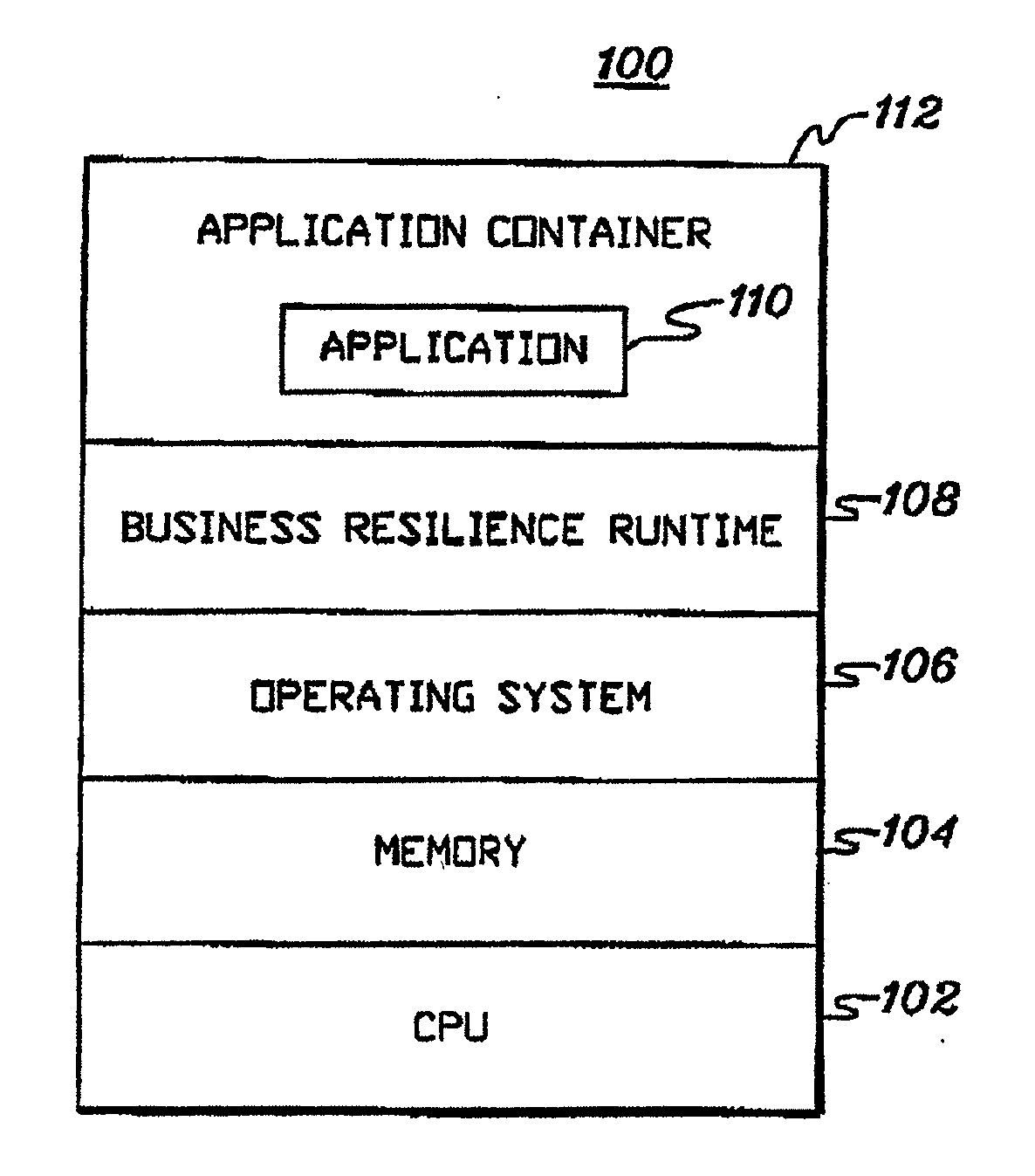
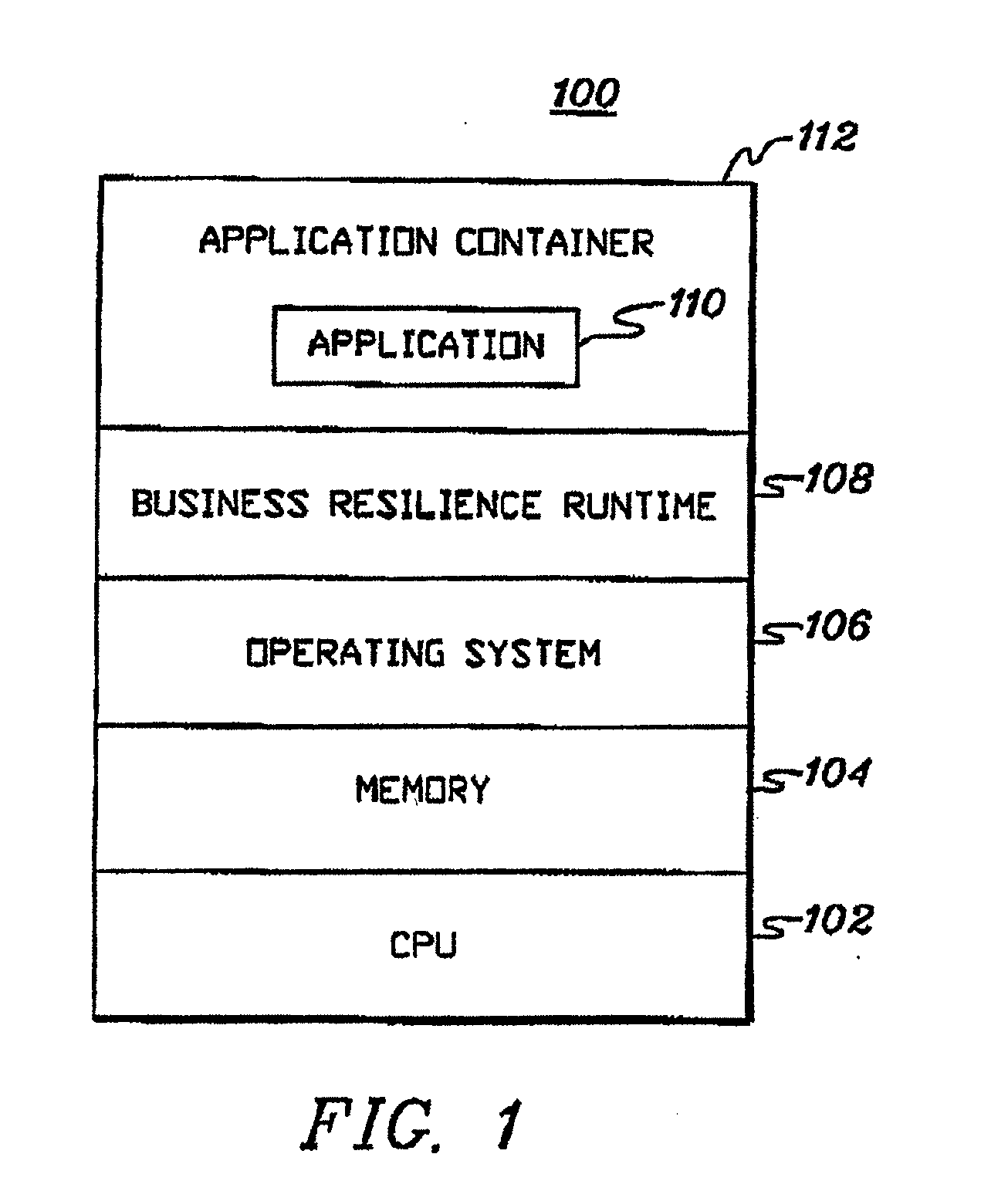
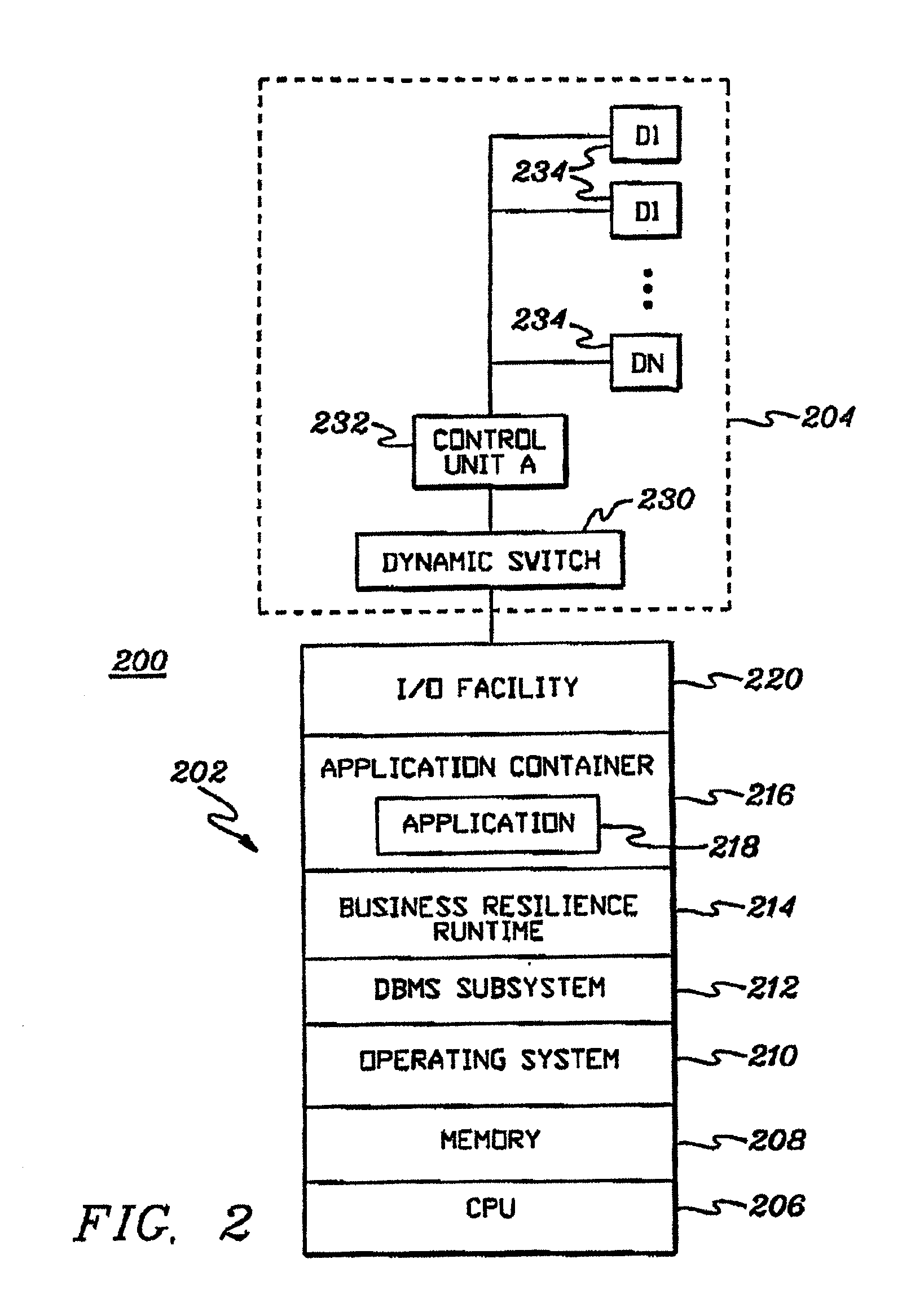
Patents
Literature
131 results about "Program validation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
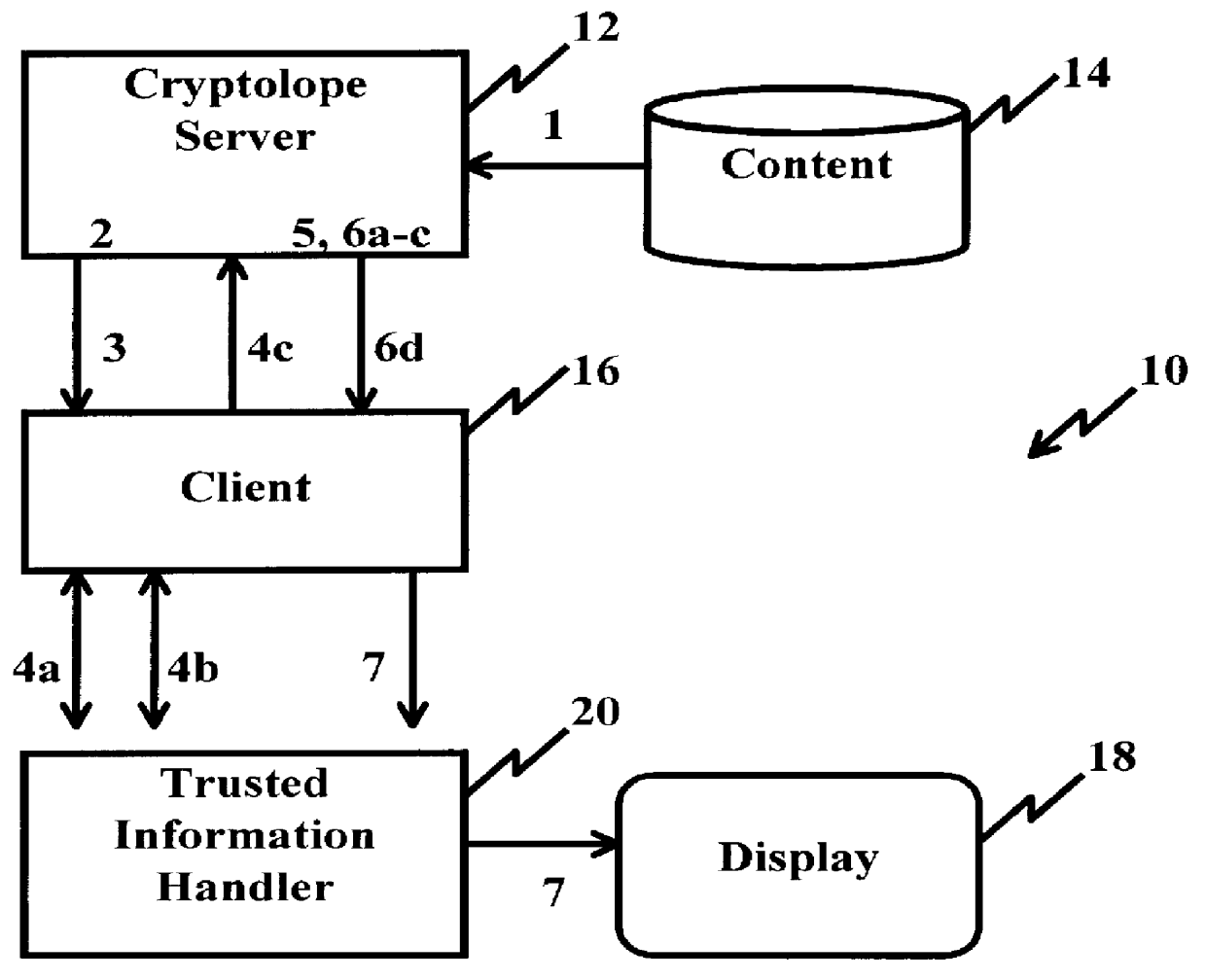
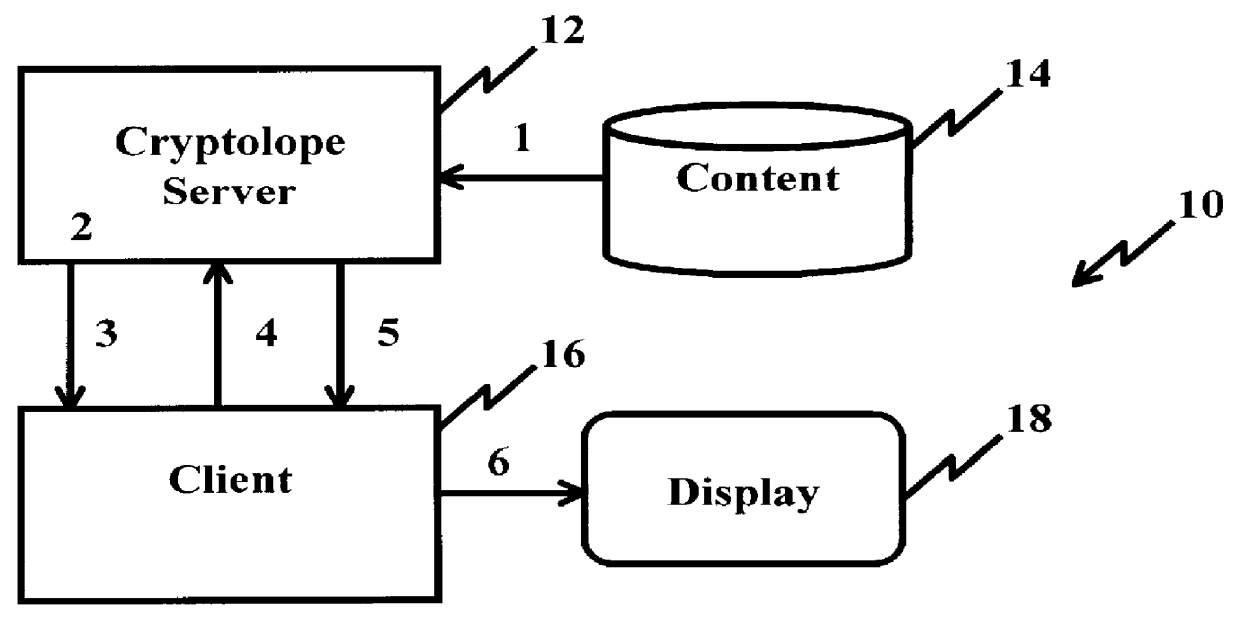
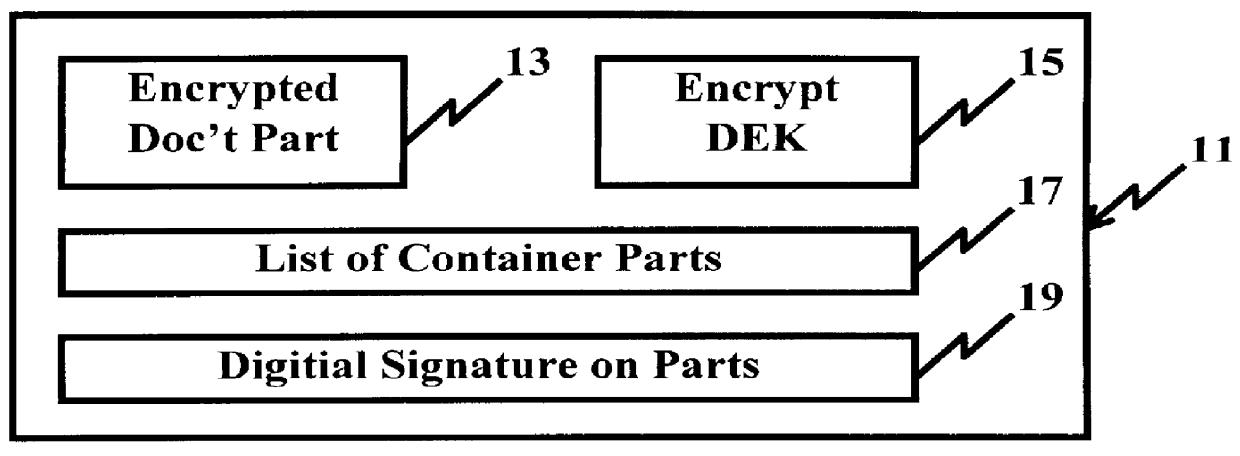
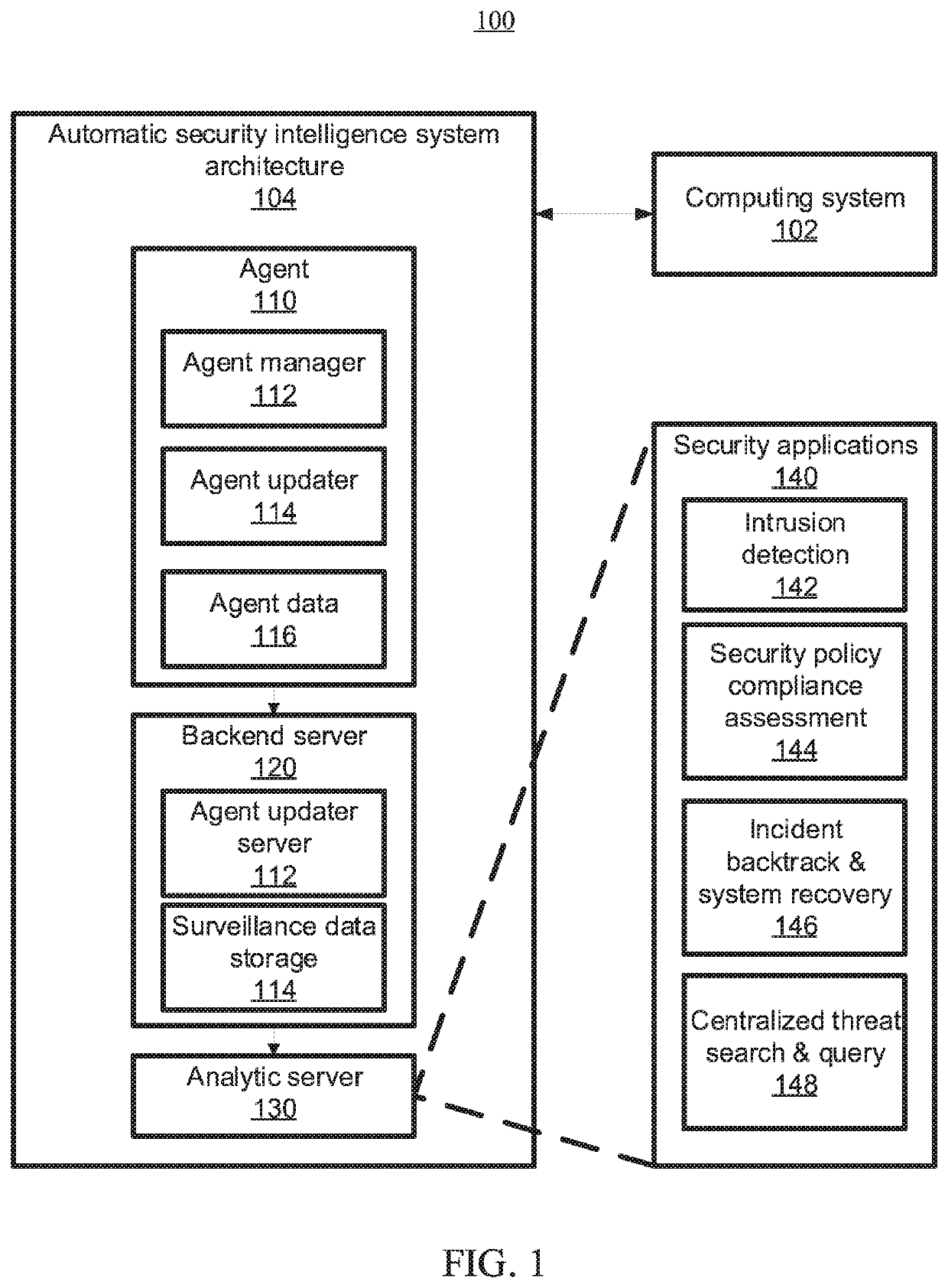
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
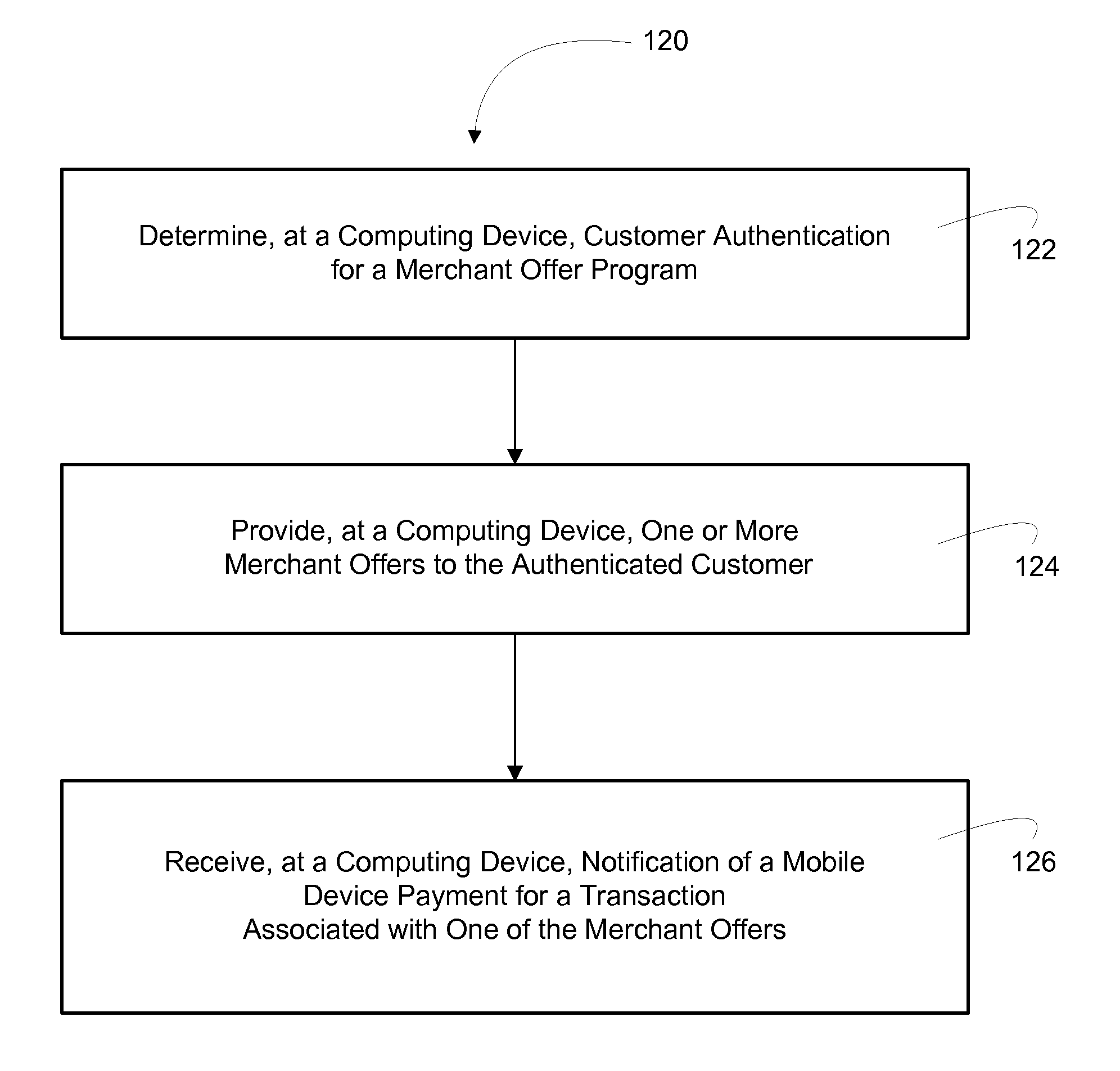
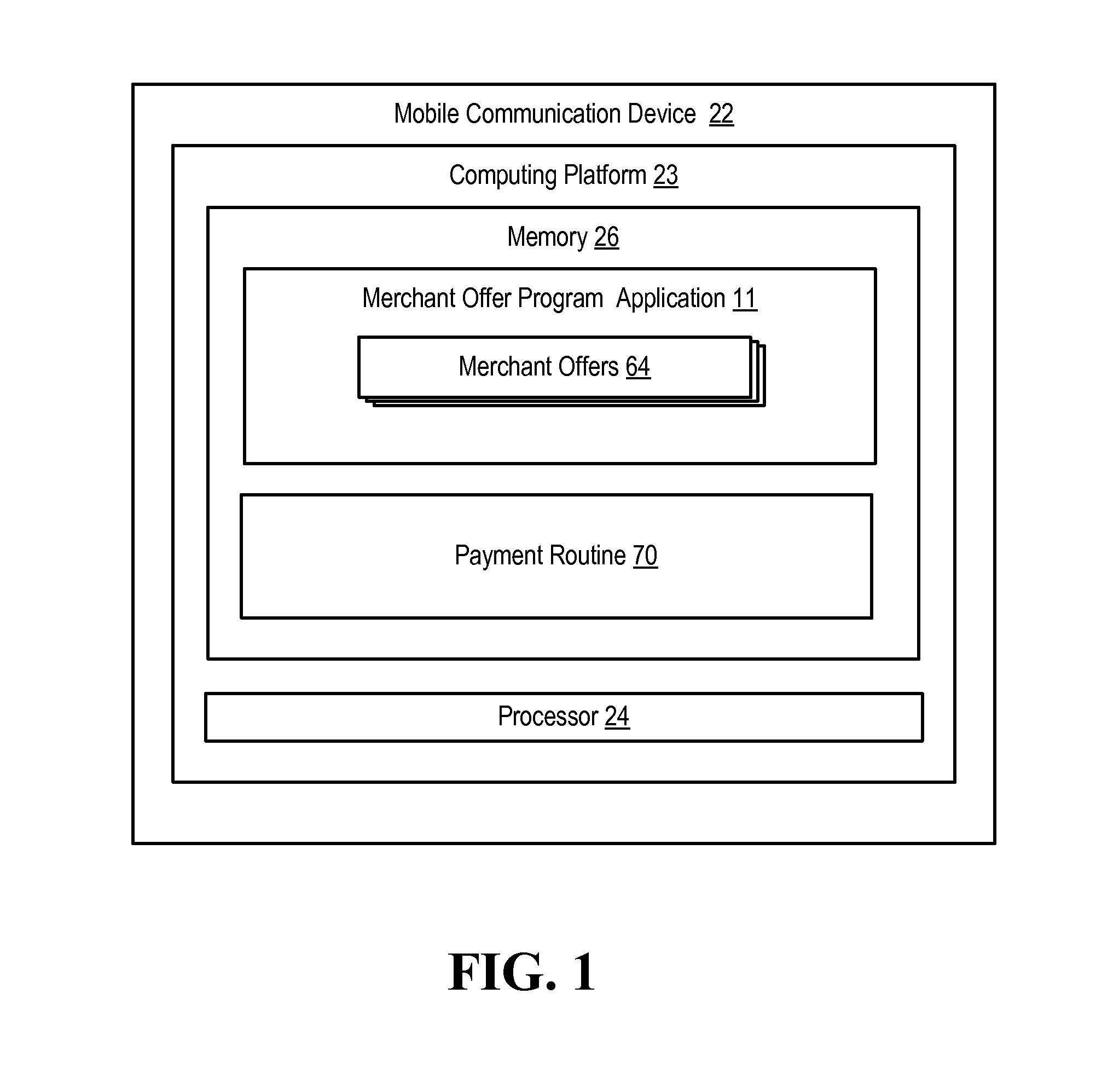
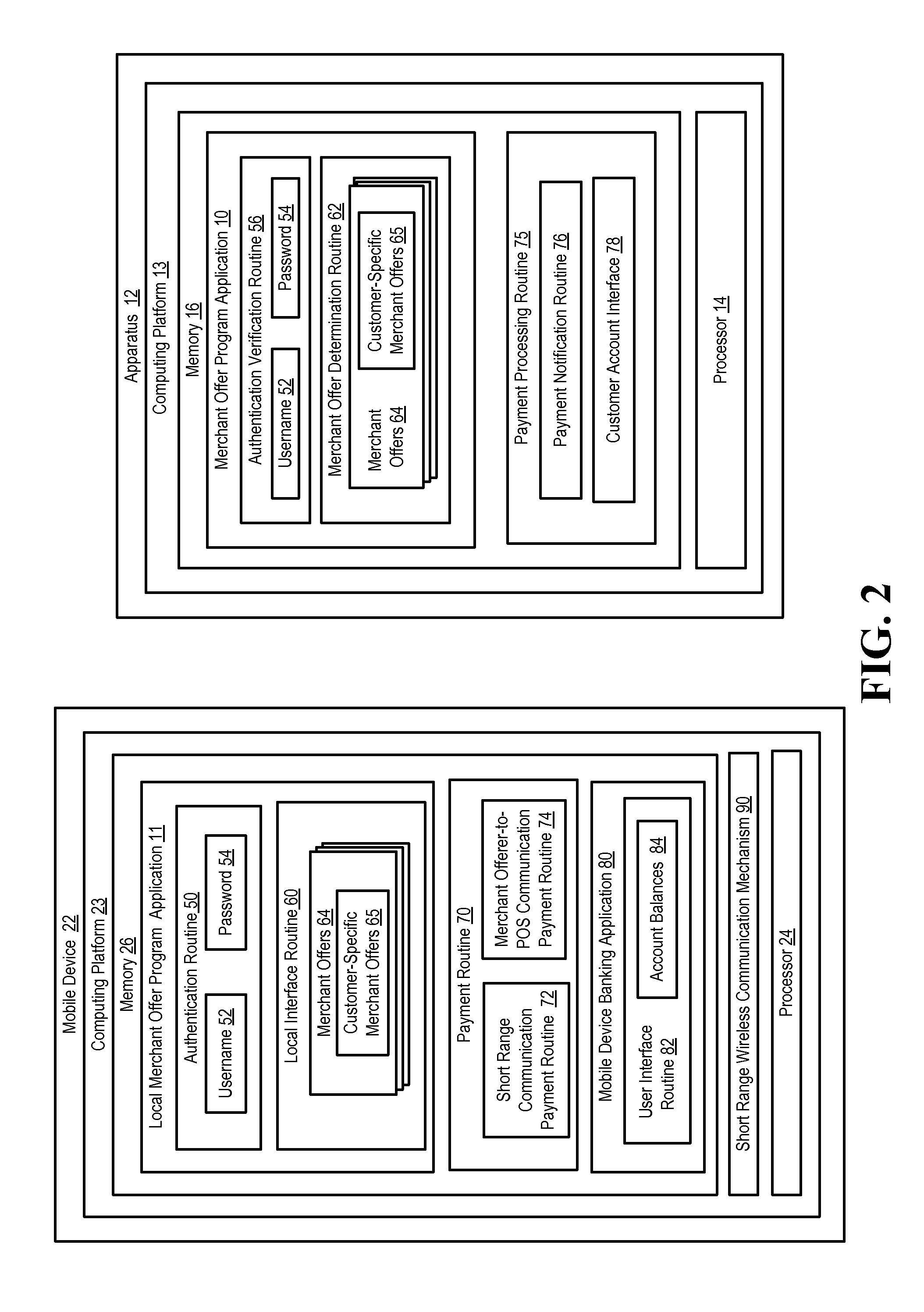
Mobile payment device for conducting transactions associated with a merchant offer program
InactiveUS20110191160A1Buying/selling/leasing transactionsPoint-of-sale network systemsProgram validationNetwork communication
Embodiments of the invention provide for a mobile payment device used to conduct transactions associated with a merchant offer program. In specific embodiments, the mobile device is equipped with short range communication mechanisms or some other form of wireless communication that allows for the mobile device to communicate customer program verification data, offer data and / or necessary payment data to a properly configured Point-Of-Sale (POS) device, such as a cash register, card reader device or the like. In other embodiments of the invention, the mobile device is in network communication with the financial institution and the financial institution is in network communication with the merchant, such that, once the customer communicates to the financial institution acceptance of an offer and the desire to conduct the corresponding transaction, the financial institution can, in turn, communicate the necessary payment data to the merchant.
