Patents
Literature
702results about How to "Avoid storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
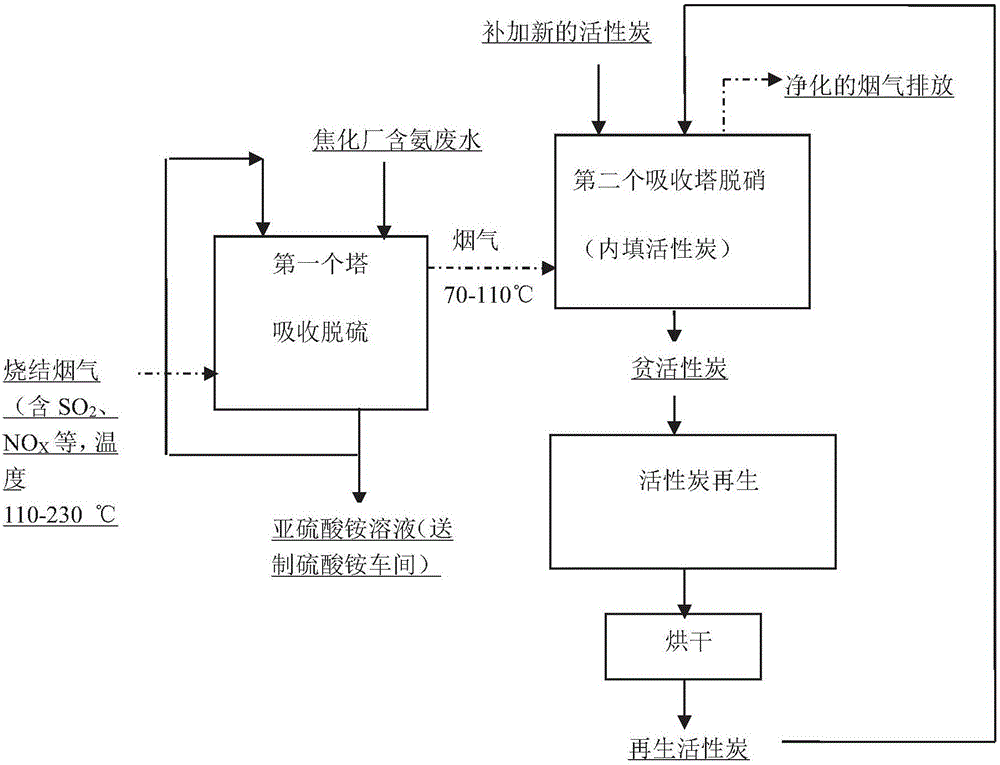
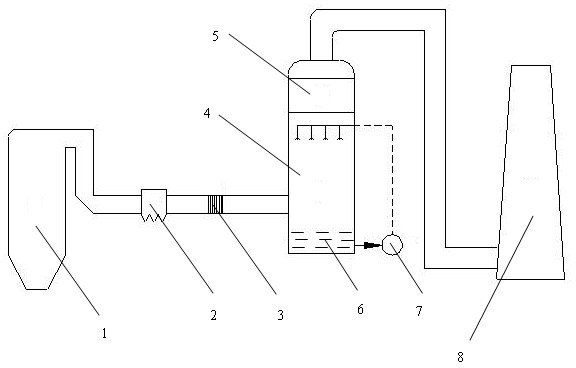
Ammonia-carbon combined desulfurization and denitration method for sintering flue gas
ActiveCN106621773AHigh mechanical strengthImprove recycling ratesGas treatmentOther chemical processesActivated carbonFlue gas
The invention discloses an ammonia-carbon combined desulfurization and denitration method for sintering flue gas. The sintering flue gas is desulfurized through ammonia-containing absorption liquid and then is adsorbed through activated carbon; the activated carbon is obtained by roasting carbonaceous materials and metallic oxide sources at a mass ratio of 2: 1 to 5: 1 at 850-1100 DEG C; the carbonaceous materials refer to semicoke or a mixture of coal and biomass. In the method, ammonia is cooperated with the activated carbon prepared through the method in use, desulfurization and denitration can be effectively achieved, secondary pollution is reduced, the process is cut short, and the treatment cost is reduced.
Owner:CENT SOUTH UNIV
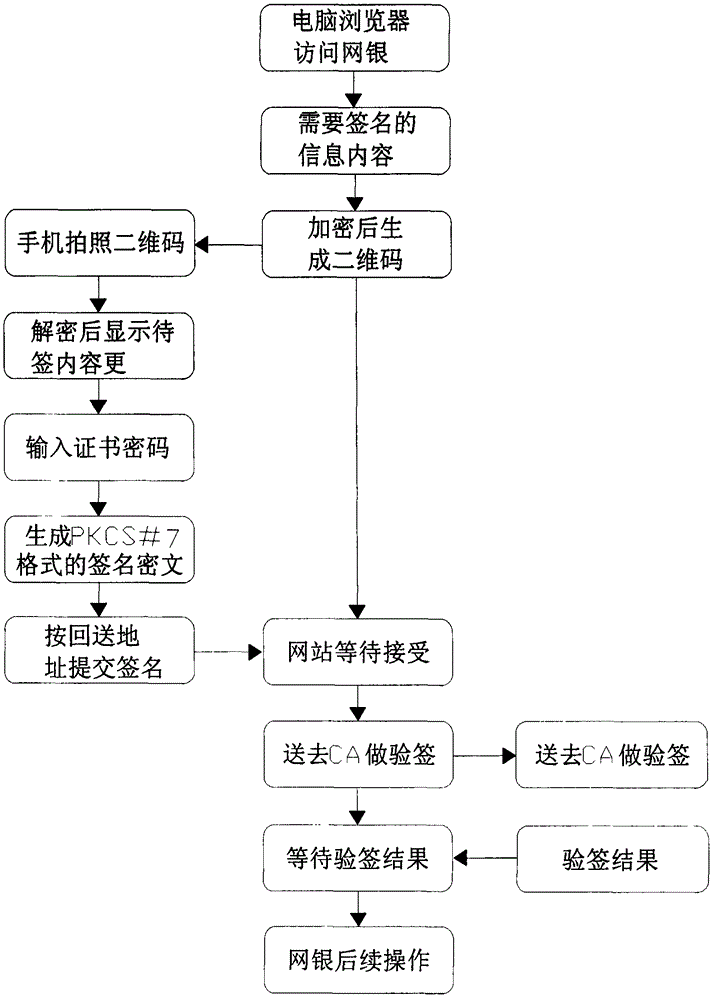
Mobile terminal digital certificate electronic signature method
ActiveCN105323062AIngenious ideaReasonable ideaUser identity/authority verificationIssuing bankInternet privacy
The invention relates to a mobile terminal digital certificate electronic signature method. According to the method, based on the characteristics of public keys and private keys and on the premise of not violating the rules prescribed by the electronic signature law, for example, a private key should be generated in a user terminal and should not leave the user terminal, a private key should not be transmitted via the network, and the like, a private key is discarded and locally and discretely stored after encryption, and the cloud uses strategies such as storing the public key and certificate to ensure that the private key is not locally cracked. In the transport layer, strategies such as double key and one-time pad are adopted to ensure that important information is not intercepted and decoded in network transmission. The identity of a certificate applicant is verified through the interface of an issuing bank, the user identity verification result of the bank counter is inherited, and therefore, remote online certificate issuing is realized in the system. The method not only can ensure that all the links of certificate applying, certificate issuing, certificate storing and certificate using are safe, but also can prevent hackers and Trojans from stealing certificate files, prevent network package-capture parsing, prevent password intercepting through screen capture and prevent an algorithm from being known through software decompiling.
Owner:BANKEYS TECH
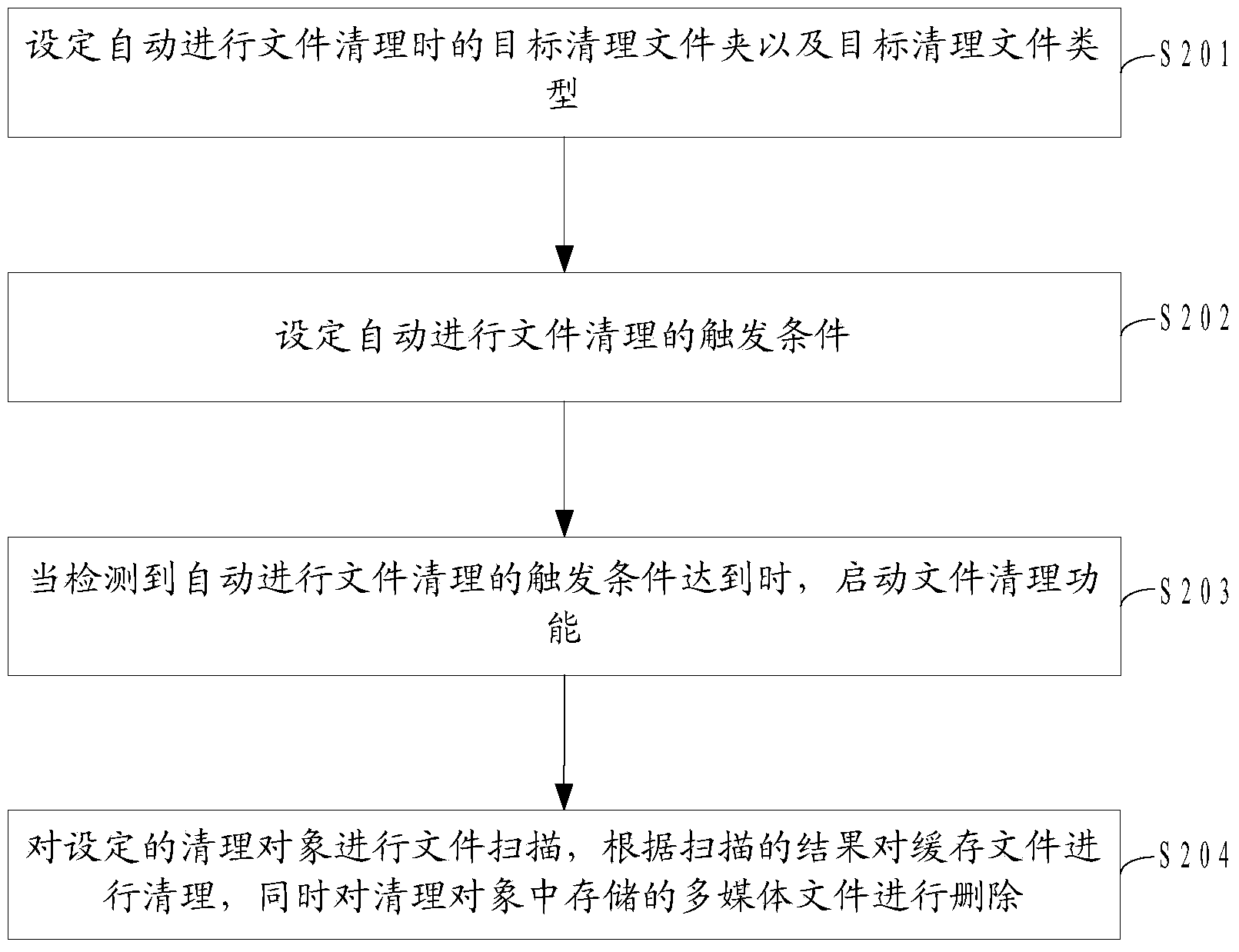
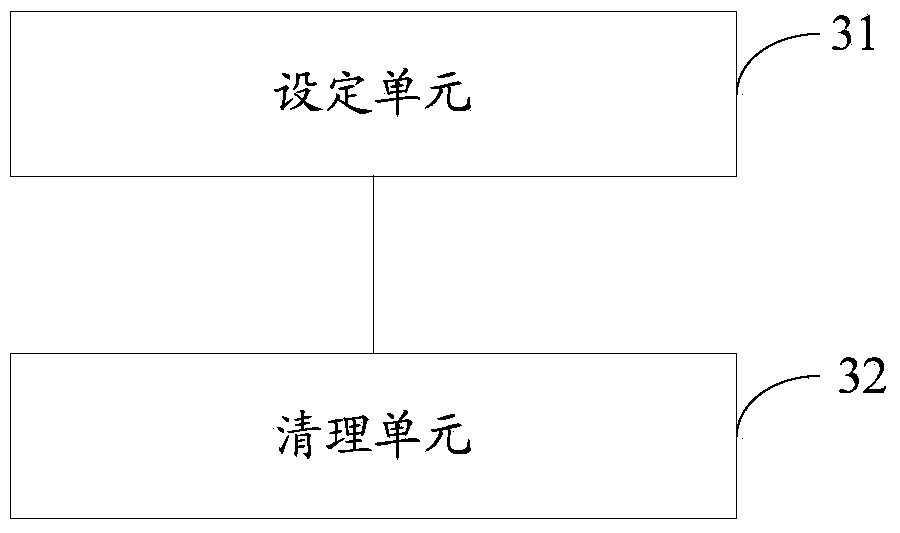
Smart terminal file cleaning method and device
ActiveCN103761306AGuaranteed uptimeAvoid storageSpecial data processing applicationsOperating system
The invention belongs to the field of mobile terminals, and provides a smart terminal file cleaning method and device. The method comprises the following steps of setting a cleaning object when file cleaning is conducted automatically and a triggering condition for automatically conducting file cleaning, starting the file cleaning function when the fact that the triggering condition for automatically conducting file cleaning is met is detected, scanning the set cleaning object, and conducting file cleaning on the cleaning object according to the scanning result. According to the smart terminal file cleaning method and device, a user sets the cleaning object and the triggering condition when file cleaning is automatically conducted, when the set triggering condition is met, a smart terminal cleans the cleaning object set by the user, and cache files and multimedia files in the smart terminal are automatically cleaned.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Data encryption/decryption using neuro and neuro-mechanical fingerprints
ActiveUS20160234174A1Exclude influenceEasy to useKey distribution for secure communicationEncryption apparatus with shift registers/memoriesXML EncryptionMulti dimensional
In accordance with one embodiment, a method for securing data is disclosed. The method includes sensing multi-dimensional motion of a body part of a user to generate a multi-dimensional signal; in response to the multi-dimensional signal and user calibration parameters, generating a neuro-mechanical fingerprint; and encrypting data with an encryption algorithm using the neuro-mechanical fingerprint as a key.
Owner:AERENDIR MOBILE INC
Spatially correlated x-ray and ultrasound mammographic imaging systems and method
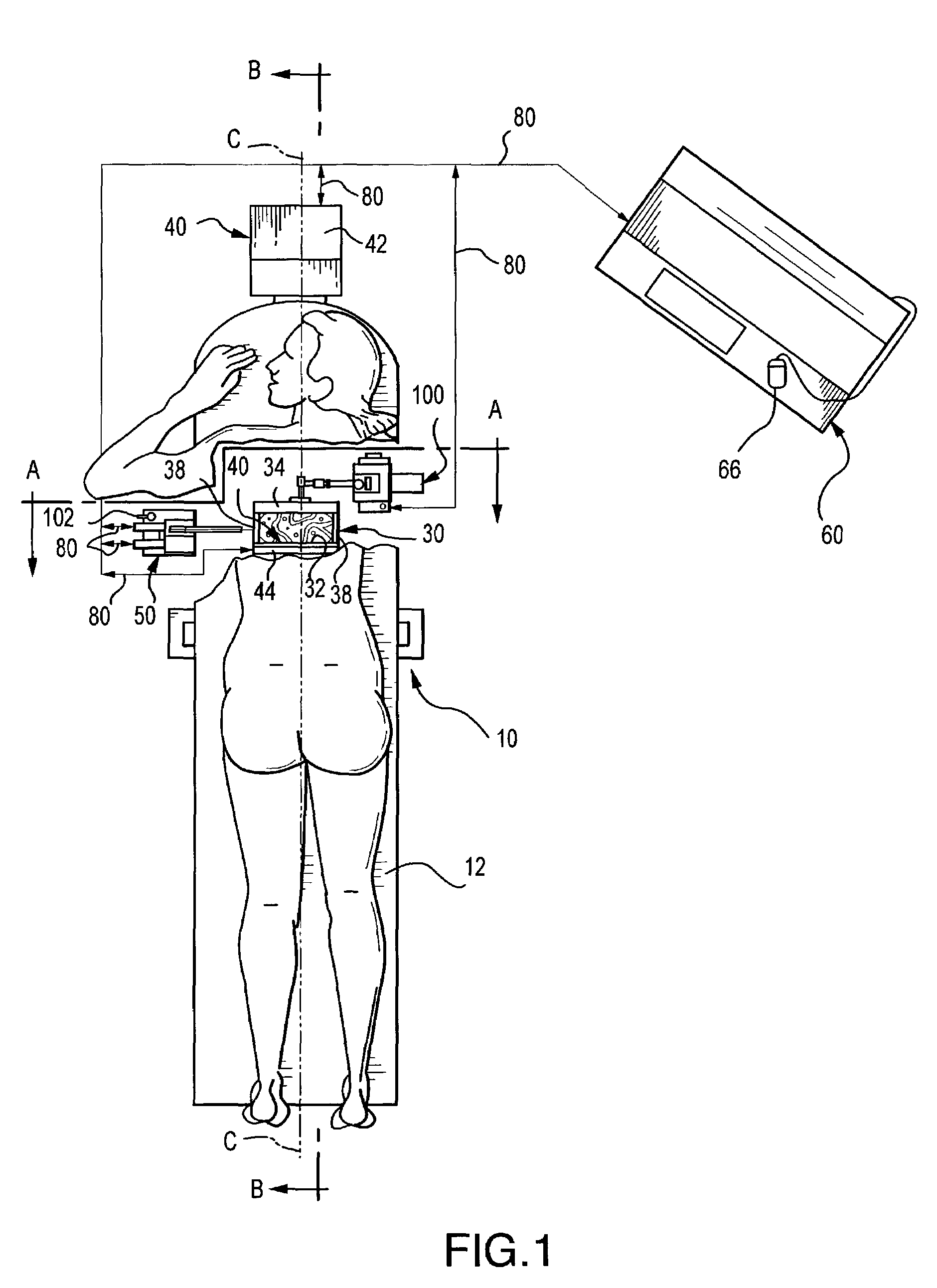
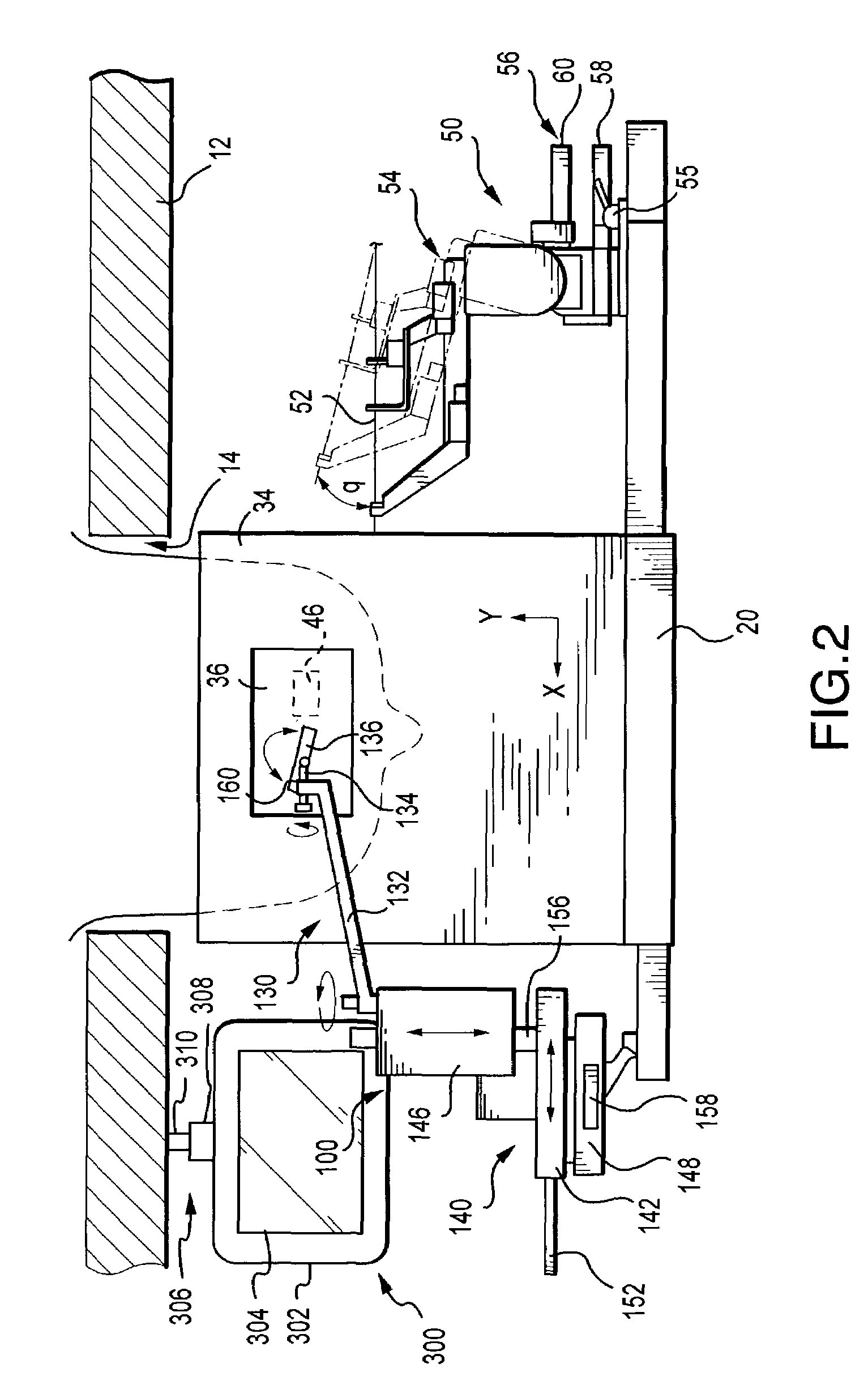
InactiveUS7496398B2Avoids acquisitionAvoid storageOrgan movement/changes detectionSurgical needlesUltrasound imagingSoft x ray
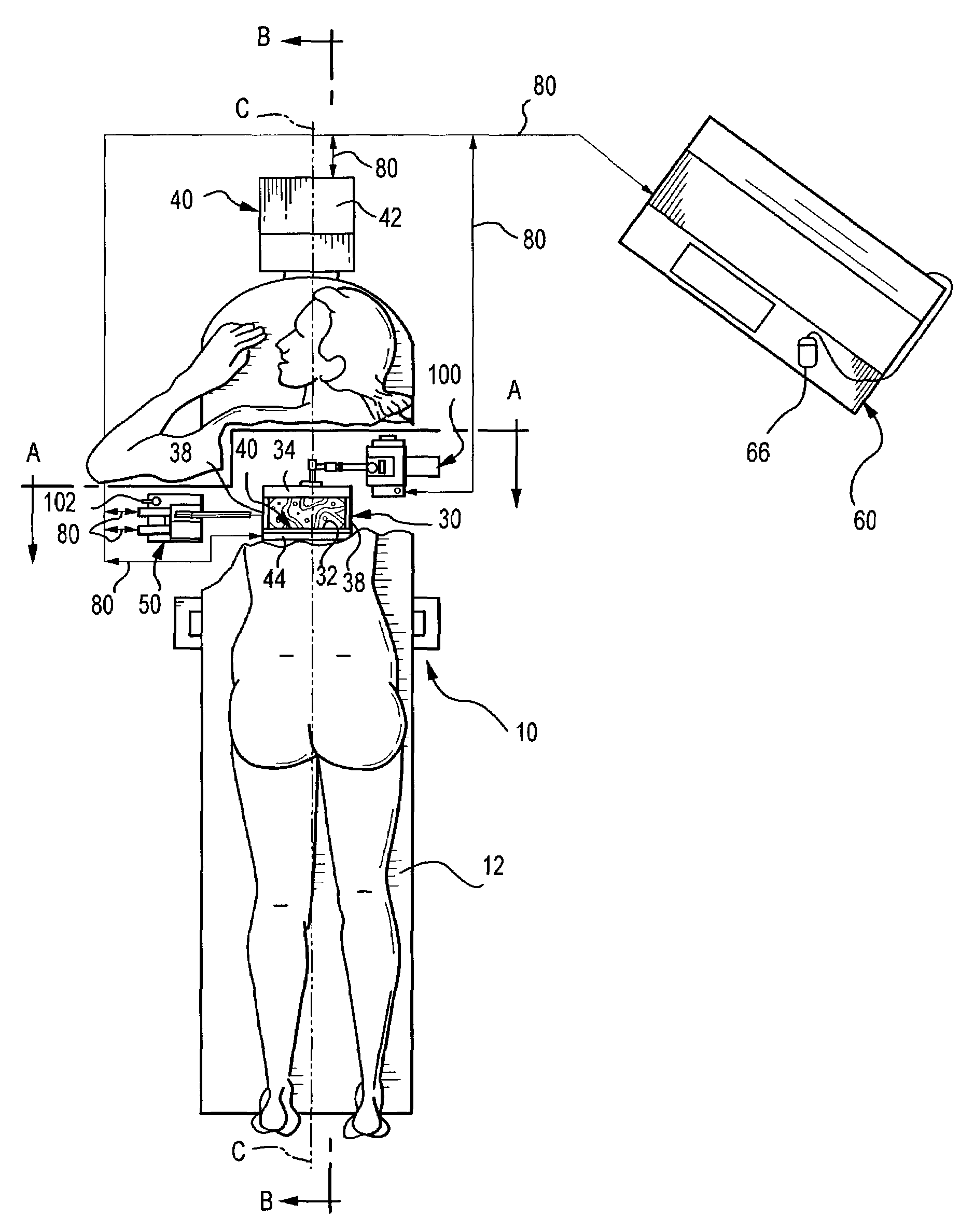
The present invention provides for x-ray imaging and ultrasound imaging of a body region of interest in a spatially correlatable manner. The resultant x-ray and ultrasound images may be combinatively employed to provide three-dimensional information regarding a location of interest within the body, and is particularly apt for use in the analysis / biopsy of potential lesions and suspicious masses in a female breast. The invention provides for direct body contact by an ultrasound imaging head, as well as targeted ultrasound imaging of a selected portion of the region from which x-ray images are obtained. A user interface system facilitates various procedures including ultrasound guided needle biopsy procedures.
