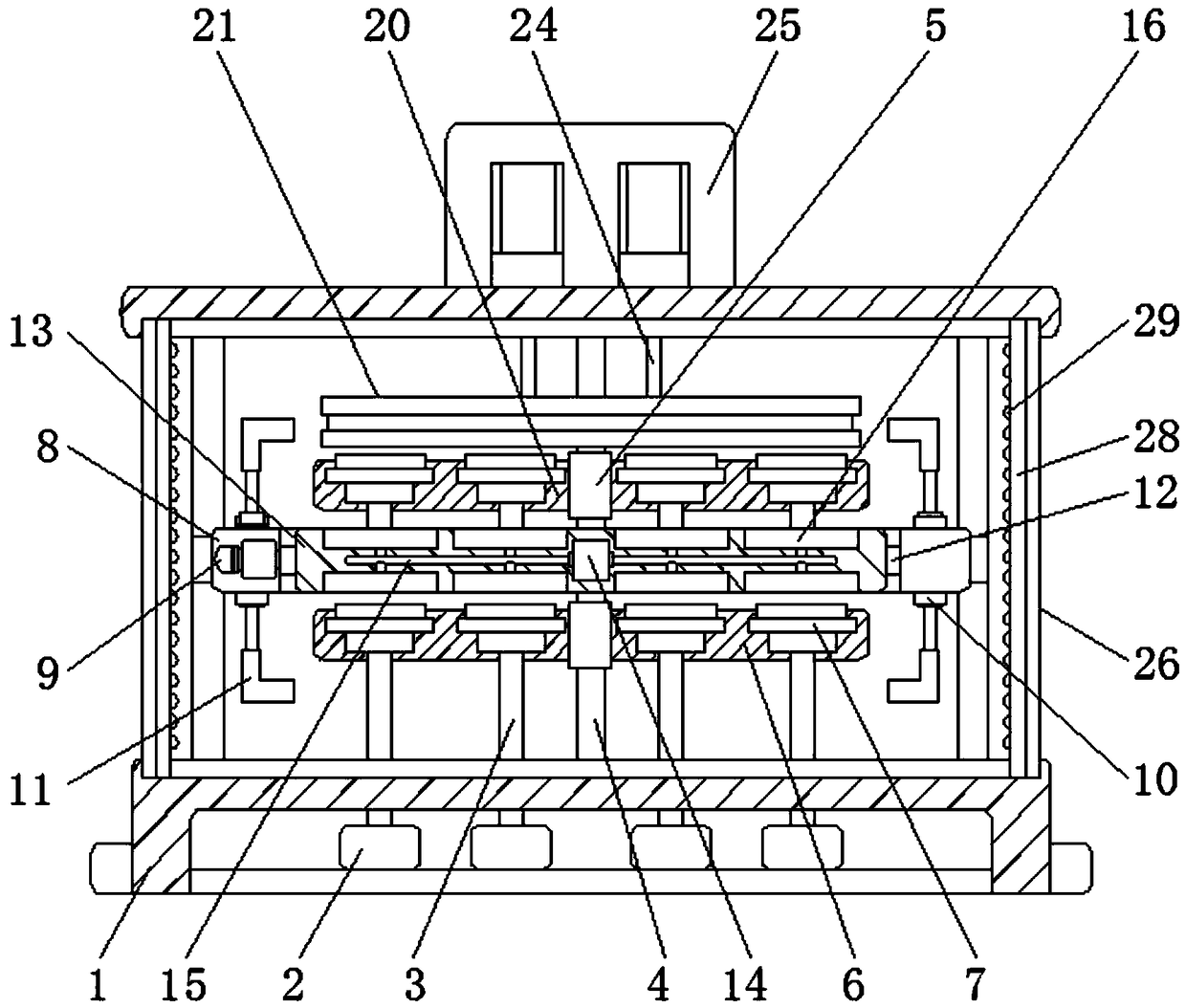
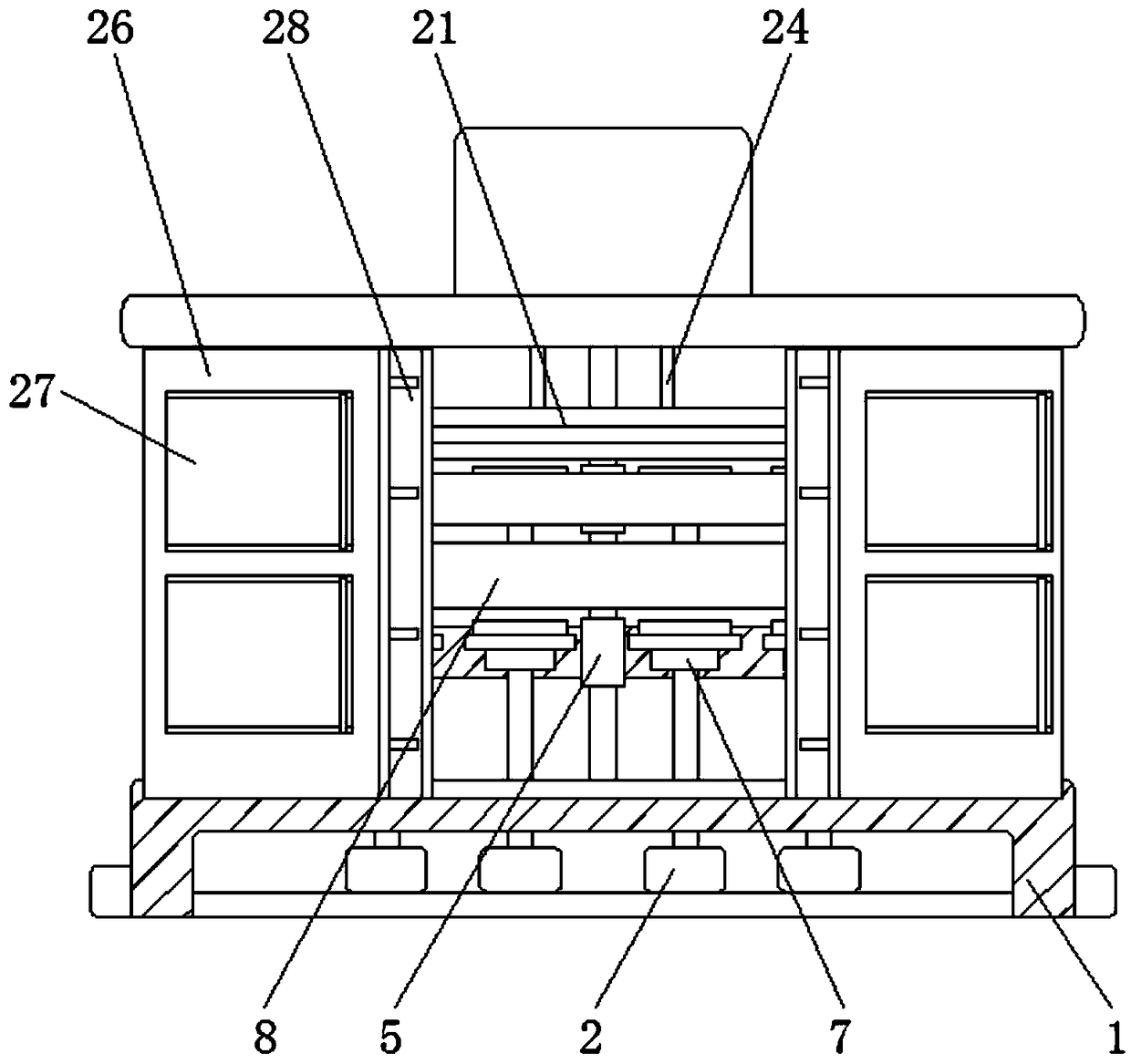
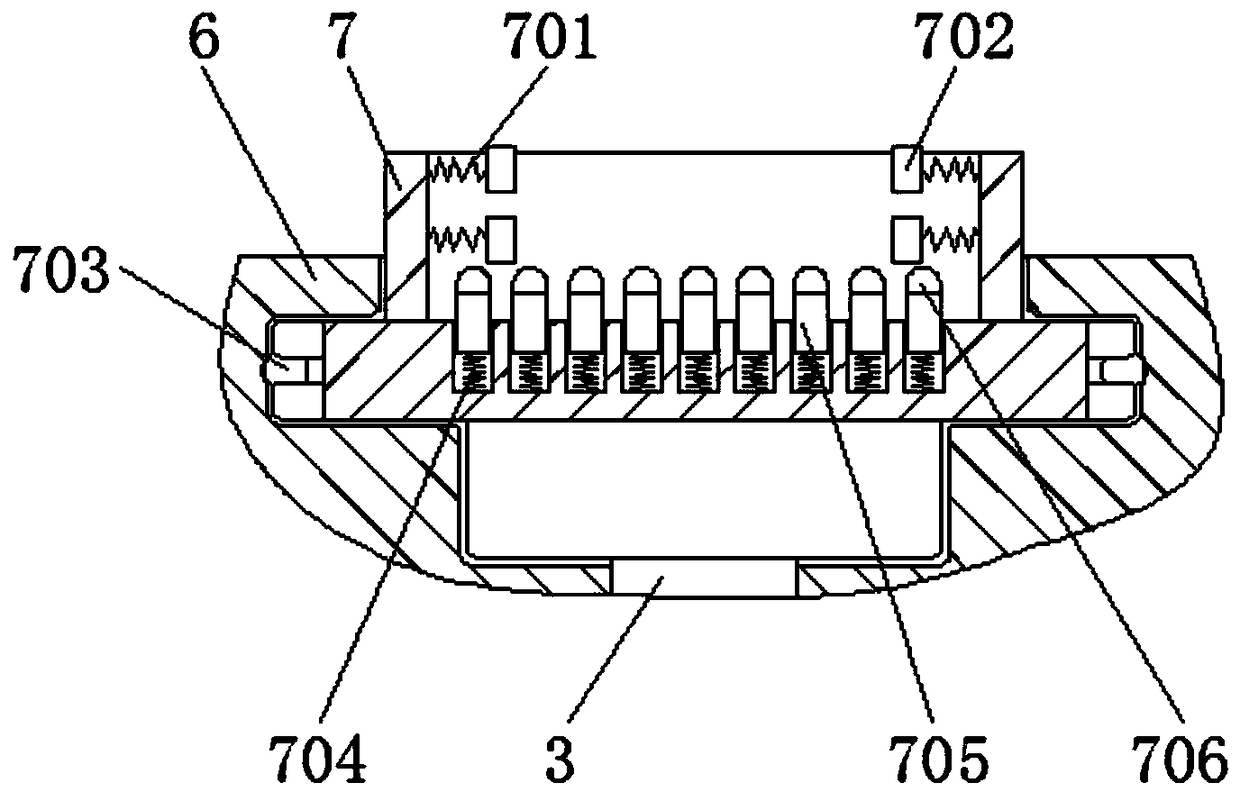
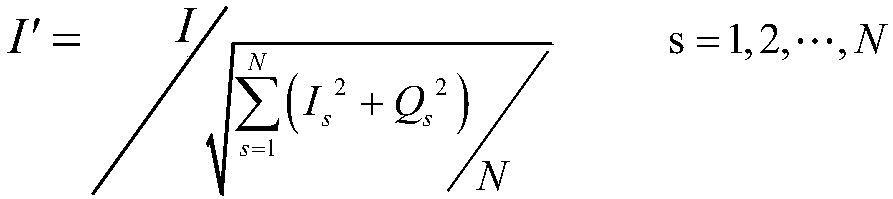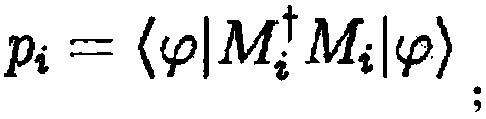Patents
Literature
163results about How to "Security threat" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
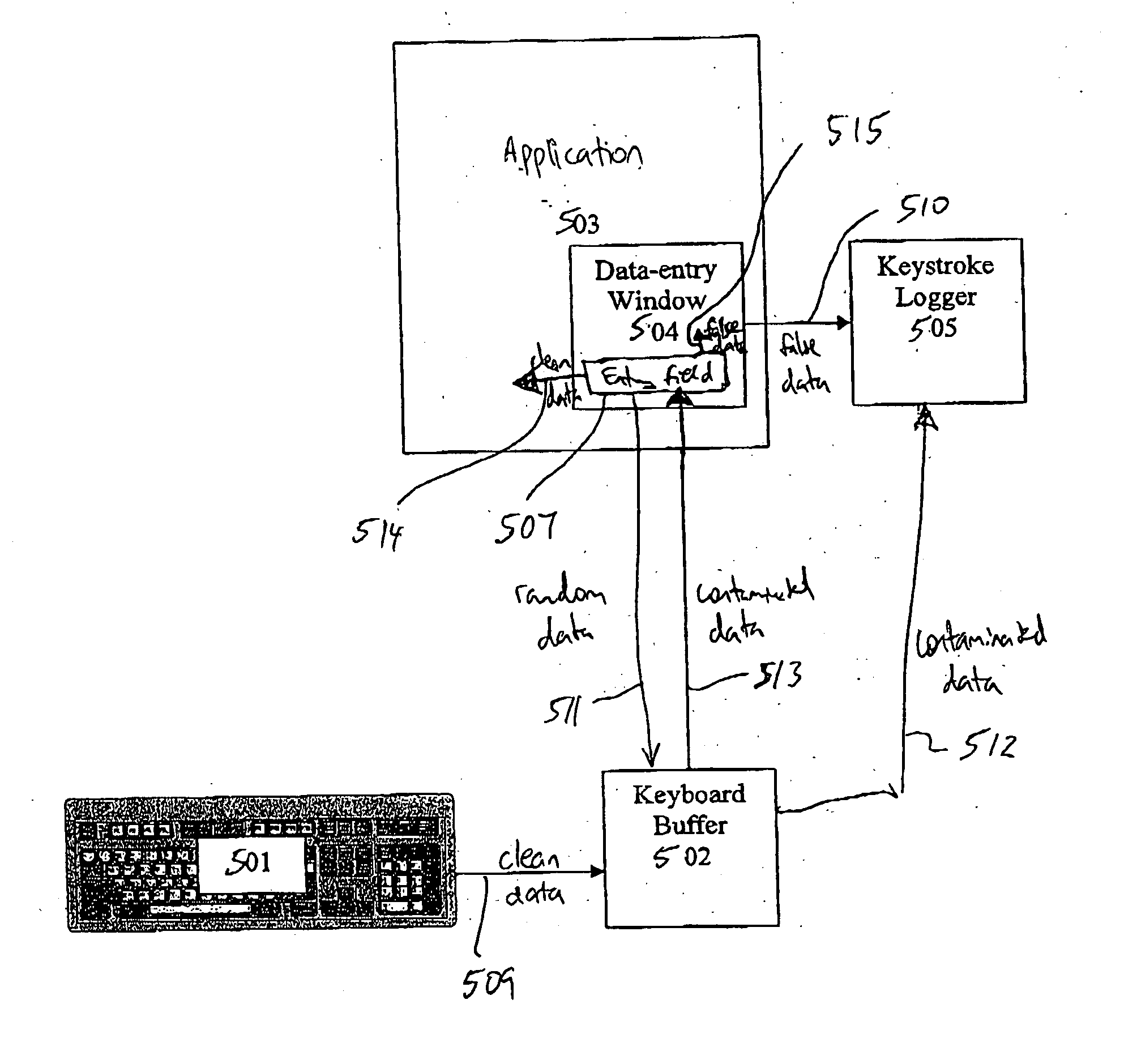
System for preventing keystroke logging software from accessing or identifying keystrokes
ActiveUS20060101128A1Invade privacySecurity threatMemory loss protectionDigital data processing detailsOperational systemUser input
A computer program is adapted for securing user entry data against keyboard login attempts. The program masks user input data, either insulating the data from vulnerable parts of the operating system or application, or contaminating user data that is supplied to those vulnerable parts of the operating system or application. The program securely stores data, either intercepted prior to reaching the vulnerable parts of the operating system or extracted from the contaminated data, and securely provides the data directly to a verified application.
