Patents
Literature
385 results about "Software as a service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
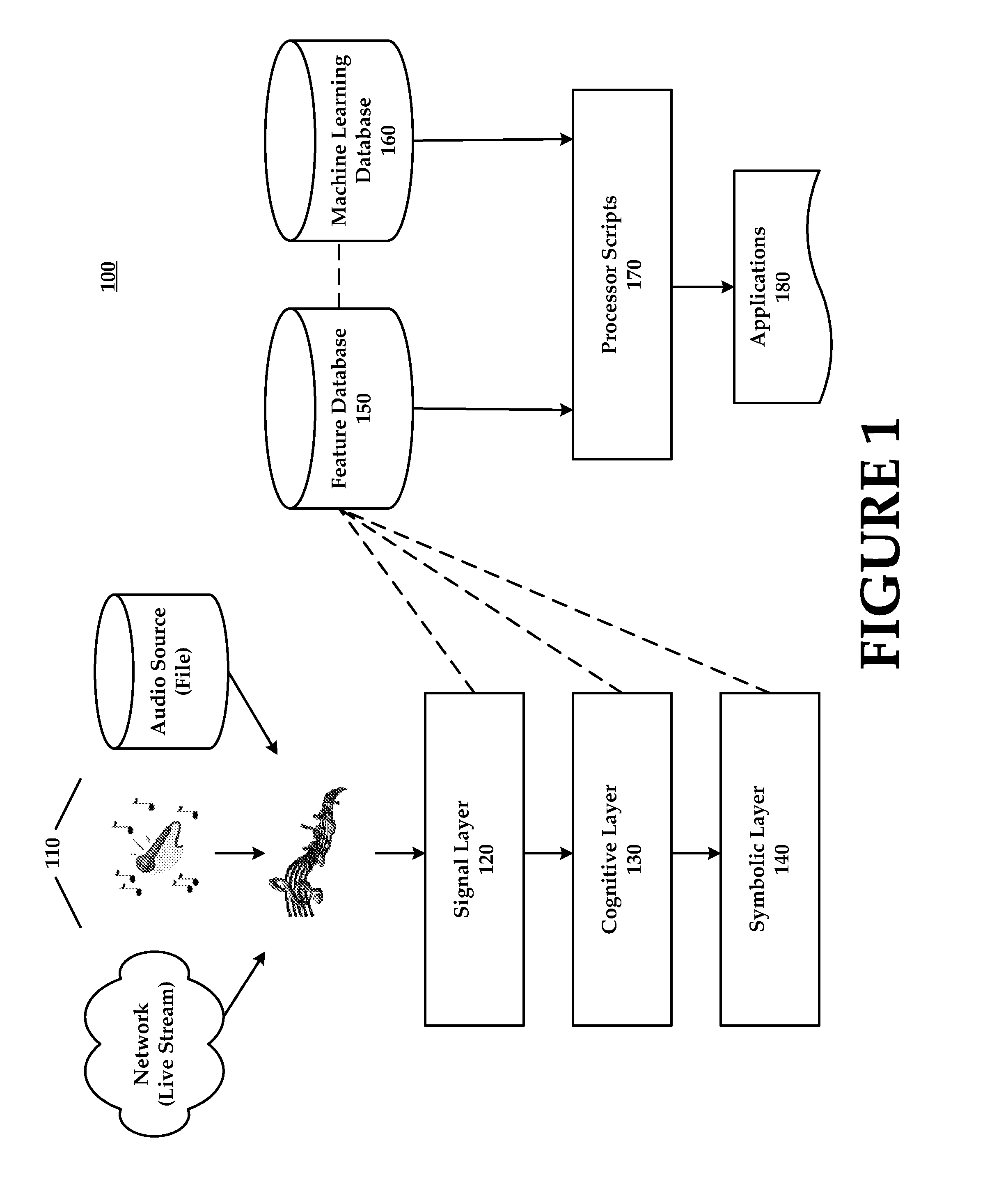
Software as a service (SaaS /sæs/) is a software licensing and delivery model in which software is licensed on a subscription basis and is centrally hosted. It is sometimes referred to as "on-demand software", and was formerly referred to as "software plus services" by Microsoft.
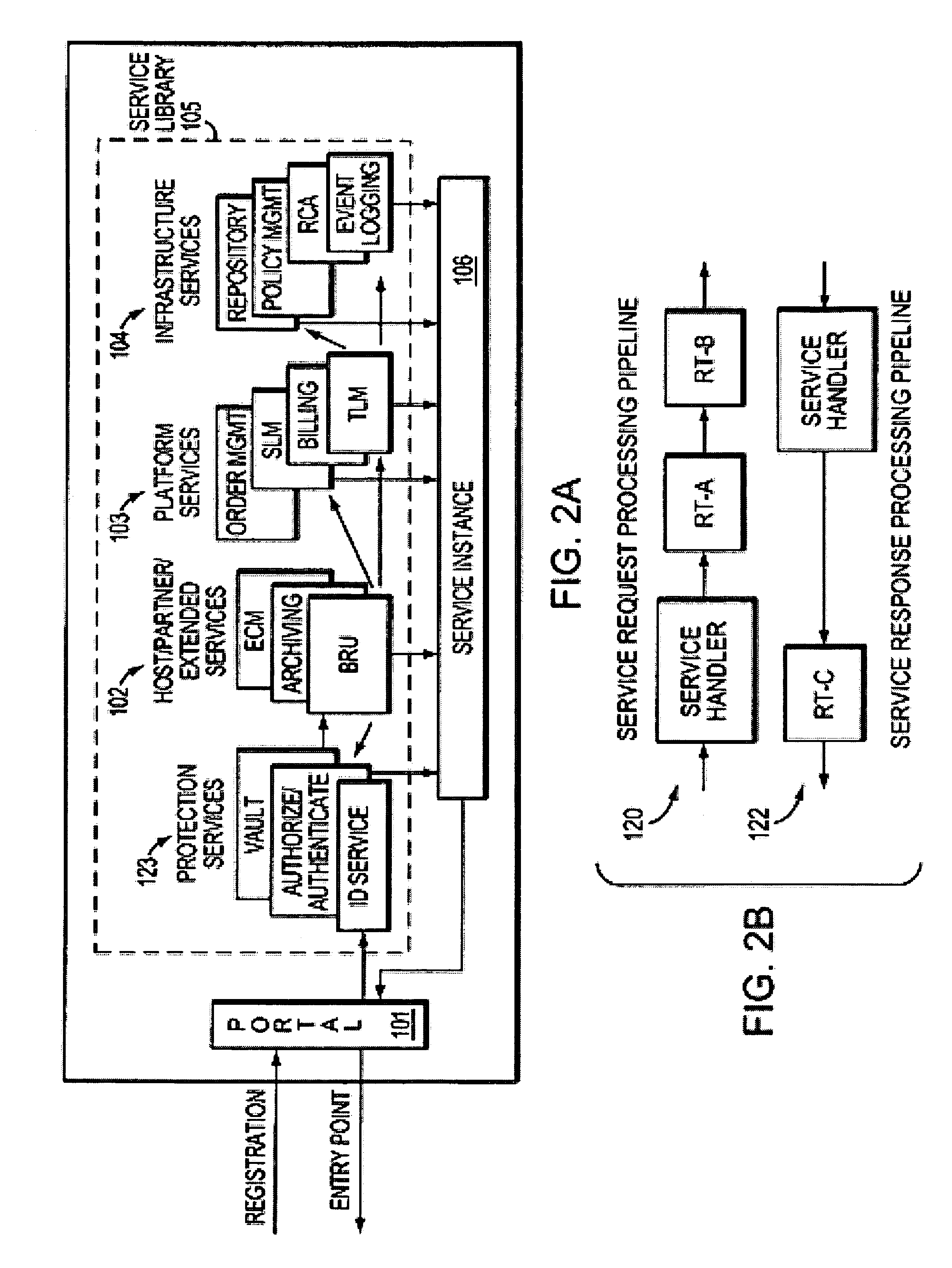
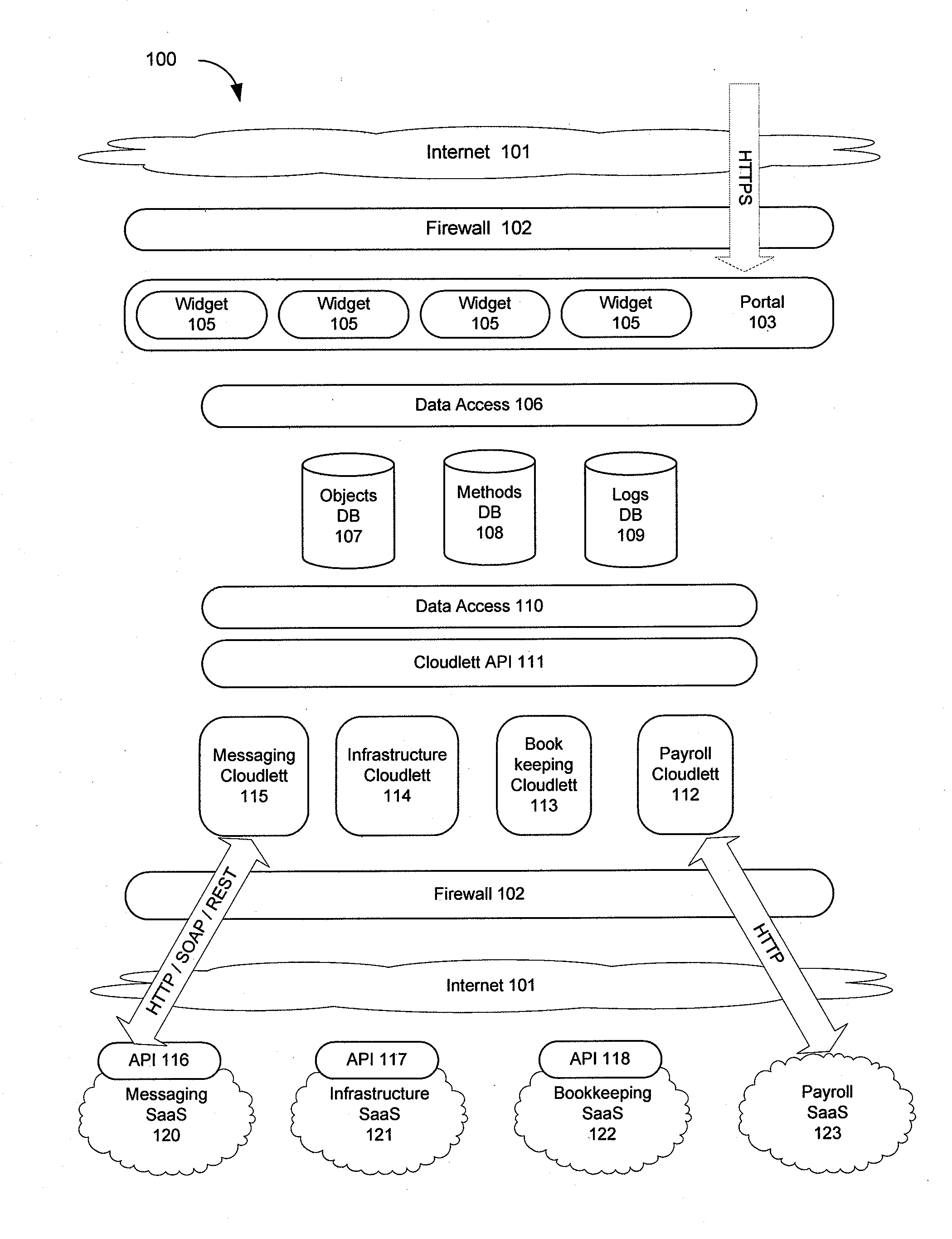
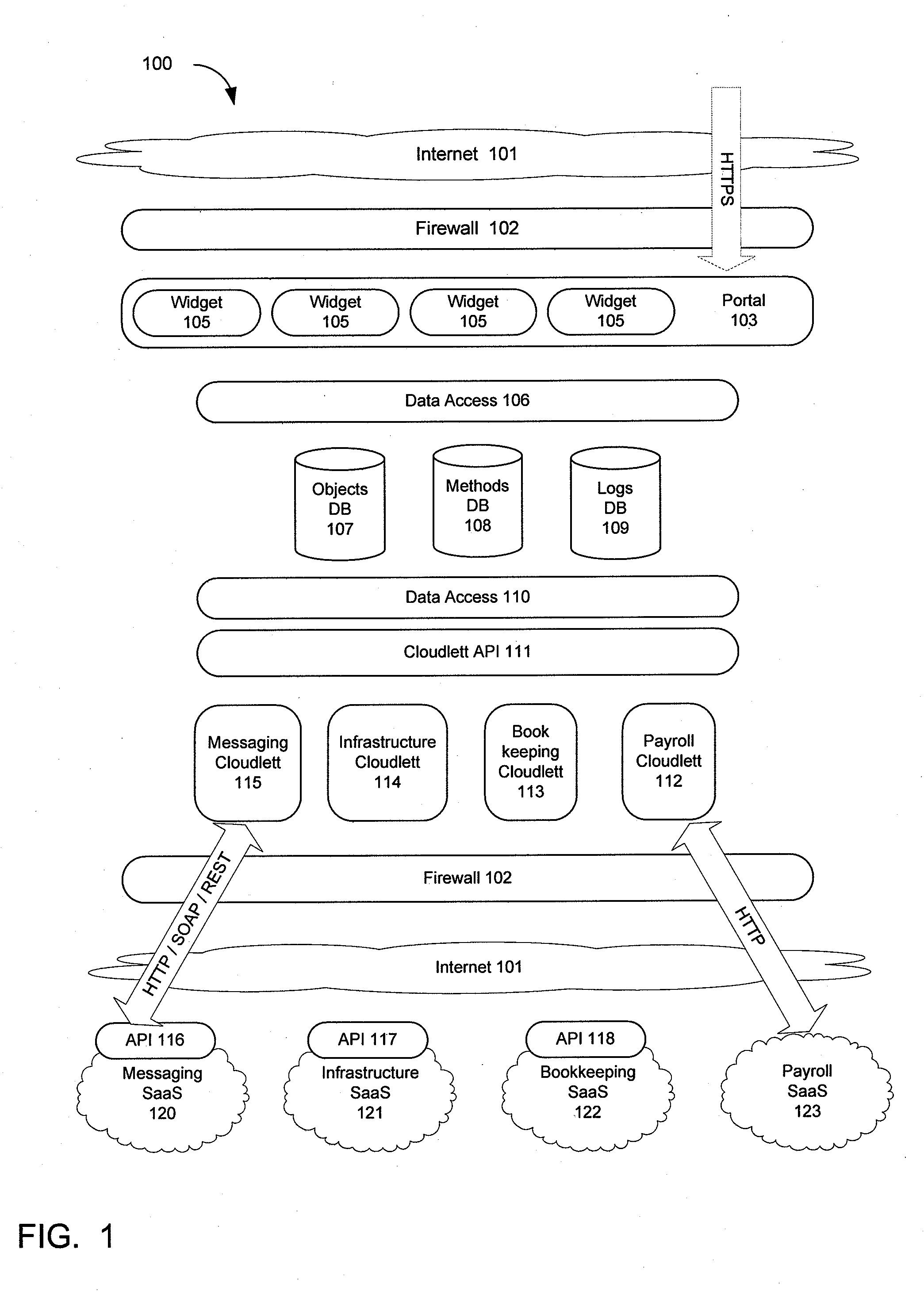
Building distributed software services as aggregations of other services
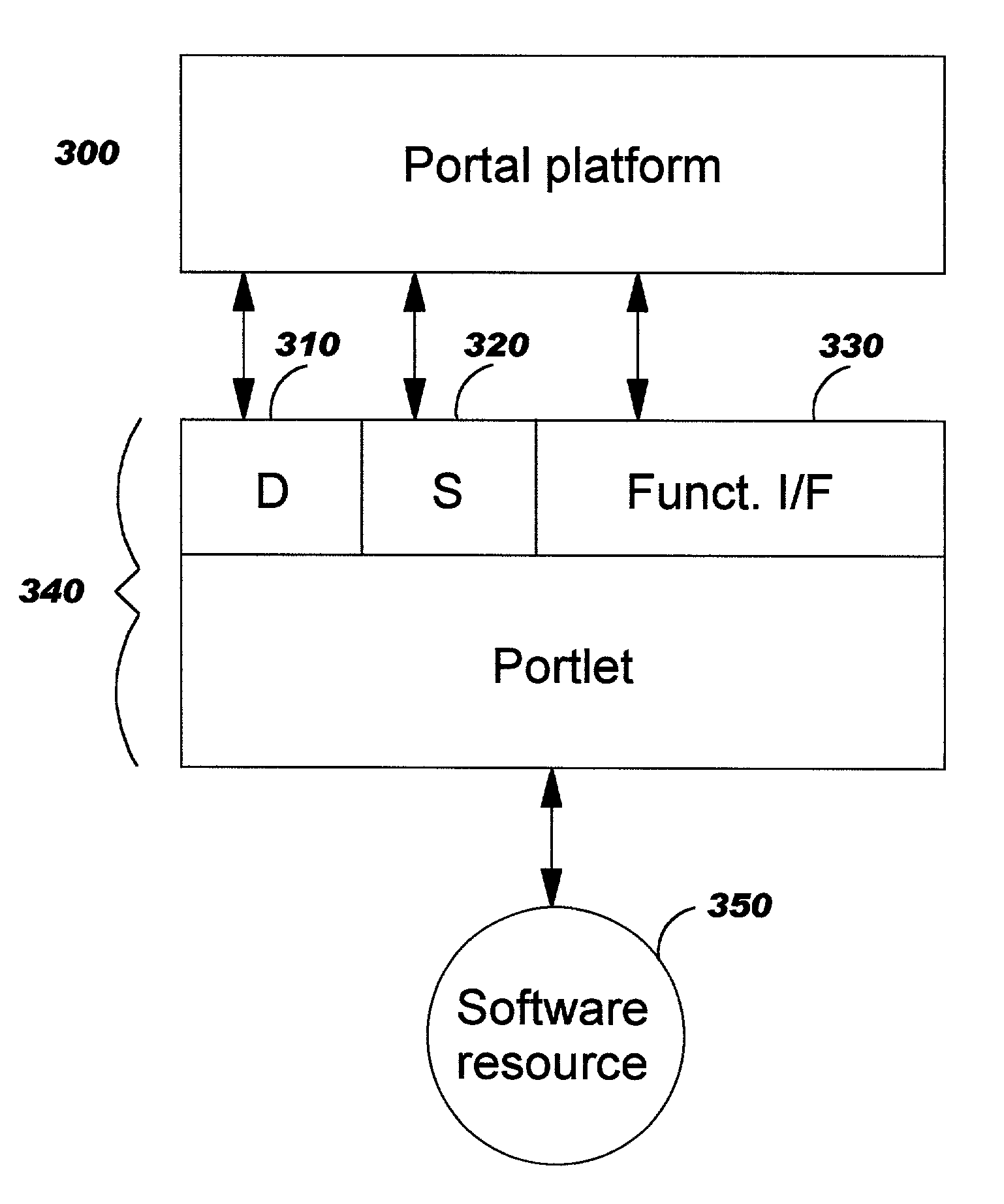
InactiveUS6985939B2Fast and efficient constructionData processing applicationsMultiple digital computer combinationsPortletWeb service
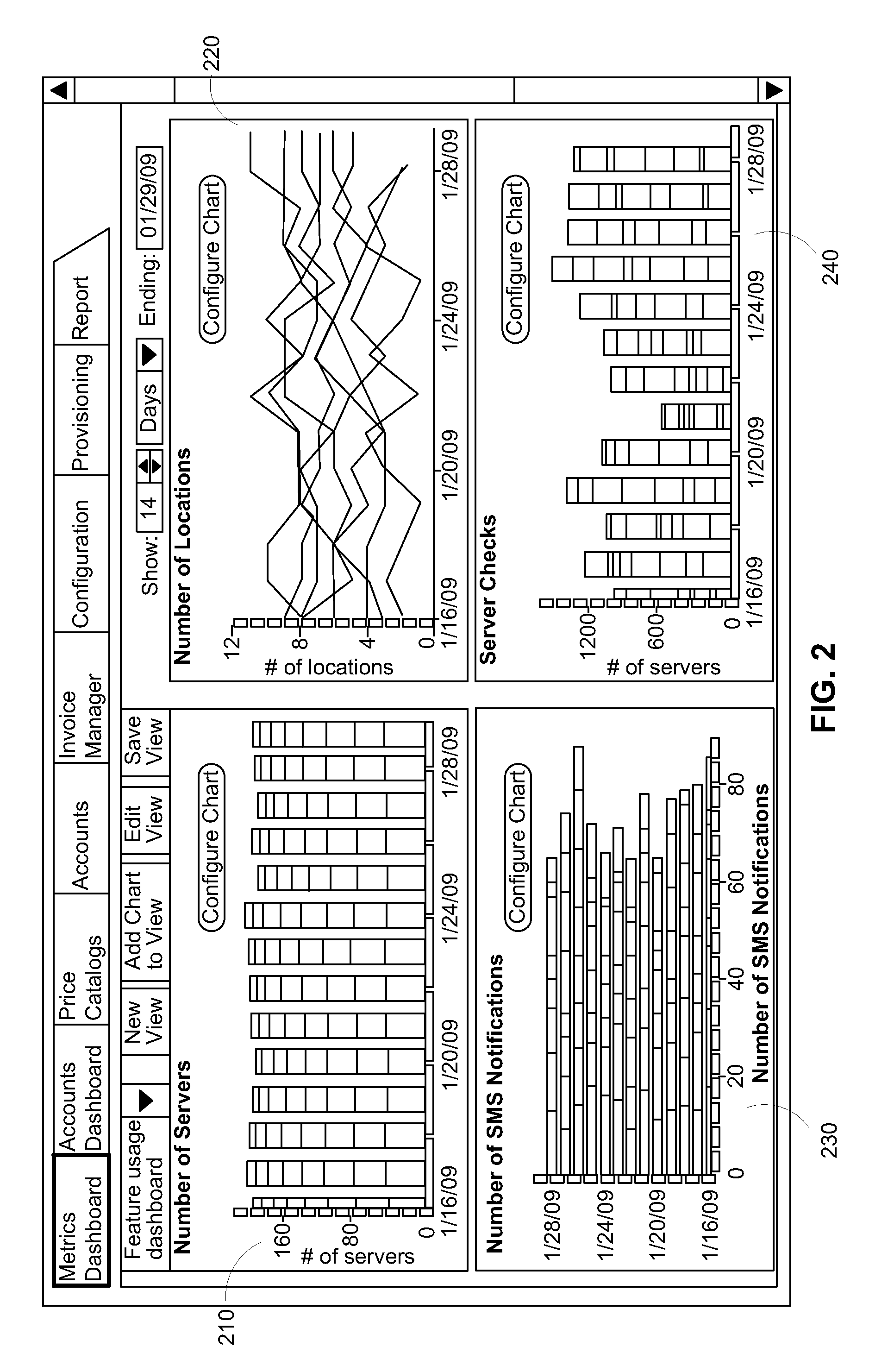
Methods, systems, and computer program products are disclosed for dynamically integrating software resources (such as web services and other back-end software resources) using the services of a content framework (such as a portal platform). A portlet model is leveraged to allow programmatic portlets to serve as proxies for web services, thereby extending portlets beyond their traditional visual role. A deployment interface and a system interface are described for these portlet proxies. The deployment interface is used for composing new web services, and a composition tool is described. The system interface allows for run-time management of the web services by the portal platform. The service provider for a particular function may be bound to the portlet proxy at development time or at run-time.
Owner:INT BUSINESS MASCH CORP
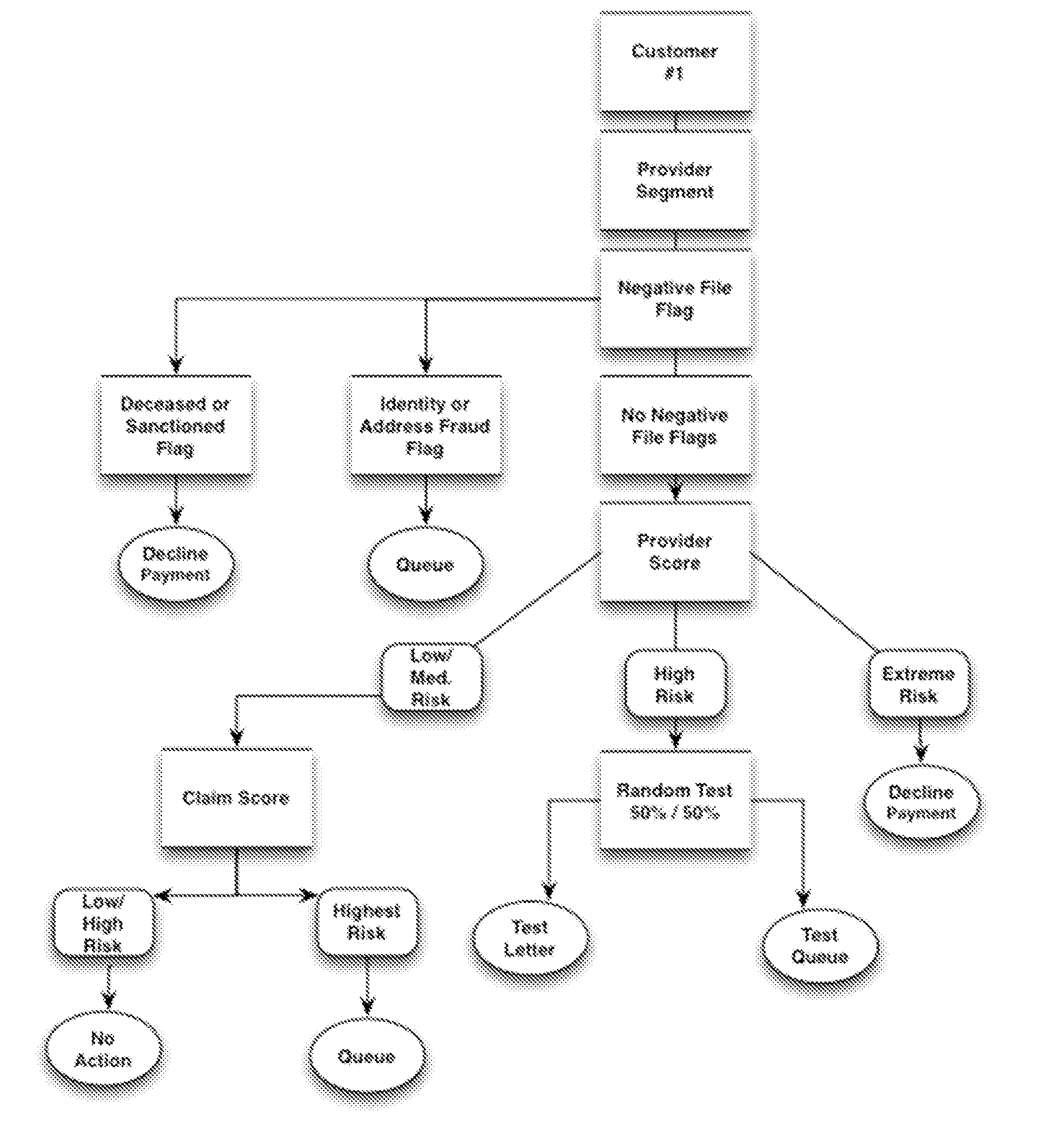
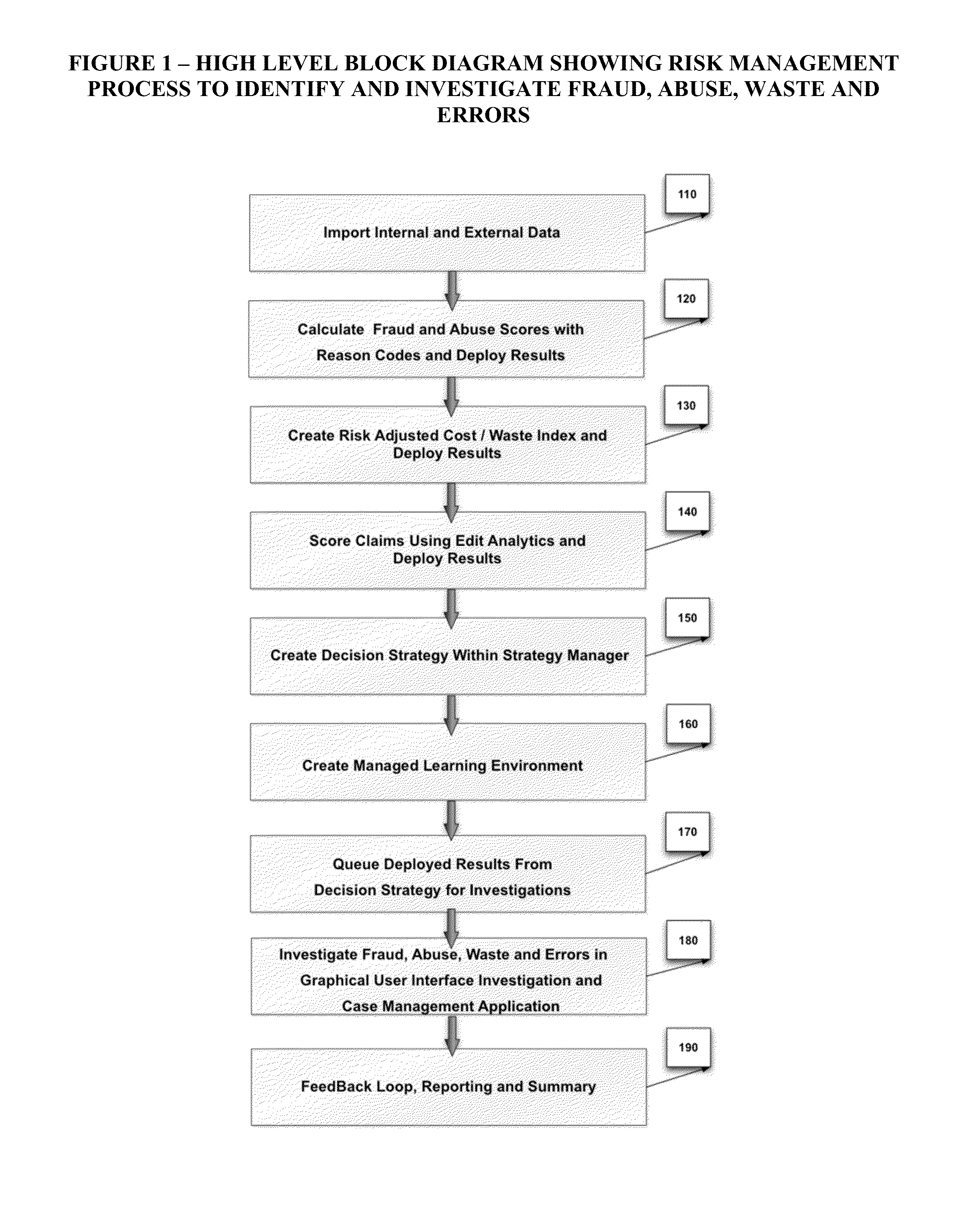
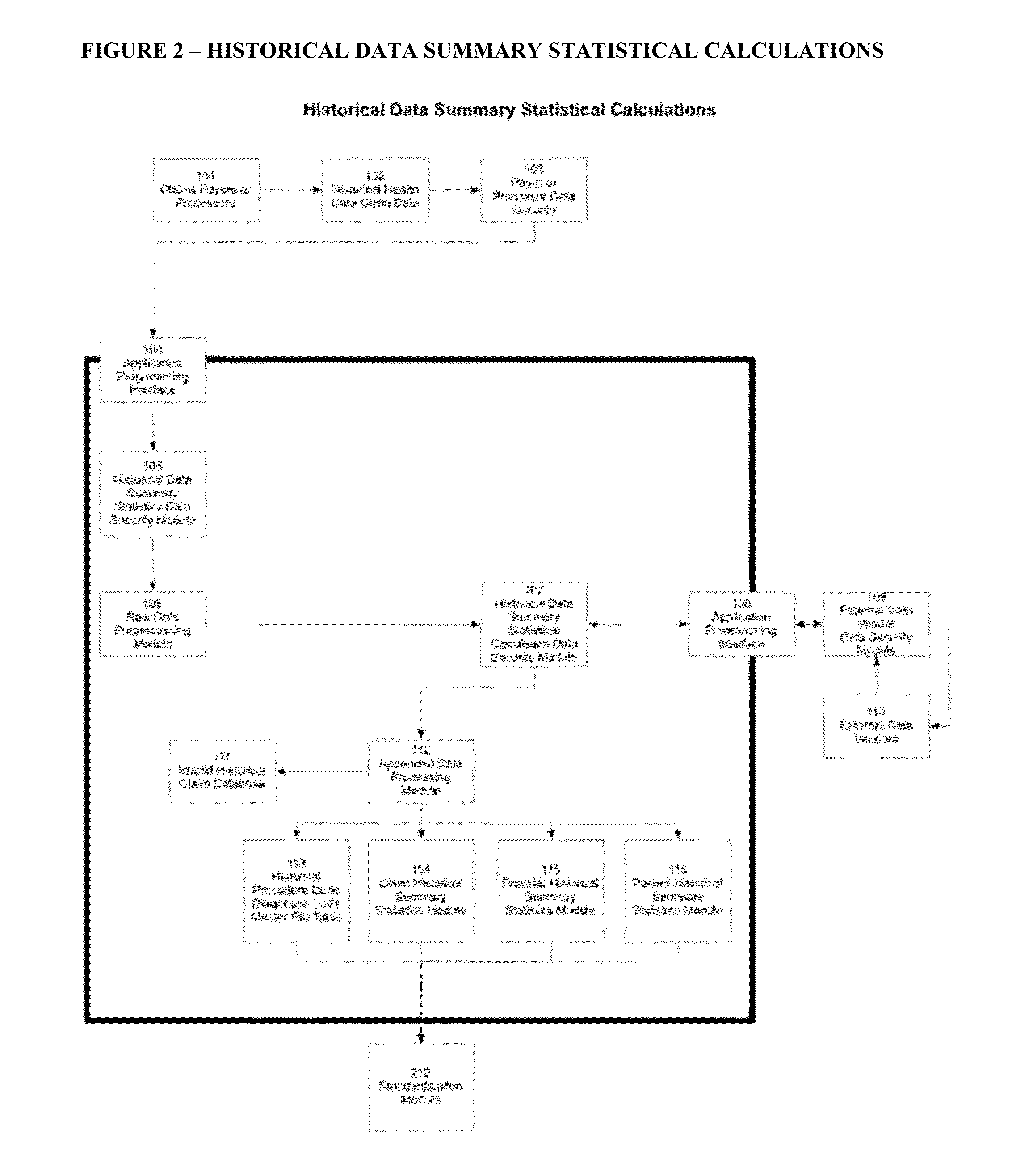
Automated Healthcare Risk Management System Utilizing Real-time Predictive Models, Risk Adjusted Provider Cost Index, Edit Analytics, Strategy Management, Managed Learning Environment, Contact Management, Forensic GUI, Case Management And Reporting System For Preventing And Detecting Healthcare Fraud, Abuse, Waste And Errors
InactiveUS20140081652A1Facilitate and enhance and implement multiple investigator decisionResource optimizationFinancePayment architectureLower riskMedical education
The Automated Healthcare Risk Management System is a real-time Software as a Service application which interfaces and assists investigators, law enforcement and risk management analysts by focusing their efforts on the highest risk and highest value healthcare payments. The system's Risk Management design utilizes real-time Predictive Models, a Provider Cost Index, Edit Analytics, Strategy Management, a Managed Learning Environment, Contact Management, Forensic GUI, Case Management and Reporting System for individually targeting, identifying and preventing fraud, abuse, waste and errors prior to payment. The Automated Healthcare Risk Management System analyzes hundreds of millions of transactions and automatically takes actions such as declining or queuing a suspect payment. Claim payment risk is optimally prioritized through a Managed Learning environment, from high risk to low risk for efficient resolution by investigators.