Owner:BANK OF AMERICA CORP
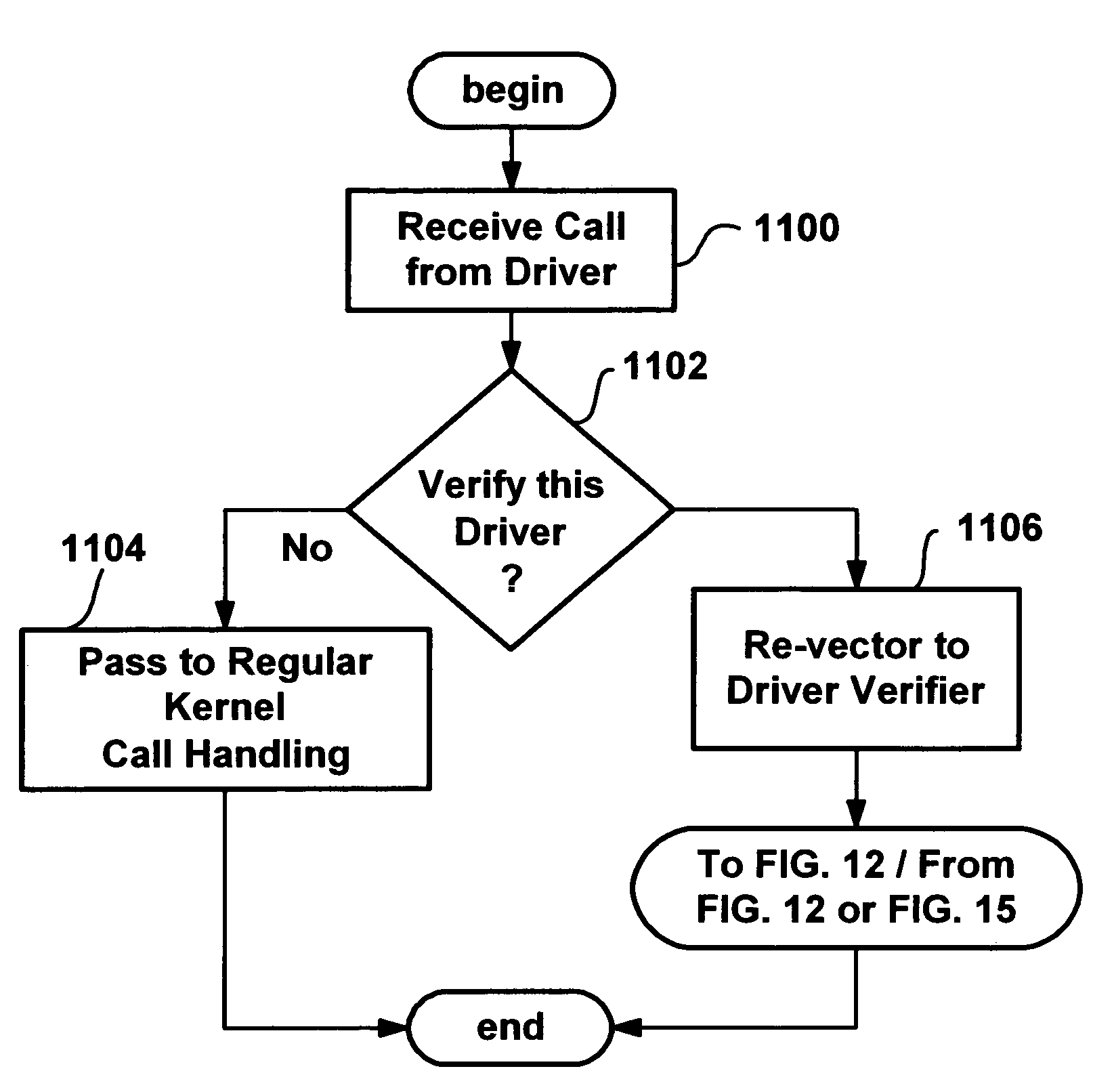
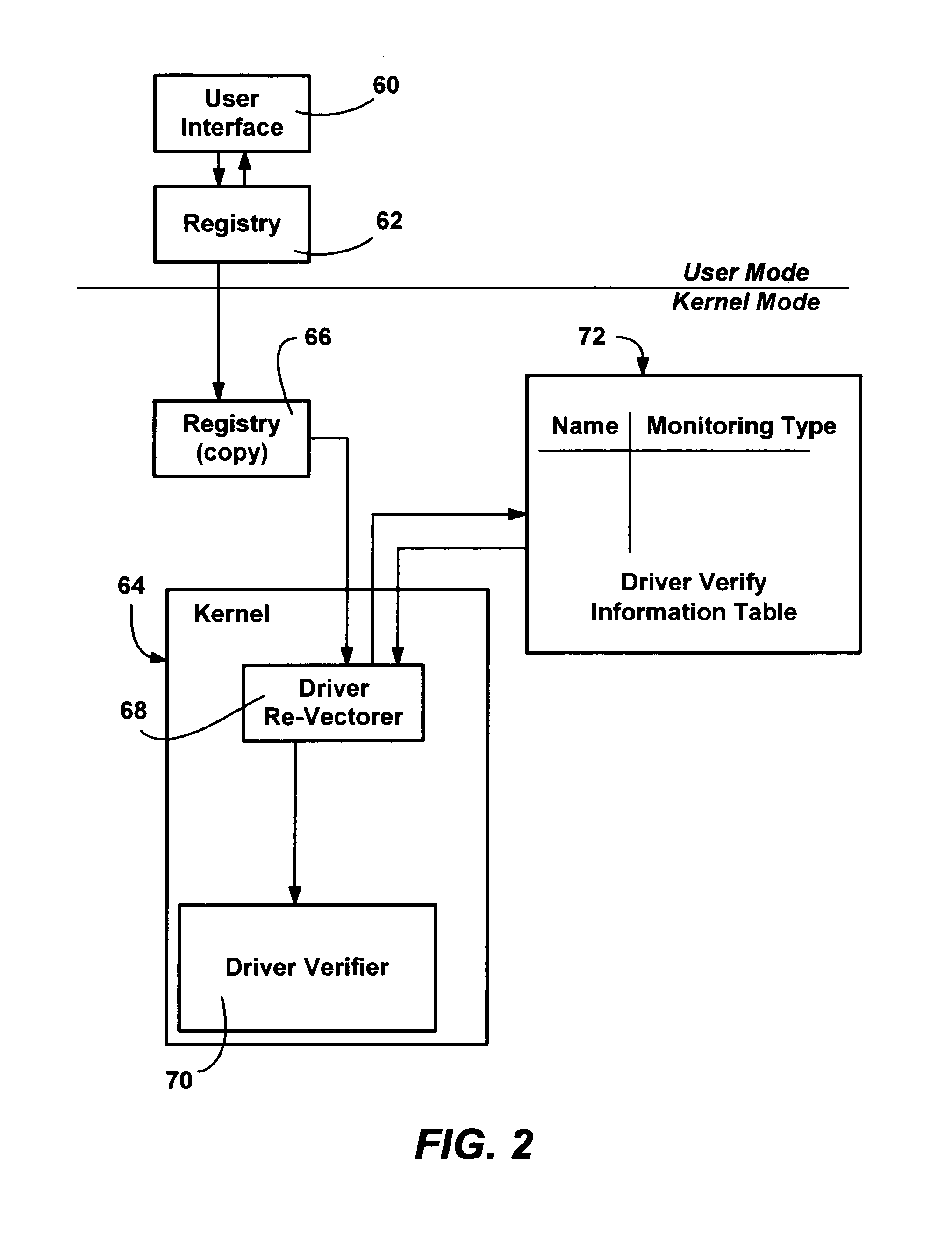
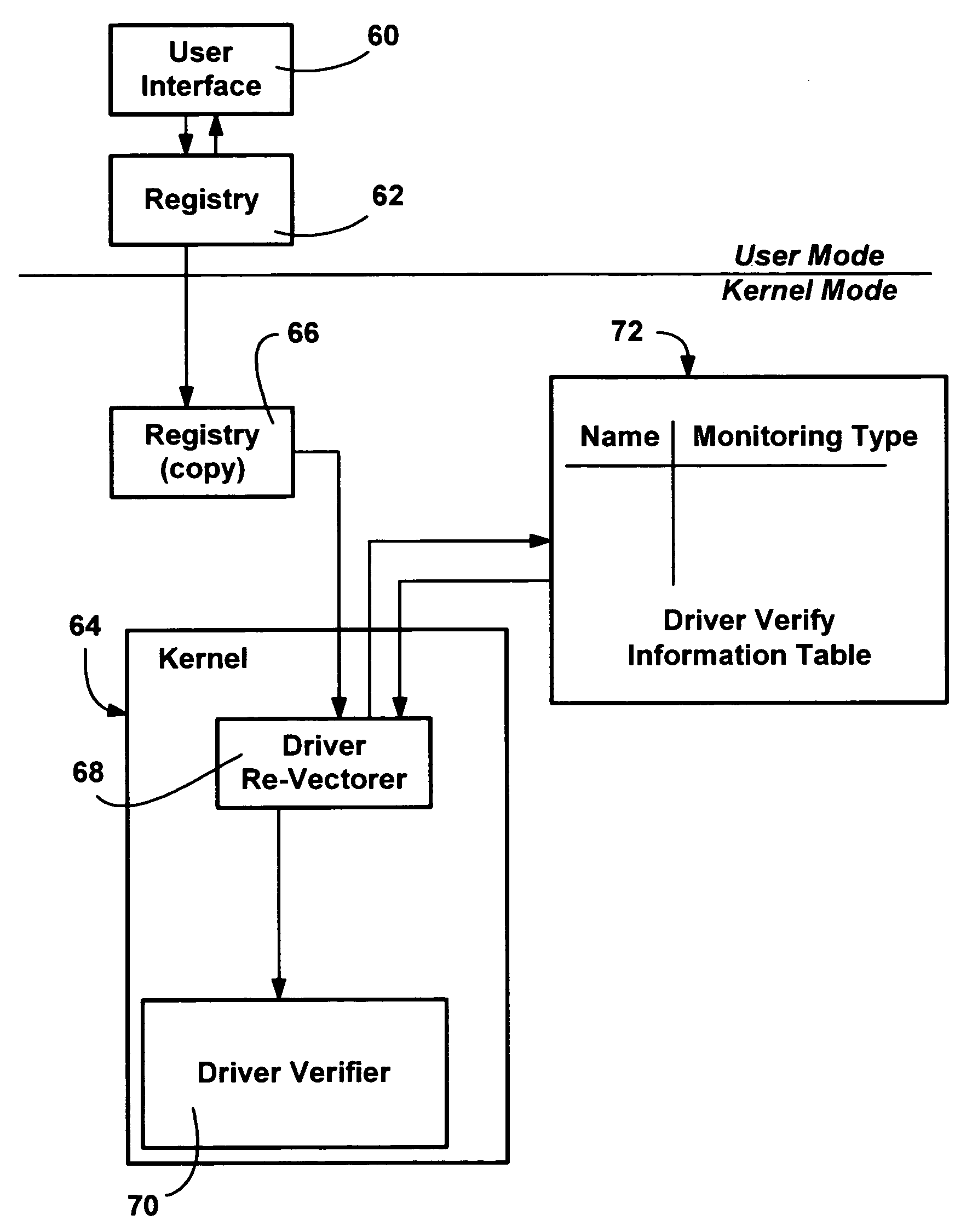
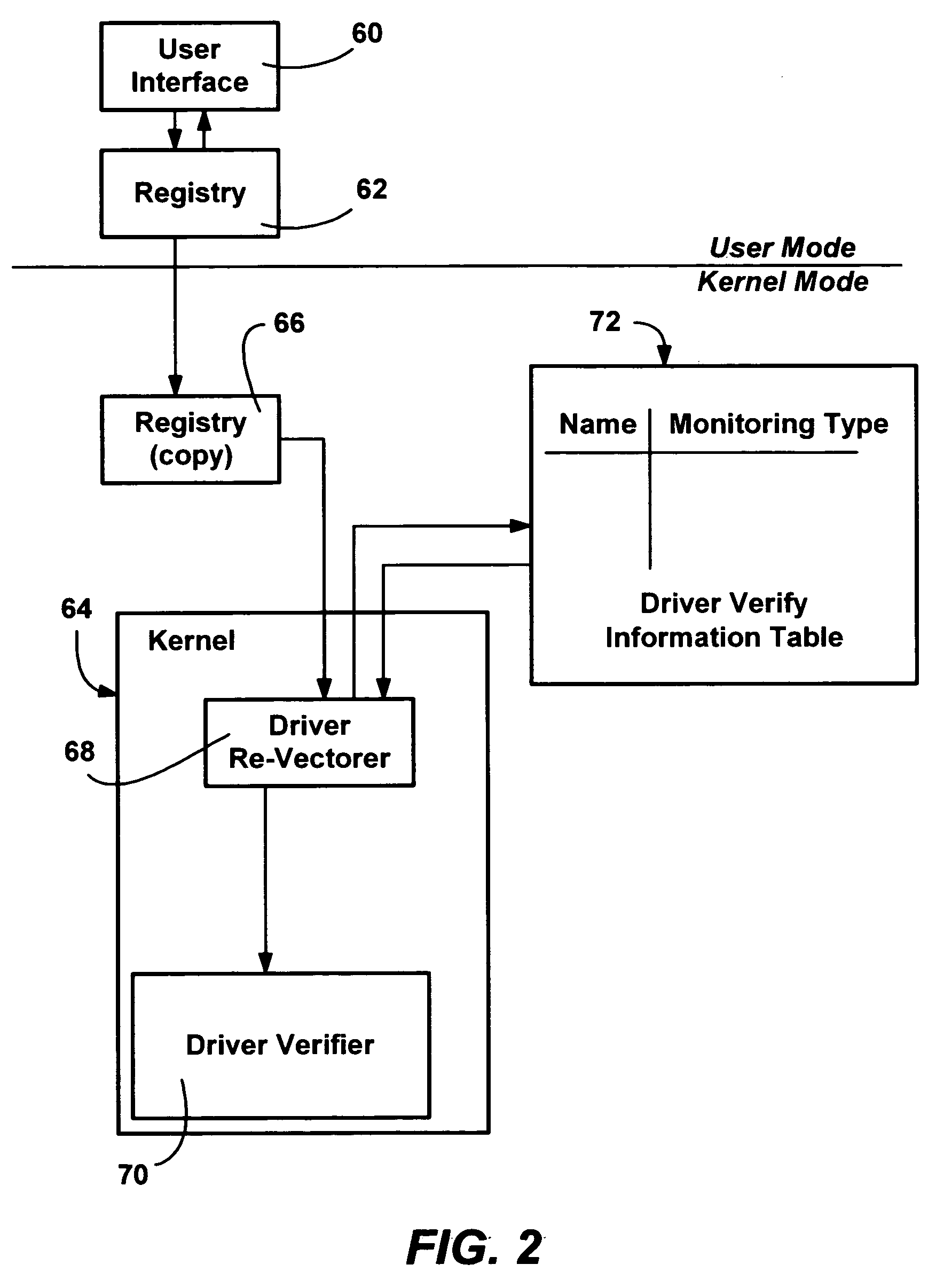
Method and system for monitoring and verifying software drivers using system resources including memory allocation and access
InactiveUS7111307B1Error detection/correctionMultiprogramming arrangementsComputer hardwareProgram validation
A method and system for verifying computer system drivers such as kernel mode drivers. A driver verifier sets up tests for specified drivers and monitors the driver's behavior for selected violations that cause system crashes. In one test, the driver verifier allocates a driver's memory pool allocations from a special pool bounded by inaccessible memory space for testing the driver's accessing memory outside of the allocation. The driver verifier also marks the space as inaccessible when it is deallocated, detecting a driver that accesses deallocated space. The driver verifier may also provide extreme memory pressure on a specific driver, or randomly fail requests for pool memory. The driver verifier also checks call parameters for violations, performs checks to ensure a driver cleans up timers when deallocating memory and cleans up memory and other resources when unloaded. An I / O verifier is also described for verifying drivers use of I / O request packets.
Owner:ZHIGU HLDG
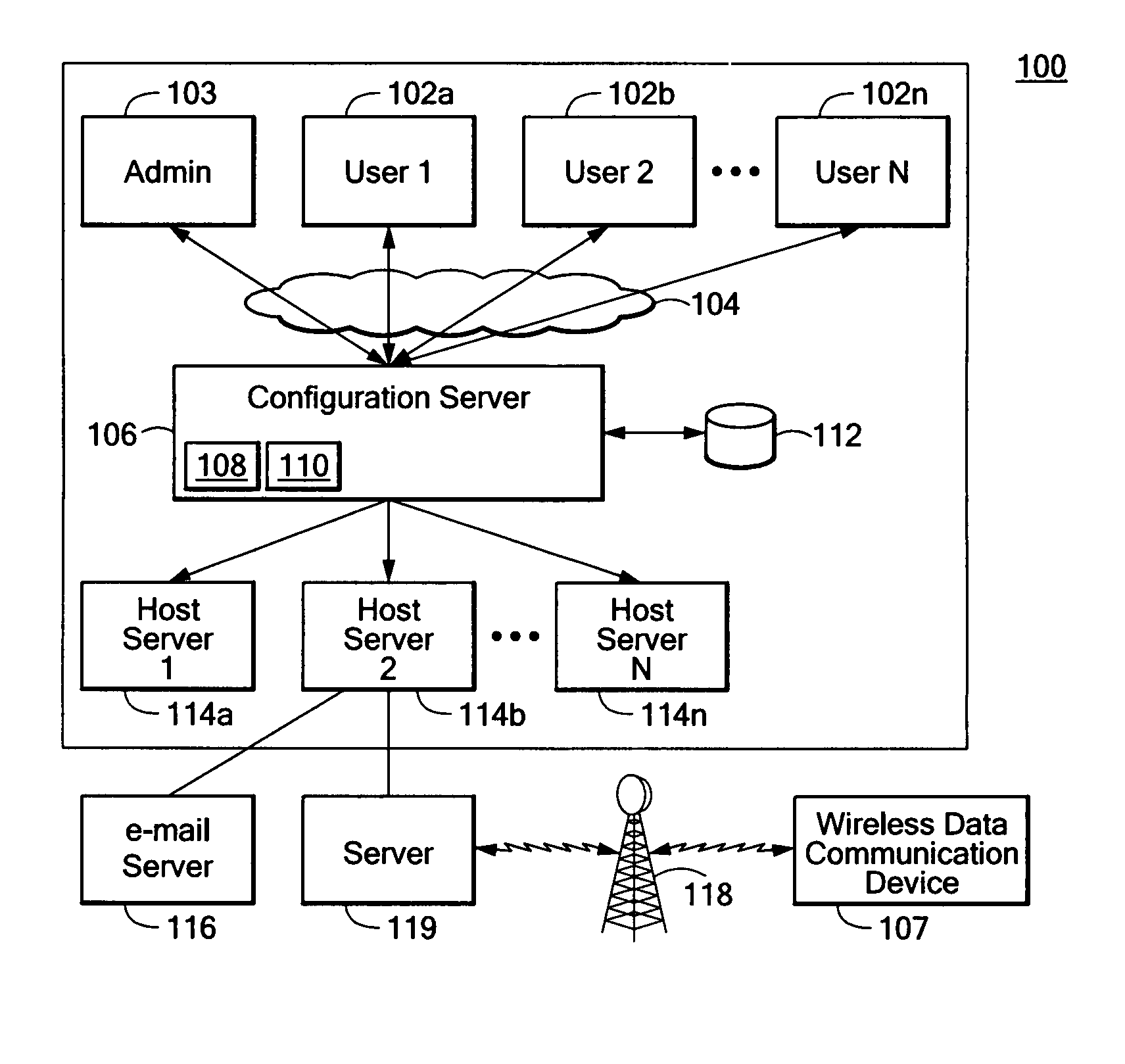
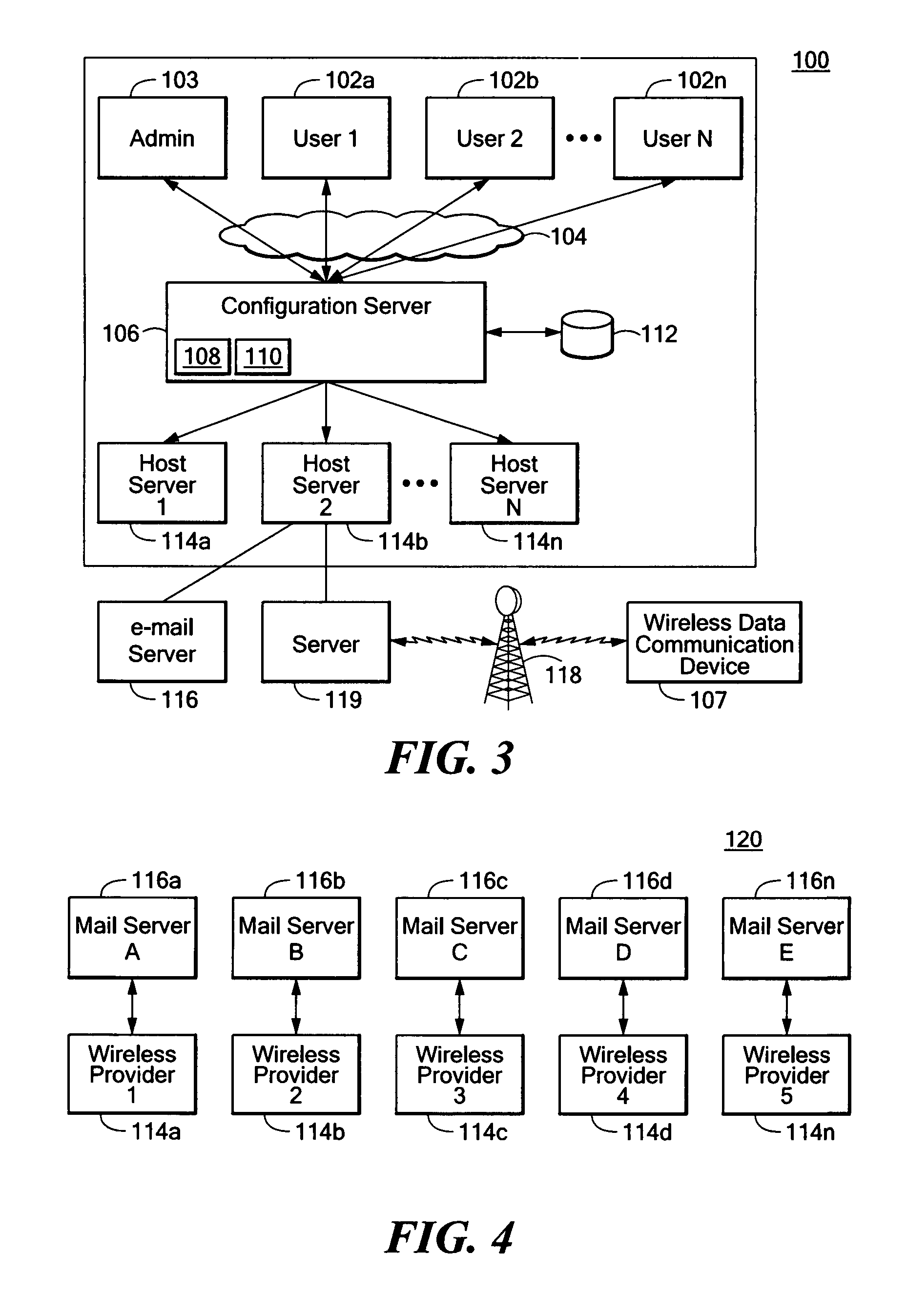
Apparatus and method for provisioning wireless data communication devices
ActiveUS7917641B2Multiple digital computer combinationsWireless commuication servicesProgram validationWireless data
A system for provisioning wireless data communication devices for a plurality of users is provided in which the system includes a configuration server having an authorization program and a configuration program, and a database. The configuration server is connectable to a network for providing a network portal for the plurality of users to allow each of them to have a wireless data communication device provisioned. The authorization program validates which one of a plurality of wireless host servers a user is authorized to use. The configuration program is configured to provision the wireless data communication device to communicate with the one of a plurality of wireless host servers to obtain email from one of a plurality of messaging servers. The database is in communication with the configuration server for storing configurations for each of the wireless host servers.
