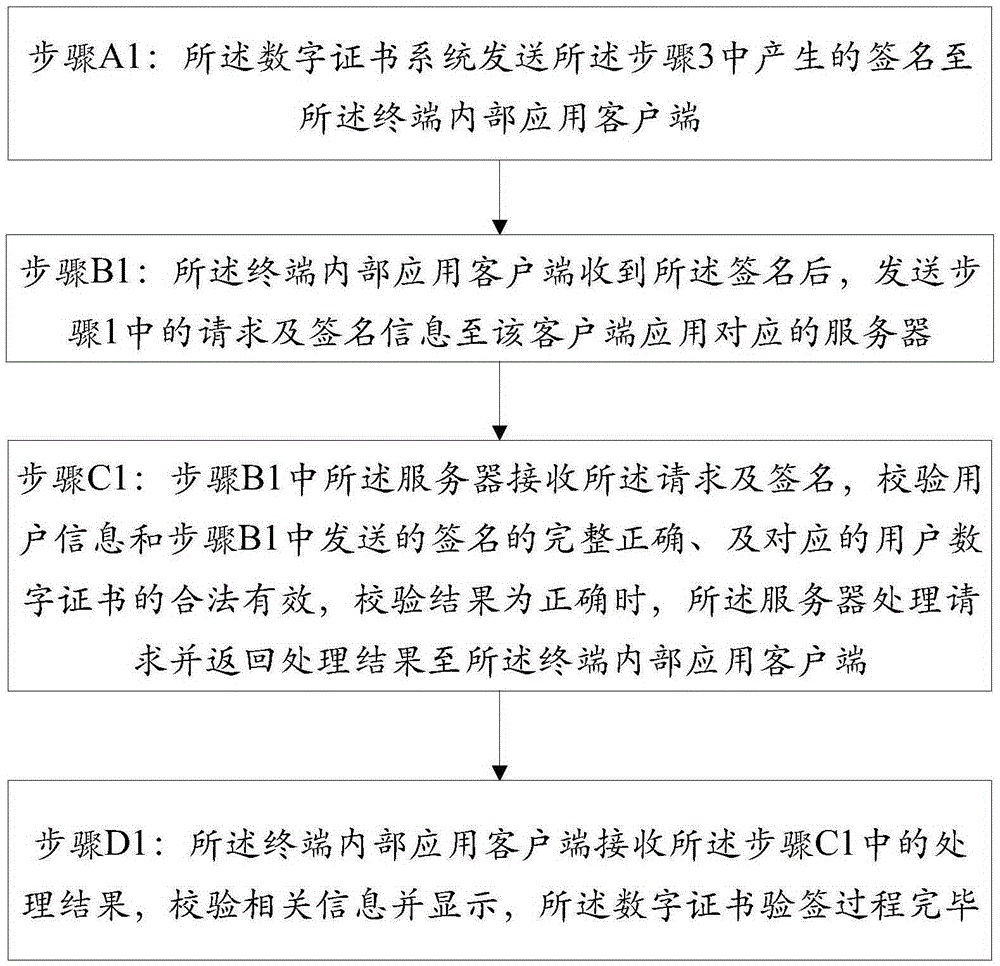
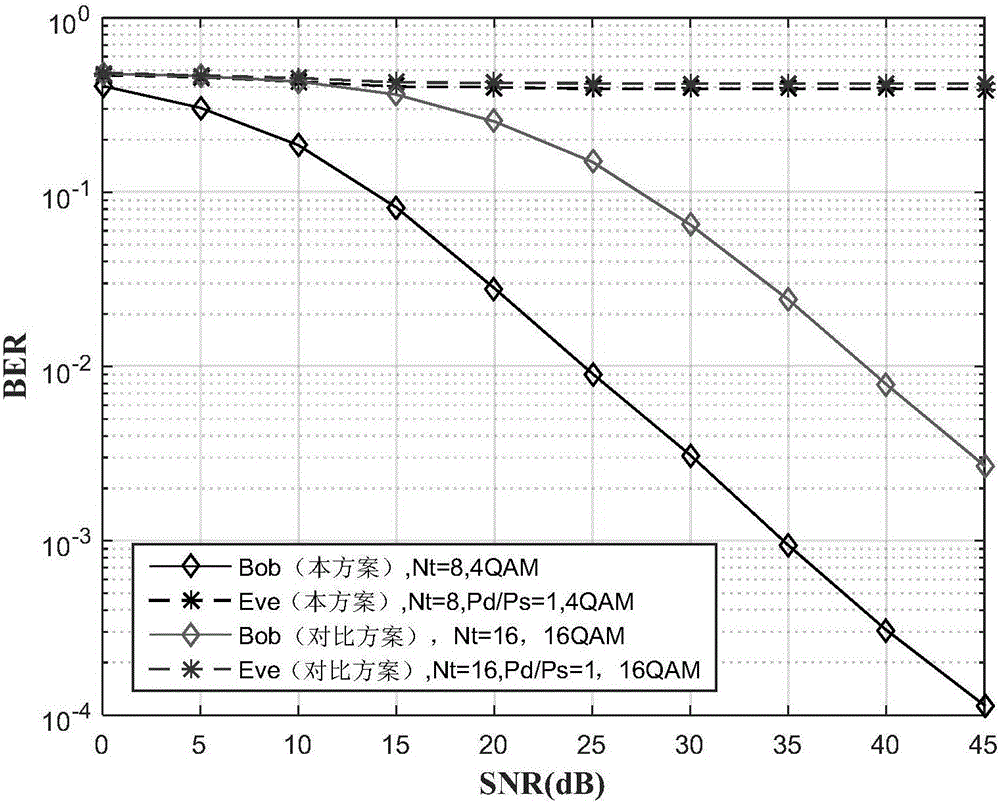
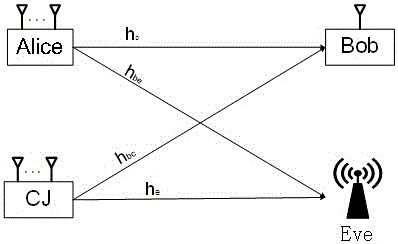
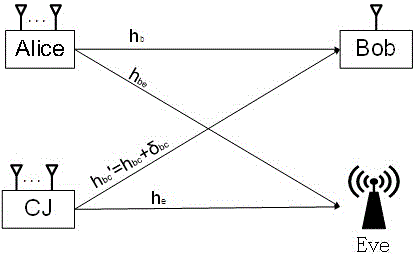
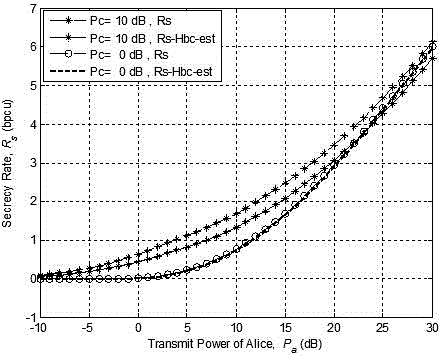
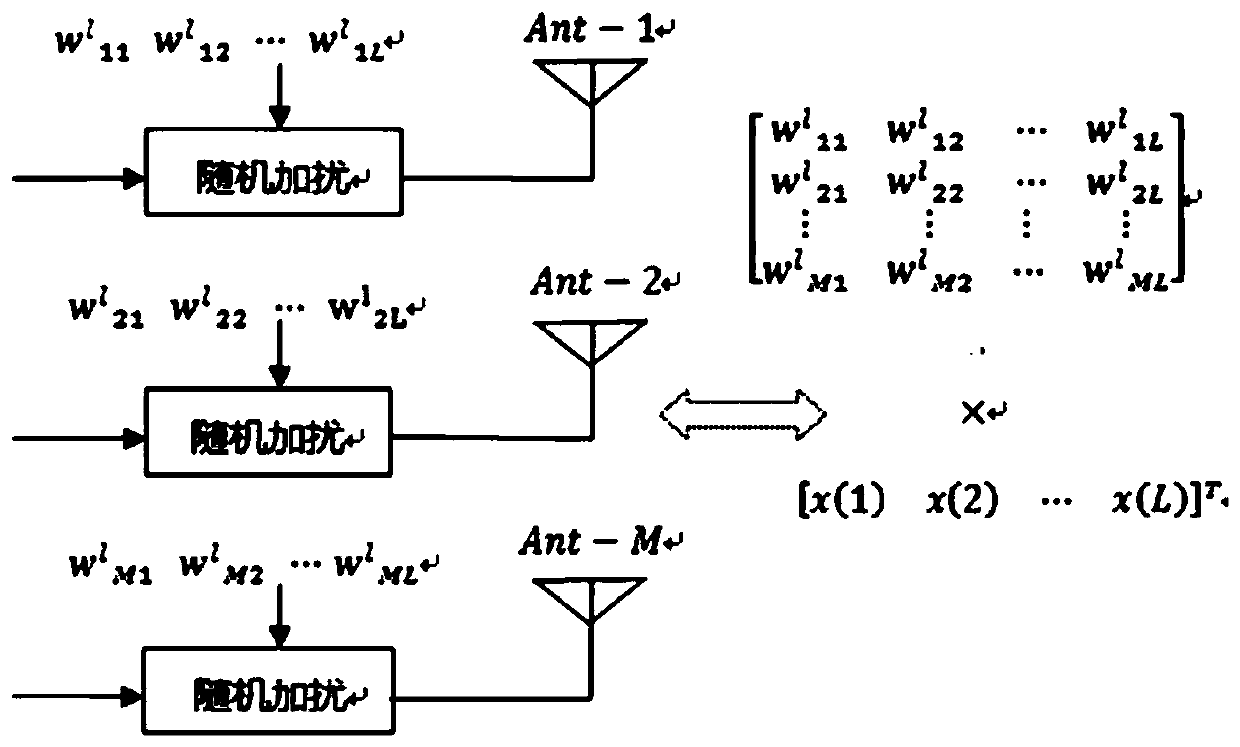
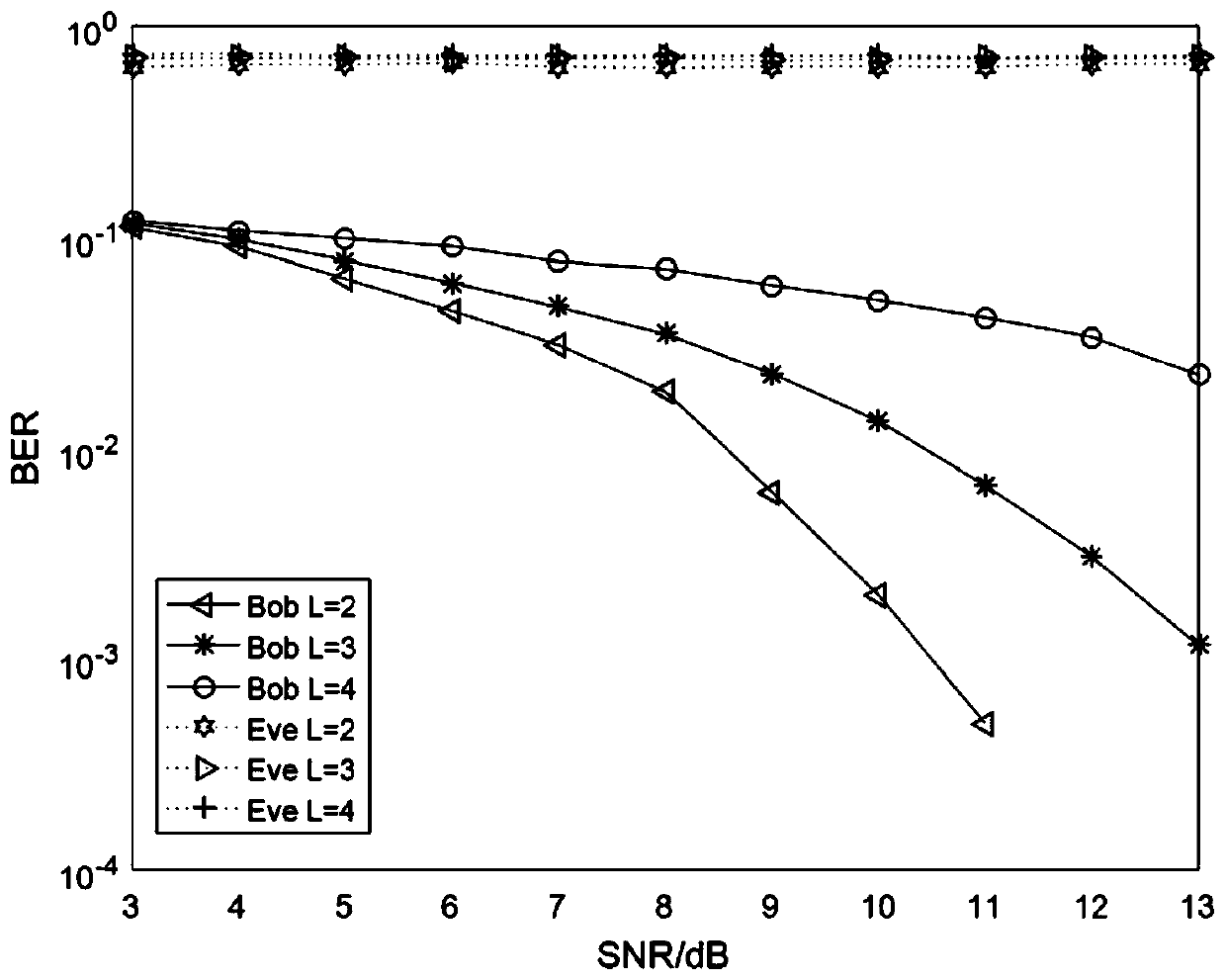
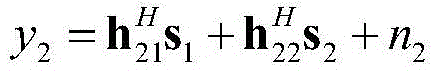Patents
Literature
212results about How to "Realize secure transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and system for identity verification of digital certificate based on TEE (Trusted Execution Environment)
ActiveCN105429760AEnsure true willEnsure that the identity verification process can reflect the true willUser identity/authority verificationPasswordPersonal identity verification
The invention discloses a method for identity verification of a digital certificate based on a TEE (Trusted Execution Environment). The method comprises pre-configuration of a digital certificate system through a terminal, a digital certificate signature process and a digital certificate signature verification process. The method is characterized in that the terminal is provided with the TEE; the digital certificate signature process is carried out on the terminal and is used for utilizing a private key of the digital certificate to sign for a user request; the digital certificate signature verification process is used for authenticating identity of a requested user, and the authentication method comprises verification of validity and effectiveness of the digital certificate and integrity and correctness of the signature, wherein the digital certificate signature process is carried out under the TEE; the sensitive information, such as a user key, identity information, biological characteristic information and password information, is stored through a secure storage module, so that the problems that the signature process is carried out in REE and the sensitive information of the user is stored under the REE environment to cause privacy disclosure and stolen hidden danger of property in the prior art are avoided.
Owner:神州融安数字科技(北京)有限公司
Method and system for implementing authentication and data safe transmission
InactiveCN101483654AEnable secure interactionsEnsure safetyTransmissionSecurity arrangementSecure transmissionPassword
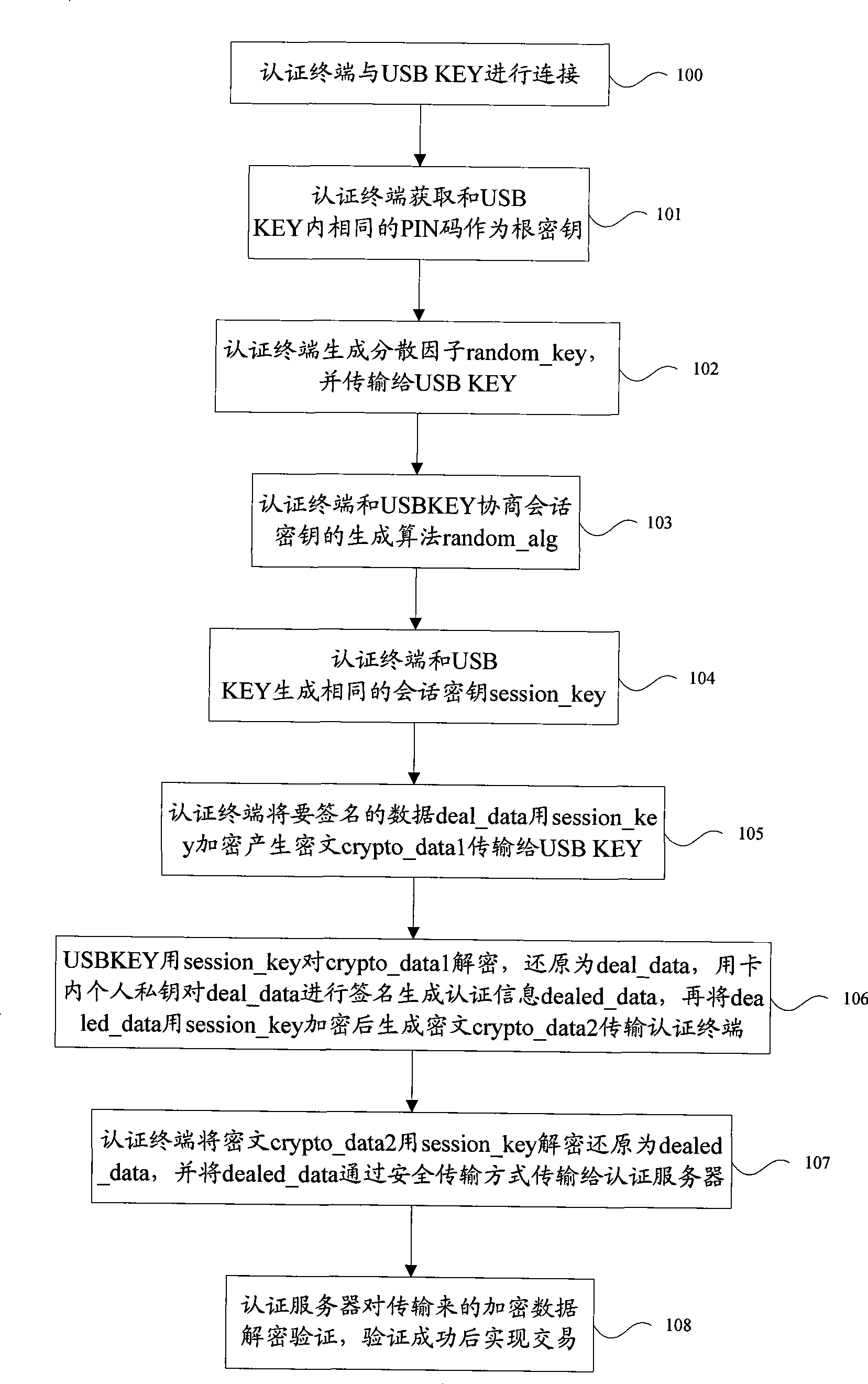
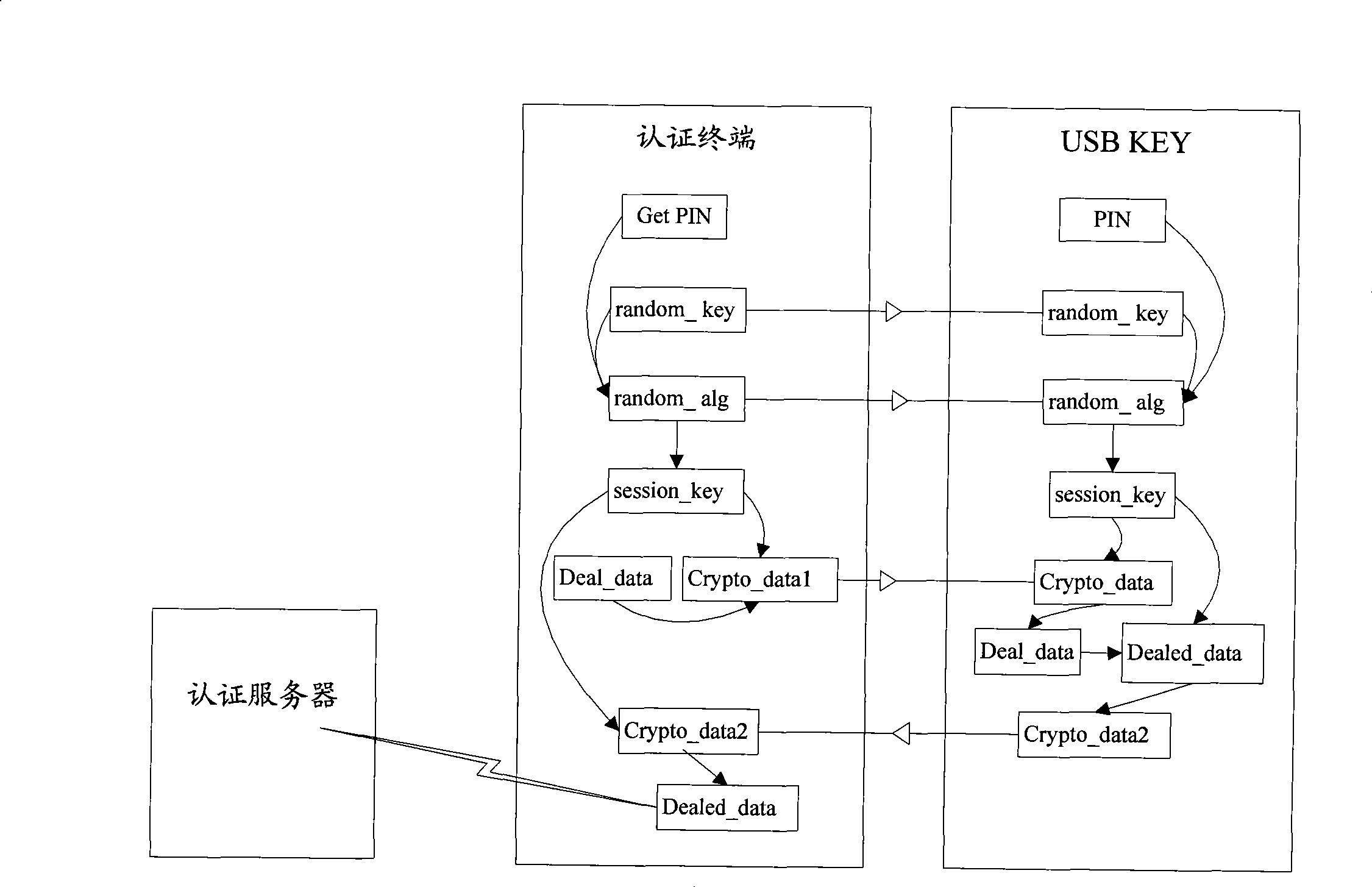
The invention discloses an authentication and safe transmission of data realizing method. A terminal safety device and an authentication terminal after being connected negotiates to have a same data to be used as a root key, and at the same time negotiates to have a same dispersion factor and a same algorithm, the negotiated root key and dispersion factor generate a same session key used as a symmetrical key by using the algorithm, and then, safety authentication and data encryption and decryption can be performed and safety data interaction between the two ends can be realized. The invention also discloses a system for realizing authentication and safe transmission of data, and the system comprises a terminal safety device, an authentication terminal and an authentication server. According to the invention, randomness of the session key for data encryption transmission can be assured, even though a session key is decrypted, the safety of the whole system can be assured, and at the same time, atom manipulation for safety authentication and safe transmission of data can be realized for avoiding that in the current authentication process, once a password is verified by the terminal safety device, limits of authority are totally released and potential safety hazard is generated, therefore, authentication safety is improved greatly.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
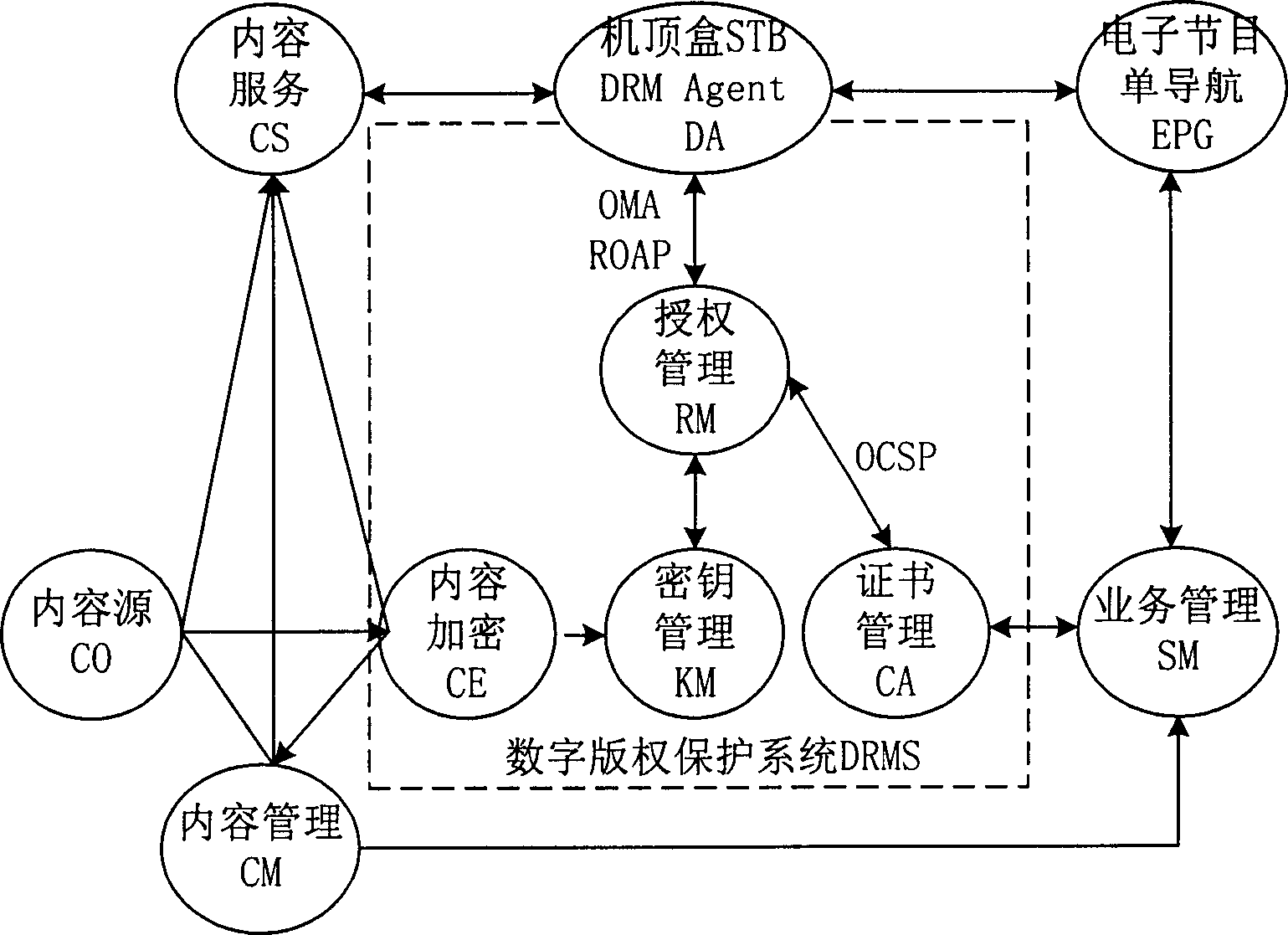
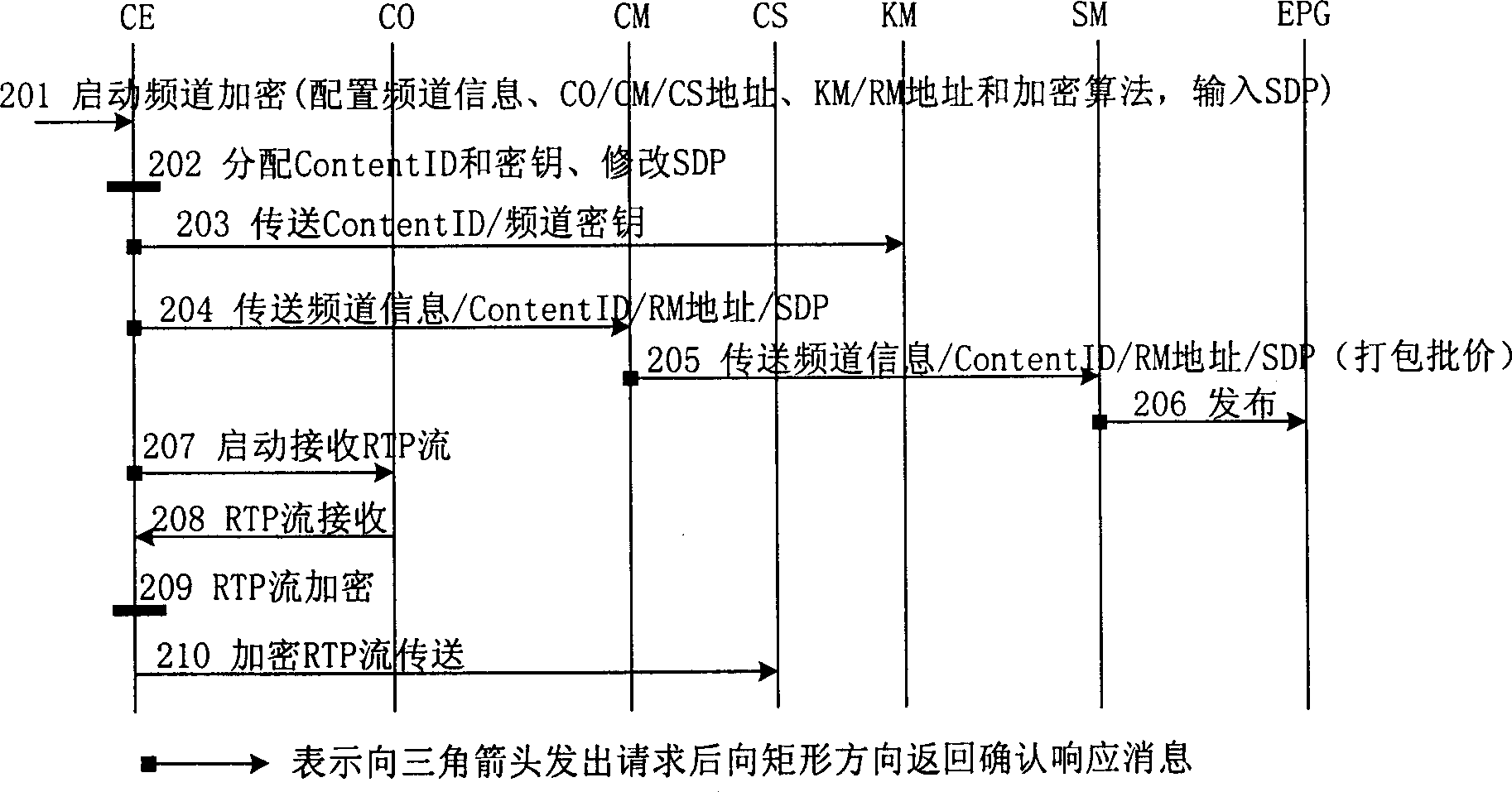
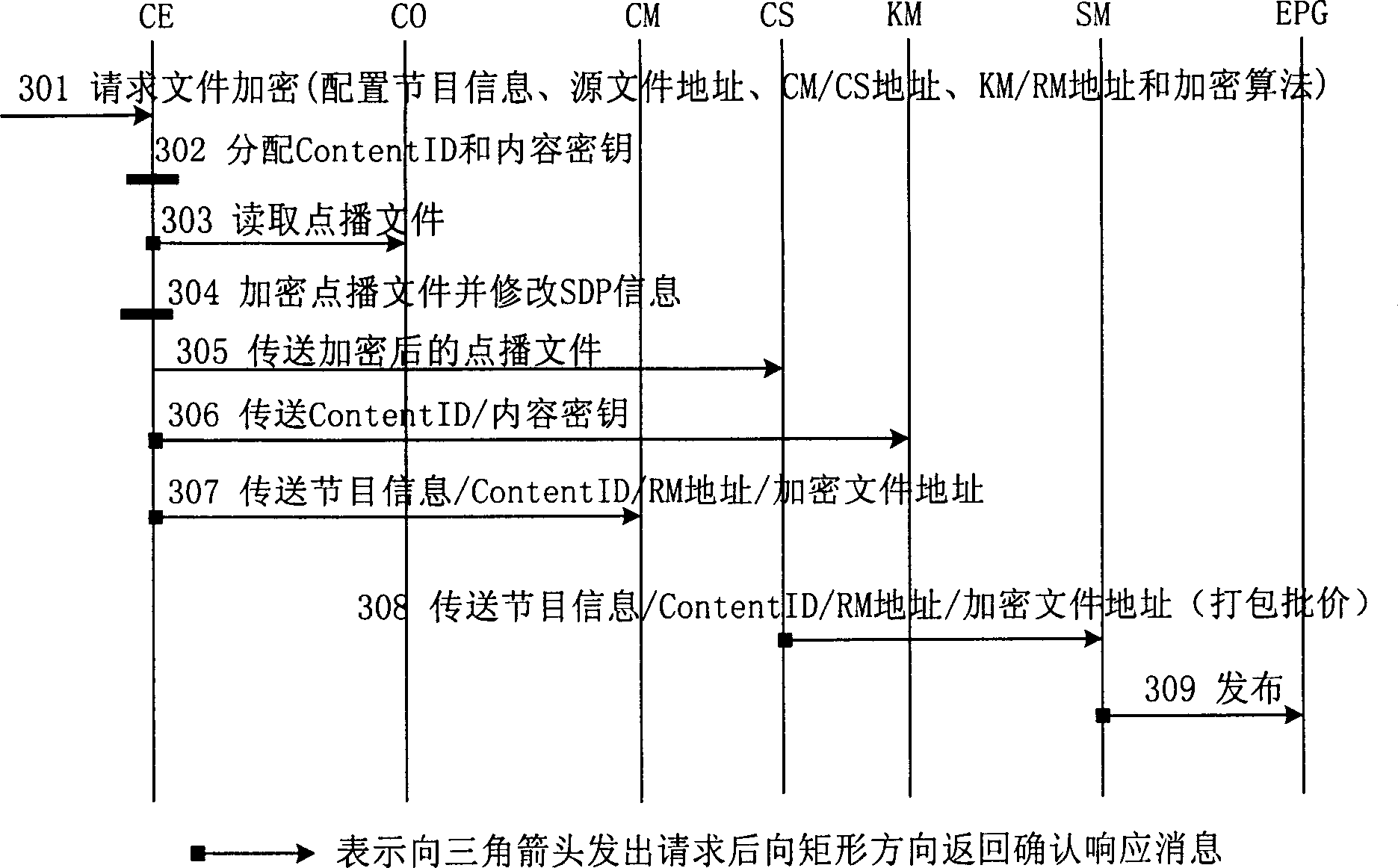
IPTV system, enciphered digital programme issuing and watching method
ActiveCN1848944APrevent leakageRealize secure transmissionAnalogue secracy/subscription systemsTwo-way working systemsContent managementAuthorization
An IPTV system comprises content source CO, content service unit CS, content management unit CM, service management unit SM, single-way guide unit EPG of electronic program, top box STB, content enciphering unit CE, cipher key management unit KM and authorization management unit RM for providing enciphered program. The method of issuing and viewing enciphered program is also disclosed.
Owner:HUAWEI TECH CO LTD
Network authentication service system and method
The present invention embodiment relates to system and method for network authentication service. The network authentication service system is used in network application layer, which includes network service safety device for holding up interactive packet of network application layer and executing authentication process for the packet. The network authentication service method includes holding up interactive packet of network application layer and executing authentication process for the packet. Transmitted packet can be executed safe process by the invention embodiment, and safe authentication modus is variety.
