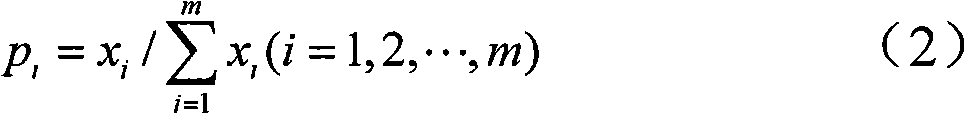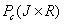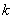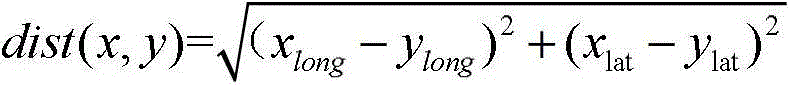Patents
Literature
464 results about "Misinformation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Misinformation is false or inaccurate information. Examples of misinformation include false rumors, insults and pranks, while examples of more deliberate disinformation include malicious content such as hoaxes, spearphishing and propaganda. News parody or satire may also become misinformation if it is taken as serious by the unwary and spread as if it were true. The terms "misinformation" and "disinformation" have been associated with the neologism "Fake News," defined by some scholars as “fabricated information that mimics news media content in form but not in organizational process or intent.”
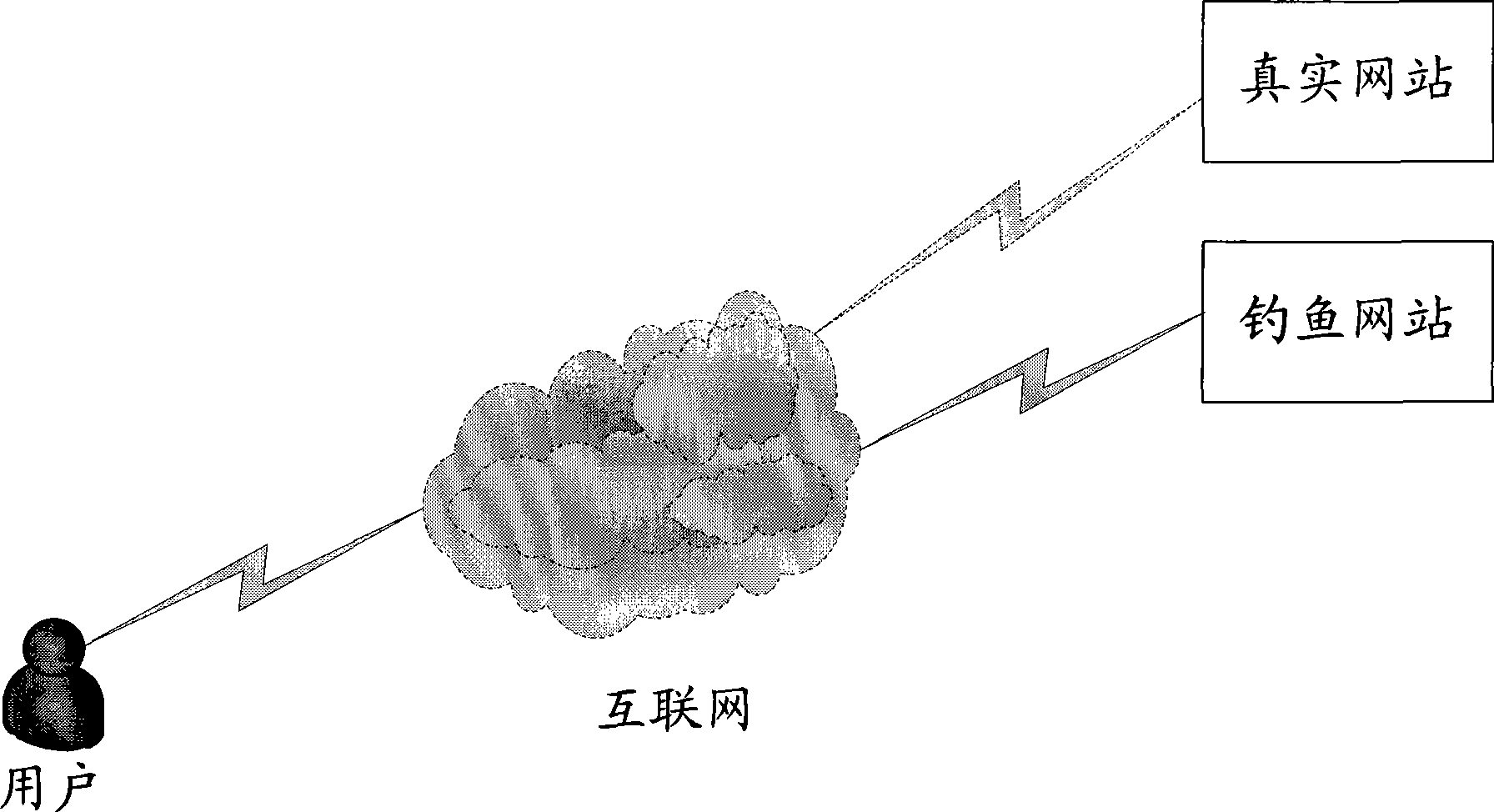
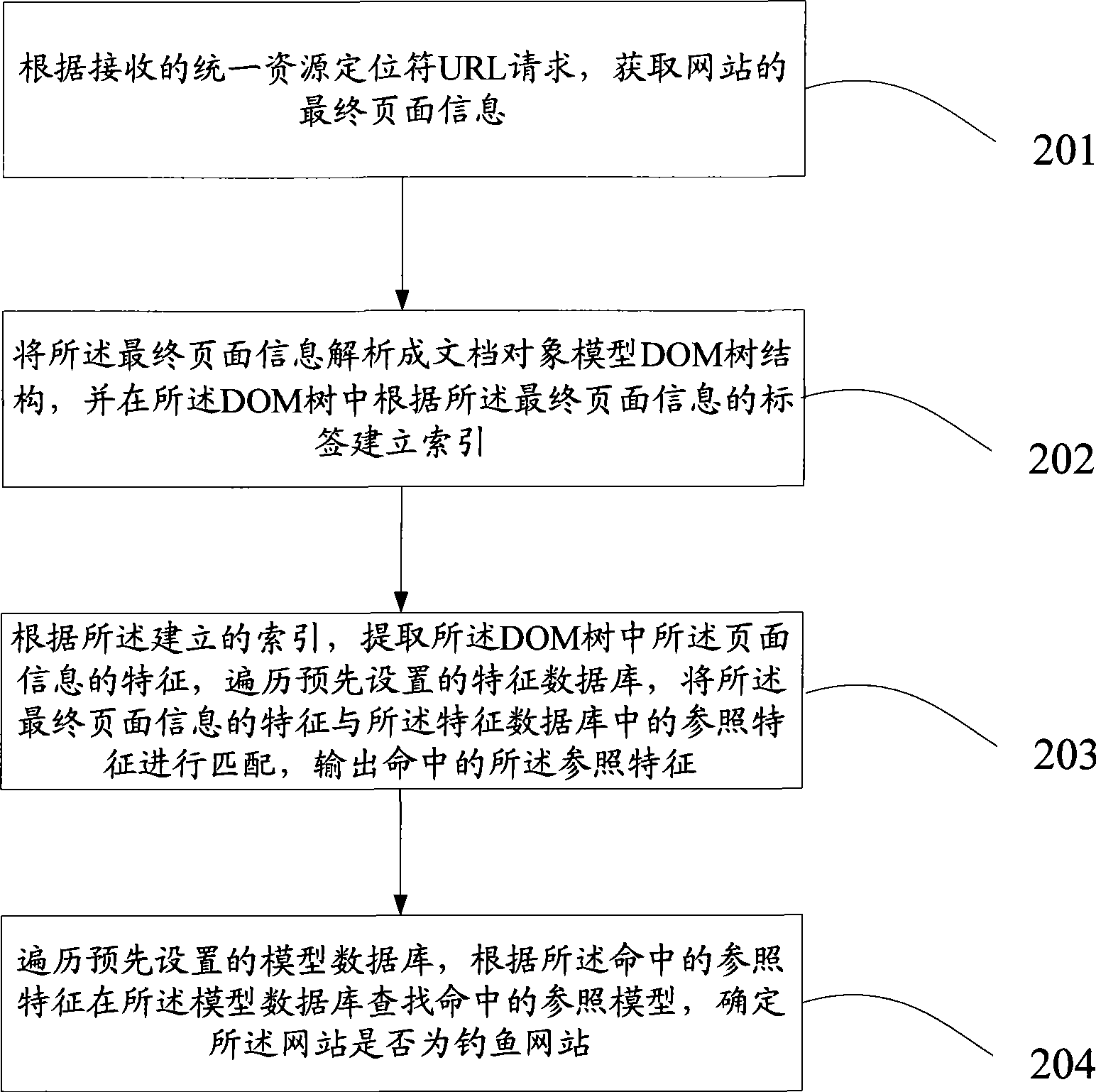
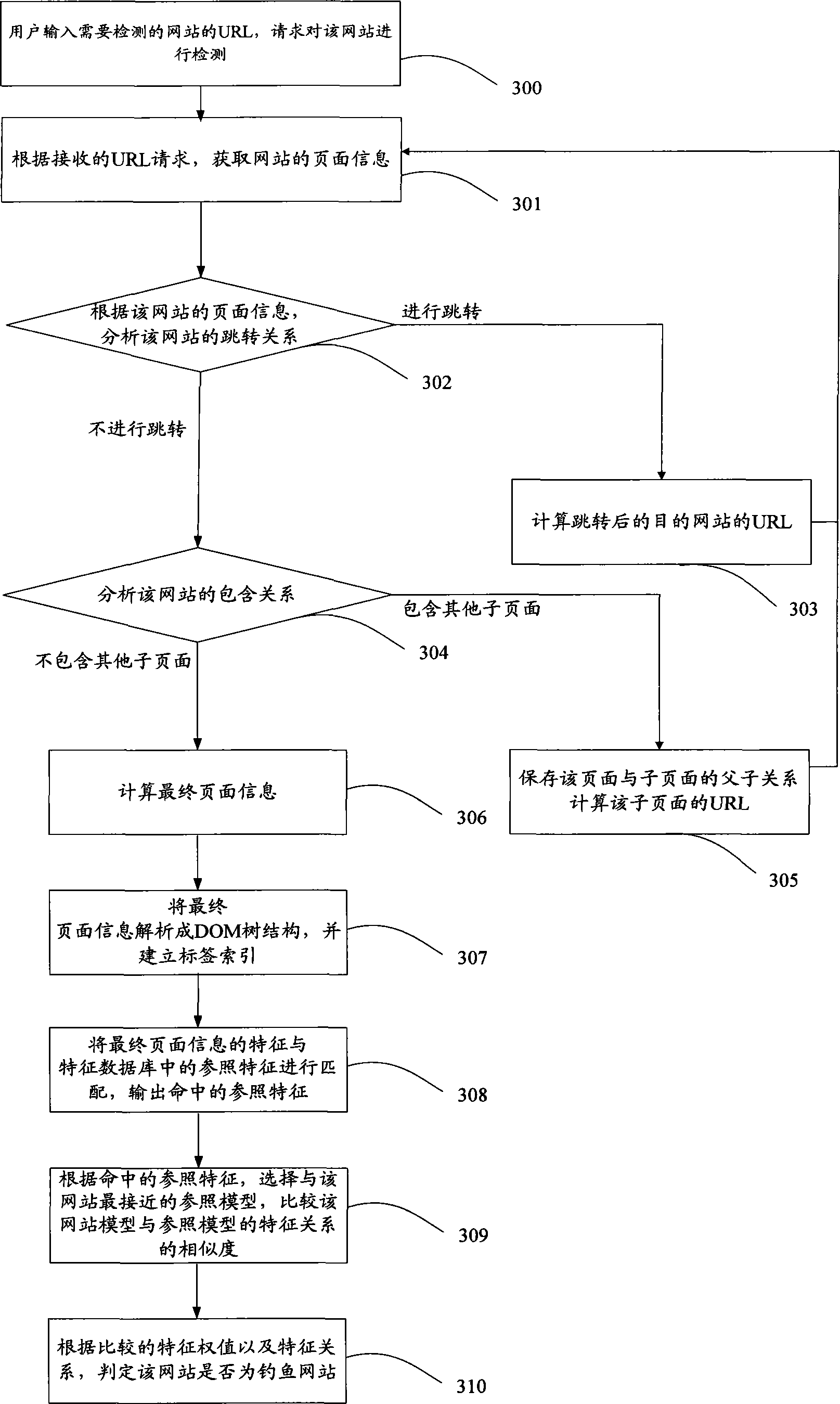
Detecting method and a device for fishing website
ActiveCN101534306AImprove the accuracy of judgmentQuick responseData switching networksSpecial data processing applicationsMisinformationUniform resource locator
The invention discloses a detecting method and a device for fishing website. The method comprises the following steps: detecting device obtains the final page information according to the received URL request; analyzing the final page information of the website; as the DOM tree structure and building the index for the label according to the final page information in DOM tree structure; extracting the characteristic of the final page information n the DOM tree structure according to the built index, traveling the pre-set characteristic database and matching the characteristic of the final page information and the referred characteristic in the database, outputting the referred characteristic; travelling the pre-set model database and finding the referred object in the model database according to the referred characteristic to confirm whether the website is the fishing website. The invention processes the detection for the page information by the website, which avoids the misinformation phenomenon in judging the page information to enhance the judging accuracy of the fishing website.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
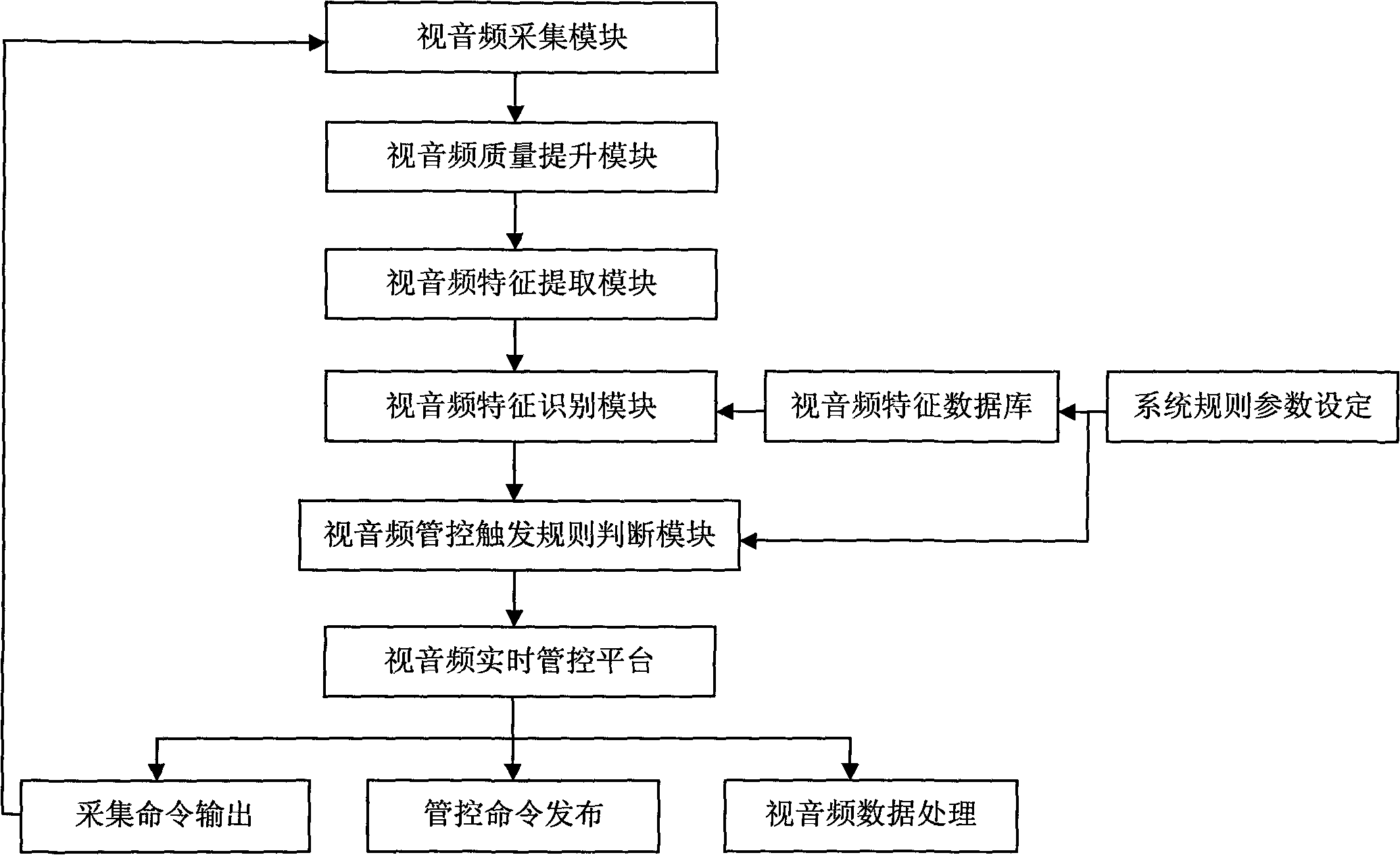
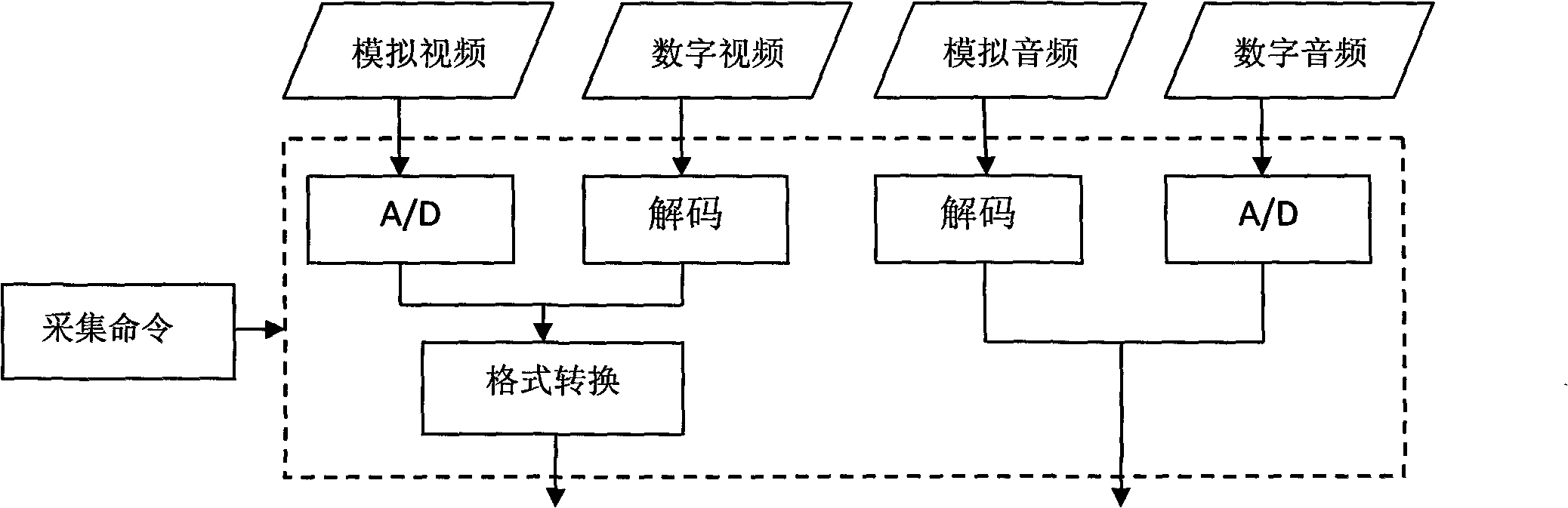
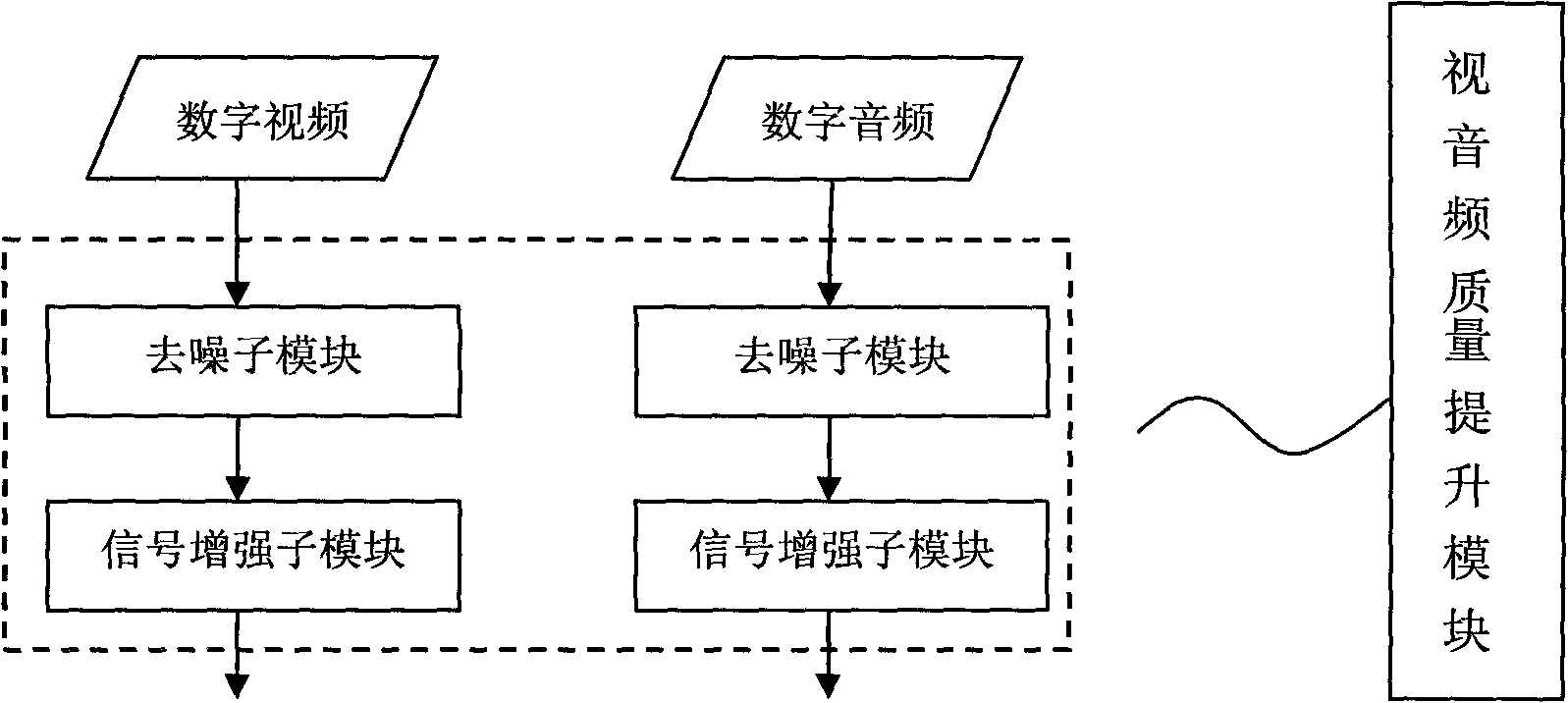
Video/audio intelligent analysis management control system
InactiveCN101799876AGood auxiliary effectEliminate false positivesCharacter and pattern recognitionClosed circuit television systemsFeature extractionControl system
The invention relates to the fields of computer vision and artificial intelligence, in particular to the field of intelligent video analysis, and provides a video / audio intelligent analysis management control system. The invention aims to solve the problems of the existing intelligent video analysis system of high misinformation rate, high report missing rate, low accuracy, single working mode, failure of realizing transmission and storage as required, and the like. The system comprises a video / audio feature database, a video / audio acquisition module, a video / audio quality improvement module, a video / audio feature extraction module, a video / audio feature recognition module, a video / audio management control trigger rule judgment module and a video / audio real-time management control platform. The system has three working modes: front-end analysis, back-end analysis and distributed analysis. The system combines voice information and image information for intelligent analysis, thereby effectively reduces the misinformation rate and report missing rate of the intelligent video analysis system. The invention enhances the quality of the video / audio information and establishes a large target and behavior feature database, thereby enhancing the system accuracy and realizing management control as required.
