Dynamic authentication method of client side suitable for mobile cloud
A dynamic authentication and mobile cloud technology, applied in user identity/authority verification, transmission systems, electrical components, etc., can solve the problem that mobile cloud applications cannot resist equipment attacks and are not involved
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
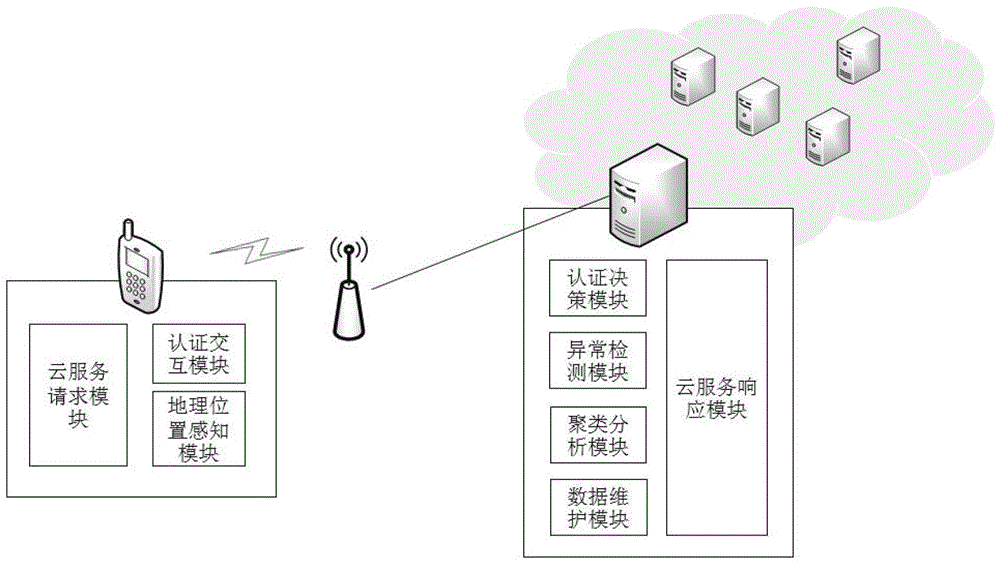
[0089] We use the login process of the mobile cloud application to illustrate the flow of the dynamic authentication solution of the present invention, but it is not limited to the login process. After logging in, we will still periodically upload location information to detect anomalies. Once an exception occurs, execute the verification process in the program flow.
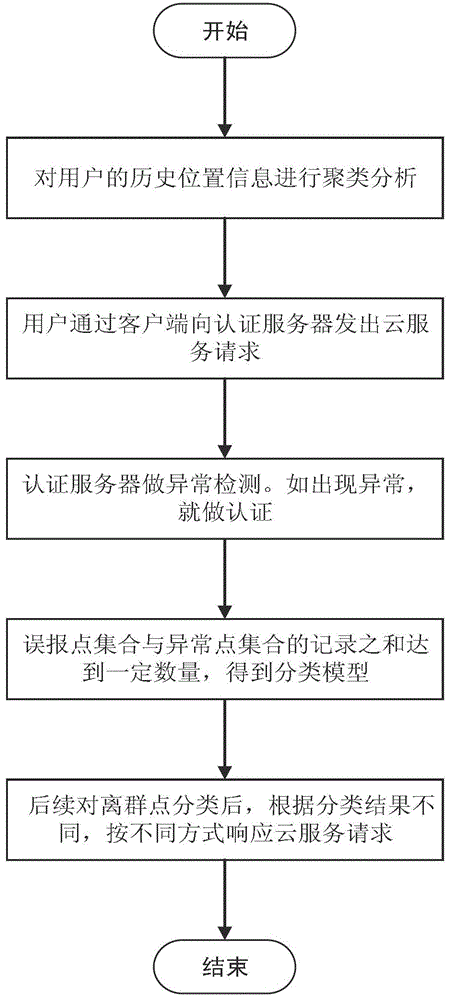
[0090] Such as figure 1 As shown, the flow of the entire authentication scheme is as follows:
[0091] ① The user sends a service request to the nearest server through the client. This mode is applicable to any connection model of mobile cloud computing. At this point, since the user has not logged in, similar to the current application, the user needs to be authenticated. The client sends the account and password information (input by the user or bound to the application) together with the geographic location information to the authentication server.
[0092] ②After receiving the user request, the authentic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com