Owner:HOLOGIC INC
Weight-loss health-care food and preparation method thereof
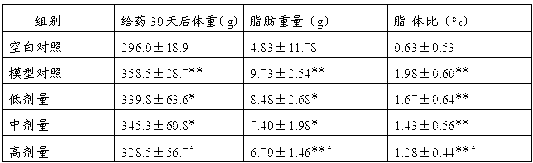
ActiveCN103230021AReduce emptyingHinder or delay digestion and absorptionFood preparationDiet controlledVitamin
The invention discloses a weight-loss health-care food which is prepared from the main raw materials of, by weight, 1-60% of a white kidney bean extract, 1-50% of L-malic acid, 1-65% of L-carnitine tartrate, and 1-40% of konjac powder. The invention also discloses a preparation method of the weight-loss health-care food. The method comprises the step that: the main materials of the white kidney bean extract, L-malic acid, L-carnitine tartrate, and konjac powder are well mixed, such that the health-care food with weight-loss function is obtained. With the health-care food, starchy substance absorption is inhibited, body metabolism is promoted, and energy conversion is promoted, such that fat consumption is increased, fat formation is prevented, and a weight-loss function is achieved. With the preparation method, absorption of nutrients such as proteins and vitamins is not influenced, diet control is not needed, and weight can be naturally controlled and reduced. The preparation method provided by the invention has the advantages of simple process, no high-temperature operation, convenient operation, and energy saving.
Owner:GUANGZHOU SAIJIAN BIO TECH
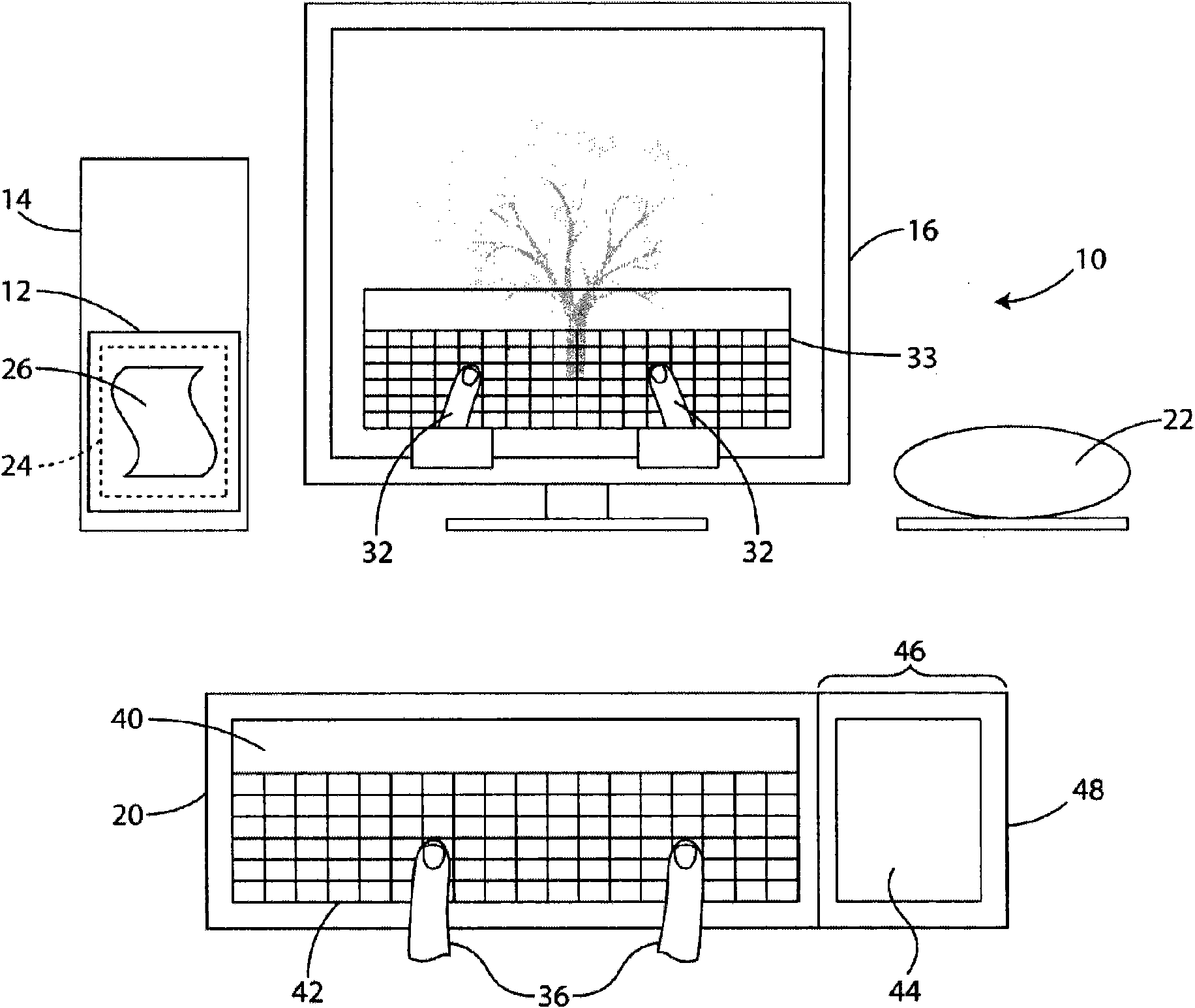
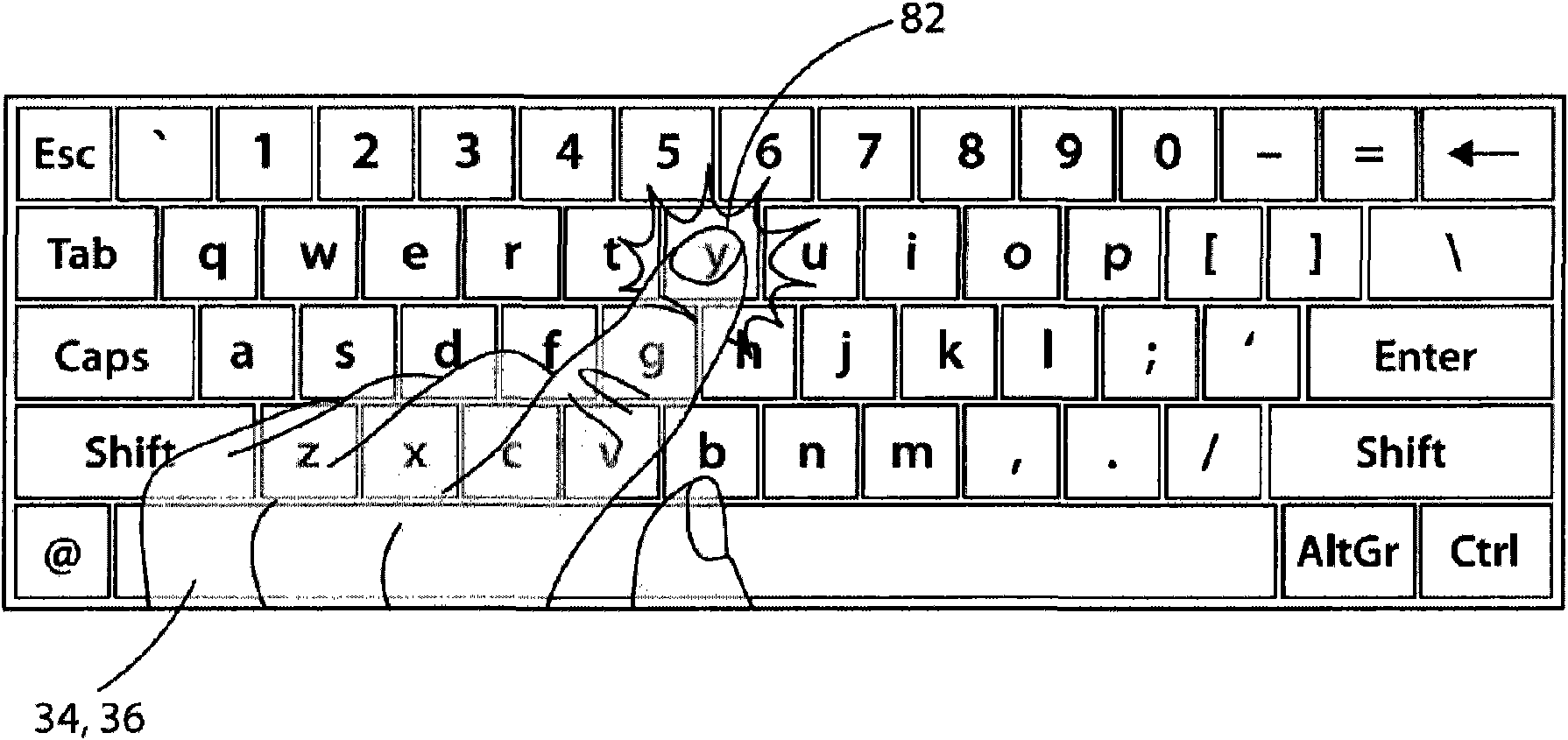
System and method for remote, virtual on screen input
ActiveCN101963840AAvoid typographyAvoid makingInput/output for user-computer interactionGraph readingData connectionProximity sensor
A system, apparatus, and method of remote, virtual on screen data input includes a peripheral data input device (PDID) made up of a proximity sensor and data communications means. The proximity sensor is adapted to dynamically recognize the movement of a target in the proximity of the peripheral device. The data connection device is adapted to transmit signals from the proximity sensor to a processor communicatively coupled to the remote display. The processor constructs a representation of input fields on the display, and, when detected, overlays a real-time, virtual representation of the target over the representation of the input fields.
Owner:LOGITECH EURO SA
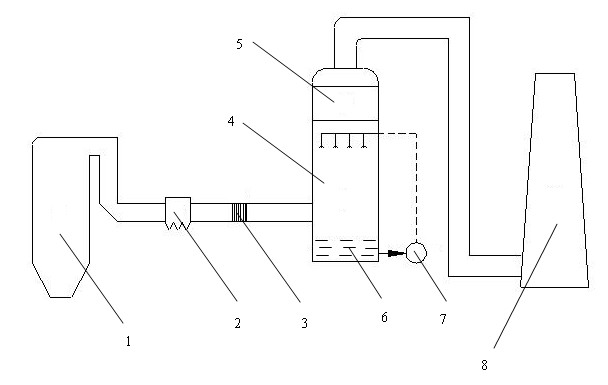
Method and system for simultaneously removing sulfur, niter and mercury from smoke based on catalytic oxidation
ActiveCN102527205AAvoid preparationImprove safety and economyDispersed particle separationEnvironmental chemistryDust control
The invention discloses a method for simultaneously removing sulfur, niter and mercury from smoke based on catalytic oxidation. The method is characterized by comprising the following steps of: (1) arranging a catalytic reactor in a dust-removed smoke duct, wherein a catalyst for promoting oxidizing reaction of NO and HgO is filled in the catalytic reactor; (2) allowing the dust-removed smoke to pass through the catalytic reactor, wherein under catalysis of the catalyst, the reaction speed of the NO, the HgO and O2 is increased and the NO and the HgO are oxidized into NO2 and Hg<2+>; and (3) introducing the smoke subjected to catalytic oxidation into an absorber with an absorption solution, wherein the absorption solution is used for absorbing NO2, Hg<2+> and SO2 from the smoke. The invention also discloses a system applicable to the method. According to the method and the system, the sulfur, the niter and the mercury are removed from the smoke; external oxidant is not required to be added; preparation, transportation and storage of strong oxidant are avoided; operating cost is reduced; and economy and safety of the system are improved.