Owner:王巍
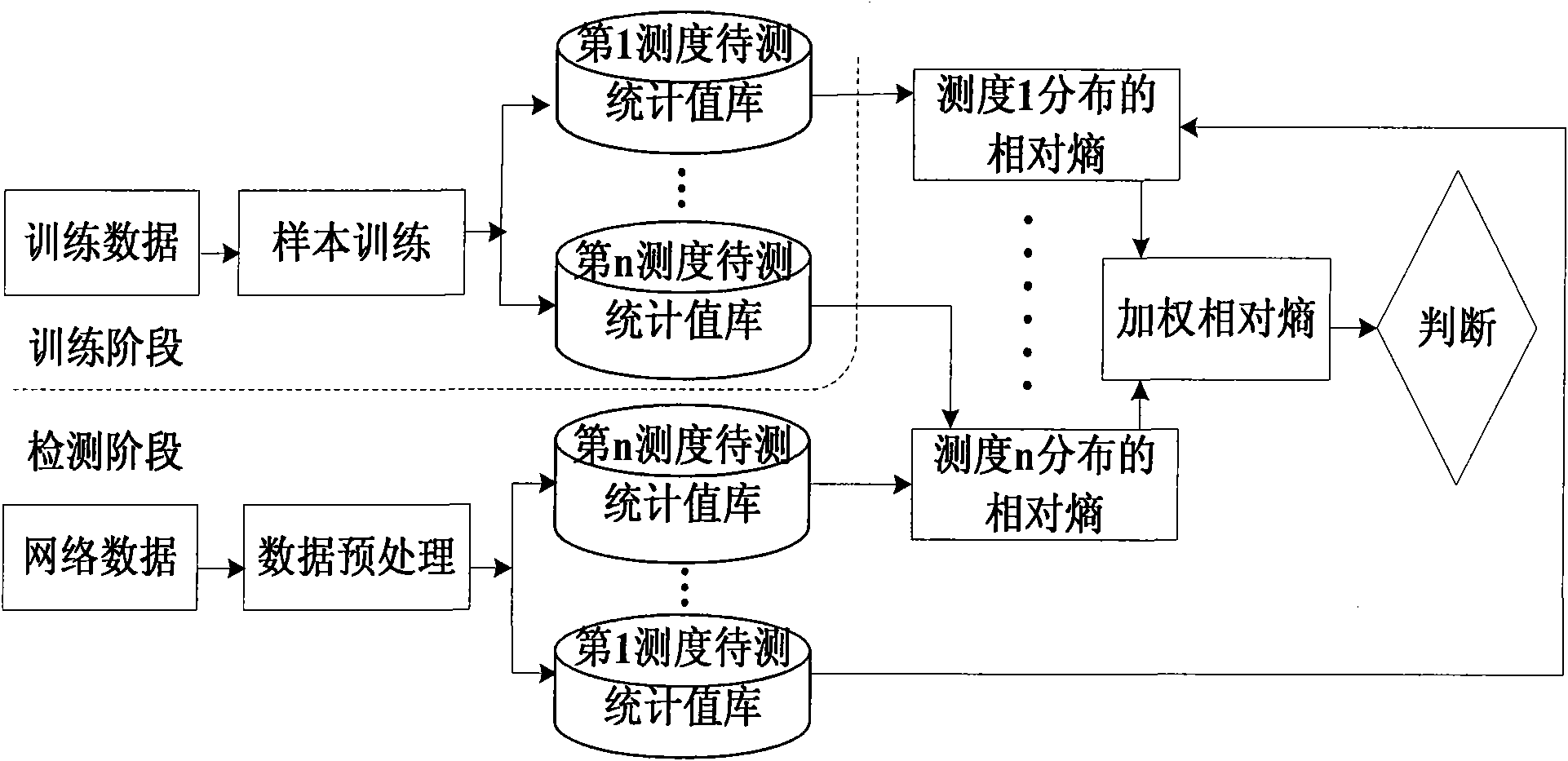
Multi-measure network abnormity detection method based on relative entropy theory
InactiveCN101645884ASolution rangeResolve detectionData switching networksAnomaly detectionSingle measure
The invention discloses a multi-measure network abnormity detection method based on a relative entropy theory. In the detection method, an integrative relative entropy is obtained by weighting the relative entropy of a plurality of measures to judge network abnormity, thereby avoiding the problem of single-point malfunction of single-measure detection under a certain specific attack; simultaneously, abnormity detection based on the relative entropy is different from the abnormity detection of the flow rate, and the abnormity of the measures can be accurately reflected. The method is concretelyactualized according to the following steps: step 1, selecting and quantifying the measures for abnormity detection; step 2, preprocessing data; step 3, training a sample; step 4, detecting the single-measure relative entropy; step 5, calculating the multi-measure weighting relative entropy; and step 6, displaying an alarm mechanism and a detection result. The technical scheme provided by the method is beneficial to solving the problems of insufficient attack detection range and contravention between the detection rate and the misinformation lowering rate existing in the prior network abnormity detection technique and can provide various network environments, such as a host machine, a local area network, a wide area network and the like, to carry out network circuit abnormity detection.
Owner:XIAN UNIV OF TECH
Financial self-service device and anti-peeping system and anti-peeping method thereof
ActiveCN102610035AImprove accuracyReduce false alarm rateComplete banking machinesATM surveillanceFace detectionImaging processing
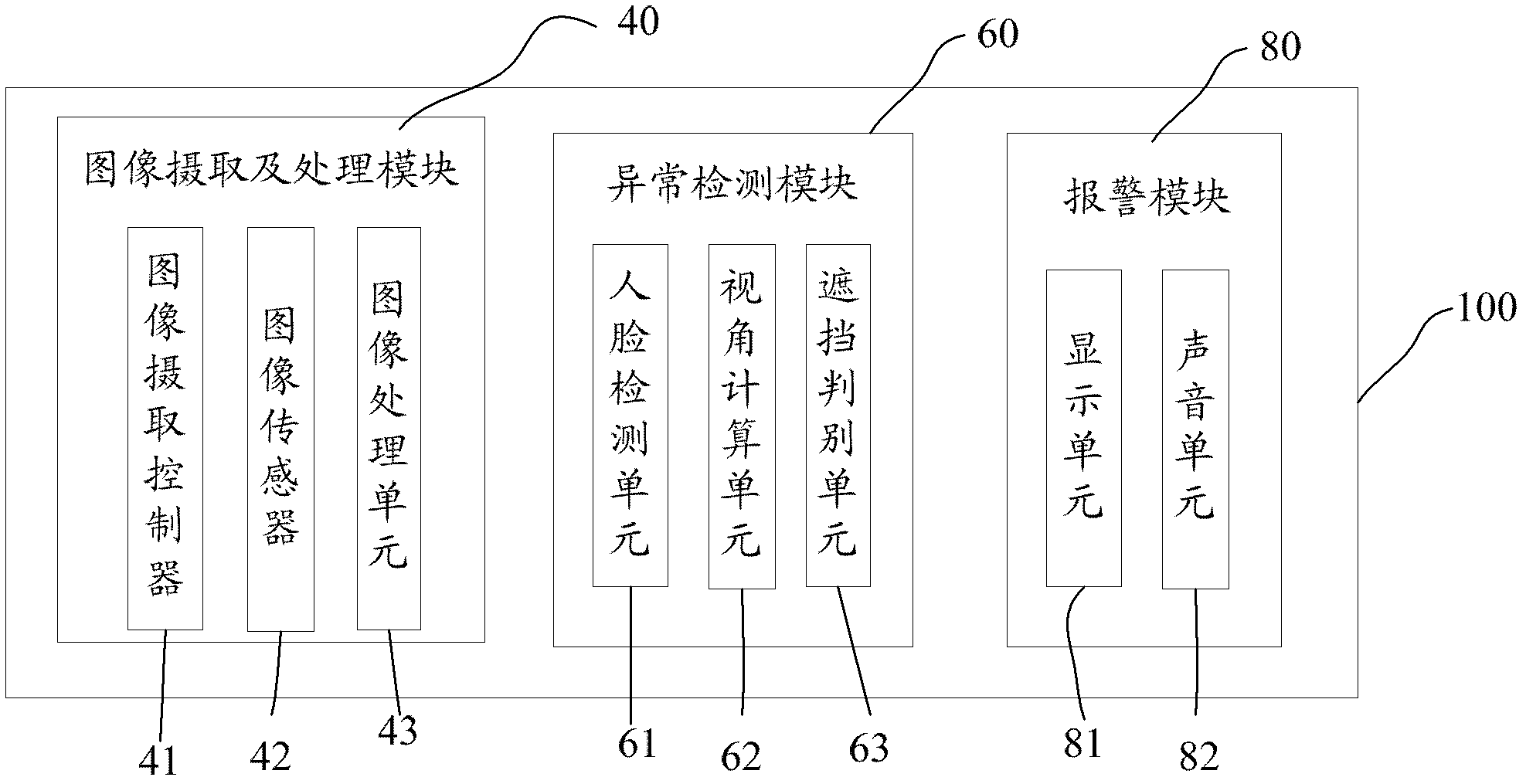
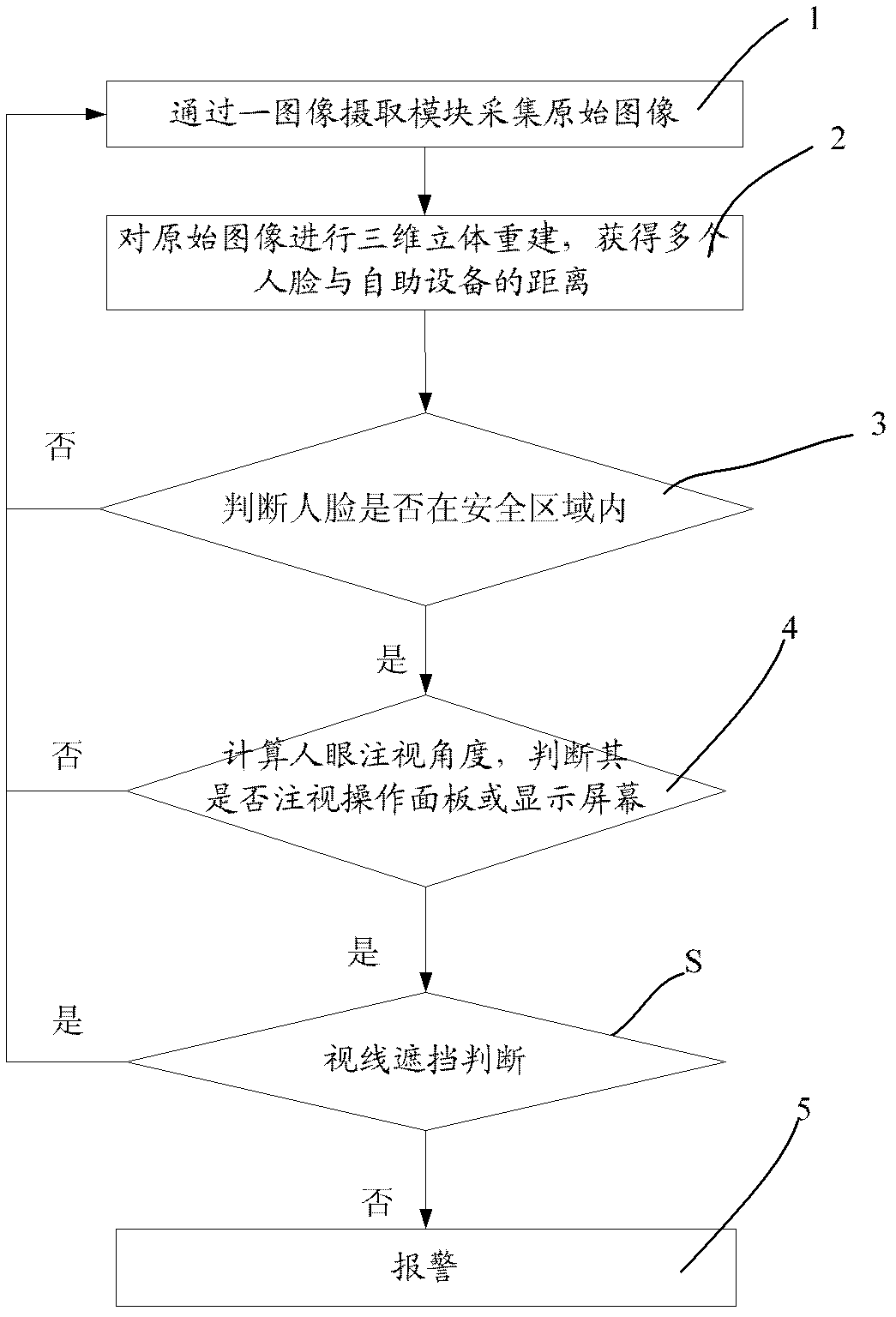
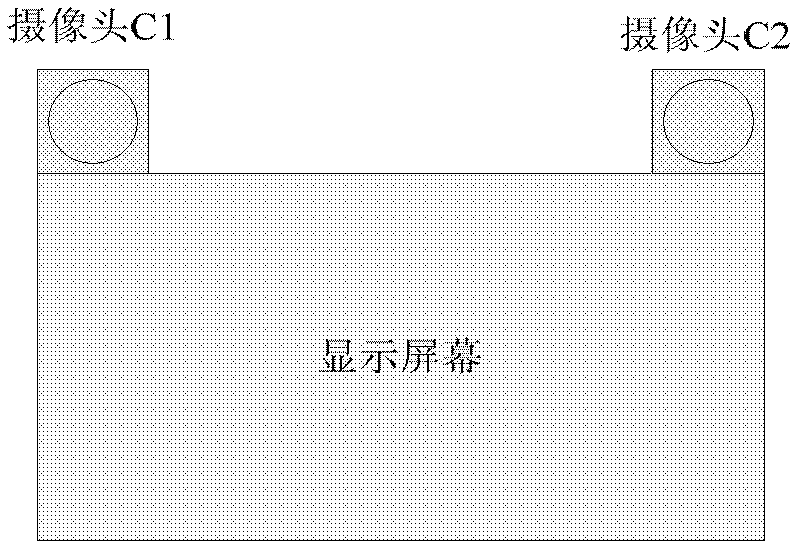
The invention provides an anti-peeping system, which is applied to a financial self-service device. The anti-peeping system comprises an image acquiring and processing module, an anomaly detection module and an alarm module. The image acquiring and processing module comprises an image acquiring controller, at least a pair of image sensors and an image processing unit and is used for acquiring original image data and rebuilding three dimension so as to acquire distance information of each image relative to the financial self-service device. The anomaly detection module comprises a human-face detection unit and a view angle calculation unit and is used for detecting whether multiple human faces exist or not and calculating a view angle range watched by human eyes so as to judge whether the human faces watch an operation panel or a display screen. The alarm module is used for conducting response to detection results of the anomaly detection module so as to warn whether current customers are peeped or not. By means of the scheme, the accuracy rate of judging peepers can be improved greatly, and the misinformation rate of an alarm is reduced.
Owner:GRG BAKING EQUIP CO LTD
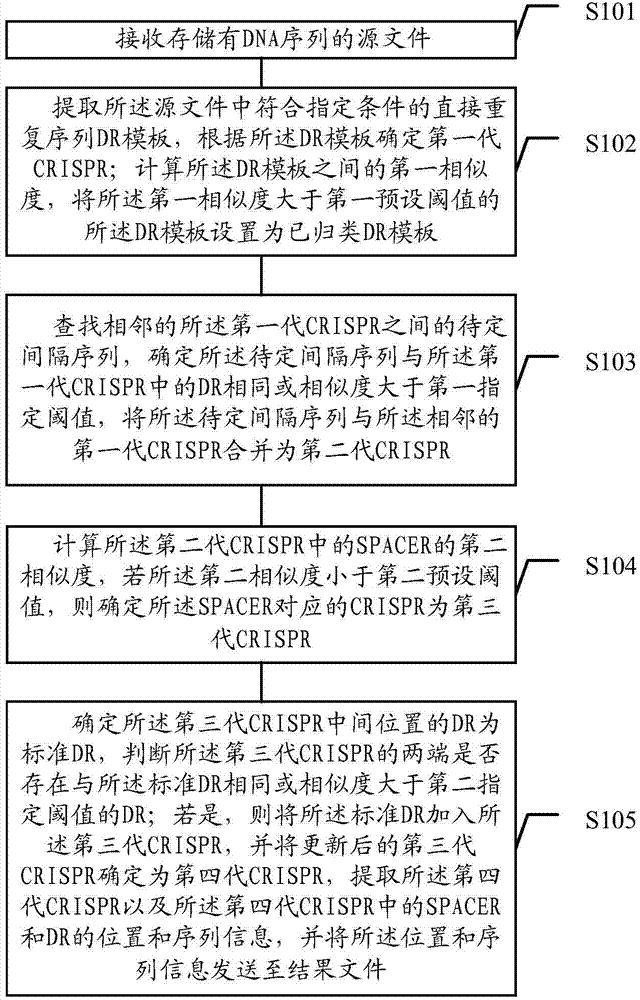
Method and device for identifying clustered regularly interspaces short palindromic repeats (CRISPR)
ActiveCN104504304AImprove accuracyIncrease diversitySpecial data processing applicationsDirect repeatFirst generation
The embodiment of the invention discloses a method for identifying clustered regularly interspaces short palindromic repeats (CRISPR). The method comprises the following steps: according to a DR (Direct Repeats) template in a source file, determining a first-generation CRISPR; after the missed DR in an undetermined spacer sequence between two pieces of adjacent first-generation CRISPR is added, determining a second-generation CRISPR; determining the CRISPR of which the SPACER similarity is lower than a preset threshold value in the second-generation CRISPR as a third-generation CRISPR; and determining the third-generation CRISPR of which two ends are provided with the DR as a four-generation CRISPR. The embodiment of the method can reduce misinformation or ignore the cut-off DR so as to improve the identification accuracy and comprehensiveness of the CRISPR.
Owner:SHENZHEN INST OF ADVANCED TECH
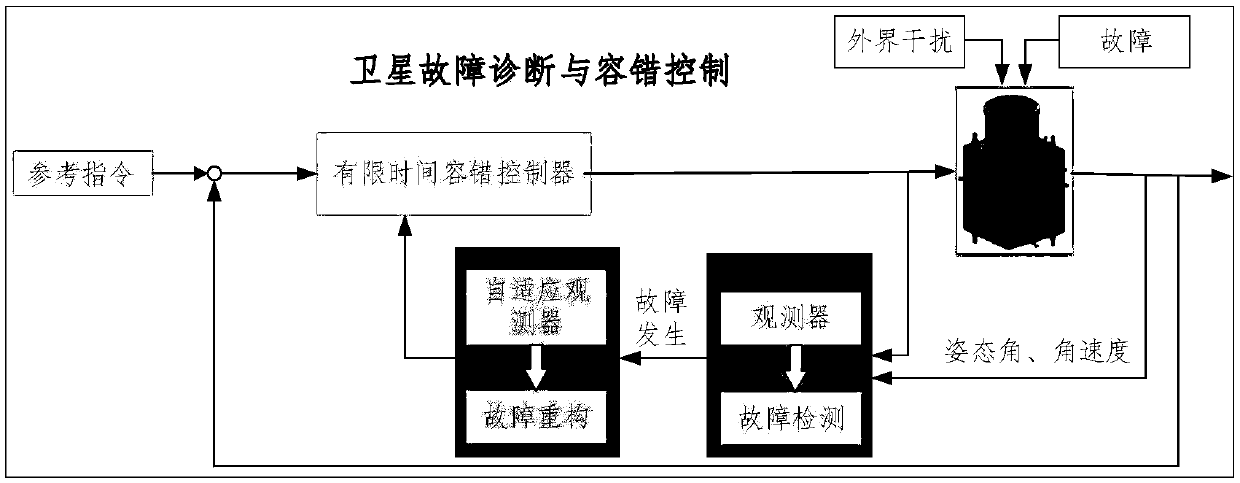
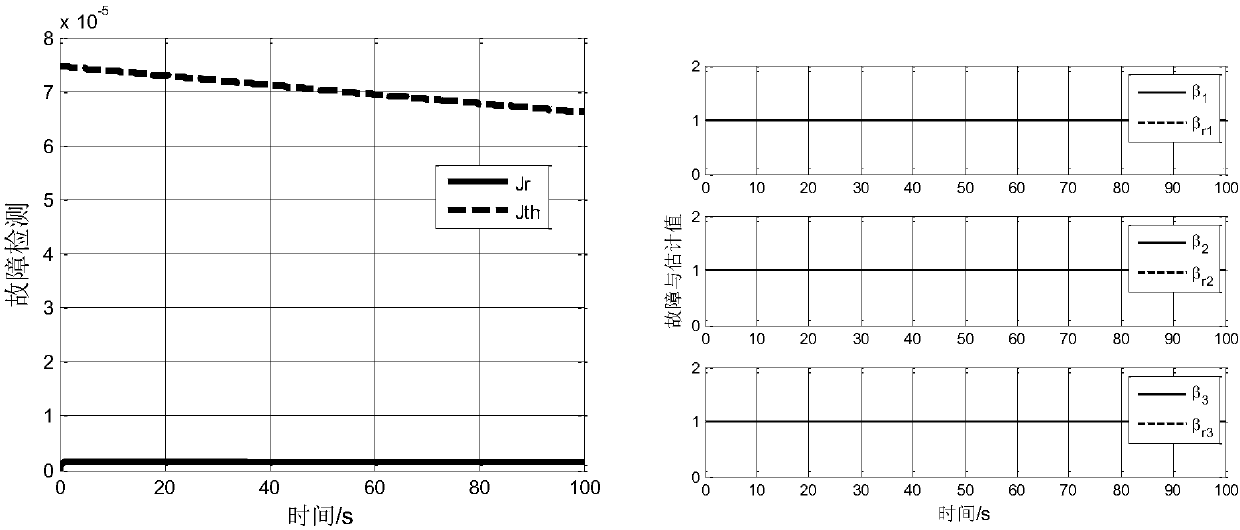
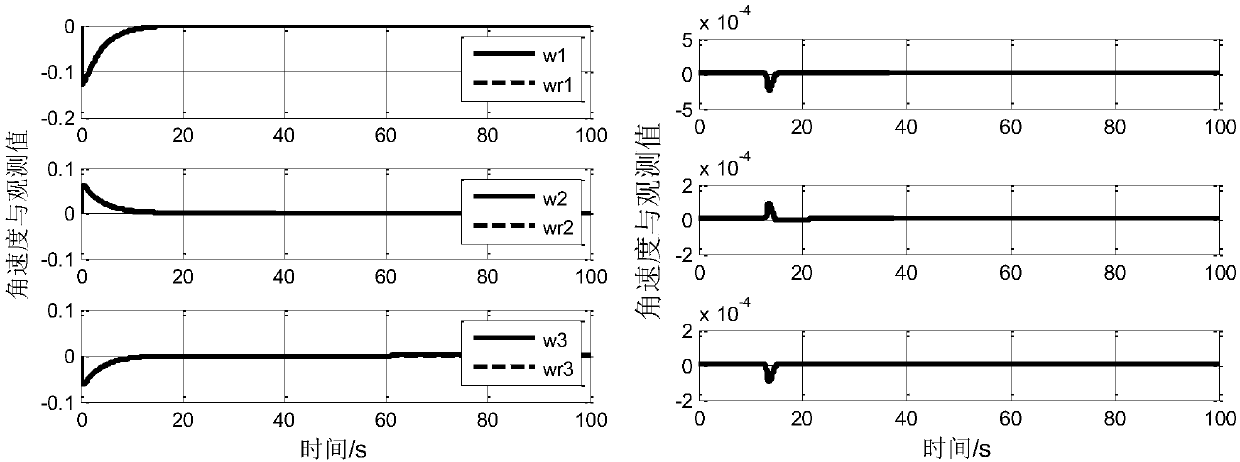
Satellite fault diagnosis and fault-tolerant control method based on self-adaptive observer
ActiveCN107861383AGuaranteed strong robustnessStrong robustnessAdaptive controlEffective factorKinematics
The invention relates to the technical field of satellite fault diagnosis and fault-tolerant control, and proposes a fault diagnosis method, which has very good robustness to external interference, isfree of influence of external interference in a fault diagnosis process, prevents generation of misinformation and missing report, and can effectively estimate fault severity. According to the satellite fault diagnosis and fault-tolerant control method based on a self-adaptive observer, first a satellite kinematics and dynamics model under an actuator fault and external interference influence isestablished to analyze influence of fault effective factors on a system; secondly, an observer is designed for a satellite fault system, a residual error evaluation function is established based on observer output and system actual output, an evaluation threshold value is obtained, and the purpose of fault detection is achieved; then, when occurrence of a fault is detected, a self-adaptive observer is designed to complete a fault diagnosis task; and finally, based on an estimated value of the fault, a finite time self-adaptive fault-tolerant controller is designed. The satellite fault diagnosis and fault-tolerant control method based on a self-adaptive observer is mainly applied to fault diagnosis and fault-tolerant control occasions.
Owner:TIANJIN UNIV
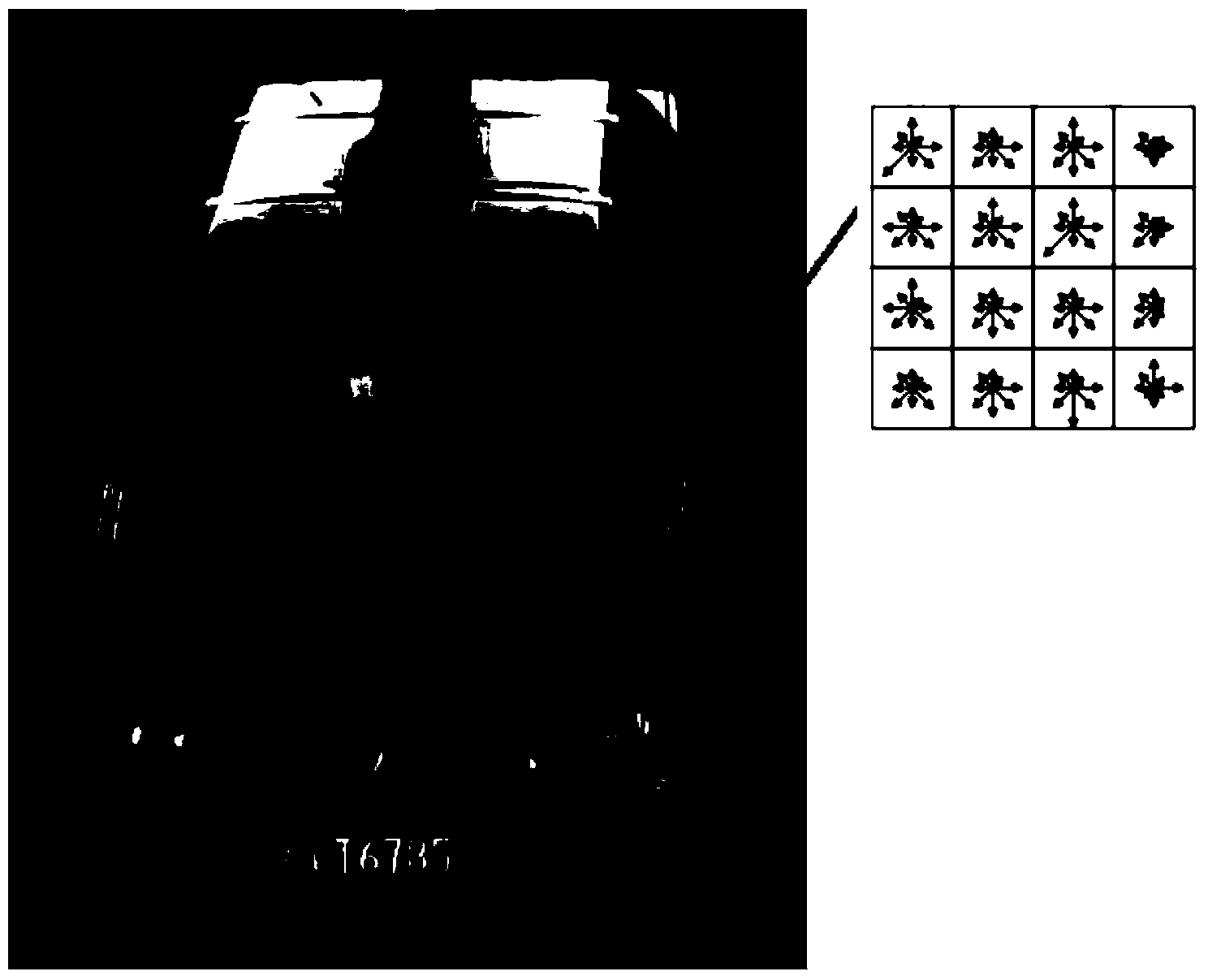
Method and system for recognizing vehicle brand based on image
ActiveCN103488973AImprove reliabilityLow costCharacter and pattern recognitionMisinformationMulti dimensional
The invention provides a method and system for recognizing a vehicle brand based on an image. The method and system can carry out multi-dimensional position detection in the image to fast recognize the vehicle brand, are high in detection rate and have little misinformation.
