Patents
Literature
133results about How to "High false positive rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
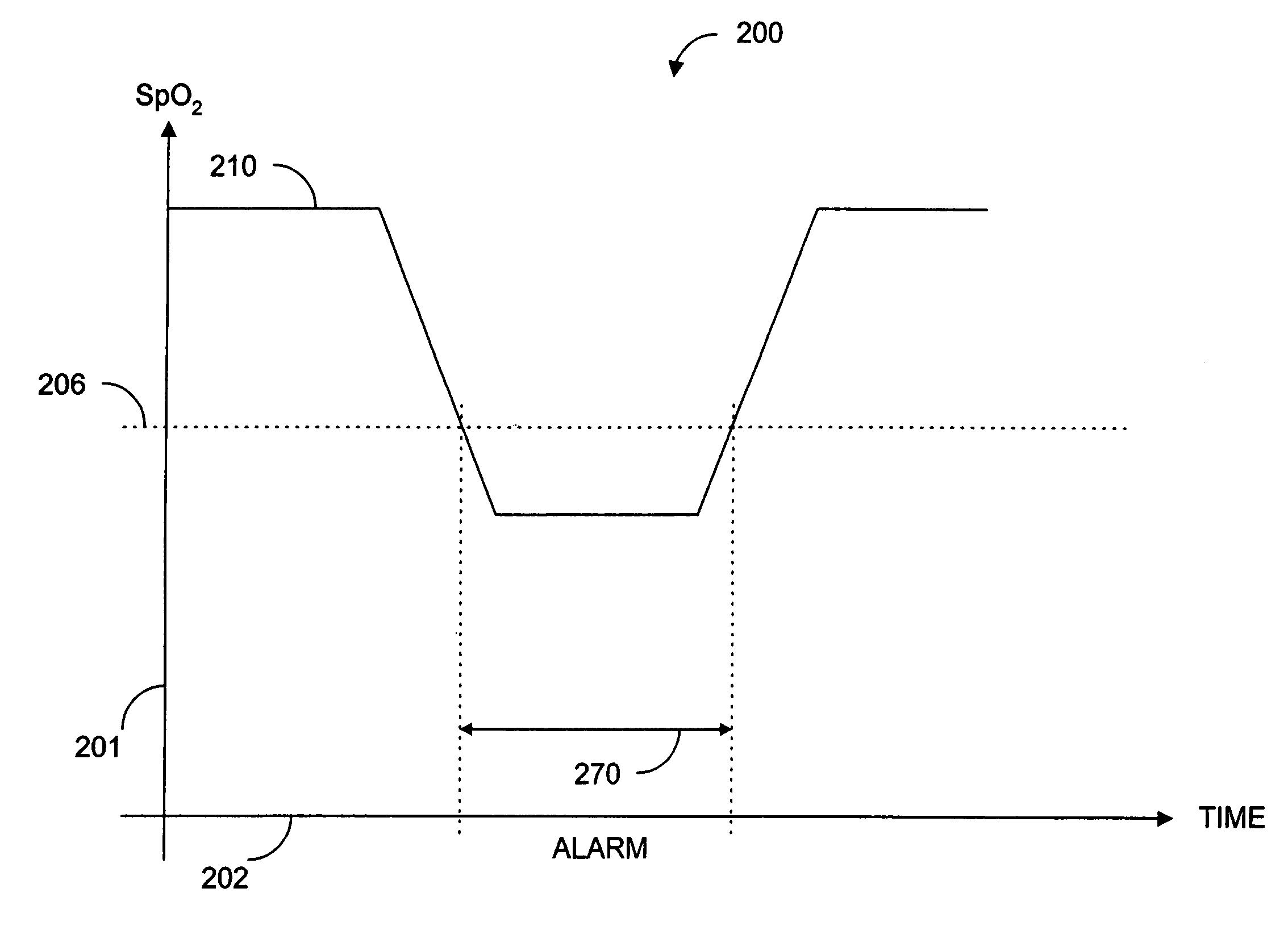
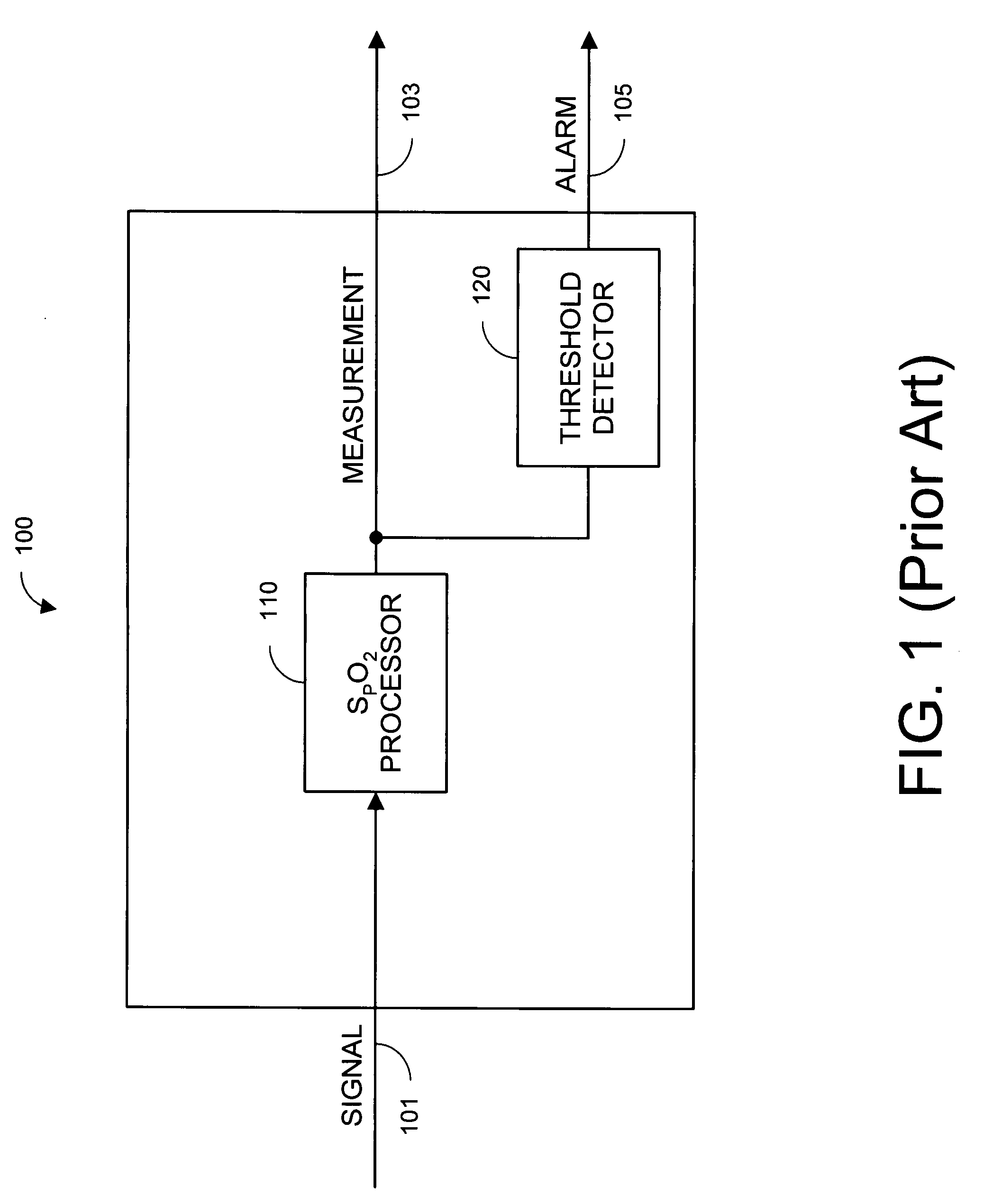
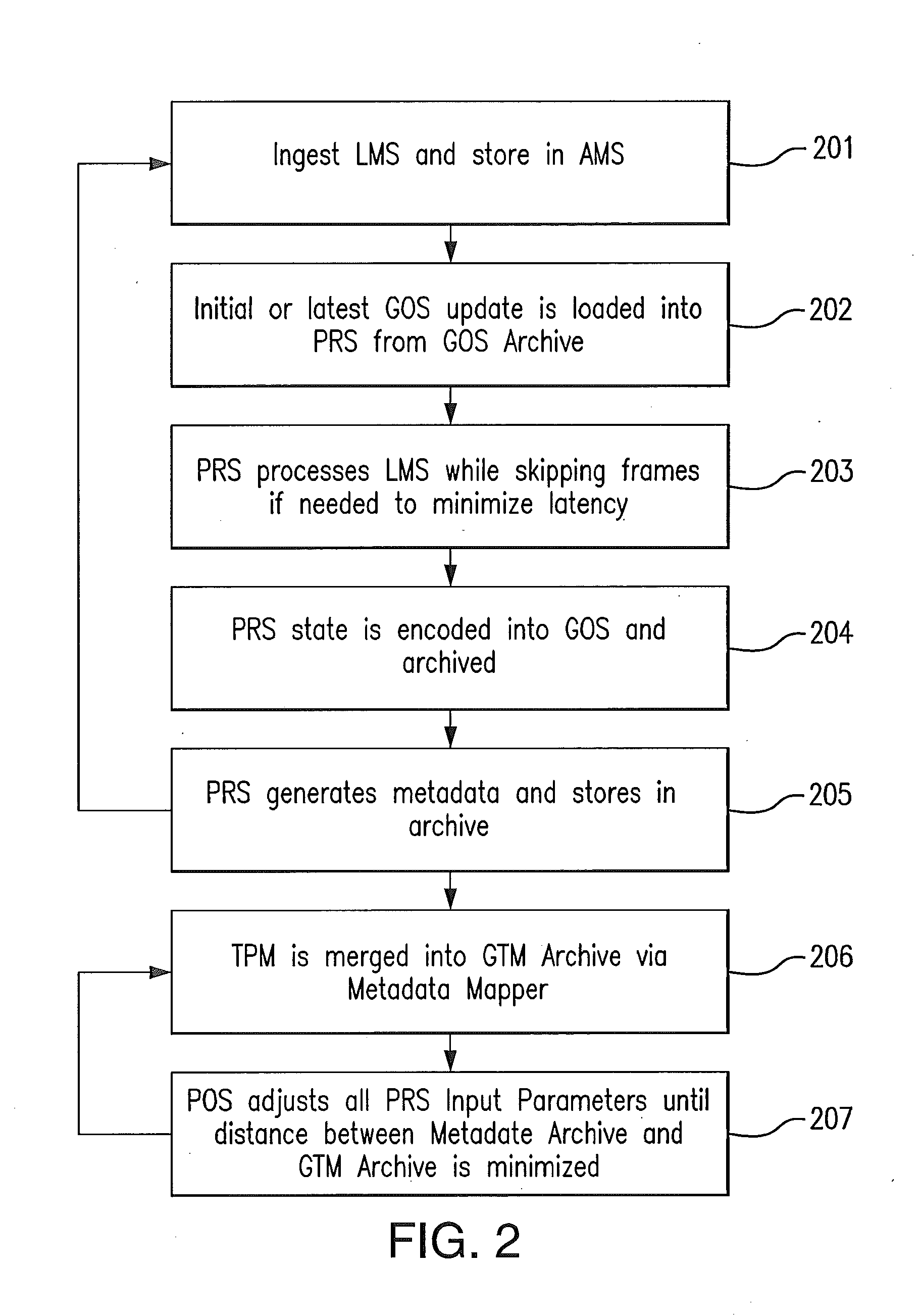
Parallel measurement alarm processor
InactiveUS7030749B2Waste caregiver resourcesReduce false alarm rateComputer controlResistance/reactance/impedenceNormal rangeComputer science
An alarm processor suppresses alarms when a physiological parameter is below a predetermined value but recovering toward a normal range.
Owner:JPMORGAN CHASE BANK NA
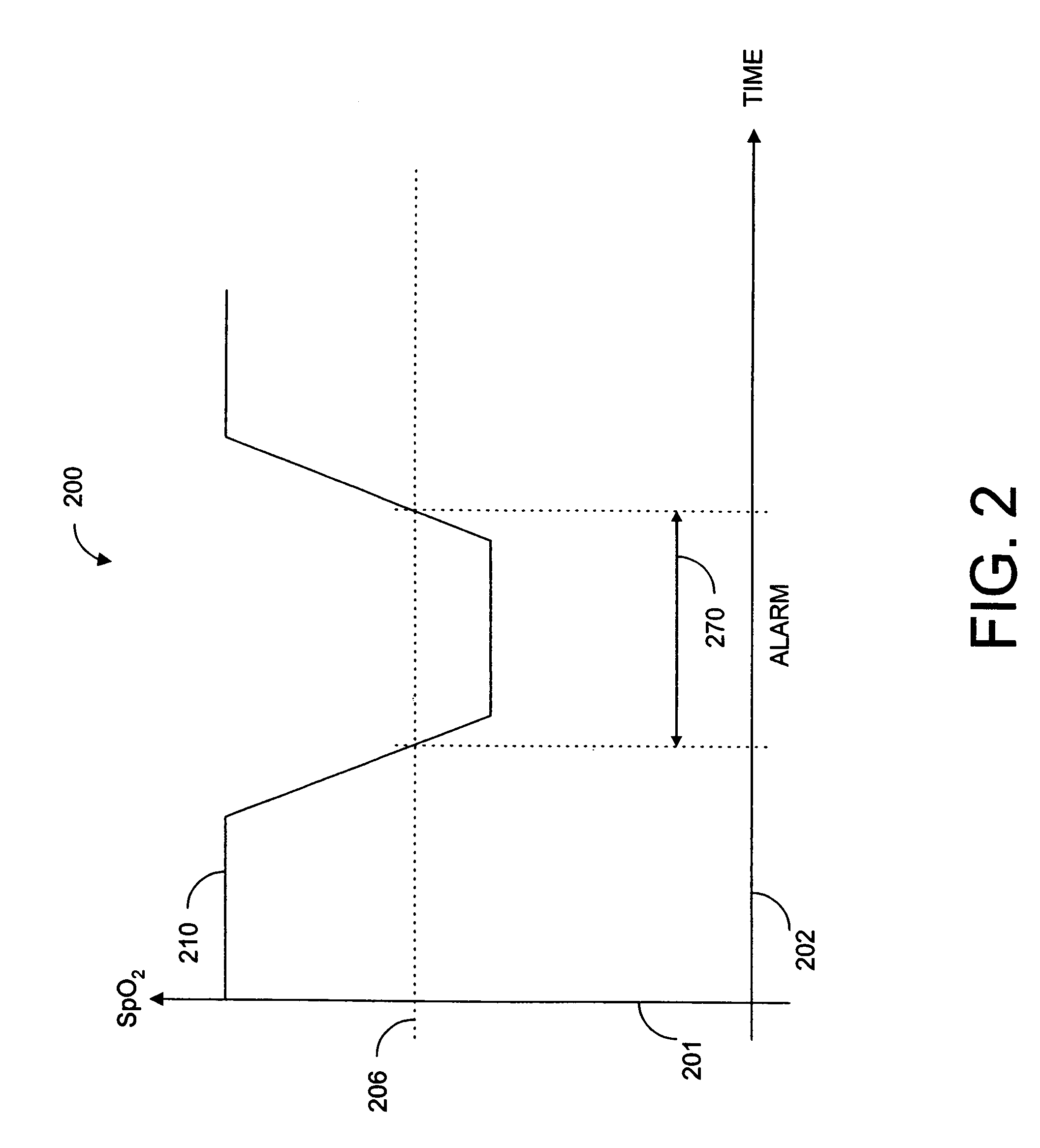
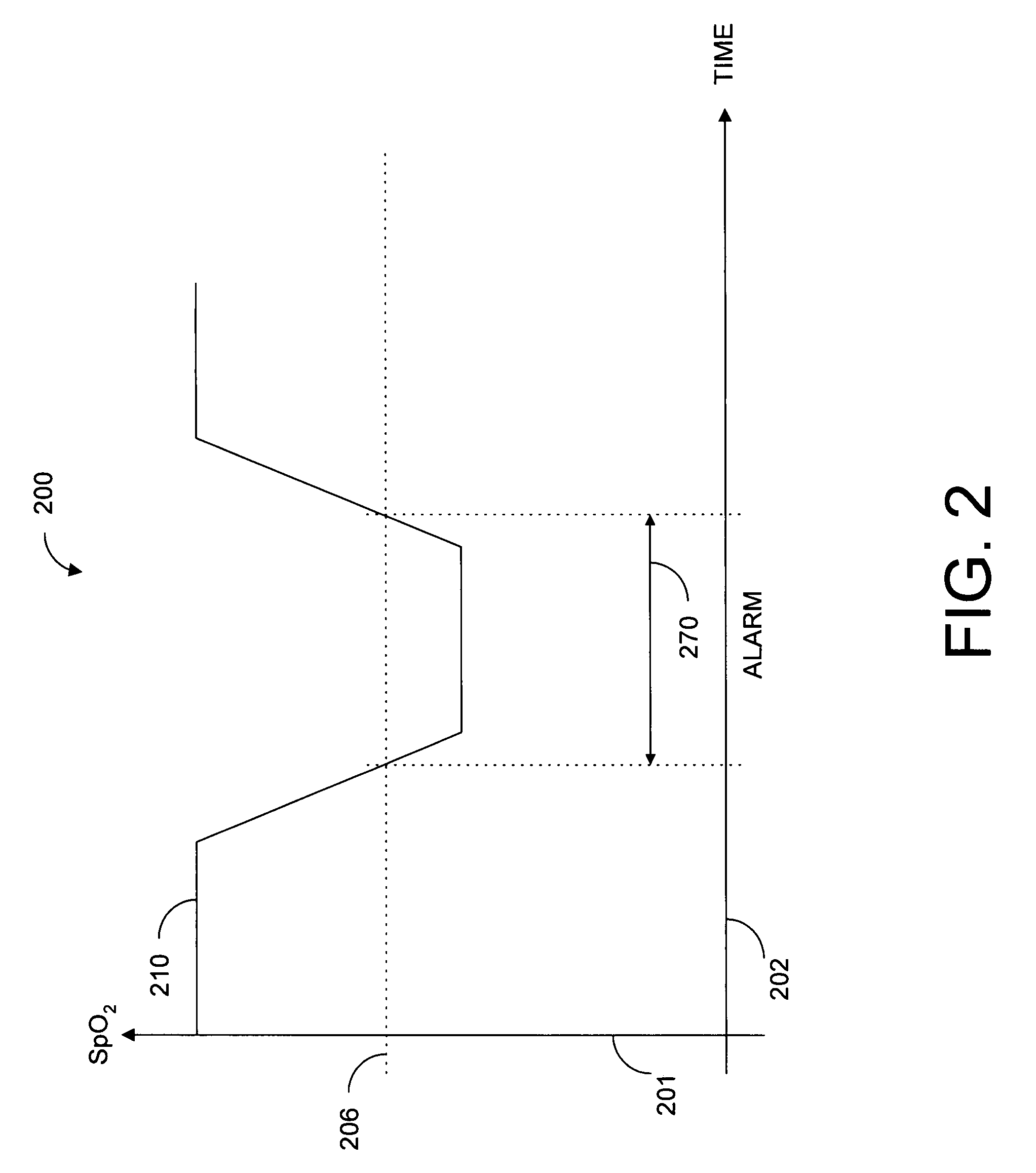
Parallel alarm processor
InactiveUS7355512B1Waste caregiver resourcesReduce false alarm rateEvaluation of blood vesselsSensorsLower limitOxygen Saturation Measurement
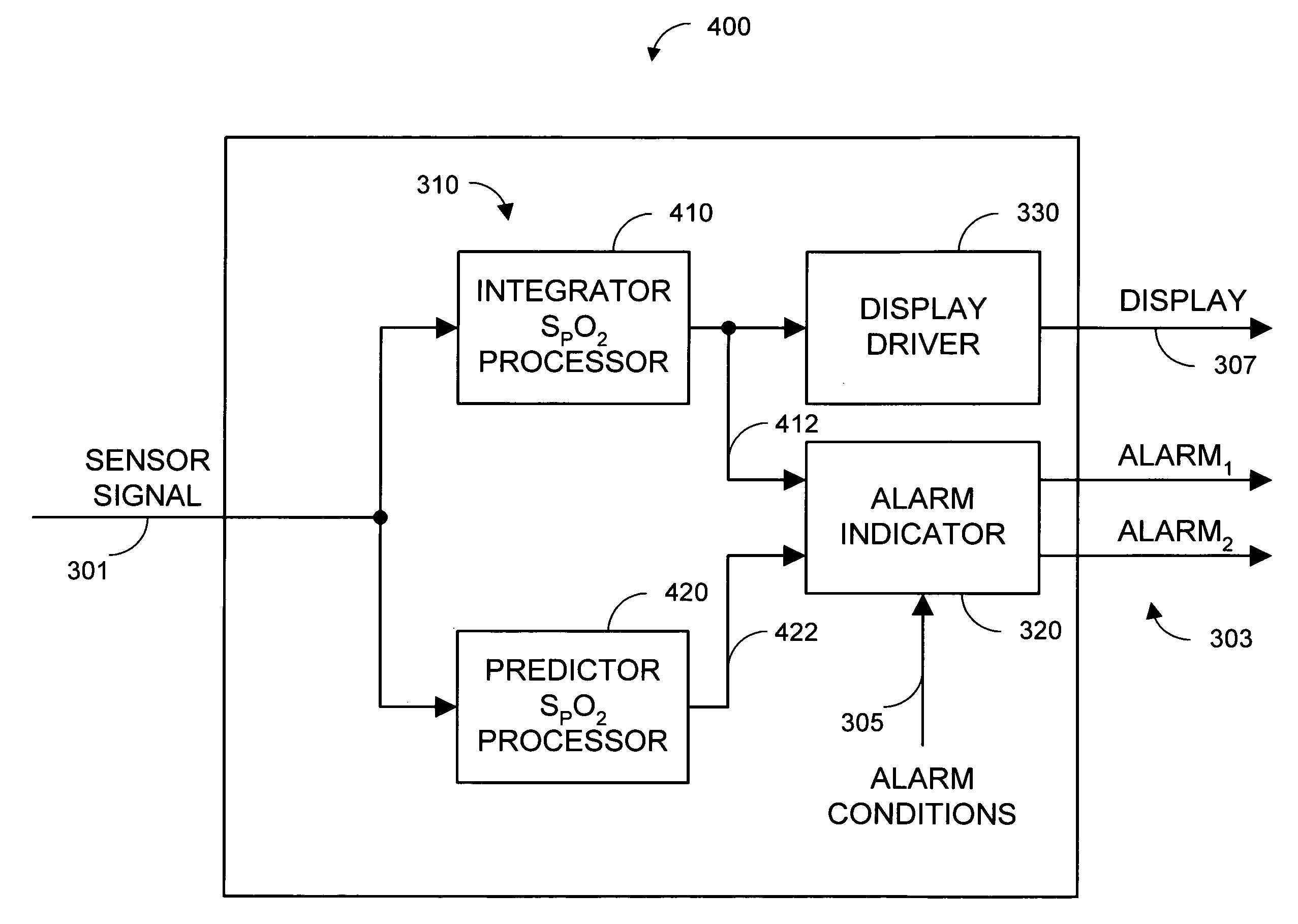
A parallel alarm processor has a threshold detector, a pattern extractor, a predetermined reference pattern, a first alarm and a second alarm. The threshold detector has a first output responsive to relatively long duration oxygen desaturations. The pattern extractor has a second output responsive to relatively short duration oxygen desaturations. The predetermined reference pattern is indicative of a series of intermittent oxygen desaturations. A first alarm is triggered when the first output crosses a lower limit threshold. A second alarm is triggered when the second output matches the predetermined reference pattern. In an embodiment, an integrator inputs smoothed oxygen saturation measurements to the threshold detector, and a predictor inputs predictive oxygen saturation measurements to the pattern extractor.
Owner:JPMORGAN CHASE BANK NA
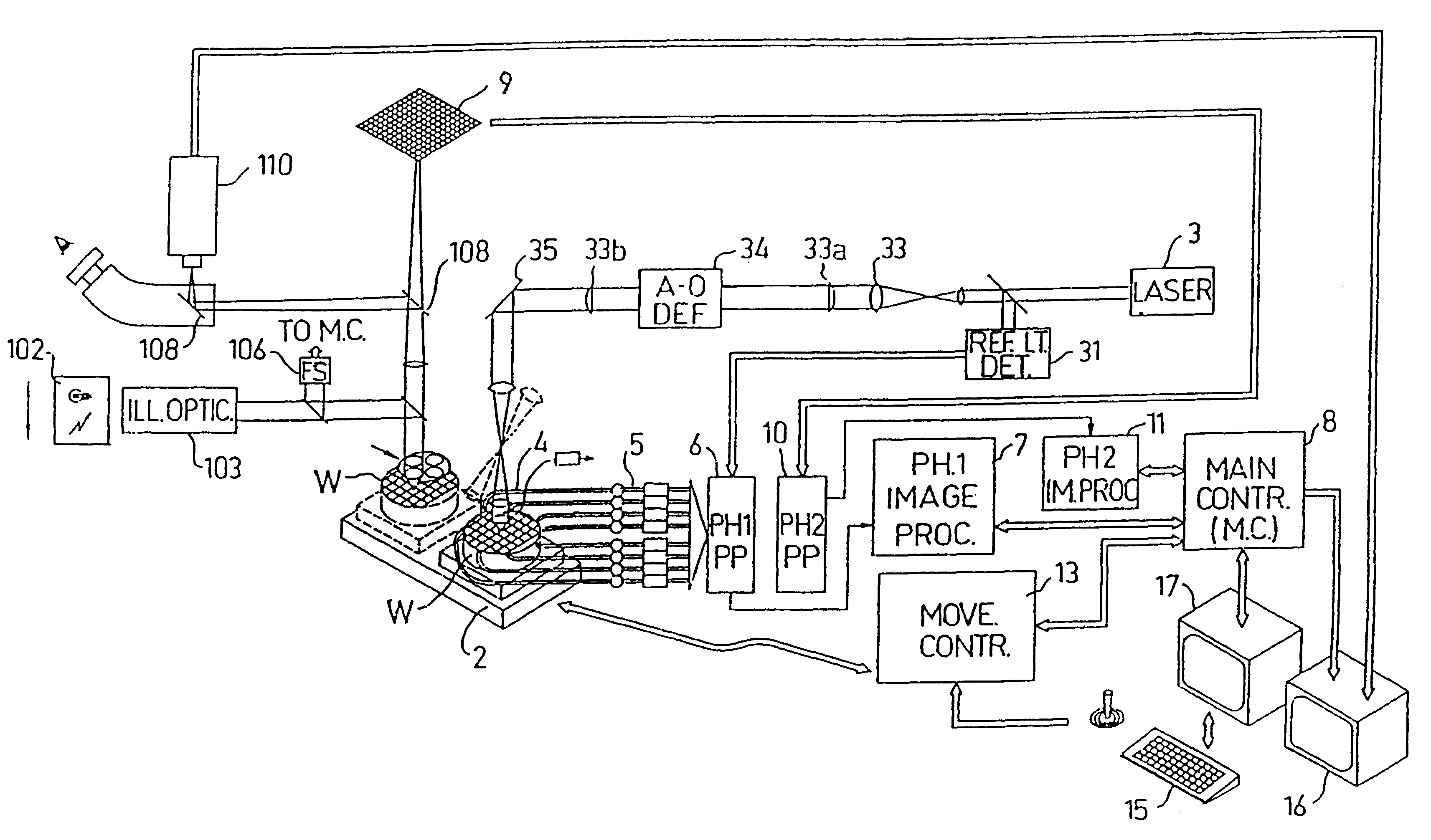
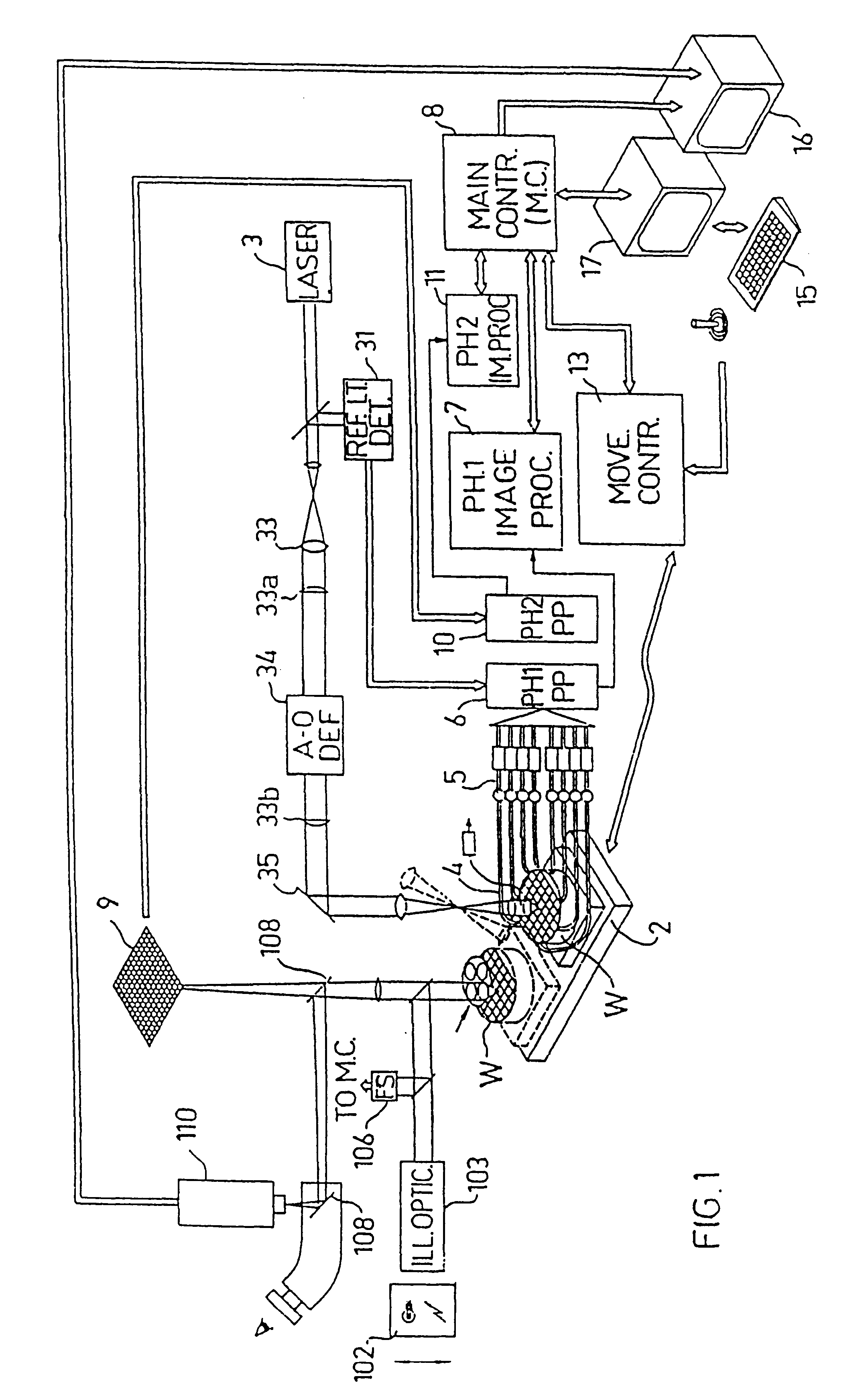
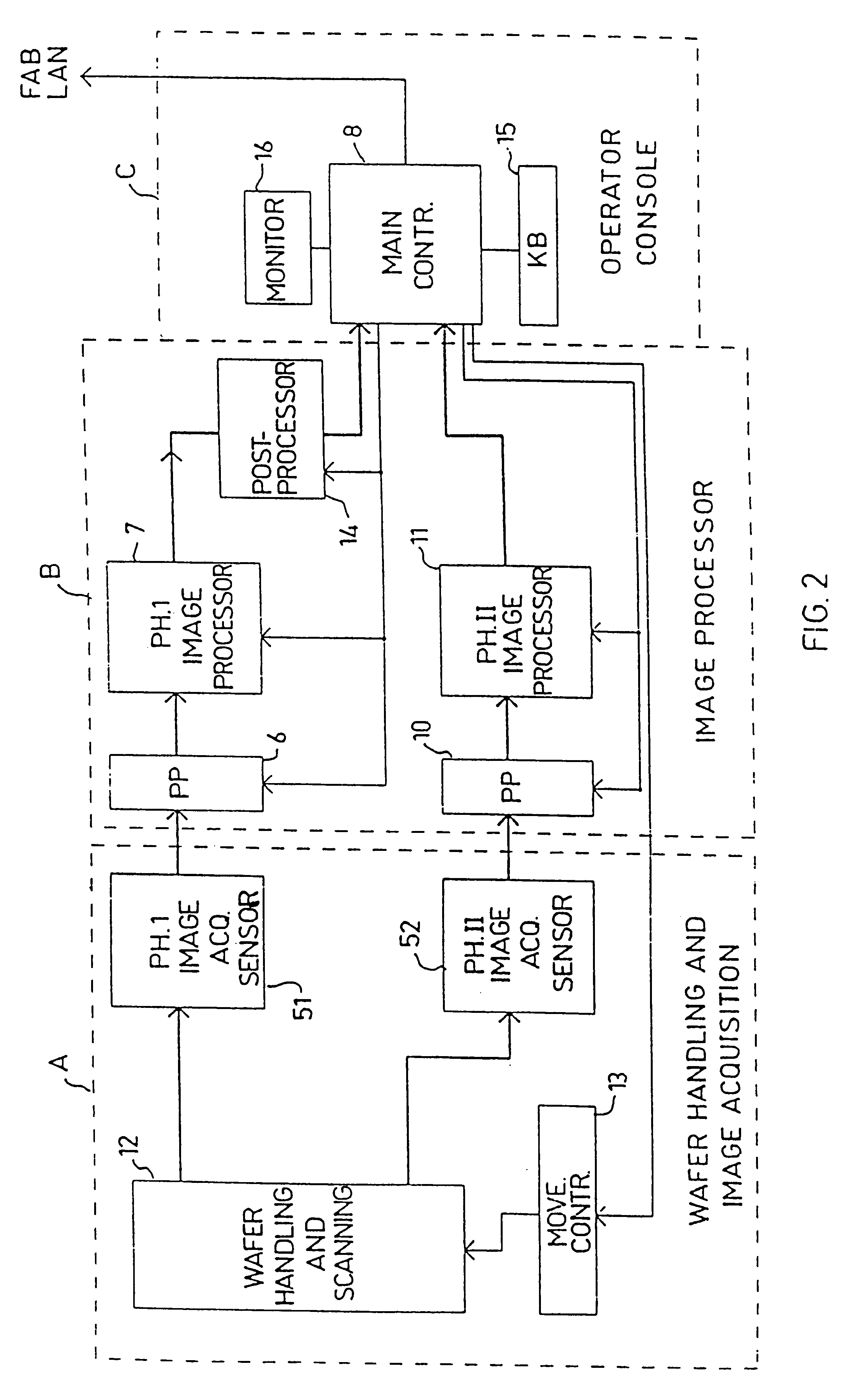
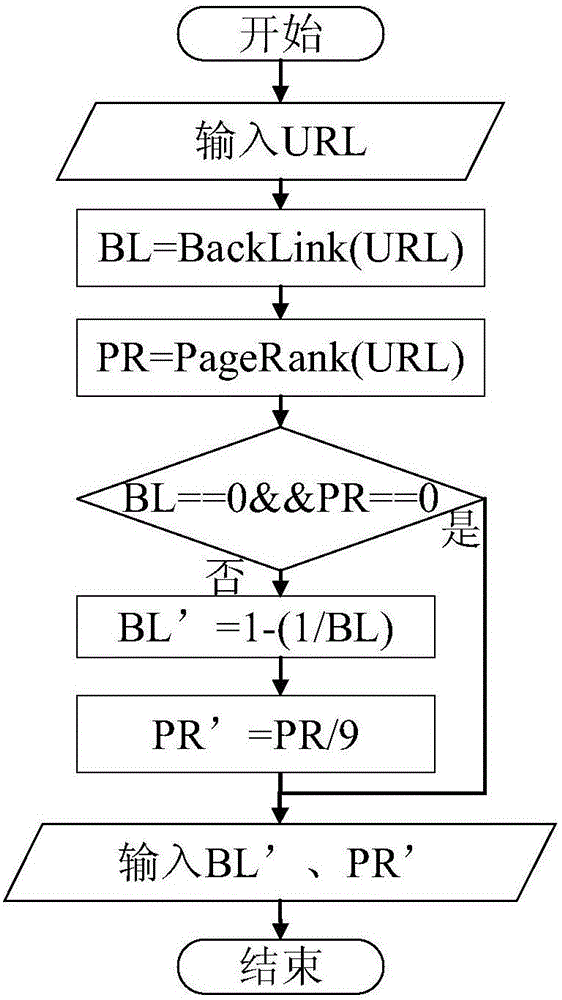
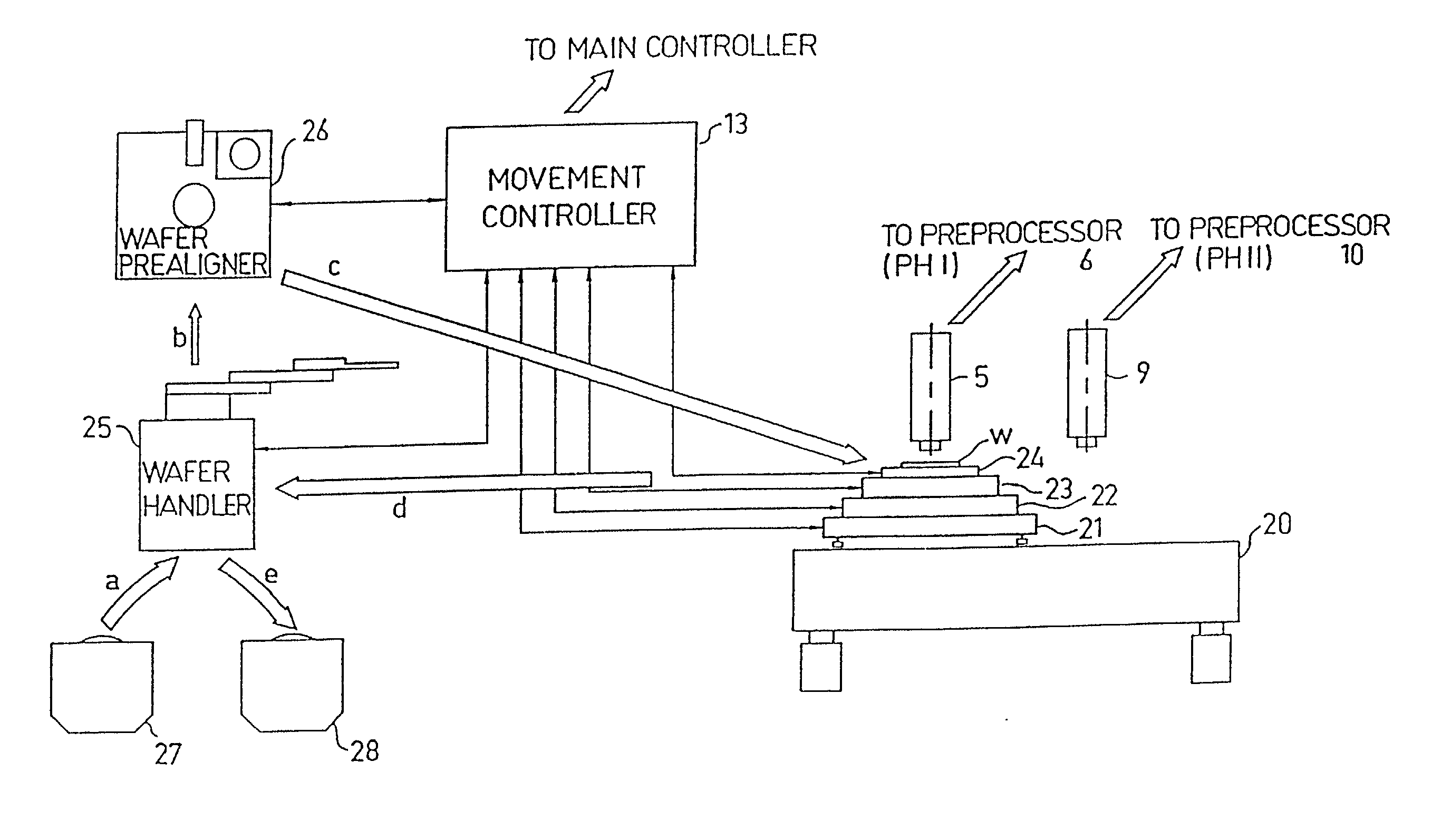
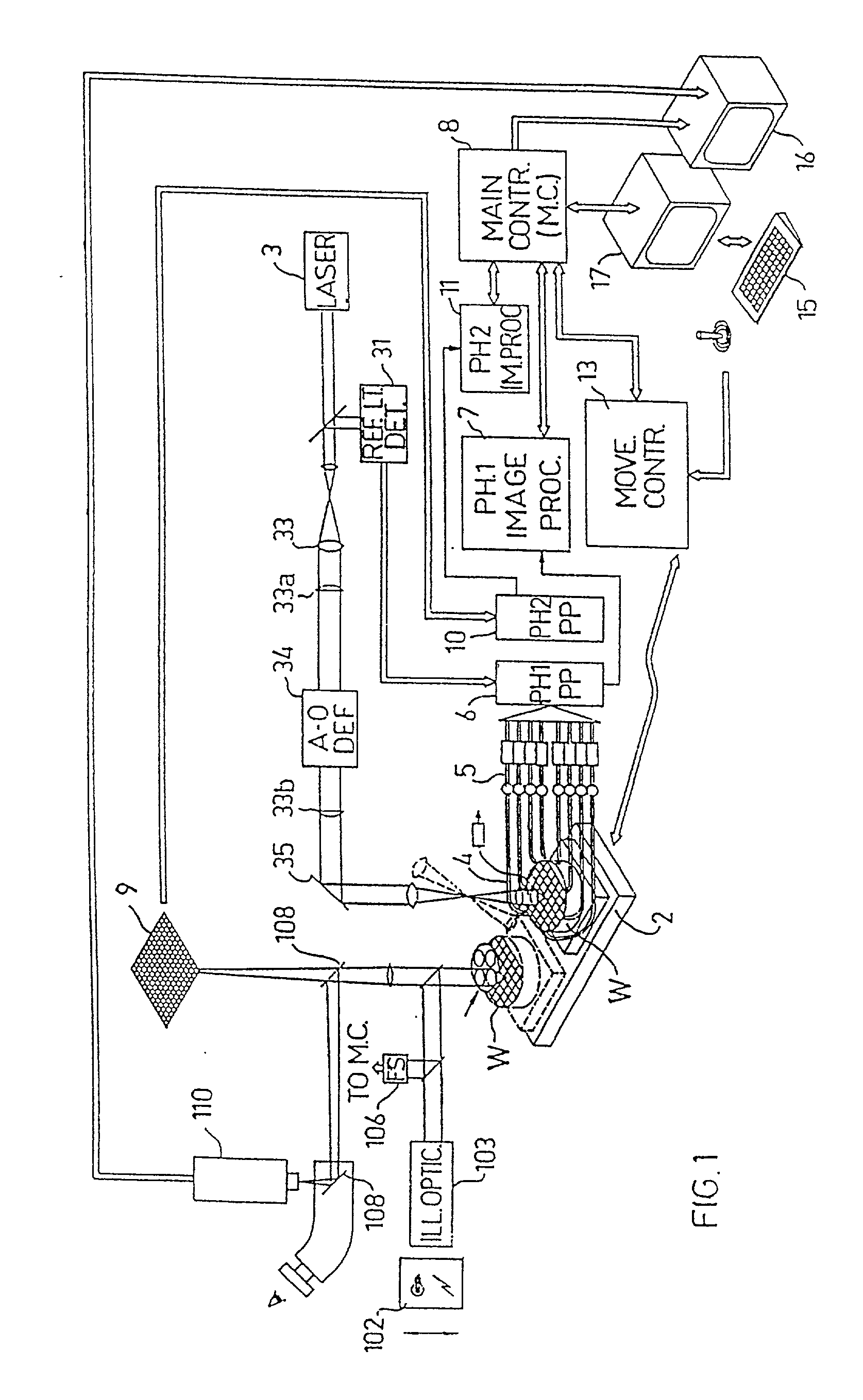
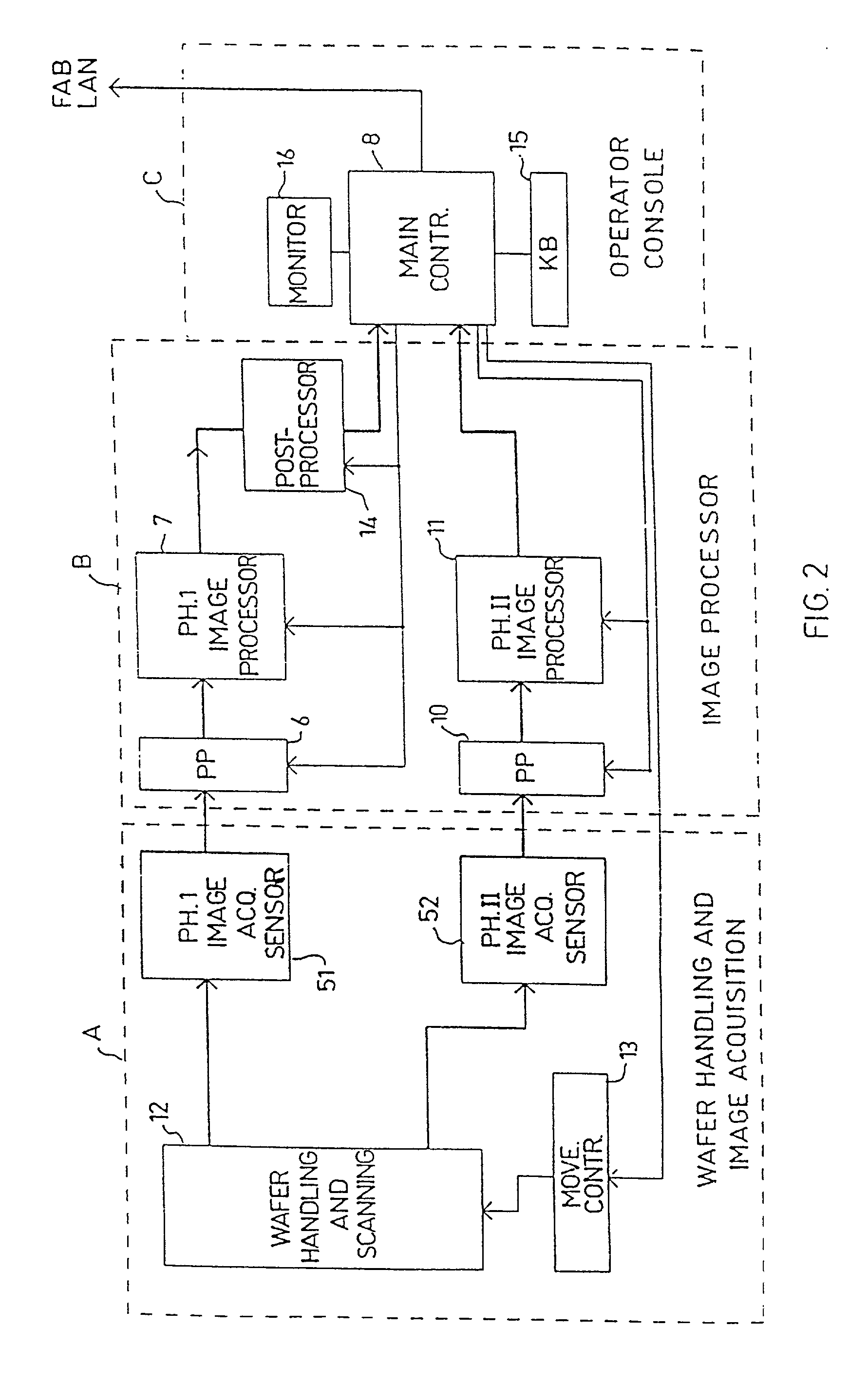
Substrate inspection method and apparatus
InactiveUS6178257B1High throughputIncrease sensitivityCharacter and pattern recognitionOptically investigating flaws/contaminationImage resolutionHigh spatial resolution
A method and apparatus for inspecting the surface of articles, such as chips and wafers, for defects, includes a first phase of optically examining the complete surface of the article inspected at a relatively high speed and with a relatively low spatial resolution, and a second phase of optically examining with a relatively high spatial resolution only the suspected locations for the presence or absence of a defect therein.