Owner:GUANGDONG ELECTRIC POWER SCI RES INST ENERGY TECH CO LTD
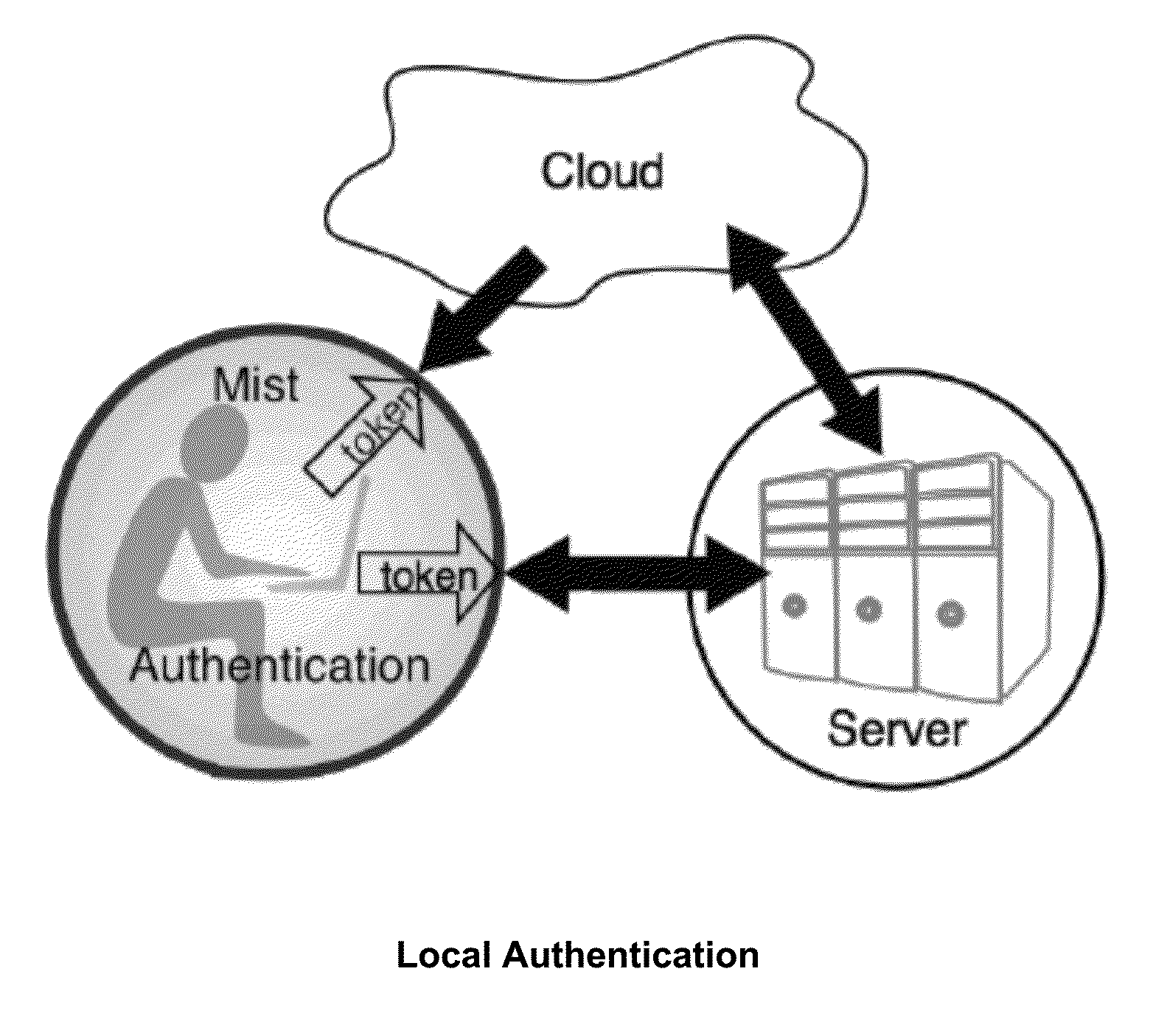
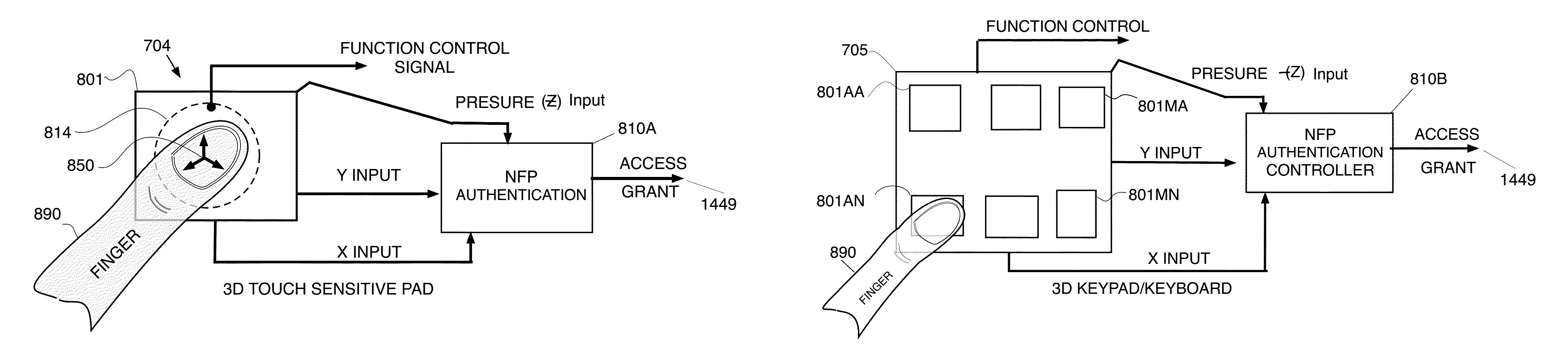
Local user authentication with neuro and neuro-mechanical fingerprints
ActiveUS20160241554A1Easy to useLow powerAcquiring/recognising eyesDigital data authenticationUser authenticationBody region
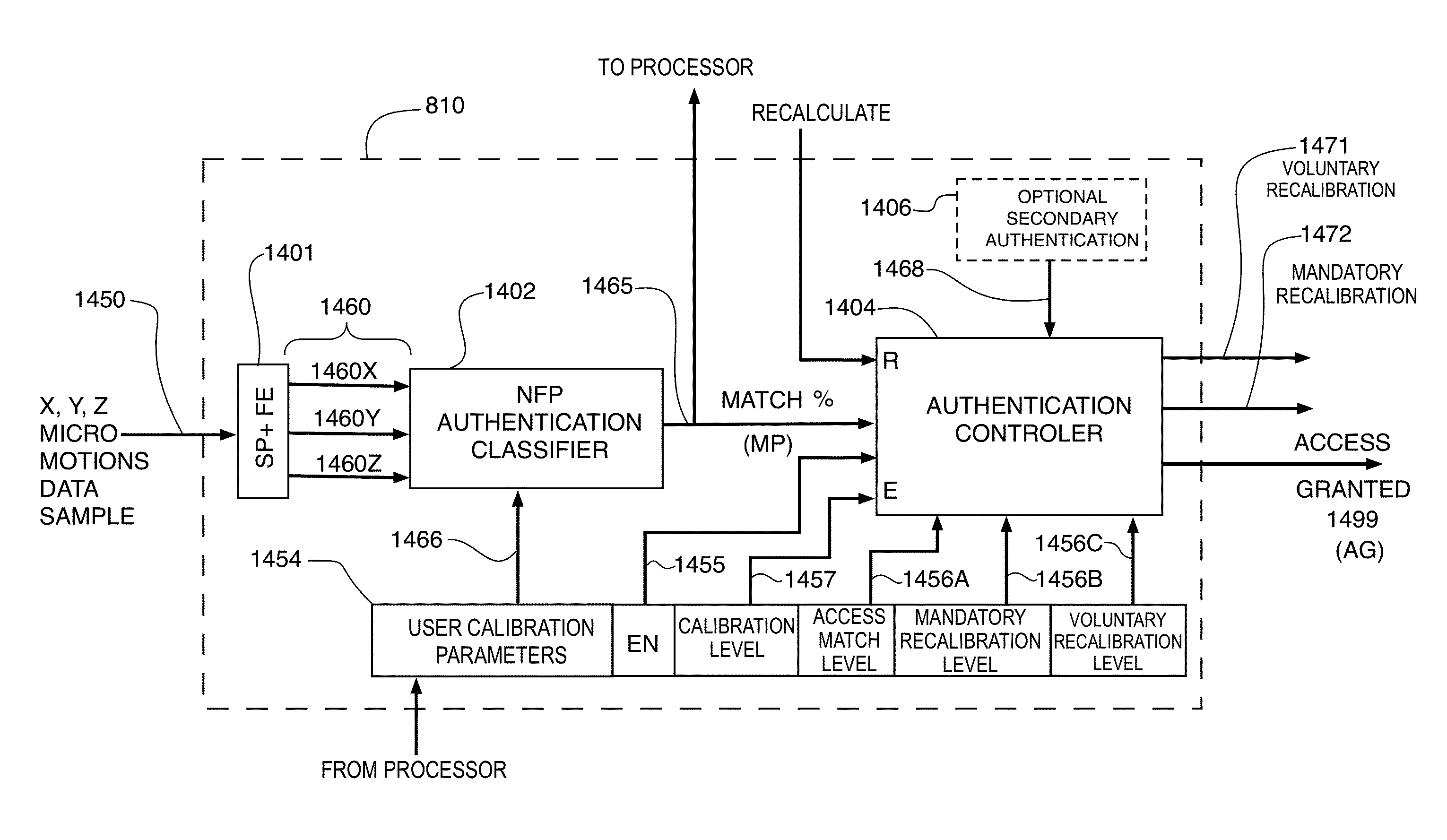
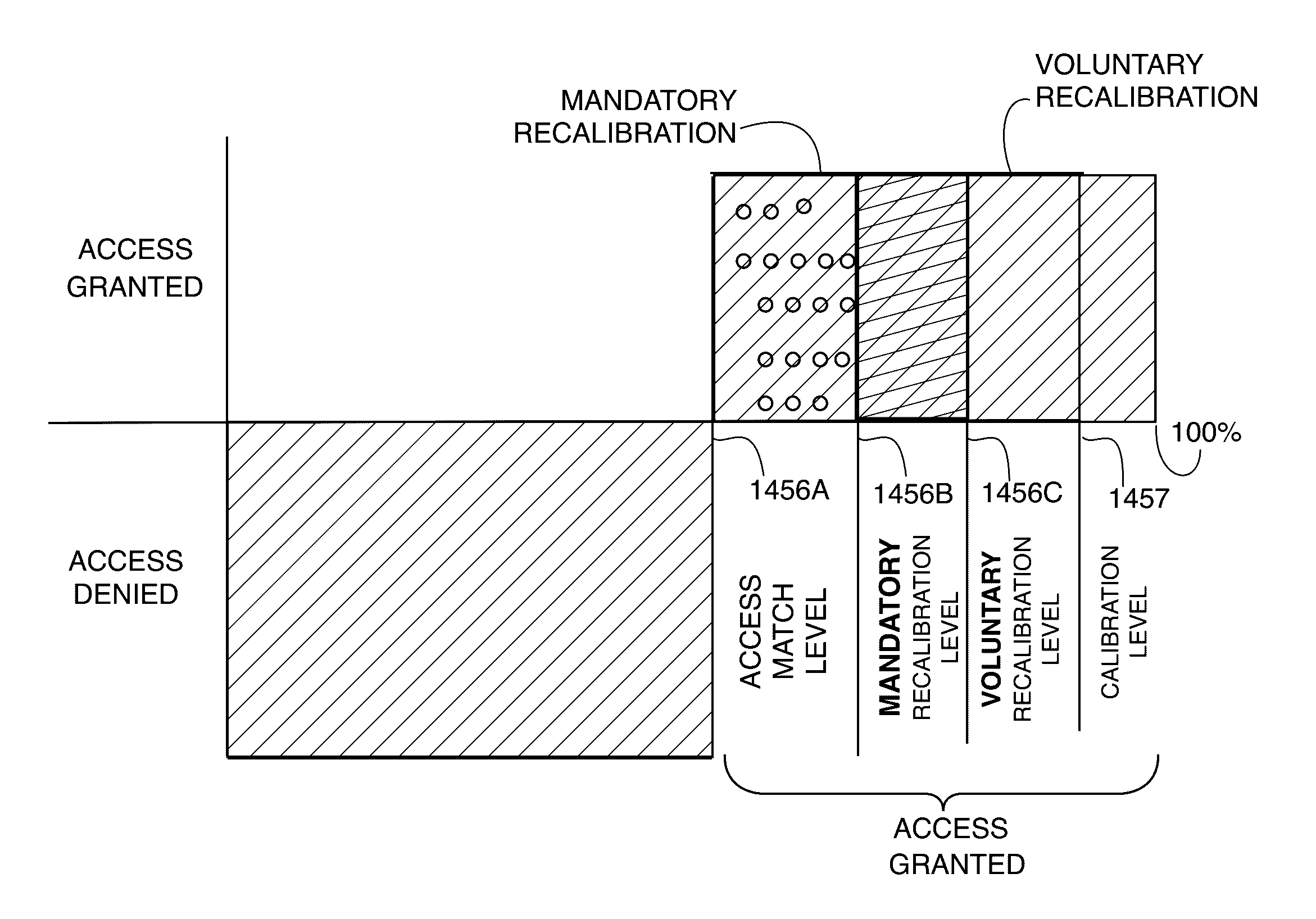
In accordance with one embodiment, a method for locally verifying the identification of a user with an electronic device is disclosed. The method includes regenerating a neuro-mechanical fingerprint (NFP) in response to a micro-motion signal sensed at a body part. In response to a plurality of authorized user calibration parameters, a match percentage of the neuro-mechanical fingerprint is determined. The match percentage is determined without the use of a calibration NFP that was previously used to generate the user calibration parameters. Access to the electronic device and its software applications is then controlled by the match percentage. If the match percentage is greater than or equal to an access match level, access to the electronic device is granted. If the match percentage is less than the access match level, access is denied. Subsequent access requires further regeneration of the NFP and a determination of its match percentage in response.
Owner:PROPRIUS TECH S A R L
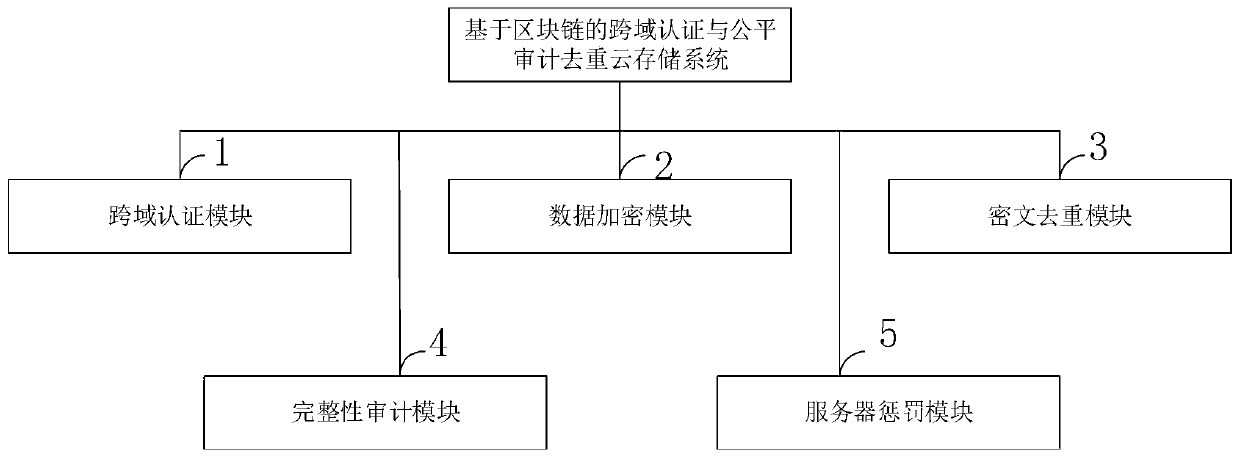
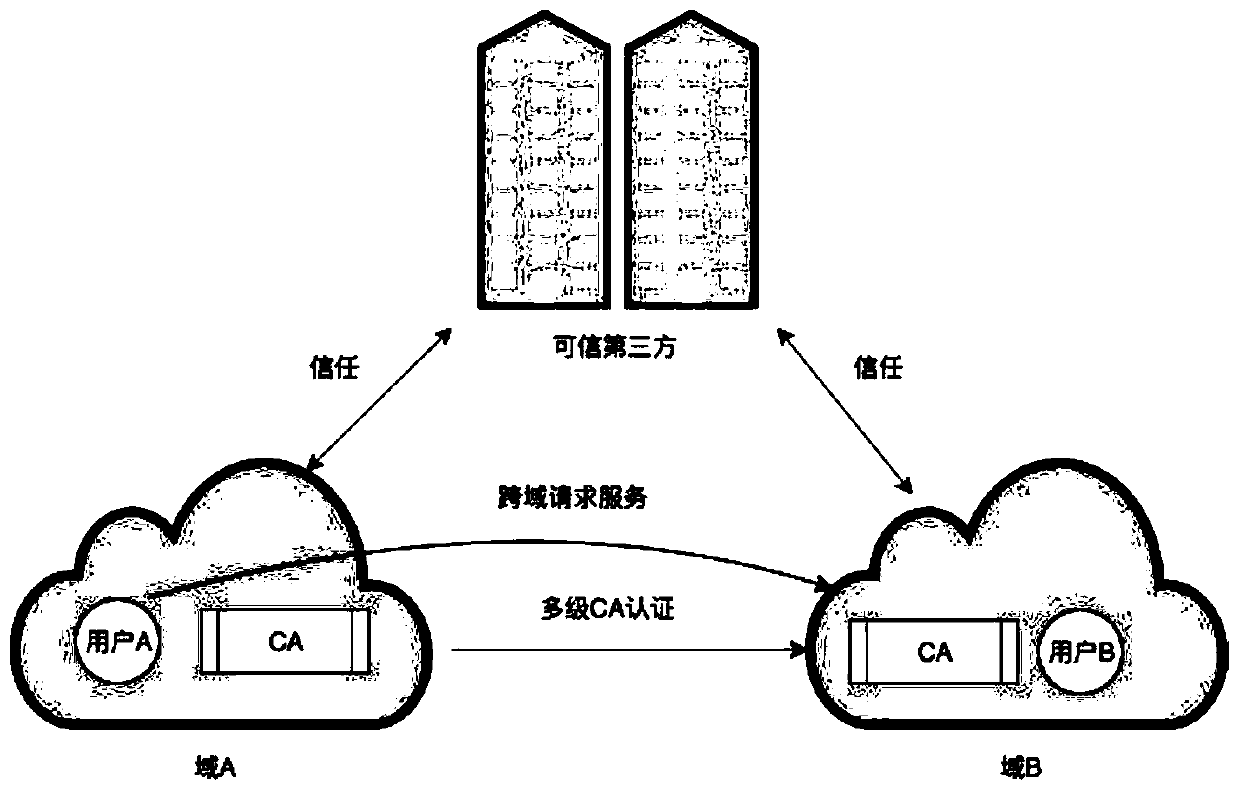
A cross-domain authentication and fair audit deduplication cloud storage system based on a block chain
ActiveCN109829326AResolve dependenciesProtect interestsDigital data information retrievalDigital data protectionCiphertextAuthentication server
The invention belongs to the technical field of cloud computing, and discloses a cross-domain authentication and fair audit duplicate removal cloud storage system based on a block chain. The system comprises a cross-domain authentication module, a data encryption module, a ciphertext duplicate removal module, an integrity audit module and a server punishment module. In the authentication module, acloud user generates a certificate at a client in a self-signed mode, the certificate is stored in a block chain network after being verified by an authentication server, the user is verified to compare information such as the certificate and a block, and whether the certificate is valid or not is verified. According to the method, the problem of hierarchical query verification of a traditional PKI structure is avoided, the authentication frequency is greatly reduced, and the verification cost is reduced; By using an intelligent contract, a malicious server is punished to receive certain penalties and compensate users with impaired benefits under the condition that user data is damaged; And in the duplicate removal module, a data duplicate removal function is realized by using a convergence encryption technology, so that the cloud server is prevented from storing too much duplicate data, and the user and the cloud server are prevented from consuming a large amount of calculation expenditure and storage expenditure.
Owner:XIDIAN UNIV
Keyless access control with neuro and neuro-mechanical fingerprints
ActiveUS20160232726A1Easy to useLow powerVoting apparatusDigital data authenticationControl systemMulti dimensional
In accordance with one embodiment, an access control system is disclosed. The access control system comprises an access control panel including a touchable surface, a multi-dimensional touch sensor under the touchable surface, and a processor coupled to the multi-dimensional touch sensor. The multi-dimensional touch sensor captures a multi-dimensional motion signal including a micro-motion signal component representing neuro-mechanical micro-motions of a user touching the multi-dimensional touch sensor. The processor performs signal processing of the multi-dimensional motion signal to obtain the micro-motion signal component; and extracts unique values of predetermined features from the micro-motion signal component to form a neuro-fingerprint (NFP) that uniquely identifies the user. The NFP can be used as a gatekeeper to control entry into homes, offices, buildings, or other real properly typically protected by access control.
