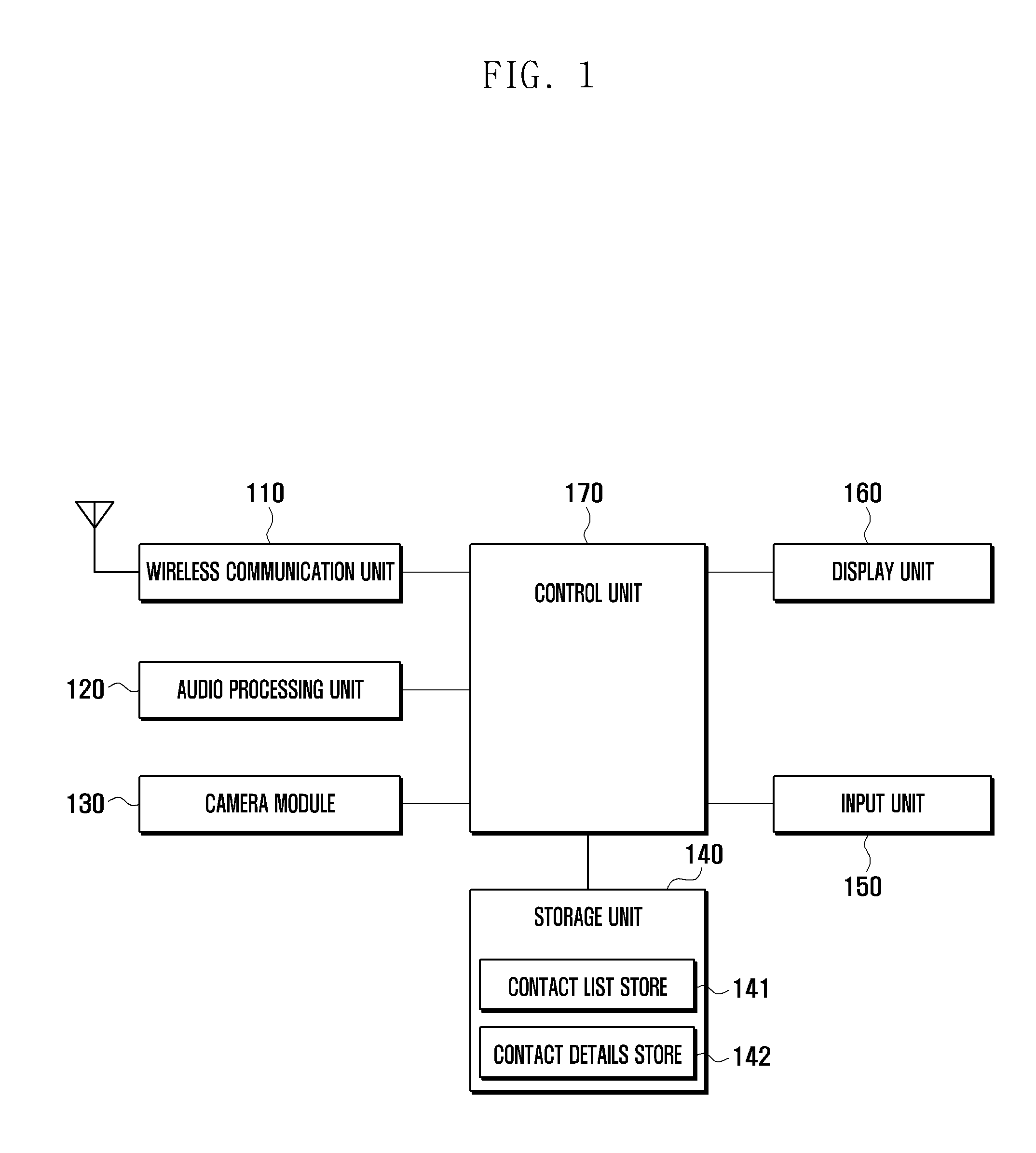
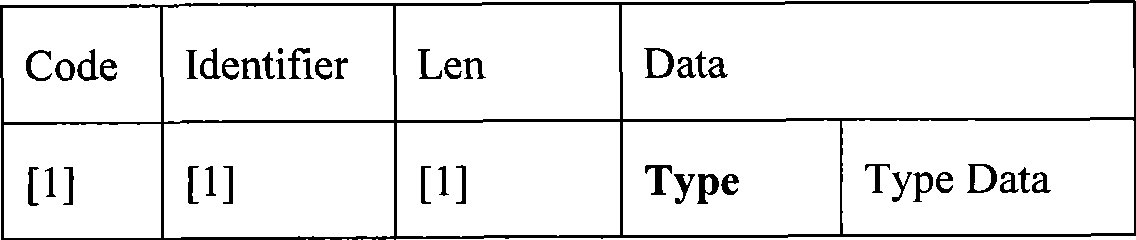
Patents
Literature
224 results about "Information privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
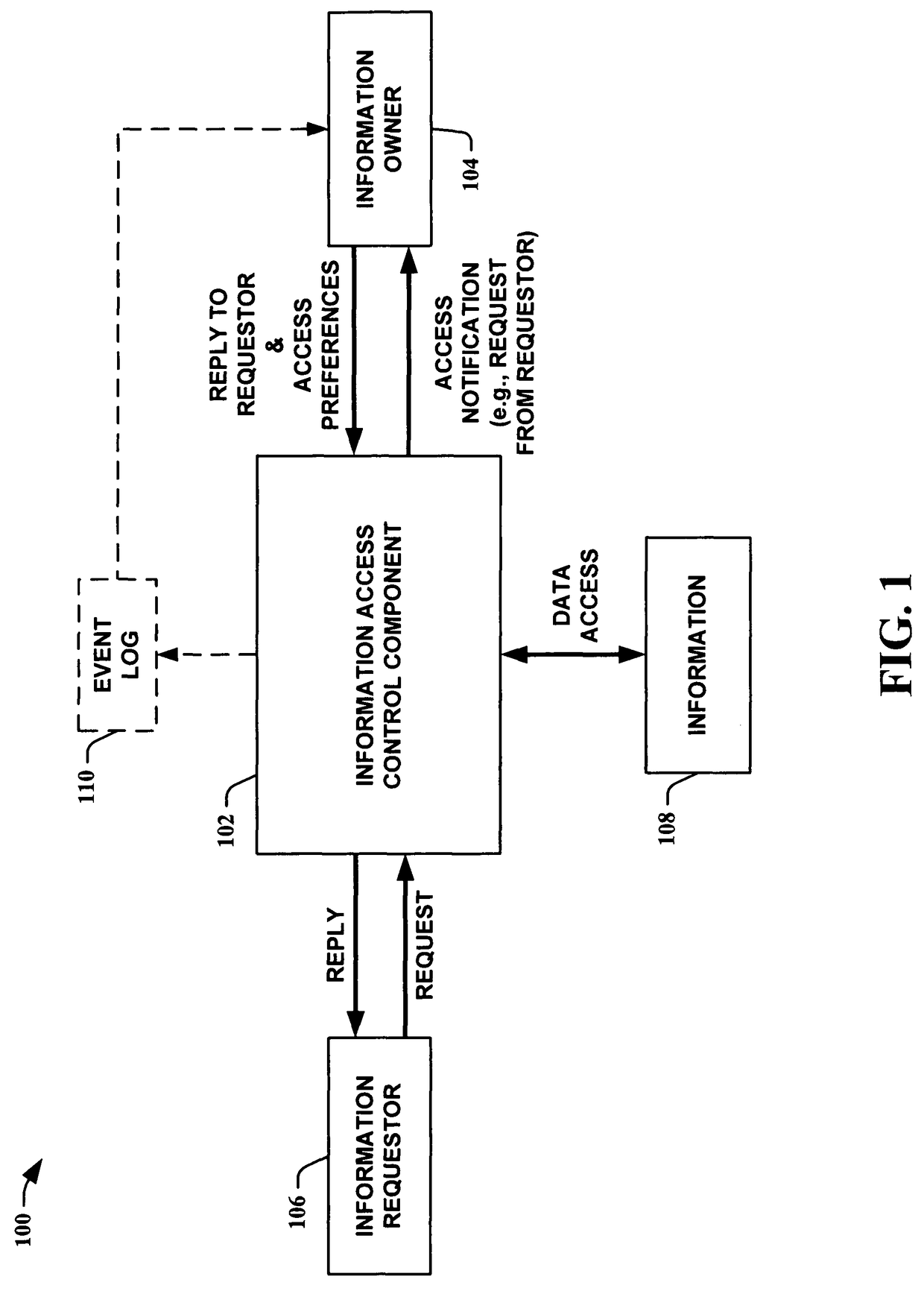
Information privacy is the relationship between the collection and dissemination of data, technology, the public expectation of privacy, legal and political issues surrounding them. It is also known as data privacy or data protection.
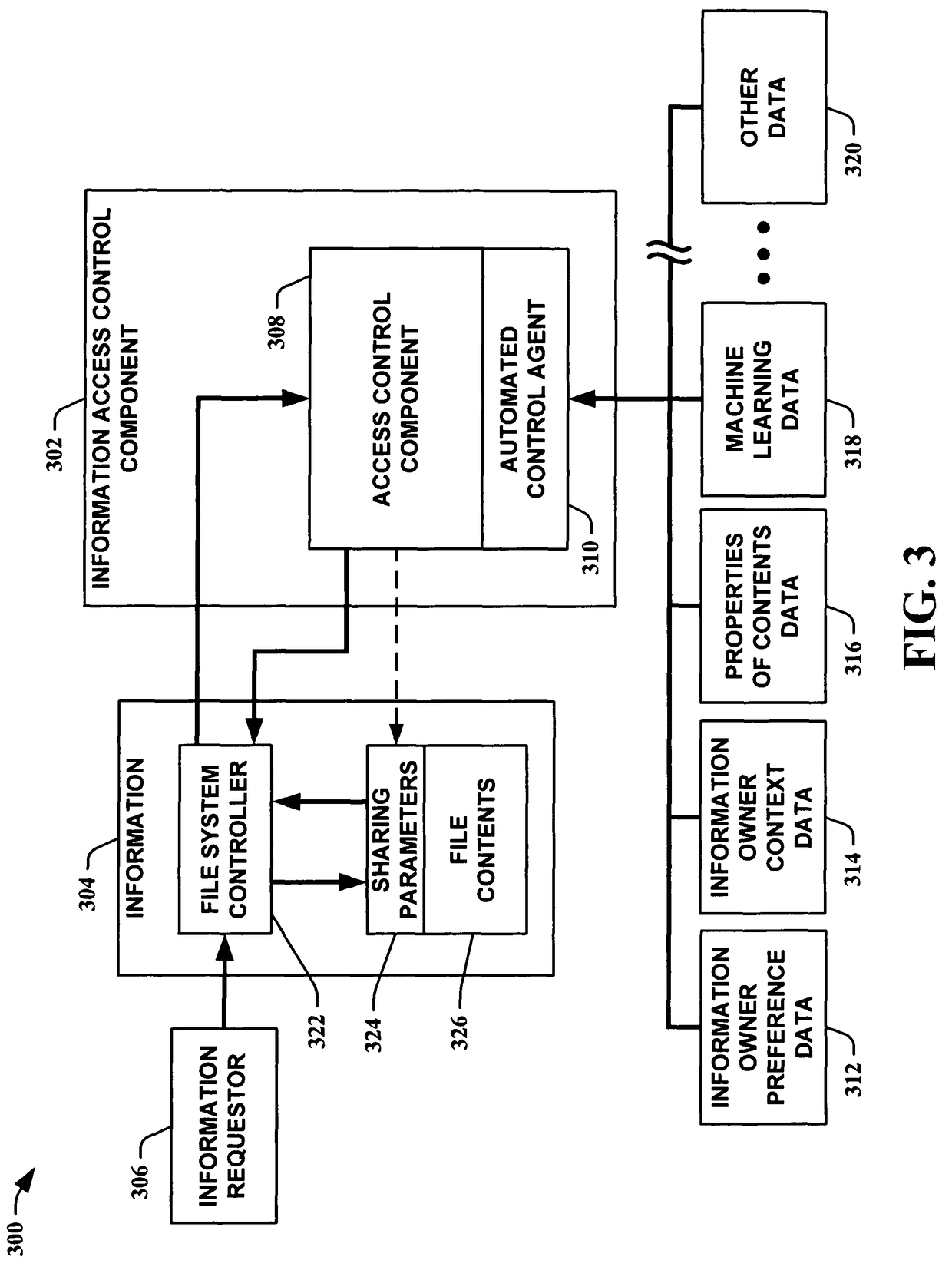
Abstractions and automation for enhanced sharing and collaboration
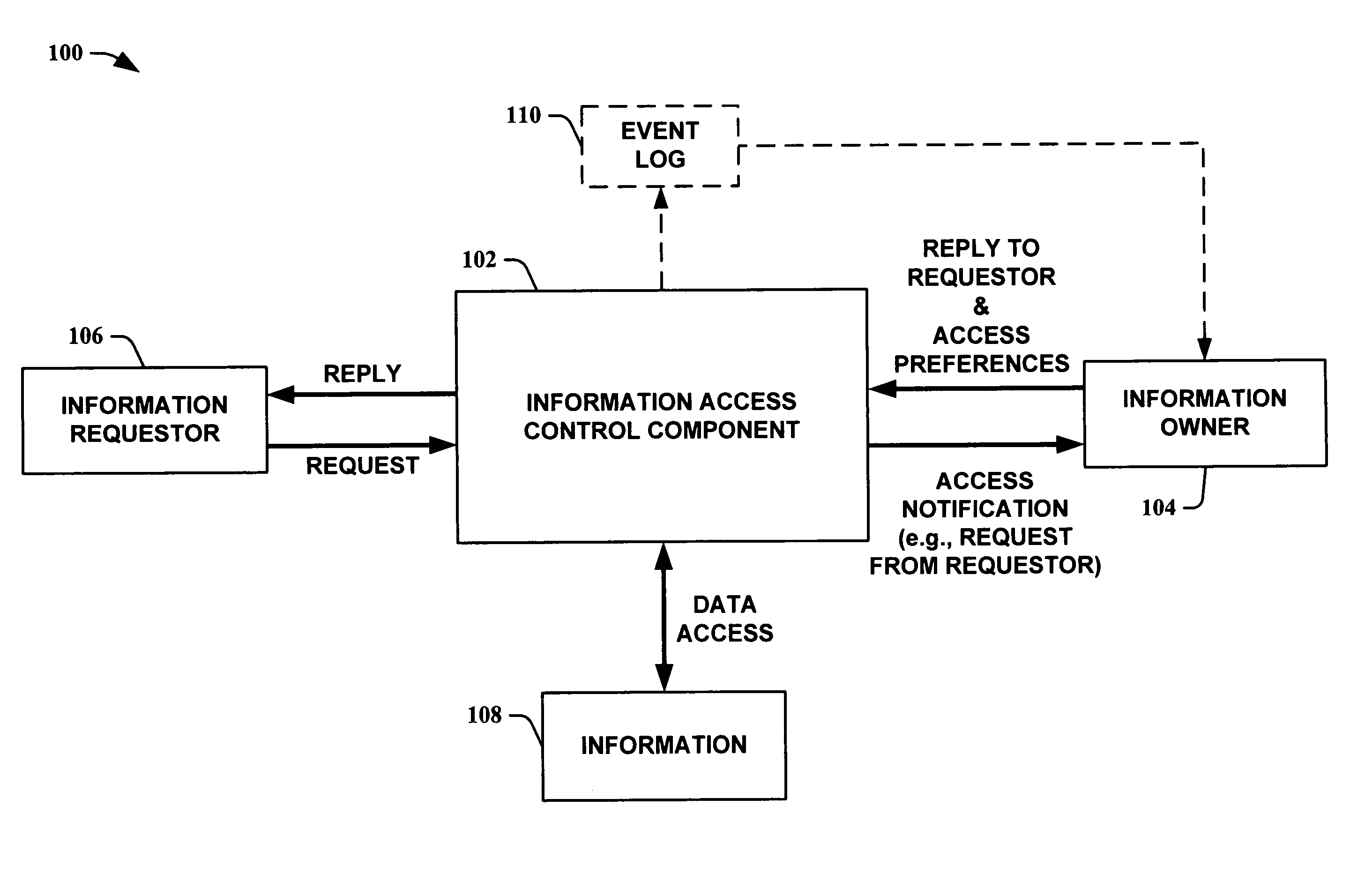
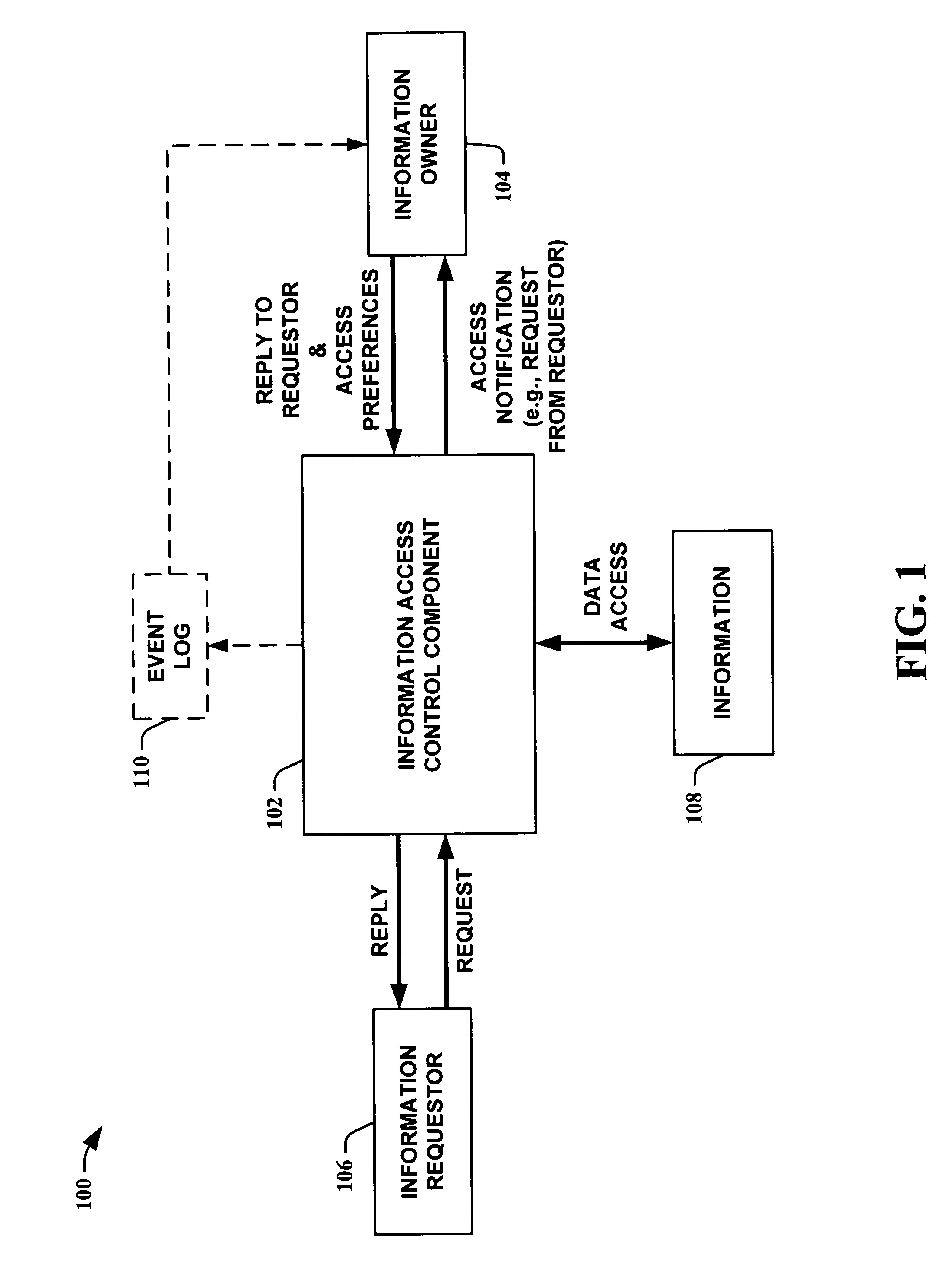
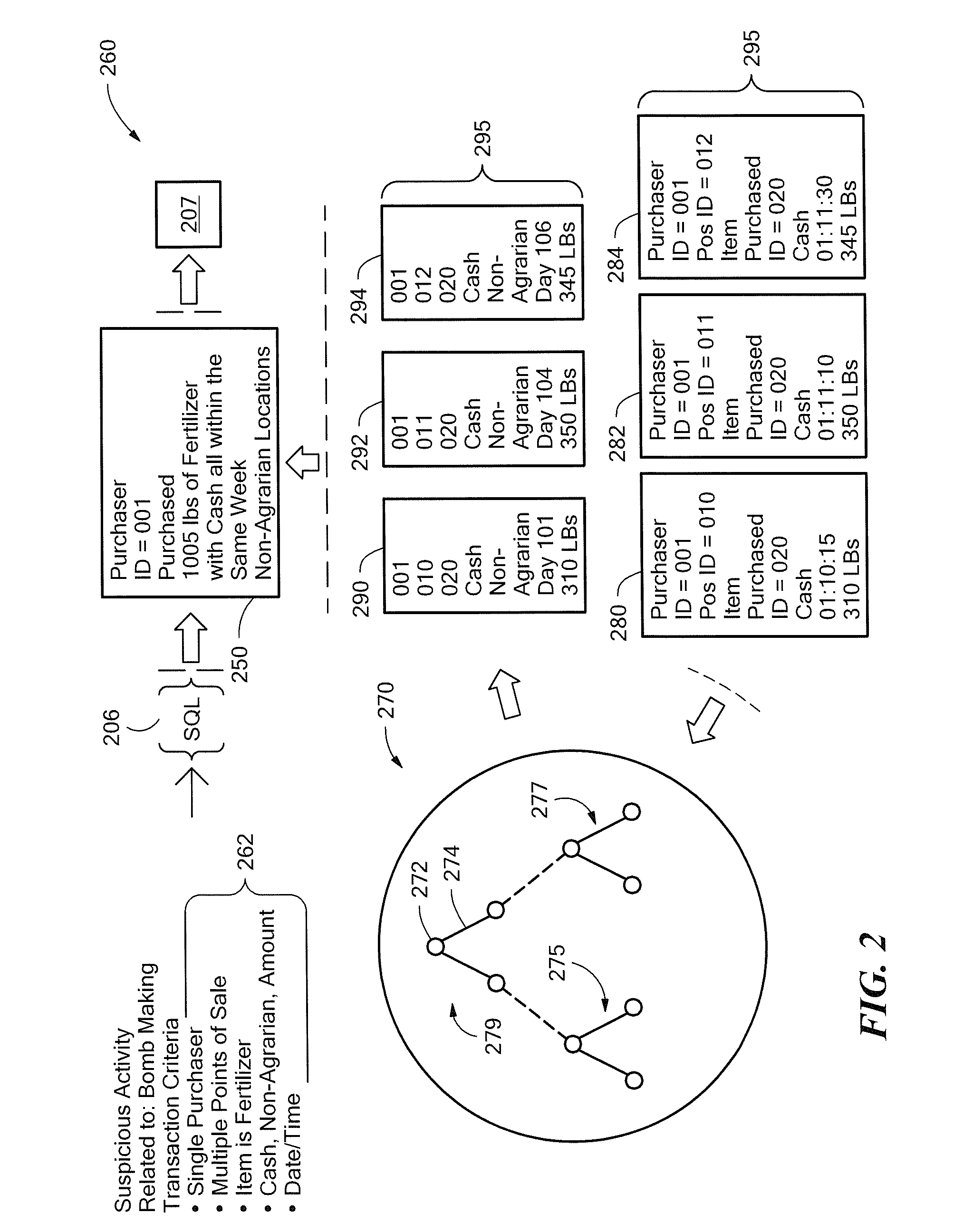
InactiveUS20050232423A1Optimal information privacyReduce the burden onDigital data processing detailsUser identity/authority verificationInformation sharingCrowds
The present invention provides methods for using abstractions of people, including dynamic and static groups of people, to enhance the efficiency of the specification and automation of policies for sharing information between users with a “need-to-know.” An instance of the present invention can also provide these users information based on a “time-to-know.” By providing access to information based on group affiliation and properties of the content of the information, the present invention maintains optimal information privacy while minimizing encumbrances to sharing data with appropriate users and even at appropriate times. The present invention can be integrated with other communication technologies to facilitate access to information in a time appropriate manner. Other instances of the present invention employ automated and semi-automated, mixed-initiative techniques, to make information-sharing decisions. Additional instances of the present invention include the employment of machine-learning techniques to facilitate construction of access policies from the actions or profile of a single user or a community of users, including the construction of automated sharing agents that work in an automated or mixed-initiative manner to respond to real-time requests for information.