Owner:SHANGHAI YITU NETWORK SCI & TECH
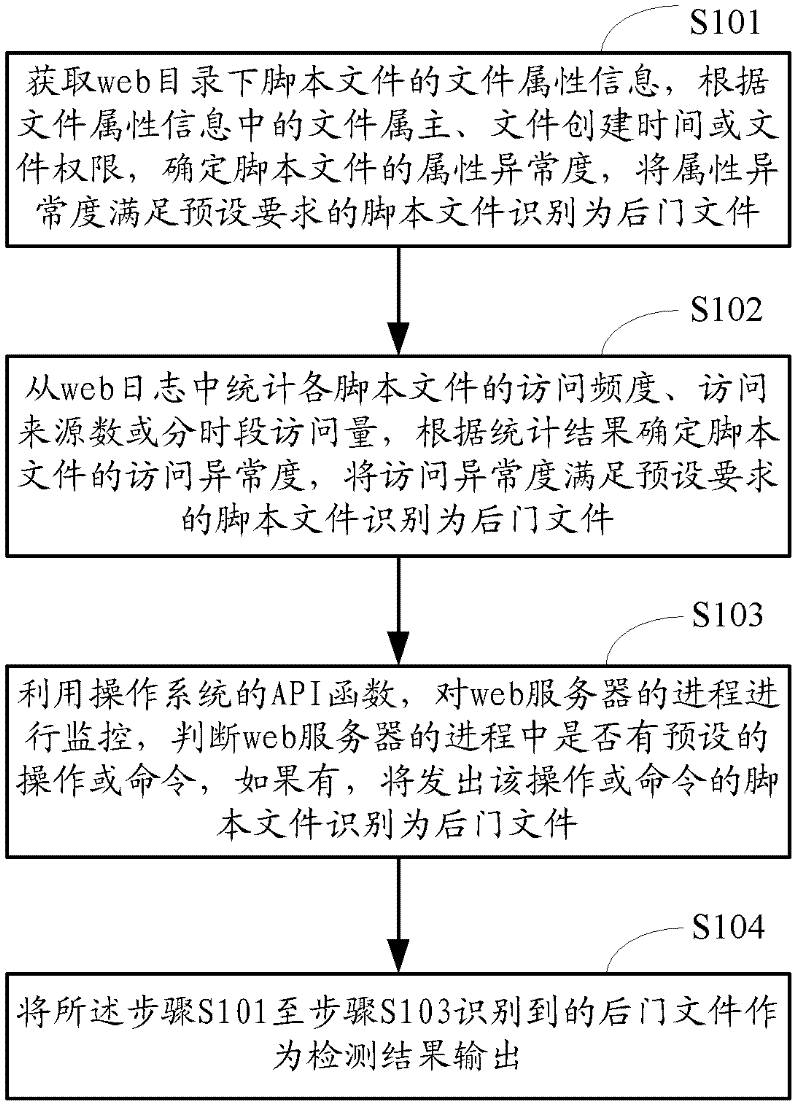
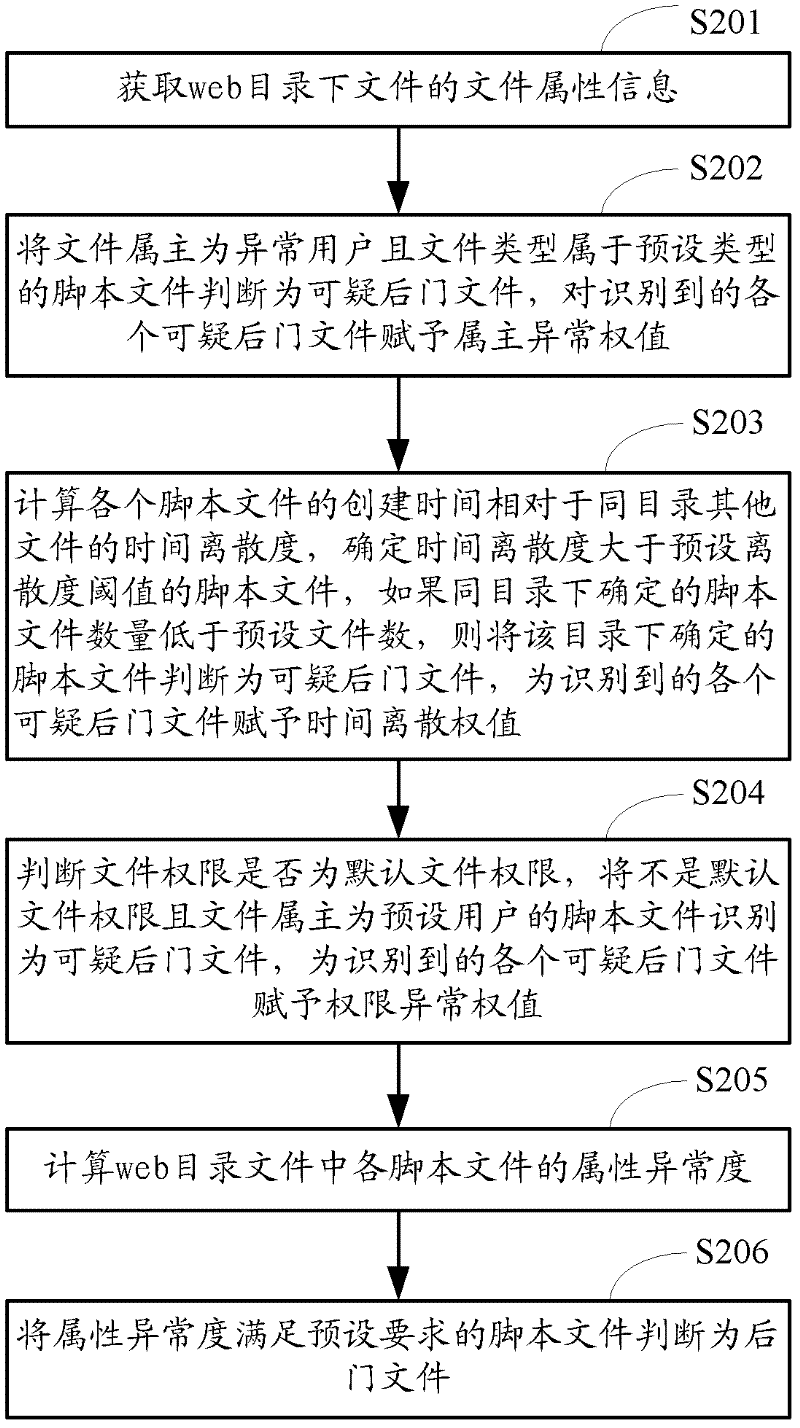
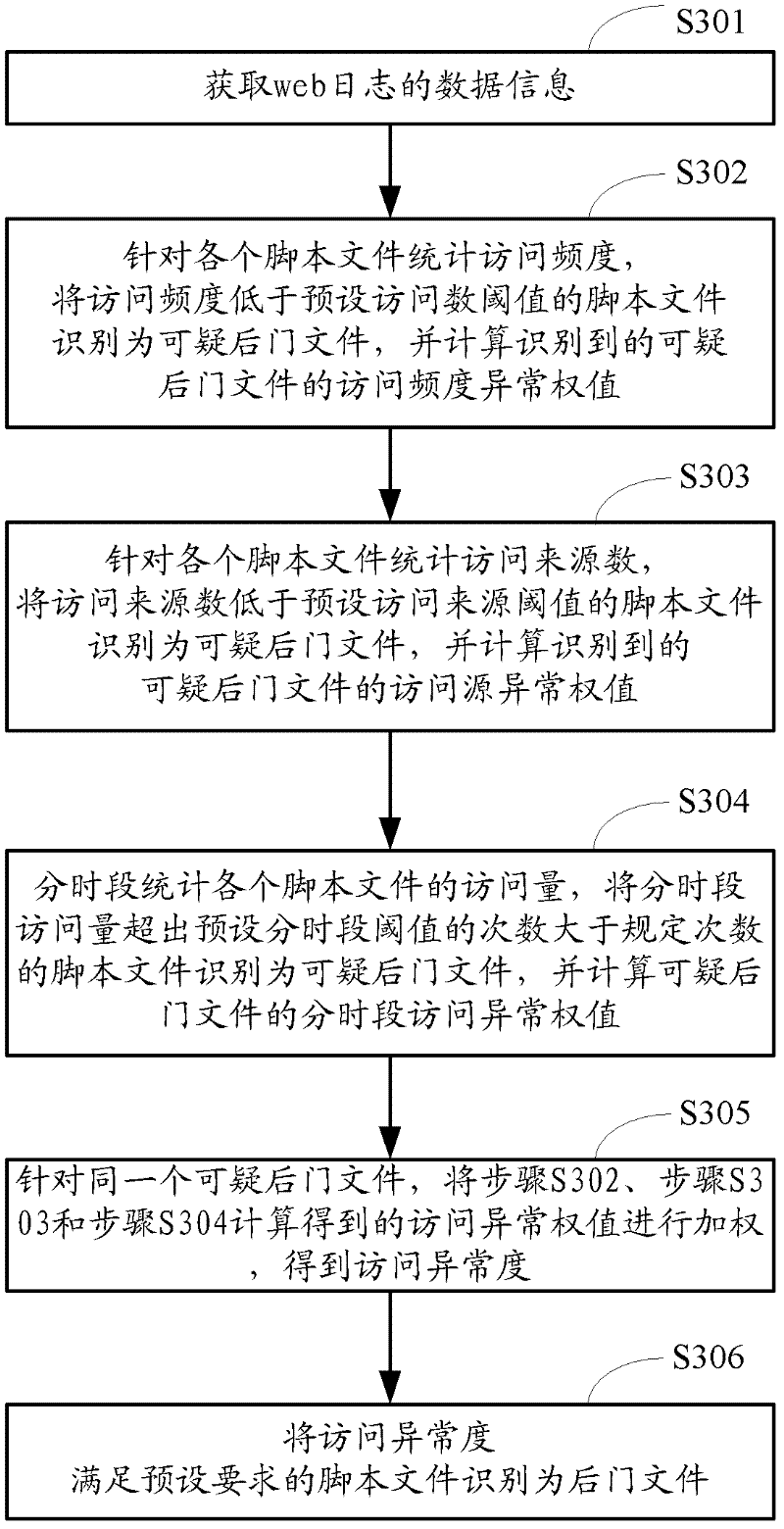
Web back door detection method and device based on behavioral characteristics
ActiveCN102647421AEfficient detectionImprove the detection rateTransmissionOperational systemWeb service
The invention provides a web back door detection method and device based on behavioral characteristics. The method comprises the following steps of: step S1_1, obtaining file attribute information of a script file under a web catalogue; determining an attribute abnormality of the script file according to file establishing time, a file owner or a file authority limit in the file attribute information; and identifying the script file with the attribute abnormality which meets pre-set requirements into a back door file; step S1_2, counting an accessing frequency, accessing source quantity or different-time accessing amount of each script file from a web log and determining an accessing abnormality; and identifying the script file with the accessing abnormality which meets pre-set requirements as the back door file; and step S1_3, utilizing an operating system to monitor a progress of a web server; judging whether a pre-set operation or order exists; and if so, identifying the script file which sends out the operation or the order as the back door file. The web back door detection method and device based on the behavioral characteristics can effectively detect an encrypted and deformed wed back door based on a detection manner of the behavioral characteristics, so that the relevance ratio and the detection efficiency are improved and the misinformation rate is reduced.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
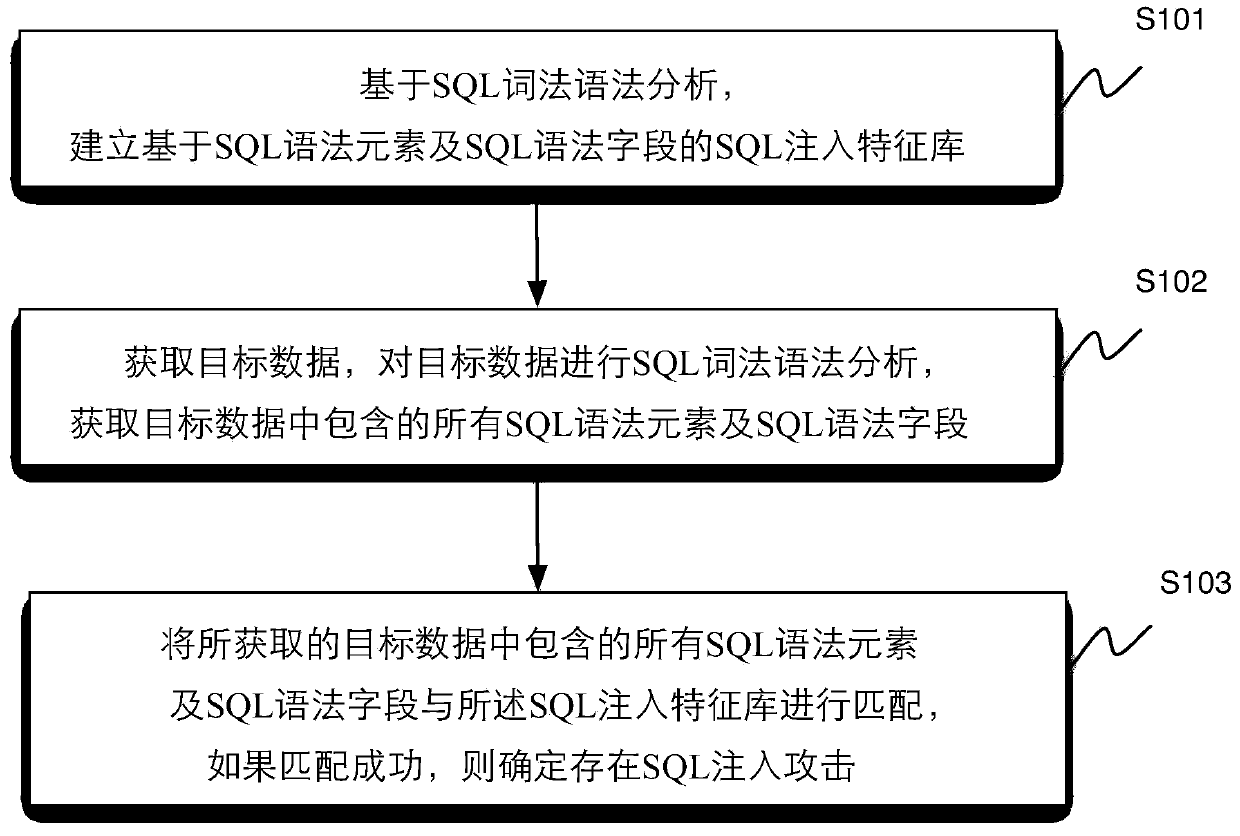
Method and device for identifying SQL injection attacks
ActiveCN103744802AImprove efficiencyReduce false positivesUnauthorized memory use protectionMultiple digital computer combinationsSQL injectionMisinformation
The invention discloses a method and a device for identifying SQL (Structured Query Language) injection attacks, wherein the method comprises the steps of establishing an SQL injection feature library based on SQL syntax elements and SQL syntax fields through SQL lexical and syntactic analysis, obtaining target data, performing the SQL lexical and syntactic analysis on the target data and obtaining all SQL syntax elements and SQL syntax fields included in the target data, next, matching all of the obtained SQL syntax elements and SQL syntax fields included in the target data with the SQL injection feature library, and if matching is successful, determining the existence of the SQL injection attacks. The method and the device are capable of improving the efficiency of identifying SQL injection and reducing misinformation and failures in report.
Owner:BEIJING QIANXIN TECH
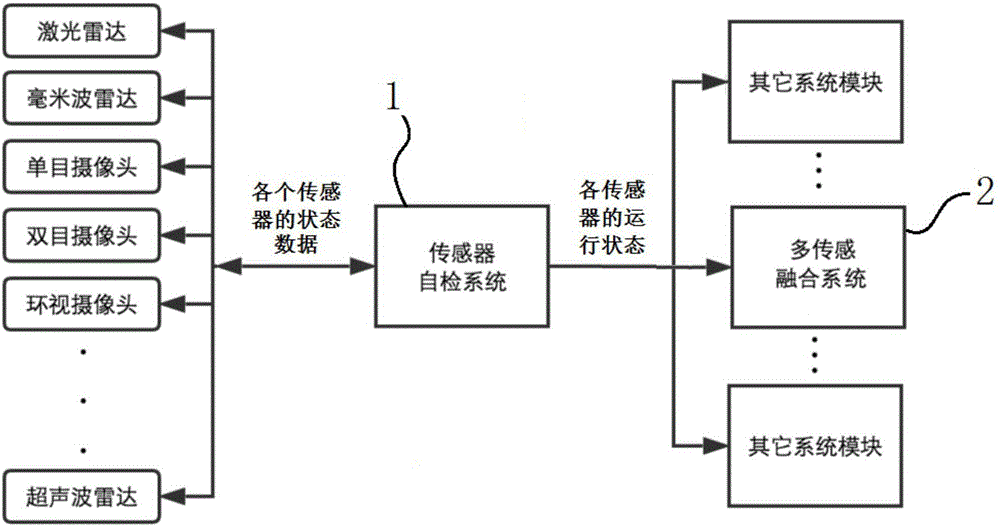
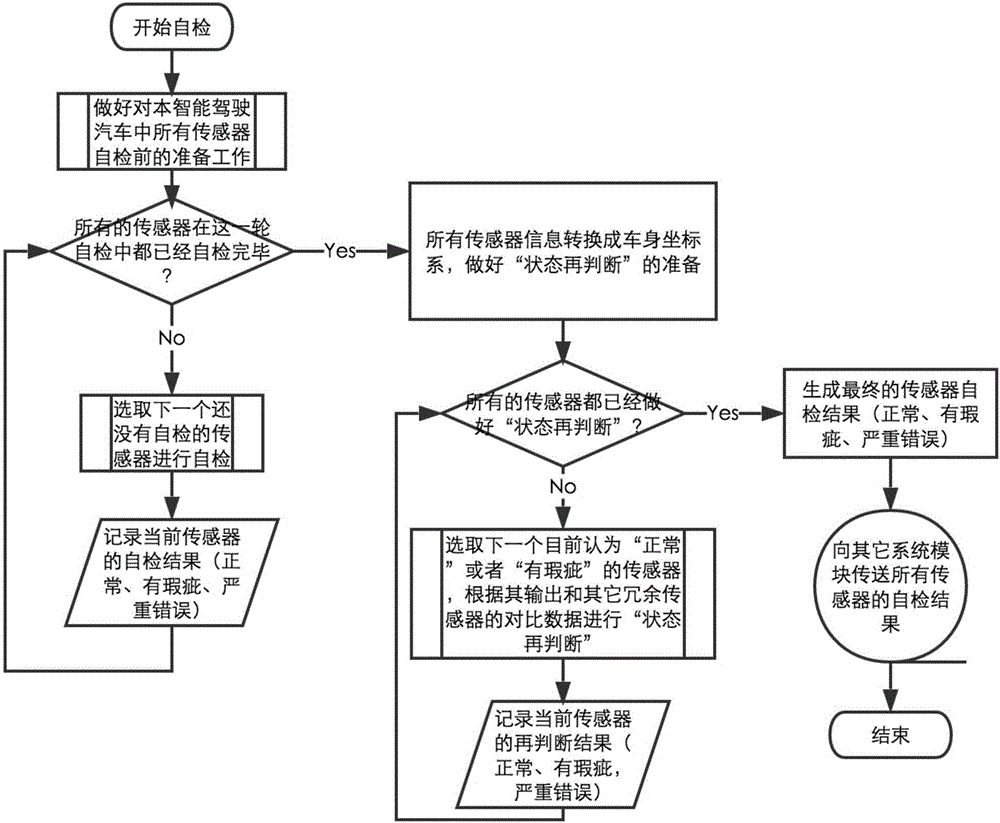
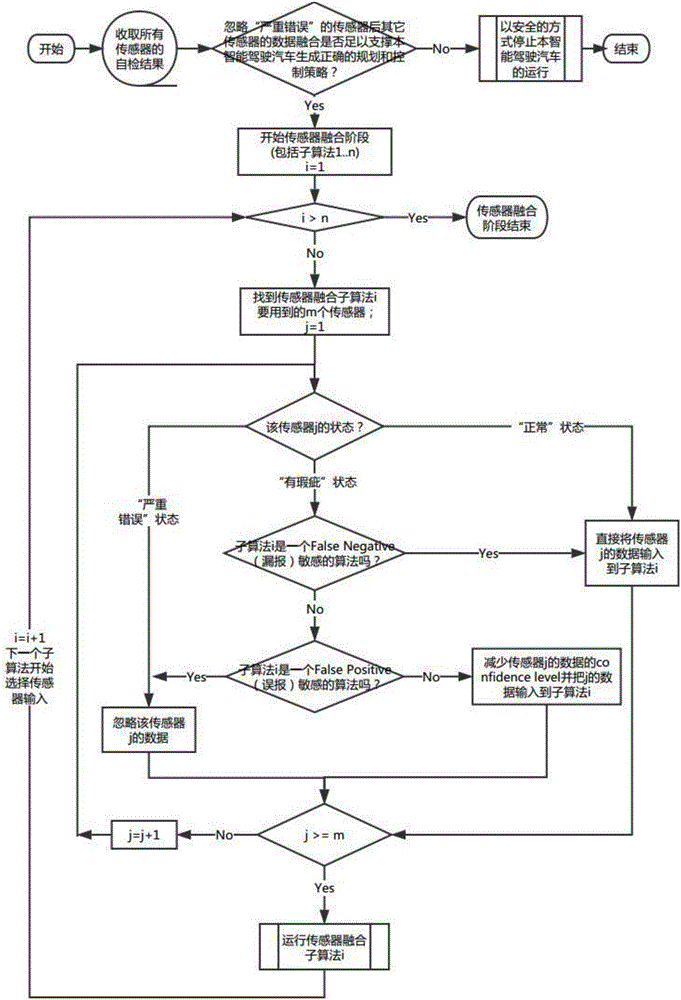
Sensor self-checking system of intelligent driving vehicle and multi-sensing fusing system
ActiveCN106840242AImprove securityImprove efficiencySafety arrangmentsCharacter and pattern recognitionMultiple sensorMisinformation
The invention discloses a sensor self-checking system of an intelligent driving vehicle. The sensor self-checking system is an integrated multi-sensor self-checking system, when states of all sensors of the intelligent driving vehicle are detected, self-checking results of all the sensors are integrated, the checking results are classified, sense redundancy brought by multiple sensors with the same classification is utilized, sensor fault testing and detection are further conducted, and the comprehensive sensor state of the intelligent driving vehicle is reasonably judged. The invention further provides an intelligent driving vehicle multi-sensing fusing system, the sensor self-checking system completes self-checking and state judgment of an integrated sensor, and self-checking information sent by the sensor self-checking system is utilized to be subjected to information fusing processing at the same time, according to a dynamic result of sensor self-checking and with the combination of a planning controlling algorithm, a sensitive degree of misinformation and a missing report are subjected to intelligent fusing, and the intelligent driving vehicle is helped to make a more reasonable plan and controlling strategy.