Owner:AERENDIR MOBILE INC
Identity authentication method, device and system
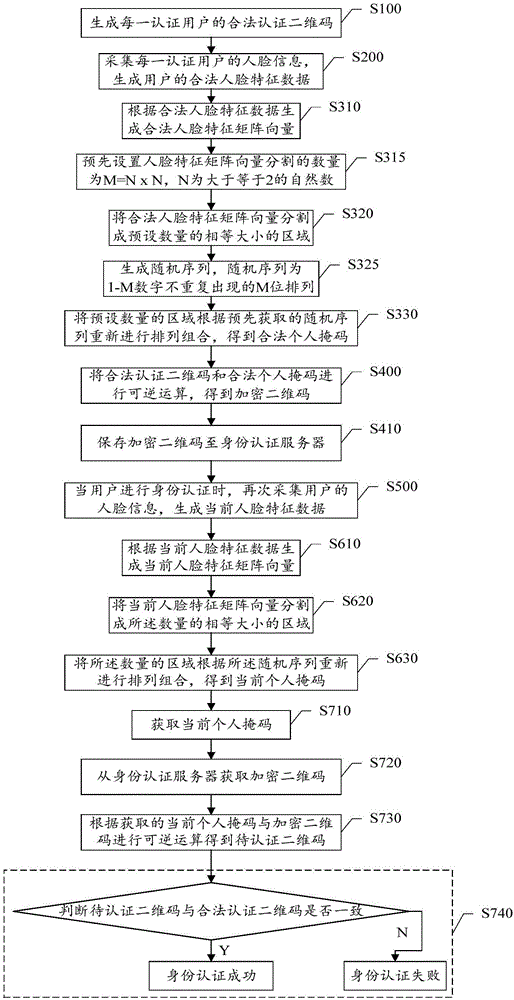
ActiveCN106330464AUniqueness guaranteedEnsure safetyKey distribution for secure communicationUser identity/authority verificationGraphicsFeature data
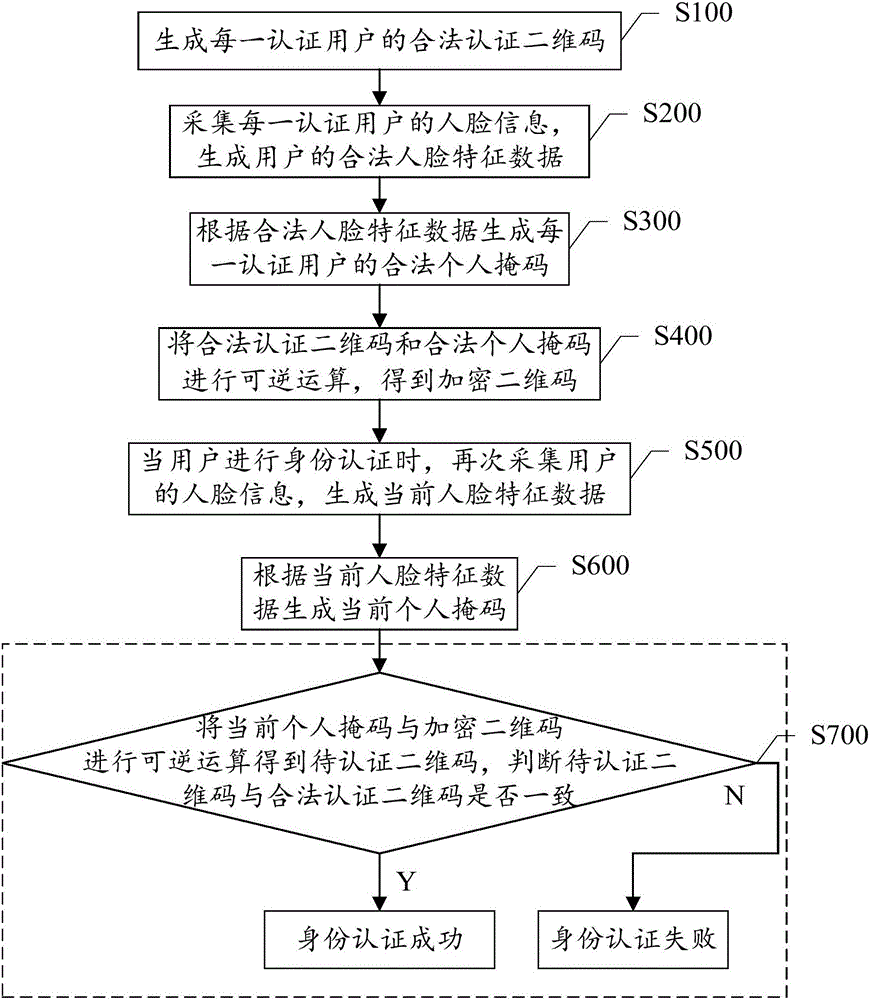
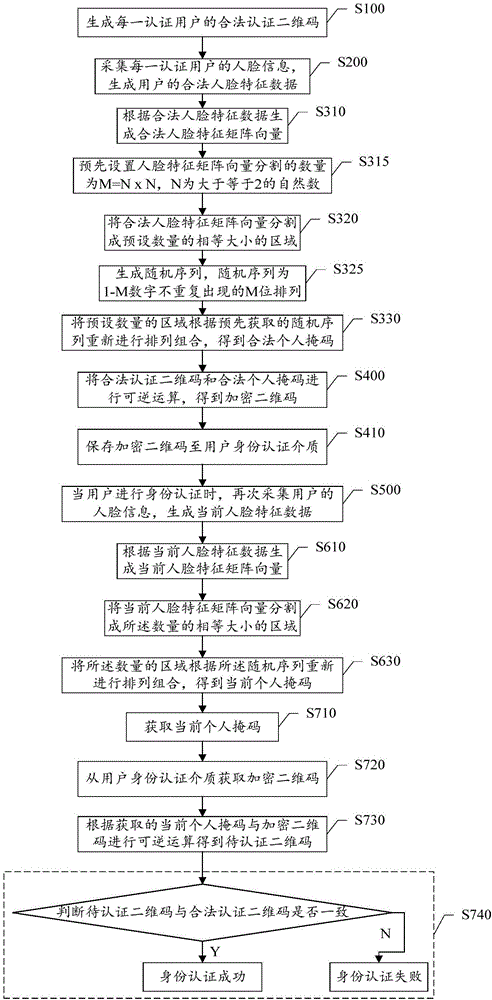
The invention discloses an identity authentication method, device and system. The method includes the steps that legal authentication two-dimensional codes of authentication users are generated, face information of the authentication users is collected to generate legal face feature data of the users, legal personal mask codes of the authentication users are generated according to the legal face feature data, and the legal authentication two-dimensional codes and the legal personal mask codes are subjected to reversible operation to obtain encrypted two-dimensional codes; when the users are subjected to identity authentication, face information of the users is collected again to generate current face feature data, current personal mask codes are generated according to the current face feature data, the current personal mask codes and the encrypted two-dimensional codes are subjected to reversible operation to obtain two-dimensional codes to be authenticated, and whether the two-dimensional codes to be authenticated are consistent with the legal authentication two-dimensional codes is judged. The problem of user information leakage caused by storage of face recognition images is avoided, and the intensity and safety of identity authentication are improved.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Distributed cache method and system
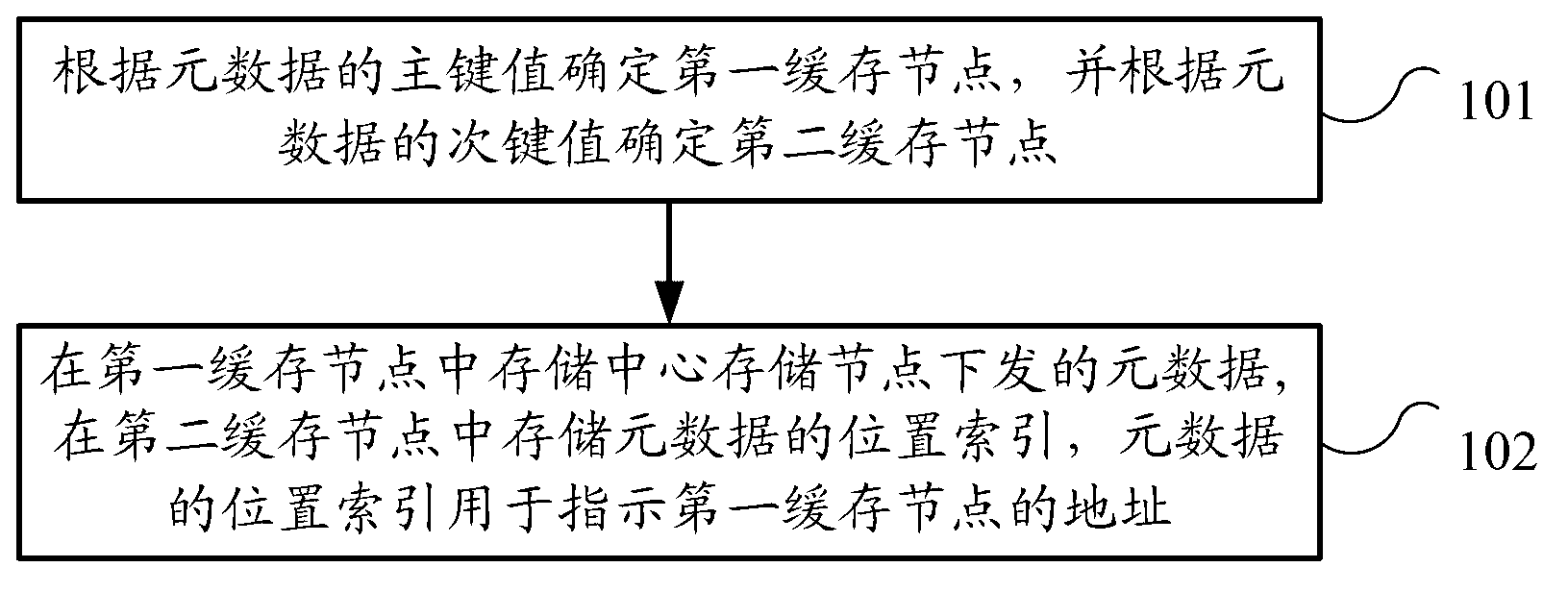
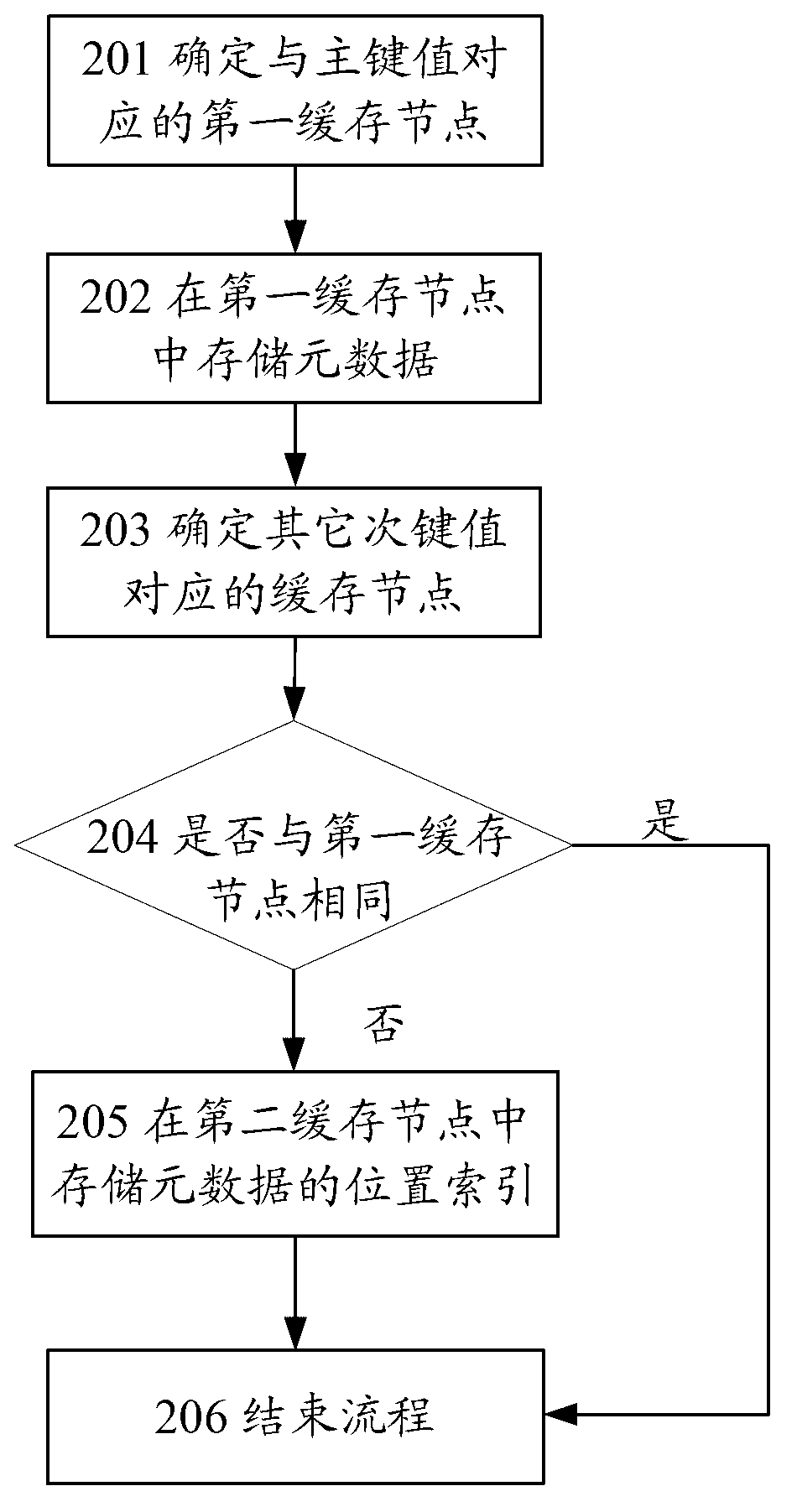
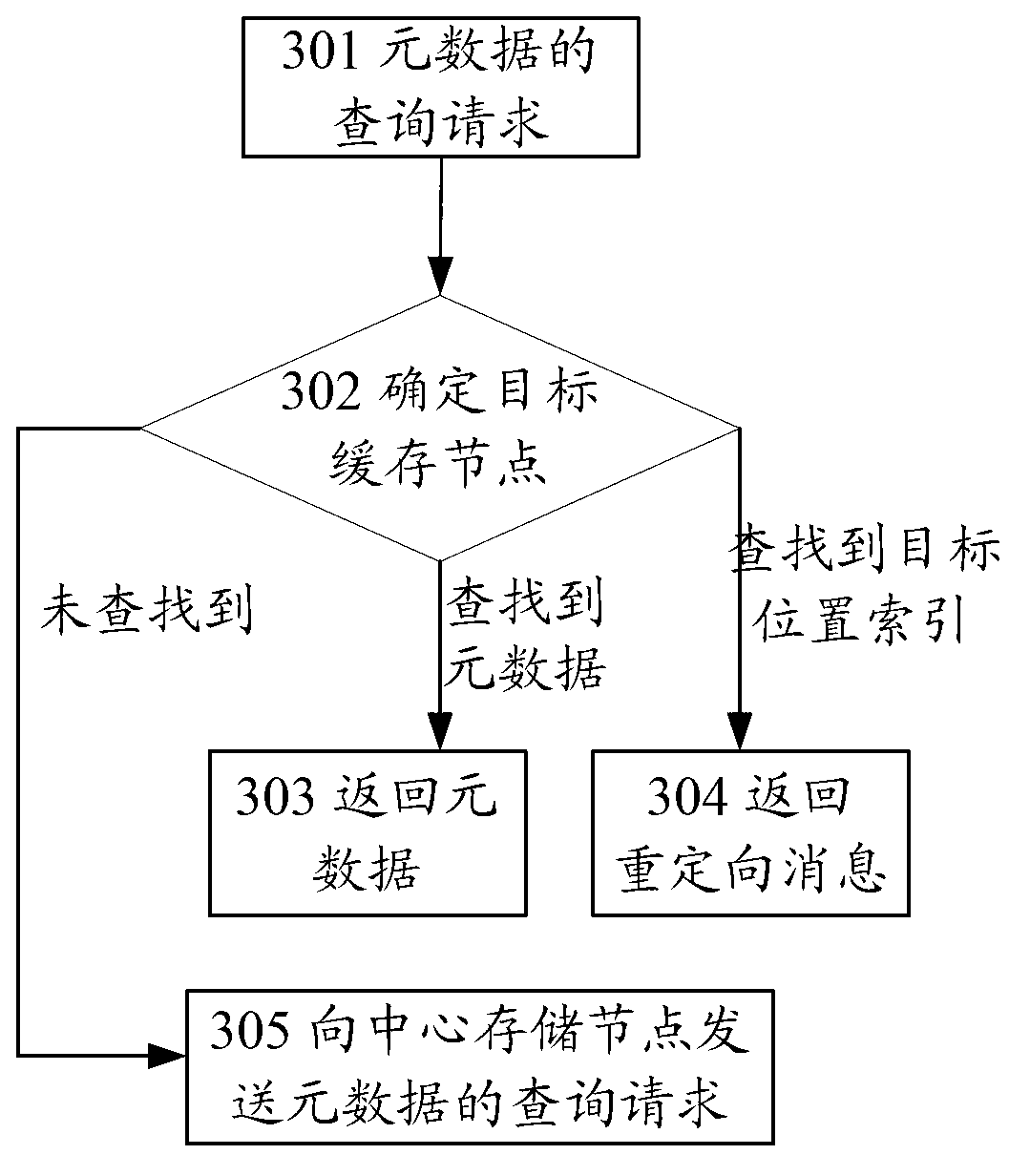
ActiveCN103019960AAvoid redundant storageSave storage spaceInput/output to record carriersMemory adressing/allocation/relocationMetadataPrimary Key
The embodiment of the invention provides a distributed cache method and system. The method comprises the following step: determining a first cache node according to a primary key value of metadata, and determining a second cache node according to a secondary key value of the metadatathe; and storing metadata issued by center storage node in the first cache node and storing index position of the metadata in the second cache node, wherein the index position of the metadata is used for indicating addresses of the first cache node. According to the invention, the access of the metadata can be achieved by the index position of the metadata, so that the same metadate stored in a plurality of cache nodes is avoided, thereby avoiding redundant storage of the metadata, saving storage space and ensuring the data access consistency.
Owner:浙江杭海新城控股集团有限公司
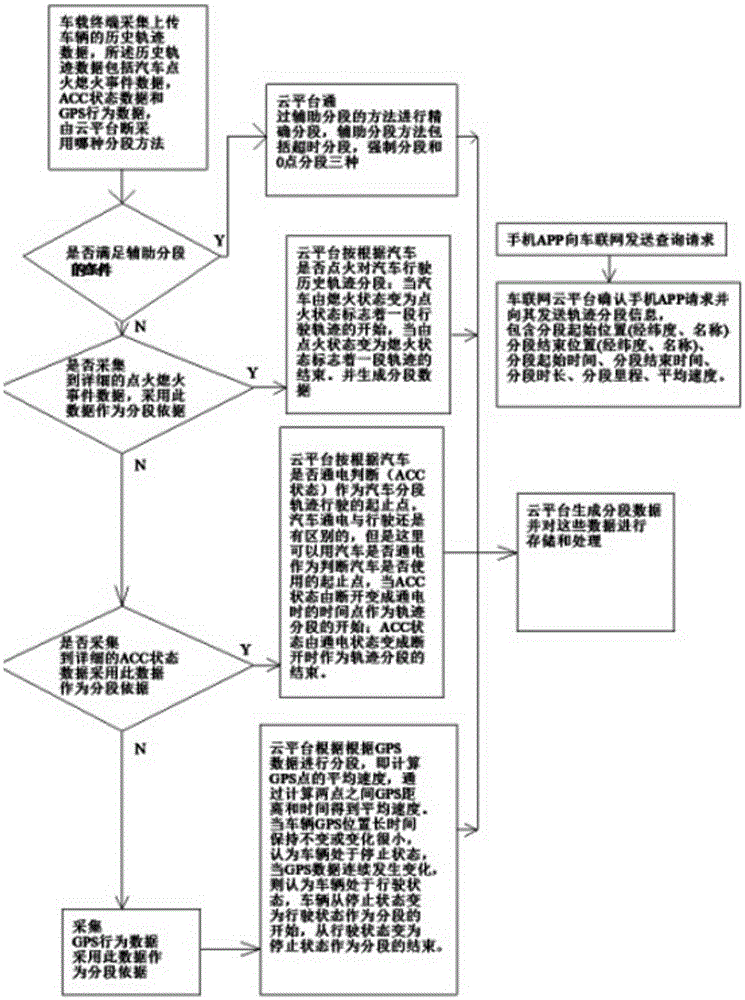
Automobile driving recorder locus segmentation method
ActiveCN105354896AAvoid storageAccurate and reasonable timeRegistering/indicating working of vehiclesSpecial data processing applicationsCar drivingComputer terminal
The invention relates to an automobile driving recorder locus segmentation method and belongs to the field of automobile driving historical locus recording in a vehicle network system. The method utilizes an improved terminal-tube-cloud three layer structure and realizes automobile driving historical locus segmentation according to a vehicle ignition loss event, an ACC state and GPS behavior characteristics. Different vehicle terminals dynamically select segmentation methods according to a vehicle state. Through combination with three auxiliary segmentation methods such as timeout segmentation, forced segmentation and zero segmentation, the segment data is uploaded to a database of a car networking cloud platform in real time and a user can inquire detailed segment information.
Owner:JIANGSU DIGITAL DNA TECH CO LTD
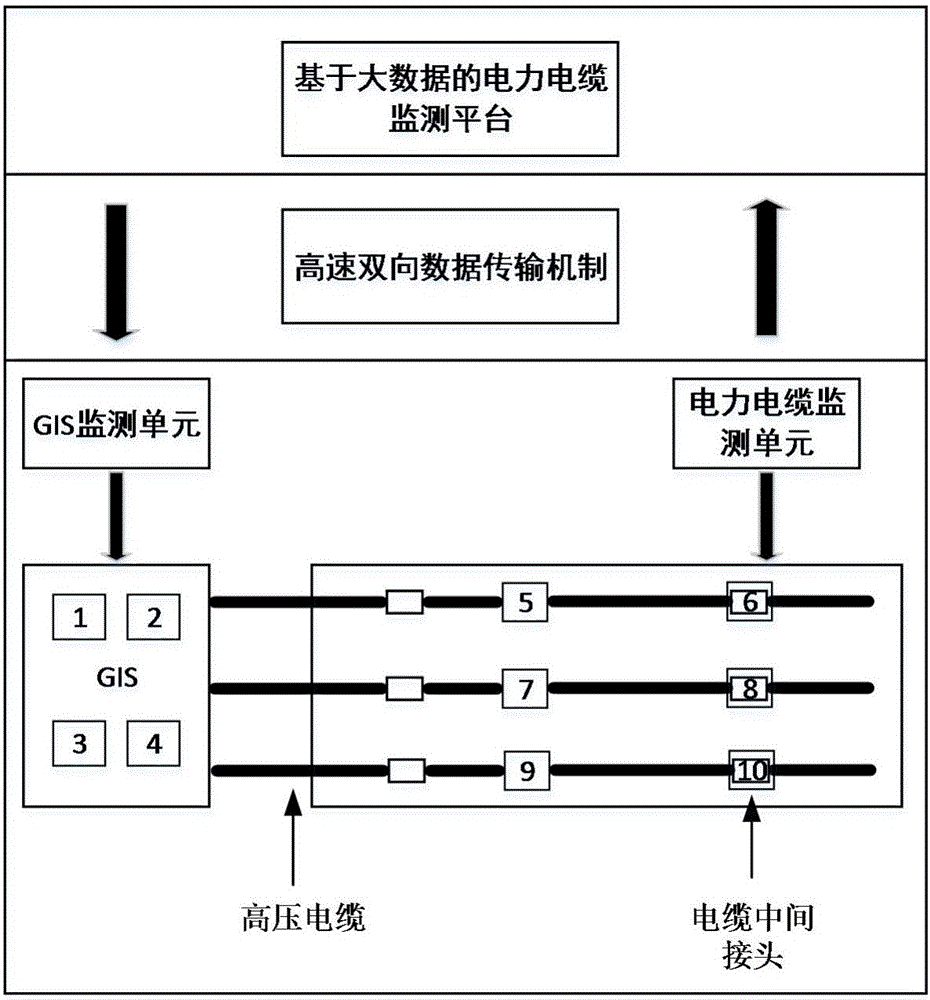
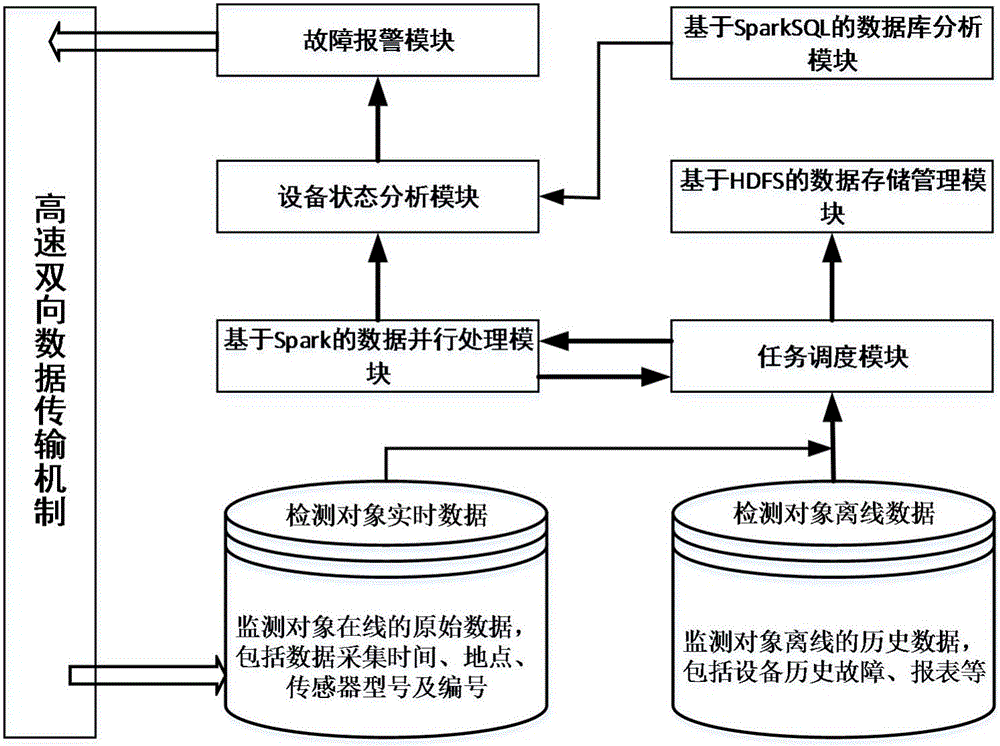
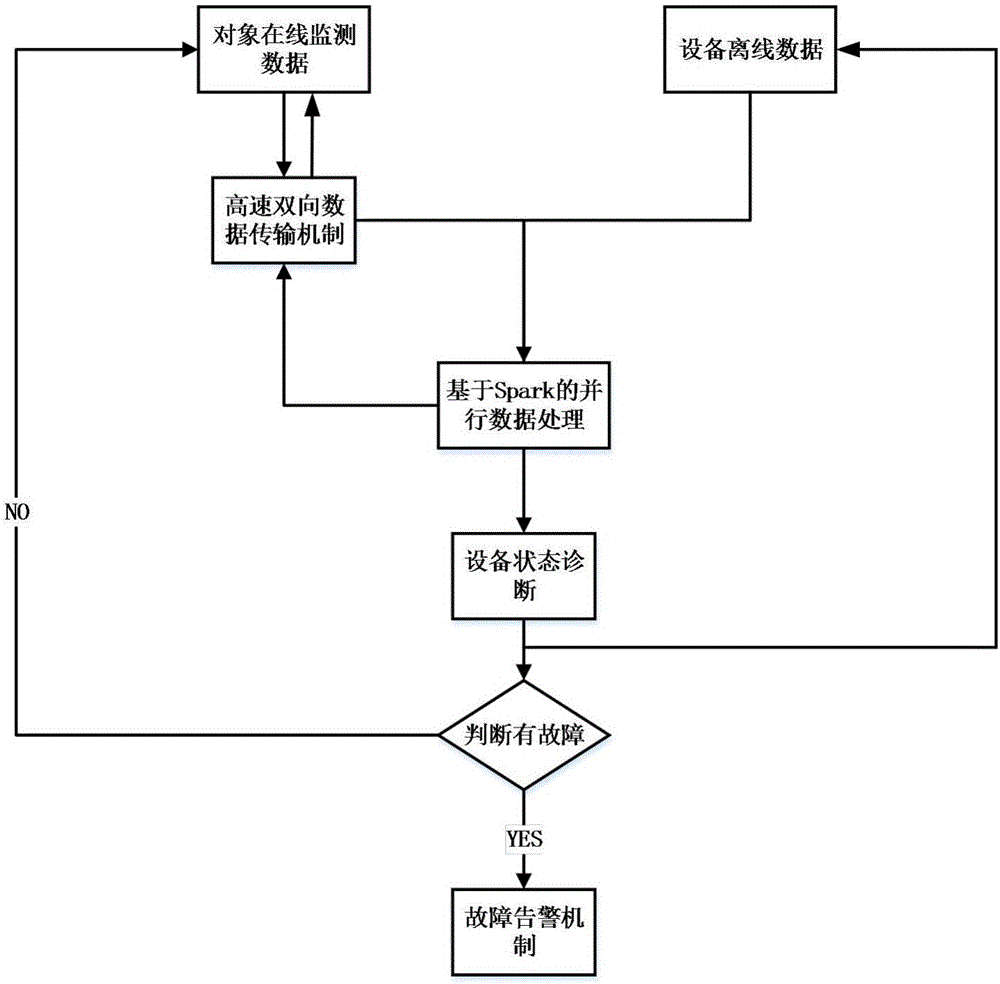
Big data-based power cable monitoring system and monitoring method
InactiveCN106324428AAvoid storageHighly redundant and scalableFault location by conductor typesPower cableTreatment results
The present invention discloses a big data-based power cable monitoring system and monitoring method. The system comprises a sensor module, a task scheduling module, a storage module, a cable comprehensive diagnosis module and a monitoring module. The sensor module is used for acquiring the data of a monitored object. The task scheduling module is used for starting the task scheduling operation according to an operation request submitted by a user. The storage module is used for storing real-time monitoring data and off-line historical data. The cable comprehensive diagnosis module is used for analyzing and processing data and sending out a fault alarm. The monitoring module is used for displaying and monitoring the treatment result of the cable comprehensive diagnosis module. According to the technical scheme of the invention, based on the HDFS, massive text data are stored and managed. Based on the k-means clustering algorithm in combination with a Spark computing engine, the collected massive data are subjected to the clustering treatment and analysis. Therefore, the fault point of a power cable can be quickly positioned.