Owner:MICROSOFT TECH LICENSING LLC
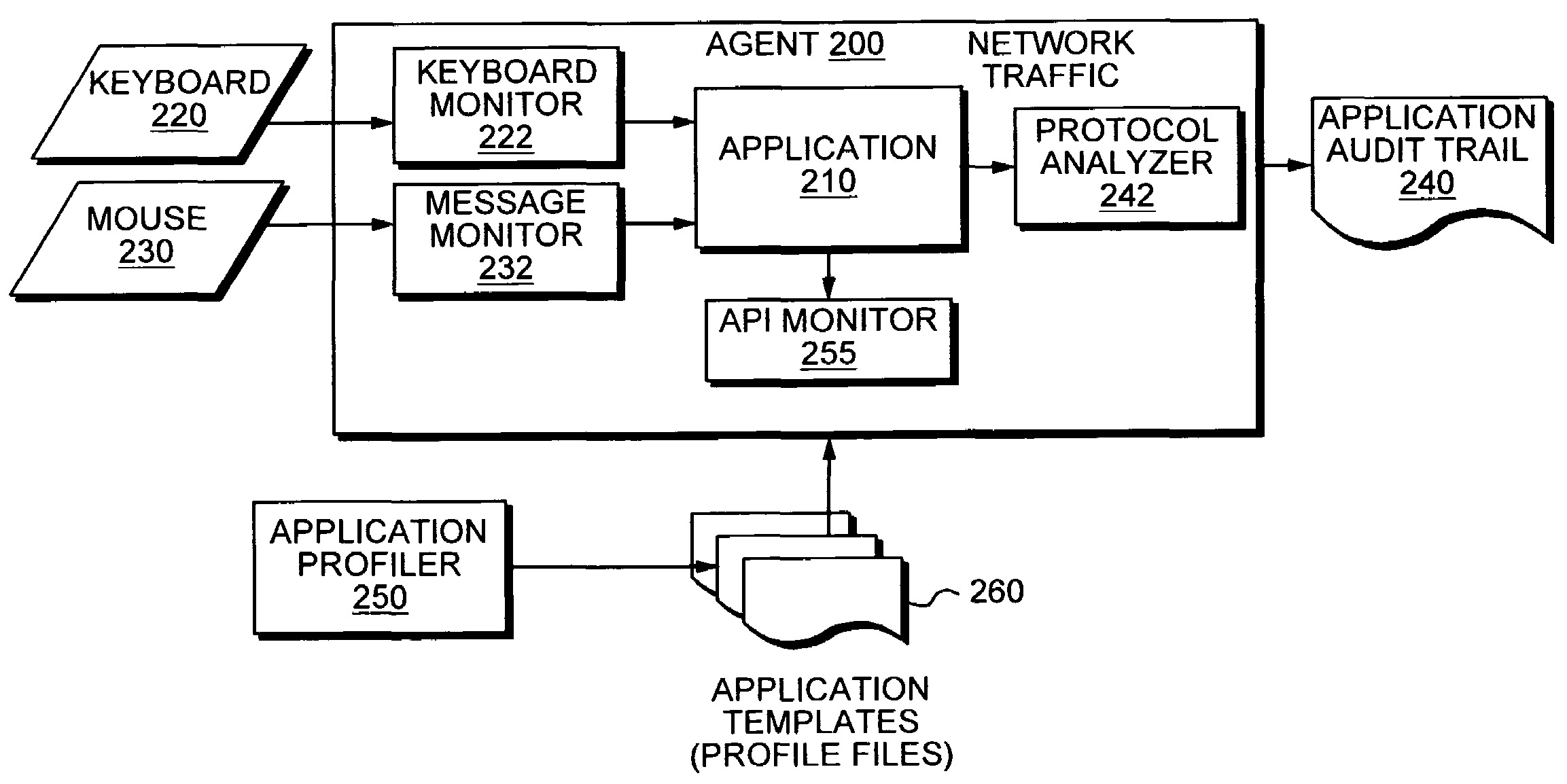
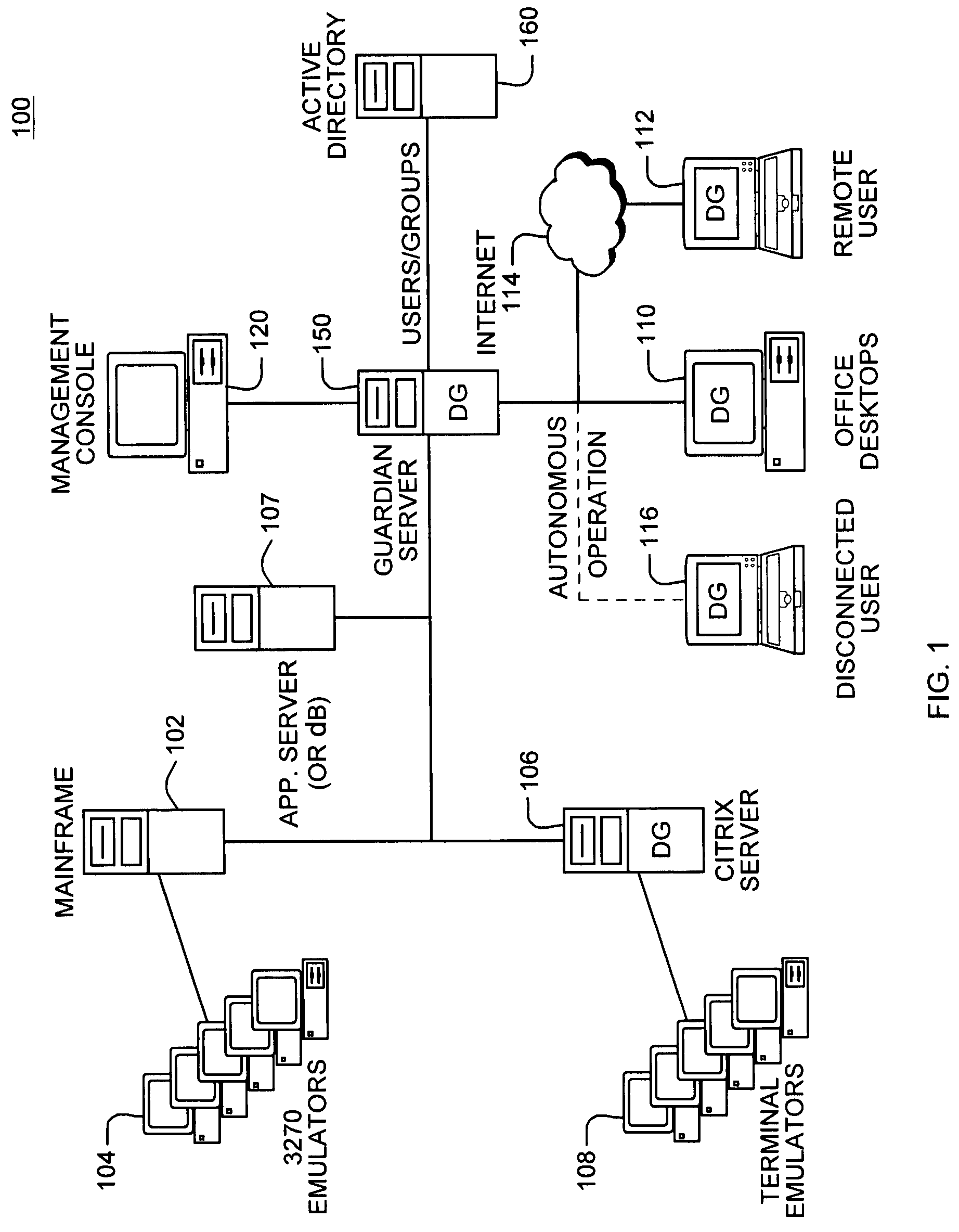
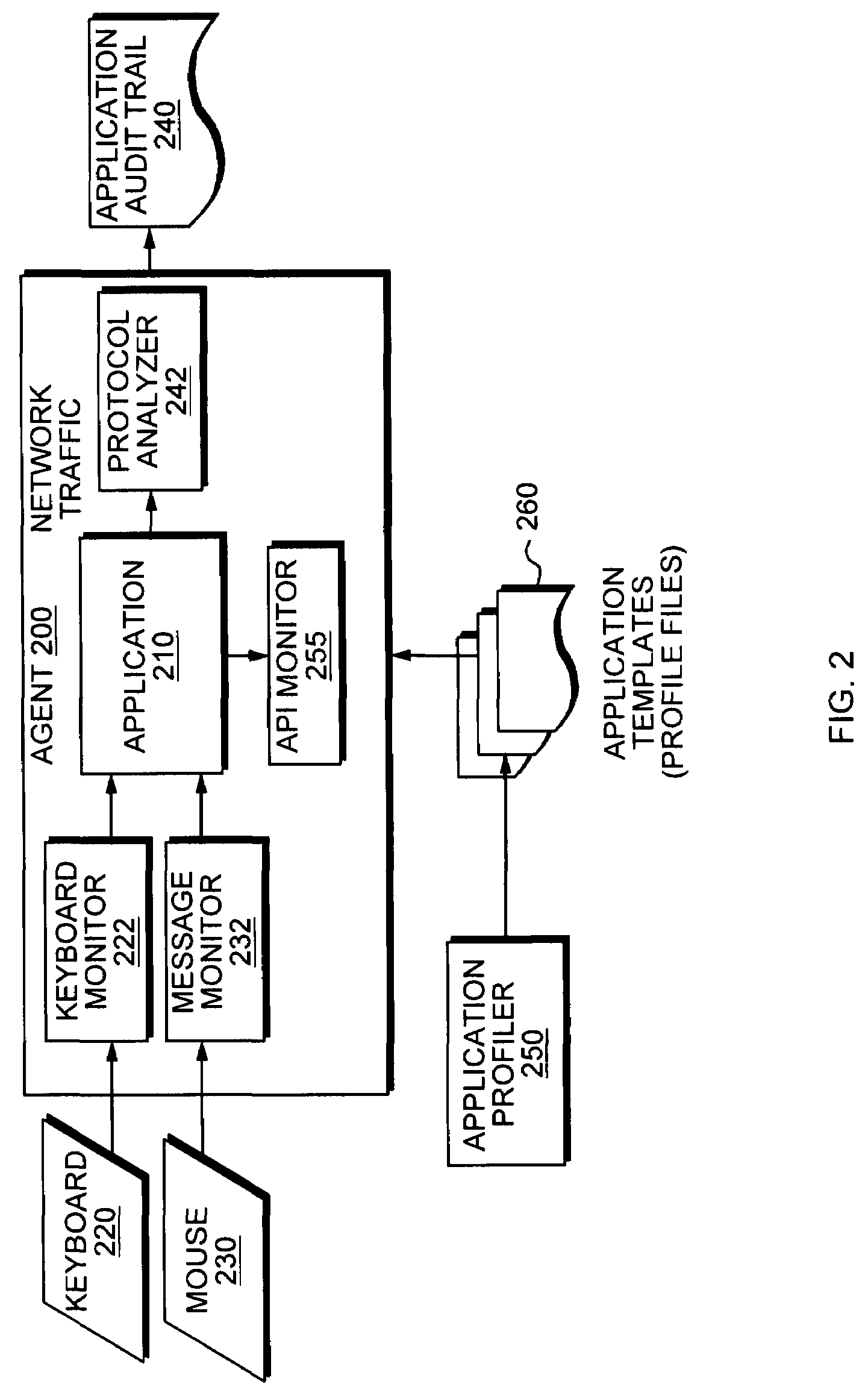
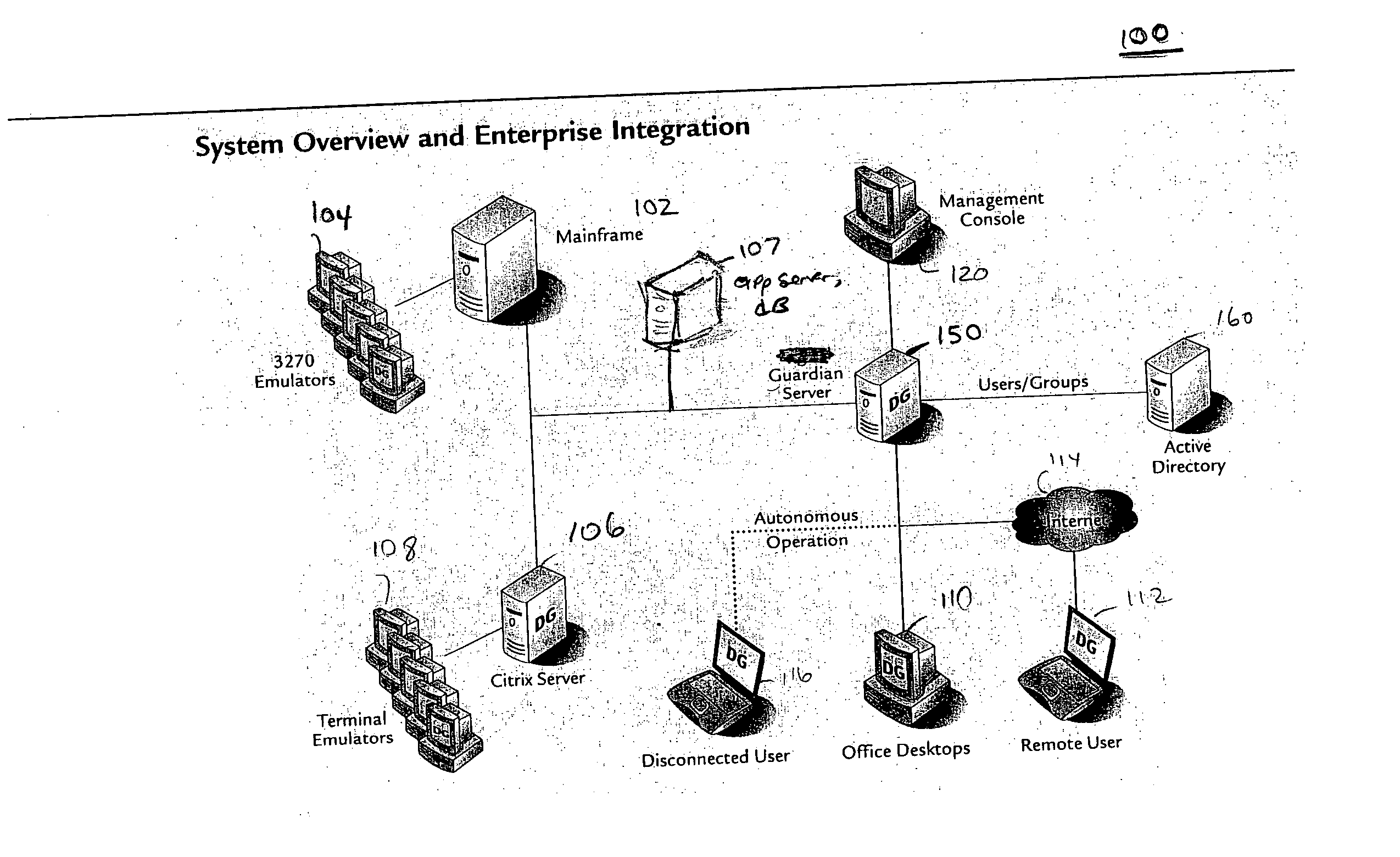
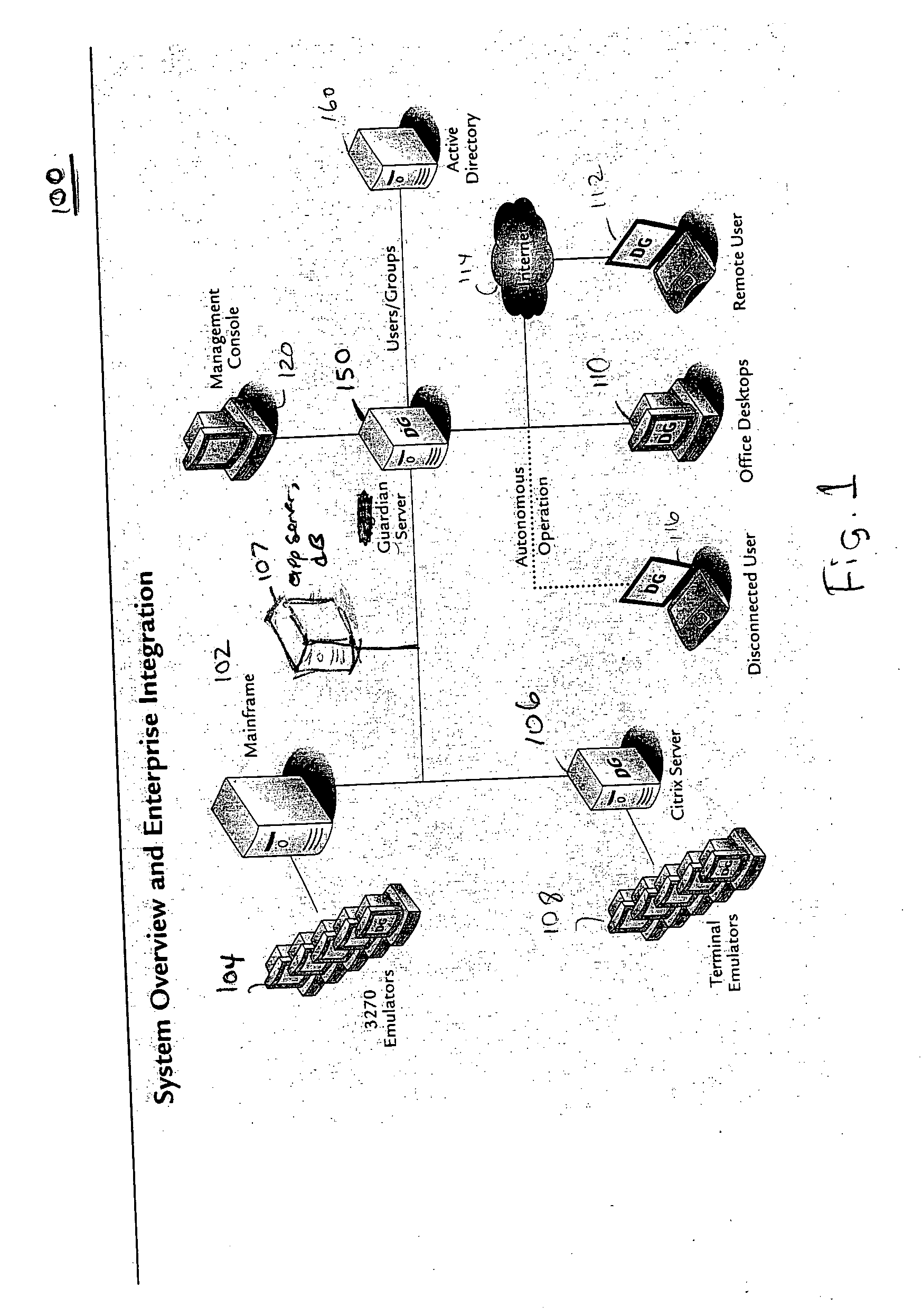
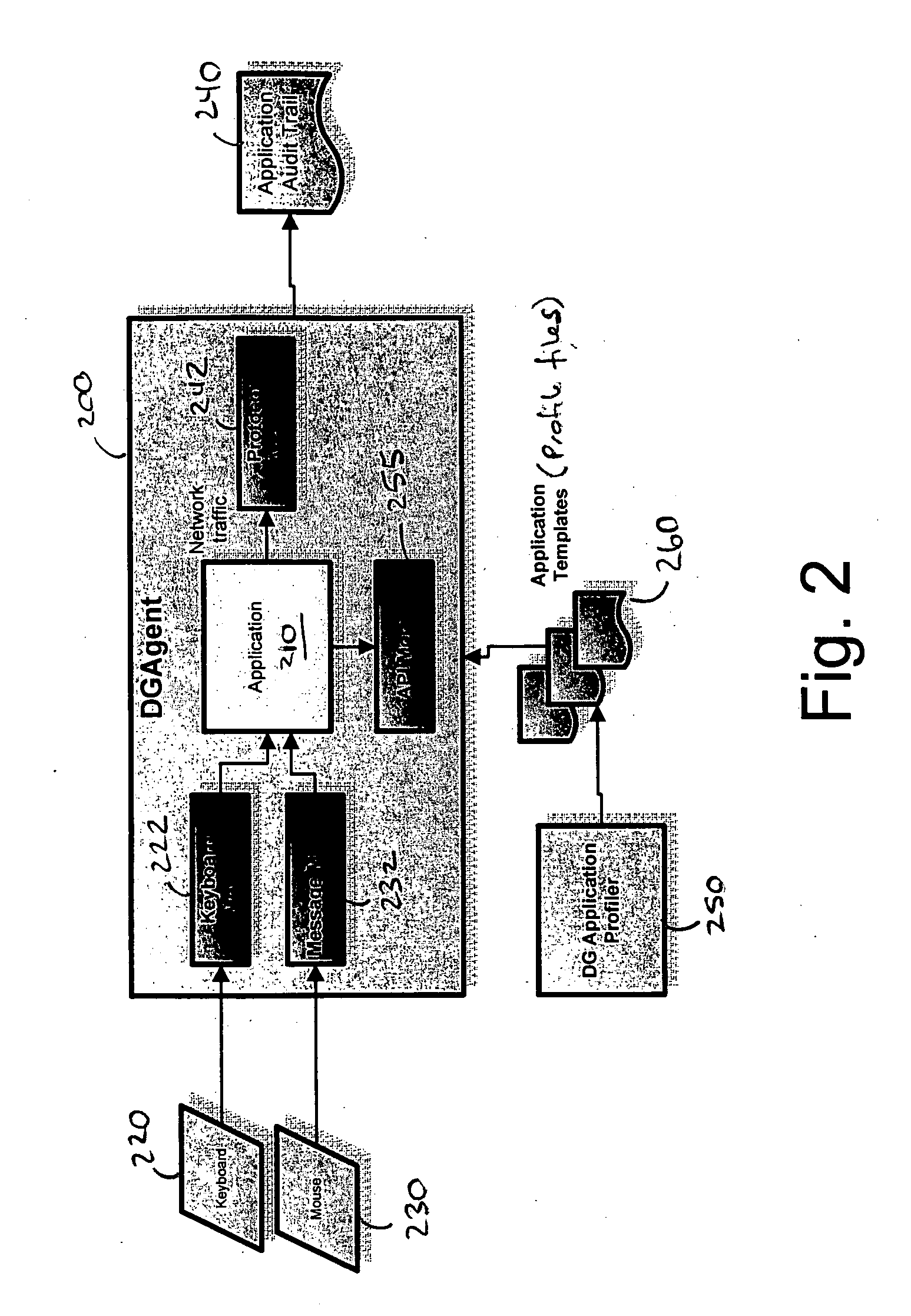
Application instrumentation and monitoring
ActiveUS7496575B2Cost effectiveAvoid the needDigital data processing detailsDigital computer detailsApplication softwareData store
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
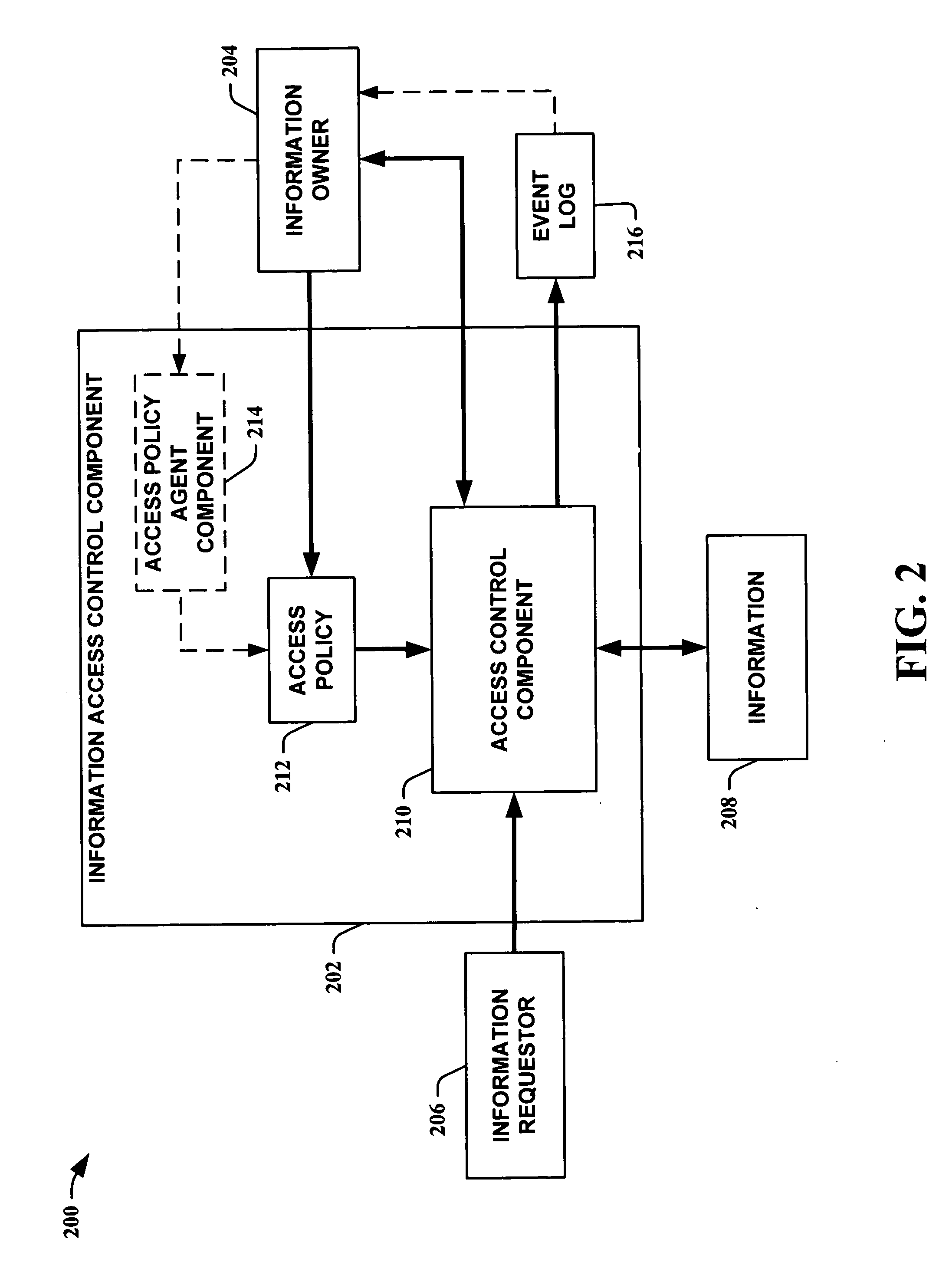
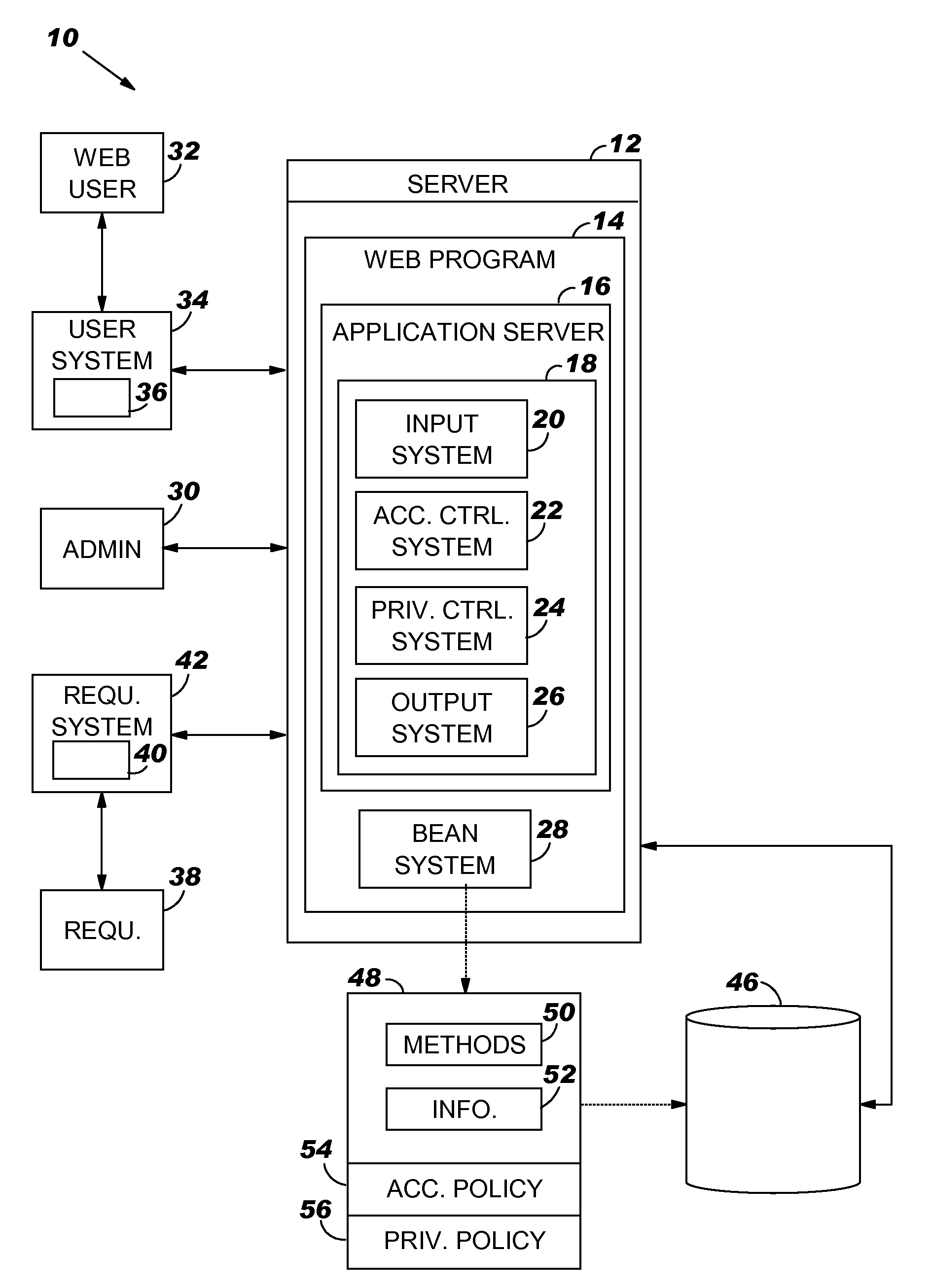
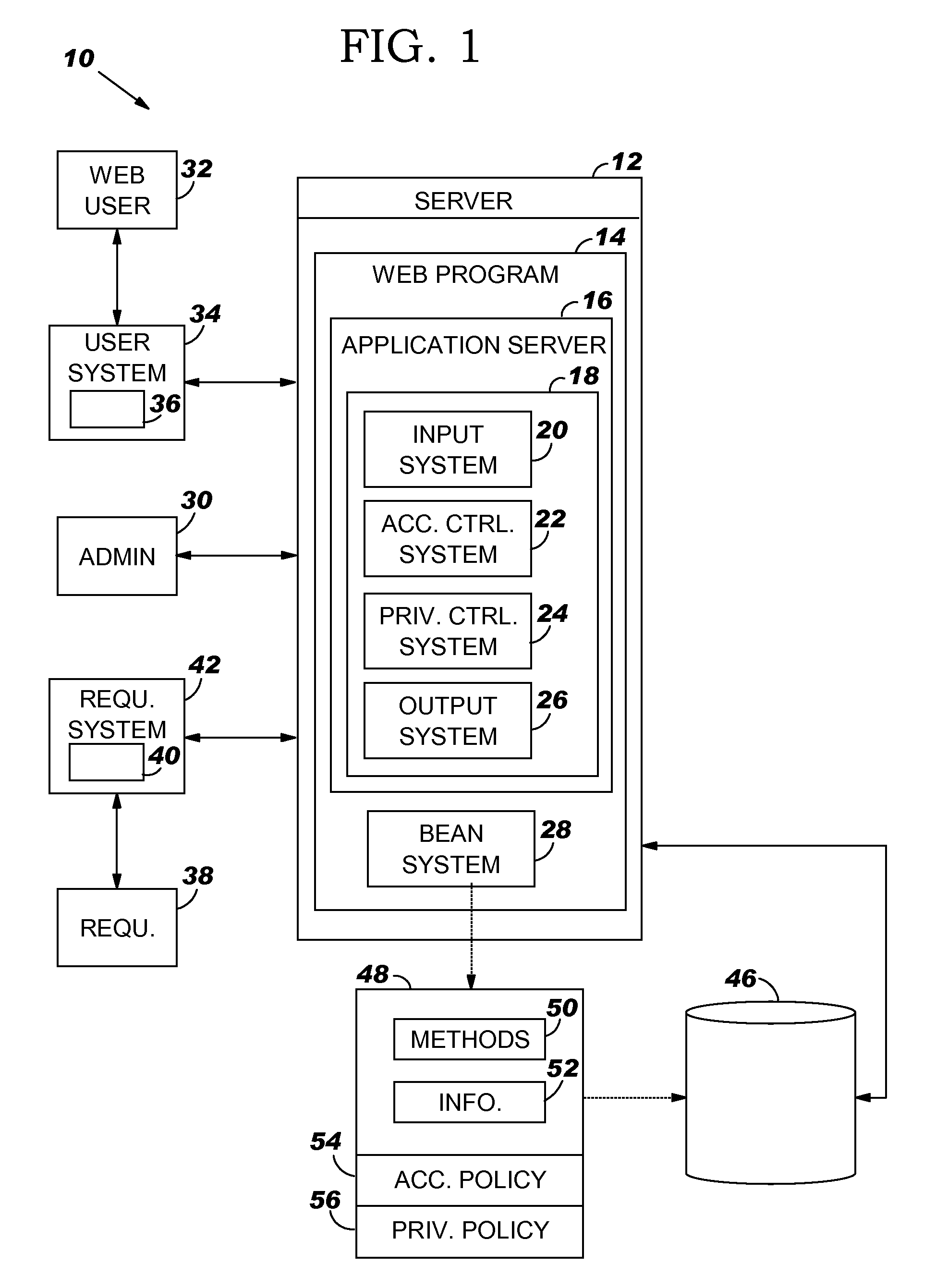
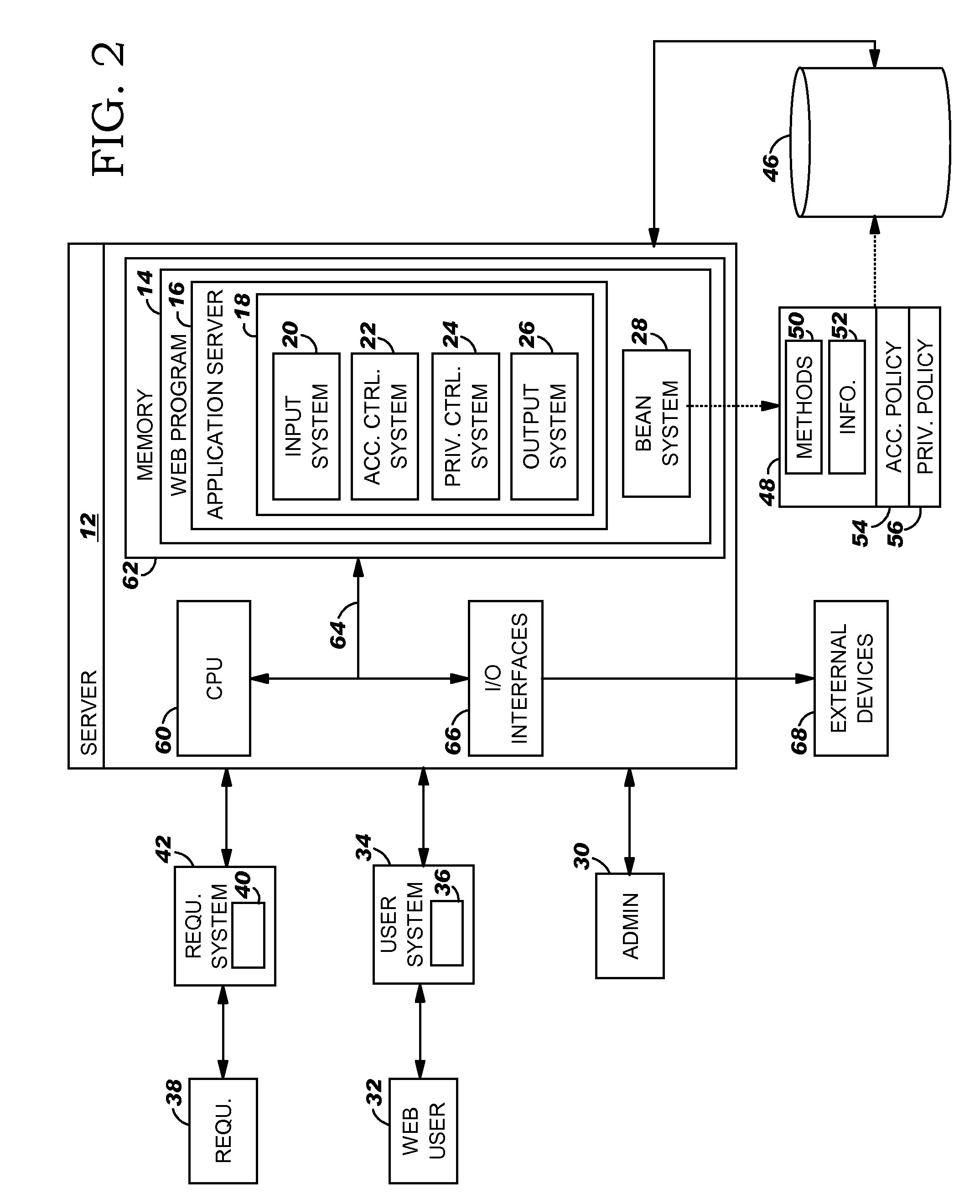
System and program product for automatically managing information privacy
A request including a call for the information in a bean and a purpose for the call is received. Upon receipt, the purpose is compared to a privacy control policy that is packaged with the bean. If the purpose complies with the privacy control policy, the requested access and / or use of the information is permitted.
