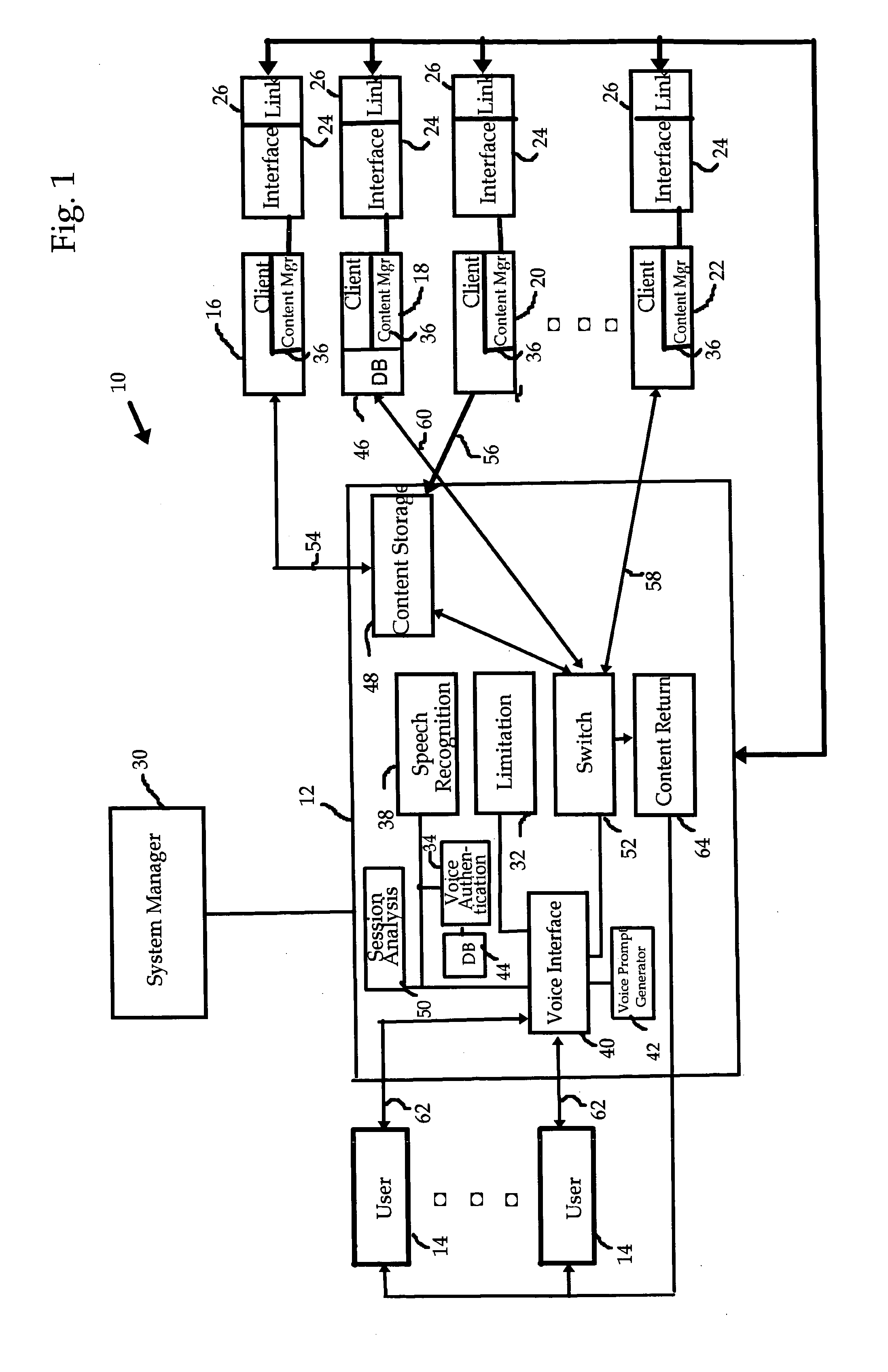
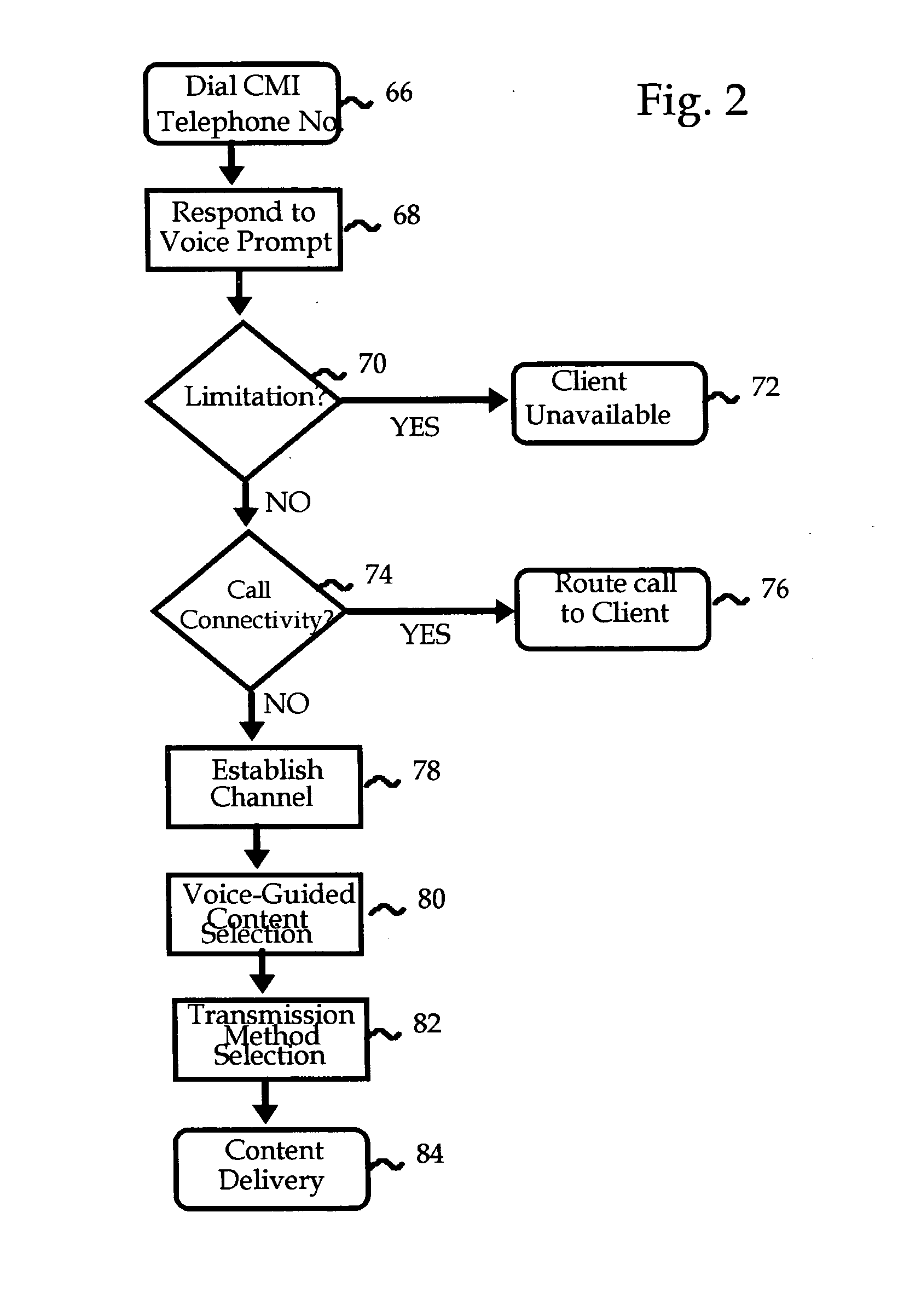
Content management interface
InactiveUS20060165104A1Easy accessDevices with voice recognitionData switching by path configurationSpeech identificationClient-side
A platform is provided to respond to data inquiries from callers or users that are directed to one of a plurality of clients or subscribers. A user is guided to a selected client's area on the platform using voice menus and prompts together with speech recognition and database search techniques. The voice prompts are adaptively generated according to the client's policies and the kind of content it offers, and the platform's experience with the user's speech patterns. The content is returned to the caller using a transmission method that is selected in response to voice prompts.
Owner:KAYE ELAZAR MOSHE
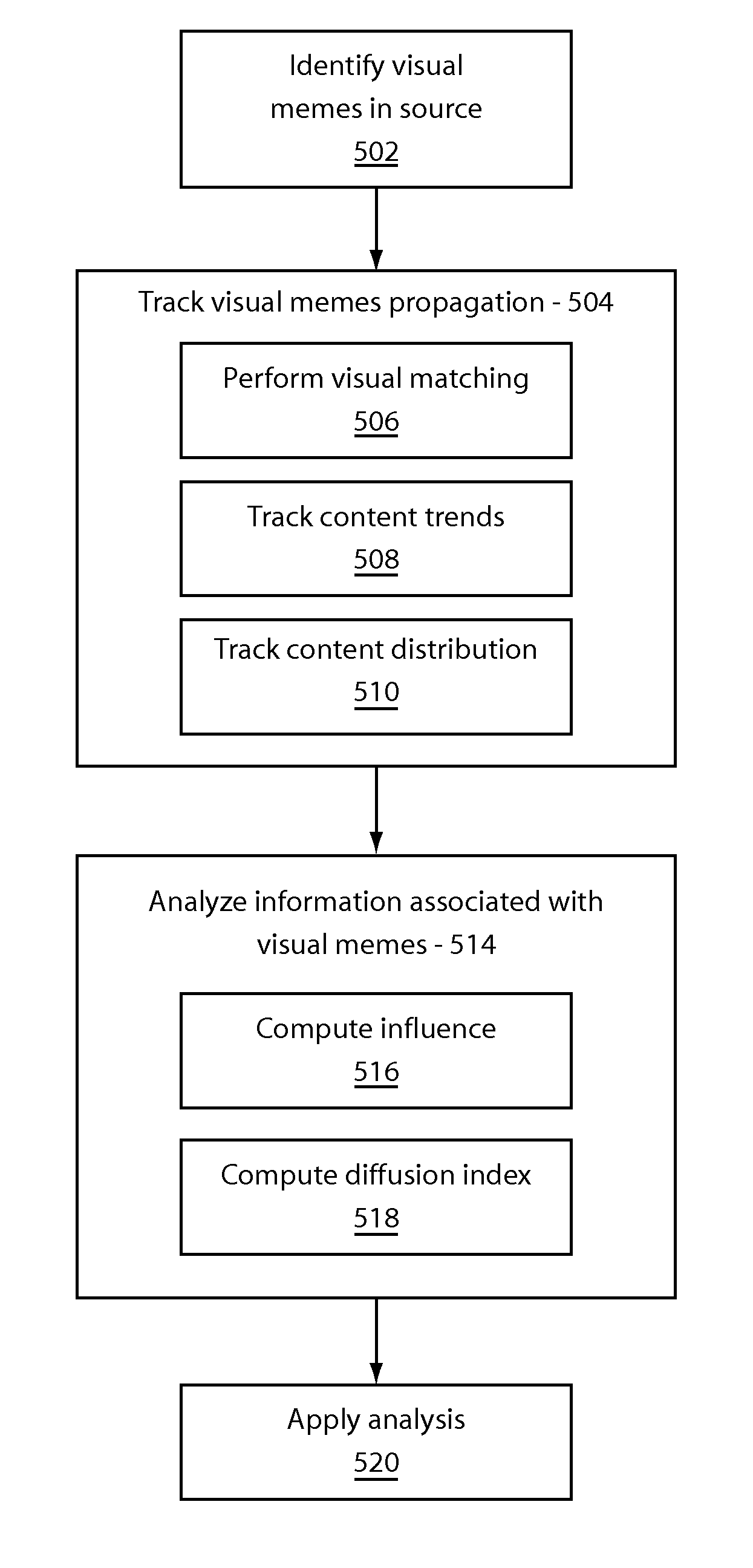
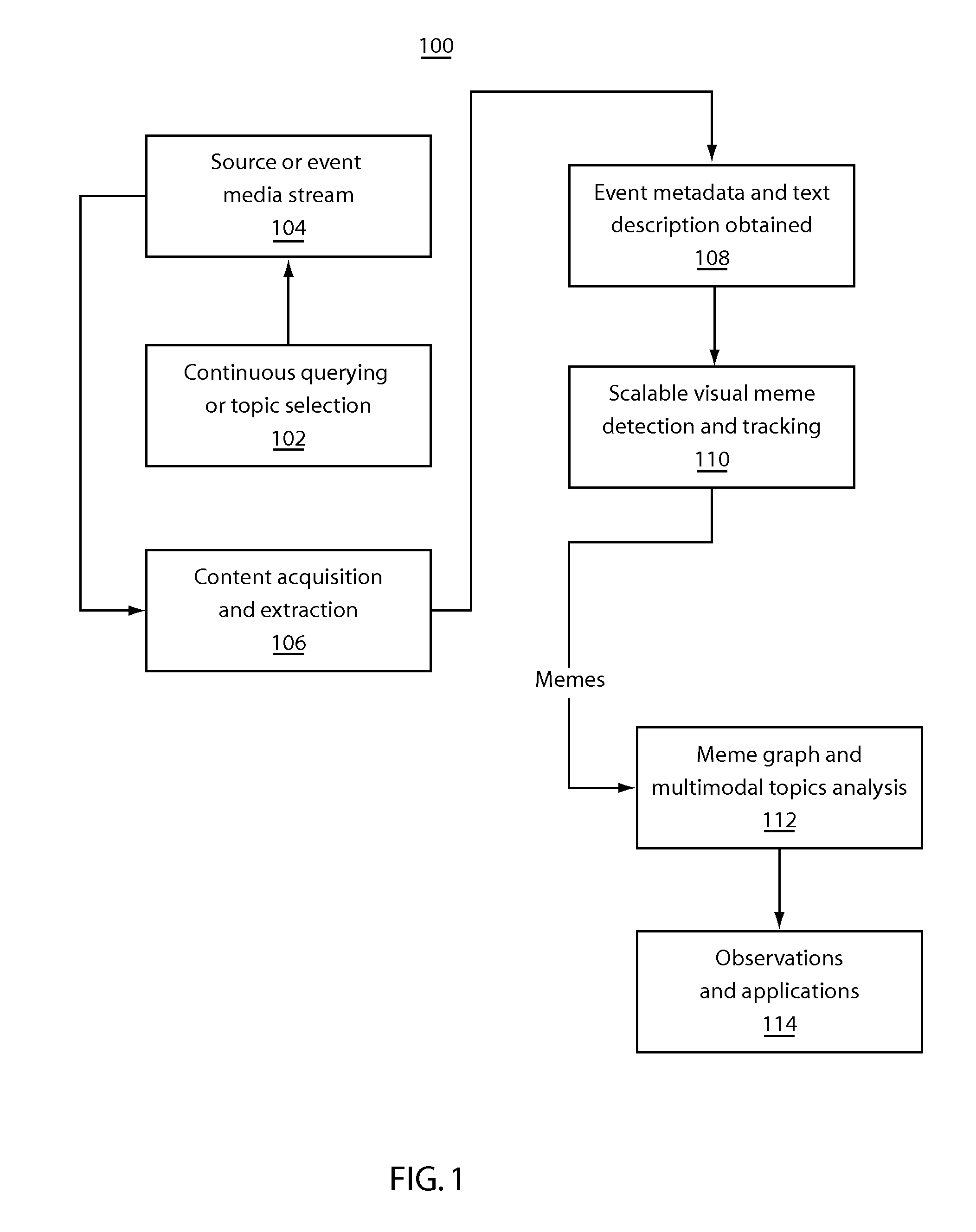
Visual meme tracking for social media analysis
ActiveUS20120102021A1Digital data processing detailsMetadata multimedia retrievalData sourceSubject matter
A system and method for analyzing visual memes includes identifying visual memes associated with at least one topic in a data source. The visual memes propagated over time are tracked to extract information associated with identified visual memes. The information associated with the visual memes is analyzed to determine at least one of generation, propagation, and use of the identified memes.