Owner:UISEE TECH BEIJING LTD
Forward collision early-warning method and system based on curve self-adaption
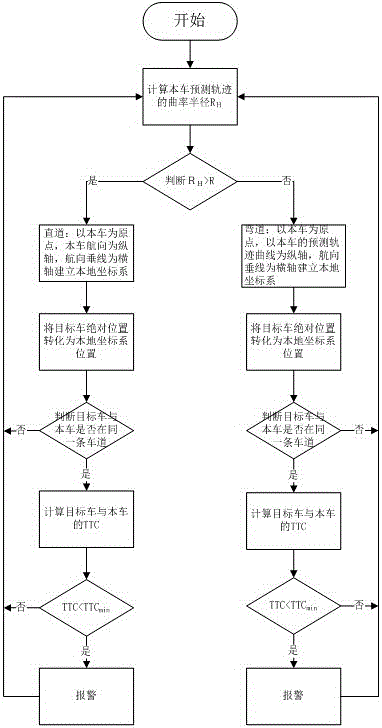
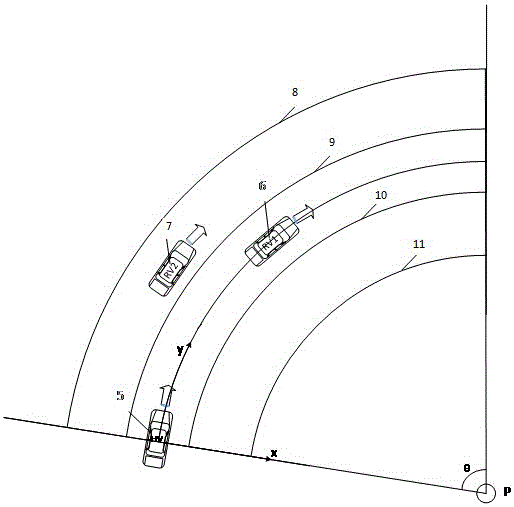
InactiveCN106601029AAvoid False Positive SituationsAnti-collision systemsEarly warning systemEngineering
The invention discloses a forward collision early-warning method and a forward collision early-warning system based on curve self-adaption, which can prevent the misinformation condition of listing vehicles in lateral lanes as early-warning vehicles through judging whether a target vehicle and a present vehicle are in the same lane after determining whether a horizontal coordinate distance between the two vehicles is within a set lane width. Moreover, a prediction trajectory of the present vehicle serves as a vertical axis of a local coordinate system, so that the vertical axis of the local coordinate system can change along with the road profile automatically, therefore, the forward collision early-warning system can adapt to a curve scene.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
Self-adaptive warning system for intelligently addressing circumferential intrusions of fiber Bragging grating
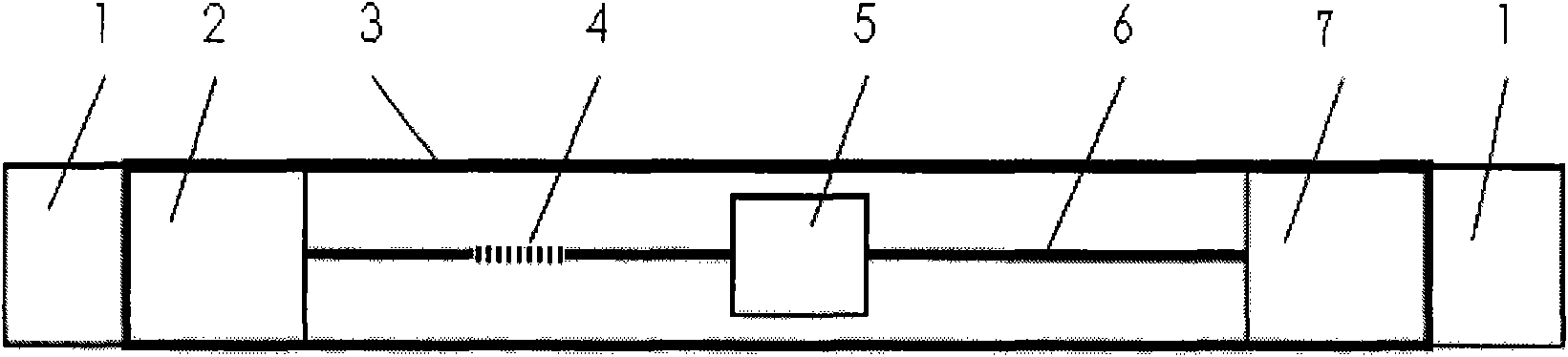
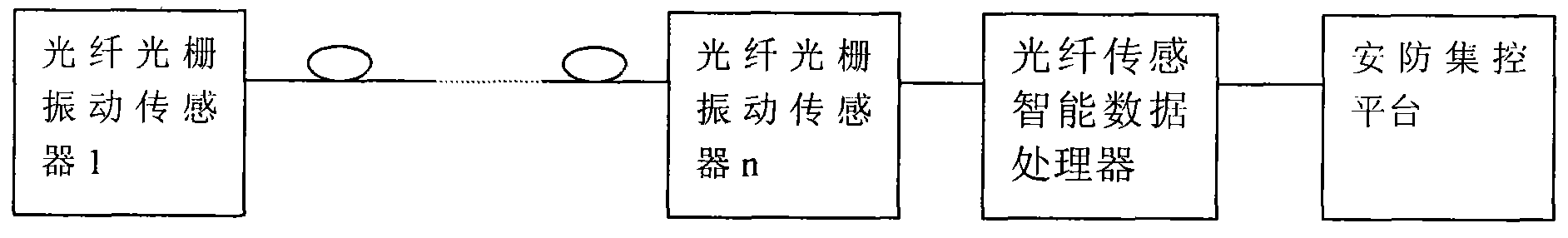
InactiveCN101840615AEasy to install on siteAvoid false positives and false negativesBurglar alarm short radiation actuationFiberGrating
The invention discloses a self-adaptive warning system for intelligently addressing circumferential intrusions of fiber Bragging grating. The self-adaptive warning system consists of a fiber Bragging grating vibration sensor, an optical transmission cable, a fiber grating signal demodulator and a security centralized control platform. When in detection, a plurality of the fiber Bragging grating vibration sensors with different wavelengths are connected in series with one optical fiber by the wavelength division multiplexing technology to acquire the distributed information; by acquiring and processing the fiber grating signals, the fiber Bragging grating vibration sensors are integrated with the application software of an upper computer into an intelligent management system to form a set of ideal and complete self-adaptive warning system for the fiber circumferential intrusion security. The system can be applied to the circumference intrusion warning guard, and can be used as the environmental sensing device by the circumferential intrusion of the intelligent addressing. The invention adopts the outdoor all-passive network type transmission system, so that the sensing region can be addressed freely. The passive transmission and the optical cable laying are applied to the system, so that the system is convenient for the on-site installation and no device debugging is needed on site; in particular, the invention has the advantages of suitability of the outdoor laying, lightning and flash resistance and anti-electromagnetic interference, capability of sufficiently meeting and being applied to the circumference security in various complex environments, capability of accurately solving the misinformation and the report missing and the like.
Owner:WUHAN UNIV OF TECH
Attack detection method and system for WEB
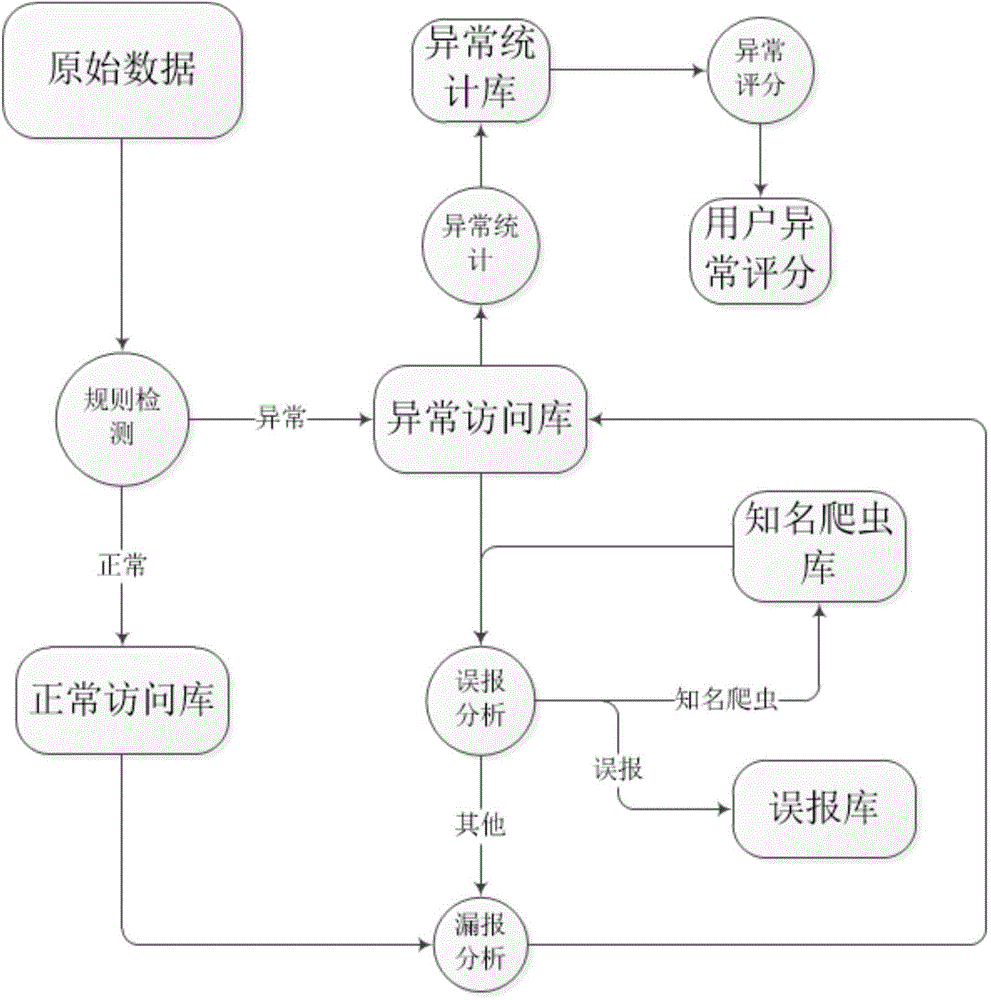
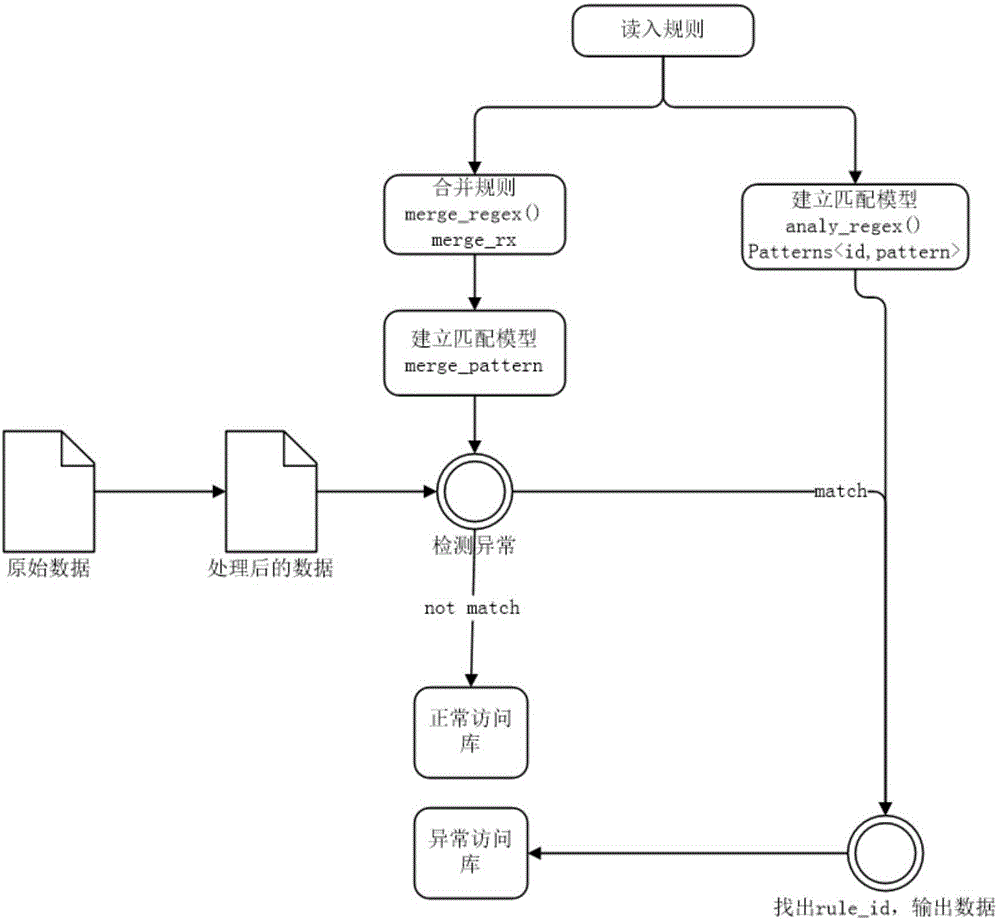
The invention discloses an attack detection method and system for WEB; the method comprises the following steps: firstly implementing attack characteristic detection to the url accessed by a user; then implementing misinformation analysis and fail-to-declare analysis treatment to the detection result, wherein the misinformation analysis mainly solves the misinformation caused by normal embedded resources of the website and the web crawlers, the fail-to-declare analysis is to treat the undetected abnormal behaviors conducted by the detected abnormal users. Based on the results of the treatment above, calculating the total normal access time of each abnormal user under each domain name; when the access time is less than the average value of all users, taking the ratio between the access time and the average value as an abnormality scoring index of the abnormal user; otherwise, the abnormality score is a weighted value w of the ratio between the access time and the maximum access time of all users. By the misinformation analysis and fail-to-declare analysis treatment, the efficiency of the attack detection method and system for WEB is significantly increased.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
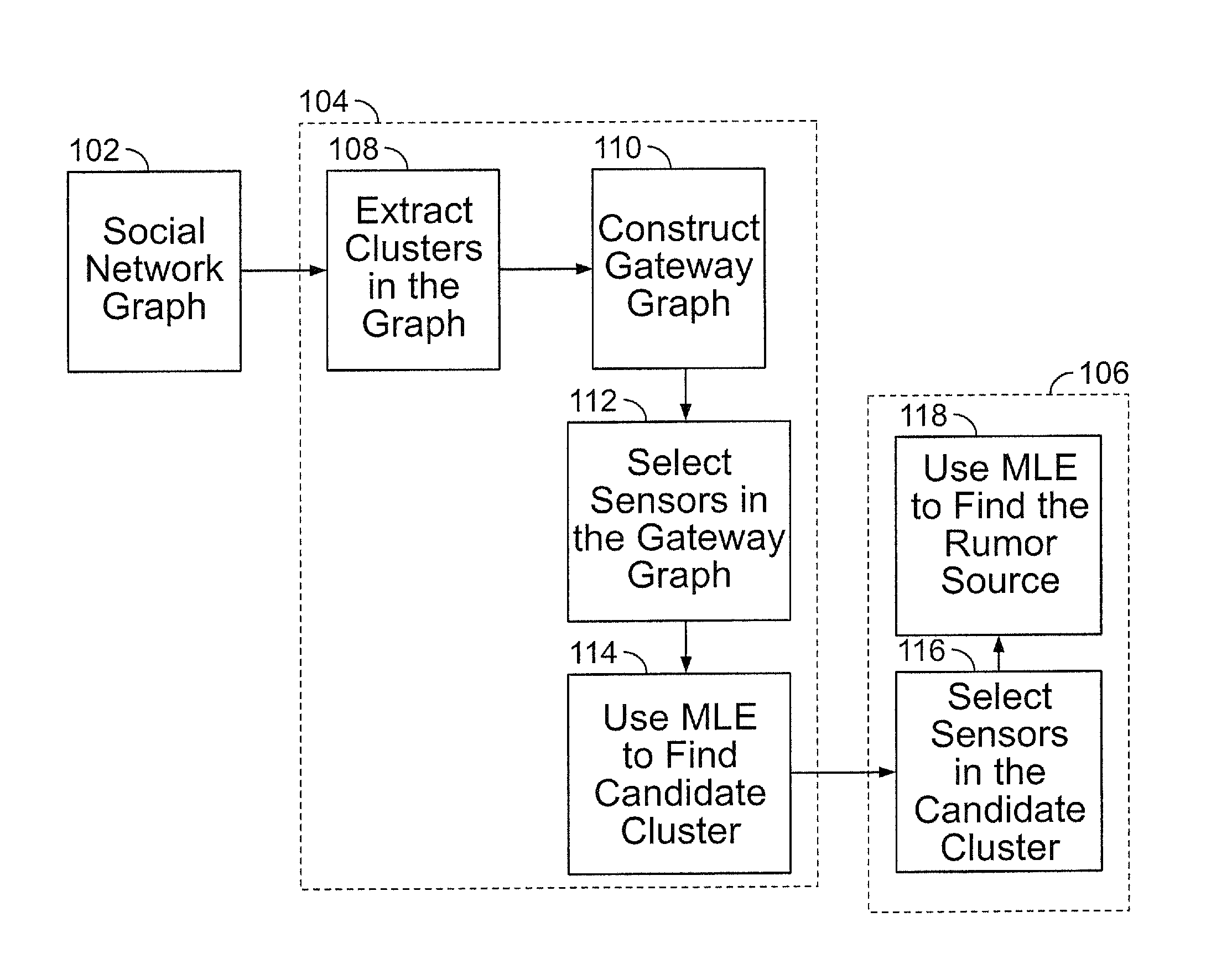
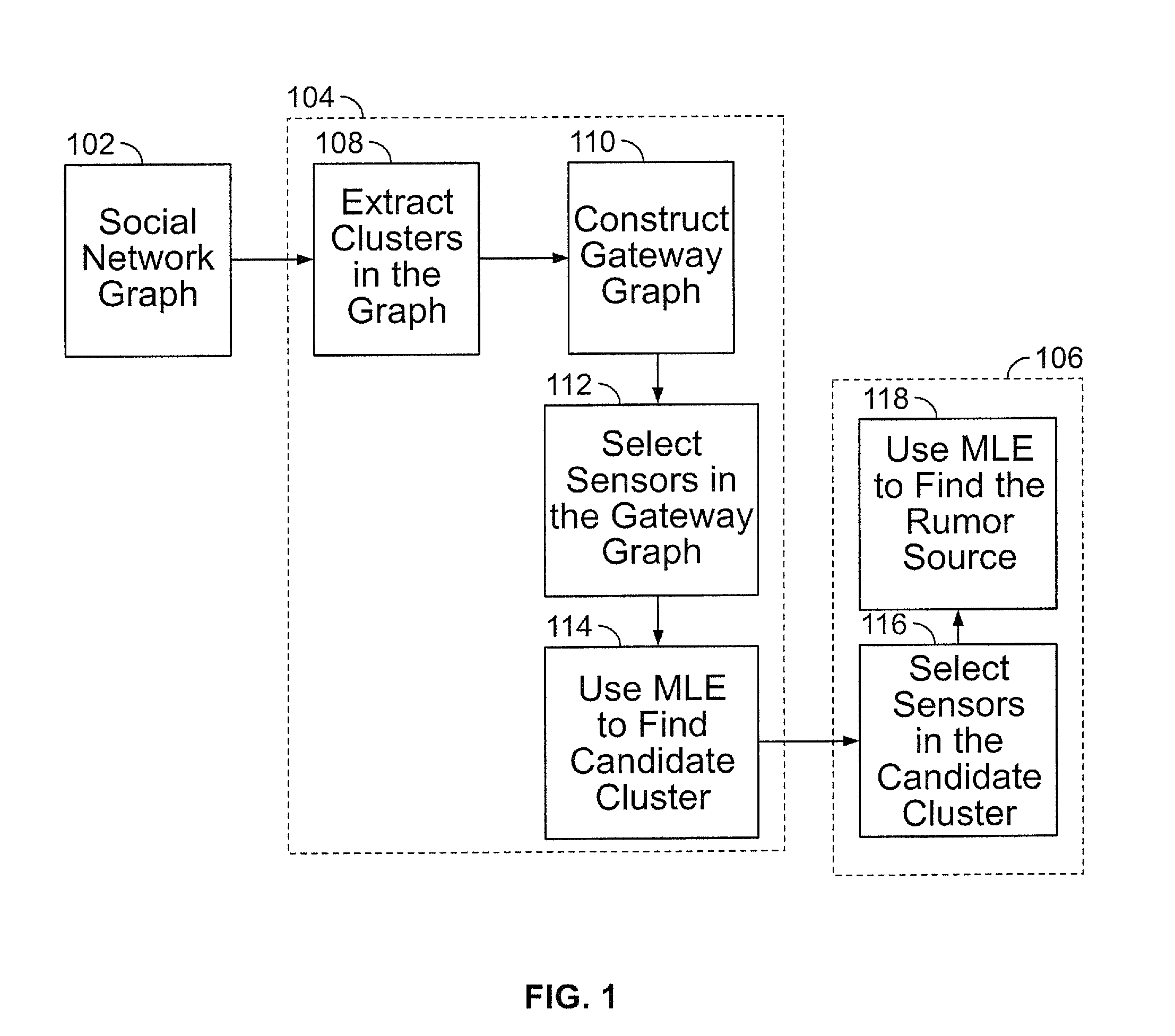
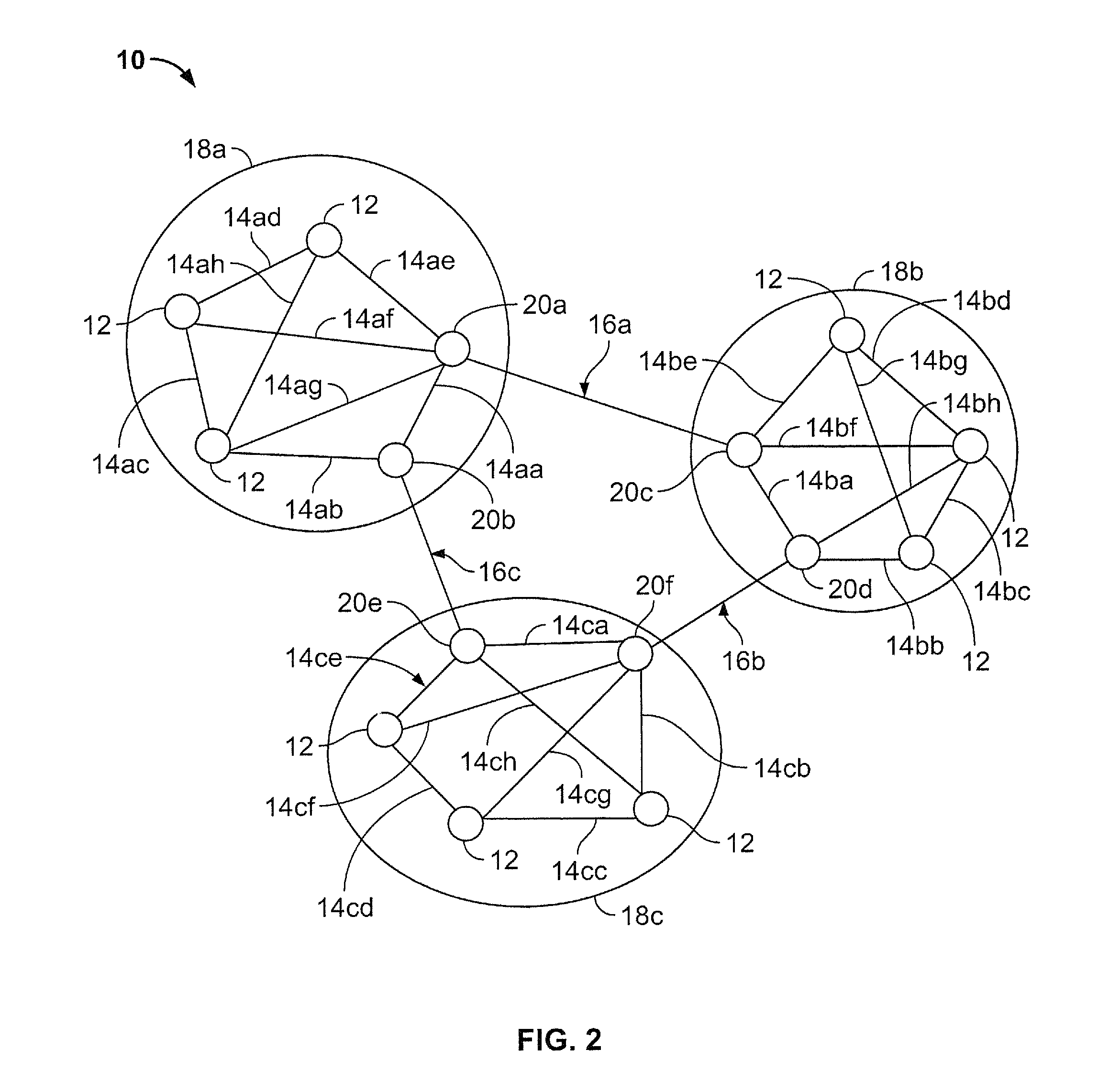
Method and Apparatus to Identify the Source of Information or Misinformation in Large-Scale Social Media Networks
ActiveUS20160212163A1Increase probabilityDigital data information retrievalMemory loss protectionNode clusteringHigh probability
A system and method of detecting a source of a rumor in a social media network is disclosed. The social media network includes a plurality of node clusters, each of the plurality of nodes therein having at least one edge connection to a corresponding number of different nodes in the same cluster. The system identifies a plurality of gateway nodes, each having at least one weak tie connection with a corresponding gateway node from a different node cluster; selects a subset of gateway nodes as sensors to measure arrival times of a rumor; and selects a candidate node cluster based on these arrival times. From there, the system selects a set of nodes in the candidate cluster to measure arrival times of a rumor from a source node, and selects a candidate node from the candidate cluster as having a high probability of being the source node.