Owner:DAEDALUS BLUE LLC
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
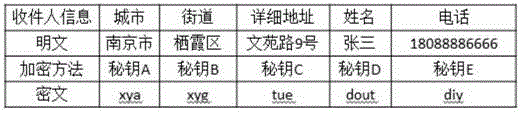
Logistics personal information privacy protection system based on multilayer-encrypted two-dimensional code
ActiveCN104933371APrevent leakageImplement query authentication mechanismDigital data protectionRecord carriers used with machinesLogistics managementPrivacy protection
The invention discloses a privacy protection system based on a two-dimensional code multilayer encryption technology for personal information in a logistics process. A two-dimensional code encryption technology and a layered extraction technology are combined in order to solve the problem of leakage of logistics platform personal information. The privacy protection system mainly comprises a two-dimensional code layered encryption printing module of a sending service department, a layered two-dimensional code decryption information extraction scanning module for use in a logistics transfer process, and a personal information verification module of a logistics distribution end. Through adoption of the privacy protection system, a logistics information inquiry authentication mechanism is implemented, and the contradiction between address information leakage and incapability of inquiring after encryption in logistics number inquiry is solved.
Owner:NANJING UNIV OF POSTS & TELECOMM
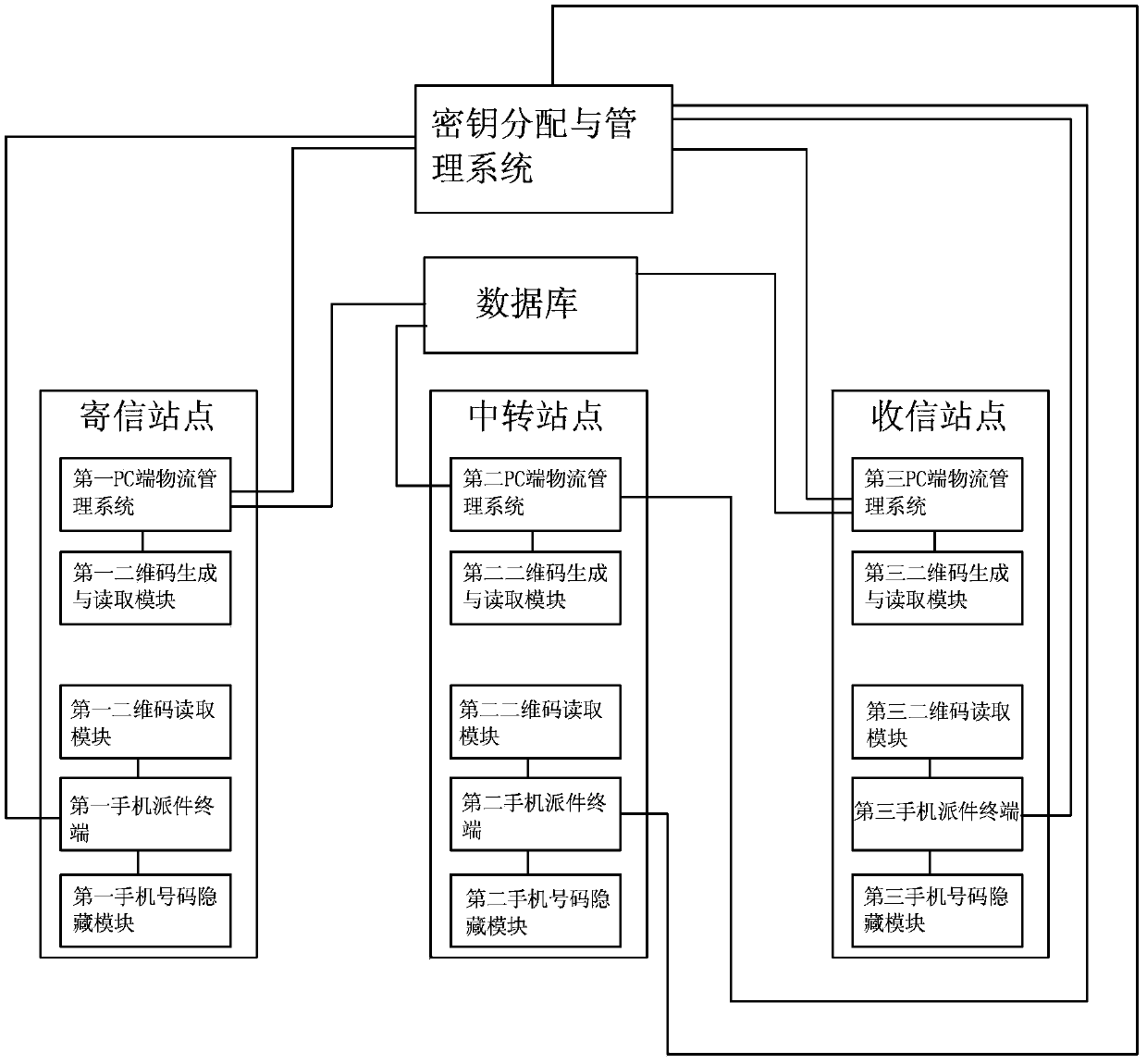
Two-dimensional barcode-based logistics industry personal information privacy protection system and method
InactiveCN103401676ATroubleshoot access rights assignmentsPrevent leakageLogisticsSecuring communicationProtection systemInformation privacy
The invention discloses a two-dimensional barcode-based logistics industry personal information privacy protection system. The system comprises a key distribution and management system, a database, a first PC (Personal Computer) side logistic management system, a first two-dimensional barcode generation and reading module, a first two-dimensional barcode reading module, a first mobile phone delivery terminal, a first mobile phone number hiding module, a third PC side logistic management system, a third two-dimensional barcode generation and reading module, a third two-dimensional barcode reading module, a third mobile phone delivery terminal and a third mobile phone number hiding module, wherein the first PC side logistic management system is positioned at a letter sending site; and the third PC side logistic management system is positioned at a receiving site. According to the two-dimensional barcode-based logistic personal information privacy protection scheme design, the two-dimensional barcode technology and an encryption technology are applied to the logistics industry to try to solve the problem of personal information leakage. The functions such as two-dimensional barcode generation and reading, sensitive information encryption protection, and key distribution and management are realized, and the problem of privacy information leakage is solved better.
Owner:NAVAL UNIV OF ENG PLA
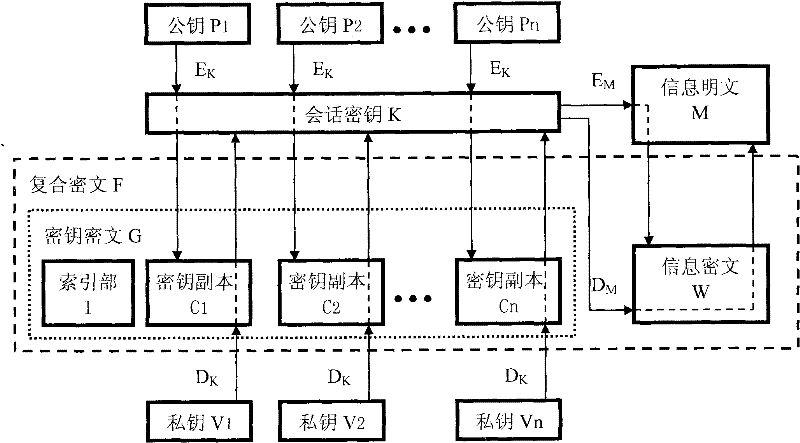
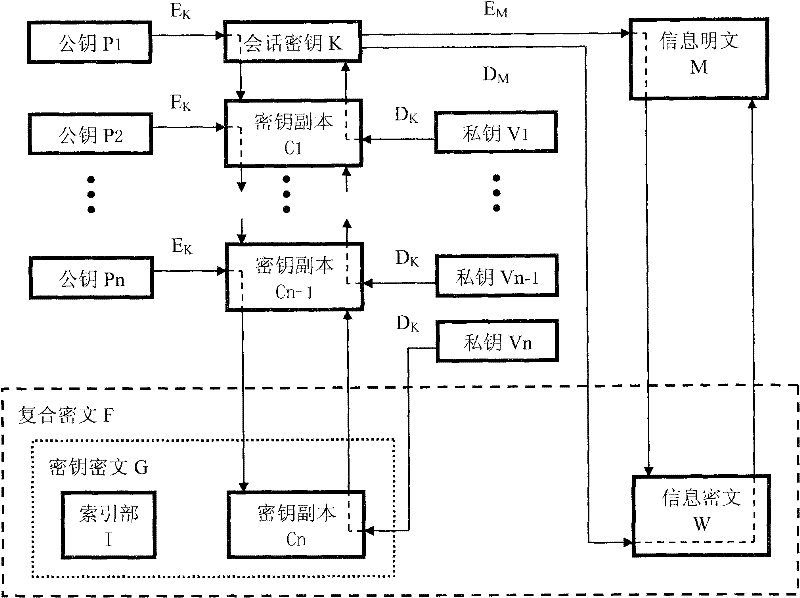
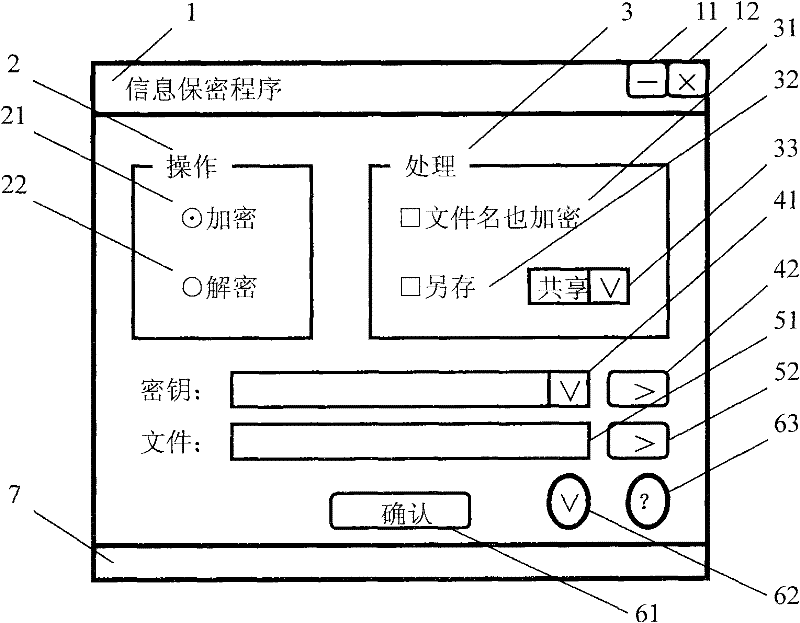
Information privacy and identity authentication method and digital signature program
InactiveCN101753311AUniversalPublic key for secure communicationUser identity/authority verificationConfidentialityCiphertext
The invention provides an information privacy and identity authentication method and a digital signature program, which relate to the technical filed of computer software, network communication and information safety and are particularly used for the information privacy of instant messaging, electronic mails and file information. A symmetrical cryptographic algorithm and an unsymmetrical cryptographic algorithm are combined, and a key ciphertext and an information ciphertext form a complex ciphertext. The effect of text confidentiality and sharing is reached through the integration of effects of multiple keys, and the effect of text confidentiality interlocking is realized through the effect of the combination of multiple keys. The signature is used for challenging the response mechanism, more than two cipher devices are compatible, the effect of automatic identification distinction and / or self-customization by users can be realized, and the identity authentication is more flexible and complete. A convenient and practical data signature program is also designed, and the convenient and practical data signature program assists a target program for use and runs independently for realizing the instant signature and the instant verification on window text information.
Owner:杨筑平
Apparatus and method for information sharing and privacy assurance
InactiveUS20120131189A1Maintain privacyIncrease probabilityDigital data processing detailsDigital computer detailsInformation sharingData source
An apparatus for information privacy assurance includes a data processing engine to restrict access to data received from a plurality of data sources and to a predefined data relationship query. The data processing engine includes a data input component restricted to receive the data from the plurality of data sources, a data relationship component configured to generate data relationships associated with the data, a query input component restricted to receive the predefined data relationship query associated with the data relationships, a query execution component configured to execute the predefined data relationship query, and a data output component restricted to render a result including information associated with an execution of the predefined data relationship query.
Owner:RAYTHEON CO
Information privacy method and electronic terminal
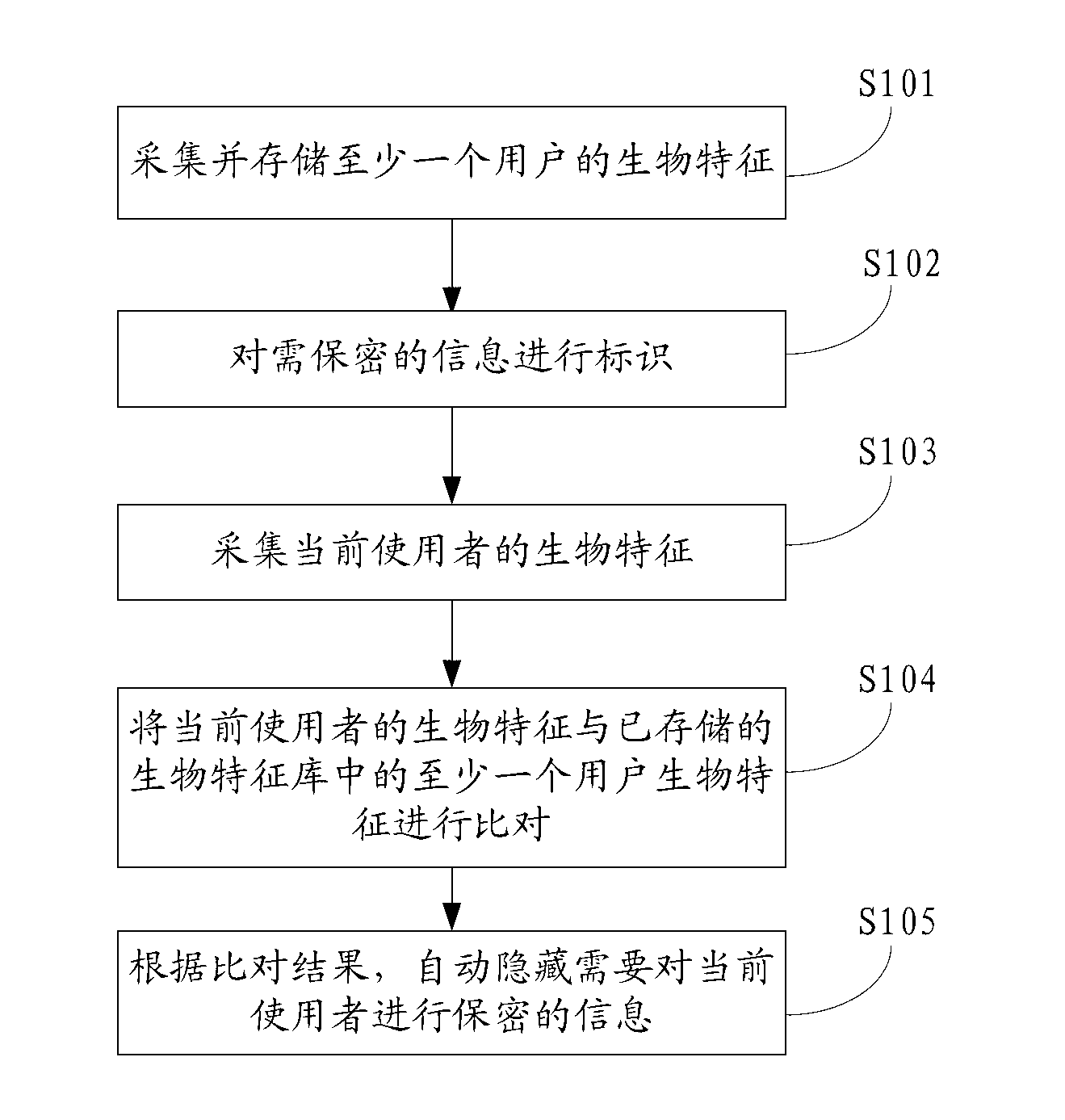
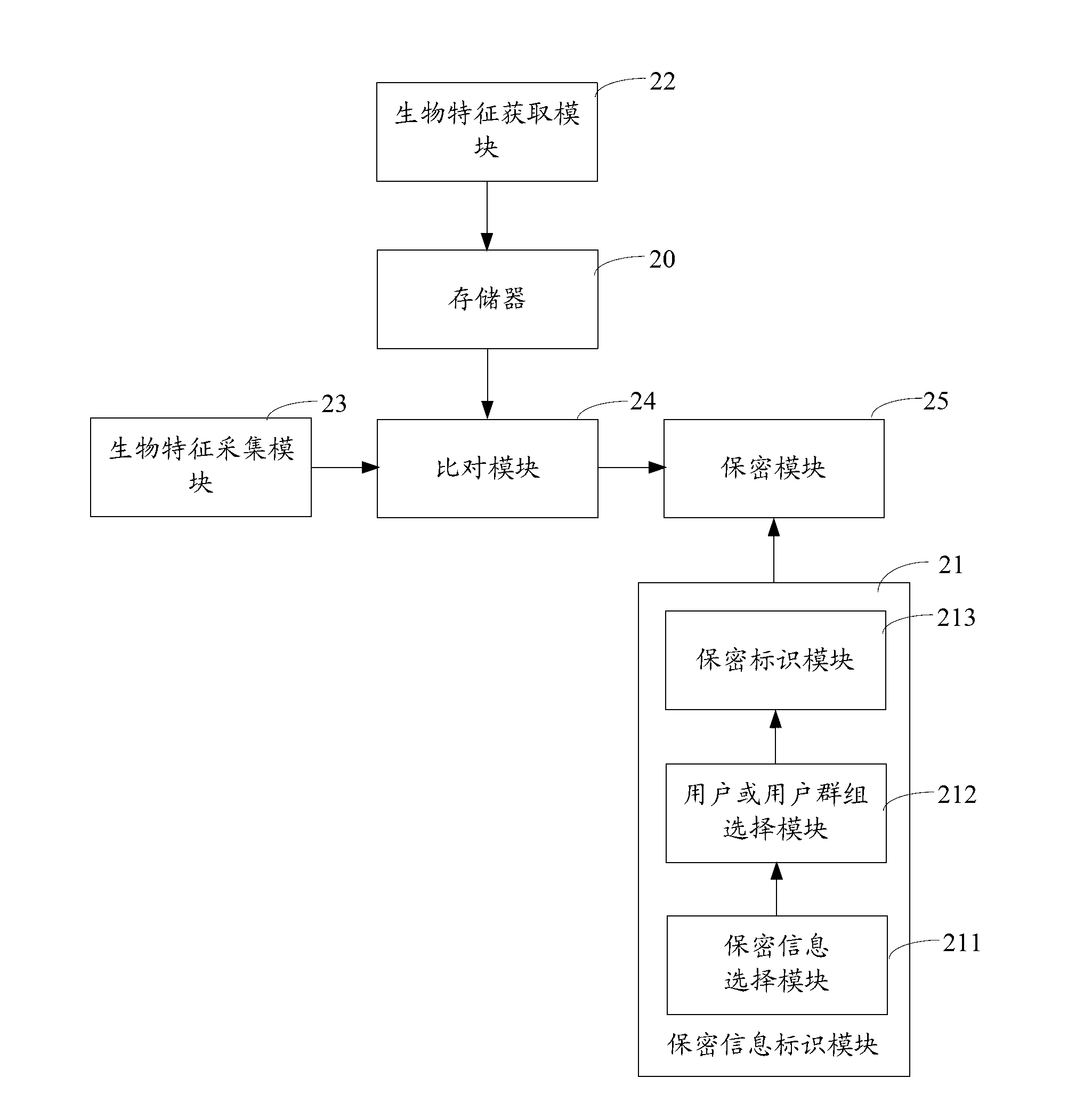
InactiveCN103177206AAvoid identificationConfidentiality is concealedDigital data protectionDigital data authenticationComputer terminalInformation confidentiality
The invention belongs to the field of communication and provides an information privacy method and an electronic terminal. The information privacy method includes the following steps. Biological characteristics of a current user are collected. The biological characteristics of the current user are compared with at least one user biological characteristic stored in a biological characteristic base. The user biological characteristic is correlated with operation authority of information privacy. According to a comparison result, information that the current user is not supposed to know is automatically hidden. The biological characteristics of the current user are collected and compared with the stored biological characteristics. Based on the comparison result, the information that the current user is not supposed to know is automatically hidden. Thus, automatic identification can be performed without tedious log-in and code entering. Private information can be automatically hidden and a privacy manner is invisible and not easily observed by people.
Owner:NUBIA TECHNOLOGY CO LTD
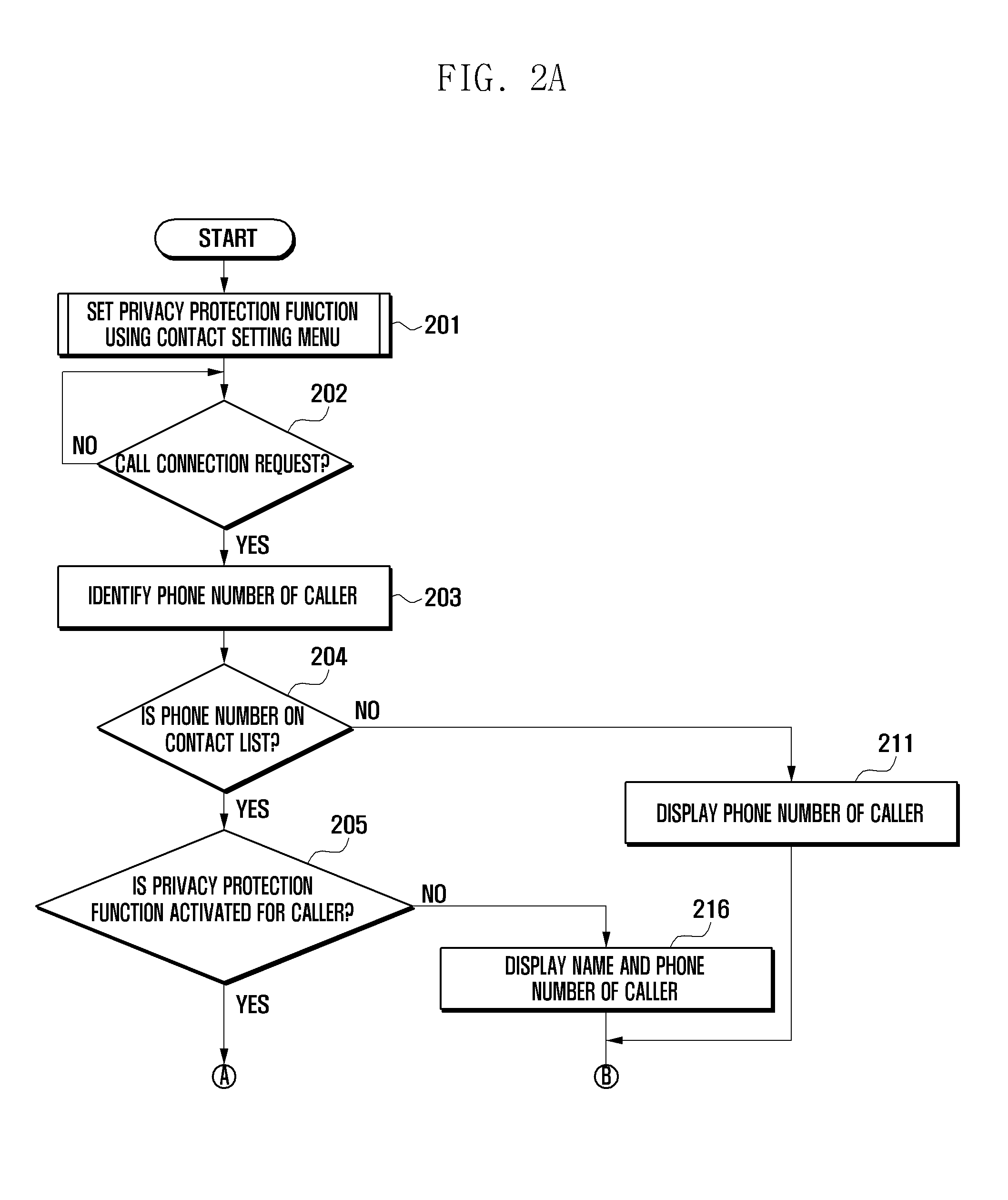
Privacy protection method and apparatus for mobile terminal
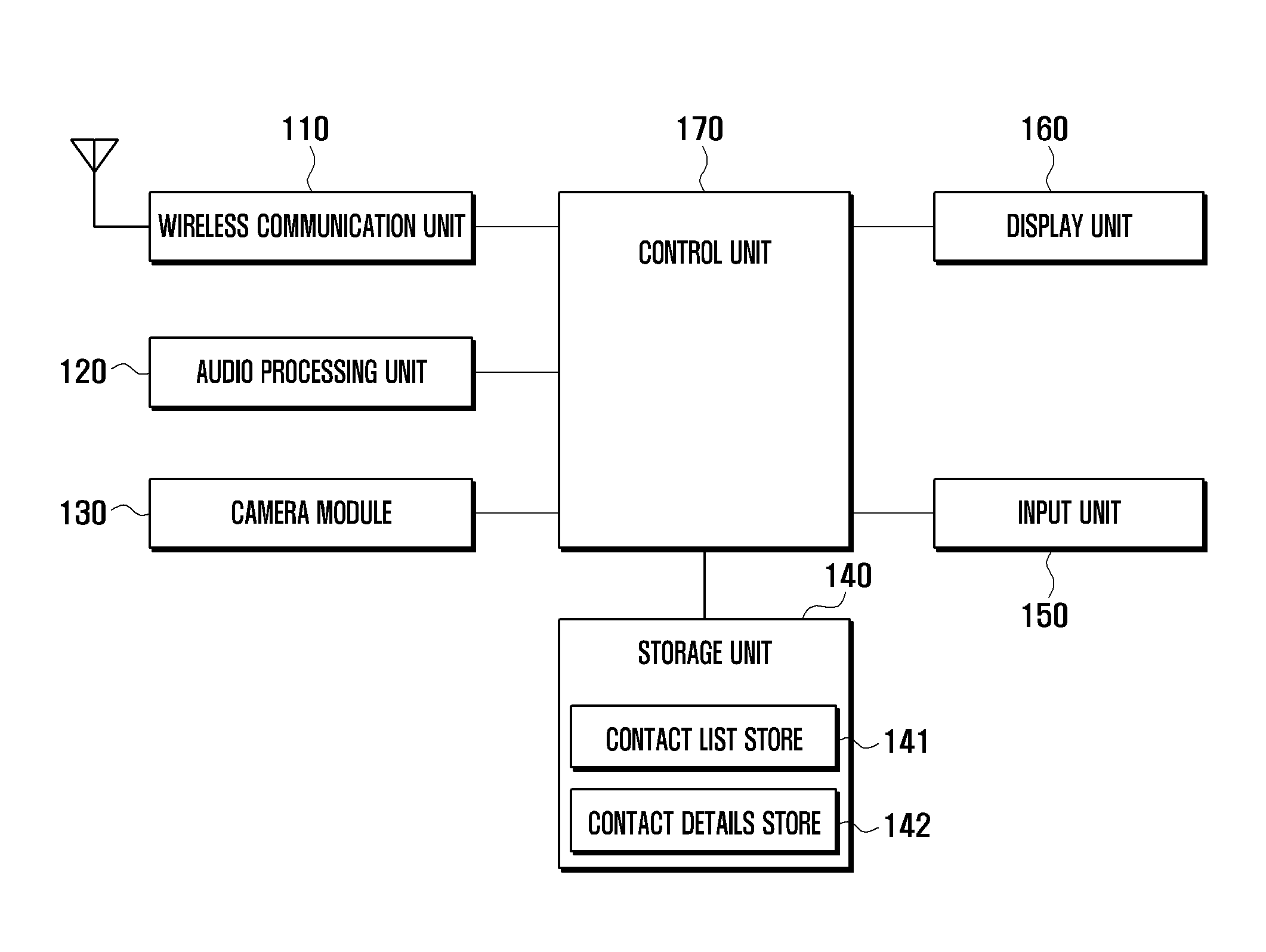
ActiveUS20120142316A1Prevent leakageUnauthorised/fraudulent call preventionEavesdropping prevention circuitsPrivacy protectionContact list
A privacy protection method and apparatus for a mobile terminal are provided. The method includes specifying basic information, privacy protection indication, and fictitious information of a contact item to be recorded in a contact list, determining, when a contact is received from an external terminal, whether a privacy protection function is activated for the external terminal, and outputting, when the privacy protection function is activated for the external terminal, a contact reception screen and a contact handling screen that include pre-specified fictitious information of the external terminal and exclude pre-specified basic information thereon. As a result, when a contact is received from a counterpart, information on the counterpart can be prevented from being displayed on the screen. Hence, it is possible to prevent inadvertent disclosure of counterpart information.