Owner:AIRBNB
Automated occupant tracking systems and methods
ActiveUS20190122322A1Reduce contactDatabase updatingData processing applicationsElectronic communicationData mining
An occupancy database is in electronic communication with a plurality of location-specific distributed computing entities to maintain real-time update occupancy data for various entities. As those entities relocate from one location to another (e.g., moving from one apartment to another), distributed computing entities associated with both the prior and new location of the entity transmit information to the occupancy database to reflect the changed location for the entity. The occupancy database also maintains communication data for the entities and / or locations associated with the entities, and the occupancy database may share that communication data with authorized mobile / user computing entities to enable communication between those authorized mobile / user computing entities and the particular entity or devices located at the entity's location.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
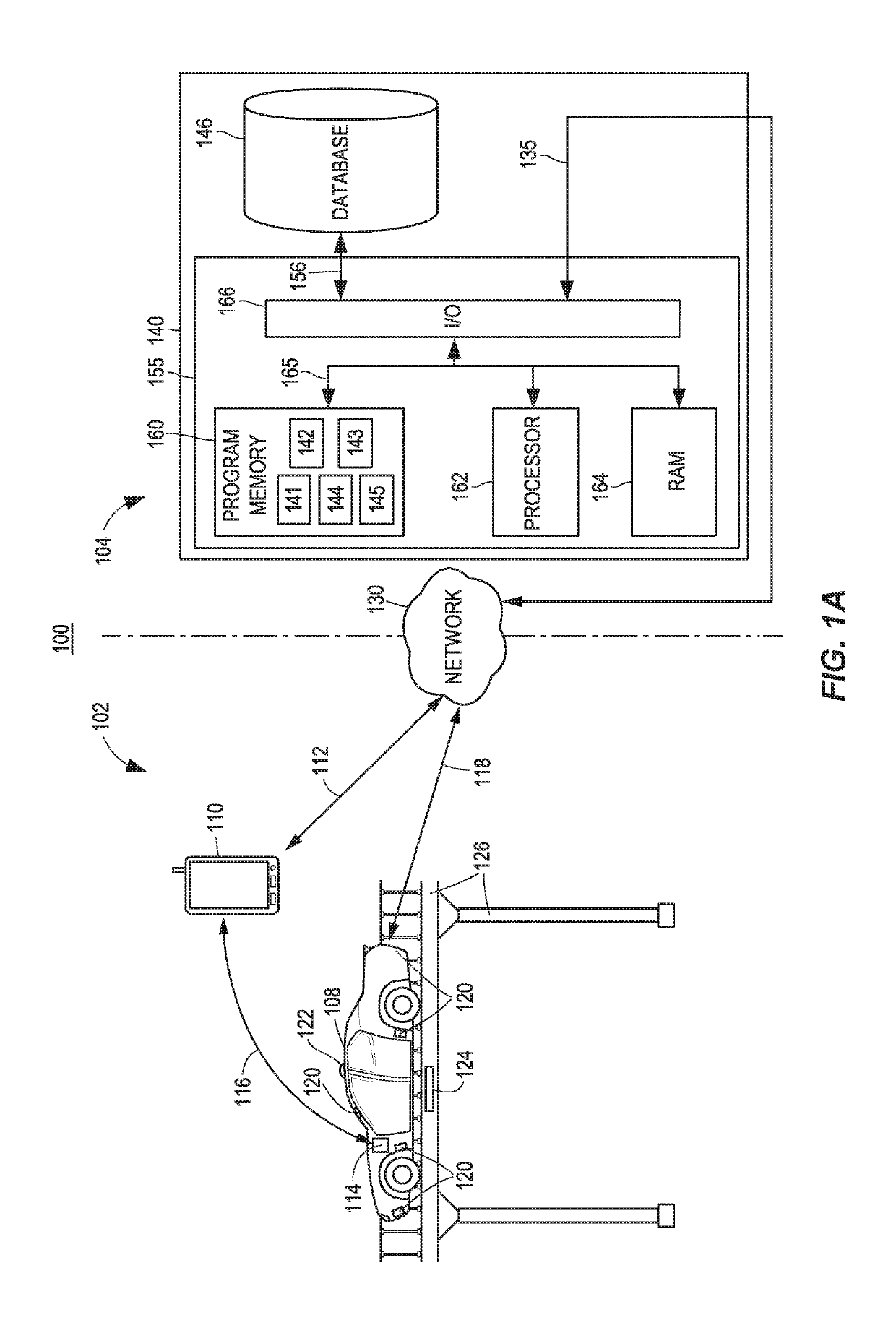
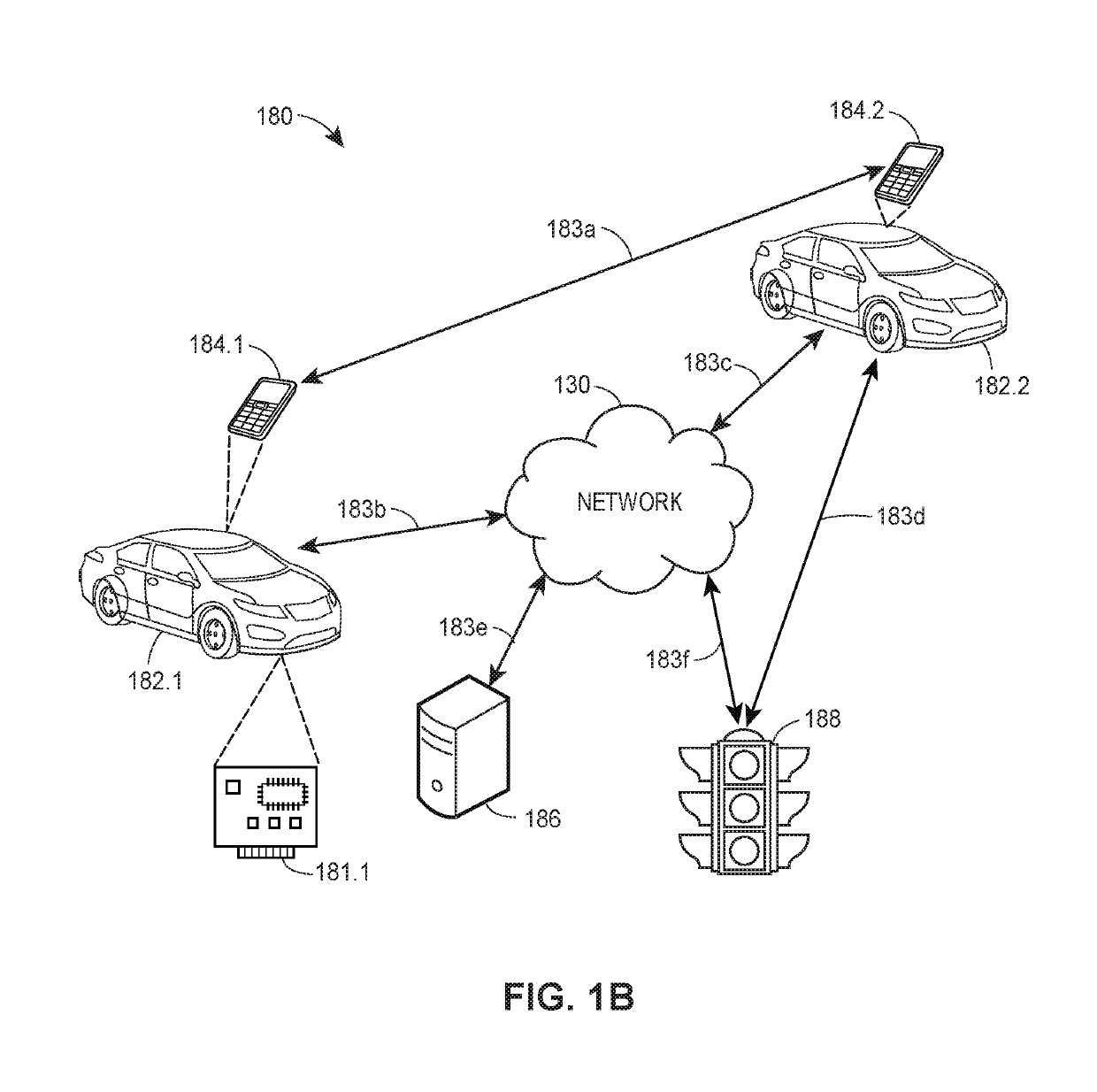
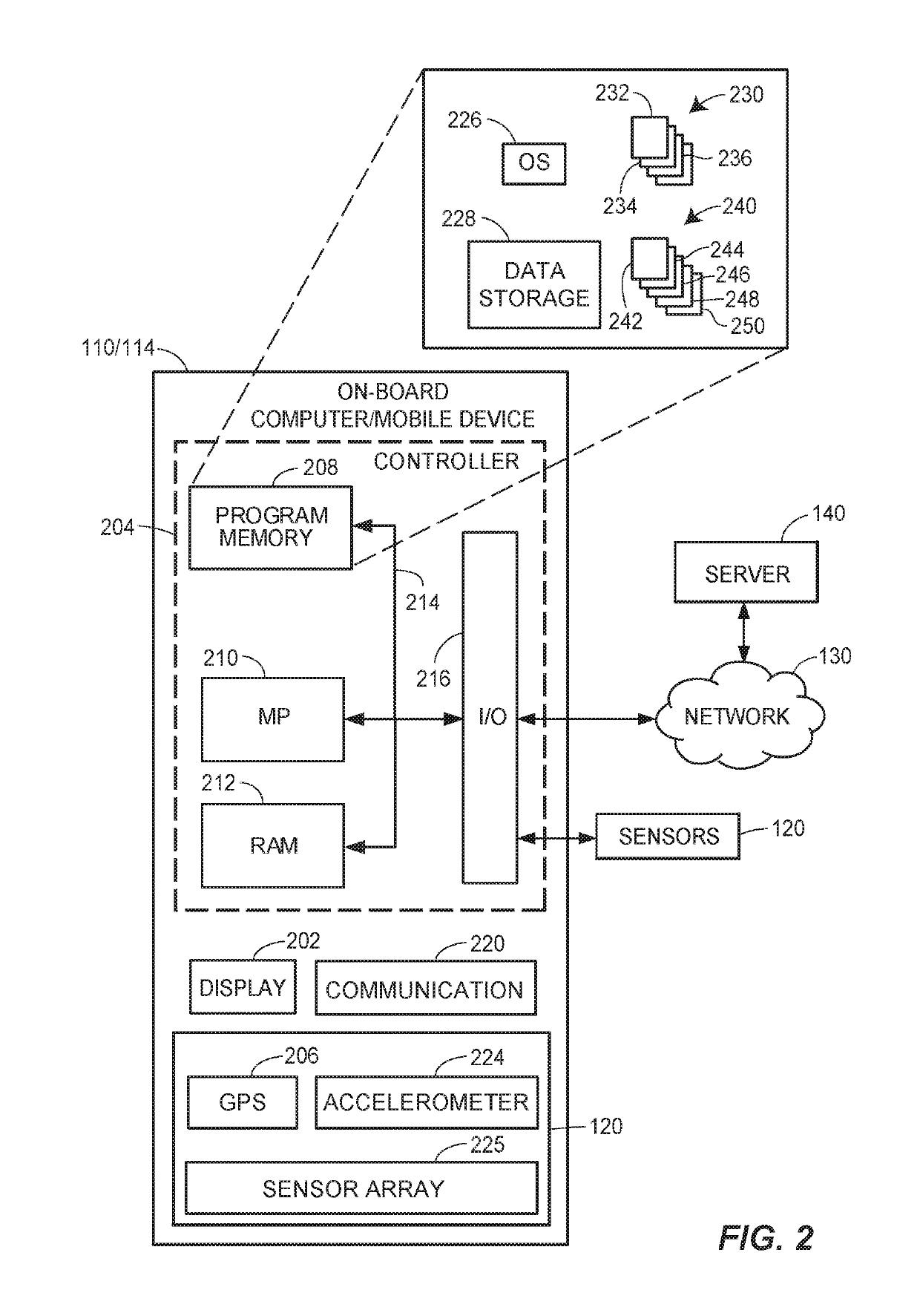
Coordinated autonomous vehicle automatic area scanning
Methods and systems for autonomous and semi-autonomous vehicle control, routing, and automatic feature adjustment are disclosed. Sensors associated with autonomous operation features may be utilized to search an area for missing persons, stolen vehicles, or similar persons or items of interest. Sensor data associated with the features may be automatically collected and analyzed to passively search for missing persons or vehicles without