Information privacy system and method
A privacy system and privacy technology, applied to instruments, digital data authentication, computing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
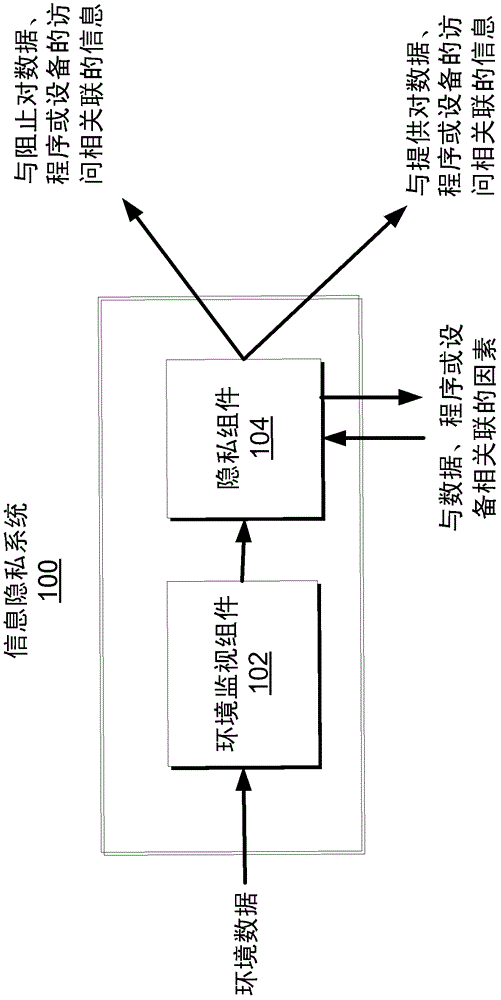
[0021] information privacy
[0022] It is to be understood that the non-limiting examples provided herein are not intended to be limited to any information privacy system or environment implementation unless expressly stated otherwise. Furthermore, unless otherwise stated, the appended claims are not intended to be limited to the claimed information privacy systems or methods.
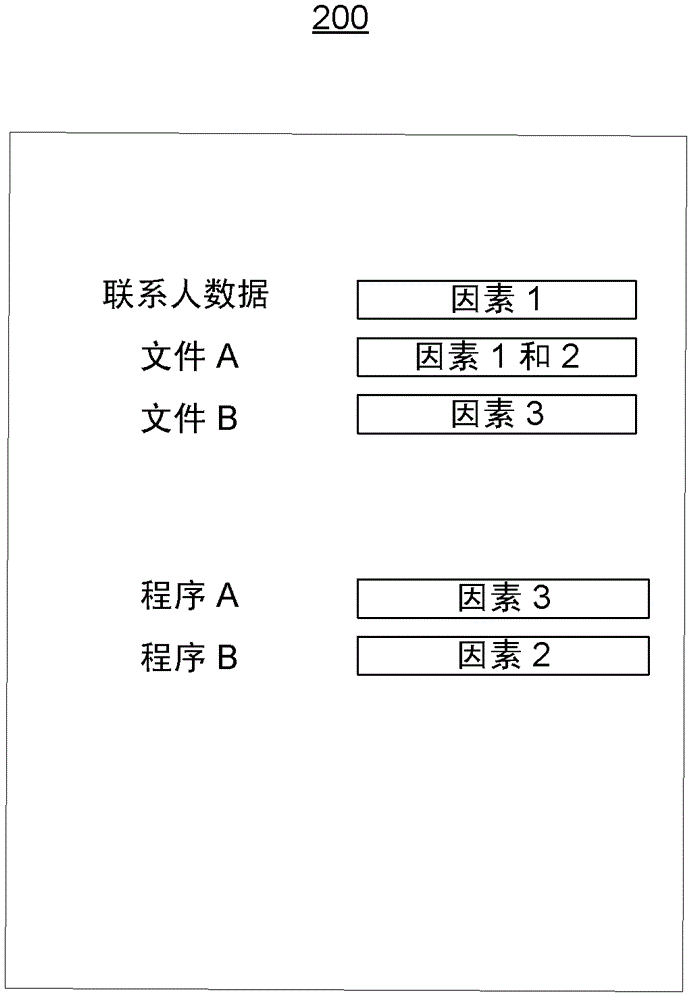
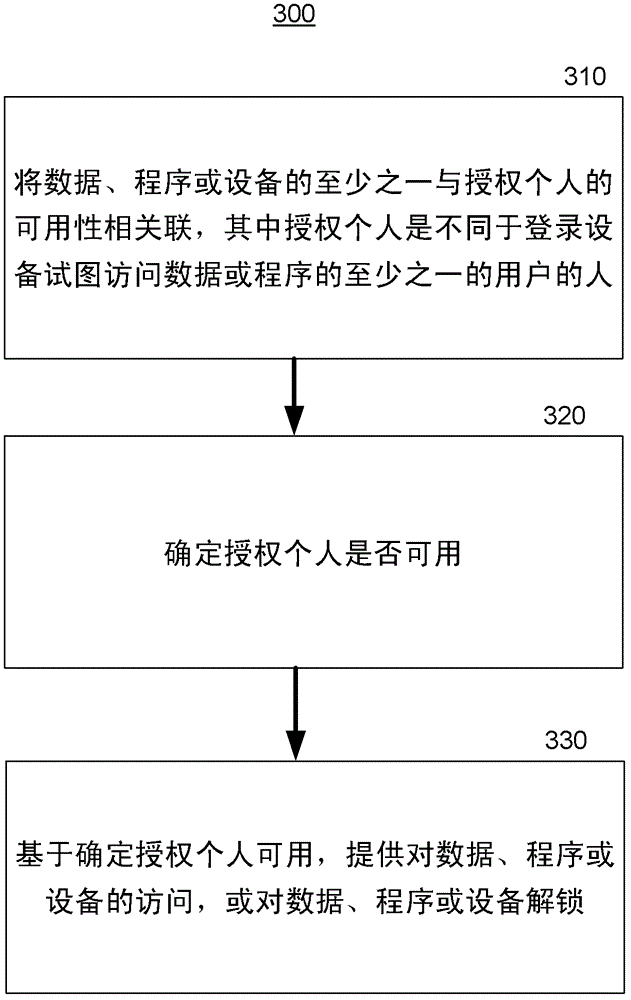
[0023] By further describing one or more non-limiting aspects of information privacy systems and methods, it is revealed that such access to data, programs, and / or devices may be permitted or prevented based on a number of factors considered individually or in combination. systems and methods. By way of example, and not limitation, factors may include time or location of a device configured with an information privacy system, whether an authorized individual other than the device user is within a particular proximity of the user or is logged into a specified network, and / or is within the user's Motio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com