Patents
Literature
66results about How to "Implement encrypted transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
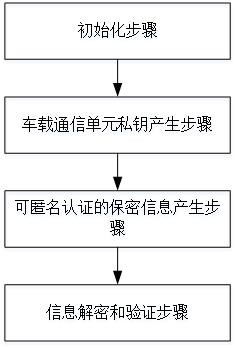
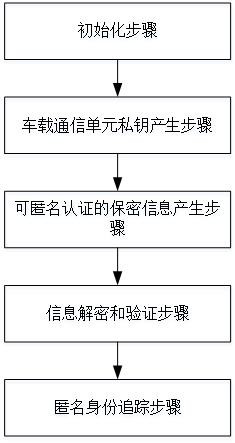
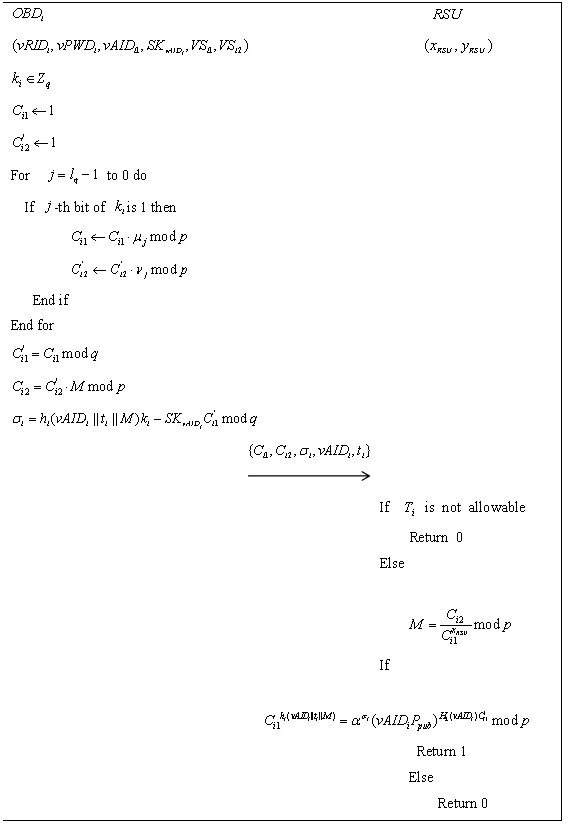
Lightweight anonymity authentication method with privacy protection and based on Internet of Vehicles
ActiveCN108964919AImplement encrypted transmissionSatisfy forward securityUser identity/authority verificationData privacy protectionCommunication unit
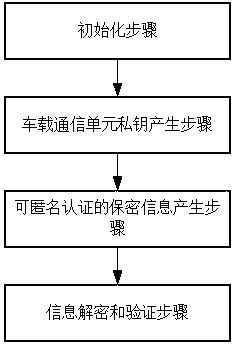
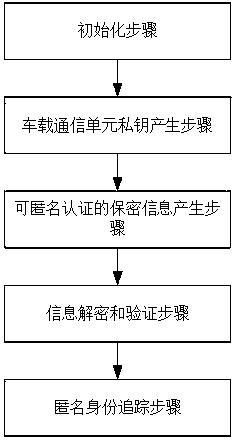
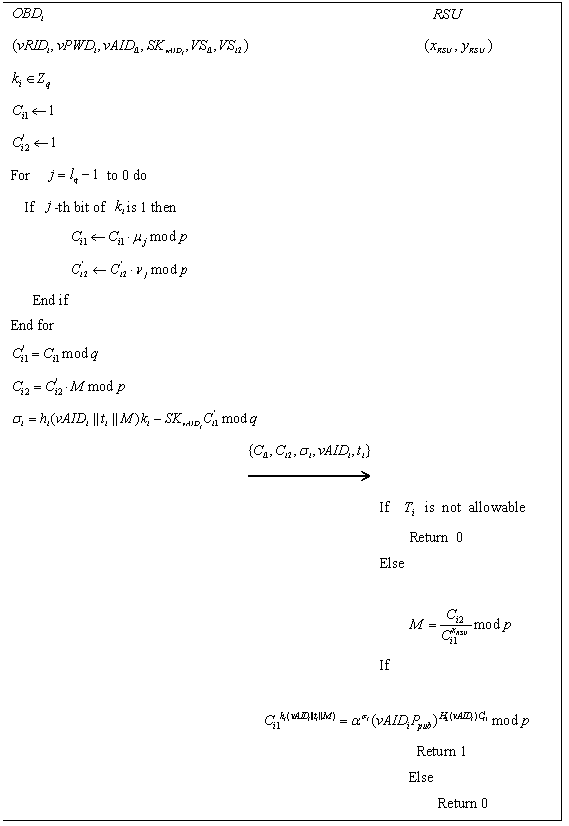
The invention discloses a lightweight anonymity authentication method with privacy protection and based on Internet of Vehicles. The method comprises the steps of initialization, generation of a private key of a vehicle-mounted communication unit, generation of secrecy information capable of anonymity authentication, information decryption and verification, and tracking of anonymous identity. A trustable center generates an anonymous identity for an intelligent vehicle as well as the private key of the anonymous identity, an ElGamaL encryption algorithm and a modified Schnorr signature algorithm are combined to generate the information capable of anonymity, transmission information is transmitted in an encrypted way in authentication protocols, and the information cannot be decrypted unless using the secret key of a roadside base station unit; when a dispute of a traffic accident occurs, the anonymous identity can be tracked; and the method has prospects in practical application.
Owner:SOUTHWEST PETROLEUM UNIV
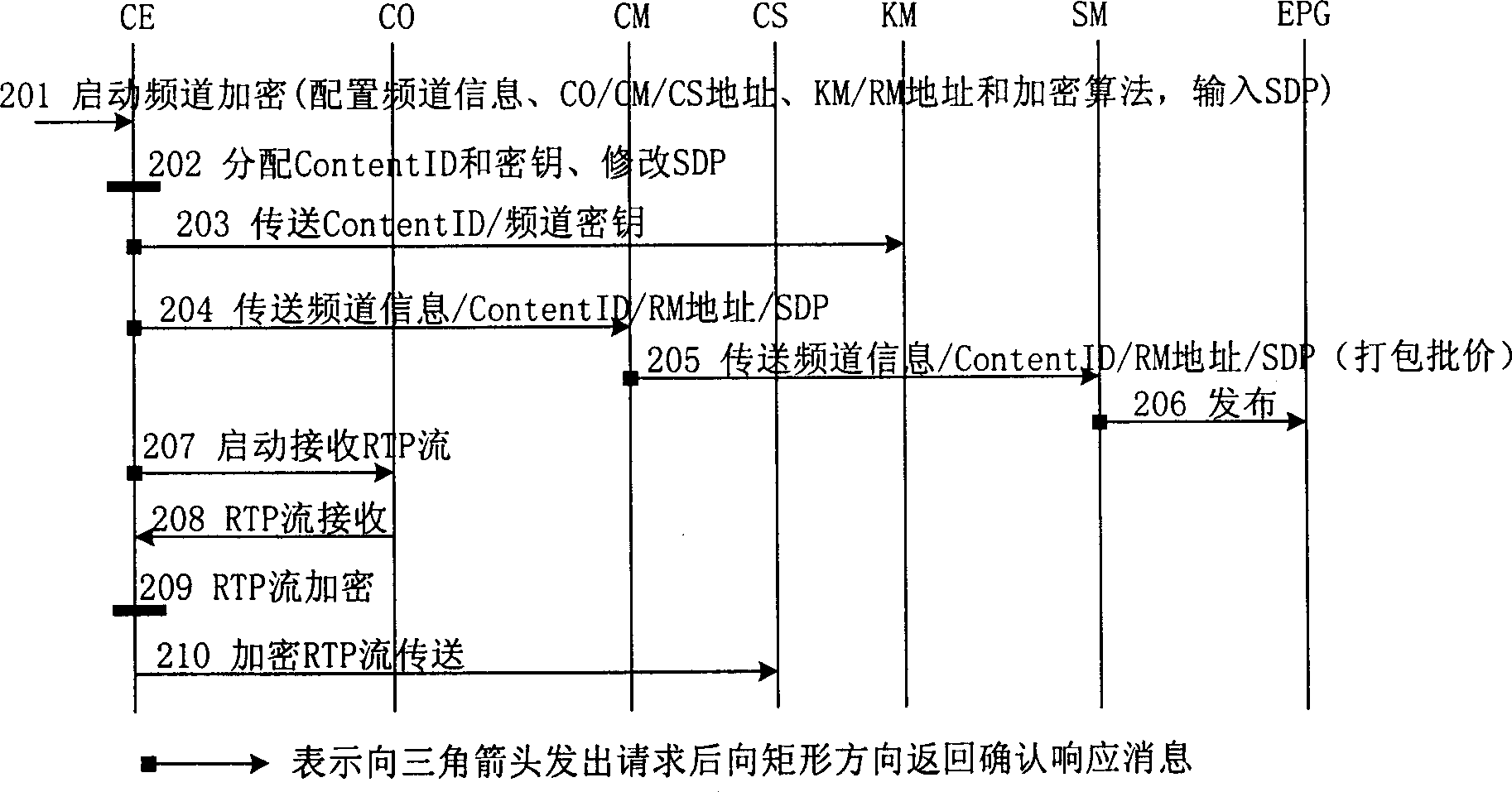
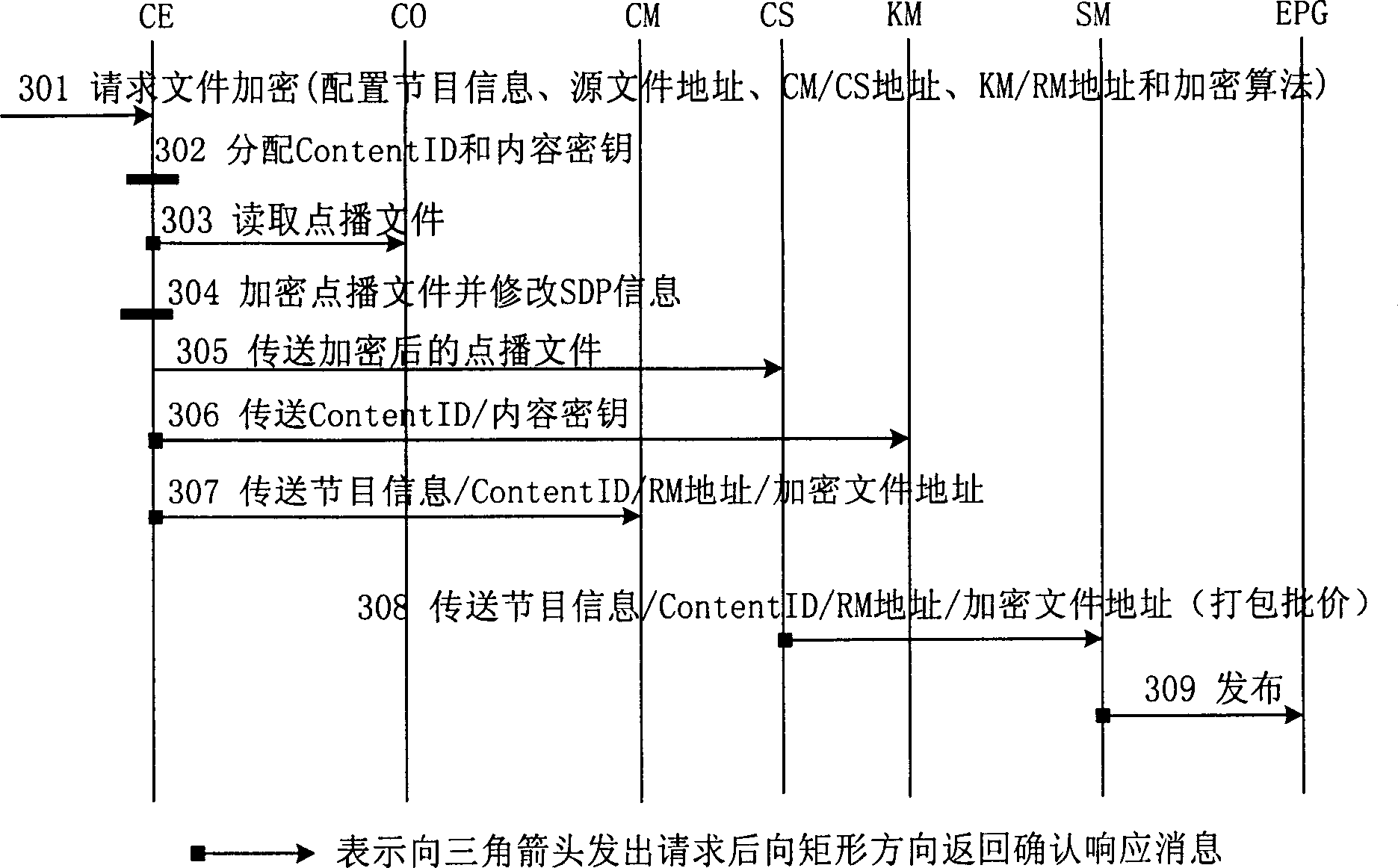
IPTV system, enciphered digital programme issuing and watching method
ActiveCN1848944APrevent leakageRealize secure transmissionAnalogue secracy/subscription systemsTwo-way working systemsContent managementAuthorization
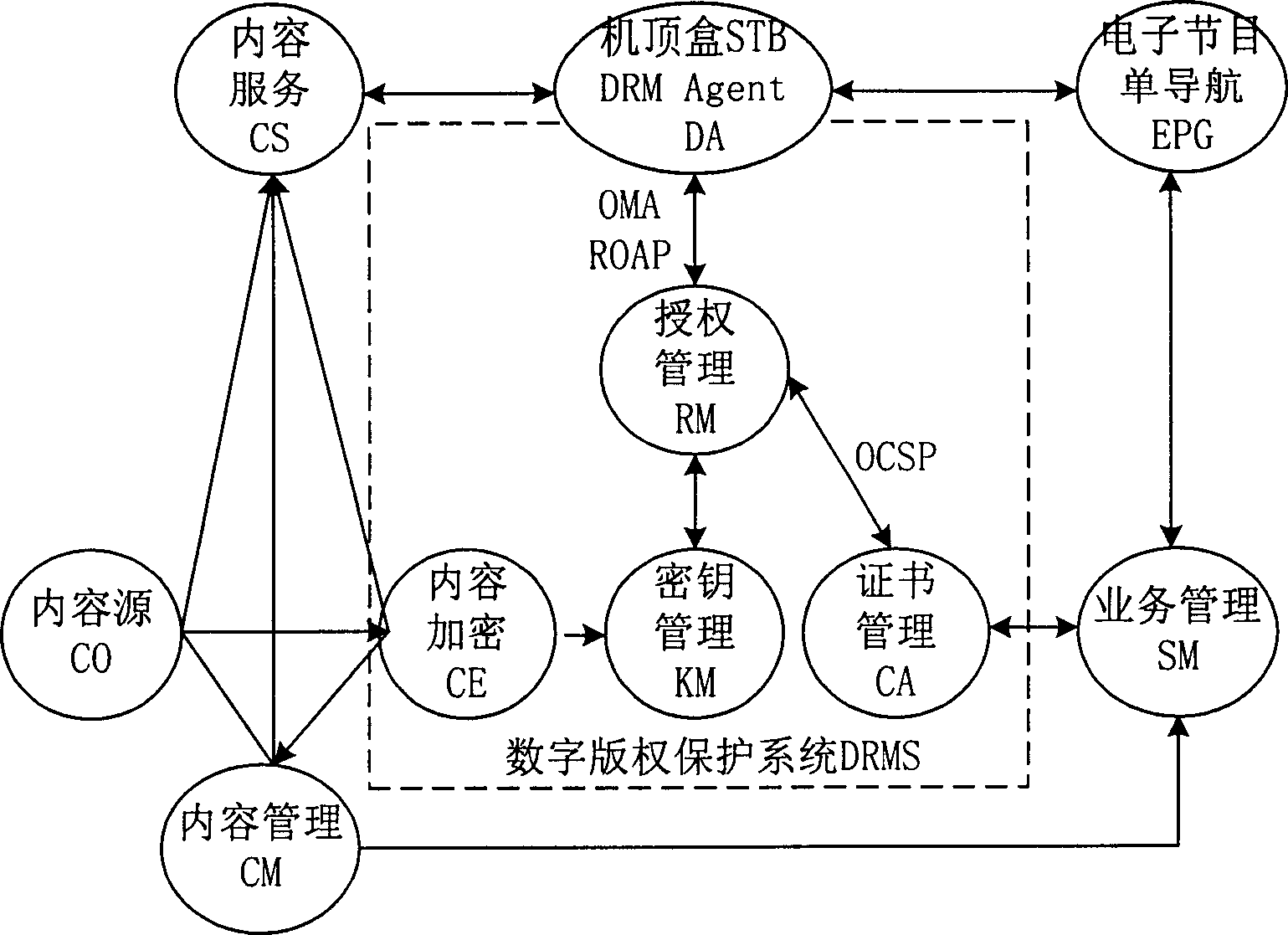
An IPTV system comprises content source CO, content service unit CS, content management unit CM, service management unit SM, single-way guide unit EPG of electronic program, top box STB, content enciphering unit CE, cipher key management unit KM and authorization management unit RM for providing enciphered program. The method of issuing and viewing enciphered program is also disclosed.
