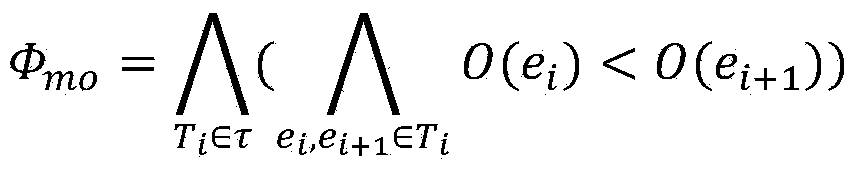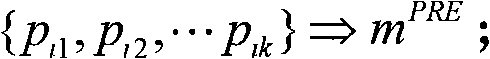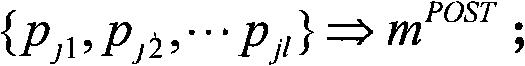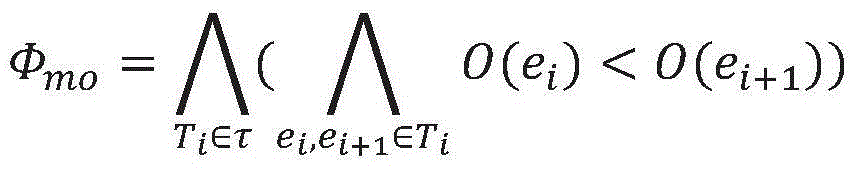Patents
Literature
56 results about "First-order logic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
First-order logic—also known as predicate logic, quantificational logic, and first-order predicate calculus—is a collection of formal systems used in mathematics, philosophy, linguistics, and computer science. First-order logic uses quantified variables over non-logical objects and allows the use of sentences that contain variables, so that rather than propositions such as Socrates is a man one can have expressions in the form "there exists x such that x is Socrates and x is a man" and there exists is a quantifier while x is a variable. This distinguishes it from propositional logic, which does not use quantifiers or relations; in this sense, propositional logic is the foundation of first-order logic.
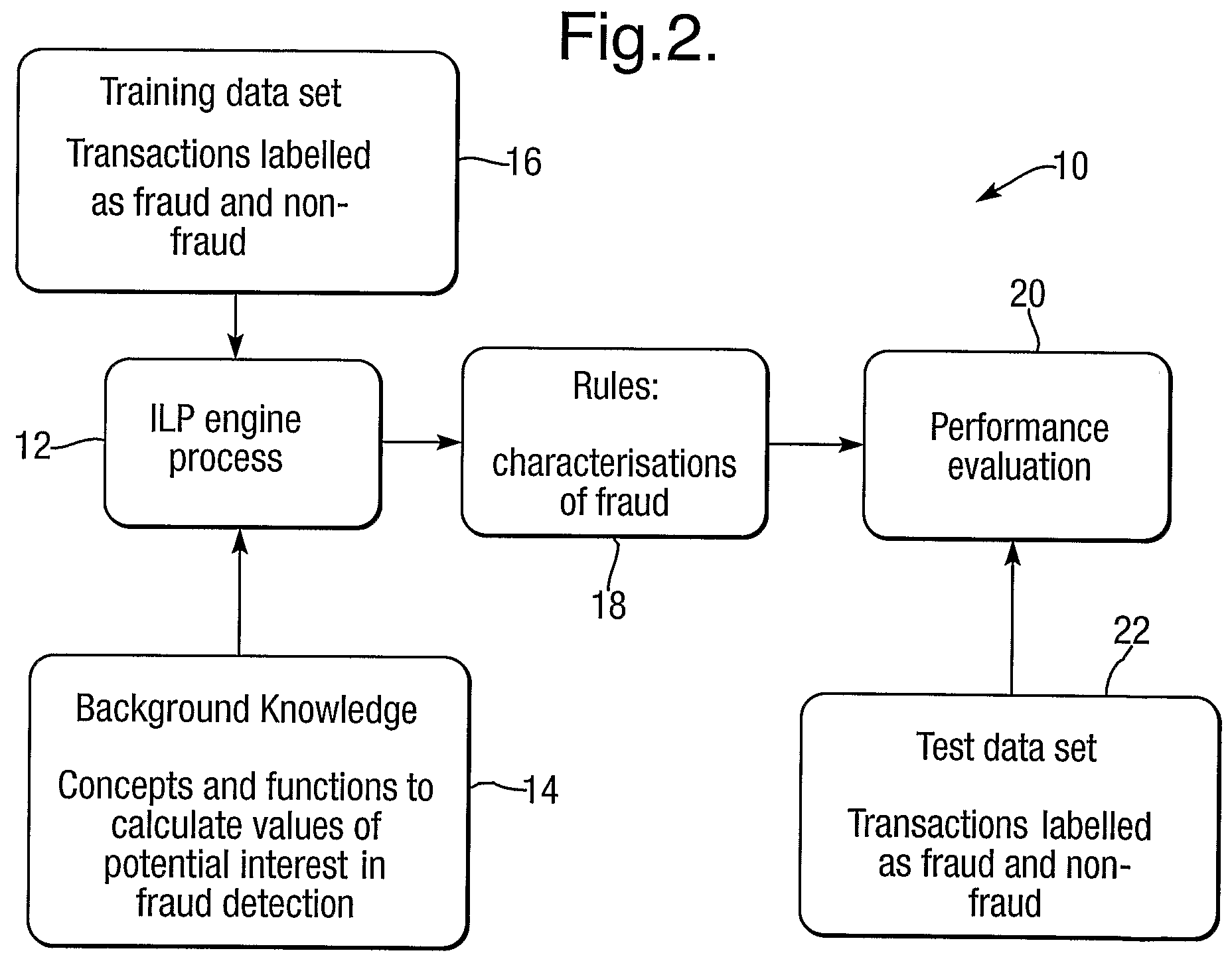
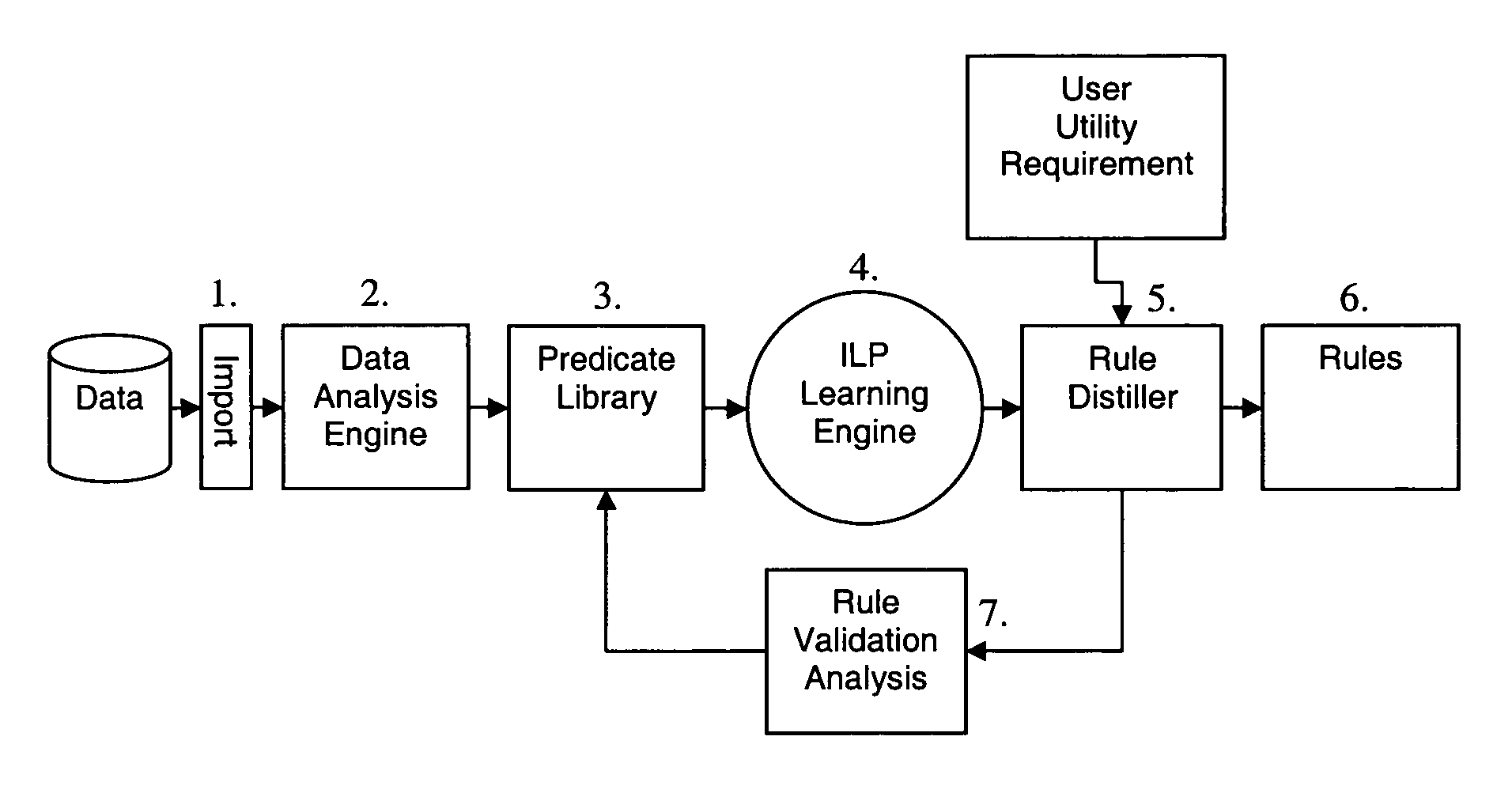
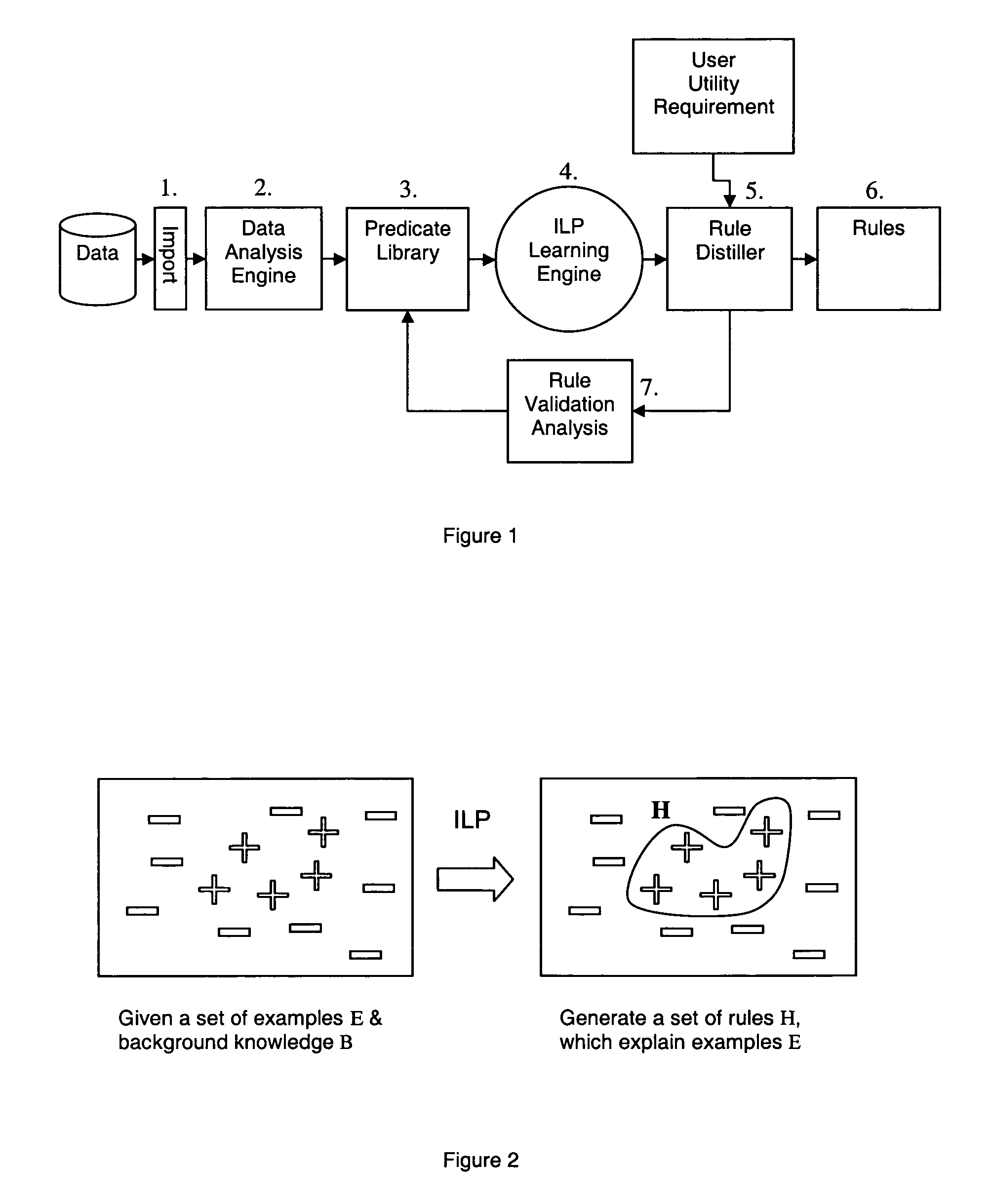
Analytical system for discovery and generation of rules to predict and detect anomalies in data and financial fraud
InactiveUS20070027674A1Effective and optimal analysis of dataSimple strategyNatural language data processingKnowledge representationFirst-order logicAlgorithm
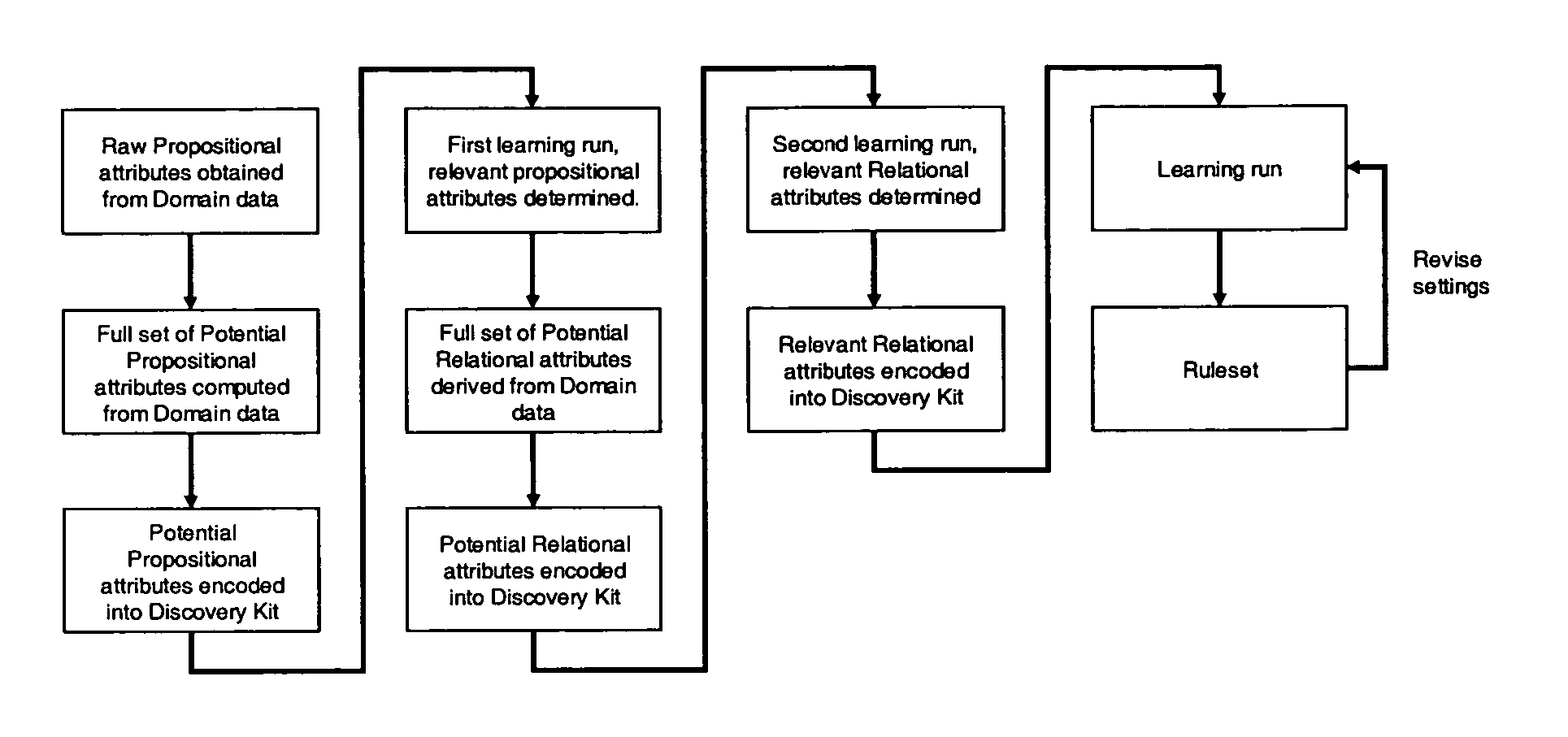
Methods and computer apparatus are disclosed for deriving first order logic language rules for use in analysing new data to identify anomalies in the new data. Historical data is formatted to be in a form suitable for application of a machine-learning algorithm thereto. The machine-learning algorithm is applied to the formatted historical data to generate a set of first order logic language rules that cover the formatted historical data. The set of first order logic language rules are analysed to obtain a subset of said set of first order logic language rules which can be used as first order logic language rules in analysing new data.
Owner:VALIDIS UK LTD
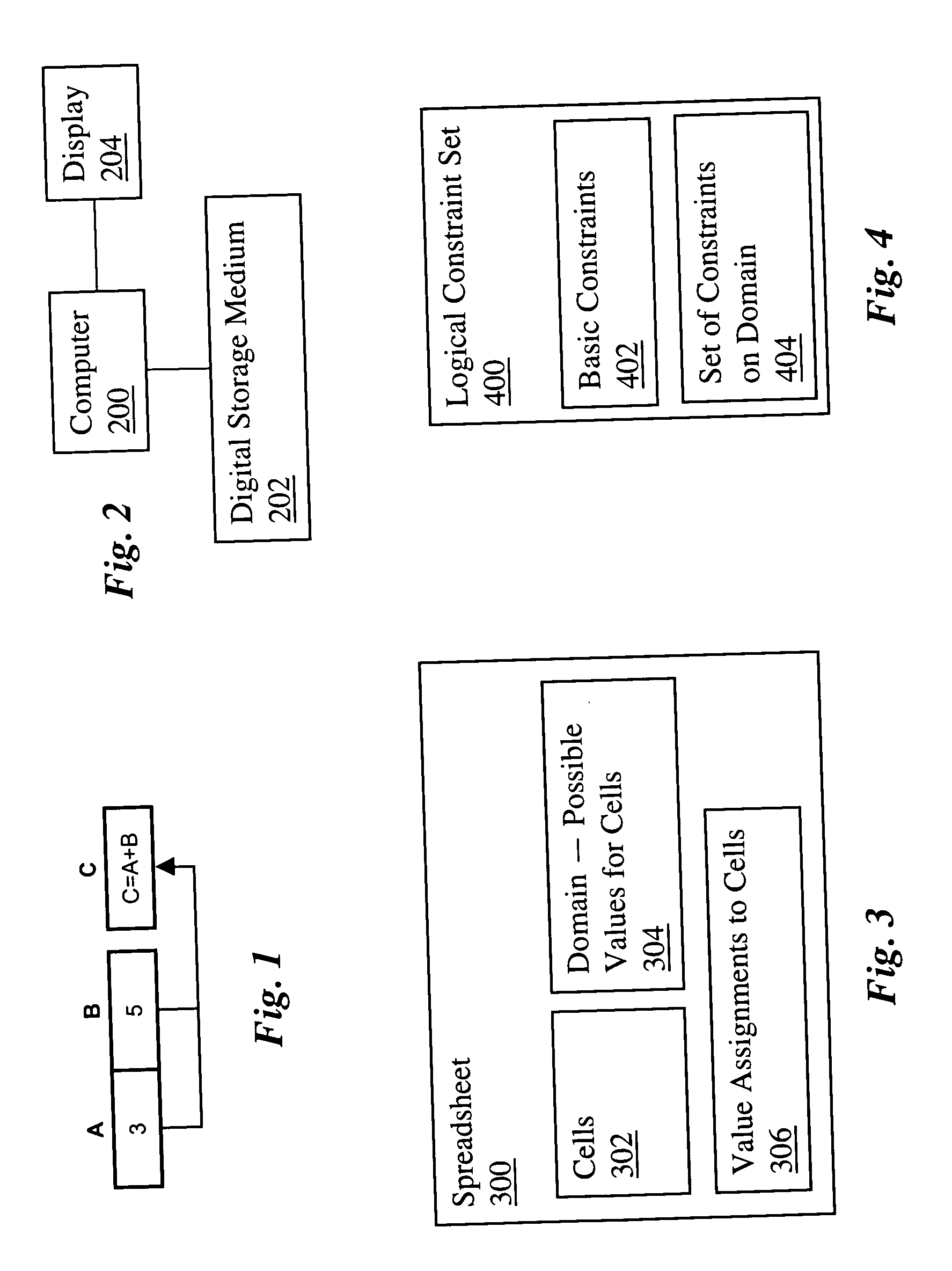
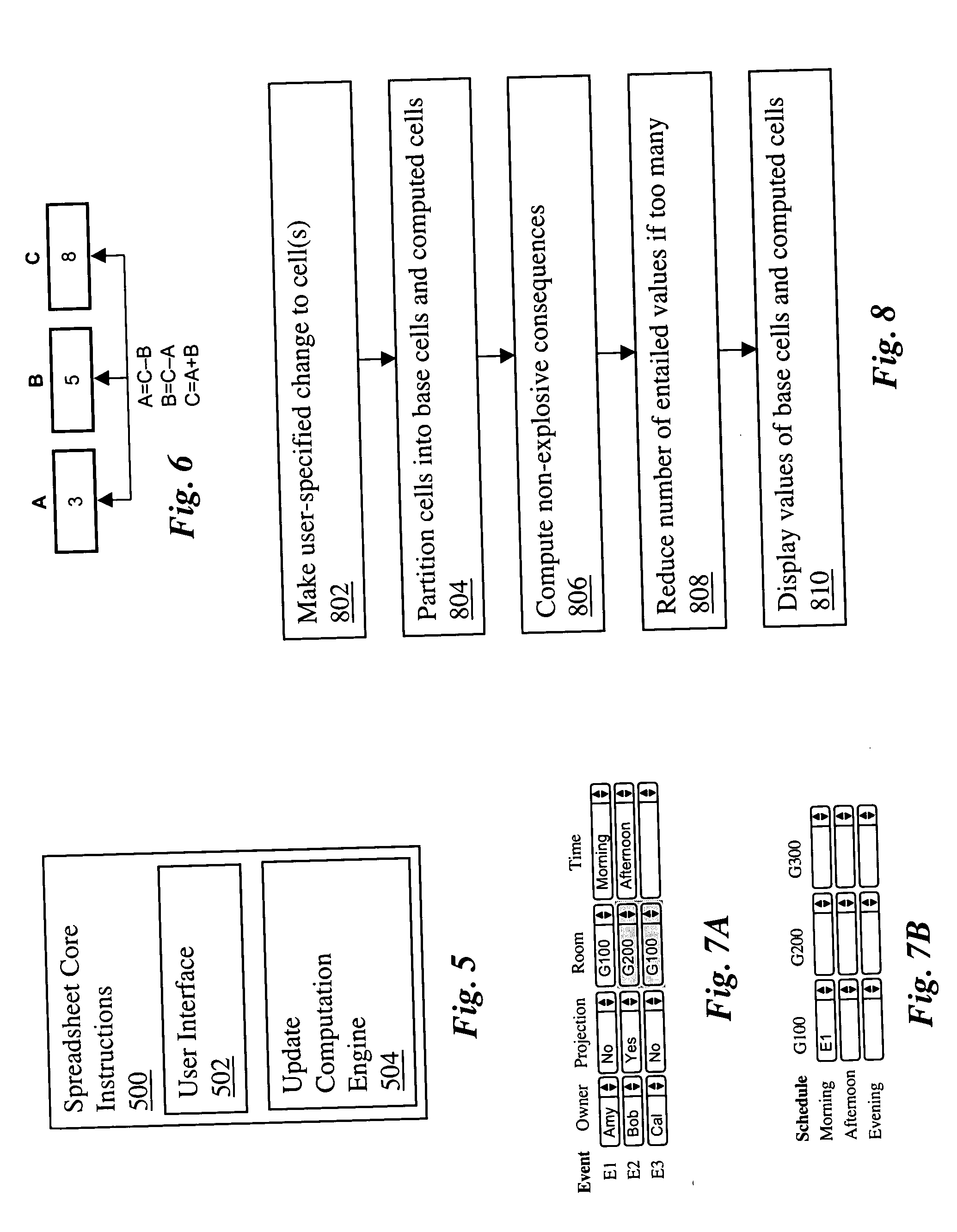
