Multi-user cloud encryption keyboard searching method capable of verifying integrity and completeness
A search method and keyword technology, applied in the field of multi-user cloud encryption keyword search, can solve problems such as insufficient query efficiency to meet cloud applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
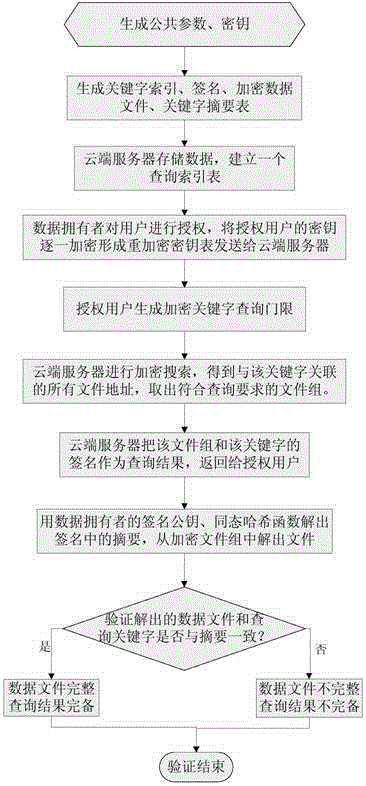
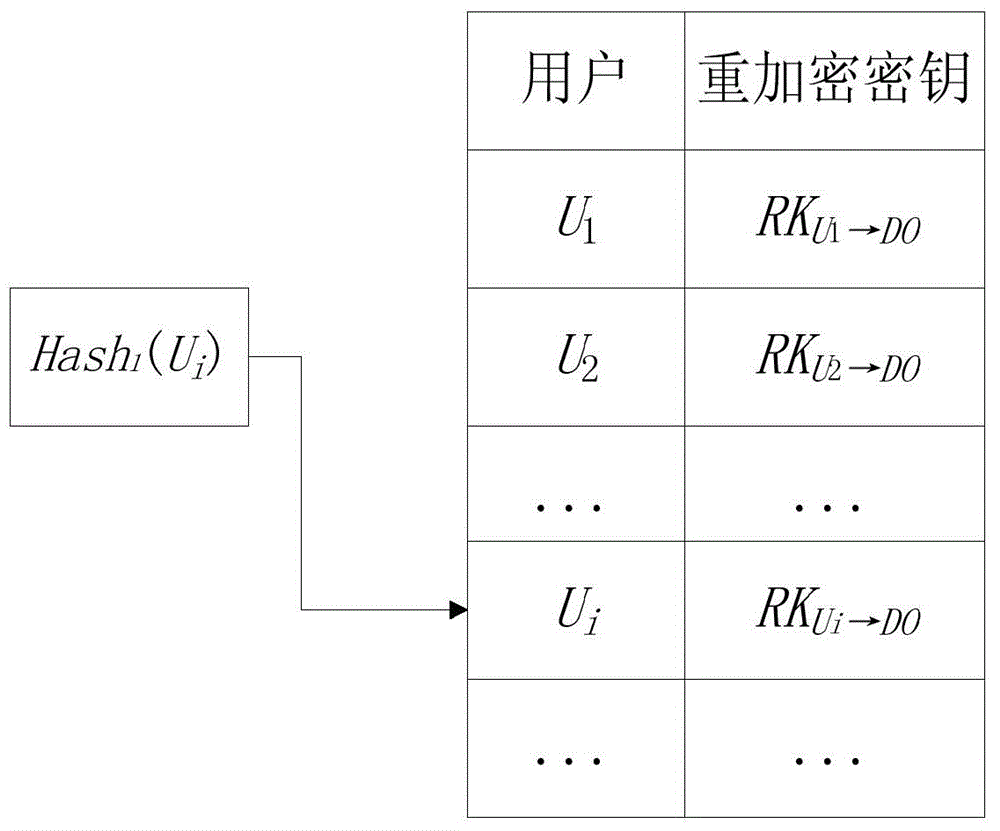
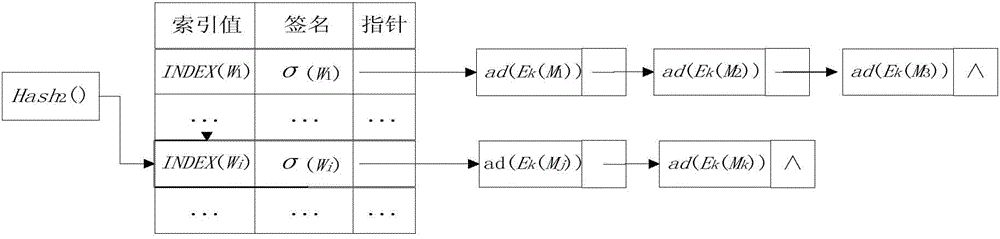
[0062] The present invention mainly studies the searchable encryption technology under the public key cryptography system, and proposes a multi-user cloud encryption keyword search method that can verify integrity and completeness. This method realizes the query and retrieval function of encrypted data, and protects The user's query privacy is guaranteed. On the basis of realizing the basic encrypted search, the present invention aims at the characteristics of multi-user access and large data volume storage in the cloud environment, proposes multi-user query settings, optimizes the index structure and query mechanism of encrypted files, and realizes dynamic user authority control and The ability to quickly retrieve encrypted data. The invention also designs a verification mechanism for completeness of query results and integrity of outsourced data, and uses homomorphic hash functions, signature binding keyword indexes and associated encrypted files to provide verification func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com