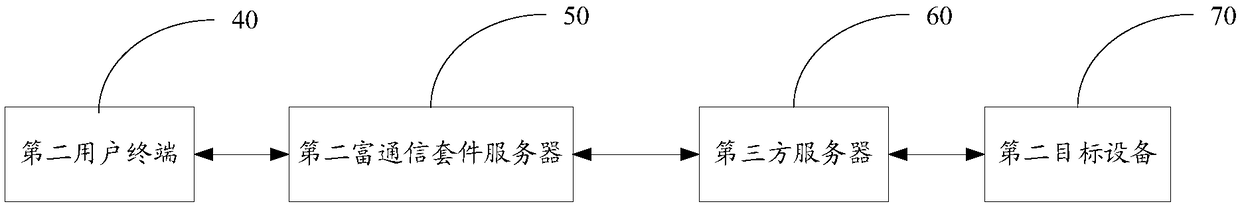
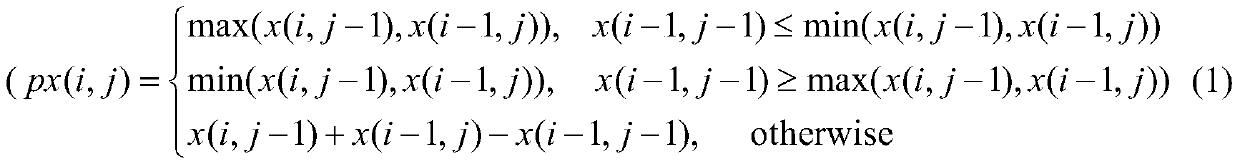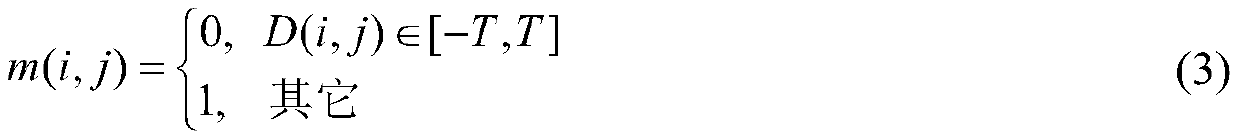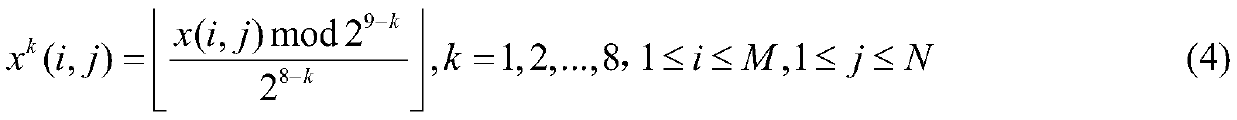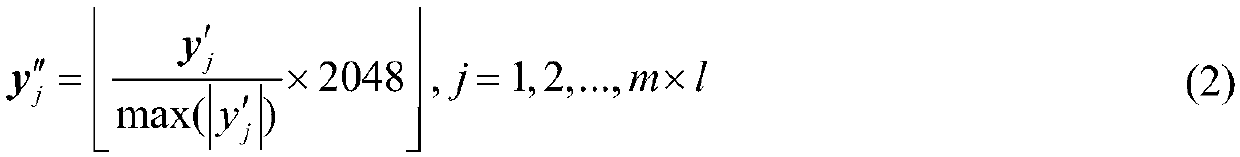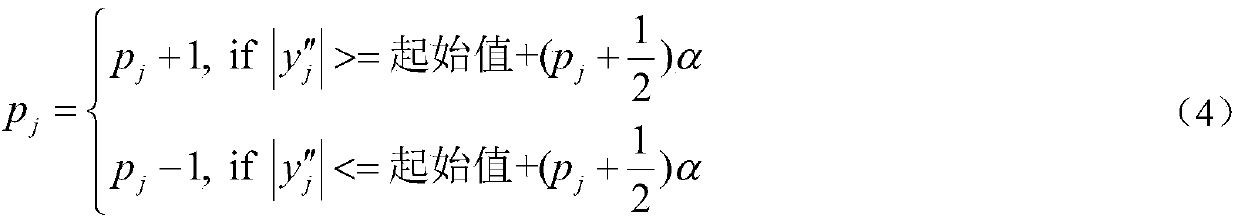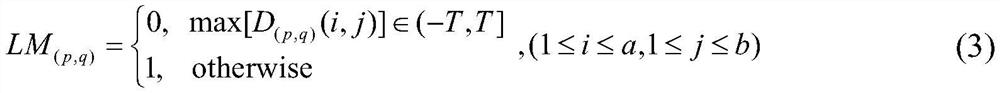Patents
Literature
79results about How to "Implement security authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and system for implementing authentication and data safe transmission
InactiveCN101483654AEnable secure interactionsEnsure safetyTransmissionSecurity arrangementSecure transmissionPassword
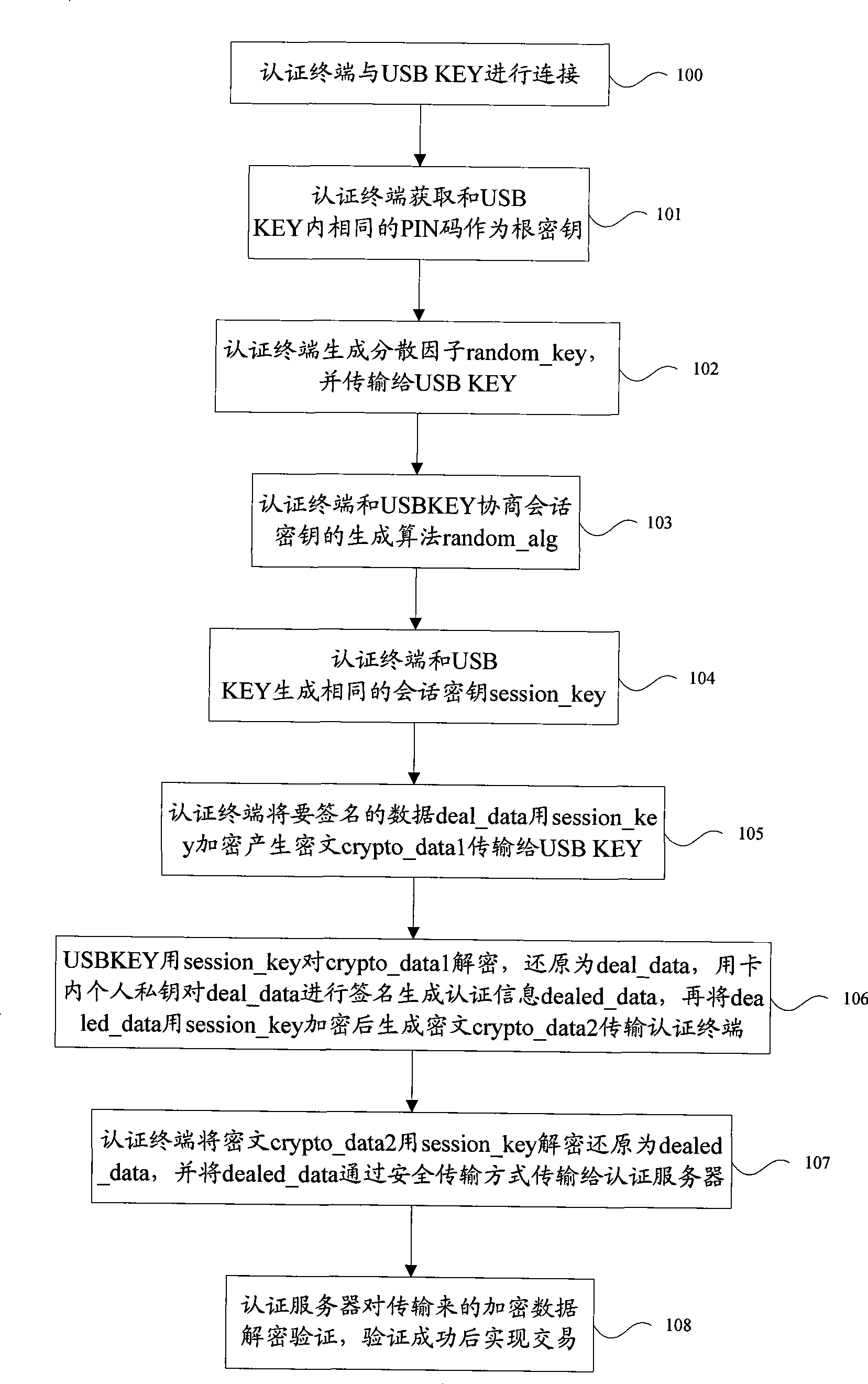
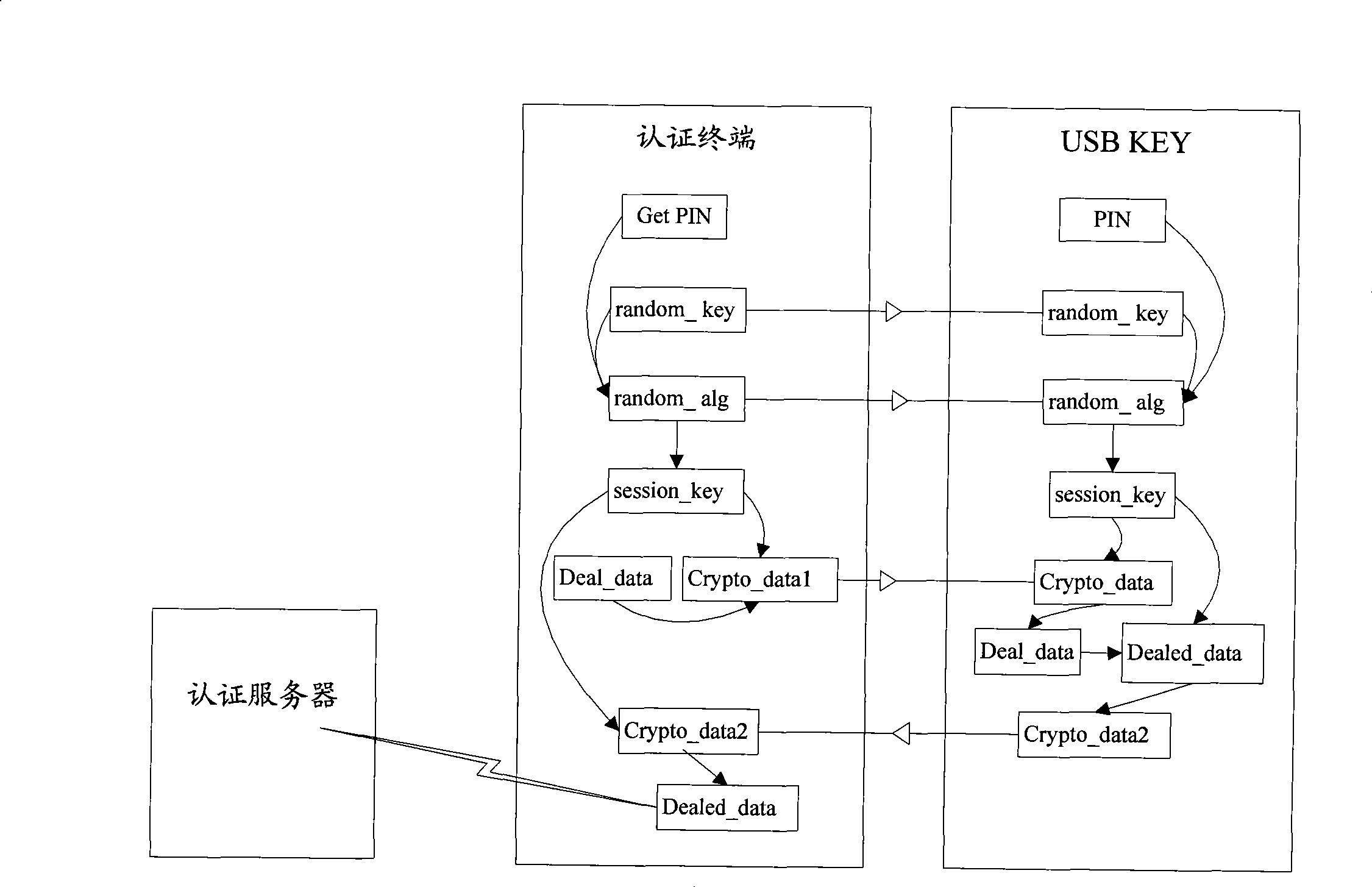
The invention discloses an authentication and safe transmission of data realizing method. A terminal safety device and an authentication terminal after being connected negotiates to have a same data to be used as a root key, and at the same time negotiates to have a same dispersion factor and a same algorithm, the negotiated root key and dispersion factor generate a same session key used as a symmetrical key by using the algorithm, and then, safety authentication and data encryption and decryption can be performed and safety data interaction between the two ends can be realized. The invention also discloses a system for realizing authentication and safe transmission of data, and the system comprises a terminal safety device, an authentication terminal and an authentication server. According to the invention, randomness of the session key for data encryption transmission can be assured, even though a session key is decrypted, the safety of the whole system can be assured, and at the same time, atom manipulation for safety authentication and safe transmission of data can be realized for avoiding that in the current authentication process, once a password is verified by the terminal safety device, limits of authority are totally released and potential safety hazard is generated, therefore, authentication safety is improved greatly.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST
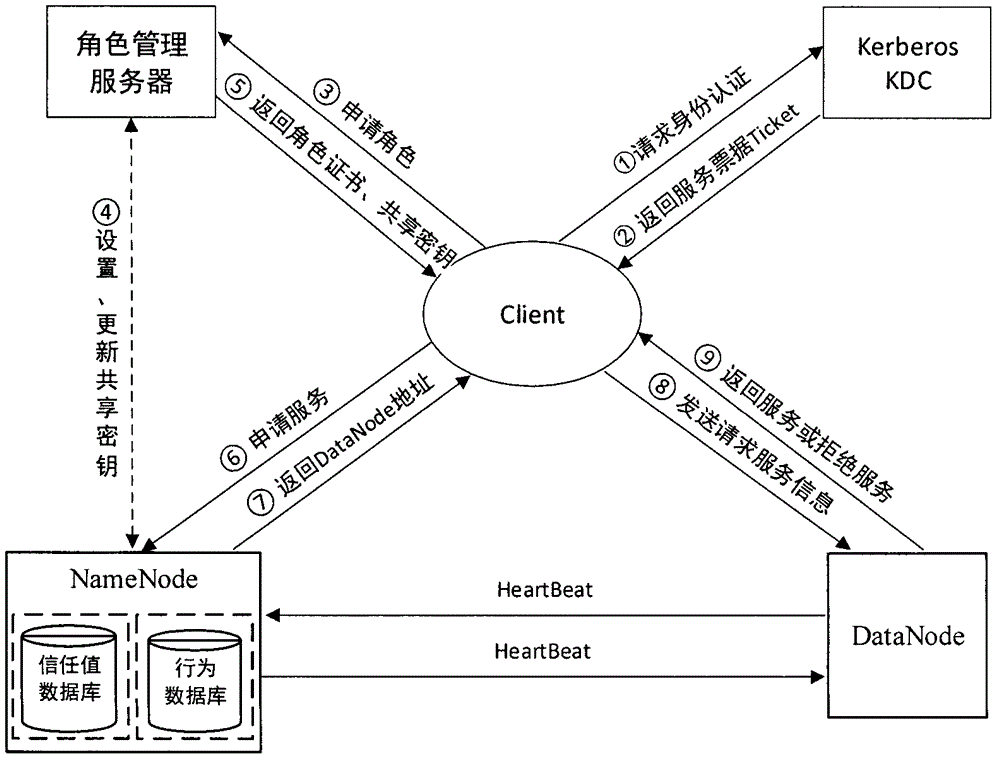
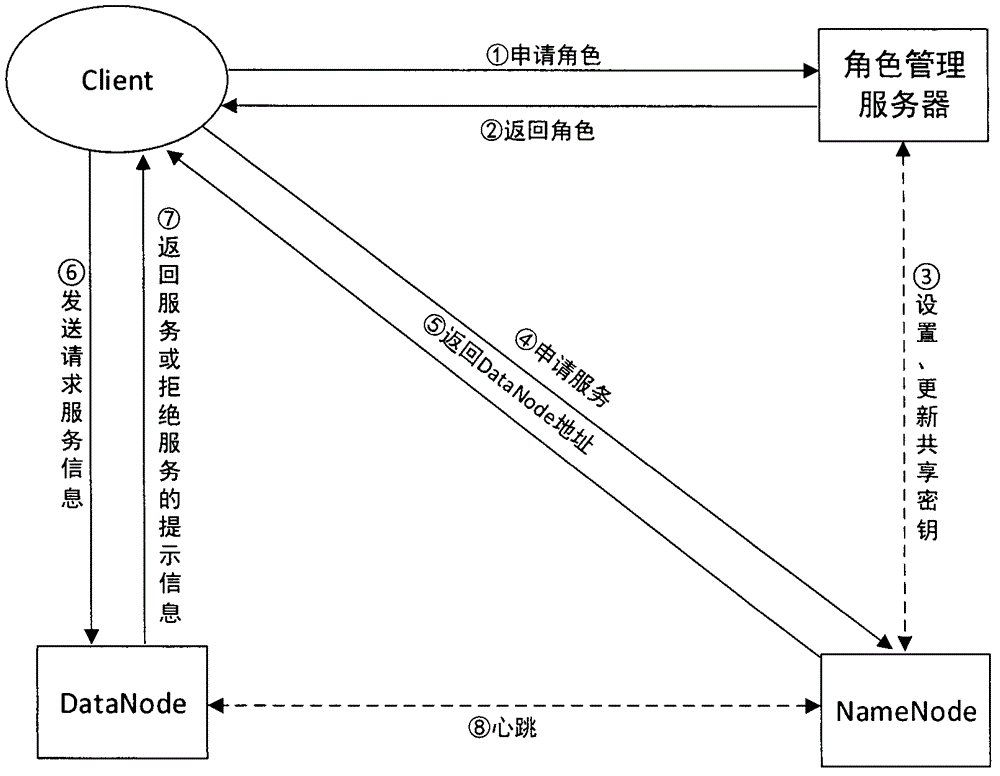
HDFS access control method based on role and user trust value
InactiveCN104935590AReduce complexityReduce administrative overheadUser identity/authority verificationCloud storageDiscretionary access control
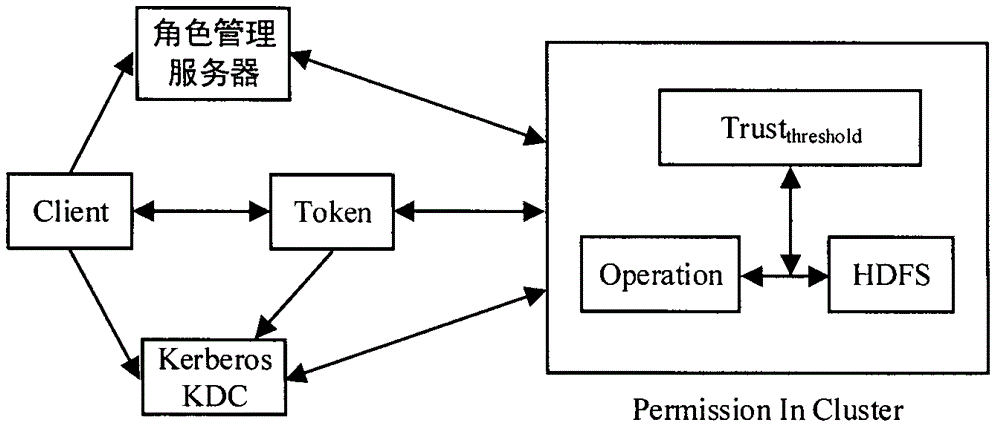
The invention provides an HDFS access control method based on a role and a user trust value and belongs to the field of computer cloud storage access control. The HDFS access control method of the invention firstly combines with a role-based access control policy RBAC to replace a discretionary access control policy of an HDFS, thereby reducing complexity and management expenditure of HDFS authorization management and improving flexibility of the authorization management. When a user accesses the HDFS for the first time, a role is granted to the user, so that users are isolated from authorization through roles, and the management is facilitated. On this basis, the HDFS access control method of the invention further introduces a concept of the user trust value and sets one trust value for each user so that different users with the same role could obtain different access permissions because of their different trust values, and the trust value of the user is dynamically updated according to the later behavior of the user, thereby dynamically and effectively controlling the access of the user to a resource in the HDFS.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
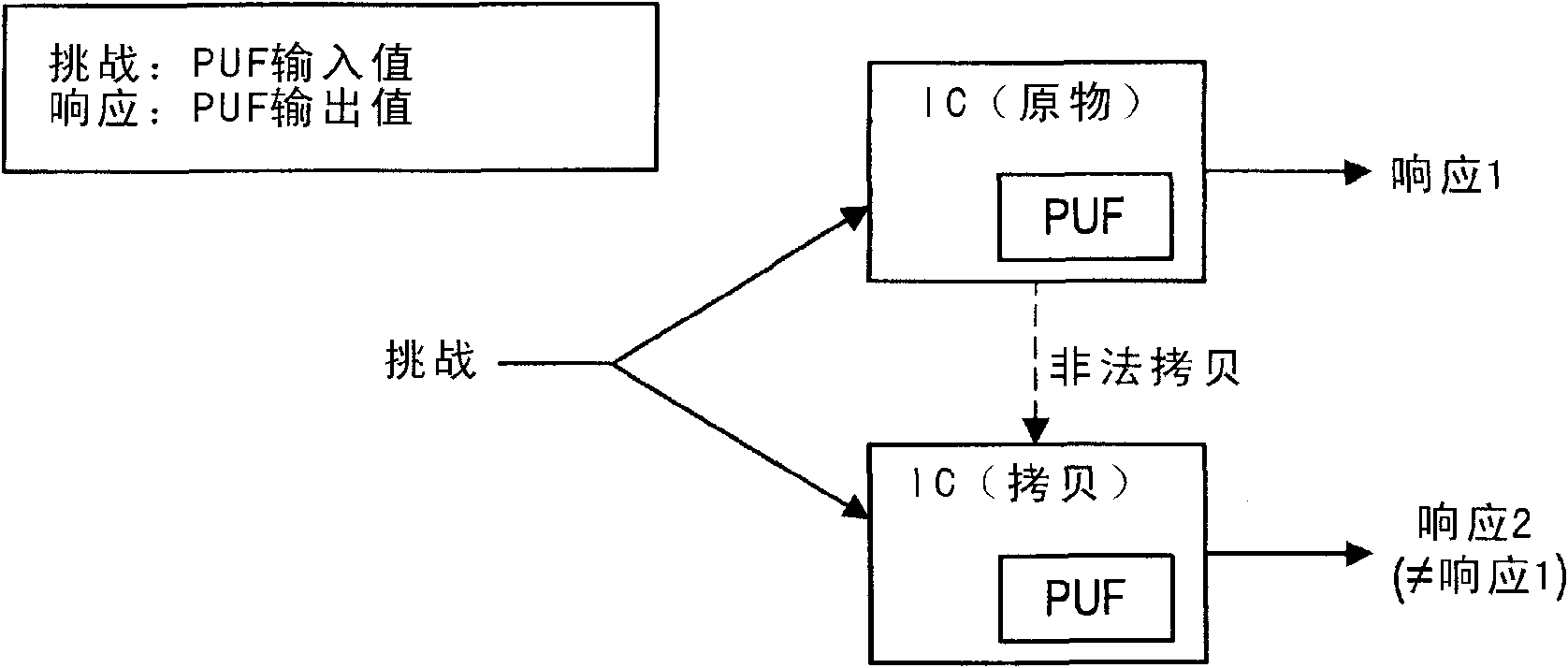
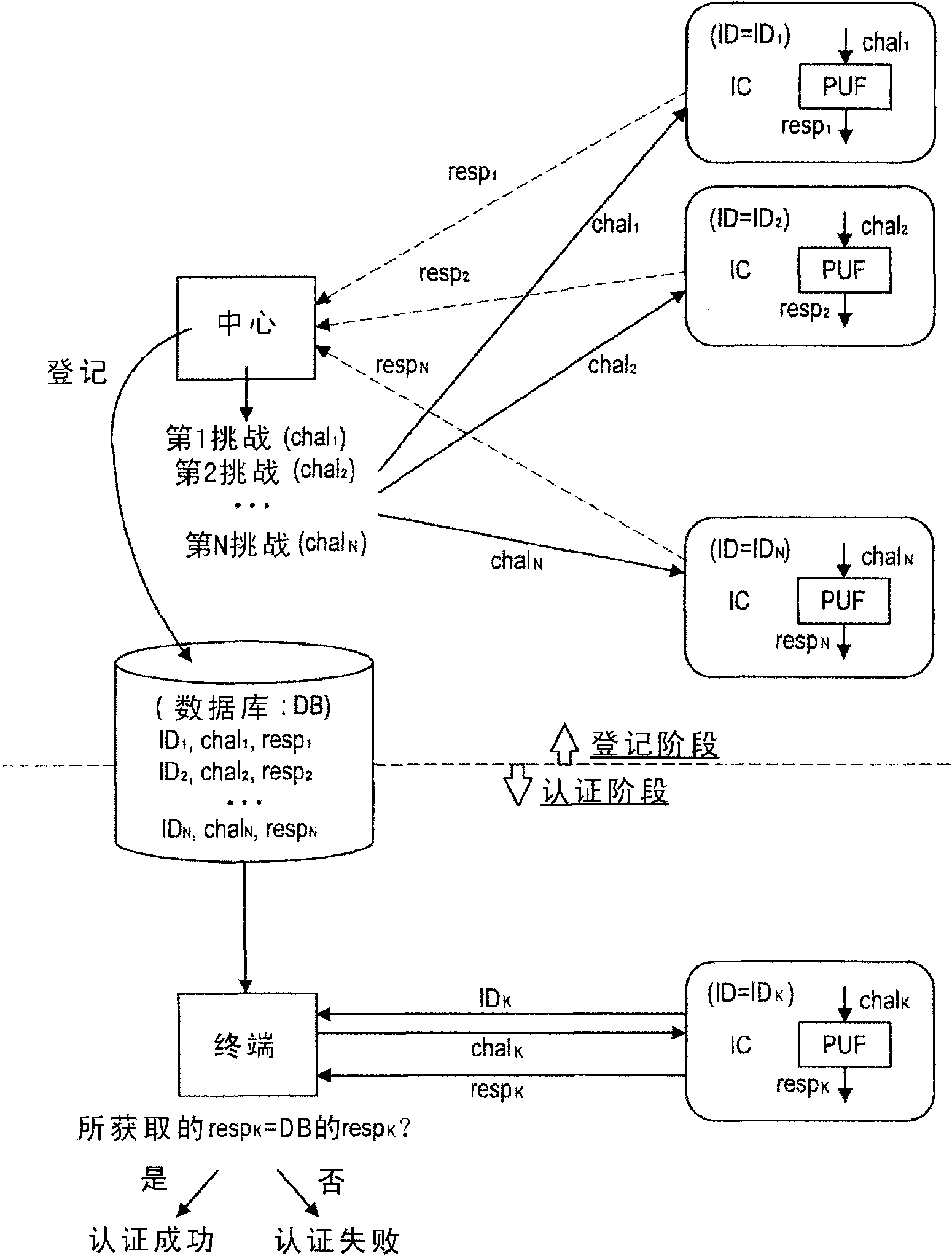
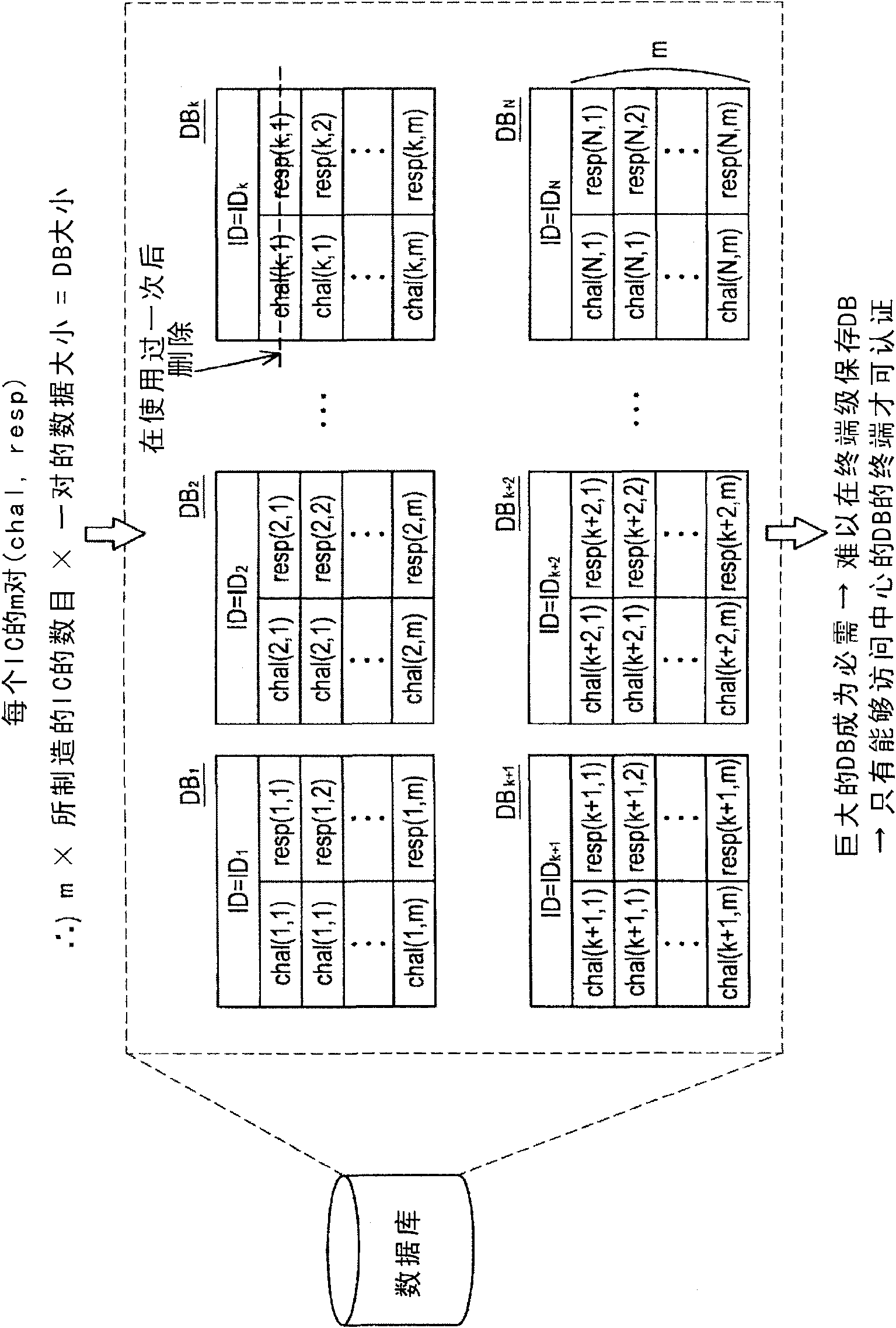
Integrated circuit, encryption communication apparatus, encryption communication system, information processing method and encryption communication method
InactiveCN101847296AImplement security authenticationRecord carriers used with machinesCoded identity card or credit card actuationComputer hardwareInformation processing
The invention provides an integrated circuit, an encryption communication apparatus, an encryption a communication system, an information processing method and an encryption communication method. The integrated circuit includes an arithmetic circuit having input / output characteristics determined by element-specific physical characteristics; a storage unit having cipher text obtained by performingencryption processing on predetermined secret information using an output value output from the arithmetic circuit with respect to input of a predetermined value and the predetermined value input into the arithmetic circuit stored therein; and a decryption unit that restores the predetermined secret information by inputting the predetermined value stored in the storage unit into the arithmetic circuit and decrypting the cipher text stored in the storage unit using the output value output from the arithmetic circuit when the predetermined secret information is used.