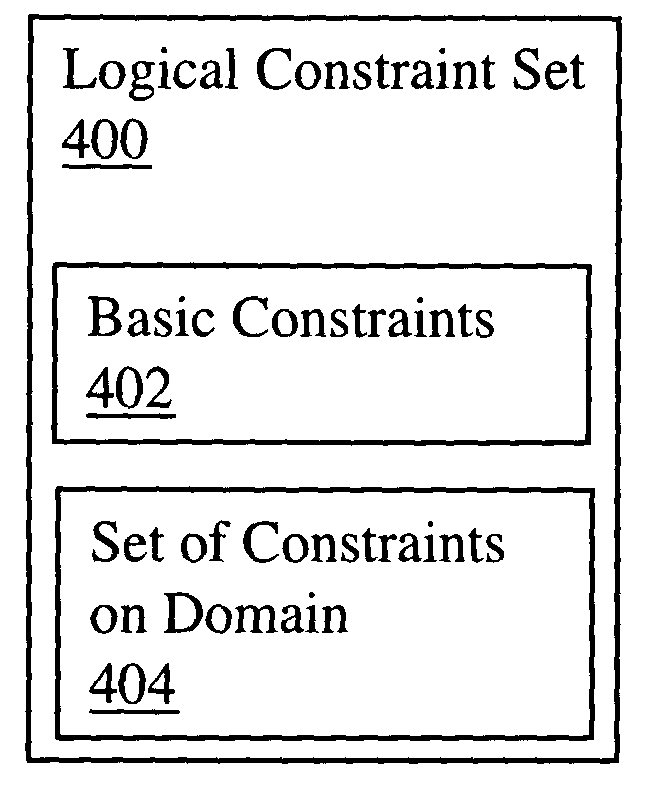
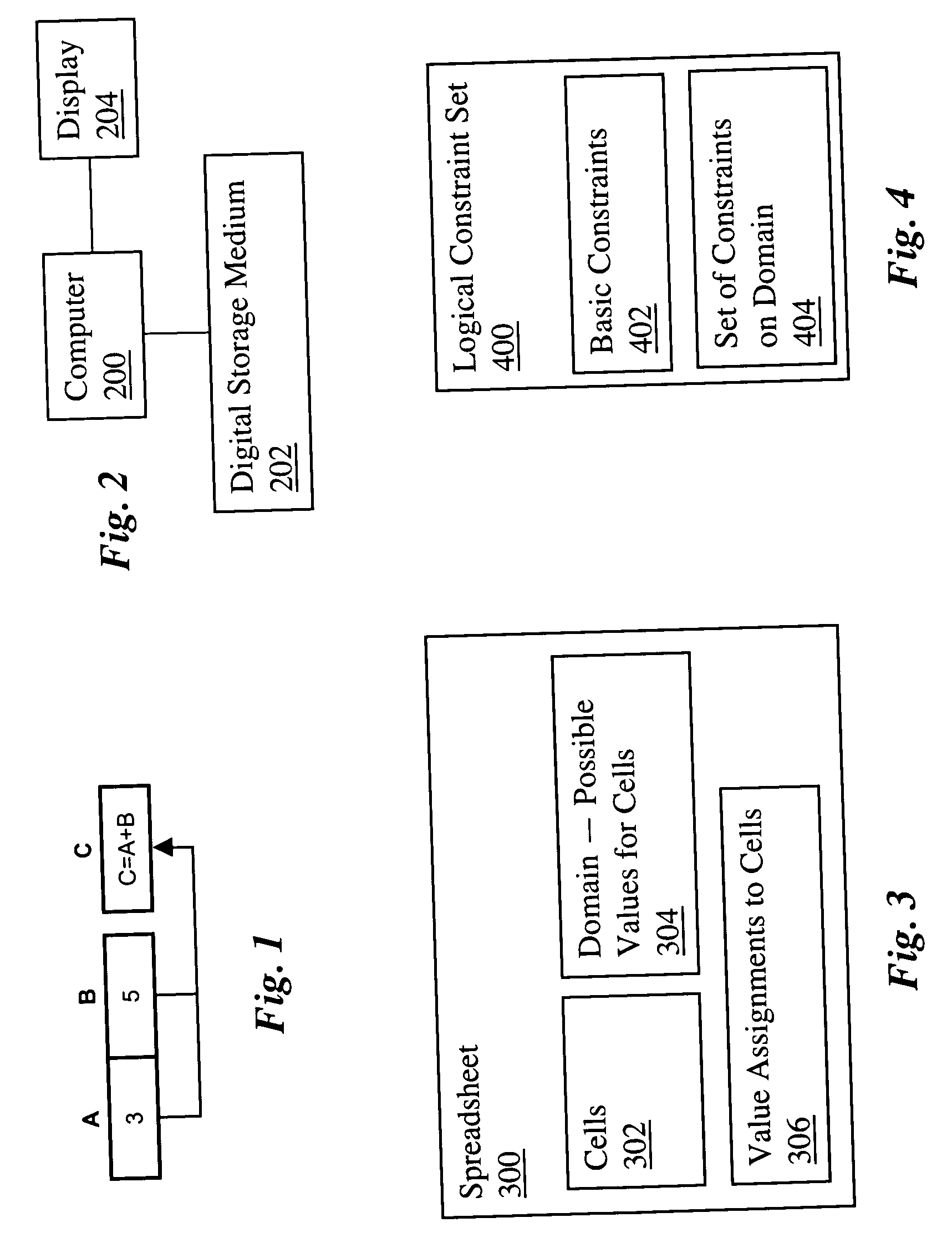
Logical spreadsheets
ActiveUS20060048044A1Improve welfareText processingSpecial data processing applicationsFirst-order logicTheoretical computer science
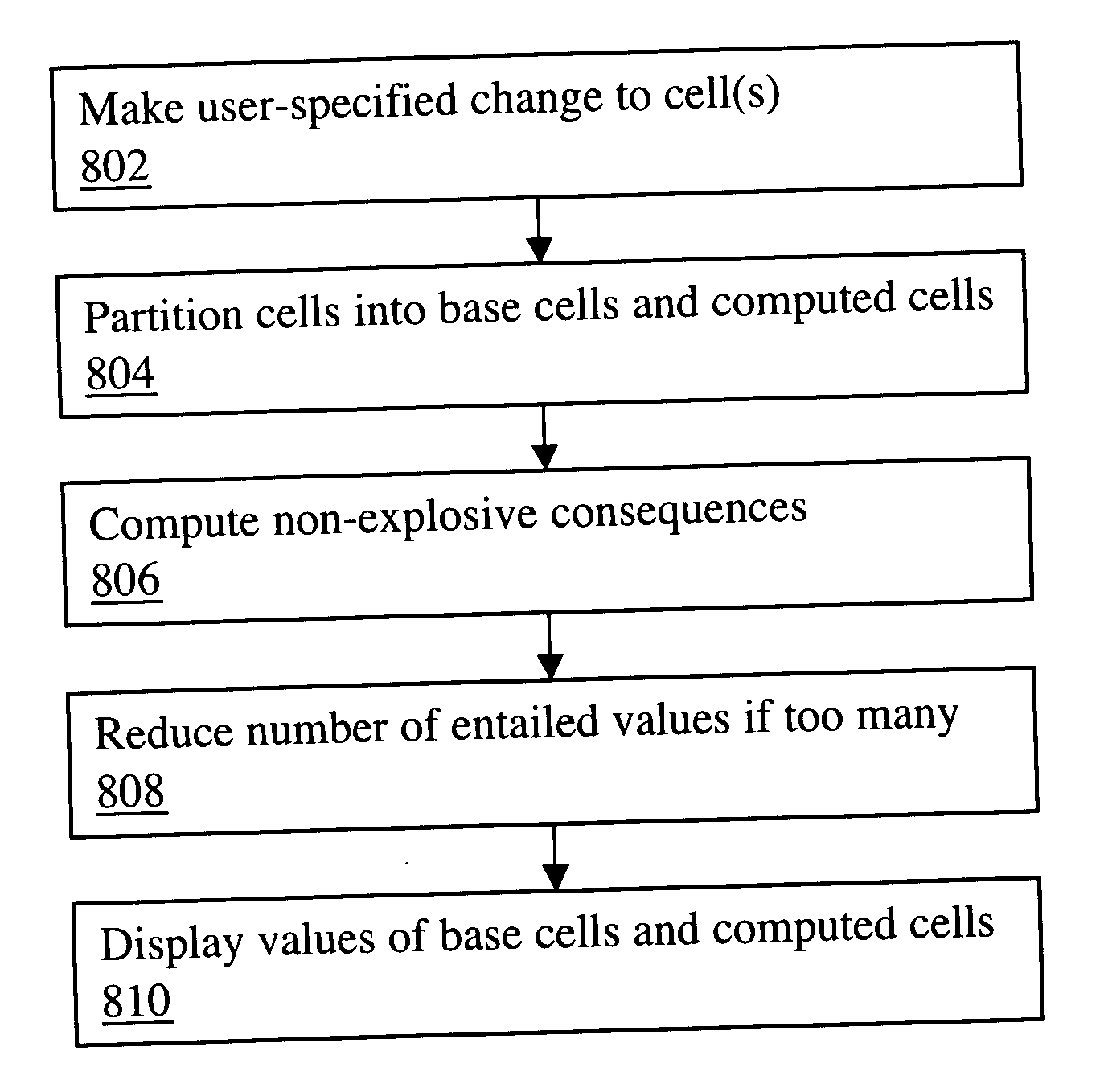
A computerized spreadsheet system includes a set of cells and a separate set of logical constraints on the values of cells. The constraints may be many-to-many relationships that permit omni-directional propagation of values between cells. The constraints may be expressed in a language encompassing first-order logic. Cells are dynamically reclassified as base cells or computed cells as a user specifies values for cells. Non-explosive consequences of the base cell values are computed and displayed in computed cells, even when the values in the base cells are inconsistent with the constraints. The spreadsheet system may also include an auto-complete feature that automatically fills in empty cells with values consistent with the logical constraints and an auto-deconflict feature that automatically changes values in cells to reduce conflicts with the logical constraints.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
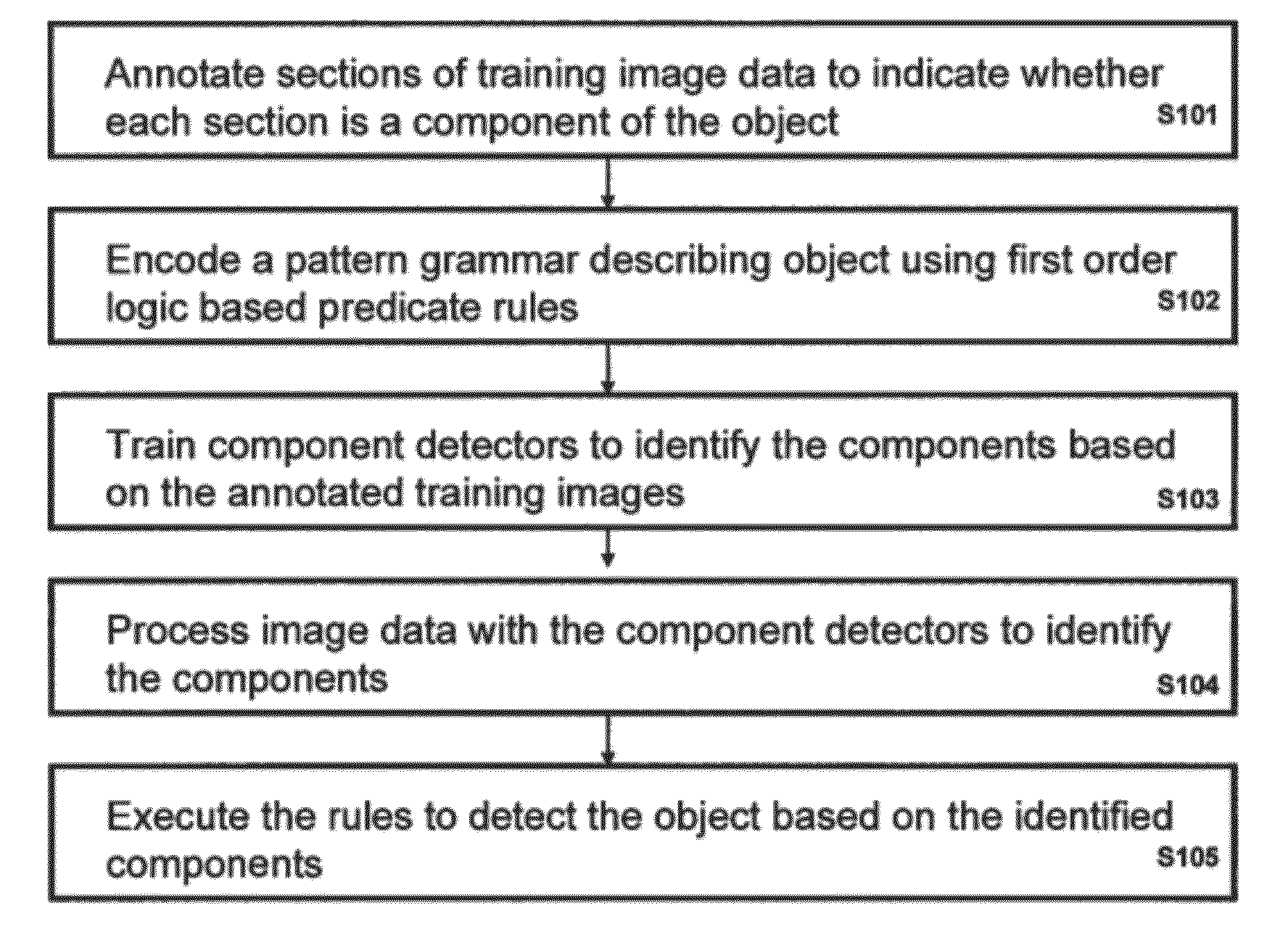
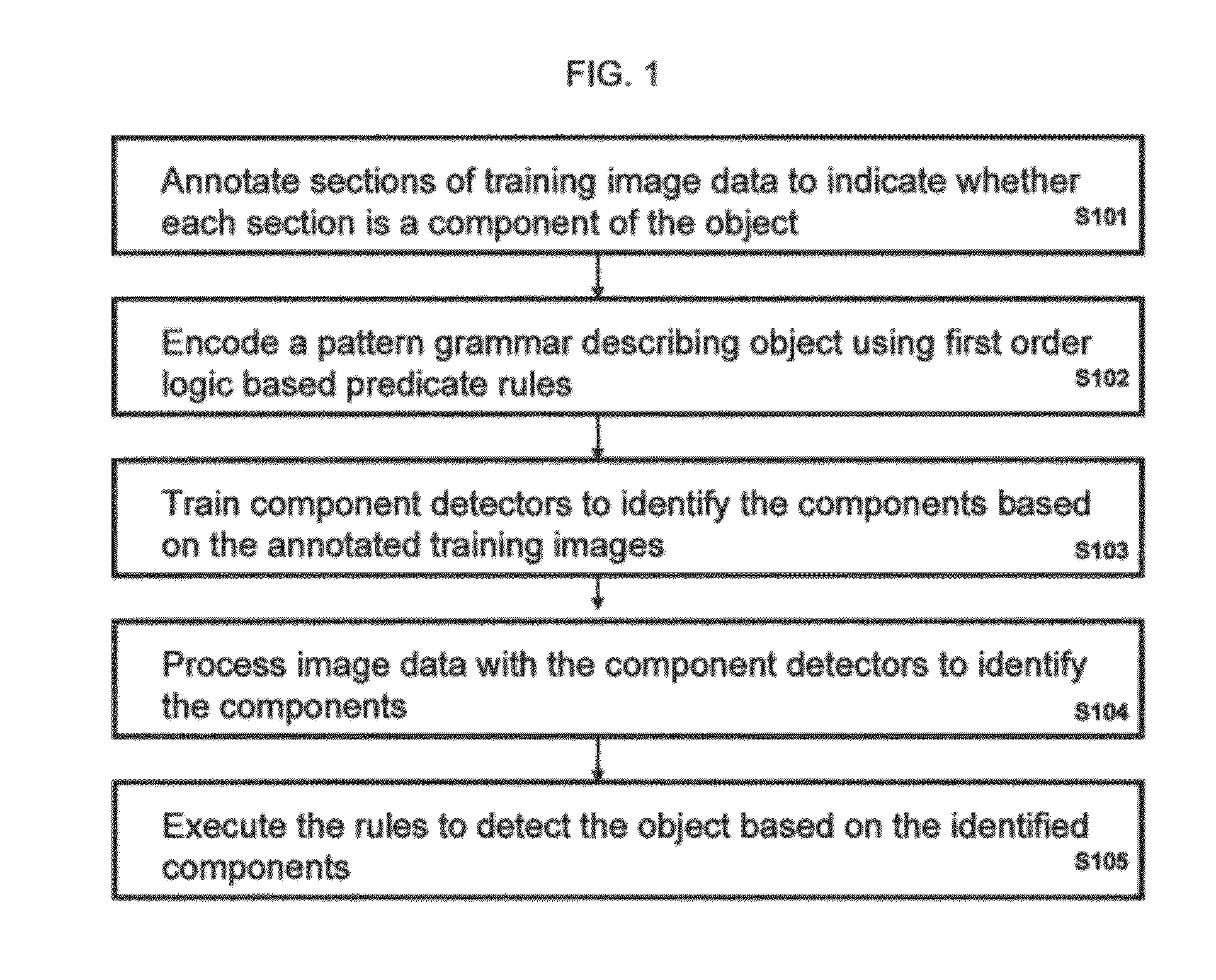
Object Recognition For Security Screening and Long Range Video Surveillance
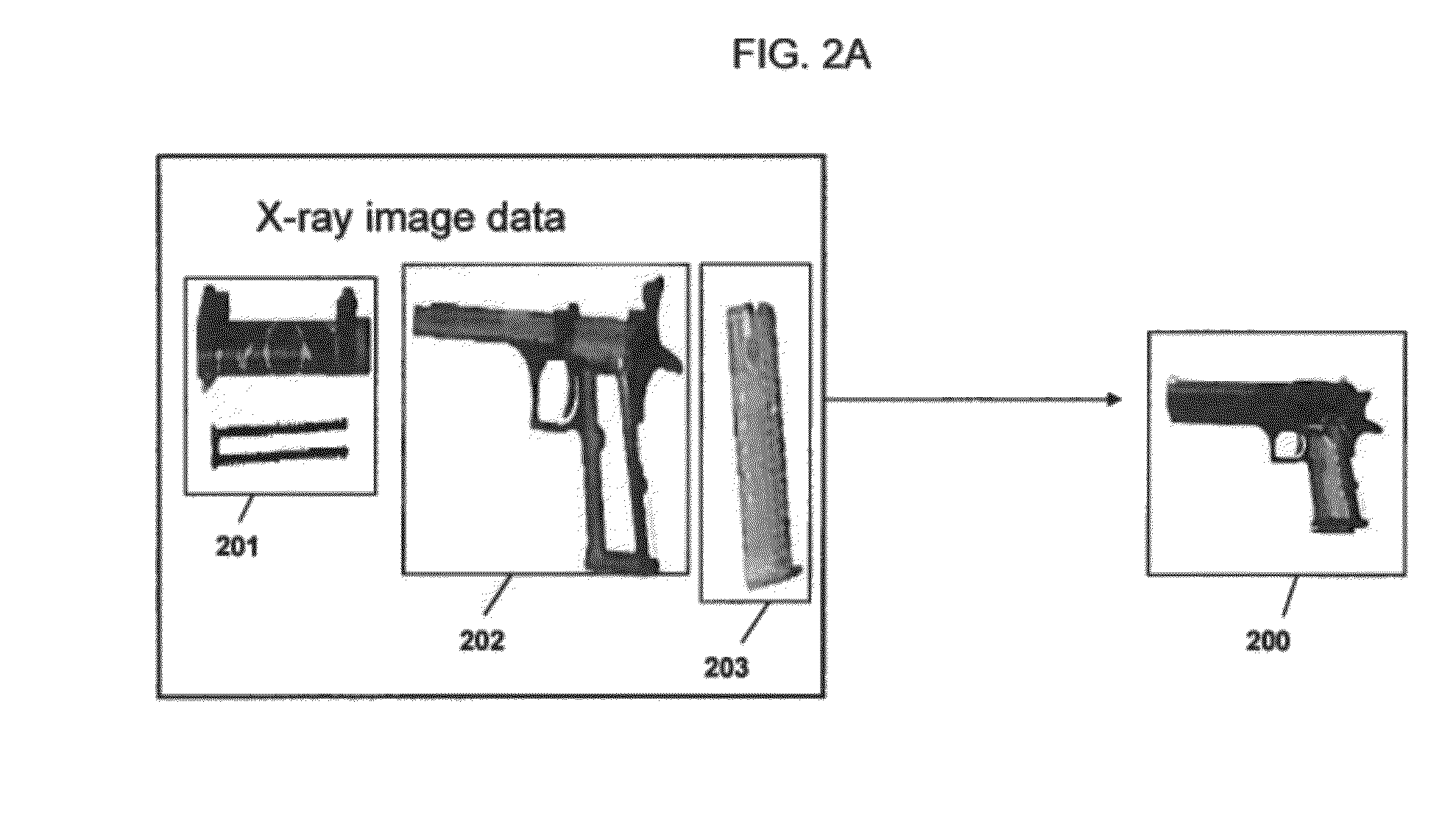
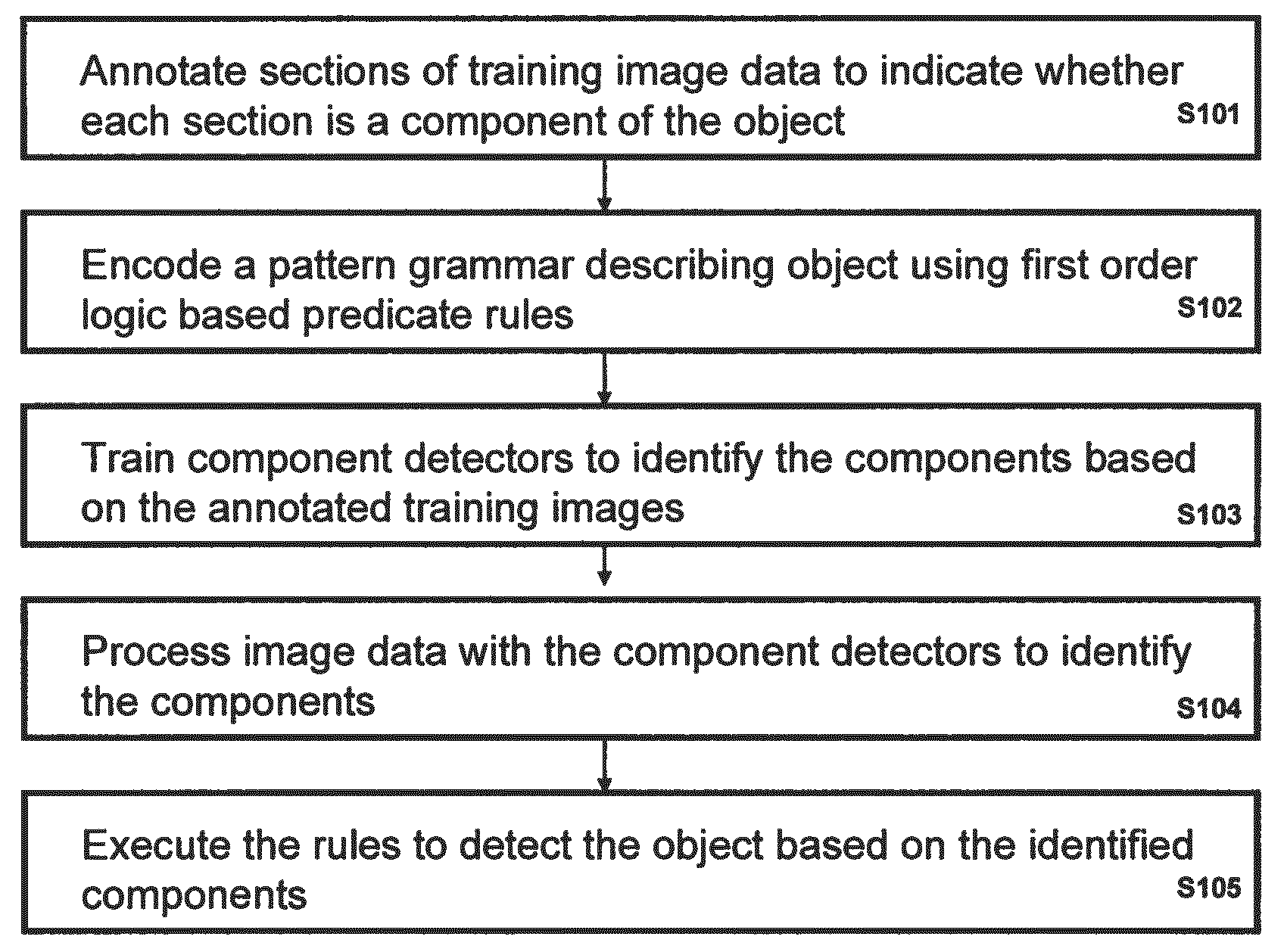
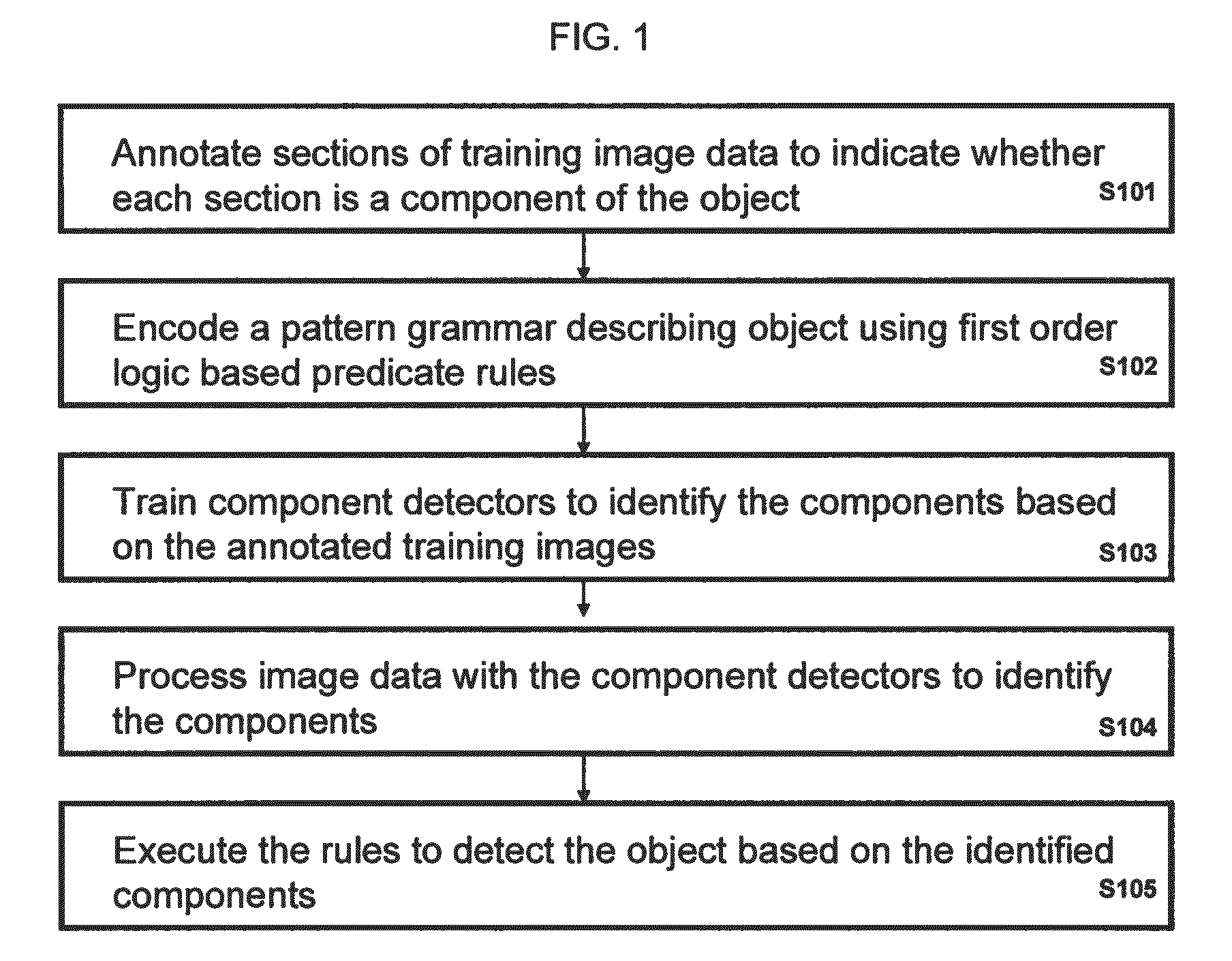
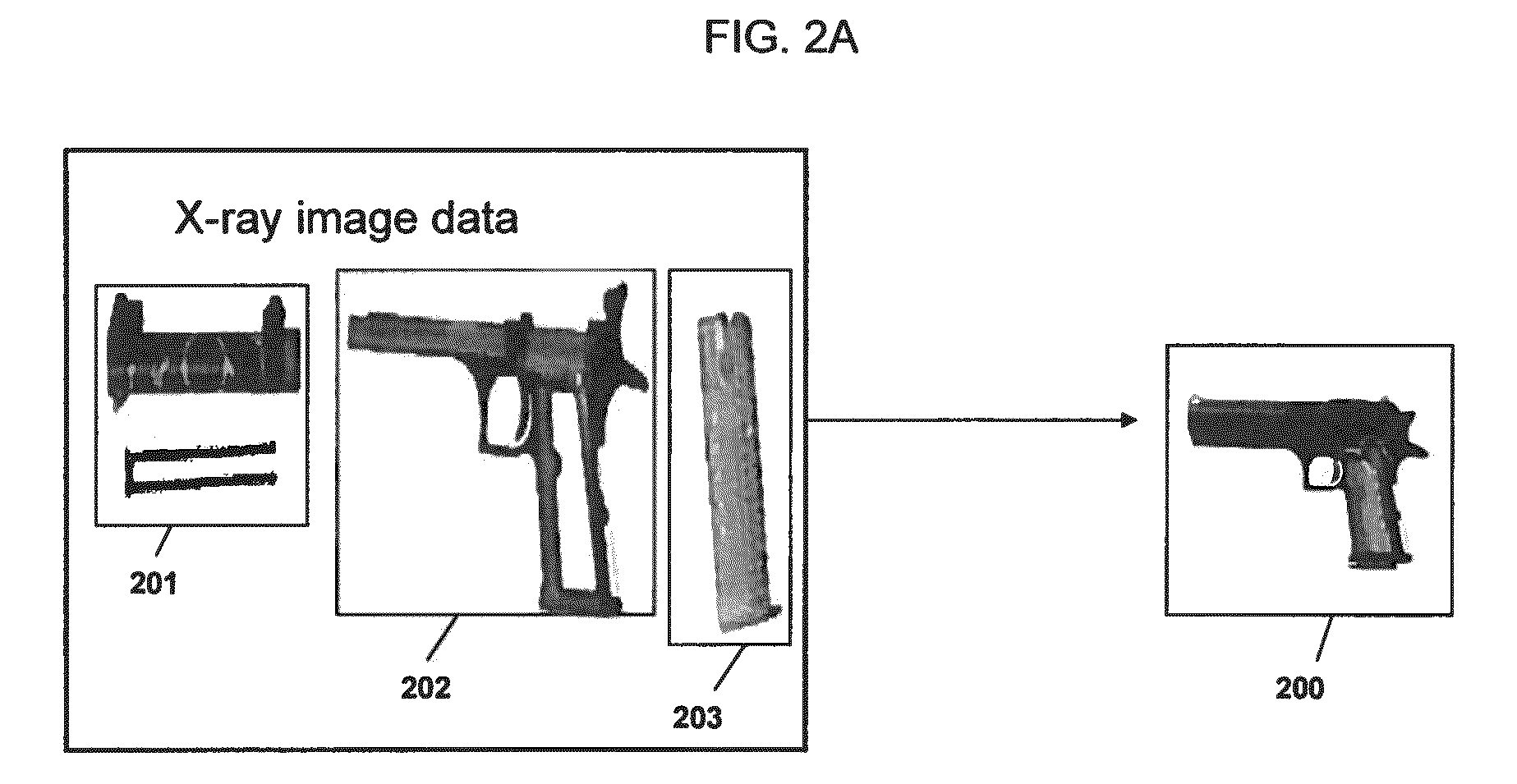
A method of detecting an object in image data that is deemed to be a threat includes annotating sections of at least one training image to indicate whether each section is a component of the object, encoding a pattern grammar describing the object using a plurality of first order logic based predicate rules, training distinct component detectors to each identify a corresponding one of the components based on the annotated training images, processing image data with the component detectors to identify at least one of the components, and executing the rules to detect the object based on the identified components.