Owner:ZHEJIANG 1ONE TECH CO LTD
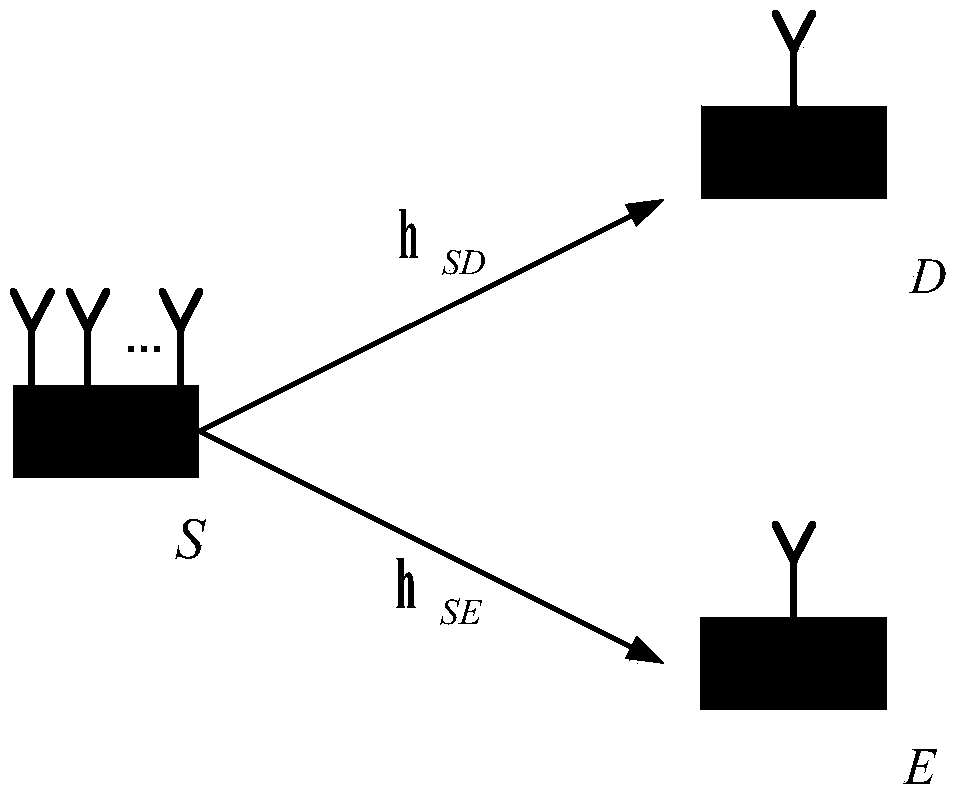
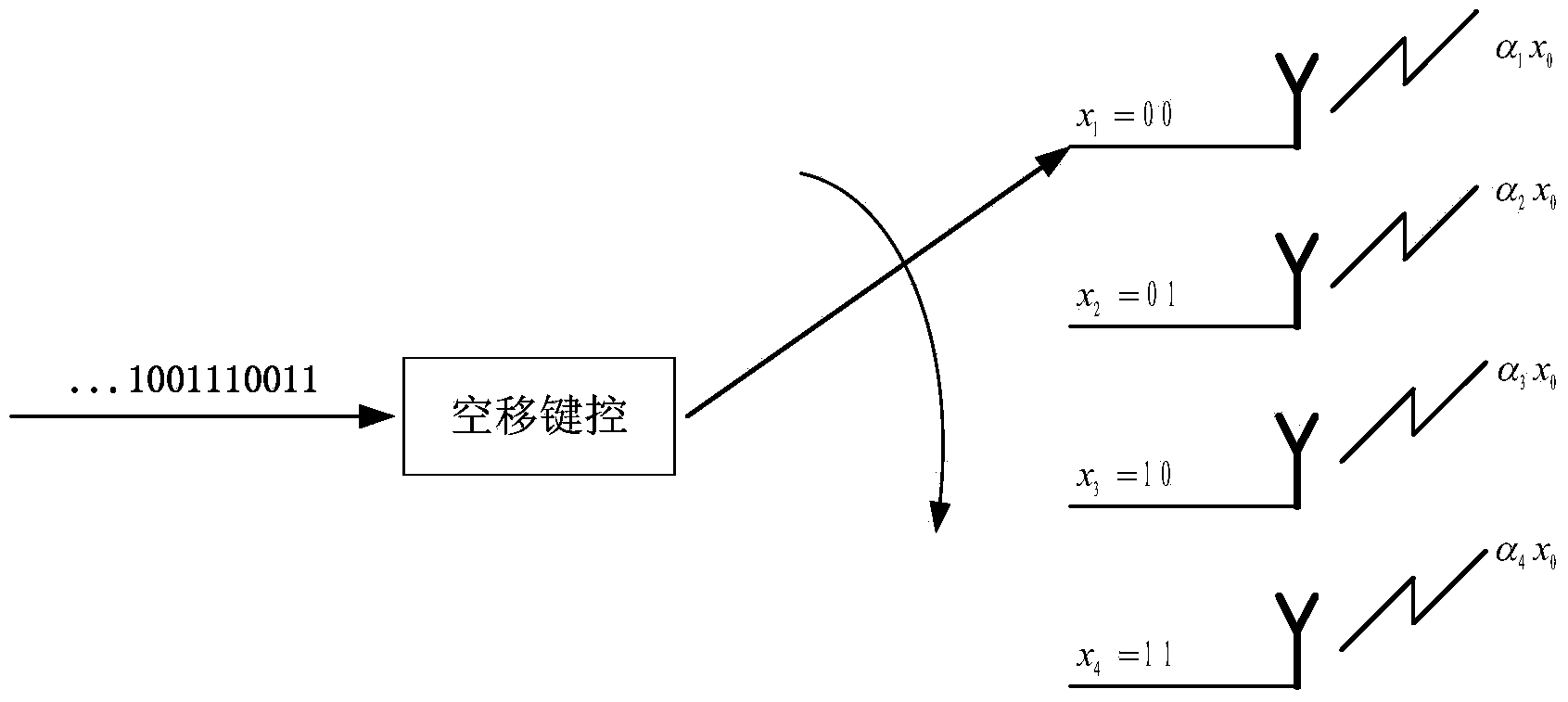
Physical layer secure transmission method for resisting information eavesdropping of eavesdropping node
InactiveCN105790818ARealize secure transmissionResistance to eavesdroppingSpatial transmit diversityInformation transmissionSecure transmission
The invention discloses a physical layer secure transmission method for resisting information eavesdropping of an eavesdropping node. The physical layer secure transmission method comprises the steps that: 1) a source node and a target node sequentially send a training sequence before the beginning of information transmission, so that the source node and the target node estimate equivalent channel information h<n, k> from the source node to the target node, wherein n is contained in {1, ... , Nr}, k is contained in {1, ... , Nt}, Nt is antenna number set by the source node, and Nr is antenna number set by the target node; 2) the source node encodes to-be-transmitted data, obtains a to-be-transmitted symbol and an antenna serial number for transmitting the to-be-transmitted symbol, then adds artificial noise into the to-be-transmitted symbol, and transmits the to-be-transmitted symbol added with the artificial noise to the target node through a selected antenna; 3) and the target node receives the symbol transmitted by the source node, decodes the symbol transmitted by the source node by means of a maximum likelihood decoder, and completes physical layer secure transmission of information. The physical layer secure transmission method can achieve physical layer secure transmission of the information.
Owner:XI AN JIAOTONG UNIV
Collaboration network power distribution method based on artificial noise under nonideal channel estimation condition of collaboration channel
ActiveCN106131941AReduce distractionsImprove reliabilityPower managementChannel estimationEstimation methodsDistribution method
The invention discloses a collaboration network power distribution method based on artificial noise under a nonideal channel estimation condition of a collaboration channel. The method comprises the steps that S1, a legal receiving end sends pilot sequences to a transmitting end of an transmitting source, and a collaboration jammer; S2, the transmitting end receives the pilot sequence and carries out ideal channel estimation, and the collaboration jammer receives the pilot sequence and carries out nonideal channel estimation; S3, the transmitting end and the collaboration jammer design respective transmitting signals; S4, the transmitting end and the collaboration jammer transmit signals to the legal receiving end and an eavesdropping end at the same time; S5, the optimum transmitting power distribution ratio and the maximum safe transmission rate under the nonideal channel estimation condition of the collaboration channel are calculated; S6, the optimum transmitting power distribution ratio and the maximum safe transmission rate under an ideal channel estimation condition of the collaboration channel are calculated; and S7, the maximum safe transmission rates under the nonideal channel estimation condition and the ideal channel estimation condition are compared. According to the collaboration scheme provided by the method, the condition that an error exists in the channel estimation method of the collaboration channel is taken into full consideration, and the practical power distribution scheme for realizing system safety is proposed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
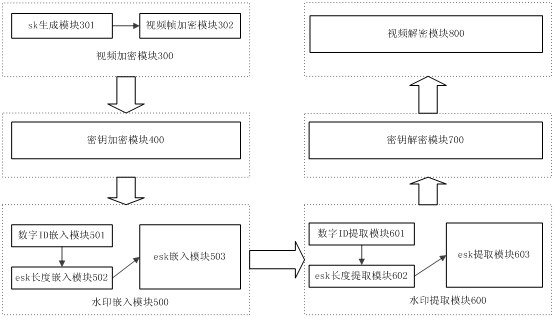
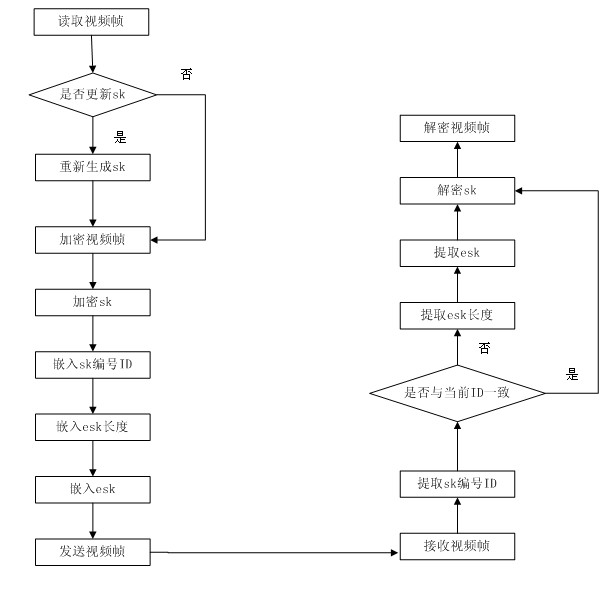
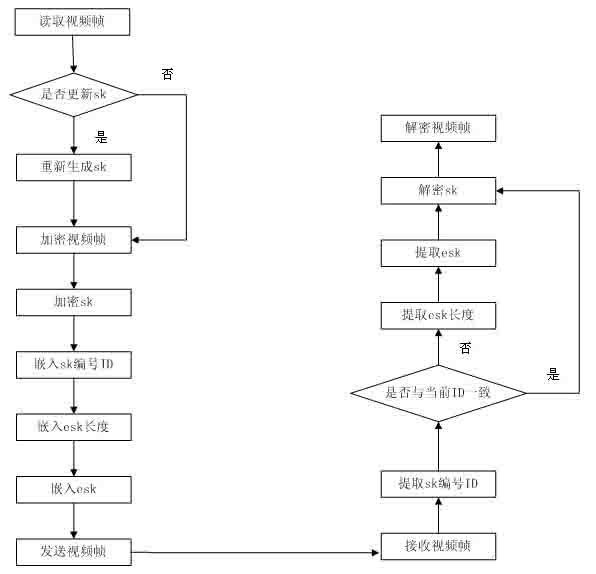
Digital watermarking-based high-definition video encrypted transmitting method and system
InactiveCN102014266AImplement secure encryptionEnsure safetyTelevision system detailsPulse modulation television signal transmissionComputer hardwareSecure transmission
The invention discloses a video watermarking-based high-definition video encrypted transmitting method. In the method, a random number generated by a random number generator is taken as a video scrambling key; the video scrambling key is encrypted by adopting an RSA algorithm to ensure that the video scrambling key cannot be captured in the transmitting process; and the encrypted video scrambling key is taken as a watermark to be embedded into the encrypted video by using a least significant bit (LSB) algorithm so as to realize secure encryption of the high definition video. The invention has higher security and lower computational complexity, and ensures the transmission quality of the high definition video content on the premise of secure transmission.