Owner:SONY CORP
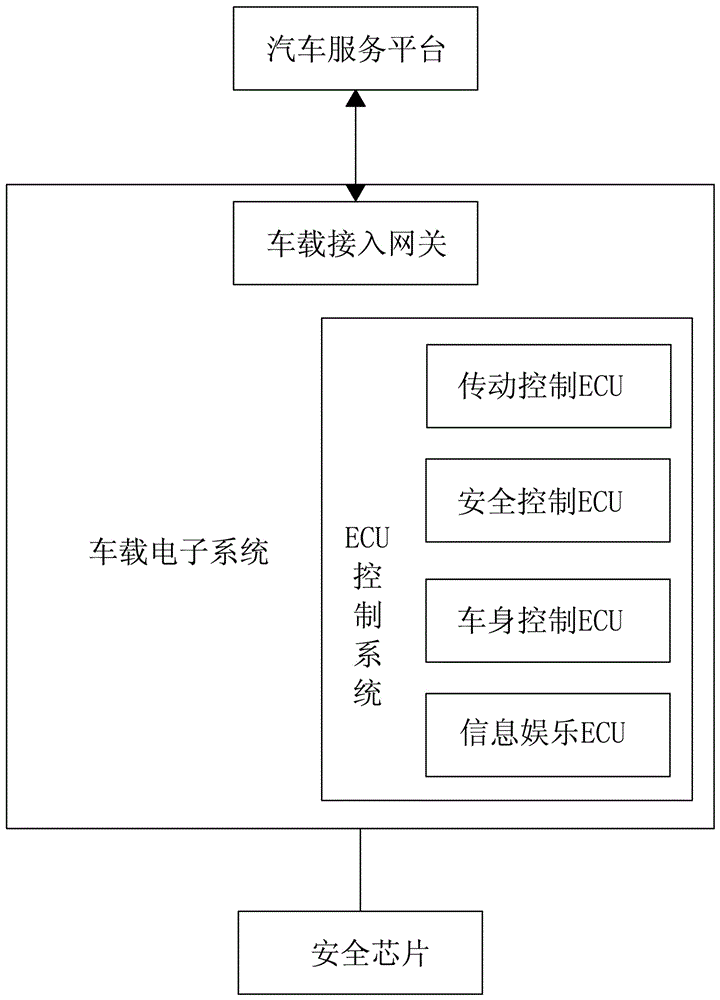
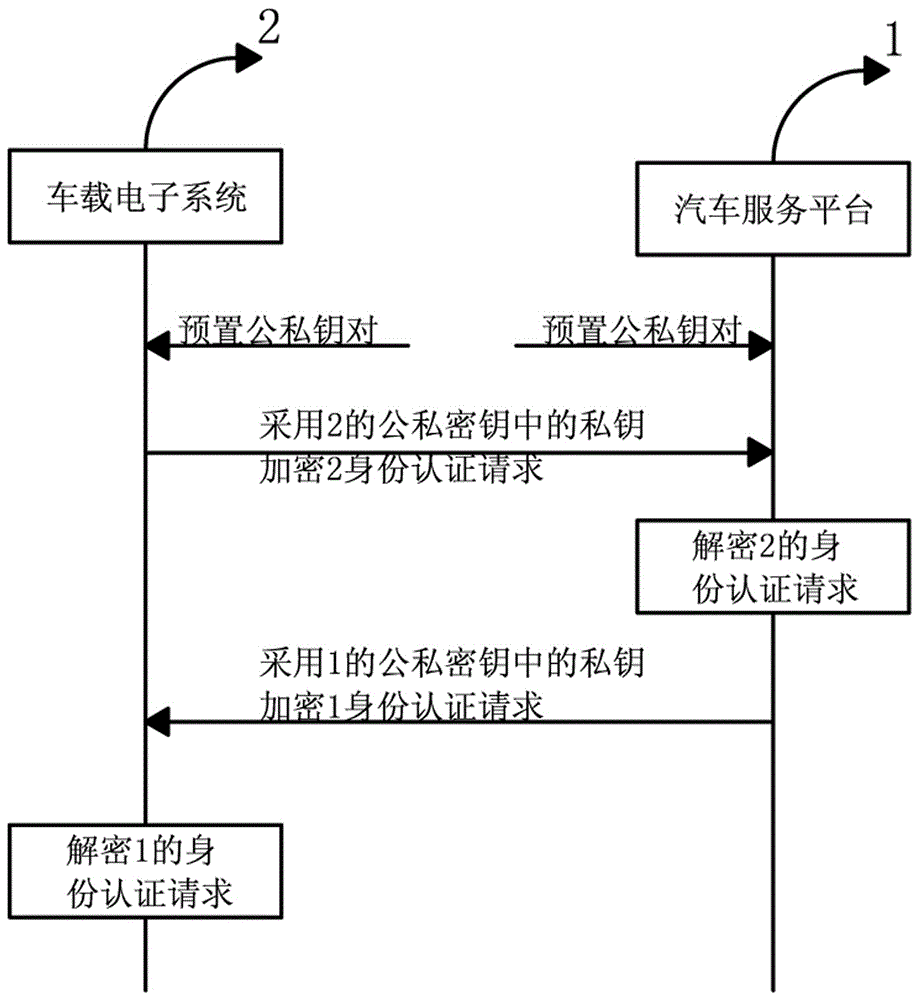
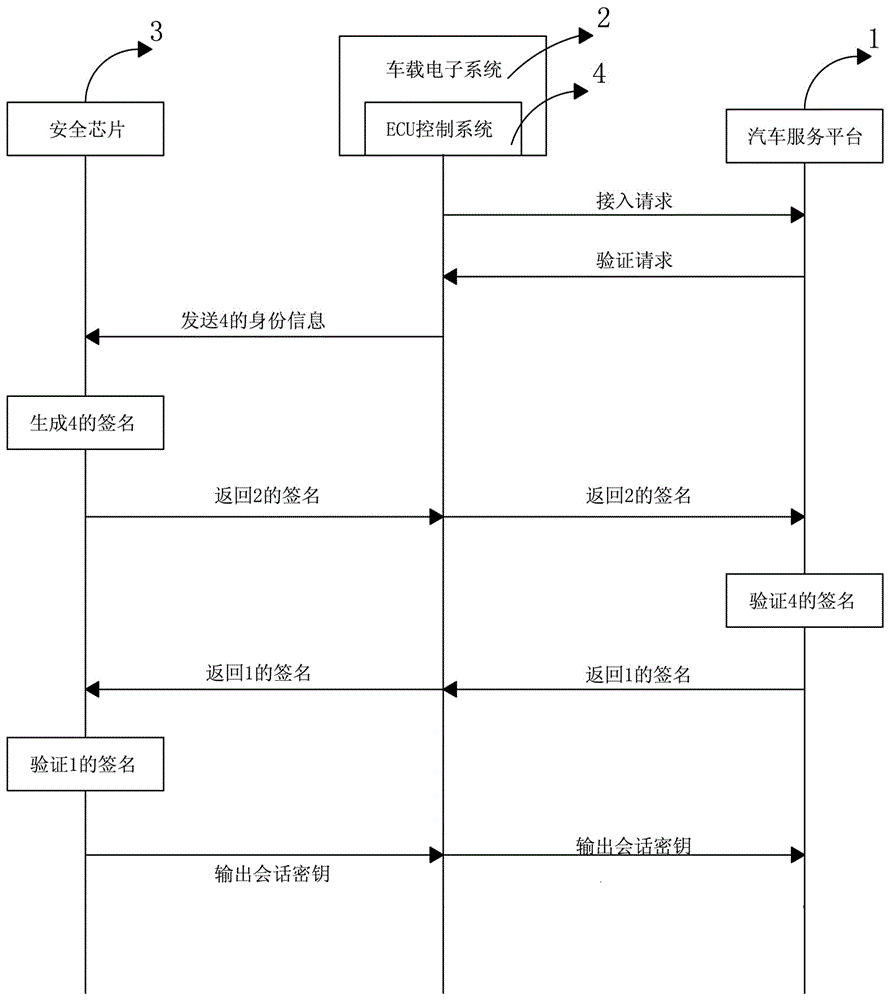
Vehicular electronic secure communication system and communication method
ActiveCN106101111AImprove securityImplement security authenticationTransmissionSecure communication systemEngineering
The invention provides a vehicular electronic secure communication system. The vehicular electronic secure communication system comprises a secure chip, a vehicular electronic system and an automobile service platform; the vehicular electronic system and the automobile service platform perform bidirectional identity authentication; the vehicular electronic system comprises an ECU control system; the ECU control system and the automobile service platform perform bidirectional signature authentication through the secure chip; and, after bidirectional signature is successfully verified, the automobile service platform and the ECU control system are in encrypted communication. The invention further provides a communication method of the vehicular electronic secure communication system. The communication method comprises the following steps that: (1), the vehicular electronic system and the automobile service platform perform bidirectional identity authentication; (2), after verification is successful, the ECU control system of the vehicular electronic system and the automobile service platform perform bidirectional signature authentication through the secure chip; and (3), after verification is successful, the automobile service platform and the ECU control system are in encrypted communication through a session key output by the secure chip.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
User registration and user identification method and user registration and user identification system
ActiveCN104219228AImplement security authenticationKeep the low cost advantageUser identity/authority verificationPasswordClient-side
The invention discloses a user registration and user identification method and a user registration and user identification system and aims to provide a HTTP (hyper text transfer protocol)-based encrypted client register and user identification method. The method is technically characterized by including: step 1, a client encrypts a user name and a password according to symmetric encryption and decryption algorithms; step 2, the client transmits the encrypted user name and password to a server according to the HTTP; step 3, the server decrypts the received user name and password according to the symmetric encryption and decryption algorithms; searching a database to determine whether the user name already exists or not; if not, the server encrypts a register success message and a public key of an asymmetric cryptography according to the symmetric encryption and decryption algorithms and writes the user name and the password into the database; if yes, the server encrypts a to-be-returned register failure message according to the symmetric encryption and decryption algorithms; step 4, the server transmits the encrypted message acquired at the step 3 to the client according to the HTTP.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
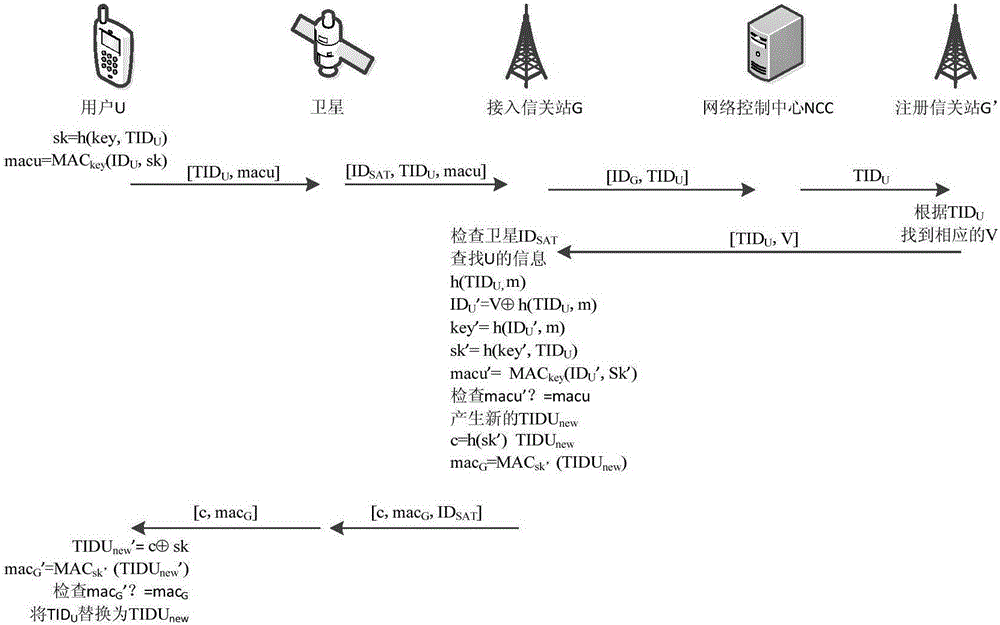
Gateway station-based satellite network anonymous authentication method
ActiveCN105827304AImprove securityImplement anonymous authenticationRadio transmissionSecurity arrangementNetwork controlAnonymous authentication
The present invention provides a gateway station-based satellite network anonymous authentication method. The conventional satellite network authentication methods all adopt a network control center (NCC) to authenticate users, and in order to reduce the authentication calculation amount of the NCC, the gateway station-based satellite network anonymous authentication method of the present invention enables an authentication function to transfer to a gateway station G, thereby relieving the burdens of the NCC. The gateway station-based satellite network anonymous authentication method of the present invention adopts a message authentication code (MAC) during an authentication process, thereby realizing the anonymous authentication of the users, and protecting the privacy of the users. According to the present invention, after the security authentication of a satellite network to the users is realized, the security authentication of the users to the satellite network is finished, thereby achieving a bidirectional authentication purpose, and further improving the network security. The authentication method of the present invention mainly comprises two stages, namely a registration stage and an authentication stage.
