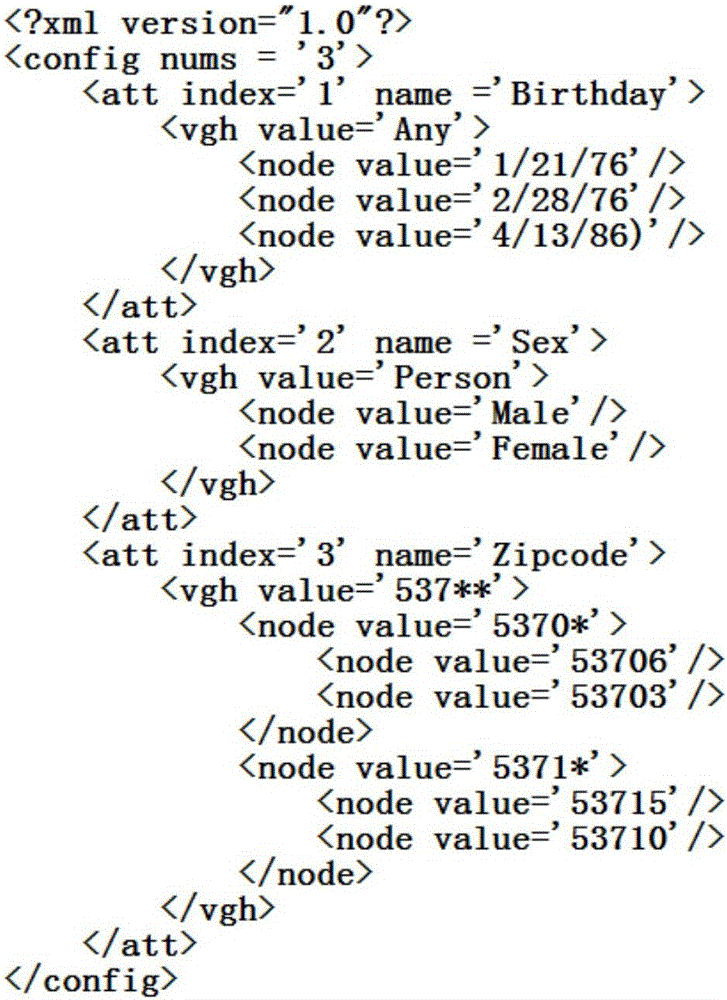
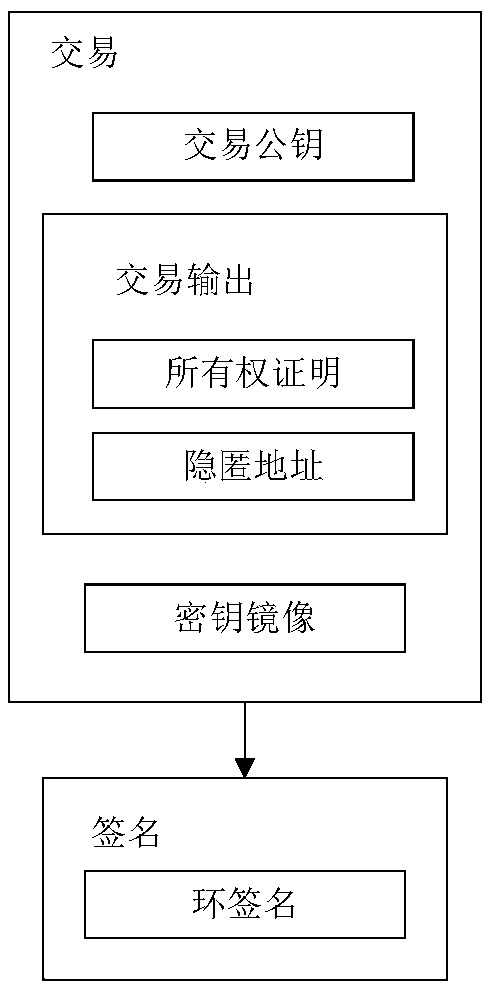
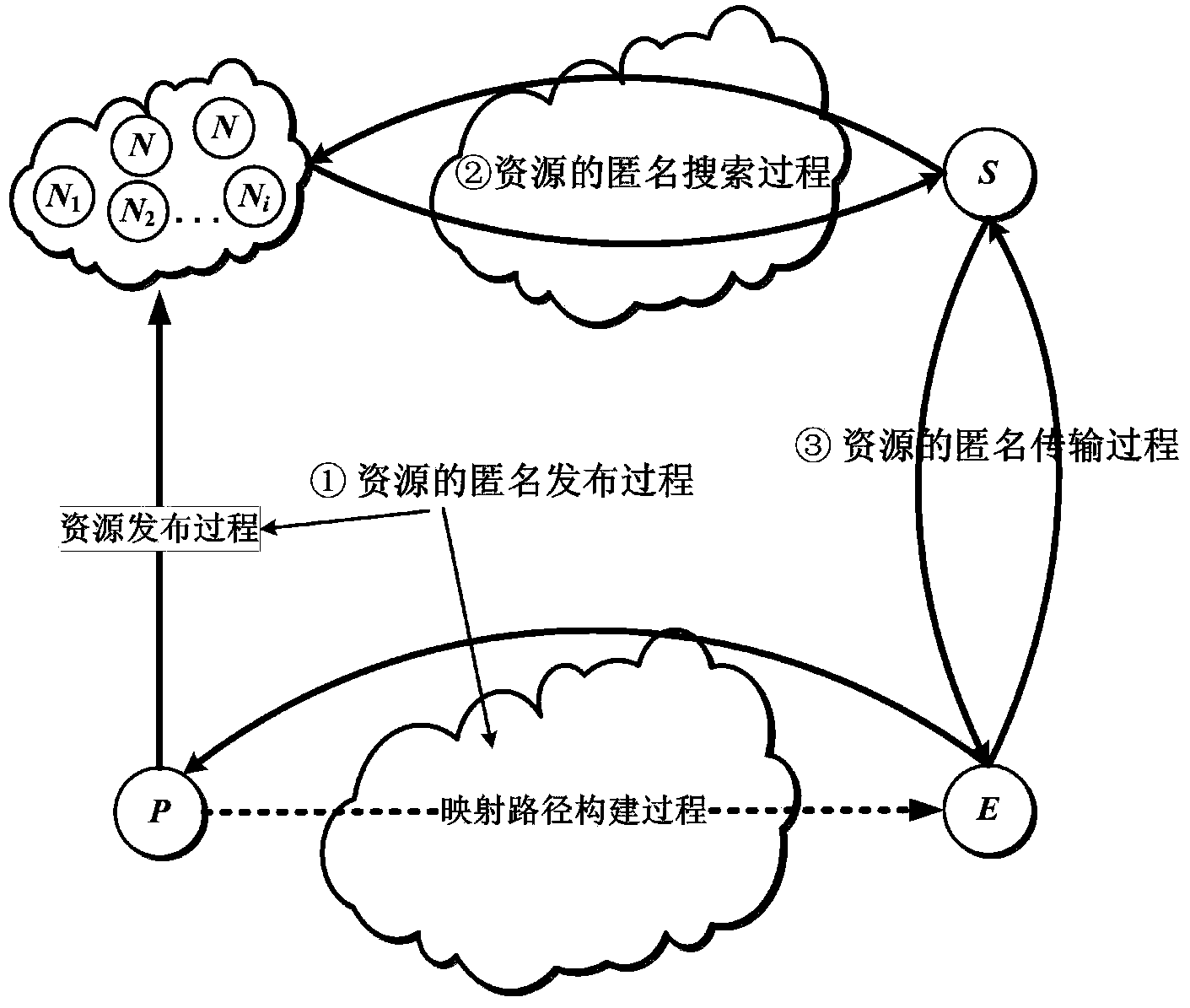
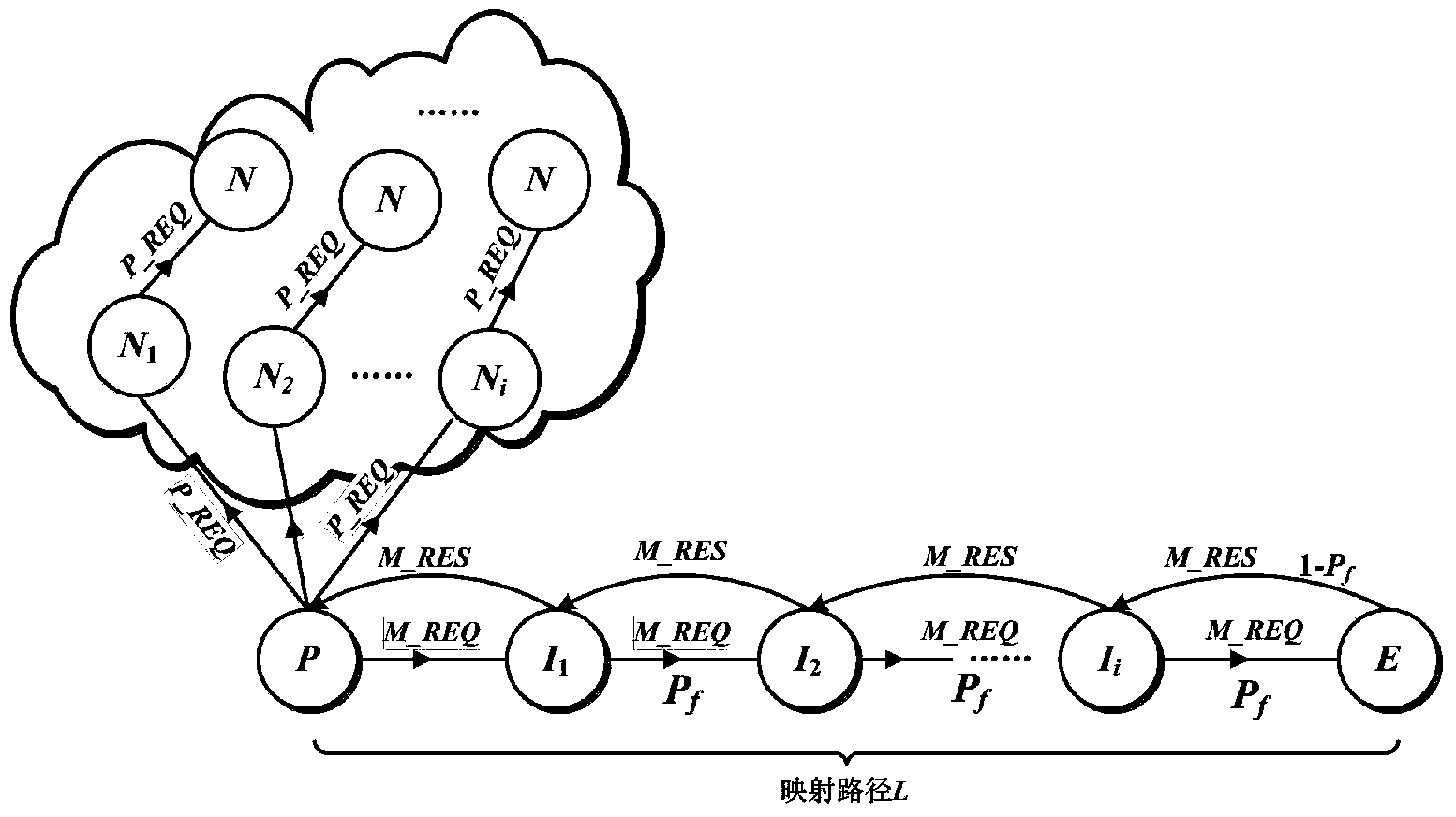
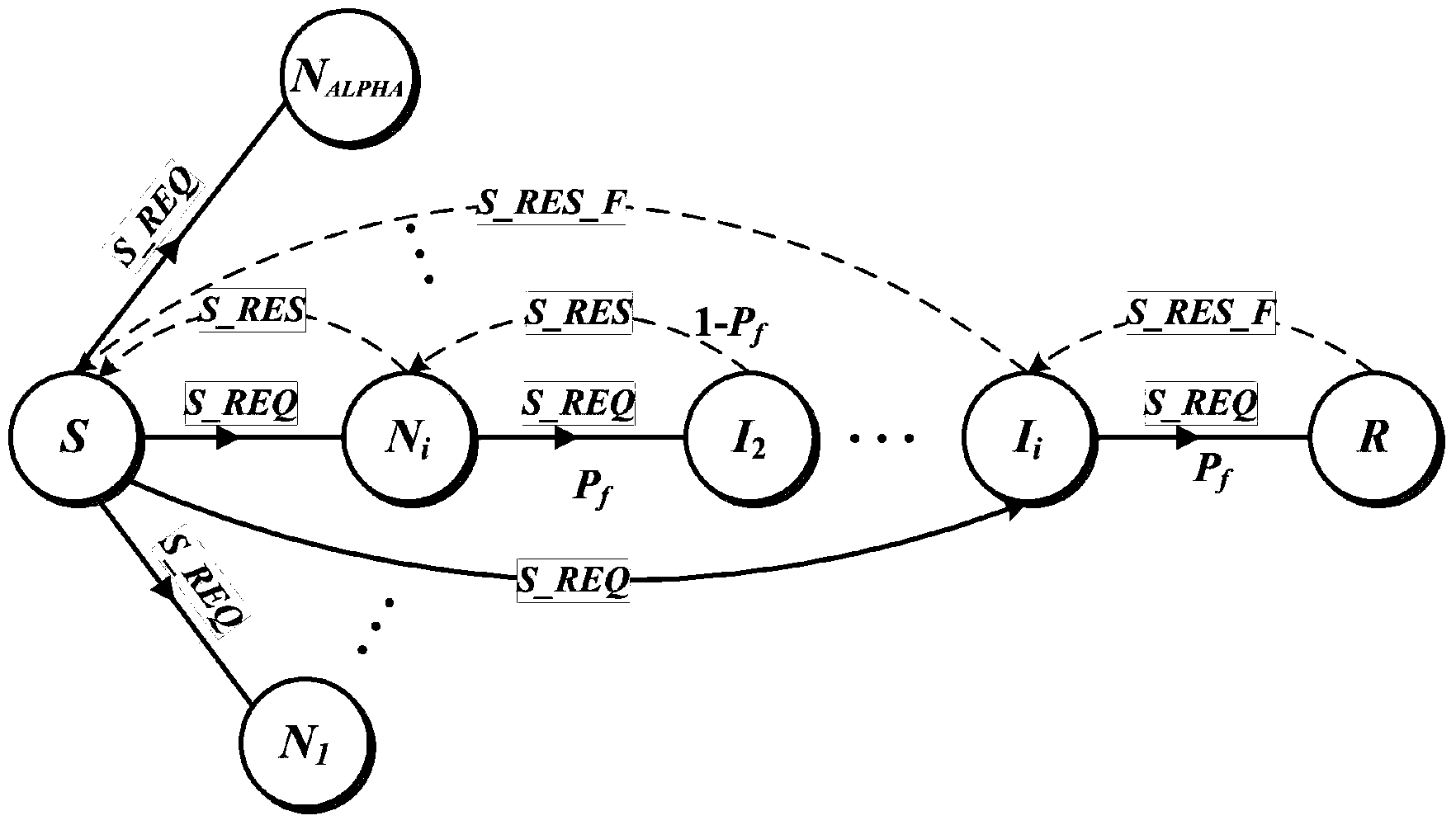
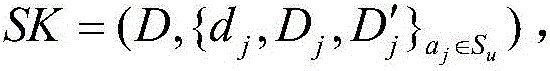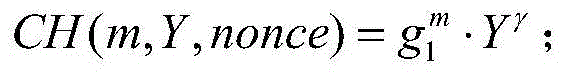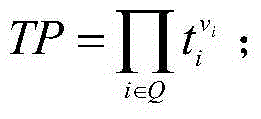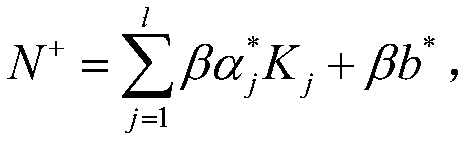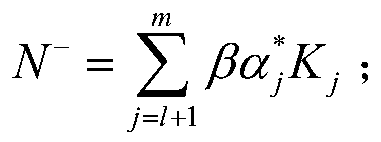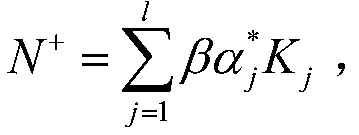Patents
Literature
331results about How to "Realize privacy protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
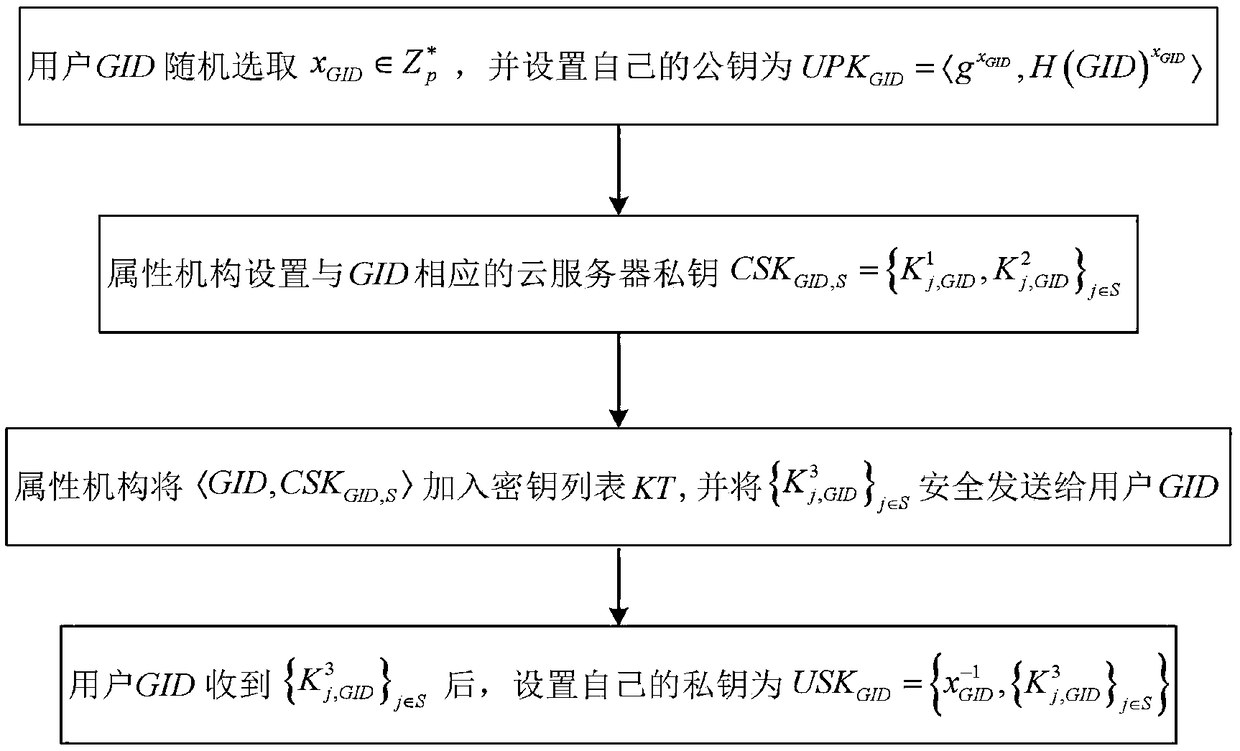
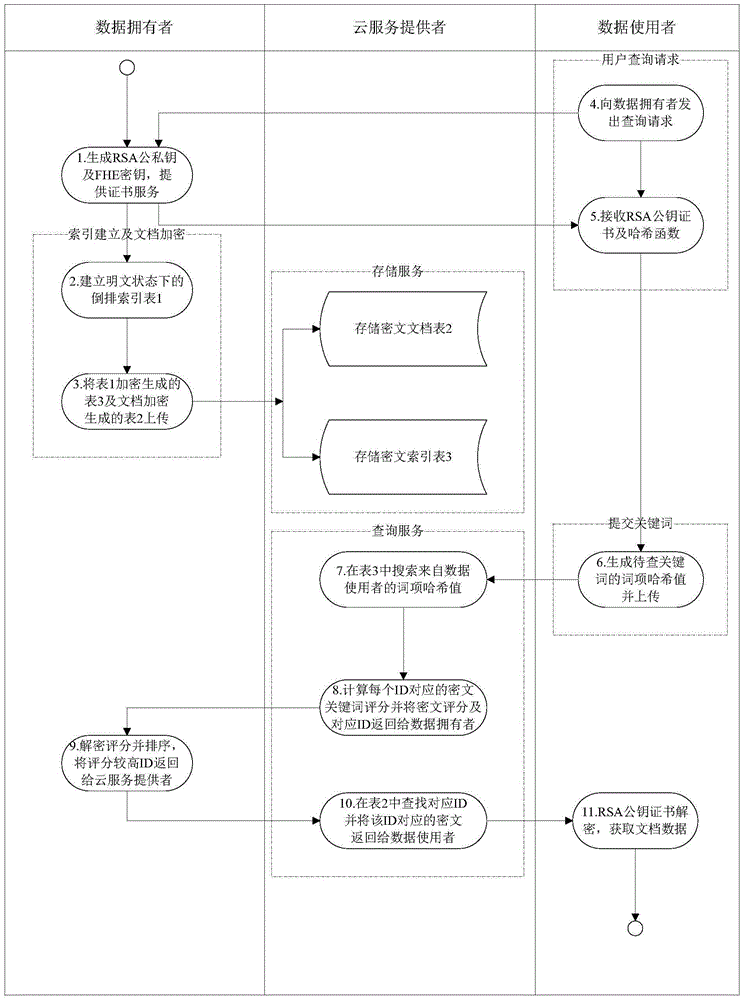
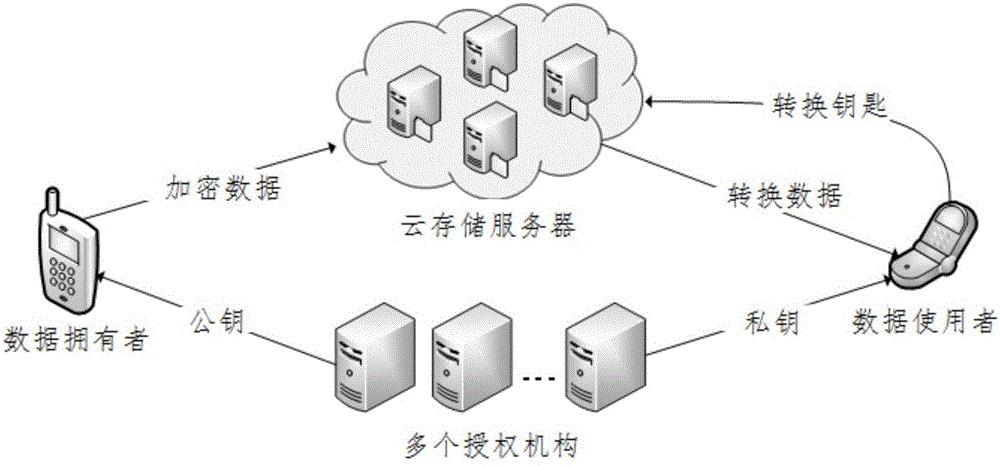
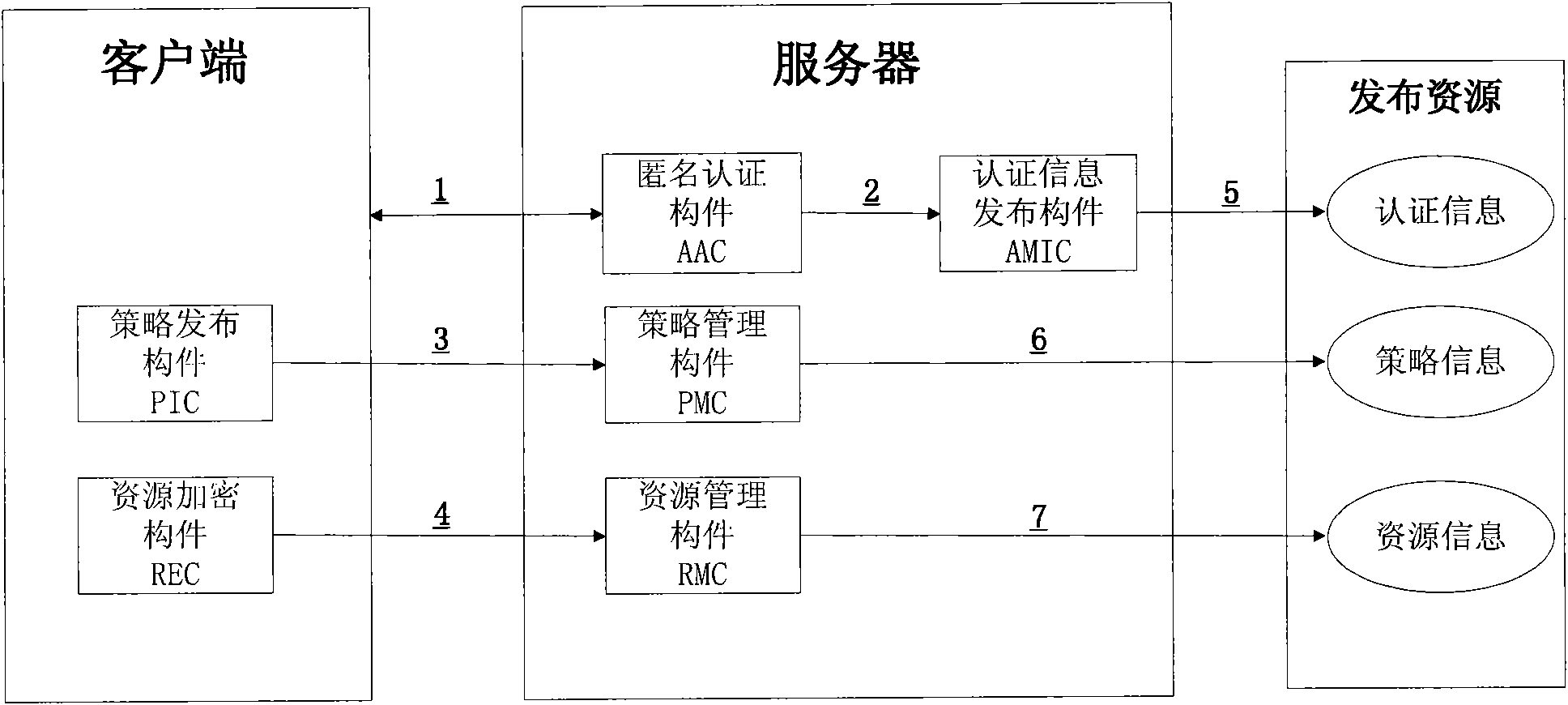
Block chain privacy data access control method based on attribute encryption
ActiveCN106503994AAddress privacy breachesRealize privacy protectionKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
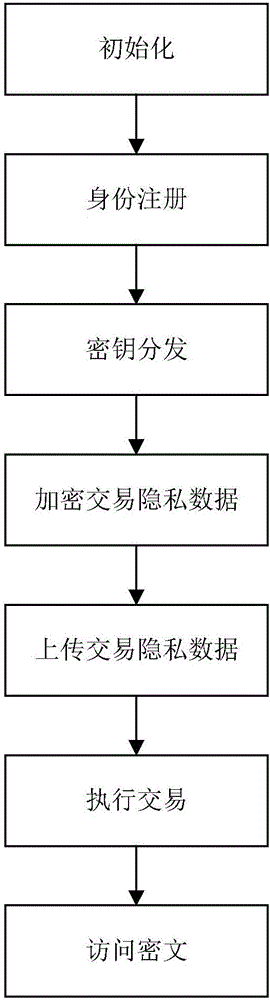
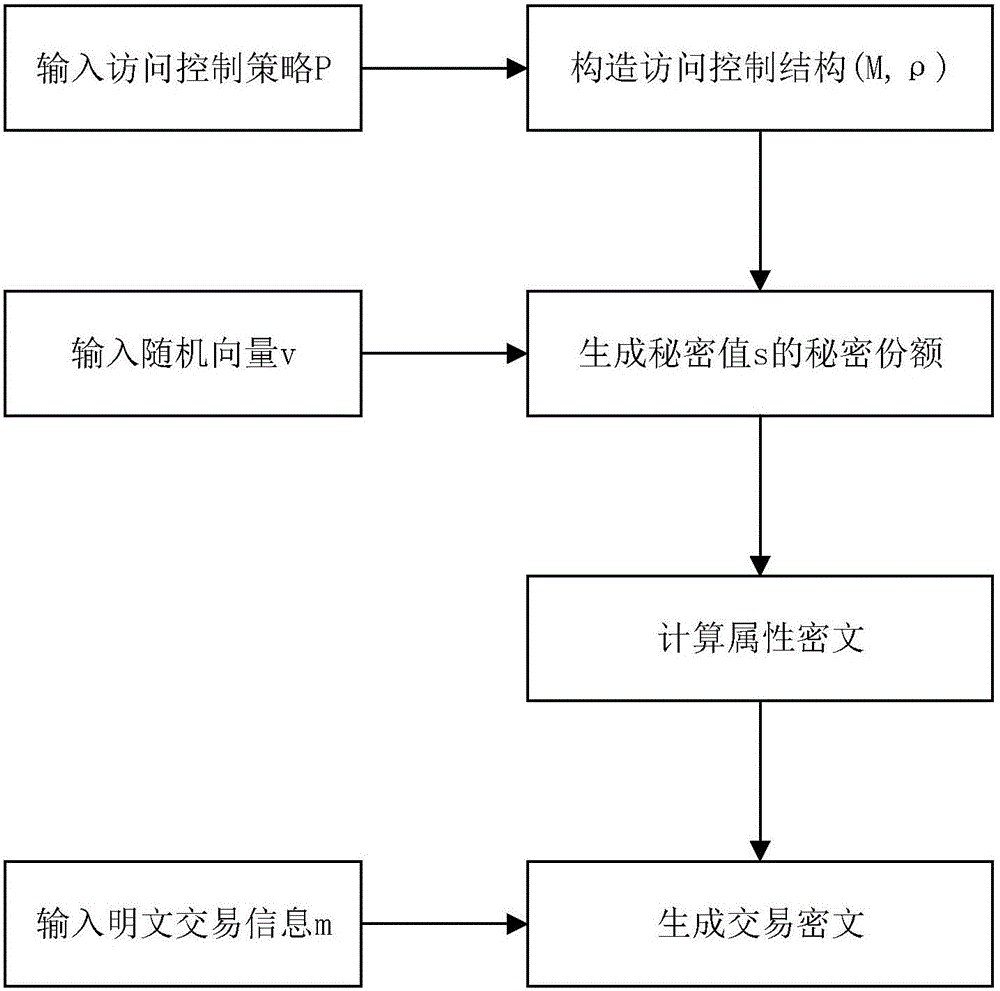
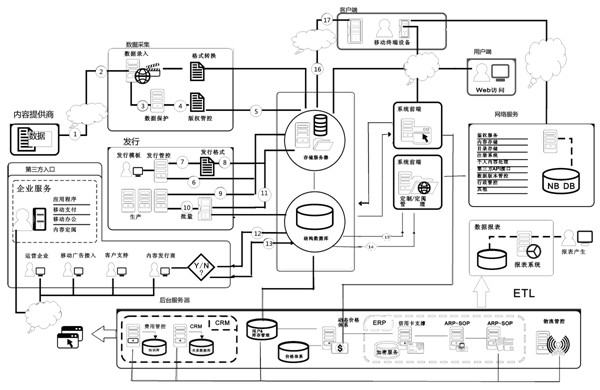
The invention discloses a block chain privacy data access control method based on attribute encryption, which mainly solves a problem in the prior art that the real identity of a user in the block chain is anonymously protected but the and transaction privacy information is not encrypted so as to cause privacy leakage. The method comprises the steps that 1. a system is initialized; 1, a user registers to obtain attribute information; 3, an authoritative center, according to the user attribute information, distributes a user private key; 4 a transaction party encrypts transaction privacy data and uploads the transaction privacy data to a block chain; 5, an accountant verifies the transaction information and performs the transaction; 6, a supervisory center is authorized to use the authorized private key to decrypt and check the transaction ciphertext. The method encrypts the transaction privacy information, avoids the leakage of data privacy and can be used for privacy protection of the virtual asset transaction data in the block chain.
