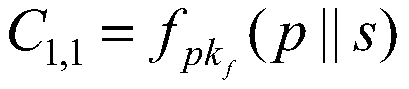Fully homomorphic data packaging method for lightweight single-user multi-data
A data encapsulation, single-user technology, used in digital data protection, electrical digital data processing, computer security devices, etc., can solve problems such as inability to meet objective performance requirements, high algorithm complexity, huge computing overhead and communication overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
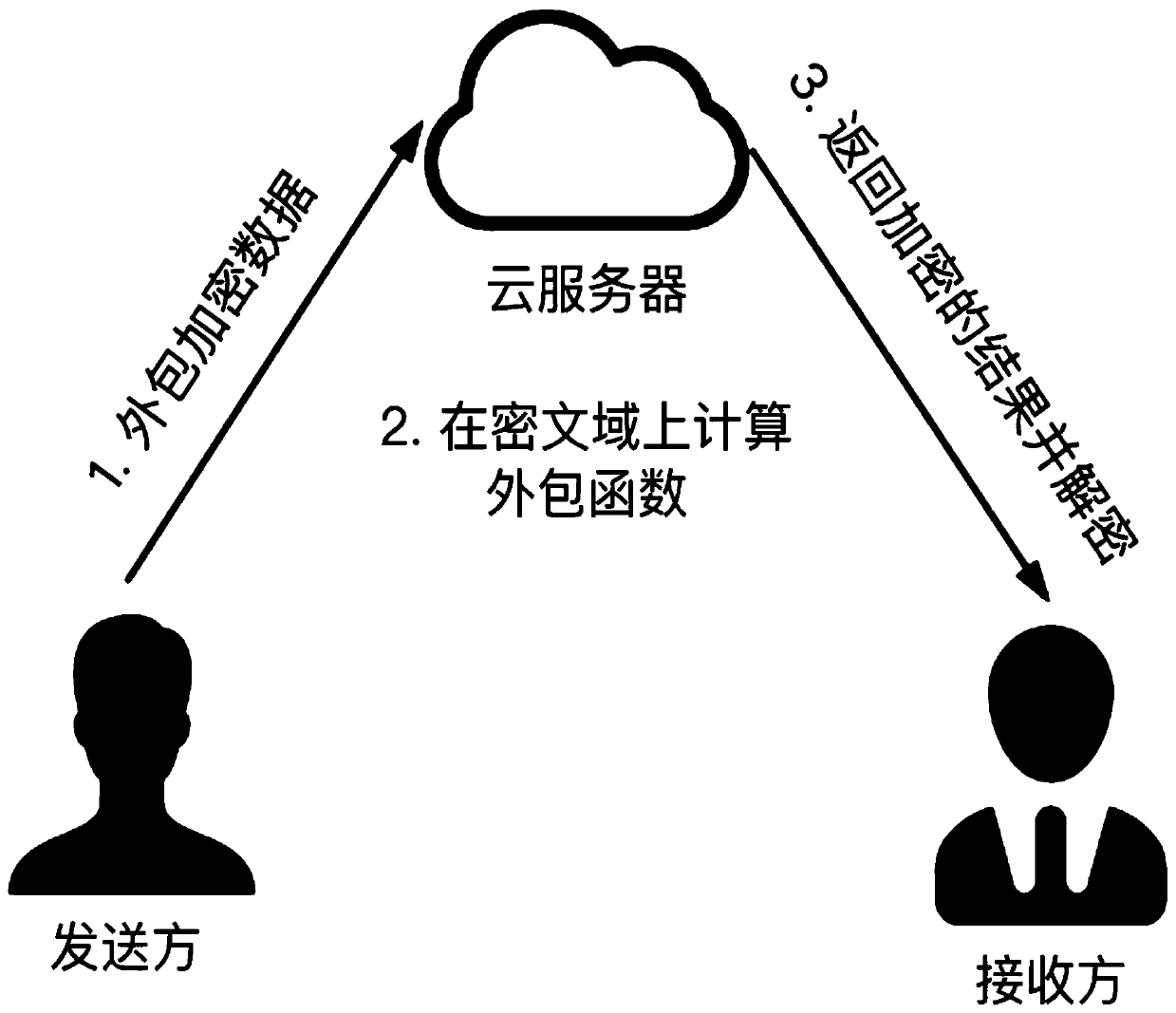
[0094] See attached figure 1 , the present invention generates public parameters and keys by the system (trusted third party), the sender encrypts the message, the cloud server performs addition and multiplication operations on the encrypted data in the cipher text domain, and the receiver performs calculation results decrypt. The invention is based on an arbitrary one-way trapdoor replacement implementation, which can be flexibly used in different network scenarios, meets the requirements of high efficiency and privacy, and can achieve unconditional security and security in terms of input privacy and calculation result privacy. Adaptive Chosen Ciphertext Security (CCA2 Security).
