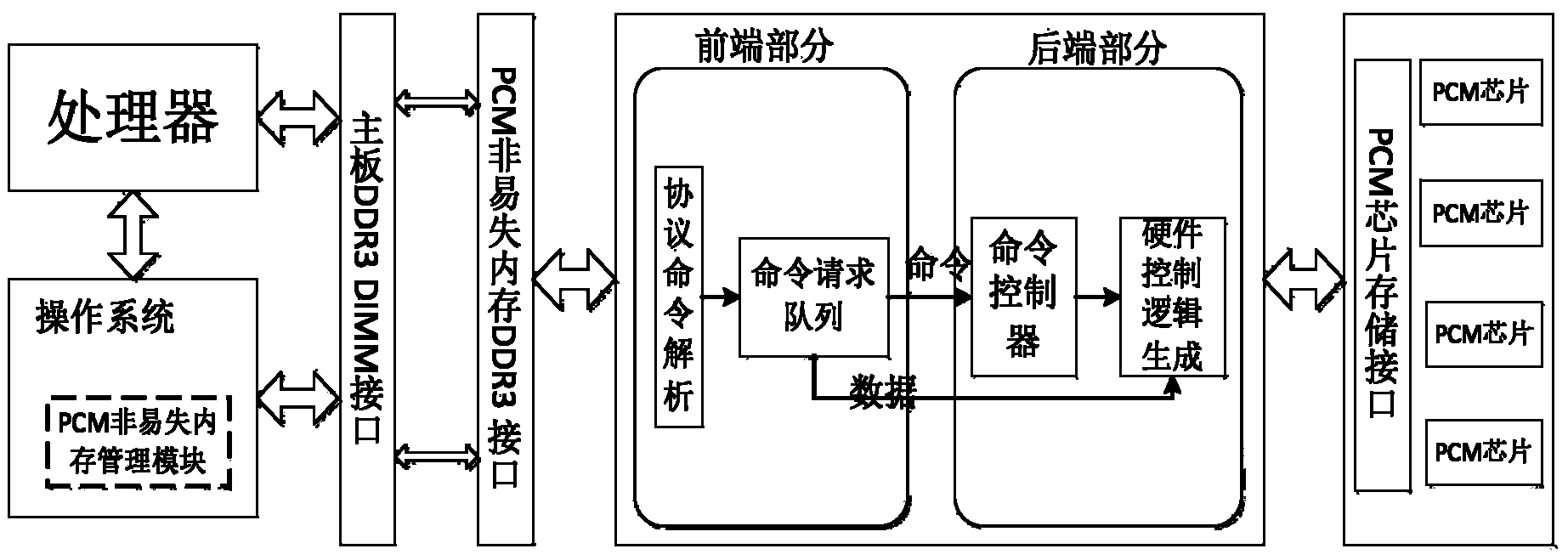
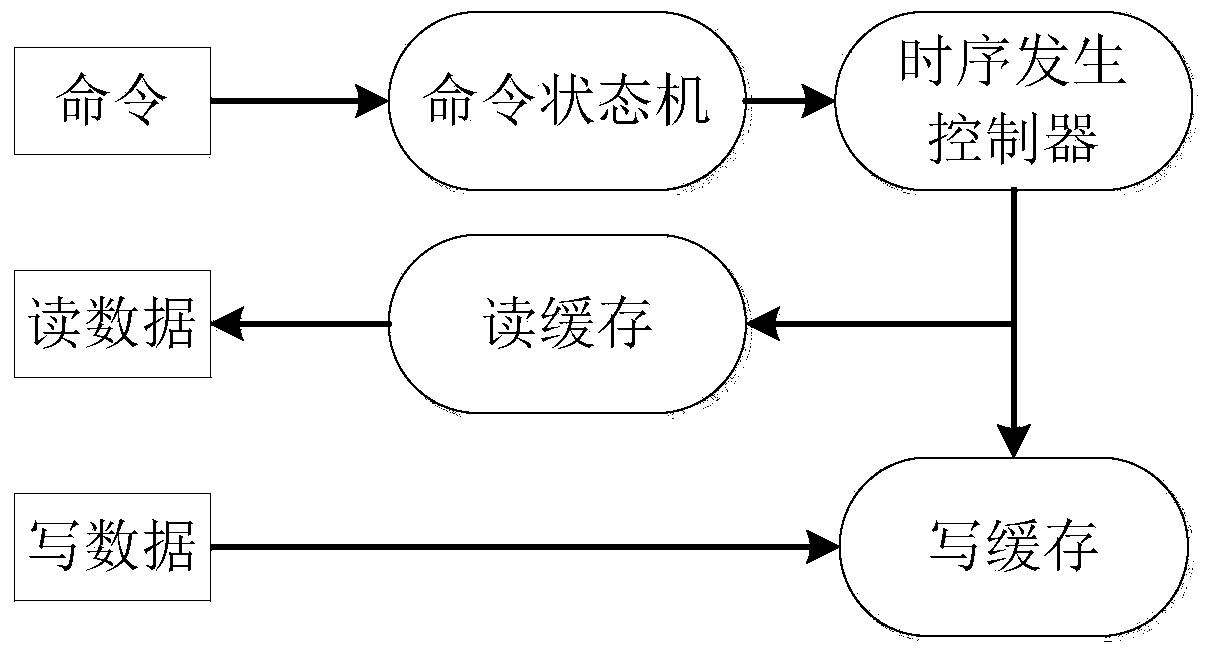
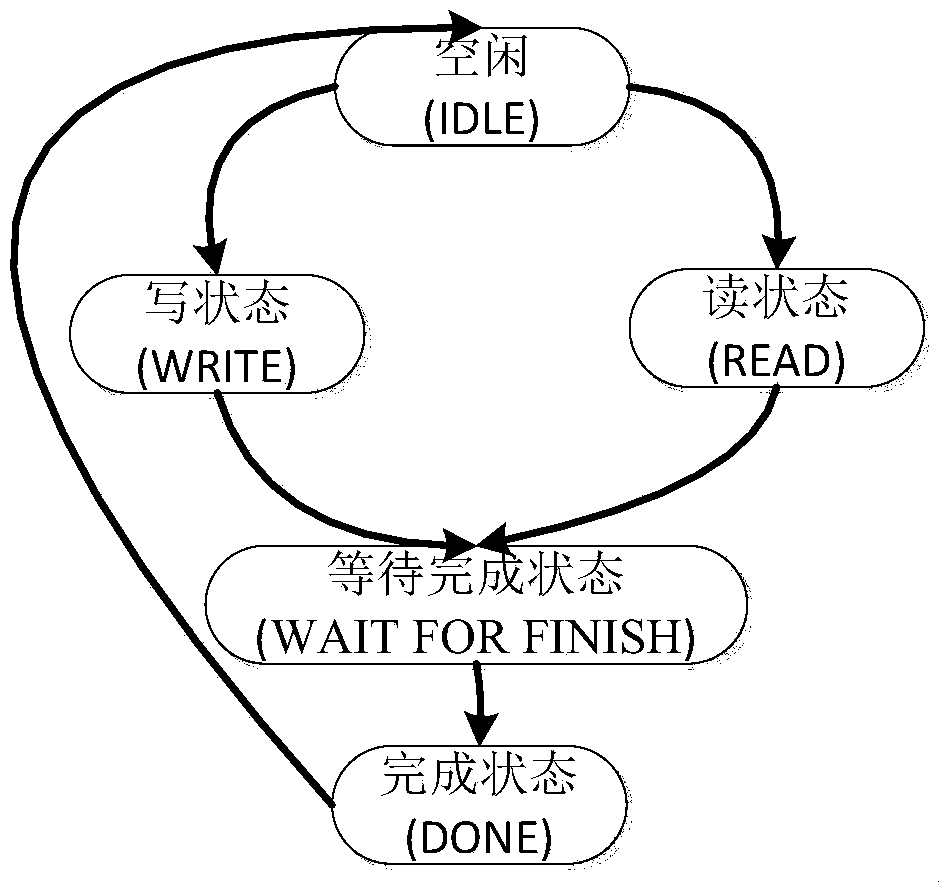
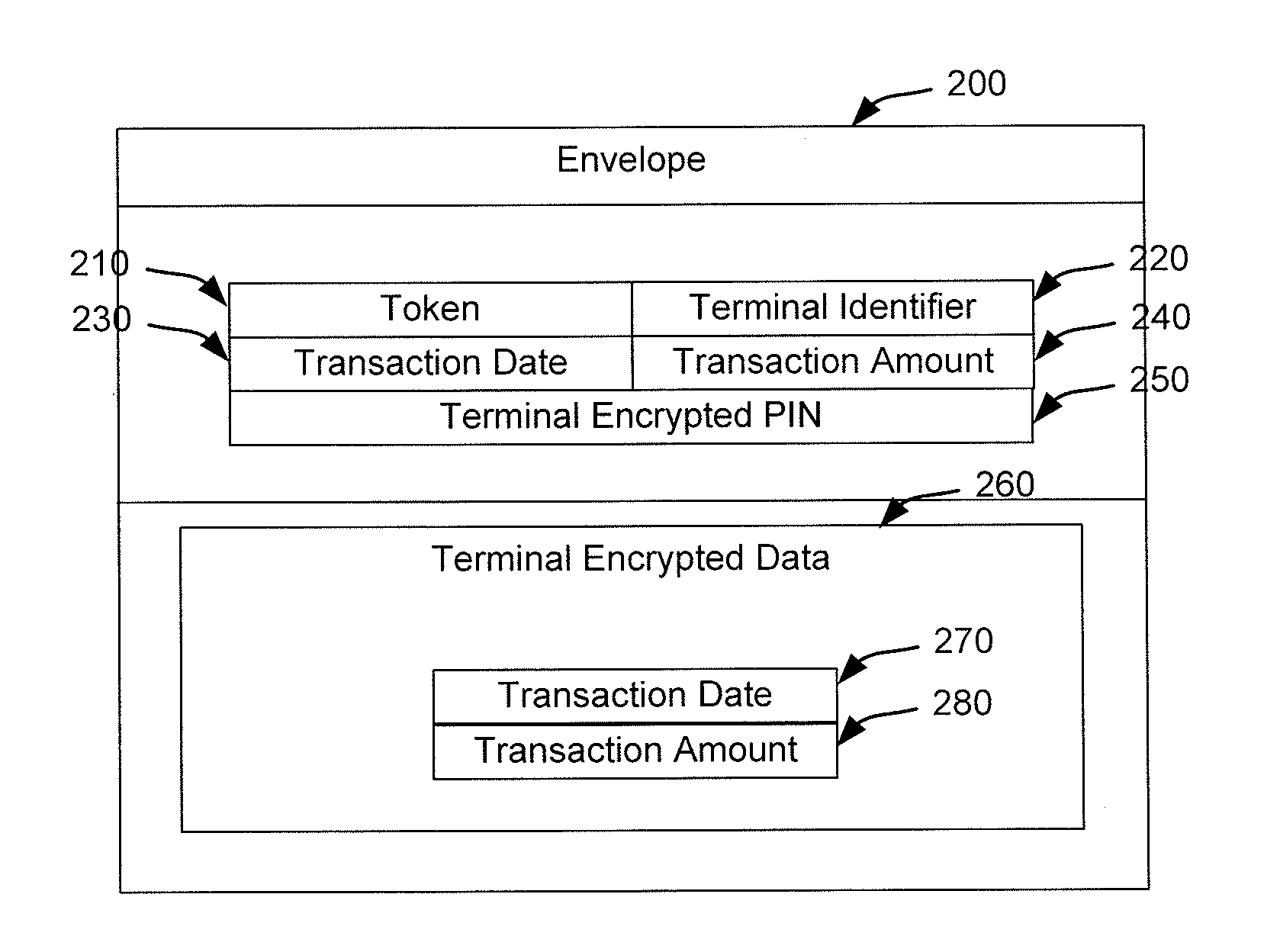
Patents
Literature
860results about How to "Ensure data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
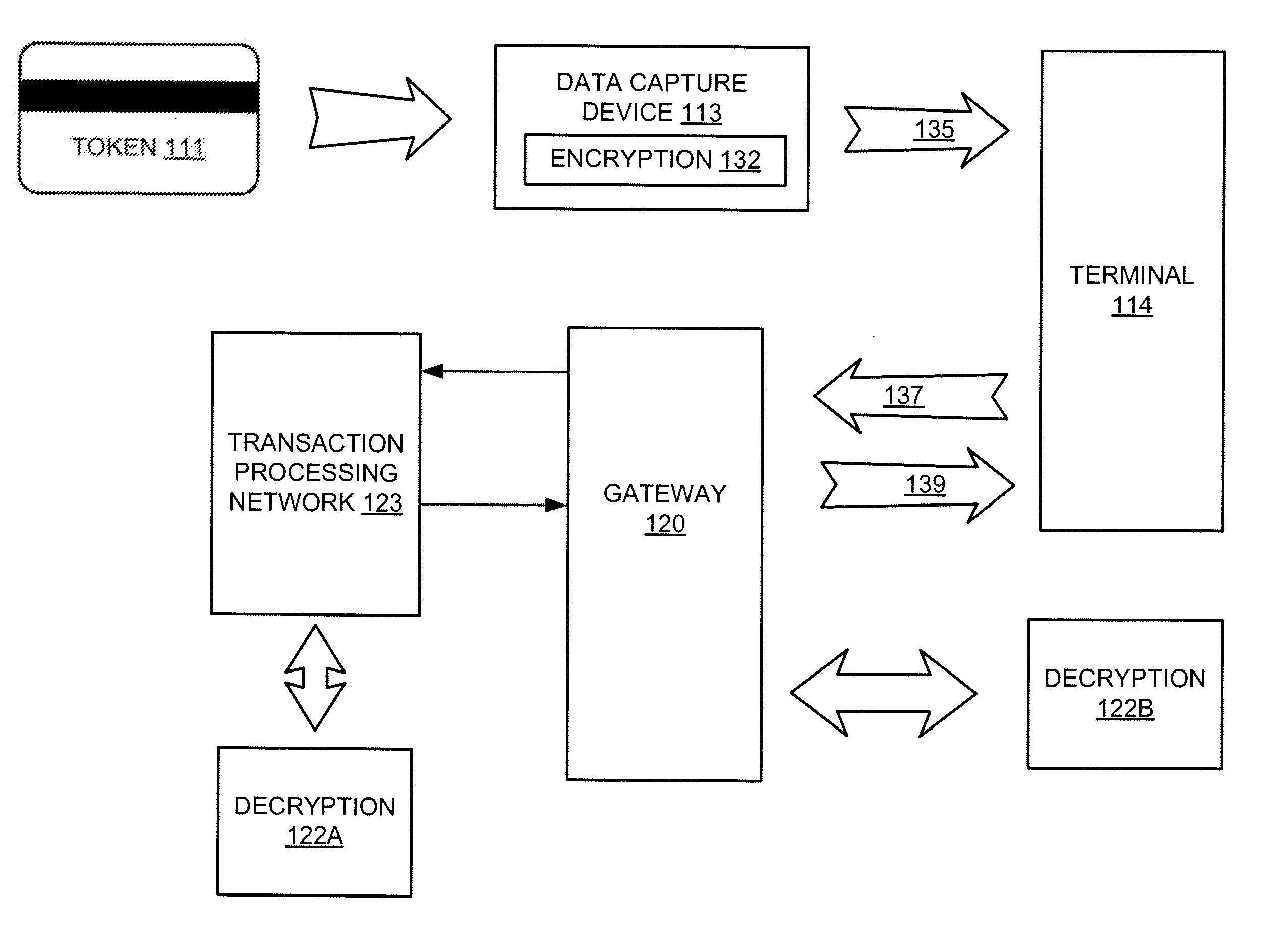
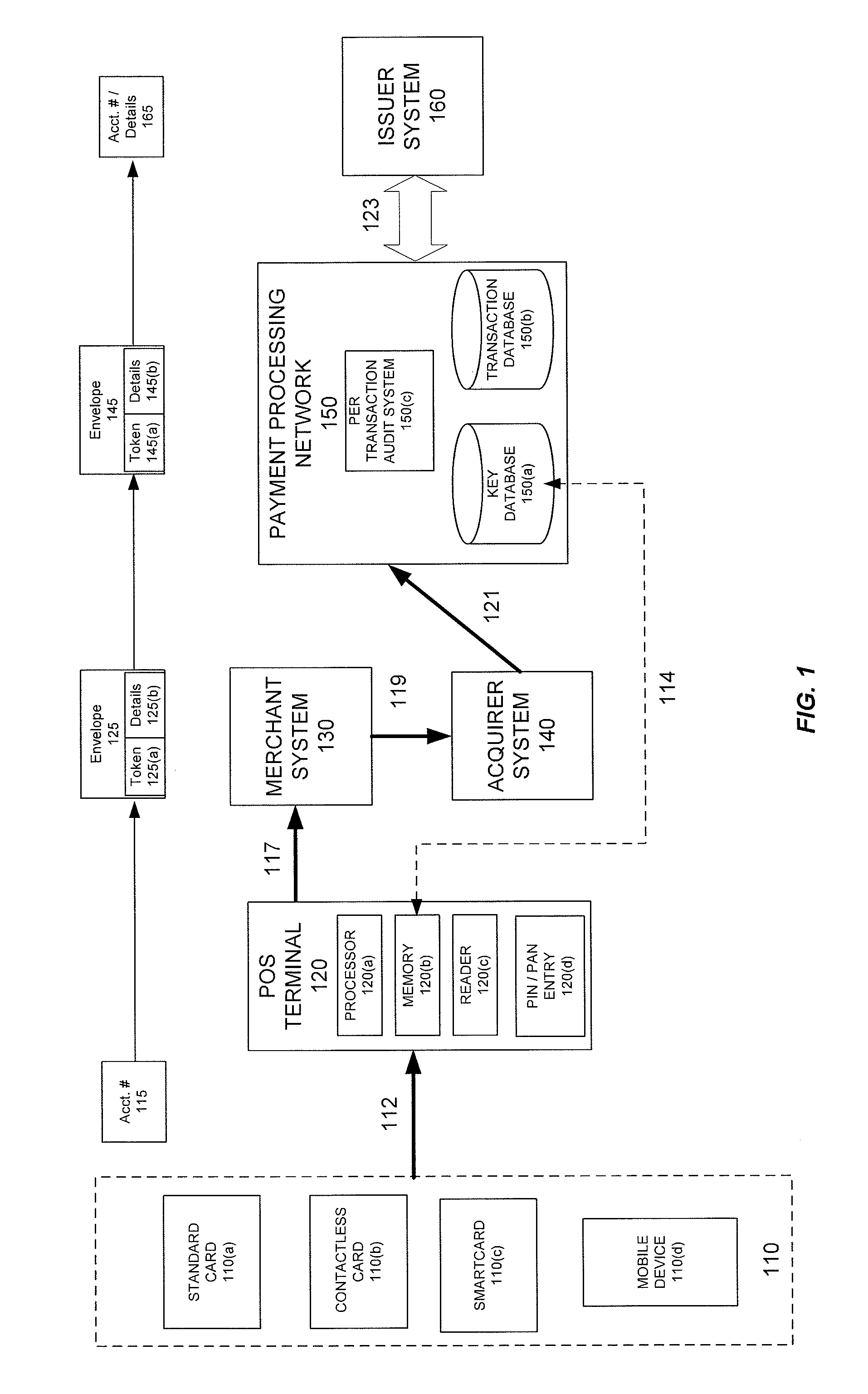
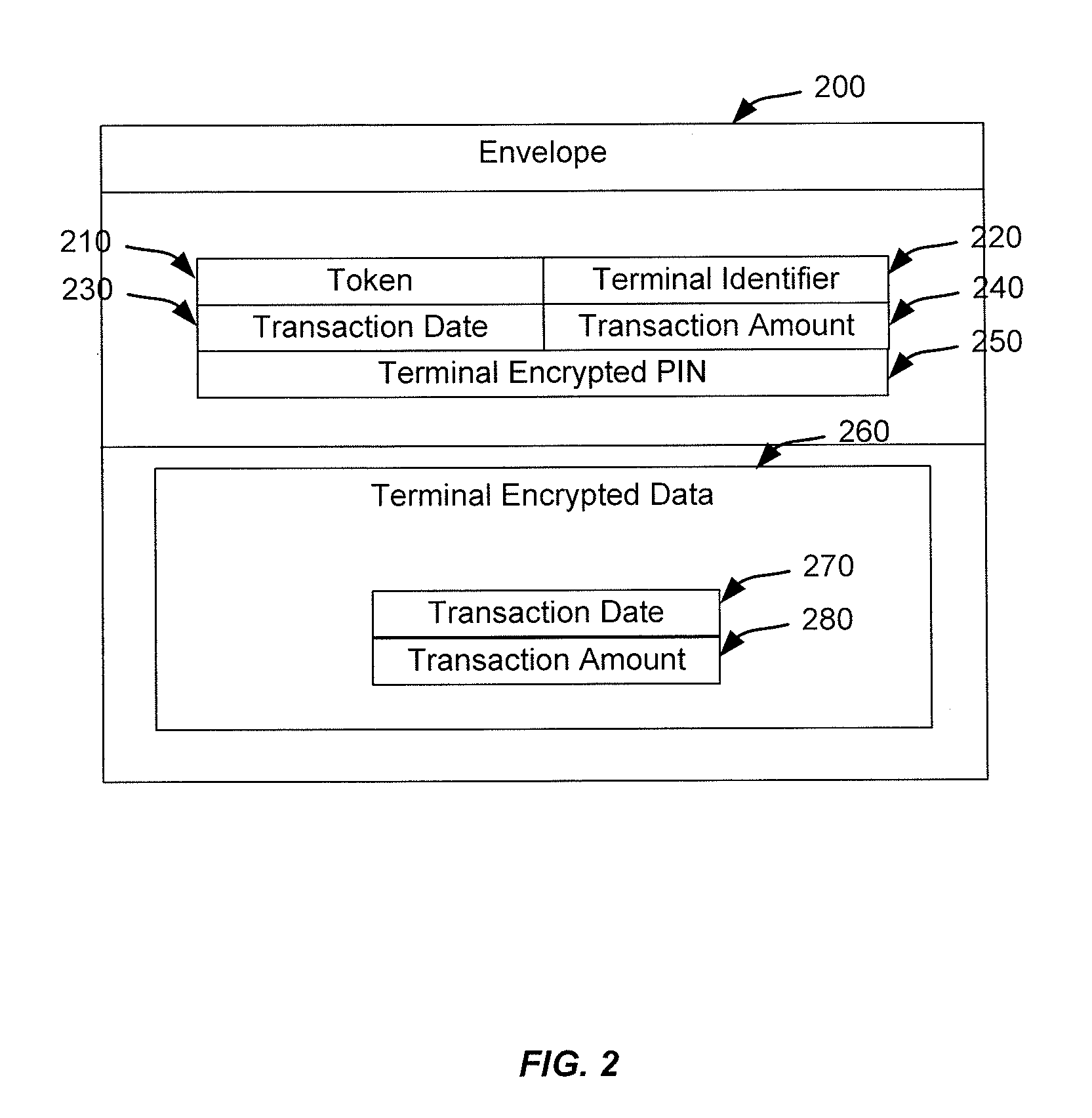
Metrics systems and methods for token transactions
ActiveUS20090048953A1Ensure data securityImprove securityAcutation objectsFinanceOperating systemE infrastructure
Systems and methods for monitoring token access transactions are provided. In one embodiment, the invention provides receiving transaction records for a plurality of bank card transactions, wherein the transaction records include transaction information and infrastructure information; determining whether a reportable event has occurred based on the transaction information with the transaction records; and providing an alert representing the reportable event.