vehicle operator involvement. Search criteria may be determined by a remote server and communicated to a plurality of vehicles within a search area. In response to which, sensor data may be collected and analyzed by the vehicles. When sensor data generated by a vehicle matches the search criteria, the vehicle may communicate the information to the remote server.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
Total Property Intelligence System
ActiveUS20180211115A1Multiple keys/algorithms usagePublic key for secure communicationPhysical securityApplication software
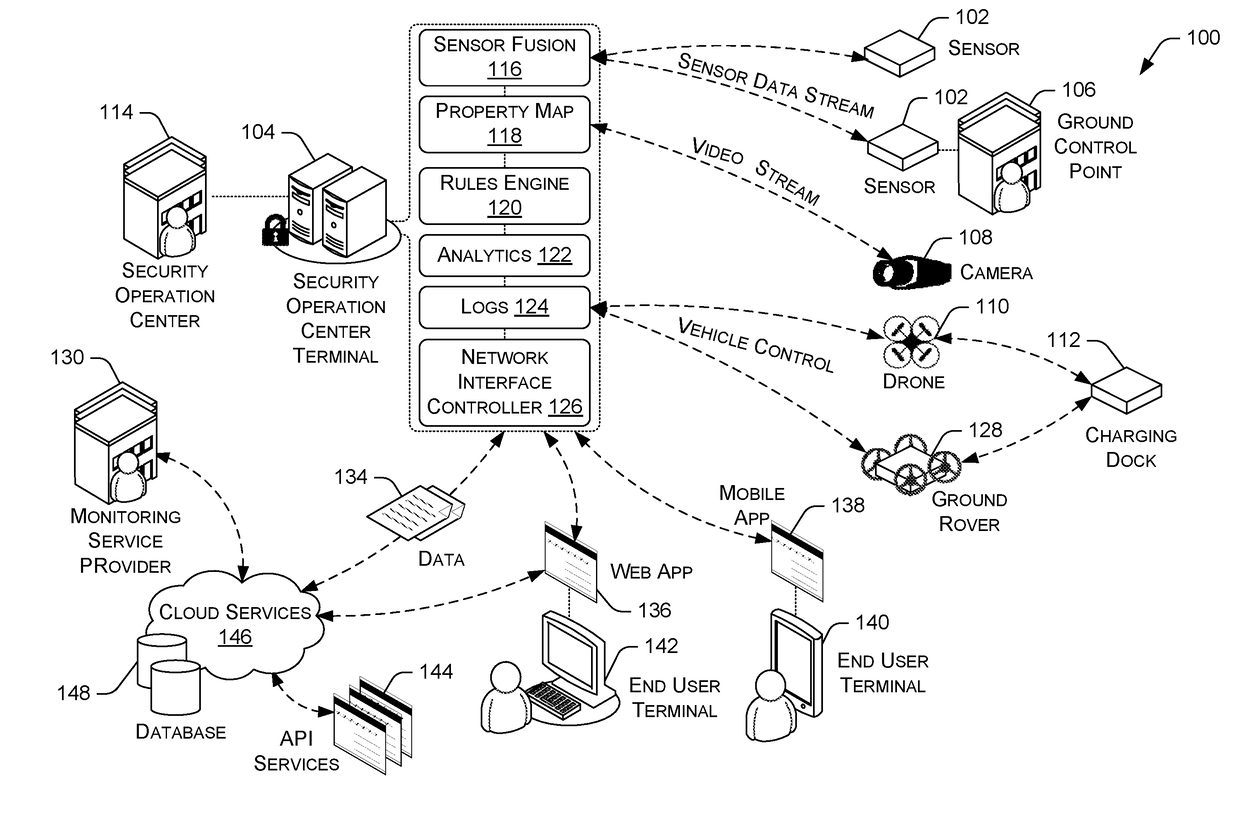
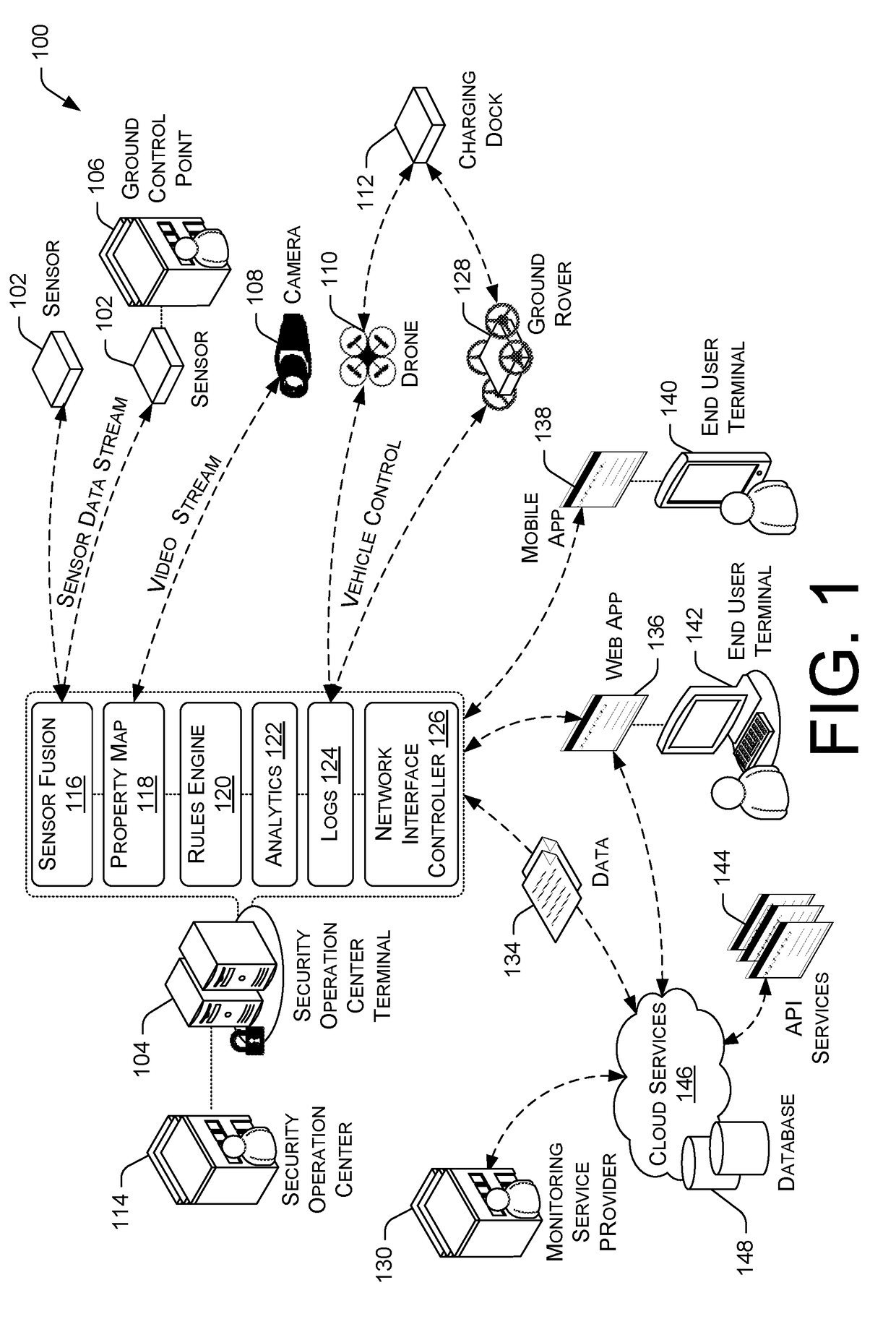
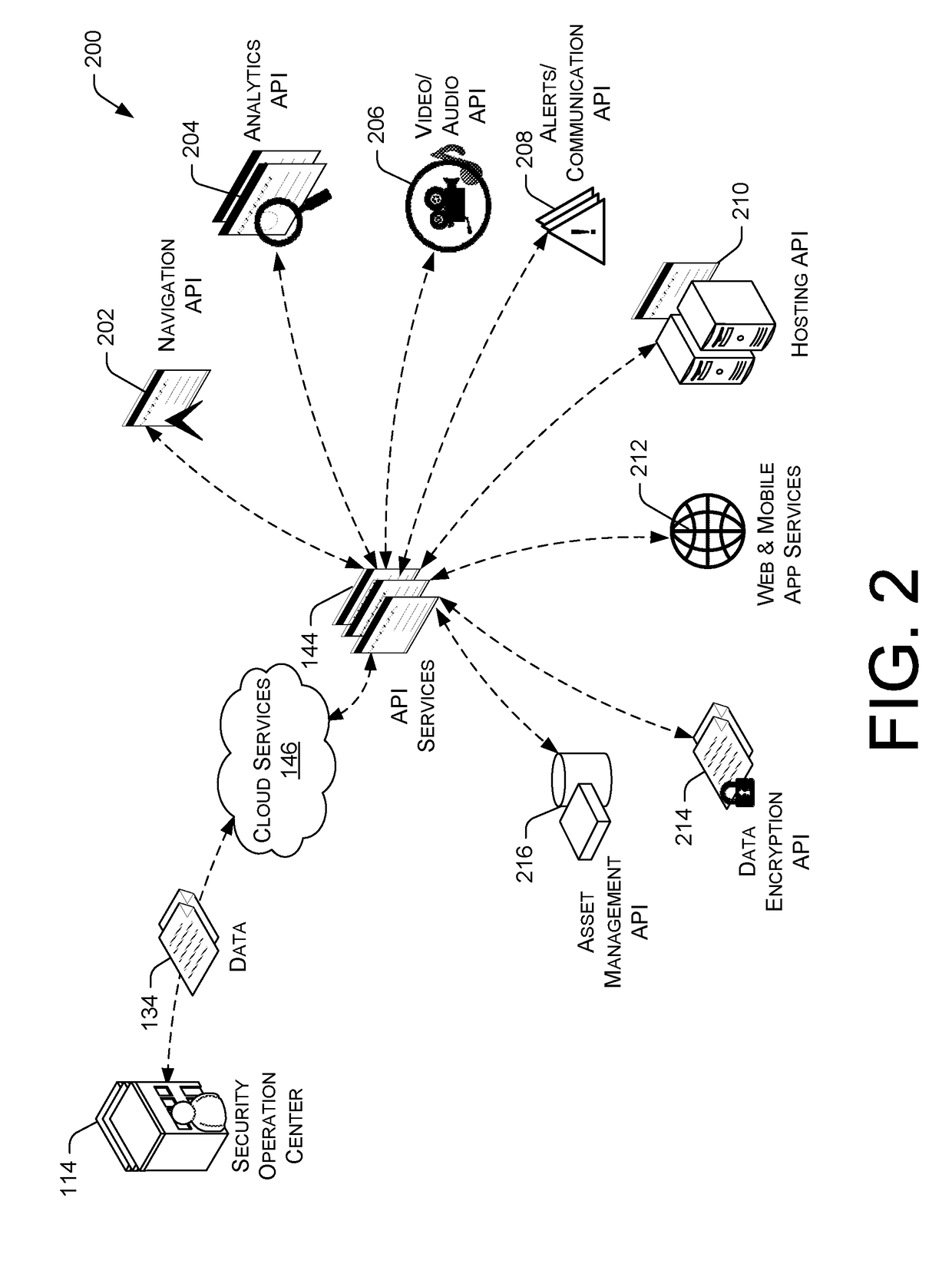
A total property security system may be implemented to conduct security and surveillance operations. The system includes security operations centers that are connected to one or more sensors and vehicles for collecting and transmitting surveillance data to a database hosted on cloud services. The collected surveillance data is analyzed in order to automatically deploy security measures and / or recommend courses of action using a rules engine that can be configured to client-specific or user-specific security needs. The cloud services can provide a set of application program interface services that can act on the surveillance operations center. Sensor fusion data and other surveillance data can be also transmitted to vetted monitoring service providers on a subscription basis to provide physical security services to the area within the property perimeter. During the subscription period, the selected monitoring service providers can obtain time-based encryption token for accessing surveillance data.
