Patents
Literature
265 results about "Physical security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques.
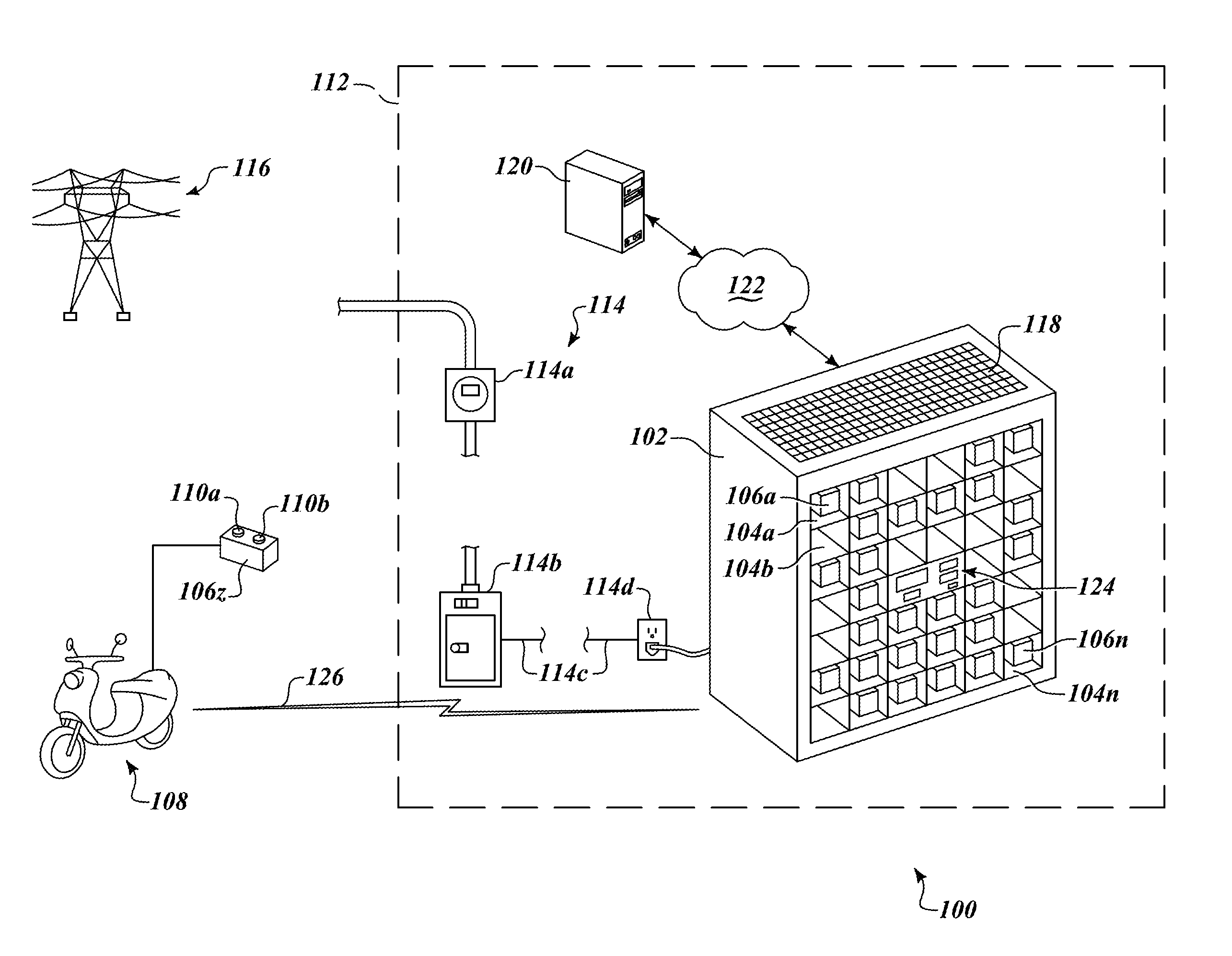
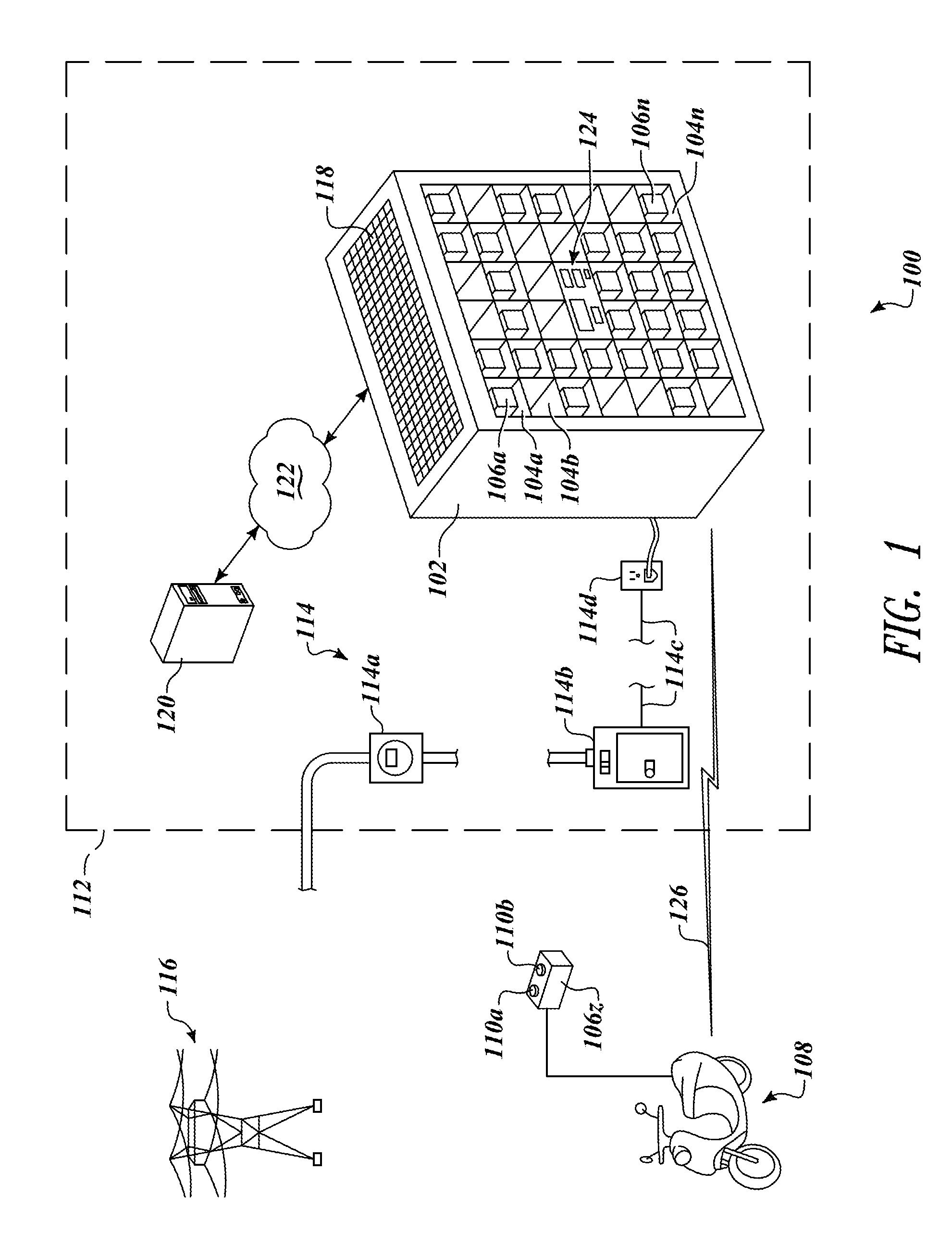
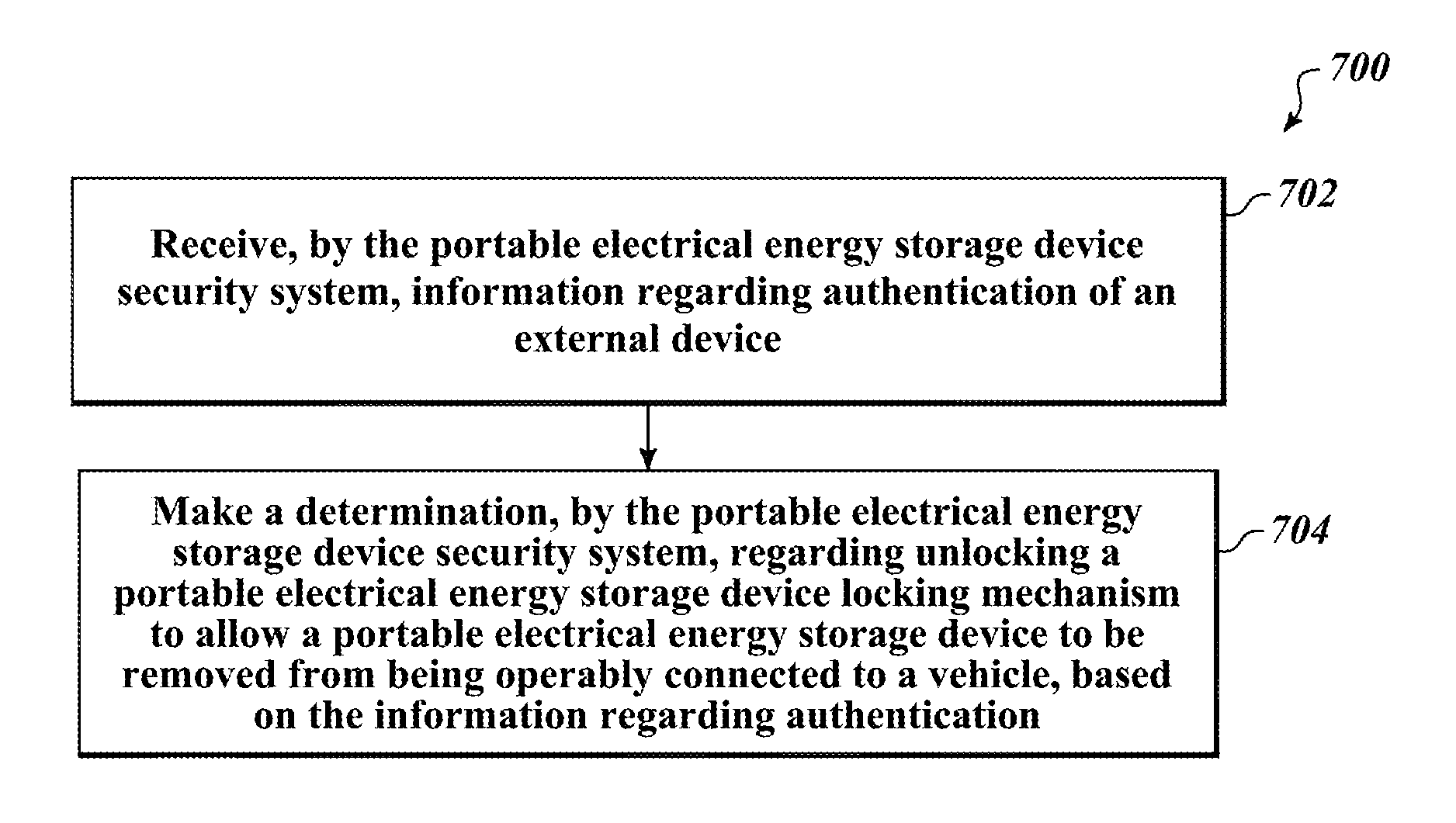
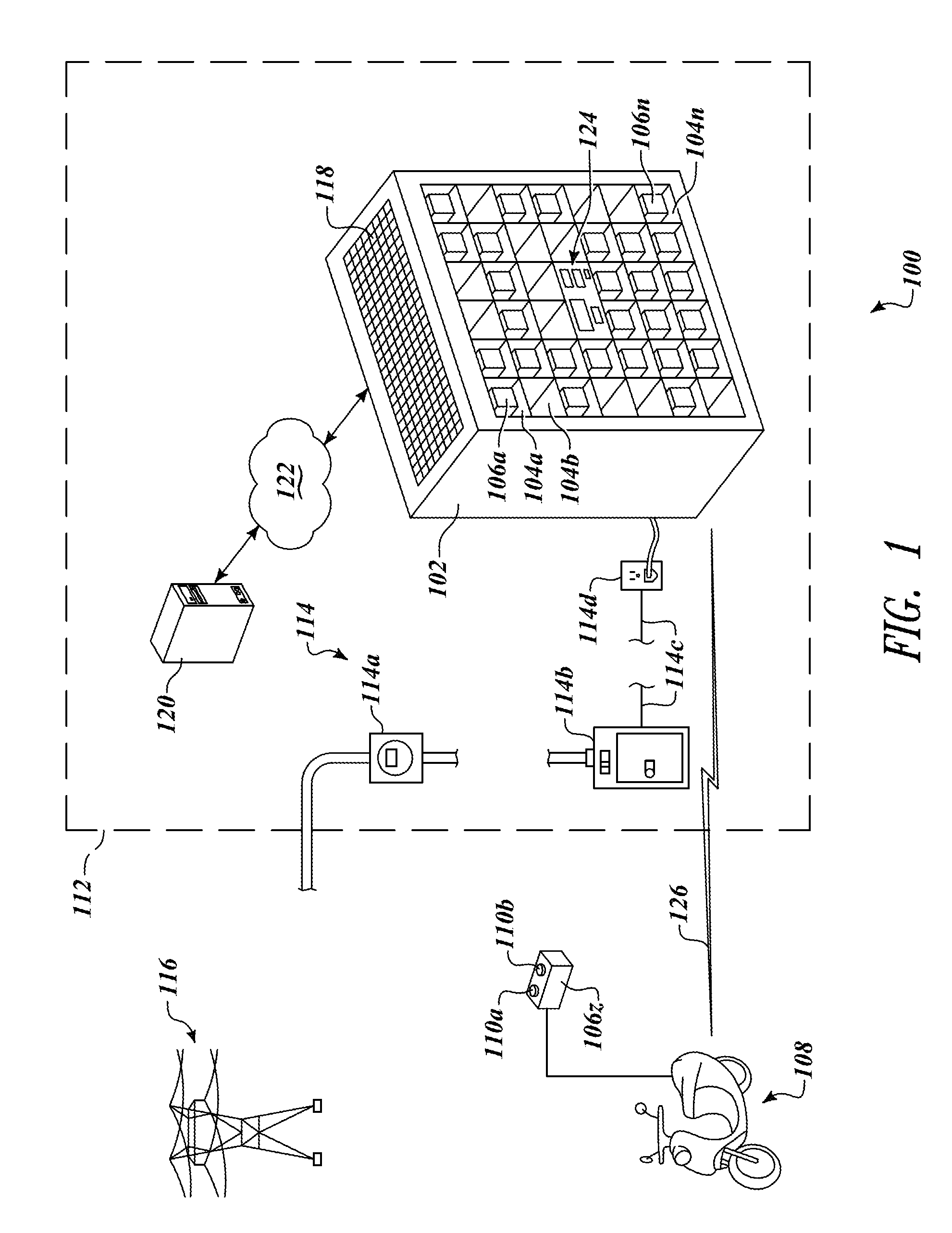
Apparatus, method and article for physical security of power storage devices in vehicles
ActiveUS8560147B2Registering/indicating working of vehiclesNavigation instrumentsPhysical securityIn vehicle
A network of collection, charging and distribution machines collect, charge and distribute portable electrical energy storage devices (e.g., batteries, supercapacitors or ultracapacitors). To avoid theft and tampering of the portable electrical energy storage devices, by default, each portable electrical energy storage device is locked in and operably connected to the vehicle to which it provides power unless the vehicle comes within the vicinity of a collection, charging and distribution machine or other authorized external device such as that in a service center. Once within the vicinity of a collection, charging and distribution machine or other authorized external device a locking mechanism in the vehicle or within the portable electrical energy storage device unlocks and allows the portable electrical energy storage device to be exchanged or serviced.
Owner:GOGORO
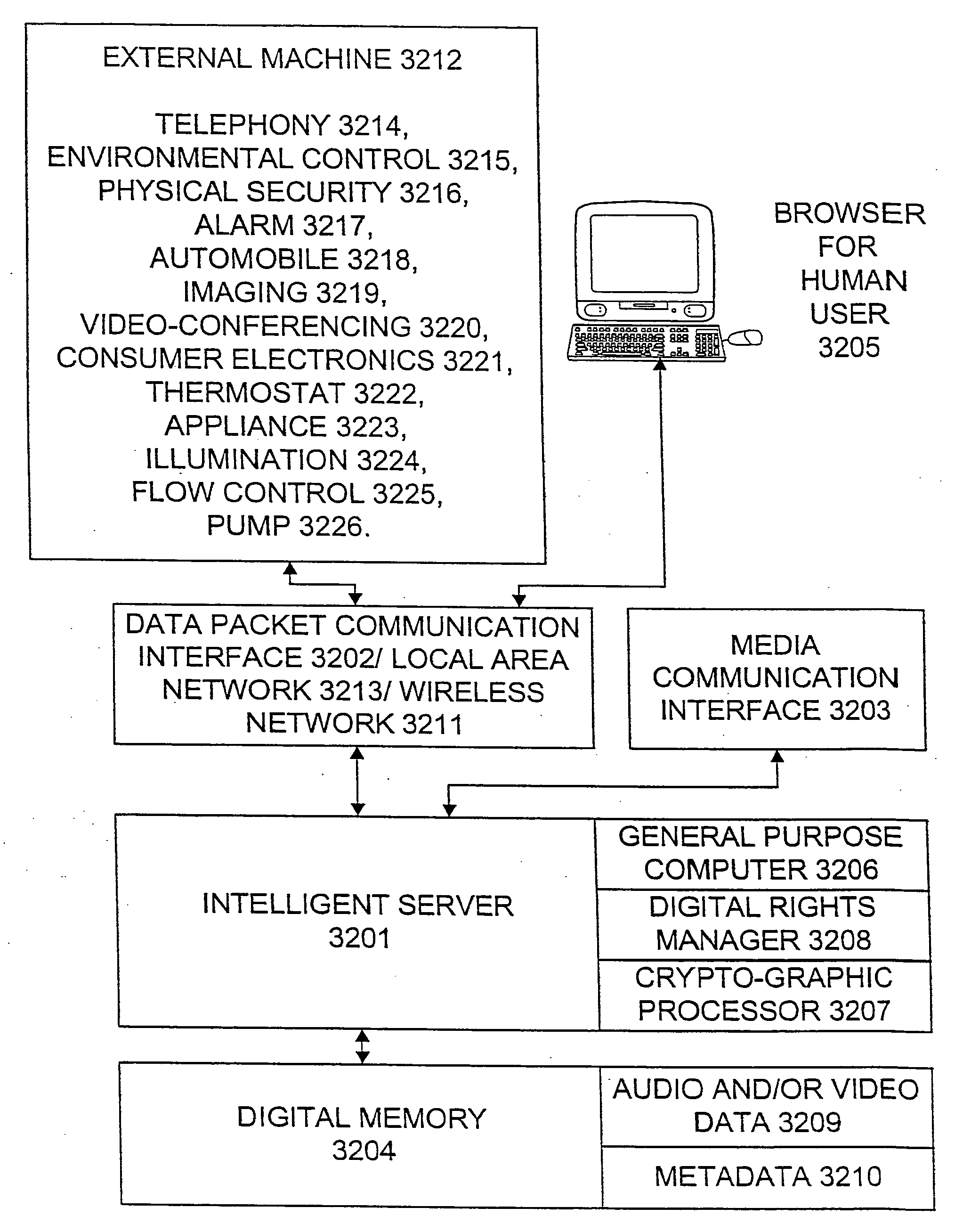
Internet appliance system and method
InactiveUS20060200253A1Minimize timeTelevision system detailsAdvertisementsPhysical securityThe Internet
An Internet appliance, comprising, within a single housing, packet data network interfaces, adapted for communicating with the Internet and a local area network, at least one data interface selected from the group consisting of a universal serial bus, an IEEE-1394 interface, a voice telephony interface, an audio program interface, a video program interface, an audiovisual program interface, a camera interface, a physical security system interface, a wireless networking interface; a device control interface, smart home interface, an environmental sensing interface, and an environmental control interface, and a processor, for controlling a data transfer between the local area network and the Internet, and defining a markup language interface communicated through a packet data network interface, to control a data transfer or control a remote device.
Owner:BLANDING HOVENWEEP
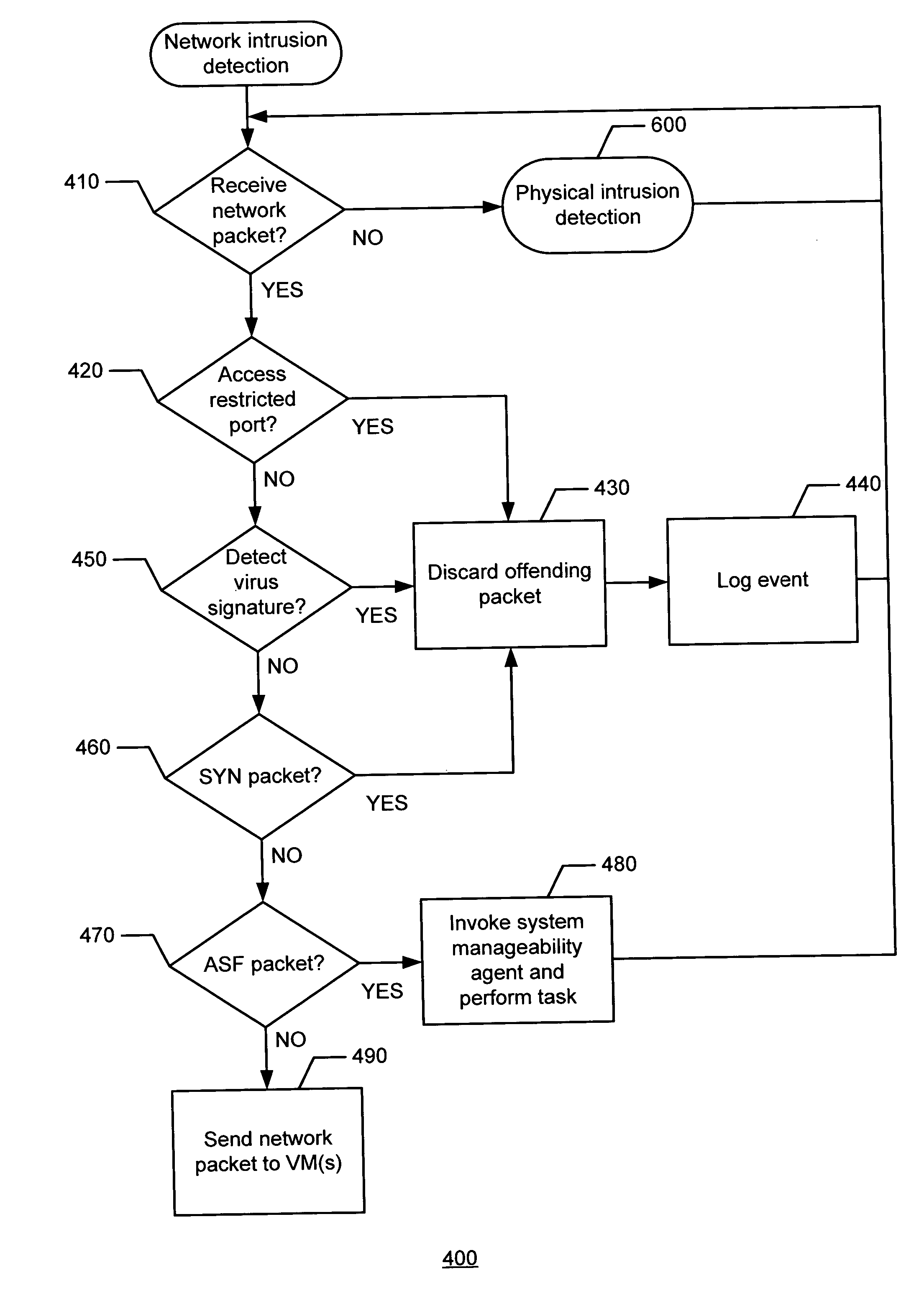
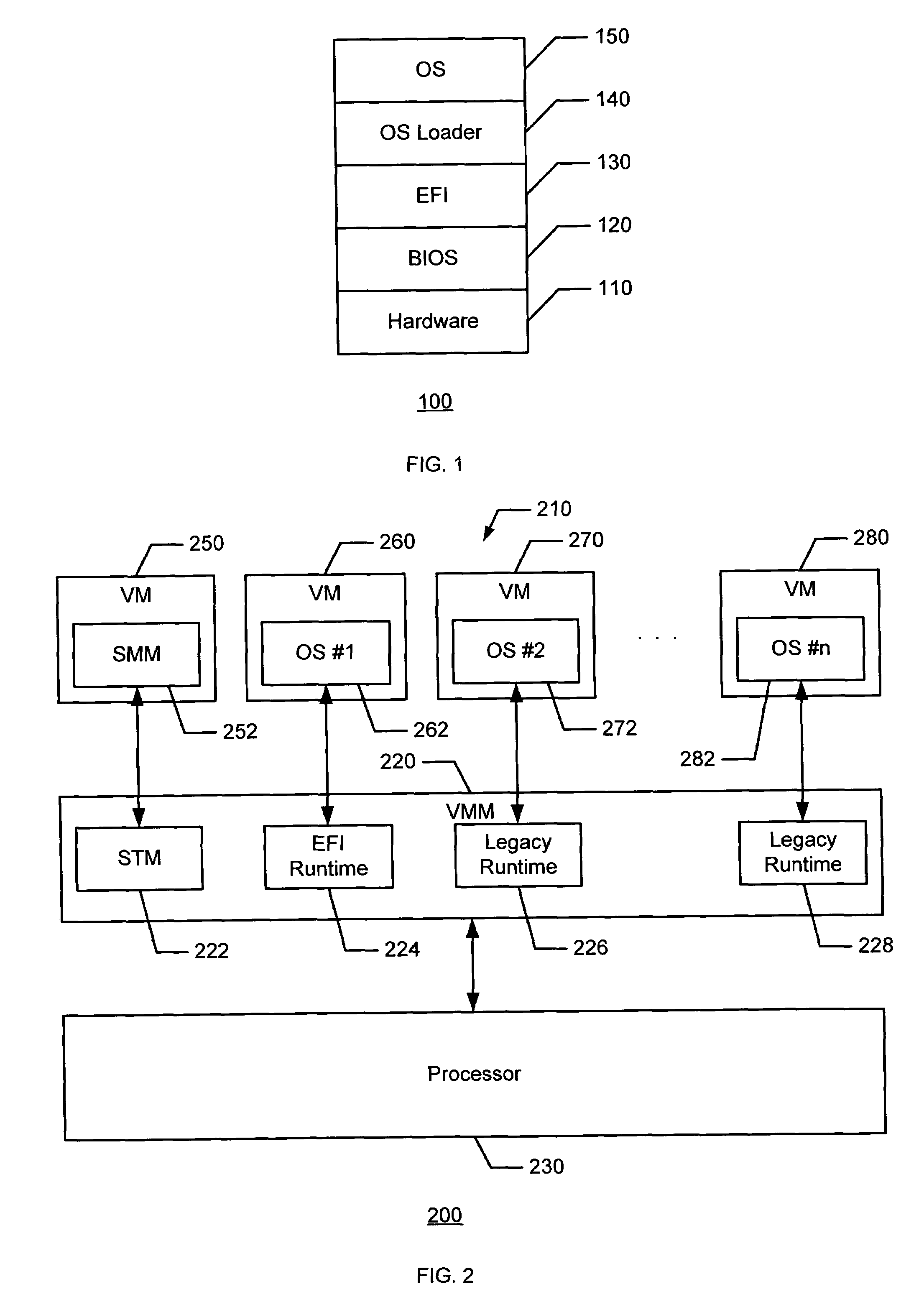
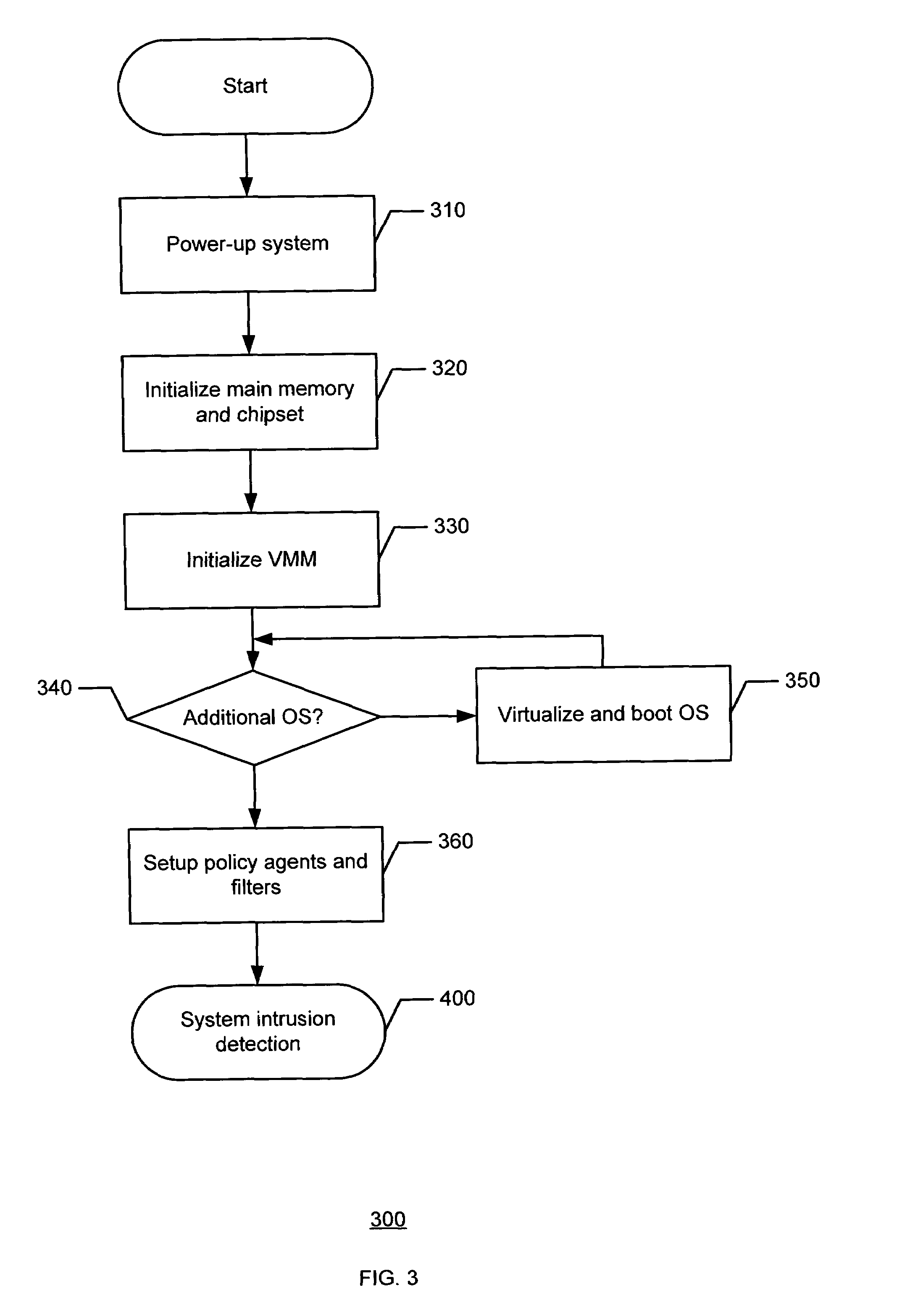
Methods and apparatus to provide network traffic support and physical security support
InactiveUS7496961B2Memory loss protectionVolume/mass flow measurementTraffic capacityPhysical security
Methods and apparatus to provide network traffic support and physical security support are described herein. In an example method, a virtual machine monitor (VMM) in a processor system is initialized. At least one of a network traffic intrusion event and a physical security intrusion event is identified by the VMM. At least one of a network traffic support and a physical security support is implemented in response to at least one of the network traffic intrusion event and the physical security intrusion event.
Owner:INTEL CORP
Apparatus, method and article for physical security of power storage devices in vehicles
ActiveUS20130030608A1Registering/indicating working of vehiclesNavigation instrumentsPhysical securityIn vehicle
A network of collection, charging and distribution machines collect, charge and distribute portable electrical energy storage devices (e.g., batteries, supercapacitors or ultracapacitors). To avoid theft and tampering of the portable electrical energy storage devices, by default, each portable electrical energy storage device is locked in and operably connected to the vehicle to which it provides power unless the vehicle comes within the vicinity of a collection, charging and distribution machine or other authorized external device such as that in a service center. Once within the vicinity of a collection, charging and distribution machine or other authorized external device a locking mechanism in the vehicle or within the portable electrical energy storage device unlocks and allows the portable electrical energy storage device to be exchanged or serviced.
Owner:GOGORO
Systems and methods for document verification
InactiveUS20060157559A1Absence in detectionEliminate needAcutation objectsCo-operative working arrangementsPhysical securityPaper document
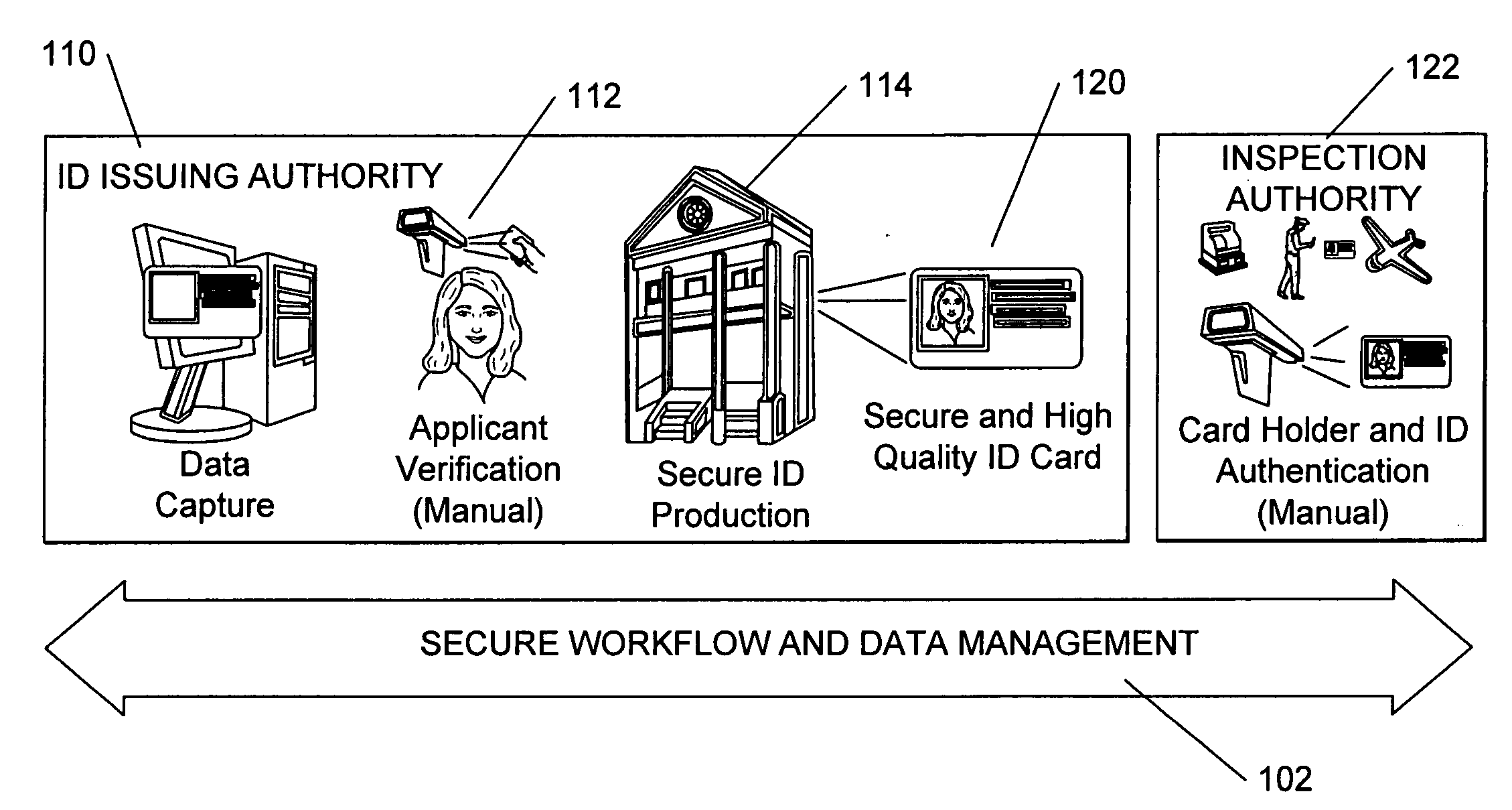
A method for issuing a credential includes scanning in documents (e.g., breeder or ID documents) used to verify the applicant of the credential and creating data records including the image of the documents. As a means to reduce fraud, these data records are linked to the credential and to the issuer location, operator and time and place of issuance. If the document includes machine readable information, the method automatically reads the machine readable information from the document and uses at least part of the machine readable information from the document to pre-populate a form used to create a credential, such as an identification document. The method includes applying a transformation to the image of the document that enables protection against fraudulent use. The transformation secures the image of the document from tampering and / or enables tracking of the use of the document image to deter fraud. A method of verifying a credential comprises reading a physical security feature attribute on the credential, reading a logical attribute on the credential, and comparing information from the physical security feature with the logical storage element on the credential to verify the credential.