Owner:VERIFONE INC
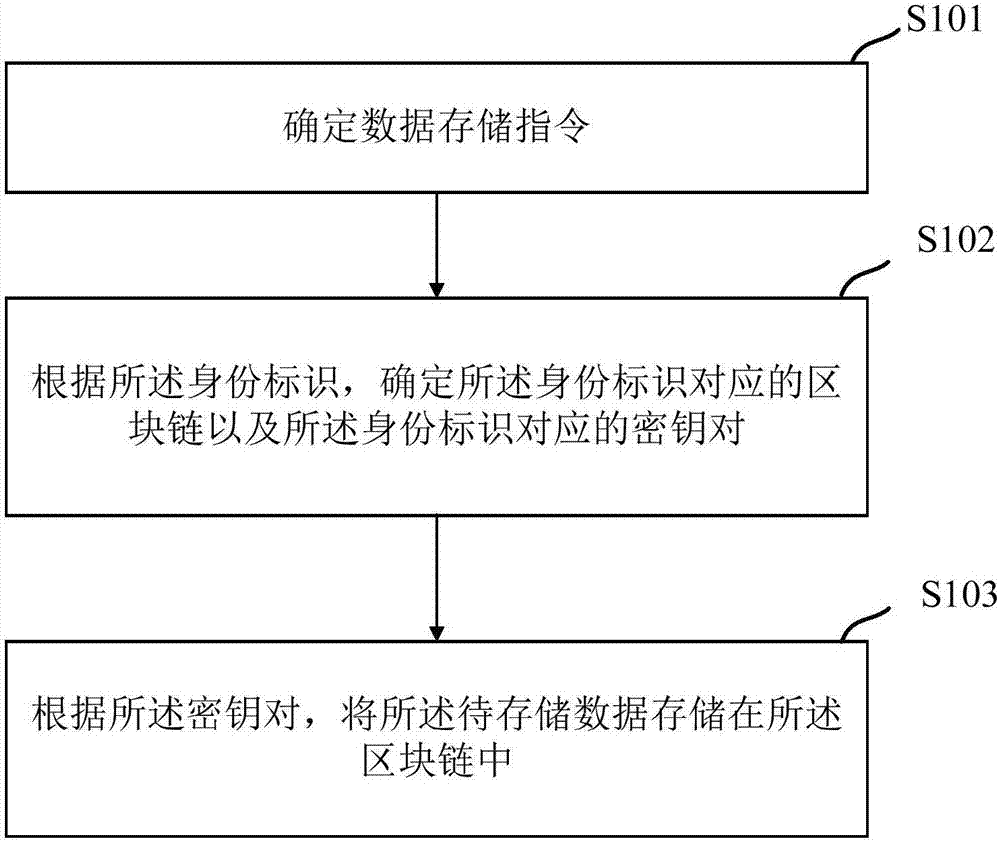
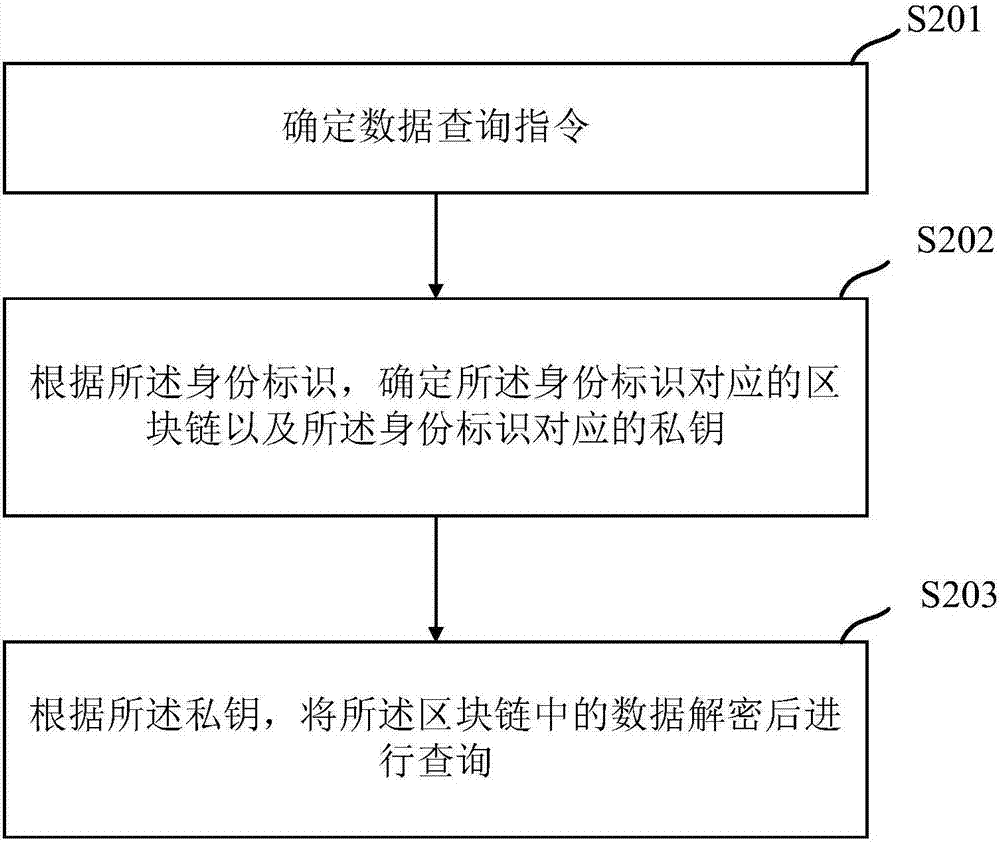
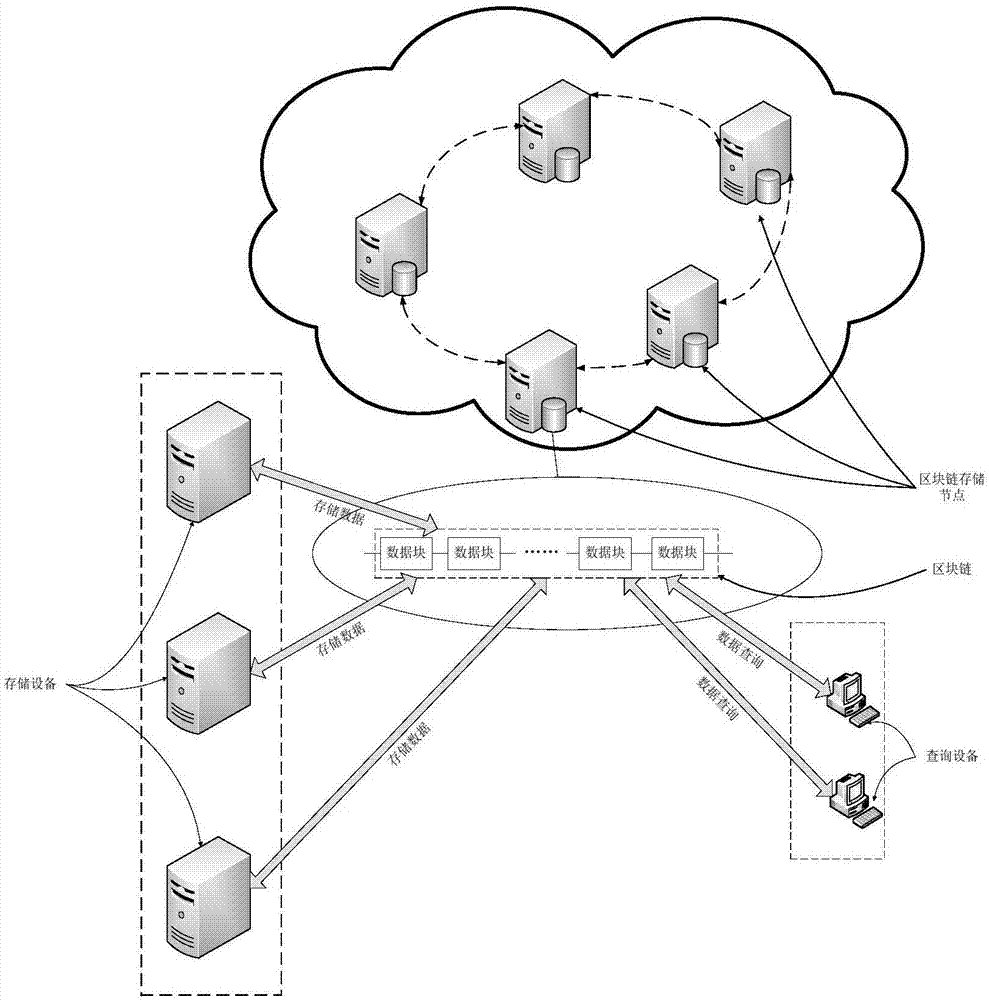
Data access method, system and device
ActiveCN106991334AEnsure data securitySimplify complexityPublic key for secure communicationDigital data protectionData queryBlockchain
The invention discloses a data access method, system and device. The data access method includes: determining a data storage command during data storage; determining a block chain corresponding to an identity identifier and a secret key pair according to the identity identifier arranged in the data storage command; storing data to be stored in the block chain according to the secrete key pair; determining a data query command during data query; determining a block chain corresponding to an identity identifier and a private key according to the identity identifier corresponding to the data query command; and decrypting data in the block chain according to the private key, and querying the data. It is thus clear that the data access method can access data corresponding to the identity identifier without accessing a plurality of databases, can only access the block chain corresponding to the identity identifier, can perform data storage through the secrete key, can ensure the security of the data, can simplify the complexity of operations, and can improve the efficiency of data access.
Owner:ADVANCED NEW TECH CO LTD
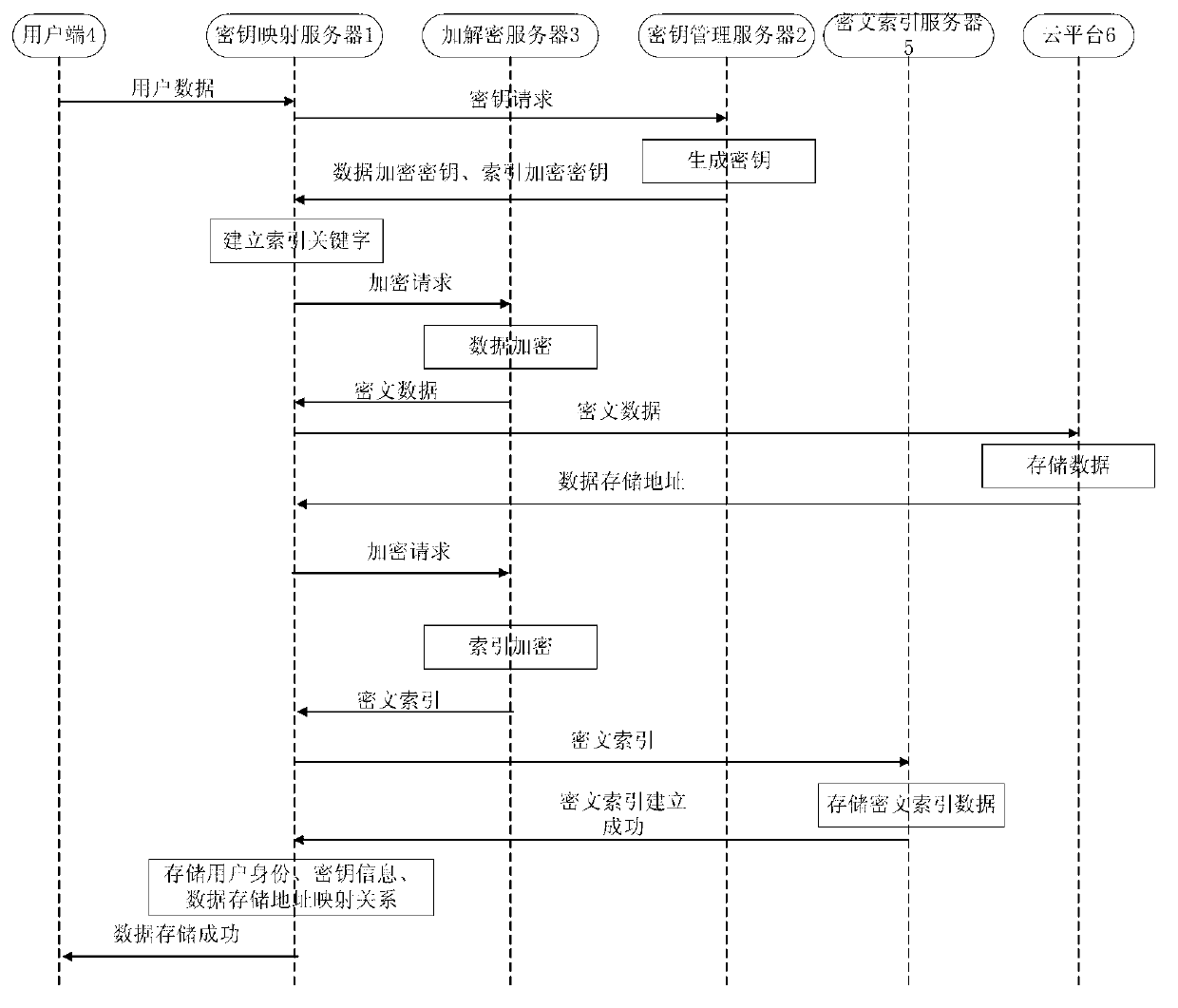
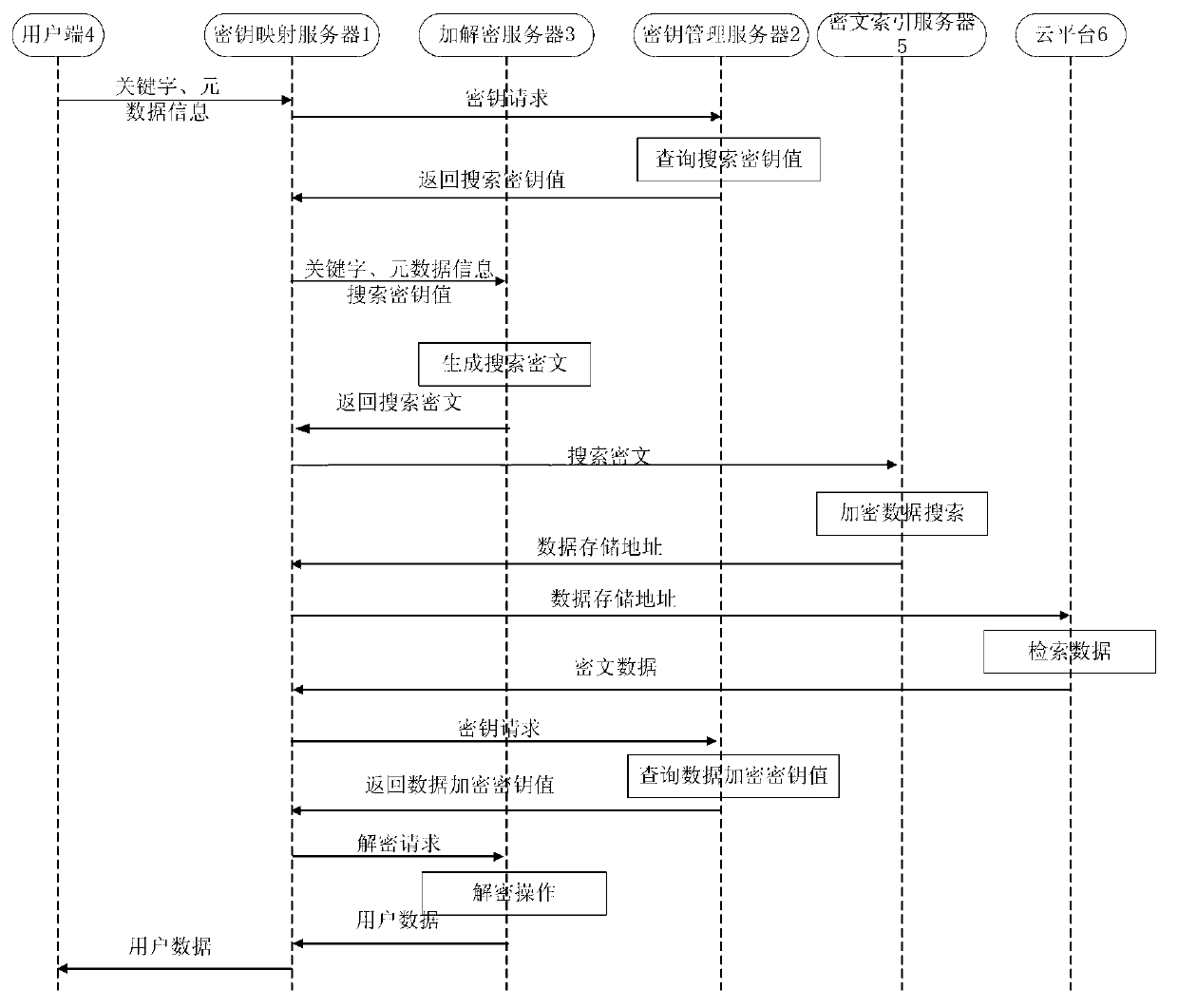
System and method for cloud computing environment data encryption storage and capable of searching
ActiveCN103107889AImprove work efficiencyEnsure data securityUser identity/authority verificationCiphertextData interchange
The invention relates to a system and a method for cloud computing environment data encryption storage and capable of searching. The system for cloud computing environment data encryption storage comprises a key management server, an encryption and decryption server, a user side, a ciphertext indexing server and a cloud platform which are all respectively connected with a key mapping server and exchange data with the key mapping server. Due to the fact that only mapping relation of user identification, key identification and data storage addresses is stored in the key mapping server, only the key identification and key values are stored in the key management server, only ciphertext index containing relative relation of indexing key words and data storage address is stored in the ciphertext indexing server, and only ciphertext data is stored in the cloud platform, so that direct relation between the key values and the ciphertext data which are used in the encryption and decryption server is broken. The key values and the ciphertext data do not exist simultaneously in the position storing the key mapping relation, the key values and the key mapping relation do not exist simultaneously in the position storing the ciphertext data and the key mapping relation and the ciphertext data do not exist simultaneously in the position storing the key values.
Owner:CEC CYBERSPACE GREAT WALL
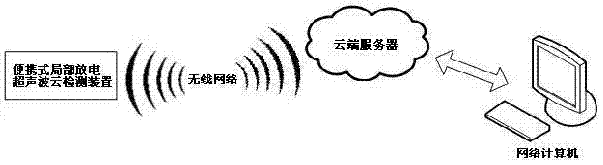
Portable partial discharge ultrasonic cloud detection device
InactiveCN102298107ARealize online detectionEasy to carryTesting circuitsUltrasonic sensorDisplay device
The invention discloses a portable partial discharge ultrasonic cloud detection device, which comprises an ultrasonic sensor, a temperature sensor, a humidity sensor, an atmospheric pressure sensor, a signal processing module, a wireless network device, a display and an earphone. The sensor transmits the signal to the signal processing module, and the processed signal is transmitted to the cloud server through the wireless network device, and the signal is subjected to anti-interference processing and characteristic parameters are extracted and stored in the partial discharge signal characteristic database. For analysis, the operator monitors the sound in the earphone and makes a diagnosis based on the results of the cloud server. The diagnosis result is displayed on the monitor, and the device detects and alarms at the same time. The invention uses the data analysis, processing and storage capabilities of the cloud detection principle to detect the partial discharge in the equipment early and prevent the occurrence of major accidents through online monitoring or inspection of the partial discharge of the high-voltage equipment.
Owner:SOUTH CHINA UNIV OF TECH
Intelligent electromechanical equipment management system and method based on BIM (building information modeling)
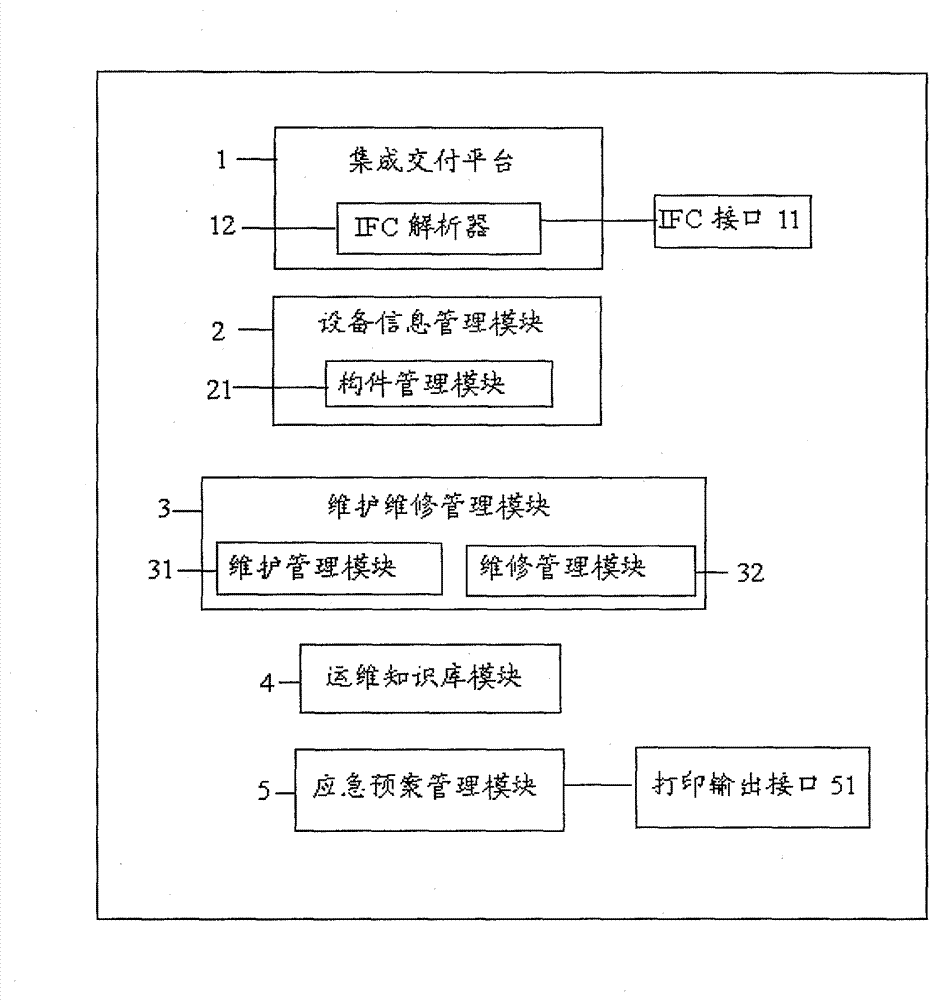
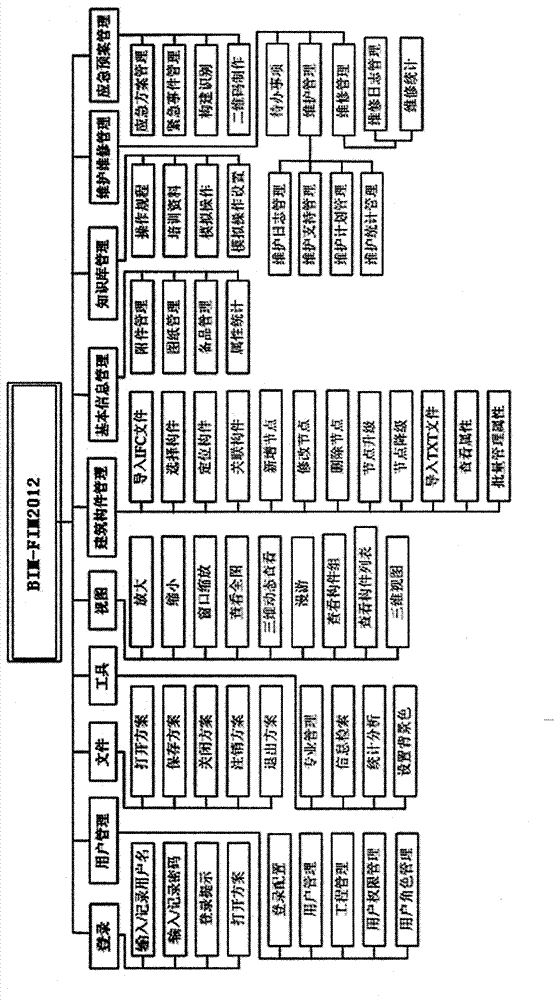
InactiveCN103246951AEnsure data securityAchieve sharingResourcesManagement systemMaintenance management
The invention discloses an intelligent electromechanical equipment management system and method based on BIM. The intelligent electromechanical equipment management system comprises an integrated delivery platform, an equipment information management module, a maintenance management module, an operation and maintenance knowledge base module and an emergence plan management module. By virtue of the system and the method, a property management practitioner can efficiently realize management of equipment information, maintenance, an operation and maintenance knowledge base and an emergence plan of a large number of complex electromechanical equipment of a building.
Owner:NO 1 CONSTR ENG CO LTD OF CHINA CONSTR THIRD ENG BUREAU CO LTD
Data protection transmission method of P2P network
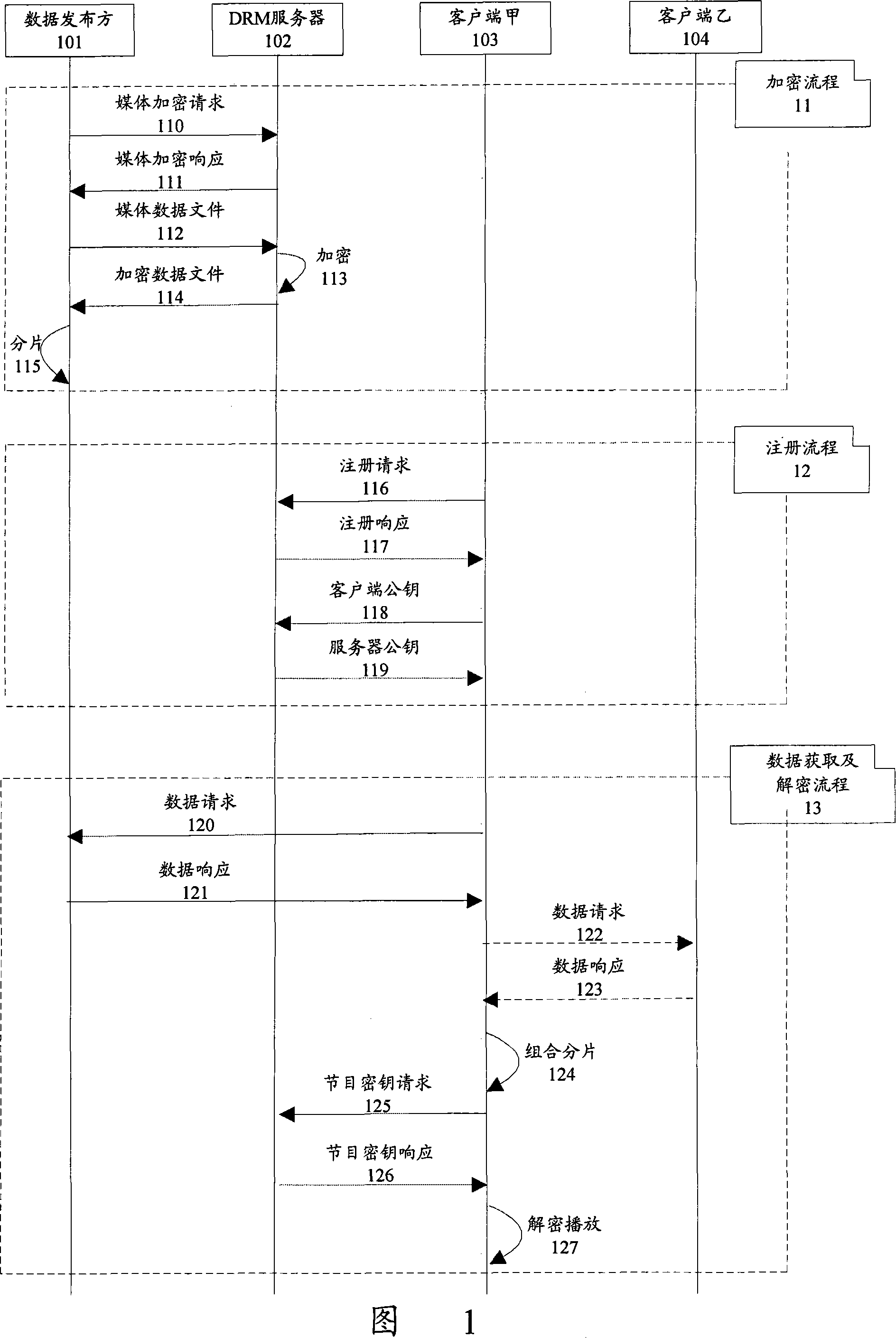
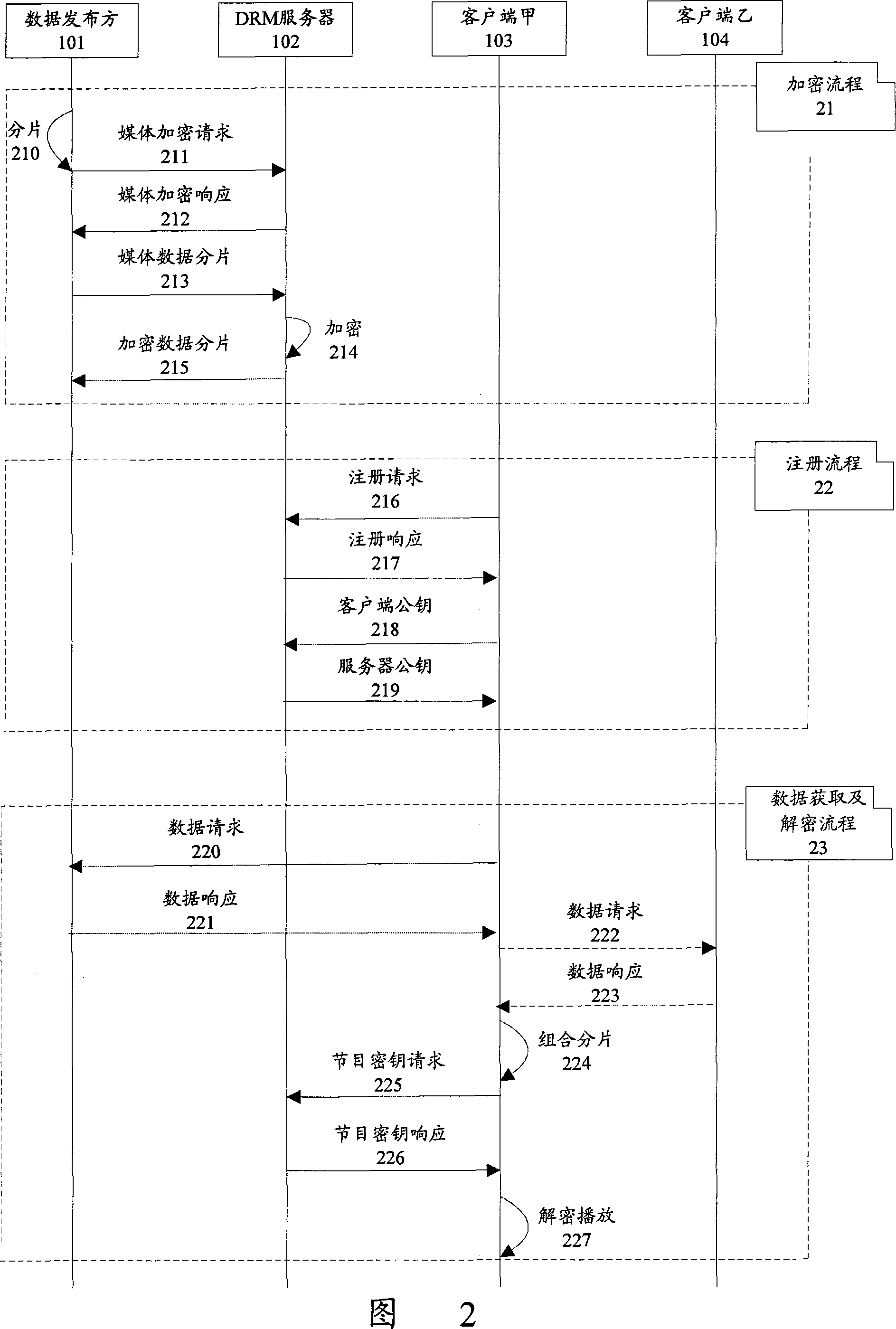
The present invention discloses a data protection transmission method for peer-to-peer network. The method has an encryption server arranged in a peer-to-peer network, and comprises following the steps that: A. a data publication party sends data needing to be published to the encryption server; B. the encryption server encrypts the data needing to be published, saves a corresponding key and returns the encrypted data to the data publication party; C. the data publication party publishes the encrypted data in different pieces; D. a data request client collects the published encrypted data pieces through the peer-to-peer network; the data request client acquires the corresponding key from the encryption server and decrypts the collected encrypted data pieces according to the key. The present invention can be applicable to the characteristics of the peer-to-peer network, improve the data transmission security of the peer-to-peer network, prevent hackers from attacking the peer-to-peer network data and guarantee the rights and benefits of data owners and users.