Owner:NANJING UNIV OF POSTS & TELECOMM
High-capacity image encryption domain information hiding method
ActiveCN111311474ASimple technical solutionPractical and convenientDigital data protectionImage data processing detailsPattern recognitionData ingestion
The invention belongs to the technical field of information hiding, and aims to provide a high-capacity encrypted domain information hiding method capable of separating a carrier image decryption process from a secret data extraction process. According to the specific technical scheme, the high-capacity image encryption domain information hiding method is composed of the following four parts: 1, calculation of a prediction difference value and generation of a label map; 2, encrypting a carrier image; 3, storing a prediction difference value and embedding secret information; 4, reversible recovery of the carrier image and lossless extraction of secret information; the whole technical scheme is simple and easy to implement, information such as user copyright, identity authentication or content retrieval can be hidden in the encrypted image according to different requirements of a user for image protection, and management of copyright protection, security authentication, retrieval, classification and the like of the image is achieved.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
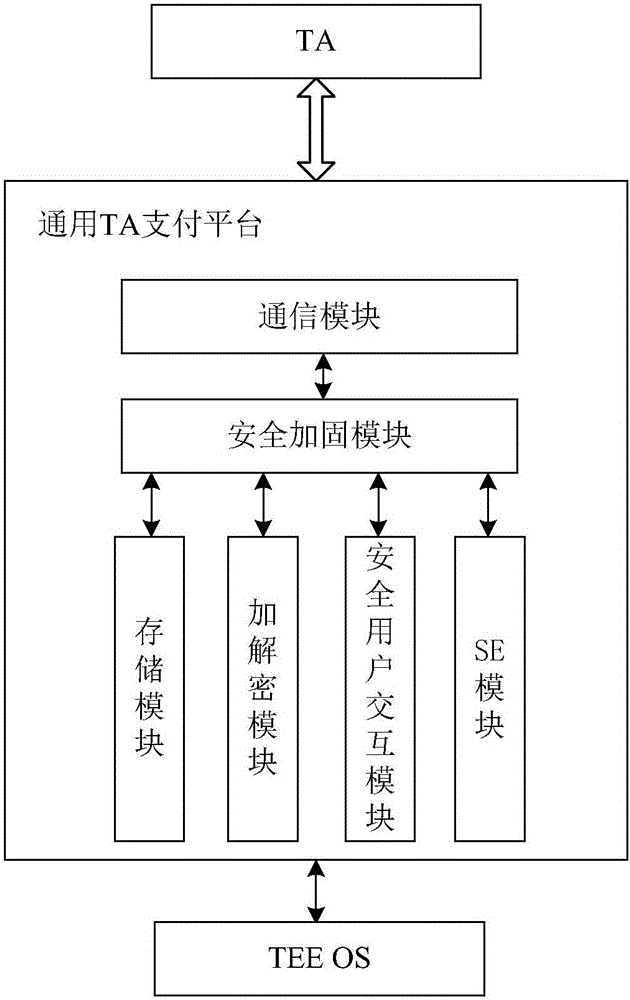
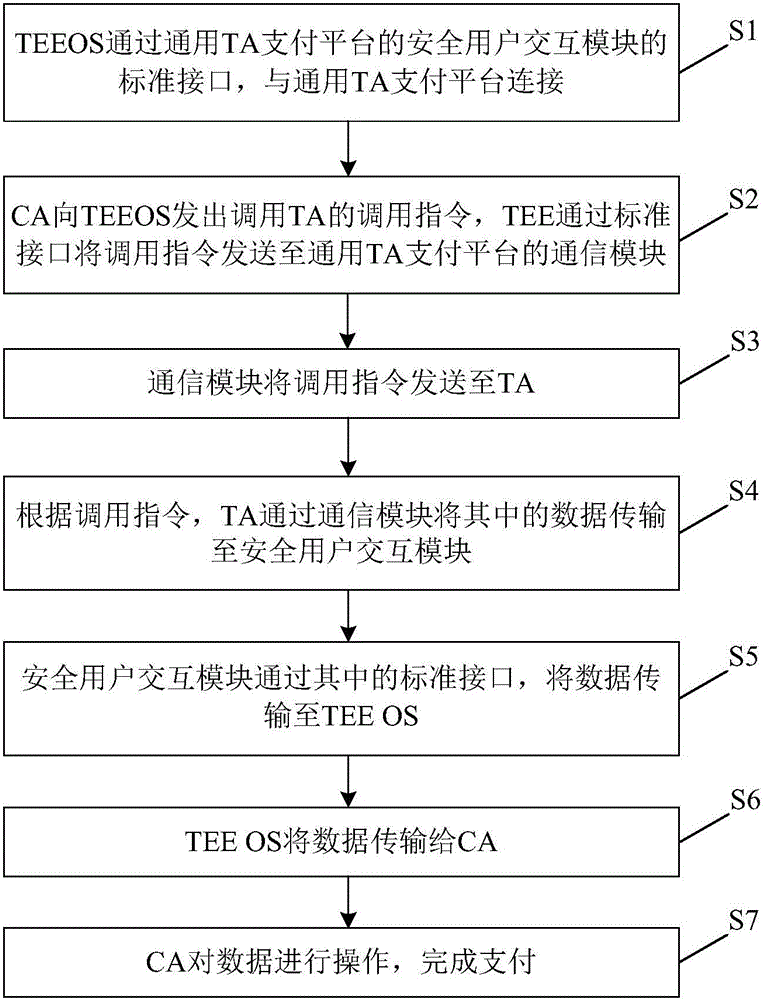
Universal TA (trusted application) payment platform and payment method
InactiveCN106228072AImplement security authenticationPlatform integrity maintainancePayment circuitsGeneral purposeMobile payment
Owner:HENGBAO
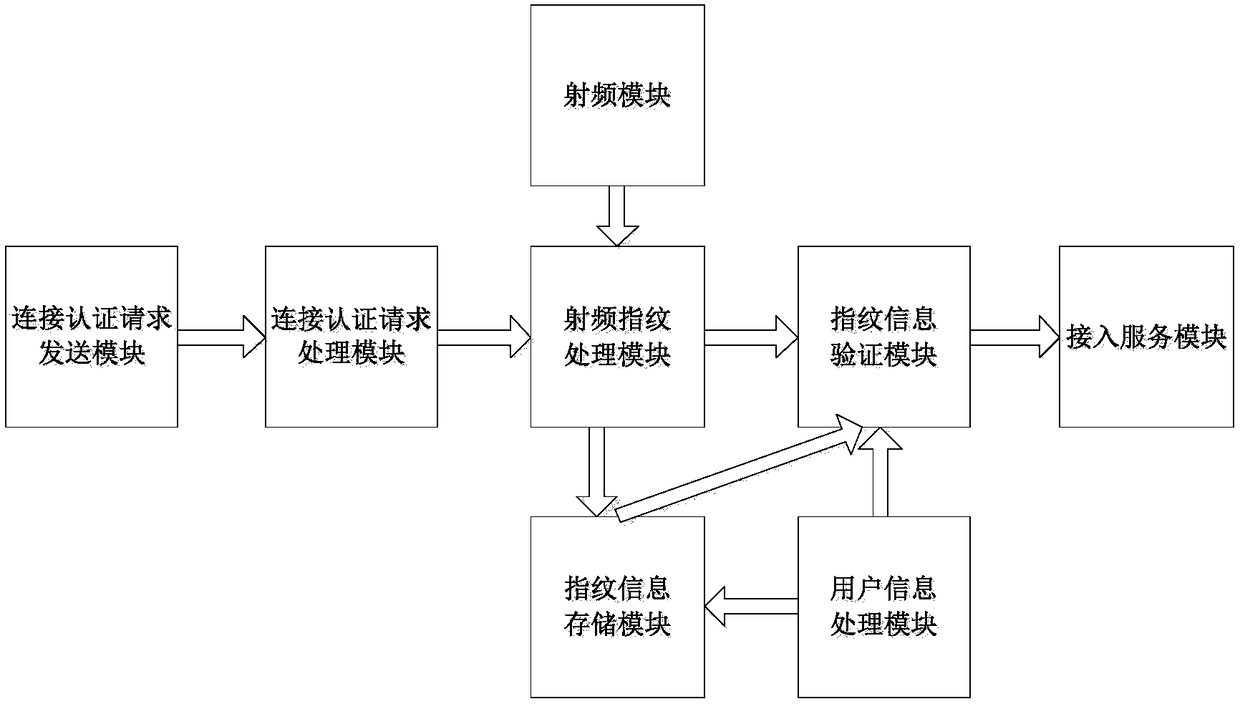
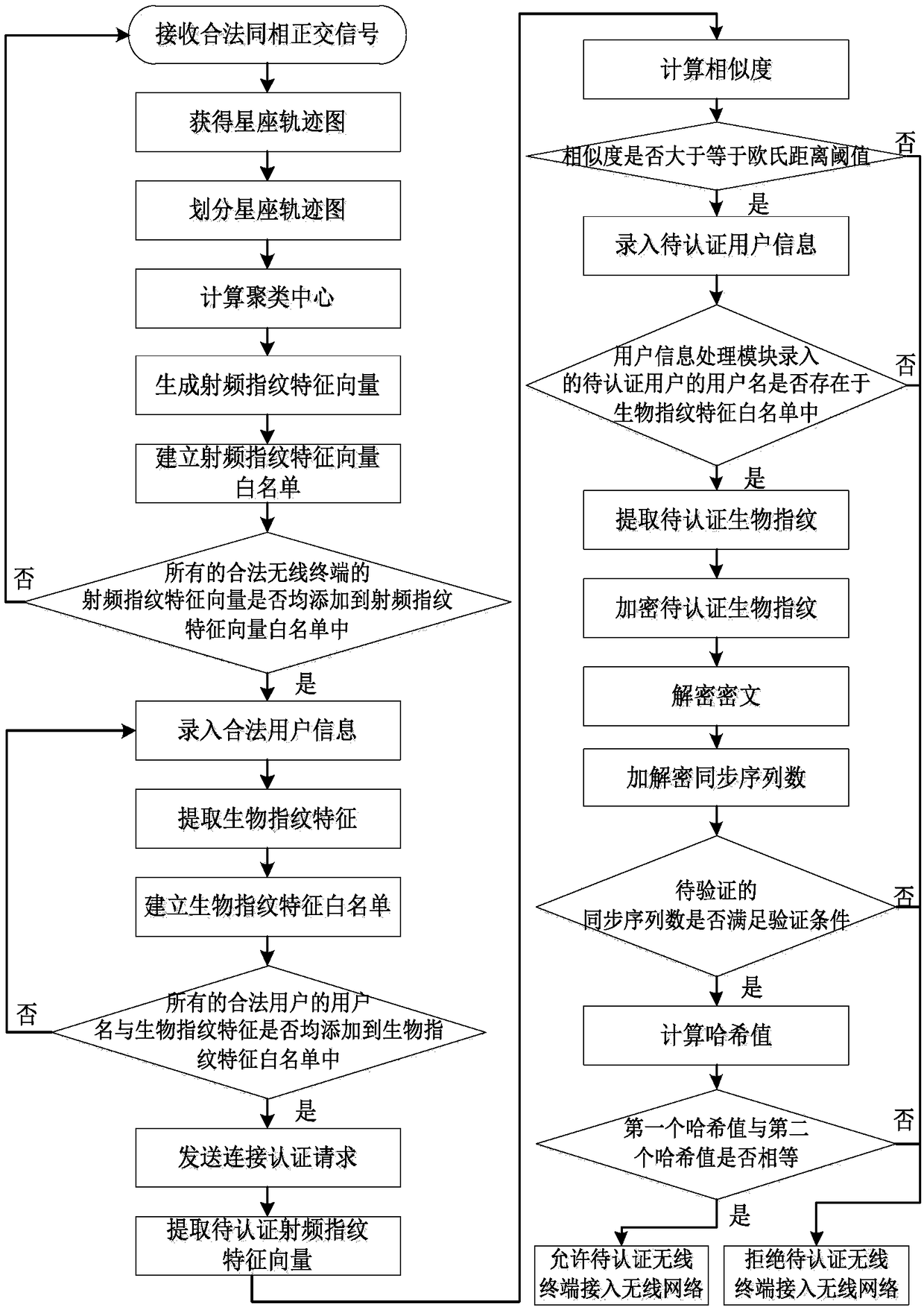
Wireless network access authentication system and method based on radio frequency fingerprint and biological fingerprint
ActiveCN108173871AAchieve authenticationImprove securityTransmissionAuthentication systemRadio frequency
The invention discloses a wireless network access authentication system and a wireless network access authentication method based on a radio frequency fingerprint and a biological fingerprint. The system provided by the invention comprises a radio frequency module, a radio frequency fingerprint processing module, a fingerprint information storage module, a user information processing module, a fingerprint information authentication module, a connection authentication request sending module, a connection authentication request processing module and an access service module. According to the method provided by the invention, the radio frequency fingerprint of a wireless terminal used by a user for applying for accessing a wireless network is authenticated, after the radio frequency fingerprint is authentication, the biological fingerprint of the user using the wireless terminal to access the wireless network is authentication, and after the biological fingerprint of the user is authenticated, the user is allowed to use the wireless terminal to access the wireless network. According to the system and the method provided by the invention, the secure access to the wireless network is achieved through authenticating the wireless terminal and the user applying for using the network.
Owner:XIDIAN UNIV
Switching method and equipment between heteroid systems
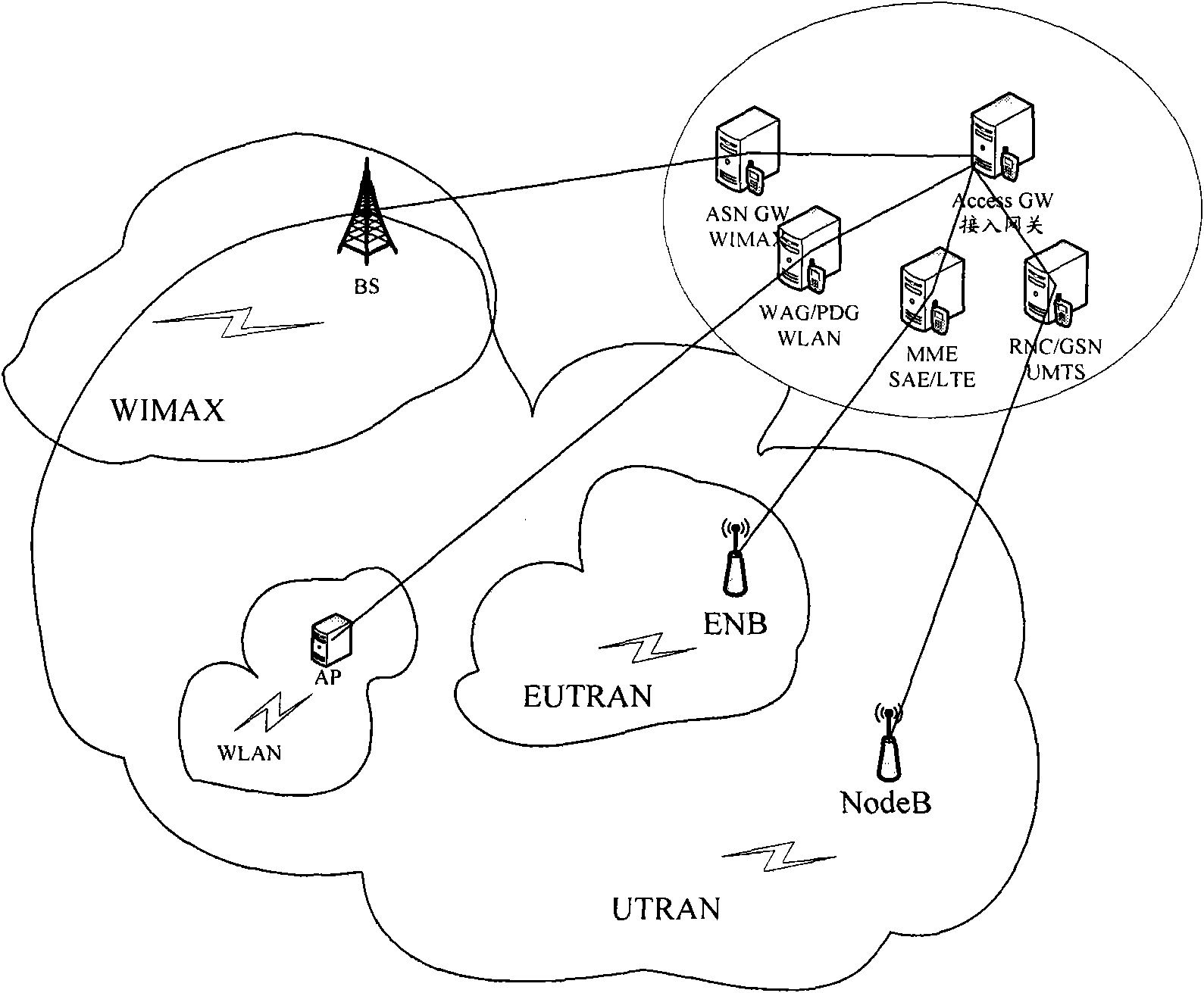
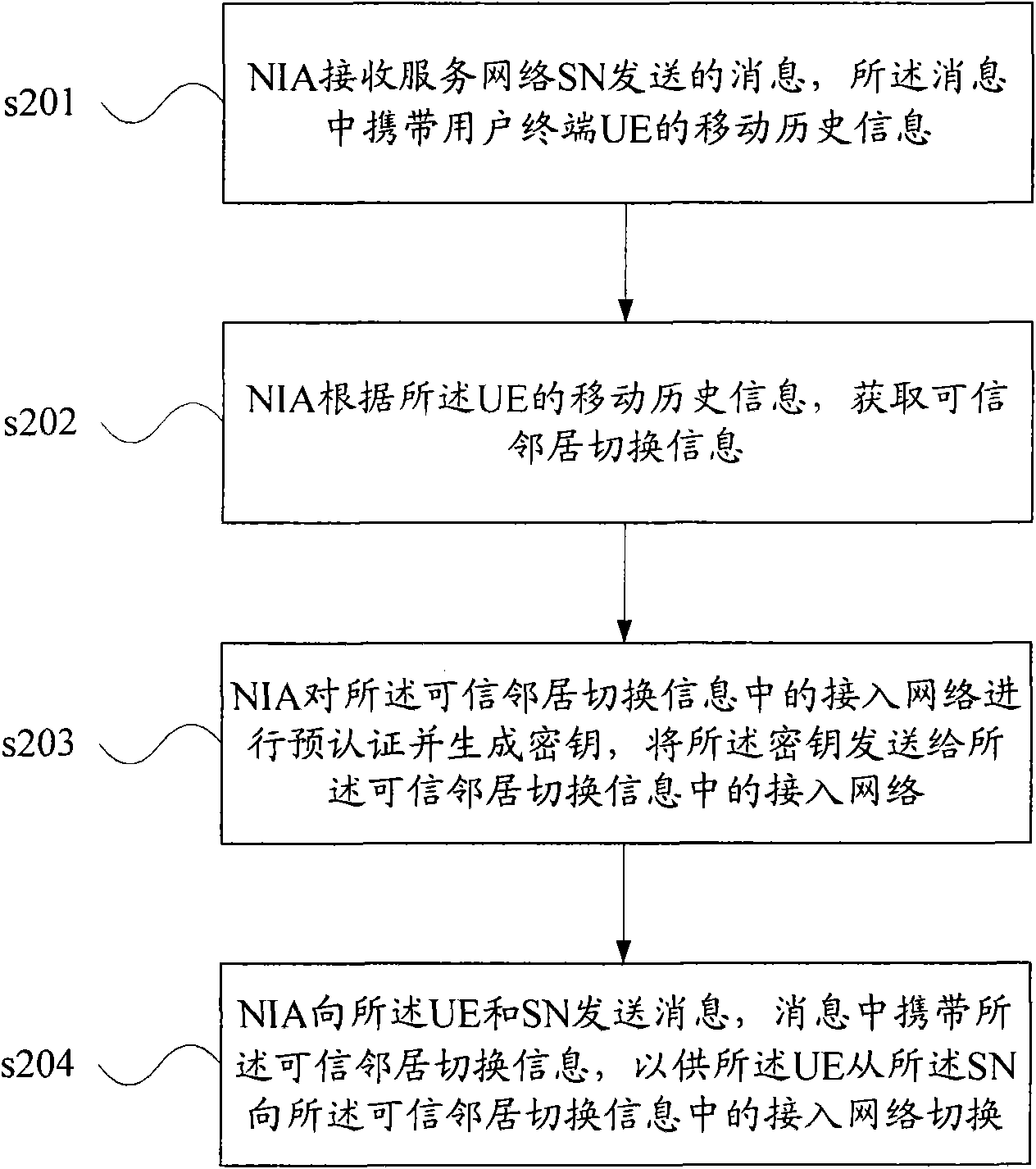
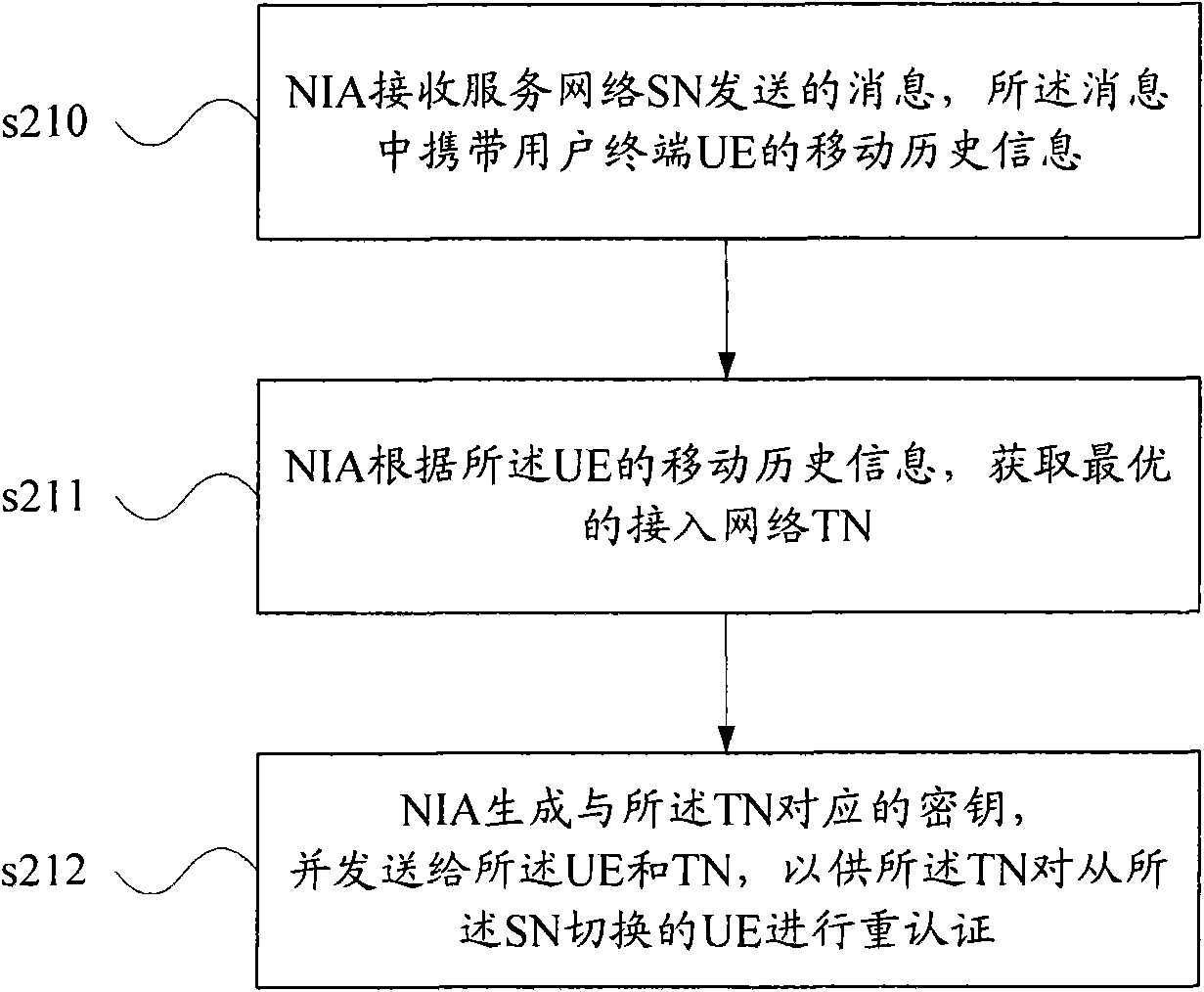
ActiveCN101568108AReduce switching delayImplement security authenticationAssess restrictionSecurity arrangementAdaptive securitySelf adaptive
The embodiment of the invention discloses a switching method and equipment between heteroid systems. The method comprises a self-adapting safety protocol based on advance certification and a self-adapting safety protocol based on repeated certification. The embodiment is dynamically suitable for a safety structure accessed to a network technology by the self-adapting protocol, introduces a restructurable technology based on cognitive radio to the system, simultaneously imports an interconnection acting NIA entity, obtains latest trusty neighbor switching information by mobile historical information of a subscriber, realizes safety certification among different networks by adopting the advance certification and a safety context transmission technology, and also reduces the switching time delay. In addition, the invention can also use a method of the repeated certification, dynamically selects an optimal neighbor switching network from NIA and realizes the safety certification among different networks.