Owner:APPLIED MATERIALS INC
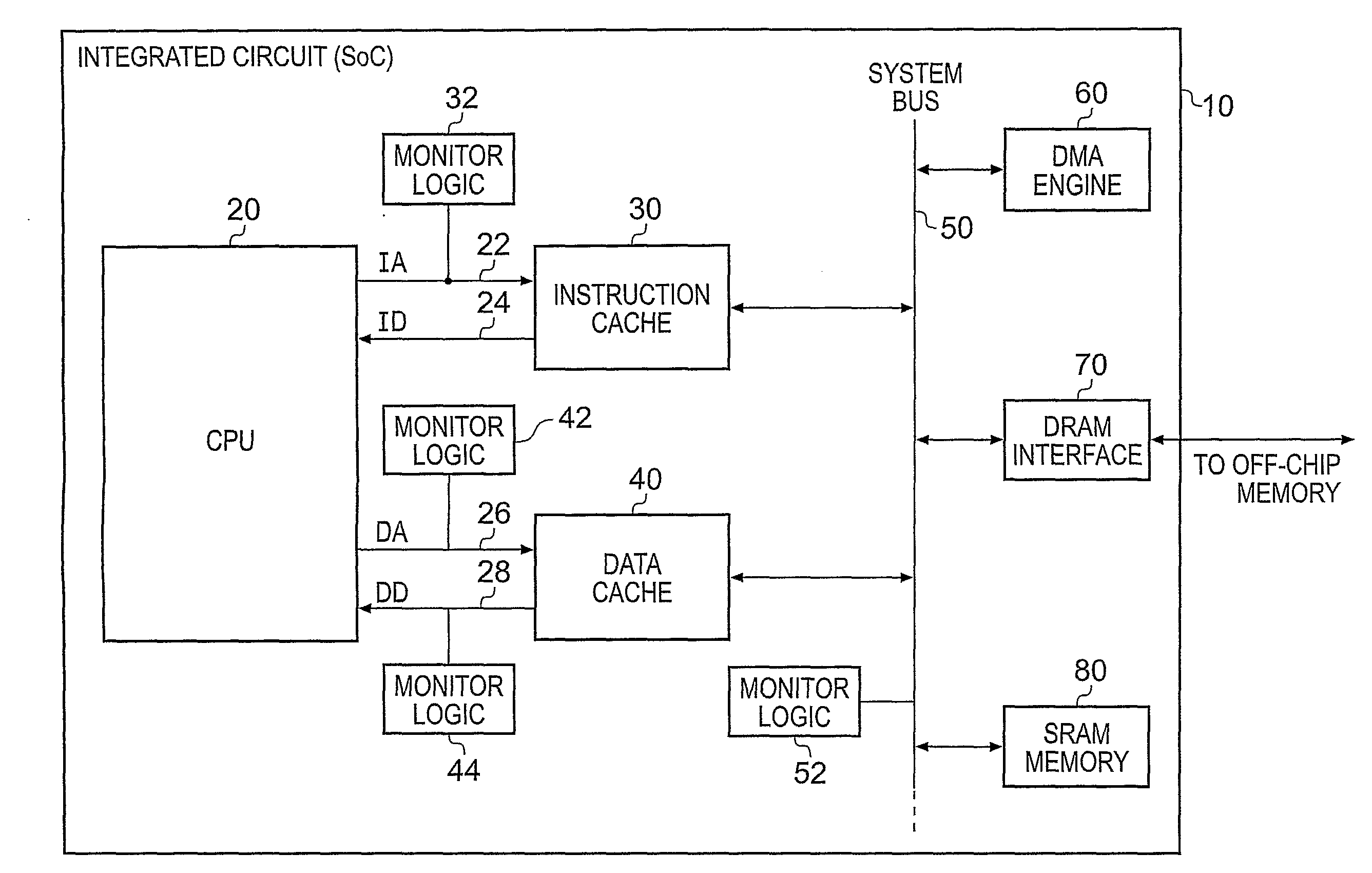
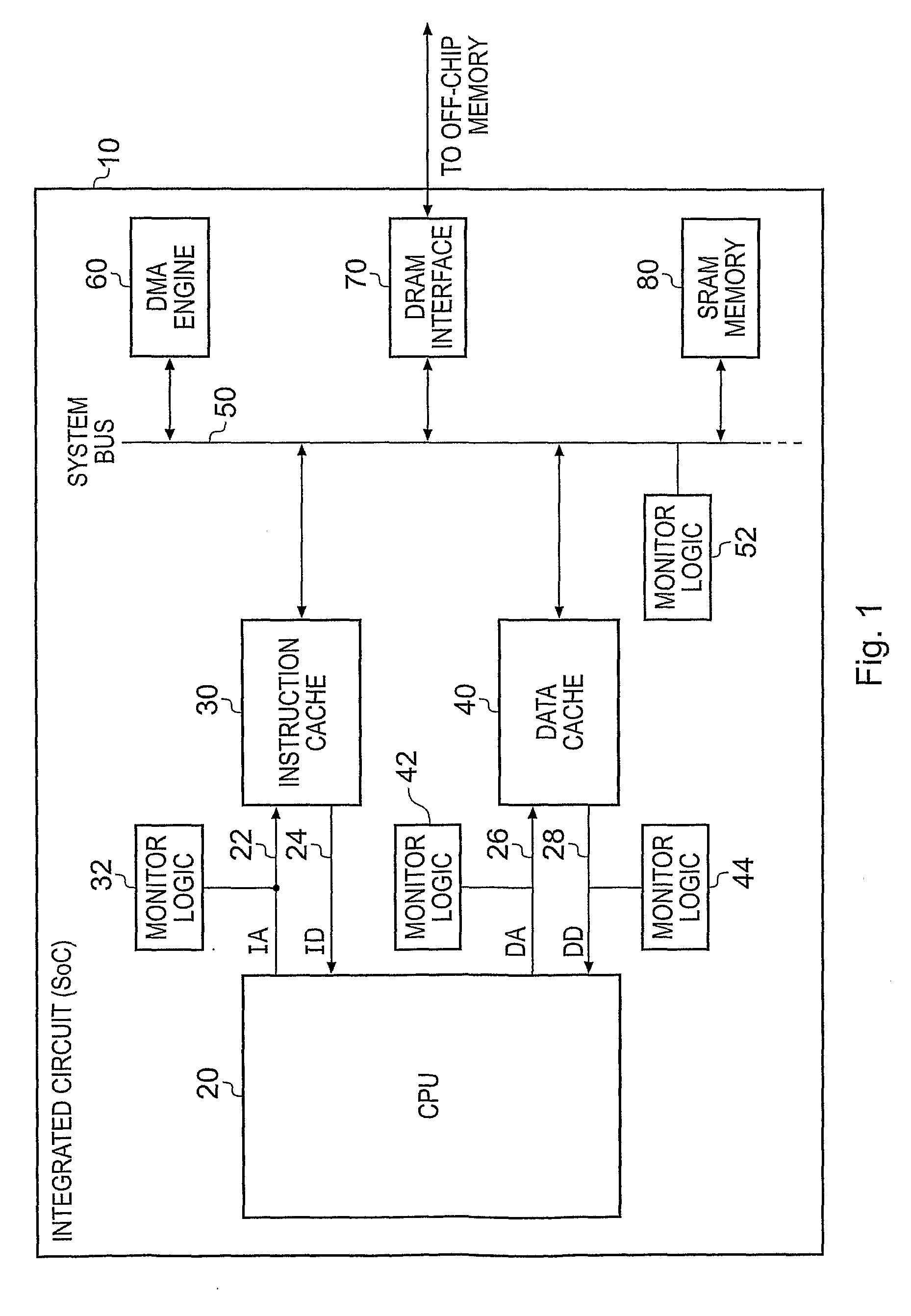
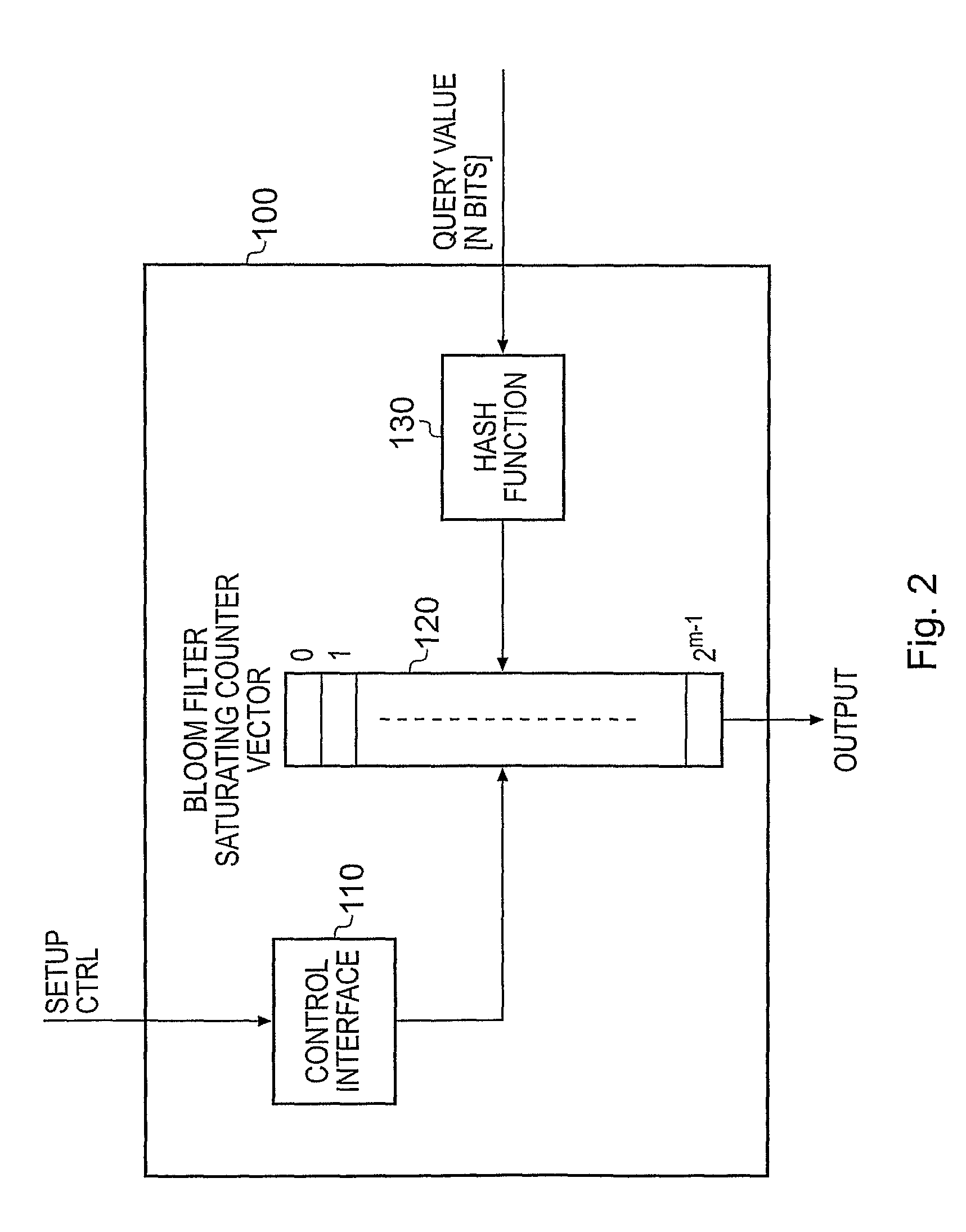
Monitoring Values of Signals within an Integrated Circuit
InactiveUS20090043993A1Achieve balanceLow false hit rateDigital computer detailsHardware monitoringComputer hardwareSignal correlation
An integrated circuit, and method of reviewing values of one or more signals occurring within that integrated circuit, are provided. The integrated circuit comprises processing logic for executing a program, and monitoring logic for reviewing values of one or more signals occurring within the integrated circuit as a result of execution of the program. The monitoring logic stores configuration data, which can be software programmed in relation to the signals to be monitored. Further, the monitoring logic makes use of a Bloom filter which, for a value to be reviewed, performs a hash operation on that value in order to reference the configuration data to determine whether that value is either definitely not a value within the range or is potentially a value within the range of values. If the value is determined to be within the set of values, then a trigger signal is generated which can be used to trigger a further monitoring process.
Owner:ARM LTD
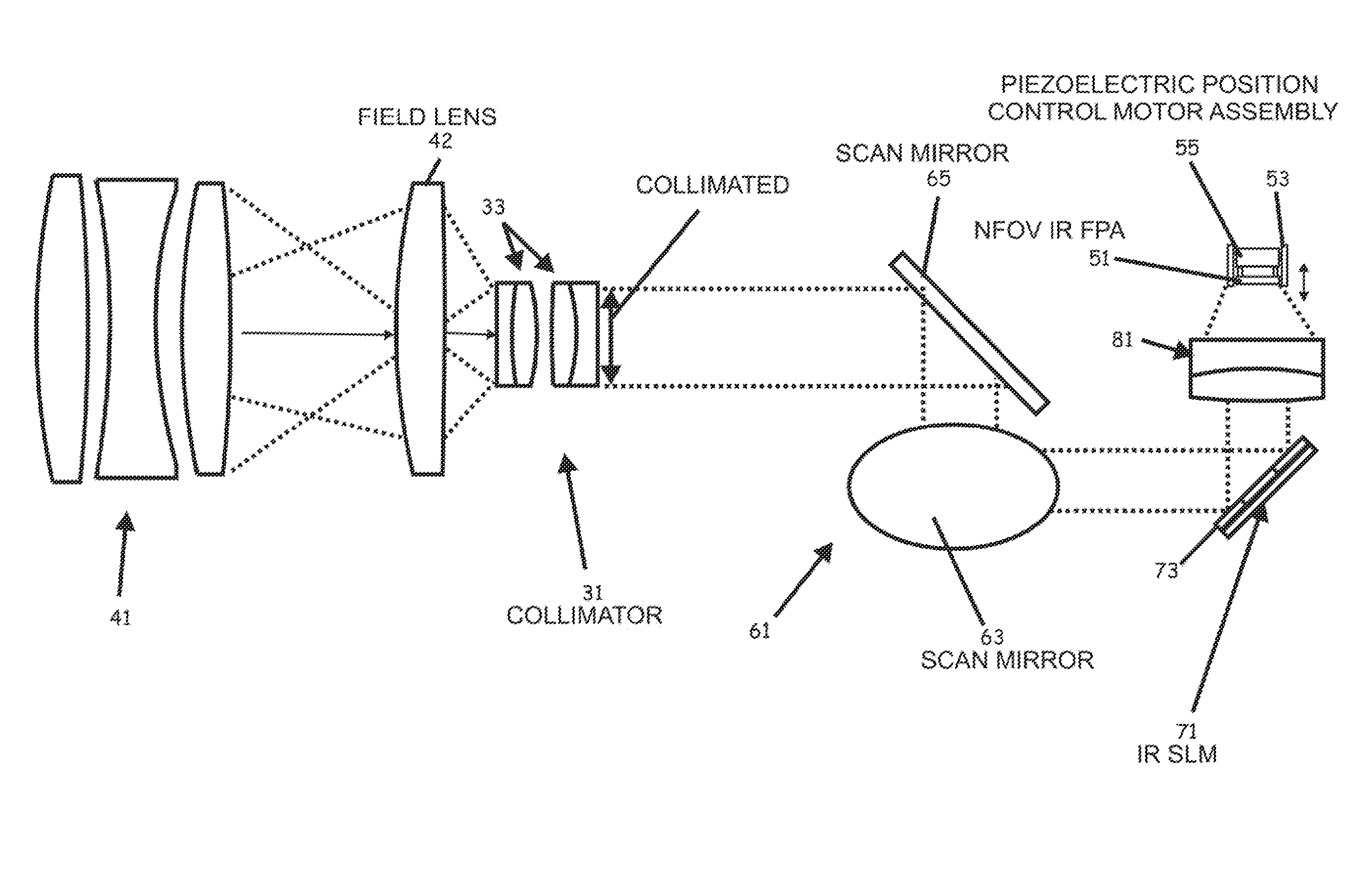
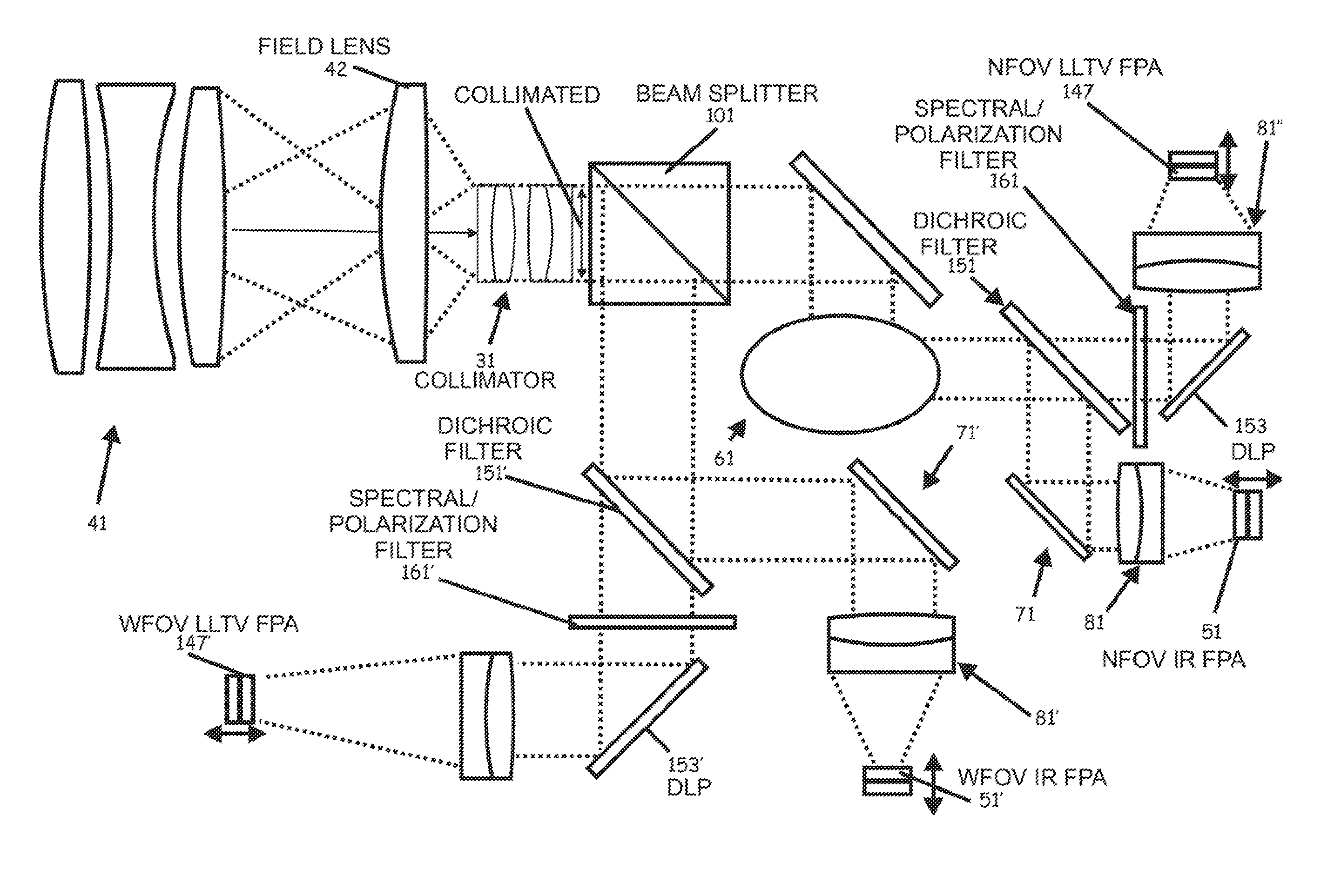
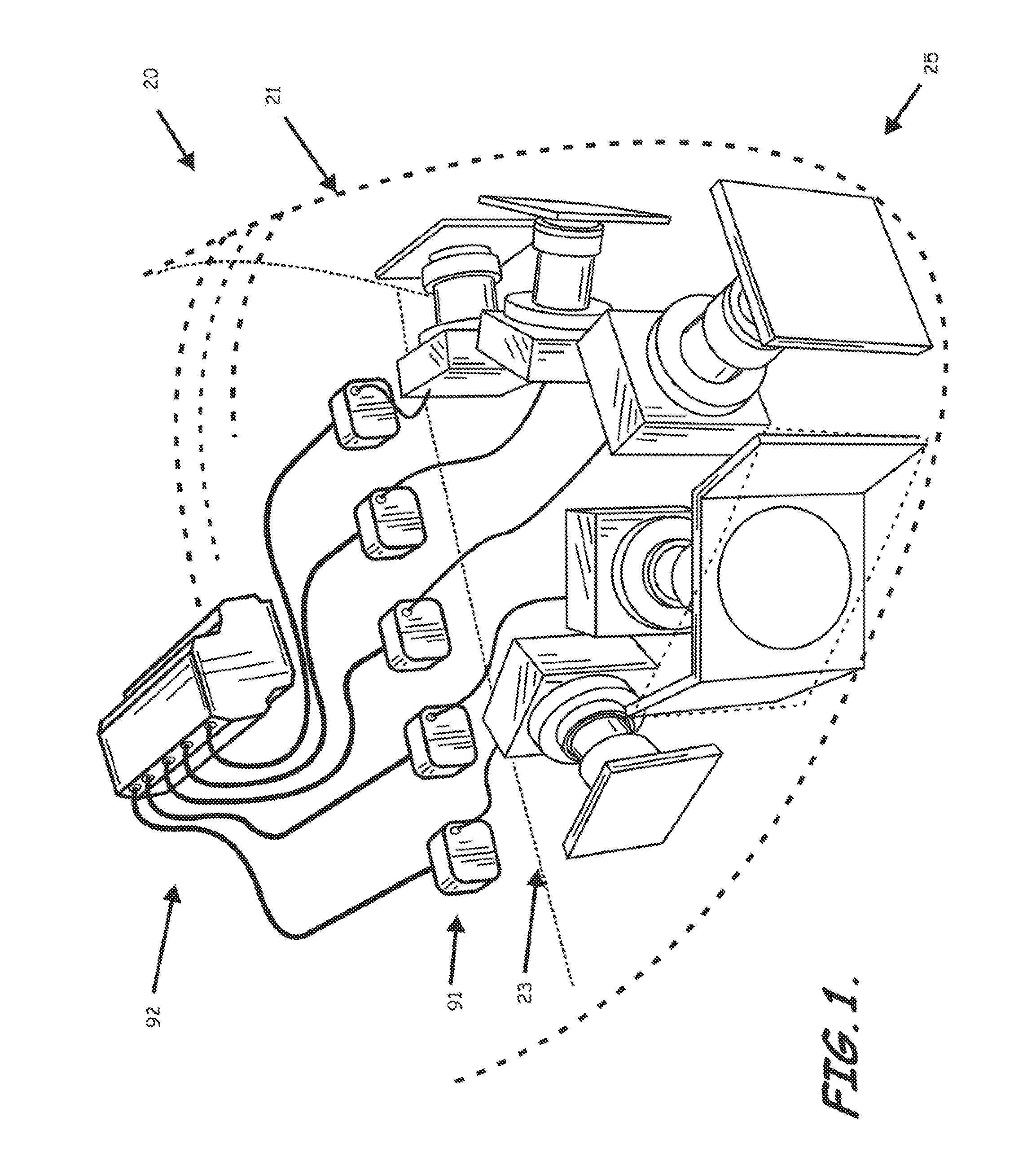
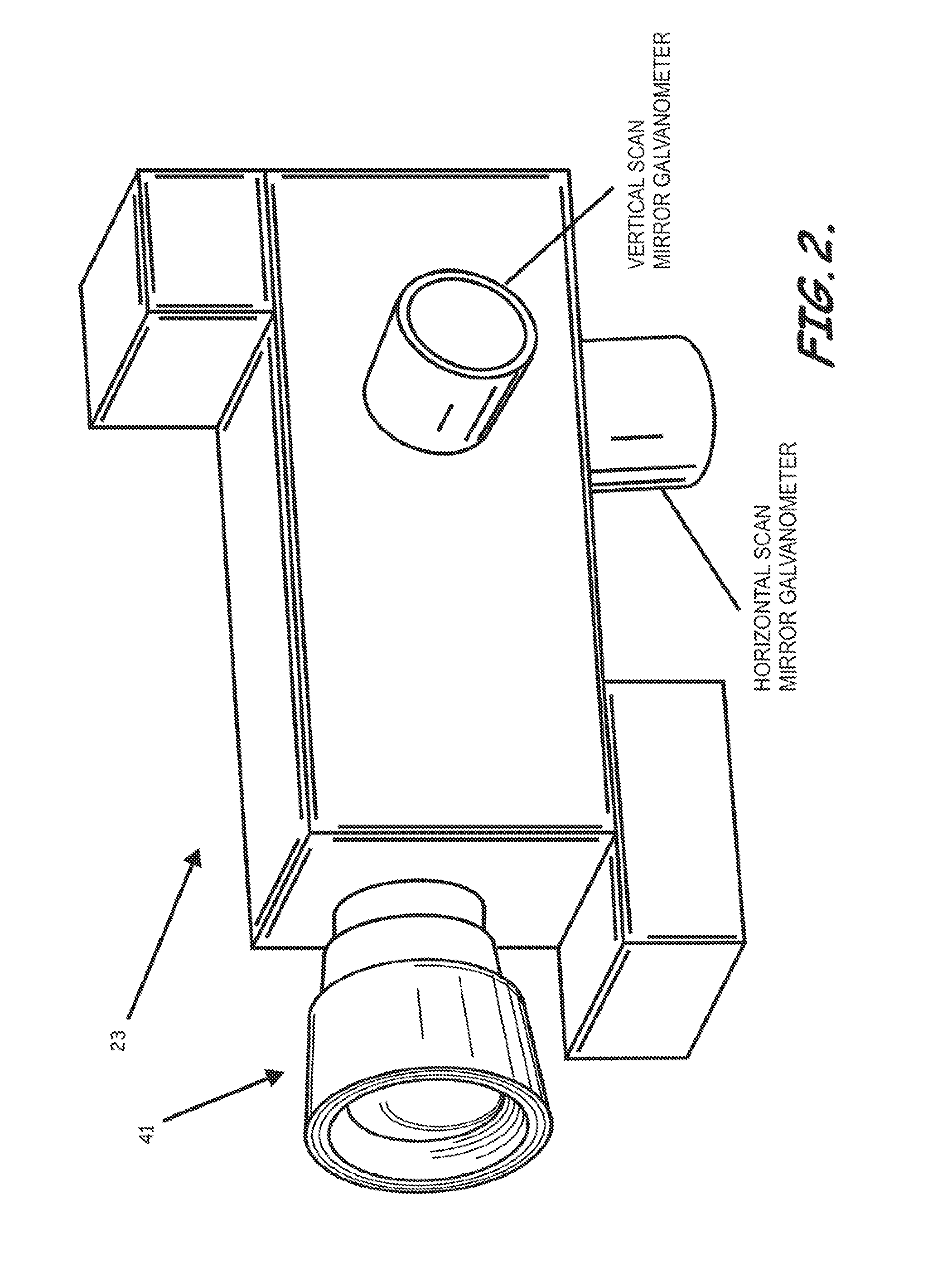
Optical Detection and Ranging Sensor System For Sense and Avoid, and Related Methods
ActiveUS20110134249A1Small lossConvenient distanceTelevision system detailsOptical rangefindersSense and avoidWide field
An apparatus carried by an unmanned vehicle to provide passive sensing and facilitate avoiding airborne aerial obstacles is provided. The apparatus can include at least one, but typically multiple optical systems installed, for example, in the nose of the aerial vehicle to passively sense and determine a range, direction, and velocity of the airborne obstacles to allow the aerial vehicle to avoid the airborne obstacles. The typical optical system includes at least one focal plane array or other imaging device configured to receive a wide field of view and at least one focal plane array or other imaging device configured to receive a steerable narrow field of view within the wide field of view to allow concentrated determination of the range, direction, and / or velocity of obstacles detected by the wide field of view imaging devices.