Owner:新疆新颖电子科技有限公司
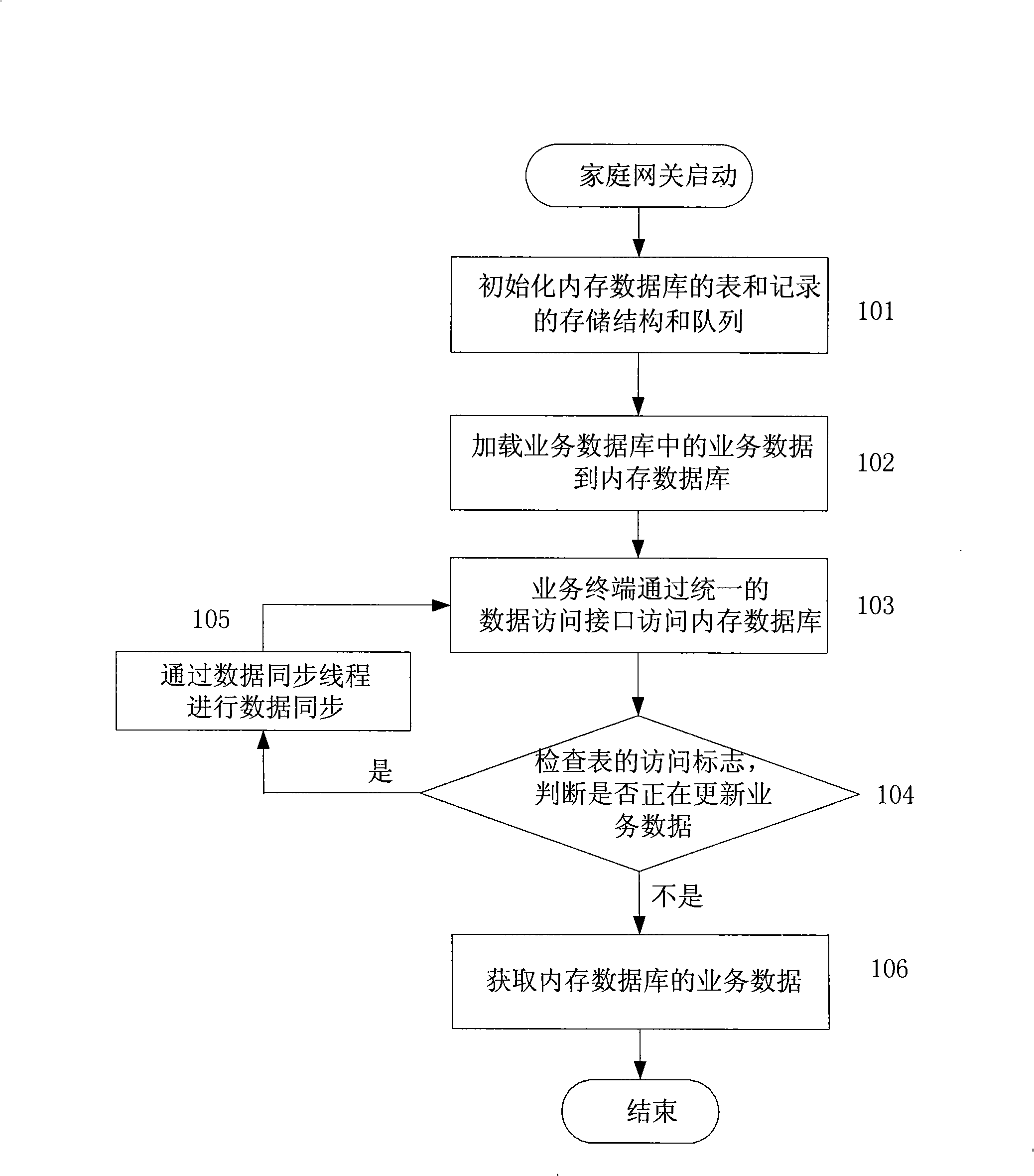
Implementing method of memory database on household gateway
InactiveCN101329685AFast accessEnsure data securitySpecial data processing applicationsData synchronizationIn-memory database
The invention discloses a realization method of a memory database on a home gateway. The method of the invention comprises the steps: 1. the storage structure and queue of data sheets and records in the memory database are initialized; 2. on the basis of the establishment of the storage structure of the memory database, the business data in a business database are uploaded to the memory database on the home gateway, while before the business data are uploaded, the business data are filtered; 3. data synchronization: when the data in business database are changed, the given data in the memory database are backed up; data synchronization is carried out by adopting a synchronous module, and if the synchronization succeeds, the backup data are cleared; 4. data access: a unified access interface of the memory database is provided for inquiring, adding, deleting and modifying, etc. Compared with the realization method of the existing memory database, the realization method of the invention requires few resources, has high data storage efficiency and is especially suitable for the business application that is based on a home gateway and has high requirement for data real time.
Owner:FENGHUO COMM SCI & TECH CO LTD
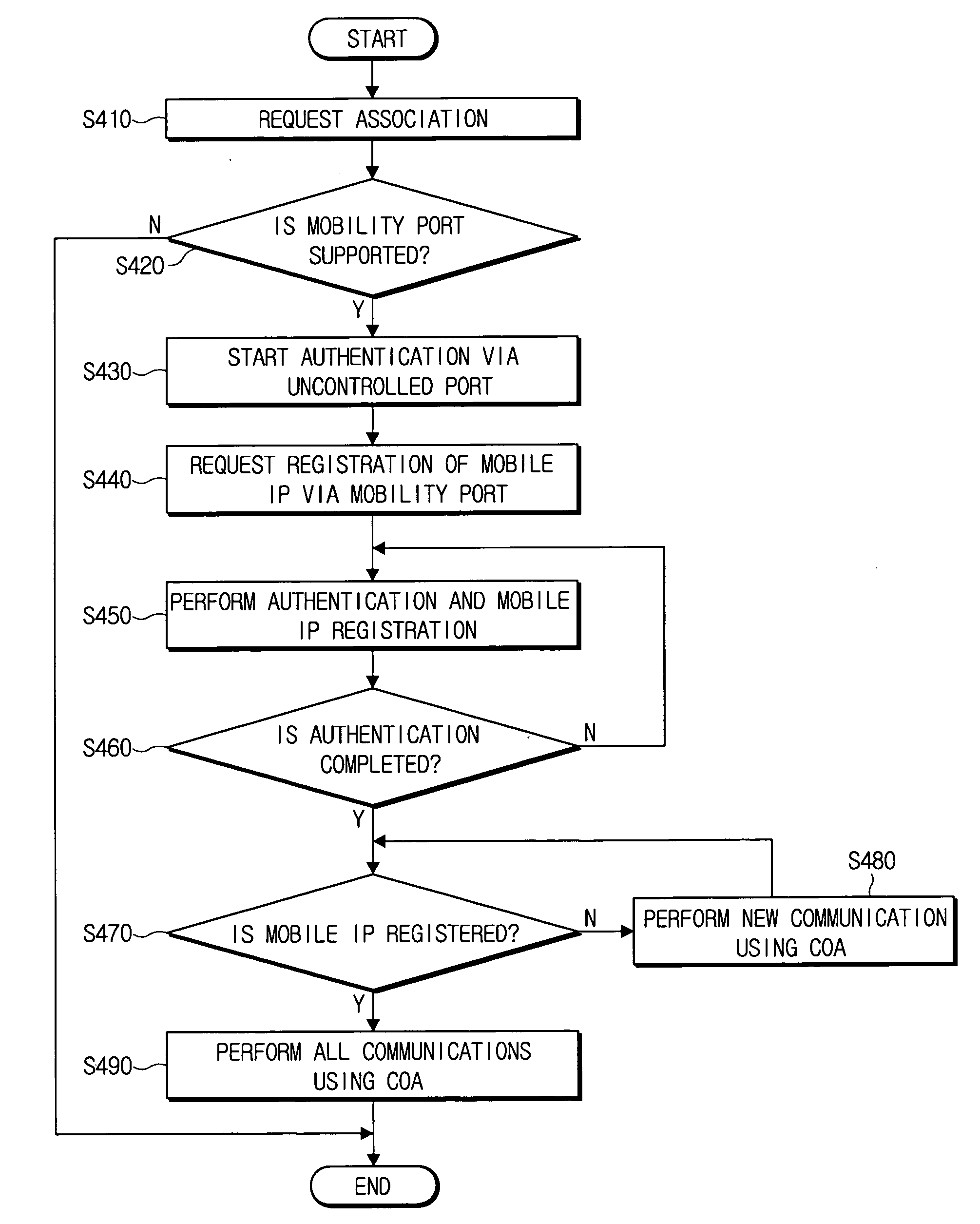
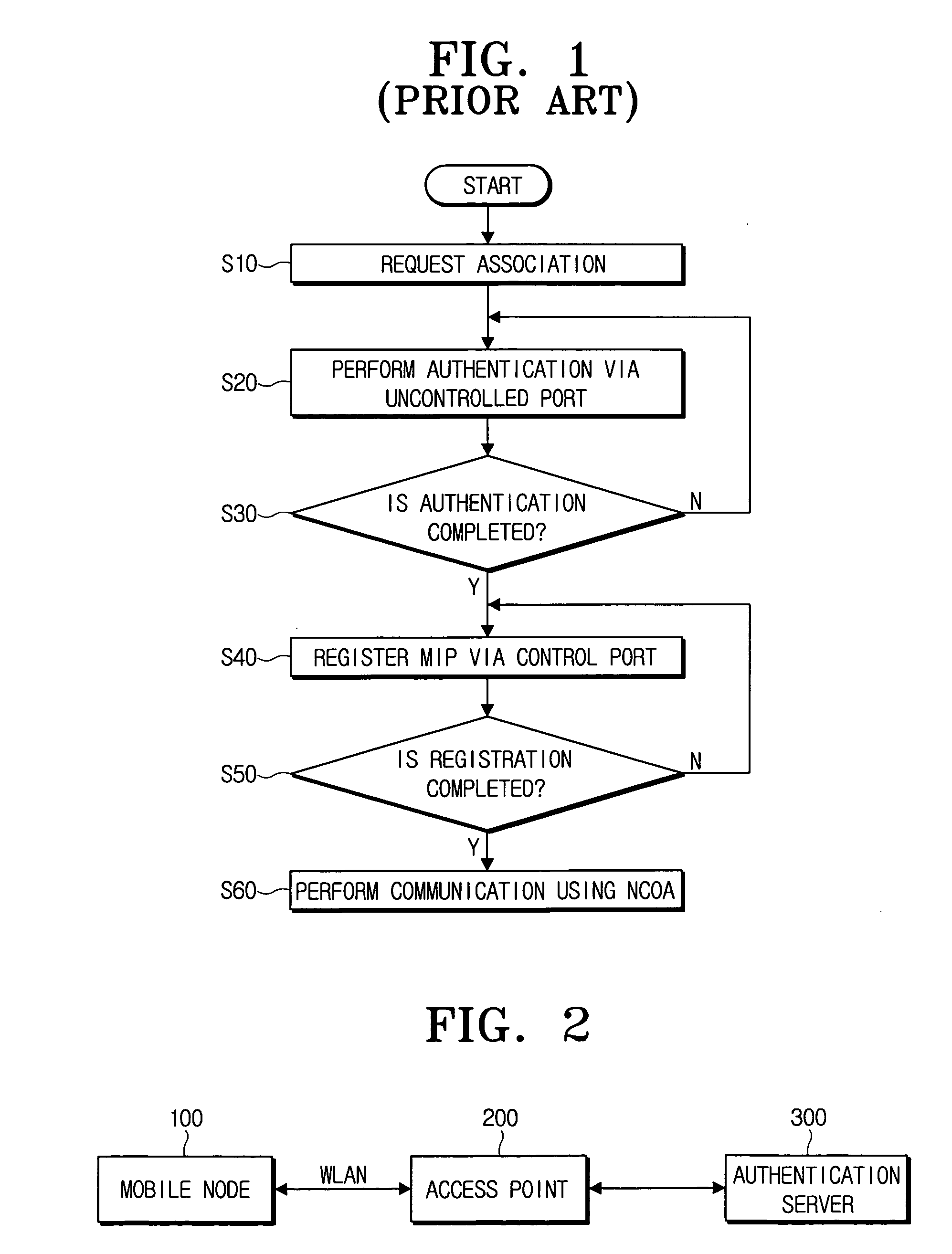
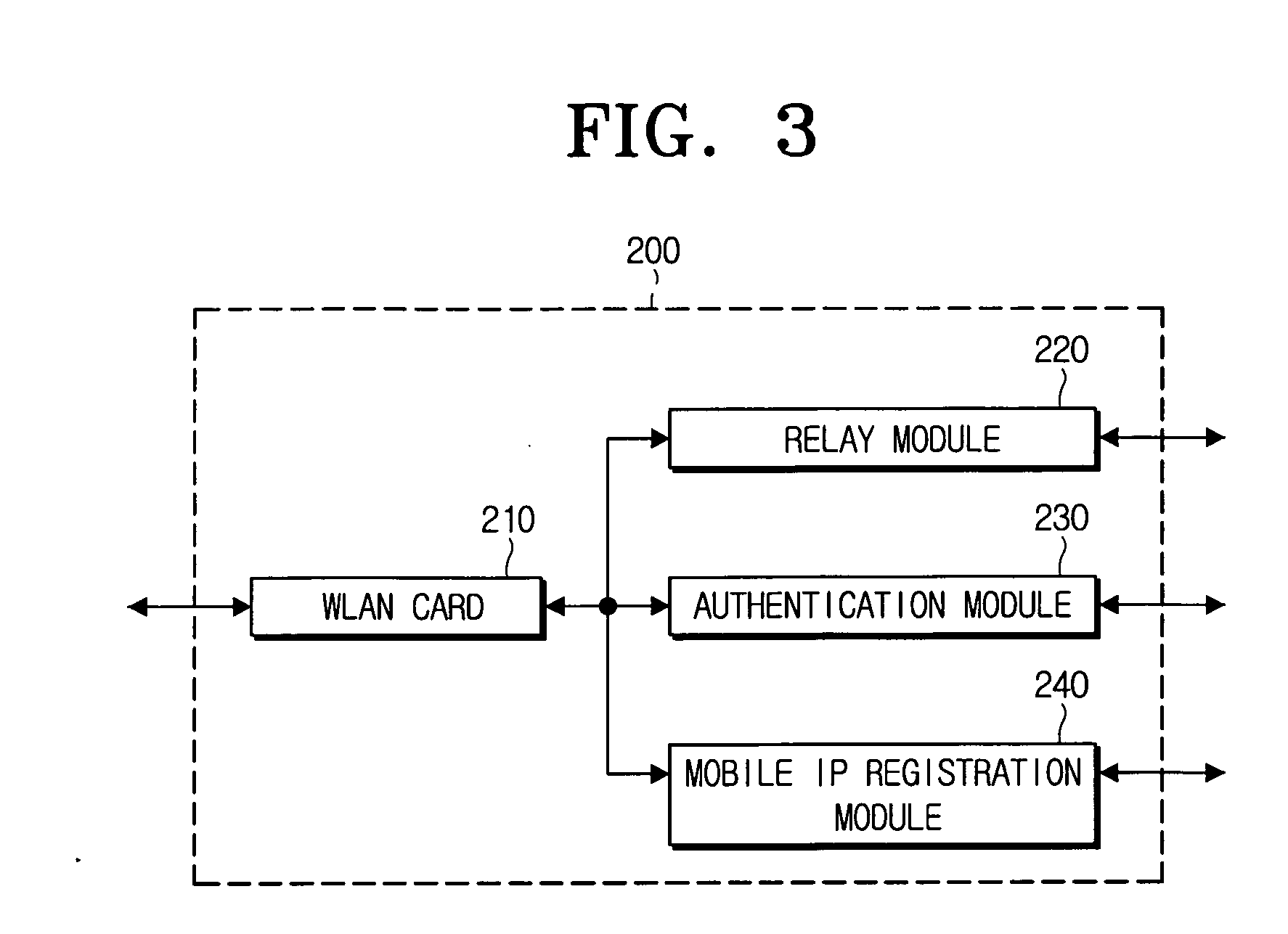
Method for fast handover
ActiveUS20060146752A1Handoff time of be minimizeFaster handoverError preventionFrequency-division multiplex detailsWireless securityCare-of address
Disclosed is a method for fast handover in a wireless security data communication environment. The fast handover method for a mobile node connected to a network via an access point to perform a data communication in a wireless communication environment according to the present invention includes: performing an authentication while communicating with an authentication server having registration information about the mobile node via an uncontrolled port of the access point so as to make the mobile node connected to the network; performing a mobile Internet Protocol (IP) registration for binding a Care-of-Address (CoA) to a home agent and a correspondent node (CN) via the access point in parallel with performing the authentication; and opening a control port of the access point and relaying data transceived at the mobile node using the CoA when the authentication and the registration being successfully completed. Accordingly, a fast handover of the mobile node can be supported.
Owner:SAMSUNG ELECTRONICS CO LTD
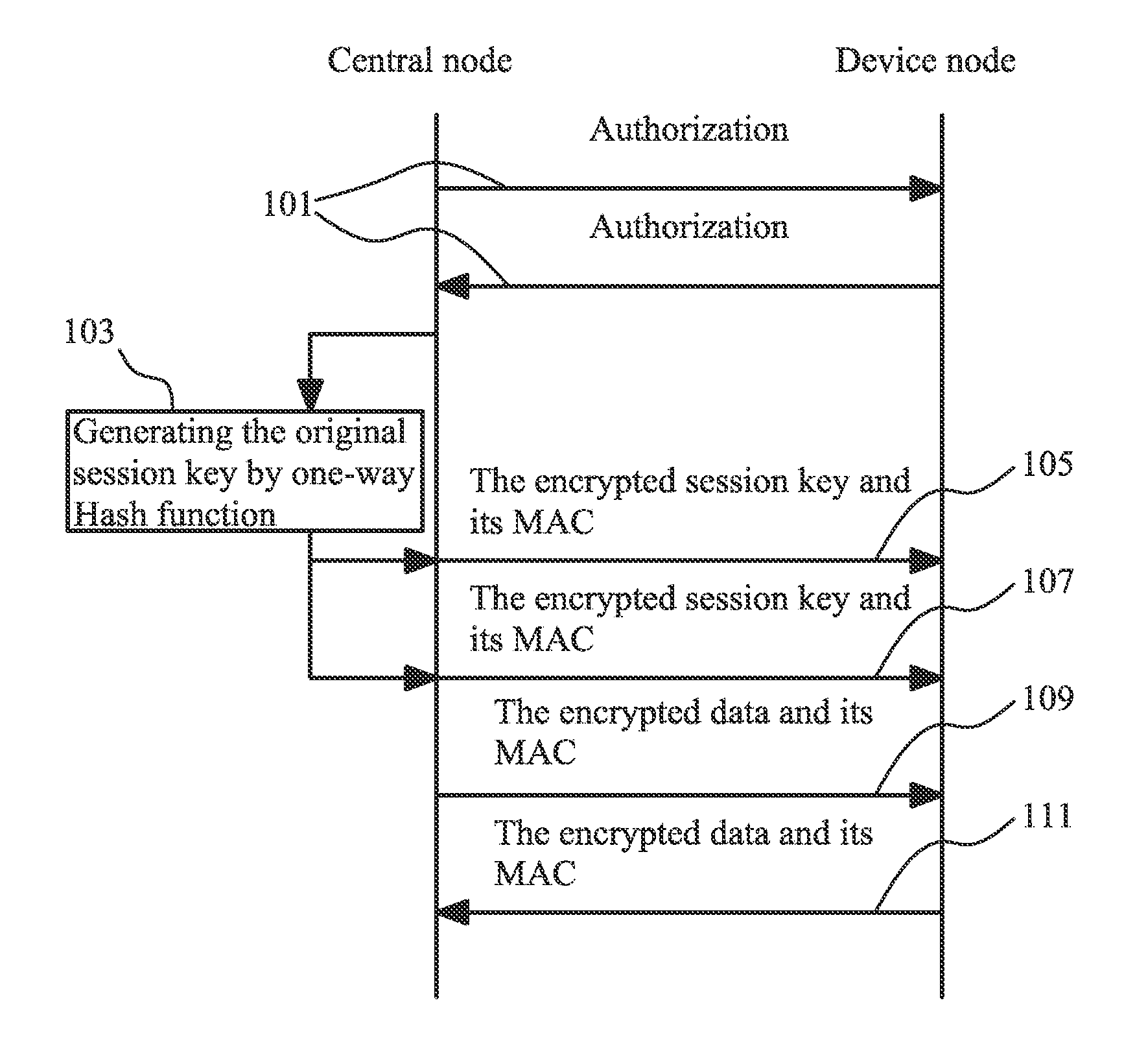
Method for secure data transmission in wireless sensor network
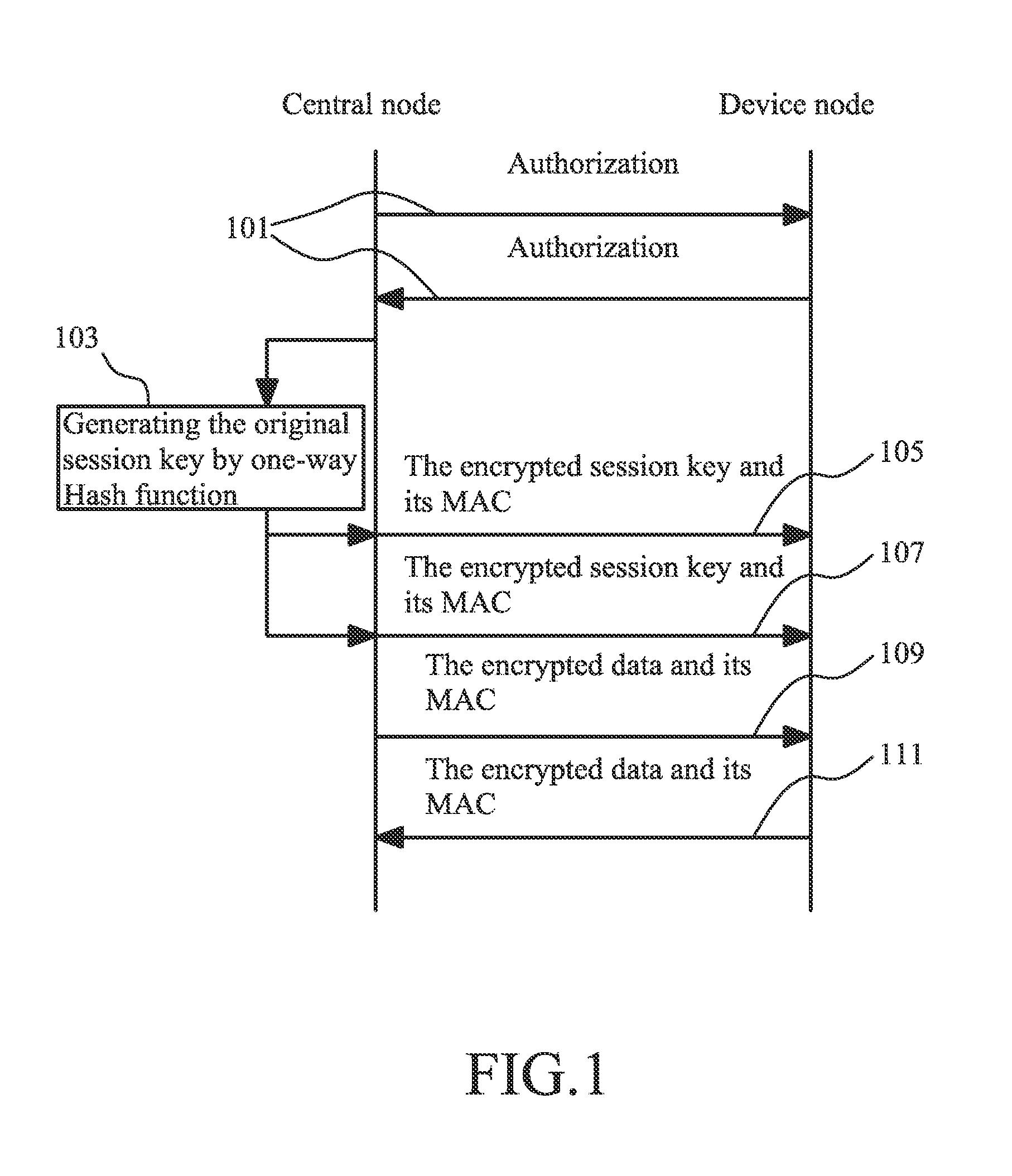
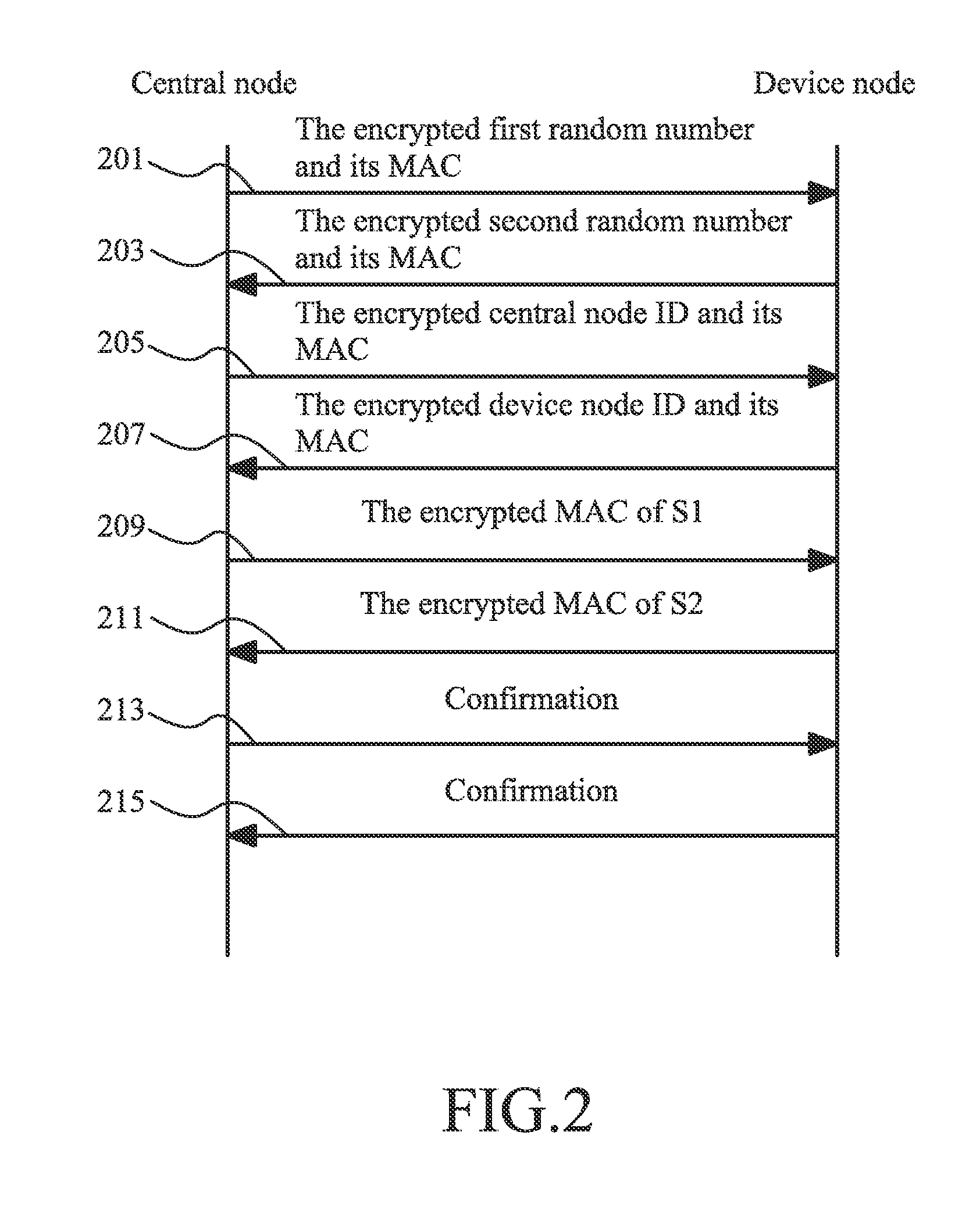
InactiveUS20100293379A1Data security be ensureEnsure data securityKey distribution for secure communicationUser identity/authority verificationData transmissionData validation
A method for secure data transmission in wireless sensor network includes that: the network user determines a master key and inputs it into a central node and a device node; after the central node and the device node have authorized each other, the central node generates a new session key and sends it to the device node; while the central node and the device node communicate with each other, the data sending party uses the new session key to encrypt the data for transmission and verify the integrity of the data, and the data receiving party uses the session key to decrypt the data and verify the integrity of the data. The advantages of the present invention are that: the consumption of computation resource and the communication overhead are greatly reduced without affecting the security performance of the network, the problem of the authorization between the central node and the device node is solved, and the method for generating, transmitting and updating the key realizes the encryption of the data for transmission and the verification of the data integrity, and thus it ensures the security of the data transmission in wireless sensor network.