Owner:SIEMENS MOBILITY GMBH
Method for establishing fault diagnosis technique based on contingent Bayesian networks
ActiveUS20190087294A1Good effectProbabilistic networksDetecting faulty hardware using expert systemsFirst-order logicMarkov chain
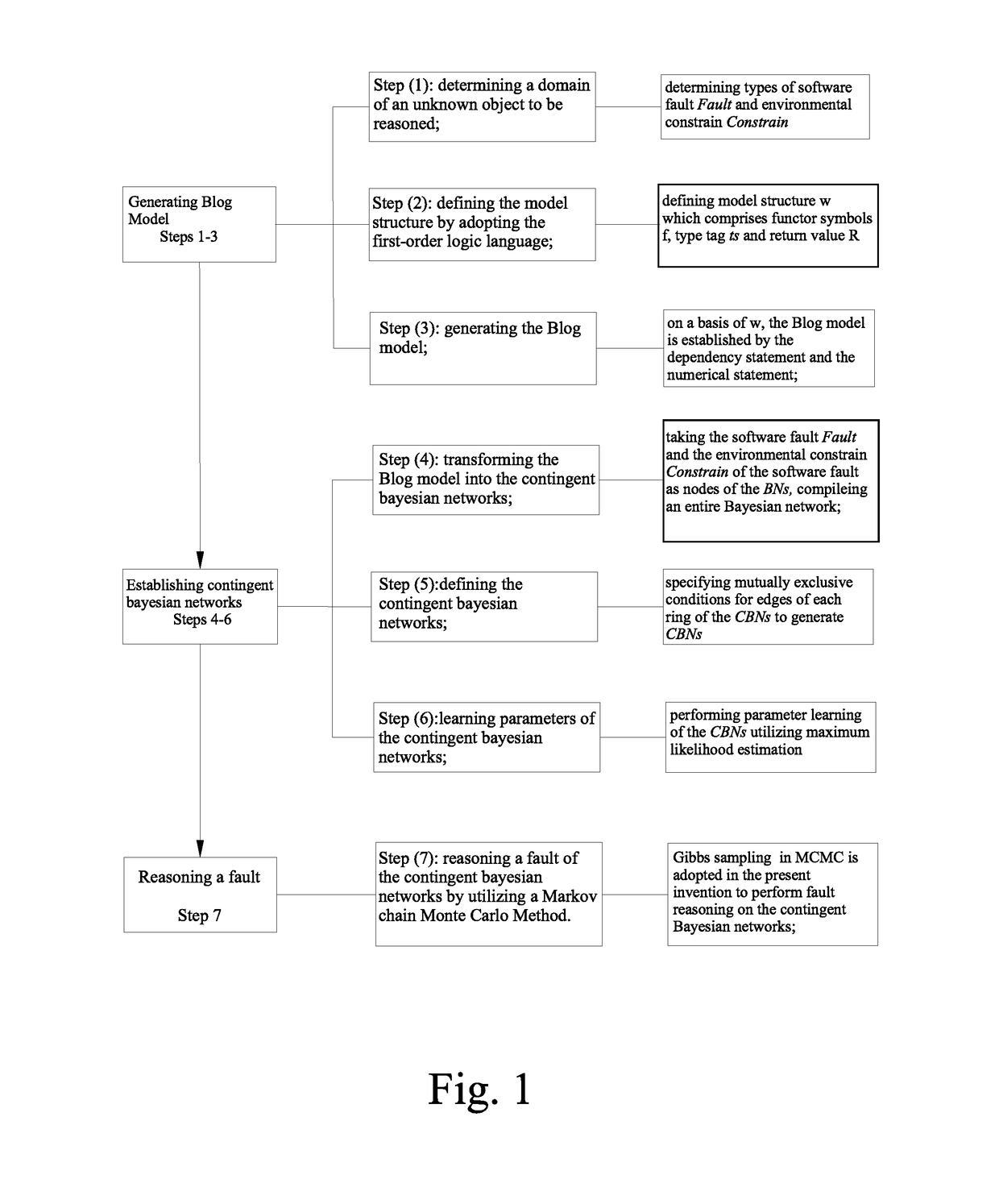
A method for establishing fault diagnosis technique based on contingent Bayesian networks, comprising steps of: step (1) determining a domain of an unknown object to be reasoned; step (2) defining a model structure by adopting a first-order logic language; step (3) generating a Blog model; step (4) transforming the Blog model into the contingent Bayesian networks; step (5) defining the contingent Bayesian networks; step (6) learning parameters of the contingent Bayesian networks; and step (7) reasoning a fault of the contingent Bayesian networks by utilizing a Markov chain Monte Carlo Method. By the steps mentioned above, establishing fault diagnosis technique based on contingent Bayesian networks is achieved.
Owner:BEIHANG UNIV
Object recognition for security screening and long range video surveillance
A method of detecting an object in image data that is deemed to be a threat includes annotating sections of at least one training image to indicate whether each section is a component of the object, encoding a pattern grammar describing the object using a plurality of first order logic based predicate rules, training distinct component detectors to each identify a corresponding one of the components based on the annotated training images, processing image data with the component detectors to identify at least one of the components, and executing the rules to detect the object based on the identified components.
Owner:SIEMENS MOBILITY GMBH
Automated anomaly detection
ActiveUS7627543B2Avoid overfitting noisy dataError detection/correctionDigital computer detailsData setNoisy data
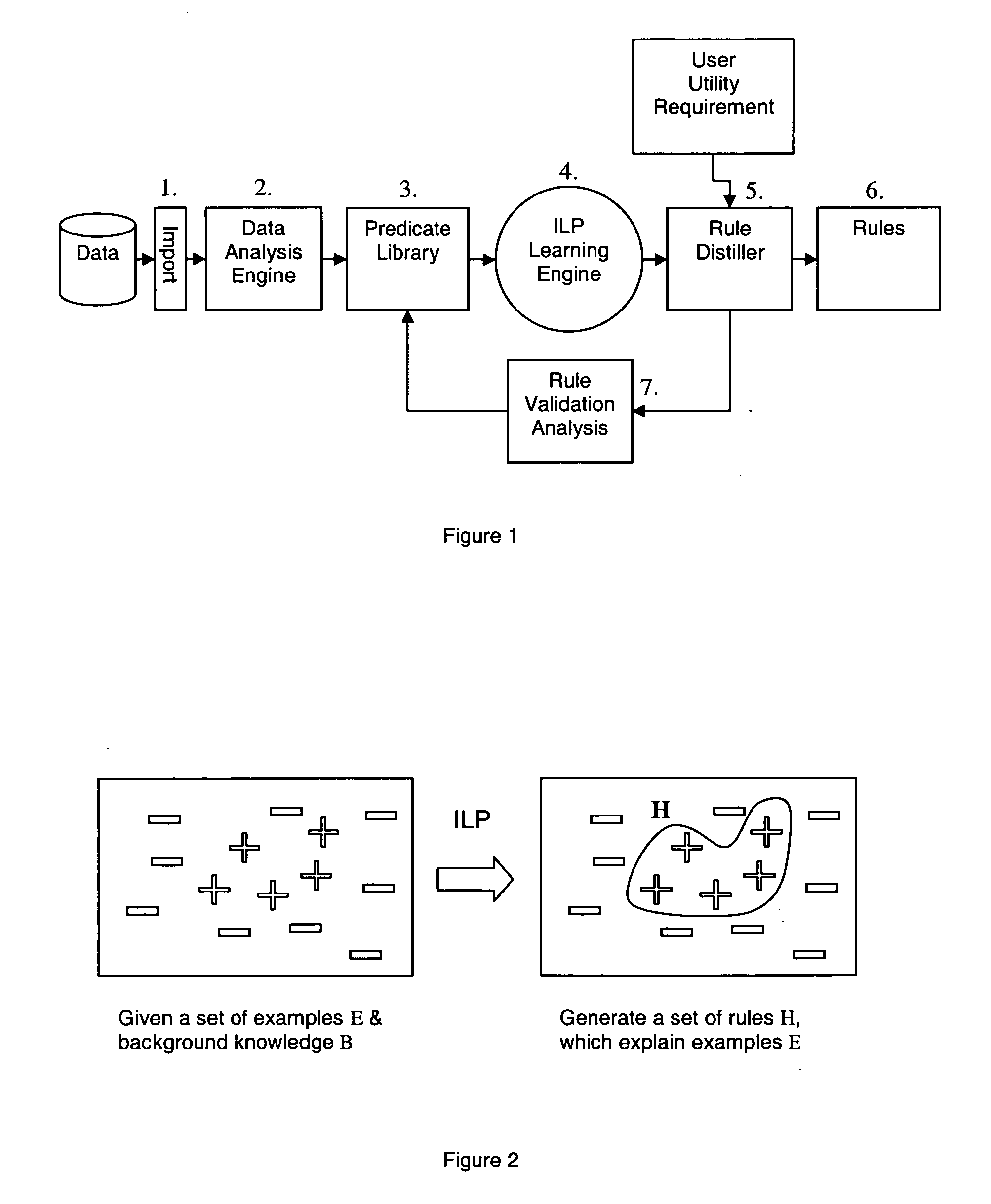
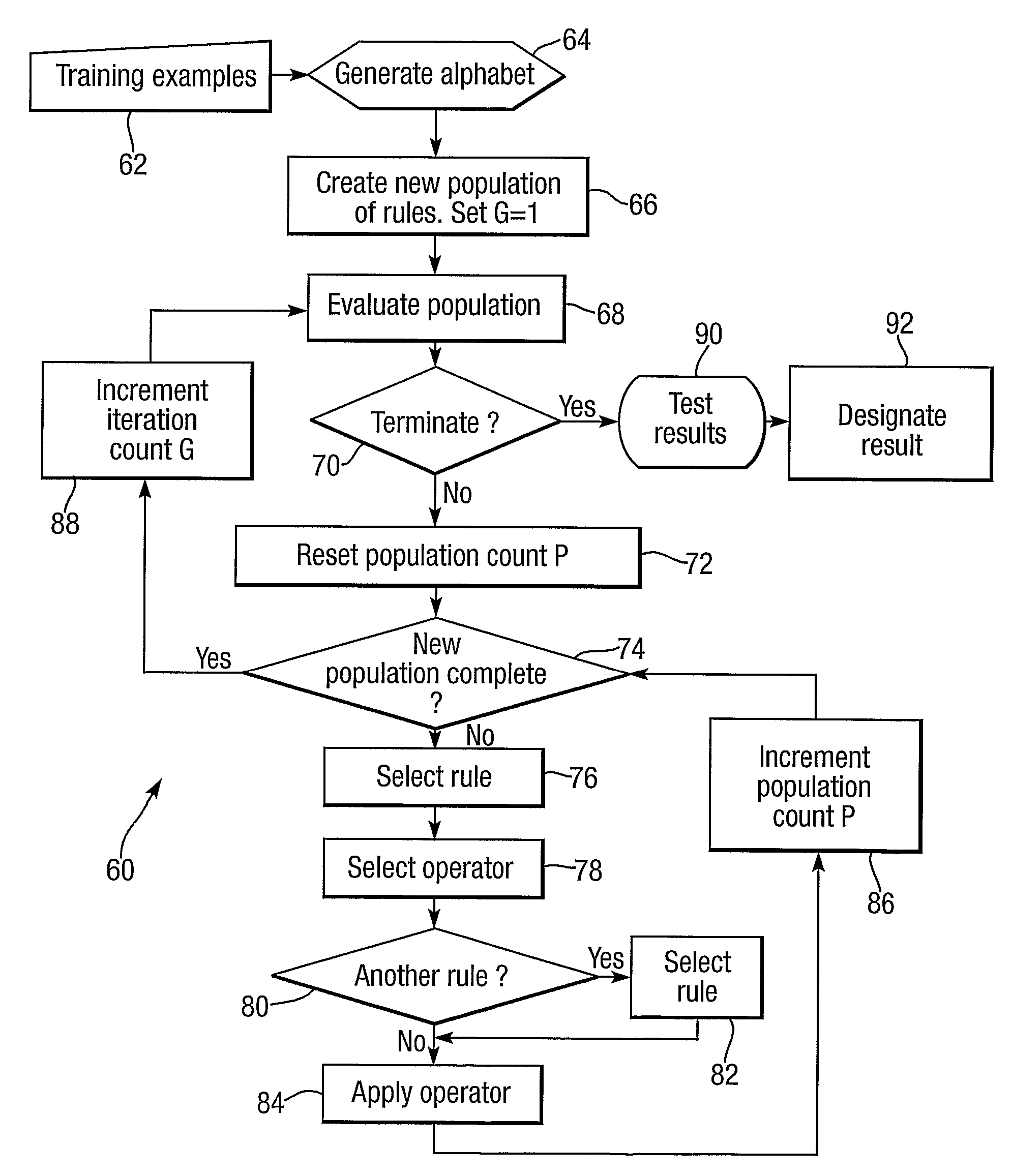
A method of anomaly detection applicable to telecommunications or retail fraud or software vulnerabilities uses inductive logic programming to develop anomaly characterization rules from relevant background knowledge and a training data set, which includes positive anomaly samples of data covered by rules. Data samples include 1 or 0 indicating association or otherwise with anomalies. An anomaly is detected by a rule having condition set which the anomaly fu,lfils. Rules are developed by addition of conditions and unification of variables, and are filtered to remove duplicates, equivalents, symmetric rules and unnecessary conditions. Overfitting of noisy data is avoided by an encoding cost criterion. Termination of rule construction involves criteria of rule length, absence of negative examples, rule significance and accuracy, and absence of recent refinement. Iteration of rule construction involves selecting rules with unterminated construction, selecting rule refinements associated with high accuracies, and iterating a rule refinement, filtering and evaluation procedure to identify any refined rule usable to test data. Rule development may use first order logic or Higher Order logic.
