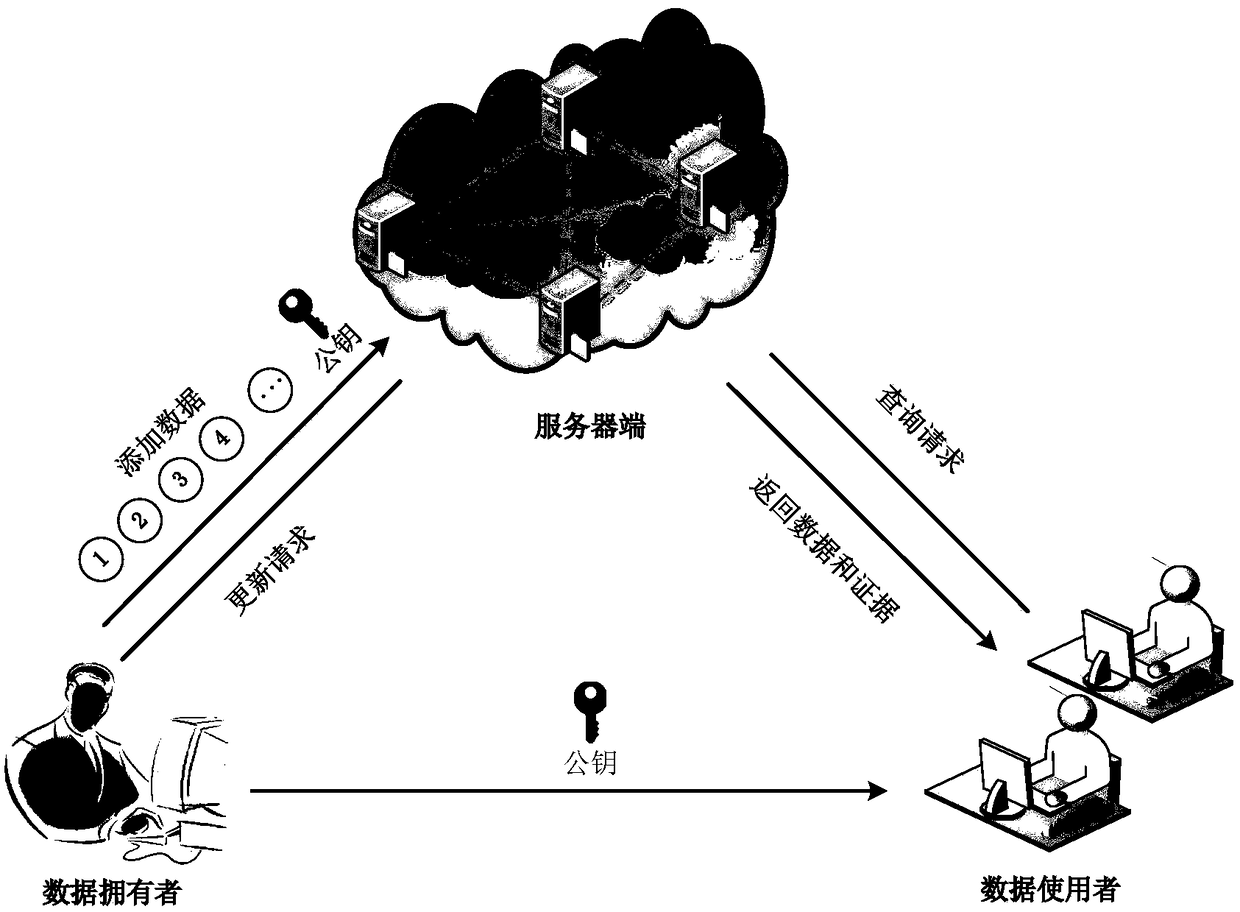
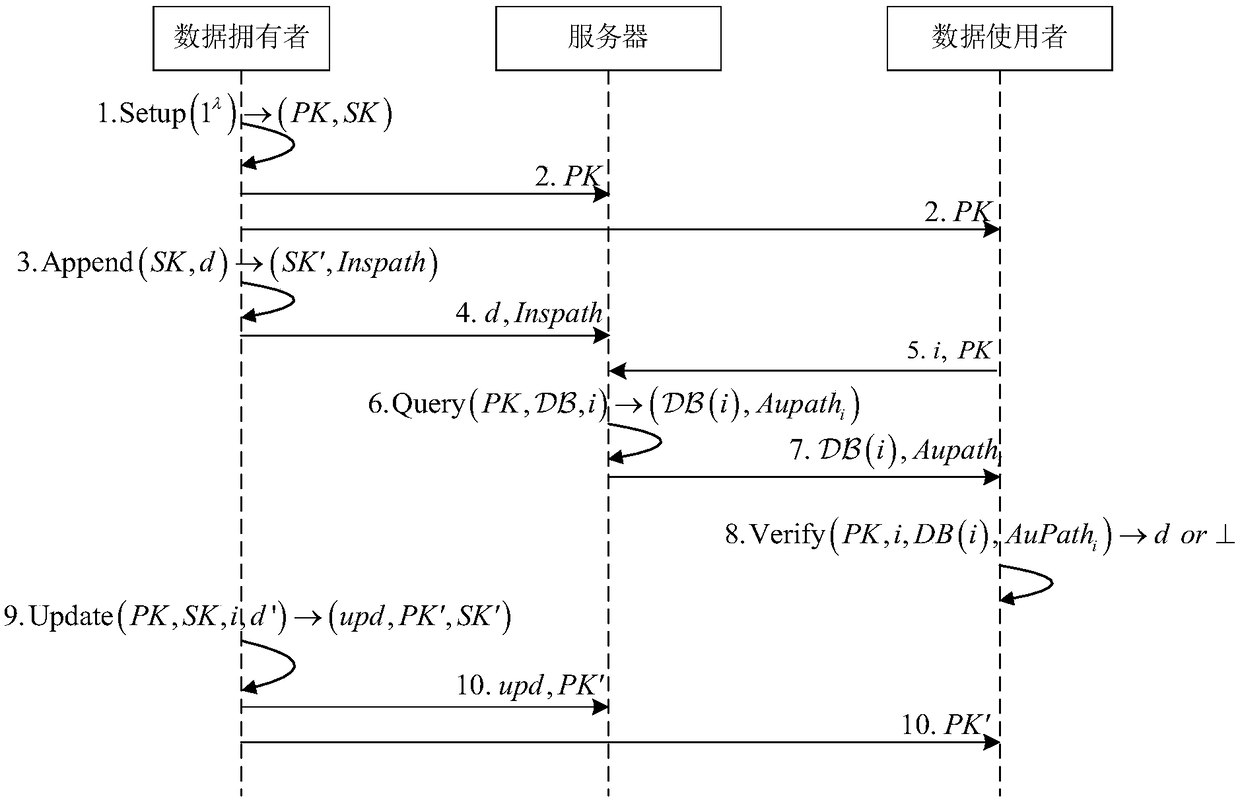
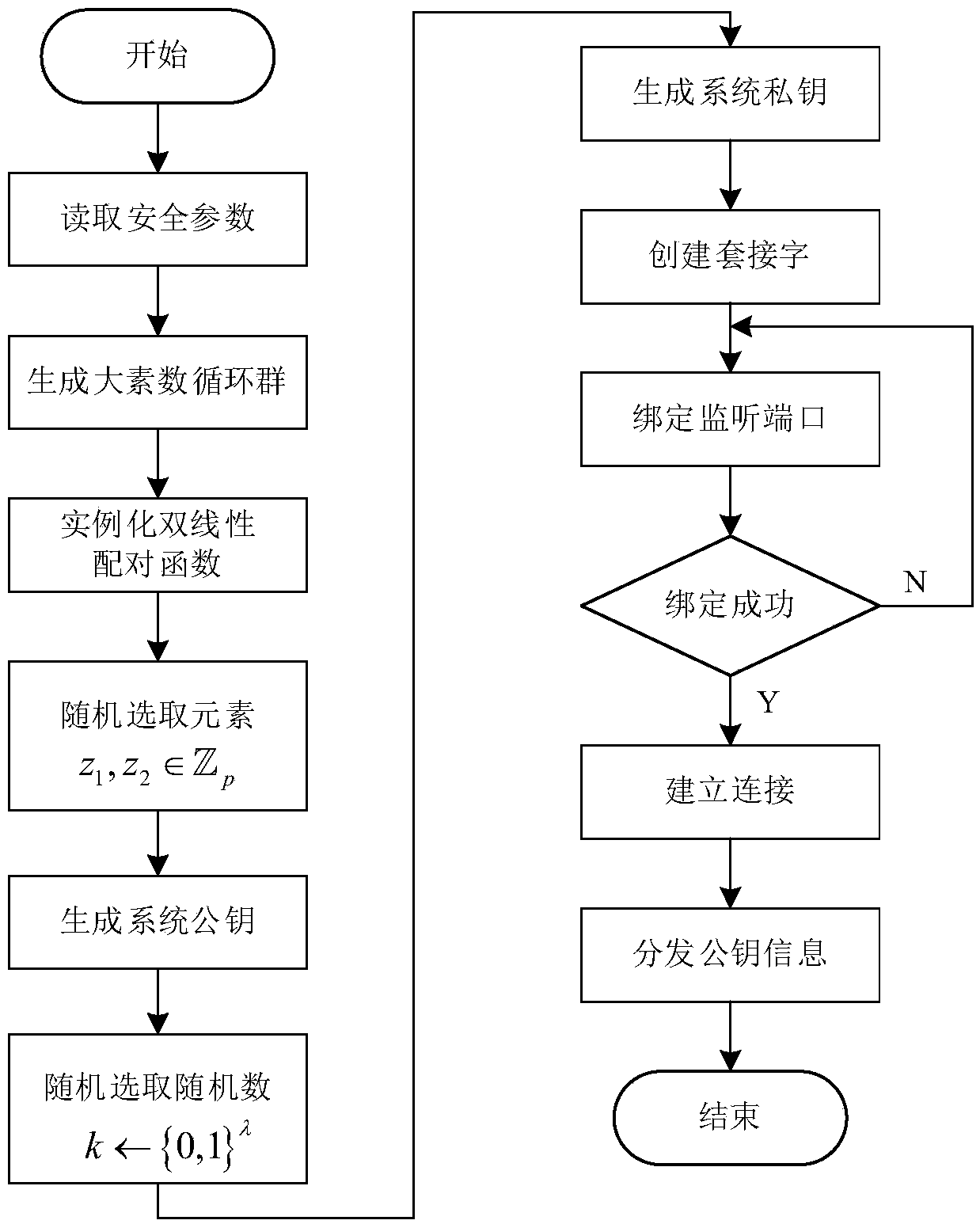
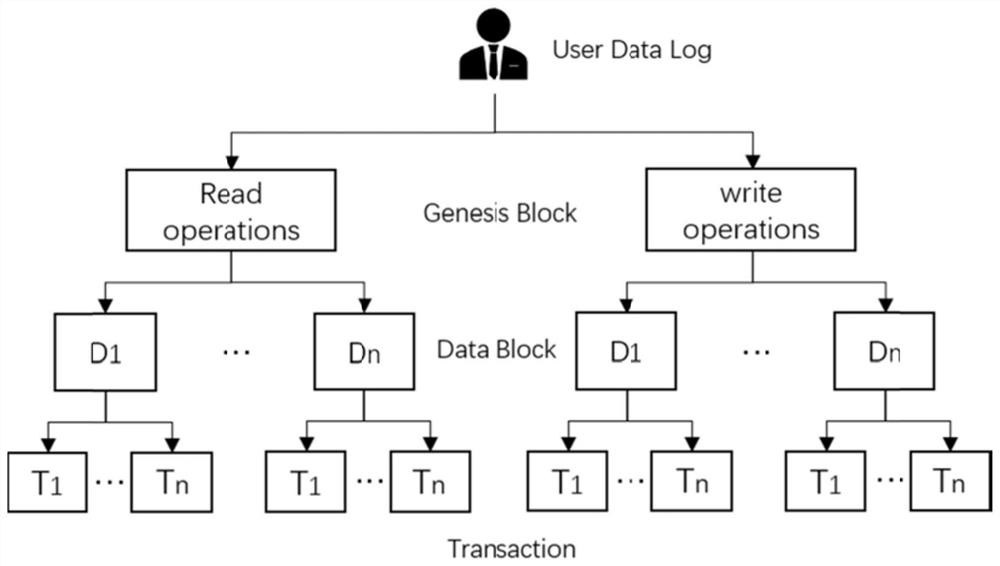
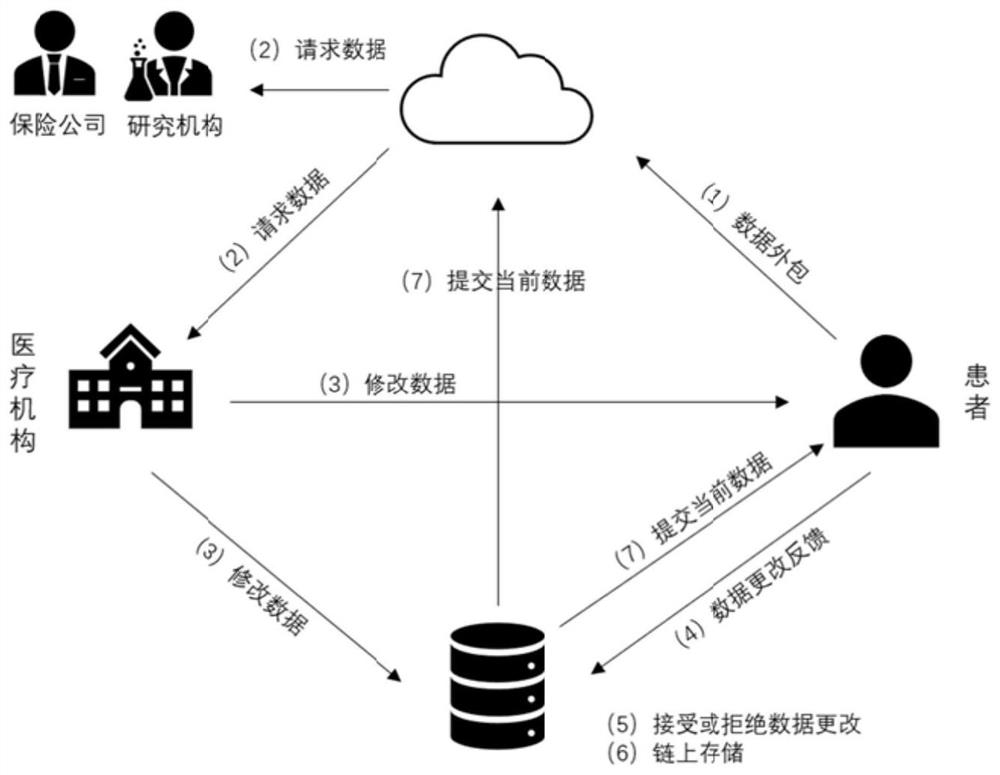
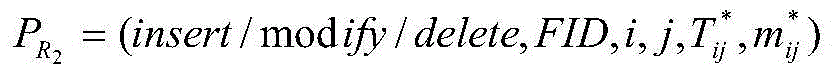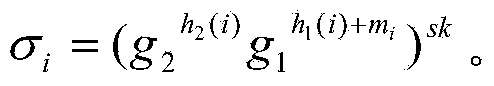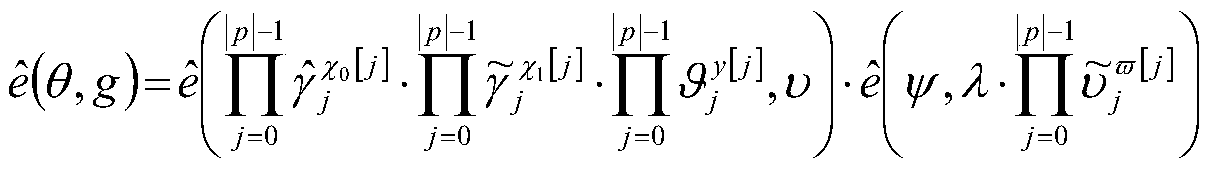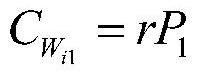Patents
Literature
57 results about "Data outsourcing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
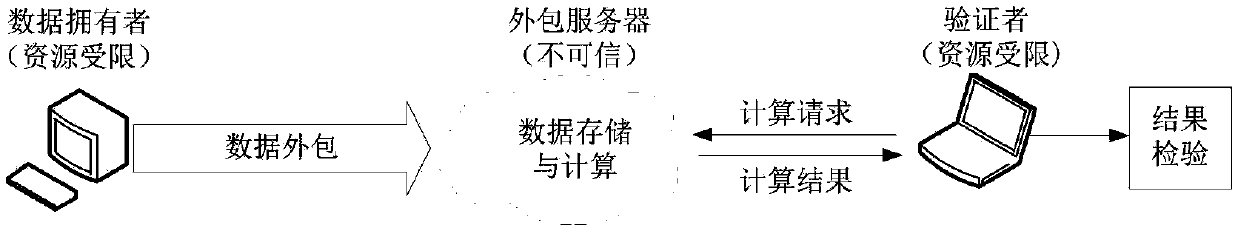
Data Outsourcing is all about maintaining the data of business that they have collected such as customer address, e-mail, telephone number, reviews, etc, in the proper format by converting into digitized form.