Owner:HUAWEI TECH CO LTD
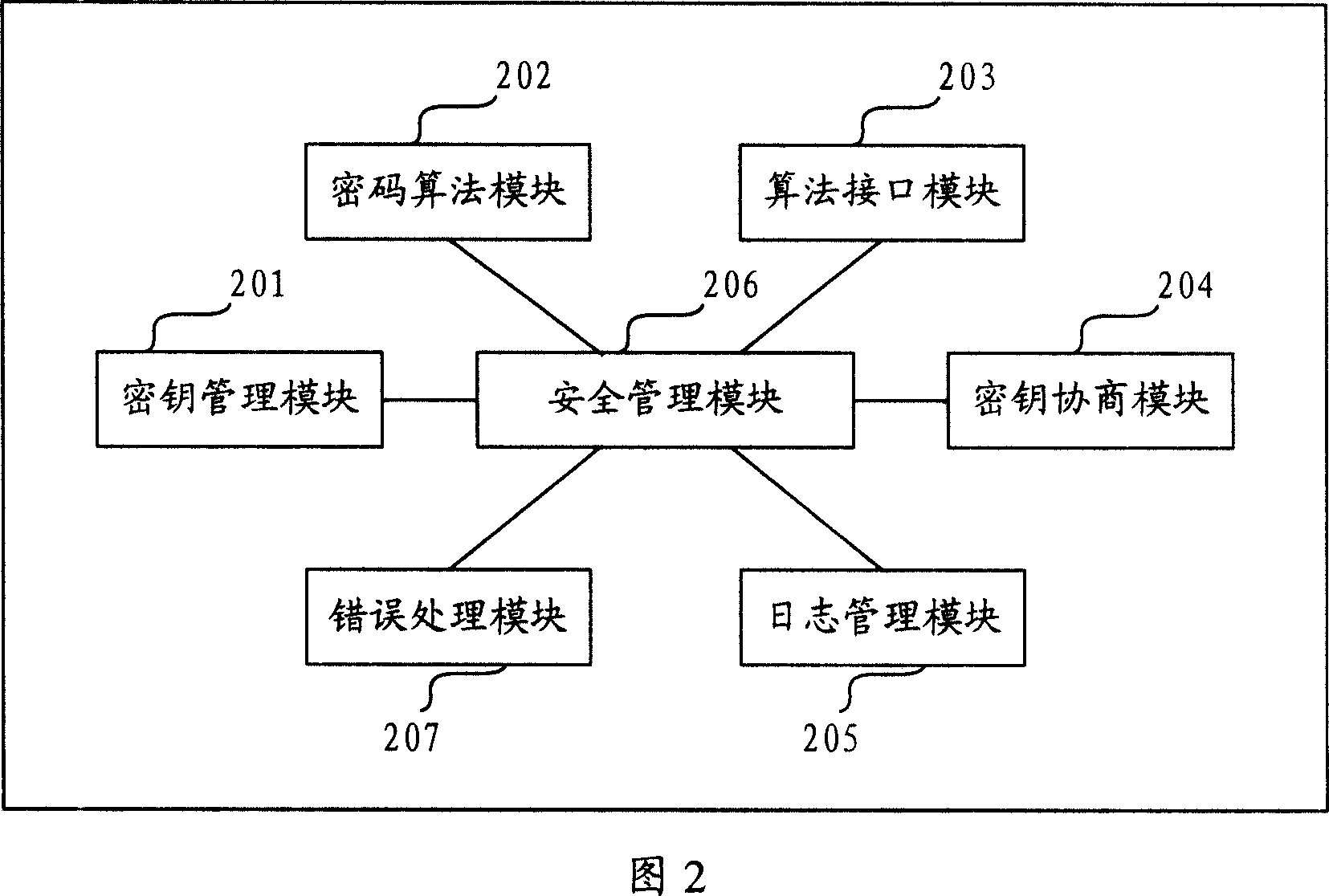
Information security control system
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
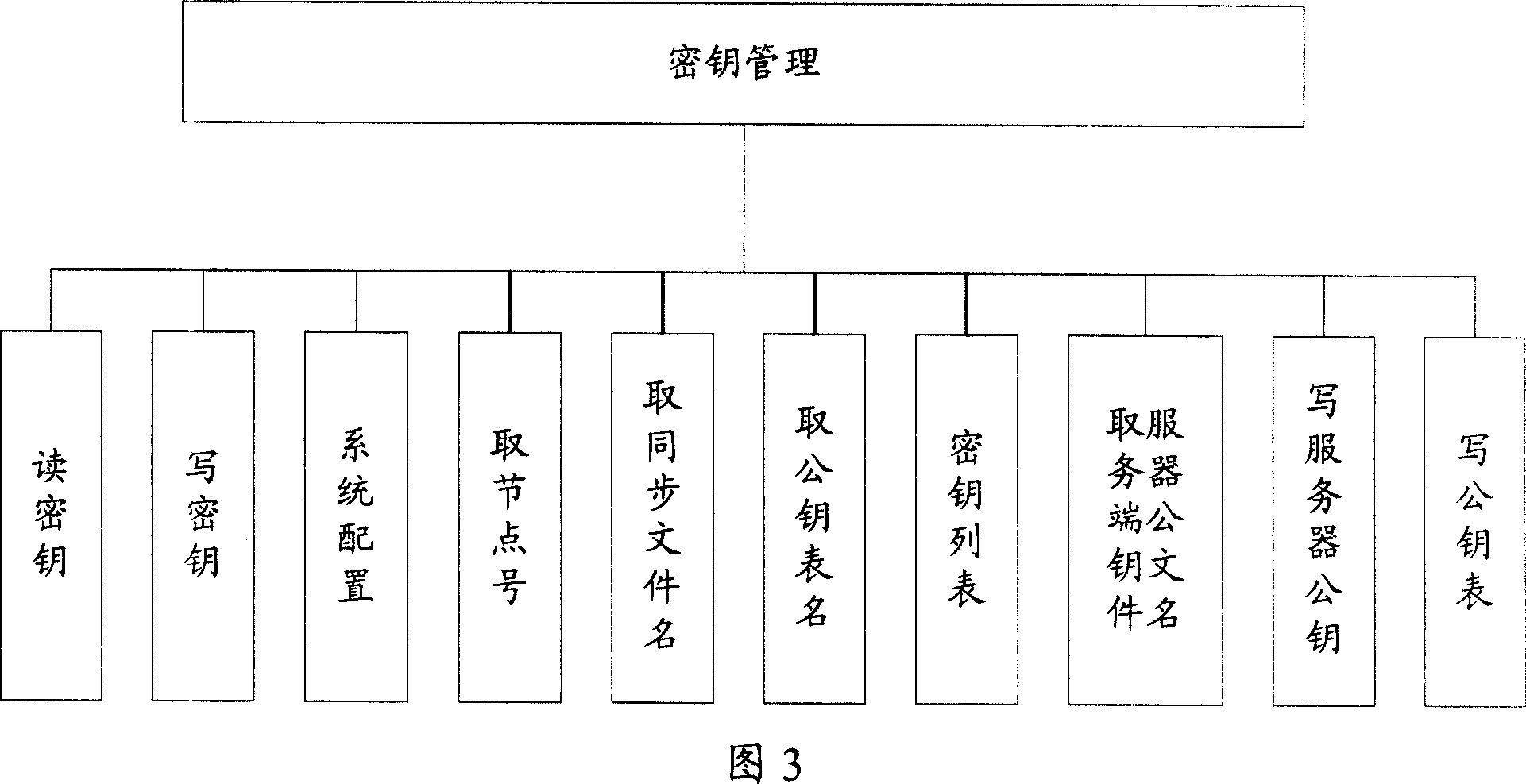
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
Webpage tamper-proofing device and method based on access control and directory protection
InactiveCN103236932APrevent tamperingTampering will notUser identity/authority verificationTamper resistanceMedia access control
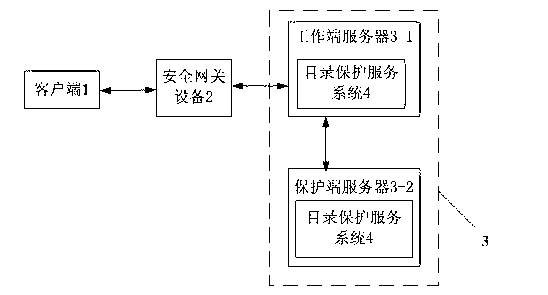
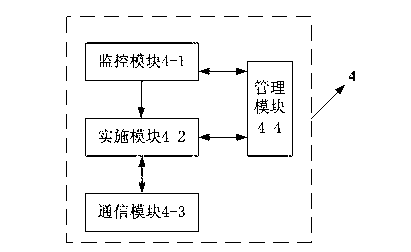
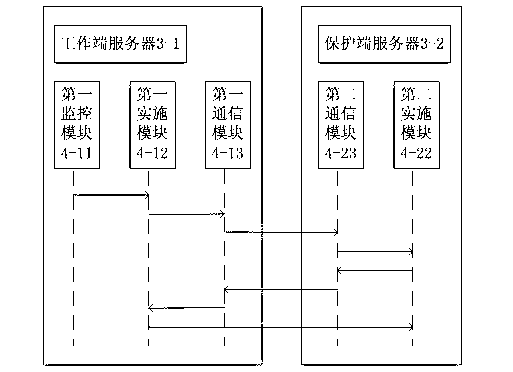
The invention provides a webpage tamper-proofing device and a webpage tamper-proofing method based on access control and directory protection. The webpage tamper-proofing device comprises a client end and a service end, wherein security gateway equipment is arranged between the client end and the service end, the service end comprises a work end server and a protecting end server, the work end server and the protecting end server are connected in an interactive manner, the work end server is communicated with the client end, and directory protection service systems are respectively arranged inside the work end server and the protecting end server. The webpage tamper-proofing device and the webpage tamper-proofing method comprise two parts that 1, the access control is realized through the security gateway equipment, an internal website and an external website are separated, the access authority of users is determined, and the users are prevented from illegally accessing and modifying application system and data; and 2, the directory protection function is realized through the directory protection service systems, the real-time deletion and recovery is realized, and the real reliability of files is ensured.
Owner:ANHUI HIGHGUARD NETWORKS TECH
Optical frequency hopping system based on optical circulator and transmitter
ActiveCN109981174AImplement encrypted transmissionReliable transmissionRing-type electromagnetic networksEncryption apparatus with shift registers/memoriesConfidentialityCarrier signal
The invention discloses an optical frequency hopping system based on an optical circulator and a transmitter. The optical frequency hopping system includes: an annular modulation unit, whereinthe annular modulation unit comprises a plurality of optical circulators; the first port of each optical circulator receives different optical carriers; a second port of each optical circulator is connected with an optical coupler, each optical coupler is connected with a phase modulator and is combined with frequency hopping coding in a pseudo-random code generator to realize coding modulation of an optical carrier signal, and a third port of each optical circulator respectively outputs the coded and modulated optical carrier signal; a transmitter which is internally provided with the annular modulation unit and is used for transmitting the optical carrier signal encrypted by the annular modulation unit; a receiver which is used for receiving the encrypted optical carrier signal and decrypting the encrypted optical carrier signal through frequency hopping coding; and an optical fiber which is used for realizing carrier communication between the transmitter and the receiver. According to the invention, high-speed optical frequency hopping coding can be realized, a flexible and simple unit structure is provided, expansion to a multi-channel optical frequency hopping system is facilitated, and a communication system with higher confidentiality is provided.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI +1
Image coding and decoding methods and devices, electronic equipment and computer readable medium
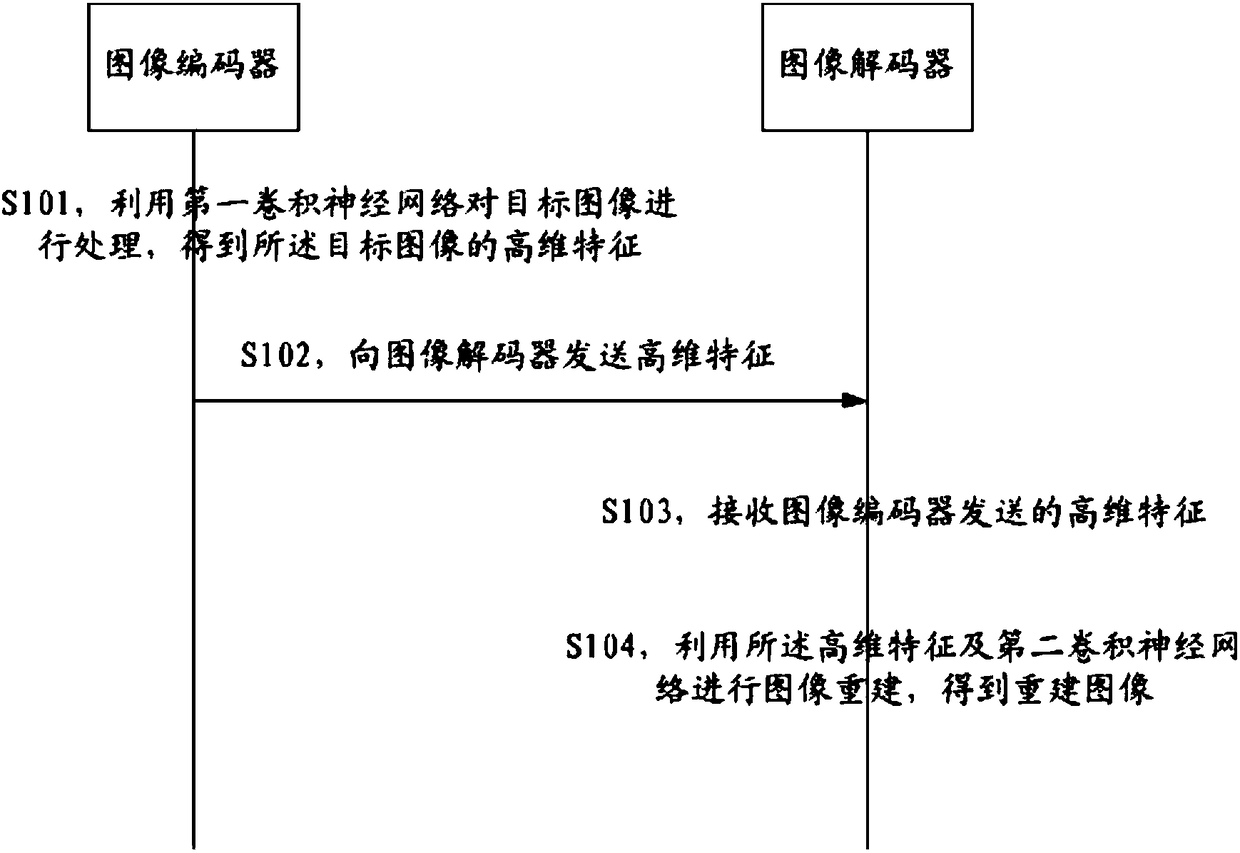
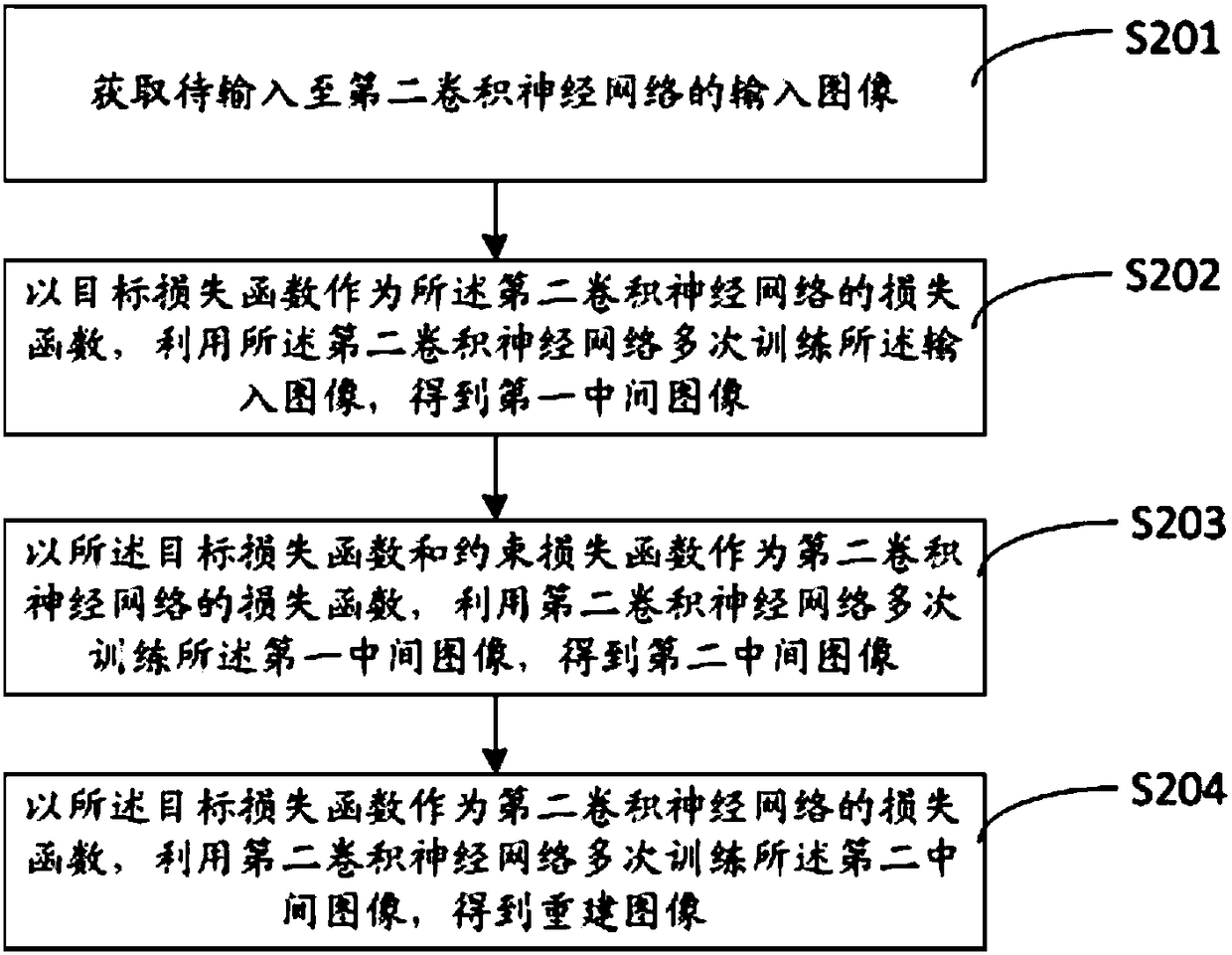
The invention provides image coding and decoding methods and devices, electronic equipment and a computer readable medium. The image coding method comprises the steps that an image coder processes a target image by utilizing a first convolutional neural network to obtain high-dimensional features of the target image, wherein network structure parameters of the first convolutional neural network are randomly generated in advance; and the high-dimensional features are sent to an image decoder. The technical effects, that only the high-dimensional features are transmitted in the process of transmitting the image to the image decoder by the image coder, the image decoder can reconstruct the target image based on the high-dimensional features only by using a second convolutional neural networkconfigured according to the network structure parameters sent by the image encoder, a third party cannot reconstruct the target image even if part or all of the high-dimensional features are capturedin the image transmission process, and encrypted transmission of the image is realized, are achieved.
Owner:BEIJING KUANGSHI TECH +1
Software-defined Internet of Things network topology data transmission security management method and system
ActiveCN112565230AReduce control overheadGuaranteed safe transmissionKey distribution for secure communicationUser identity/authority verificationGlobal topologyTopology information
The invention provides a software-defined Internet of Things network topology data transmission security management method and system, and the method comprises the steps: deploying common nodes and aggregation nodes at Internet of Things network nodes, and enabling the nodes to communicate with each other; performing encryption algorithm configuration on common nodes and aggregation nodes; each adjacent node performing bidirectional identity authentication and key agreement, and each node recording credible nodes passing authentication around itself and suspicious nodes failing to be authenticated; periodically executing topology discovery, collecting topology information of common nodes by the aggregation nodes, forwarding messages of trusted nodes among the aggregation nodes, establishing a trusted path, and constructing a global topology view; sequentially forwarding and aggregating the topology state messages according to the determined trusted path; and determining newly added nodes and malicious nodes based on the global topology view, broadcasting, and updating the network topology structure of the Internet of Things. According to the invention, the security and reliabilityof data transmission can be effectively improved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
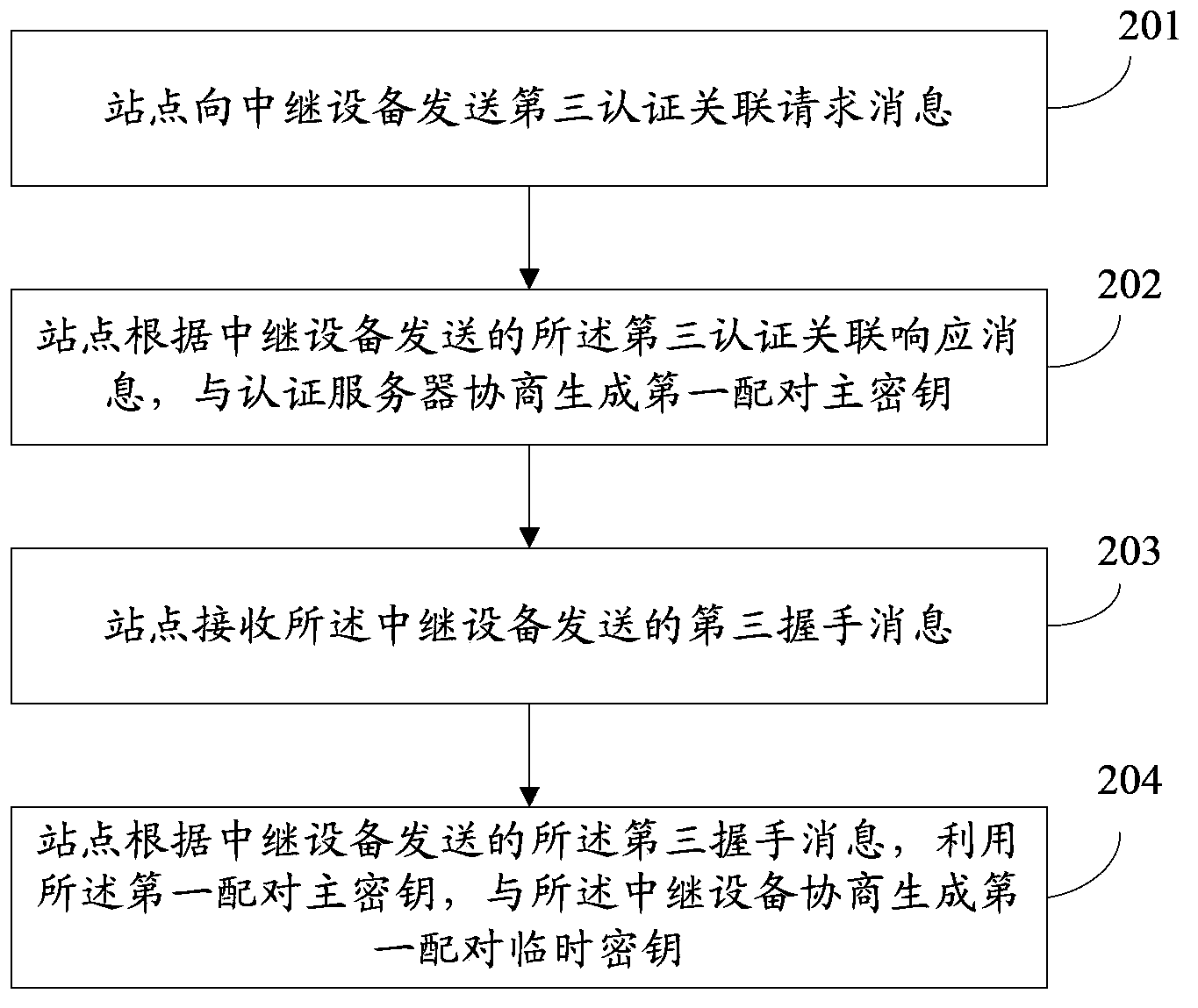
Relay equipment-based security association, data transmission method, device and system
ActiveCN103905389AReduce workloadImplement encrypted transmissionKey distribution for secure communicationSecurity associationData transmission
The embodiment of the invention discloses a relay equipment-based security association, data transmission method, a device and a system. Certification association operation is carried out between a site and an access point via the relay equipment to obtain a first matching main key, and the first matching main key is the matching main key between the site and the access point. Further, the site uses the first matching main key via the relay equipment to carry out handshaking interaction operation negotiation with the access point to generate a first matching temporary key, the first matching temporary key is the matching temporary key between the site and the access point and is used for protecting data transmitted between the site and the access point. Thus, the problems that the work load of the relay equipment is added and the data transmission efficiency is influenced due to the fact that security association can not be carried out between the site and the access point when the relay equipment is added between the site and the access point can be solved.