Owner:RISK MANAGEMENT SOLUTIONS
Integrated system for software application development
InactiveUS10001975B2Equally distributedProgram initiation/switchingVersion controlIntegrated softwareProject management
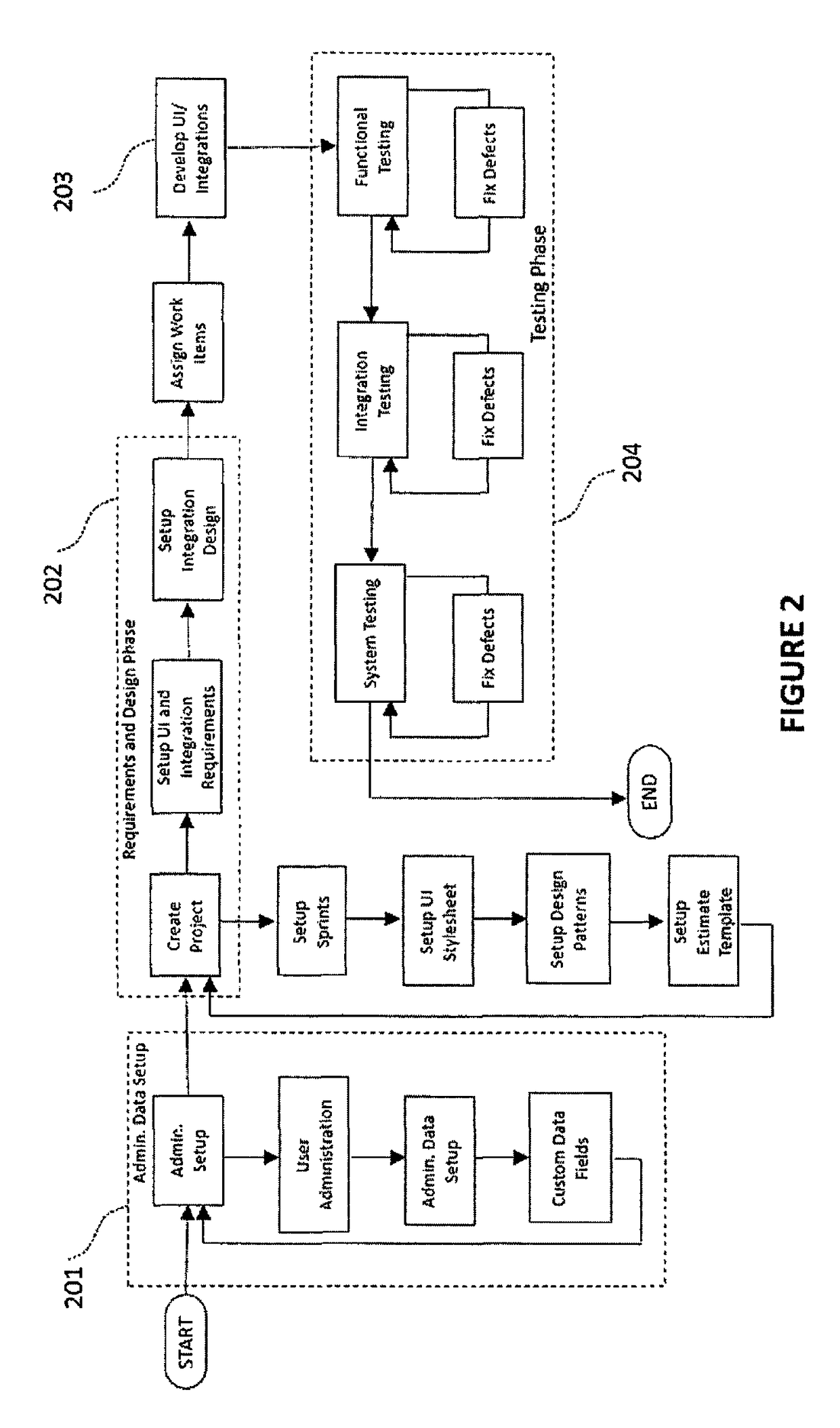
Methods and systems are disclosed for developing a software application through requirements specification, design, effort estimation, assigning and tracking work items, development, testing, collaboration and project management. The system is structured as an integrated software development system allowing for structured, systematic and user friendly set up of requirements specification (including workflow, user interface, business rules and integrations), technical design for UI features and integrations using design patterns, automated effort estimation, automated story card and task creation. The system also provides a novel, audio-video playback capability for workflow visualization. Further, the system provides visual depiction of defects and changed items side-by-side with requirements, as well as predictive modeling of defects that allows for forecasting of defect completion rate. In the preferred embodiment, the system is delivered as a multi-tenant Software as a Service.
Owner:BHARTHULWAR SHRIDHAR V
Network Access Control with Compliance Policy Check
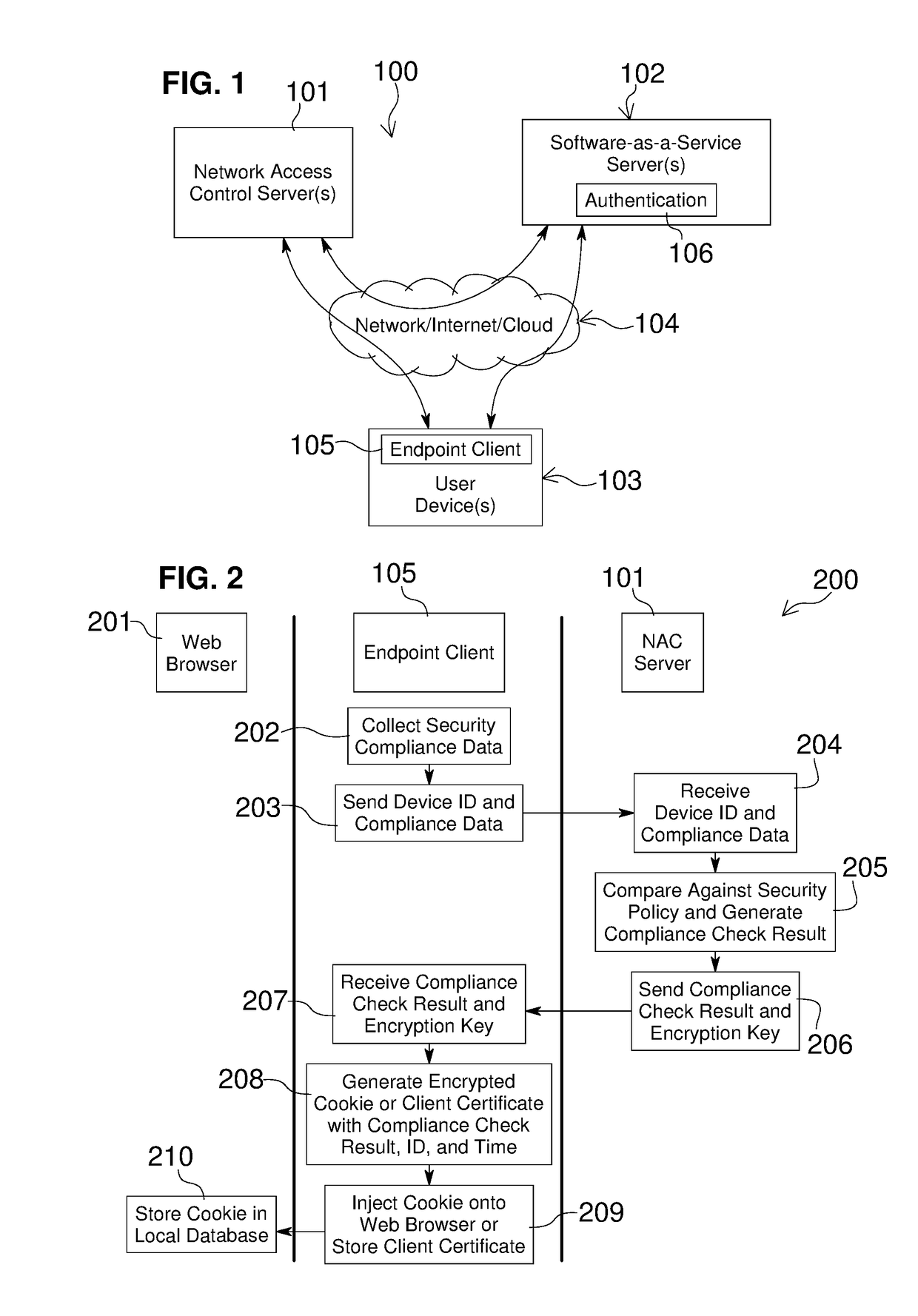
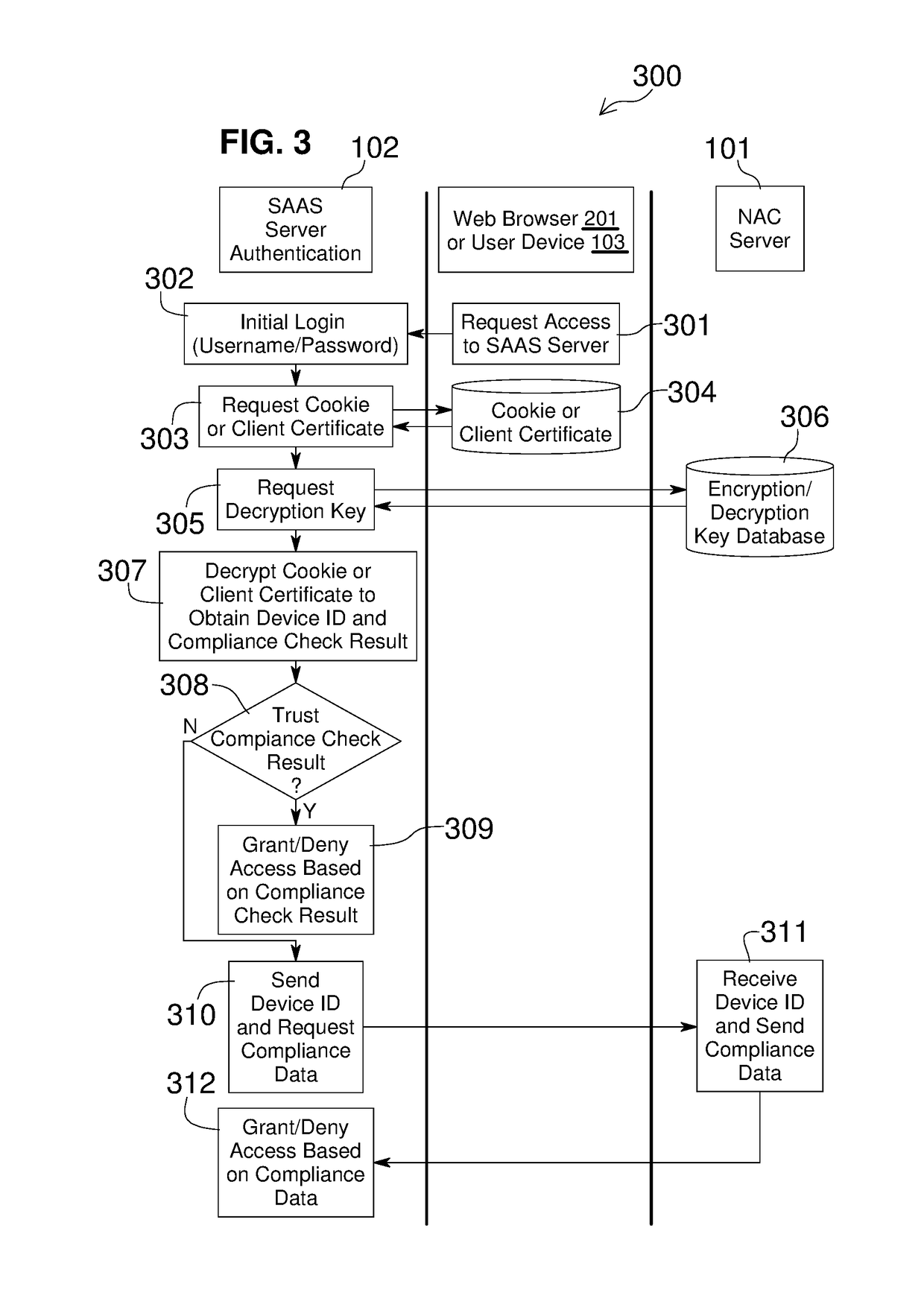
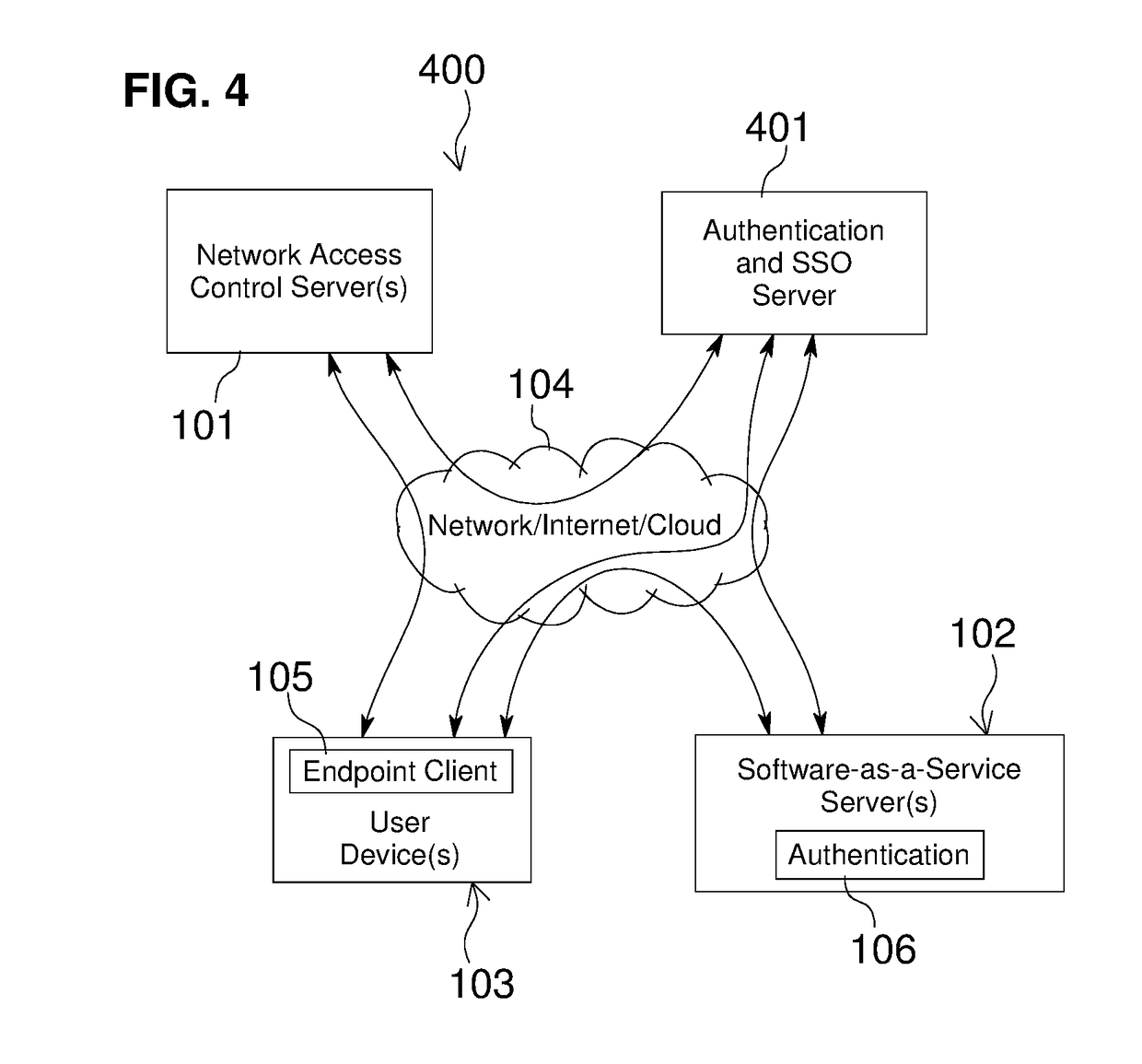
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT INC
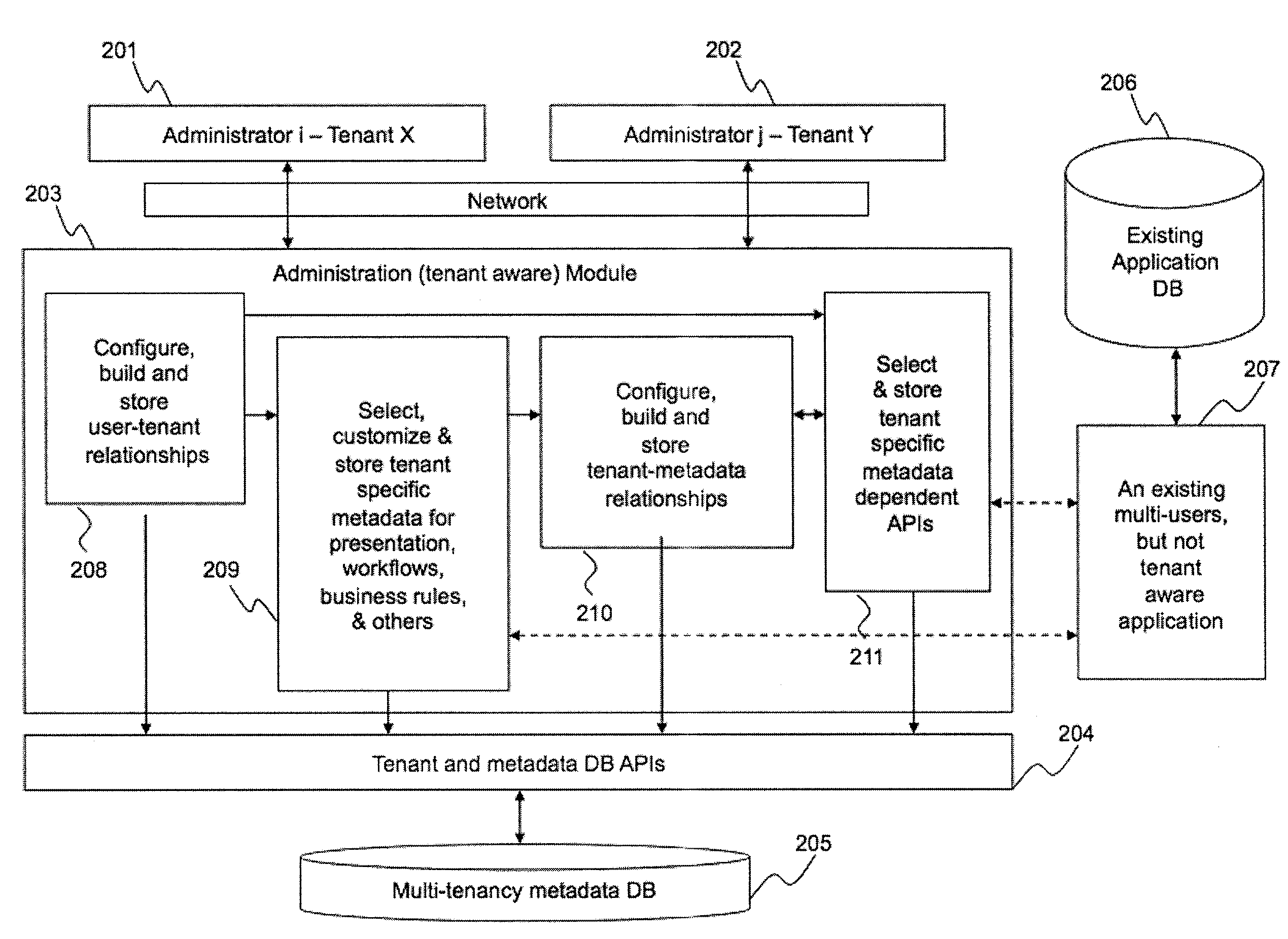
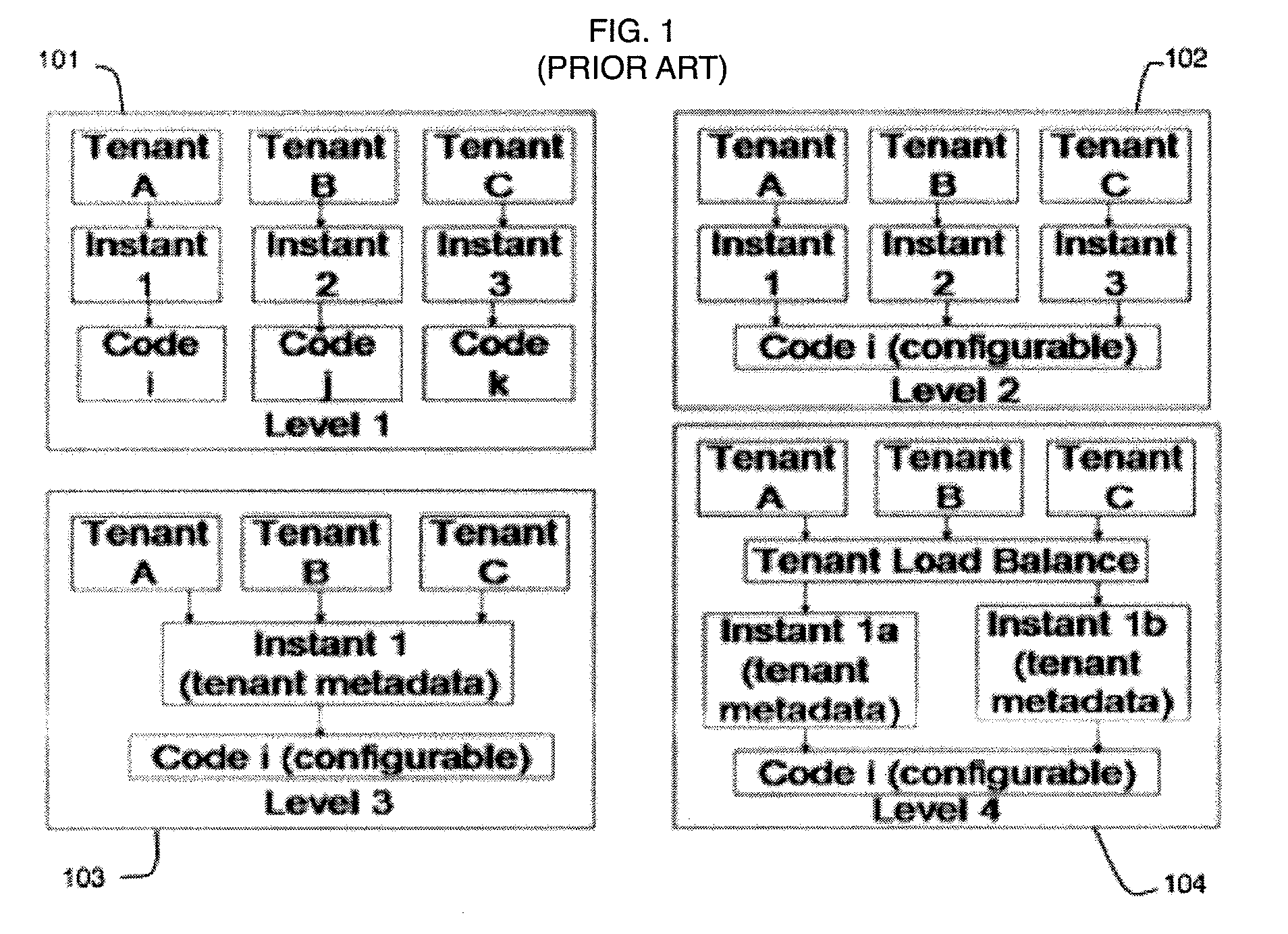
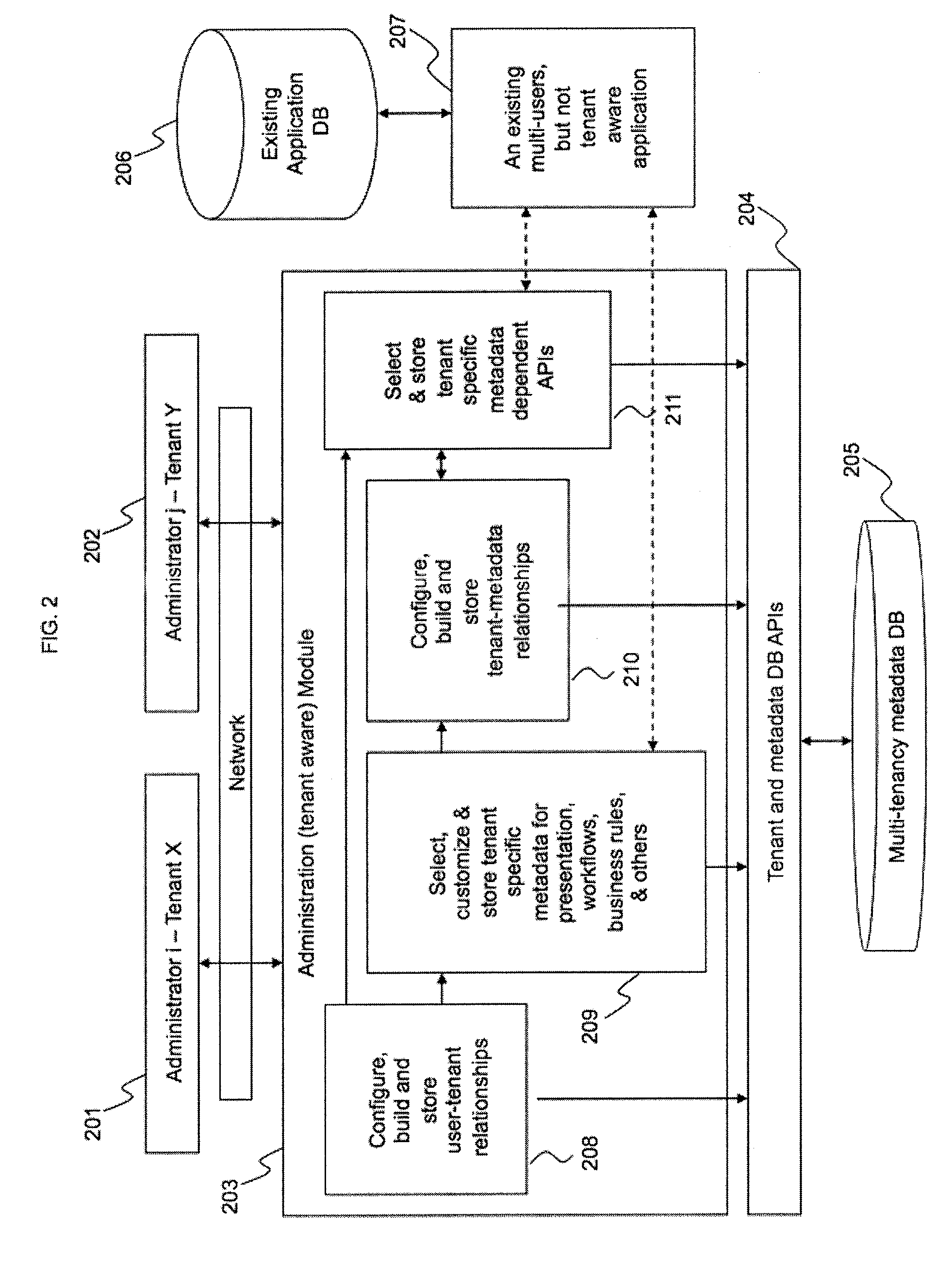
Framework for facilitating implementation of multi-tenant saas architecture
ActiveUS20140289391A1Facilitates monitoring and controllingFacilitate monitoring and controlling of featuresDigital computer detailsData switching networksWeb applicationSoftware as a service
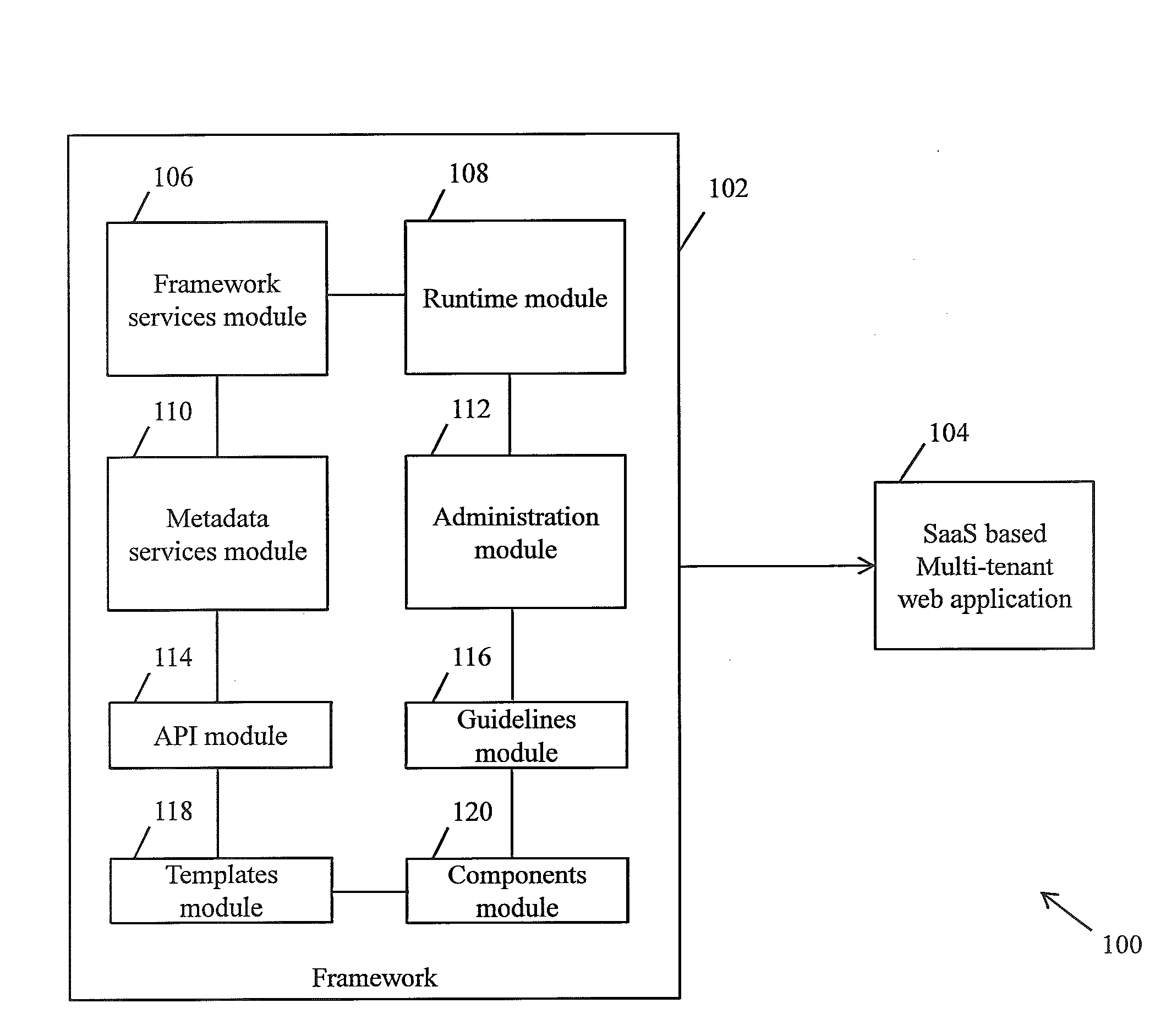
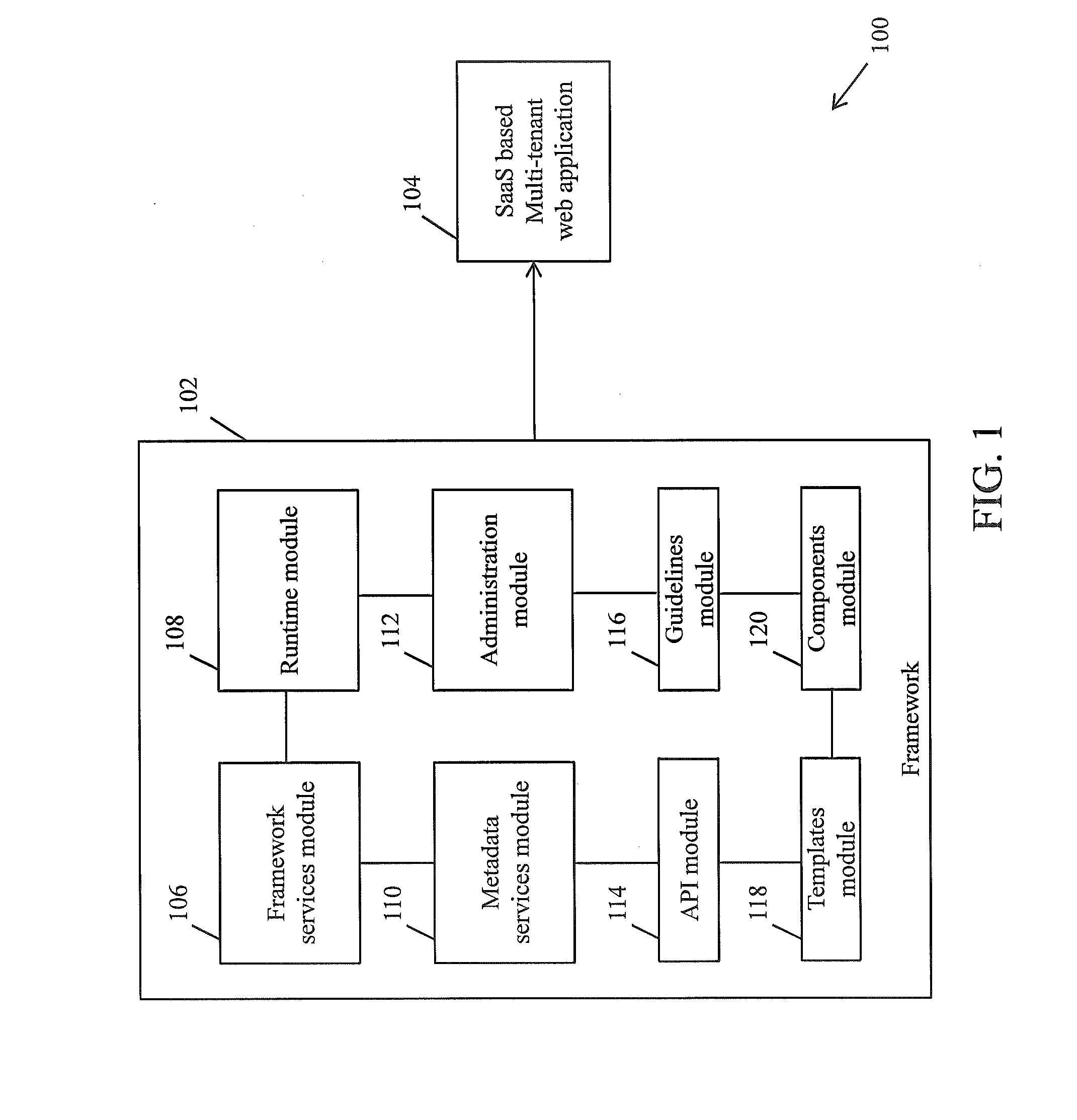
A framework for implementing multitenant architecture is provided. The framework comprises a framework services module which is configured to provide framework services that facilitate abstraction of Software-as-a-Service (SaaS) services and crosscutting services for a Greenfield application and a non SaaS based web application. Further the abstraction results in a SaaS based multitenant web application. The framework further comprises a runtime module configured to automatically integrate and consume the framework services and APIs to facilitate monitoring and controlling of features associated with the SaaS based multitenant web application. The framework further comprises a metadata services module configured to provide a plurality of metadata services to facilitate abstraction of storage structure of metadata associated with the framework and act as APIs for managing the metadata. The framework further comprises a role based administration module that facilitates management of the metadata through a tenant administrator and a product administrator.
