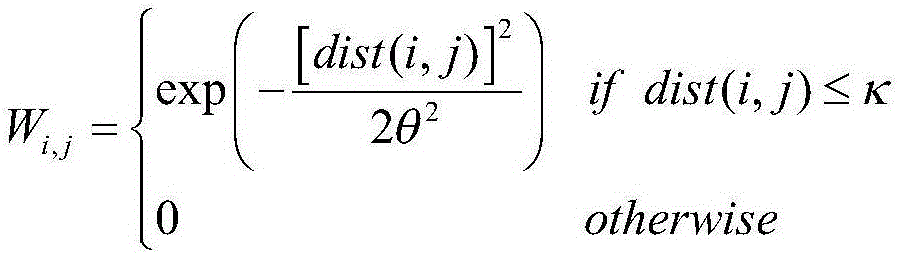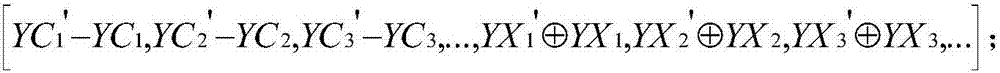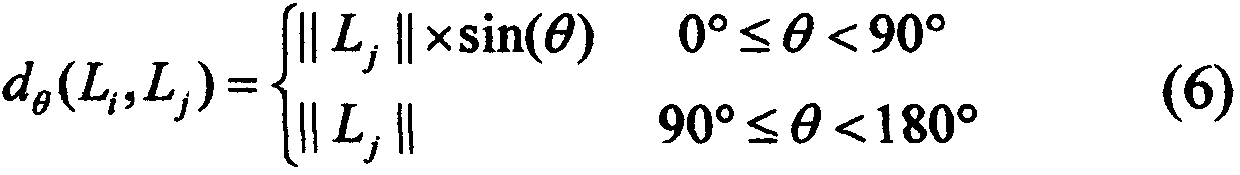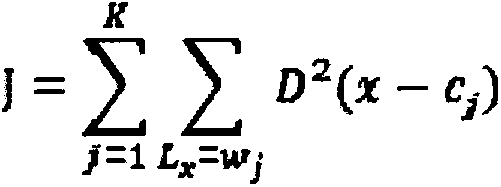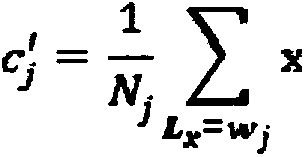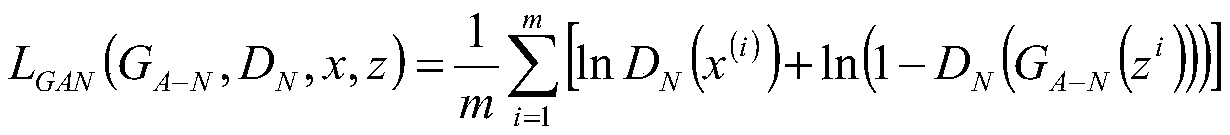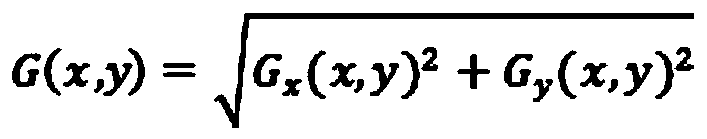Patents
Literature
266 results about "Anomaly detection algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Anomaly Detection Algorithms. Outliers and irregularities in data can usually be detected by different data mining algorithms. For example, algorithms for clustering, classification or association rule learning. Generally, algorithms fall into two key categories – supervised and unsupervised learning.
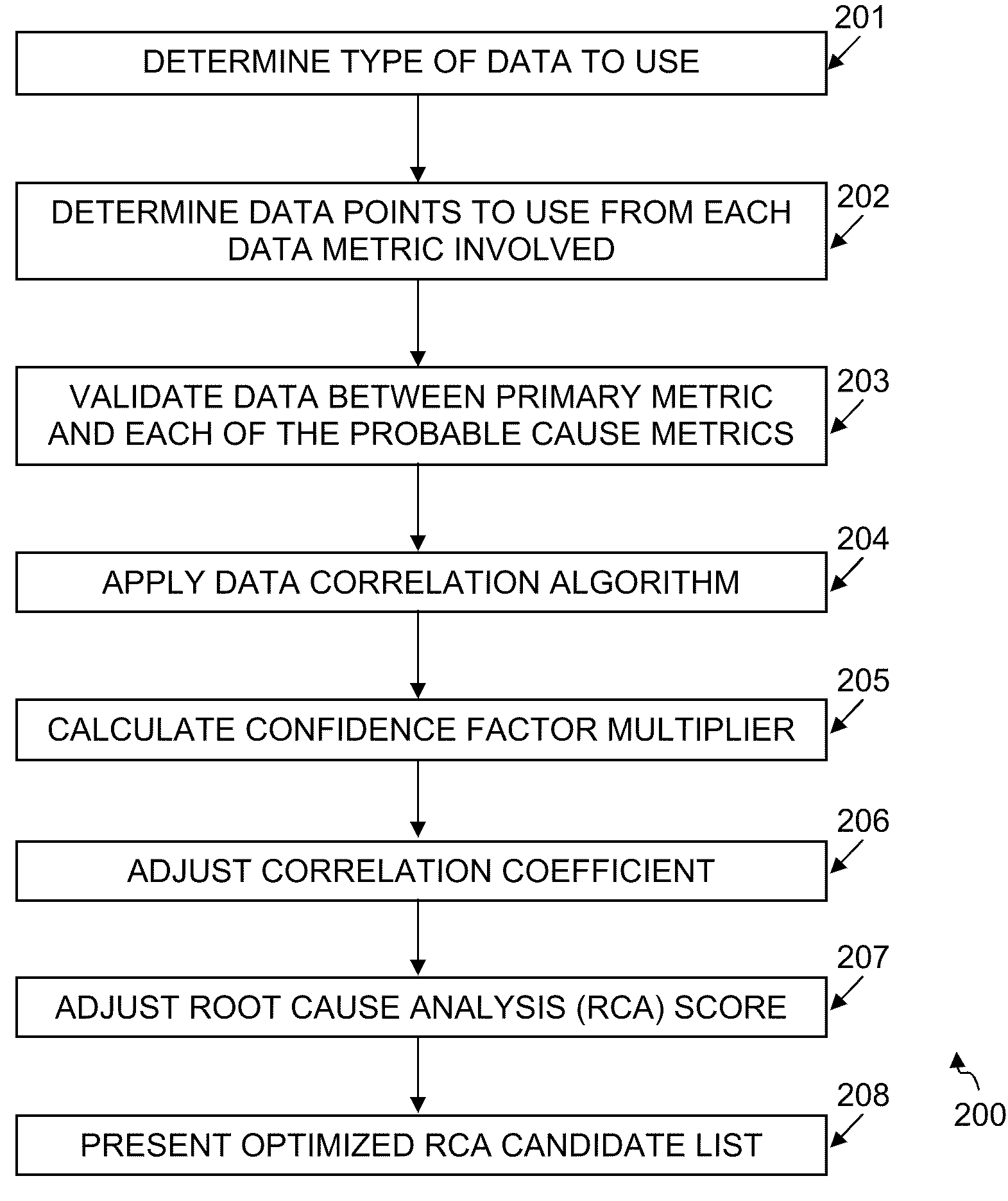
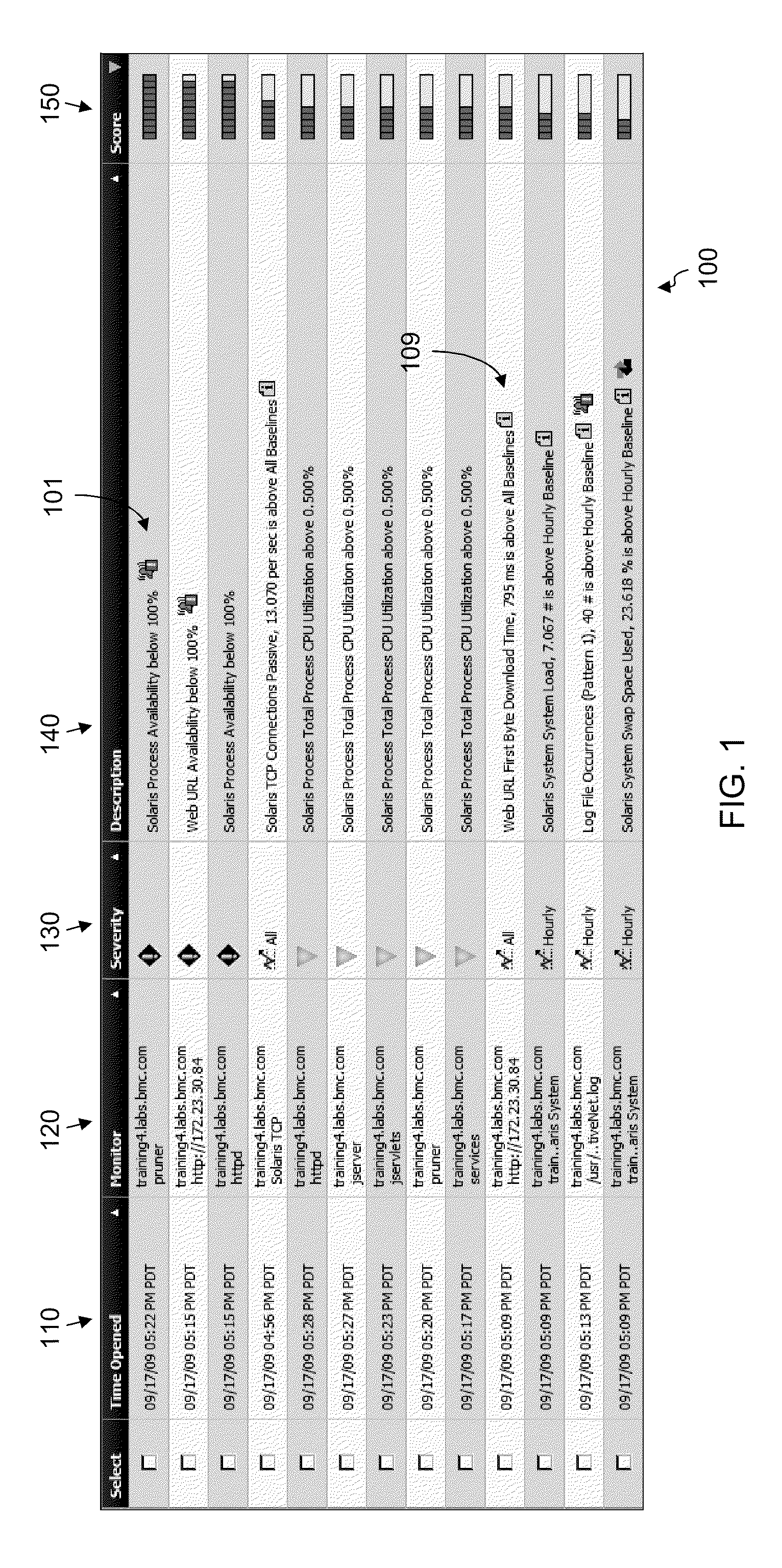
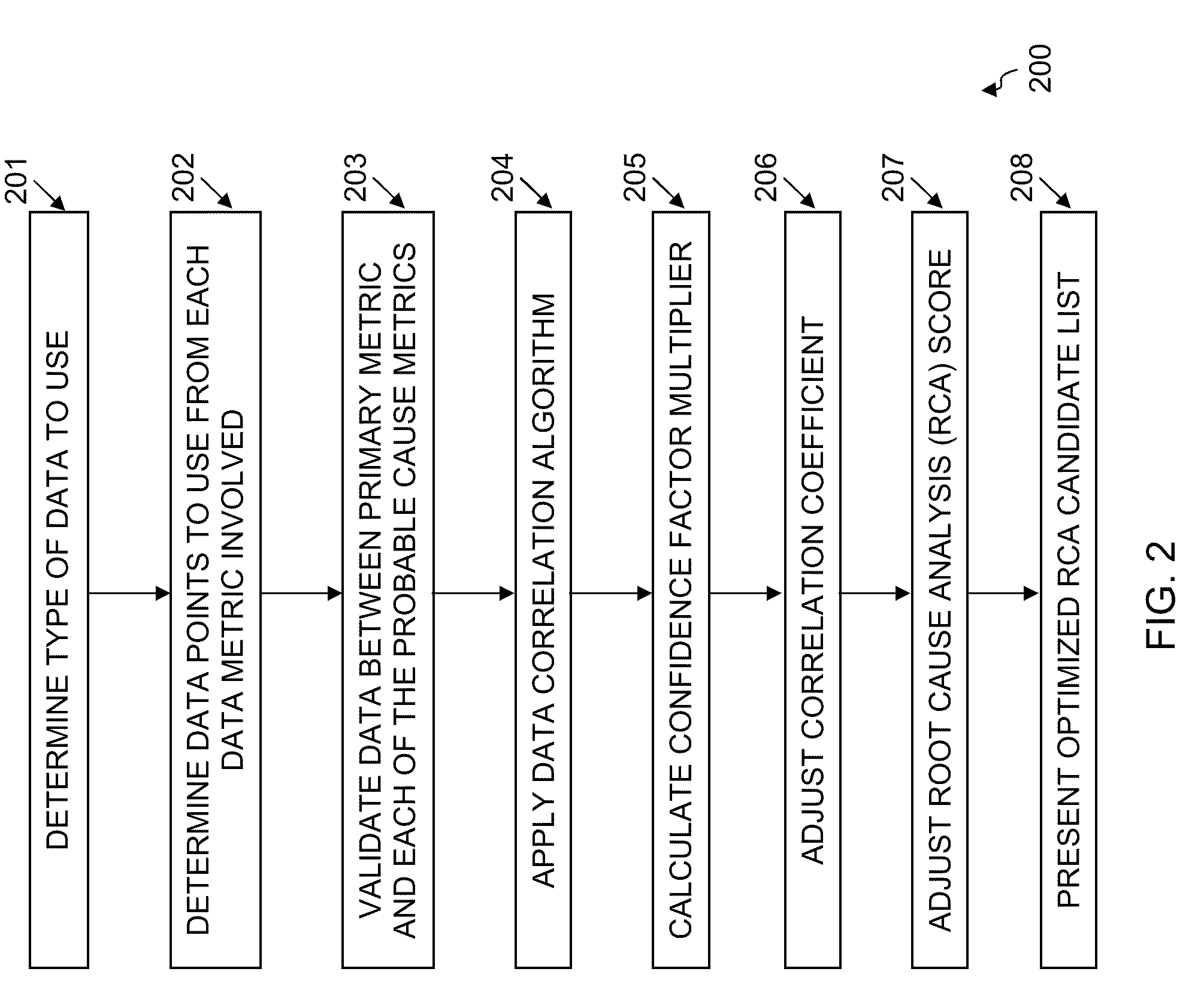
System, method and computer program product for optimized root cause analysis
ActiveUS20100050023A1Shorten the timeReduce comparisonDigital computer detailsNon-redundant fault processingRoot causeRoot cause analysis
Embodiments disclosed herein can significantly optimize a root cause analysis and substantially reduce the overall time needed to isolate the root cause or causes of service degradation in an IT environment. By building on the ability of an abnormality detection algorithm to correlate an alarm with one or more events, embodiments disclosed herein can apply data correlation to data points collected within a specified time window by data metrics involved in the generation of the alarm and the event(s). The level of correlation between the primary metric and the probable cause metrics may be adjusted using the ratio between theoretical data points and actual points. The final Root Cause Analysis score may be modified depending upon the adjusted correlation value and presented for user review through a user interface.