Owner:QINETIQ LTD
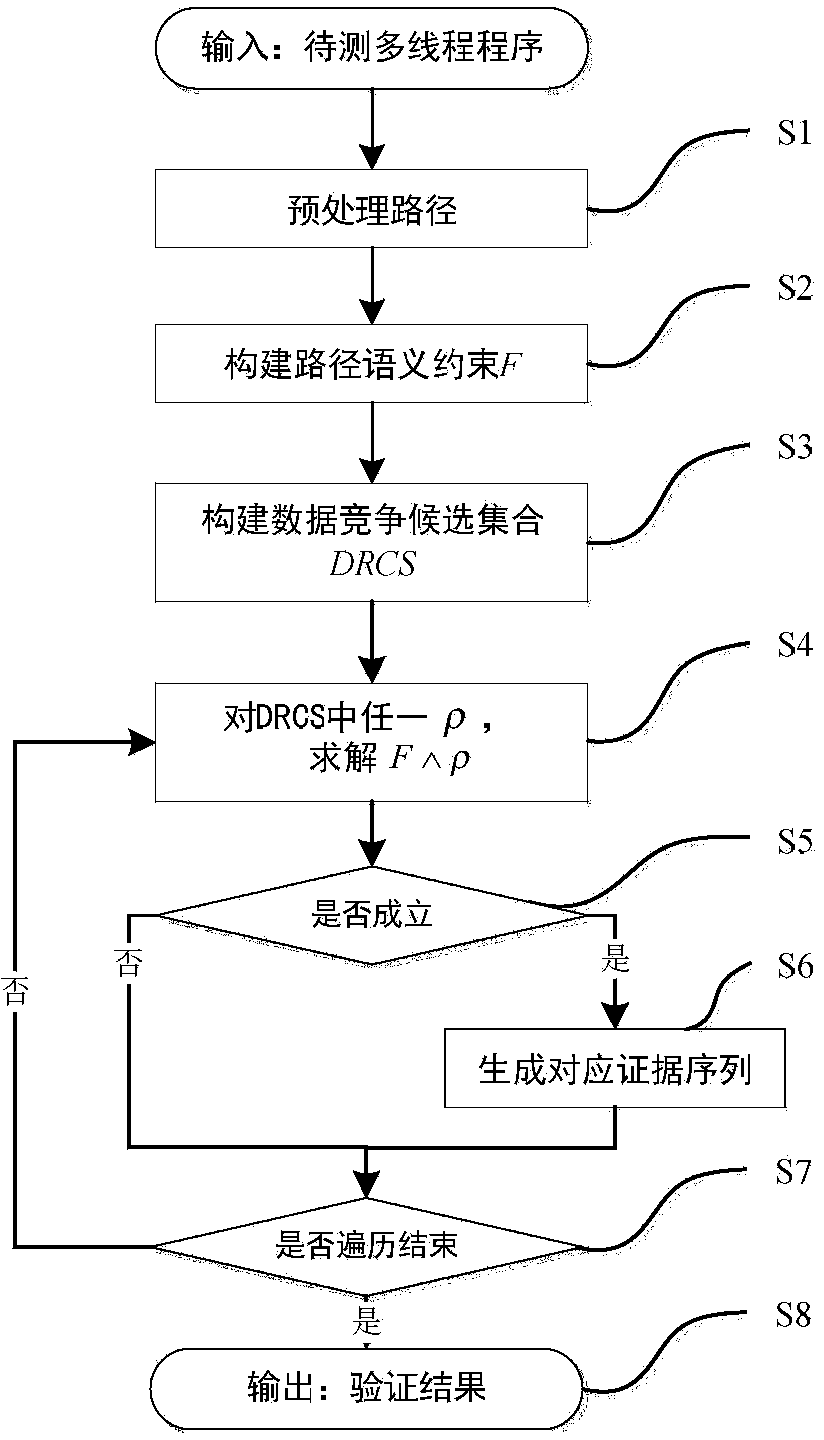
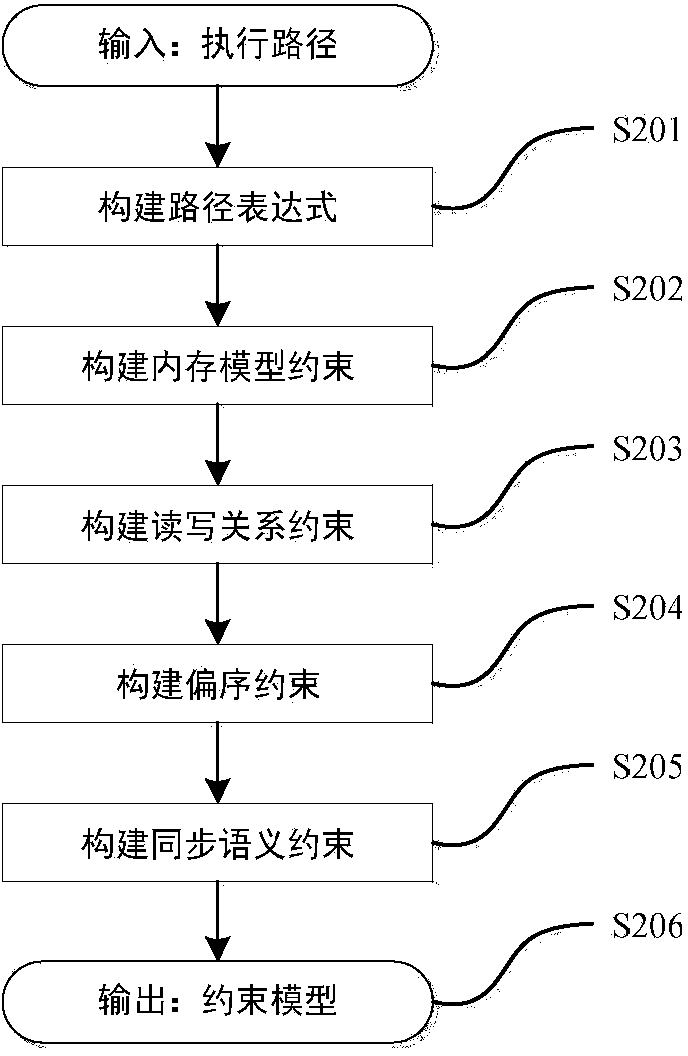
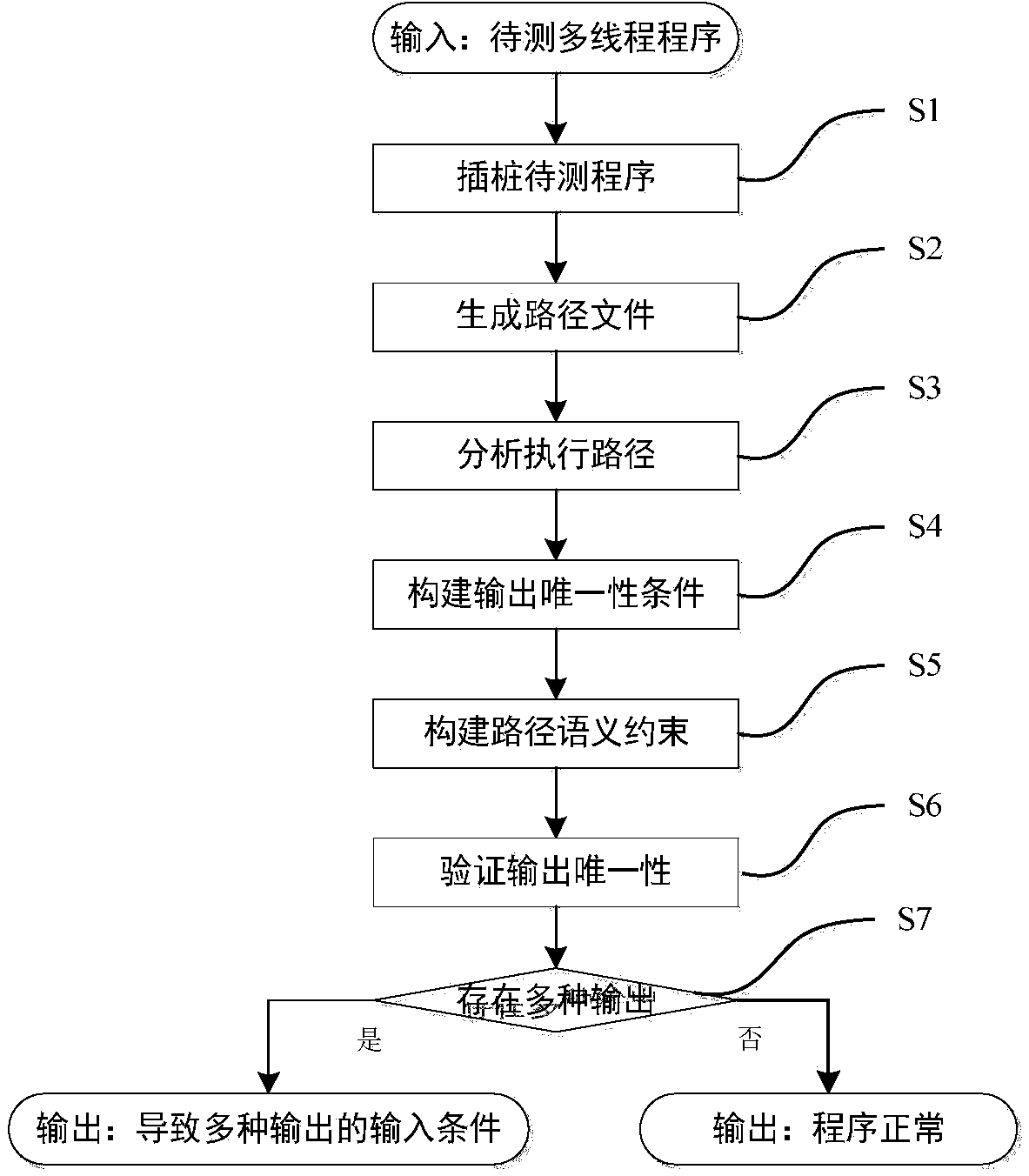
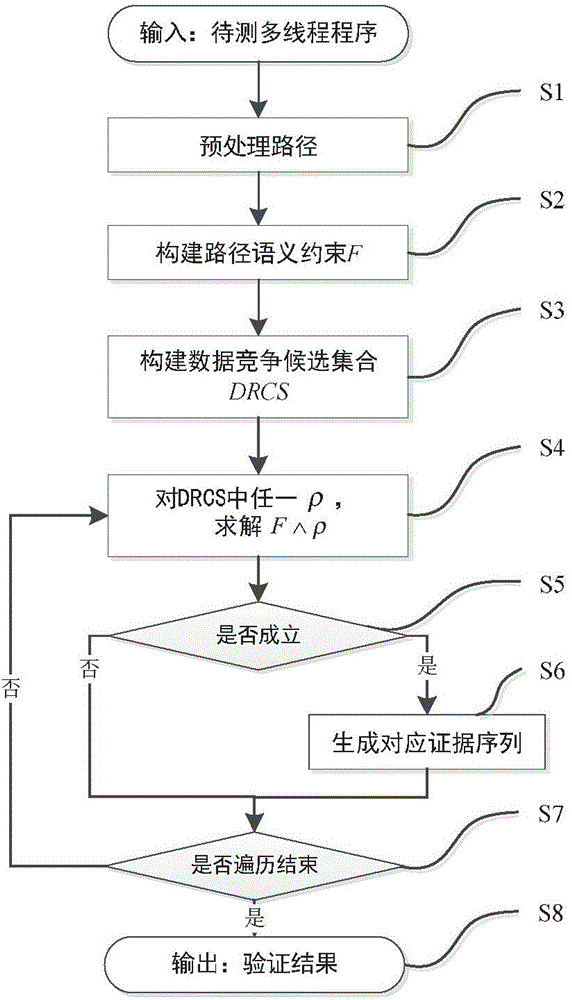
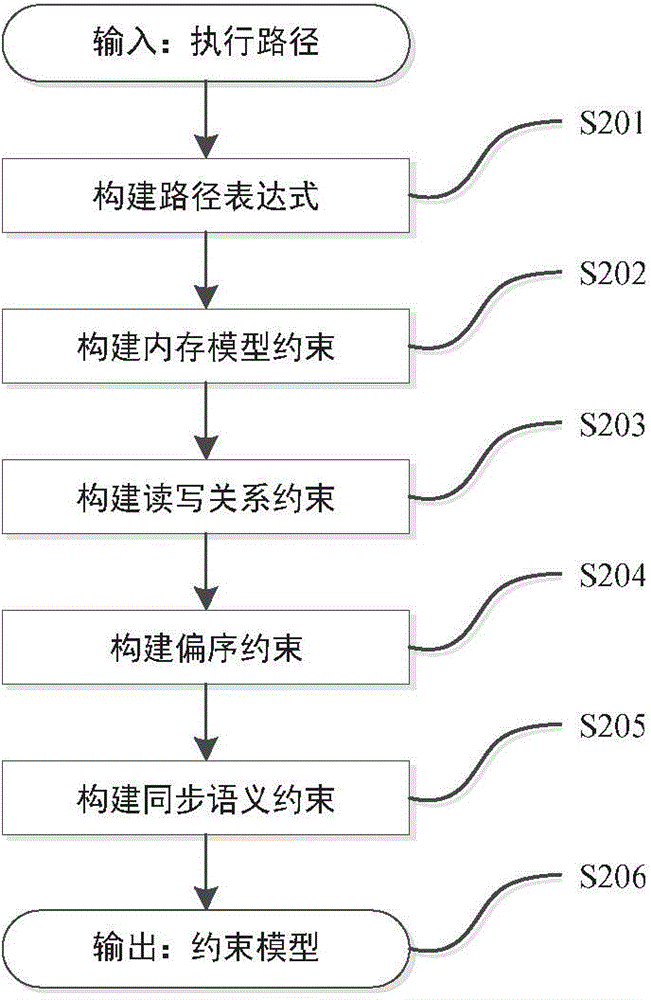
Data race detection and evidence generation method based on multithreaded program constraint building
ActiveCN104077144ANo overheadSoftware testing/debuggingSpecific program execution arrangementsFirst-order logicOccurrence data
The invention provides a data race detection and evidence generation method based on multithreaded program constraint building. The data race detection problem is converted into a constraint solving problem by building a constraint expression according to the multithreaded program semanteme, a constraint solver is used for detecting possible data races and program execution paths triggering the data races are generated; the data race detection and evidence generation method comprises the steps of firstly, carrying out the instrumentation of the detected program, executing the program and obtaining an execution path, secondly, converting the execution path into a quantifier-free first-order logic expression covering all feasible thread interleaving according to the multithreaded program execution semanteme, thirdly, building a data race candidate set according to the sequential relationship of statements when a data race happens and generating candidate conditions for races, and finally, traversing the candidate set to determine whether the data race exists, and if so, generating a corresponding evidence sequence. The method is capable of finding out all data races in once operation without misinformation; for each data race, the evidence sequence indicating the trigger process of the data race is generated.
Owner:XI AN JIAOTONG UNIV
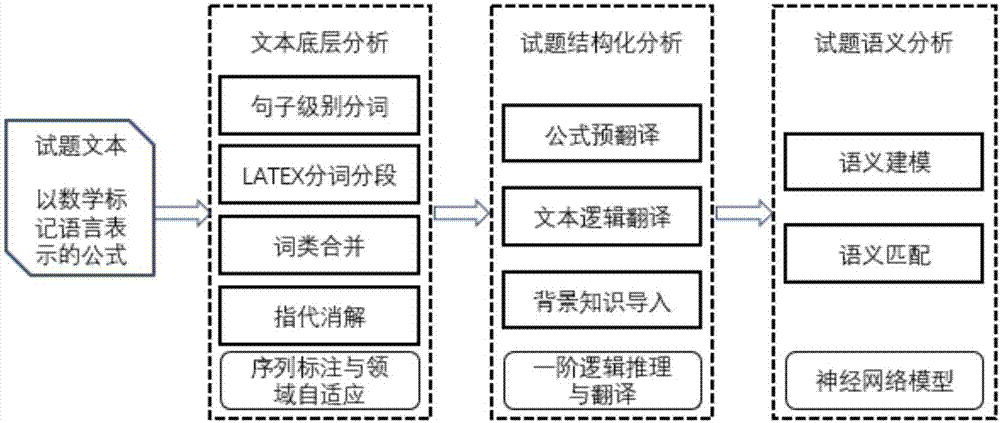
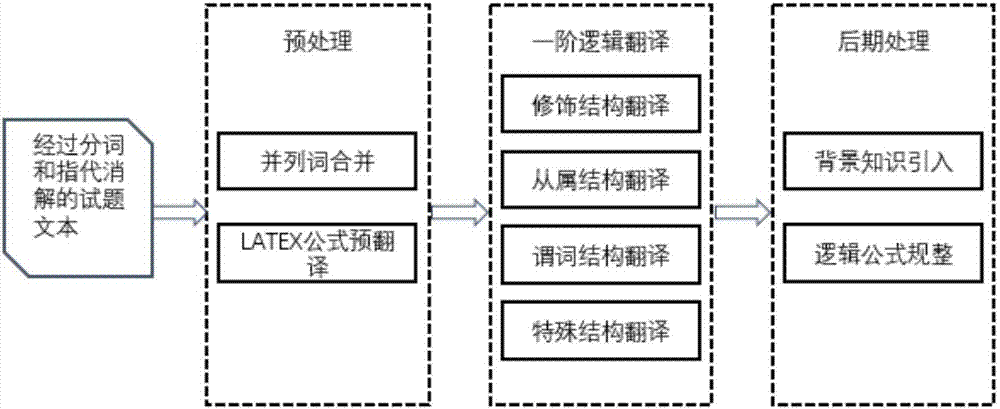
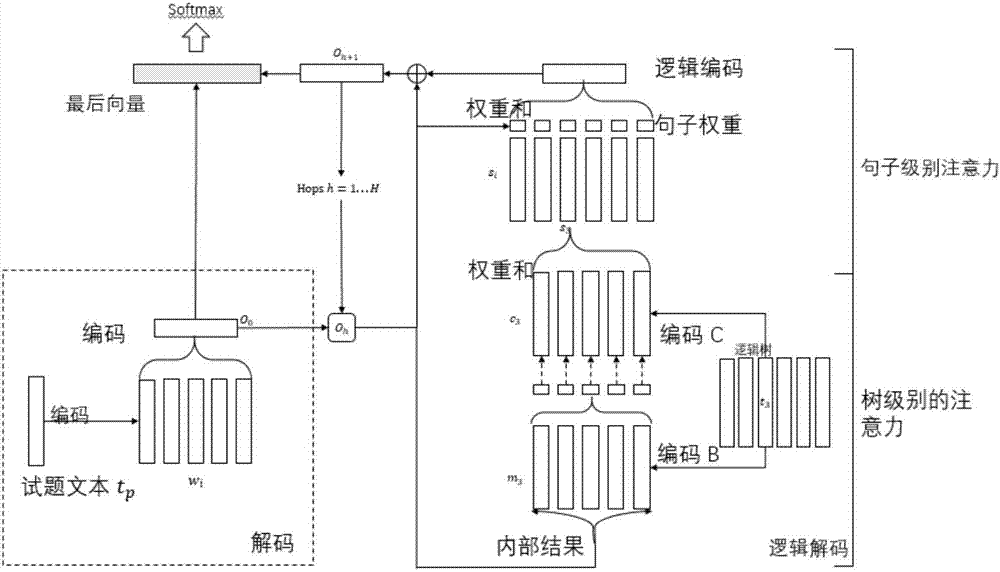
Extraction, expression and modeling method and system of text semantics aimed at elementary mathematical questions
ActiveCN107463553AAccurate Semantic Modeling ResultsSemantic analysisSpecial data processing applicationsFirst-order logicPart of speech
The invention belongs to the technical field of natural language processing for mathematics, in particular to an extraction, expression and modeling method of text semantics aimed at elementary mathematical questions and a corresponding question meaning analysis system of elementary mathematics. The method includes the following steps: as for an inputted mathematical question, using a combination of a word segmentation lexicon and a regular expression to segment words, as for the result after segmenting the words, conducting word conversion and word group combination, and conducting object replacement of reference words through anaphora resolution; then using the information obtained after processing to extract and translate mathematical formulas by virtue of a first-order logic, obtaining a mathematical question expression based on the first-order logic; finally, using deep neural networks to conduct semantic modeling and semantic fusion to the natural language and formulas of the question. The effective expression and modeling method of elementary mathematical questions proposed by the extraction, expression and modeling method and system of text semantics aimed at elementary mathematical questions can convert the mathematical question to a semantic representation which can be processed by a computer and conduct a more precise semantic modeling of mathematical questions.
Owner:FUDAN UNIV
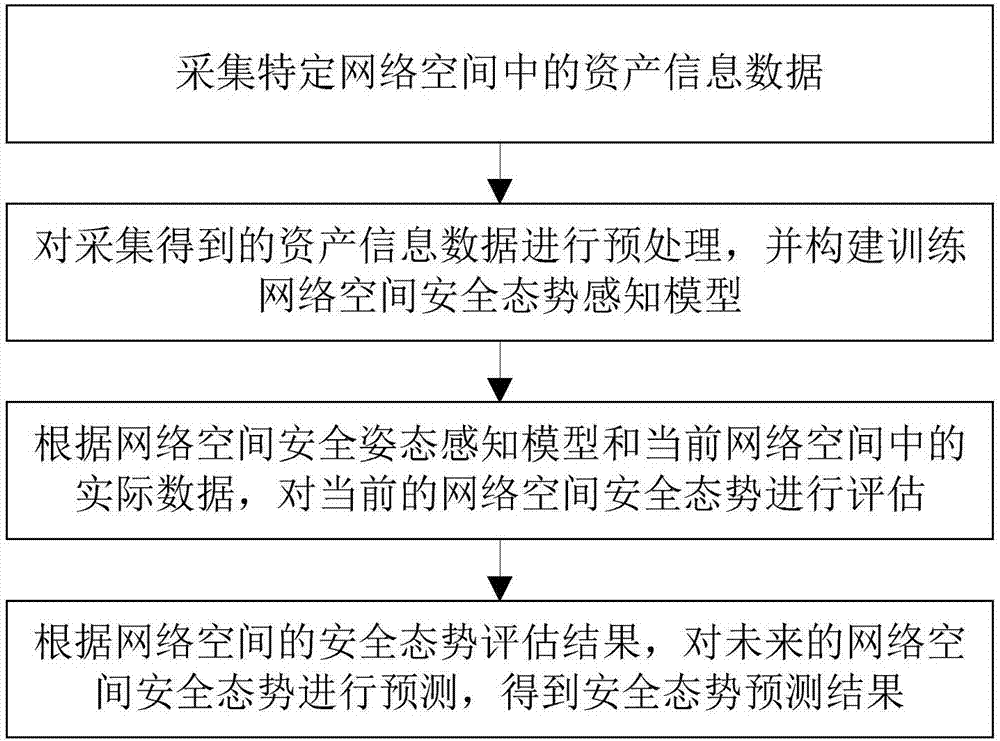
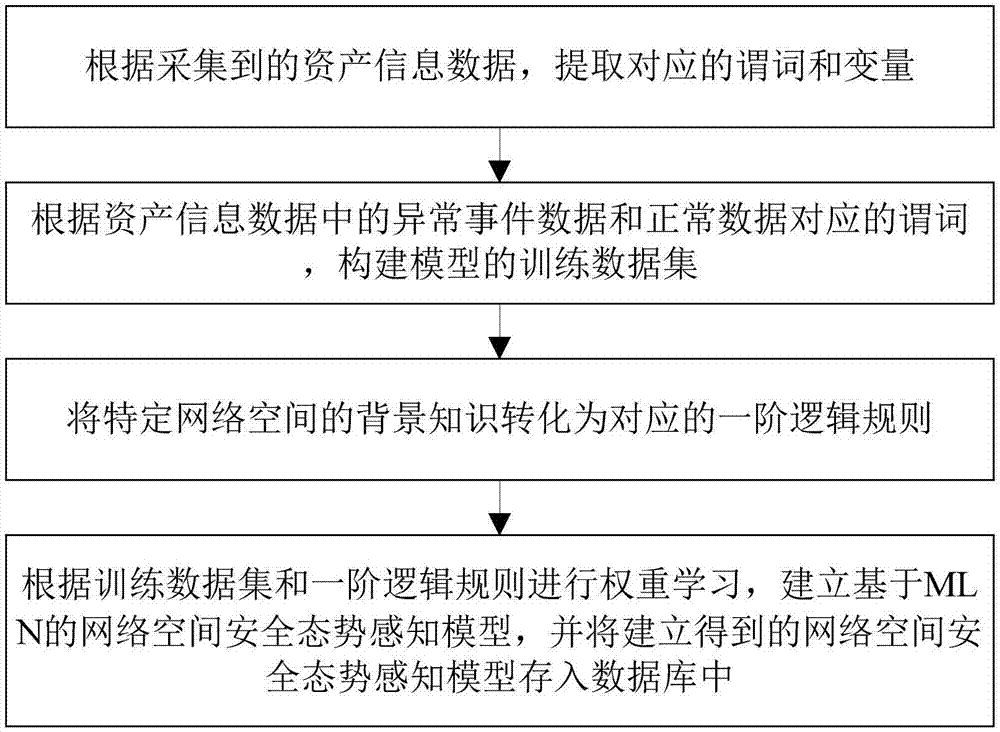
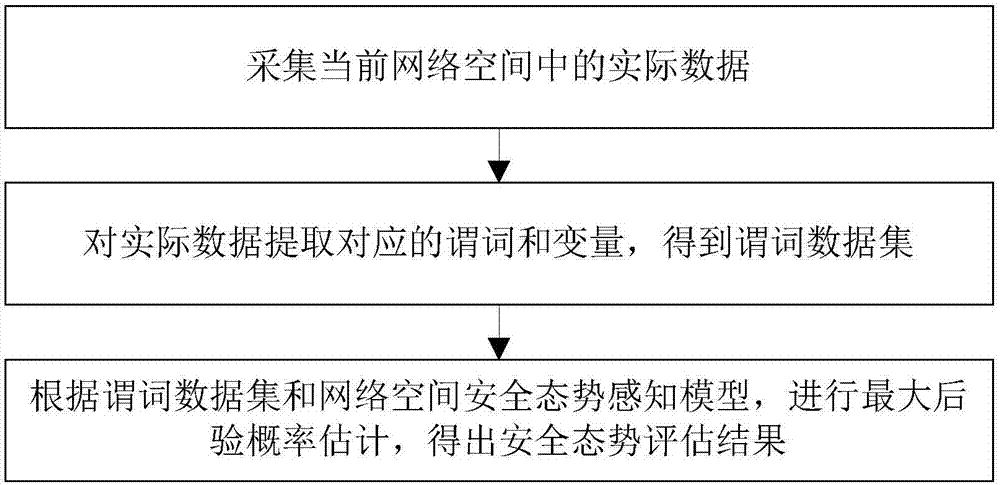
MLN-based network space security situation prediction method and system
InactiveCN107147515AAccurateImprove accuracyData switching networksFirst-order logicEvaluation result
The invention discloses an MLN-based network space security situation prediction method and system. The method comprises the steps that asset information data in a specific network space is collected; the collected asset information data is preprocessed, and a network space security situation perception model is constructed and trained; the current network space security situation is evaluated according to the network space security situation perception model and actual data in the current network space; and the future network space security situation is predicted according to a security situation evaluation result of the network space to obtain a security situation prediction result. According to the method, the relation between objects and object properties can be easily represented according to a first-order logic rule by applying a Markov logic network; and in addition, by introducing background knowledge, the object relation in the network space can be mastered more accurately, and then the evaluation accuracy rate is effectively increased. The method and system can be widely applied to the computer network field.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Analytical system for discovery and generation of rules to predict and detect anomalies in data and financial fraud
InactiveUS7885915B2High precisionLow false positive rateNatural language data processingKnowledge representationFirst-order logicAlgorithm
Methods and computer apparatus are disclosed for deriving first order logic language rules for use in analyzing new data to identify anomalies in the new data. Historical data is formatted to be in a form suitable for application of a machine-learning algorithm thereto. The machine-learning algorithm is applied to the formatted historical data to generate a set of first order logic language rules that cover the formatted historical data. The set of first order logic language rules are analyzed to obtain a subset of said set of first order logic language rules which can be used as first order logic language rules in analyzing new data.