Owner:SOUTHEAST UNIV
Key managing project for virtual organization under gridding computer environment
InactiveCN1801696AEasy to implement authenticationResistance to security risksKey distribution for secure communicationComputer scienceVirtual organization
The key management scheme for virtual organization in grid computation environment comprises: generating and updating the key; communicating and identifying based on threshold scheme. Based on schemes of centralization and distribution, it provides a new layer-cluster key management frame to solve the security problem and improve execution efficiency.
Owner:NANJING UNIV OF POSTS & TELECOMM
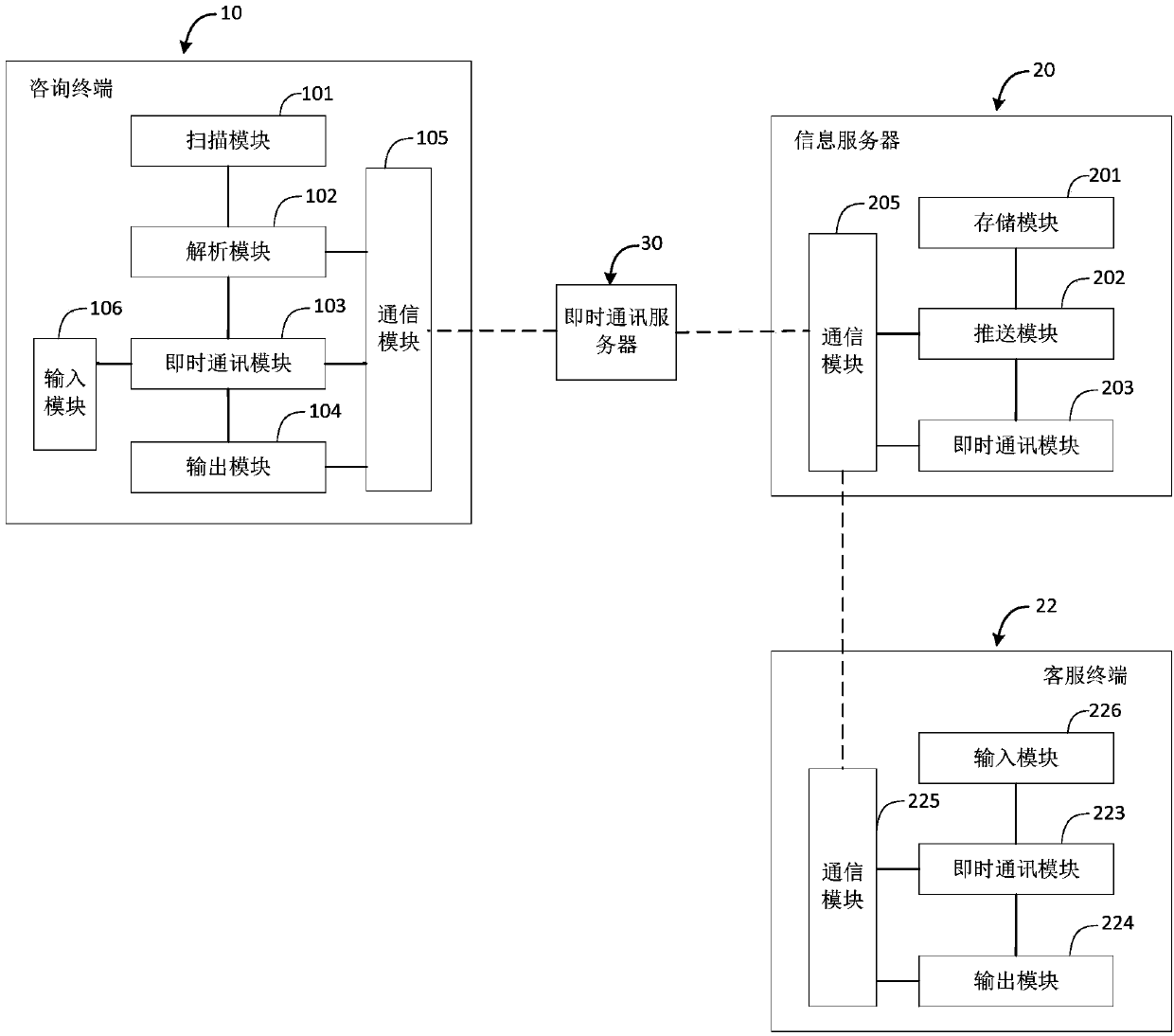
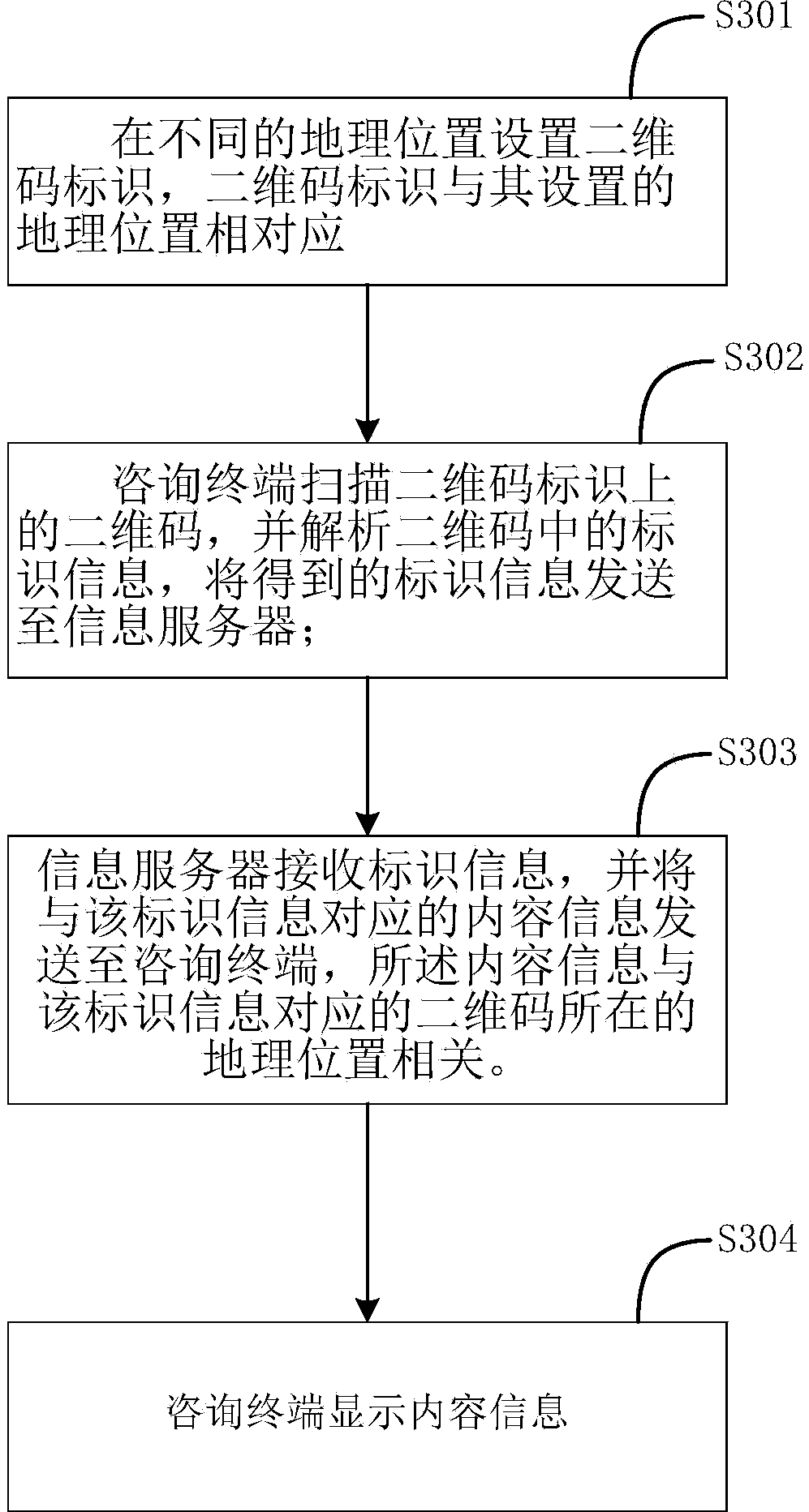
Information pushing method and system and platform
ActiveCN104184655AAvoid storageAvoid cumbersomeData processing applicationsData switching networksData informationGeolocation
The invention provides an information pushing technical scheme so as to solve the information pushing accuracy problem under the condition that enough historical data of a user to information preference lack. The information pushing method includes the following steps that two-dimensional code identifications are set at different geographic positions, and the two-dimensional code identifications correspond to the geographic positions where the identifications are set; a consulting terminal scans two-dimensional codes on the two-dimensional code identifications, identification information in the two-dimensional codes is analyzed, and the acquired identification information is sent to an information server; the information server receives the identification information, content information corresponding to the identification information is sent to the consulting terminal, and the content information is related to the geographic positions where the two-dimensional codes corresponding to the identification information are placed. According to the technical scheme, the tedious locating process of the geographic positions is avoided, storage processing of a large amount of geographic data information is also avoided, and configuration is flexible and convenient.
Owner:FUJIAN JIANKANGZHILU INFORMATION TECH CO LTD
VOC (volatile organic compound) waste gas treatment system
ActiveCN104028086AEasy to handleImprove efficiencyCombination devicesUsing liquid separation agentActivated carbonEnvironmental engineering
The invention discloses a VOC (volatile organic compound) waste gas treatment system. The VOC waste gas treatment system sequentially comprises a fan, a padding spray tower device, an ultraviolet activated carbon integrated device and a purified gas discharge opening, wherein the fan is connected with a VOC waste gas source; the padding spray tower device is connected with an air outlet of the fan; the ultraviolet activated carbon integrated device is connected to an air outlet of the padding spray tower device; the purified gas discharge opening is connected to the ultraviolet activated carbon integrated device. Waste gas is treated efficiently by the design of combining the padding spray tower with the ultraviolet activated carbon integrated purifier. Firstly, the padding spray tower is used for spraying washing; organic waste gas is dissolved into a purifying liquid well by multi-surface hollow spheres; then air water of a defogging layer is matched to share efficiently, so that gas after primary treatment is obtained by the padding spray tower. The gas after primary treatment is treated by the ultraviolet activated carbon integrated purifier, and clean gas reaching the standard is discharged out. The size of the device is reduced; the waste gas treatment efficiency is high; the purification cost is reduced; the purification standard reaching effect is ensured.
Owner:DONGGUAN CITY HUANSHUN ENVIRONMENTAL PROTECTION EQUIP IND
Control apparatus and method of flash memory
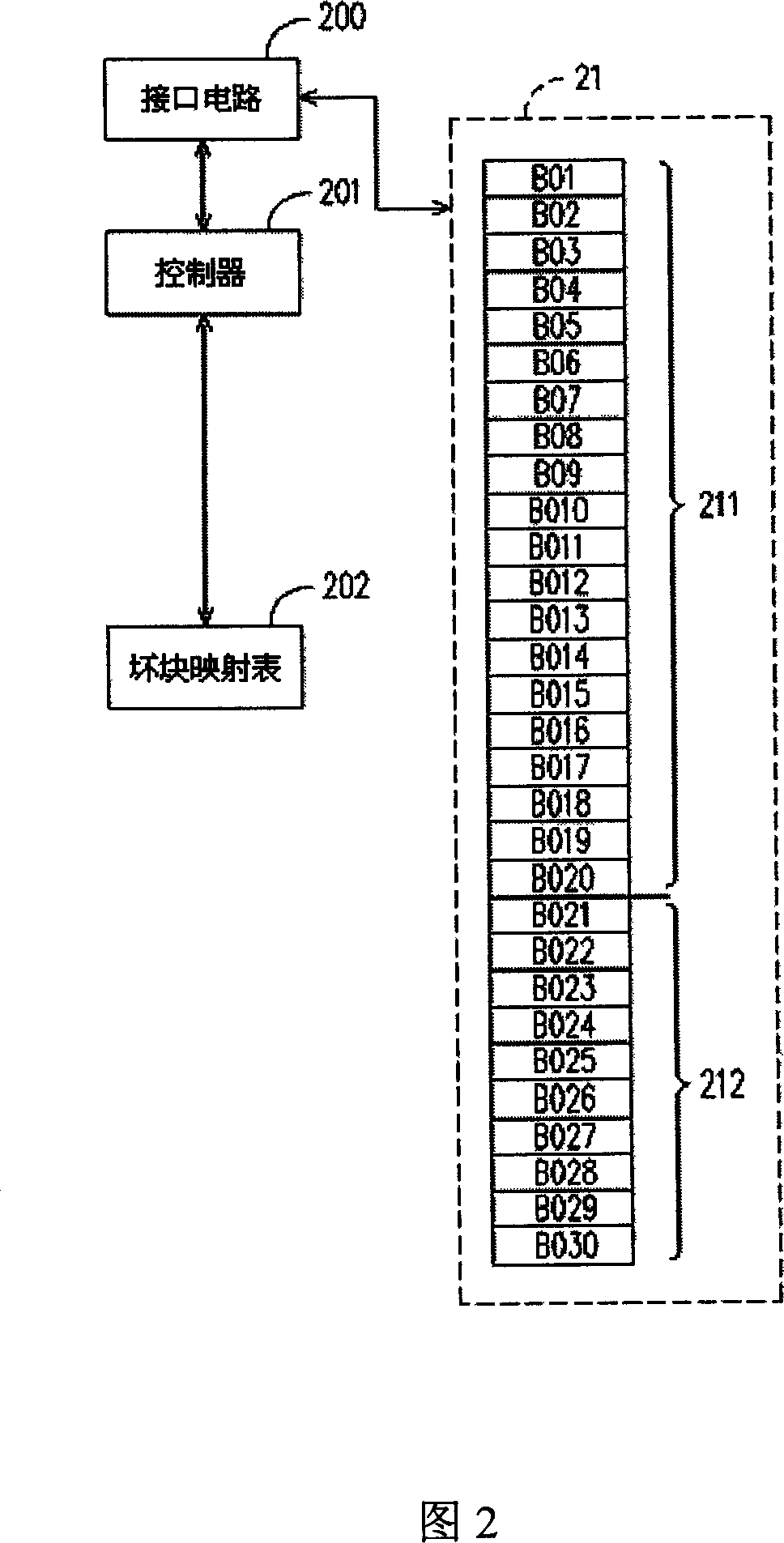
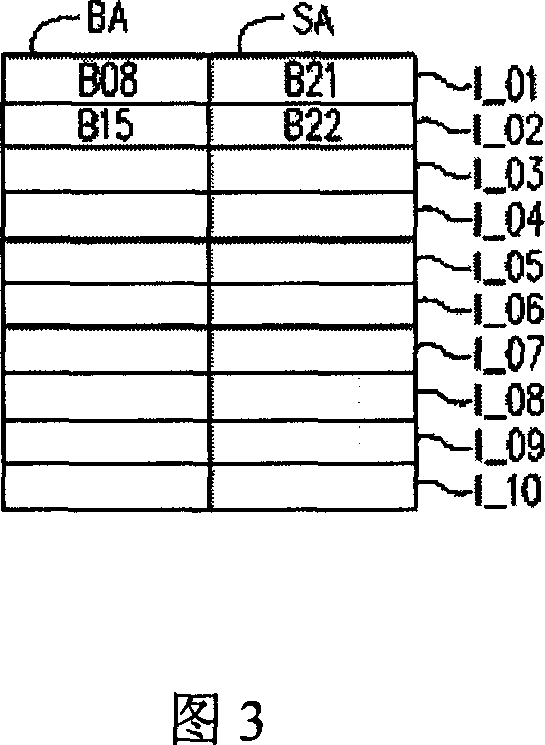
InactiveCN1967504AAvoid using corrupt blocksReduce hardware costsMemory adressing/allocation/relocationRead-only memoriesParallel computingFlash memory
A flash control device and method. The flash includes a number of flash memory blocks, in which these blocks are divided into a number of storage blocks, and several reserved blocks. This control device includes a bad block mapping table and a controller. When to access to the data by the block addresses, the controller judges whether the block corresponding to the block addresses is a damage block. When the controller determines the block corresponding to the block addresses is a damage block, it replaces the access block address to the corresponding reserved block address by finding the bad block mapping table. Next, the controller repeats the above operation until the reserved block corresponding to the access block address is the normal block, and access to data with the access block address.