Owner:DIGIMARC CORP
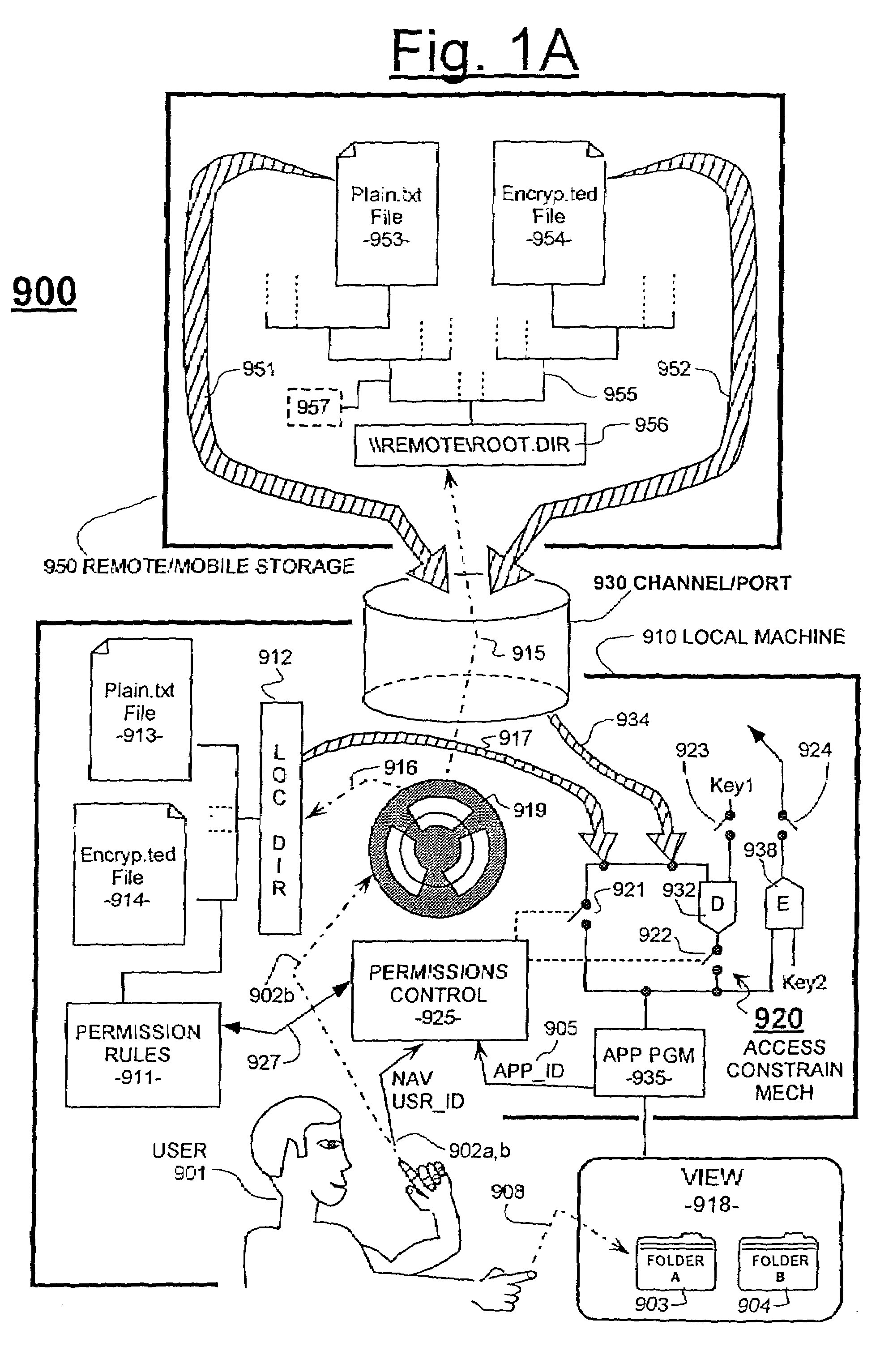
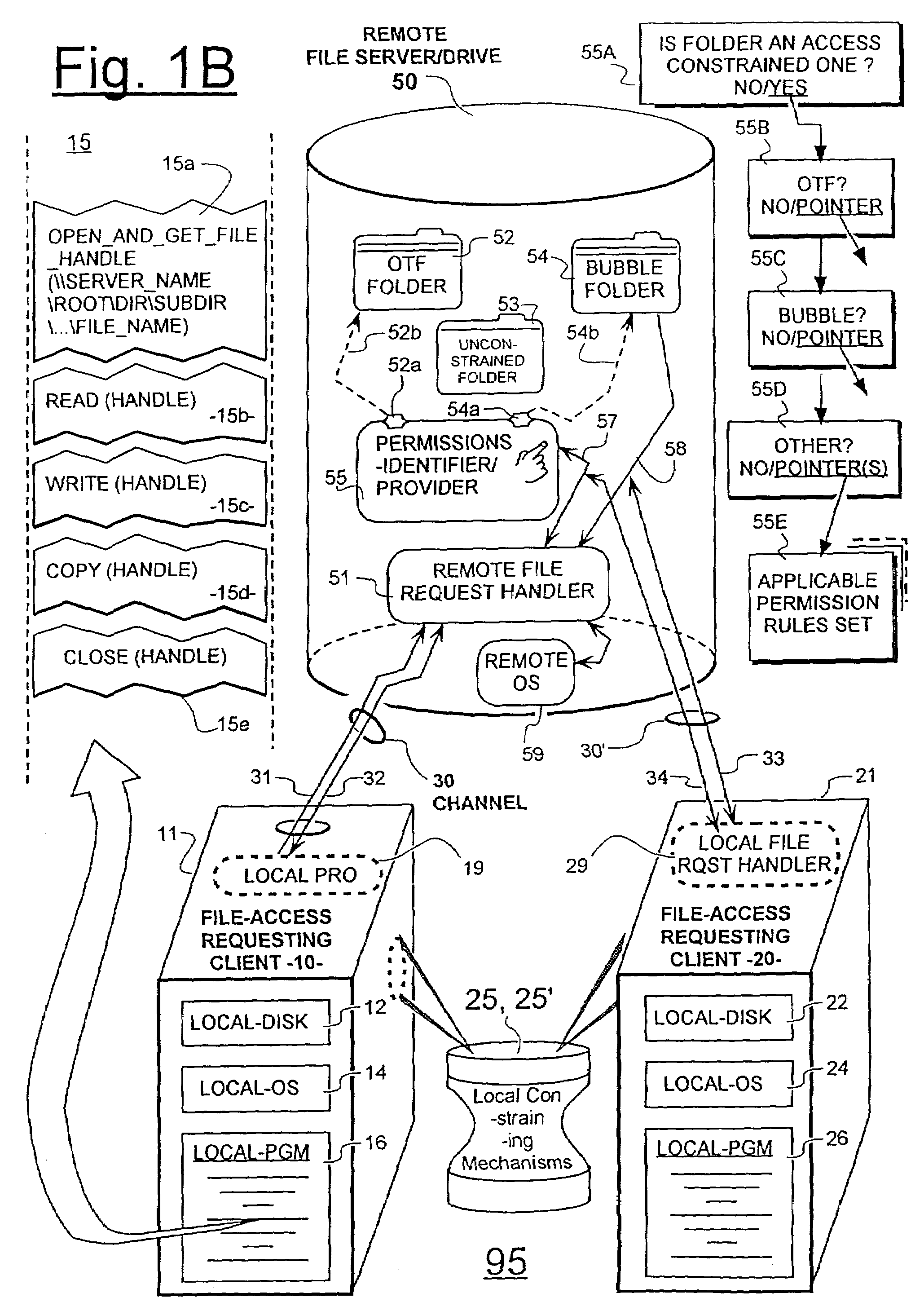
Unified permissions control for remotely and locally stored files whose informational content may be protected by smart-locking and/or bubble-protection
ActiveUS7197638B1Reduce in quantityImprove system response timeDigital data processing detailsAnalogue secracy/subscription systemsPhysical securityNon local
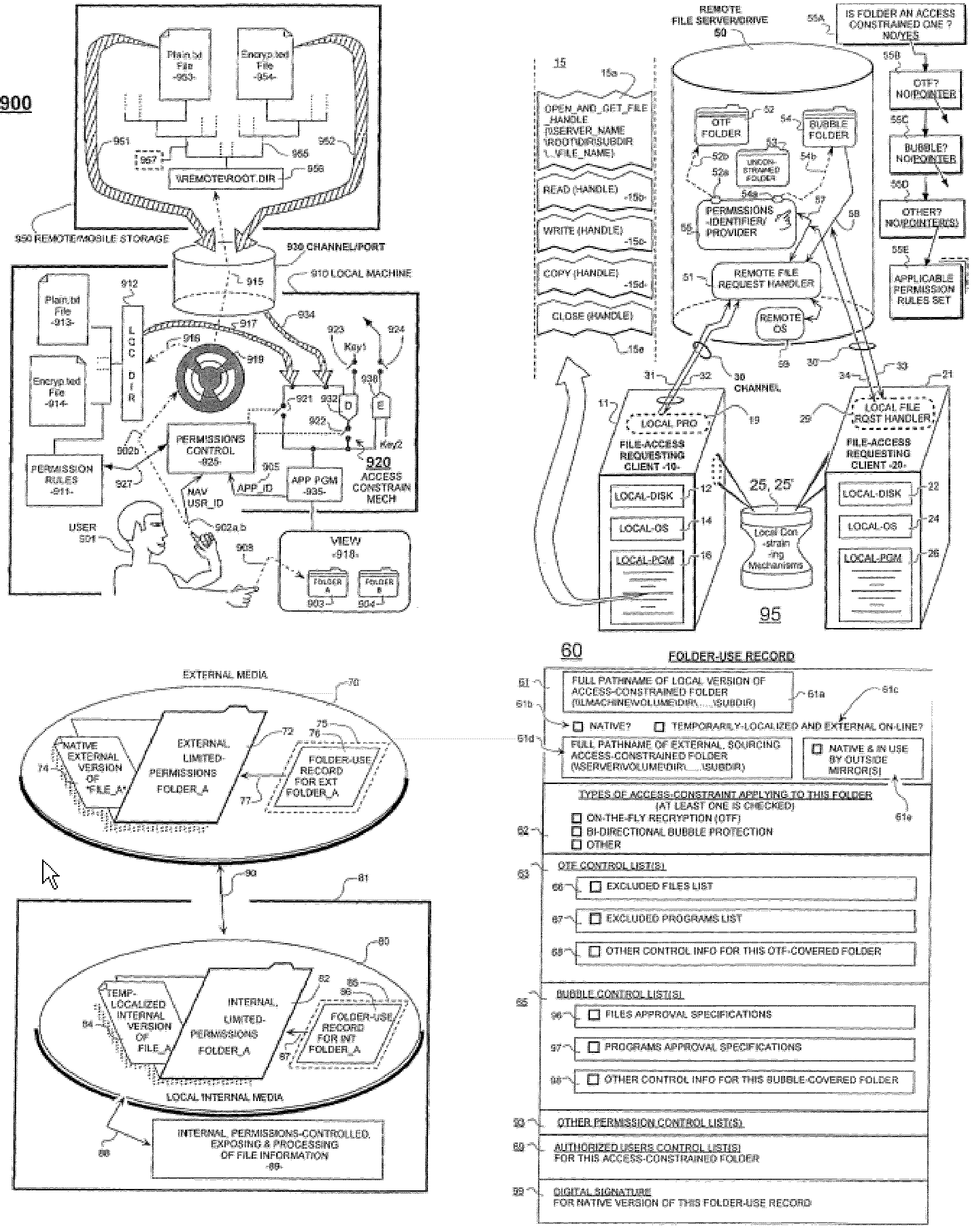
A machine system includes access-constraining mechanisms for protecting the information of certain classes of files from unauthorized intelligible access or from other kinds of access by way of requests supplied from unauthorized classes of programs which may be made at unauthorized periods of time and / or from unauthorized locations and / or under association with unauthorized users. Permission rules are provided for what constitutes an unauthorized access attempt for intelligible or another kind of access to the data of a given file. The given file may be a native one stored in a local machine or an external file stored in a remote server and / or on easily removable media. The machine system includes localizing means for Transparently and Temporarily Localizing (TTL'ing) external files and their respective access permission rules so that such may be processed within relatively physically-secure confines of the local machine. Such localized processing may include automatic decryption of confidential file data on a per-use basis and automatic later re-encrypting of modified data. Modified ones of TTL'ed files may be returned back to their non-local home after such processing.
Owner:CA TECH INC
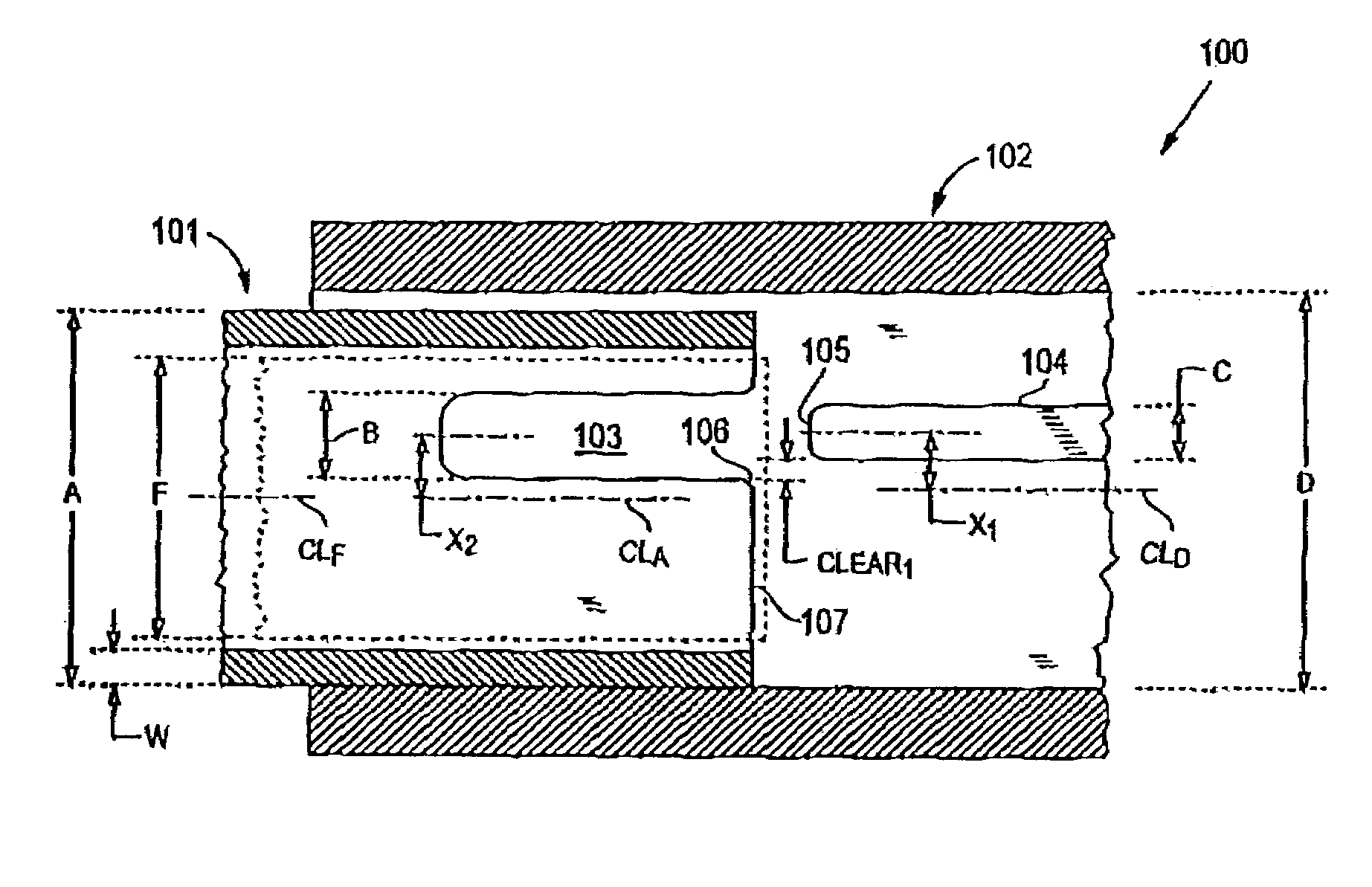
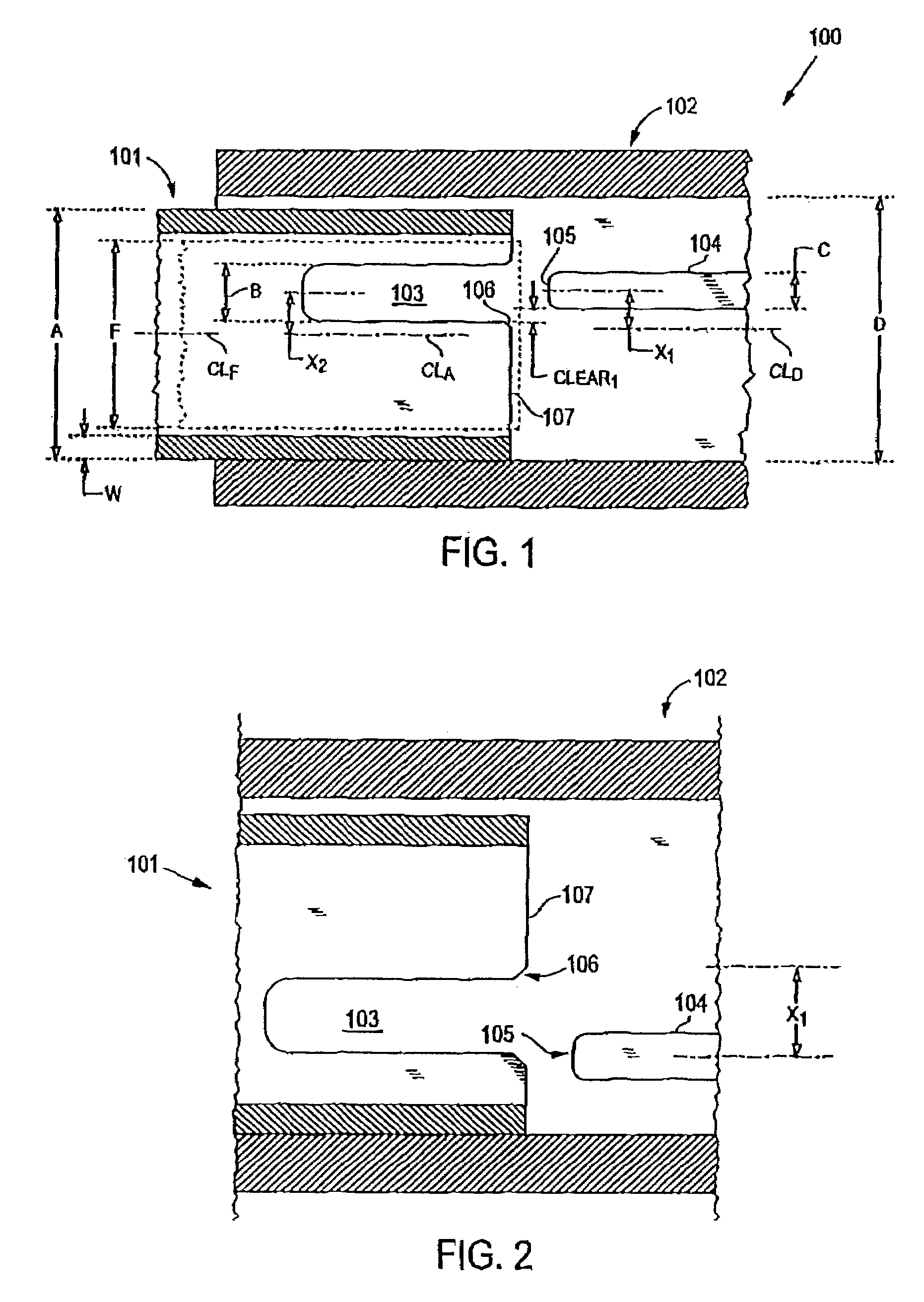
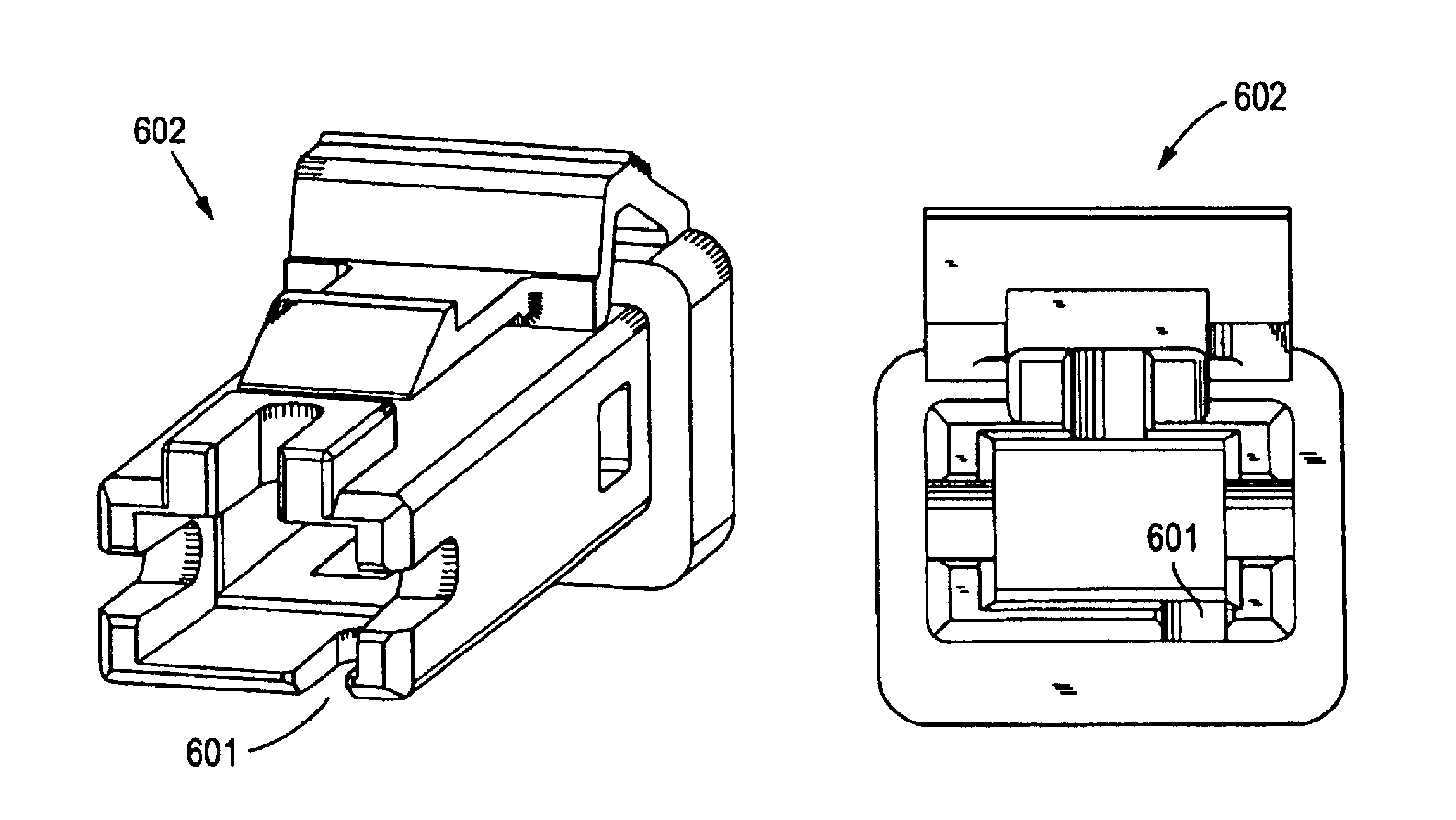
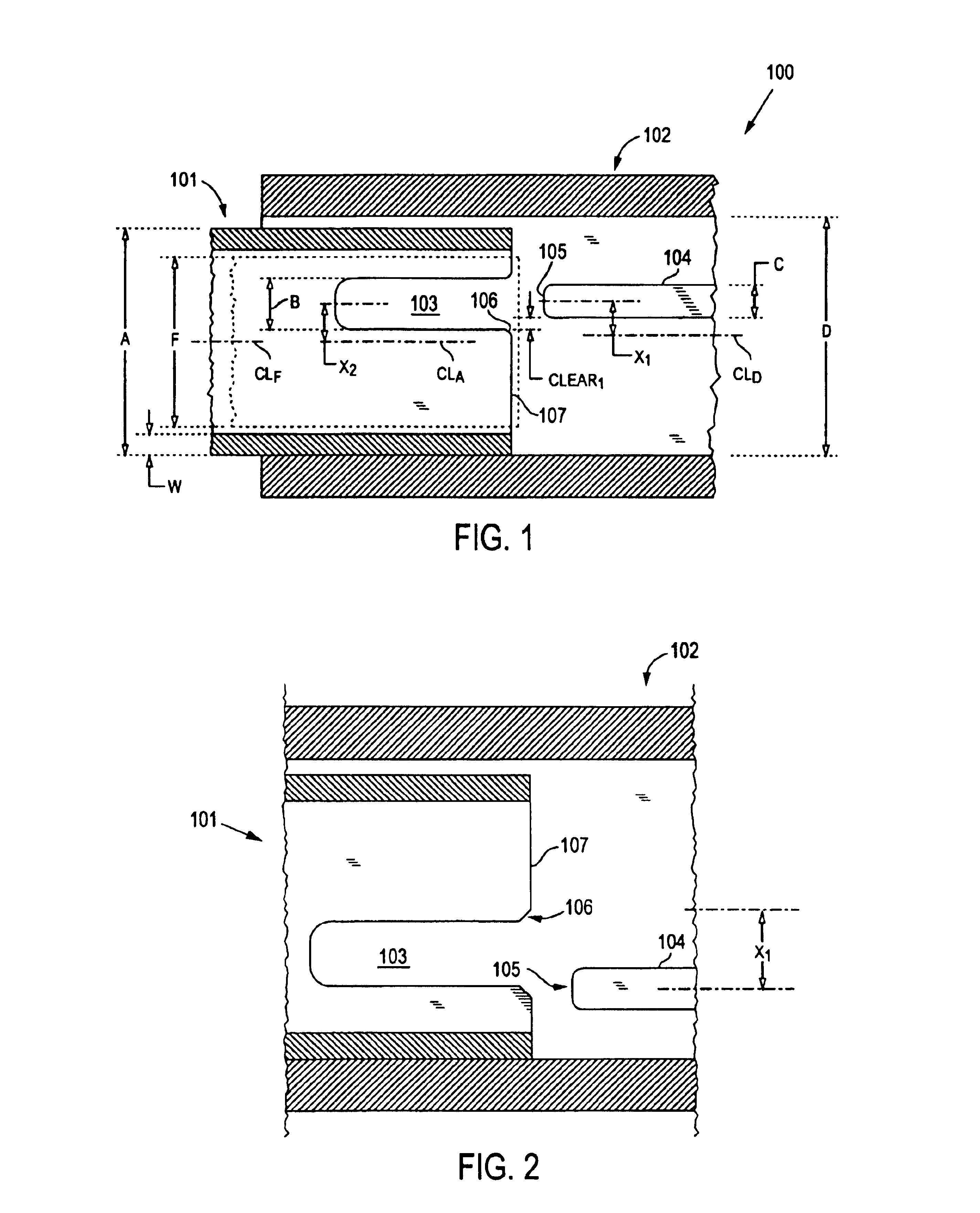
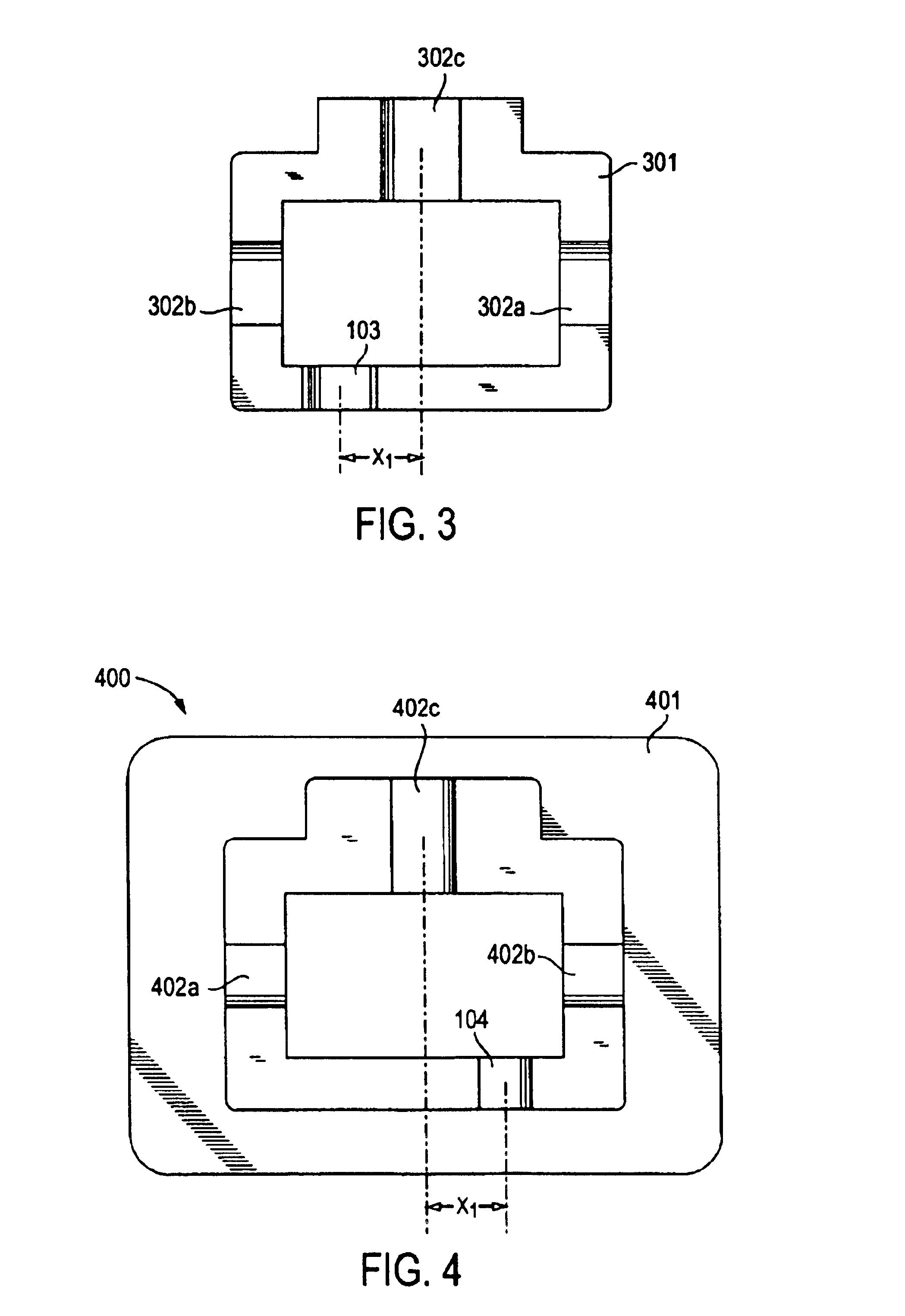
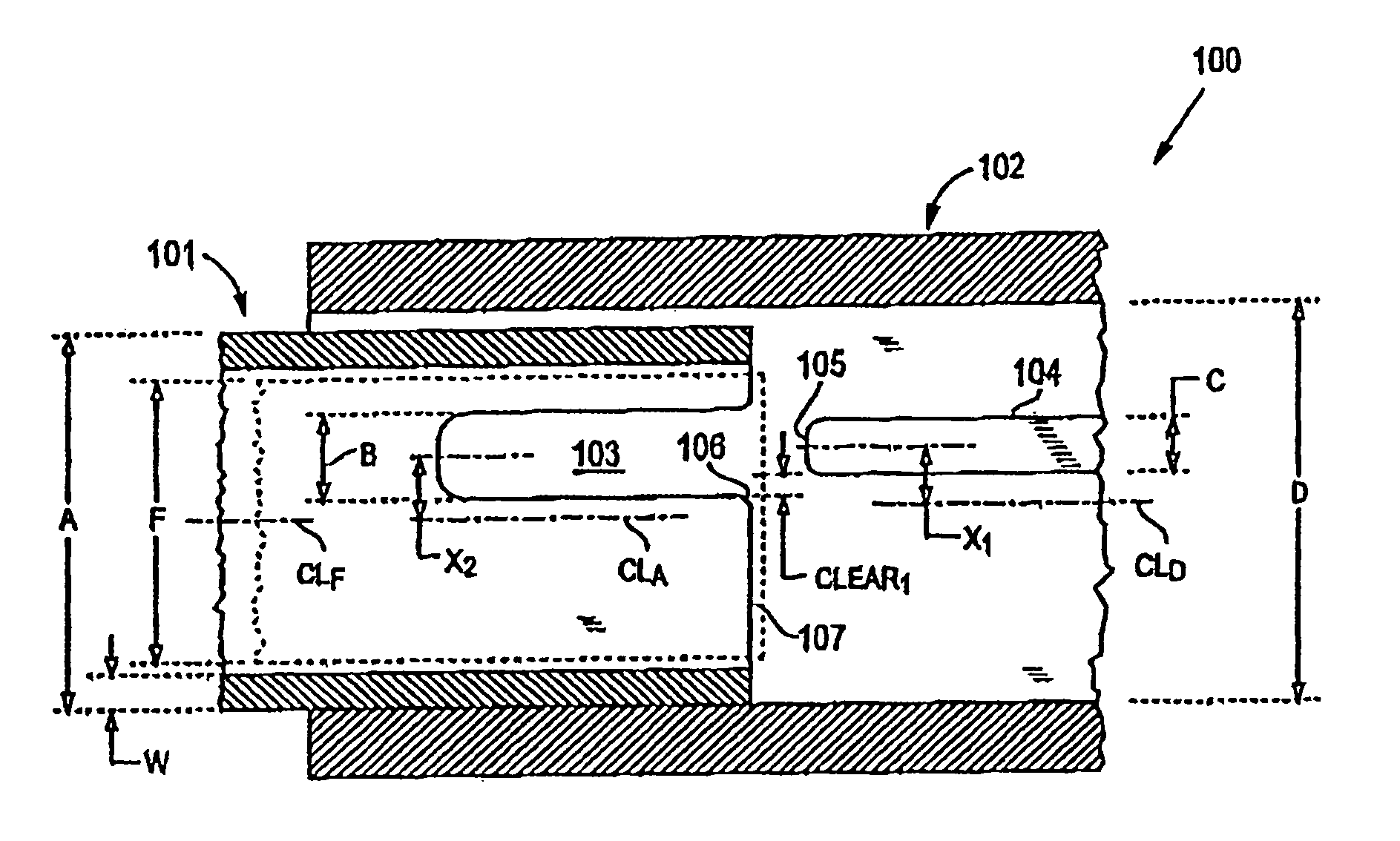
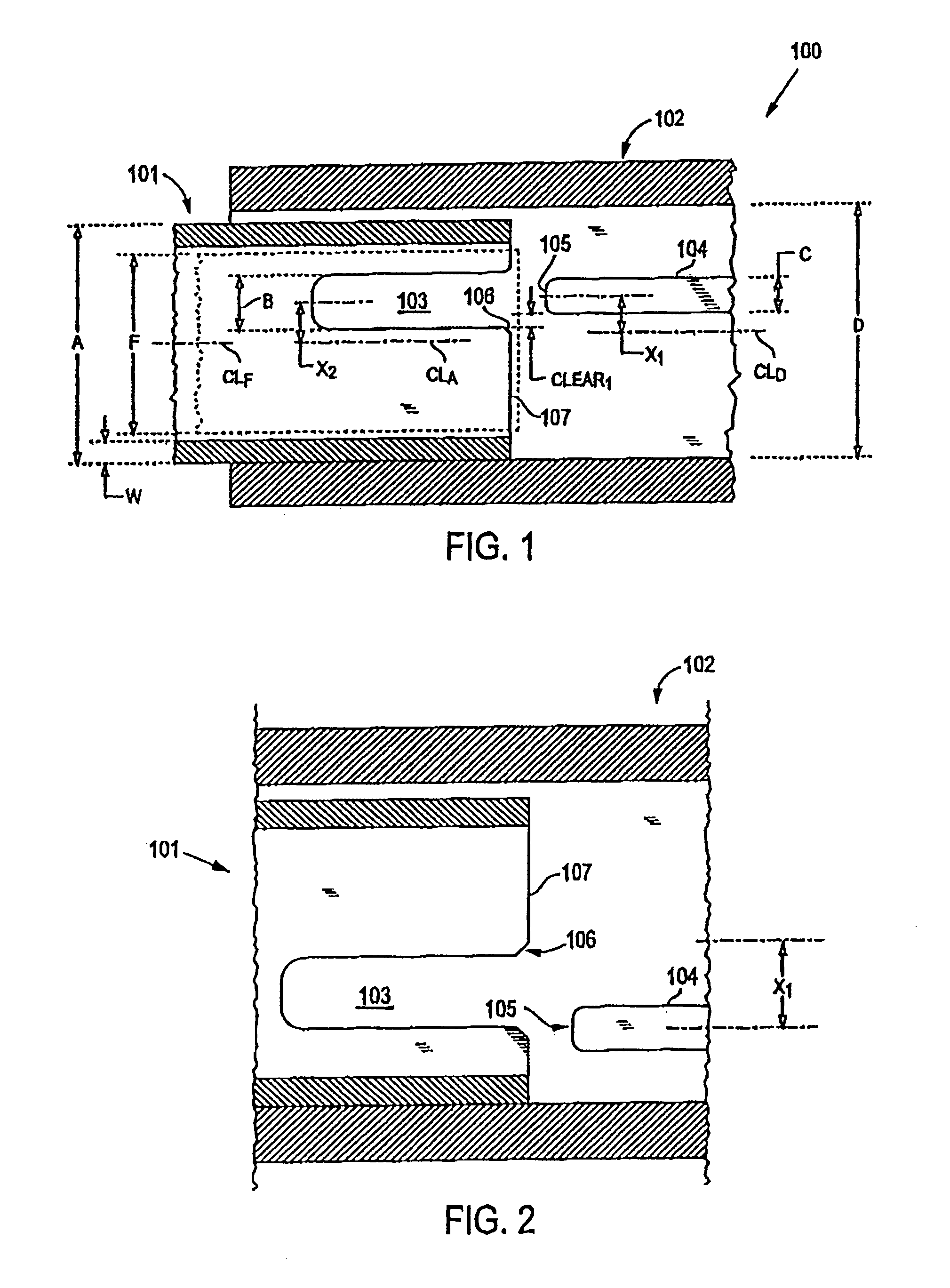
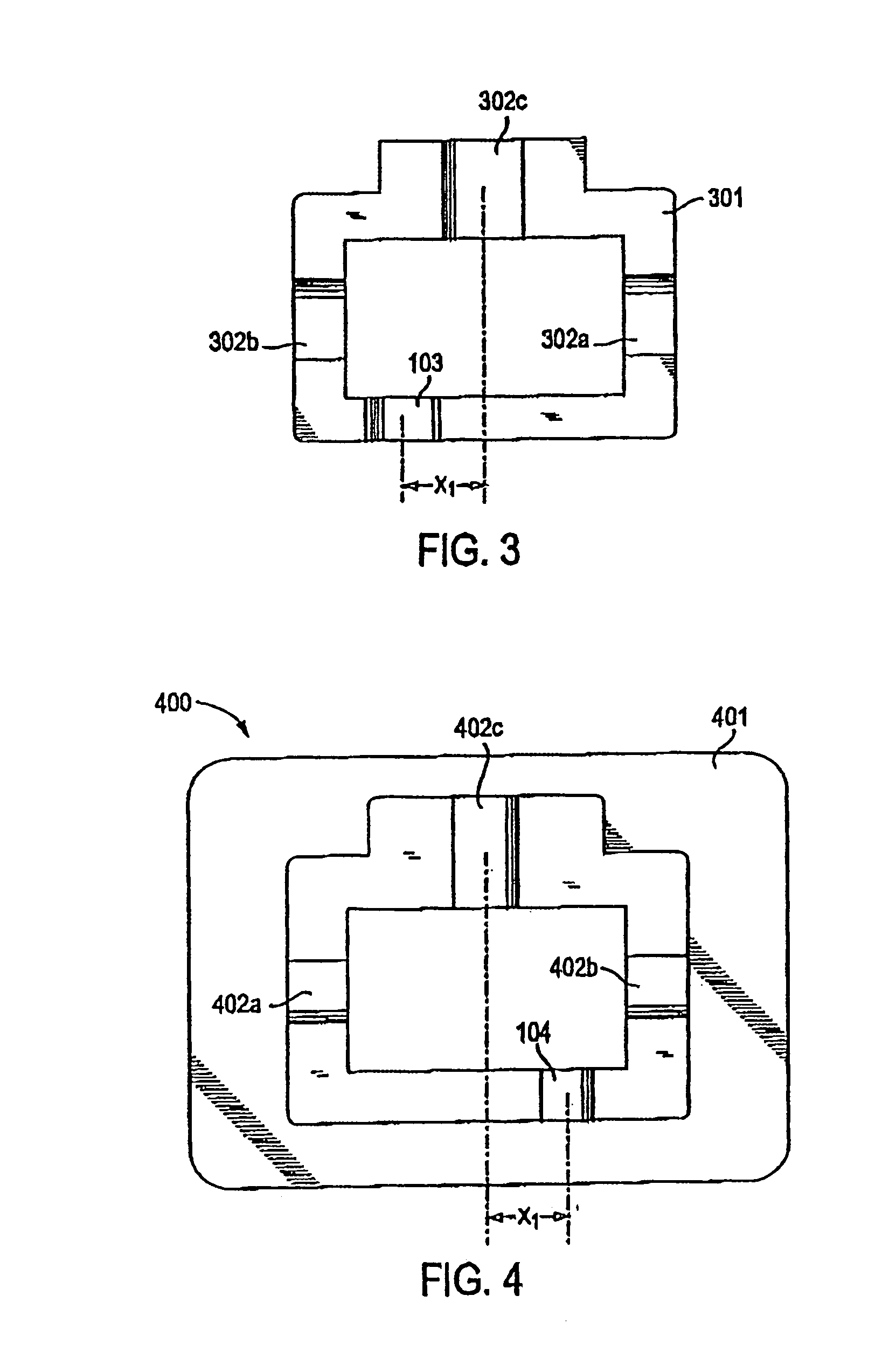
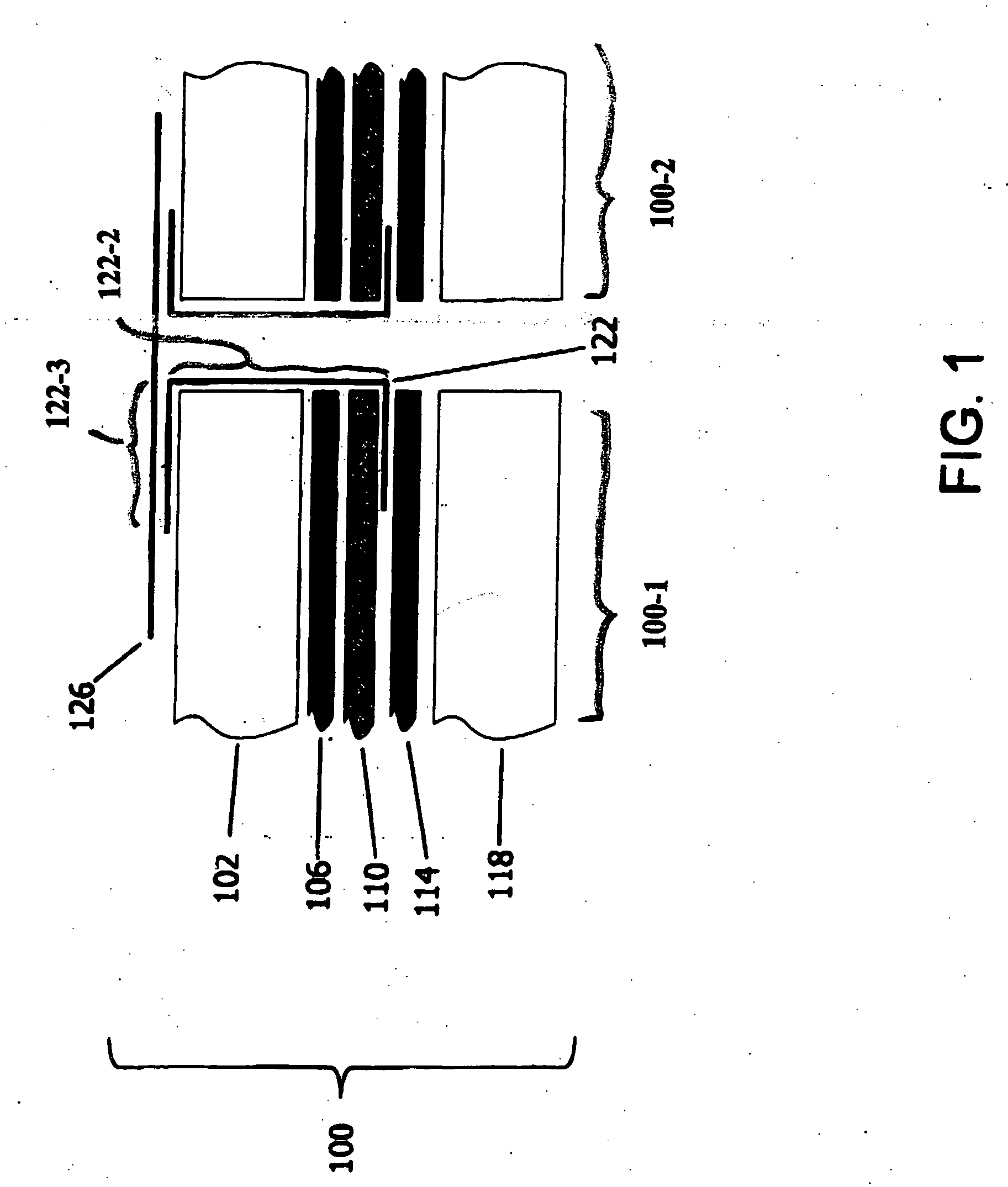
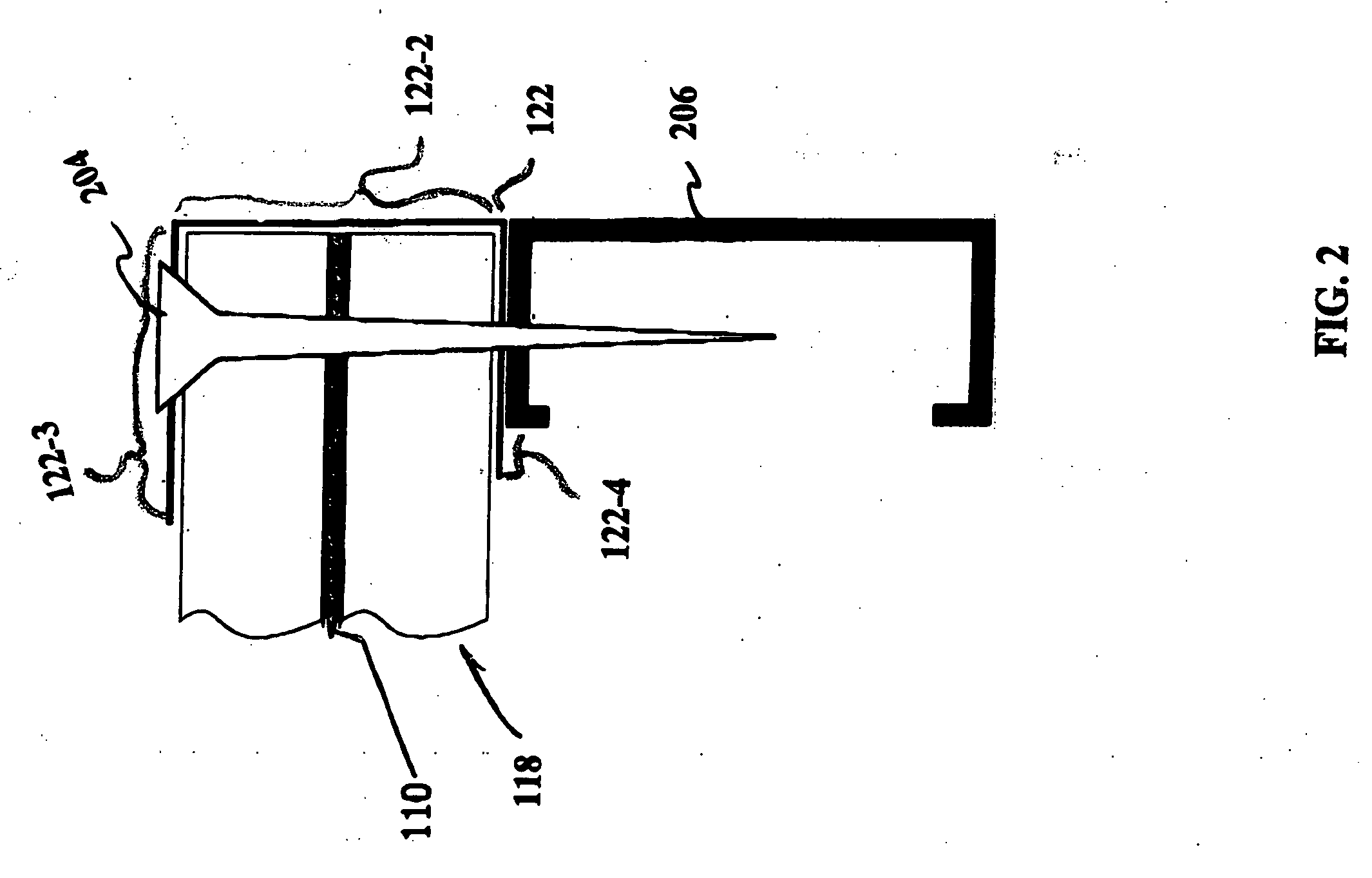
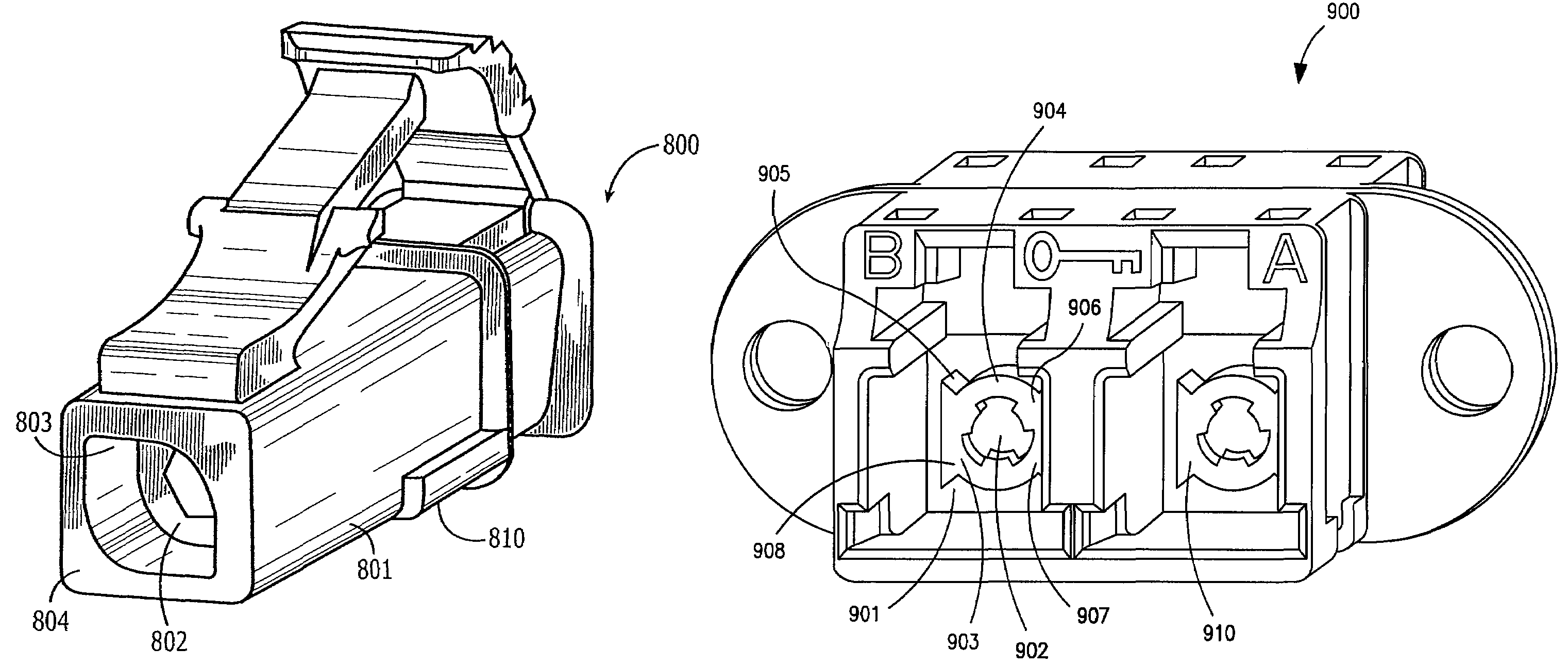
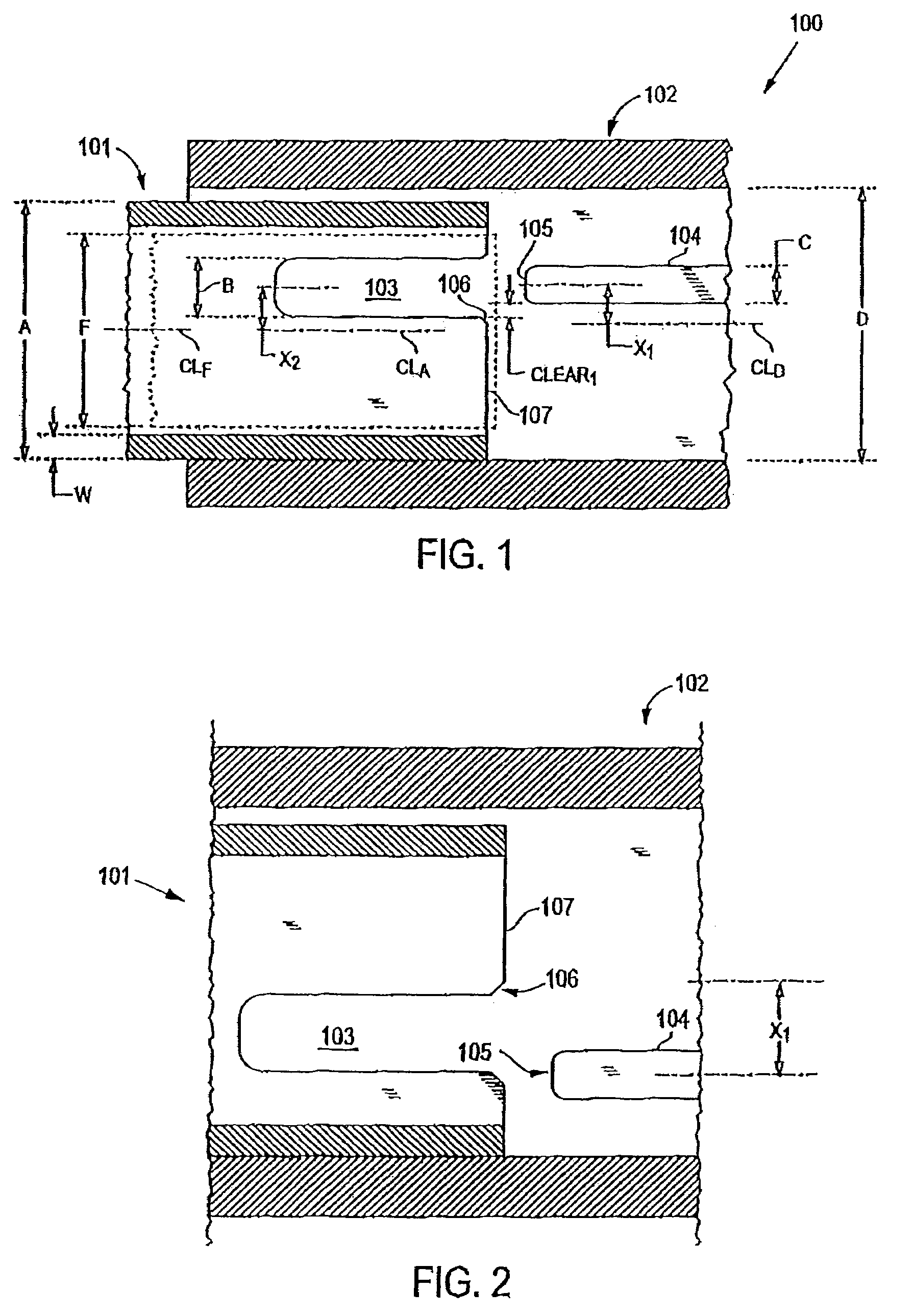
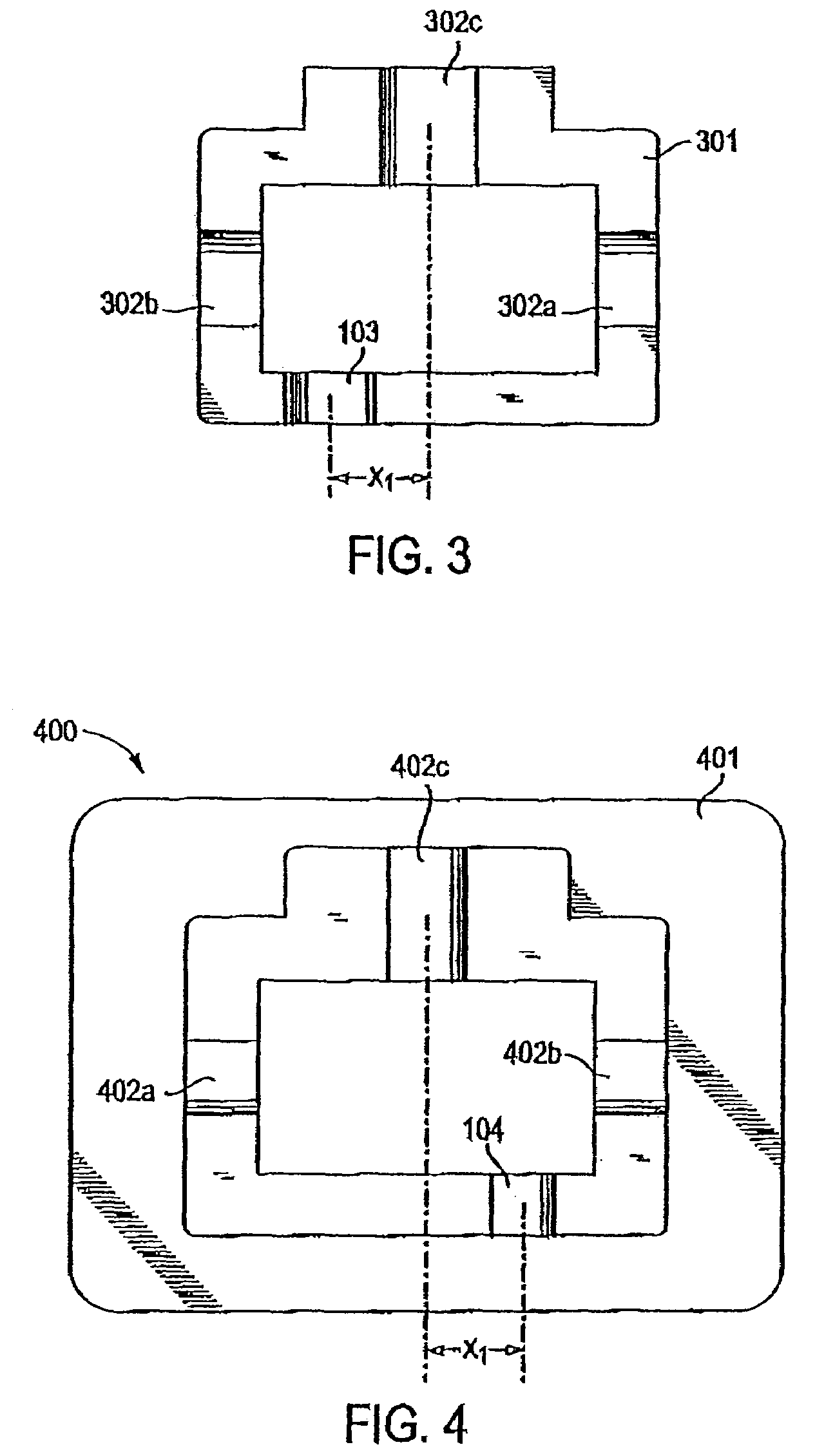
Connector and receptacle containing a physical security feature
InactiveUS7325976B2Imparts physical securityFacilitates discriminationIncorrect coupling preventionCoupling light guidesPhysical securityInformation networks
A network comprising: (a) a plurality of different receptacles for facilitating an optical connection to different information networks requiring different access authorization, each different receptacle coupled to one and only one different information network, each receptacle having an inner surface with a first geometry, the first geometry comprising at least a slot, a certain number of receptacles having different first geometries in which the slots are in different positions; and (b) a plurality