Alarm and response system for inner-mesh network aggression detection
A network attack, intranet technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of difficult deployment and increased deployment costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] An embodiment of an alarm and response system and implementation method for intranet network attack detection of the present invention will be described in detail below with reference to the accompanying drawings.
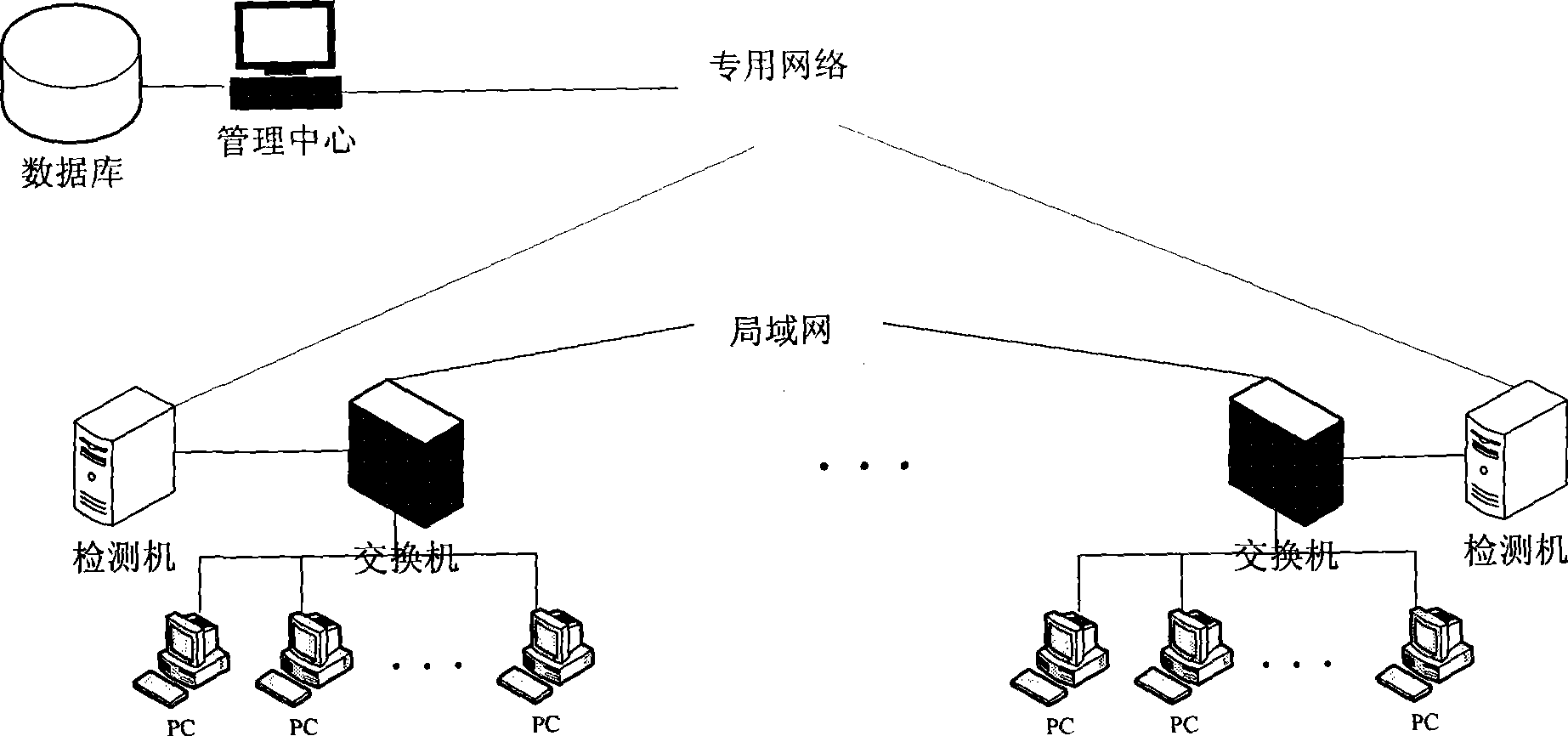
[0058] like figure 1 As shown in , an alarm and response system for intranet network attack detection in the intranet, the system includes a management center, a detection machine and a database.