Owner:VALIDIS UK LTD
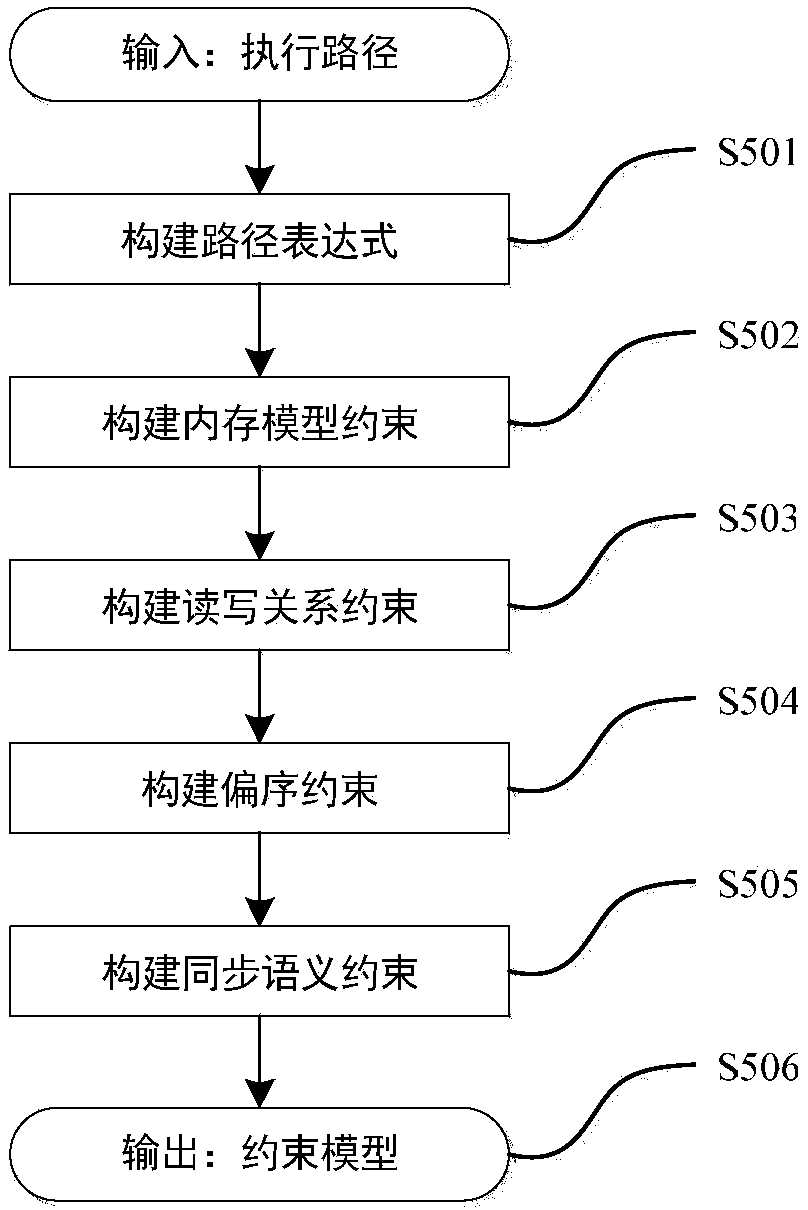
Multithreaded program output uniqueness detection and evidence generation method based on program constraint building
Owner:XI AN JIAOTONG UNIV
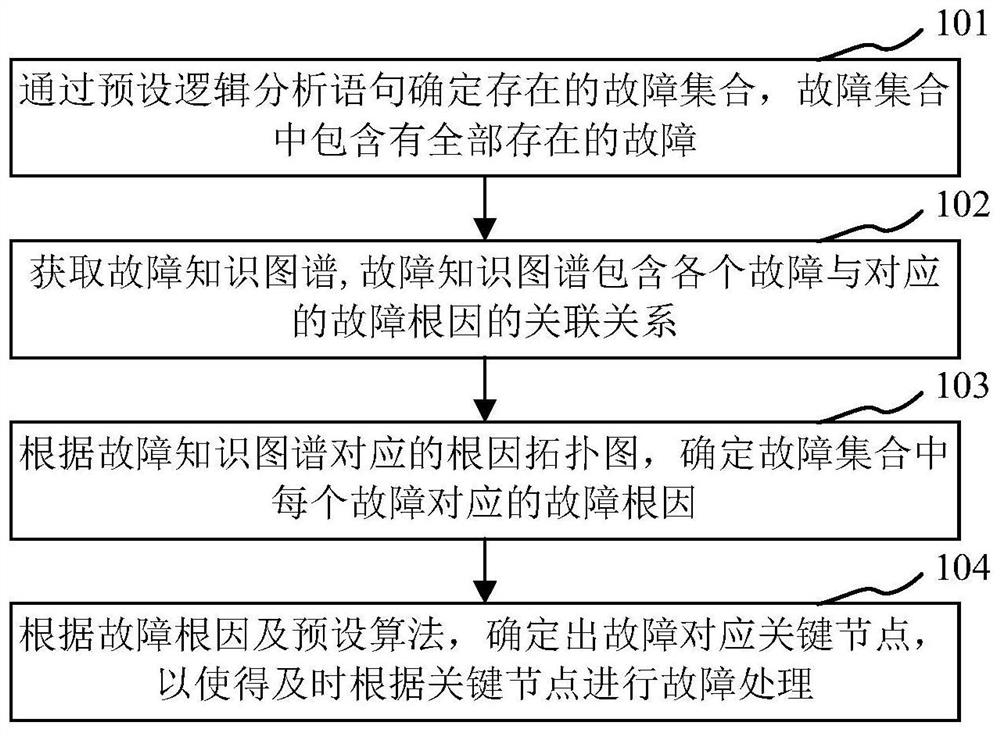
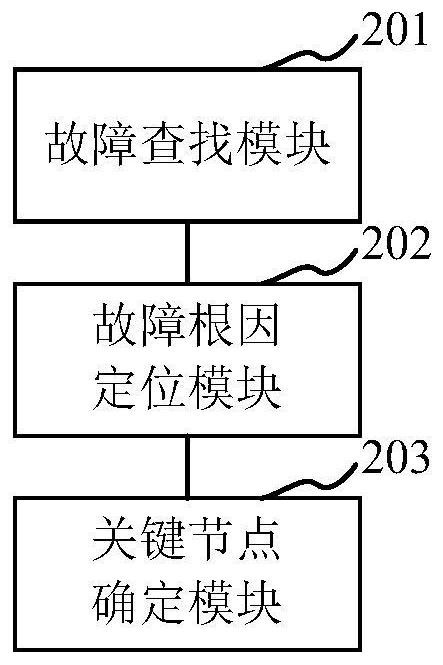
Fault root cause inference positioning method and device based on artificial intelligence
ActiveCN112416645APrecise positioningTimely processingNon-redundant fault processingInference methodsFirst-order logicGraph spectra
The embodiment of the invention provides a fault root cause inference positioning method and device based on artificial intelligence. The method comprises the steps of determining an existing fault set through a preset logic analysis statement, wherein the fault set comprises all existing faults; obtaining a fault knowledge graph, wherein the fault knowledge graph comprises an association relationship between each fault and the corresponding fault root cause; determining a fault root cause corresponding to each fault in the fault set according to the root cause topological graph correspondingto the fault knowledge graph; and according to the fault root cause and a preset algorithm, determining a key node corresponding to the fault so as to carry out fault processing in time according to the key node. A derivation relation between faults is established through carding based on the knowledge graph and applying a preset artificial intelligence first-order logic algorithm. According to the method, rules are defined for the fault, the root cause is searched for according to the rules and the currently sampled data, and finally the fault root cause is visually displayed through the topological graph of the software, so that the fault root cause can be rapidly, timely and accurately positioned to facilitate the technicians to process in time.
Owner:广州云岫信息科技有限公司
Logical spreadsheets
A computerized spreadsheet system includes a set of cells and a separate set of logical constraints on the values of cells. The constraints may be many-to-many relationships that permit omni-directional propagation of values between cells. The constraints may be expressed in a language encompassing first-order logic. Cells are dynamically reclassified as base cells or computed cells as a user specifies values for cells. Non-explosive consequences of the base cell values are computed and displayed in computed cells, even when the values in the base cells are inconsistent with the constraints. The spreadsheet system may also include an auto-complete feature that automatically fills in empty cells with values consistent with the logical constraints and an auto-deconflict feature that automatically changes values in cells to reduce conflicts with the logical constraints.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
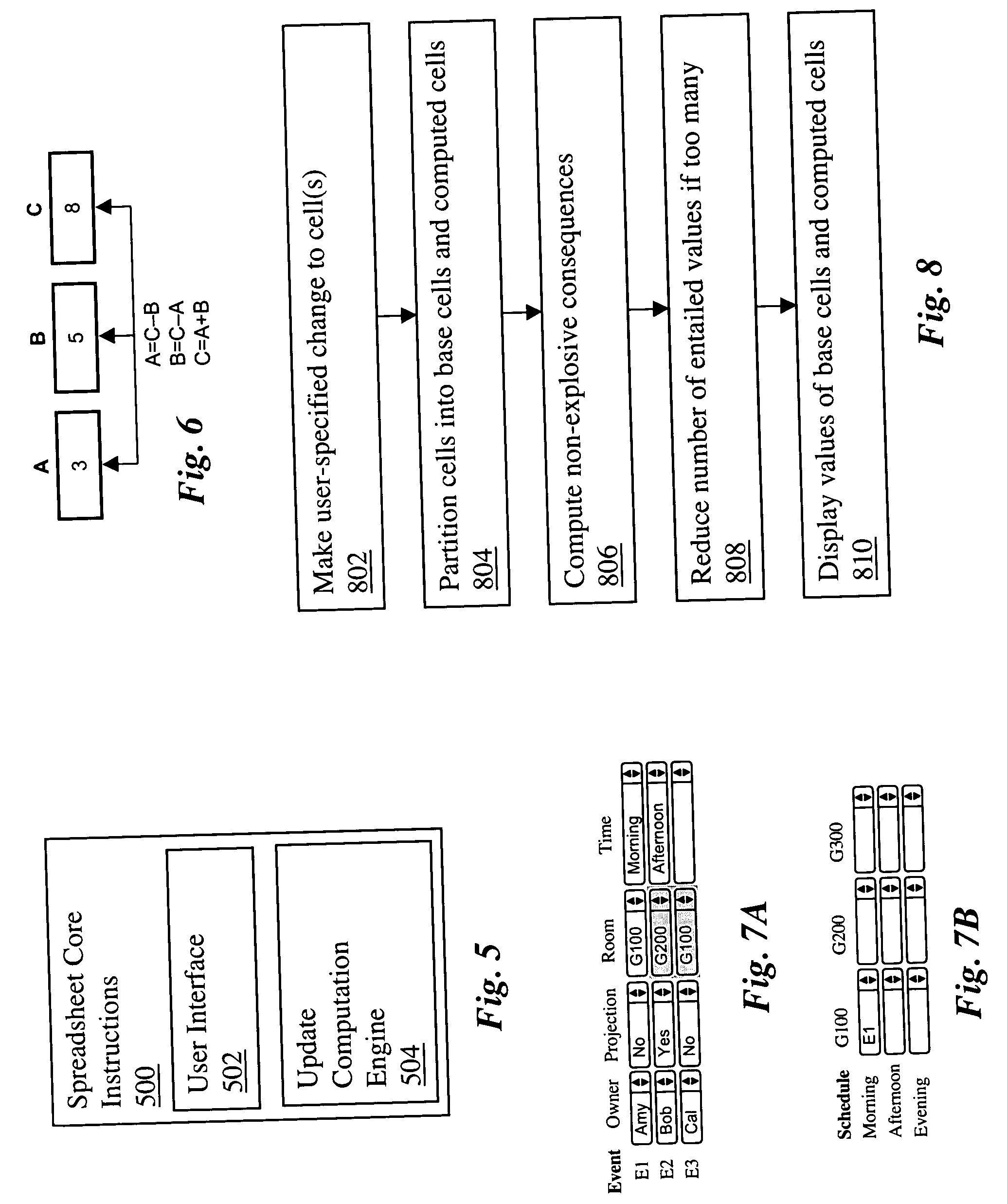
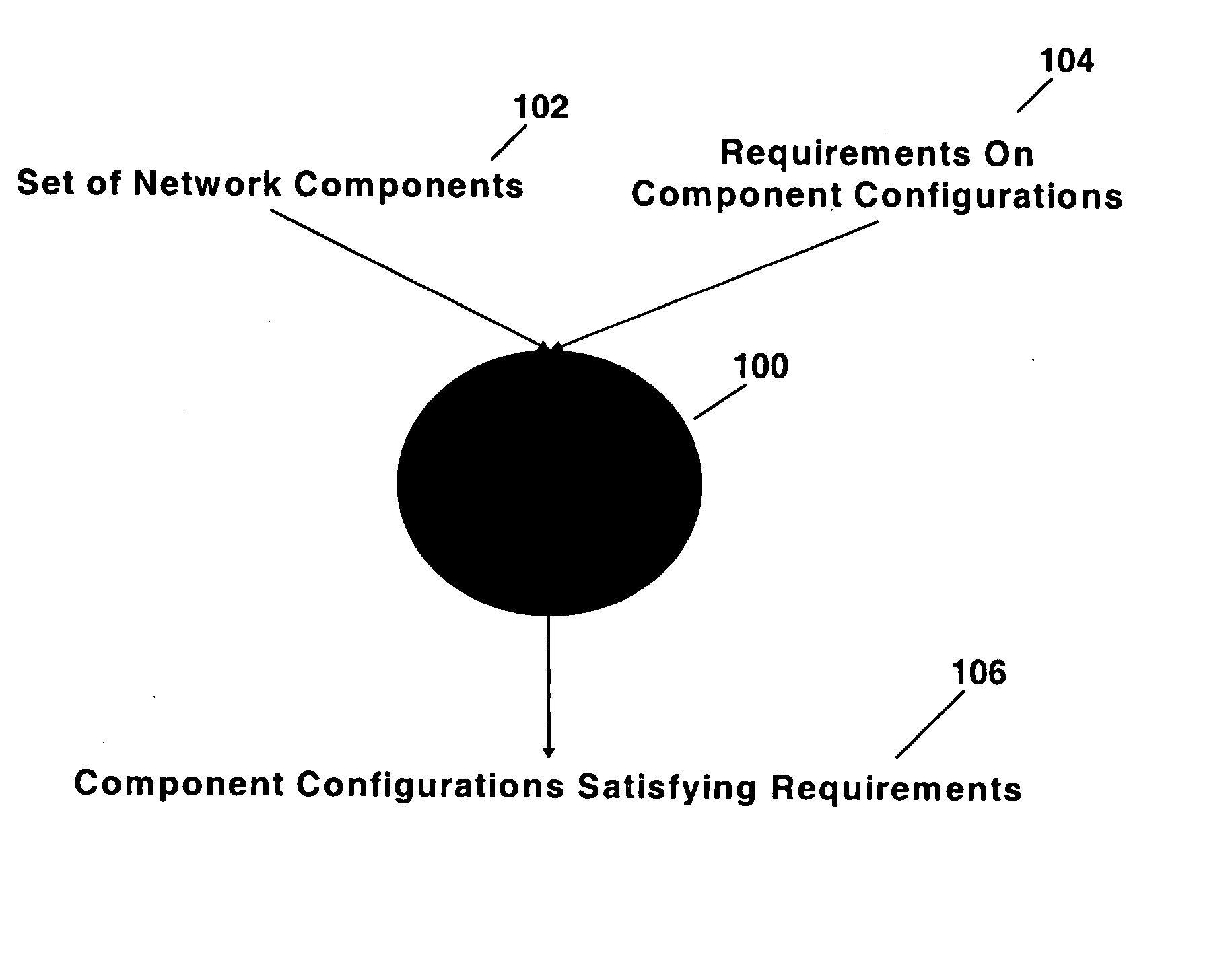
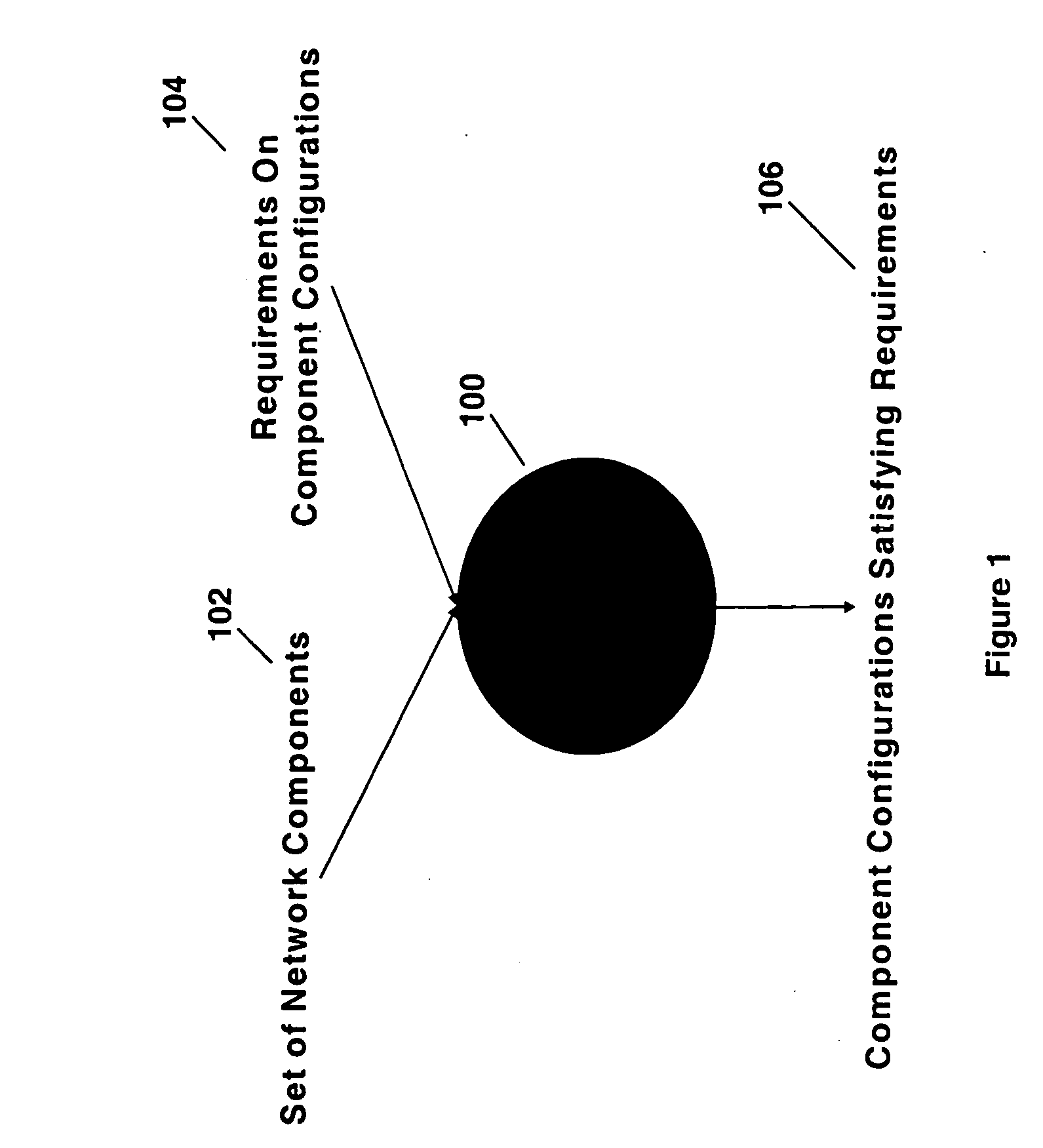
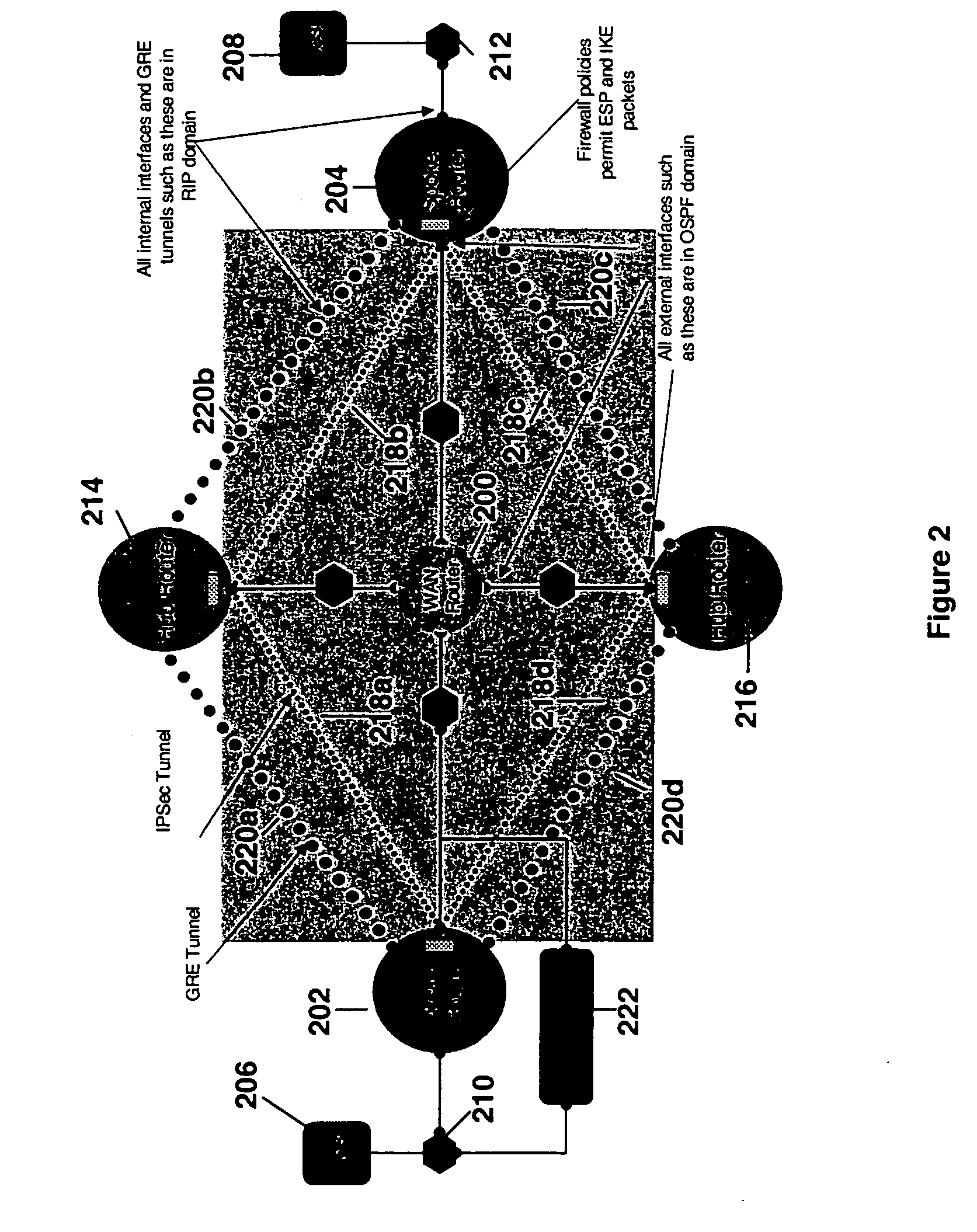
Network configuration management by model finding
InactiveUS20060184342A1Minimizing quantifierAvoiding unintended answerComputation using non-denominational number representationData switching networksFault toleranceSystem call
Complex, end-to-end network services are set up via the configuration method: each component has a finite number of configuration parameters each of which is set to definite values. End-to-end network service requirements can be on connectivity, security, performance and fault-tolerance. A number of subsidiary requirements are created that constrain, for example, the protocols to be used, and the logical structures and associated policies to be set up at different protocol layers. By performing different types of reasoning with these requirements, different configuration tasks are accomplished. These include configuration synthesis, configuration error diagnosis, configuration error fixing, reconfiguration as requirements or components are added and deleted, and requirement verification. A method of performing network configuration management by model finding formalizes and automates such reasoning using a logical system called Alloy. Given a first-order logic formula and a domain of interpretation, Alloy tries to find whether the formula is satisfiable in that domain, i.e., whether it has a model. Alloy is used to build a Requirement Solver that takes as input a set of network components and requirements upon their configurations and determines component configurations satisfying those requirements. This Requirement Solver is used in different ways to accomplish the above reasoning tasks.
Owner:TT GOVERNMENT SOLUTIONS
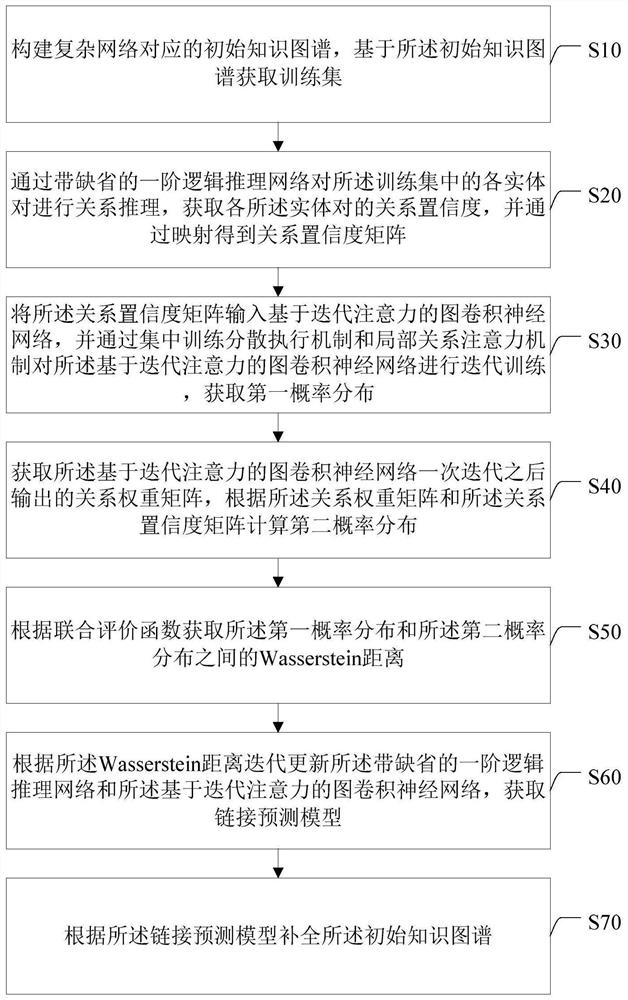
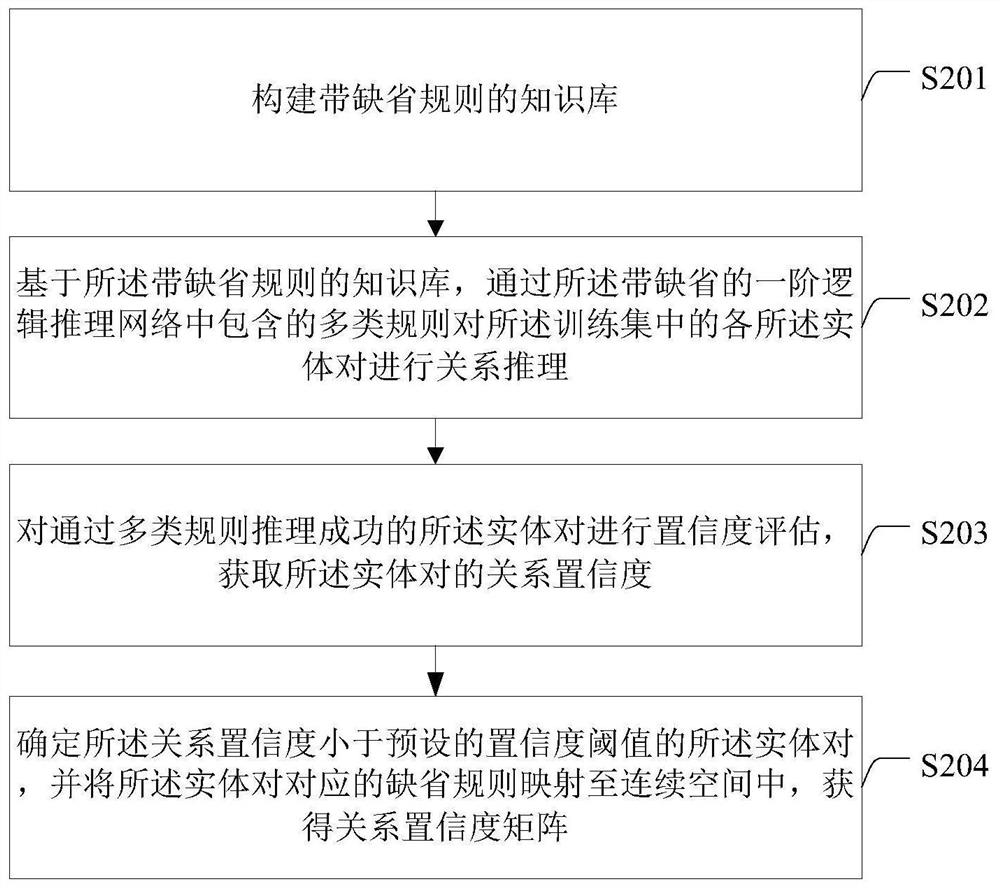
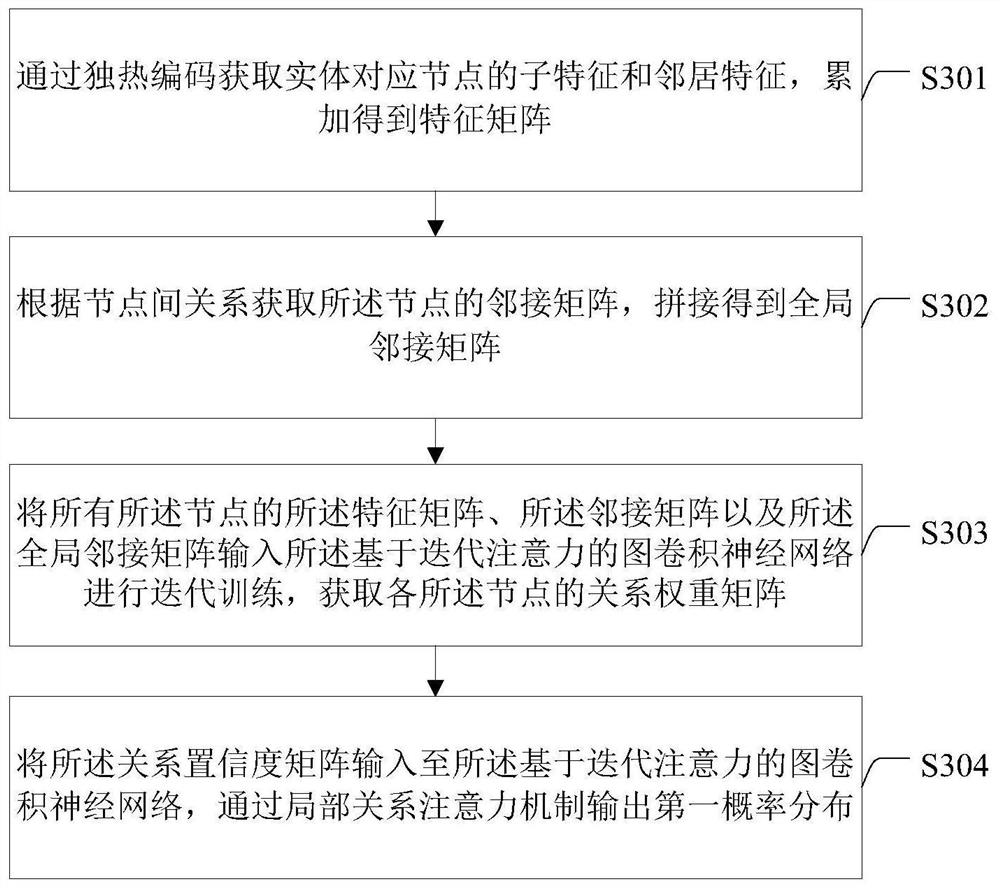
Complex network link prediction method and system based on logical reasoning and graph convolution
ActiveCN113190688ARich Entity FeaturesImprove linking efficiencyNeural architecturesInference methodsAlgorithmTheoretical computer science
The invention discloses a complex network link prediction method and system based on logical reasoning and graph convolution. The method comprises the following steps: constructing a knowledge graph corresponding to a complex network, and obtaining a training set; performing relation reasoning on each entity pair in the training set through a first-order logical reasoning network with default, and obtaining a relation confidence coefficient matrix through mapping; based on the relation confidence coefficient matrix, performing iterative training on a graph convolutional neural network based on iterative attention through a centralized training decentralized execution mechanism and a local relation attention mechanism to obtain first probability distribution; calculating second probability distribution according to a relation weight matrix and a relation confidence coefficient matrix output by network iteration; obtaining a Wasserstein distance between the first probability distribution and the second probability distribution according to a joint evaluation function; iteratively updating the two networks according to a Wasserstein distance to obtain a link prediction model; and complementing the knowledge graph according to the link prediction model. The link prediction efficiency is high.