Owner:HUAWEI TECH CO LTD +1
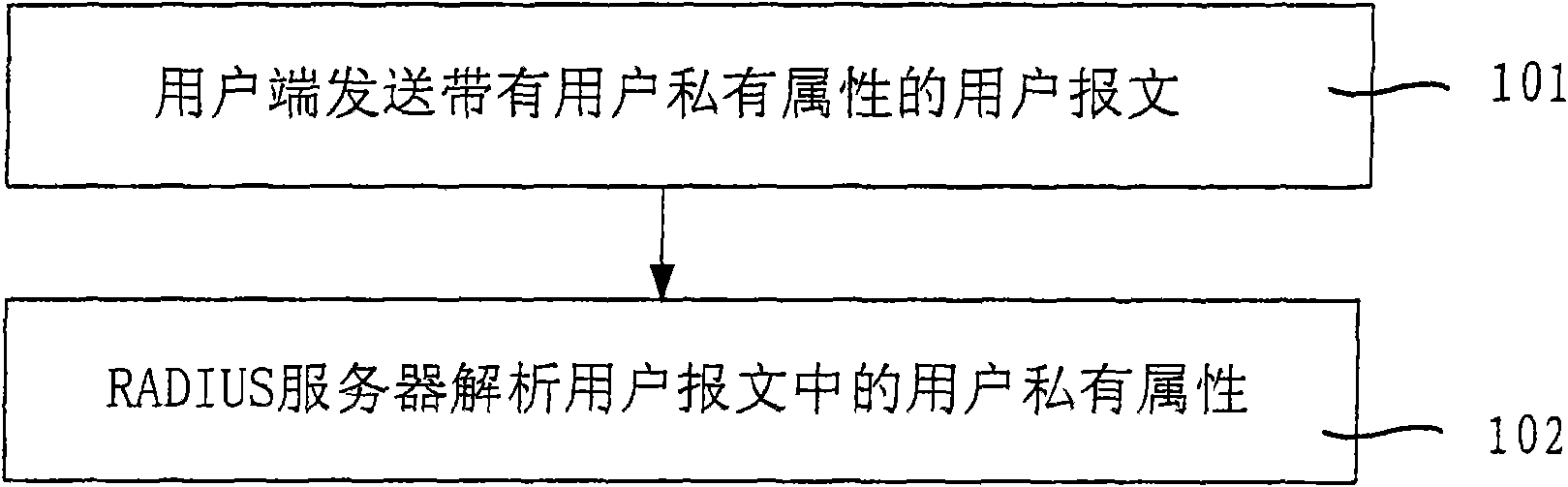
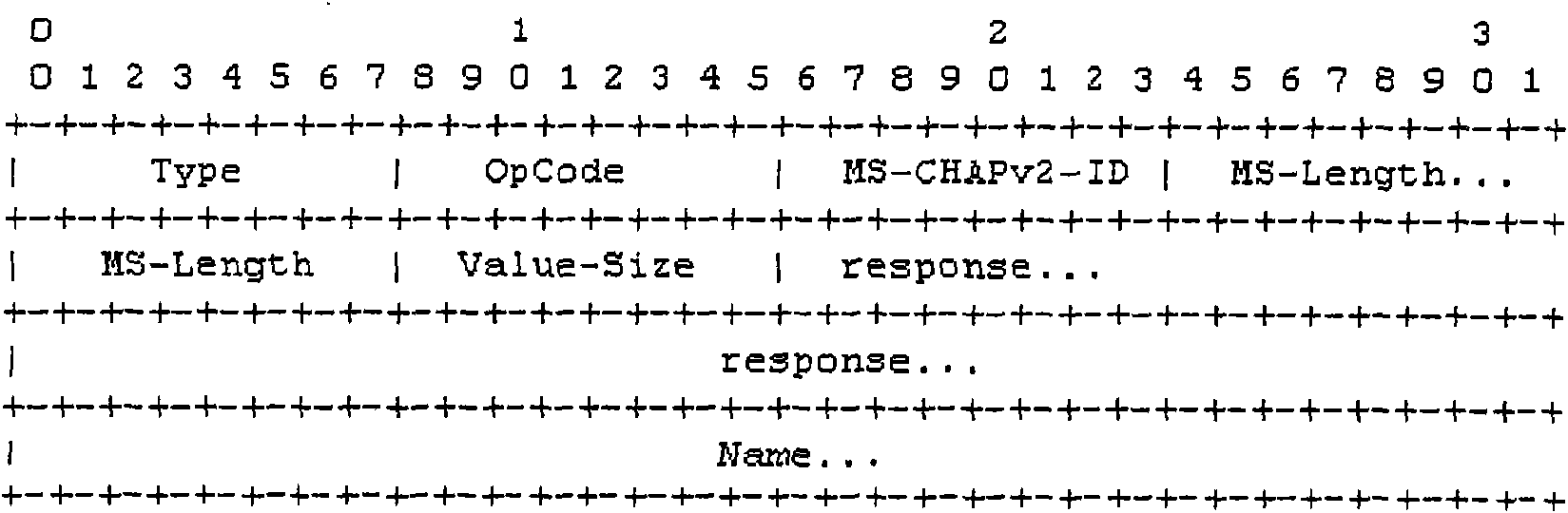
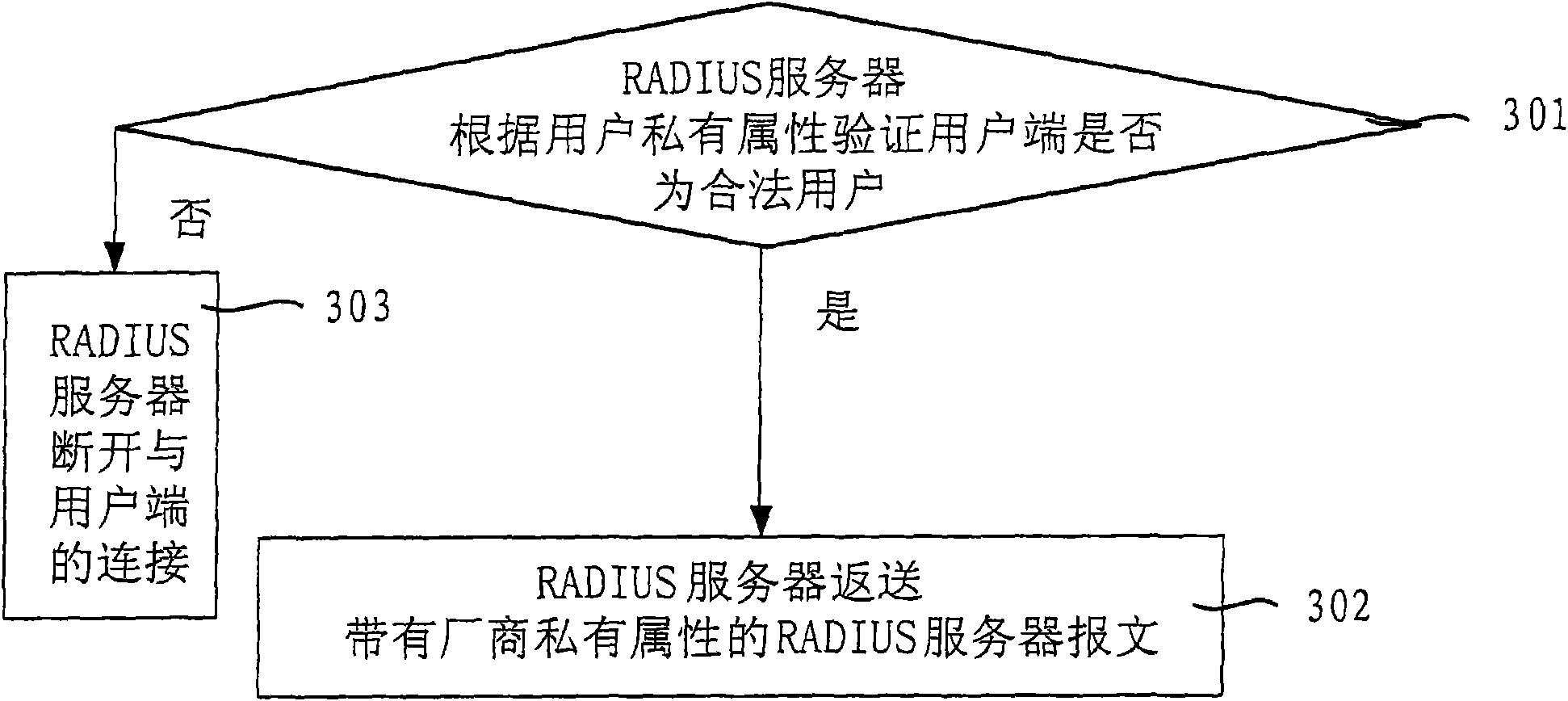
Method and system for delivering private attribute information
InactiveCN101640685AImprove securityImprove compatibilityUser identity/authority verificationOperational systemMessage delivery
The invention relates to a method and a system for delivering private attribute information, wherein the method comprises the following steps: a user terminal sends a user message with user private attribute; and a RADIUS server analyzes the user private attribute in the user message. The user private attribute is sent to the RADIUS server by the user message and the RADIUS server sends private attribute of a manufacturer to the user terminal, therefore, the embodiment of the invention enhances the safety and the compatibility of the user terminal and the RADIUS server during the delivery ofthe message comprising the private attribute and improves the capacity and the efficiency of message delivery. The user terminal obtains the address of a downloaded software, a user terminal system upgrading or anti-agent identifier and the like according to the private attribute of the manufacturer, thereby ensuring that the version of an operating system of the user terminal can be updated in time and the system is upgraded successfully, preventing the operating system of the user terminal from easily being attacked by virus, and avoiding the information of the user terminal being cracked or pirated by other persons.
Owner:RUIJIE NETWORKS CO LTD
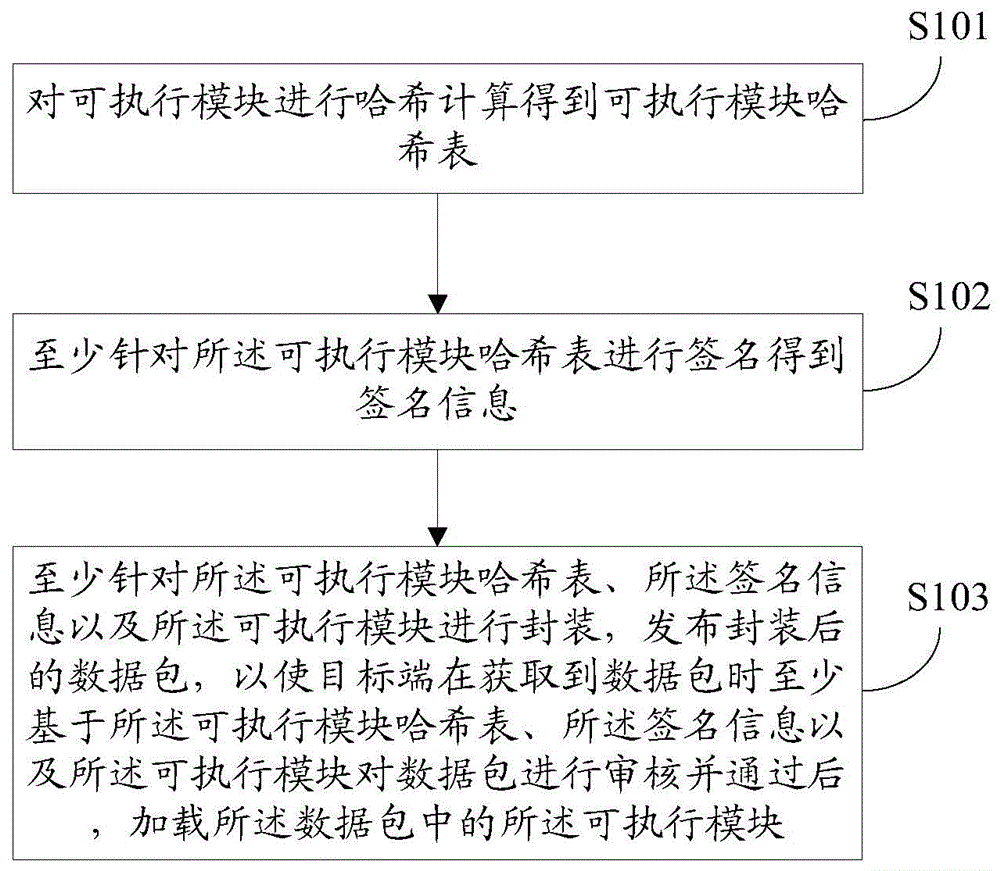
Method and terminal for provision and loading of executable module
InactiveCN105787352AImplement safe loadingImplement security authenticationDigital data protectionComputer hardwareNetwork packet
The invention provides a method and terminal for provision and loading of an executable module. Processes executed by the provision method on a host computer end comprise that Hash calculation is carried out to the executable module, so that a Hash table of the executable module can be obtained; signing is carried out at least aiming at the Hash table of the executable module, so that signing information can be obtained; and packaging is carried out at least aiming at the Hash table of the executable module, the signing information and the executable module, and a packaged data packet is issued, so that a target end can load the executable module in the data packet after the target end checks the data packet at least based on the Hash table of the executable module, the signing information and the executable module and after the data packet passes the checking. The method and terminal disclosed by the invention are applied in issuance and loading of the executable module, wherein the signing is carried out to the information such as the Hash table of the executable module, and the mobile communication terminal carries out authentication before loading the executable module, so that safety certification of the executable module can be implemented, and injective attacks made by the executable module to a system can be avoided.
Owner:ZTE CORP
Virtual special terminal, network service system and service access method
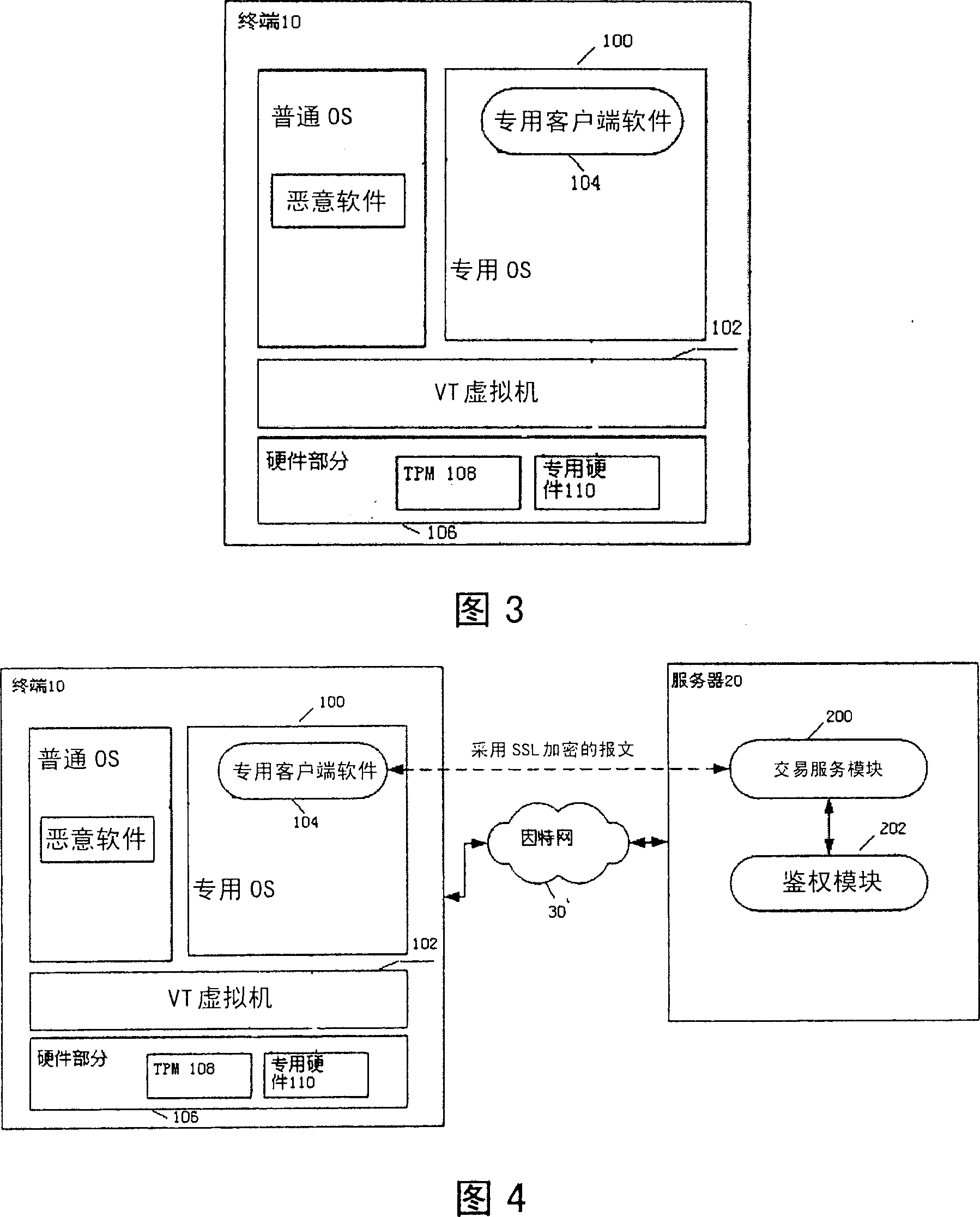
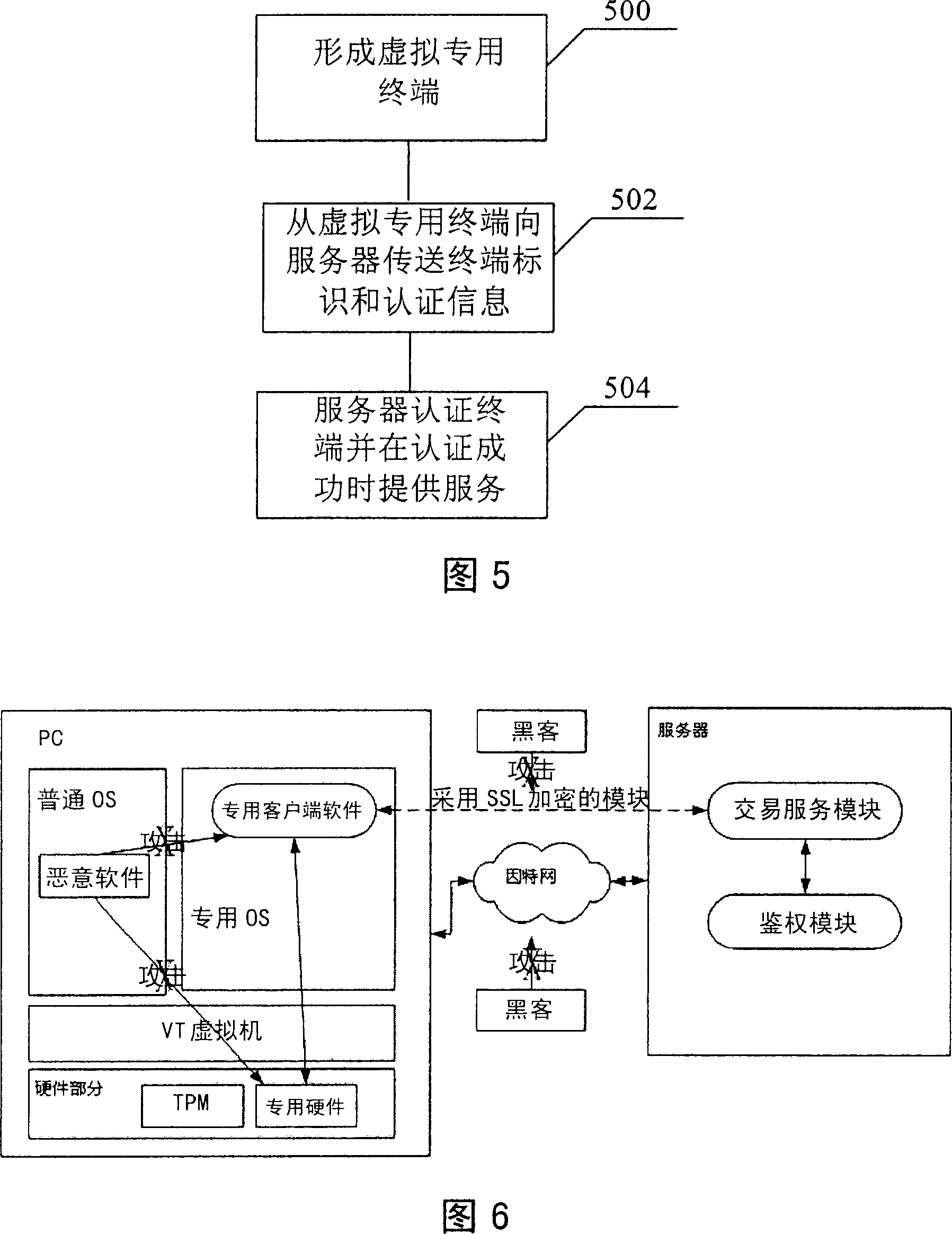
ActiveCN101155112AImplement security authenticationUser identity/authority verificationNetworks interconnectionOperational systemAccess method
The invention provides a virtual specialized terminal used in network service system of server containing terminal as client-side and for providing network service, comprising a VT virtual machine, a specialized operation system on the VT virtual machine; a specialized client-side software operated on the specialized operation system; and a hardware part containing safety chip and hardware part of specialized hardware, wherein the said safety chip stores a terminal identification for terminal authentication and the said specialized hardware stores authentication information for authenticating. The said VT virtual machine makes the specialized hardware virtual for the specialized operation system therefore the said specialized operation system can visit to the specialized hardware, so that the specialized client-side software is accessed to network service using terminal identification and authentication information in the specialized hardware.