Owner:SUNPLUS TECH CO LTD
Streptococcus-A quantum dot immunochromatographic detection reagent card and preparation method thereof
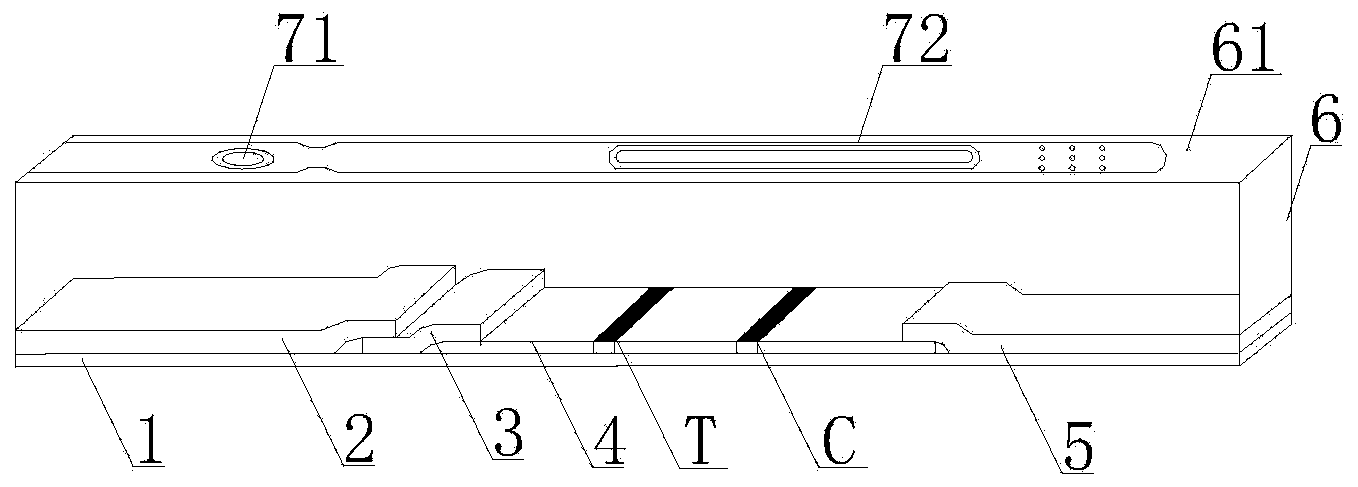
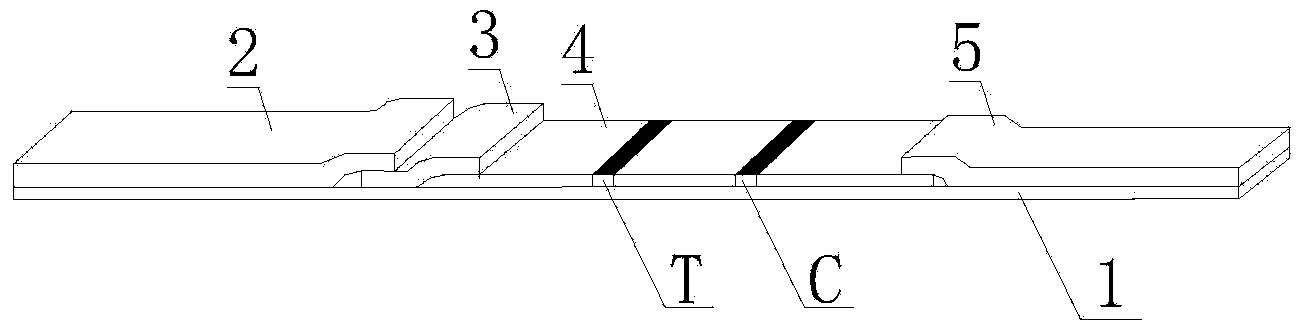
ActiveCN103926403AImprove the detection rateOptimal treatment timeBiological material analysisFluorescence immunoassayFluorescence
The invention discloses a streptococcus-A quantum dot immunochromatographic detection reagent card and a preparation method of the streptococcus-A quantum dot immunochromatographic detection reagent card, and aims to provide the streptococcus-A quantum dot immunochromatographic detection reagent card which is simple, high in sensitivity and reliable in detection results. The detection reagent card comprises a box body (6), wherein a piece of detection test paper is arranged in the box body (6); the detection test paper comprises a bottom plate (1); a sample pad (2), an anti-streptococcus-A quantum dot anti-body markup pad (3), a coating film (4) and a water absorption pad (5) are connected with the bottom plate (1) in sequence; a streptococcus-A quantum antibody detection area line T and a goat anti-rabbit polyclonal anti-body quality control area line C are arranged on the coating film (4); the two lines are arranged in parallel; the streptococcus-A quantum dot immunochromatographic detection reagent card and the preparation method thereof belong to the field of fluorescence immunoassay.
Owner:GUANGZHOU WEIMI BIOLOGICAL SCI & TECH
LED supplementary lighting and image clipping evaluation system in standard image acquisition device
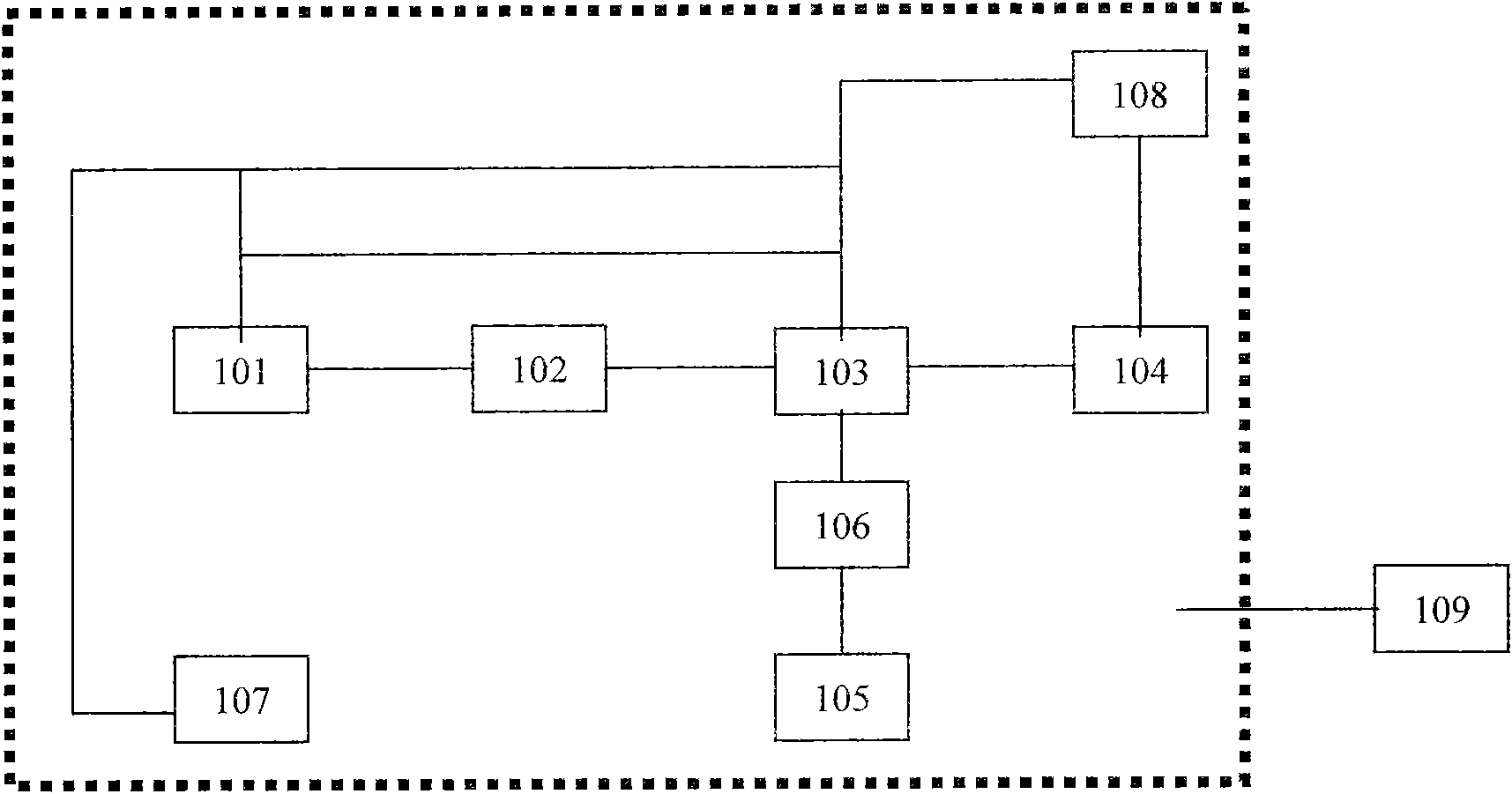
ActiveCN102466945AReduce feverReduce power consumptionCharacter and pattern recognitionClosed circuit television systemsImaging qualityEffect light
The invention relates to an LED supplementary lighting and image clipping evaluation system in standard image acquisition device, comprising an LED light source (101), a 1-120 VDC (Voltage-to-Digital Converter) power supply (102), a control circuit board (103), an image acquisition system (105), an LED light source switch (106), and an LED light source controller (301); the LED light source (101)is connected with the control circuit board (103) via an analog circuit, a digital circuit or an integrated circuit; the LED light source (101) is connected with the 1-120 VDC power supply (102) via the analog circuit, the digital circuit or the integrated circuit; the control circuit board (103) is connected with the image acquisition system (105) via the analog circuit, the digital circuit or the integrated circuit; and the technology of the invention is applicable to the public security image acquisition system, and improves the operation efficiency and image quality.
Owner:BEIJING HISIGN TECH
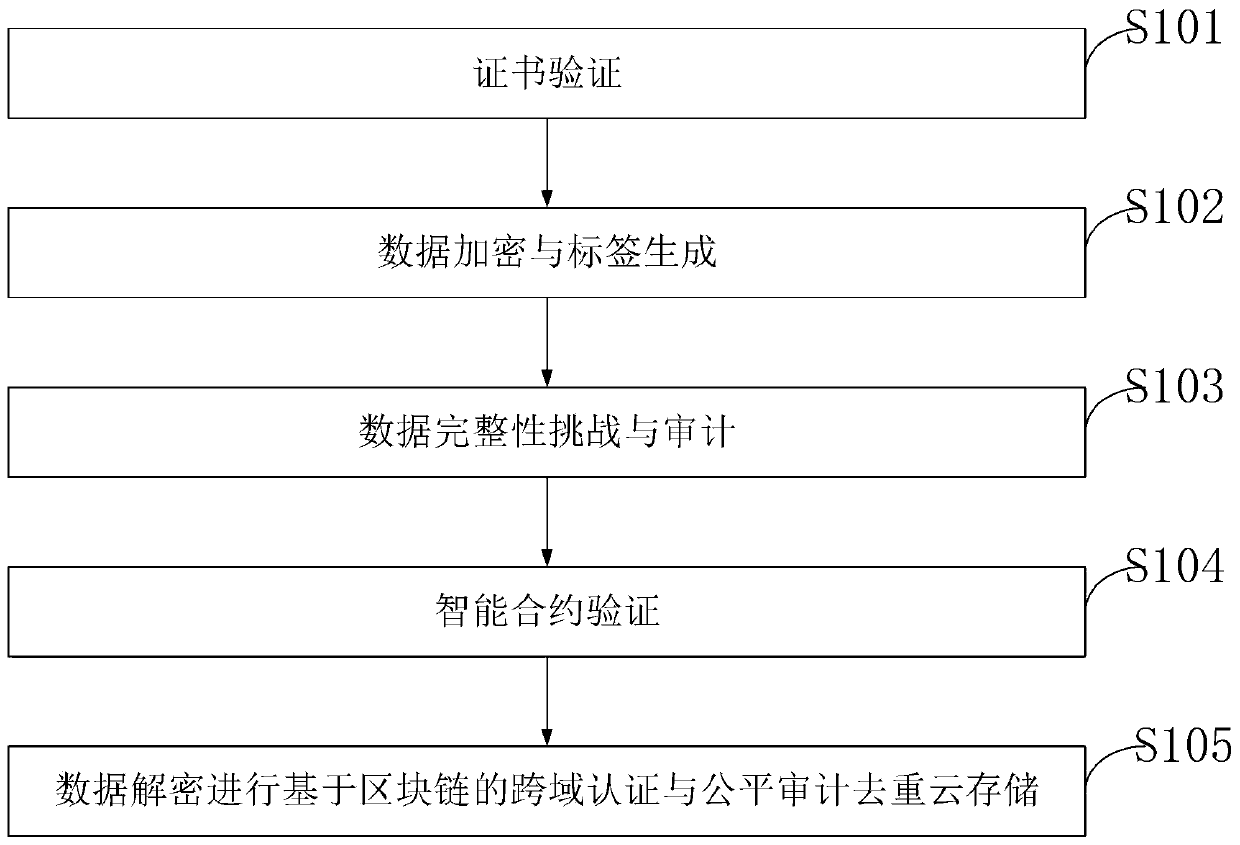
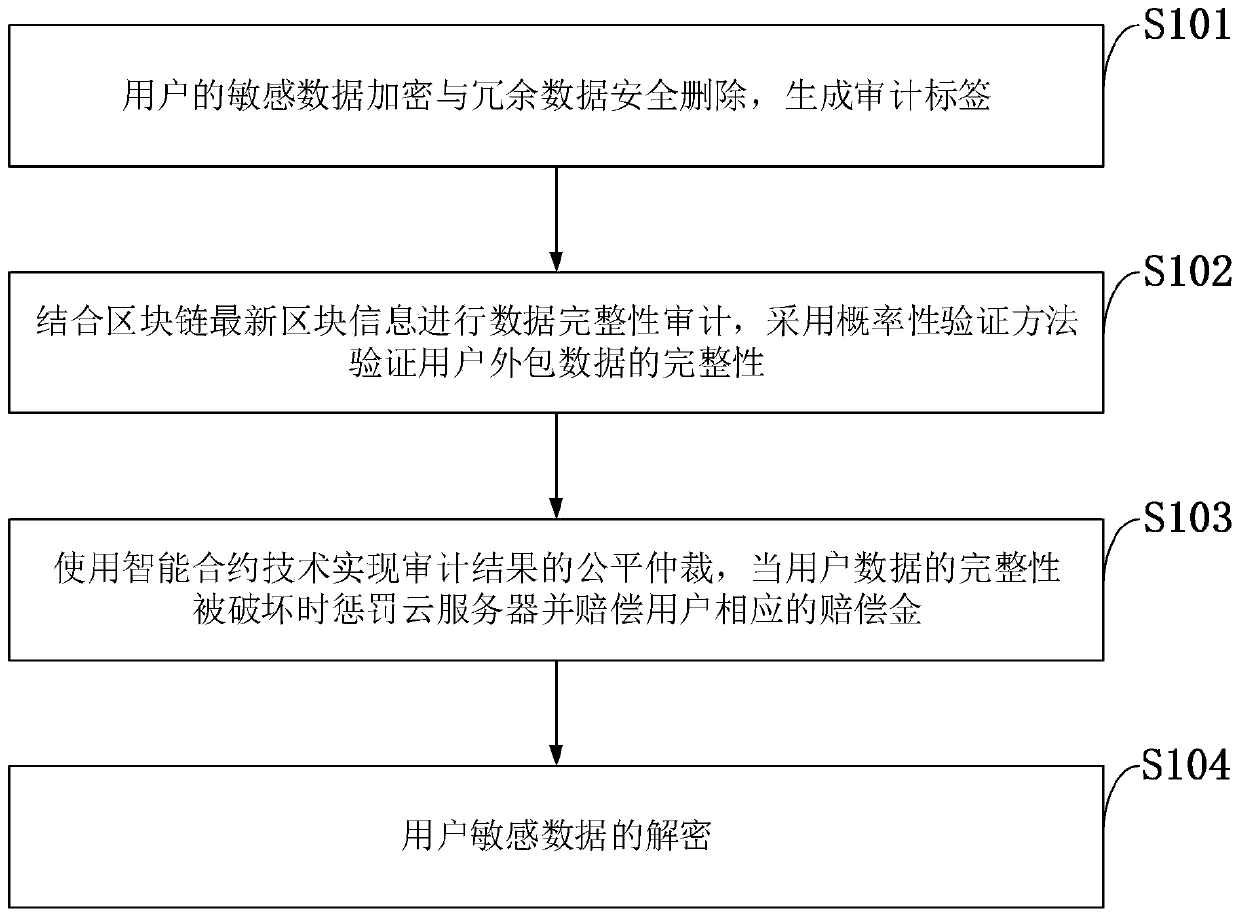
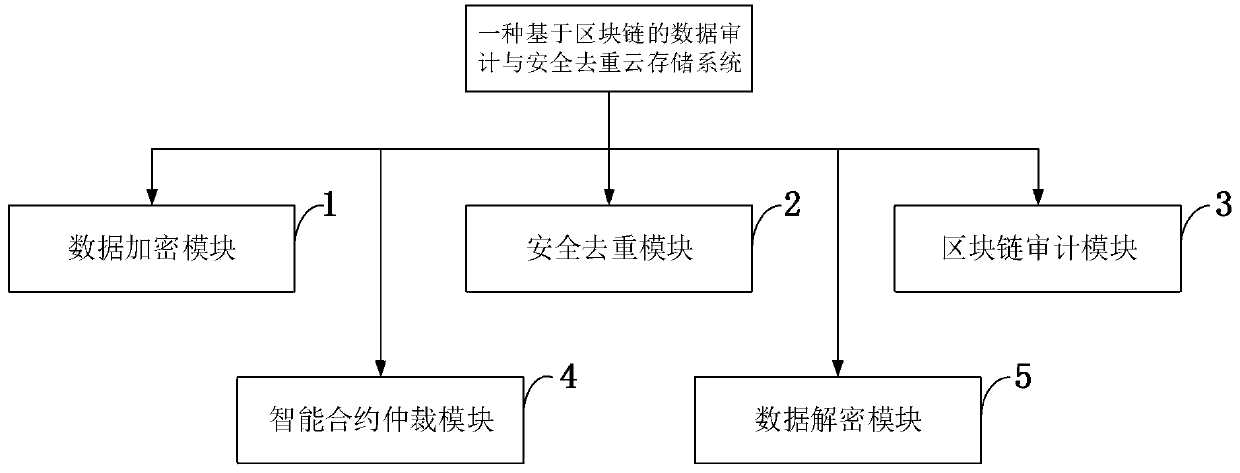
Data auditing and security deduplication cloud storage system and method based on block chain
ActiveCN111355705AAvoid storageReduce consumptionDigital data information retrievalEncryption apparatus with shift registers/memoriesData securityEngineering
The invention belongs to the technical field of cloud computing, and discloses a data auditing and security deduplication cloud storage system and method based on a block chain. The method comprises four processes of data security deduplication and auditing label generation, probabilistic integrity auditing, intelligent contract arbitration and data decryption. Before data outsourcing, enabling auser to encrypt data by adopting a convergence encryption technology and delete redundant data on a cloud server; verifying the integrity of the outsourcing data by adopting a probabilistic verification method; enabling the intelligent contract to automatically execute verification and fair arbitration of an integrity auditing result, punish the cloud server and compensate corresponding compensation money of the user when the integrity is damaged; and obtaining original plaintext data after the user downloads the data and carries out data decryption operation. The problem that arbitration cannot be automatically executed in traditional data auditing is solved. In addition, the method also supports a ciphertext data deduplication function for protecting the consistency of user data, so thata user can effectively obtain correct plaintext data after decryption is completed.