Owner:XIDIAN UNIV
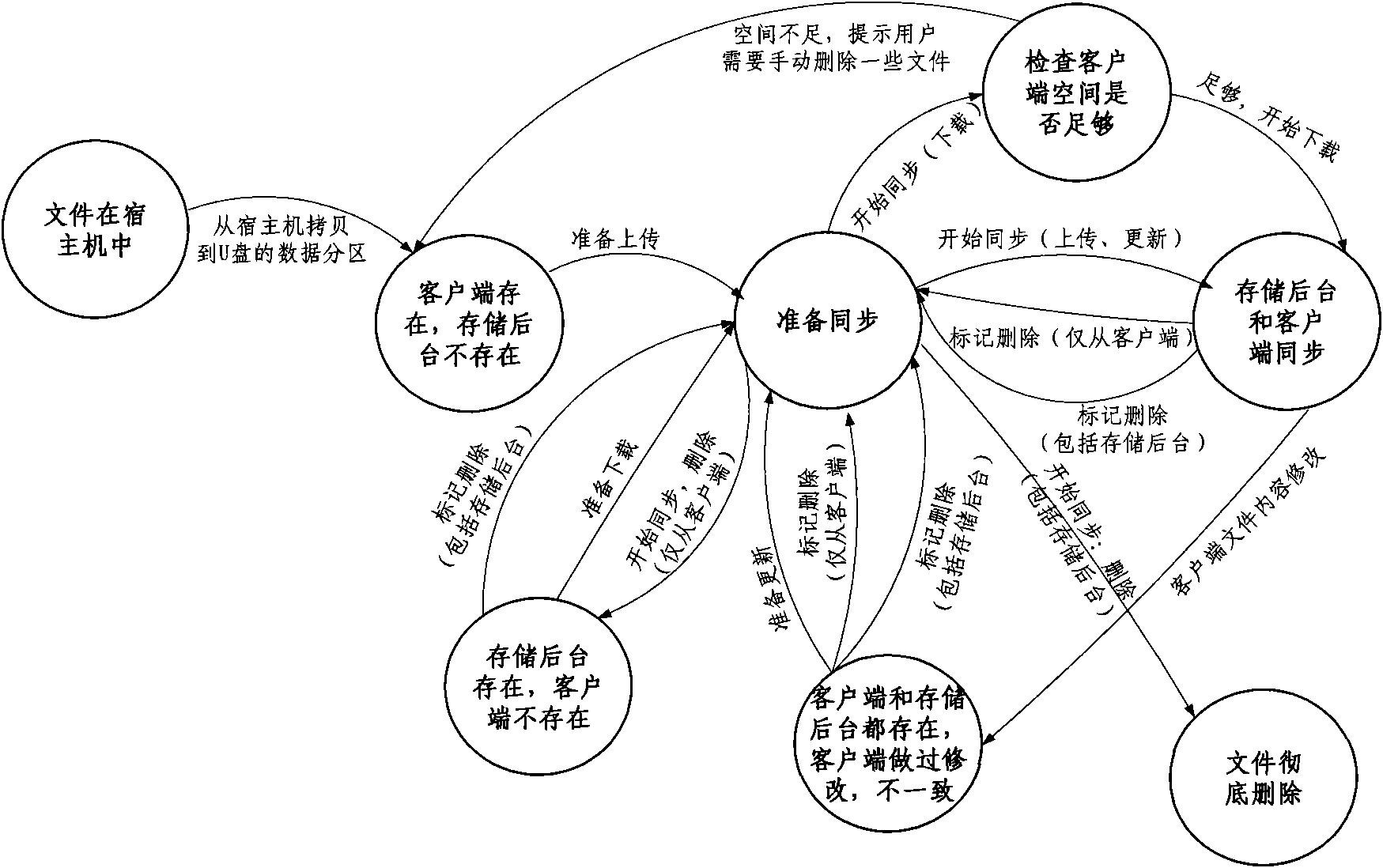
Personal data management method based on cloud computing environment
ActiveCN101854392ARealize privacy protectionEnsure data synchronizationInput/output to record carriersTransmissionClient-sideCloud computing
The invention discloses a personal data management method based on cloud computing environment. The method takes the server cluster of the cloud computer environment as a background server, a removable storage device as a client and a computer connected with the removable storage device as a host. The method comprises the following steps: the removable storage device is configured to be a disk which can be visited through a driver letter on the host, through the disk, documents are uploaded and downloaded to the background server, the disk is read and written and a green software is used, at the same time, in the document uploading and downloading and the disk reading and writing process, the data is encrypted and decrypted and the document of the background server is kept synchronous with document of the removable storage device client. The invention adopts the removable storage device as the storage client, the data on the removable storage device is encrypted, the green software can be used portably, no mark is left on the host, and the privacy protection of the user is realized. When the data is backed up, the data synchronism of the client and the background server is ensured.
Owner:上海浩方信息技术有限公司
Identity authentication method based on biological feature encryption and homomorphic algorithm
InactiveCN102664885AImprove privacyAvoid crackingUser identity/authority verificationTimestampAlgorithm
The invention discloses an identity authentication method based on biological feature encryption and a homomorphic algorithm. The method is quicker than a normal password method by using biological features of users as passwords to log in a system through a mobile device, using an encrypted biological template is safer, and privacy of the users can be guaranteed as information is transmitted in a ciphertext form. By adding factors such as timestamps, tri-party authentication among the users, a provider server and a cloud computing server is realized, and reliability among the three parties is enhanced. Legal users can be prevented from using resources in the cloud computing environment illegally to better manage the resources by means of user authentication operation according to attribution predicate encryption and real-time updating of permission information. Operation without encryption can be realized by the aid of the homomorphic algorithm, same effects as decrypting before operation can be achieved, time and space expenses can be saved, system efficiency is greatly improved, and the identity authentication method has high safety and efficiency.
Owner:南京邦普信息科技有限公司
Control system based on cloud computing encryption storage service
InactiveCN102143188ARealize privacy protectionEnsure data synchronizationTransmissionSpecial data processing applicationsData synchronizationThird party
The invention discloses a control system based on cloud computing encryption storage service, comprising a cloud computing processor, a cloud computing storage, a cloud computing user access front end, a cloud computing backstage controller module and a cloud computing third-party access end, wherein, a company or a content provider is connected with the system through a third-party access port; and a mobile terminal is interconnected with the cloud computing encryption through wireless manners of 2G, 3G or WIFI and the like. The movable encryption storage equipment is adopted as the stored mobile terminal, the interactive data is the encryption data, and a decryption secret key is controlled by a user; the data at a client side can not be decrypted by the system side under the non-authorized condition, thus realizing the private protection of users, also realizing the safety protection of the company level, and simultaneously ensuring the data synchronism of the client side and the backstage server when the data is backed up.
Owner:SHANGHAI QINGLONG COMM TECH
Efficient privacy protecting audit scheme based on chameleon hash function of cloud storage
InactiveCN104601605AImplement integrity verificationRealize privacy protectionTransmissionData labelingUser privacy
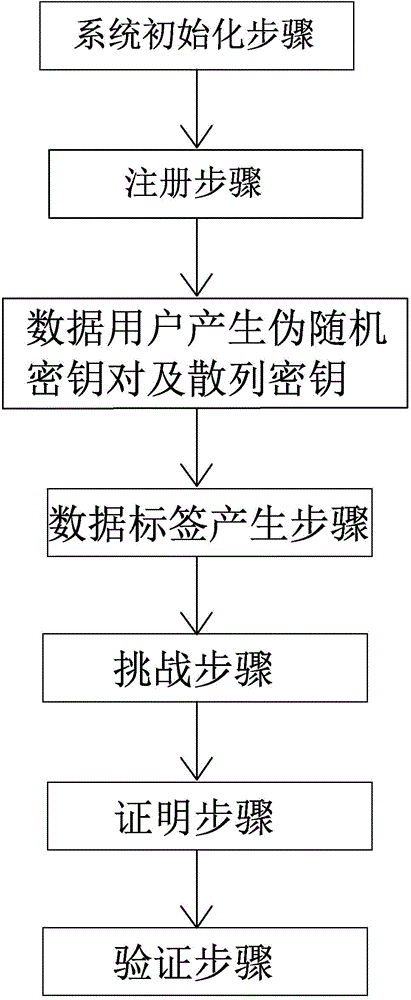
The invention provides an efficient privacy protecting audit scheme based on the chameleon hash function of cloud storage. The scheme includes (1) a system initialization step; (2) a registration step; (3) a pseudo-random key pair and hash key generation step for data users; (4) a data label generation step; (5) a challenge step; (6) a proof step; (7) a validation step. According to the scheme, on the basis of the decidable Diffie-Hellman problem and a chameleon digital signature, a privacy protecting public audit scheme is established, and high efficiency, low safety assumptions and wide application range are provided; according to a cloud server, the identity privacy of the data users is protected, and the outsourcing data integrity is protected; according to auditors, the data user privacy is protected in the whole auditing process.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Cloud-oriented interactive privacy protection method and system
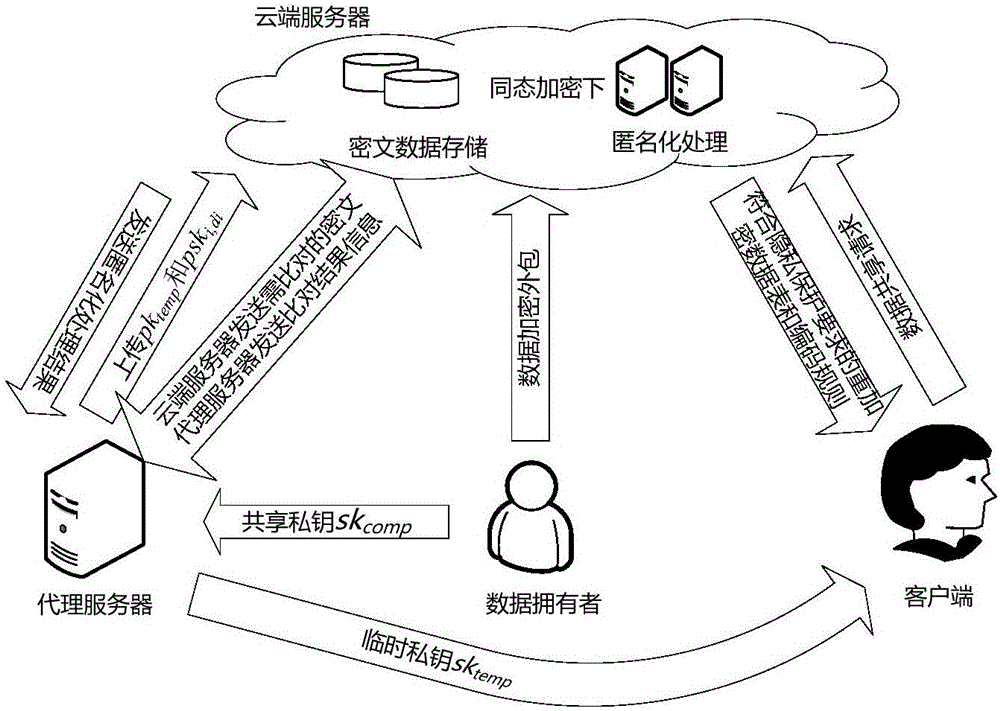
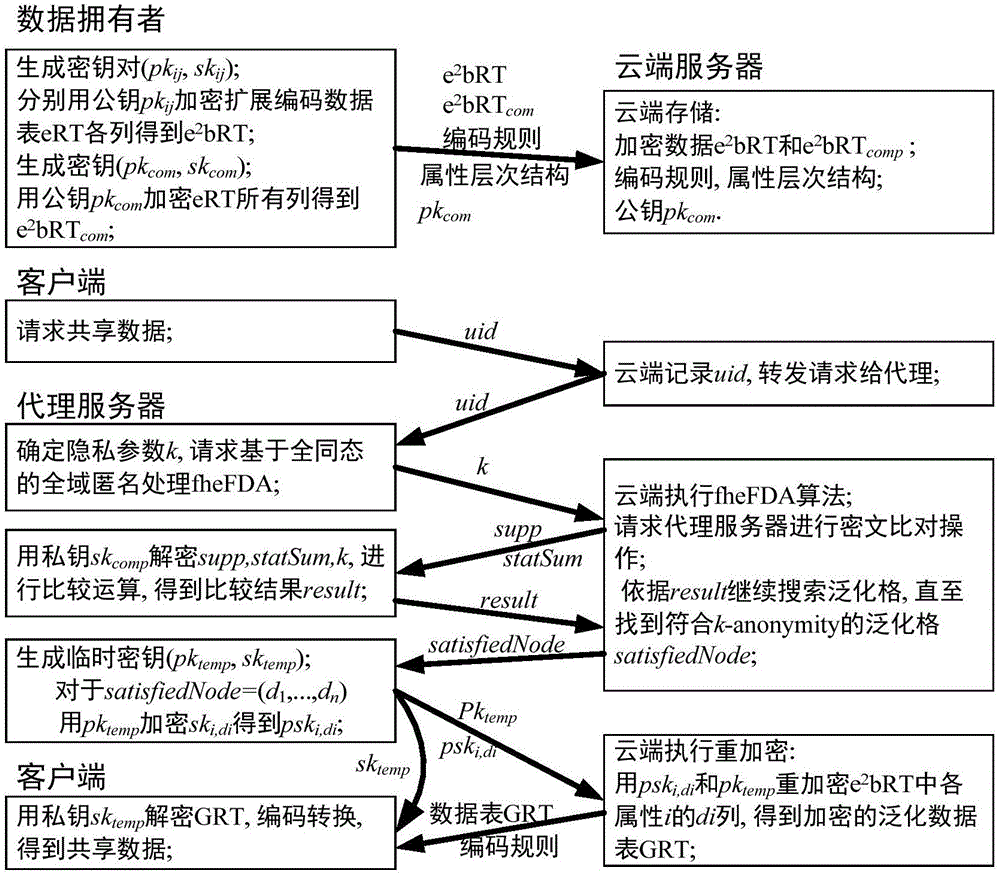
ActiveCN106533650AEnsure safetyRealize privacy protectionDigital data protectionCommunication with homomorphic encryptionThird partyCiphertext
The invention discloses a cloud-oriented interactive privacy protection method and system. The privacy protection method is characterized in that a data owner uploads encrypted data and stores the encrypted data on a cloud server for a long time, and data sharing services meeting privacy protection requirements are provided; when a client sends a data request, anonymization processing of the encrypted data is directly carried out on the cloud server, and the data meeting the privacy protection requirements is output; and during the anonymization processing, the cloud server can interact with a proxy server for comparison processing of ciphertext data. The method has the advantages that the data stored in an encrypted manner can serve multiple purposes; and diversified privacy protections can be easily achieved. The privacy protection system has two preconditions: a cloud service provider may be a privacy attacker, but the services must be provided according to a protocol; and the client promises not to forward an obtained data sheet to any unauthorized third party (including the cloud service provider), so that conspiratorial attacks are prevented.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
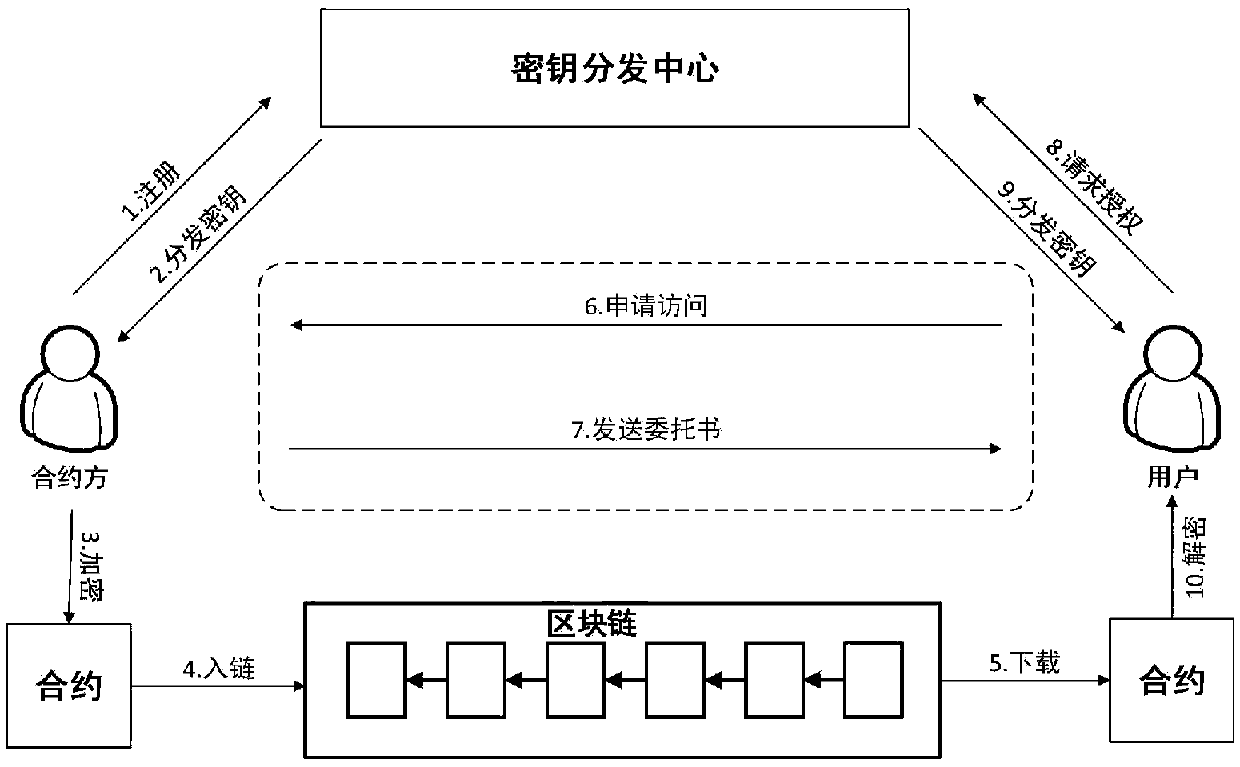
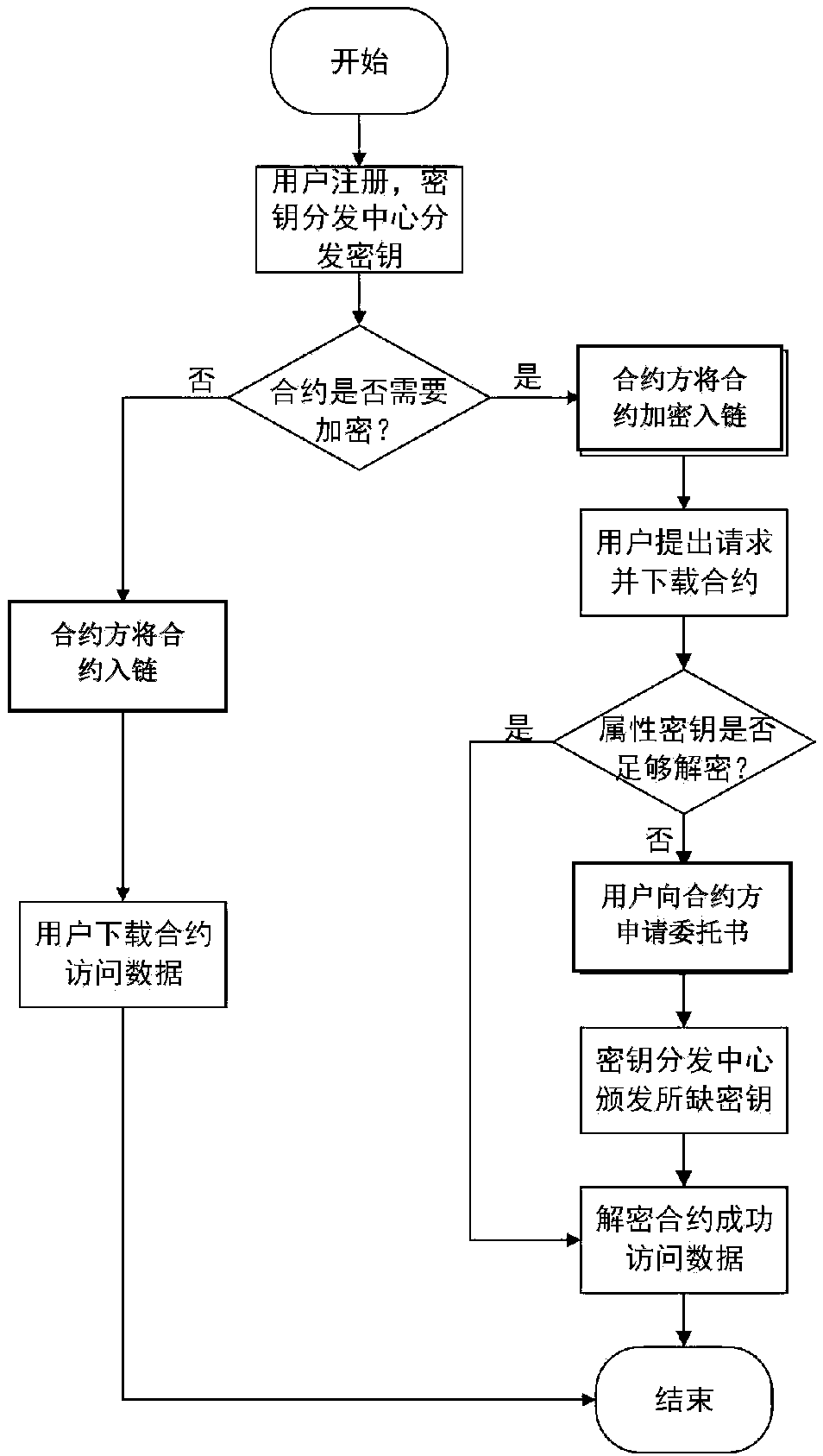
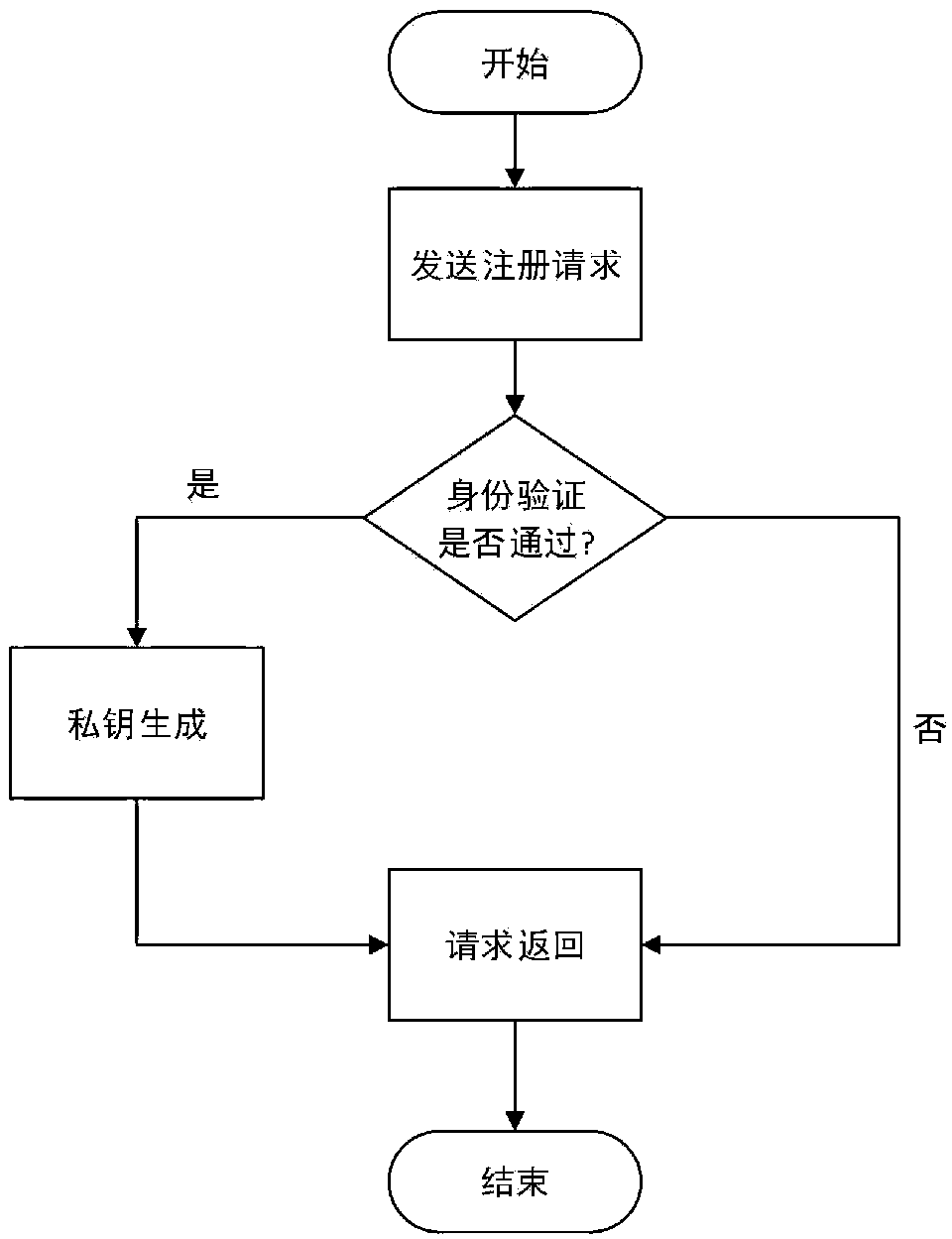
Block chain contract privacy protection method and system based on attribute-based encryption
ActiveCN109559117ARealize privacy protectionFinancePayment protocolsAttribute-based encryptionChain system
The invention belongs to the technical field of information, and particularly relates to a block chain contract privacy protection method and system based on attribute-based encryption. The system comprises a key distribution center KDC, a user and a block chain system. The key distribution center KDC is used for establishing an attribute-based encryption system supporting an attribute-based access strategy, user key distribution, public key management and authorization check and revocation. The whole block chain system adopts one attribute-based encryption system, and one key distribution center (KDC) is adopted to carry out key management. According to the method, the attribute-based encryption is adopted to realize privacy protection on sensitive information in a block chain contract; and the attribute key in the access control strategy can be dynamically generated and cancelled, and the contract party dynamically controls the access permission of the private data on the block chain.