Owner:BEIJING YUDONG TECH DEV
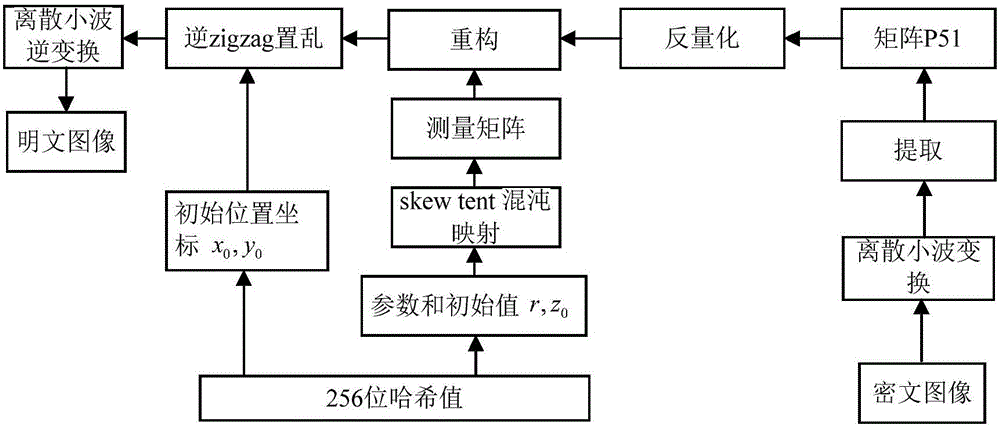
Image encryption method and image decryption method with visual security and data security based on compressed sensing
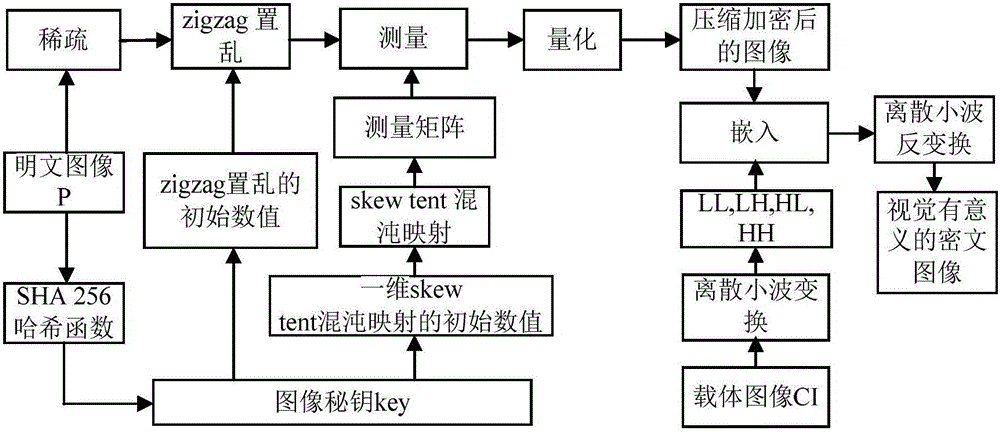
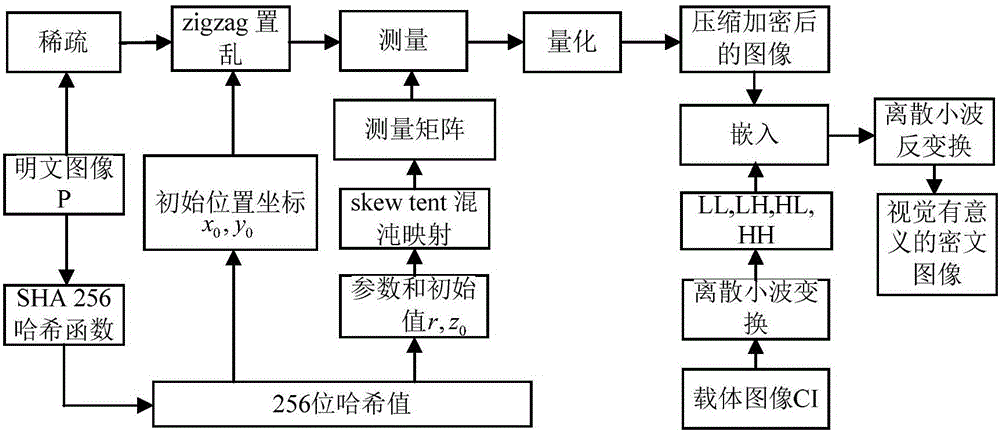
ActiveCN106600518AIncrease spaceEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackHash function
The invention relates to an image encryption method and an image decryption method with visual security and data security based on compressed sensing. The image encryption method comprises the steps of: firstly, utilizing an SHA 256 hash function to obtain a 256-bit hash value of a plaintext image as an image secret key, and calculating initial numerical values of one-dimensional skew tent chaotic mapping and zigzag scrambling; carrying out sparse processing on the plaintext image, and carrying out zigzag scrambling on a coefficient matrix; and then utilizing the one-dimensional skew tent chaotic mapping to generate a measurement matrix, measuring and quantifying a scrambling matrix to obtain a compressed and encrypted image, and embedding the image into a carrier image with visual significance to obtain a final ciphertext image with visual significance. The image encryption method realizes the visual security and data security of the plaintext image, has large secret key space, is highly sensitive to plaintext, has higher capacity of resisting brute-force attack, chosen-plaintext attack and known-plaintext attack, does not need an additional storage space, and can transmit and store the ciphertext image quickly and effectively.
Owner:HENAN UNIVERSITY
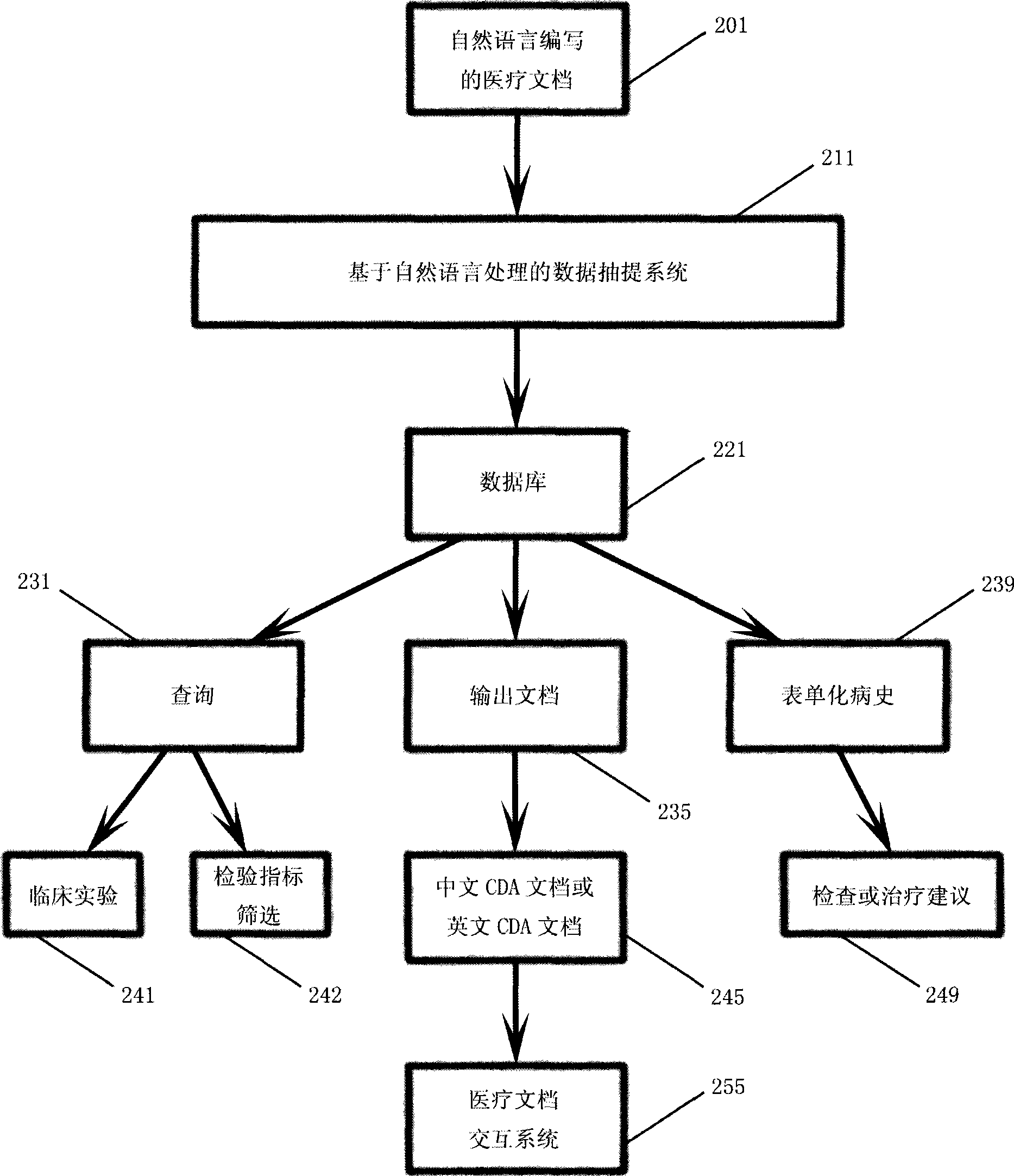
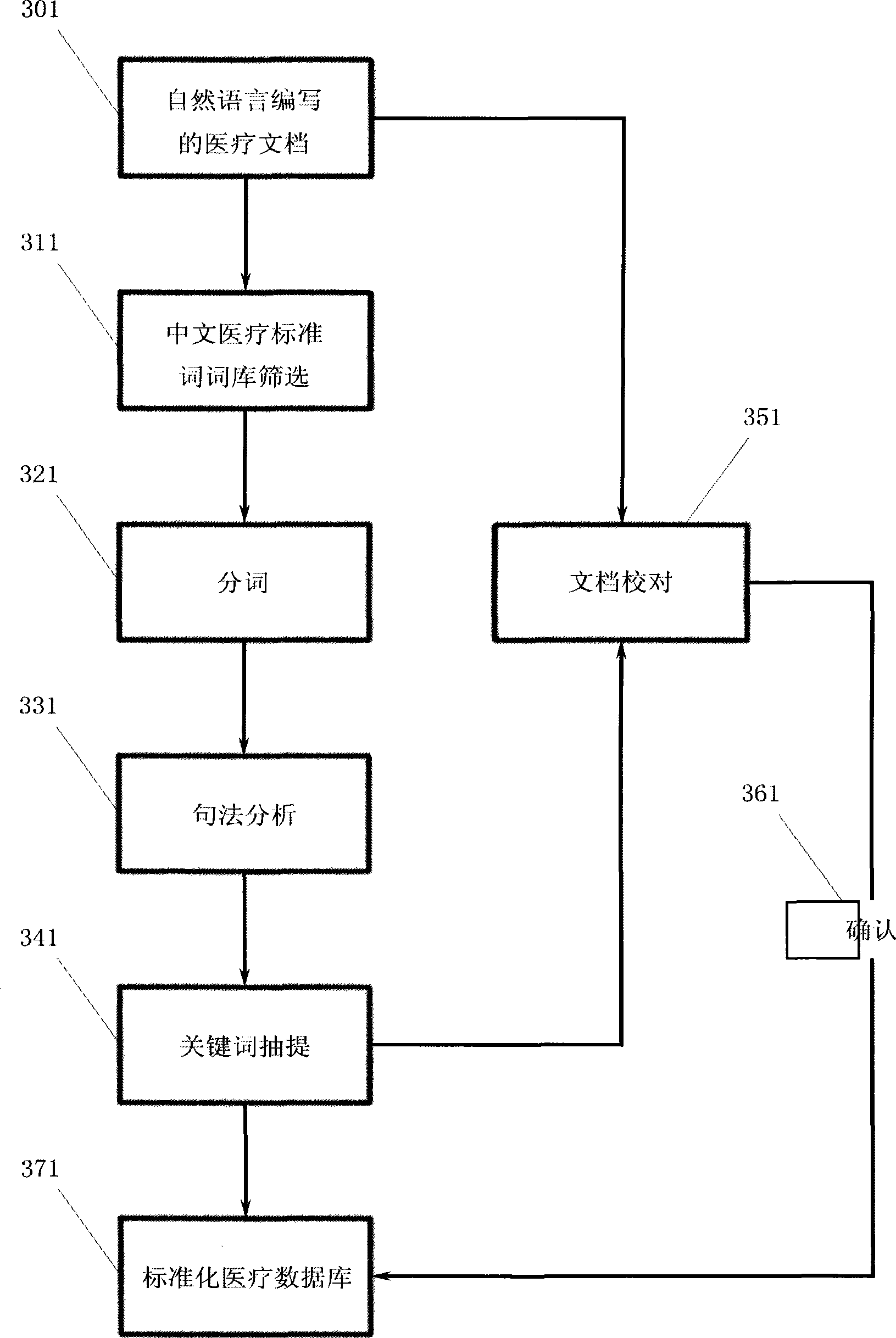
Information abstracting and format conversion system of medical document based on natural language compile
InactiveCN101441686AMeet the needs of communicationEnsure data securitySpecial data processing applicationsMedical recordDocument preparation
The invention provides a device for automatically formatting and unionizing medical documents written in natural language. The device comprises medical documents which are based on electric case history systems used in Chinese hospitals and written in the natural language, a Chinese medical standard word library which is classified according to disease type, a natural language analysis based data pick-up system which is used for converting the documents written in the natural language into the standard formatting document, a database which is classified according to the disease type and used for clinical scientific research, a document conversion system used for automatically converting the formatting document into the standard document with consolidation form, and a privilege system used for protecting private information of patients and doctors treating the patients. The device has the advantages of realizing automatization of the medical information management, making the doctors conveniently and quickly look up information related to certain disease, greatly saving time and making the doctors have more energy to be put in the disease research.
Owner:ZHONGSHAN HOSPITAL FUDAN UNIV +1
Petrochemical engineering equipment supervision information management system
InactiveCN106503927AOptimize workflowReduce management costsOffice automationResourcesWeb servicePetrochemical
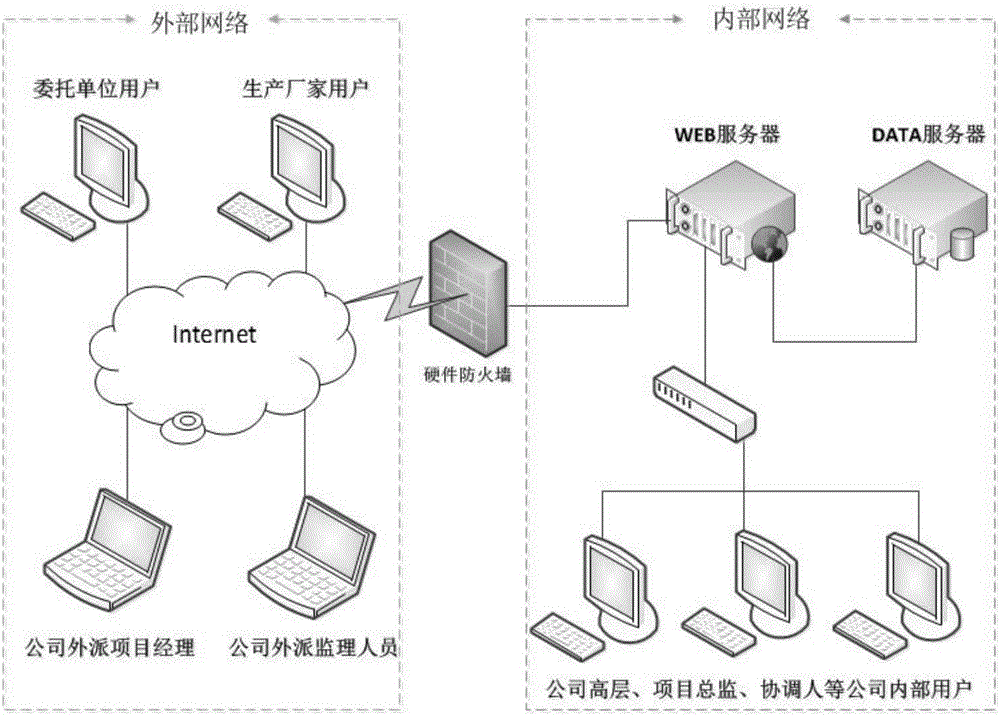
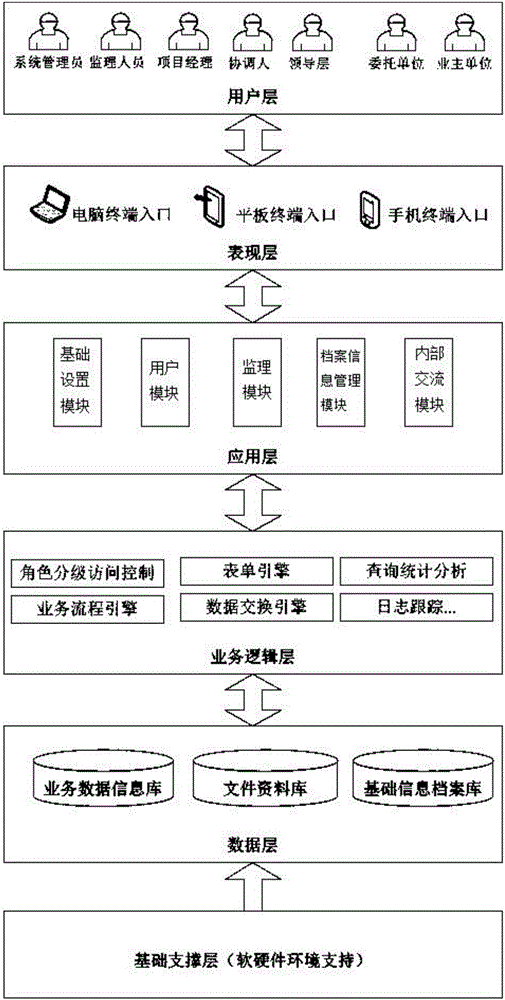
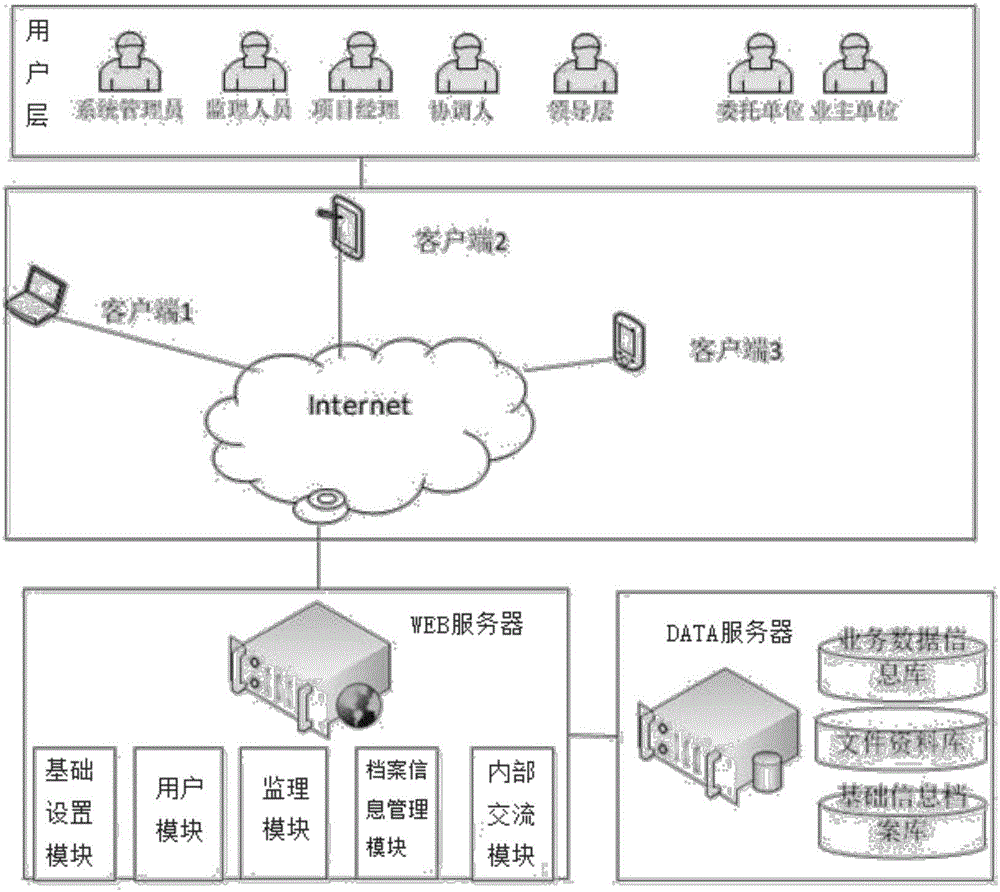
The invention relates to a petrochemical engineering equipment supervision information management system. The system comprises an external network subsystem and an internal network subsystem which are connected through a hardware firewall; the external network subsystem comprises an external network terminal which accesses the system through Internet; a WEB server and a DATA server are erected in the internal network subsystem; the DATA server stores data-layer data, the WEB server is in communication connection with the hardware firewall and a switch, and the switch is in communication connection with an internal network terminal for performing internal communication; the system employs a six-layer architecture which successively comprises a basic support layer, a data layer, a service logic layer, an application layer, a presentation layer and a user layer from the bottom layer to the top layer; and the application layer provides application service for the presentation layer and is internally integrated with various function modules including a user module, a supervision module, a basic setting module, an archive information management module and an internal exchange module. The system provided by the invention integrates an enterprise OA system and supervision service into one platform, supports multi-terminal registration, optimizes the work flow, decreases the management cost and improves the work efficiency.