Owner:COGNIZANT TECH SOLUTIONS INDIA PVT
Cloud plarform for managing software as a service (SAAS) resources
InactiveUS20110126168A1Ensure availabilityEnsure data securityMultiple digital computer combinationsSpecific program execution arrangementsApplication softwareData availability
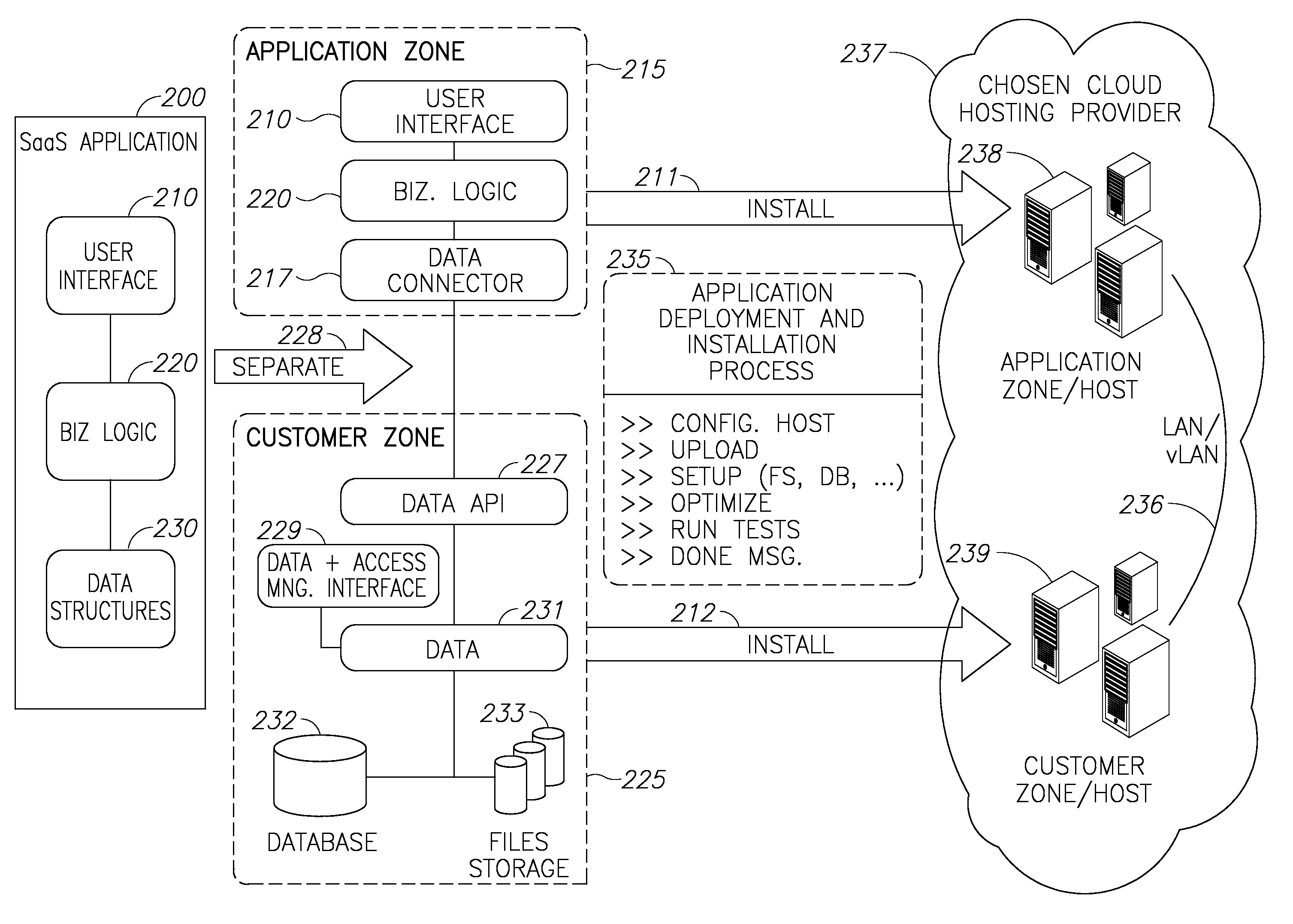
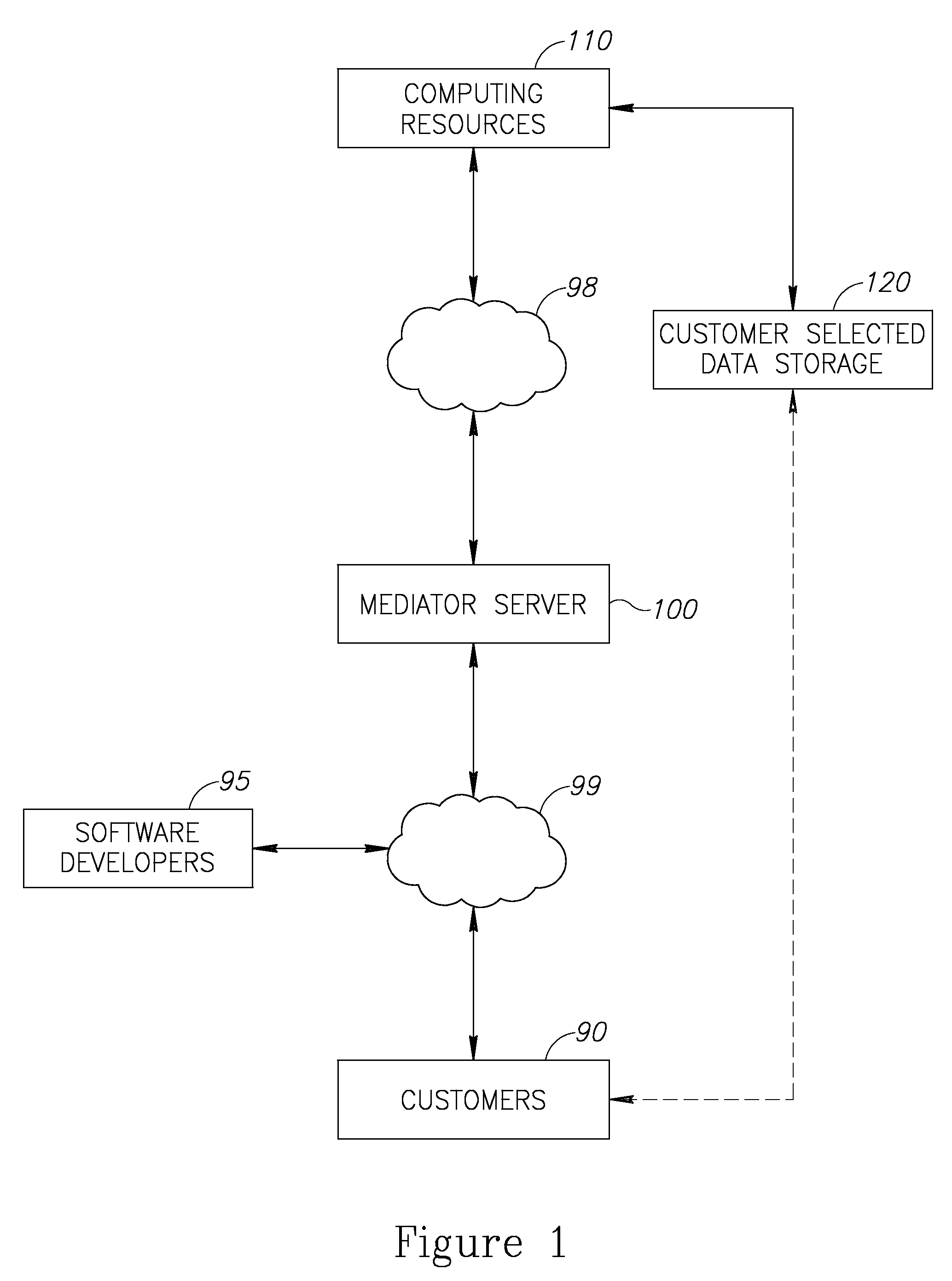
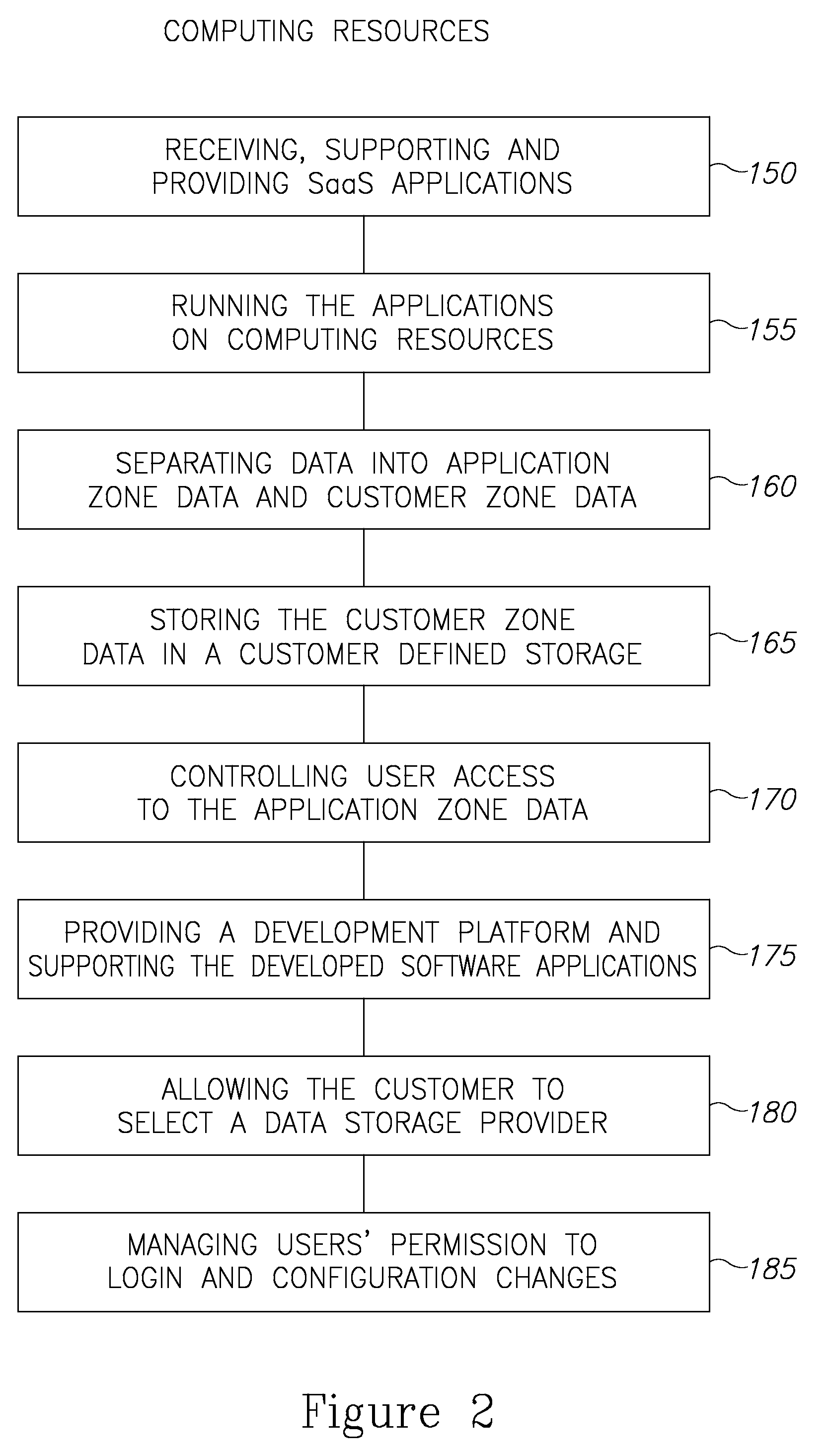
A cloud platform for managing Software as a Service (SaaS) resources is provided herein. The platform includes: a mediator server connected to computing resources, arranged to provide software developers a platform to develop SaaS applications, operable on the computing resources, wherein the SaaS applications and customer data are stored logically and physically independent of the computing resources, and data of SaaS application and the customer data are logically and physically separated. SaaS platform allows developers to provide software solutions via the mediator server directly to customers, and ensures data availability and data security. Access policy of users and developers to SaaS applications is centrally supervised and capable of integrating with other applications on the site of the customer. Upgrades to SaaS applications are performed in a predefined order of customers. Further, the SaaS platform facilitates selection and replacement of data storage provider.
Owner:CROWDSOURCE TECH
Systems and methods for metered software as a service
InactiveUS20090271324A1Good serviceComplete banking machinesError detection/correctionPaymentInvoice
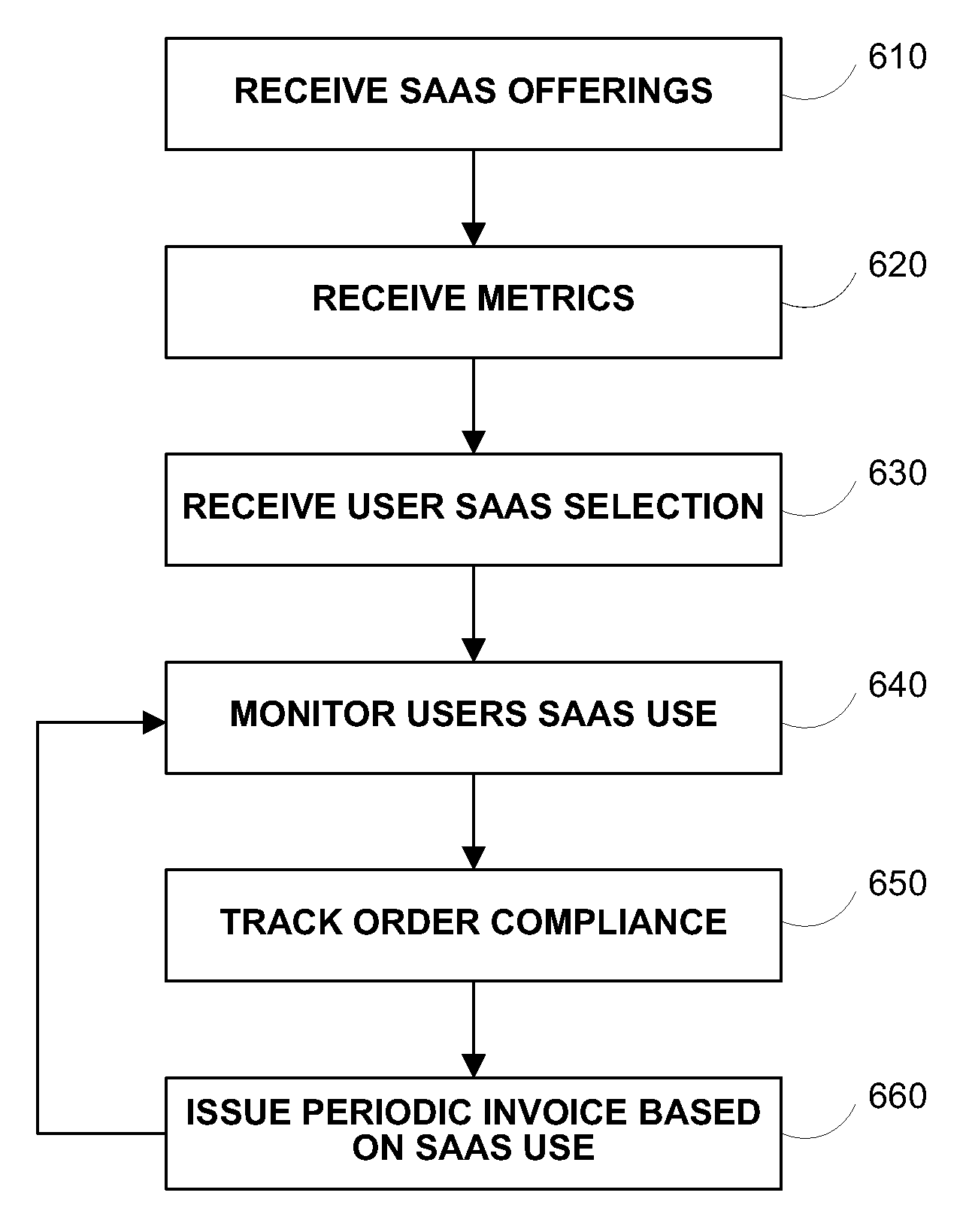
Systems and methods are provided for facilitating software as a service (SAAS) by receiving information of SAAS offerings and metrics for tracking a users use of the SAAS offerings. The systems may be used to create SAAS orders and provide compliance and auditing of the SAAS, as well as generating invoices and receiving payment for the SAAS.
Owner:EVAPT
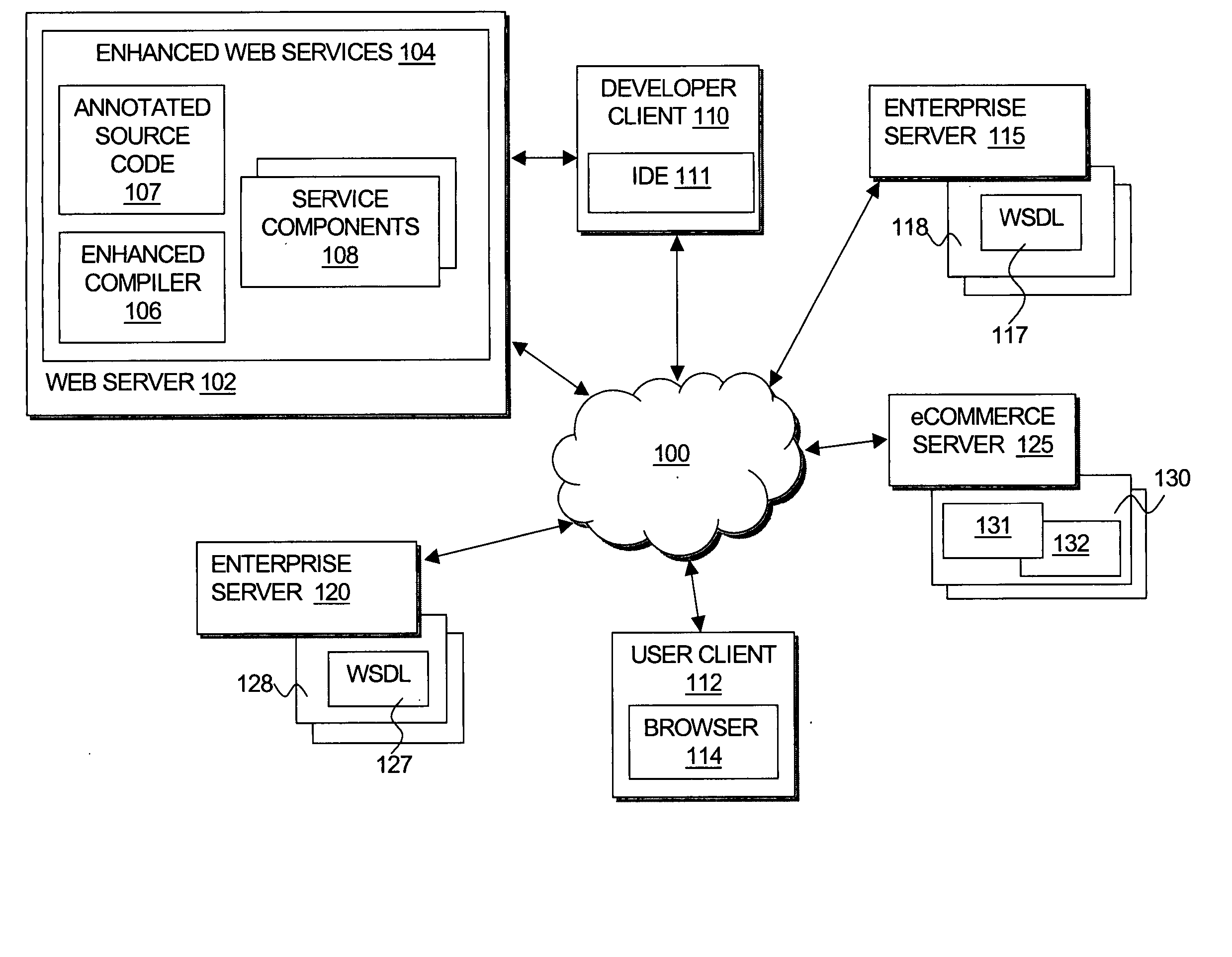
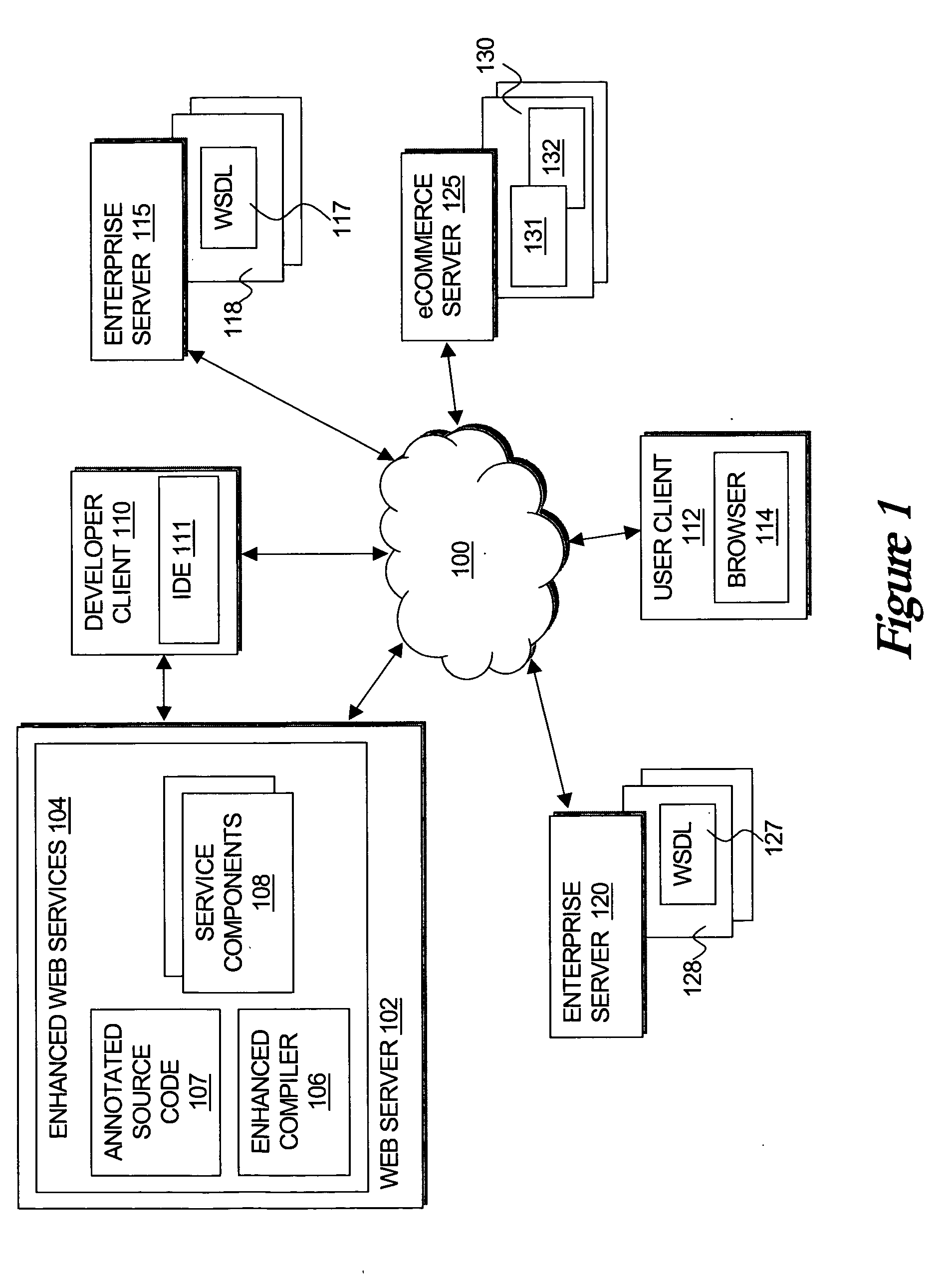
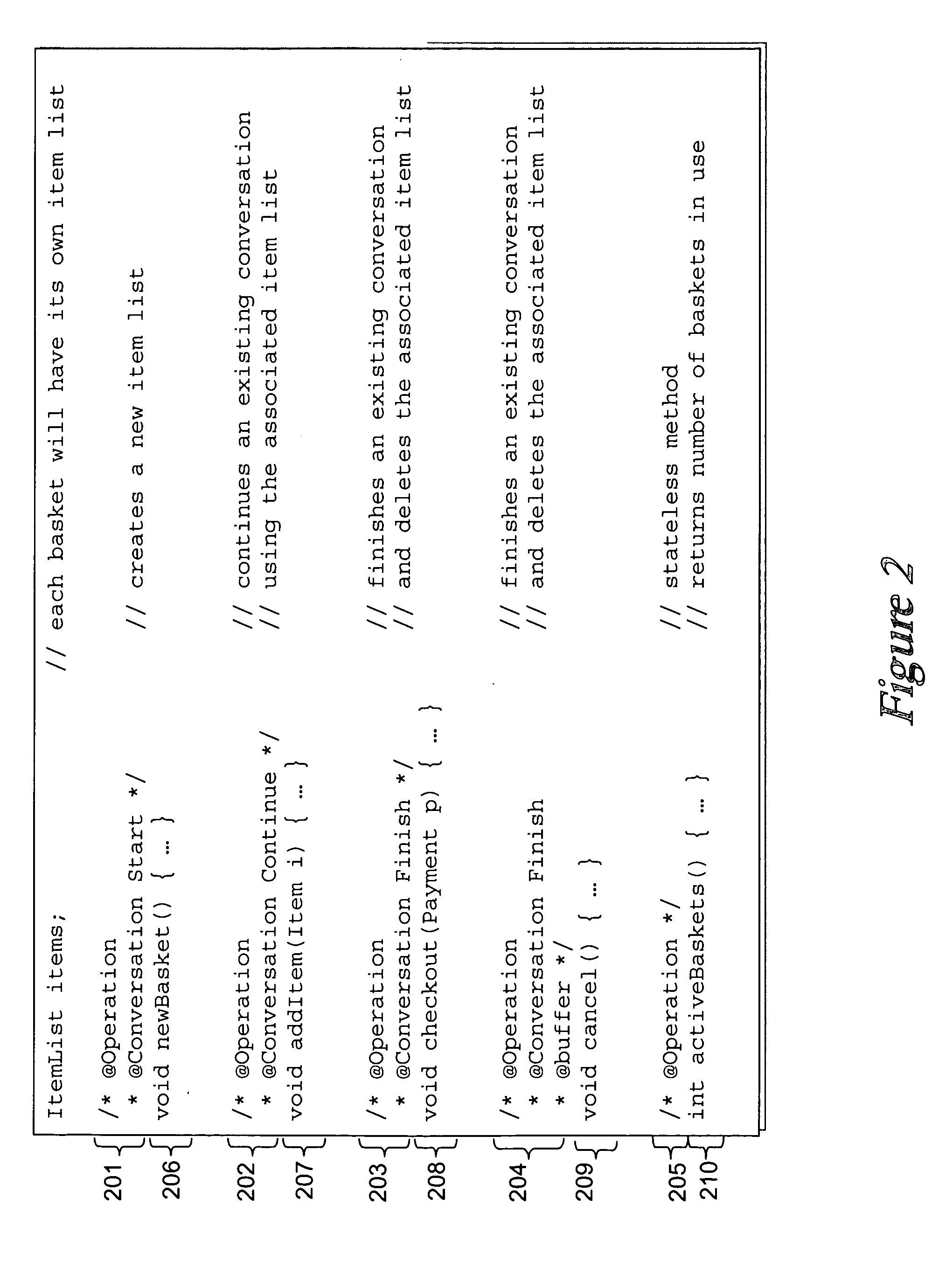
Systems and methods for creating network-based software services using source code annotations
ActiveUS20050021689A1Digital data processing detailsUnauthorized memory use protectionWeb serviceDEVS
A developer can express the logic offered by a Web service, or other network accessible service, using a standard programming language augmented with declarative annotations specifying preferences for exposing that logic as a Web service. At compile time, an enhanced compiler can analyze the annotated source file and automatically generate the mechanisms required to expose its functionality as a Web service or network accessible service. Because the annotations are declarative, they may be easily visualized, created, and modified such as by using a graphical user interface, further simplifying the developer's task. Thus, such an approach decreases the time, knowledge, skill and ultimately cost required to develop the complex support required to proved services in these environments. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
System and method to support subscription based Infrastructure and software as a service
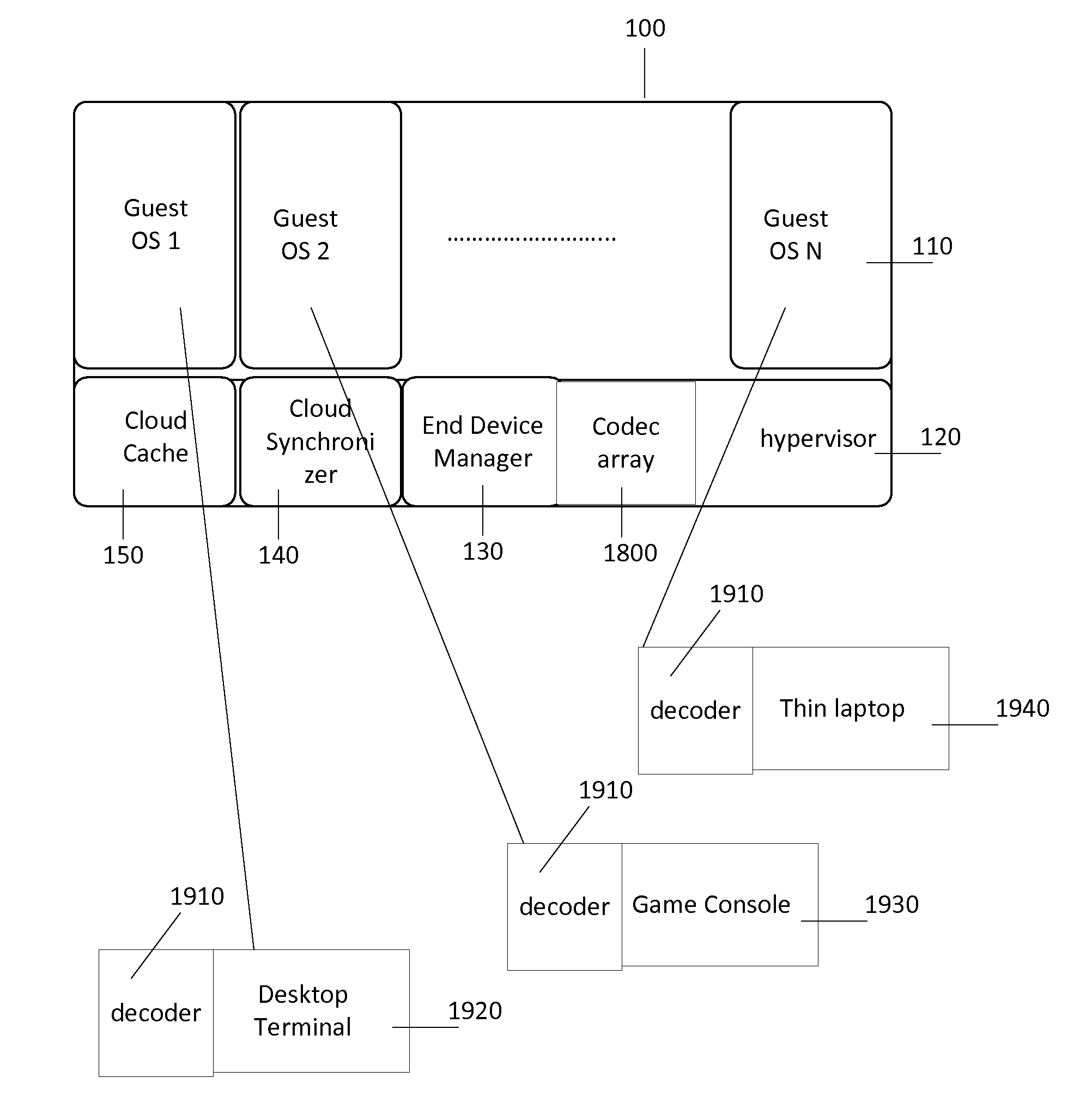
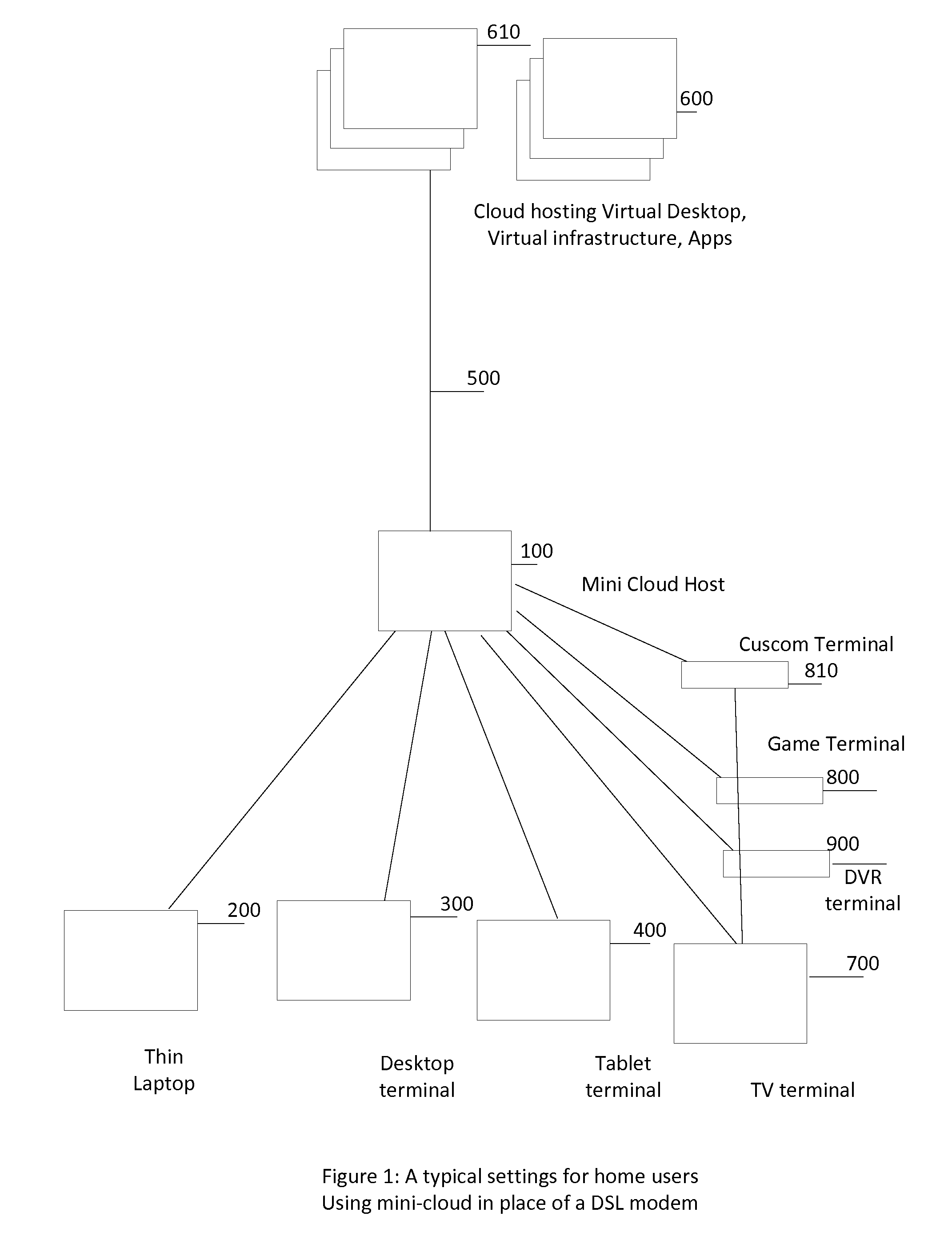
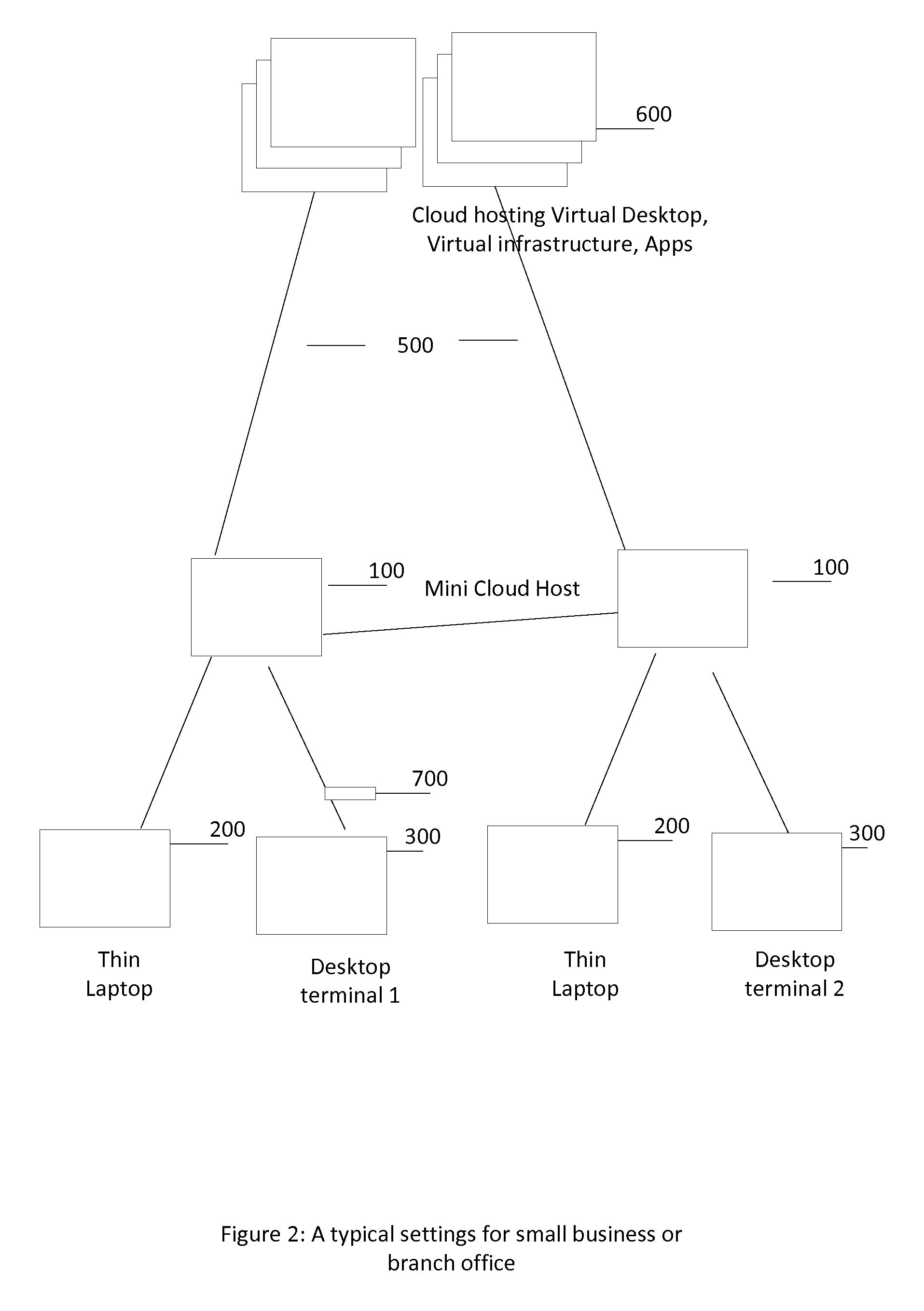
A mini-cloud system has been described to enable subscription or service model for computing infrastructure, software and Digital content. The mini-cloud system work as a pipe line for information delivery connecting end user, infrastructure provider, content provider, and retailer offering automatic provisioning of infrastructure, content lifecycle management, automatic upgrade, servicing, license managements based on subscription model. Mini-cloud system uses a subscription management component, virtualization host to back computing environment, then add routing component to connect to backend cloud infrastructure along with a digital content delivery framework. The system allow a user to subscribe a computing environment, preferred software applications, and digital content like move and pay a monthly utility bill.