Owner:SENTRYBAY
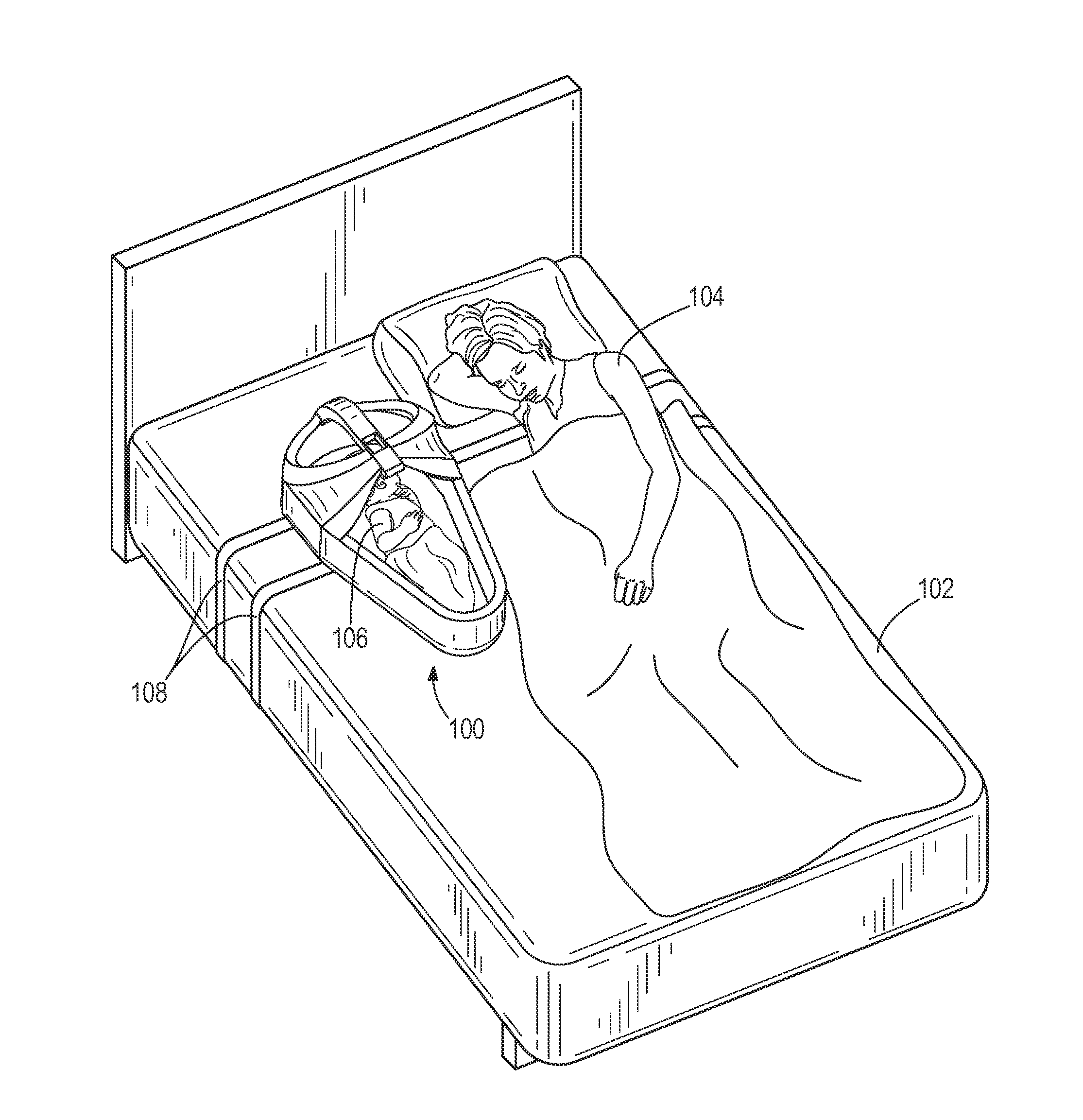
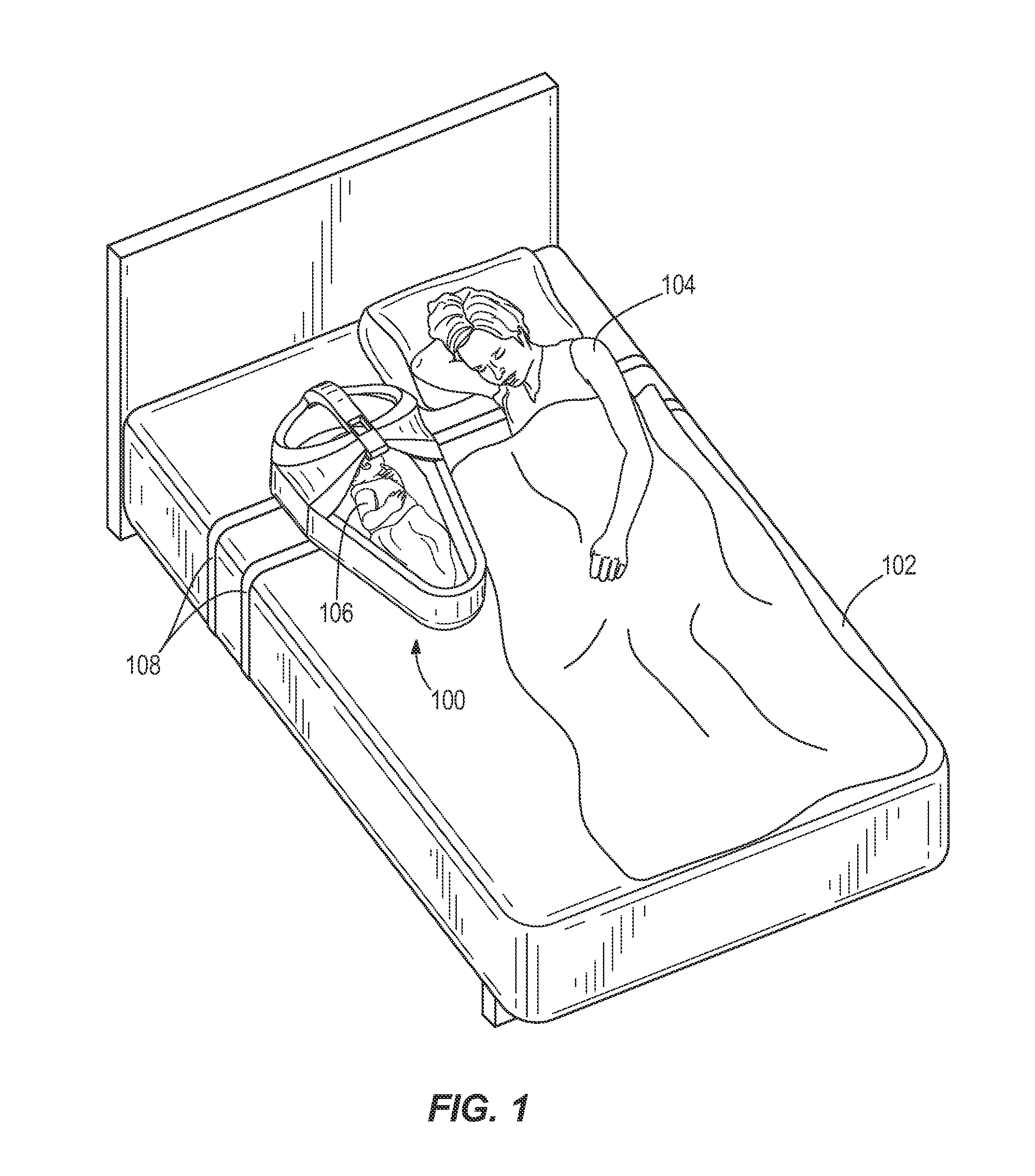
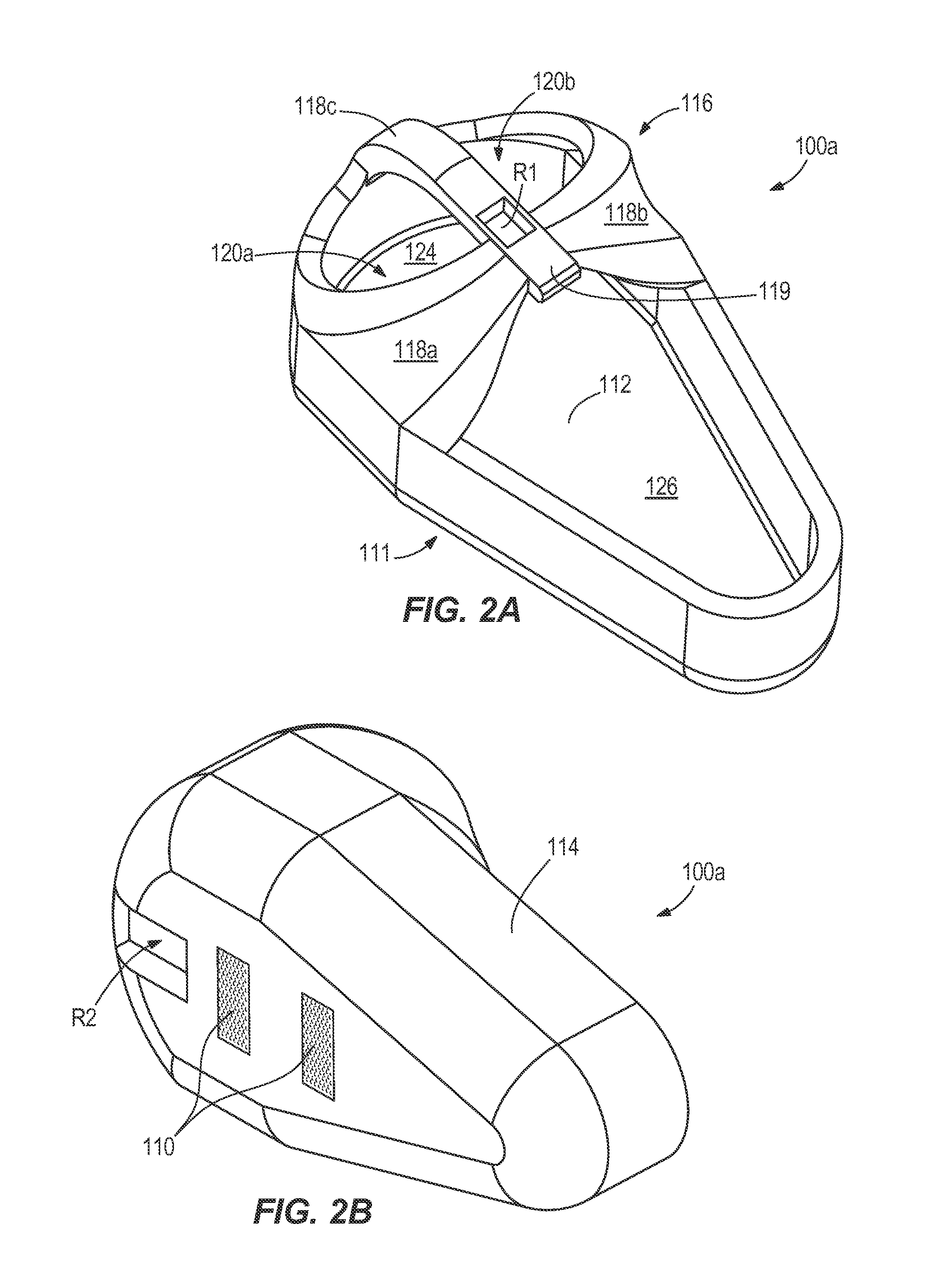
Infant sleep pod
An infant sleep pod providing passive and / or active safety features. The infant sleep pod provides a safe sleeping environment for infants sharing sleep areas with adults. The infant sleep pod provides a firm, flat, separate, portable, and dedicated sleep space for an infant. The infant sleep pod includes a base with a bed and sidewall, and a bridge extending across the bed. The bridge covers a head portion of the bed, while a foot portion of the bed is left open for inserting and removing the infant. The bridge prevents pillows and blankets from covering the bed and infant. The infant sleep pod also includes electronics for monitoring the sleep pod. The electronics include a sensor unit in the bridge and a control unit in communication with the sensor unit. The control unit and sensor unit are operable to detect unsafe conditions and, in response, generate alerts.
Owner:UMW RES FOUND INC
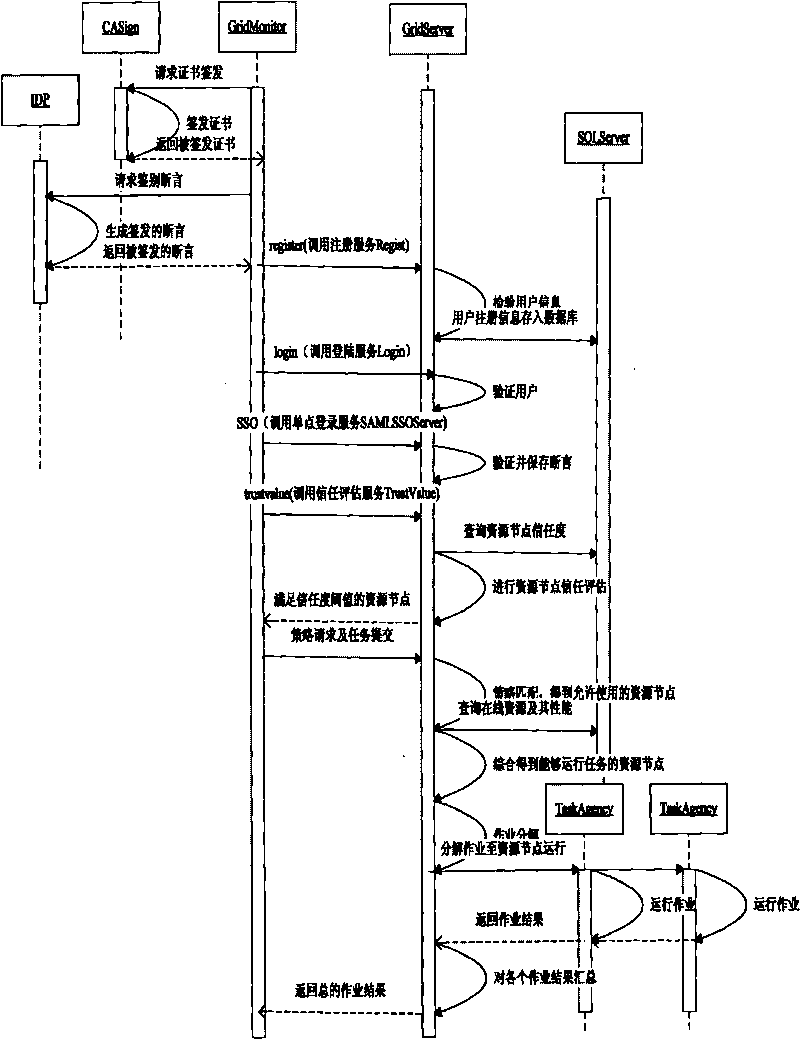
Single sign on based grid authentication trust model
InactiveCN101707594ASolve authentication problemsTo achieve the purpose of access controlUser identity/authority verificationGrid resourcesVirtual organisation
A single sign on (SSO) based grid authentication trust model is a solution for objective authentication of trusted entities under open grid environment and is mainly used for solving the following problem: how users carry out identity authentication and can launch grid application after passing primary authentication. When continuously using the grid resources, users can access various legal resources in the computational grid after passing the identity authentication without repeated authentication. Under the grid computing environment, the invention solves the problems of collaboration between the grid users and the grid entities in the virtual organization and the entities in other virtual organizations, and security and dynamics of the shared resources, and constructs the security architecture for authorizing the users under the grid computing environment.
Owner:NANJING UNIV OF POSTS & TELECOMM
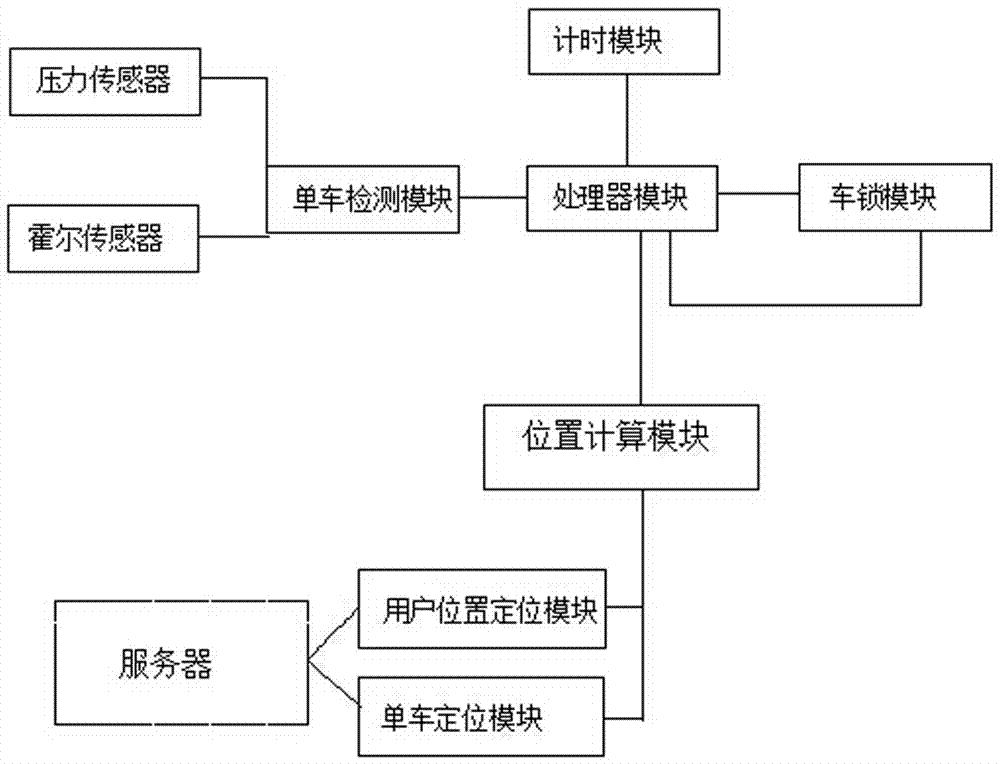
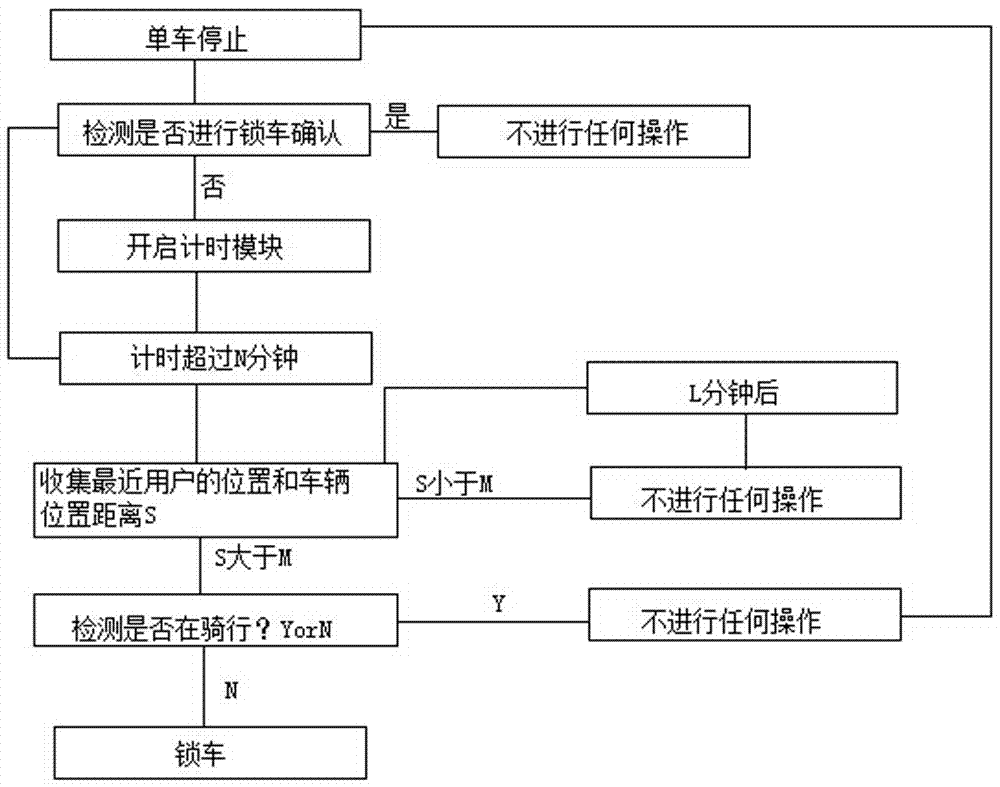
Automatic locking system and locking method for shared bicycle
PendingCN106926815ASecurity threatAnti-theft devicesIndividual entry/exit registersComputer hardwareEmbedded system
The invention discloses an automatic locking system and locking method for a shared bicycle, belongs to the field of shared bicycles and aims at safely solving the problem that a user forgets to lock the bicycle. The automatic locking system comprises a bicycle lock module, a processor module and a timing module, wherein the bicycle lock module is used for controlling opening and closing of a bicycle lock and detecting the state of the bicycle lock; the processor module is capable of obtaining state information of the bicycle lock and controlling opening and closing of the bicycle lock; the processor module is connected with the bicycle lock module; the timing module is used for timing the state information of the bicycle and transmitting the timing result to the processor module; and the timing module is connected with the processor module.
Owner:CHENGDU WENGWENG TECH CO LTD
Method for root authority management and control in Android platform
ActiveCN105045625AImprove convenienceEnsure safetyPlatform integrity maintainanceProgram loading/initiatingSoftware engineeringInit
The present invention provides a method for root authortity management and control in an Android platform. The management and control method comprises: establishing and storing a rootagent executable file that is added with a package name of an application program allowed to be granted a root authority; an Android init process enabling a rootagent service corresponding to the rootagent executable file by reading a configuration file; before the application program applies for the root authority, judging whether a rootagent service process is running or not first; and the rootagent service process matching a process ID of the application program that submits an application with a process ID corresponding to the package name of the application program allowed to be granted the root authority in the rootagent service process, and if the matching is successful, then granting the application program, that submits the application, the root authority, or otherwise, rejecting. By using the method, the fact that only individual application is subjected to root authorization can be accurately limited, and at the same time, opening and closing operations of the root authority can be performed conveniently and quickly by setting system attributes.
Owner:湖州帷幄知识产权运营有限公司
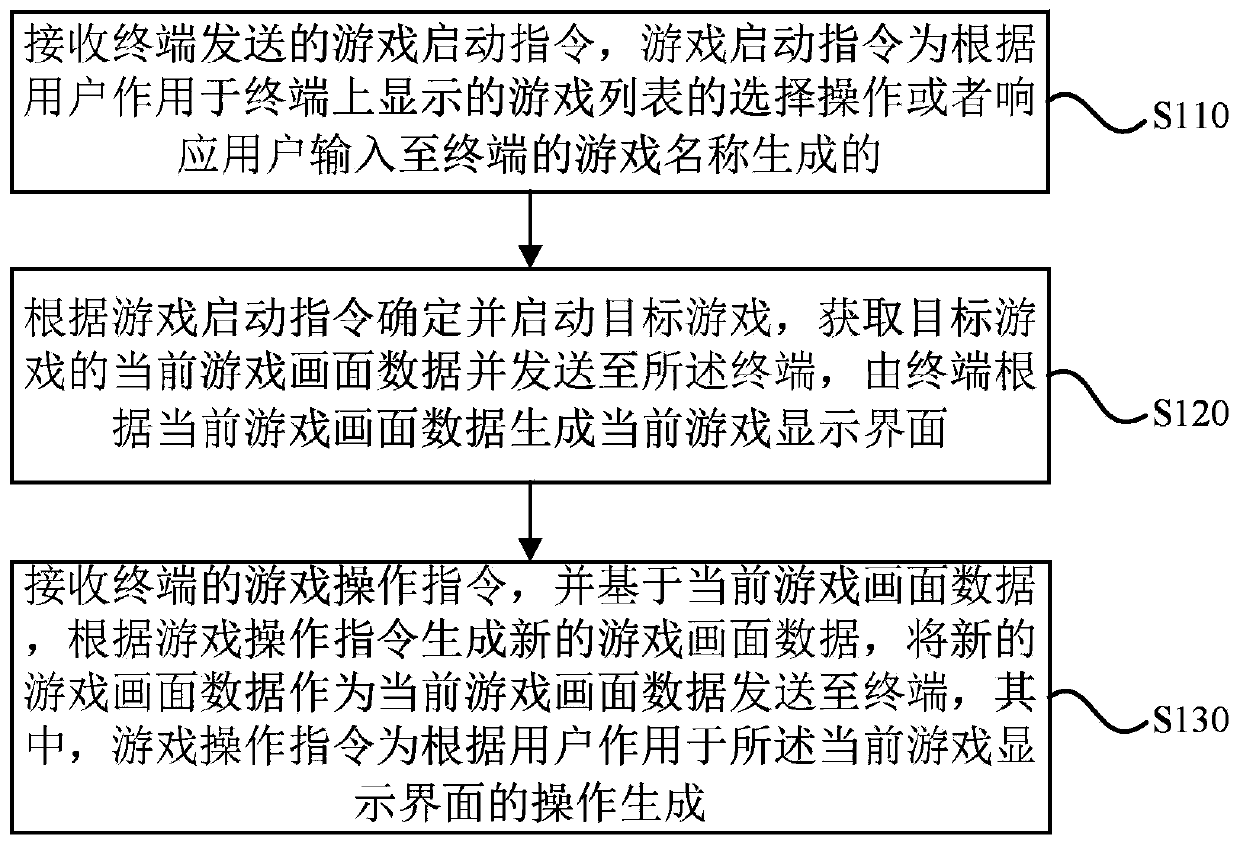
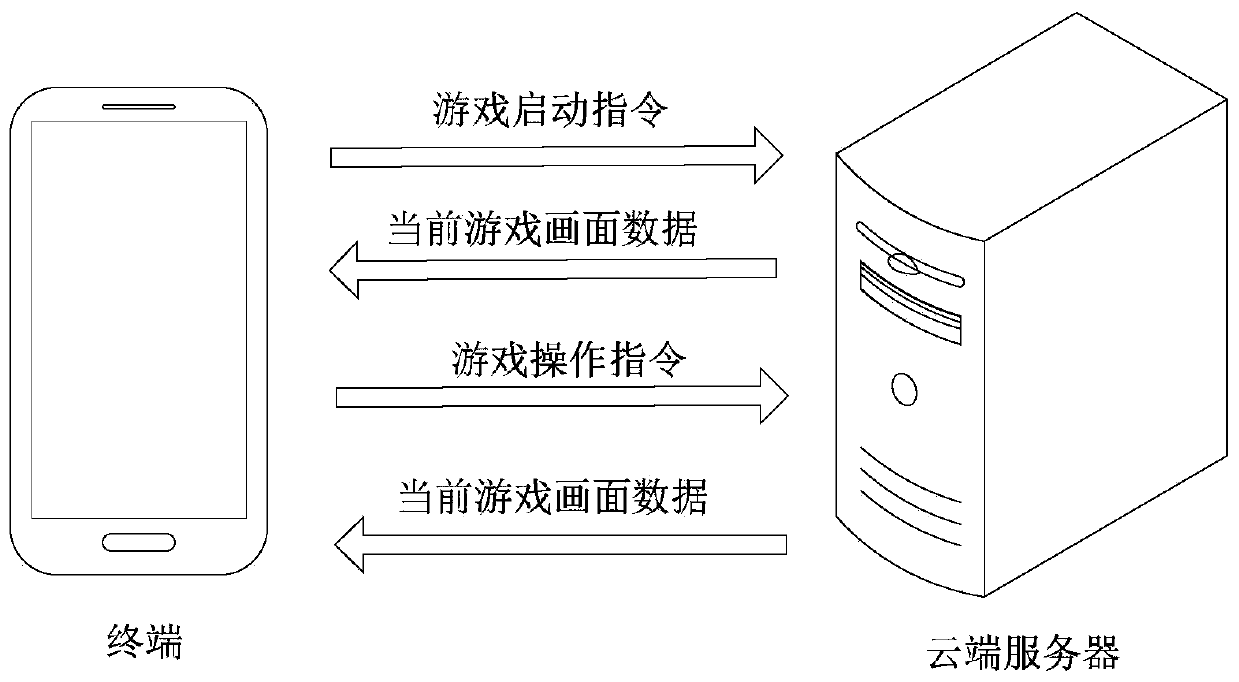
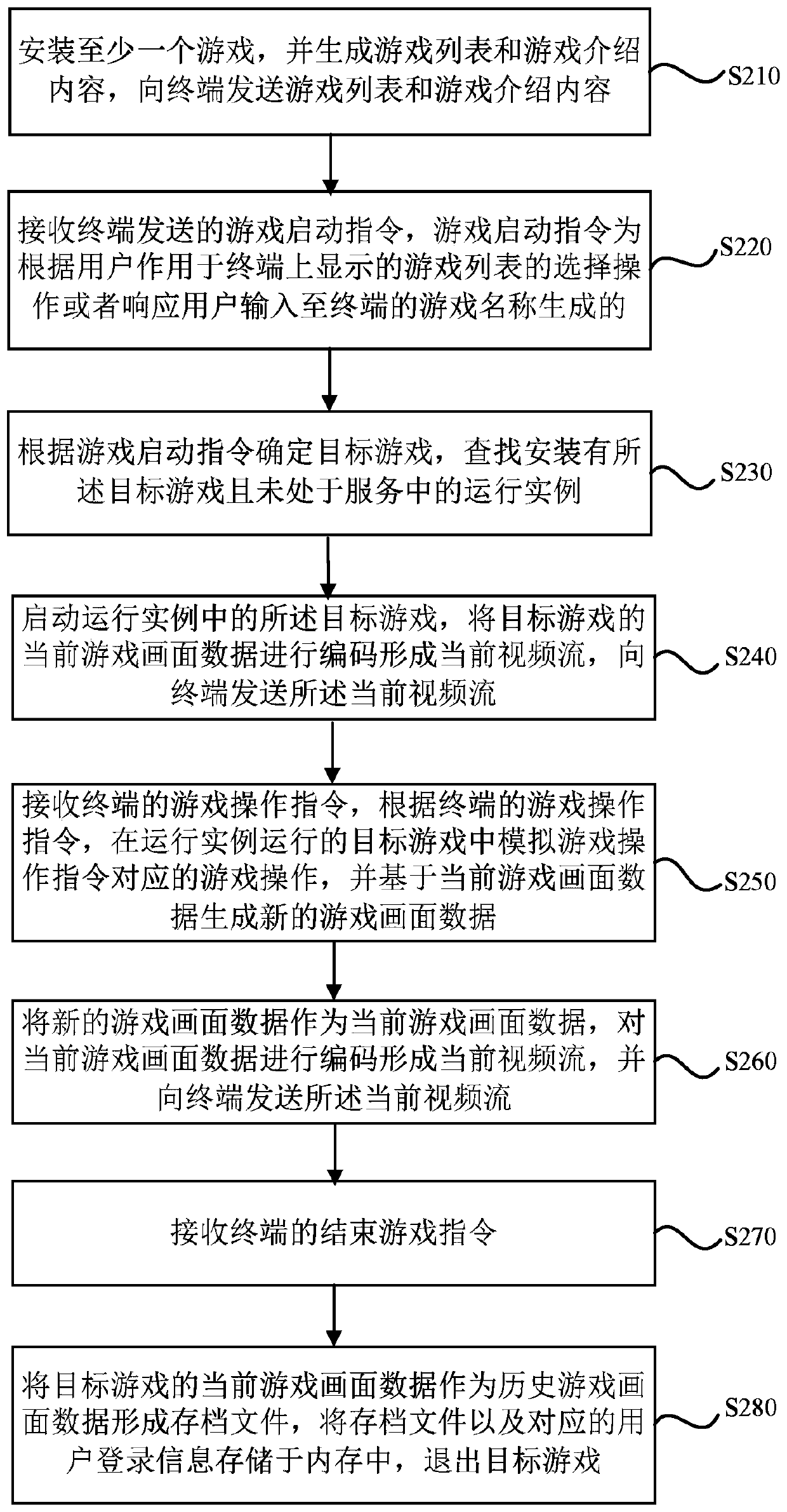
Cloud game realizing method and device, cloud server, terminal and medium
PendingCN110368686AReduce configuration requirementsSecurity threatVideo gamesTransmissionMultimedia
The embodiment of the invention discloses a cloud game realizing method and device, a cloud server, a terminal and a medium. The method is executed by the cloud server. The method comprises the stepsof receiving a game start instructionsent by a terminal; confirming and starting a target game according to the game start instruction; acquiring current game image data of the target game and sendingthe data to the terminal; generating a current game display interface by the terminal according to the current game image data; receiving the game operation instruction of the terminal; based on thecurrent game image data, generating new game image data according to the game operation instruction; and sending the new game image data as the current game image data to the terminal. By the adoptionof the method provided by the scheme, the user can play a variety of games without loading or installing the game application in the terminal; the terminal configuration required by the game operation is reduced; the safety of the terminal is not threatened by the advertising Trojan and so on carried in the installation file; and thus, the safety of the terminal is improved.