Owner:SAMSUNG ELECTRONICS CO LTD
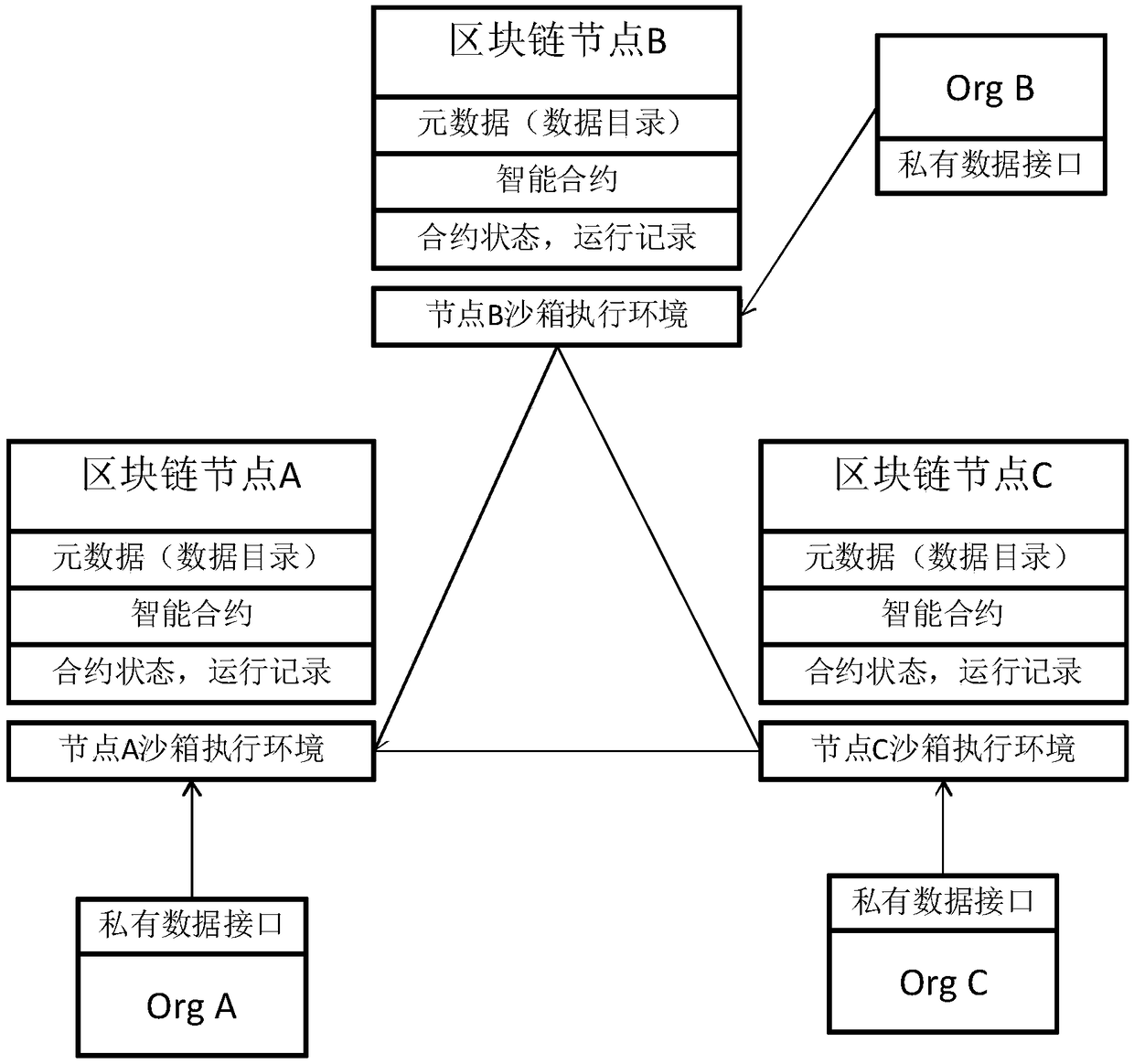
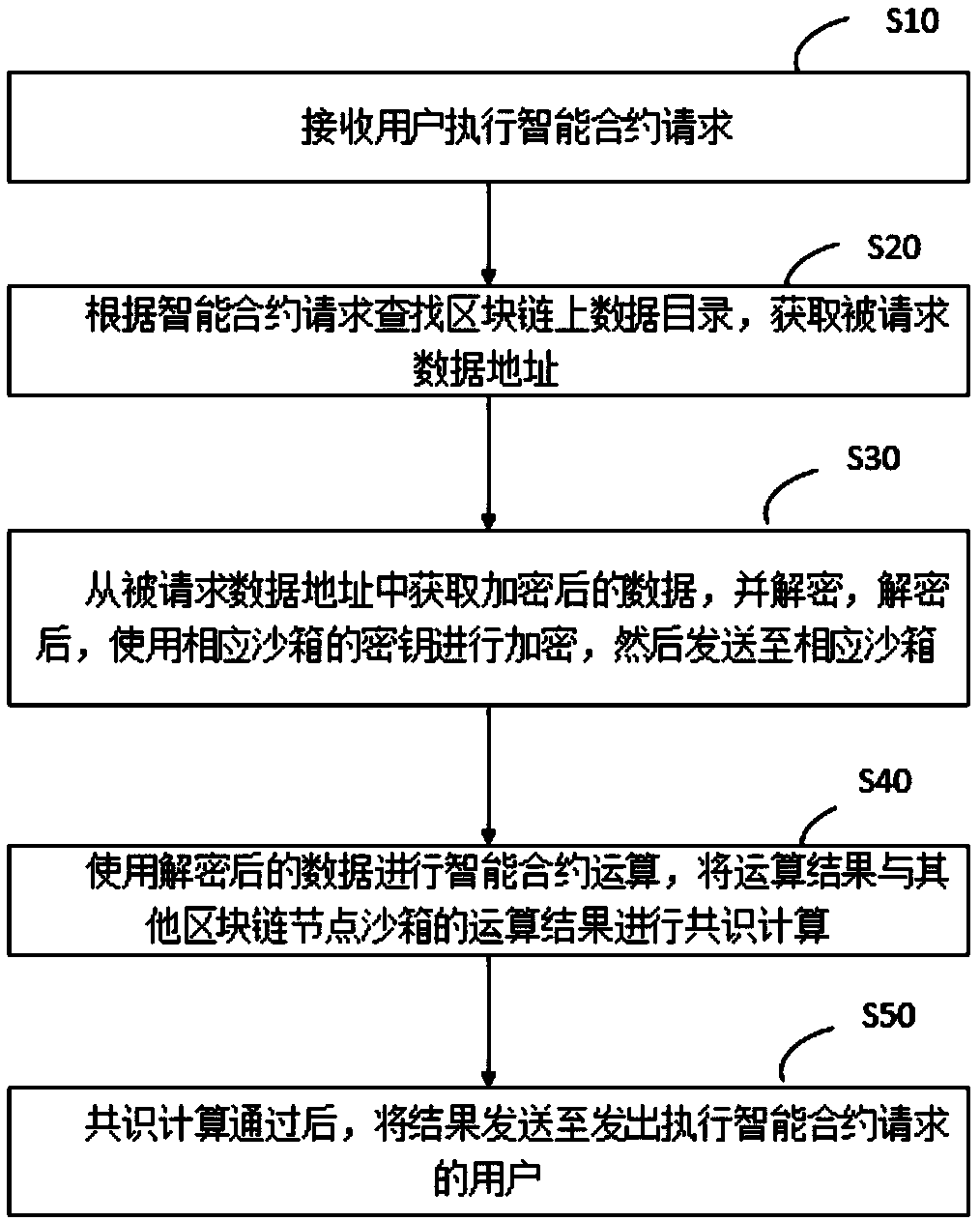
Blockchain-based smart city information safety using method and system
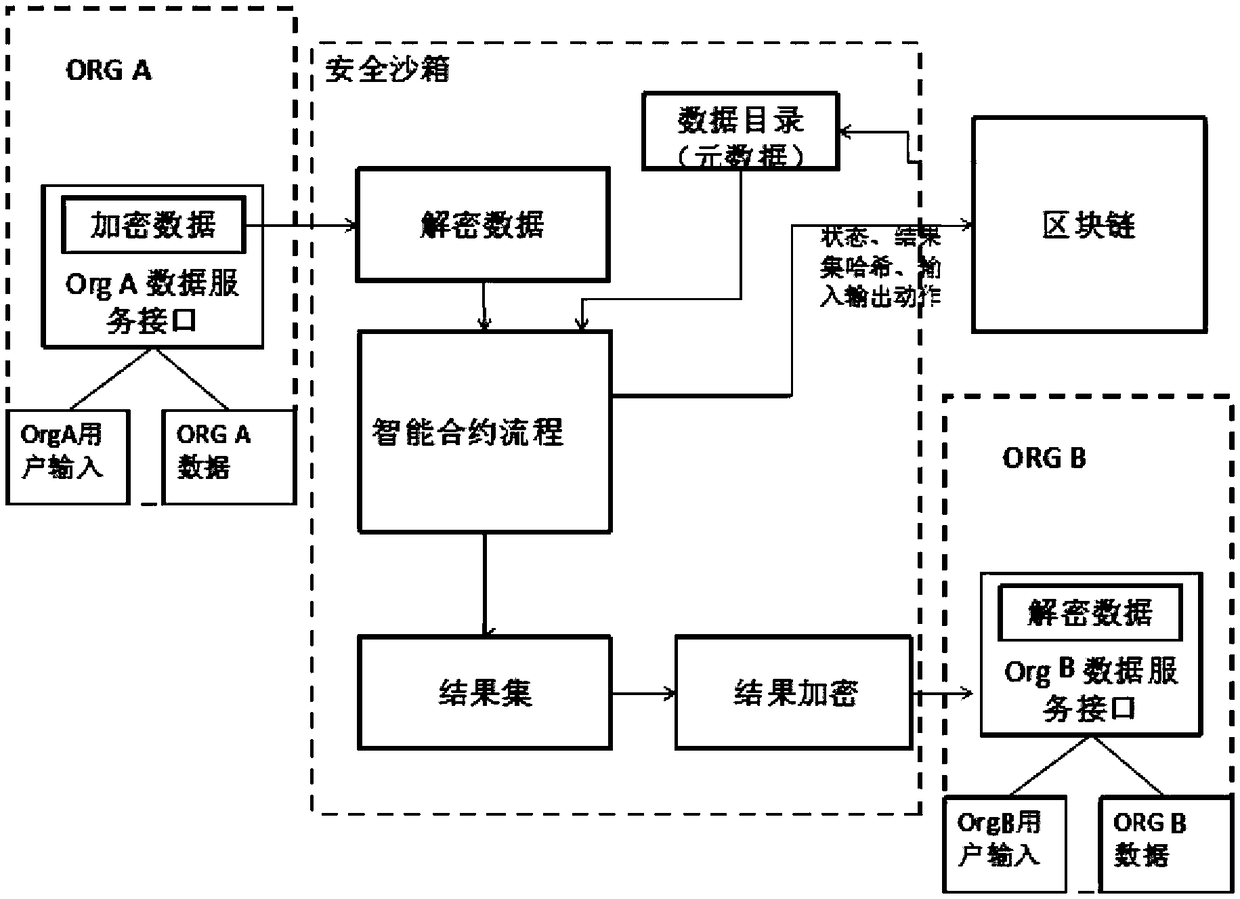
ActiveCN108830601ARealize privacy protectionFacilitates safe sharingPayment protocolsPlatform integrity maintainanceInformation sharingSmart city
The invention relates to a blockchain-based smart city information safety using method and system. The blockchain-based smart city information safety using method according to the present invention includes the following steps: receiving a request for executing a smart contract from a user; searching for a data directory on a blockchain according to the smart contract request and obtaining a requested data address; obtain encrypted data from the requested data address, decrypting the encrypted data, encrypting the decrypted data with the secret key of a corresponding sandbox, and then sendingthe data to the corresponding sandbox; performing an smart contract operation by using the decrypted data, performing consensus calculation on an operation result and the operation results of other blockchain node sandboxes; after the consensus calculation is passed, sending a result to the user who issues the request for executing the smart contract. The blockchain-based smart city information safety using method realizes effective information sharing and sensitive information privacy protection among multiple physical organization in a smart city.
Owner:SHANGHAI YANHUA HEALTH TECH
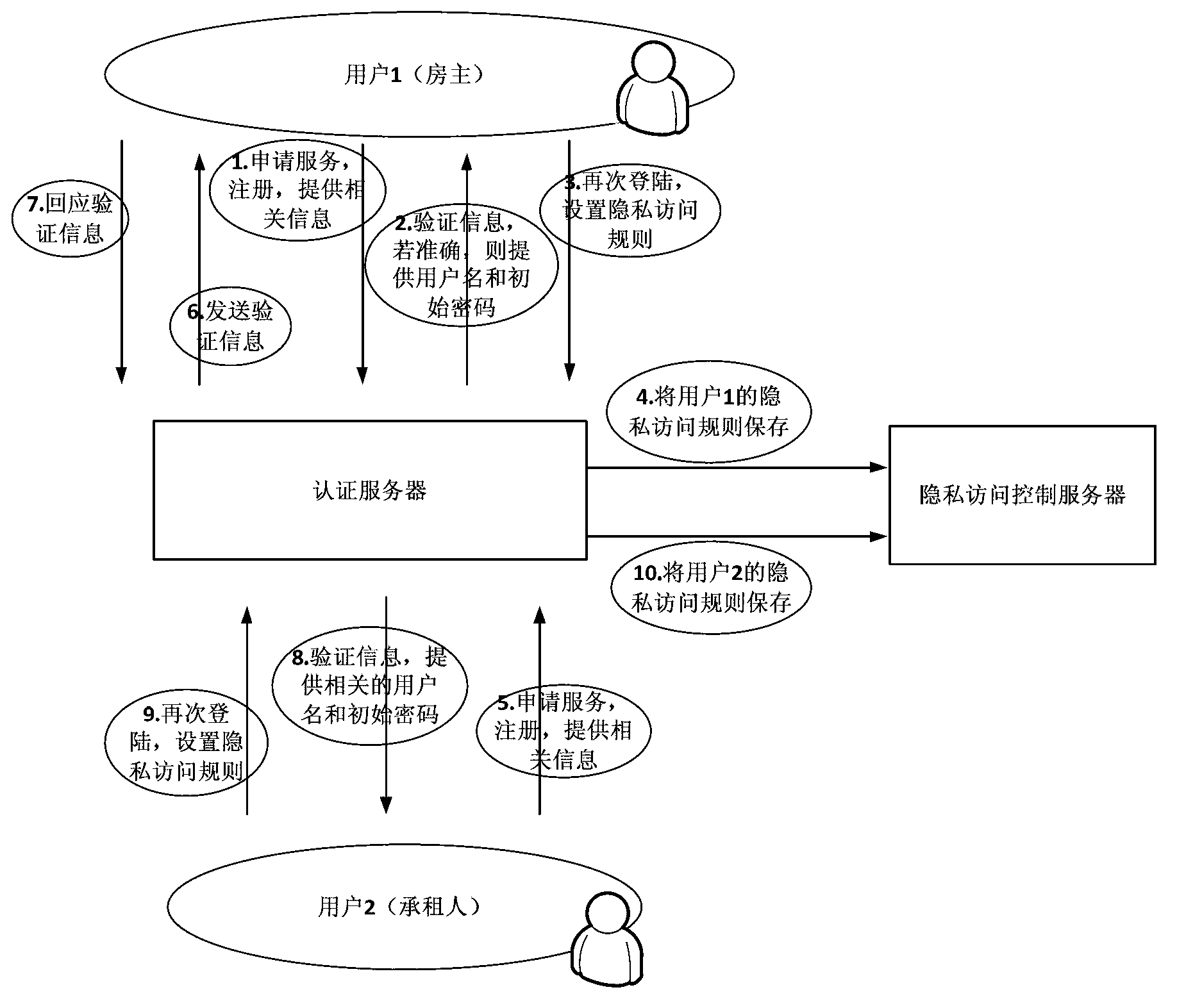
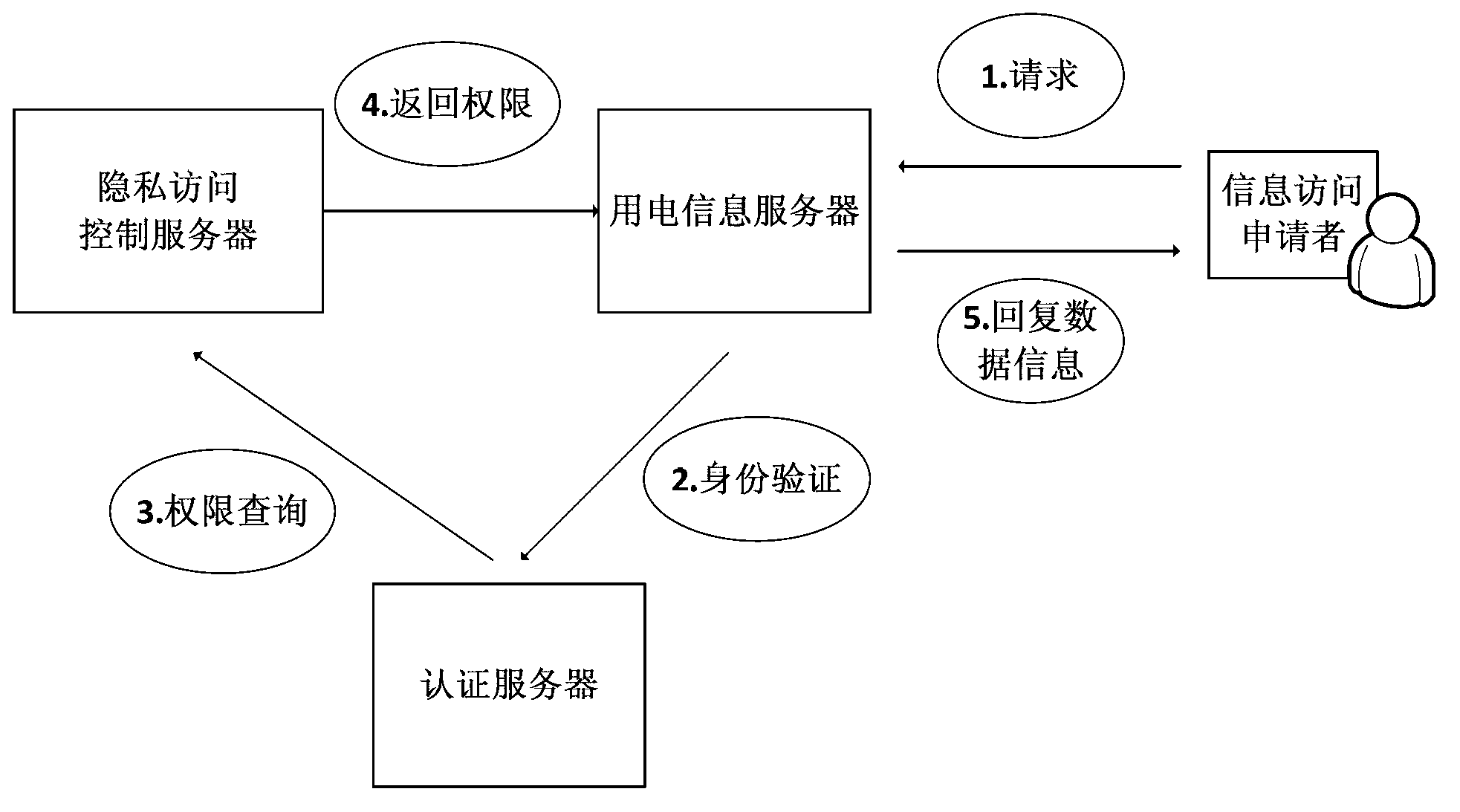
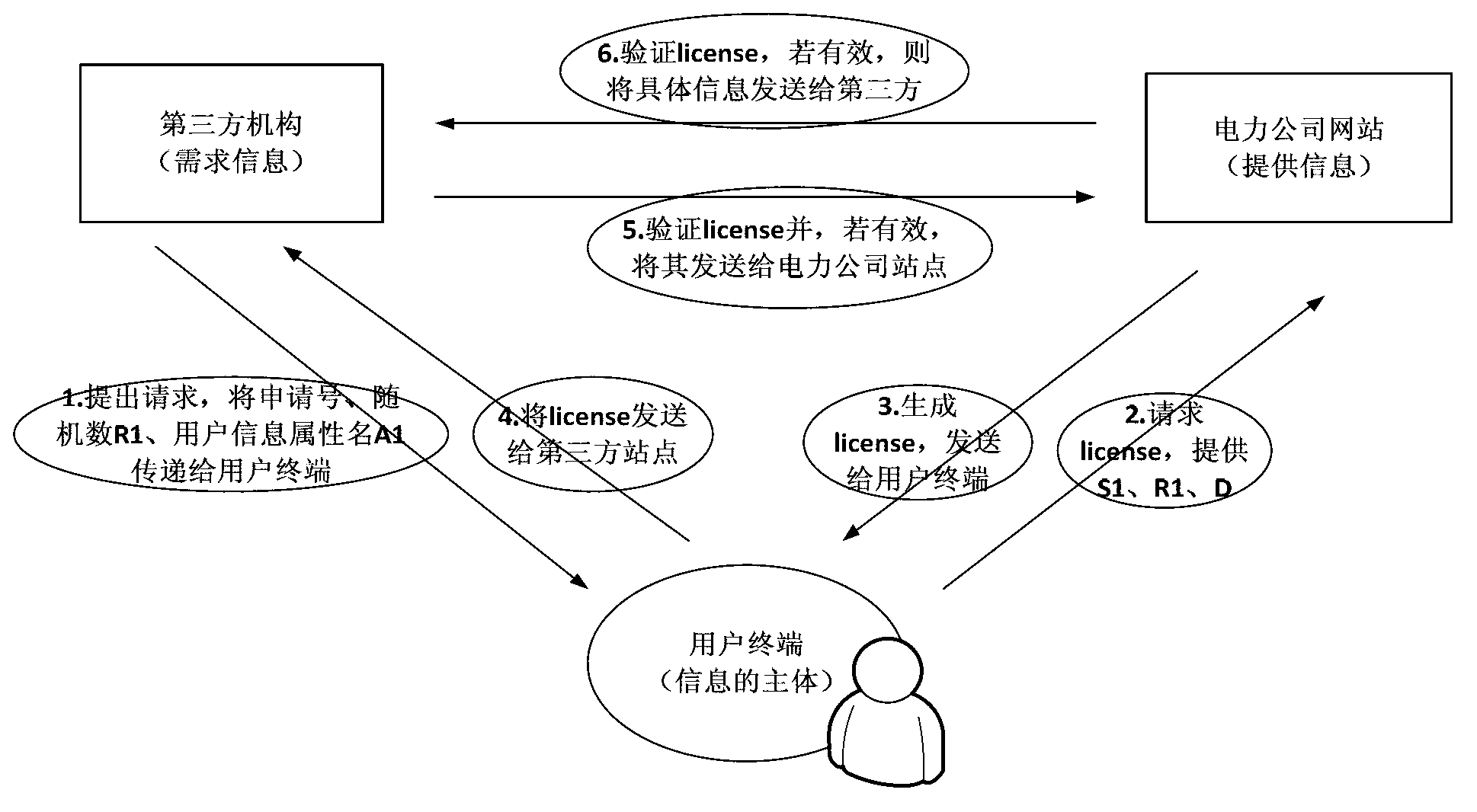
Intelligent grid electricity information privacy protection method based on multi-party interaction
The invention provides an intelligent grid electricity information privacy protection method based on multi-party interaction. The method comprises the following steps that the user sets a privacy access rule; the user requests to access the electricity information; the third party requests to obtain the electricity information. With the adoption of the method, the user can make an access control aiming at his / her own electricity information and prevent others from getting the detailed electricity information without the consent, and meanwhile, the third party gets permit through users when requiring to get the electricity information, and the corresponding safety mechanism is provided, thereby effectively protecting the privacy of the user.
Owner:CHINA ELECTRIC POWER RES INST +2
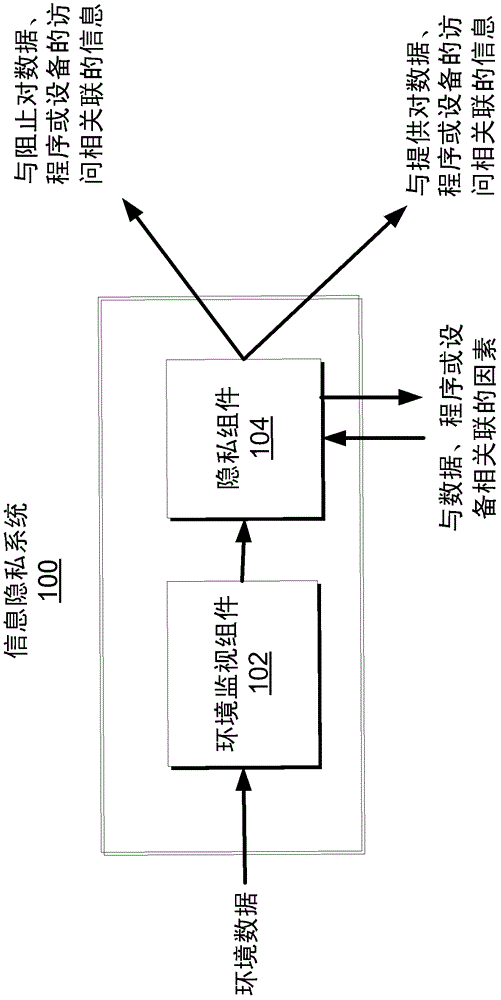
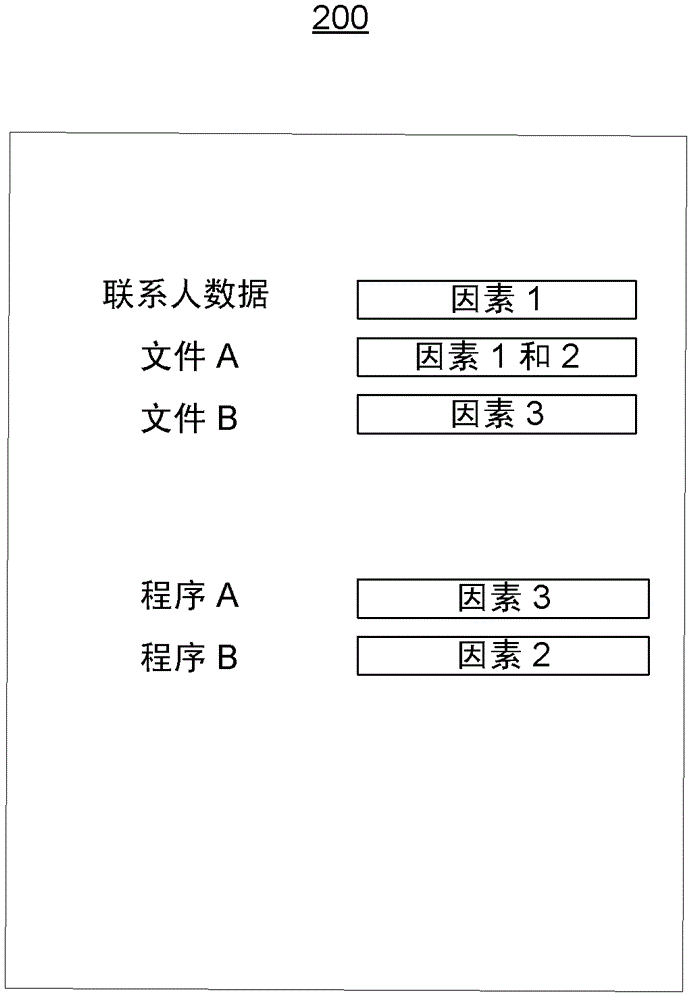
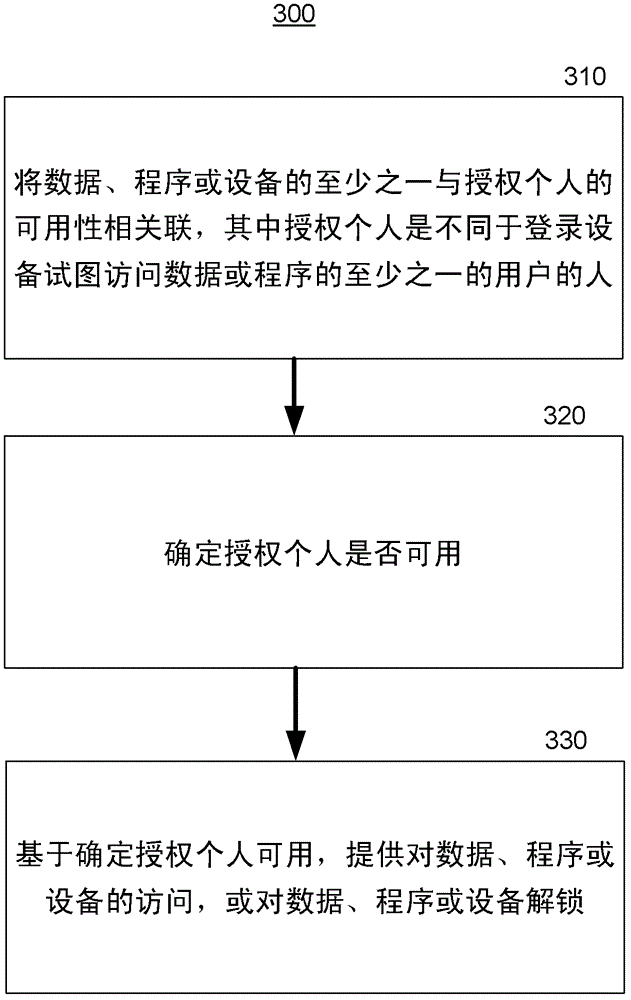
Information privacy system and method
The subject disclosure relates to systems and methods for providing privacy for information. In one non-limiting embodiment, a system includes an environment monitoring component configured to monitor an aspect of an environment; and a privacy component configured to: determine whether factors associated with the environment are triggered; and obscure access or provide access to data or a program associated with the factors based on determining that the factors are triggered. Factors can be based on the time and the location or network connectivity of a device associated with the system, the detected presence or absence of an authorized person other than the user logged into the device or the privacy state of the user logged into the device. Motion detectors, cameras, biometric sensors and other devices can be employed in the determination of whether to provide or obscure access to the information.