Owner:TANGOE US INC
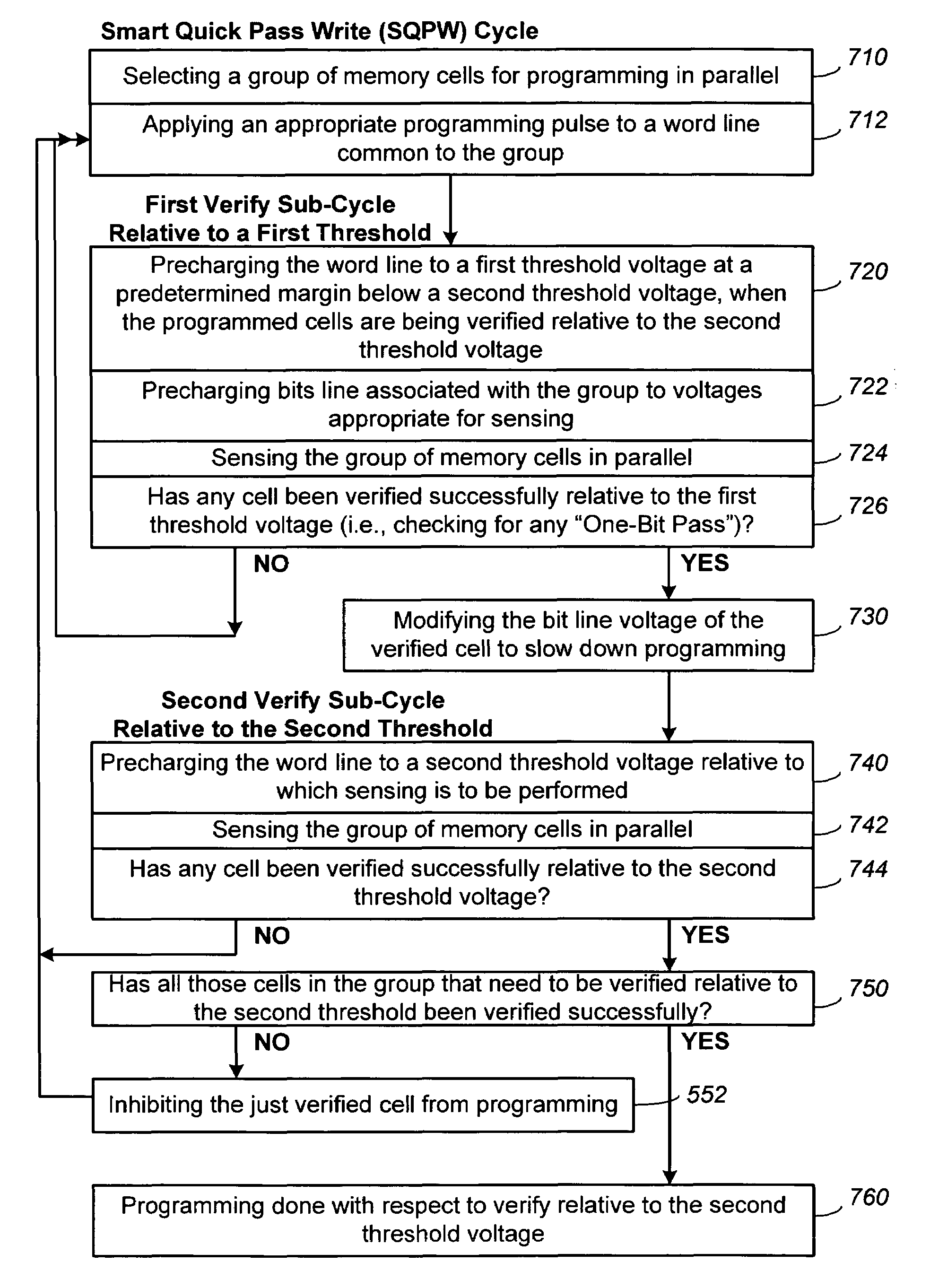
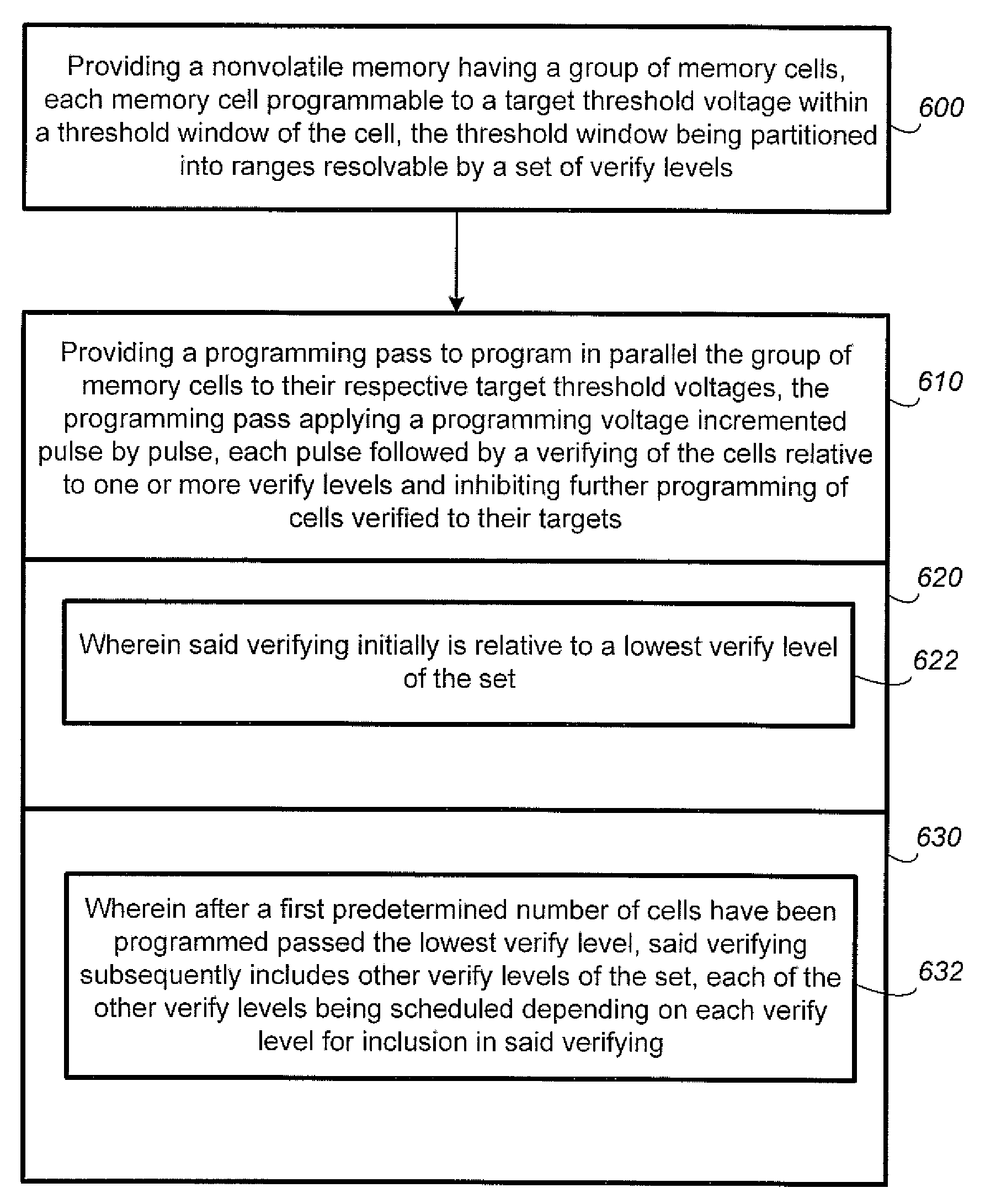
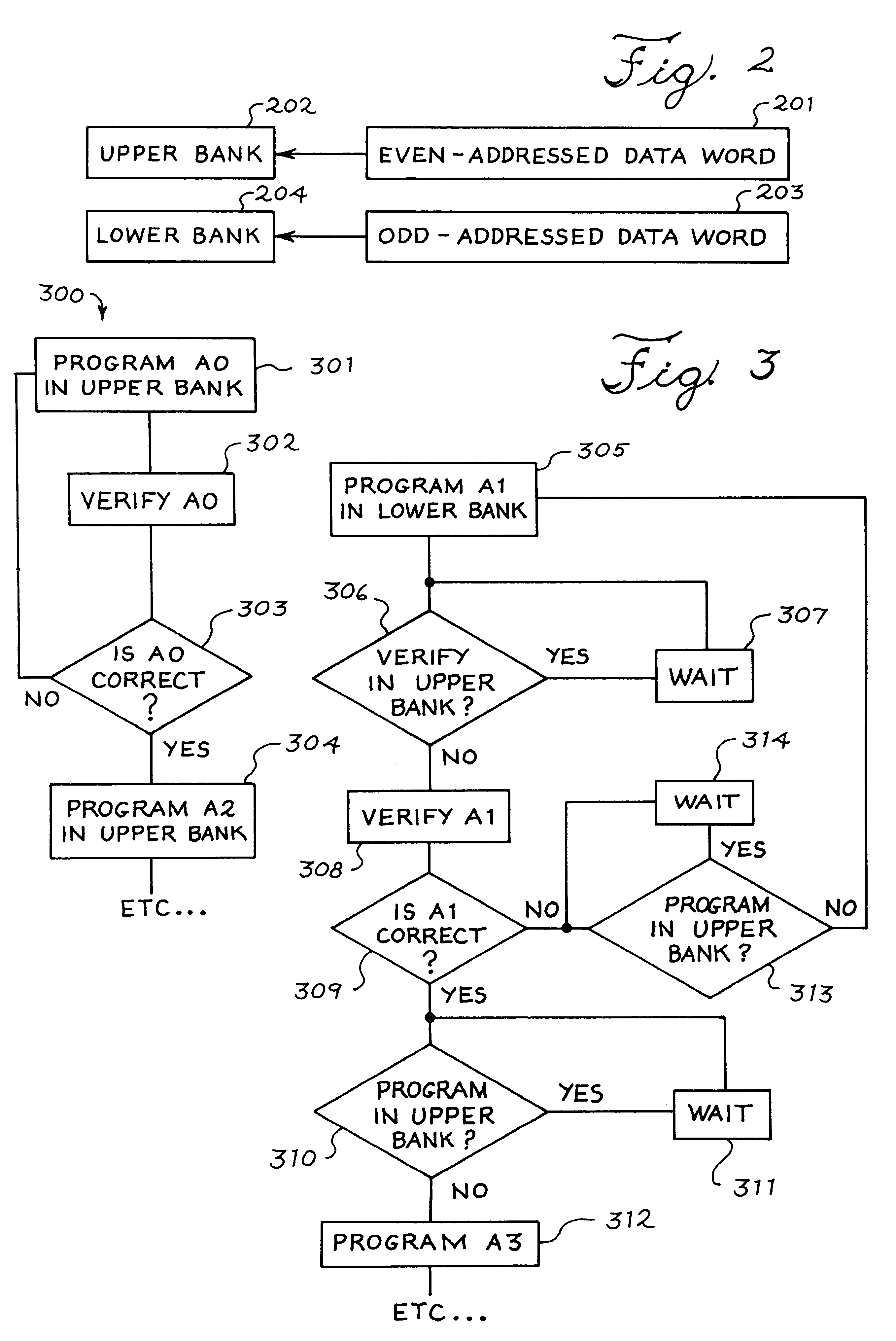
Methods for improved program-verify operations in non-volatile memories
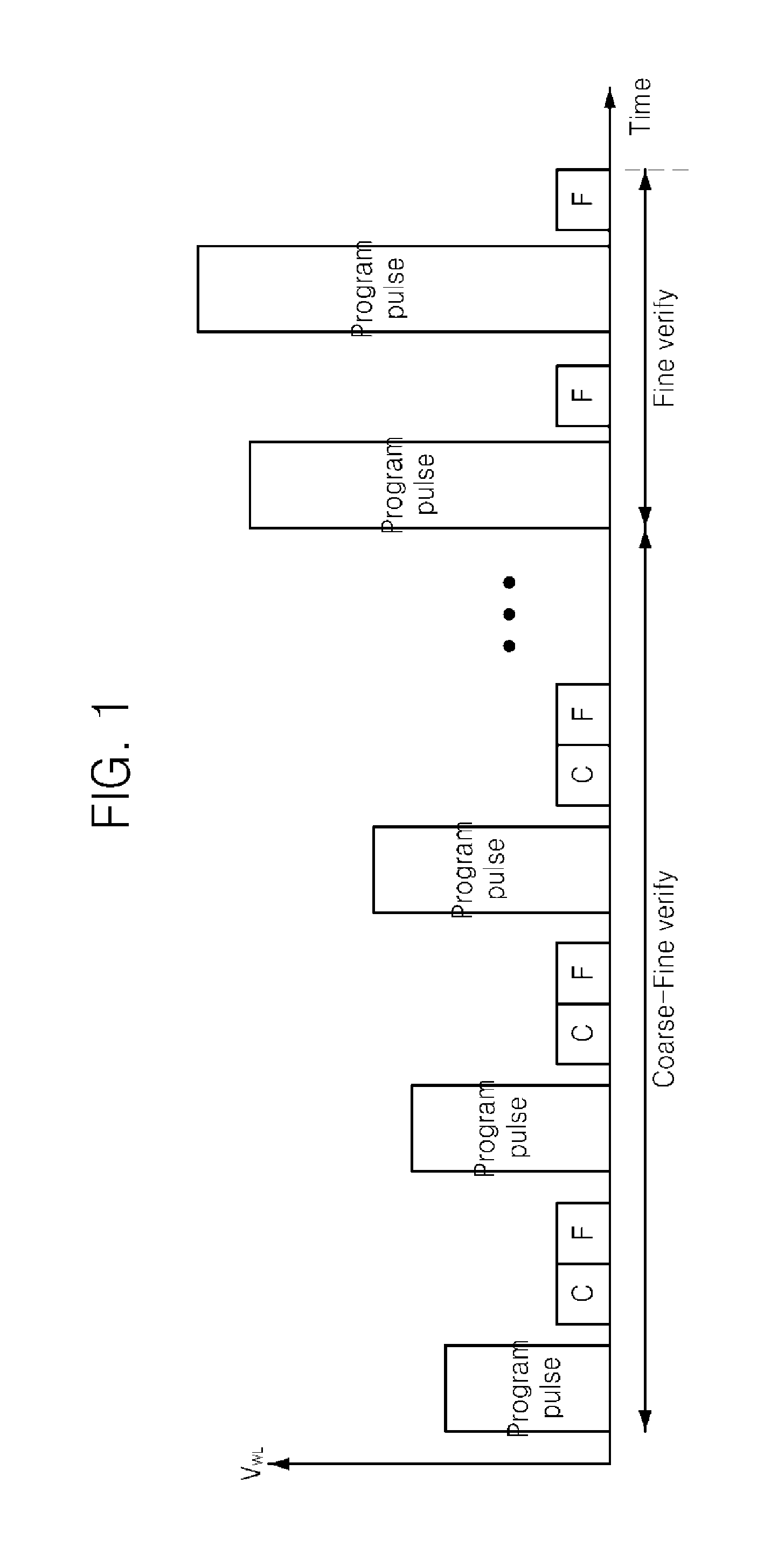
In programming a non-volatile memory involving alternately applying a programming pulse and verifying the programming, time is saved in the program verify portion when, depending on the states of the memory cells, a portion of the verify operation is recognized to be superfluous and skipped. Preferably, in a program verify operation relative to a demarcation threshold level for demarcating between two memory states, the verify operation includes a sequence of two verify sub-cycles, the first sub-cycle performing a verify relative to a first threshold level at a predetermined margin below the demarcation threshold level and the second sub-cycle performing a verify relative to a second threshold level which is identical to the demarcation threshold level. Unlike conventional cases, the second sub-cycle is not performed until any one memory cell of the group has been verified to pass the first threshold.