Owner:KLEIN MATIAS
Methods and apparatuses for pay-per-call advertising in mobile/wireless applications
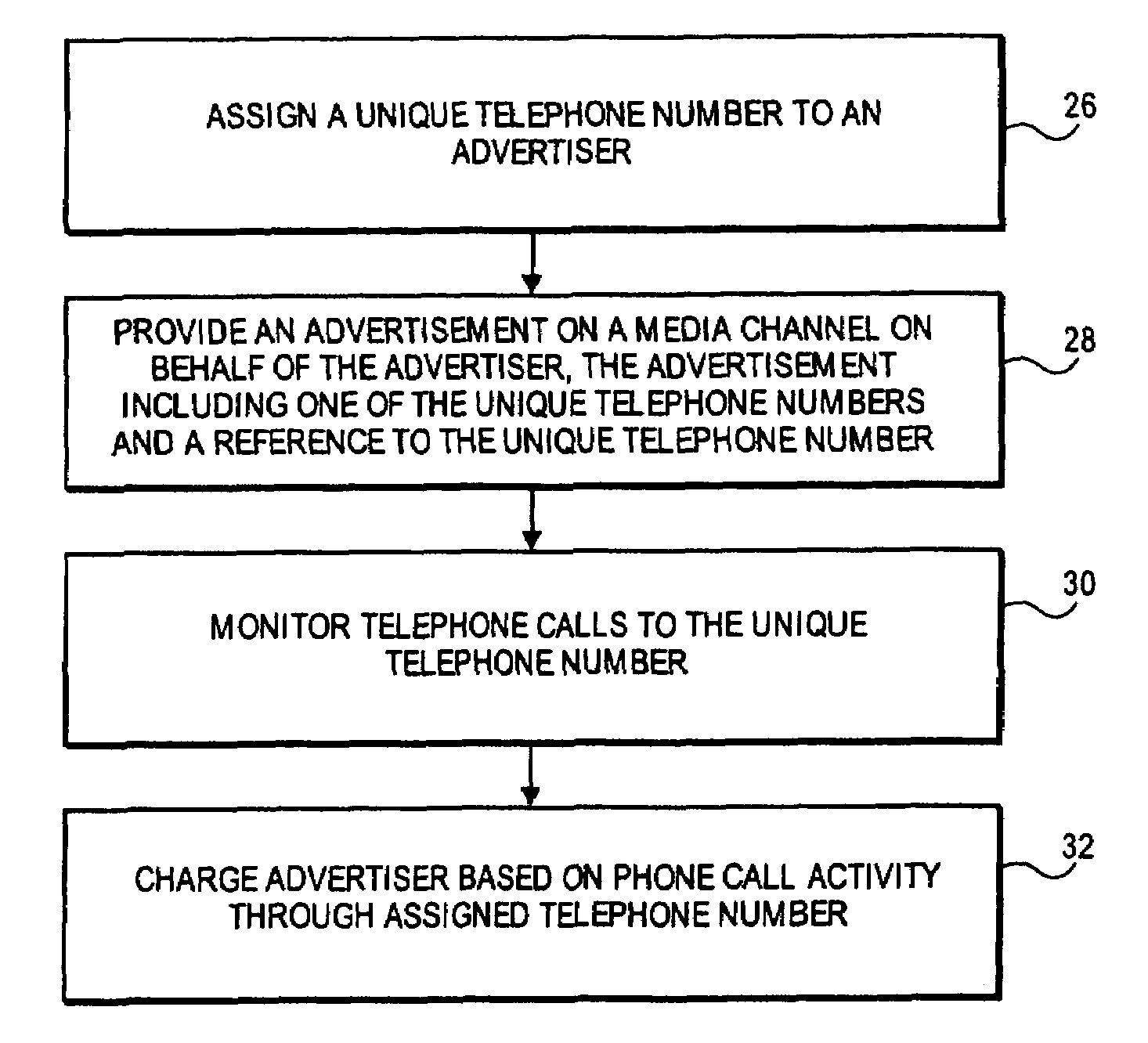
Methods and apparatuses to connect telephone calls and track information about the telephone calls resulting from advertisements on mobile / wireless media channels. In one embodiment, a method includes: assigning a telephone number to an advertiser, one of the telephone number and a reference to the telephone number to be included in an advertisement provided to an end user via a wireless media; and, monitoring telephone connections to the telephone number to bill the advertiser for the advertisement in response to each telephone connection to the telephone number. In one embodiment, a method includes: a first party providing an advertisement to a mobile device on behalf of an advertiser, the advertisement to include at least a reference to a telephonic connection with the advertiser; and, the first party collecting a fee from the advertiser in response to a telephonic connection being established between the advertiser and customer.
Owner:THRYV INC
Natural language dialogue method and natural language dialogue system
ActiveUS20140188478A1Easy to useNatural language data processingSpeech recognitionSpeech inputSpeech sound
A natural language dialogue method and a natural language dialogue system are provided. In the method, a first speech input is received and parsed to generate at least one keyword included in the first speech input, so that a candidate list including at least one report answer is obtained. According to a properties database, one report answer is selected from the candidate list, and a first speech response is output according to the report answer. Other speech inputs are received, and a user's preference data is captured from the speech inputs. The user's preference data is stored in the properties database.
Owner:VIA TECH INC
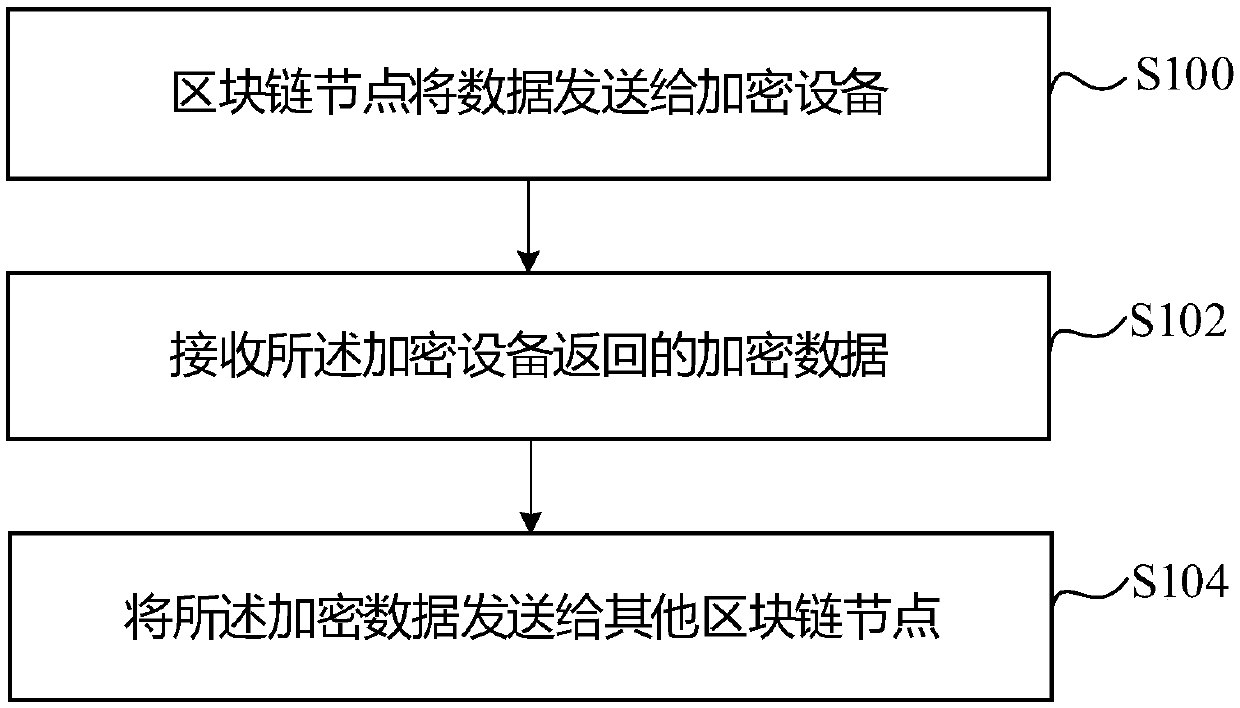
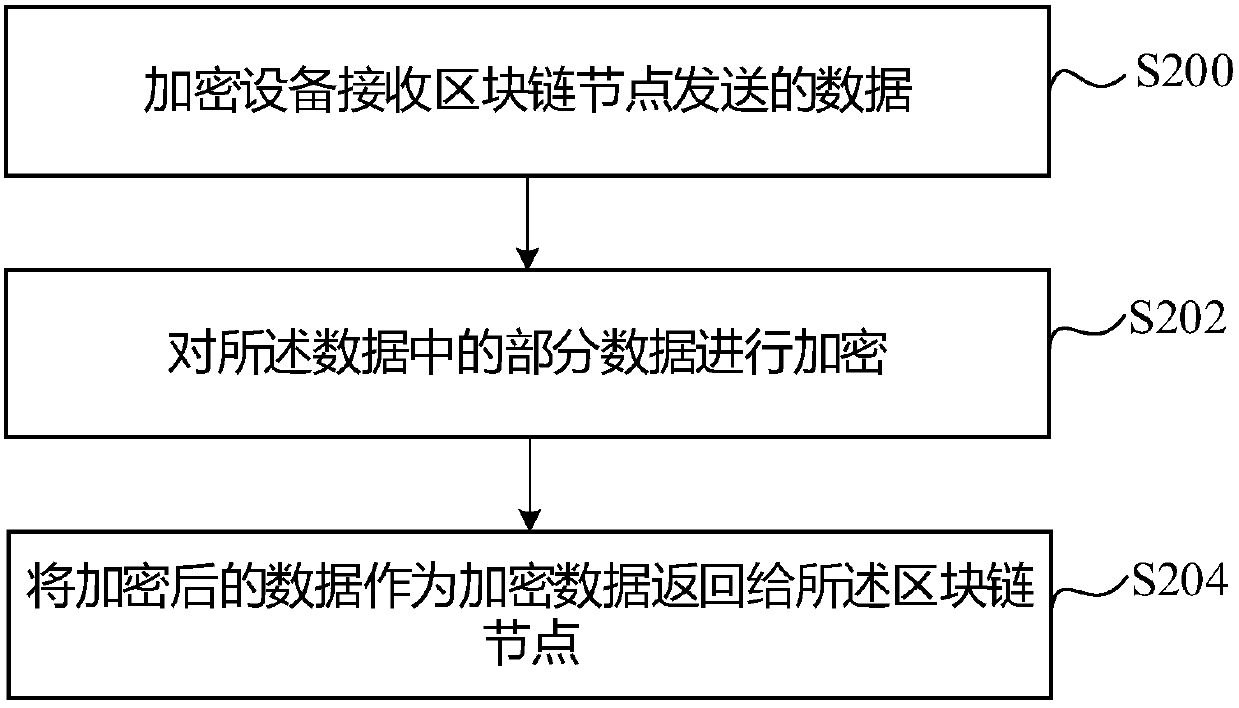
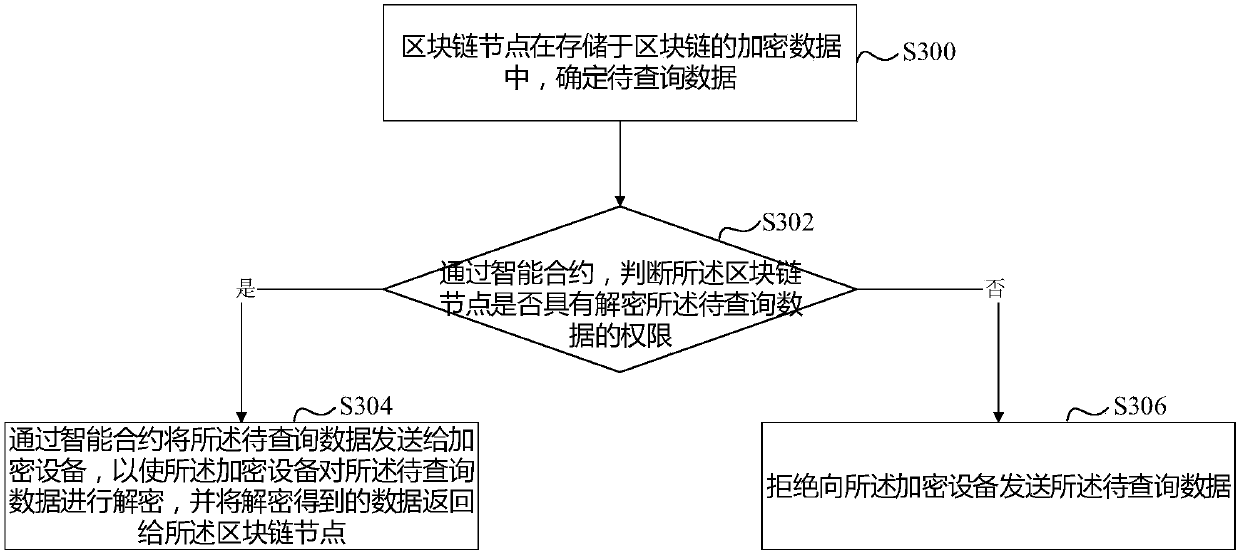
Data storage method and apparatus, and data query method and apparatus
ActiveCN107862215AImprove securityEasy accessUser identity/authority verificationDigital data protectionSmart contractChain network
Embodiments of the invention disclose a data storage method and apparatus, and a data query method and apparatus. Each institution serves as a block chain node to form a block chain network. For any block chain node, on one hand, the block chain node can send data to an encryption device for performing encryption and receive encrypted data returned by the encryption device, the encrypted data is sent to each block chain node for consensus verification, and the encrypted data passing the consensus verification is stored in a block chain; and on the other hand, through an intelligent contract, the block chain node only can obtain the data in a permission range from the block chain.