Owner:HUAZHONG UNIV OF SCI & TECH
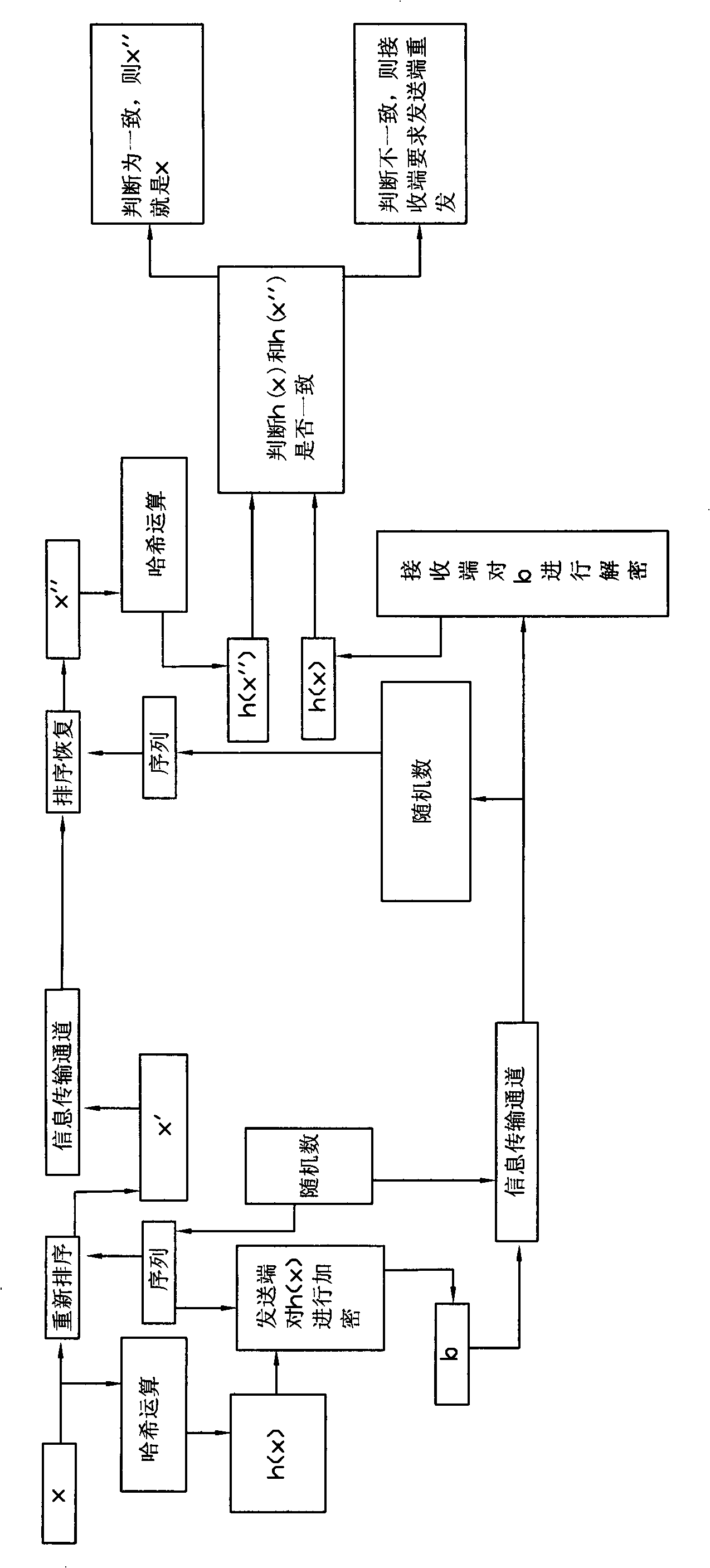
Data transmission method for remote meter reading system
ActiveCN101360101ASecure transmissionRealize secure transmissionTransmission systemsSecuring communicationData transmissionComputer science
The invention discloses a data transmission method of the remote meter reading system, comprising the following: a sender firstly conducts hash operation on x to yield h(x); at the same time, the sender generates a random number which one to one corresponds to sequences pre-stored inside memories of the sender and a receiver; then the sender takes the sequences as keys to encrypt the h(x) with a one time encrypting method to yield b; the b and the random number are transmitted to the receiver; the receiver determines the corresponding sequences according to the random number, and then the receiver takes the sequences as the keys to decrypt the b with the one time encrypting method to yield h(x); at the same time, the sender sorts the x according to the sequences to yield x` which is transmitted to the receiver, and the receiver sorts the x` to yield x``, and then conducts hash operation on x`` to yield h(x``); and the receiver compares the h(x) with the h(x``): if the h(x) is consistent with the h(x``), the x`` is the x, and otherwise, the receiver discards the received data and demands that the sender resend the x according to the above processes.
Owner:NINGBO SANXING MEDICAL & ELECTRIC CO LTD
Rail transportation ticket-card processing intelligent system and data encryption auditing method
InactiveCN101826219AImprove consistencyGuaranteed to be strictly enforcedRegistering/indicating time of eventsTicket-issuing apparatusServices computingTransaction log
The invention discloses a rail transportation ticket-card processing intelligent system, which comprises a sorting center and an automatic ticketing system for a plurality of rail transportation lines. The sorting center comprises a set of service computers, and the automatic ticketing system comprises a set of equipment computers and a ticket-card processing intelligent terminal connected with the equipment computers; and the card processing intelligent terminal is used for processing of ticket transaction flow, issuing of single ticket transaction keys, online authentication of value-stored ticket recharge and generation and verification of transaction logs. The sorting center also comprises an encryption computer which is connected with the ticket-card processing intelligent terminal and is used for receiving an encryption certification request of the ticket-card processing intelligent terminal; and the equipment computers are used for transmitting service commands to the ticket-card processing intelligent terminal and receiving the service command processing result. The modification of the ticket-card processing service is realized through the online update function of the parameters or ticket-card processing programs and the maintenance cost due to the updated card processing programs is reduced. The invention also discloses a data encryption auditing method.
Owner:NANJING PANDA INFORMATION IND +1
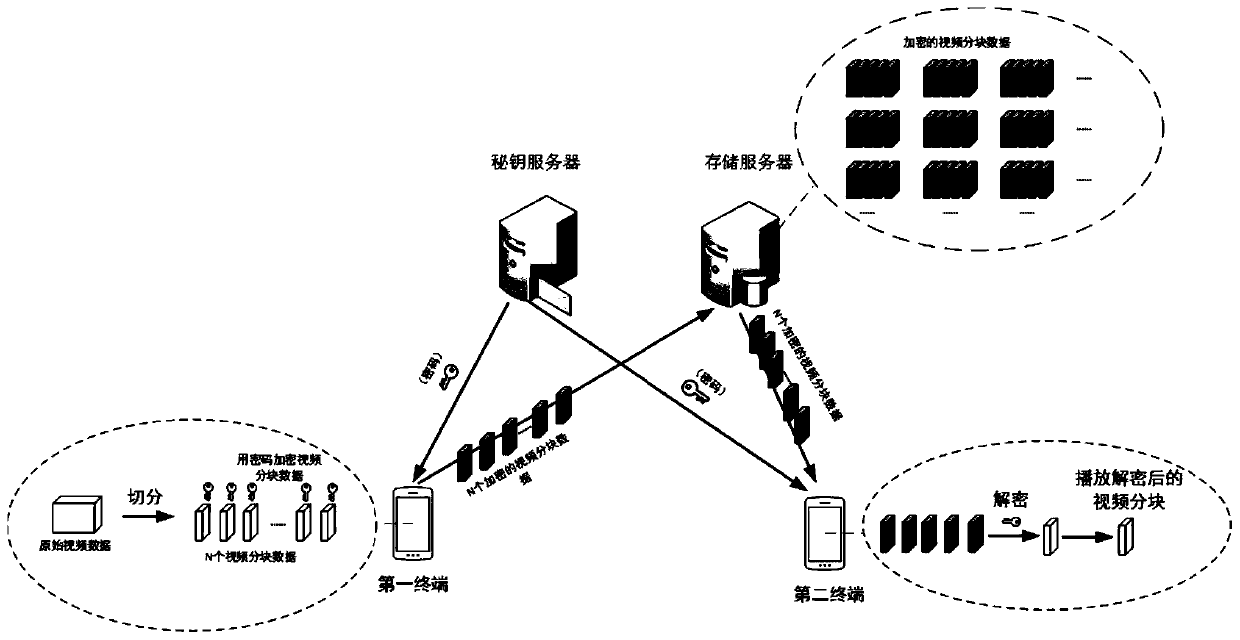
Data security protection method and related device
The embodiment of the invention discloses a data security protection method and a related device. The method comprises the steps that a first terminal sends the first ciphertext information to a secret key server, wherein the first ciphertext information is obtained by encrypting a first password by the first terminal according to a public key from the secret key server; the first terminal receives the second ciphertext information sent by the secret key server, wherein the second ciphertext information is obtained by encrypting a second password of the key server according to the first password after the key server decrypts the first ciphertext information according to the private key corresponding to the public key to obtain the first password; the first terminal decrypts the second ciphertext information according to the first password to obtain a second password; and the first terminal sends the data encrypted by the second password to a storage server. Through the implementation of the embodiment, the security of the personal data of the user during the cloud backup process can be improved, and the data leakage risk is avoided.
Owner:PETAL CLOUD TECH CO LTD
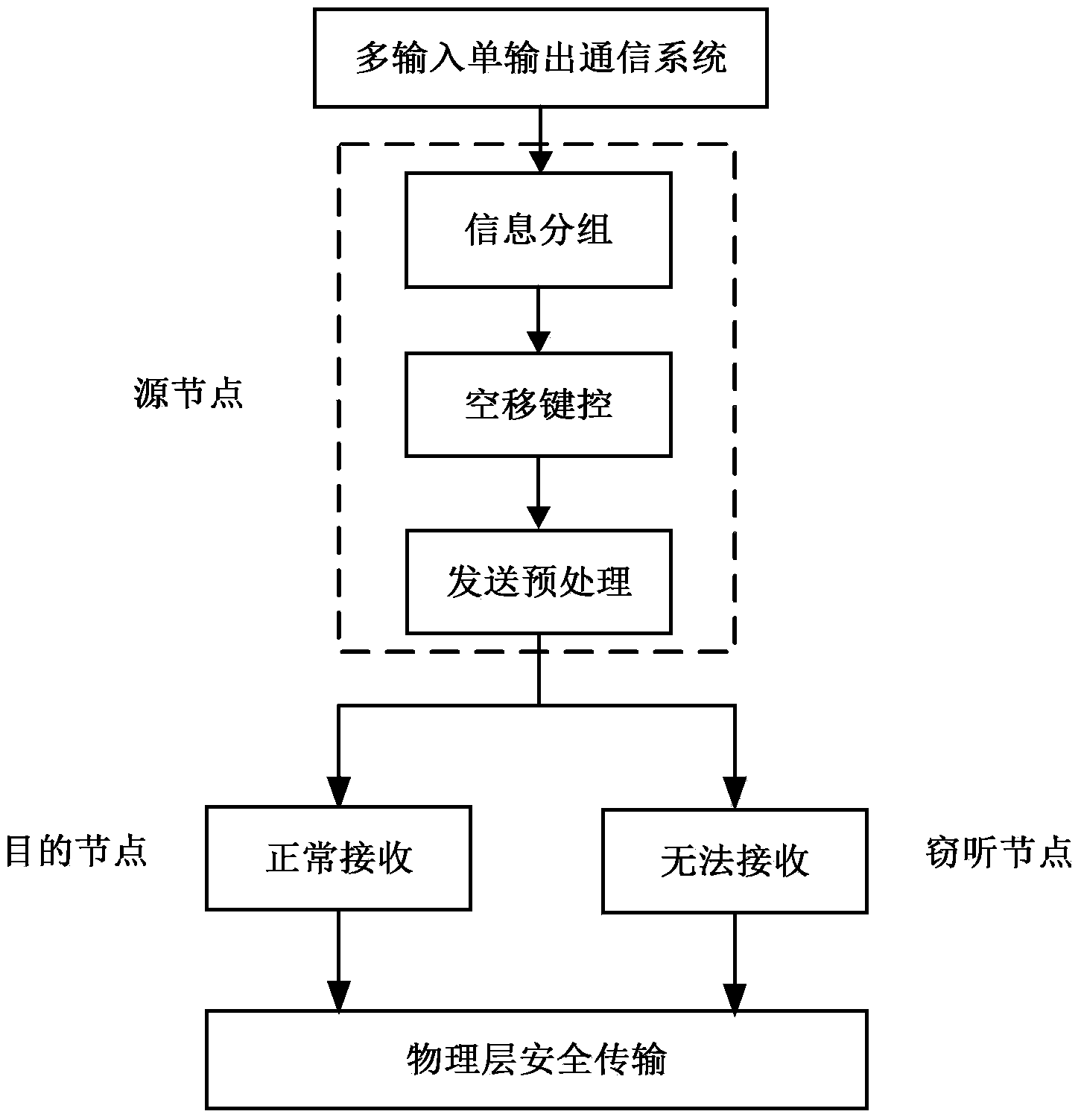
Null-shift-keying-based physical layer safety transmission method in multi-input single-output system
ActiveCN104270227ARealize secure transmissionOvercome the shortcoming that security is restricted by the channelSpatial transmit diversityError prevention/detection by diversity receptionMulti inputPrecoding
The invention discloses a null-shift-keying-based physical layer safety transmission method in a multi-input single-output system. The physical layer safety transmission method includes the steps that (1) the multi-input single-output communication system comprises a source node, a destination node and a wiretapping node, M transmitting antennas are assembled on the source node, and the destination node and the wiretapping node are each provided with an antenna; (2) information of the source node is grouped, wherein bit grouping is carried out on bit information sequences to be transmitted through the source node according to the same bit length; (3) null shift keying is carried out, wherein bit information contained in information bit groups is mapped to the transmitting antennas with the corresponding serial numbers through the source node, and the source node transmits antenna serial numbers to serve as carriers of information source information through null shift keying; (4) precoding processing is carried out, wherein precoding processing is carried out on symbols transmitted by the transmitting antennas through the source node. According to the null-shift-keying-based physical layer safety transmission method, limitation of a single-antenna system to the physical layer safety can be broken, the structure of a transceiver can be simplified, and defects in a traditional multi-antenna physical layer safety transmission method are overcome.