Owner:LENOVO (BEIJING) LTD
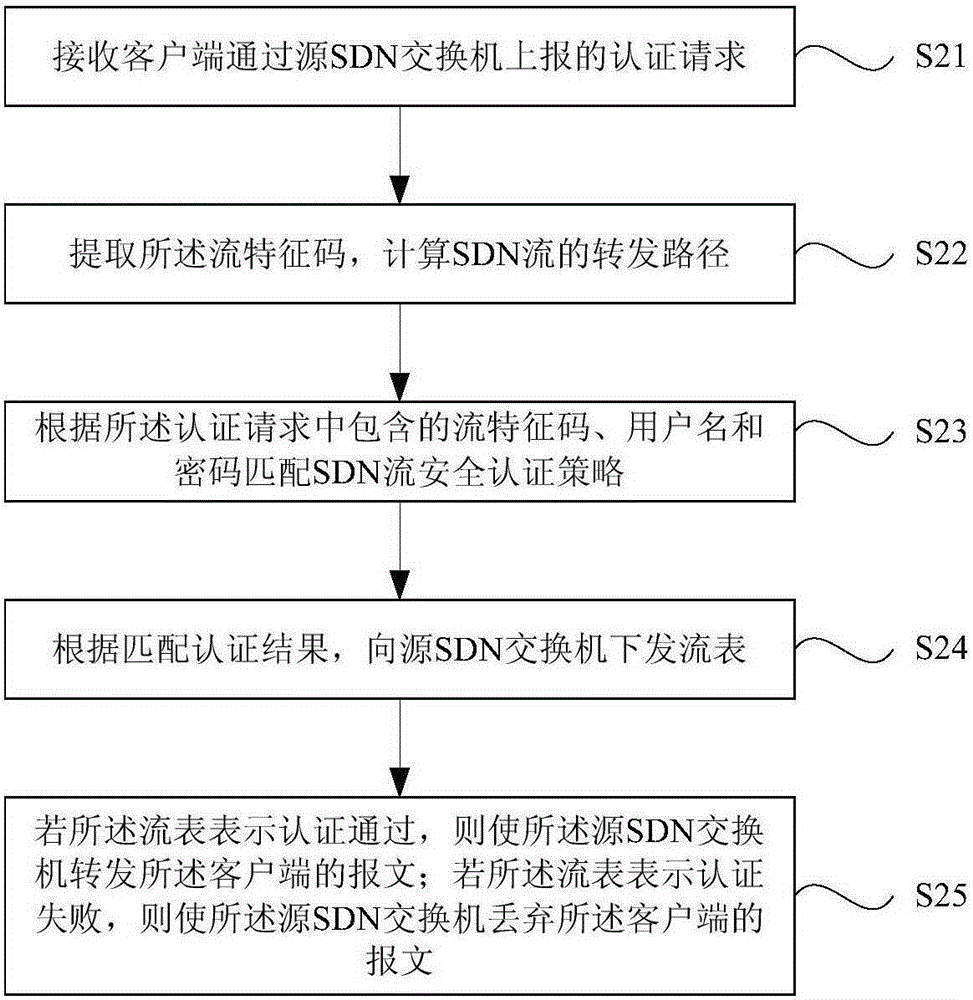
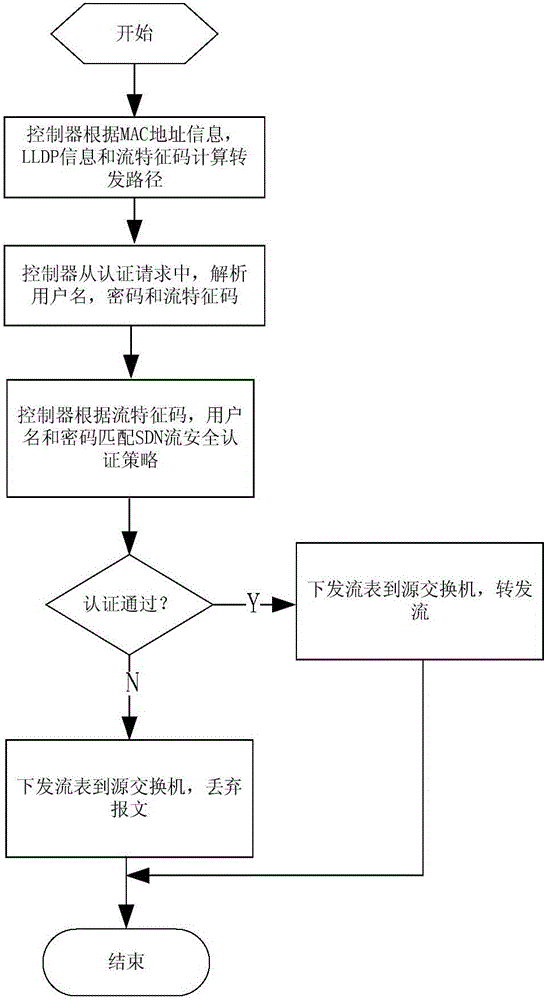
Safety authentication method and system based on SDN flow
ActiveCN105119911ASimple and Smart ManagementSimple and Smart ConfigurationData switching networksPasswordAuthentication
The invention provides a safety authentication method and system based on an SDN flow. The method comprises the following steps of receiving an authentication request reported by a client through a source SDN switch, wherein, the authentication request includes a flow feature code, a user name and a password; extracting the flow feature code and calculating an SDN flow forwarding path; matching an SDN flow safety authentication strategy according to the flow feature code, the user name and the password contained in the authentication request; according to the matching authentication result, sending a flow table down, wherein, the flow table includes the SDN flow forwarding path; if the flow table indicates that the authentication is passed, then making the source SDN switch forward the message of the client; otherwise, making the source SDN switch drop the message of the client. An SDN architecture is adopted. An SDN controller can sense the message forwarding path and network changes. Dynamic safety authentication on the SDN flow is achieved by sending the flow table down. Safety authentication on whole-network SDN flows is thus achieved.
Owner:湖州帷幄知识产权运营有限公司
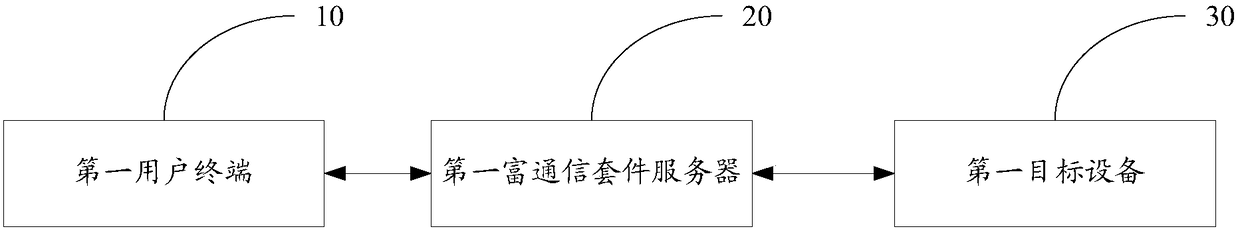
Internet of Things authentication system and Internet of Things authentication method
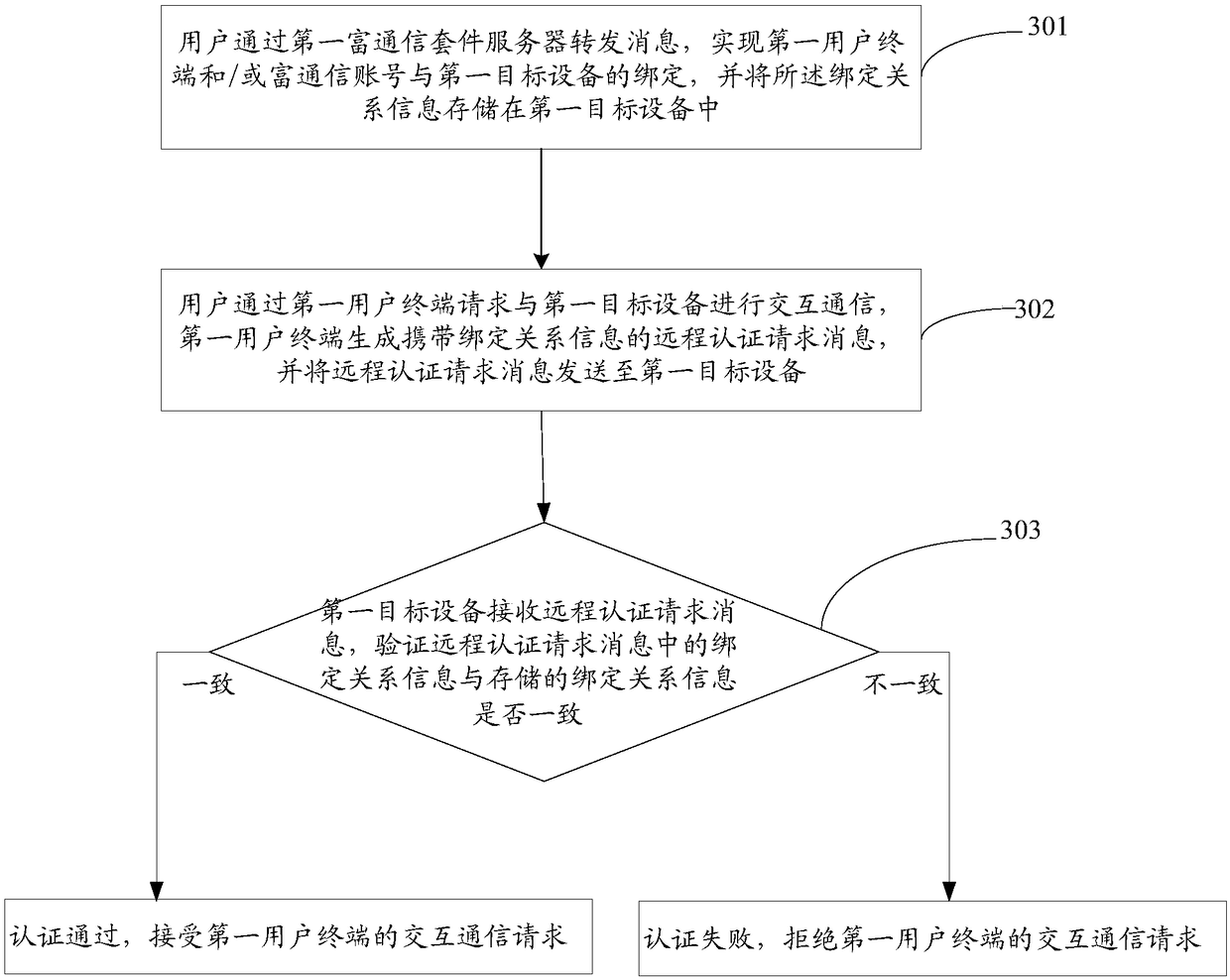
InactiveCN108696479AEnable secure interactionsAvoid analysisDigital data authenticationTransmissionThe InternetComputer terminal
The invention discloses an Internet of Things authentication system and an Internet of Things authentication method. The Internet of Things authentication system comprises a first user terminal for accepting an interactive communication request of a user, generating a remote authentication request message carrying binding relationship information, and sending the remote authentication request message to a first target device; a first rich communication suite server for realizing message forwarding between the first user terminal and the first target device in a process of establishing establishing a binding relationship among the first user terminal and / or a rich communication account and the first target device, and authenticating the binding relationship; and the first target device forstoring the binding relationship information, receiving the remote authentication request message, detecting whether the binding relationship information is consistent with the stored binding relationship information, if yes, indicating that the authentication is passed, and accepting the interactive communication request of the first user terminal. The Internet of Things authentication system disclosed by the invention can conveniently and effectively realize the secure interaction between a user and the device and between the device and the device in the Internet of Things environment by means of the instantaneity, security and standardability of the RCS service.
Owner:ZTE CORP
Method based on IOT Hub service of industrial internet platform
InactiveCN108737539AImplement security authenticationImplement subject permission definitionsNetwork connectionsData acquisitionThe Internet
The invention provides a method based on an IOT Hub service of an industrial internet platform, and belongs to the field of a computer. According to the invention, by the IOT Hub service of the industrial internet platform, equipment management is carried out, and an equipment certificate and a strategy are generated and issued to an industrial gateway; and the industrial gateway is a data acquisition entry and carries out data submission to the IOT Hub service according to a rule. Finally, the industrial internet platform collects industrial data by the IOT Hub service to carry out big data analysis so as to implement creative application of an industrial APP.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
A safety certification method, device and system for a client end
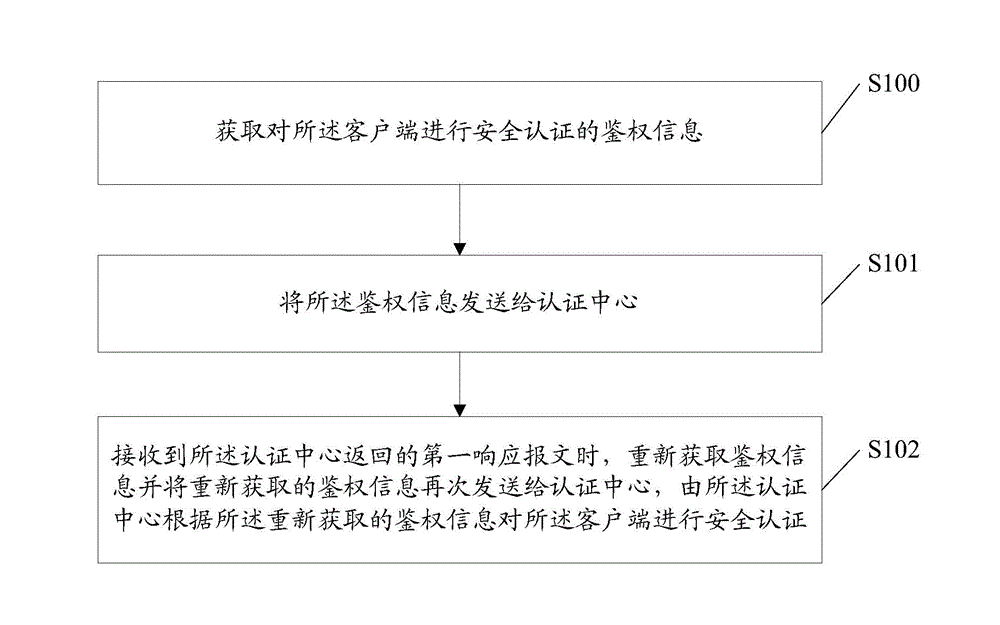
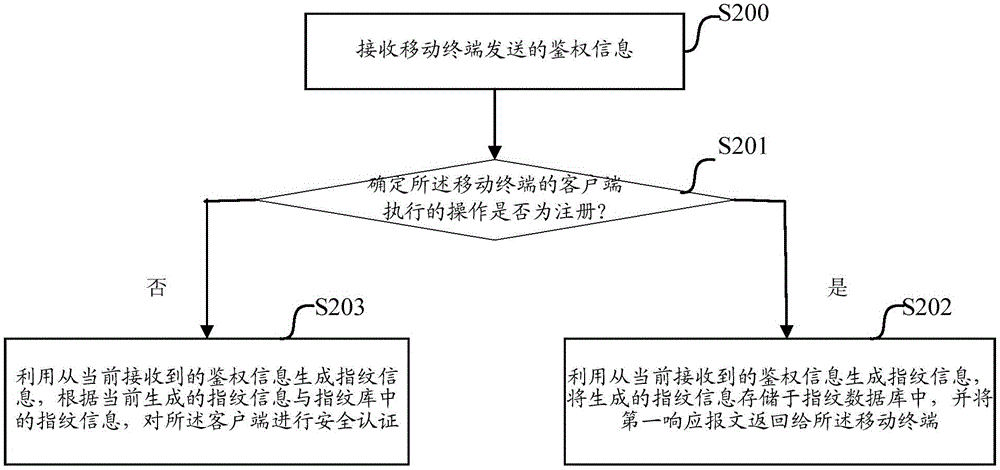
InactiveCN104796255AEnsure information securityEnsure safetyUser identity/authority verificationClient-sideSecure authentication
The invention discloses a safety certification method for a client end. The method comprises: acquiring authentication information for executing safety certification for the client end; sending the authentication information to a certification center; and when a first response message returned by the certification center is received, reacquiring the authentication information, resending the reacquired authentication information to the certification center, and executing safety certification for the client end according to the reacquired authentication information by the certification center. Meanwhile, the invention also discloses another safety certification method for a client end, a safety certification system for a client end, a mobile terminal, and a certification center. Adopting the safety certification method, device and system for a client end, safety certification can be executed for the client end by establishing a unified certification center for the client end; and it can be realized that safety certification is executed for the client end without connecting the mobile terminal to any external equipment or changing any internal software of the mobile terminal.
Owner:CHINA MOBILE GROUP ANHUI
Method and system for realizing sound control based on NFC
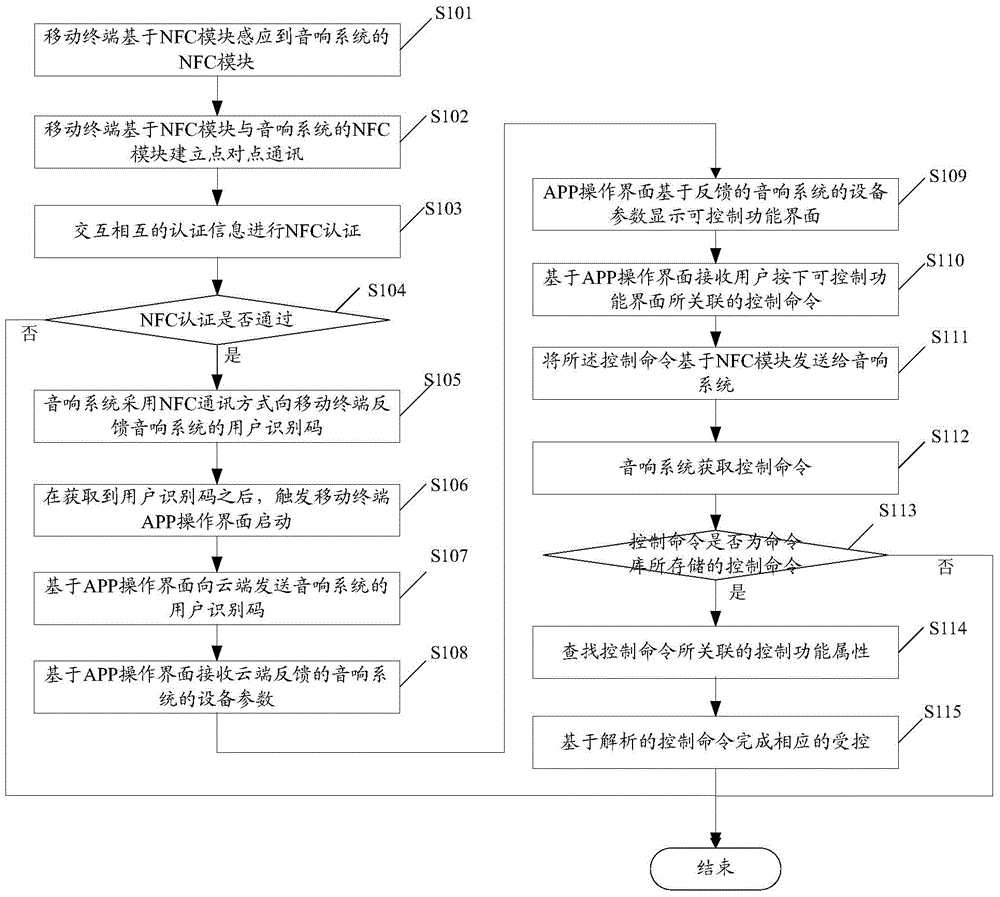
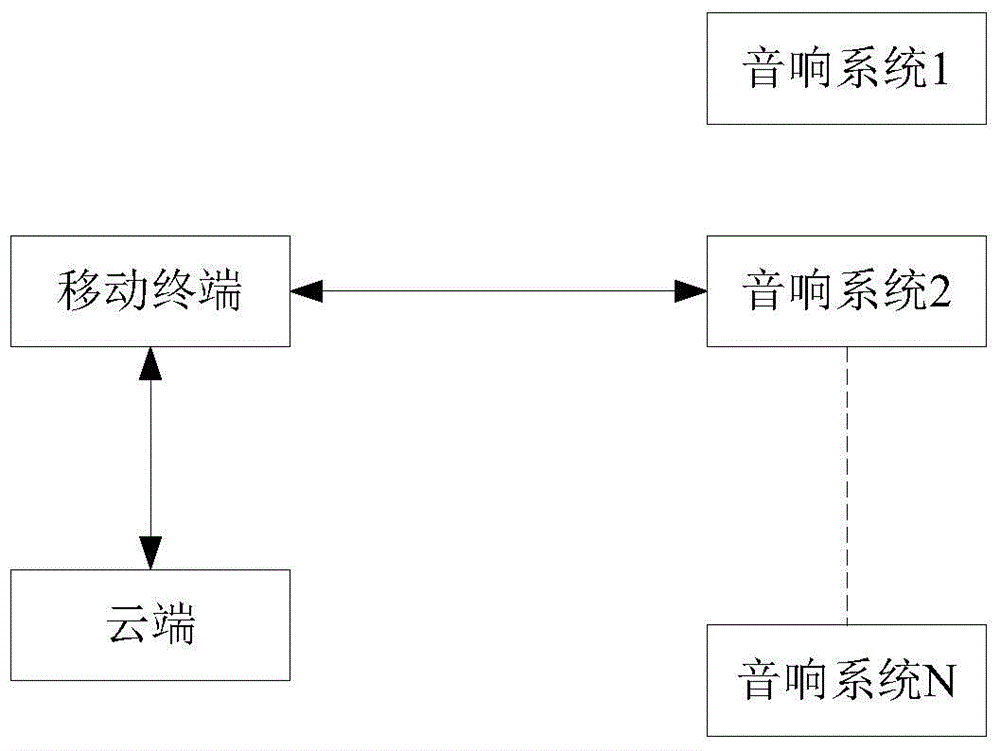
InactiveCN104936094AImplement Security AuthenticationSecurityTransducer circuitsEmbedded systemSound system
The invention discloses a method and a system for realizing sound control based on NFC. The method includes: a mobile terminal inducts an NFC module of a sound system based on an NFC module; the mobile terminal establishes point-to-point communication based on the NFC module and the NFC module of the sound system and interacts with each other about mutual authentication information for NFC authentication; the sound system employs the NFC communication mode to feed back user identification codes of the sound system to the mobile terminal; the mobile terminal obtains a control interface of the sound system from a cloud terminal based on the user identification codes; the mobile terminal employs the NFC communication mode to send a control instruction to the sound system based on the control interface; and the sound system parses the control instruction and is correspondingly controlled based on the parsed control instruction. According to the method and the system, the security of the communication mode is guaranteed, the user identification codes of the sound system are obtained based on the NFC technology, the triggering of an operation interface of the mobile terminal is completed, and operation convenience is realized.