Owner:SHANGHAI WINGTECH INFORMATION TECH CO LTD
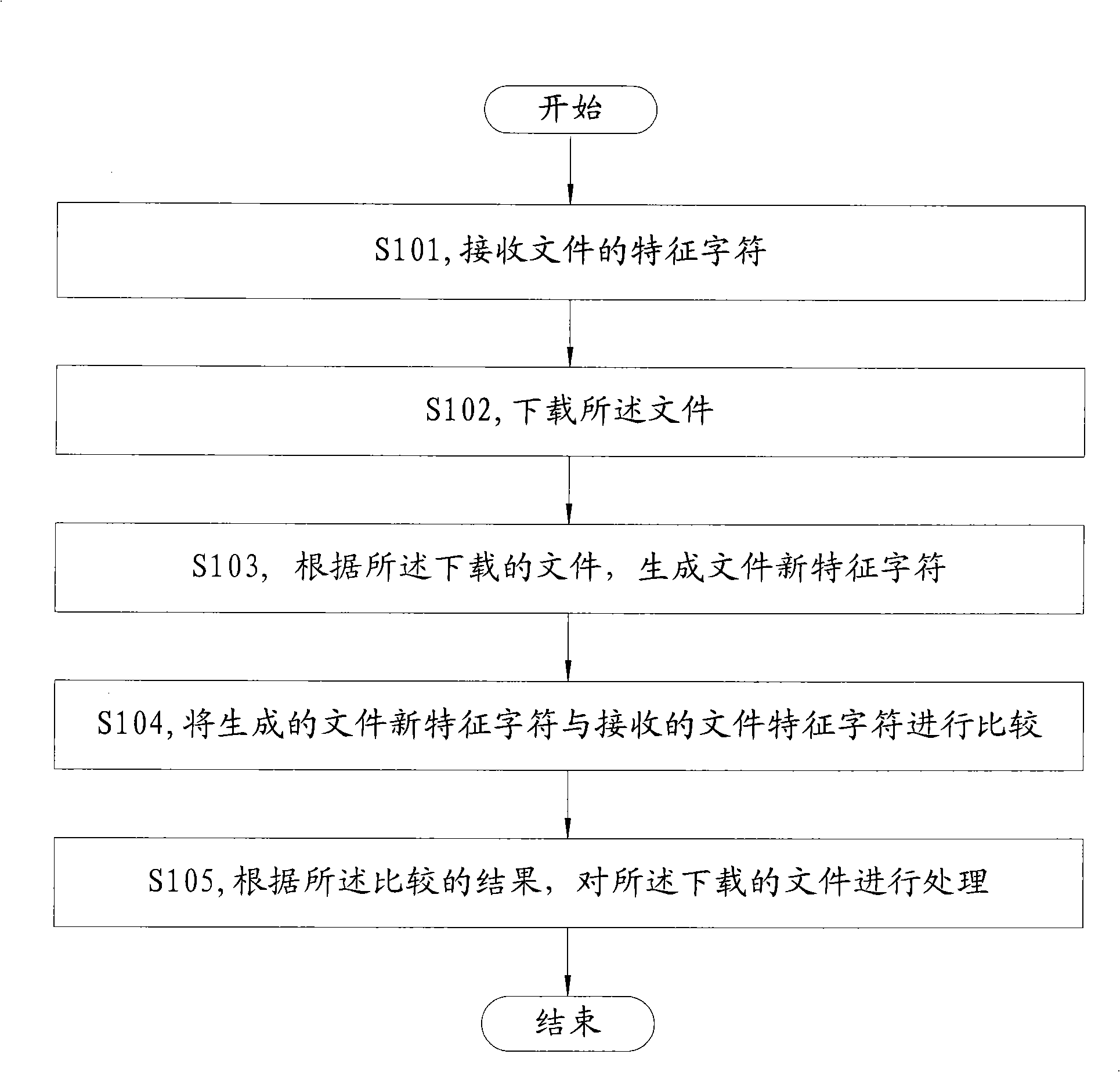
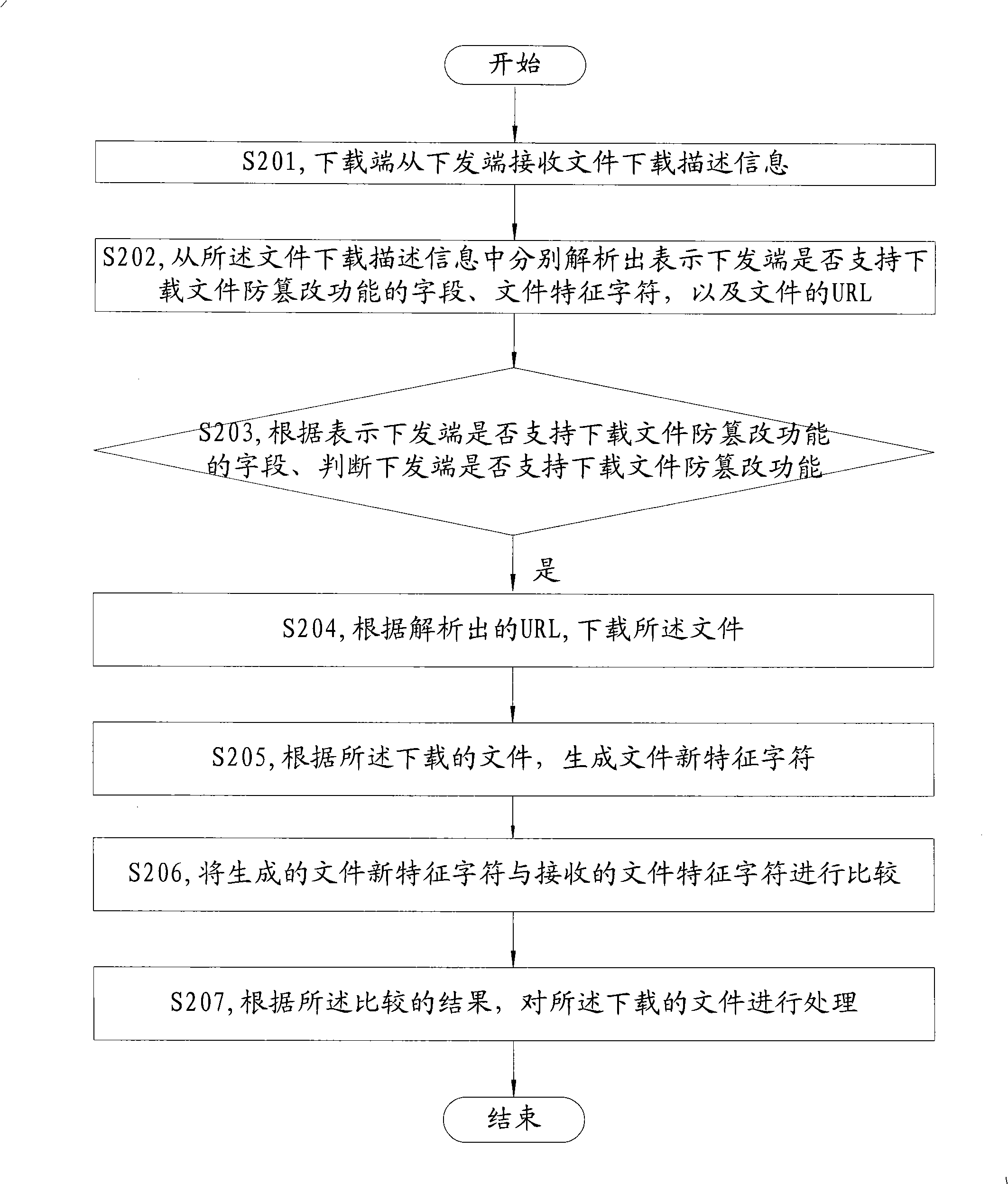
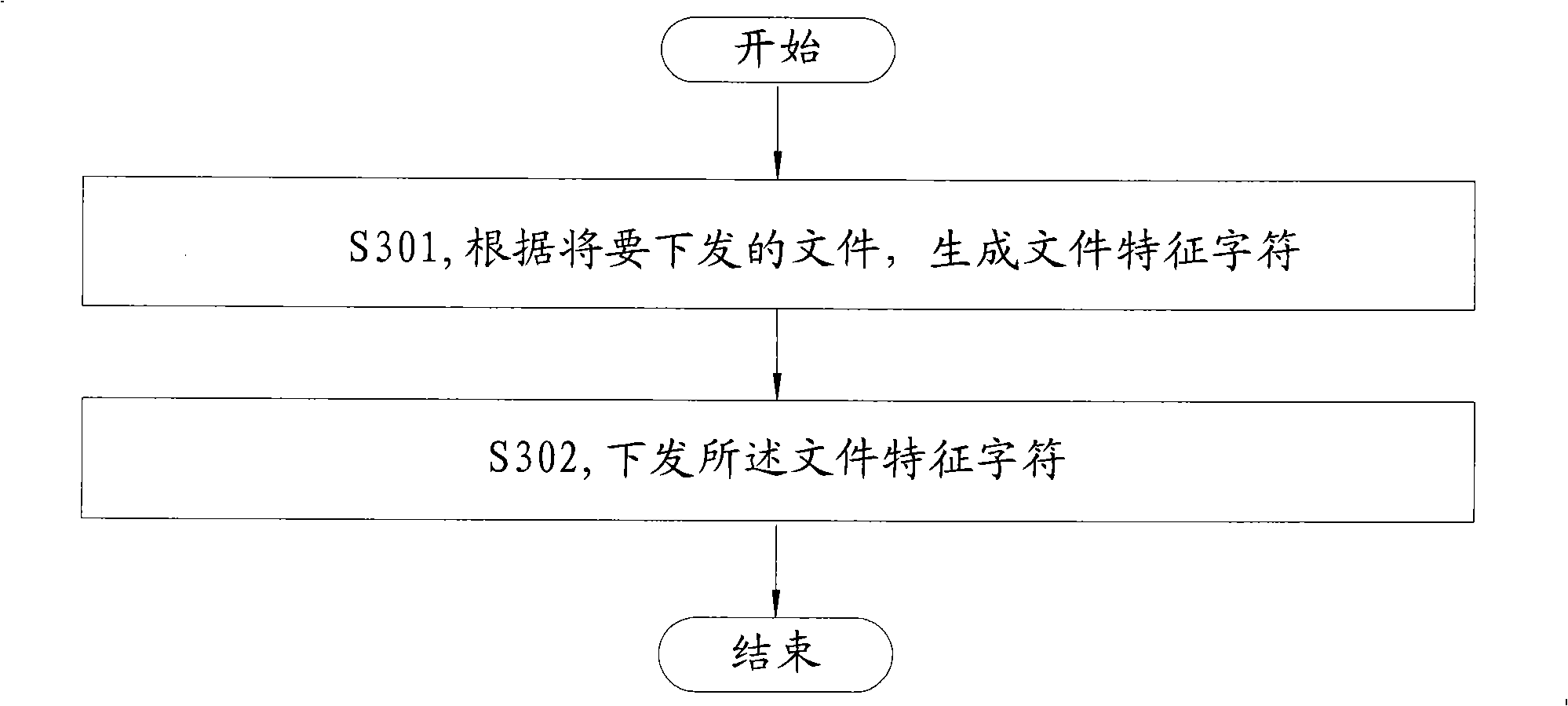
Method and apparatus for processing download and dispatching file as well as transmission file system
InactiveCN101330524AImprove securitySecurity threatComputer security arrangementsTransmissionFile systemComputer science
The embodiment of the invention discloses a processing method for downloading a file and a device thereof, a processing method for assigning a file and a device thereof, and a system for transmitting a file, and belongs to the communication field. The processing method for downloading the file comprises the steps of receiving the feature characters of the file; downloading the file; generating the new feature characters of the file according to the downloaded file; comparing the generated new feature characters of the file and the received feature characters of the file; and performing processing to the downloaded file according to compared results. The embodiment of the invention can be suitable for the processing procedures during the file downloading process, and improve the security of users.
Owner:HUAWEI TECH CO LTD
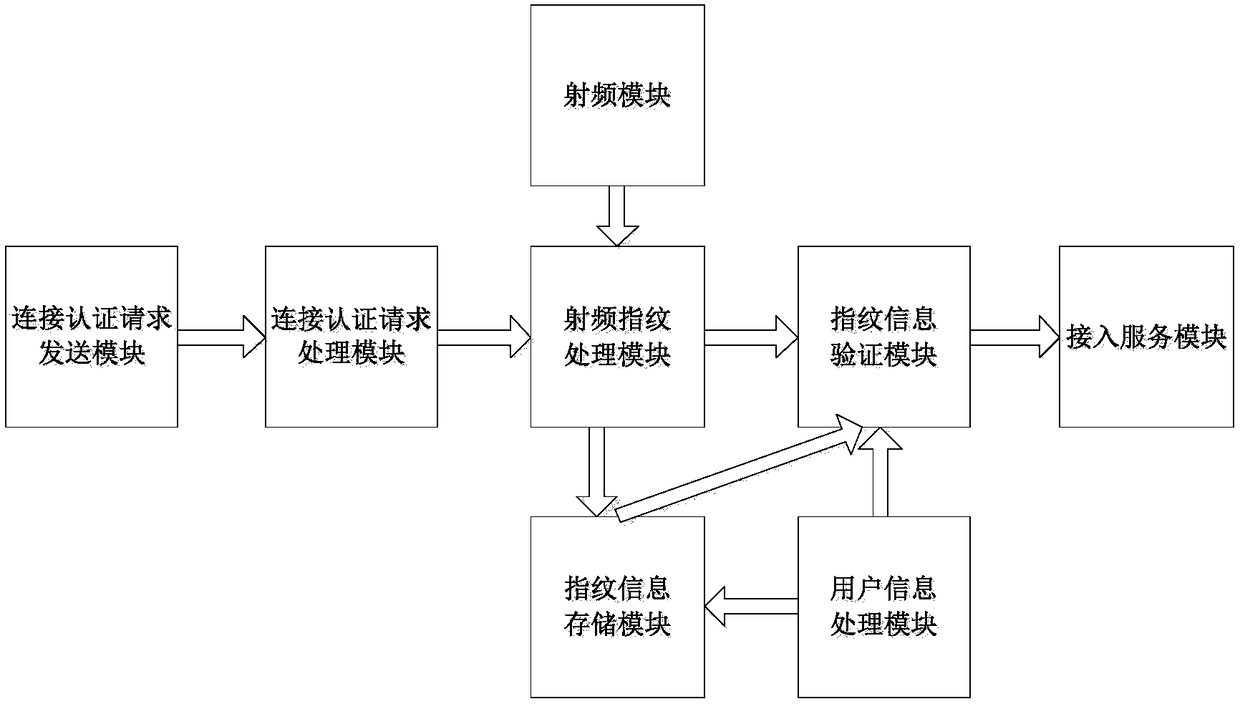
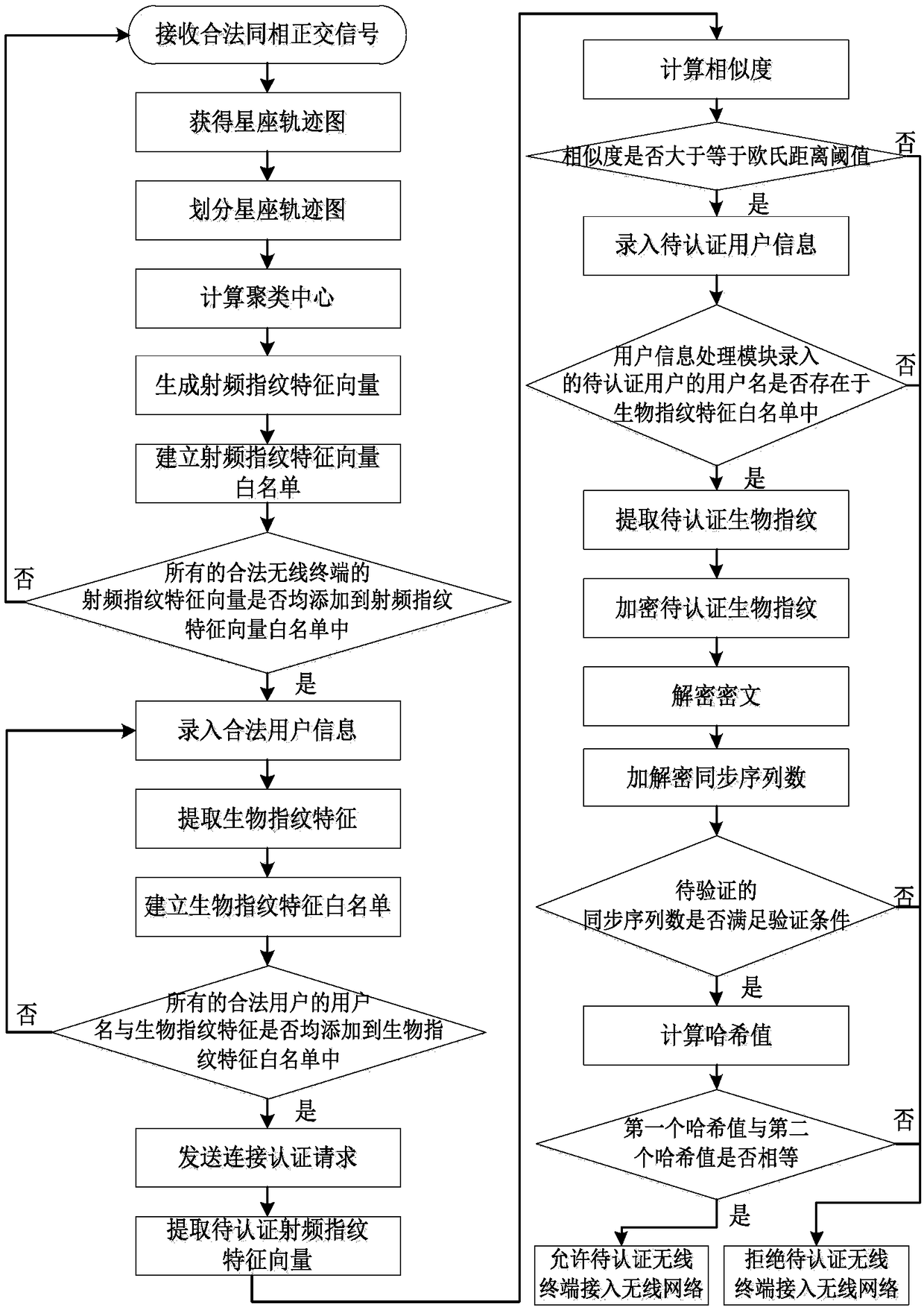
Wireless network access authentication system and method based on radio frequency fingerprint and biological fingerprint
ActiveCN108173871AAchieve authenticationImprove securityTransmissionAuthentication systemRadio frequency
The invention discloses a wireless network access authentication system and a wireless network access authentication method based on a radio frequency fingerprint and a biological fingerprint. The system provided by the invention comprises a radio frequency module, a radio frequency fingerprint processing module, a fingerprint information storage module, a user information processing module, a fingerprint information authentication module, a connection authentication request sending module, a connection authentication request processing module and an access service module. According to the method provided by the invention, the radio frequency fingerprint of a wireless terminal used by a user for applying for accessing a wireless network is authenticated, after the radio frequency fingerprint is authentication, the biological fingerprint of the user using the wireless terminal to access the wireless network is authentication, and after the biological fingerprint of the user is authenticated, the user is allowed to use the wireless terminal to access the wireless network. According to the system and the method provided by the invention, the secure access to the wireless network is achieved through authenticating the wireless terminal and the user applying for using the network.