Owner:HUAWEI DEVICE CO LTD
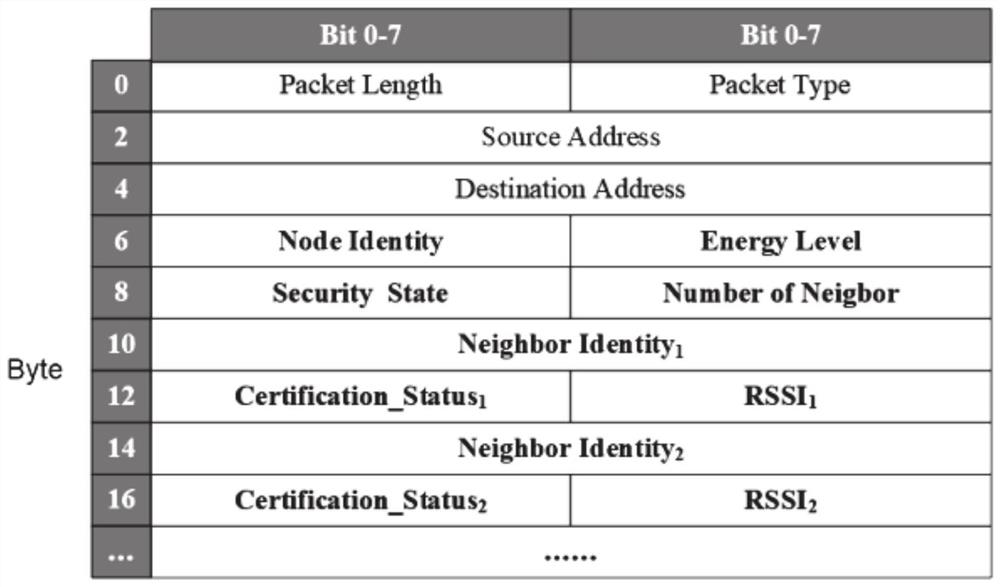
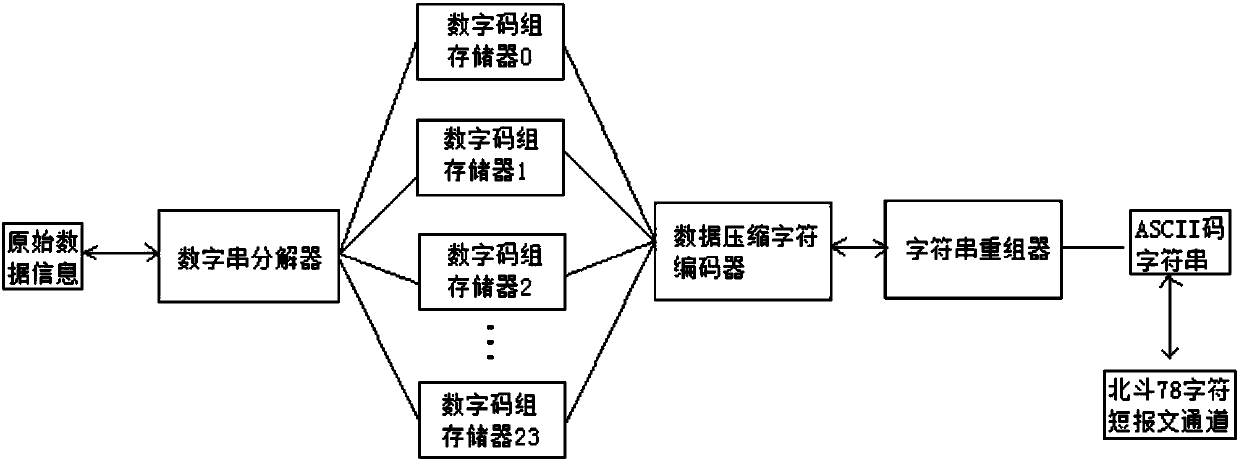
Beidou short message data compression-encryption method and apparatus, and processor
InactiveCN107566999AImplement encrypted transmissionIncrease flexibilityMessaging/mailboxes/announcementsTransmissionData compressionComputer hardware
The invention discloses a Beidou short message data compression-encryption method and apparatus, and a processor. The method comprises the following steps: step 1, integrating original data information, and respectively storing integrated data; step 2, performing encoding processing on the integrated data, and performing character string recombination on encoded data; and step 3, transmitting an obtained character string to a Beidou short data channel. According to the Beidou short message data compression-encryption method and apparatus, and the processor, the encrypted transmission for equal-height dynamic-target total-factor information of three aircrafts can be implemented using one Beidou short message limited by seventy-eight characters, and the time interval for flight path points of the aircrafts is shortened from 60s to 20s; and meanwhile, the encoding and decoding of the Beidou short message data compression-encryption method and apparatus, and the processor to data information do not rely on ID information of a Beidou device card, and the relatively good flexibility is achieved.
Owner:山东东进航空科技有限公司
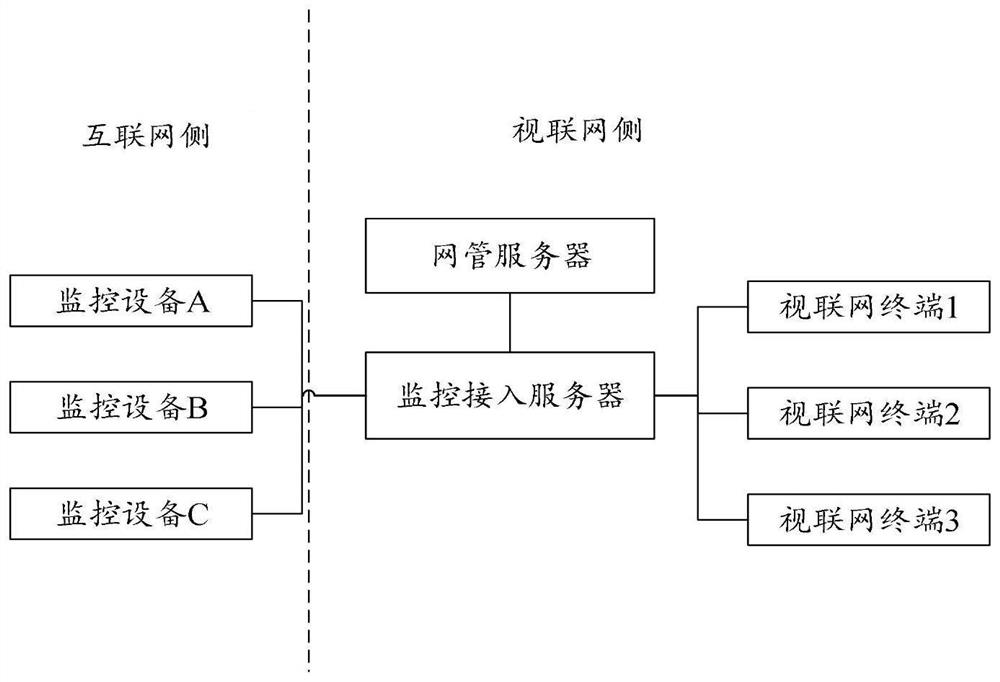
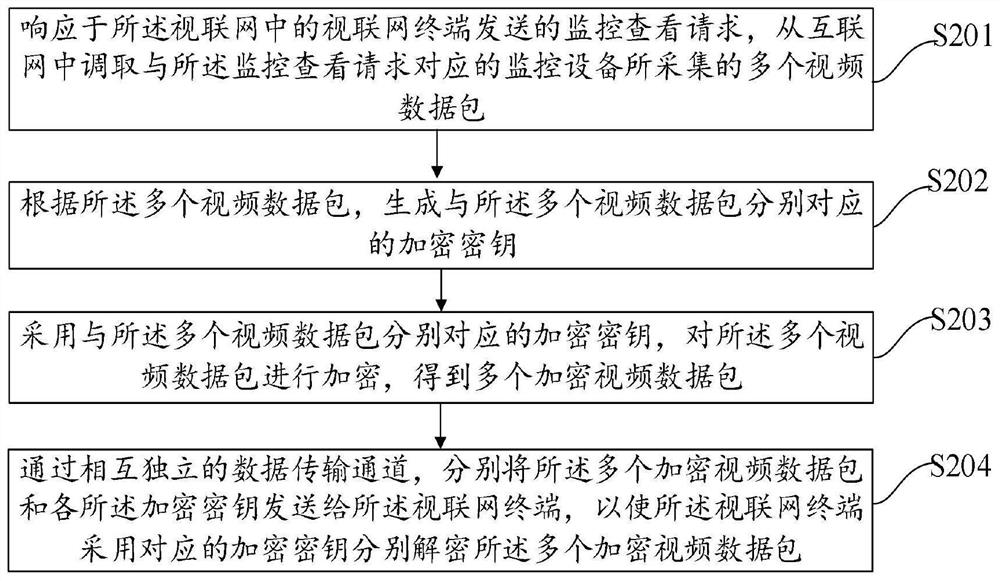
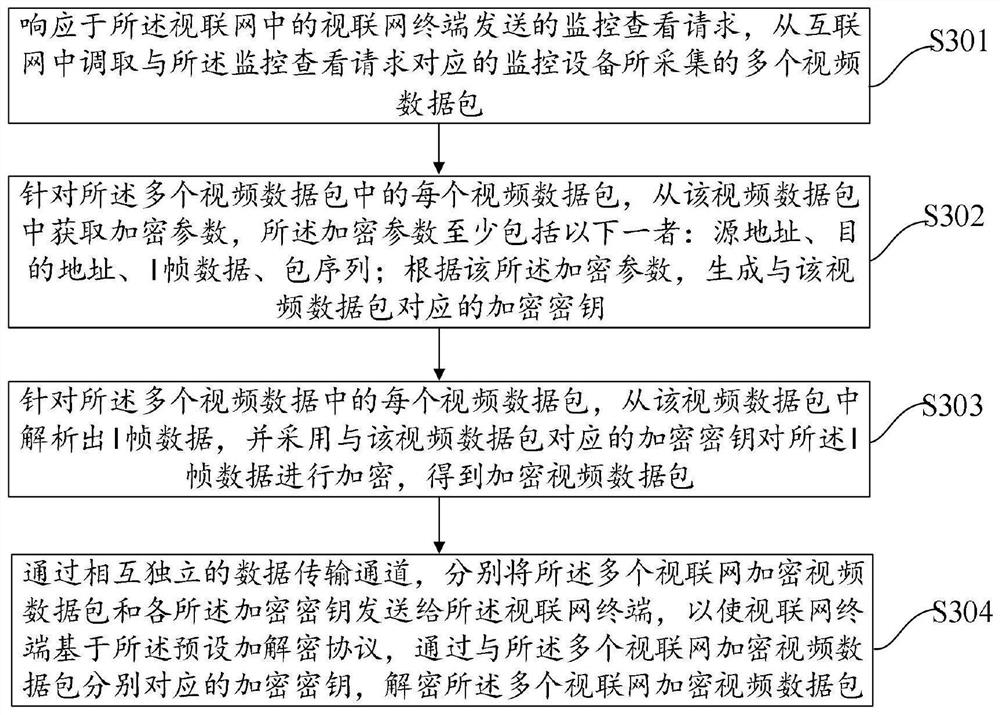
Monitoring video encryption transmission method, device, equipment and medium
PendingCN111953656AGuaranteed transmission securityEnsure safetyMultiple keys/algorithms usageData packThe Internet
The embodiment of the invention provides a monitoring video encryption transmission method and device, electronic equipment and a storage medium, and is applied to a monitoring access server in the articulated naturality web, and the method comprises the steps: responding to a monitoring check request transmitted by an articulated naturality web terminal in the articulated naturality web, callinga plurality of video data packets acquired by monitoring equipment corresponding to the monitoring check request from the Internet; generating encryption keys respectively corresponding to the plurality of video data packets according to the plurality of video data packets; encrypting the plurality of video data packets by adopting encryption keys respectively corresponding to the plurality of video data packets to obtain a plurality of encrypted video data packets; and respectively sending the plurality of encrypted video data packets and each encryption key to the articulated naturality webterminal through mutually independent data transmission channels, so that the articulated naturality web terminal respectively decrypts the plurality of encrypted video data packets by adopting the corresponding encryption keys. By adopting the technical scheme of the invention, the security of calling the monitoring video from the Internet can be improved.
Owner:VISIONVERA INFORMATION TECH CO LTD
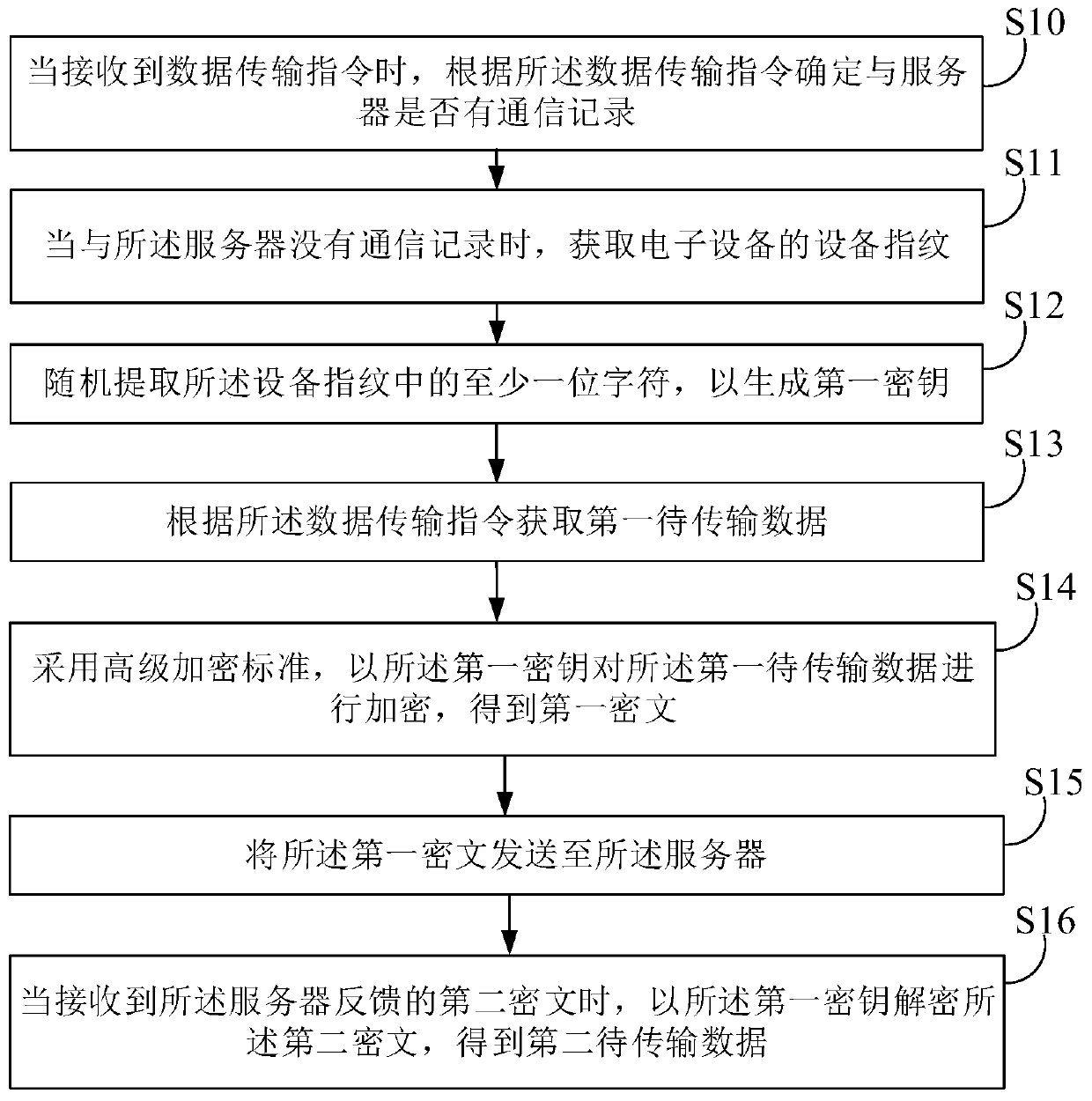
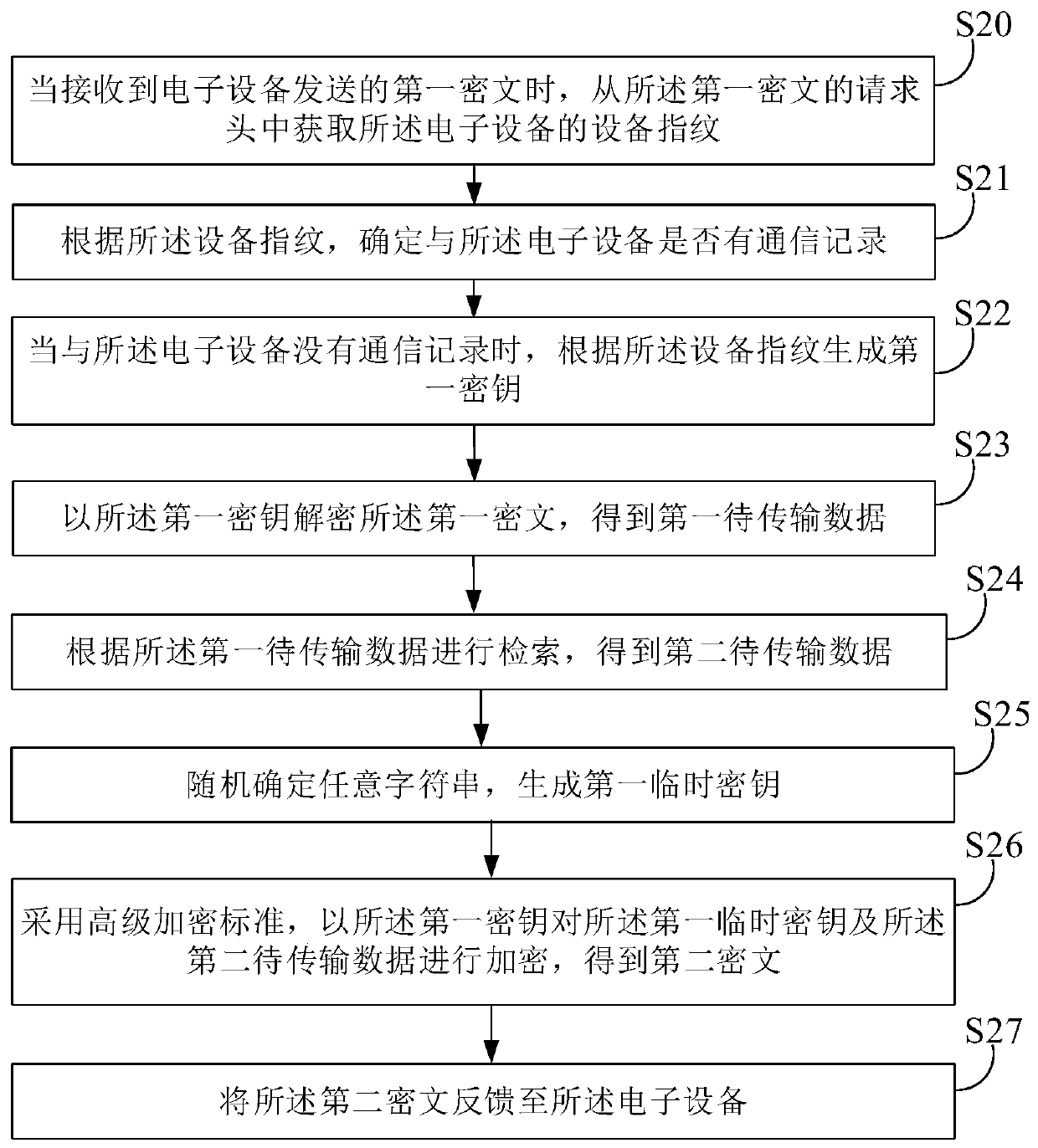
Data transmission method, electronic equipment and storage medium
ActiveCN110324143AIncreased complexityImplement encrypted transmissionKey distribution for secure communicationComputer hardwareCiphertext
The invention provides a data transmission method, electronic equipment and a storage medium. The data transmission method includes: determining whether there is a communication record with the serveraccording to a received data transmission instruction; when no communication record exists with the server, acquiring a device fingerprint of the electronic device, randomly extracting at least one character in the equipment fingerprint; generating a first key, acquiring first to-be-transmitted data according to the data transmission instruction, using advanced encryption standards to encrypt thefirst to-be-transmitted data by using the first secret key, and obtaining a first ciphertext; sending the first ciphertext to the server; and when a second ciphertext fed back by the server is received, decrypting the second ciphertext by using the first key to obtain second to-be-transmitted data, thereby realizing data processing, achieving encrypted transmission of the data between the electronic equipment and the server, and further improving the security of data transmission due to the complexity of an encryption mode.