Owner:XENCARE SOFTWARE
Automatic labeling and control of audio algorithms by audio recognition
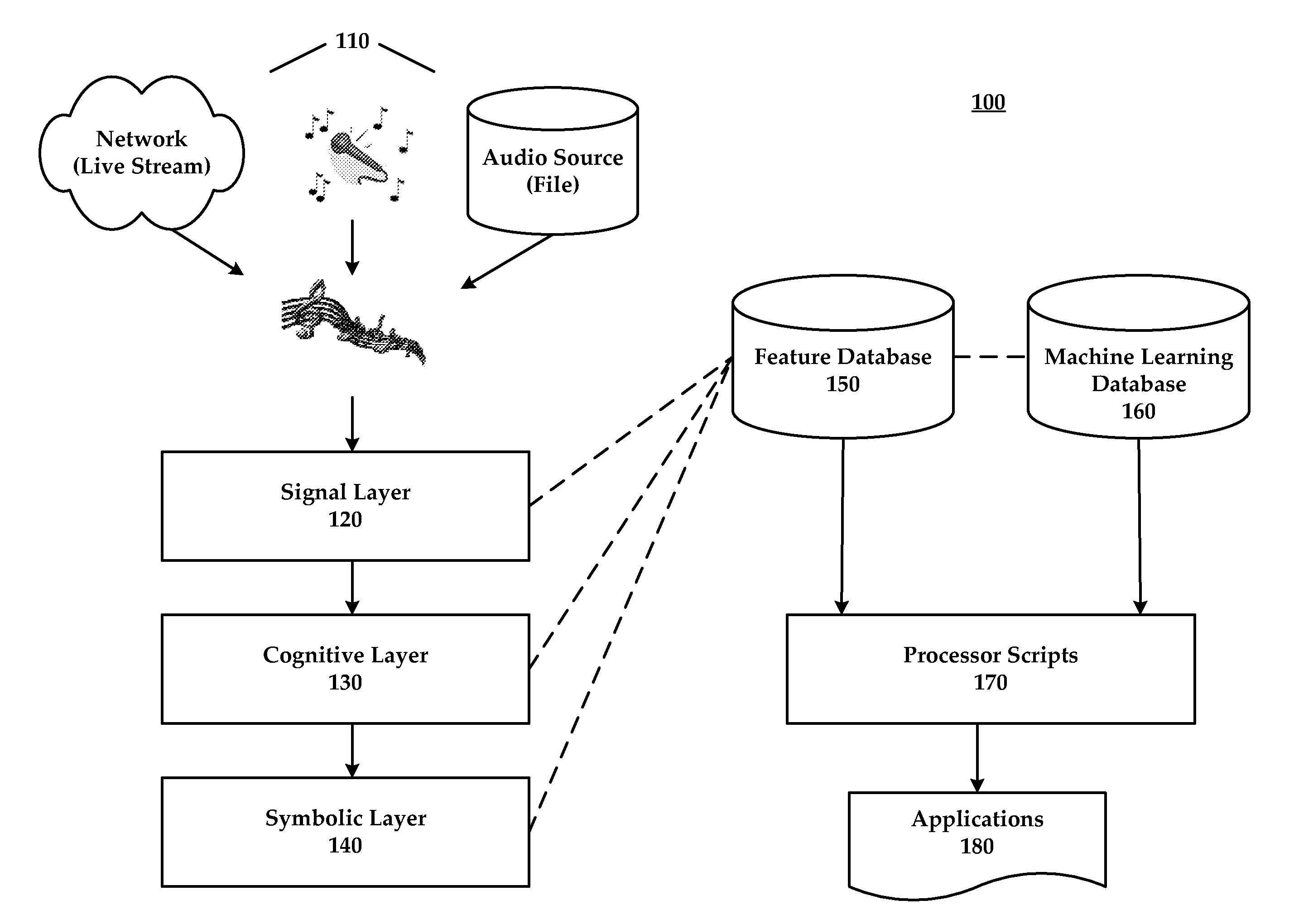
ActiveUS20110075851A1Better-sounding audioFaster and more creative work flowElectrical apparatusSpeech analysisMultimedia softwareApplication software
Owner:IZOTOPE
Tenant life cycle management for a software as a service platform
ActiveUS8291490B1Digital data processing detailsUnauthorized memory use protectionApplication specificApplication software
Managing user access to application-specific capabilities of a system includes maintaining data correlating application-specific capabilities for each of the applications of the system, where the application-specific capabilities of different applications are independent of each other. Managing user access also includes maintaining data correlating user identifiers with user roles, maintaining data correlating user roles with application-specific capabilities, and managing the data using a security module that accesses the data correlating application-specific capabilities, data correlating user identifiers, and the data correlating user roles. The system may have a plurality of tenants and wherein each of the tenants subscribes to one or more of the applications. Each of the users may correspond to a particular one of the tenants. Each tenant may subscribe to a particular set of applications / features.
Owner:EMC IP HLDG CO LLC
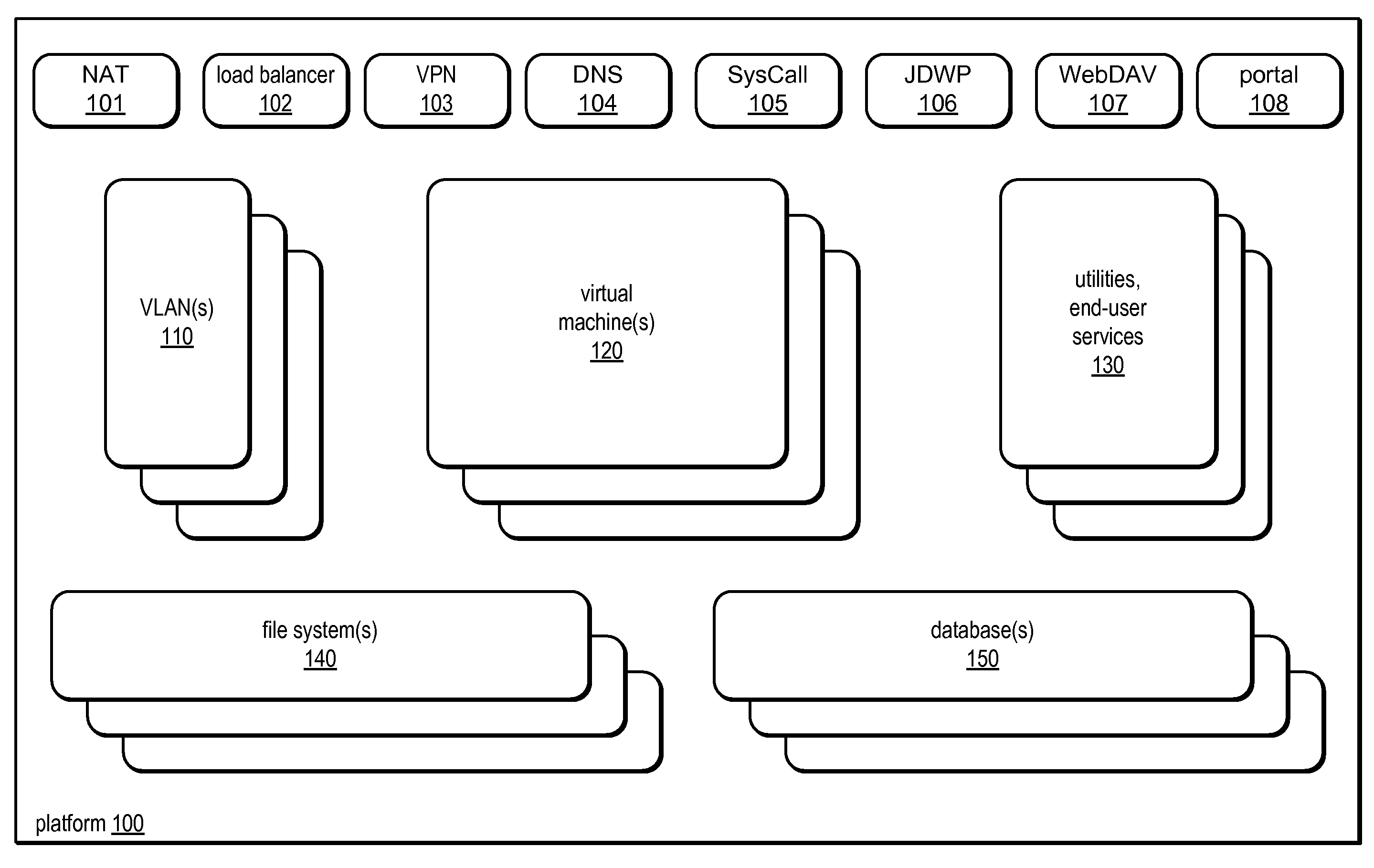
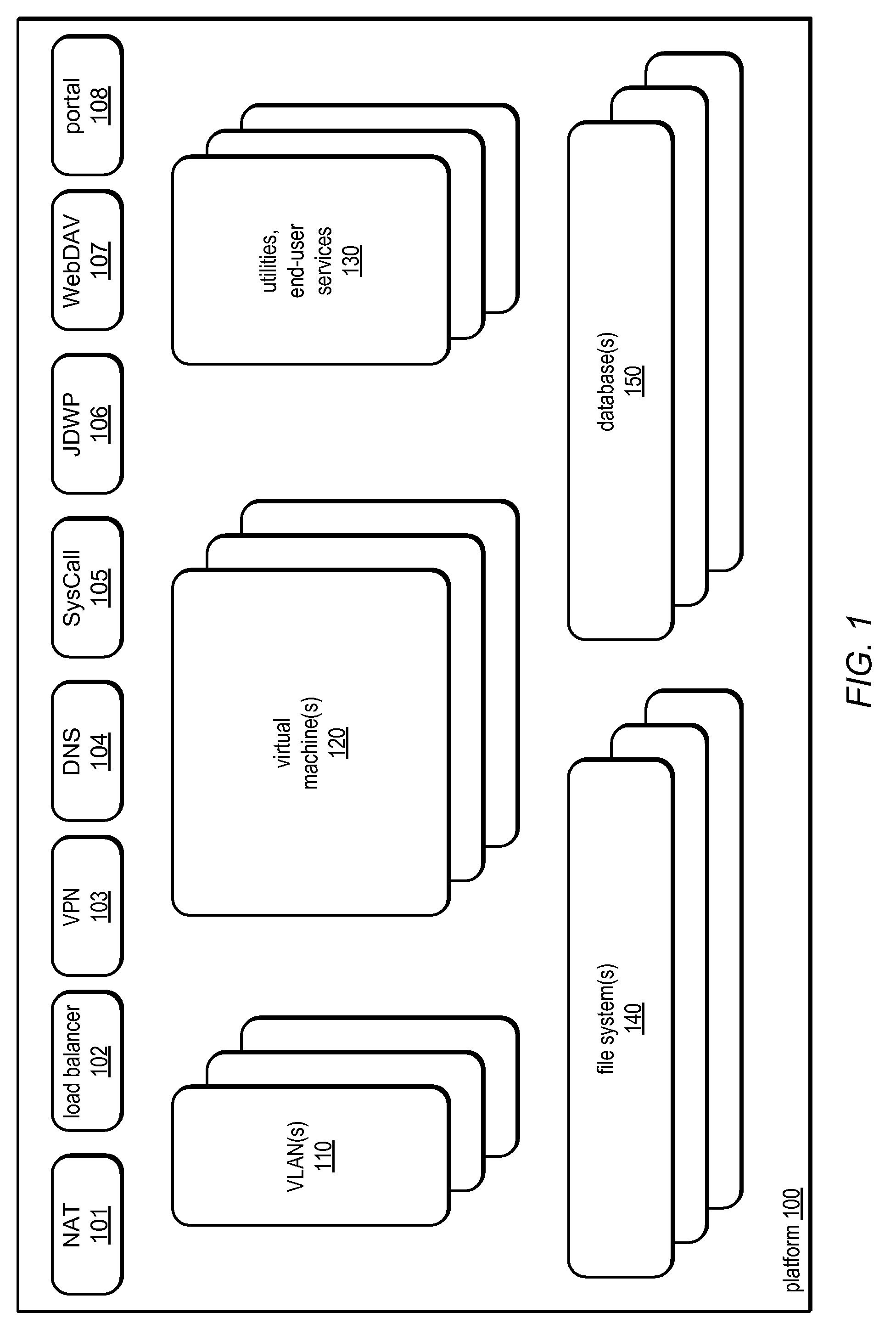
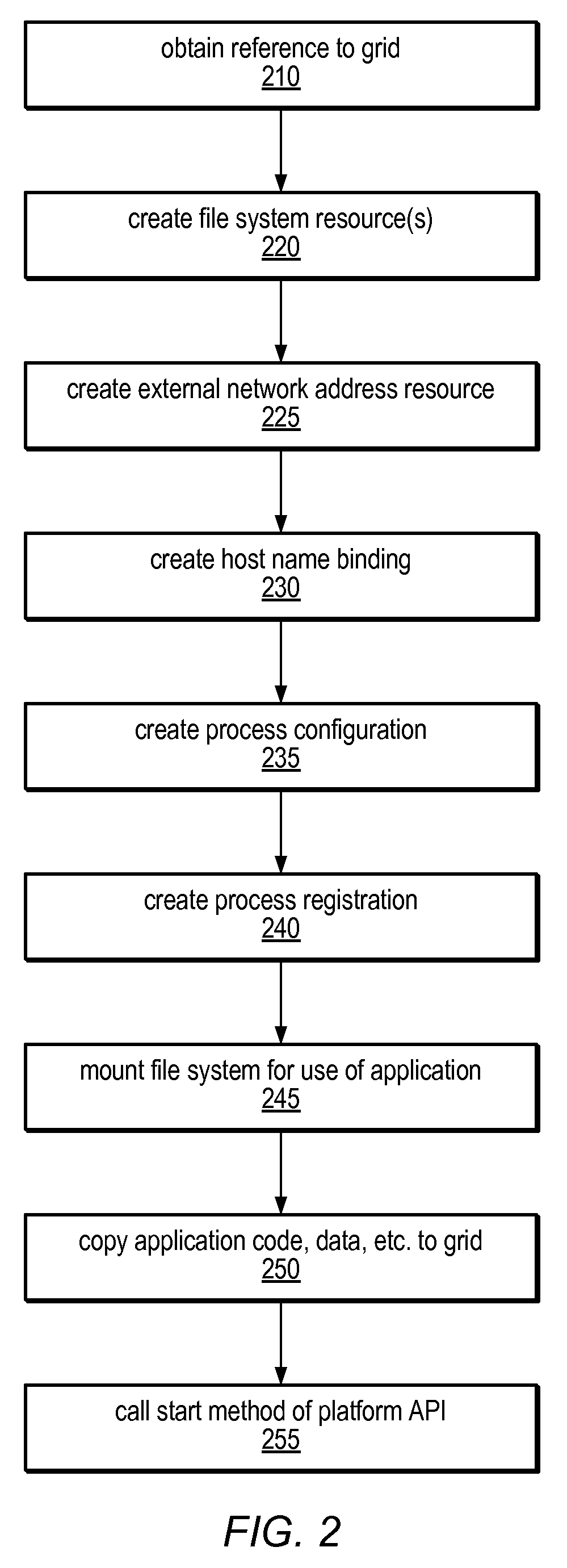
System and method for programmatic management of distributed computing resources
ActiveUS7886021B2Speed up developmentSpeeding up deliveryMultiple digital computer combinationsProgram controlWeb serviceStructure of Management Information
Systems and methods for providing a development and deployment platform for Software as a Service (SaaS) providers are disclosed. The platform may provide an application programming interface (API) through which customers may configure virtualized grids of language-level virtual machines (VMs), networks, and storage resources. A grid may be horizontally