Owner:LOCKHEED MARTIN CORP
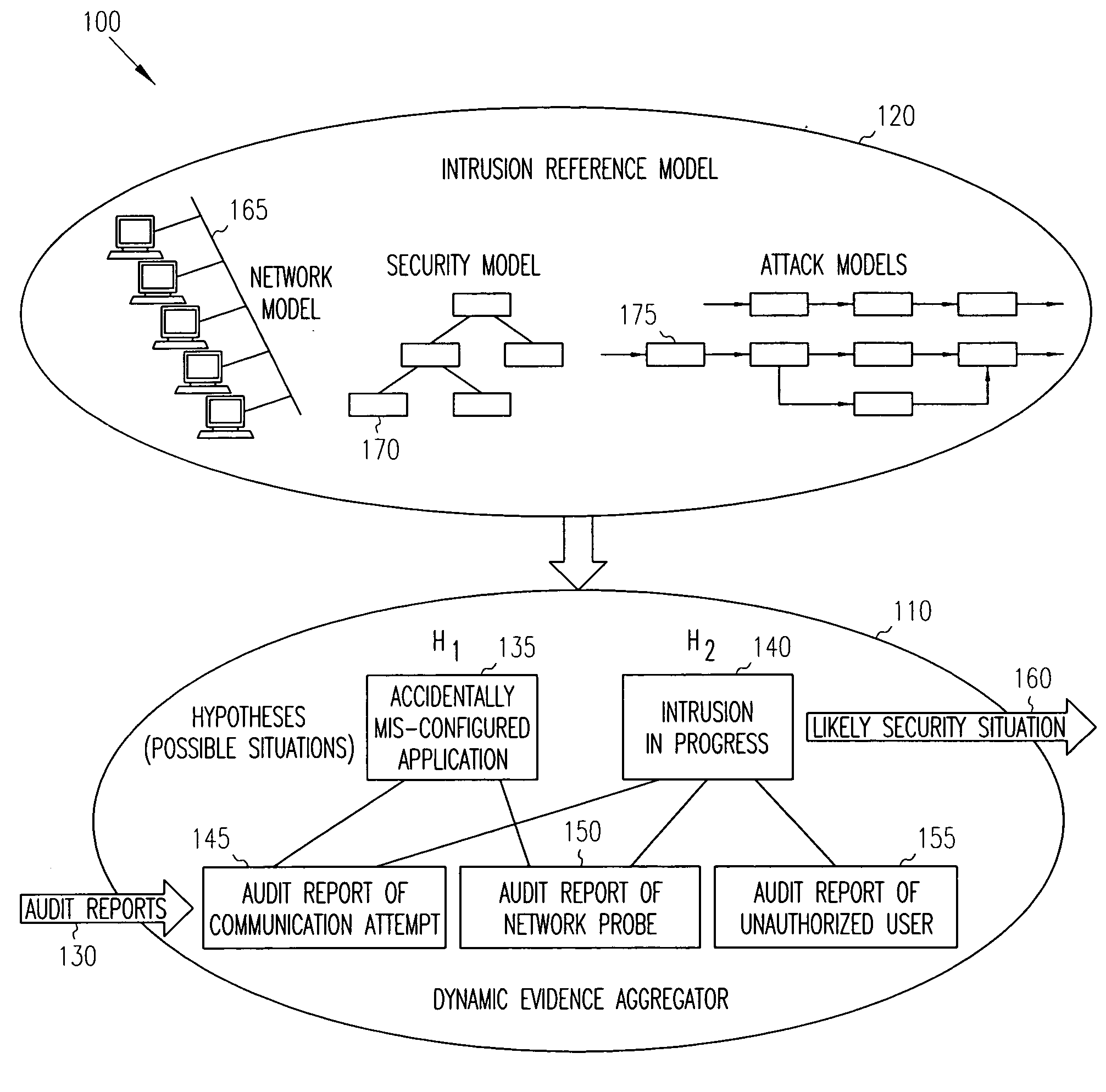
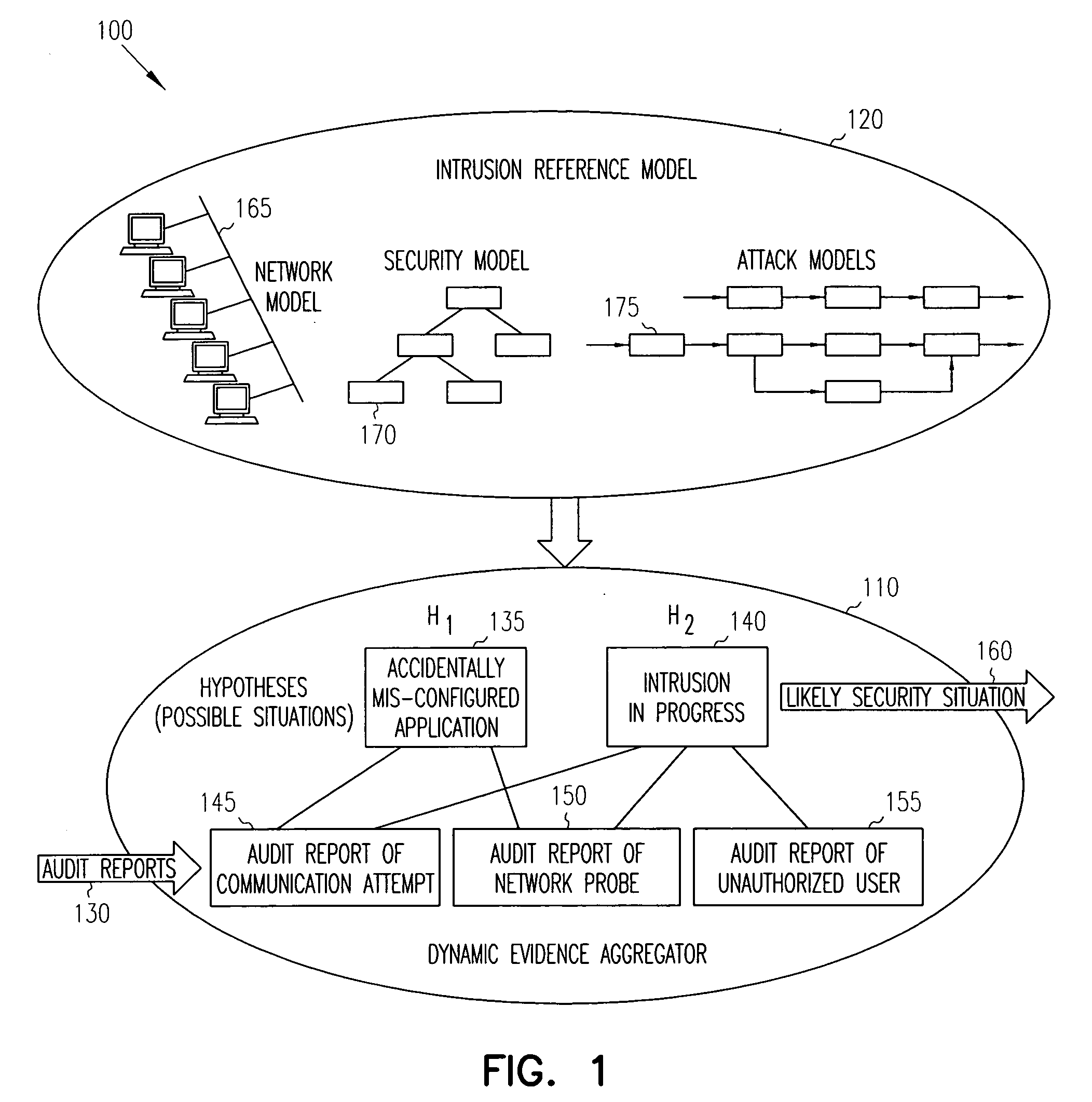
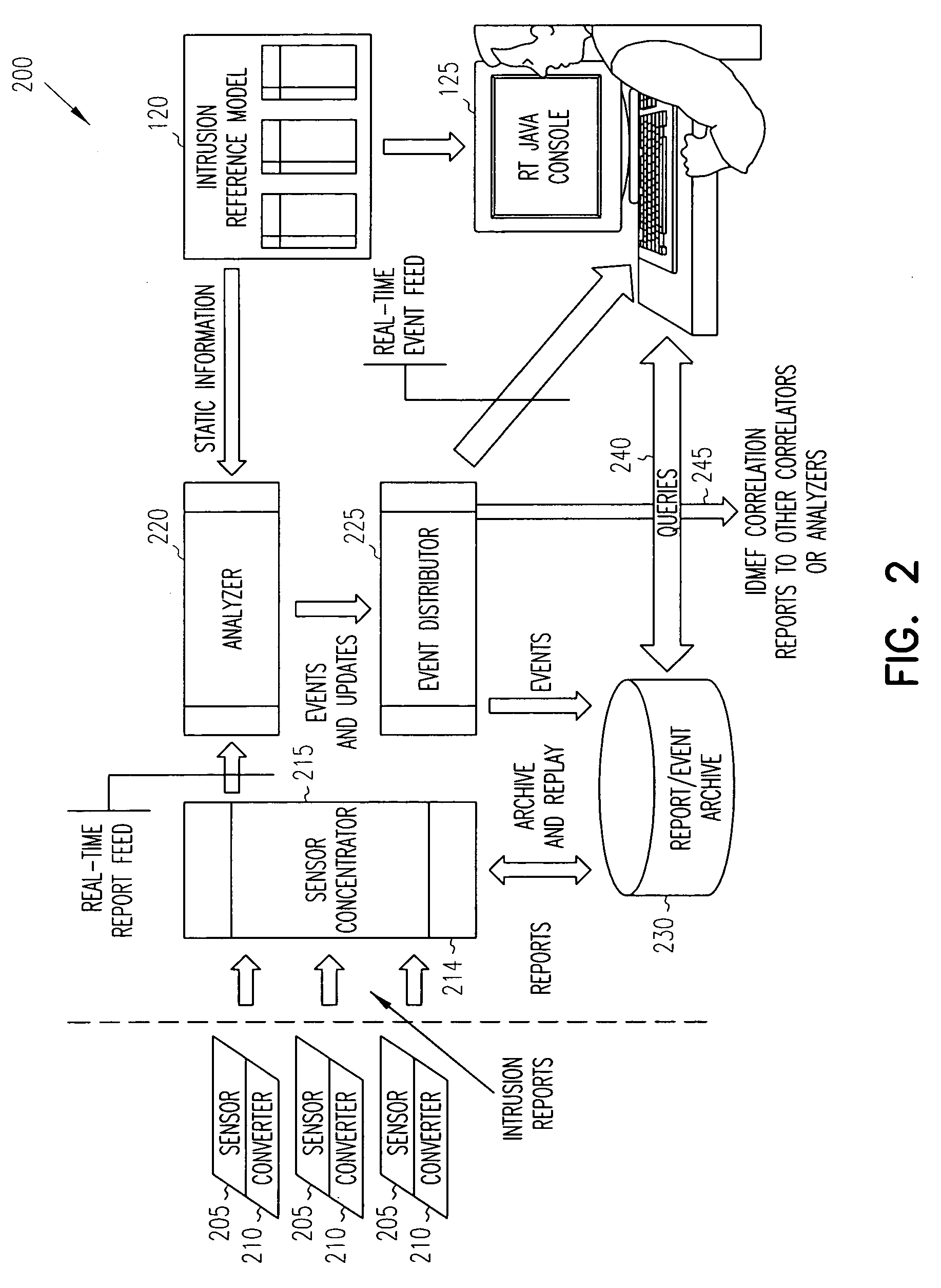
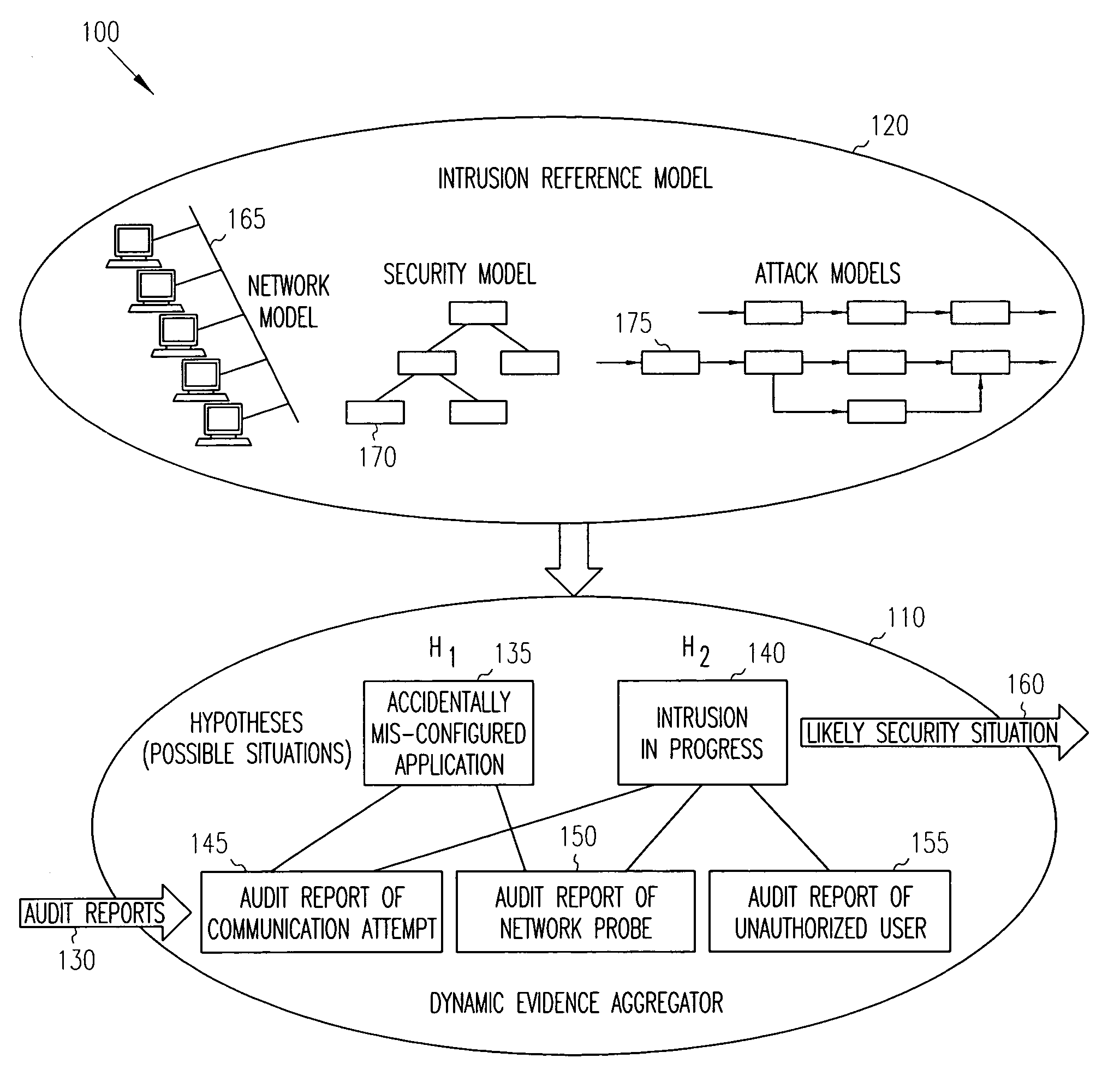
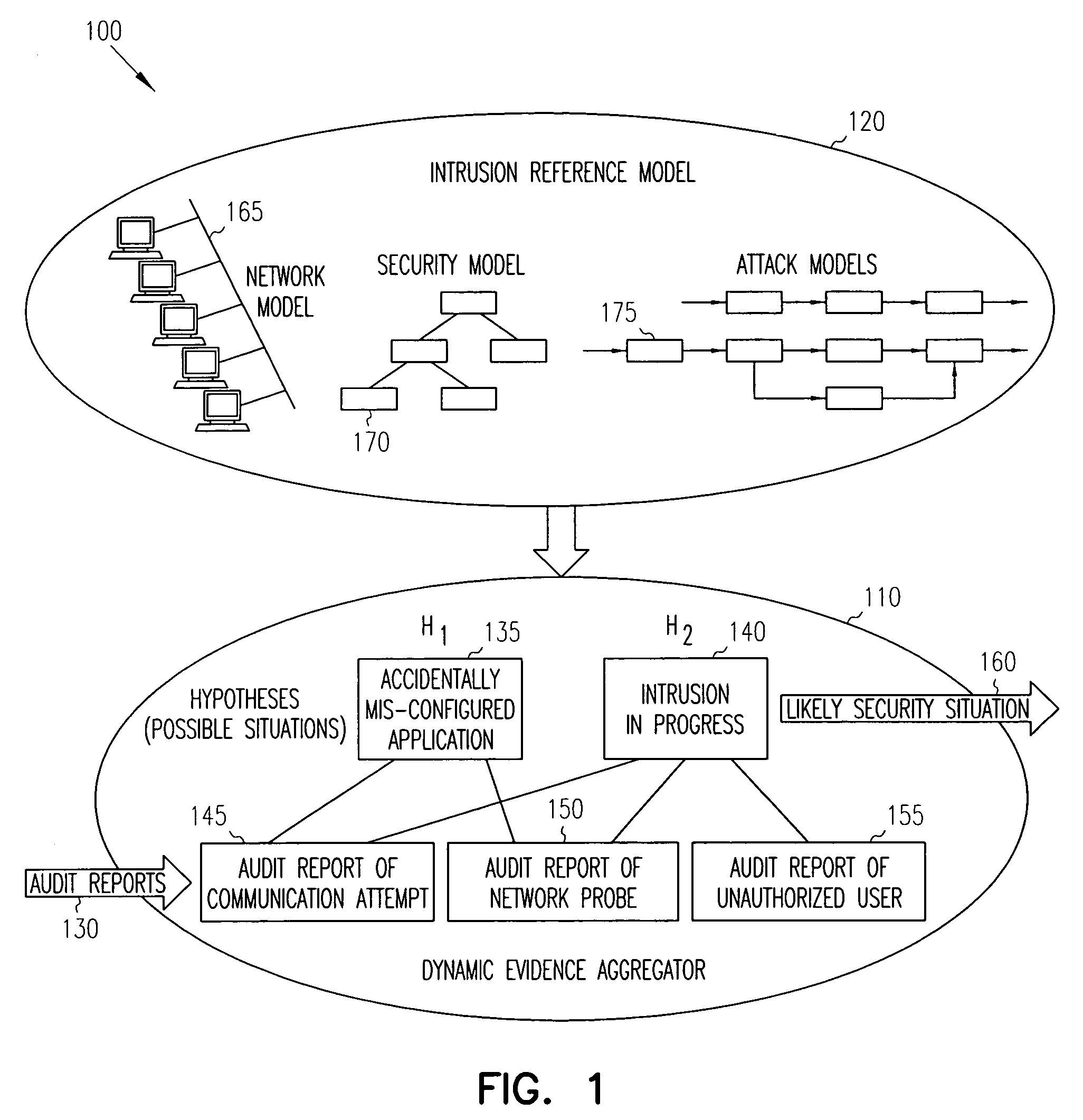
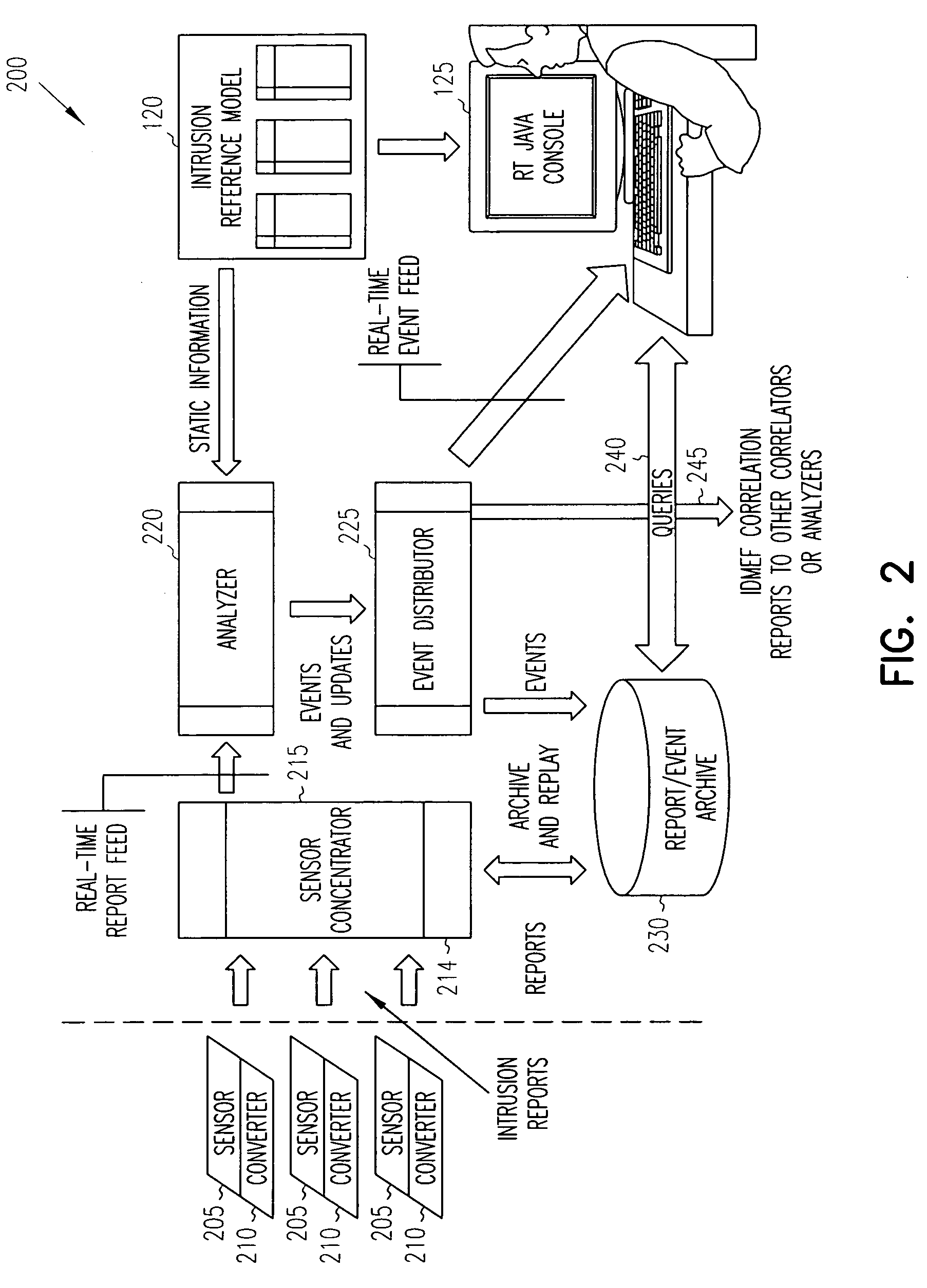
Intrusion detection report correlator and analyzer
ActiveUS20060070128A1Reduce high false positive rateEasy to detectMemory loss protectionError detection/correctionAlert managementFalse alarm
A computer / computer network security alert management system aggregates information from multiple intrusion detectors. Utilizing reports from multiple intrusion detectors reduces the high false alarm rate experienced by individual detectors while also improving detection of coordinated attacks involving a series of seemingly harmless operations. An internal representation of a protected enclave is utilized, and intrusion detection system (IDS) information is correlated to accurately prioritize alerts. In one embodiment, the system is capable of utilizing data from most existing IDS products, with flexibility to add further IDS products.
Owner:HONEYWELL INT INC
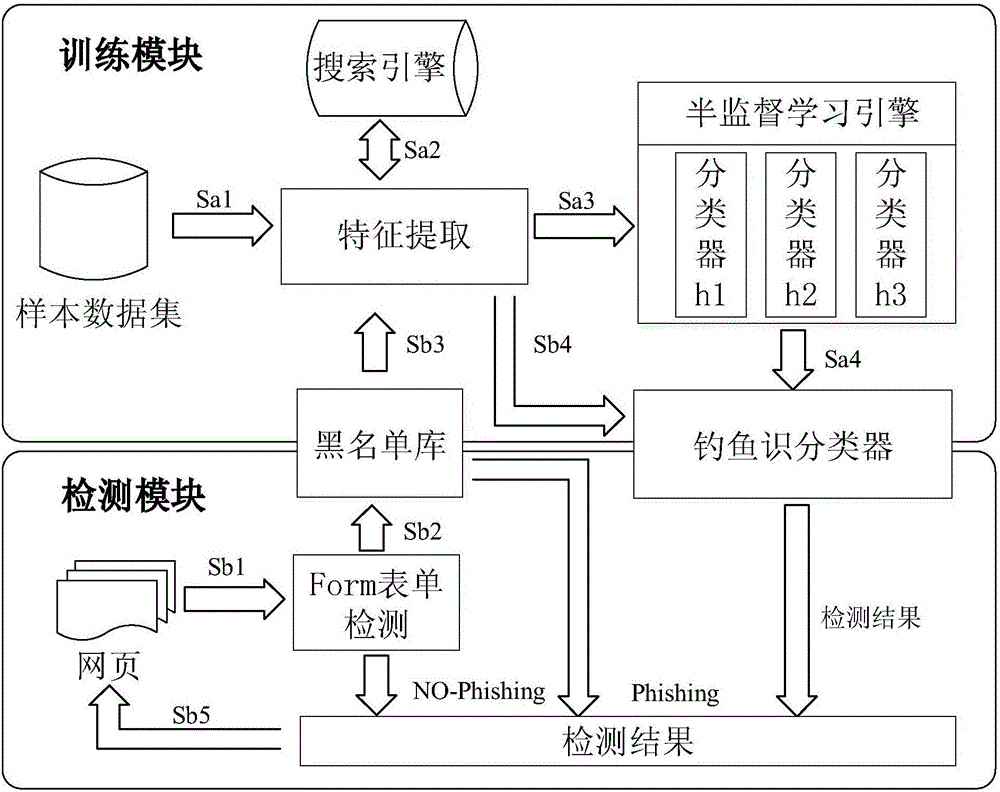
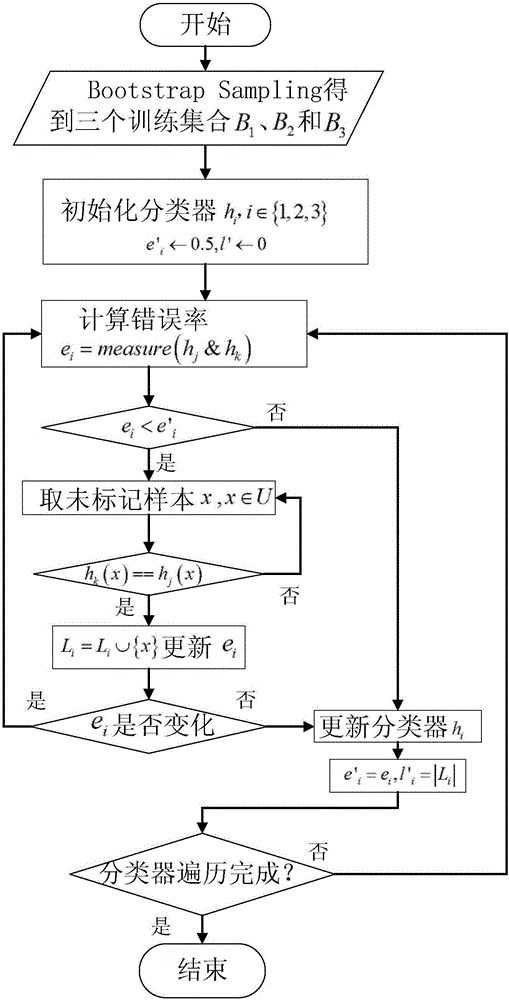
Multi-feature fusion phishing webpage detection method
ActiveCN106789888AEasy economic lossHigh false positive rateWeb data retrievalTransmissionManual annotationCategorical models
The invention relates to a multi-feature fusion phishing webpage detection method, which comprises two parts such as a training process and a detection process. The multi-feature fusion phishing webpage detection method integrates three views of phishing webpage characteristics by combining a semi-supervised learning tri-training method, and mainly solves a problem that the existing phishing webpage detection methods mostly need to perform classification model training by using supervised learning through a large amount of annotation data. The method provided by the invention mainly combines a coordinated training algorithm, starts from webpage URL characteristics, webpage information characteristics and webpage search information characteristics, applies the idea of multiple views and multiple classifiers to phishing webpage detection, and achieves the purposes of reducing the total numbers of manual annotation training samples and timely recognizing a phishing webpage through coordinated training and learning of different classifiers.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Optical inspection apparatus for defect detection
InactiveUS20020039436A1Increase speedLow rateCharacter and pattern recognitionColor television detailsImage resolutionHigh spatial resolution
A method and apparatus for inspecting the surface of articles, such as chips and wafers, for defects, includes a first phase of optically examining the complete surface of the article inspected at a relatively high speed and with a relatively low spatial resolution, and a second phase of optically examining with a relatively high spatial resolution only the suspected locations for the presence or absence of a defect therein.