Owner:PLA UNIV OF SCI & TECH
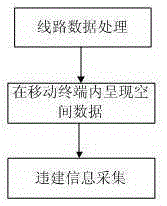
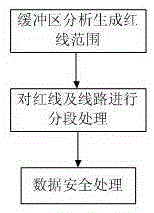
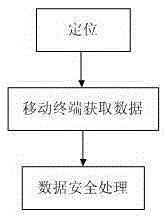
Unapproved construction information high precision acquisition method based on mobile terminal
InactiveCN106709837ARaise the spotlightRealize secure transmissionData processing applicationsData displaySecure transmission
The invention discloses an unapproved construction information high precision acquisition method based on a mobile terminal, and relates to the information acquisition technology field. The unapproved construction information high precision acquisition method comprises steps: processing of line data, spatial data displayed in the mobile terminal, and acquisition of unapproved construction information. The unapproved construction information high precision acquisition method is advantageous in that a method of acquiring, integrating, and pushing information for location awareness in different environments is used to effectively support integration of audio and video information, image information, position information, and attribute information by taking place name and address data as a basis, and the multidirectional comprehensive acquisition and collection of the unapproved construction information is realized; during the data acquisition, automatic acquisition is carried out, and range value precision is high, and a range value is precise to a centimeter level, and therefore the high precision position locating and the acquisition of the related data are realized; before the data pushing, the safety of the data is guaranteed by adopting an information encryption pushing strategy based on the position and a mobile terminal data strategy, and therefore safe transmission of a line and red line data during a mobile inspection process is realized, and the currency of the unapproved construction data acquisition is improved.
Owner:星际空间(天津)科技发展有限公司
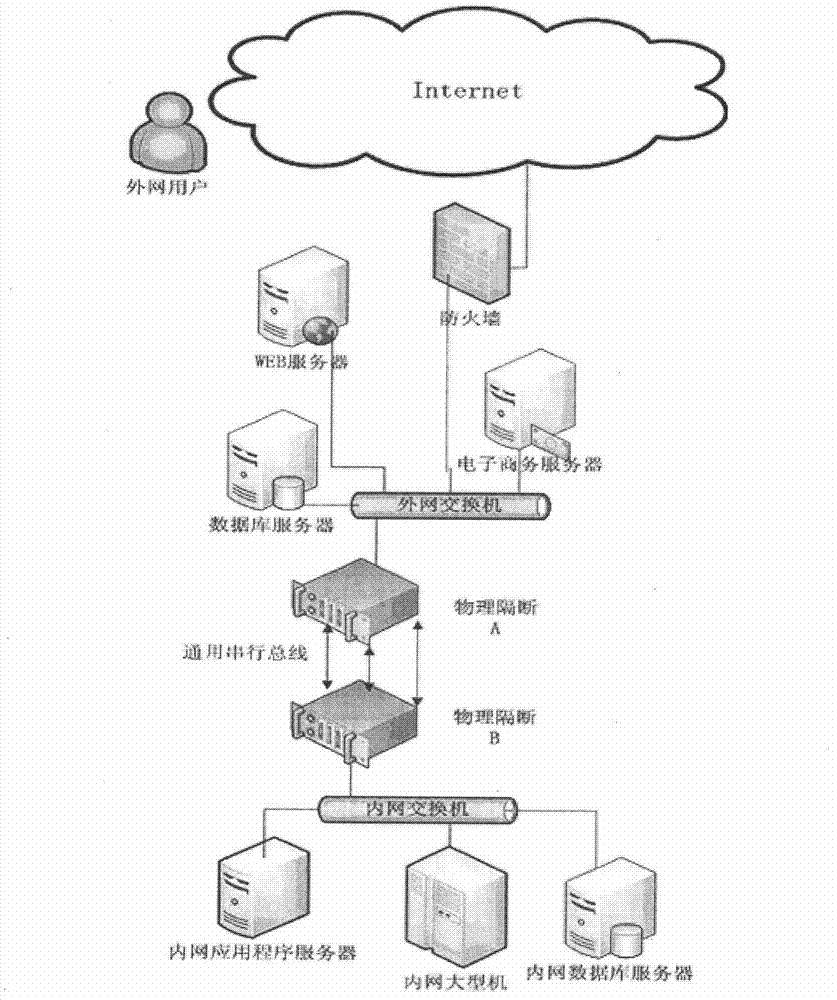
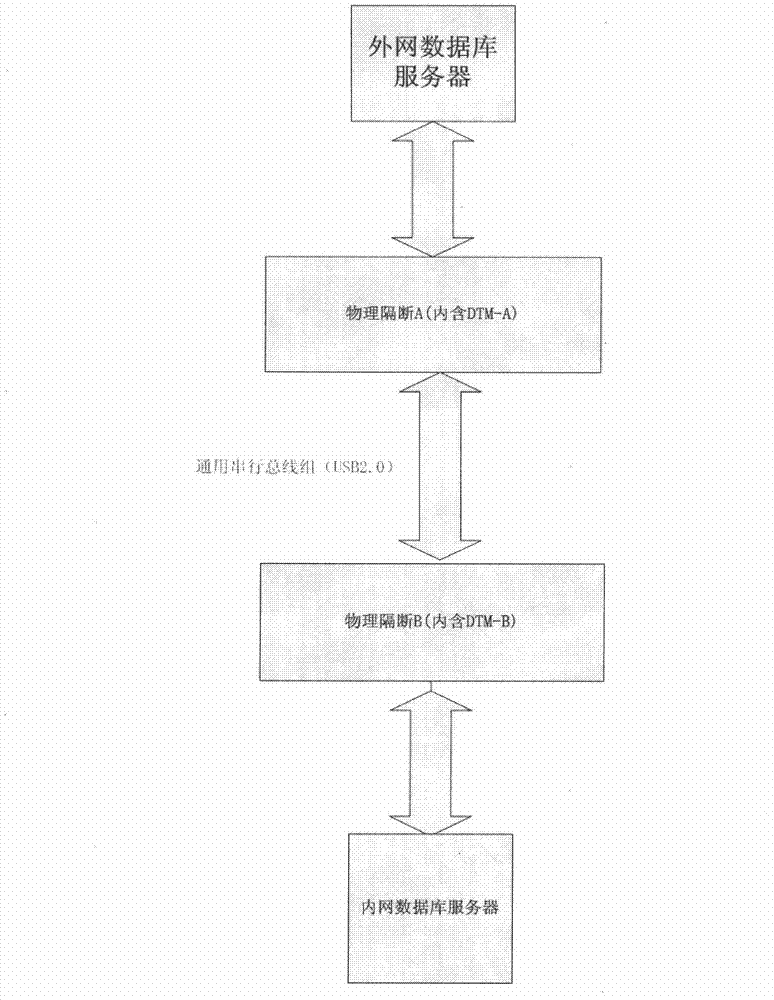
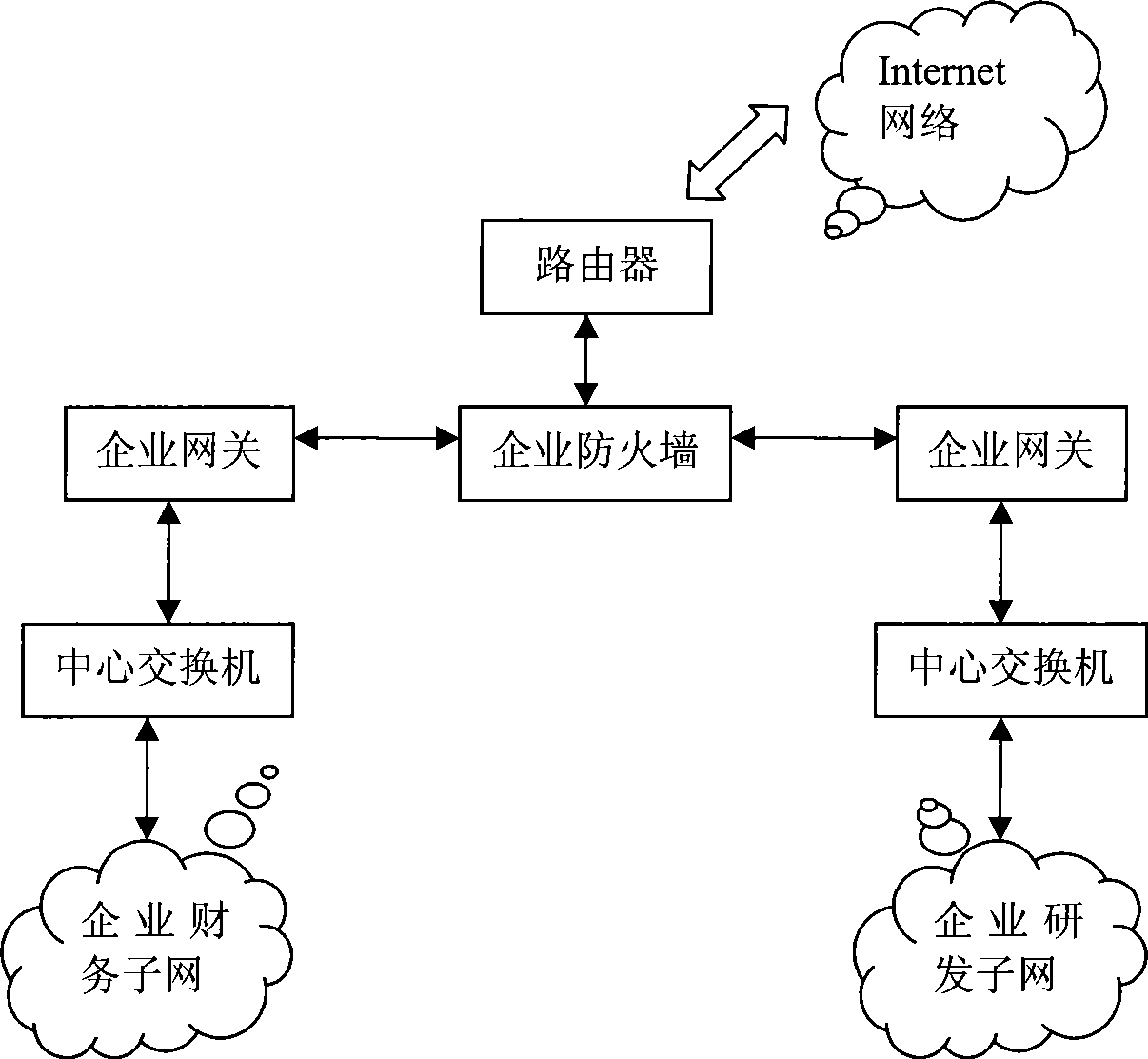
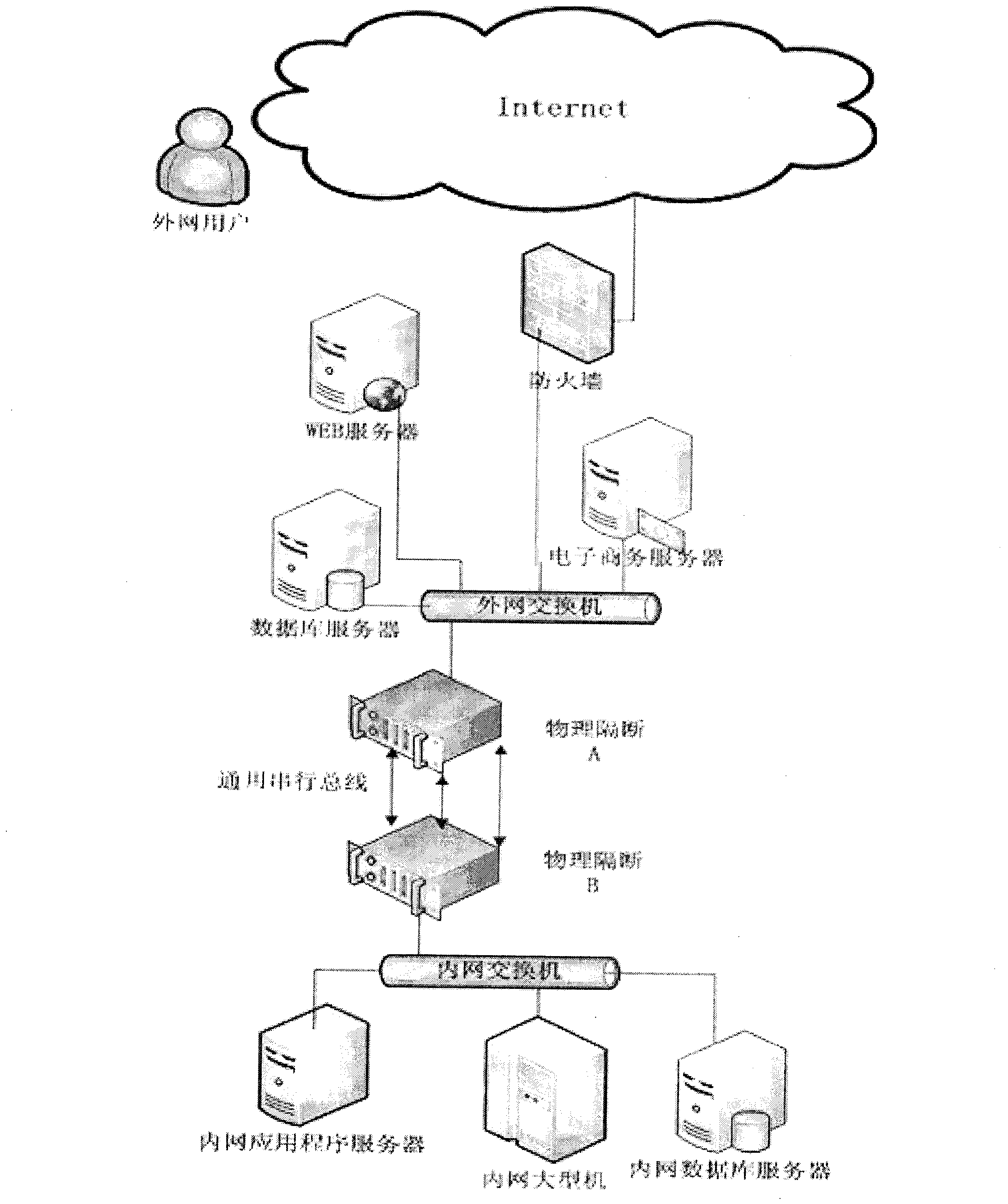
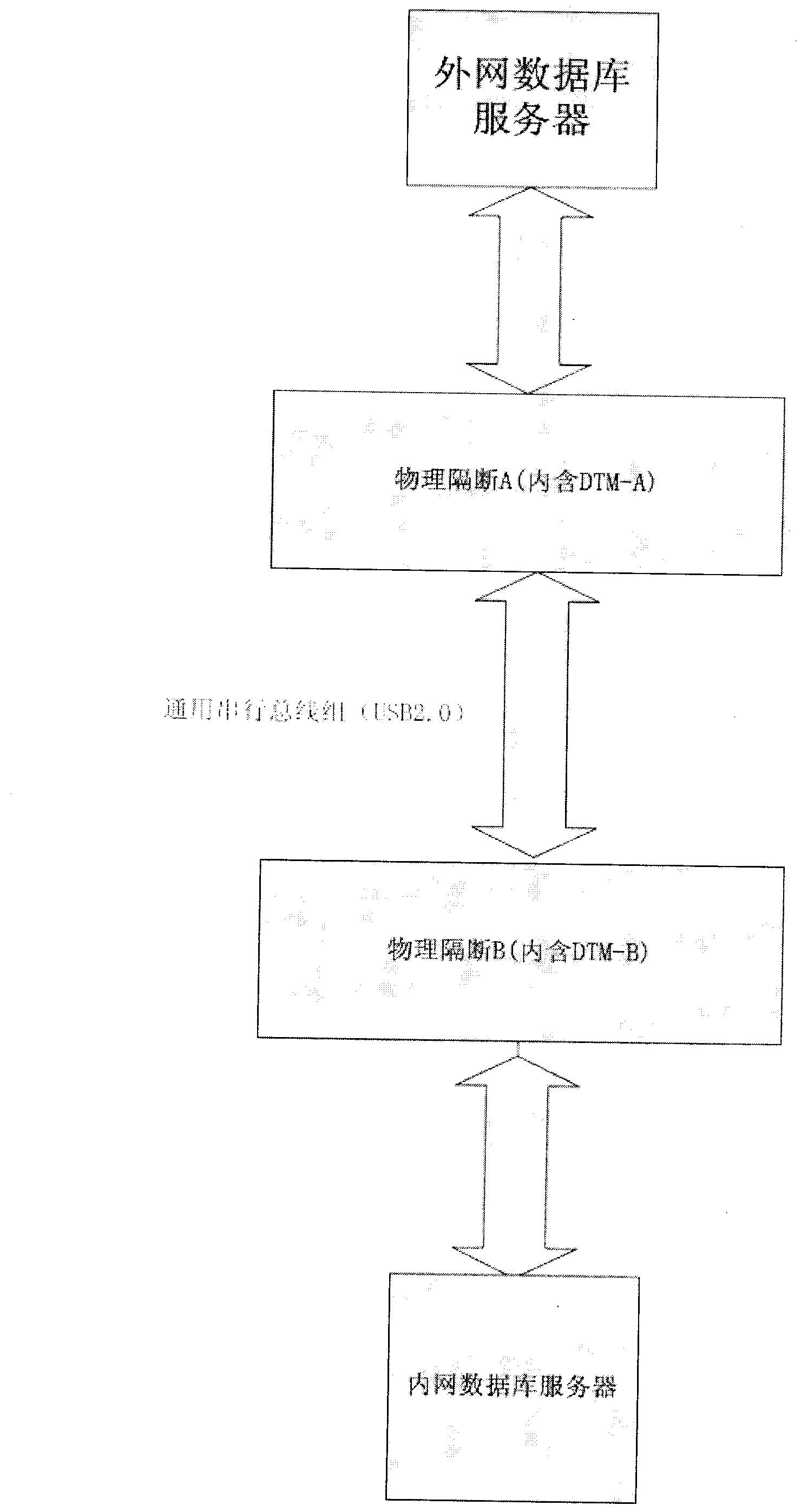
Method for realizing physical partition of internal and external networks
InactiveCN103209191AEnhanced real-time responsivenessReal-time communicationTransmissionReal time data transmissionComputer hardware
The invention provides a method for realizing physical partition of internal and external networks, and belongs to the field of network security. The method comprises the steps that the external network is provided with first physical partition equipment; the internal network is provided with second physical partition equipment; communication between the internal network and the external network is realized through the first physical partition equipment and the second physical partition equipment; at least one universal serial bus is arranged between the first physical partition equipment and the second physical partition equipment; and the communication between the first physical partition equipment and the second physical partition equipment is realized through the universal serial bus. The method realizes real-time data transmission between the internal network and the external network based on ensuring the security, and improves the real-time data responsiveness of the internal network and the external network greatly.
Owner:TIANJIN POLYTECHNIC UNIV
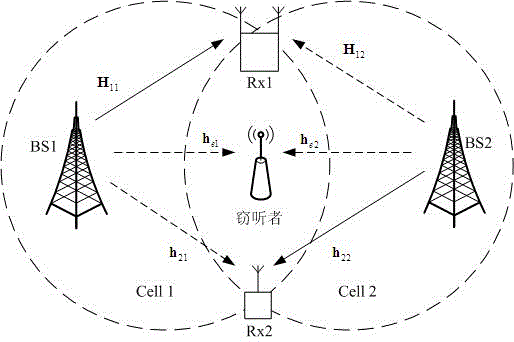
Security transmission method based on cooperation interferences in multi-cell network
InactiveCN105657698ARealize secure transmissionReliable service qualityPower managementSecurity arrangementQuality of serviceSecure transmission
The invention discloses a security transmission method based on cooperation interferences in a multi-cell network. It is assumed that a base station BS 1 and a target user Rx1 in a first cell are legal communication parties; the BS1 transmits a secrete message to the Rx1; in order to improve the security of the secrete message, the BS1 builds a cooperation relationship with the base station of other cell; an eavesdropping node is interfered by using the artificial noises AN generated by the cooperation base station; moreover, the cooperation base station adjusts the powers between usable signals and AN signals; on the basis of ensuring security performance, the service quality assurance is provided for the users of the local cell as much as possible; under a condition that a transmitter only knows the statistic channel information of the eavesdropping node, the secrete message is transmitted securely in the multi-cell network; further, on the basis of ensuring the security performance, the target users of the cooperation base station are ensured to obtain reliable service quality as much as possible; in consideration of the dynamic changes of channel gains in a wireless fading environment, the cooperation scheme provided by the invention is featured by dynamic self-adaption.
Owner:江苏星地通通信科技有限公司
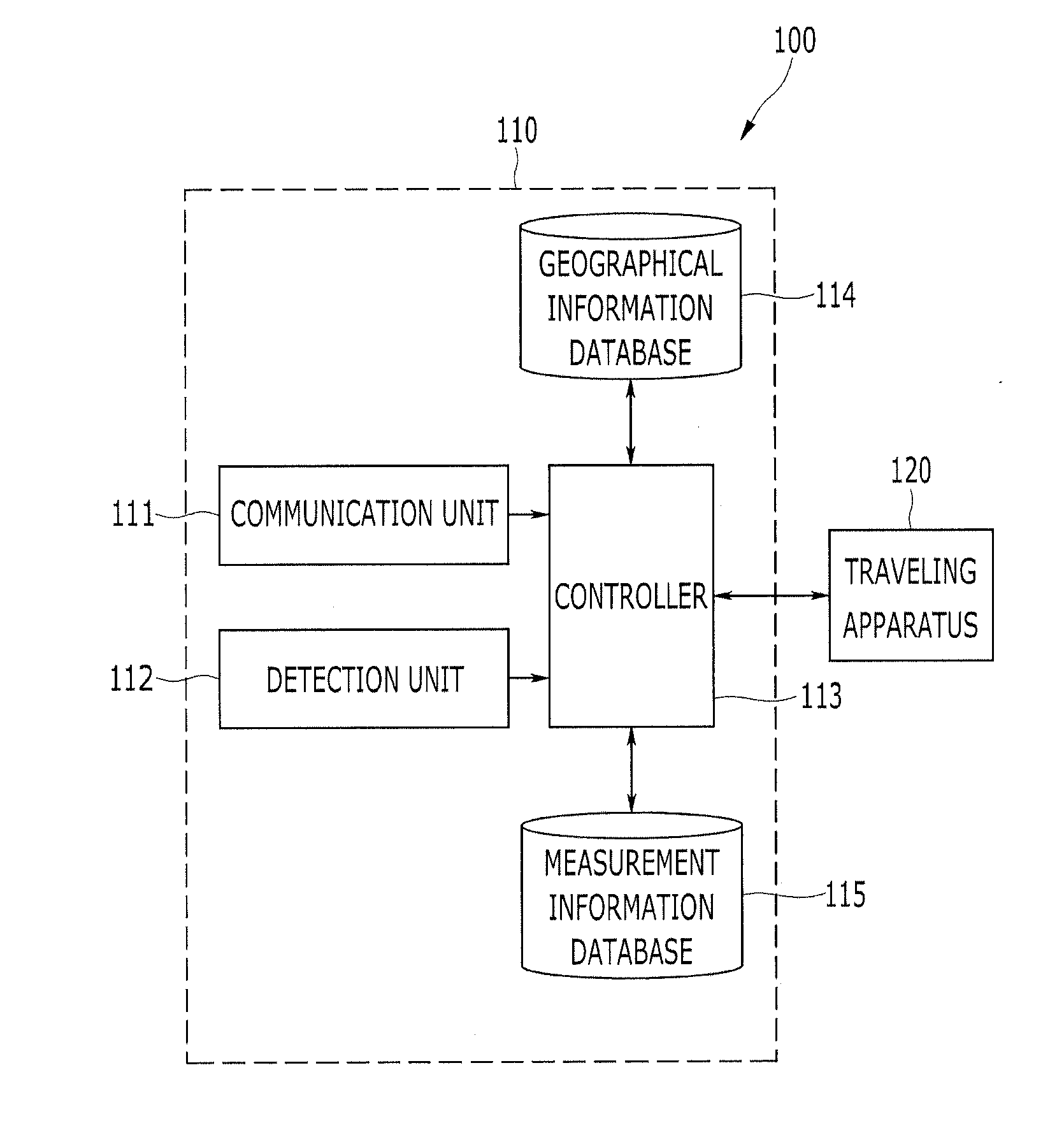
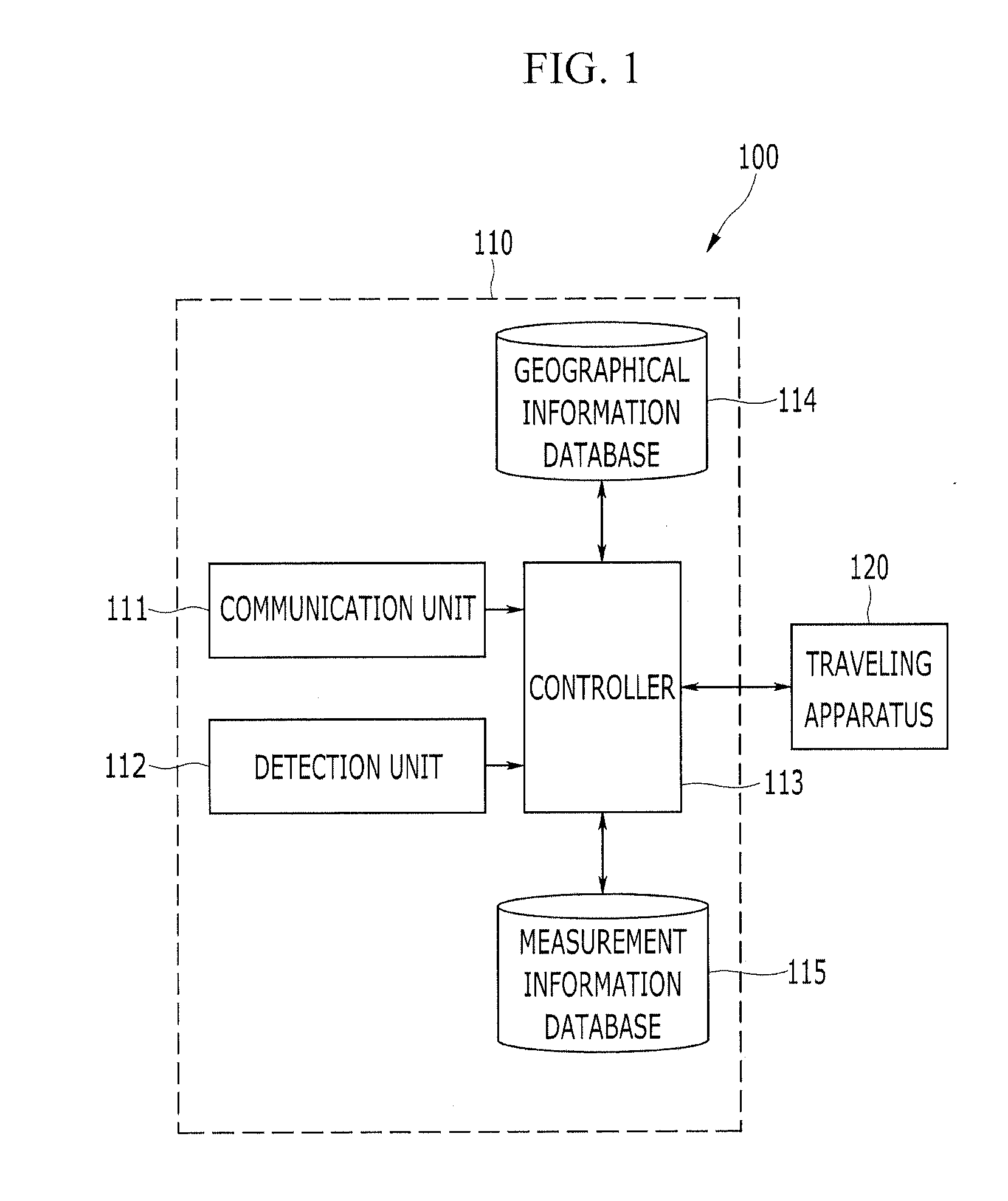
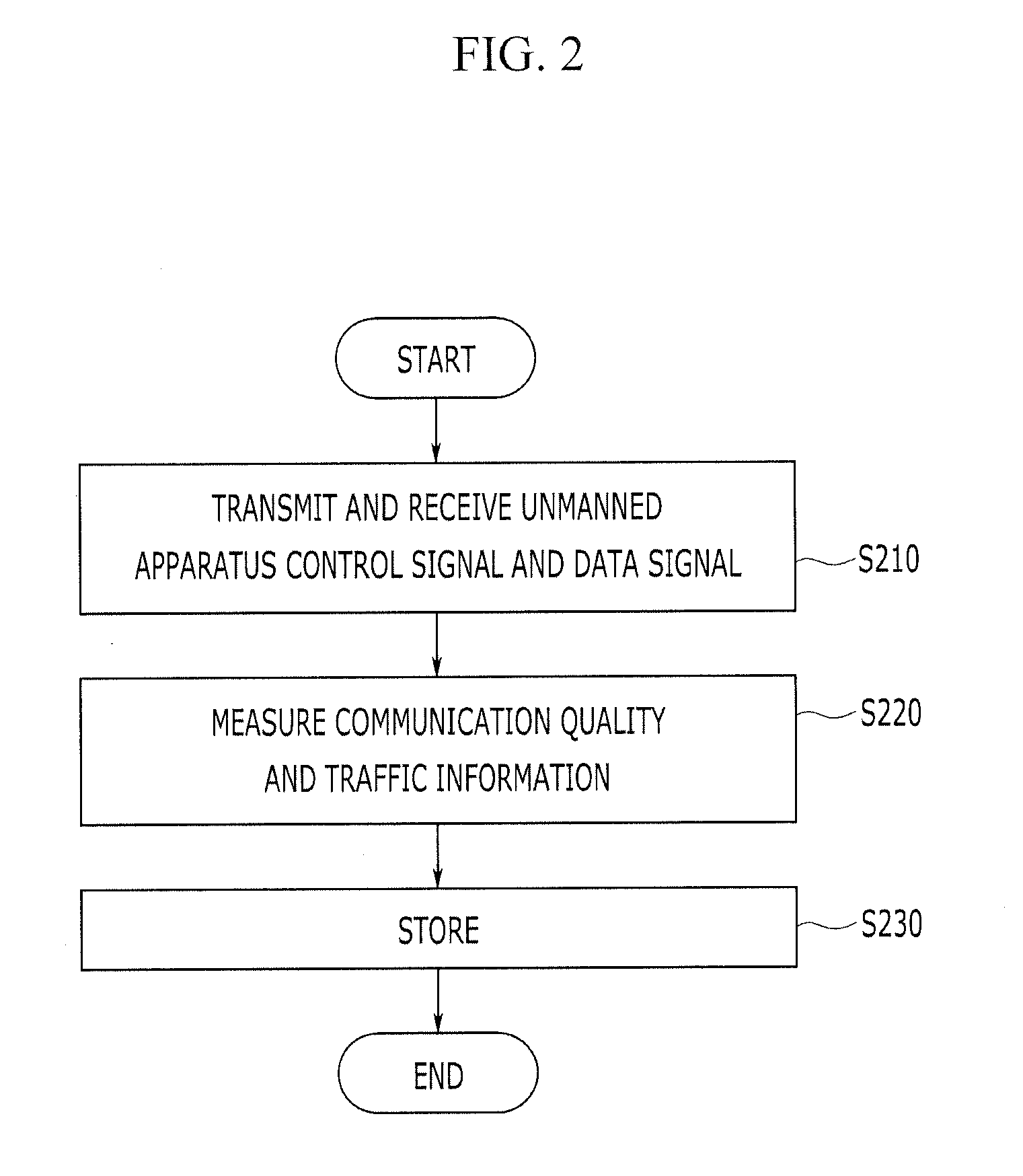
Unmanned apparatus and method of driving the same
InactiveUS20120158237A1Safe transferPerformed quickly and accuratelyVehicle position/course/altitude controlDistance measurementCommunication qualityElectronic map
An unmanned apparatus obtains position information and communication quality and traffic information while traveling, synchronizes the position information with the communication quality and traffic information, maps the communication quality and traffic information for each poison, synchronized with the position information, to geographical information, displays the geographical information on an electronic map, and sets a traveling path using the electronic map.