Owner:广州番禺巨大汽车音响设备有限公司
TrustZone-based secure intelligent mobile terminal trust train transfer method and system
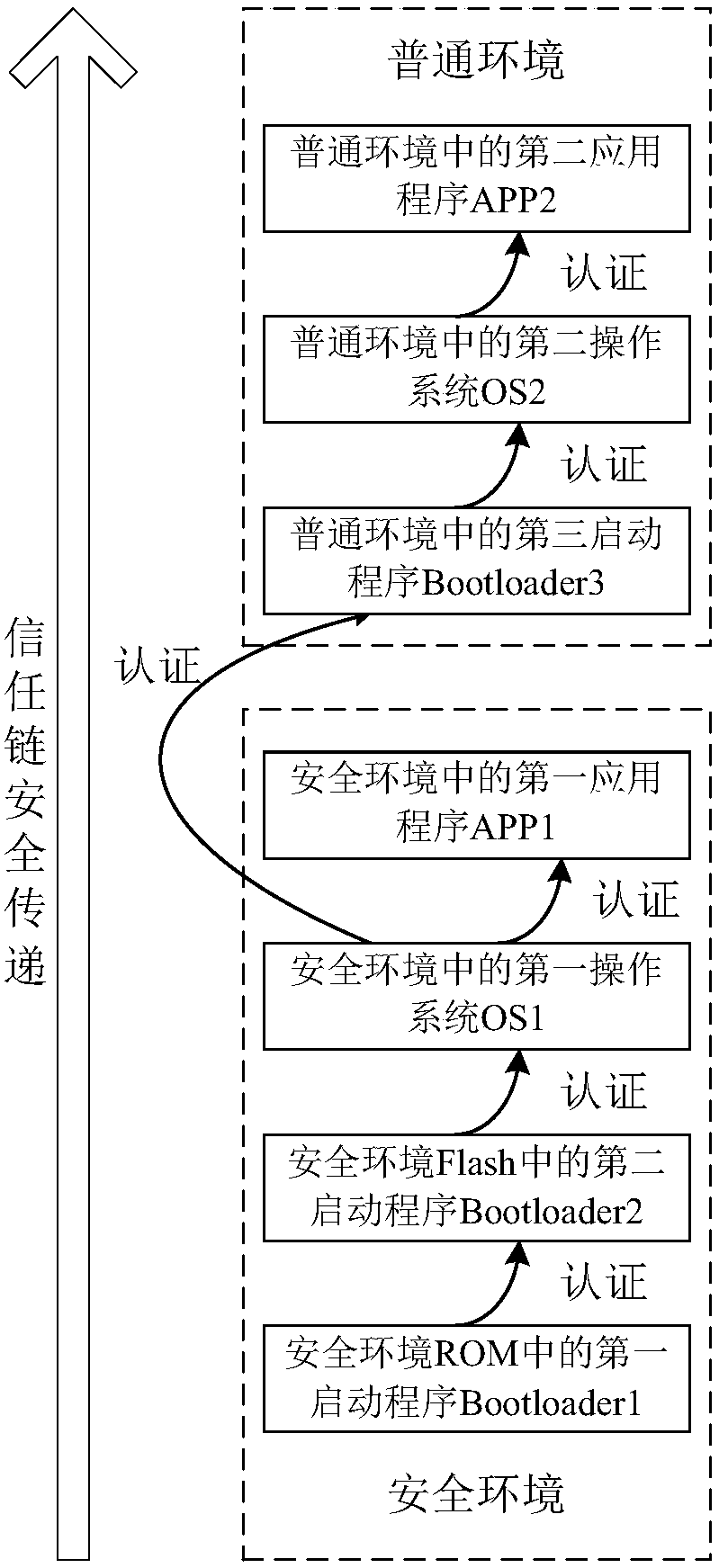
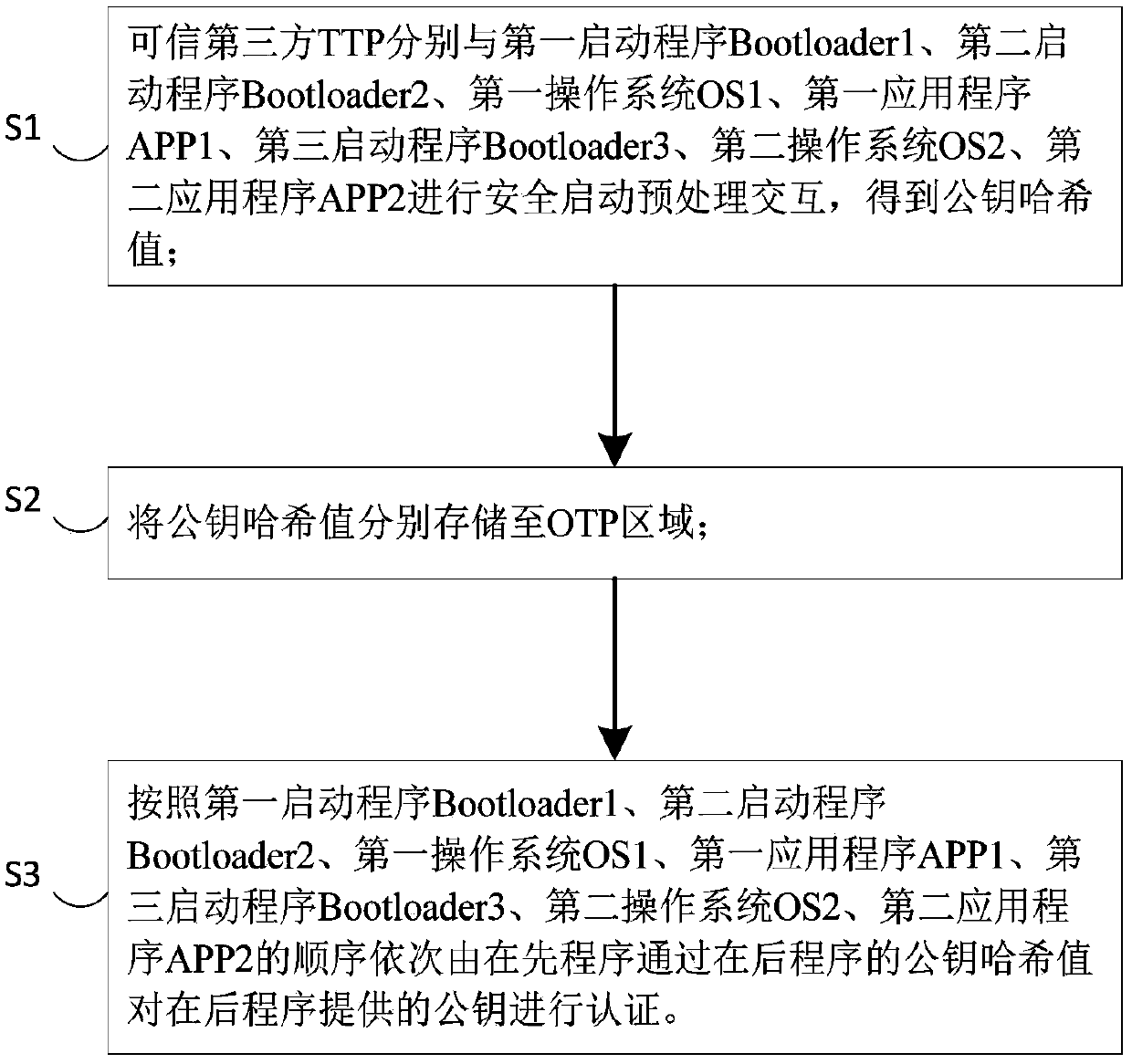
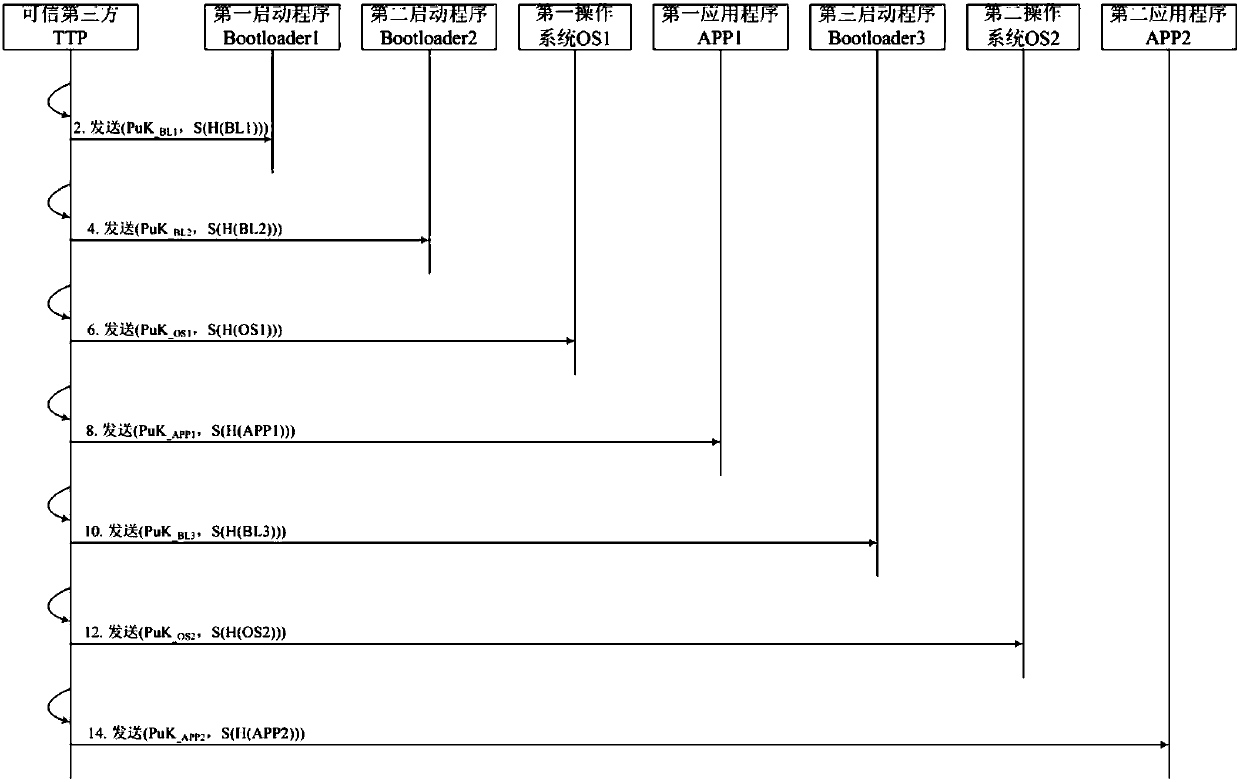
ActiveCN107908977AEnhanced Security AuthenticationImplement security authenticationDigital data protectionInternal/peripheral component protectionTrusted third partyComputer terminal
The invention discloses a TrustZone-based secure intelligent mobile terminal trust train transfer method and system. The method comprises the following steps of: carrying out secure startup preprocessing interaction with Bootloader 1, Bootloader 2, OS1, APP1, Bootloader 3, OS2 and APP2 by a trusted third party TTP, so as to obtain public key hash values; respectively storing the public key hash values to an OTP area; and authenticating public keys provided by posterior programs by prior programs through the public key hash values of the posterior programs in sequence according to a startup sequence. According to the method and system, a secure trust chain transfer process from a secure environment to a common environment is established through secure authentication startup, and the publickey hash values are stored to the OTP area according to the fact that OTP has a once programmable characteristic, so that uniqueness of public keys is ensured, the security of the intelligent mobile terminal startup process is ensured, and software attacks and hardware attacks can be defensed.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
Separable encryption domain information hiding method
ActiveCN109547797AQuality improvementImplement encryptionKey distribution for secure communicationDigital video signal modificationCiphertextInformation hiding
The invention provides a separable encryption domain information hiding method, and belongs to the technical field of the information hiding. The method is characterized by comprising the following steps: firstly reading in an image needing to protect and blocking the image, selecting an appropriate observation rate according to storage space and a user demand to perform the observation, quantitatively encoding the obtained observation values, and embedding secret information (such as copyright and identity authentication) into low 4-bit of each observation value in the encoding process, thereby producing a ciphertext image containing the secret information. Through the method provided by the invention, the extraction of the secret information and the reconstruction of the protected imageare separable; if a user extracts a key, the secret information can be directly and nondestructively extracted from the ciphertext image containing the secret information; if the user is authorized toreconstruct the image, the protected image can be reconstructed in high quality; if both key extraction and image reconstruction are existent, the secret information and the reconstructed image can be acquired at the same time.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Method for generating ID code containing human body information
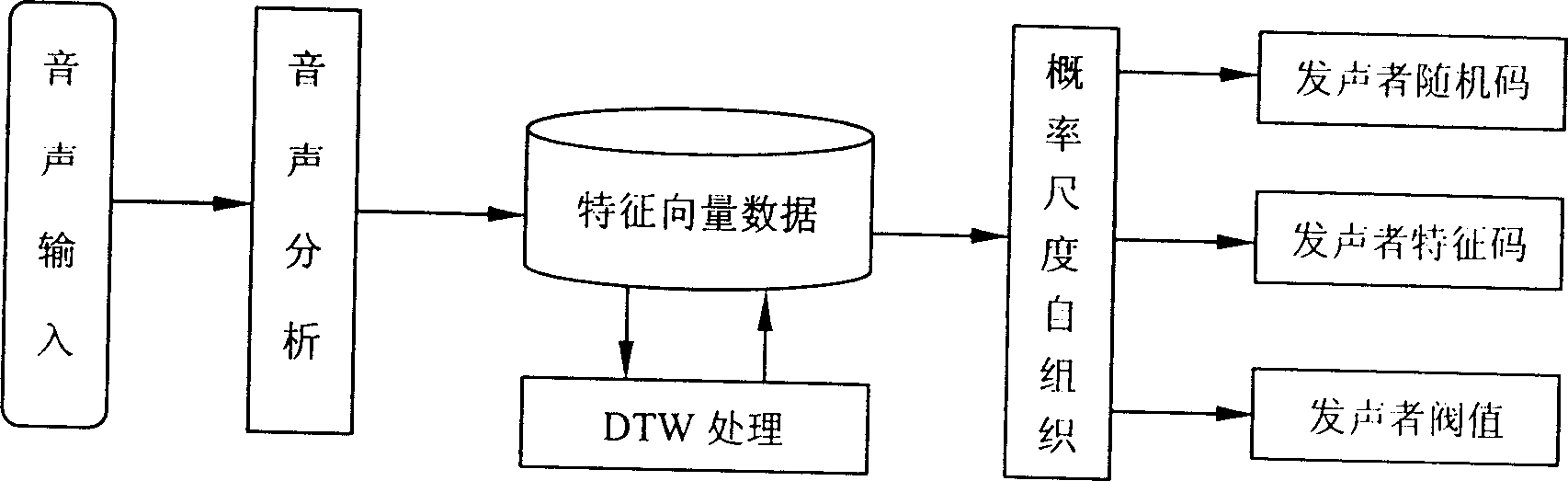
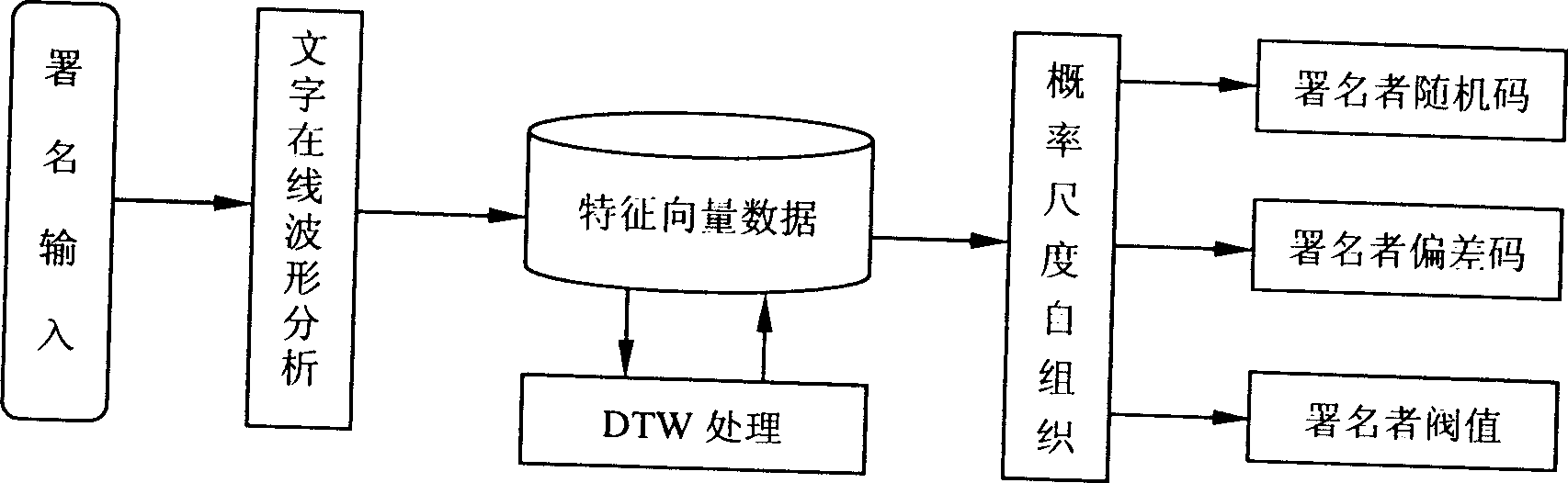
InactiveCN1424691AImplement Security AuthenticationIncrease randomnessCharacter and pattern recognitionComplex mathematical operationsHuman bodyComputer science
This invention relates to a method for generating ID codes containing human body information. 1. generating ID codes with signing information of sound type; 2. ID codes contain the random codes, value of difference and threshold of the interested party; 3. self-organizing algorithm of probability scale; 4. processing course and processing contents of ID codes generated based on signing in sound ripple type. The interested party himself can be identified using only the ID codes stored in computer, achieving attestation of safety without increasing more hardware; because the sound and the content of signing have pretty large random, the generated ID codes have necessity difficult to uncover for computer; the interested party can be identified most effectively using the ID codes; these is no need for special apparatus, so it is easy to popularize, specifically, it can be used in mobile phone.
Owner:天津市阿波罗信息技术有限公司
Wireless tool control system and method for vehicle assembly and fabrication technique
InactiveCN101470441AImplement security authenticationIncrease the difficulty of malicious damageTotal factory controlProgramme total factory controlQuality controlData processing
Disclosed are a wireless tool control system for automobile assembling and manufacturing techniques and a method thereof, which realize self-adaptive safety certification, working data tracking, preventing and collecting errors in the producing process of all wireless tools on the automobile assembling and manufacturing line, and realize real-time control, data process and working record storage simultaneously. The wireless tool control system comprises at least one wireless tool, an Ethernet network of the automobile manufacture production line, an enterprise firewall embedded in the Ethernet network of the automobile manufacture production line, and a production line monitor center which is connected with the Ethernet network of the automobile manufacture production line and is provided with a human-machine interface, wherein a control system of the wireless tool is provided with a quality control servo unit, the quality control servo unit is provided with a data storage system, the data storage system is provided with a quality data base, the control system of the wireless tool is equipped with at least one Ethernet serial server and is embedded with a safety certification system, and the safety certification system allocates one identification certificate for each wireless tool, and each identification certificate is different from each other.