Owner:APPLIED MATERIALS INC
Alarm and response system for inner-mesh network aggression detection
InactiveCN101414927AHigh false positive rateReduce the degree of manual interventionData switching networksIp addressNetwork attack
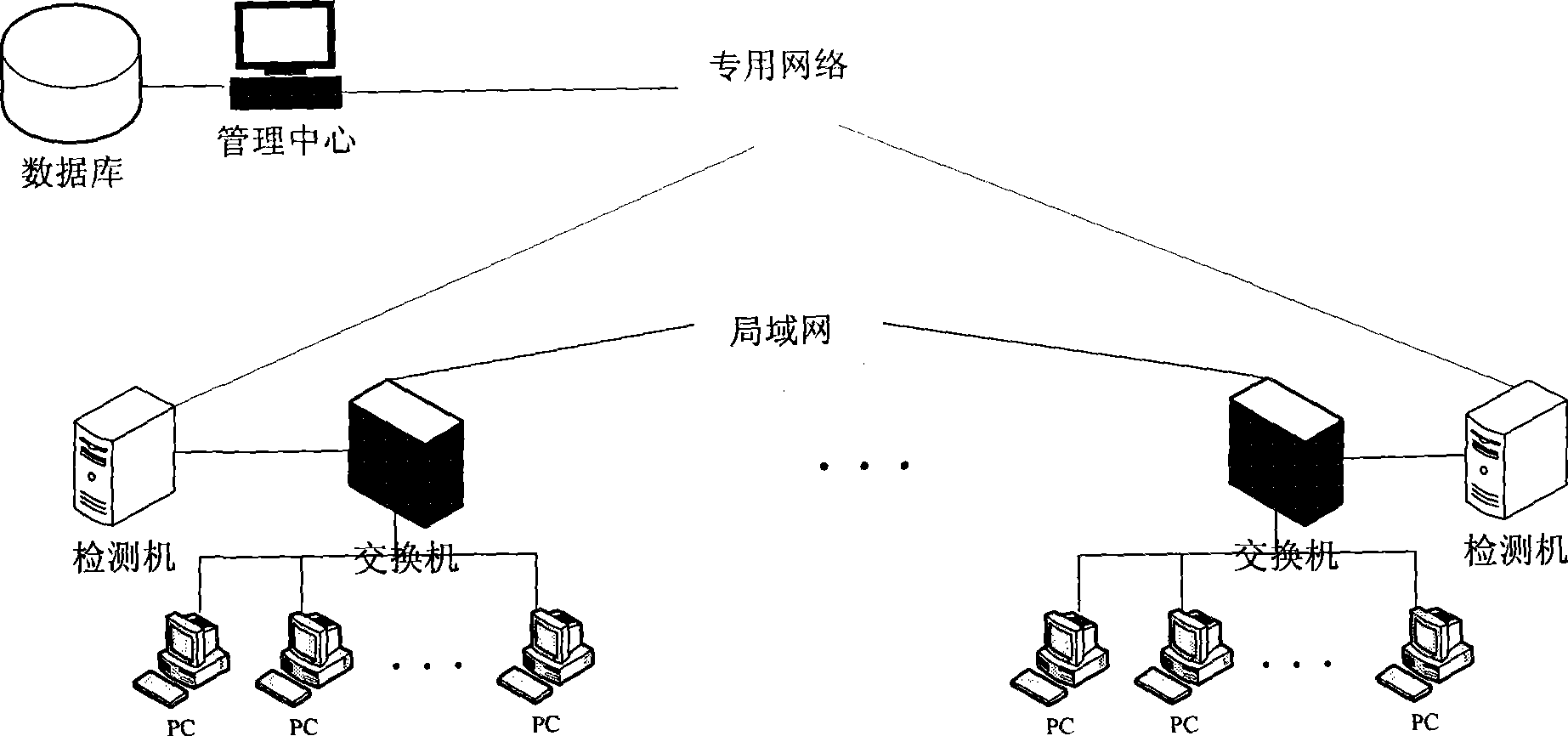
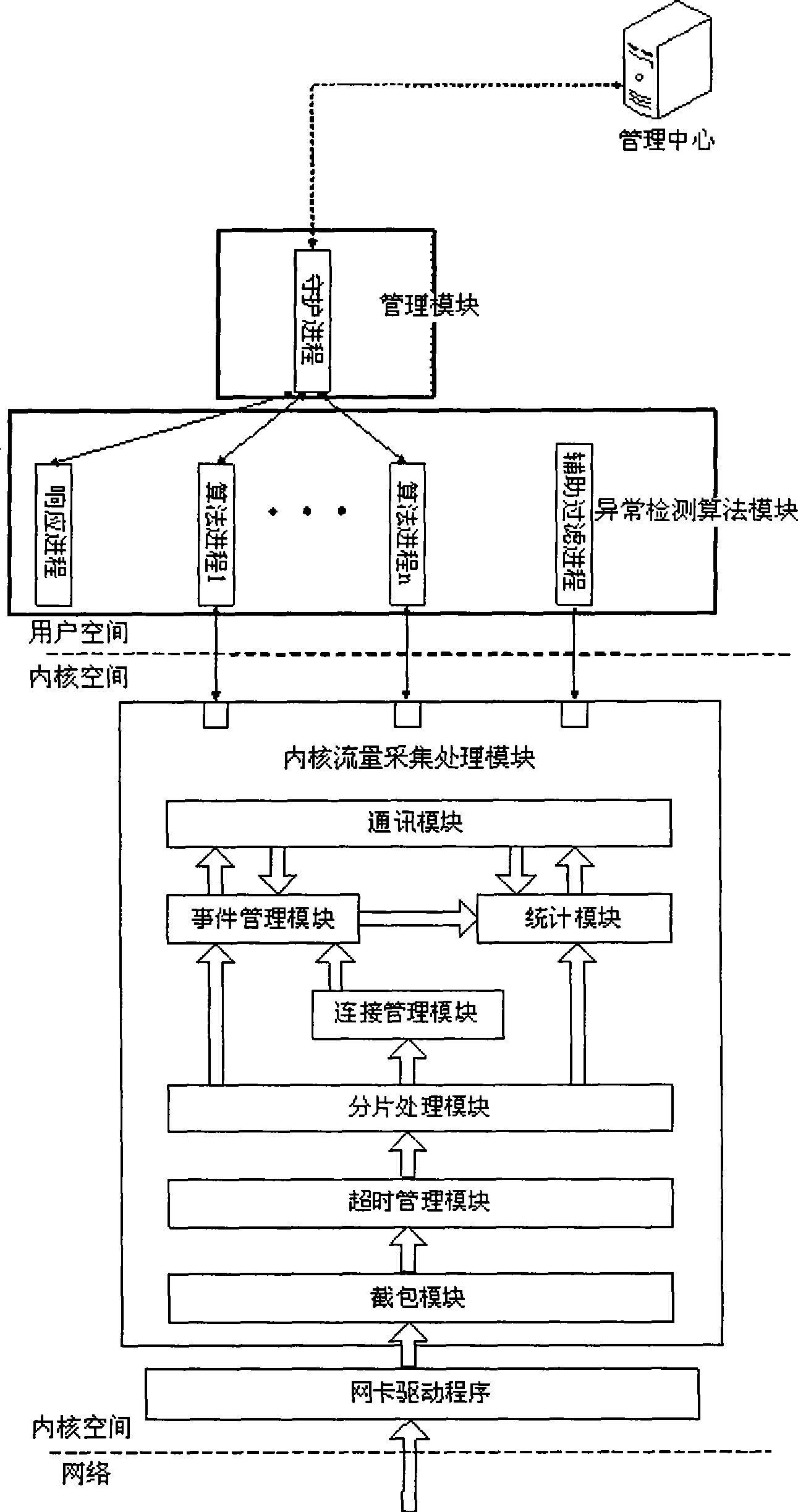
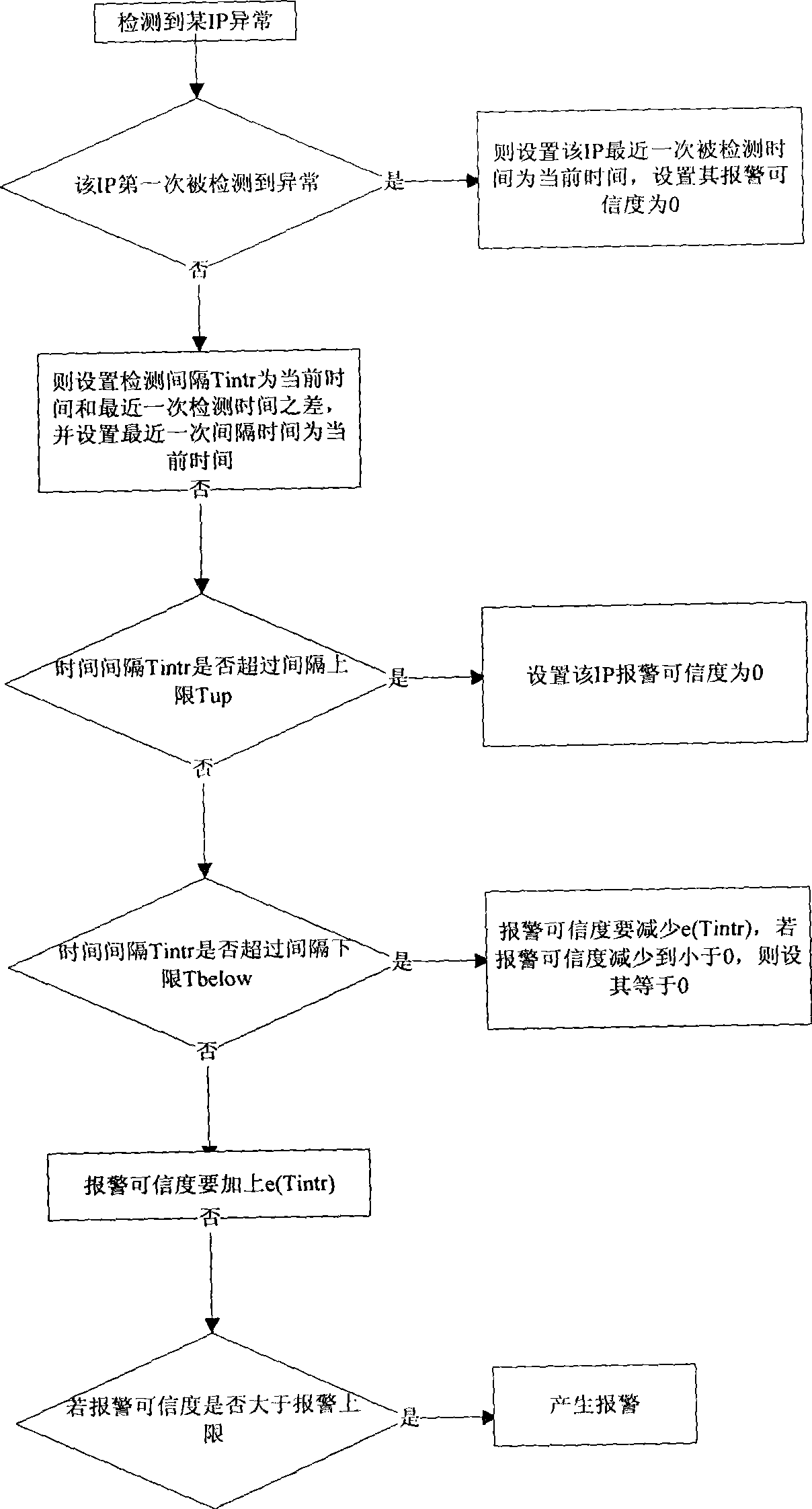
The invention discloses a warning and responding system used for intranet network attack detection. The system comprises a management center, a detecting machine and a database. The management center is used for configuring and amending each parameter of the detecting machine, receiving and storing warning message sent by the detecting machine and inquiring the state of the detecting machine. Anomaly information detection is carried out on an intranet network by an anomaly detection algorithmic module of the detecting machine, the anomaly detection algorithmic module obtains anomaly detection information and confirms the reliability of the information. When the reliability of the anomaly detection information reaches a preset value, the warning message is sent. The isolation time and the isolation form of an IP address generating the anomaly detection information are confirmed according to the warning message, and the IP address is isolated. The IP address that the isolation time reaches the preset value is released from isolation. The method can detect and prevent the attack from an intranet mainframe to outer net or other intranet mainframes exactly and effectively in time.
Owner:ZHEJIANG UNIV
Method for web application layer attack detection and defense based on behavior characteristic matching and analysis
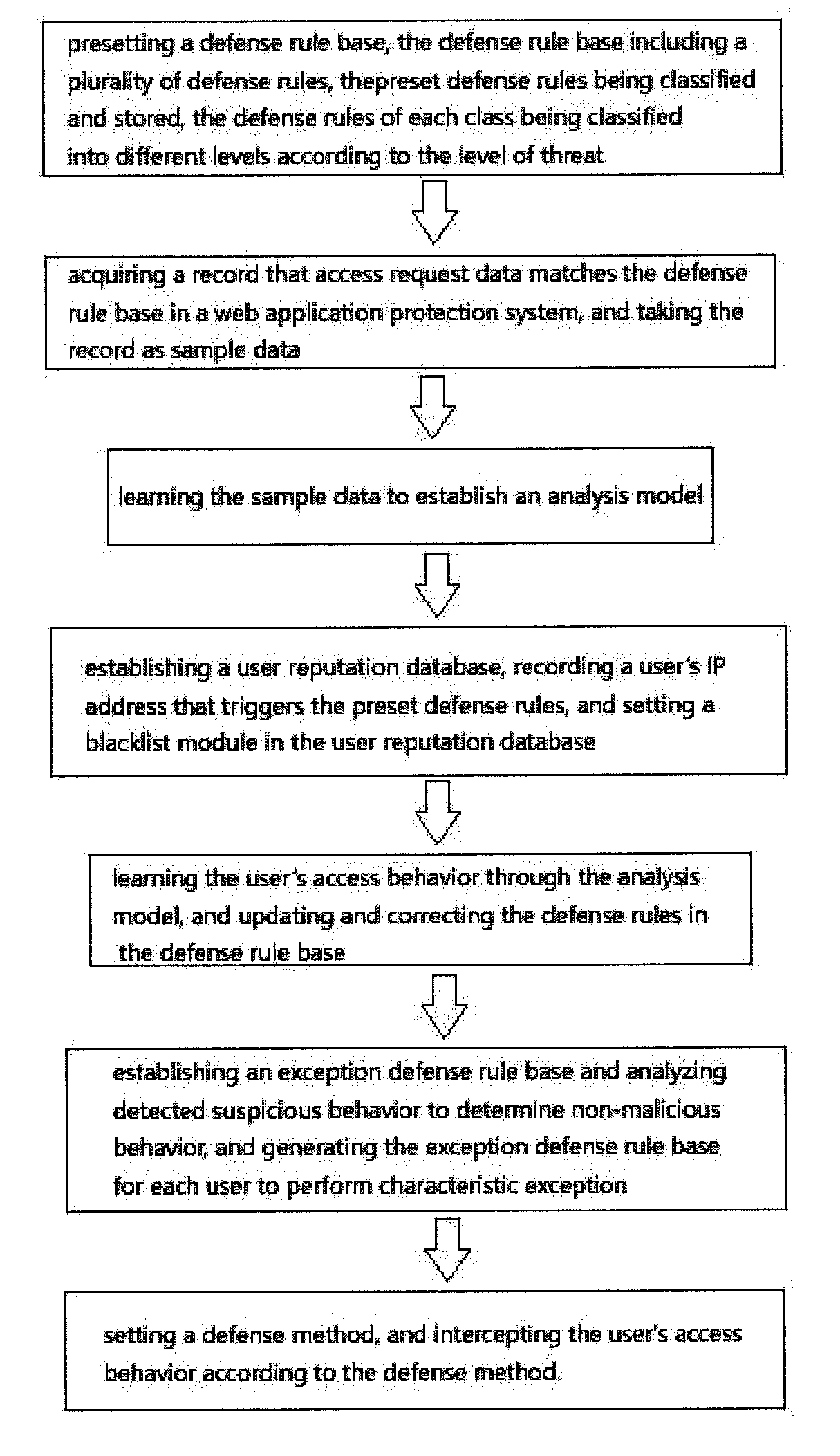
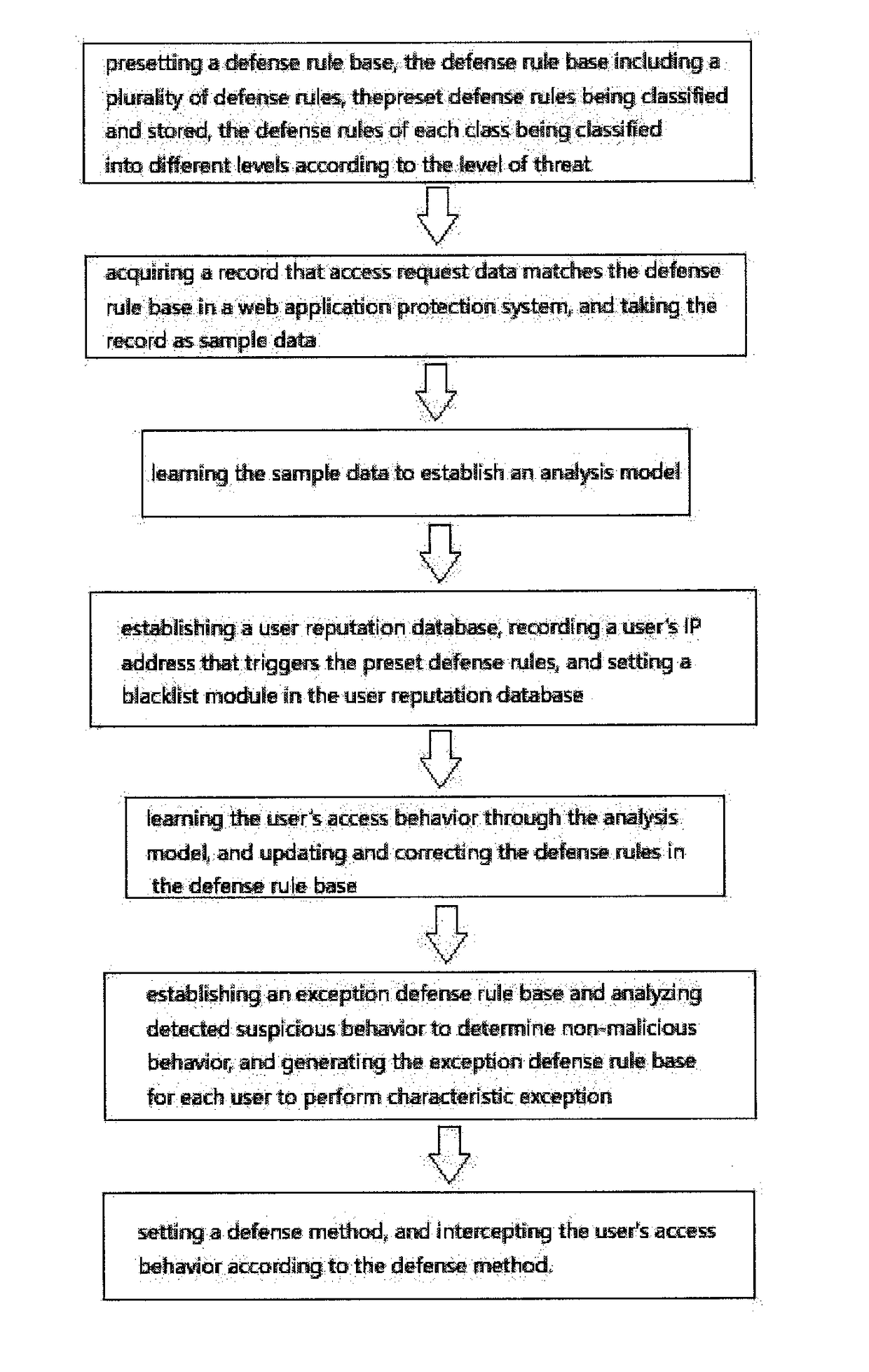
ActiveUS20180262521A1High false alarm rateLow efficiencyMathematical modelsTransmissionWeb serverApplication software
A method for web application layer attack detection and defense based on behavior characteristic matching and analysis includes presetting a defense rule base, the defense rule base including a plurality of defense rules; acquiring a record that access request data matches the defense rule base in a web application protection system and taking the record as sample data; learning the sample data to establish an analysis model; establishing a user reputation database and setting a blacklist module in the user reputation database; learning the user's access behavior through the analysis model and updating and correcting the defense rules in the defense rule base; establishing an exception defense rule base; and setting a defense method and intercepting the user's access behavior according to the defense method. By intelligently learning the user's behavior, threat behavior can be identified and intercepted quickly to ensure the security of the web server.
Owner:MOLBASE SHANGHAI BIOTECH CO LTD
Intelligent gloves, method and system for calorie consumption and hand posture recognition
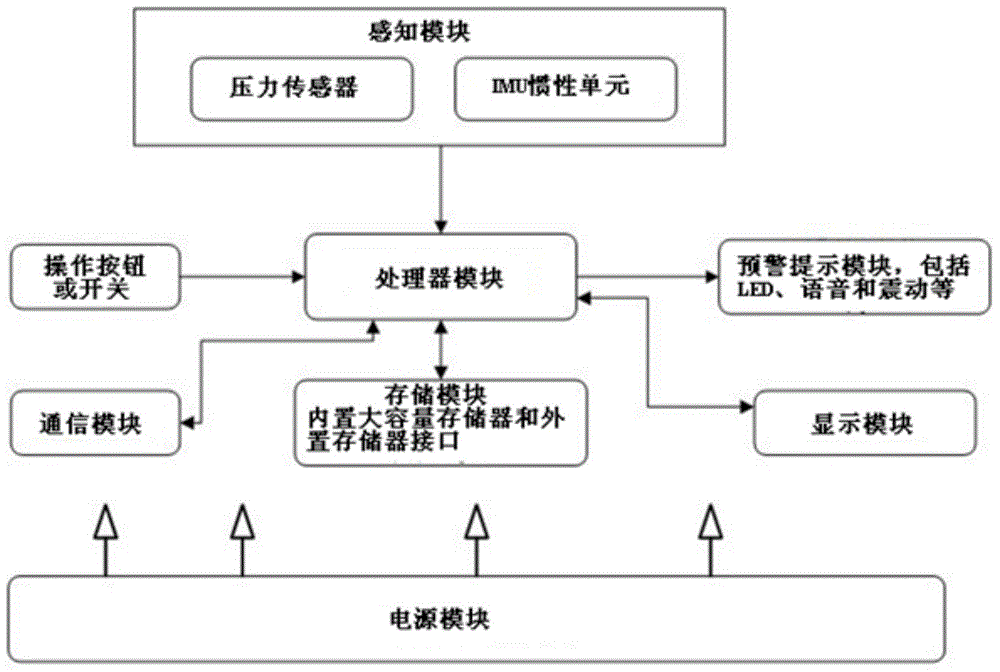
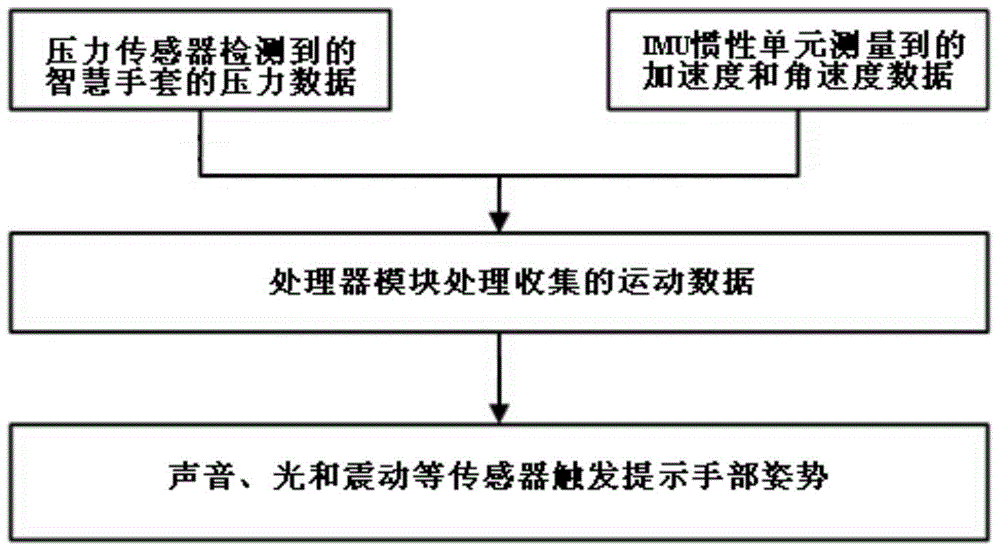
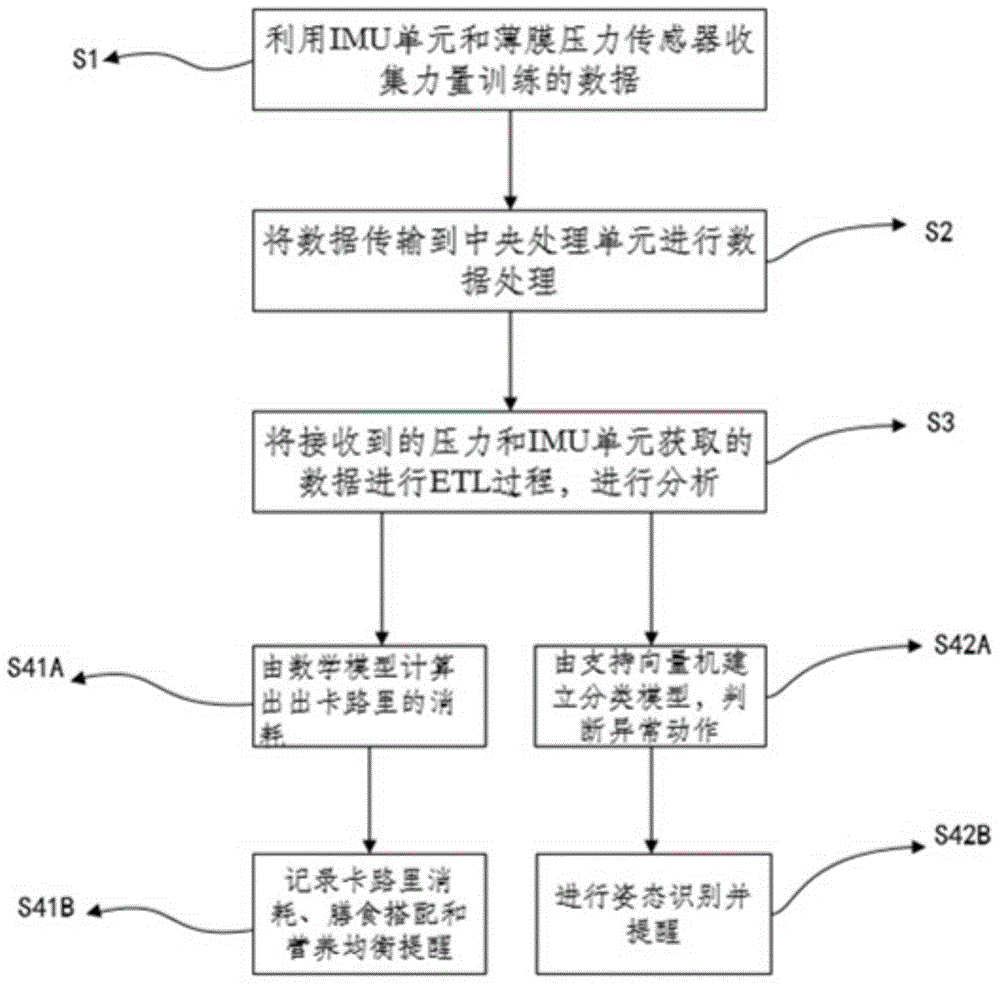
ActiveCN104888444ALow detection accuracyReduce false alarm rateGlovesSport apparatusStress strengthLarge Calorie
The invention provides a pair of intelligent gloves, method and system for calorie consumption and hand posture recognition. The pair of intelligent gloves comprises a processor module, a memory module, a communication module, an induction module, an early warning prompt module, a display module, a power module, a switch module and a cloud server. The memory module, the communication module, the induction module, the early warning prompt module, the display module, the power module, the switch module and the cloud server are respectively connected with the processor module. The induction module comprises a pressure sensor and an IMU. The pressure sensor and the IMU are respectively used for being responsible for sensing hand stress strength and IMU data in users' fitness process, collecting source data according to user strength training and sending the source data to the processor module. The processor module is responsible for preprocessing of the source data. According to the pair of intelligent gloves, in the strength training process, the detection accuracy rate of detected motions is high, the rate of false alarm is low, and alarm signals can be sent when the hand posture is deviated.
Owner:SHENZHEN UNIV
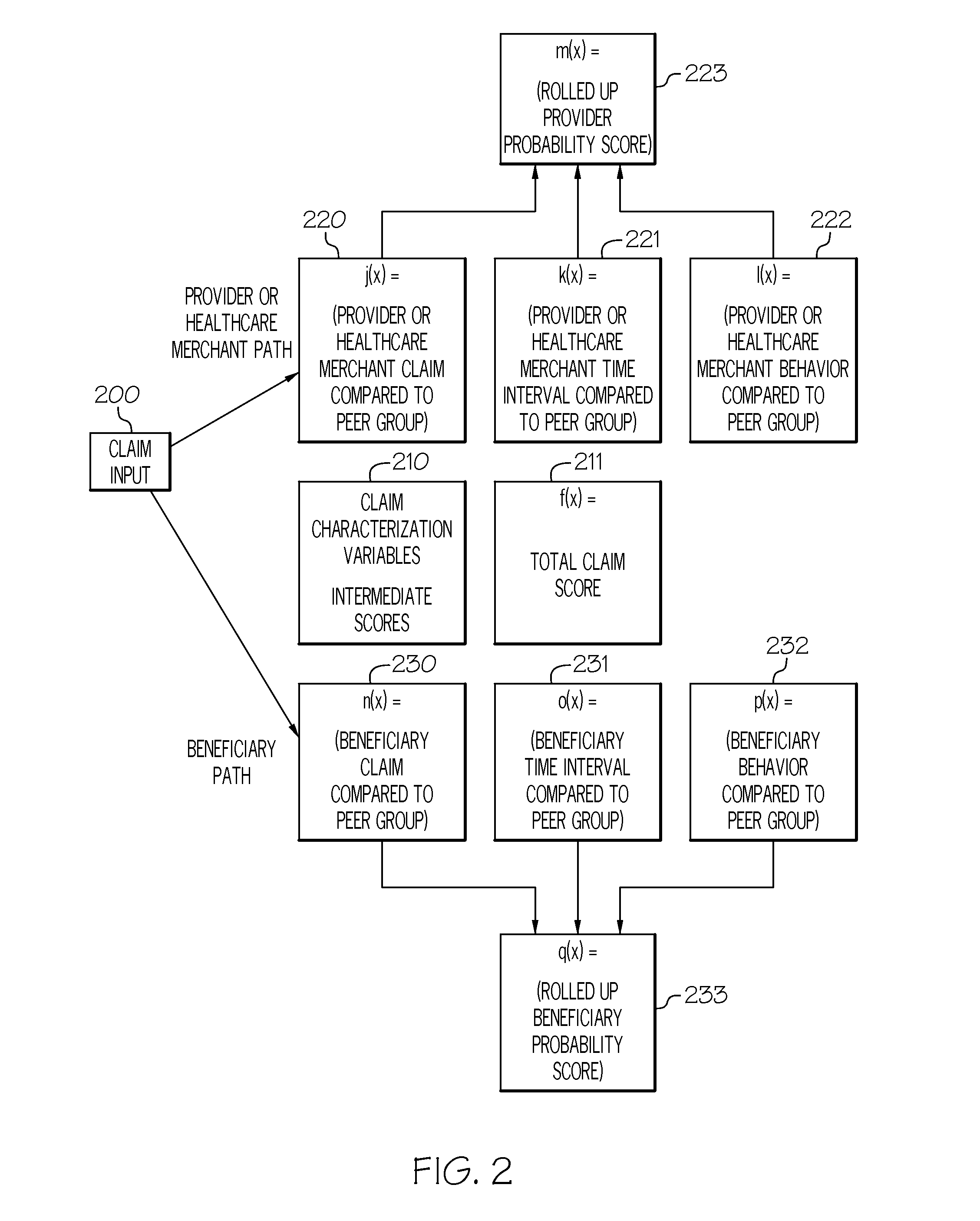
Characterizing healthcare provider, claim, beneficiary and healthcare merchant normal behavior using non-parametric statistical outlier detection scoring techniques
InactiveUS20130085769A1Predictive performanceHigh false positive rateOffice automationPatient-specific dataScalar ValueCrowds
This invention uses non-parametric statistical measures and probability mathematical techniques to calculate deviations of variable values, on both the high and low side of a data distribution, from the midpoint of the data distribution. It transforms the data values and then combines all of the individual variable values into a single scalar value that is a “good-ness” score. This “good-ness” behavior score model characterizes “normal” or typical behavior, rather than predicting fraudulent, abusive, or “bad”, behavior. The “good” score is a measure of how likely it is that the subject's behavior characteristics are from a population representing a “good” or “normal” provider, claim, beneficiary or healthcare merchant behavior. The “good” score can replace or compliment a score model that predicts “bad” behavior in order to reduce false positive rates. The optimal risk management prevention program should include both a “good” behavior score model and a “bad” behavior score model.
Owner:RISK MANAGEMENT SOLUTIONS
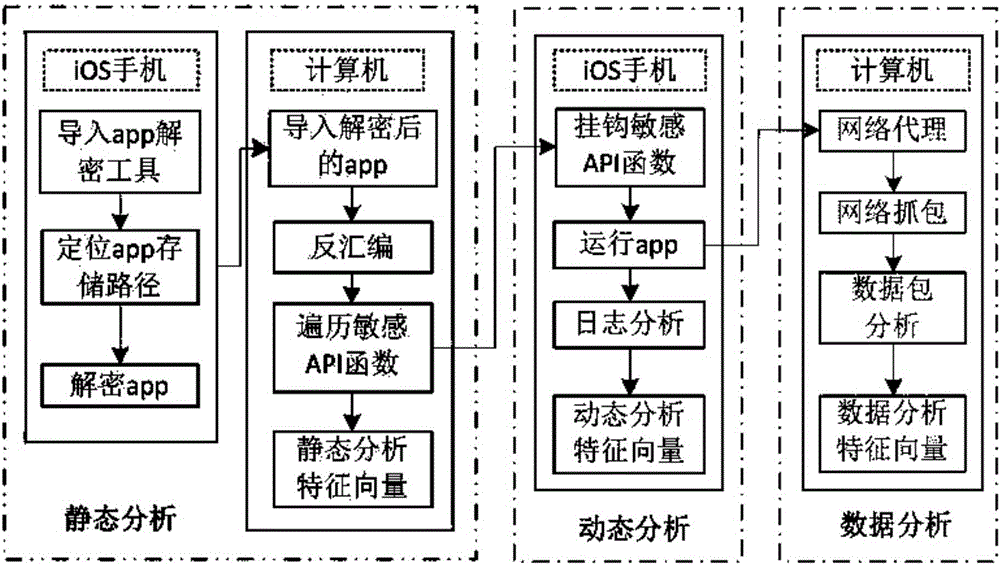
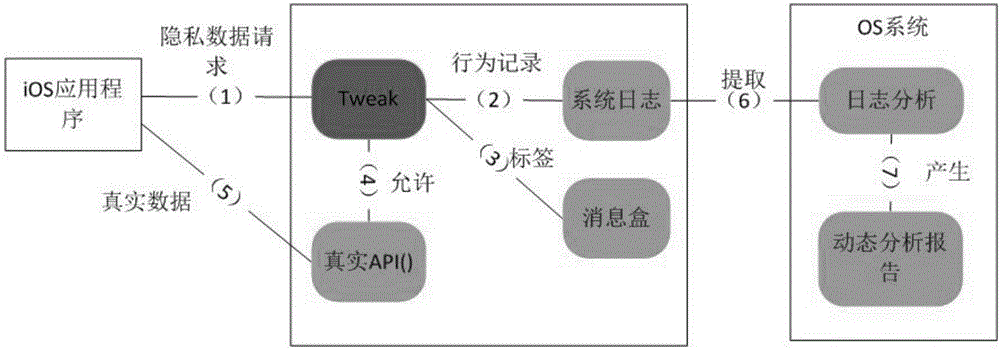
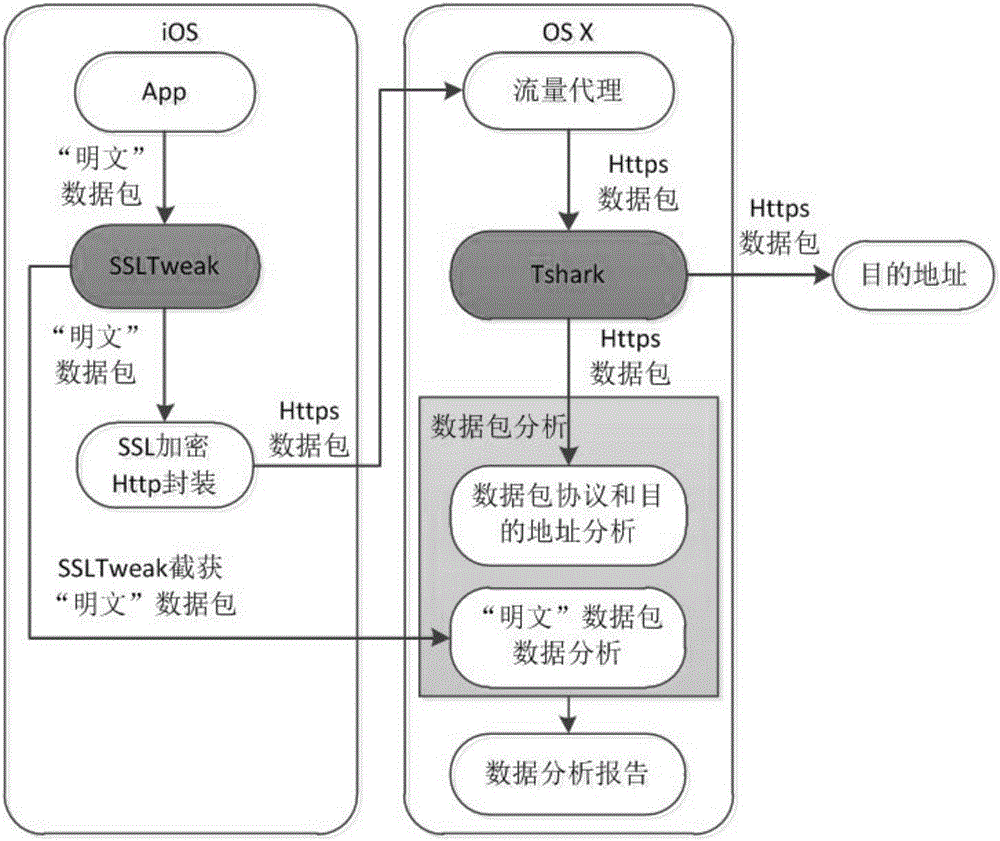
Application multidimensional privacy leak detection method and system for iOS platform
InactiveCN106845236AImprove scienceImprove rigorPlatform integrity maintainanceStatic timing analysisInternet privacy
The invention discloses an application multidimensional privacy leak detection method and system for iOS platform; privacy leak detection is provided for iOS applications from the three dimensions, static analysis, dynamic analysis and data analysis, wherein the static analysis incudes the steps of application decrypting, app storage path locating, disassembling, and disassembly source code sensitive API (application program interface) analysis; the dynamic analysis includes the step of allowing Hook-sensitive API function to acquire a log record by running an application, and acquire a sensitive API calling sequence through log analysis; the data analysis incudes the steps of capturing application network data packets, and analyzing data packet protocol, address and content. The method and system of the invention can provide comprehensive detection for data privacy leaks of iOS applications to obtain complete privacy leak event data.