of different plugs for coupling with the different receptacles, each plug having a second geometry, the second geometry comprising at least a key in a certain position, the certain number of plugs having different second geometries in which the keys are in different positions, each different first geometry corresponding to one and only one second geometry such that the plugs and receptacles of corresponding first and second geometries are mating pairs.
Owner:COMMSCOPE TECH LLC
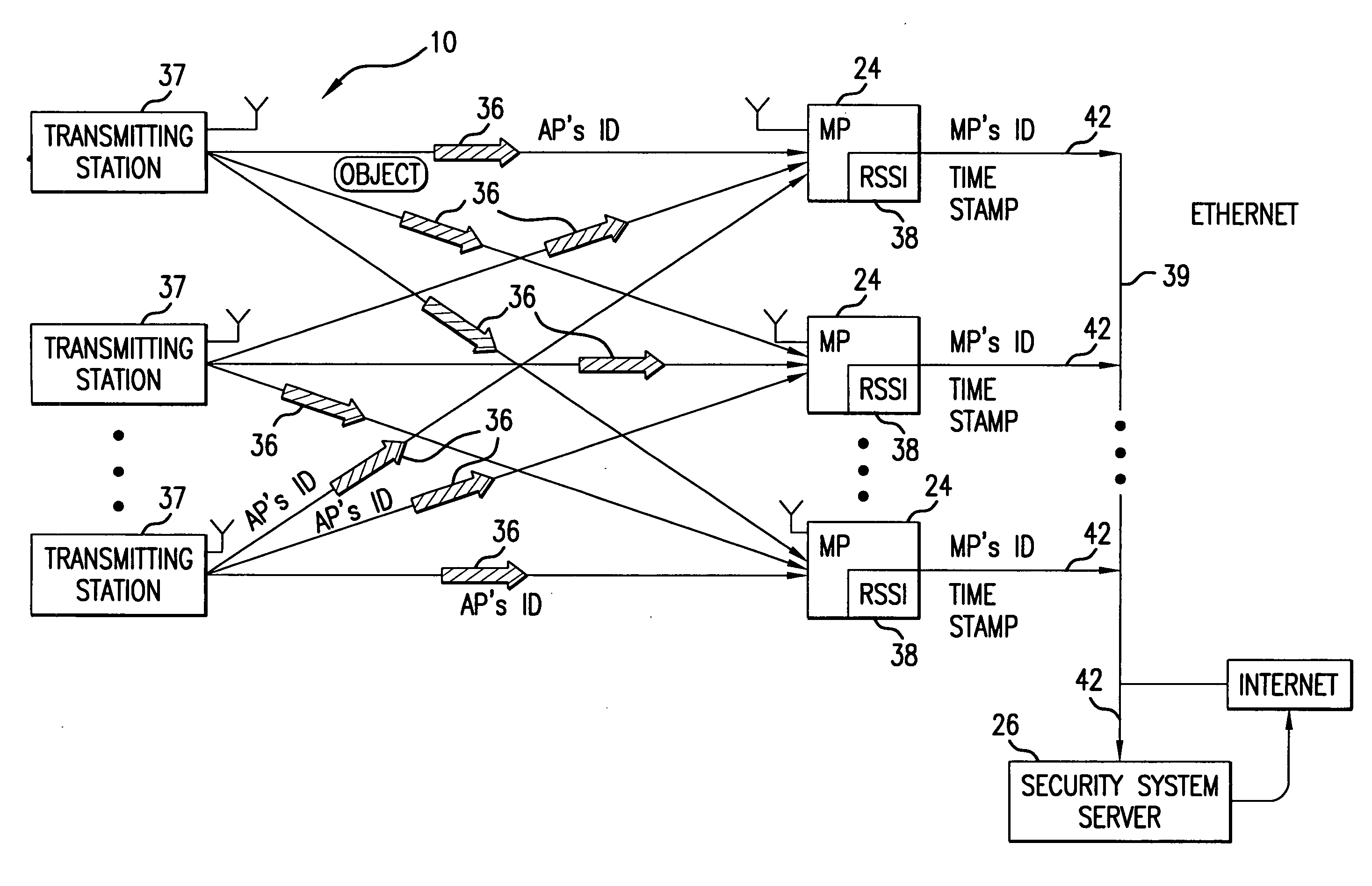
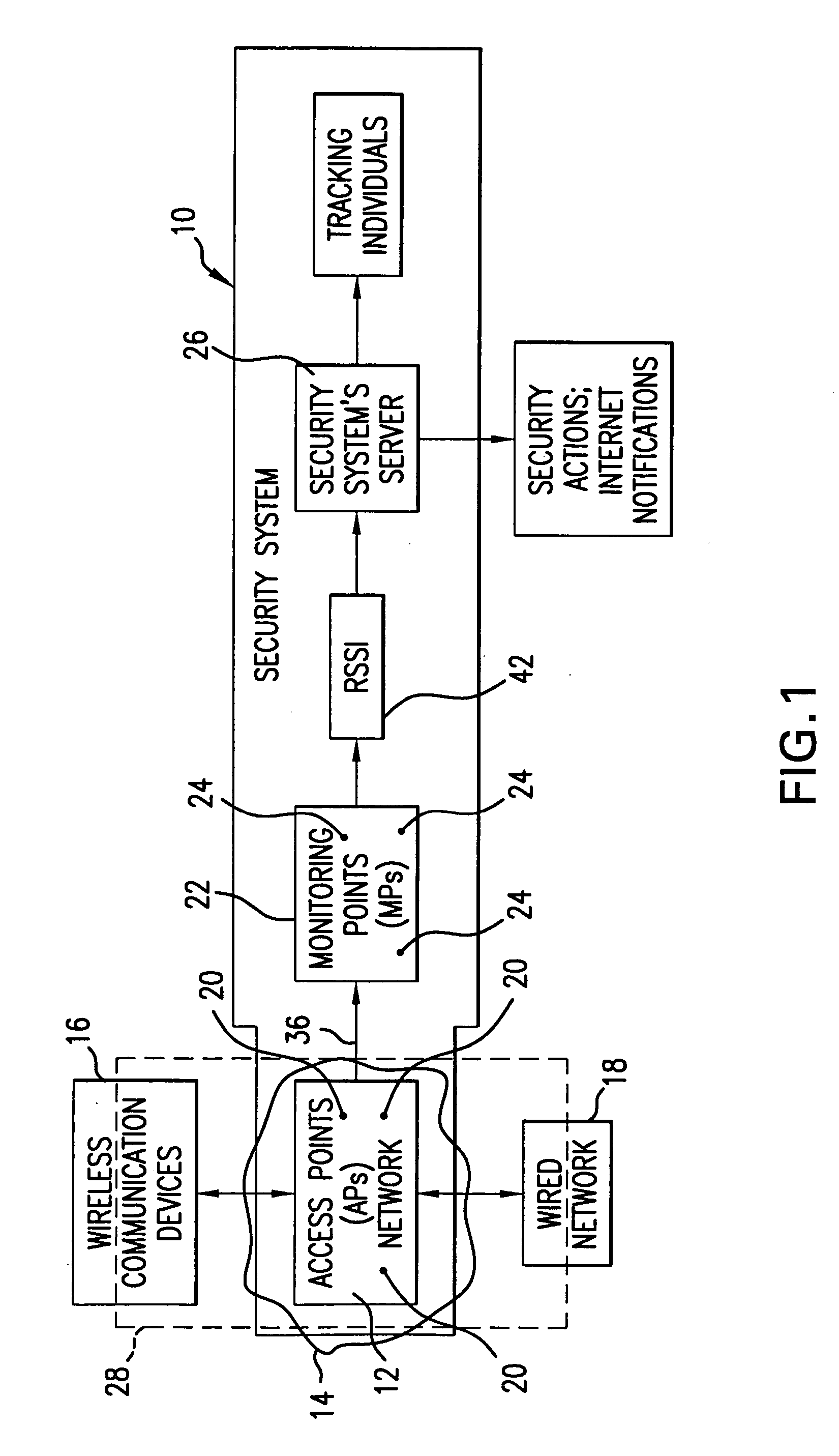
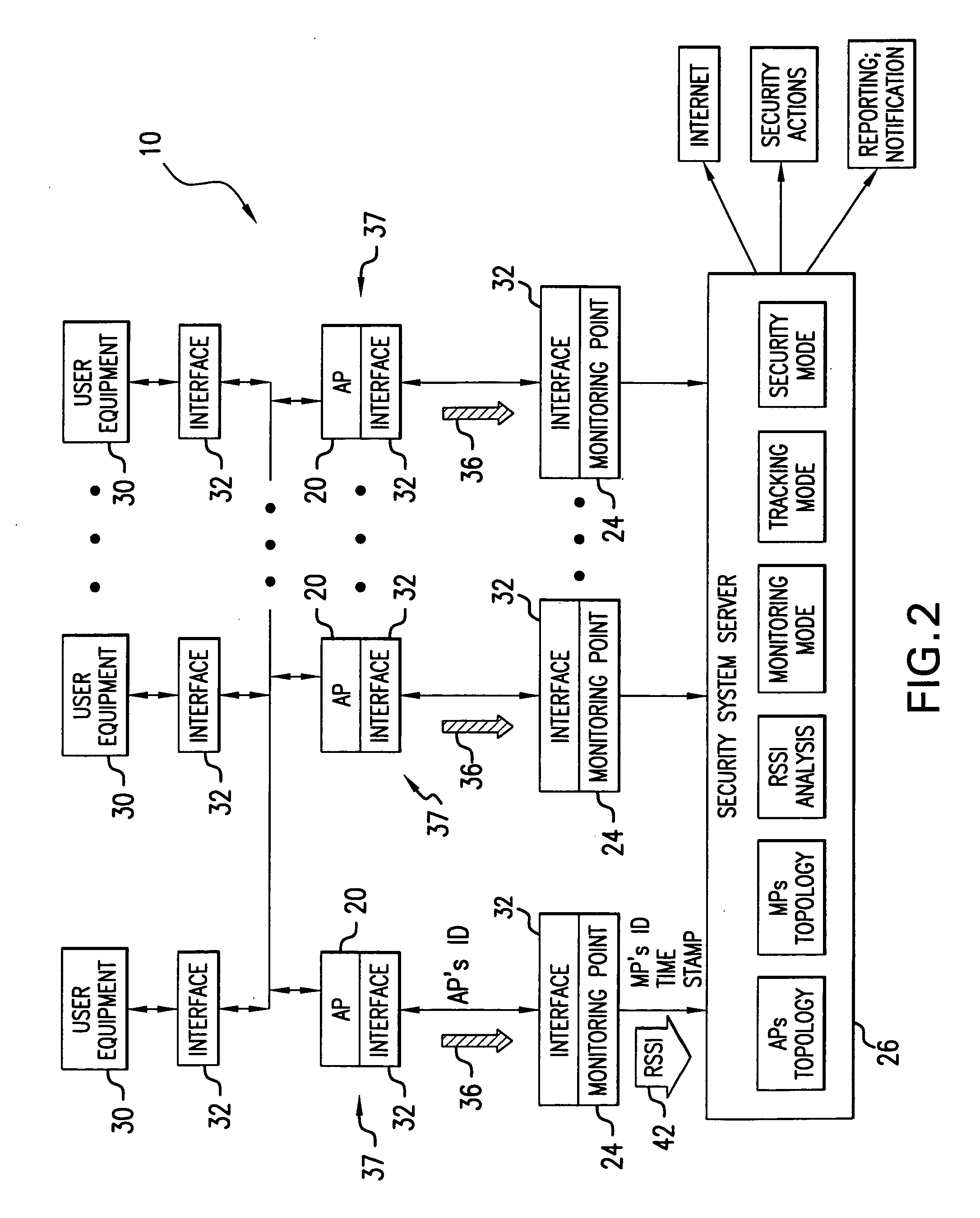
Method and system for providing physical security in an area of interest
InactiveUS20050055568A1Keep trackDigital data processing detailsHardware monitoringWi-FiPhysical security
A system for detecting the presence of an intruder in a protected area utilizes a received signal strength indicator (RSSI) value of signals broadcast from transmitting stations deployed in the protected area. The system includes monitoring points for receiving broadcast signals, measuring the RSSI values of the received signals, and transmitting the measured RSSI values to a security system server. The security system server analyzes the RSSI values, and initiates security measures when the physical security of the protected area is violated which is detected when the measured RSSI values deviate from a predetermined strength of the broadcast signals. The security system also has the ability to track objects in the protected area and keep track of their movement in real time and report such movement. The system may be based on a Wi-Fi infrastructure in the protected area.
Owner:UNIV OF MARYLAND
Simulacrum of physical security device and methods
ActiveUS20120117635A1Service provisioningDigital data processing detailsSoftware emulationPhysical security
A simulacrum security device and methods. In one embodiment, a simulacrum or likeness of a physical security device is provided for use in conjunction with a software emulation of the security device. In one implementation, a “faux SIM card” is provided that does not contain Subscriber Identification Module (SIM) information itself, but instead enables a user to download Electronic SIM (eSIM) information (e.g., from a network or eSIM server) which is loaded into a software emulation of a Universal Integrated Circuit Card (UICC) device. The faux card is printed with an activation code, scan pattern, or other activation or access information. The subscriber purchases the faux card, and enters the activation code into a device; the entered activation code enables the device to log onto a network, and download the appropriate eSIM data. Delivery of eSIM information as enabled by the faux card addresses deficiencies in existing SIM distribution schemes, provides users with an enhanced perception of security, and further addresses various legal requirements.