Safe data-outsourcing machine learning and data analysis method
ActiveCN107124276AReduce complexityFix security issuesPublic key for secure communicationDigital data protectionCiphertextDecision taking
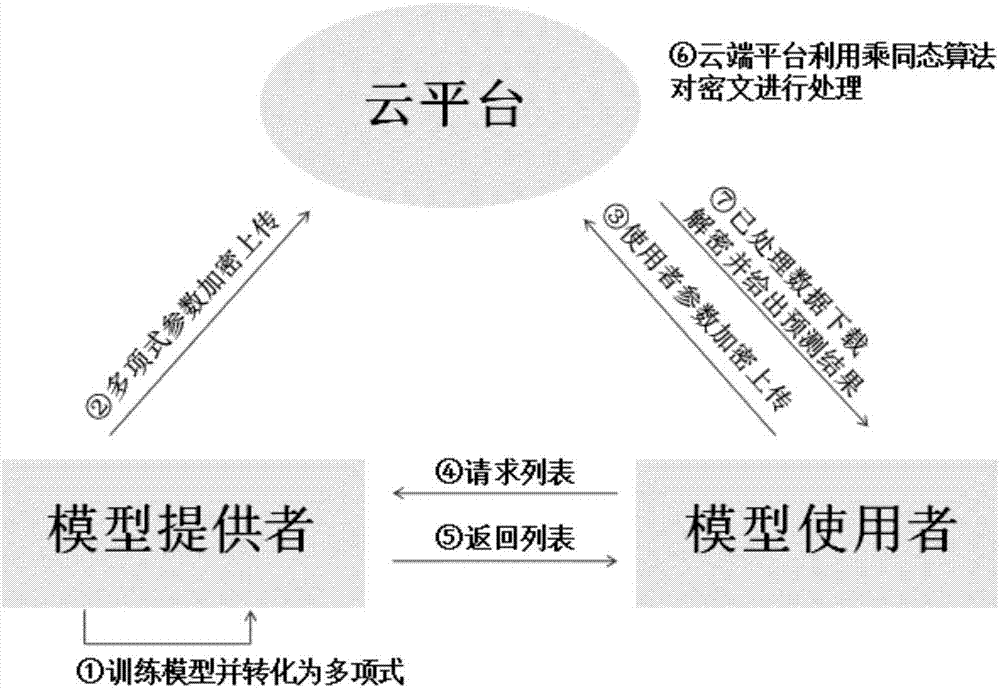
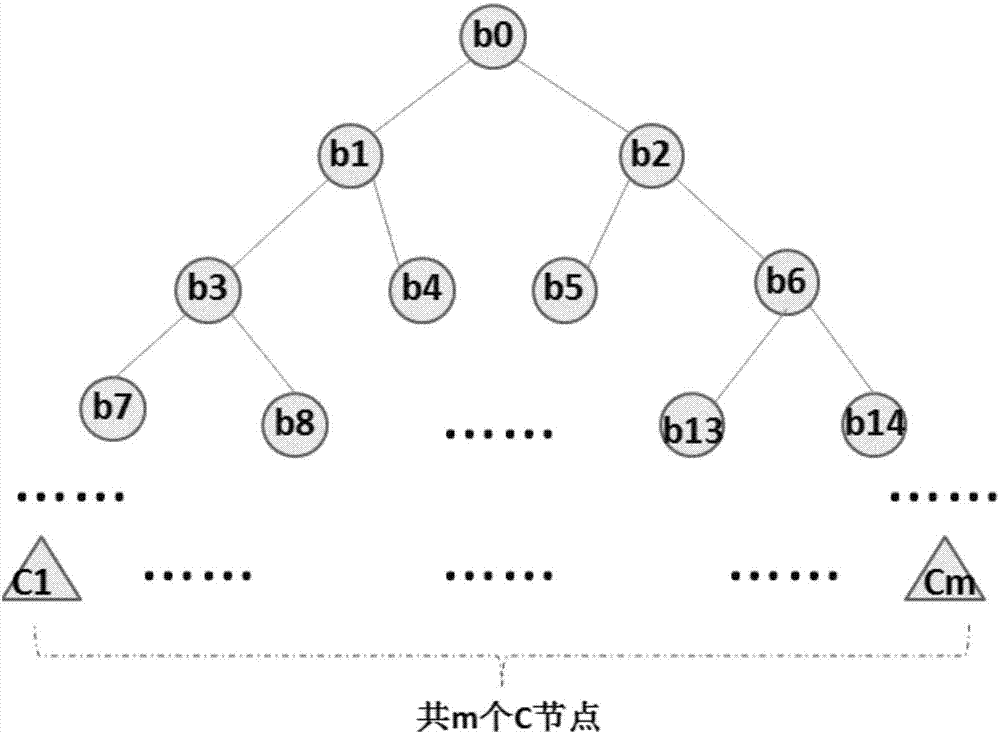
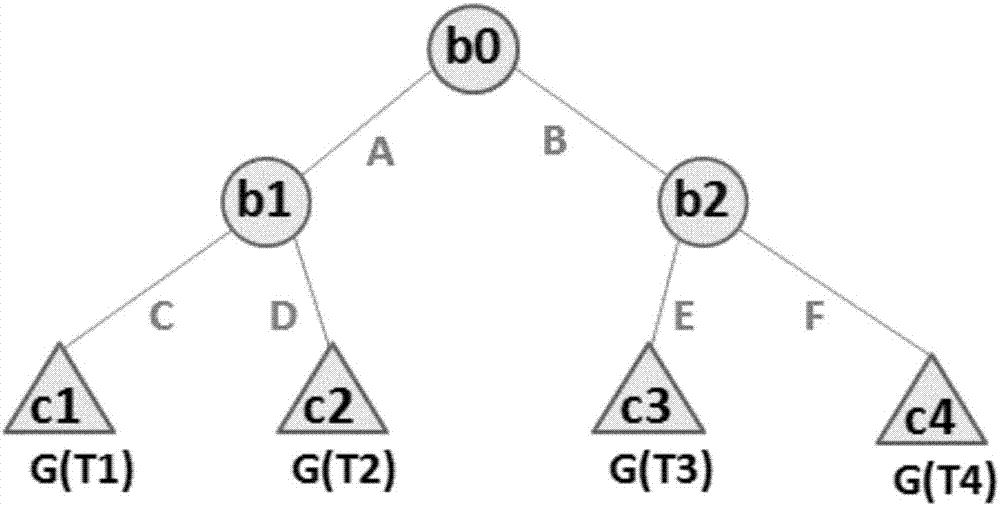
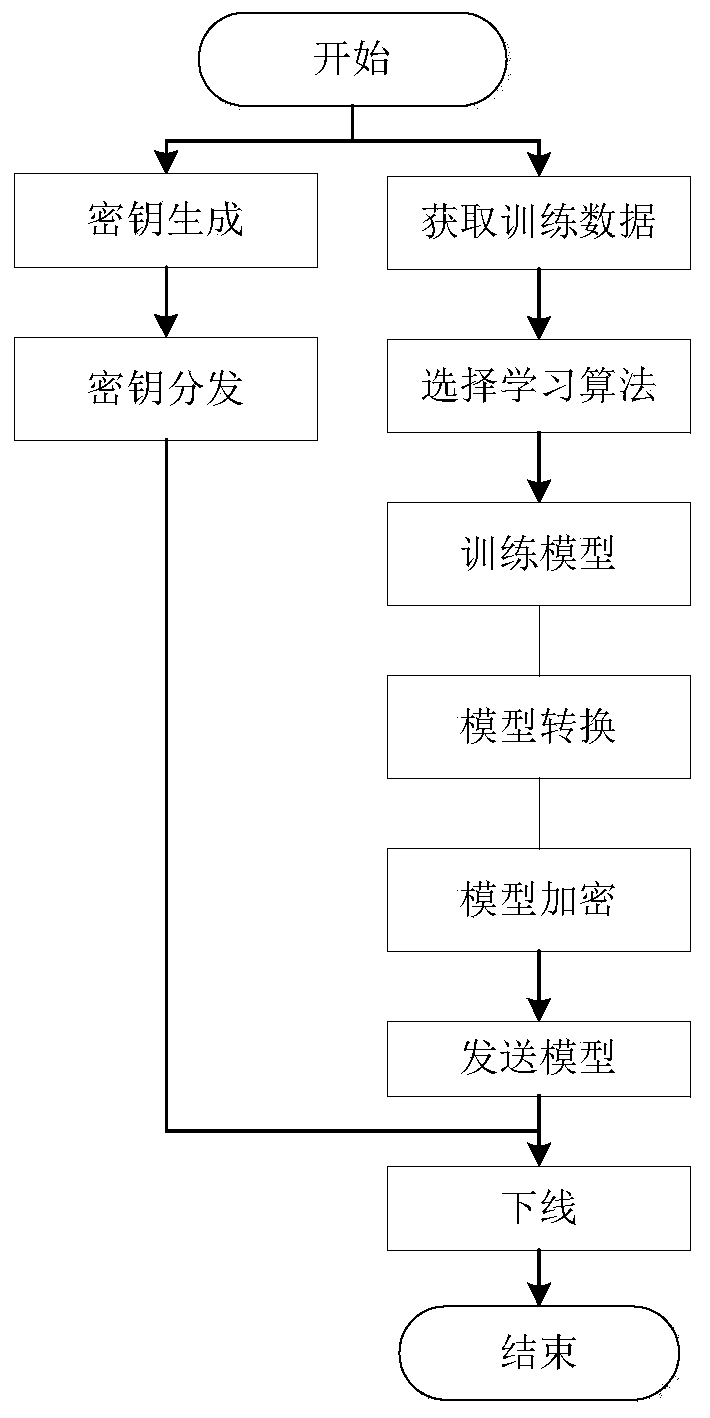
The invention discloses a safe data-outsourcing machine learning and data analysis method. A random tree is transformed in a homoenergetic mode into properties of a binary tree; a trained decision tree prediction model is transformed into the binary tree, the binary tree is induced into a special polynomial of which a shape is a sum of an infinite number of multiplier items, and each piece of data in the model is encrypted by an RSA and is uploaded to a cloud platform; then data which needs to be decided is also encrypted by the RSA and is uploaded to the cloud platform; the encrypted data of the model and the encrypted data which needs to be decided are correspondingly computed by utilizing the multiplication homomorphic encryption property of the RSA to obtain a ciphertext result of each multiplier item; and the results are returned to a data user for decryption so as to obtain a decision result. By transforming the binary tree into the polynomial, a decision tree which originally can be implemented by various computations is transformed into the decision tree which can be implemented by one computation, so that the machine learning process of the decision tree can be rapidly completed by using a multiplication homomorphic algorithm, a complex degree of carrying out such decision tree machine learning algorithm on a ciphertext is greatly reduced, and computing efficiency is promoted.
Owner:XIDIAN UNIV
Decision tree classification service system and method supporting privacy protection
The invention belongs to the field of machine learning and privacy protection, and particularly relates to a decision tree classification service system and method supporting privacy protection. The service system comprises a model owner module, a client module, a cloud service module and a ciphertext operation module. The method comprises a preparation stage and a classification stage. The invention provides a decision tree classifier supporting privacy protection orienting cloud encryption data, and designs and implements a decision tree classification service system supporting privacy protection. Original data cannot be recovered through encrypted data uploaded by a user, privacy protection in the outsourcing calculation process is guaranteed, large-scale data are outsourced to a third-party server which is high in storage and calculation resource, local infrastructure investment and management of the user are reduced, and then more economic benefits are generated.
Owner:NORTHEASTERN UNIV
System and method for high-efficiency data integrity auditing supporting safety duplication eliminating in cloud environment
ActiveCN107483585AReduce redundancyGuaranteed correctnessDigital data protectionTransmissionThird partyData integrity
The present invention belongs to the cloud data technology field, and discloses a system and method for high-efficiency data integrity auditing supporting safety duplication eliminating in a cloud environment. A data owner module is configured to store local data after safety duplication eliminating on cloud, submit a data management task to a cloud service provider module and submit a data auditing task to a third-party audit module; the cloud service provider module is configured to provide data outsourcing storage and integrity auditing service to take the user' place to perform data storage and management; the third-party audit module is configured to replace the data owner module to provide the data integrity auditing service and return back an auditing result; and a certificate authority module is configured to generate a data owner module anonymous public key certificate, track the real identities of malicious users and generate public parameters and label aggregation secret keys. The safety duplication eliminating and high-efficiency data integrity auditing are realized so as to reach the expected safety target and improve the efficiency of the integrity auditing.
Owner:XIDIAN UNIV
Cloud storage service-oriented dynamic data integrity auditing program
InactiveCN104902027AOvercoming Insufficient Support for Dynamic OperationsHonest updateTransmissionData integrityCloud data
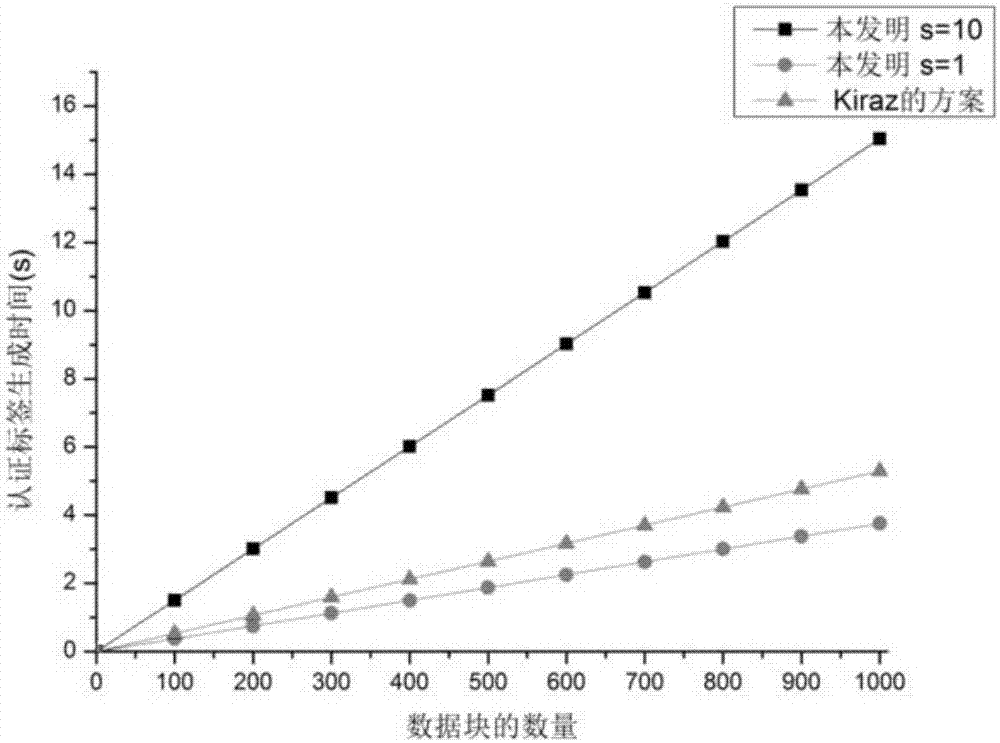
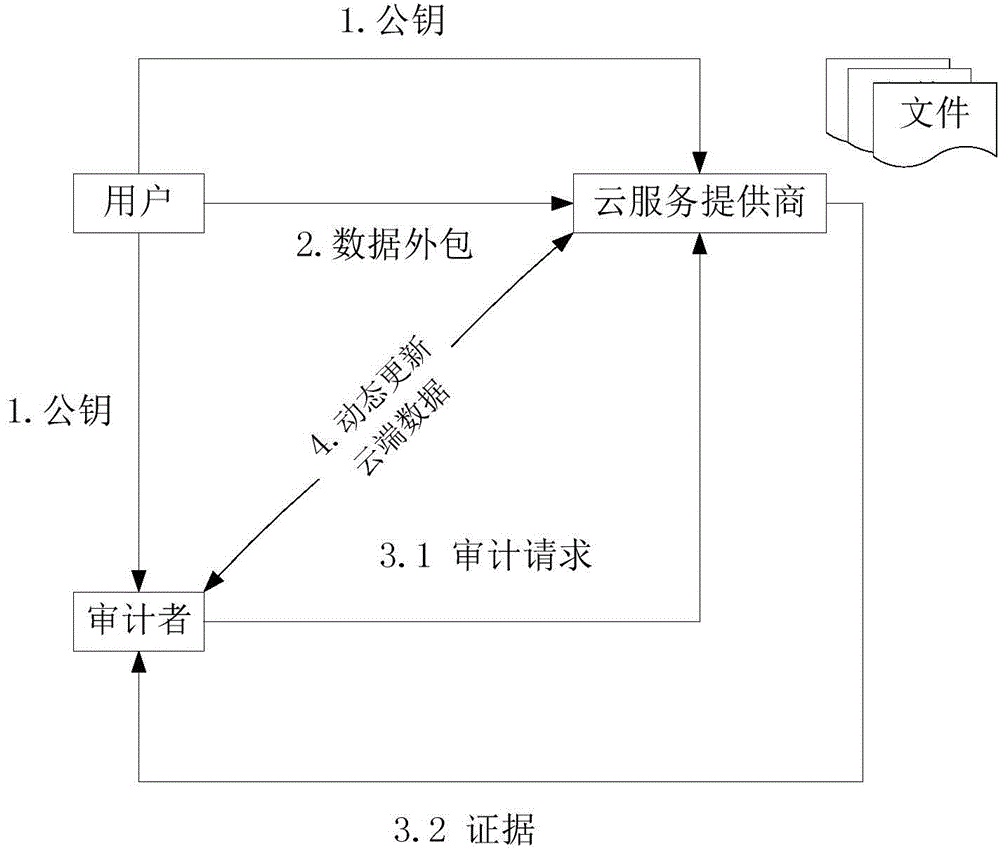
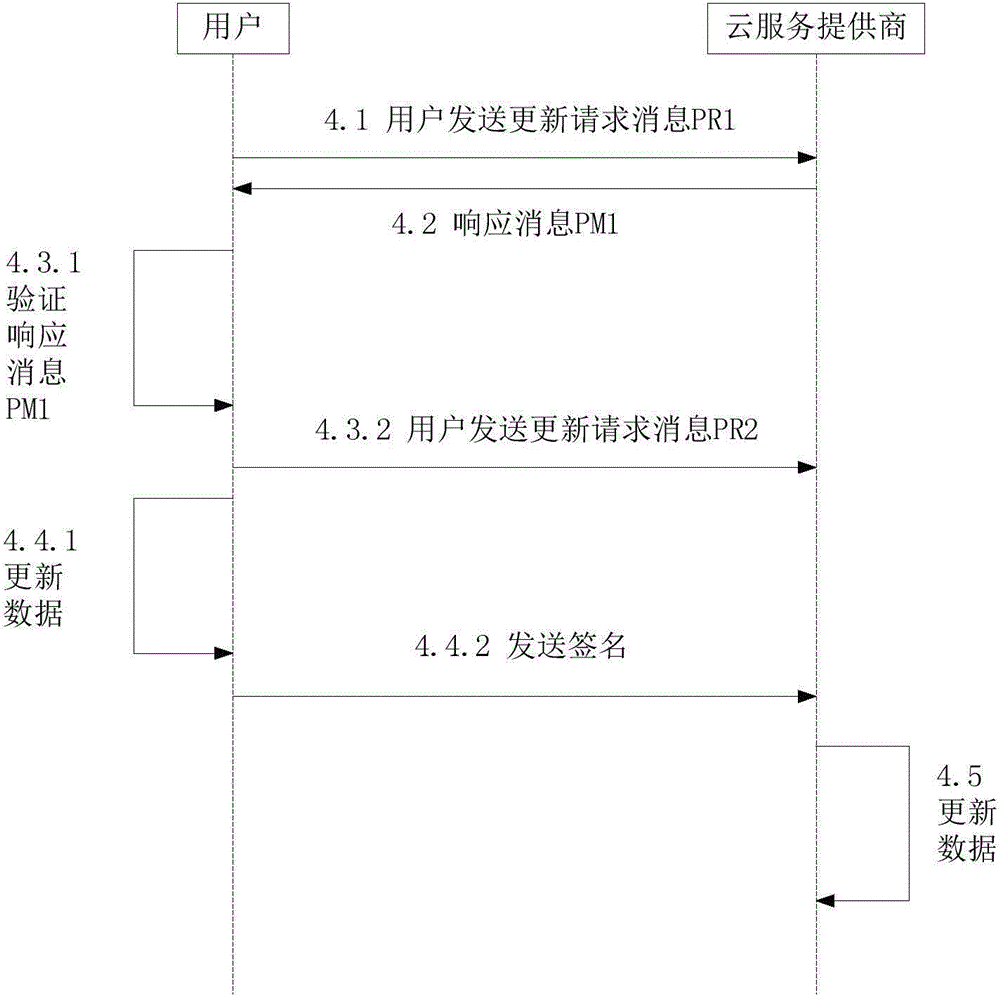
The invention discloses a cloud storage service-oriented dynamic data integrity auditing program, and aims to overcome the deficiency of an existing data integrity examination program of the cloud storage service in supporting the user dynamic operation. The cloud storage service-oriented dynamic data integrity auditing program includes a key generation phase in which a user generates a pair of public and private keys and transmits the public key to a cloud service supplier and an auditor; a data outsourcing phase in which the user transmits data blocks and labels to the cloud service supplier, and the cloud service supplier verifies the correctness of the labels; a cloud data integrity auditing phase in which the auditor transmits an audit request to the cloud service supplier, and a cloud server computes an evidence and returns the evidence to the auditor, and finally the auditor verifies the correctness of the evidence; and a cloud data dynamic updating phase in which the user transmits the data blocks and the labels to the cloud service supplier, and the cloud service supplier performs update operation and informs the user of an updated result. The cloud storage service-oriented dynamic data integrity auditing program can not only effectively satisfy a safety requirement of the data integrity auditing program of the cloud storage service but also effectively support dynamic operations of users.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
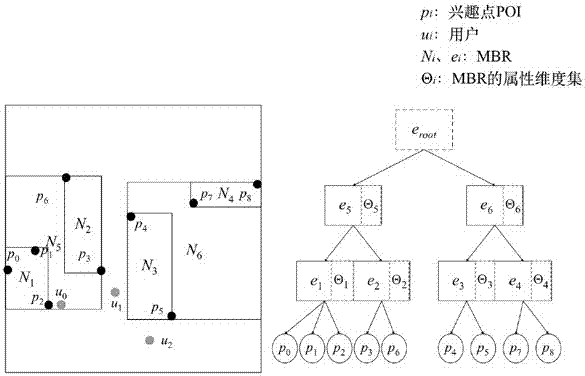
Merkle tree structure-based space inquiring integrity verification method
InactiveCN104750784AEasy to storeIncreased maintenance overheadSpecial data processing applicationsNODALTheoretical computer science
The invention discloses a Merkle tree structure-based space inquiring integrity verification method. Based on an existing quadtree node generated by a self-adaption Hilbert curve, a Merkle tree structural construction method for supporting the inquiring integrity verification is provided, and an integrity verification method for range inquiring and KNN inquiring is provided, so that an integrity verification result provided by the Merkle tree structure-based space inquiring integrity verification method is free of phenomena of the misinformation and the false-information, and malevolence changing is difficult to carried out on a user inquired result by a service supplier. Under the mode of space data outsourcing service, the method can provide an efficient verification structural generating function, accurate range inquiring and a KNN inquiring integrity verification function for a user, and therefore the quality of space inquiring service can be guaranteed.