Owner:SOUTHEAST UNIV +1
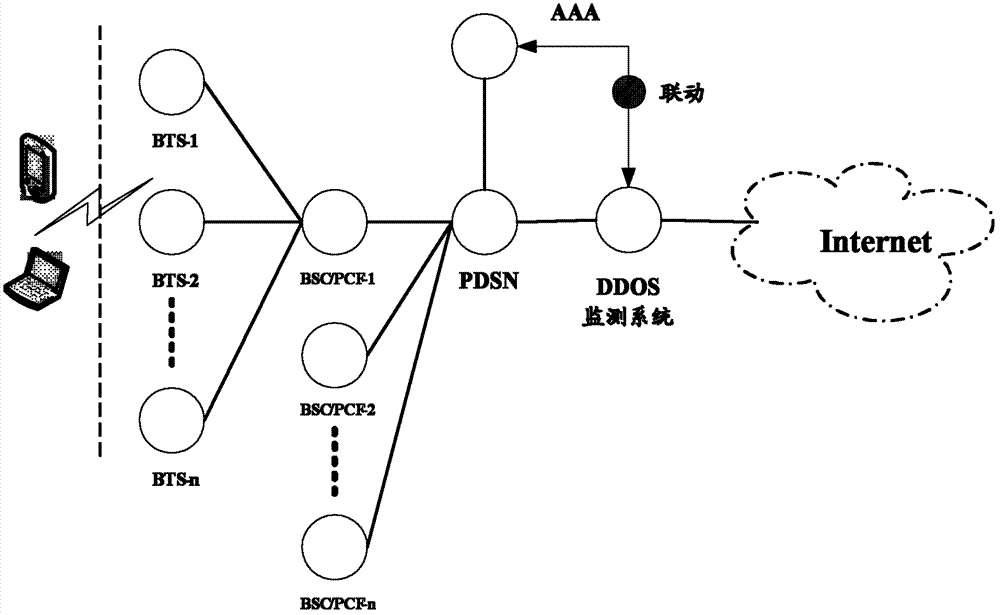
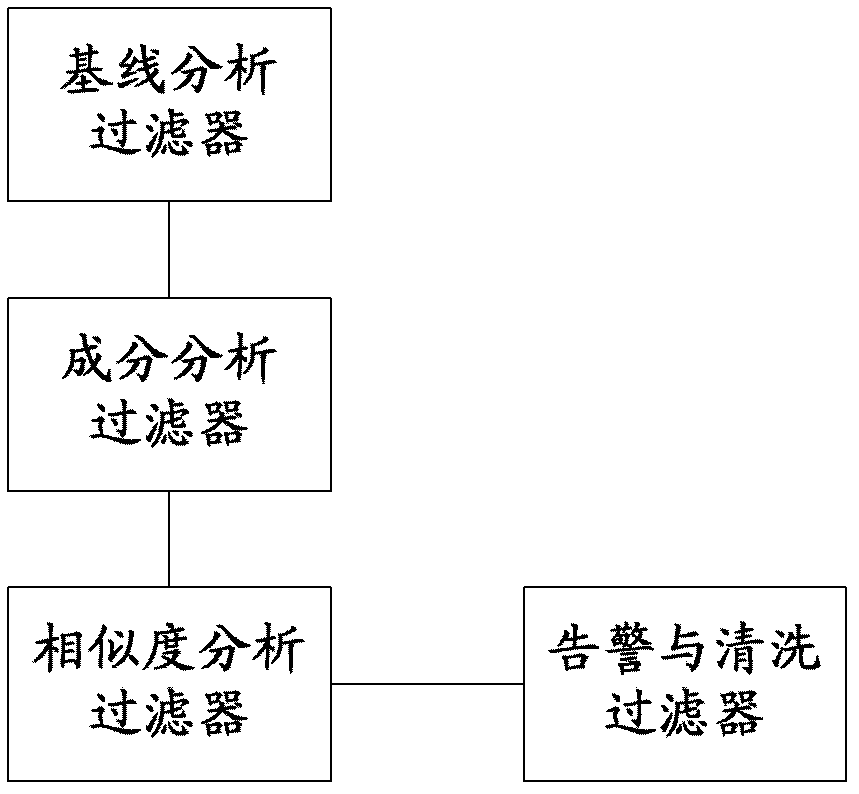
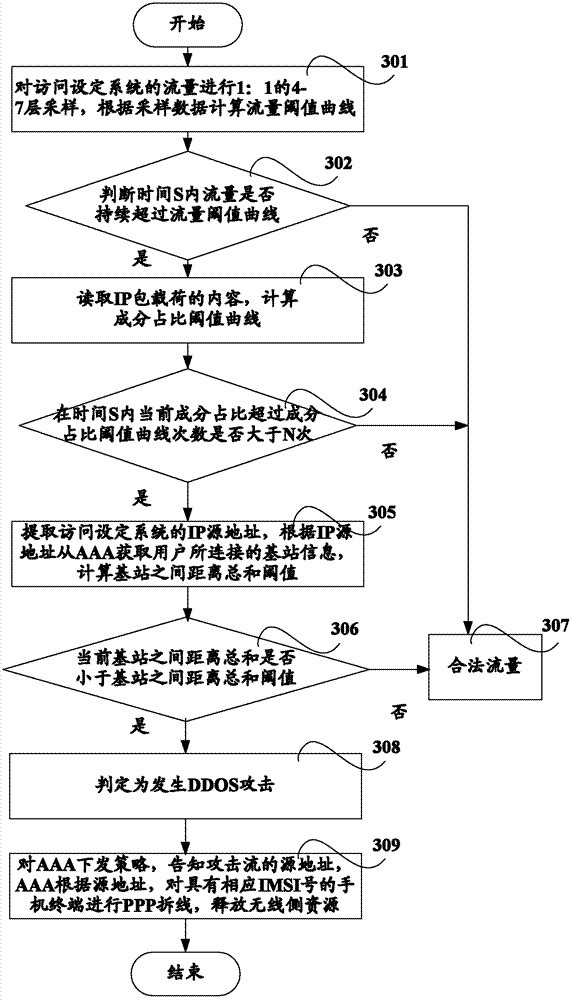
Method and system for monitoring DDOS (distributed denial of service) attacks in small flow
ActiveCN102821081AMake up for the inability to detect low-rate DDoS attacksHigh false positive rateData switching networksSimilarity analysisProtocol Application
The invention discloses a method and a system for monitoring DDOS (distributed denial of service) attacks in small flow, solves the problems that the existing DDOS attack detection technology is high in cost, complex to implement and high in misjudgment rate, cannot respond to DDOS attacks aiming at an application layer and the like, and provides the monitoring scheme of an integrated DPI (dots per inch) technology. A baseline analysis, component analysis and similarity analysis method is used to establish a normal use model, characteristics are accurately matched to detect the attacks in small flow and the application layer attacks, deployment at one point of an operator network and complete coverage of the operator network are achieved, and detection accuracy is increased.
Owner:CHINA TELECOM CORP LTD
Subsurface intrusion detection system
ActiveUS20110169638A1Accurately indicatedReduce false alarm rateAcoustic presence detectionBurglar alarmRelative magnitudeAcoustics
A system to detect subsurface activity. The system employs vibration sensor pairs, with each sensor pair having a shallow sensor and a deep sensor. Outputs of the sensors of a pair are processed together and events are detected based on the relative values detected by the sensors of the pair. When signal energy departs from a detected background level, the relative amplitude and frequency content of vibrations measured at the shallow and deep sensors may be compared. The comparison may be performed, at least in part, using a classifier that discriminates between subsurface activity and surface to activity. The outputs of sensor pairs may be aggregated to make a determination of whether subsurface activity exists and / or its location. Aggregation may involve comparing the outputs of the same sensor pair at multiple time intervals or may involve comparing the outputs of arrayed sensor pairs.
Owner:RAYTHEON BBN TECH CORP +1
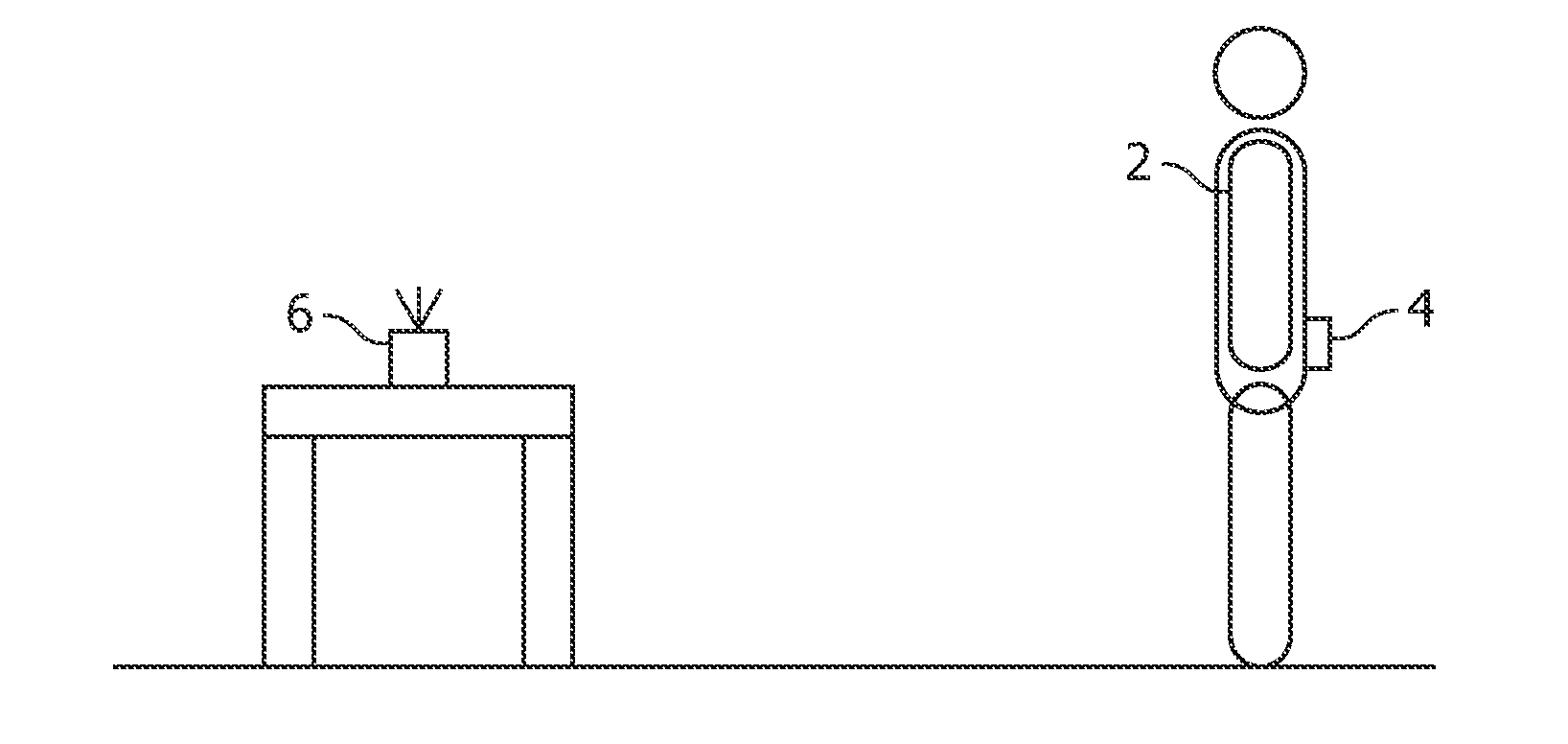
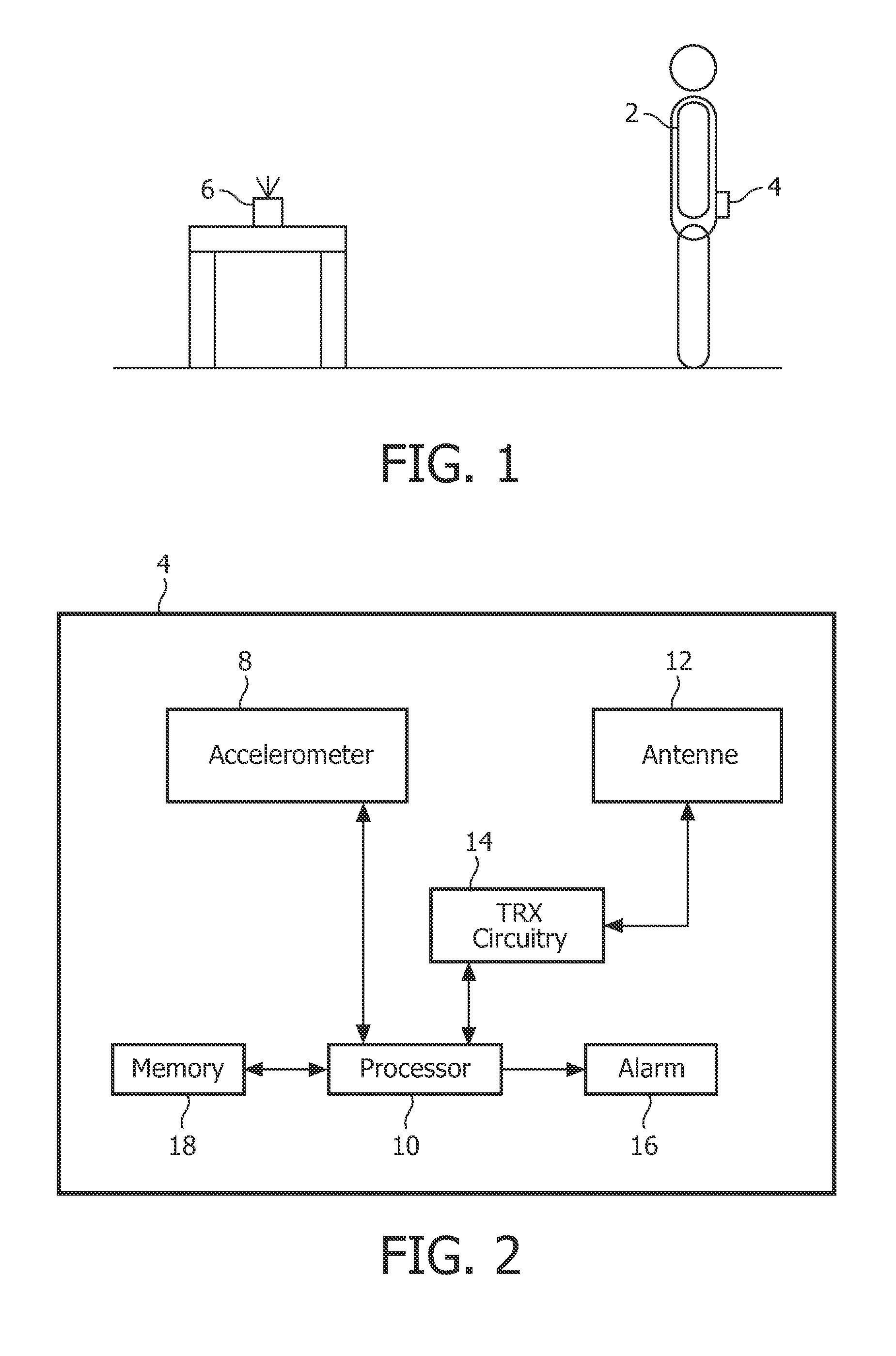
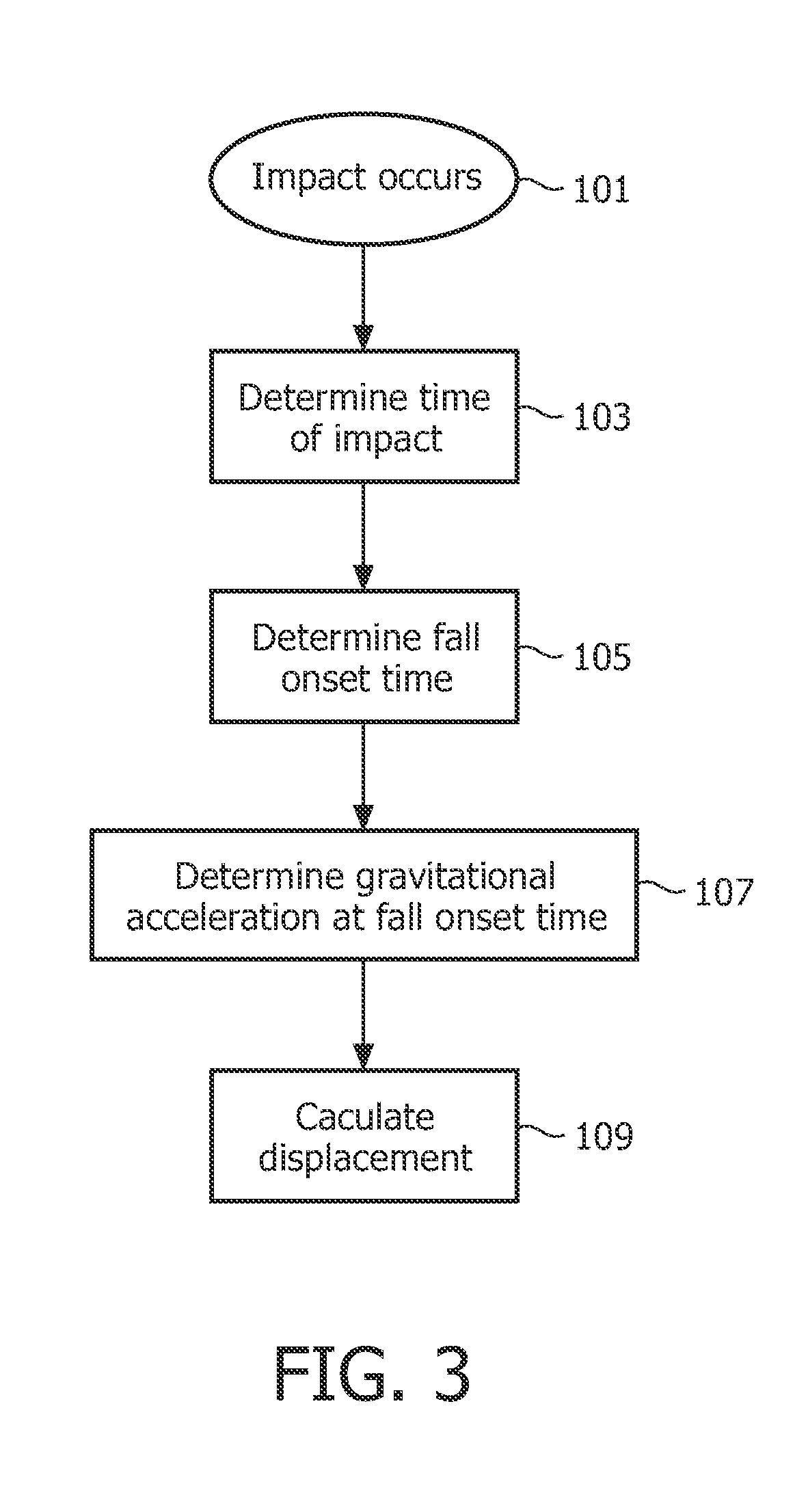
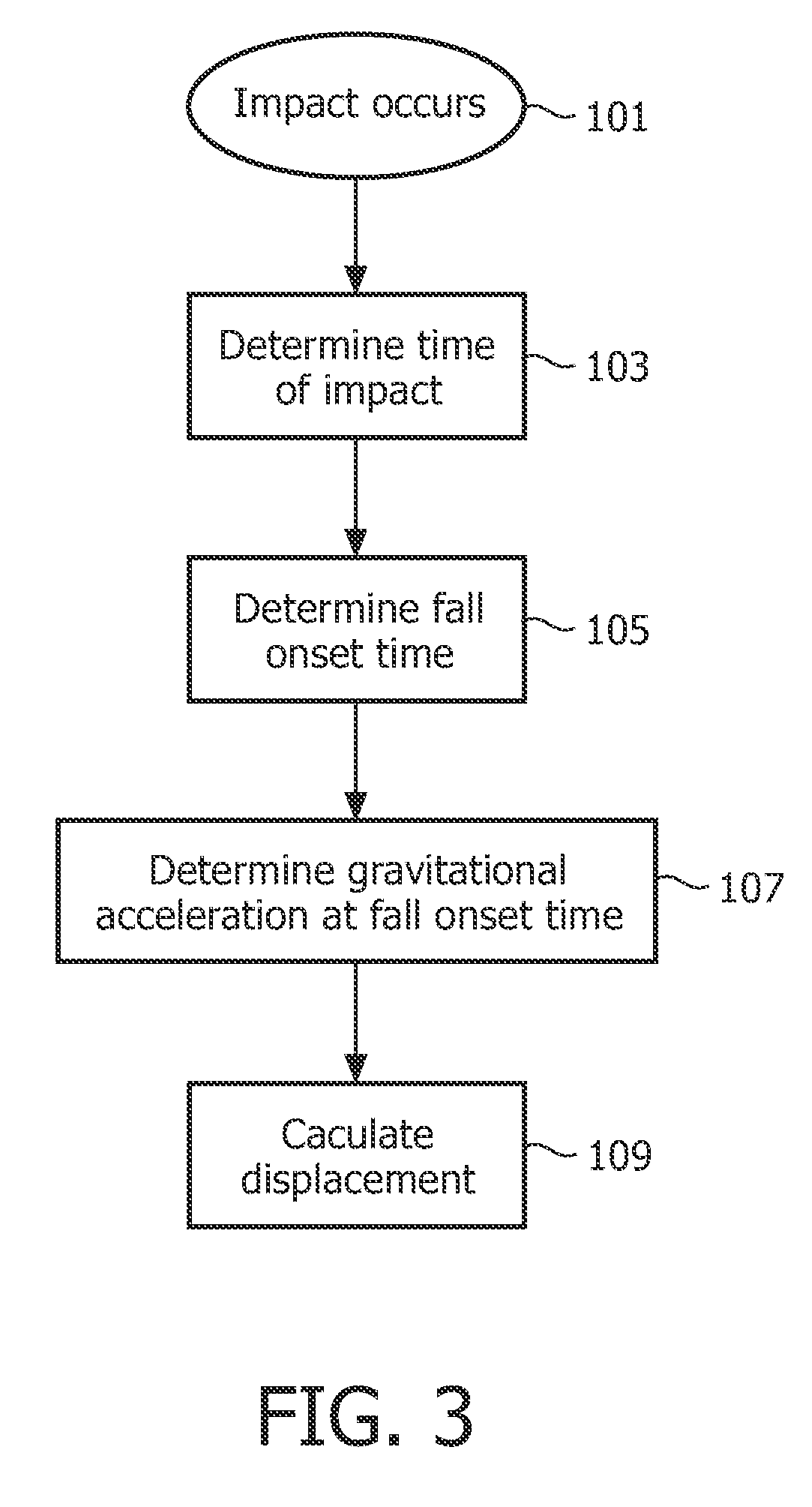
Displacement measurement in a fall detection system
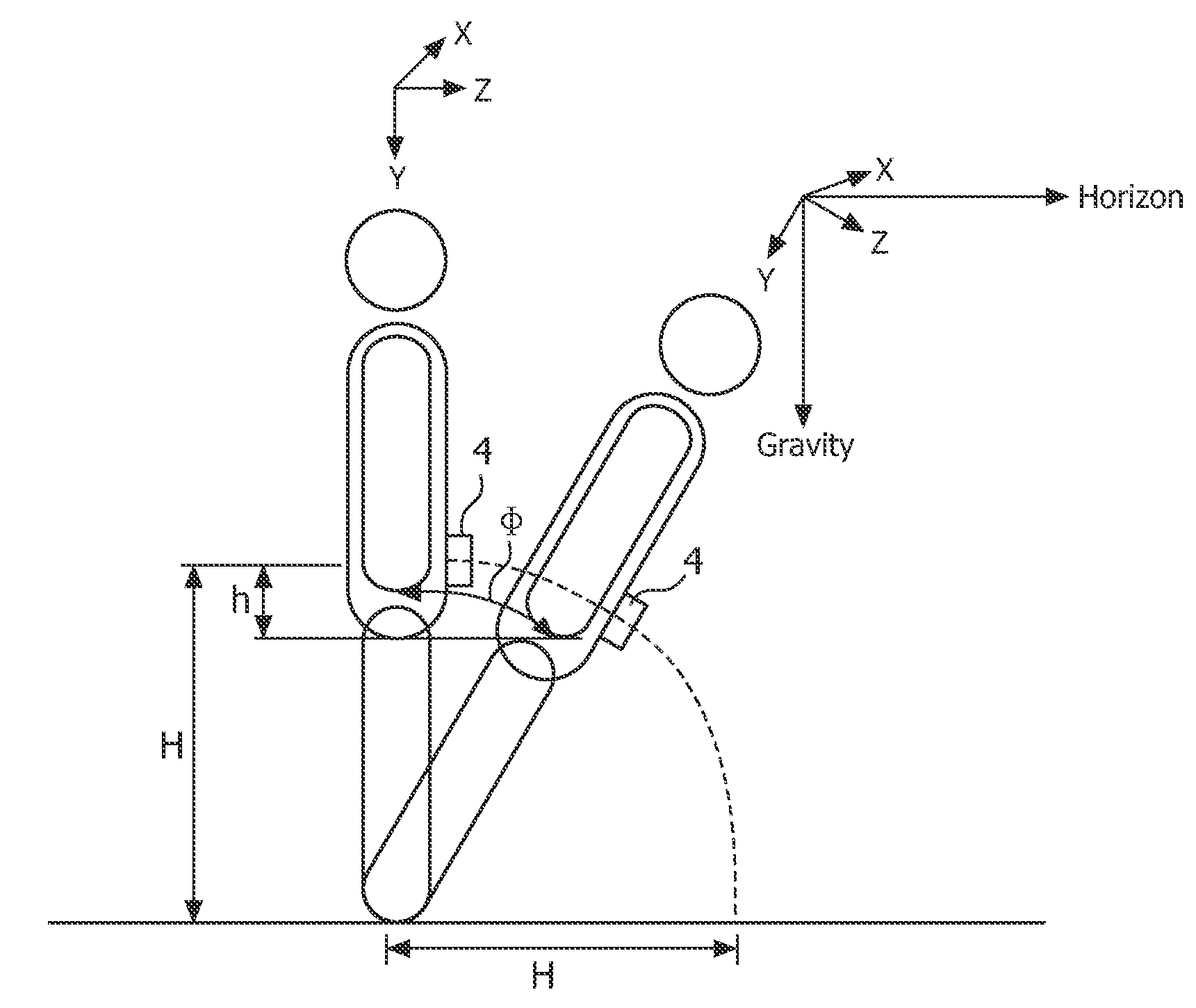
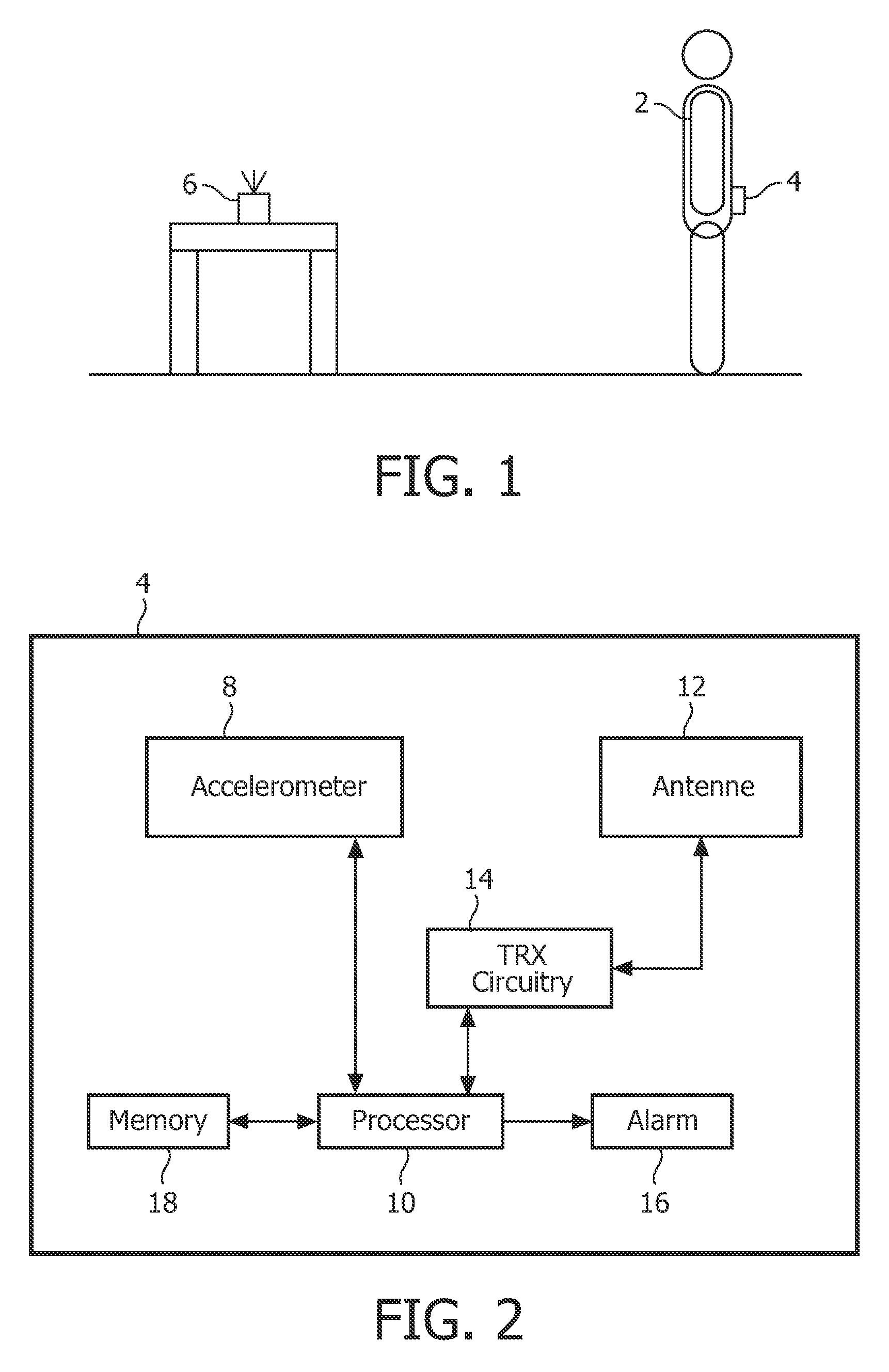
ActiveUS20110144542A1Increase consumptionIncrease volumePerson identificationInertial sensorsEngineeringVertical displacement
There is provided a personal fall detection system comprising a sensor module that is suitable for attachment to a user, the sensor module comprising an accelerometer for measuring accelerations acting on the sensor module; and a processor for analyzing the measured accelerations to determine if the sensor module has suffered an impact, and for estimating a vertical displacement of the sensor module during a time period immediately before the impact; wherein the processor estimates the vertical displacement of the sensor module by twice integrating the measurements from the accelerometer.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Intrusion detection report correlator and analyzer
ActiveUS8191139B2Easy to detectHigh false positive rateMemory loss protectionError detection/correctionAlert managementFalse alarm
A computer / computer network security alert management system aggregates information from multiple intrusion detectors. Utilizing reports from multiple intrusion detectors reduces the high false alarm rate experienced by individual detectors while also improving detection of coordinated attacks involving a series of seemingly harmless operations. An internal representation of a protected enclave is utilized, and intrusion detection system (IDS) information is correlated to accurately prioritize alerts. In one embodiment, the system is capable of utilizing data from most existing IDS products, with flexibility to add further IDS products.