Owner:BMC SOFTWARE
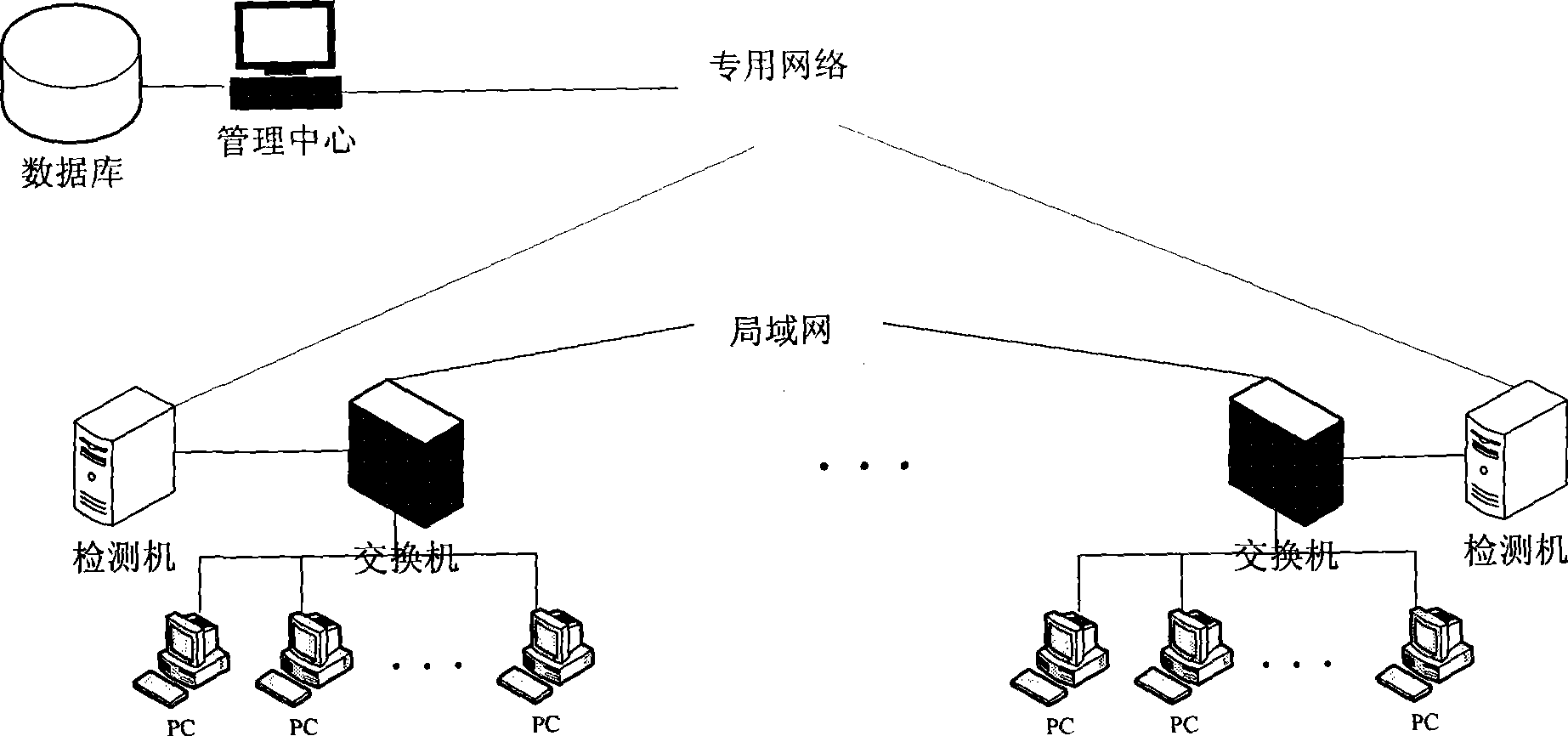
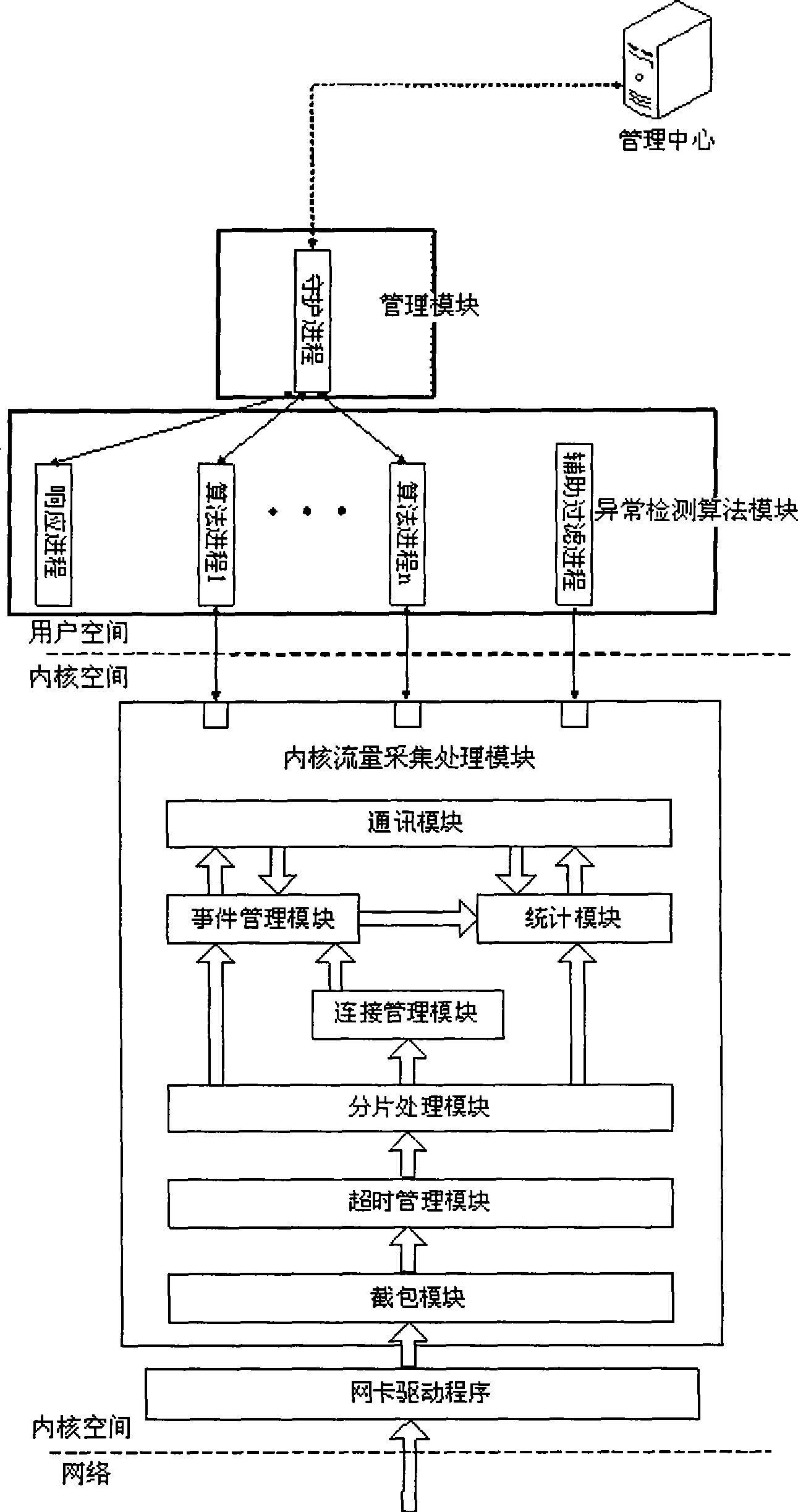
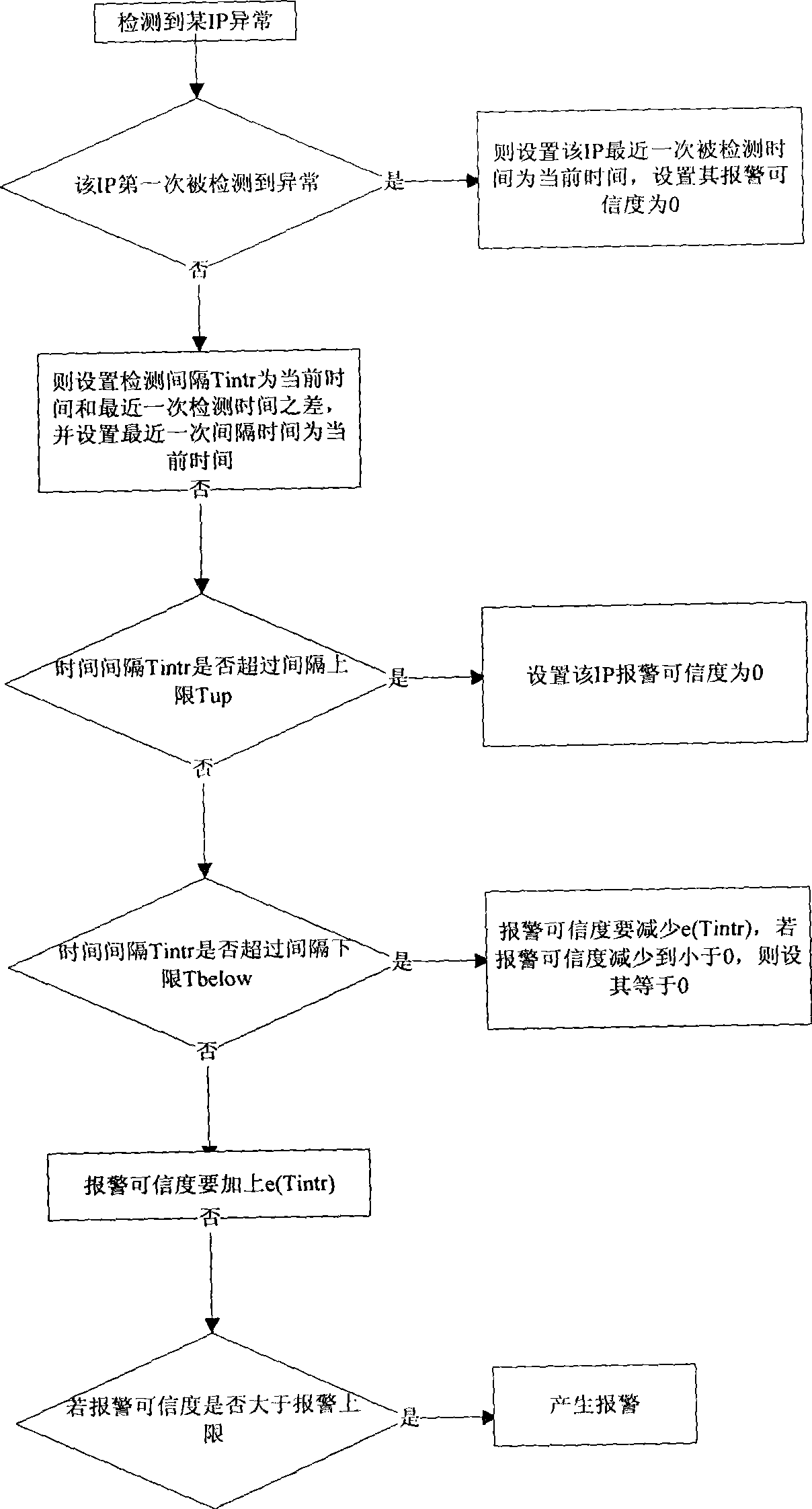
Alarm and response system for inner-mesh network aggression detection
InactiveCN101414927AHigh false positive rateReduce the degree of manual interventionData switching networksIp addressNetwork attack
The invention discloses a warning and responding system used for intranet network attack detection. The system comprises a management center, a detecting machine and a database. The management center is used for configuring and amending each parameter of the detecting machine, receiving and storing warning message sent by the detecting machine and inquiring the state of the detecting machine. Anomaly information detection is carried out on an intranet network by an anomaly detection algorithmic module of the detecting machine, the anomaly detection algorithmic module obtains anomaly detection information and confirms the reliability of the information. When the reliability of the anomaly detection information reaches a preset value, the warning message is sent. The isolation time and the isolation form of an IP address generating the anomaly detection information are confirmed according to the warning message, and the IP address is isolated. The IP address that the isolation time reaches the preset value is released from isolation. The method can detect and prevent the attack from an intranet mainframe to outer net or other intranet mainframes exactly and effectively in time.
Owner:ZHEJIANG UNIV
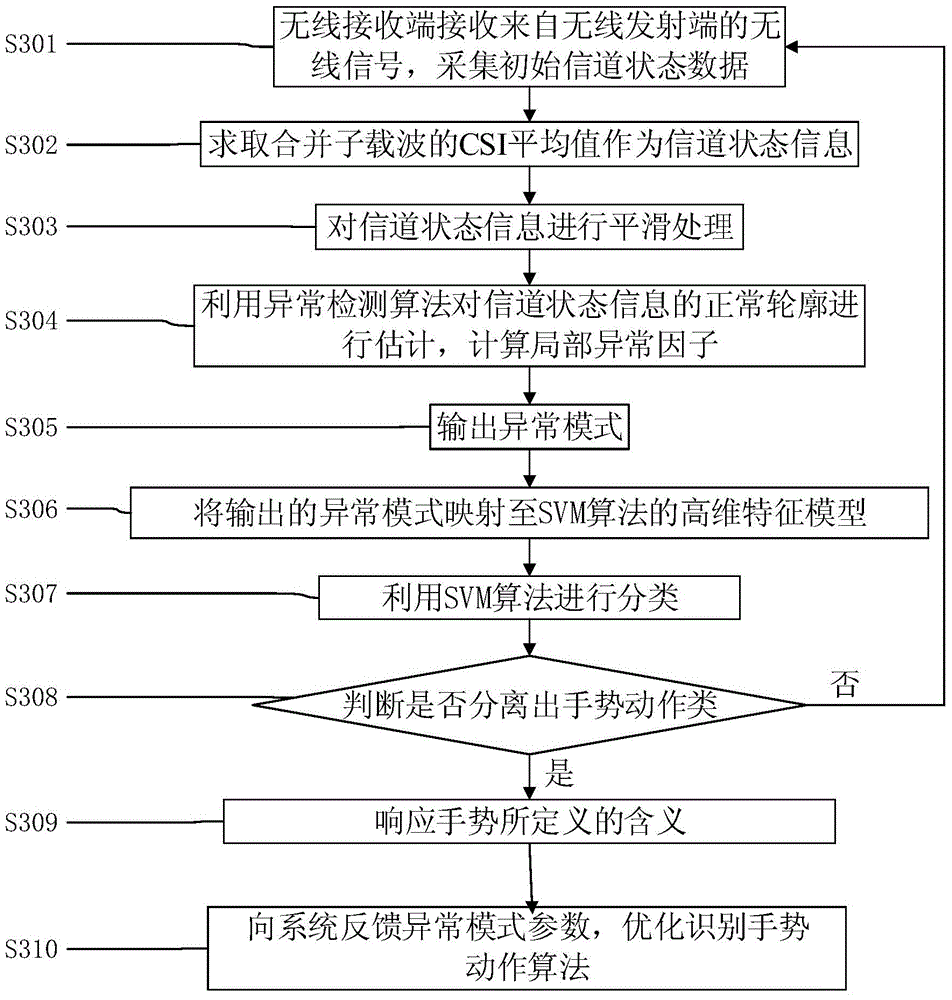
Automatic gesture recognizing method and system
InactiveCN104615244AAvoid inconvenienceReduce false alarm rateInput/output for user-computer interactionCharacter and pattern recognitionChannel state informationWireless mesh network
The invention discloses an automatic gesture recognizing method and system based on the wireless network signal transmission technology. The method comprises the following steps that firstly, a wireless receiving end receives a wireless signal from a wireless transmitting end and assesses channel state information; the changing abnormality of the channel state information is recognized through an abnormality detection algorithm; the gesture action is recognized based on an SVM algorithm capable of distinguishing a plurality of target action types and with the mode that the human body gesture action causes the channel state information change as the target action type, and if recognition can be achieved, the definition of the gesture can be answered. According to the recognizing method, the false alarm rate is low; an existing wireless network and an existing device are utilized, other specific detecting devices do not need to be installed, and high popularity is achieved. Meanwhile, a detected person does not need to carry any additional sensing devices, and inconvenience caused when the detected person carries the detecting devices is avoided.
Owner:SHENZHEN UNIV
Automatic detection method and system for human body falling-over
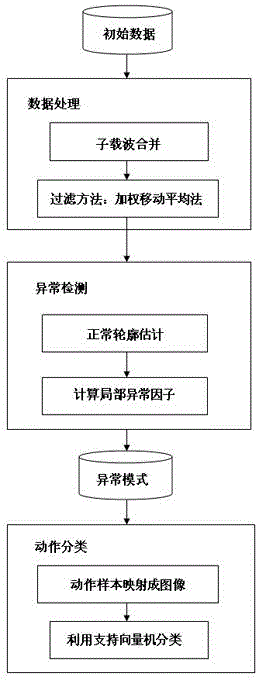
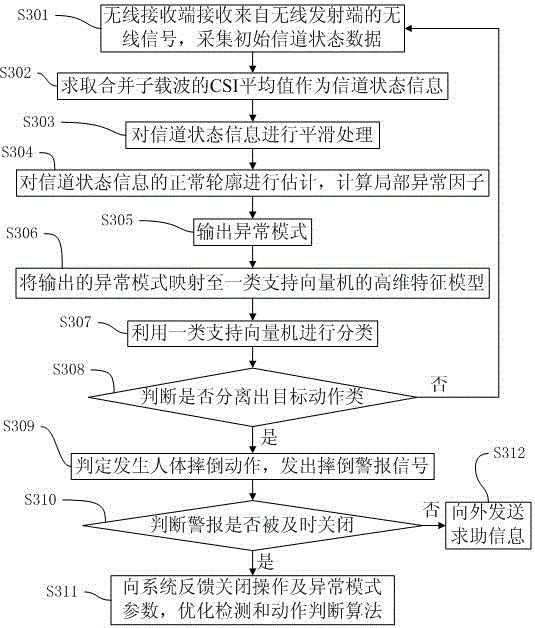