Owner:XI AN JIAOTONG UNIV
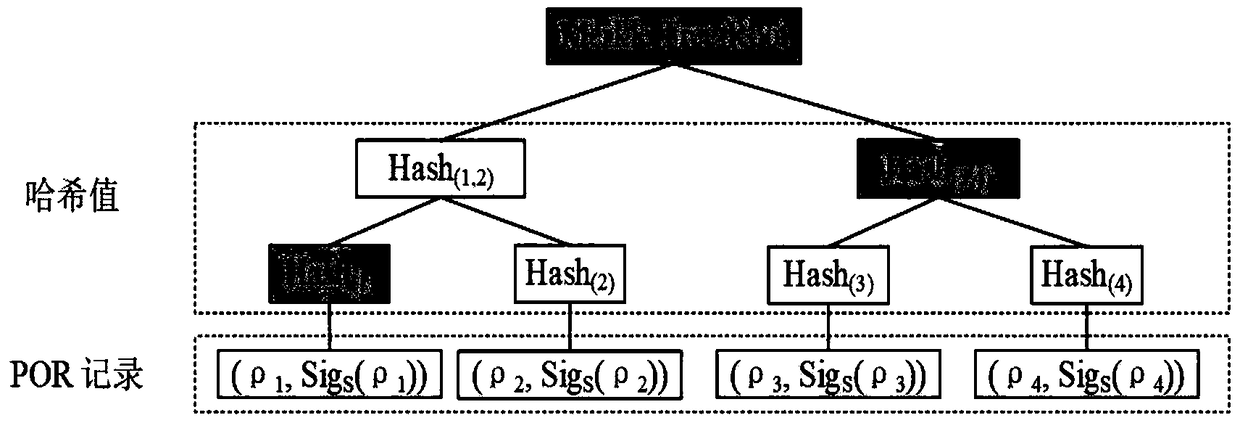
Decentralized collaborative verification model and verification algorithm
ActiveCN108923932AImprove securityImprove efficiencyUser identity/authority verificationData validationSource Data Verification
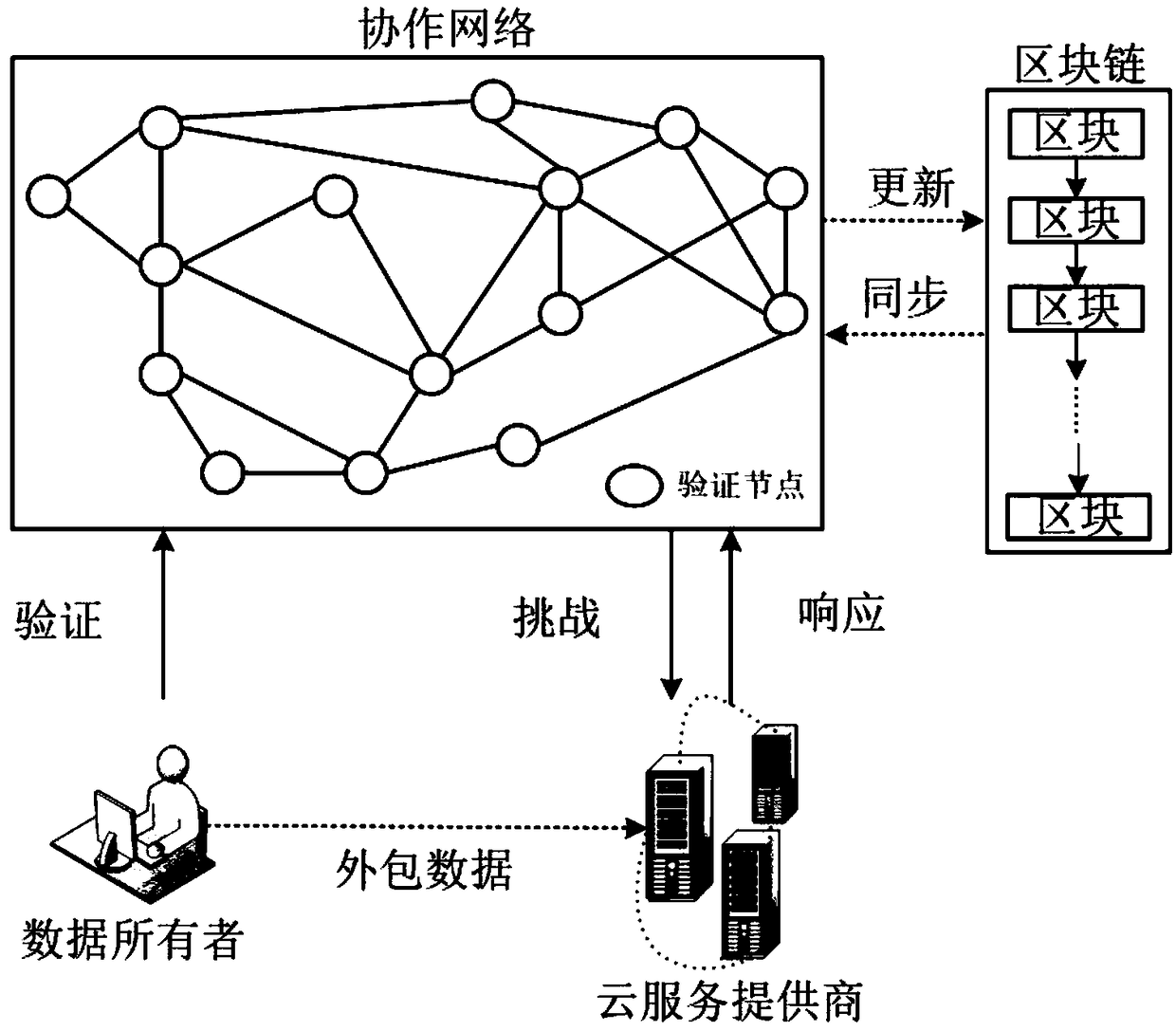
The invention discloses a decentralized collaborative verification model and verification algorithm. The model comprises four key components: a data owner, a cloud service provider, a collaboration network and a blockchain, wherein the block storage of the blockchain is composed of a POR Merkle tree generated by a POR record, a leaf node of the POR Merkle tree consists of a two-tuples, and the two-tuples records the POR record and a digital signature of the data owner. The decentralized collaborative verification model disclosed by the invention brings the characteristics of the blockchain into the process of outsourcing data storage and verification in an untrusted environment, so that the data security can be improved, the security problem that may be caused by handing over a data verification process to a third party in the traditional data outsourcing service is avoided, the efficiency is improved, and the security is improved.
Owner:NORTHEASTERN UNIV
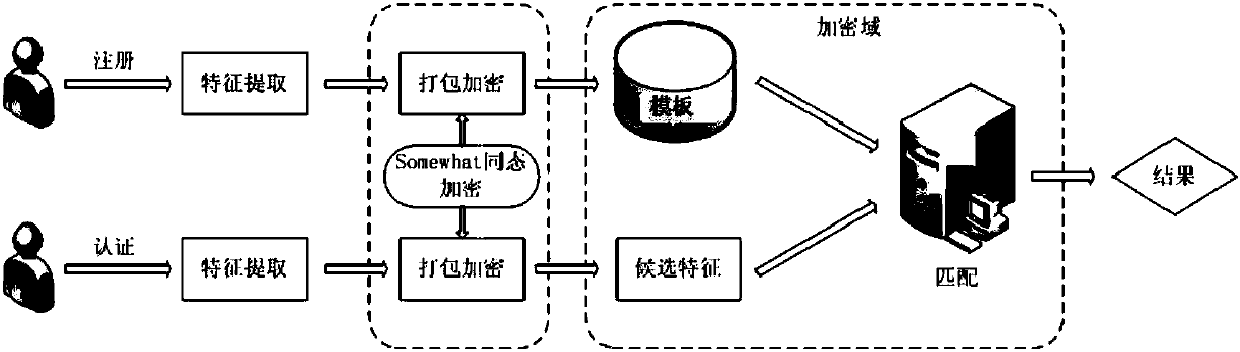
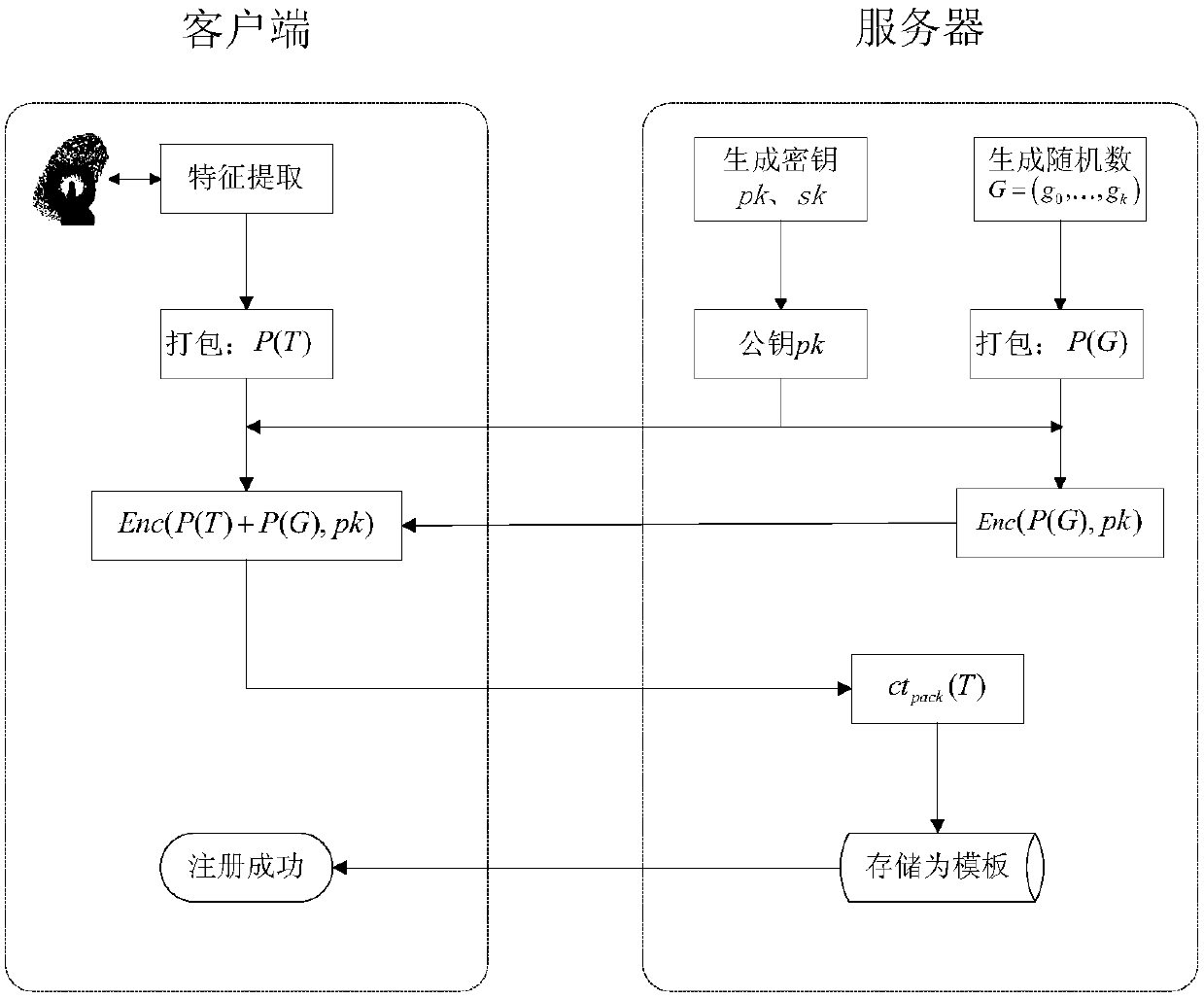
Biological characteristic sensitive information outsourcing identity authentication method based on homomorphic encryption
ActiveCN107919965AImprove securityImprove efficiencyKey distribution for secure communicationUser identity/authority verificationData privacy protectionData transmission
The invention relates to a biological characteristic sensitive information outsourcing identity authentication method based on homomorphic encryption, to provide users with a more secure identity authentication method based on biological characteristics. Compared with a traditional biological characteristic authentication method, the method includes a Somewhat homomorphic encryption method based on RLWE construction and a message coding method, which can conduct fast computation processing on the biological characteristic information after user encryption, and effectively solve the secure privacy problem brought by data outsourcing. The transmission, storage and computation of user biological characteristic information are under an encrypted state in a register stage and an authenticationstage, and the replay attack can be effectively resisted by the random number bought in a data transmission process. As a result, the method can realize secure identity authentication based on biological characteristic sensitive information outsourcing in the case of user data privacy protection.
Owner:HANGZHOU DIANZI UNIV
Multiple users-based outsourcing database audit method
InactiveCN106452748AImprove privacy protectionReduce the burden onKey distribution for secure communicationUser identity/authority verificationPlaintextData privacy protection
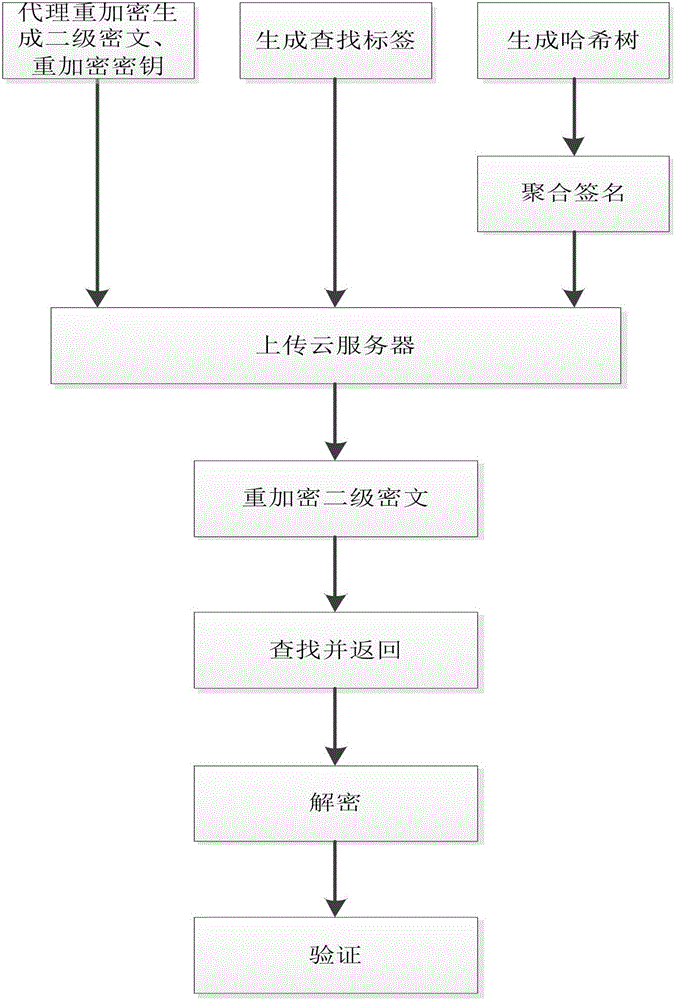
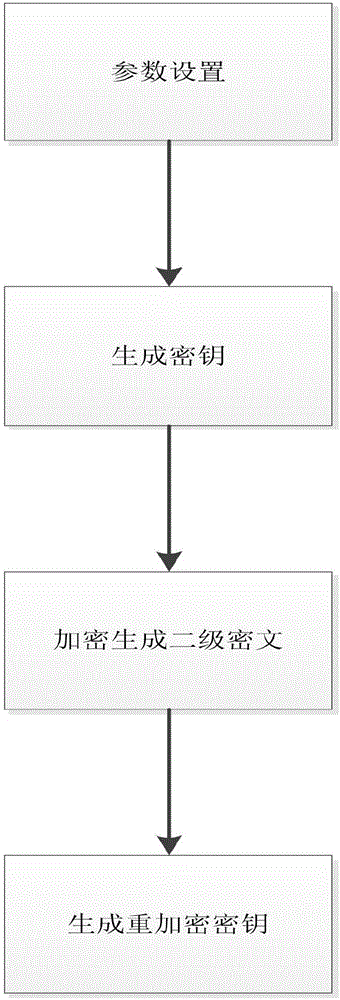
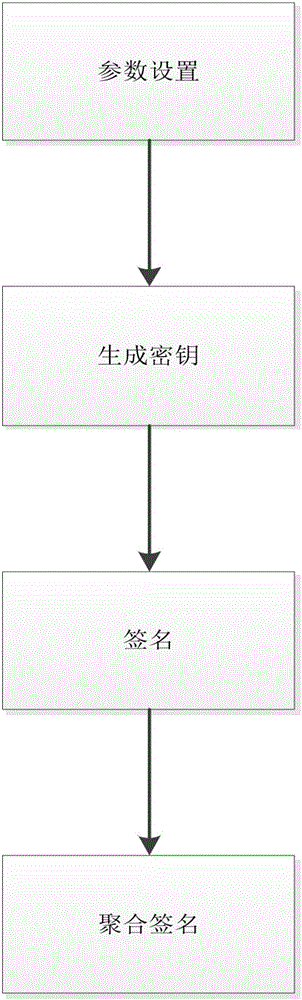
The present invention discloses a multiple users-based outsourcing database audit method, aiming to solve problems of low signature verification efficiency and complex decryption in the prior art. The method comprises a first step that a data owner encrypts data by using a proxy re-encryption method so as to form a second-level ciphertext, generates a re-encryption secret key by inquiring a public key of a user, generates a searching label by using an Evdokimov encryption manner, and generates hash tree root signature by using aggregate signature; and the signature, second-level ciphertext, re-encryption secret key and the searching label are transmitted to a cloud server; a second step that the cloud server encrypts the second-level ciphertext so as to generate a first-level ciphertext; a third step that a user sends a search request to the cloud server, and the cloud server searches and returns a corresponding first-level ciphertext; and a fourth step that the user decrypts the first-level ciphertext so as to form a plaintext, and performs aggregate verification on the plaintext. Through adoption of the method, the burden on the data owner is greatly reduced, interaction is reduced for one time, data privacy protection is improved, and the method can be applied to safe data outsourcing in a cloud calculation environment.