Owner:PING AN TECH (SHENZHEN) CO LTD
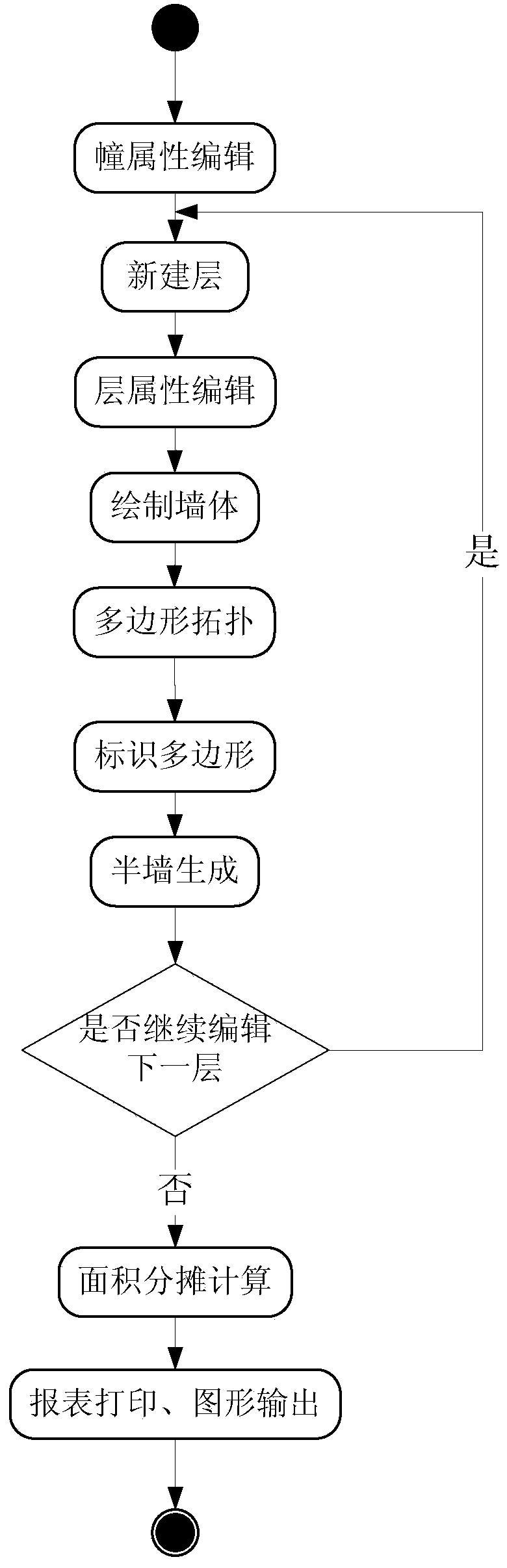
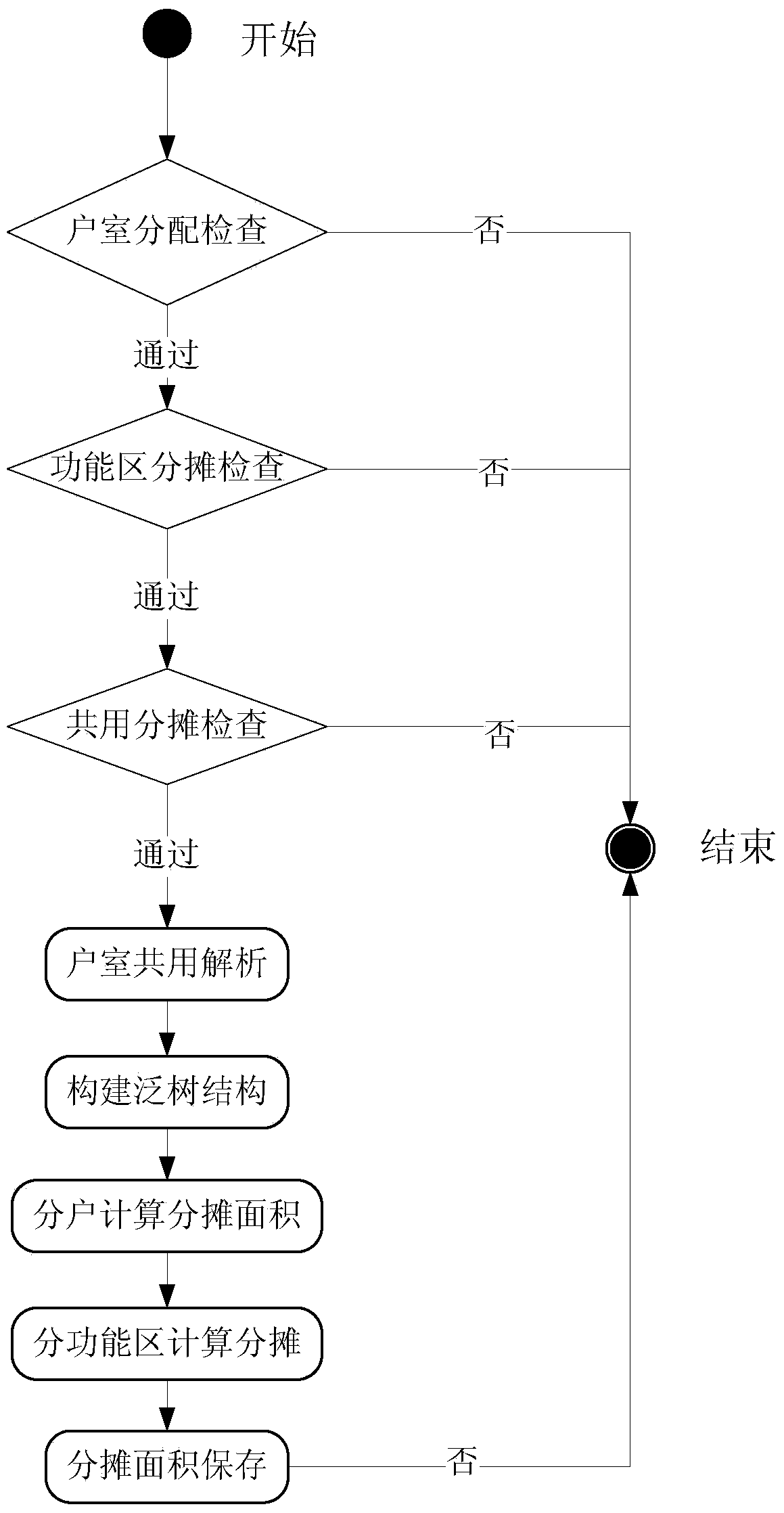
Storied household graph management system based on generic tree apportionment model
ActiveCN103824157AAchieve seamless connectionReduce manual intermediate linksResourcesGraphicsSurveyor
The invention discloses a storied household graph management system based on a generic tree apportionment model. The system comprises a house wall editing module, a room definition module, an area apportionment calculating module and a house graph making and printing module. The house wall editing module is used for drawing house walls, defining the width of the walls and establishing the topological relation between the walls. The room definition module is used for automatically working out a room graph of a house according to wall data formed by the house wall editing module and classifying rooms of the house according to functional zones where the rooms of the house belong. The area apportionment calculating module is used for performing apportionment calculation according to the functional zones where the rooms of the house belong and calculating apportioned area and apportioned zones of all households. The house graph making and printing module is used for making and printing graphs according to a measuring scale, printing house household area list and the like, wherein the graphs are formed according to user house graph data. The dynamic error correction technology is adopted in the system, shared area apportionment is performed according to the standard apportionment model, and the accuracy and the reliability of area calculation in house property surveying and mapping management are improved.
Owner:NANJING NORMAL UNIVERSITY
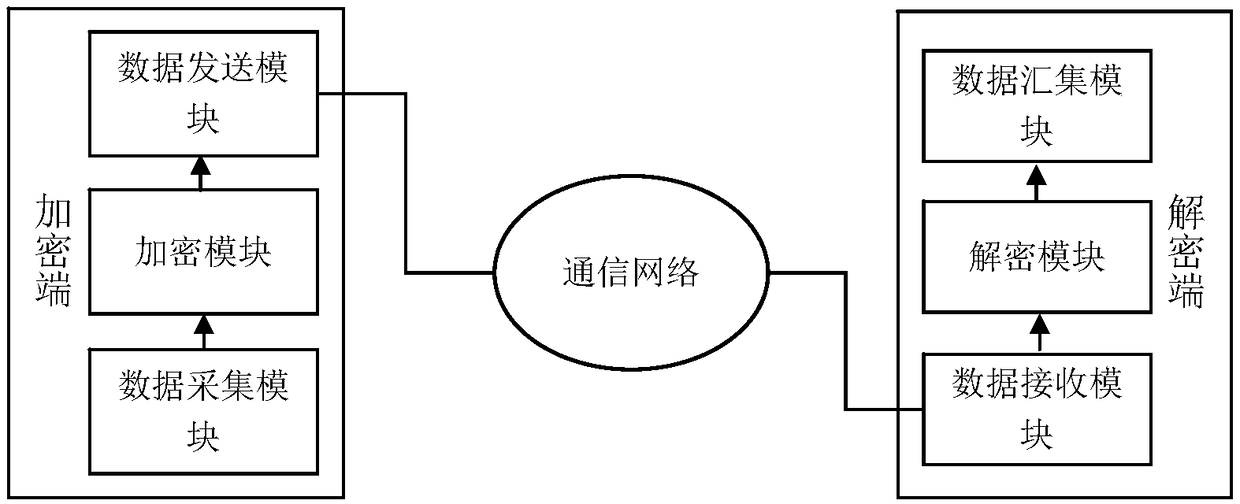
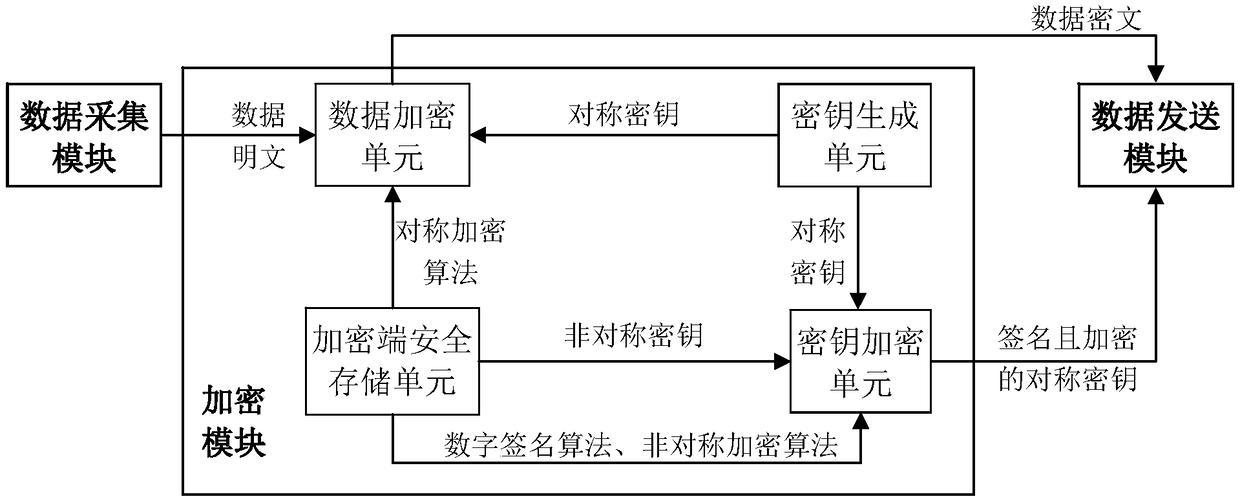
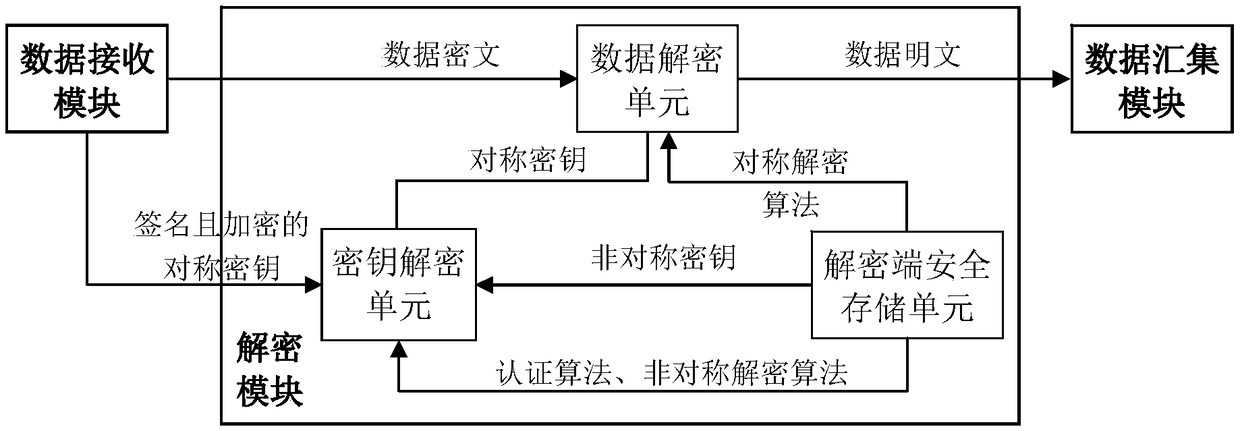
Encrypted transmission method and encrypted transmission system for marine environment detection data
InactiveCN108881318AImplement encrypted transmissionReduce communication costsKey distribution for secure communicationMultiple keys/algorithms usagePlaintextSecure communication
The invention discloses an encrypted transmission method and encrypted transmission system for marine environment detection data. Encrypted transmission and decryption processing of the collected marine environment data plaintext are completed through one-time communication. An encryption end uses the marine environment data plaintext to generate a data ciphertext by adopting a symmetric encryption method, and the symmetric secret key are safely processed by adopting a digital signature and an asymmetric encryption mechanism. The data ciphertext and the symmetric secret key which are subjectedto safety processing are packaged into a communication data packet to be transmitted to a decryption end. After receiving the data, the decryption end firstly performs decryption and authentication processing on the symmetric secret key, and then decrypts the data ciphertext by the processed symmetric secret key. The data plaintext is restored. The method and system disclosed by the invention areused for safe communication of observation data of ocean sensors, and have small communication cost. The effects of safety, low power consumption and high efficiency of marine environment detection data transmission are guaranteed.
Owner:程杰
Network data file storing method and device based on WEB application
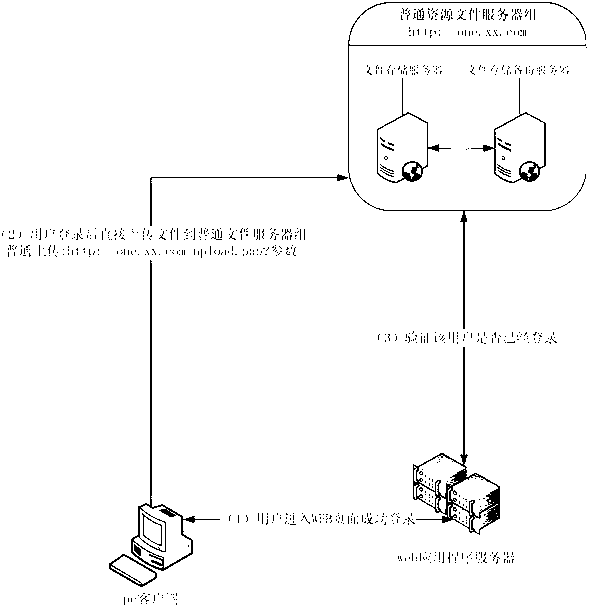
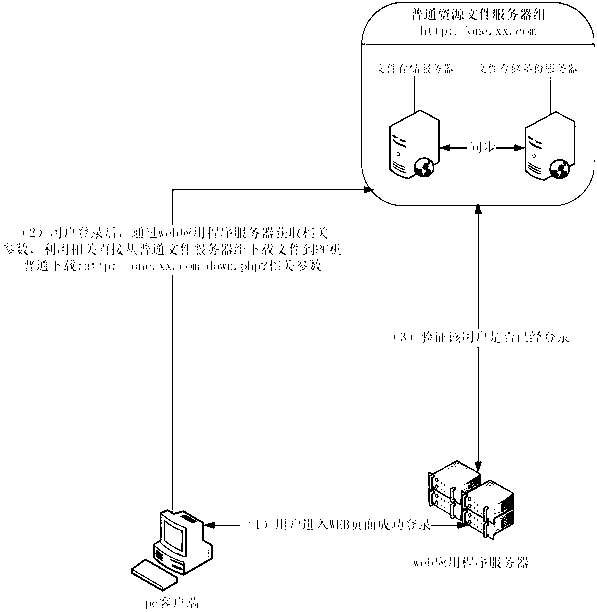
ActiveCN103024020ARealize ordinaryImplement encrypted transmissionTransmissionData fileApplication software
The invention discloses a network data file storing device based on WEB application. The device comprises a WEB application server, a common resources file server group, an encrypted resources file server group and a hot spot resources file server group. The WEB application server is written in PHP (Professional Hypertext Preprocessor) and provides relative information of websites. When the resource reading is involved, a request will be sent to the resources file server group. If the data are encrypted, the encrypted resources file server group is needed to be read. The network data file storing device based on WEB application can effectively achieve mass data common transmission and encryption transmission based on HTTP (Hyper Text Transport Protocol) and can achieve user permission limit to resource data, thereby achieving the purpose of load balancing. General control of common data and encryption transmission data is achieved by choosing different transmission ways according to different business requirements, thereby resources uploading and downloading websites have a more flexible and appropriate framework way.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
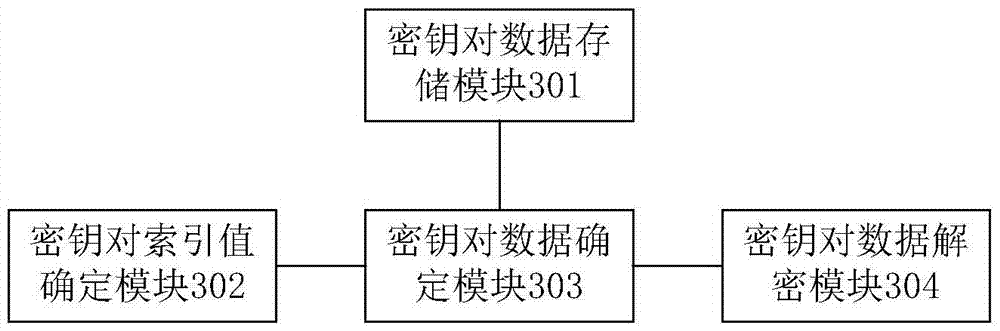
Method and device for determining key pair and data processing method
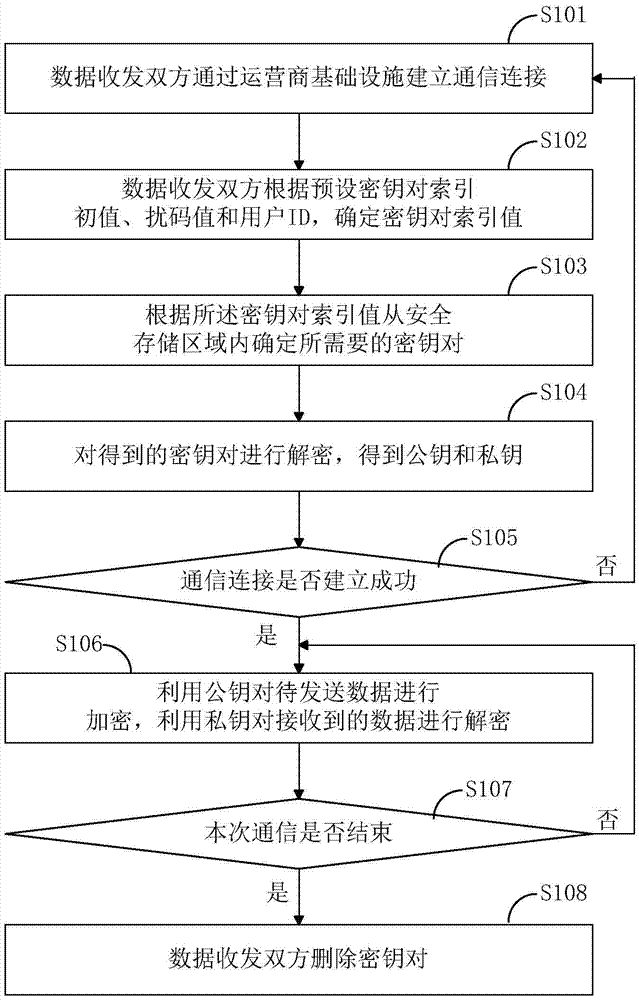
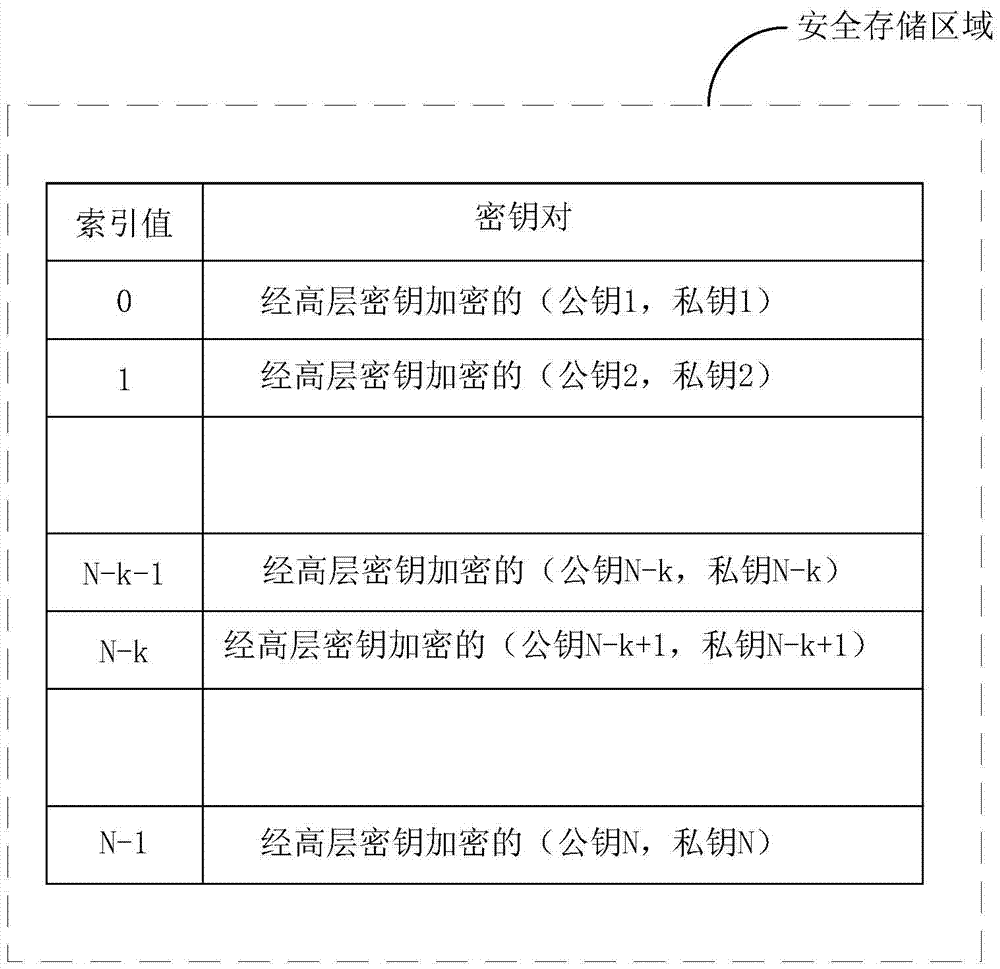
ActiveCN105450392AImplement encrypted transmissionSolve the leakage problemKey distribution for secure communicationMultiple keys/algorithms usagePaired DataData information
The invention discloses a method and a device for determining a key pair and a data processing method. The method for determining the key pair comprises: a key pair index value generating step of generating a key pair index value according to a preset key pair index initial value, a scrambling value and an ID or multicast / broadcast ID of equipment performing data communication; a key pair data determining step of determining required key pair data in a secure storage area according to the key pair index value; and a key pair determining step of decrypting the key pair data with a preset high-level key to obtain a required key pair. Through adoption of the method for determining the key pair, an encryption key can be appointed by a data receiving party and a data transmitting party without key management entities such as KTC / KDC, so that encryption transmission of voice and data information is realized, and the problem of information leakage in a current wireless communication process is solved.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
Internet of Things data encryption transmission method and system
InactiveCN111431922AImprove securityImprove reliabilityKey distribution for secure communicationThe InternetHealth examination
The embodiment of the invention provides an Internet of Things data encryption transmission method and system, and the method comprises the steps: calling a health examination assembly corresponding to a target micro-service architecture system, wherein the health examination assembly comprises a preset health examination core assembly and a received pluggable health examination assembly defined by a user; performing health examination on each target service component corresponding to the target micro-service architecture system by applying the health examination assembly to obtain a health examination result corresponding to each target service component; and determining whether the health examination result corresponding to each target service component meets a preset health condition ornot, and if so, scheduling each target service component based on a preset scheduling rule. According to the application, encrypted transmission of the Internet of Things data can be realized by effectively utilizing a data encryption mode, the encrypted transmission process is high in reliability and high in security, and the security and reliability of the Internet of Things data can be effectively improved.