An automatic detection method and a system for human body falling-over are based on a wireless network signal transmission technology. The method comprises the following steps: a wireless receiving terminal receives wireless signals from a wireless transmitting terminal and assesses channel state information; abnormity of the channel state information change is identified by using an abnormity detection algorithm; based on a one-class support vector machine which distinguishes a target motion kind from other motion kinds, an abnormity mode that a human body falling-over motion leads to a channel state information change is set as the target motion kind to determine whether a human body falling-over motion happens; if the human body falling-over motion happens, a falling-over alarm signal is emitted. The false alarm rate of the detection method provided by the invention is low; by utilizing a present wireless network and a device, other specific detection devices are not needed, and the detection method is high in universality; and at the same time people to be detected do not need to carry any extra sensing equipment, and inconvenience caused by that people to be detected carry detection equipment is avoided.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
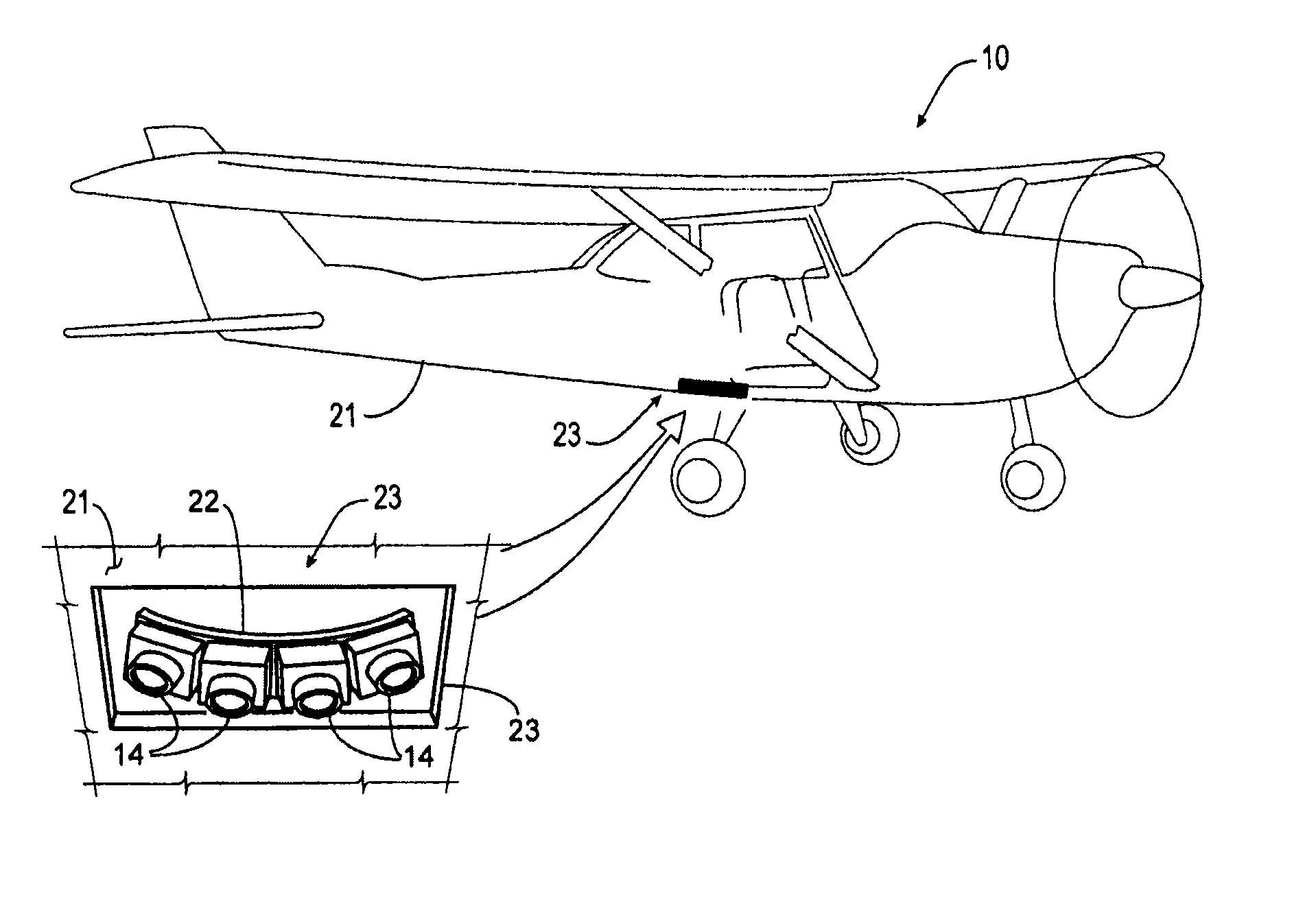
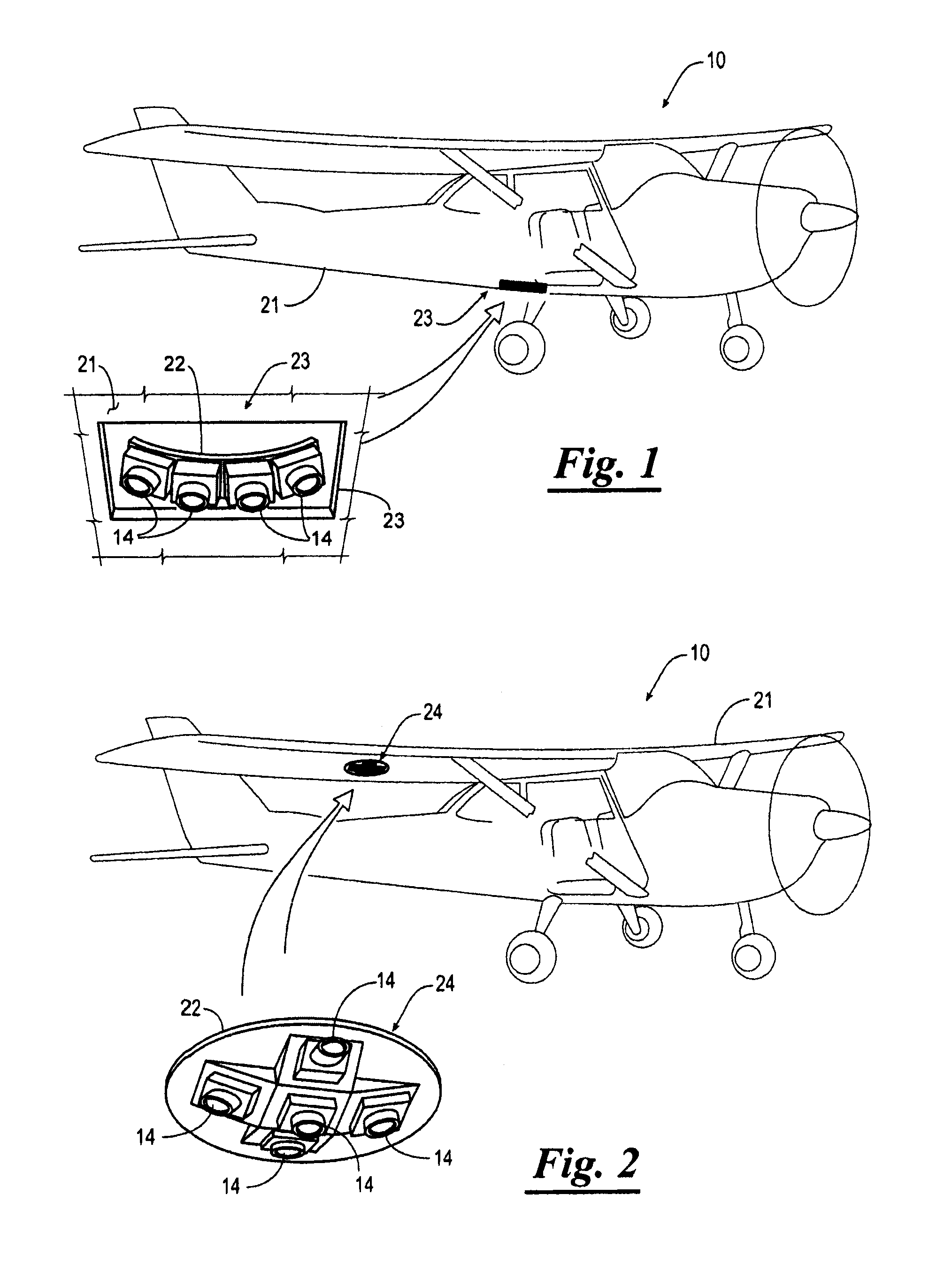
System for Detecting Image Abnormalities
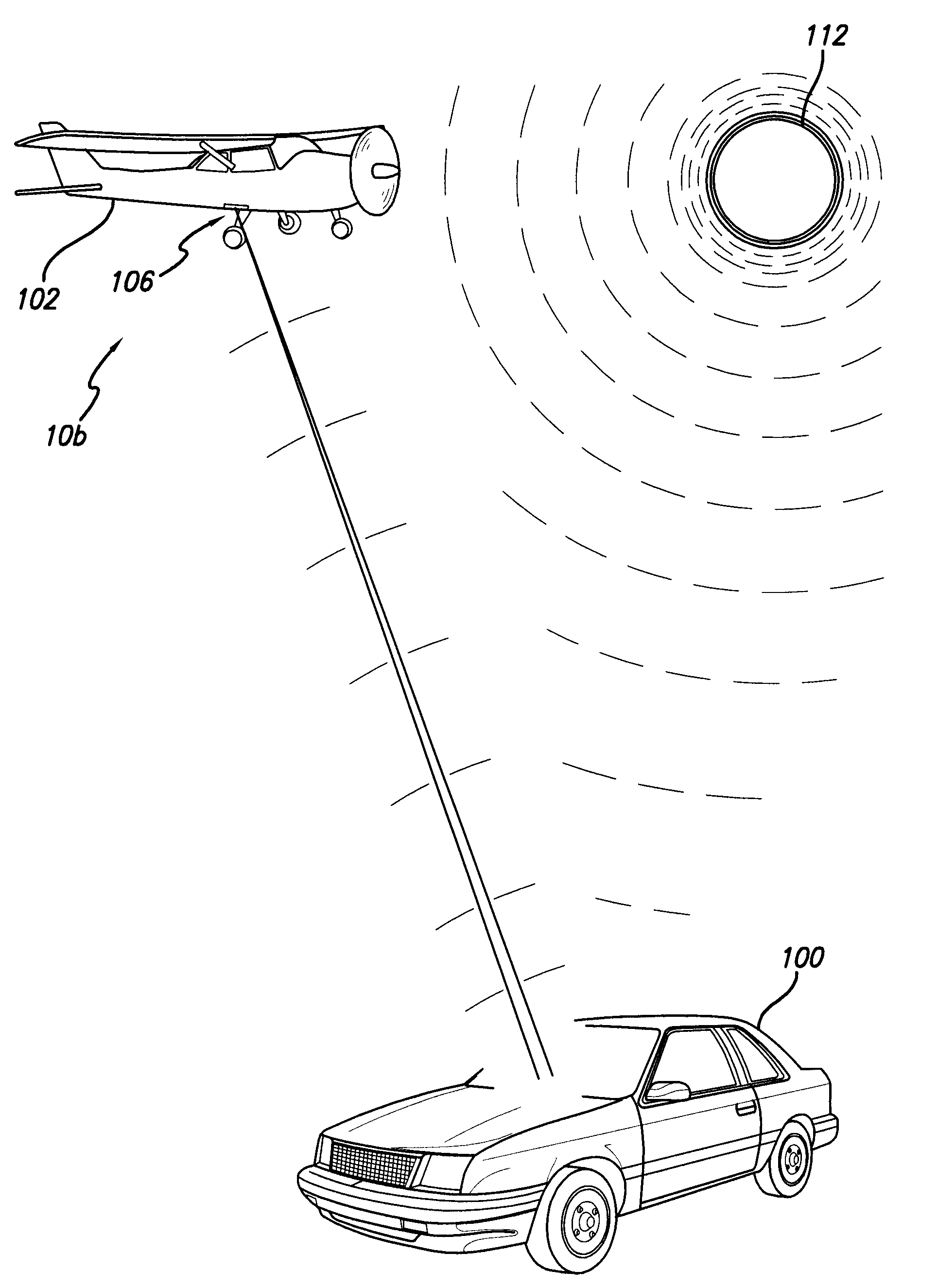
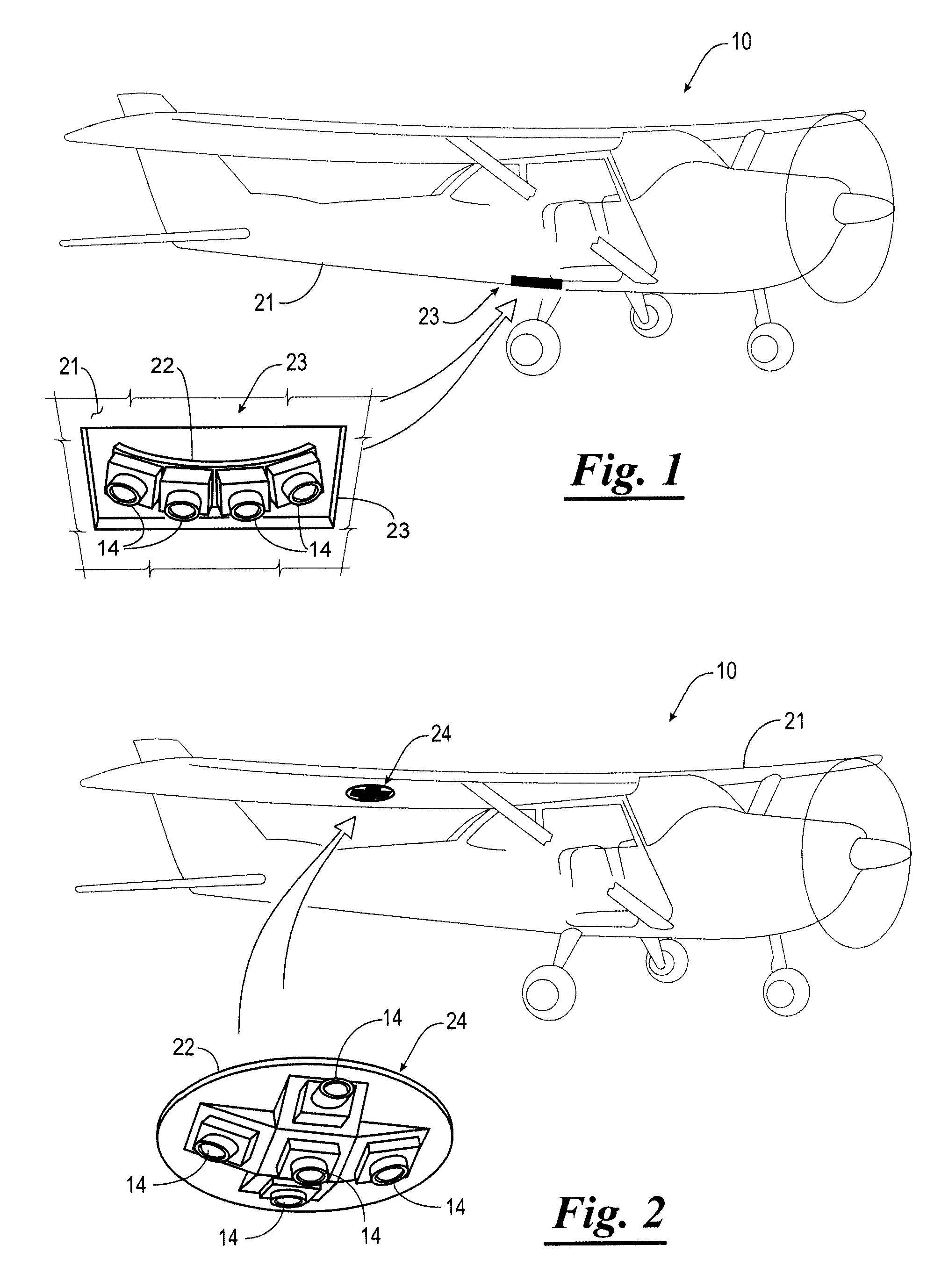
An image capture system for capturing images of an object, the image capture system comprising a moving platform such as an airplane, one or more image capture devices mounted to the moving platform, and a detection computer. The image capture device has a sensor for capturing an image. The detection computer executes an abnormality detection algorithm for detecting an abnormality in an image immediately after the image is captured and then automatically and immediately causing a re-shoot of the image. Alternatively, the detection computer sends a signal to the flight management software executed on a computer system to automatically schedule a re-shoot of the image. When the moving platform is an airplane, the detection computer schedules a re-shoot of the image such that the image is retaken before landing the airplane.
Owner:PICTOMETRY INTERNATIONAL CORPORATION
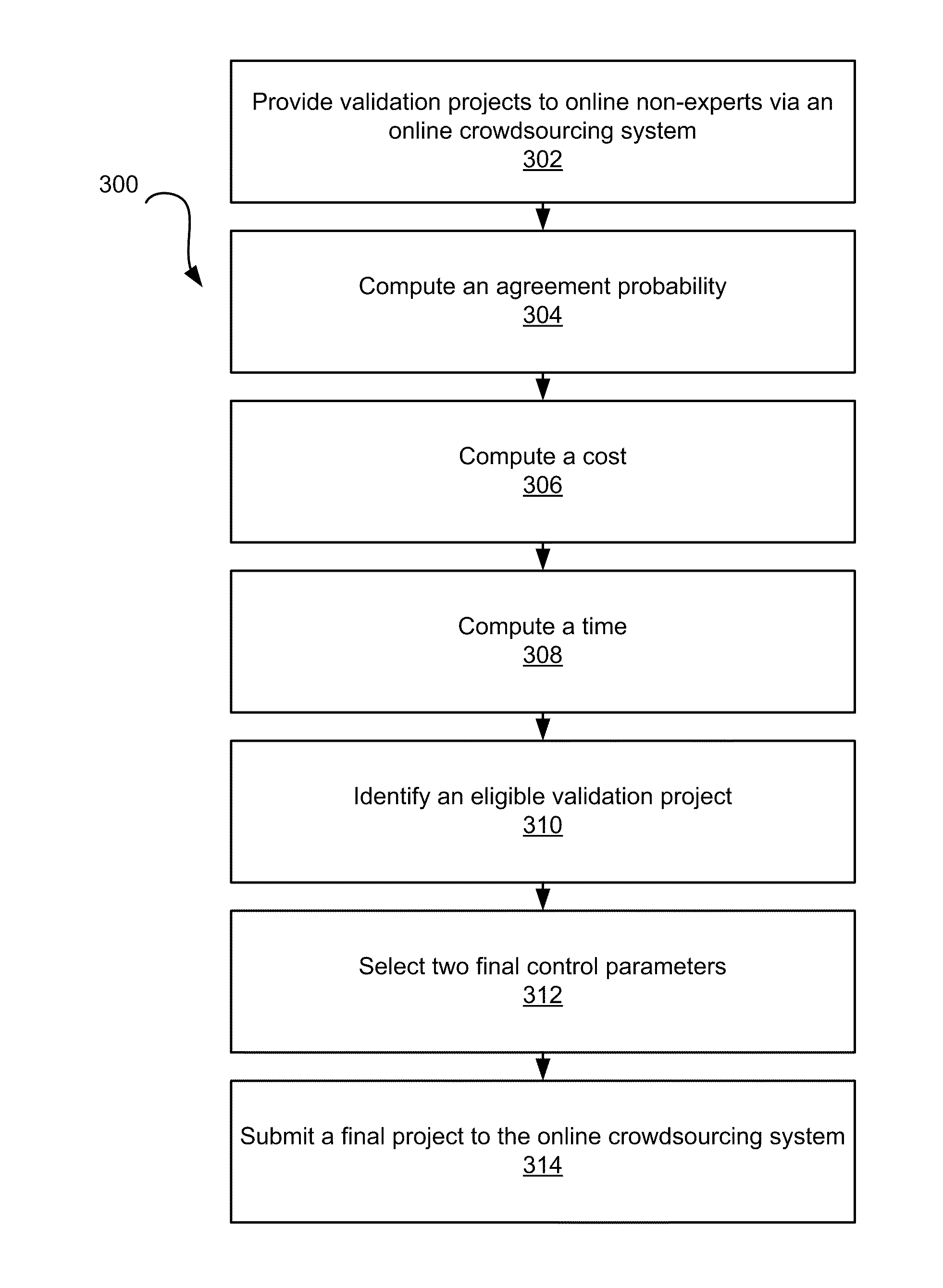
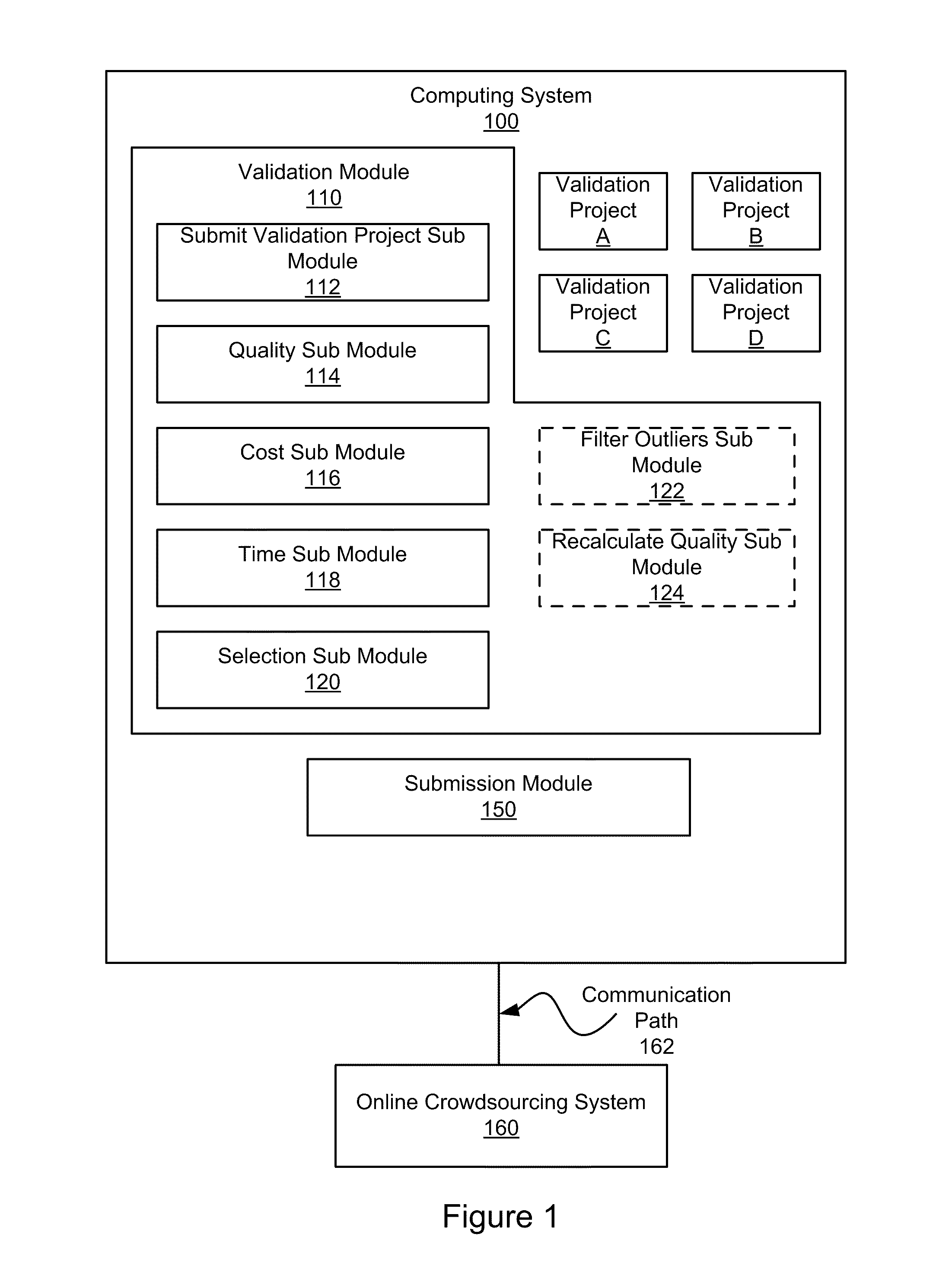
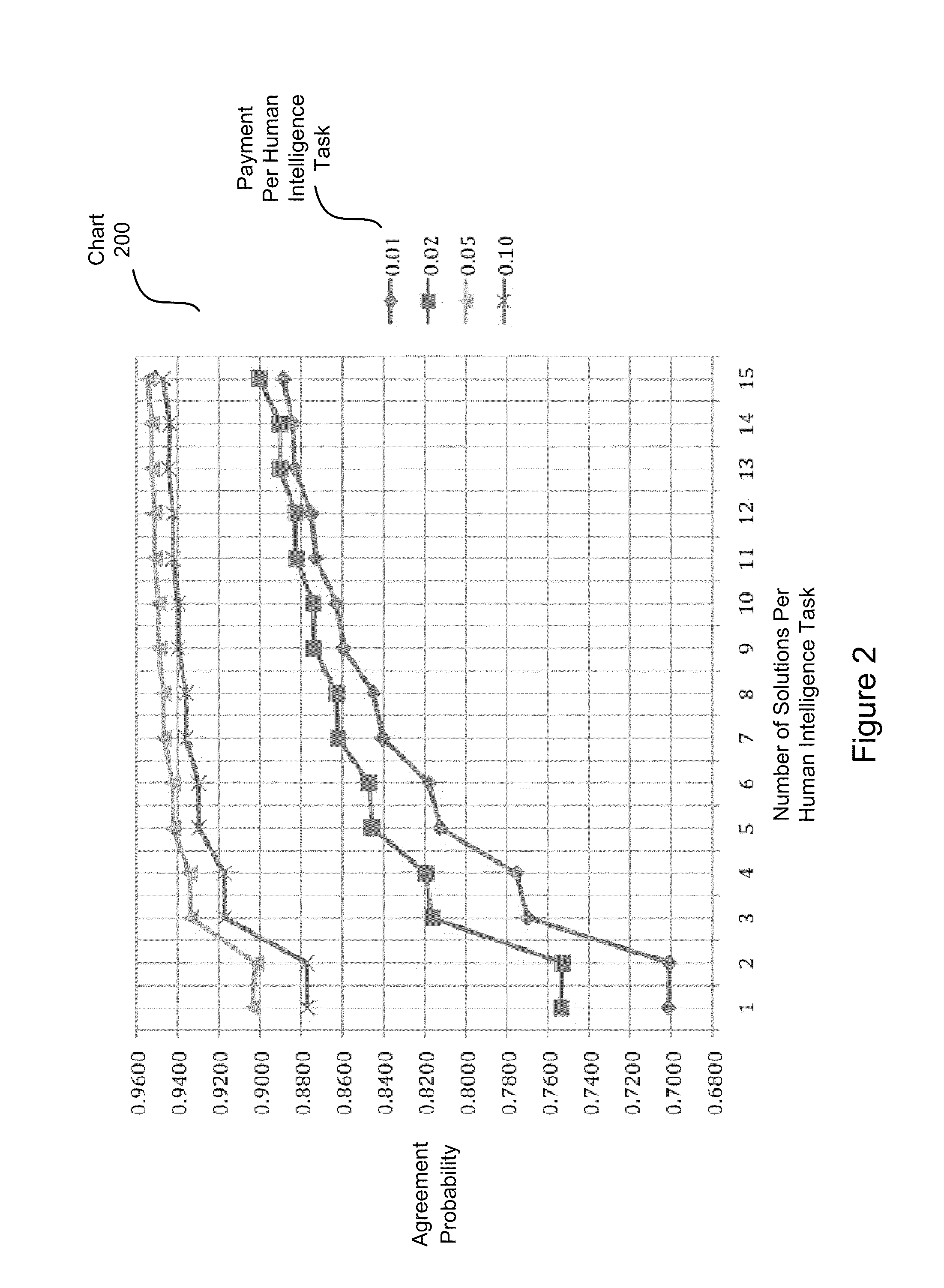
Method and System for Acquiring High Quality Non-Expert Knowledge from an On-Demand Workforce
ActiveUS20110145156A1Quality improvementImprove accuracyBuying/selling/leasing transactionsPaymentCompletion time
Systems and computer-implemented methods include a validation phase in which validation projects are submitted to an online crowdsourcing system. The validation projects each have different combinations of the two validation control parameters, payment per human intelligence task (“HIT”) and number of solutions per HIT. By analyzing the solutions for the validation projects, final control parameters can be selected from the validation project having the best combination of high quality, low cost, and short time to completion. The final control parameters can be submitted along with a final project to the online crowdsourcing system. In addition, a novel outlier detection algorithm enables the system to detect outlier workers based on the distribution of non-experts' agreement probabilities, reject outlier workers' results, and thus save labeling cost.