Owner:南京三方化工设备监理有限公司
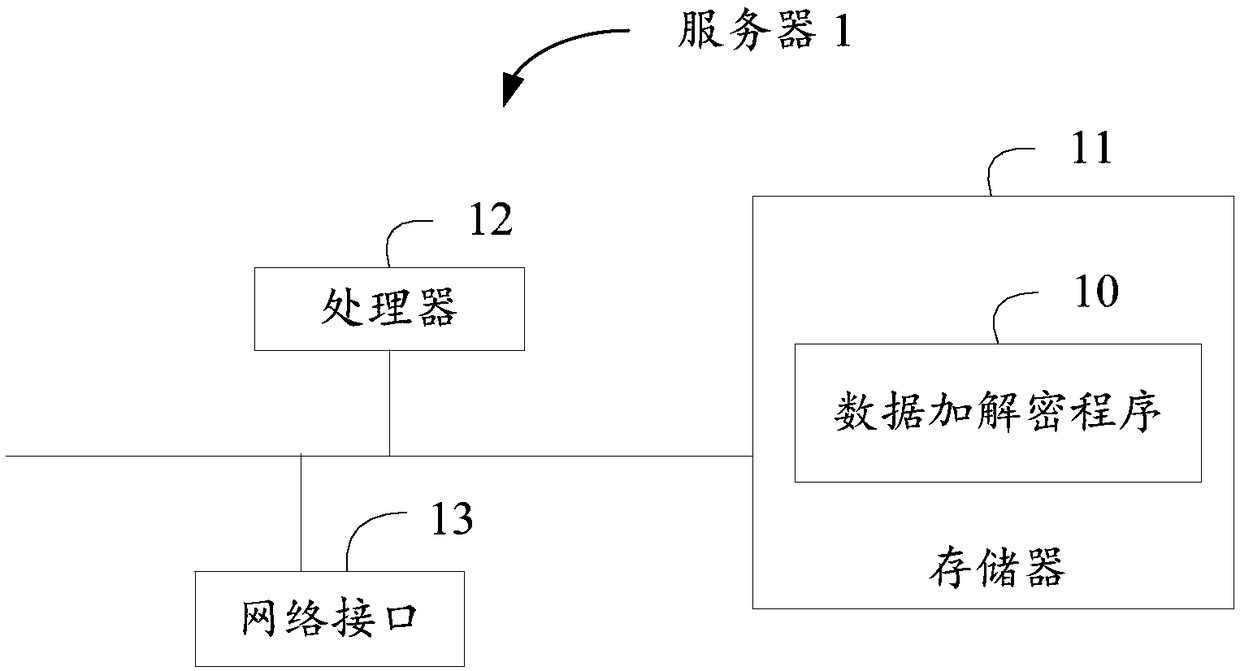
Data encryption and decryption method, server and storage medium
ActiveCN109474423AImprove securityEnsure data securityKey distribution for secure communicationCiphertextPassword
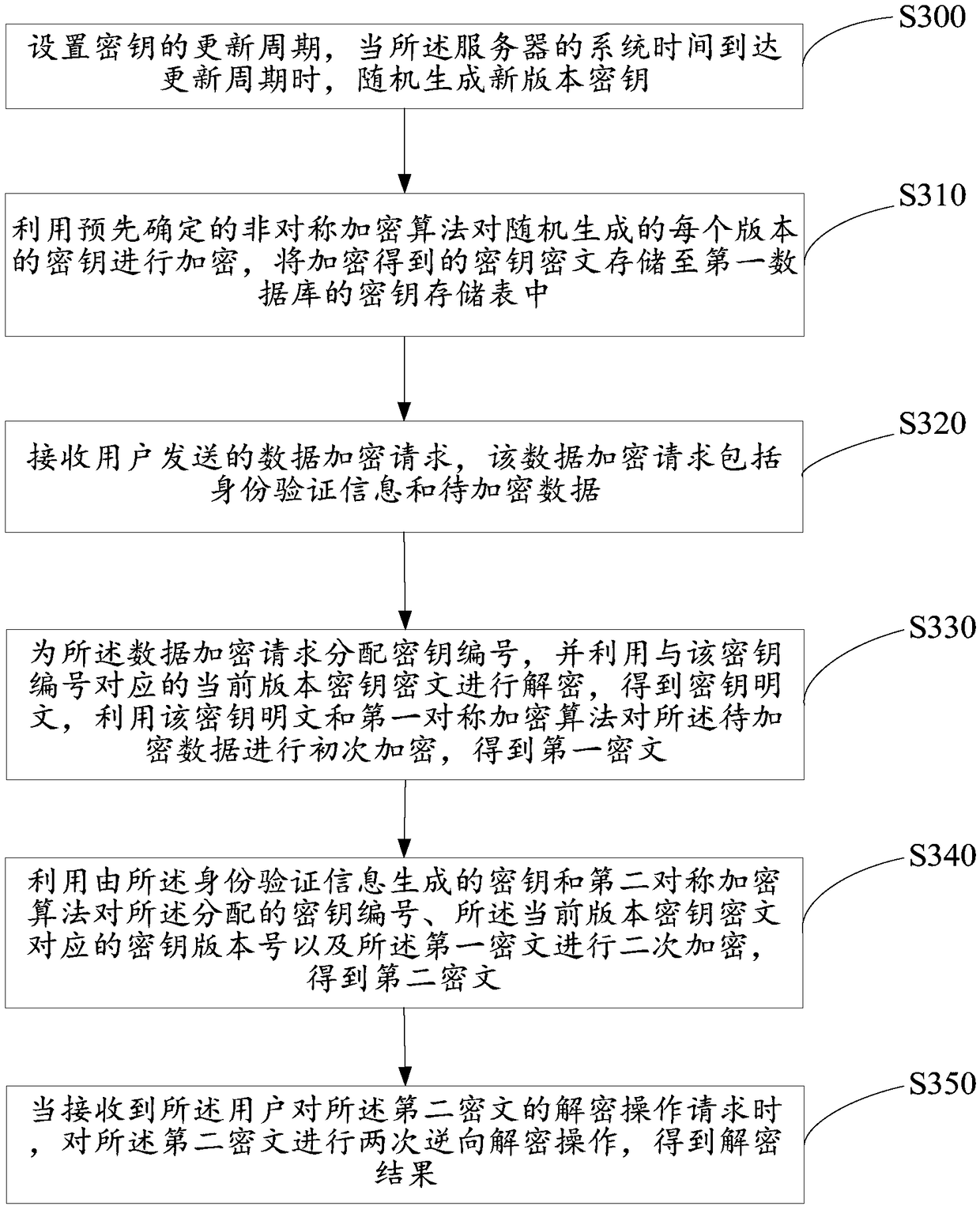
The invention relates to a password technology, and provides a data encryption and decryption method, a server and a storage medium. The method comprises the steps of setting an update period of a key, and generating and storing multi-version keys; receiving a data encryption request, including identity authentication information and data to be encrypted, sent by the user; distributing a key number for the data encryption request, and primarily symmetrically encrypting the data to be encrypted by using a current-version key corresponding to the key number, to acquire a first ciphertext; secondarily symmetrically encrypting the key number, the key version number of the current-version key and the first ciphertext by using the identity authentication information, to acquire a second ciphertext; and receiving a data decryption request sent by the user, and performing an inverse decryption operation on the second ciphertext, to acquire a decryption result. By using the method, server and medium provided by the invention, the key can be periodically updated, and the key security is enhanced.
Owner:PING AN TECH (SHENZHEN) CO LTD
Data sharing method and system under cloud computing environment
ActiveCN103457733AImprove securityReduce duplicationUser identity/authority verificationData ingestionCiphertext
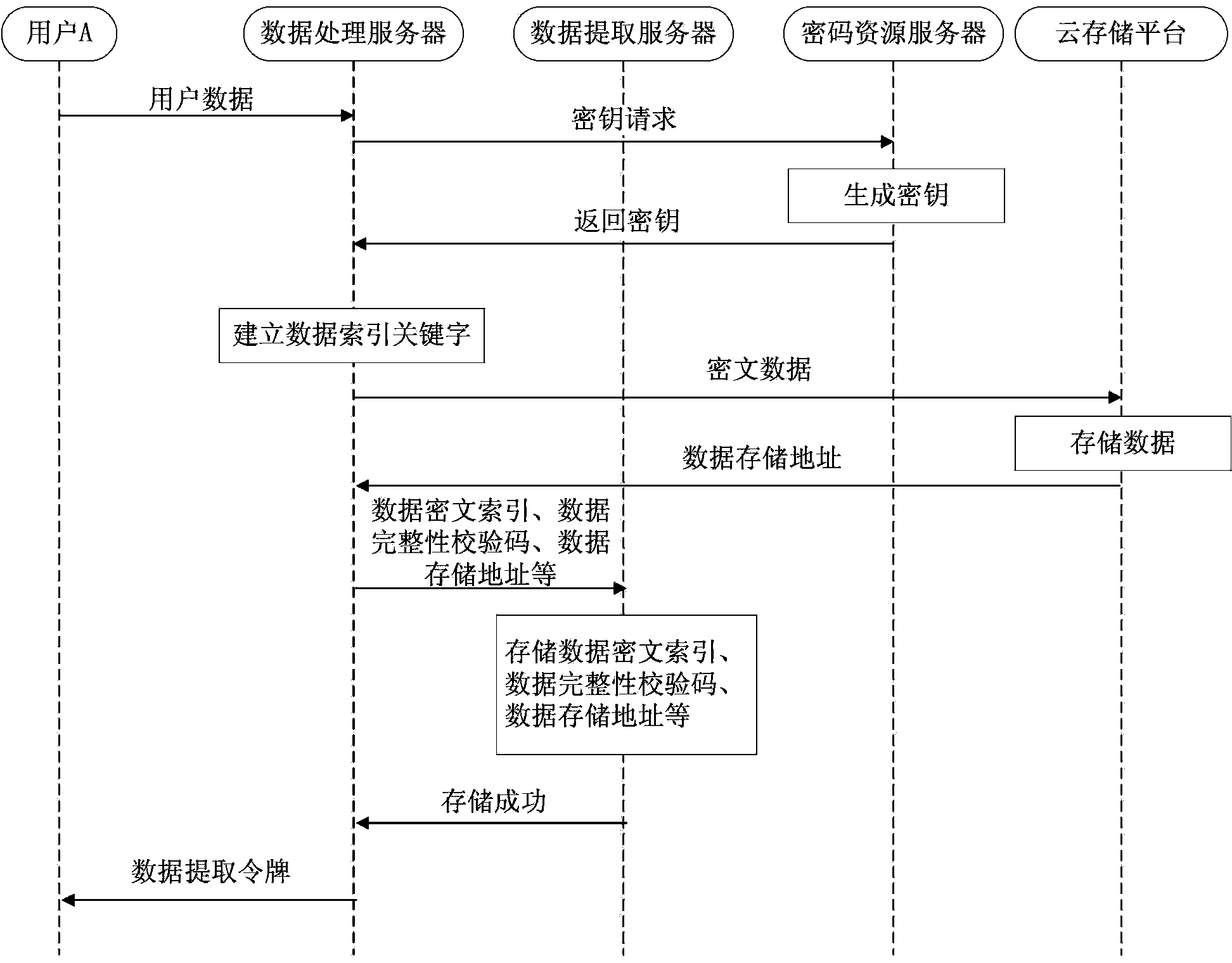
The invention relates to a data sharing method and system under the cloud computing environment. The method comprises the user data encryption storage step and the user data extraction step. The user data encryption storage step comprises the particular steps that a data processing server sets up data index keyword information for user data and generates a matched data ciphertext index and a matched data extraction token, the user data are stored in a cloud storage platform after being encrypted, the data ciphertext index and a data storage address are stored in a data extraction server, and the data extraction token is transmitted to a user. The user data extraction step comprises the particular steps that after receiving the data extraction token, the data extraction server verifies the legality of the data extraction token, extracts data from the cloud storage platform according to the data storage address, and the data are returned to the user by the data extraction server after being decrypted by the data processing server. According to the data sharing method and system, the data storage safety under the cloud computing environment is ensured, and meanwhile the problem of user data sharing is conveniently solved.
Owner:CEC CYBERSPACE GREAT WALL
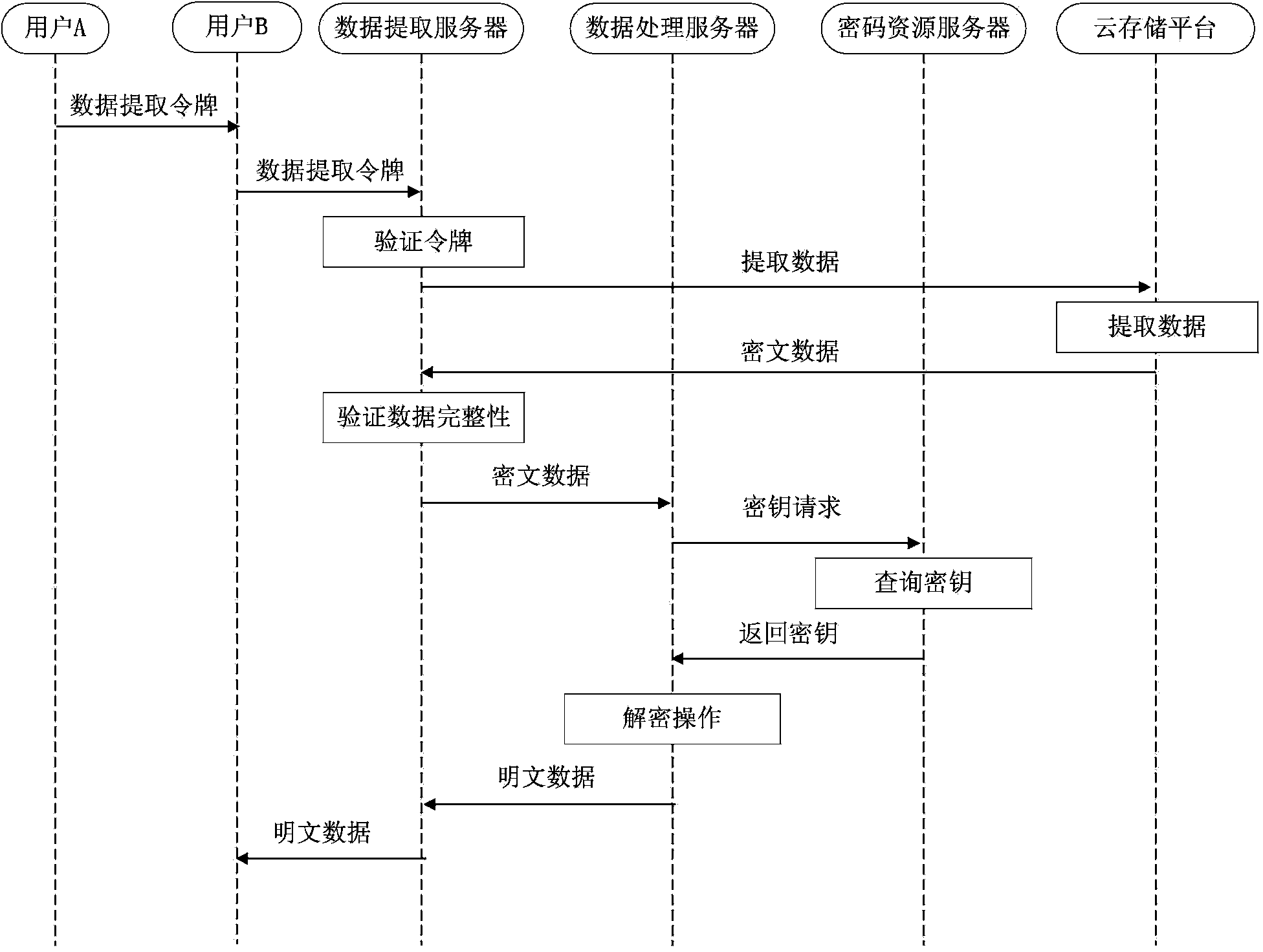
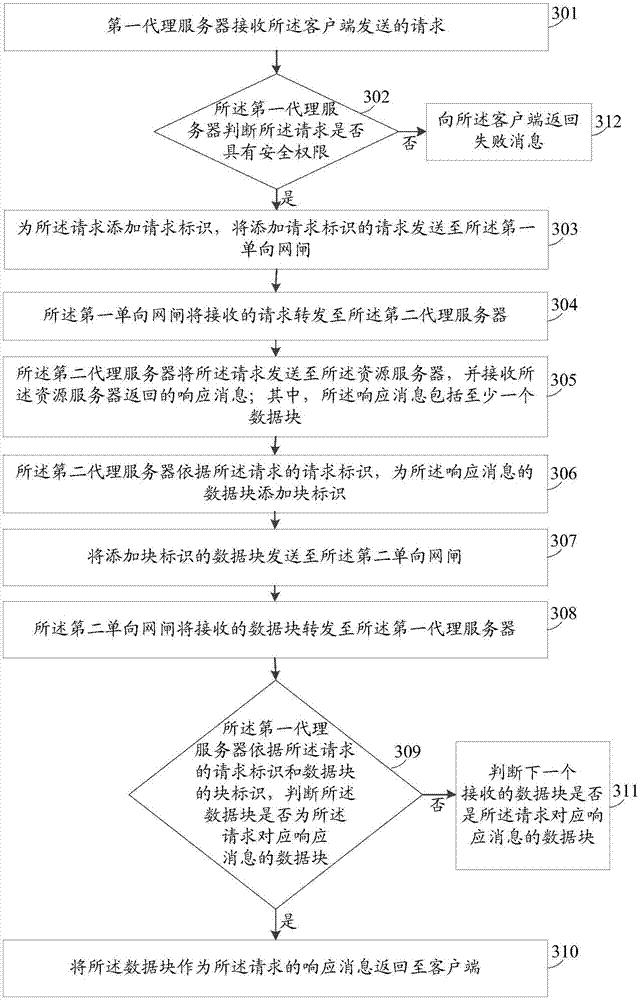
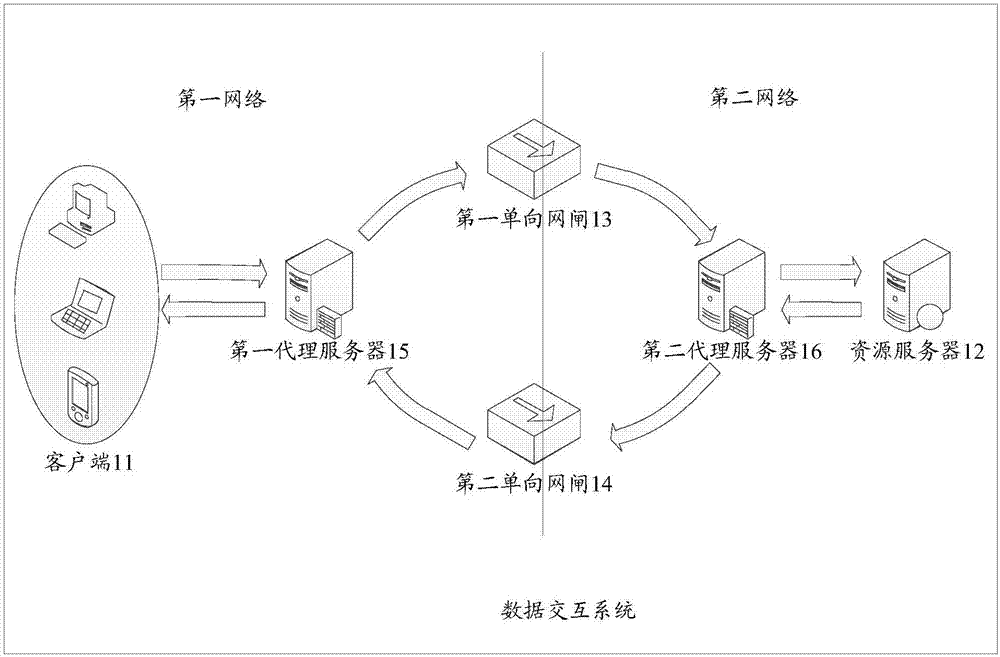
Data interaction method and system
The embodiment of the invention provides a data interaction method and system. The system includes a first unidirectional gatekeeper, a second unidirectional gatekeeper, a first proxy server, a second proxy server, a resource server, and a client. The first proxy server and the client are both located in a first network. The second proxy server and the resource server are both located in a second network. The first network is physically isolated from the second network. The first proxy server is configured to receive a request sent by the client, to send the request to the second proxy server via the first unidirectional gatekeeper, and to send a response message to the client. The second proxy server is configured to send the request to the resource server and to receive a response message returned from the resource server, and to send the response message to the first proxy server via the second unidirectional gatekeeper. Because the unidirectional gatekeepers transmit data unidirectionally, the first network and the second network are safely isolated, thereby ensuring the data security of the first network during data interaction.
Owner:北京明朝万达科技股份有限公司
Key management system and method for bank terminal security equipment
InactiveCN101877157AImprove development efficiencySave human resourcesComplete banking machinesMultiple keys/algorithms usageComputer terminalManagement system
The invention relates to a key management system and a key management method for bank terminal security equipment. The system comprises a bank service terminal and a bank service background; the bank service terminal comprises the bank terminal security equipment and a key management agent component; and the bank service background comprises a KMC, a key database, an encoder and a service application system server, wherein the key management agent component is used for acquiring a working key from the KMC and writing the working key into the bank terminal security equipment; and the KMC provides registration service, key transmitting service and automatic key update service for the bank terminal security equipment. The key management system and the key management method for the bank terminal security equipment can effectively realize key management of the bank terminal security equipment, and separate the key management from a bank service application system at the same time so that each service application system does not need to implement complex key management logics any more and the implementing complexity of the service application system is reduced.
Owner:戴宇星
Method for data security transmission and key exchange
ActiveCN103618607ASimple and efficient operationIncreased security levelUser identity/authority verificationData securityAuthorization
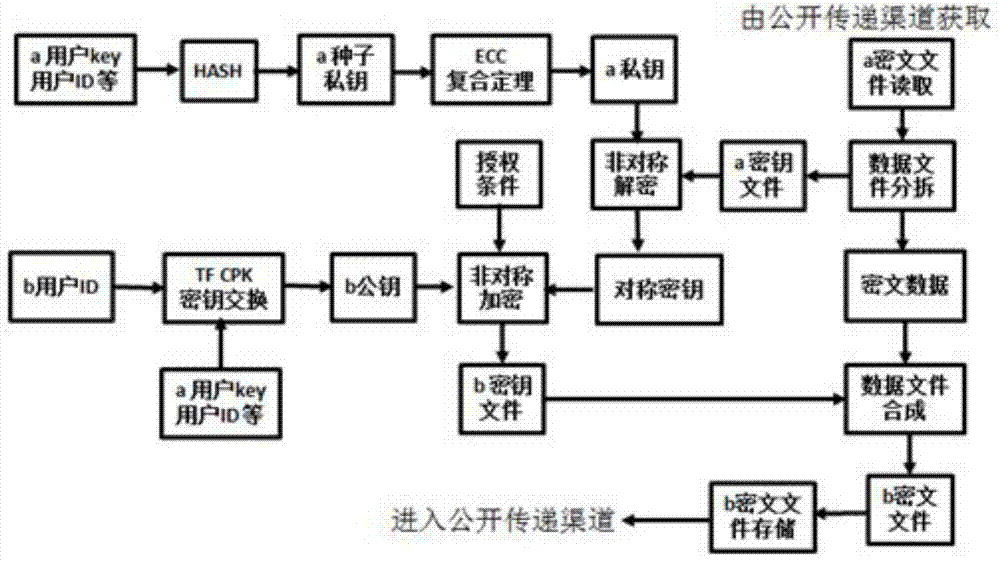
The invention provides a method for data security transmission and key exchange and relates to the technical field of information security. The method solves the problems that in the prior art, due to the fact that a mobile storage device is used for transmitting data, a file is divulged; when the data are transmitted through the internet, online supporting by a third-party CA center is needed; when the data are transmitted through a special security hardware device, cost is high and compatibility is poor. The method comprises a cleartext file encryption process, a decryption authorization process and a ciphertext file decryption process. According to the method for data security transmission and key exchange, the technical scheme that a high-intensity symmetric encryption algorithm and an asymmetric cryptographic algorithm are combined is adopted, mark extraction can be conducted, a public key and private key pair is generated and extracted, a key file is synthesized into ciphertext data, and therefore a file can be formed. Meanwhile, a reversible process can also be achieved, wherein one file is divided into the key file and the ciphertext data, and therefore the method for data security transmission and key exchange is easy and convenient to operate and high in security level.
Owner:北京信长城科技发展有限公司
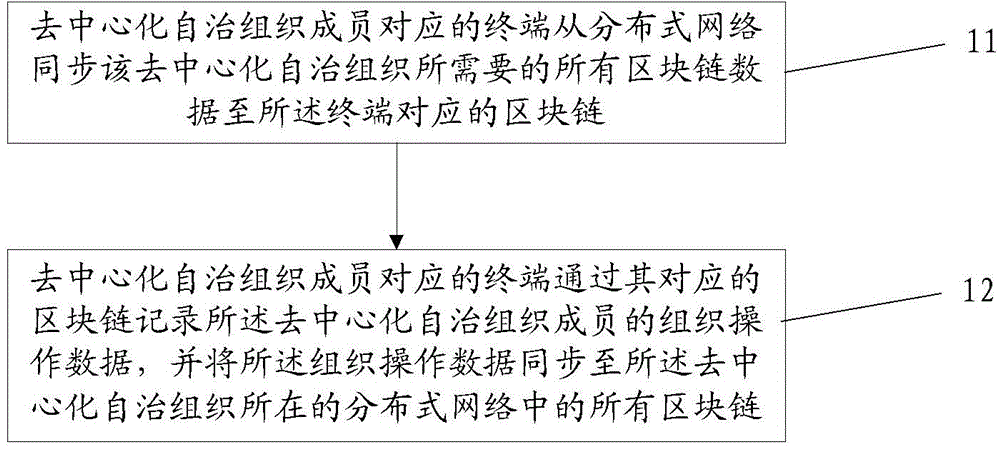
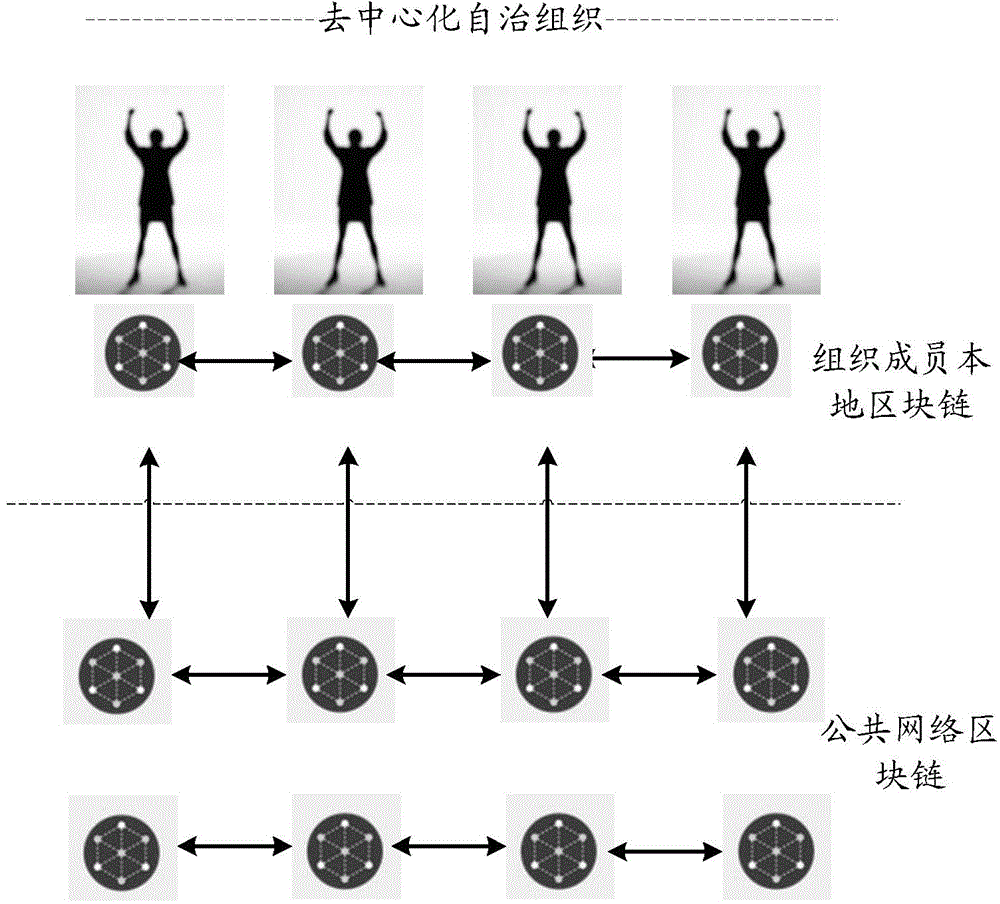
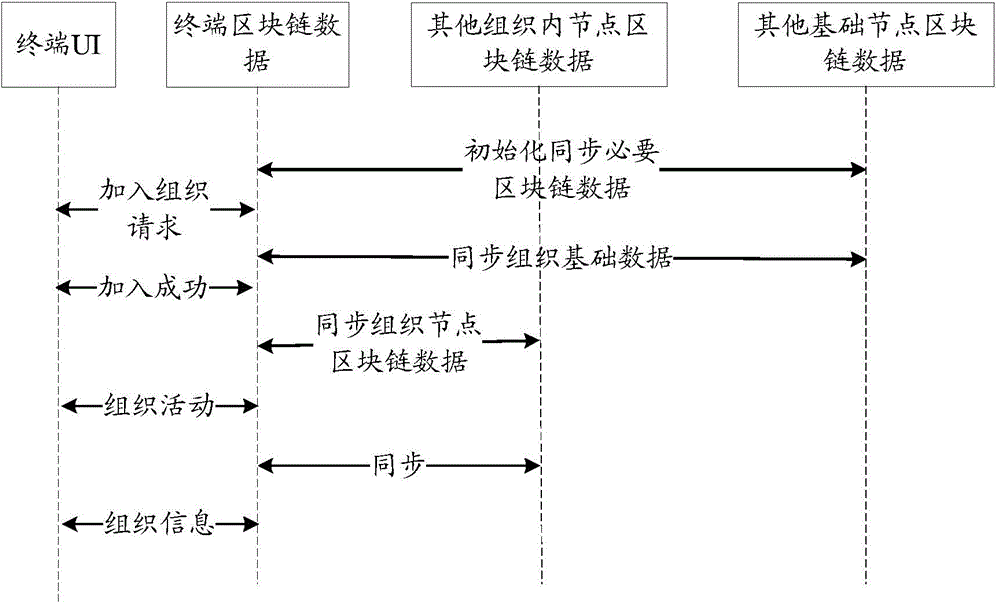
Method and system for data processing for decentralized autonomous organization
The invention discloses a method and a system for data processing for a decentralized autonomous organization, which are applied to a block chain-based distributed network. The method comprises steps: a terminal corresponding to the decentralized autonomous organization member synchronizes all block chain data needed by the decentralized autonomous organization to a block chain corresponding to the terminal from the distributed network; and the terminal corresponding to the decentralized autonomous organization member records organization operation data of the decentralized autonomous organization member through the corresponding block chain and synchronizes the organization operation data to all block chains in the distributed network where the decentralized autonomous organization is. The method and the system for data processing for the decentralized autonomous organization disclosed by the invention can solve problems of information storage security and data security existing in a centralized system architecture of a client / server in the prior art.