Owner:APPLE INC
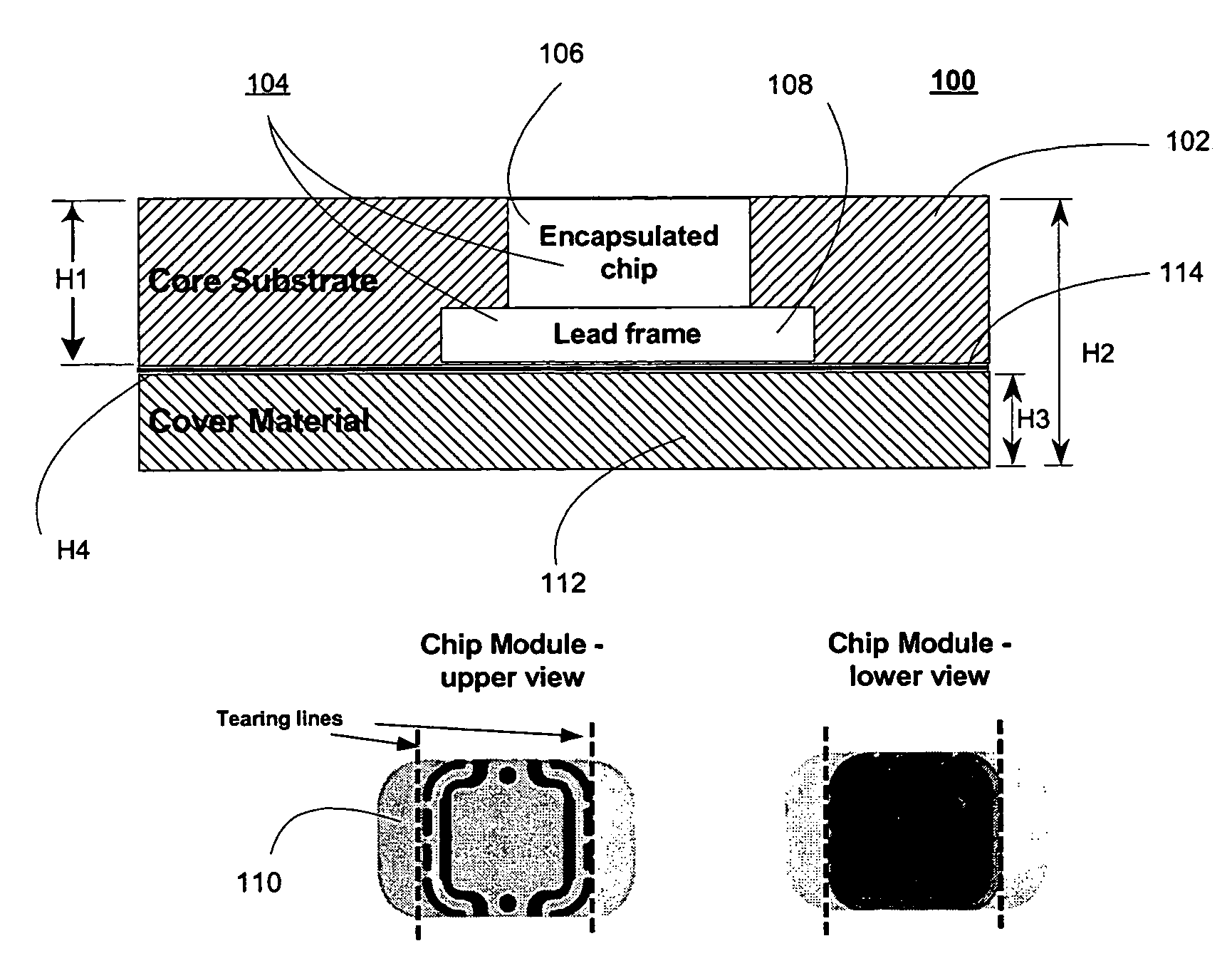
Tamper-free and forgery-proof passport and methods for providing same
InactiveUS20060005050A1Prevent tamperingUnauthorized memory use protectionHardware monitoringTamper resistancePhysical security
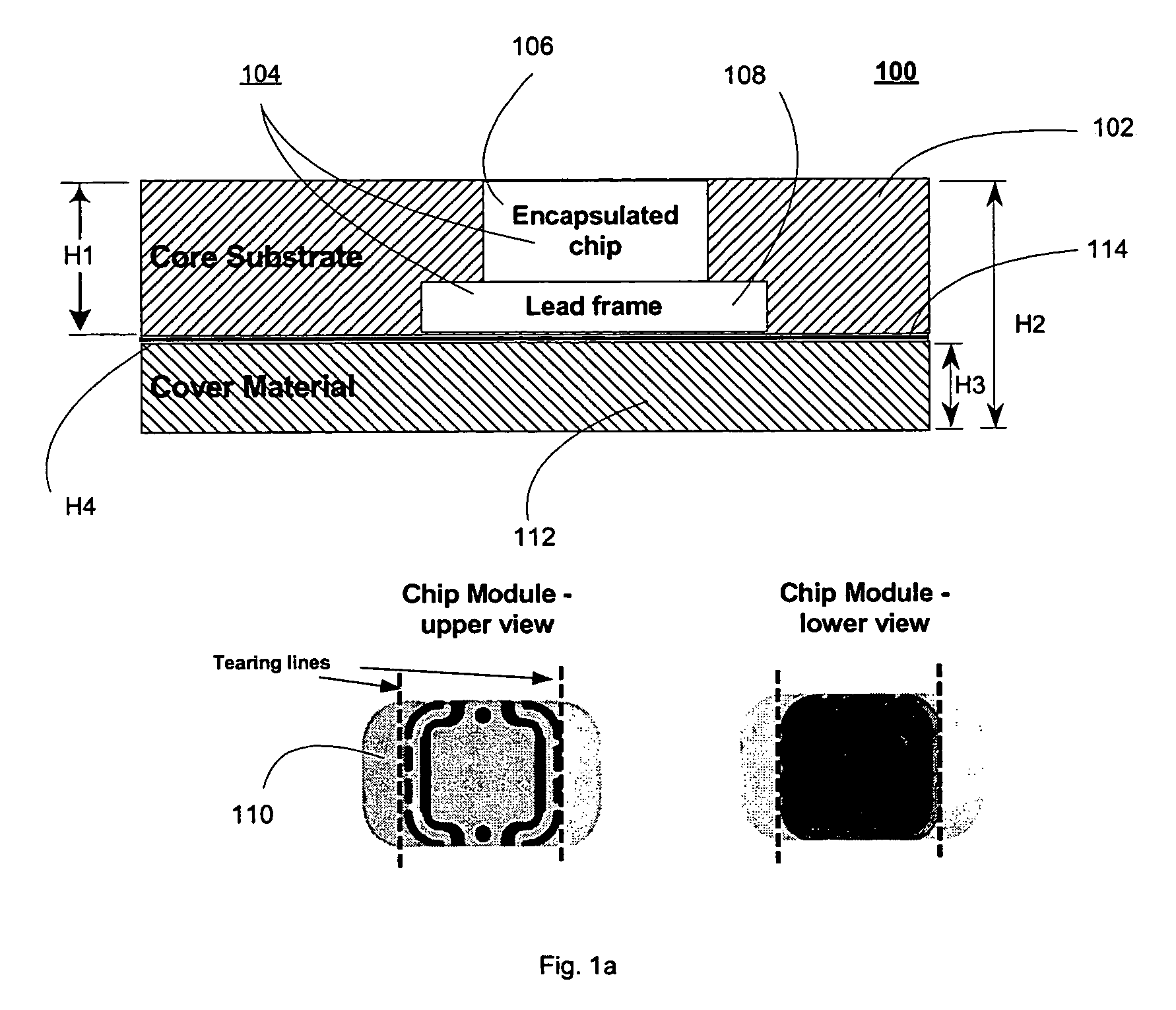
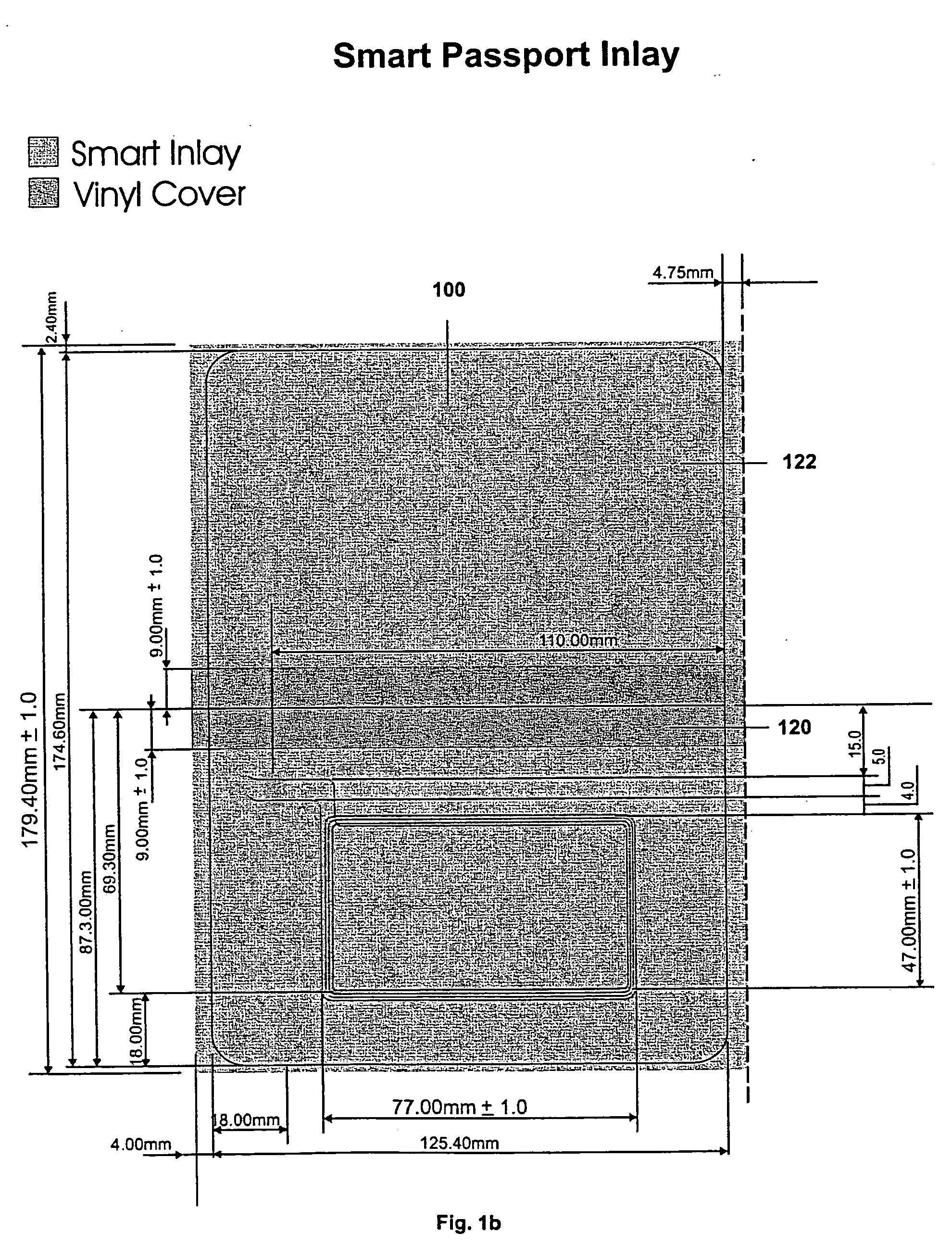
A smart passport comprising a smart inlay that includes a core substrate operative to store and exchange information contactlessly with an external reader, at least one physical security component coupled to the core substrate and operative to render the smart inlay and thereby the passport tamper-proof, and a logical security component incorporated in the core substrate and operative to render the smart inlay and thereby the passport forgery-proof. The physical security component is preferably selected from the group at least one tear line and at least one patterned adhesive, both operative to cause irreversible damage to the information storage and communication capabilities of the passport in case of tampering.
Owner:SUPERCOM IP LLC +1
Total Property Intelligence System
ActiveUS20180211115A1Multiple keys/algorithms usagePublic key for secure communicationPhysical securityApplication software
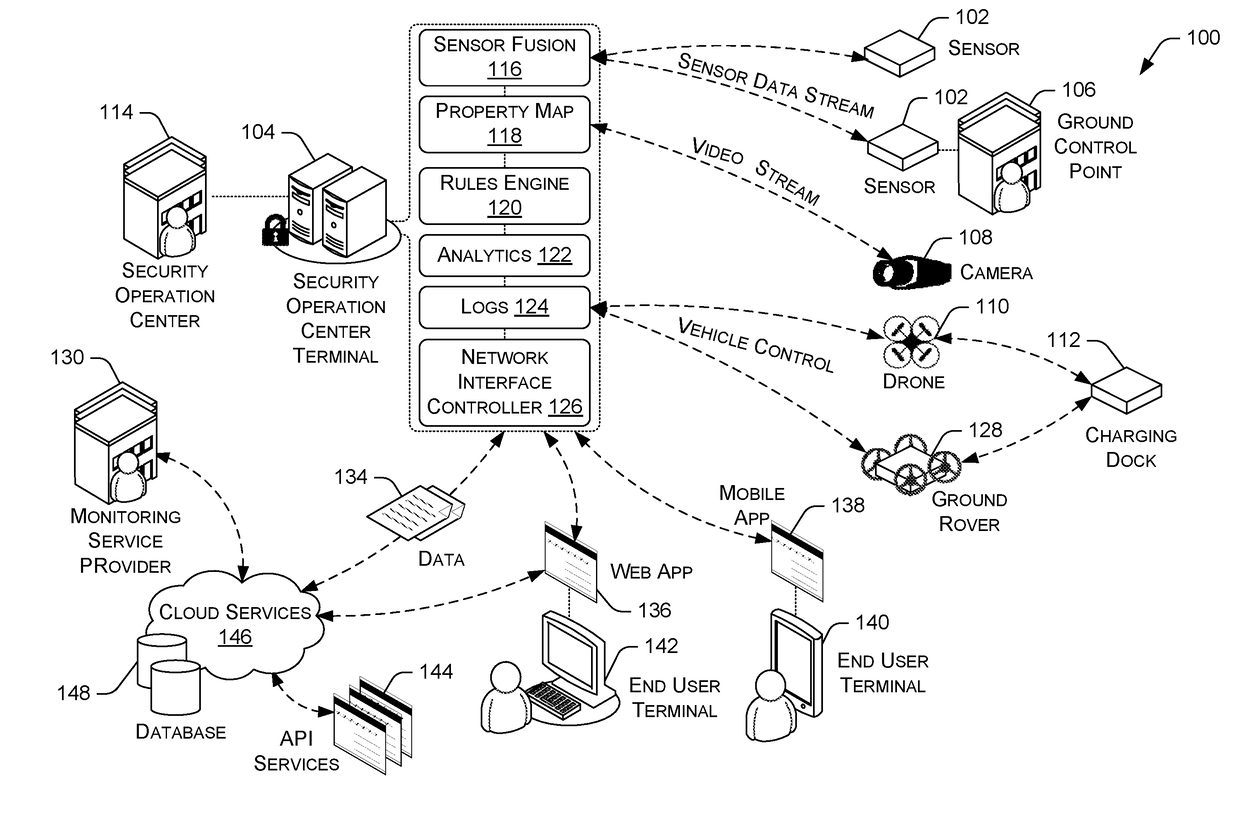
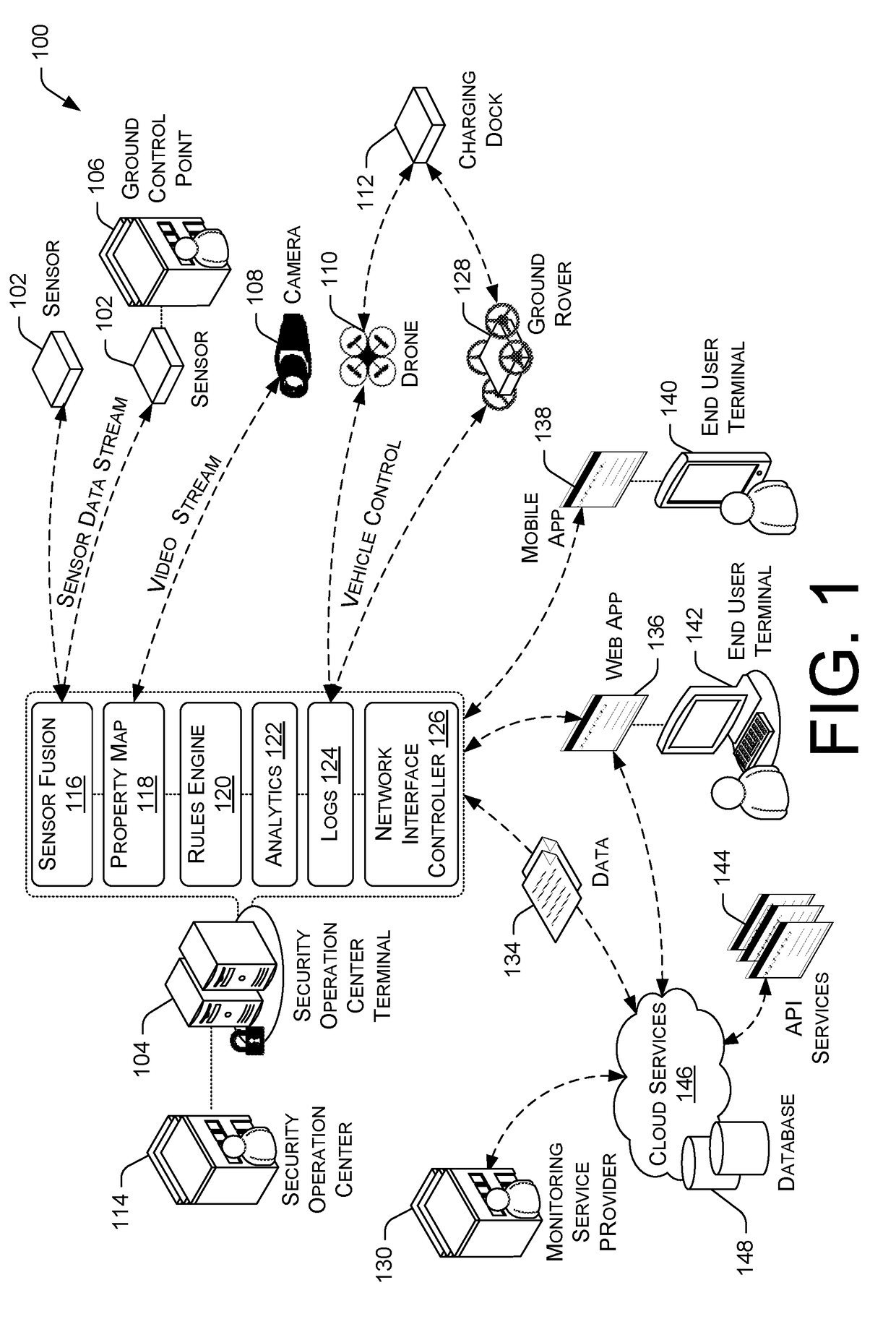
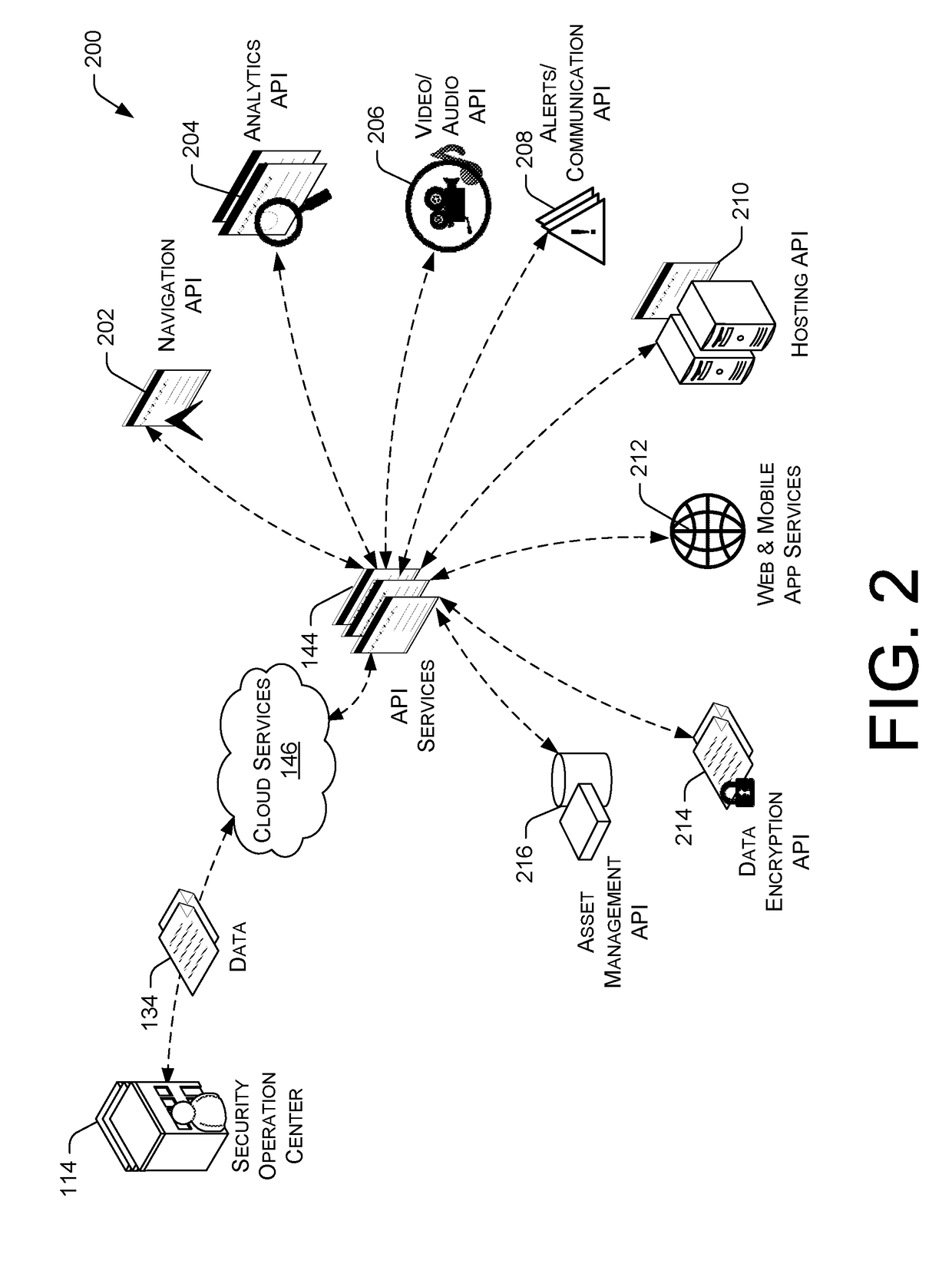
A total property security system may be implemented to conduct security and surveillance operations. The system includes security operations centers that are connected to one or more sensors and vehicles for collecting and transmitting surveillance data to a database hosted on cloud services. The collected surveillance data is analyzed in order to automatically deploy security measures and / or recommend courses of action using a rules engine that can be configured to client-specific or user-specific security needs. The cloud services can provide a set of application program interface services that can act on the surveillance operations center. Sensor fusion data and other surveillance data can be also transmitted to vetted monitoring service providers on a subscription basis to provide physical security services to the area within the property perimeter. During the subscription period, the selected monitoring service providers can obtain time-based encryption token for accessing surveillance data.
Owner:KLEIN MATIAS
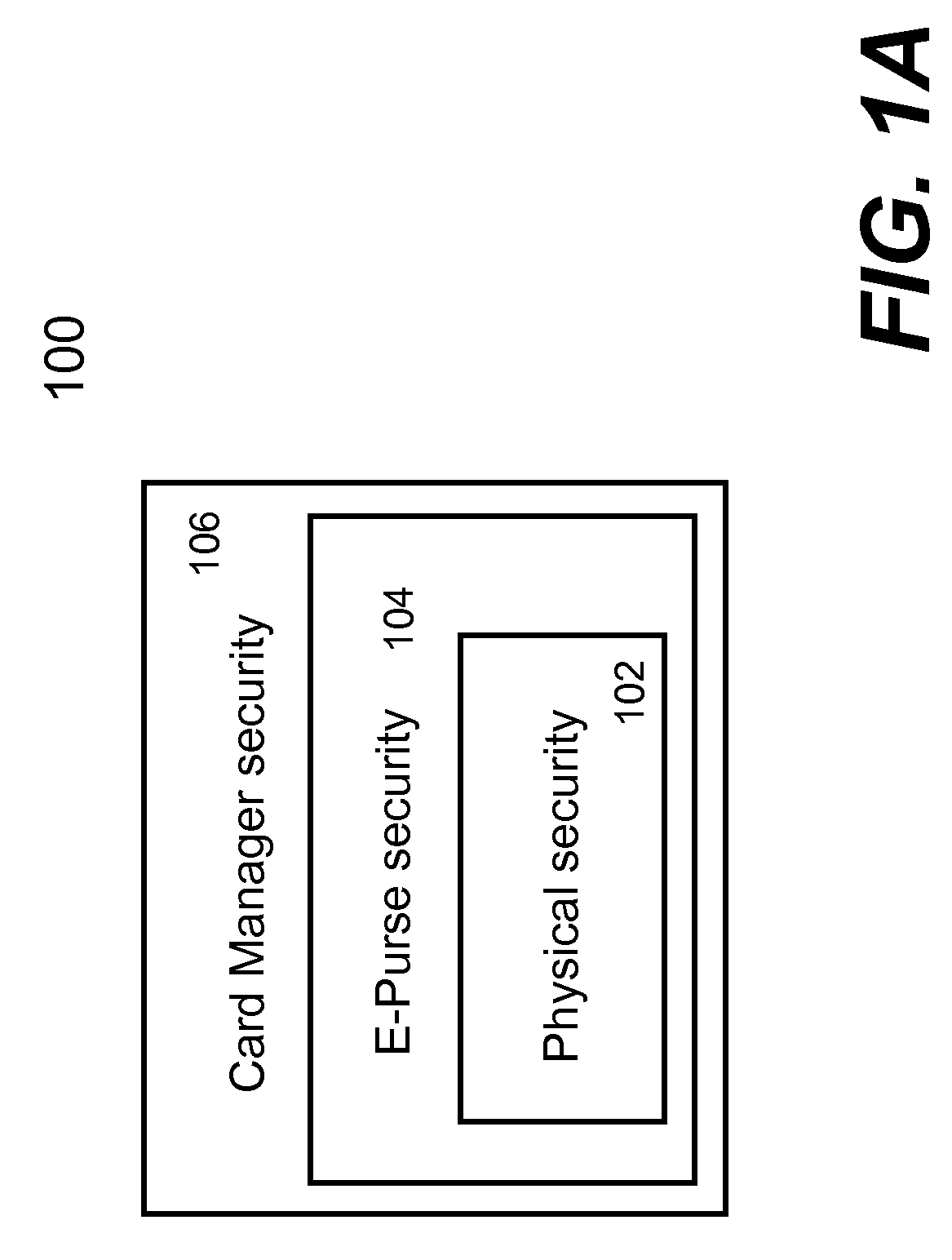
Method and apparatus for providing electronic purse
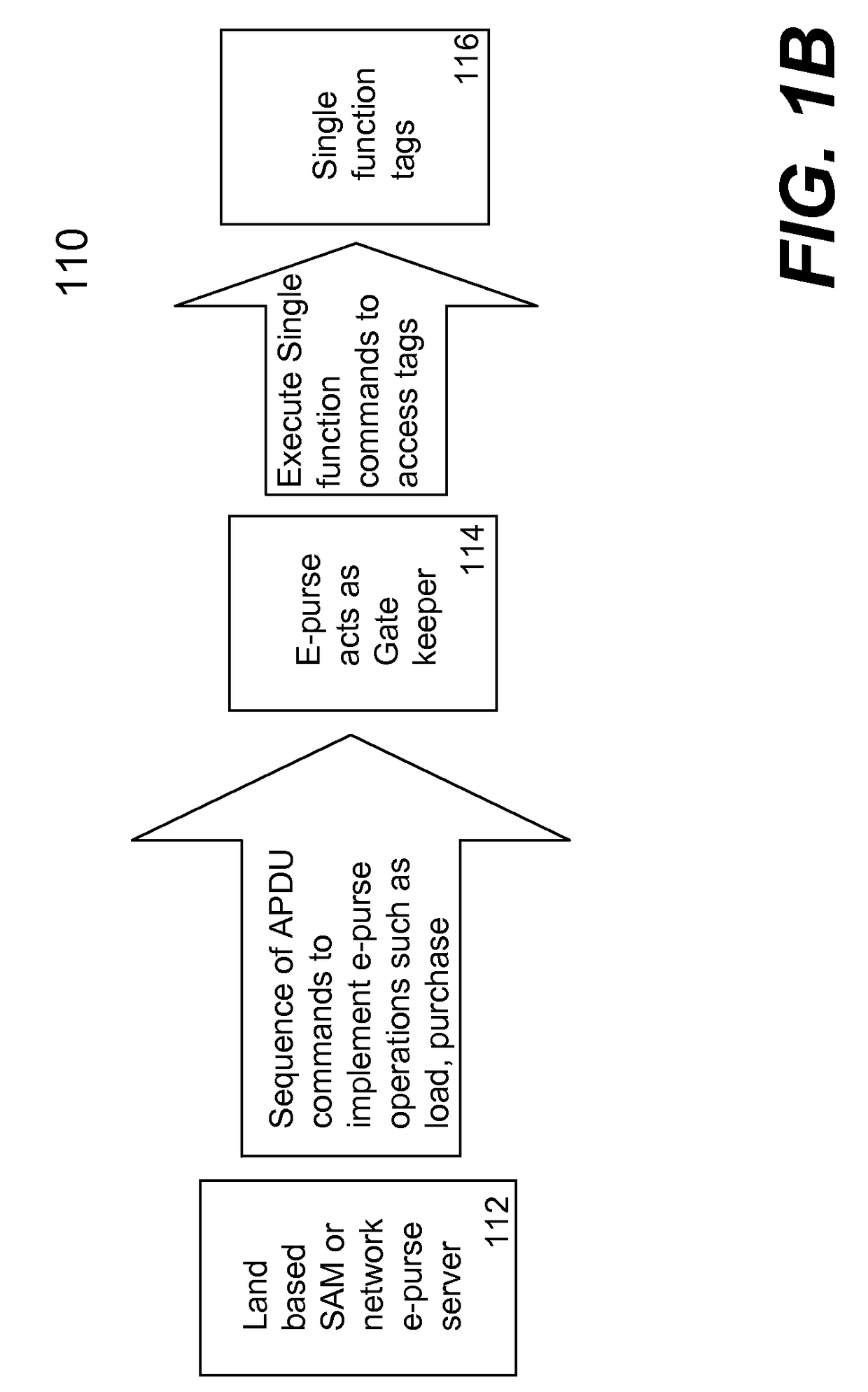
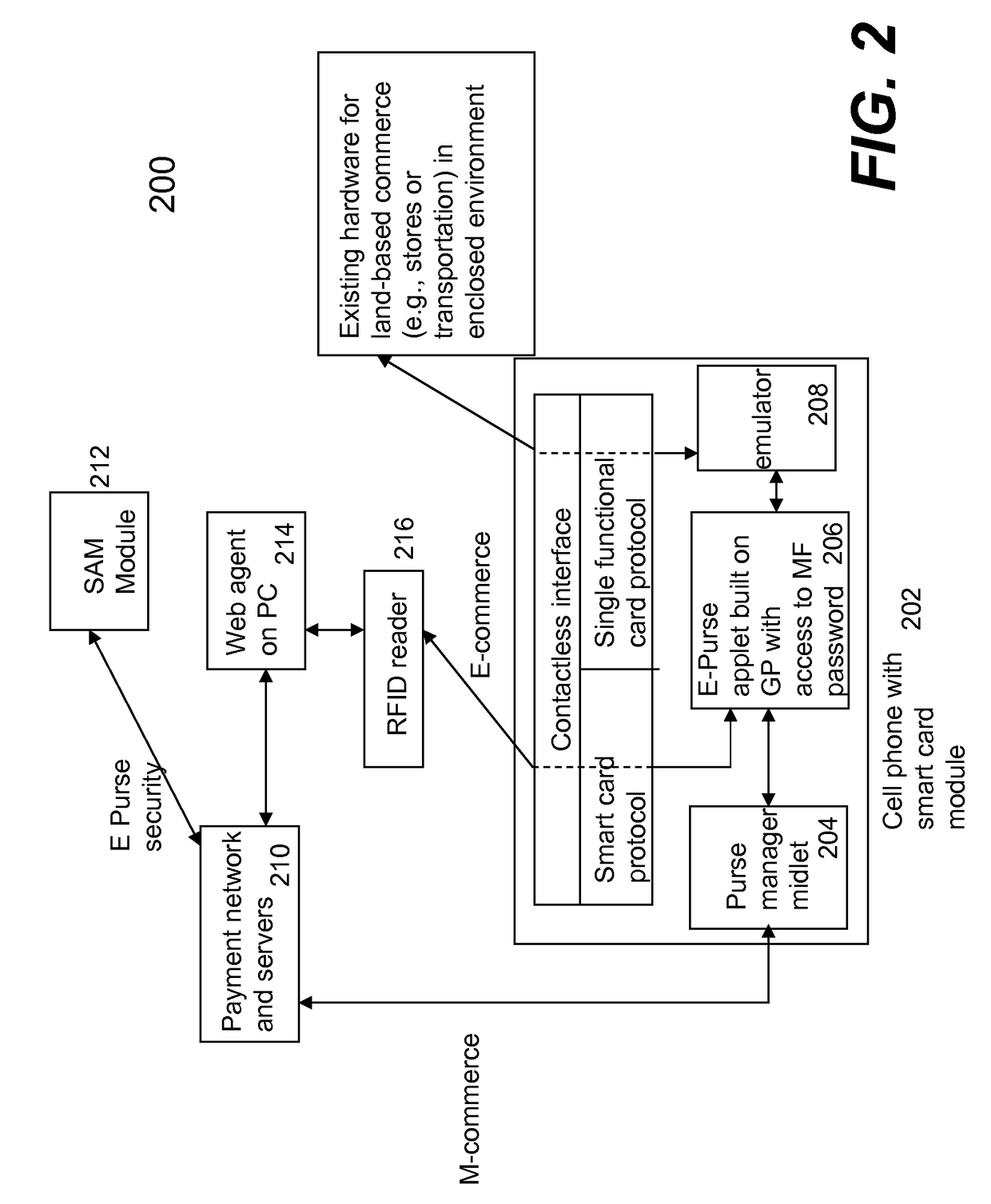
ActiveUS20080073426A1Facilitate communicationWithout compromising securityFinancePayment protocolsPersonalizationPhysical security
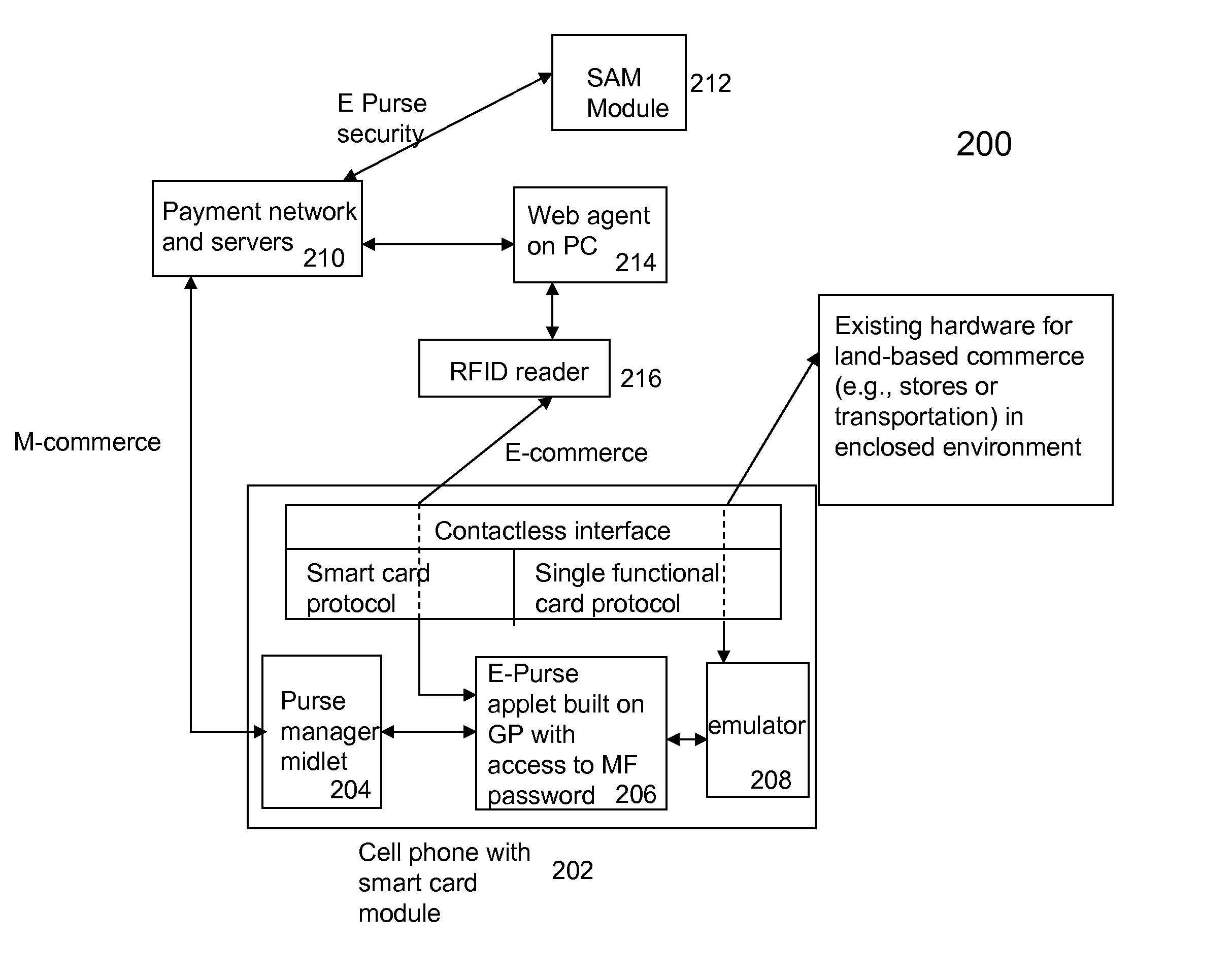
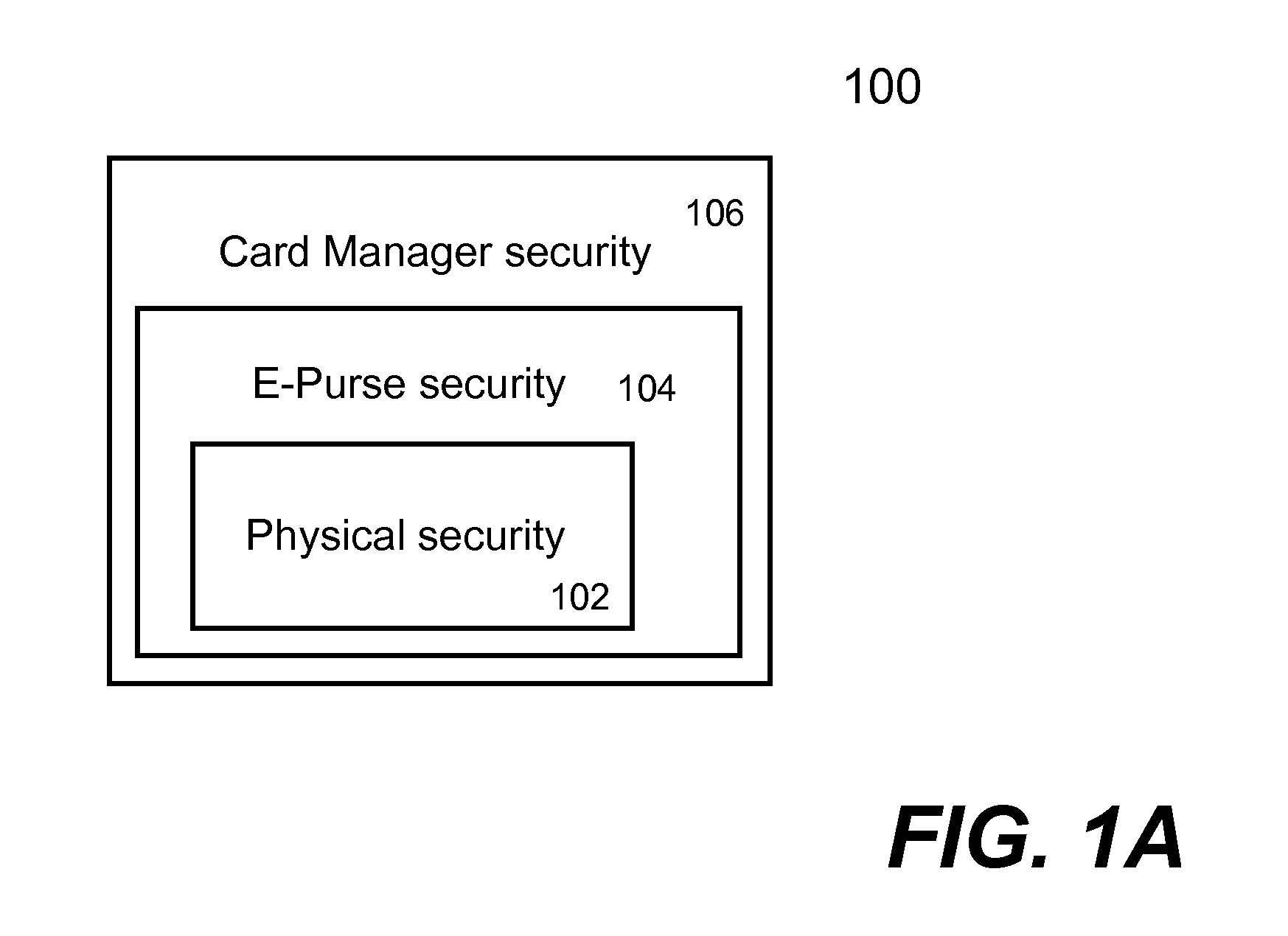
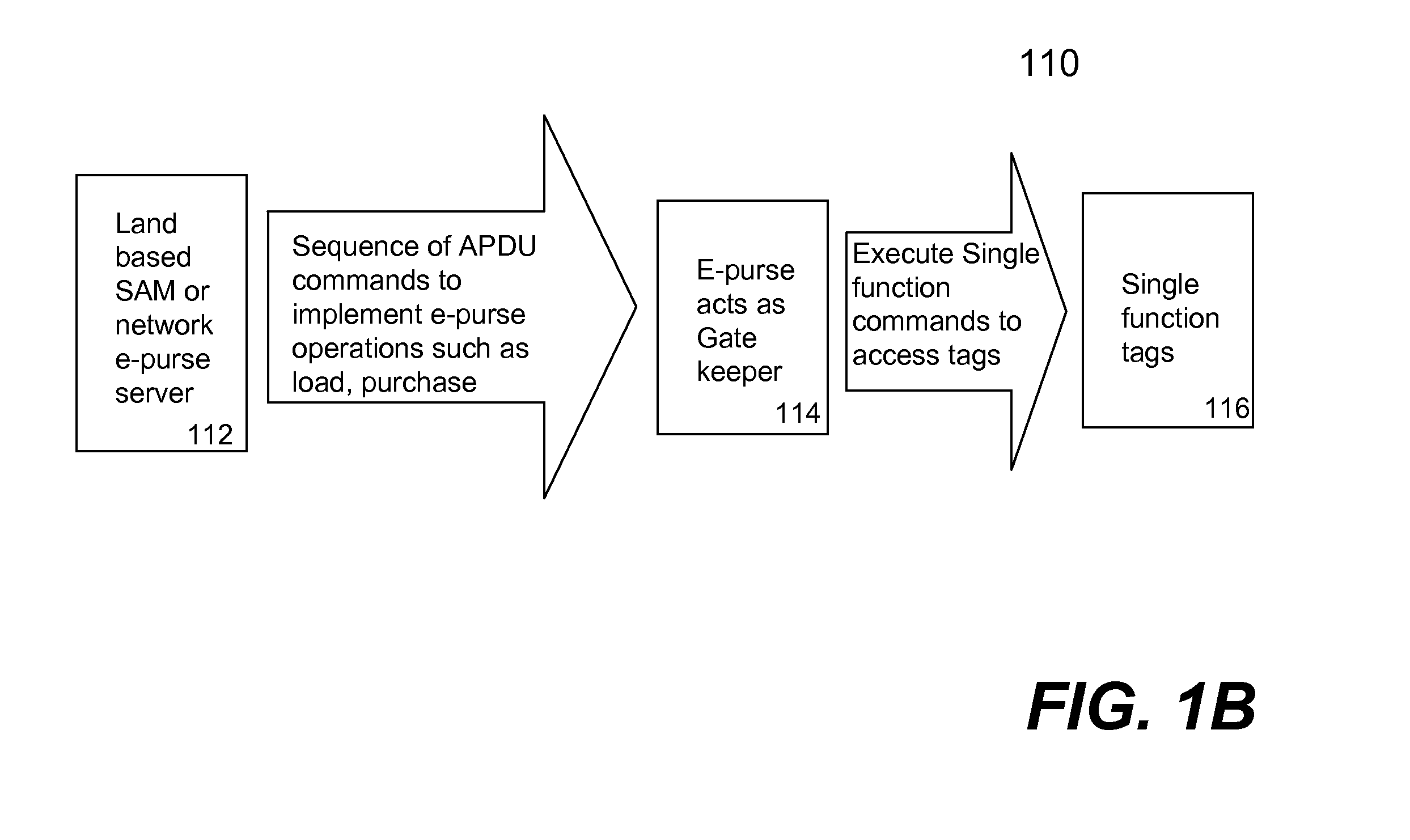
Techniques for portable devices functioning as an electronic purse (e-purse) are disclosed. According to one aspect of the invention, a mechanism is provided to enable a portable device to conduct transactions over an open network with a payment server without compromising security. In one embodiment, a device is loaded with an e-purse manager. The e-purse manager is configured to manage various transactions and functions as a mechanism to access an emulator therein. The transactions may be conducted over a wired network or a wireless network. A three-tier security model is contemplated to support the security of the transactions from the e-purse. The three-tier security model includes a physical security, an e-purse security and a card manager security, concentrically encapsulating one with another. Security keys (either symmetric or asymmetric) are personalized within the three-tier security model.