Owner:ADVANCED NEW TECH CO LTD
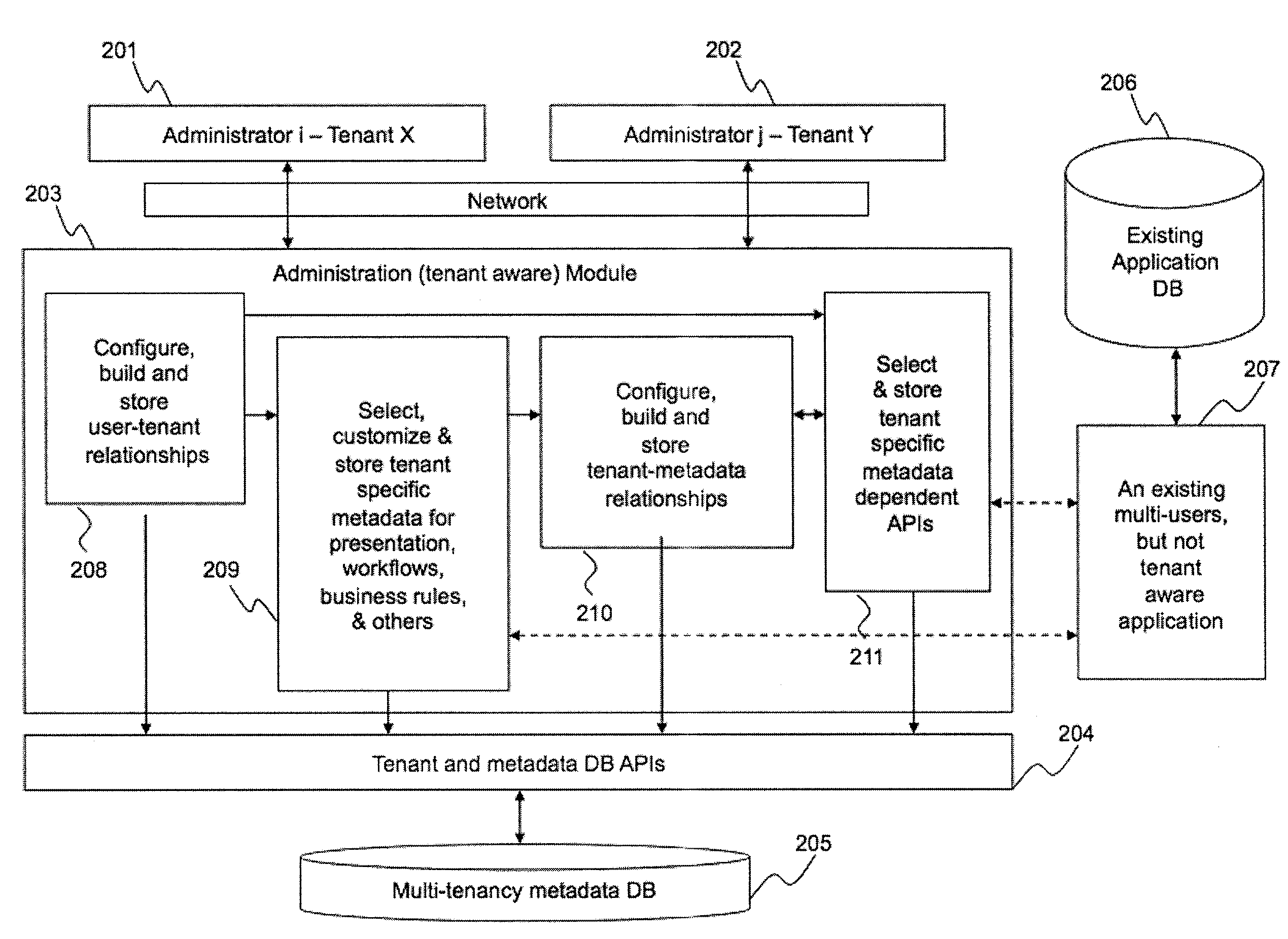
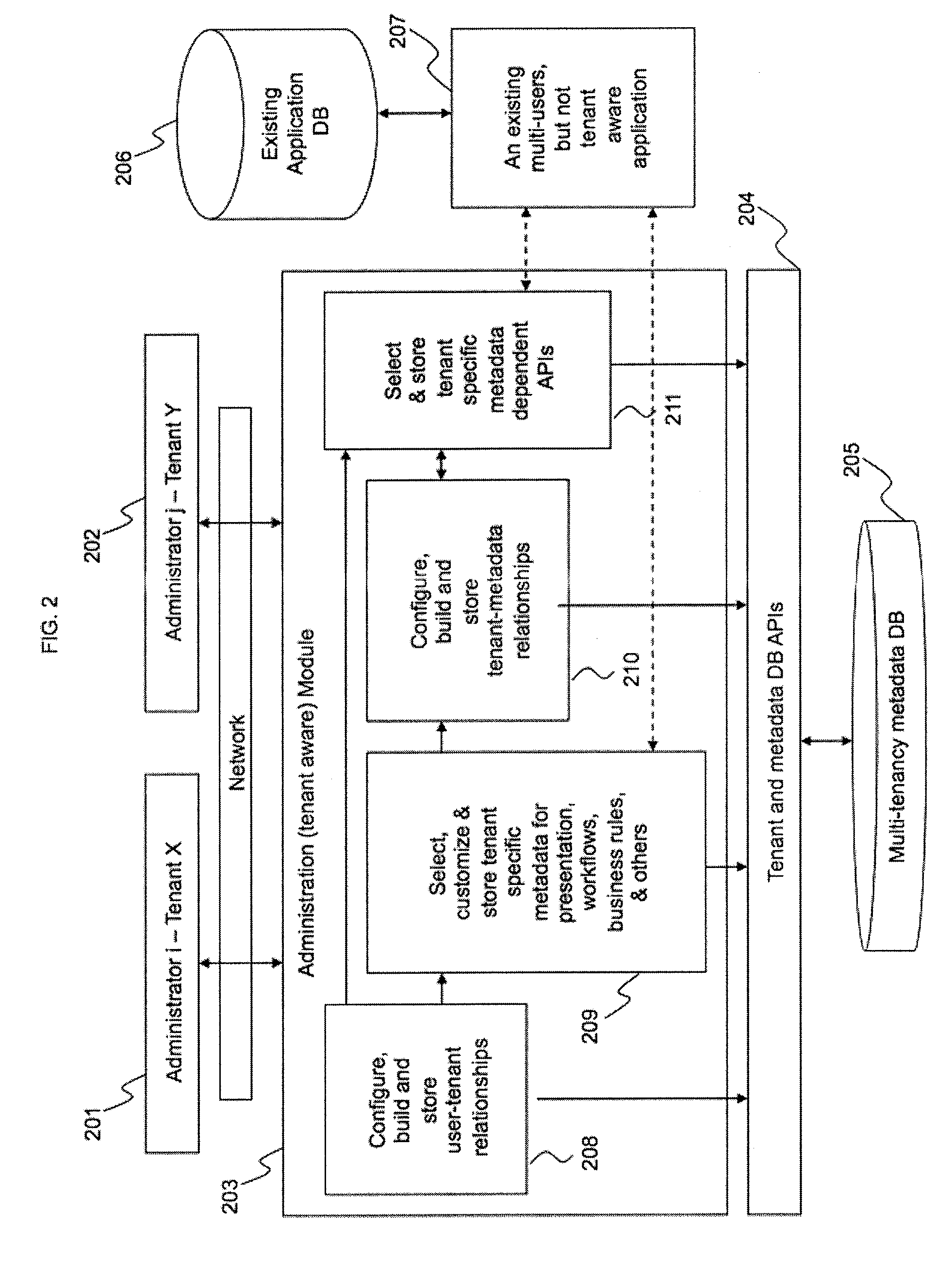
System and Methods to Create a Multi-Tenancy Software as a Service Application
ActiveUS20100005443A1Office automationOther databases queryingApplication softwareSoftware as a service
Owner:SERVICENOW INC
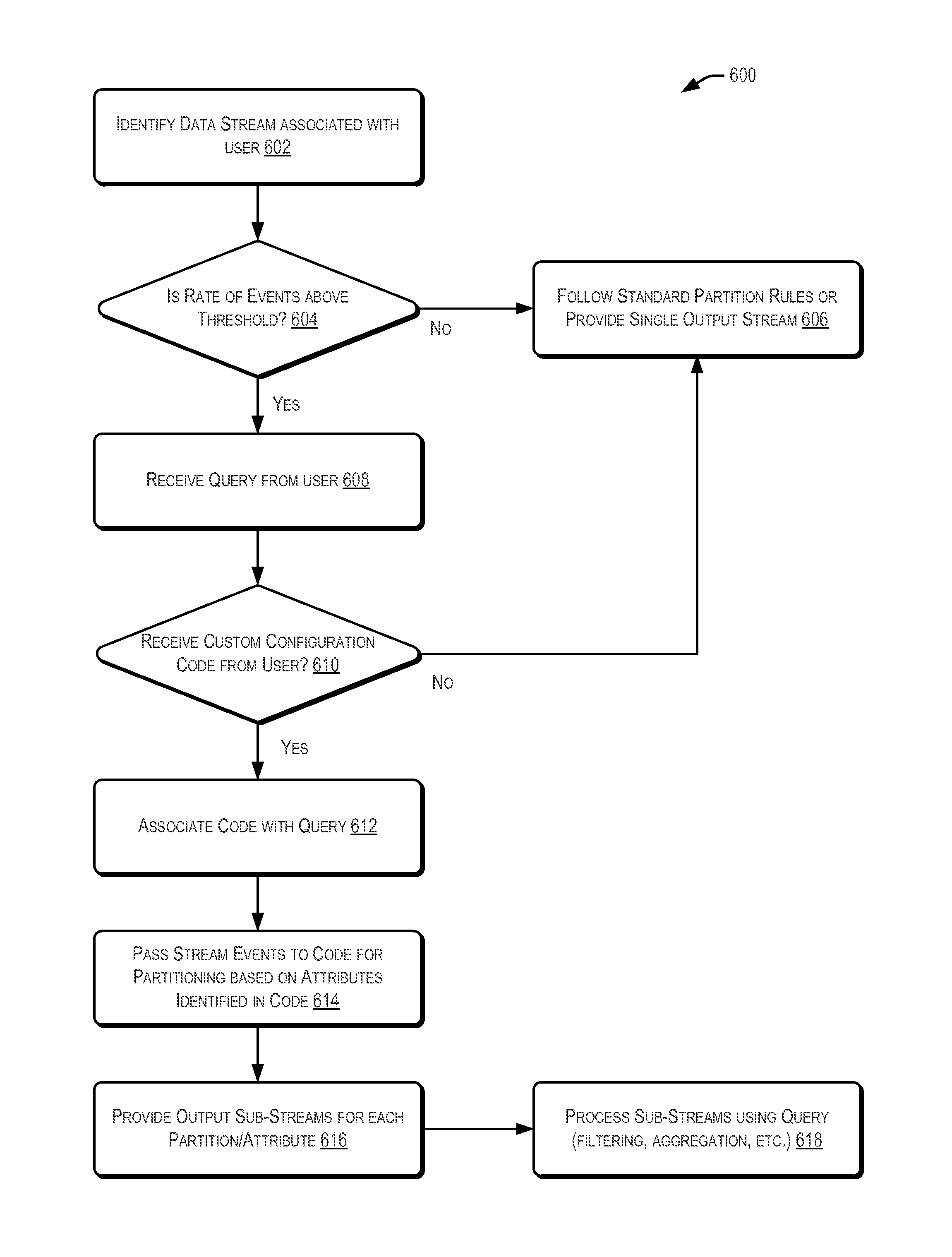
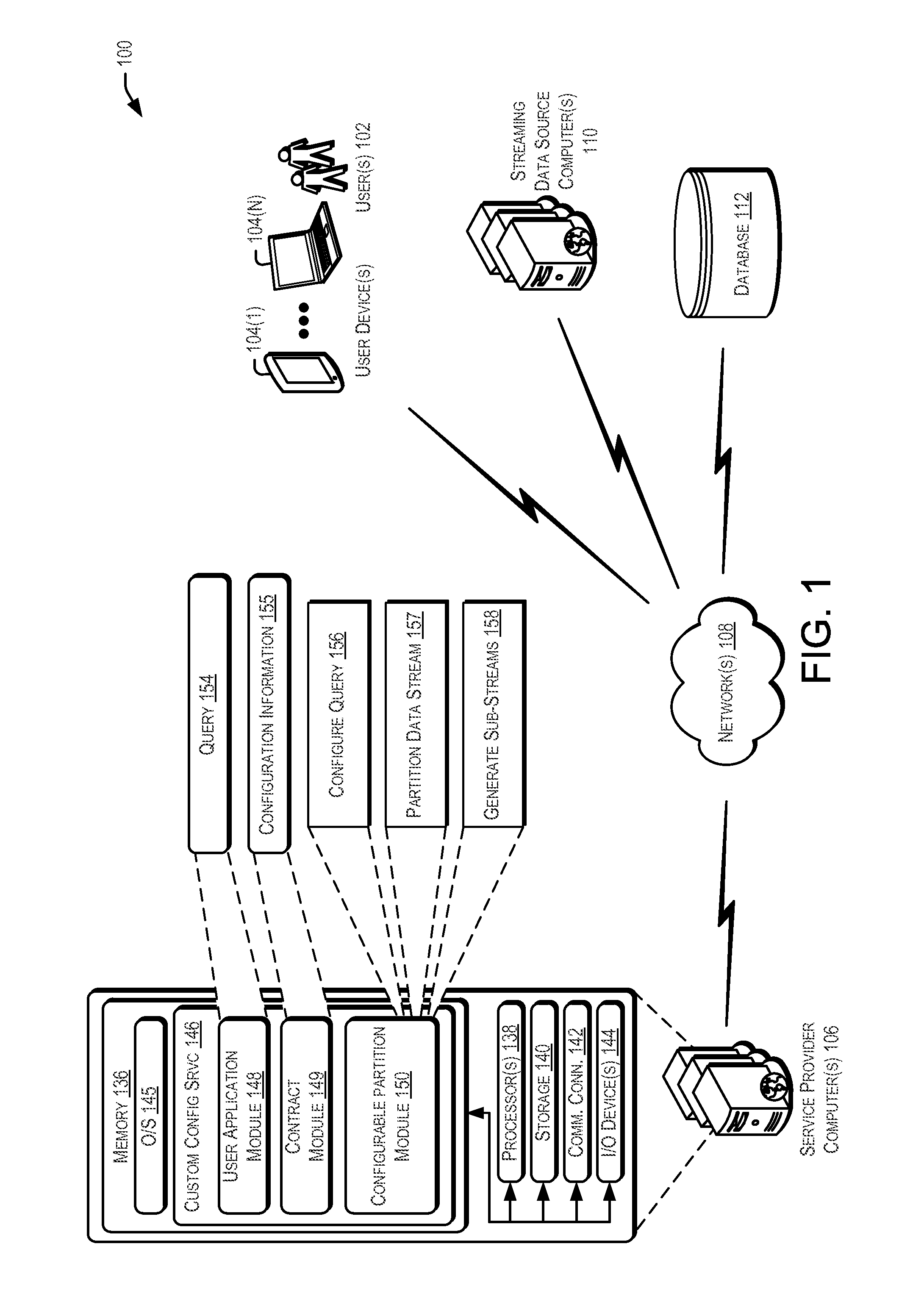
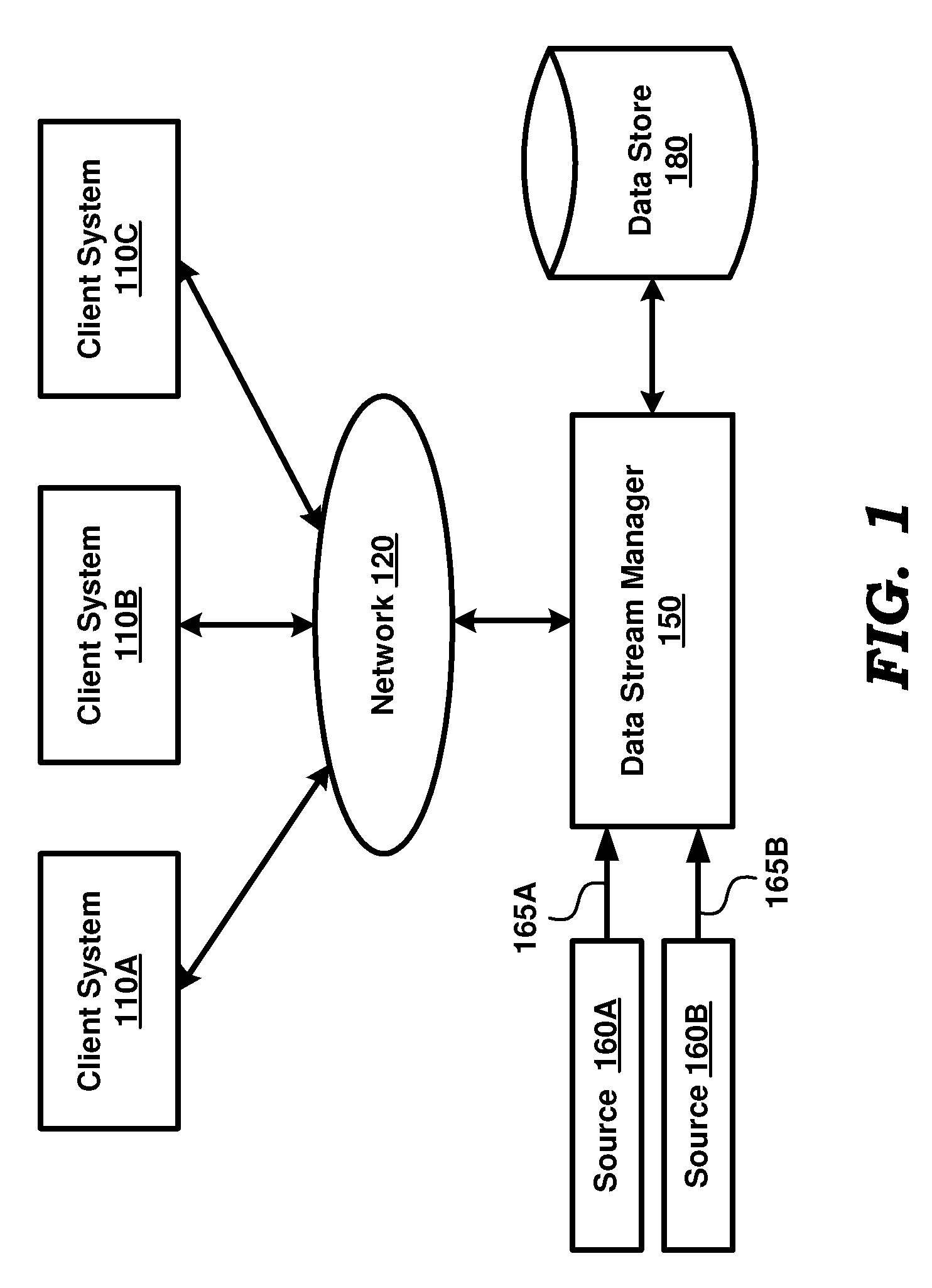
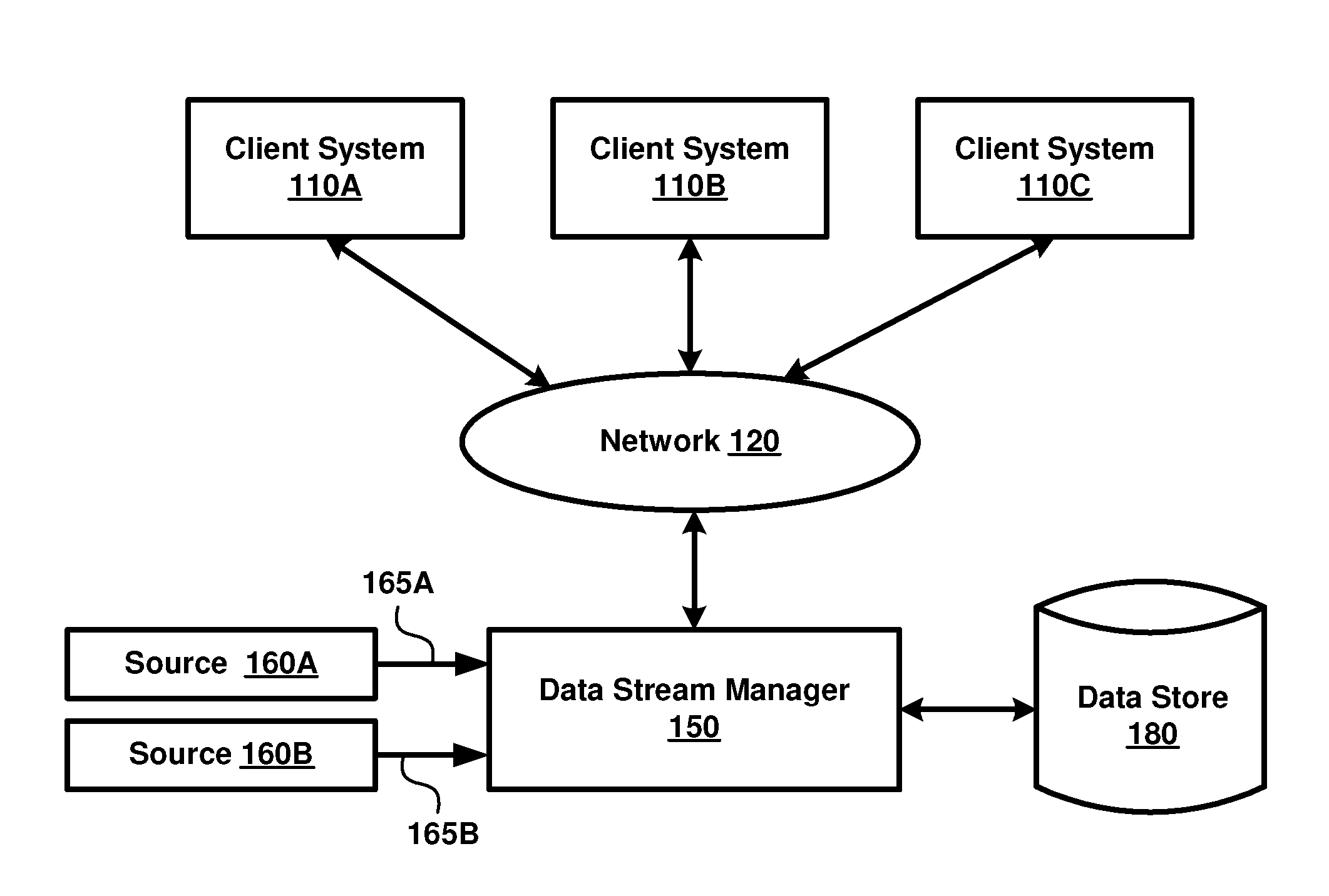
Custom partitioning of a data stream
ActiveUS9244978B2Other databases queryingSpecial data processing applicationsComputer hardwareData stream
Techniques for partitioning data streams are provided. In some examples, a query for processing at least a portion of a data stream may be identified. The data stream may be associated with a user. Additionally, in some examples, code identifying an attribute of the identified stream may be received. The code may be capable of configuring the query based at least in part on the attribute. Further, in some aspects, the code may be configured to partition the data stream into at least a sub-stream based at least in part on the attribute.
Owner:ORACLE INT CORP
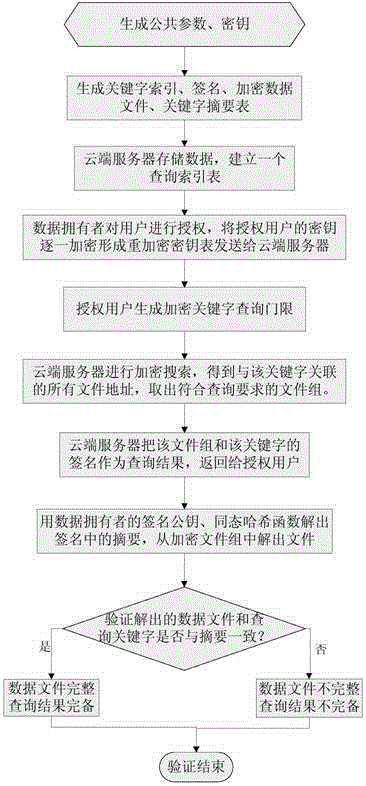
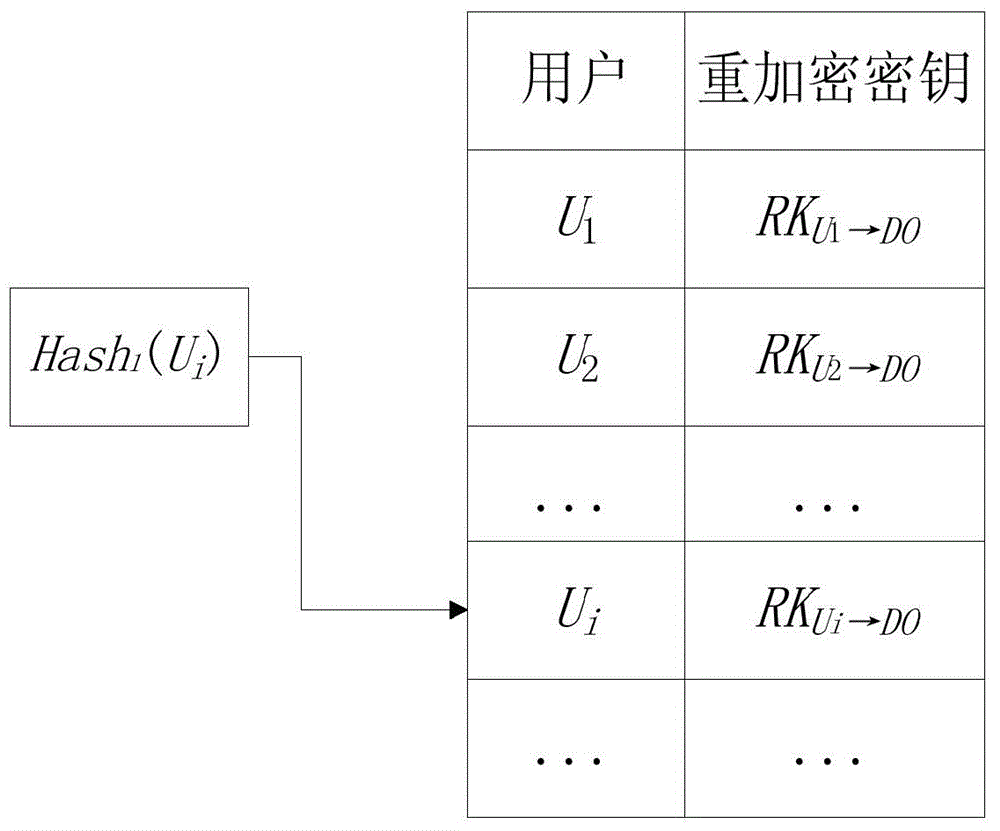