scalable and programmatically configurable by a customer and / or customer code. The platform may allow dynamic scaling of resources (up and down) to match changing demands, by allowing customers and / or customer code to programmatically alter their own system level structure at runtime, through the API. The grid may be accessed by both on-grid and off-grid processes, through internal and external connectivity resources provided by the platform. The platform may provide common utilities for end-user services, deployment operations, and development tasks (e.g., debugging), and may include frameworks and macro-components (e.g. web servers). The platform may host long-running Internet-based services and / or one-shot computational services.
Owner:ORACLE INT CORP
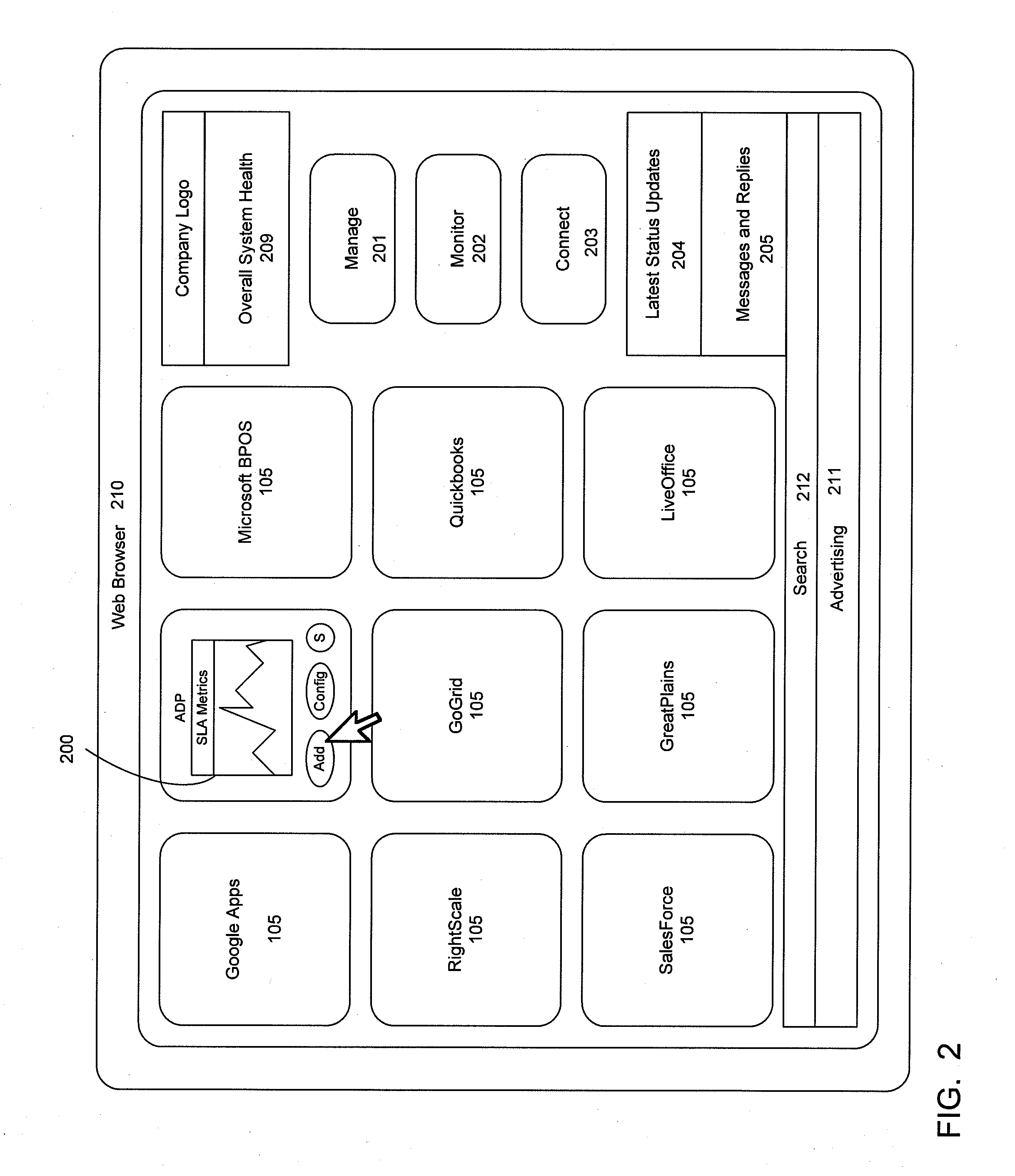
Centrally managing and monitoring software as a service (SAAS) applications
ActiveUS20100250712A1Data processing applicationsMultiple digital computer combinationsApplication softwareCentralized management
An apparatus, system, method and program providing a multi-tenant software as a service (SaaS) application that manages and monitors the use of other SaaS applications via a common connection and database framework. An Internet-based interface is provided as a single portal for monitoring and managing the use of SaaS applications. Objects and the state of these objects including all associated attributes related to the SaaS applications are stored in databases associated with the Internet-based interface. The Internet-based interface also provides a social networking infrastructure and an application exchange infrastructure that allows sharing of information related to the SaaS applications.
Owner:III HLDG 1
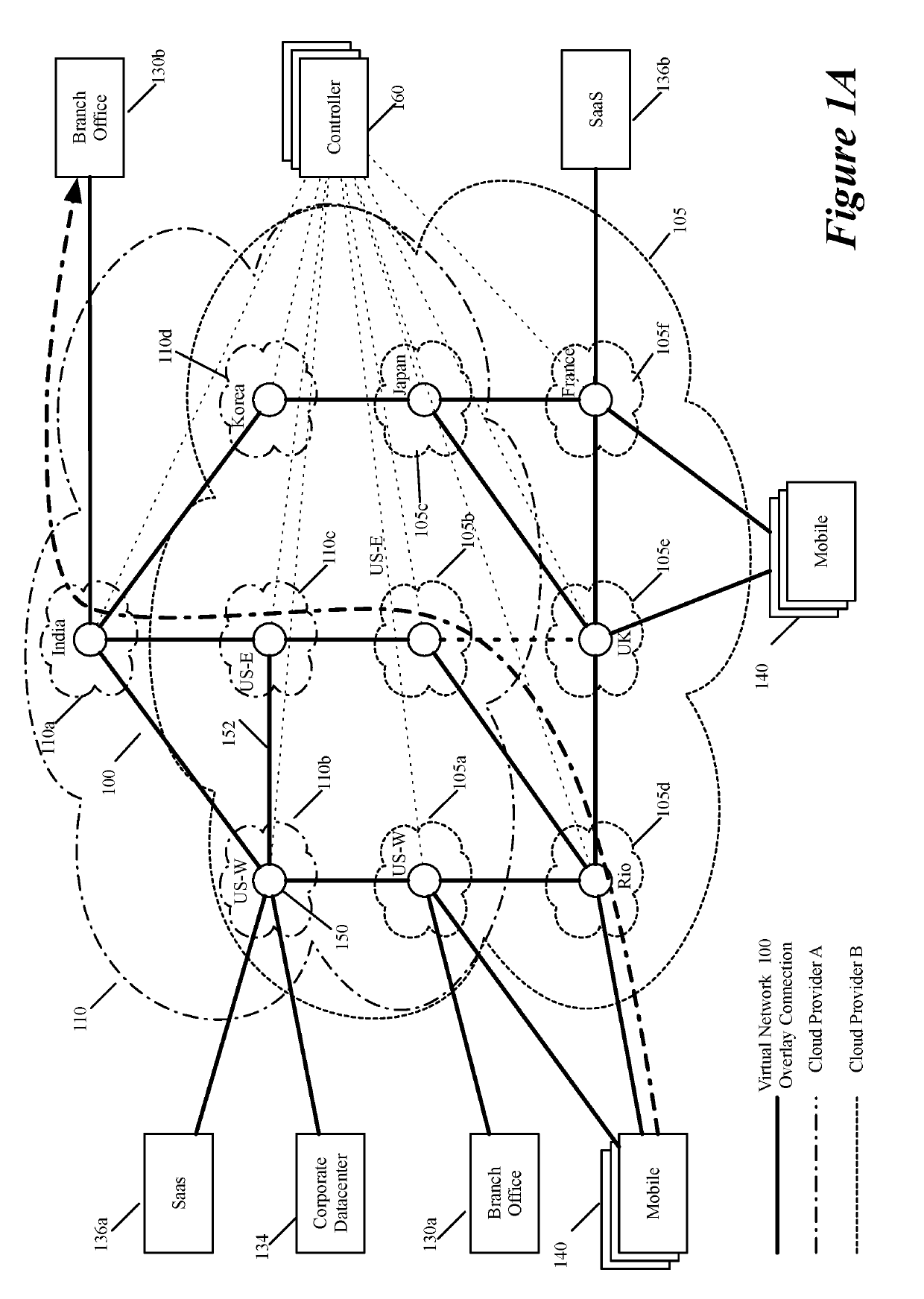
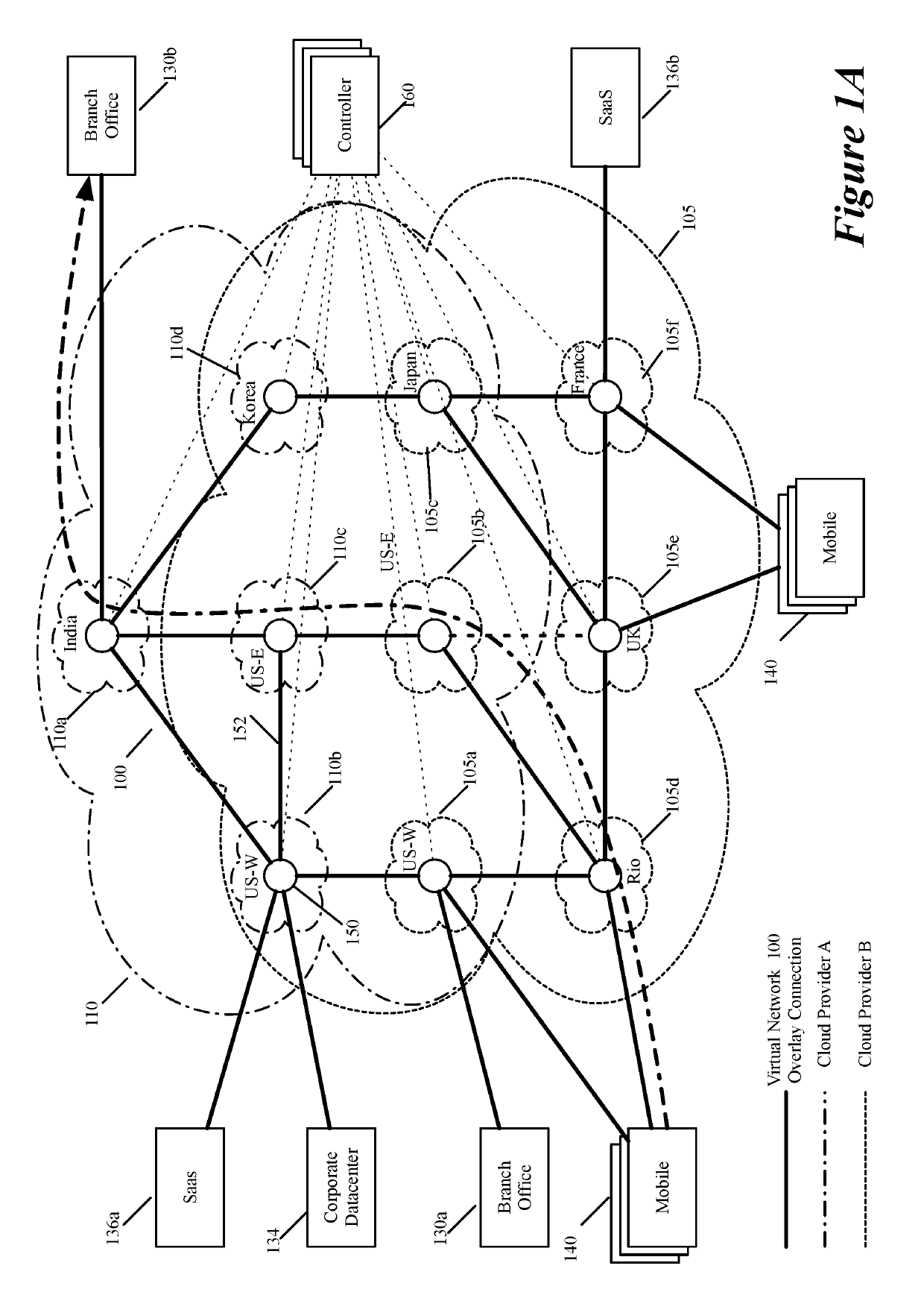
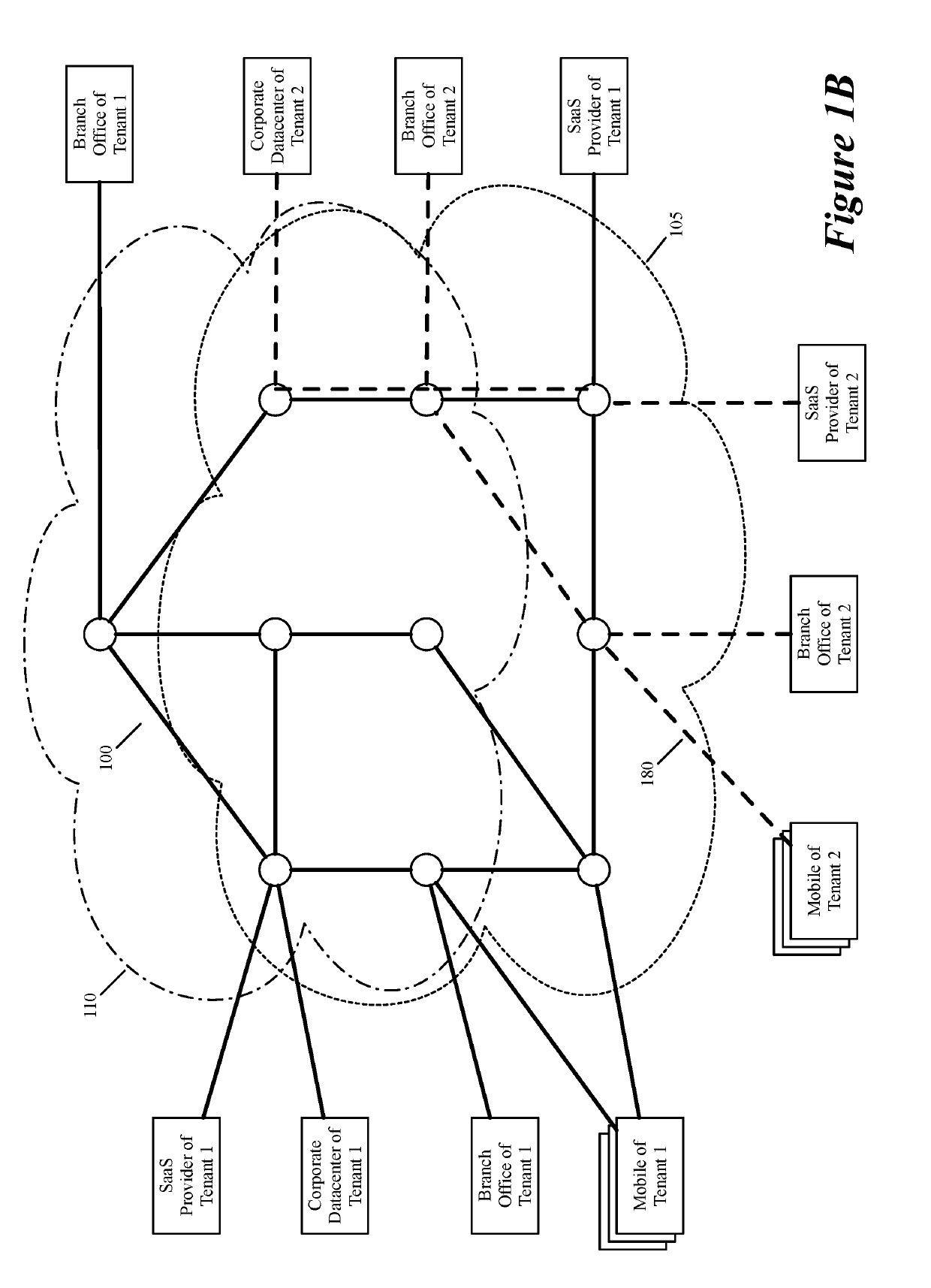
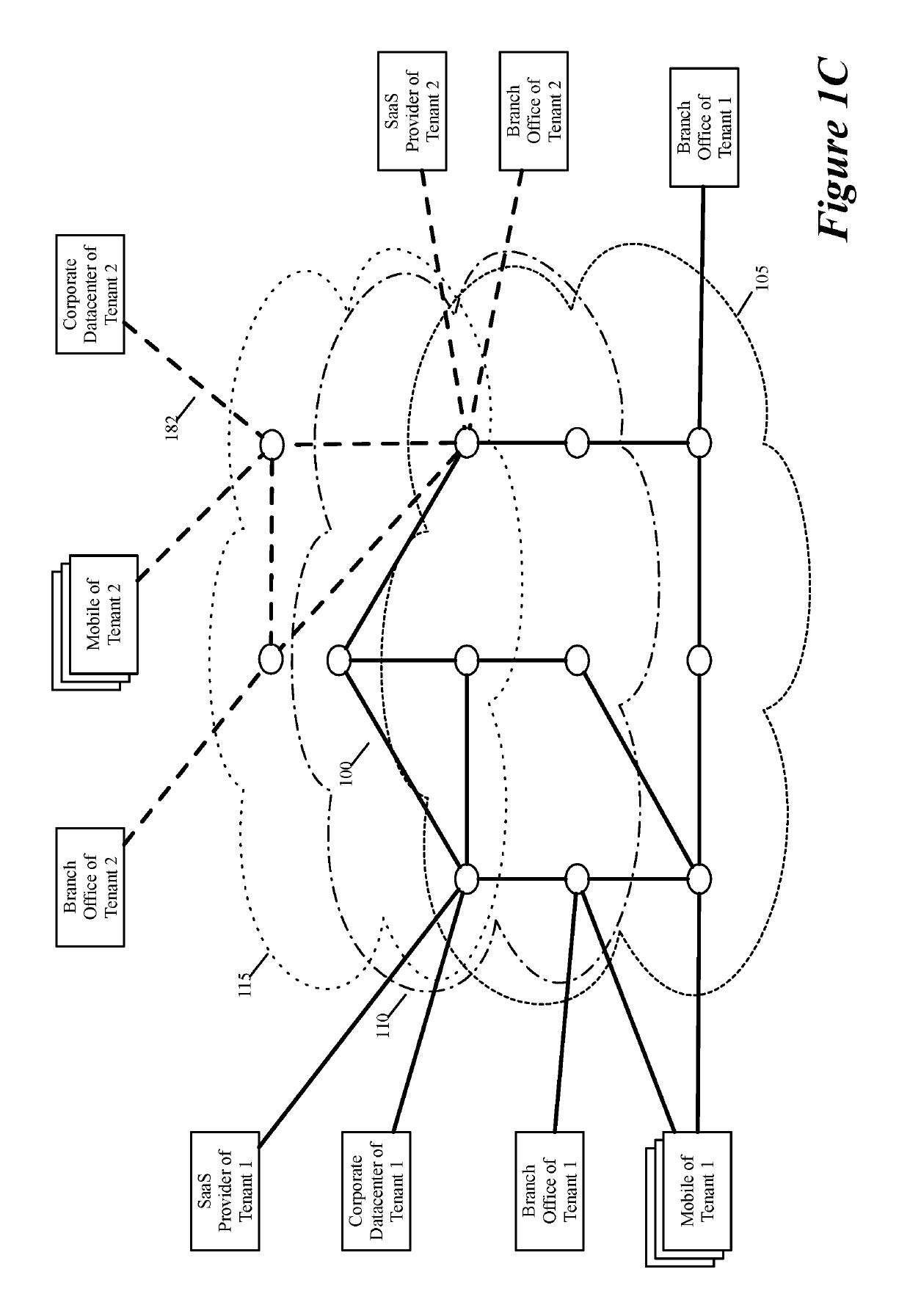
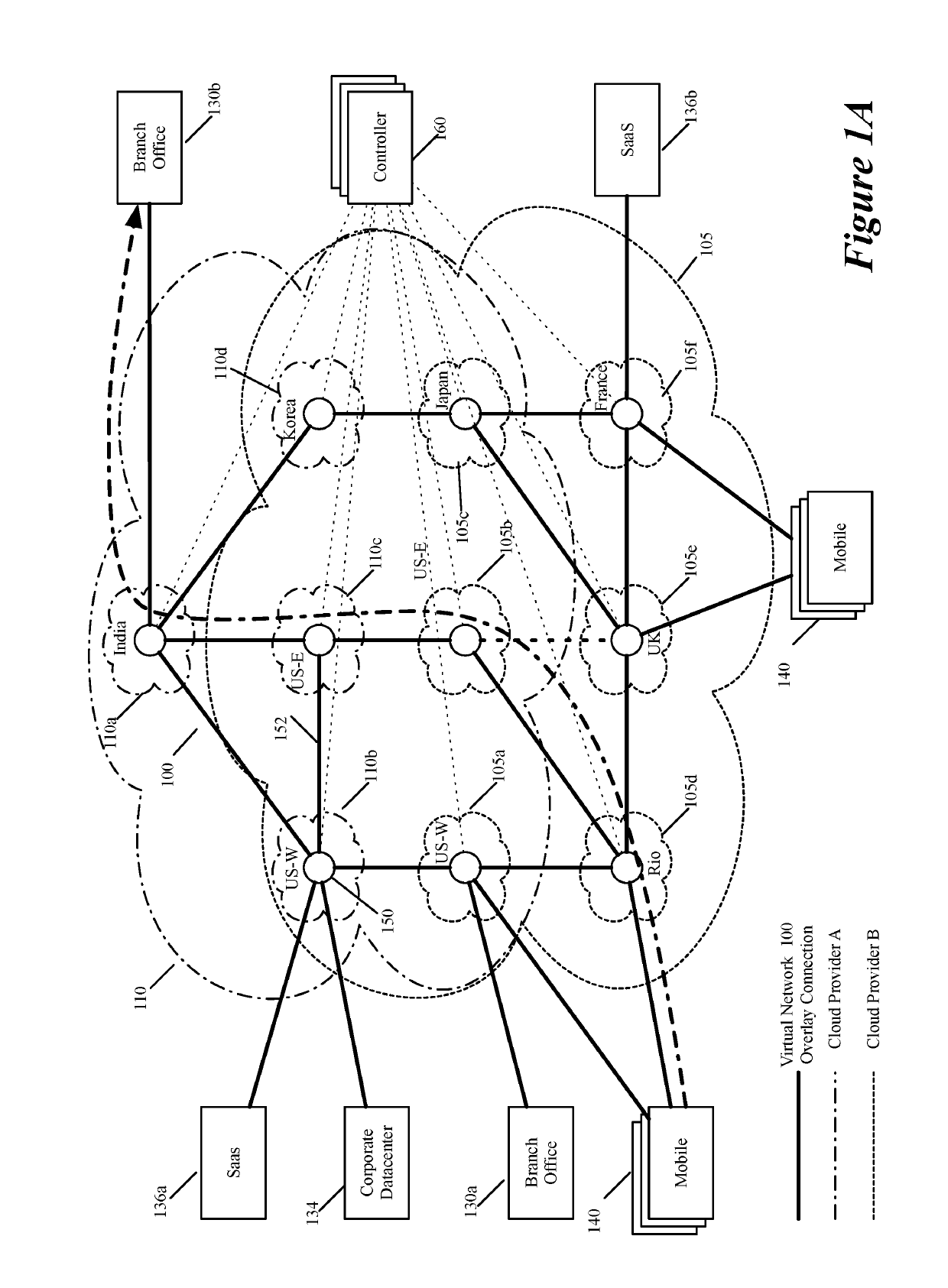
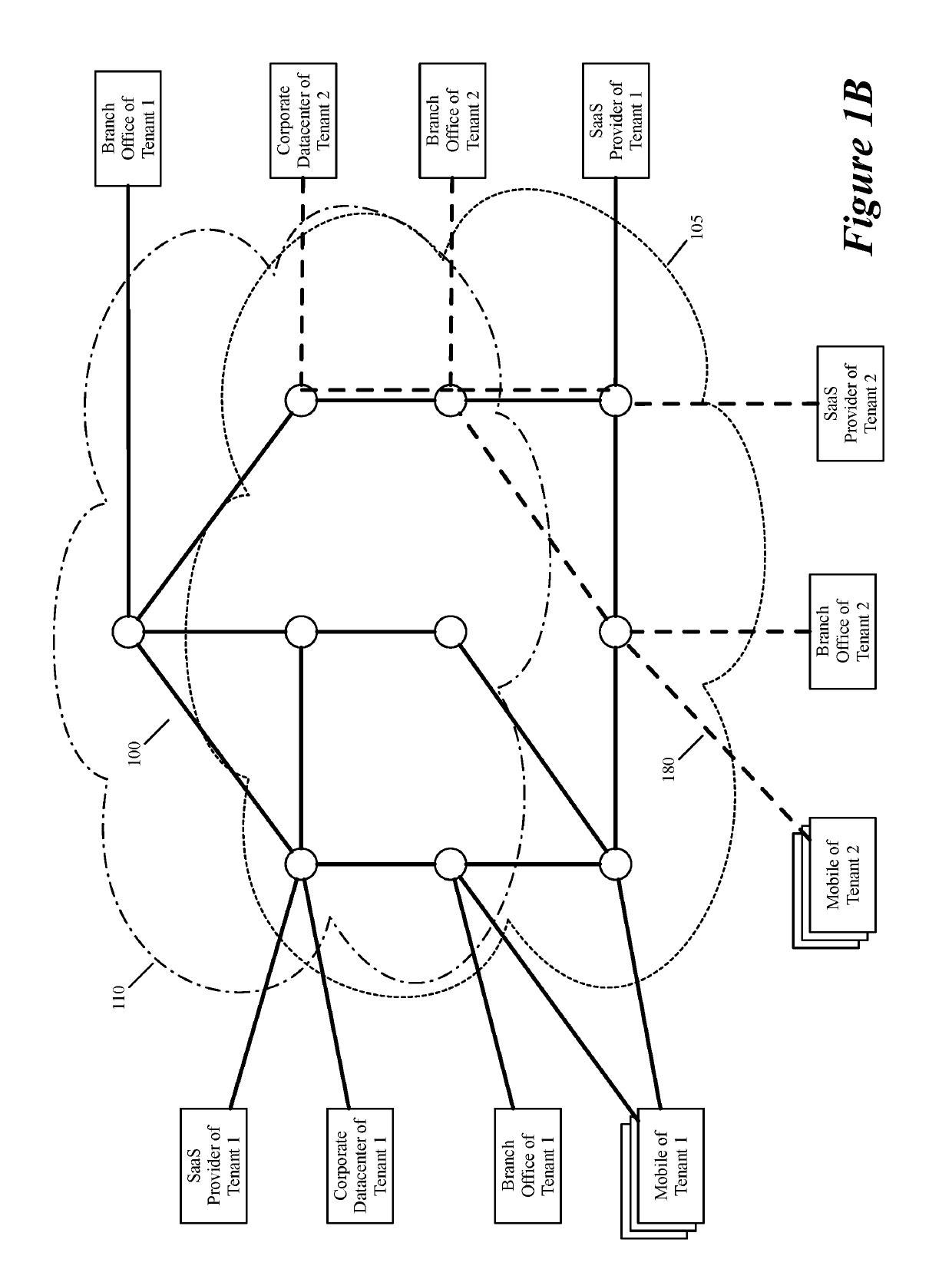
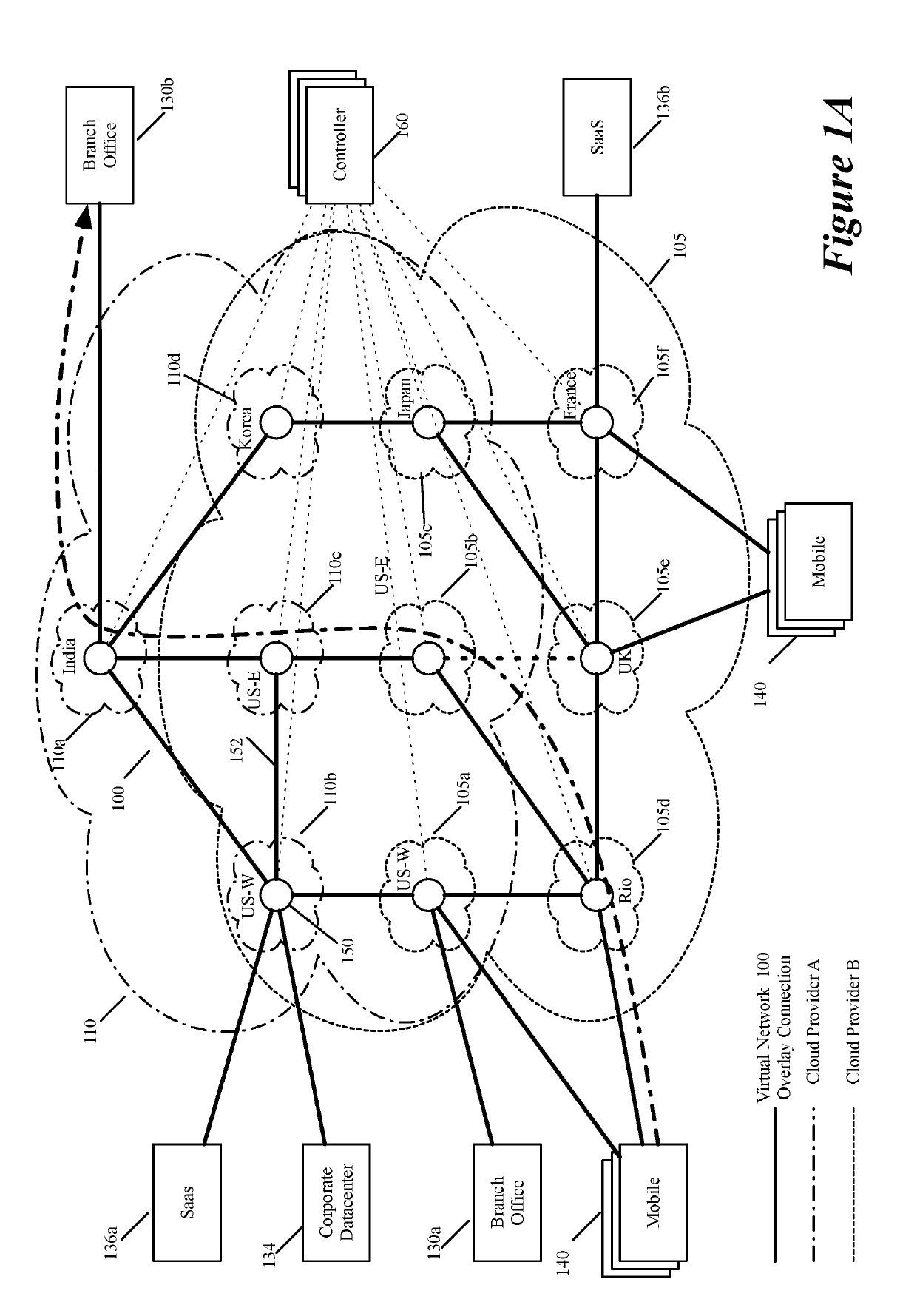
Layer four optimization for a virtual network defined over public cloud
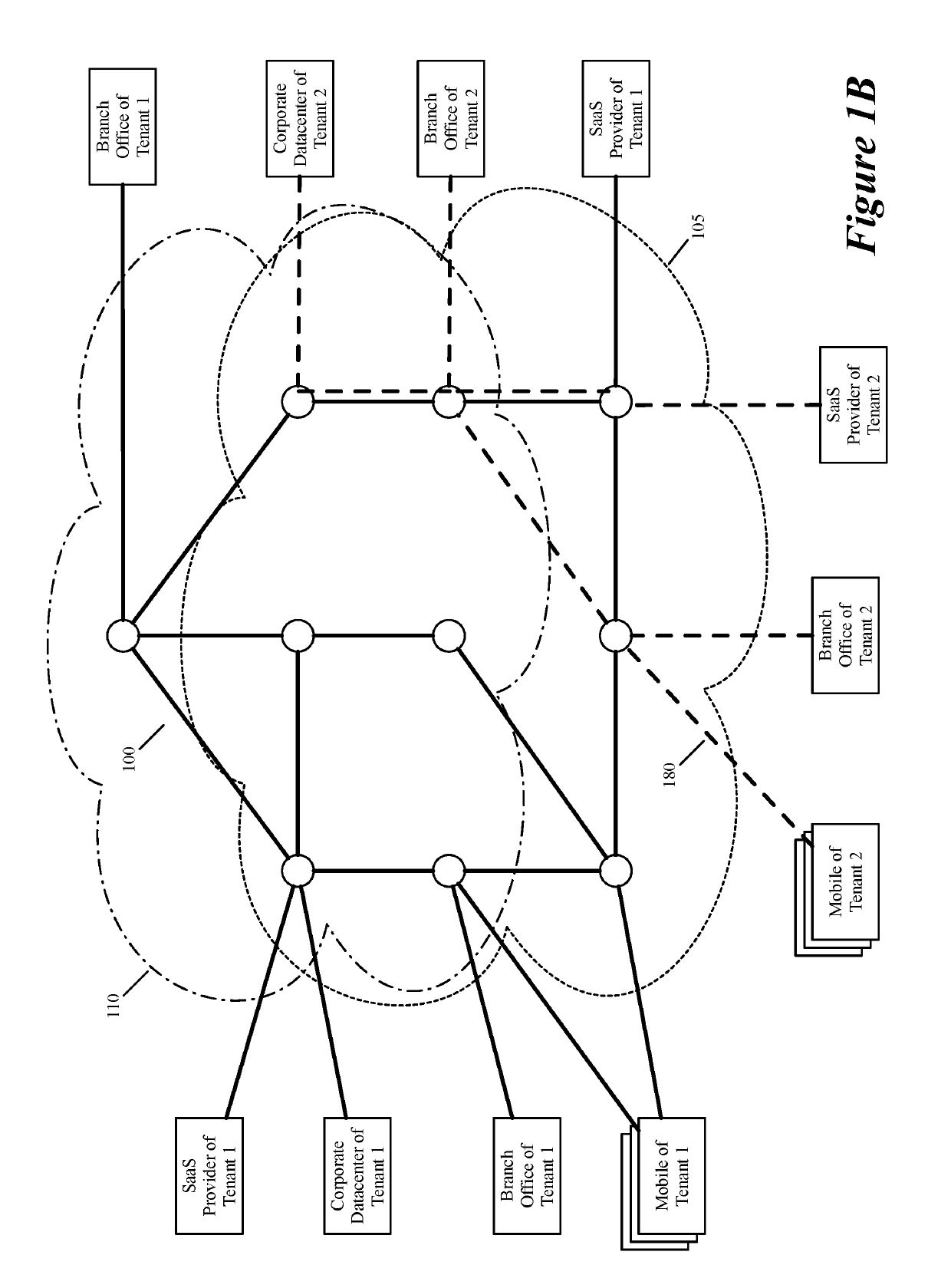
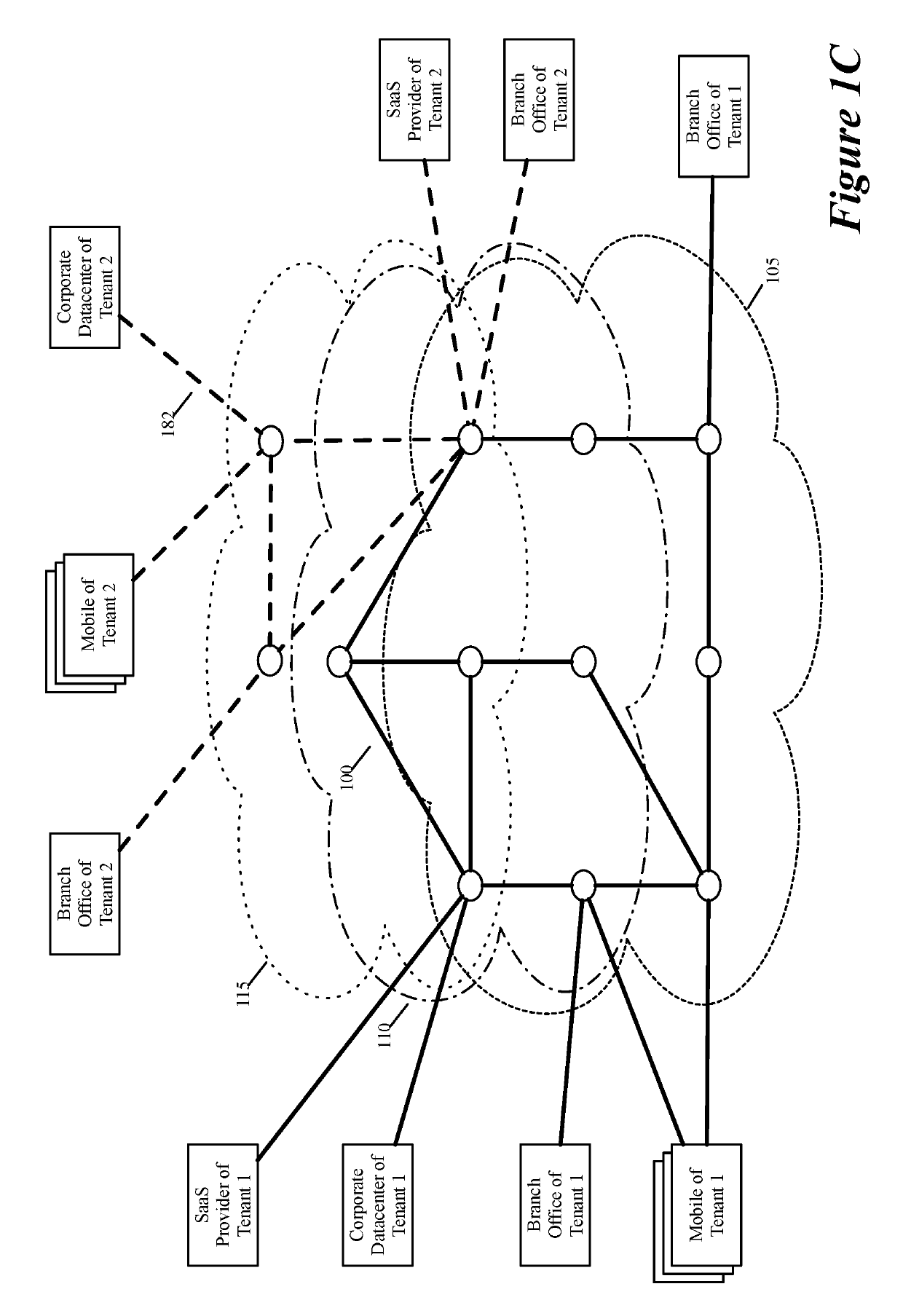