Owner:THRYV INC
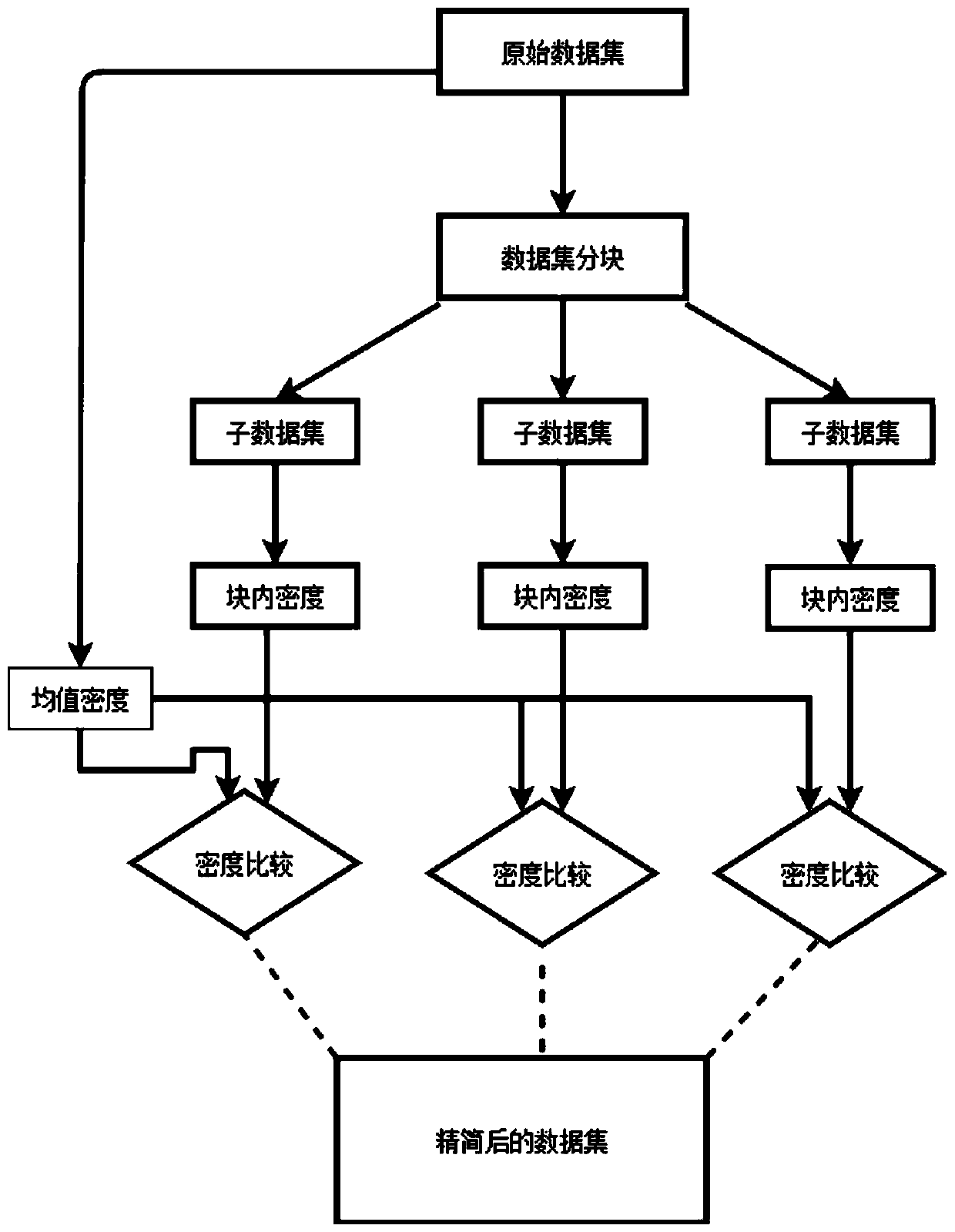
Isolated forest-based binary classification abnormal point detection method and information data processing terminal
InactiveCN110046665AImprove accuracyImprove robustnessCharacter and pattern recognitionData setFeature extraction
The invention belongs to the technical field of communication control and communication processing, and discloses an isolated forest-based binary classification abnormal point detection method and aninformation data processing terminal. The method comprises the steps of carrying out initial static average blocking on an original data set, and calculating the density in the block and the mean density; after calculating the density in each block of the static block, reducing the data set by taking the mean density of the original data set as a threshold value; constructing an isolated forest byusing a node recursion method; performing corresponding feature extraction and datamation on the original data set, and calculating the spatial position distances between the clustering center pointand other points; adding the abnormal score calculated on the basis of the density and the distance and the abnormal score calculated on the basis of the proof information and comparing with a corresponding threshold value. According to the method, the accuracy of an abnormal point detection algorithm is effectively improved, the actual data size in the abnormal detection process can be greatly reduced, the calculation resources are saved, and the abnormal detection efficiency is improved, and the robustness of an abnormal detection algorithm is enhanced.
Owner:CHENGDU UNIV OF INFORMATION TECH
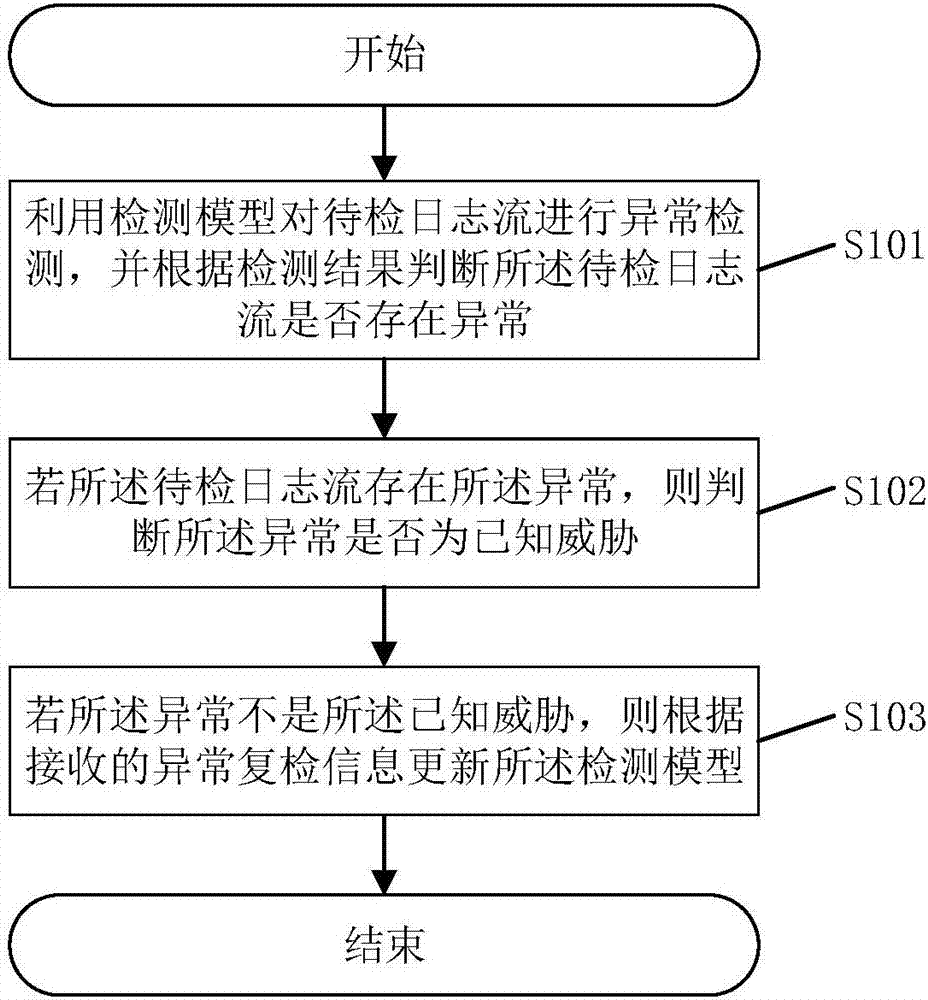
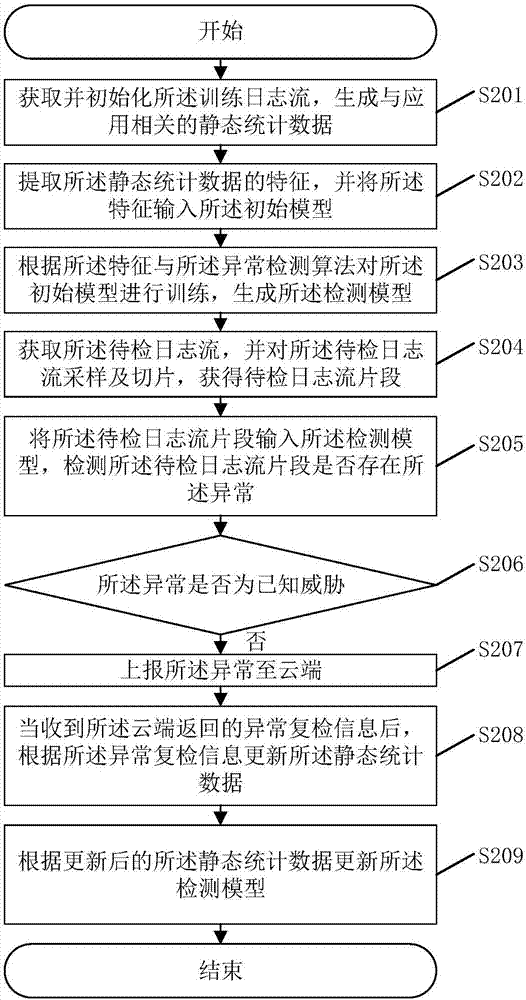
Log stream anomaly detecting method and system
The invention discloses a log stream anomaly detecting method. The method comprises the steps of utilizing a detecting model to perform anomaly detection on log stream to be detected and judging whether the log stream to be detected is abnormal or not according to detection results, wherein the detecting model is obtained by training an initial model according to training log stream and an anomaly detecting algorithm; if the log stream to be detected has anomaly, judging whether the anomaly is a known threat or not; if the anomaly is not the known threat, updating the detecting model according to received anomaly rechecking information. The method can recognize the anomaly in the log stream and autonomously learn the new anomaly, not only recognizes the known threat, but also can learn unknown events and improves safety of a network environment. The invention further discloses a log stream anomaly detecting system which also has the beneficial effects.
Owner:SANGFOR TECH INC
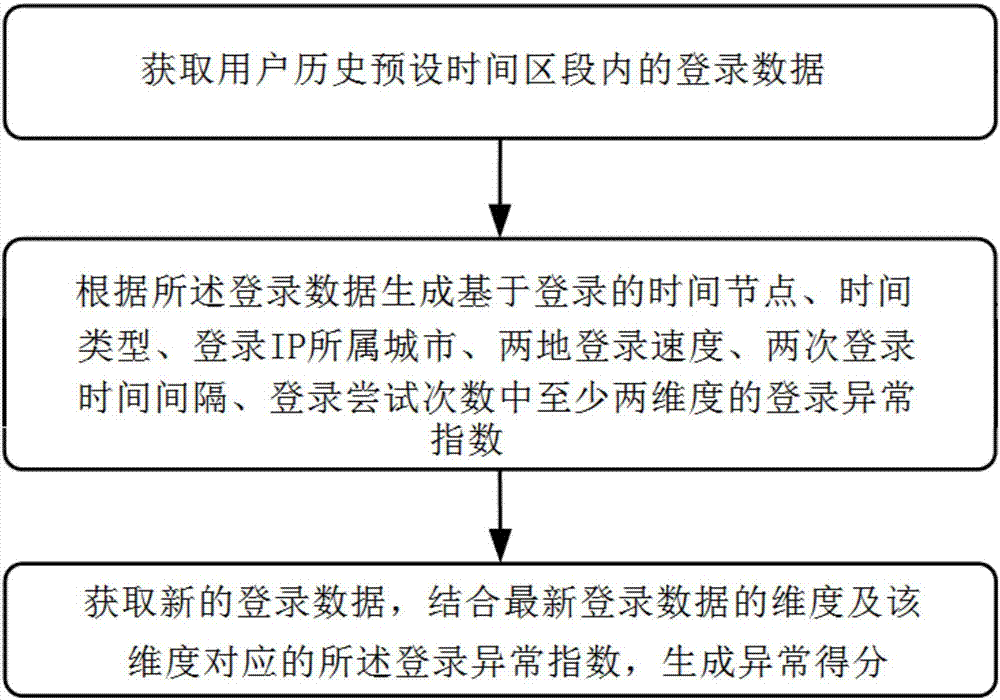
Login abnormity detection method, system and device
ActiveCN107172104AImprove the hit rate of abnormal loginImprove securityTransmissionMisinformationAnomaly detection algorithm
The invention relates to a login abnormity detection method, system and device. The login abnormity detection method comprises steps of obtaining login data of a user history preset time interval, generating a login abnormity index based on at least two dimensions of a time node, a time type, a city that a login IP belongs to, two place login speeds, a time interval between two login times and times of trying to login according to the login data, wherein at least one of the dimensions of the login time node, the time type and the city where the login IP belongs to exists, obtaining new login data and generating an abnormal score by combining with a newest login data dimension and a login abnormal index corresponding to the dimension. Multi-dimension aggregation solves a problem of one-dimension misinformation. The login abnormity detection method, system and device can overcome current dimension deficiency through more dimension detection, improve abnormal login hit rate, screen out high score data to investigate through grading the login data according to weights / and abnormity detection algorithm and can fundamentally eliminate misdetection and leak detection of login through combining multiple detection modes.
Owner:SF TECH
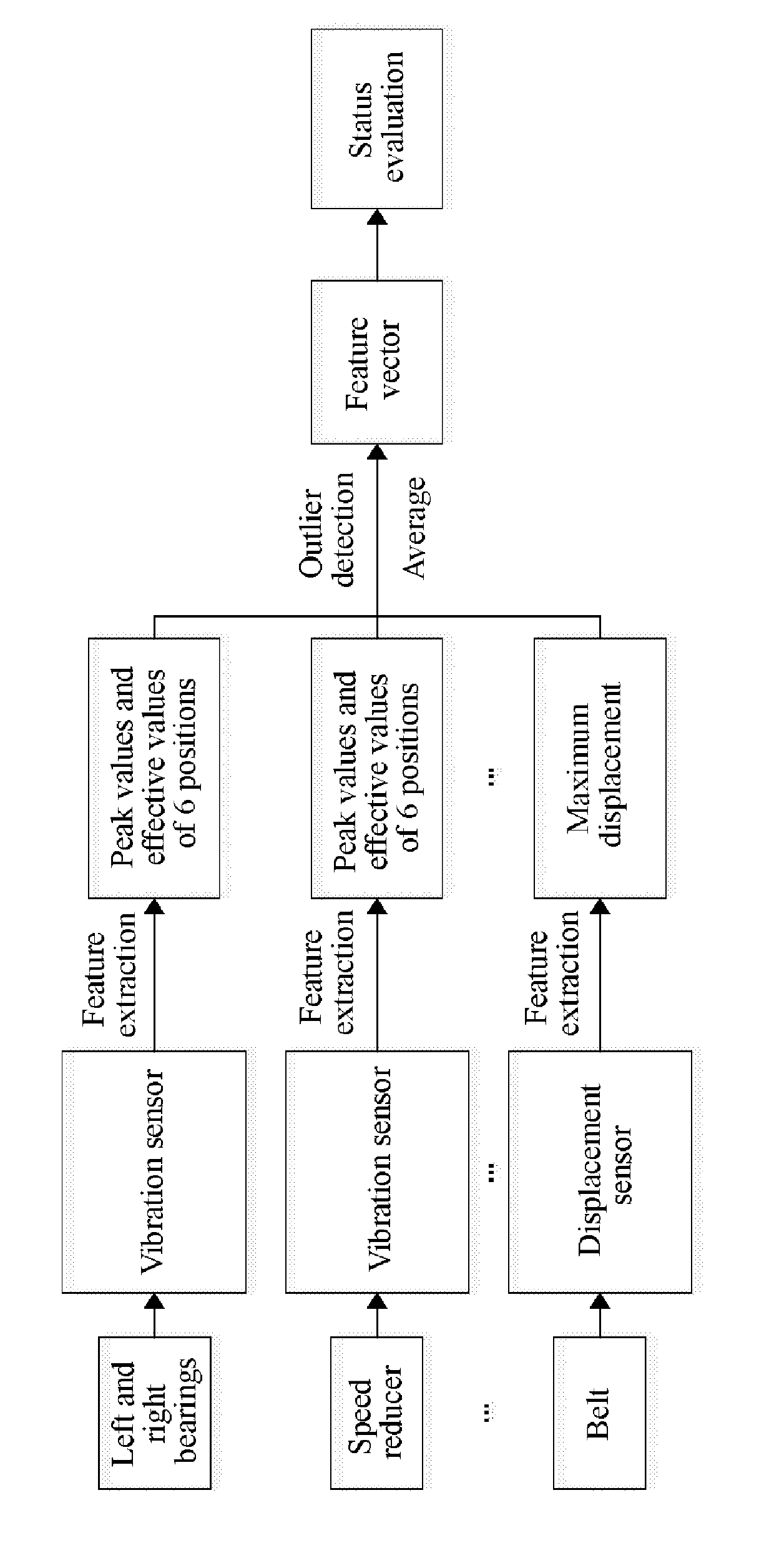
Method for evaluating health status of mechanical equipment
InactiveUS20190285517A1Testing/monitoring control systemsStructural/machines measurementSelf organizing map neural networkNerve network
Disclosed is a method for evaluating a health status of mechanical equipment. Firstly, status data of main components on mechanical equipment are collected by a sensor, and feature extraction is performed to obtain feature parameters. Then, noise data and fault data are extracted by an outlier detection algorithm, and only the fault data are retained. Subsequently, dimension reduction processing is performed to obtain a feature vector for final evaluation. Finally, equipment status evaluation is performed, a self-organizing map neural network model is established by health status data and failure status data, rate impact factors of each group of data to be evaluated are calculated by an entropy weight theory, and the rate impact factors are introduced into a neural network to perform health factor calculation. The present invention implements overall status evaluation for mechanical equipment, provides a basis for health maintenance of the mechanical equipment, and avoids unnecessary economic losses.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS +1
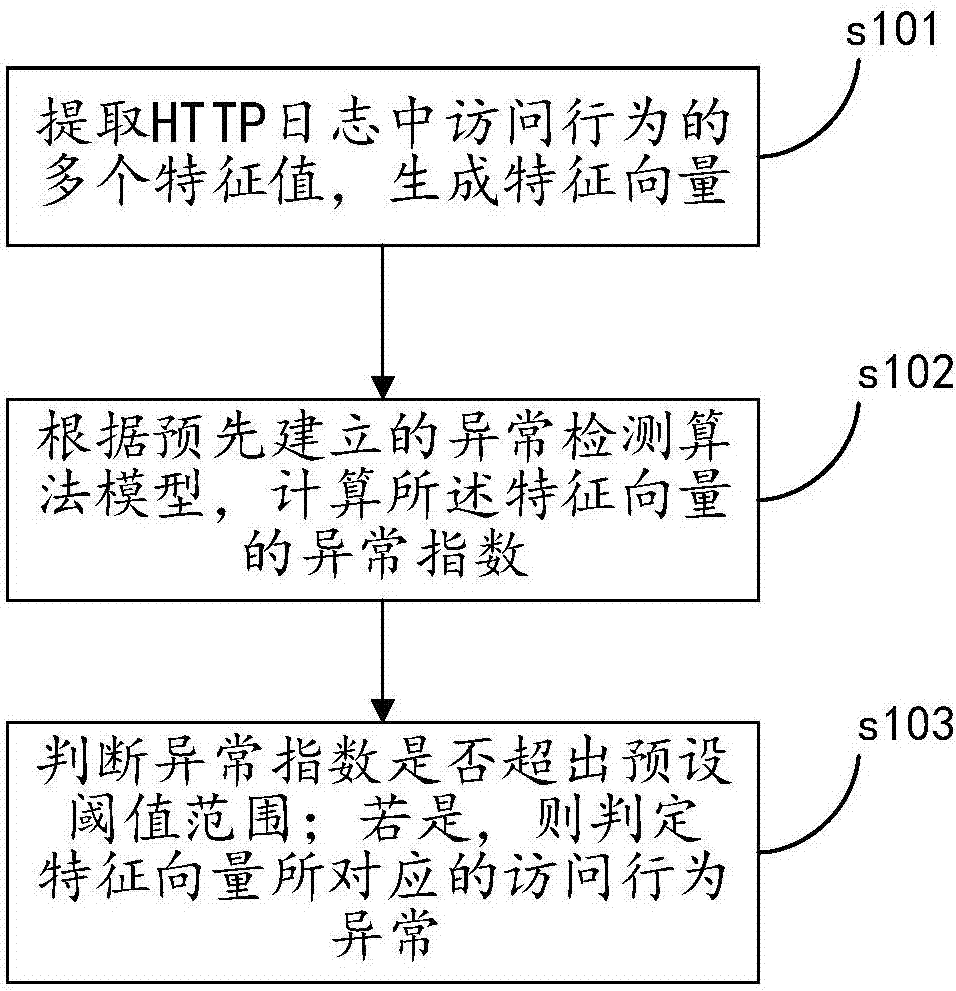
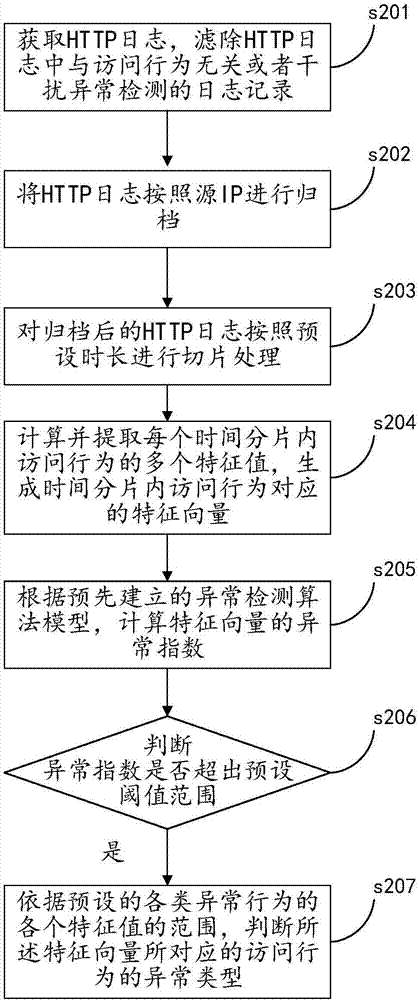
Web business abnormality detection method and apparatus
The invention discloses a web business abnormality detection method. The web business abnormality detection method comprises the following steps: extracting a plurality of feature values of an access behavior in an HTTP log, and generating a feature vector; calculating an abnormal index of the feature vector according to a pre-established abnormality detection algorithm model; determining whether the abnormal index goes beyond a preset threshold value range; and if the abnormal index goes beyond the preset threshold value range, determining the access behavior corresponding to the feature vector to be abnormal. According to the method, by extracting and analyzing the feature value of an access record in the HTTP log, the abnormal behavior can be detected without a rule base, so that the detection capacity for an unknown type of abnormal behavior can be effectively improved. The invention also discloses a web business abnormality detection apparatus which has the same beneficial effects.