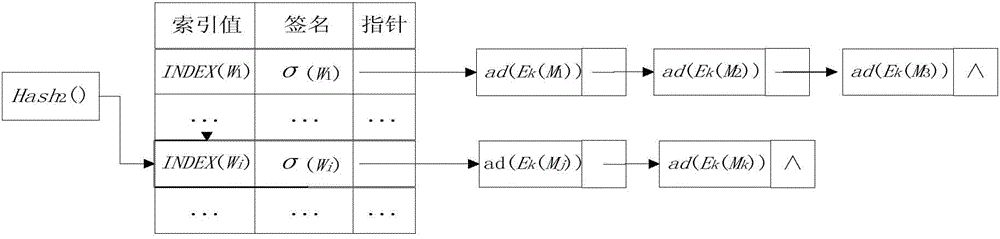
Multi-user cloud encryption keyboard searching method capable of verifying integrity and completeness
ActiveCN104394155AQuery does not affectCompleteness verificationUser identity/authority verificationOther databases queryingData integrityPassword
The invention is mainly used for searching a searchable encryption technology under a public key password system, and discloses a multi-user cloud encryption keyboard searching method capable of verifying integrity and completeness. The method can be used for verifying the search result completeness and the outsourced data integrity under the cloud environment and setting the multi-user authority. The method can be used for realizing the verification of the search result completeness and the outsourced data integrity by using signatures to bind keyword indexes and associated encryption files thereof, realizing multi-user privacy query by using a re-encryption technology and dynamically updating the query authority of the user. Moreover, the index structure and the query mechanism of the encrypted file are further optimized, so that the query efficiency is improved by using hash query in the query process, and the rapid access to the cloud data is realized.