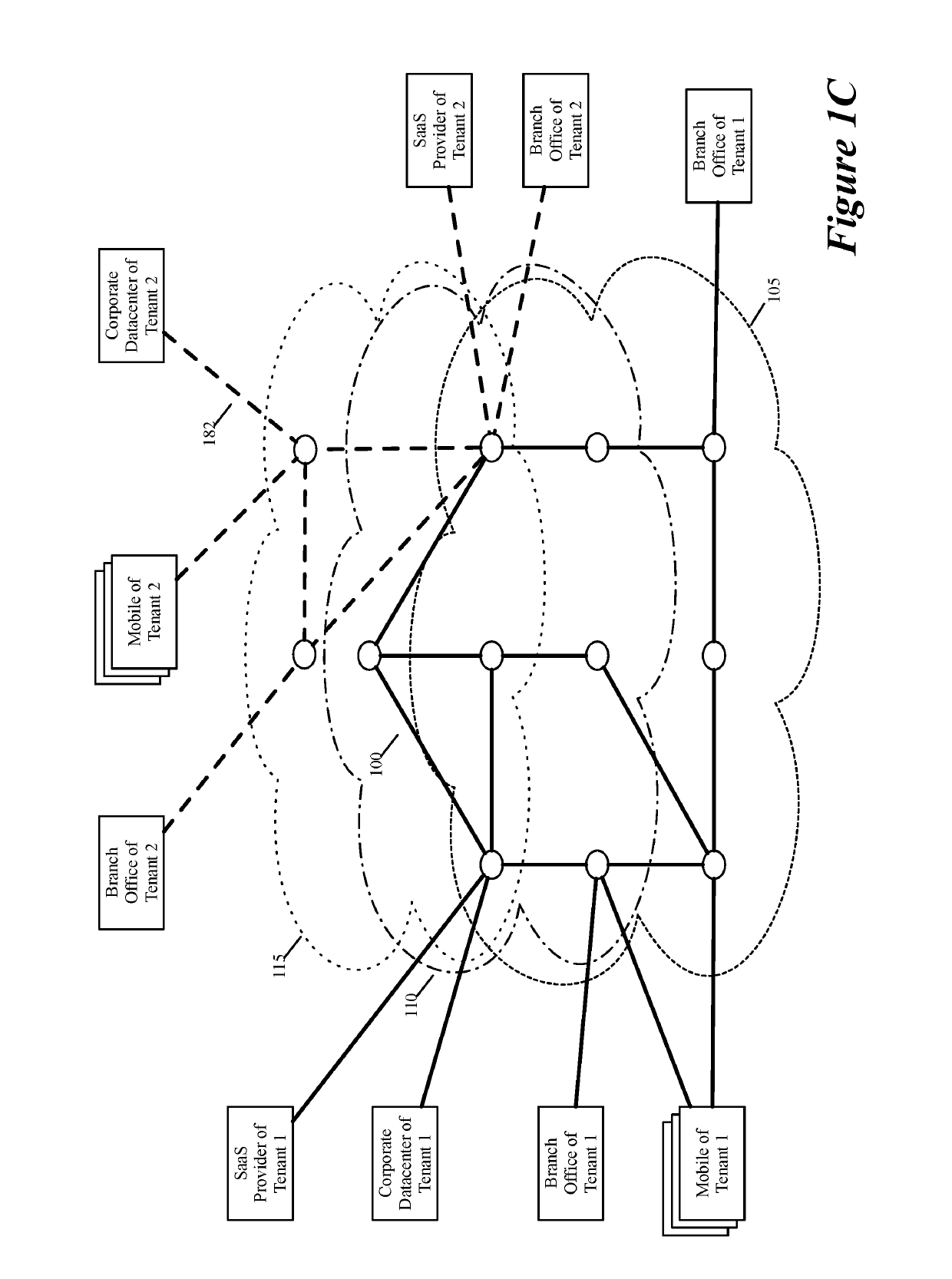
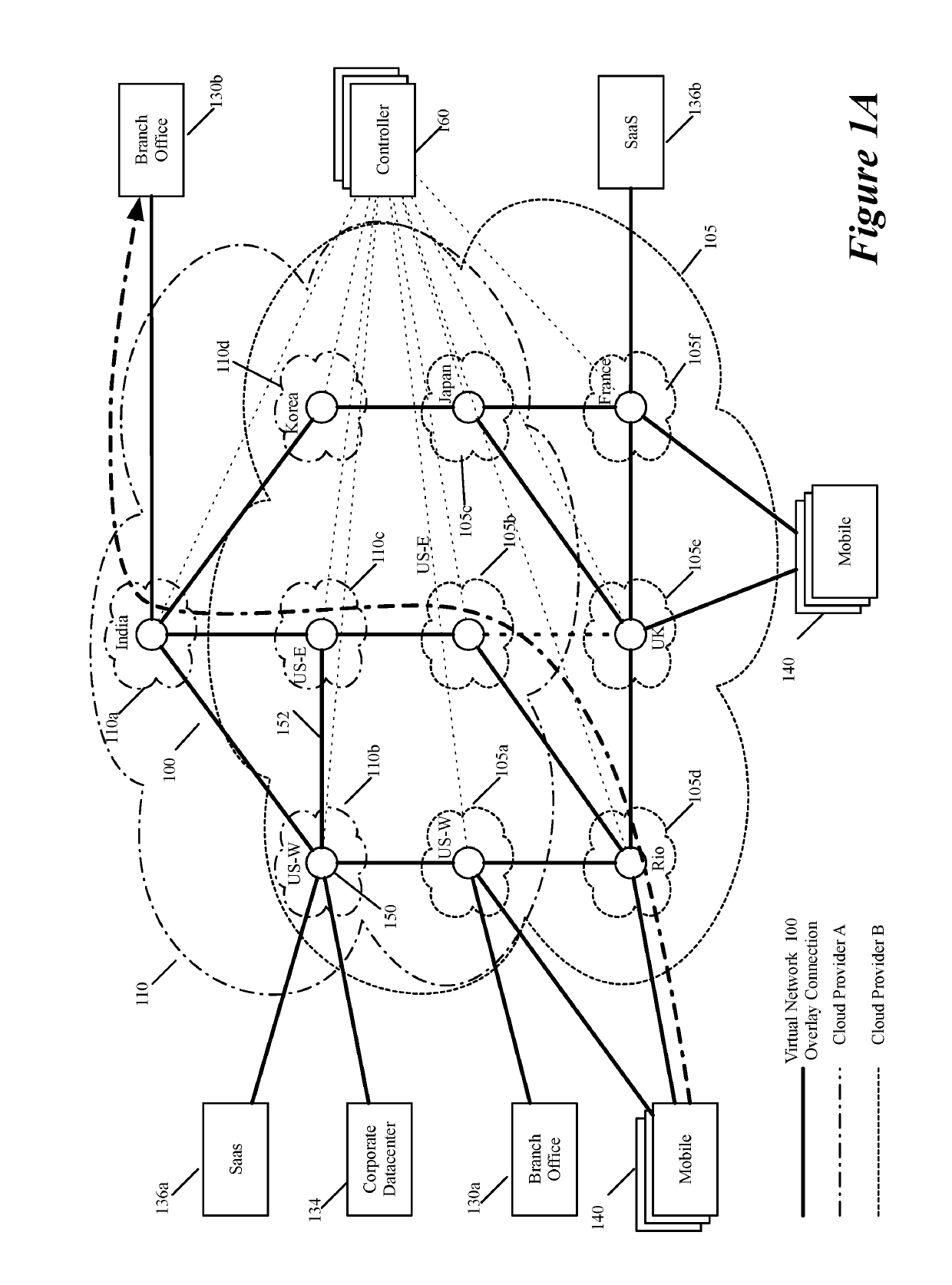
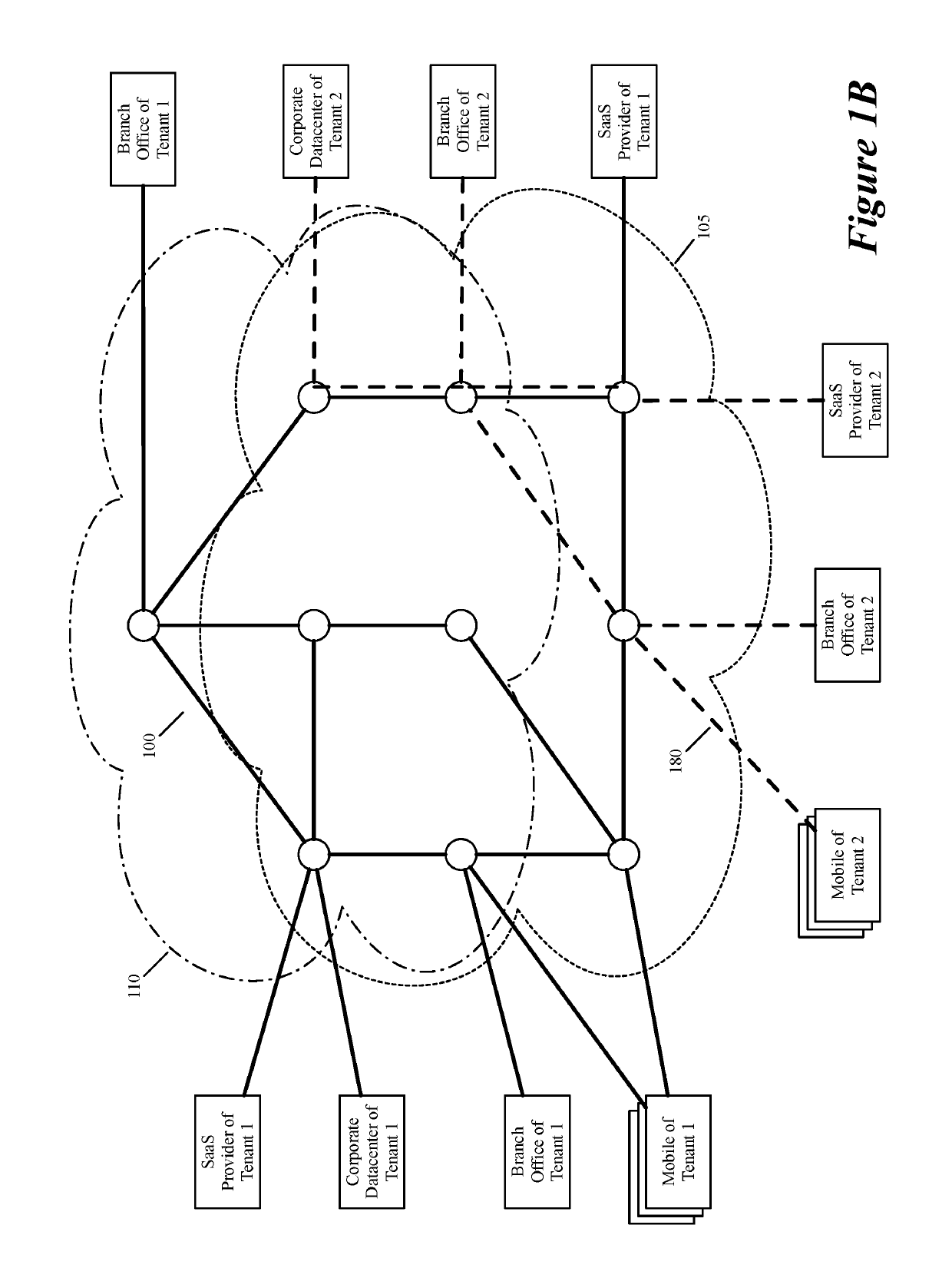
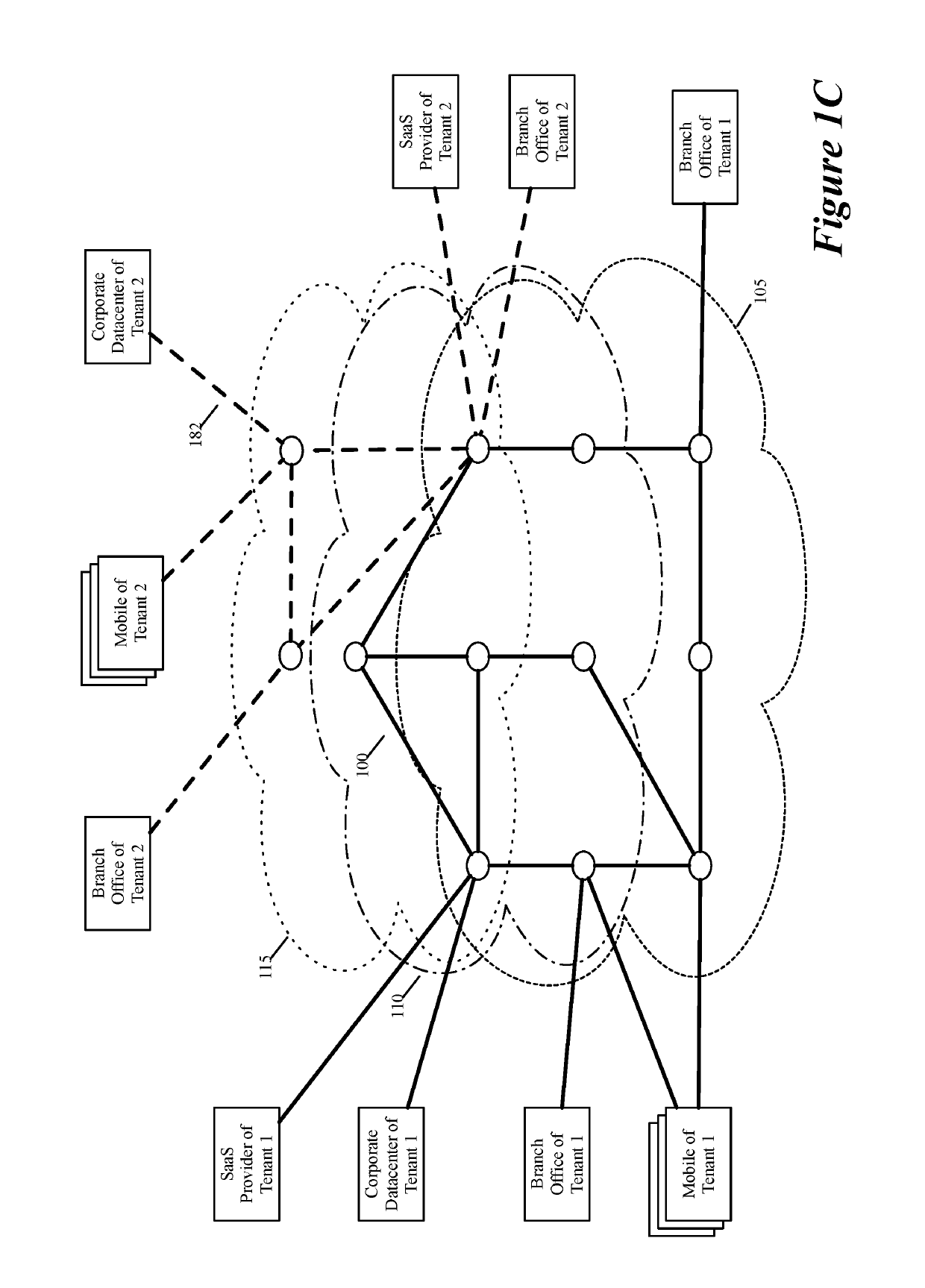
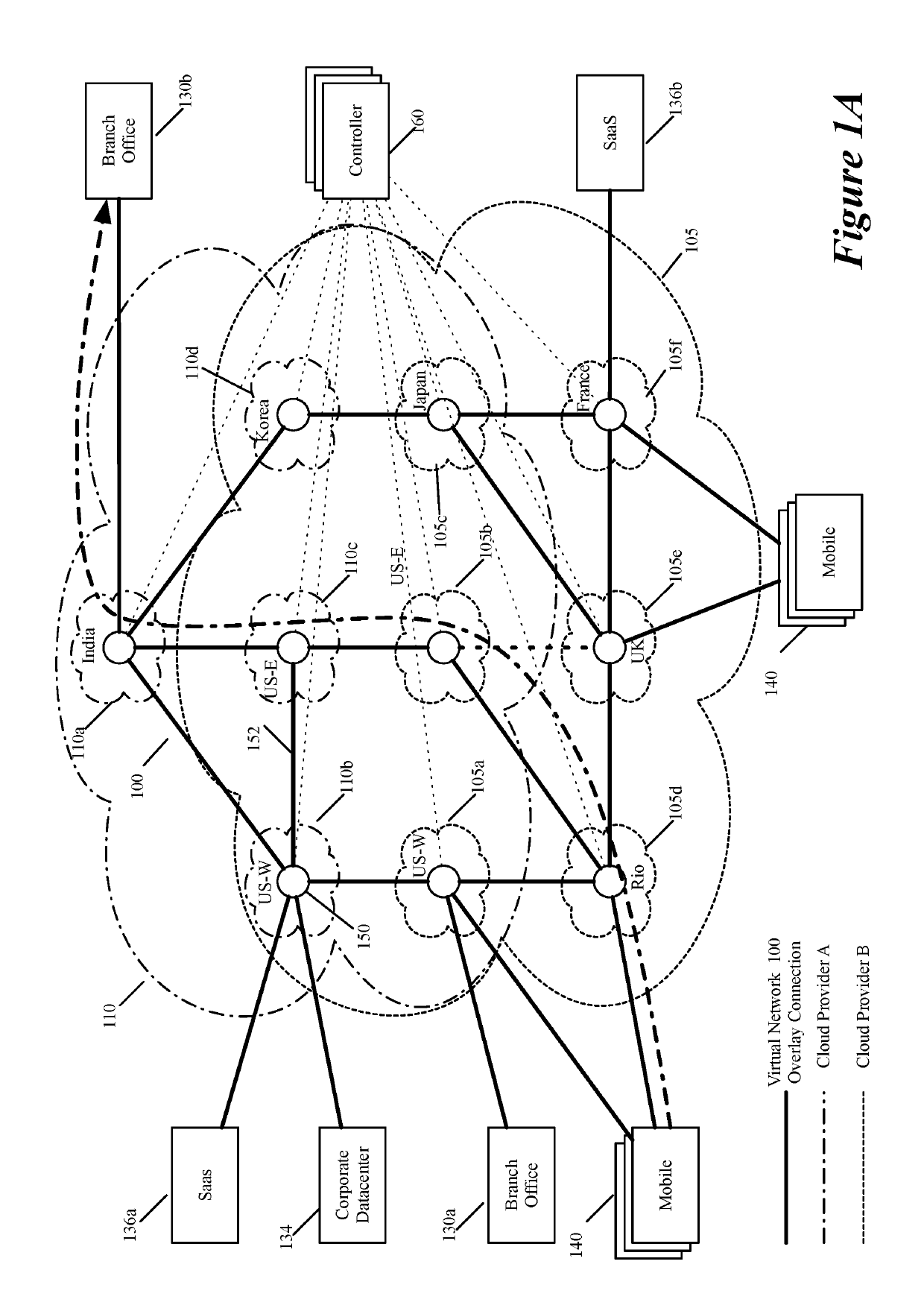
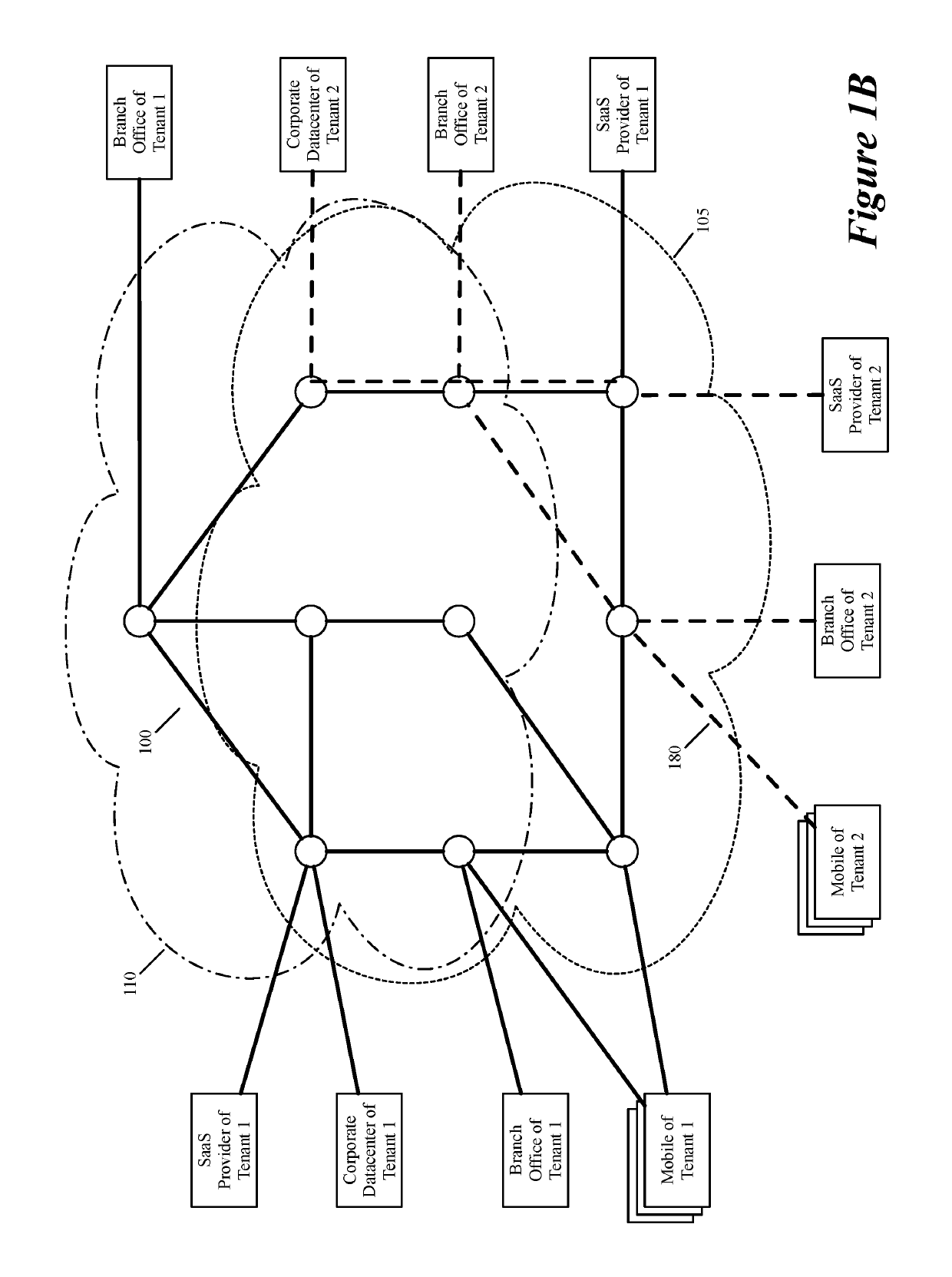
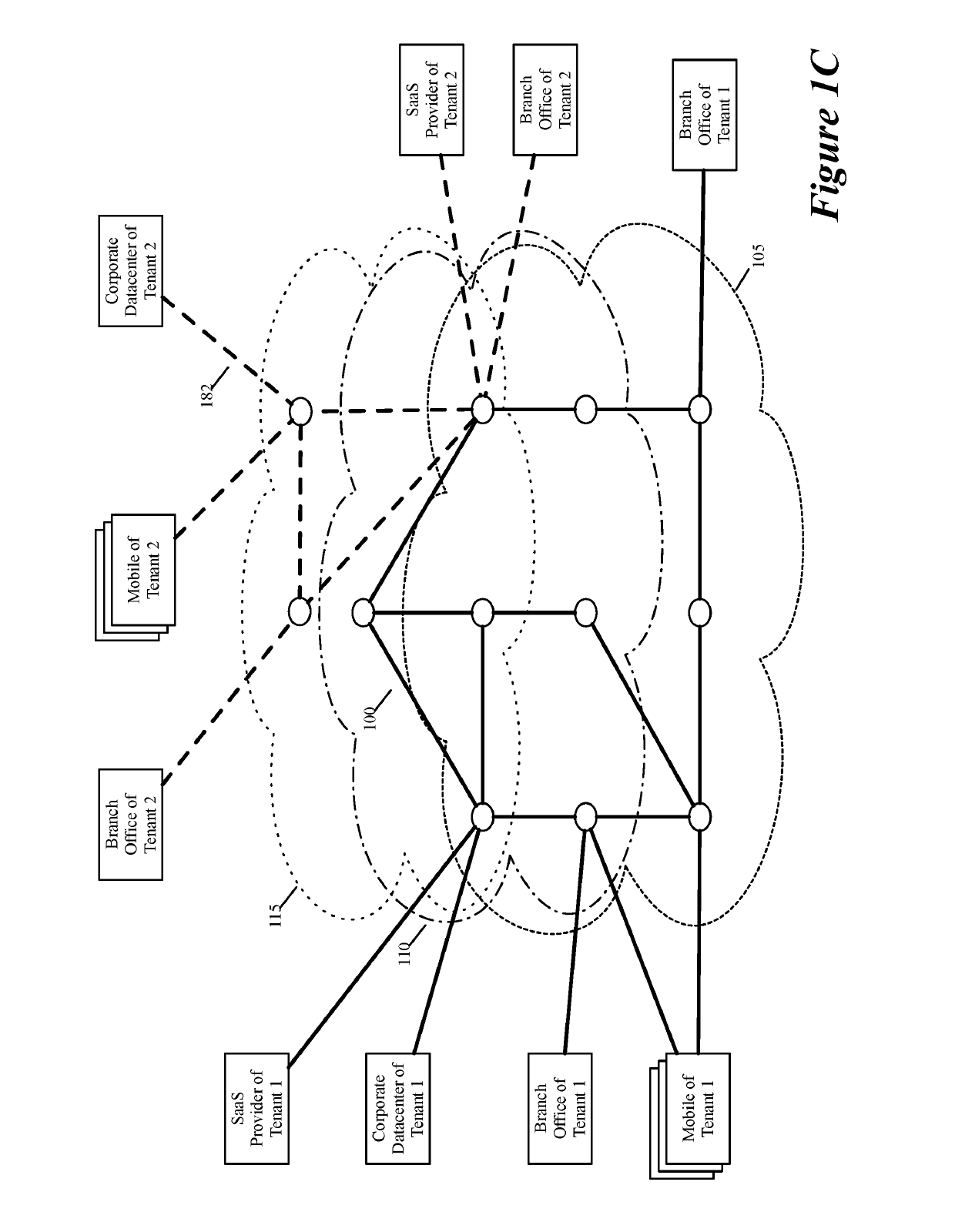
ActiveUS20190158605A1Better download timeImprove performanceData switching networksWeb applicationPrivate network
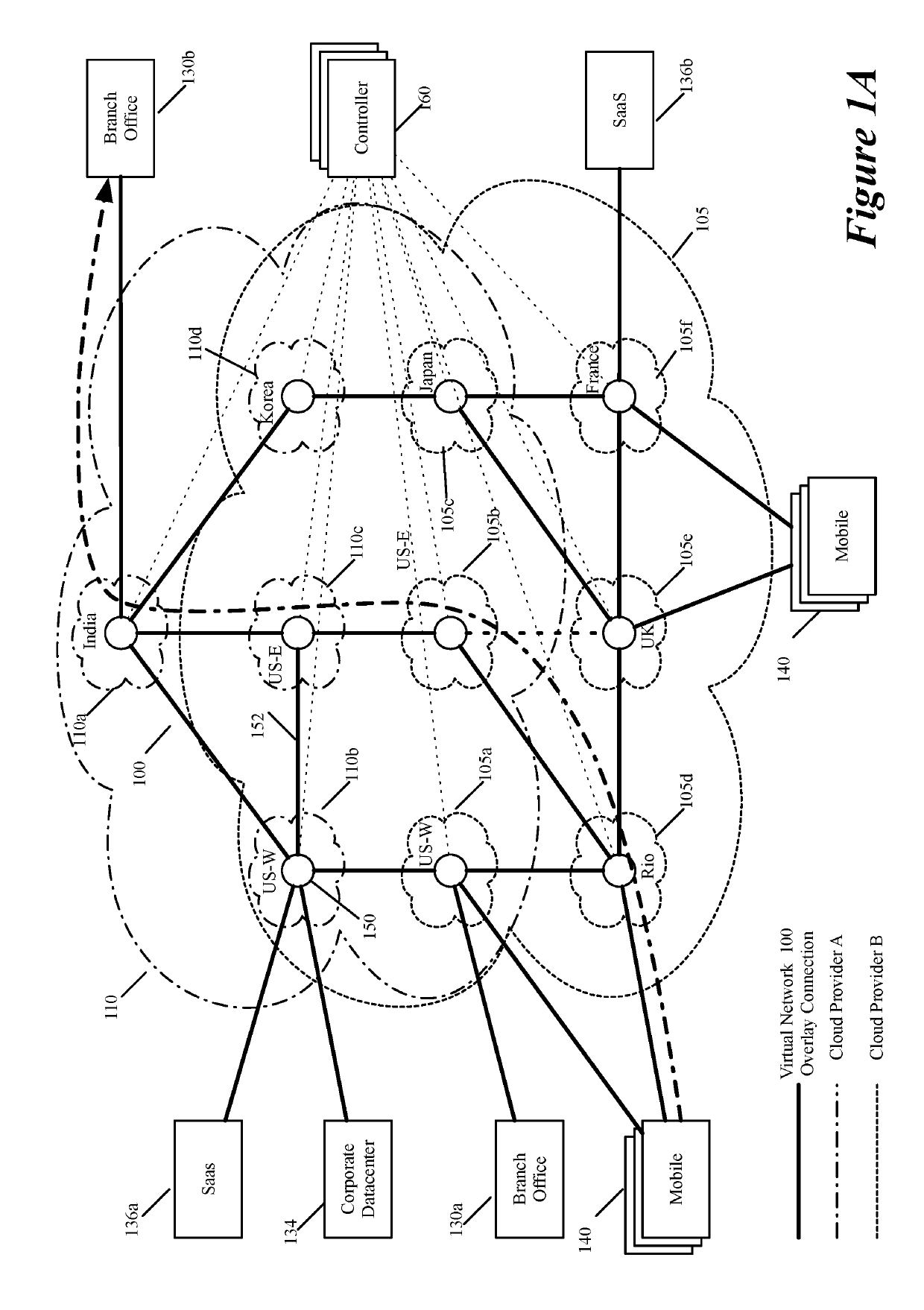
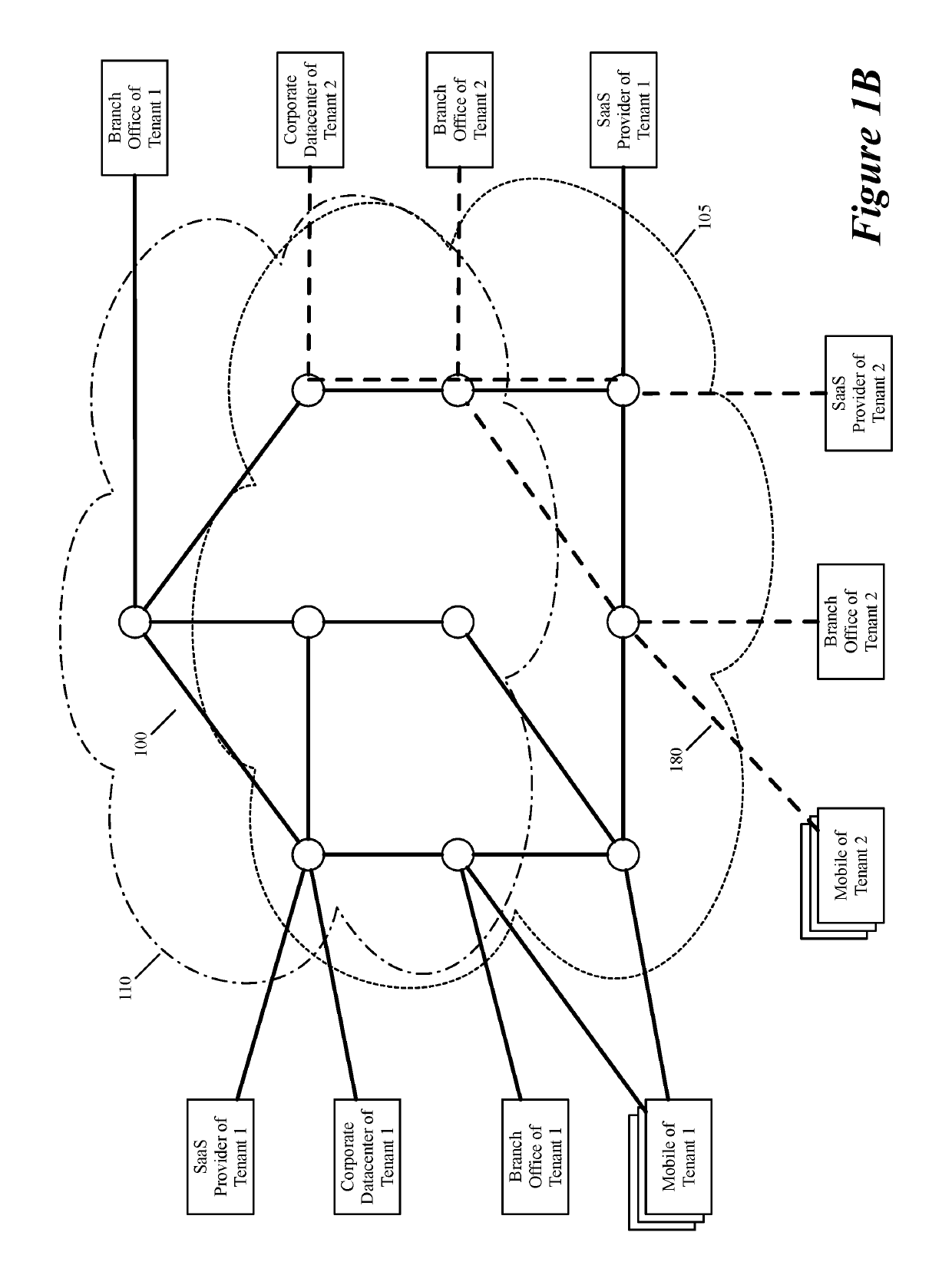
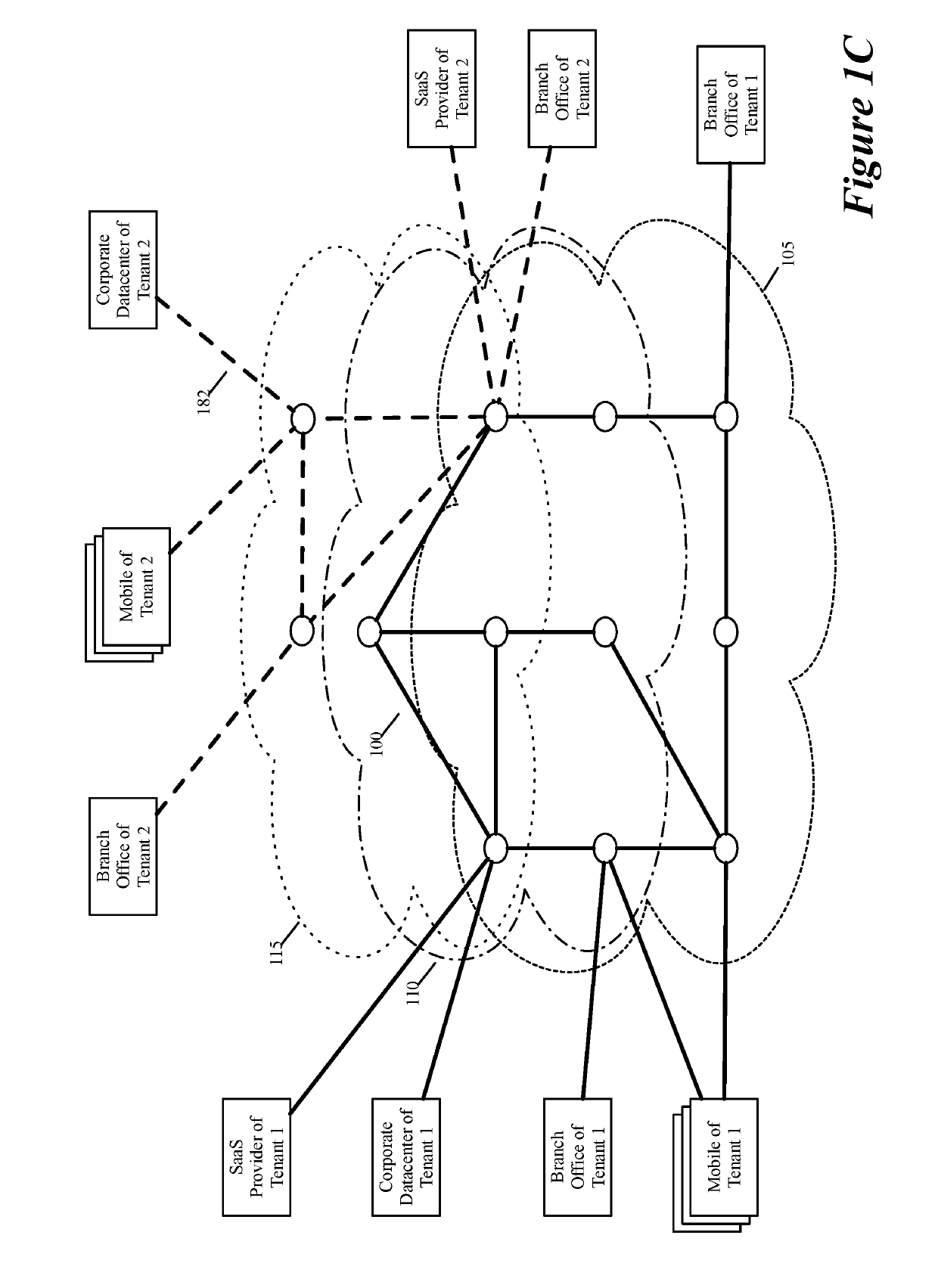
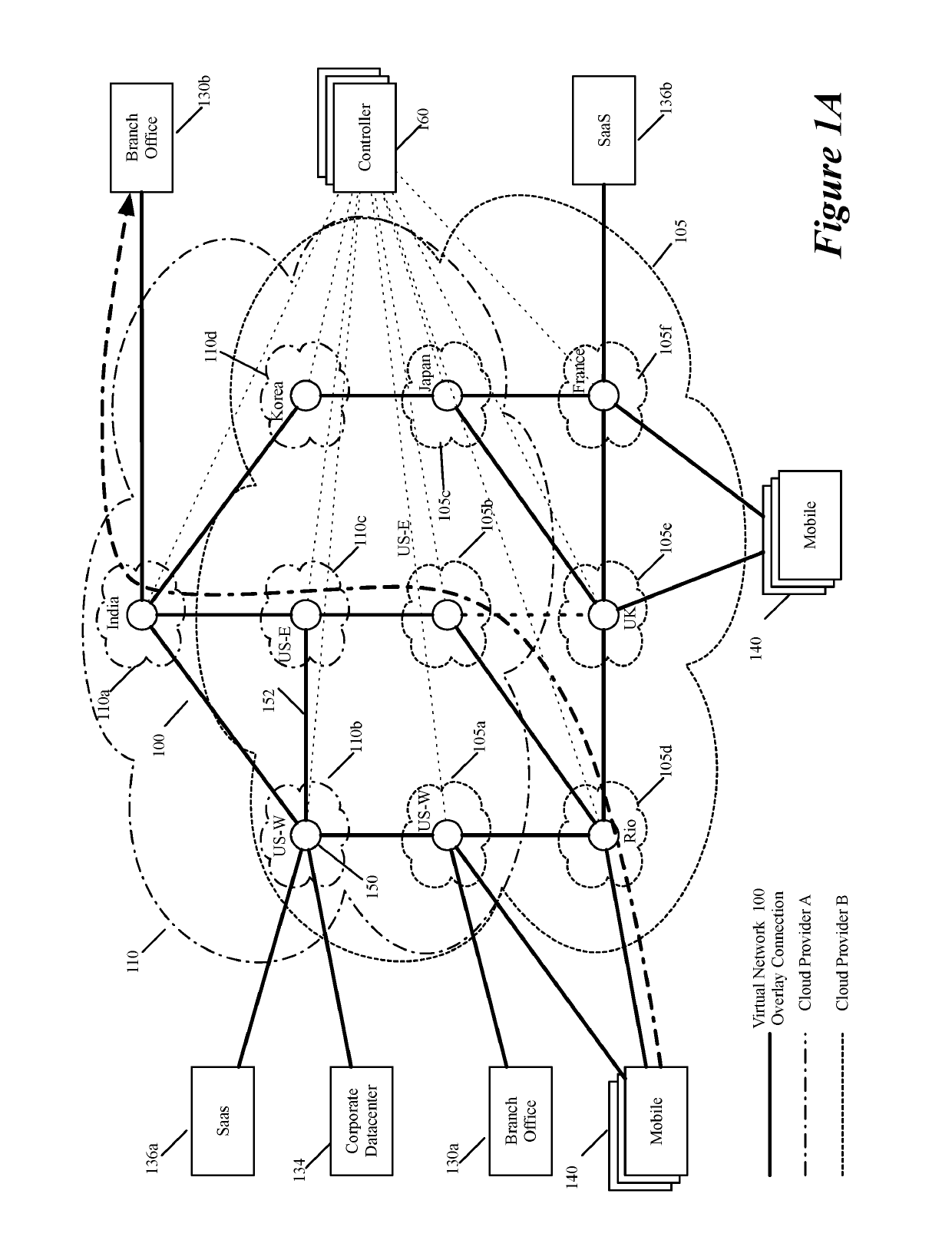
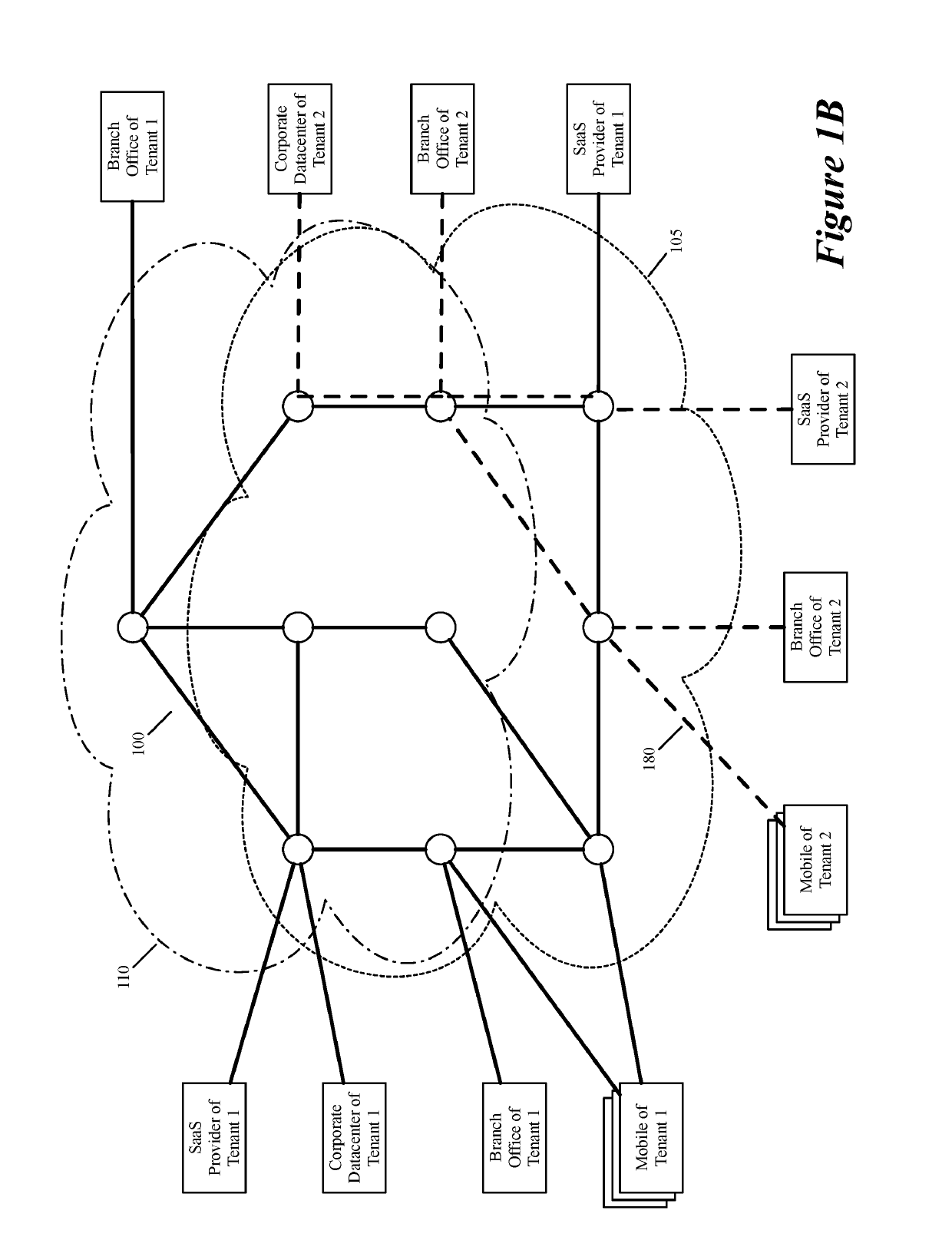
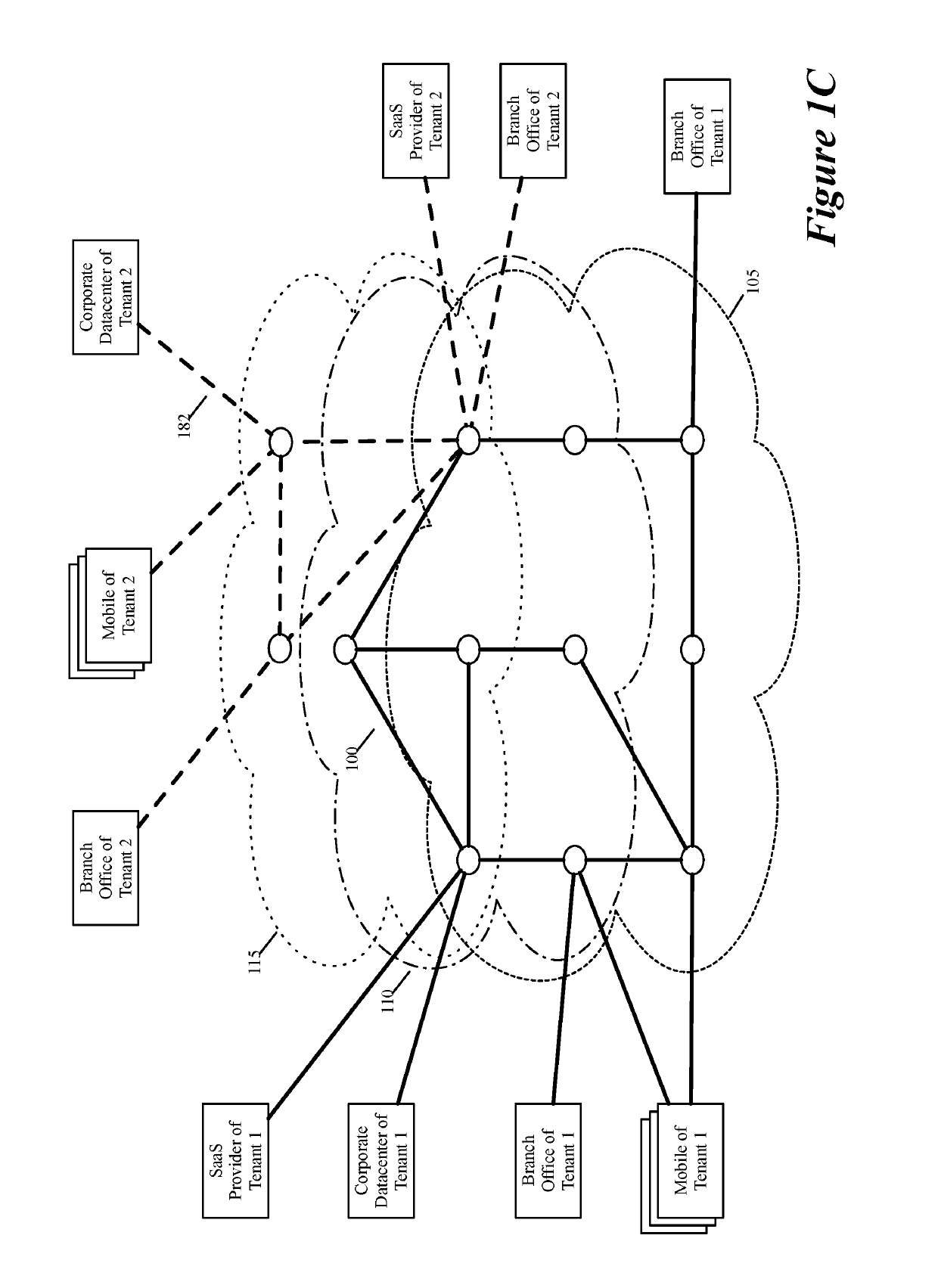
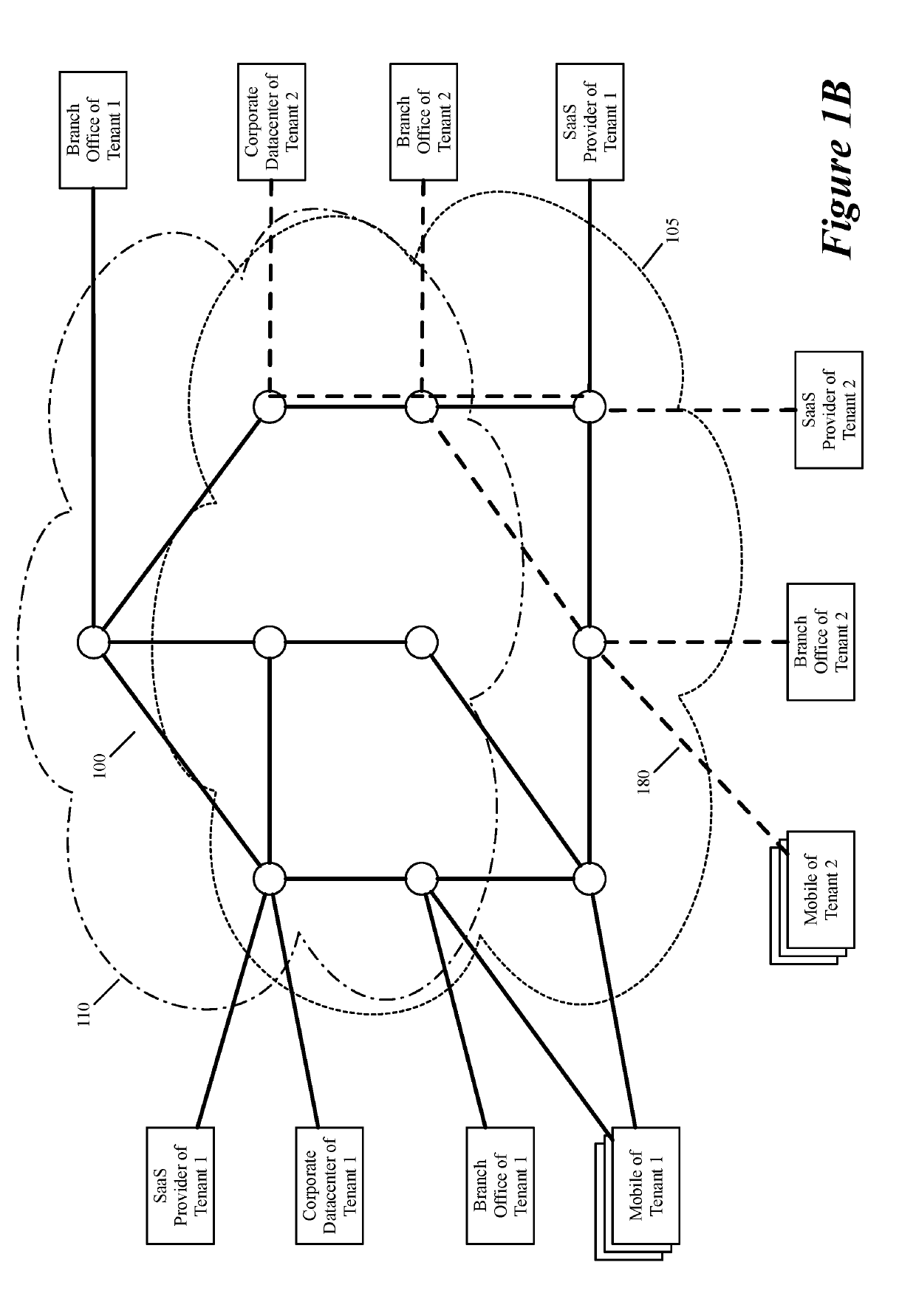
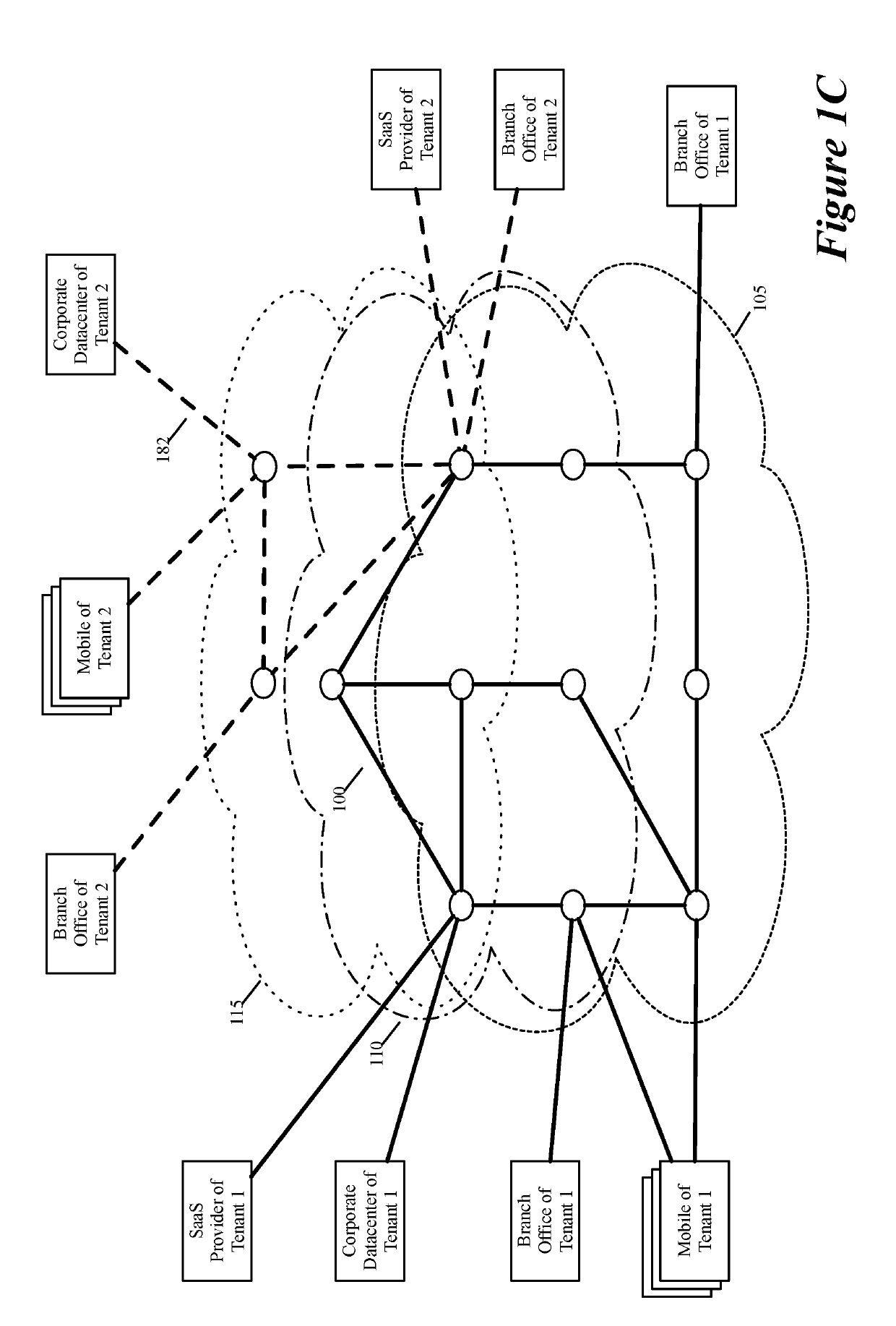
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
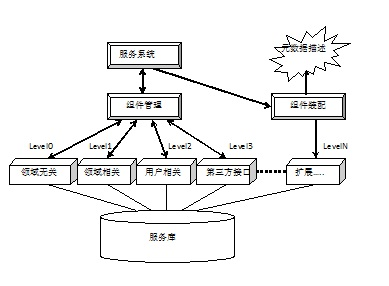
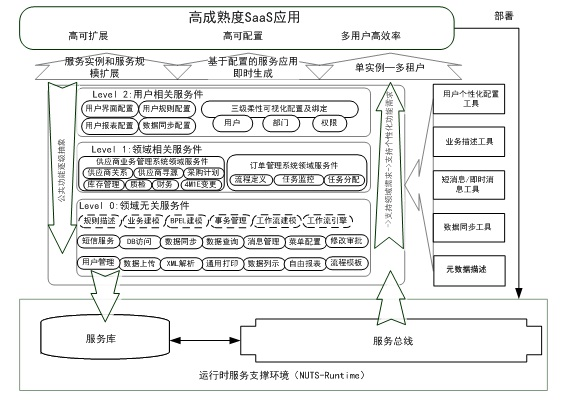
Service software construction method and system adapting to multiple business abstraction levels
InactiveCN101794226AReduced domain knowledge requirementsImprove reusabilityData switching networksSpecific program execution arrangementsAbstraction layerService-orientation
The invention discloses a service software construction method and a system adapting to multiple business abstraction levels. The invention is based on business-oriented frameworks, and constructs the service component resources by a stage-by-stage abstraction method, and a software system is constructed on the basis. According to the application requirements of different business abstraction levels, the invention also provides construction way atom component unrelated to the field, a composite component reconstruction way related to the field, and a configuration way related to the user business. Thus, the construction and the management of the software can aim at different business requirements and abstraction levels, and a proper method can be utilized to adapt to quick reconstruction of large-scale multiple tenants and software, namely quick reconstruction of service mode applications, thereby ensuring the efficiency, economical efficiency and reliability of software production.