Owner:CHINA CONSTRUCTION BANK +1
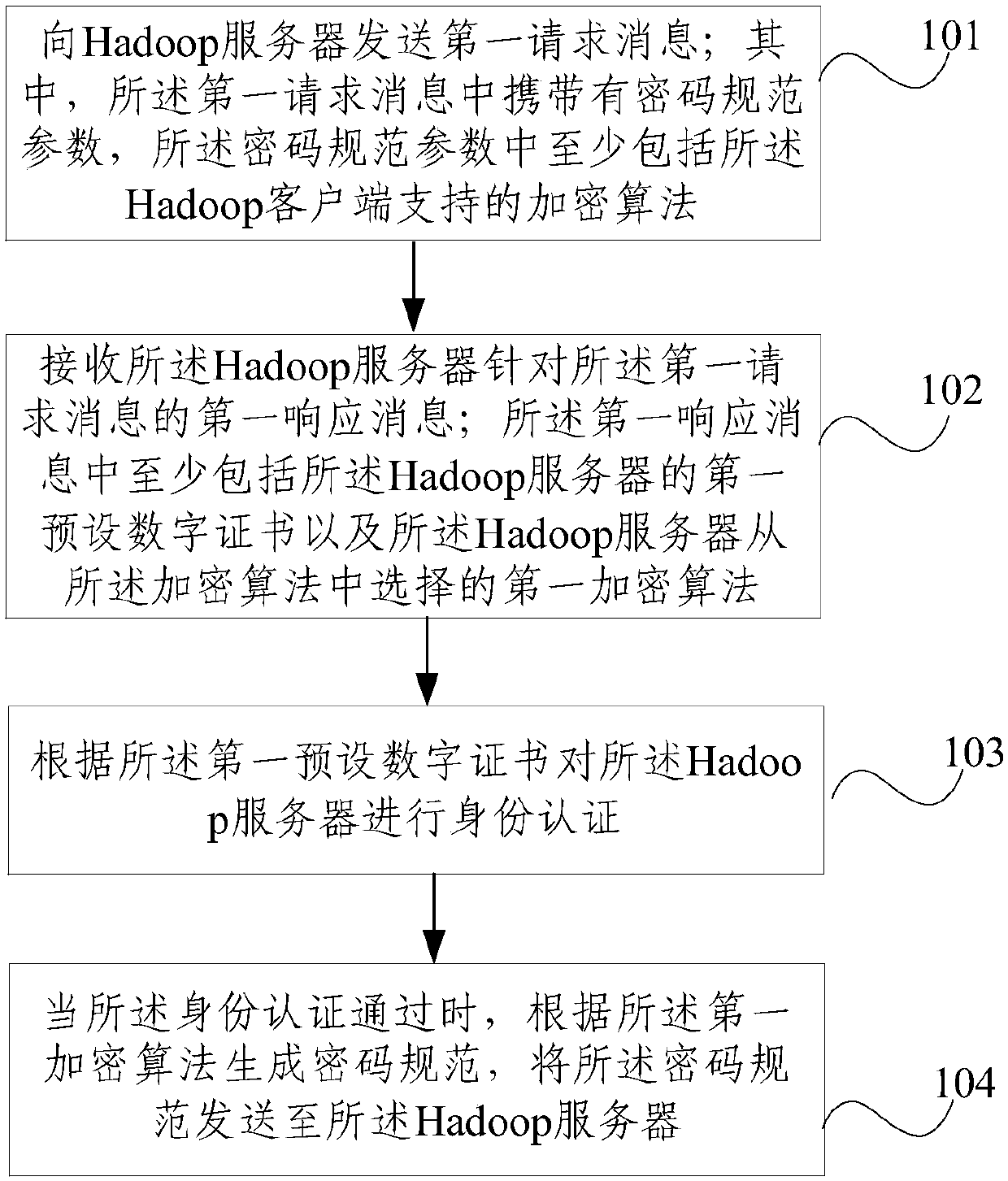
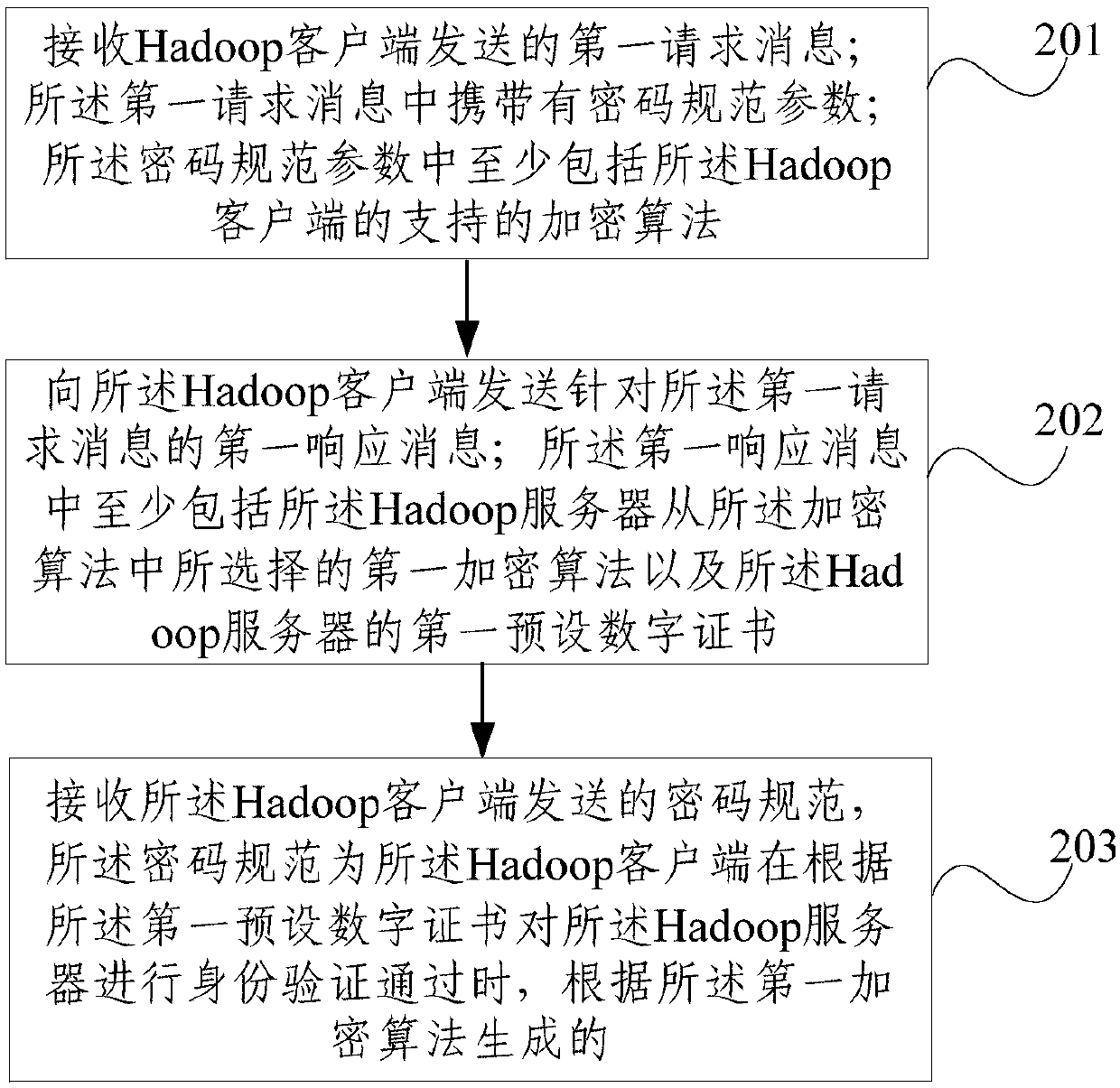
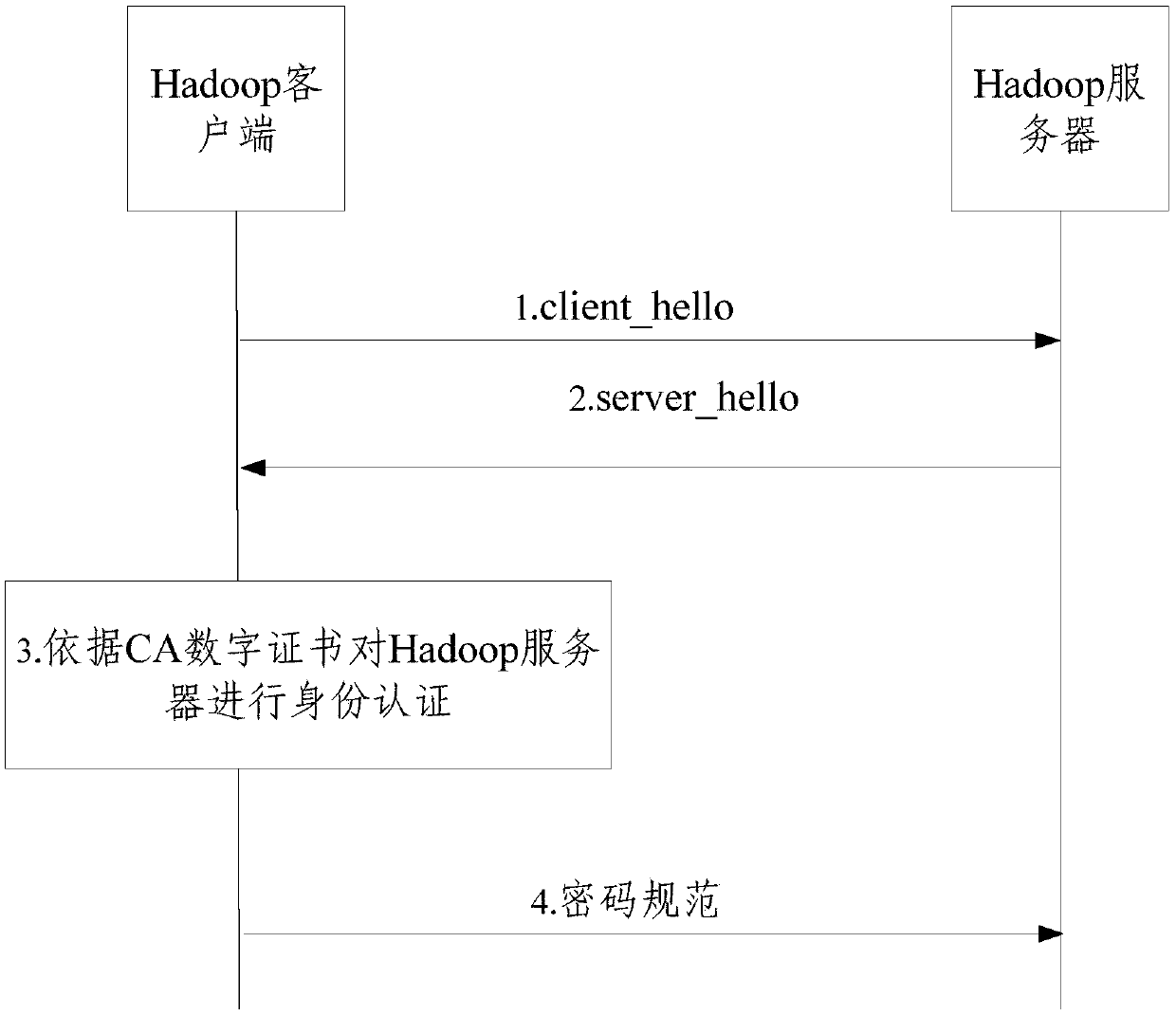
Communication method and device
InactiveCN110581829AImprove securityImplement encrypted transmissionKey distribution for secure communicationTransfer procedurePassword
The embodiment of the invention provides a communication method and device. The method is applied to a Hadoop client, and comprises the following steps: sending a first request message to a Hadoop server, wherein the first request message carries a password specification parameter, and the password specification parameter at least comprises an encryption algorithm supported by the Hadoop client; receiving a first response message of the Hadoop server for the first request message, wherein the first response message at least comprises a first preset digital certificate of the Hadoop server anda first encryption algorithm selected by the Hadoop server from the encryption algorithms; performing identity authentication on the Hadoop server according to the first preset digital certificate; and when the identity authentication is passed, generating a password specification according to the first encryption algorithm, and sending the password specification to the Hadoop server. According tothe embodiment of the invention, the encrypted transmission of the data in the Hadoop cluster is realized, and the data encryption technology is utilized to ensure that the data cannot be interceptedor eavesdropped in the transmission process on the network.
Owner:CHINA MOBILE COMM GRP CO LTD +1
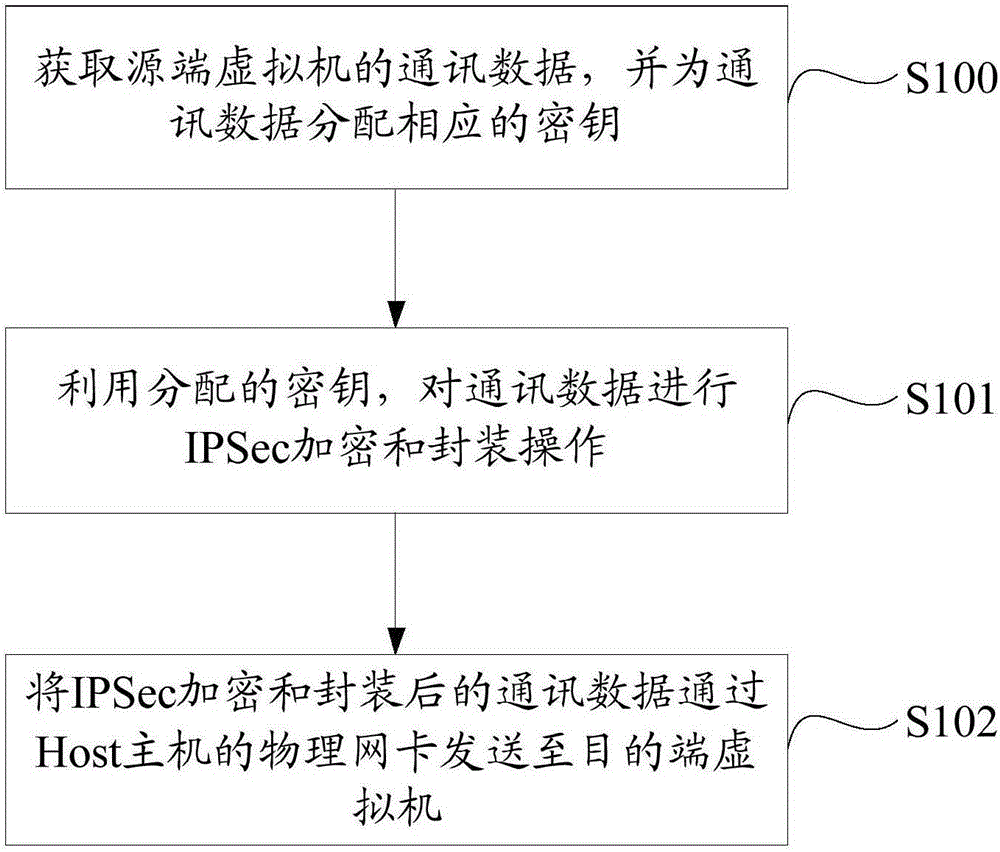
Virtual machine communication data encryption method and system
InactiveCN105245430AImplement encrypted transmissionImprove transmission securityNetworks interconnectionNetwork interface controllerPhysical network
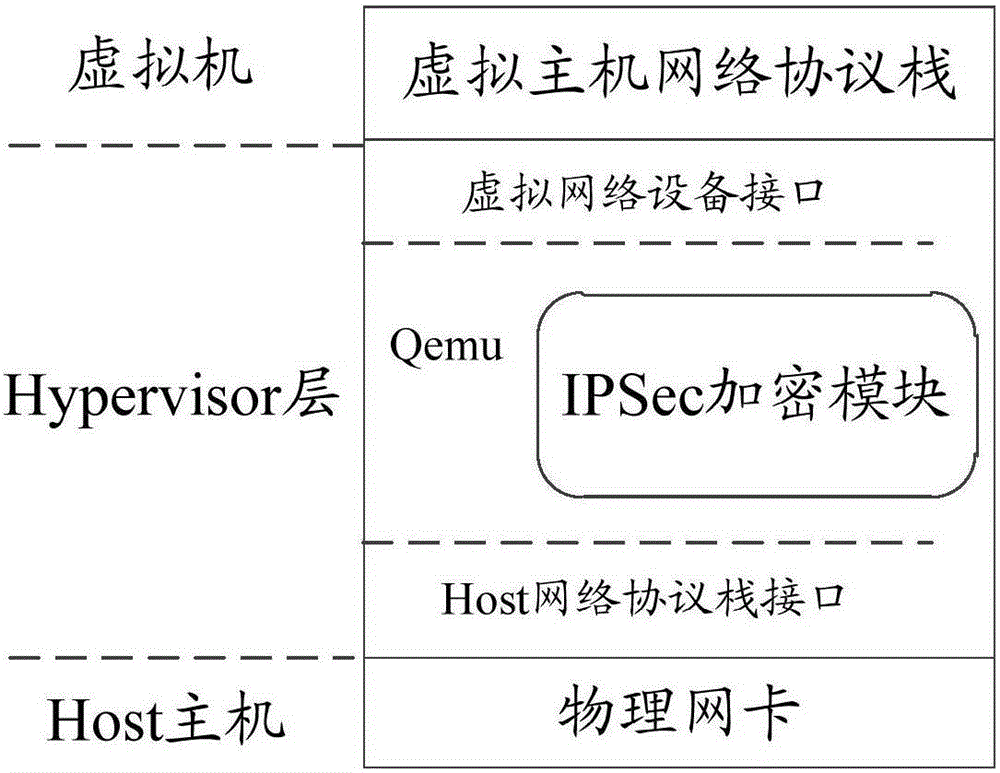
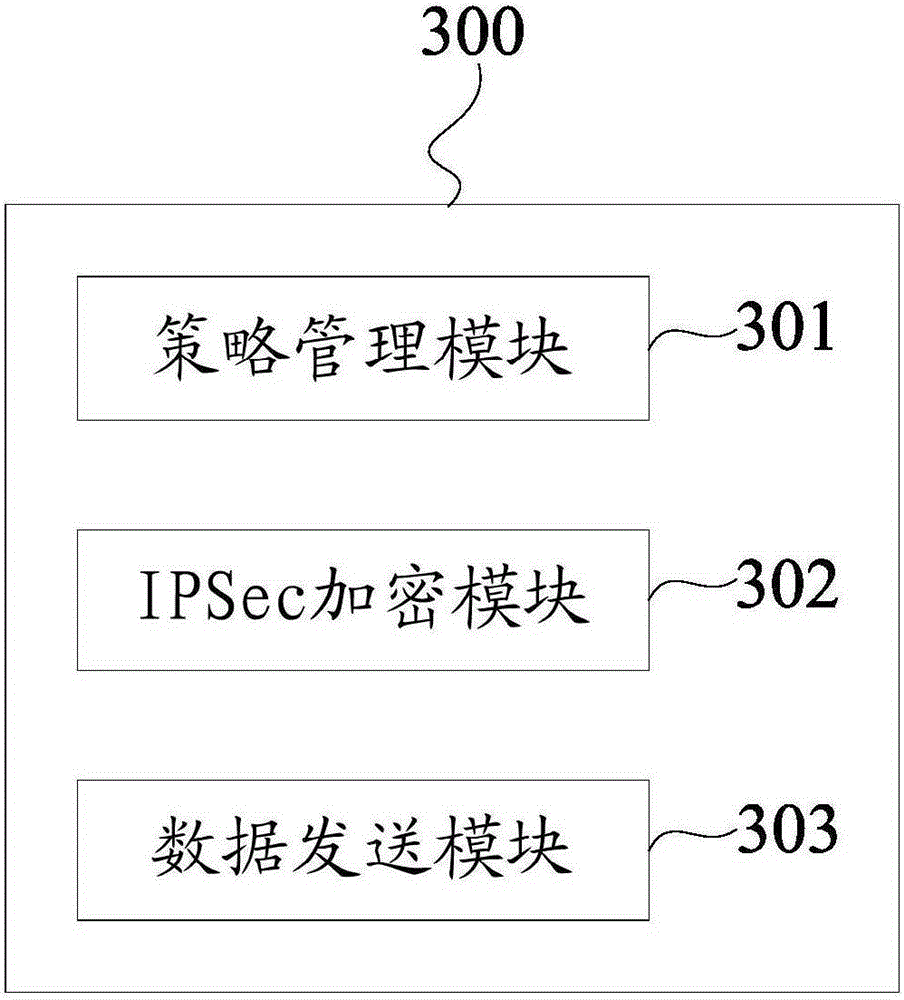
The invention discloses a virtual machine communication data encryption method and system. The method comprises the following steps: acquiring communication data of a source-end virtual machine, and allocating a corresponding key to the communication data, wherein the communication data is an IP (Internet Protocol) message of the source-end virtual machine on a network layer; performing IPSec encryption and encapsulation operations on the communication data by using an allocated key; and transmitting the communication data being subjected to IPSec encryption and encapsulation to a destination-end virtual machine through a physical network card of a Host. Through adoption of the method and the system, encryption transmission of the communication data between the source-end virtual machine and the destination-end virtual machine is realized, and the aims of enhancing isolation of communication data among different tenant virtual machines and enhancing transmission security of the communication data among the virtual machines are fulfilled.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Big data security system based on financial service management
InactiveCN109246088AImplement encrypted transmissionImprove securityFinanceData switching networksBig data securityThe Internet
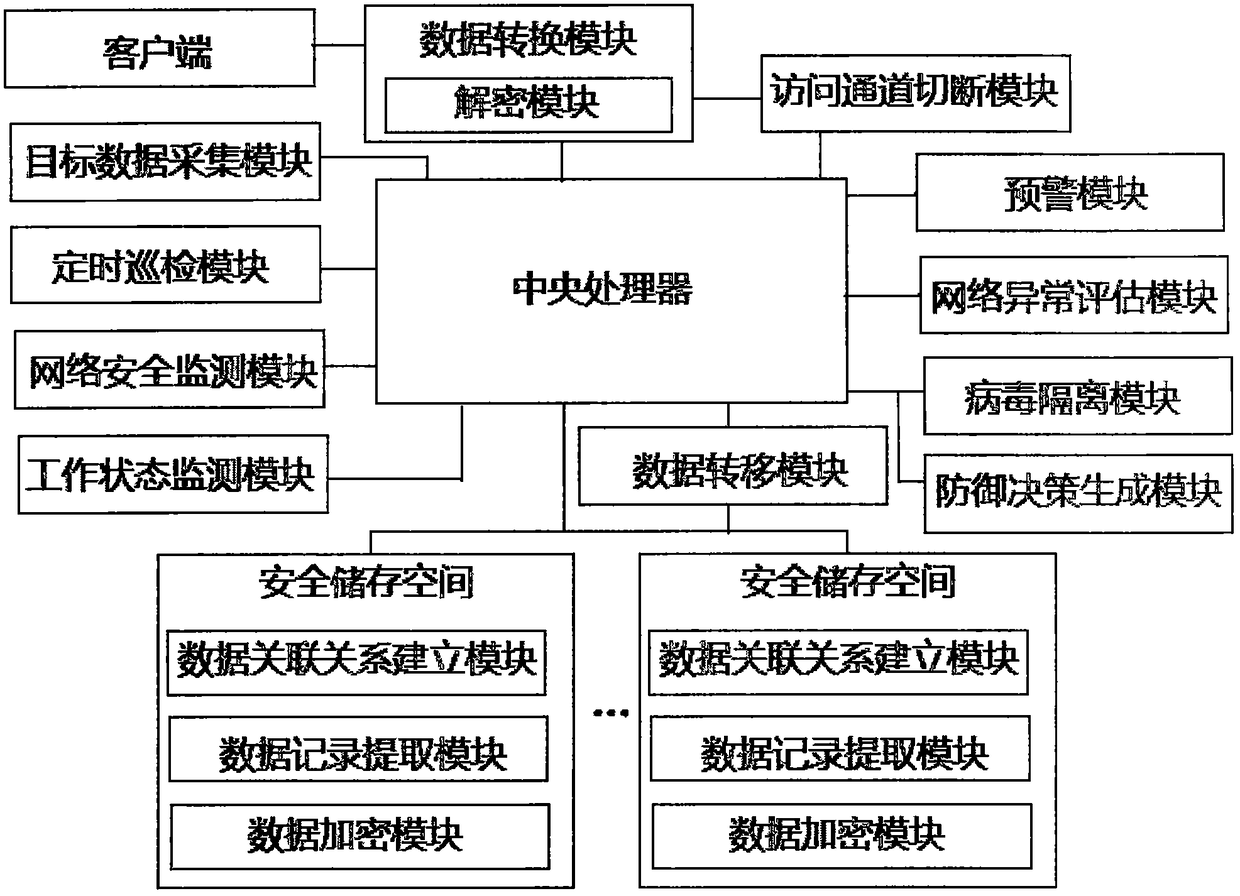
The invention discloses a big data security system based on financial service management, and the system comprises a target data acquisition module, a safety storage space, a data conversion module, aworking state monitoring module, an early warning module, an access channel cutting module and a central processing unit. The system realizes the encrypted transmission, encrypted storage and sharingof data within the authority, and the system has the function of monitoring the working state of each module, and can perform the corresponding decision execution according to different monitoring results, thereby greatly improving the security of the data. Meanwhile, the access to a database does not directly depend on the Internet, thereby blocking the possibility of hackers directly in attacking a database system, and avoiding the performance loss caused by the attack while ensuring the security of the database system.