Owner:广州市瑞玛信息技术有限公司 +1
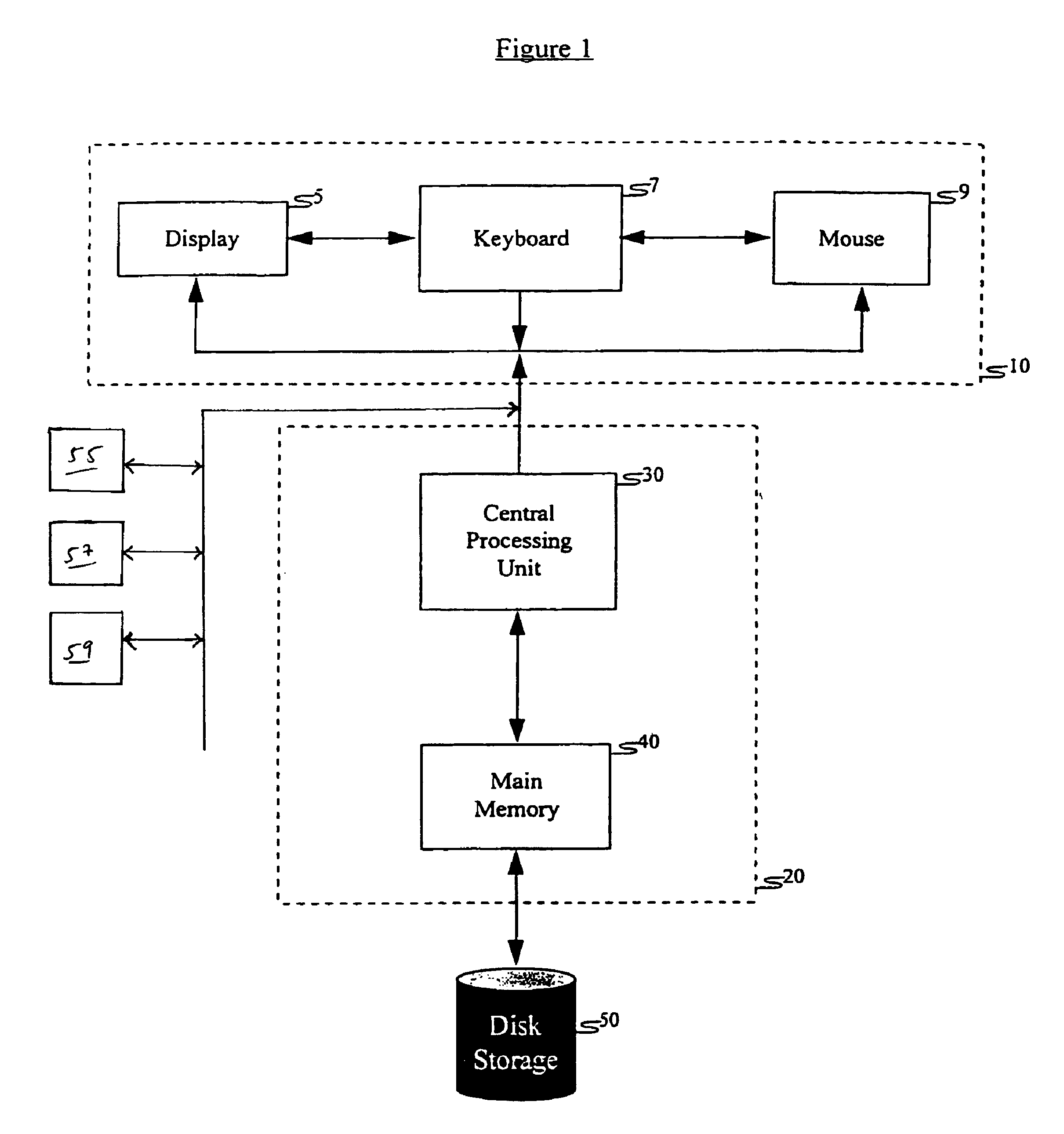
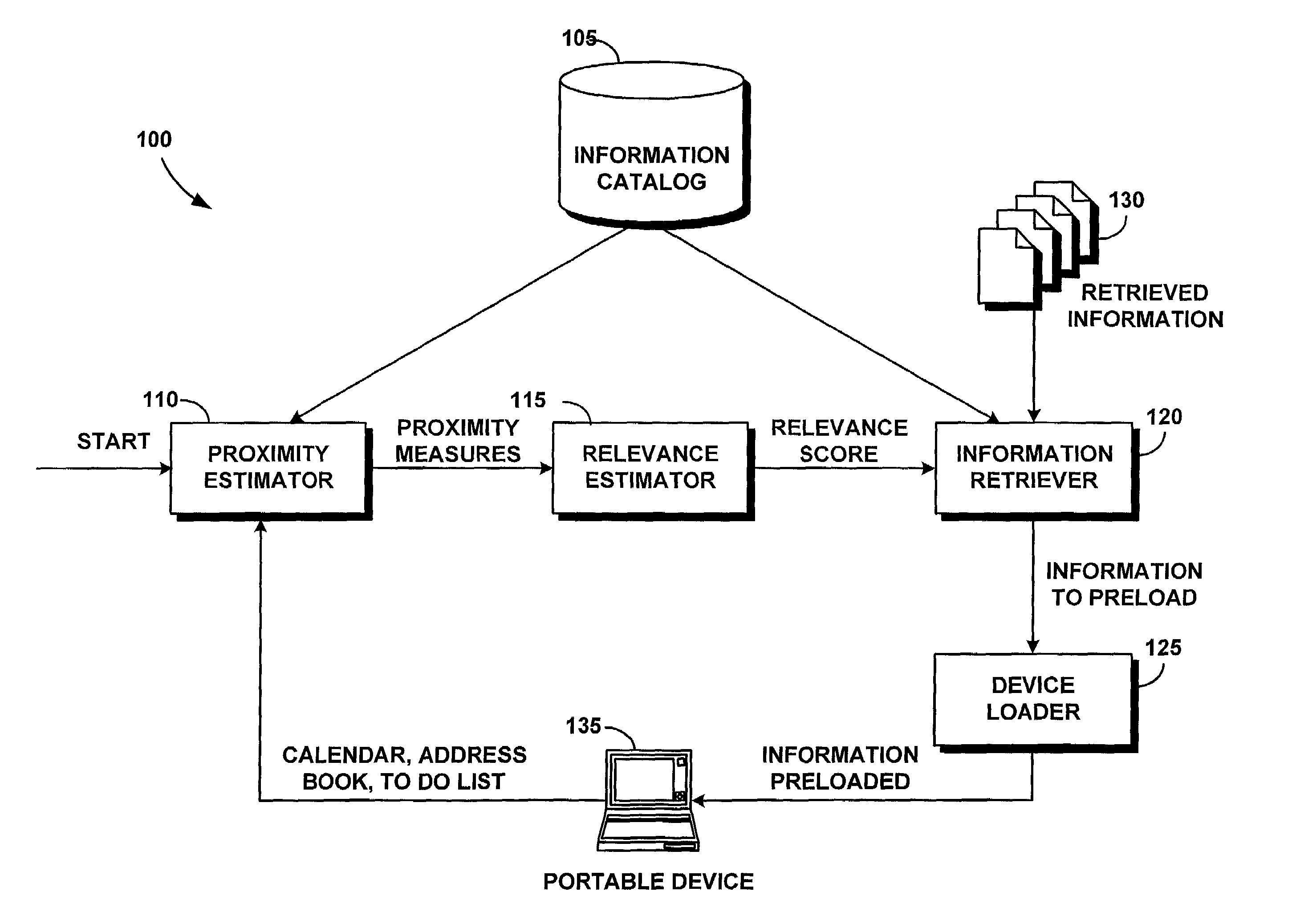
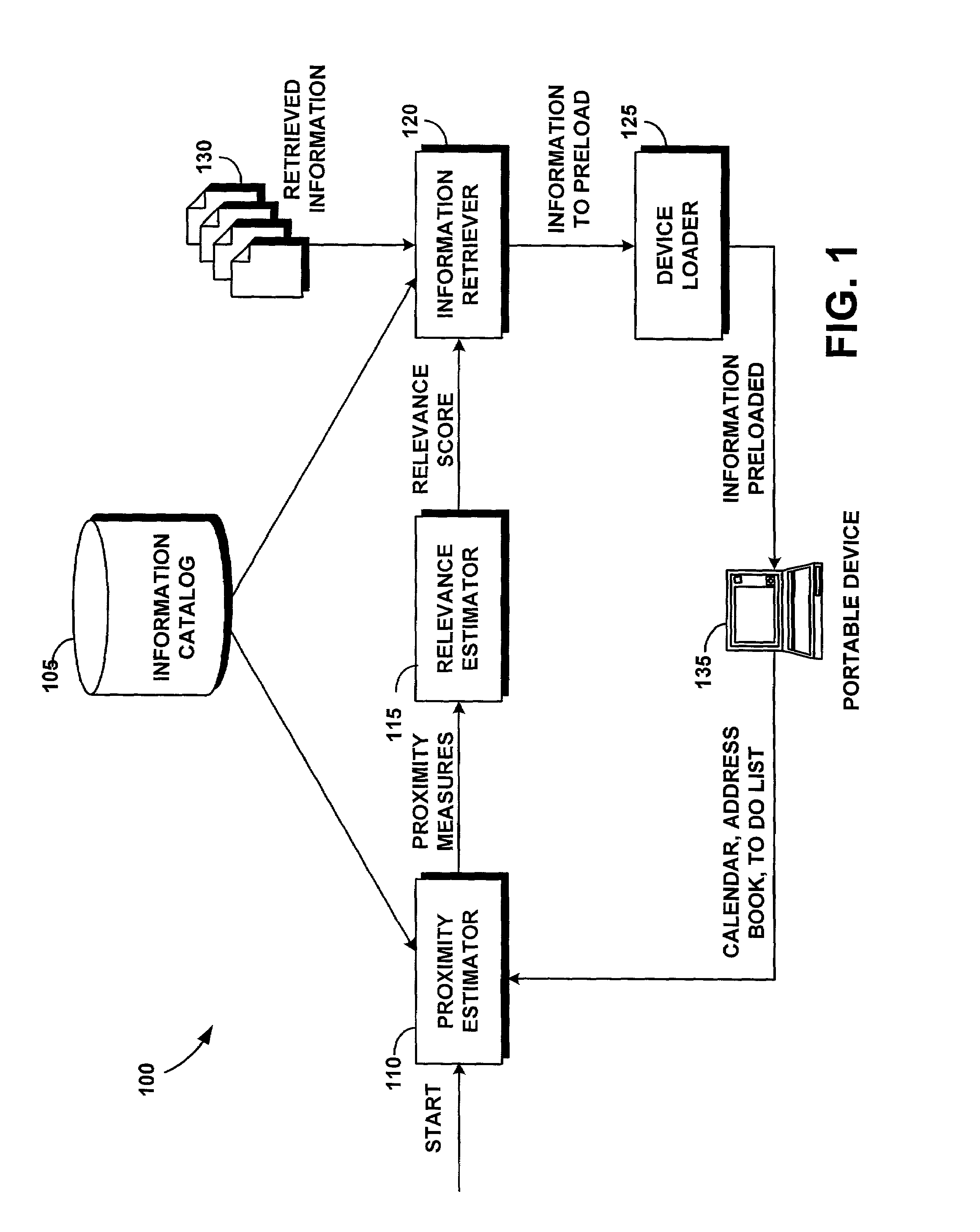
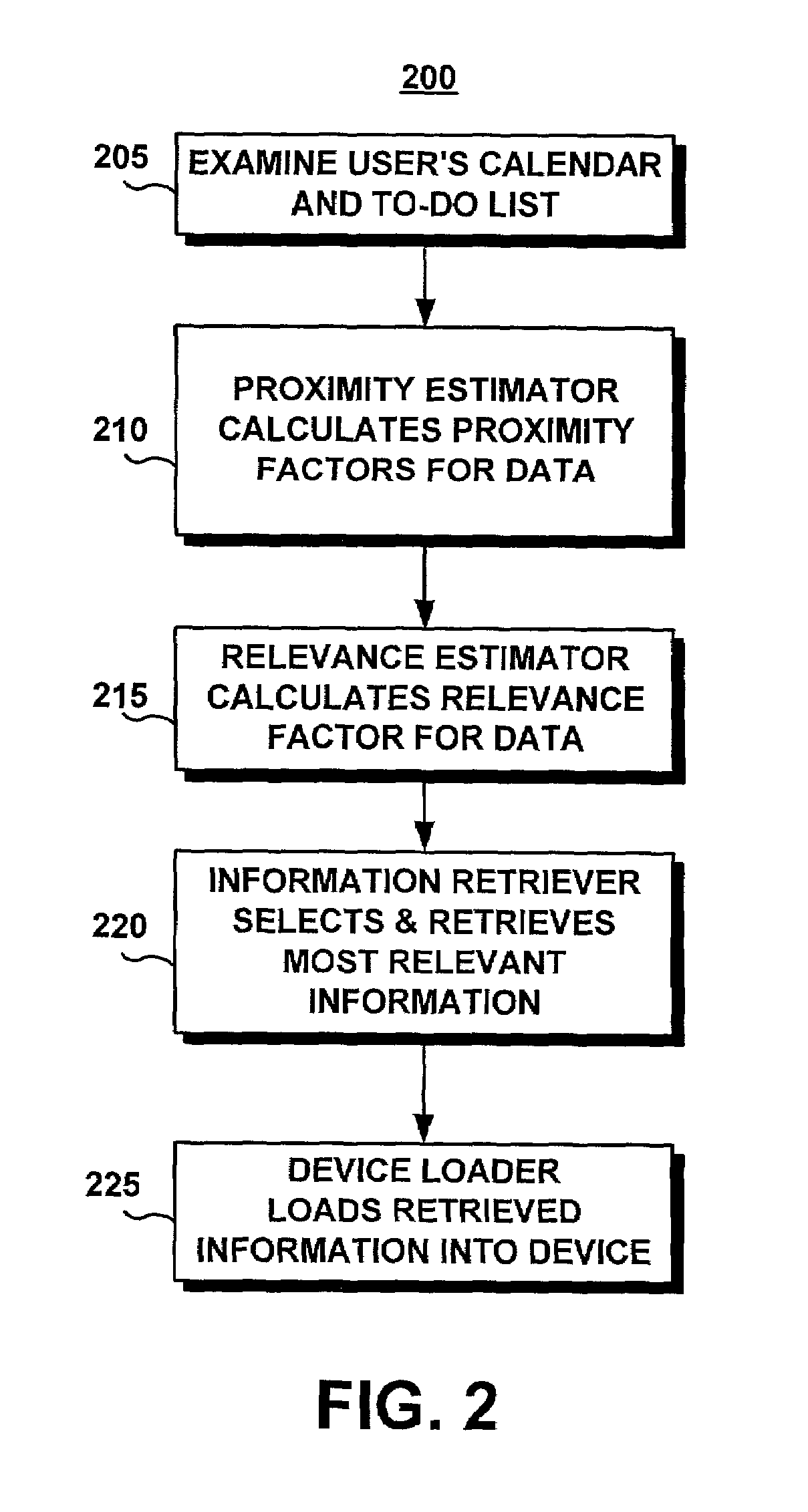
Automatic relevance-based preloading of relevant information in portable devices
ActiveUS7610365B1Facilitate actionMinimal effortReservationsMultiple digital computer combinationsRelevant informationProximity measure
A system for automatic proximity-based preloading of relevant information in portable devices pre-loads a portable device such as a mobile telephone, a personal digital assistant (PDA) or portable computer before the occurrence of a trip or event, with information relevant to the user's current or upcoming tasks. The system locates and loads into the portable device only the information required by the user for near term projects, meetings, or trips. The system is generally comprised of an information catalog, a proximity estimator, a relevance estimator, an information retriever, and a device loader. The information catalog contains a list of the information sources and items to which the user has access and from which the system of the invention will retrieve data to be loaded into the mobile device. The proximity estimator determines the proximity of various relevant information items to the user's tasks based on distance, time, and / or association. The relevance estimator combines these proximity measures into a single relevance score. The most relevant information is retrieved by the information retriever and loaded onto the portable device by the device loader.