Owner:HONEYWELL INT INC
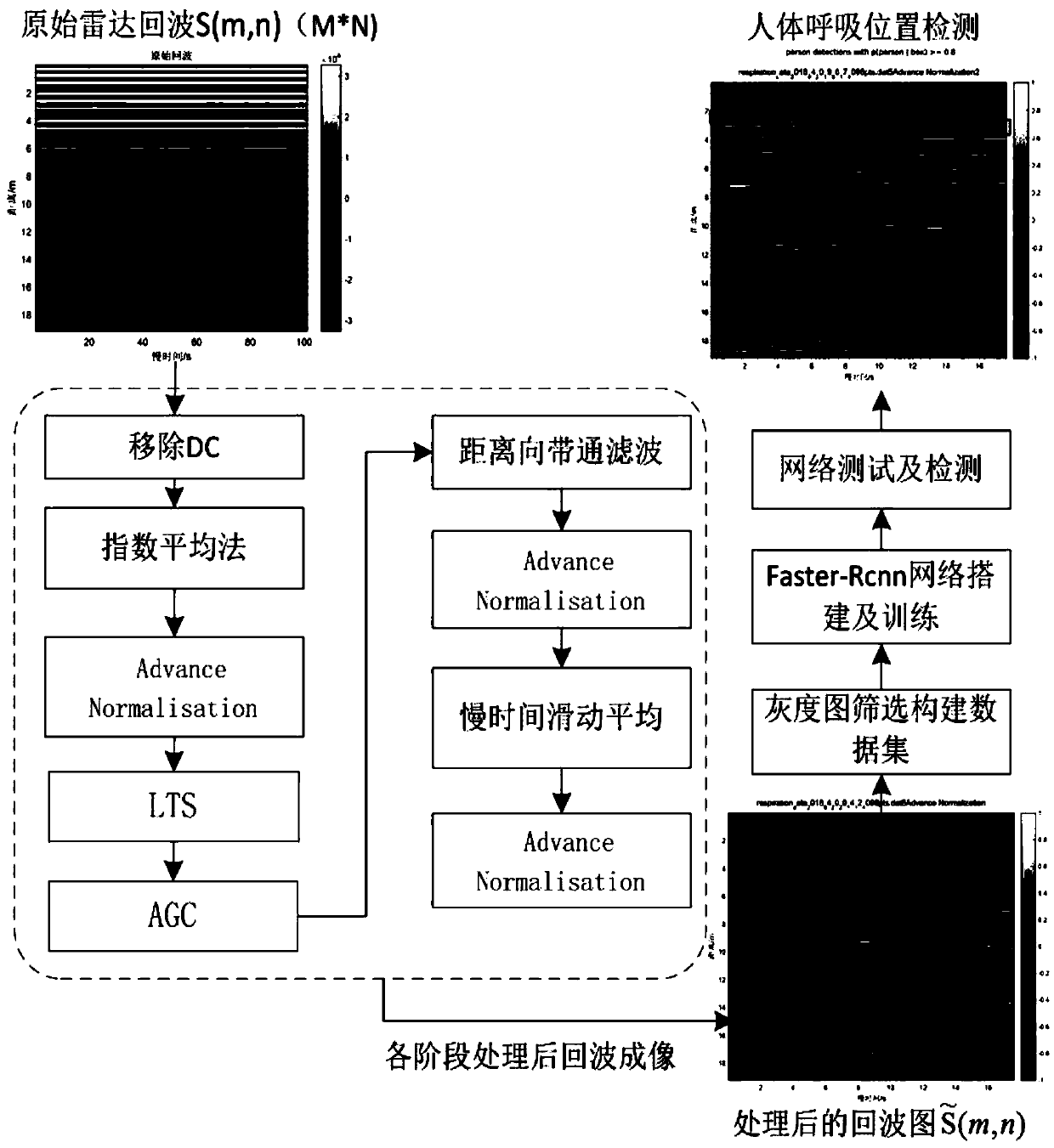
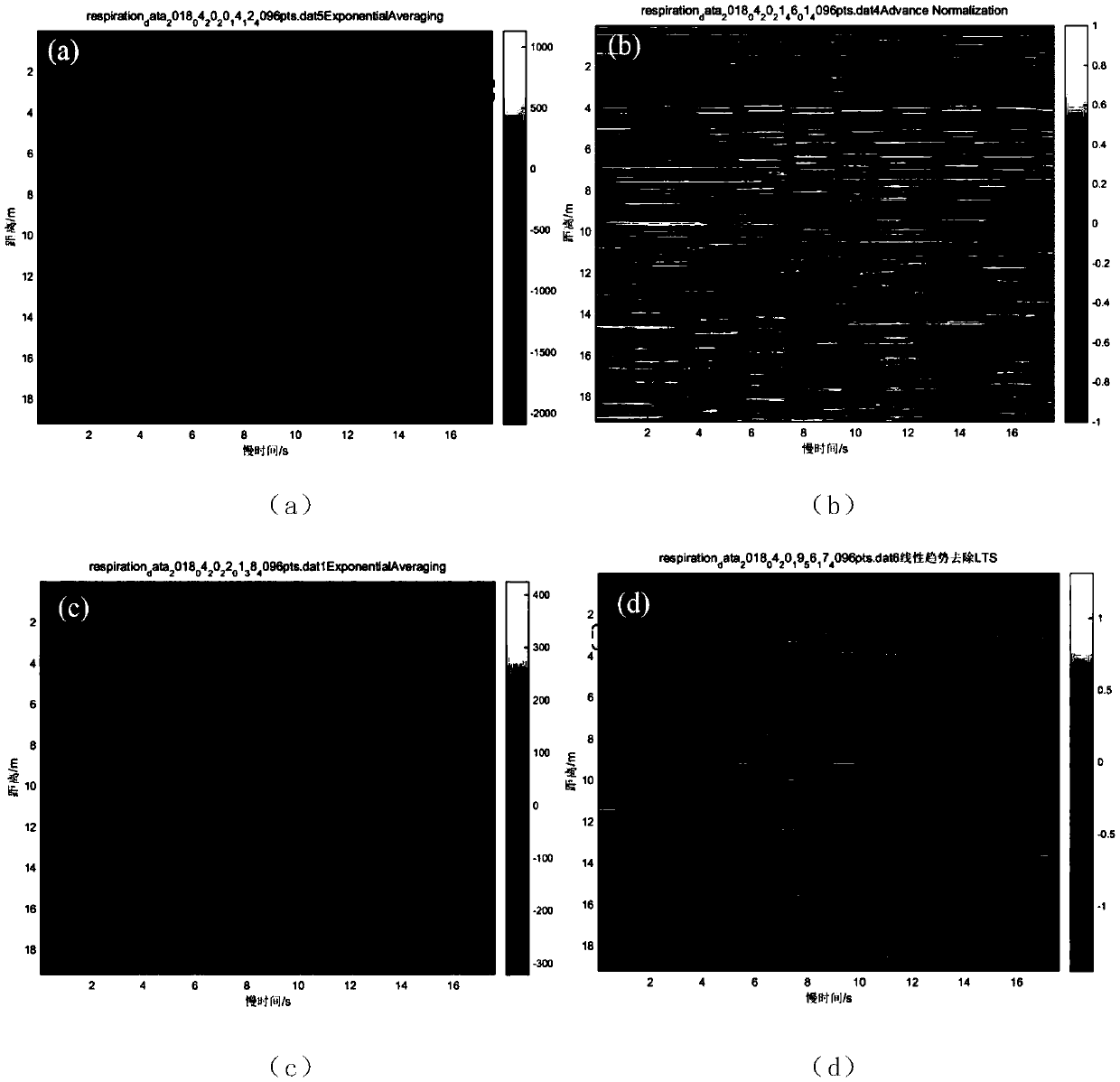
Through-wall ultra-wideband radar human body respiration signal detection method based on Faster-RCNN network
ActiveCN109031287AInsufficient avoidance of misjudgmentImprove signal-to-noise ratioRespiratory organ evaluationSensorsPattern recognitionData set
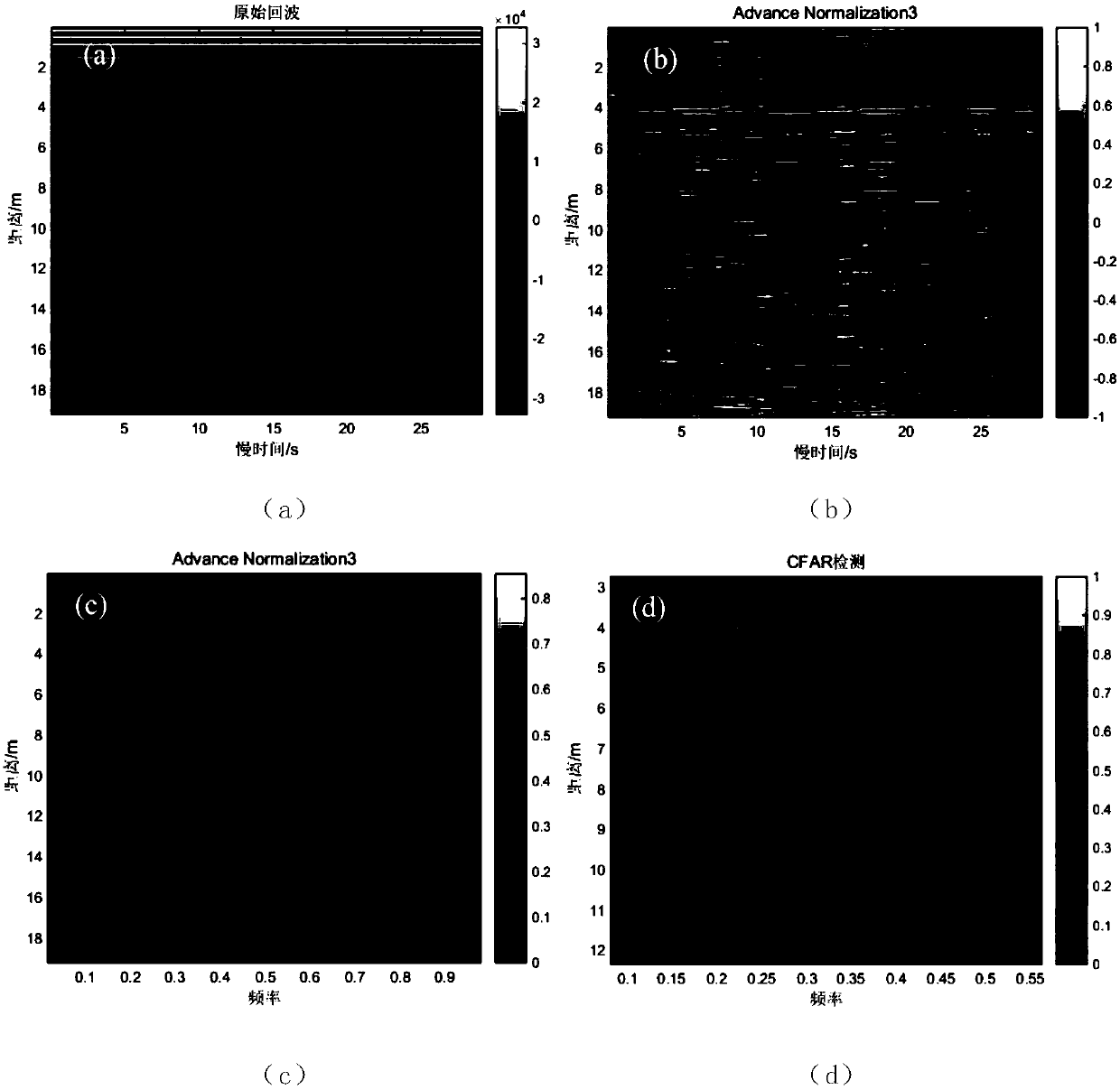
The invention discloses a through-wall ultra-wideband radar human body respiration signal detection method based on a Faster-RCNN network. The method comprises the following steps: performing denoising and weak signal enhancement preprocessing on an original slow time-distance two-dimension ultra-wideband radar echo signal; and then continuously performing signal enhancement and denoising on the processed echo by adopting an Advance Normalisation method; imaging the echo signal in the preprocessing process as a gray image by adopting MATLAB, wherein the image width is corresponding to the echoslow time direction, and the image height is corresponding to the echo distance direction; and screening the obtained gray image, annotating a data set, and training a Faster-RCNN network model to perform human body respiration weak signal identification. The method disclosed by the invention is high in identification accuracy rate, high in detection speed, and capable of providing better technical support for the radar echo target detection, the life detection and practical technologies in actual applications.
Owner:XI AN JIAOTONG UNIV
Synthetic aperture radar (SAR) image change detection difference chart generation method based on contourlet transform
InactiveCN102800074AHigh false positive rateEnhanced change areaImage enhancementImage analysisSynthetic aperture radarContourlet
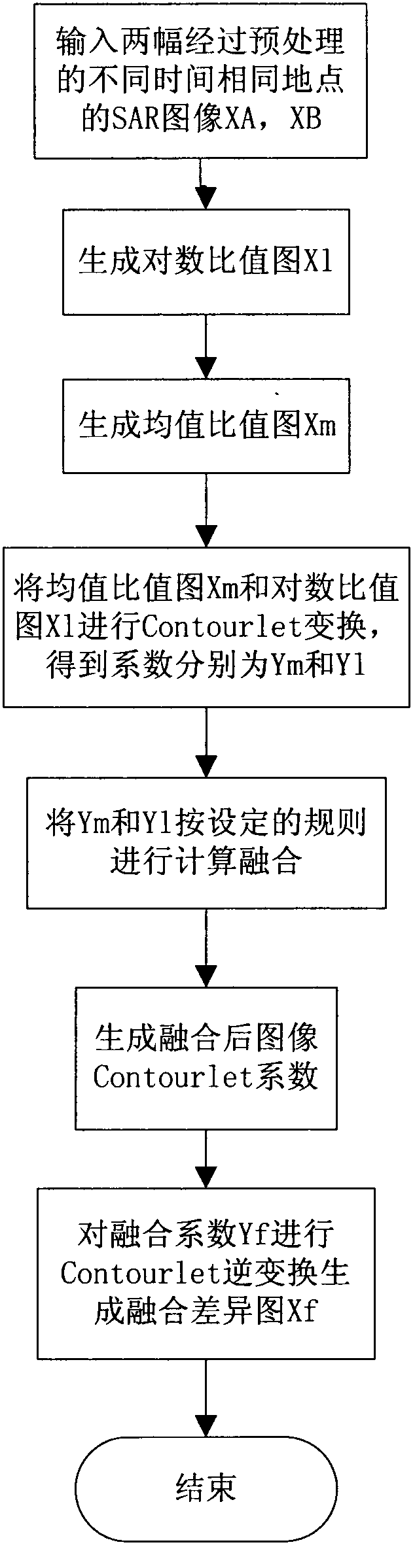
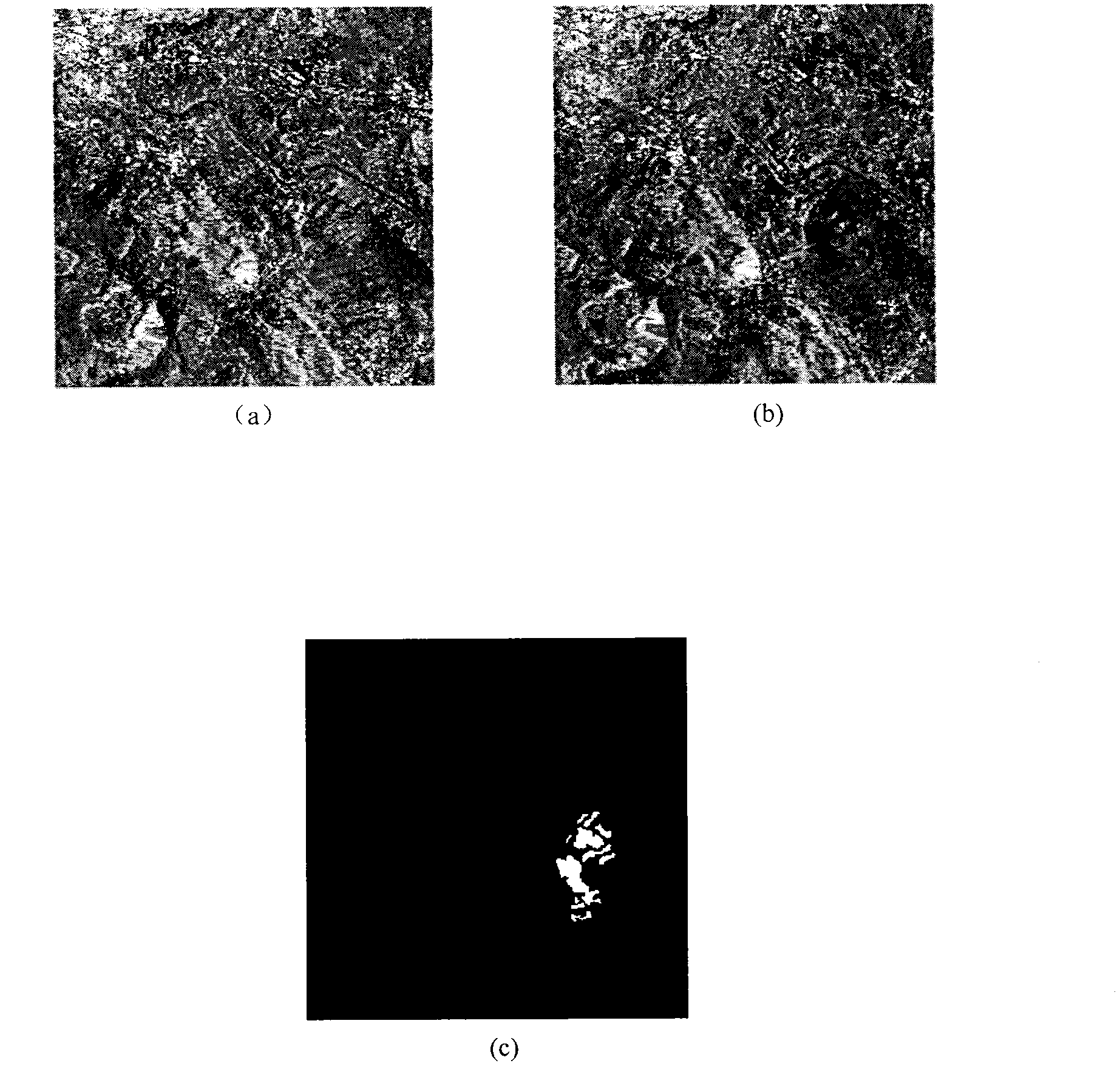
The invention discloses a synthetic aperture radar (SAR) image change detection difference chart generation method based on contourlet transform. A realization process mainly comprises the following steps of: firstly, constructing a logarithmic ratio image and a mean ratio image on two SAR images which are preprocessed and obtained at different time and in a same region; generating corresponding Contourlet coefficients by Contourlet transform processing; respectively calculating the coefficients of the two images in a high-frequency mode and a low-frequency mode according to different fusion rules; performing inverse Contourlet transform on the fused Contourlet coefficients to generate a change difference chart. The different characteristics of high frequency and low frequency are respectively extracted by the mean ratio image and the logarithmic ratio image, and complementation information of the source images is fully utilized by the image fusion based on the Contourlet transform, so that the SAR image change detection can have a better result, the detection error ratio is low, the image noise is inhibited, and the analysis precision is improved. Compared with other difference chart generation methods, the method disclosed by the invention is high in noise inhibition and good in edge maintenance, and can reserve change information to the maximum extent.
Owner:XIDIAN UNIV
Method of detecting and recognizing target by using police video monitoring fuzzy image
InactiveCN107169993AHigh speedRapid positioningImage enhancementImage analysisVideo monitoringAngle of view
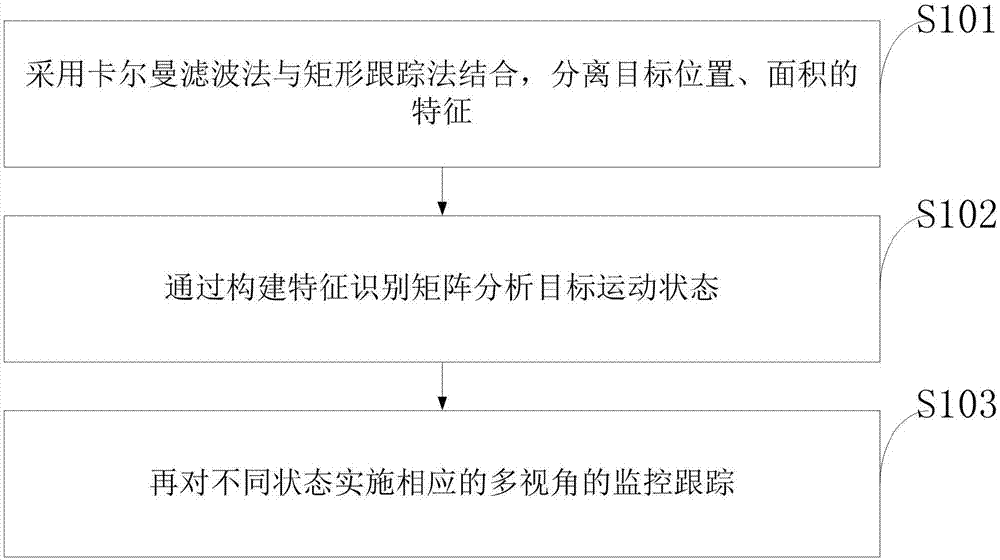
The invention discloses a method of detecting and recognizing a target by using a police video monitoring fuzzy image. A Kalman filtering method and a rectangle tracking method are combined, and target position and area features are separated; through constructing a feature recognition matrix, the motion state of the target is analyzed; and corresponding multi-angle of view monitoring tracking is executed on different states. As for the police video monitoring fuzzy image, a fuzzy neural network and an RS theory are adopted, the target is detected and recognized, a new algorithm is improved and put forward, and the fuzzy image recognition rate is improved; effective information is subjected to fusion processing, the features of the target object are dynamically extracted, and dynamic capturing and early warning are carried out, and the advanced level of the country is reached; and the problem that the current video monitoring image is fuzzy can be solved.
Owner:GANSU INST OF POLITICAL SCI & LAW
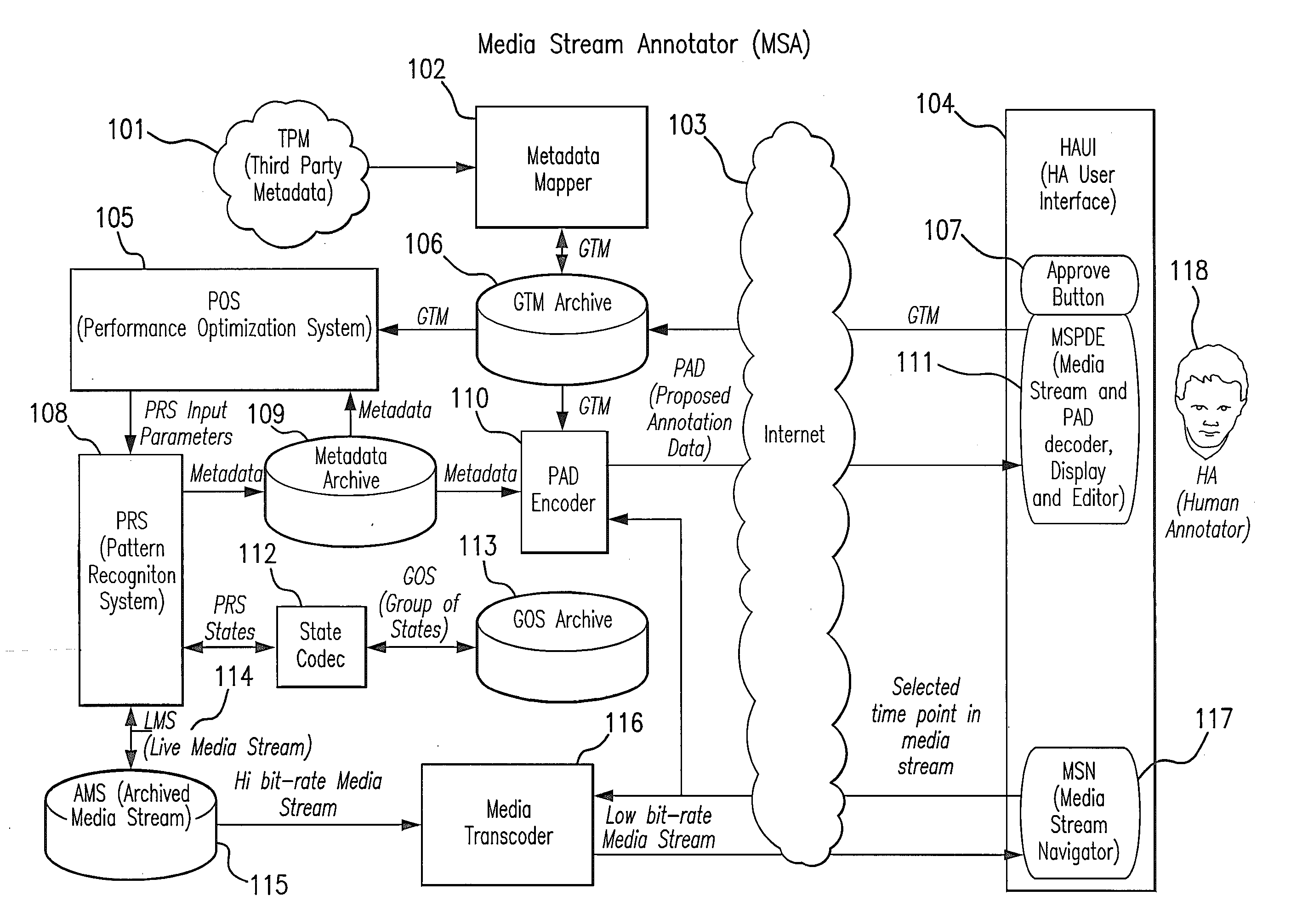
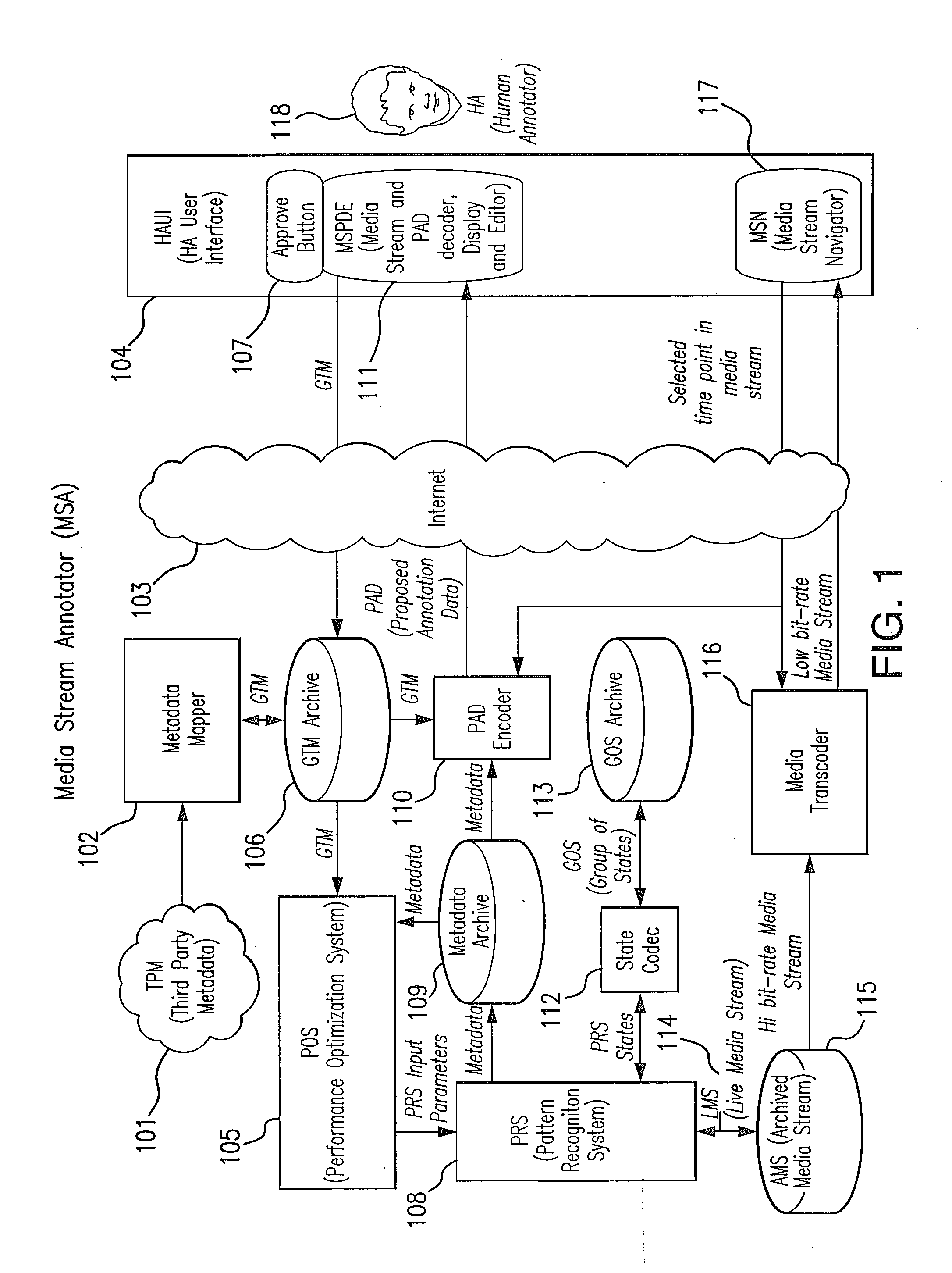
System for Annotating Media Content for Automatic Content Understanding
ActiveUS20140168517A1Shorten the timeReduce effortTelevision system detailsImage analysisData streamHigh probability
A method to correct for temporal variability in incoming streams of media and data to optimize the performance of a pattern recognition system includes the steps of receiving from one of the incoming streams a point in time when an event is announced, applying a probability distribution about the point in time, shifting a point of highest probability of the probability distribution back in time by an amount effective to accommodate for a delay between the event and the announcement, comparing a detected pattern of the event to a stored pattern of similar events and applying a confidence value to the comparison, and confirming to the pattern recognition system that the event occurred at the point of highest probability when the confidence score exceeds a predefined threshold. The method is useful to determine the time at which a particular play occurs during a sporting event, such as the time of a shot-on-goal in a soccer match.
Owner:LIVECLIPS
Optical detection and ranging sensor system for sense and avoid, and related methods
ActiveUS8400511B2Rapidly optimize blur differentialIncrease rangeTelevision system detailsOptical rangefindersSense and avoidWide field
An apparatus carried by an unmanned vehicle to provide passive sensing and facilitate avoiding airborne aerial obstacles is provided. The apparatus can include at least one, but typically multiple optical systems installed, for example, in the nose of the aerial vehicle to passively sense and determine a range, direction, and velocity of the airborne obstacles to allow the aerial vehicle to avoid the airborne obstacles. The typical optical system includes at least one focal plane array or other imaging device configured to receive a wide field of view and at least one focal plane array or other imaging device configured to receive a steerable narrow field of view within the wide field of view to allow concentrated determination of the range, direction, and / or velocity of obstacles detected by the wide field of view imaging devices.
Owner:LOCKHEED MARTIN CORP
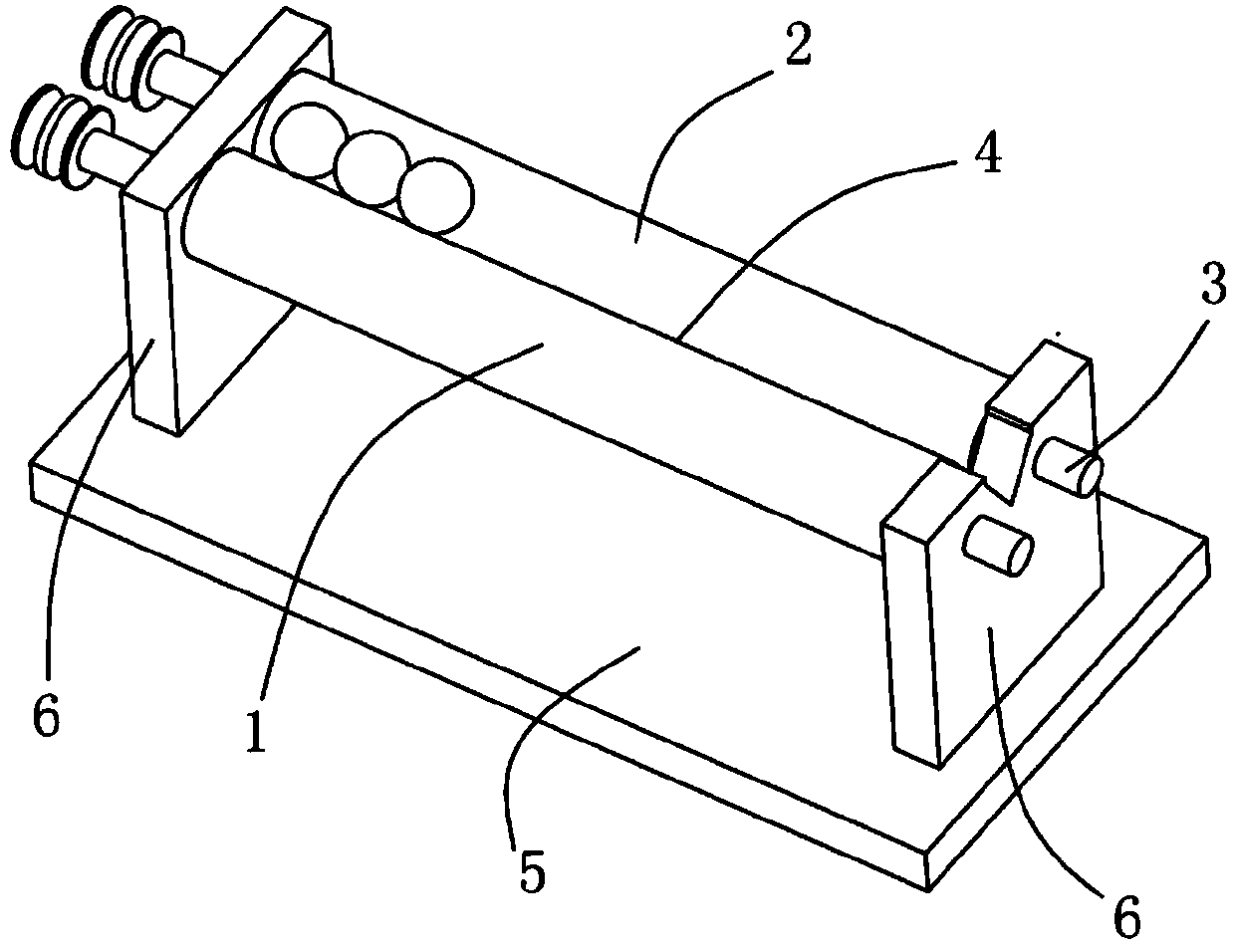
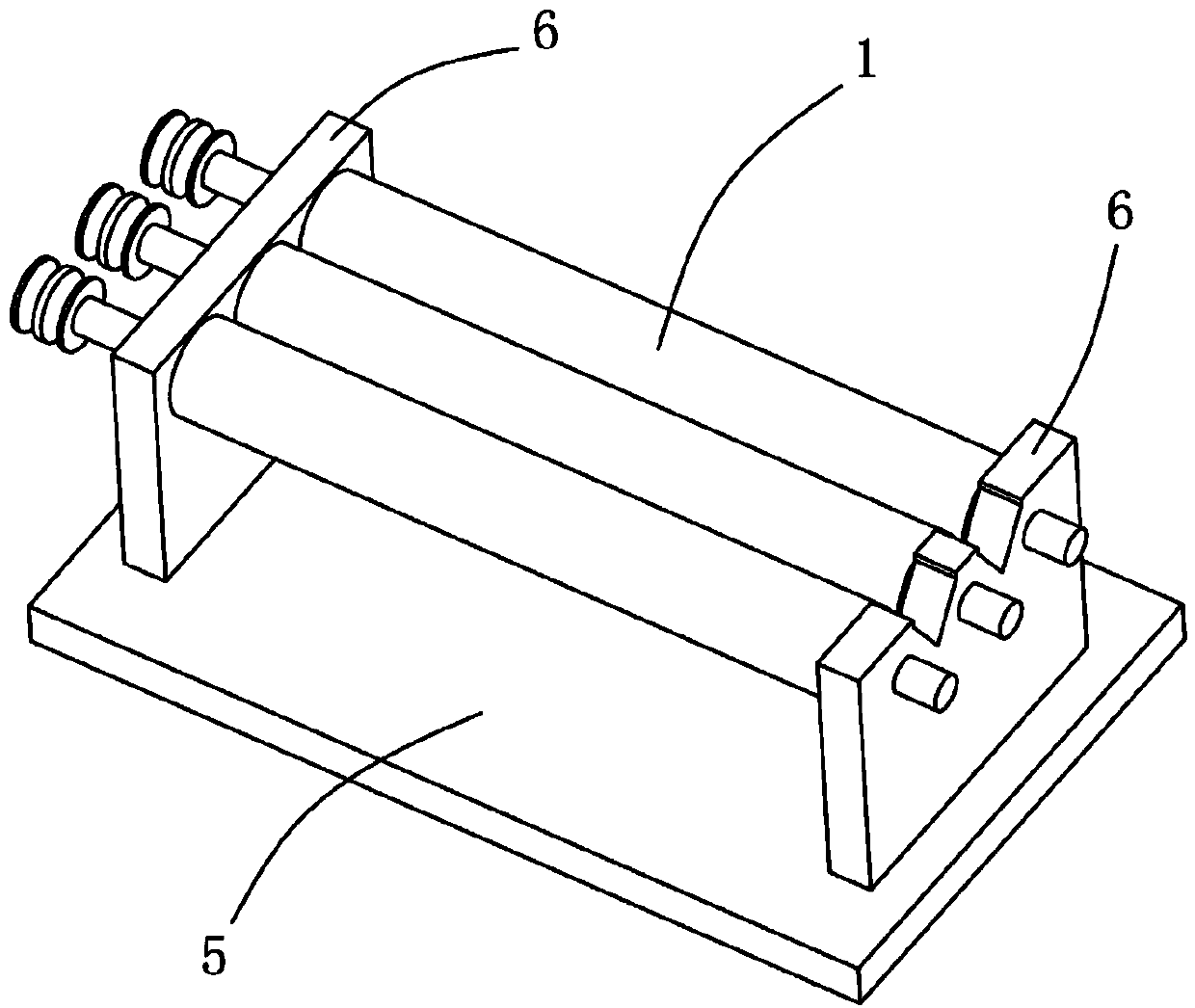
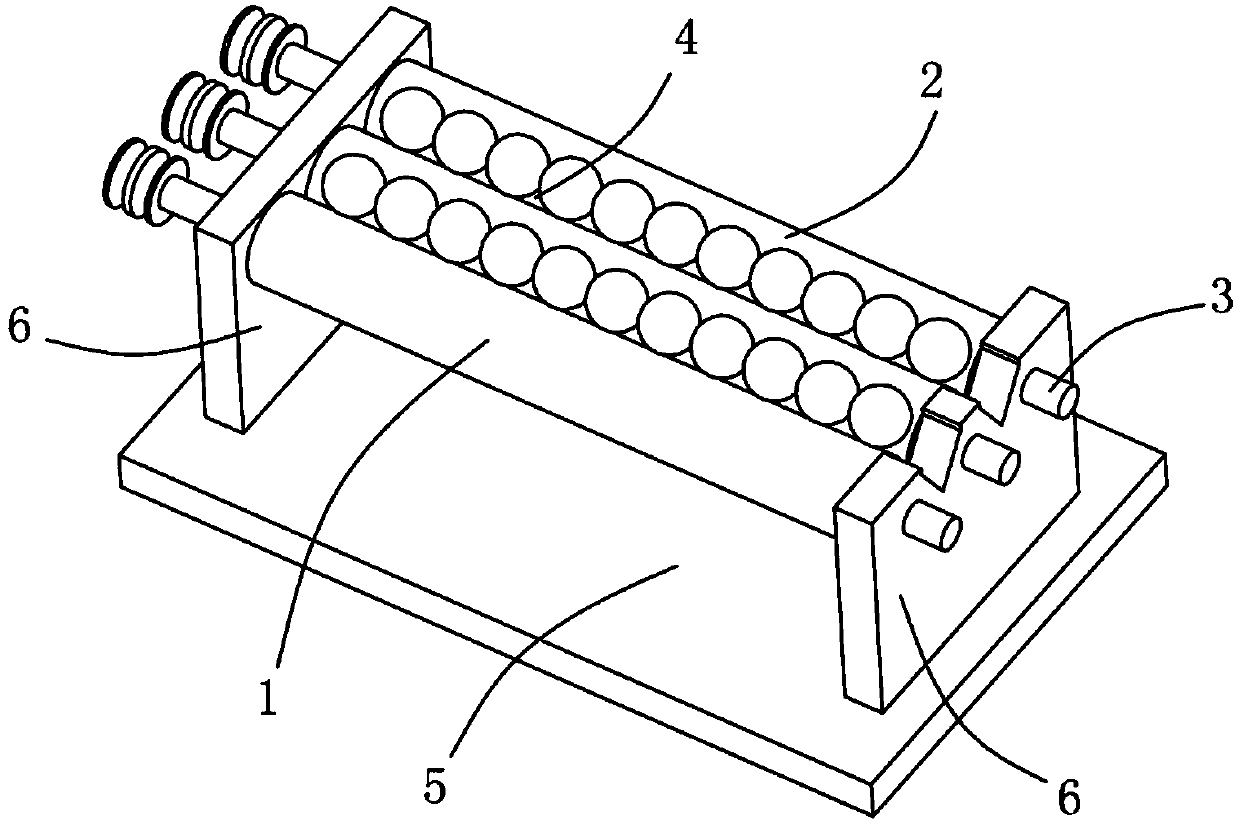
Steel ball surface defect detection sorting equipment
ActiveCN104190634AImprove fullyHigh false positive rateOptically investigating flaws/contaminationCleaning using toolsMetallurgySurface cleaning
The invention discloses steel ball surface defect detection sorting equipment. The steel ball surface defect detection sorting equipment comprises a steel ball size screening device, a steel ball surface cleaning device, a steel ball surface unfolding device, a camera, a sorting device and a control module, wherein the steel ball size screening device comprises two parallel rolling shafts; the steel ball surface cleaning device comprises a trapezoid rotary table and a rotary sleeve covering the rotary table; the steel ball surface unfolding device comprises at least two rolling bars, wherein a containing groove is formed between two adjacent rolling bars, and at least one rotatable rolling bar in the two adjacent rolling bars can be used for driving steel balls to roll in the containing groove in synchronism with the rolling bars. The equipment disclosed by the invention can screen out the out-of-size steel balls and can clean the surfaces of the steel balls so as to prevent the false detection caused by blots on the surfaces of the steel balls; in combination with the specific steel ball surface unfolding device, the steel ball surface defect detection storing equipment can rapidly and accurately sort the steel ball sizes and the steel ball surface defects, and the steel ball sorting efficiency is greatly promoted.