Owner:XIDIAN UNIV
Publicly verifiable outsourcing statistical method
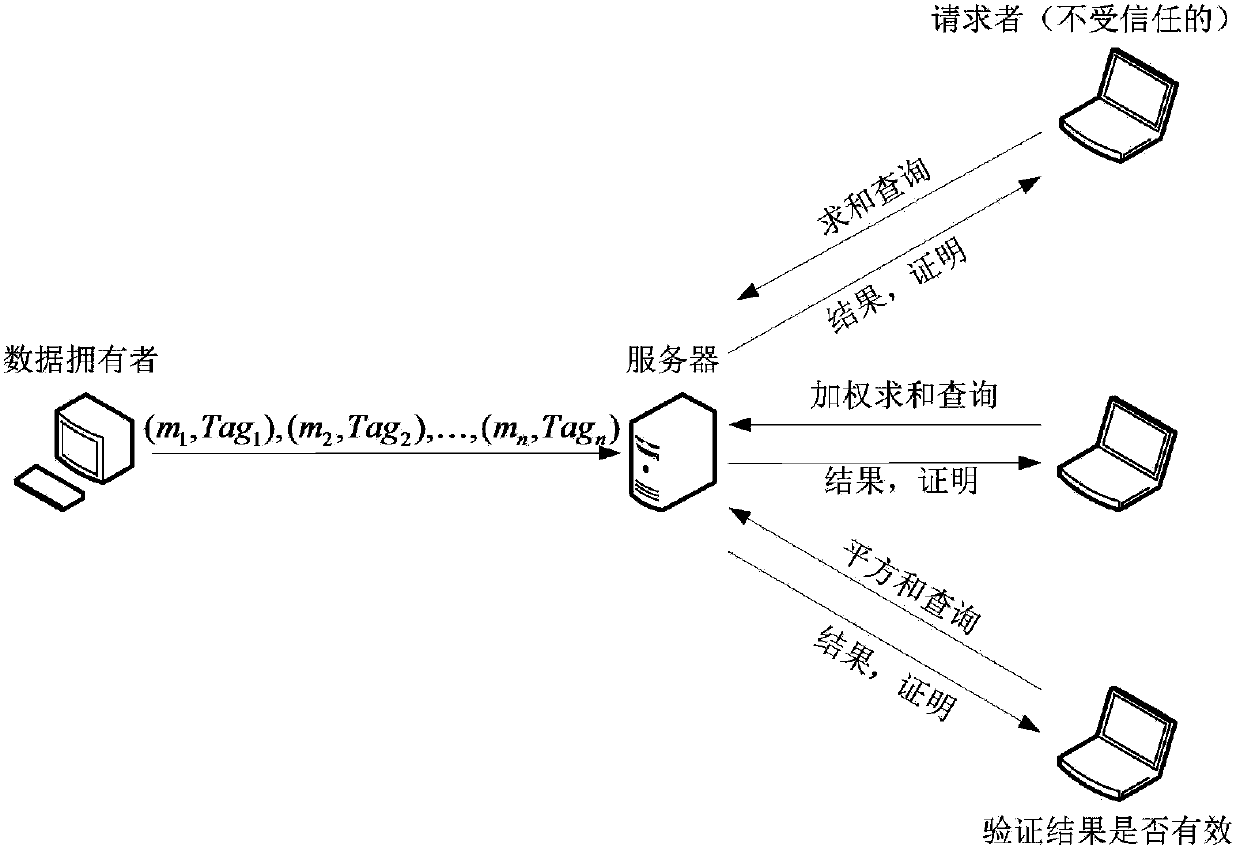
The invention discloses a publicly verifiable outsourcing statistical method. Three entities of a data owner, an outsourcing server and a requester are included, first the data owner uploads data to the outsourcing server, then the outsourcing server conducts statistical operation on the data according to the need of the requester, finally the requester detects and verifies effectiveness of the statistical result. By means of the method, the requester can conducts various statistical operations on data under the condition that massive data are not downloaded locally, and the method has good safety, effectiveness, function independence and variability. On one hand, the requester can verify correctness of response returned by the outsourcing server, the expenses of calculation and communication are irrelevant with the amount of data input by verification, and the algorithm time complexity is maintained in the O (1) range; on the other hand, the data owner can conduct data outsourcing under the condition that the function details to be calculated are not required to be understood. In addition, statistical operation can be conducted on the whole both on the whole and partially through the function.
Owner:XIDIAN UNIV
Data integrity verification method supporting key updating and third-party privacy protection
InactiveCN108768975AMeet safety goalsReduce computational overheadKey distribution for secure communicationUser identity/authority verificationThird partyComputer hardware
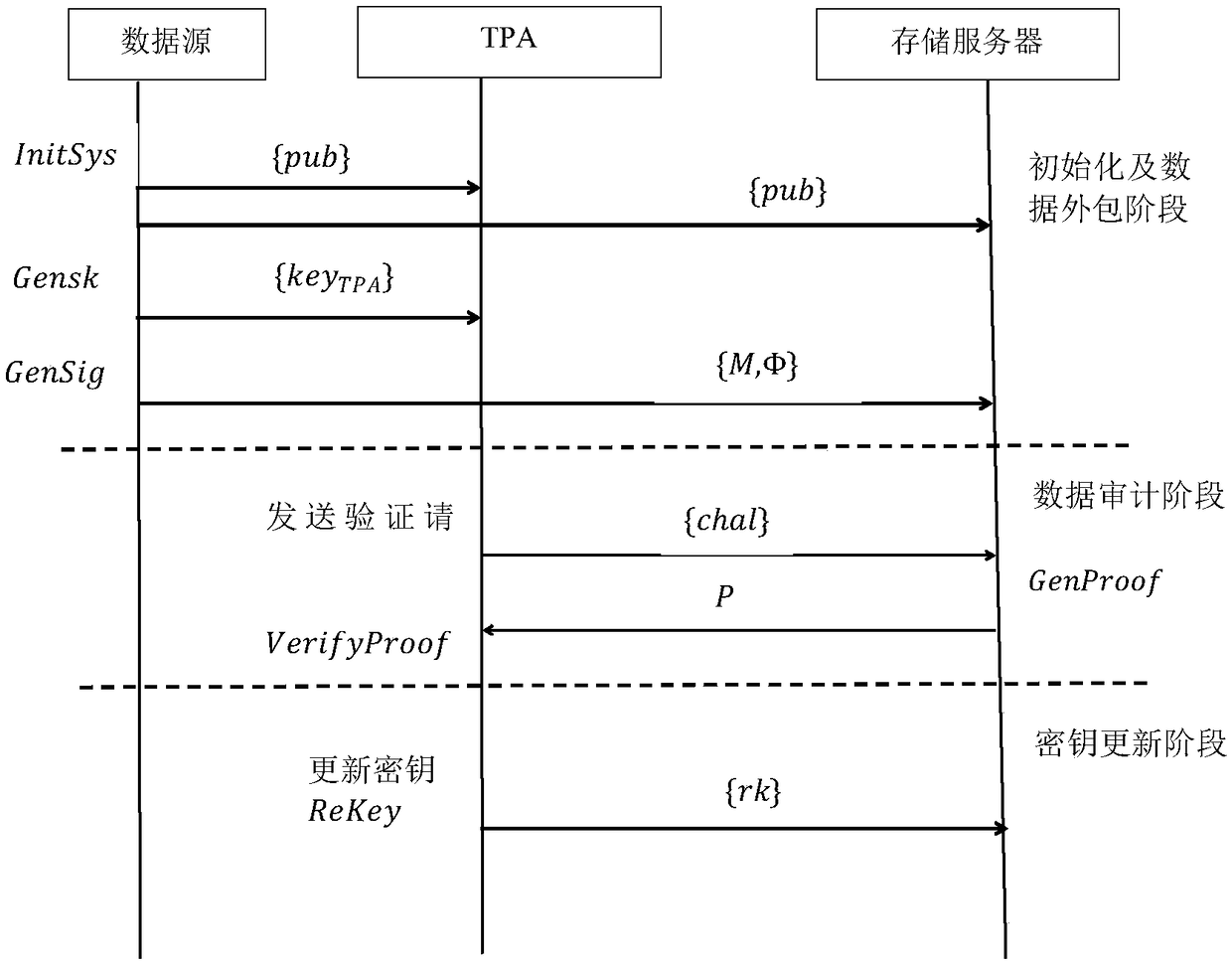
The invention discloses a data integrity verification method supporting key updating and third-party privacy protection. The data integrity verification method comprises an initialization and data outsourcing stage, a data auditing stage and a key updating stage. On the basis that a proxy re-signature technology substitutes a traditional key updating method in an existing scheme, a storage serverutilizes a re-signature key to achieve updating of data block signature, the computation cost and the communication cost of data sources are effectively lowered, and it can be ensured that TPA cannotobtain privacy data contents of the data sources in the process of integrity verification; and thus the data integrity verification method achieves the safety purpose required by data integrity verification.
Owner:SOUTHEAST UNIV
Data structure construction and matching method for secure character string pattern matching
ActiveCN110176984AProtect privacy and securityImprove efficiencyKey distribution for secure communicationDigital data protectionOriginal dataTheoretical computer science
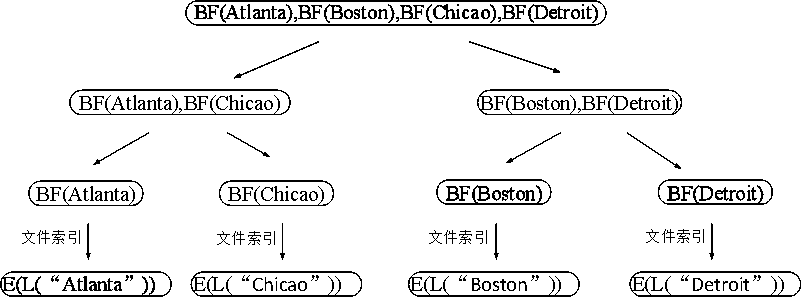
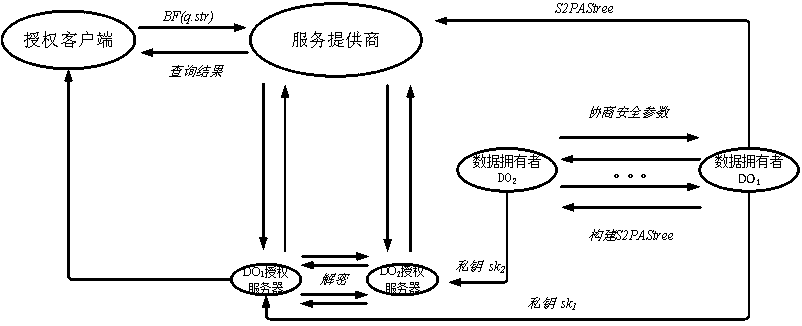
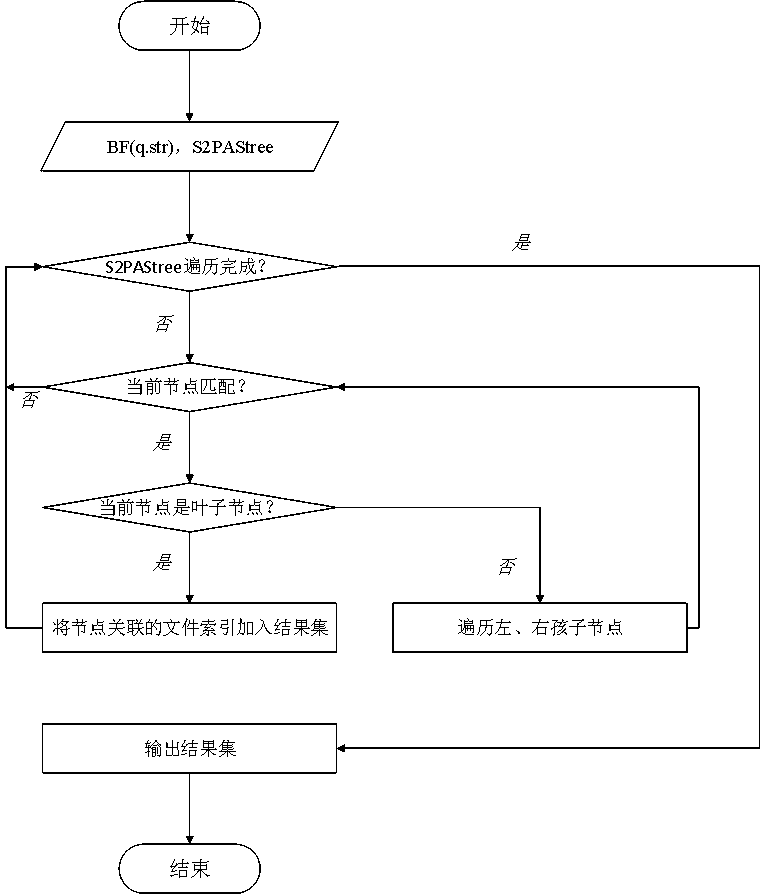
The invention discloses a data structure construction and matching method for secure character string pattern matching. The method comprises a construction method of a data structure S2PASTree and a method for carrying out character string mode matching based on the data structure. The data structure comprises a group of keywords, so that a program applying the data structure can quickly respond to a character string mode matching query requirement supporting privacy protection, and the memory resource expenditure of a service provider and an authorized user is reduced. Based on the construction method, aiming at cloud computing and data outsourcing situations, a service provider can quickly respond to the requirements of an authorized client for security character string mode matching query on the premise of protecting the privacy security of original data, query conditions and query results. Based on the matching method, compared with a common character string mode matching query method, the query speed is higher, the communication overhead is lower, and the query processing efficiency and the service quality of a service provider are improved.