Owner:SANDISK TECH LLC
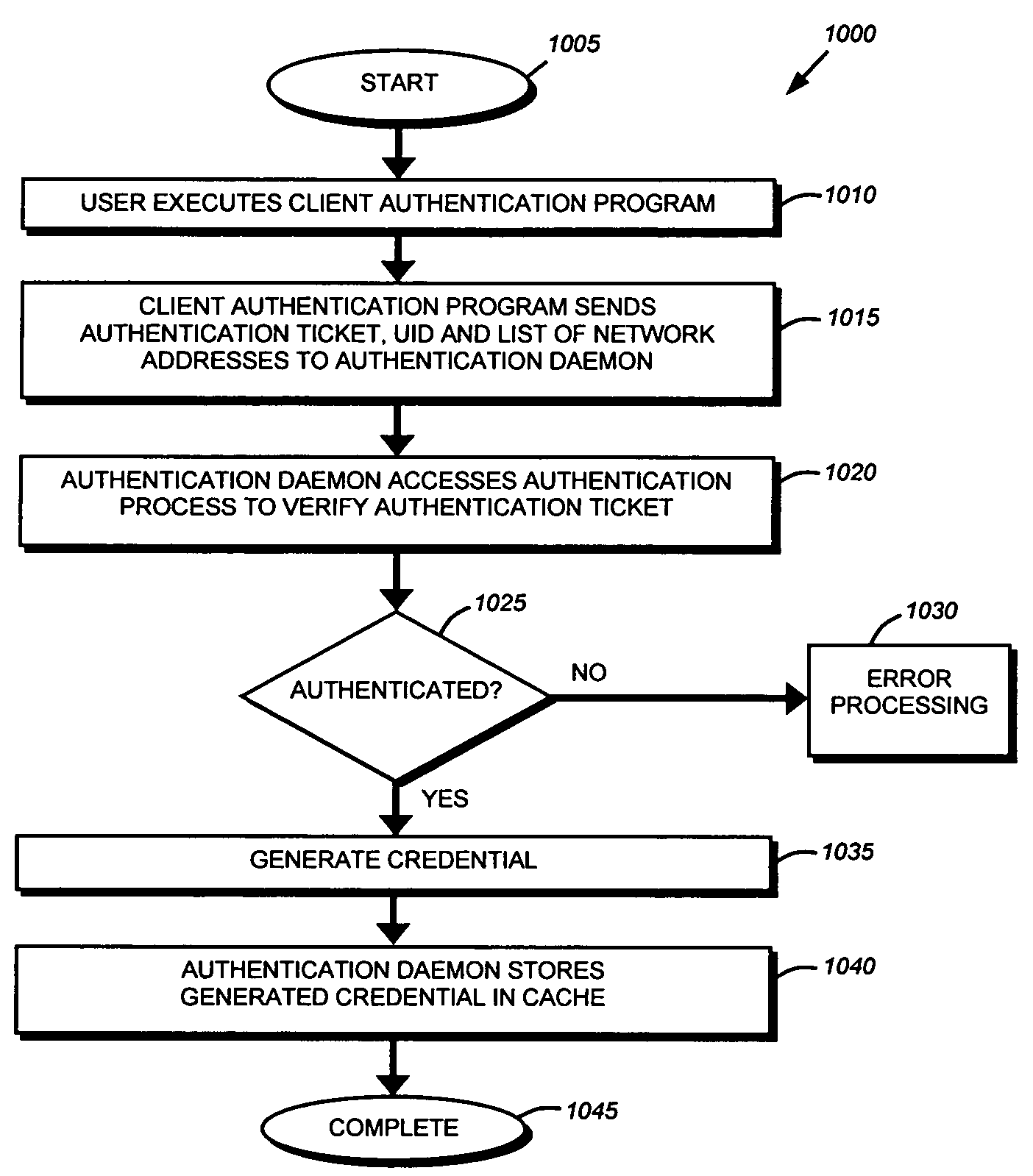
System and method for a sidecar authentication mechanism
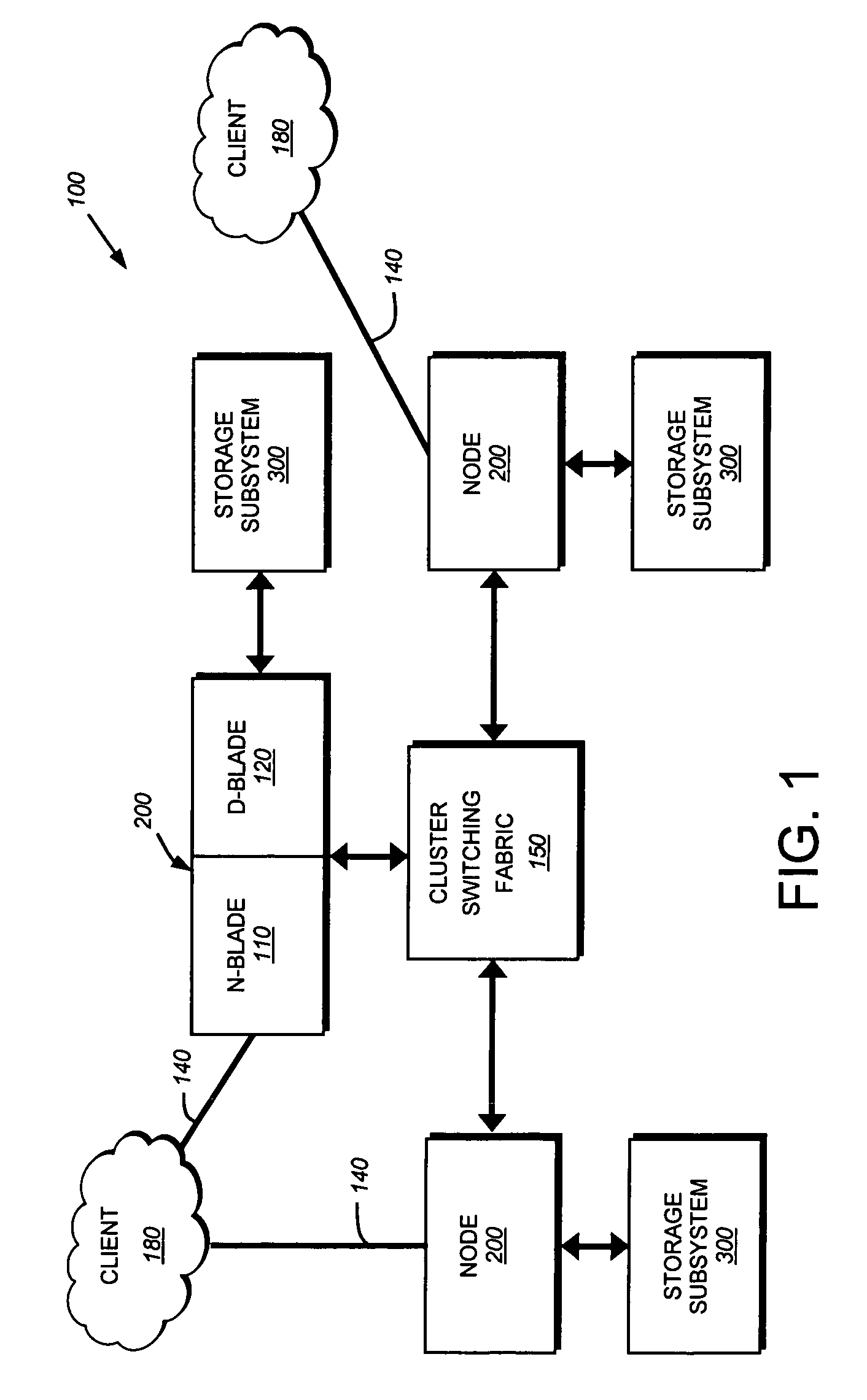
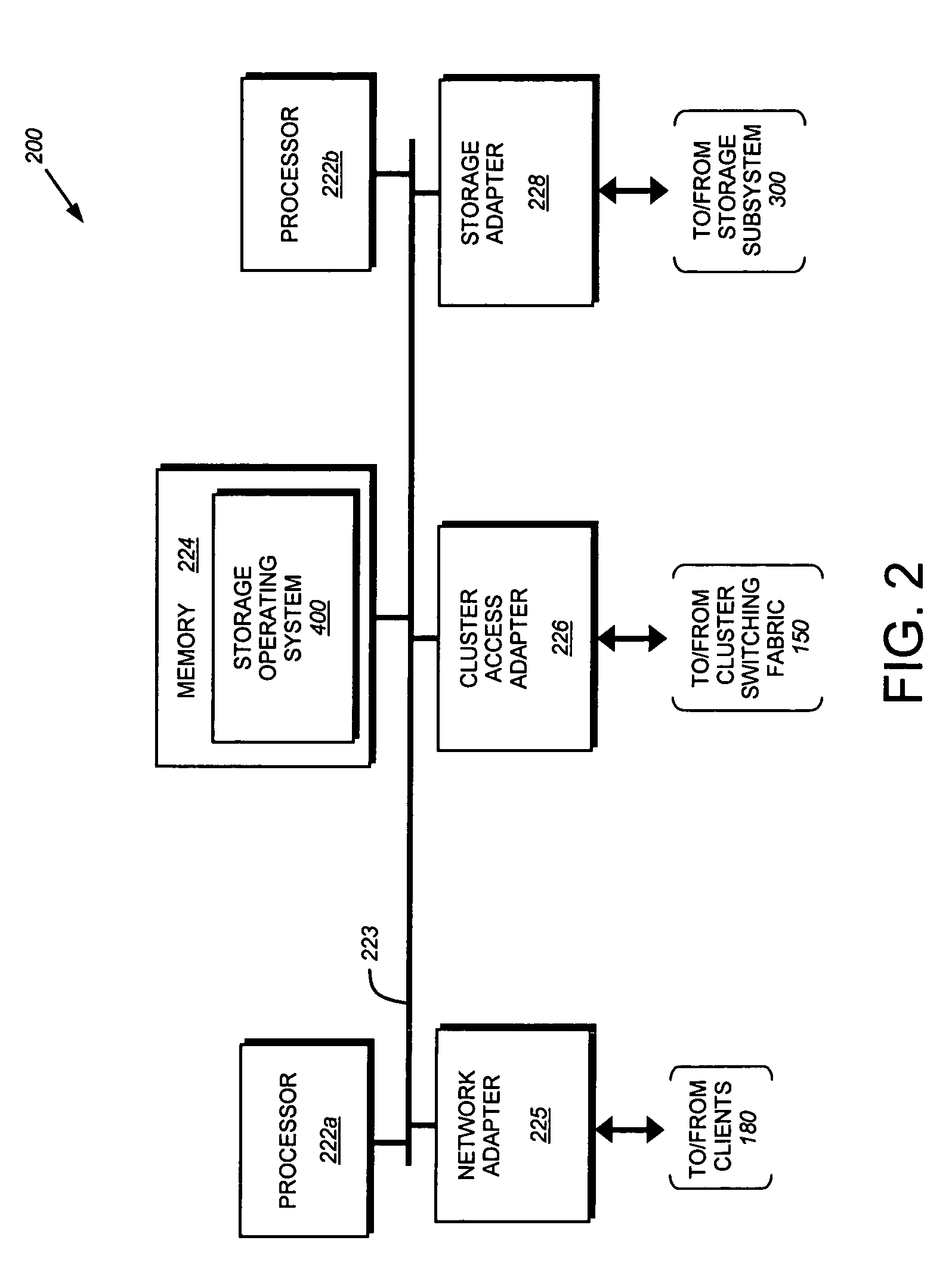
ActiveUS7519813B1Improve securityExpand accessDigital data processing detailsUser identity/authority verificationProgram validationFile system
A system and method for authenticating an unauthenticated file level protocol using a sidecar authentication mechanism. A client transmits an authentication ticket, UID and list of network addresses to an authentication daemon of a storage system. The authentication daemon verifies the user identity and generates a file system credential that is stored in a cache indexed by an authentication tuple. Received data access operations from a client are compared to authentication tuples by UID and network address and the file system utilizes the stored credential for processing the data access operation.