Owner:NINGBO BAIJIABAI MEASUREMENT & CONTROL EQUIP
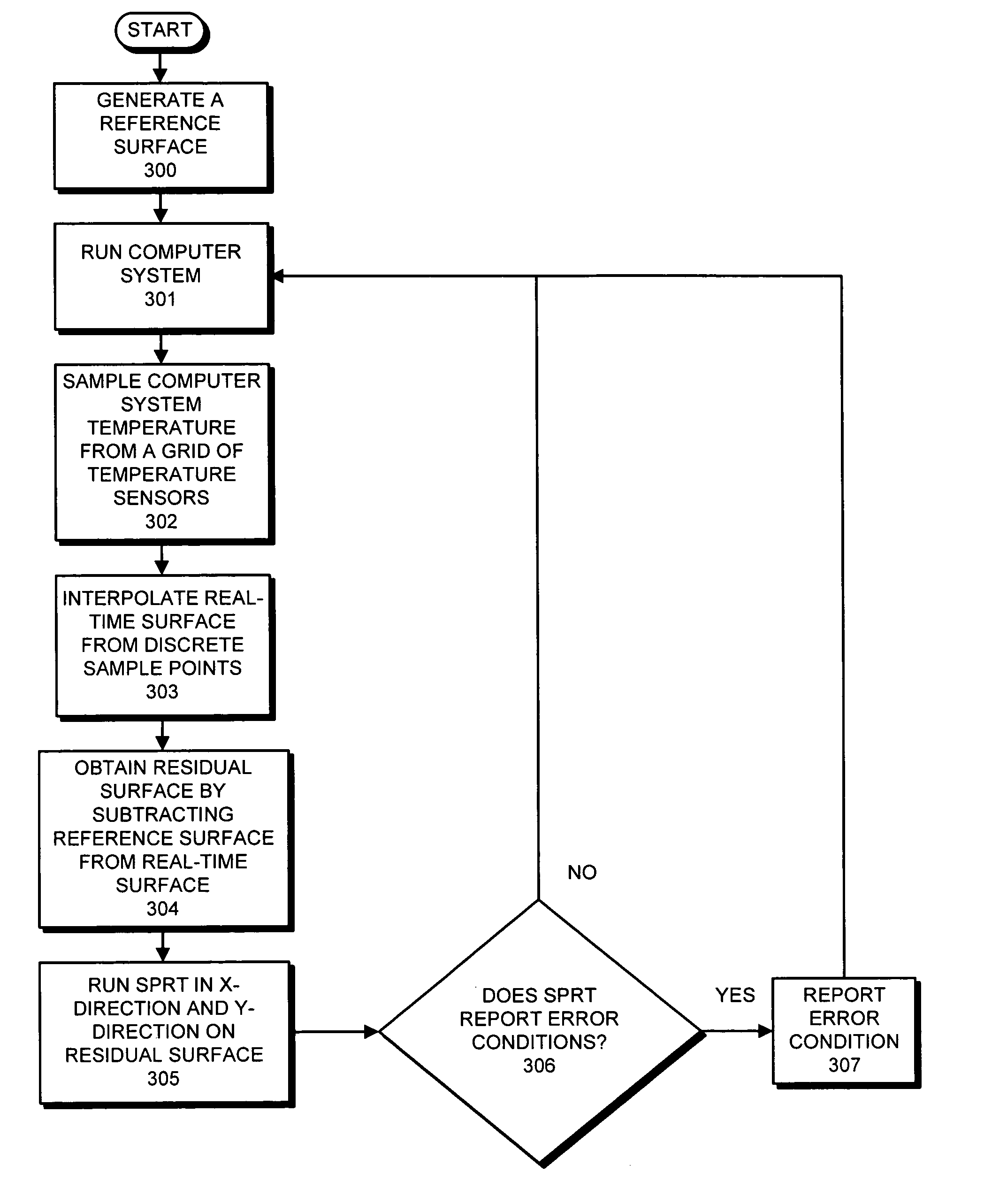
Multi-dimensional sequential probability ratio test for detecting failure conditions in computer systems
ActiveUS7191096B1High sensitivityHigh false positive rateDigital computer detailsNuclear monitoringComputerized systemMonitoring system
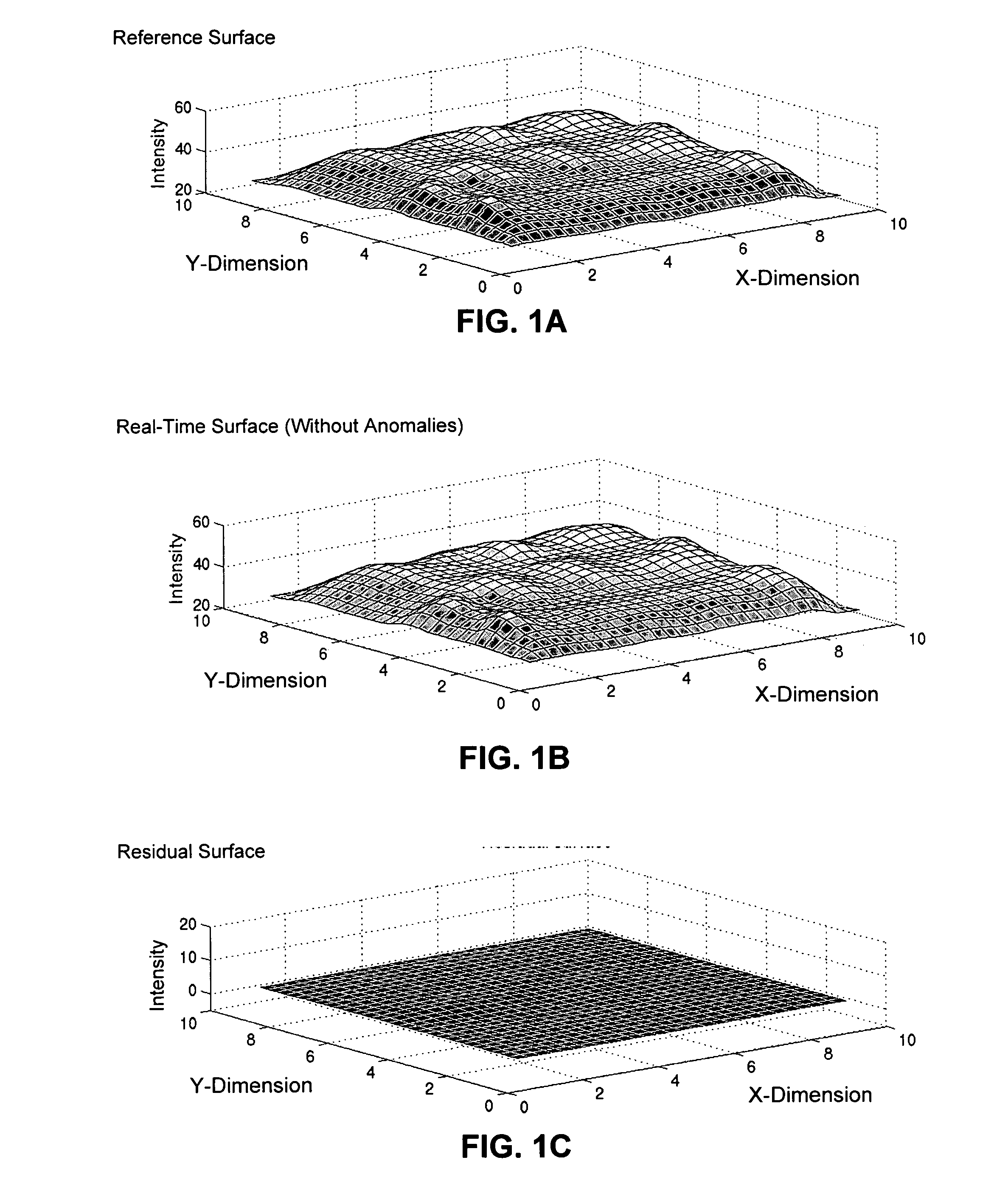
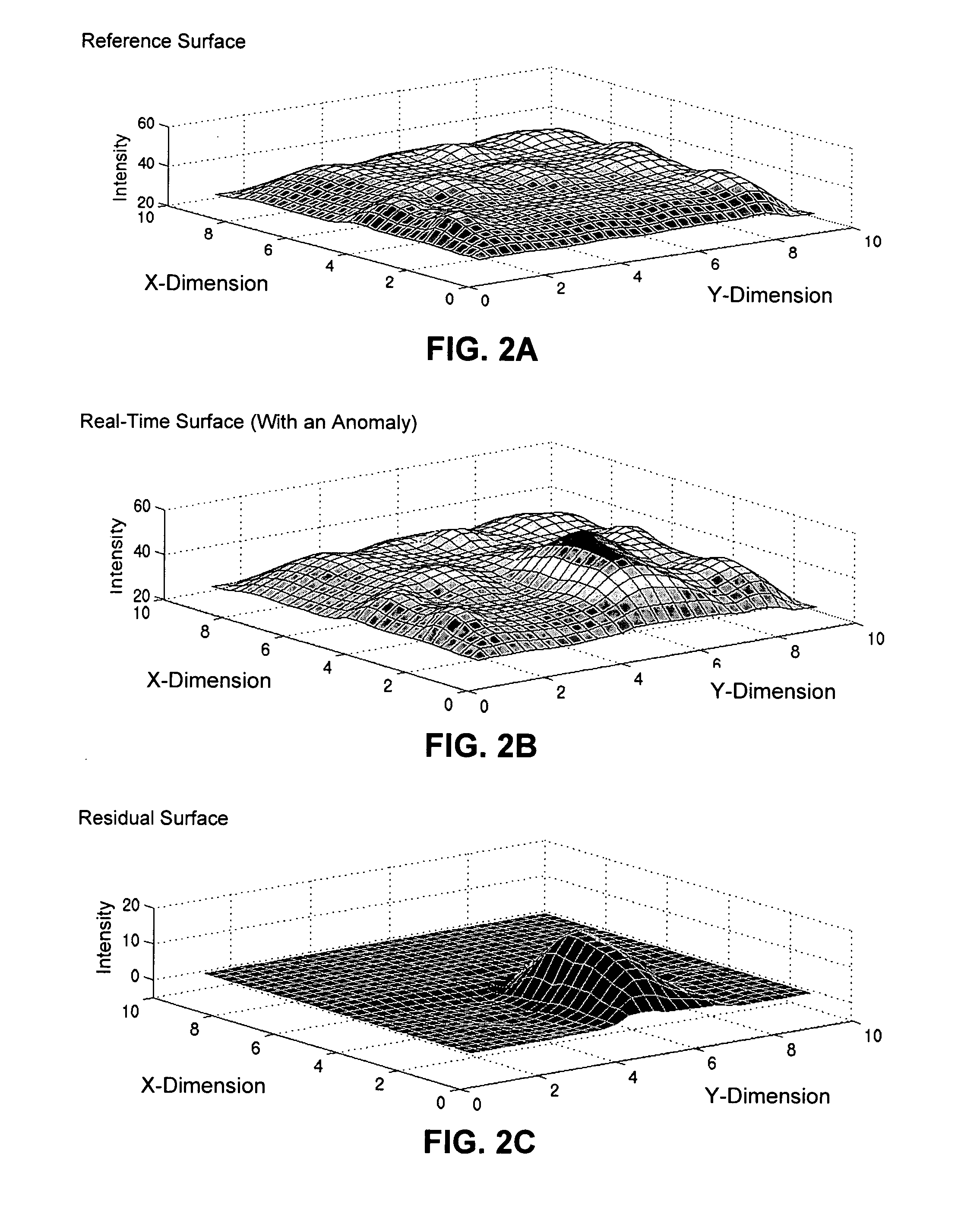
One embodiment of the present invention provides a monitoring system that detects anomalies in data gathered from sensors in a computer system. During operation, the monitoring system samples data from a plurality of sensors located at various sampling points throughout the computer system. Next, the monitoring system interpolates the data from the sampling points to produce a real-time digitized surface. The monitoring system then subtracts a reference digitized surface from the real-time digitized surface to produce a residual digitized surface. Finally, the monitoring system applies a multi-dimensional sequential probability ratio test (SPRT) to the residual digitized surface to detect anomalies in the residual digitized surface which indicate an impending failure of the computer system.
Owner:ORACLE INT CORP
Displacement measurement in a fall detection system
ActiveUS9138174B2Increase consumptionIncrease volumePerson identificationInertial sensorsComputer moduleEngineering
There is provided a personal fall detection system comprising a sensor module that is suitable for attachment to a user, the sensor module comprising an accelerometer for measuring accelerations acting on the sensor module; and a processor for analyzing the measured accelerations to determine if the sensor module has suffered an impact, and for estimating a vertical displacement of the sensor module during a time period immediately before the impact; wherein the processor estimates the vertical displacement of the sensor module by twice integrating the measurements from the accelerometer.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
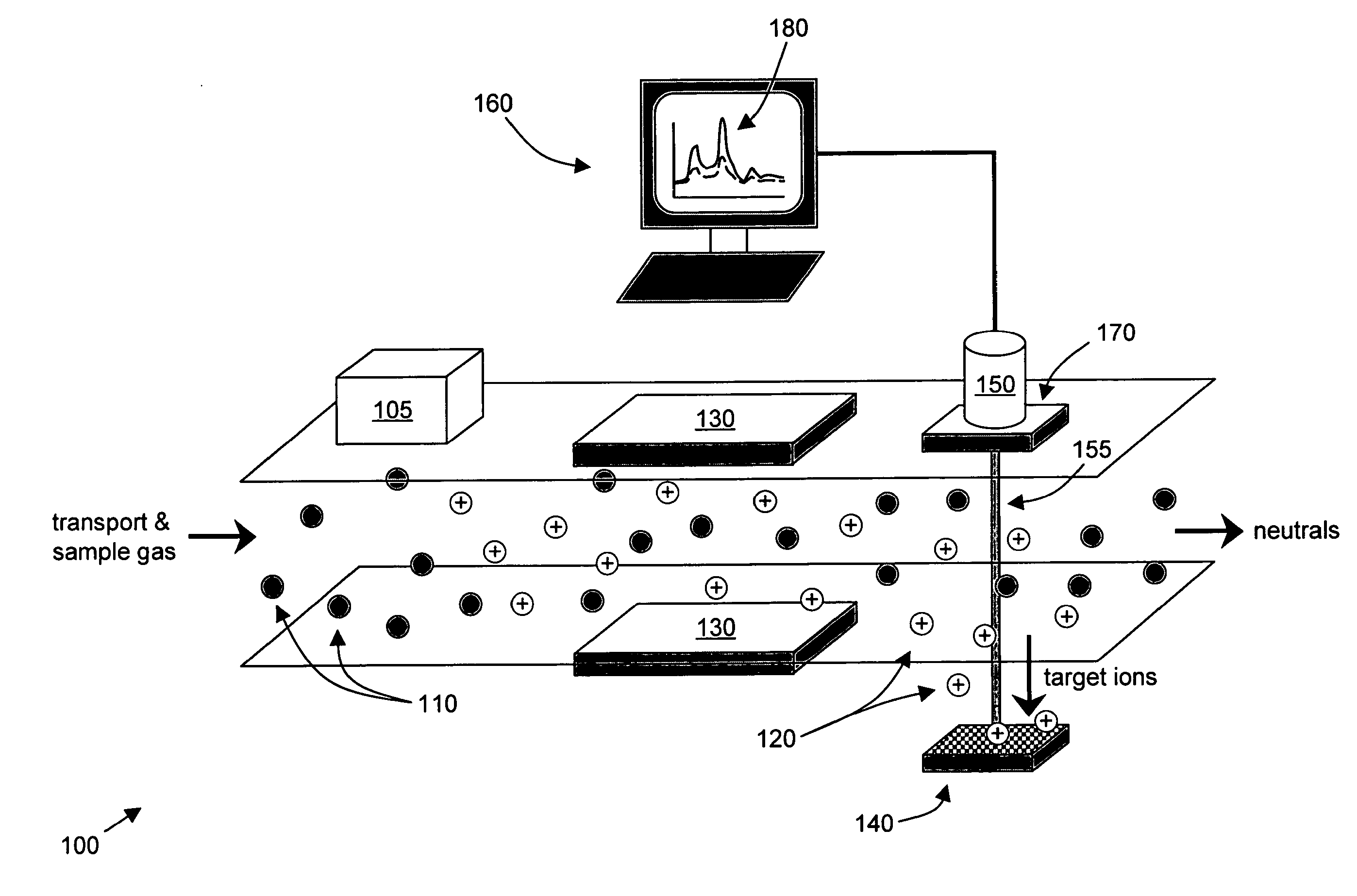
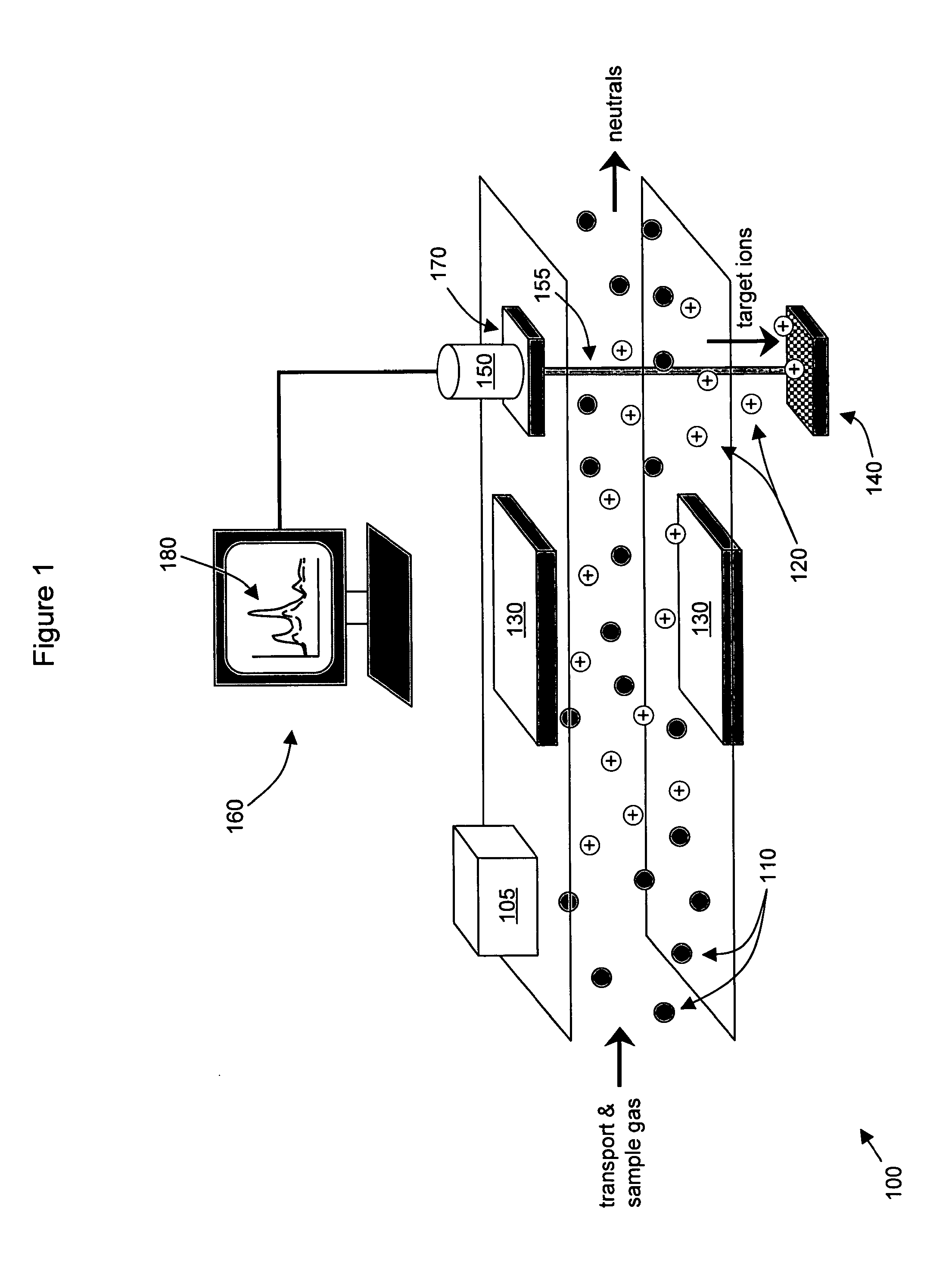
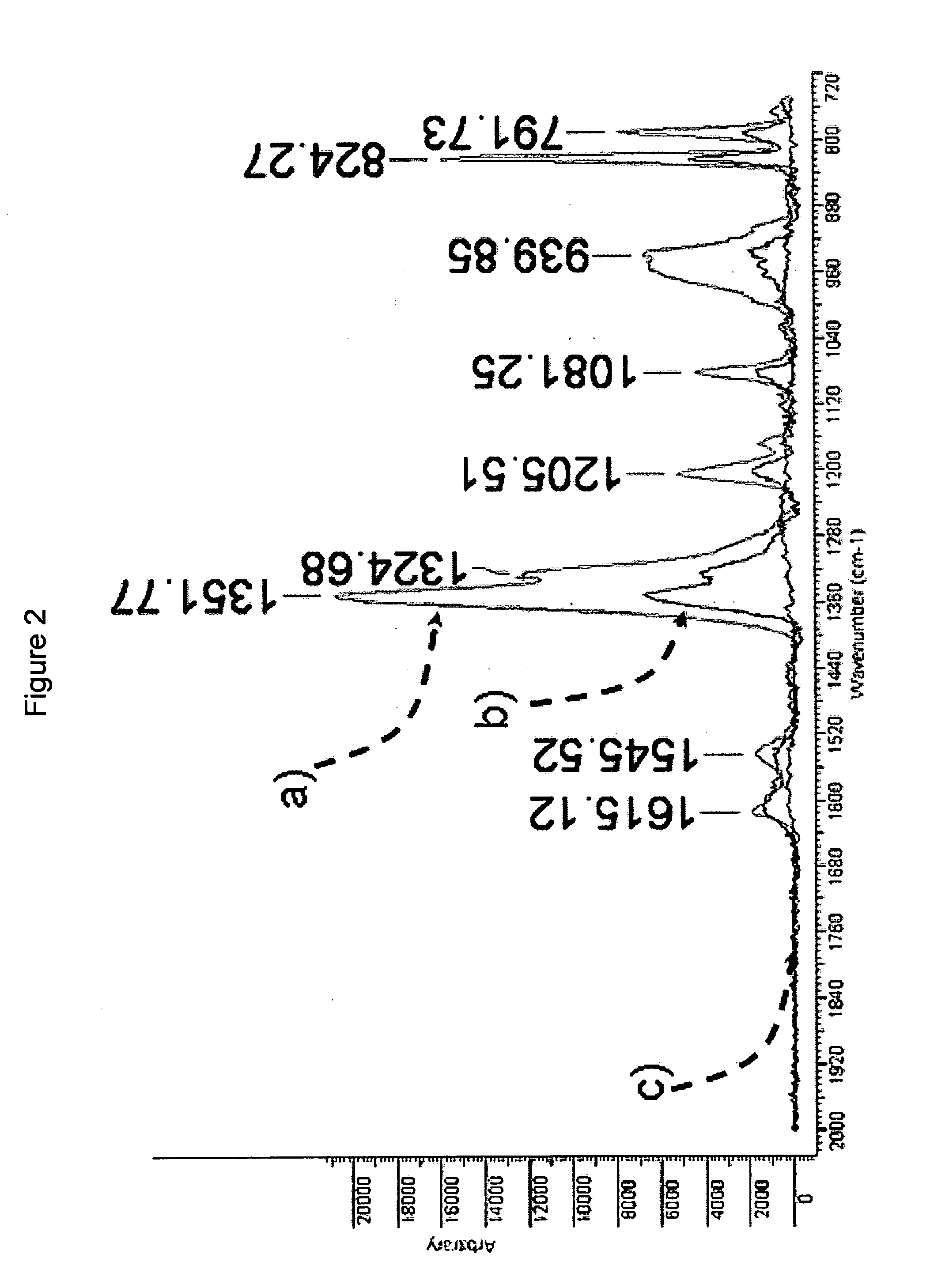
Surface enhanced raman spectroscopy detection with ion separation pre-filter
InactiveUS20110266429A1Effectively distinguish and separateEasy to measureRadiation pyrometryTime-of-flight spectrometersIon currentPower flow
Detecting and identifying ions using surface enhanced Raman spectroscopy (SERS) and an ion separation pre-filter, such as an ion spectrometer, are provided. The combination of an ion separator as a pre-filter for SERS provides a highly sensitive detector with very low false alarm rates. Target ions from an ionized sample are identified and separated by the ion separator. The target ions are steered and deposited onto a SERS substrate for Raman spectroscopic analysis with an optical probe. The Raman spectrum is compared with reference spectra and the composition of the sample is identified. The ion current from the target ions can also be measured, preferably concurrently with the Raman spectrum measurement. Types of ion separators include a differential ion mobility spectrometer, an ion mobility spectrometer, or a mass spectrometer.