Owner:SANGFOR TECH INC
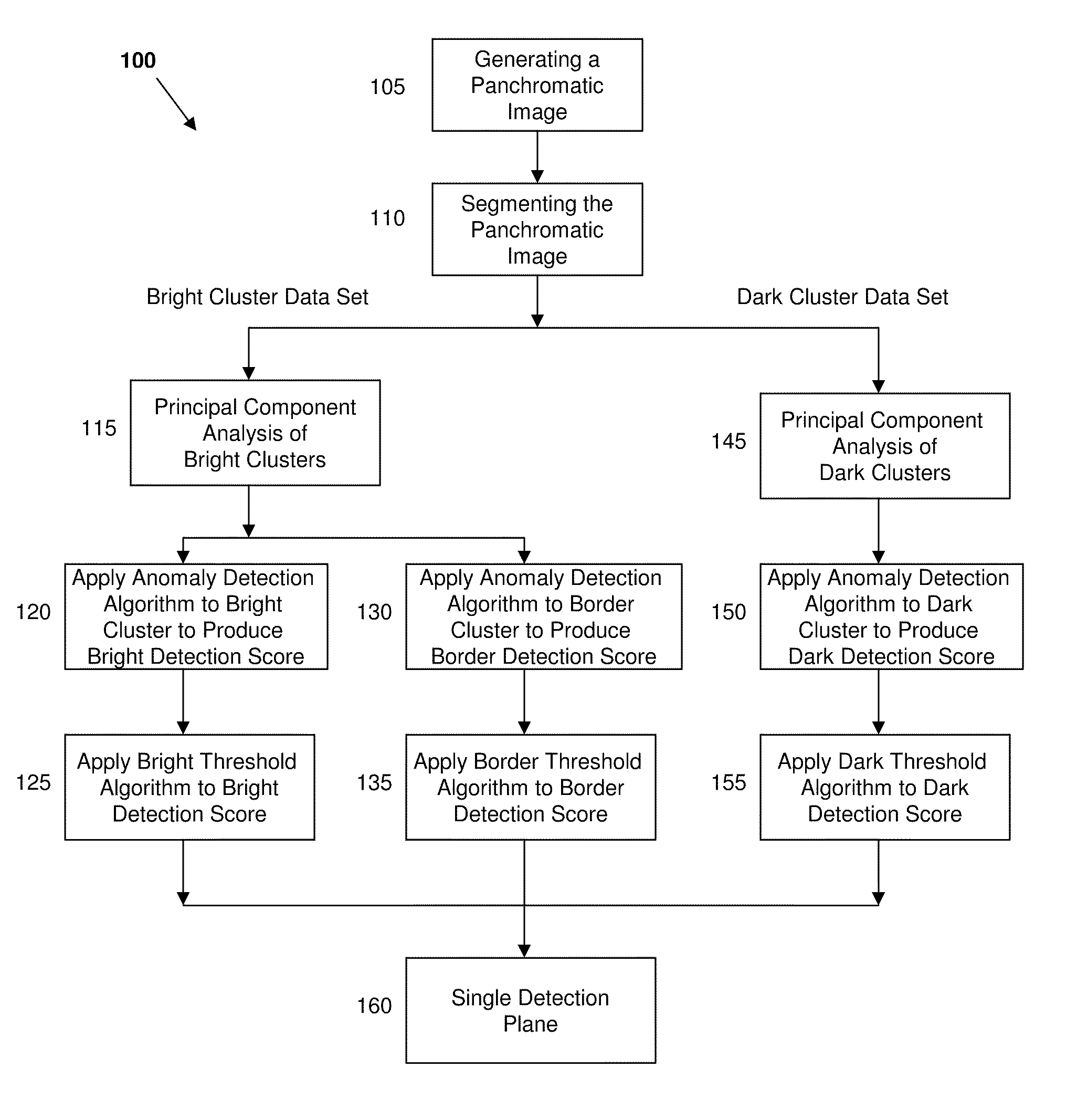
Spectral Anomaly Detection in Deep Shadows
InactiveUS20110221926A1Image enhancementTelevision system detailsKernel principal component analysisData set
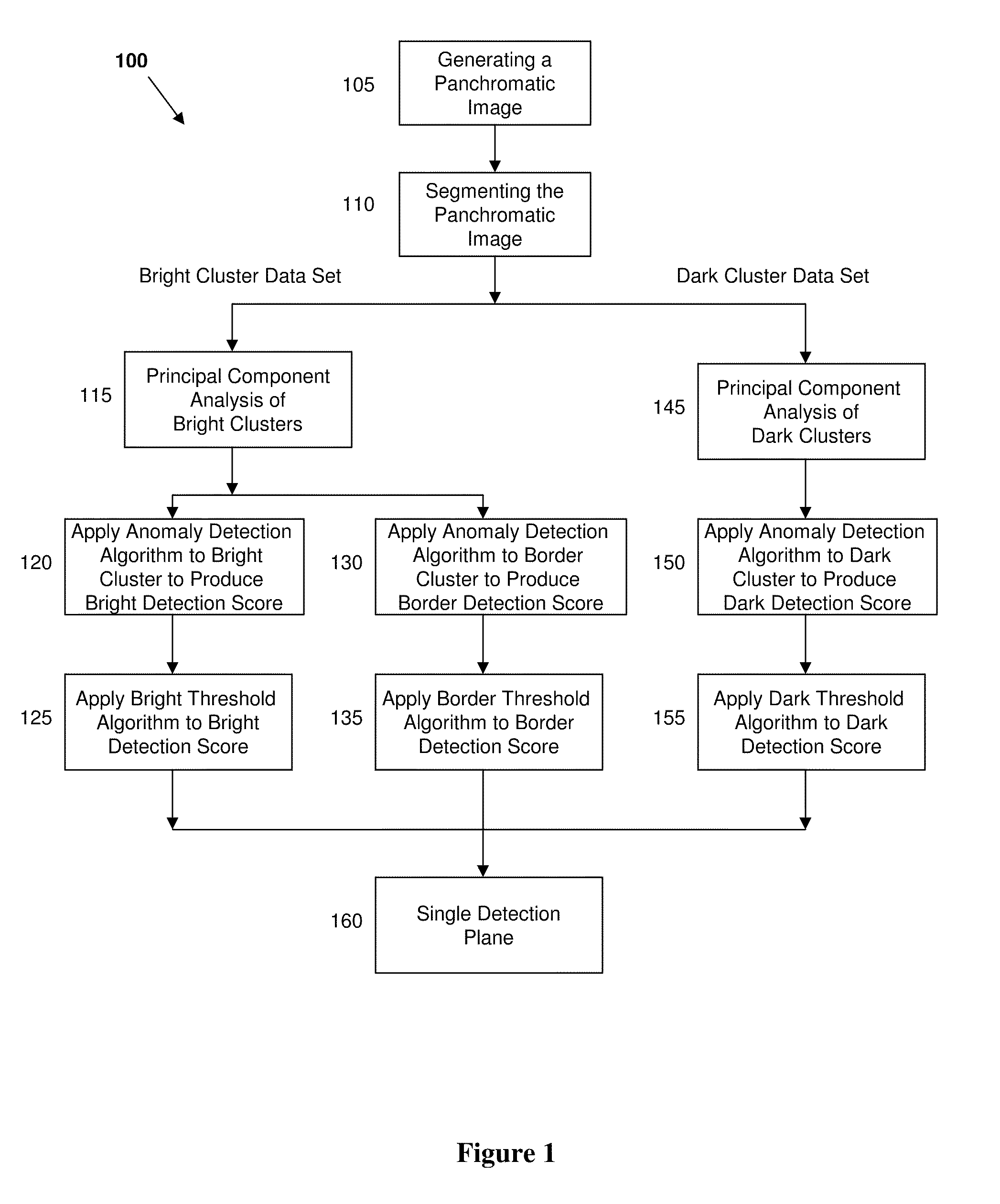
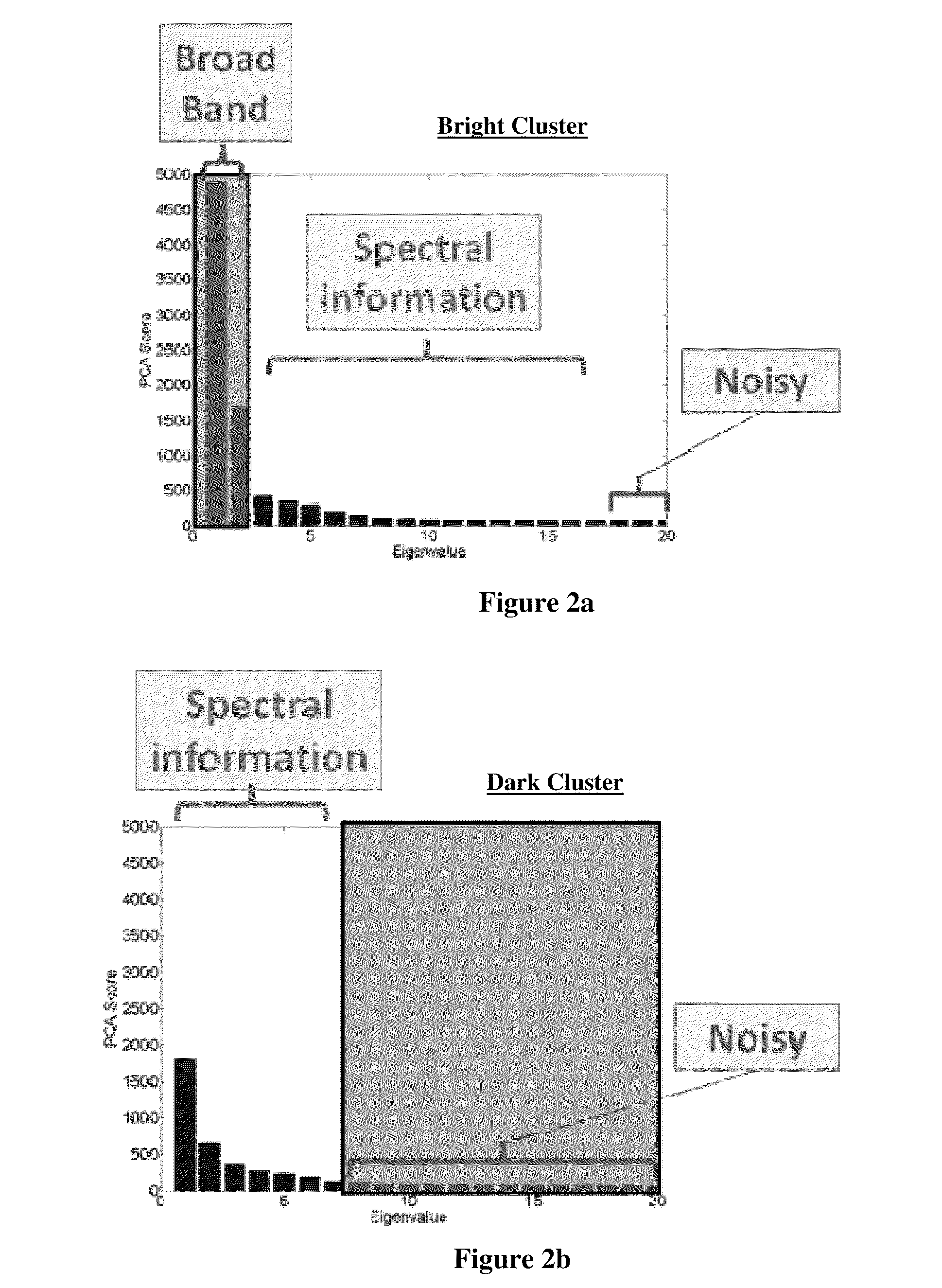
A spectral anomaly detection method includes the steps of segmenting a panchromatic image, obtained from a hyperspectral sensor into cluster data sets. Principal component analysis can be separately performed on each of the cluster data sets to produce a plot of principal components. An anomaly detection algorithm can be applied to an adaptively selected subset of principal components for each of the cluster data sets to produce cluster detection scores. Finally, separate detection thresholding algorithms can be applied to each of the cluster detection scores, and the results of the detection thresholding algorithms can be combined into a single detection plane.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Video abnormity detection method based on graph structure under multi-scale transformation
ActiveCN106548153AImprove computing efficiencyReduce the number of optical flow featuresCharacter and pattern recognitionSpatial correlationOptical flow
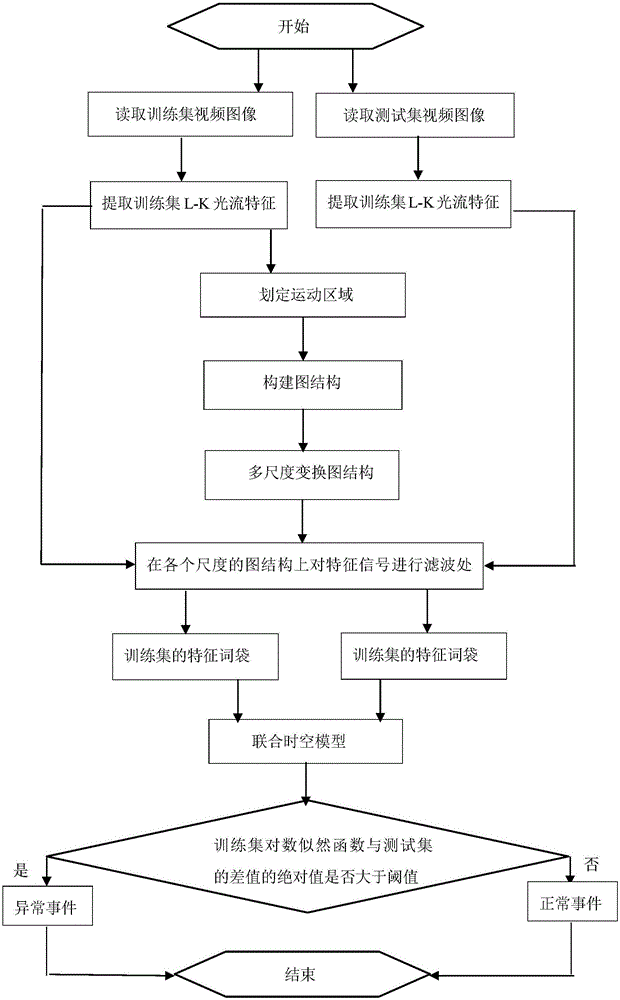
The invention discloses a video abnormity detection method based on a graph structure under multi-scale transformation. First of all, video abnormity detection is carried out by use of an optical flow feature, and spatial correlation scales of video abnormity association optical flow features in different scenes are different. Under the condition that the spatial correlation structure of the video abnormity association optical flow features is maintained, since the calculation efficiency of video abnormity detection can be effectively improved by reducing the quantity of the optical flow features, it is brought forward that a network graph structure of the optical flow features is constructed based on spatial correlation, by use of multi-scale transformation of the graph structure under correlation constraints, the quantity of the optical flow features in the video abnormity detection is effectively reduced, under the condition that the detection precision is slightly reduced, the calculation efficiency of a video abnormity detection algorithm can be substantially improved, and detection of event abnormities is more rapid and reasonable.
