A cross-domain authentication and fair audit deduplication cloud storage system based on a block chain
A cloud storage system and blockchain technology, applied in the field of cloud computing, can solve problems such as unfair storage costs, damage to certificate certification centers, high payment, etc., to save storage costs and management costs, reduce storage costs and management costs , the effect of reducing network overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
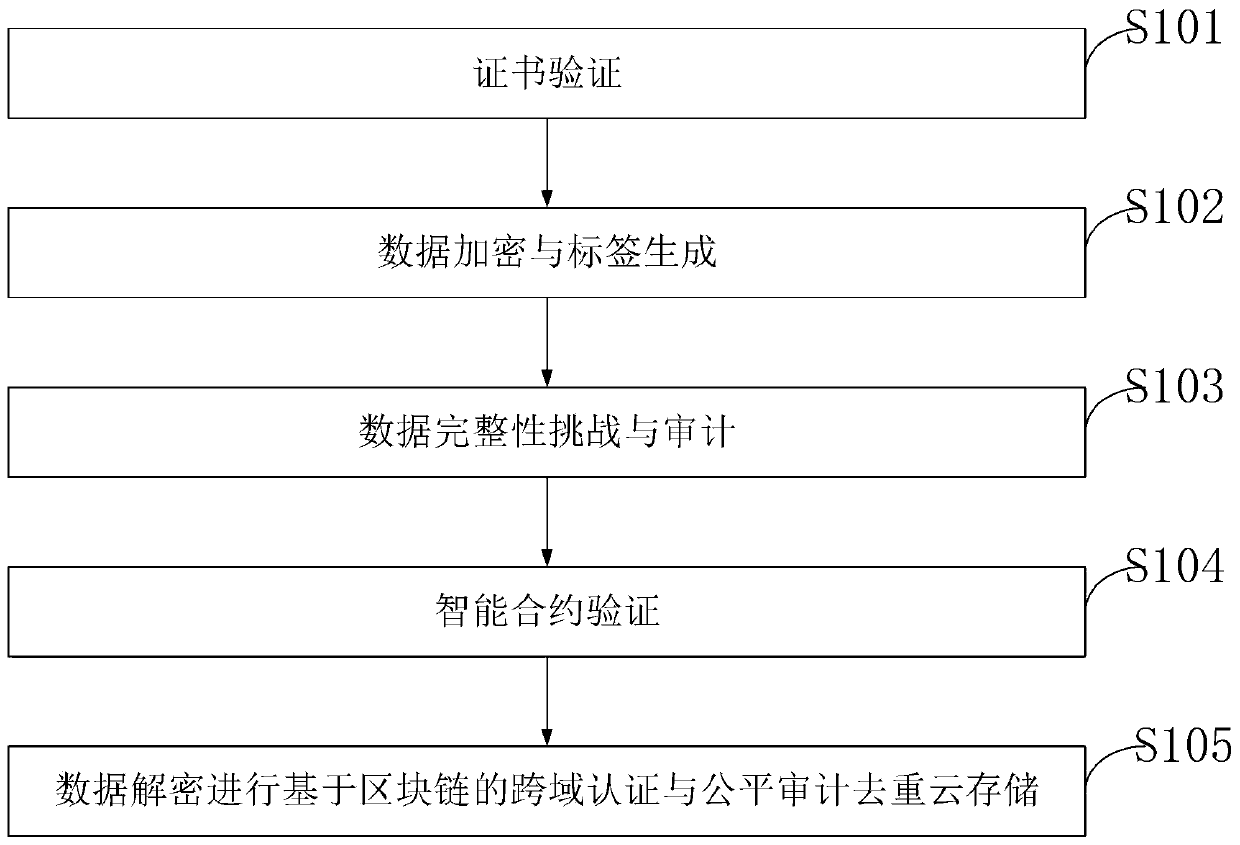
[0079] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
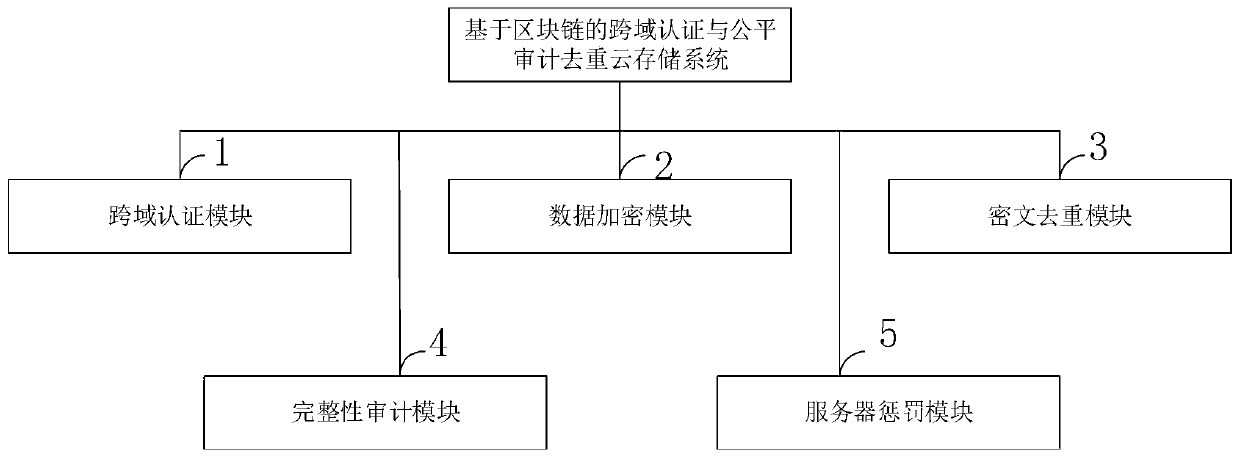
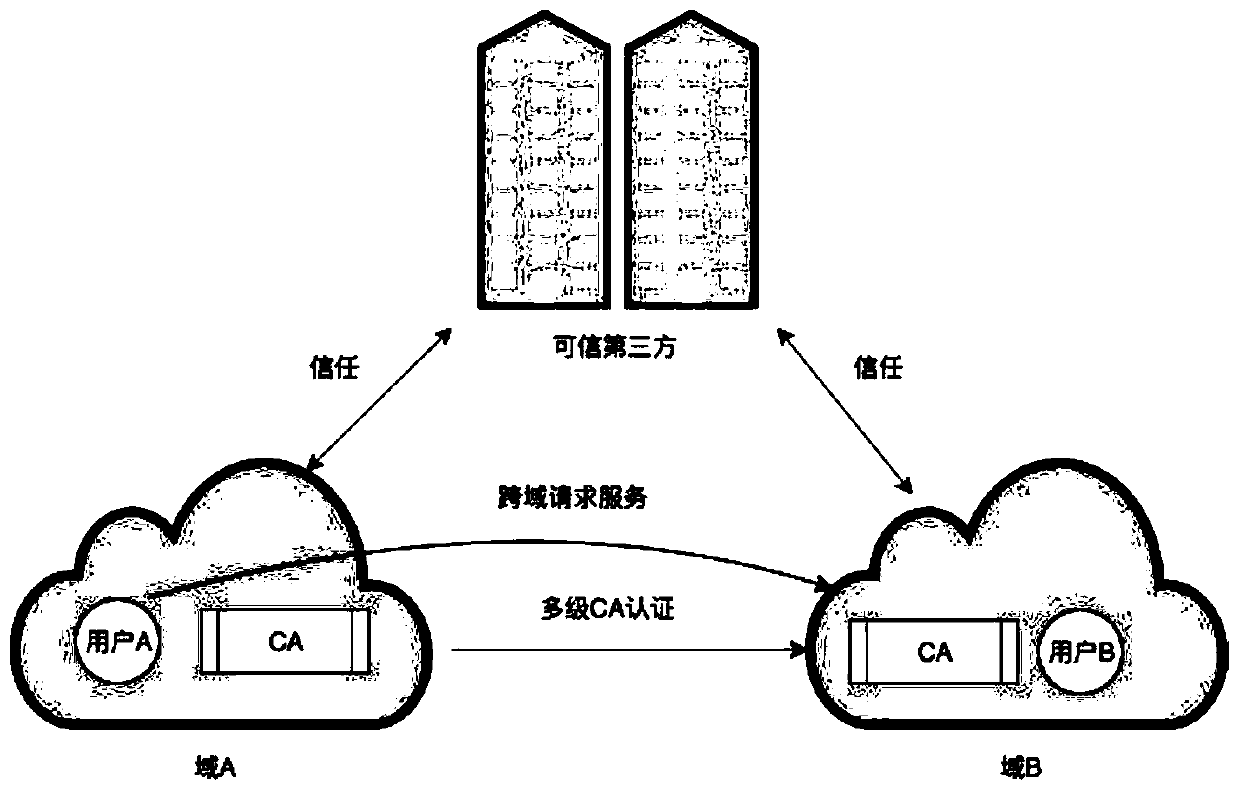
[0080] With the rapid development of cloud computing technology and the explosive growth of user data, more and more enterprises and individuals tend to outsource and store data on cloud servers and exchange and share data by using the cloud. Since users need to authenticate their identities before exchanging data, the certificate authentication center that traditional cross-domain authentication schemes rely on in the cloud environment is easily damaged, which makes traditional cross-domain authentication schemes not only inefficient but also huge in the verification process. security risks. On the other hand, due to vari...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com