Owner:SRI INTERNATIONAL +2
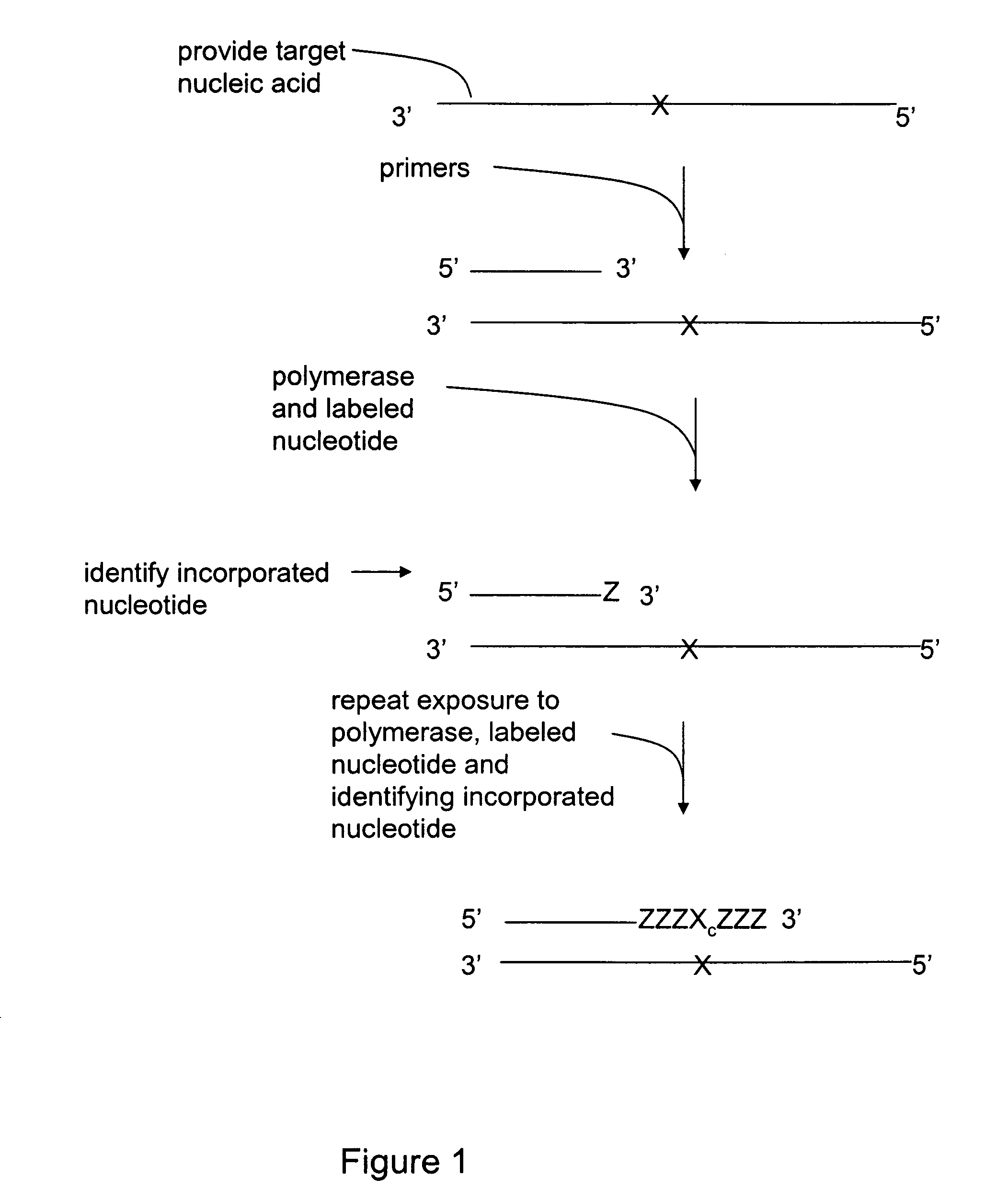
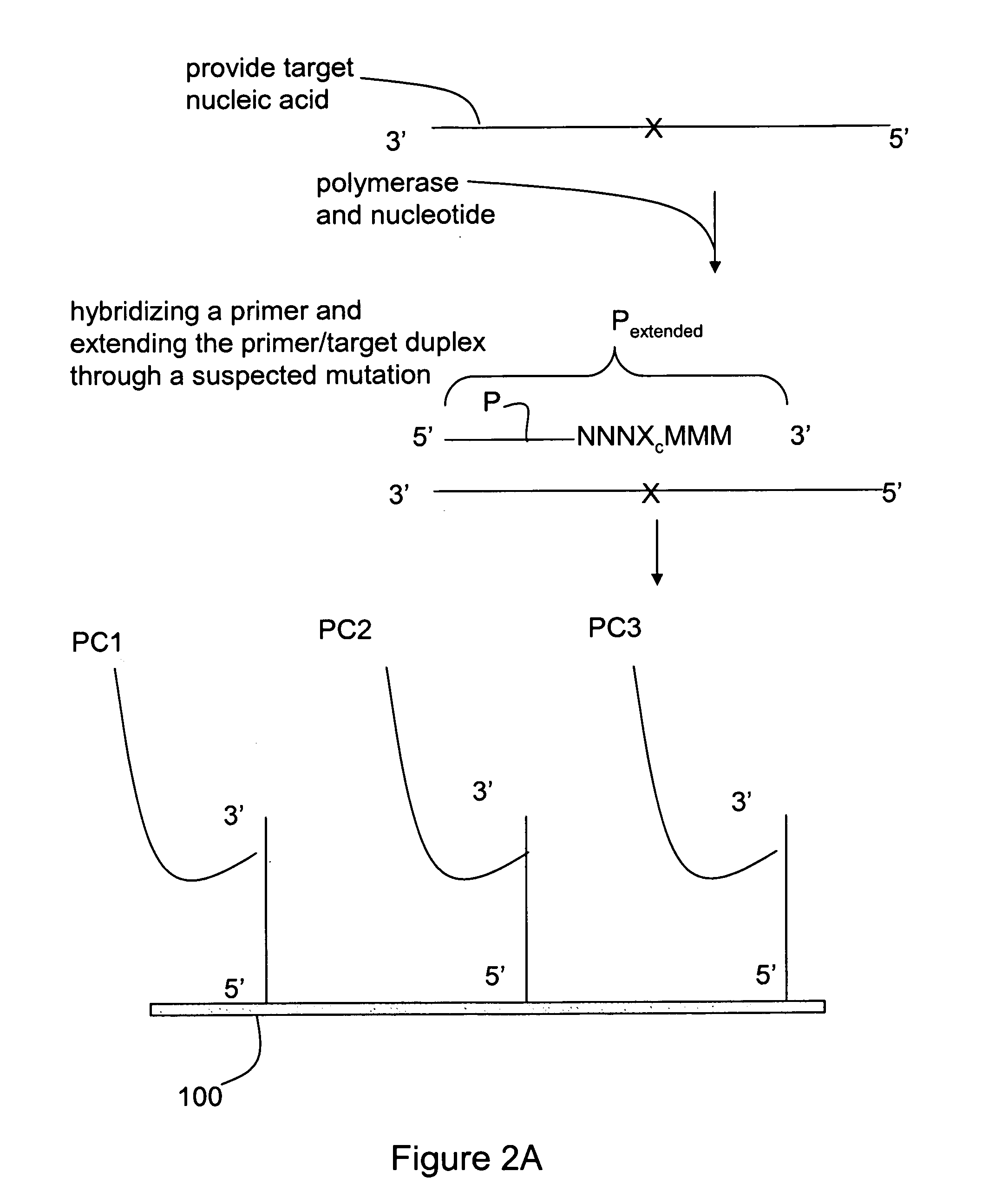
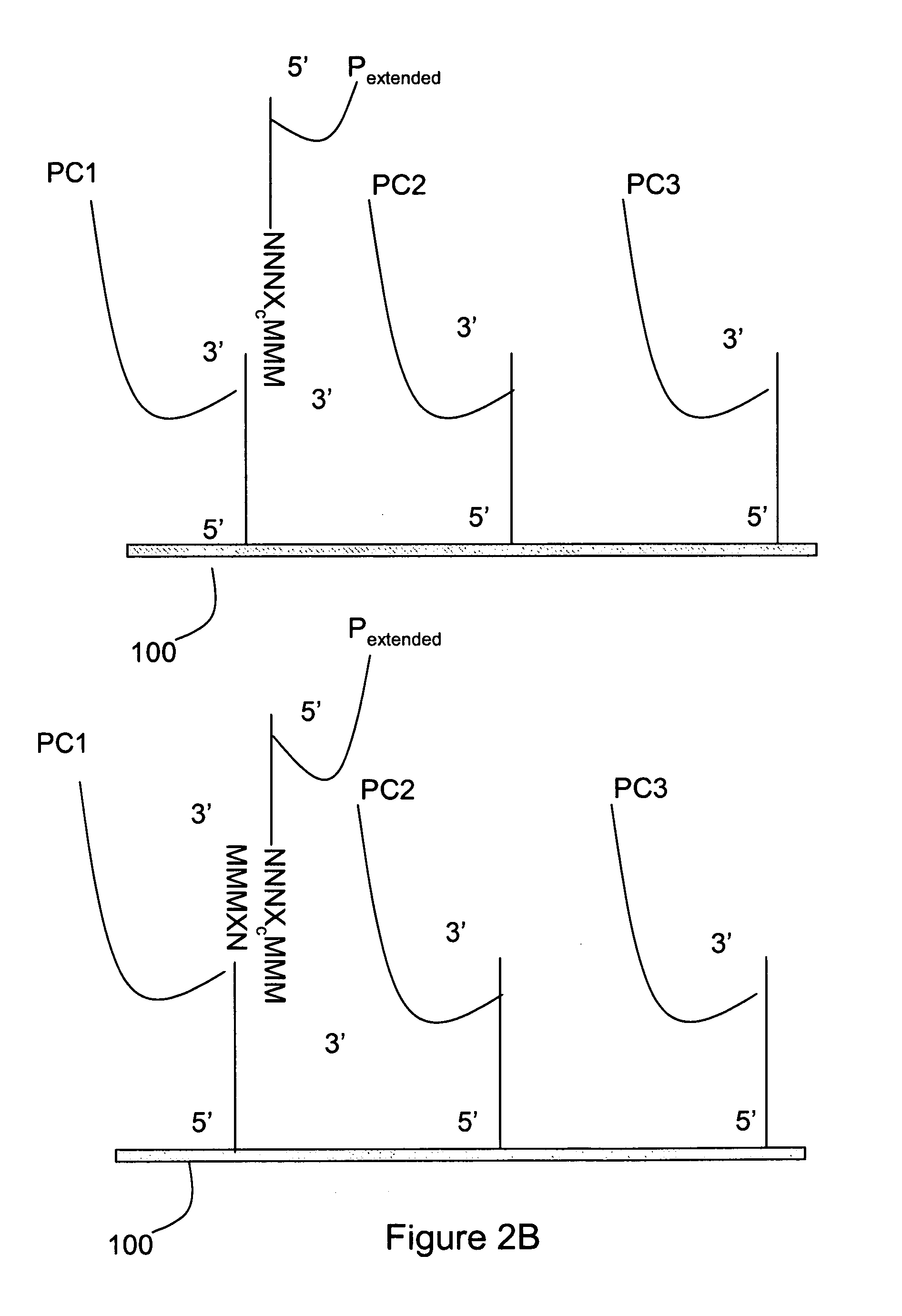
Methods for mutation detection
InactiveUS20070196832A1Strong specificityHigh false positive rateMicrobiological testing/measurementFermentationMutation detectionBiology
The invention relates to methods for detecting a mutation in a nucleic acid. Methods of the invention are useful for detecting and identifying mutations that are indicative of disease or the predisposition for disease.
Owner:FLUIDIGM CORP
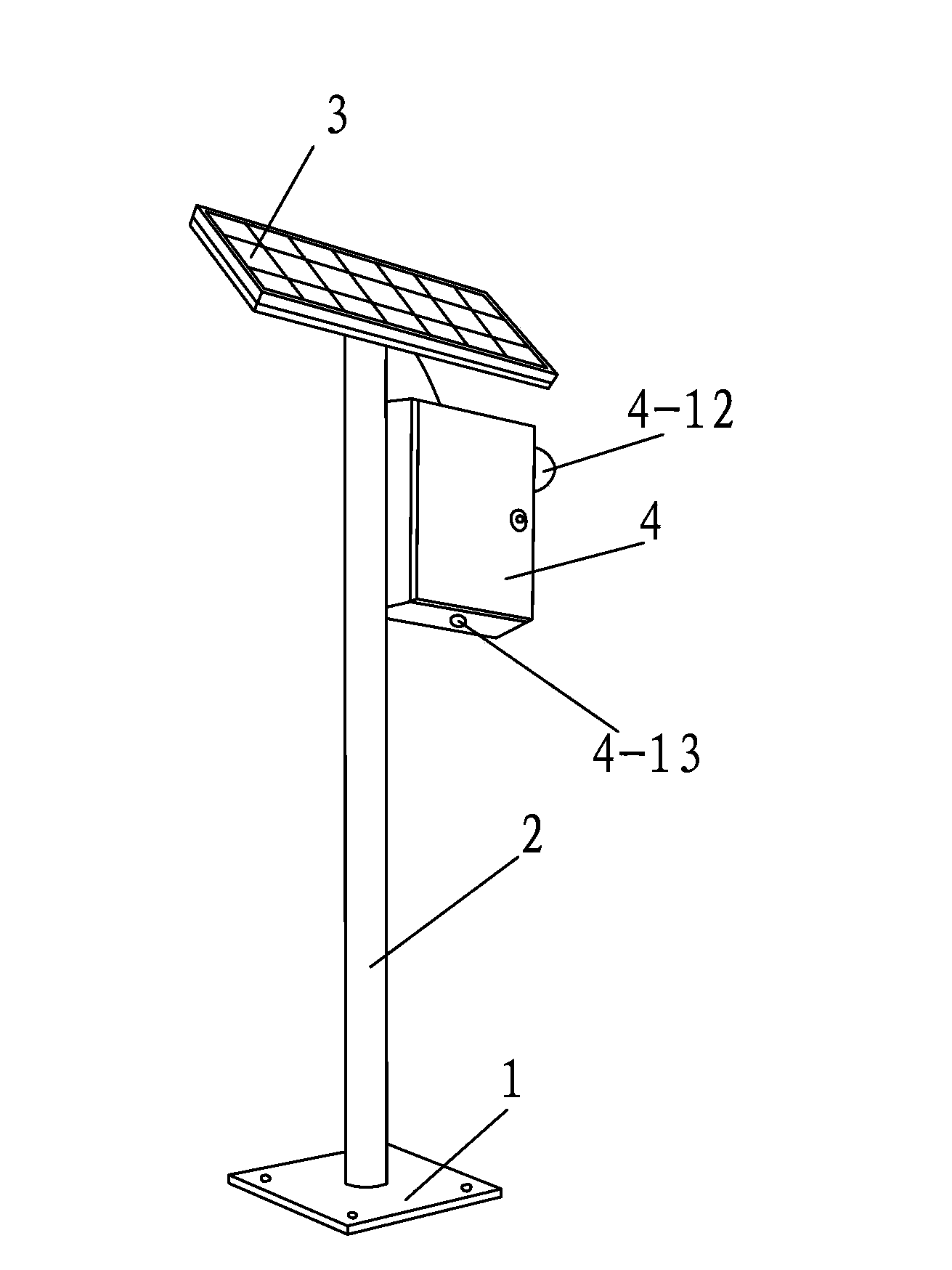
Forest fire detection device
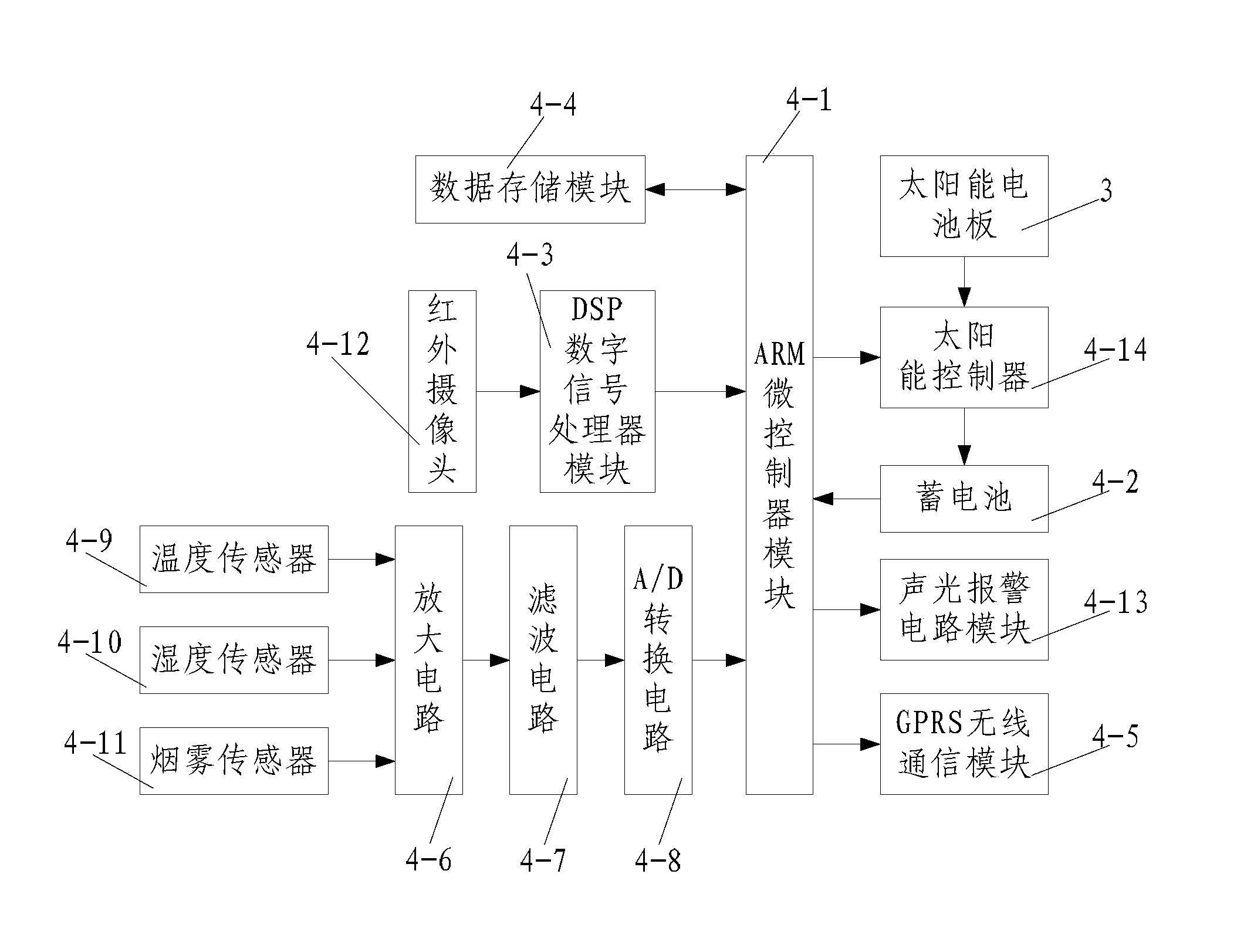
InactiveCN103824412ASimple structureReasonable designClimate change adaptationFire alarmsVIT signalsSmoke
The invention discloses a forest fire detection device. The forest fire detection device comprises a base, a pillar arranged at the bottom end of the base, a solar cell panel arranged at the top end of the pillar, and a forest fire detection box arranged on the pillar; a forest fire detection system is arranged in the forest fire detection box; the forest fire detection system comprises an ARM (Advanced RISC Machine) microcontroller module, a storage battery, a DSP (Digital Signal Processor) module, a data storage module, a GPRS (General Packet Radio Service) wireless communication module, and a signal conditioning circuit module; an amplification circuit, a filter circuit and an A / D (Analog-to-Digital) converting circuit are connected with one another sequentially so as to form the signal conditioning circuit module; input ends of the amplification circuit are connected with a temperature sensor, a humidity sensor and a smoke sensor; an input end of the DSP module is connected with an infrared camera; and output ends of the ARM microcontroller module are connected with a sound-light alarm circuit module and a solar controller. The forest fire detection device of the invention has the advantages of high intelligence, capacity for realizing 24-hour uninterrupted effective monitoring, and excellent energy-saving effect.
Owner:XIAN ZHONGZHI HUIZE PHOTOELECTRIC TECH
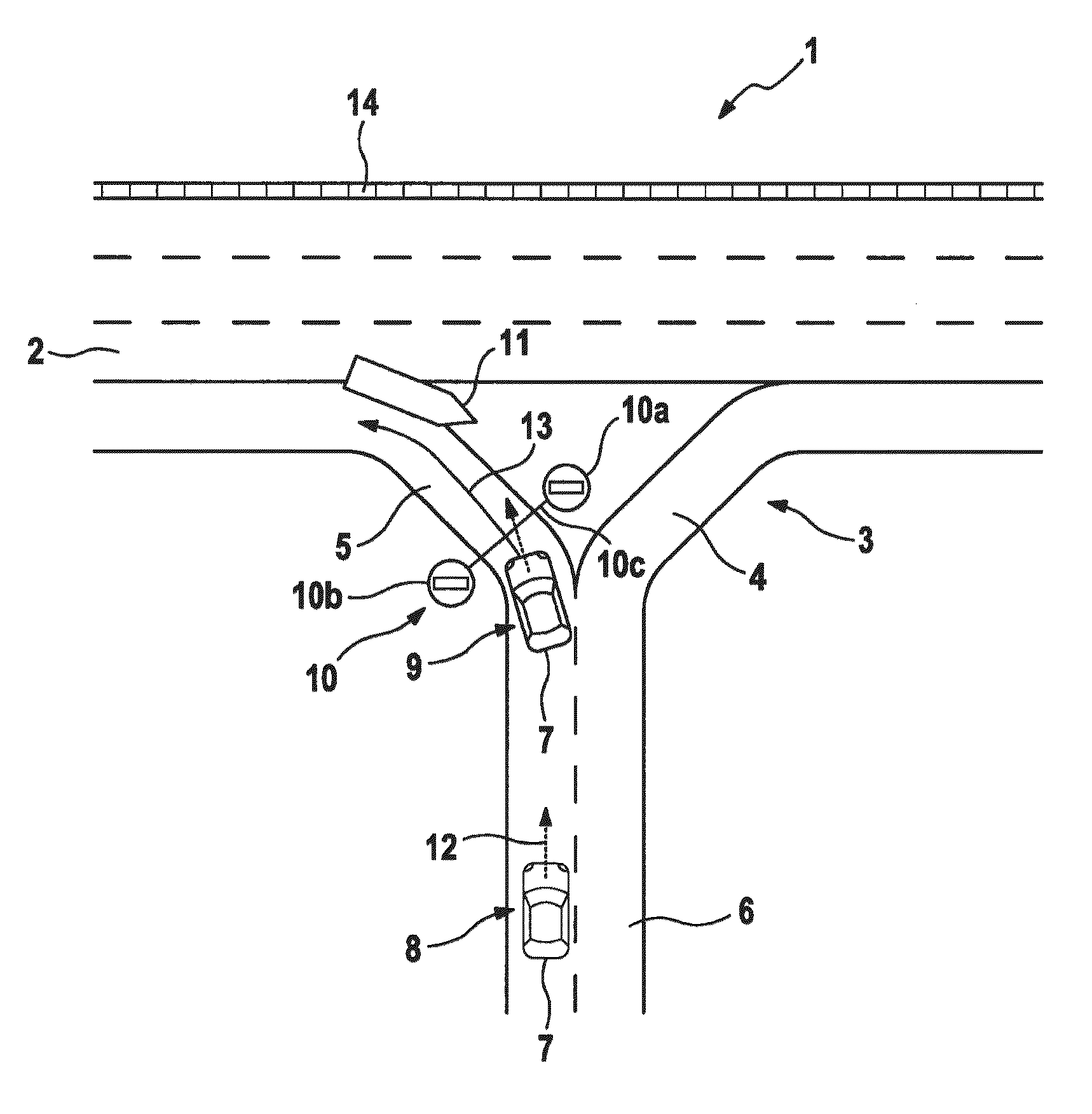
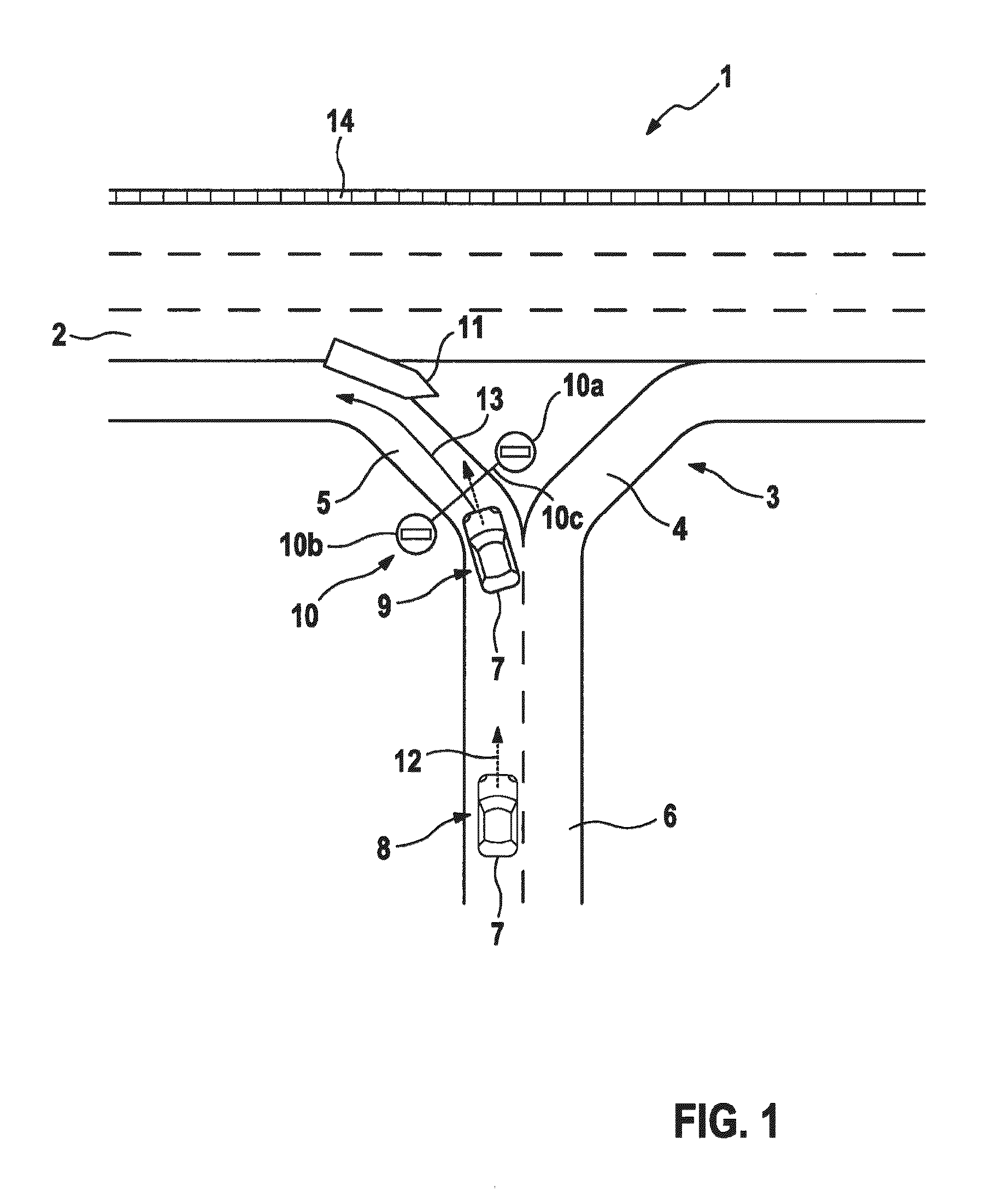
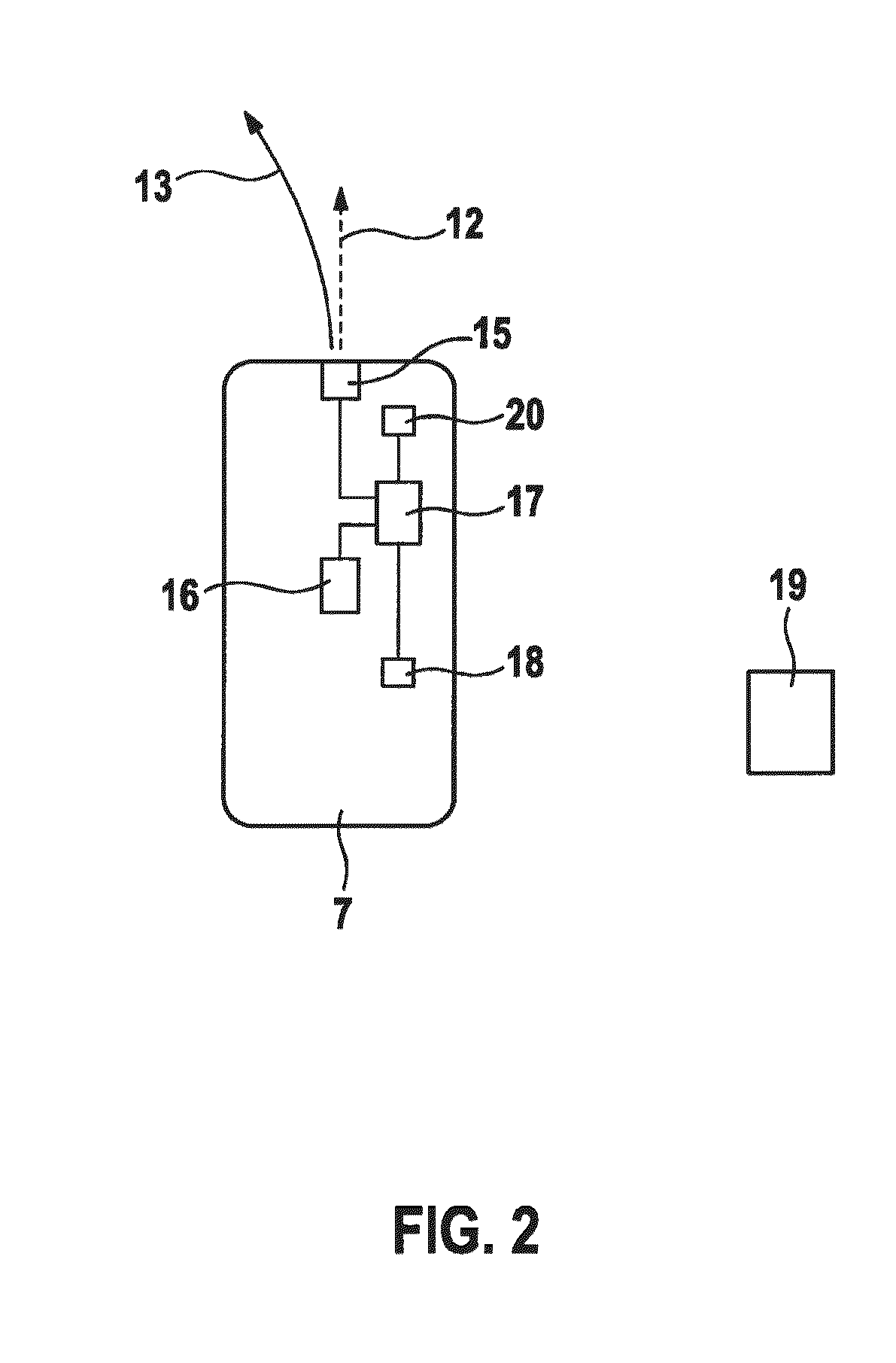
Method and control and detection device for a plausibility check of a wrong-way driving indcident of a motor vehicle
ActiveUS20160225256A1Easy to detectEasy to determineRoad vehicles traffic controlCharacter and pattern recognitionWrong-way drivingAutomotive engineering
A method and a control and detection device for a plausibility check of a wrong-way driving incident of a motor vehicle at a junction of a unidirectional roadway of a road, in which the plausibility check is activated by recognizing a direction feature of a roadway of the junction, and in which it is determined whether a current driving direction of the motor vehicle leads in the direction of a roadway having at least one prohibition sign, indicating that entry is prohibited, and / or in which it is determined whether a predicated driving route of the motor vehicle leads in the direction of a roadway having at least one prohibition sign.
Owner:ROBERT BOSCH GMBH
Vulnerability scanning method and related device
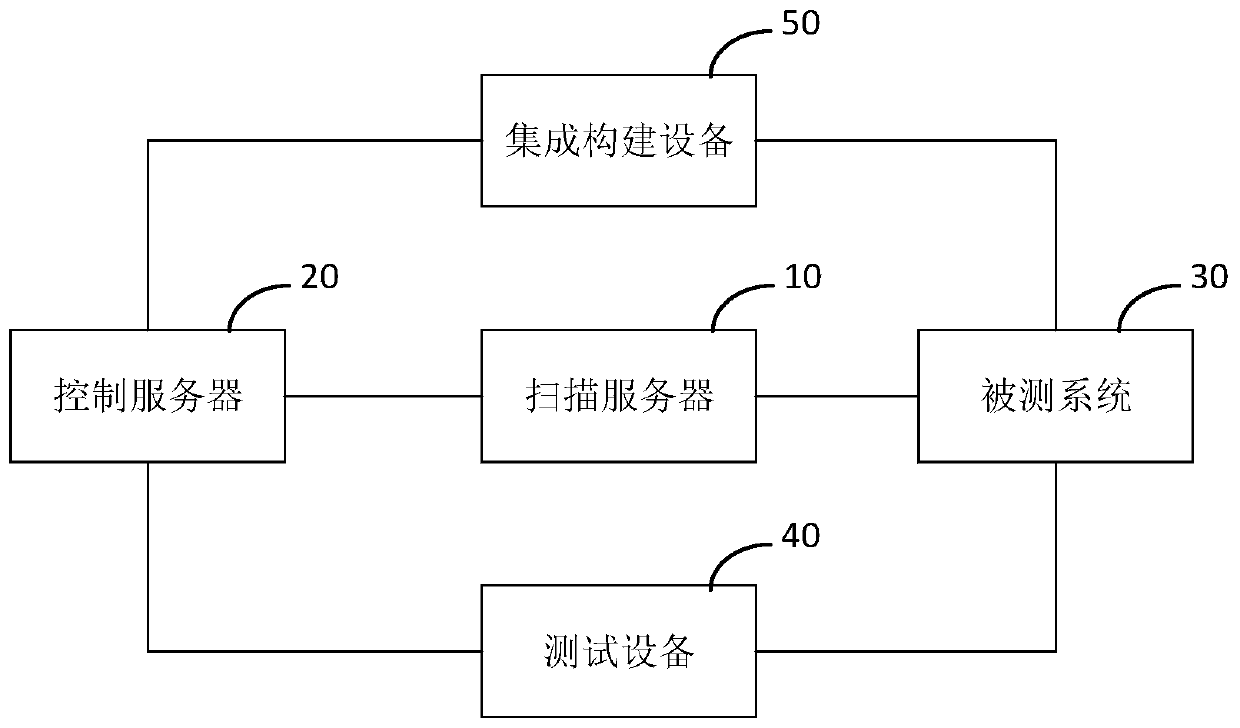
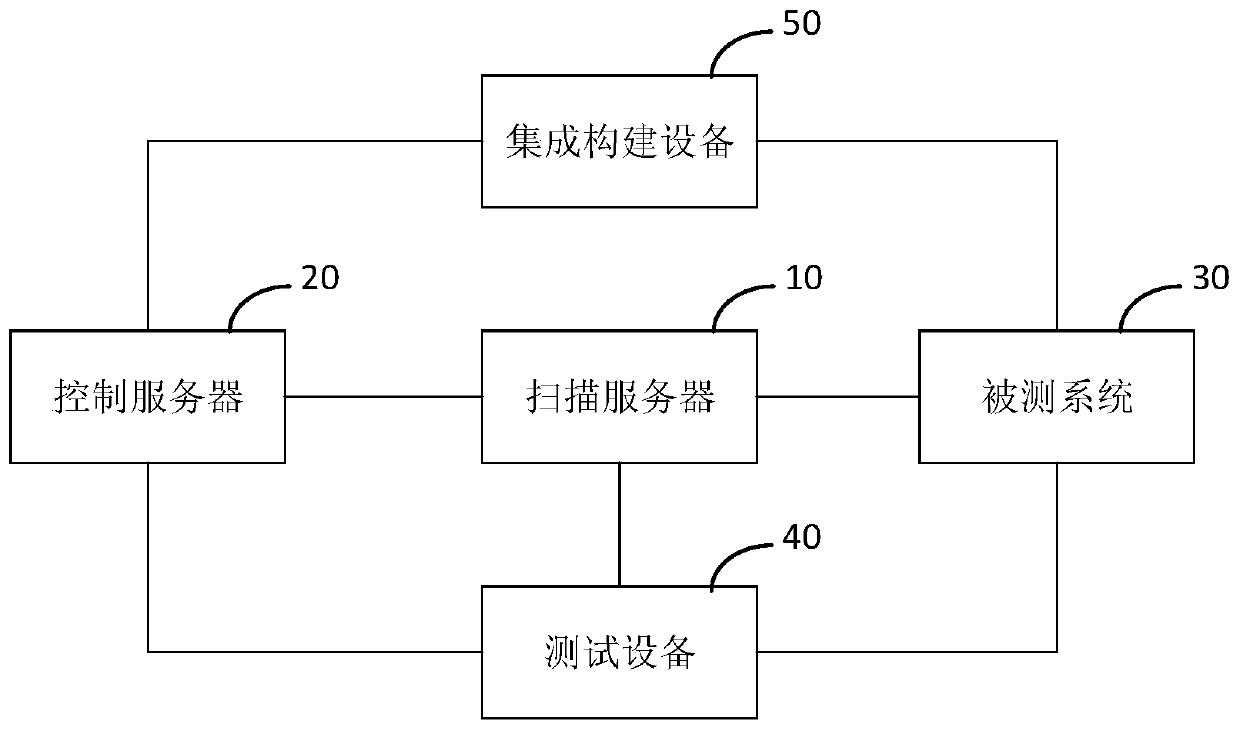
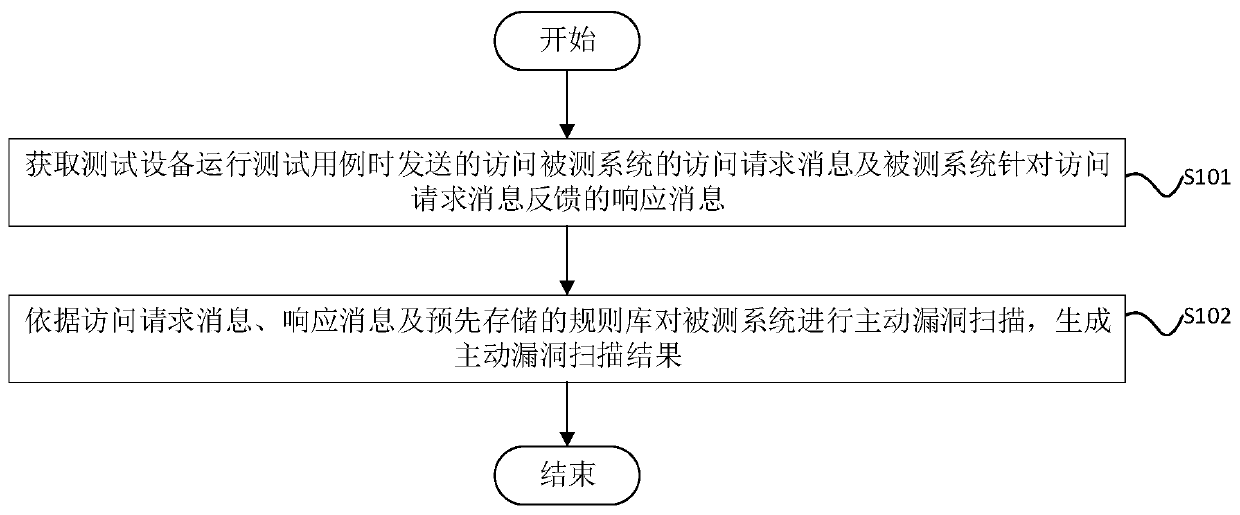
ActiveCN110704847AAvoid false negatives and false positivesLow false negative and false positive ratesPlatform integrity maintainanceTransmissionComputer securityVulnerability scanning
The embodiment of the invention relates to the technical field of computer security, and provides a vulnerability scanning method and a related device. The vulnerability scanning method comprises: obtaining an access request message for accessing a tested system and a response message fed back by the tested system for the access request message when a test device runs a test case; and performing active vulnerability scanning on the tested system according to the access request message, the response message and a pre-stored rule base to generate an active vulnerability scanning result, whereinrules in the rule base are acquired from a preset vulnerability information platform in advance and stored locally. Active vulnerability scanning is performed on a tested system based on an access request message and a response message which are actually generated when a test case is operated in a CI environment, and meanwhile, a richer rule base and a containerized operation mode are adopted, sothat the missing report rate and the false alarm rate are greatly reduced.
Owner:重庆紫光华山智安科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com