Owner:XIDIAN UNIV
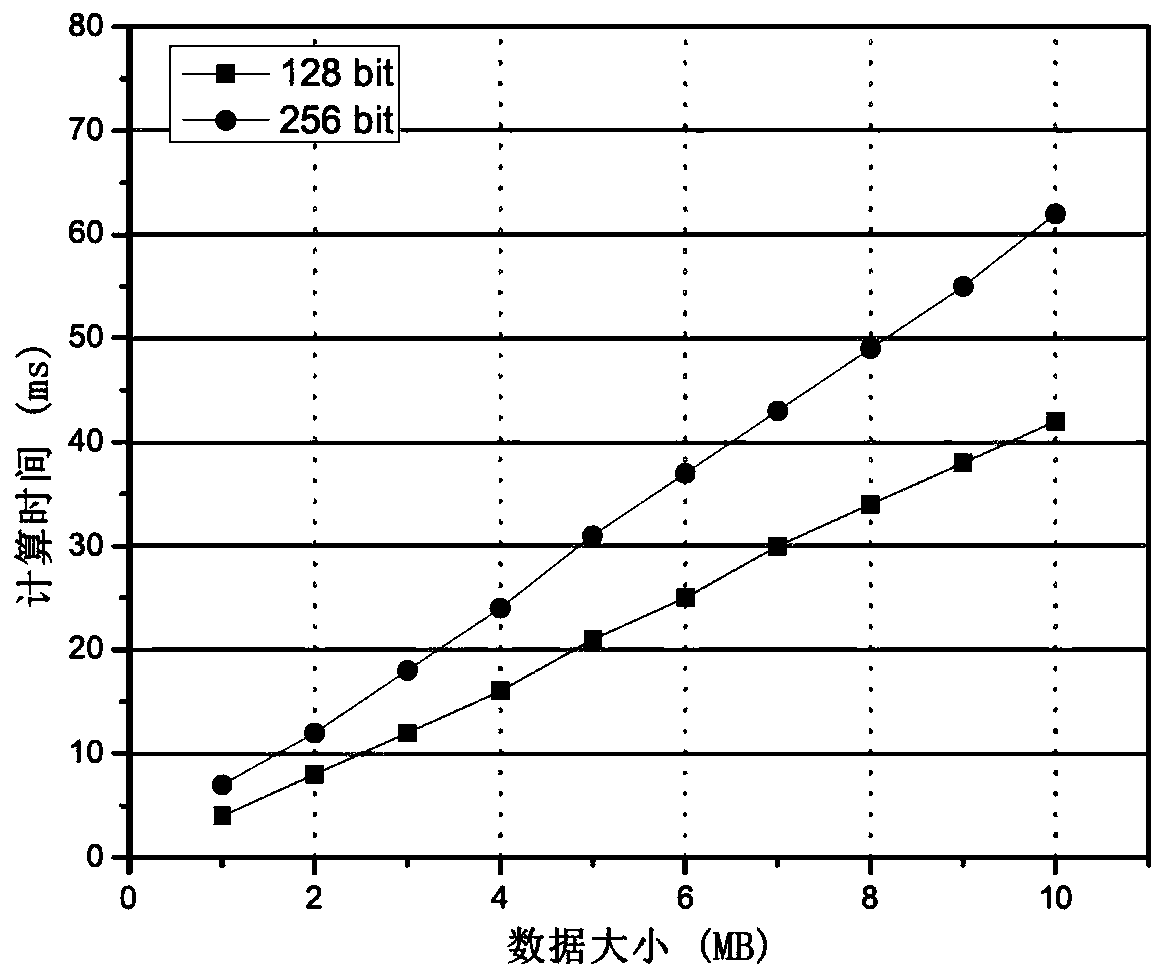
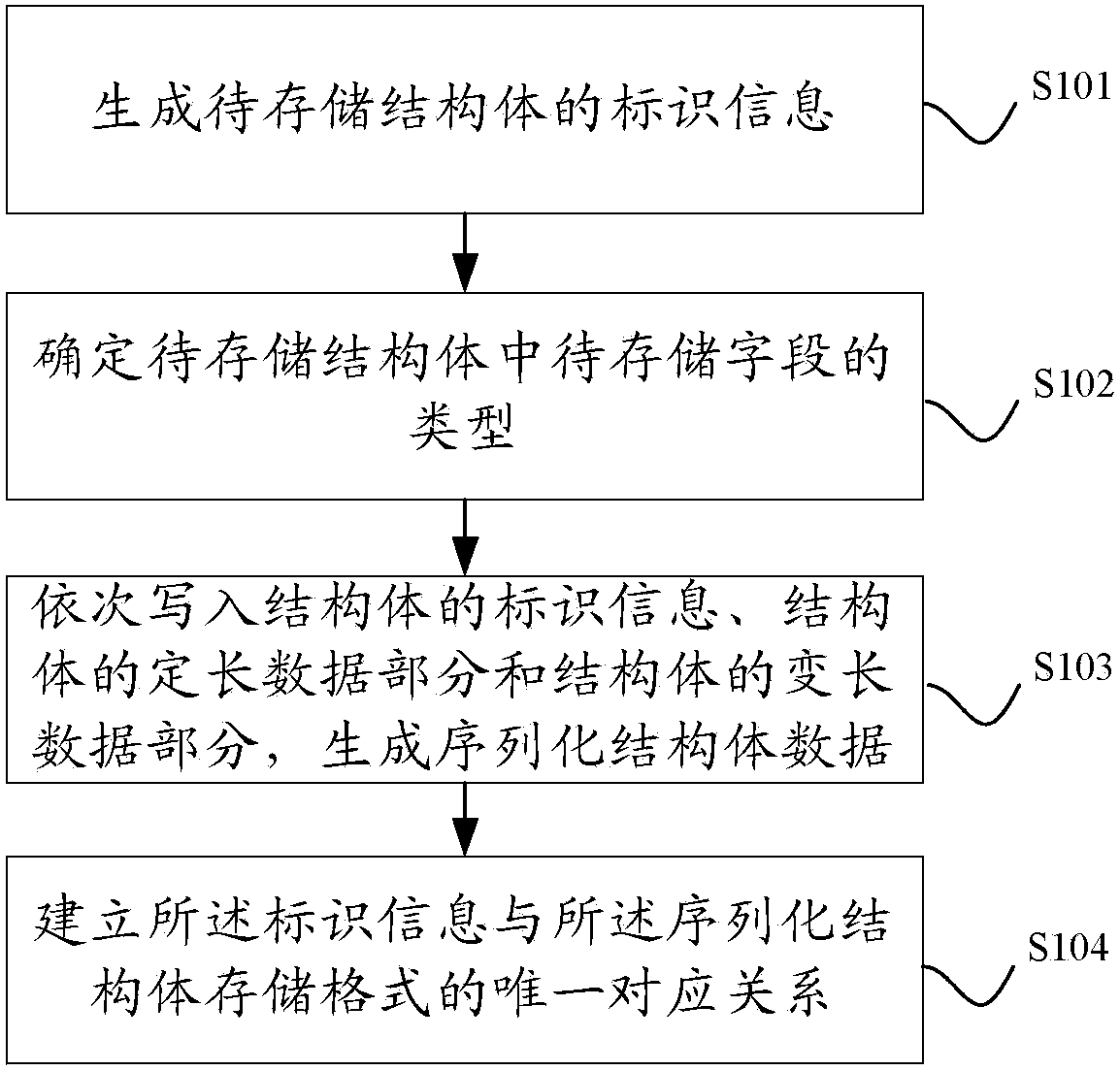
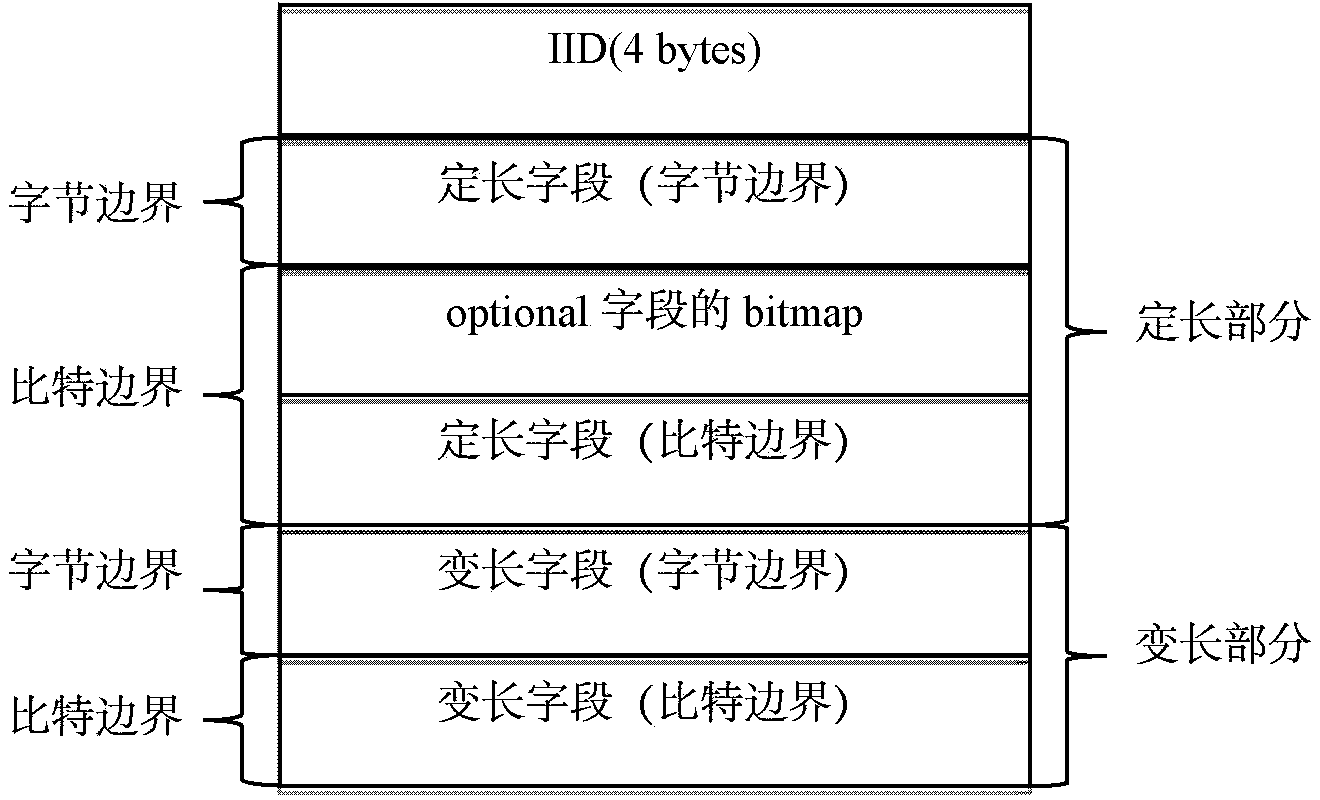
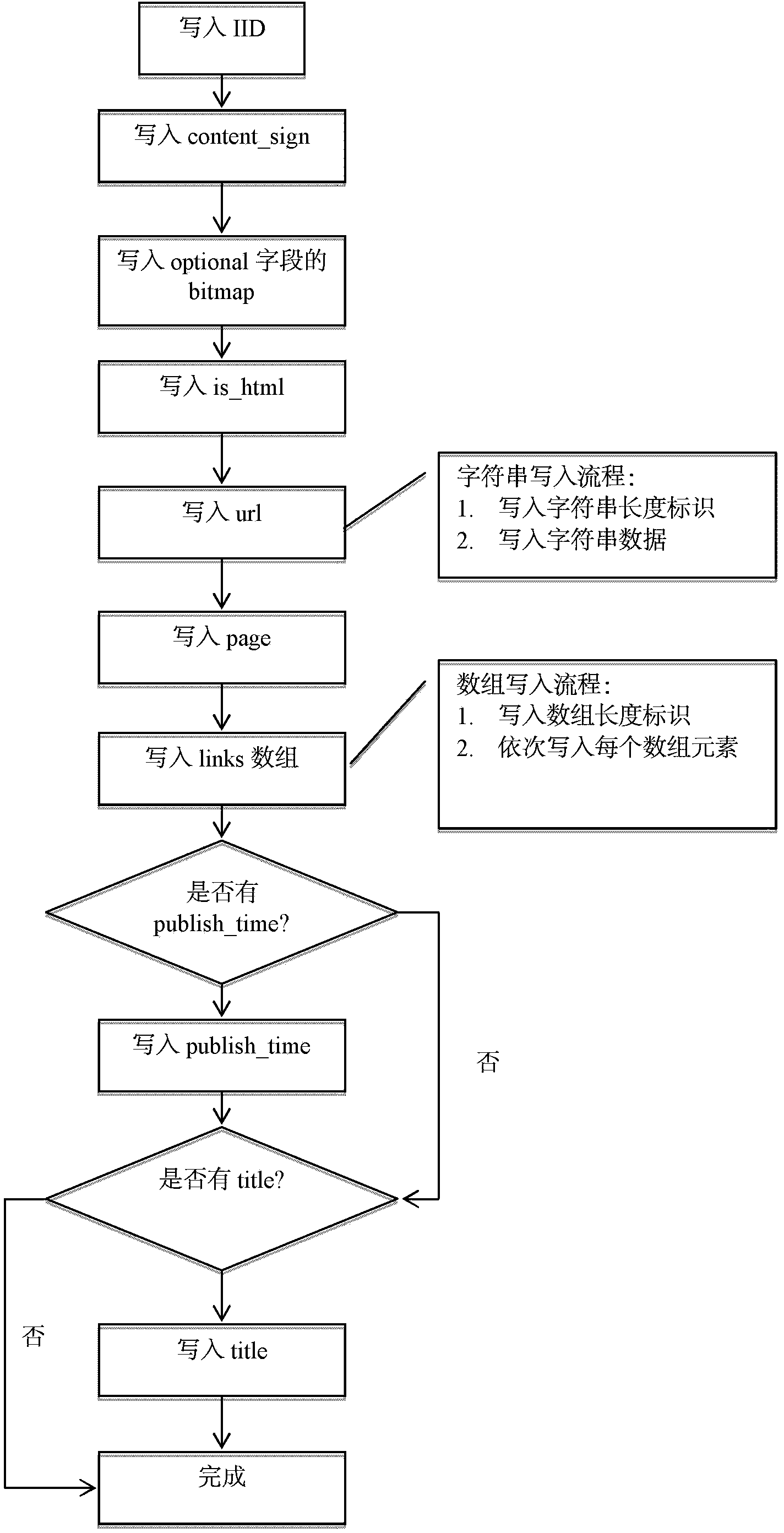
Structured data storage method and device
InactiveCN103389992AAvoid storageRealize flexible adaptationSpecial data processing applicationsSerializationVariable length
The invention discloses a structured data storage method and a structured data storage device. The structured data storage method comprises the following steps: generating identification information of a structural body to be stored; determining the type of a field to be stored in the structural body to be stored; writing the identification information of the structural body, a fixed-length data part of the structural body and a variable-length data part of the structural body in sequence to generate serialized structural body data in a storage space; and establishing unique correspondence of the identification information and a storage format of the serialized structural body. By applying the scheme provided by the invention, high efficiency close to compact binary storage can be provided by using a compact storage scheme without losing the flexibility similar to that of protobuf, so that flexible adaptation of structural body data of different versions can be realized.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Four-stage addressing method for tile recording disk
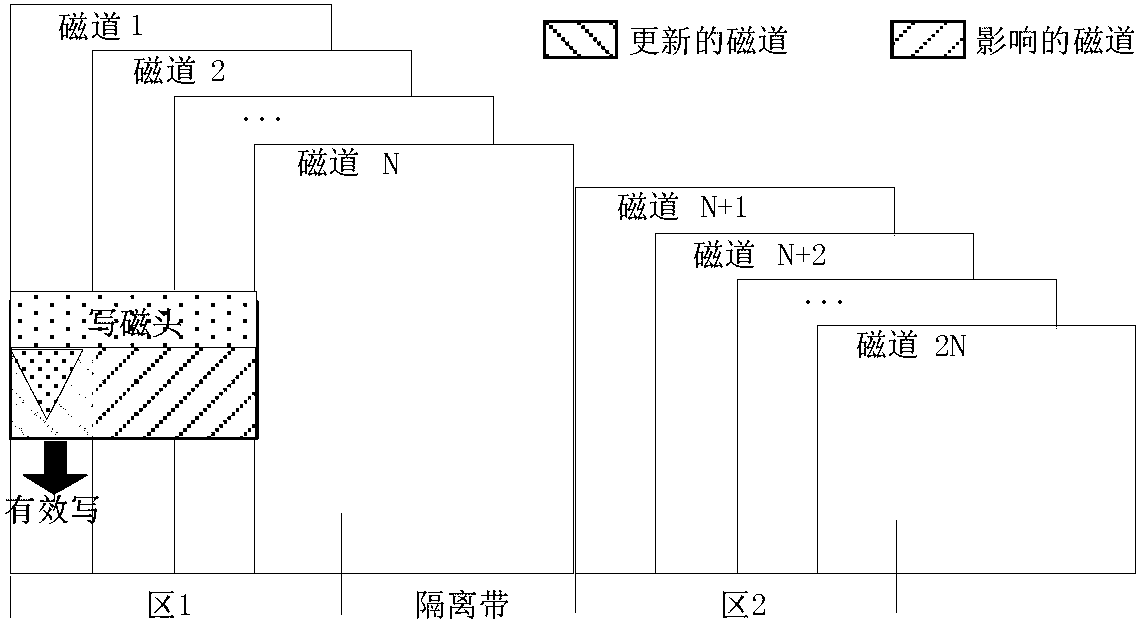
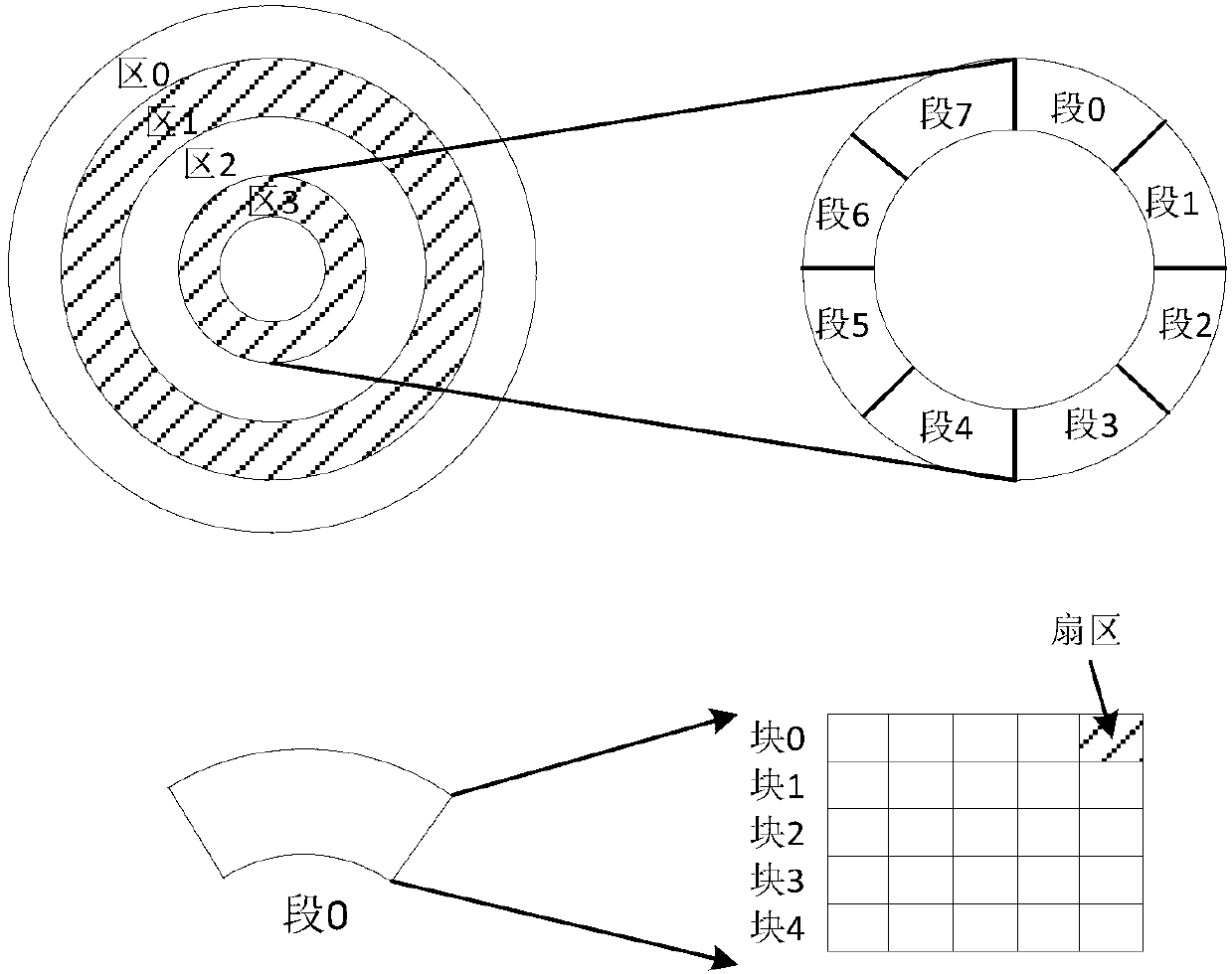
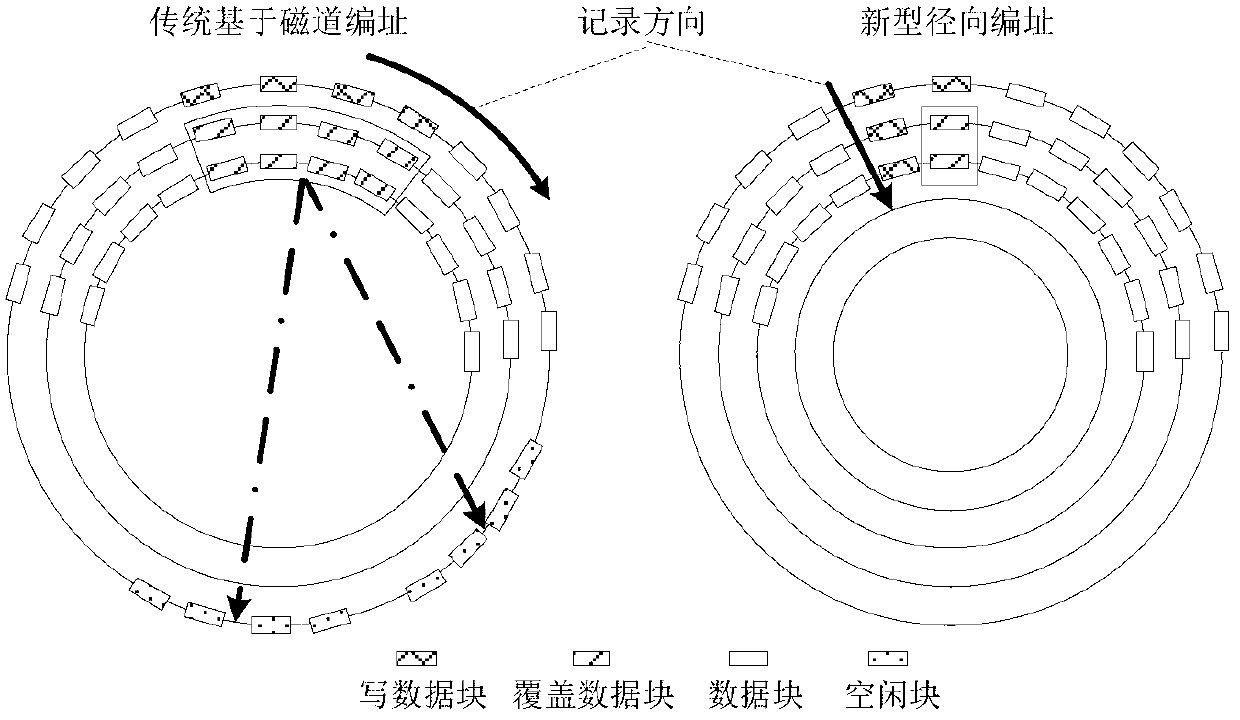
InactiveCN102999428AAvoid managementAvoid storageMemory adressing/allocation/relocationThree stageAddressing mode
The invention discloses a four-stage addressing method for a tile recording disk. The four-stage addressing method comprises the following steps of: dividing a logic space of the tile recording disk into a four-stage structure comprising a region, a section, a block and a sector; addressing the divided four-stage structure by a radial addressing mode; optimizing region intervals of the divided four-stage structure by adopting symmetric stack type magnetic track arrangement; and performing read-write operation on the tile recording disk with the addressed four-stage structure. Aiming at tile recording disk random write limitation, a data structure and the track arrangement of the tile recording disk are optimized; due to the advantages of high read-write speed of a flash memory and a memory, a tile recording disk system with a three-stage architecture is formed, so that the problem of low random write performance of the conventional tile recording disk is solved; the available capacity of the disk can be multiplied, and the performance can be prevented from being reduced; and the read-write speed is increased.