Owner:XIDIAN UNIV
Robot for preventing senile dementia mainly based on mental stimulation
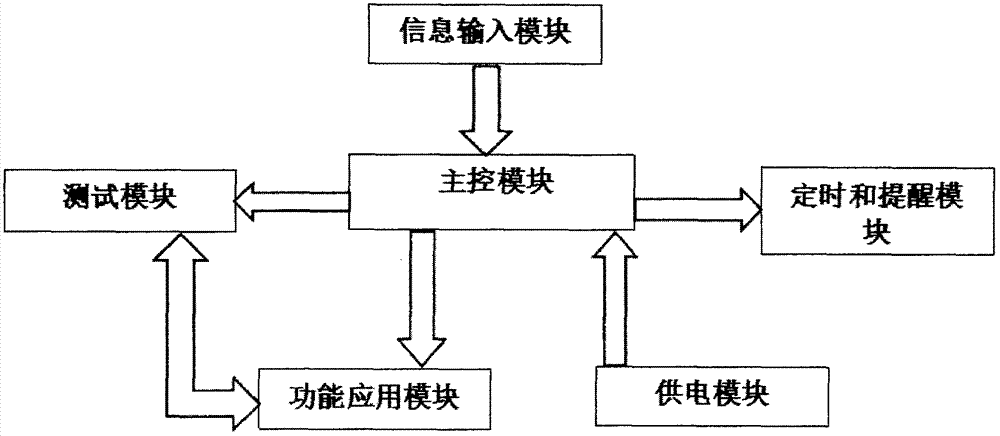
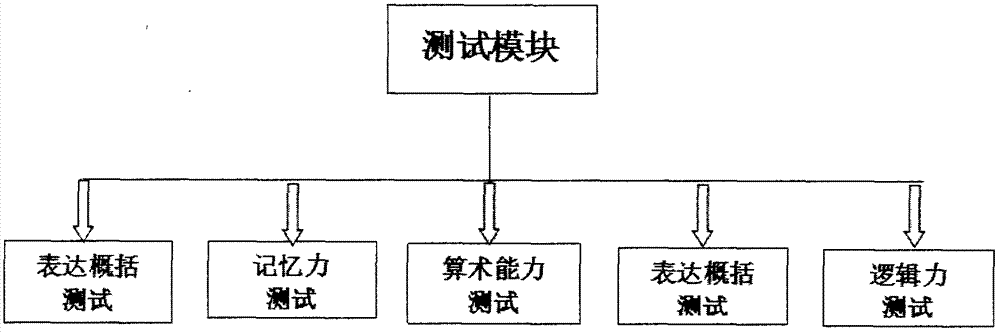
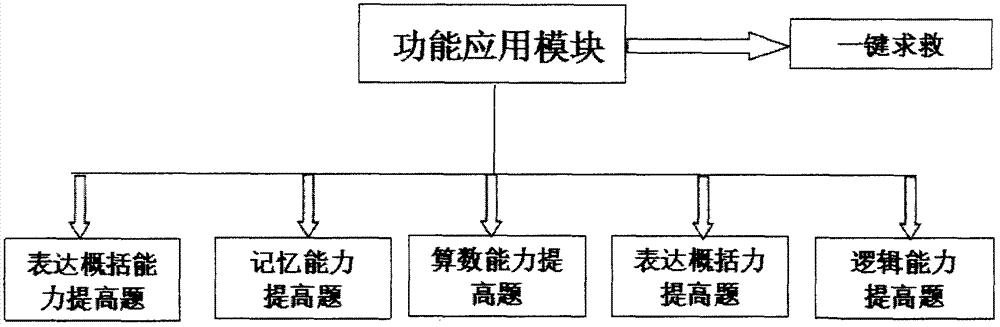
InactiveCN107186722AImprove computing powerImprove generalizationManipulatorMental functionsOlder people
The invention relates to the field of robots, and discloses a robot for preventing senile dementia mainly based on mental stimulation. The robot mainly comprises an information input module, a testing module, a main control module, a function application module, a timing and reminding module, an interaction module, and a shape designing and moving module. The information input module is mainly used for inputting basic information of old people; the testing module tests mental functions of the old people; the main control module can store information and process the information; the function application module can realize various manners of the mental stimulation; the timing and reminding module can finish functions of medicine taking, exercising and position reminding; the interaction module can realize function interaction with the old people; and for the shape designing and moving module, a tumbler base and idler wheels capable of realizing differential steering ensure safety and movability. A power supply module provides energy required by the system, and the robot realizes the function of preventing the senile dementia from the metal stimulation.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Pressure control valve for controlling opening degree of valve core through utilization of sensing element and refrigeration system
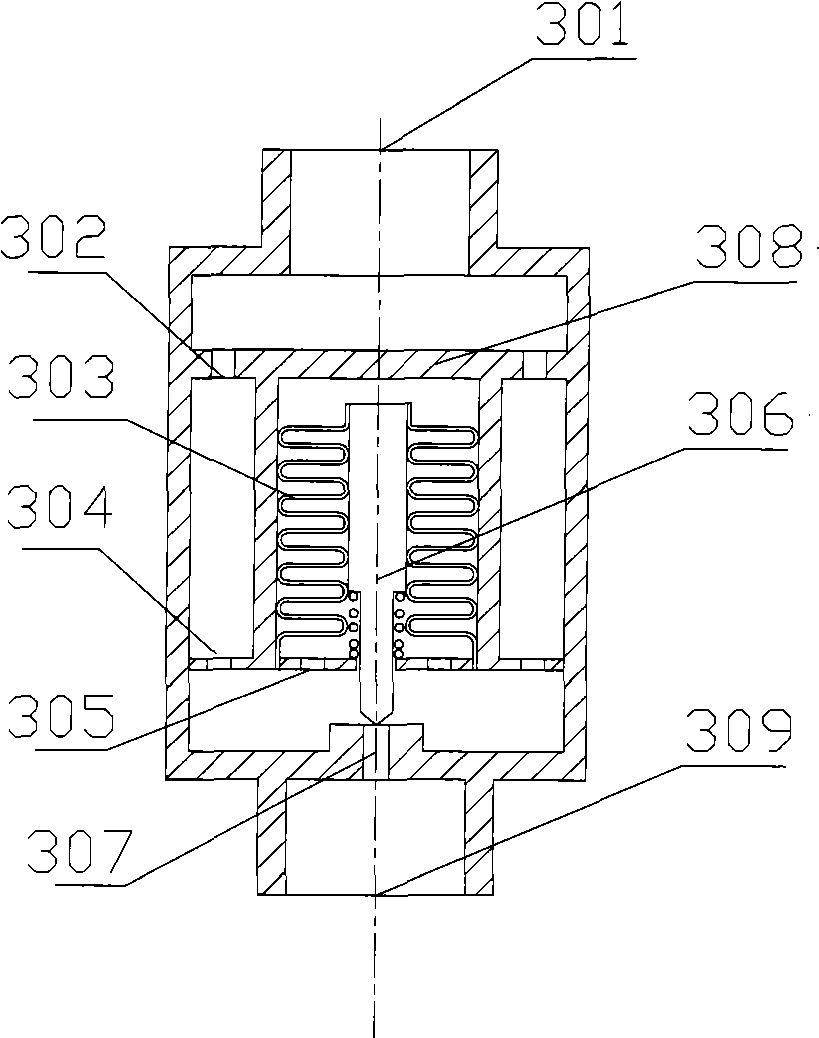
ActiveCN101545555AHigh compressive strengthEasy to manufactureCompression machines with non-reversible cycleEqualizing valvesVapor–liquid separatorEngineering
The invention relates to a pressure control valve for controlling the opening degree of a valve core through utilization of a sensing element and a refrigeration system. The pressure control valve comprises a valve body, a Bourdon tube and a conversion part; the conversion part comprises a connecting bar transmission mechanism, a gear transmission mechanism and a thread transmission mechanism; the Bourdon tube and the conversion part convert the pressure change into the corresponding motion of the valve core so as to realize the control of the opening degree of a valve port; the valve body and a cover body form a cavity for sealing the Bourdon tube and the conversion part so as to enhance the safety of the control valve; and a damping hole between an inner cavity of the Bourdon tube and an inlet of the valve body ensures the stability of the operation of the control valve. The disclosed refrigeration system comprises a compressor, a gas cooler, an inner heat exchanger, an evaporator, a gas-liquid separator and the disclosed pressure control valve. The provided pressure control valve is suitable for controlling the pressure of a high-pressure refrigeration working substance, in particular the pressure of the refrigeration working substance in a supercritical carbon dioxide refrigerating circulation system.
Owner:ZHEJIANG SANHUA AUTOMOTIVE COMPONENTS CO LTD
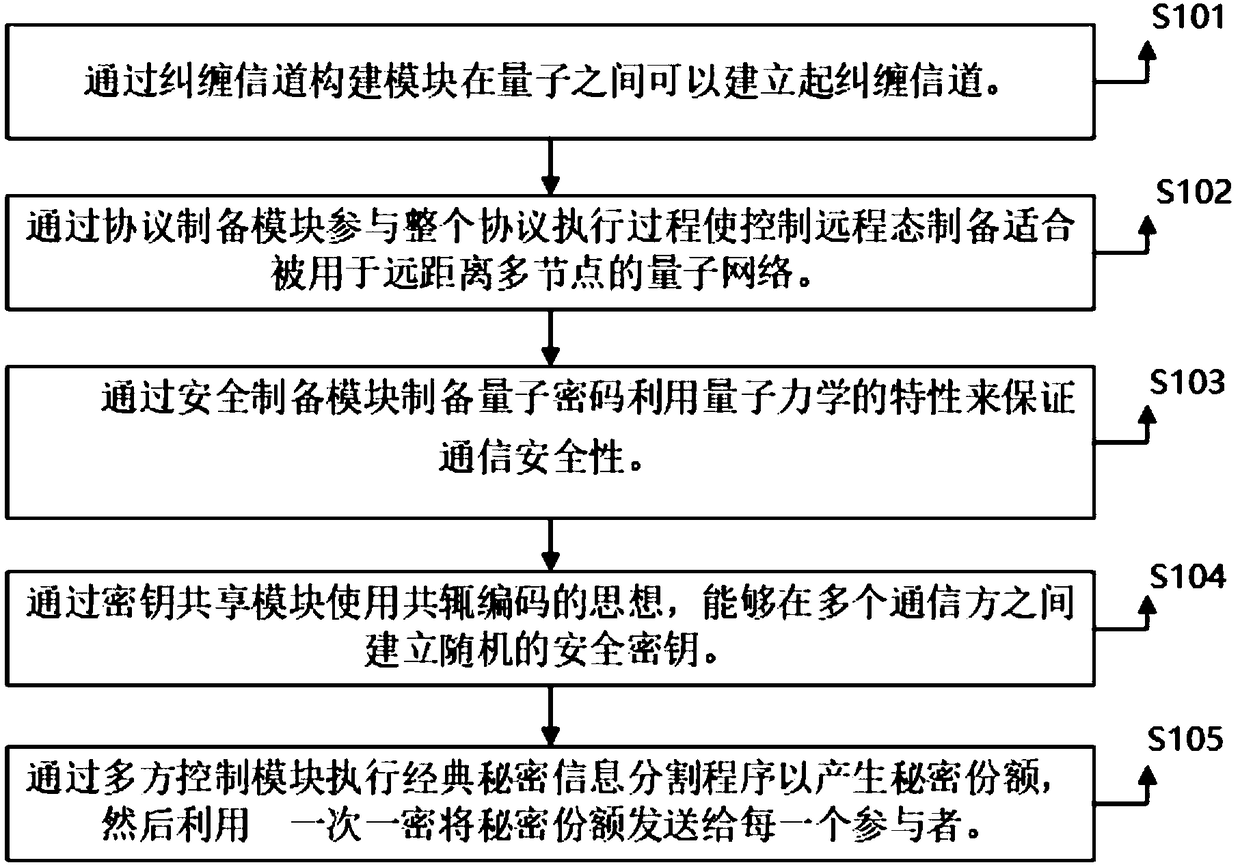
A method and system for realizing a multi-party controlled quantum communication protocol
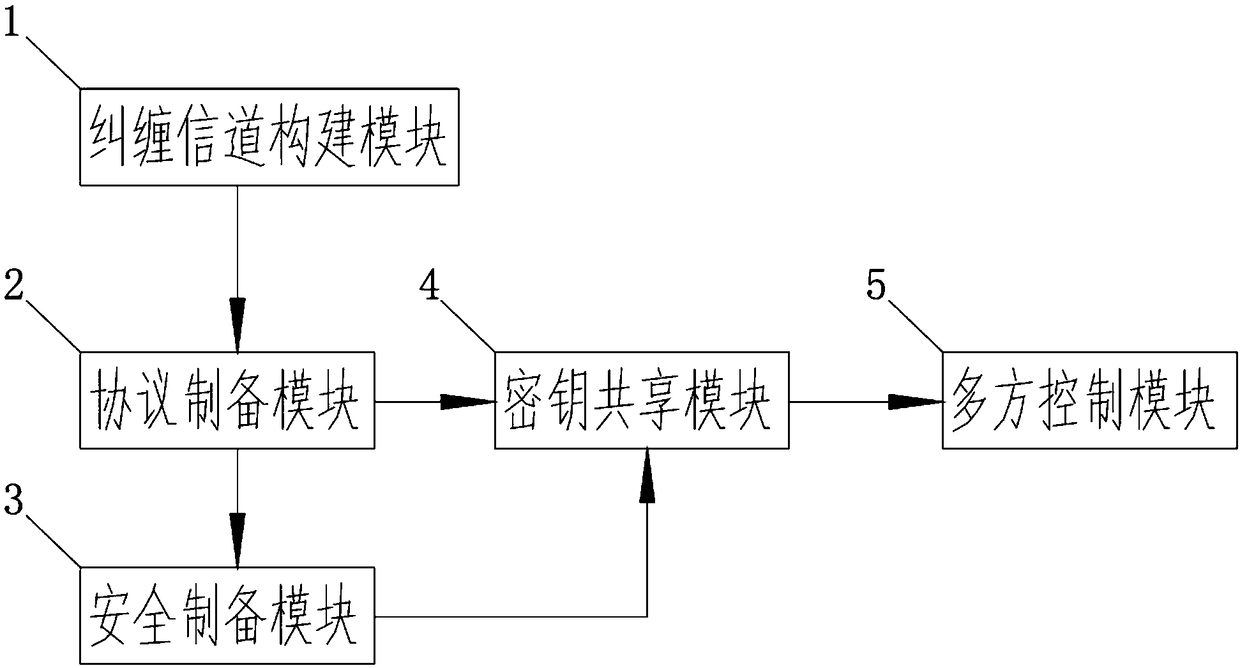
InactiveCN109257108ASufficient security and confidentialityEnsure safetyKey distribution for secure communicationPhotonic quantum communicationCommunications securityCryptosystem
The invention belongs to the technical field of computer software and discloses a method and a system for realizing multi-party control quantum communication protocol. The system is provided with an entanglement channel construction module, a protocol preparation module, a safety preparation module, a secret key sharing module and a multi-party control module. The invention establishes an entanglement channel between the quanta through an entanglement channel construction module. The protocol preparation module participates in the whole protocol execution process without knowing any information of the target state, which makes the remote state preparation suitable for the remote multi-node quantum network. The quantum cryptography is prepared by the secure preparation module, and the quantum mechanics is used to ensure the communication security. It solves the problem of security distribution of key in classical cryptosystem. Firstly, the multi-party control module executes a classic secret information partitioning procedure to generate secret shares, and sends the secret shares to each participant one-at-a-time by using and one-at-a-time encryption. Secret distribution and eavesdropping detection are simultaneously realized by using multi-particle entangled states.
Owner:GUANGDONG TECHN COLLEGE OF WATER RESOURCES & ELECTRIC ENG
Automatic detection device for toy production
ActiveCN108645713AImprove work efficiencyHelp to installMaterial strength using tensile/compressive forcesMaterial testing goodsElectric machineryEngineering
The invention discloses an automatic detection device for toy production. The device comprises a base, a detecting table, an appearance detecting table and first protective doors, cylinders are mounted in the base, pneumatic telescopic rods are arranged above the cylinders, a support rod is fixed above the base, a sleeve sleeves above the support rod, a first horizontal platform is fixed at the outer side of the sleeve, fixed plates are mounted at the left side and the right side of the first horizontal platform, a motor is arranged in the left side of the detecting table, the detecting tableis located above the first horizontal platform, connecting pieces are mounted in the appearance detecting table, the appearance detecting table is located above the second horizontal table, glass windows are arranged in the outside surface of every first protective door, and the first doors are respectively located at the left side and the right side of the base. The automatic detection device fortoy production has the advantages of high working efficiency, completeness in obtained detection data, realization of simultaneous detection of a plurality of sets of toys, and realization of continuous detection.
Owner:ZHEJIANG LAISIAO ELECTRIC
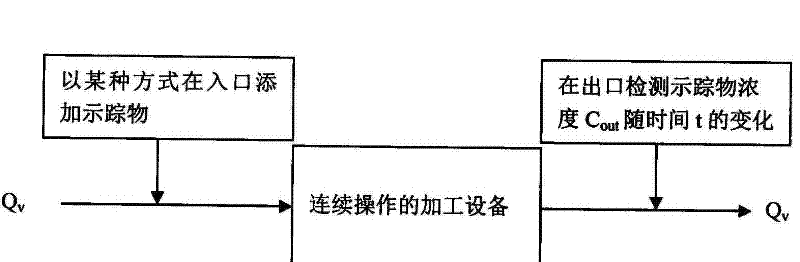
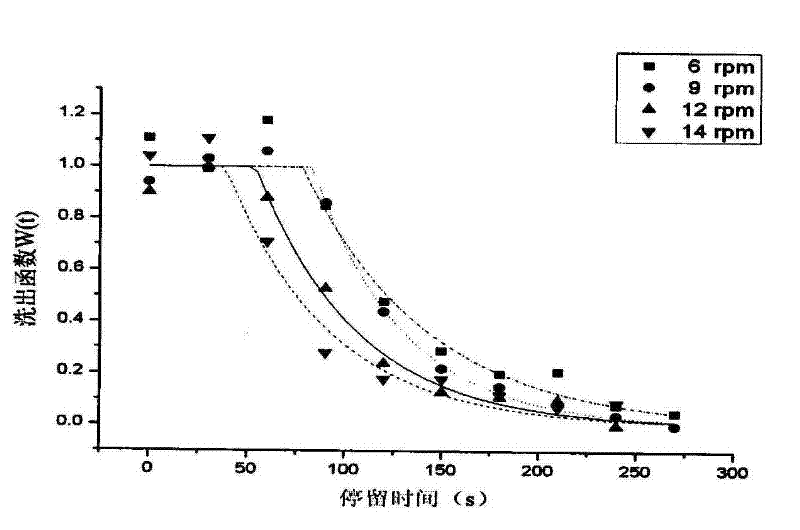
Method for measuring residence time distribution of tobacco material in processing equipment
A method for measuring residence time distribution of tobacco material in processing equipment comprises the following steps: a, a common component is selected from the tobacco material to work as a tracer to meet accuracy detection requirements; b, the tracer is added into a stably working material flow at the equipment inlet through adopting a tracing method, and response value of the variationon the concentration of the tracer along with time is detected with a certain time interval at the outlet, so as to get a residence time distribution (RTD) function; and c, the function is fitted in a nonlinear manner by a proper flowing model to get the model equation of the function, as well as the average residence time of the material and blending rate in the axial direction of the equipment.The invention has the advantages that firstly, a common component is selected from the tobacco material to work as the tracer for measuring the RTD of tobacco material in processing equipment, so that the testing time is short, the influenced area is small, the detect method has high accuracy, less influence is caused to the product quality, and no threatening is caused to the safety of consumers; and secondly, by adopting the method, the WIP (work in process) quality can be predicted, optimized, and controlled.