Owner:杭州软库科技有限公司
Abnormity detection method for enterprise industry classification
ActiveCN109657947AAccurate dataReliable dataCharacter and pattern recognitionNeural architecturesOriginal dataBusiness enterprise
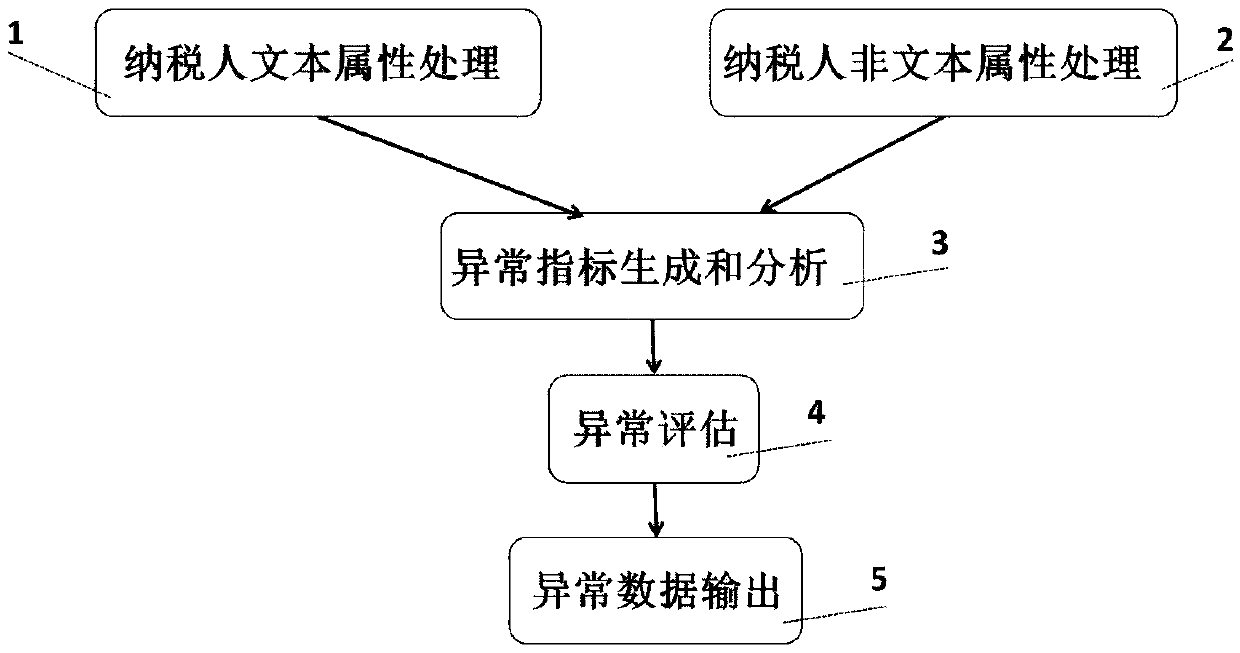
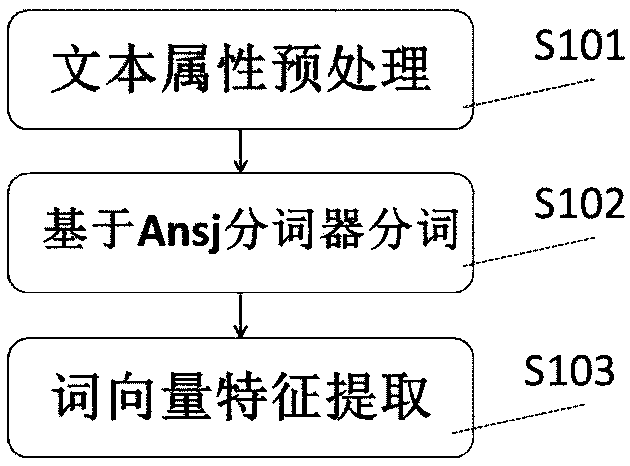
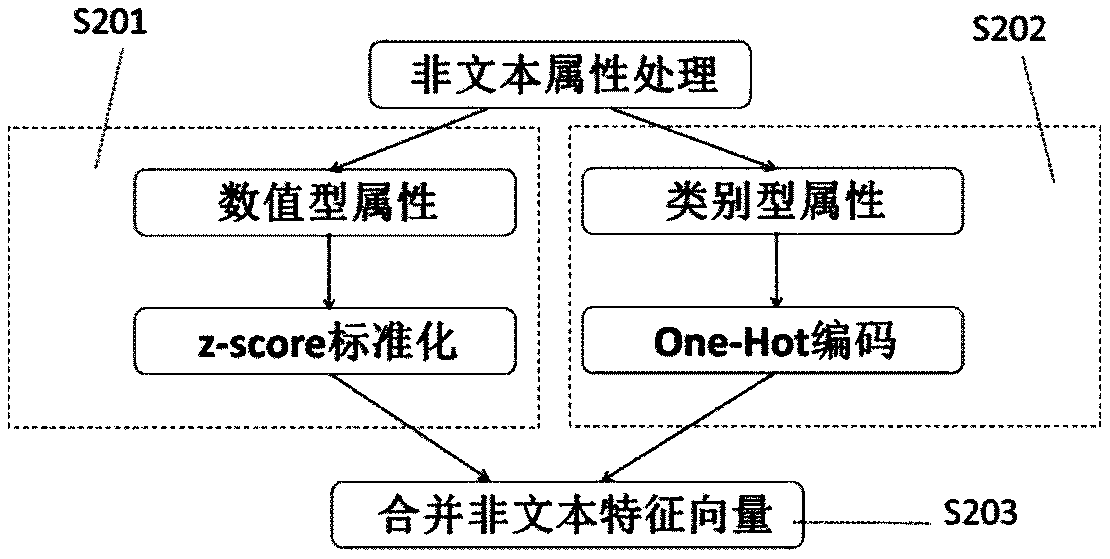
The invention discloses an abnormity detection method for enterprise industry classification, which comprises the following steps of: firstly, extracting to-be-mined text and non-text information in taxpayer industry information, and carrying out feature processing and coding processing; Secondly, constructing a deep network structure conforming to the industry classification abnormity detection problem, and determining the number of neurons of an input layer and an output layer of the network according to the characteristic dimension of the coded data; Thirdly, on the basis of the constructeddeep network structure, adopting different training strategies to train the industry large-class network and the industry detail network through cross validation; And finally, carrying out abnormitydetection on the industry large class by using dimension reduction characteristics of the industry large class network in combination with an SOS abnormity detection algorithm, and carrying out abnormity detection on industry details according to reconstruction characteristics of the industry detail network. According to the invention, the TADM model is utilized to carry out abnormal detection onthe original data, and macroscopic management work such as national statistics, tax collection and industrial and commercial management can be analyzed more reasonably and accurately.
Owner:XI AN JIAOTONG UNIV
Noise diagnosis algorithm for rolling bearing faults of rotary equipment
ActiveCN110132598AEffective diagnosisEfficient detectionMachine part testingCharacter and pattern recognitionPrincipal component analysisEngineering
The invention discloses a noise diagnosis algorithm for rolling bearing faults of rotary equipment. Firstly, a sound pick-up device collects running noise signals of a rolling bearing, and the signalsare subjected to preliminary fault judgment through a bearing normality and anomaly pre-classification model based on an anomaly detection algorithm; secondly, according to a fault pre-judgment result, the abnormal signals (the faults occur) pass through a neural network filter to filter normal components in the signals of the bearing, the output net abnormal signals are connected to a subsequentfeature extraction module, and the normal signals (no faults occur) are directly connected to the feature extraction module; the feature extraction module extracts Mel-cepstrum coefficients (MFCC) ofthe signals to serve as eigenvectors, feature reconstruction is carried out by utilizing a gradient boosted decision tree (GBDT) to form composite eigenvectors, and principal component analysis (PCA)is used for carrying out dimensionality reduction on features; and finally, feature signals are input into an improved two-stage support vector machine (SVM) ensemble classifier for training and testing, and at last, high-accuracy fault type diagnosis is achieved. According to the algorithm, the bearing faults can be effectively detected and relatively high fault identification accuracy is kept;and the algorithm has relatively high effectiveness and robustness for detection and classification of the bearing faults.
Owner:CHINA UNIV OF MINING & TECH
Improved local anomaly factor algorithm-based power grid topology identification method
InactiveCN107123989AImprove accuracySimplify complexityCharacter and pattern recognitionAc network circuit arrangementsTopology identificationDensity based
The invention provides an improved local anomaly factor algorithm-based topology identification method. The method comprises the steps of firstly, based on the statistical theory, acquiring the operating state change information of a to-be-predicted device object, such as a switch, a disconnecting link or the like; secondly, according to the acquired data, modeling a to-be-identified data object, and respectively establishing an object set for each device object, wherein the object set represents the operating state change condition of the device object within a certain period of time; thirdly, based on the grid reduction theory in the GDLOF algorithm, reducing data objects in the object set to reduce identification objects and improve the efficiency of the algorithm; fourthly, for non-excluded data objects, subjecting each attribute of each object to weighted treatment by adopting a relative entropy in considering different influences of the telemetry and remote signaling information on topology error identification. In this way, the reliability and the execution efficiency of the algorithm are improved, and the identification topology error of a local anomaly factor is finally confirmed. According to the technical scheme of the invention, the density-based anomaly detection algorithm is applied to the topology error identification of the power grid, so that the application field of the anomaly detection algorithm is expanded. Meanwhile, the topology error problem of the power grid and the identification problem of telemetry bad data in the prior art are solved at the same time.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +3
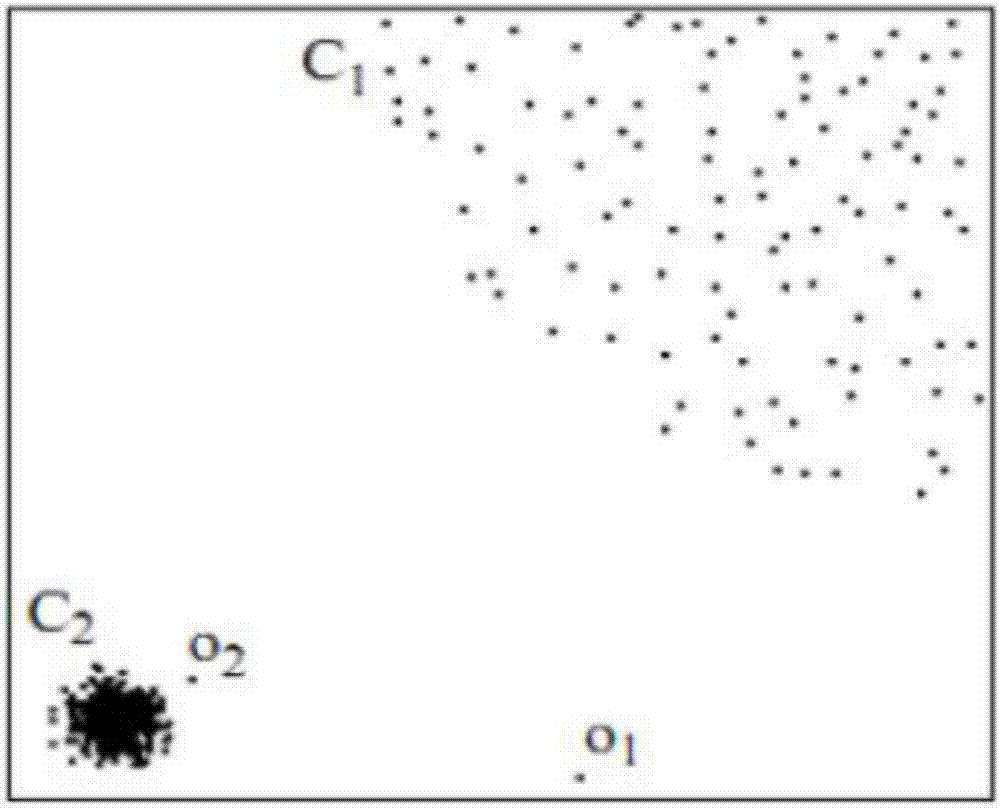
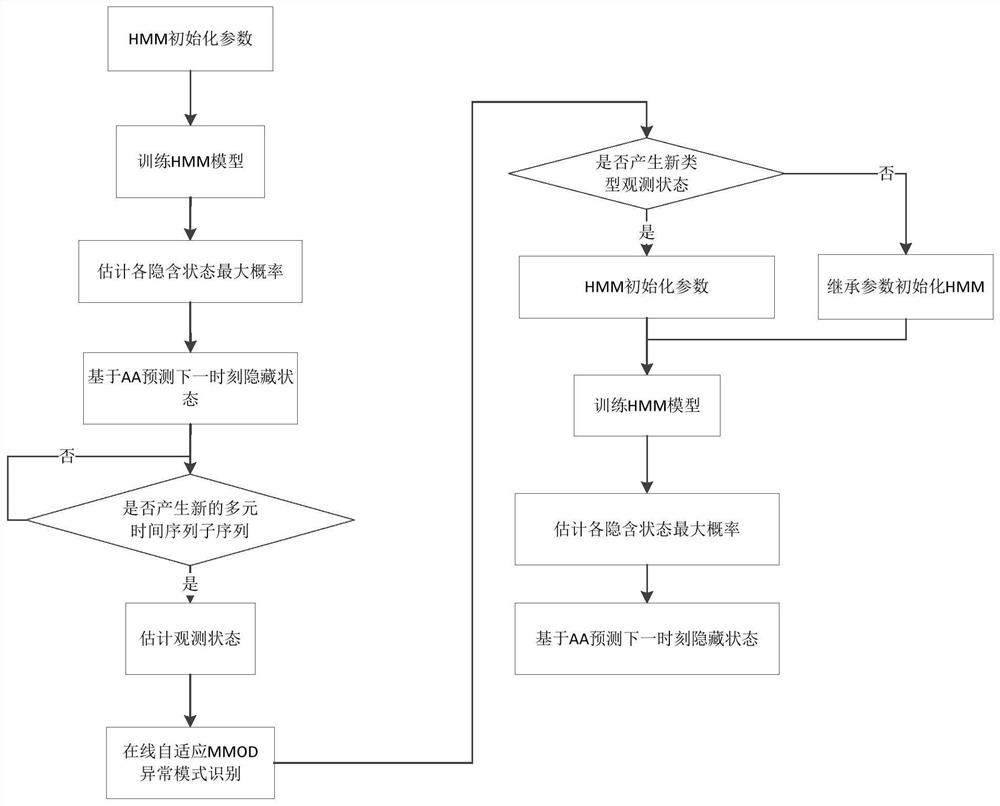
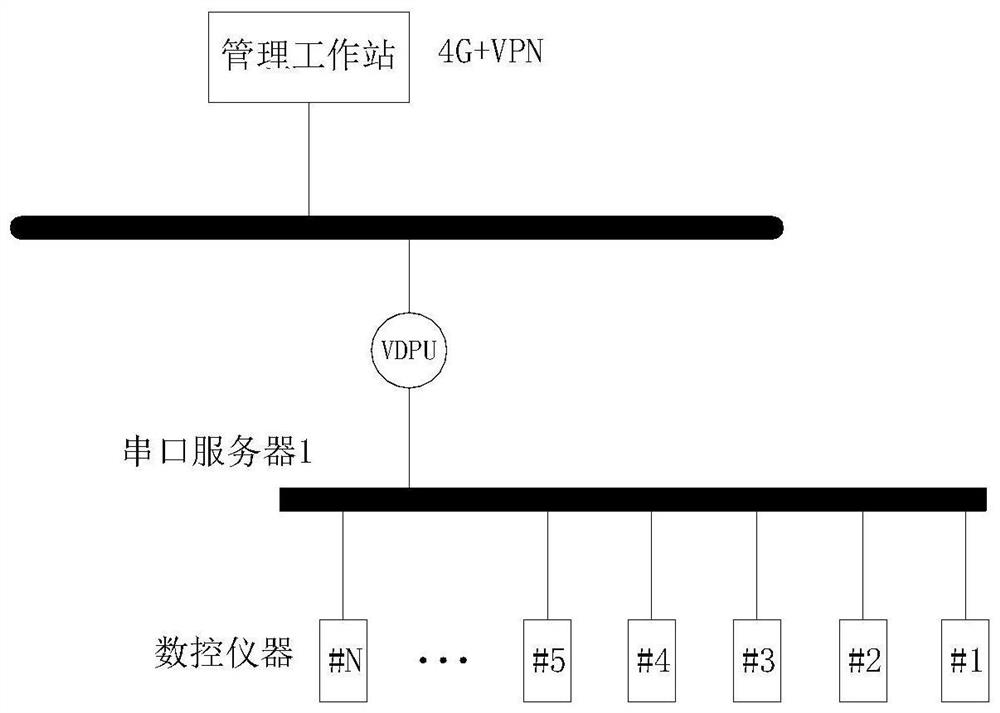
Multivariate time series abnormal mode prediction method and data acquisition monitoring device
ActiveCN111694879AEnables real-time forecastingEasy to monitor in real timeRelational databasesData miningHide markov modelData acquisition
The invention provides a multivariate time series abnormal mode prediction method and a data acquisition monitoring device. The method comprises the steps of obtaining an optimal k value of an MMOD algorithm based on historical data according to a natural neighbor principle; carrying out online expansion on the MMOD algorithm to achieve online identification of a multivariate time sequence abnormal mode; and according to an incremental fuzzy adaptive clustering algorithm, achieving conversion from the multivariate time series sub-sequence to the observation sequence, constructing a hidden Markov model based on a Baum-Welch algorithm and all the observation sequences, and achieving online prediction of the multivariate time sequence abnormal mode based on the constructed hidden Markov model. Through the multivariate time series data acquisition system of the cloud platform, related data needing to be mined can be better acquired, and real-time prediction of the abnormal mode of the multivariate time series can be achieved by utilizing an online density difference anomaly detection algorithm and a Markov prediction model algorithm. A monitoring system APP is constructed, so that real-time monitoring is facilitated.
Owner:UNIV OF SCI & TECH BEIJING
SAM weighted KEST hyperspectral anomaly detection algorithm
The invention discloses an SAM weighted KEST hyperspectral anomaly detection algorithm (SKEST). The method includes the steps: firstly, deducing the SKEST algorithm; and secondly, calculating the SKEST value of each image element in a hyperspectral image by the aid of a double-rectangular window, performing threshold segmentation and detecting abnormal points. In the SKEST algorithm, based on the KEST (kernel Eigen space separation transformation) algorithm, a weight factor is introduced into each sample in a DCOR (difference correlation) matrix of a high-dimensional Eigen space detection point neighborhood by means of SAM (spectral angle mapper) measurement, and the weight factor of each sample depends on an included angle between the spectral vector of the sample and a data center of the detection window. Therefore, abnormal data in the detection window are suppressed, the contribution of main compositional data is highlighted, and the DCOR matrix can more effectively describe target and background data distribution difference. Besides, the SAM is robust to spectral energy, and by the aid of a radial basis function, the SKEST algorithm considers both spectral energy difference and spectral curve shape difference of signals, and accordingly conforms to hyperspectral data characteristics more effectively.
Owner:NANJING UNIV OF SCI & TECH
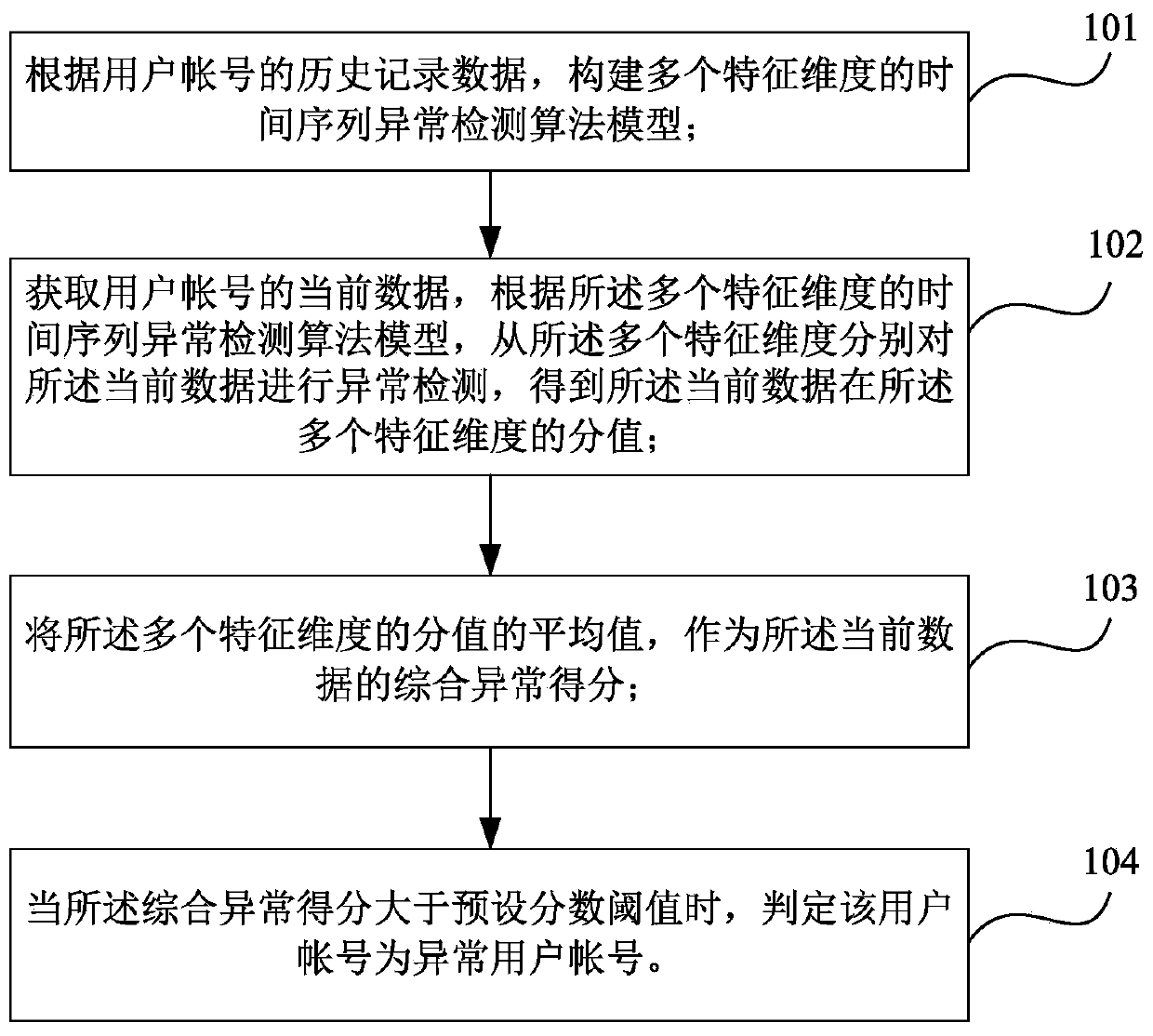
A user account abnormity detection method and device based on time sequence characteristics
ActiveCN109818942AGood explainabilityImprove detection accuracyData switching networksFeature DimensionFeature set
The embodiment of the invention provides a user account abnormity detection method based on time sequence characteristics, and the method comprises the steps: building a time sequence abnormity detection algorithm model with a plurality of characteristic dimensions according to the historical record data of a user account; Obtaining current data of a user account, and according to the plurality ofanomaly detection algorithm models, respectively carrying out anomaly detection on the current data from the plurality of feature dimensions to obtain scores of the current data in the plurality of feature dimensions; Taking the average value of the scores of the plurality of feature dimensions as a comprehensive abnormal score of the current data; And when the comprehensive abnormal score is greater than a preset score threshold, judging that the user account is an abnormal user account. According to the technical scheme, dynamic behavior changes of a user are captured through user account evaluation based on a time sequence model and abnormal feature set matching based on association rule analysis, and the accuracy and interpretability of abnormal account detection in practical application are improved.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
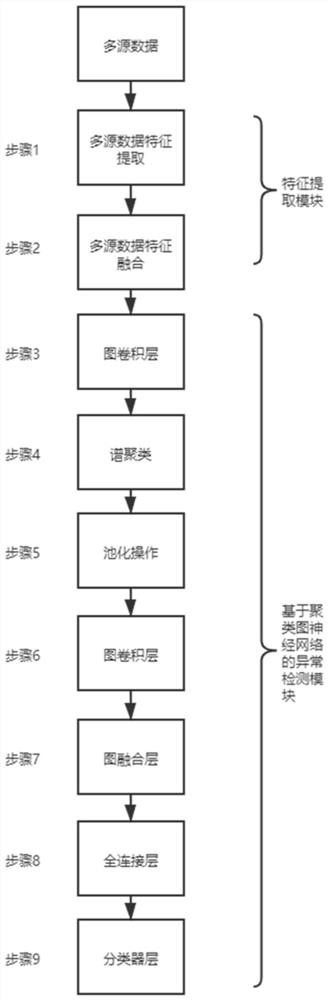
Network security anomaly detection algorithm and detection system based on clustering graph neural network
ActiveCN112165496ACharacter and pattern recognitionNeural architecturesPattern recognitionCluster algorithm
The invention discloses a network security anomaly detection algorithm based on a clustering graph neural network. The algorithm comprises the following steps: describing a network topology structureby using a graph model, optimizing node characteristics by using a graph neural network convolution layer, segmenting a graph into a plurality of disjoint sub-graphs by using a graph clustering algorithm, regarding each sub-graph as a node, regarding an adjacency relationship of the sub-graphs as an edge, forming a sub-graph, learning a weight for each node by utilizing a graph attention layer, performing weighted summation on features of all nodes in each sub-graph to form features of the nodes in the sub-graph, and finally judging whether a network is attacked or not by utilizing a full connection layer and a classifier layer. According to the method, a hierarchical graph neural network is constructed, node features in a graph are optimized through a graph convolution layer, local features on the graph are captured through a pooling layer based on a graph clustering algorithm, high-level semantic features are generated, situation features of the whole network are generated through afusion layer, and network situations are classified through a classifier.