Owner:NETWORK APPLIANCE INC
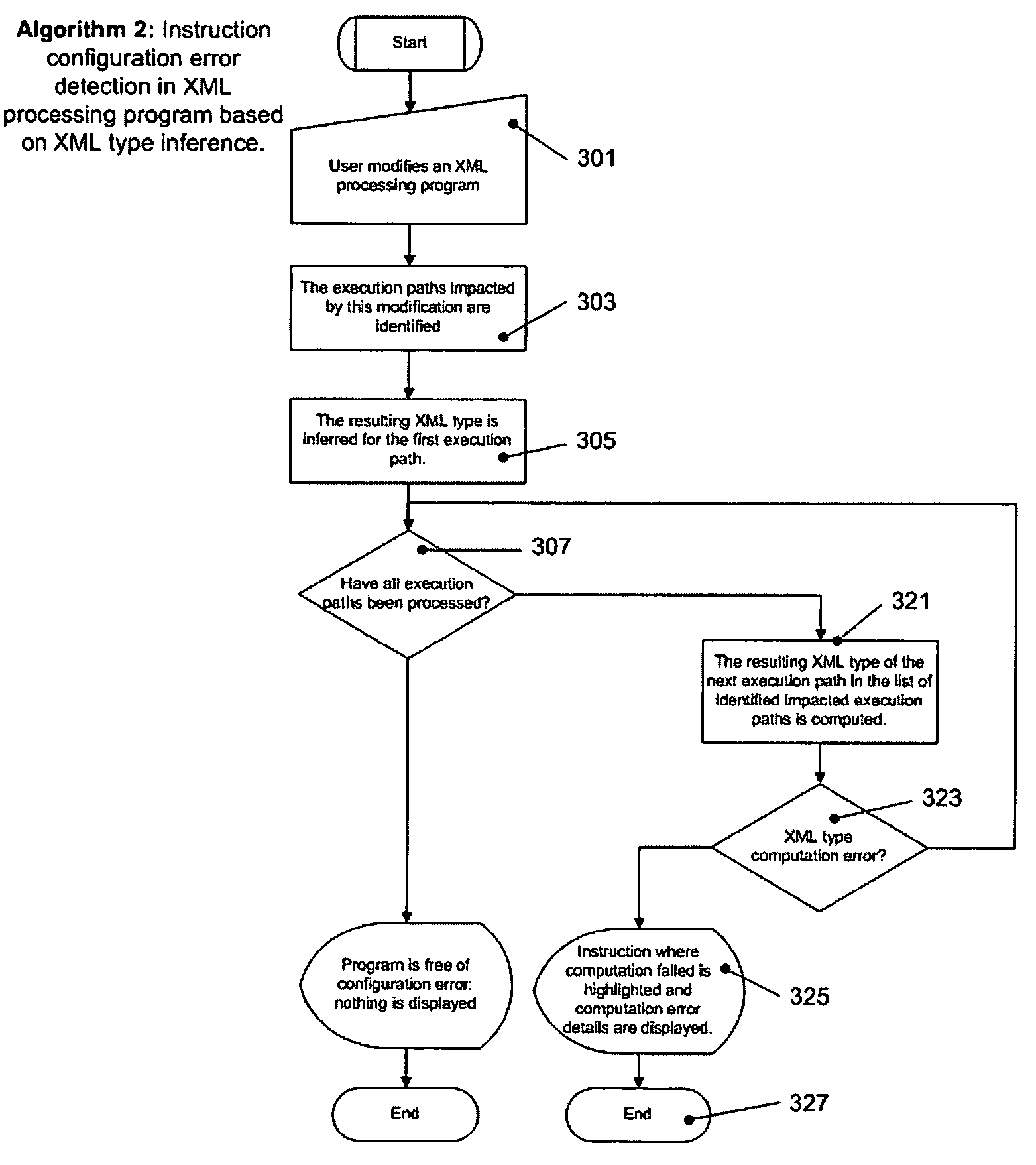
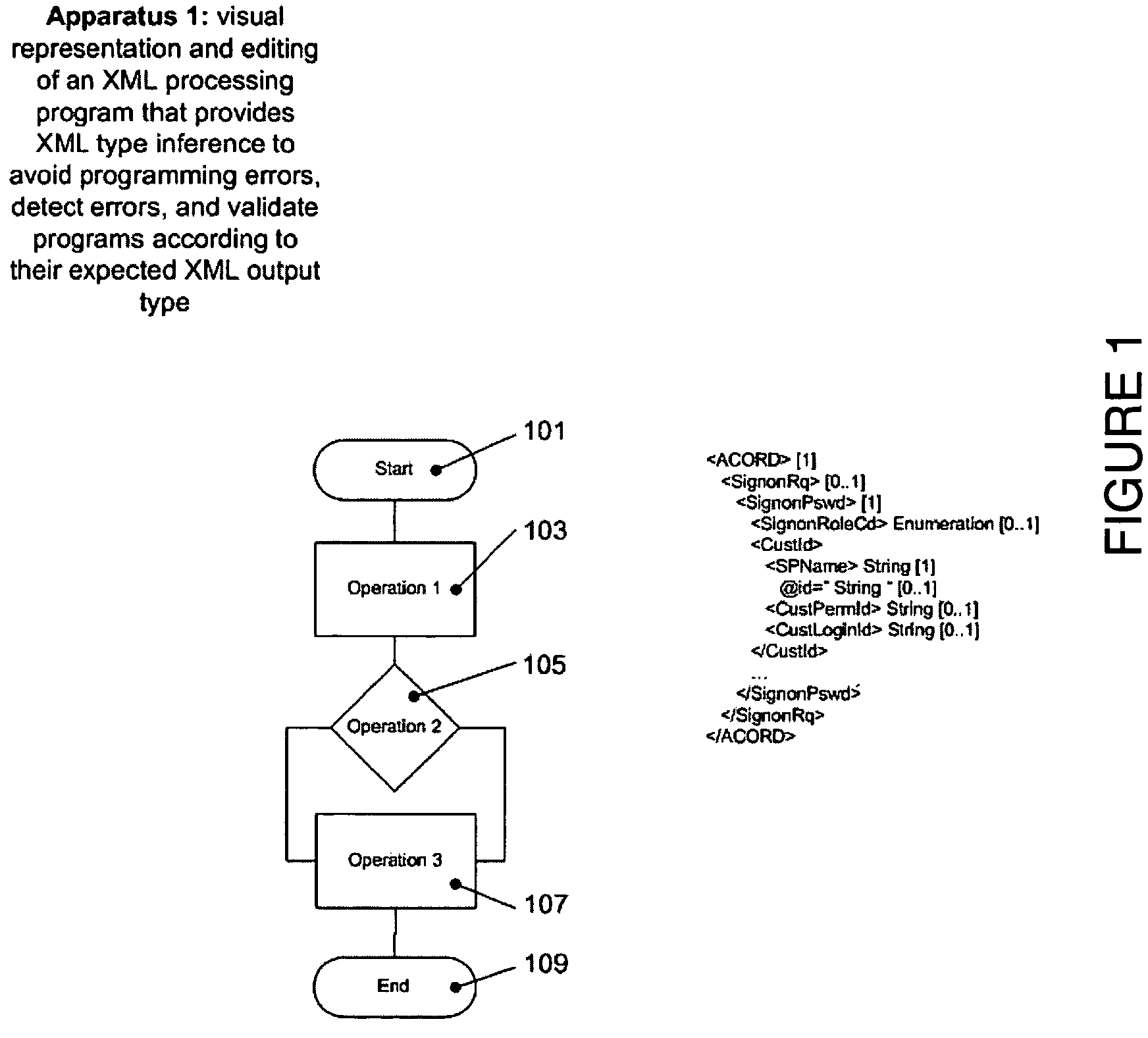
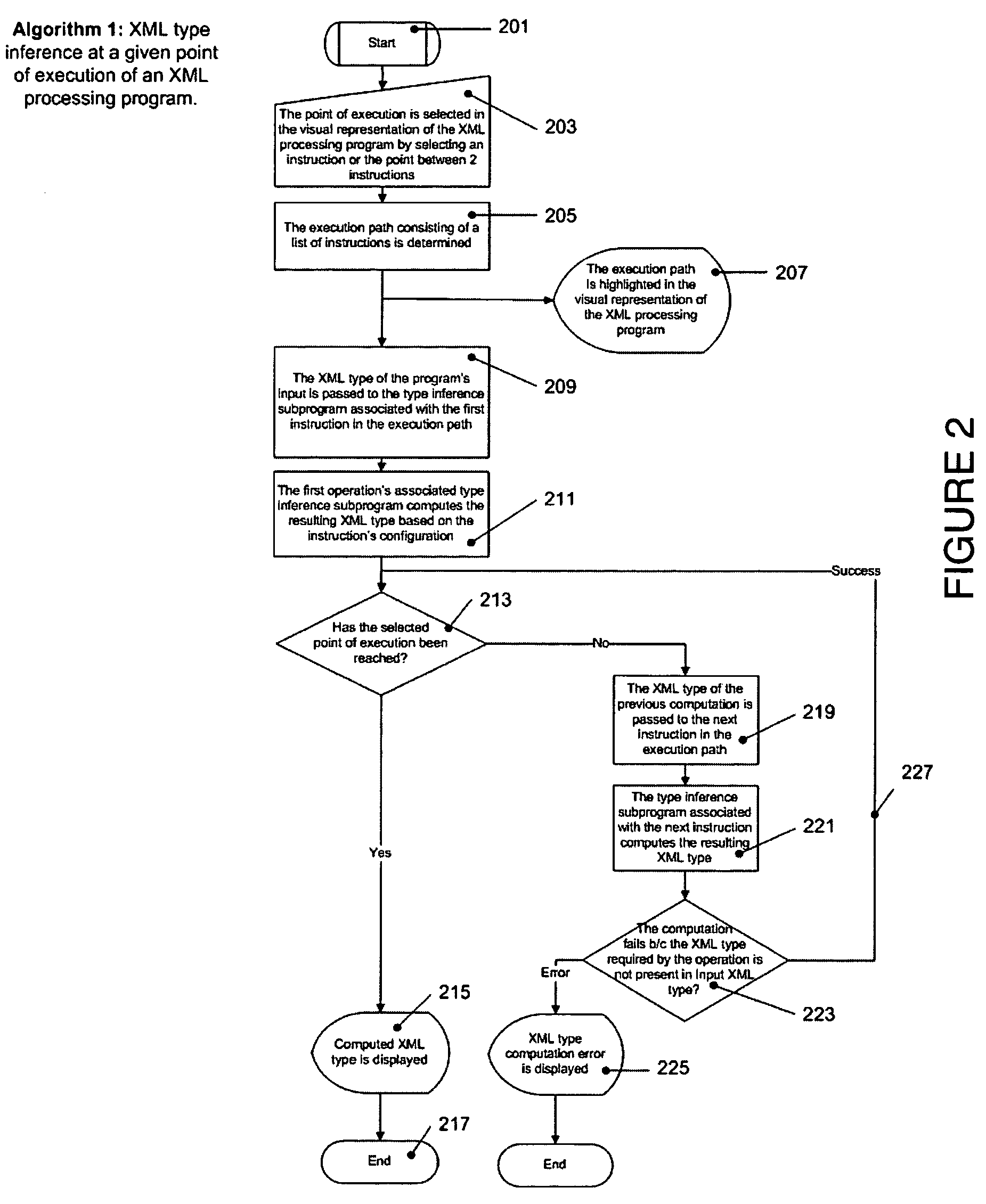
Graphical XML programming system and engine where XML processing programs are built and represented in a graphical fashion
ActiveUS20060075387A1Fix bugsDesign errorNatural language data processingVisual/graphical programmingChange managementWeb service
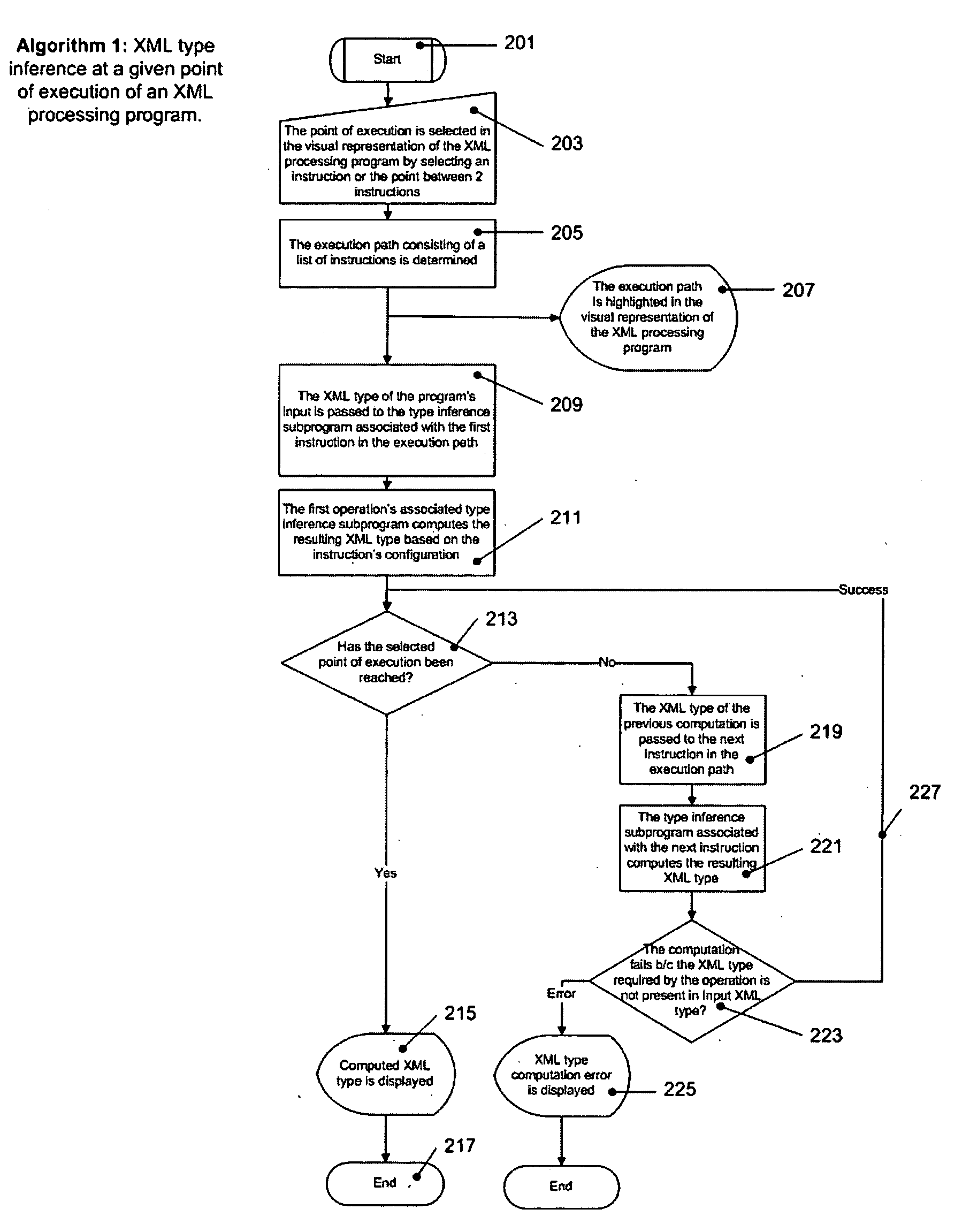
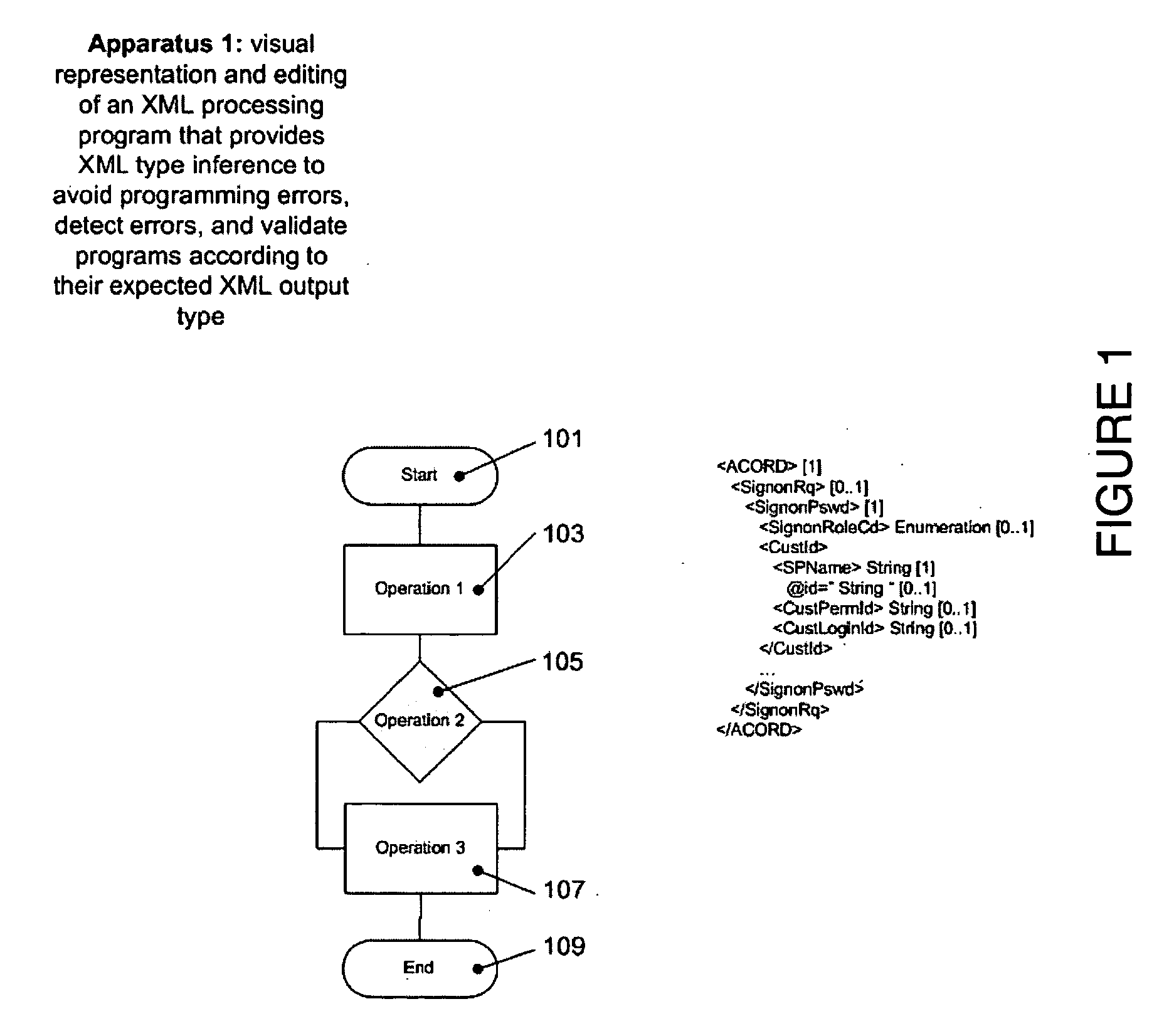
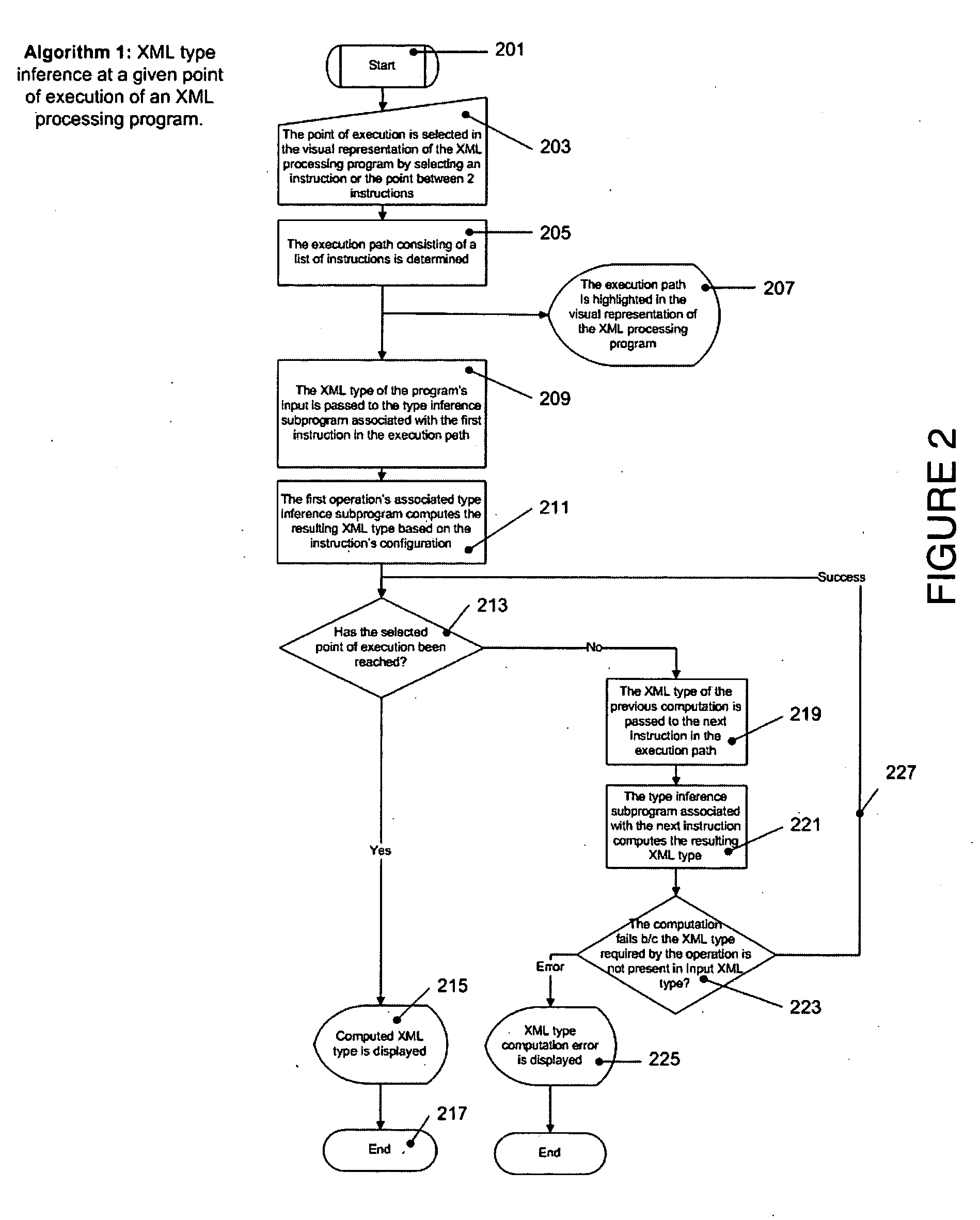
A system and methods are provided for operating and building graphically XML processing programs, guiding the user in development of the program, preventing and detecting development errors as the program is being designed, ensuring that the program is valid, i.e. satisfies required input and output constraints at all times, i.e. from the time it is developed to when it is deployed in a production environment, ensuring the automated change management if the internal logic of the Web service, or data sources called by the service or the schema that underlies the Web service are modified. The system includes a graphical XML Programming system where XML processing programs are built and represented in a graphical fashion, a real-time metadata computation and visualization method for each selected execution point in the visual program that provides guided programming, error prevention and detection, and change impact analysis and change management, and, an automated execution path exploration method that enables overall program validation and error identification. The system and methods allow a user to reduce by at least a factor of 2 the costs of development and maintenance of reliable XML processing programs such as Web Services.