Owner:SHENZHEN RFCYBER ASSET MANAGEMENT
Connector and receptacle containing a physical security feature
Owner:COMMSCOPE TECH LLC
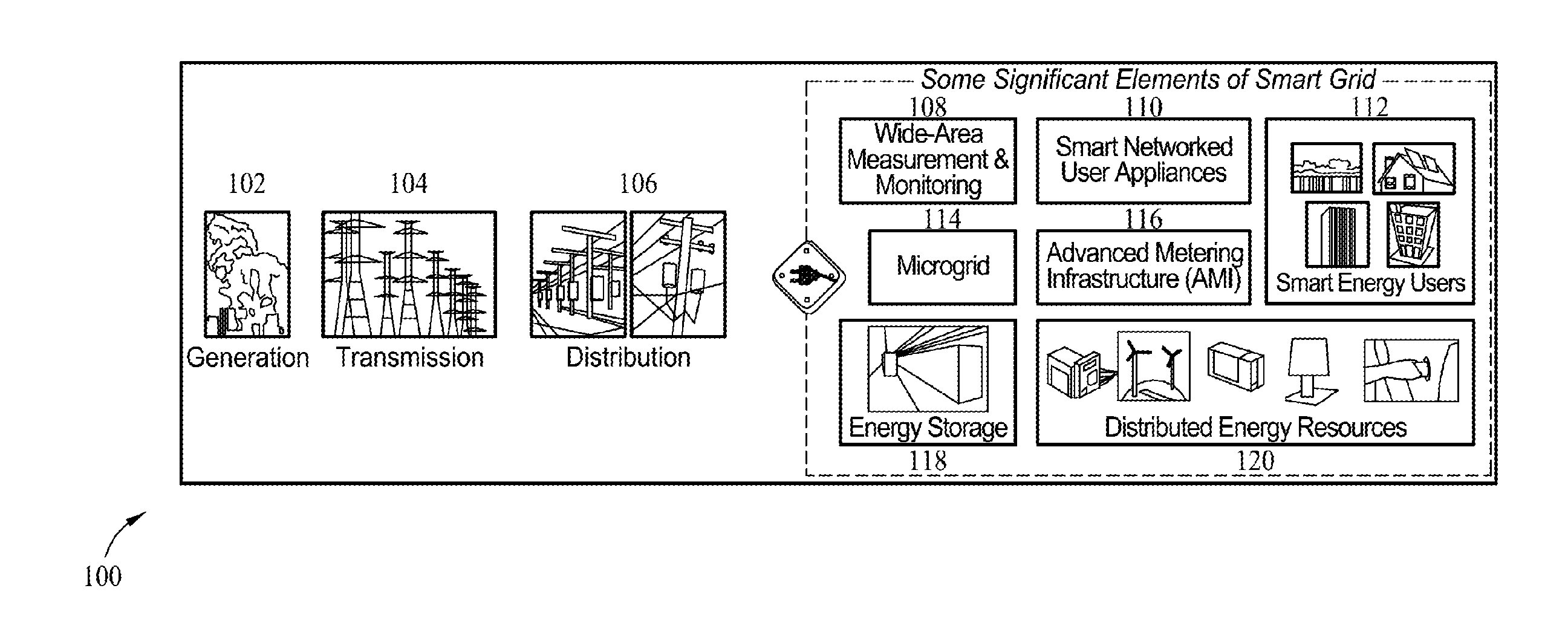
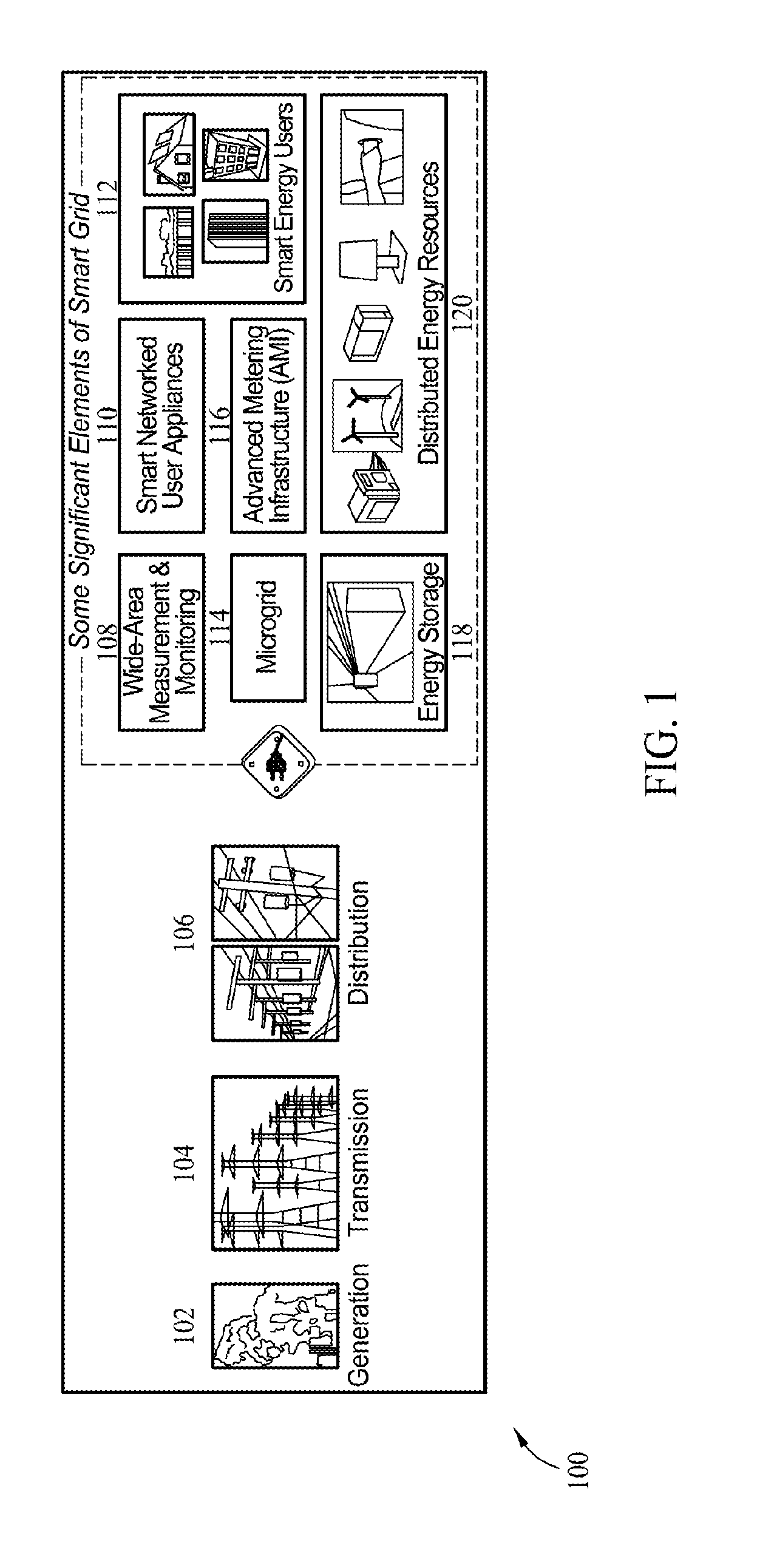
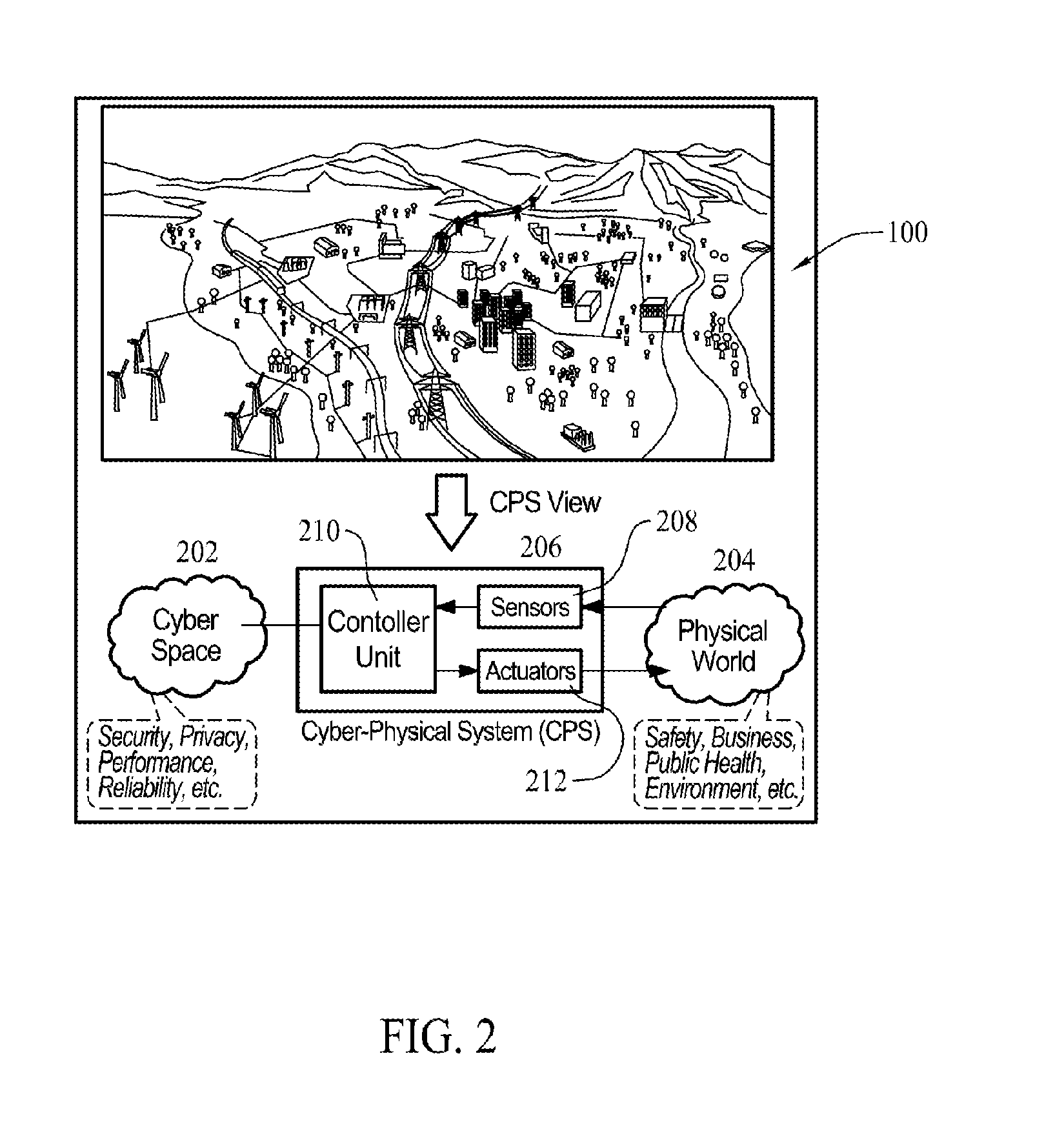
Methods and systems for cyber-physical security modeling, simulation and architecture for the smart grid
ActiveUS20130198847A1Memory loss protectionError detection/correctionInteractive softwarePhysical security
A computer-implemented method for use in evaluating at least one threat to a complex system includes identifying one or more physical components of the complex system and modeling the one or more physical components with interactive software multi-agents. The multi-agents are programmed to monitor and control at least one function of the modeled physical components. One or more threats to a target of the complex system are identified. Each threat is defined as a cyber threat or physical threat and the target is defined as a cyber component or physical component. The method includes simulating an attack on the complex system by the identified threat and assessing an impact of the attack on the complex system.
Owner:THE BOEING CO
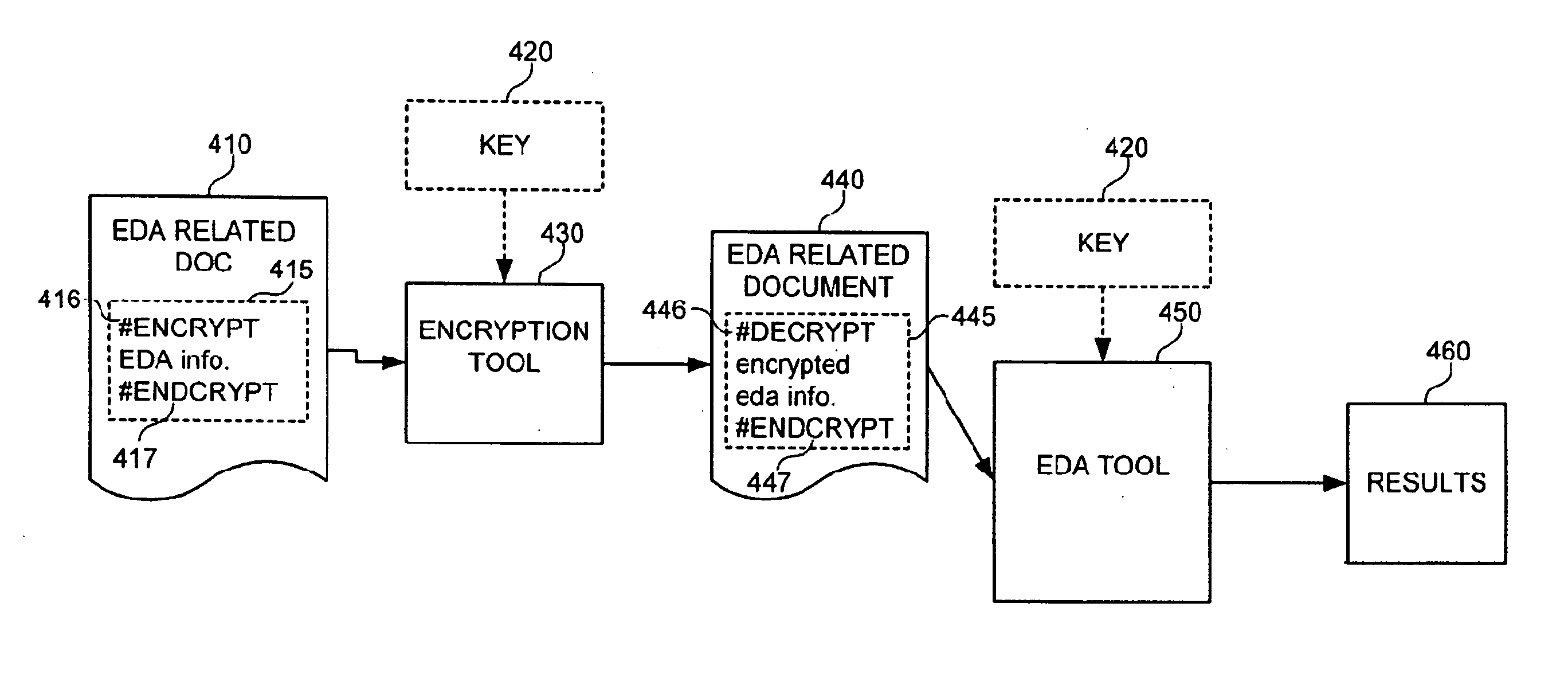
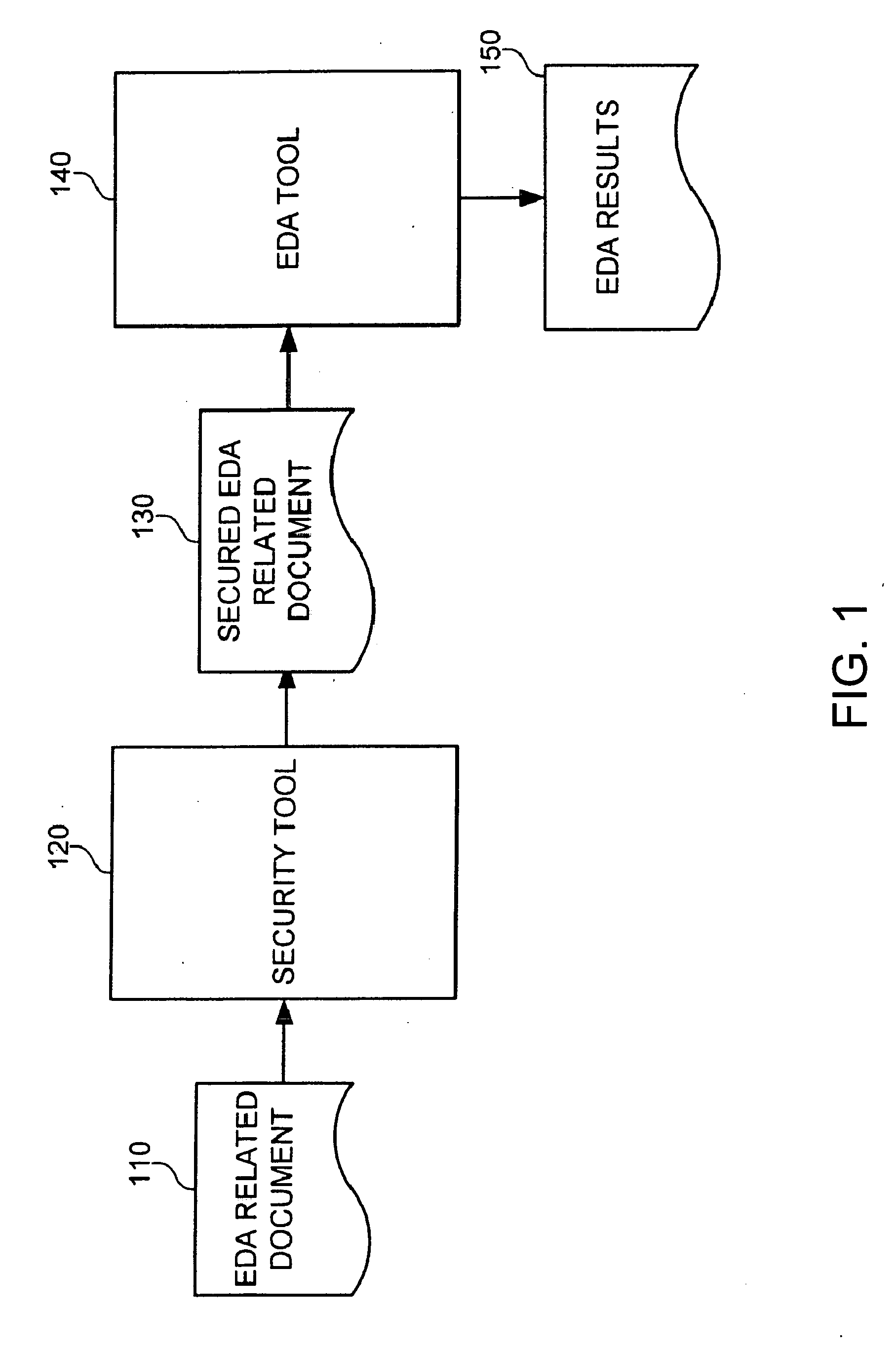
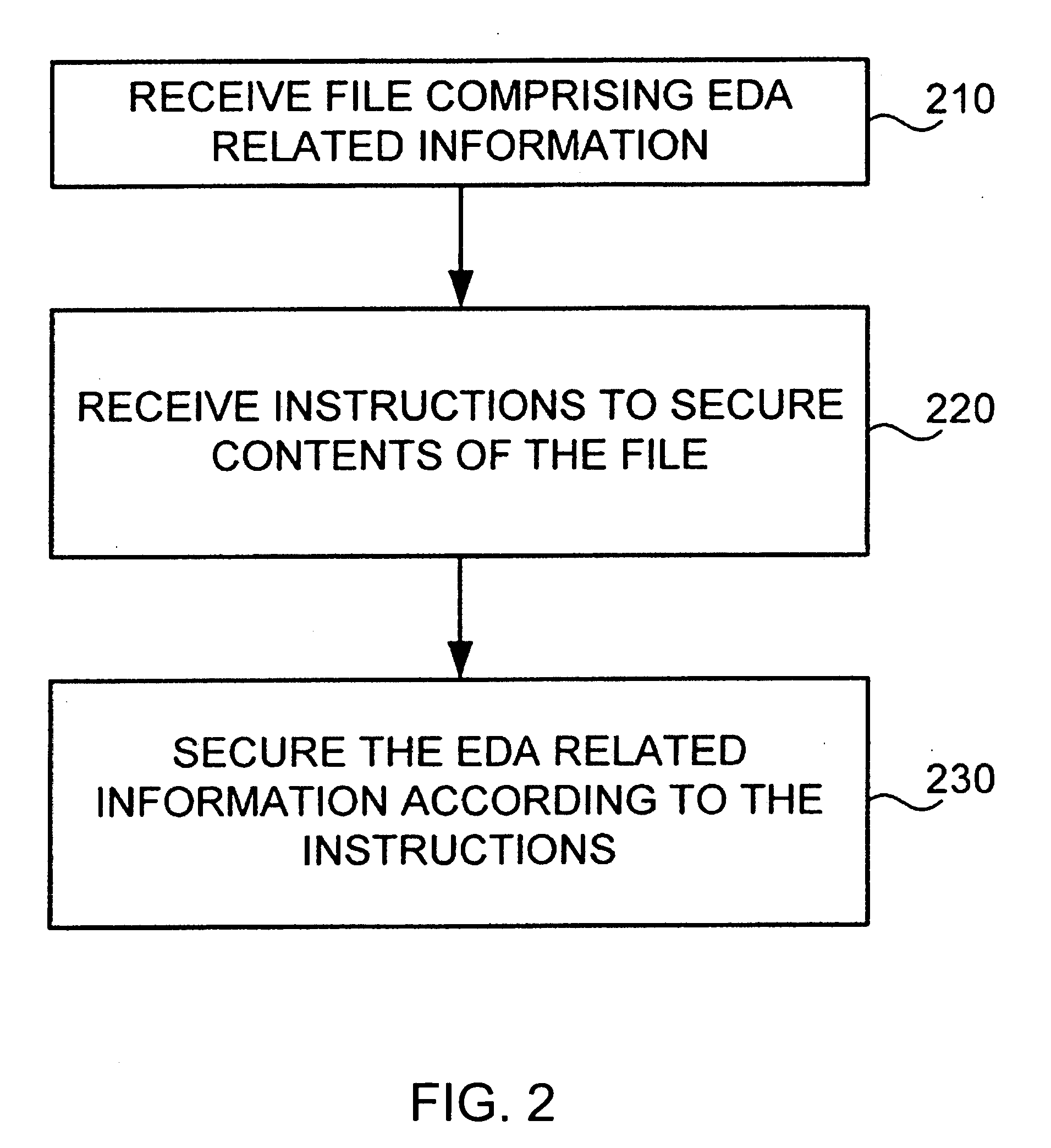
Concealment of information in electronic design automation
InactiveUS20070055892A1Digital data processing detailsUser identity/authority verificationEngineeringInformation hiding
An electronic design automation tool may receive information related to electronic design automation that contains secured information, such as physically secured information, and annotations to indicate the secured portions of the information. Upon receiving such information, the electronic design automation tool may identify those portions of the information comprising secured information related to electronic design automation, and unlock the secured information for processing. The electronic design automation tool may process at least some of the secured electronic design automation information without revealing that secured information to unauthorized persons, tools, systems, or otherwise compromising the protection of that secured information. That is, the design automation tool may process the secured electronic design automation information so that the secured information is concealed both while it is being processed and by the output information generated from processing the secured information.
Owner:MENTOR GRAPHICS CORP
Connector and receptacle containing a physical security feature
ActiveUS7182523B2Personal safetyImpede matingIncorrect coupling preventionCoupling light guidesPhysical securityInformation networks
An optical network comprising: (a) a plurality of different optical fiber receptacles for facilitating an optical connection to different information networks requiring different access authorization, each different optical fiber receptacle optically coupled to one and only one different information network, each optical fiber receptacle having an inner surface with a first geometry, the first geometry comprising at least a slot, a certain number of optical fiber receptacles having different first geometries in which the slots are in different positions; and (b) a plurality of different optical fiber plugs for optically coupling with the different optical fiber receptacles, each optical fiber plug having a second geometry, the second geometry comprising at least a key in a certain position, the certain number of optical fiber plugs having different second geometries in which the keys are in different positions, each different first geometry corresponding to one and only one second geometry such that the optical fiber plugs and receptacles of corresponding first and second geometries are mating pairs.
Owner:COMMSCOPE TECH LLC
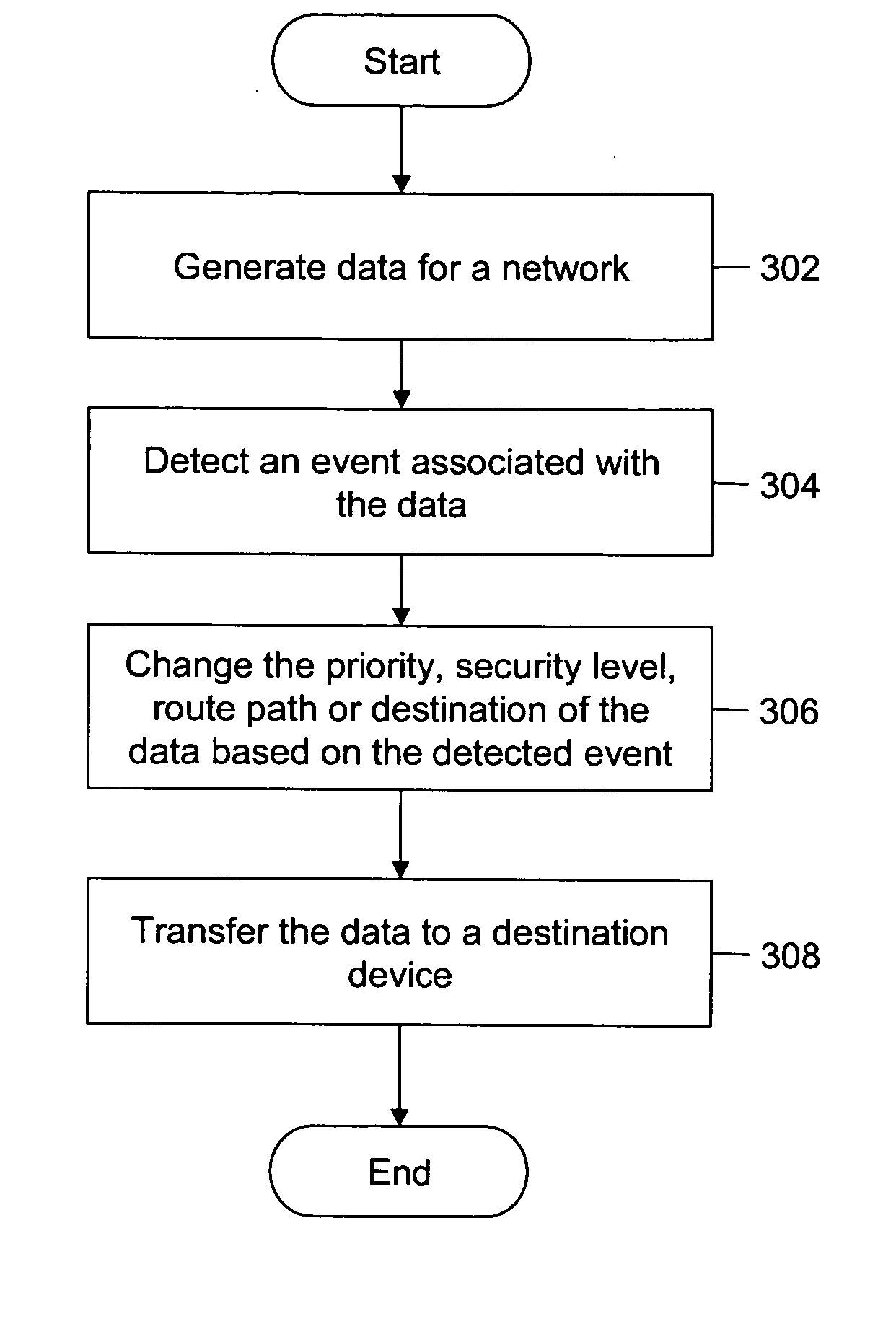
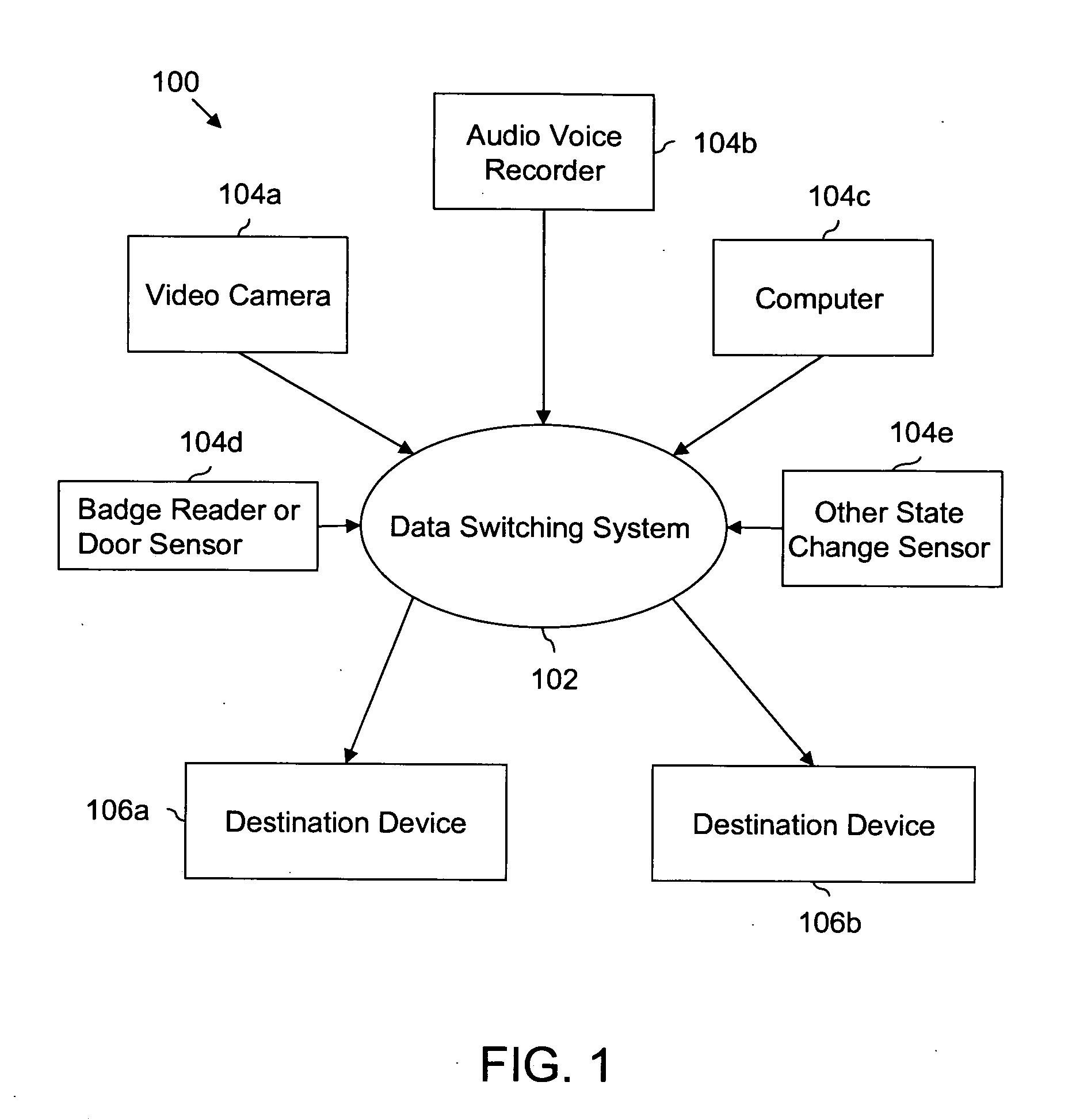
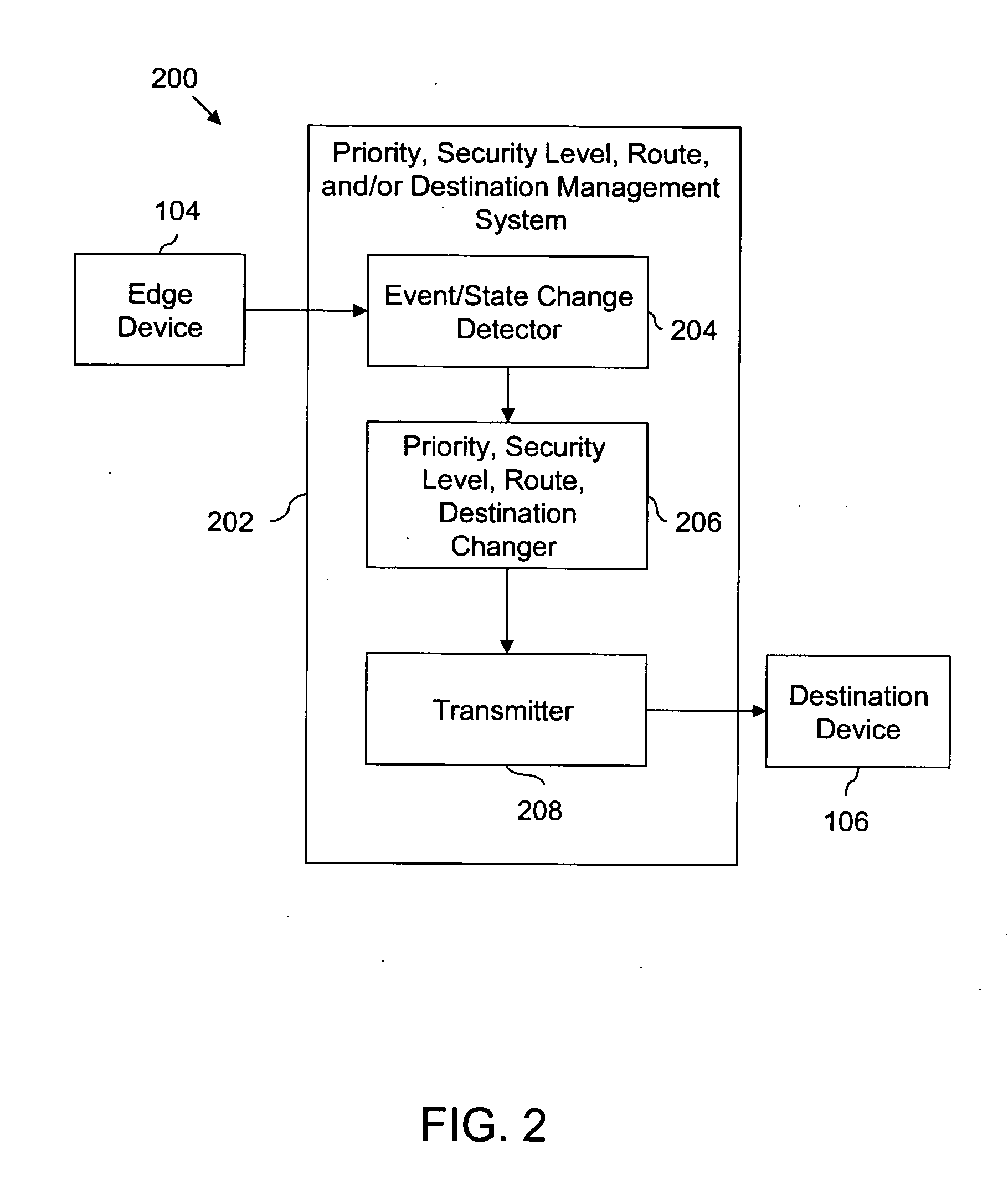
Method and system for transmitting data over a network based on external non-network stimulus
Method, system and apparatus are provided for transmitting data over a network based on external, non-network oriented (external to the network) stimulus. A facility's physical security, environment monitoring / management, or production control system utilizing a frame-based / packet-based network includes a number of edge devices, an event / state change detector, a priority, security level, route specification, destination changer, a transmitter, and a number of destination devices. Edge devices generate data for the network; the event / state change detector identifies an event associated with the data; the priority, security level, route specification, destination changer changes the priority, security level, route, destination of the data, based on the detected event or state change; and the transmitter then transmits the data to an intended destination device, based on the changed priority, security level, route, and destination.
