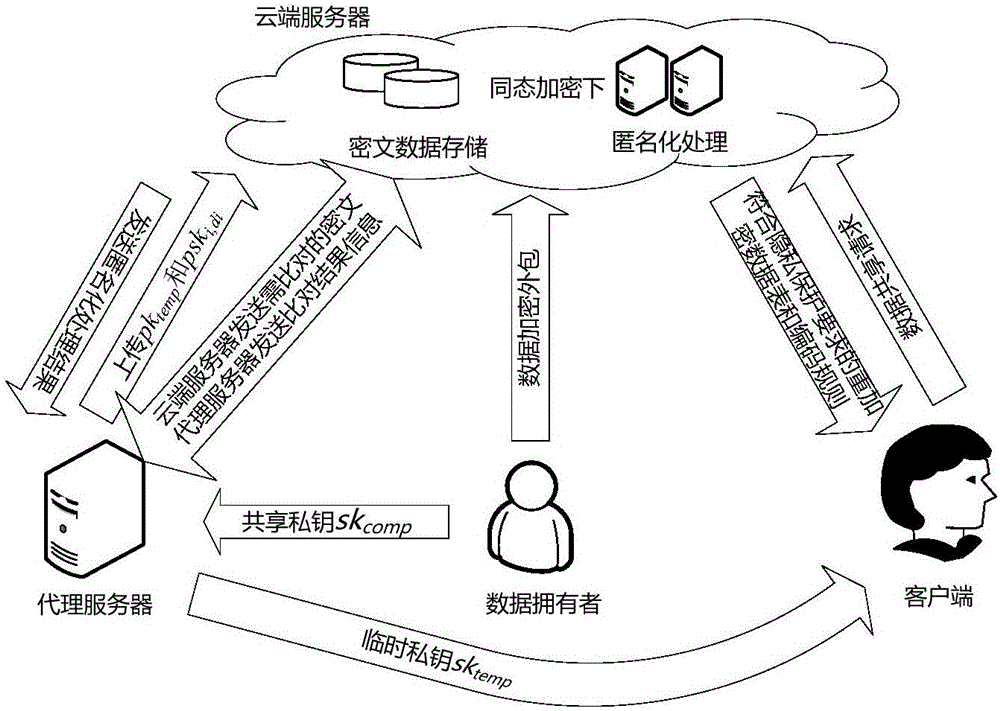
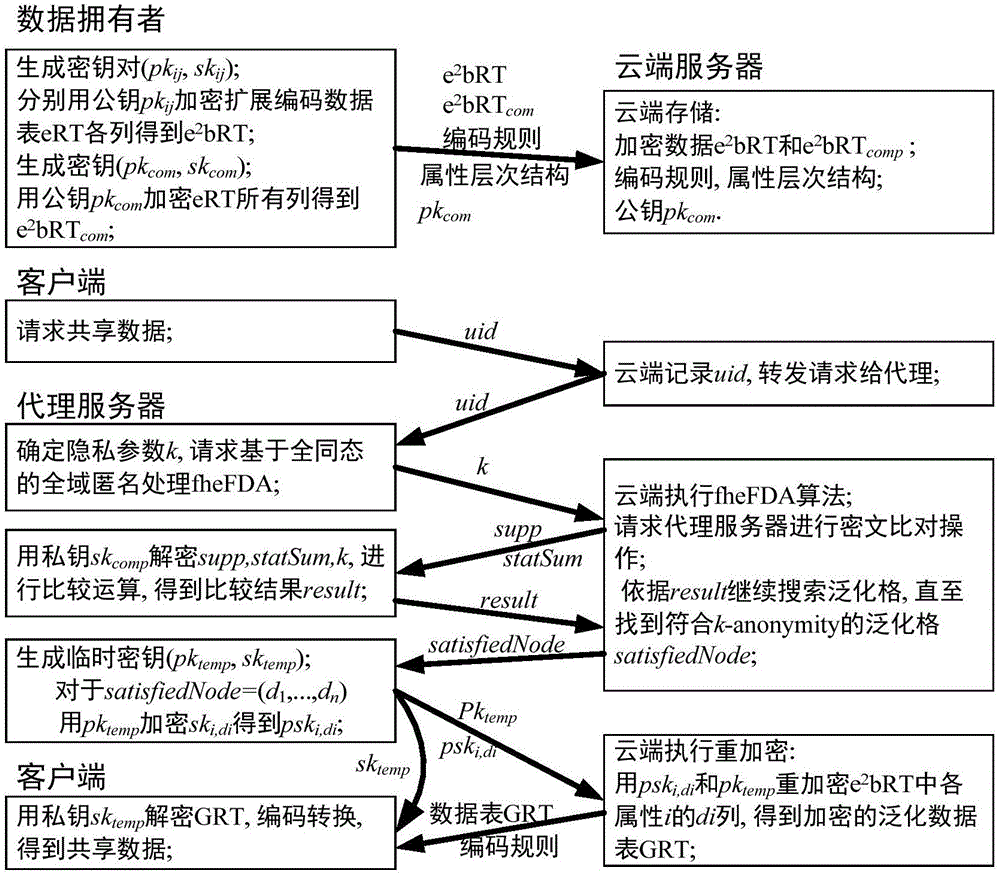
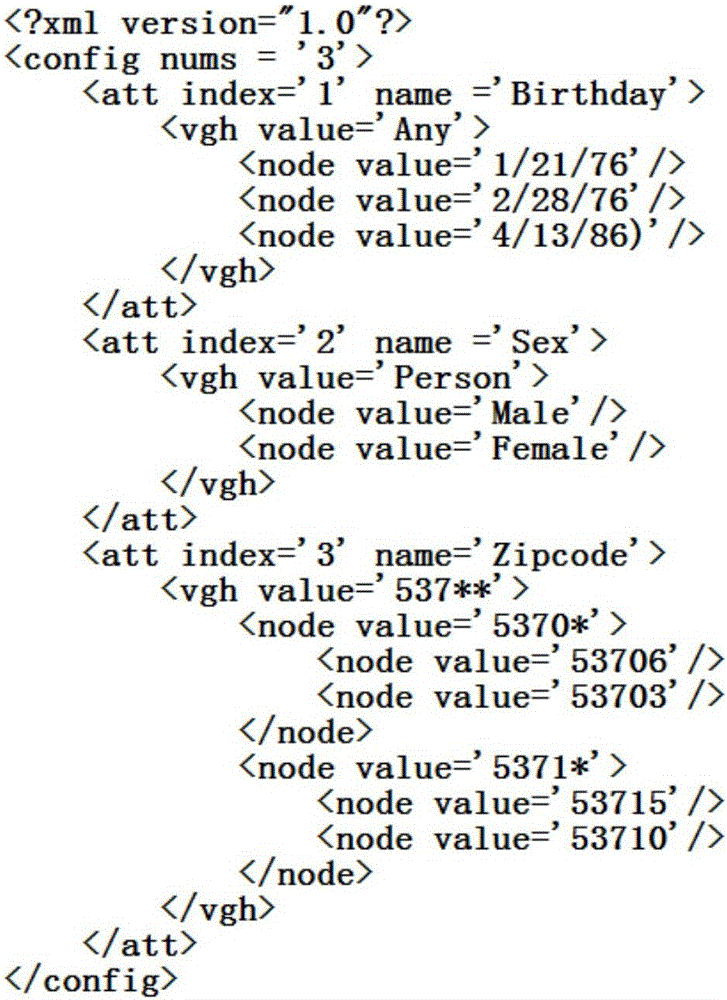
Cloud-oriented interactive privacy protection method and system
A privacy protection, interactive technology, applied in the field of interactive privacy protection, can solve problems such as research, difficult ciphertext, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034]What the present invention adopts is the BGV fully homomorphic encryption scheme (Z.Brakerski, C.Gentry, and V.Vaikuntanathan.(leveled) fully homomorphic encryption without bootstrapping.TOCT, 6(3): 13, based on RLWE with higher efficiency at present. 2014.Preliminary version in ITCS 2012.), in order to facilitate understanding, the principle of fully homomorphic encryption will be introduced first.
[0035] First, parameter setting. The fully homomorphic encryption scheme adopted in the present invention is based on a polynomial ring, and the polynomial ring d is the power of 2, λ is the security parameter of the homomorphic encryption scheme, the ciphertext polynomial coefficient is the modulus q of μ bits, L is the depth of the binary operation circuit, other parameters (d=d(λ,μ,b), n=n(λ,μ,b), χ=χ(λ,μ,b)) to ensure that 2 λ security. n=1 is to set instantiation based on RLWE. In order to make fully homomorphic encryption suitable for the global anonymous algor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com