Owner:田金荣
A Computer Data Protection System
InactiveCN109145557AImplement encrypted transmissionImprove securityDigital data protectionInternal/peripheral component protectionStructure of Management InformationProtection system
The invention discloses a computer data protection system, comprising a security storage space, which is used for storing data; a man-machine operation module, configured to pre-record and verify theaccess authority of the biometric model controlling the secure storage space; an encryption module for encrypting data; a data conversion module, configured to decrypt the data according to the biometric model input by the man-machine operation module; an operation state monitoring module, which is used for recording the operation state of the user, performing real-time evaluation on the operationstate of the current user, and obtaining a monitoring result; a data transfer module used for receiving the monitoring result obtained by the operation state monitoring module and judging whether tocarry out data transfer operation or not. The invention realizes the data encryption transmission, encryption storage and sharing within the authority, and the system has the safety monitoring function of the operation state, which greatly improves the safety of the data, greatly improves the storage of the structural grid and the physical quantity, localizes the accessing storage data, and further ensures the safety of the data.
Owner:XIAN AERONAUTICAL POLYTECHNIC INST
Method of connecting to WIFI network by mobile terminals and system thereof
ActiveCN106792687AImprove securityImprove convenienceAssess restrictionNetwork topologiesWifi networkAuthorization
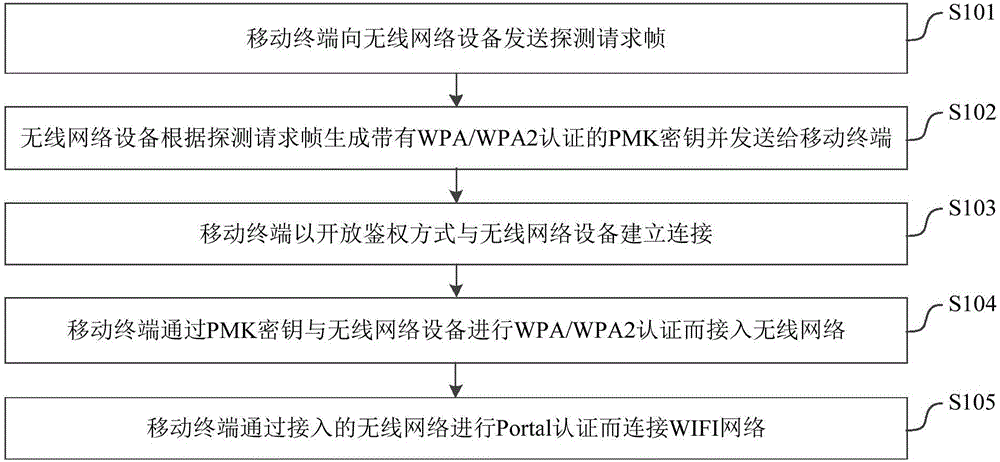
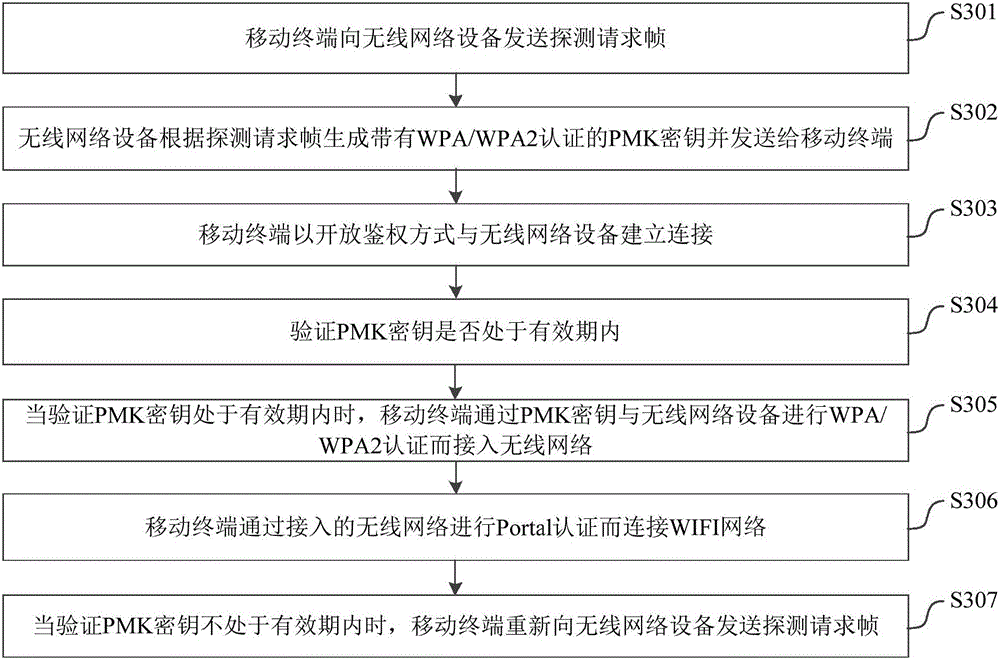
The invention relates to the field of wireless network connection technology, which discloses a method of connecting to WIFI networks by mobile terminals and a system thereof. The method of connecting to WIFI networks by mobile terminals comprises steps as follows. A detection request frame is sent to a wireless network device by a mobile terminal. A PMK key with WPA / WPA2 certification is generated by the wireless network device according to the detection request frame and sent to the mobile terminal. The mobile terminal is connected to the wireless network device by using the method of open authorization. The mobile terminal accesses the wireless network by WPA / WPA2 authentication with the wireless network device by using the PMK key. Then the mobile terminal is connected to the WIFI network by Portal authentication through the accessed wireless network. Compared with the prior art, the invention realizes WIFI wireless network connection and encryption transmission of network data conveniently and quickly. The security, convenience and privacy of connecting to the WIFI networks by the mobile terminals are improved.
Owner:台州市吉吉知识产权运营有限公司
Network secret key interaction system, device and method
ActiveCN108777678AImplement encrypted transmissionImprove securityKey distribution for secure communicationInteraction systemsNetwork key
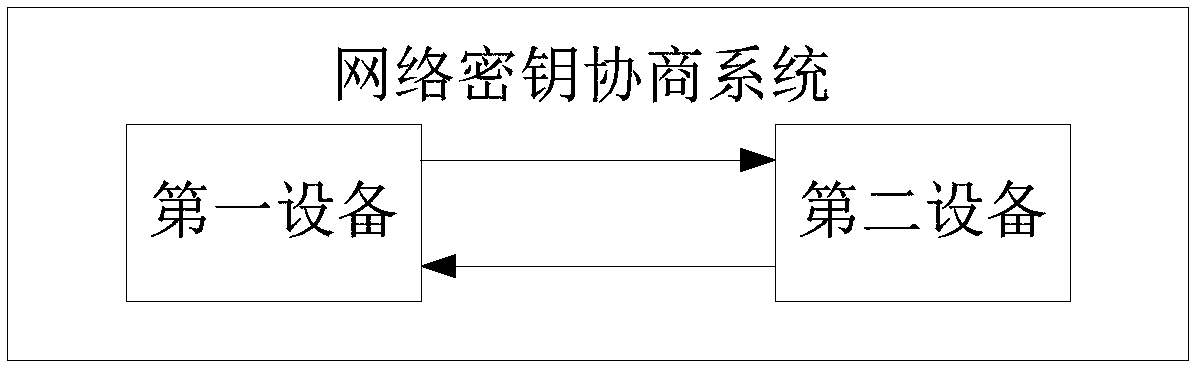
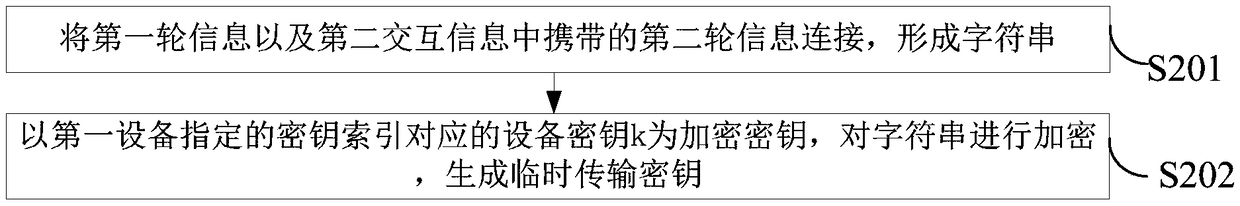
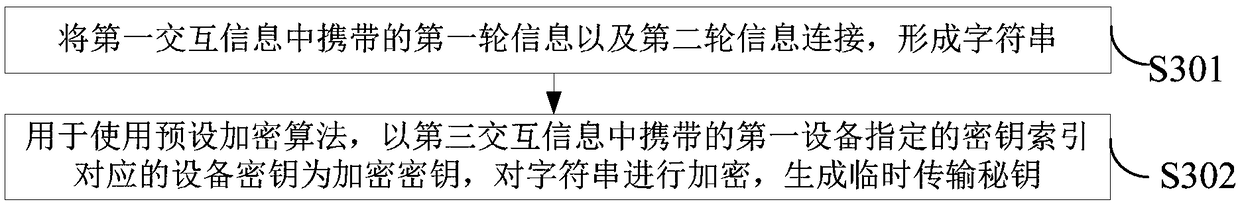
The invention provides a network secret key interaction system, device and method. The system comprises a first device and a second device, wherein the first device is used for sending the generated first interaction information to the second device; the second interaction information sent by the second device after reception of the first interaction information is received; based on the first round of information contained by the first interaction information and the second round of information contained by the second interaction information, a temporary transmission secret key is generated;after the temporary transmission secret key is utilized to encrypt a randomly-generated network secret key, the network secret key is contained in the third interaction information, and the third interaction information with the network secret key is sent to the second device; after the third interaction information is received by the second device, a temporary transmission secret key is generatedbased on the first round of information contained by the first interaction information and the locally-generated second round of information, and the generated temporary transmission secret key is utilized to obtain the network secret key contained in the third interaction information. The system is advantaged in that the network secret key can be negotiated by multiple handshakes, the network secret key can be replaced in time when the network secret key is stolen, and security of wireless network communication is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
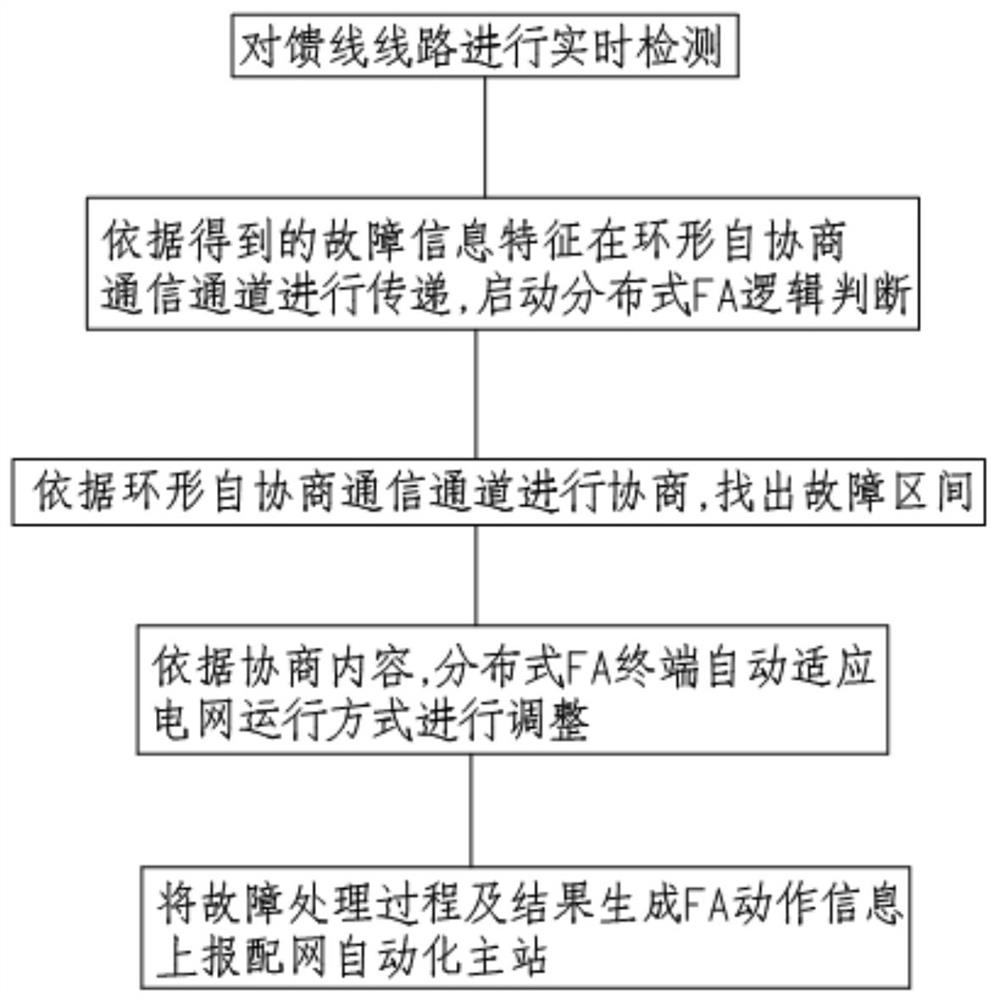
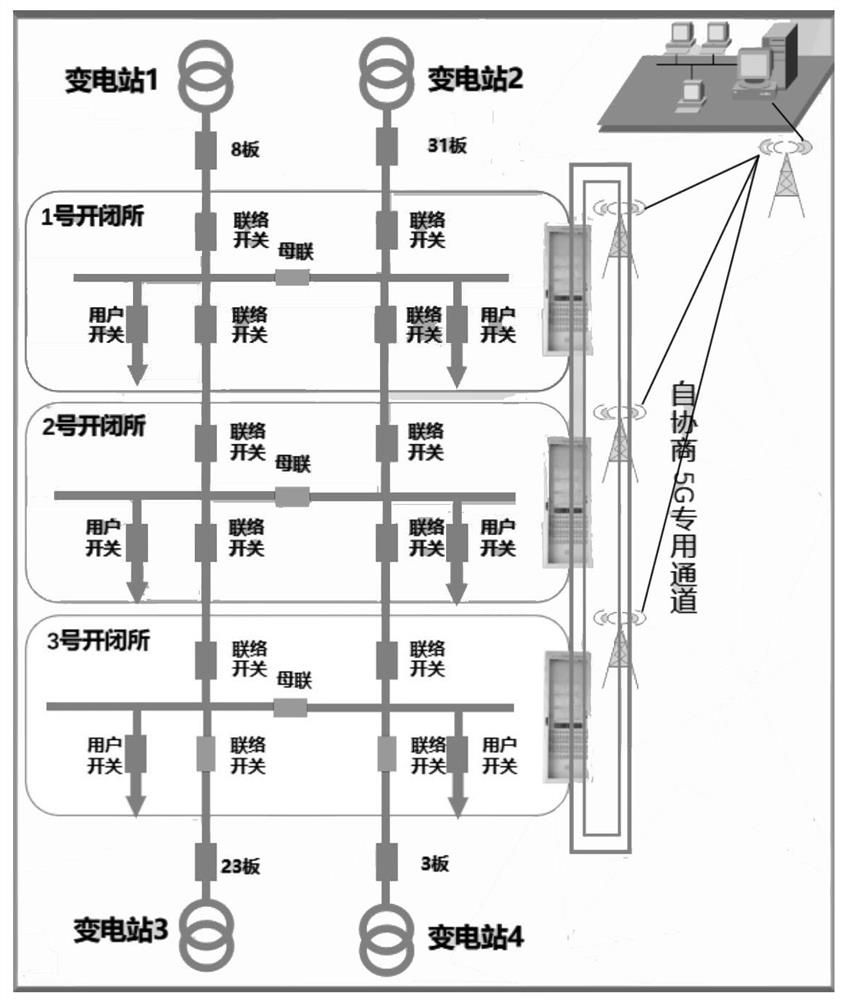
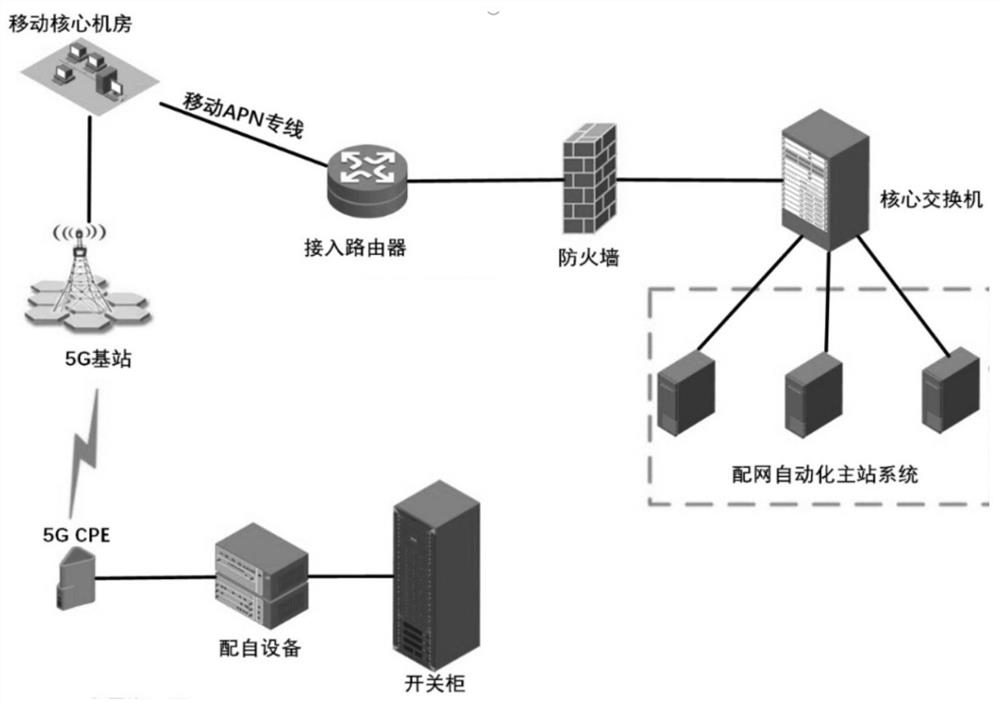
Intelligent distributed feeder method and device based on 5G communication
PendingCN113131448AAccurate discriminationRealize fault locationEmergency protective circuit arrangementsData switching networksFiber-optic communicationHigh bandwidth
The invention discloses an intelligent distributed feeder method and device based on 5G communication. The device comprises at least one switching station comprehensive intelligent terminal, a feeder switch, and a distributed FA terminal, the distributed FA terminal is installed at the switching station comprehensive intelligent terminal and a power distribution terminal in an overhead line, and is used for detecting the electric signal and the on-off state information of the feeder switch, and the switching station comprehensive intelligent terminal forms an annular auto-negotiation communication channel through the 5G wireless data terminal, and is communicated with the distribution network automation master station through the 5G communication topology network. Communication between power distribution terminals and communication of a master station are realized by utilizing the technical characteristics of low time delay and high bandwidth of a 5G network, wireless communication interaction can be realized after a line fault occurs, positioning, isolation and power transfer of a fault section can be automatically completed, the defects of long isolation and removal time existing in traditional feeder protection can be overcome, meanwhile, differential protection based on optical fiber communication can be replaced, and laying of optical fiber lines in engineering construction is not needed.