Owner:NAT UNIV OF DEFENSE TECH
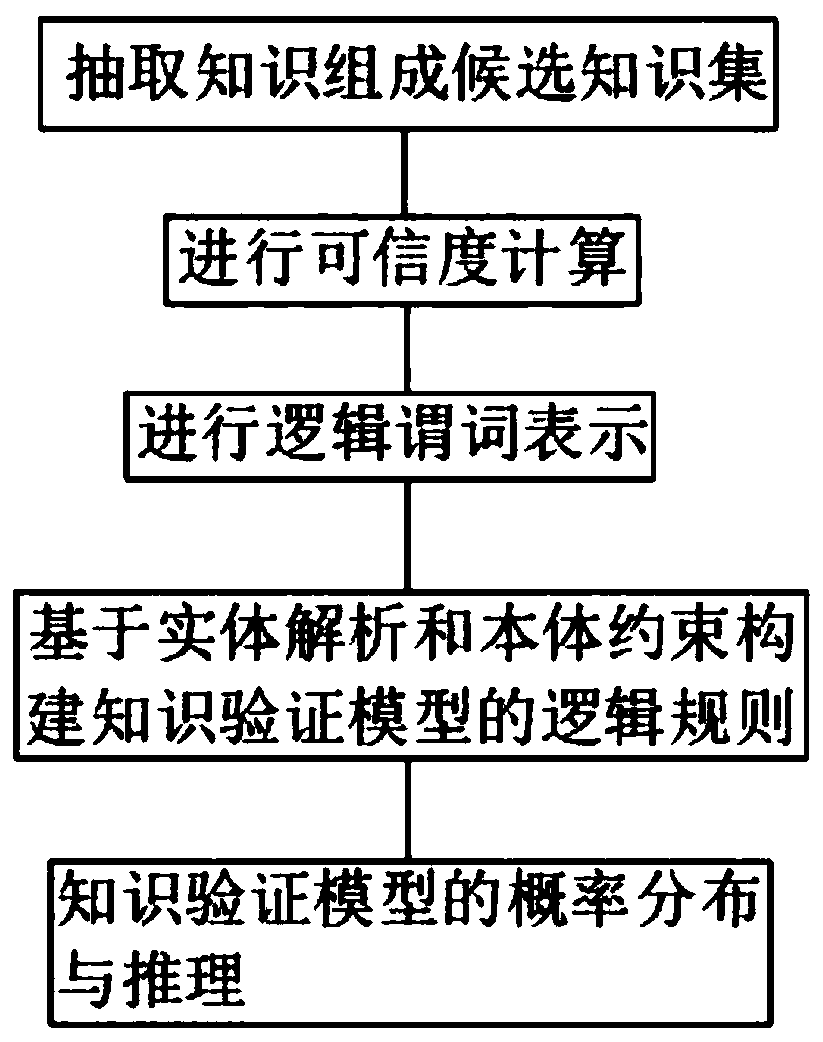
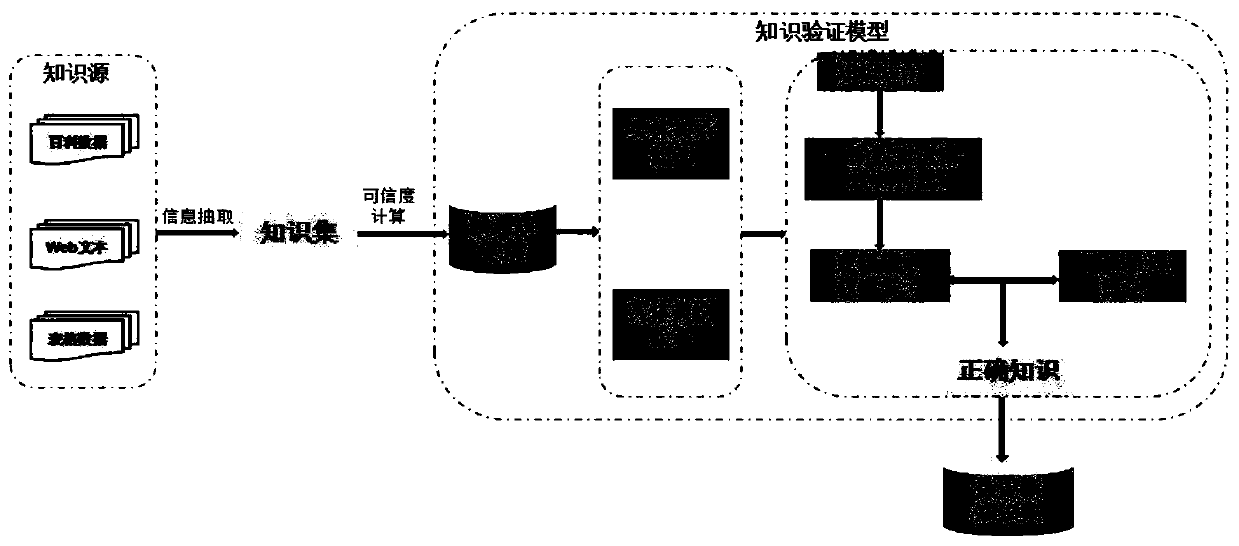
Knowledge verification model construction and analysis method based on probability soft logic
PendingCN111026877AImprove accuracyTroubleshoot issues such as errorsMathematical modelsKnowledge representationTheoretical computer scienceEngineering
The invention belongs to the technical field of information extraction, and particularly relates to a knowledge verification model construction and analysis method based on probability soft logic, which comprises the following steps of: a, forming a candidate knowledge set by knowledge extracted from webpage web texts of a plurality of data sources by an information extraction system; b, carryingout credibility calculation on the candidate knowledge set; c, performing logic predicate representation on each entity in the candidate knowledge set; d, constructing a first-order logic rule of theknowledge verification model based on the entity analysis and the ontology constraint, generating the first-order logic rule in the probability soft logic model through the constructed logic rule, andachieving entity relationship and entity label verification in the candidate knowledge set; and e, setting probability distribution of the knowledge verification model, and calculating and selectingcorresponding knowledge to be updated through an inference algorithm. According to the method, the candidate knowledge set is verified, so that the accuracy of the candidate knowledge set is greatly improved.
Owner:INST OF ELECTRONICS & INFORMATION ENG OF UESTC IN GUANGDONG
Data association method based on first-order logic and nerve network
InactiveCN102799627AShorten the timeImprove efficiencySpecial data processing applicationsNeural learning methodsFirst-order logicNerve network
The invention belongs to the field of data migration and data integration, and in particular relates to a data association method based on a first-order logic and a nerve network. The data association method is high in matching efficiency and high in accuracy. The method comprises the following steps of: (1) analyzing a matched data mode; (2) converting the mode into a table vector, and storing into a table training set to be matched; (3) performing characteristic extraction on tables in the set; (4) storing the extracted characteristics of the tables; (5) matching a table to be matched in a mode to be matched; (6) training fields in the matched mode, and correcting an expression of the fields and the constructed nerve network; and (7) performing field matching on the matched table by using the trained nerve network and the corrected field expression format. By the method, the time during data association is shortened, and the matching efficiency and the accuracy are improved.
Owner:三亚哈尔滨工程大学南海创新发展基地
Collaborative first order logic system with dynamic ontology
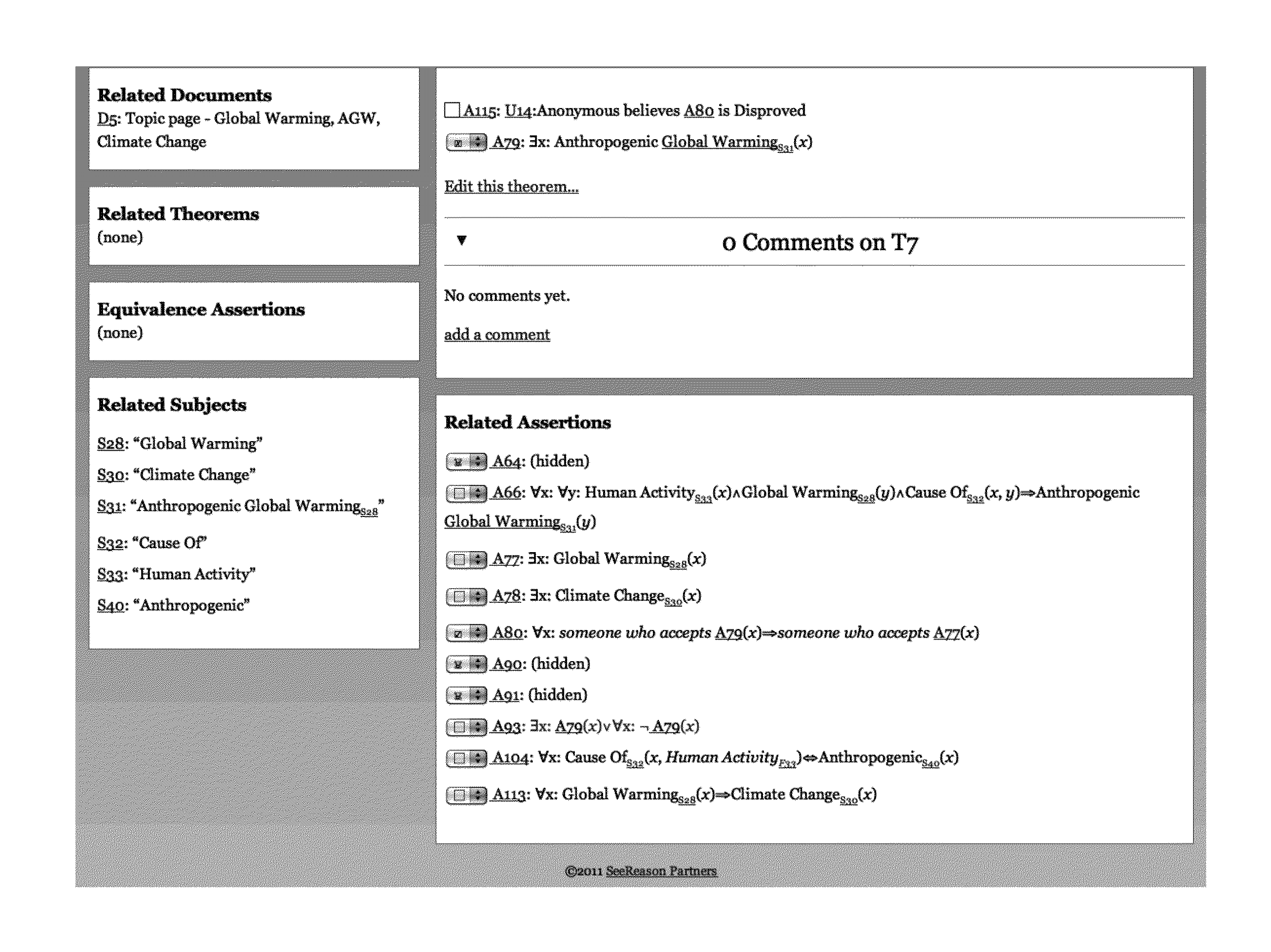
ActiveUS20130124397A1Improve practicalityFinanceDigital data processing detailsFirst-order logicDocument preparation
A collaborative first order logic system with dynamic ontology for example that enables collaborative discussion of documents, subjects associated within the documents, assertions about the subjects and theorems that utilize the assertions along with dynamic creation and association of two or more subjects that may represent the same thing. Enables geographical and temporal displays of assertions and opinions regarding the assertions.
Owner:SEEREASON PARTNERS
Method for solving reading comprehension question based on semantic analysis and SMT solution
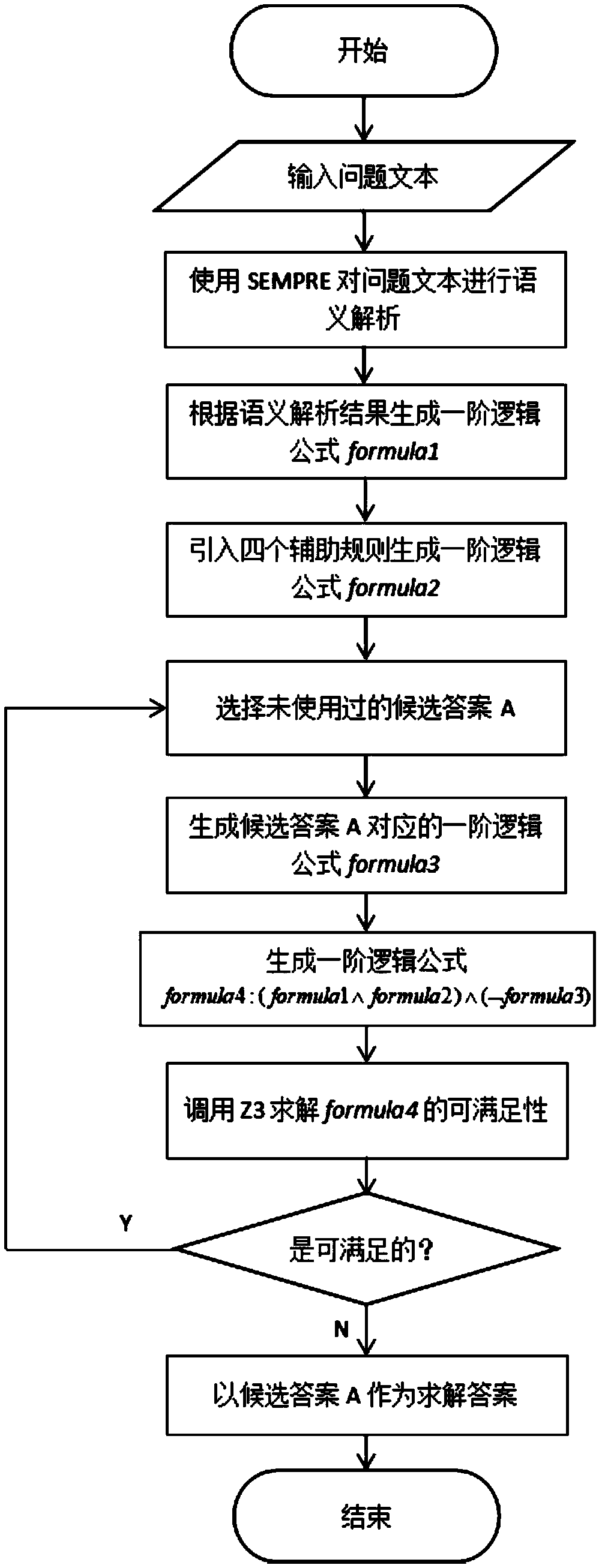
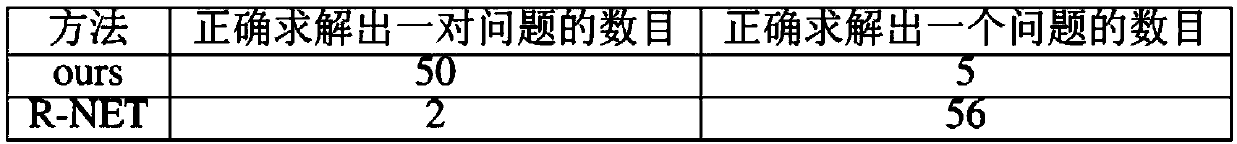
ActiveCN108829666AEasy to parseStrengthen reasoning and solving abilitySemantic analysisSpecial data processing applicationsFirst-order logicClosed world
The invention provides a method for solving a reading comprehension question based on semantic analysis and SMT solution. The method comprises the following steps: firstly, performing semantic parsingon the reading comprehension question to generate a first-order logic formula corresponding to the reading comprehension question, then introducing four hypotheses, namely, a unique name hypothesis,a closed world hypothesis, a closure cause hypothesis and a unique answer hypothesis, to generate a first-order logic formula corresponding to candidate answers; and finally, verifying whether a knowledge base contains the first-order logic formula corresponding to the candidate answers by using a SMT solver, and then figuring out the answer. Compared with the existing methods of expressing textsby using neural network models and word vectors, the method provided by the invention has the advantages being able to better establish the relationship between the events described in the reading comprehension question, thereby giving a reading comprehension system a stronger expression ability and reasoning ability.