Owner:ZTE CORP
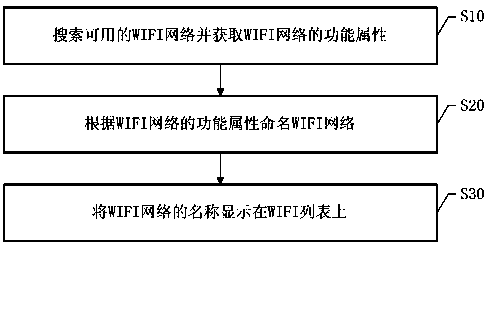
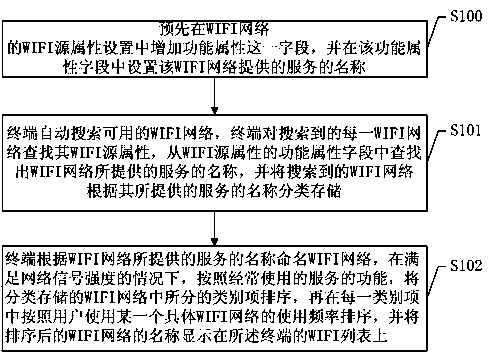
Method and system for displaying WIFI (wireless fidelity) names
InactiveCN103686941AEnsure data securityImprove securityAssess restrictionSubstation equipmentComputer networkWifi network
The invention discloses a method and a system for displaying WIFI (wireless fidelity) names. The method includes searching available WIFI networks and acquiring functional attributes of the WIFI networks; naming the WIFI networks according to the functional attributes of the WIFI networks; displaying the names of the WIFI networks on a WIFI list. By the method and the device for displaying the WIFI names according to user preferences, mobile terminals can have a new function of naming the WIFI networks according to the functional attributes of the WIFI networks; the method and the system have high convenience and safety and bring convenience to users.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
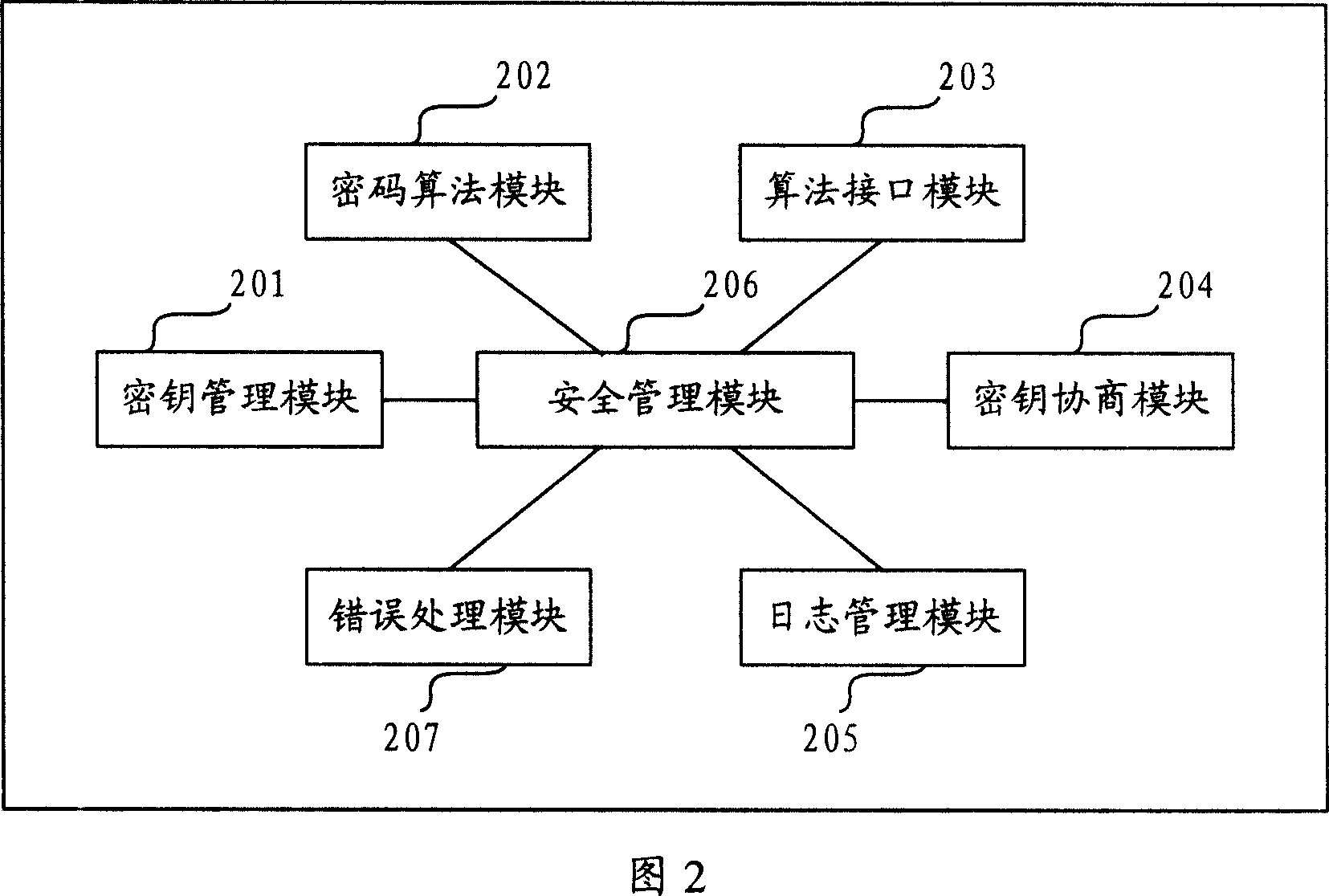
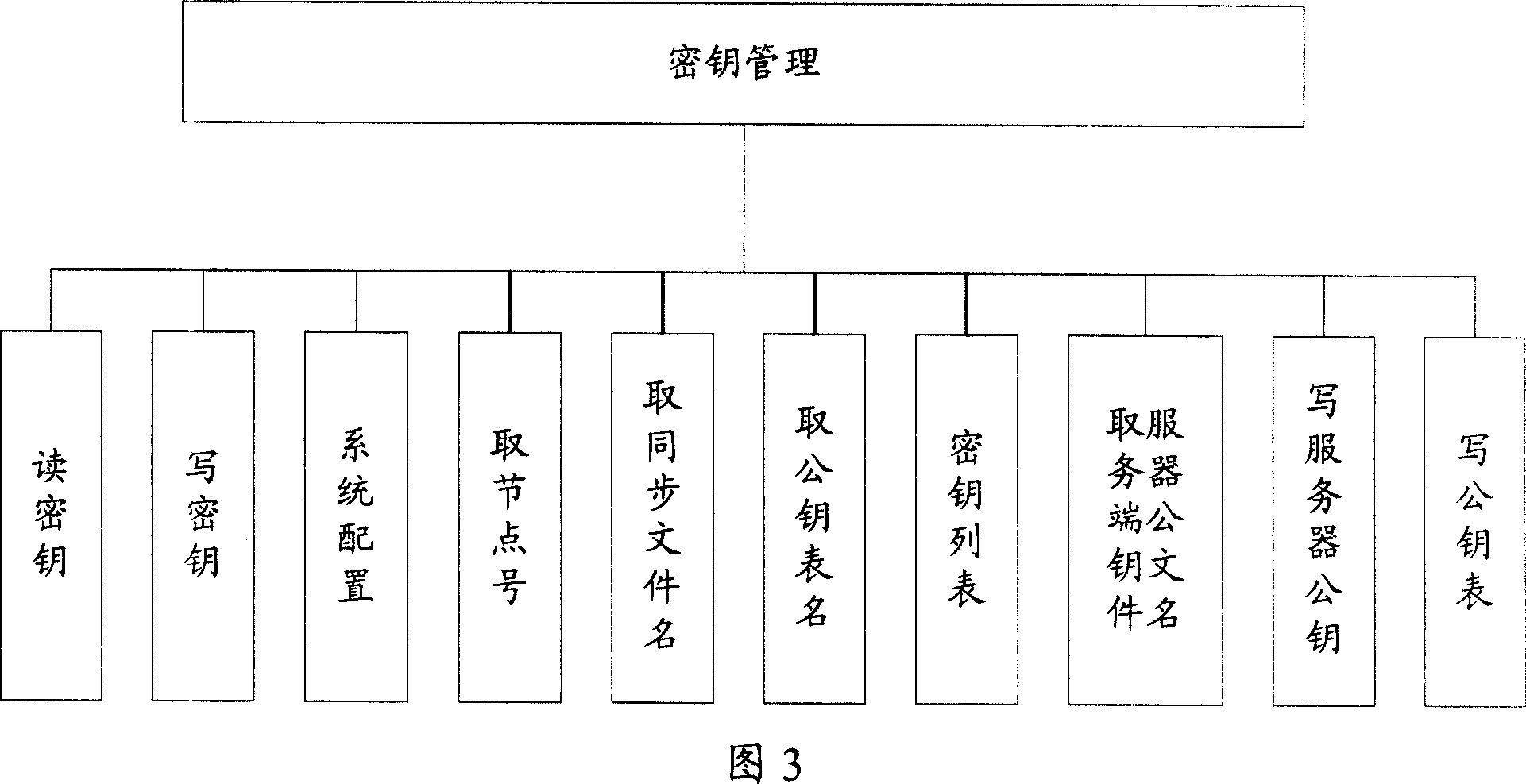
Information security control system
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
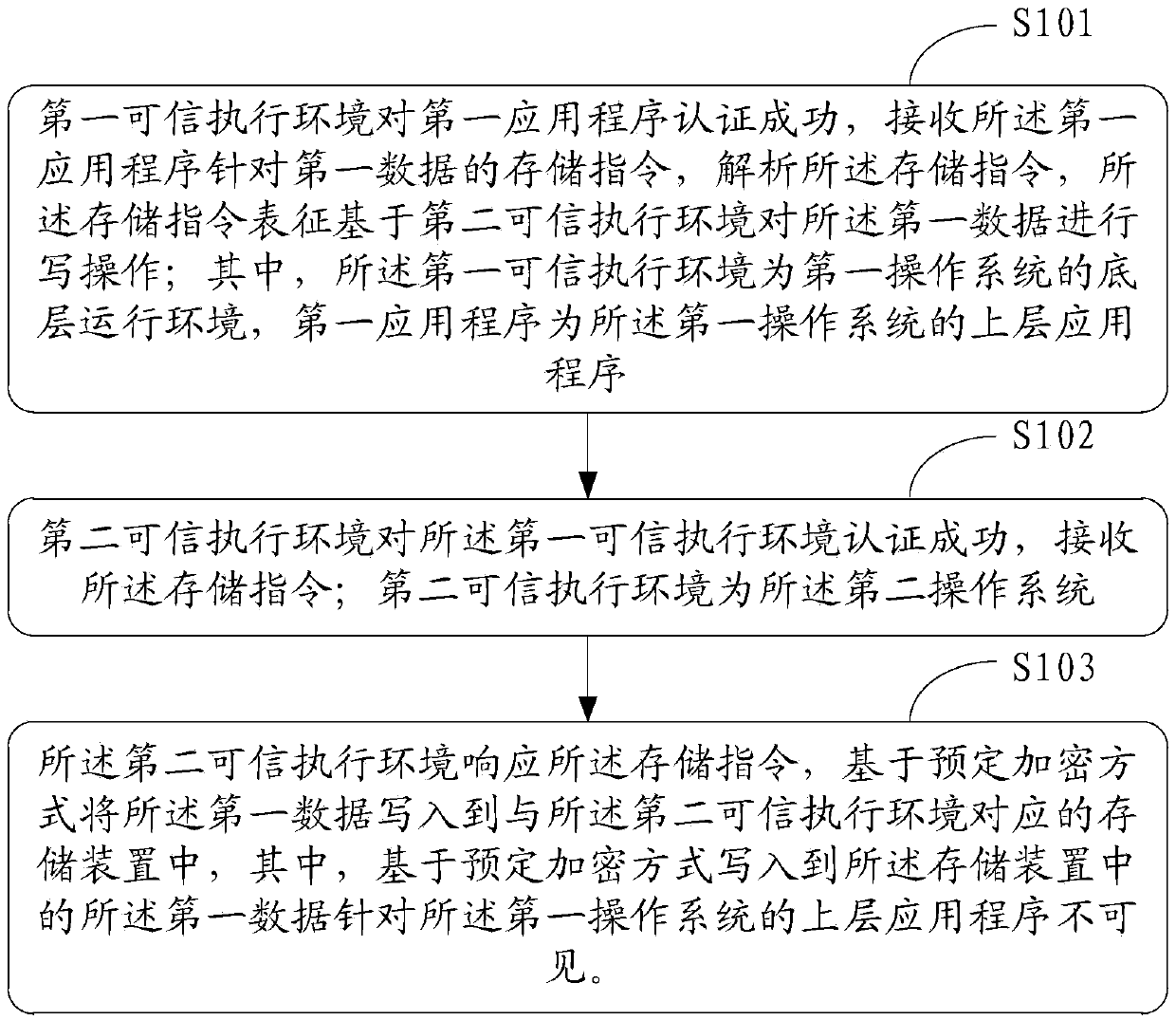
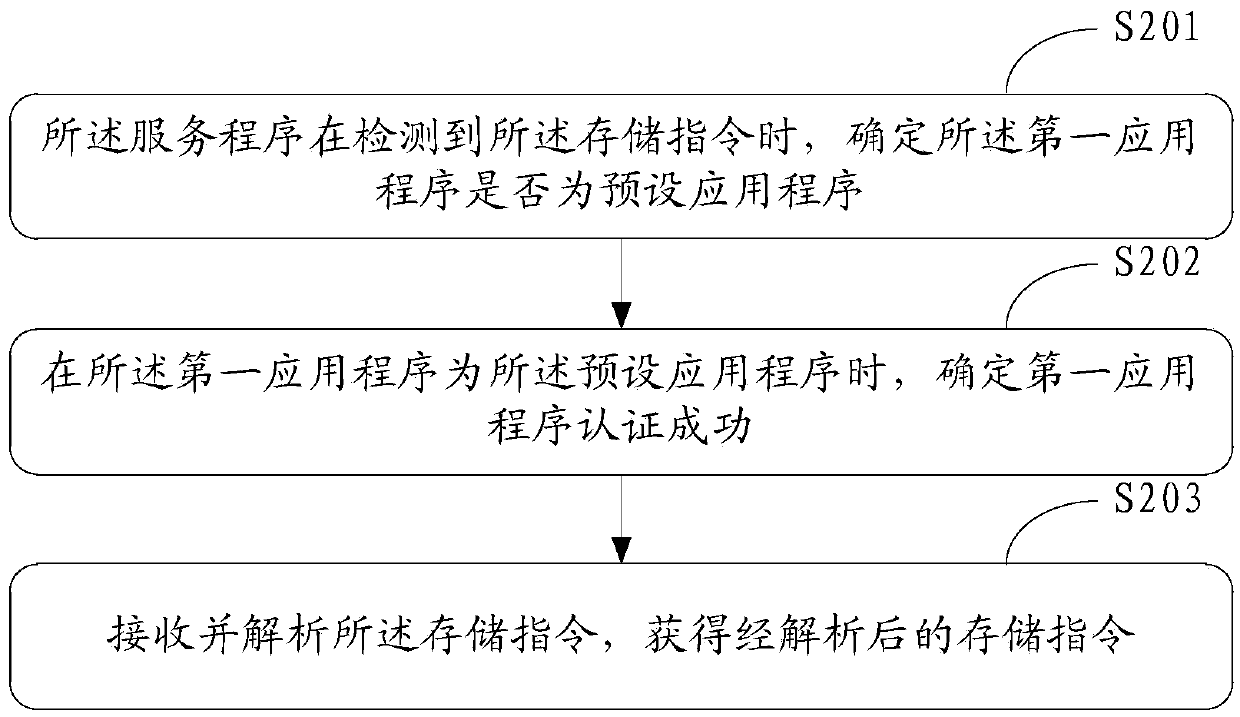
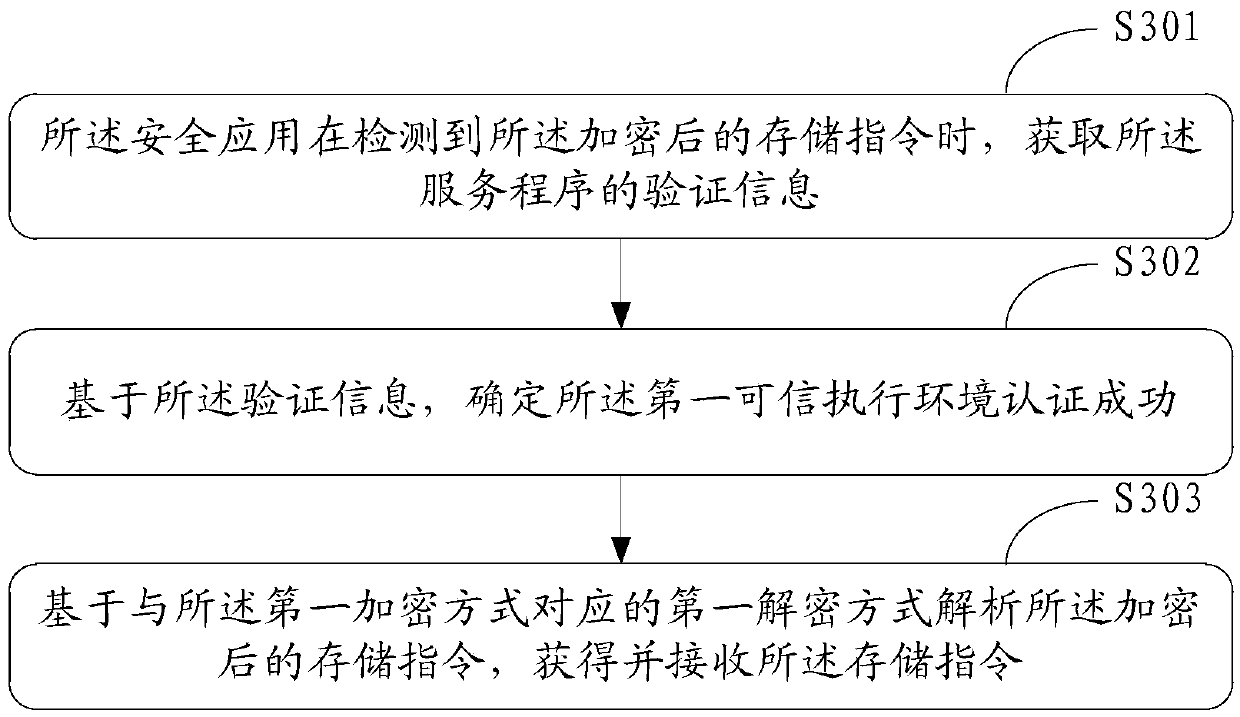
Method for secure storage of data and electronic equipment
InactiveCN105512576AEnsure communication securityEnsure safetyInternal/peripheral component protectionDigital data authenticationOperational systemApplication software
The invention discloses a method for secure storage of data and electronic equipment. The method comprises steps as follows: a first credible execution environment authenticates a first application successfully, receives a storage instruction of the first application for first data and analyzes the storage instruction, and the storage instruction represents to perform write operation on the first data on the basis of a second credible execution environment; the second credible execution environment authenticates the first credible execution environment successfully and receives the storage instruction; the second credible execution environment is a second operation system; the second credible execution environment responds to the storage instruction and writes the first data in a storage device corresponding to the second credible execution environment in a preset encryption mode, and the first data written in the storage device in the preset encryption mode are invisible to an upper-layer application of a first operation system.
Owner:LENOVO (BEIJING) CO LTD
A distributed big data computing engine and an architecture method
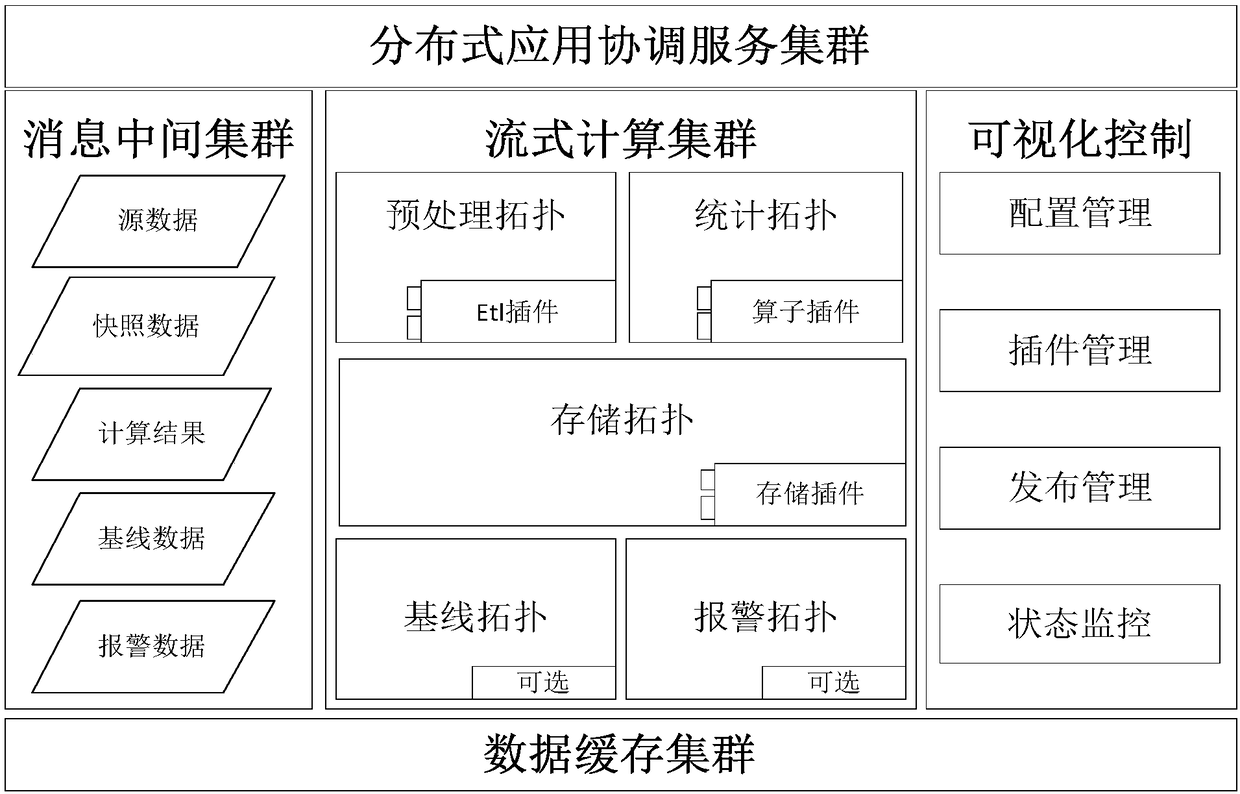
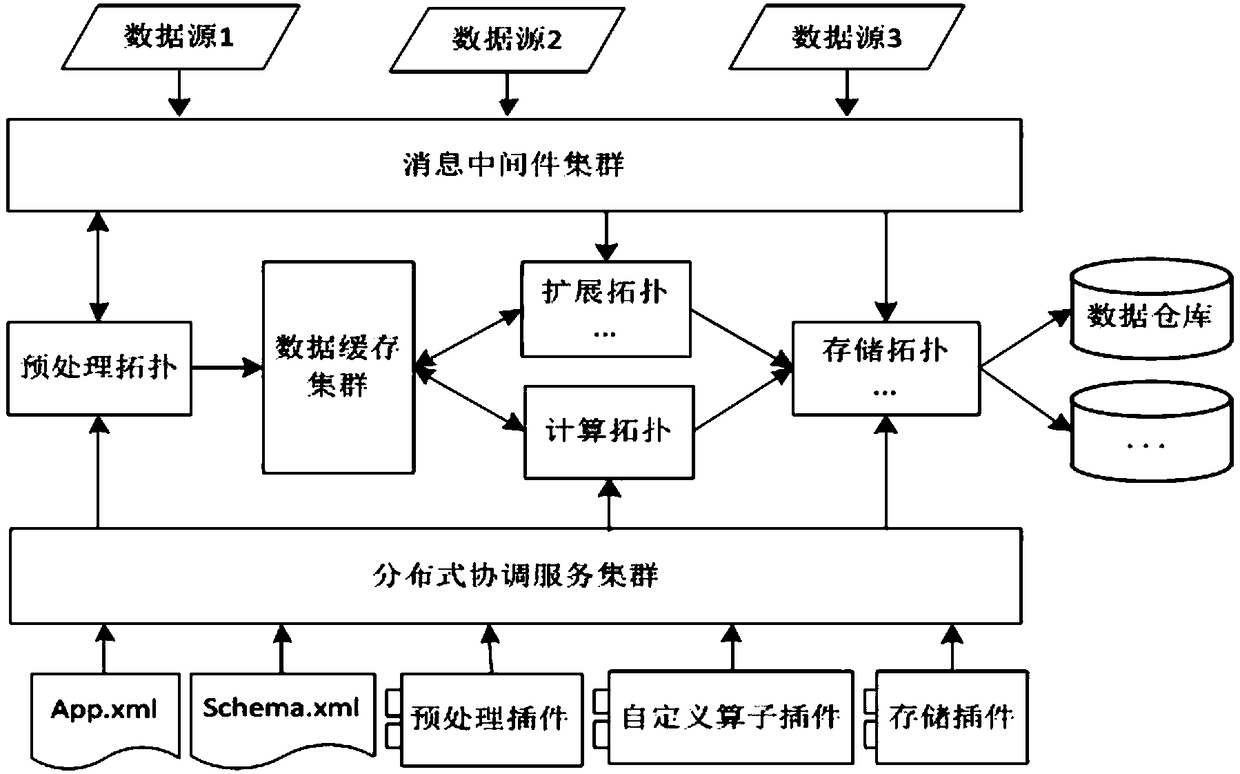
ActiveCN109189589AFunction increaseIncrease flexibilityInterprogram communicationTransmissionBaseline dataOriginal data
The invention discloses a distributed big data computing engine and an architecture method. The computing engine includes: a distributed coordination service cluster, which is used to provide coordination service for distributed applications, stores schema configuration files of related plug-ins and business database objects; a message intermediate cluster for transmitting different types of service data, the service data comprising raw data, calculation results, snapshot data, baseline data and alarm data; a streaming computing cluster, which is based on Storm bottom computing framework and is used to abstract the processing process of temporal index big data into several processes; a visual control module, which is used to display and manage the data through the way of web; a data cachecluster used to reduce the memory overhead of the streaming computing cluster in large-batch computing. The invention can help the enterprise with less accumulation of big data technology, or the project team with shortage of project cycle and manpower can realize online streaming processing of massive time series index data conveniently and quickly.