Owner:ZHENGZHOU ELECTRIC POWER COLLEGE
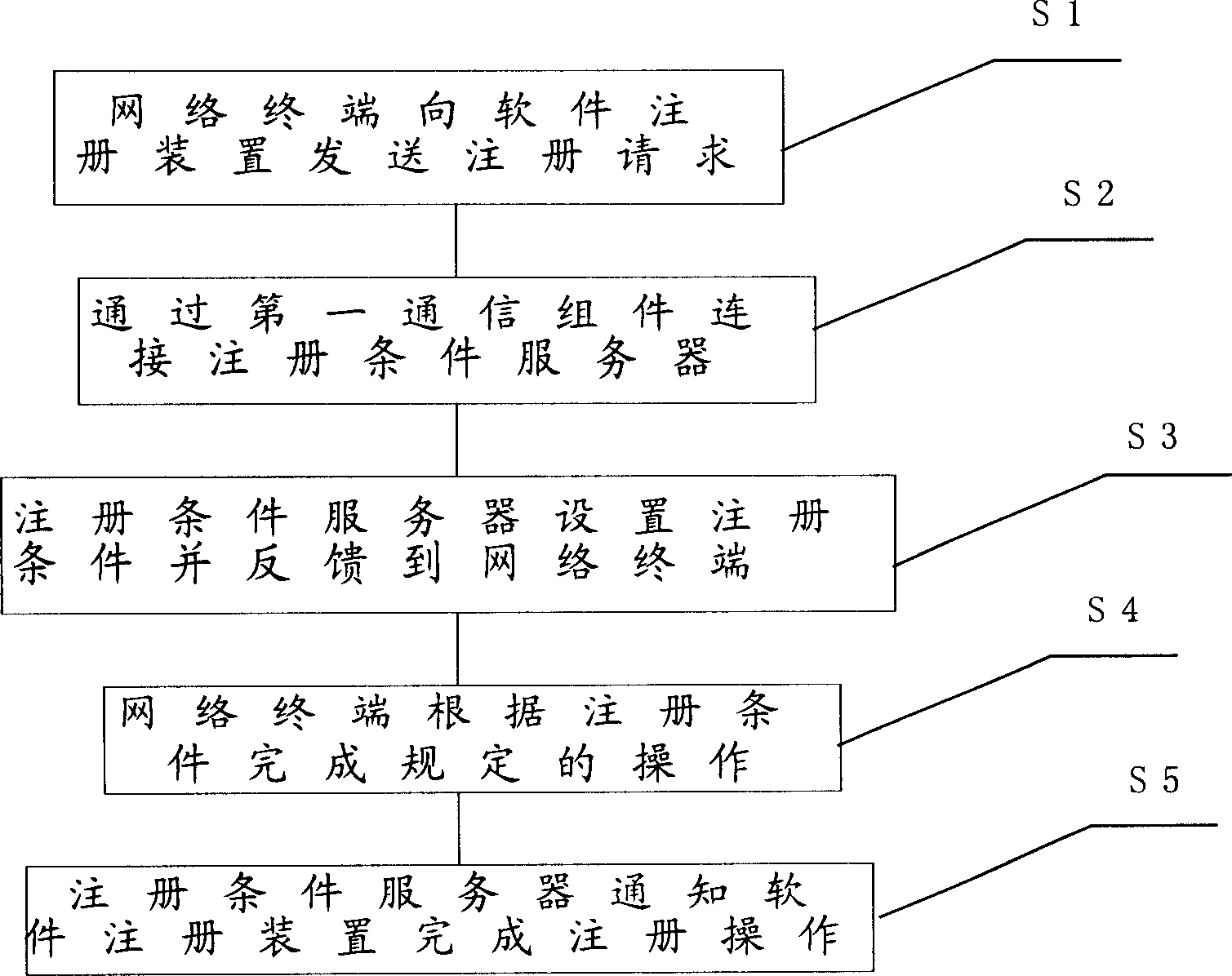
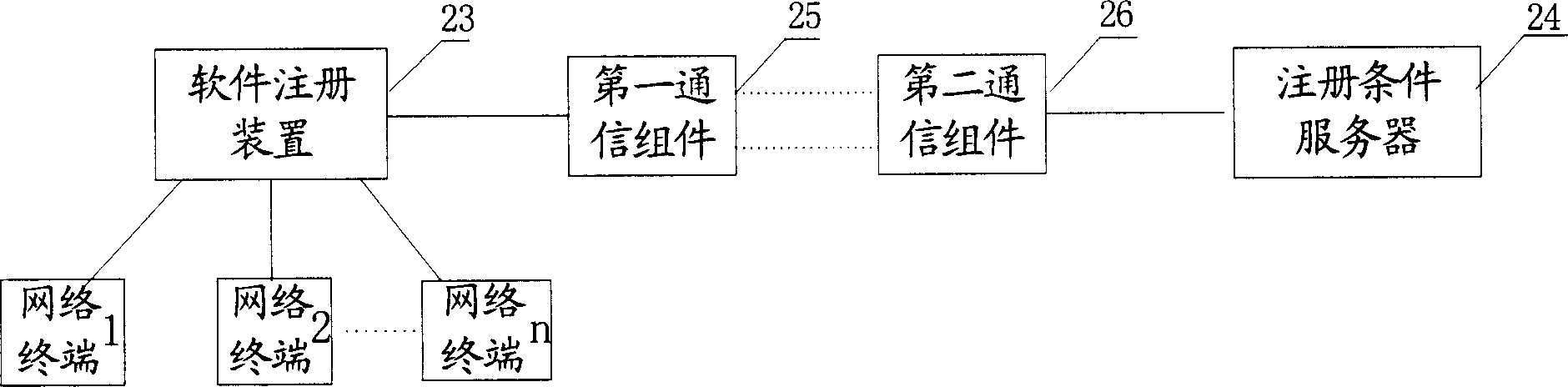
Network-based software registration method and system
ActiveCN1852205AFix security issuesNon-unique solutionData switching by path configurationNetwork terminationSoftware engineering
The method includes following steps: through first communication module, software registration unit sends registering request to server of registration condition; based on the said registering request, the server of registration condition sets up registering condition, which is fed back to network terminal of requesting registration; according to registering condition, the network terminal accomplishes stated opertions; the server of registration condition informs software registration unit that registering operation is completed. Through receiving and recognizing notice message of satisfying registration condition sent by server of registration condition, the invention carries out software registration directly. In procedure of registering software, the invention cancels use of license, or hides license so as to solve the issue of poor security and anti decipherment in procedure of registering software caused by not uniqueness of license.
Owner:ADVANCED NEW TECH CO LTD
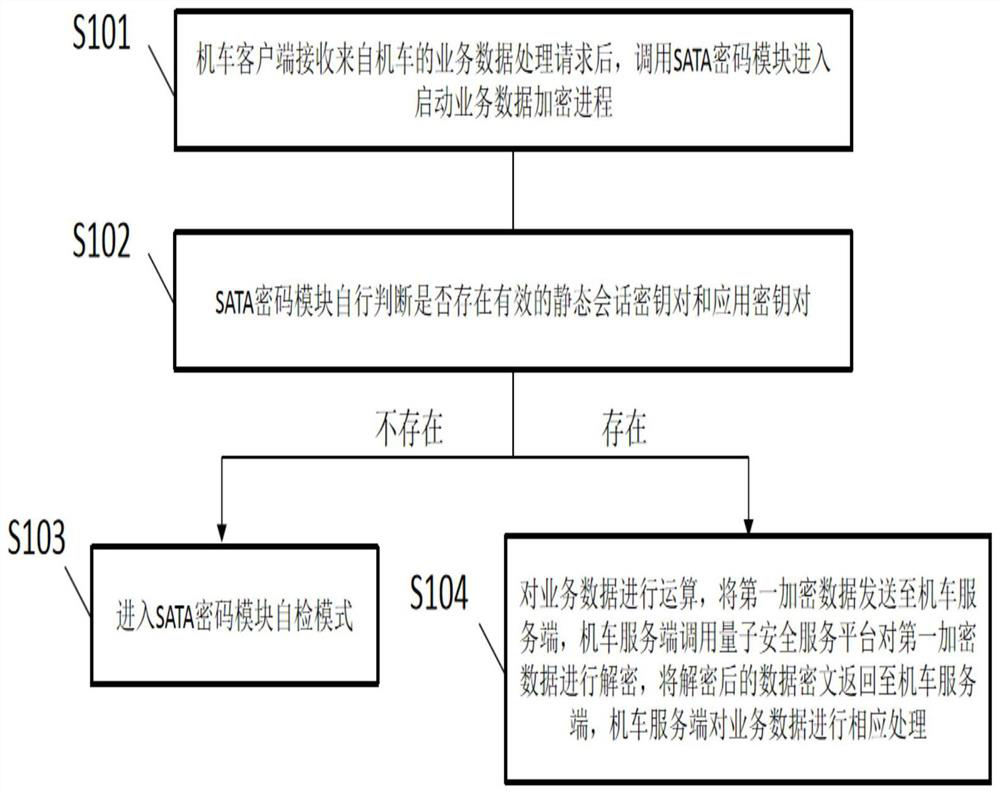
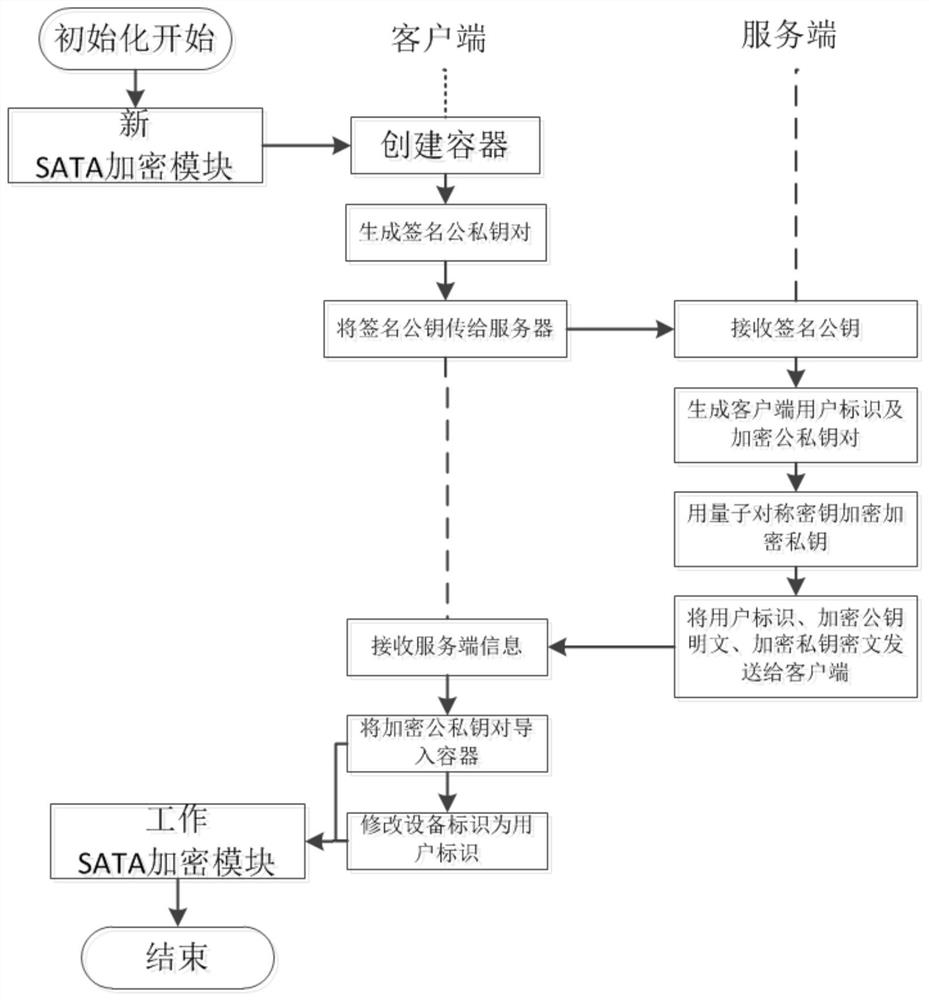
Train service data processing method and system based on quantum key
ActiveCN112865965AImplement encrypted transmissionImprove security levelKey distribution for secure communicationUser identity/authority verificationCiphertextData transport
The invention provides a train service data processing method and system based on a quantum key, and the method comprises the steps: a locomotive client receives a business data processing request from a locomotive, and then calls an SATA password module to enter a business data encryption starting process; the SATA cryptographic module automatically judges whether effective static session key pairs and application key pairs exist or not, if not, entering an SATA cryptographic module self-checking mode, if yes, encrypting service data and subjecting to signature operation, wherein the encrypted first encrypted data are sent to the locomotive server side from the locomotive client side, and the locomotive server calls the quantum security service platform to decrypt the first encrypted data and returns the decrypted data ciphertext to the locomotive server, and the locomotive server correspondingly processes the business data. According to the invention, data encryption transmission of train operation production data from a train end to a business background is realized, so that comprehensive password protection is provided for locomotive operation control, state acquisition and sensitive data transmission.
Owner:安徽量安通信息科技有限公司
Consultation service control system and method for enterprise e-commerce
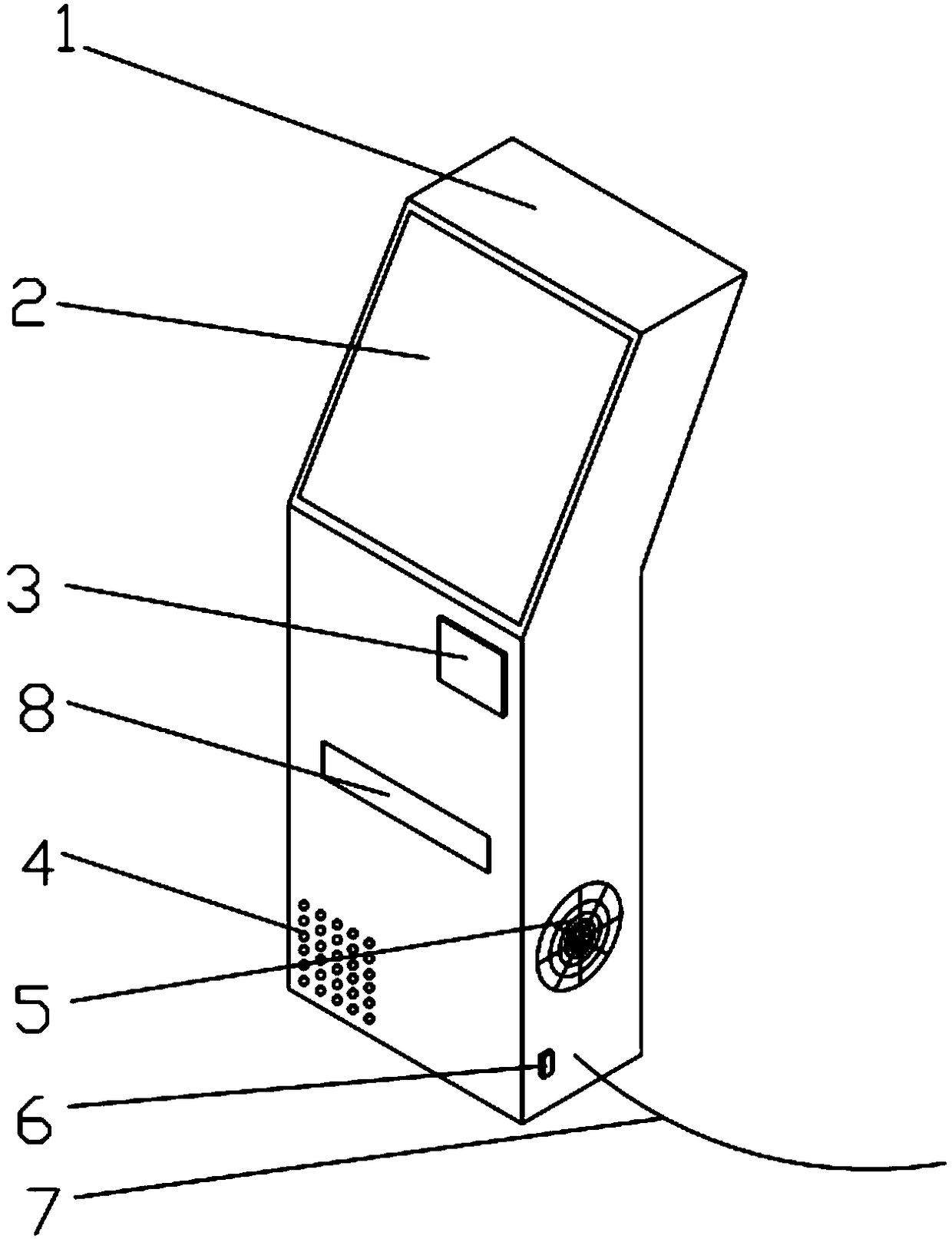
InactiveCN109326238AEasy to operateEasy to learnAdvertisingDigital data authenticationControl systemService control
The invention belongs to the technical field of consultation devices and discloses a consultation service control system and method for enterprise e-commerce. The system includes a machine box, a touch screen, a card swiping area, loudspeaker ports, a heat dissipation port, a power source switch, an external connecting wire, a printing outlet, a card reader, a printer, a central processor, a loudspeaker and a heat dissipation device. Consultation about correlated information is carried out through the touch screen, the operation is convenient, training is substituted, convenience is provided for staff to understand and learn different kinds of information of the e-commerce, and therefore all the staff of an enterprise can acquire some knowledge about the e-commerce, so that the e-commerce,regarded as a constantly developing concept, becomes an everlasting unchangeable advantage of the enterprise, and the enterprise keeps pace with the time and grasps the opportunity to the time. A card swiping login system for internal staff can obtain information of the staff and monitor the study process of the staff. The results of mobile reading can be printed out, and printed files can be taken away after users finish reading for better self-examination.