Owner:ELECTRONICS & TELECOMM RES INST
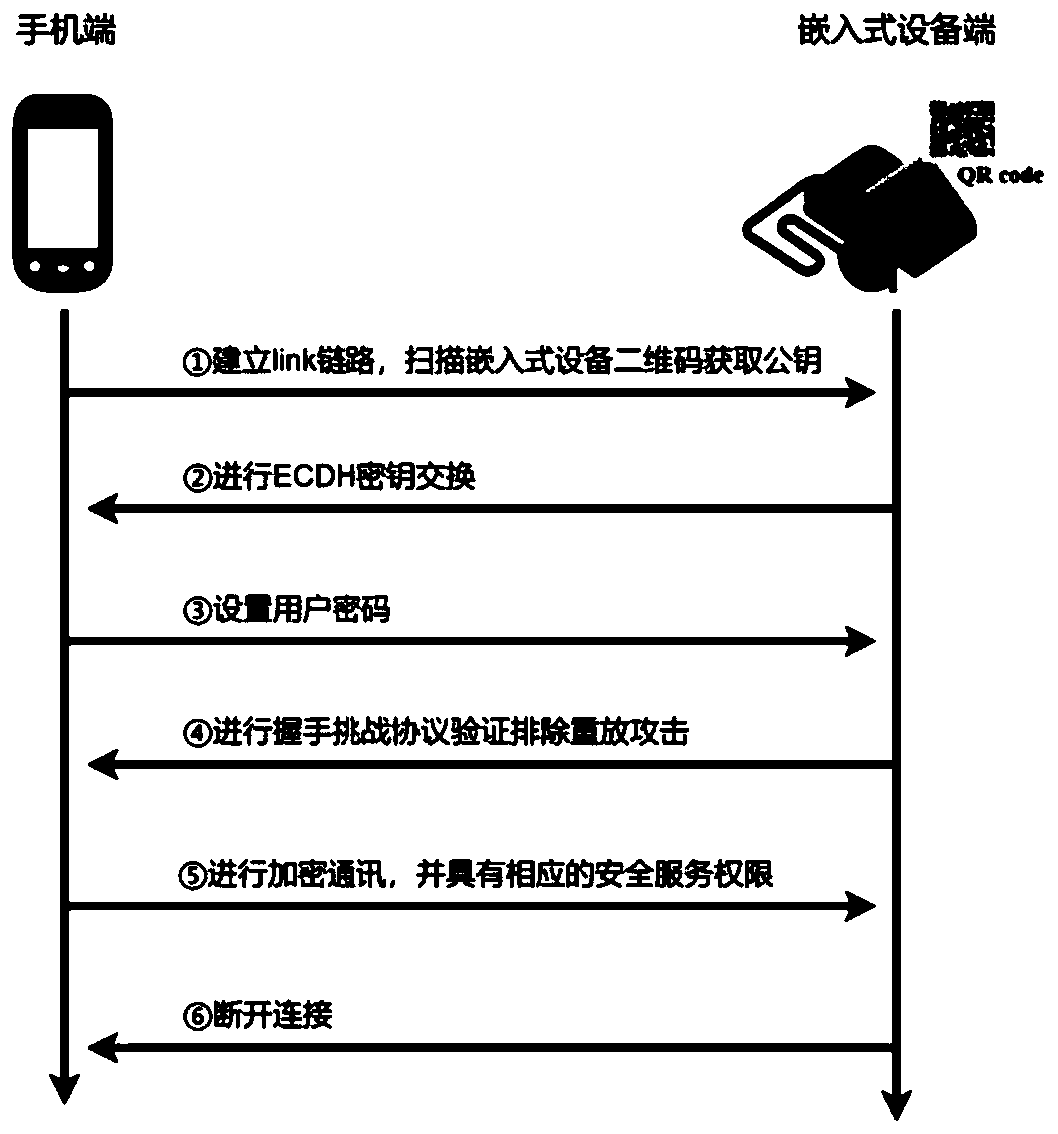
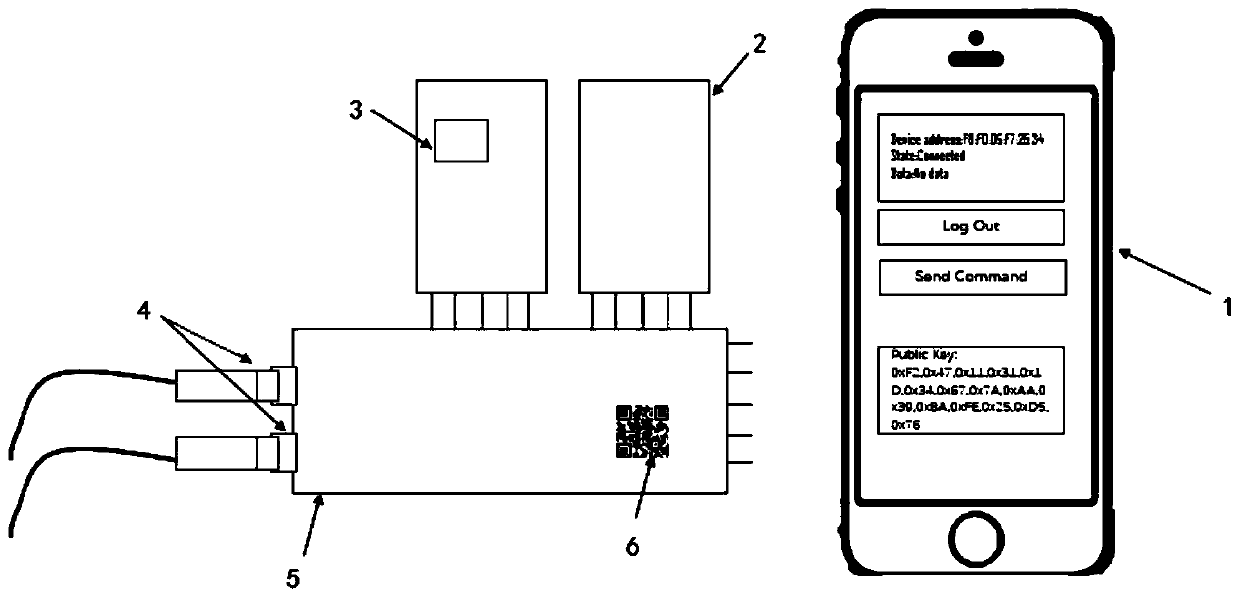
Bluetooth communication authentication request, receiving and communication method, mobile terminal and equipment terminal
ActiveCN110572804AWill not visitEnsure safetyShort range communication serviceSecurity arrangementKey exchangeTelecommunications link
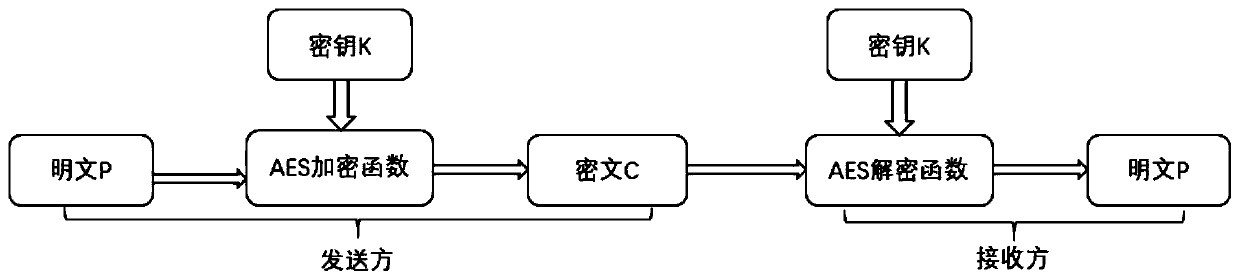
The invention discloses a Bluetooth communication authentication request, receiving and communication method, a mobile terminal and an equipment terminal, and the Bluetooth communication authentication request and communication method comprises the steps: carrying out the Bluetooth scanning with the equipment terminal, and establishing a communication link on a link layer; obtaining an equipment end public key; performing ECDH key exchange, and generating an ECDH Base AES Key symmetric key K; acquiring a user password, and sending the user password to the equipment end; after the equipment terminal passes user authentication, performing data communication with the equipment terminal, and disconnecting connection after communication is completed; in the user password sending process and thedata communication process, an AES encryption channel is adopted for encryption and decryption transmission, and a secret key of an AES encryption function is a symmetric secret key K. According to the method, the secret keys of the two communication parties are stored in the application layer, detection and verification are carried out on the application layer through the ECDH secret key exchange technology, it is guaranteed that the secret keys are stored in a protected thread, and data cannot be accessed by other malicious programs.
Owner:JINAN UNIVERSITY
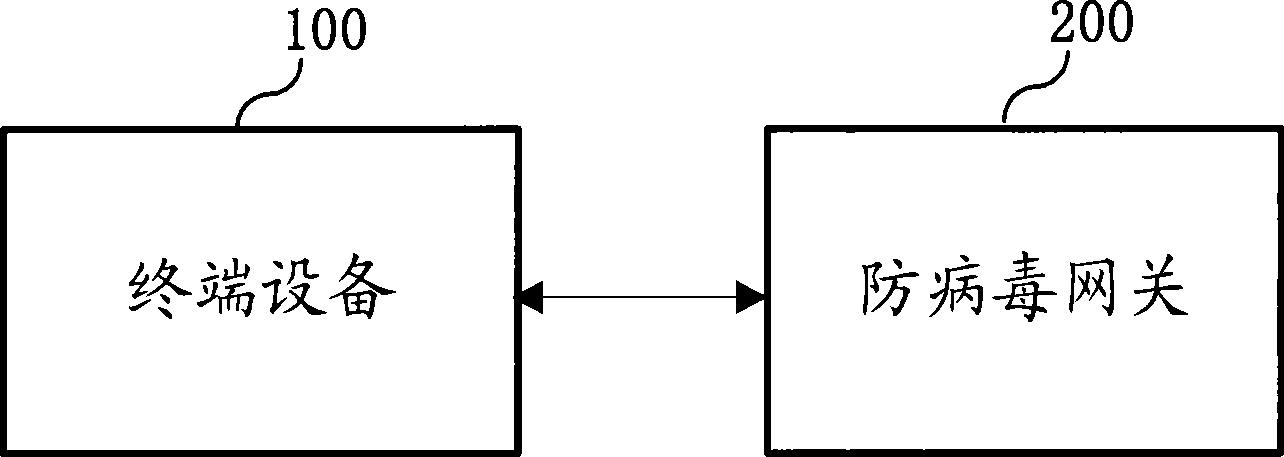
Method, apparatus and system for network safe transmission
InactiveCN101399786ADoes not take up resourcesSolve the problem of intruding into the network and blocking the networkNetwork connectionsAnti virusSecure transmission
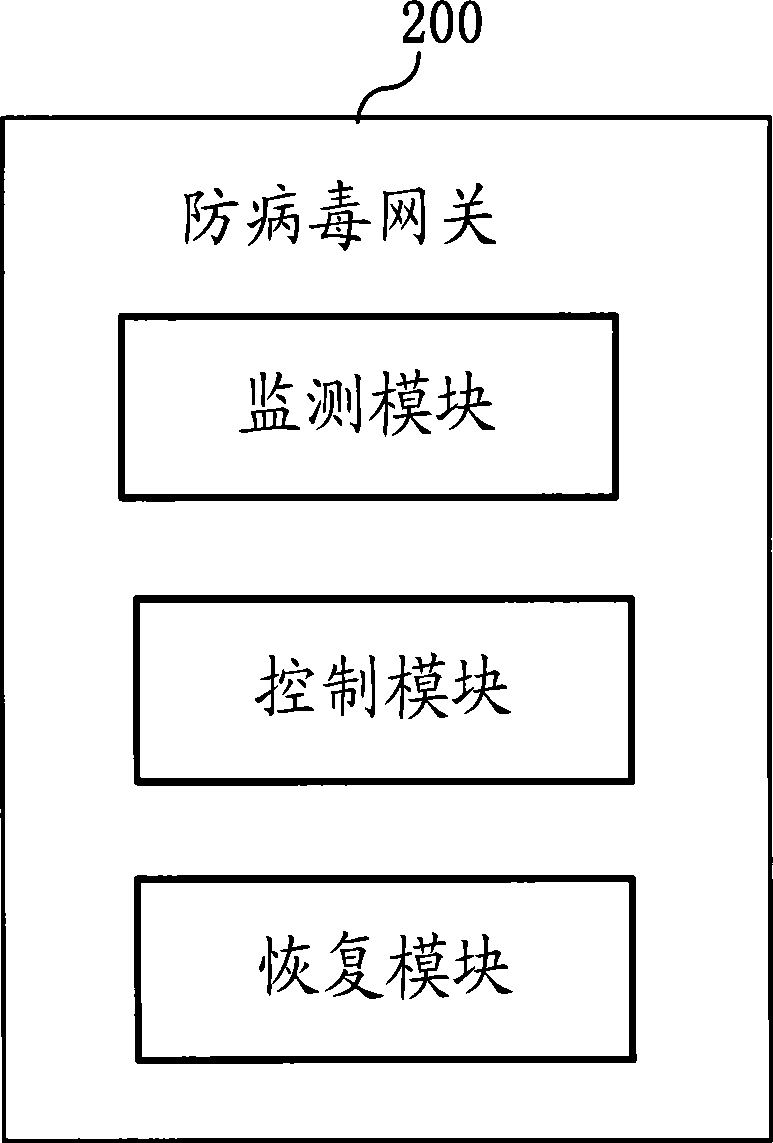
The invention provides a network security transmission method, a device and a system thereof. The method of the invention comprises that: an anti-virus gateway is used for monitoring the security state of terminal equipment, so as to judge whether security hidden troubles exit in the terminal equipment; when the security hidden trouble exits in the terminal equipment, the network transmission of the terminal equipment is controlled according to the security control policy and a control command is transmitted to the terminal equipment to cause the terminal equipment to search and kill virus and remove the hidden trouble. The anti-virus gateway equipment comprises a monitoring module, a transmission module and a control module. By adopting the invention, the problem that the network virus utilizes the security hidden trouble of the terminal equipment to invade the network and block the network is solved, and meanwhile, the mutual transmission between terminal equipment can be avoided; therefore, the network security transmission can be realized.
Owner:HUAWEI TECH CO LTD
Method applying SIP signaling to quantum secure communication system, integrated access quantum gateway and system
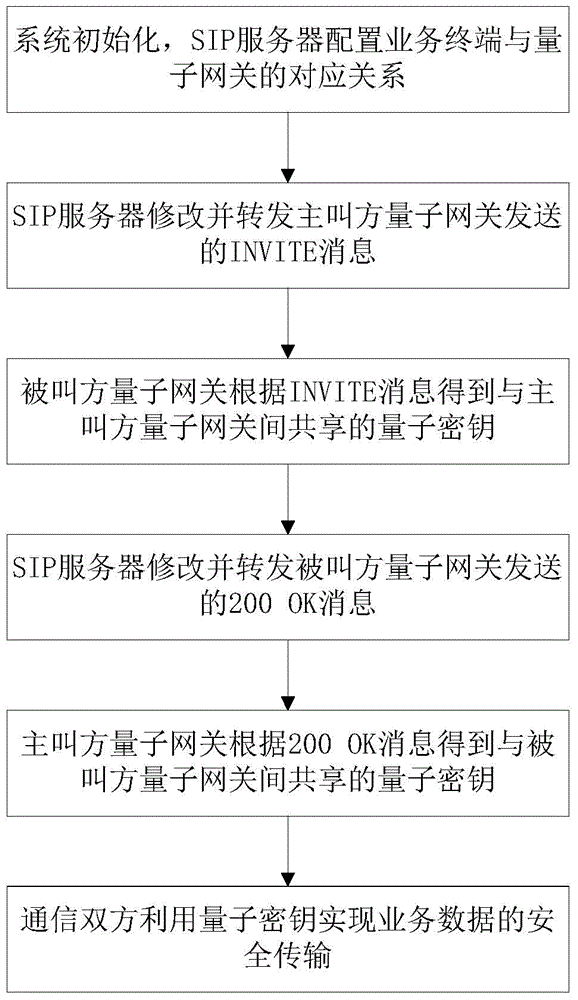
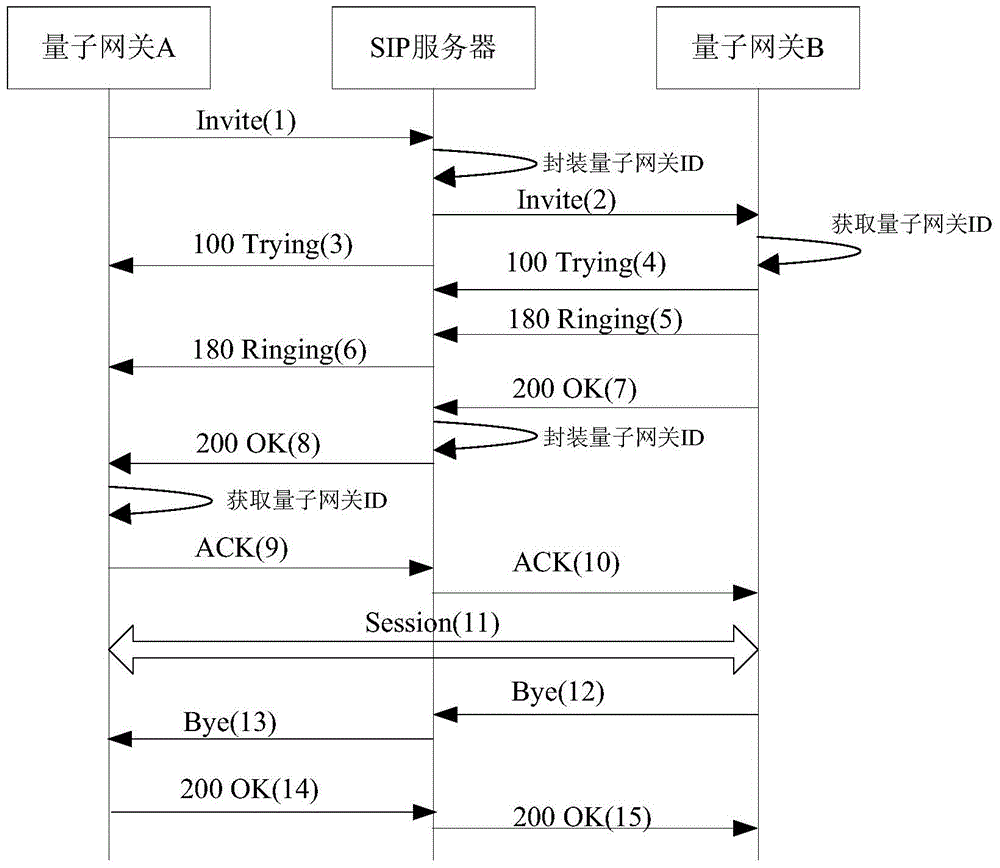
ActiveCN104618387AImprove securityRealize secure transmissionTransmissionCommunications systemBusiness data
The invention discloses a method applying SIP signaling to a quantum secure communication system. Aiming at the widely used SIP system, quantum gateway ID information is added on the basis that little SIP protocol instruction field is modified so that a quantum gateway can accurately identify and use a shared quantum secret key, encryption and decryption services can be provided for the business data of the SIP system, and dynamic integration of the SIP signaling business system and the quantum communication technology can be realized. Moreover, the invention further provides an integrated access quantum gateway and the quantum secure communication system which take the SIP signaling business as the basis, convert various business types into SIP signaling business, conduct encryption and decryption on each business data through the quantum secret key, and ensure the high safety of the business data transmission.
Owner:QUANTUMCTEK +1
Design method of collaborative unmanned aerial vehicle data acquisition system based on physical layer security
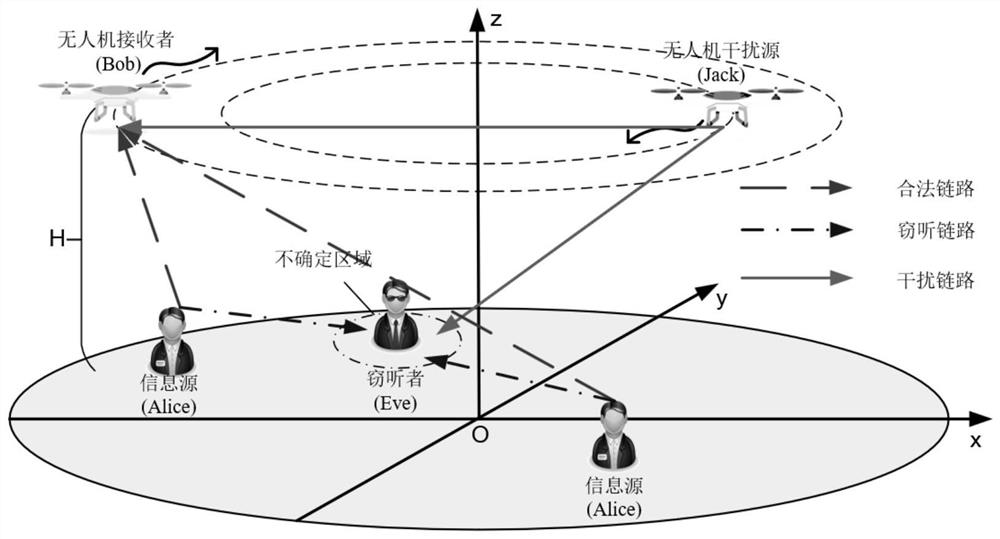
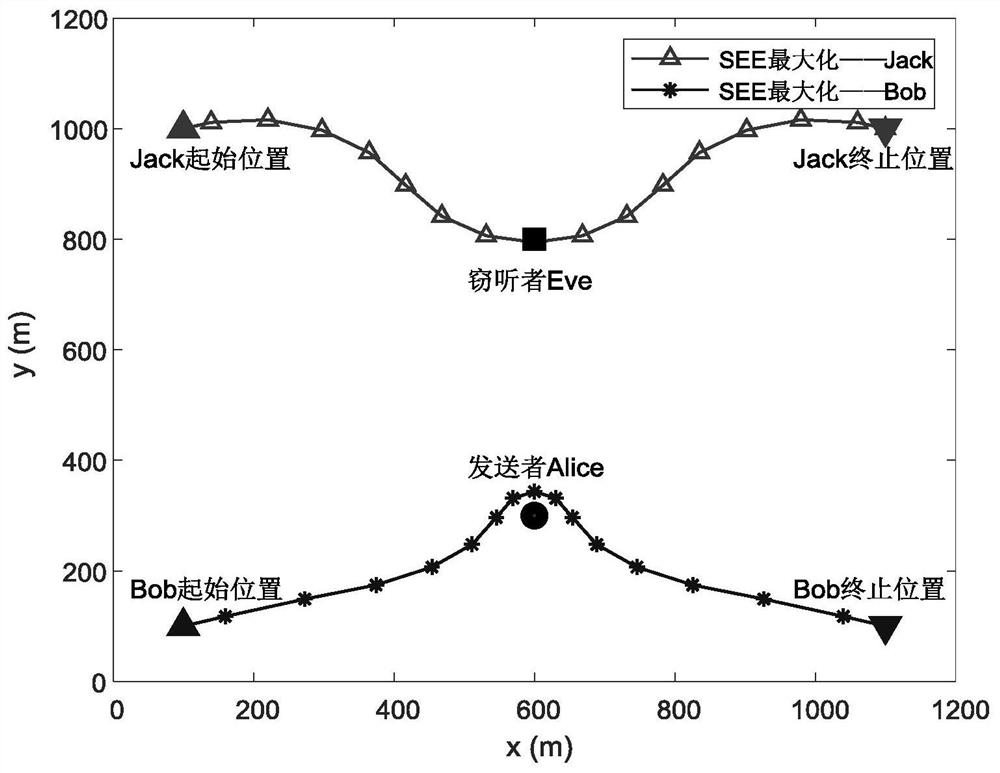
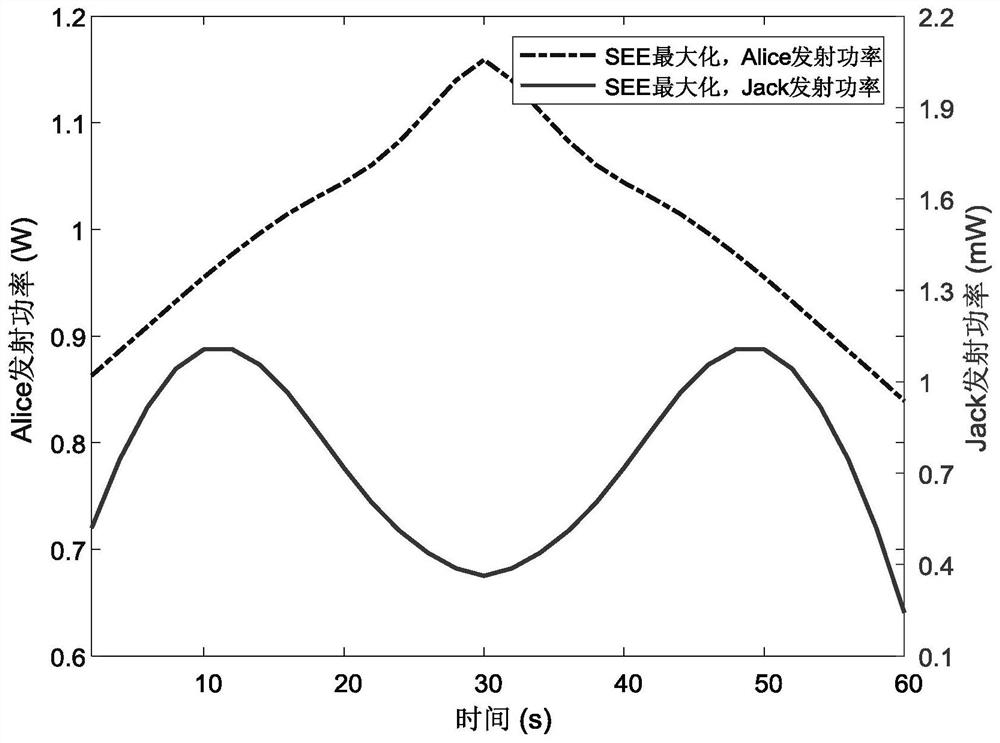
ActiveCN112383935AMaximize safety and energy efficiencyRealize secure transmissionPower managementCommunication jammingSimulationUncrewed vehicle
The invention provides a design method of a cooperative unmanned aerial vehicle data acquisition system based on physical layer security, and belongs to the field of energy efficiency optimization ofunmanned aerial vehicle uplink communication. When the unmanned aerial vehicle collects information, a potential eavesdropper tries to monitor the transmitted information, and another interference unmanned aerial vehicle is set to realize cooperative communication by utilizing the sight distance characteristic of an air-ground link so as to improve the system security. Based on the model, the invention provides a design method for joint optimization of the unmanned aerial vehicle trajectory, the unmanned aerial vehicle speed, the information source transmitting power and node scheduling. The method can generate the optimal motion trajectory of the unmanned aerial vehicle according to model parameters to maximize the safety energy efficiency of the system.