Owner:MICROSOFT TECH LICENSING LLC
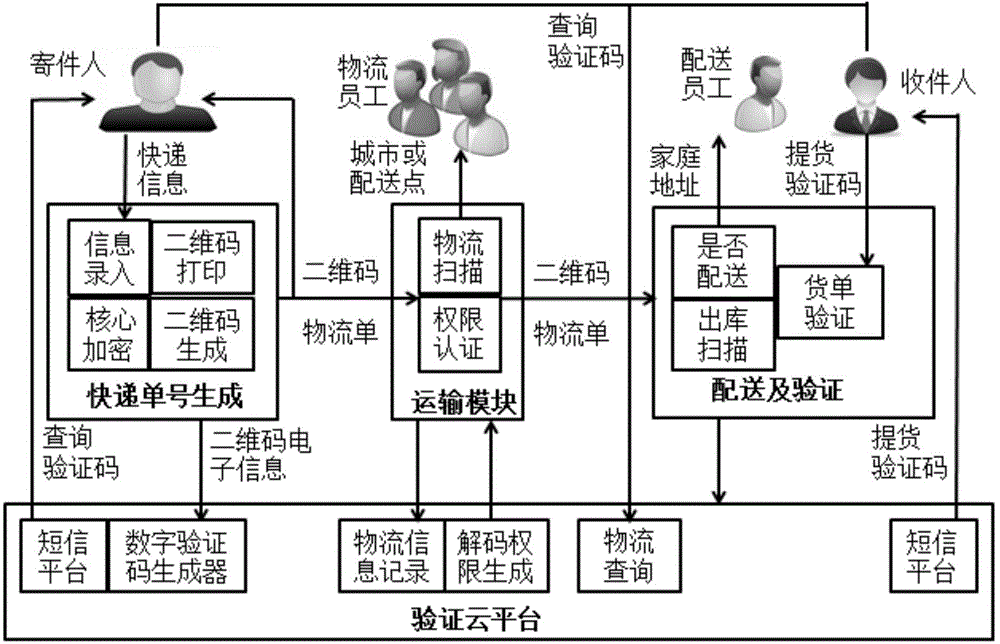
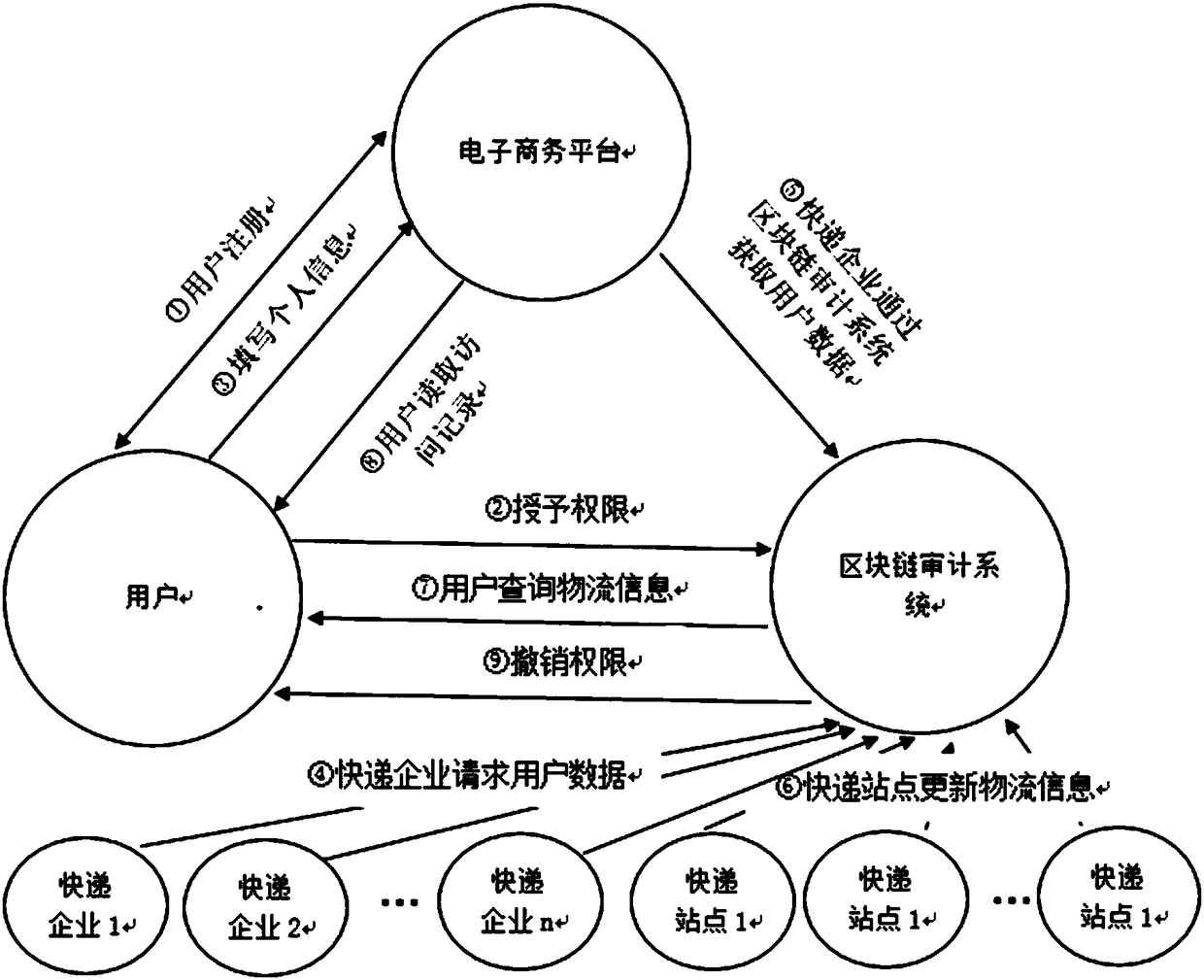
Express delivery information privacy protection system based on blockchain, and protection method thereof
ActiveCN108614974AEnhancing Operational ComplianceAvoid illegal acquisitionDigital data protectionDigital data authenticationPlaintextLogistics management
The invention discloses an express delivery information privacy protection system based on a blockchain, and a protection method thereof. The method records all operational motions of an express delivery enterprise for user data through a blockchain auditing platform, the operation compliance of the express delivery enterprise is enhanced, and the express delivery enterprise can be effectively prevented from illegally obtaining personal information. Meanwhile, a user can read a user data visitor record through an authorization record recorded in the blockchain, the access permission of the express delivery enterprise for the user data is revoked, and the sense of control of the user for personal data is enhanced. In addition, a ciphertext express waybill is used for replacing a plaintext express waybill, so that a possibility that the user data is leaked in each link of an express delivery business process can be lowered. An express delivery package logistics tracking scheme based on the blockchain can assist the user in checking the logistics situation of the express delivery package at any time in a blockchain system, and logistics information which can not be tampered on the blockchain can provide proof-providing information for disputes including delivery losing claims and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
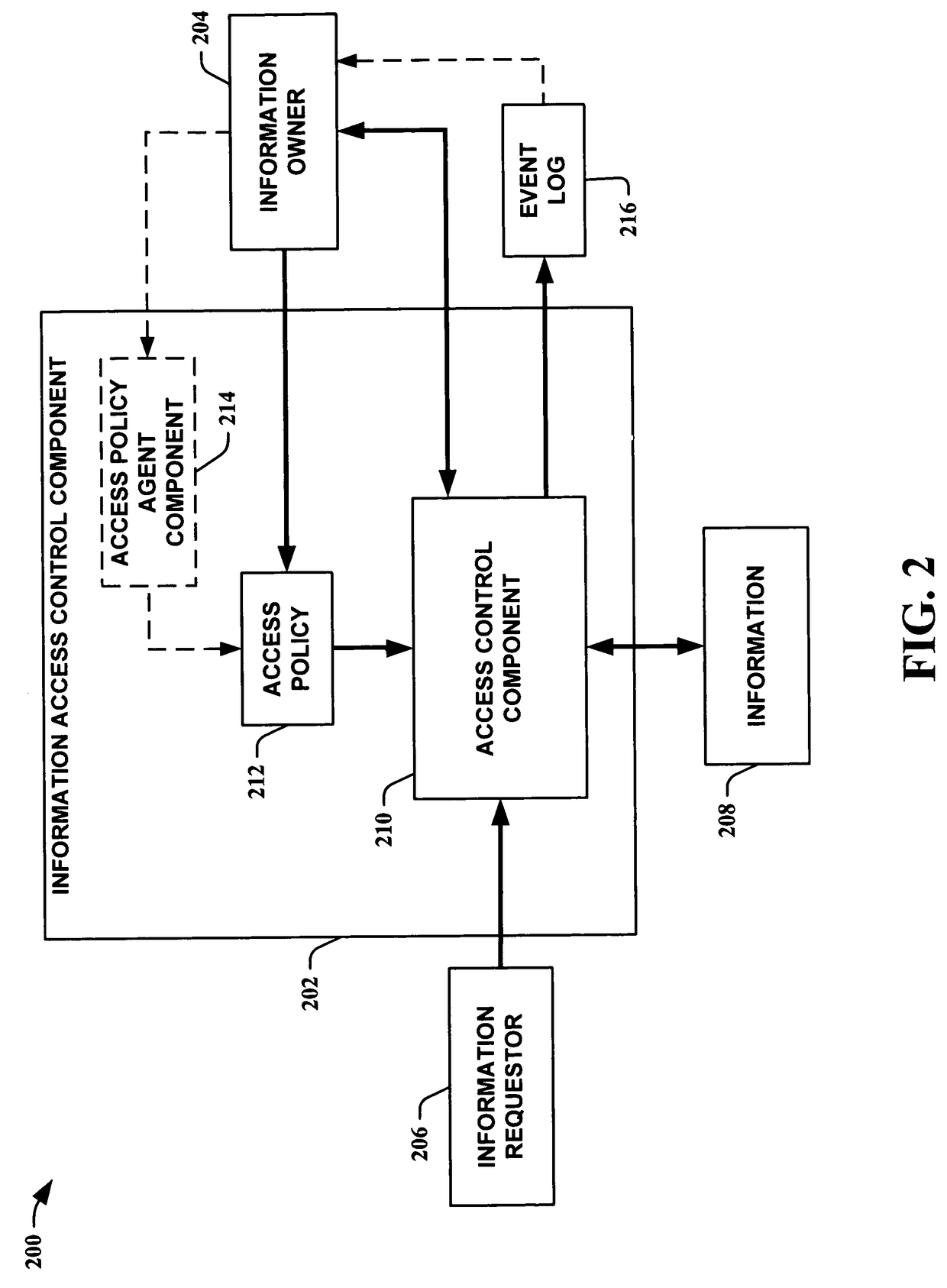
Abstractions and automation for enhanced sharing and collaboration
InactiveUS7908663B2Reduce the burden onImprove privacyDigital data processing detailsUser identity/authority verificationInformation sharingDecision taking
The present invention provides methods for using abstractions of people, including dynamic and static groups of people, to enhance the efficiency of the specification and automation of policies for sharing information between users with a “need-to-know.” An instance of the present invention can also provide these users information based on a “time-to-know.” By providing access to information based on group affiliation and properties of the content of the information, the present invention maintains optimal information privacy while minimizing encumbrances to sharing data with appropriate users and even at appropriate times. The present invention can be integrated with other communication technologies to facilitate access to information in a time appropriate manner. Other instances of the present invention employ automated and semi-automated, mixed-initiative techniques, to make information-sharing decisions. Additional instances of the present invention include the employment of machine-learning techniques to facilitate construction of access policies from the actions or profile of a single user or a community of users, including the construction of automated sharing agents that work in an automated or mixed-initiative manner to respond to real-time requests for information.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and method used for transparent window intimacy protection of on-line help
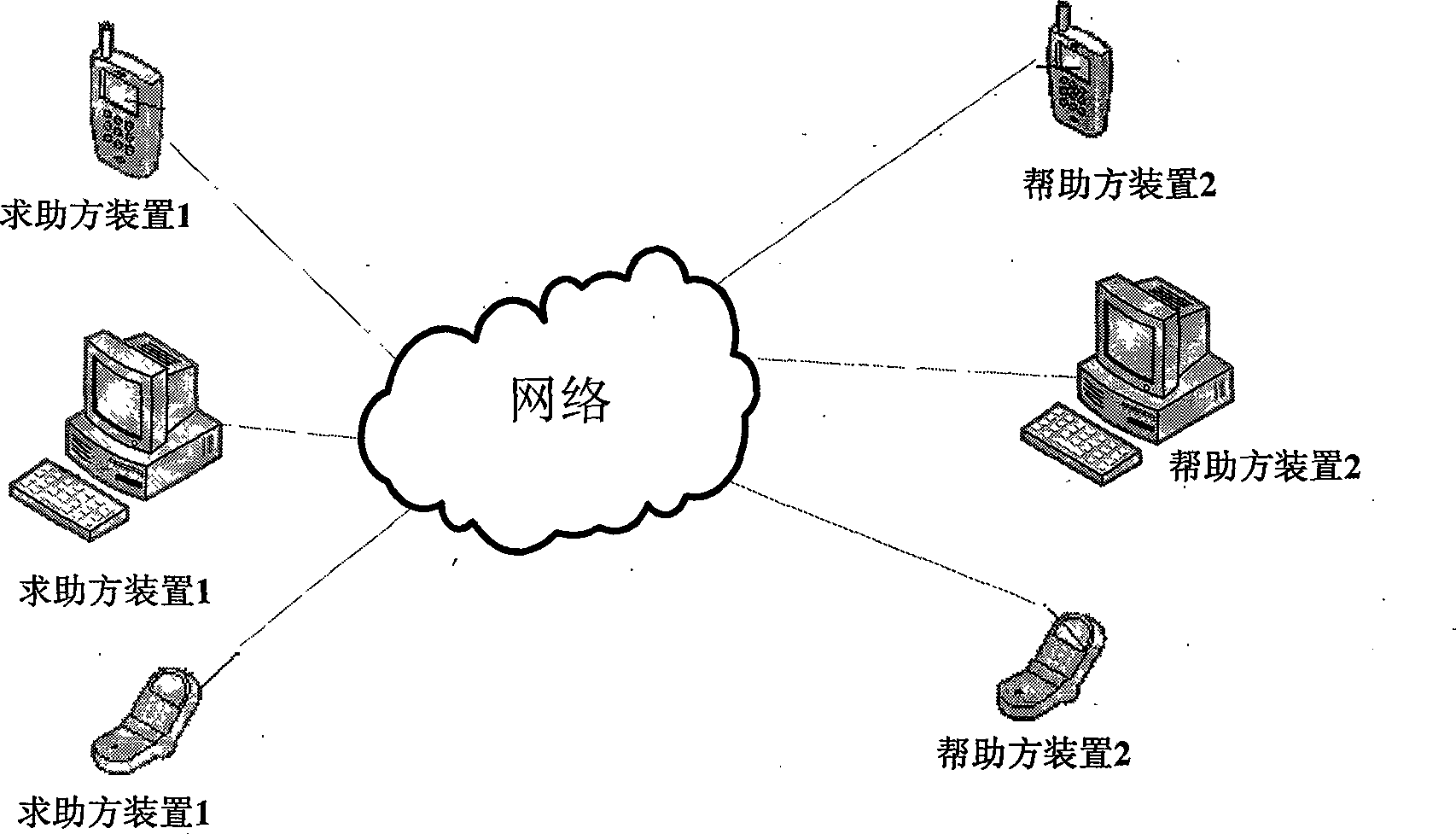
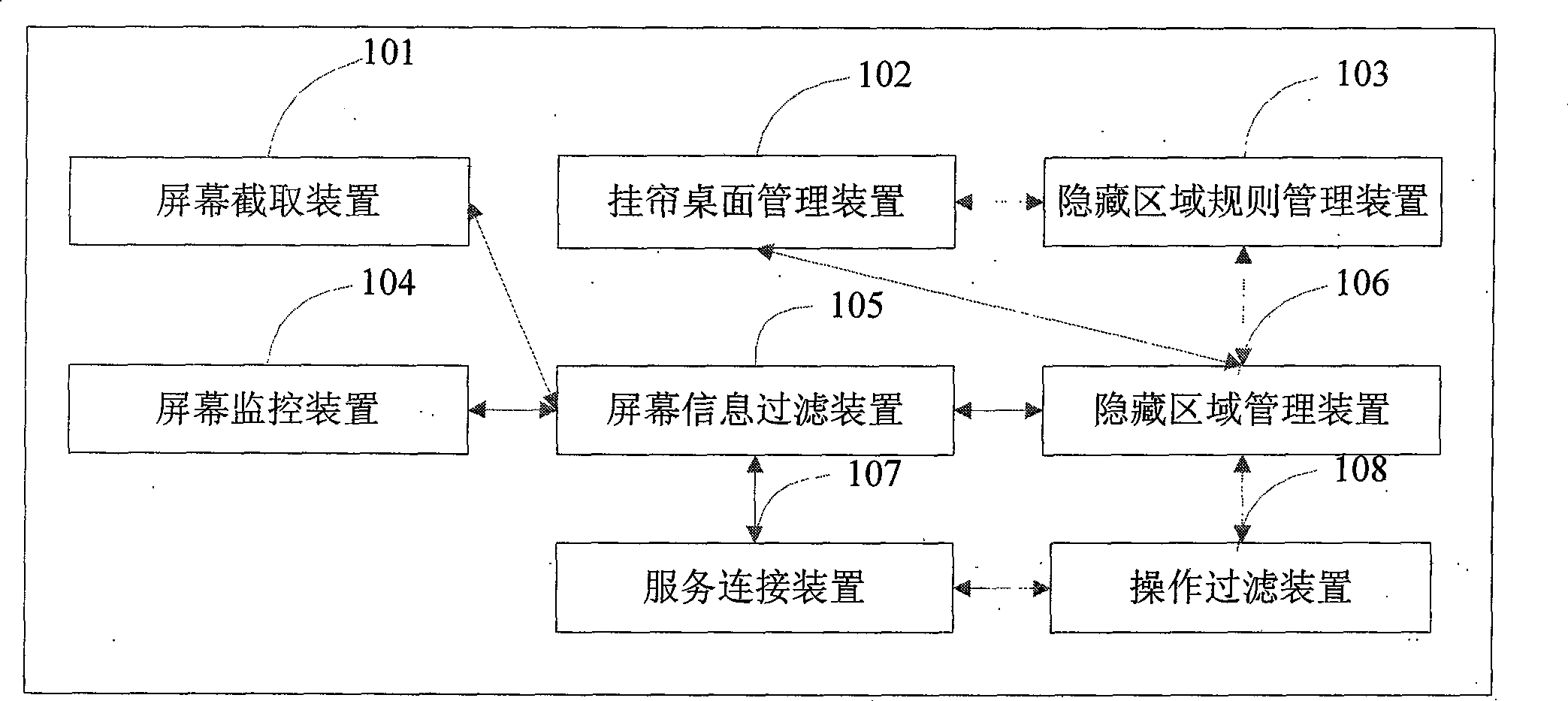
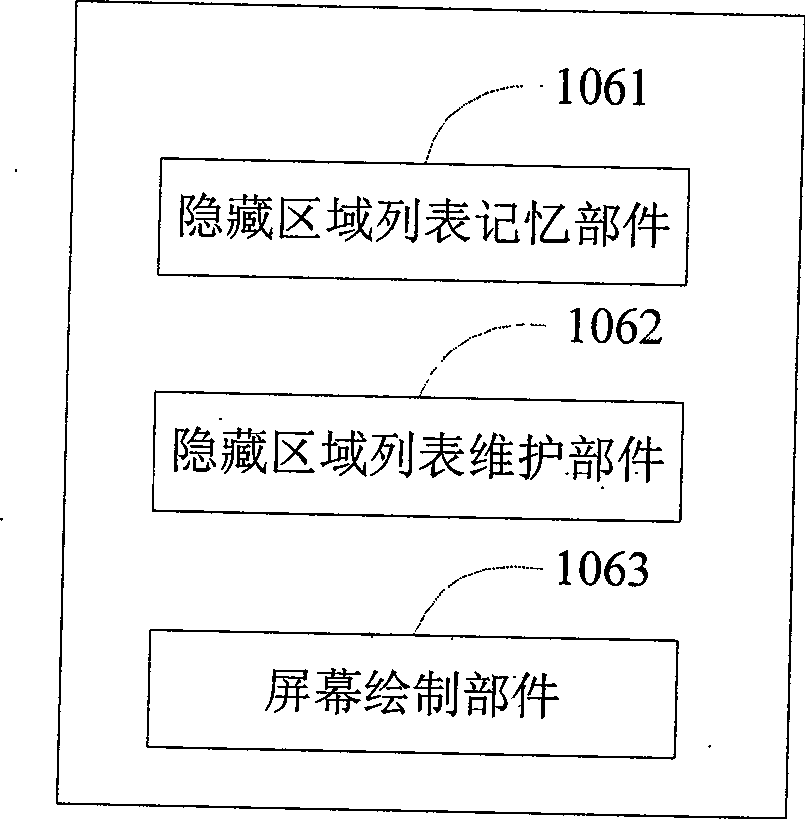
InactiveCN101470787AWide range of applicationsSpecial service provision for substationDigital data protectionOnline helpPrivacy protection
The invention discloses a window message privacy protection device and a method for on-line help, which belong to the privacy protection of computer field. The main use of the invention is to help the privacy protection of a person who asks for help in a system on line. The invention has the advantages that a person who asks for help can do privacy protection to the window message of an application program on a device of a person who asks for help. A plurality of windows can be manually selected or automatically arranged according to a protection rule system to protect privacy, wherein the windows can be integral application program windows, or one sub window of an application program, screen information which can be seen by a person who asks for help and a helper is symmetrical or is not symmetrical (namely a person who asks for help can select whether itself can see the privacy information which can not be seen or not), when in on-line help, a person who asks for help can operate the contents in a protected zone, and the information can not be transmitted to a helper device, and the person who asks for help can monitor screen images which can be seen by a helper.
Owner:北京帮助在线信息技术有限公司
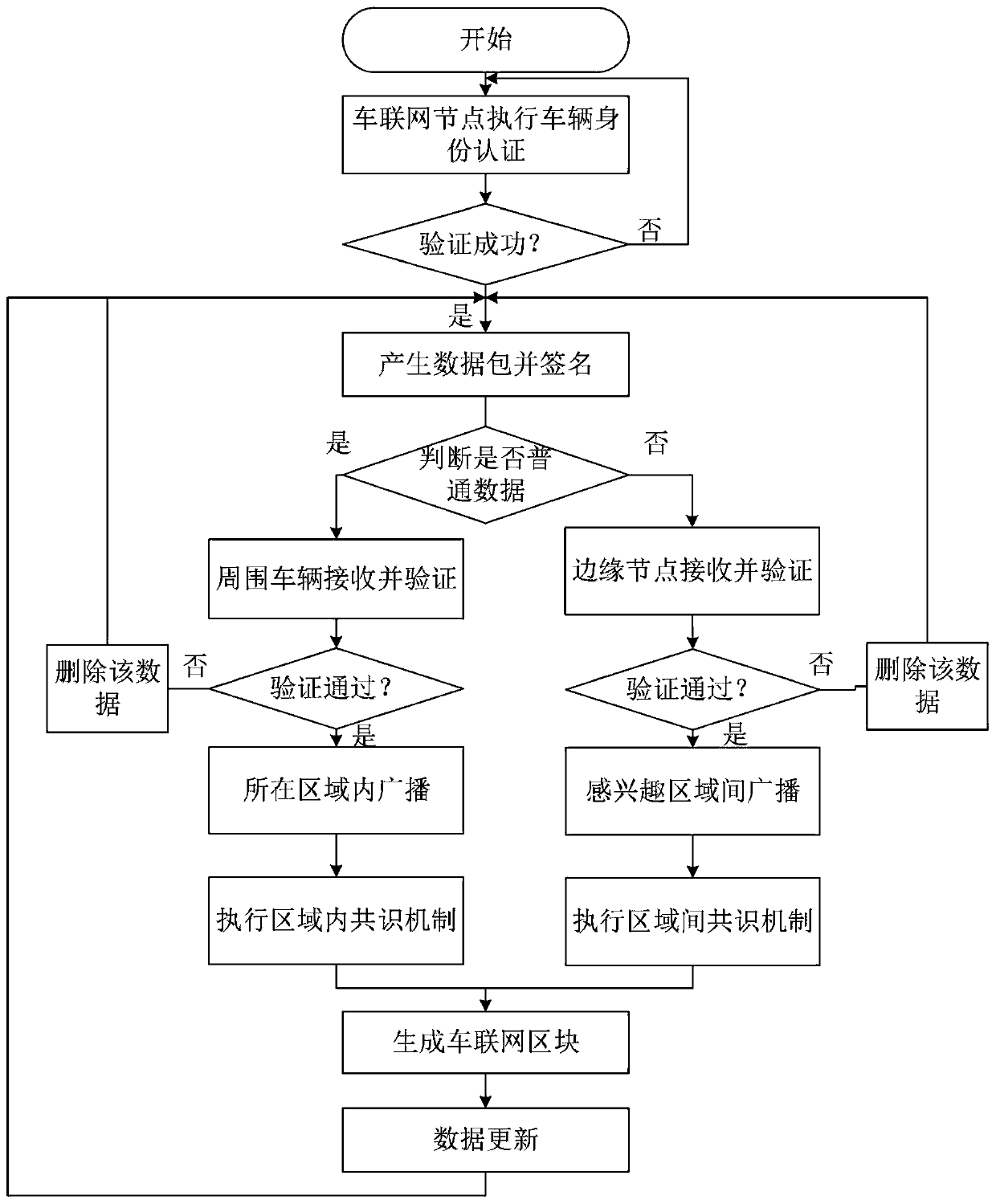
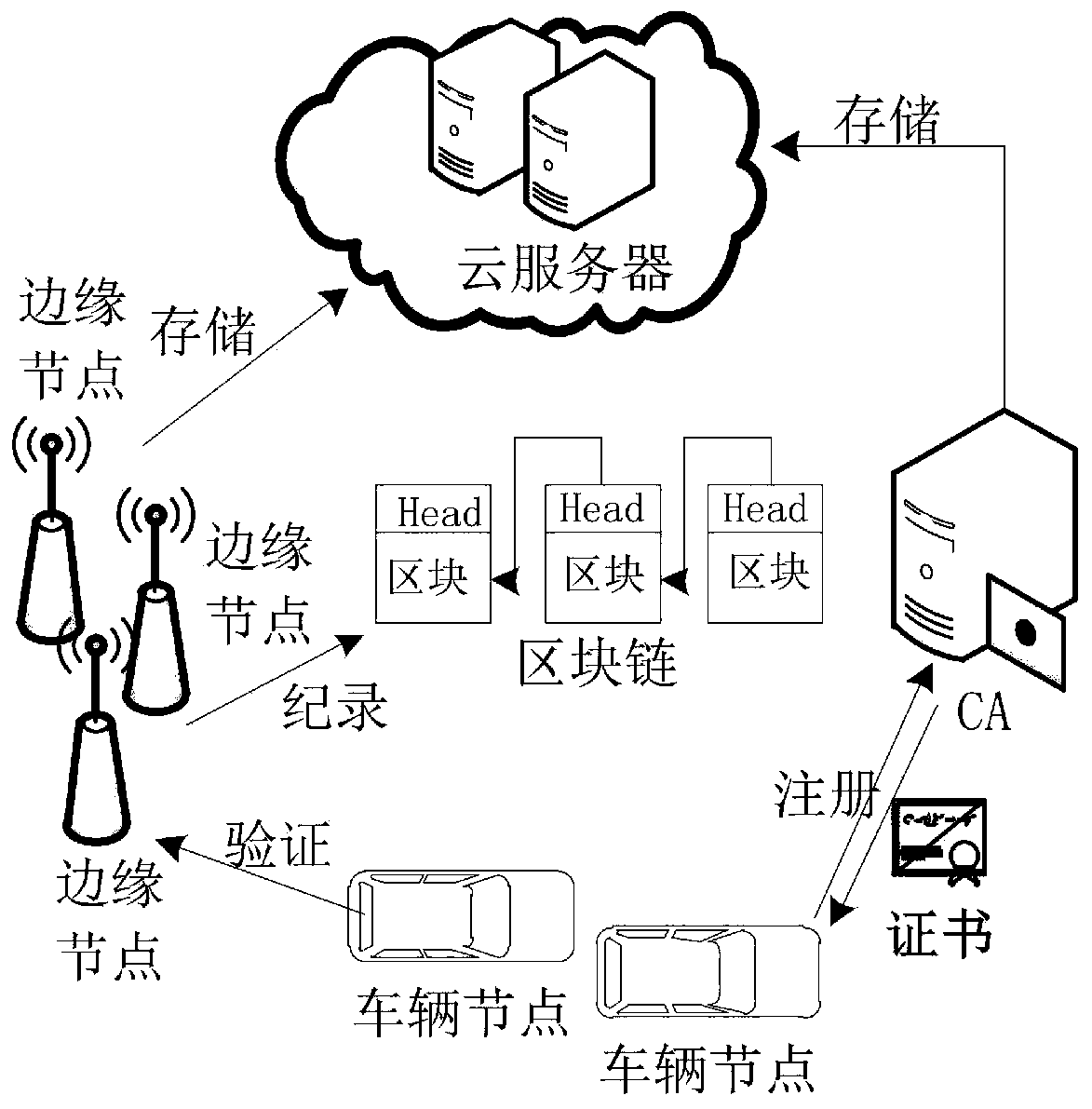
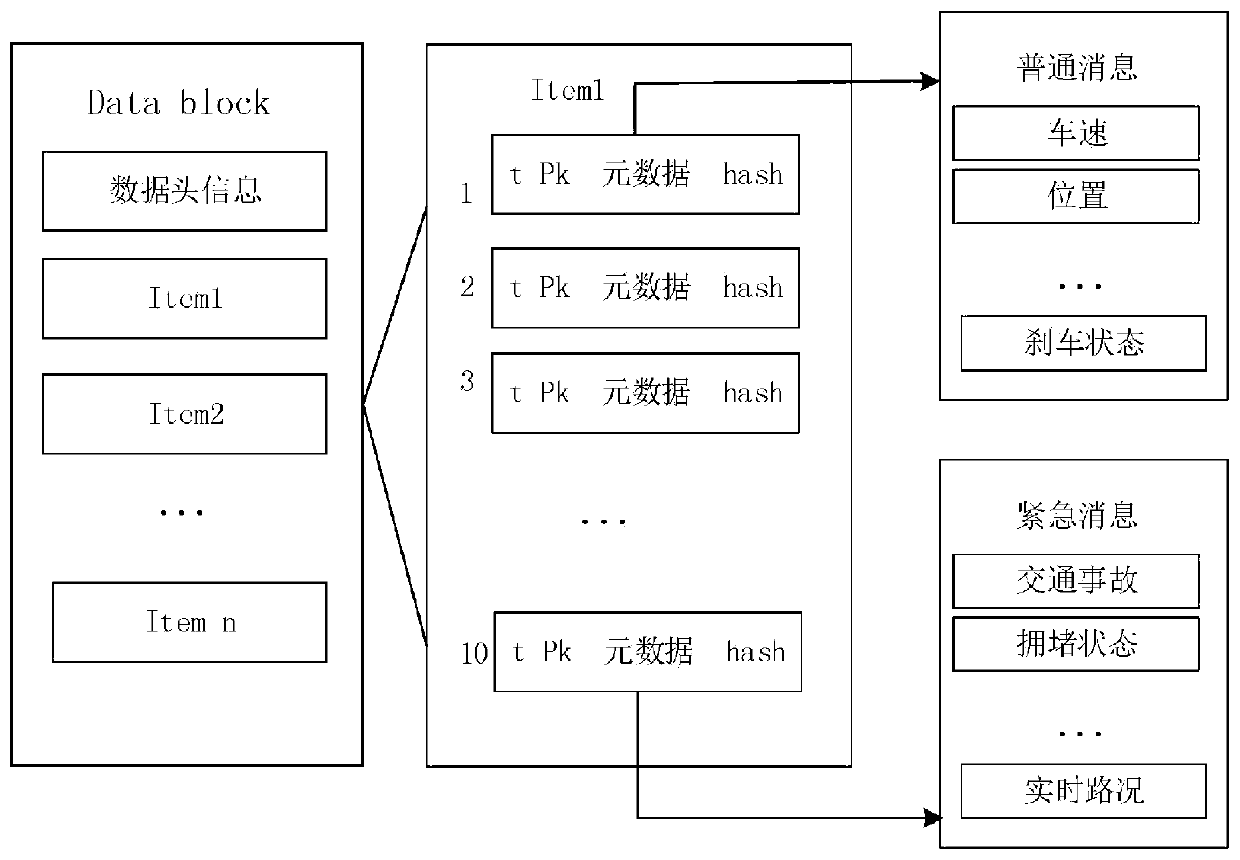
Internet of Vehicles node data security communication method based on block chain
ActiveCN111601258AGuaranteed traceabilityImprove consensus efficiencyParticular environment based servicesBroadcast service distributionSecure communicationThe Internet
The invention relates to an Internet of Vehicles node data security communication method based on a block chain, and the method comprises the steps: dividing a whole network into honeycomb regions with the same size, designing an Internet of Vehicles alliance chain and an inter-region public chain in units of regions, guaranteeing the data traceability, and improving the data consensus efficiency;in the vehicle data communication process, mutual trust between nodes is guaranteed through vehicle identity authentication, data is divided into common data and emergency data according to differenturgency of the data, the common data are communicated in areas, the emergency data is communicated among multiple areas, different data classifications adopt different block structures, and the dataconsensus efficiency is improved; and meanwhile, the motion condition of the Internet of Vehicles node is also considered, and an improved practical Byzantine fault-tolerant consensus method is adopted to realize data security communication of the Internet of Vehicles node, so that the data security risk caused by centralized data storage can be resisted. The consensus speed is high, data securityand information privacy can be protected, the data storage space is reduced, and the communication efficiency is high.