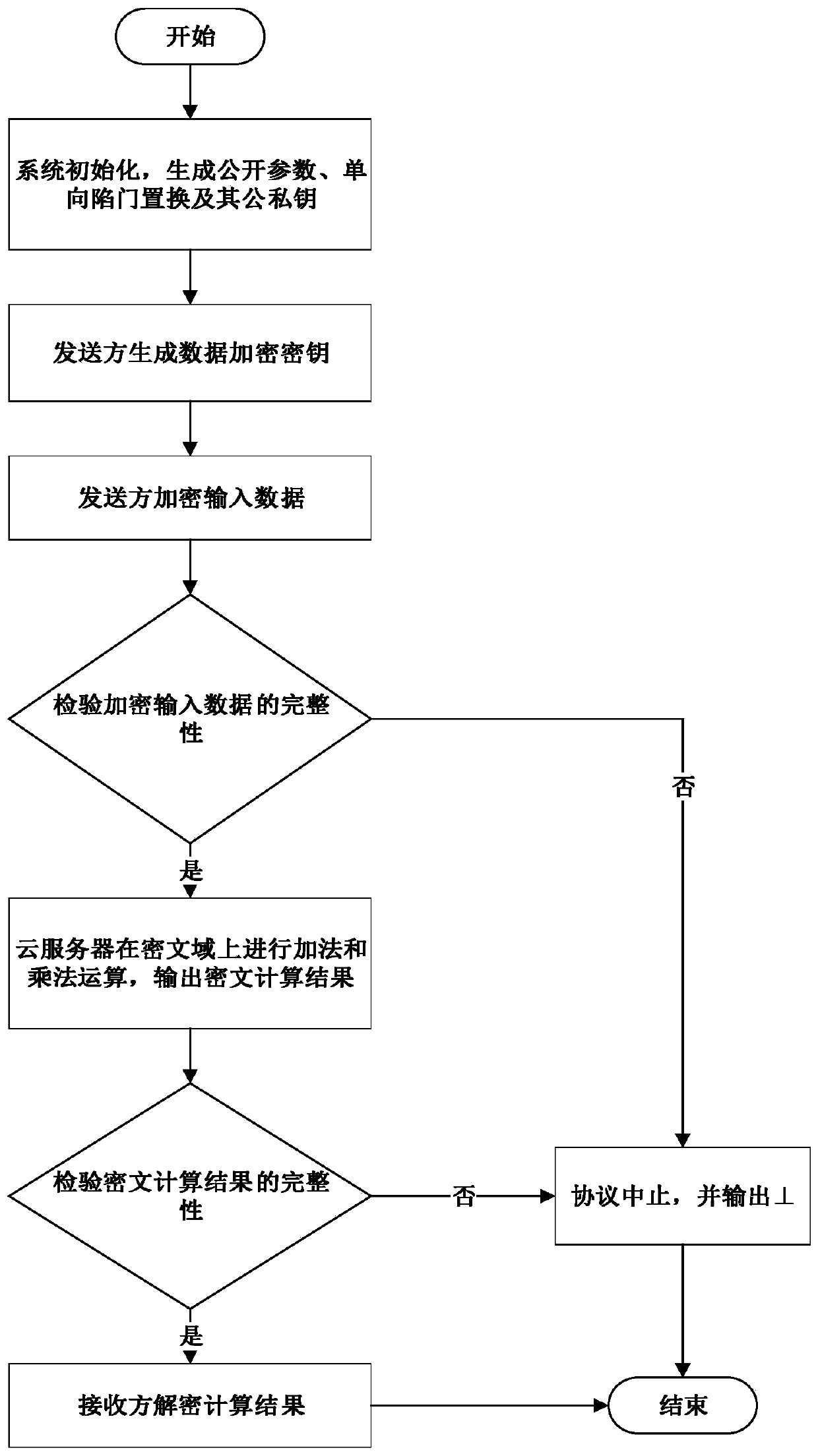
[0095] See attached figure 2 , the concrete realization process of the present invention is as follows:
[0096] Step 1: System (trusted third party) initialization
[0097] a) Enter 1 λ , where λ is a security parameter, take λ=512;
[0098] b) The system (trusted third party) runs the prob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com