Owner:CISCO TECH INC
Radio frequency wave reducing material and methods for manufacturing same
ActiveUS20070107350A1Improve abilitiesReduce transmissionScreening rooms/chambersCeilingsUltrasound attenuationPhysical security
An improved radio frequency wave attenuating wall (ceiling or floor) or door material comprises a laminated structure having as an integral part thereof one or more layers of a viscoelastic material which also functions as a glue and one or more electrically conducting layers. An electrically conducting material such as tape or a formed metal channel provides an electrical connection between the electrically conducting material and an exposed outer surface of the laminated structure. In one embodiment the electrically conducting material is paint. In one embodiment , standard wallboard, typically gypsum, comprises the external surfaces of the laminated structure and one or more conductive layers are constructed between the gypsum exterior. In one embodiment, the conducting layer material is selected to provide physical security in addition to radio frequency wave attenuation. The construction is such that acoustical attenuation is also achieved.
Owner:PACIFIC COAST BUILDING PRODS
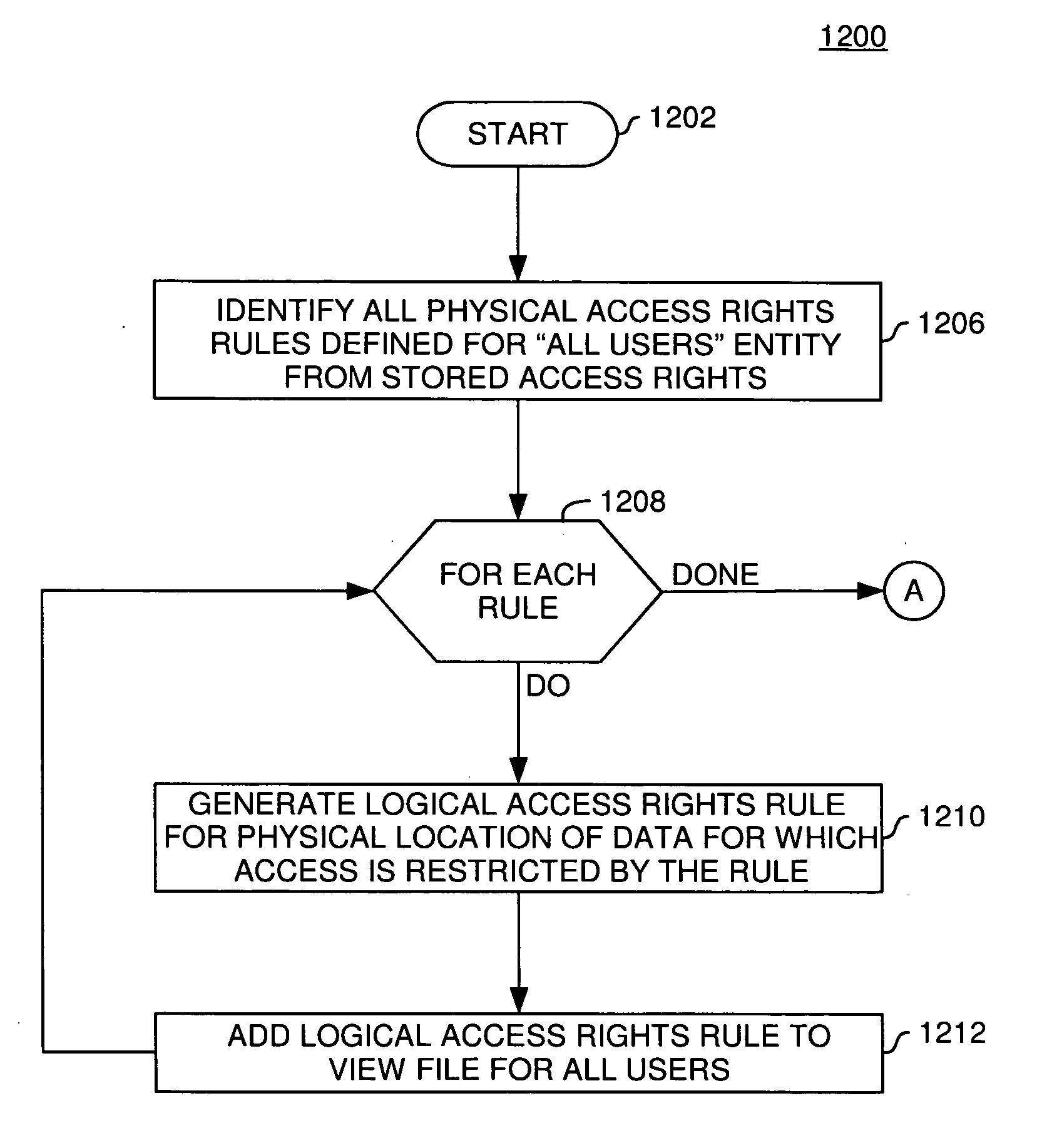
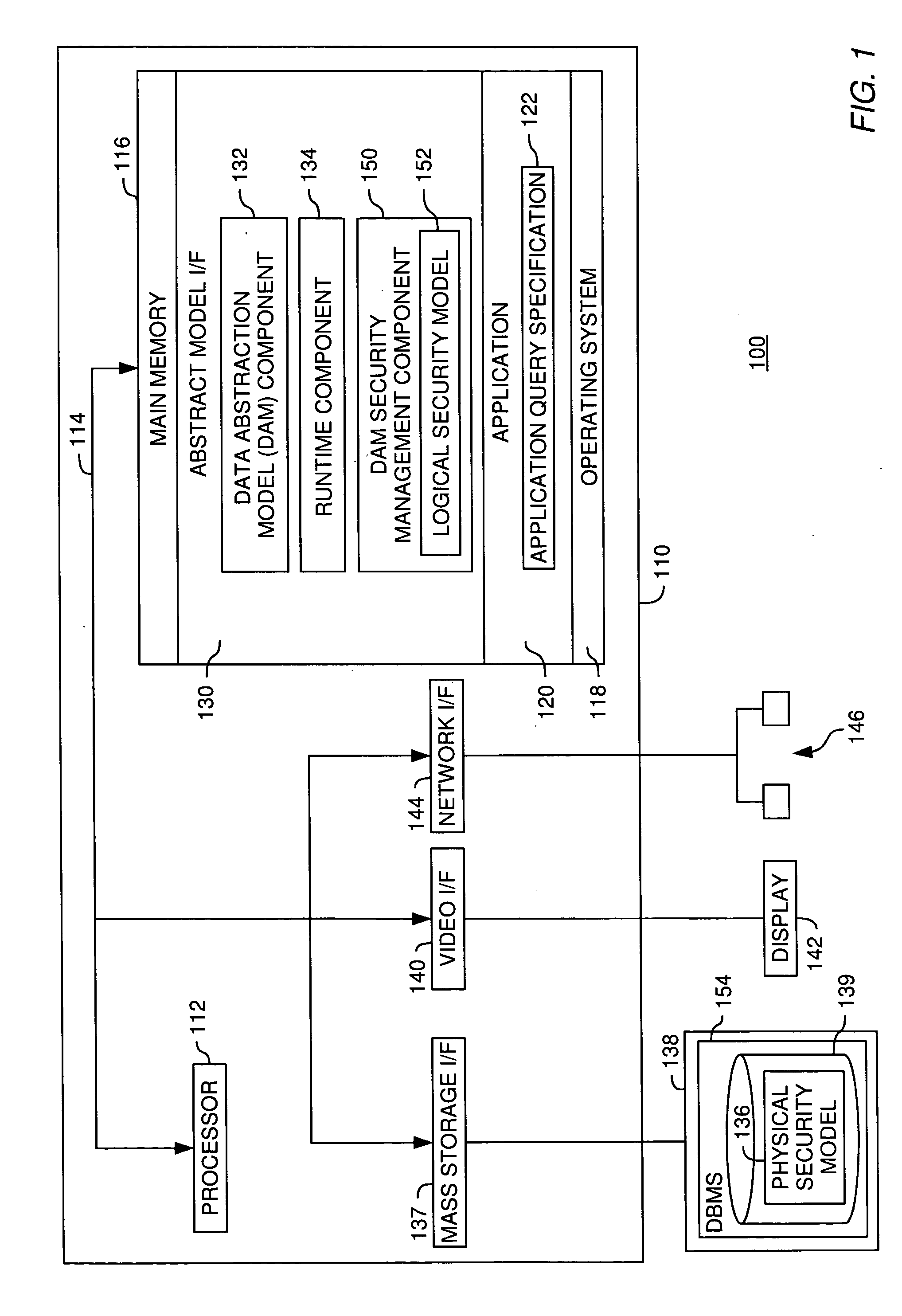
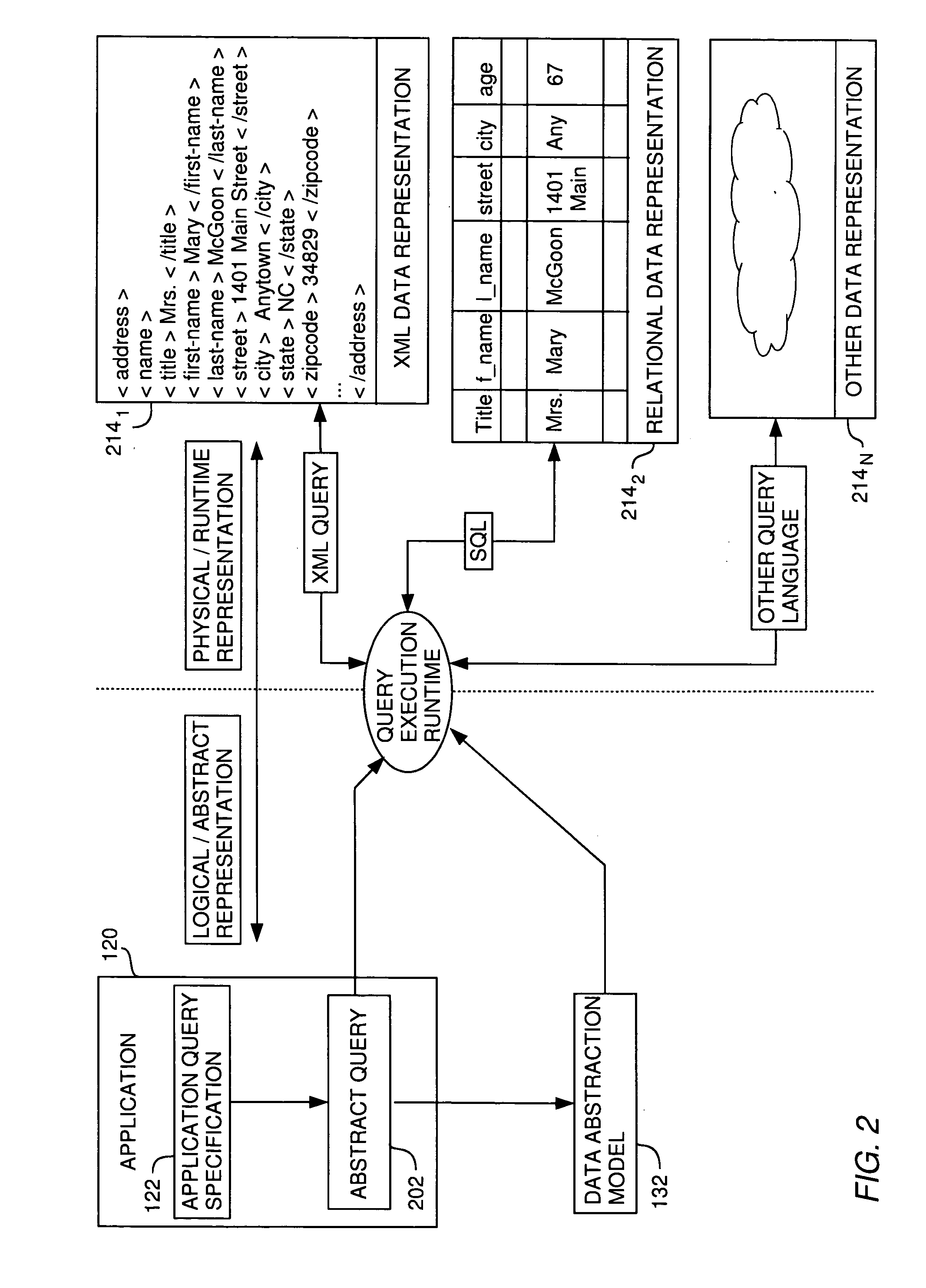
Techniques for managing access to physical data via a data abstraction model
InactiveUS20060137019A1Limited accessDigital data processing detailsUser identity/authority verificationData abstractionPhysical security
A method, system and article of manufacture for managing access to a data abstraction model abstractly describing physical data and, more particularly, for creating a logical security model for a data abstraction model abstractly describing data in a database. One embodiment provides a computer-implemented method for creating a logical security model based on a physical security model defining user access rights to physical data. The method comprises, for each of the user access rights defined by the physical security model, creating a logical access right definition for a logical model. The logical model comprises a plurality of logical field definitions each comprising a field name and access information for accessing a field of the physical data. The logical access right definitions are applied to the logical model so that the logical model reflects the user access rights to the physical data.
Owner:IBM CORP
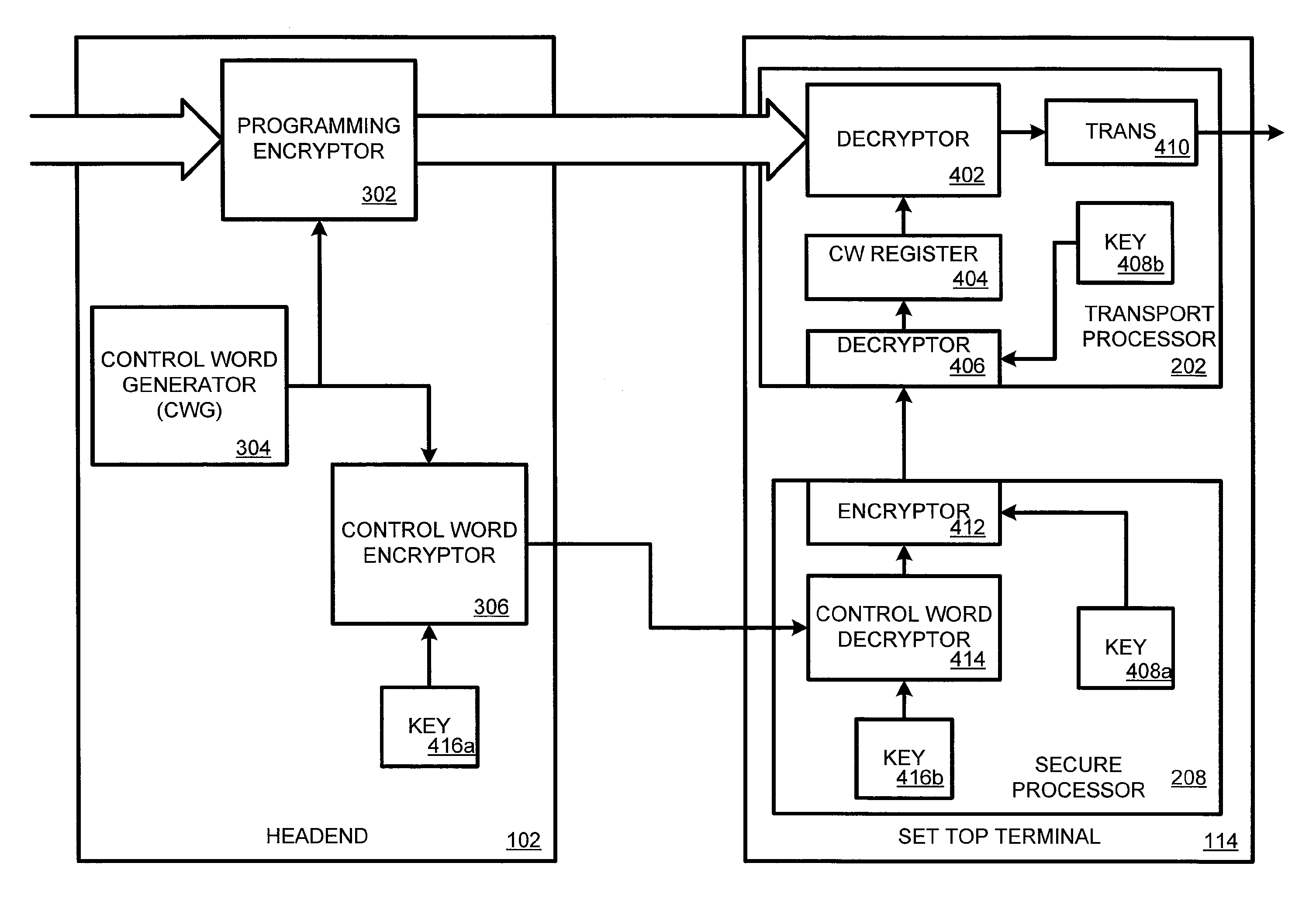
Data authentication with a secure environment
InactiveUS7715552B2Key distribution for secure communicationUnauthorized memory use protectionPhysical securitySecure cryptoprocessor
Included are systems and methods for data authentication. At least one embodiment of a system includes a secure processor configured as a physically secure environment, the secure processor further configured to receive a control word from a headend, the secure processor further configured to encrypt the received control word using a first encryption key. Other embodiments of a system includes a transport processor configured to receive the encrypted control word, the transport processor further configured to decrypt the received control word using a first decryption key, wherein the first decryption key is compatible with the first encryption key.
Owner:CISCO TECH INC
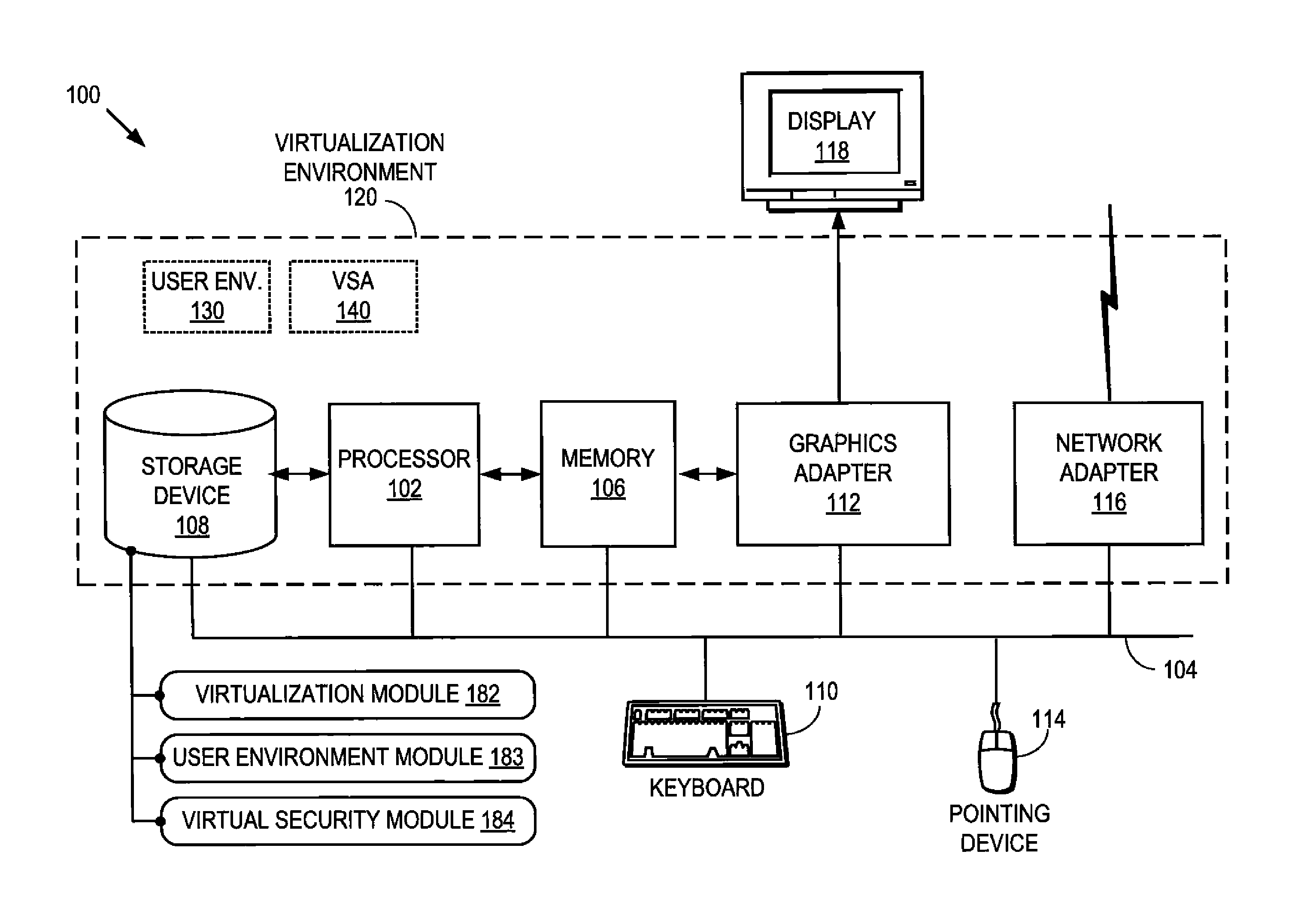
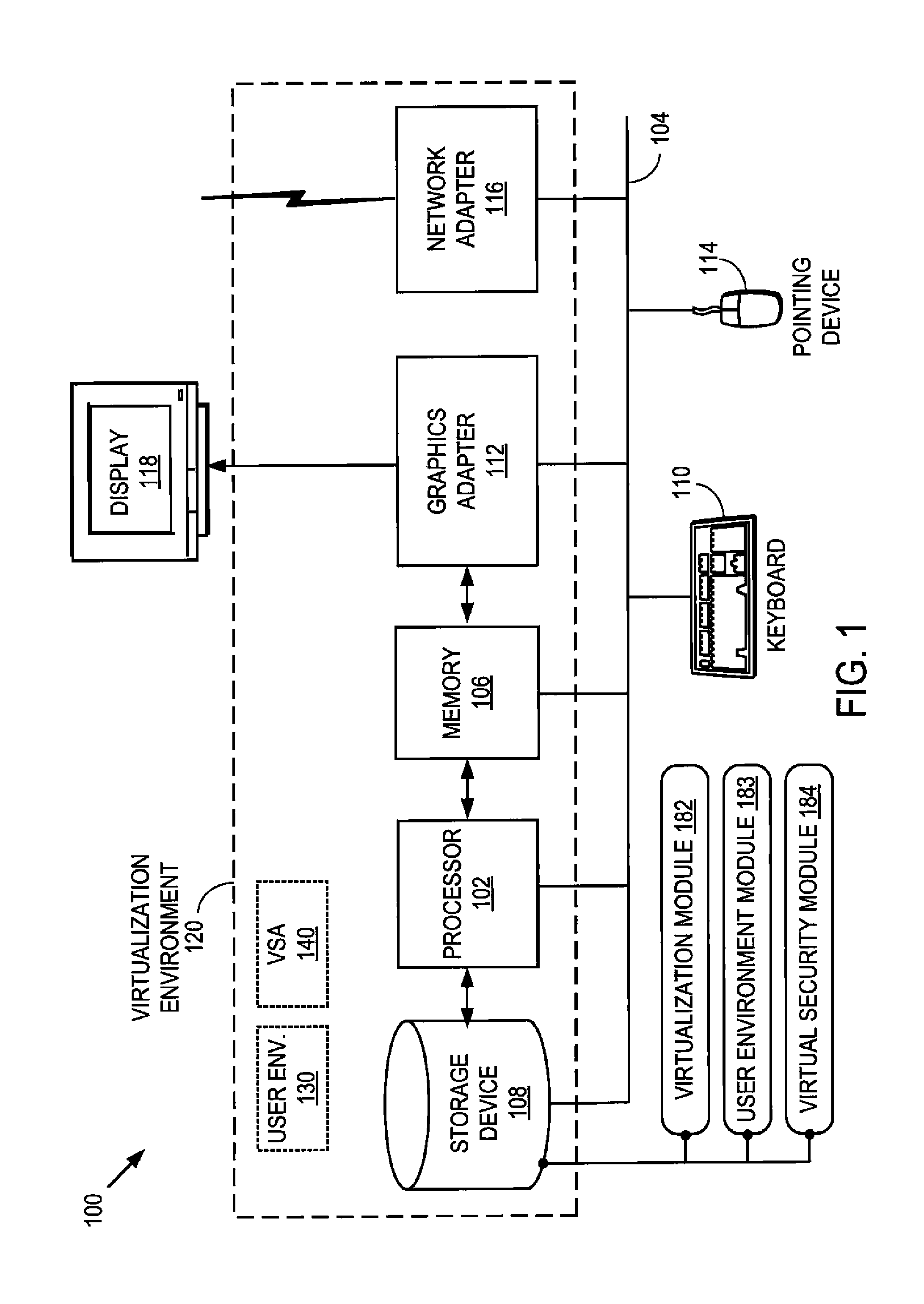
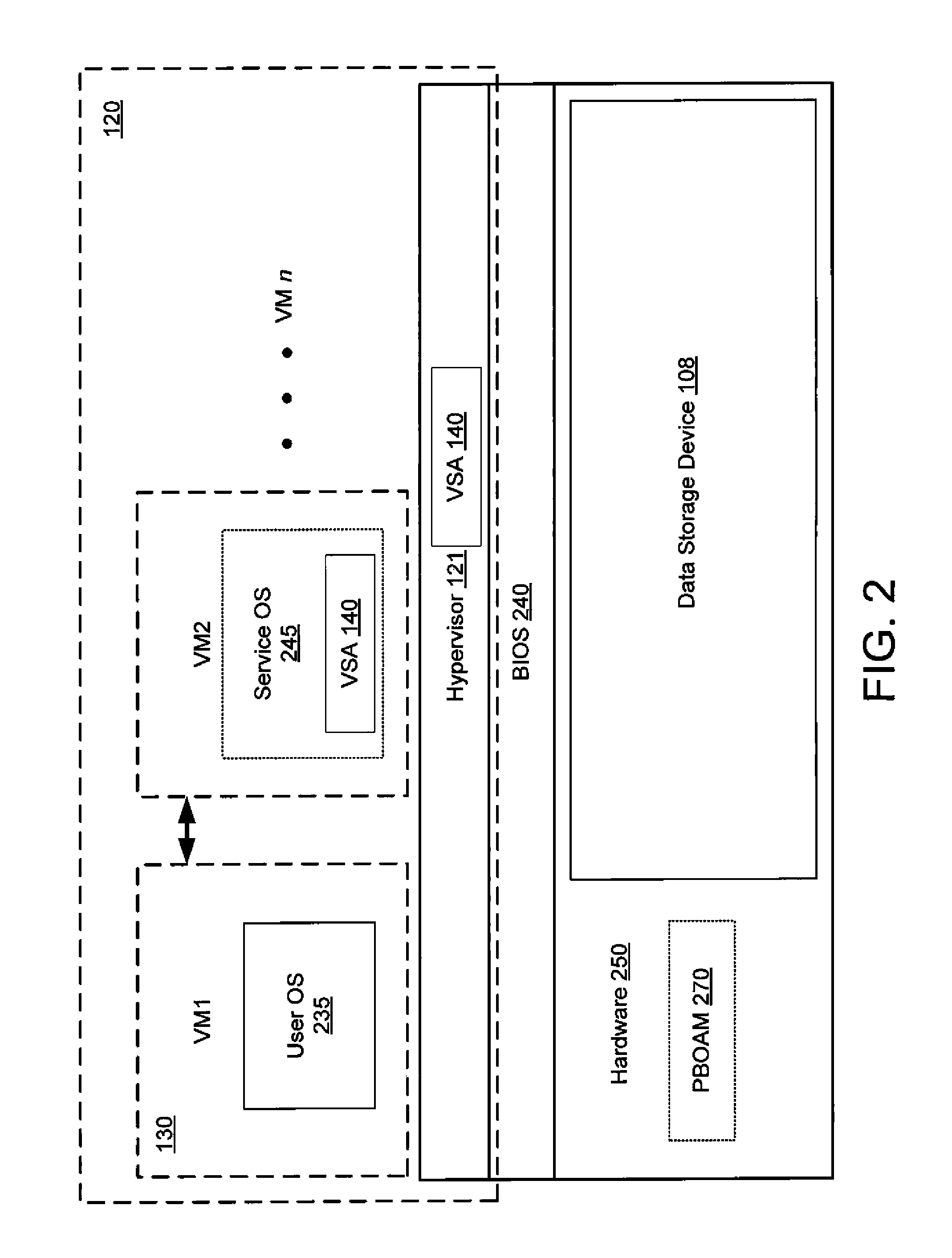
Virtual security appliance
ActiveUS8353031B1Expensive to manageHighly inaccessibleMemory loss protectionError detection/correctionVirtualizationPhysical security
Security from malicious attack is provided for a user environment running in a virtualized environment by a virtual security appliance (VSA) running outside of the user environment, but on the same computer system as the user environment. For example, a VSA running in a virtual machine can provide security for a user environment running in a second virtual machine. The separation of the VSA from the user environment enhances the robustness of the VSA against malicious attacks seeking to disable / bypass the protections of the VSA, while avoiding the costs and complexities of a physical security appliance.
Owner:NORTONLIFELOCK INC
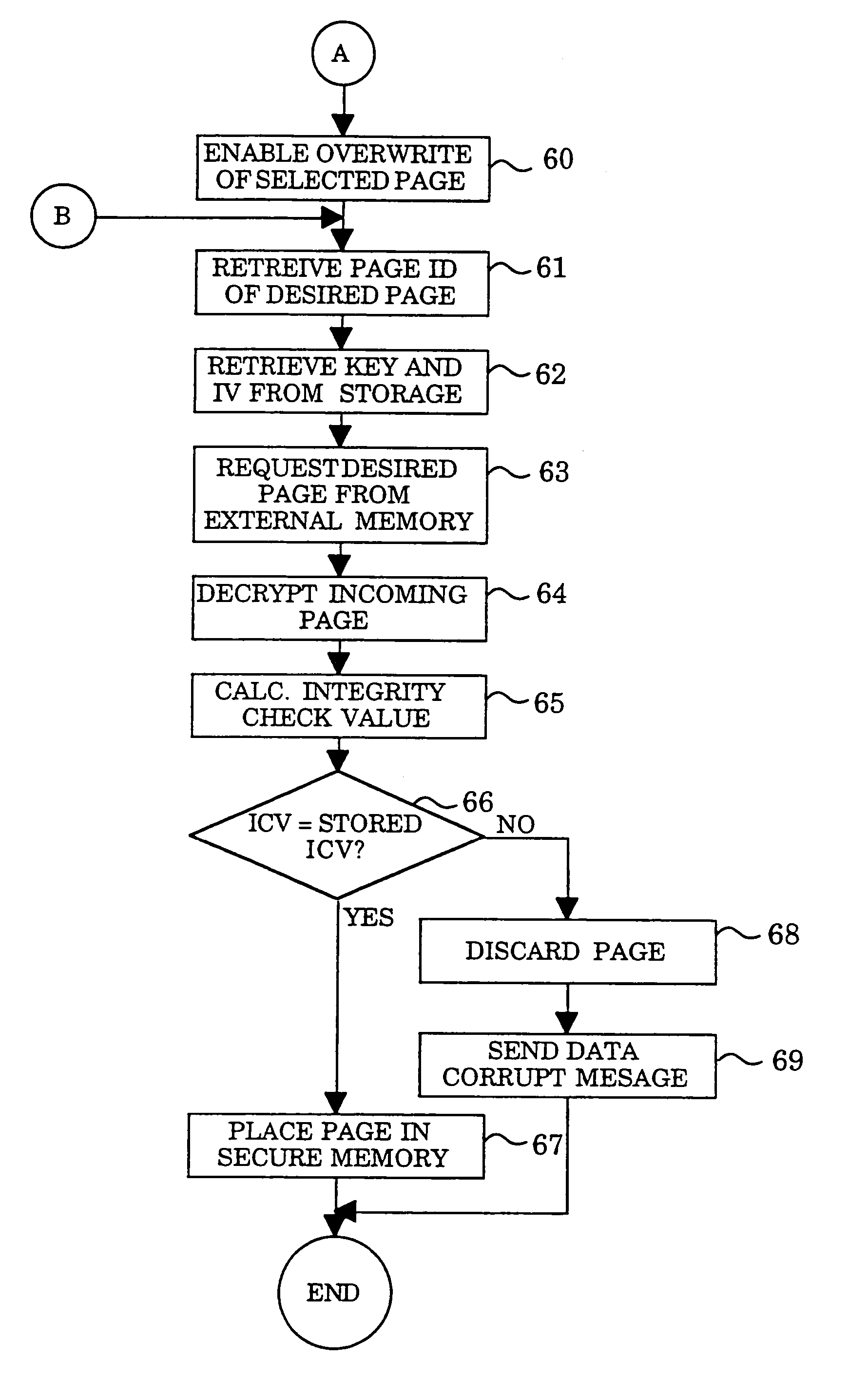
Cryptographically protected paging system
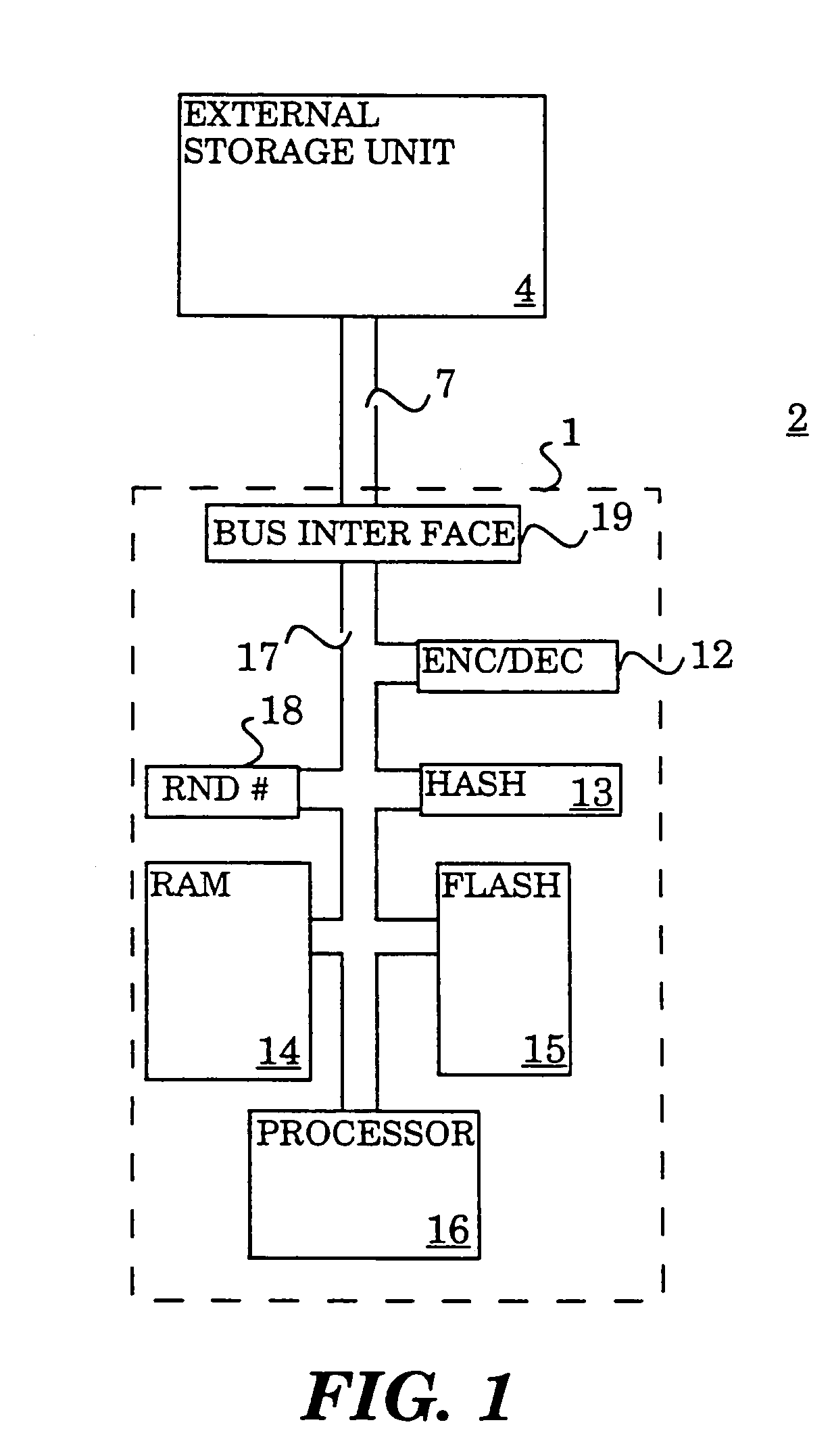
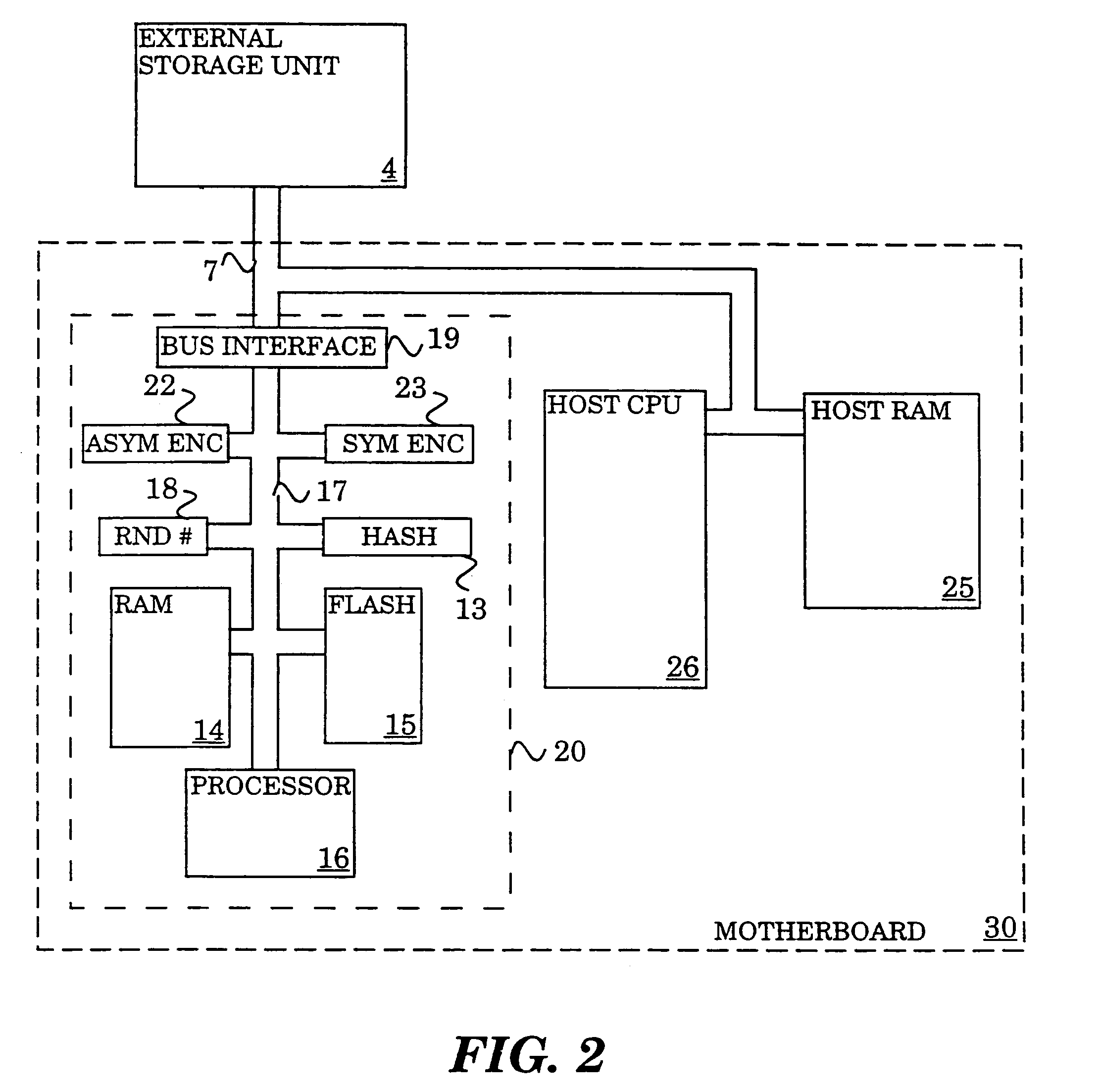
InactiveUS7149901B2Maintain confidentialityMaintain integrityMemory architecture accessing/allocationDigital data processing detailsHash functionPhysical security
A method and system for maintaining integrity and confidentiality of pages paged to an external storage unit from a physically secure environment. An outgoing page is selected to be exported from a physically secure environment to an insecure environment. An integrity check value is generated and stored for the outgoing page. In one embodiment, this takes the form of taking a one-way hash of the page using a well-known one-way hash function. The outgoing page is then encrypted using a cryptographically strong encryption algorithm. Among the algorithms that might be used in one embodiment of the invention are IDEA and DES. The encrypted outgoing page is then exported to the external storage. By virtue of the encryption and integrity check, the security of the data on the outgoing page is maintained in the insecure environment.