Owner:STEVENS INSTITUTE OF TECHNOLOGY
Security signal alarm system
InactiveCN101246627AKnow instantlyReal-time observationBurglar alarm short radiation actuationMonitoring siteThe Internet
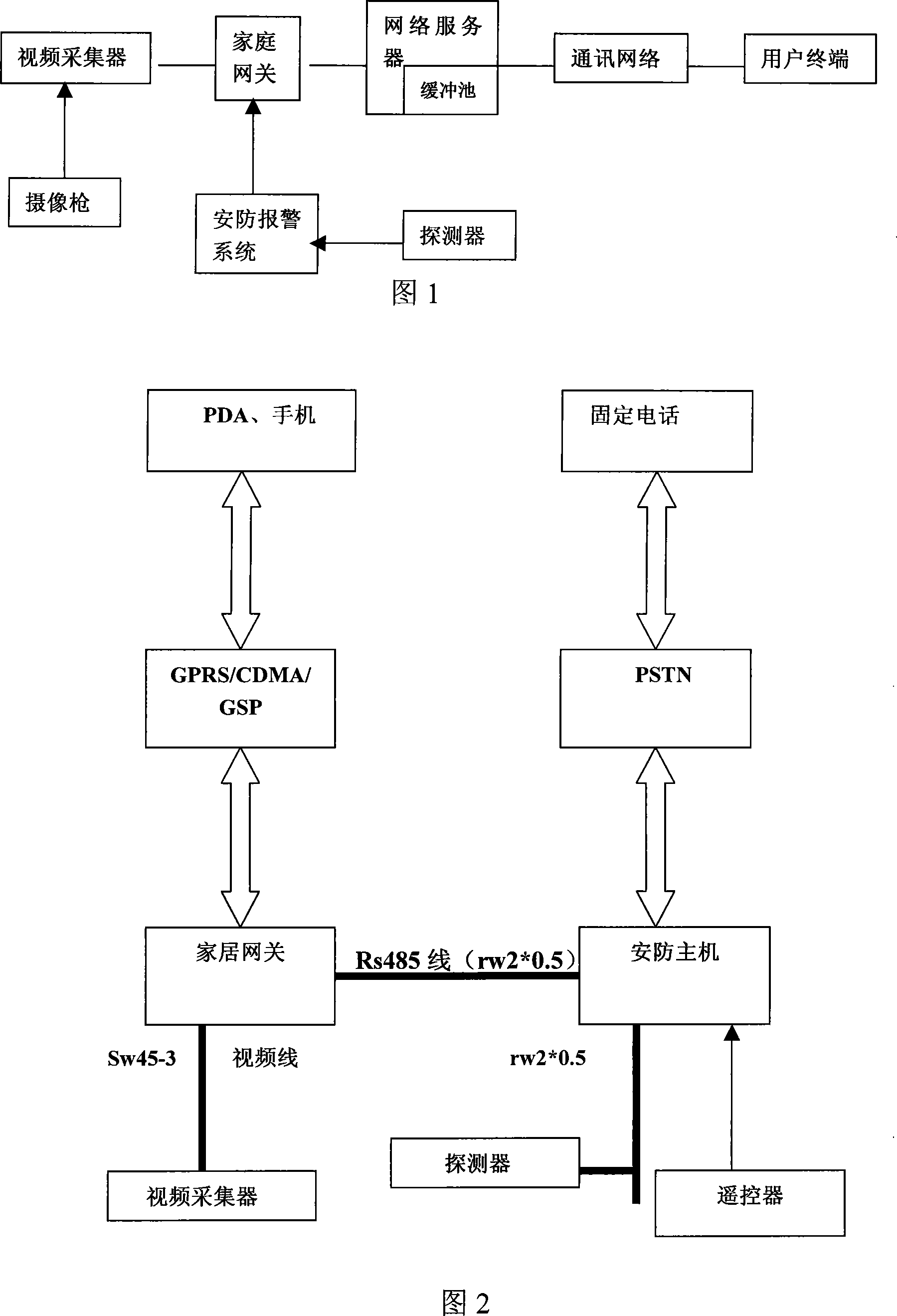
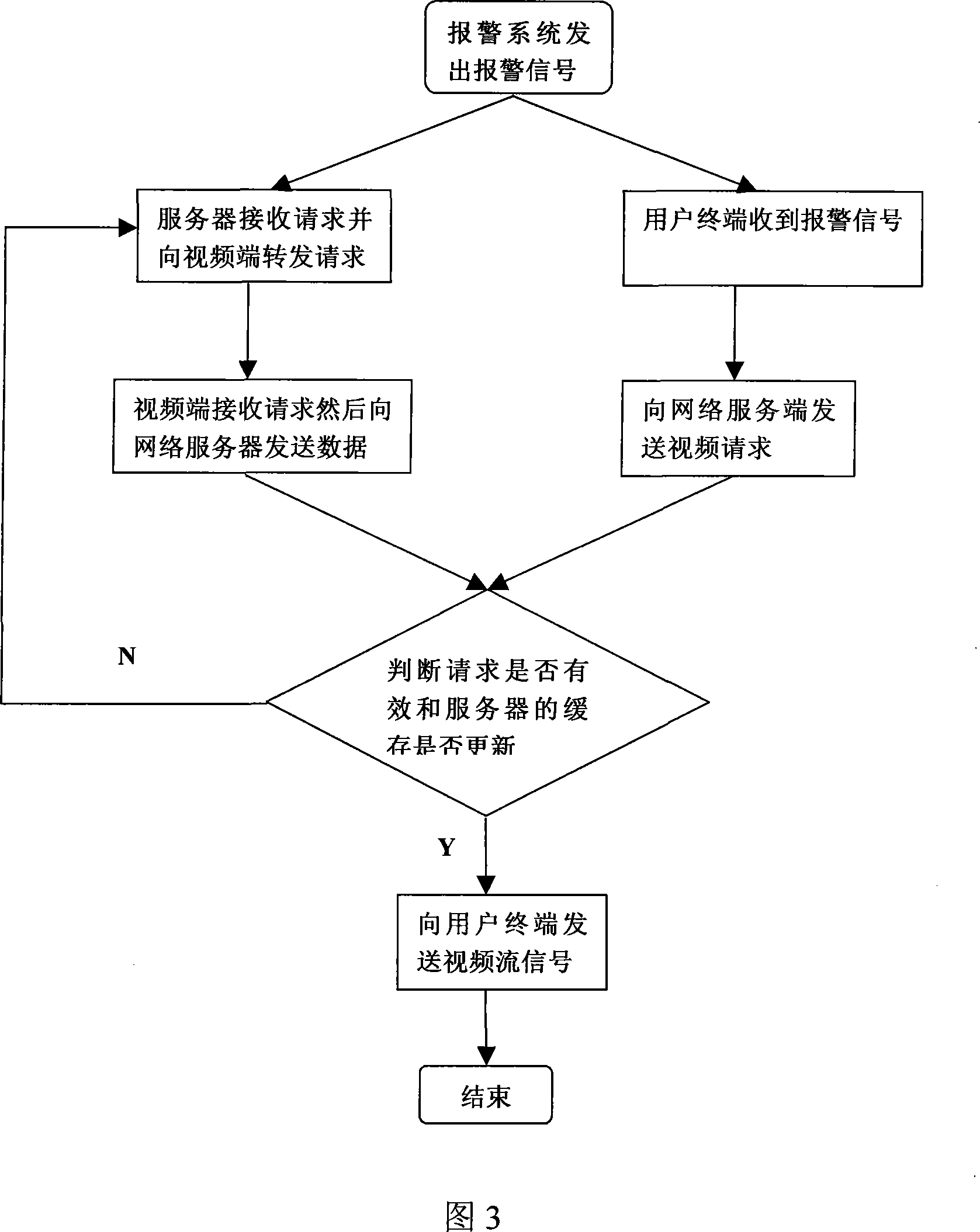
The present invention provides a security signal alarming system, mainly including a detector, a security alarming system, multiple camera guns, a video collector, a family gateway, a network server, a communication network and an user terminal, the camera gun is connected to the video collector via common analog video wire, the video collector and the family gateway are connected by unshielded twisted pair, the gateway is accessed in internet by radio card and communicated with the network server, the network server is communicated with the user terminal by the communication network. When the security alarming system alarms, the system processes alarming signal by family gateway, at the same time collecting video signal and sending alarming information to user, sending request video information by mobile phone or PDA terminal, observing condition of the monitoring site at any time and strengthening interactive of the security system and human, resolving the fateful fault of the misinformation in the present alarming system, and grasping the condition of monitoring point when the user not in the site.
Owner:GUANGDONG TRI SUN ELECTRONICS TECH +1
Method of monitoring faults in sections for intermittent control system
InactiveCN103279123AThe phase division complies withThe phase division is more in line with the batch process actually in line withElectric testing/monitoringFuzzy clustering analysisPrincipal component analysis
The invention discloses a method of monitoring faults in sections for an intermittent control system and relates to a fault monitoring method. Firstly, a plurality of batches of collected intermittent process data are standardized in a way of expanding variables, and a data matrix on each sampling time is subjected to principal component analysis; secondly, a fuzzy C-means clustering is a fuzzy clustering analysis method which is suitable for soft partition and is generated through combining a fuzzy set theory and a k-means clustering; and thirdly, after segmentation is finished, an improved MPCA (Multiway Principal Component Analysis) model with a time varying principal element covariance on the basis of expanding variables is established on each subphase, then when on-line monitoring is carried out, which phase a new batch of data belongs to is judged, whether the data exceeds the fault monitoring control limit or not is calculated and judged, if so, a fault occurs, and the fault monitoring in sections ends. According to the invention, process multi-phase partition is more accurate, misinformation and missing report rates in monitoring are reduced, and the practical application and operability are strong.
Owner:SHENYANG INSTITUTE OF CHEMICAL TECHNOLOGY
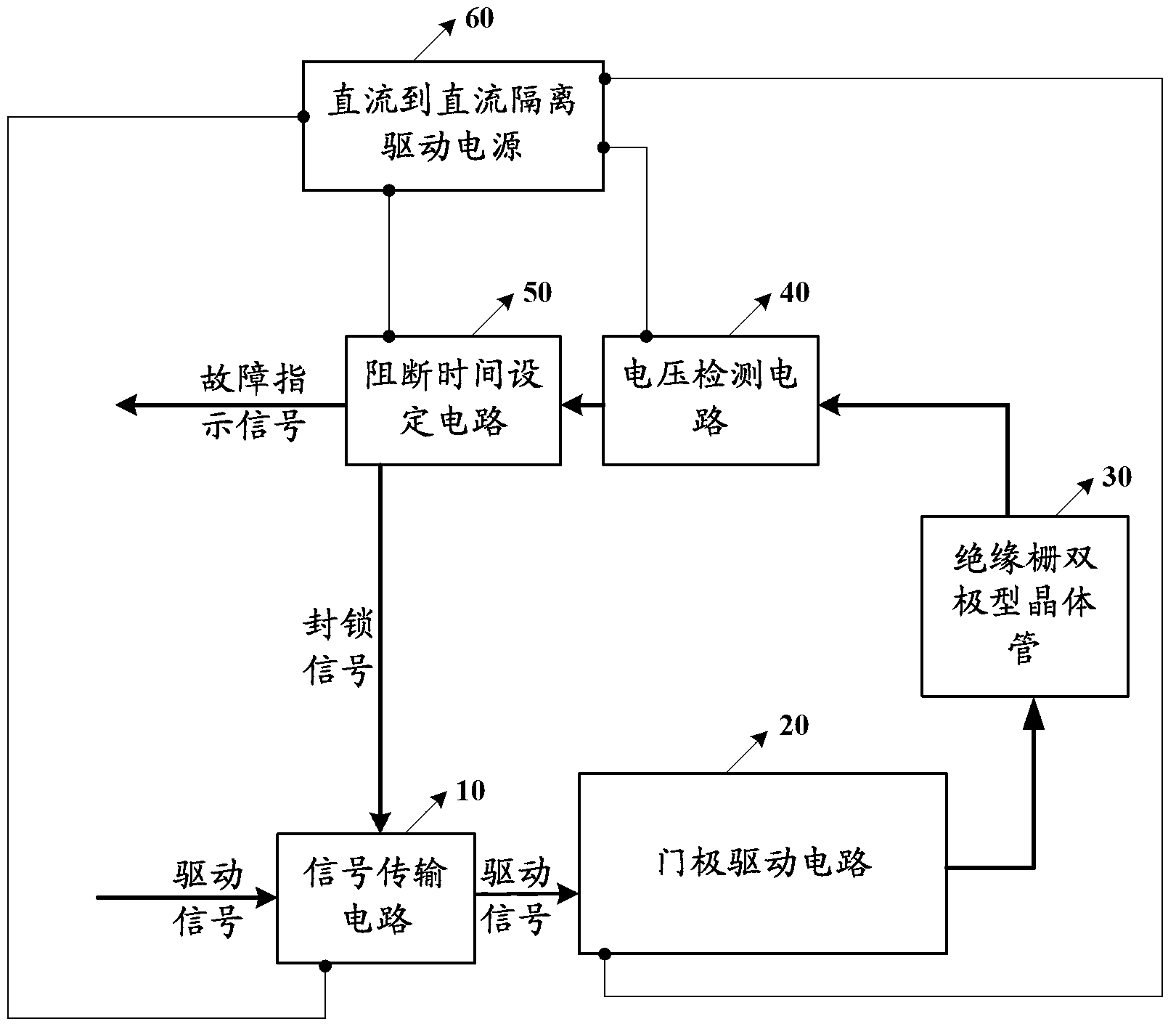
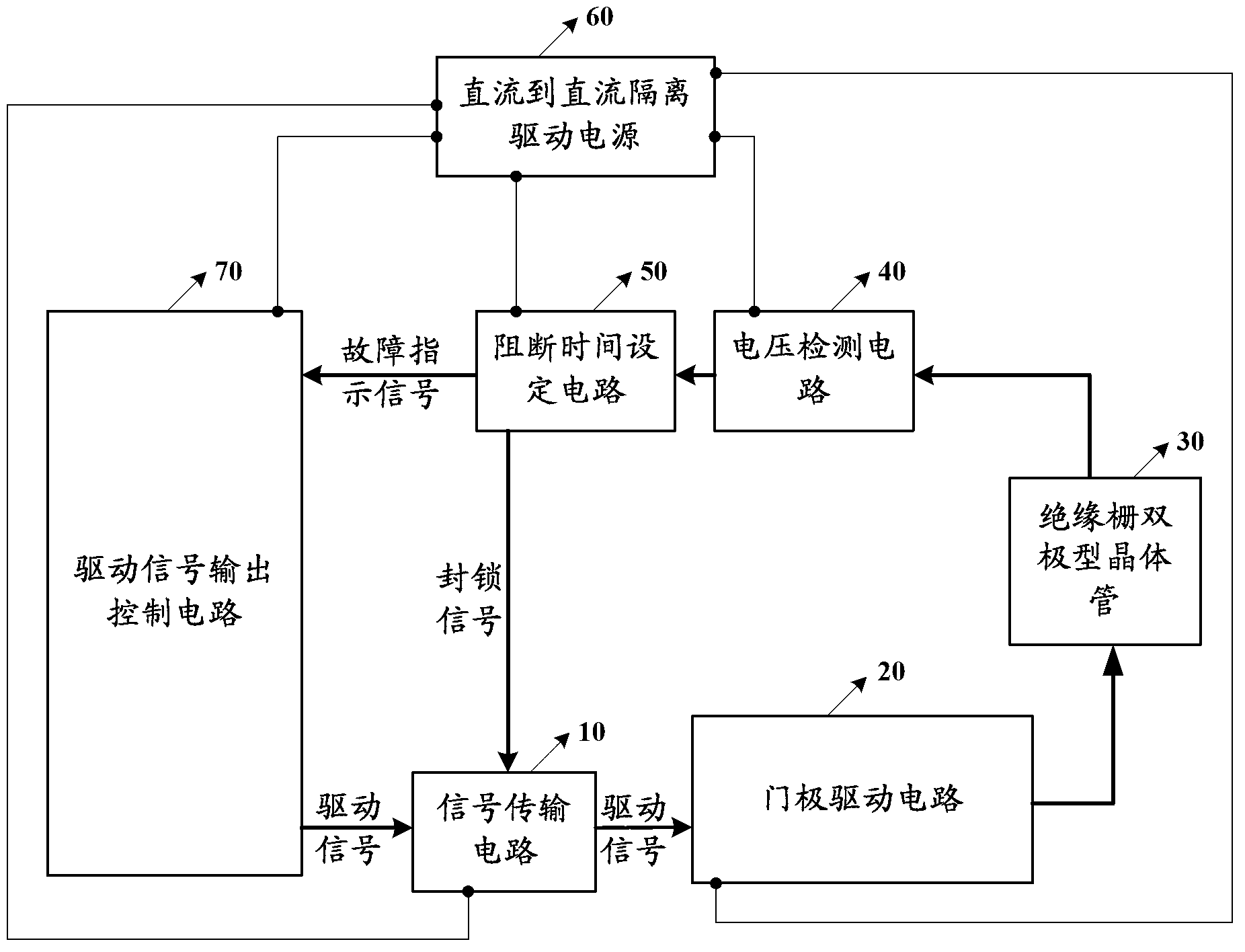
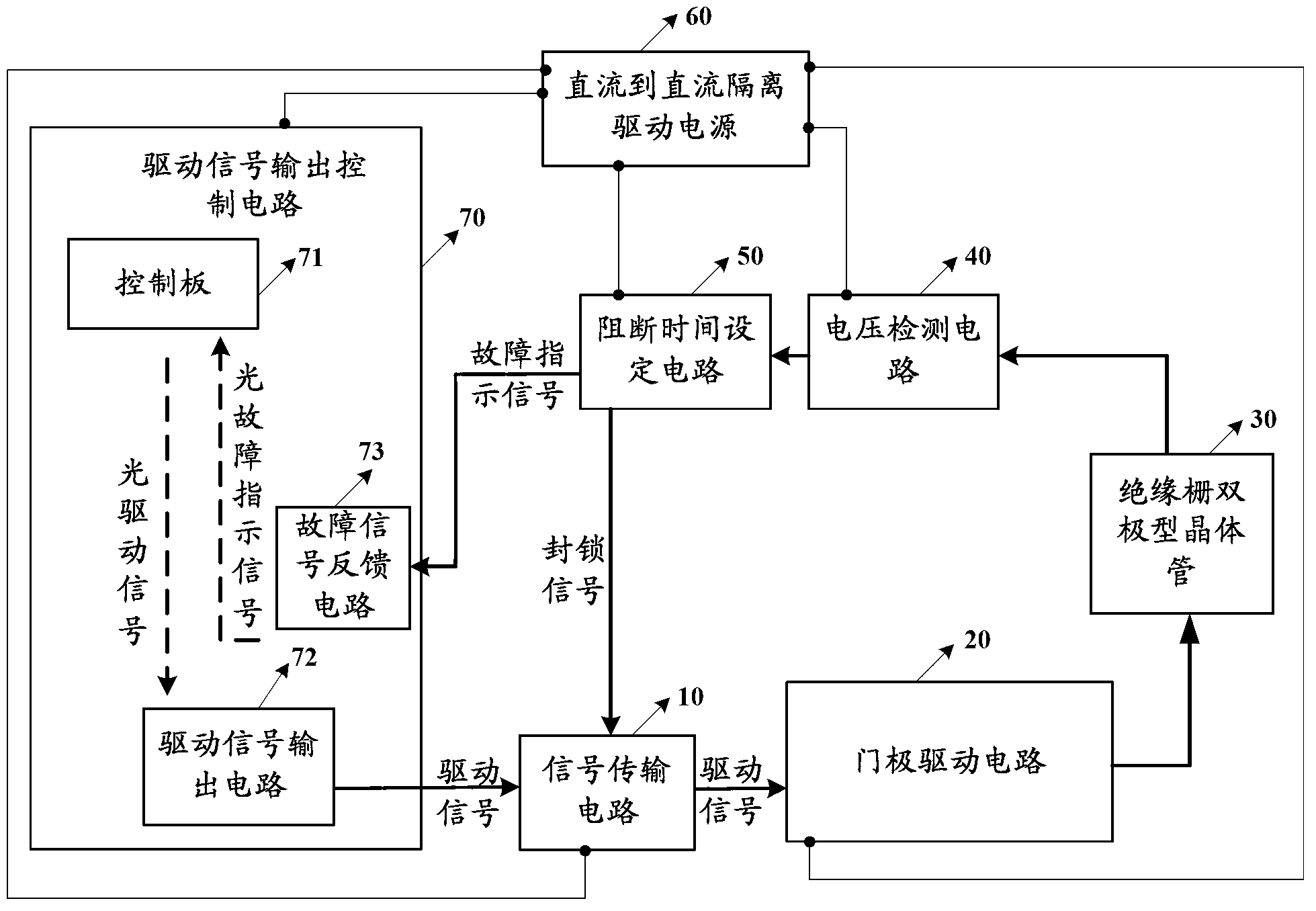
Insulated gate bipolar transistor-driven protective circuit
ActiveCN102801142AEffective protectionDo not falsely report short-circuit faultsCurrent/voltage measurementEmergency protective circuit arrangementsFault indicatorEngineering
The embodiment of the invention discloses an insulated gate bipolar transistor-driven protective circuit which comprises a signal transmission circuit, a gate pole driving circuit, a voltage detecting circuit and a blocking time setting circuit, wherein the signal transmission circuit is used for transmitting a driving signal to the gate pole driving circuit; the gate pole driving circuit is used for amplifying the driving signal from the signal transmission circuit, and then driving an insulated gate bipolar transistor to act through the amplified driving signal; the voltage detecting circuit is used for transmitting a fault indicator signal to the blocking time setting circuit once the voltage between a collecting electrode and an emitting electrode of the insulated gate bipolar transistor is detected over a set voltage threshold, wherein the voltage threshold is more than the driving voltage of the insulated gate bipolar transistor; the blocking time setting circuit is used for transmitting a locking signal to the signal transmission circuit after receiving the fault indicator signal from the voltage detecting circuit; and the signal transmission circuit also can be used for blocking and outputting the driving signal to the gate pole driving circuit after receiving the locking signal from the blocking time setting circuit. With adoption of the insulated gate bipolar transistor-driven protective circuit, misinformation of a short circuit fault can be avoided.
Owner:SHENZHEN INVT ELECTRIC
Inflection point compensation of vehicle track information
InactiveCN103697897AReduce the amount of data transferredAvoid false positivesInstruments for road network navigationNavigational calculation instrumentsGeneral Packet Radio ServiceContinuous measurement
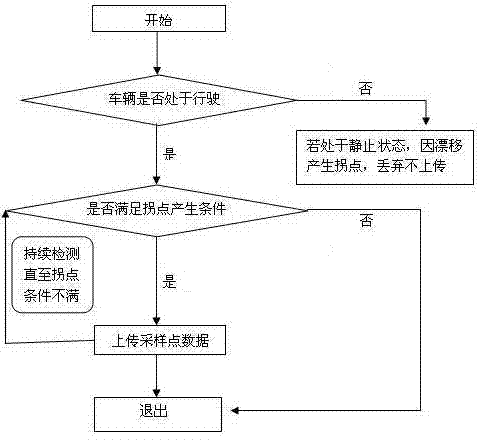
The invention discloses an inflection point compensation measurement method of vehicle track information. The method comprises a vehicle state judging step, an inflection point judging step and a data uploading step, wherein the inflection point judging step comprises: continuously measuring the turning angle between each two points, calculating the sum alpha of the turning angles of N continuous measurement points, and determining to enter a turning state if the absolute value of alpha is larger than beta; the data uploading step comprises: intermittently uploading data with frequency K1 after entering the turning state, and recovering the data uploading frequency to default frequency K0 when the turning state is finished, wherein K1 is larger than K0; beta is a preset angle threshold, and N is a preset judging number. By adopting the inflection point compensation measurement method of vehicle track information disclosed by the invention, the inflection point compensation mechanism is increased on the basis of isochronous or equidistant collection, a collection point is increased only when vehicle turning is detected so as to reduce the transmission data size of GPRS (General Packet Radio Service), and angles of continuous sampling points are accumulated and calculated to overcome the possible misinformation under small curvature and large turning radius.
Owner:CHENGDU YIMENG HENGXIN TECH
Monitoring and alarm device for fatigue driving of automobile
InactiveCN103021134AEasy extractionExtract valid reviewsDiagnostic recording/measuringSensorsEcg signalMicrocontroller
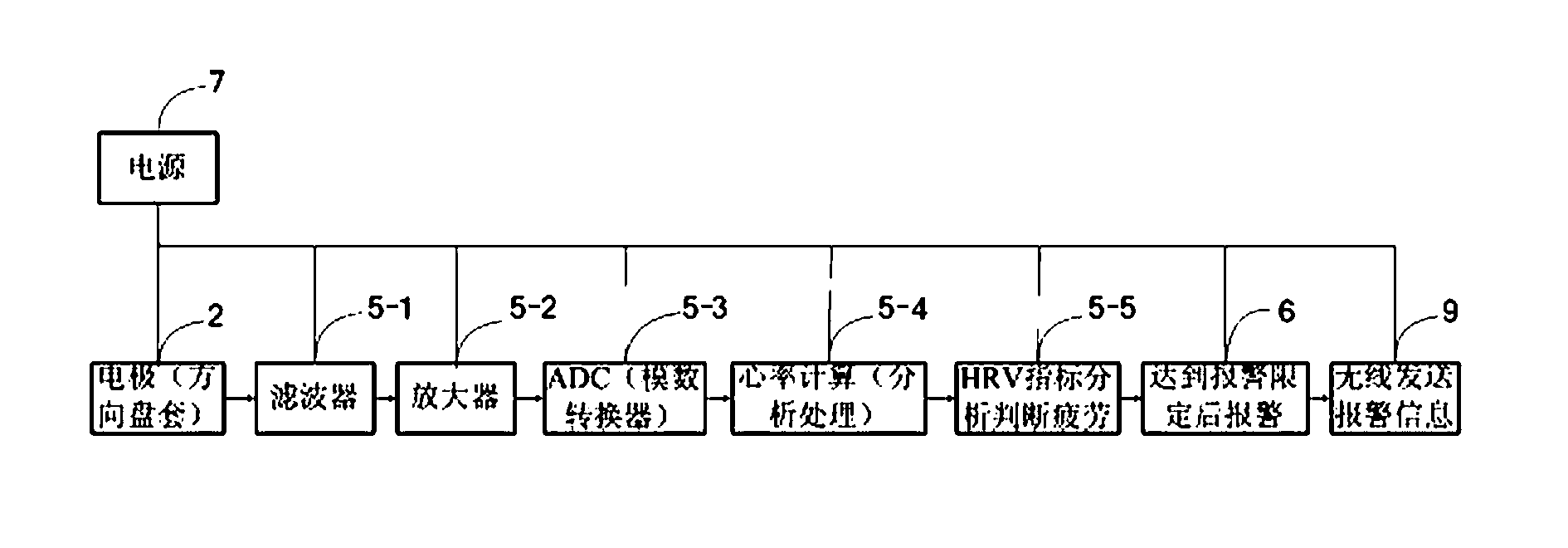
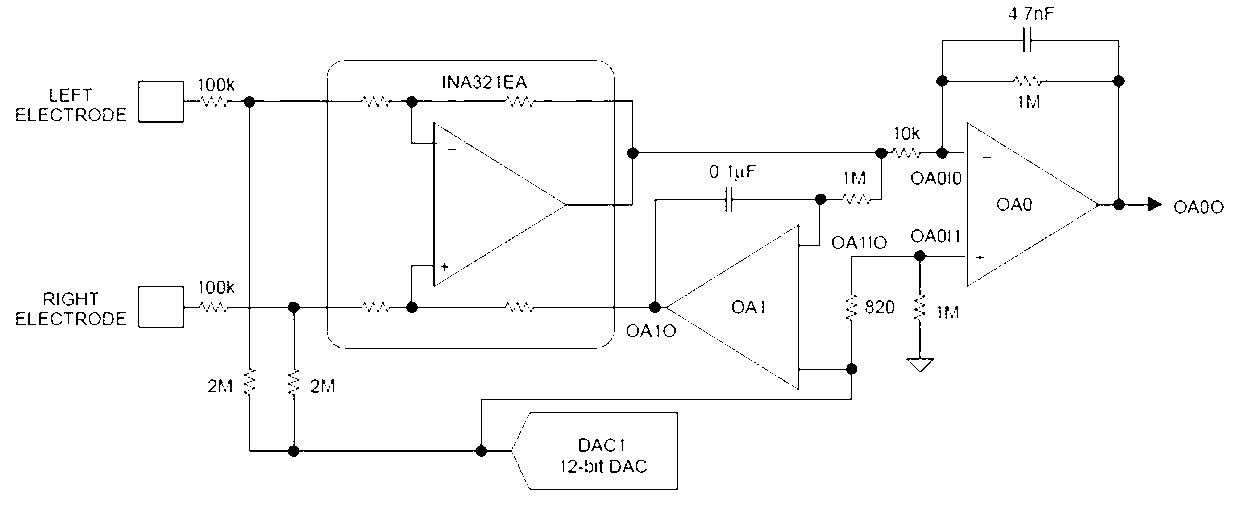
A monitoring and alarm device for fatigue driving of an automobile is used for monitoring and prompting the fatigue state of a driver and overcomes the defects of misinformation and concealed information of the existing monitoring devices caused by changes of surroundings, operating states and driver's positions. The monitoring and alarm device is composed of an electrocardiosignal acquisition electrode, an electrocardiosignal processor, an alarm, a work power supply and connecting wires among the parts, wherein the electrocardiosignal acquisition electrode is in a wire mesh structure and divided into two sections which are bilaterally and symmetrically attached to the surface of a steering wheel sleeve, and two sections of electrodes are mutually insulated. The electrocardiosignal processor comprises a filter, an amplifier, an analog digital converter (ADC) conventional electric signal sorting circuit and a single chip microcomputer (SCM) which is used for calculating and analyzing heart rates and heart rate variability (HRV) index signals. The alarm uses a sound and light alarm module. The monitoring and alarm device has the advantages that physical states of drivers are reflected accurately; information extraction and processing and alarm processes are convenient, quick and not easy to interfere; and failed information and misinformation can be avoided.