Owner:DIEBOLD NIXDORF
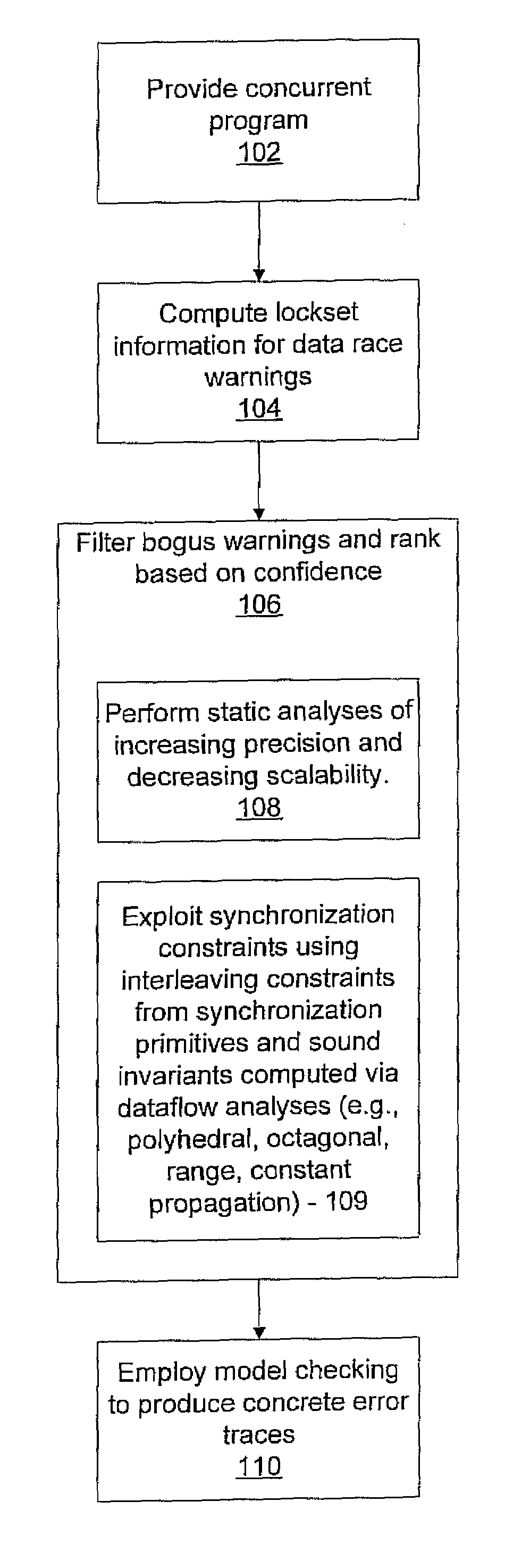
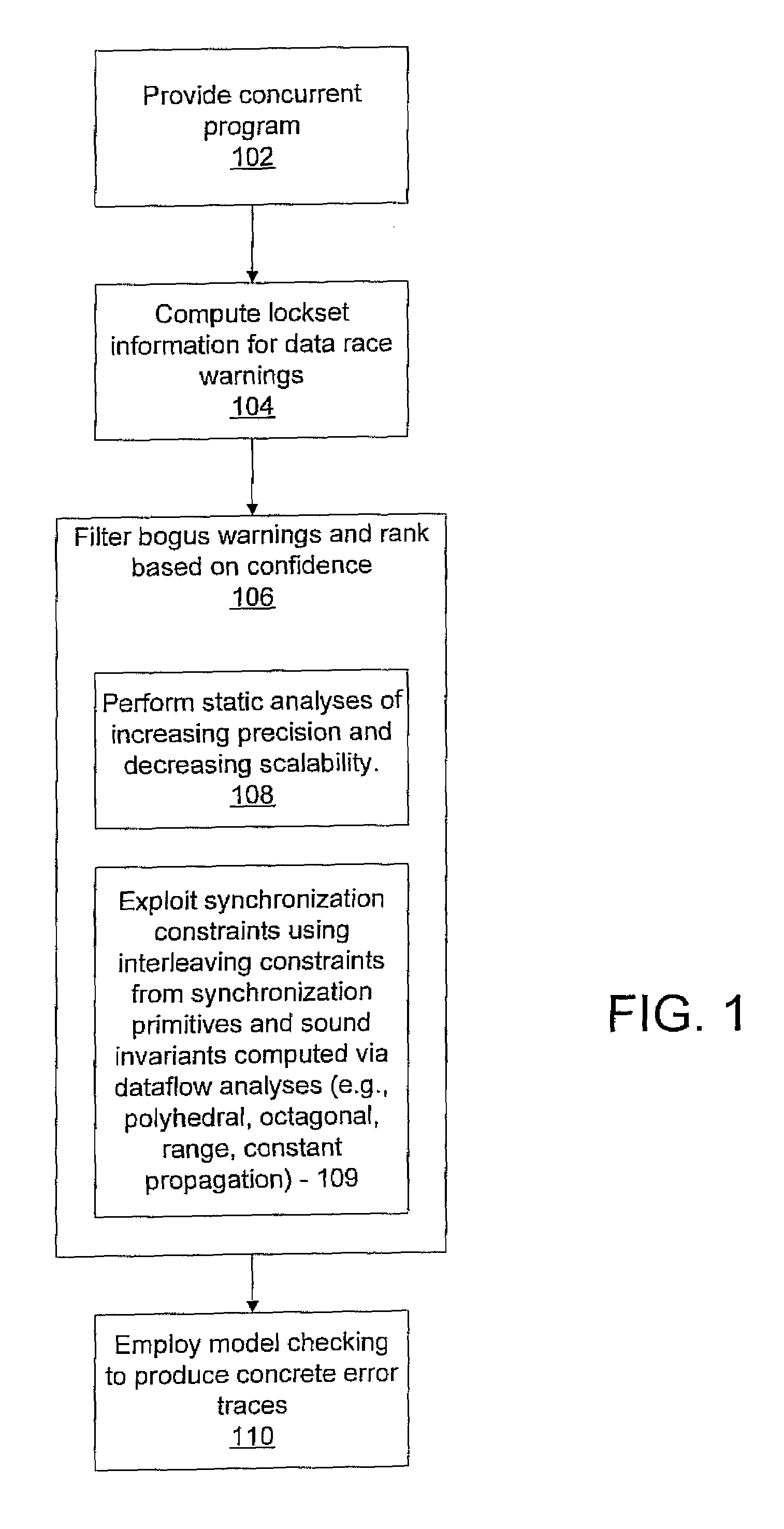
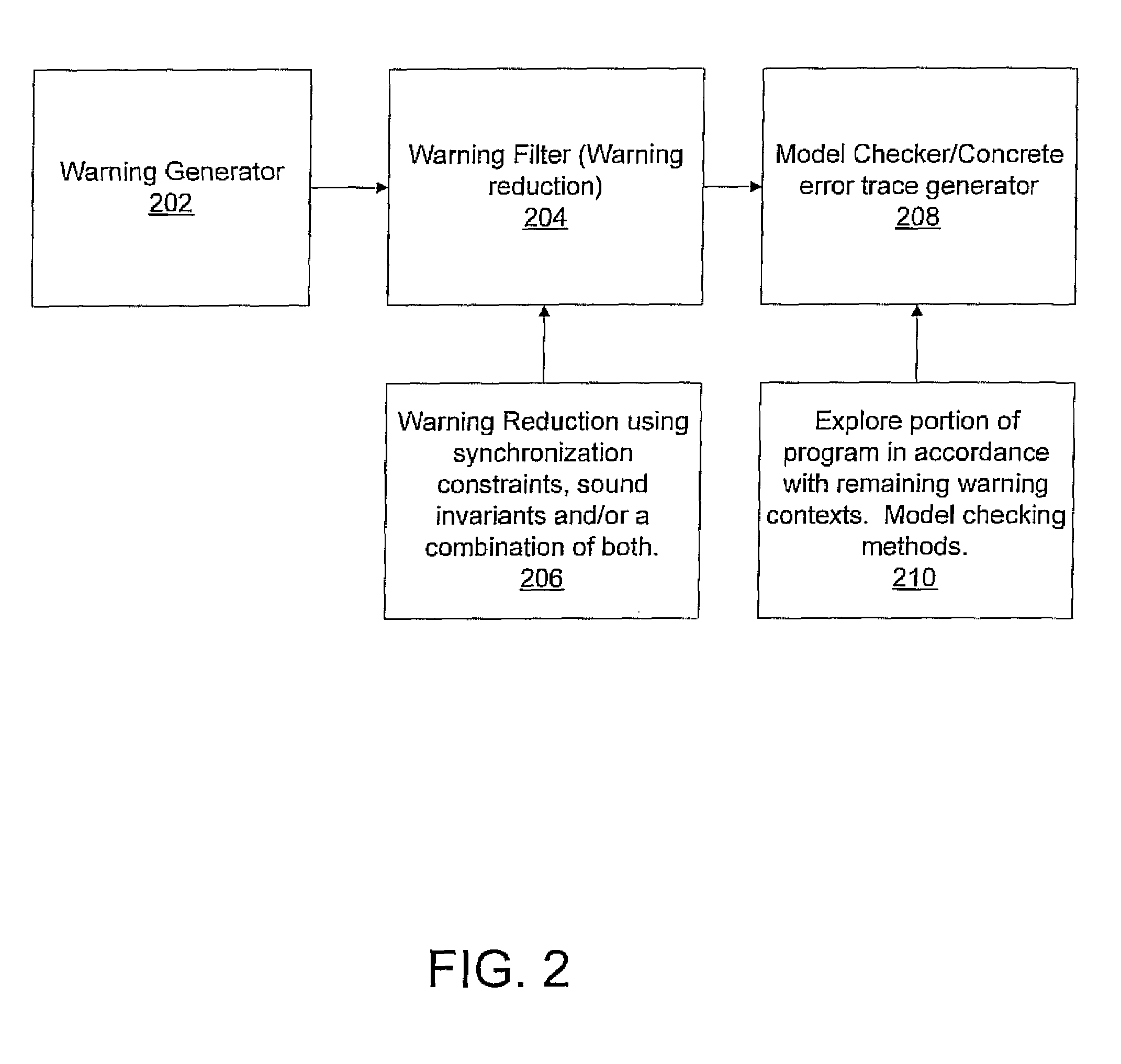
System and method for generating error traces for concurrency bugs
ActiveUS20090125887A1Error detection/correctionSpecific program execution arrangementsData streamProgram validation
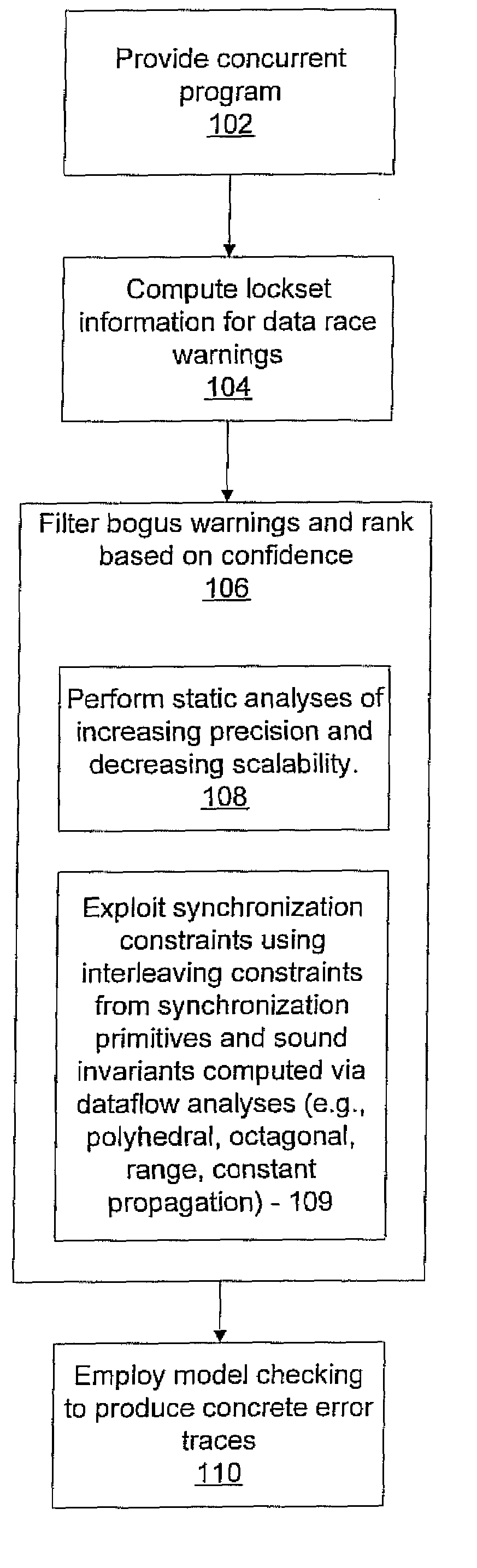
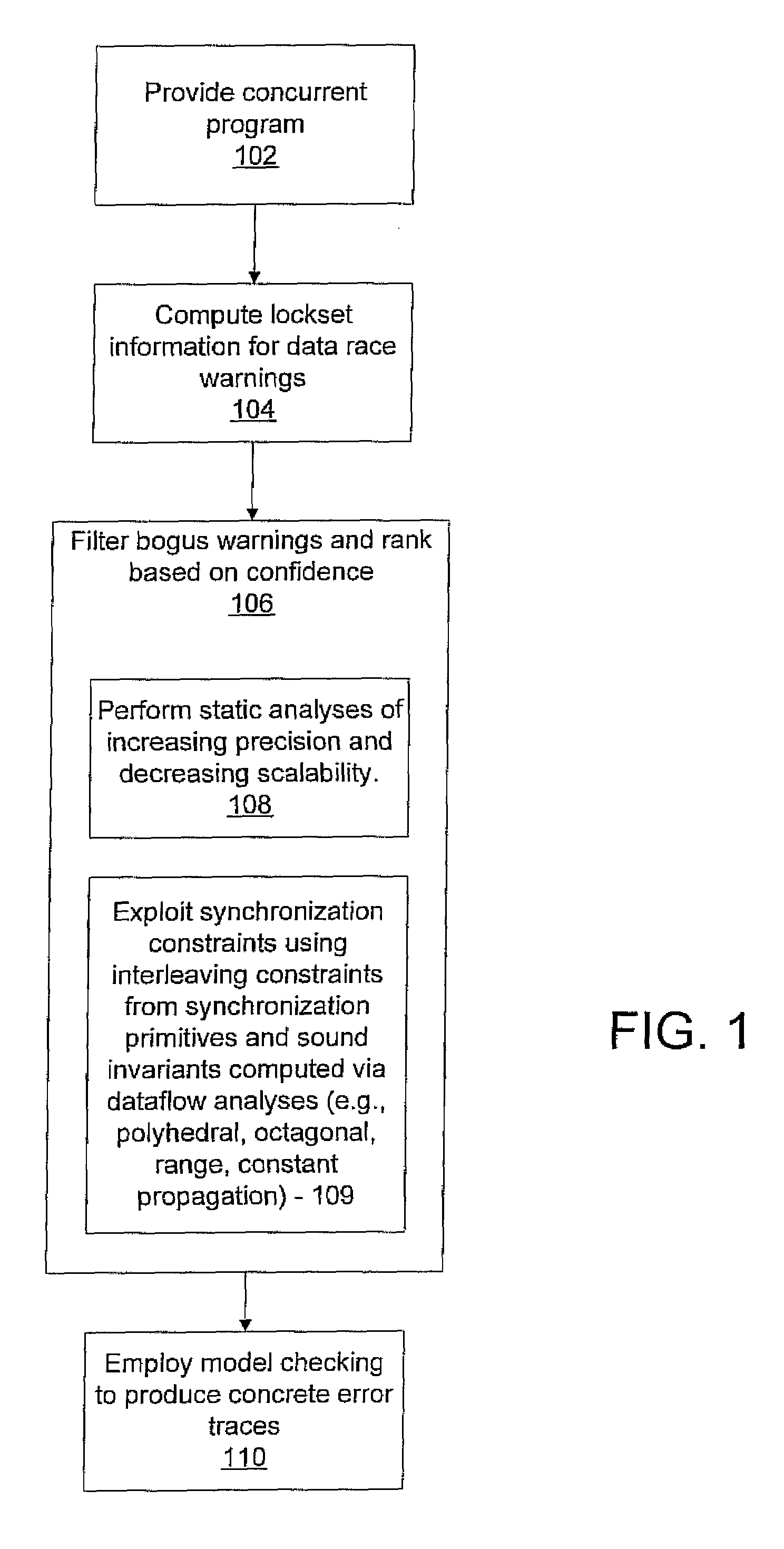
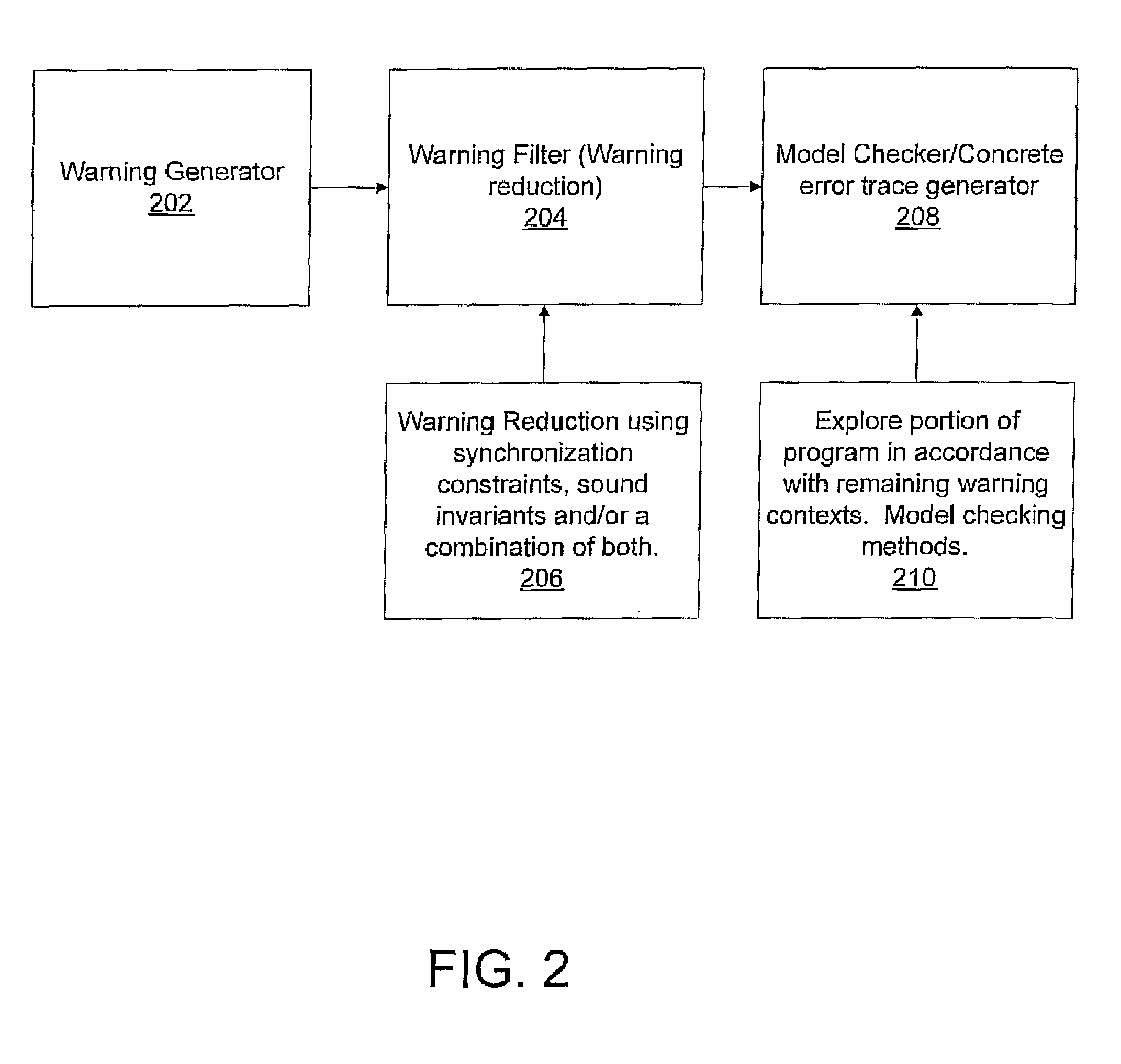
A system and method for program verification includes generating a product transaction graph for a concurrent program, which captures warnings for potential errors. The warnings are filtered to remove bogus warnings, by using constraints from synchronization primitives and invariants that are derived by performing one or more dataflow analysis methods for concurrent programs. The dataflow analysis methods are applied in order of overhead expense. Concrete execution traces are generated for remaining warnings using model checking.