Owner:UNIV OF SCI & TECH BEIJING
Two-way privacy protective system and method for inquiring medical diagnostic service
ActiveCN105577368ARealize privacy protectionGuaranteed privacy protectionKey distribution for secure communicationData processing applicationsDiseaseService provision
The invention discloses a two-way privacy protective system and method for inquiring a medical diagnostic service, used for mainly solving the problem that privacy protection of inquiry information of medical users and data resources of service providers are not related in the prior art. The system comprises a medical diagnostic server and a medical user terminal; the medical diagnostic server completes system initialization, provides login and distributes a secrete key to the medical user terminal, stores data of a nonlinear SVM model built by using the existing medical database, provides a privacy protective medical diagnostic service for the medical user terminal, and sends an inquiry response result to the user terminal; and the medical user terminal sends a service inquiry request to the medical diagnostic server and performs decryption and polynomial aggregation operation of the inquiry response result returned by the medical diagnostic server, such that a pre-diagnosis result is obtained. According to the invention, privacy protection of the inquiry information of the medical users and the data of the nonlinear SVM model can be realized; and the system and the method can be used for providing an online disease prediction service for the medical users.
Owner:XIDIAN UNIV
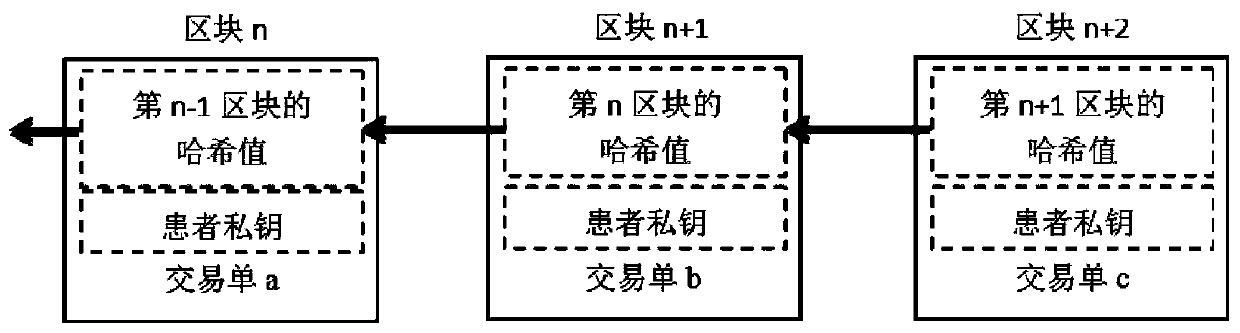
Electronic medical record access control method based on block chain
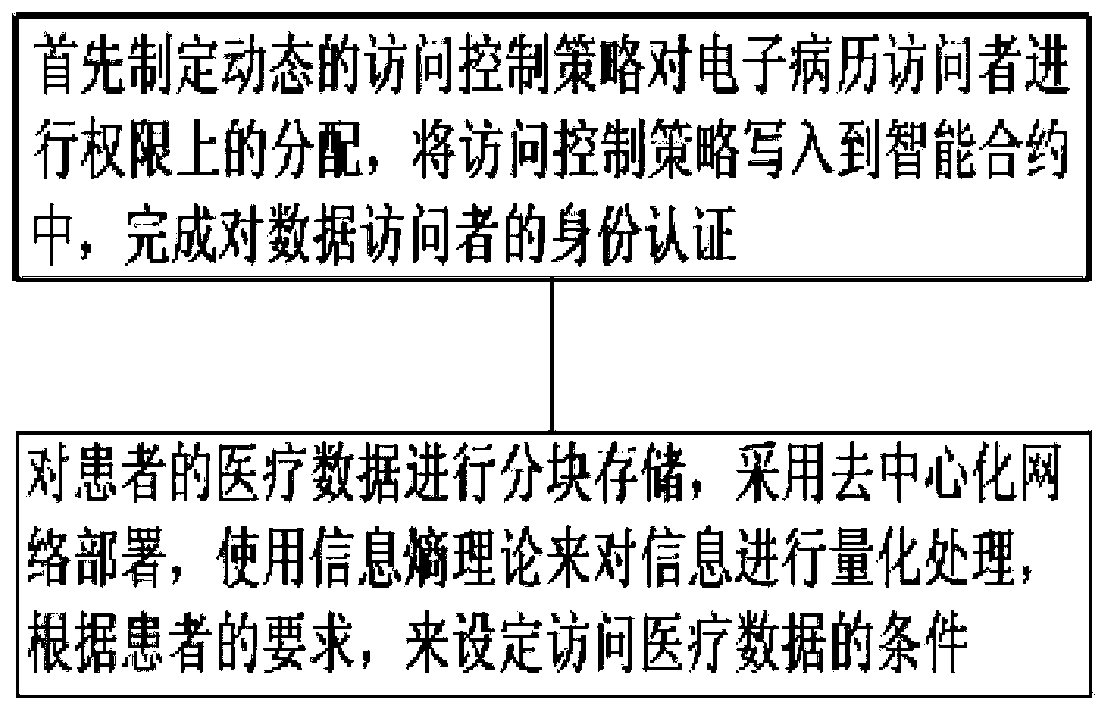
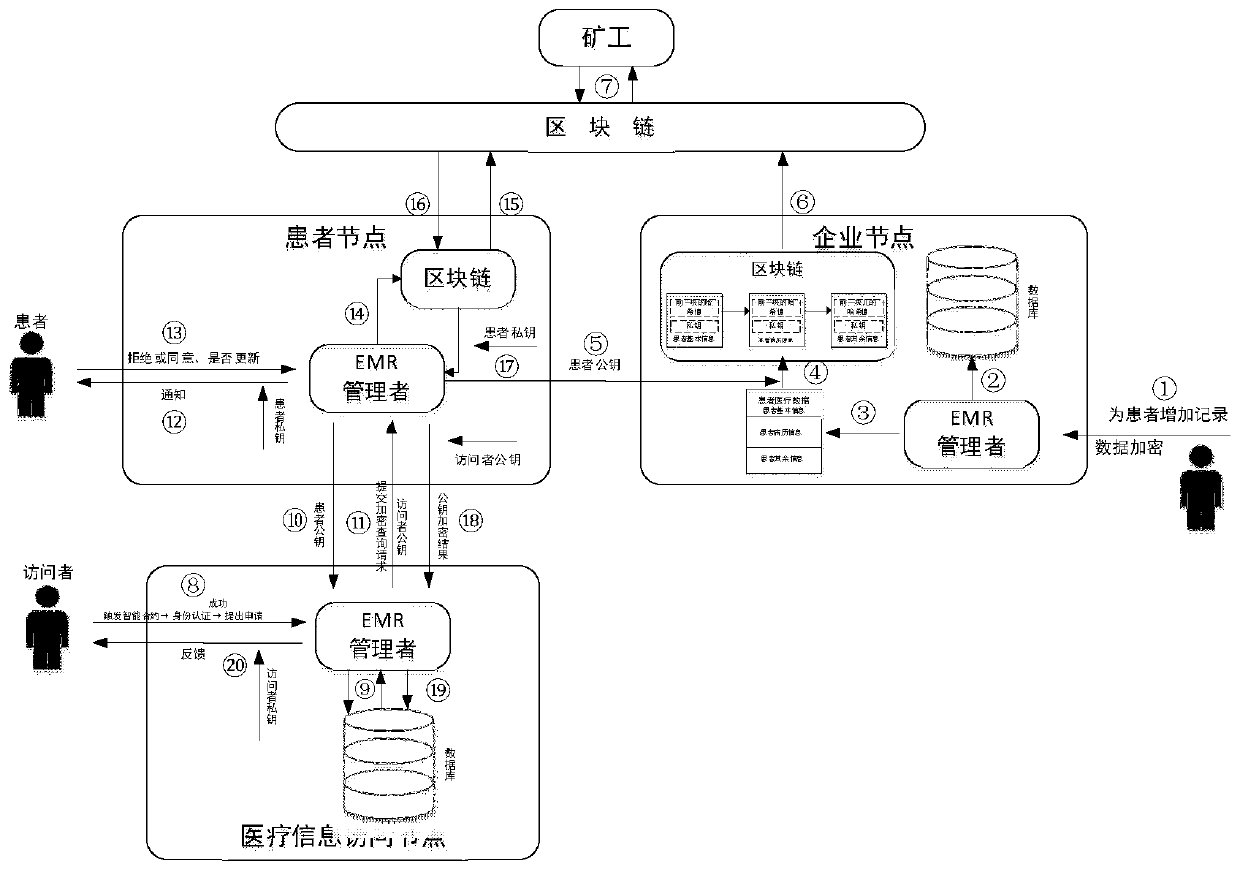
ActiveCN110321721AFix the leakAchieve protectionDigital data protectionPatient-specific dataMedical recordData access
The invention discloses an electronic medical record access control method based on a block chain, and relates to the technical field of medical data sharing methods. The method comprises the following steps: firstly, formulating a dynamic access control strategy to carry out authority distribution on an electronic medical record visitor, and writing the access control strategy into an intelligentcontract to complete identity authentication on a data visitor; storing medical data of a patient in blocks, adopting decentralized network deployment, using an information entropy theory for carrying out quantitative processing on information, and setting conditions for accessing the medical data according to the requirements of the patient. According to the method, the medical privacy information protection of the user in the service process can be realized, the patient can autonomously manage own medical data, and the privacy protection method under medical data sharing is favorably realized.
Owner:西康软件有限责任公司
Block chain transaction settlement method and system, and related equipment
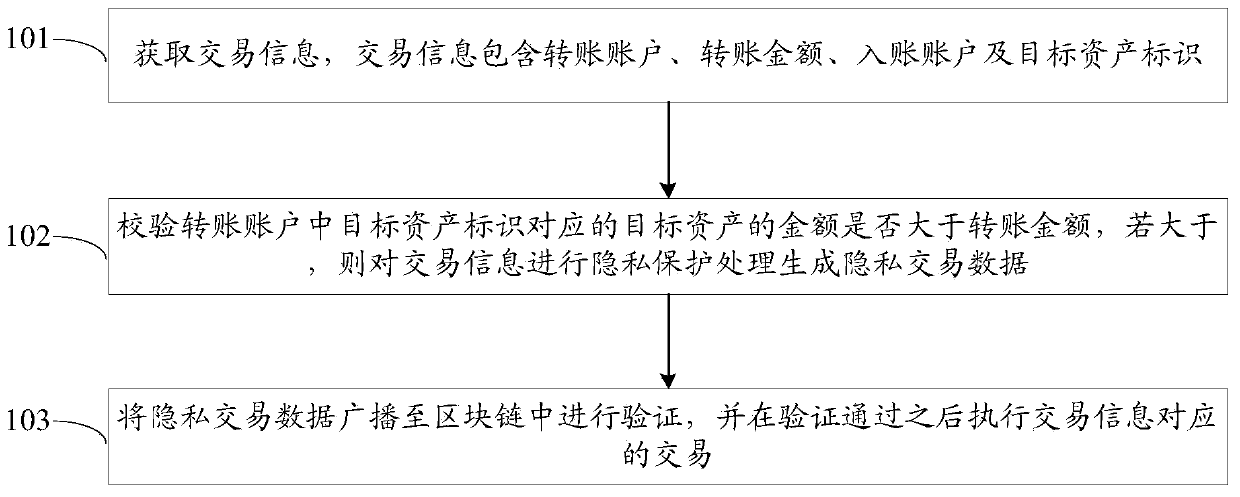
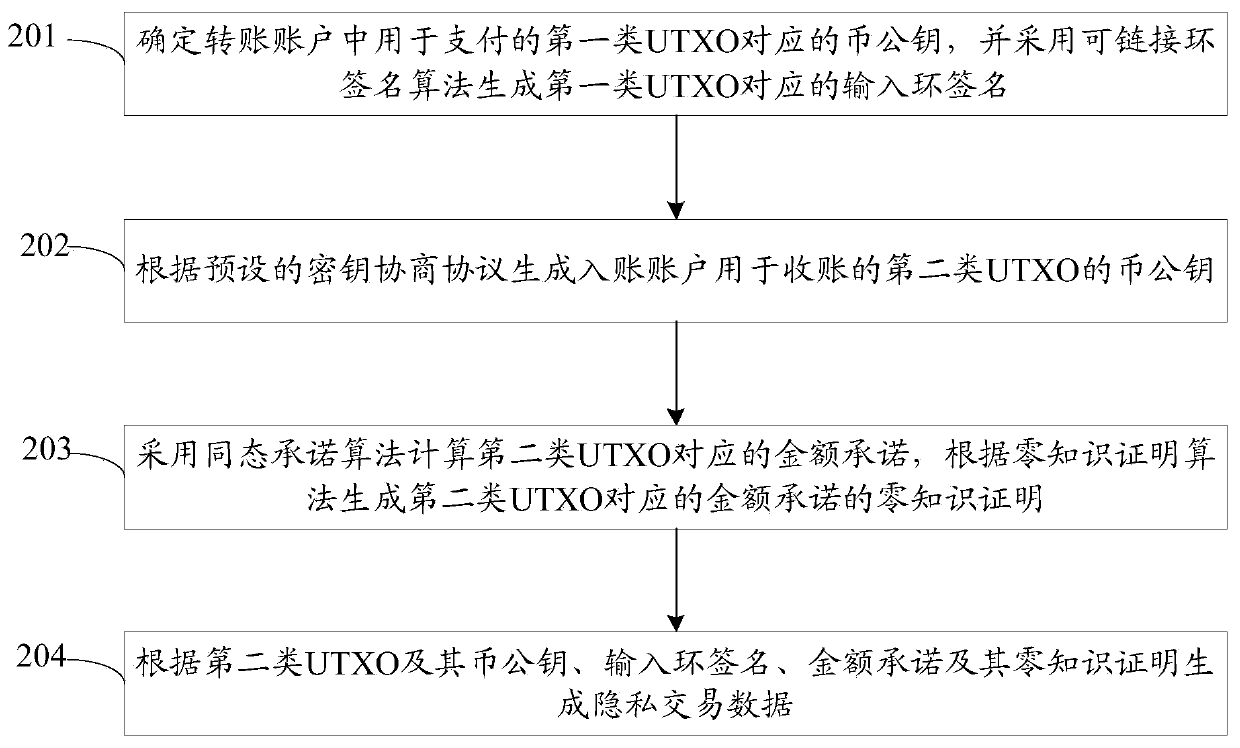
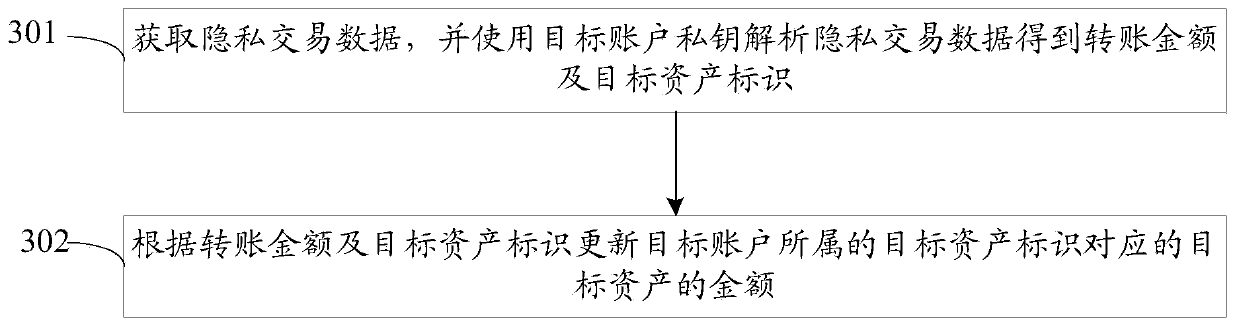
The embodiment of the invention provides a block chain transaction settlement method and system and related equipment, which are used for realizing compatibility and transaction privacy protection ofvarious asset transactions on the same block chain. The method comprises steps that transaction information is acquired, the transaction information comprises an account transfer account, an account transfer amount, an account entry account and a target asset identifier, and the target asset identifier is one of multiple preset asset identifiers; whether the amount of the target asset corresponding to the target asset identifier in the transfer account is greater than the transfer amount or not is verified, and if so, privacy protection processing is performed on the transaction information togenerate private transaction data, so that the transaction information cannot be analyzed without private keys of both transaction parties; and the private transaction data is broadcast to a block chain for verification, and a transaction corresponding to the transaction information is executed after the verification is passed.
Owner:SHENZHEN THUNDER NETWORK TECH +1
Blockchain-based smart city information safety using method and system
ActiveCN108830601ARealize privacy protectionFacilitates safe sharingPayment protocolsPlatform integrity maintainanceInformation sharingSmart city
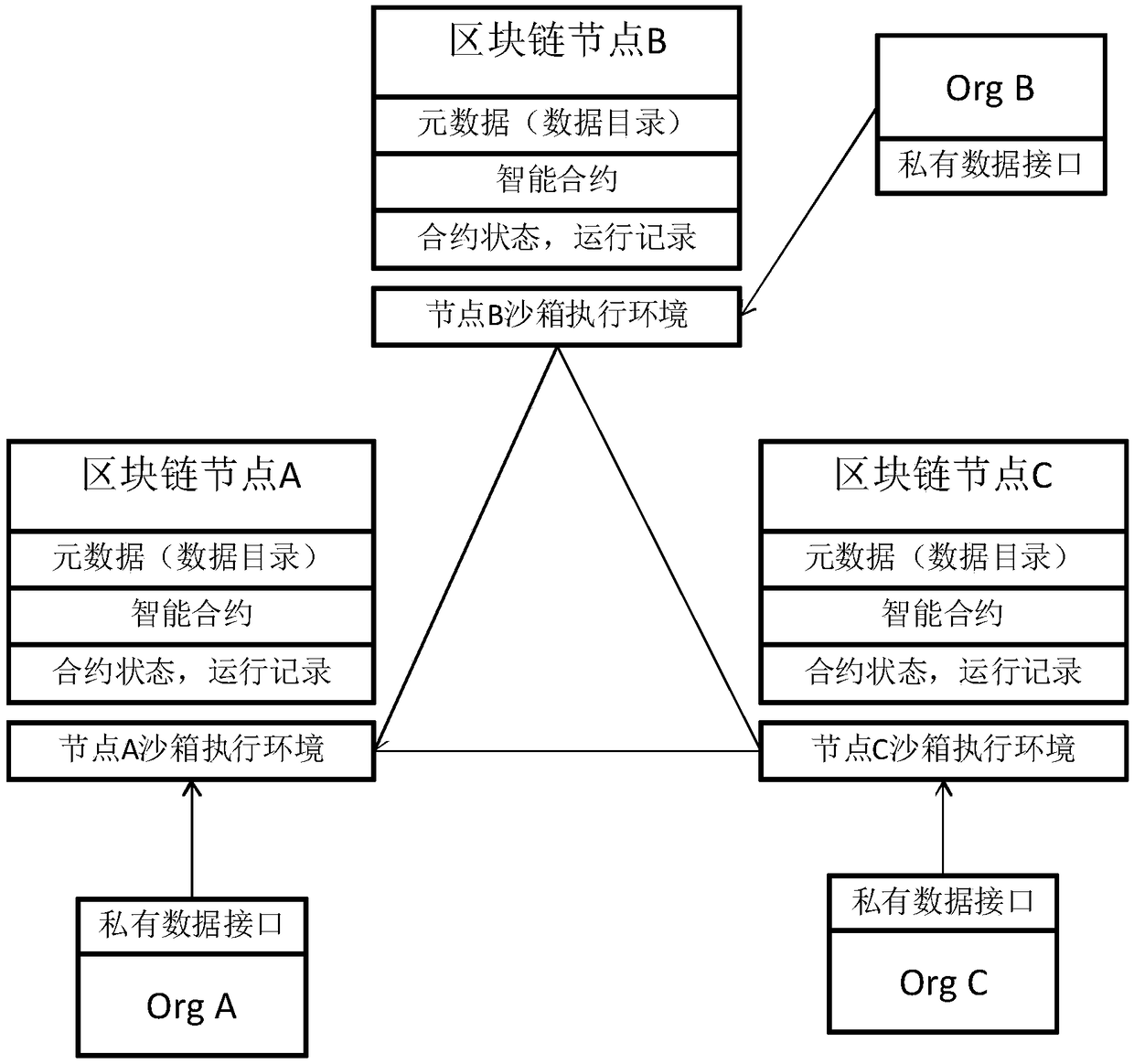
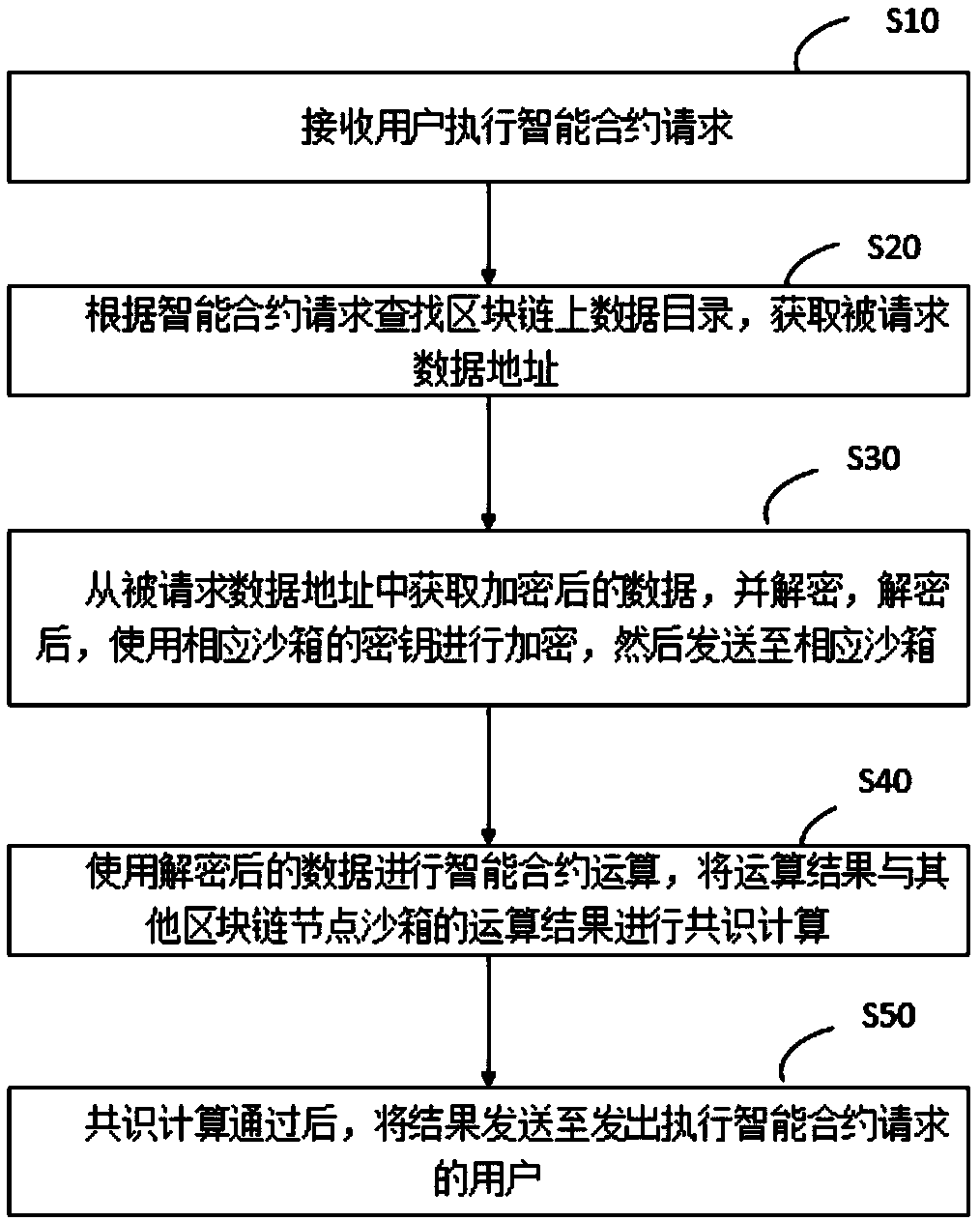
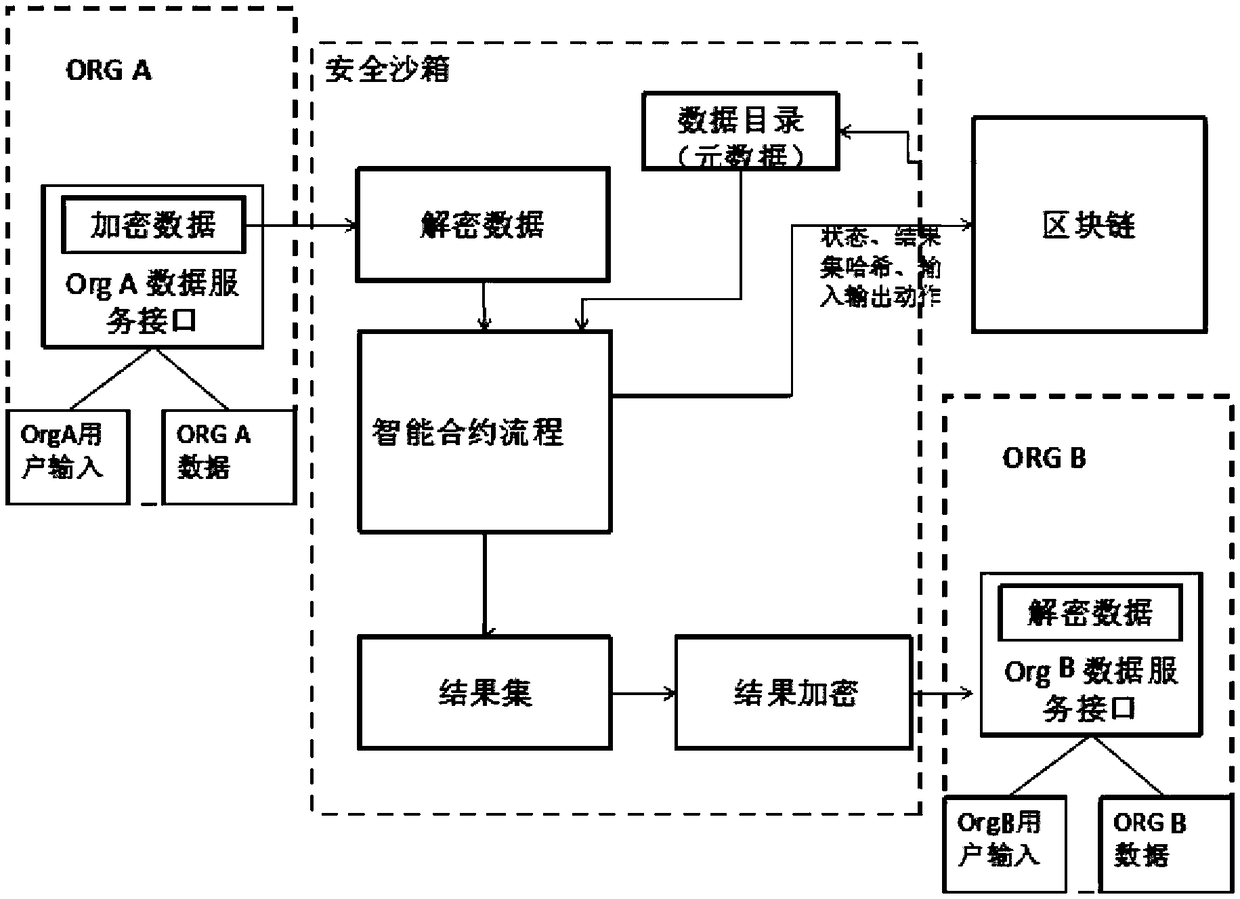
The invention relates to a blockchain-based smart city information safety using method and system. The blockchain-based smart city information safety using method according to the present invention includes the following steps: receiving a request for executing a smart contract from a user; searching for a data directory on a blockchain according to the smart contract request and obtaining a requested data address; obtain encrypted data from the requested data address, decrypting the encrypted data, encrypting the decrypted data with the secret key of a corresponding sandbox, and then sendingthe data to the corresponding sandbox; performing an smart contract operation by using the decrypted data, performing consensus calculation on an operation result and the operation results of other blockchain node sandboxes; after the consensus calculation is passed, sending a result to the user who issues the request for executing the smart contract. The blockchain-based smart city information safety using method realizes effective information sharing and sensitive information privacy protection among multiple physical organization in a smart city.