Owner:TSINGHUA UNIV
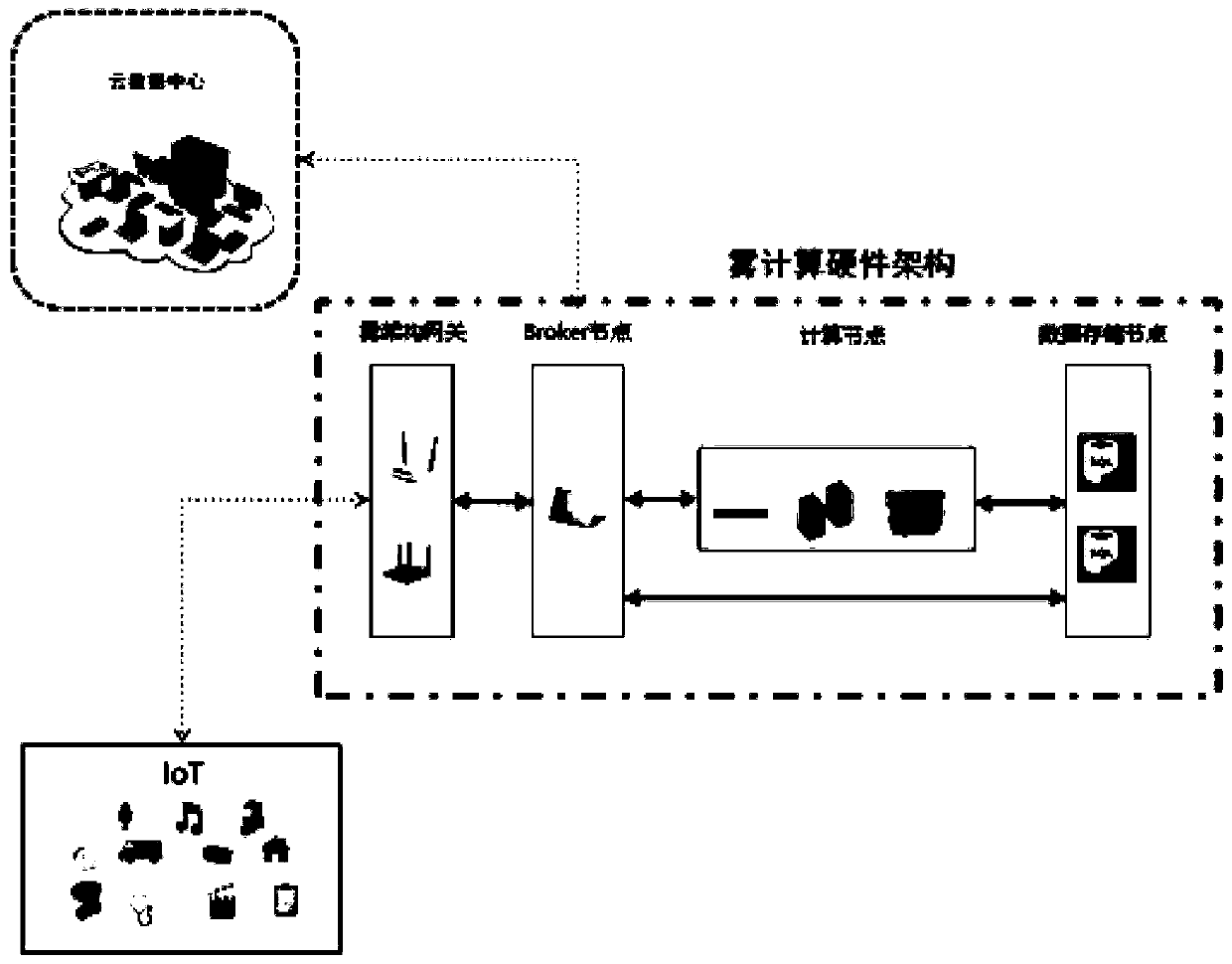
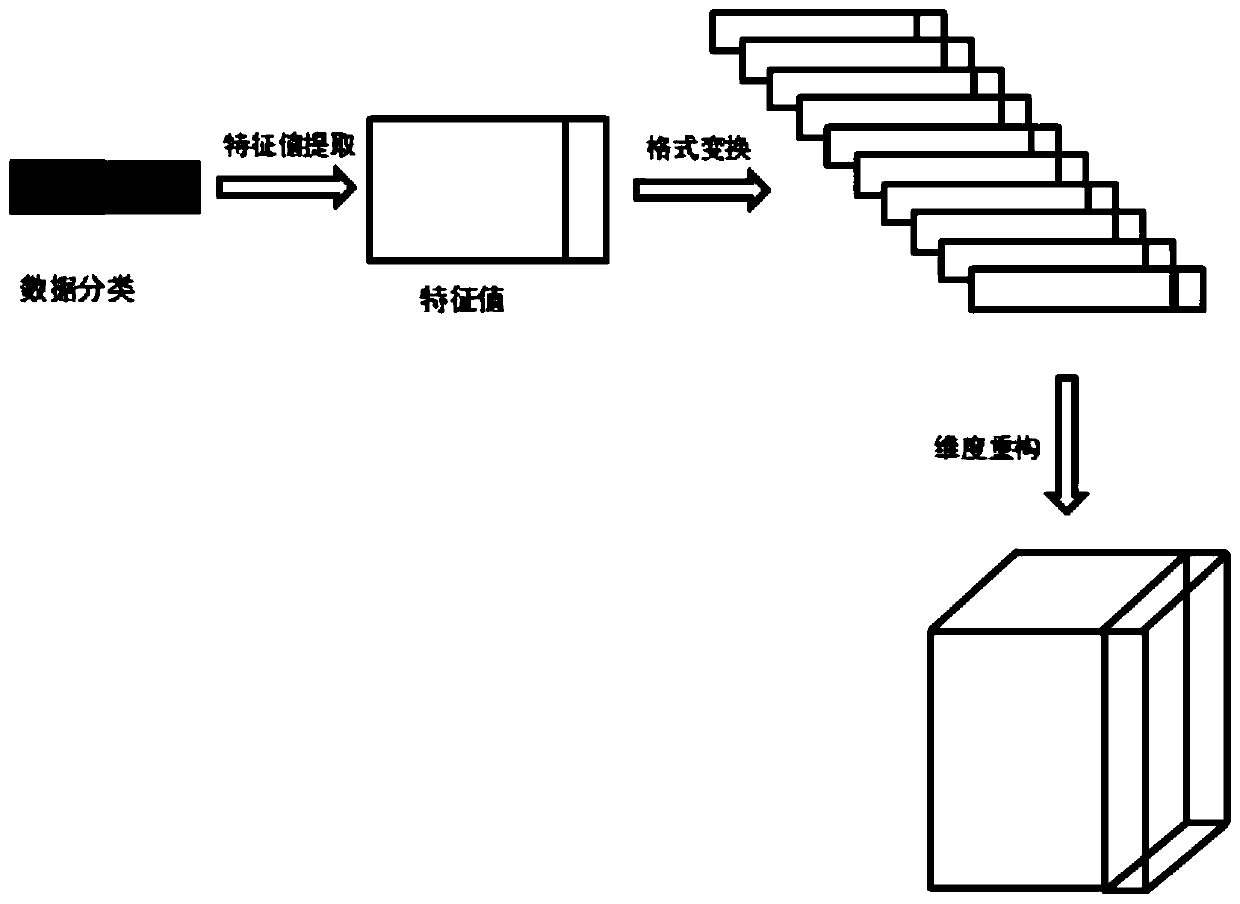
Internet of Things malicious traffic detection method based on fog computing platform
ActiveCN111510433AImprove recognition rateOvercoming delays and other issuesNeural architecturesTransmissionData packAttack
The invention relates to an Internet of Things malicious traffic detection method based on a fog computing platform, and the detection method is operated based on the fog computing platform, and comprises the steps: (1) building an experimental network, and building a feature extraction module which is used for collecting a traffic data packet of IoT equipment under jurisdiction; building a Miraibotnet environment, and obtaining a traffic data packet when a DDoS attack is initiated; (2) performing feature value classification and extraction on the traffic data packet by using a feature extraction module to generate feature data; (3) by a data processing module, performing data dimension reconstruction on the feature data; and (4) building a convolutional neural network on the fog computing node. According to the method, the convolutional neural network anomaly detection algorithm is transplanted to the field of IoT botnets, so that the identification rate of DDoS malicious traffic ofIoT equipment is improved; based on fog computing platform architecture construction, real-time detection of abnormal traffic of IoT equipment under jurisdiction is realized, and consequences of DDoSattacks are reduced.
Owner:SHANDONG UNIV
Prediction method of carbide blade chemical-mechanical polishing surface roughness
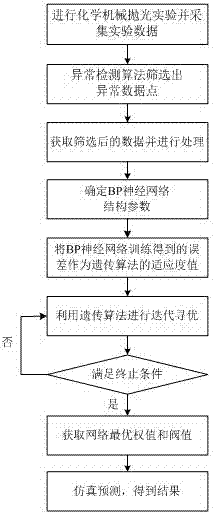
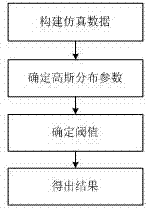
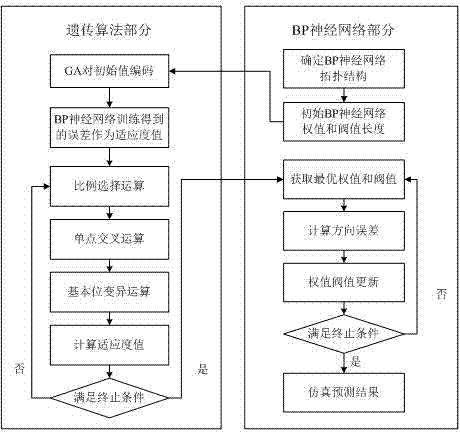
InactiveCN107292051ADecreased prediction accuracyHigh precisionGeometric CADDesign optimisation/simulationAlgorithmGenetic algorithm
The invention discloses a prediction method of carbide blade chemical-mechanical polishing surface roughness. The prediction method comprises the following steps of 1, designing experiment parameters, an experiment scheme and collection of experiment data of chemical-mechanical polishing carbide blades, 2, adopting an anomaly detection algorithm based on the gaussian function to preprocess experiment sample data and 3, constructing a prediction model in which a genetic algorithm optimizes a BP neural network, utilizing the preprocessed experiment sample data to conduct learning training on the prediction model, and thereby obtaining the prediction model of the carbide blade surface roughness under different conditions. According to the prediction method of the carbide blade chemical-mechanical polishing surface roughness, the anomaly detection algorithm based on the gaussian function is used for preprocessing the experiment sample data and eliminating anomaly data groups, then, the threshold value and weight value of the BP neural network are optimized by the genetic algorithm, so that a high-precision surface roughness prediction model is constructed, and the chemical-mechanical polishing efficiency is improved.
Owner:XIANGTAN UNIV
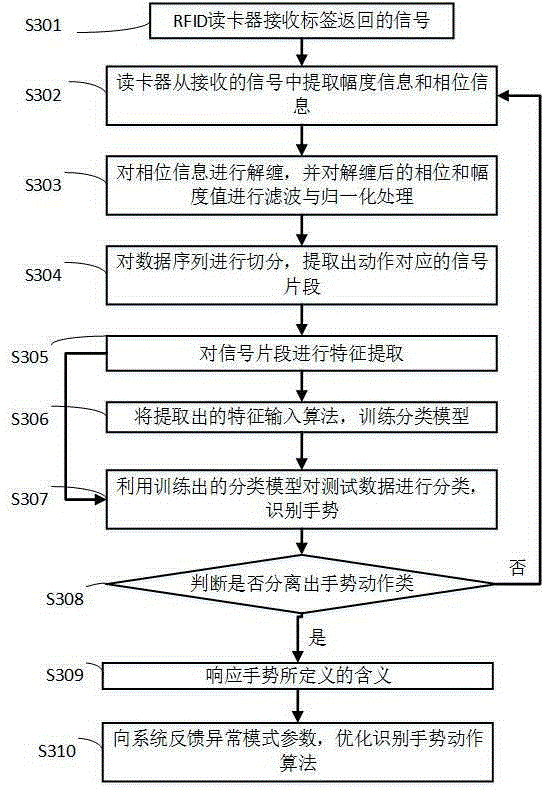
Gesture recognition method and system based on RFID (radio frequency identification devices)
ActiveCN105353881AAvoid inconvenienceHigh popularityInput/output for user-computer interactionSensing record carriersInformation processingTarget–action
The invention relates to an information processing technology, and discloses a gesture recognition system based on RFID (radio frequency identification devices). The gesture recognition system comprises an RFID signal information acquisition module used for receiving a wireless signal from a reader by a transponder, and preprocessing an RFID signal; an anomaly detection and extraction module used for using an anomaly detection algorithm to recognize and extract abnormal changes of RFID signal state information; an action recognition module used for recognizing a gesture action by taking an abnormal segment caused by the gesture action as a target action class based on a matching algorithm; and a response recognition module used for executing a meaning that the gesture represents when recognizing a target gesture action. The gesture recognition method and system based on the RFID provided by the invention have the following beneficial effects that the universality is very high, and people subjected to detection do not need to carry any extra equipment, so that the inconvenience caused by carrying detection equipment by people subjected to detection can be avoided.