Owner:INTEL CORP
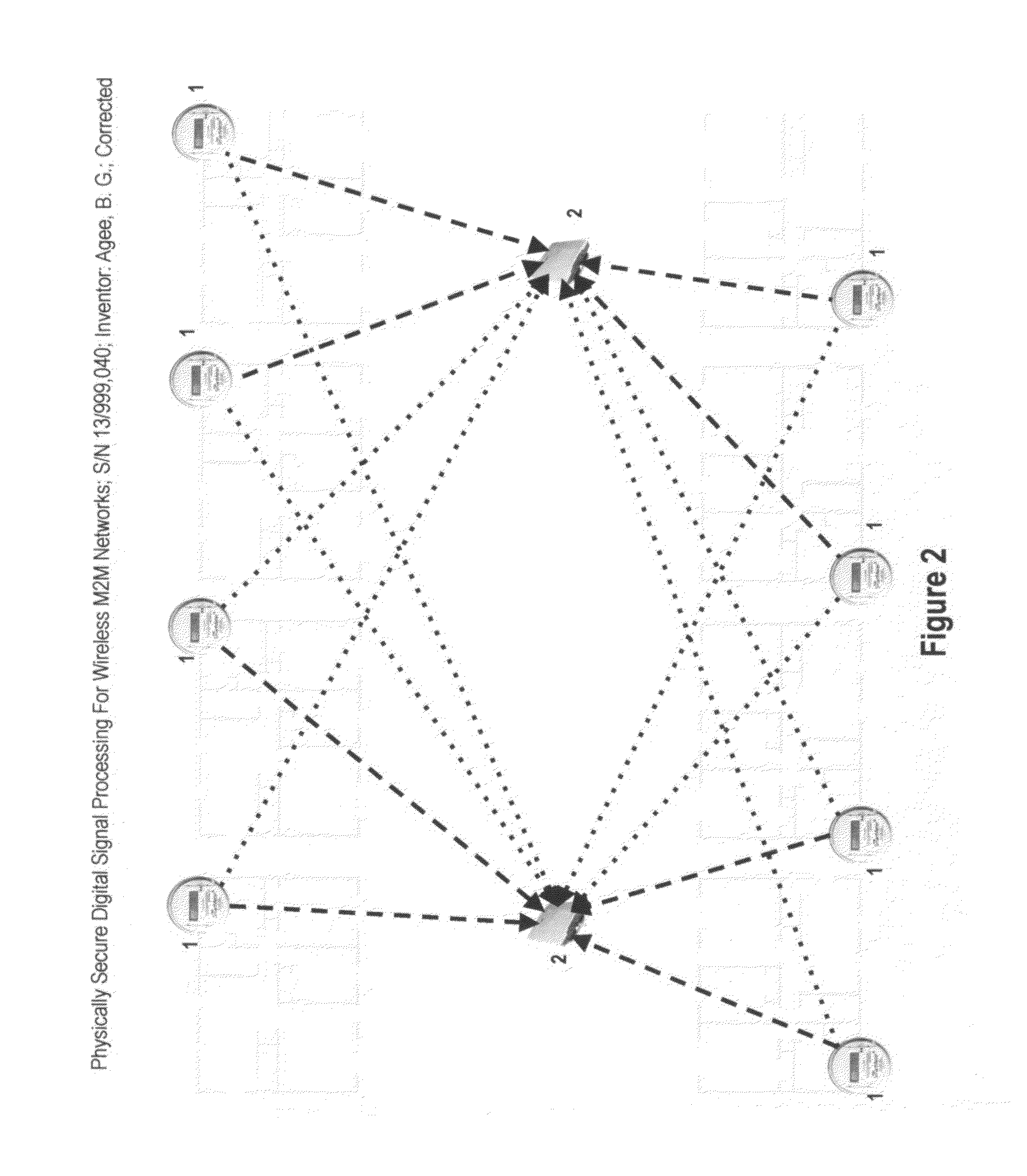
Physically secure digital signal processing for wireless M2M networks
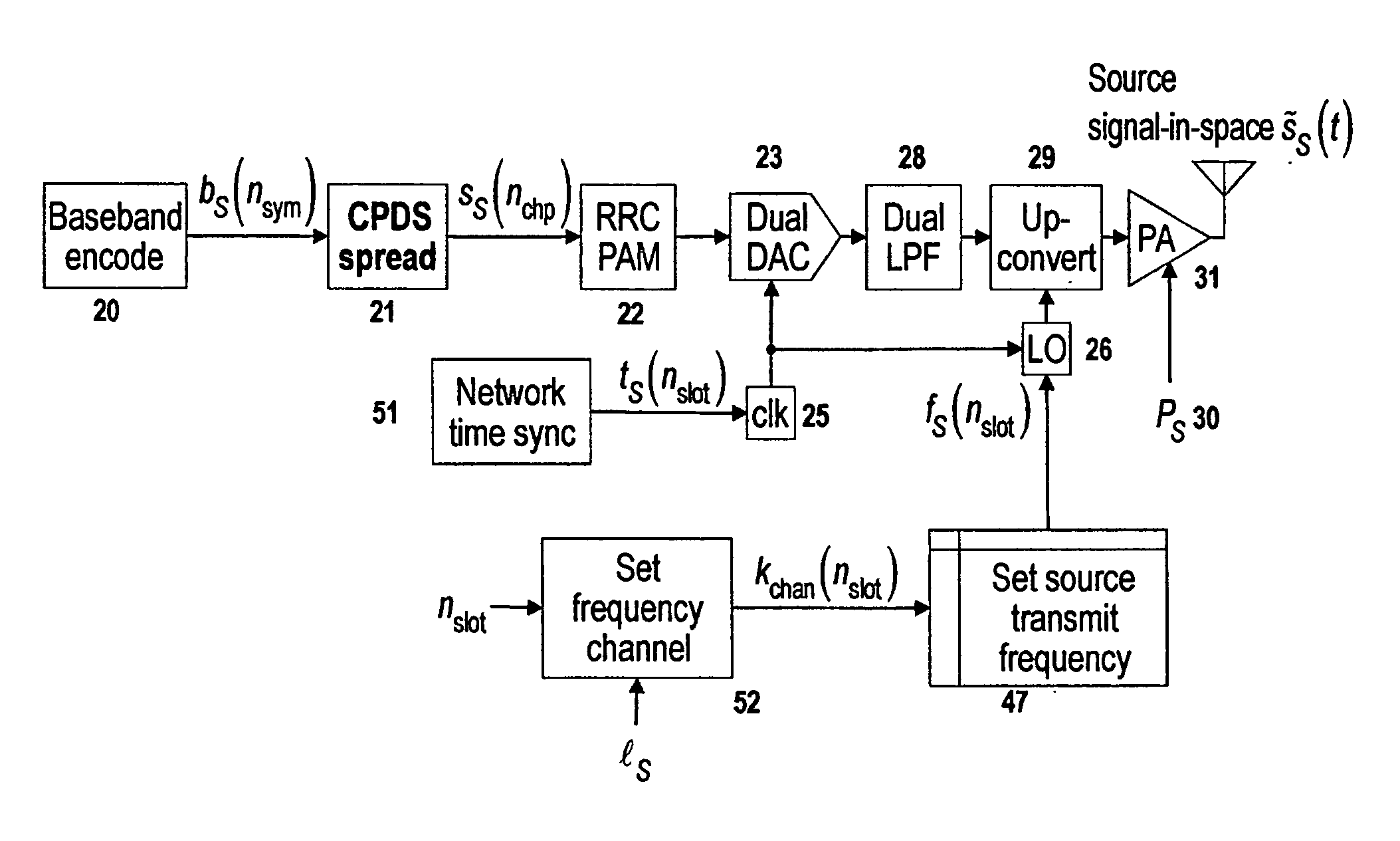
ActiveUS20150195670A1Avoid overheadReduce data transferWireless commuication servicesTransmissionDigital signal processingPhysical security
A method and apparatus for physically secure communication over machine-to-machine (M2M) networks is claimed, through the use of frequency-hop and random access spread spectrum modulation formats employing using truly random spreading codes and time / frequency hopping and receiver selection strategies at the transmitters in the M2M network, blind signal detection and linear signal separation techniques at the receivers in the M2M network, completely eliminating the ability for an adversary to predict and override M2M transmissions. Additional physical security protocols are also introduced that allow the network to easily detect and identify spoofing transmissions on uplinks and downlinks, and to automatically excise those transmissions as part of the despreading procedure, even if those transmissions are received at a much higher power level than the intended transmissions. Extensions to weakly and strongly macrodiverse networks are also described, which provide additional efficiency and security improvements by exploiting the route diversity of the network.
Owner:AGEE BRIAN G
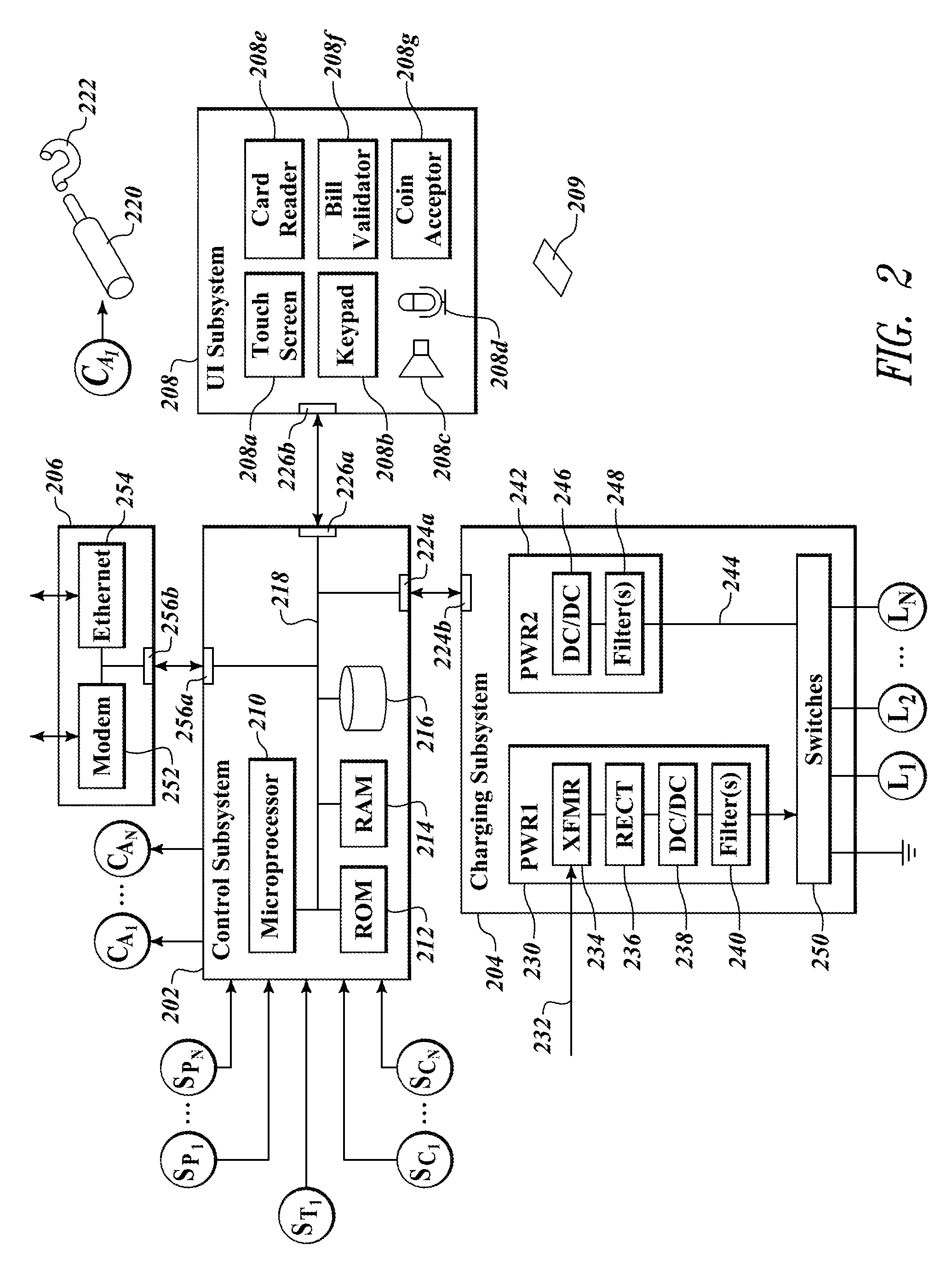
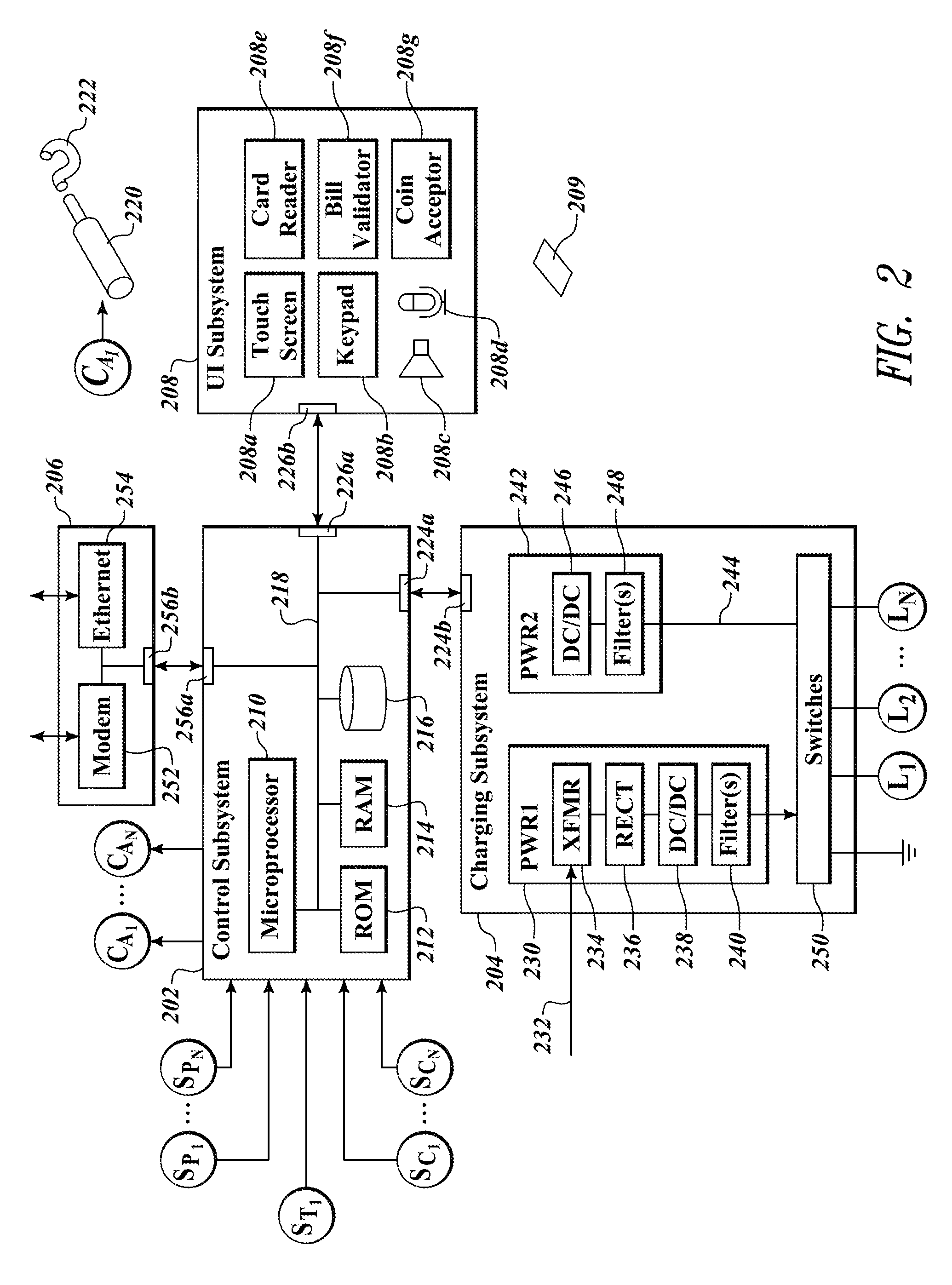
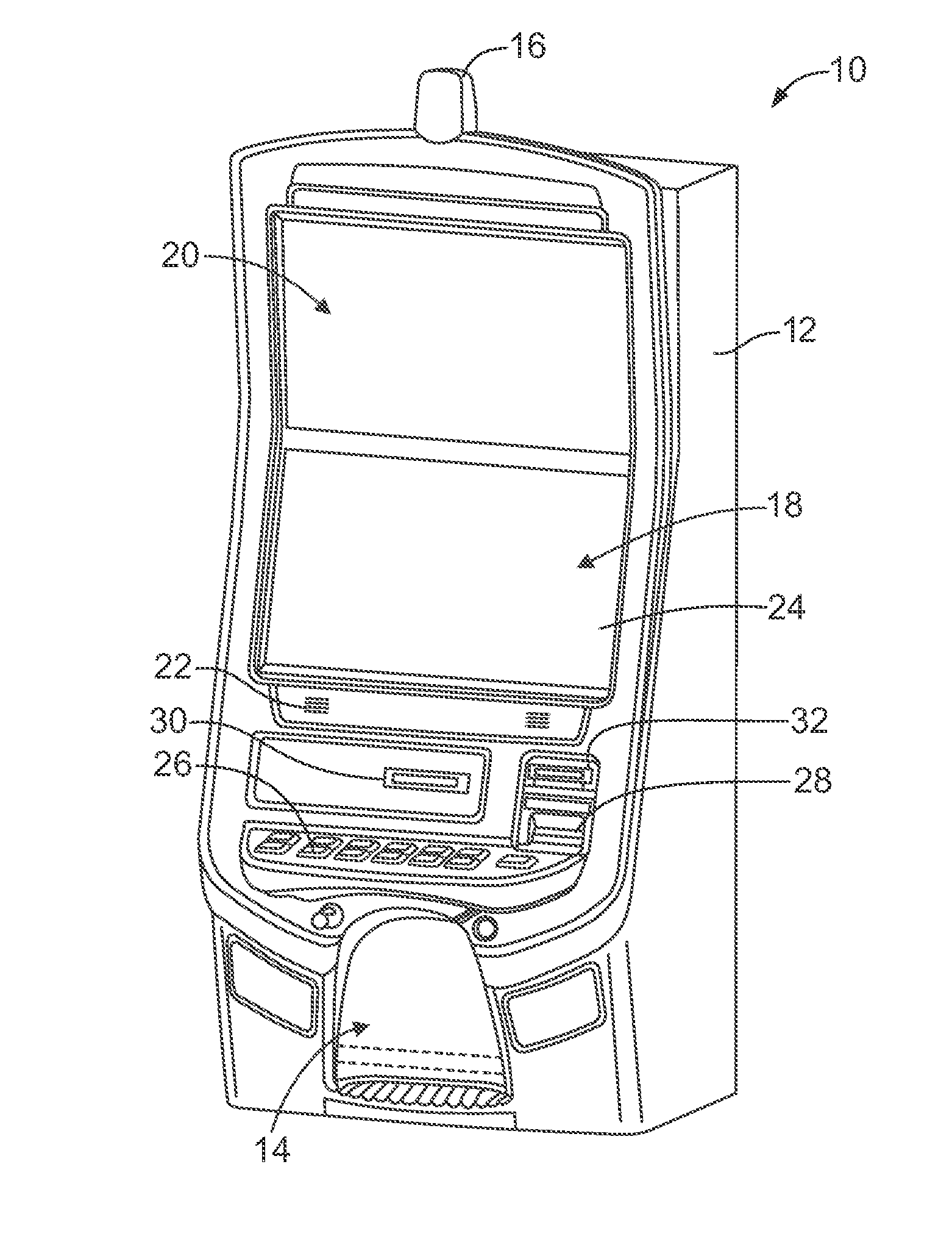
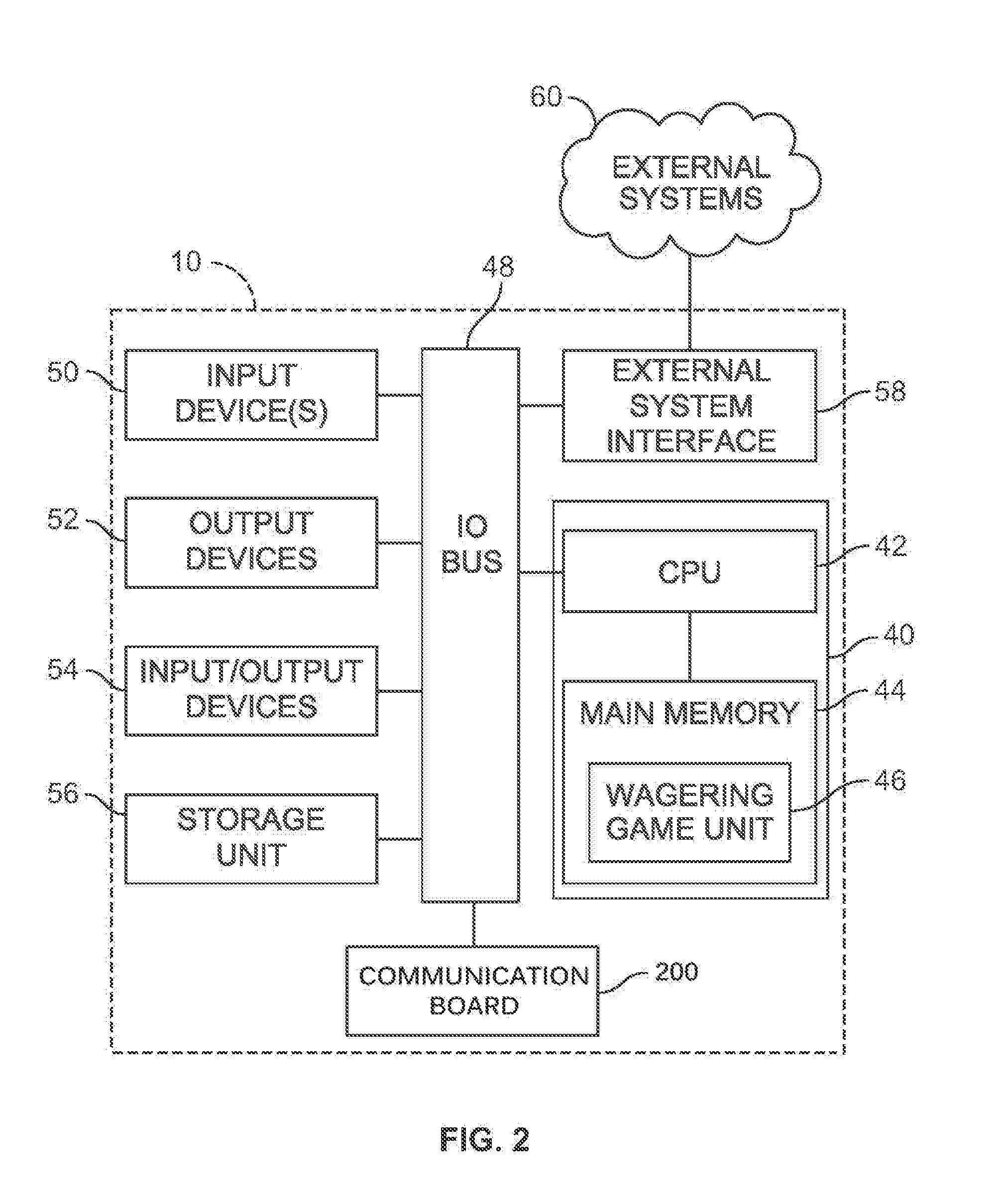
System and method for selective power and secure communications via an electronic gaming machine interface
ActiveUS20160180656A1Apparatus for meter-controlled dispensingVideo gamesSecure communicationMicrocontroller
A gaming system includes a secure communication board having a Universal Serial Bus (USB) interface and / or a wireless interface accessible externally to players and administrators of the gaming system. The secure communication board selectively provides power and communication between a coupled or proximate mobile device and the gaming system. The secure communication board includes a microcontroller to selectively control both power and communication flow through the secure communication board to the external interfaces. The microcontroller is responsive to the physical state of gaming system components and gaming system processor events and control signals. A wagering game event, user authentication, and / or specific states of one or more physical security switches of the gaming system may be required to provide power and data via the external interfaces.