Owner:SHANGHAI YANHUA HEALTH TECH
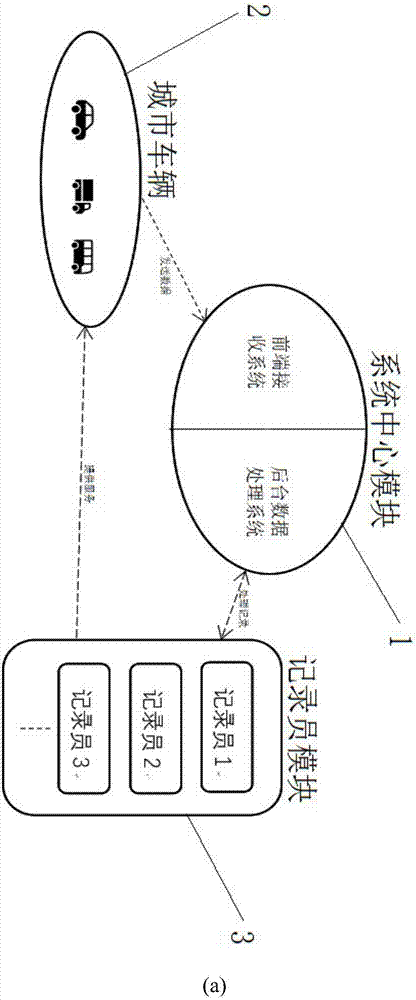
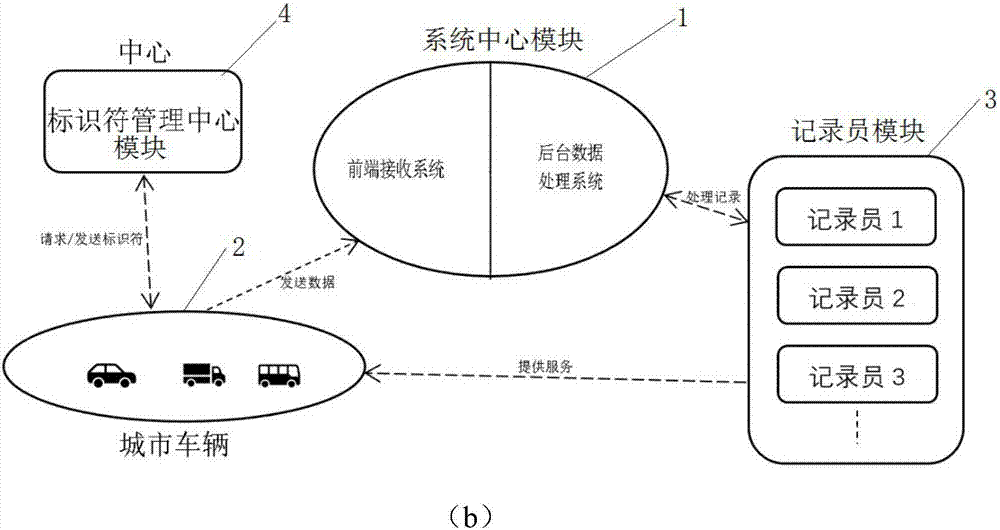
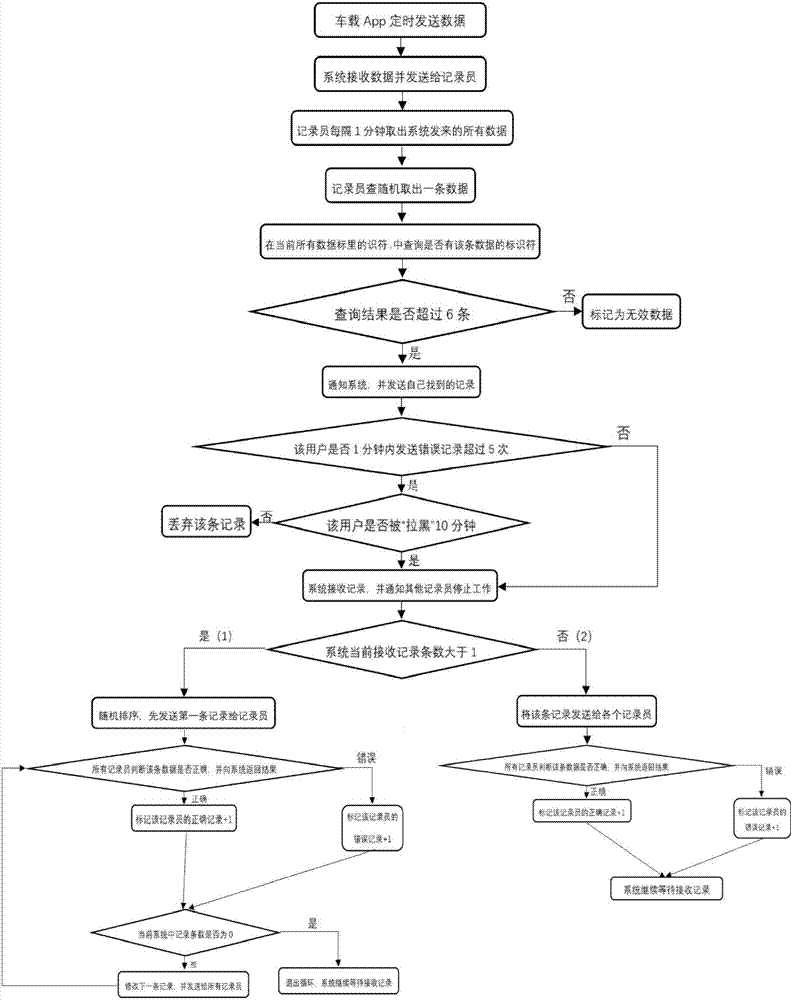
Urban real-time traffic system and method capable of realizing privacy protection based on block chains
ActiveCN107067720ARealize privacy protectionMap real-time traffic conditionsDetection of traffic movementConfidentialityPrivacy protection
The invention relates to two systems which are an urban real-time traffic system capable of realizing privacy protection based on block chains of a public chain and an urban real-time traffic system capable of realizing vehicle monitoring based on block chains of a private chain. The urban real-time traffic system capable of realizing privacy protection based on the block chains of the public chain comprises a system center module, urban vehicles and a recorder module. The urban real-time traffic system capable of realizing vehicle monitoring based on the block chains of the private chain is additionally provided with a center which is responsible for managing identifiers of the vehicles. According to the invention, the block chain is adopted as a core technology, a record book of the block chain is utilized to store and record driving records of each automobile in a distributed manner, each automobile is recorded by adopting a mode of the automobile identifier in the record book, each identifier generates a random character string by adopting an encryption algorithm and varies in a timed manner, and privacy protection for an automobile owner or vehicle monitoring is realized according to the confidentiality of the identifiers. The recorder draws real-time traffic conditions according to data of the record book.
Owner:CHENGDU UNIV OF INFORMATION TECH
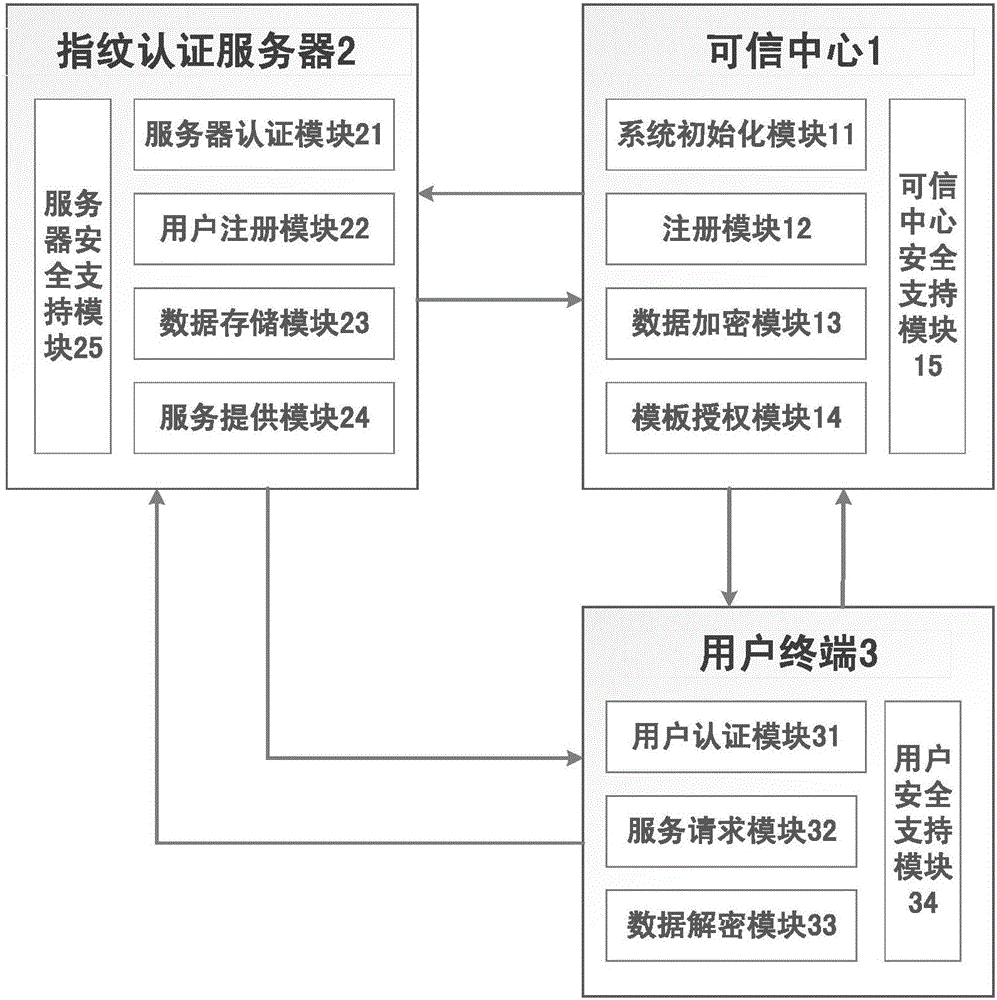
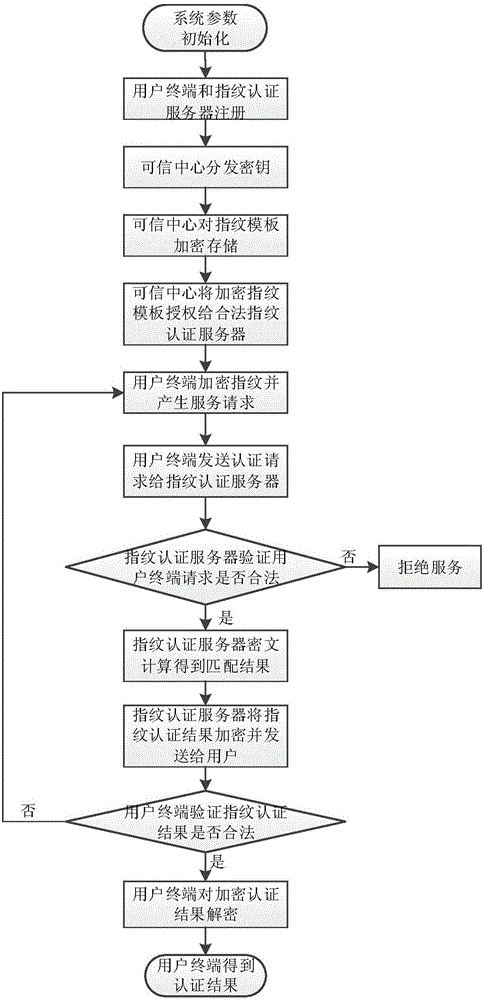
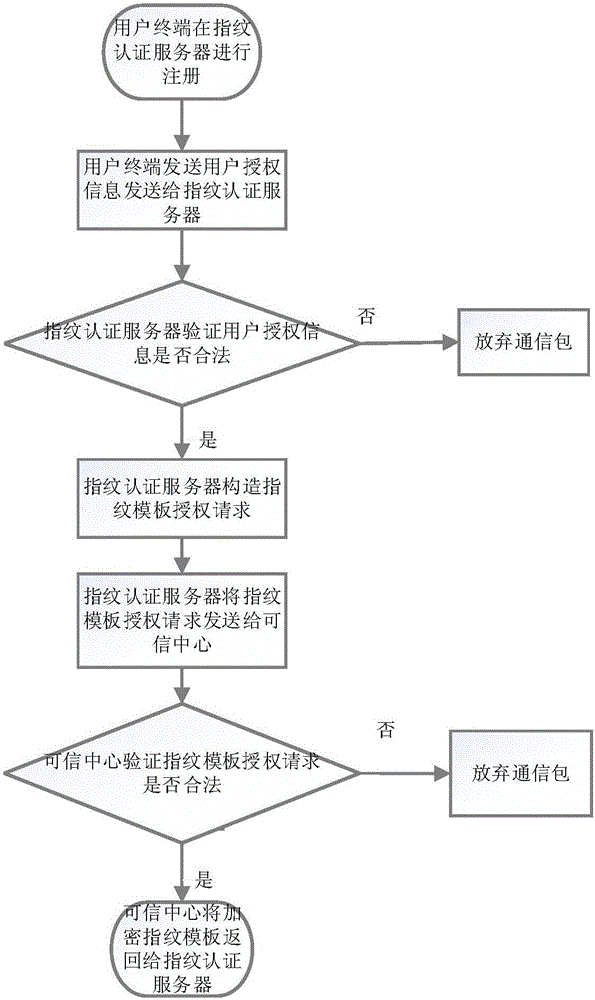
On-line fingerprint authentication system and method based on bidirectional privacy protection
ActiveCN106411533ARealize privacy protectionGuaranteed privacy protectionUser identity/authority verificationInternet Authentication ServiceCiphertext
The invention discloses an on-line fingerprint authentication system and method based on bidirectional privacy protection. With the system and method, a problem that bidirectional privacy protection of fingerprint data of the user and fingerprint template data is not involved in the prior art can be solved. The system is composed of a trusted center (1), a fingerprint authentication server (2), and a user terminal (3). The trusted center (1) completes system initialization, provides registration and secret key distribution for a user terminal and the fingerprint authentication server, collects a user fingerprint as an authentication template, and gives authorization of the template to a legal fingerprint authentication server in a ciphertext mode; the fingerprint authentication server (2) provides an on-line encryption fingerprint authentication service with privacy protection and returns an authentication result to the user terminal; and the user terminal (3) sends an encrypted fingerprint authentication request to the fingerprint authentication server and decrypts the reply of the fingerprint authentication server to obtain an authentication result. According to the invention, bidirectional privacy protection of the user fingerprint data and the fingerprint template data is realized and a secure on-line fingerprint authentication service is provided.
Owner:陕西嵩远明瑞信息技术有限公司
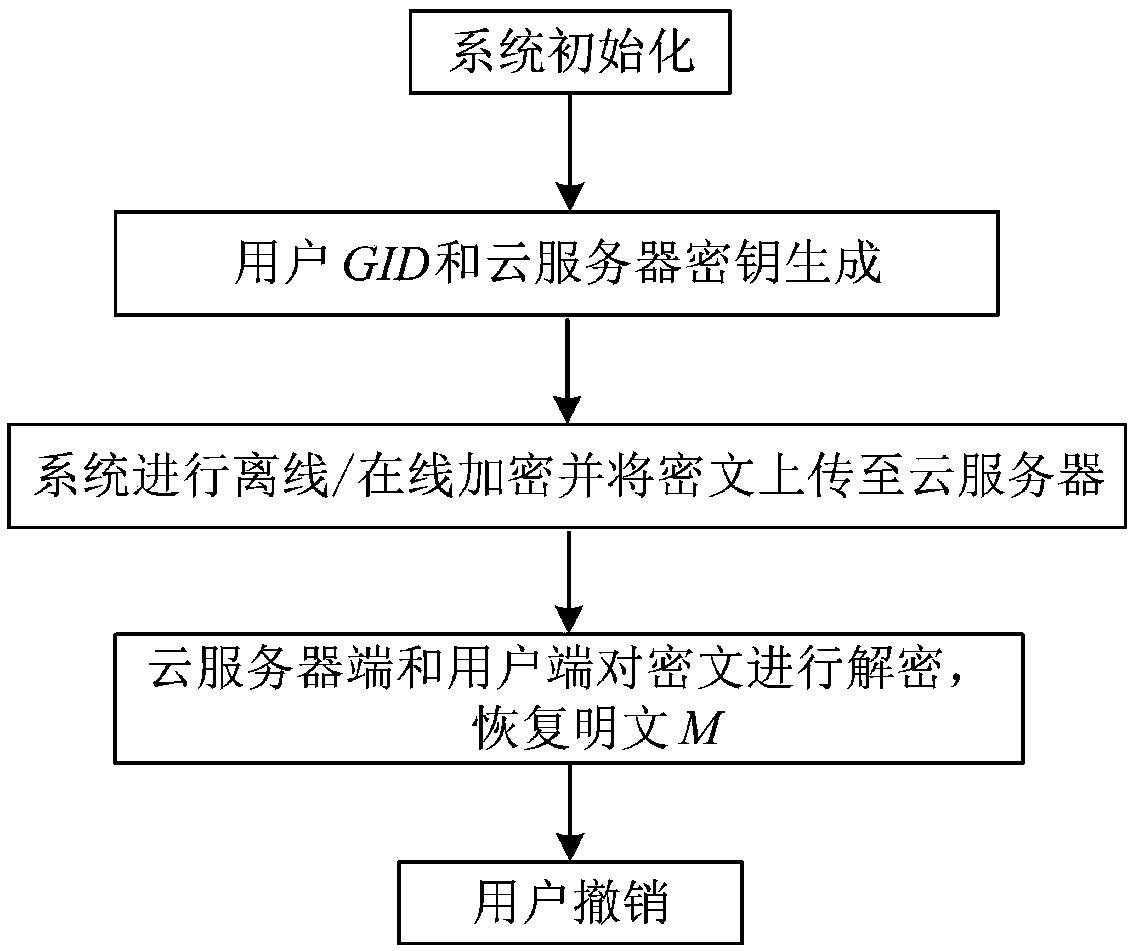
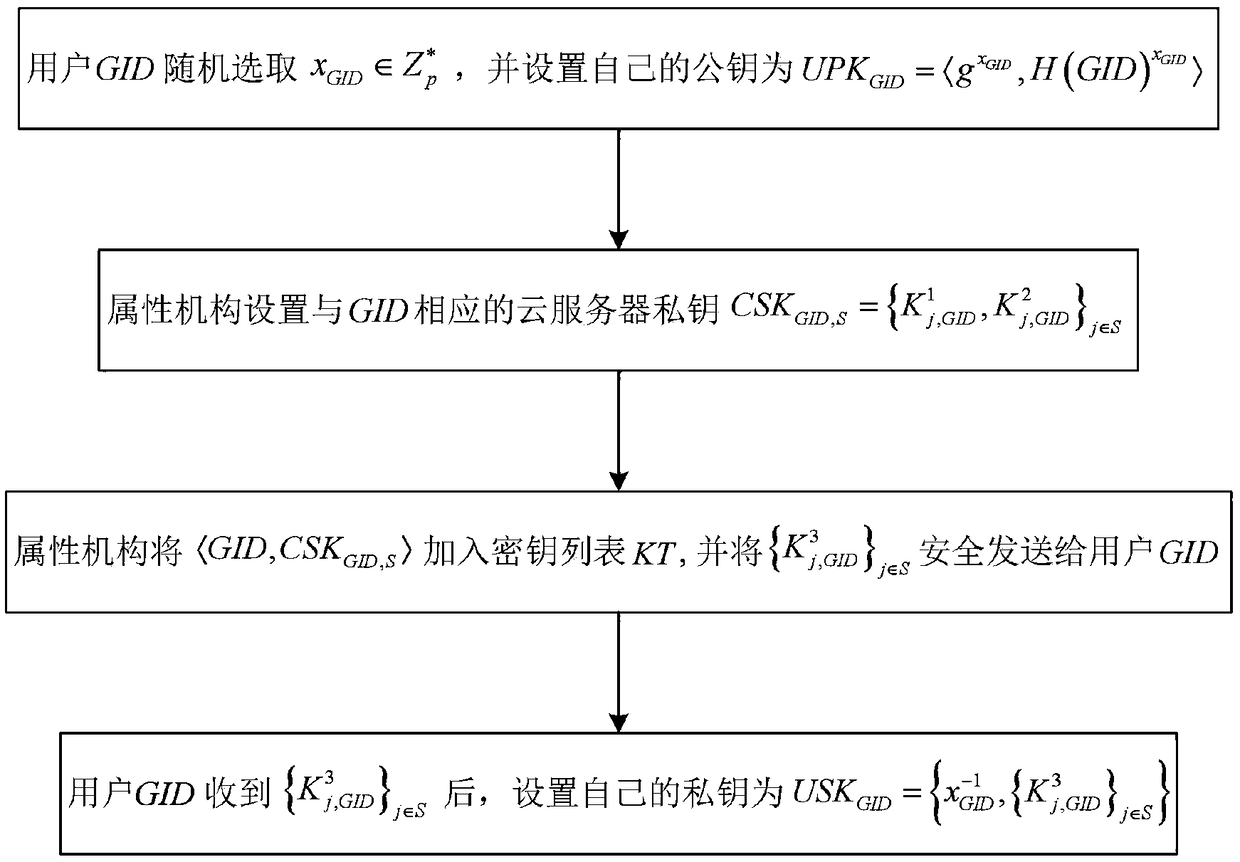
Multifunctional fine-grained access control method for cloud storage
The invention discloses a multifunctional fine-grained access control method for cloud storage, and solves the problem of fine-grained access control of data in cloud storage. The implementation stepsof the method are as follows: performing global initialization and attribute organization initialization; generating the public and private keys of a user and a private key of a cloud server; enabling a system to perform offline / online encryption, wherein the system is provided with a strategy hiding mechanism; uploading a final ciphertext to the cloud server; enabling the cloud server and a userterminal to decrypt and verify the correctness of the keys; enabling the cloud server to delete the corresponding entry from a key list for user revocation. The invention proposes a multi-system CP-ABE scheme with multiple characteristics, and the offline / online encryption mechanism is constructed in detail, which greatly reduces the computational cost of the user. The method has the functions ofattribute revocation, keyless collocation problem, the offline / online encryption mechanism, the strategy hiding and verifiability, and can be applied to fine-grained access control of data in cloud environments such as education, business and medical fields.