Owner:SHENZHEN UNIV
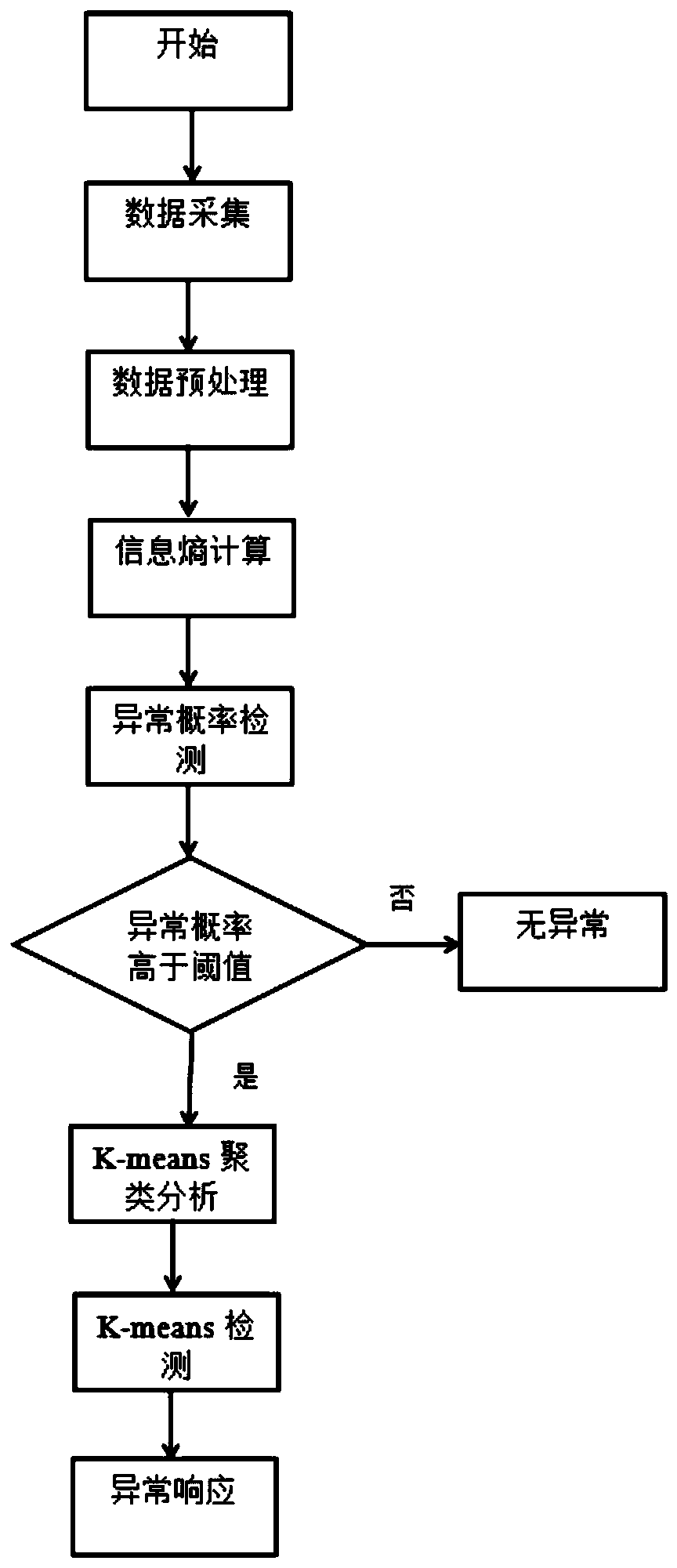
A Correction Method for Data Abnormality in Atmospheric Monitoring System
PendingCN110895526AReduce resource consumptionImprove accuracyRelational databasesCharacter and pattern recognitionFeature vectorAlgorithm
The invention discloses a data anomaly correction method in an atmospheric monitoring system. The method uses a minimum-maximum normalization method to preprocess feature data, and then combines the historical data of the node with the first-level anomaly detection algorithm based on information entropy to calculate The abnormal probability of the sensor node is obtained. When the abnormal probability of the node is higher than the threshold, the second level of abnormal detection algorithm based on K-means is executed to obtain the feature vector of the adjacent nodes of the node, and the clustering of the node and the adjacent nodes is performed. , calculate the distance between the node feature vector and the cluster center based on the clustering results, and judge whether the sensor node is normal or not. The method of the invention can detect the data collected by the sensor, and can also detect the abnormality occurring in the data transmission path of the atmospheric monitoring system, and can improve the data accuracy of the atmospheric monitoring system.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
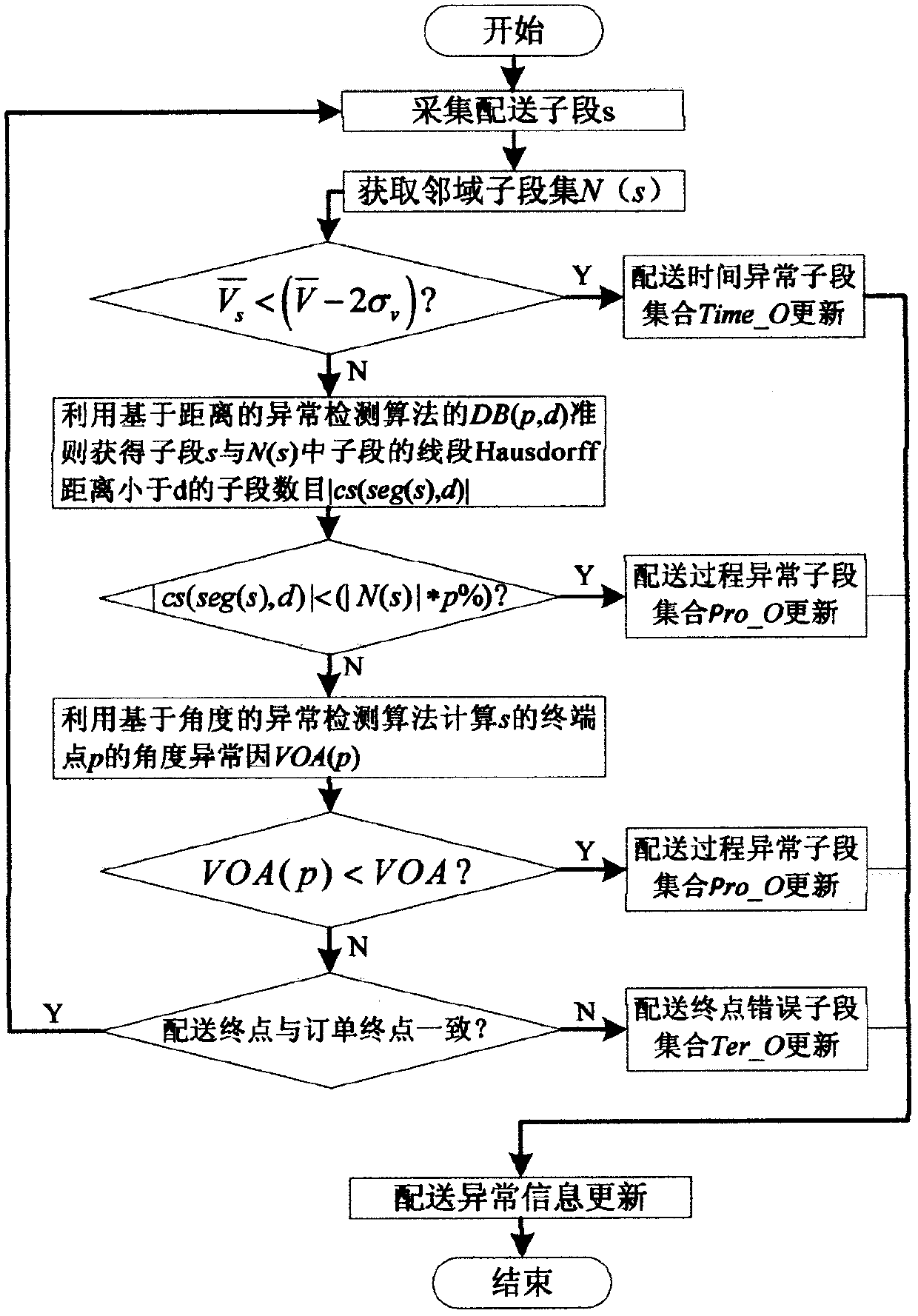
Express and logistics distribution anomaly detection method
ActiveCN107153931AAccurately obtain distance outlier factor valuesAccurately obtain angular outlier factor valuesLogisticsLogistics managementTime delays
An express and logistics distribution anomaly detection method is used to quickly and effectively discover the abnormal distribution conditions of delivery time delay, process error (detour), end point error (non-delivery of the correct destination) and so on in the distribution process. The method comprises steps of analyzing the multi-attribute characteristic of the express and logistics distribution trajectory data, proposing a method combining ideals of the distance and angle-based anomaly detection algorithms to measure the abnormal degree of each trajectory sub-segment; converting detection of the delivery time delay into detection of the average speed of the delivery process; and detecting the distribution end point error by using the position coordinates, city number, city level and other attributes of the trajectory data. With the method, it is possible to quickly and accurately discover the abnormal distribution of the express and logistics, timely feedback to the logistics enterprise for processing, reduce the economic loss, and create the conditions for improving the competitiveness of the logistics enterprise.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
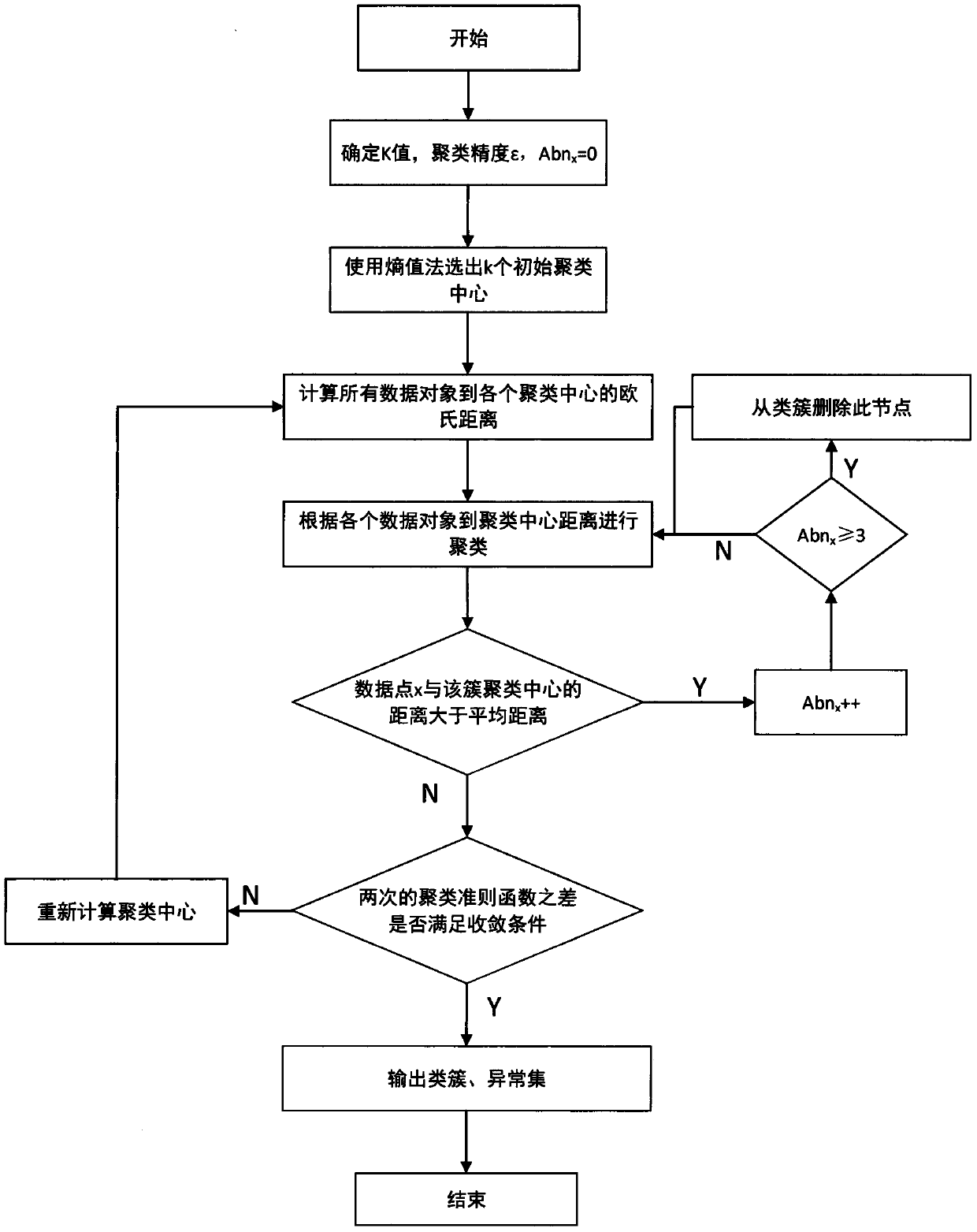
Anomaly detection method based on information entropy clustering
InactiveCN109522926AImprove clustering effectEasy to detectCharacter and pattern recognitionLocal optimumCluster algorithm
The invention discloses an anomaly detection method based on information entropy clustering, which belongs to the field of machine learning and data mining. The anomaly detection algorithm of the invention is based on the idea of the clustering algorithm, and overcomes the shortcomings of the traditional K. Means clustering algorithm randomly selects the initial clustering centers, which easily leads to the clustering results into the local optimal problem. A method based on information entropy to select the initial clustering centers is proposed. The invention provides a method for dividing adata set into data blocks with more than K value, Then the entropy method is used to get the target value function of each data block, and the centroid corresponding to the first k data blocks with the smallest value of the target value function is selected as the initial clustering center. The entropy method is used to ensure the efficiency of selecting the initial clustering center, and the function of anomaly detection is realized in the iterative process of the algorithm. Compared with the traditional K-based clustering algorithm of means, the clustering effect and the anomaly detection ability of the algorithm proposed by the invention are higher than those of the traditional K. Means clustering algorithm. It has certain practical significance.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Electric power data parallelization anomaly detection method based on MapReduce
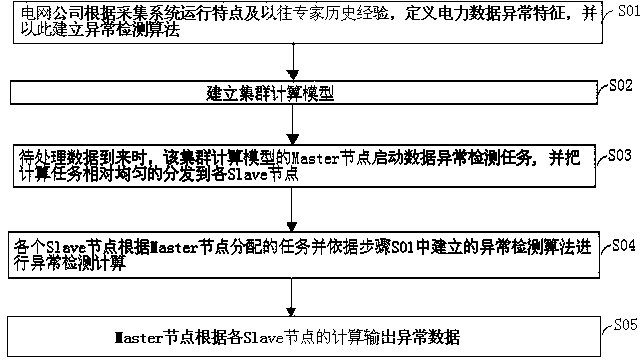
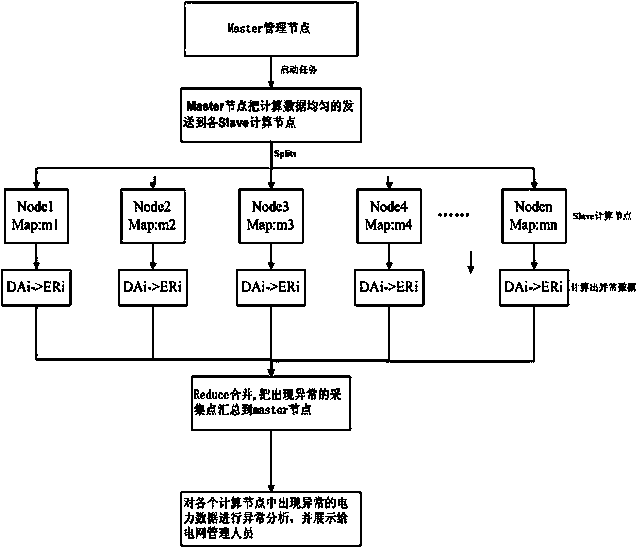
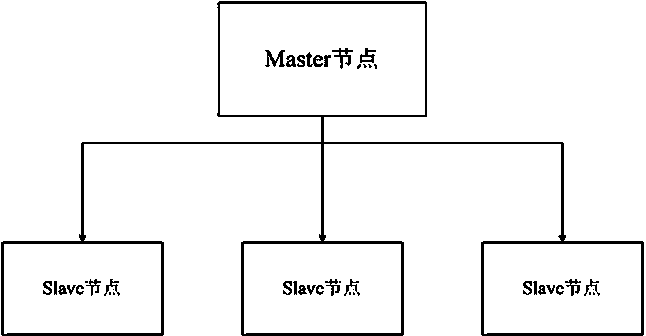
InactiveCN103761685AHealthy and stable operationHigh speedData processing applicationsSystems intergating technologiesNODALPower grid
The invention relates to an electric power data parallelization anomaly detection method based on a MapReduce. The method comprises the following steps that first, electric power data anomaly characteristics are defined by a grid company according to the operation feature of an acquisition system and expert historical experience before, and accordingly an anomaly detection algorithm is established; second, a cluster calculation model is established; third, when processing data arrive, a Master node of the cluster calculation model starts a data anomaly detection task and distributes the calculation task to all Slave nodes in a relatively even mode; fourth, all the Slave nodes conduct anomaly detection calculation according to the task distributed by the Master node and the anomaly detection algorithm established in the step S01; fifth, the Master node outputs abnormal data according to the calculation of all the Slave nodes. By means of the electric power data parallelization anomaly detection method based on the MapReduce, the problem that the calculating and analyzing efficiency is low under the background of a huge quantity of electric power data in the prior art can be solved, and a forceful guarantee is provided for improving power grid efficiency and reducing loss.
Owner:STATE GRID CORP OF CHINA +4
Transformer substation environment anomaly detection system, method and device
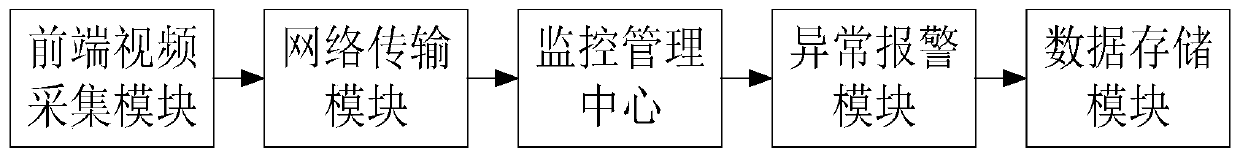
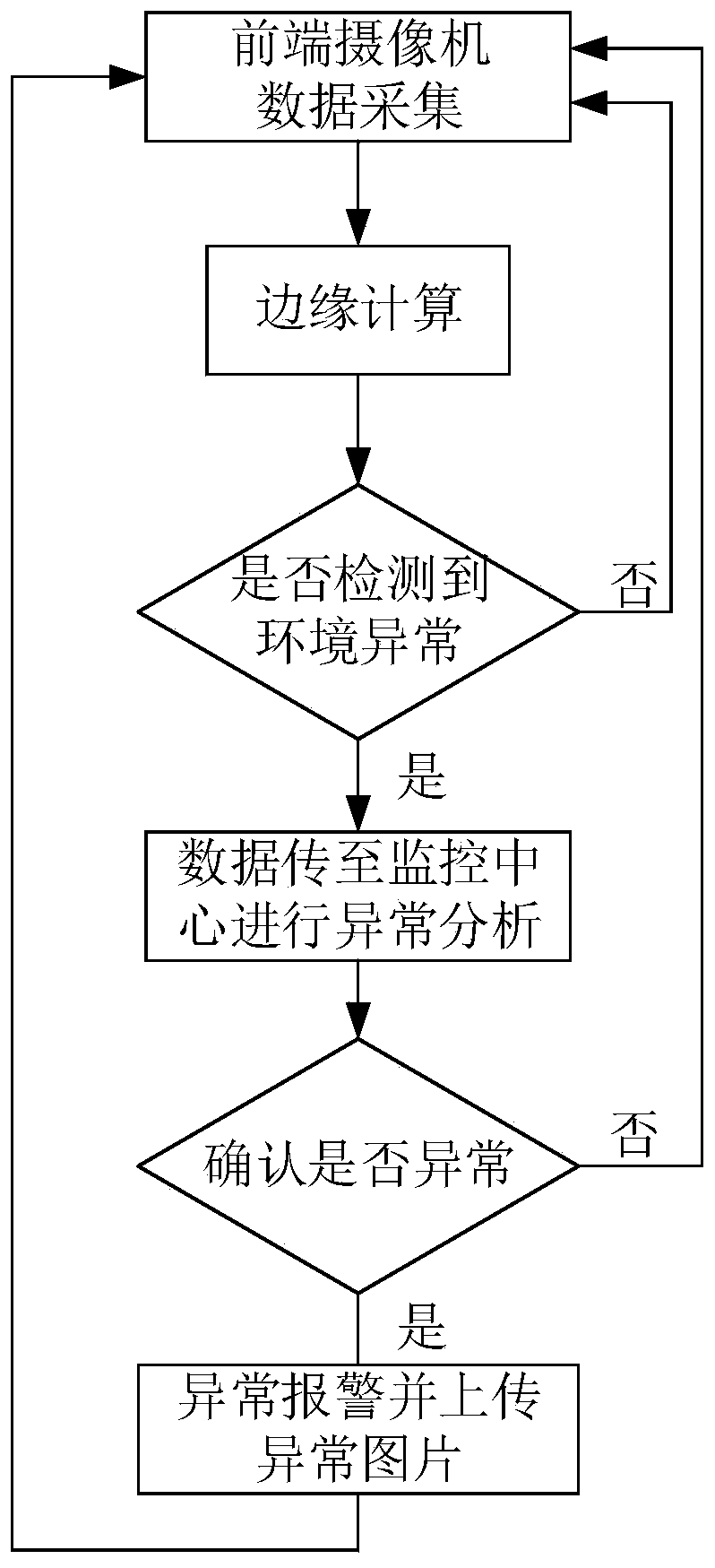
PendingCN110351536AEasy transferReduce security risksCharacter and pattern recognitionClosed circuit television systemsTransformerData transmission
The invention discloses a transformer substation environment anomaly detection system, method and device. The transformer substation environment anomaly detection system comprises a front-end video acquisition module, a network transmission module, a monitoring management center, an anomaly alarm module and a data storage module, wherein the front-end video acquisition module comprises a network camera with an intelligent detection function, an intelligent algorithm module is integrated in the network camera, the intelligent algorithm module adopts an unsupervised anomaly detection algorithm based on generative adversarial learning, and the intelligent algorithm module is used for quickly detecting the anomaly of the surrounding environment of the equipment. According to the invention, thenetwork camera with an intelligent detection function is adopted to carry out anomaly detection on the collected environment information, and only picture information which may have anomaly is output, so that data transmission is facilitated. Compared with a traditional abnormal target detection algorithm, the method has better robustness and adaptability, has the advantages of being uninterrupted and timely, reduces the probability of missed detection and untimely discovery of manual monitoring, and reduces the potential safety hazard of a transformer substation.
Owner:SHENZHEN JIANGXING INTELLIGENCE INC
System for Detecting Image Abnormalities
An image capture system for capturing images of an object, the image capture system comprising a moving platform such as an airplane, one or more image capture devices mounted to the moving platform, and a detection computer. The image capture device has a sensor for capturing an image. The detection computer executes an abnormality detection algorithm for detecting an abnormality in an image immediately after the image is captured and then automatically and immediately causing a re-shoot of the image. Alternatively, the detection computer sends a signal to the flight management software executed on a computer system to automatically schedule a re-shoot of the image. When the moving platform is an airplane, the detection computer schedules a re-shoot of the image such that the image is retaken before landing the airplane.
Owner:PICTOMETRY INTERNATIONAL CORPORATION
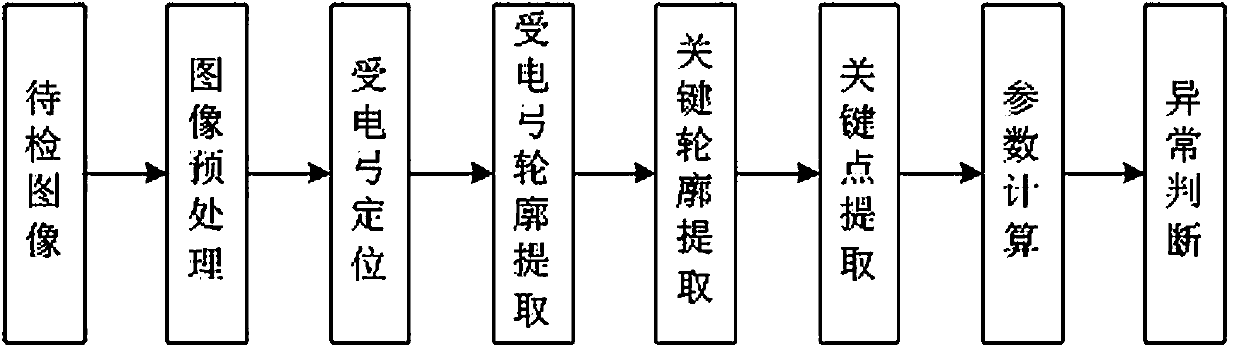
Pantograph structure abnormity detection algorithm based on image processing
PendingCN111260629AMeet the needs of online testingImage enhancementImage analysisImaging processingEngineering
The invention belongs to the technical field of pantograph structure anomaly detection, discloses a pantograph structure abnormity detection algorithm based on image processing. The method comprises an image preprocessing step, a pantograph positioning step, a pantograph contour extraction step, a key contour extraction step, a key point extraction step and a parameter calculation and abnormity judgment step. Positioning a pantograph image contained in the to-be-identified image subjected to the image preprocessing step by adopting an HOG + SVM method; the pantograph structure abnormity detection algorithm provided by the invention has good adaptability to images with complex backgrounds, uneven illumination, noise and the like, is high in algorithm detection accuracy, and improves the detection efficiency of pantograph structure abnormity faults.
Owner:成都地铁运营有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com