Owner:LNW GAMING INC
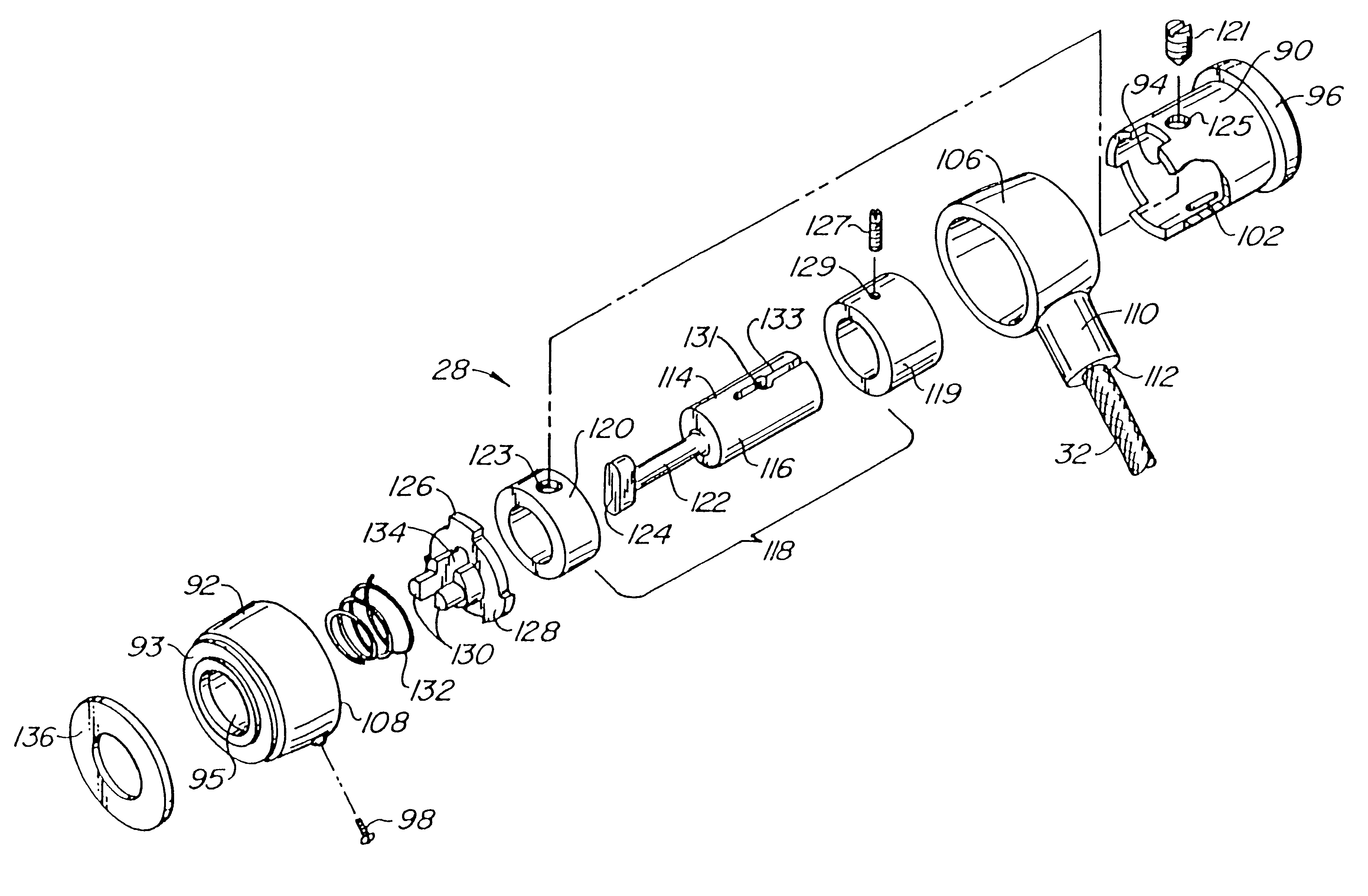
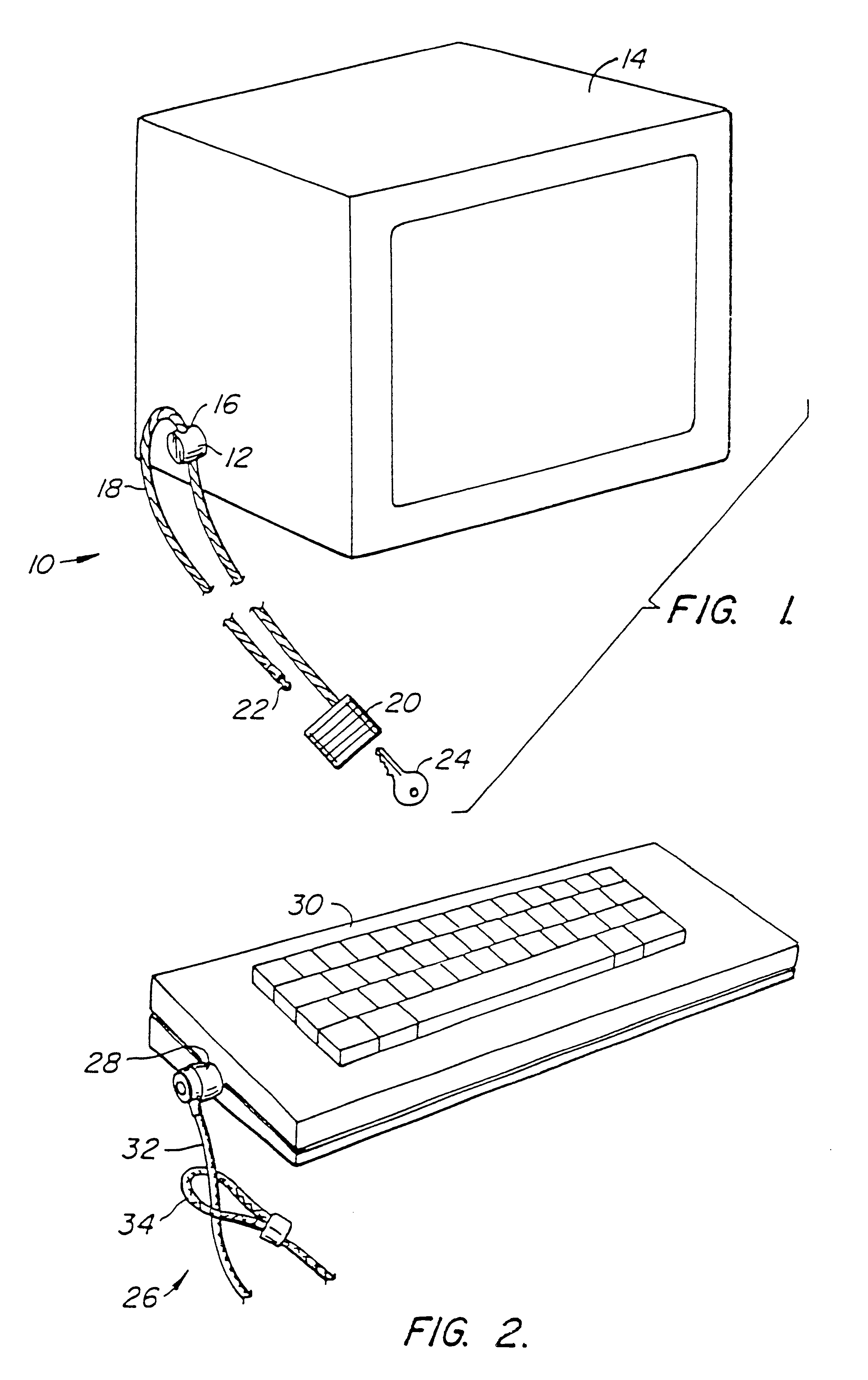
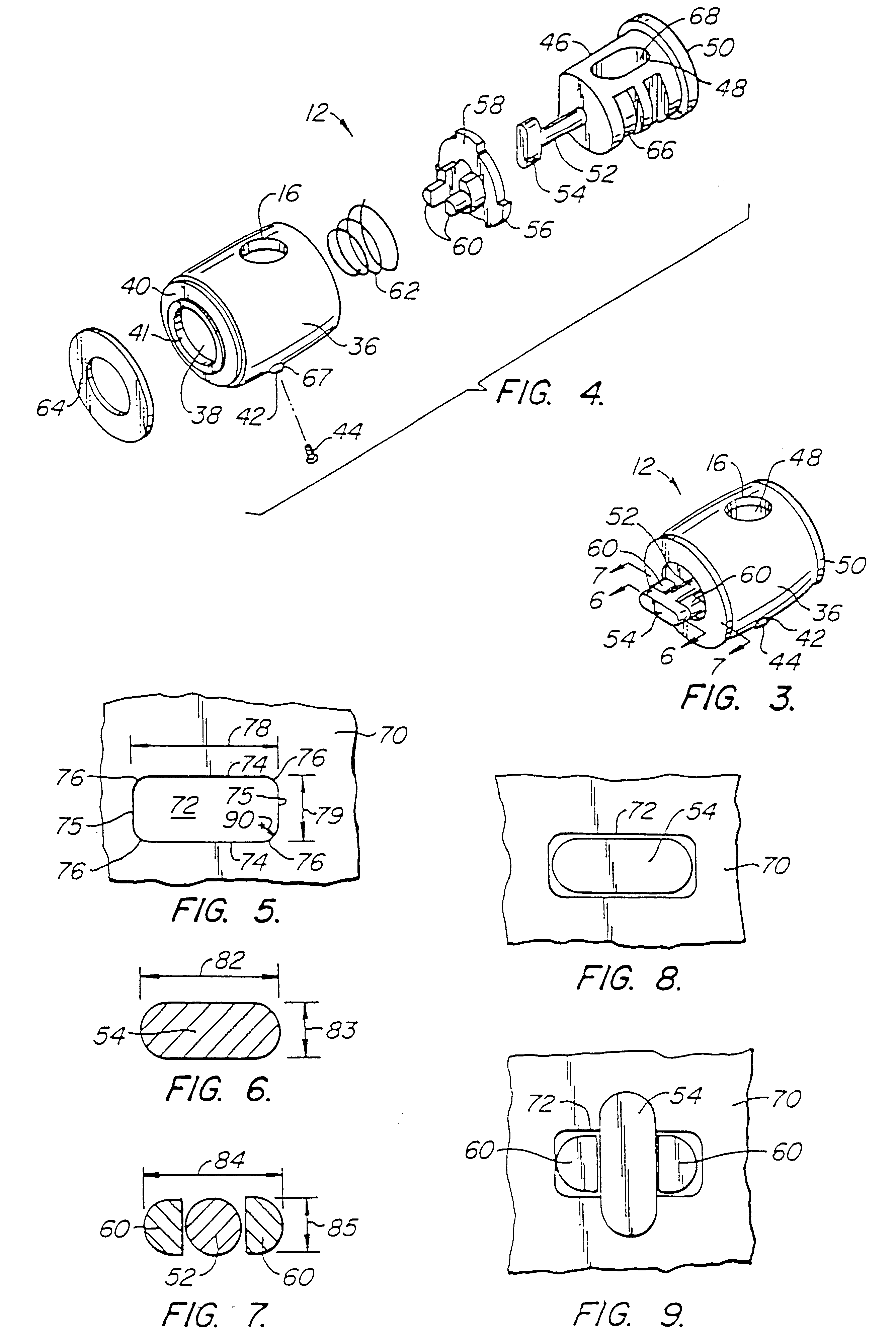
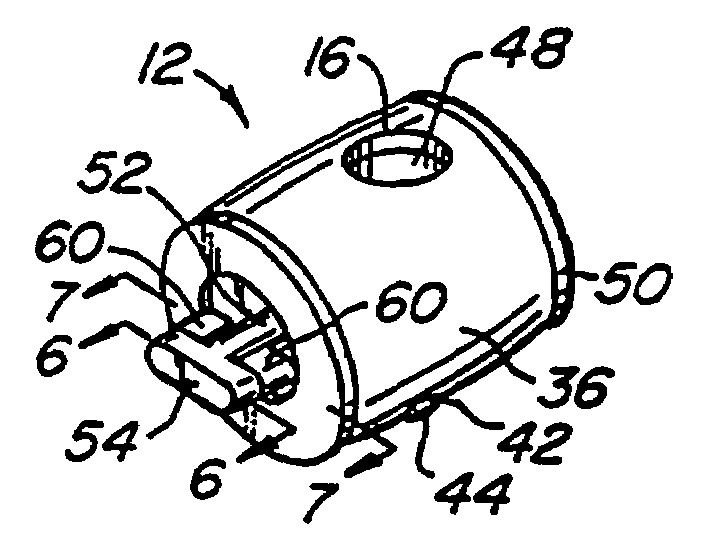
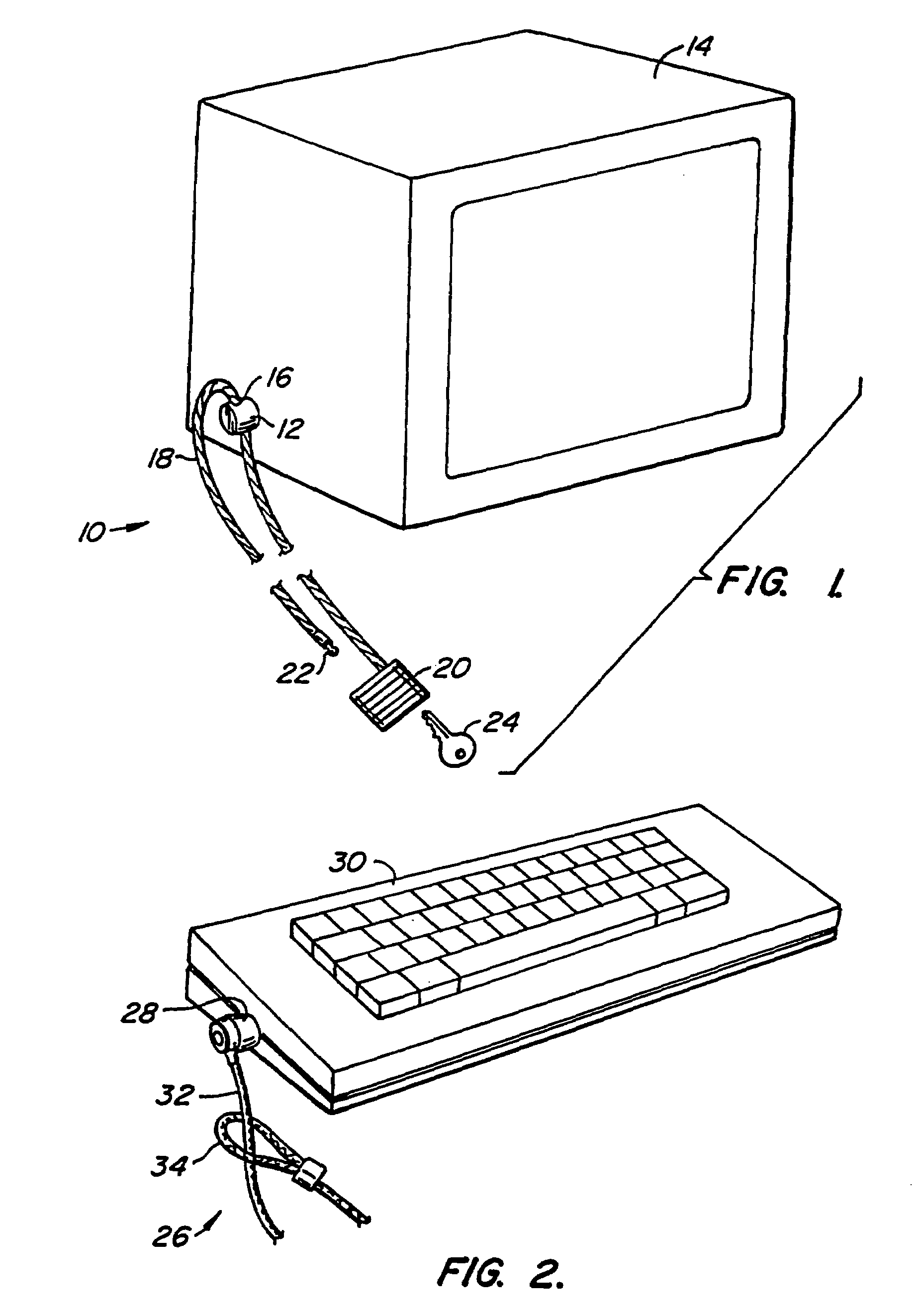
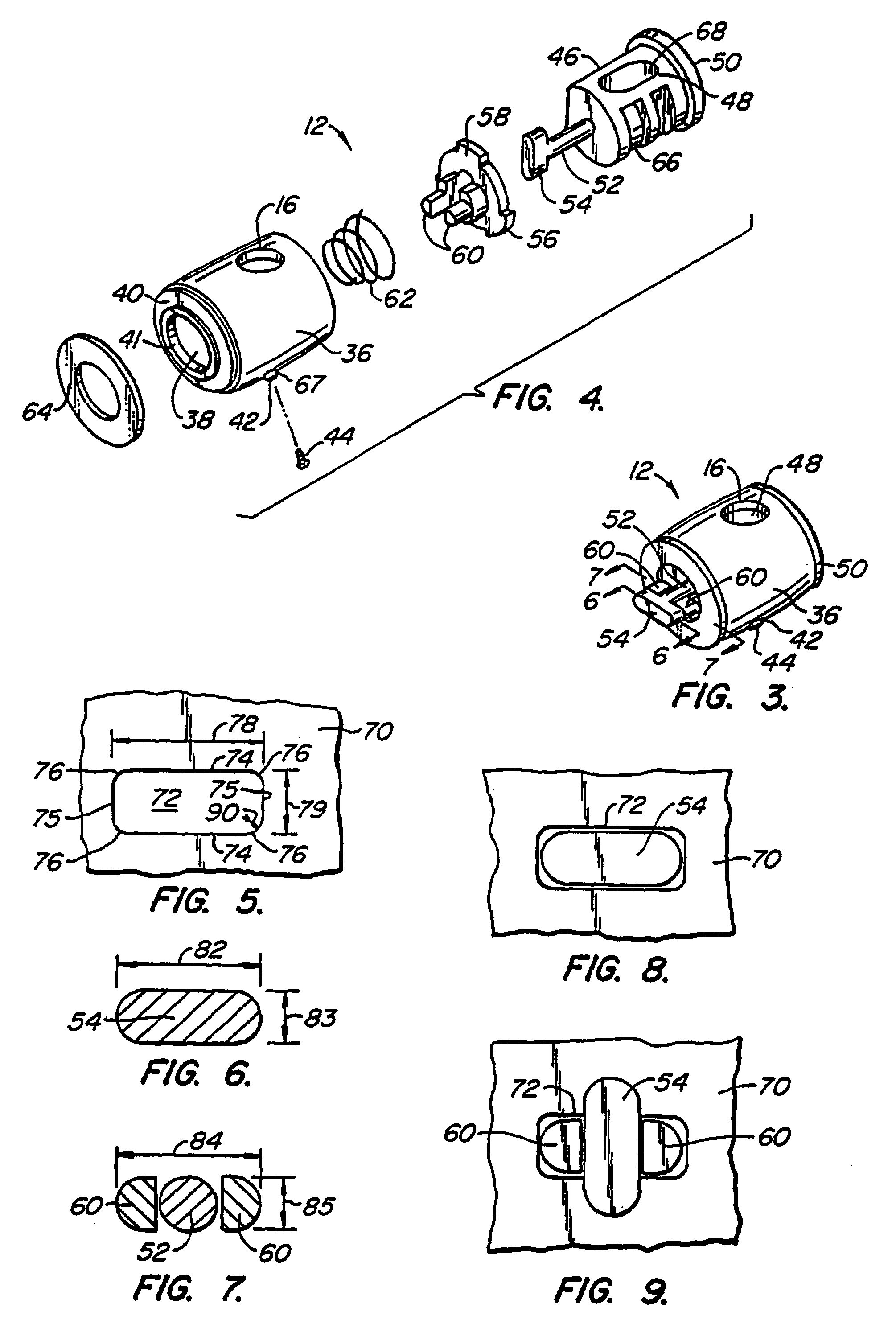
Computer physical security device
InactiveUS7111479B2Prevent theftEasily be molded into computer systemClothing locksLocks for portable objectsPhysical securityPersonal computer
An apparatus which inhibits the theft of equipment such as personal computers is disclosed. The equipment must have an external wall provided with a specially designed, approximately rectangular slot having preselected dimensions. An attachment mechanism includes a housing for a spindle having a first portion rotatable within the housing, a shaft extending outwardly from the housing, and a crossmember at the end of the shaft having peripheral dimensions closely conforming to the internal dimensions of the slot. An abutment mechanism also emanates from the housing, and is located on opposite sides of the shaft intermediate the housing and the crossmember. The peripheral cross-sectional dimensions of the abutment mechanism and the shaft in combination closely conform to the dimensions of the slot. The length of the shaft from the housing to the crossmember is approximately equal to the thickness of the external wall of equipment. The crossmember is aligned with the abutment mechanism so that the crossmember can be inserted through the slot with the shaft and the abutment mechanism occupying the slot. The spindle is then rotated 90° to misalign the crossmember with the slot, thereby attaching the attachment mechanism rigidly to the external wall. A cable is secured to the housing and to an immovable object so that the equipment cannot be stolen.
Owner:ACCO BRANDS USA LLC
Method and apparatus for providing electronic purse
ActiveUS8118218B2Facilitate communicationWithout compromising securityFinancePayment protocolsPersonalizationPhysical security
Techniques for portable devices functioning as an electronic purse (e-purse) are disclosed. According to one aspect of the invention, a mechanism is provided to enable a portable device to conduct transactions over an open network with a payment server without compromising security. In one embodiment, a device is loaded with an e-purse manager. The e-purse manager is configured to manage various transactions and functions as a mechanism to access an emulator therein. The transactions may be conducted over a wired network or a wireless network. A three-tier security model is contemplated to support the security of the transactions from the e-purse. The three-tier security model includes a physical security, an e-purse security and a card manager security, concentrically encapsulating one with another. Security keys (either symmetric or asymmetric) are personalized within the three-tier security model.
Owner:SHENZHEN RFCYBER ASSET MANAGEMENT
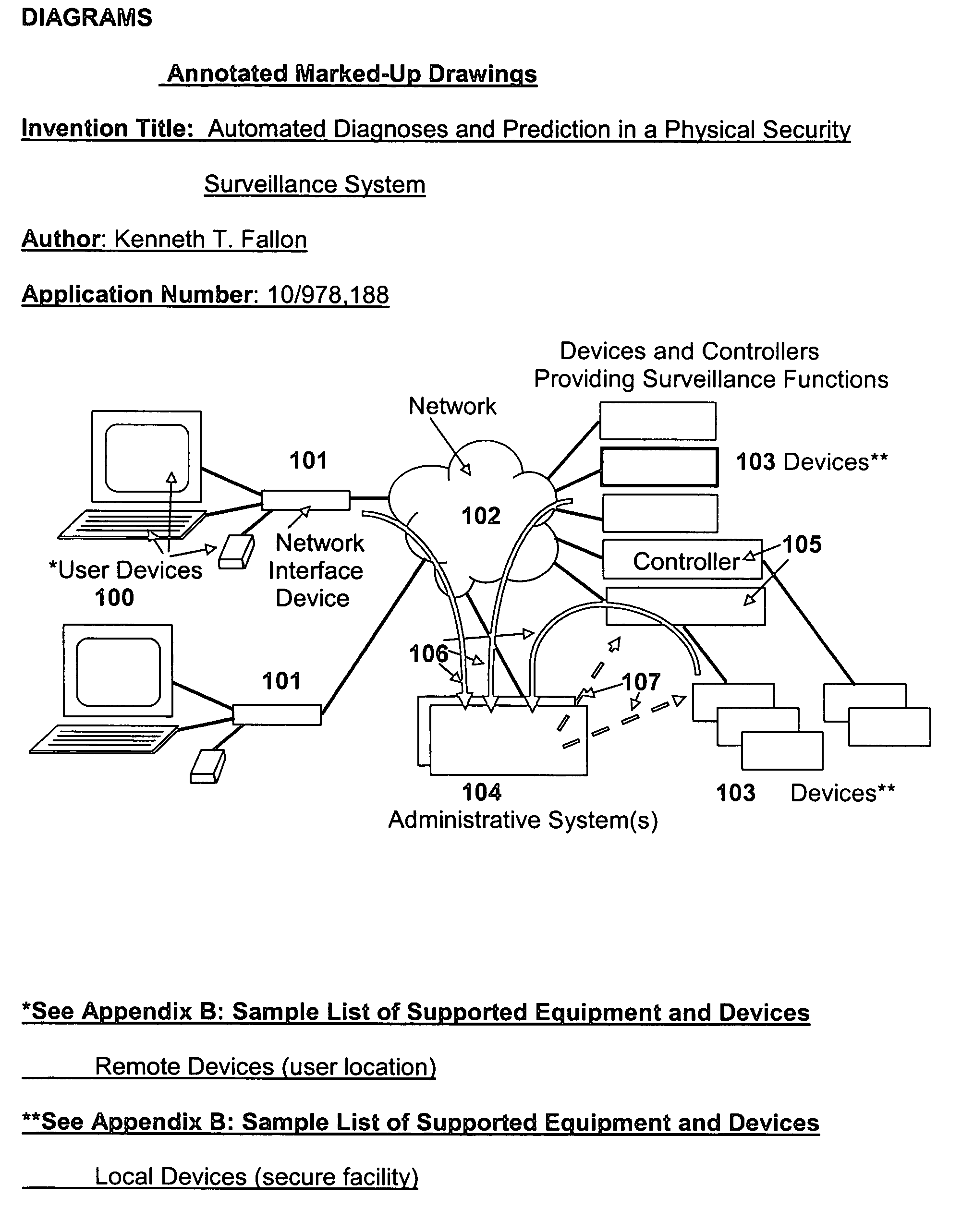
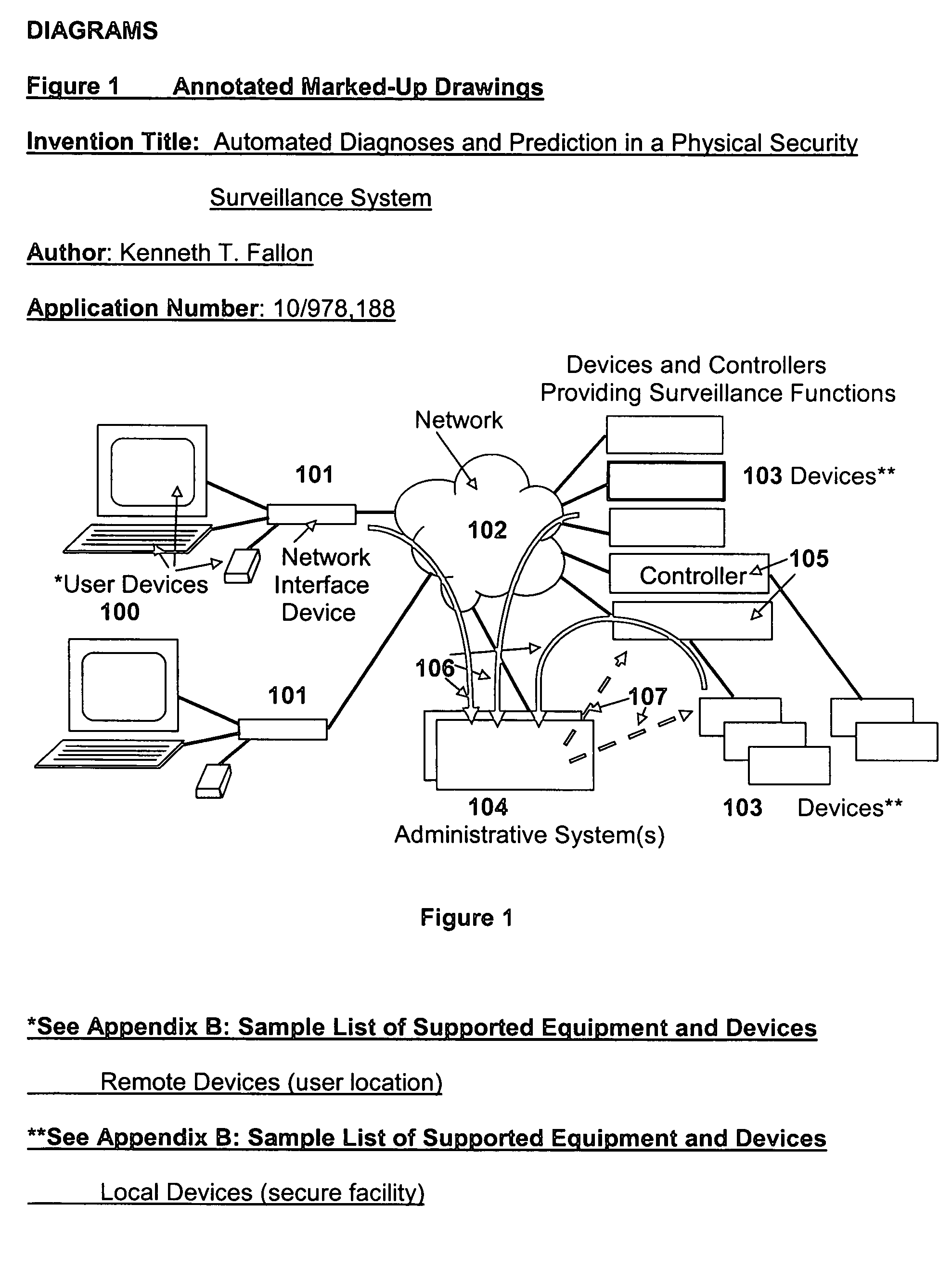
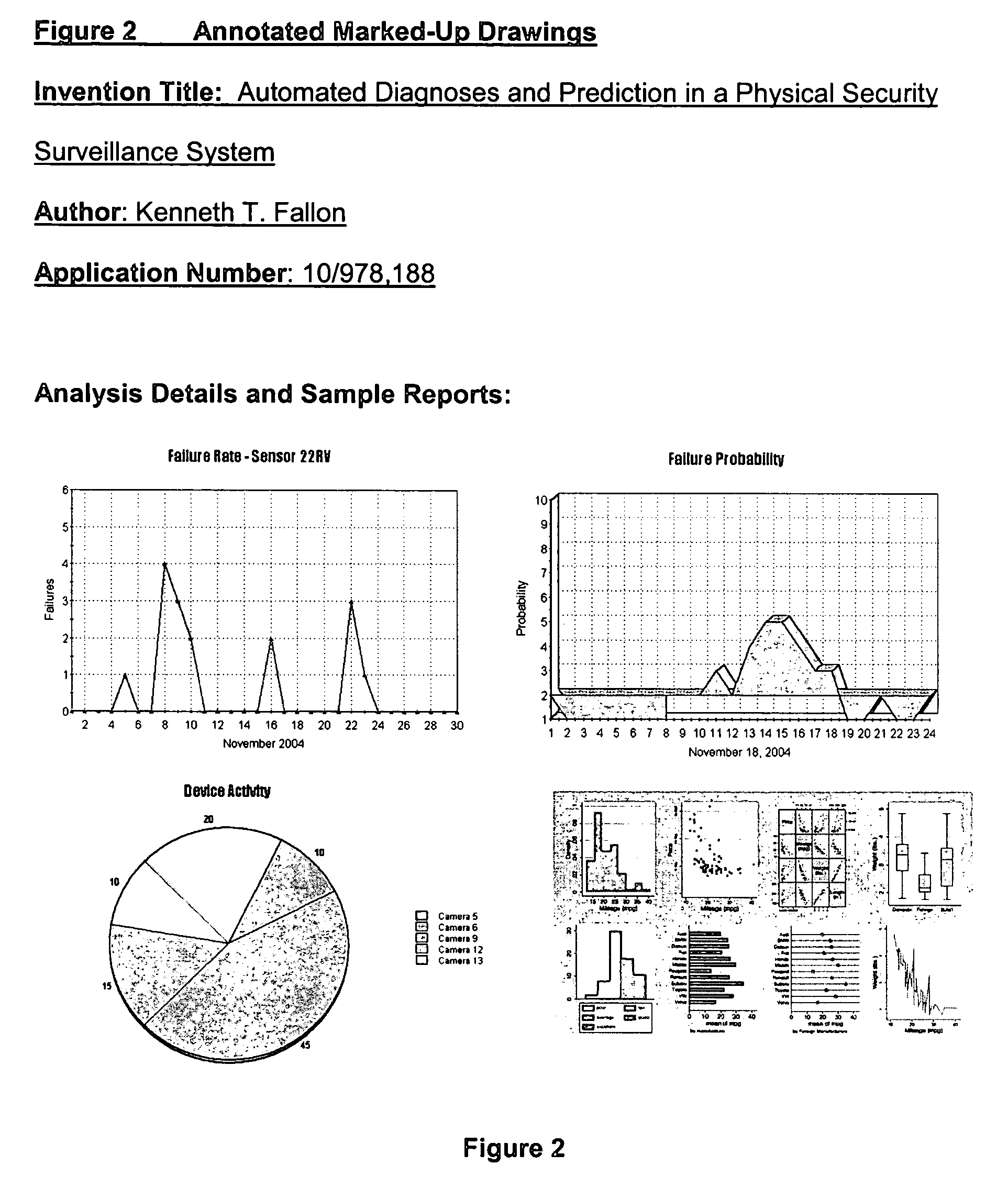
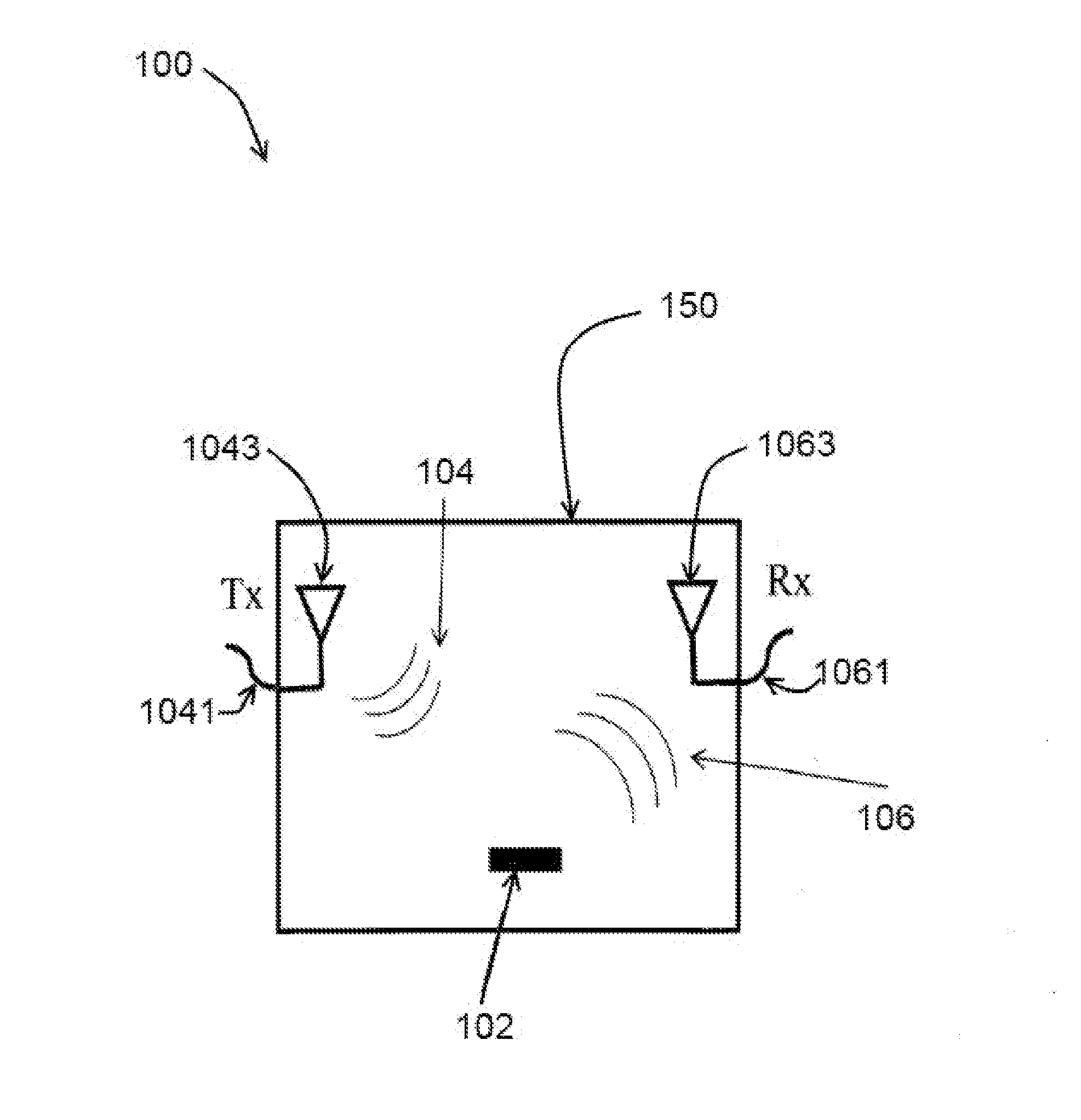
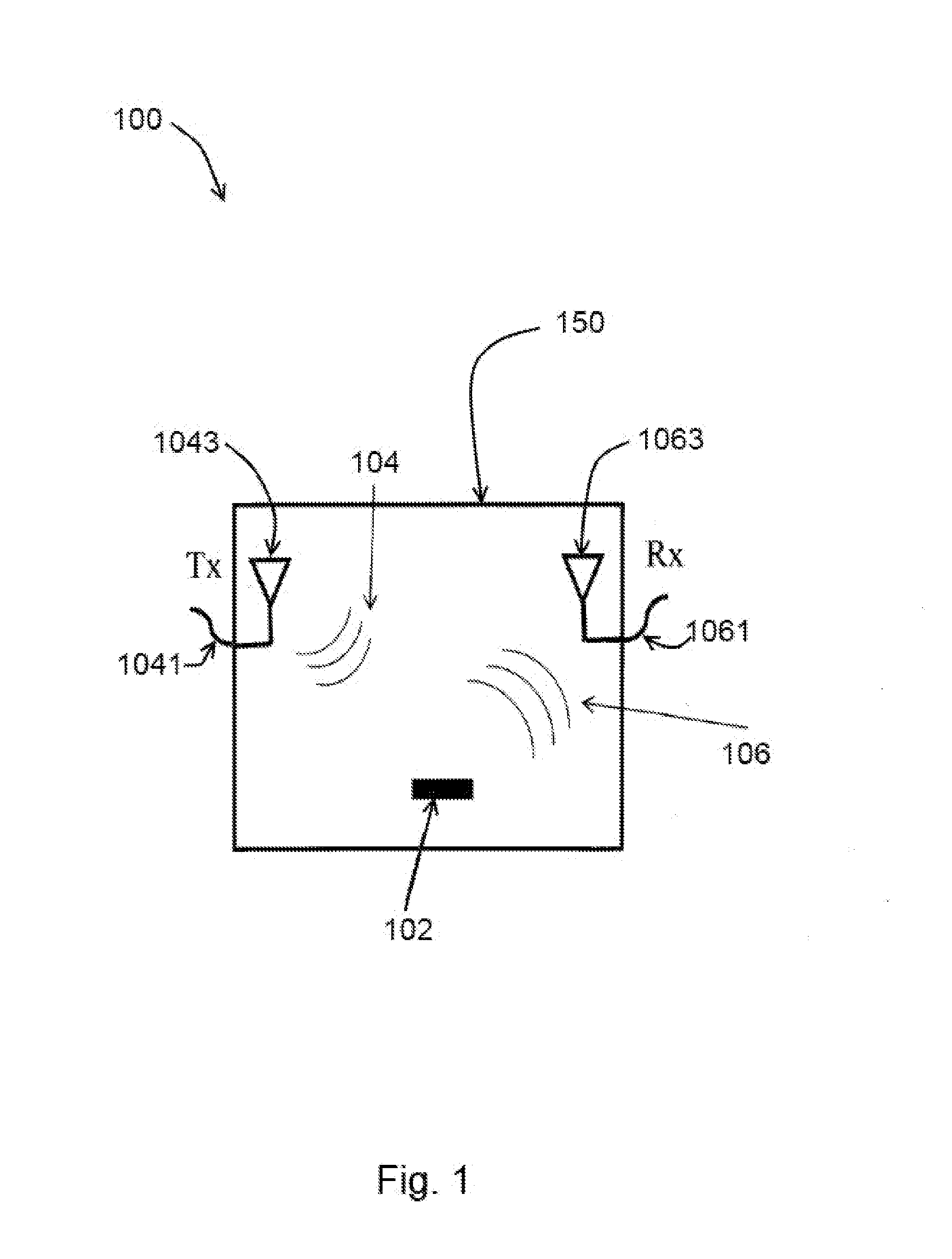
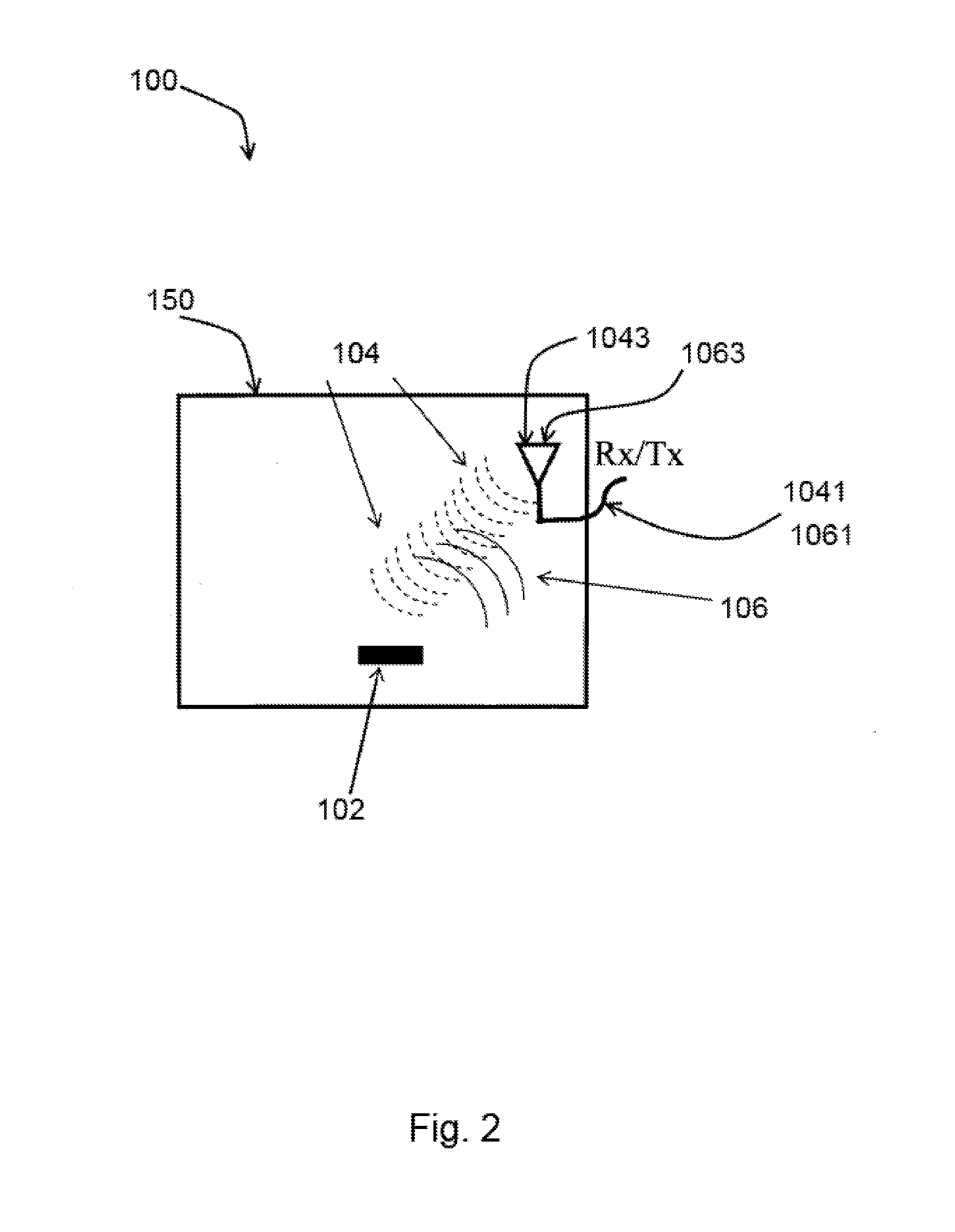
Automated diagnoses and prediction in a physical security surveillance system
Owner:FALLON KENNETH T
Non-contact electromagnetic illuminated detection of part anomalies for cyber physical security
An apparatus for testing, inspecting or screening an electronic device for electrical characteristics, modified or unmodified hardware, or firmware modifications including Malware, Trojans, improper versioning, and the like, includes a transmitting antenna positioned at a distance from the electronic device and a electromagnetic energy receiver or sensor for examining a resulting unintentional derived electromagnetic energy from the electronic device. The receiver collects unintentional RF energy components emitted by the device and includes a processor and executable instructions that perform analysis in a response to the acquired electromagnetic energy input. The characteristics of the collected RF energy may be compared with RF energy characteristics of an exemplary device. The analysis determines one of a modified, unmodified or score of certainty of discerned condition of the device.
Owner:NOKOMIS
Computer physical security device
InactiveUS7100403B2Prevent theftEasily be molded into computer systemClothing locksLocks for portable objectsPhysical securityPersonal computer
An apparatus which inhibits the theft of equipment such as personal computers is disclosed. The equipment must have an external wall provided with a specially designed, approximately rectangular slot having preselected dimensions. An attachment mechanism includes a housing for a spindle having a first portion rotatable within the housing, a shaft extending outwardly from the housing, and a crossmember at the end of the shaft having peripheral dimensions closely conforming to the internal dimensions of the slot. An abutment mechanism also emanates from the housing, and is located on opposite sides of the shaft intermediate the housing and the crossmember. The peripheral cross-sectional dimensions of the abutment mechanism and the shaft in combination closely conform to the dimensions of the slot. The length of the shaft from the housing to the crossmember is approximately equal to the thickness of the external wall of equipment. The crossmember is aligned with the abutment mechanism so that the crossmember can be inserted through the slot with the shaft and the abutment mechanism occupying the slot. The spindle is then rotated 90° to misalign the crossmember with the slot, thereby attaching the attachment mechanism rigidly to the external wall. A cable is secured to the housing and to an immovable object so that the equipment cannot be stolen.
Owner:ACCO BRANDS USA LLC
Connector and receptacle containing a physical security feature
InactiveUS7651277B2Imparts physical securityFacilitates discriminationIncorrect coupling preventionOptical articlesPhysical securityInformation networks
A network comprising: (a) a plurality of different receptacles for facilitating an optical connection to different information networks requiring different access authorization, each different receptacle coupled to one and only one different information network, each receptacle having an inner surface with a first geometry, the first geometry comprising at least a slot, a certain number of receptacles having different first geometries in which the slots are in different positions; and (b) a plurality of different plugs for coupling with the different receptacles, each plug having a second geometry, the second geometry comprising at least a key in a certain position, the certain number of plugs having different second geometries in which the keys are in different positions, each different first geometry corresponding to one and only one second geometry such that the plugs and receptacles of corresponding first and second geometries are mating pairs.
Owner:COMMSCOPE TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com