Owner:陕西链诚致远科技有限公司
Epidemic infectious disease virus field visualization method and system based on space-time trajectory data
PendingCN111261302ABlock the route of infectionRealize privacy protectionEpidemiological alert systemsICT adaptationMedicineAlgorithm
The invention discloses an epidemic infectious disease virus field visualization method based on space-time trajectory data. The method comprises the following steps: S1, airspread infectious diseaseurban diffusion modeling; s2, collecting, cleaning and processing space-time trajectory data and infection attack data of virus carrying crowds; s3, obtaining position semantic information of a viruscarrier; s4, calculating the virus distribution density by taking the virus carrier as the position center; s5, mapping the time, space and virus distribution density data of the virus carrying population; and S6, constructing an epidemic infectious disease virus field cloud platform based on temporal GIS. The invention further provides an epidemic infectious disease virus field visualization system based on the space-time trajectory data. According to the method, space-time trajectory data and infection attack data of virus carrying crowds are processed into a virus distribution density map with the virus carrier as the position center, spatial position semantic information is added and mapped to a temporal GIS, and an epidemic infectious disease virus field is visually processed.
Owner:汤一平
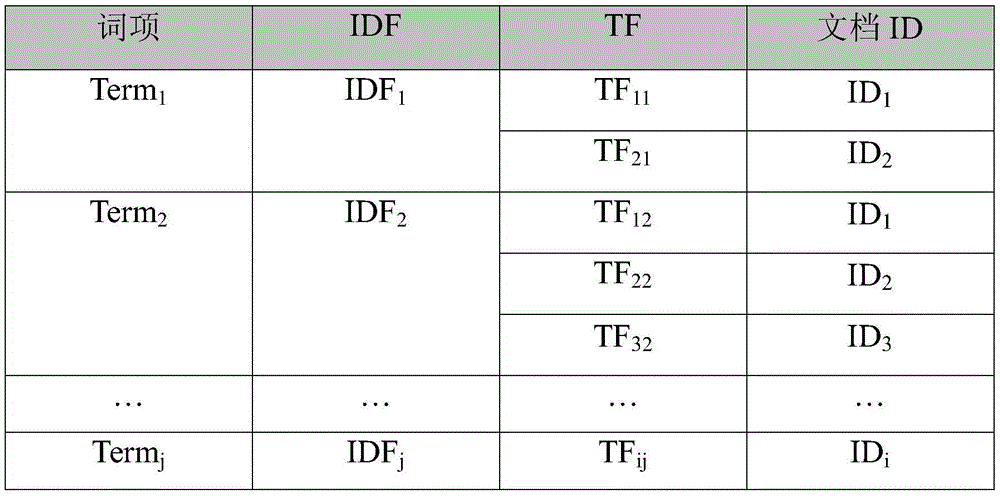
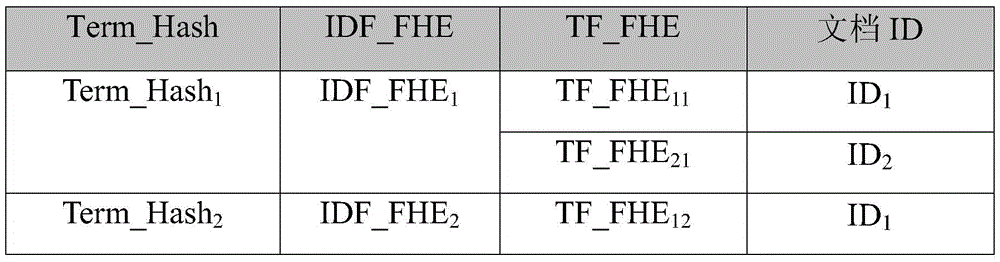
Cloud storage oriented ciphertext full-text search method and system based on full homomorphic ciphers
ActiveCN105610910ARealize privacy protectionImprove data confidentialityDigital data protectionTransmissionFull text searchCiphertext
The invention discloses a cloud storage oriented ciphertext full-text search method and system based on full homomorphic ciphers. The method comprises that a data owner uploads document IDs, encrypted document ciphertexts and an encrypted document inverse index table to a cloud server; hash operation is carried out to the document terms on the inverse index table; TF (Term frequency) and IDF (Inverse document frequency) values are encrypted by a full homomorphic technique on integers; a public key certificate is issued to a data user; the data user carries out hash operation to to-be queried keywords and uploads to a cloud service provider; the cloud service provider compares and searches the hash operation values of the to-be queried keywords and the hash operation values of the document terms on the inverse index table; and the cloud service provider carries out full homomorphic multiplication and add operations. According to the method and the system of the invention, the calculation is carried out in a ciphertext state; in the calculation process, any information related to the documents will not be leaked to the cloud service provider and other attackers; the data privacy of the data owner and the query data privacy of the data user are protected; and moreover, the controllability of the data right of use is realized.
Owner:SOUTH CENTRAL UNIVERSITY FOR NATIONALITIES
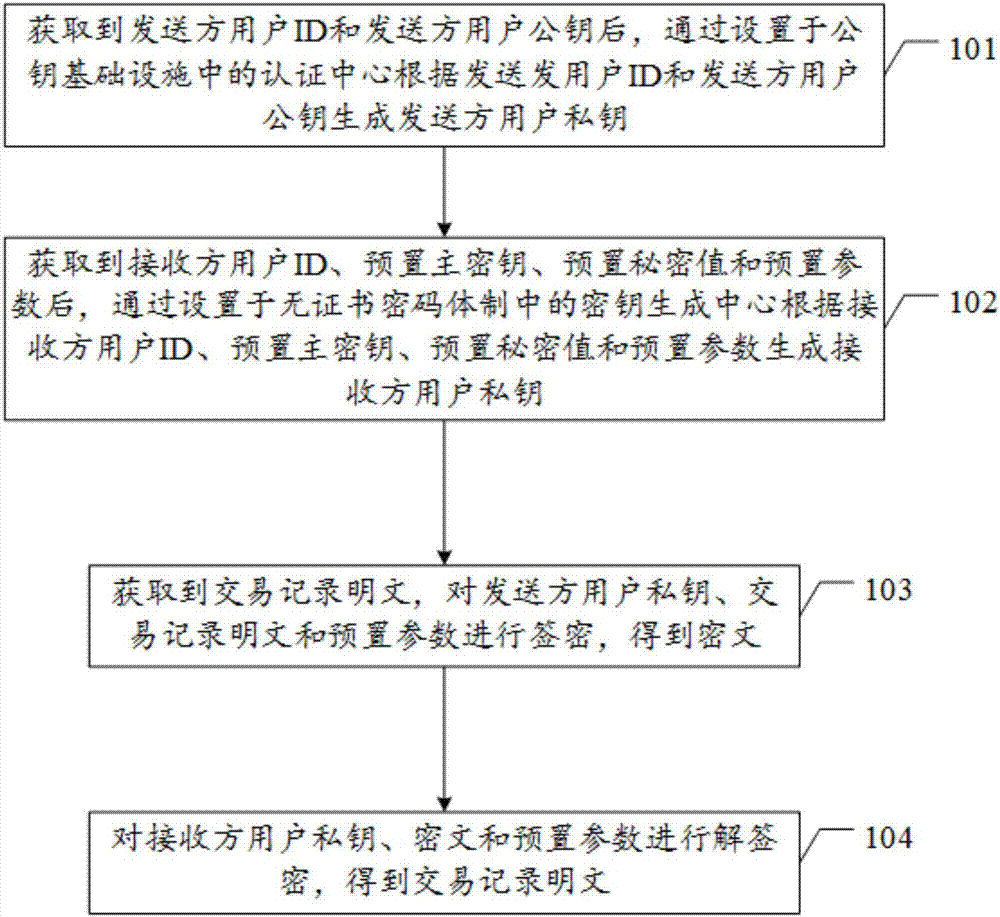
Block chain encryption method based on PKI-CLC heterogeneous aggregation signcryption algorithm
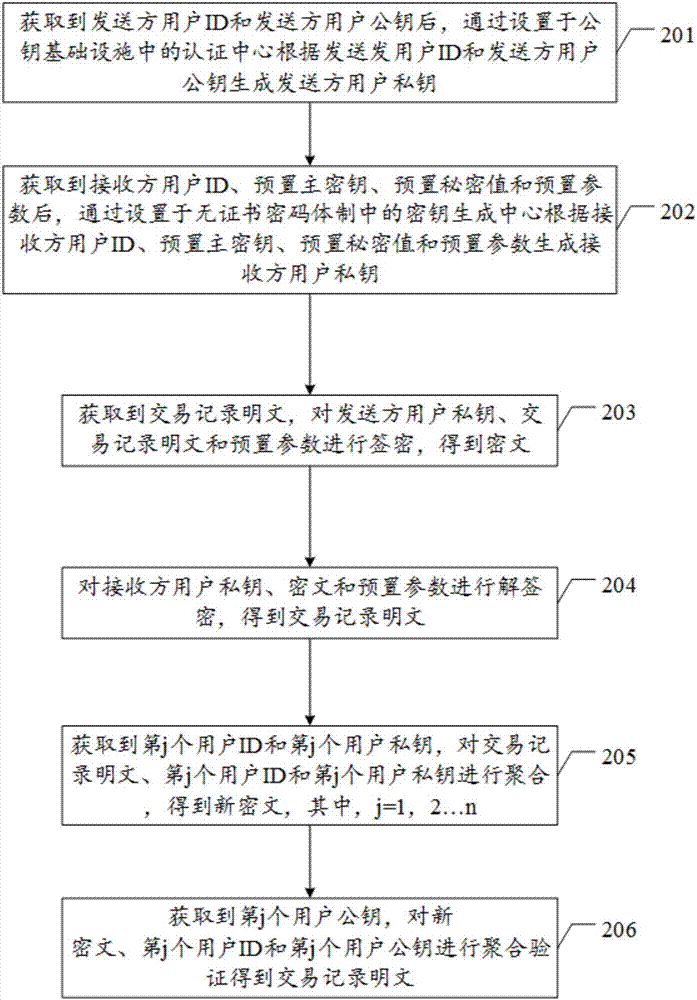
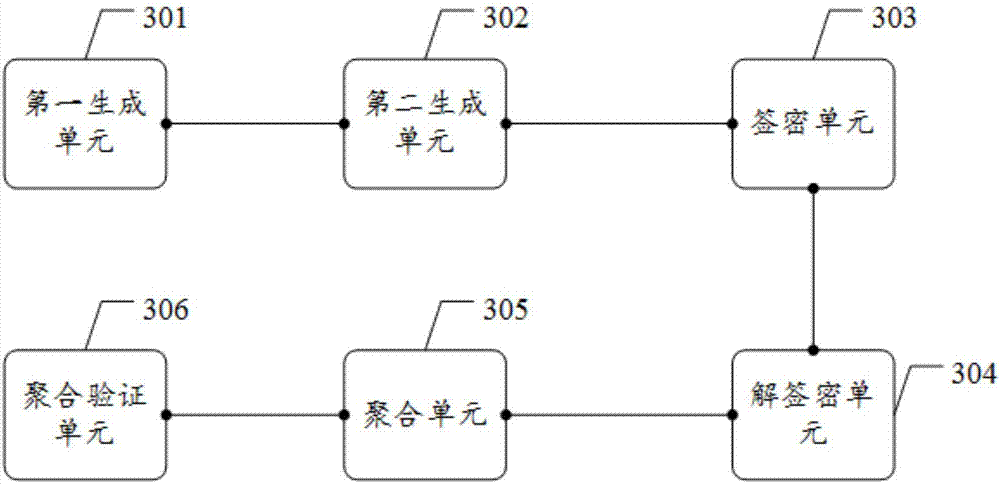
The embodiment of the invention discloses a block chain encryption method based on a PKI (public key infrastructure)-CLC (certificateless cryptography) heterogeneous aggregation signcryption algorithm. The method comprises: generating, after a sender user ID and a sender user public key are obtained, a sender user private key by using an authentication center in the PKI according to the sender user ID and the sender user public key; generating, after a receiver user ID, a preset master secret key, a preset secret value, and a preset parameter, a receiver user private key by using a secret key generation center in the CPC according to the receiver user ID, the preset master secret key, the preset secret value, and the preset parameter; obtaining a transaction record plaintext, subjecting the sender user private key, the transaction record plaintext, and the preset parameter to signcryption to obtain a ciphertext; and subjecting the receiver user private key, the ciphertext, and the preset parameter to unsigncryption to obtain the transaction record plaintext.
Owner:GUANGDONG UNIV OF TECH
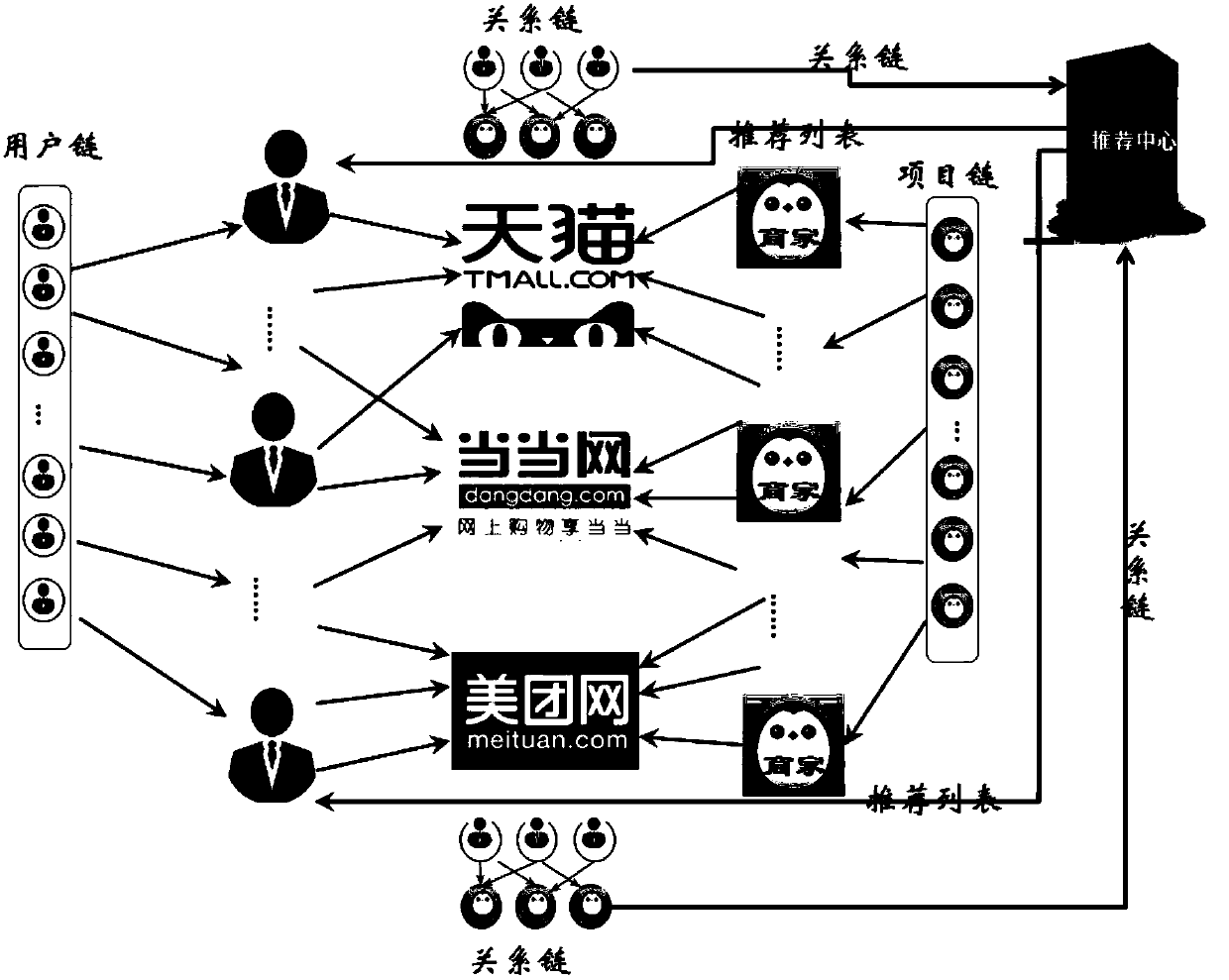
Anonymous Cross-domain Recommendation Based on Block Chain Technology
ActiveCN109523341AGuaranteed privacy and securityReduce storage pressureBuying/selling/leasing transactionsDatabase indexingTransaction dataData aggregator
The invention discloses an anonymous cross-domain recommendation method based on block chain technology, A technology base on block chain adopts heterogeneous multi-link data structure to carry out data storage, Users, merchandise and transaction relationship data are stored on users, merchants and platforms respectively. Transaction relationship does not store specific user and commodity information. Recommendation center can only obtain the relationship chain stored by each platform to ensure that an attacker cannot associate a user with a commodity. Aiming at the cold start problem caused by data sparseness, the invention performs data aggregation and similarity calculation based on accurate transaction data, and adopts a mixed recommendation strategy based on users and commodities to perform cross-platform recommendation, so as to achieve a safe and accurate win-win recommendation effect.
Owner:GUANGXI NORMAL UNIV
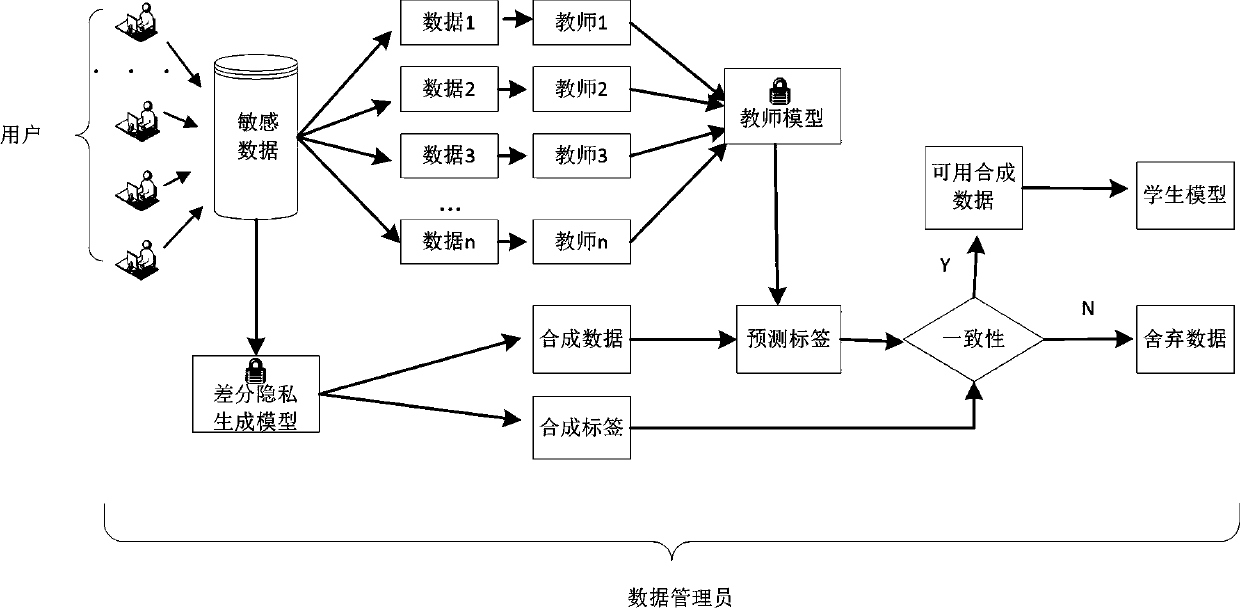
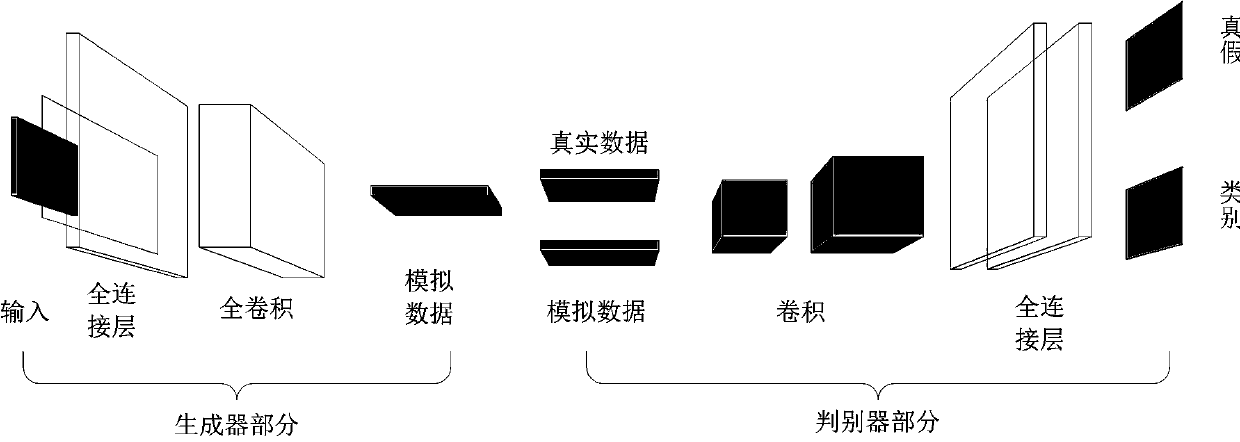
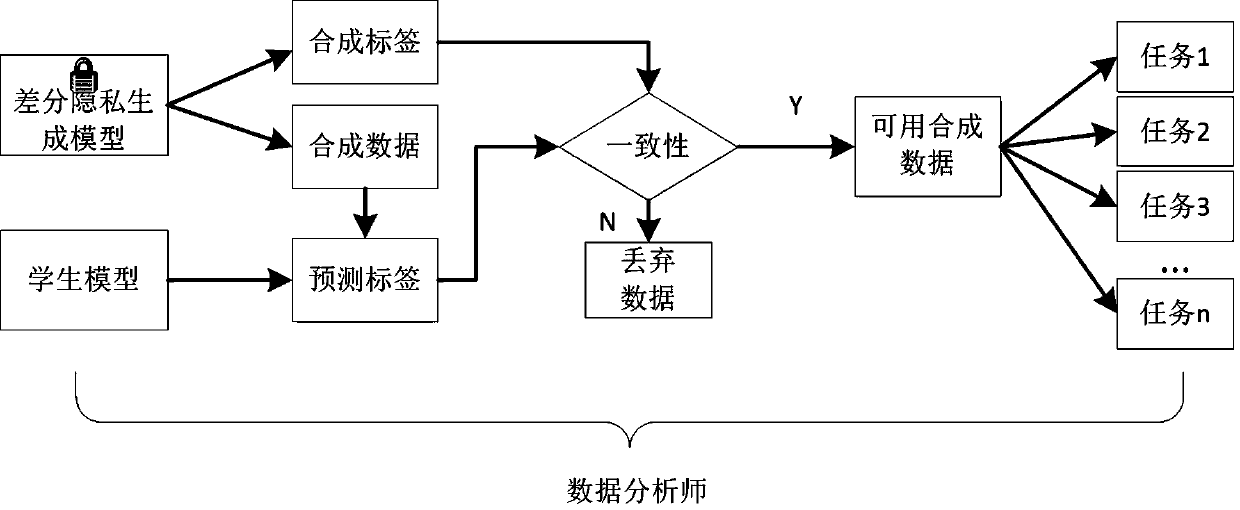
Form data privacy protection method fusing differential privacy GAN model and PATE model
ActiveCN109784091ARealize privacy protectionCharacter and pattern recognitionDigital data protectionData privacy protectionData set
The invention relates to a form data privacy protection method fusing a differential privacy GAN model and a PATE model. The method comprises the steps of 1, training a differential privacy generationmodel by using original table data; 2, training a teacher classifier under the differential privacy budget by using the original table data; Step 3, generating 'false' table data by using the generation model, predicting labels of the 'false' table data by using a teacher classifier, selecting data with consistent prediction labels and generated labels, defining an 'available' data set, and training a student classifier by using the 'available' data set; and step 4, releasing the generation model and the student classifier, synthesizing data by using the generation model, selecting the data by using the student model, and finishing a data analysis task. According to the method, privacy protection is carried out on the table data in the data release stage, a data analyst cannot restore original training data through a generation model and cannot speculate the original training data through a student model, protection on the original table data is achieved, and the requirement of the data analyst for the data is met.