Owner:广州信邦智能装备股份有限公司
Separable ciphertext domain reversible data hiding method
The invention relates to a separable ciphertext domain reversible data hiding method, which comprises three parts of a content owner, a secret data hider and a receiver, and is characterized in that the content owner preprocesses a carrier image to vacate a spare space to hide secret data; the secret data hider can directly hide secret data without knowing the content of the carrier image; after the receiver obtains the encrypted image with the secret data, the receiver can extract the secret data and recover the carrier image. According to the invention, a separable ciphertext domain reversible digital hiding method is realized. The authorized user can recover the carrier image in a lossless manner or extract the secret data in a lossless manner according to own needs or own held secret keys.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
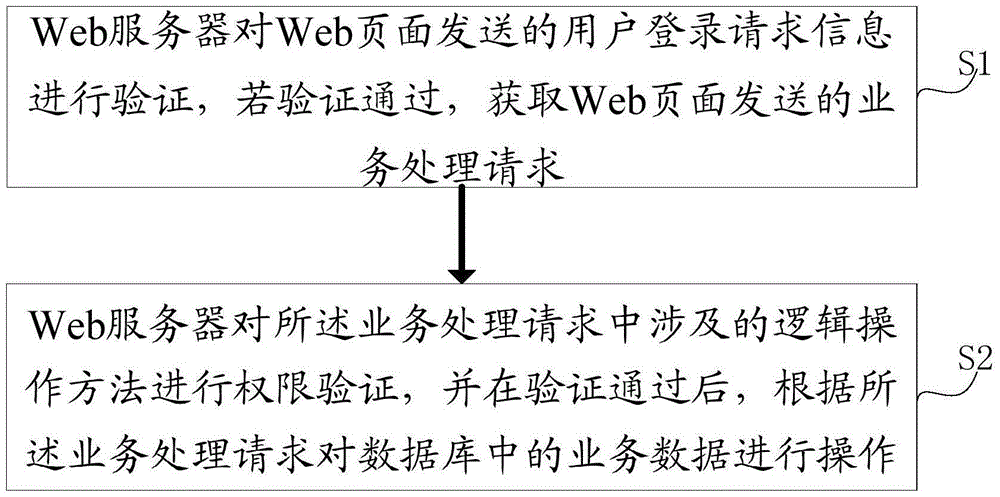
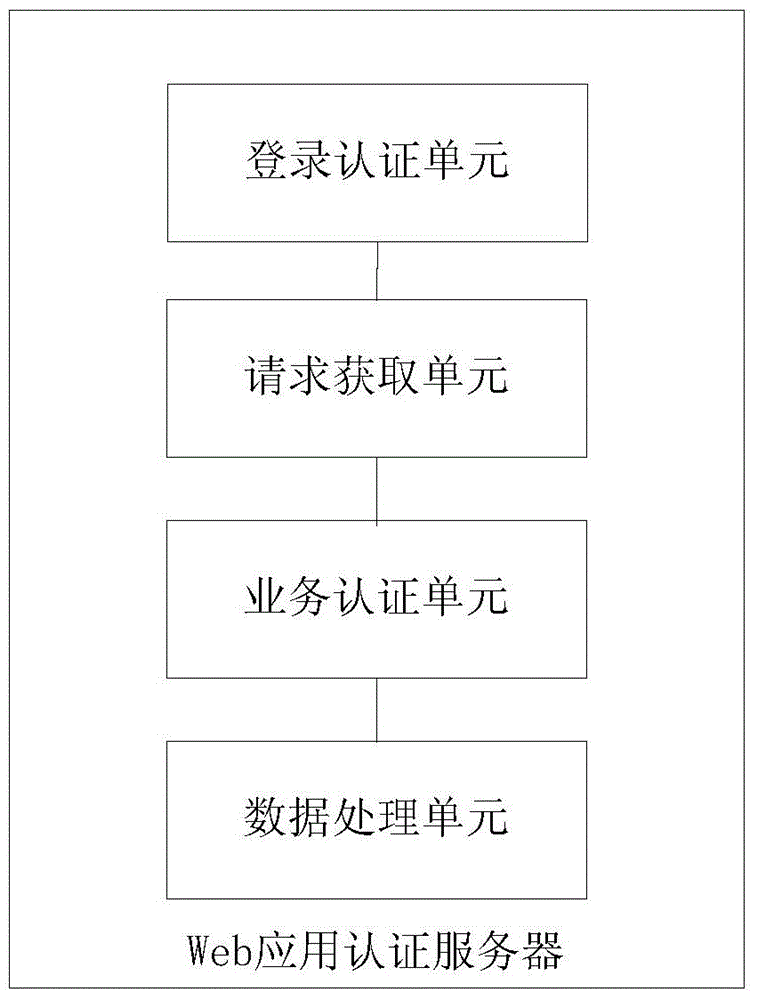
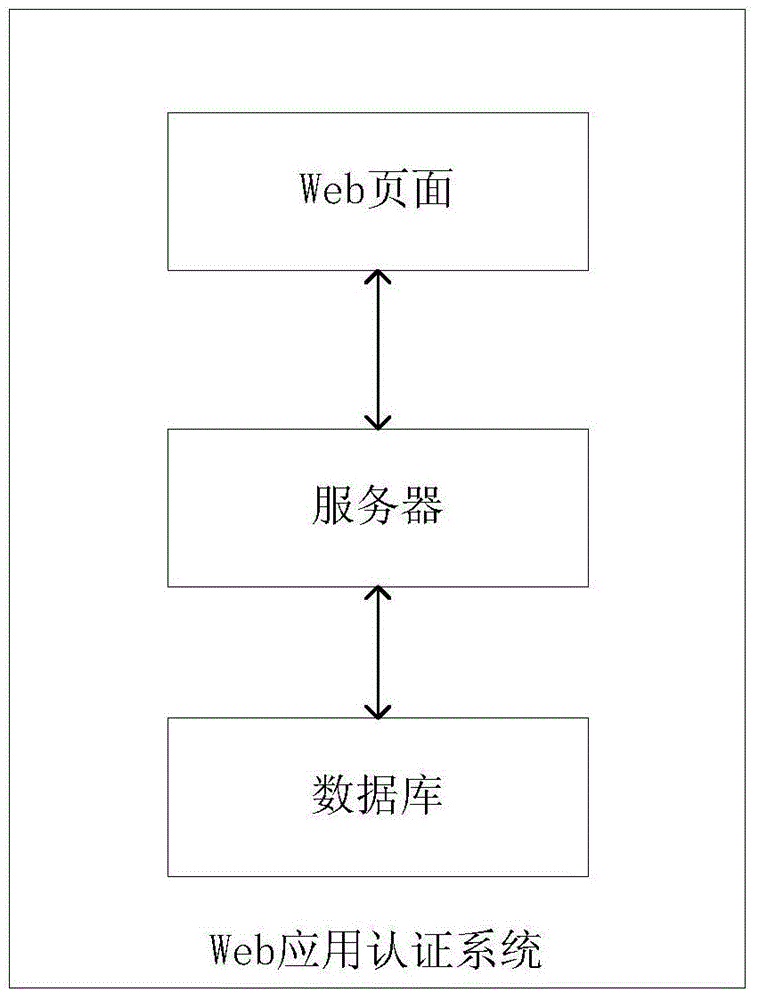
Web application authentication method, server and system
ActiveCN105227315AProtect personal privacyImplement security authenticationUser identity/authority verificationWeb applicationWeb service
The invention discloses a Web application authentication method, server and system. The method comprises the following steps that: a Web server verifies user login request information transmitted by a Web page, and acquires a service processing request sent by the Web page if the verification is passed; and the Web server performs permission verification on a logical operation method involved in the service processing request, and operates service data in a database according to the service processing request after the verification is passed. According to the web application authentication method, server and system, the logical operation method involved in the service processing request is further authenticated from a service logical processing layer, so that malicious access and illegal operation can be effectively intercepted; data is protected from being damaged; and the data safety and reliability are enhanced.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
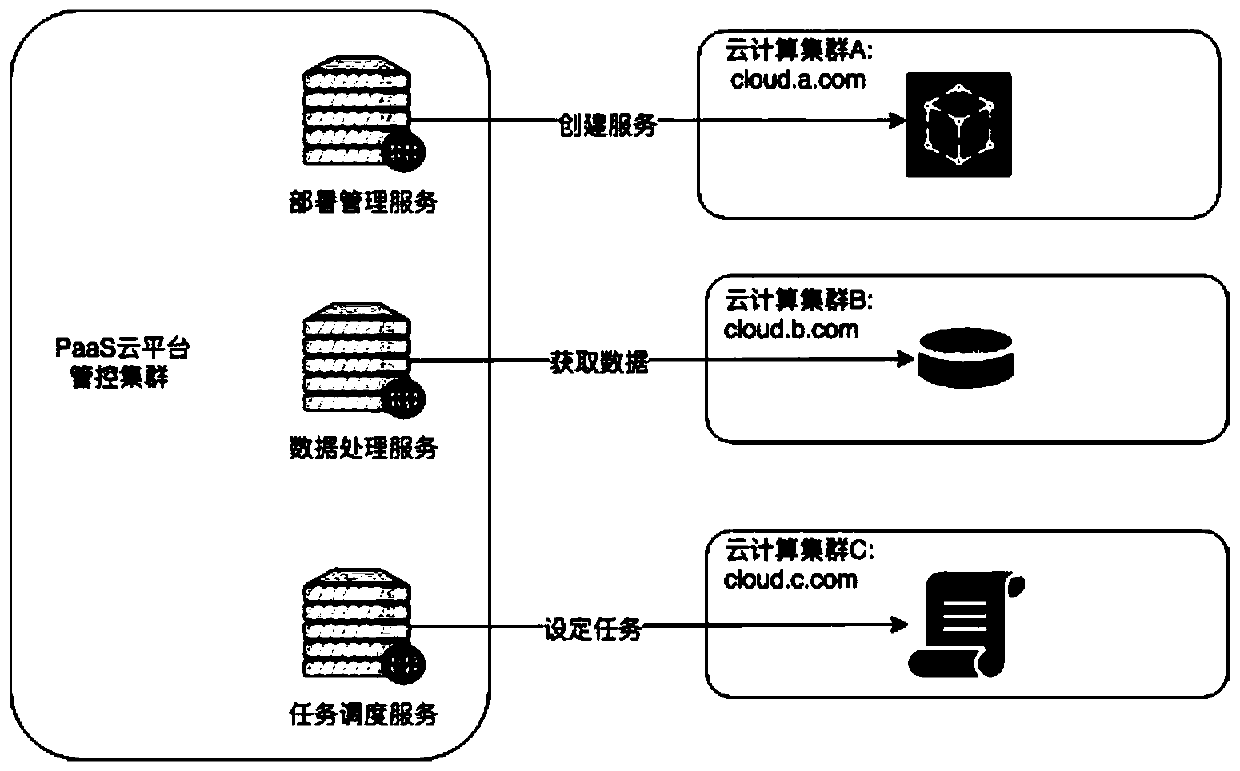
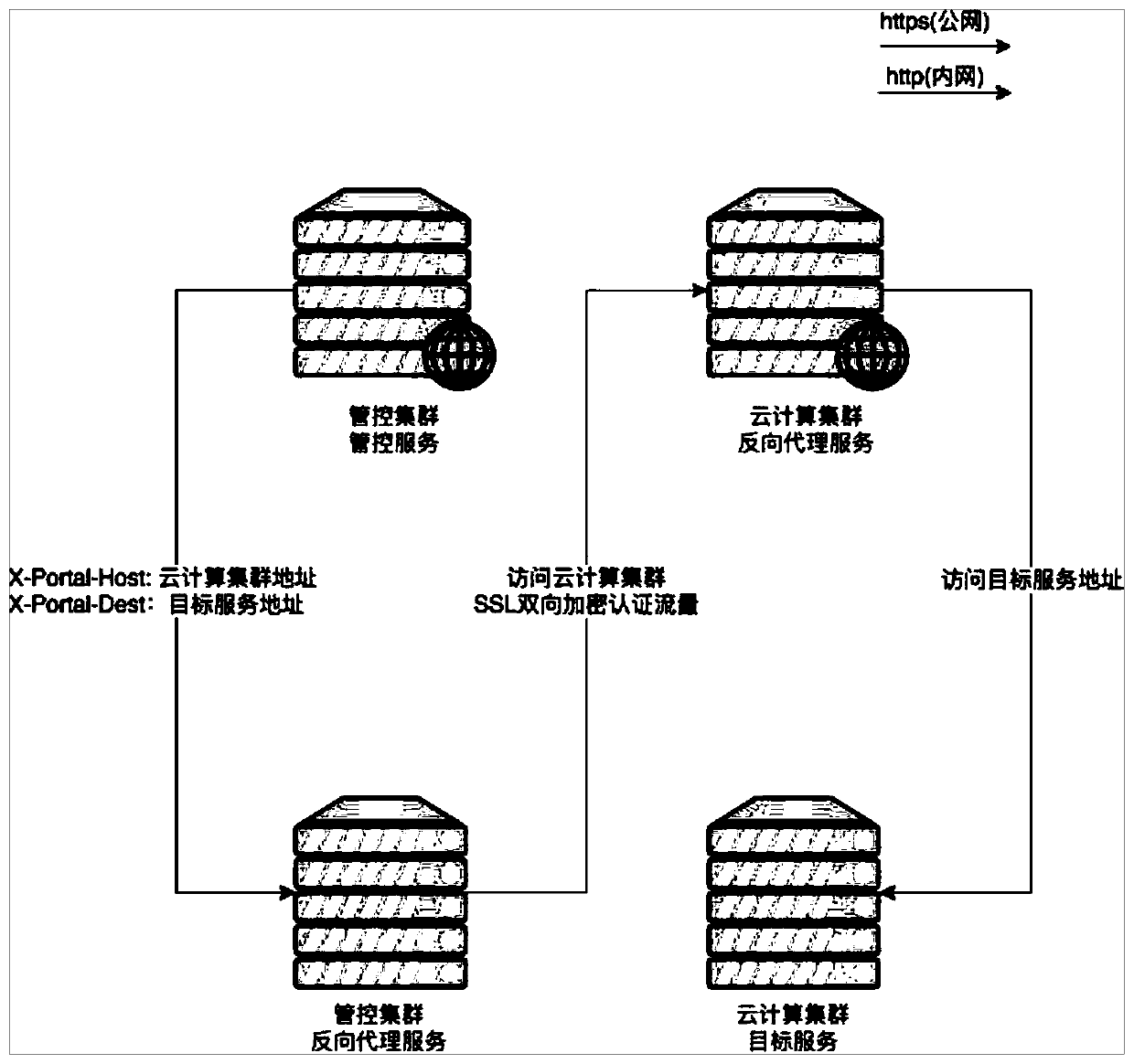
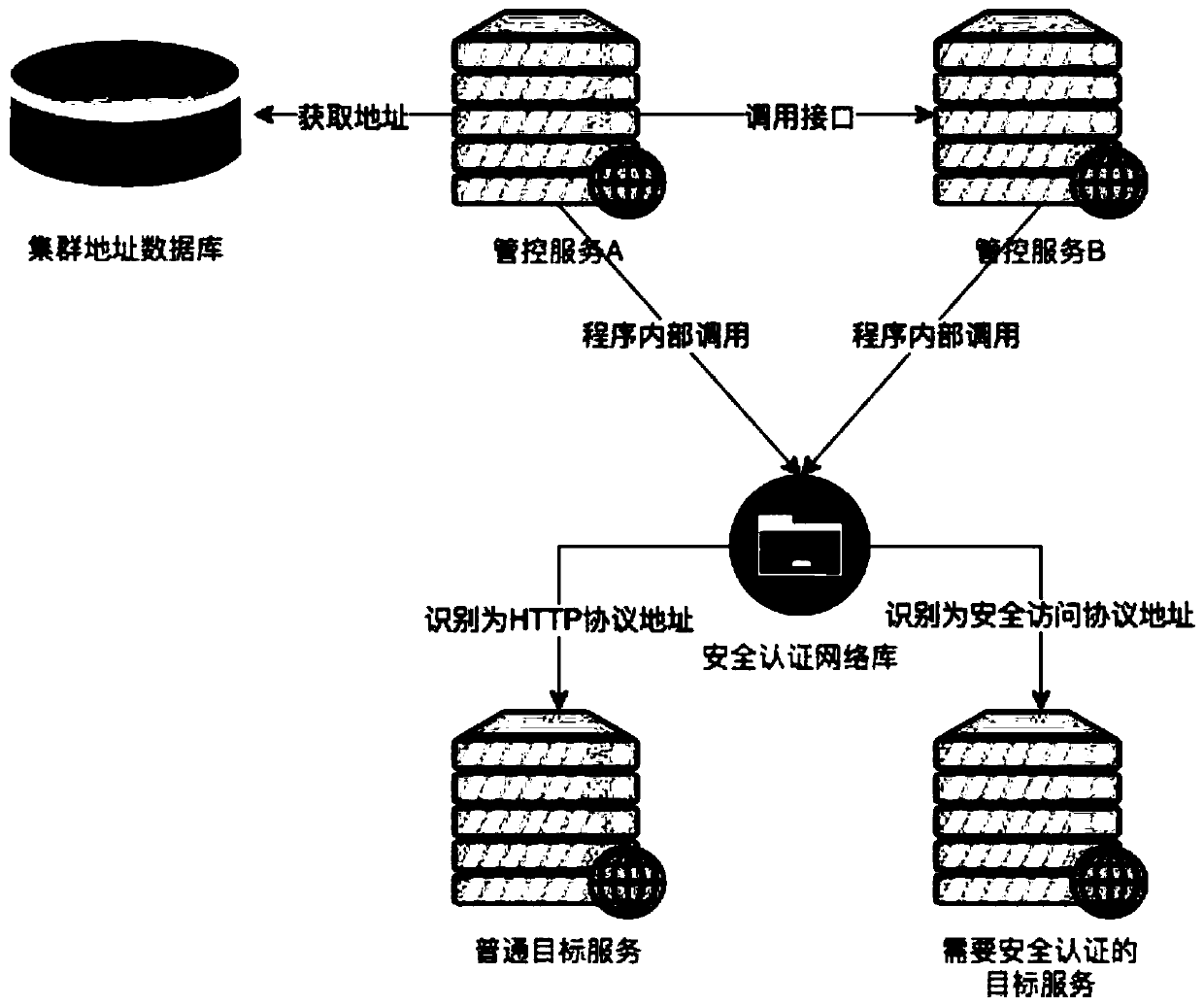
Security authentication method for realizing multi-cloud management and control across public network
InactiveCN110855700AReduce operation and maintenance costsSave human and financial resourcesTransmissionSelf-signed certificateProxy service
The invention discloses a security authentication method for realizing multi-cloud management and control across a public network. The method specifically comprises the following steps: establishing abidirectional authentication network channel between a management and control cluster and a cloud computing cluster through a group of reverse proxy servers; in the management and control cluster, the management and control service directly uses an HTTP protocol to access the reverse proxy service; after the management and control cluster reverse proxy server receives the request, a self-signed SSL client certificate is used to access the reverse proxy server of the cloud computing cluster through HTTPS to complete authentication of the management and control cluster; meanwhile, the cloud computing cluster returns a self-signed server certificate, and the management and control cluster also uses the same self-signed CA certificate to complete authentication of the cloud computing cluster;and after the bidirectional authentication is completed, unloading the HTTPS protocol by the cloud computing cluster reverse proxy service, and accessing the target service by using the HTTP protocolto realize security management and control. According to the method, manpower and financial resources can be saved, the method is safer, meanwhile, the control service can realize control by directlyusing the HTTP protocol to access the reverse proxy service, and the control is flexible and convenient.