Owner:TROY INFORMATION TECHNOLOGY CO LTD
Fully homomorphic data packaging method for lightweight single-user multi-data
ActiveCN110851845AImprove securityHigh computational complexityDigital data protectionHigh level techniquesAlgorithmCiphertext
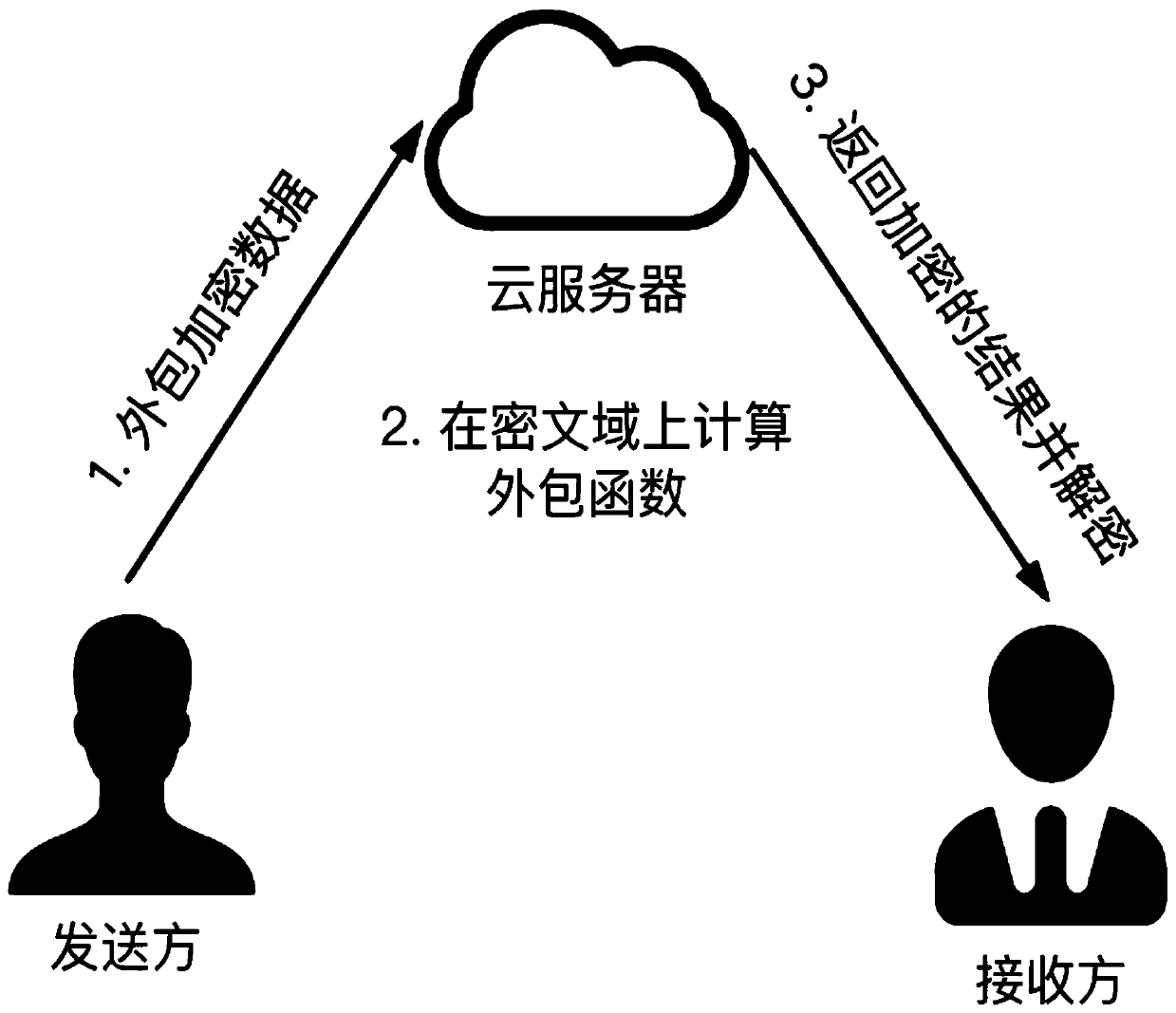
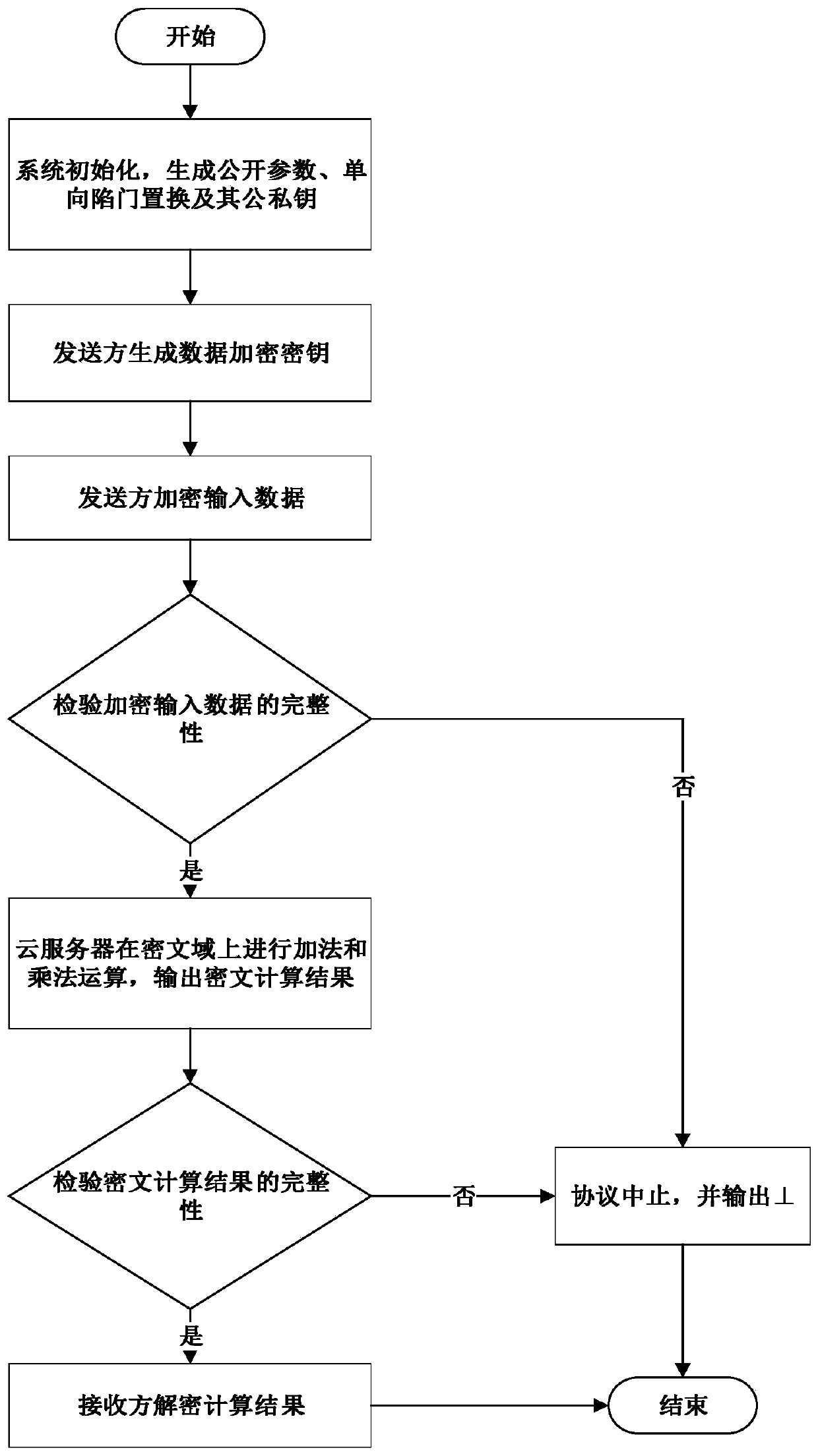
The invention discloses a fully homomorphic data packaging method for lightweight single-user multi-data, which is characterized by comprising the following five stages of system initialization, key generation, data encryption, encryption data outsourcing calculation and decryption. Compared with the prior art, the method is simple and easy to implement, the efficiency is high, and efficient privacy protection outsourcing calculation is realized in a scene of a single user and a plurality of input data; according to the method, a cloud server and an unauthorized receiver are combined, additionand multiplication operations on a ciphertext domain are supported at the same time, input privacy can achieve unconditional security (information theory security) under collusion attacks of the cloud server and the unauthorized receiver, calculation result privacy can achieve adaptive ciphertext security selection (CCA2 security) for the unauthorized receiver, and the requirements for high efficiency and privacy are met.
Owner:EAST CHINA NORMAL UNIV
Privacy-protecting outsourcing Internet-of-things data based on blockchain and backup integrity checking method thereof
ActiveCN112054897AImprove securityKey distribution for secure communicationUser identity/authority verificationThird partyData integrity
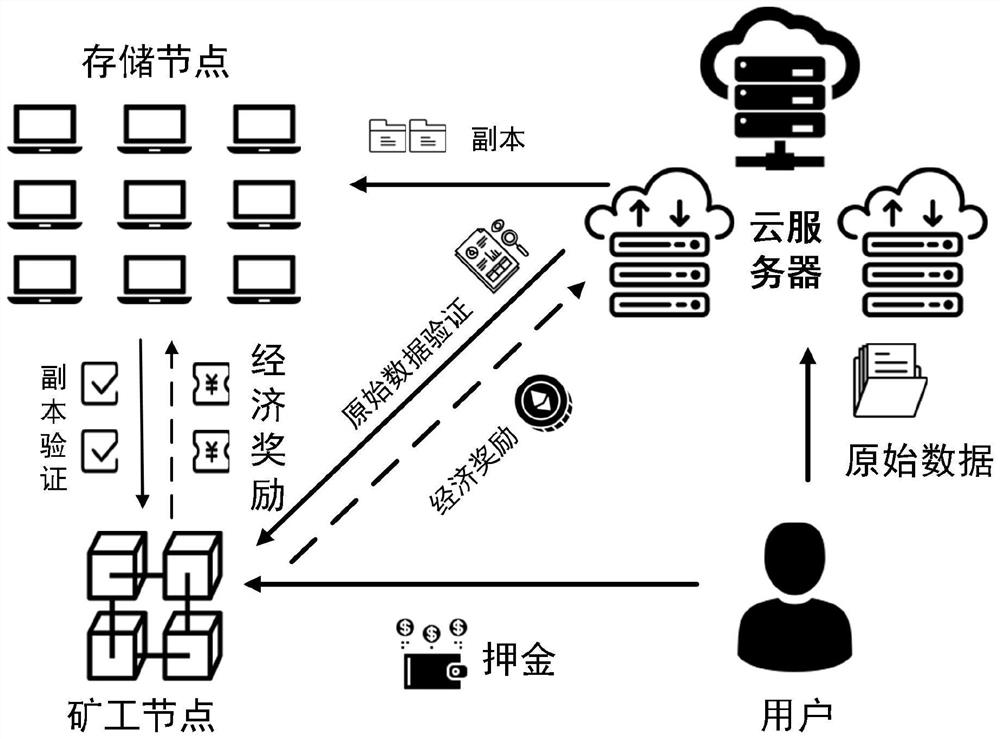
The invention provides a privacy-protecting outsourcing data and backup integrity checking method based on a blockchain for an Internet-of-things scene by utilizing the characteristics of openness, tamper resistance and the like of the blockchain and combining related knowledge of smart contracts and cryptography. Compared with an existing data outsourcing and outsourcing data integrity checking process, the method solves the problem that the expenditure of self-verification data of a user is too large, or outsourcing depends on a trusted third party; in addition, the invention provides a newcontribution degree measurement standard and a reward distribution mechanism, so that each participant can obtain corresponding incentives.
Owner:WUHAN UNIV
Method for realizing and using MRS tree data structure under multi-user space query
InactiveCN107193980AImprove operational efficiencyImprove scalabilityDigital data protectionGeographical information databasesValidation methodsService quality
The invention discloses a data structure. The data structure comprises a property dimension set. Through the data structure, a readable storage medium storing a data structure program can respond to multi-user space query, a multi-dimension query request is processed quickly and efficiently, the extendibility of the readable storage medium is enhanced, and memory resource expenditure is reduced for a service provider and users. The invention furthermore discloses a method for processing an external multi-user query request based on the data structure. Through the method, diversified query demands of a large number of users can be correctly reflected, the blank of multi-user space query processing in a data outsourcing scene is filled up, and the query processing efficiency and service quality of the service provider are improved. The invention furthermore discloses a verification method. Through the verification method, the authenticity, correctness and integrity of multi-user space query can be verified at the same time, and the reliability of data, used by the users, of the service provider is ensured. In the data outsourcing scene, the invention furthermore provides a multi-user space query verification method according to user preferences, an application device and a query verification system.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
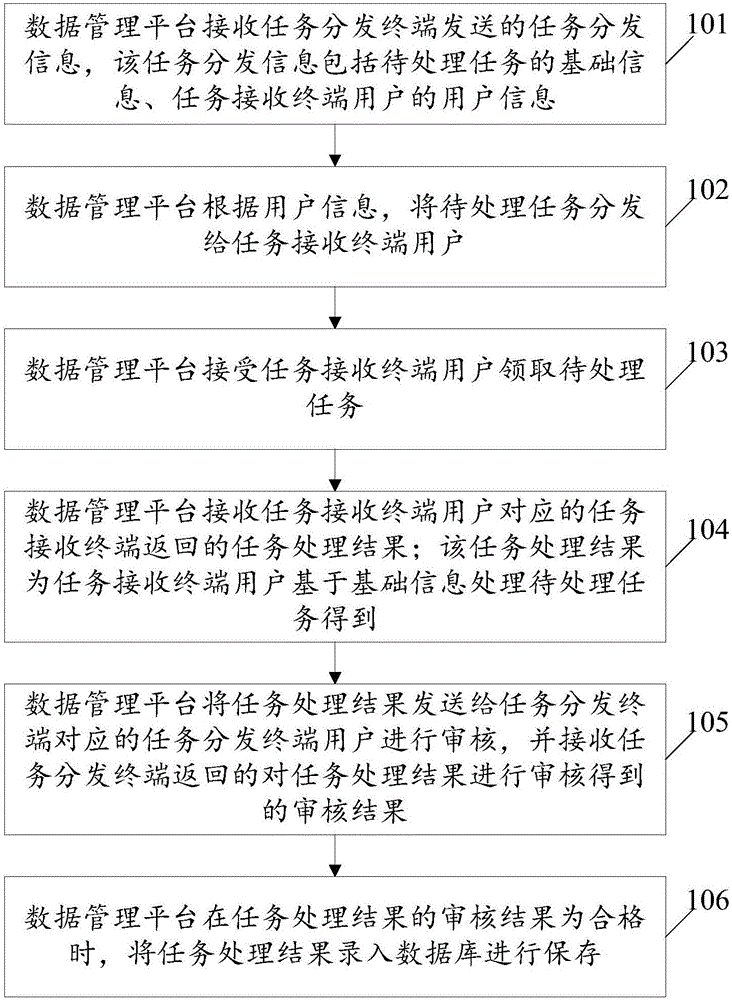
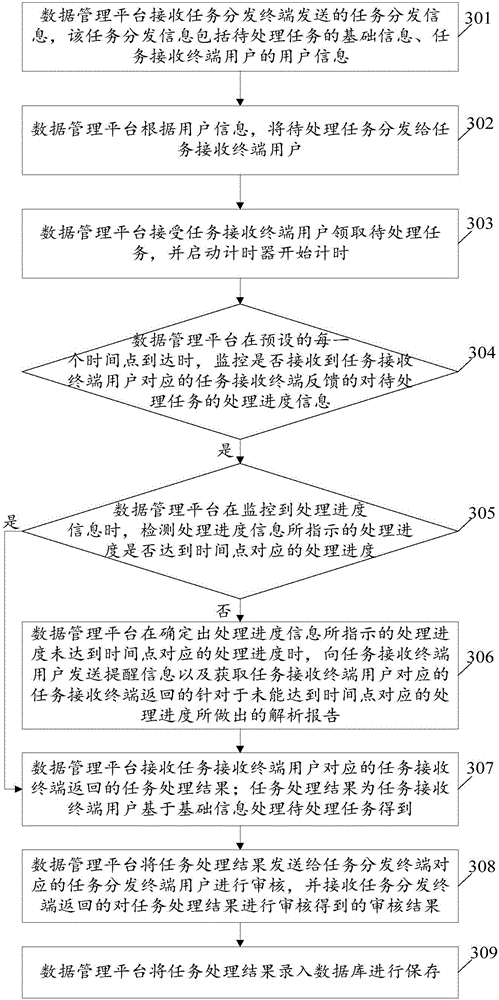
Data management implementation method based on data management platform, and data management platform
The embodiment of the invention relates to the technical field of data processing, and discloses a data management implementation method based on a data management platform, and the data management platform. The method comprises the following steps: receiving task distribution information sent by a task distribution terminal by the data management platform; distributing to-be-processed tasks to task receiving terminal users according to user information; allowing the task receiving terminal users to obtain the to-be-processed tasks; receiving task processing results returned by the task receiving terminals corresponding to the task receiving terminal users; sending the task processing results to a task distribution terminal user corresponding to the task distribution terminal for auditing, and receiving auditing results of the task processing results returned by the task distribution terminal; and when it is determined that the auditing results of the task processing results are qualified, recording the task processing results in a database for storage. By implementation of the data management implementation method provided by the embodiment of the invention, unified and transparent management and monitoring of data outsourcing are realized, and the security and stability in a data delivery process are improved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
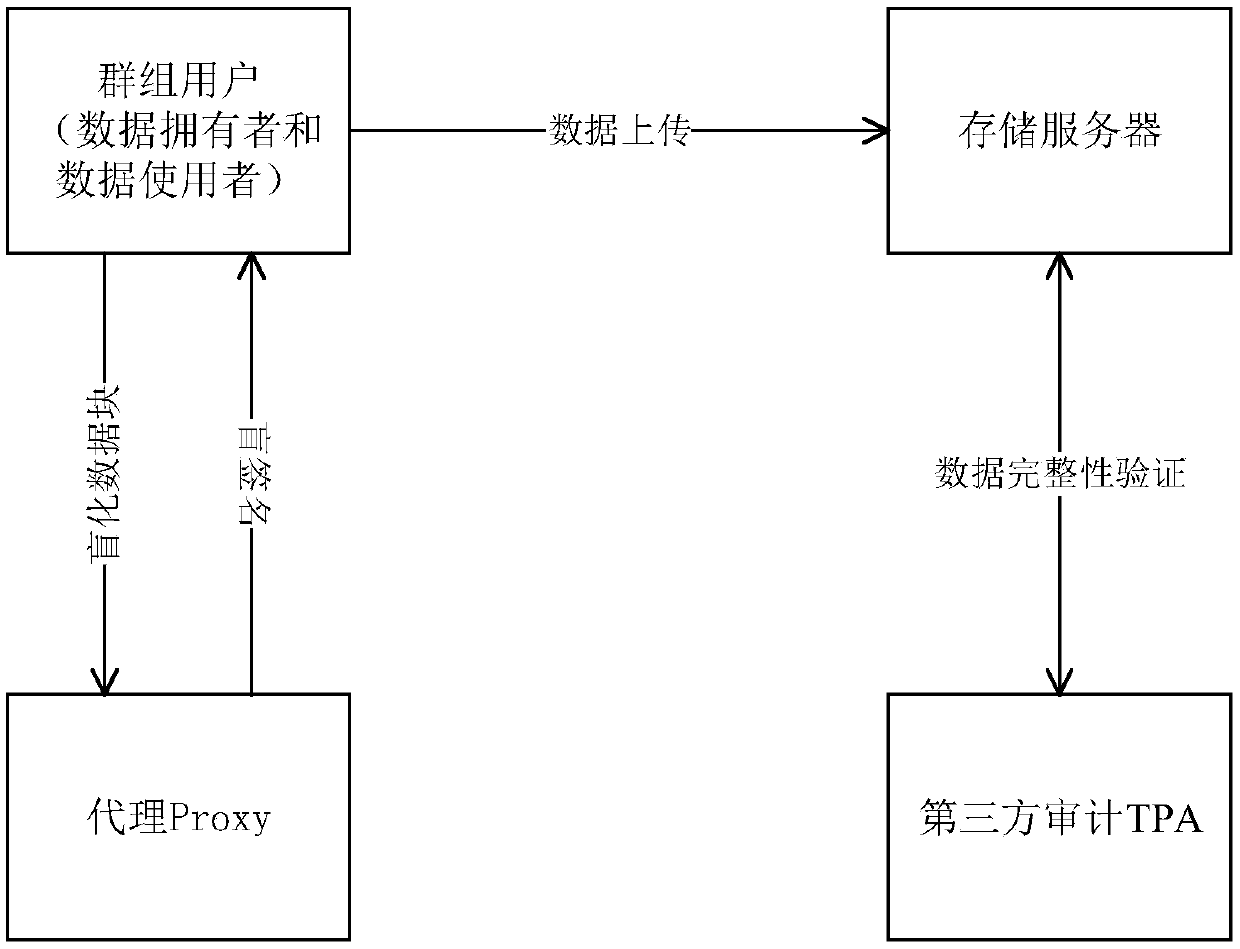
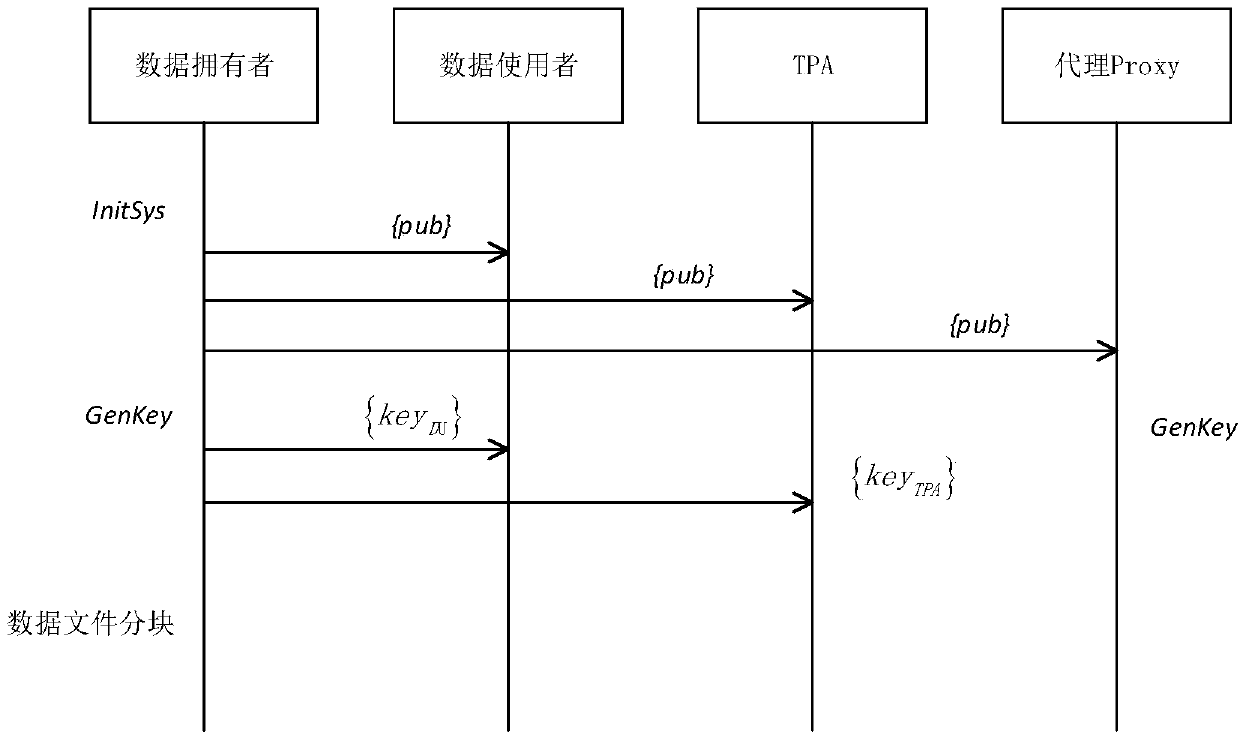
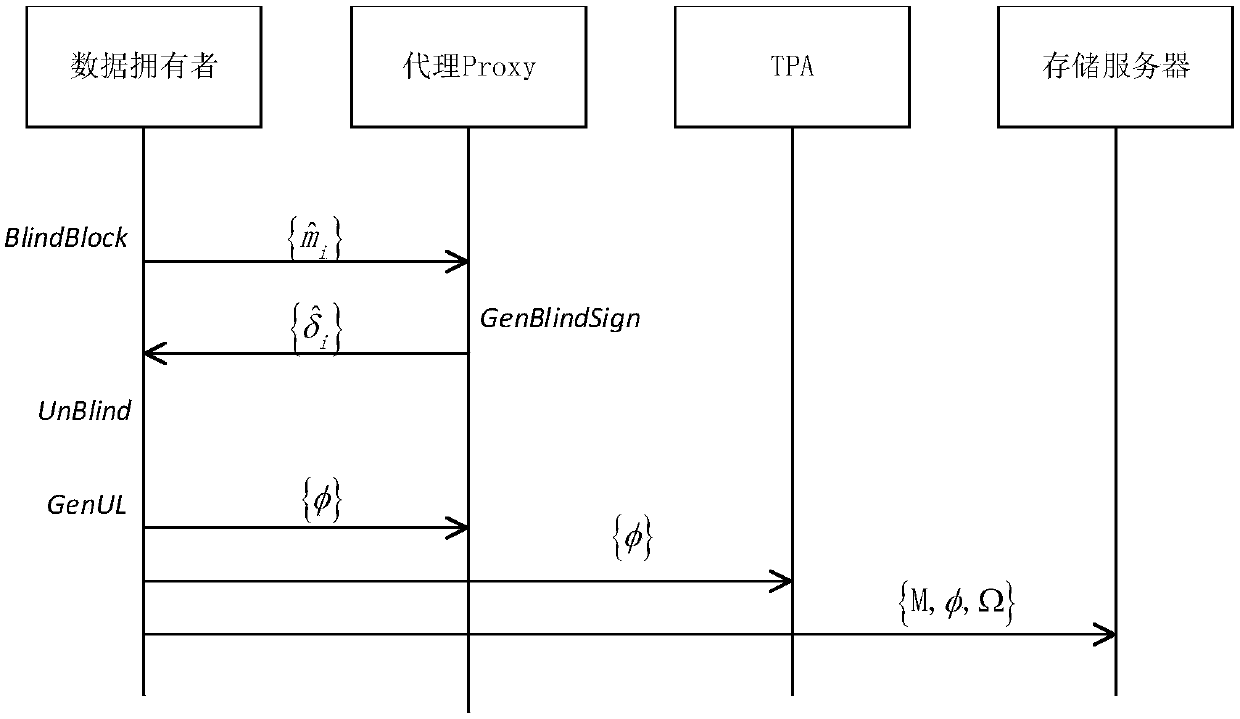
Group data completeness verification method based on proxy
ActiveCN108664814AGuaranteed identity privacyReduce overheadDigital data protectionData integrityData mining
The invention provides a group data completeness verification method based on a proxy. The method comprises an initializing stage, a data outsourcing stage, a completeness verification stage and a group user member updating stage. According to the method, users (owners and users of data) of each group are helped in data block signature computing by introducing a proxy Proxy in a system model, whendata completeness verification is conducted by TPA, any identification information of group users is not needed, completeness verification can be conducted by using the public key of the proxy Proxy,and therefore the identification privacy of group users is effectively guaranteed. The data block signatures of the group members are calculated through the proxy Proxy, the private key of the proxyProxy is unknown, so that even the originally uploaded data block signatures which are revoked of the group members are still illegal, the data block signatures do not need to be computed through other group legal members again, expenditure is reduced, and dynamic groups can be efficiently supported.