Owner:张珈瑞
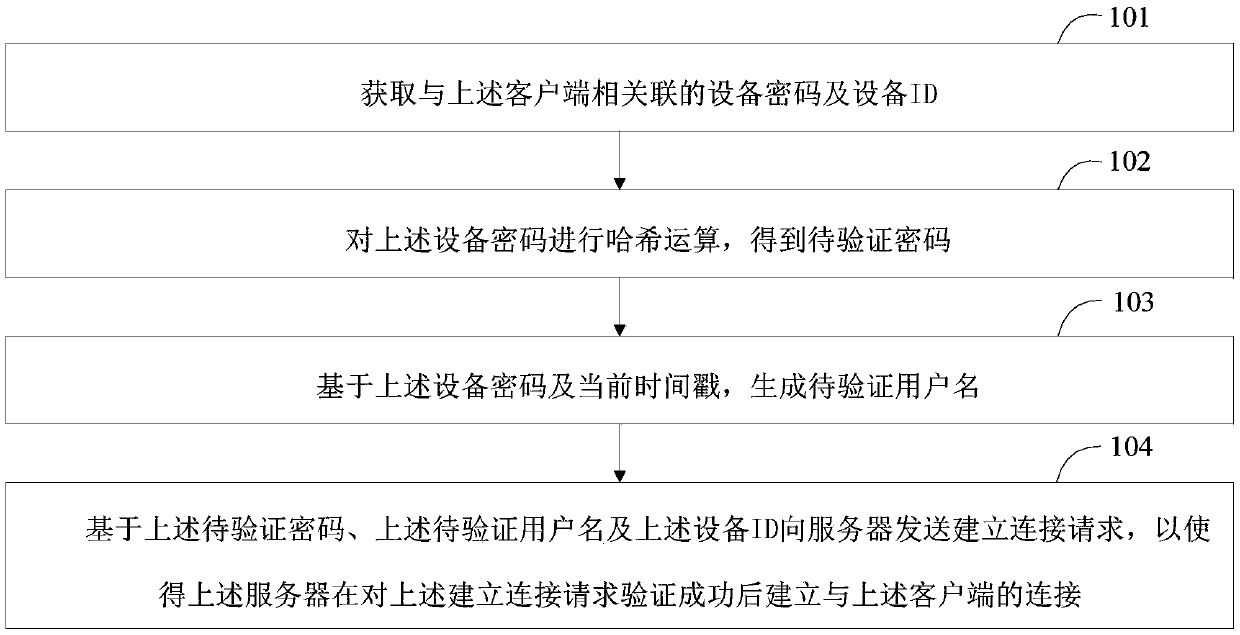
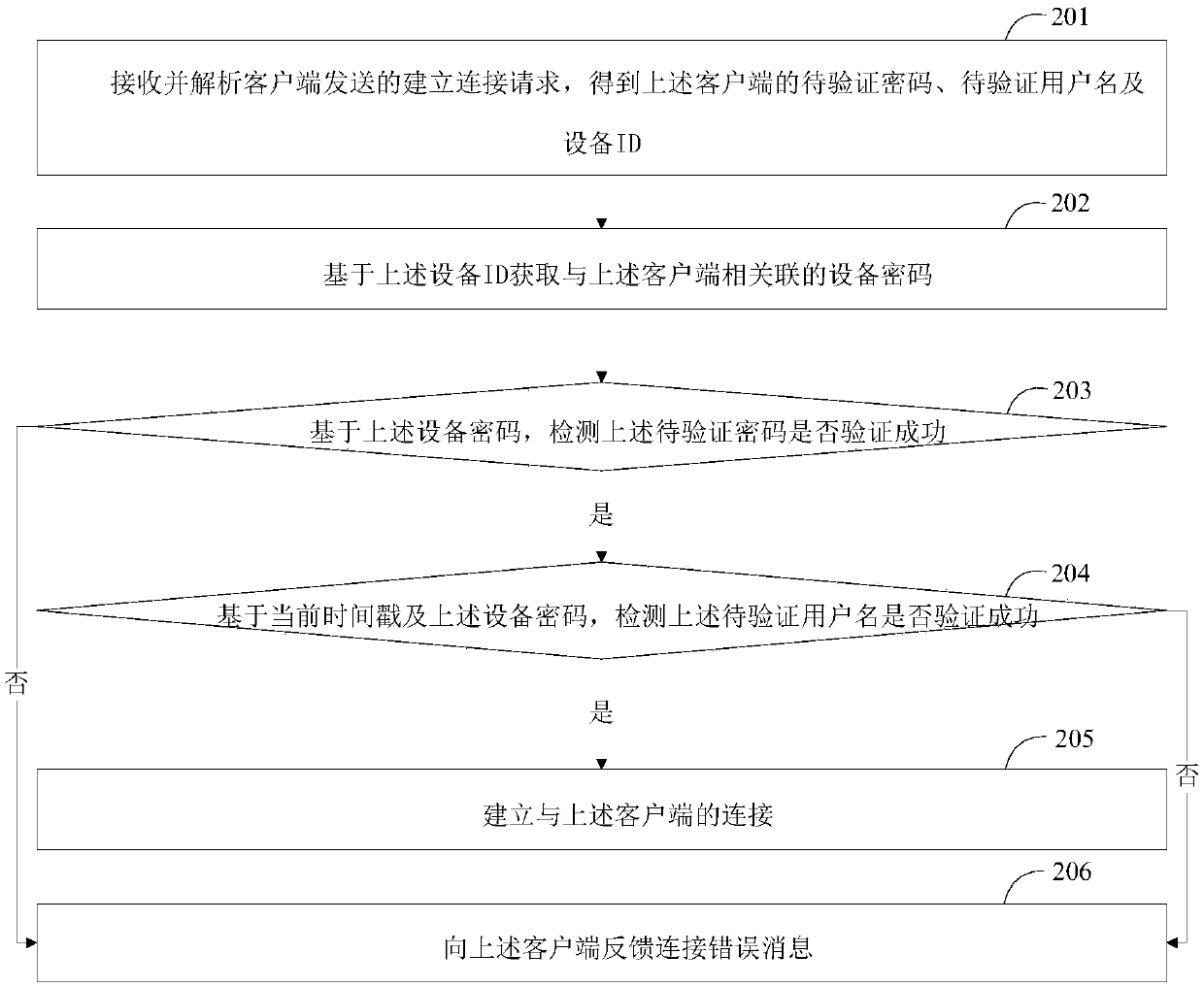
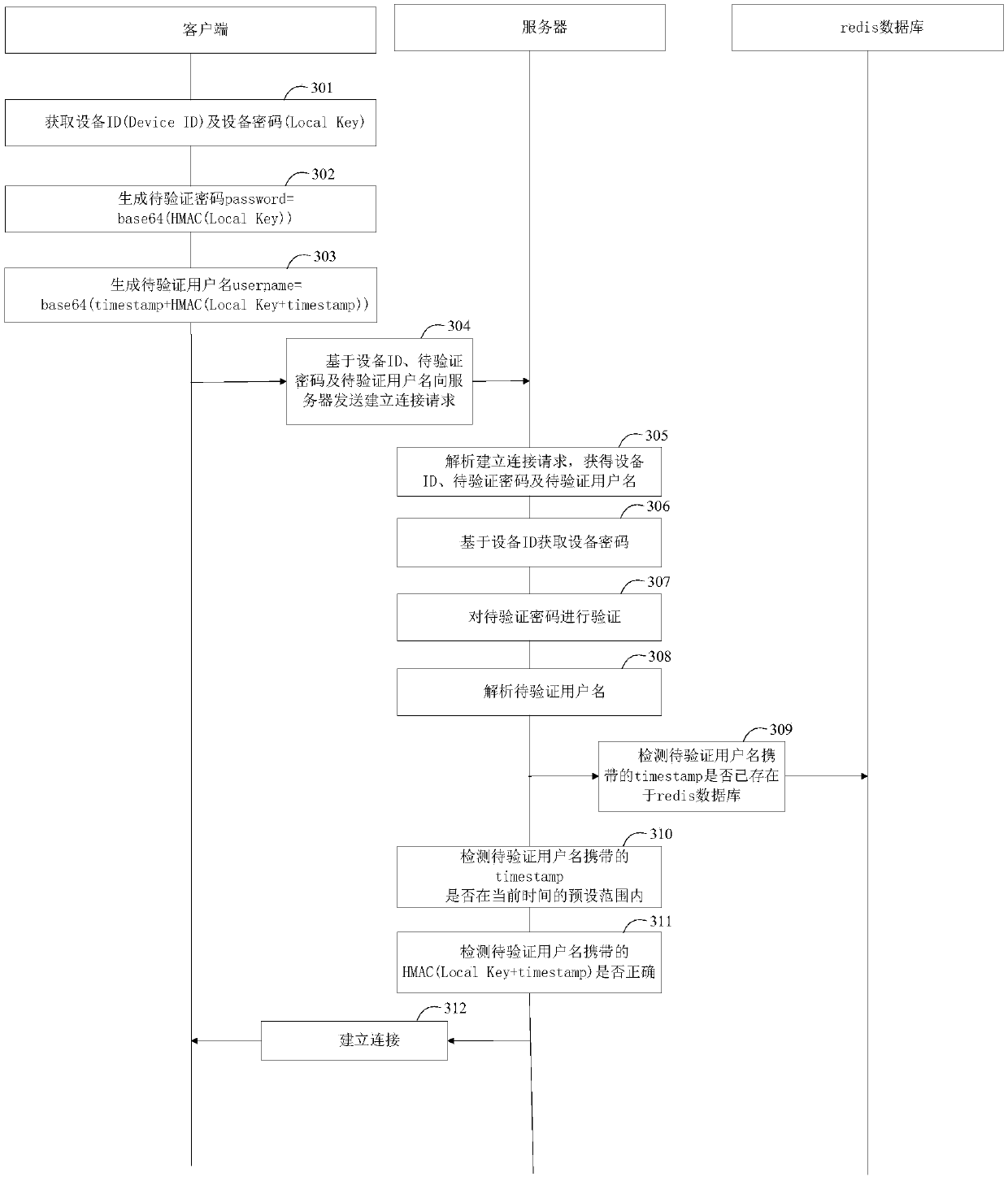
Method for establishing connection, client and server
ActiveCN109587180AImplement encrypted transmissionImprove securityEncryption apparatus with shift registers/memoriesClient-sideTimestamp
The application discloses a method for establishing a connection, a client and a server. The method for establishing a connection includes the following steps: acquiring a device password and a deviceID associated with a client; hashing the device password to obtain a password to be verified; generating a user name to be verified based on the device password and the current timestamp; and sendinga connection establishment request to a server based on the password to be verified, the user name to be verified and the device ID so that the server can establish a connection with the client afterverifying the connection establishment request. Through the scheme of the application, encrypted transmission of the user name and password during the establishment of a connection is realized, and the security of the connection establishment process is improved.
Owner:HANGZHOU TUYA INFORMATION TECH CO LTD
A Lightweight Anonymous Authentication Method with Privacy Protection Based on Internet of Vehicles
ActiveCN108964919BImplement encrypted transmissionSatisfy forward securityUser identity/authority verificationCommunication unitIn vehicle
The invention discloses a lightweight anonymous authentication method with privacy protection based on the Internet of Vehicles, which includes: an initialization step, a private key generation step for a vehicle communication unit, a confidential information generation step that can be anonymously authenticated, an information decryption and verification step, and an anonymous authentication step. Identity Tracing Steps. The invention generates anonymous identity and private key of anonymous identity for intelligent vehicles through trusted center, combines ElGamal encryption algorithm and modified Schnorr signature algorithm to generate anonymous information, and realizes encrypted transmission of transmitted information in authentication protocol , only the private key of the roadside base station unit can be decrypted; when a dispute arises, the anonymous identity can also be tracked, which has important practical application prospects.
Owner:SOUTHWEST PETROLEUM UNIV
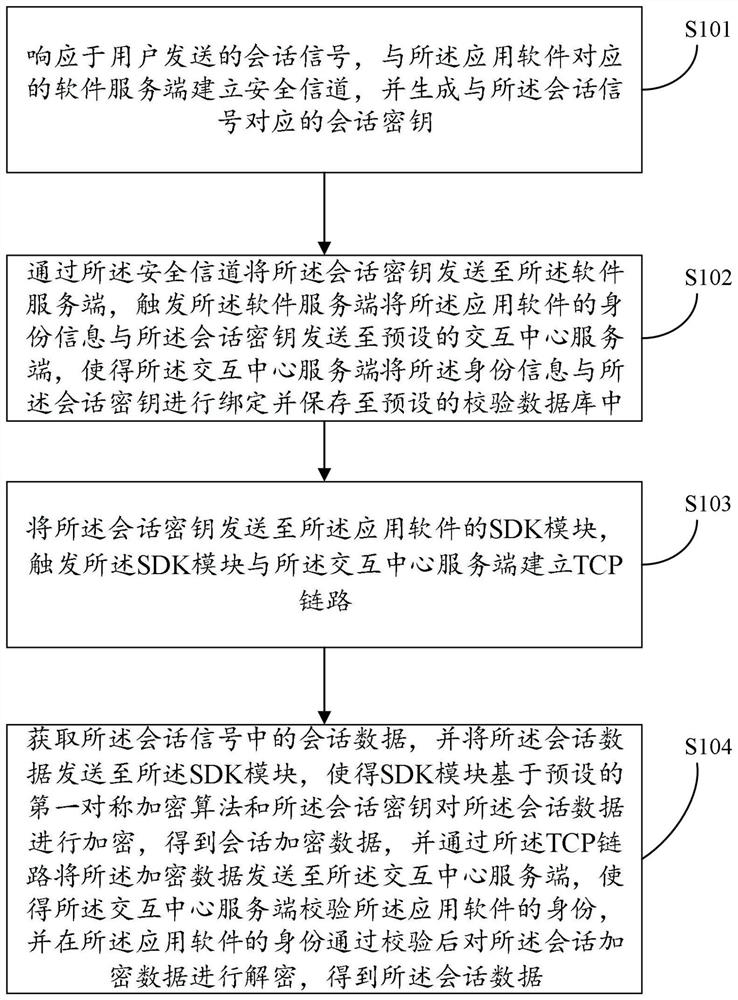
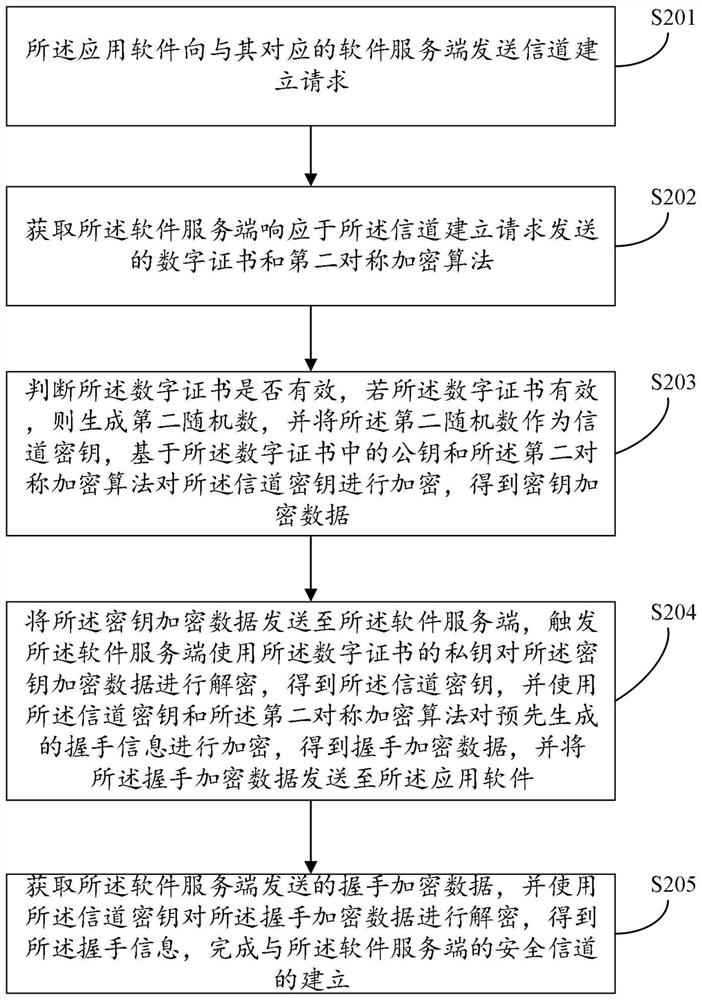
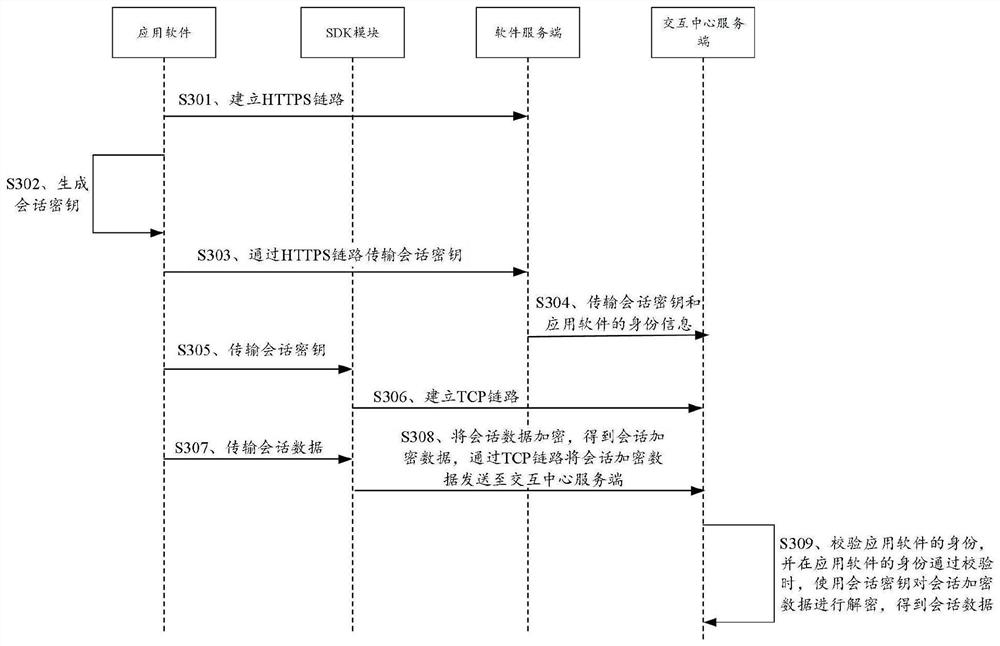
Session data transmission method and device
ActiveCN112738048AImprove session securityReduce the risk of theftKey distribution for secure communicationEngineeringApplication software
The invention provides a session data transmission method and device applied to application software. The session data transmission method comprises the steps that: the application software responds to a session signal sent by a user, generates a session key, builds a safety channel with a software server, and sends the session key to the software server through the safety channel, so that the software server sends the session key and identity information of the application software to an interaction center server; and an SDK module of the application software encrypts the session data based on the session key and a first symmetric encryption algorithm to obtain session encrypted data and sends the session encrypted data to the interaction center server through a TCP link, and the interaction center server decrypts the session encrypted data by using the session key after passing the identity verification of the application software, so as to obtain the session key. The session data transmission method and the device realize encrypted transmission of the session data between the application software and the interaction center server, use different keys in each session, improve the session security, and prevent the session data from being stolen.
Owner:AGRICULTURAL BANK OF CHINA
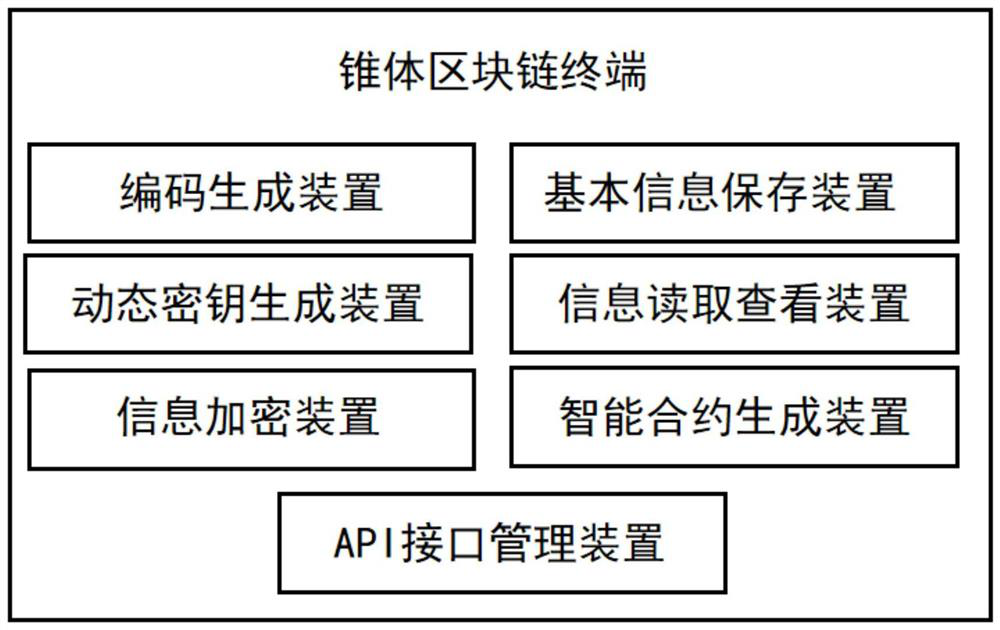
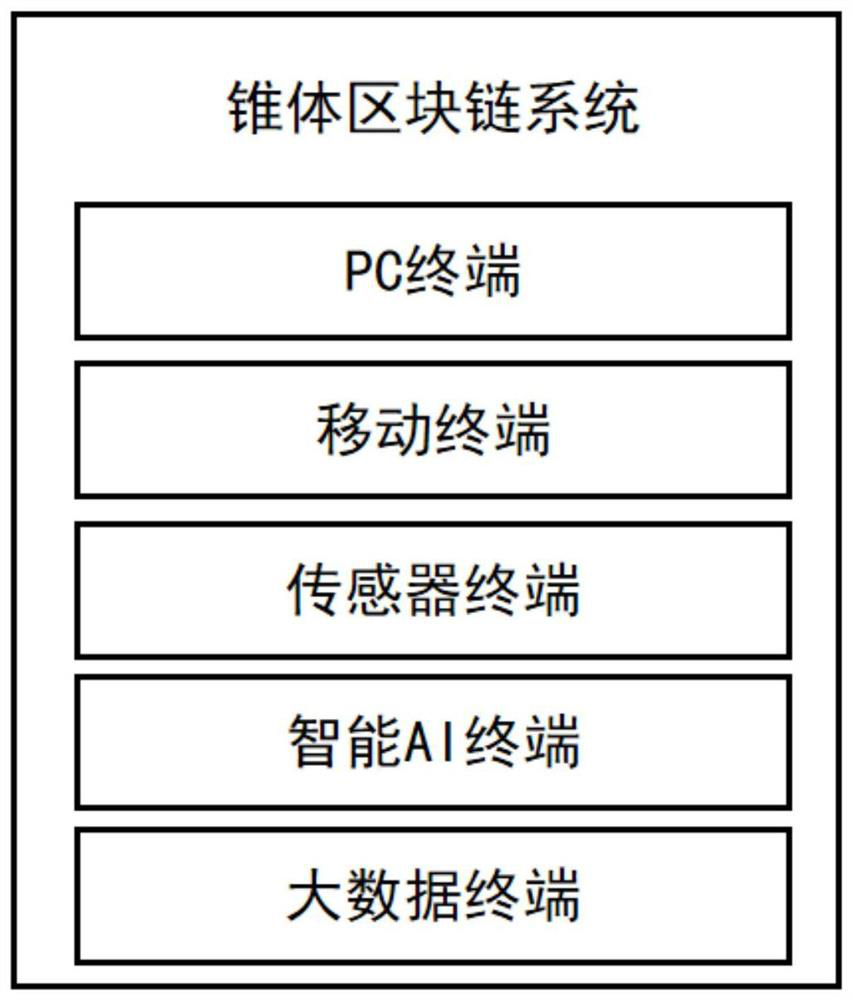
Cone block chain terminal and access method thereof
InactiveCN112637274AAdd real-name authenticationEasy to superviseTransmissionData terminalAccess method
The invention belongs to the technical field of block chains, and particularly relates to a cone block chain terminal and an access method thereof, comprising a terminal and a terminal device provided with the terminal, the terminal comprises a terminal code generation device, a dynamic secret key generation device, an information encryption device, a terminal information storage device, an information reading and viewing device, an intelligent contract generation device and an application programming interface management device. The terminal device comprises at least one of a PC terminal, a mobile terminal, a sensor terminal, an AI terminal and a data terminal. Each terminal is used for collecting data and transmitting the data to the cone block chain, and the output data is stored in the cone block chain block and is subjected to authentication and consensus storage respectively. A user can freely select the cone block chain system on the terminal, so that the degree of freedom of user selection is improved, and the application effect of the block chain is better played.
Owner:GLOBAL PRESTIGE INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com