Owner:SUN YAT SEN UNIV
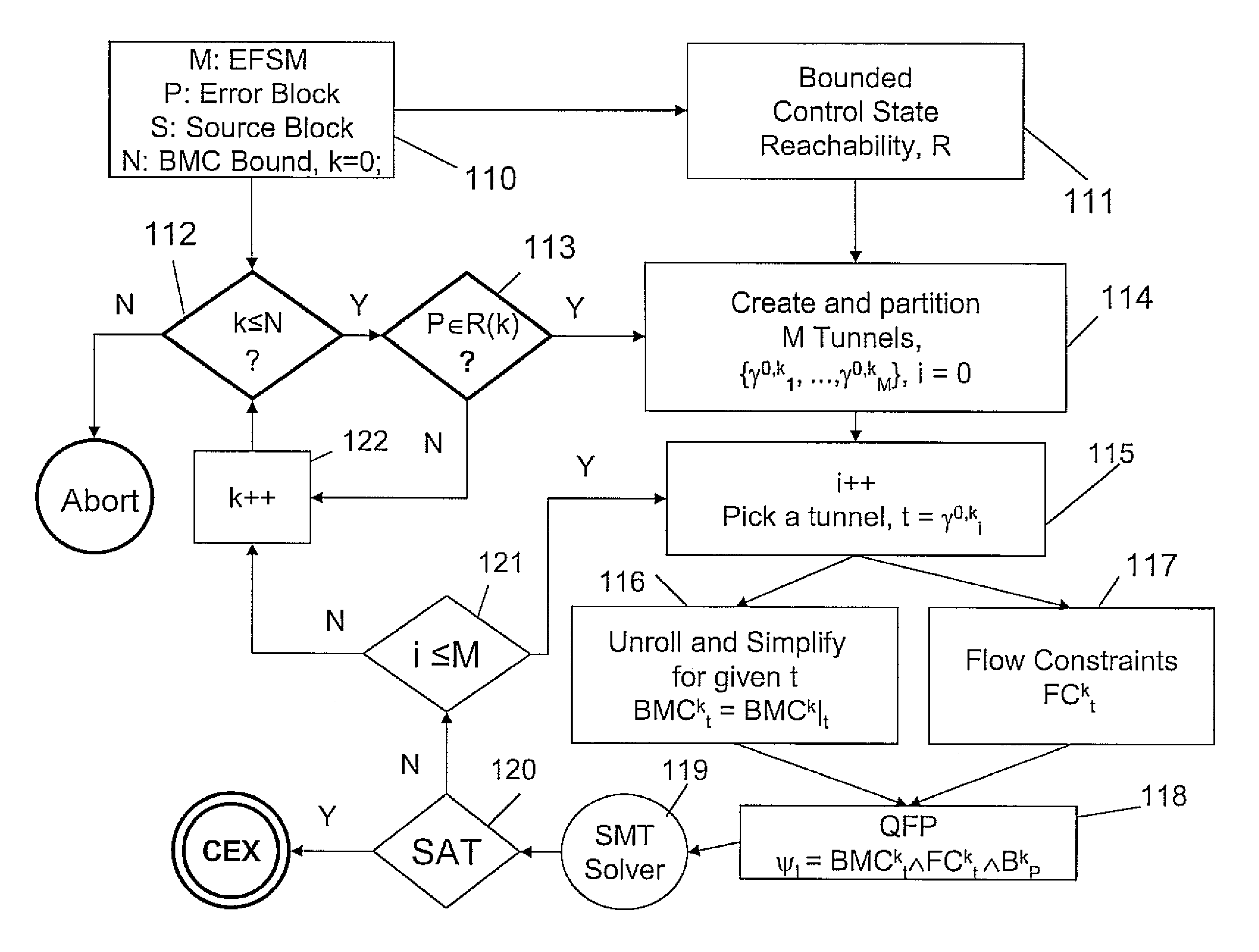
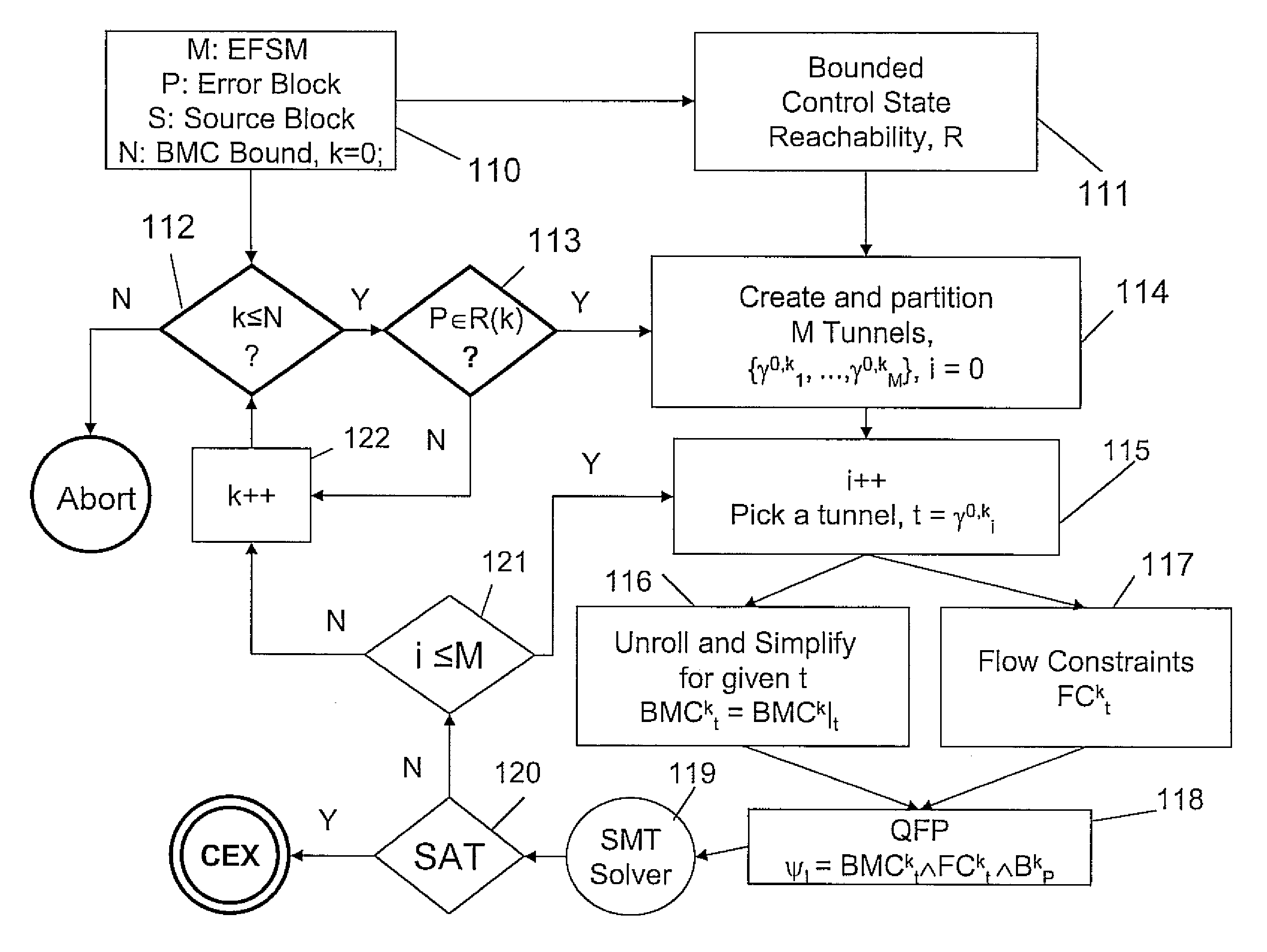
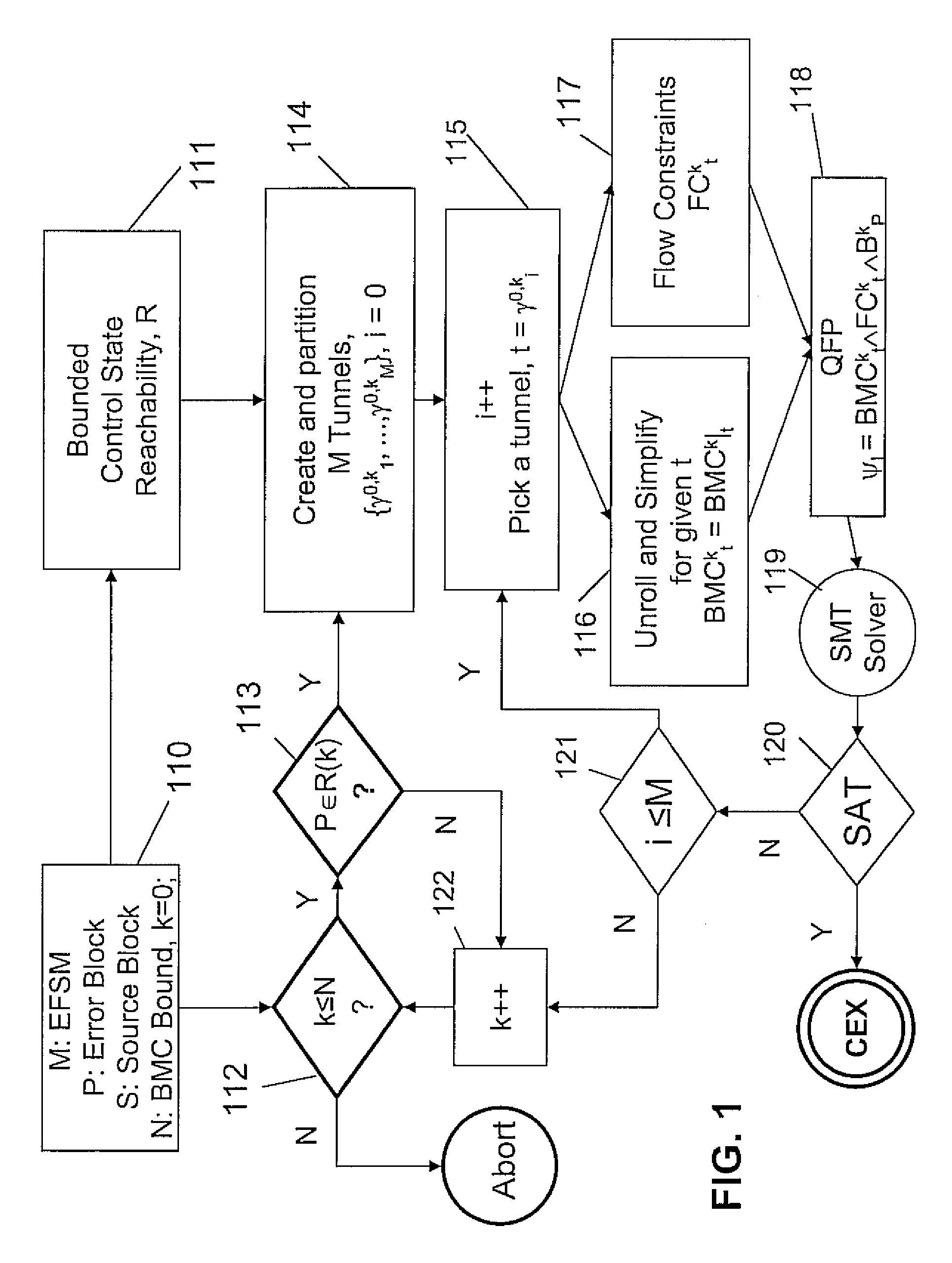
System and method for tunneling and slicing based BMC decomposition
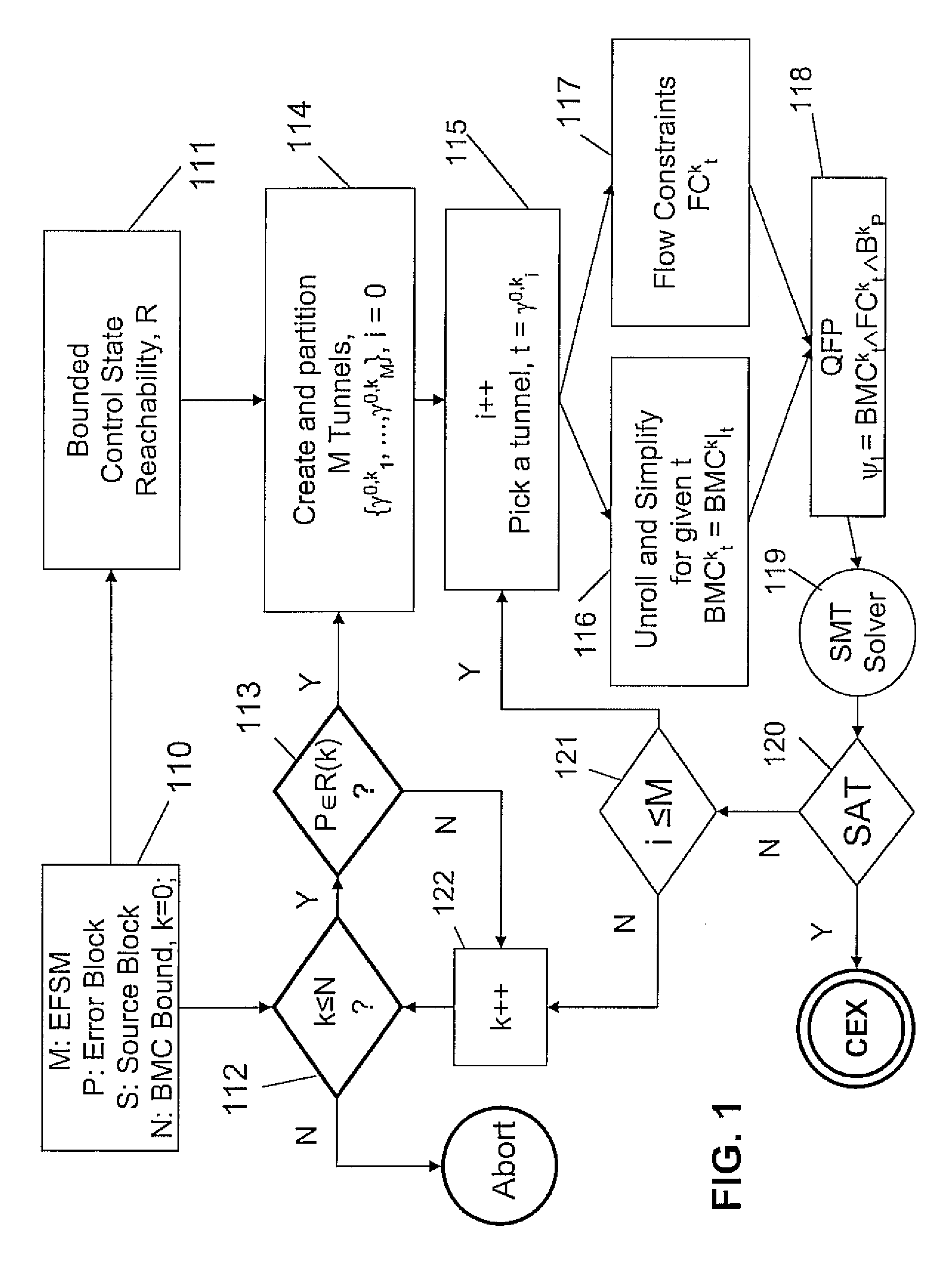
InactiveUS7949511B2Avoid explosionReduce usageError detection/correctionProgram loading/initiatingFirst-order logicDecomposition
A system and method for bounded model checking of computer programs includes providing a program having at least one reachable property node. The program is decomposed for bounded model checking (BMC) into subproblems by creating a tunnel based on disjunctive control paths through the program. A reduced BMC sub-problem obtained using BMC unrolling, while using path constraints imposed by the at least one tunnel. For the reachable property node, determining a quantifier-free formula (QFP) in a decidable subset of first order logic. Satisfiability of the QFP is checked, independently and individually, to determine whether the QFP is satisfiable for the subproblem. The decomposing is continued until the a BMC bound is reached.
Owner:NEC CORP
Data association method, system and device based on Markov logic network
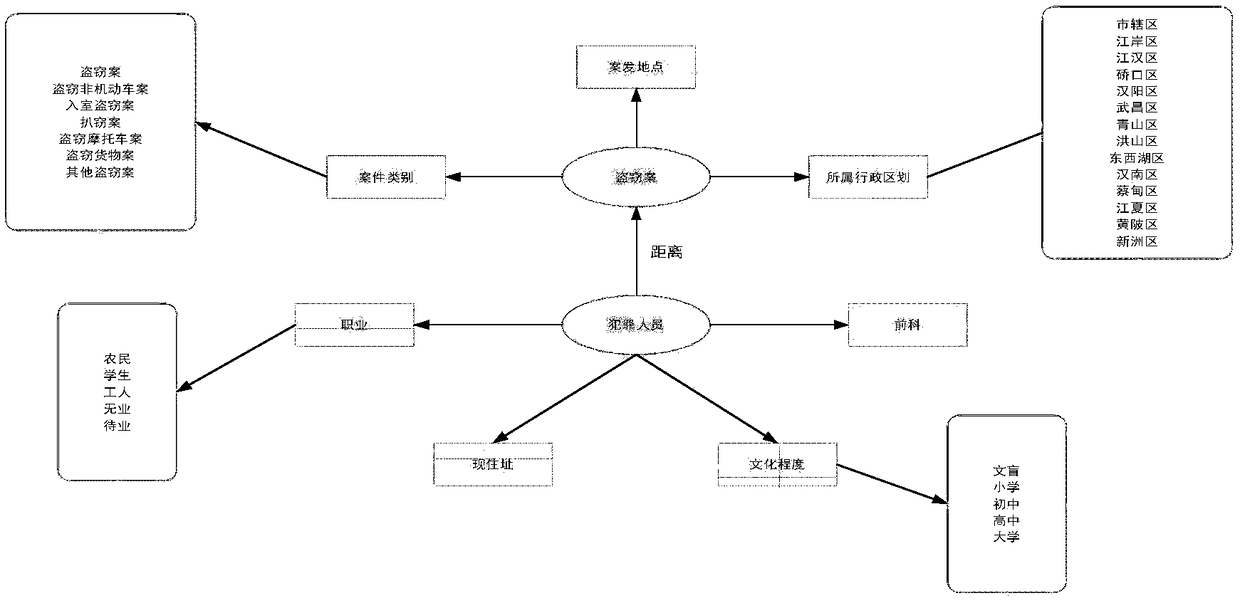
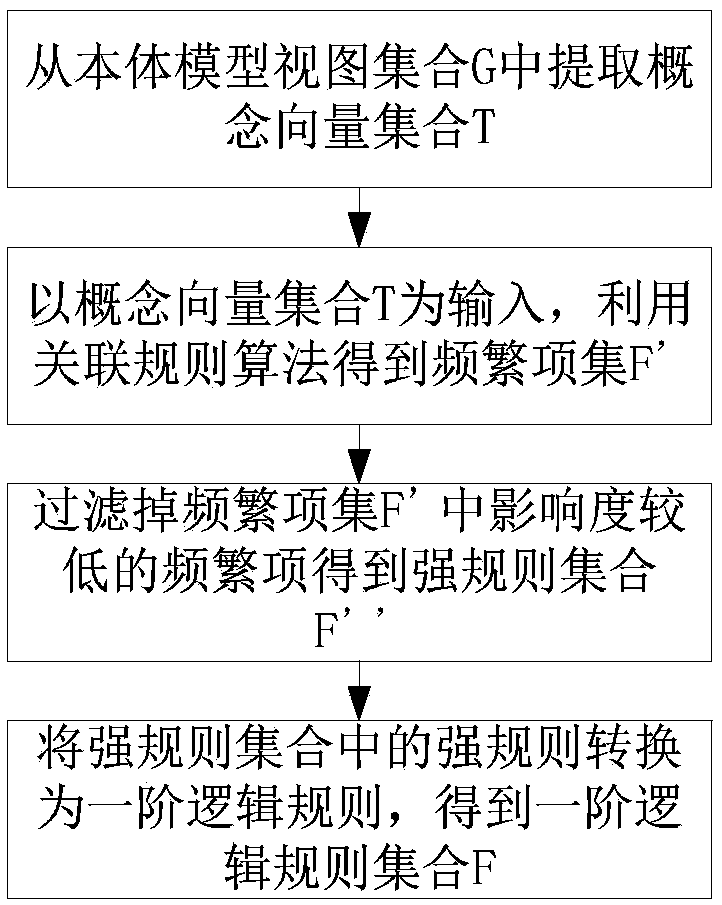
ActiveCN109166069AData association is fast and efficientReduce time complexityData processing applicationsCharacter and pattern recognitionFirst-order logicAlgorithm
The invention discloses a data association method, system and device based on a Markov logic network. The method includes: utilizing key personnel database, case to be solved and its corresponding weighted rule database to construct the model of obtaining crime probability based on Markov logic network, obtaining the probability of each key personnel committing the case to be solved, thereby screening out the target object, and realizing the data association between the target object and the case to be solved; the method for obtaining the weighted rule base includes: the ontology model view set is constructed by using the data of the solved case which is the same as the main type of the case to be solved, the first-order logic rule set and predicate atom set are extracted, and then the rule weight learning model based on Markov logic network is constructed by using the two extracted sets, the rule weights are obtained by training the model, and thus the weighted rule base composed of the first-order logic rule and the corresponding rule weights is obtained. The acquisition of the rules in the invention does not depend on manpower, and the accuracy rate of data association can be improved.
Owner:HUAZHONG UNIV OF SCI & TECH +1
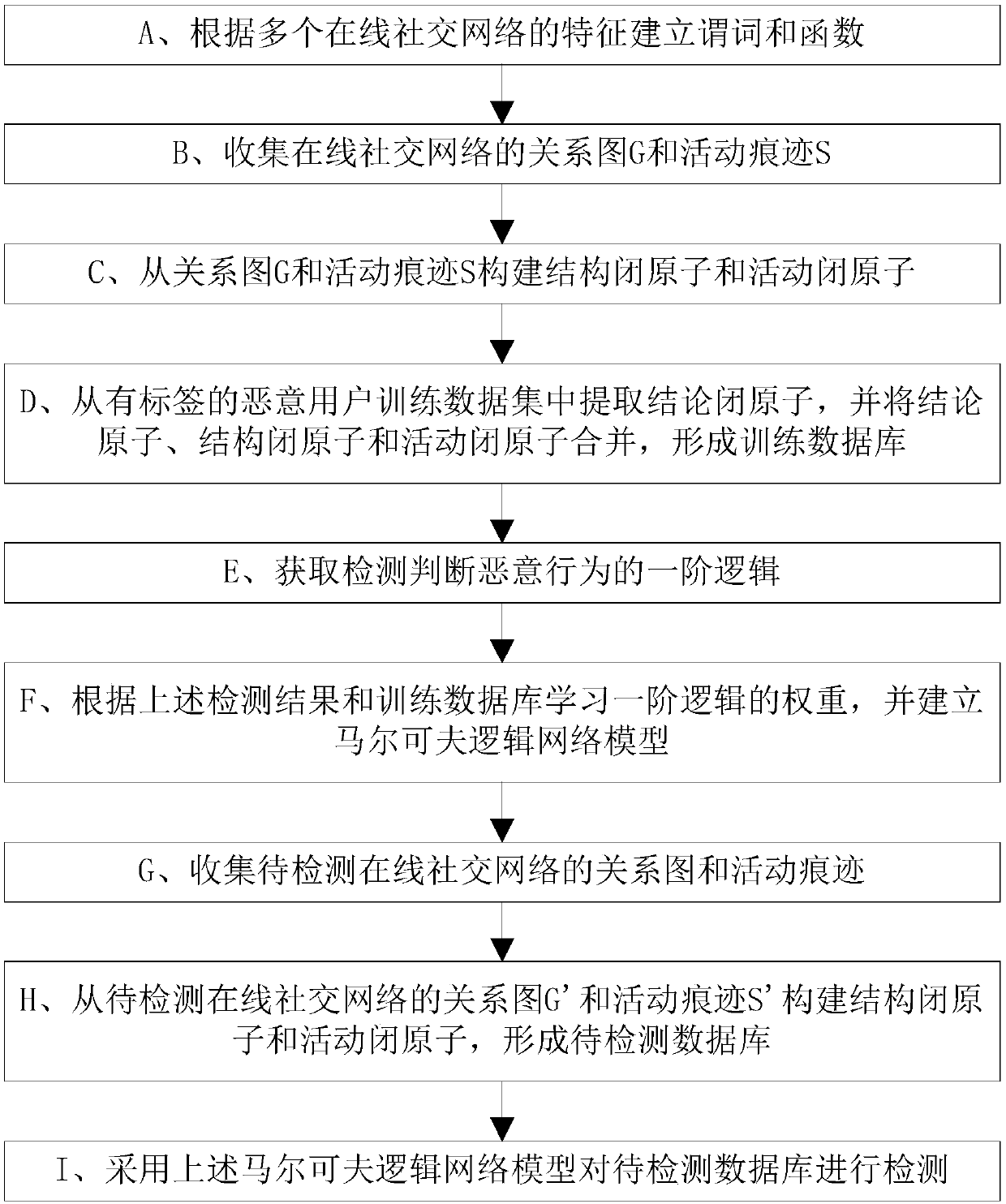
Unified user malicious behavior detecting method and system in social network
InactiveCN108536776AImprove detection accuracyPlatform integrity maintainanceData switching networksFirst-order logicInformation security
The invention discloses a unified user malicious behavior detecting method and system in a social network. The method comprises the steps of: establishing predicates and functions according to characteristics of multiple OSNs, collecting relation graph G and activity traces S, and constructing structural closed atoms and active closed atoms, then extracting the structural closed atoms, and mergingto form a training database; obtaining the first-order logic detecting and judging the malicious behavior; learn the weight of the first-order logic rule based on detecting results and the training database and establishing an MLN model; collecting a relationship diagram and activity traces of to-be-detected OSN and constructing structural closed atoms and active closed atoms, forming a to-be-detected database, and using the MLN model for detection. The unified user malicious behavior detecting method and system in the social network combines the OSN malicious behavior detection methods through the MLN model, realizes the joint detection of multiple malicious behaviors at the same time, and achieves higher detection accuracy. The unified user malicious behavior detecting method and systemin the social network can be widely applied in the field of information security.
Owner:王欣明
System and method for tunneling and slicing based bmc decomposition
InactiveUS20090125294A1Reduce model sizeEliminate redundant checkError detection/correctionSoftware simulation/interpretation/emulationFirst-order logicDecomposition
A system and method for bounded model checking of computer programs includes providing a program having at least one reachable property node. The program is decomposed for bounded model checking (BMC) into subproblems by creating a tunnel based on disjunctive control paths through the program. A reduced BMC sub-problem obtained using BMC unrolling, while using path constraints imposed by the at least one tunnel. For the reachable property node, determining a quantifier-free formula (QFP) in a decidable subset of first order logic. Satisfiability of the QFP is checked, independently and individually, to determine whether the QFP is satisfiable for the subproblem. The decomposing is continued until the a BMC bound is reached.
Owner:NEC CORP
Automatic threat ensuring method facing to network security risk assessment based on first order logic predicate reasoning
The invention discloses an automatic threat ensuring method facing to network security risk assessment based on first order logic predicate reasoning. The method uses a first order logic predicate descriptive language Datalog to formally describe network security state information and attack rule knowledge base information, uses a logic reasoning engine XSB to automatically reason, and analyzes the evidence files in a reasoning result to obtain threat information in a current network system; wherein, the threat information comprises a threat potential attack source, a corresponding loophole and a possible attack action. By adopting the logical reasoning engine, the automatic threat ensuring method can automatically and effectively ensure the attack threat in a large-scale network system, greatly reduce the working pressure of network administrators, and help the network administrators to purposely adopt preventive measures to protect the network system.
Owner:BEIHANG UNIV
Weak supervision relation extraction method based on multi-source semantic representation fusion
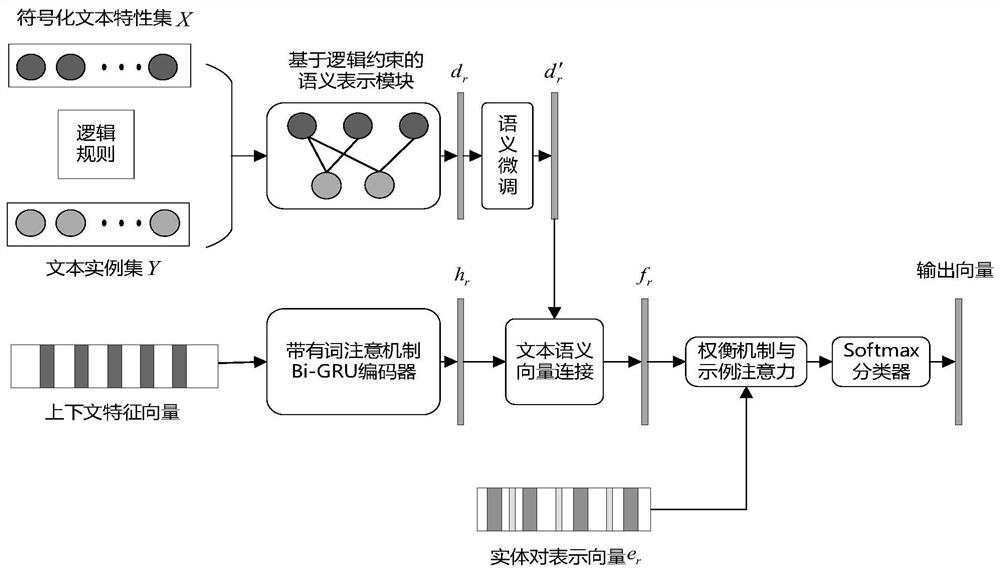
ActiveCN111737497AFlexible writingFacilitate adoptionSemantic analysisNeural architecturesSemantic vectorSemantic feature
The invention provides a weak supervision relation extraction method based on multi-source semantic representation fusion. Firstly, distributed word vectors are adopted to initialize context semanticfeatures of text statements, a natural language processing tool is adopted to analyze mass discretized symbol features describing the text features, and a universal first-order logic rule between statement instances and features in a relation extraction task is designed; then, a logic rule is combined with the factor graph to establish a relationship between the text characteristics and the statement instances, modeling is performed from the perspective of human perception through joint statistical reasoning, and a low-dimensional relationship semantic vector for describing the text characteristics is learned; and the semantic information of the statement content encoded by the bidirectional gating loop unit is used as a context content semantic vector. And finally, text characteristic semantic vectors are finely adjusted in the neural network, vector representations of two different characteristic sources are fused to obtain text semantic characteristic representations with higher robustness, and weak supervision relationship extraction work is guided together with entity pair embedded representations.
Owner:DALIAN UNIV OF TECH
Data race detection and evidence generation method based on multithreaded program constraint building
ActiveCN104077144BNo overheadSoftware testing/debuggingSpecific program execution arrangementsFirst-order logicTheoretical computer science
The invention provides a data race detection and evidence generation method based on multithreaded program constraint building. The data race detection problem is converted into a constraint solving problem by building a constraint expression according to the multithreaded program semanteme, a constraint solver is used for detecting possible data races and program execution paths triggering the data races are generated; the data race detection and evidence generation method comprises the steps of firstly, carrying out the instrumentation of the detected program, executing the program and obtaining an execution path, secondly, converting the execution path into a quantifier-free first-order logic expression covering all feasible thread interleaving according to the multithreaded program execution semanteme, thirdly, building a data race candidate set according to the sequential relationship of statements when a data race happens and generating candidate conditions for races, and finally, traversing the candidate set to determine whether the data race exists, and if so, generating a corresponding evidence sequence. The method is capable of finding out all data races in once operation without misinformation; for each data race, the evidence sequence indicating the trigger process of the data race is generated.
Owner:XI AN JIAOTONG UNIV
Collaborative first order logic system with dynamic ontology
ActiveUS8996989B2Improve practicalityFinanceDigital data processing detailsFirst-order logicDocument preparation
A collaborative first order logic system with dynamic ontology for example that enables collaborative discussion of documents, subjects associated within the documents, assertions about the subjects and theorems that utilize the assertions along with dynamic creation and association of two or more subjects that may represent the same thing. Enables geographical and temporal displays of assertions and opinions regarding the assertions.