Owner:SOUTHEAST UNIV
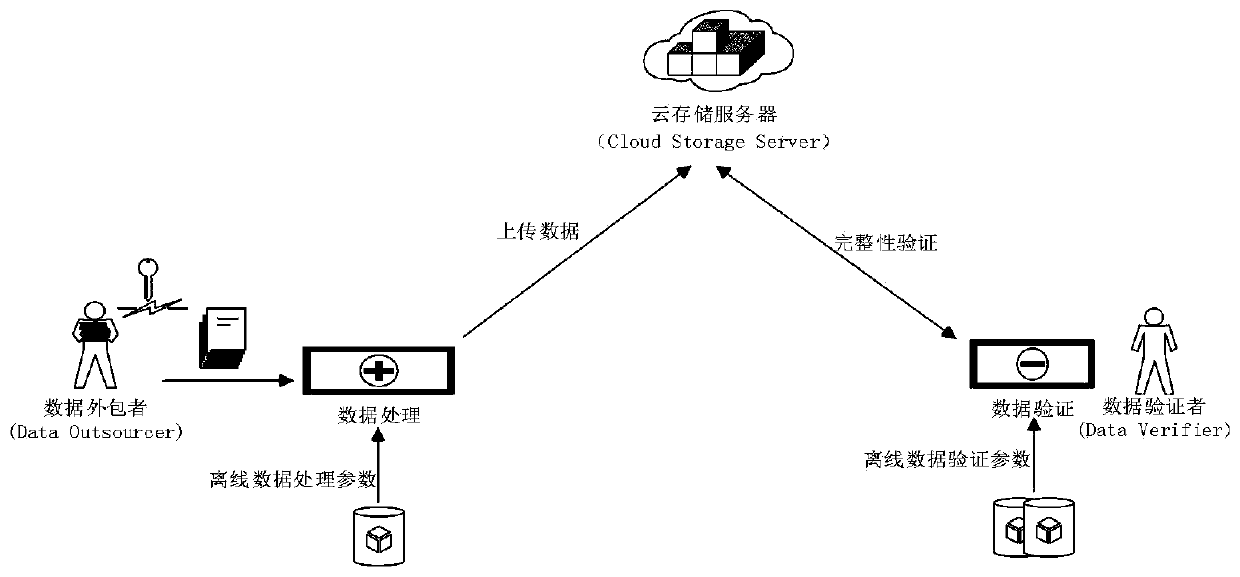
A cloud data outsourcing and integrity verification method and device supporting preprocessing
ActiveCN109818944AReduce the burden onKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData validationHash function
The invention provides a cloud data outsourcing and integrity verification method supporting preprocessing, which comprises the following steps that: a data outsourcer selects a security parameter andan anti-collision hash function to generate a public key and a private key; The data outsourcer executes a first pre-calculation process according to the public key to generate offline data processing parameters; The data outsourcer executes a data processing process according to the private key and the offline data processing parameters, generates processed data and data labels and uploads the processed data and data labels to the cloud storage server; The data verifier executes a second pre-calculation process according to the public key and the data label to generate an offline data verification parameter; The data verifier verifies the data label of the outsourced data according to the public key of the data outsourcer and the offline data verification parameter, and generates a challenge if the data label of the outsourced data is legal; The cloud storage server responds to the received challenge calculation according to the stored outsourcing data; And the data verifier verifiesthe received response according to the public key and the offline data verification parameters so as to judge the integrity of the corresponding outsourcing data.
Owner:GUILIN UNIV OF ELECTRONIC TECH
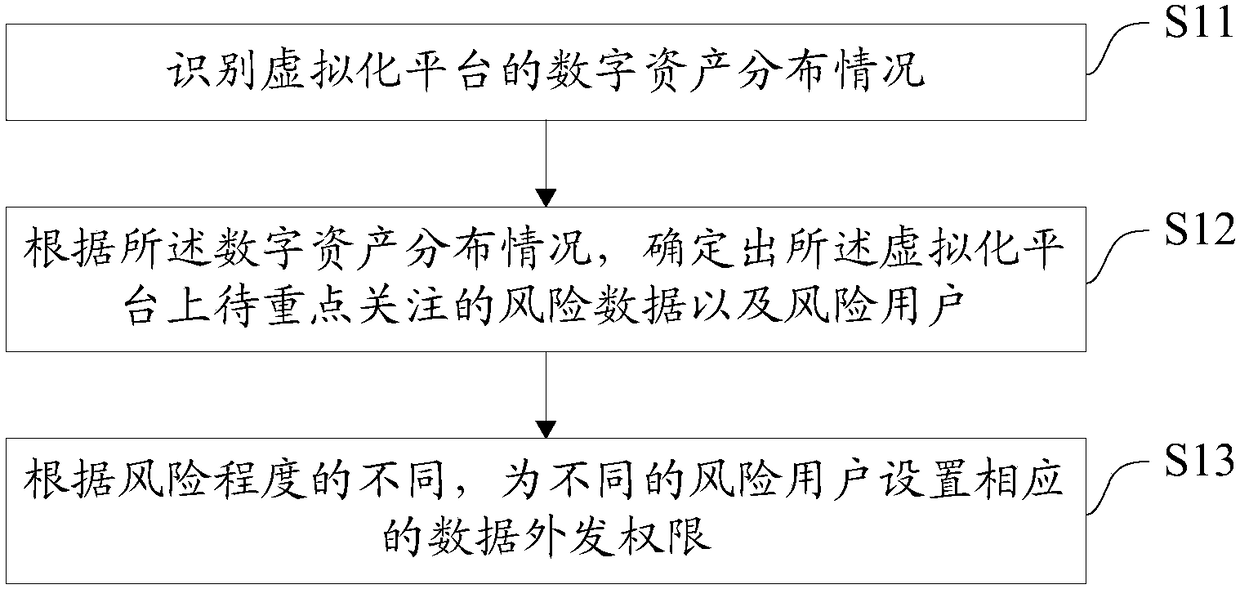
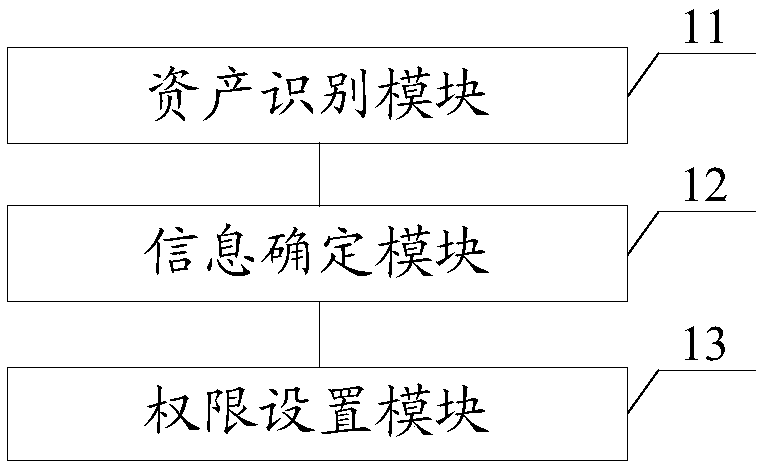
Data monitoring method, data monitoring system, data monitoring equipment based on virtualization technology, and storage medium
ActiveCN108494797AImprove securityReduce leakageDigital data protectionTransmissionVirtualizationData outsourcing
The invention discloses a data monitoring method, a data monitoring system, data monitoring equipment based on virtualization technology, and storage medium. The data monitoring method comprises stepsthat a digital asset distribution condition of a virtualization platform is identified; according to the digital asset distribution condition, to-be-emphasized risk data and risk users on the virtualization platform are determined; according to different risk degrees, corresponding data outsourcing authorities are set for different risk users. By using the identified digital asset distribution condition of the virtualization platform, the to-be-emphasized risk data and the corresponding risk users on the virtualization platform are determined, and based on the different risk degrees, the corresponding data outsourcing authorities are set for the different users, and then the risk users are prevented from having unmatched data outsourcing authorities, and therefore data safety performanceis improved, and data leakage conditions are reduced.
Owner:SANGFOR TECH INC
Hierarchical security multi-party calculation method and device based on Chinese remainder theorem
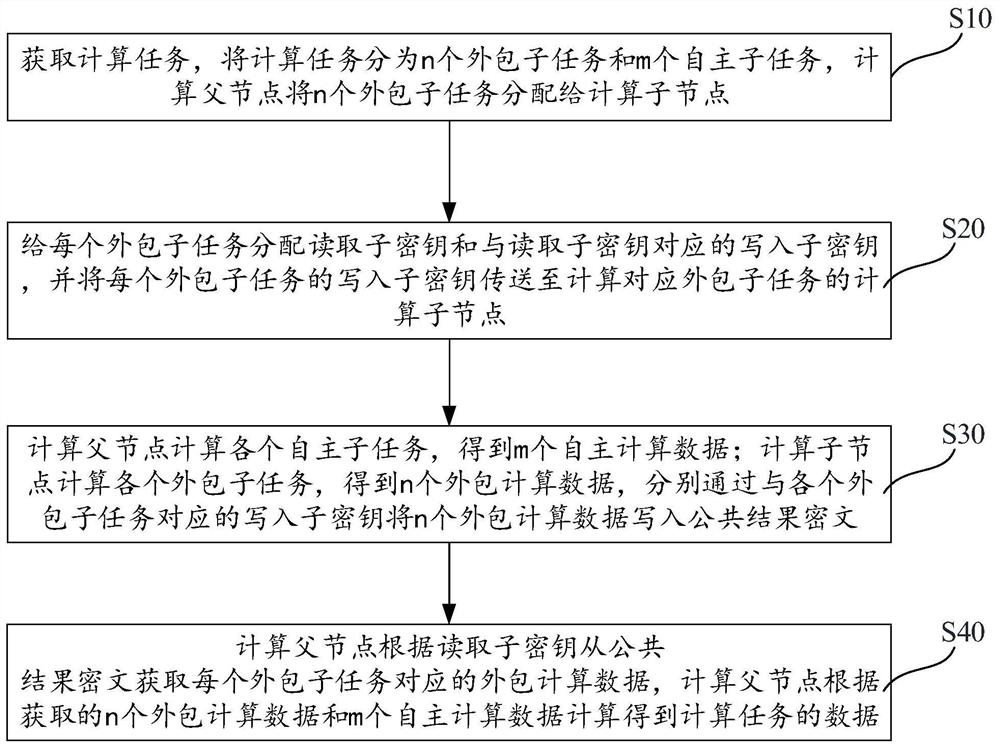
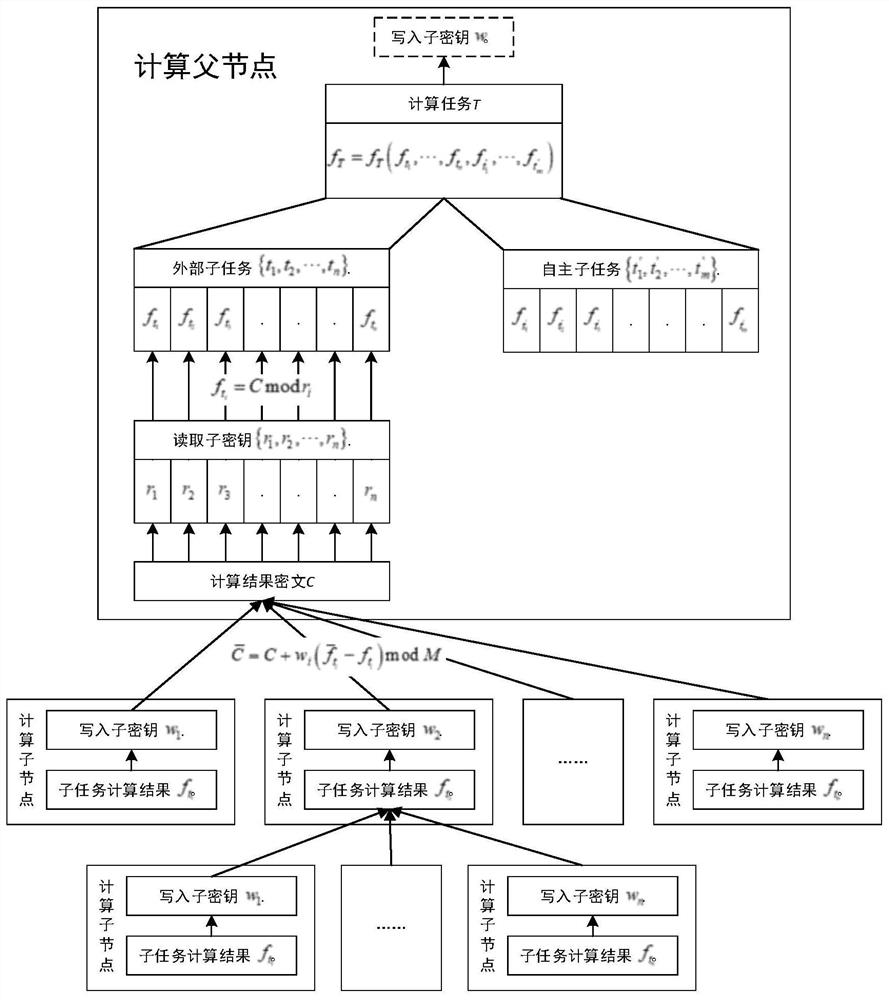
ActiveCN112700152AAchieve the purpose of computingDigital data protectionResourcesCiphertextChinese remainder theorem
The invention relates to a hierarchical security multi-party computing method and device based on the Chinese remainder theorem, and the method comprises the steps: enabling a computing task to be divided into an outer package subtask and an autonomous subtask through a computing father node, and distributing a writing subkey and a reading subkey for each outer package subtask; sending each outer packet sub-task and the corresponding write-in sub-key to each computing sub-node in a safe mode; enabling the computing father node and the computing child nodes to obtain data of respective child tasks through computing, and storing outsourcing computing data in a public result ciphertext through writing of child keys and sharing and transmitting the outsourcing computing data in the public result ciphertext; enabling the computing father node to obtain outsourcing computing data calculated by each computing child node from the public result ciphertext by reading the child key, and calculating a final result of the calculation task. According to the method, the computing sub-nodes can assist each other to complete the computing task together, but the computing data of other computing sub-nodes and the final computing data of the computing task cannot be obtained, so that secure multi-party computing is realized.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Circular range query method and system in cloud environment based on position privacy protection
ActiveCN111555861AAvoid safety hazardsCircular range query implementationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData setConfidentiality
The invention provides a circular range query method and system in a cloud environment based on position privacy protection. The method and the system belong to the technical field of location privacyprotection. The method comprises the steps of converting a relational expression between the spatial data point and a circular range which takes the query position as a circle center and r as a radius into an inner product of two vector sums, and judging a relationship between the inner product and zero by utilizing SSW confidentiality, so as to determine the relationship between the spatial datapoint and the circular range under the condition of not leaking the spatial data point and the query position; meanwhile, a Hilbert curve is used for dividing a region into atomic regions, and a spatial data set is stored and managed according to the atomic regions, so that the query efficiency is improved; the circular range query can be realized while the query privacy of the position query terminal and the data privacy of the position server are protected, and the potential safety hazard caused by spatial data outsourcing is solved.