Owner:DALIAN UNIV OF TECH +1
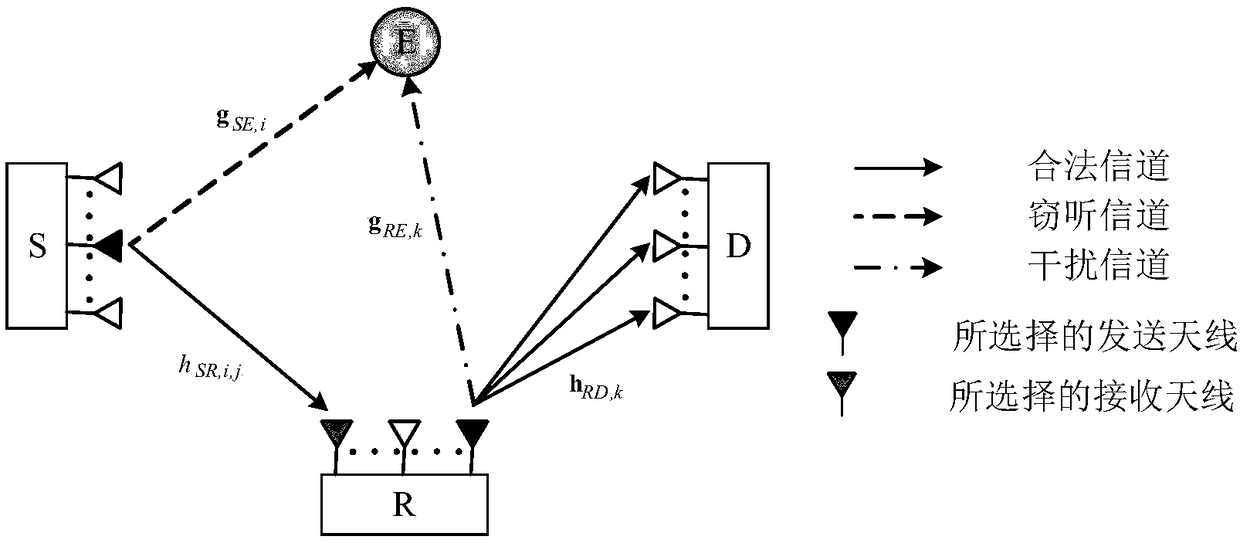
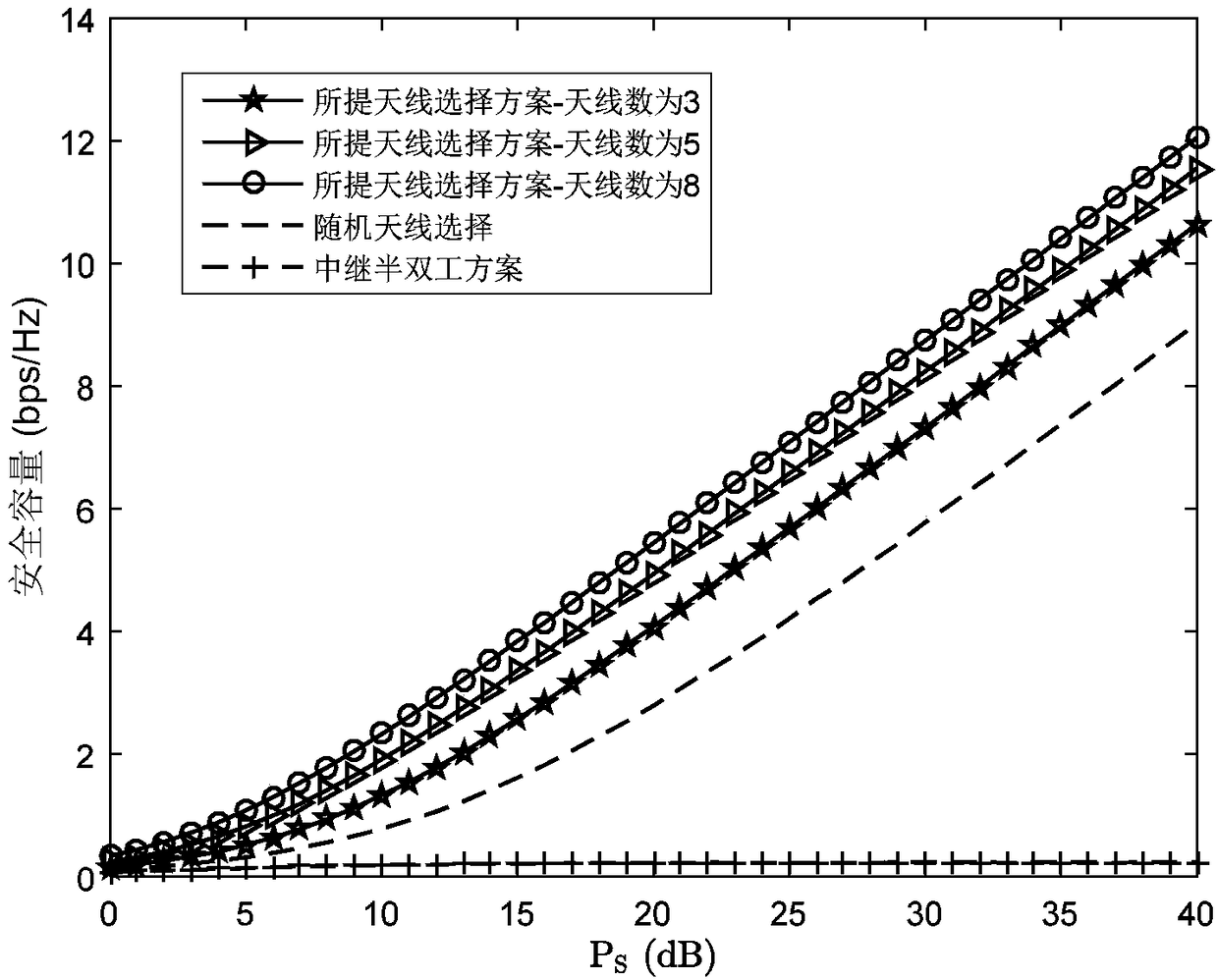
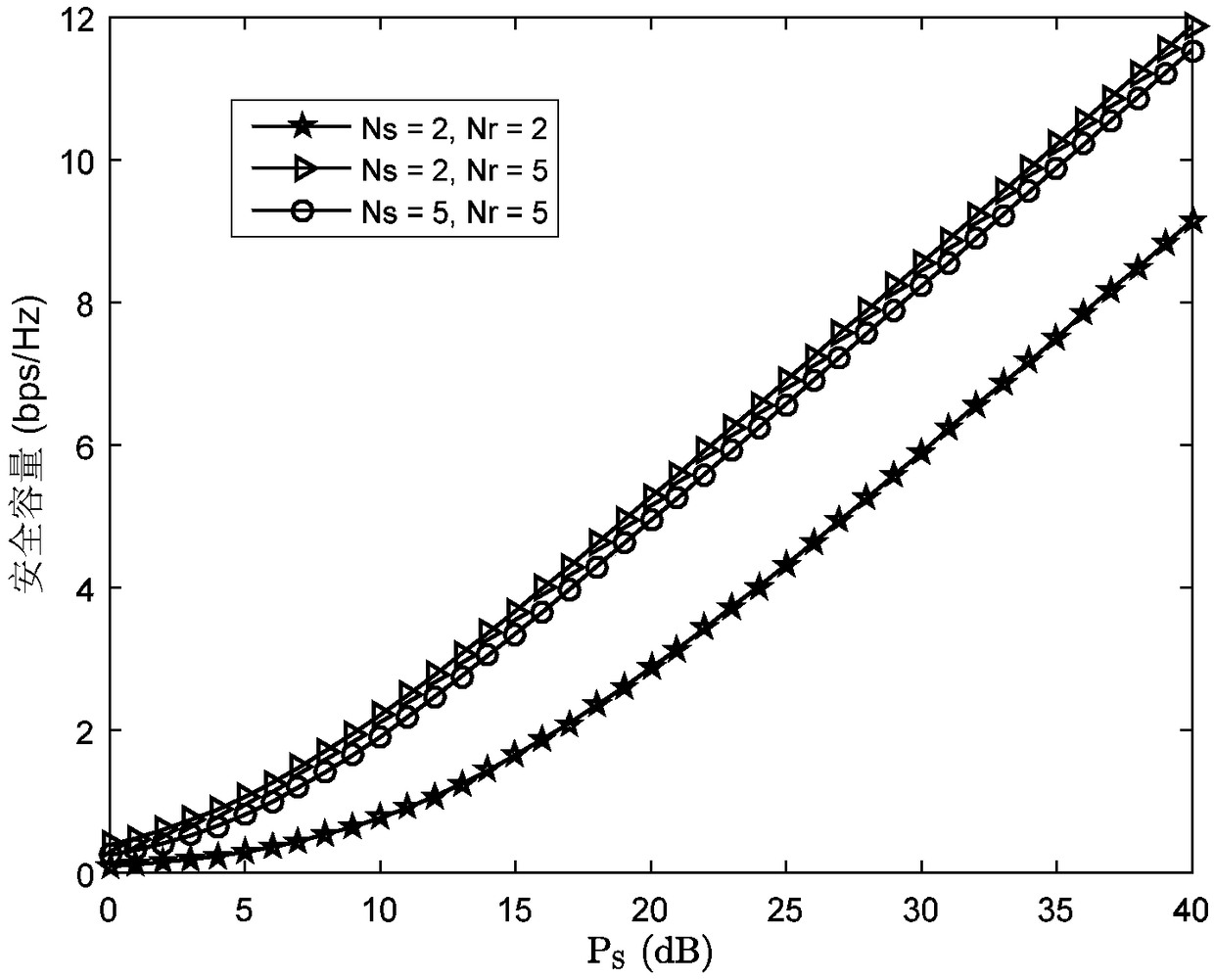
A method for selecting secure transmission of unidirectional full-duplex MIMO relay antennas
ActiveCN109039411AIncrease channel capacityOptimizing Receive Signal-to-Noise RatioSite diversitySpatial transmit diversityMultiple antennaSignal-to-noise ratio (imaging)
A method for selecting safe transmission of one-way full-duplex MIMO relay antenna is disclosed. The full-dual MIMO relay system comprises a source, a relay, a destination node and an eavesdropper. The source, the relay, the destination node and the eavesdropper are configured with multiple antennas. The transmission of information is completed in one time slot, comprising the following steps: acquiring the number of transmitting antennas of the source and the number of receiving antennas of the relay; obtaining the number of transmit antennas for the relay; based on the number of transmittingantennas of the source, the number of receiving antennas of the relay and the number of transmitting antennas of the relay, obtaining the reception signal-to-noise ratio of the destination and the reception signal-to-interference-noise ratio of the eavesdropper; obtaining the instantaneous safety capacity of the full-duplex MIMO relay system based on the received signal-to-noise ratio of the destination and the received signal-to-interference-noise ratio of the eavesdropper. By selecting the optimal transmitting and receiving antennas, the method of the invention not only optimizes the signal-to-noise ratio of the relay reception, but also takes into account the weakening of the signal-to-interference-to-noise ratio of the eavesdropper reception, thereby effectively improving the safety capacity of the whole system.
Owner:HUAQIAO UNIVERSITY
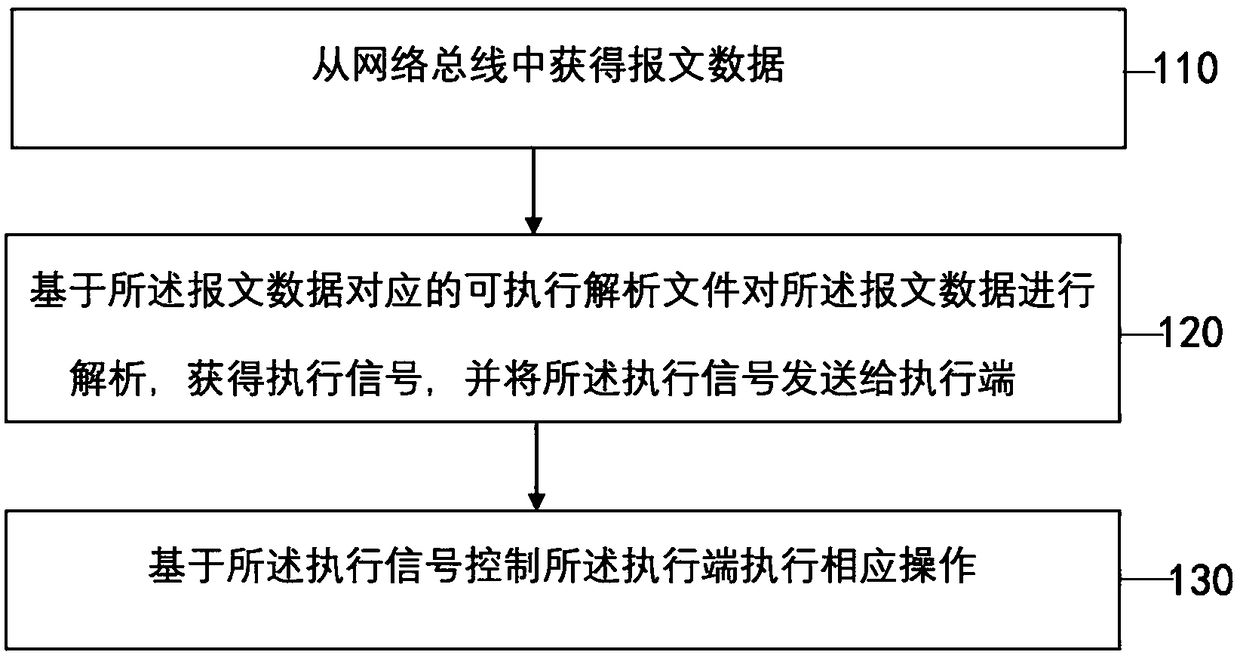
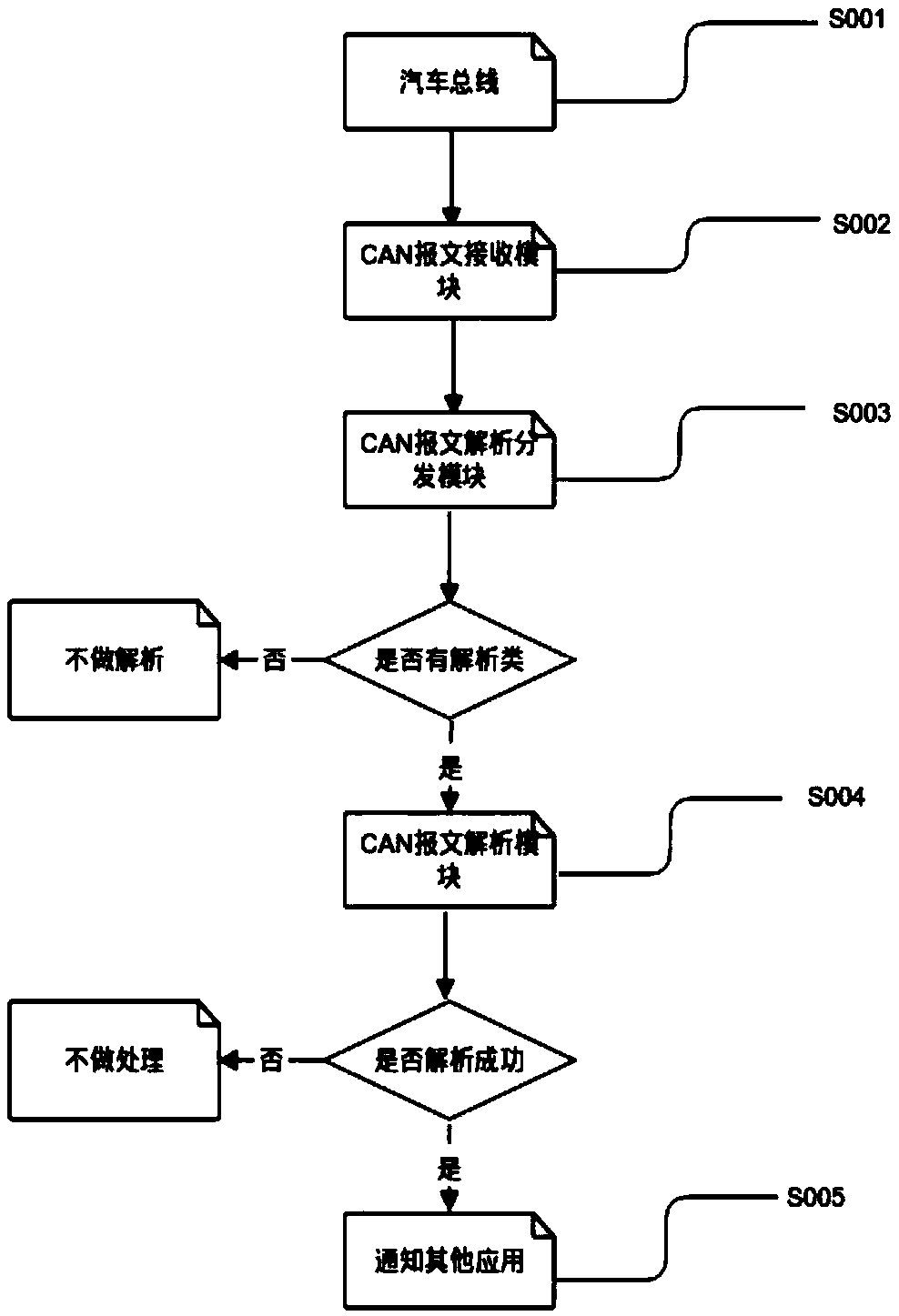
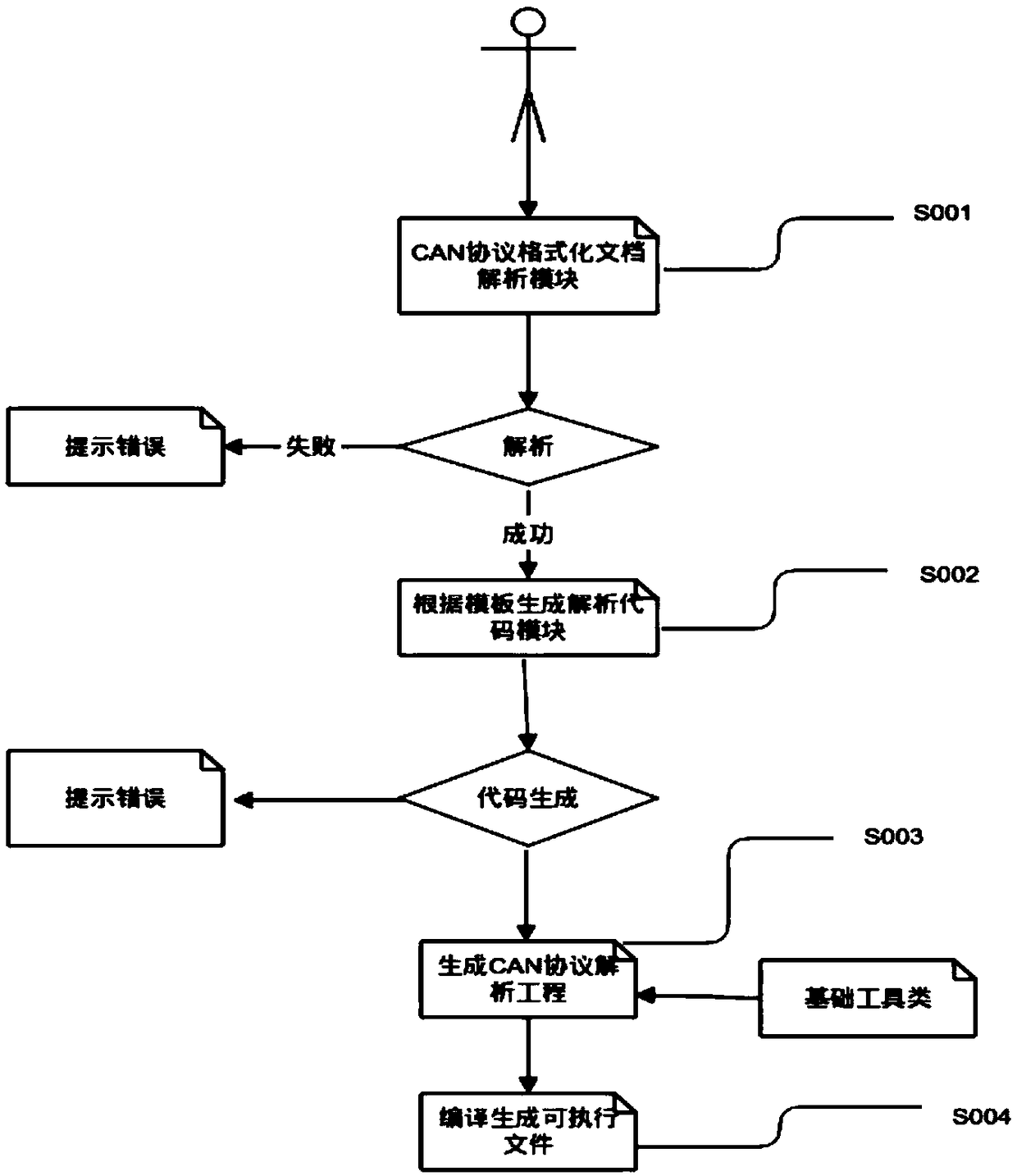
Message parsing method and apparatus, and electronic device
ActiveCN108965293AImprove driving safety and driving experienceRealize secure transmissionBus networksDriving safetyComputer hardware
The embodiment of the invention discloses a message parsing method and apparatus, and an electronic device. The method comprises the following steps: obtaining message data from a network bus; parsingthe message data based on an executable parsing file corresponding to the message data to obtain an execution signal, and transmitting the execution signal to an execution terminal; and controlling the execution terminal to perform a corresponding operation based on the execution signal. By adoption of the message parsing method and apparatus disclosed by the embodiment of the invention, secure transmission of the message data on the network bus can be realized, and the message data can be parsed to obtain the accurate execution signal so as to improve the driving safety and the driving experience.
Owner:ZHICHEAUTO TECH BEIJING
Device for realizing physical partition of internal and external networks
The invention provides a device for realizing physical partition of internal and external networks, and the device belongs to the field of network security. The device comprises first physical partition equipment and second physical partition equipment; the first physical partition equipment is arranged in an external network, and the second physical partition equipment is arranged in an internal network; the external network and the internal network communicate with each other through the first physical partition equipment and the second physical partition equipment; and the first and second physical partition equipment communicate at least through a universal serial bus. According to the device for realizing the physical partition of the internal and external networks, the real-time transmission of data between the internal and external networks is realized on the premise of ensuring security, and the real-time response of the data of the internal and external networks is greatly improved.