Owner:FUZHOU UNIV
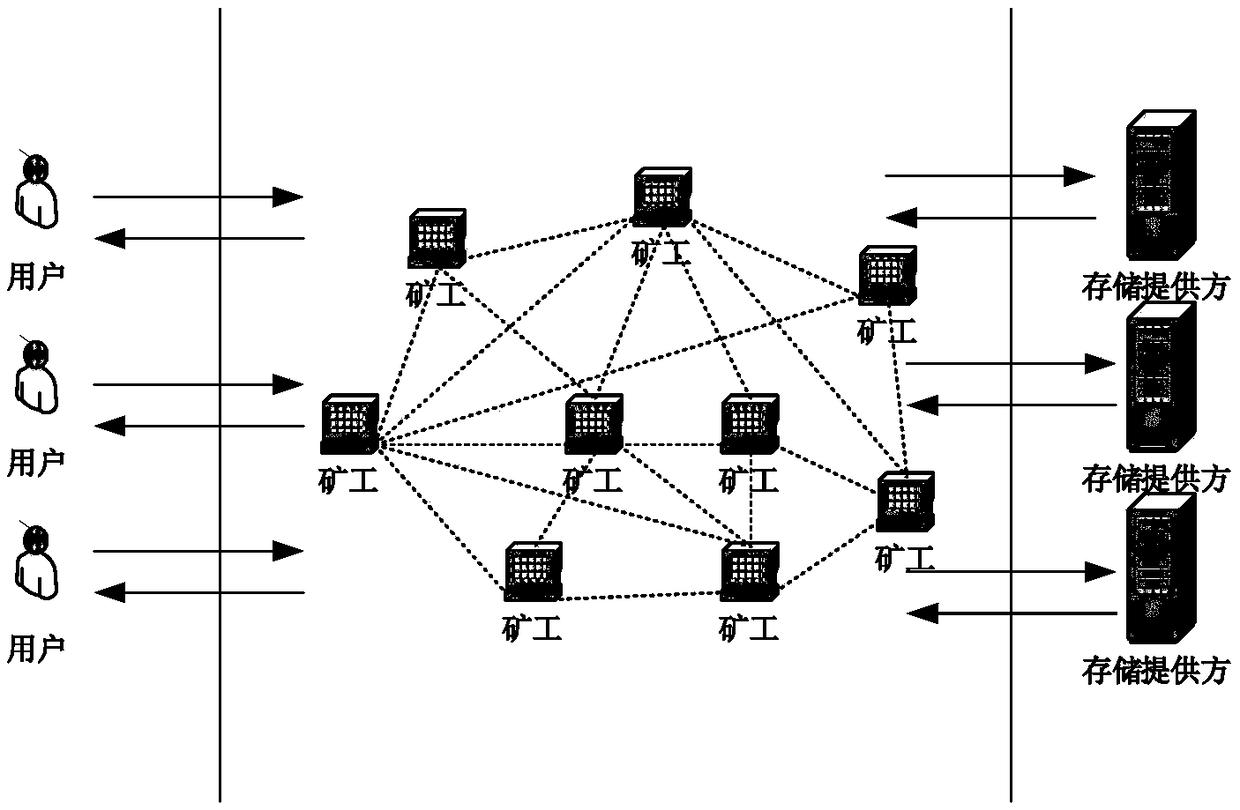
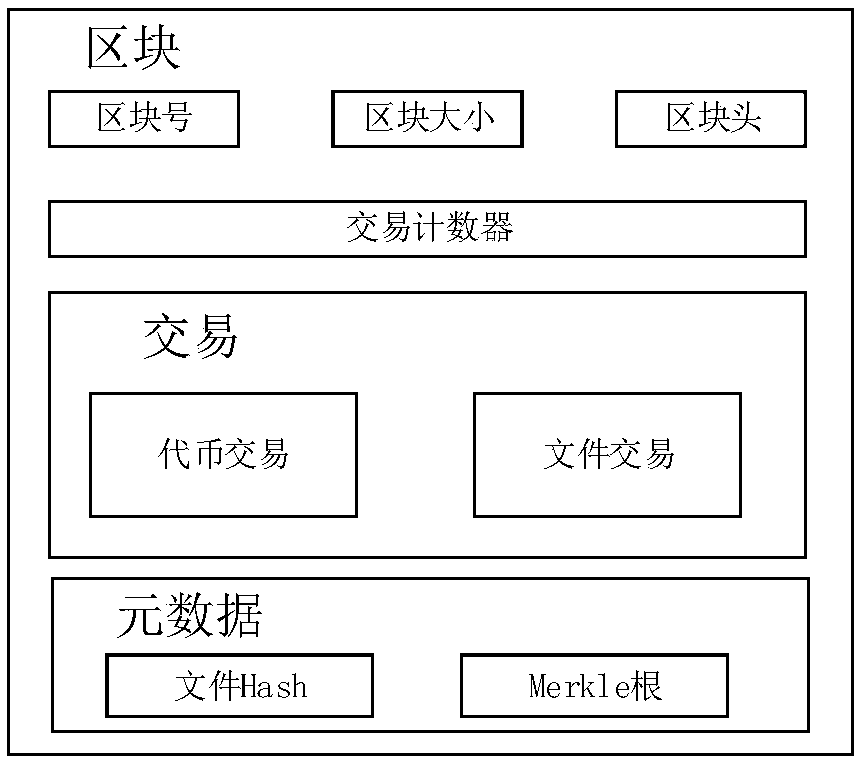
Privacy protection method of distributed cloud storage system
ActiveCN109508552APrecise positioningRealize privacy protectionFinanceDigital data protectionPrivacy protectionCloud storage system
The invention discloses a privacy protection method of a distributed cloud storage system, comprising a user, a miner, a storage provider, system initialization, file uploading, file sharing, file downloading, file deletion and the like. The invention combines the distributed cloud storage system with the block chain technology, and regards the file ownership processing process as the transactionprocessing, thereby realizing the privacy protection of the file ownership processing process in the distributed cloud storage system, including the hiding of the sender, the receiver and the transaction content. In addition, the invention can effectively resist the replay attack and the data forgery attack while ensuring the privacy of the user.
Owner:JIANGSU BOZHI SOFTWARE TECH CO LTD
Distributed hash table network-based anonymous communication method
ActiveCN104168265AAchieve the purpose of normal operationRealization of anonymous communicationTransmissionSecure transmissionUser privacy
The invention relates to a distributed hash table (DHT) network-based anonymous communication method. With regard to three kinds of basic operations, including the resource publishing operation, the resource searching operation, and the resource transmission operation, of the traditional DHT network, a certain anonymous mechanism and security mechanism are introduced, thereby solving an anonymous communication problem in the DHT network. An anonymous mapping path is constructed at the resource publishing stage and a mapping node is determined, so that an anonymous base is provided for the resource publishing operation; a probabilistic forwarding strategy is used at the resource searching stage, so that the resource searching operation has the anonymous property; and at the resource loading and transmission stage, the mapping node is used as a relay node to carry out data transmission and combination with the session key encryption data is used, thereby guaranteeing the anonymous transmission and secure transmission of data. On the basis of combination of the three parts, sender anonymity, receiver anonymity, and communication relation anonymity are realized, thereby achieving objectives of user privacy protection and secure and stable operation of the whole DHT network.
Owner:NANJING UNIV OF POSTS & TELECOMM
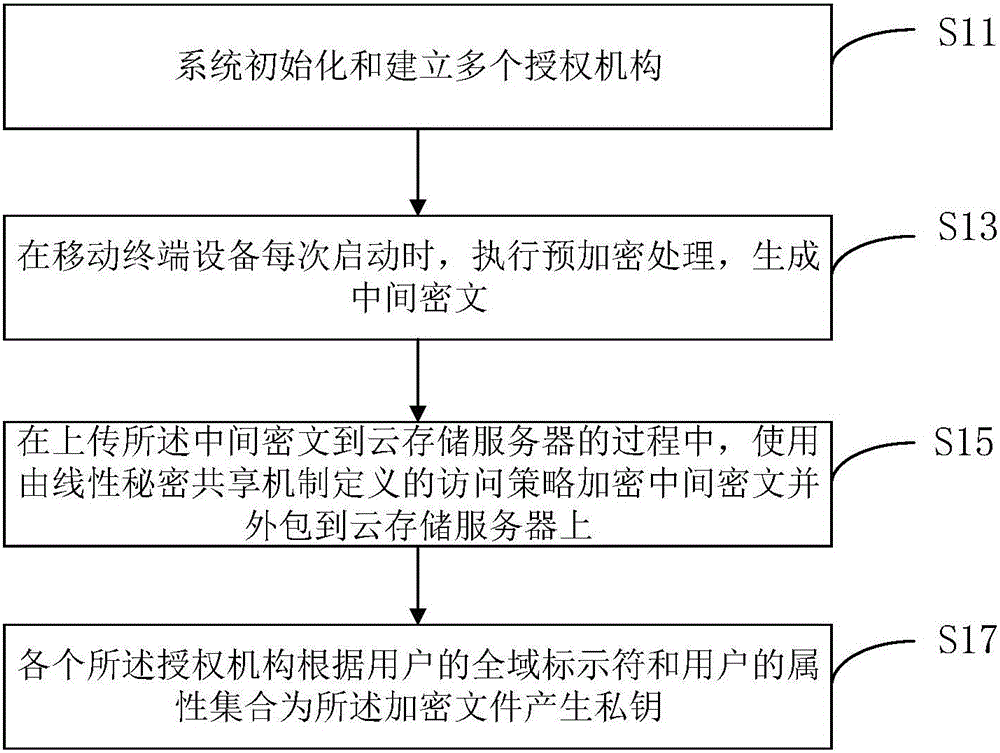
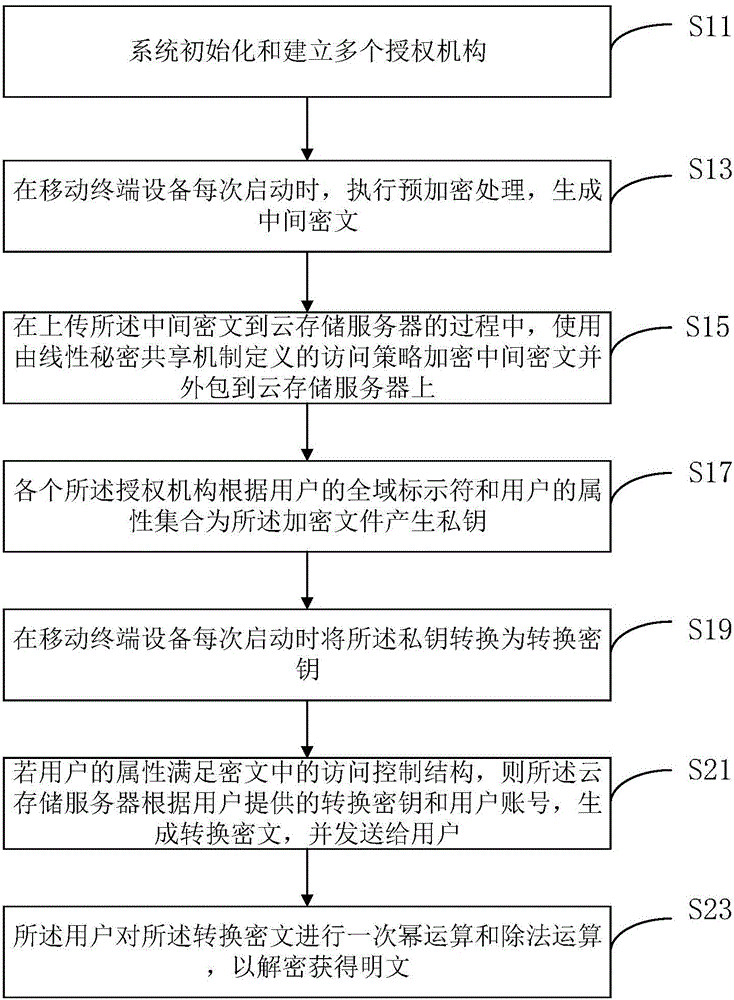
Multi-authority ciphertext-policy attribute-based encryption method
ActiveCN106230590AEnsure safetyImprove battery lifeKey distribution for secure communicationPublic key for secure communicationAttribute-based encryptionMobile cloud
The invention discloses a multi-authority ciphertext-policy attribute-based encryption method. The method includes following steps: step 1, performing system initialization and establishing a plurality of authorities; step 2, before each starting of a mobile terminal device, executing pre-encryption treatment, and generating an intermediate ciphertext; step 3, in a process of uploading the intermediate ciphertext to a cloud storage server, encrypting the intermediate ciphertext by employing an access policy defined by a linear secret sharing mechanism, and outsourcing the intermediate ciphertext to the cloud storage server; and step 4, generating a private key for an encryption file according to global identifiers of users and an attribute set of the users by each authority. According to the method, aiming at the mobile cloud storage environment, on the premise of guaranteeing the data security, a lot of pairing operations are pre-processed in advance by employing the encryption pre-processing technology so that the calculation cost of online encryption is minimum; and by employing the secret key transformation technology and decryption outsourcing, a lot of pairing operations are outsourced to the cloud storage server so that the decryption calculation cost of the mobile terminal is reduced.
Owner:ANHUI UNIVERSITY
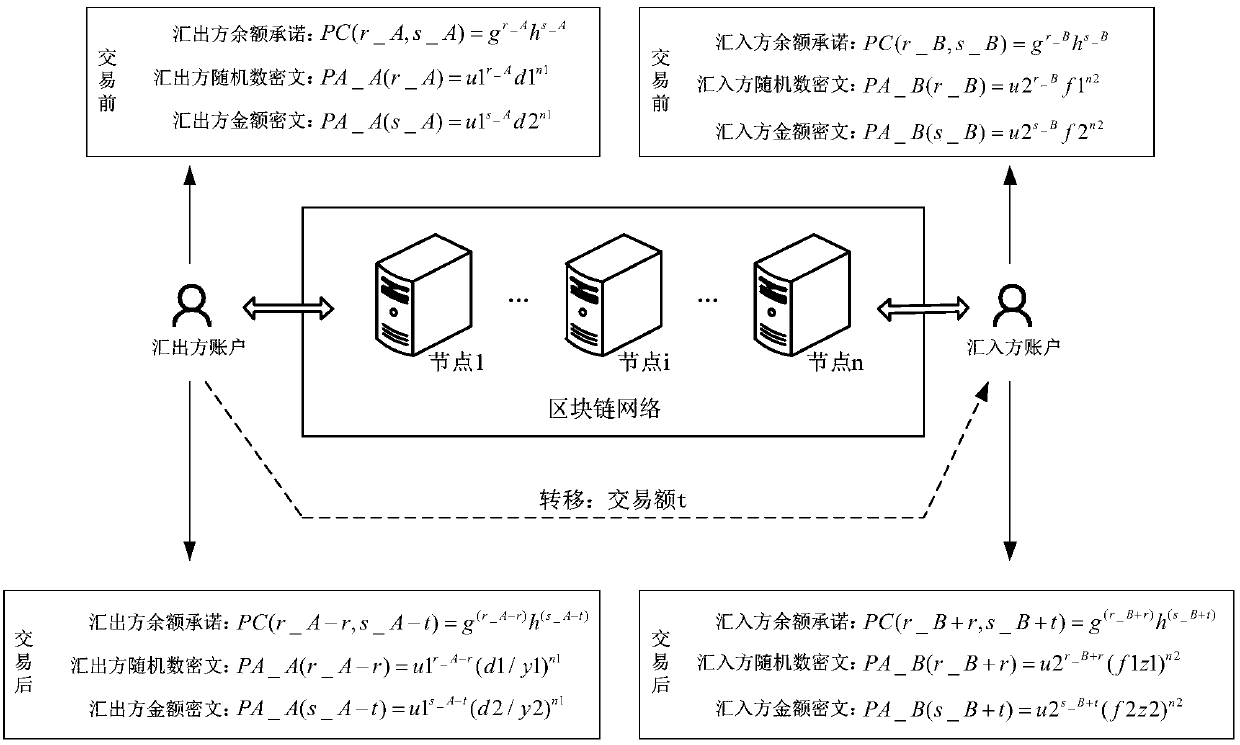
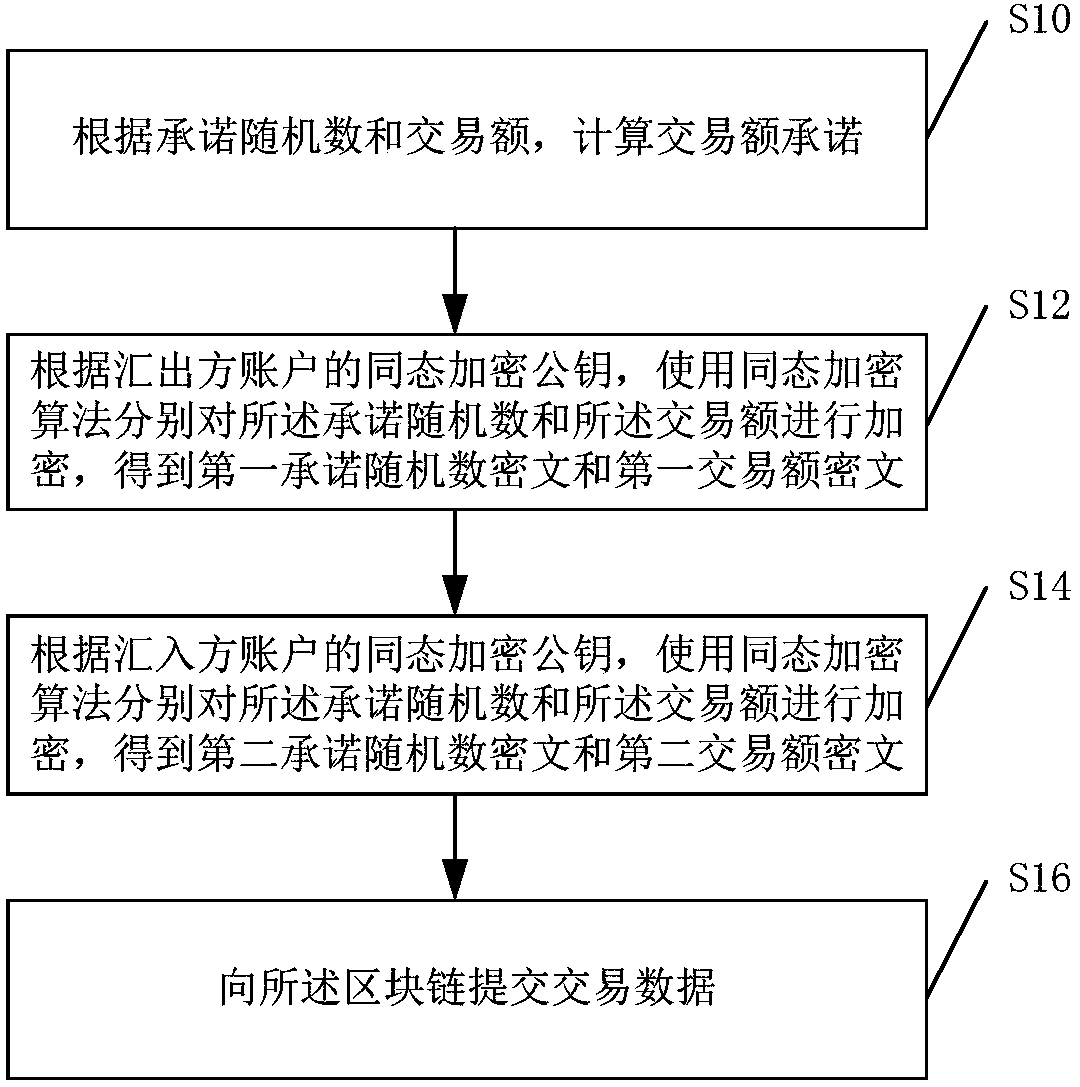
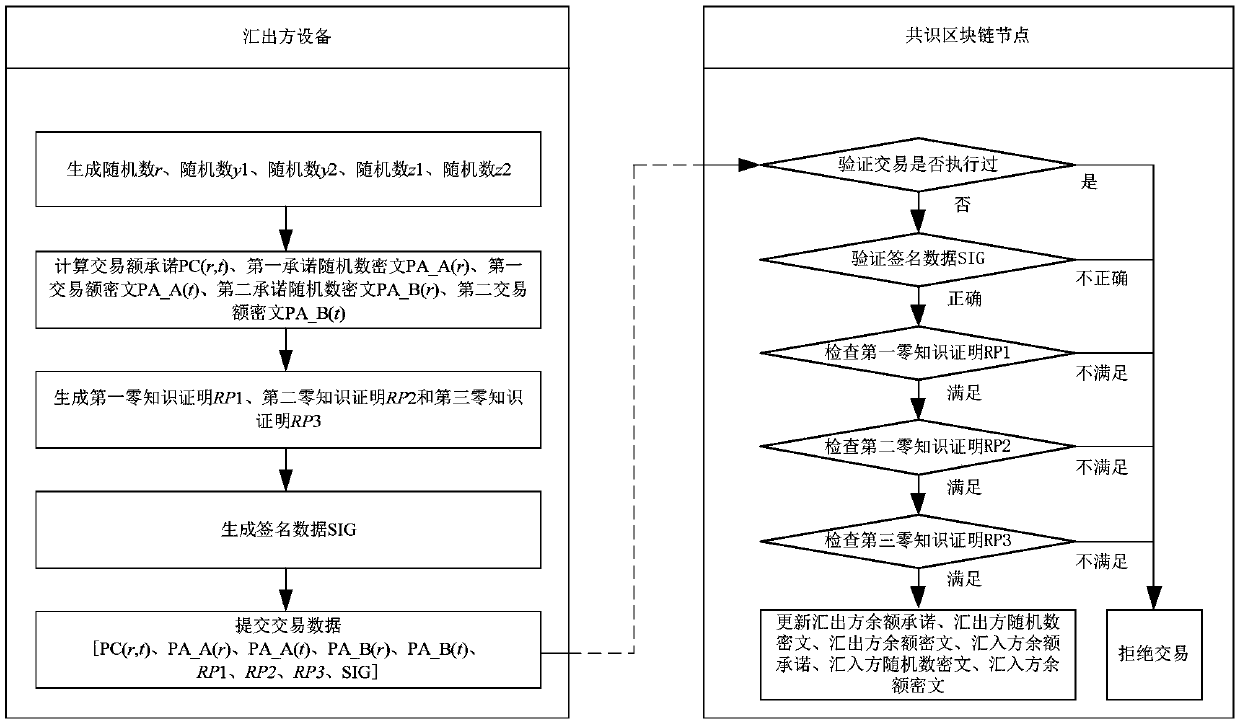
Transaction method and device based on block chain and exporter equipment
ActiveCN109584055ARealize privacy protectionFinanceDigital data protectionCiphertextTransaction data
The embodiment of the invention provides a Transaction method and device based on block chain and exporter equipment. The method comprises the following steps: calculating a transaction amount commitment, a first commitment random number ciphertext, a first transaction amount ciphertext, a second commitment random number ciphertext and a second transaction amount ciphertext; Submitting transactiondata to the block chain; Wherein the transaction data comprises the transaction amount commitment, the first commitment random number ciphertext, the first transaction amount ciphertext, the second commitment random number ciphertext and the second transaction amount ciphertext; And recording the transaction amount commitment, the first commitment random number ciphertext and the first transaction amount ciphertext into the remitter account, and recording the transaction amount commitment, the second commitment random number ciphertext and the second transaction amount ciphertext into the remitter account.
