User registration and user identification method and user registration and user identification system
A user and user name technology, applied in the field of network security, can solve the problems of increasing the service cost of manufacturers and increasing the consumption of server resources, and achieve the effect of ensuring reliability and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
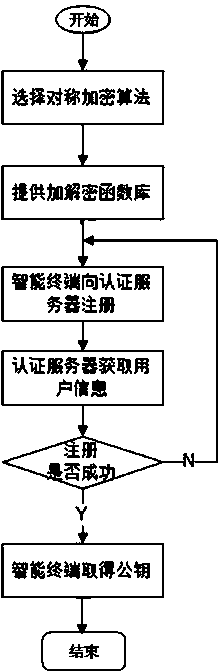
[0057] Such as figure 1 , a user registration method, the client and the server both contain the same symmetric encryption and decryption algorithm, and both parties follow the http communication protocol, including:
[0058] Step 1: the client uses the symmetric encryption and decryption algorithm to encrypt the username and password;
[0059] Step 2: The client transmits the encrypted user name and password to the server according to the http protocol;
[0060] Step 3: The server uses the symmetric encryption and decryption algorithm to decrypt the received user name and password; check whether the user name already exists in the database of the server, if not, the server uses an asymmetric encryption algorithm to generate a password for the user. A key pair of public key / private key, and the server uses the symmetric encryption and decryption algorithm to encrypt the returned registration success information and the public key, and at the same time, the server writes the u...
no. 2 example
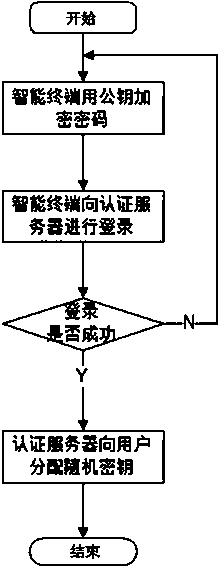
[0068] Such as figure 2 After the registration is completed, the user logs in to the server through the user name and login password. The specific process is as follows: First, both the client and the server contain the same symmetric encryption and decryption algorithm, including:
[0069] Step 1: The client uses the symmetric encryption and decryption algorithm to encrypt the user name and login password;
[0070] Step 2: The client transmits the encrypted user name and login password to the server according to the http protocol;
[0071] Step 3: The server uses the symmetric encryption and decryption algorithm to decrypt the received username and login password; then compare the decrypted login password with the login password corresponding to the username in the database of the server, if they are the same, the server Generate a random key and use the symmetric encryption and decryption algorithm to encrypt the login success information and the random key; if they are di...
no. 3 example
[0077] In this embodiment, steps 1 and 3 are improved on the basis of the second embodiment.
[0078] Step 1 further includes: the client first encrypts the login password with the public key obtained during registration, and then uses the symmetric encryption and decryption algorithm to encrypt the login password encrypted by the user name and the public key;
[0079] Correspondingly, step 3 further includes: using the symmetric encryption and decryption algorithm to decrypt the received information to obtain the ciphertext of the user name and login password; and then decrypting the ciphertext using the private key corresponding to the user name in the database , to obtain the user’s login password, compare the decrypted login password with the login password stored corresponding to the user name in the server’s database, if they are the same, it means that the user’s login is successful, the server generates a random key and uses the The symmetric encryption and decryption ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com