Owner:TIANJIN POLYTECHNIC UNIV
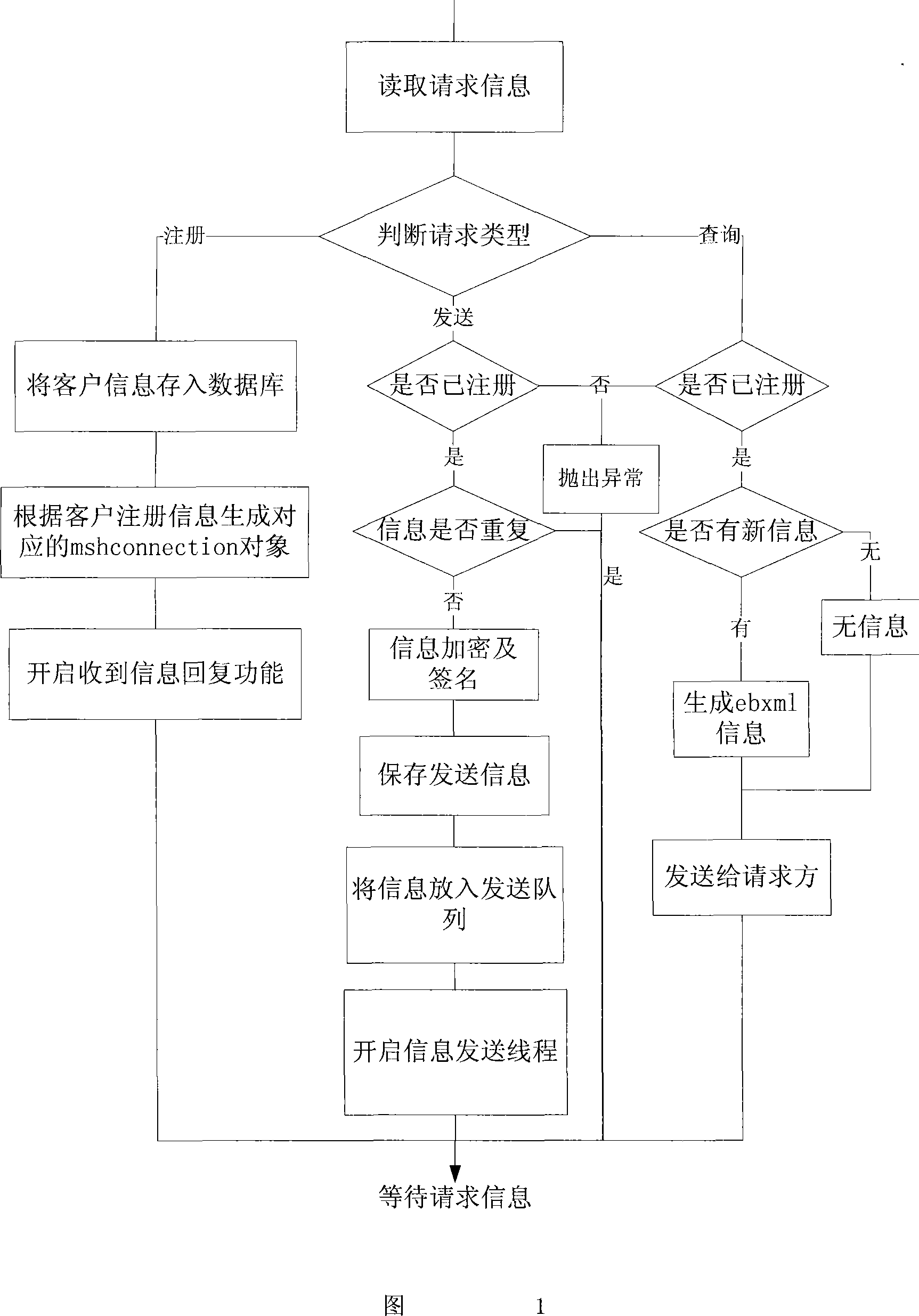
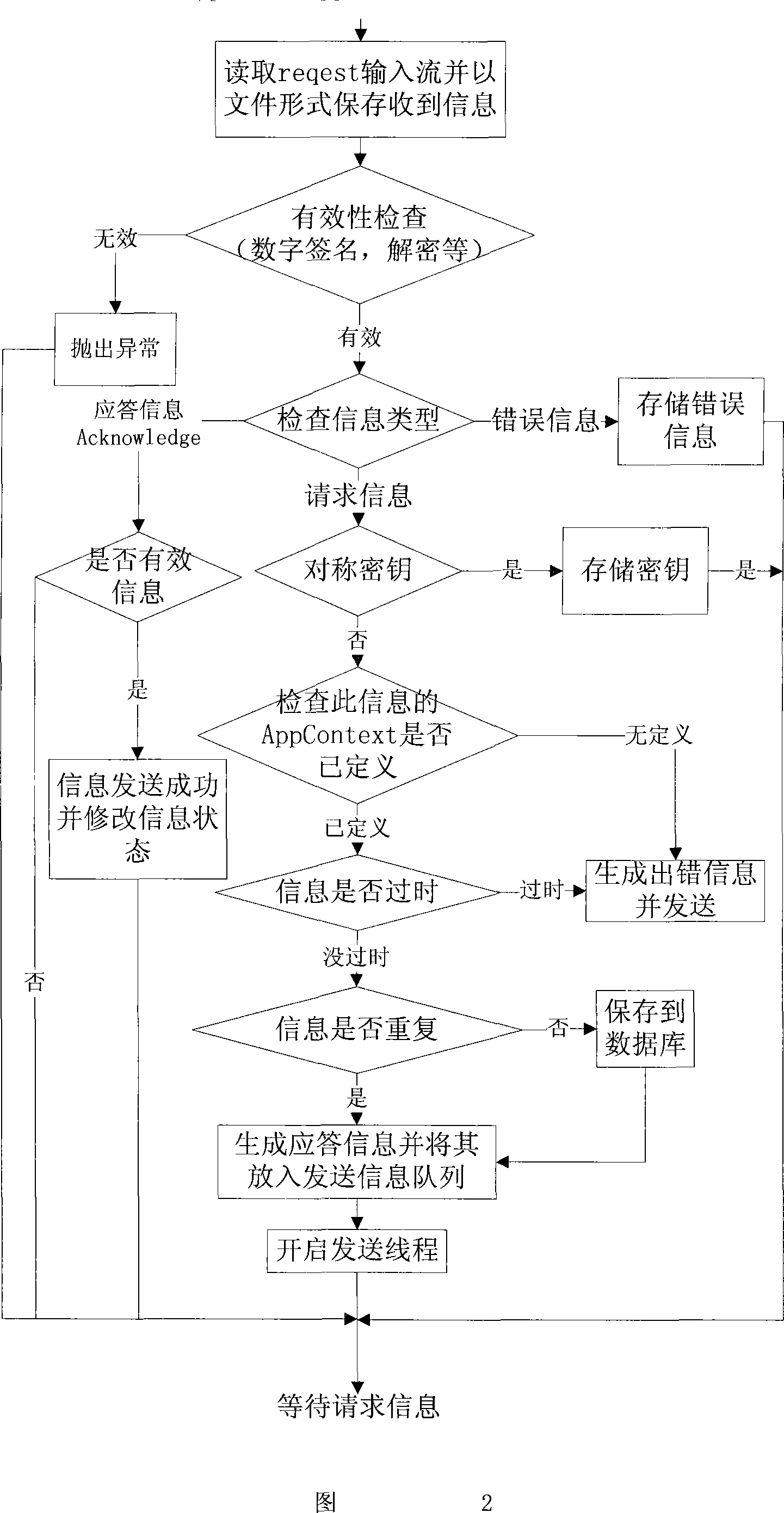
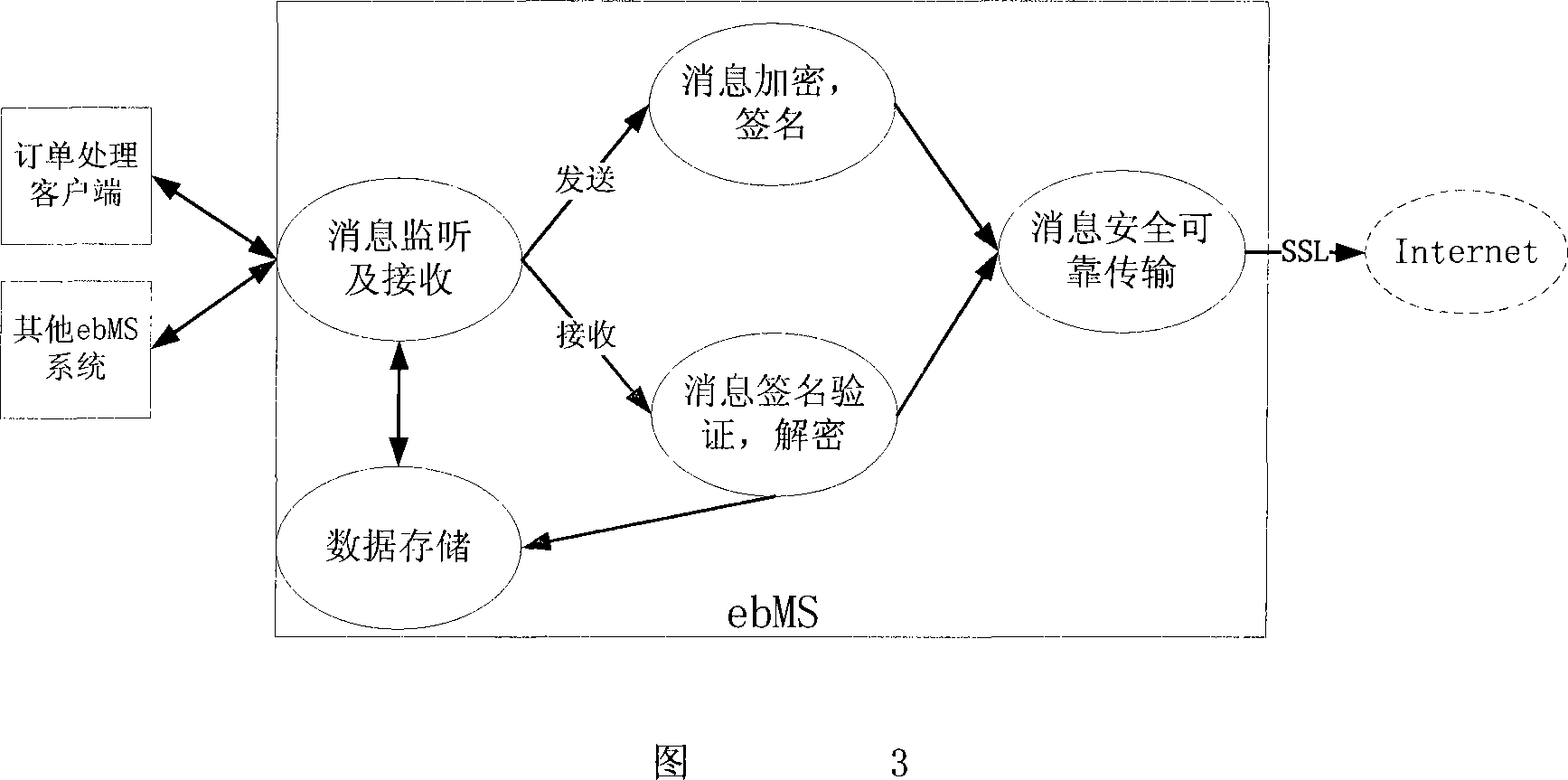
An electronic order secure transmission method based on ebMS
InactiveCN101145912AImprove efficiencyRealize secure transmissionPublic key for secure communicationUser identity/authority verificationClient-sideInformation type
The invention discloses an electronic order security transmission method based on ebMS, which includes the steps as follows: (1) a local trade client end registers on an ebMS message server; (2) after the client end generates the order in XML format, an ebXML message is constructed by using SOAP technology, and the order is packed into the ebXML message as an attachment and the message is delivered to the ebMS message server in a HTTP way; (3) the ebMS message server encrypts or decrypts the XML message of the order; (4) when receiving the request message from other ebMS message servers, the ebMS message server verifies the message by signature, encrypts and judges the message type, if the message is an order message, the message is saved in a file format and recorded in the data base, and if the message is a symmetric key message, the message is saved in the data base. The invention enhances the order processing efficiency and realizes order message security transmission between heterogeneous platforms.
Owner:ZHEJIANG UNIV OF TECH
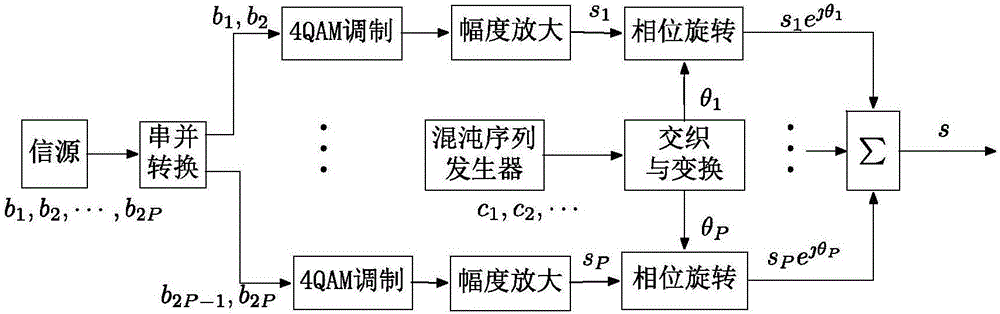
Physical layer secret communication method based on modulation symbol phase rotation
ActiveCN107181732ARealize secure transmissionImprove securityPhase-modulated carrier systemsSecuring communication by chaotic signalsPhysical layer secrecyPhysical layer
A physical layer secret communication method based on modulation symbol phase rotation is provided; a rectangular MQAM symbol is formed by stacking P mutually independent 4QAM symbols; the P 4QAM symbols phases are rotated in random, thus safely transmitting data between users; the method comprises the following steps: legal users use channel state information, and use a channel reciprocity theorem and a negotiation mechanism to determine the seed number of a chaotic sequencer used for generating a random number; the method periodically updates the seed number, resets the chaotic sequencer so as to generate a new chaotic sequence, and uses an interleaver to process the generated chaotic sequence set, thus obtaining approximately independent P groups of uniform distributed random sequences. The channel reciprocity and negotiation mechanism can ensure the dual-party phase rotation consistency, and the channel randomness can ensure a wiretapper cannot obtain a random rotation phase consistent with a sending terminal. The method allows legal users to safely transmit data under static state or quasi-state channel environments with high safety.
Owner:ZHEJIANG POLICE COLLEGE
Video processing method and system, mobile terminal, server and storage medium
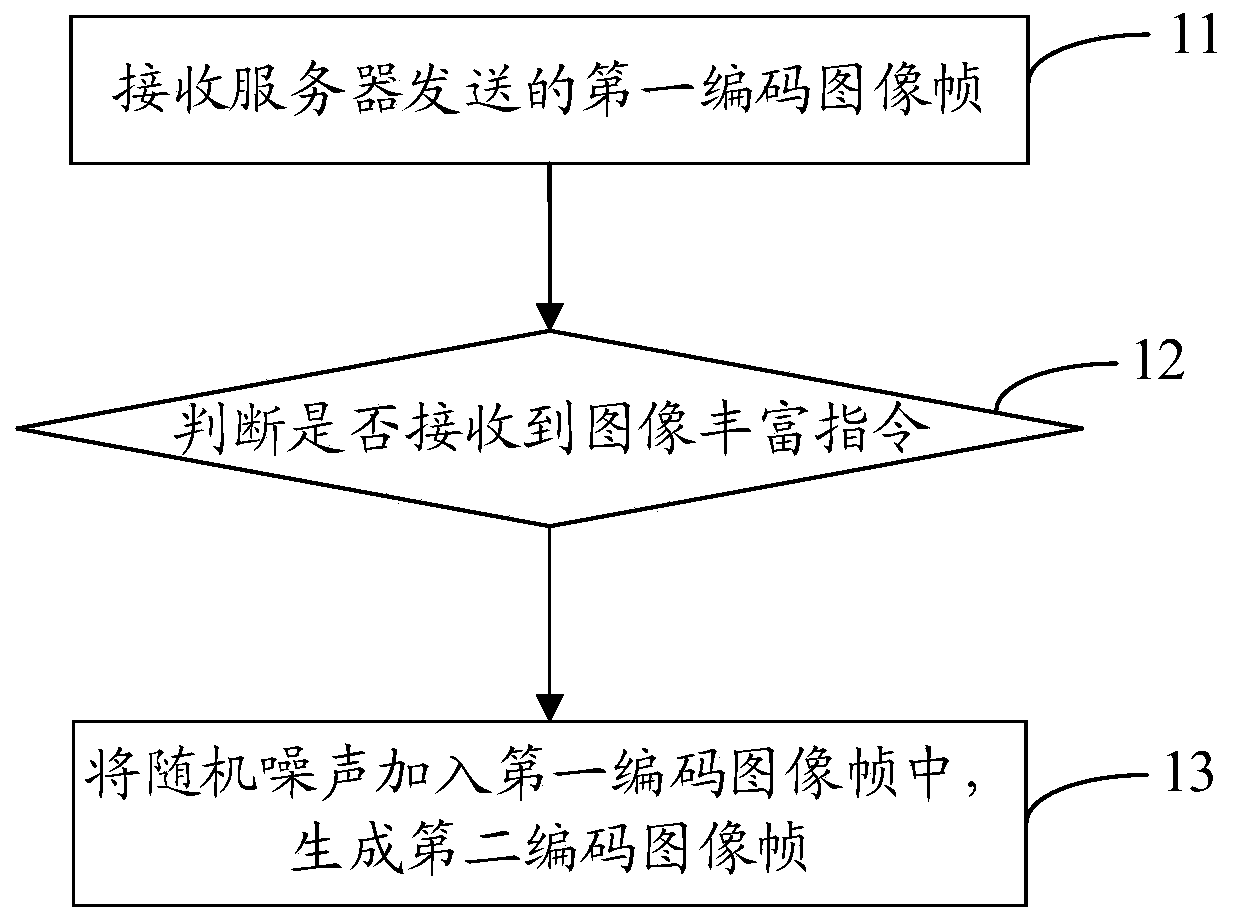
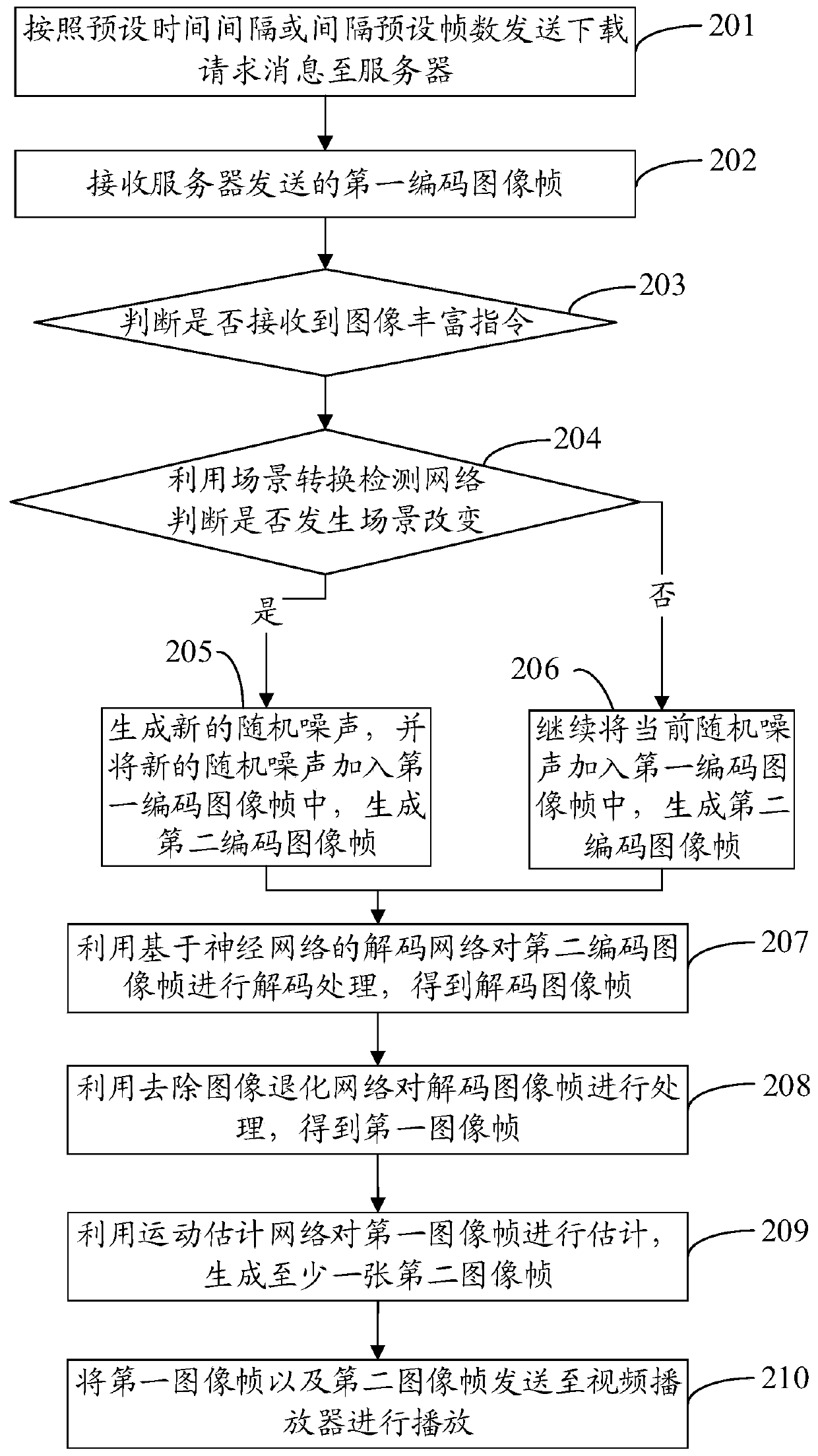
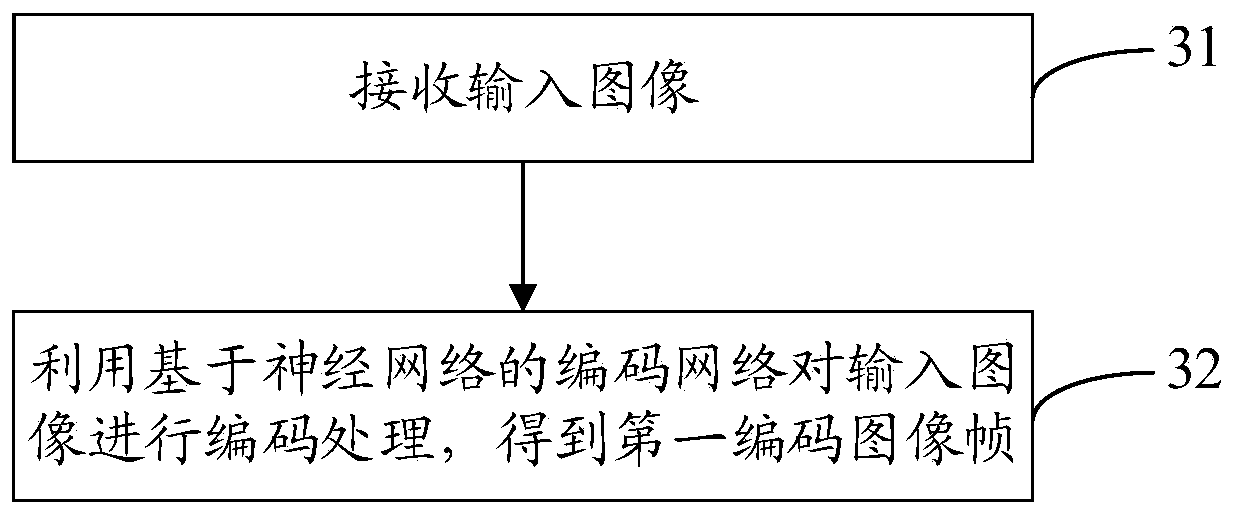
ActiveCN110139147ARealize secure transmissionImprove freshnessImage enhancementImage analysisComputer graphics (images)Video processing
The invention discloses a video processing method and system, a mobile terminal, a server and a storage medium, the video processing method is applied to a client, and the method comprises the following steps: receiving a first coded image frame sent by the server; judging whether an image enrichment instruction is received or not; if an image enriching instruction is received, adding random noiseinto the first coded image frame to generate a second coded image frame, wherein the first coded image frame is floating point type data, and the difference value between the first coded image frameand the second coded image frame is within a preset range. By means of the mode, the floating point type data can be decoded into the image, safe transmission of the image is achieved, and the decodedimage can be enriched.