Owner:ZHENGZHOU TOBACCO RES INST OF CNTC +1
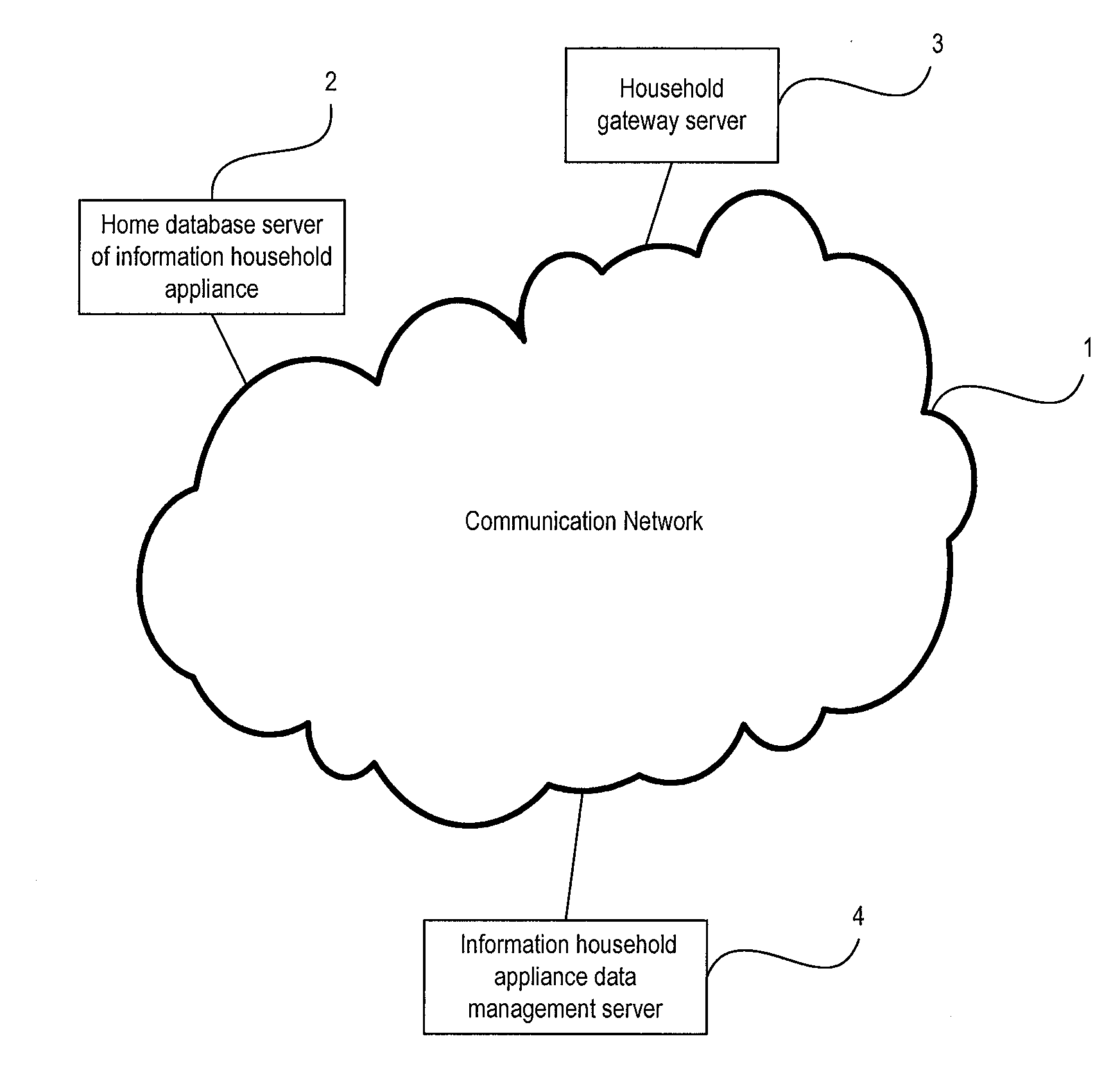
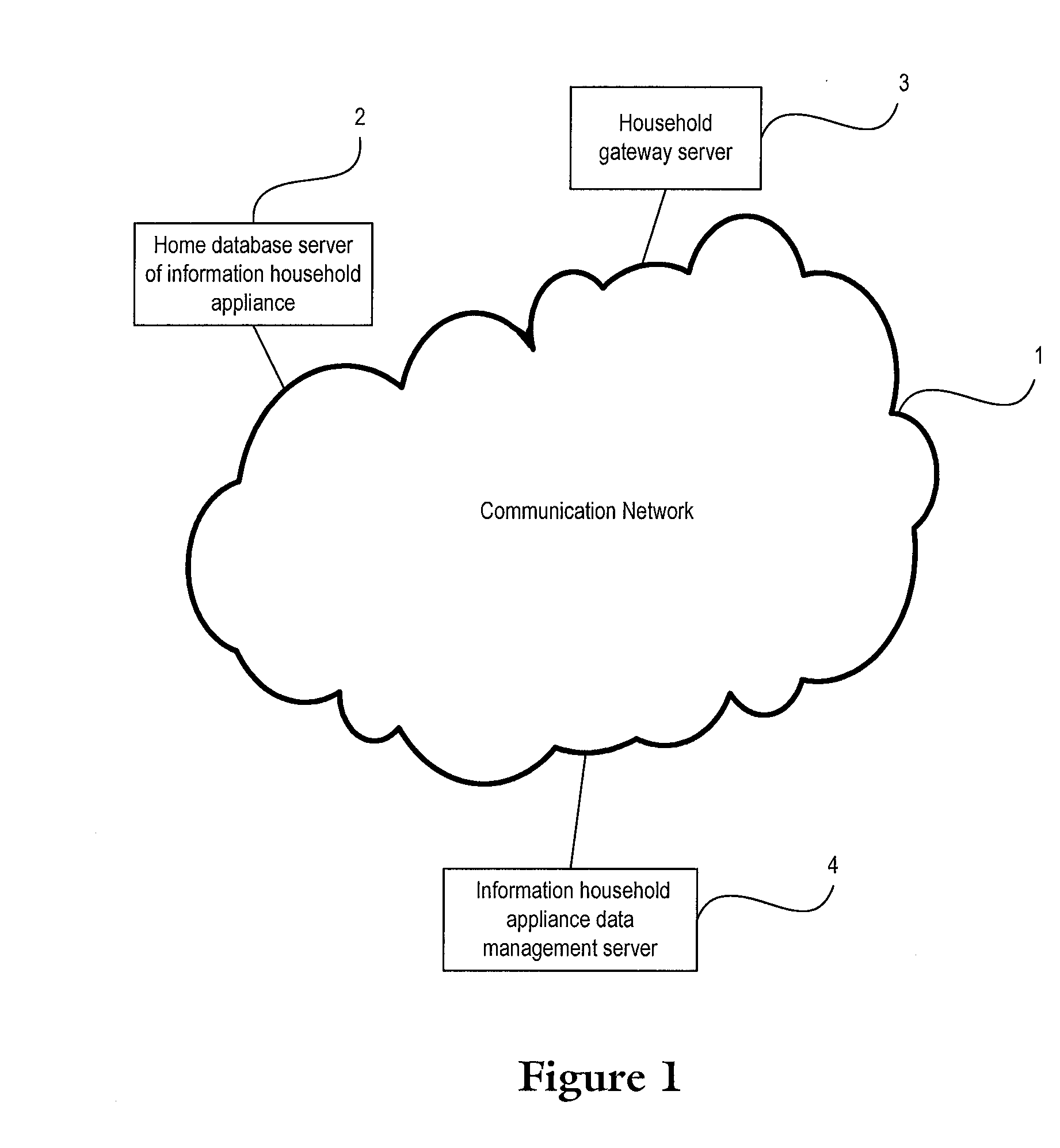
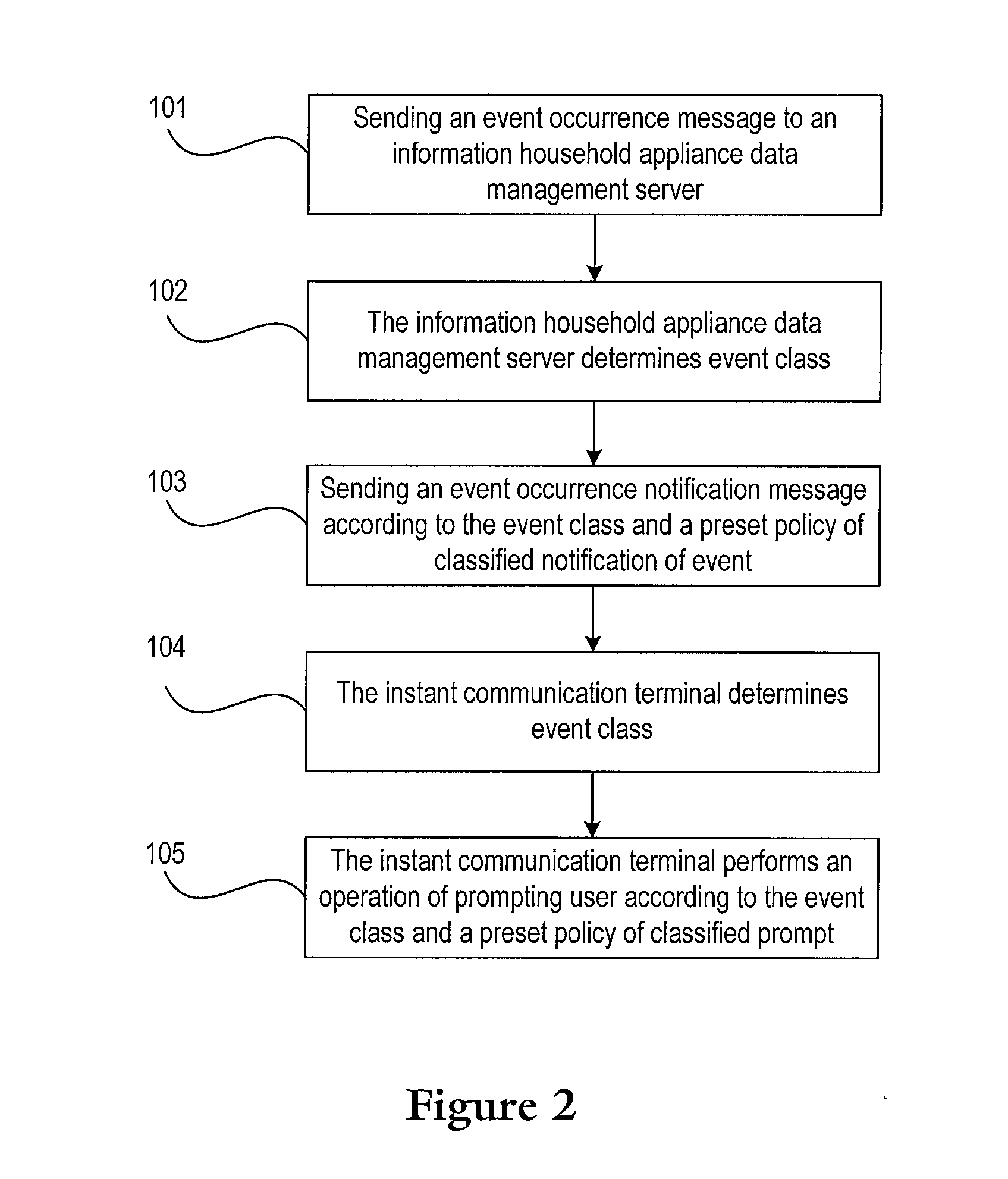
Classified processing method for event message of information household appliances
InactiveUS20100262665A1Reducing potential threat against safetyConveniently obtainSpecial service provision for substationSubstation remote connection/disconnectionEngineeringData management
The invention provides a classified processing method for an event message of an information household appliance including: a house gateway server sends an event occurrence message to an information household appliance data management server; according to an event class and a policy of classified notification of event, the information household appliance data management server sends an event occurrence notification message to an instant communication terminal, or sends an event occurrence notification message to an instant communication terminal and notifies a communication device at a preset communication destination; according to an event class and a policy of classified prompt, the instant communication terminal performs an operation of prompting the user. The method in the invention, the user can obtain the current status of the information household appliances, and the user or the related department may know the emergency or abnormal events in time, thus reducing the potential threat against safety.
Owner:CHINA MOBILE COMM GRP CO LTD
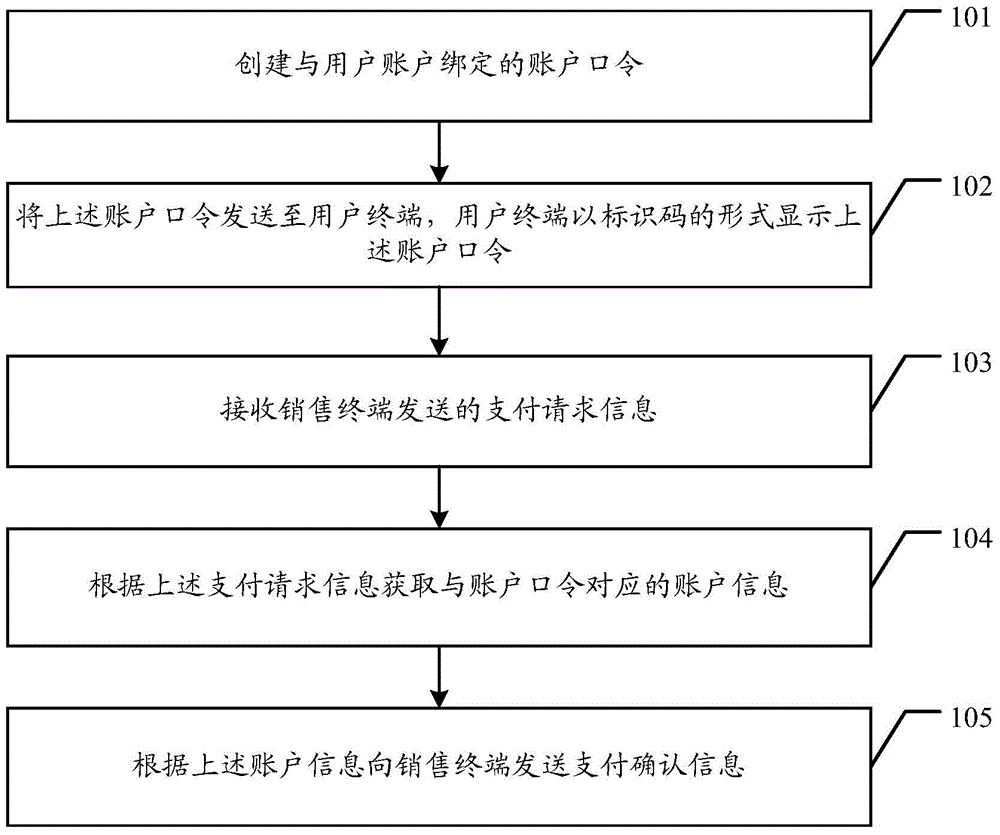
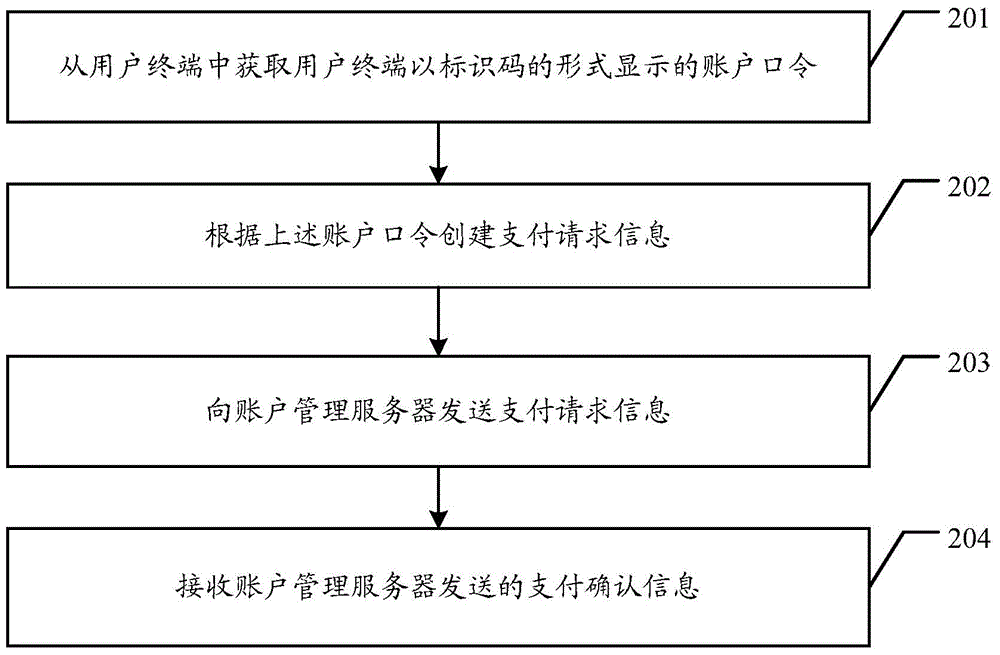
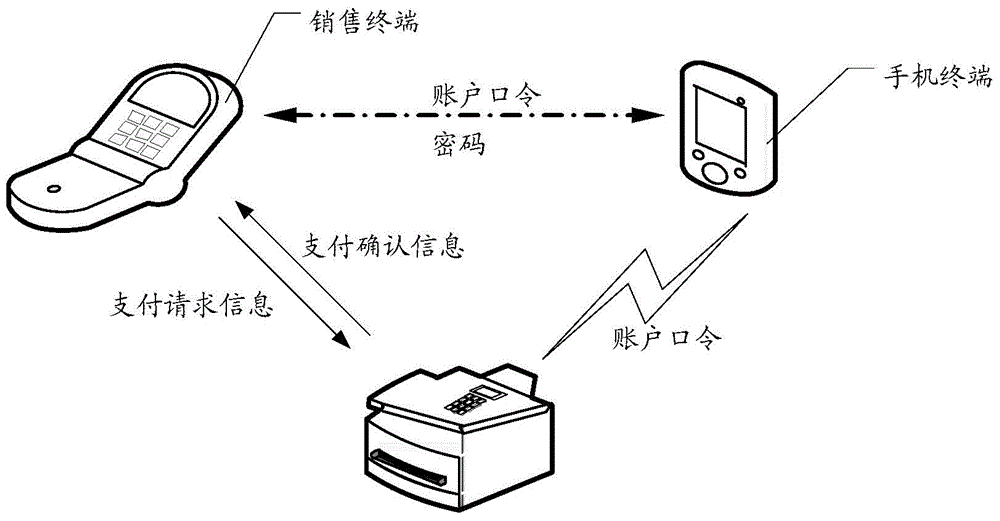
Management method for account information, account management server and a POS terminal and system
A method of protecting account information at an account management server having one or more processors, and memory, comprising: receiving, from a portable electronic device associated with a first user account, a request to make a payment at the portable electronic device. In response to the payment request, creating a temporary first account access code associated with the first user account, storing a copy of the first account access code at the server and sending the first account access code to the portable electronic device. The method including receiving a transaction confirmation request sent from a sales terminal, wherein the transaction confirmation request comprises a second account access code, and in accordance with a determination that the second account access code matches the first account access code stored at the server, sending a transaction confirmation message to the sales terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD
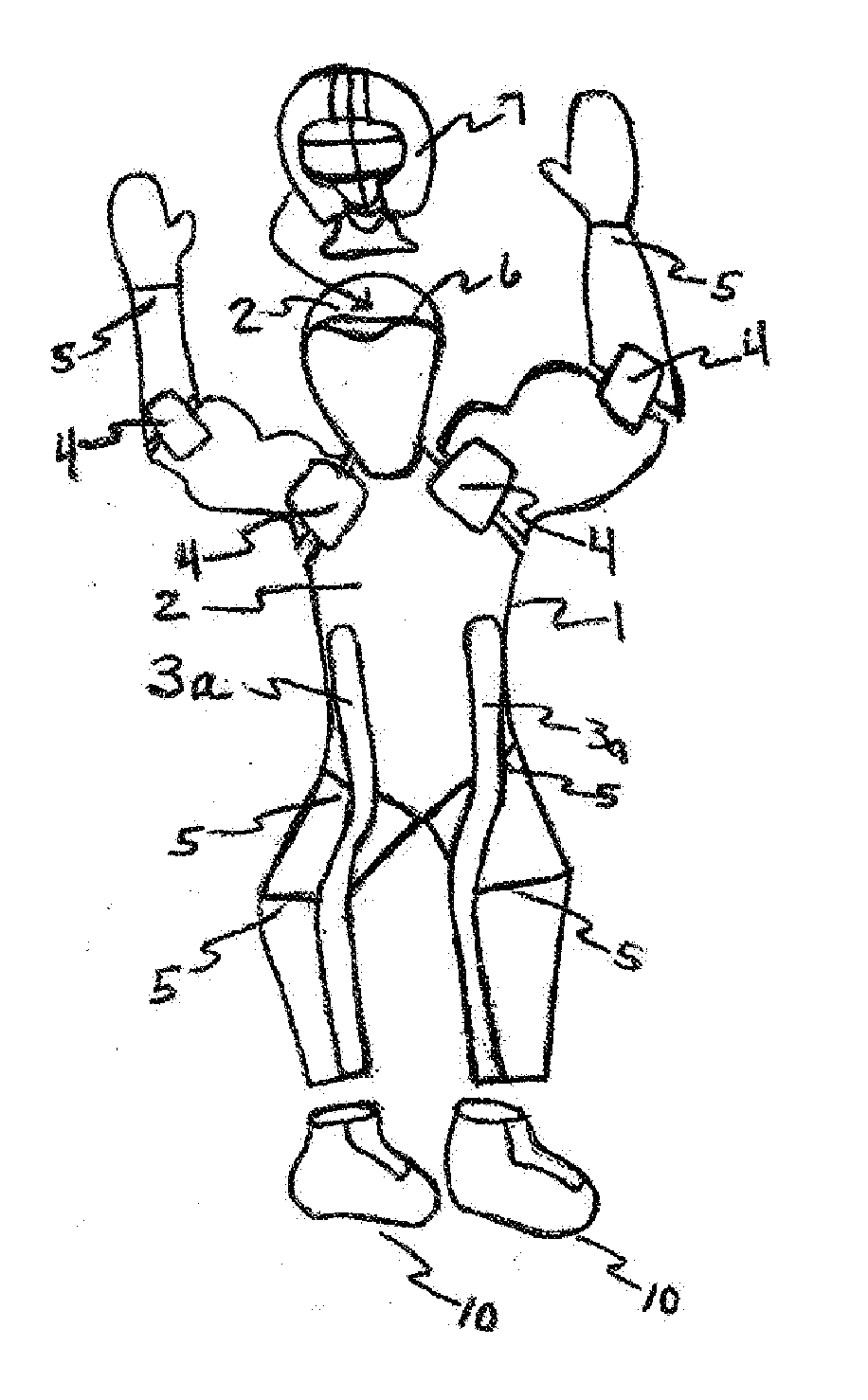
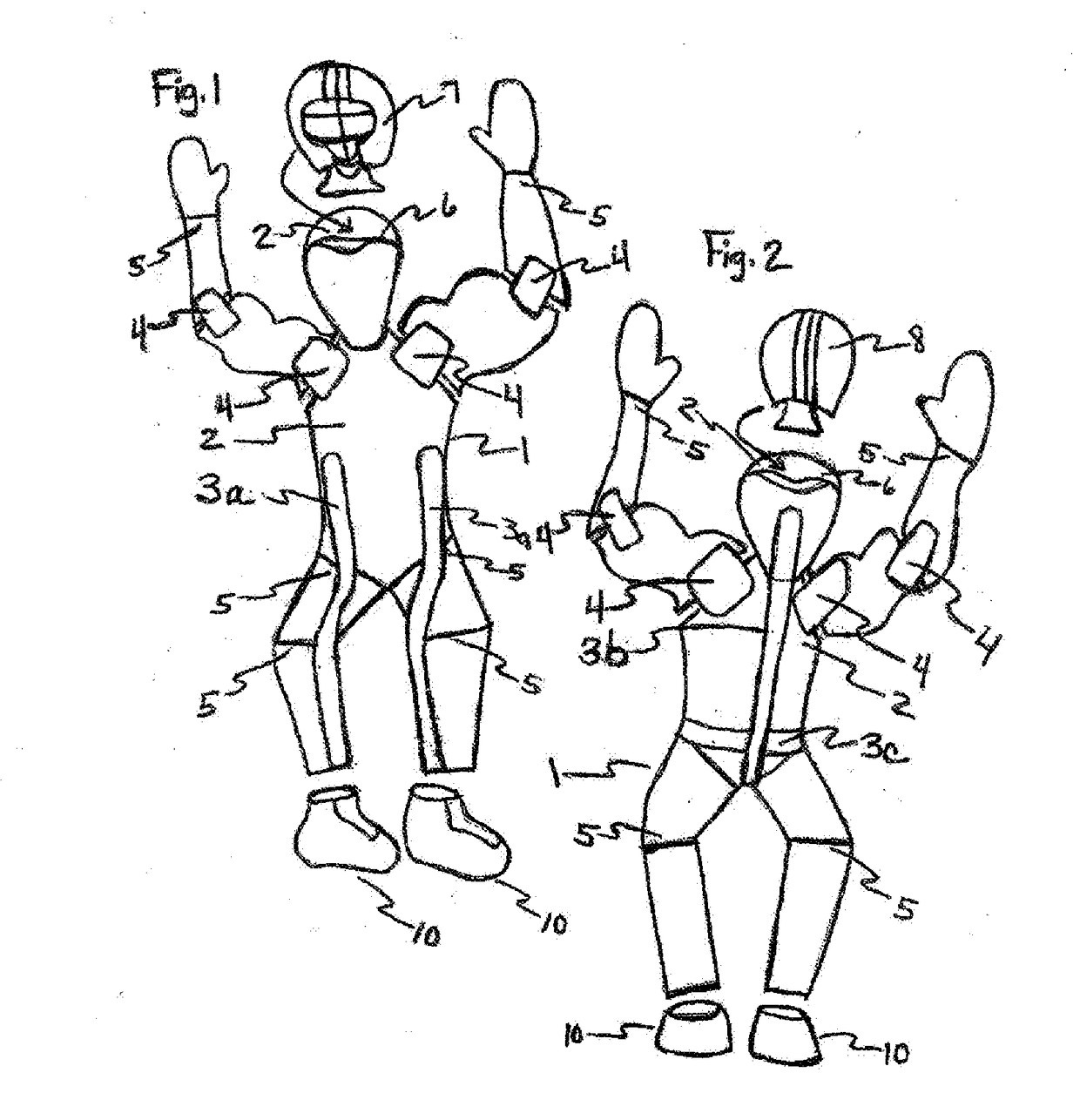
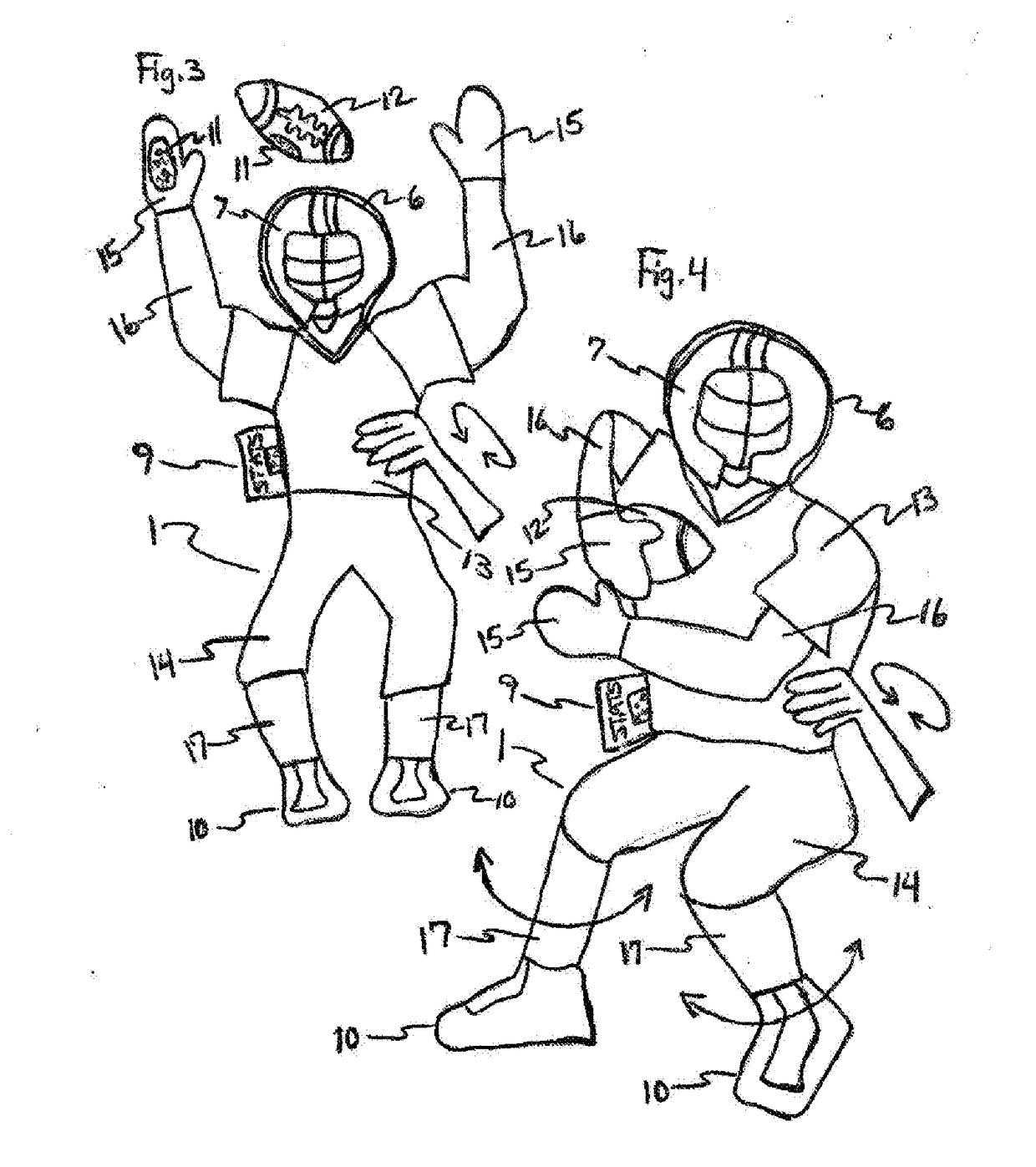
Sports and Entertainment Action Figure Doll & Trading Card
The New Improved Sports and Entertainment Action Figure Doll that is wave-able and motion-able and has a body that is made flat like a trading card and made flat for security reasons due to high security risks at sport and event venues and complexes. The action figure doll can be made with trading card attached or with trading card features like stats card and picture graphics printed on doll and doll is made of flexible material that uses one or more folds and one or more items that can be used as a weight or weights such as game gear or equipment that allow movement when doll is waved and action figure doll can be made to use one or more flexible supports that help provide structure to doll and