Owner:HUAZHONG UNIV OF SCI & TECH
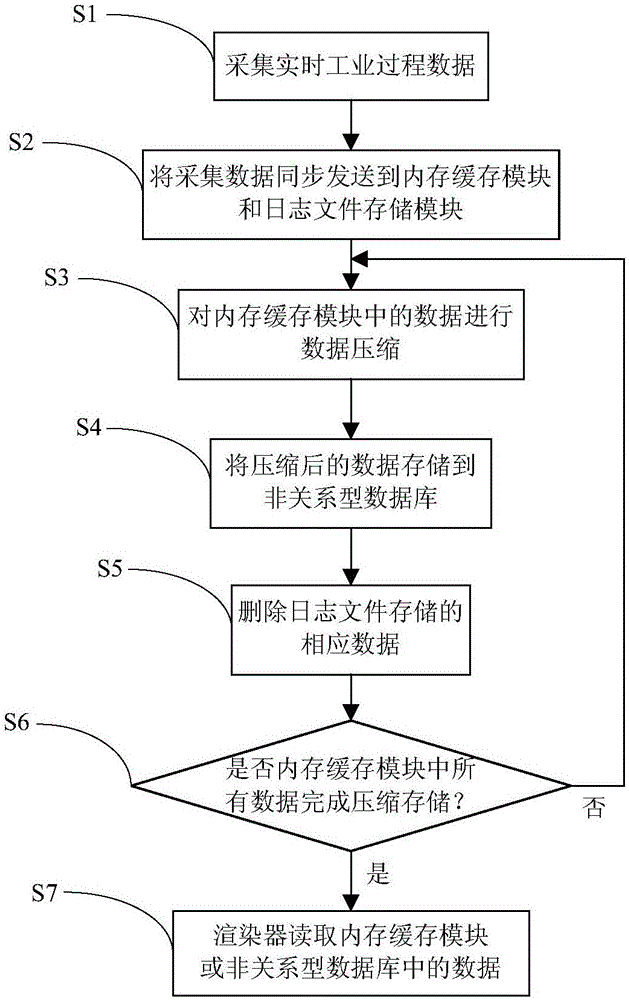
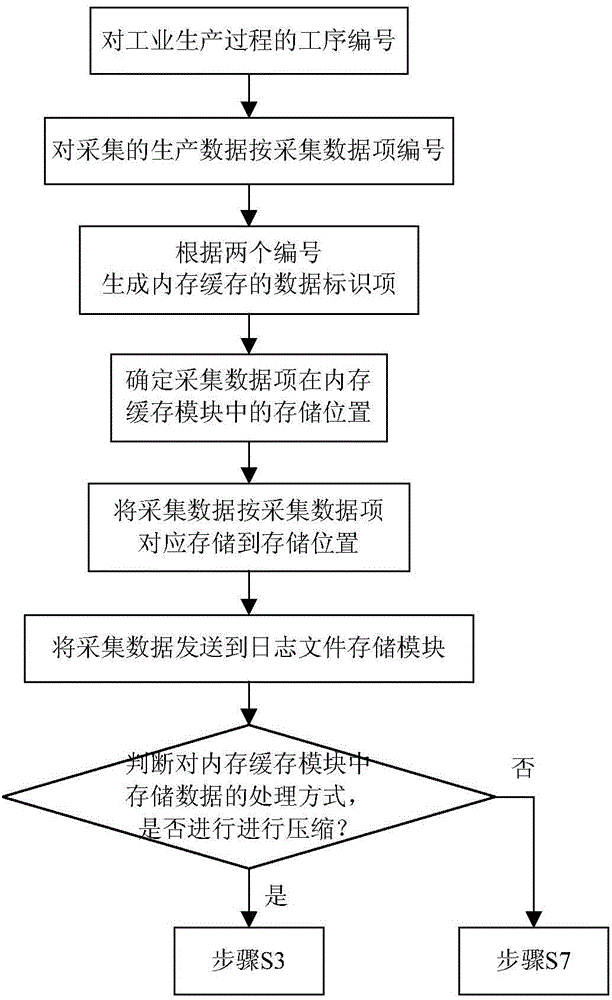
Real-time industrial process big data compression and storage system and method
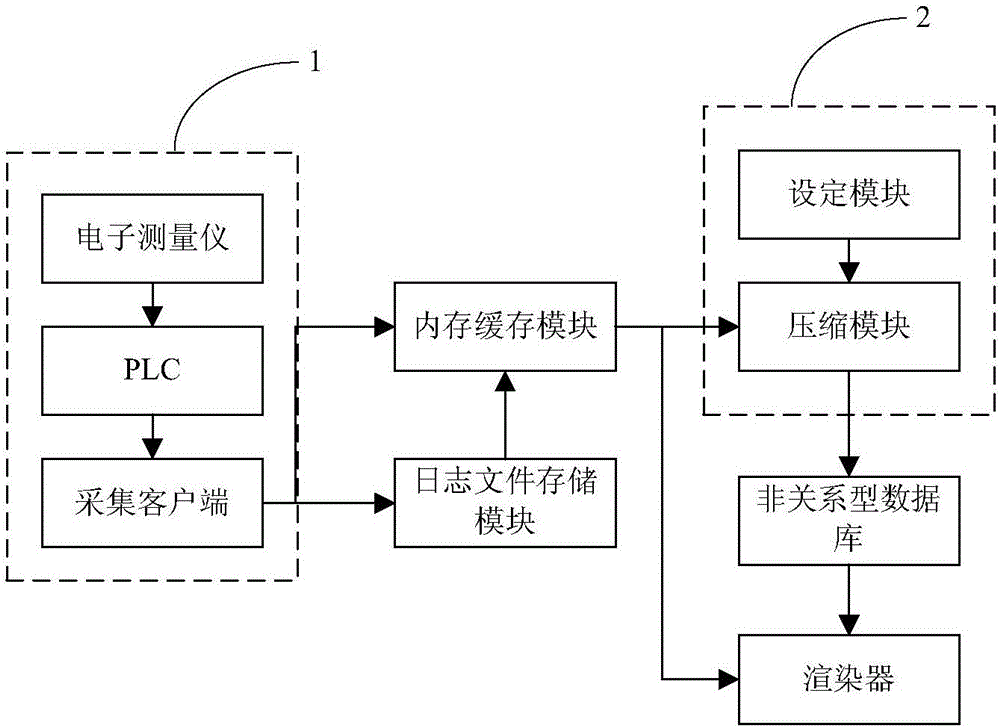
ActiveCN106354774AAvoid storageSolve storage problemsSpecial data processing applicationsData compressionRelational database
The invention provides a real-time industrial process big data compression and storage system and method and relates to the technical field of big data analysis. The system comprises a data acquisition module, a log file storage module, a memory cache module, a data compression module, a non-relational database and a rendering device. The data acquisition module is used for acquiring real-time industrial process data and synchronously sending the real-time industrial process data to the memory cache module and the log file storage module, data in the memory cache module is compressed, and the compressed data is stored in the non-relational database. By means of the real-time industrial process big data compression and storage system and method, the purpose of storing real-time industrial process big data can be effectively achieved, the real-time industrial process big data is compressed to the maximum and stored with the non-relational database, the real-time industrial process big data is effectively stored, the huge cost generated for storing the real-time industrial process big data can be reduced for enterprises, and online inquiry, calculation and the like of data can be quickly responded to.
Owner:NORTHEASTERN UNIV
Intelligent medical service method based on undistinguishable confusion
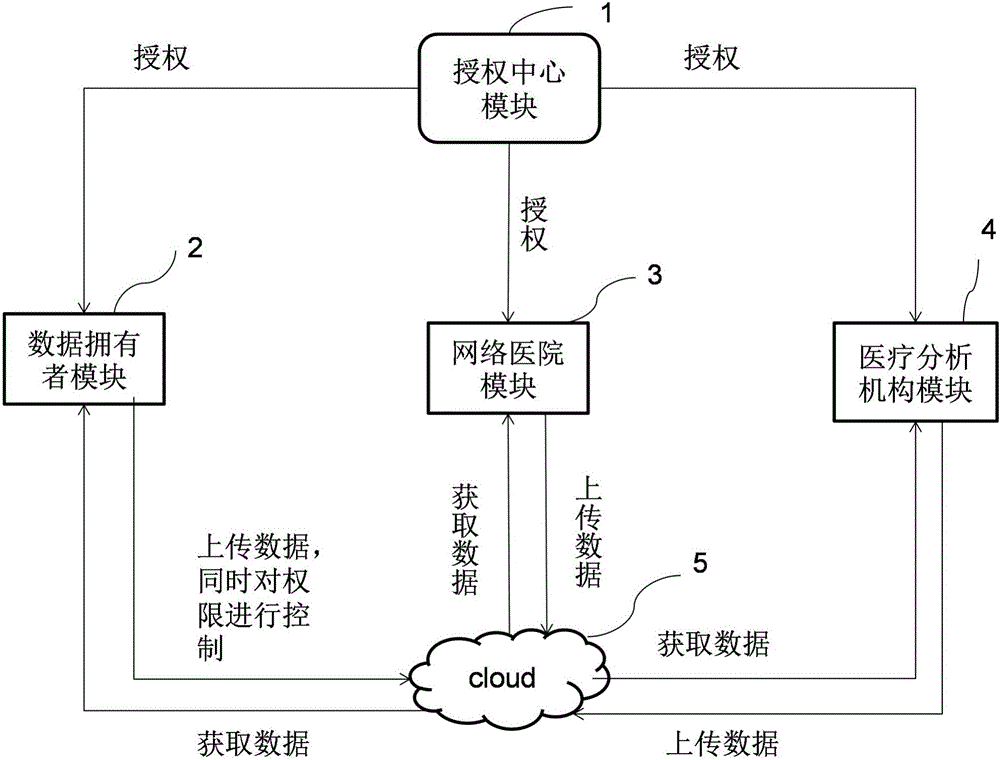
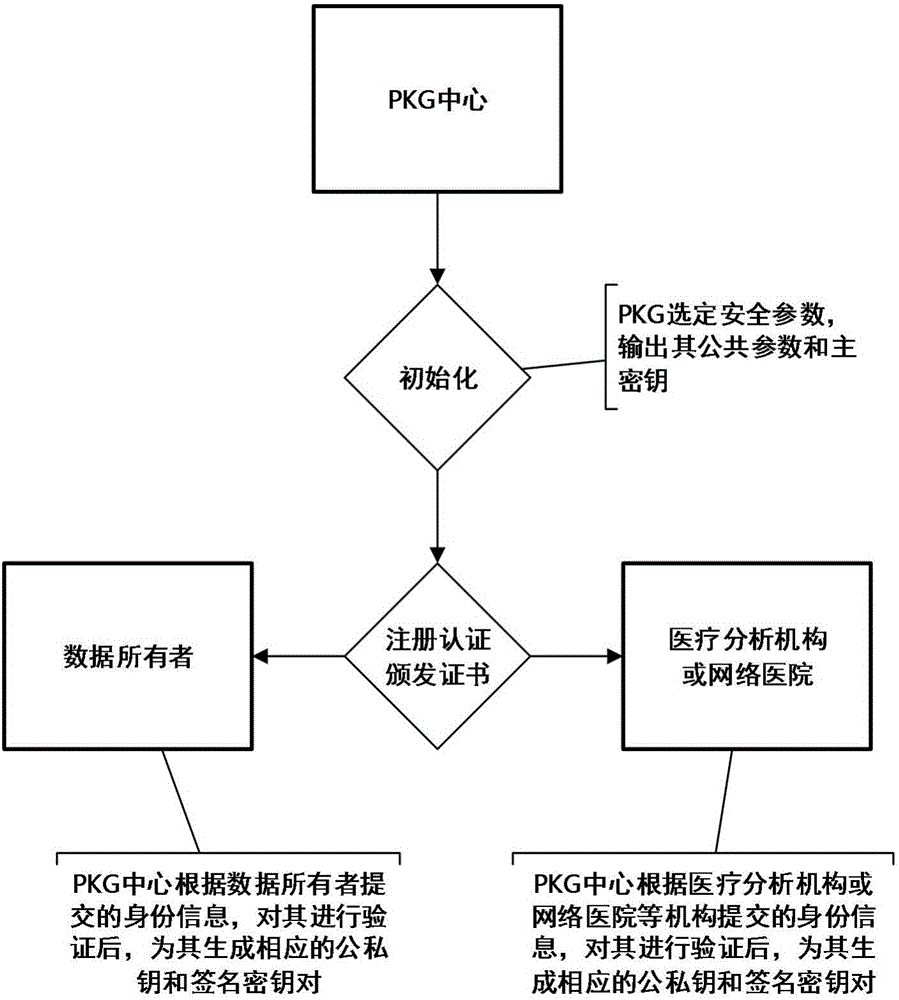
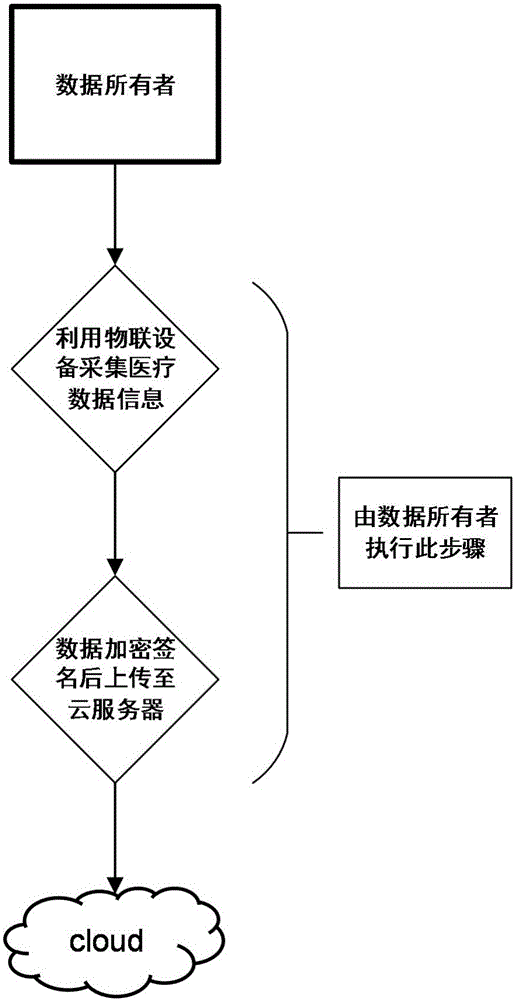
ActiveCN105978854AFlexible Control AllocationAssignment Convenience ControlKey distribution for secure communicationData processing applicationsCiphertextData access
The invention discloses an intelligent medical service method based on undistinguishable confusion, which is characterized in that a data owner independently decides allocation for the medical data access authority through carrying out security symmetric encryption on medical information uploaded to a cloud server; a medical data analysis mechanism carries out confusion on a medical data analysis program by using an undistinguishable confusion technology, the confused program is deployed to the cloud server, and security analysis is carried out on the medical data by using a confusion program so as to acquire a correct medical analysis result; and the access authority of other related mechanisms for a ciphertext can be controlled conveniently without changing the ciphertext structure by using a key sharing scheme. According to the invention, the privacy of data is realized, interaction of keys is reduced, and storage and management of a great number of keys are avoided; the integrity and the effectiveness of data can be verified; and the access type of medical data is decided by the user, the overall structure of an algorithm is not change at the same time, and the expansibility of the scheme is enhanced.
Owner:XIDIAN UNIV
Local user authentication with neuro and neuro-mechanical fingerprints
ActiveUS9590986B2Easy to useLow powerAcquiring/recognising eyesDigital data authenticationUser authenticationBody region
In accordance with one embodiment, a method for locally verifying the identification of a user with an electronic device is disclosed. The method includes regenerating a neuro-mechanical fingerprint (NFP) in response to a micro-motion signal sensed at a body part. In response to a plurality of authorized user calibration parameters, a match percentage of the neuro-mechanical fingerprint is determined. The match percentage is determined without the use of a calibration NFP that was previously used to generate the user calibration parameters. Access to the electronic device and its software applications is then controlled by the match percentage. If the match percentage is greater than or equal to an access match level, access to the electronic device is granted. If the match percentage is less than the access match level, access is denied. Subsequent access requires further regeneration of the NFP and a determination of its match percentage in response.
Owner:PROPRIUS TECH S A R L
In-situ preparation method of nanofiber antibacterial dressing
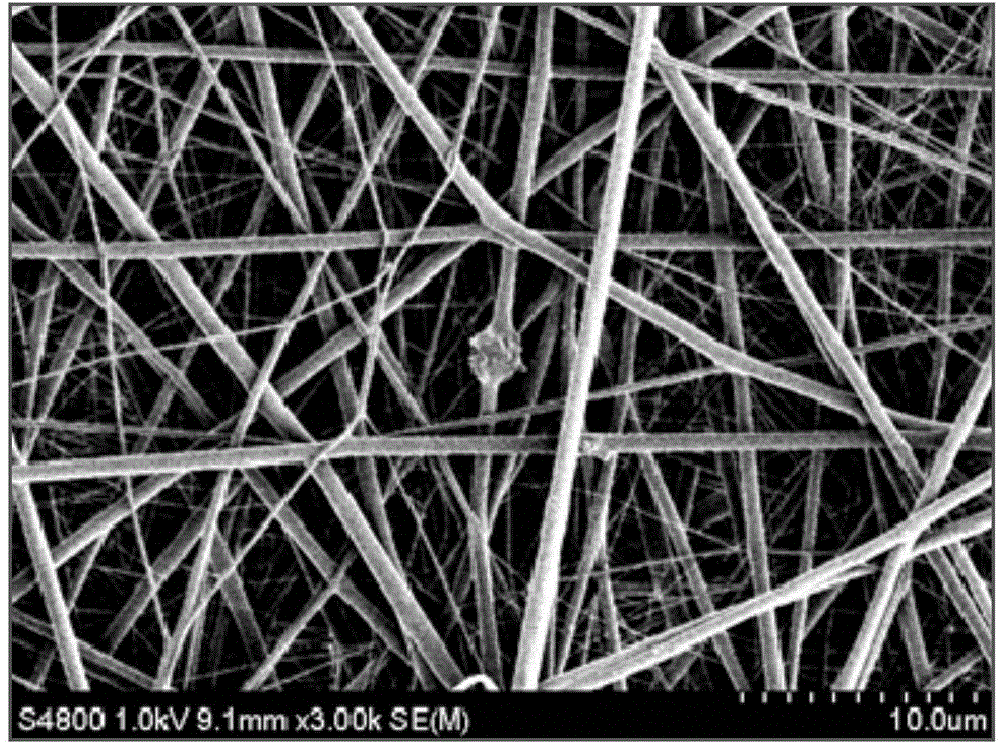
ActiveCN104667338AEasy to useImprove antibacterial propertiesAbsorbent padsBandagesBiocompatibility TestingHand held
The invention discloses an in-situ preparation method of a nanofiber antibacterial dressing and belongs to the field of medical dressing. According to the method, a nanofiber antibacterial dressing containing a silver-supported nano particle is electrically spun directly on a wound surface by virtue of handheld electrostatic spinning equipment, wherein the high polymer material for electric spinning is a water-soluble or degradable biocompatibility material; the solvent is a medical solvent, and is safe and effective when directly sprayed on the wound surface; the used silver-supported nano particle is the nano particle with nano silver particles or silver ions adsorbed and loaded on the surface. By virtue of a doping manner, the antibacterial effect of the nano silver particles or silver ions is reserved; the problems of oxidation and agglomeration of silver nano particles are effectively overcome; the preparation method disclosed by the invention is simple and convenient to operate, is not limited by an operation site, and can be applied to acute trauma emergency treatment on various occasions; and the obtained dressing is stable in antibacterial property, does not need to be fixed extra, and is applicable to wound surfaces with various shapes, depths and sizes on different parts.
Owner:QINGDAO KANGYUAN JULI BIOTECH CO LTD
Data storage method and storage equipment
ActiveCN107092439AReduce lookup timeShorten access timeInput/output to record carriersAccess timePhysical address
The embodiment of the invention provides a data storage method and storage equipment. The method is applied to the storage equipment and comprises the following steps that: the storage equipment receives a write request message, wherein the write request message comprises data and the keyword of the data, and the keyword is used for identifying the data type of the data; the storage equipment determines the data type of the data according to the keyword; then, the storage equipment searches a target physical storage block matched with the data type according to the data type, wherein the target physical storage block is a physical storage block of which the physical address is continuous; then, the storage equipment stores the data to the target physical storage block; and the storage equipment determines the data type of the data according to the keyword, and stores the data of the same data type into the target physical storage block of which the address is continuous so as to prevent from randomly storing the data of the same type. If the data of the same type needs to be searched or accessed, not all stored data need to traversed, data searching and accessing time is shortened, and data searching and accessing efficiency is improved.
Owner:CHENGDU HUAWEI TECH
Broadband grid antenna array
InactiveCN104319491AIncrease Radiation BandwidthAvoid storageAntenna arraysRadiating elements structural formsAcoustic transmission lineRadiating element
The invention discloses a broadband grid antenna array. The broadband grid antenna array comprises a reflection floor and a plurality of radiating elements uprightly arranged on the reflection floor, wherein a plurality of micro strip transmission lines respectively connected with all the radiating elements are arranged on the upper layer of the reflection floor, the plurality of the radiating elements on the reflection floor form a grid antenna array in surrounding mode, radiation patches cover the obverse side and the reverse side of each radiating element, a section of each radiation patch, located on the lower portion of each of the obverse side and the reverse side of each radiating element, is corroded so as to expose a medium portion, metal slices are respectively pasted at the left end and the right end of each exposed medium portion, the metal slices are respectively connected with the radiation patches and the micro strip transmission lines, a plurality of via holes are formed in the periphery of each radiating element, and the plurality of the via holes penetrate through the radiation patches on the obverse sides and the reverse sides of each radiating element. The broadband grid antenna array is provided with a simple feed network, has the advantages of being large in bandwidth, easy to process, low in cost and the like, and can meet requirements of a broadband communication system.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com