Owner:SHENZHEN INST OF ADVANCED TECH
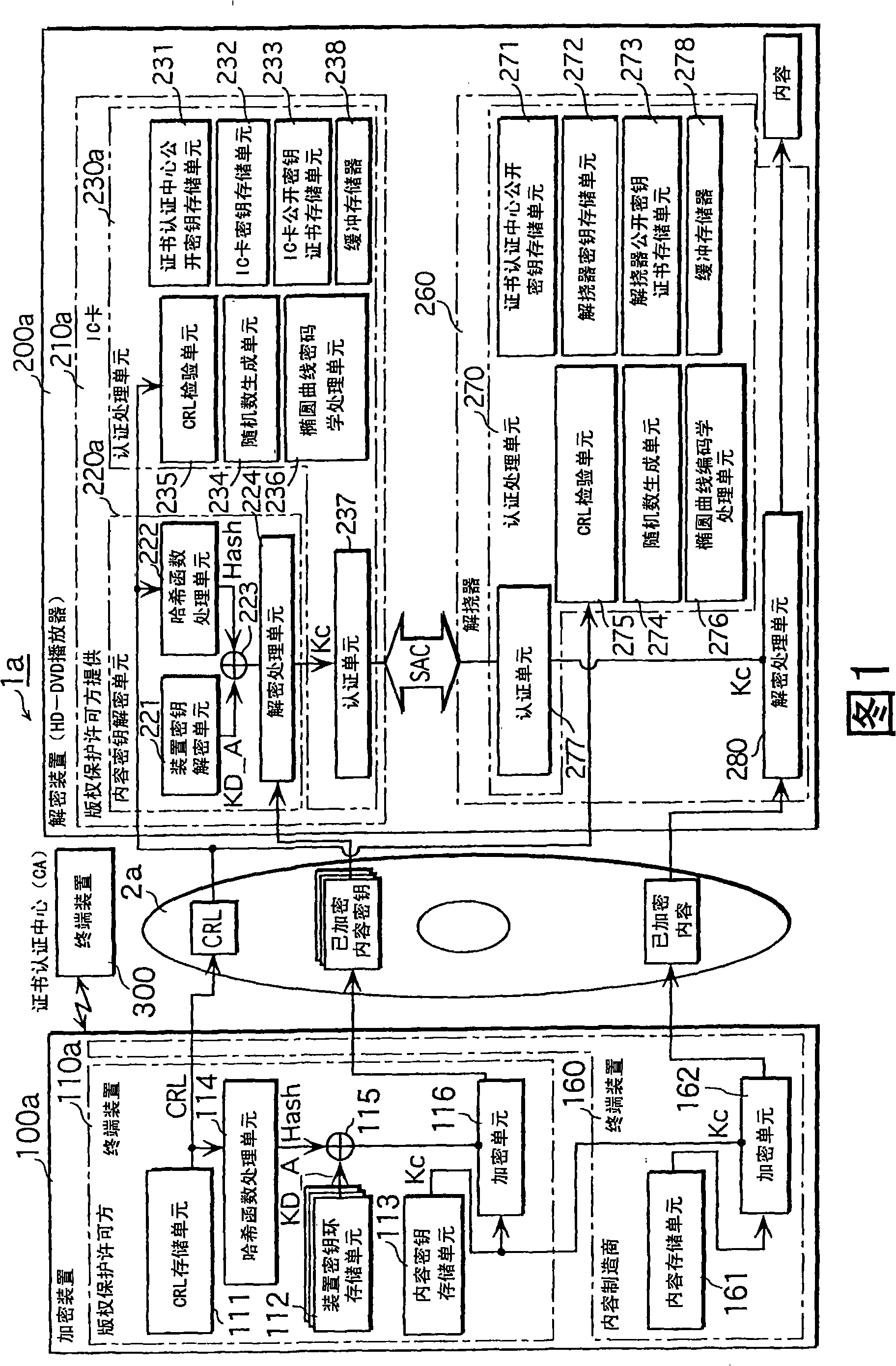
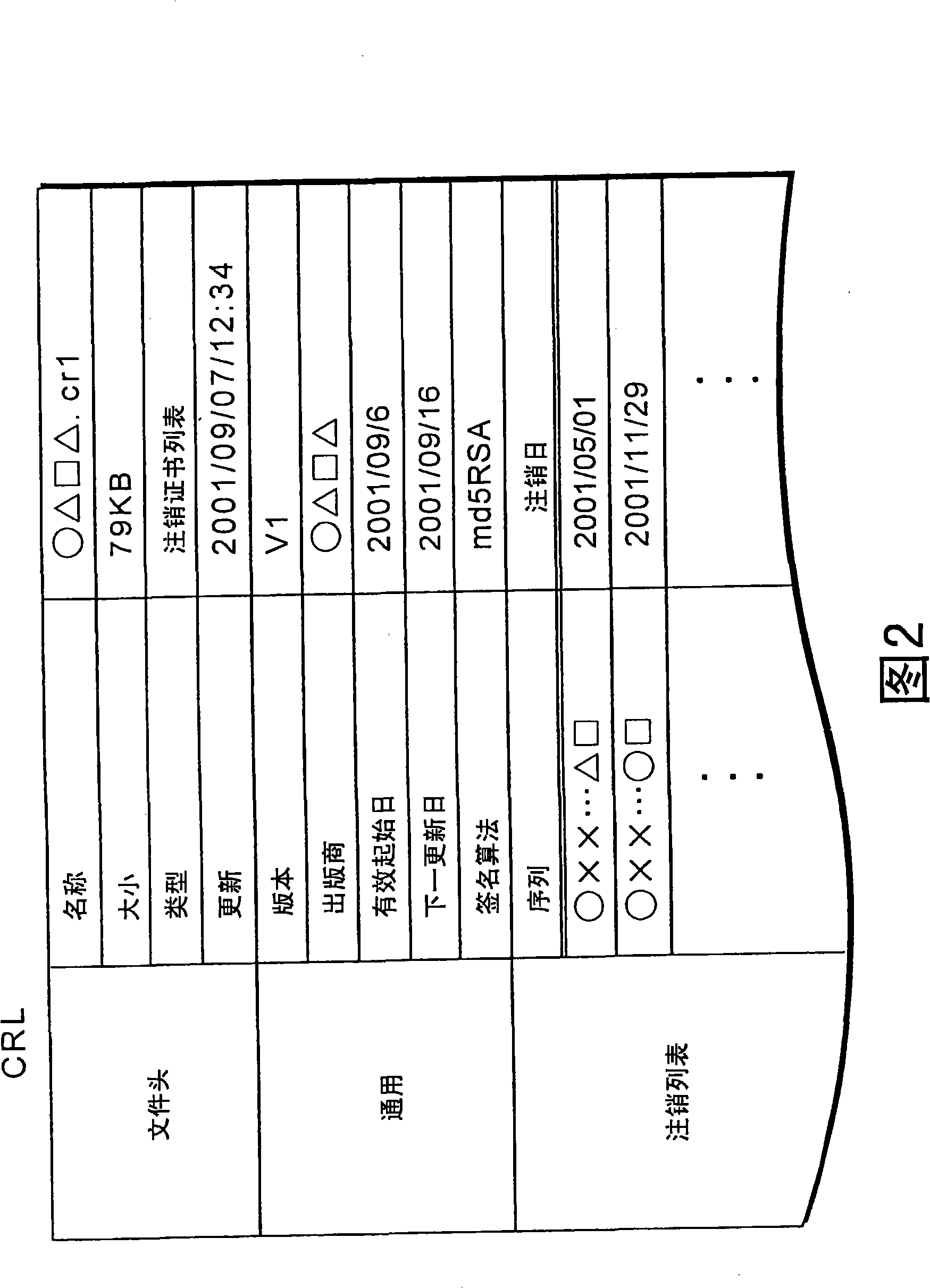
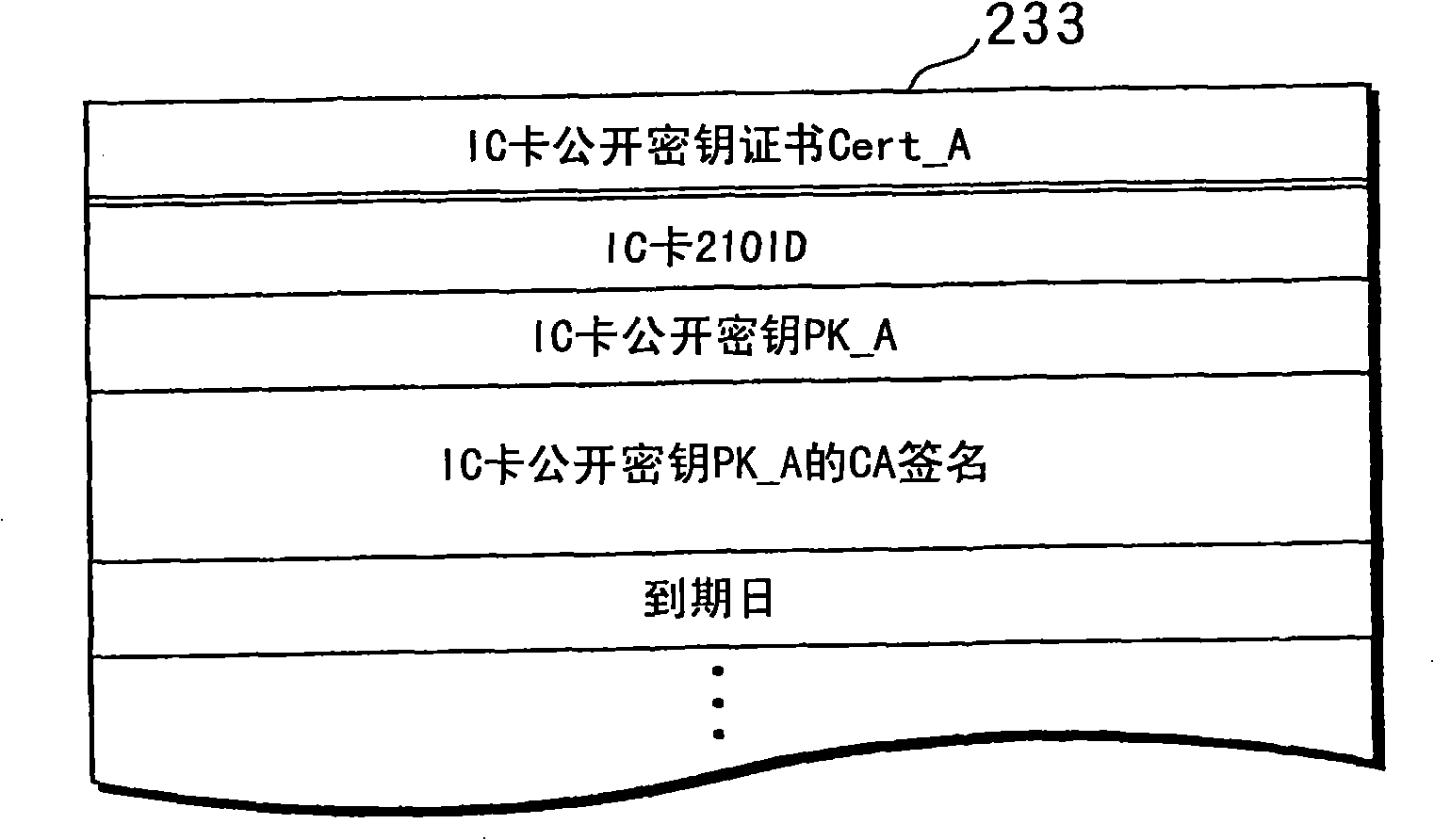
An encryption device, a decrypting device, a secret key generation device,a copyright protection system and a cipher communication device
InactiveCN101262339ARealize secure transmissionAvoid attackKey distribution for secure communicationPublic key for secure communicationComputer hardwareHash function
An encryption device, a decrypting device, a secret key generation device, a copyright protection system and a cipher communication device comprise: a CRL memory unit 111 that memorizes a CRL, a device key ring memory unit 112 that memorizes a peculiar device key KD A in every IC card 210a used in a decrypting device 200a, a content key memory unit 113 that memorizes a content key Kc which is a secret key for decrypting content, a hashing function processing unit 114 that calculates a hashing value of the CRL memorized in the CRL memory unit 111, an Ex-OR unit 115 that carries out an exclusive OR between the hashing value and the device key KD A memorized in the device key ring memory unit 112, and an Enc unit 116 that encrypts the content key Kc memorized in the content key memory unit 113 with an output value of an Ex-OR unit 115.
Owner:PANASONIC CORP
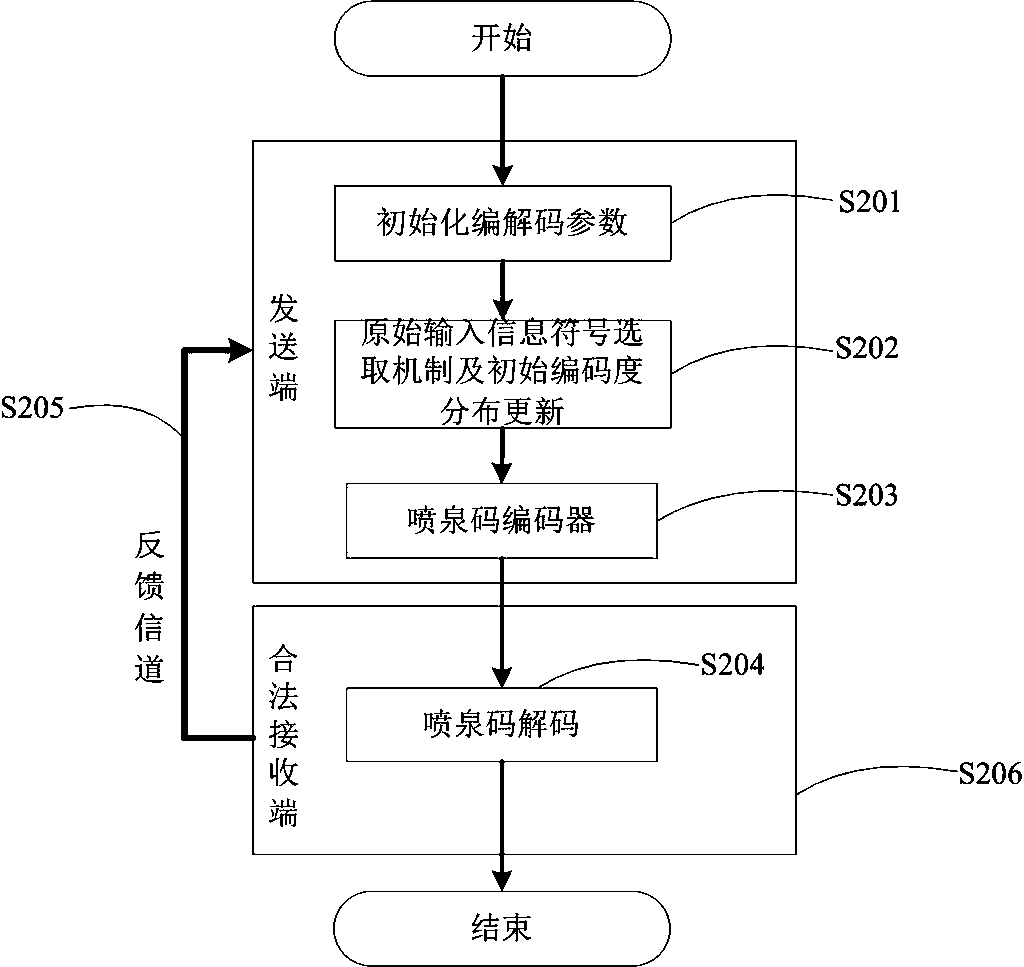
Secure transmission method using fountain code for multiple feedbacks
InactiveCN108259138ASecure transmissionWithout sacrificing transmission reliabilityChannel coding adaptationComputer hardwareReliable transmission
The invention belongs to the technical field of communications, and particularly relates to a secure transmission method using a fountain code for multiple feedbacks. According to the scheme of the invention, a fountain code encoding and decoding process is updated by using the feedback, the purpose of continuously accumulating the legitimate channel advantages can be achieved, the gap between a legitimate receiver and the eavesdropper translation rate can be maximized, and thus a relatively more secure transmission can be implemented. Compared with a common fountain code security transmissionmethod, the scheme of the invention can be tightly coupled with channels, the entire encoding and decoding process is operated on the basis of guaranteeing the reliable transmission, and the transmission reliability cannot be sacrificed due to the pursuit of security performance; moreover, only a small number of feedbacks are needed, and the phenomenon of channel congestion caused by a large number of feedbacks similar to that of the traditional communication cannot occur; and the requirement for channel conditions is low, and strong adaptability and practicability can be achieved in both wired and wireless environments.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
A method and system for realizing live stream distribution
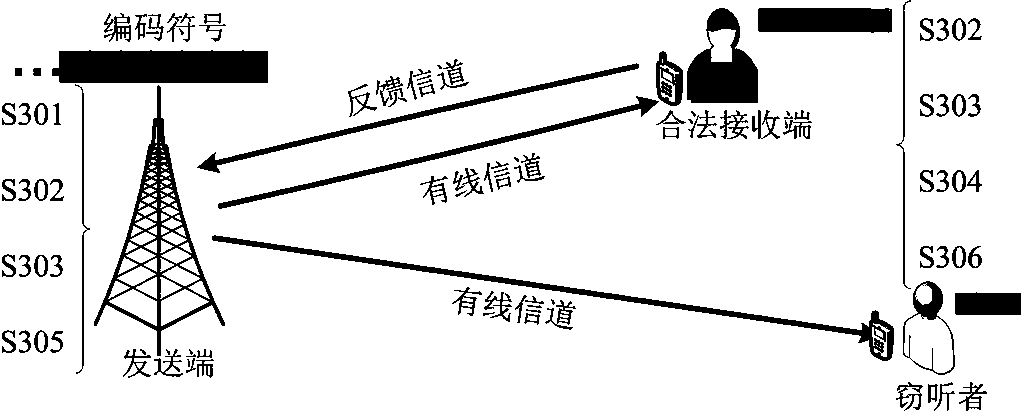
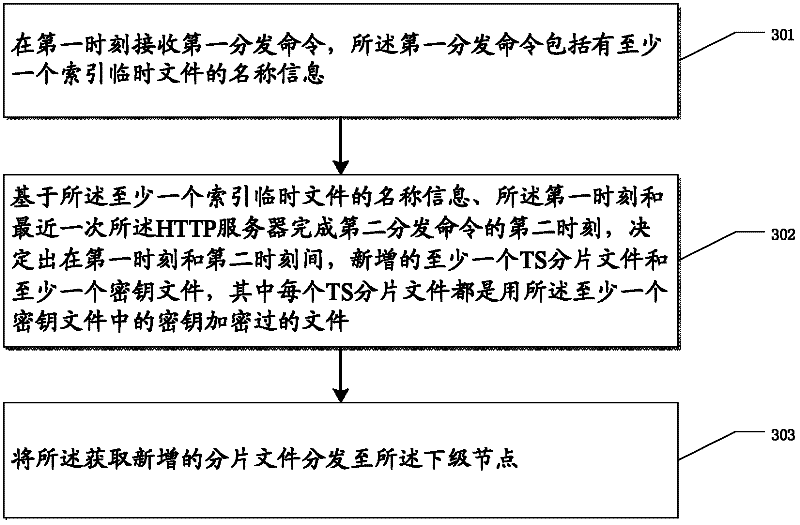
The present application discloses a method and system for realizing distribution of live code streams, wherein the method for distributing live code streams is used to obtain new files and distribute them to the next-level nodes by analyzing HTTP messages, including the following steps: Receive a first distribution command at the first moment, the first distribution command includes name information of at least one index temporary file; based on the name information of the at least one index temporary file, the first moment and the latest HTTP server At the second moment when the second distribution command is completed, at least one TS segment file and at least one key file are newly added between the first moment and the second moment, wherein each TS segment file uses the A key-encrypted file in at least one key file; and distributing the newly added at least one TS segment file and at least one key file to the lower-level nodes.
Owner:ZTE CORP
Method and equipment for implementing safety access
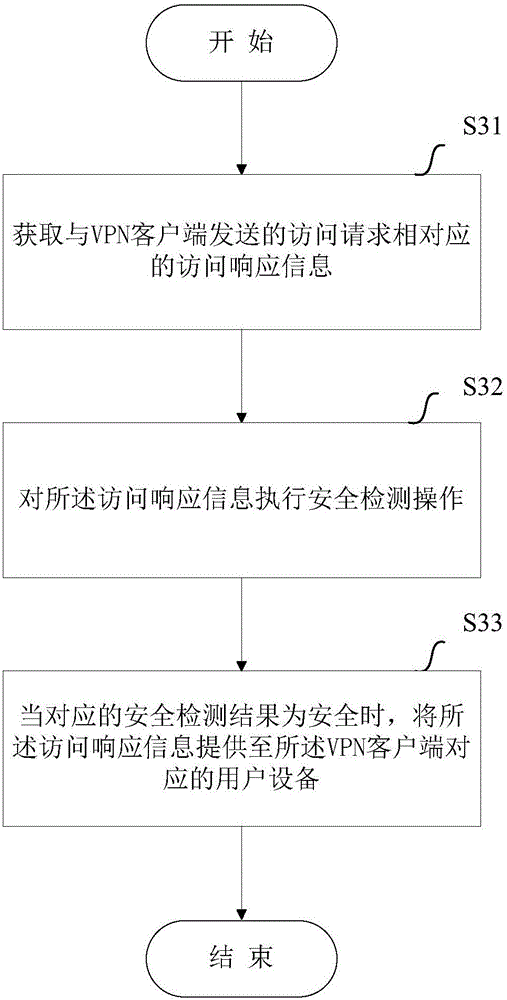
ActiveCN106101075AReduce security risksAvoid constraintsData switching networksPrivate networkClient-side
The application aims to provide a method and equipment for implementing safety access. The method comprises the steps of: acquiring access response information corresponding to an access request sent by a VPN (Virtual Private Network) client; executing a safety detection operation on the access response information; and when a corresponding safety detection result is that the access response information is safe, providing the access response information to user equipment corresponding to the VPN client. Compared with the prior art, according to the method and equipment provided by the application, the acquired access response information corresponding to the access request sent by the VPN client of the user equipment is subjected to the safety detection operation by network equipment, and the access response information, of which the safety detection result is that the access response information is safe, is sent to the user equipment, thereby avoiding direct acquisition of the user equipment on network transmission data which is not subjected to safety detection, effectively implementing interception on access response information with the safety problem and preventing the potential safety hazard brought to the user equipment by the access response information.
Owner:SHANGHAI LIANSHANG NETWORK TECHNOLOGY CO LTD
Cooperative vector secure transmission method and system for resisting pilot pollution attack
InactiveCN109905203ARealize secure transmissionPracticalError preventionBaseband system detailsPrecodingThird party
The invention discloses a cooperative vector secure transmission method and system for resisting pilot frequency pollution attacks, which resist the pilot frequency pollution attacks in a mode of cooperative fusion detection of a receiver and a third-party trusted node and realize secure transmission. According to the invention, the device has the following advantages, a pilot frequency sequence and a current channel estimation mode do not need to be changed; the sender does not need to know the priori knowledge of a legal channel and an eavesdropping channel; It is not needed to detect whether pilot frequency pollution exists or not and distinguish a legal receiver from an attacker, a polluted channel and a channel of a credible auxiliary node are directly used for safe transmission scheme design, a random weight coefficient matrix used for precoding does not need to be transmitted to a receiver, and practicability is high.
Owner:伍仁勇
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com