Owner:ADVANCED NEW TECH CO LTD
Method and system for sharing anonymous resource
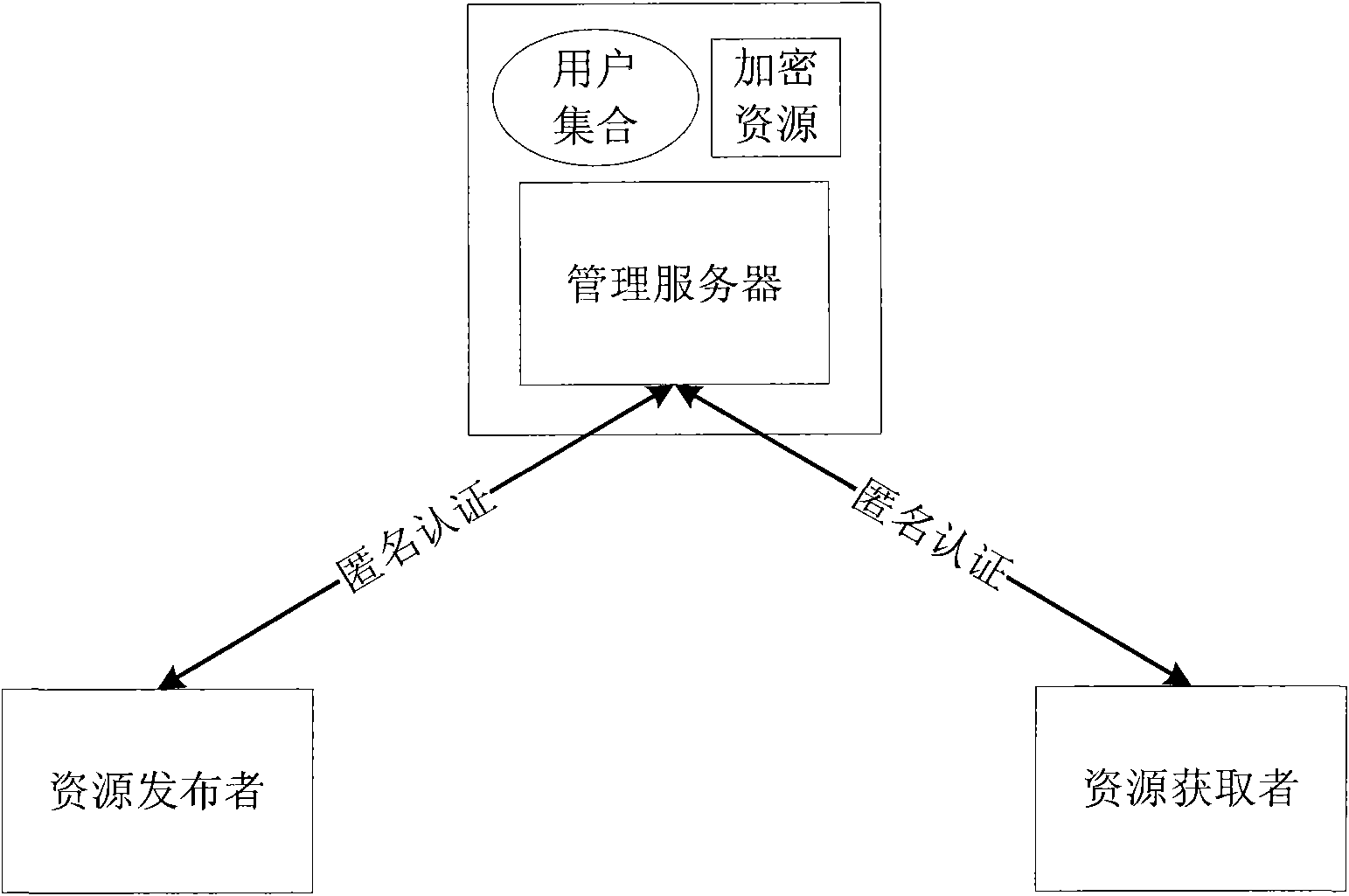
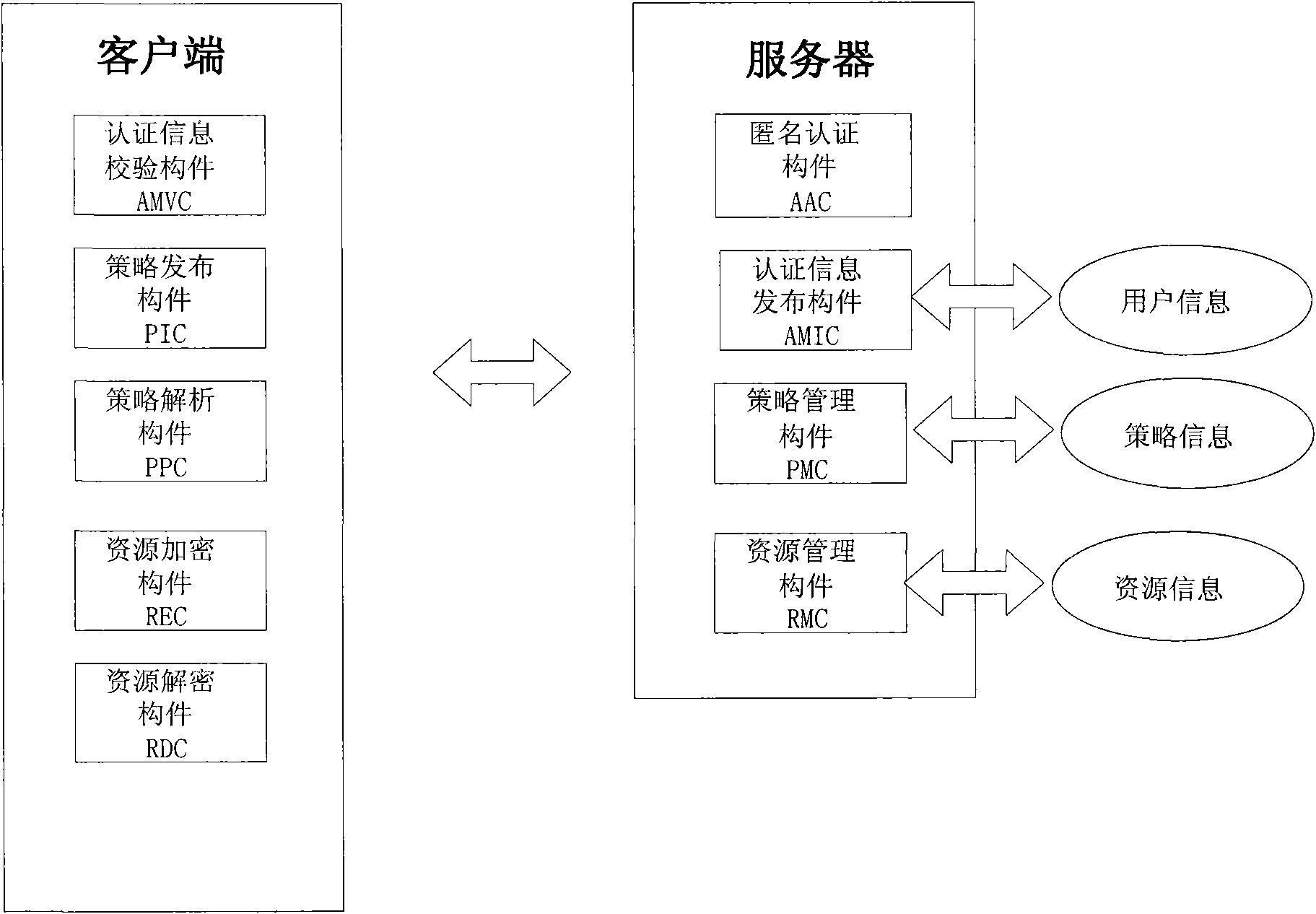
InactiveCN101834853AProtect personal privacyProtection of personal informationTransmissionResource managementResource Provider
The invention discloses a method and a system for sharing an anonymous resource, which belong to the technical field of computer information. The method for sharing the resource comprises the following steps that: a resource provider initiates a resource publishing request to a resource management server; the resource management server performs an anonymous authentication on the request; the resource provider generates a resource acquisition strategy, uses the resource acquisition strategy as a cipher key to encrypt the resource, and sends the acquisition strategy and the encrypted resource to the resource management server; the resource management server stores a binary group and releases resource description information; a resource acquirer retrieves the resource description information and initiates a resource acquisition request; the resource management server performs the anonymous authentication on the resource acquirer; and the resource acquirer acquires and decrypts the resource after acquiring a strategy verification. The invention also discloses a system sharing the resource, which corresponds to the method. The method and the system can be used for computer information technical application such as network resource sharing and the like.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
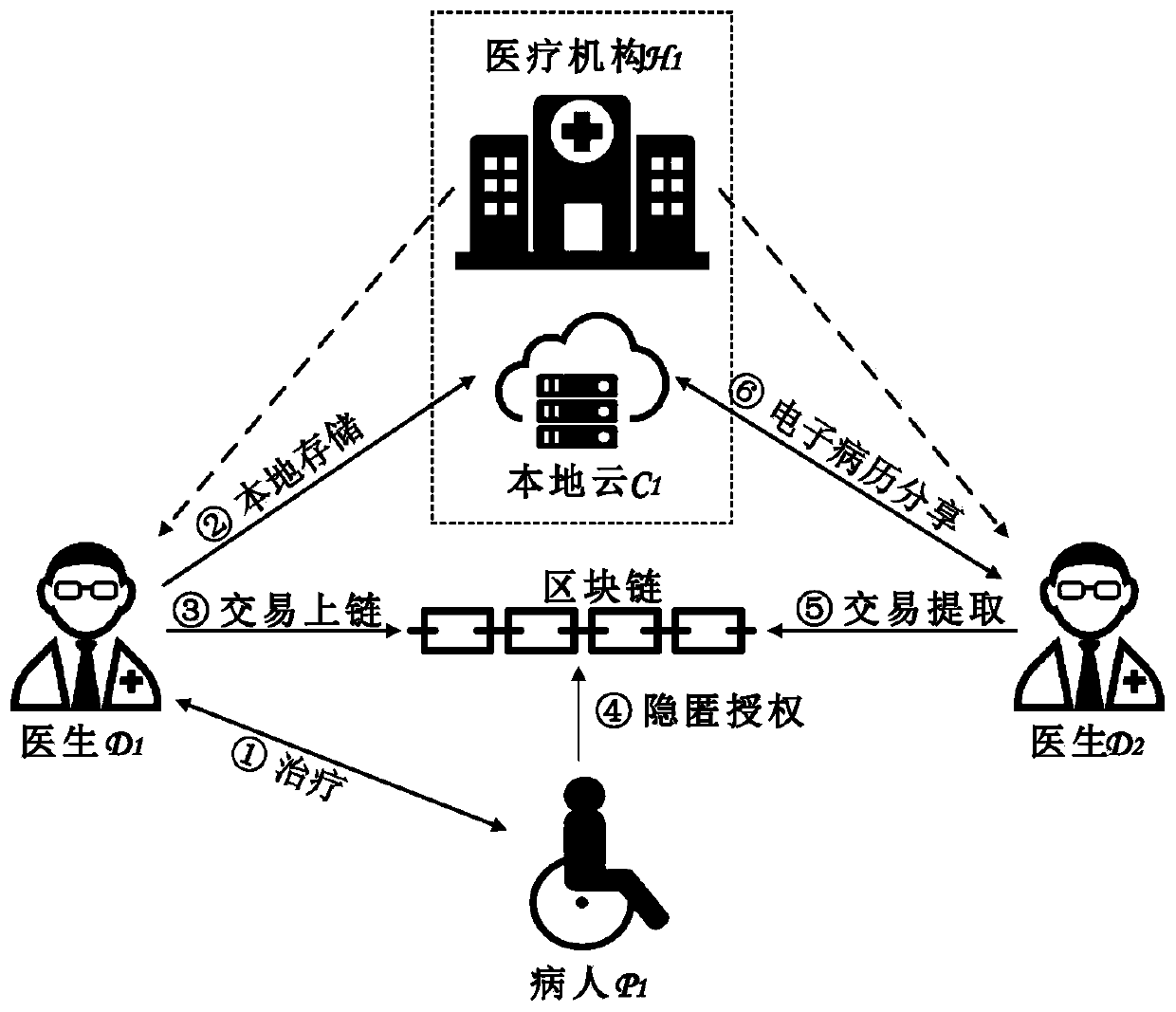
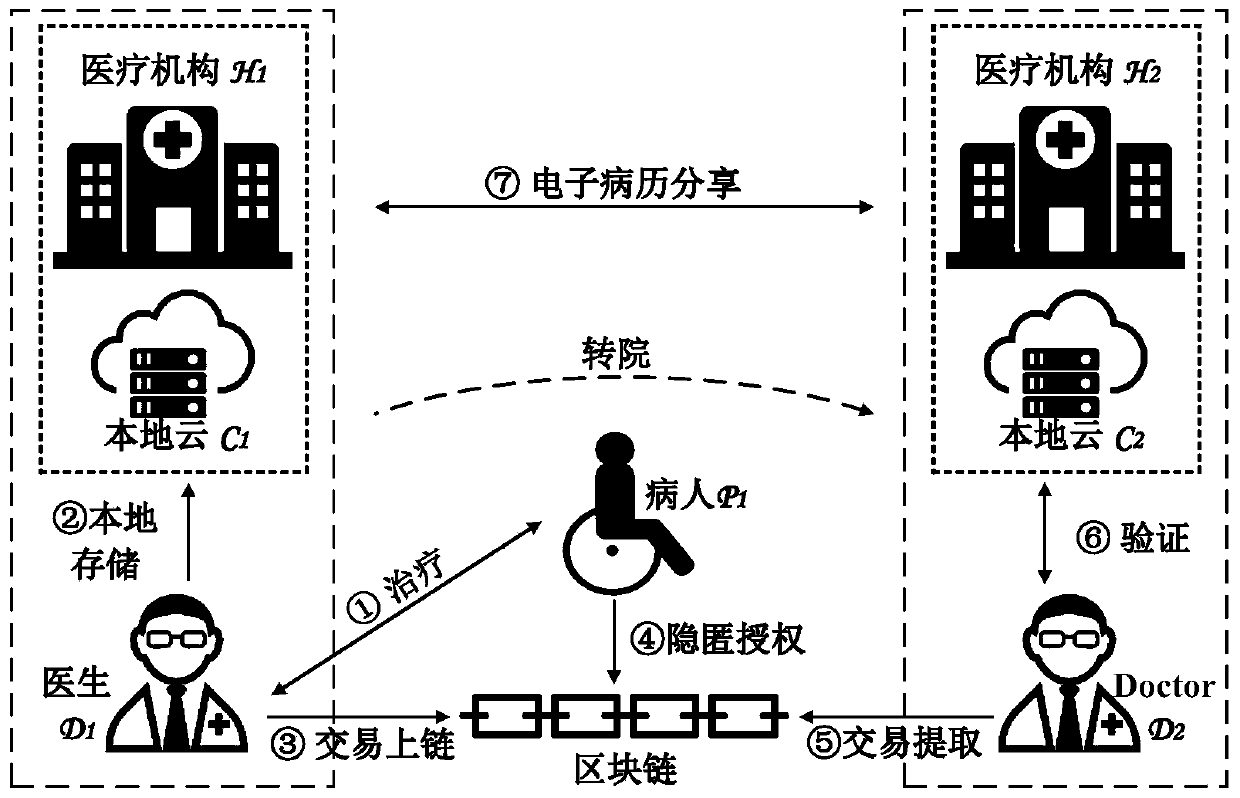
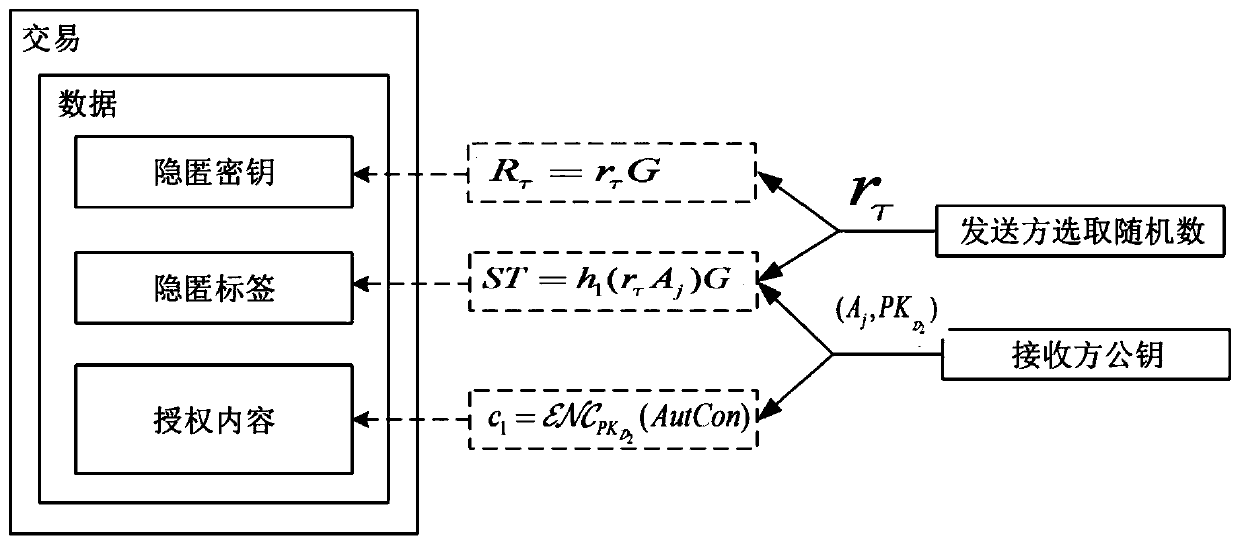
Electronic medical record sharing system with privacy protection function based on alliance chain and application method
ActiveCN110299195ARealize privacy protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMedical recordPrivacy protection
The invention discloses a blockchain-based electronic medical record sharing system with a privacy protection function and an application method, and the system comprises a medical management department, a medical institution and a medical service receiver, and achieves the operations of system initialization, registration, electronic medical record sharing and electronic medical record deletion.According to the invention, through a hidden authorization mechanism, the system achieves the privacy protection in the electronic medical record sharing process, and can achieve the electronic medical record sharing under two scenes: electronic medical record sharing among different doctors in the same hospital and electronic medical record sharing among different doctors in different hospitals;in the electronic medical record sharing process, a patient has complete control right on electronic medical records of the patient. In addition, after the electronic medical record exceeds the validity period, the local cloud and the blockchain of each medical institution delete the electronic medical record.
Owner:CHINA UNIV OF MINING & TECH
User data anonymous sharing method based on league chain encryption
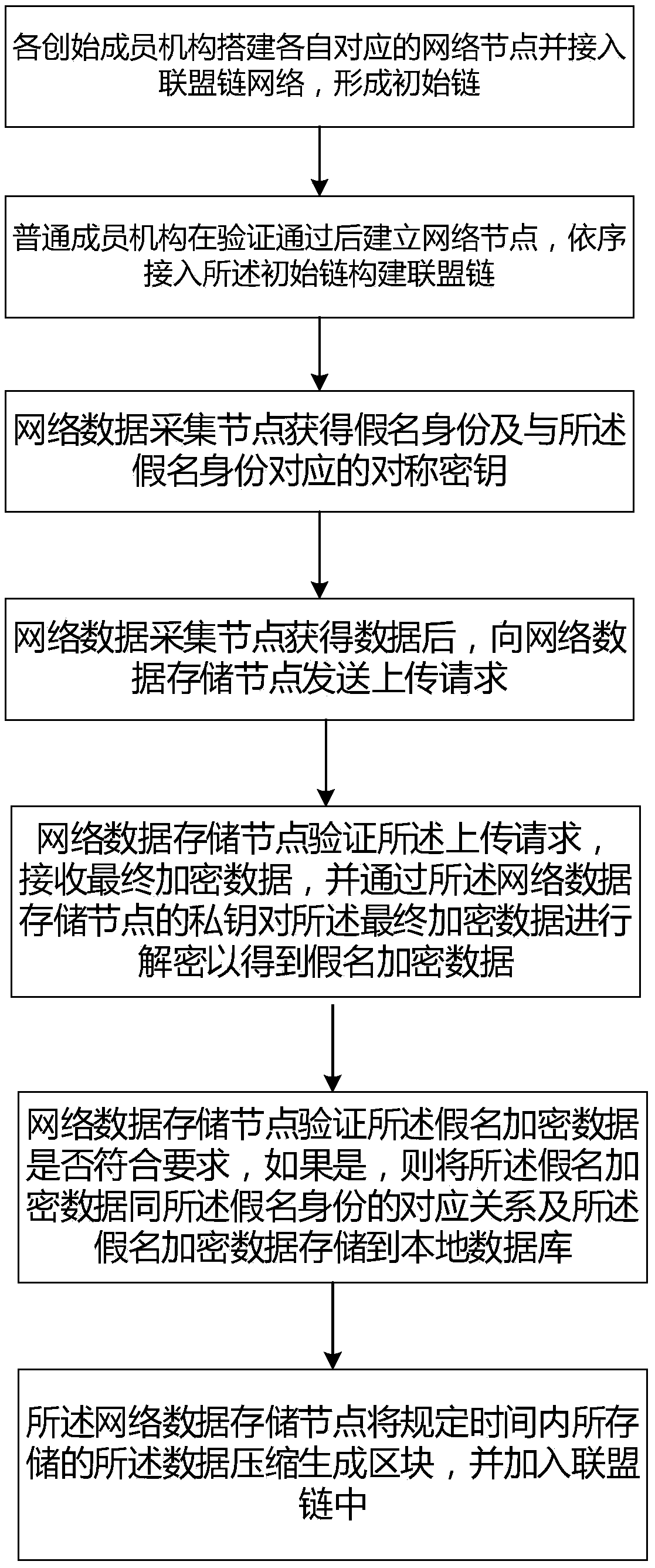
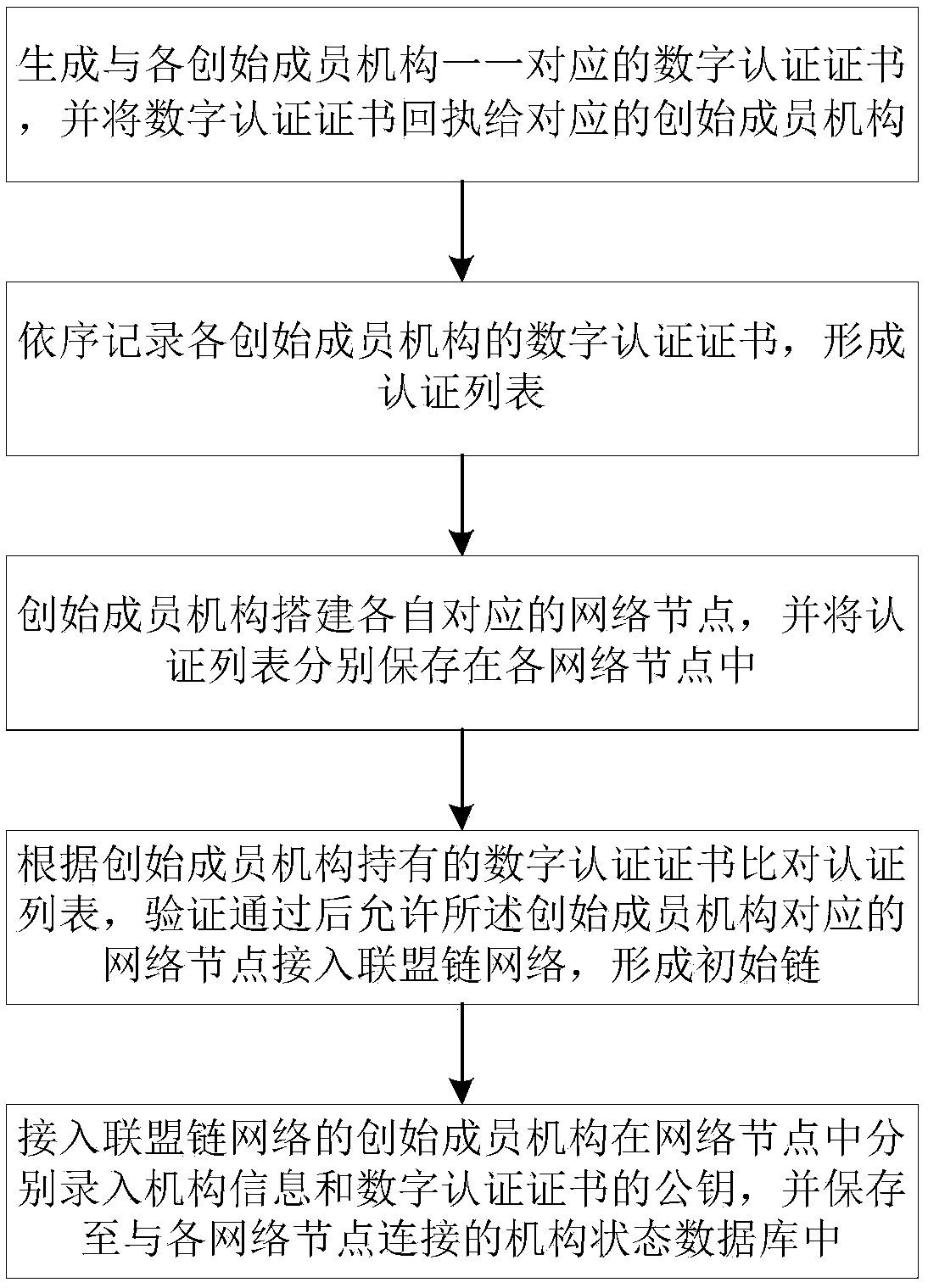
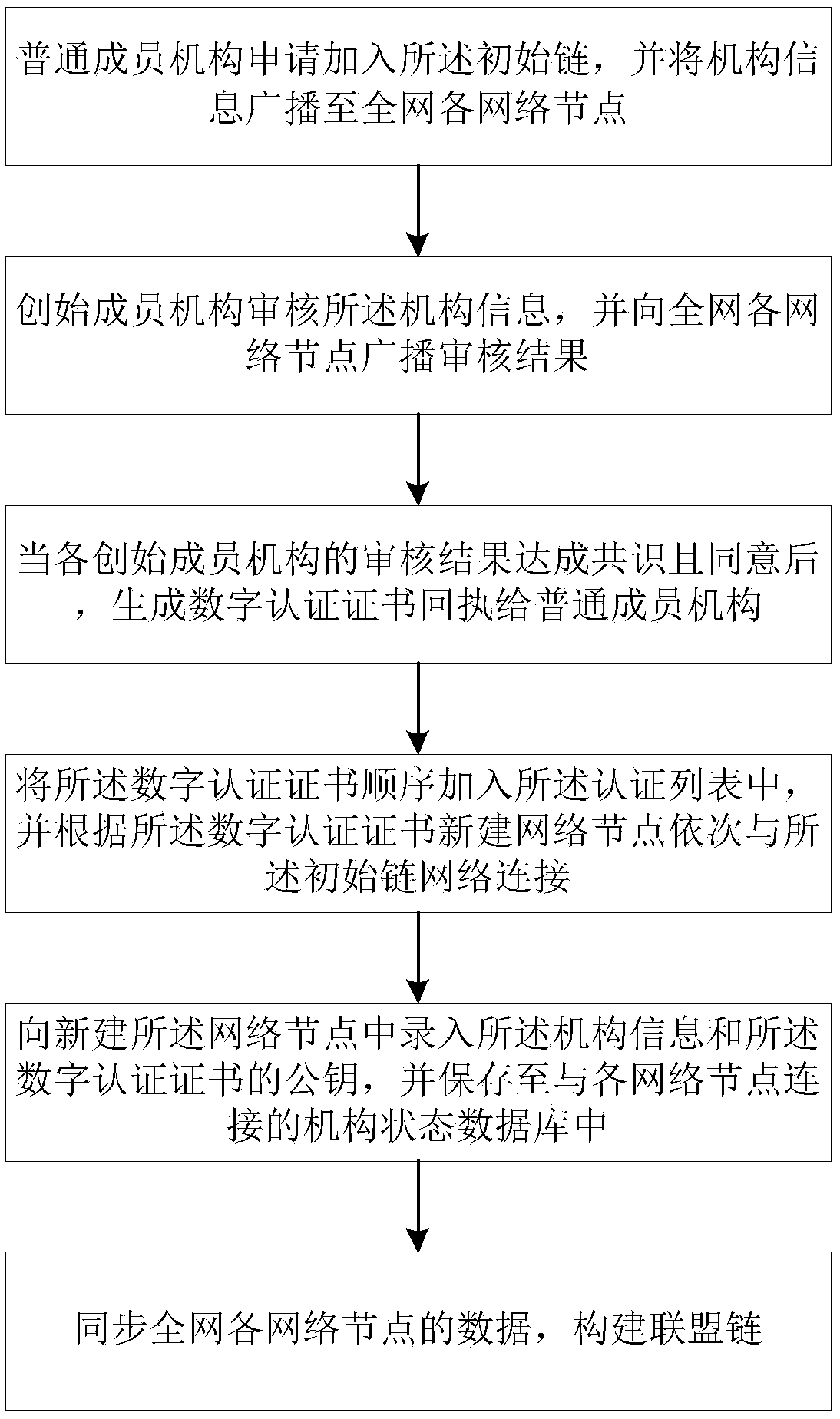
InactiveCN108833385ARealize privacy protectionLimit Access ThresholdTransmissionData compressionChain network
The invention discloses a user data anonymous sharing method based on league chain encryption. The method comprises the steps as follows: each founding member mechanism builds a respectively corresponding network data collection node and accesses a league chain network, to form an initial chain; a common member mechanism builds the network data collection node after passing through verification, and sequentially accesses the initial chain to build a league chain; the network data collection node acquires a pseudonym identity and symmetric keys corresponding to the pseudonym identity; after acquiring data, the network data collection node sends an uploading request to a network data storage node; the final encrypted data is decrypted via the private key pair of the network data storage nodeto acquire pseudonym encryption data; the network data storage node stores a corresponding relationship between the pseudonym encryption data and the pseudonym identity into a local database; and thenetwork data storage node compresses the data stored within set time into a block, and adds the block into the league chain. Through building the league chain, the permissions of the common member mechanisms are effectively controlled, and the privacy of each member mechanism is ensured.
Owner:深圳崀途科技有限公司
Vehicular ad hoc network group awareness data report duplication eliminating method
InactiveCN108377264ARealize privacy protectionResist Forgery AttacksPublic key for secure communicationParticular environment based servicesPrivacy protectionNODAL
The invention discloses a vehicular ad hoc network group awareness data report duplication eliminating method. According to the method, through adoption of an ECC algorithm, secure and reliable task distribution is realized, a label part of a ciphertext is hidden in a communication process, and fog nodes detect awareness report uniqueness and does not detect specific content of reports, so the privacy protection in a data duplication eliminating process can be realized, and a data counterfeiting attack can be resisted. According to the method, in order to record vehicle contributions in a report duplication eliminating process, signature aggregation is supported through adoption of an improved multi-signature scheme based on identities. According to the scheme, an efficient and secure aggregation confirmation function can be realized, and moreover, vehicles making contributions to the group awareness reports also can be recorded.