gives support against wear and tear of doll due to motion. The action figure doll makes controlled motions when waved or shaken or moved about in the air to make it appear as if the action figure doll is performing one or more tasks while user is cheering or jeering. Also, the motion made by action figure doll is designed to lure or attract the attention of camera operator or others at game or event. Further, the action figure doll can be made with attachable and detachable game gear or equipment and paraphernalia. Also, the action figure doll can be made to stand upright so that it can stand on desk, shelf or some other flat surface.
Owner:VINCENT THOMAS M
Apparatus and method for protecting asset in computer system
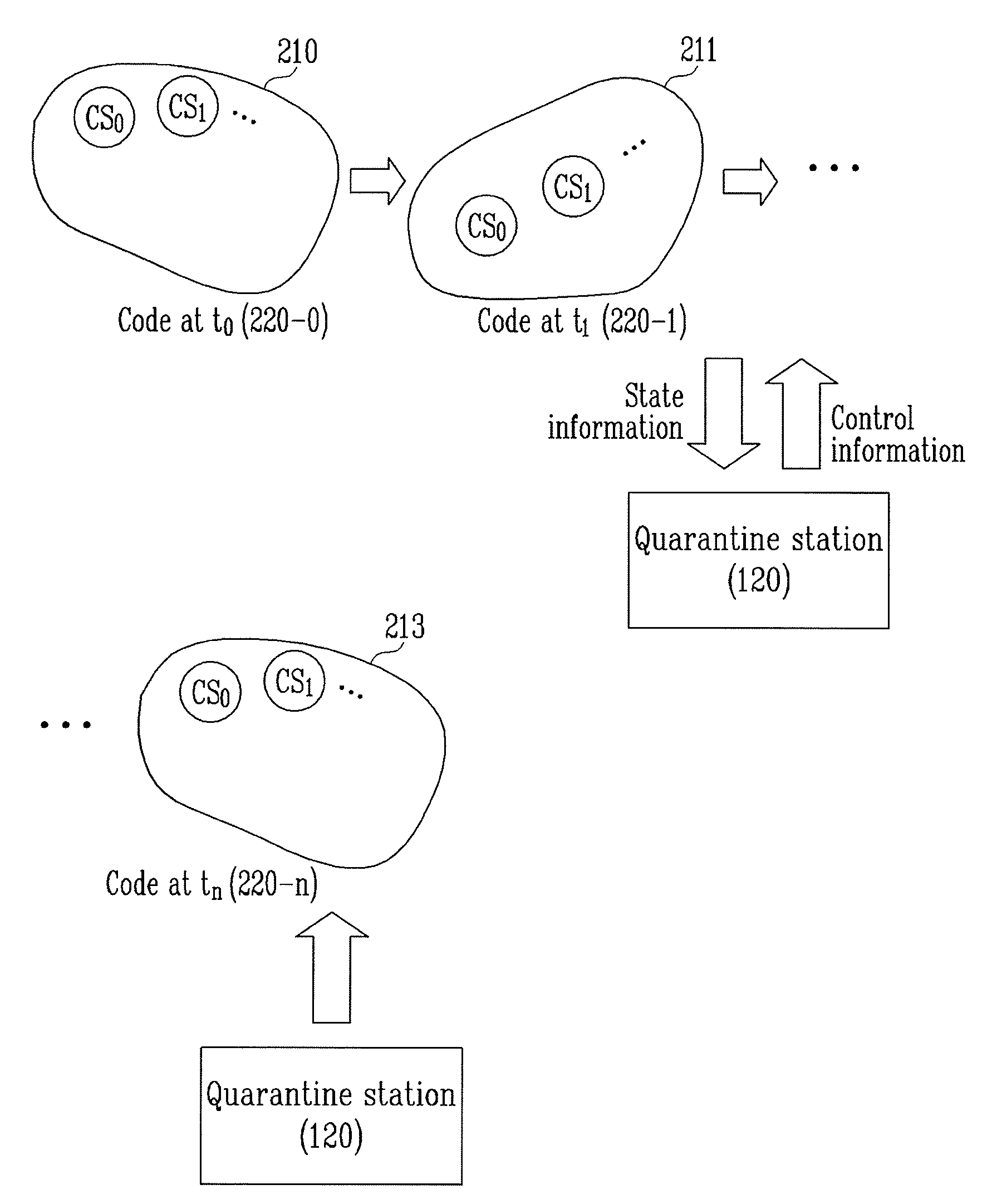
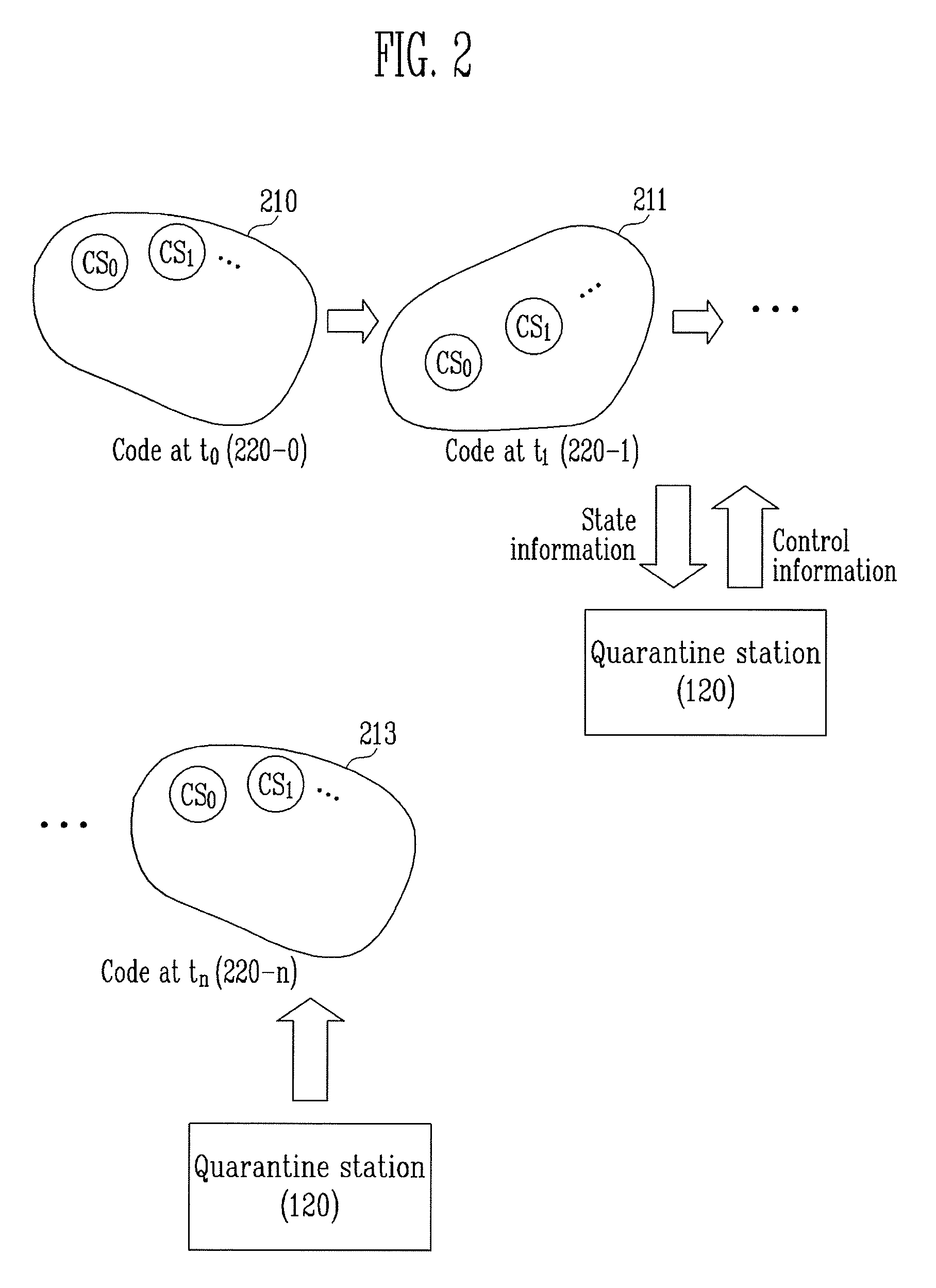
ActiveUS20100162397A1Eliminating security threat elementPrevent hackingMemory loss protectionDigital data processing detailsInformation controlCommunication unit
Provided are an apparatus and method using spatial and temporal quarantine expansion to prevent important information from being leaked due to attacks such as viruses, hacking, and the like. The apparatus includes a state change unit for changing a state of at least one of a memory, a register, and a port in the computer system; a state calculation unit for calculating information on the changed state of the computer system; a security-threat-element elimination unit for eliminating security threat elements from the computer system; a communication unit for transmitting the state information calculated by the state calculation unit to the quarantine station, or receiving control information for controlling the computer system based on the state information, from the quarantine station; and a security execution unit for receiving security information from the quarantine station to execute a specific program when the computer system is faultless, wherein the state information and the control information are transmitted or received until the computer system is faultless repeatedly.
Owner:ELECTRONICS & TELECOMM RES INST
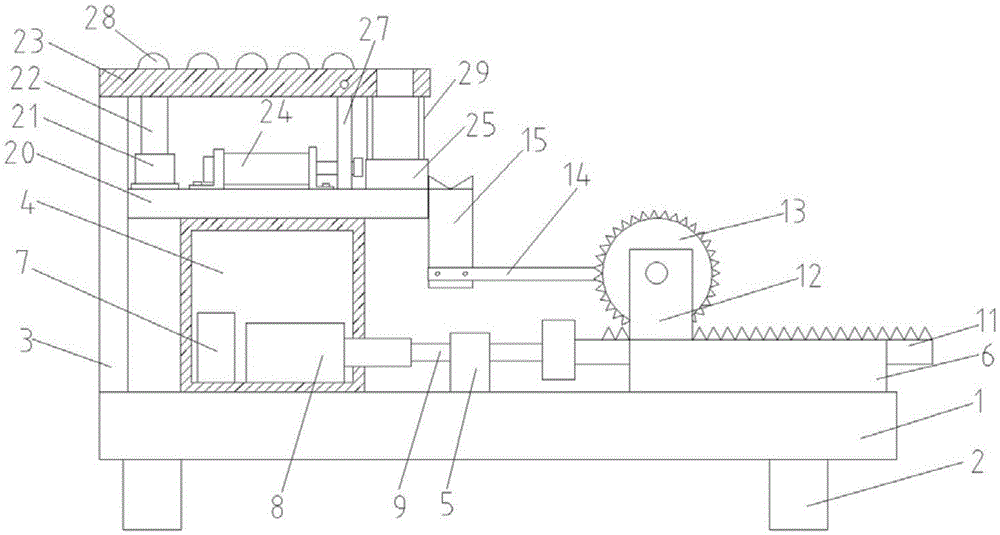
Automatic pipe fitting feeding and grinding device
InactiveCN105538137AImprove securitySecurity threatRevolution surface grinding machinesGrinding feed controlPipe fittingEngineering
The invention discloses an automatic pipe fitting feeding and grinding device. The feeding and grinding device comprises a feeding device, a supporting device, a grinding device and a measuring device. The supporting device is located at the discharging end of the feeding device, and the grinding device is located above the supporting device; the measuring device is located at the discharging end of the grinding device; through the feeding device, automatic feeding is achieved, a supporting mechanism with the adjusting function is adopted, the structure is simple, operation is convenient, and the adjustable effect is achieved; a lifting device is arranged to enable a whole grinding head mechanism to be capable of vertically moving and moving laterally, use limitation is avoided, and after grinding, the measuring device enables a steel pipe to rotate during clamping through cooperation of a first clamping device and a second clamping device; and multi-angle measuring can be achieved, vibration and shaking of the steel pipe can be reduced, and a bearing plate is arranged, so that the steel pipe is placed more stably and is more accurately measured, error generation is reduced, and the steel pipe measuring effect is better.