Owner:郭文浩
Dynamic authentication method of client side suitable for mobile cloud
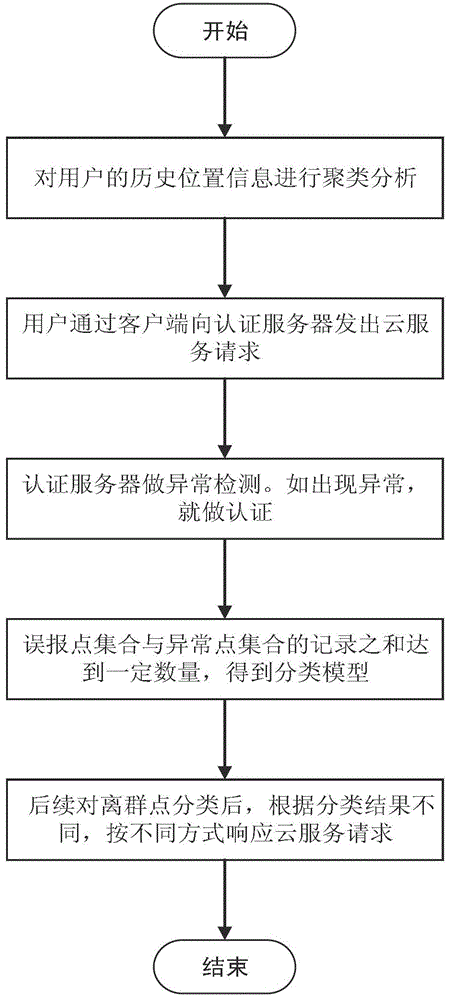
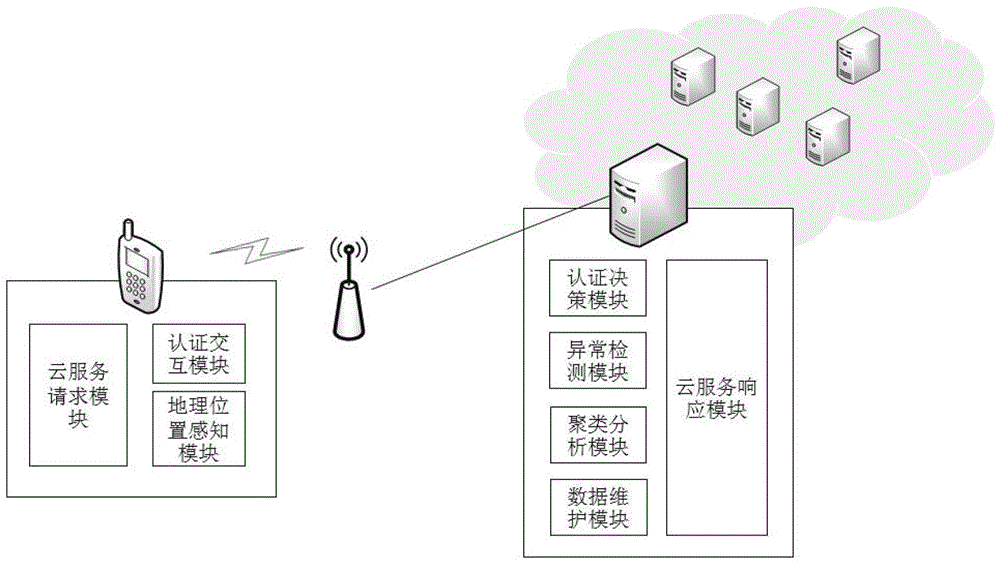
InactiveCN103338188AHigh precisionAvoid risk of lossUser identity/authority verificationMobile cloudOutlier
The invention discloses a dynamic authentication method of a client side suitable for a mobile cloud. The method comprises the following steps: 1) conducting cluster analysis of historical location information of a user; 2) sending a cloud service request / requests to an authentication server through the client side by the user; 3) confirming a cluster A to which the current location information of the client side corresponds by the authentication server, if the ratio of the number of data points in the cluster A to a sum is less than a threshold value t, deciding that the current location information is an outlier and conducting authentication, if the authentication is passed, recording the current location information in a misinformation point collection and responding to the request, otherwise, refusing the request, and recording the current location information in an outlier collection; 4) if the sum of the recorded misinformation point collection and the recorded outlier collection is greater than a threshold value L, marking and combining the sum to be used as a training data of classification to obtain a classification model; and 5) as for subsequent cloud service requests of the user, utilizing the classification model to conduct classification for outliers to respond to the cloud service request. The method improves the data security and account security of the user.
Owner:PEKING UNIV
Method and device for detecting worm virus and gateway equipment
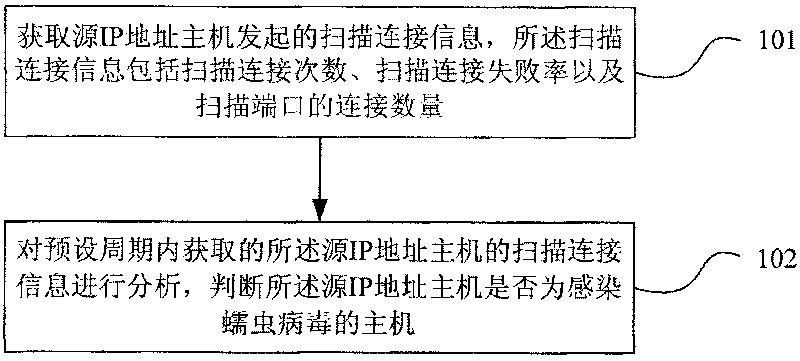
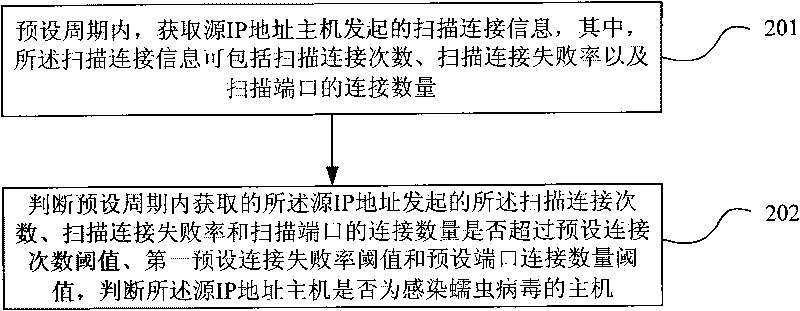
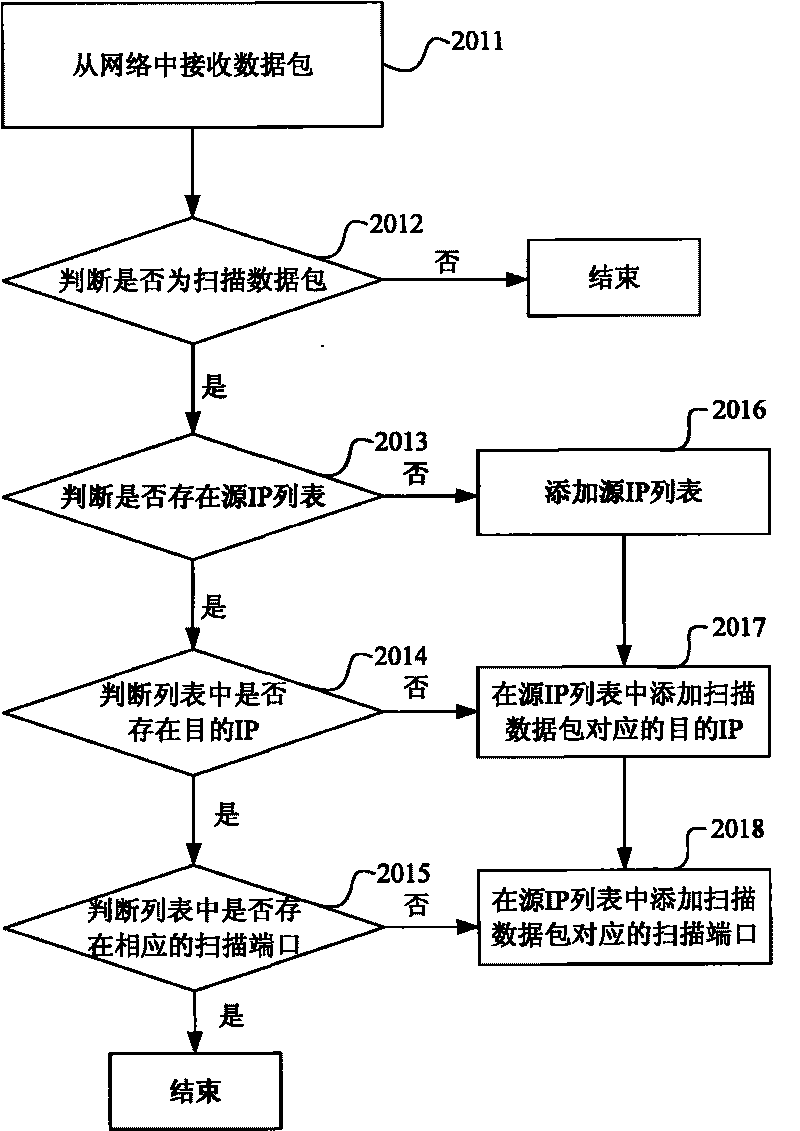
InactiveCN101707539AImprove detection efficiencyReduce false positive rateData switching networksFailure rateIp address
The embodiment of the invention relates to a method and a device for detecting a worm virus and gateway equipment. The method comprises the following steps: obtaining scanning connection information initiated by a source IP address host computer, wherein the scanning connection information comprises scanning connection times, a scanning connection failure rate and the connection number of scanning ports; and analyzing the obtained scanning connection information of the source IP address host computer in a preset period and judging whether the source IP address host computer is a host computer infected with the worm virus or not. By analyzing the scanning connection information, the technical scheme of the embodiment of the invention can effectively detect whether the source IP address host computer is the host computer infected with the worm virus or not, and has higher virus detection efficiency and lower virus detection misinformation rate.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Mixing-method-based method and system applied to defect detection of printed circuit board
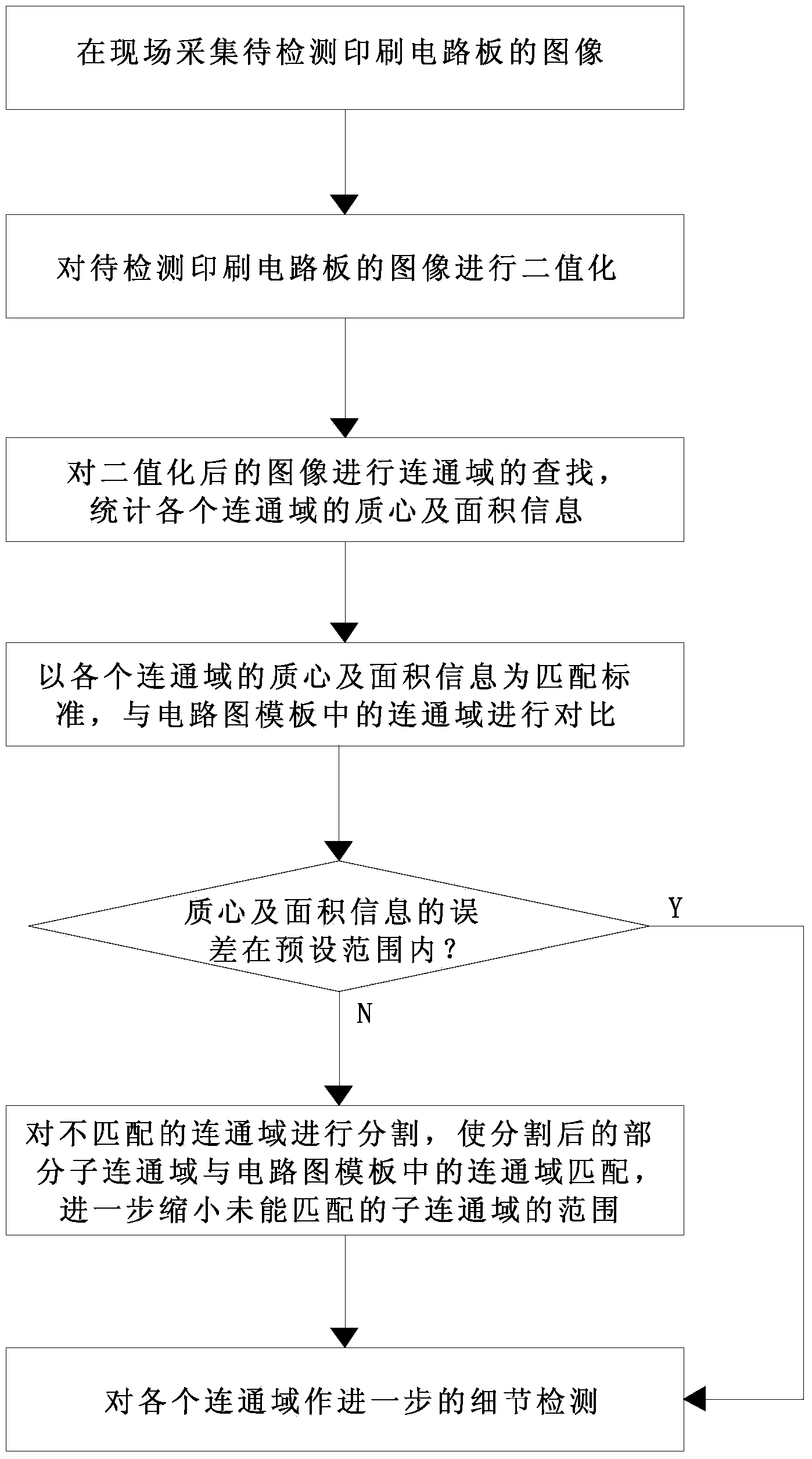
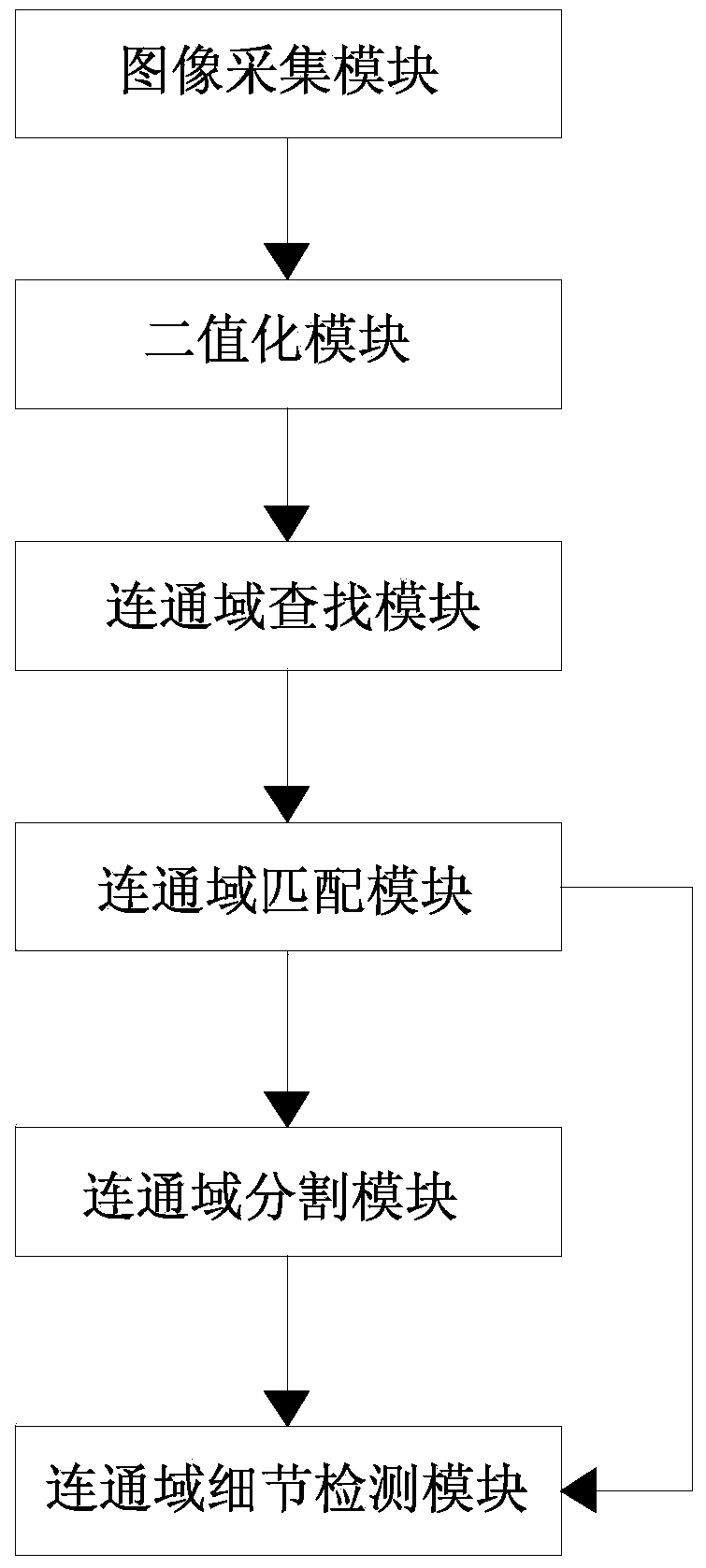
ActiveCN104297254AMeet defect detection needsGood distinctionOptically investigating flaws/contaminationMisinformationPrinted circuit board
The invention discloses a mixing-method-based method and a mixing-method-based system applied to defect detection of a printed circuit board. The method comprises the following steps: collecting an image of a to-be-detected printed circuit board in the field; carrying out binaryzation on the image of the to-be-detected printed circuit board; searching communication domains of the binaryzated image and counting information of mass center and area of each communication area; comparing each communication area with communication domains in a circuit diagram template by taking the information of mass center and area of each communication area as a matching standard, determining that the communication domains are matched with one another if the error of the information of mass center and area is in a predetermined range, or determining that the communication domains are unmatched with one another; cutting the unmatched communication domains, enabling part of secondary communication domains after cutting to be matched with the communication domains in the circuit diagram template, and further diminishing the range of the unmatched secondary communication domains; and further detecting each communication domain in detail. By virtue of the method and the system, the defect misinformation caused by rotating, horizontally moving, extending and retracting, inclining and the like can be well avoided; the reasonable deformation and defects can be well distinguished.
Owner:SOUTH CHINA UNIV OF TECH
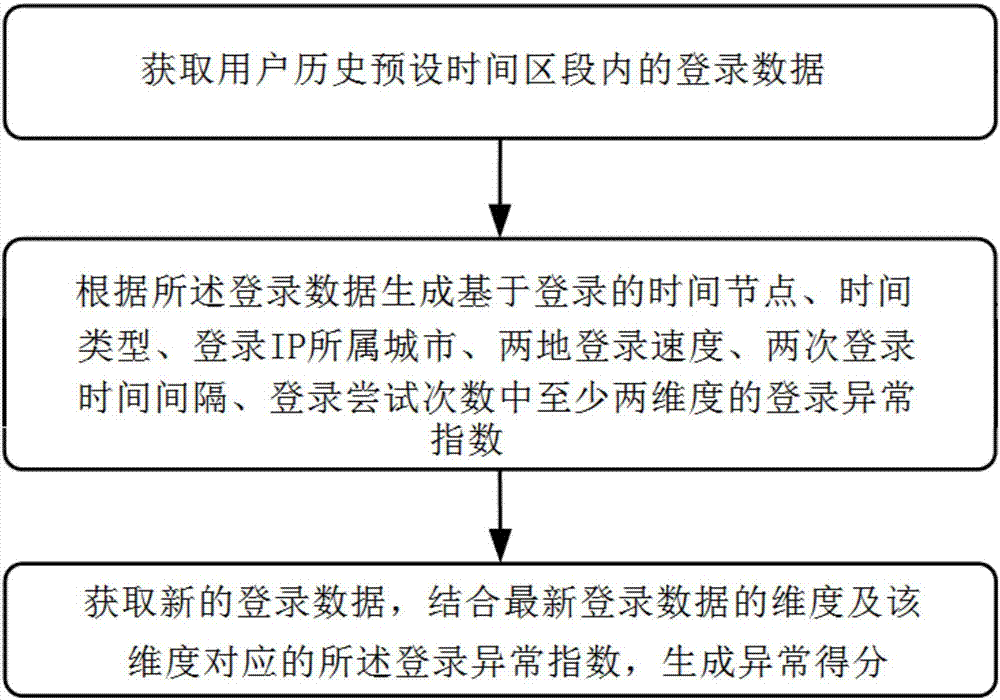
Login abnormity detection method, system and device
ActiveCN107172104AImprove the hit rate of abnormal loginImprove securityTransmissionMisinformationAnomaly detection algorithm
The invention relates to a login abnormity detection method, system and device. The login abnormity detection method comprises steps of obtaining login data of a user history preset time interval, generating a login abnormity index based on at least two dimensions of a time node, a time type, a city that a login IP belongs to, two place login speeds, a time interval between two login times and times of trying to login according to the login data, wherein at least one of the dimensions of the login time node, the time type and the city where the login IP belongs to exists, obtaining new login data and generating an abnormal score by combining with a newest login data dimension and a login abnormal index corresponding to the dimension. Multi-dimension aggregation solves a problem of one-dimension misinformation. The login abnormity detection method, system and device can overcome current dimension deficiency through more dimension detection, improve abnormal login hit rate, screen out high score data to investigate through grading the login data according to weights / and abnormity detection algorithm and can fundamentally eliminate misdetection and leak detection of login through combining multiple detection modes.