Owner:北京博睿宏远数据科技股份有限公司
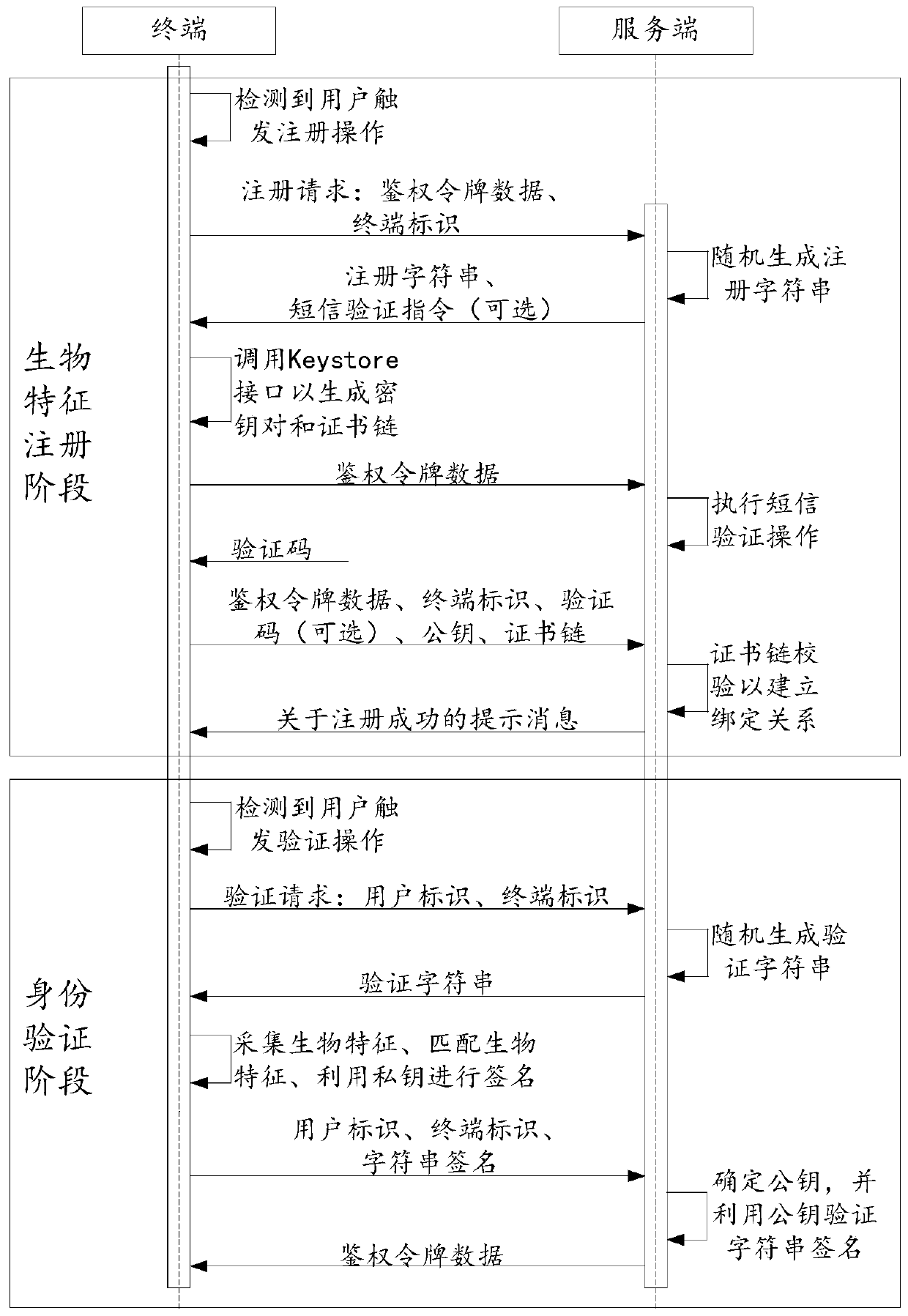
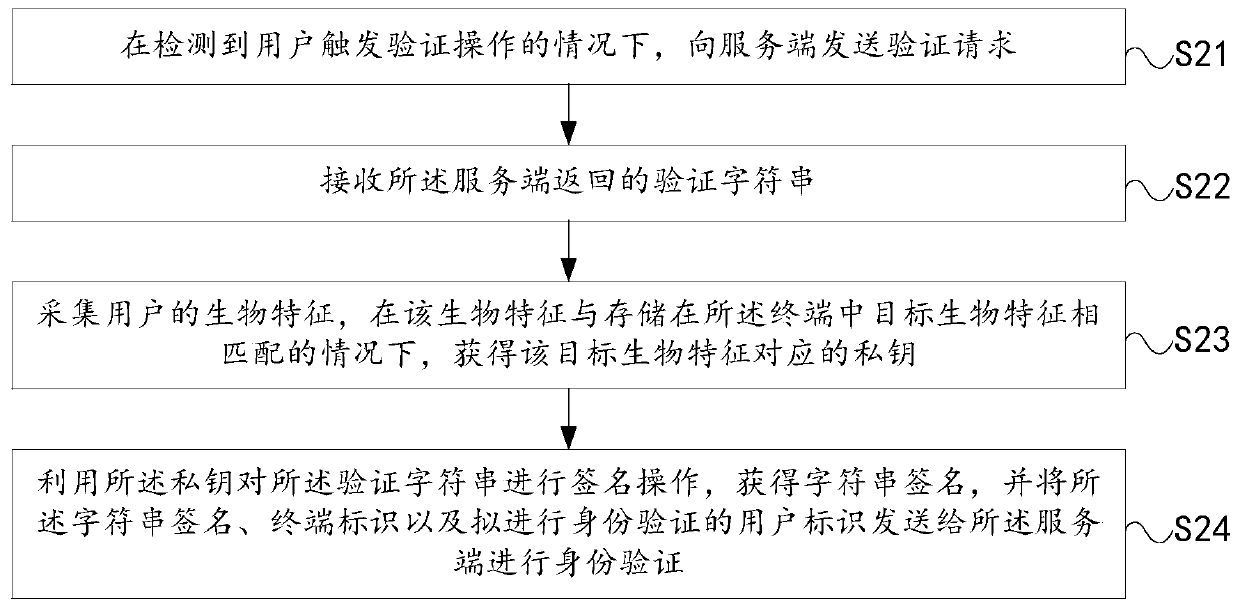
Identity verification method and device, terminal, server and readable storage medium
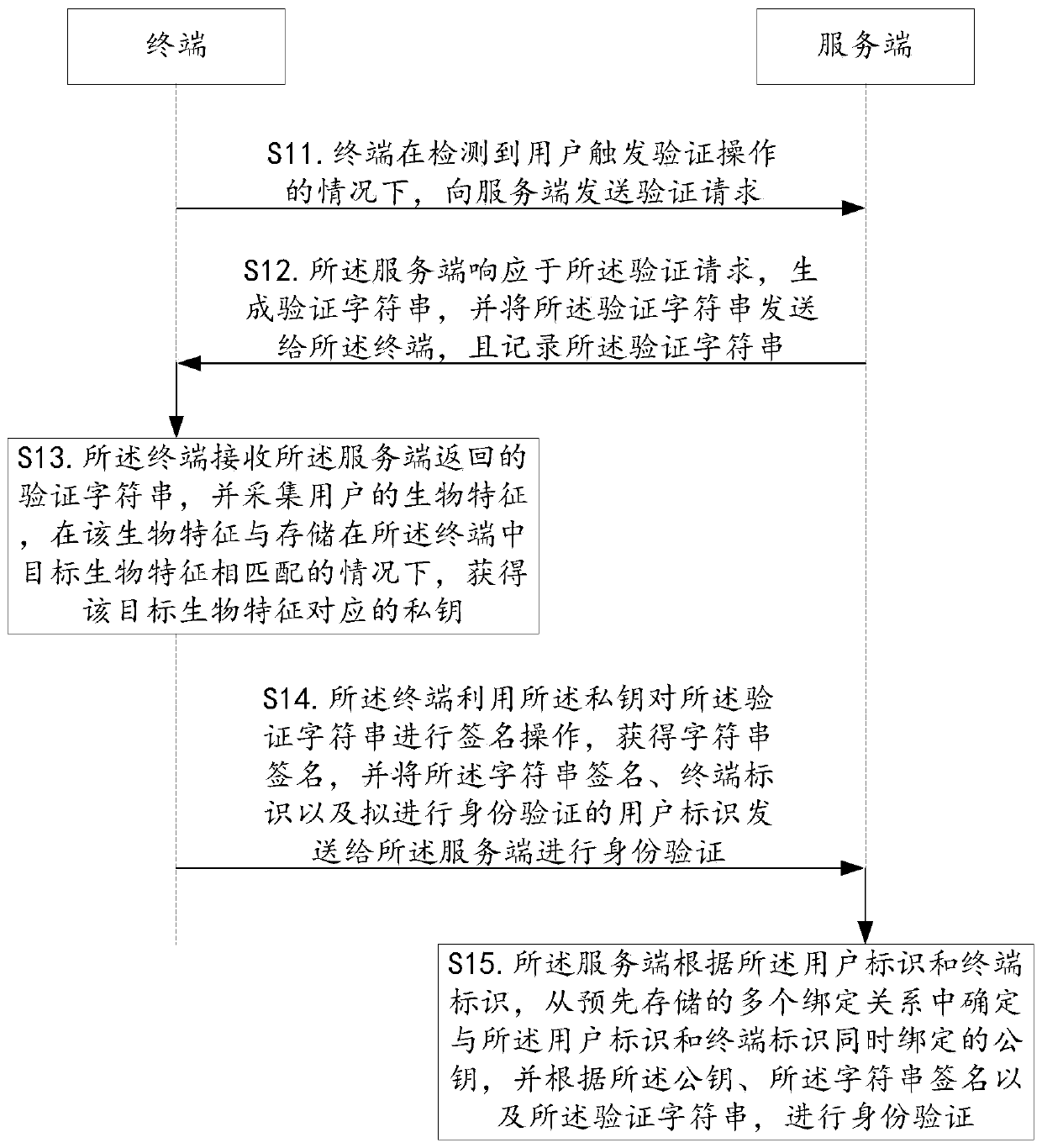
PendingCN111414599AImprove securityEnsure data securityKey distribution for secure communicationDigital data authenticationEngineeringUser identifier
The embodiment of the invention provides an identity authentication method and device, a terminal, a server and a readable storage medium, and aims to improve the security of identity authentication.The identity authentication method is applied to the terminal. The method comprises: sending an authentication request to a server under the condition of detecting that a user triggers an authentication operation; receiving a verification character string returned by the server; collecting biological characteristics of a user, and obtaining a private key corresponding to target biological characteristics under the condition that the biological characteristics are matched with the target biological characteristics stored in the terminal; and performing signature operation on the verification character string by using the private key to obtain a character string signature, and sending the character string signature, a terminal identifier and a user identifier to be subjected to identity verification to the server for identity verification.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
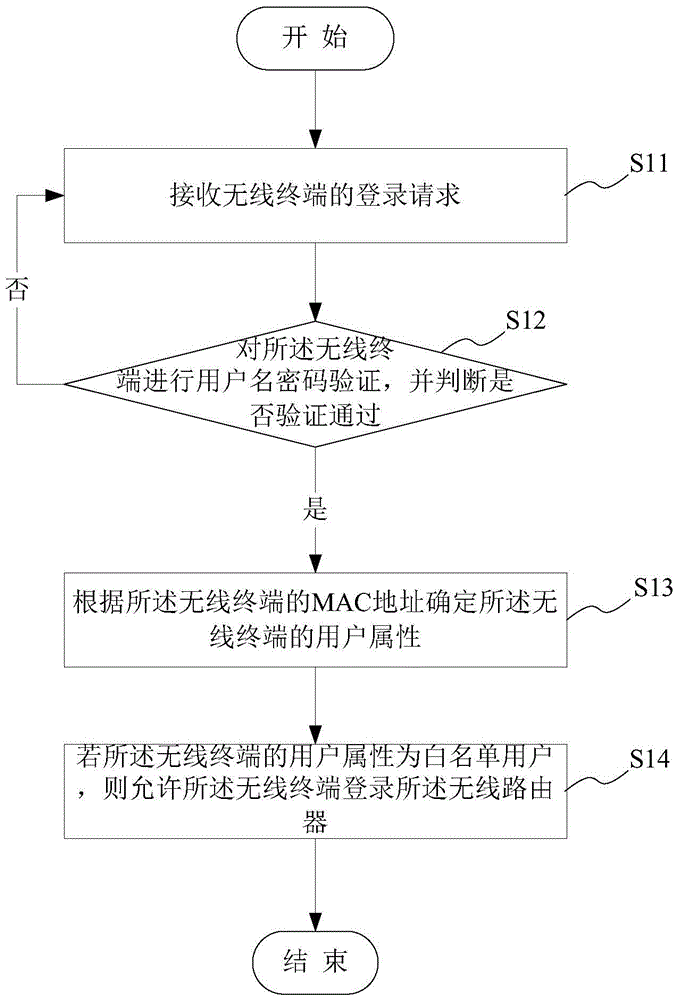
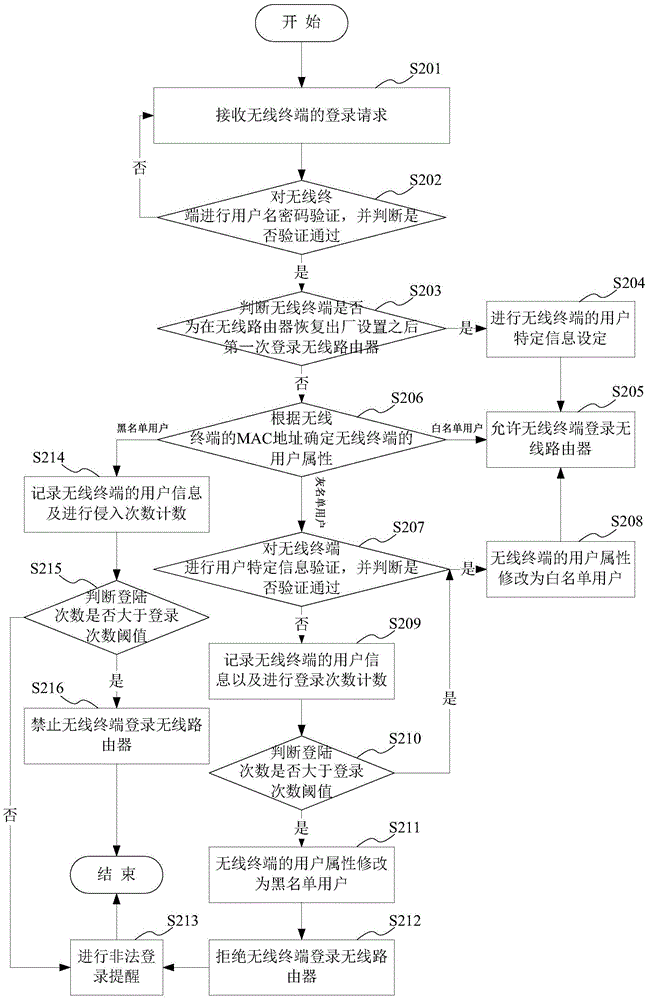
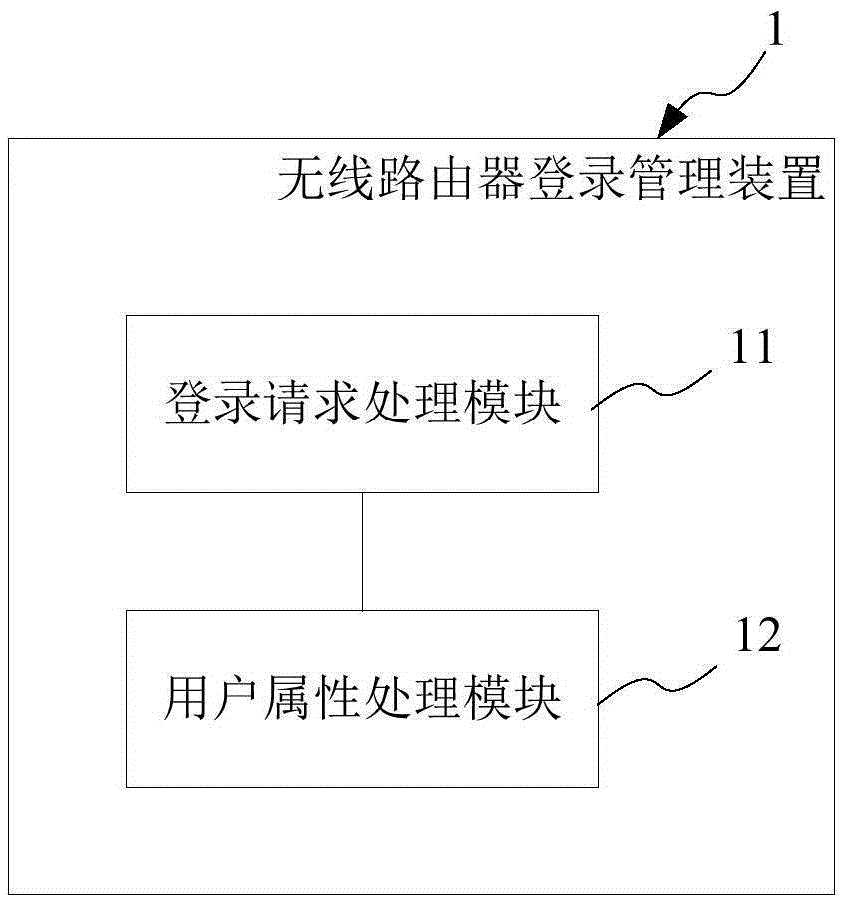
Logging-in management method and apparatus of wireless router
InactiveCN105472610AImprove securityGuarantee continuous and stable operationTransmissionSecurity arrangementWireless routerPassword
The invention provides a logging-in management method and apparatus of a wireless router. The method comprises: a logging-in request of a wireless terminal is received and user name and password verification is carried out on the wireless terminal; if the verification is done successfully, a user attribute of the wireless terminal is determined according to an MAC address of the wireless terminal, wherein the user attribute includes a white list user, a grey list user, and a black list user; and if the user attribute of the wireless terminal is a white list user, the wireless terminal is allowed to log in the wireless router. With the method, the safe logging-in mechanism is enhanced; flexibility of safe logging-in management of the wireless rout4er is improved; and the cost of safe monitoring of the wireless router is reduced.
Owner:PHICOMM (SHANGHAI) CO LTD
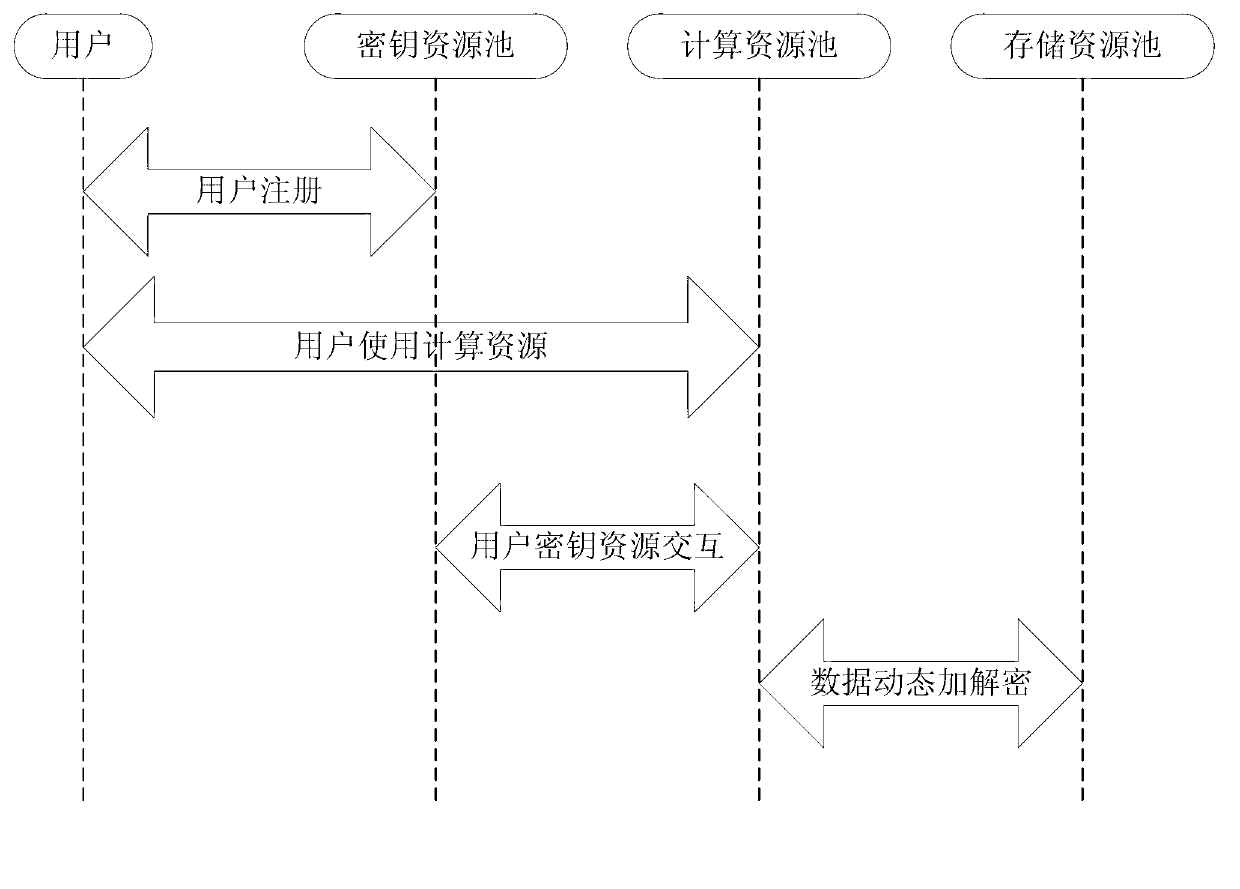
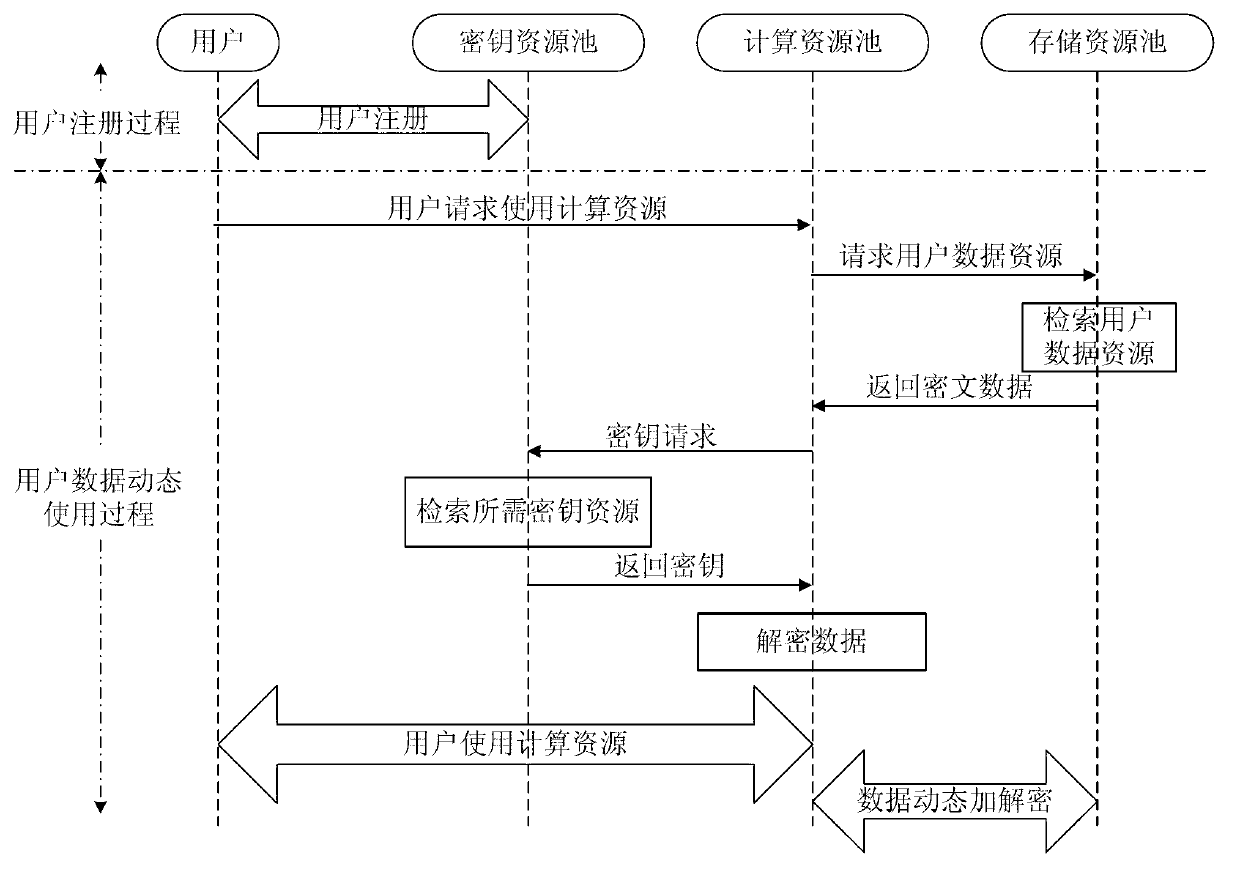
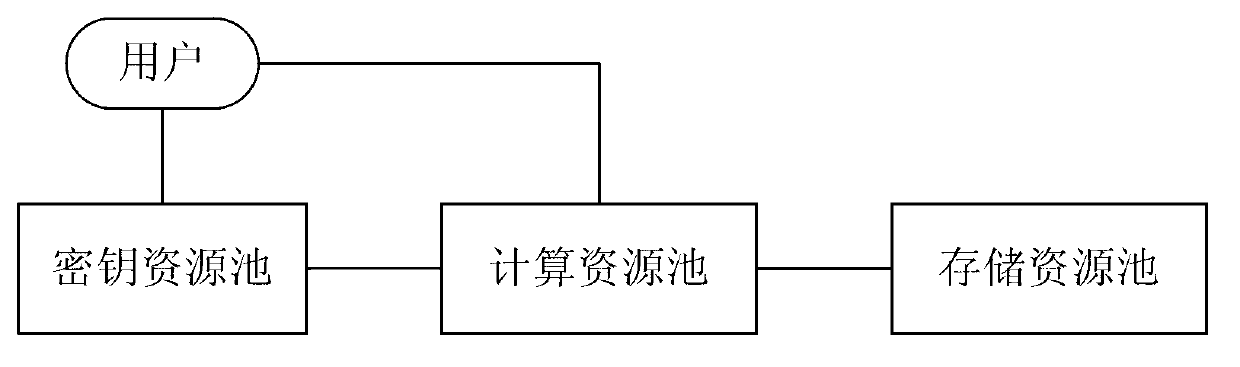
Vitualization environment data security partition method and system
ActiveCN103107994AImprove experienceGuaranteed experienceUser identity/authority verificationResource poolVirtualization
The invention relates to a vitualization environment data security partition method and a system. According to the method, a secret key resource pool is used for storing user information and supplying generation and management service of secret key resources for a user, a computation resource pool is used for supplying computation resources and carrying out deciphering before use on virtual machine image data trends of the stored user through the secret key resources generated by the secret key resource pool by adopting data dynamic transparent encryption and decryption technology, data encryption is carried out after computation resource operation, and the resources are used as stored resources to be stored in a stored resource pool. By means of the vitualization environment data security partition method and the system, through combination of the data dynamic transparent encryption and decryption technology and user secret key resource generation and management technology, virtual machine mirror data of the user can be partitioned safely, and good user experience can be achieved while user data security can be guaranteed.