Owner:CITRIX SYST INT
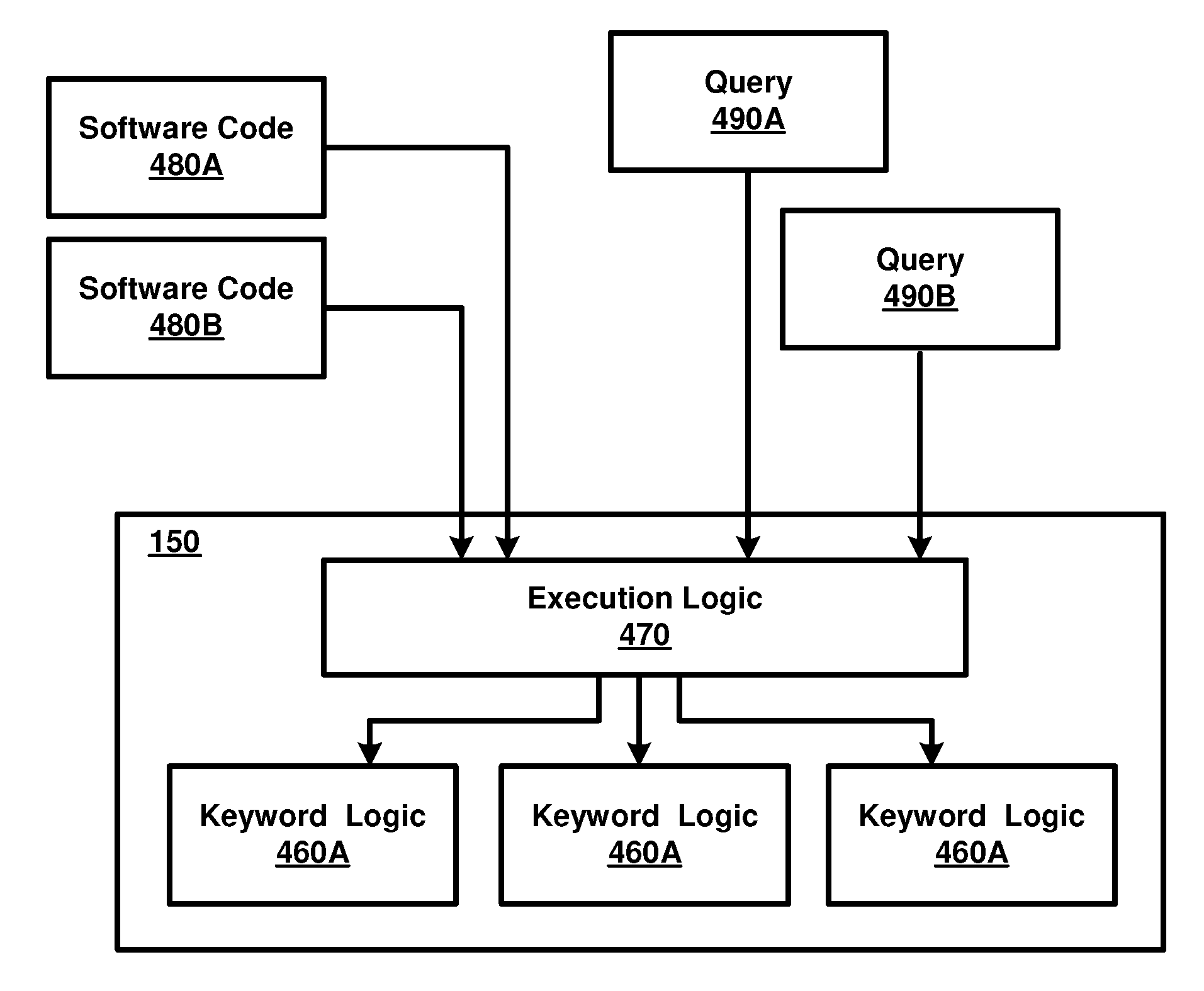
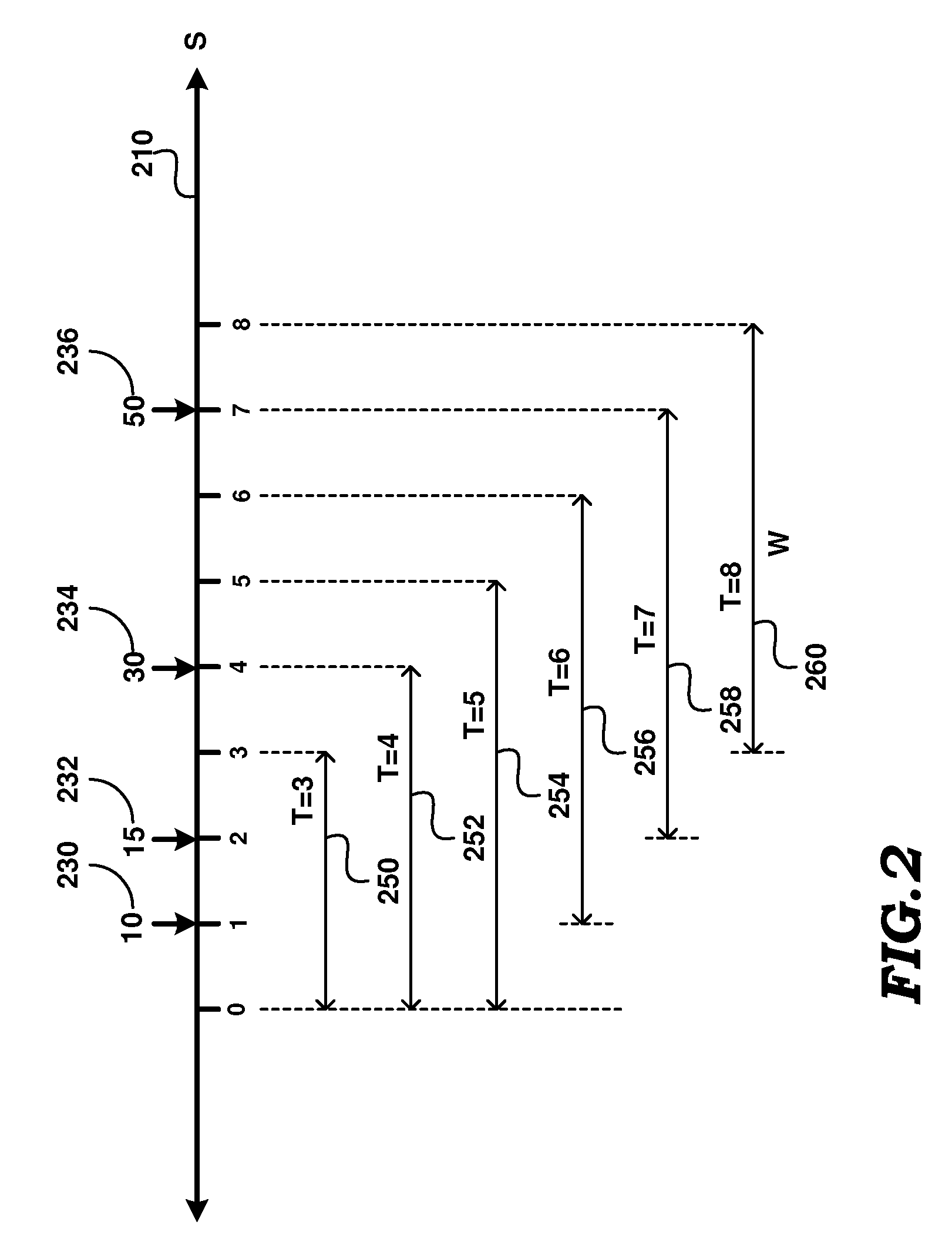
Facilitating Flexible Windows In Data Stream Management Systems
Facilitating flexible windows in querying continuous data streams. In one embodiment, a software code is associated with a window, wherein execution of the software code determines the values to be included in the window. On receiving a query indicating the window, the result of the query is generated based on the values in the window determined by execution of the software code. The software code may be identified by an identifier and thus used for different queries on the same or different continuous data streams.
Owner:ORACLE INT CORP
Specifying A Family Of Logics Defining Windows In Data Stream Management Systems
ActiveUS20090112803A1Digital data processing detailsOther databases queryingComputer scienceContinuous data
Simplifying a user's task in specifying a family of logics, with each logic designed to potentially select different subsets of values from the same continuous data stream at the same time instant. In one embodiment, all the logics are together specified by a common user specified software code design to accept a set of parameters, with different logics resulting from execution of the software code with different parametric values. Thus, when closely related family of logics are to be developed, the common software code may be formulated, with the code being designed to accept parameters and providing different logics for different sets of parametric values corresponding to the parameters.
Owner:ORACLE INT CORP
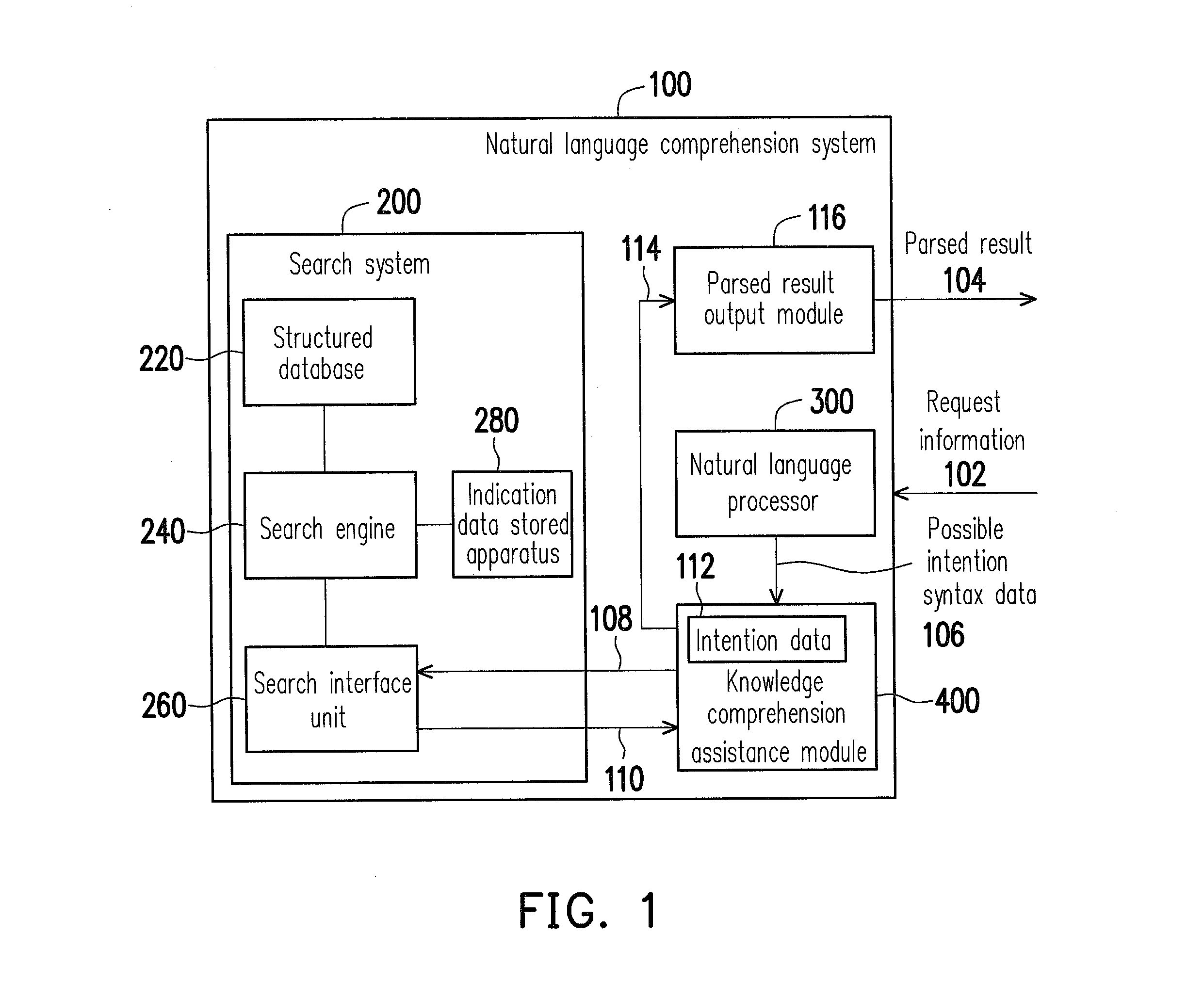
Method and device for monitoring and analyzing signals
InactiveUS20080109417A1Data processing applicationsDigital data processing detailsReference databaseData mining
A method and system for monitoring and analyzing at least one signal are disclosed. An abstract of at least one reference signal is generated and stored in a reference database. An abstract of a query signal to be analyzed is then generated so that the abstract of the query signal can be compared to the abstracts stored in the reference database for a match. The method and system may optionally be used to record information about the query signals, the number of matches recorded, and other useful information about the query signals. Moreover, the method by which abstracts are generated can be programmable based upon selectable criteria. The system can also be programmed with error control software so as to avoid the re-occurrence of a query signal that matches more than one signal stored in the reference database.
Owner:WISTARIA TRADING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com