Login abnormity detection method, system and device
An anomaly detection and anomaly index technology, which is applied in the field of login anomaly detection, can solve problems such as unsolvable, false alarms, multiple access failures, etc., and achieve the effect of improving security, increasing hit rate, and high hit rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
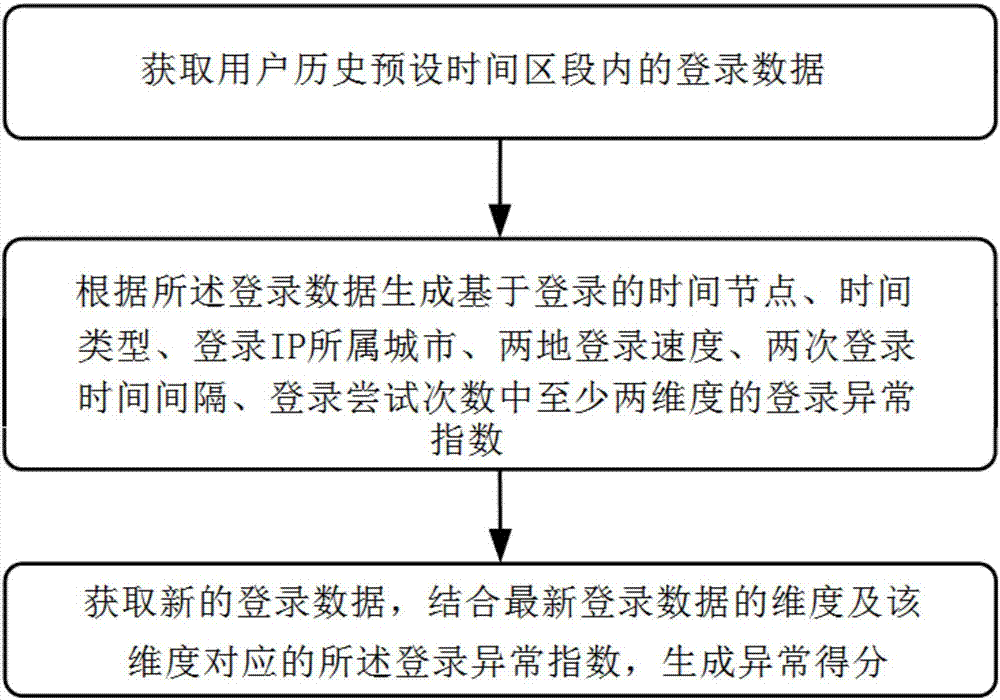
[0108] According to the user's historical data, six dimensions are established: time node, time type, city where the login IP belongs, login speed between two places, time interval between two logins, and number of login attempts.
[0109] 1 time node dimension
[0110] 1) Obtain login data for the past six months;
[0111] 2) Screen the data of successful login;
[0112] 3) According to the job number and time node (hourly), the total number of successful login times of each job number at each hour is aggregated;
[0113] 4) Calculate the average (mean) and standard deviation (sd) of the number of logins in the past six months according to the job number;
[0114] 5) Start traversing each hour from 0:00:
[0115] Define the minimum number of logins for each account Count=mean-1×sd;
[0116] First pass:
[0117] If the number of logins at this hour is greater than or equal to Count, the flag is 1;
[0118] If the number of logins at this hour is less than Count, but the ...
Embodiment 2
[0195] The features of this embodiment that are the same as those of Embodiment 1 will not be described in detail. The features of this embodiment that are different from Embodiment 1 are:
[0196] Based on the weight score or / and the results of the anomaly detection algorithm, the login data screens out high-scoring data for investigation, and judges whether it is an abnormal login.
[0197] Enter the login data into the following login record final anomaly score solution formula for weight scoring:
[0198] The final abnormal score of the login record=0.2×(the abnormal index of the time node)+0.2×(the abnormal index of the time type)+1×(the abnormal index of the city where the registered IP belongs)+0.9×(the abnormal index of the login speed of the two places) +1×(anomaly index of time interval between two logins)+1×(anomaly index of number of login attempts),
[0199] Each dimension has its own set of anomaly indices from 0-100%.
Embodiment 3
[0201] The features of this embodiment that are the same as those of Embodiment 1 will not be described in detail. The features of this embodiment that are different from Embodiment 1 are:
[0202] Based on the weight score or / and the results of the anomaly detection algorithm, the login data screens out high-scoring data for investigation, and judges whether it is an abnormal login.
[0203] Enter the login data into the following login record final anomaly score solution formula for weight scoring:
[0204] The final abnormal score of the login record = 0.2×(the abnormal index of the time node)+0.1×(the abnormal index of the time type)+0.7×(the abnormal index of the city where the registered IP belongs)+0.8×(the abnormal index of the login speed of the two places) +0.9×(anomaly index of time interval between two logins)+1×(anomaly index of number of login attempts),
[0205] Each dimension has its own set of anomaly indices from 0-100%.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com