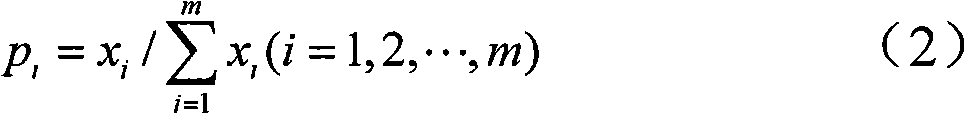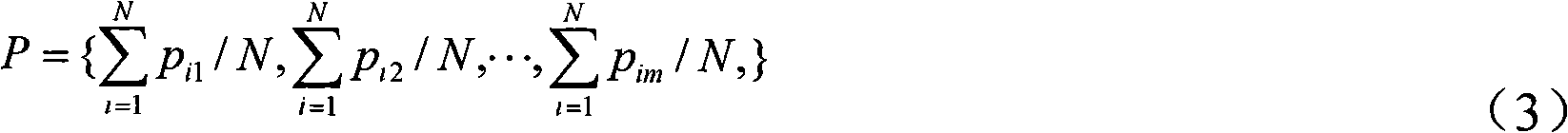Multi-measure network abnormity detection method based on relative entropy theory
A network anomaly and detection method technology, applied in the field of information security, can solve the problems of insufficient attack range detection and improvement of detection rate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
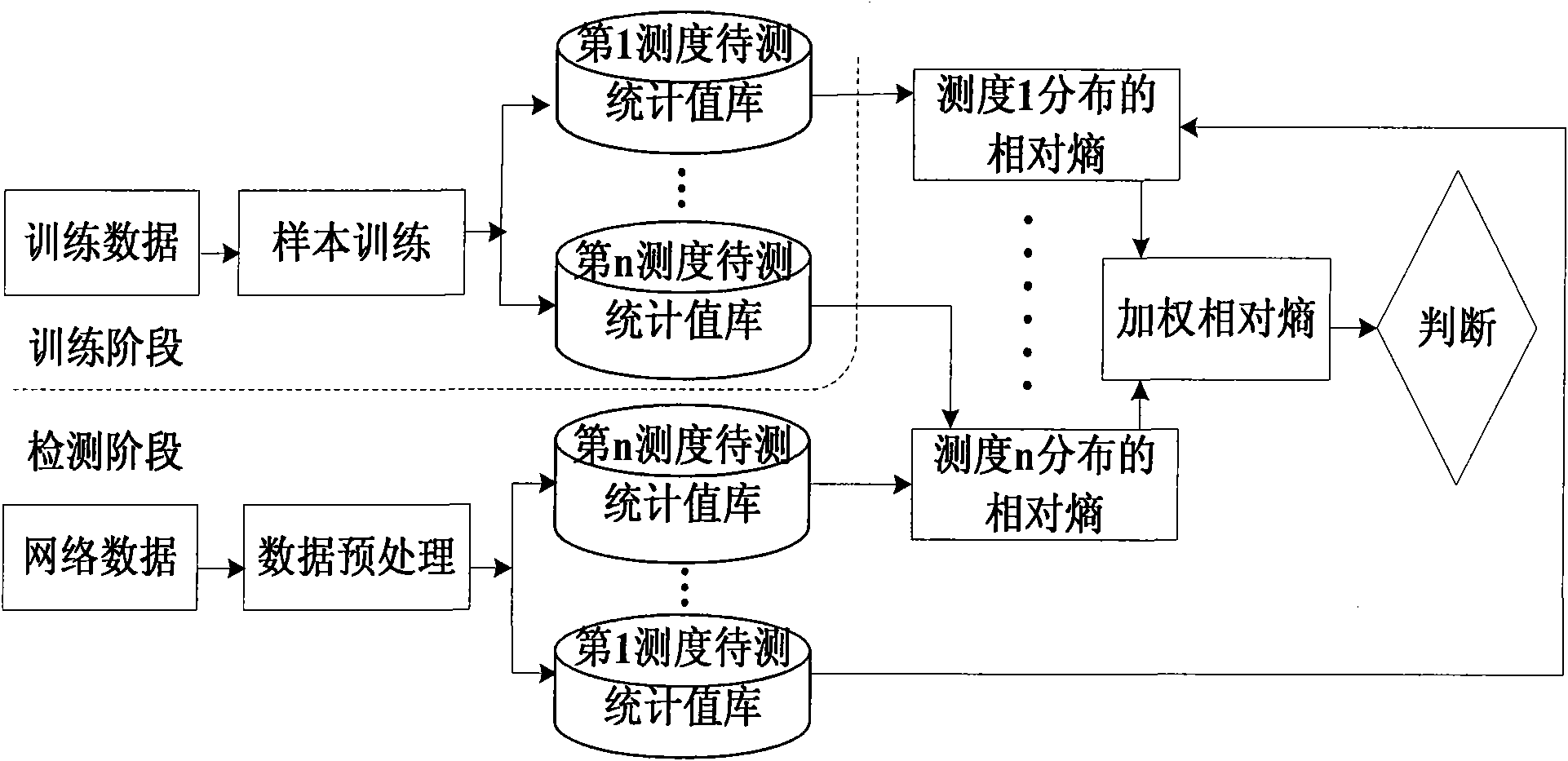
[0078] As a specific application, the present invention establishes a dual-measure network anomaly detection (RETDMAD) model based on relative entropy theory, and the measures adopted are packet length distribution and protocol distribution, and the feasibility of the RETDMAD method is verified through system implementation and testing. The two-sided degree network anomaly detection model with packet length distribution and protocol distribution as an anomaly detection measure is given below, and the model is implemented according to the following steps:
[0079] Step 1) Selection and quantification of dual measures
[0080] Divide all collected data packets into 7 categories according to the length of the packet (=1518), the first measure is each packet The ratio of data packets in the long segment to the total traffic (packet length distribution). All collected data packets are divided into four types (TCP, UDP, ICMP, and OTHER) according to the transport layer protocol. Th...
Embodiment 2
[0091] Three characteristics of packet length distribution, protocol distribution and TCP port traffic distribution are selected for network anomaly detection based on relative entropy.
[0092] When Internet users use download tools to download a large number of files, or copy files between different hosts, or send a large number of emails, etc., when these things happen, only the packet length distribution and protocol distribution are used as The measurement of anomaly detection is difficult to achieve the ideal effect of anomaly detection, and there is a high false alarm rate. When the above situation occurs, in order to accurately realize anomaly detection, the TCP port traffic distribution can be used as the third detection measure, and the commonly used TCP ports are divided into nine categories (No. 21, No. 23, No. 25, No. 53, No. 80, 4000, 8000, 6200 and others), the ratio of each type of port traffic to the total traffic is the port traffic distribution. The operati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com