Owner:ZHEJIANG SHUREN COLLEGE ZHEJIANG SHUREN UNIV
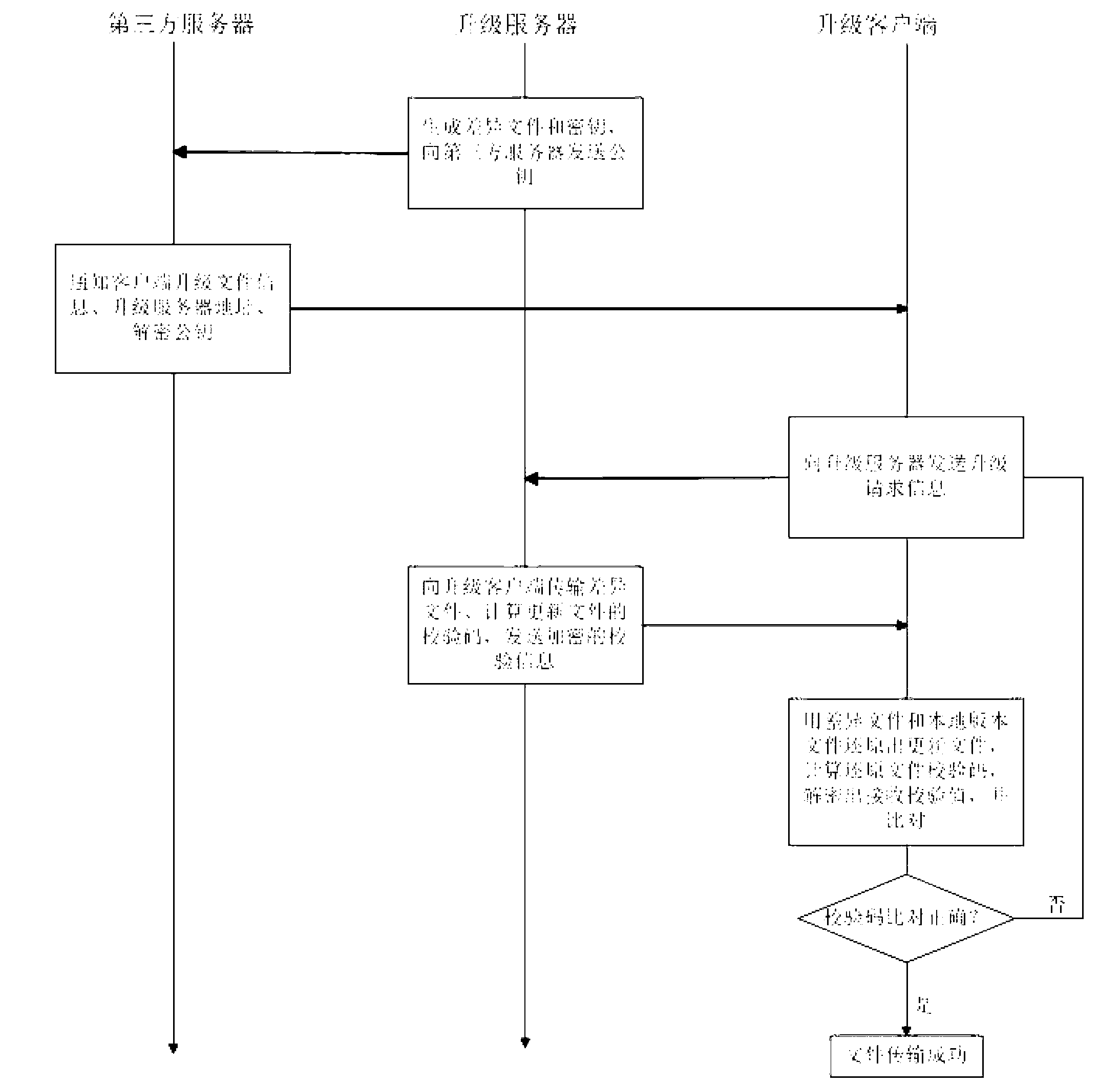
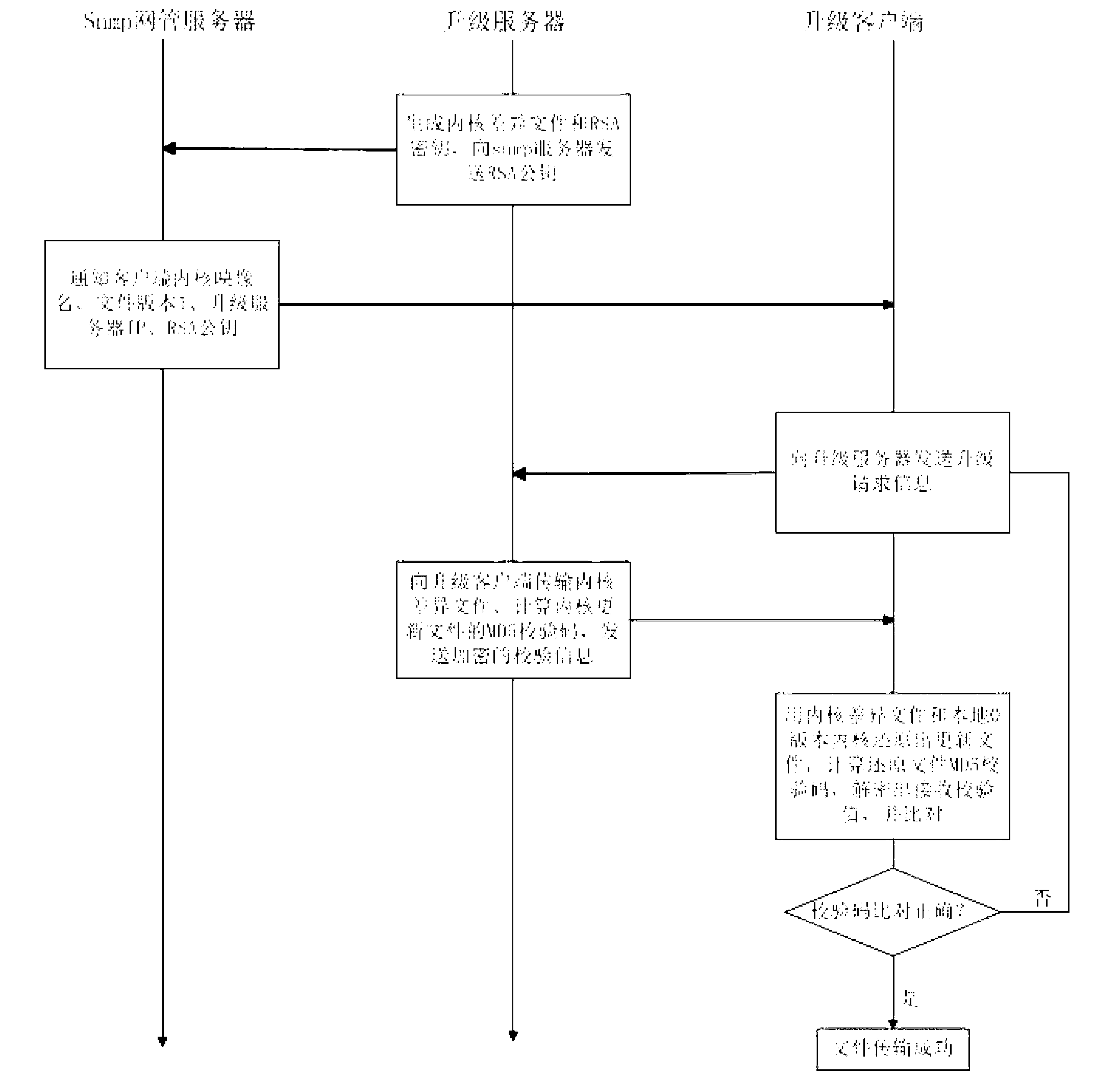
Embedded upgrading file transmission method
InactiveCN103297429AImprove transmission efficiencyHigh transmission safety factorProgram loading/initiatingTransmissionFile transmissionNetwork management
The invention relates to an embedded upgrading file transmission method. The embedded upgrading file transmission method includes steps of 1) generating upgrading file information and encryption keys by an upgrading server and transmitting decryption keys to a third-part network management server; 2) connecting the third-part network management server with an upgrading client side, and transmitting client-side upgrading file information, upgrading server address and the decryption keys to the upgrading client side; 3) transmitting upgrading request to the upgrading server through the upgrading client side, and connecting the upgrading client side with the upgrading server according to the upgrading server address, acquiring differential files on the upgrading server according to the client side upgrading file information, decrypting to acquire verifying values according to the decryption keys, and transmitting the files to complete upgrading after verifying is succeeded. The embedded upgrading file transmission method overcomes the defect that an existing embedded upgrading file transmission is low in safety and easy to be attacked and lacks of prevention of file information disclosure and the like and has the advantages of high transmission efficiency and transmission safety coefficient, information privacy and complete identity authentication mechanism and the like.
Owner:PEKING UNIV
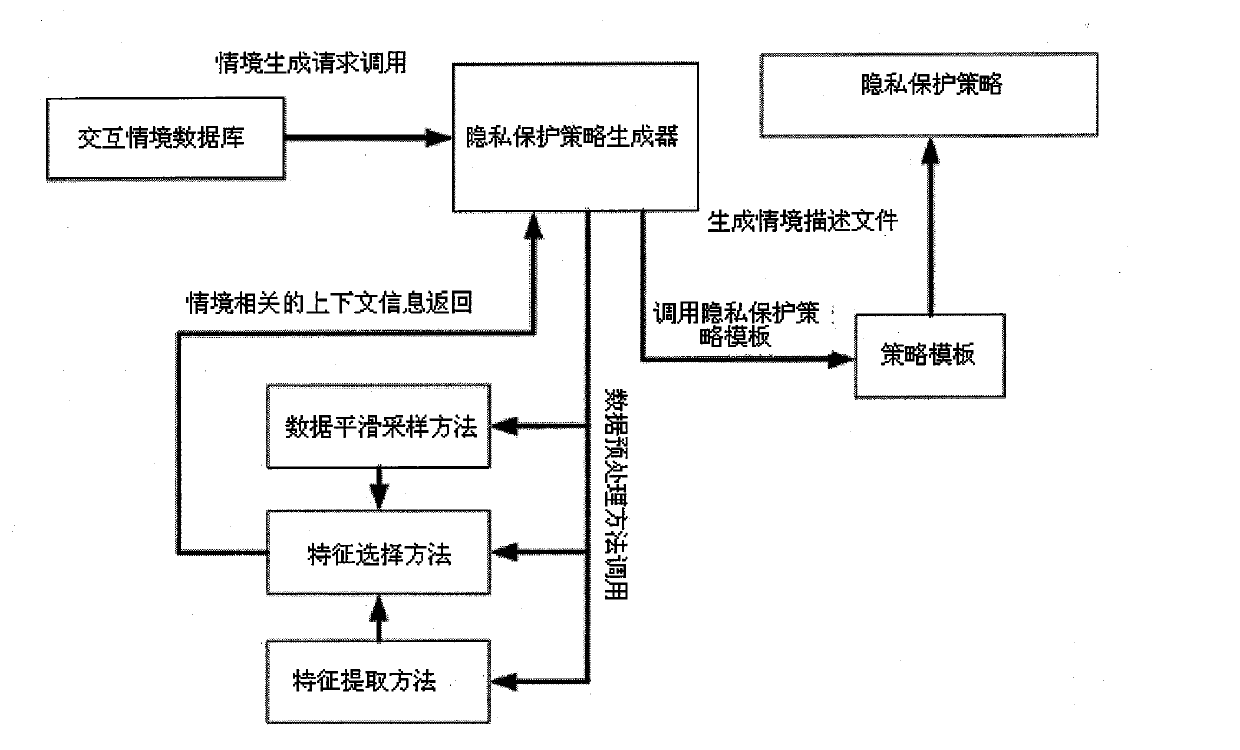
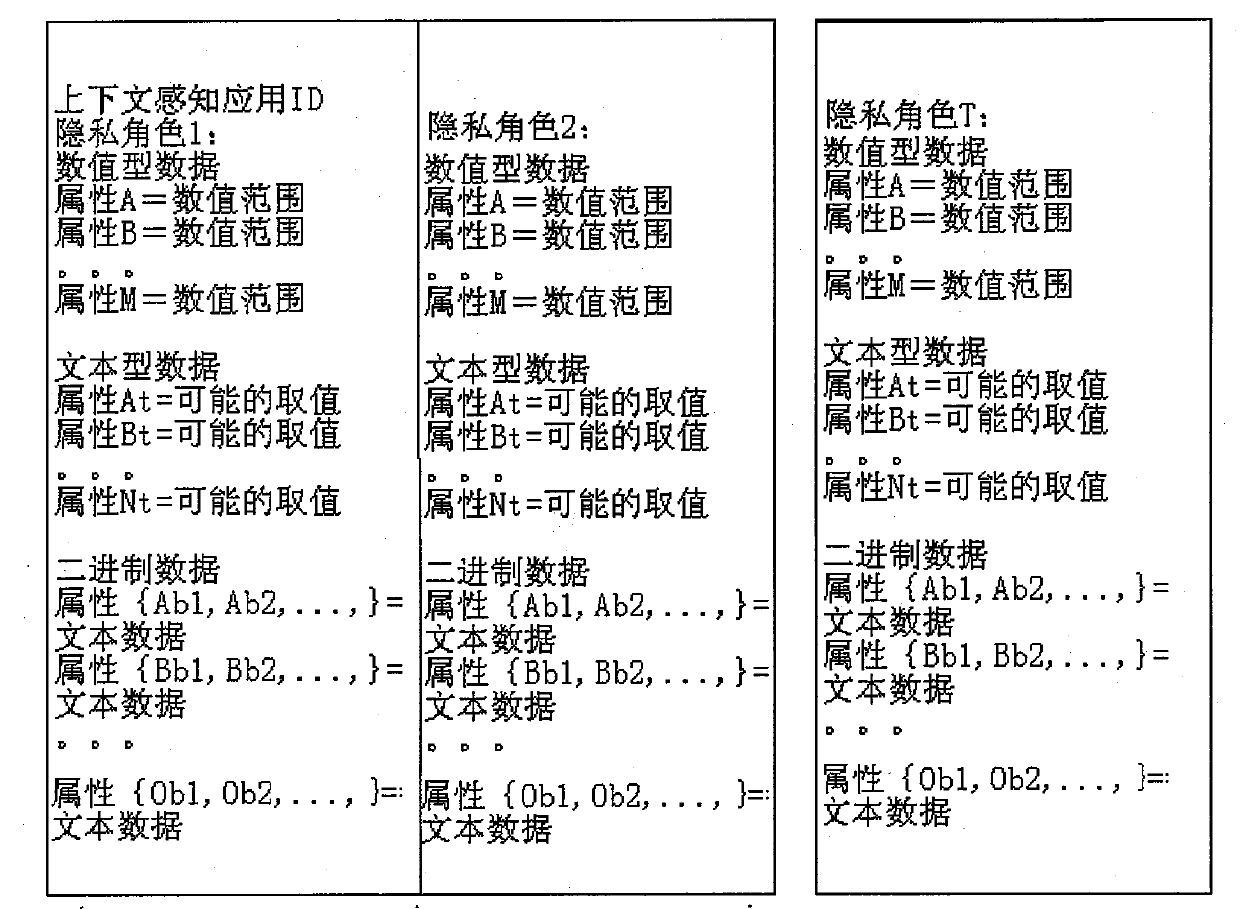
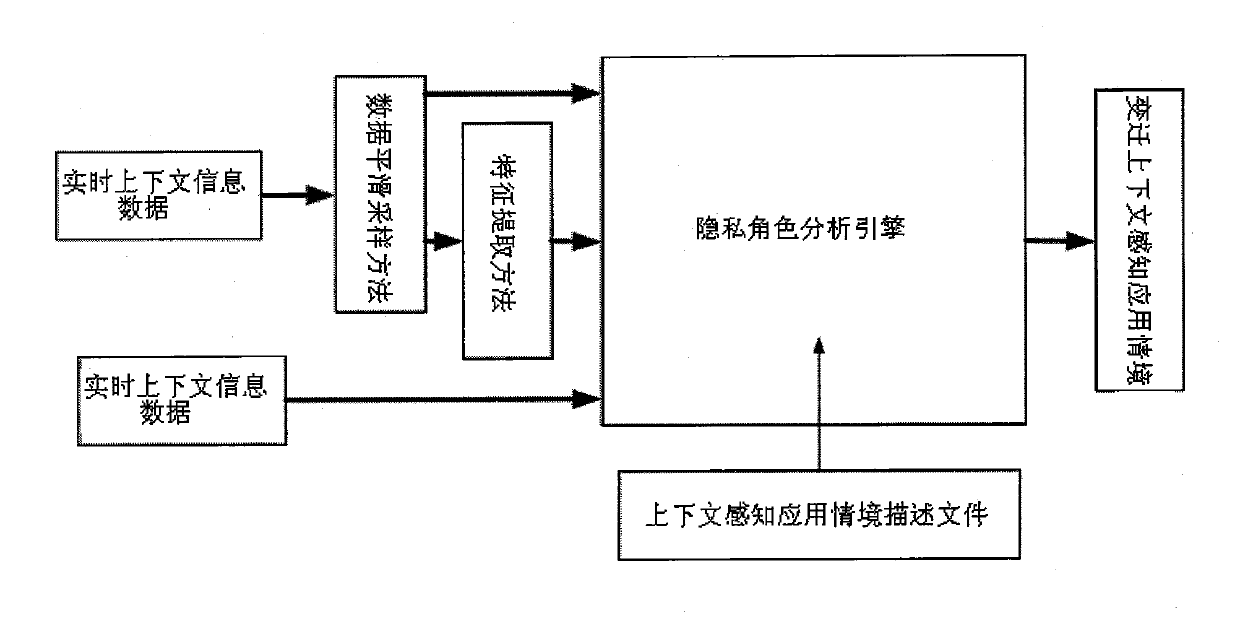
Personal context information privacy protection policy automatic generating method
The invention discloses an automatic generation method of a personal context information privacy protection strategy, which includes the steps as follows: (1) a service mode and a privacy role are analyzed and compared so as to determine the type, number and the like of the service mode; (2) a mobile agent is set as a representative in a pervasive environment for users and a system agent in the pervasive environment is set for being responsible for processing a request for personal context information of the users. Through the coordination of the mobile agent and the system agent, context information in an interactive environment is obtained; (3) various sensors in the pervasive environment can be used for obtaining the context in the interaction process of the users and a context-ware application system, namely, historical data of interaction between the users and the context-ware application system. And then the data are stored in an interactive context database; (4) a rough set algorithm is used for completing the automatic extraction of the privacy protection strategy; and (5) a privacy role analysis engine is used for automatically allocating an appropriate privacy role for the context-ware application system, namely for setting an operation mode for the context-ware application system.
Owner:XI AN JIAOTONG UNIV
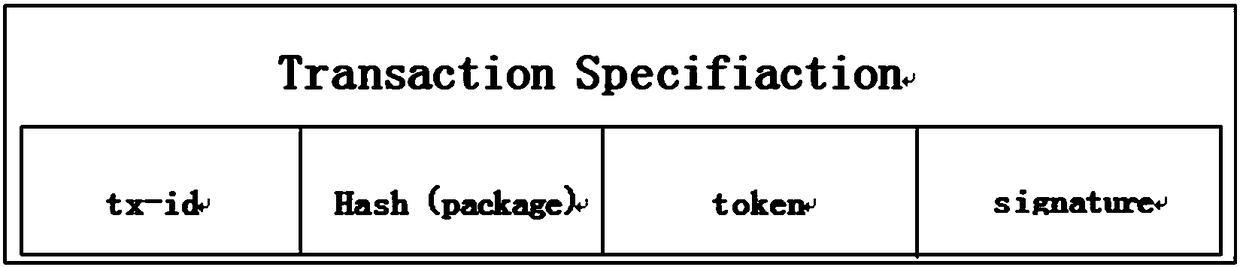
Blind signature based privacy preservation method for admissible block chains
The invention discloses a permission block chain privacy protection method based on blind signature. For transaction content, the transaction information m is encrypted blindly by Hash function, and then the transaction is signed by the address private key of both parties to ensure that the transaction information can only be viewed by both parties, and then only the unique DAID of digital assets,the blind signature of the transaction and the endorsement public key of the endorsing node are recorded on the block chain; the transaction information m is encrypted blindly by Hash function, and then the transaction is signed by both parties' address private keys. For the identity information of the transaction user, the information written into the block chain has only the blind signature andthe third-party public key address which provides the blind signature, and the ID of the digital asset. The latter two have nothing to do with the transaction information and the user information, and the blind signature is unforgeable and unextractable, so the privacy of the identity information of the user can be protected. The invention can not only protect the identity information privacy ofboth sides of the transaction, but also protect the information of the transaction during the transaction of the licensing block chain.
Owner:GUANGXI NORMAL UNIV
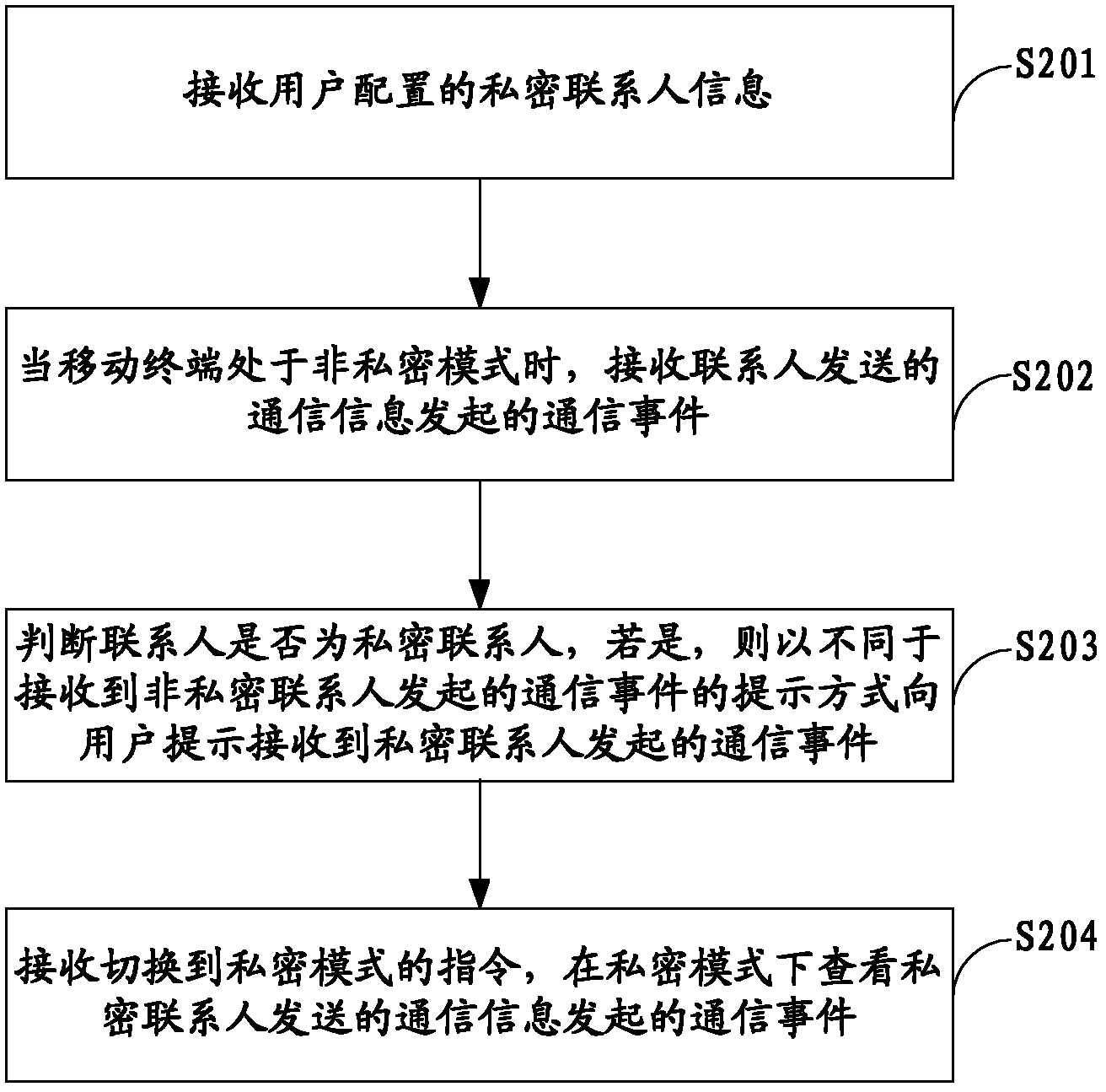
Method, system and mobile terminal for prompting private contact communication events
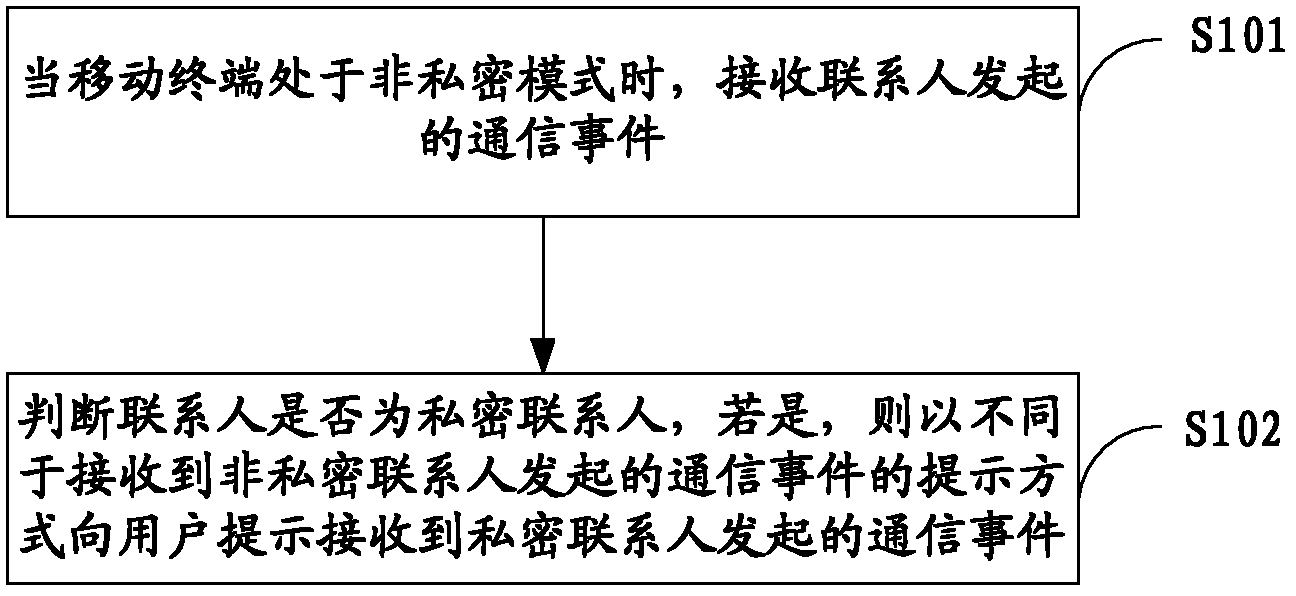
InactiveCN102291480ACalling susbscriber number recording/indicationComputer terminalComputer engineering
The present invention is applicable to the technical field of communication, and provides a method, system and mobile terminal for prompting a communication event of a private contact. The method includes the following steps: when the mobile terminal is in a non-private mode, receiving a communication event initiated by a contact ; Judging whether the contact is a private contact, if so, prompting the user to receive a communication event initiated by a private contact in a manner different from that of receiving a communication event initiated by a non-private contact. The invention enables the user to obtain the communication information of the private contact in the non-private mode, which not only ensures the privacy, but also enables the user to dynamically know the communication of the private contact.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Identification authentication method for communication entity based on combined public key
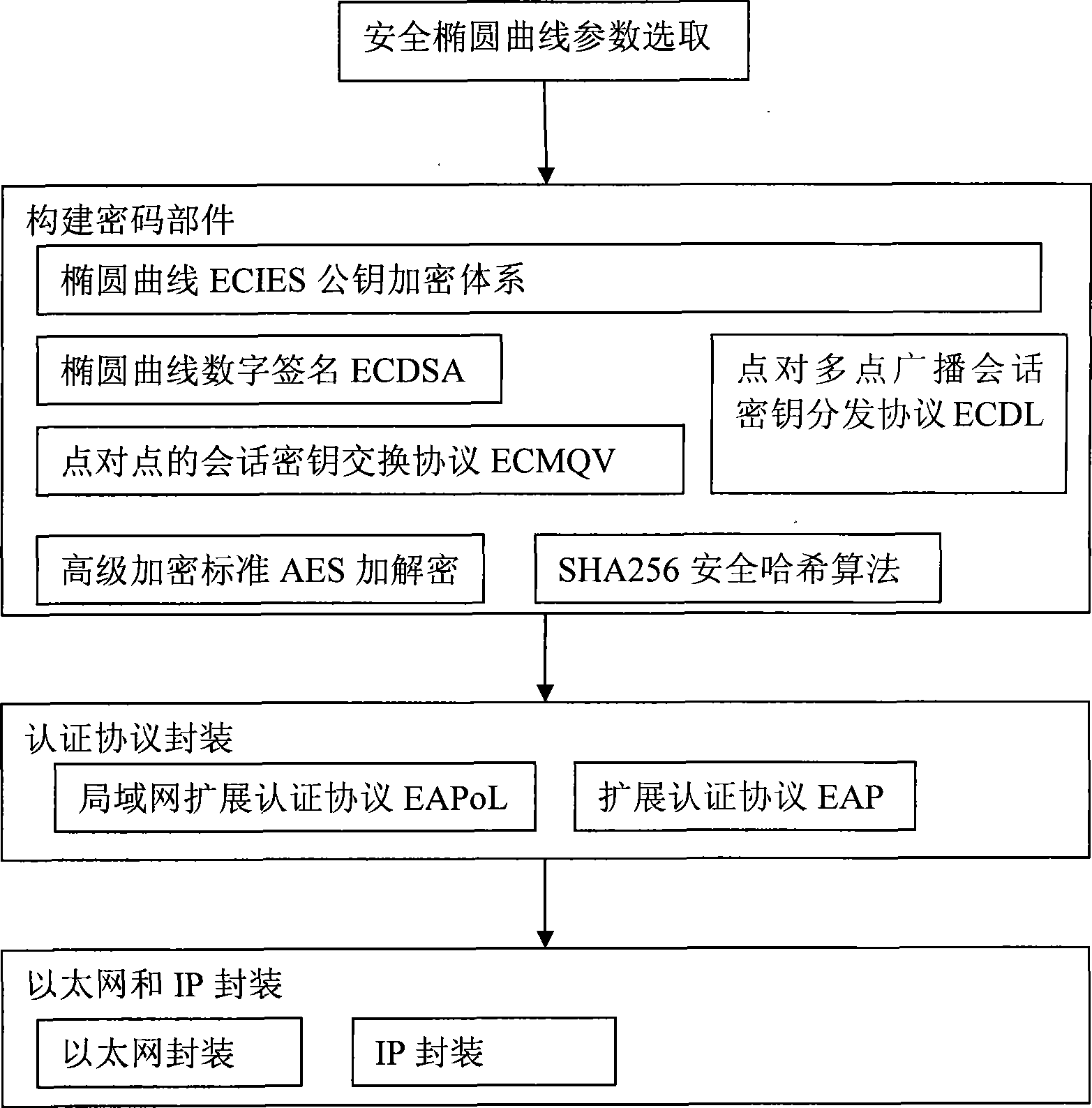
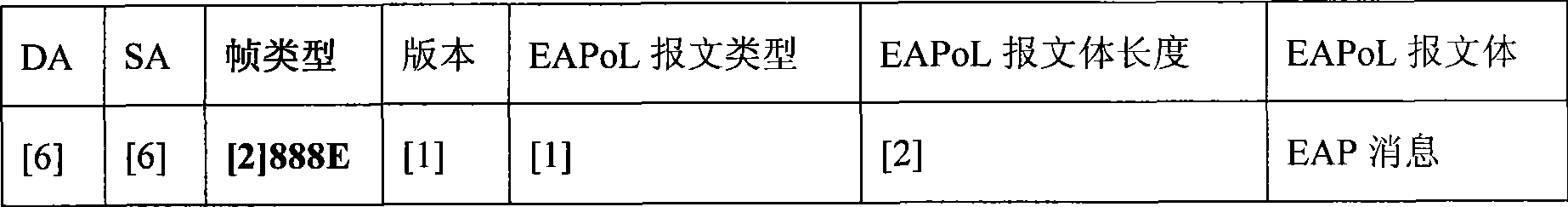
ActiveCN101442522ATake up less resourcesEase of implementation at scalePublic key for secure communicationUser identity/authority verificationInformation securityEthernet