Owner:杭州端点网络科技有限公司
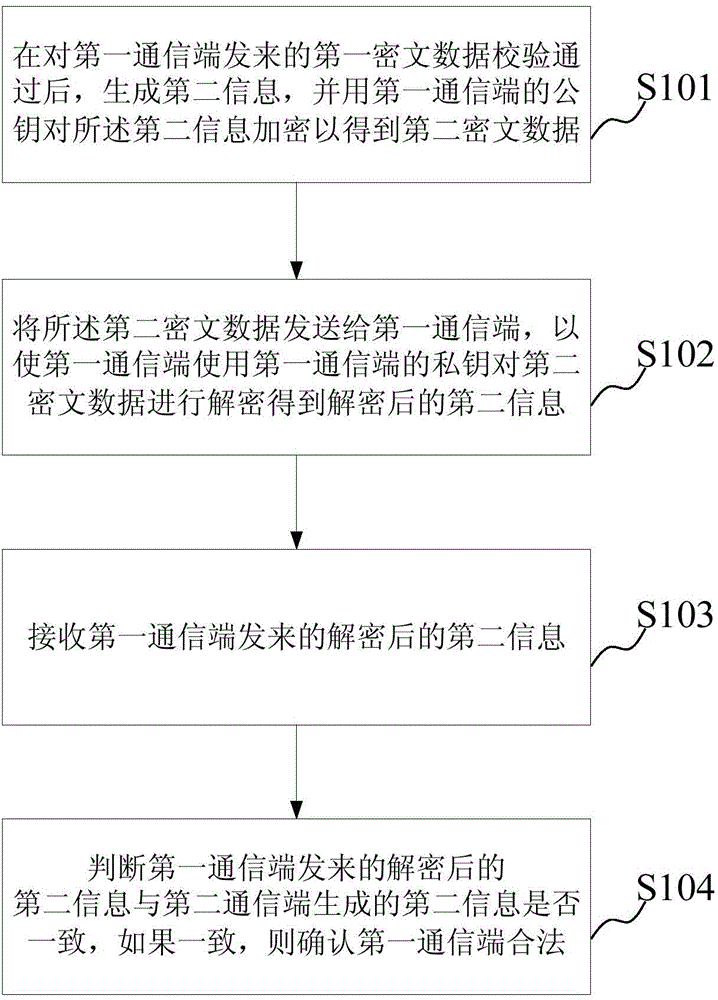
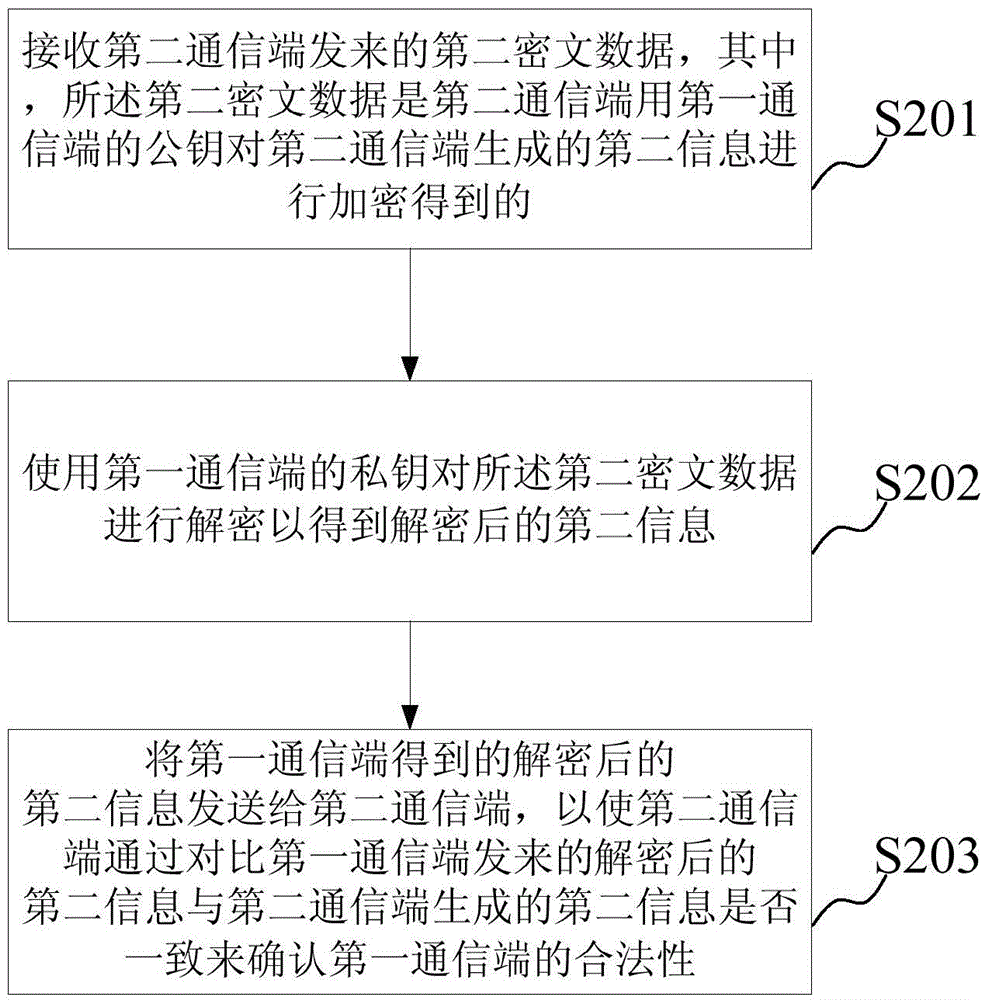
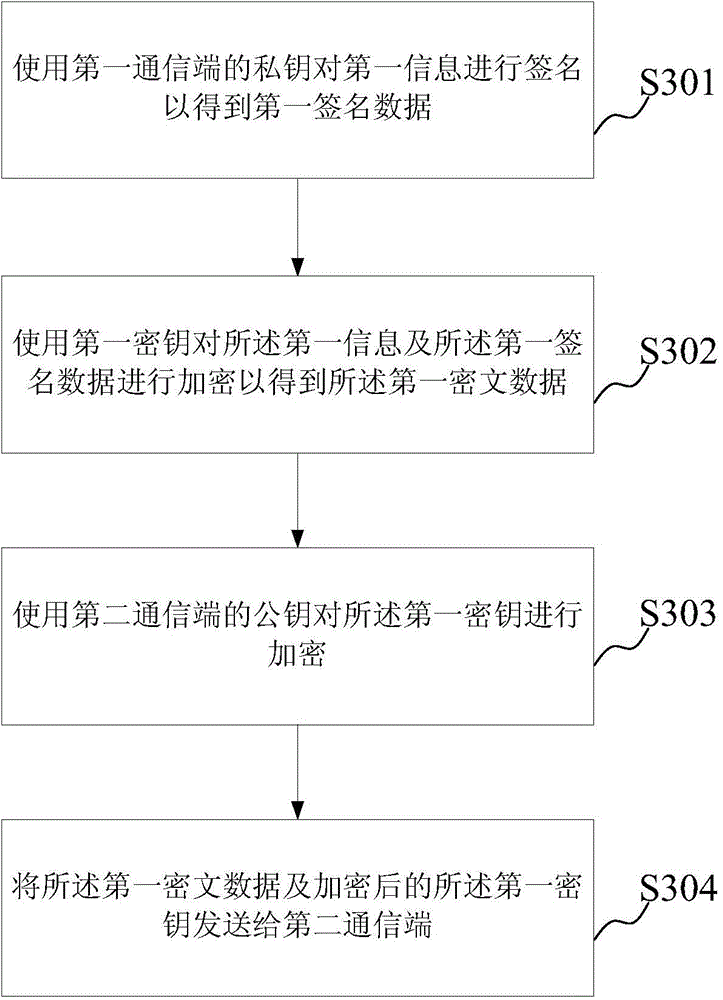
Data communication method and device
InactiveCN105450401AFast encryption and decryptionVerify legalUser identity/authority verificationCiphertext
The embodiment of the invention discloses a data communication method and device. When the method is used for a second communication end, the method comprises the steps: generating second information and carrying out the encryption of the second information through a public key of a first communication end after the verification of first ciphertext data transmitted by the first communication end is passes, so as to obtain second ciphertext data; transmitting the second ciphertext data to the first communication end, so as to enable the first communication end to carry out the decryption of the second ciphertext data through a private key of the first communication, and to obtain decrypted second information; receiving the decrypted second information transmitted by the first communication end; judging whether the decrypted second information transmitted by the first communication end is consistent with the second information generated by the second communication end or not: confirming that the first communication end is legal if the decrypted second information transmitted by the first communication end is consistent with the second information generated by the second communication end, thereby guaranteeing the safety of data communication.
Owner:NEW SINGULARITY INT TECHN DEV
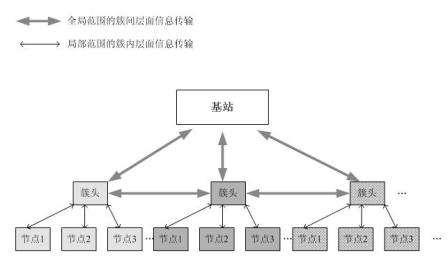
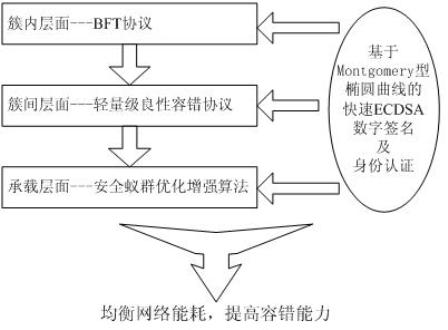
Rapid ECDSA (Elliptic Curve Digital Signature Algorithm) based lightweight byzantine fault-tolerant routing of large-scale wireless sensor network
InactiveCN101969641AImplement security authenticationIncrease credibilitySecurity arrangementDigital signatureWireless sensor networking
The invention relates to rapid ECDSA (Elliptic Curve Digital Signature Algorithm) based lightweight byzantine fault-tolerant routing of a large-scale wireless sensor network. The routing runs different fault-tolerant protocols aiming to different network layers, BFT (Byzantine Fault-Tolerant) protocols run in various clusters in a partial range, each piece of information transmitted in each cluster is signed by a threshold scheme (2f+1,3f+1) based on the lightweight optimization of the rapid ECDSA, messages transmitted outwards by all cluster heads carry digital signatures based on the rapid ECDSA, and lightweight virtuous fault-tolerant protocols run among all the clusters in the whole range. On the bearing layer of the whole network, an ant colony optimization and enhancement algorithm with added node authentication factors and confidence factors is adopted to rapidly and safely certify the nodes and search and establish reliable routing.
Owner:SHANGHAI UNIV
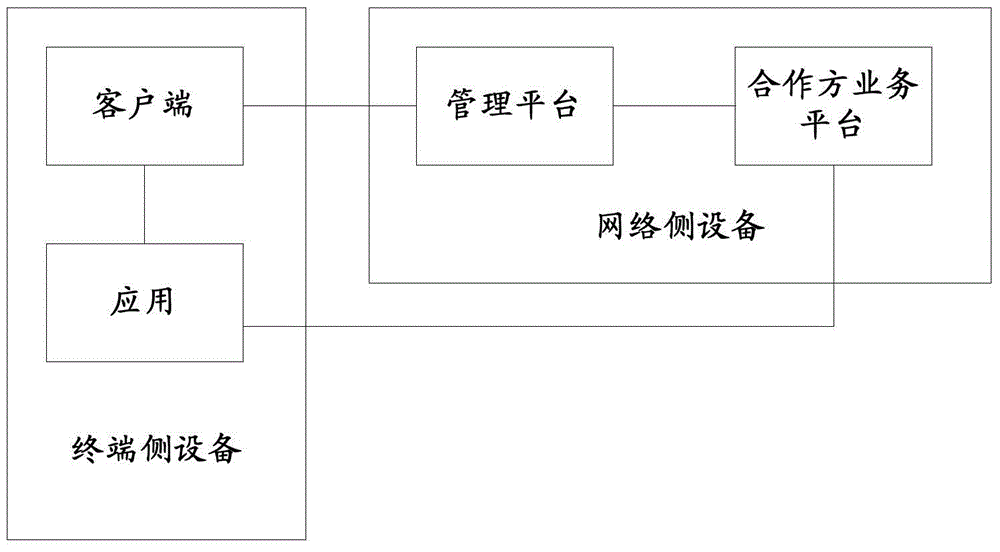
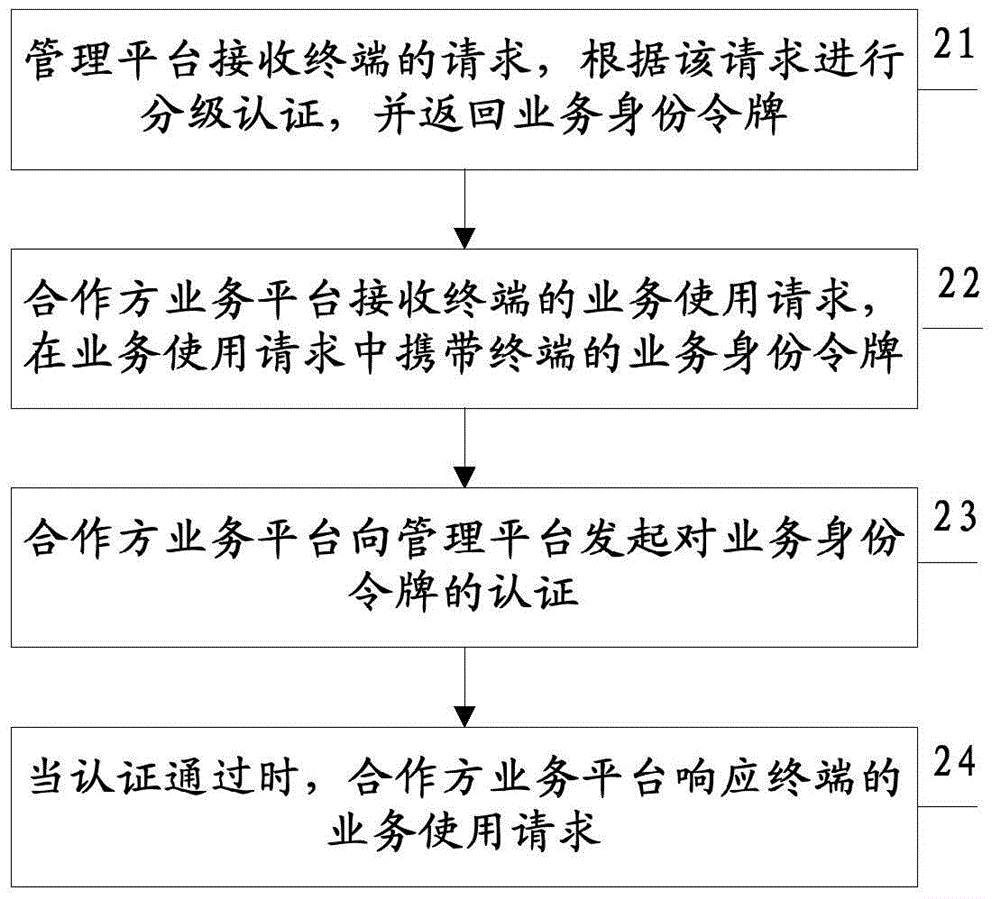
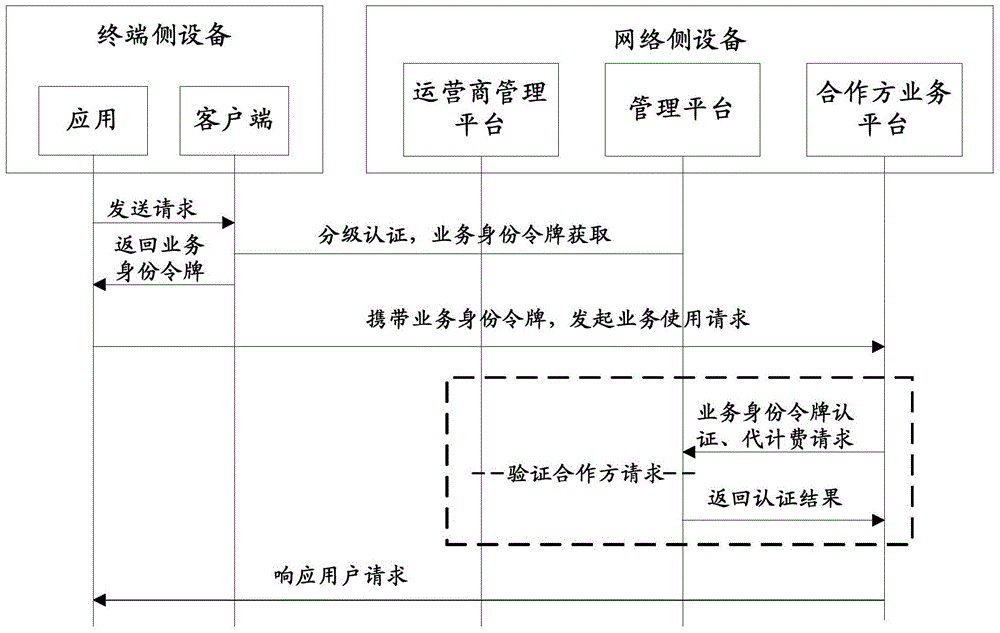
Method and system for hierarchical authentication of applications
ActiveCN104702405AImplement security authenticationUser identity/authority verificationSecure authenticationService use
The invention discloses a method and a system for hierarchical authentication of applications. The method comprises the following steps: a management platform receives a request of a terminal, carries out hierarchical authentication according to the request, and returning a service identity token; a partner service platform receives a service using request of the terminal, wherein the service using request carries the service identity token of the terminal; the partner service platform initiates authentication of the service identity token to the management platform; and the partner service platform responds to the service using request of the terminal when the service identity token passes authentication. Safety authentication of a newly introduced partner service is realized under the condition that the existing service using process of an operator is unchanged.
Owner:CHINA TELECOM CORP LTD
Method and device for securely transmitting ETC broadcast messages
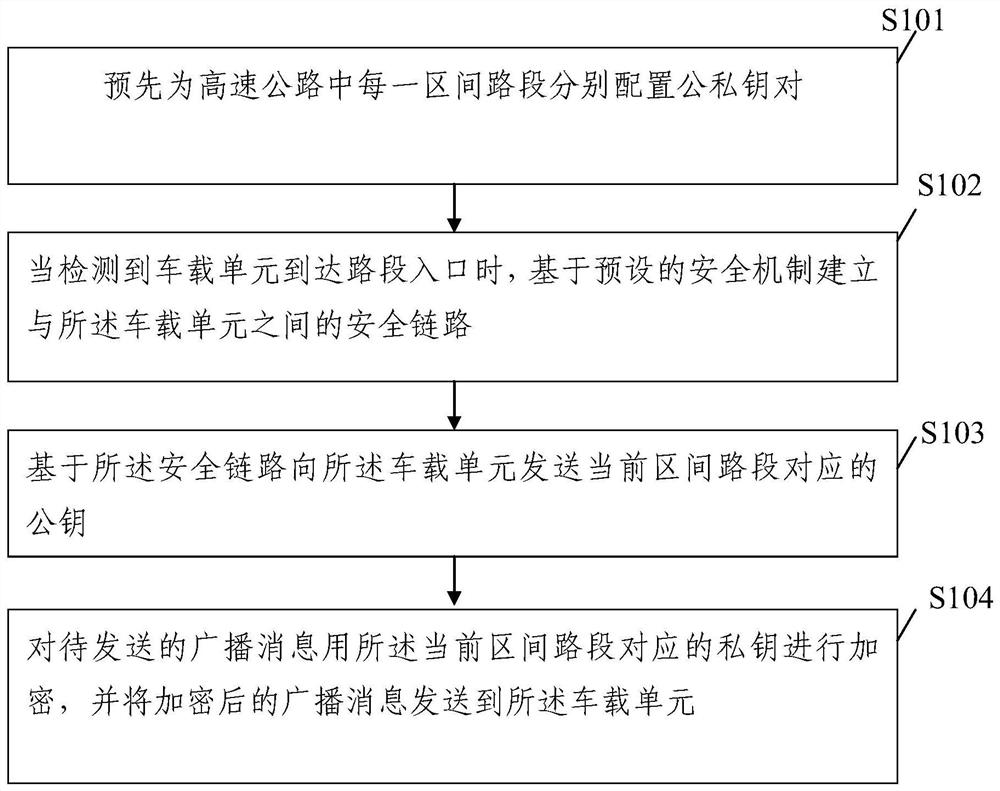
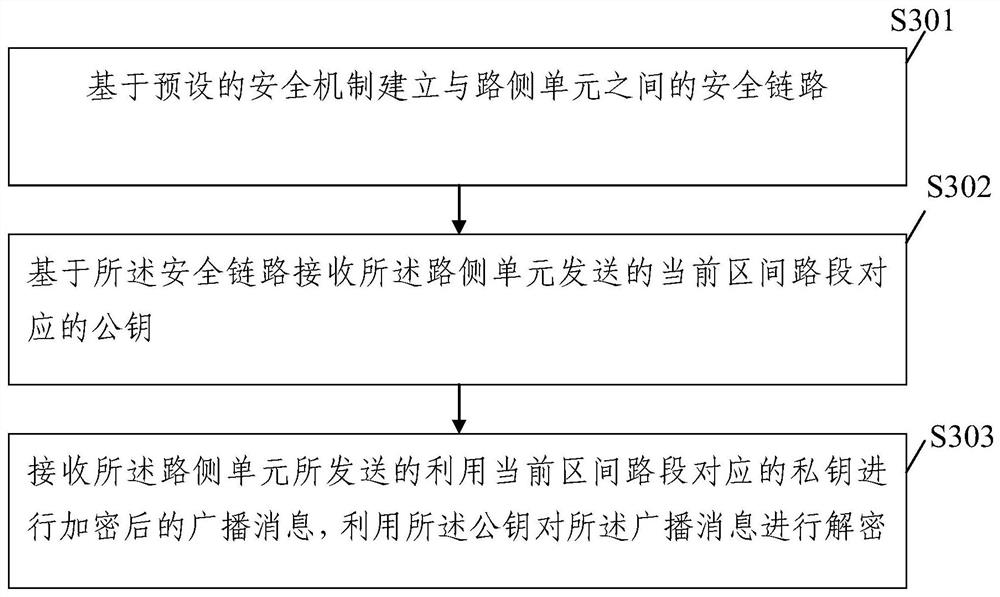
PendingCN111951420AAvoid broadcasting fake newsImprove securityTicket-issuing apparatusParticular environment based servicesIn vehicleTelecommunications
The invention discloses a method and device for securely transmitting ETC broadcast messages, and the method comprises the steps: configuring a public and private key pair for each section of a highway in advance; when it is detected that the vehicle-mounted unit arrives at the entrance of the road section, establishing a safety link with the vehicle-mounted unit based on a preset safety mechanism; sending a public key corresponding to the current section road section to the vehicle-mounted unit based on the safety link; and encrypting a to-be-sent broadcast message by using the private key corresponding to the current section road section, and sending the encrypted broadcast message to the vehicle-mounted unit. By adoption of the ETC broadcast message secure transmission method provided by the invention, the security authentication of the ETC broadcast message can be achieved, the situation that the fake road side unit broadcasts the fake message is effectively avoided, and the security of the ETC broadcast message is improved.
Owner:深圳成谷智能科技有限公司
Multi-dimensional hadoop authority control method and system
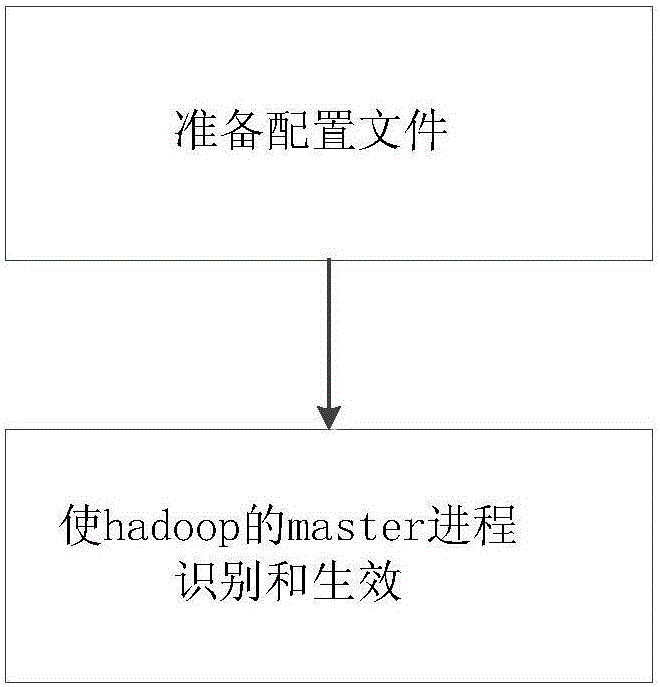
InactiveCN106250776AImplement configurationImplement security authenticationDigital data protectionControl systemWhitelist
The invention discloses a multi-dimensional hadoop authority control method. The method can be used for realizing the configuration of user groups, restricting the users to only access to hadoop clusters on fixed IPs and solving the problem that the default authorities are low in configuration flexibility, cannot control the counterfeit, carried out by the users, of super accounts and cannot restrict the users to access to the hadoop clusters from appointed IPs, so that the security certification of hadoop authorities is realized from multiple dimensions such as user, group and IP. The method comprises the following steps of: (1) preparing a configuration file, wherein the configuration file comprises an authority configuration file, an IP whitelist file and an IP blacklist file; and (2) recognizing and enforcing a master process of hadoop. The invention furthermore provides a multi-dimensional hadoop authority control system.
Owner:BEIJING GEO POLYMERIZATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com