Internet of Things malicious traffic detection method based on fog computing platform
A detection method and technology for malicious traffic, applied in the field of network security, can solve problems such as system and network security threats, limited hardware level of deployment framework, and difficulty in detecting malicious traffic.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
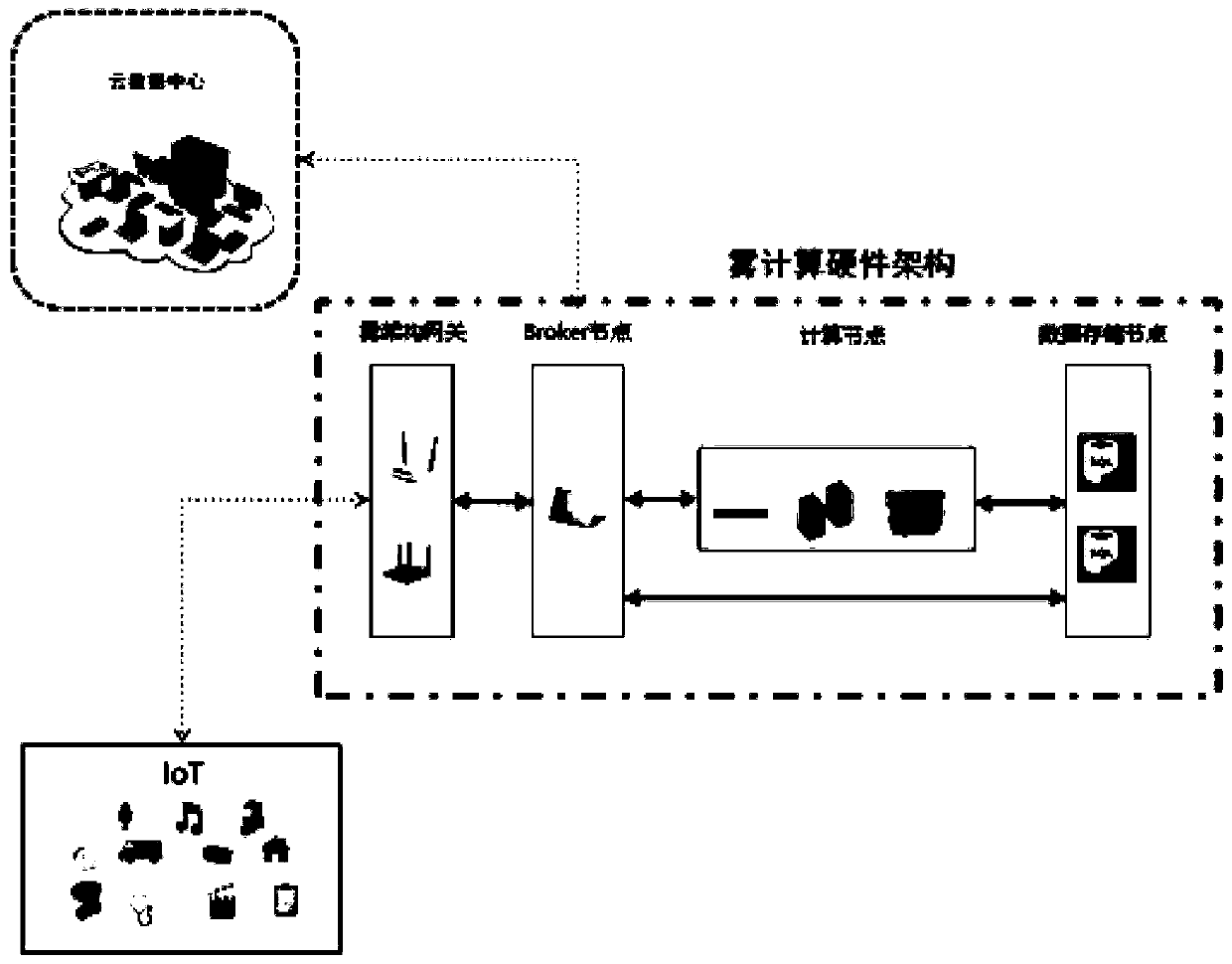
[0065] A method for detecting malicious Internet of Things traffic based on a fog computing platform. The detection method runs on a fog computing platform. The fog computing platform includes several distributed fog computing nodes, such as figure 1 As shown, the fog computing node includes a fog architecture gateway node module, an agent node module, a general computing node module and a data storage node module;
[0066] Fog Gateway Nodes (FGN) serve as a dynamic access point between the IoT device network and the local switch, and between the IoT device network and the Internet;
[0067] Agent node module (Broker Nodes), when the fog architecture gateway node module cannot meet the computing needs of IoT devices under its jurisdiction, the agent node module represents the fog architecture gateway node module, and communicates with the general computing node module or data storage node module or cloud data center Communication; to provide resources required by IoT devices; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com