Owner:RONGCHANG YONGXIN STEEL STRUCTURE PROCESSING FACTORY
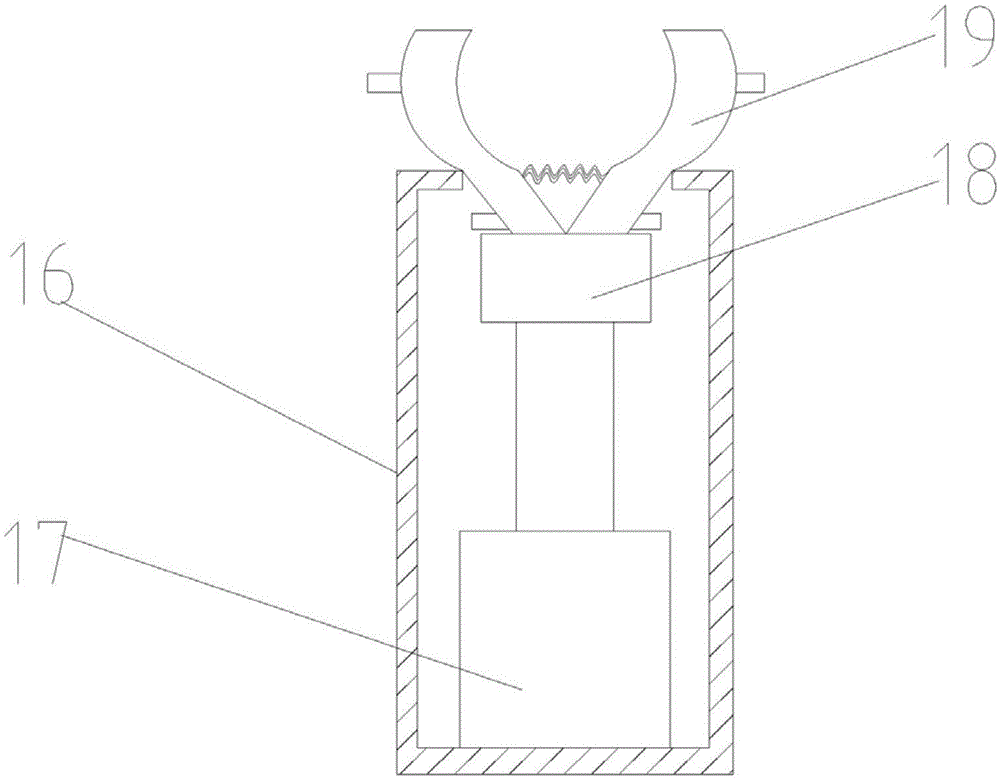
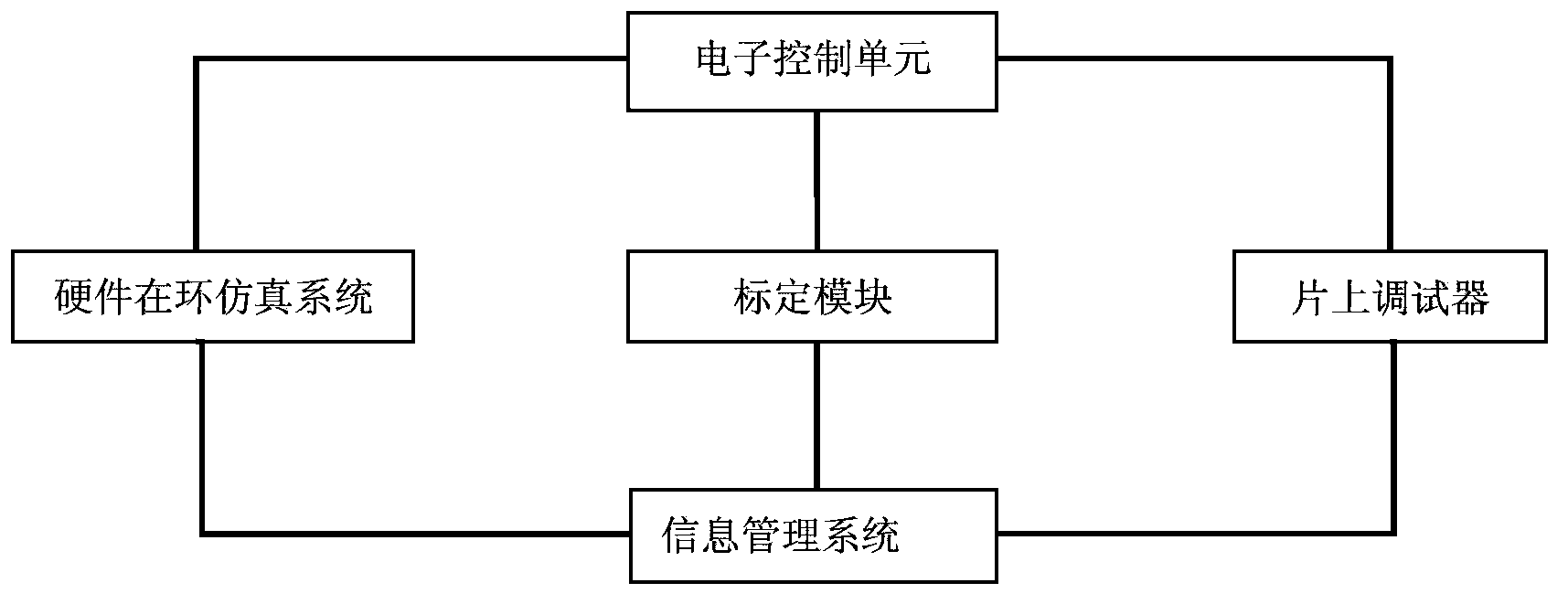
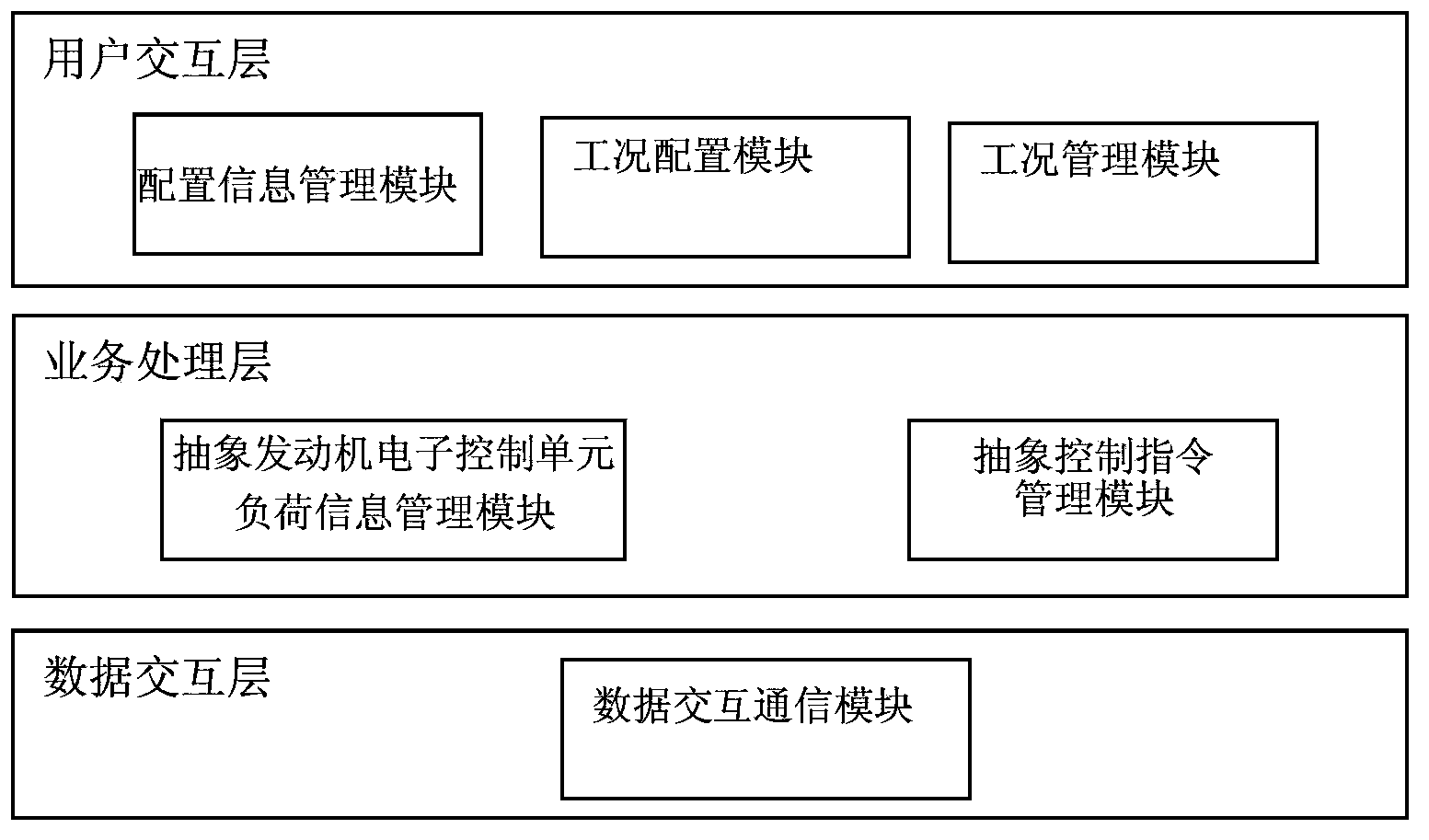
Software load testing system and method for engine ECU
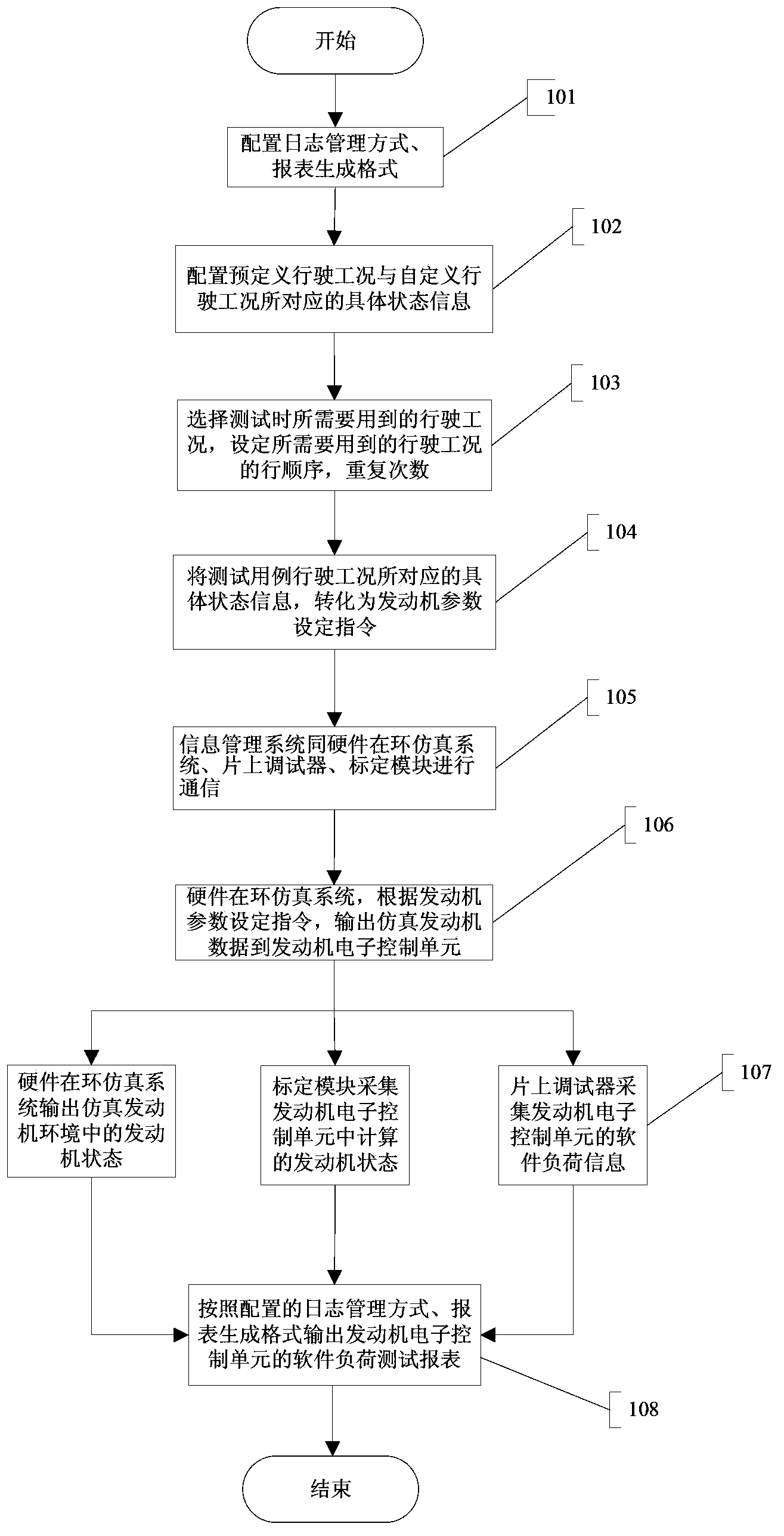
ActiveCN103853146AAvoid threatsSecurity threatElectric testing/monitoringHardware-in-the-loop simulationLoad testing
The invention discloses a software load testing system for an engine ECU. The software load testing system comprises a hardware-in-the-loop simulation system, an on-chip debugger and an information management system. The hardware-in-the-loop simulation system is used for setting instructions according to engine parameters and outputting engine simulation data to the engine ECU. The on-chip debugger is used for collecting software load information of the engine ECU and outputting the software load information of the engine ECU to the information management system. The information management system is used for configuring test cases, translating driving conditions in the test cases into engine parameter setting instructions, sending the engine parameter setting instructions to the hardware-in-the-loop simulation system and outputting load test tables according to the software load information corresponding to all the driving conditions in the test cases. The invention further discloses a software load testing method for the engine ECU. According to the software load testing system and method for the engine ECU, the truest software load conditions of the engine ECU can be comprehensively detected.
Owner:LIANCHUANG AUTOMOBILE ELECTRONICS
Symmetric encryption system and method for vehicle Bluetooth key identity authentication mode
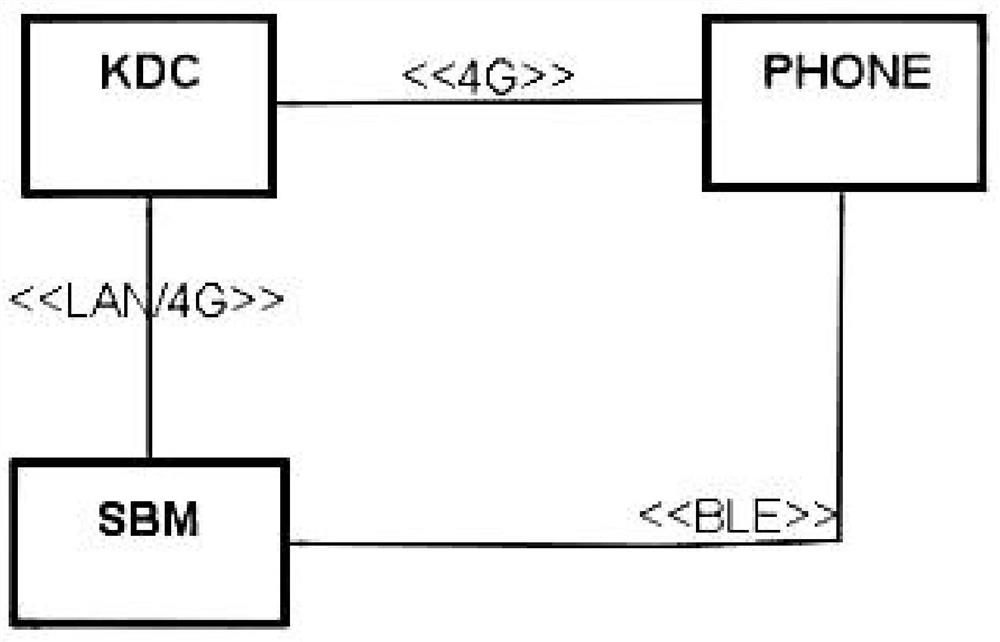
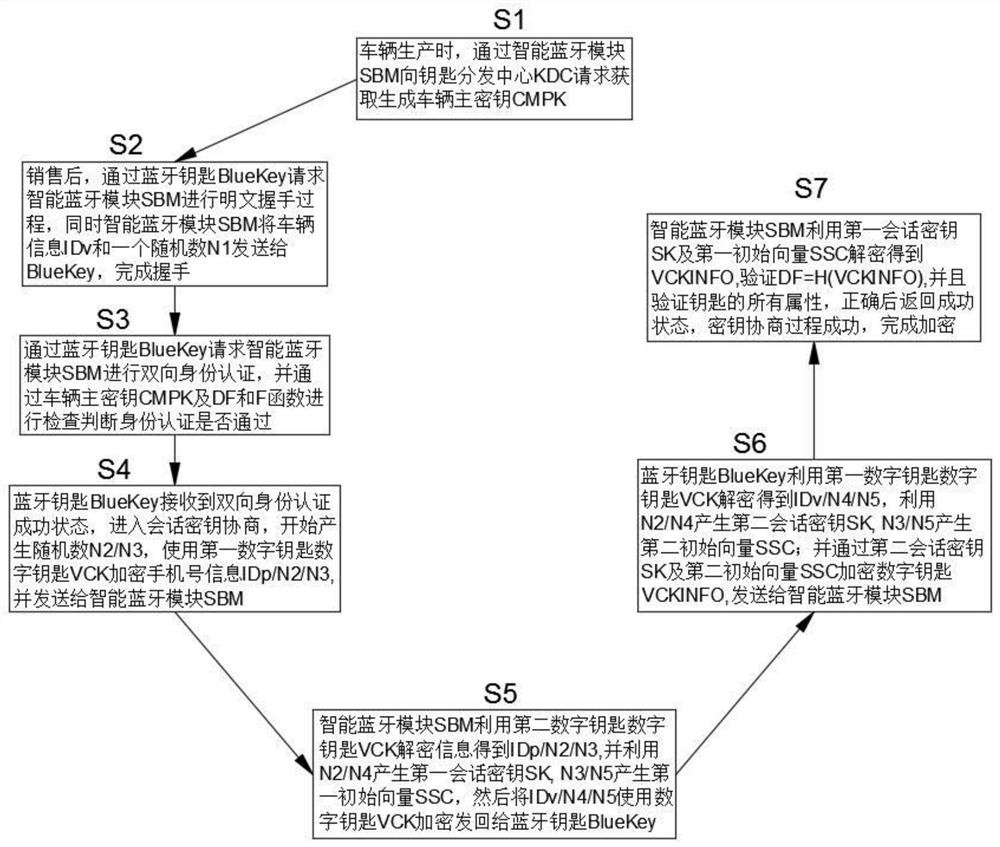
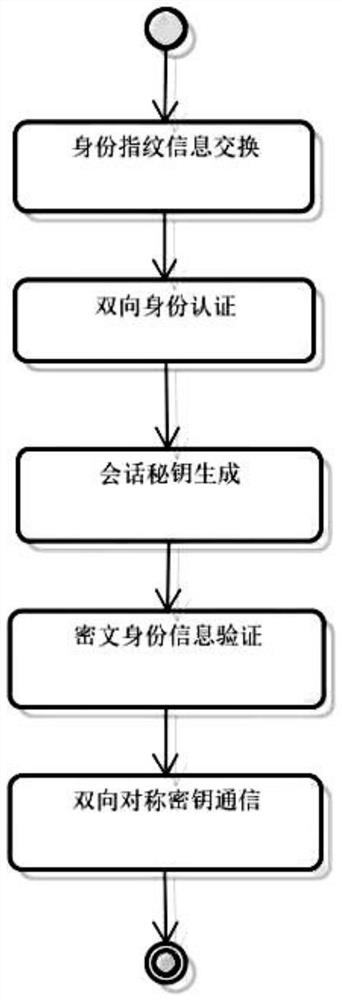
ActiveCN111669399ASecurity threatImprove securityAnti-theft devicesIndividual entry/exit registersMaster keyKey distribution center
The invention relates to the technical field of identity authentication, and relates to a symmetric encryption system and method for a vehicle Bluetooth key identity authentication mode. An intelligent Bluetooth module SBM and a Bluetooth key BlueKey are arranged, and data transparent transmission of the intelligent Bluetooth module SBM and the Bluetooth key BlueKey is achieved through a low-power-consumption Bluetooth BLE; during vehicle production, the intelligent Bluetooth module SBM is deployed on a vehicle and connected with a key distribution center KDC through an LAN or a 4G network, and a vehicle master key CMPK is obtained and generated; after sales, the Bluetooth key BlueKey is connected with a key distribution center KDC through a 4G network; a digital key VCK is generated afterobtaining, attached VCKINO information is sent back to the Bluetooth key BlueKey, and a function relation exists between the generated vehicle master key CMPK and the digital key VCK; according to the invention, the problem of information leakage is solved, the threat of replay attacks is prevented under the condition that the operation rate is not reduced, missing inspection and replay attacks are avoided, the security is higher, and the applicability is wider.
Owner:上海越域智能科技有限公司
Mechanical pressure-controlled viscous damper
PendingCN108980254ASecurity threatSpringsSprings/dampers design characteristicsMaster cylinderEngineering
The invention discloses a mechanical pressure-controlled viscous damper, and belongs to the technical field of structural vibration proofing and reducing engineering dampers. Cylinder bodies are filled with the same damping media, and the damping media are sprayed to flow through a damping hole formed in a piston to generate damping force, so that energy of input vibration is consumed. When a structure quickly vibrates under the action of external vibration, in main cylinders of the damper, due to the fact that the damping hole on the piston does not quick spray the media in time or the damping media in a left main cylinder and a right main cylinder are exchanged, the pressure intensity in the left main cylinder and the pressure intensity in the right main cylinder are increased suddenly,and the safety of the damper is possibly threatened. The mechanical pressure-controlled viscous damper is provided with a liquid through pipe, a pressure intensity adjusting device is arranged in theliquid through pipe, pressure relief can be achieved in the working process of the damper, and thus cylinder bursting is prevented. The mechanical pressure-controlled viscous damper is simple in structure, pressure intensity adjusting can be conducted, all parts and accessories can prefabricated and machined in a factory, the damping protection effect is better, the safety factor is higher, structure durability is high, and the mechanical pressure-controlled viscous damper can be used for a long time.