[0059] The management center runs on a single host, and a single management center can be connected to multiple detectors, each detector is connected to a switch, and each switch can be connected to multiple PCs at the same time.
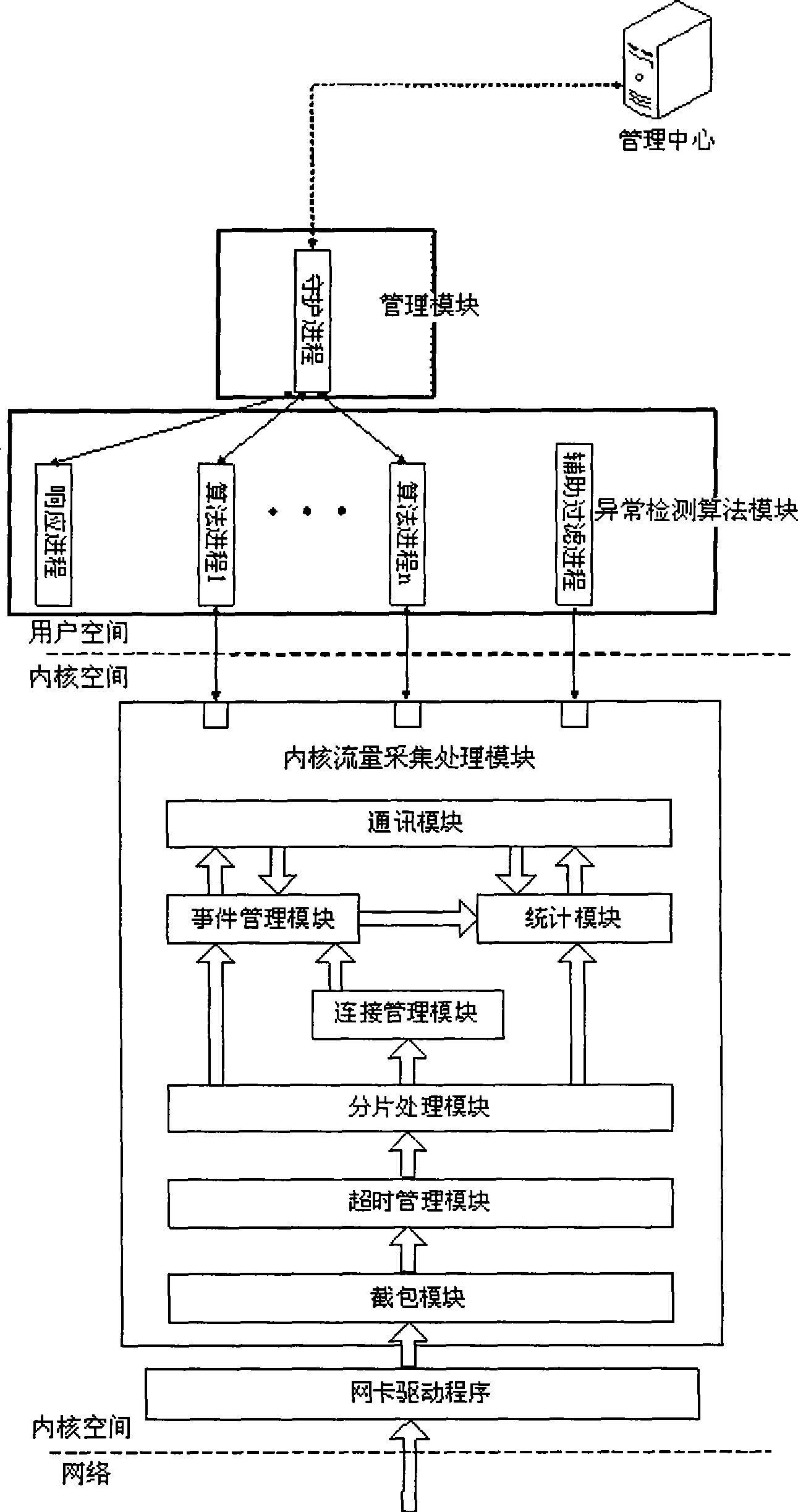
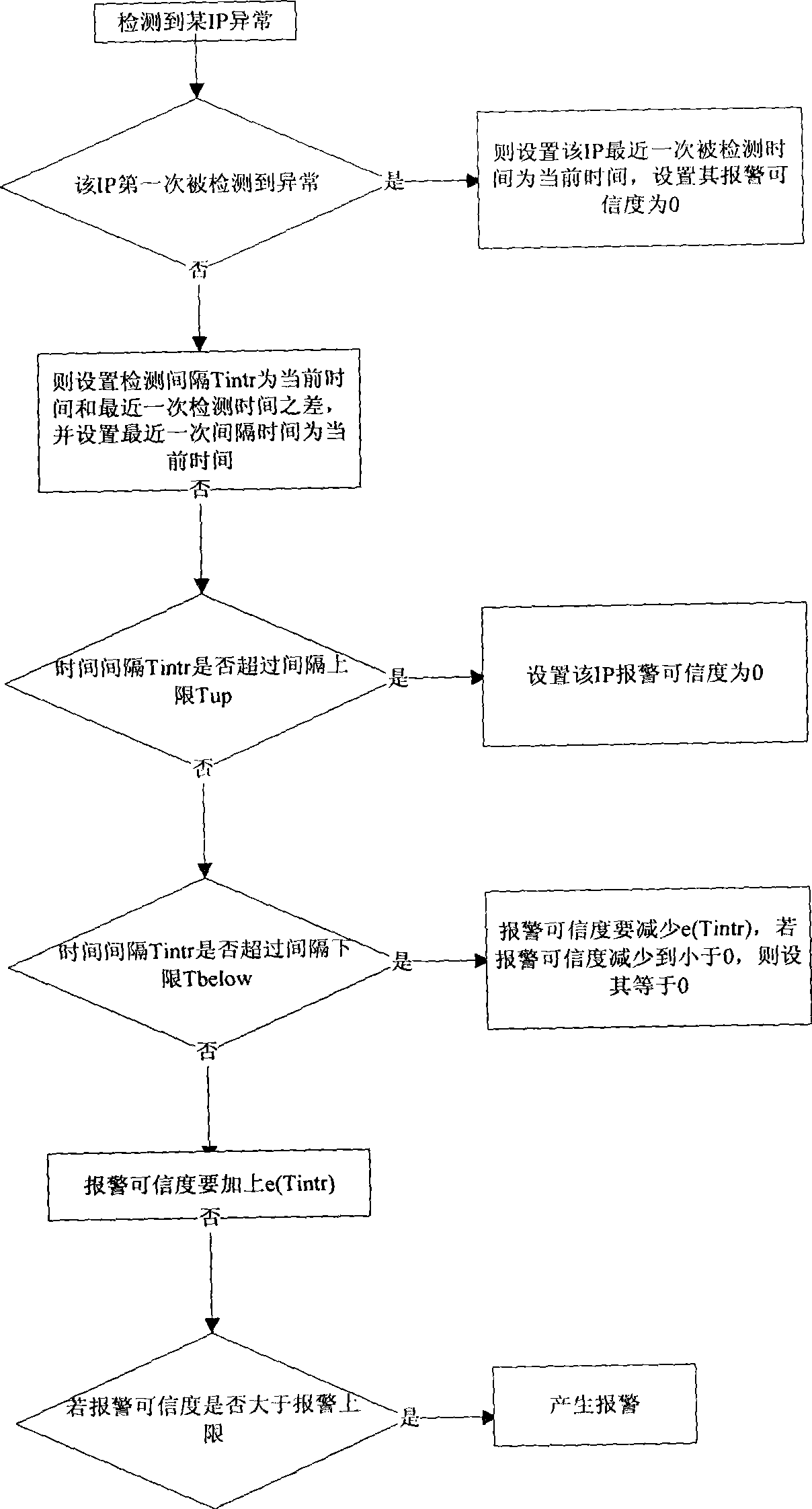
[0060] The management center receives the alarm information sent by the detector from time to time, stores the alarm information in the database of the management center, and displays it through the user interface to provide query and other functions. The management center also stores various configuration information of the detector in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com