Method and system for implementing authentication and data safe transmission
A data security and data technology, which is applied in the field of authentication and data security transmission, and can solve problems such as key security storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
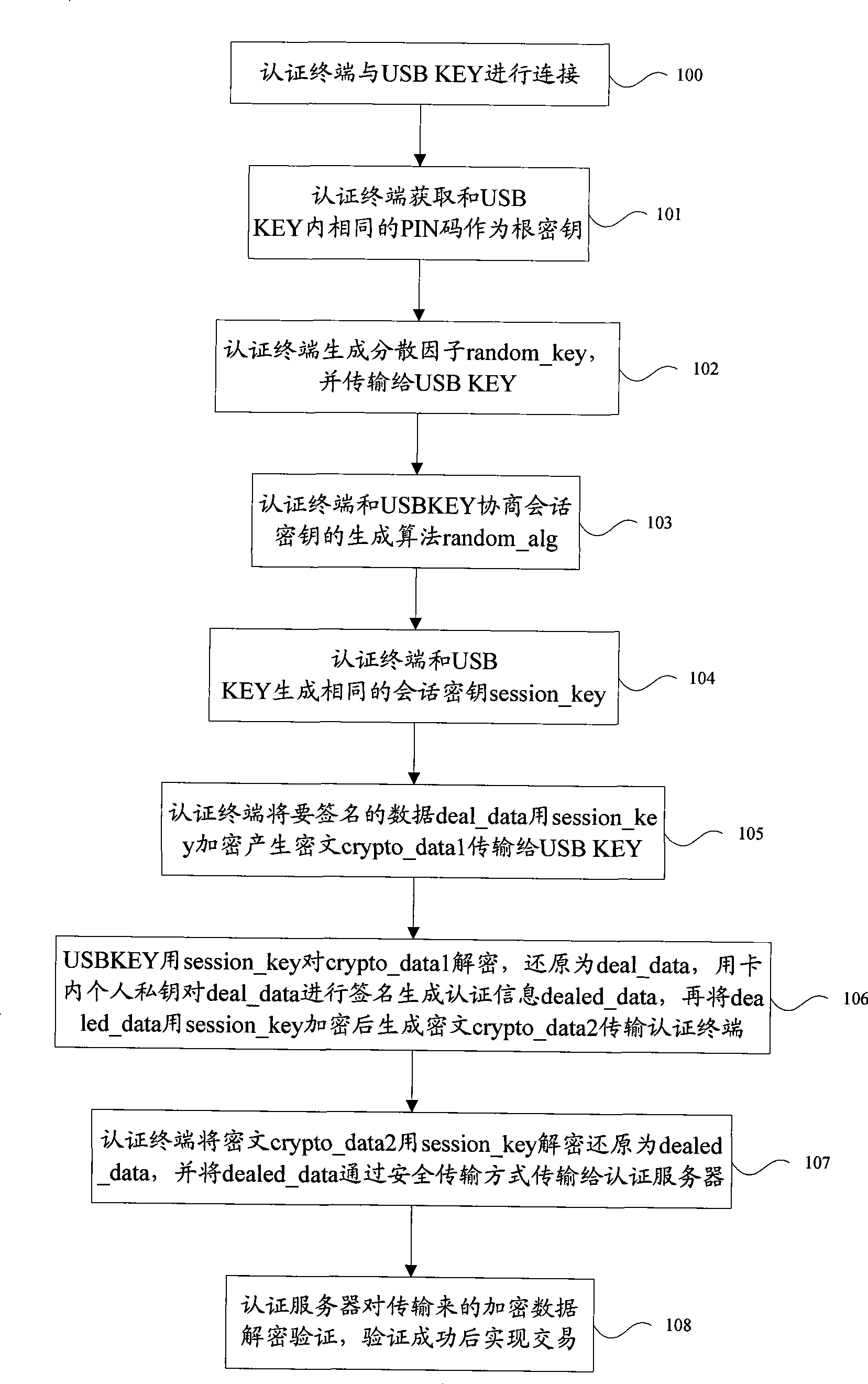
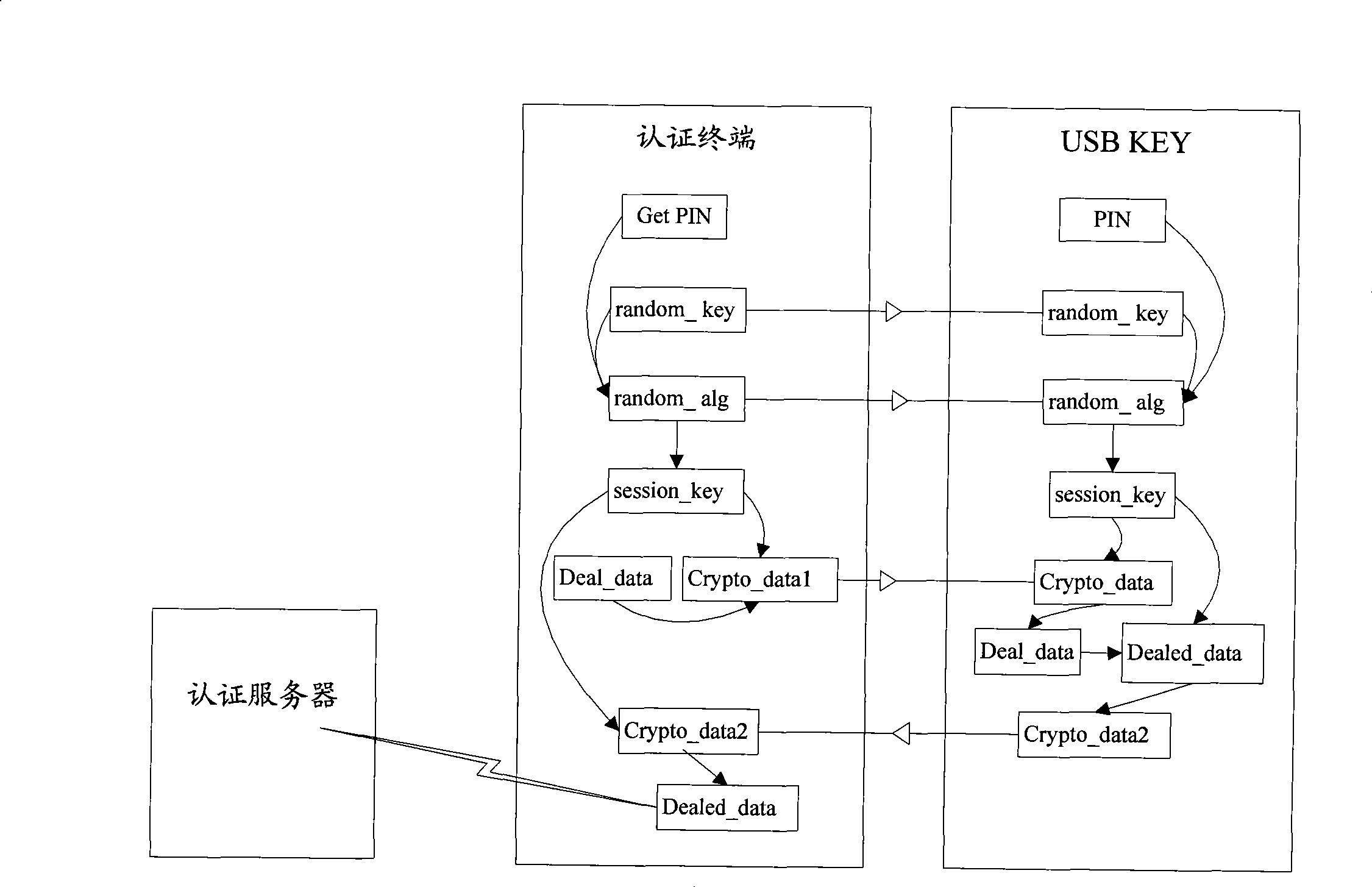
[0019] The embodiment of the present invention provides a method for data security interaction between a terminal security device and an authentication terminal, and furthermore, provides a security protection method for the used symmetric key, which can solve the problem of key security storage in the current authentication process. At the same time, it effectively prevents the plug-in "spoofing" operation, and improves the security of authentication, transaction and data transmission.
[0020] In the method and system for implementing authentication and secure data transmission provided by the embodiments of the present invention, after the terminal security device and the authentication terminal are connected, the terminal security device and the authentication terminal agree on the same data as the root key, and at the same time, both parties negotiate and agree on the same dispersion factor And algorithm, the two parties use this algorithm to generate the same session key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com