Owner:SF TECH
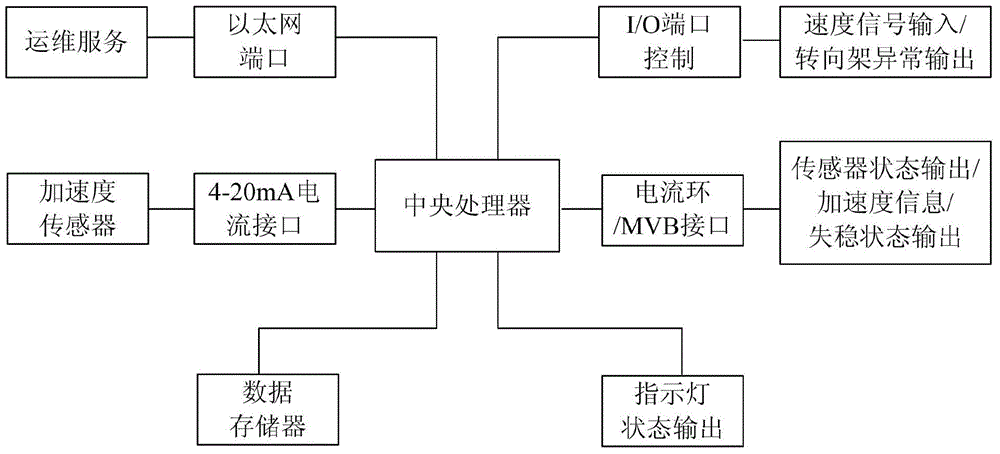
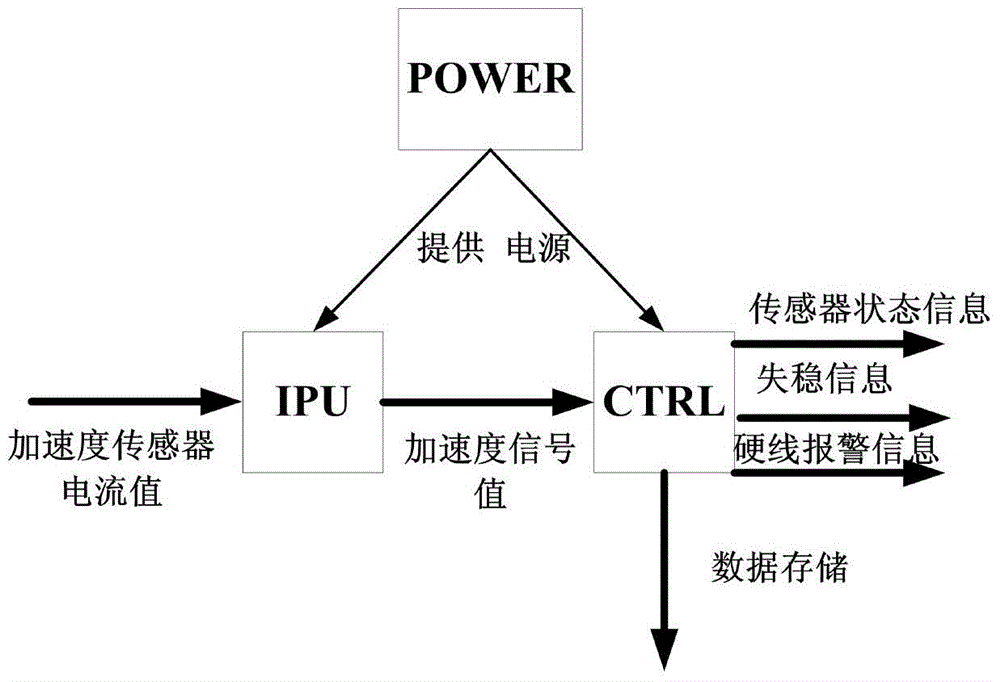
Motor train unit bogie instability detection device and realization method
ActiveCN104670249AControl false positivesReal-time display of instability status informationRailway vehicle testingRailway signalling and safetyBogieFilter algorithm
The invention provides a motor train unit bogie instability detection device and a realization method and belongs to the technical field of motor train unit control. The realization method comprises the following steps: a central processing unit is connected with an acceleration sensor by a 4-20mA current interface to obtain acceleration change information of the acceleration sensor at a detected position; a working state and instability information of the sensor are output through a current ring or an MVB interface after a filtering algorithm and instability judgment are carried out; a switching value instability signal is output by an IO port; and meanwhile, recorded data are stored in a data storage device. According to the motor train unit bogie instability detection device, acceleration information of the detected position can be fed back in real time so that the controllability and the operability are improved, misinformation can be further prevented and the train safety is improved.
Owner:北京华高世纪科技股份有限公司
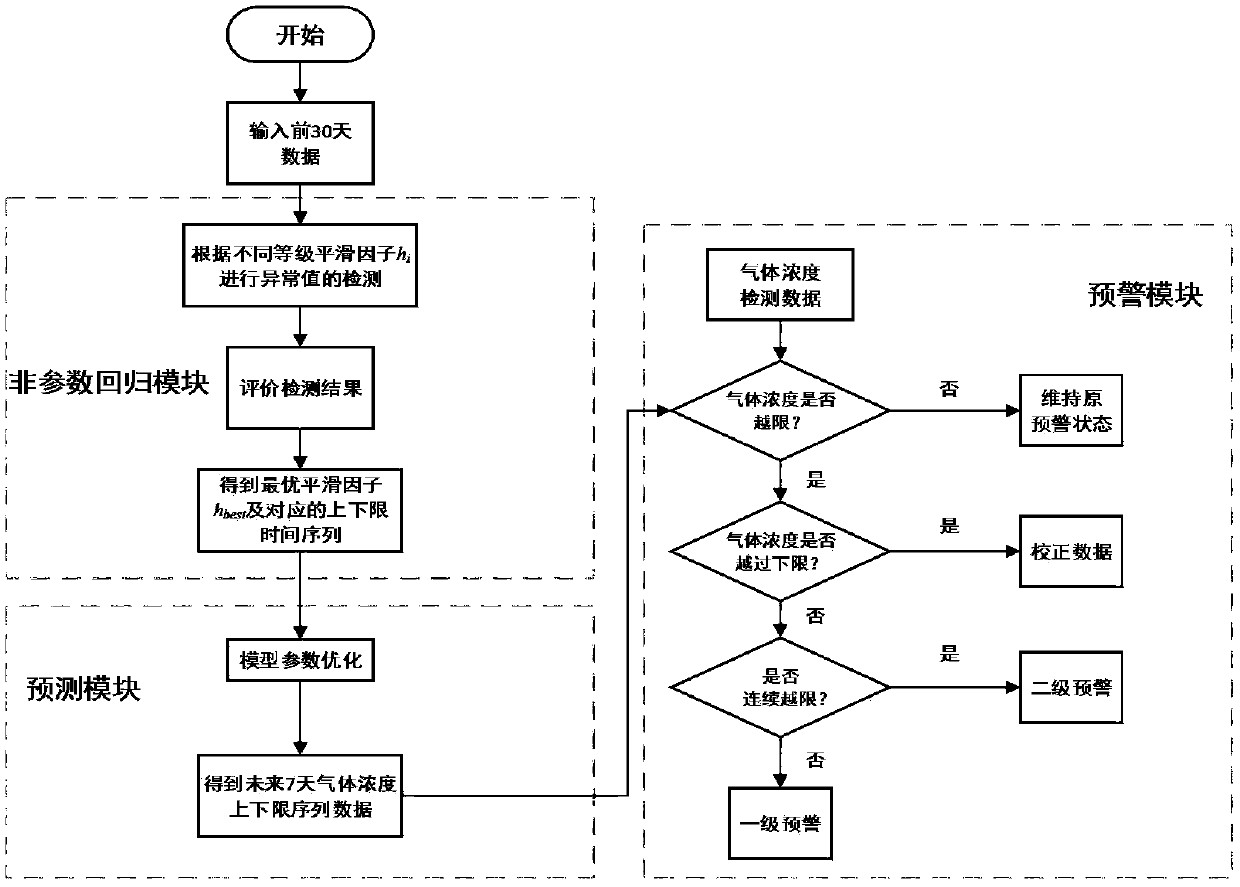
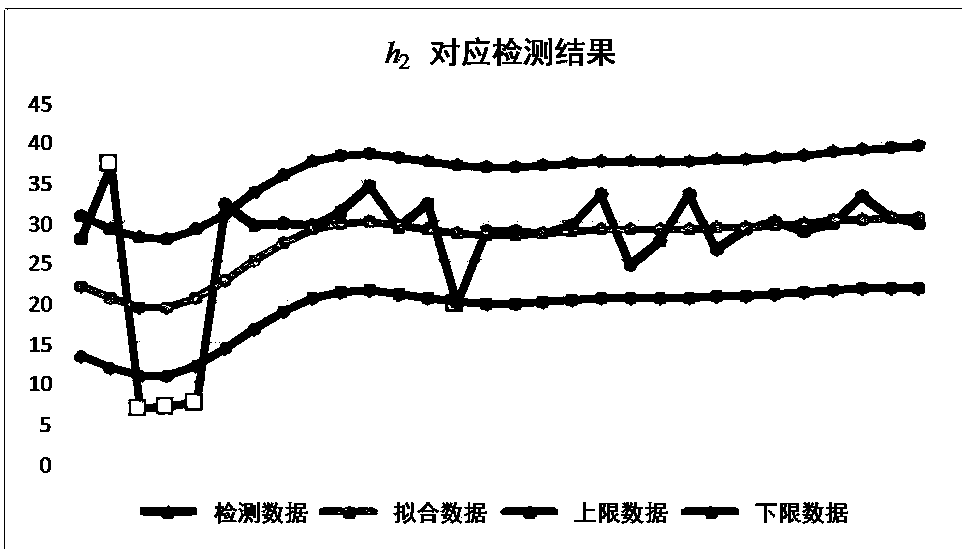
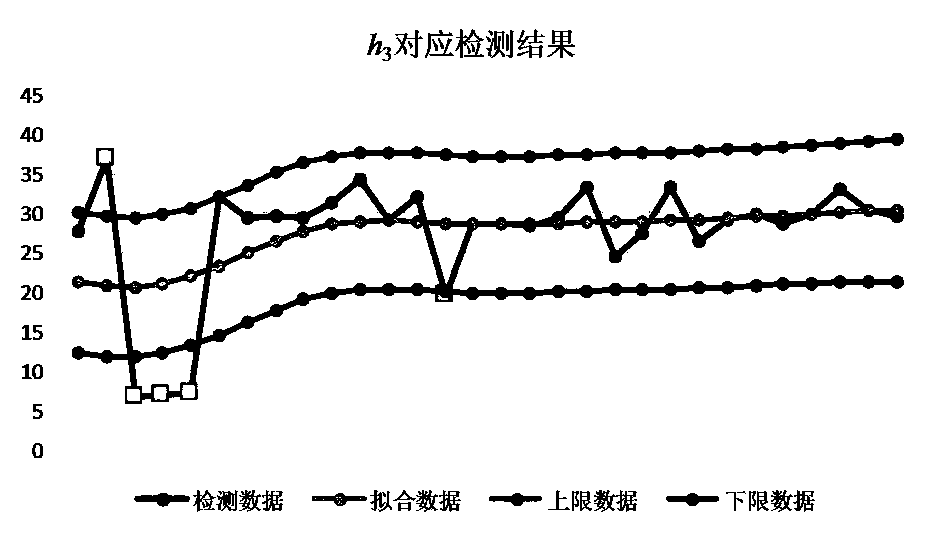
Trend analysis based transformer latent fault early warning method
InactiveCN107894969AImprove early warning reliabilitySafe and stable operationComplex mathematical operationsMaterial analysisTransformerElectric power system
The invention discloses a trend analysis based transformer latent fault early warning method. The method comprises the steps that on the basis of a non-parametric regression method, historical data issubjected to smoothing process, and by means of detection and evaluation indexes of abnormal values such as the accuracy rate, recall rate and bandwidth, an optimal smoothing factor and upper and lower limit sequence data corresponding to the optimal smoothing factor are obtained; by taking the upper and lower limit sequence data as the historical data, a gas concentration self-adaptive prediction model is built, and the upper and lower limit gas concentration data in the future time period is predicted; by means of comparison of actual detection data and predicted upper and lower limit data,an early warning strategy is determined. According to the method, the problems such as missing report and misinformation which exist in a fixed threshold value are avoided, the field application requirements can be met, the early warning reliability of transformer latent faults is improved, more reliable reference is provided for maintenance work of a transformer, and safe and stable running of the transformer and an electric power system is guaranteed.
Owner:SHANDONG UNIV
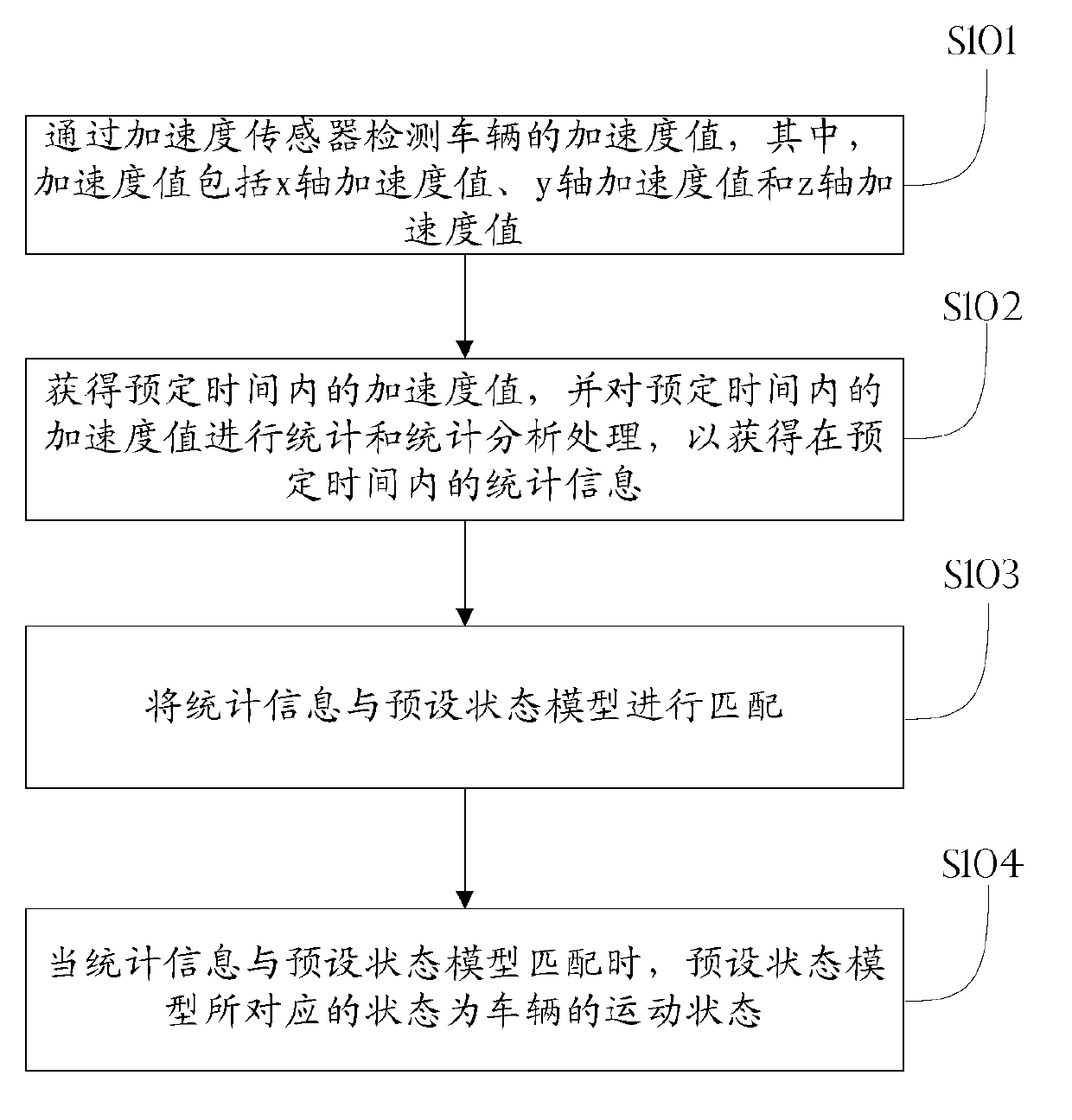
Method and device for detecting automobile motion state by using acceleration sensor
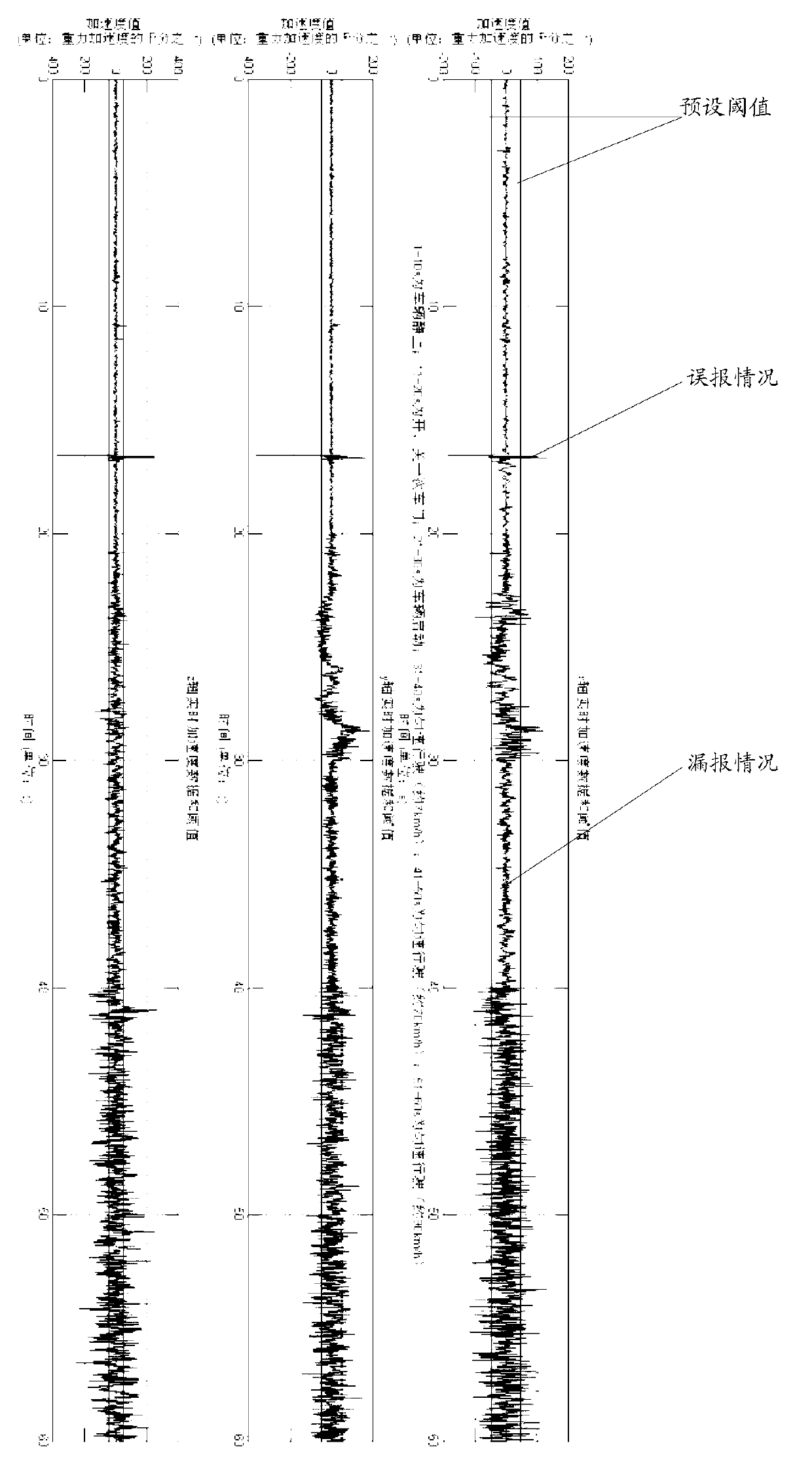
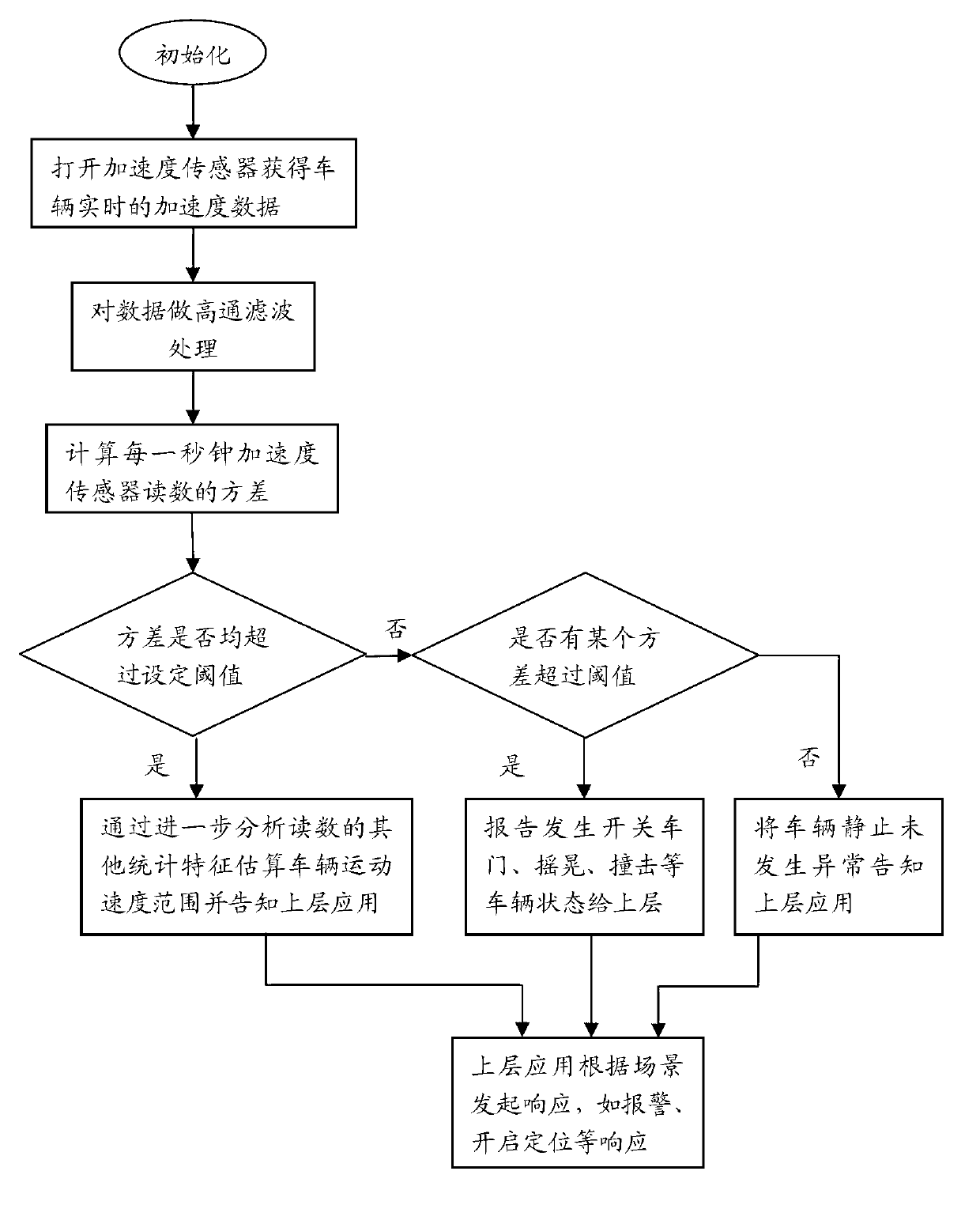
InactiveCN102967728AReduce false positivesReducer underreportingSpeed measurement using accelerationIndication/recording movementState modelClassical mechanics
The invention discloses a method and a device for detecting an automobile motion state by using an acceleration sensor. The method comprises the following steps of: detecting an acceleration value of an automobile by using the acceleration sensor, wherein the acceleration value includes an X-axis acceleration value, a Y-axis acceleration value and a Z-axis acceleration value; acquiring an acceleration value within a preset time, and carrying out statistic and statistic analysis process on the acceleration value within the preset time, so as to obtain the statistic information within the preset time; matching the statistic information with a preset state model; and determining the state corresponding to the preset state model as the motion state of the automobile when the statistic information is matched with the preset state model. According to the embodiment of the invention, the automobile state is judged according to statistic characteristics of data output from the acceleration sensor, the possibility of misinformation or report miss is reduced, and moreover, a current operation speed value of the automobile can be estimated or the state that whether the door is opened or closed can be identified.