Owner:CEC CYBERSPACE GREAT WALL
Nonvolatile memory system and management method thereof
ActiveCN103810112ASolve protection problemsPromote recoveryMemory adressing/allocation/relocationEnergy efficient computingDram memoryHost memory
The invention discloses a nonvolatile memory system and a management method of the nonvolatile memory system. A nonvolatile memory is constructed by adopting a nonvolatile PCM storage device, management on the nonvolatile memory is added to a host memory management module, unified management on the nonvolatile memory and a traditional DRAM is achieved, and the nonvolatile memory and the traditional DRAM can be fused to form a unified memory for the access of a host processor. According to the nonvolatile memory system and the management method of the nonvolatile memory system, the problem that power failure data of the traditional DRAM are lost and the problem of data consistency can be solved, and meanwhile energy consumption of the host memory can be lowered.
Owner:HUAZHONG UNIV OF SCI & TECH
Encryption switch processing
ActiveUS20110106710A1Eliminate operating expenseImprove securityFinancePoint-of-sale network systemsPaymentComputer terminal
Techniques for eliminating the need for merchants and acquirers to conduct Payment Card Industry (“PCI”) security audit procedures are provided. Merchants and acquirers can eliminate the operating expenses associated with conducting audits to ensure compliance with PCI Data Security Standards (“DSS”), while at the same time ensuring that cardholders' data remains secure, thus protecting the cardholders from fraudulent transactions. System security is further enhanced through the use of per transaction audits, with the scope of the audit being directly between the Point of Sale (POS) terminal and the payment processing network. PCI DSS compliance can thus be assured on a per transaction basis, as opposed to only ensuring compliance generally for a merchant or acquirer on a periodic basis. Per transaction PCI DSS compliance is assured, while at the same time eliminating the need for merchants or acquirers to conduct compliance audits.
Owner:VISA INT SERVICE ASSOC
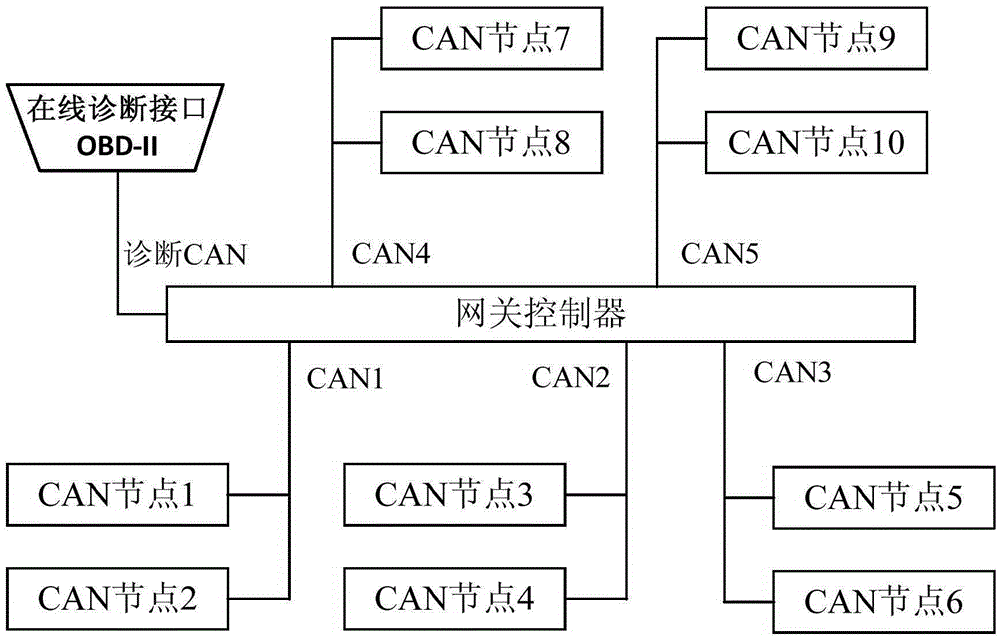
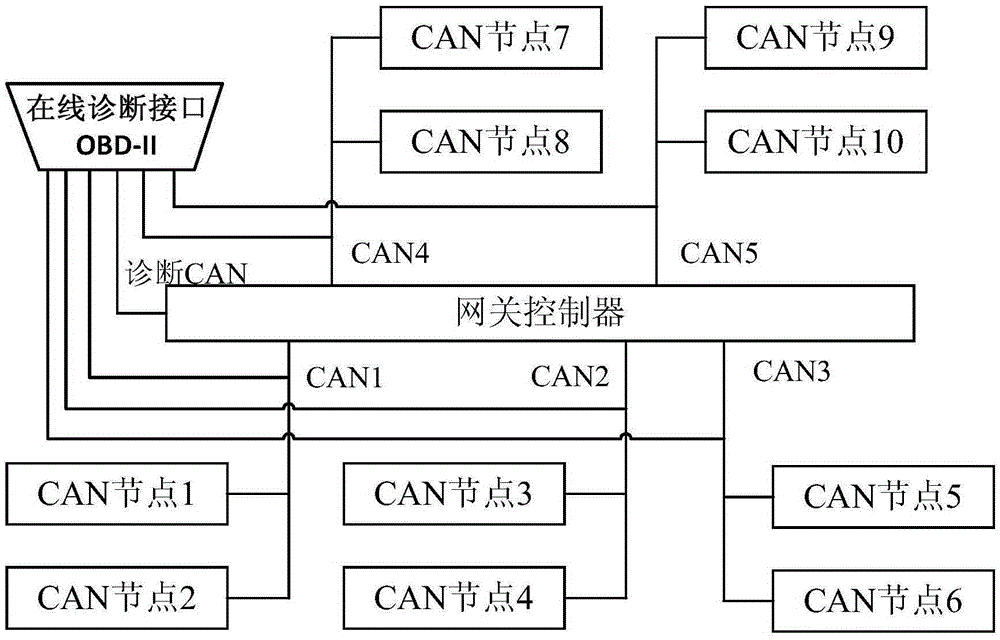
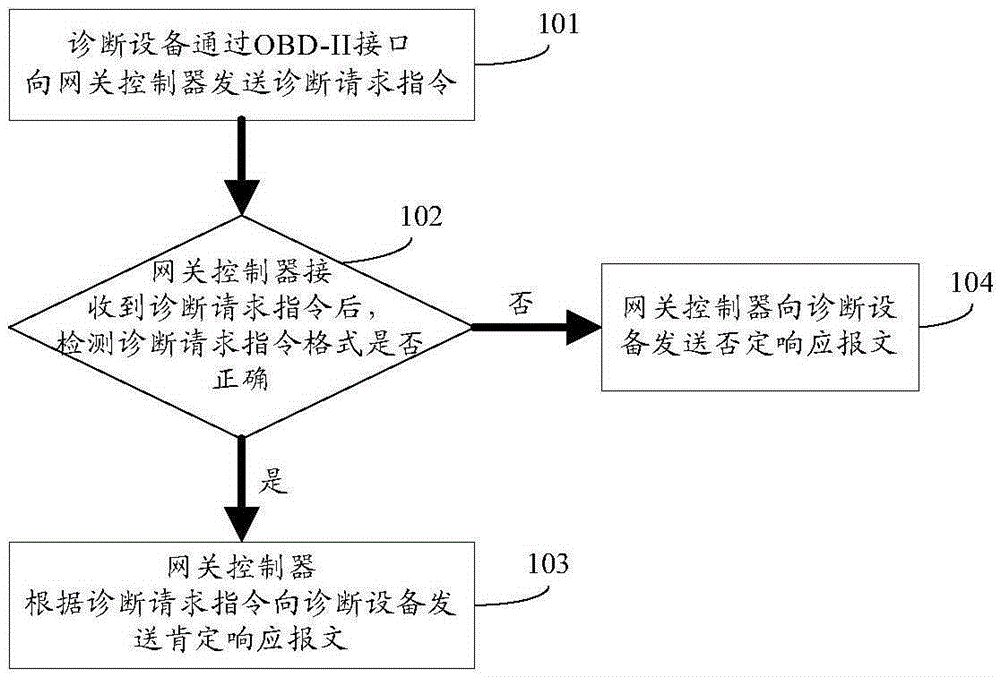
CAN communication data monitoring method and system based on OBD interface
ActiveCN105388893AEnsure data securityProgramme controlElectric testing/monitoringPositive responseNegative response
The invention relates to a CAN communication data monitoring method and system, in particular to a CAN communication data monitoring method and system based on an OBD interface. The method includes the steps that a diagnosis device sends a diagnosis request instruction to a gateway controller through the OBD-II interface; the gateway controller detects whether the format of the diagnosis request instruction is correct or not after receiving the diagnosis request instruction; if yes, the gateway controller sends a positive response message to the diagnosis device according to the diagnosis request instruction so that the diagnosis device can monitor CAN communication data of a CAN subnet; if not, the gateway controller sends a negative response message to the diagnosis device. By means of the method and the system, foundation is provided for vehicle failure checking and analyzing.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
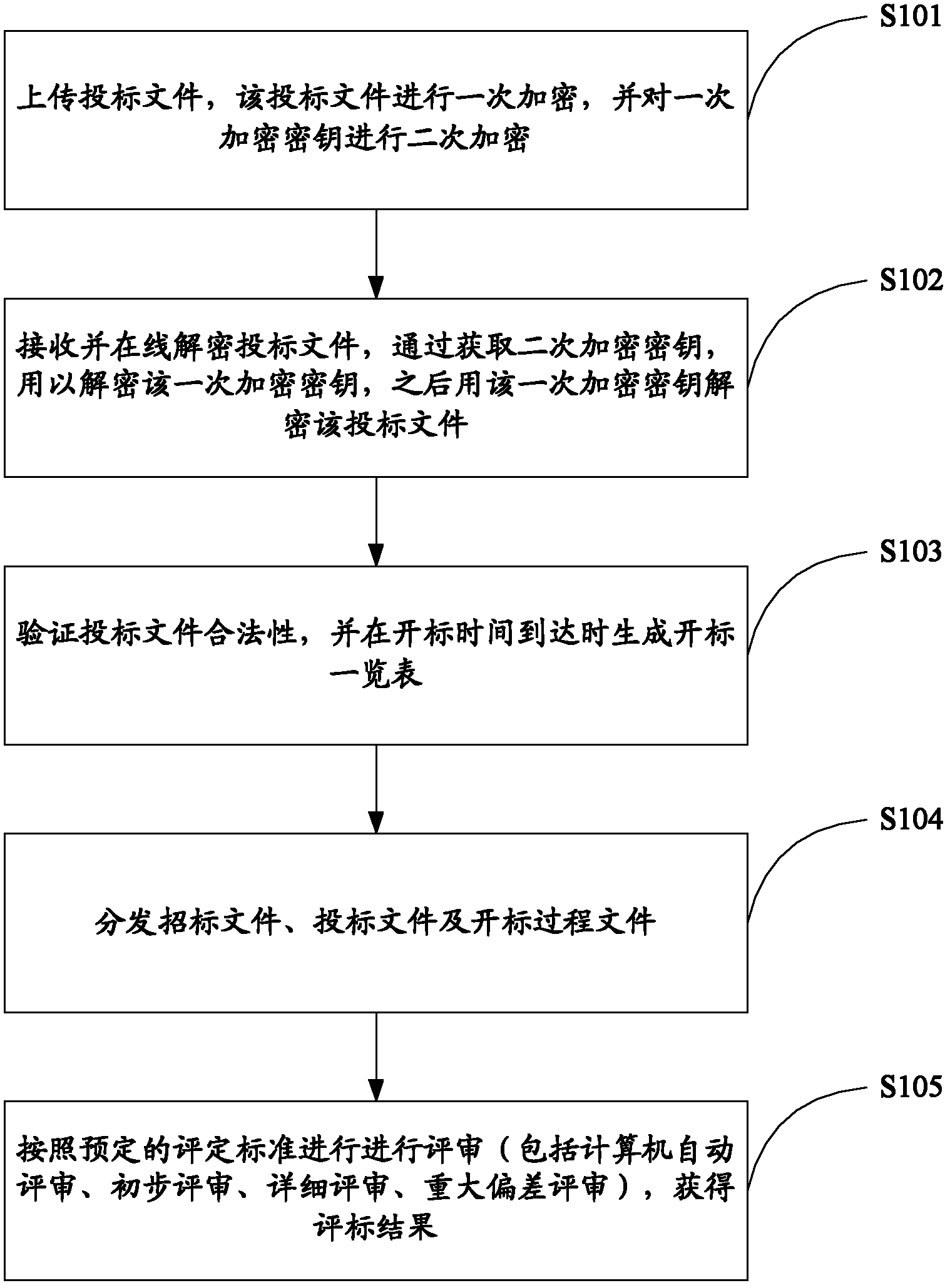
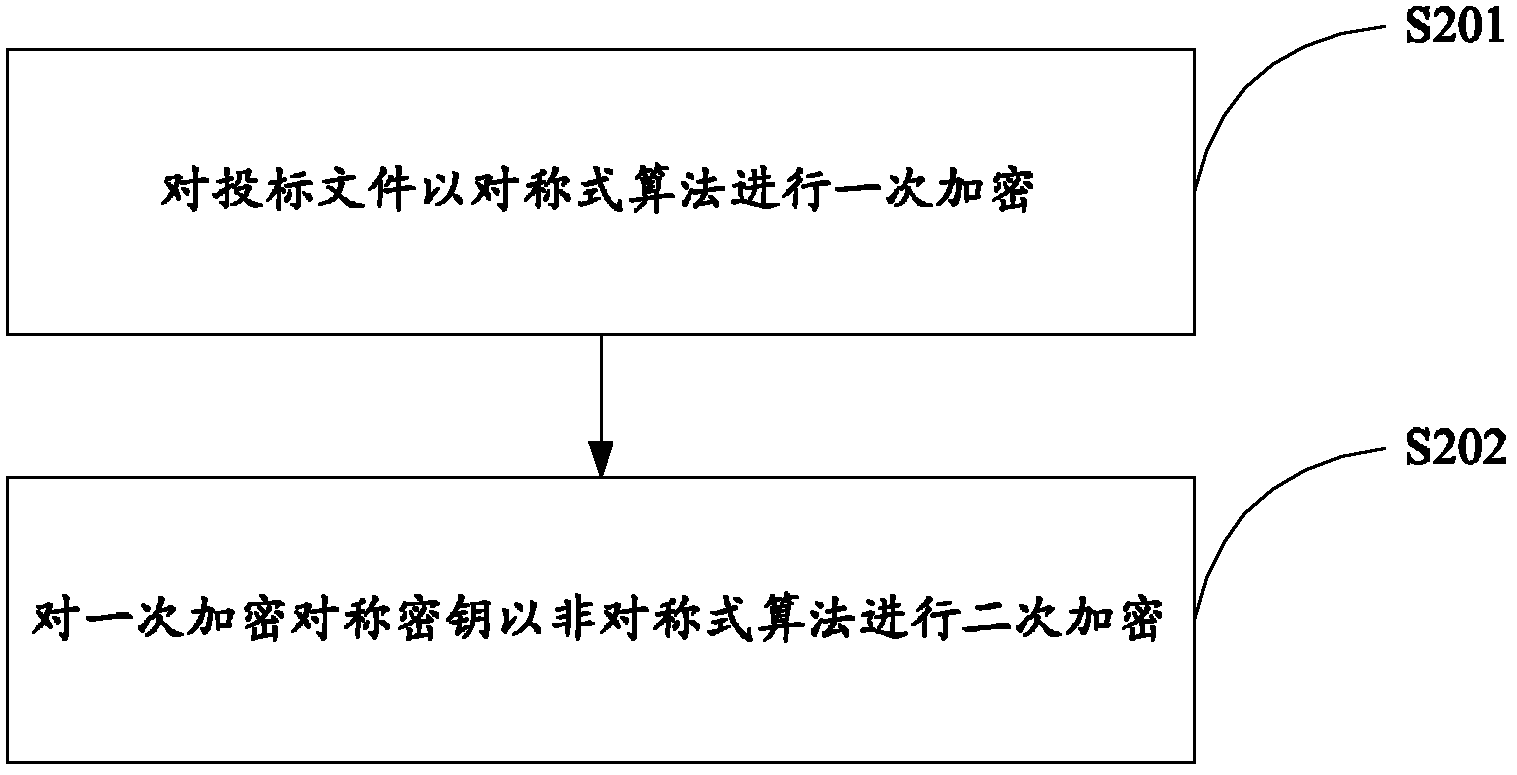
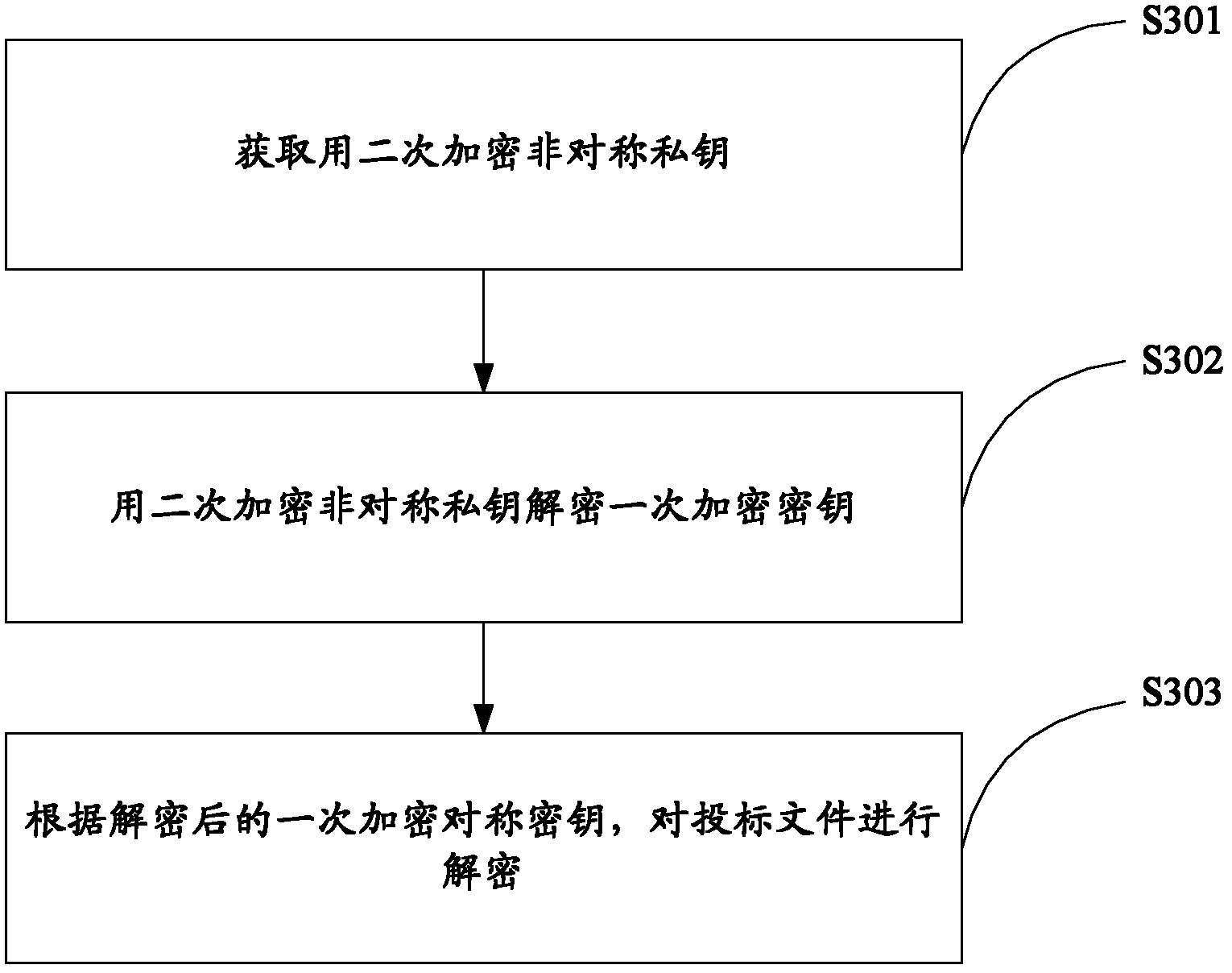
Method and system for remote bid opening and bid evaluation
InactiveCN102684879AEnsure data securityImprove data securityUser identity/authority verificationPlatform integrity maintainancePaper documentDocument preparation
The invention relates to data safety technology, and particularly discloses a method and a system for remote bid opening and bid evaluation. The method includes the steps: uploading bidding documents, primarily encrypting the bidding documents and secondarily encrypting a primary encryption key; receiving and decrypting the bidding documents in an online manner, decrypting the primary encryption key by acquiring a secondary primary encryption key, and then decrypting the bidding documents by the aid of the primary encryption key; verifying validity of the bidding documents and generating a bid opening list when bid opening time comes; distributing bid inviting documents, the bidding documents and bid opening process documents; and performing evaluation according to preset evaluation standards to obtain bid evaluation results. The system comprises a bidding service subsystem, a bid opening service subsystem and a bid evaluation service subsystem, wherein the bid opening service subsystem is capable of decrypting the secondarily encrypted bidding documents in the online manner and providing the corresponding bid inviting documents, the bidding documents and the bid opening process documents to the bid evaluation service subsystem for evaluation. By the aid of the method and the system, safety of the bidding documents is facilitated, and decrypting efficiency is improved.
Owner:SICHUAN CONSTR NETWORK
Distributed storage system based on blockchain technology and identity authentication method thereof
ActiveCN109194708AEnsure data securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationBlockchainDistributed memory systems
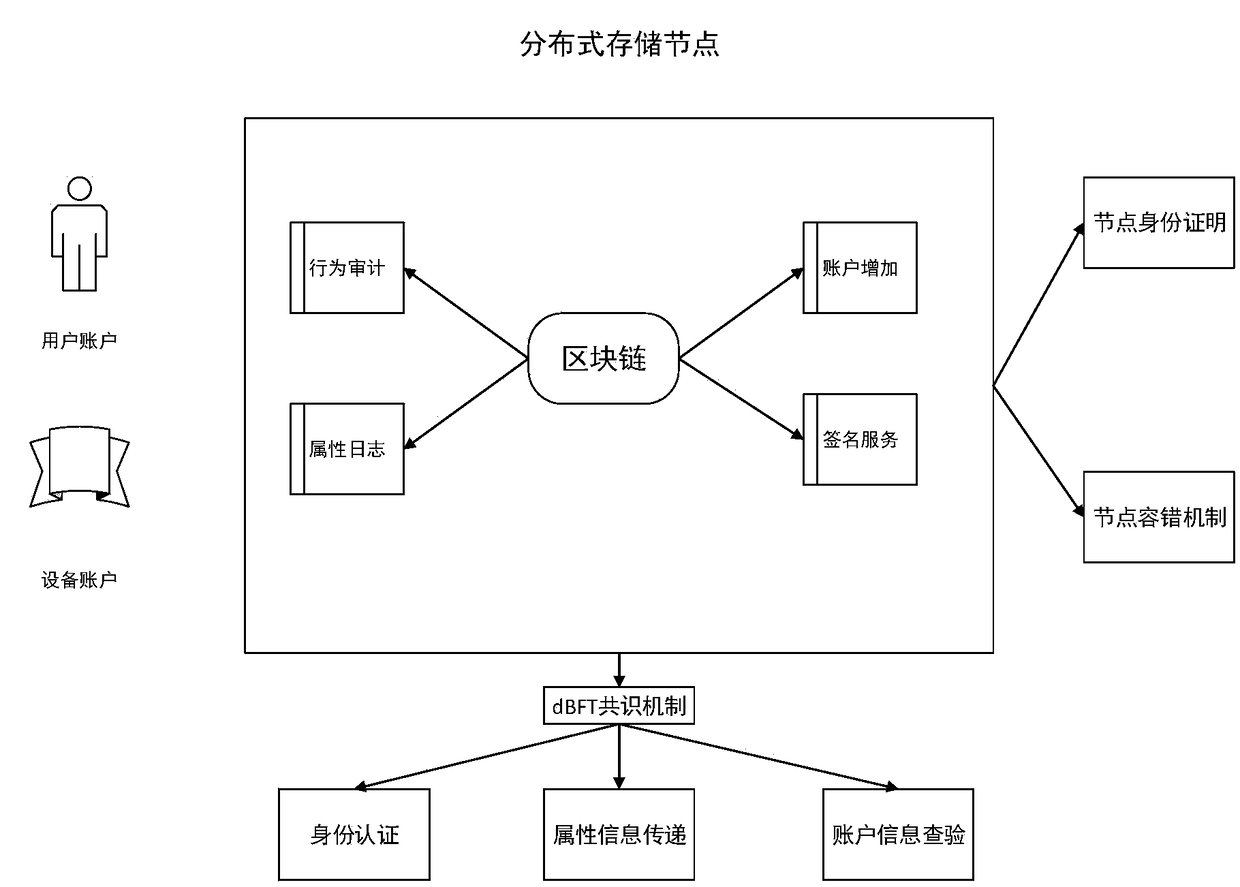
The present invention provides a distributed storage system based on a blockchain technology and an identity authentication method thereof, belonging to the field of distributed storage. There are twoclasses of identity authentication users, and the identity authentication users comprise a user account and a device account, each distributed node can achieve a node identity identification functionand a node fault-tolerant mechanism, the internal portion of each node is provided with a small area to store the content of the blockchain to record all the account data and achieve behavior auditing, attribute log recording, account information addition and signature service, nobody can tamper the user data or illegally adds accounts to the system if there is no accepting of users or an information center, and the data in the distributed storage system cannot be replaced so as to ensure the data safety of the distributed storage system.
Owner:HARBIN ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com