Owner:SHANDONG UNIV
Dynamically specifying multiple public cloud edge nodes to connect to an external multi-computer node
ActiveUS20190104413A1Traffic minimizationIncrease redundancyNetworks interconnectionSecurity arrangementData centerPrivate network
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
Layer four optimization for a virtual network defined over public cloud
ActiveUS20190268421A1Better download timeImprove performanceData switching networksPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
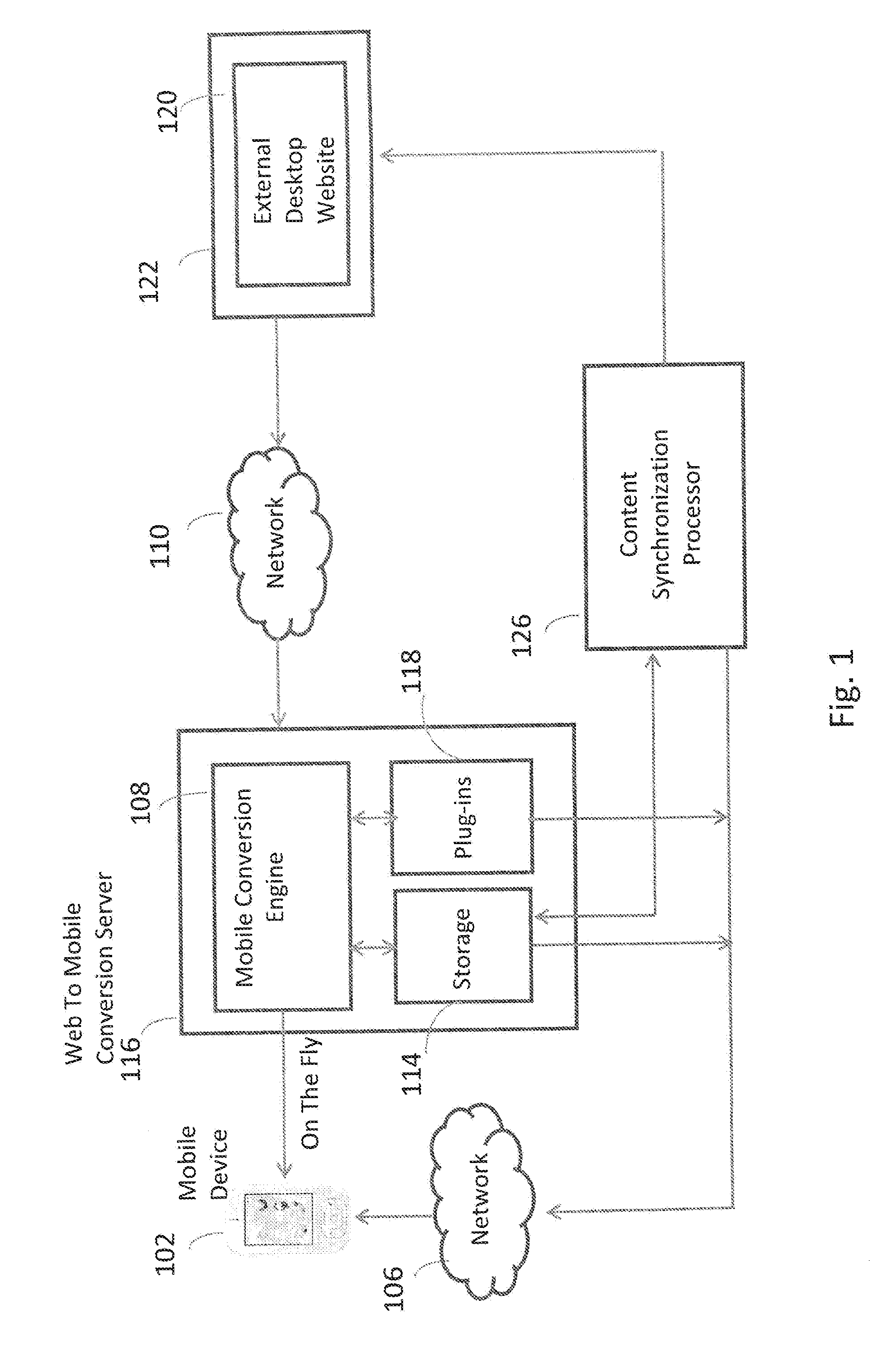
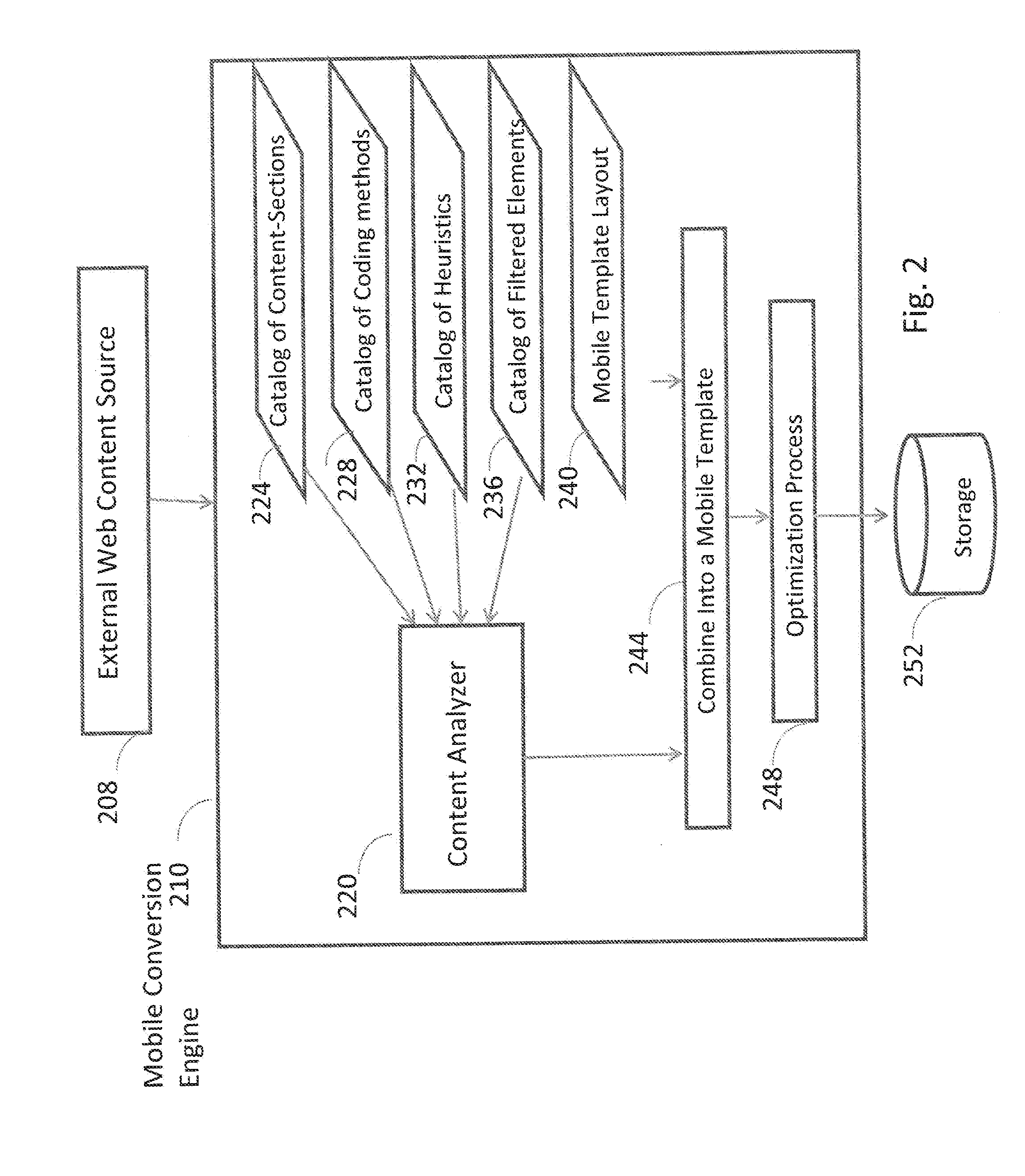
Automated Processor For Web Content To Mobile-Optimized Content Transformation
InactiveUS20140089786A1Natural language data processingWebsite content managementWeb siteSoftware as a service
A system, method, and apparatus for dynamically and automatically transforming desktop web content into a mobile-optimized version for consumption by a variety of mobile devices. The system is delivered as SaaS (Software as a Service) platform on a hosting server. Input may be provide by a user who interacts with the system by simply entering a website address, or may be provided in an automated way using a software programming interface method. The system creates the mobile-optimized version that can optionally be cached and served to mobile devices.
Owner:INSPIRITY
Three tiers of saas providers for deploying compute and network infrastructure in the public cloud
ActiveUS20190104035A1Increase redundancyImprove usabilityMetering/charging/biilling arrangementsTelephonic communicationPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
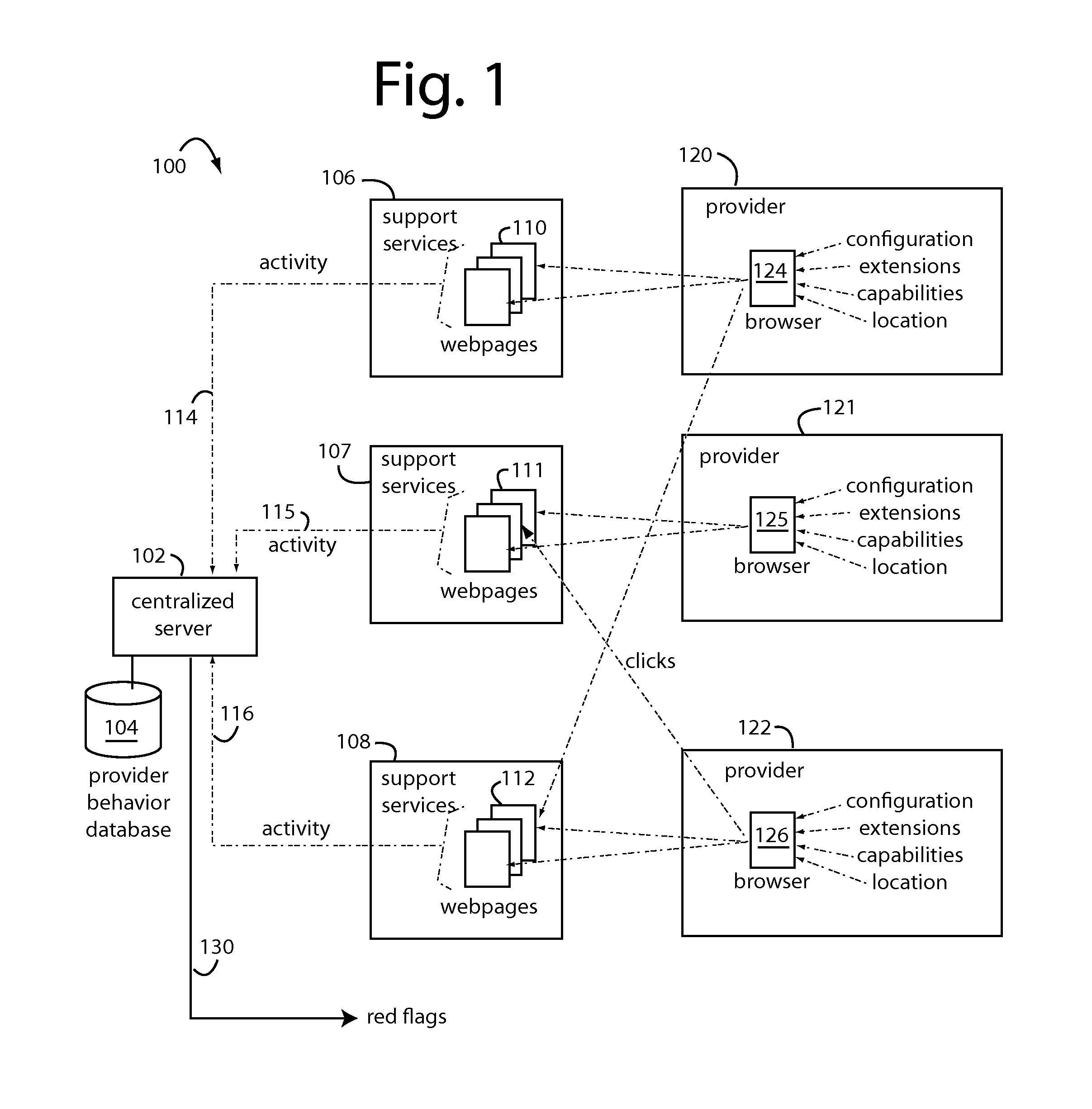
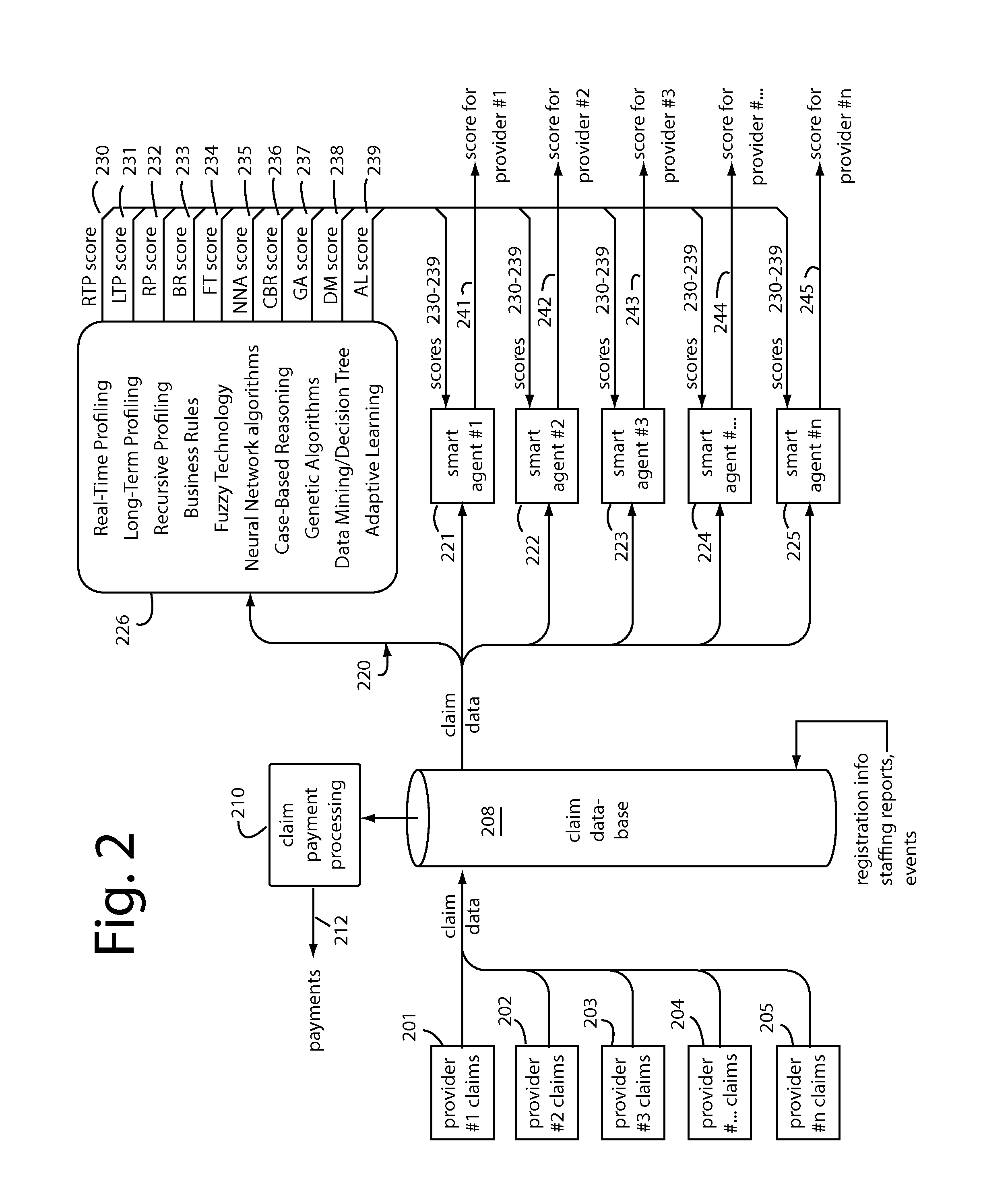
Healthcare fraud protection and management
InactiveUS20150046181A1Fraud control can be tightTight controlOffice automationInference methodsMedically unexplainedData sorting
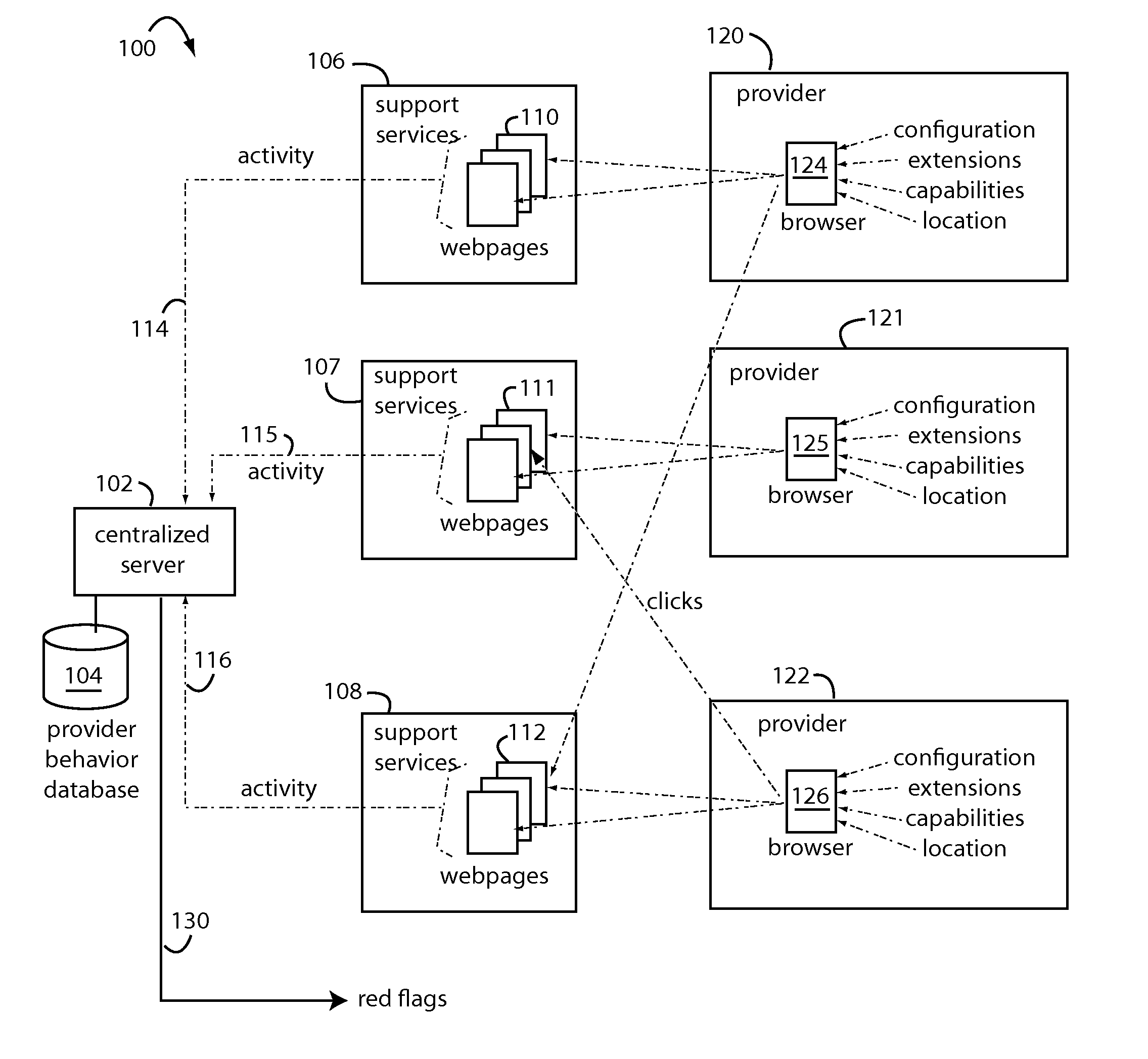
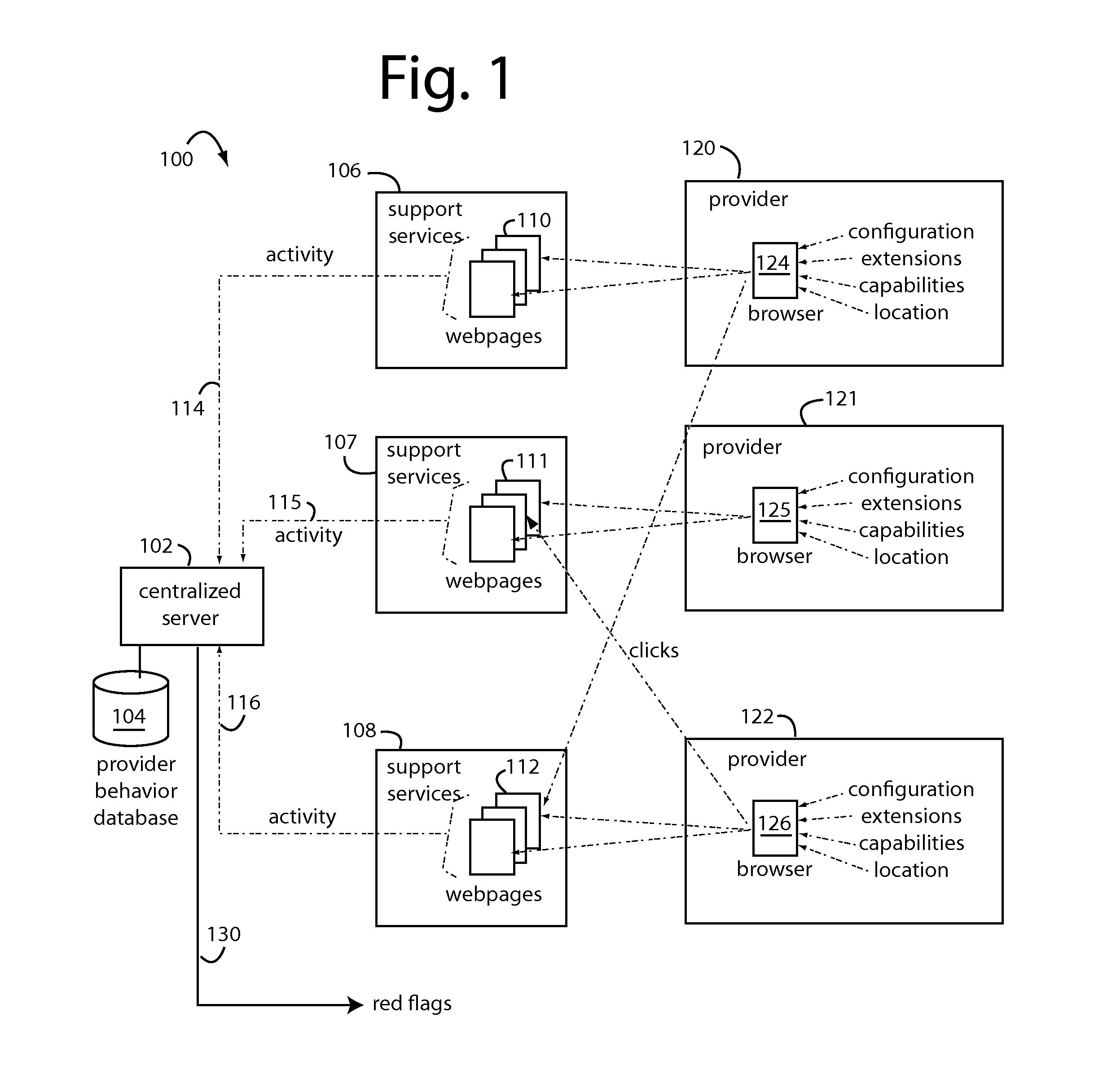
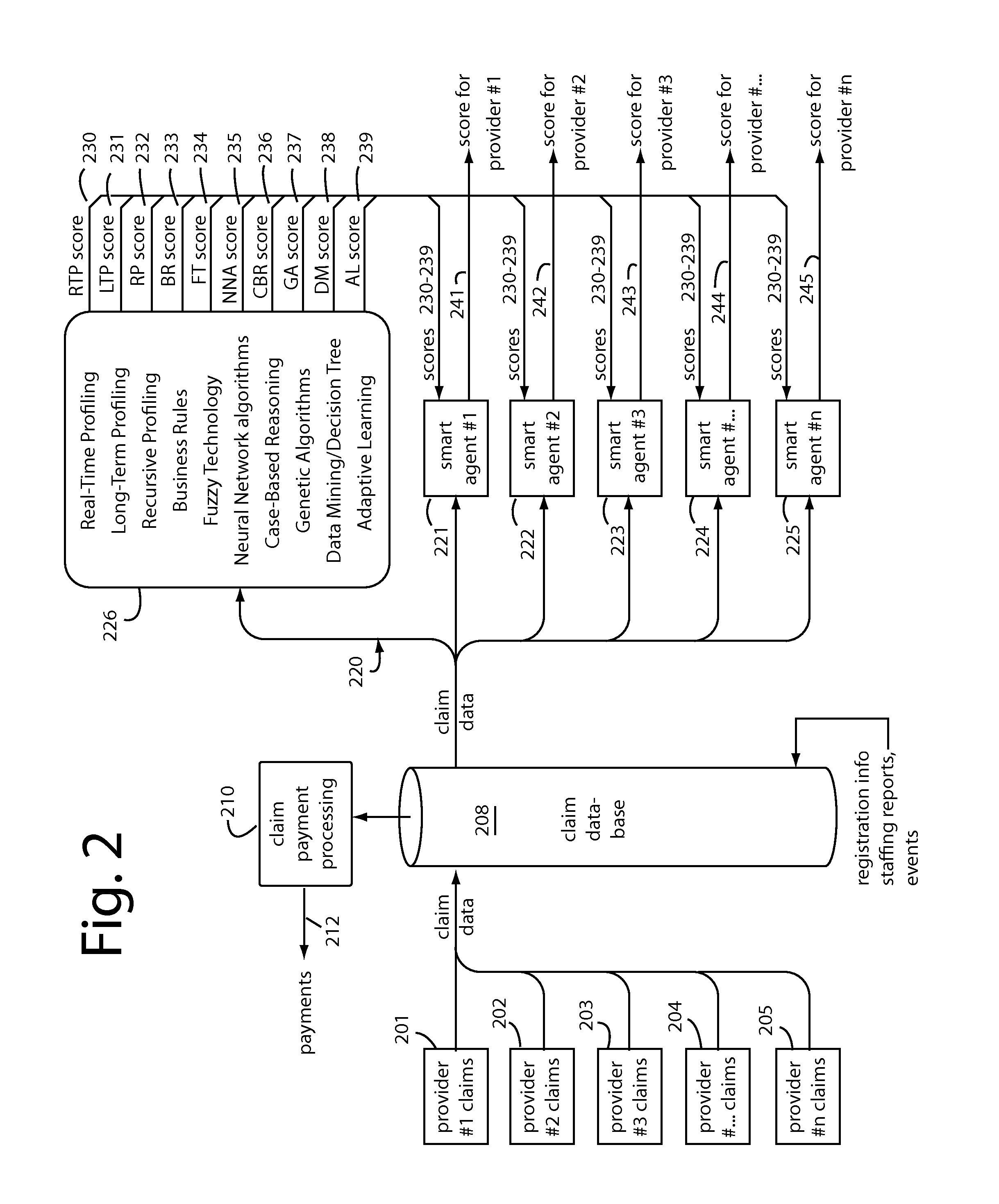
Real-time fraud prevention software-as-a-service (SaaS) products include computer instruction sets to enable a network server to receive medical histories, enrollments, diagnosis, prescription, treatment, follow up, billings, and other data as they occur. The SaaS includes software instruction sets to combine, correlate, categorize, track, normalize, and compare the data sorted by patient, healthcare provider, institution, seasonal, and regional norms. Fraud reveals itself in the ways data points deviate from norms in nonsensical or inexplicable conduct. The individual behaviors of each healthcare provider are independently monitored, characterized, and followed by self-spawning smart agents that can adapt and change their rules as the healthcare providers evolve. Such smart agents will issue flags when their particular surveillance target is acting out of character, outside normal parameters for them. Fraud controls can therefore be much tighter than those that have to accommodate those of a diverse group.
Owner:BRIGHTERION
Distributed wan security gateway
ActiveUS20190104111A1Increase redundancyImprove usabilityMetering/charging/biilling arrangementsTelephonic communicationPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
Healthcare fraud preemption
ActiveUS20150081324A1Fraud control can be tightMedical data miningFinanceMedically unexplainedData sorting
Real-time fraud prevention software-as-a-service (SaaS) products include computer instruction sets to enable a network server to receive medical histories, enrollments, diagnosis, prescription, treatment, follow up, billings, and other data as they occur. The SaaS includes software instruction sets to combine, correlate, categorize, track, normalize, and compare the data sorted by patient, healthcare provider, institution, seasonal, and regional norms. Fraud reveals itself in the ways data points deviate from norms in nonsensical or inexplicable conduct. The individual behaviors of each healthcare provider are independently monitored, characterized, and followed by self-spawning smart agents that can adapt and change their rules as the healthcare providers evolve. Such smart agents will issue flags when their particular surveillance target is acting out of character, outside normal parameters for them. Fraud controls can therefore be much tighter than those that have to accommodate those of a diverse group.