Owner:SHANDONG NORMAL UNIV
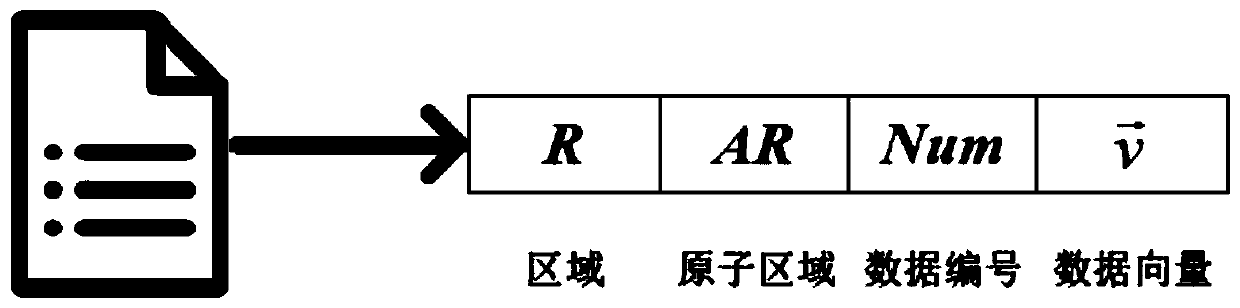
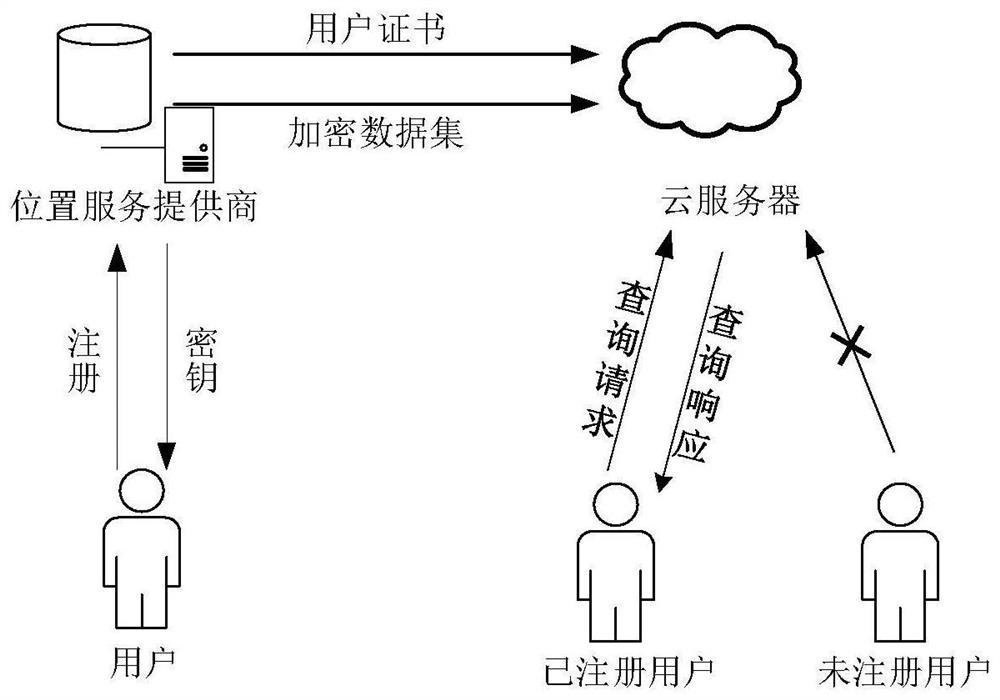
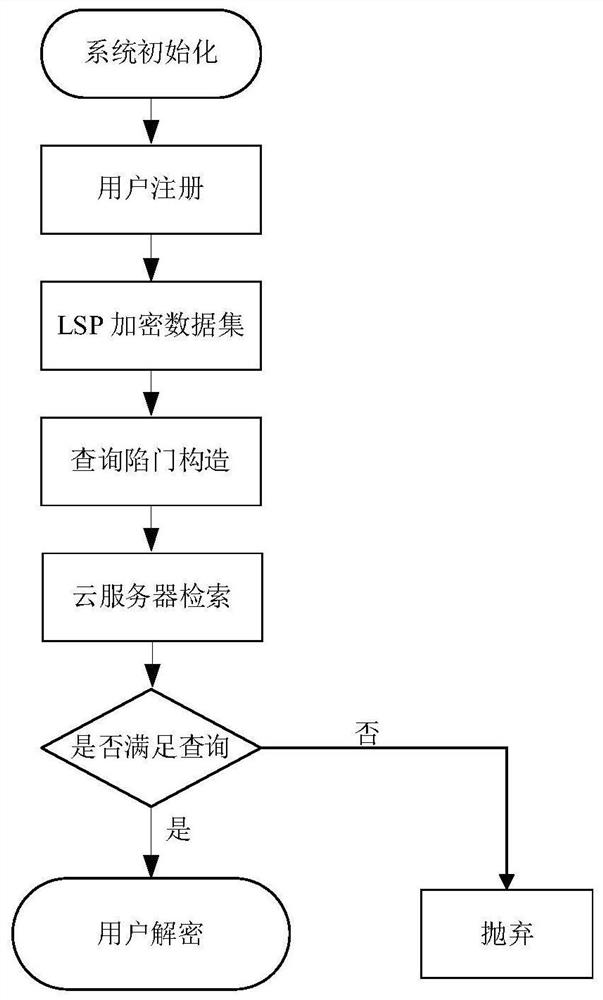
Data outsourcing privacy protection method and system and storage medium
The invention requests to protect a data outsourcing privacy protection method and system and a storage medium, and the method comprises the following steps: in a system initialization stage, a location-based service provider (LBSP) generates a system public parameter and a secret key, and then a new user registers to the LBSP to obtain the secret key to inquire a trap door structure and decrypt data; in the data encryption stage, the LBSP encrypts a location based service (LBS) data set, the LBS data confidentiality is achieved, and ciphertext data is uploaded to a cloud server. In order to protect personal privacy, a user encrypts a query request of the user and sends the query request to a cloud server for query; the cloud server performs matching calculation after receiving the LBS ciphertext data set and the query trap door, and returns ciphertext data conforming to query to the user; and finally, the user decrypts the ciphertext data to obtain actual data. According to the invention, the requirements of user interval query and privacy protection can be well met, the query efficiency is greatly improved, and the query communication overhead is remarkably reduced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A query integrity verification system and method for outsourcing streaming data
ActiveCN109274655AResist malicious behaviors such as tamperingReduce storage overheadTransmissionStreaming dataData management
The invention relates to a query integrity verification system and method for outsourcing streaming data. The system comprises an initialization module, a data management module and a query verification module. The initialization module is used to generate the public and private keys and other parameters needed by the data owner when the system starts, and distributes the public keys to the serverand the data user. The data management module is used for the data owner to outsource the real-time streaming data to the server. When the data stored before the server needs to be changed, the update data sub-module is used to update the data and the corresponding evidence. The user data user of the query verification module will query the data stored in the server, and will get the data of thecorresponding query index returned by the server and the corresponding evidence, and use the evidence returned by the server to verify whether the query result is correct.
Owner:NORTHEASTERN UNIV
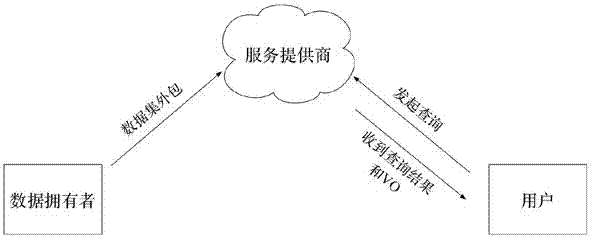
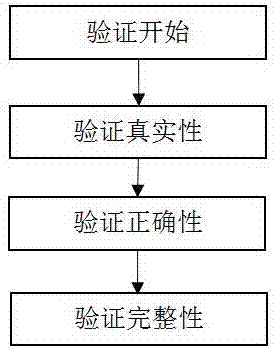
Service provider reputation-based query verification method for data outsourcing scene
ActiveCN107273444AEnsure authenticityReduce communicationSpecial data processing applicationsProgramming languageHigh probability
The invention discloses a service provider reputation-based query verification method for a data outsourcing scene. The method comprises the steps of weighing a possibility of returning a false result by a service provider by using a reputation value through a probability-based query verification policy in a query service of the data outsourcing scene; selectively requiring the service provider to return a verifiable object (VO) according to the reputation value; and verifying the authenticity, correctness and integrity of a query result by using the VO. According to the method, the communication and calculation overheads between the service provider and a user can be remarkably reduced; the efficiency of a query process is improved; and the query result is ensured to be real and reliable with high probability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Outsourcing data access control system based on block chain
ActiveCN113486082ADatabase distribution/replicationDigital data protectionData access controlEngineering
The invention discloses an outsourcing data access control system based on a block chain, and belongs to the technical field of block chains. The system comprises a user side, a cloud server and a block chain network, the user side is accessed to the cloud server and the block chain network, data interaction can be performed between the cloud server and the block chain network, and a user corresponding to the user side is a data stakeholder, comprising a data owner and a data user requesting data and operating the data, and is an entity authorized by the data owner to use the data; the cloud server is a storage end for a data owner to upload data, namely a platform for data outsourcing storage, and the data user accesses the data through the cloud server; a block chain network records logs of data access and operation of a data owner and a data user, and the security and reliability of outsourcing data access platform data are provided.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Privacy protection encrypted data query method based on fog assistance
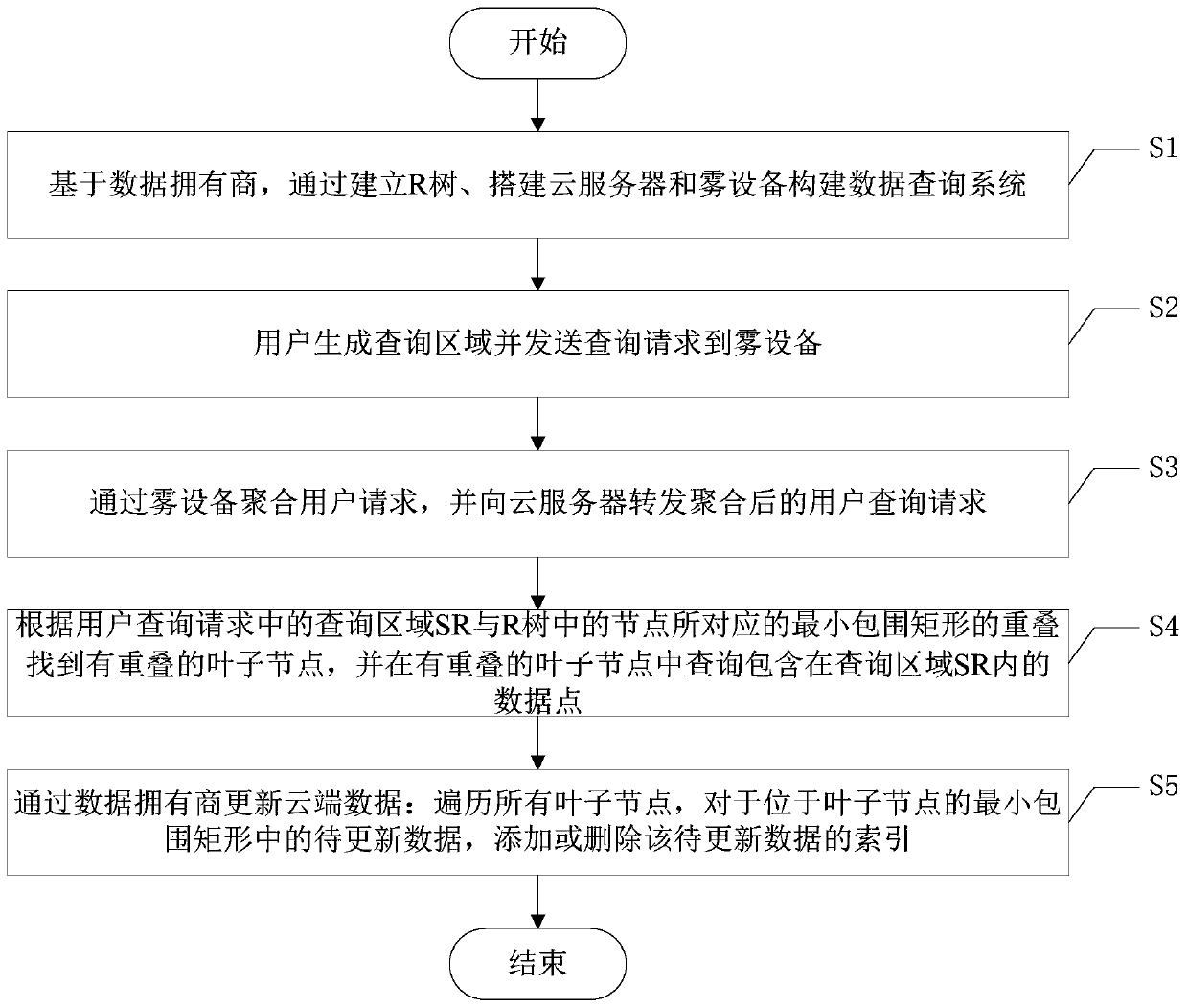
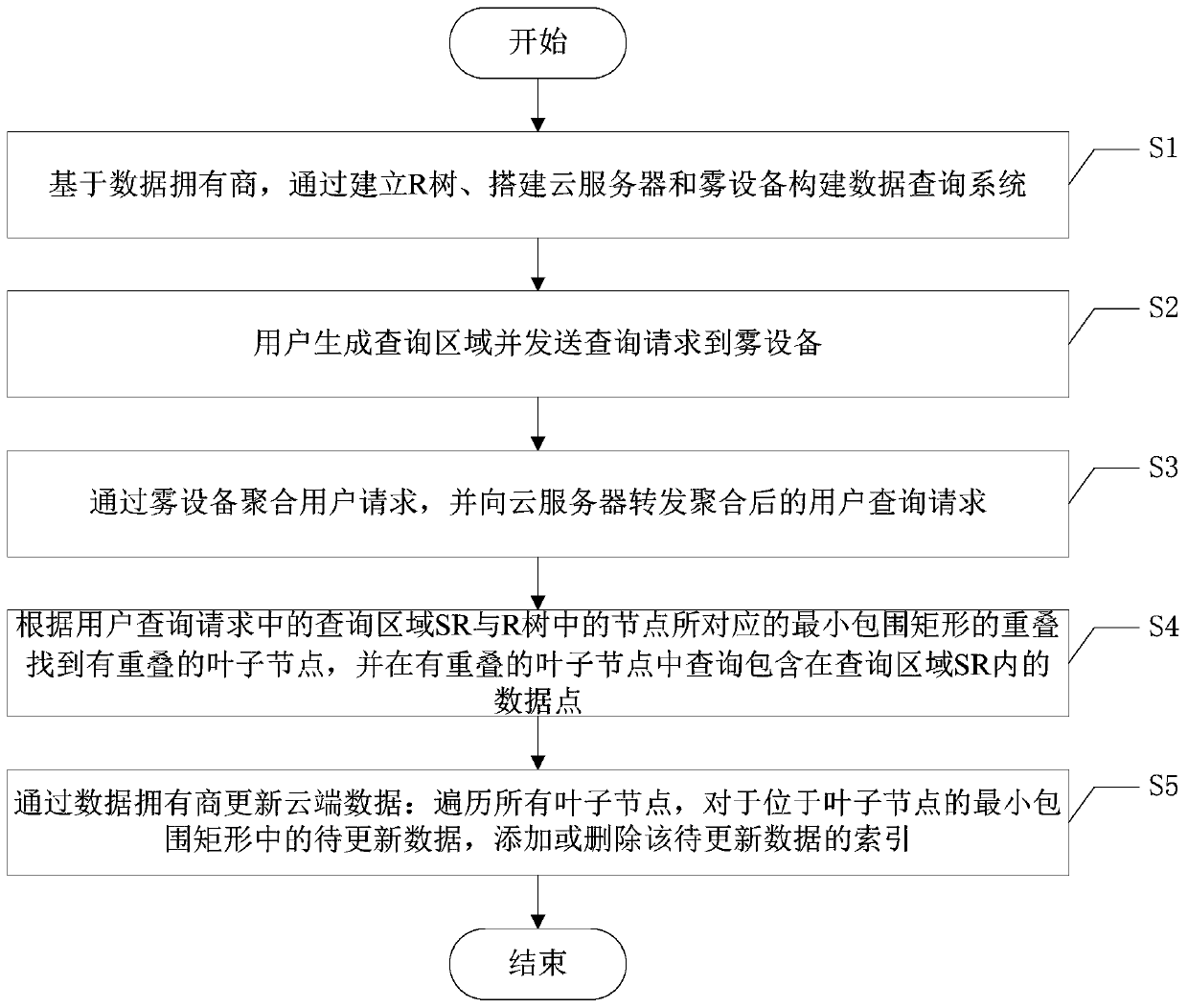
ActiveCN110601812ASolve the problem of privacy protectionImprove query efficiencyKey distribution for secure communicationDigital data protectionMinimum bounding rectangleInternet privacy
The invention discloses a privacy protection encrypted data query method based on fog assistance, and the method comprises the following steps: S1, building an R tree, a cloud server and fog equipmentbased on a data owner, and building a data query system; s2, enabling the user to generate a query area and send a query request to the fog device; s3, aggregating the user requests through fog equipment, and forwarding the aggregated user query requests to a cloud server; and S4, finding leaf nodes with overlap according to the overlap of the query area SR in the user query request and the minimum bounding rectangle corresponding to the nodes in the R tree, and querying data points contained in the query area SR in the leaf nodes with overlap. According to the invention, a light data outsourcing privacy protection structure is constructed, and the data privacy of a data owner and the query privacy of a user are protected under the structure.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
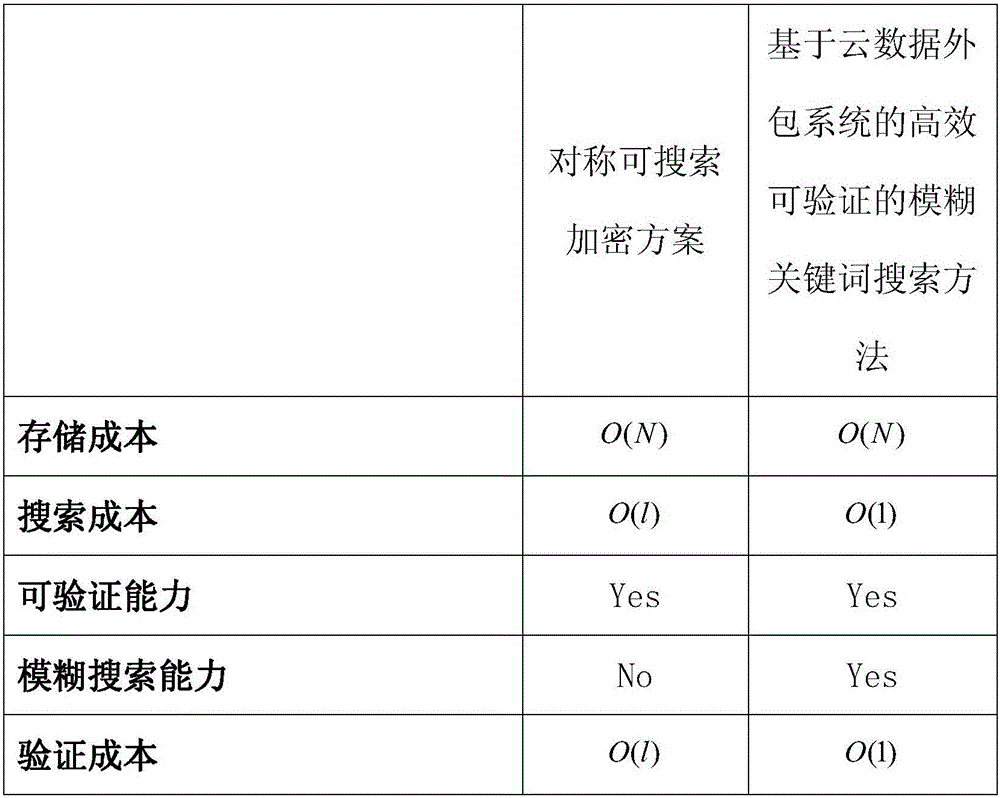
Efficient and Verifiable Fuzzy Keyword Search Method Based on Cloud Data Outsourcing System
ActiveCN102938767BVerify integrityVerify correctnessTransmissionSpecial data processing applicationsWord searchCloud data
Owner:陕西矩阵风云数据安全有限责任公司
Privacy-preserving encrypted data query method based on fog assistance
ActiveCN110601812BSolve the problem of privacy protectionImprove query efficiencyKey distribution for secure communicationDigital data protectionPrivacy protectionEngineering
The invention discloses a fog-assisted privacy protection encrypted data query method, which includes the following steps: S1, based on the data owner, constructing a data query system by establishing an R tree, building a cloud server and a fog device; S2, generating a query area by the user And send the query request to the fog device; S3, aggregate the user request through the fog device, and forward the aggregated user query request to the cloud server; S4, according to the query area SR in the user query request and the node in the R tree corresponding to the minimum The overlap of enclosing rectangles finds the overlapping leaf nodes, and queries the data points contained in the query area SR in the overlapping leaf nodes. The invention constructs a light data outsourcing privacy protection structure, and protects the data privacy of the data owner and the query privacy of the user under the framework.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
Multivariate identity authentication method and system for power grid data outsourcing calculation
PendingCN113468596AAlleviate the pressure of network securityTrue and valid identityDigital data protectionDigital data authenticationIp addressEngineering
The invention discloses a multivariate identity authentication method and system for power grid data outsourcing calculation, and the method comprises the steps: collecting various biological information of a user at the same time through a biological information collection device, transmitting the biological information to an identity authentication server, and carrying out the identity authentication of the user through the identity authentication server; enabling a calculation entrusting party and a calculation party of the power grid data to generate a session key in a mode of continuously exchanging intermediate values through a PAKE protocol, and encrypting and decrypting transmission data by using the session key to complete identity authentication between the calculation entrusting party and the calculation party; performing authentication verification on the power grid data needing to be subjected to outsourcing calculation, and performing authentication verification on a calculation result by a calculation entrusting party when a calculation party returns the calculation result; and enabling the encryption machine to write the IP address of the privacy computing server into the IP white list, and completing authentication of the privacy computing server. The method is compatible with various authentication requirements of personnel, equipment, systems, data and the like, and ensures the safety of power consumption data outsourcing calculation.