The invention discloses a communication entity identification and authentication method based on a combined public key, and relates to the information security authentication technology between communication entities in the field of communication. The invention adopts the identification and authentication technology based on the combined public key to realize authentication of the communication entities; the invention adopts an AES algorithm to encipher and decipher information data, so as to realize information privacy; and the invention adopts the Ethernet encapsulation and IP encapsulation technology to realize transparent access of an authentication device. The communication entity identification and authentication method has the characteristics of standard interface / protocol, simple access, unnecessary change of the prior communication entities, convenient use and so on, and is particularly suitable for authenticating communication terminals and communication equipment under the condition that the communication entities are not changed.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
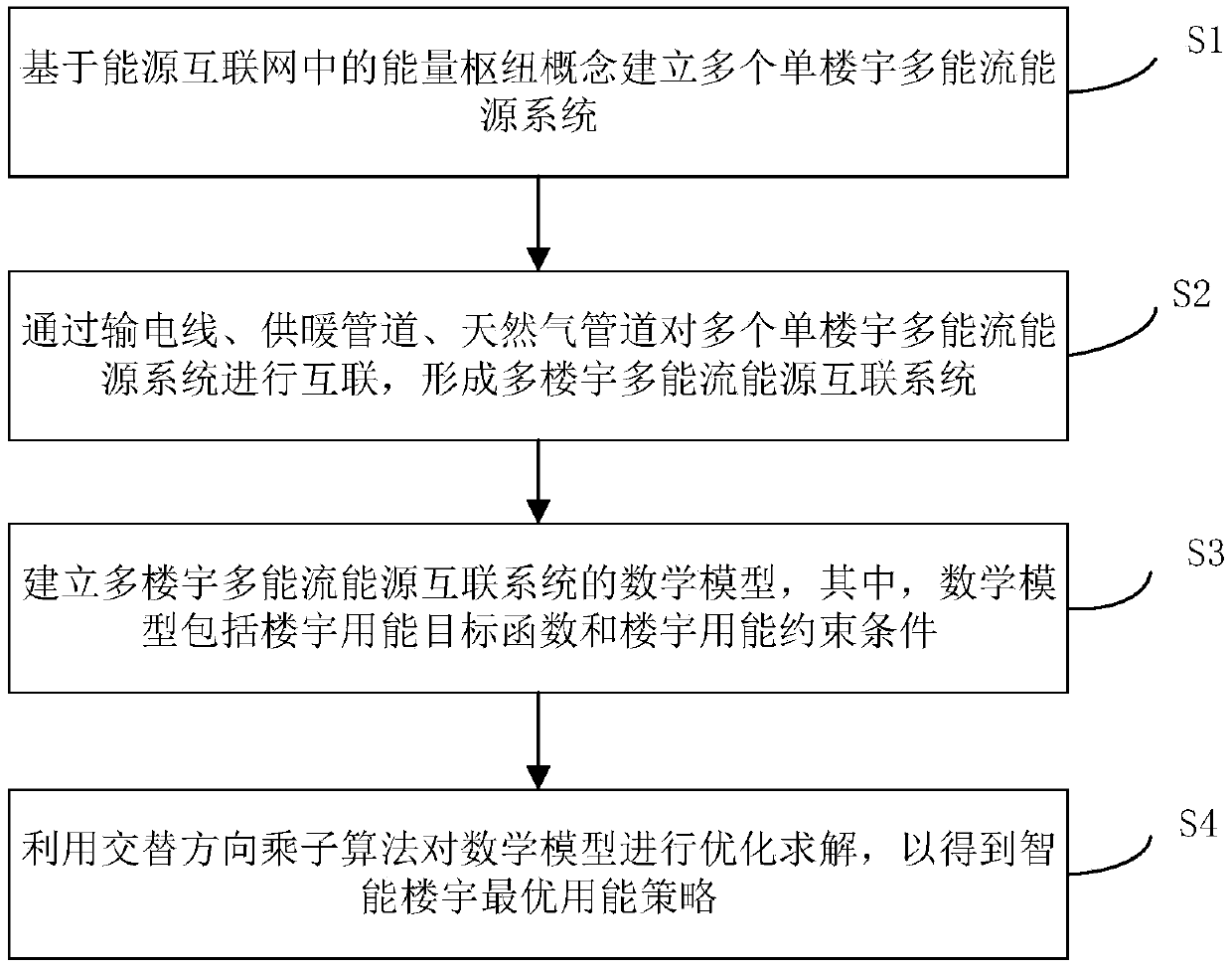
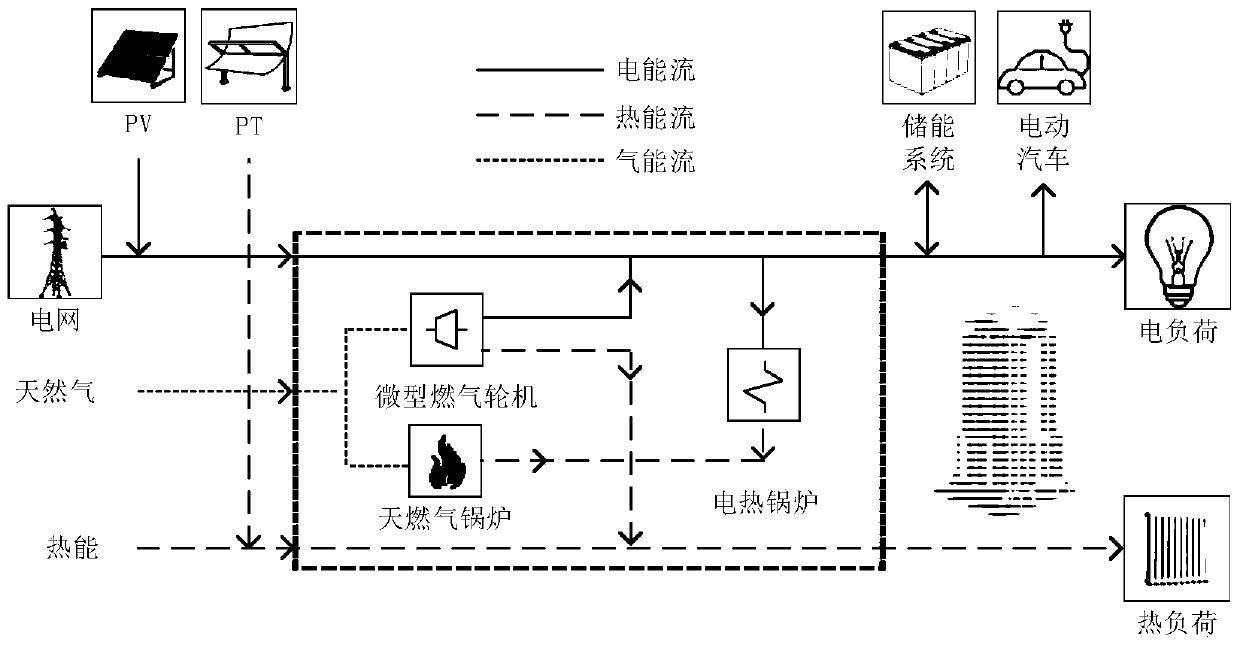
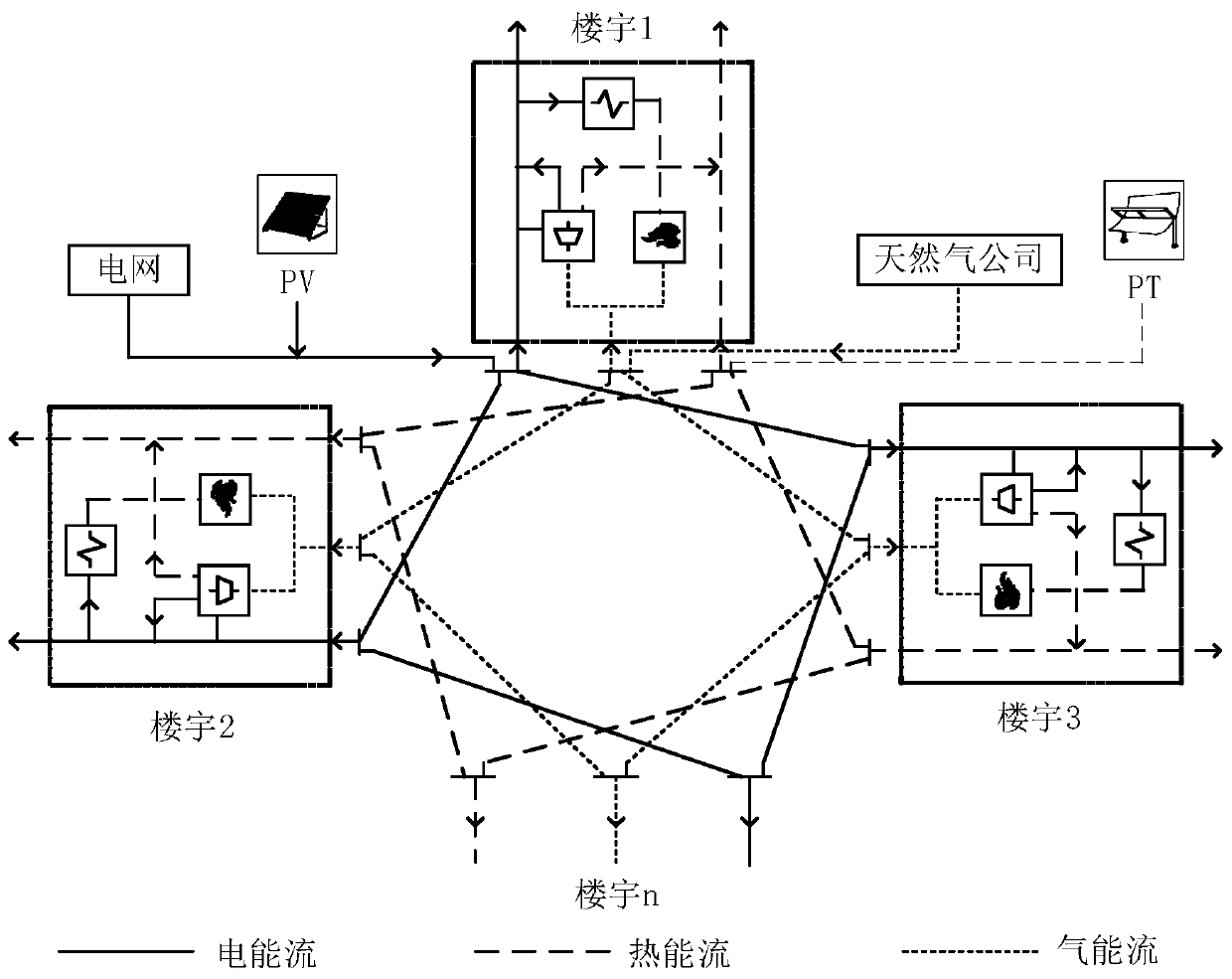
Distributed comprehensive energy demand response collaborative optimization method for intelligent building group
The invention discloses a distributed comprehensive energy demand response collaborative optimization method for an intelligent building group. The distributed comprehensive energy demand response collaborative optimization method comprises the following steps: establishing a plurality of single-building multi-energy flow energy systems based on an energy hub concept in an energy internet; interconnecting a plurality of single-building multi-energy-flow energy systems through a power transmission line, a heating pipeline and a natural gas pipeline to form a multi-building multi-energy-flow energy interconnection system; establishing a mathematical model of the multi-building multi-energy flow energy interconnection system, wherein the mathematical model comprises a building energy consumption objective function and a building energy consumption constraint condition; and carrying out optimization solution on the mathematical model by utilizing an alternating direction multiplier algorithm to obtain an intelligent building optimal energy utilization strategy. The distributed comprehensive energy demand response collaborative optimization method can effectively reduce the electrical load of a power utilization peak, optimize the energy consumption structure of a user, delay the plan of power supply and distribution equipment upgrading and capacity expansion, reduce the economic pressure of an energy supplier due to relatively high investment cost, promote information privacy protection and local decision autonomy, and greatly improve the overall scheduling decision response speed.
Owner:HXXN ELECTRICITY
Method for generating and check-controlling network identity indentification code in network electronic identification card
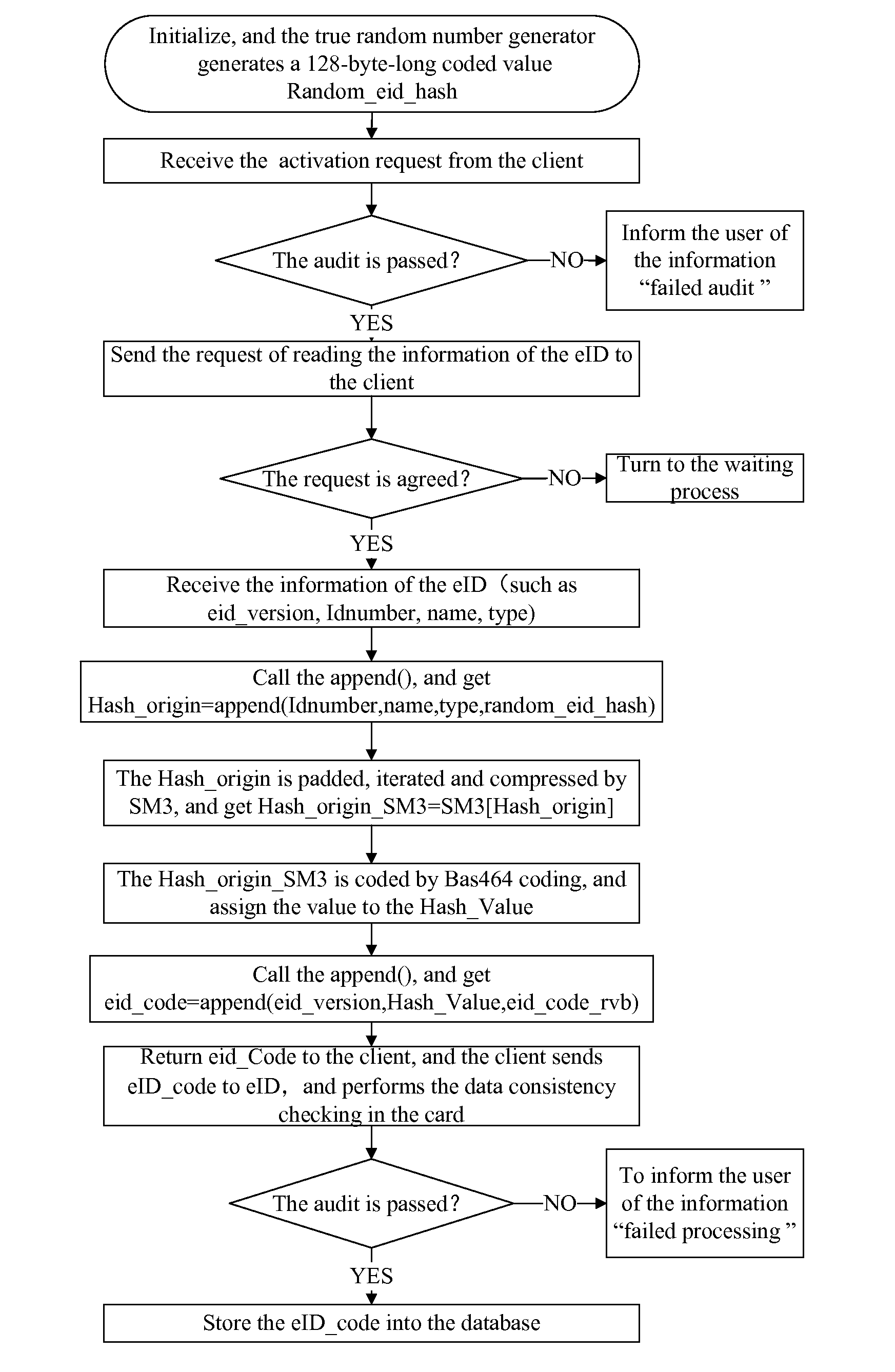
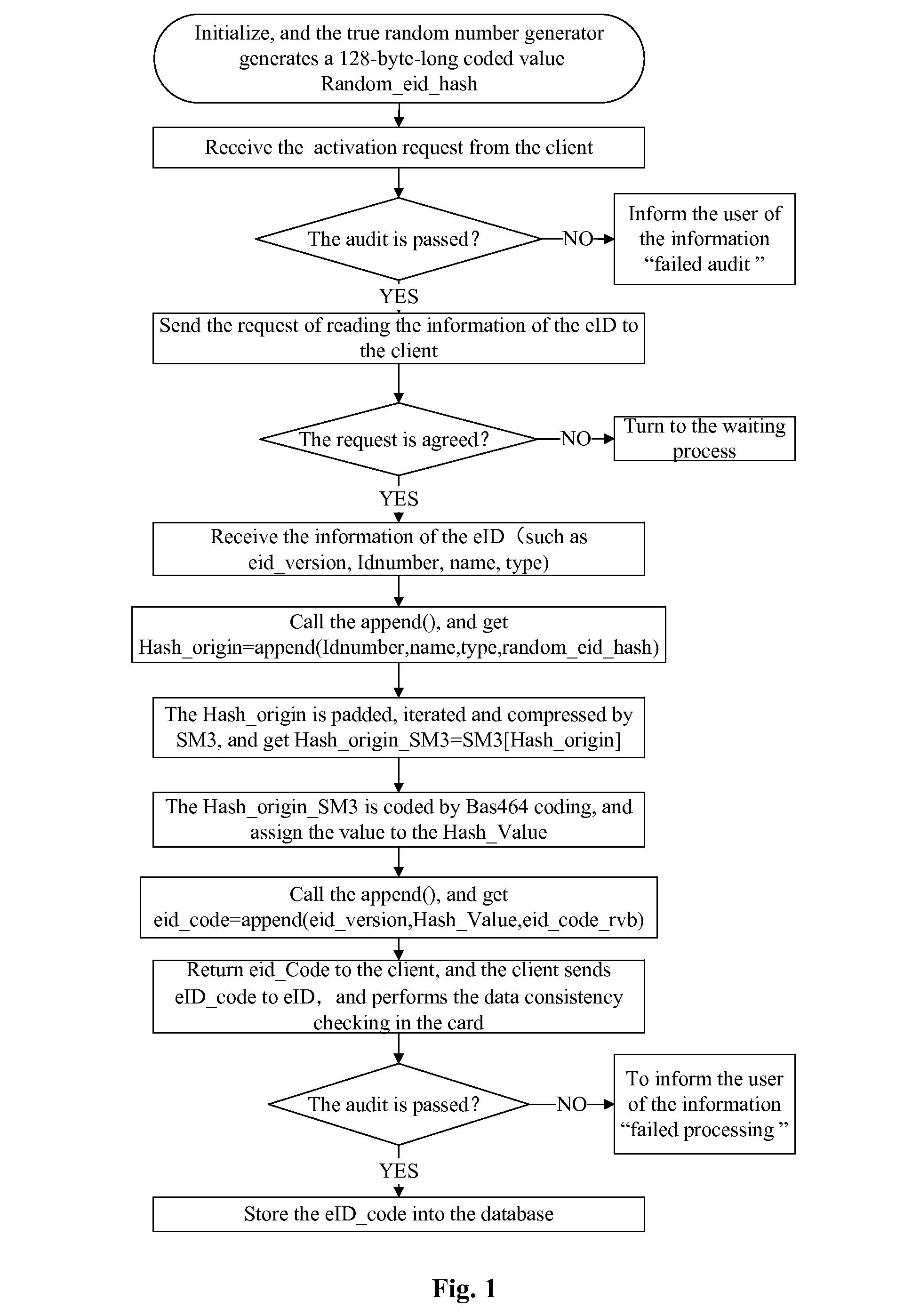
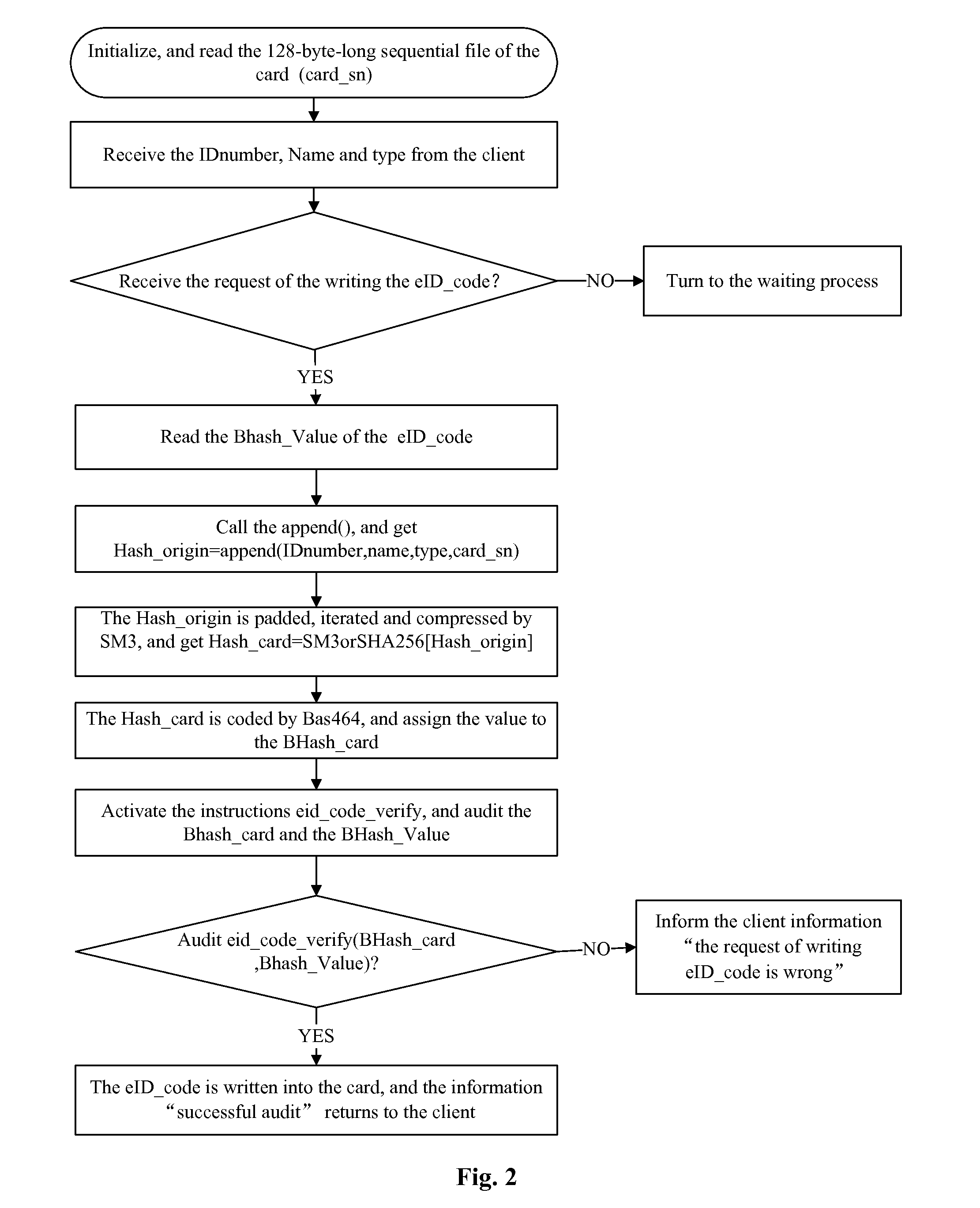
ActiveUS20140331291A1Quick and convenient in useImprove performanceDigital data processing detailsMultiple digital computer combinationsTerra firmaElectronic identification
The present invention relates to a method for generating and check-controlling a network identity identification code in a network electronic identity. The method comprises: a server performing initialization and performing generation and distribution of random numbers; receiving and auditing a request to generate the network identity identification code from a client; if the auditing is passed, performing encryption coding and generating a network identity identification code, and then sending the network identity identification code to a network electronic identification card through the client; the network electronic identification card performing the check processing of a network identity identification code, and feeding back a result to the server; the server storing the network identity identification code into a database, and informing the user. By means of the method for generating and check-controlling a network identity identification code in a network electronic identification card, the purposes of network identity management and privacy protection are both achieved, thereby effectively protecting the network application security and identity information privacy of citizens. The method is convenient and quick in use, has stable and reliable working performance, and has a wide application range, thereby laying a strong foundation for establishment of unified network identity management and service ecosystem.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Automatic screening and propelling method and system with high matching degree for managing user and confidential information
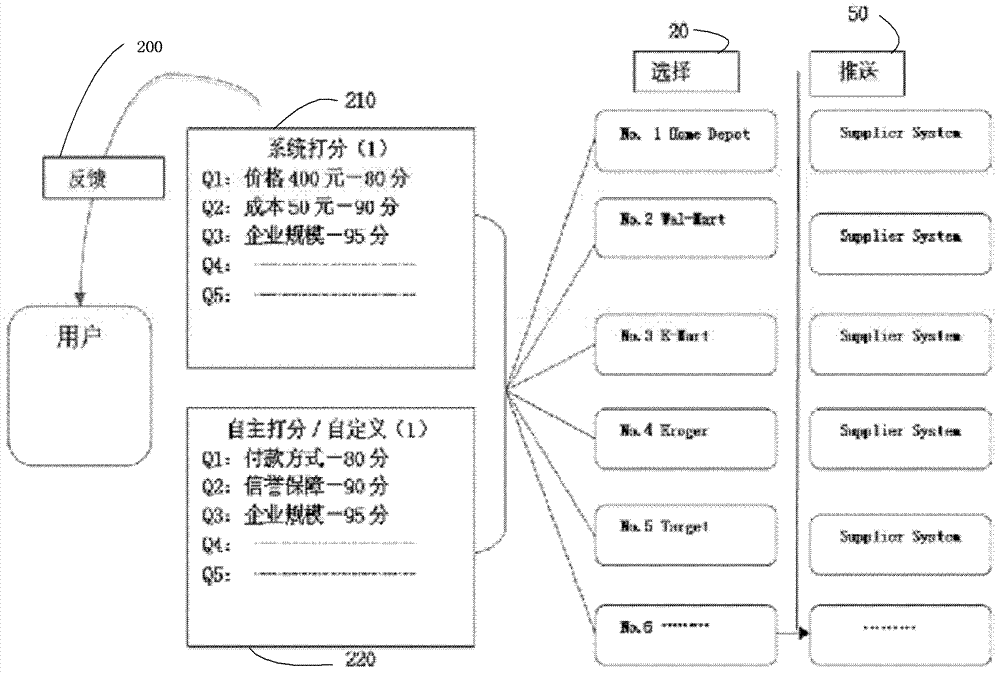
InactiveCN103034671APrevent leakageTop secret protection achievedSpecial data processing applicationsMarketingCentral databaseScreening tool
The invention provides an automatic screening and propelling method and system with a high matching degree for managing a user and confidential information. The method comprises the following steps: a step A: self-defining and screening out a target option to be screened according to a screening model of the target option; a step B, establishing a first scoring mechanism of the screening model for scoring the target option to be screened; a step C: capturing the information associated with the target option from a first database according to the scored result, and showing the scored information from high to low in sequence according to the scores; and a step D: propelling the user information to the selected target option according to the self-defined propelling mechanism. According to the automatic screening and propelling method and system provided by the invention, the conational screening tool is improved; the user-defining and quantifying function is additionally added; self-defining treatment to a plurality of objects on the basis of protecting information privacy is carried out; and all operation processes and data are stored in the central database of the system. The automatic screening and propelling method and system are suitable for high-precision matching of market development, company merger and acquisition, investment banking and commercial procurement, and even a plurality of fields such as personal employment and education, marriage dating and the like.