Owner:NANJING FORESTRY UNIV
Method of clearing material containing barrel for new material machining
InactiveCN109332319APlay a limiting effectEasy to holdHollow article cleaningEngineeringNew materials
The invention discloses a method of clearing a material containing barrel for new material machining. The clearing method is realized on the basis of a clearing device, the cleaning device comprises aworkbench, a plurality of supporting legs are fixedly connected to the side wall of the bottom of the workbench, two supporting plates are symmetrically arranged at the upper end of the workbench, and the upper ends of the two supporting plates are fixedly connected with a first fixing plate together; two supporting blocks are symmetrically arranged at the upper end of the workbench, the upper ends of the two supporting blocks are fixedly connected with a to-be-cleared barrel together, two first communicating grooves are formed in the side wall of the workbench in a penetrating mode, and a clamping mechanism is arranged on the side wall of the bottom of the workbench; the clamping mechanism penetrates through the two first communicating grooves and is in sliding connection with the side wall of the clamping mechanism, and the opposite side wall of the clamping mechanism abut against the outer side wall of the to-be-cleared barrel. According to the method, the structural design is reasonable, automatic cleaning can be realized, the safety threat to a human body is avoided, the clearing efficiency is improved, and the cleaning degree of the inner side wall of the material containingbarrel can be guaranteed.
Owner:欧彩容
Anti-silting method for ship lock passing through high-sand-content large-fall river channel
ActiveCN110904939AEffective volumeLess power requiredBarrages/weirsDry-docksMarine engineeringOceanography
The invention discloses an anti-silting method for a ship lock passing through a high-sand-content large-fall river channel. The device comprises a ship lock, a gate, a lock bottom, a water inlet gateand a water outlet gate, the gate is characterized in that a through gate width whole course is arranged below the gate; independent turn-off and turn-on, the transverse linear water inlet gate and the water outlet gate synchronously move along with the gate; water in the ship lock is injected and discharged; all the operations are realized through a water inlet gate and a water outlet gate; compared with the prior art, the ship lock has the technical advantages that the water injection and drainage processes in the ship lock pass through the linear gate; mainly, horizontal torrent flows in and out along the bottom of the lock to wash sediment settled at the bottom of the lock to enter a suspension state again to be released from the ship lock. Meanwhile, the lock is opened and closed after the water injection and water release processes are completed, resistance of static pressure and dynamic pressure is avoided, and the valve is opened more smoothly in an energy-saving mode.
Owner:董恬纲
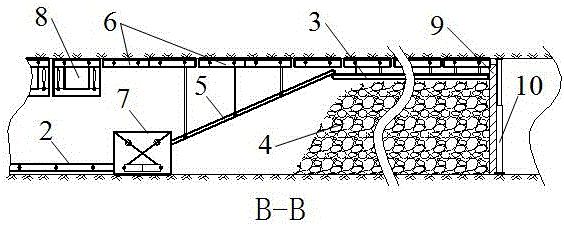
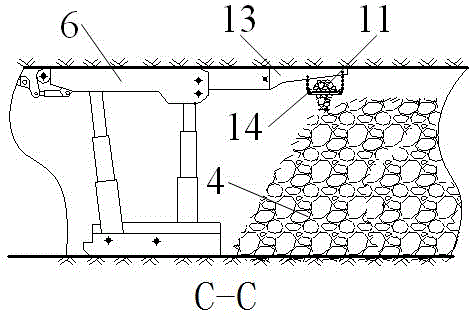
Method for gob-side entry retaining of medium-thickness coal seam
The invention relates to a method for gob-side entry retaining of a medium-thickness coal seam and belongs to the technical field of gob-side entry retaining. The method is characterized in that by taking the advantage of large space of a working face of the medium-thickness coal seam, part of a support of the working face on the gob-side entry retaining side is changed into a top coal caving support and a long tail beam support, and a scraper conveyor, a transfer crusher, a transfer belt conveyor and a downward-spreading conveyor are arranged behind the supports on the working face; and in the working face propelling process, the top coal caving support is directly adopted for conveying gangue above a gob downwards, the downwards-conveyed gangue is downwards spread to the gob area on the gob-side entry retaining side to form a beside-entry support after the procedures of conveying, crushing, transferring and downward spreading, and the whole process is carried out in the gob area. Meanwhile, before the gangue is stacked, flexible protecting plates with holes are adopted for separation in advance so as to adapt to roof settling and prevent the gangue from entering an entry, cementing material filling and reinforcing are carried out, and the flexible protecting plates with the holes can be recycled. The method has important significance to guarantee of the gob-side entry retaining stability, increase of the resource recovery rate and simplifying of a beside-entry support process.
Owner:HENAN POLYTECHNIC UNIV
An intelligent refueling system
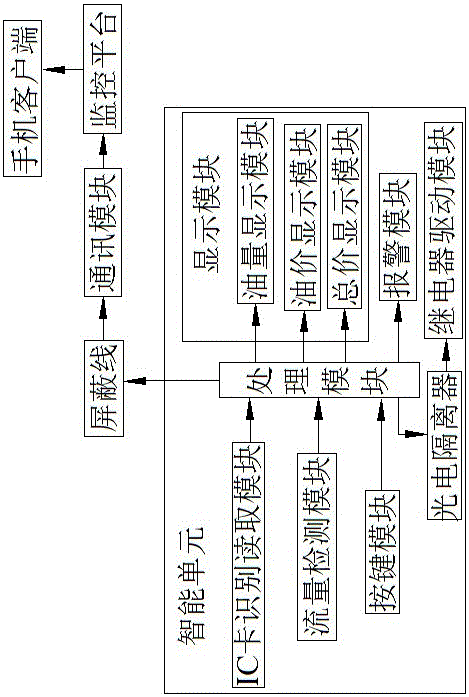
InactiveCN106127962AEasy to useEasy to viewApparatus for hiring articlesTraffic capacityComputer module
An intelligent refueling system, including a monitoring platform, a communication module and an intelligent unit arranged on the refueling equipment; the intelligent unit includes a processing module; the signal input end of the processing module is connected with a flow detection module and a button module; the signal output end of the processing module It is connected with a display module and a relay drive module, and the relay drive module controls the work of the refueling equipment; the processing module is connected to the communication module through a shielded wire, and the processing module transmits the refueling information and the working status of the refueling equipment to the monitoring platform through the communication module; the monitoring platform will The working status of the refueling equipment is transmitted to the mobile client. The invention has high safety, and the communication module, the monitoring center and the mobile phone client can make people know the working state of the refueling equipment at all times, so that when refueling, they can directly drive to the unused refueling equipment, saving time.
Owner:程子桉
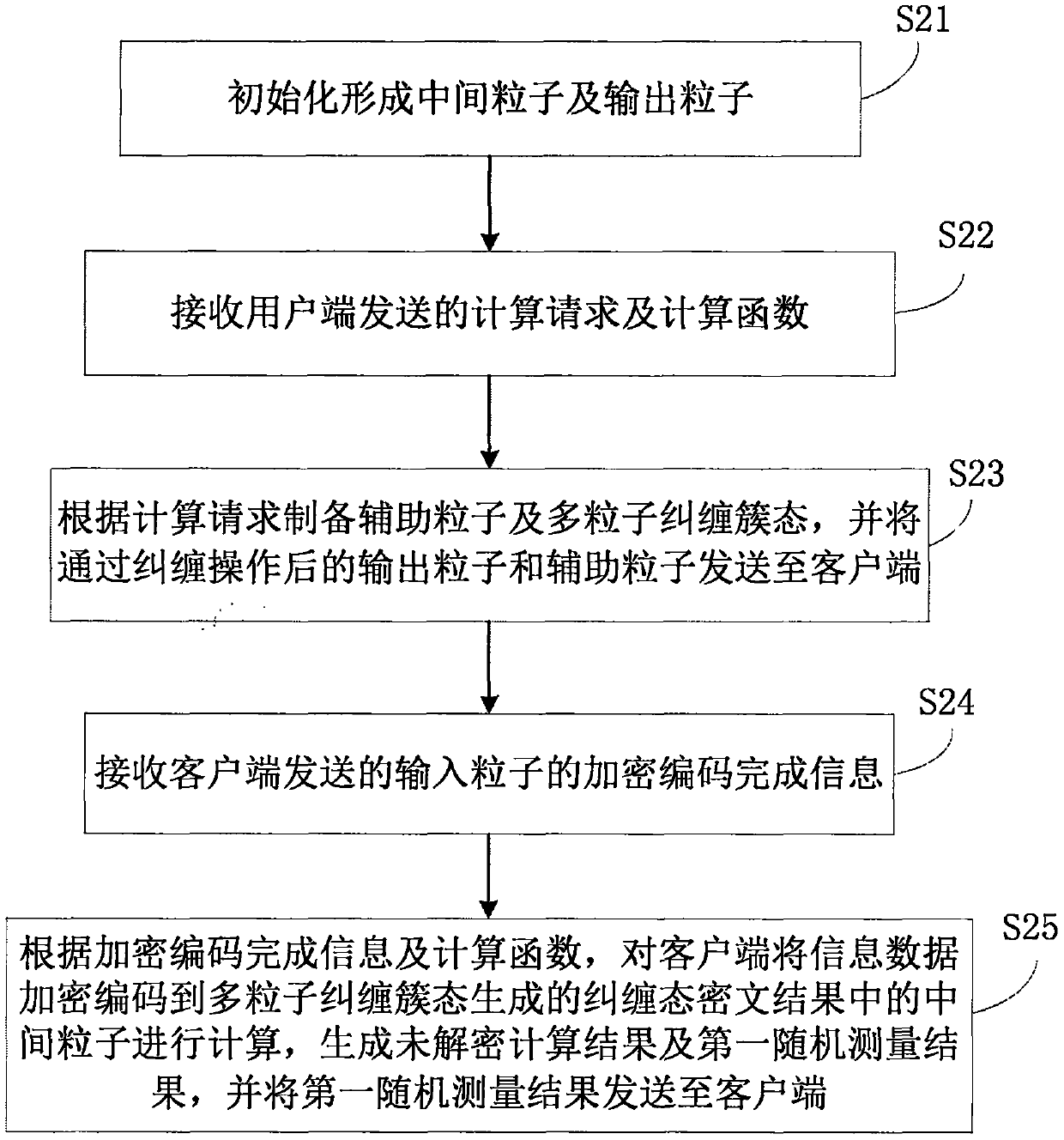
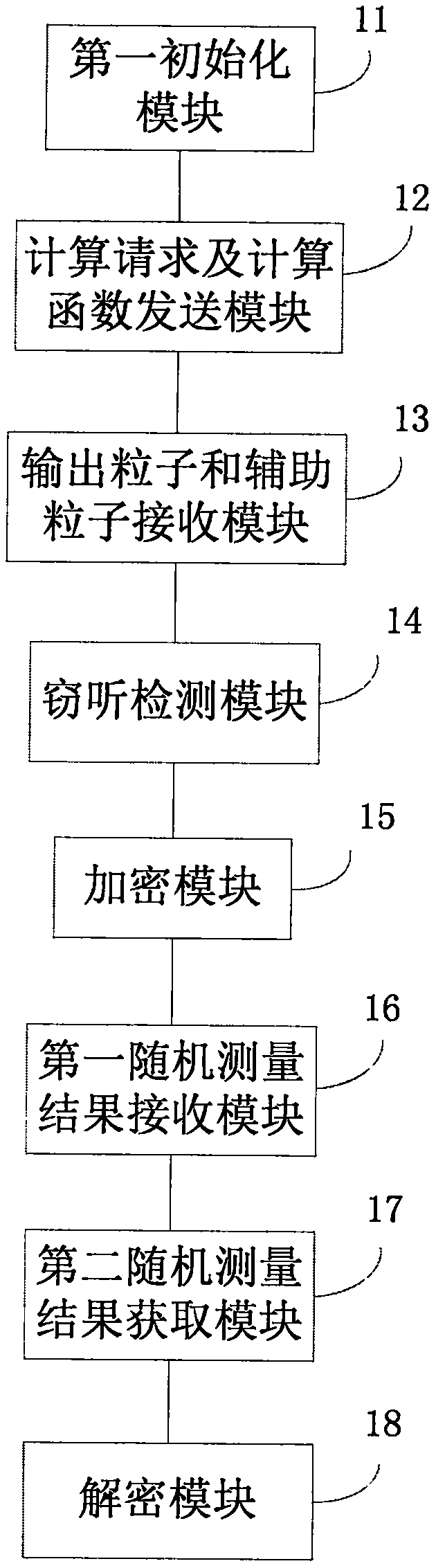
Quantum cloud computing method and system, client and cloud server
ActiveCN109560930AImplement storageSecurity threatKey distribution for secure communicationCiphertextCluster state
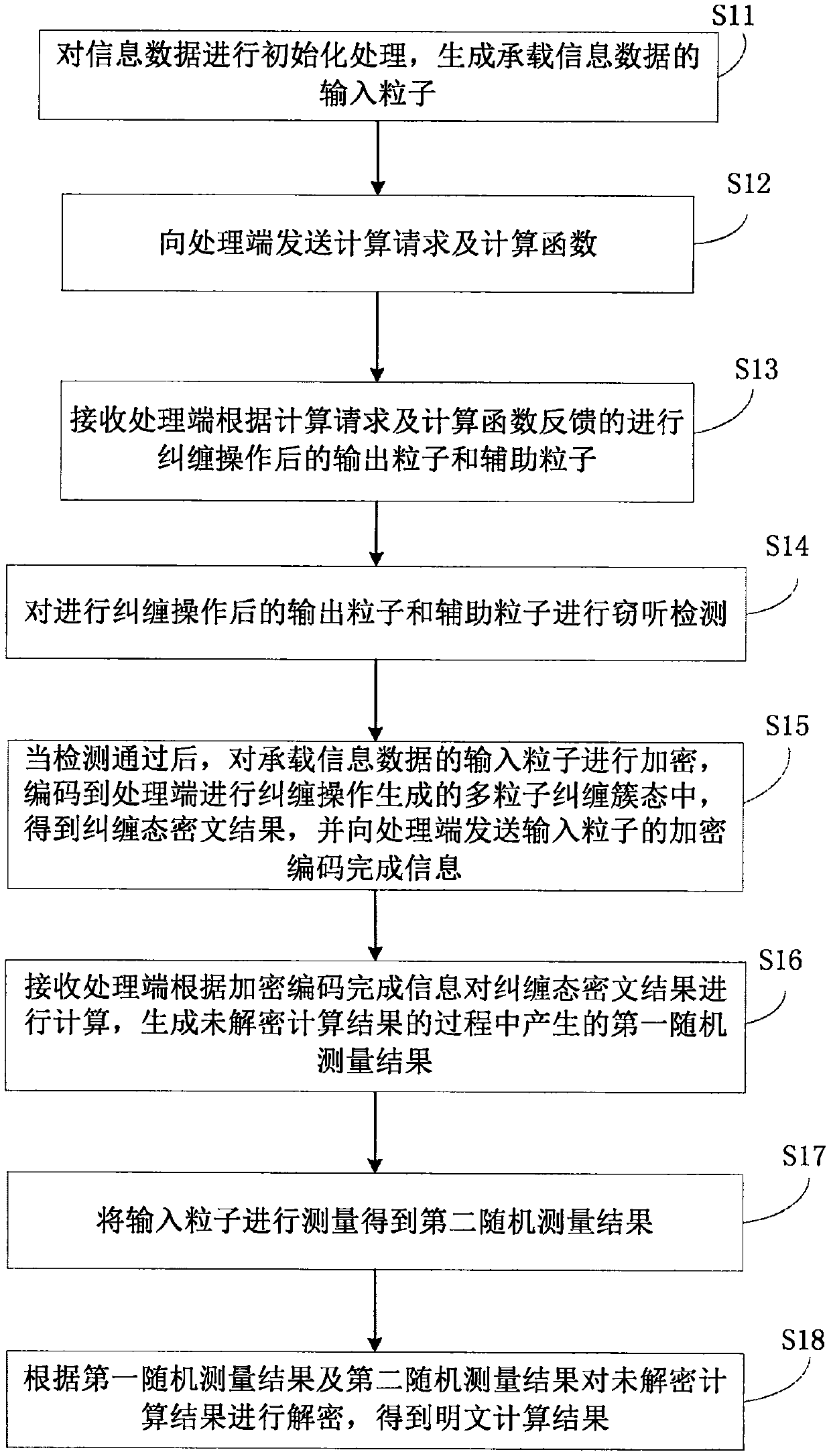
The invention discloses a quantum cloud computing method and system, a client and a cloud server. The quantum cloud computing method comprises the steps of initializing and generating an input particle carrying data; sending a computation request and a computation function to a processing terminal; carrying out eavesdropping detection on the particles after an entanglement operation; encrypting and encoding the data into an entangled cluster state after passing the detection to obtain an entangled ciphertext result, and sending encryption and encoding completion information; receiving a randommeasurement result generated in the process that the processing terminal carries out computation on the entangled ciphertext result to generate a computation result which is not decrypted; measuringthe input particle to obtain a random measurement result; and decrypting the computation result which is not decrypted to obtain a plaintext computation result according to the two measurement results. The data required to be computed and operated in the process is not actually stored in the cloud, and the storage is achieved based on the correlation between quantum states; and the operation executed by the cloud server is only related to the computation function required by the client, thereby not posing a threat to the security of the information, and ensuring the privacy and confidentialityof the client information.
Owner:国富瑞数据系统有限公司 +1
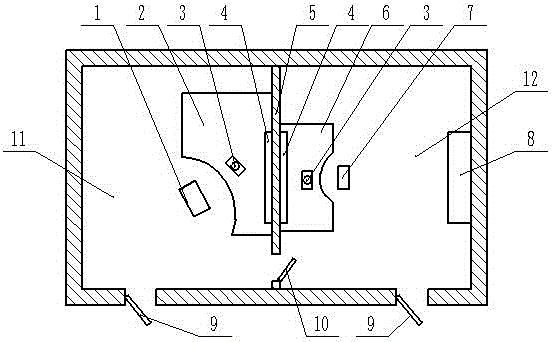
Safe and private psychological counseling room
InactiveCN105952198ASecurity threatAvoid direct face-to-face contactHospitalsSchoolsPatient roomOffice chair
The invention discloses a safe and secret psychological consultation room. The invention includes a patient room and a doctor room. Both the patient room and the doctor room are provided with access doors, and a screen is arranged between the patient room and the doctor room. Both are equipped with walkie-talkies and display screens, patient rooms are equipped with consultation tables and chairs, doctor's rooms are equipped with desks and office chairs, and connecting doors with locks are set between the doctor's room and patient room. The present invention is divided into two parts, the patient's room and the doctor's room, which avoids direct face-to-face contact between the psychological patient and the doctor when seeking medical treatment, not only allows the patient to relax, but also avoids threatening the doctor's safety when the patient has excessive emotions; the patient's room There is also a connecting door between the doctor and the doctor's room. After the doctor and the patient have a preliminary understanding and the mutual consent of the patient and the doctor, the patient can enter the doctor's room through the connecting door, and the doctor will provide further understanding and psychological counseling to the patient.
Owner:SUZHOU QIZHAN INFORMATION TECH CO LTD
Novel pipe grinding and detecting device
InactiveCN105538138AImprove securitySecurity threatRevolution surface grinding machinesGrinding feed controlMeasurement deviceMechanical engineering
The invention discloses a novel pipe grinding and detecting device. The novel pipe grinding and detecting device comprises a feeding device, a supporting device, a grinding device and a measuring device. The supporting device is located at the discharging end of the feeding device, and the grinding device is located above the supporting device; the measuring device is located at the discharging end of the grinding device; through the feeding device, automatic feeding is achieved, a supporting mechanism with the adjusting function is adopted, the structure is simple, operation is convenient, and the adjustable effect is achieved; and after grinding, the measuring device enables a steel pipe to rotate during clamping through cooperation of a first clamping device and a second clamping device; and multi-angle measuring can be achieved, vibration and shaking of the steel pipe can be reduced, and a bearing plate is arranged, so that the steel pipe is placed more stably and is more accurately measured, error generation is reduced, and the steel pipe measuring effect is better.
Owner:RONGCHANG YONGXIN STEEL STRUCTURE PROCESSING FACTORY
Automatic loading and grinding equipment for pipe fittings
InactiveCN105538139ALabor savingImprove work efficiencyRevolution surface grinding machinesGrinding feed controlEngineeringPipe fitting
The invention discloses automatic loading and grinding equipment for pipe fittings, comprising a loading device, a support device, a grinding device and a measuring device, wherein the support device is located at the discharge end of the loading device, the grinding device is located above the support device, and the measuring device is located at the discharge end of the grinding device. According to the invention, automatic loading can be realized by the loading device, a support mechanism with an adjusting function is adopted, the structure is simple, the operation is convenient, an effect of being adjustable is achieved, and after grinding is completed, due to match of a first clamping device and a second clamping device, the measuring device can carry out multi-angle measurement on a steel pipe which can be rotated when being clamped, and vibration and shake of the steel pipe can be reduced; and since a bearing plate is arranged, the steel pipe can be placed more firmly, steel pipe measurement is more accurate, errors can be reduced, and the steel pipe measuring effect is better.
Owner:RONGCHANG YONGXIN STEEL STRUCTURE PROCESSING FACTORY
Bed capable of being intelligently adjusted according to the turning over of a human body
The invention provides a bed capable of being intelligently adjusted according to the human body turning over situation. The bed includes a bed frame, multiple cameras for visual identification, a controller, a conveyor, a pair of rollers and an electric motor. The two ends of the bed frame are respectively provided with baffles extending to the top of the bed frame, the two ends of a pair of rollers are respectively rotatably connected with the baffles at the two ends of the bed frame, A pair of rollers are respectively adjacent to the two sides of the bed frame, a conveyor belt is drivably arranged on the side walls of the pair of rollers, a motor is drivingly connected with one roller of the pair of rollers, a plurality of cameras for visual identification are arranged on the two side walls of the bed frame, and the cameras for visual identification and the motors are respectively connected with the controller. The conveyor belt rolls the user back to the center of the bed so that he can roll over at will without falling under the bed. At the same time, the volume of the bed can be effectively reduced. It can also make more room for people to move around or place other objects than before, thus facilitating the life of the user.
Owner:何清华
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com