Owner:SHENZHEN POWER SUPPLY BUREAU
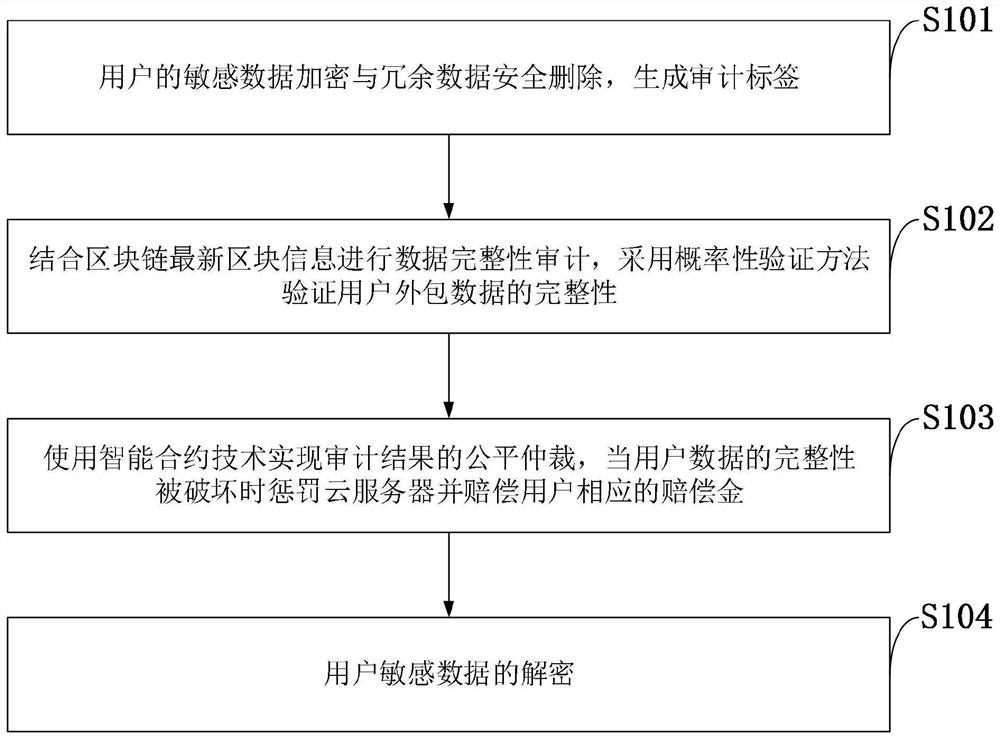
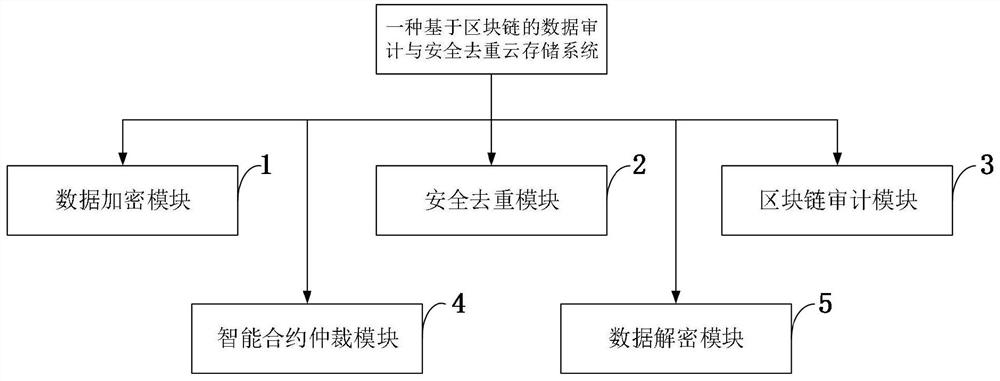
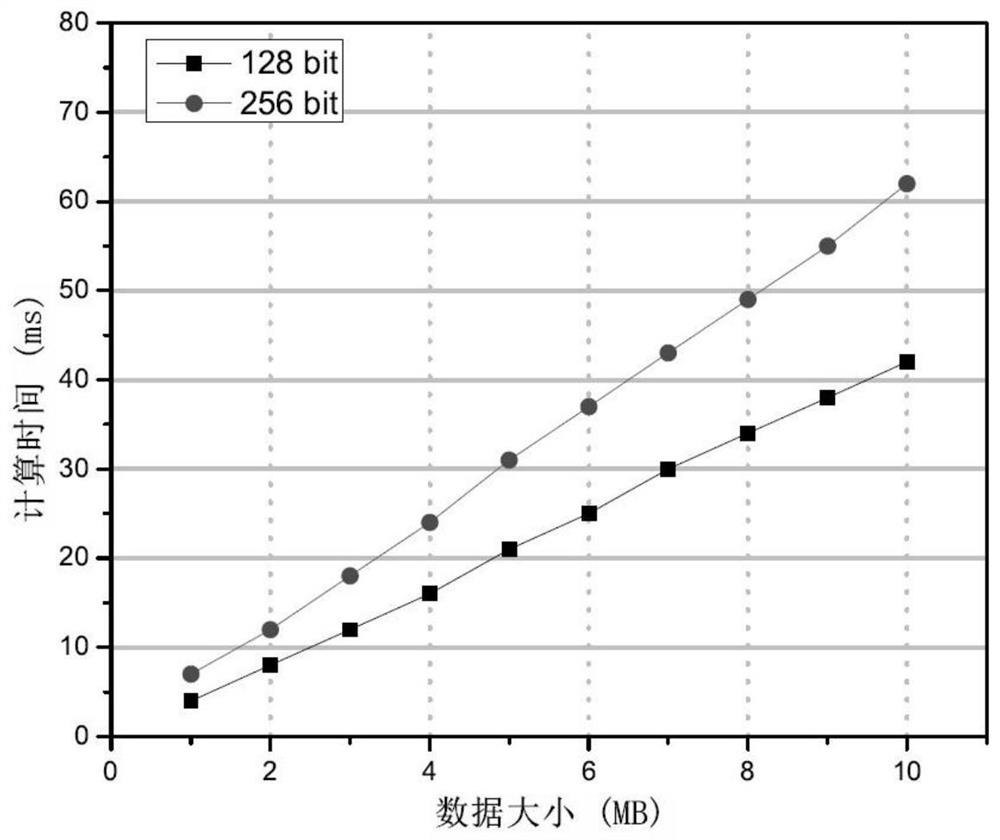
A blockchain-based data audit and security deduplication cloud storage system and method
ActiveCN111355705BAvoid storageReduce consumptionDigital data information retrievalEncryption apparatus with shift registers/memoriesCiphertextEngineering
Owner:XIDIAN UNIV
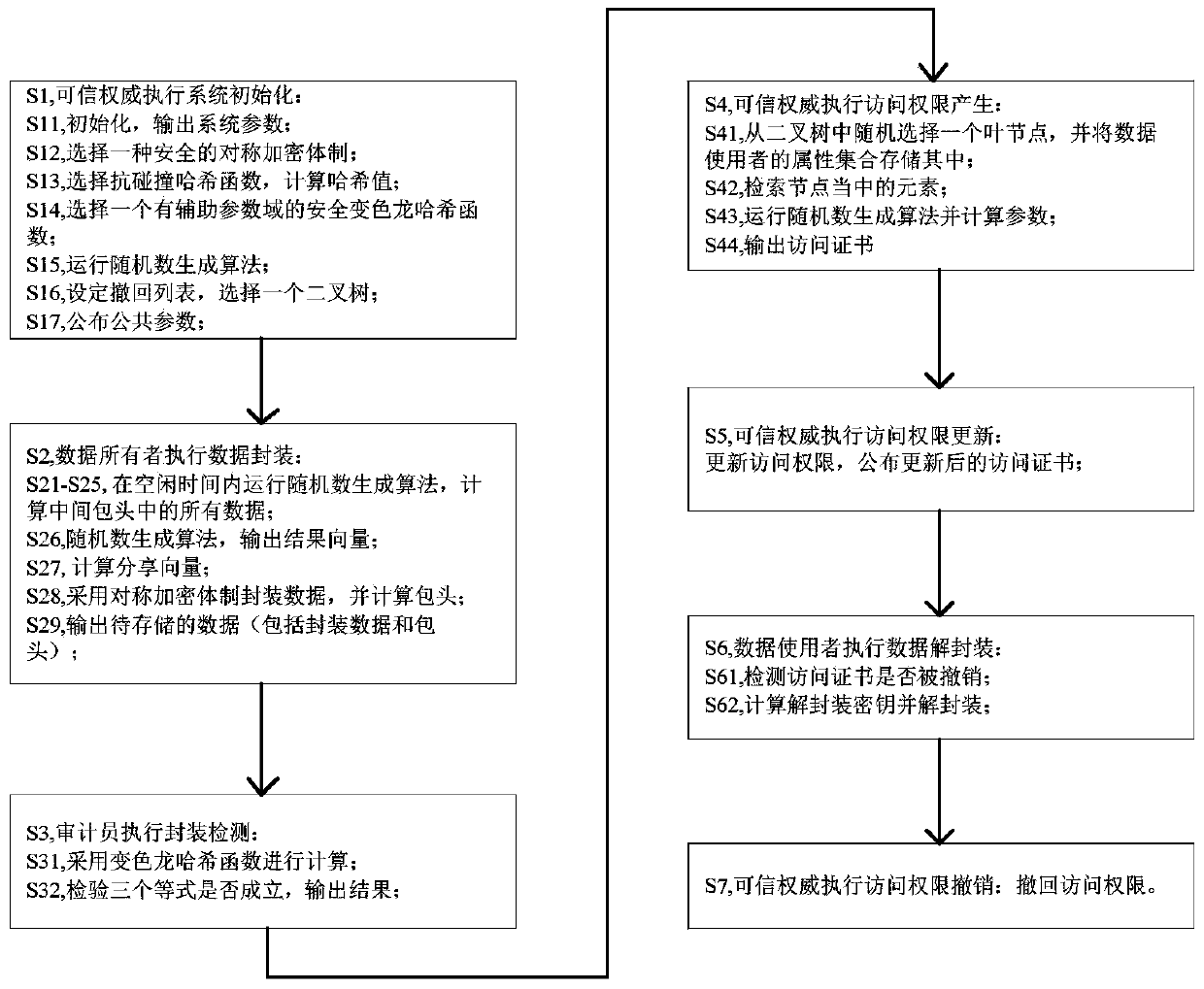
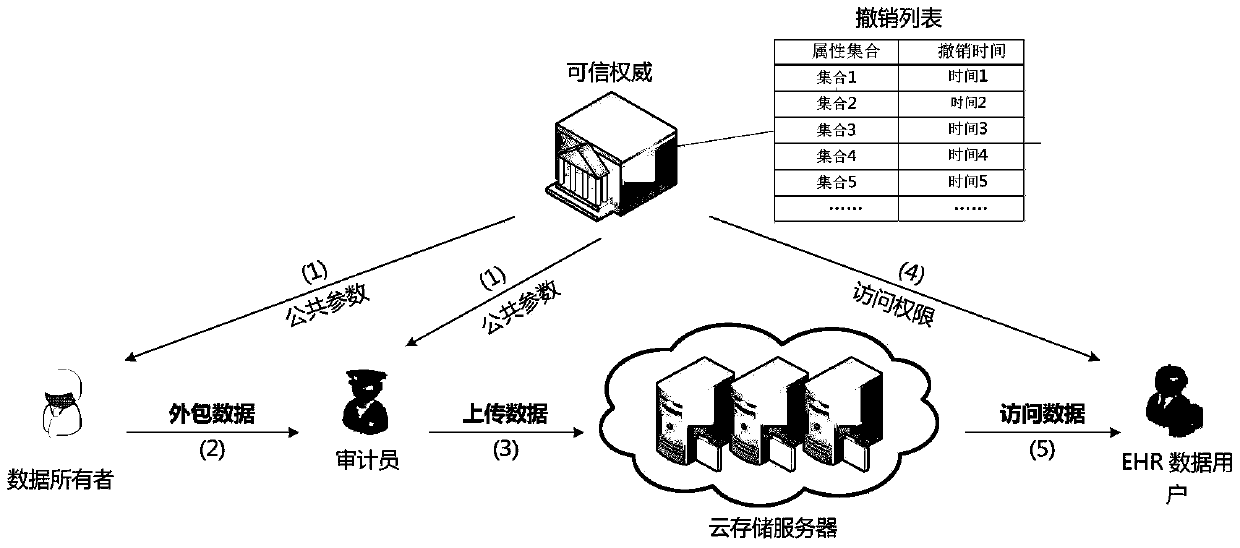
Reversible fast data outsourcing encapsulation method and device
ActiveCN105978696BEncryption apparatus with shift registers/memoriesUser identity/authority verificationTrusted authorityThird party
The invention discloses a revocable quick data outsourcing packaging method and device. The method includes initiation of trust authority is performed; a data owner performs data packaging; an auditor performs package detection, calculates and checks whether three equations hold or not by adopting a chameleon hash function and outputs a result; a trust authority execution access authority is generated and an access certificate is output; the trust authority execution access authority is updated, the access authority is updated and the updated access certificate is released; the data owner executes data de-packaging and detects whether the access certificate is cancelled and calculates a de-packaging key and de-packages; a trust authority execution access authority cancel module cancels the access authority. The method realizes effective access control and protects the safety of electronic health cases stored in third party servers that are not completely trustful in the maximal degree, and saves the decryption cost of a mobile device.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com