Owner:BRIGHTERION
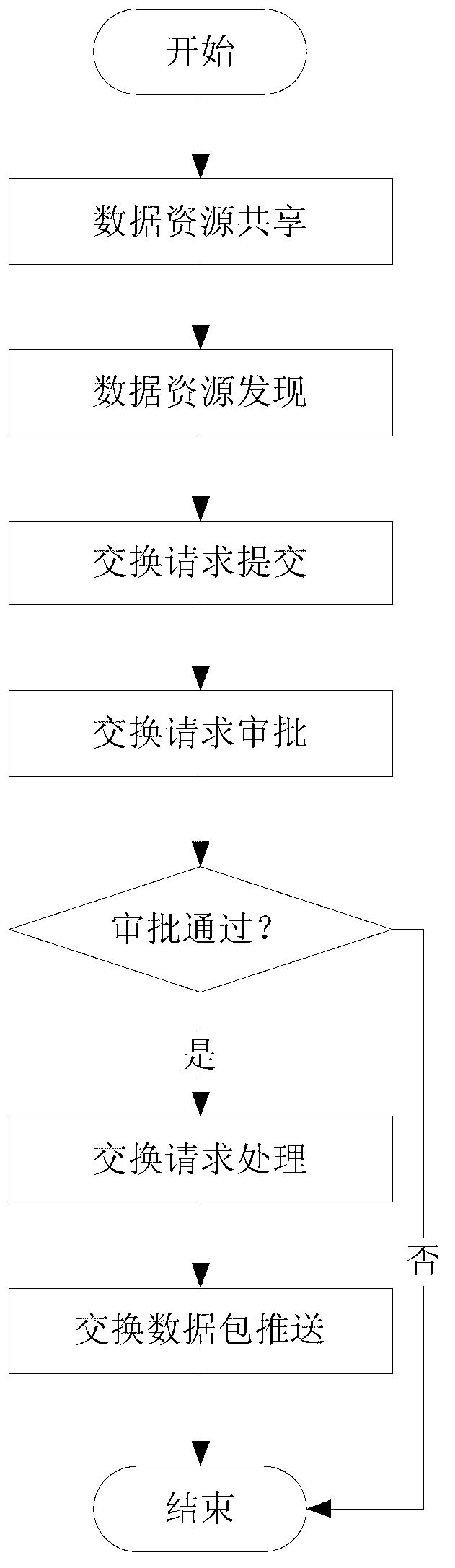
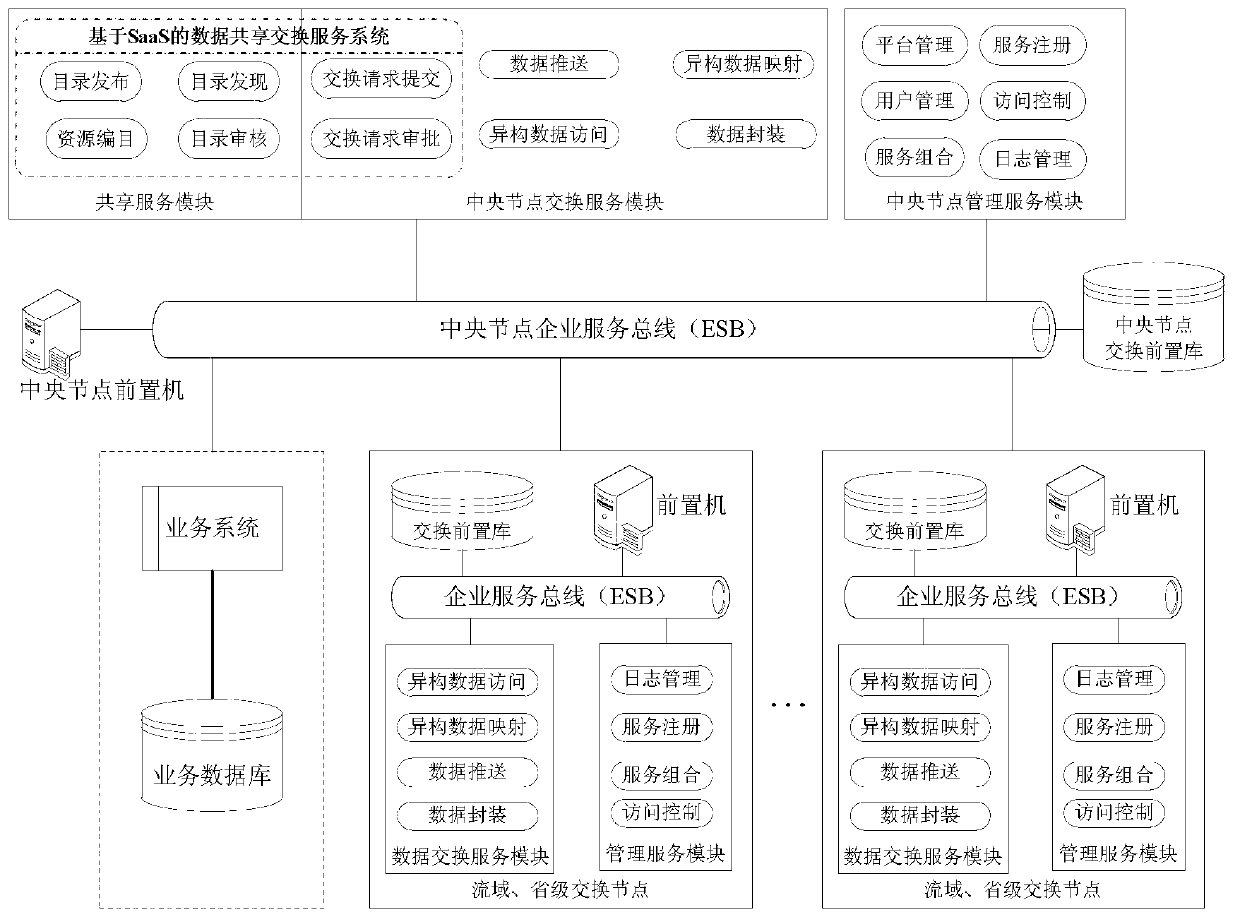
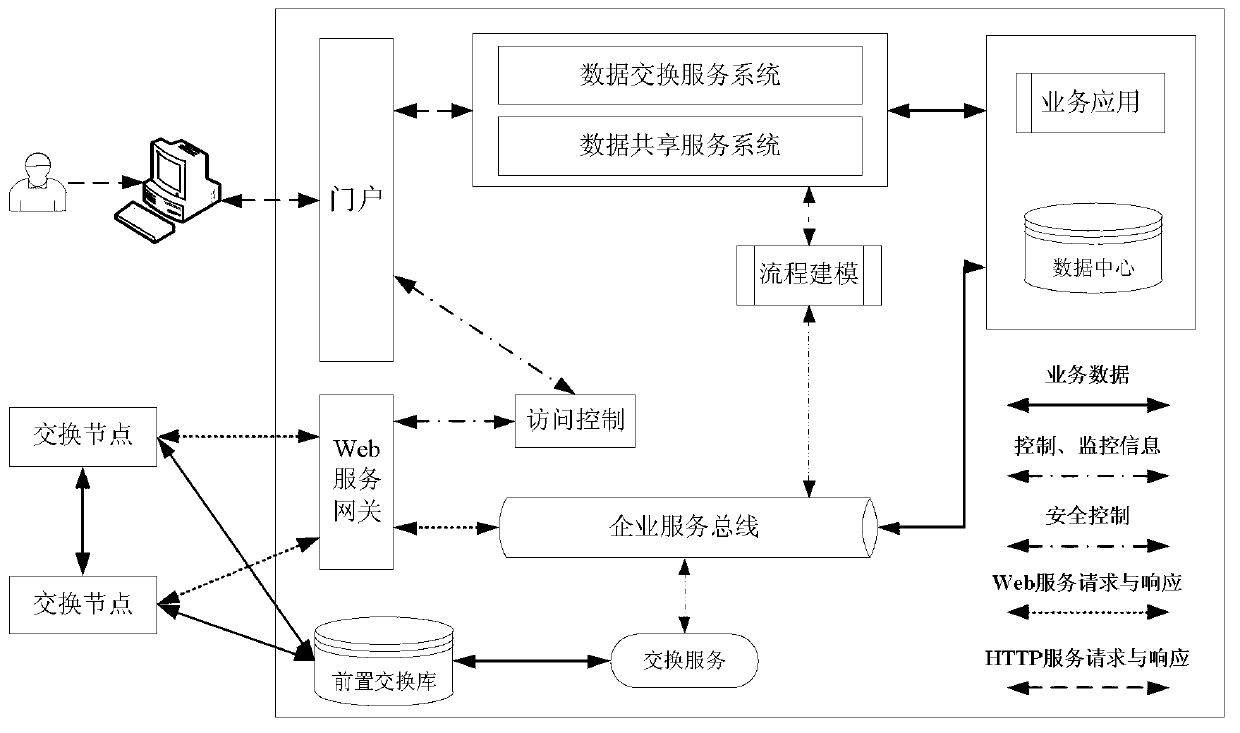
Data sharing exchange model and method based on cloud computation
The invention discloses a data sharing exchange model and a method based on cloud computation. The model comprises a data sharing service module, a data exchange service module, a management service module, an enterprise service bus, a front-end exchange database and a front-end interchanger, wherein the data sharing service module is used for realizing distributed heterogeneous data resource sharing; the data exchange service module is used for realizing a heterogeneous data exchange function; the management service module is used for realizing sharing exchange and system management; the enterprise service bus is used for realizing service registration and management; the front-end exchange database is used for realizing an intermediate storage logic information database which is established for information exchange; and the front-end interchanger is used for realizing the function of unified exchange output and input ports of exchange nodes. The method comprises the steps of constructing a data sharing exchange service system based on SaaS (Software as a Service) to share data which is stored in a business database in a distributed way and providing exchange request submission and approval service; using the enterprise service bus to conduct unified management on service and establishing a model of an exchange service business process by virtue of management service to realize dynamic combination of inter-business service; and using the front-end exchange database to conduct exchange, storage and forwarding, and pushing the data to target nodes through the front-end interchanger.
Owner:HOHAI UNIV
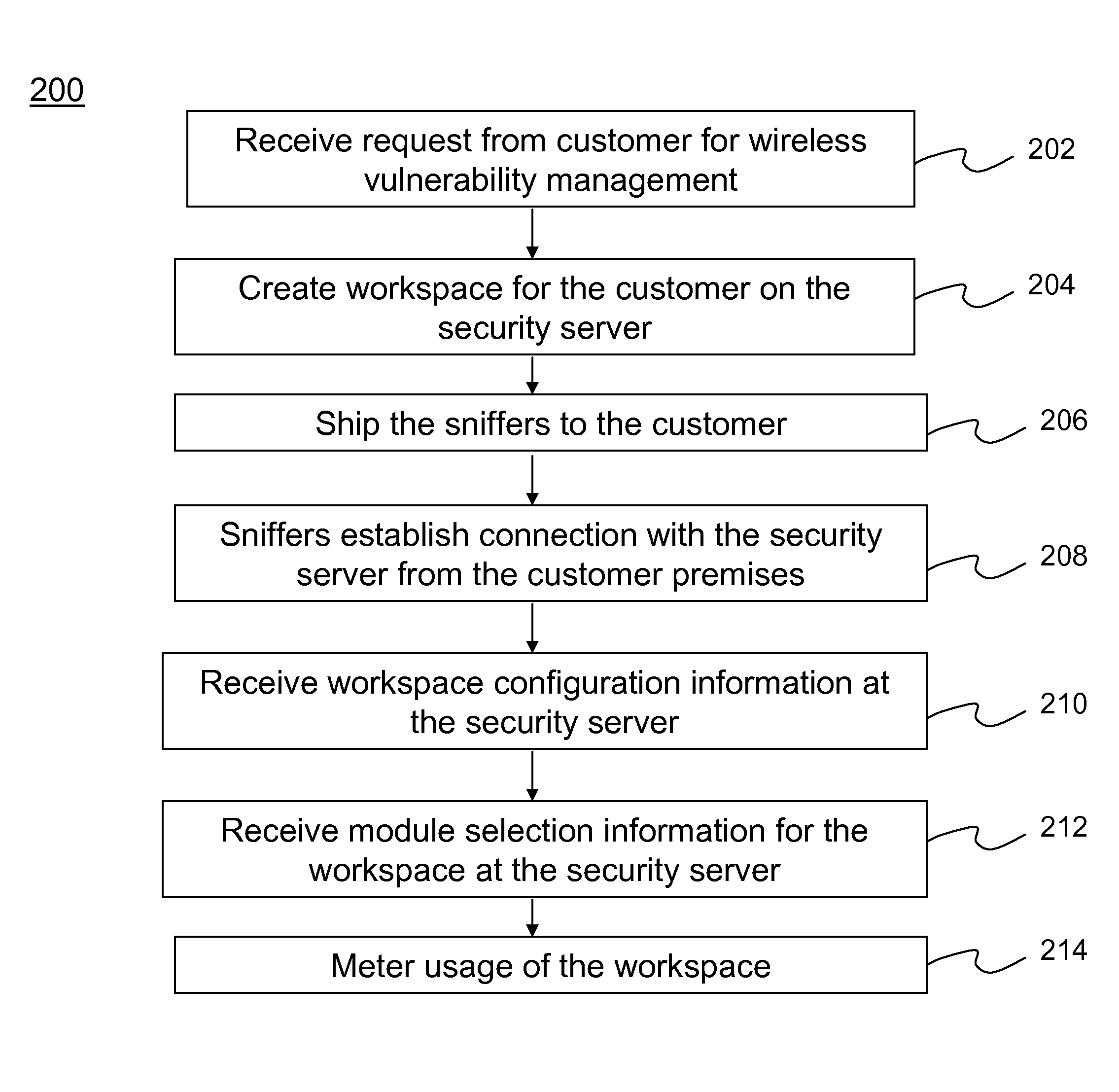
Method and system for providing wireless vulnerability management for local area computer networks
ActiveUS20090119776A1Reduce overheadEasy to customizeMemory loss protectionDigital computer detailsVulnerability managementComputer network
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:ARISTA NETWORKS
Creating virtual networks spanning multiple public clouds
ActiveUS20190103990A1Increase redundancyImprove usabilityMetering/charging/biilling arrangementsTelephonic communicationPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
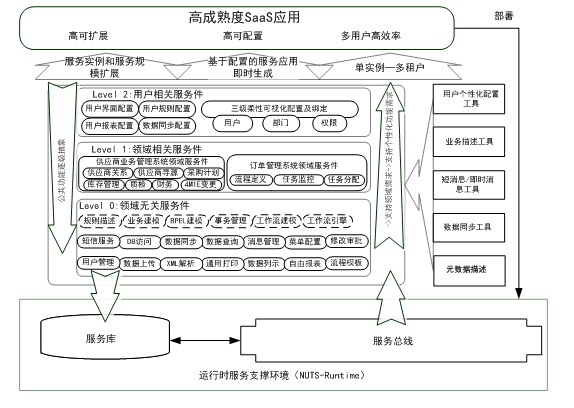
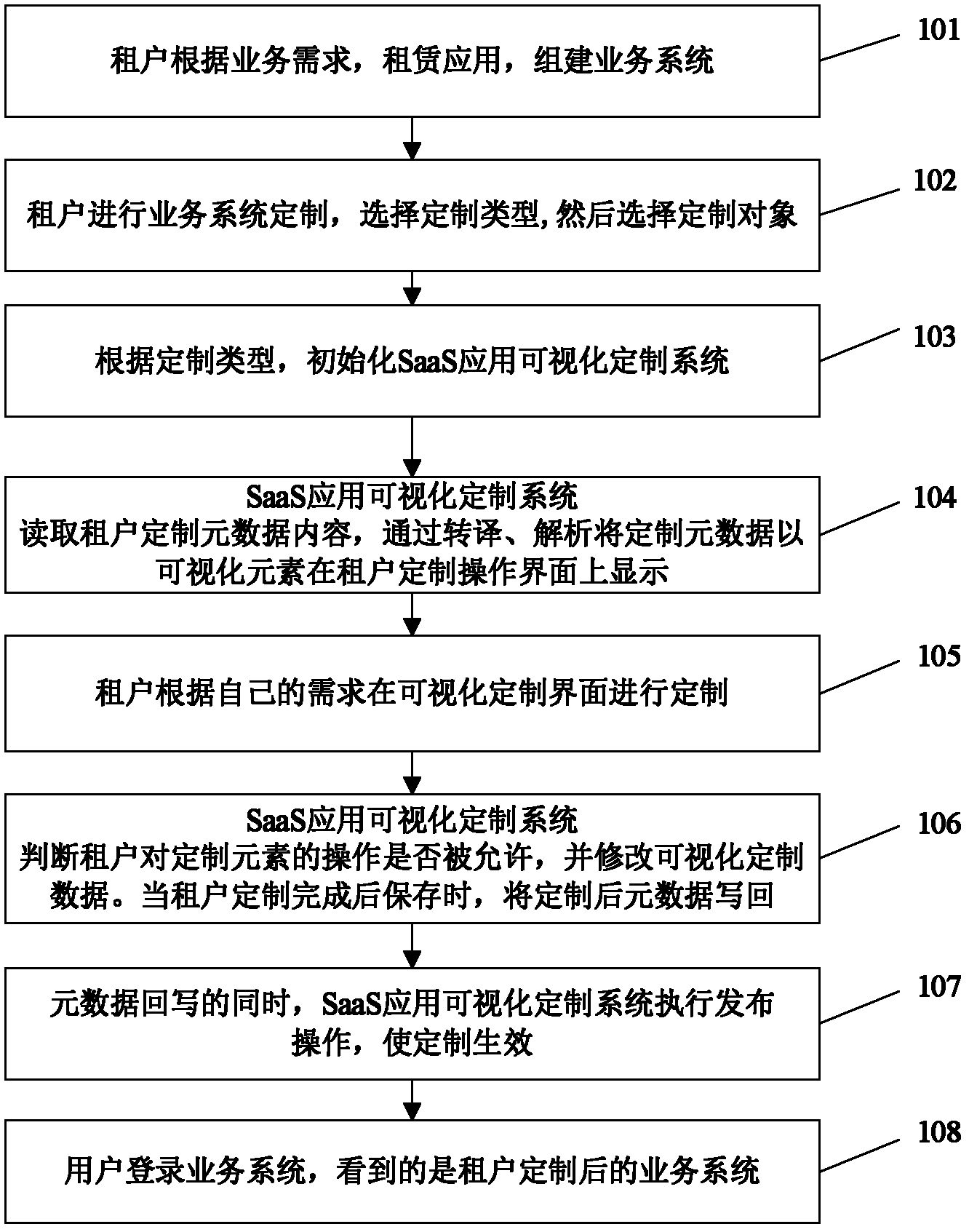
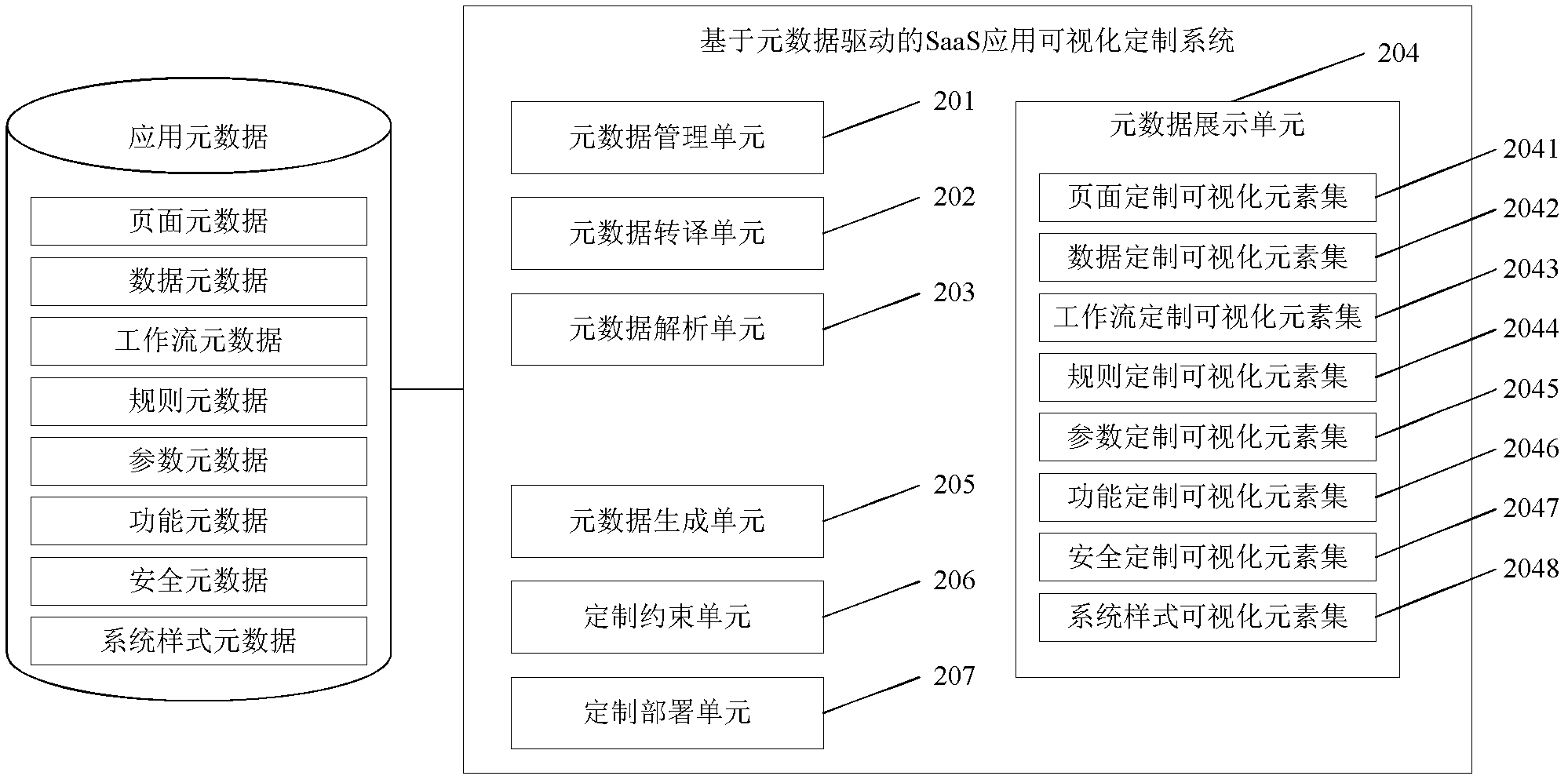
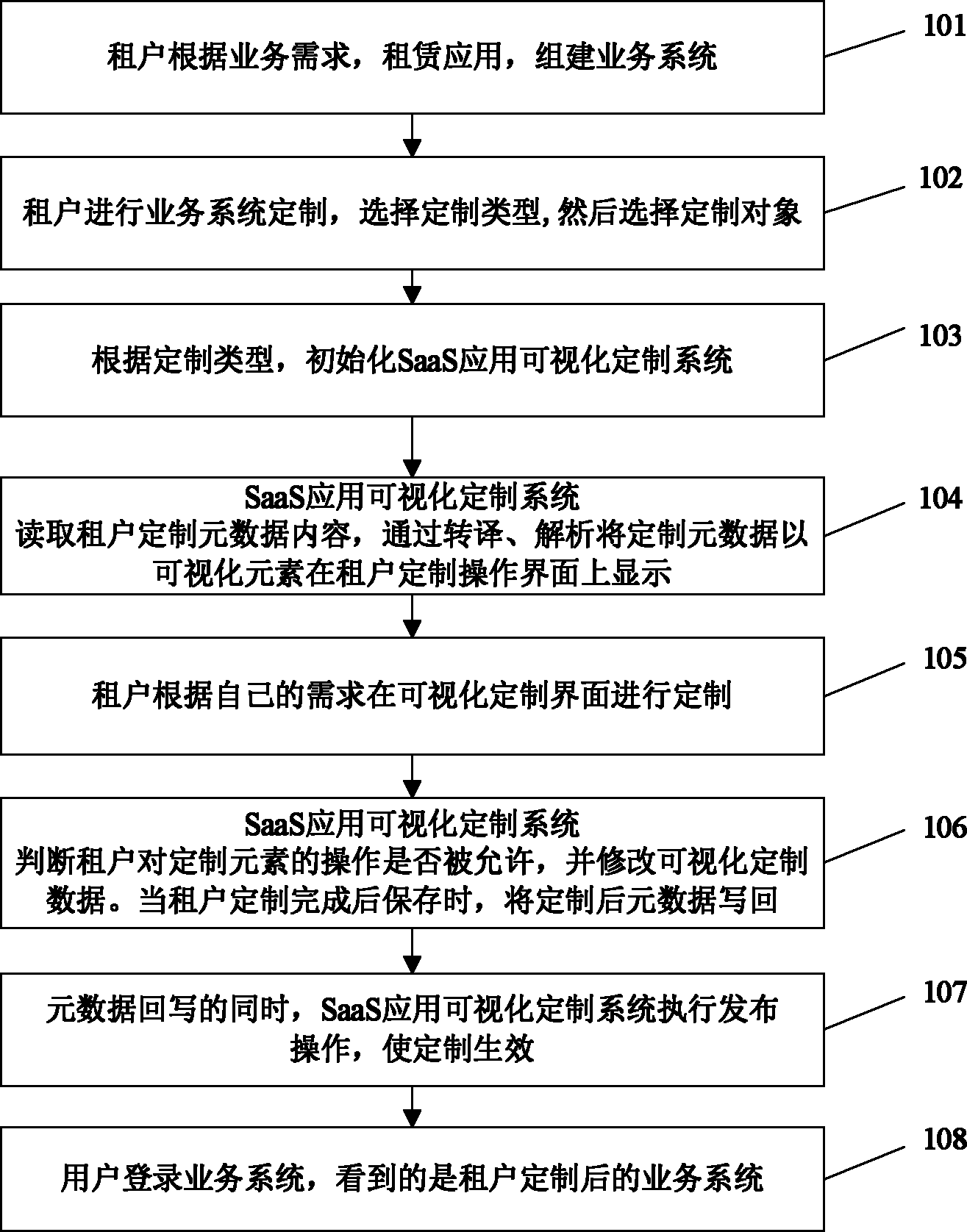
Metadata-driven visual SaaS (Software as a Service) application customizing method and metadata-driven visual SaaS application customizing system
ActiveCN102609271AImprove usabilityEasy to customizeSpecific program execution arrangementsData contentSoftware as a service
The invention relates to a metadata-driven visual SaaS (Software as a Service) application customizing method and a metadata-driven visual SaaS application customizing system, which can be used for flexibly supporting SaaS application customizing types and extension within the customizing types. The method includes the steps: A, renting an application and building a business system by a tenant; B, customizing the business system and selecting customizing types and objects by the tenant; C, initializing the visual SaaS application customizing system according to the customizing types; D, reading the content of metadata customized by the tenant and displaying the customized metadata on a customizing operation interface in the form of visual elements by means of translation and analysis by the visual SaaS application customizing system; E, customizing the elements on a visual customizing interface by the tenant according to the demand of the tenant; F, judging whether the operation of customizing the elements by the tenant is allowed or not and correcting visual customizing data by the visual SaaS application customizing system, and writing back the customized metadata when storing the data after customizing by the tenant; G, executing issue operations by the visual SaaS application customizing system while writing back the metadata so that customizing becomes effective; and H, logging in the business system by a user to see the business system customized by the tenant.
Owner:SHANDONG UNIV
Selecting one node from several candidate nodes in several public clouds to establish a virtual network that spans the public clouds
ActiveUS20190103992A1Increase redundancyImprove usabilityMetering/charging/biilling arrangementsTelephonic communicationNODALData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
System and Methods to Create a Multi-Tenancy Software as a Service Application
ActiveUS20100005443A1Office automationOther databases queryingApplication softwareSoftware as a service
Owner:SERVICENOW INC
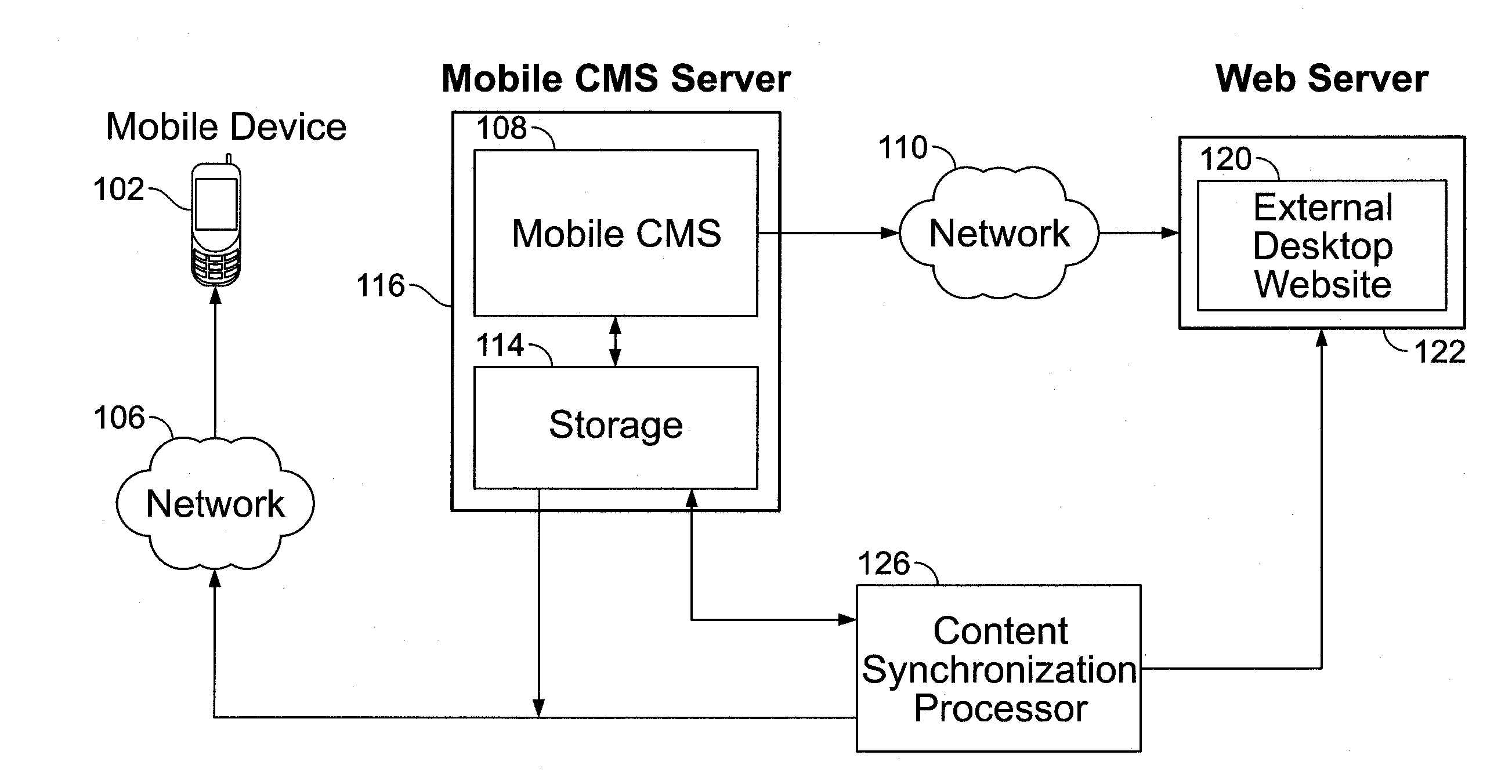
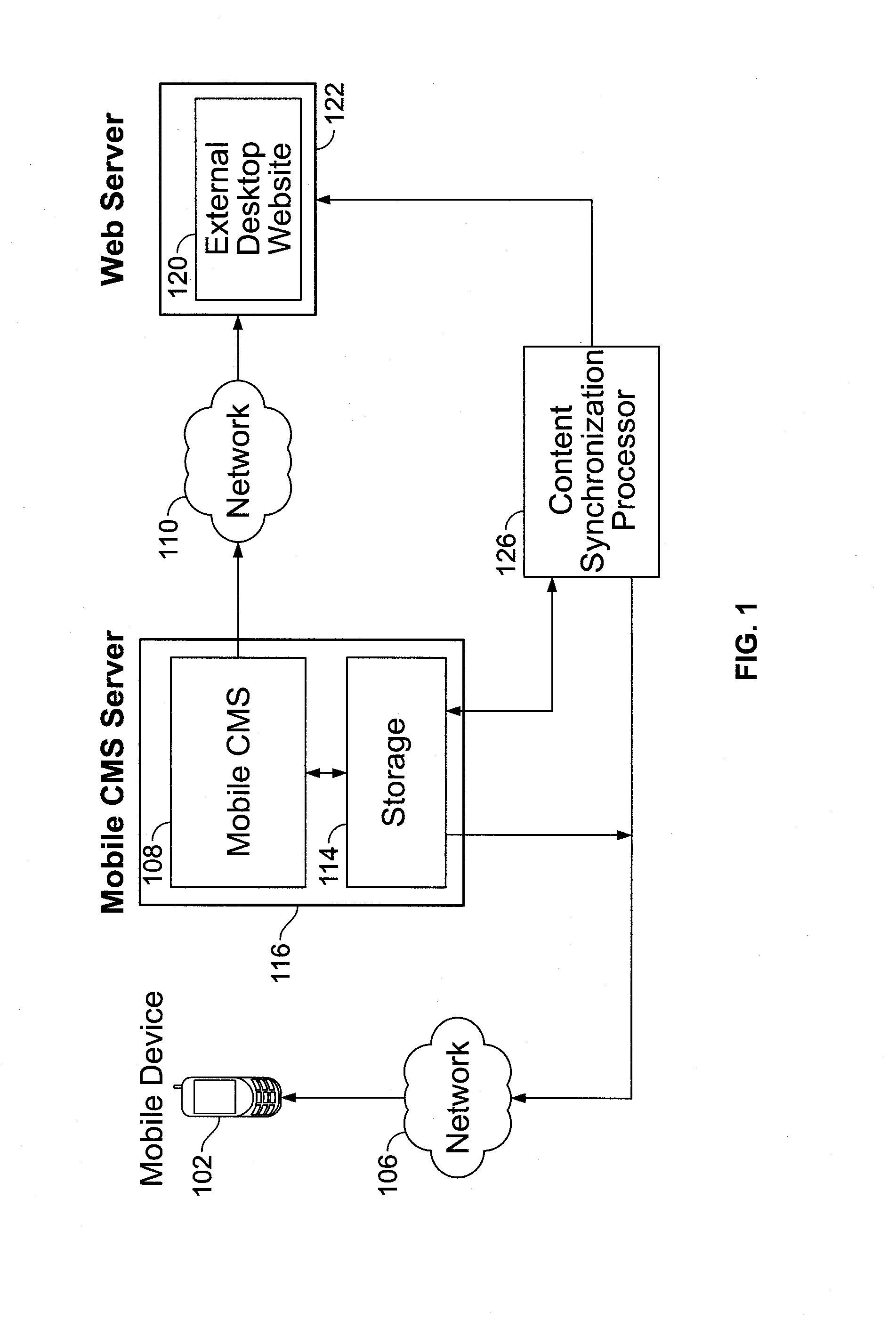
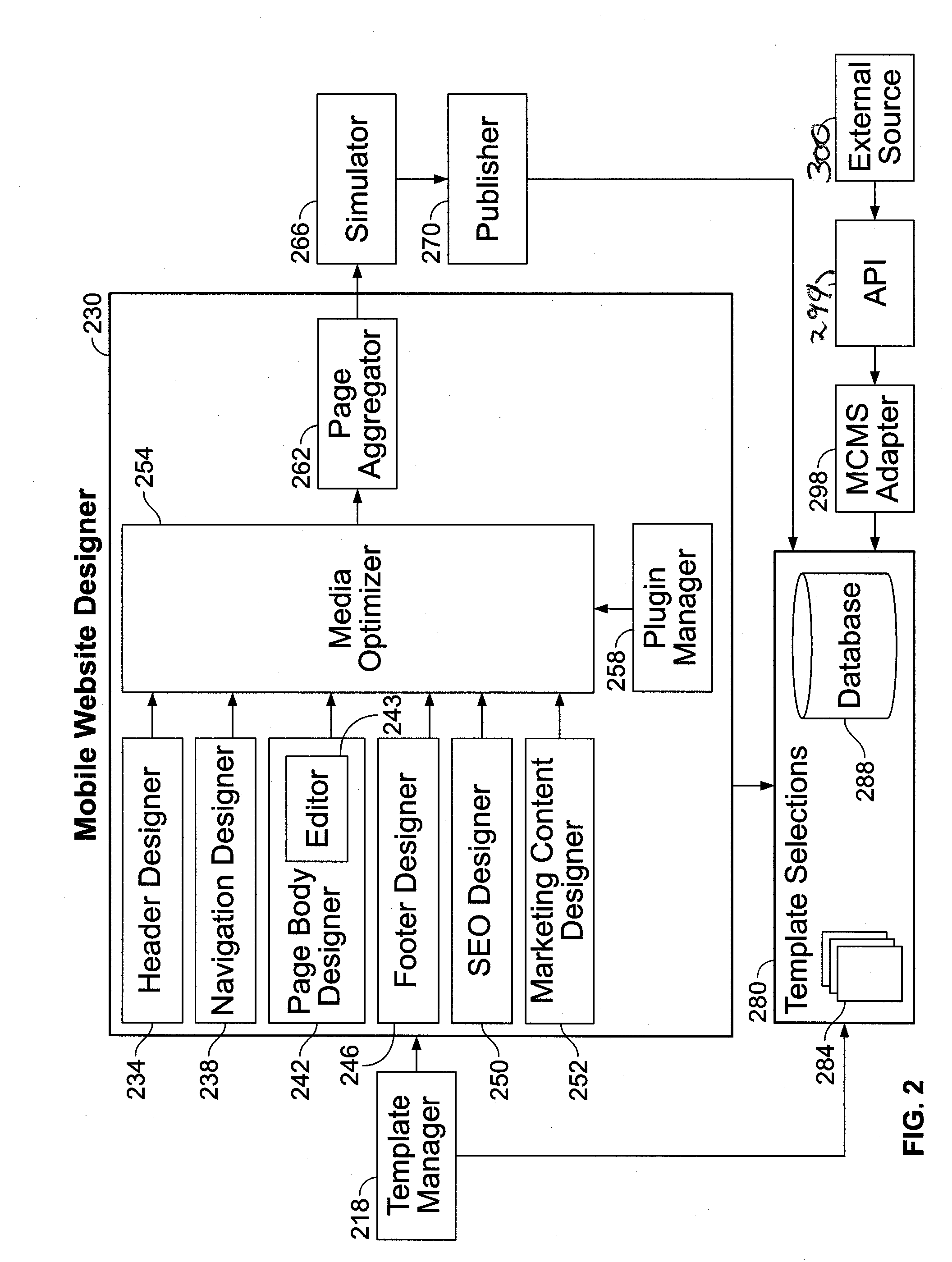
Mobile Content Management System
InactiveUS20130326333A1Useful actionThe process is convenient and fastNatural language data processingWebsite content managementWeb siteTablet computer
A system, method, and apparatus for a Mobile Content Management System that has interactive features to enable creation of Mobile Website are described. The MCMS software is cloud-based, but other versions may include standalone software that can be installed on a user's desktop or a mobile device such as a tablet or a smartphone. The system allows creating new mobile content as well as converting existing desktop websites into mobile device compatible versions. The system is delivered ON a SaaS (Software as a Service) platform on a hosting server. A user interacts with the system and utilizes various features and interfaces in the system to create the mobile website for consumption by a variety of mobile devices.
Owner:INSPIRITY
Routing data message flow through multiple public clouds
ActiveUS20190104050A1Increase redundancyImprove usabilityMetering/charging/biilling arrangementsTelephonic communicationPrivate networkData center
Some embodiments establish for an entity a virtual network over several public clouds of several public cloud providers and / or in several regions. In some embodiments, the virtual network is an overlay network that spans across several public clouds to interconnect one or more private networks (e.g., networks within branches, divisions, departments of the entity or their associated datacenters), mobile users, and SaaS (Software as a Service) provider machines, and other web applications of the entity. The virtual network in some embodiments can be configured to optimize the routing of the entity's data messages to their destinations for best end-to-end performance, reliability and security, while trying to minimize the routing of this traffic through the Internet. Also, the virtual network in some embodiments can be configured to optimize the layer 4 processing of the data message flows passing through the network.
Owner:VMWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com