Owner:GEBO INFORMATION TECH SUZHOU
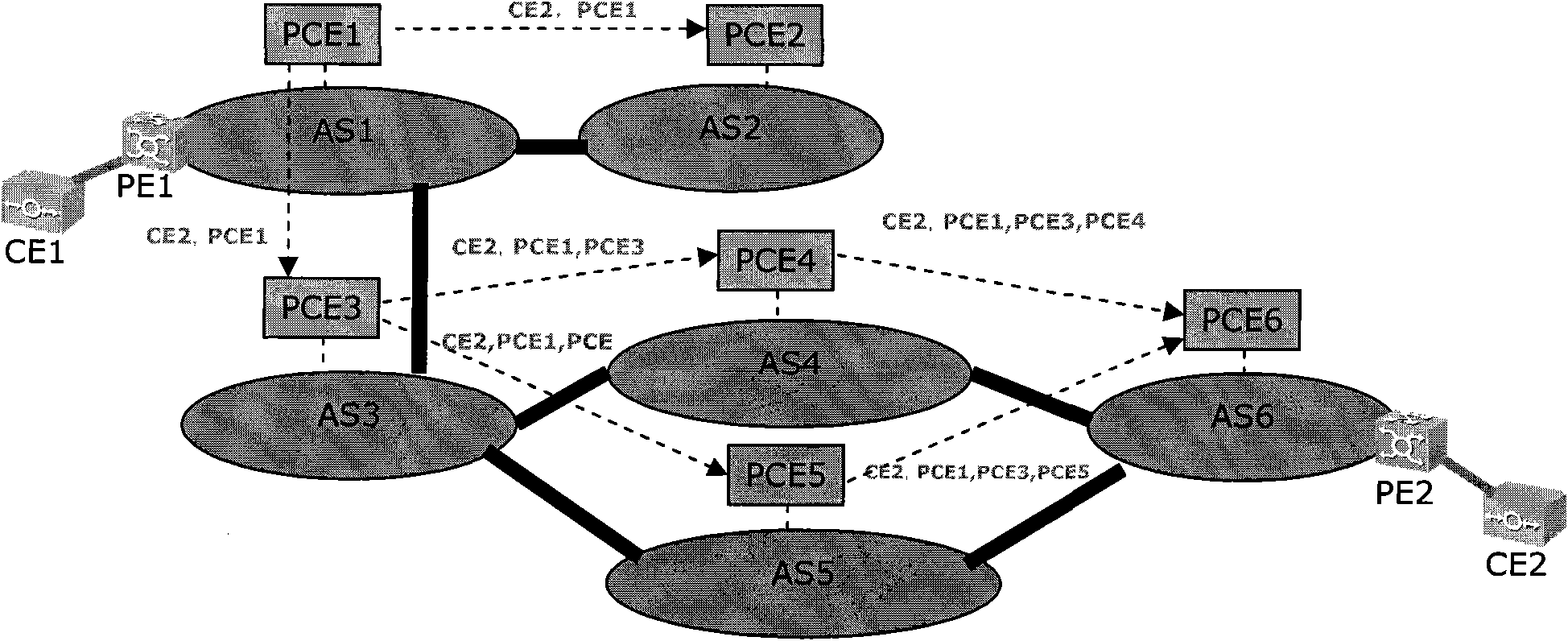
Method, device and system for calculating service path
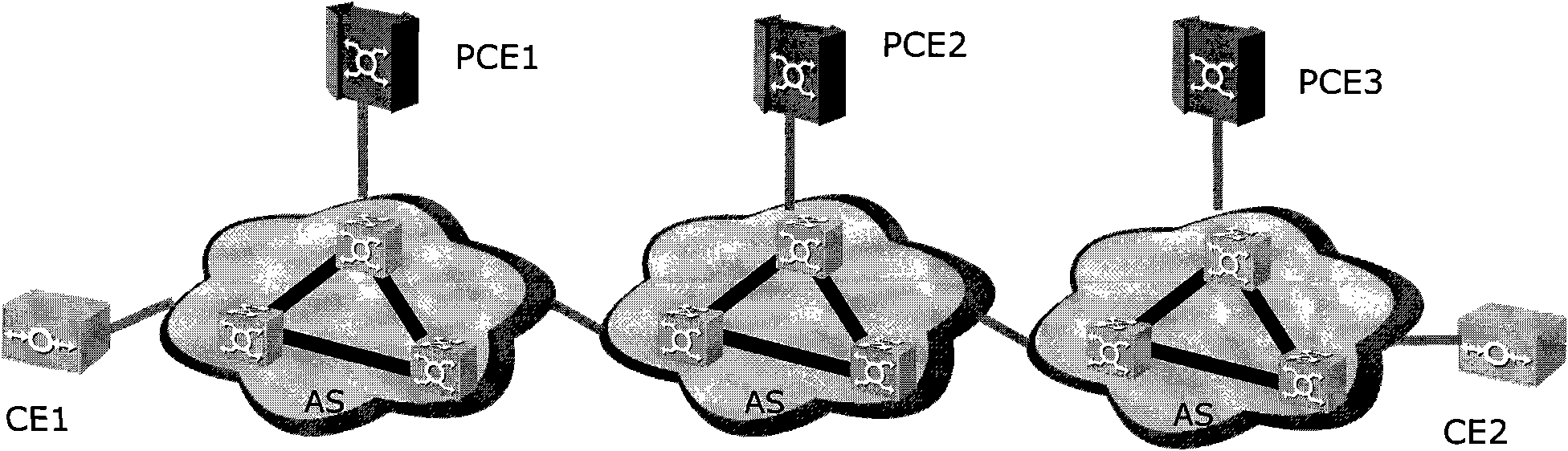
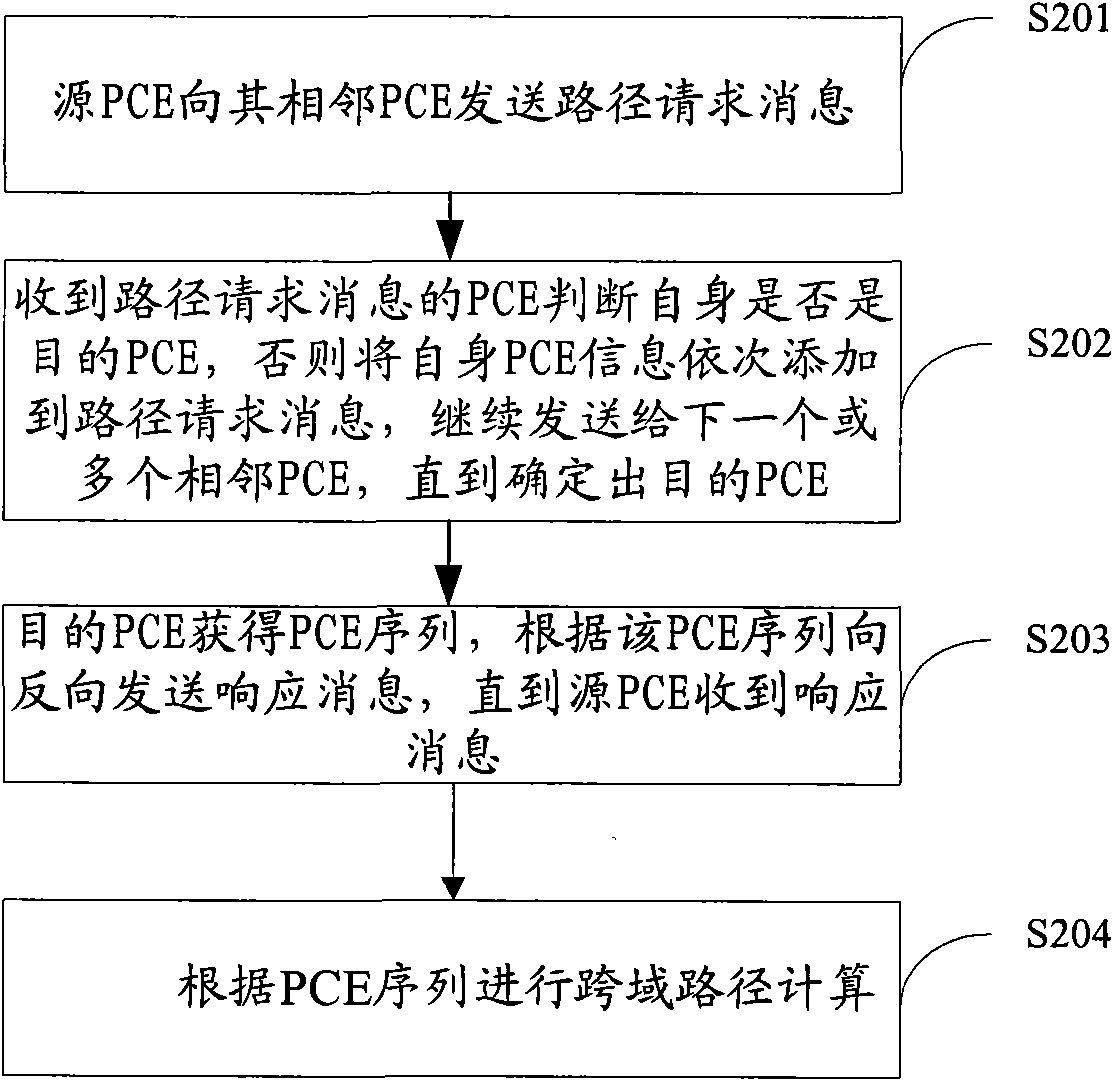
InactiveCN101552716ADon't have to spreadCalculated to reachMultiplex system selection arrangementsData switching networksPath computation elementInformation privacy
The embodiment of the invention discloses a method for calculating a service path, which comprises the following steps: a source path computation element (PCE) corresponding to a service source node sends path request messages to adjacent PCEs after receiving path request messages; each PCE receiving the path request messages judges whether the service destination node belongs to an autonomous system or not; or else, after the individual PCE information is sequentially added to the path request messages, the path request messages are continuously sent to the next or a plurality of adjacent PCEs until the destination PCE is determined; the destination PCE acquires a PCE sequence according to the individual PCE information and the received path request messages, and then, a response message carrying the PCE sequence is sent to the opposite direction according to the PCE sequence until the source PCE receives the response message; and then, the service path is calculated according to the PCE sequence. The embodiment of the invention also discloses a device and a system for achieving calculation of the service path. The effects of information privacy and optimal utilization of network resources are achieved by using the method, the device and the system.
Owner:HUAWEI TECH CO LTD
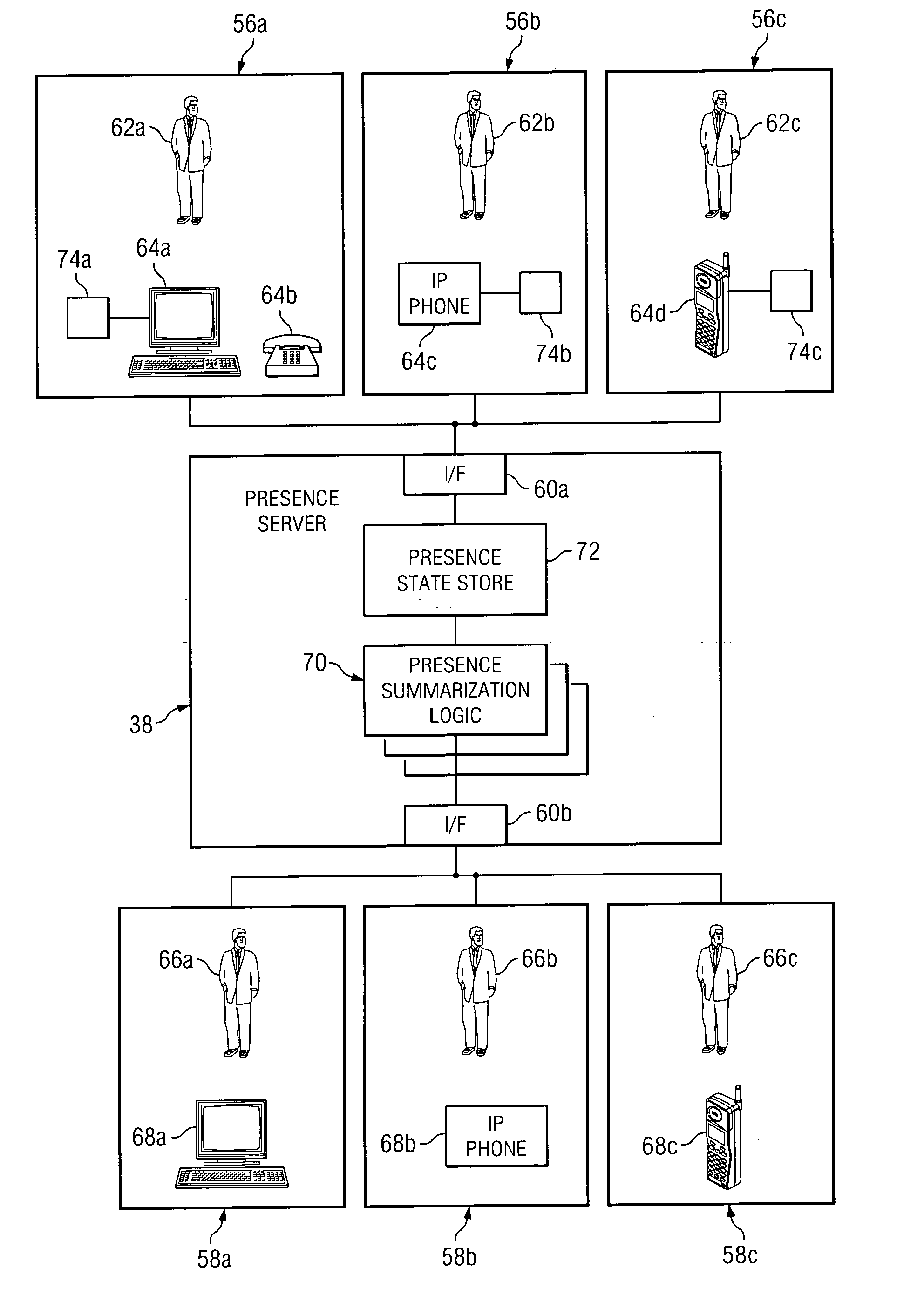
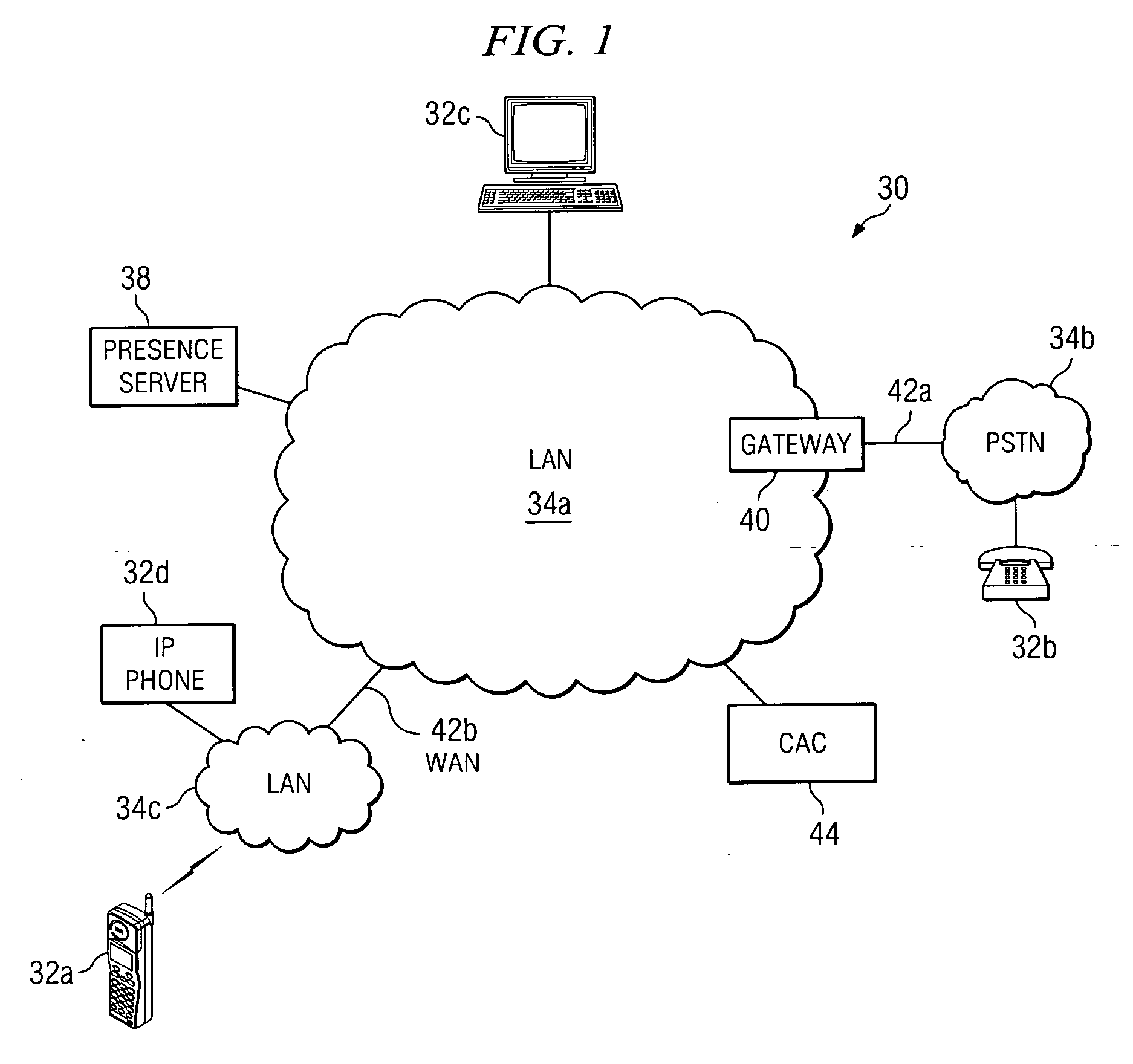
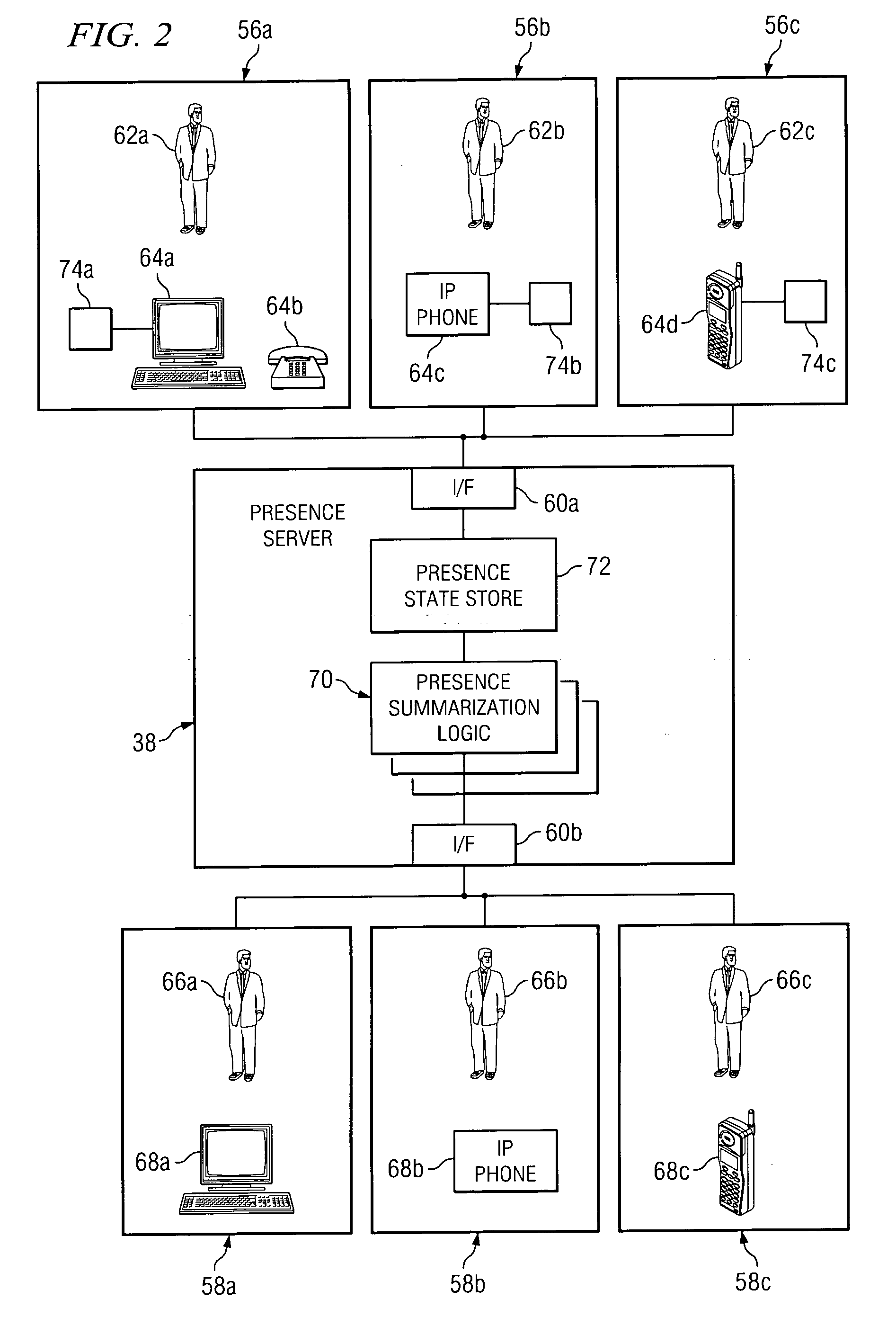
Method and system to protect the privacy of presence information for network users
ActiveUS20060258332A1Eliminates and reduces of disadvantageEliminates and reduces of and problemMetering/charging/biilling arrangementsUnauthorised/fraudulent call preventionRegistration statusPrivacy protection
In accordance with a particular embodiment of the present invention, a method for providing privacy protection to network users includes receiving a subscription request from a first end user. The subscription request identifies a second end user for whom the first end user would like to become a registered presence watcher. A cost to be assessed to become the registered presence watcher of the second end user is determined, and the first user is registered as the registered presence watcher of the second end user.
Owner:CISCO TECH INC
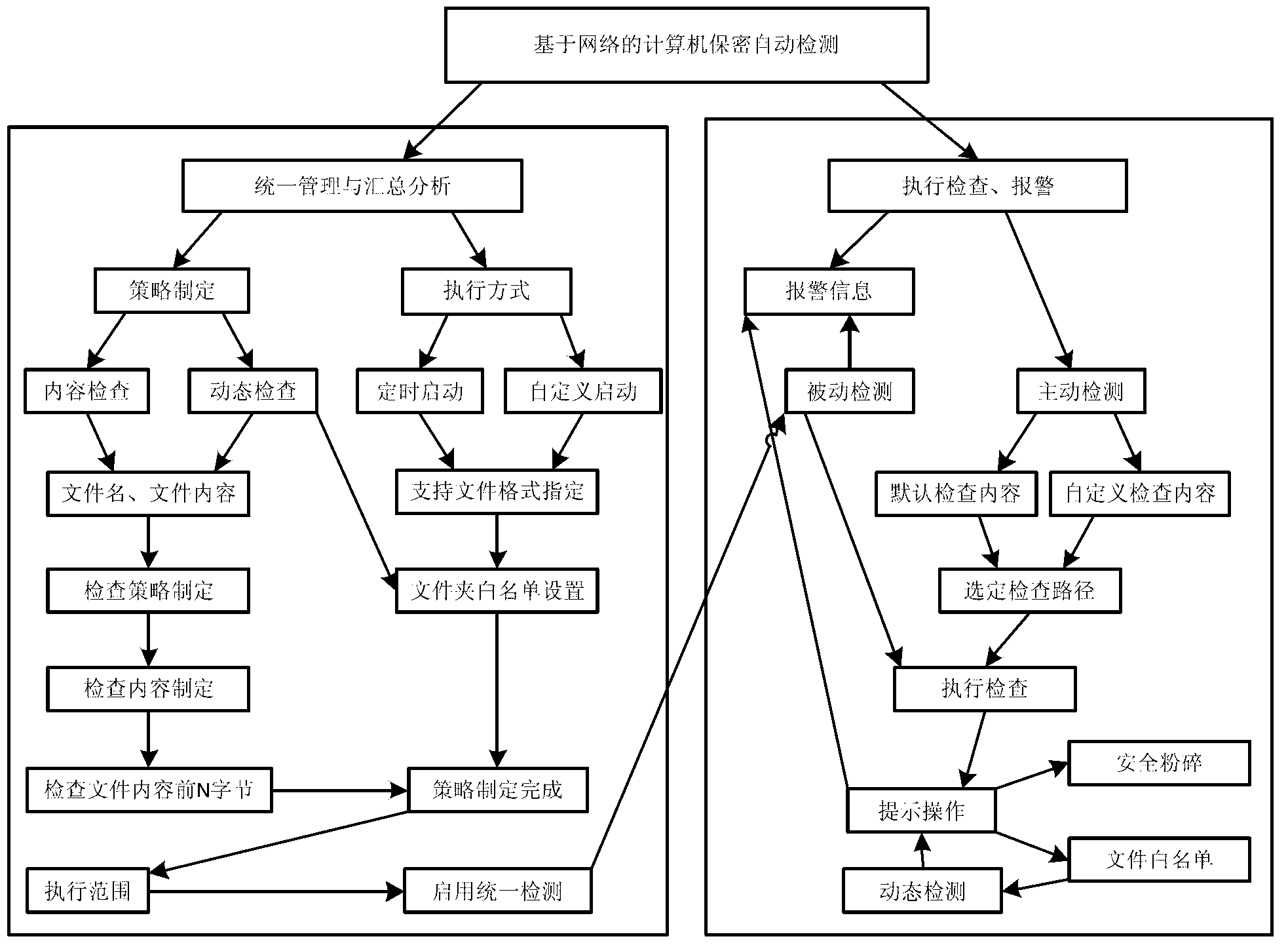
Computer information privacy detection method based on network
ActiveCN102984128AReach confidentiality checkRaise awareness of confidentialityTransmissionPassive detectionEngineering
The invention provides a computer information privacy detection method based on a network. The computer information privacy detection method based on the network comprises the following steps. A network server terminal is linked with a computer client terminal. A network server terminal detection strategy is set up. A computer client detection strategy is confirmed. Dynamics of papers are monitored in real time with alarm. Modes of positive detection and passive detection are combined, all detection results are uniformly collected and analyzed and the computer client terminal is prompted to deal correspondingly. A white list which contains sensitive word information set by the computer client terminal is utilized to improve accuracy and search efficiency of privacy detection. Through unified setting and issuing of a privacy detection strategy of the network server terminal, real time monitoring and alarming of dynamics of the papers of the computer client terminal, automatic checking and an early warning mechanism are achieved. The working staff are more aware of secrecy and prevention by a technical method and leakage risks of an enterprise are avoided.
Owner:CHINA ELECTRIC POWER RES INST +1
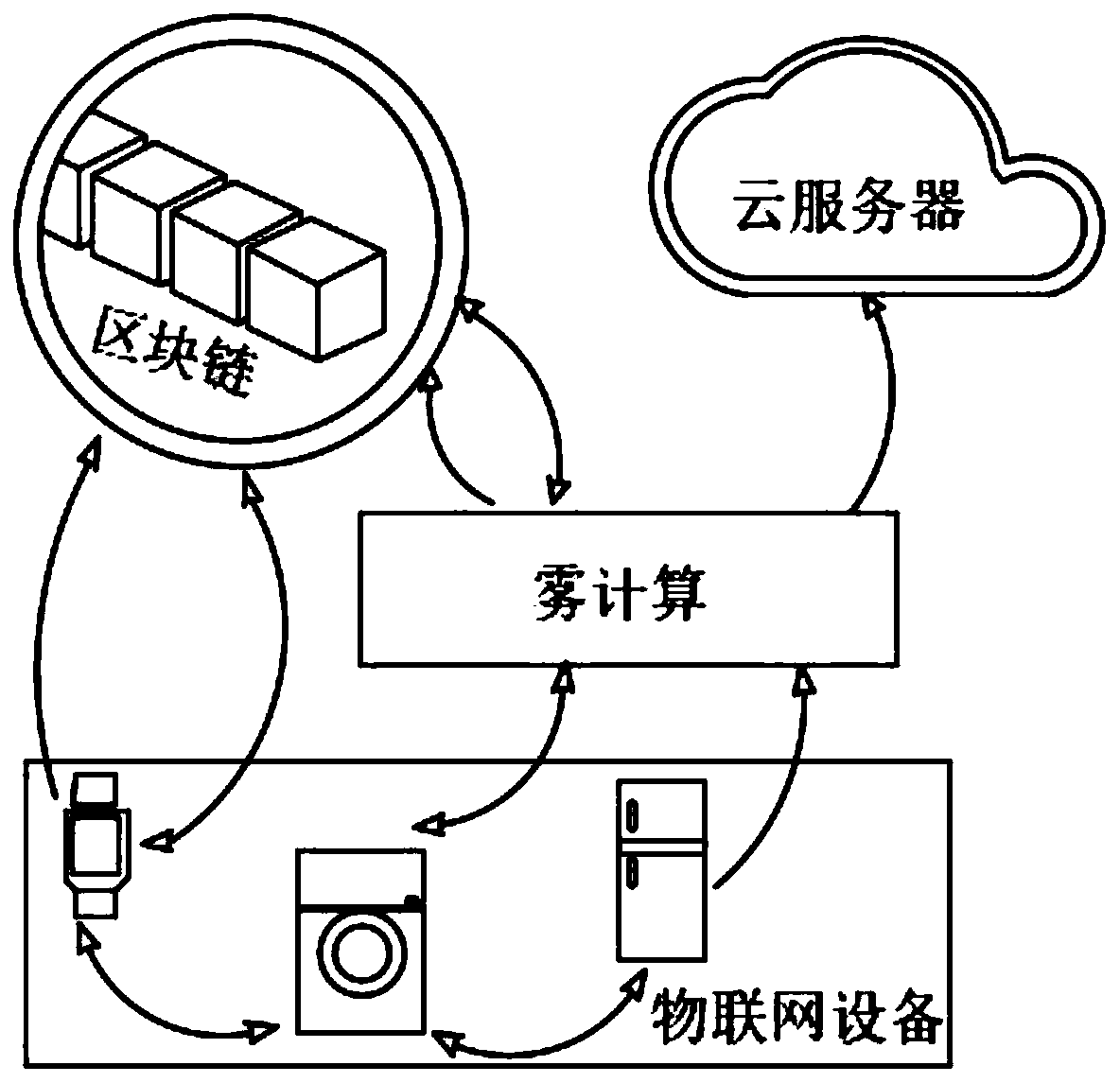
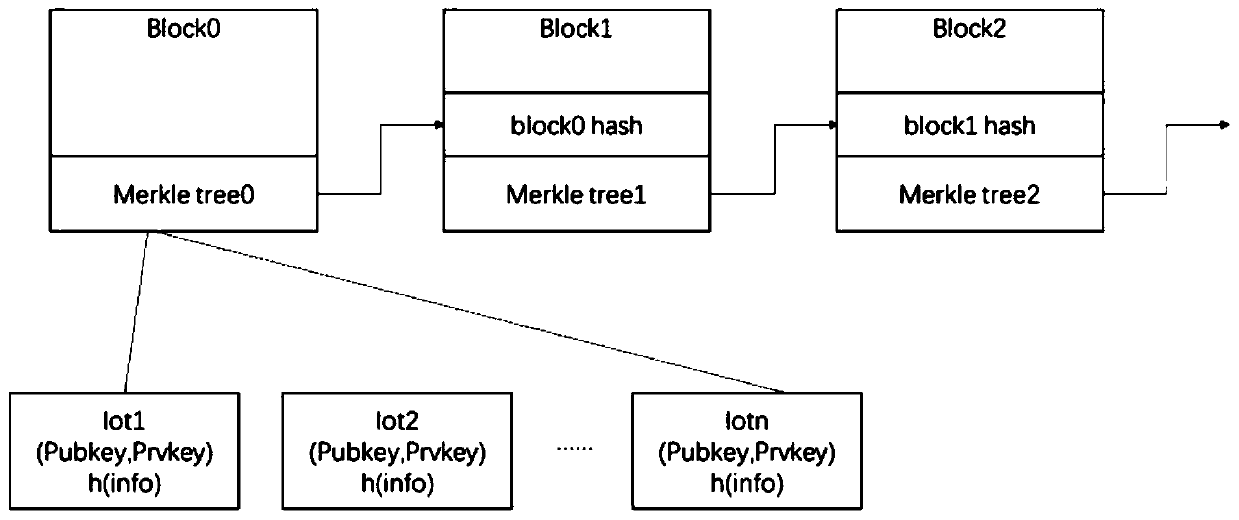
Internet of Things equipment authentication method based on block chain
The embodiment of the invention discloses an Internet of Things equipment authentication method based on a block chain. The method comprises the following specific steps: establishing a hybrid model of fog computing, a cloud server and the block chain for performing data processing on heterogeneous data generated by Internet of Things equipment connected to the Internet of Things; processing heterogeneous data generated by the Internet of Things equipment through fog calculation to form authentication data; sending a data entity of the authentication data to the cloud server through fog computing for data storage, sending an index and a Hash value of the authentication data to a blockchain for uplink, then carrying out whole-network publishing on the Internet of Things, and meanwhile, enabling the Internet of Things equipment to record a public and private key pair for identifying the identity of the Internet of Things equipment on a chain of the blockchain; enabling other Internet ofThings devices connected to the Internet of Things to perform signature verification on the Internet of Things device providing the public and private key pair in the blockchain to obtain the ownership of access and use of data, thereby realizing cooperation among multiple manufacturers and interconnection and intercommunication under the condition of device information privacy protection.
Owner:GUANGDONG POWER GRID CO LTD +1
Privacy protection reissuing method for multiple sensitive attribute data
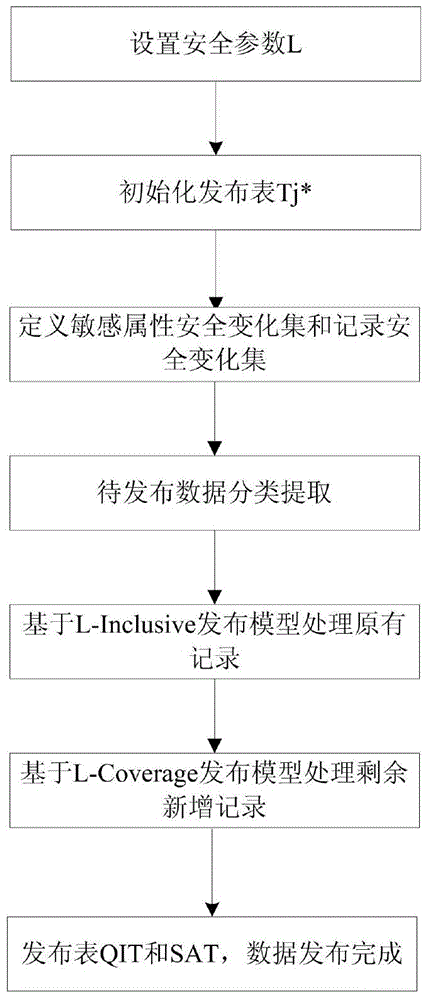
InactiveCN104156668ARelevance fully reflectsResist Privacy AttacksDigital data protectionPrivacy protectionInformation privacy
The invention belongs to the field of information privacy protection issuing safety, and relates to a privacy protection reissuing method for multiple sensitive attribute data. The privacy protection reissuing method includes the steps of dividing reissued data into retention data and refresh data and processing the retained data and the refreshed data and respectively processing the retained data and the refreshed data on the basis of defining privacy protection diversity parameters, sensitive attribute safety change sets and record safety change sets, issuing the retained data through an L-Inclusive model, and issuing the rest of refresh data through an L-Coverage model. According to the privacy protection reissuing method, relevance among the multiple sensitive attributes, relevance among different values of each sensitive attribute and relevance among multiple times of issuing of data are taken into full consideration, privacy attack can be effectively restrained, and the function of privacy protection issuing is achieved.
Owner:JIANGSU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com