Owner:JIANGSU UNIV
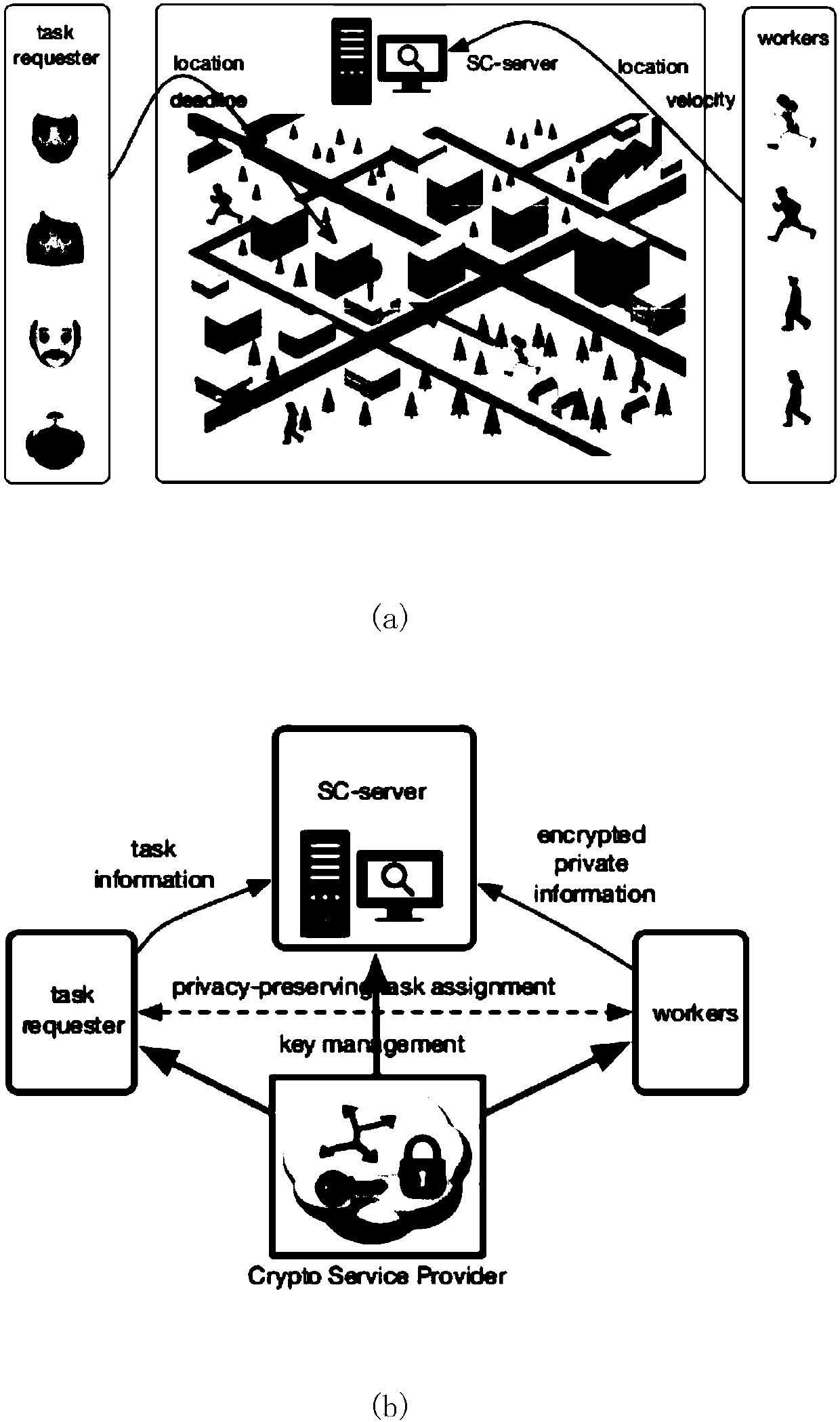
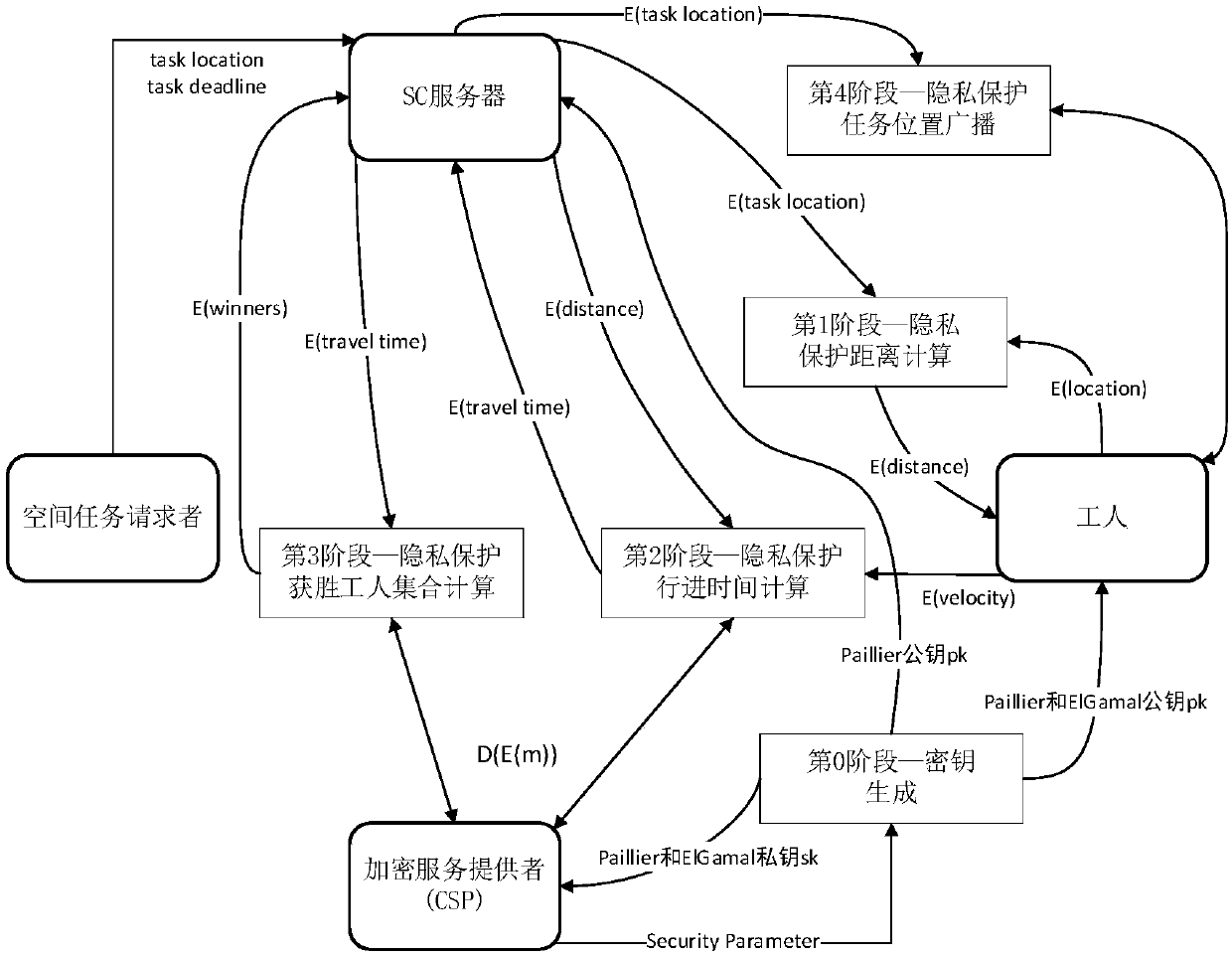
Warrantable privacy protection space crowdsourcing task distribution system and method
ActiveCN107360146APrivacy protectionStrong mutual protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDistribution systemService provider
The invention discloses a warrantable privacy protection space crowdsourcing task distribution system and method, and the system comprises an SC server, an encryption service provider, a space task requester, and workers. The encryption service provider generates a secret key, and employs a Paillier password and ElGamal password system. The space task requester creates a space task, and returns the position of the task to the SC server. The SC server encrypts the position of the task, and each worker calculates the distance between the position of the task and the position of the worker. The speed of each worker is encrypted and transmitted to the SC server, and each worker calculates the travel time of his own, and encrypts the travel time and transmits the encrypted travel time to the SC server. The SC server calculates the winning workers through the encryption service provider, and the encryption service provider enables the winning worker set comprising a plurality of winning workers to be encrypted and returned to the SC server. The SC server encrypts the position of the task, and broadcasts the encrypted position of the task to all workers, and the winning workers arrive at the specified position to execute the task. According to the invention, the system achieves the double-side privacy protection in the space crowdsourcing, greatly reduces the calculation, and can guarantee that the task is accepted at high probability.
Owner:SHENZHEN UNIV
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server
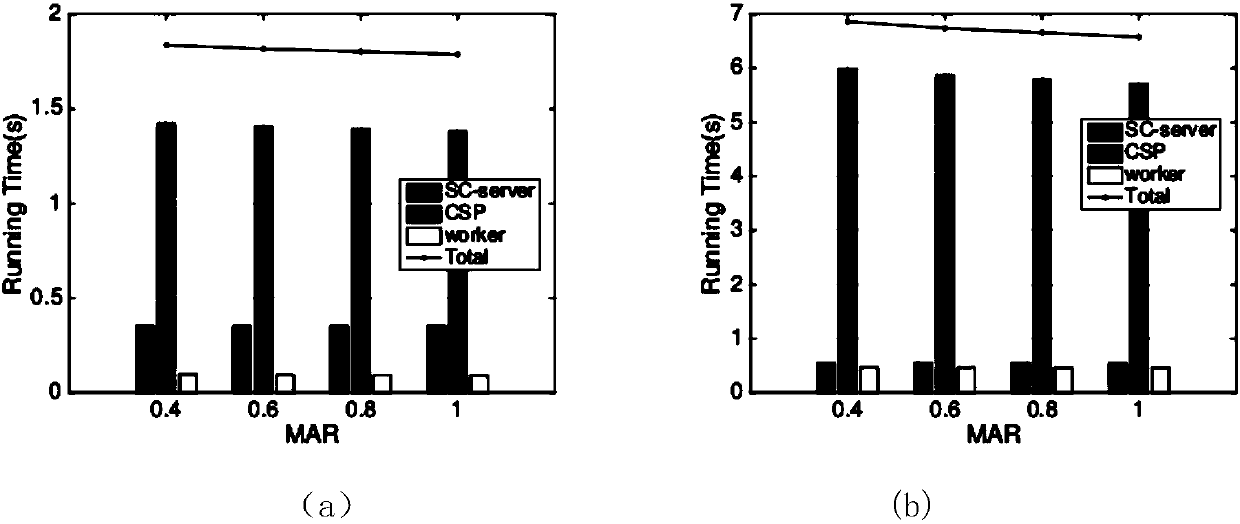
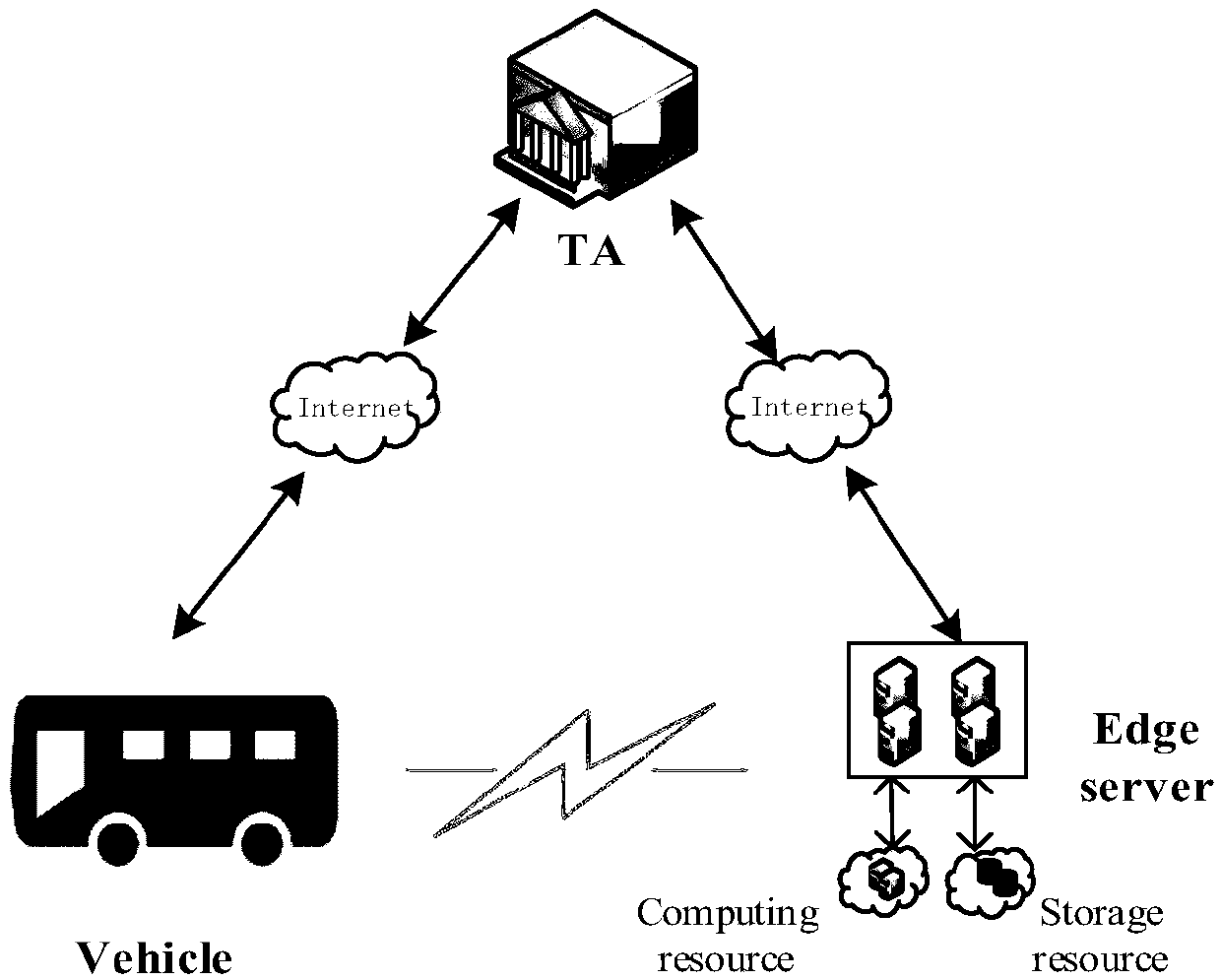
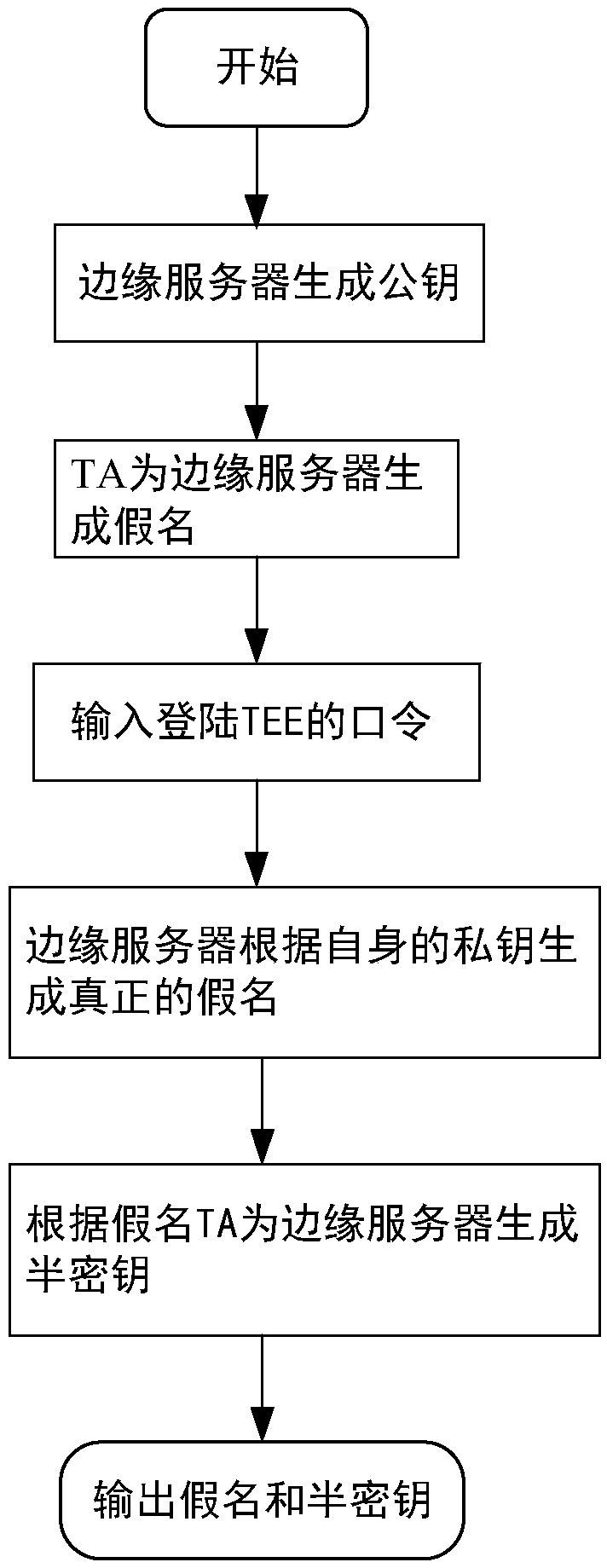
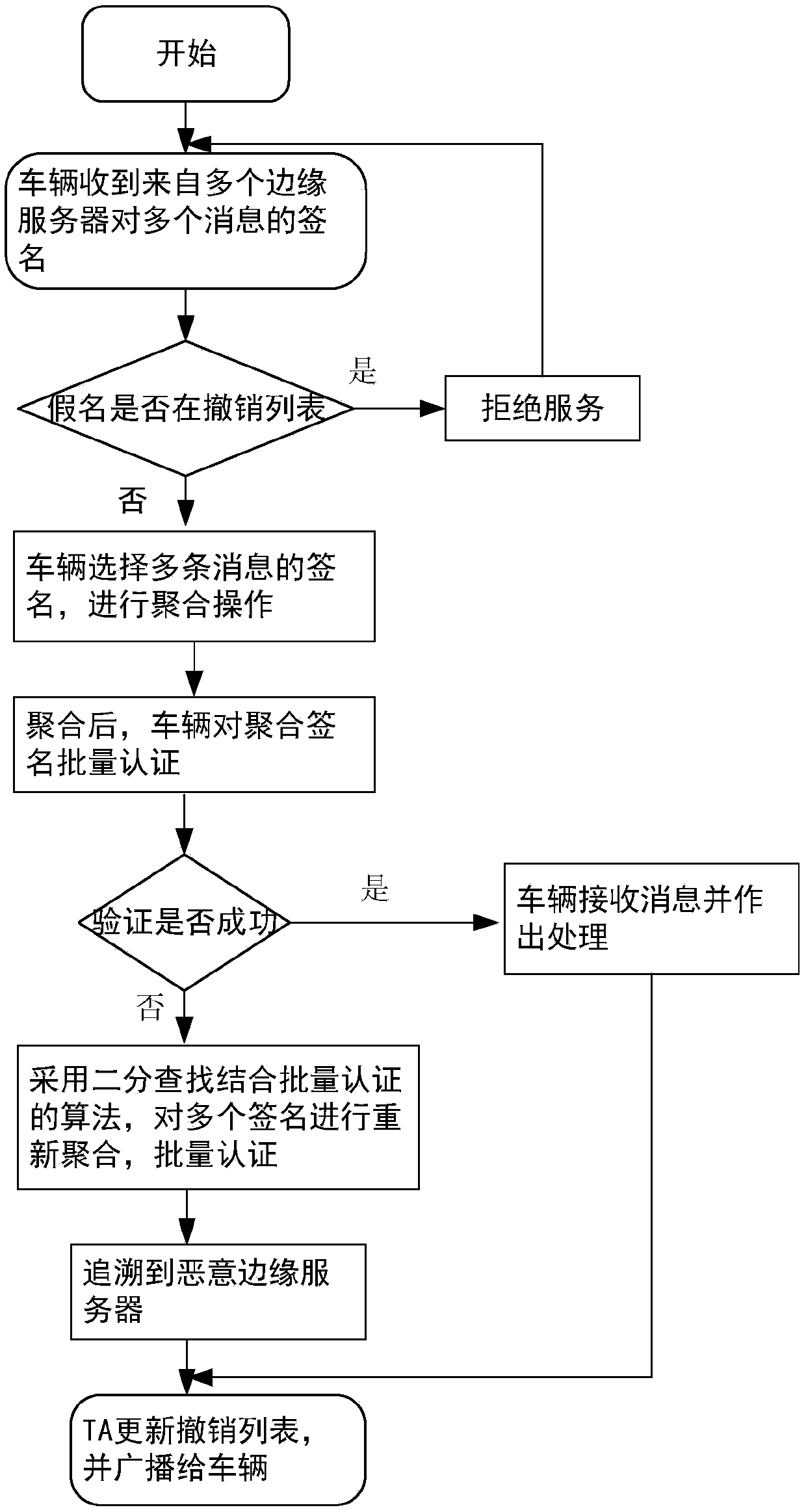
ActiveCN109005538ARealize privacy protectionReduce resource consumptionKey distribution for secure communicationUser identity/authority verificationEdge serverEdge computing
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server is disclosed. The steps are system parameter generation, pseudonym generation for a mobile edge computing server and semi-key extraction, and authentication of a message between the mobile edge computing server and the vehicle. The step comprises: the vehicle migrates a large number of calculationor stored tasks to the mobile edge computing server, the mobile edge computing server performs ring signature on the message, and the vehicle authenticates the message in batch. The invention introduces the edge computing into the traditional vehicle-mounted ad hoc network, and the vehicle can migrate the computing or storage tasks to the edge server to execute instead of sending them to the cloudend for centralized processing. In the signature part of the invention, ring signature is combined with pseudonym, and the application of ring signature effectively protects the privacy of mobile edge computing server and traces the malicious mobile edge computing server through pseudonym.
Owner:ANHUI UNIVERSITY
Security enhancement method for third-party code of Android application program
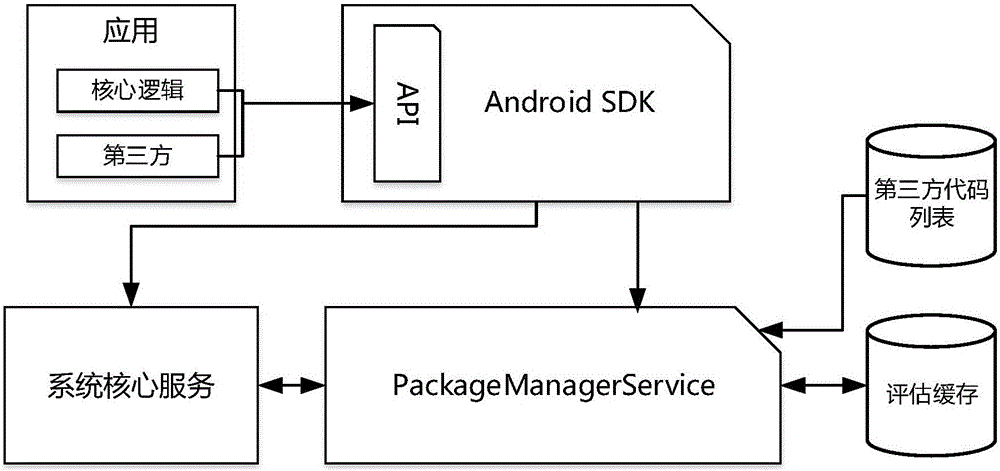
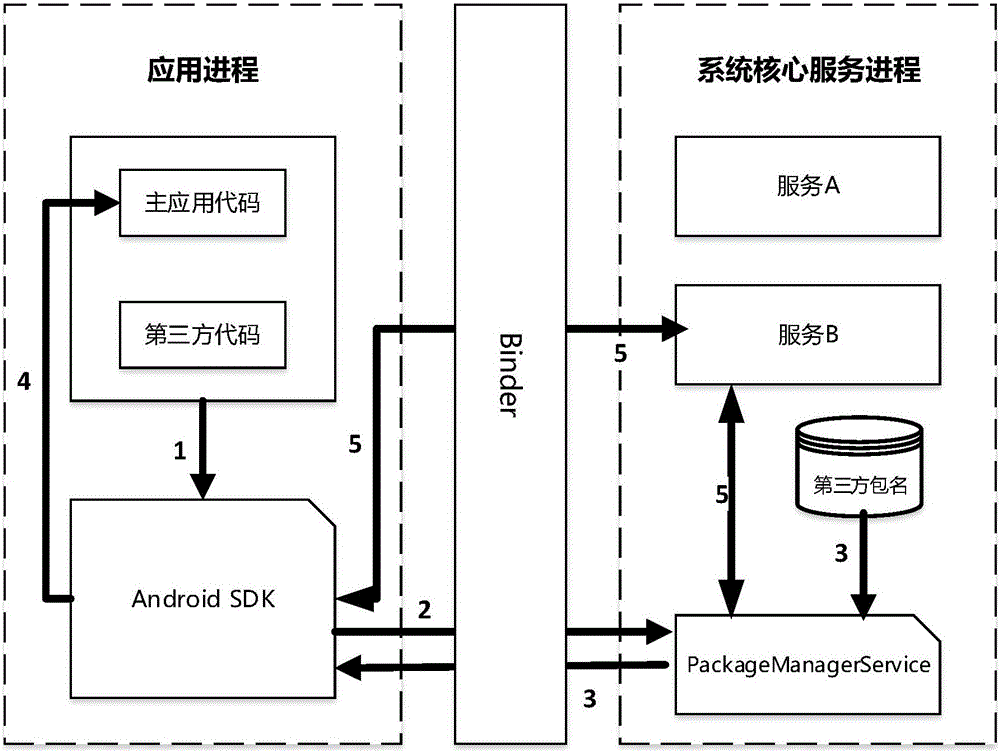
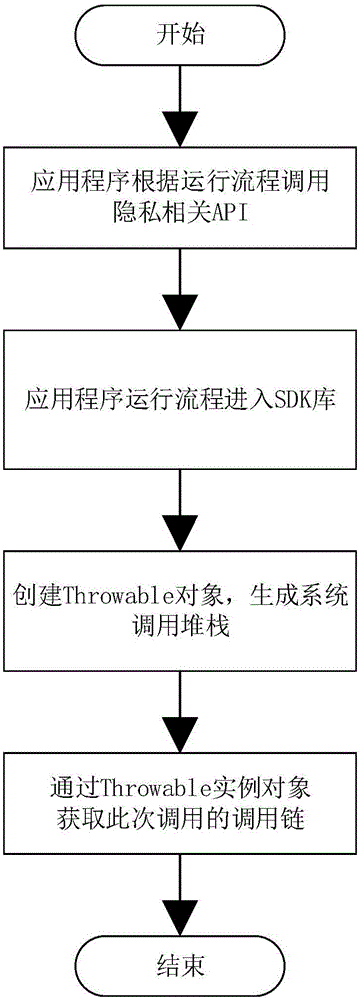
ActiveCN104992081ARealize privacy protectionReduce overheadProgram/content distribution protectionEvaluation resultThird party
The invention discloses a security enhancement method for a third-party code of an Android application program. The security enhancement method comprises the steps of: obtaining a call chain relating to user privacy data in an application program process by utilizing system exception stack data; obtaining main information of a call initiator by a system according to call chain information; sending the main information of the call initiator to a system access control evaluation engine by utilizing an inter-process communication mechanism; judging a call source by an evaluation engine according to the main information and a third-party code package list; executing a corresponding user policy according to the call source; performing permission evaluation of the call according to user selection and application program permission; caching an evaluation result; and returning corresponding data according to the evaluation result. The method is capable of realizing the security enhancement of the third-party code of the Android application program with relatively low performance cost on the basis of being compatible with an original application program structure and an original third-party code frame.
Owner:HUAZHONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com