Owner:SEEREASON PARTNERS
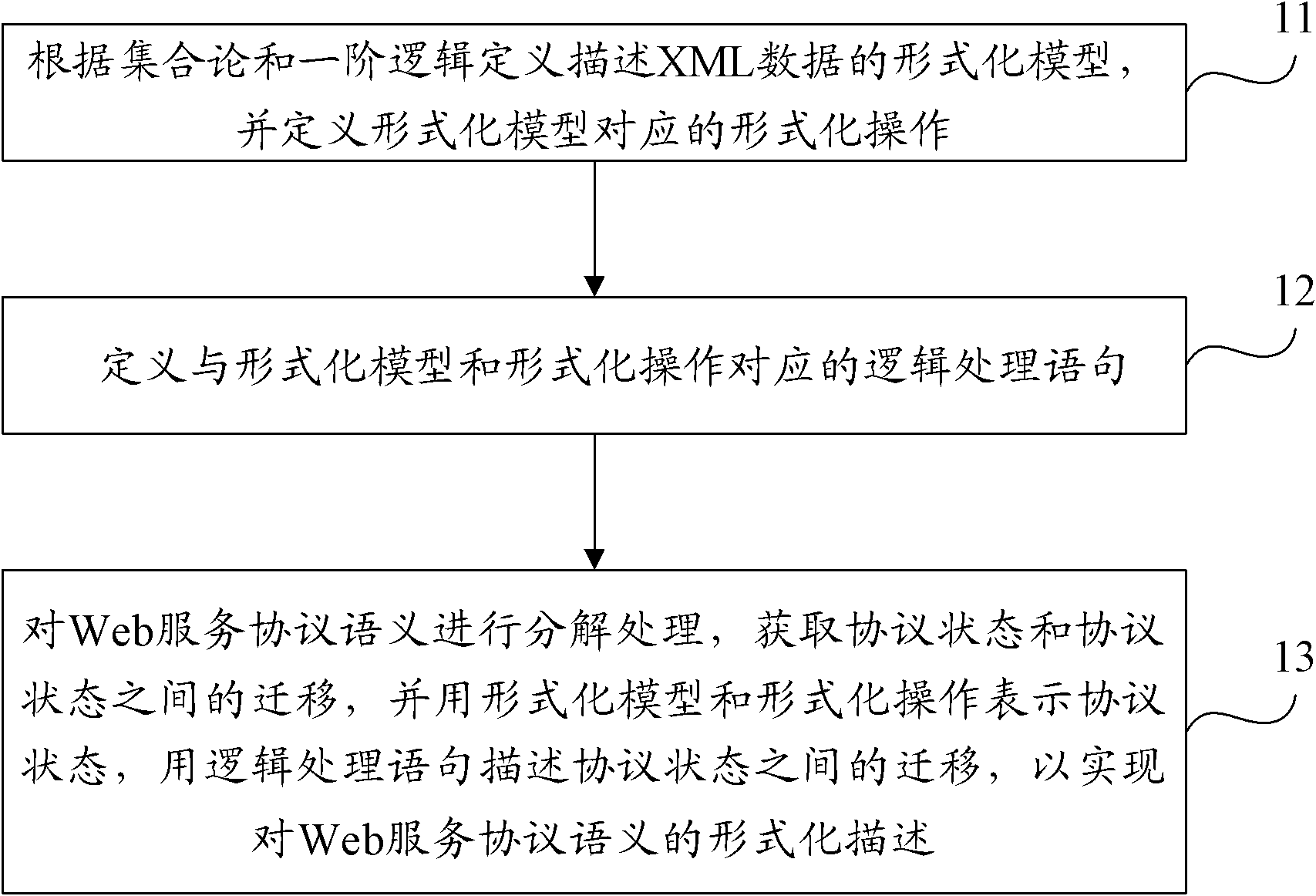
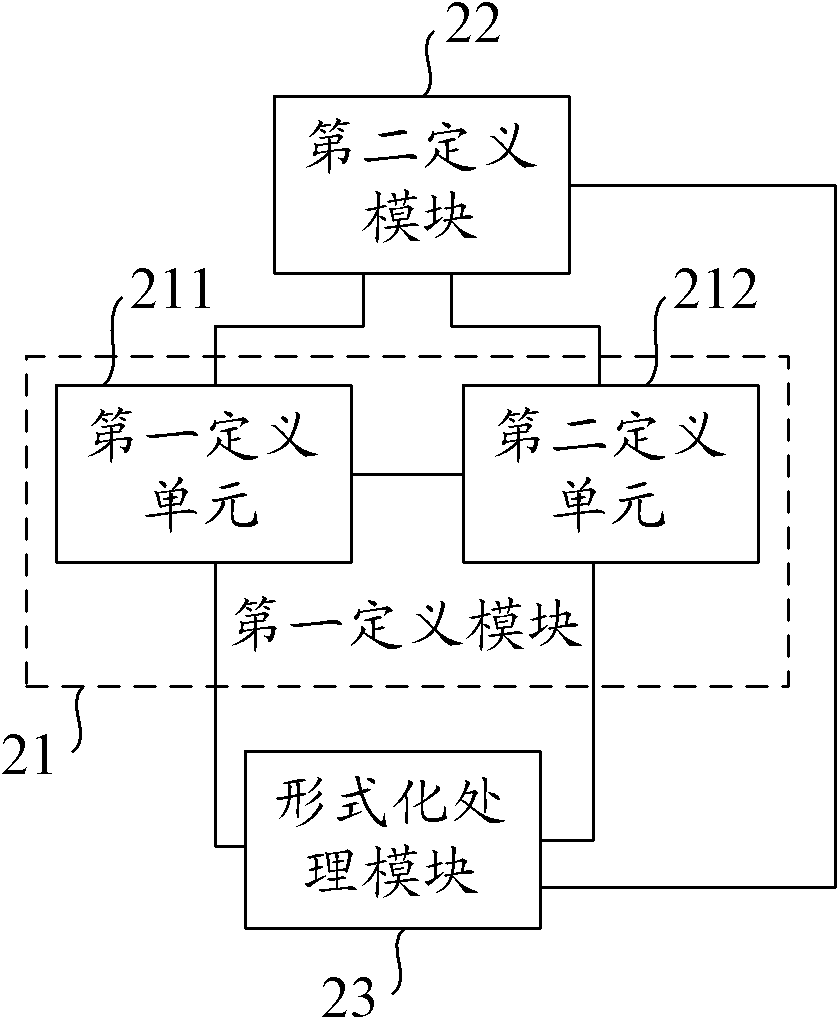
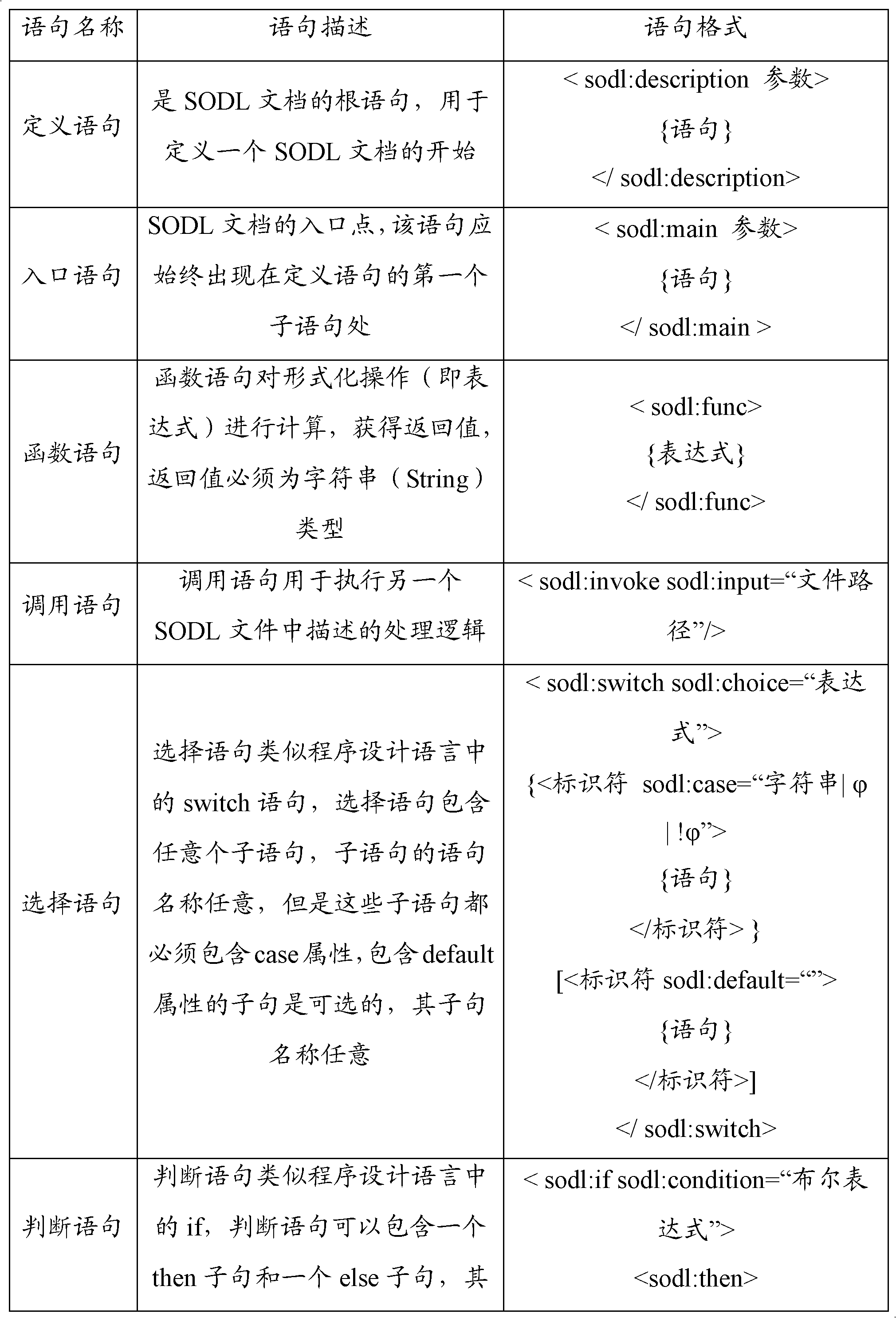
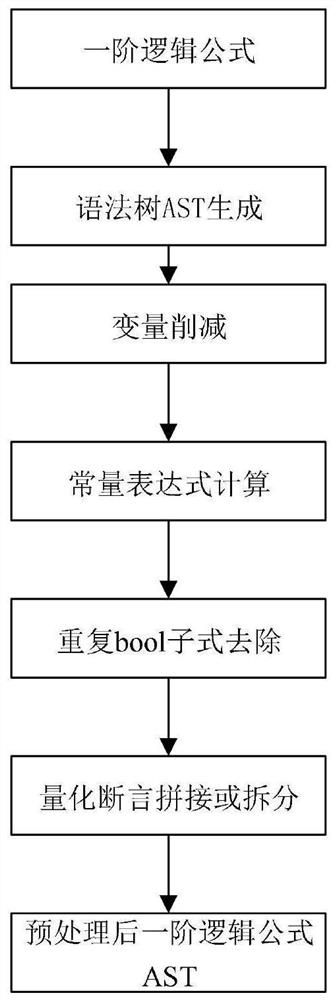
Formal description method and device of Web service protocol semantics
InactiveCN102693240AGuaranteed to implement correctlyFormal description implementationTransmissionSpecial data processing applicationsFirst-order logicWeb service
The invention provides a formal description method and device of Web service protocol semantics. The method comprises the following steps of: defining a formal model describing XML (extensible markup language) data according to the set theory and the first-order logic, and defining the formal operation corresponding to the formal model; defining the logic processing sentences corresponding to the formal model and the formal operation; decomposing the Web service protocol semantics to obtain the migration between the protocol statuses; representing the protocol status by use of the formal model and the formal operation; and describing the migration between the protocol statuses by use of the logic processing sentences to realize the formal description of the Web service protocol semantics. Through the technical scheme of the invention, the formal description of the Web service protocol semantics can be realized, and the correct realization of the Web service protocol is guaranteed.
Owner:BEIHANG UNIV
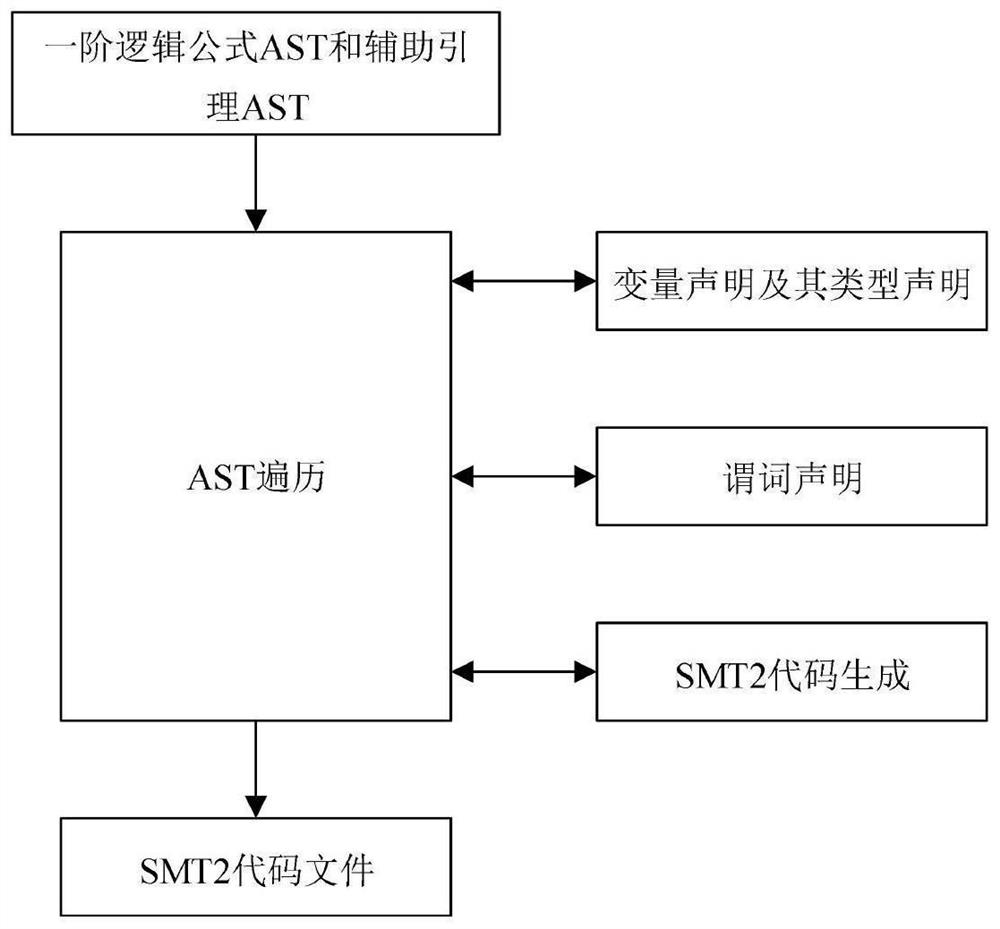
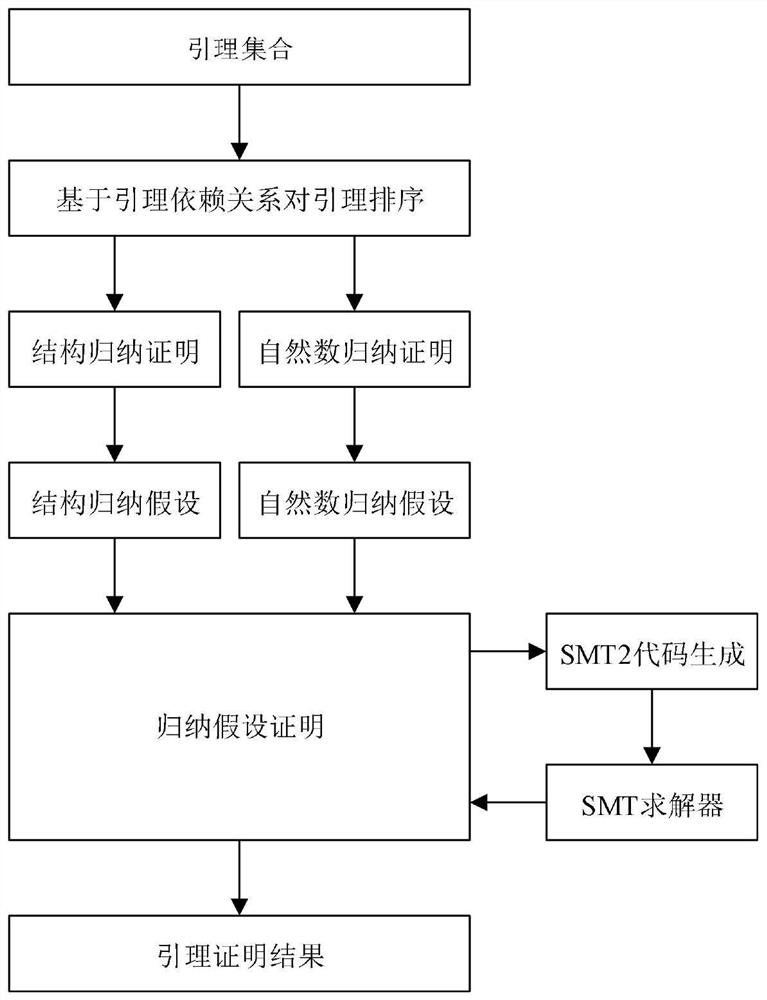
First-order logic formula program verification method and system based on SMT solver
PendingCN112231205AIncrease credibilityReduce the burden onDigital data information retrievalSoftware testing/debuggingFirst-order logicProgram validation
The invention discloses a first-order logic formula program verification method and system based on an SMT solver. The method comprises the steps: receiving a program formal verification data interaction request sent by any client in at least one client; extracting a first-order logic formula in the data verification request based on the obtained data verification request content; performing satisfiability solving on the first-order logic formula in the data verification request based on an SMT solver. According to the method, automatic certification of the first-order logic formula is realized based on the SMT solver, so that the formal verification system can automatically verify the program, and the credibility of software is improved.
Owner:安徽中科国创高可信软件有限公司 +1
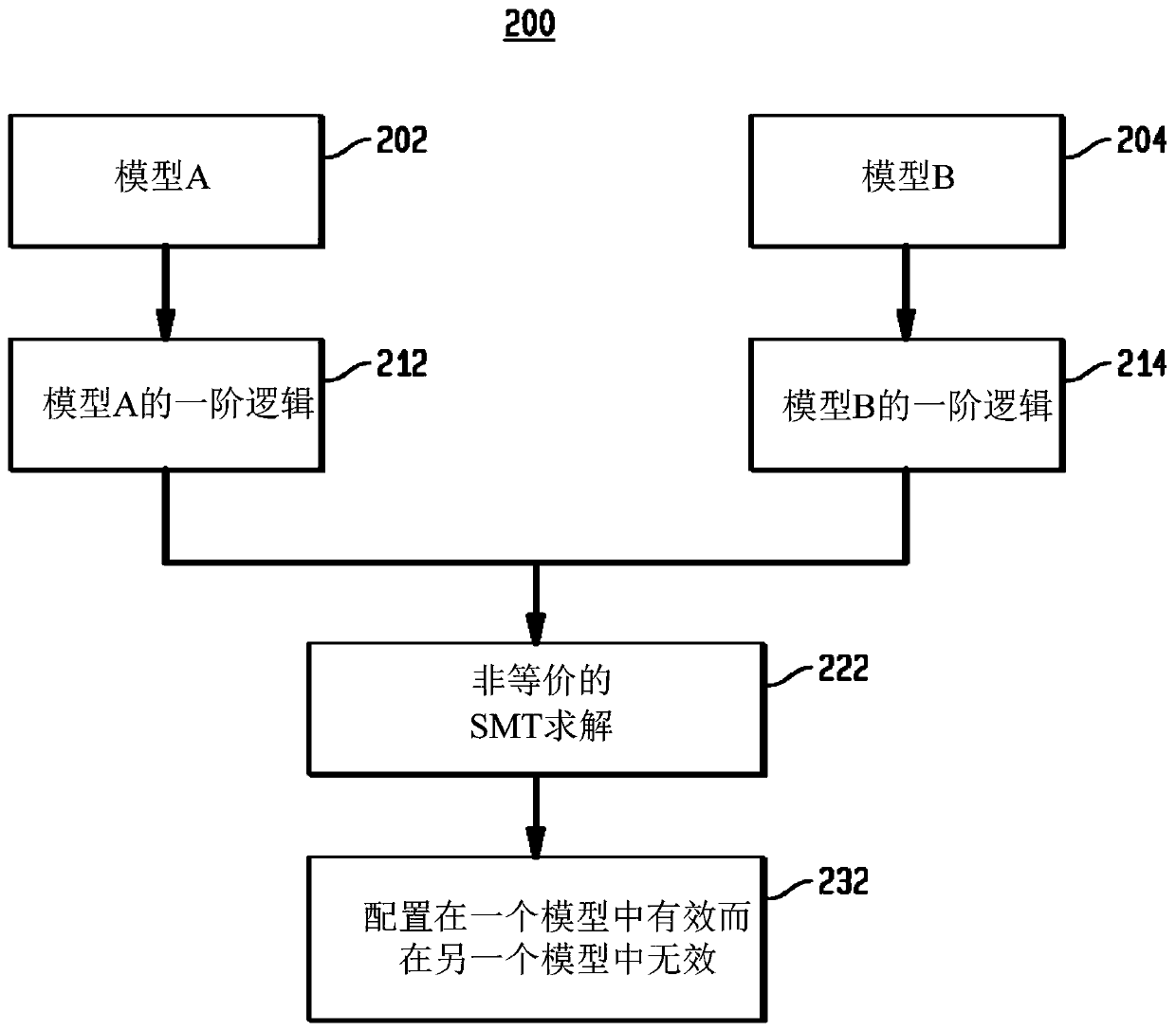
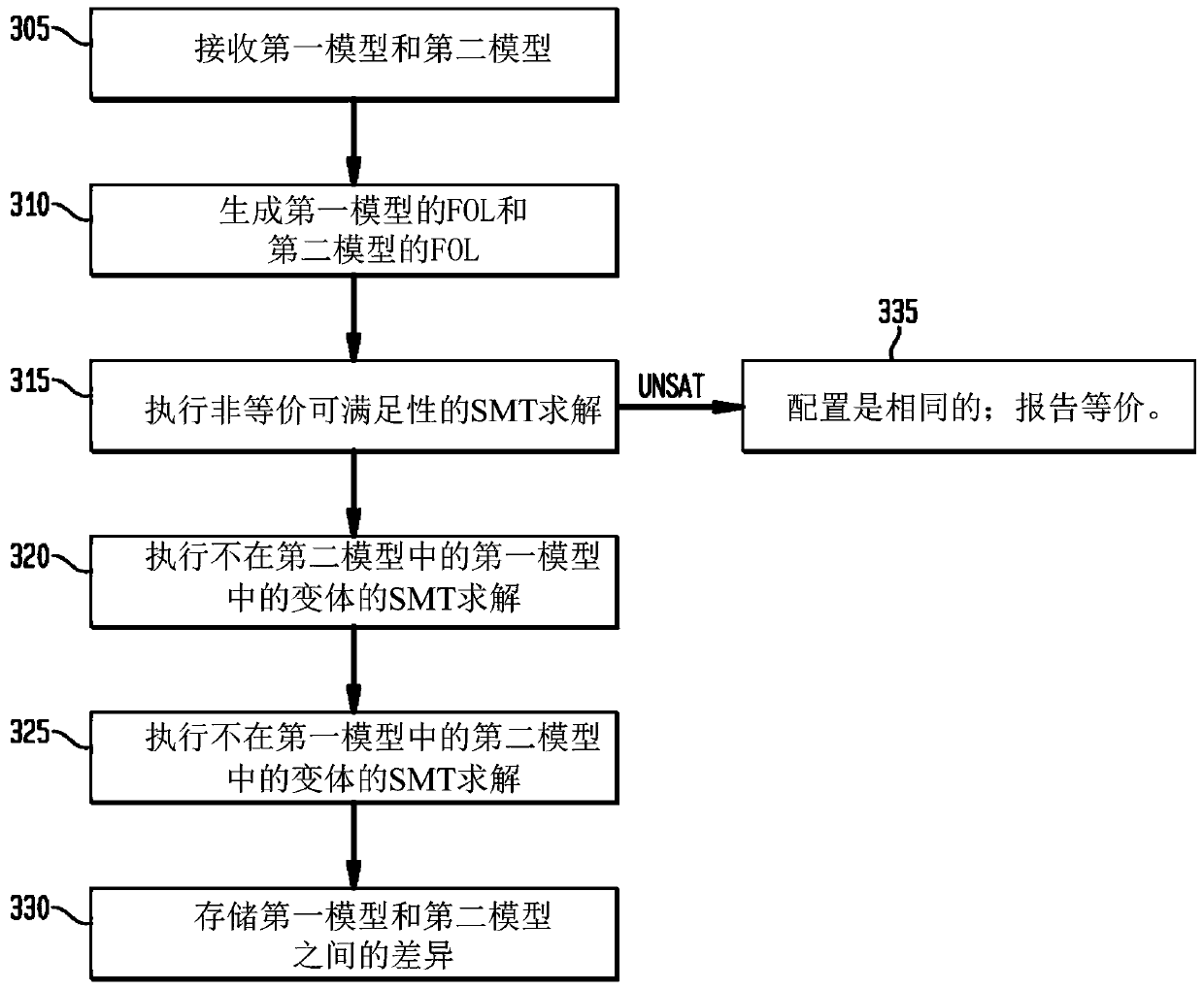
Systems and methods to semantically compare product configuration models
Owner:SIEMENS IND SOFTWARE GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com