Owner:珠海德百祺科技有限公司
Method for testing software by applying across function analysis
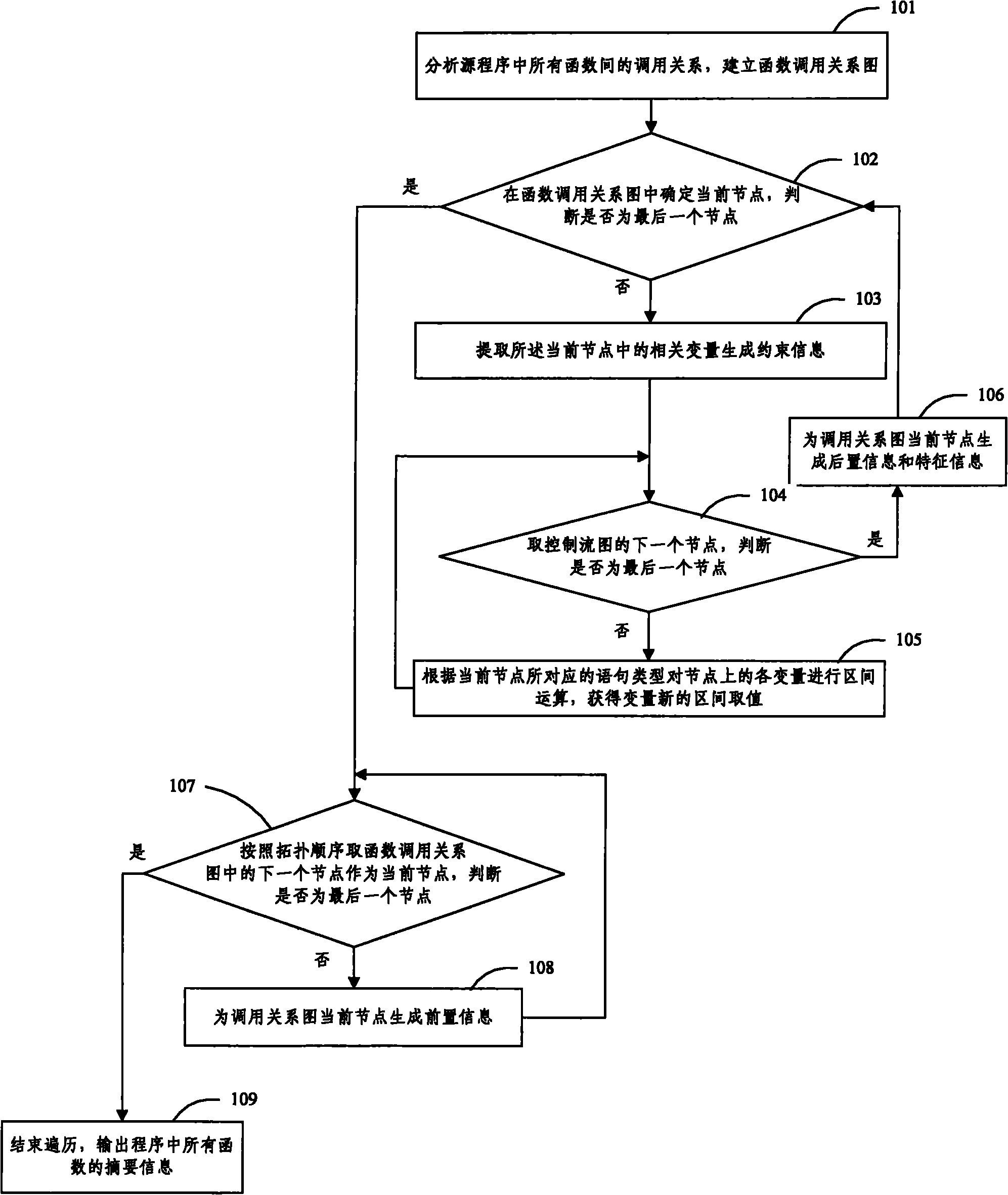
InactiveCN101894064APerfect Interval Iteration TechniqueReduce false alarm rateSoftware testing/debuggingControl flowSoftware engineering
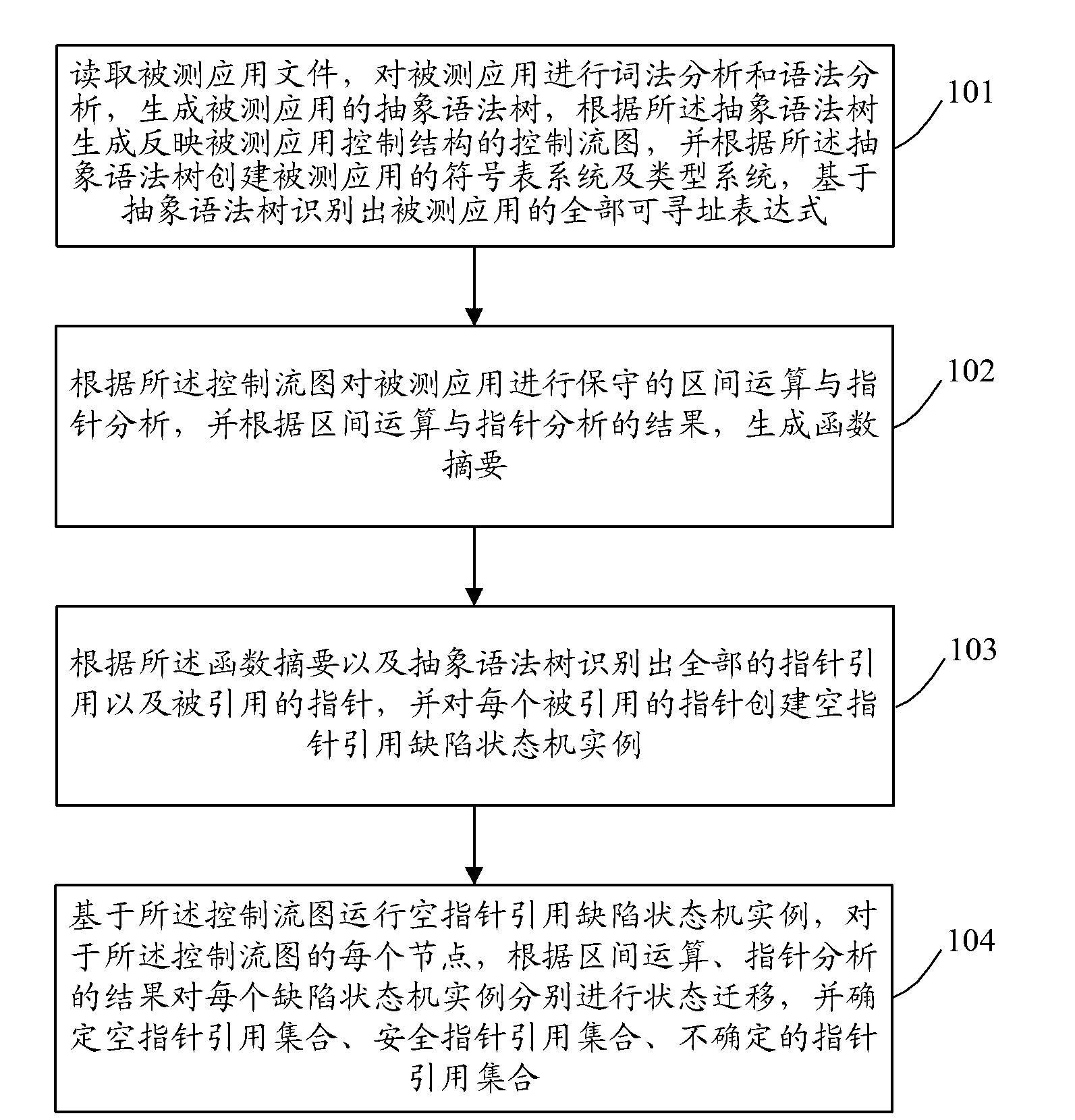
The invention discloses a method for testing software by applying across function analysis, which solves the problem of influences on interval precision caused by function calls, underutilized environment constraint information, control flow change caused by abnormal handling and the like in a software static test. Decision methods for detecting different defects in a program are correspondingly specified by defining function summary information as well as pre-information, post-information, constraint information and characteristic information of the function summary information; and the summary information of all functions in the tested program is output after the test is completed by collecting the function summary information and applying the function summary information to statement nodes of a control flow graph and the process of determining defect modes in the process of testing the software. Experiments prove that compared with the conventional testing software, the testing software of the method has the test result which has higher analysis accuracy among functions and lower misinformation rate and information missing rate.
Owner:BEIJING UNIV OF POSTS & TELECOMM
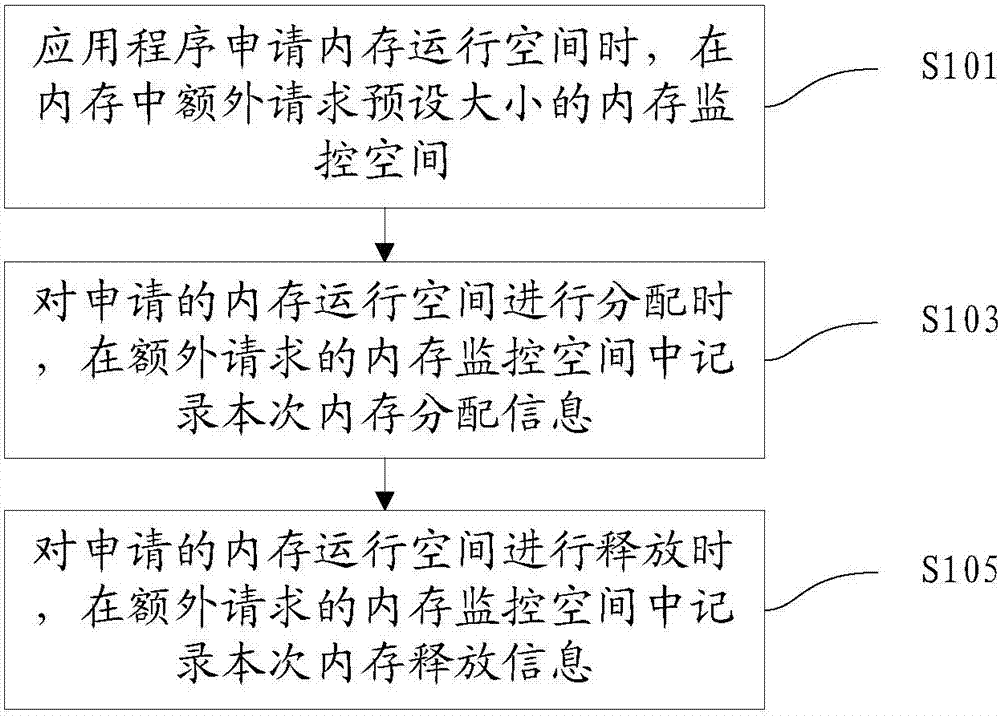
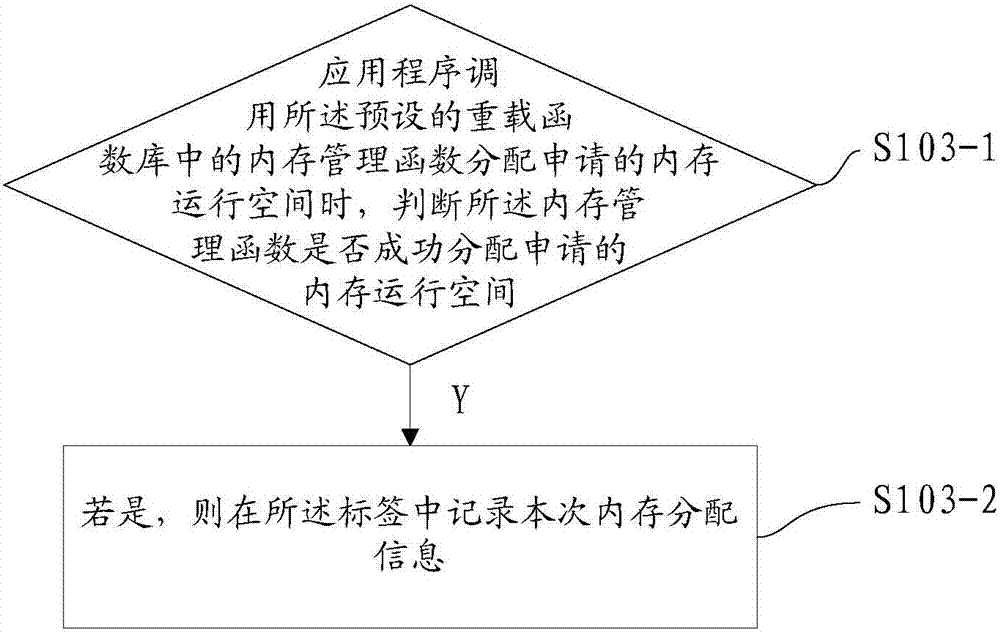
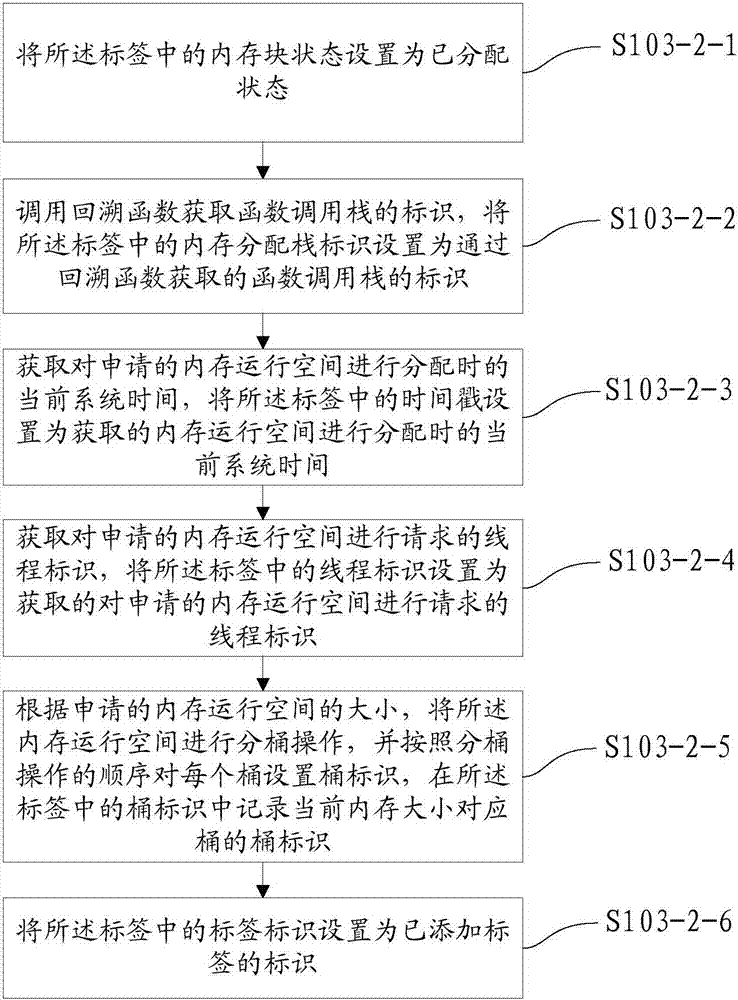
Method and apparatus for monitoring internal storage of application program and electronic equipment
InactiveCN107085548AReduced availabilityImprove reliabilityHardware monitoringUsabilityMisinformation
The invention discloses a method and an apparatus for monitoring internal storage of an application program, and electronic equipment. The method for monitoring the internal storage of the application program comprises the steps of additionally requesting an internal storage monitoring space with preset size from the internal storage when the application program applies an internal storage operating space; recording the current internal storage allocation information in the additionally requested internal storage monitoring space in allocating the applied internal storage operating space; and recording the current internal storage releasing information in the additionally requested internal storage monitoring space in releasing the applied internal storage operating space. By virtue of the technical scheme, the problem of performance degradation caused by slow program operating due to misinformation, report failure, or complexity of an instrumentation realization method or algorithm can be solved, thereby improving reliability of the result, and solving many problems existing in C / C++ program internal storage use; and in addition, high usability in complex large-scale application programs is realized, and the use cost is relatively low.
Owner:ALIBABA GRP HLDG LTD
Method of fully detecting null pointer reference defects
InactiveCN103218296ASolve the problem of false positivesAchieve zero false negativesSoftware testing/debuggingInterval arithmeticTheoretical computer science
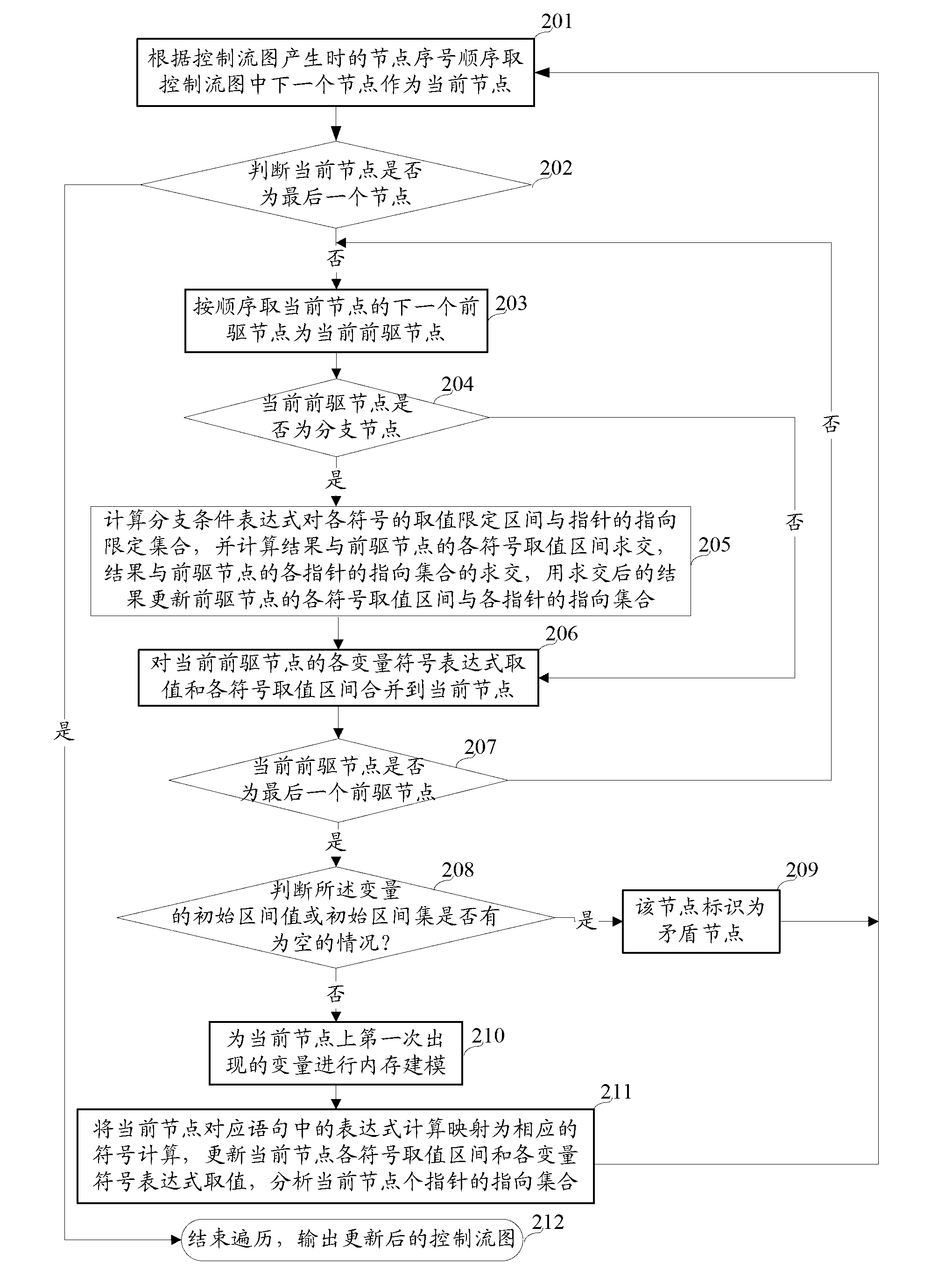
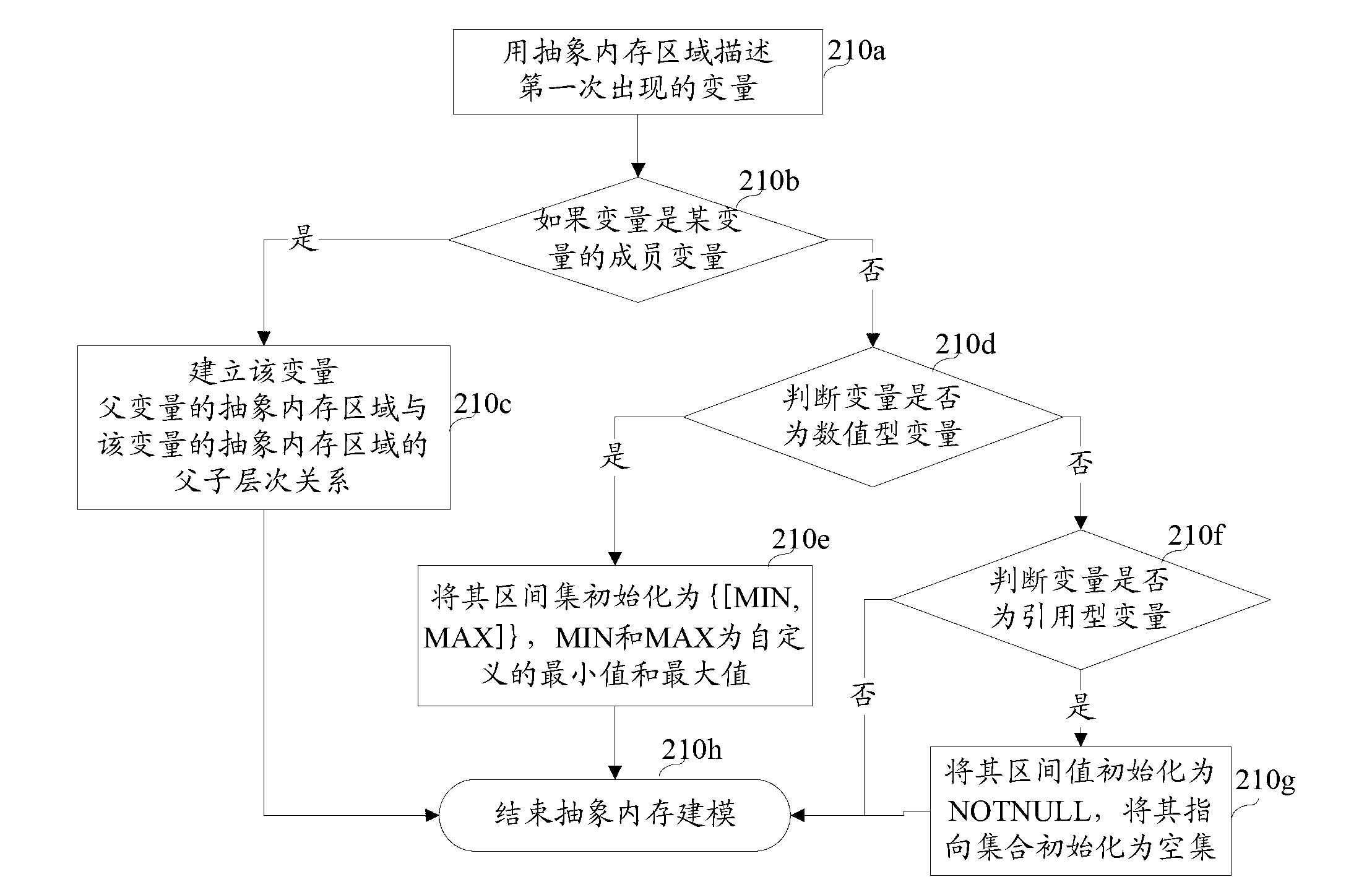
The invention discloses a method of fully detecting null pointer reference defects. The method comprises recognizing all addressable expressions of an application to be detected based on an abstract syntax tree; carrying out conservative interval arithmetic and pointer analysis on the application to be detected according to a control flow diagram, and generating a procedural summary according to results of the interval arithmetic and the pointer analysis; recognizing all pointer reference and referred pointers according to the procedural summary and the abstract syntax tree, and creating a null pointer reference defect state machine example on each referred pointer; and running the null pointer reference defect state machine examples based on the control flow diagram, carrying out state transition on each defect state machine example on each node of the control flow diagram according to the results of the interval arithmetic and the pointer analysis, and carrying out null pointer reference detection. By adopting the method of fully detecting the null pointer reference defects, the problem of failing to report the null pointer reference defects can be effectively solved, and zero omission and low misinformation of the null pointer reference defect detection are achieved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Data race detection and evidence generation method based on multithreaded program constraint building
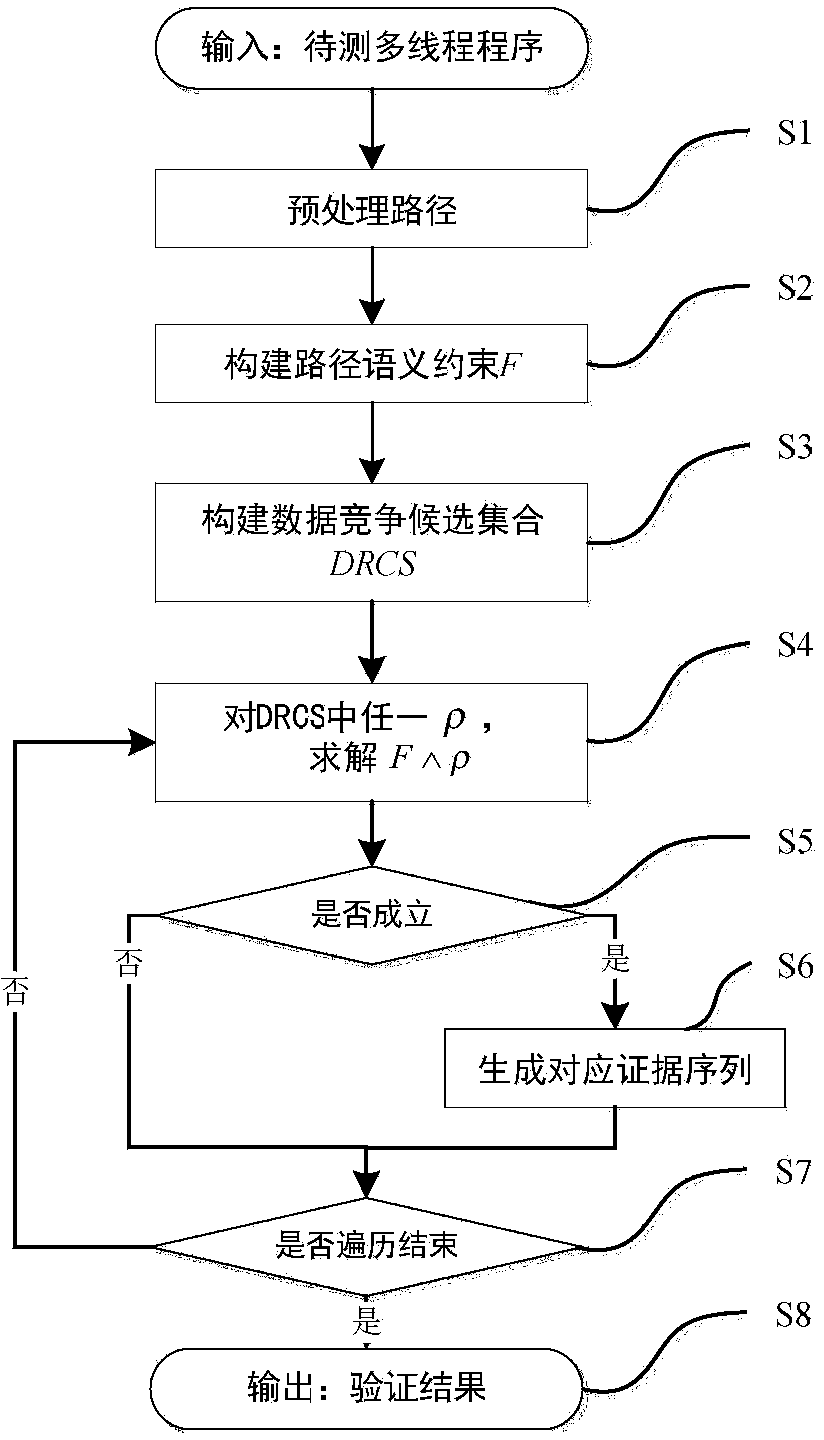
ActiveCN104077144ANo overheadSoftware testing/debuggingSpecific program execution arrangementsFirst-order logicOccurrence data
The invention provides a data race detection and evidence generation method based on multithreaded program constraint building. The data race detection problem is converted into a constraint solving problem by building a constraint expression according to the multithreaded program semanteme, a constraint solver is used for detecting possible data races and program execution paths triggering the data races are generated; the data race detection and evidence generation method comprises the steps of firstly, carrying out the instrumentation of the detected program, executing the program and obtaining an execution path, secondly, converting the execution path into a quantifier-free first-order logic expression covering all feasible thread interleaving according to the multithreaded program execution semanteme, thirdly, building a data race candidate set according to the sequential relationship of statements when a data race happens and generating candidate conditions for races, and finally, traversing the candidate set to determine whether the data race exists, and if so, generating a corresponding evidence sequence. The method is capable of finding out all data races in once operation without misinformation; for each data race, the evidence sequence indicating the trigger process of the data race is generated.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com