Owner:NEC CORP
Programmatic validation in an information technology environment
InactiveUS20090172769A1User identity/authority verificationComputer security arrangementsProgram validationApplication software
Programmatically validating service level policies established for business applications of an Information Technology environment. The programmatic validation predicts whether the policies are achievable within the environment. Examples of service level policies include quantitative goals, redundancy levels and resource use.
Owner:IBM CORP
Nonvolatile Memory And Method With Reduced Program Verify By Ignoring Fastest And/Or Slowest Programming Bits
ActiveUS20100091573A1Reduce in quantityReduce the numberRead-only memoriesDigital storageComputer scienceNon-volatile memory
A group of non-volatile memory cells are programmed in a programming pass by a series of incremental programming pulses where each pulse is followed by a program-verify and possibly program-inhibition step. Performance is improved during the programming pass by delayed starting and prematurely terminating the various verify levels that demarcate the multiple memory states. This amounts to skipping the verifying and inhibiting steps of the fastest and slowest programming (fringe) cells of the group. A reference pulse is established when the fastest cells have all been program-verified relative to a first verify level. The starting of what verify level at what pulse will then be delayed relative to the reference pulse. Verifying stops for a given verify level when only a predetermined number of cells remain unverified relative to that given level. Any errors arising from over- or under-programming of the fringe cells are corrected by an error correction code.
Owner:SANDISK TECH LLC
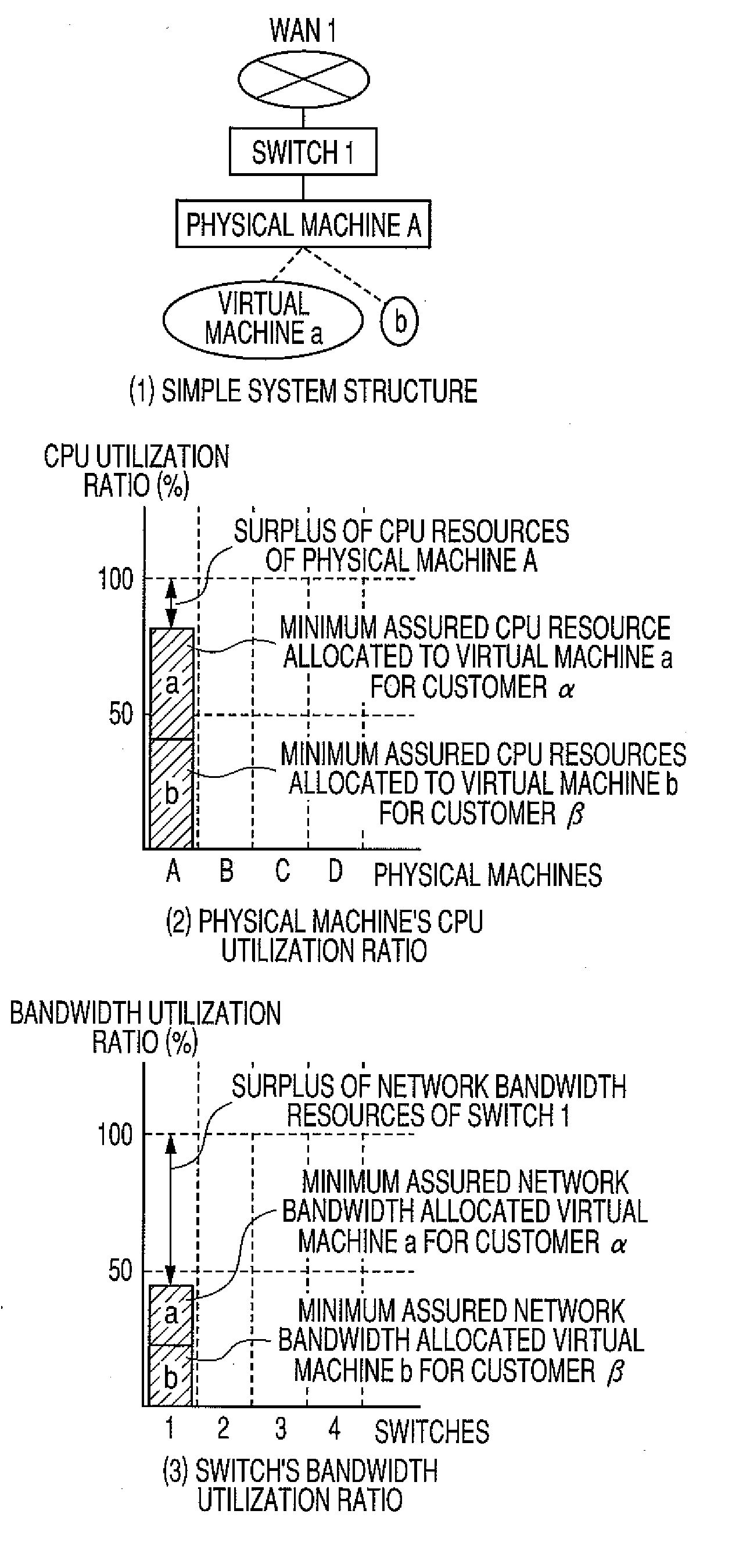
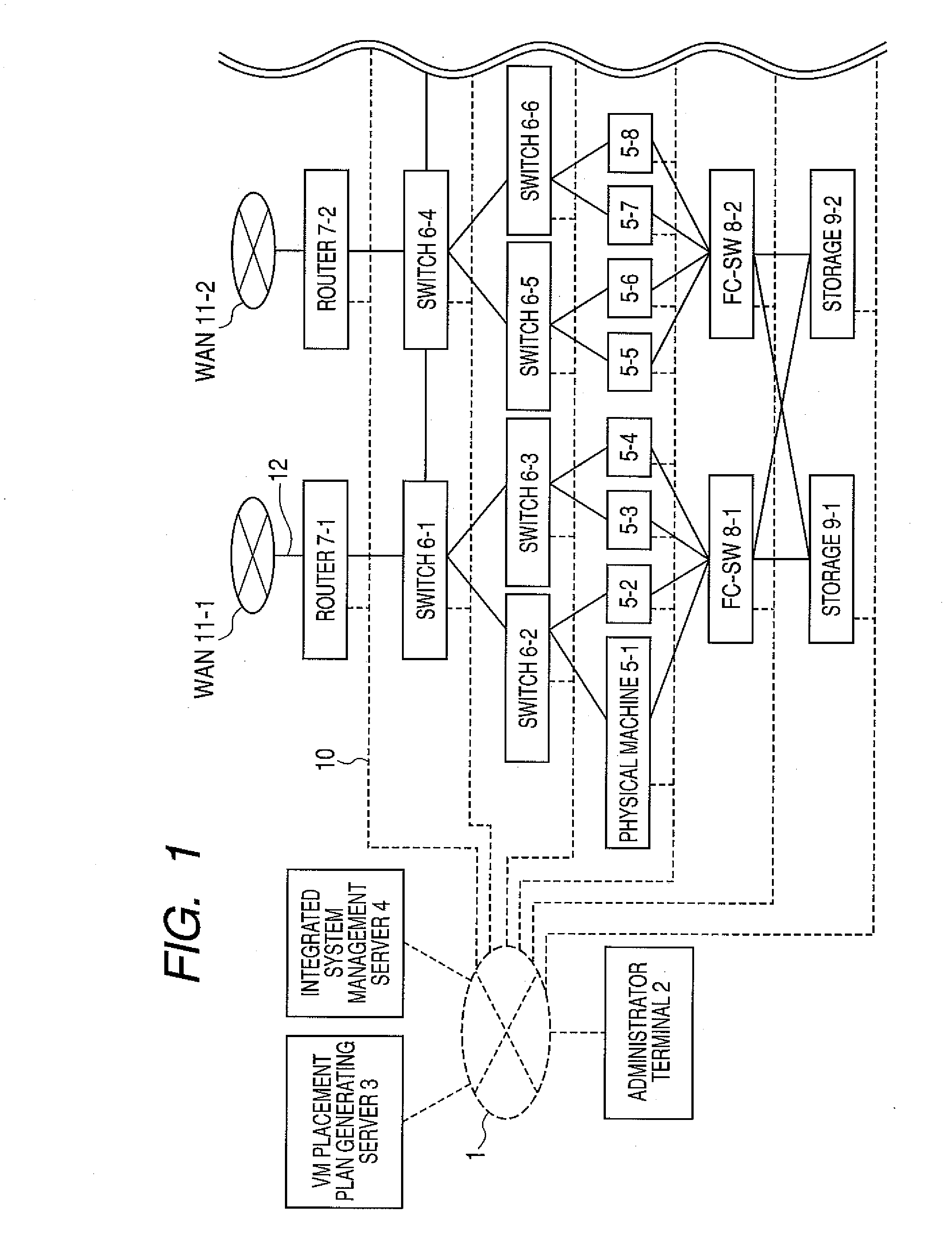
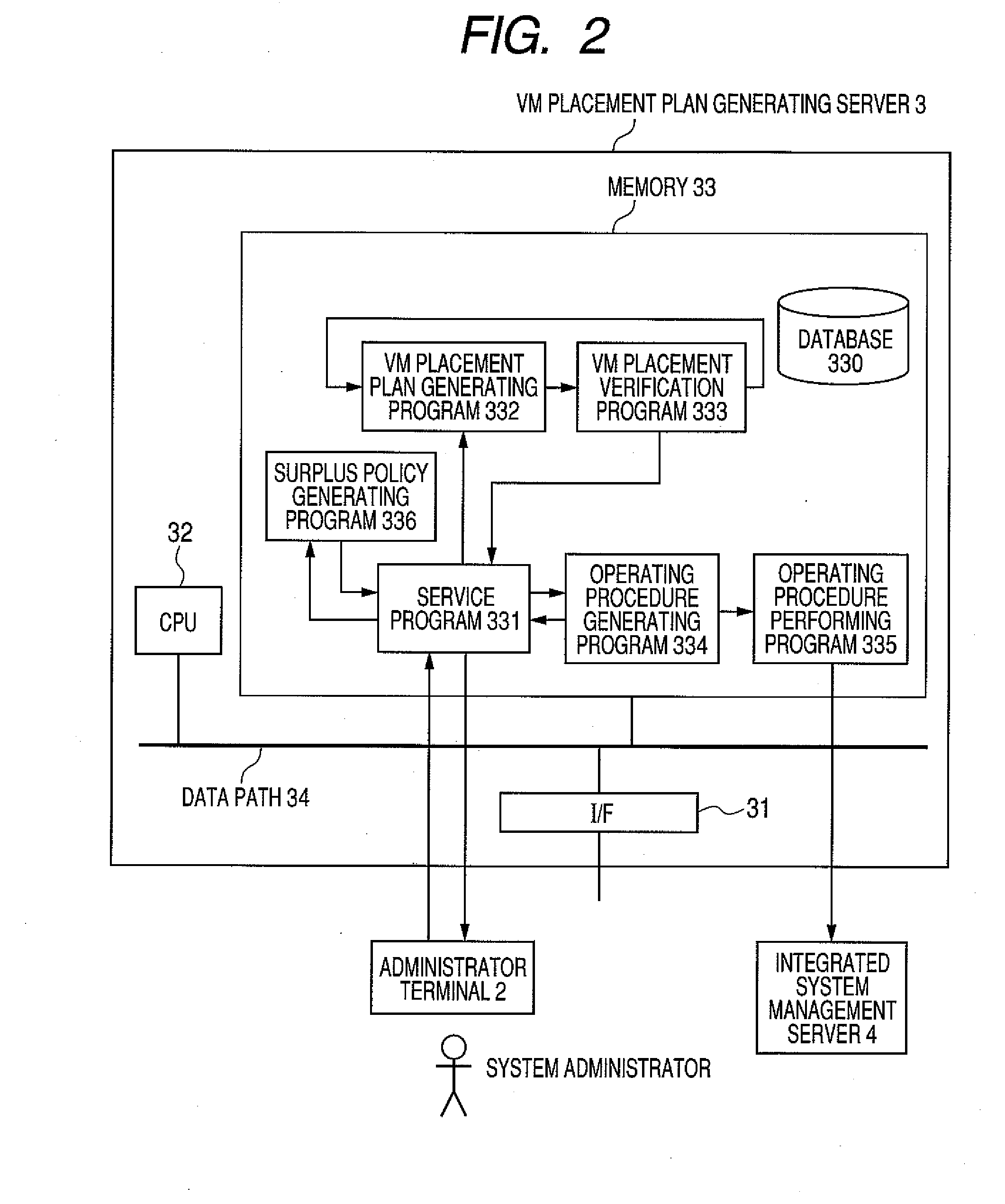
Surplus resource management system, method and server
InactiveUS20100161805A1Convenient reviewReduce the possibilityDigital computer detailsSoftware simulation/interpretation/emulationProgram validationProgram planning
In a system having physical machine resources and network component resources, a resource management technique is provided that is effective for deploying virtual machines utilizing these resources. A surplus policy regarding surplus resources is prepared as a parameter adjustable by the system administrator. A placement plan generating program at a VM placement plan generating server generates placement plans for virtual machines in response to alteration of the surplus policy. Then, a placement plan verification program at the VM placement plan generating server validates whether each of the created placement plans complies with the altered surplus policy. This validation is performed by simulating the amounts of utilization of both physical machine resources and network component resources. The VM placement plan generating server presents the placement plans that passed this validation, as those causing no problem in performance, to the system administrator through the use of an administrator terminal.
Owner:HITACHI LTD
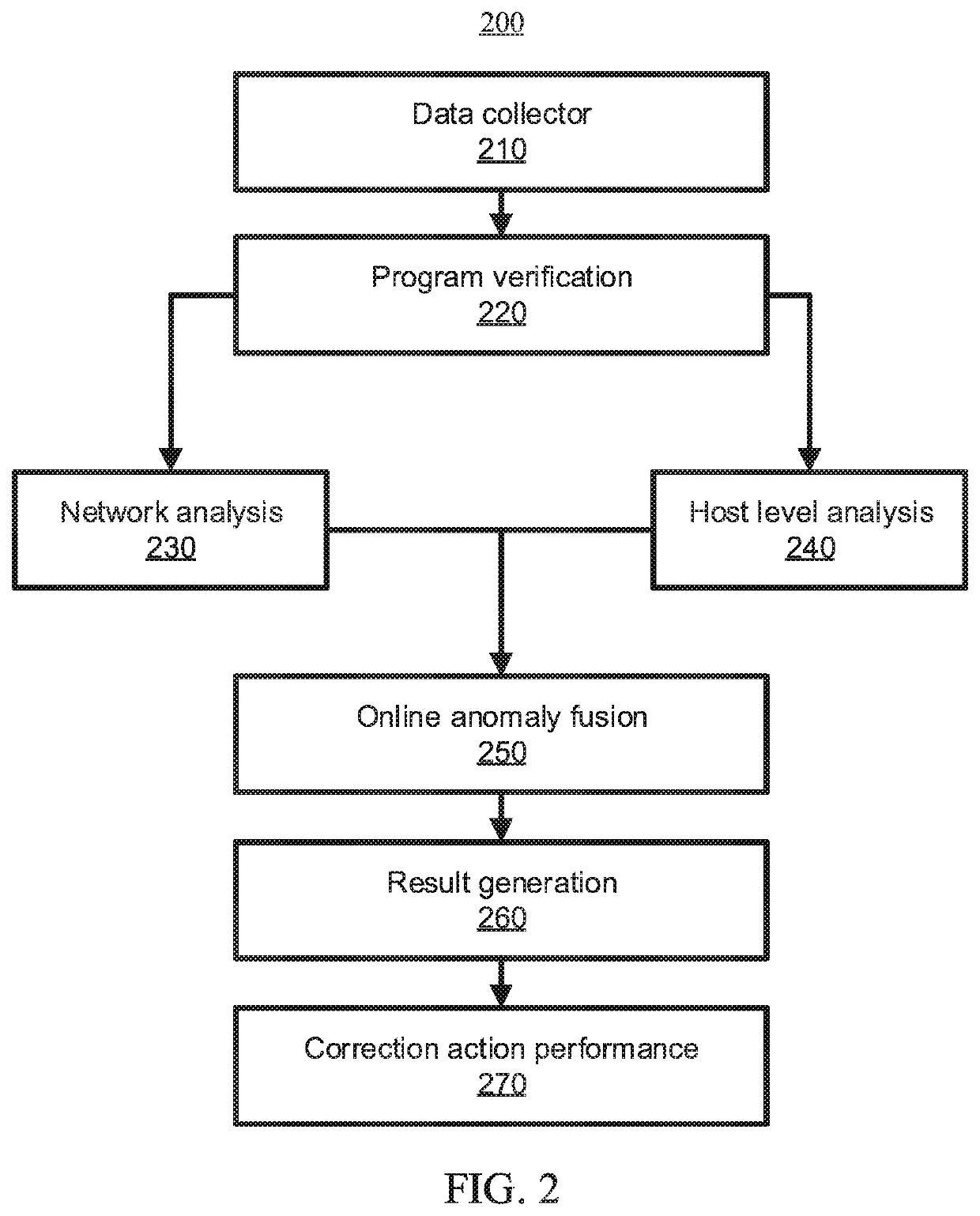
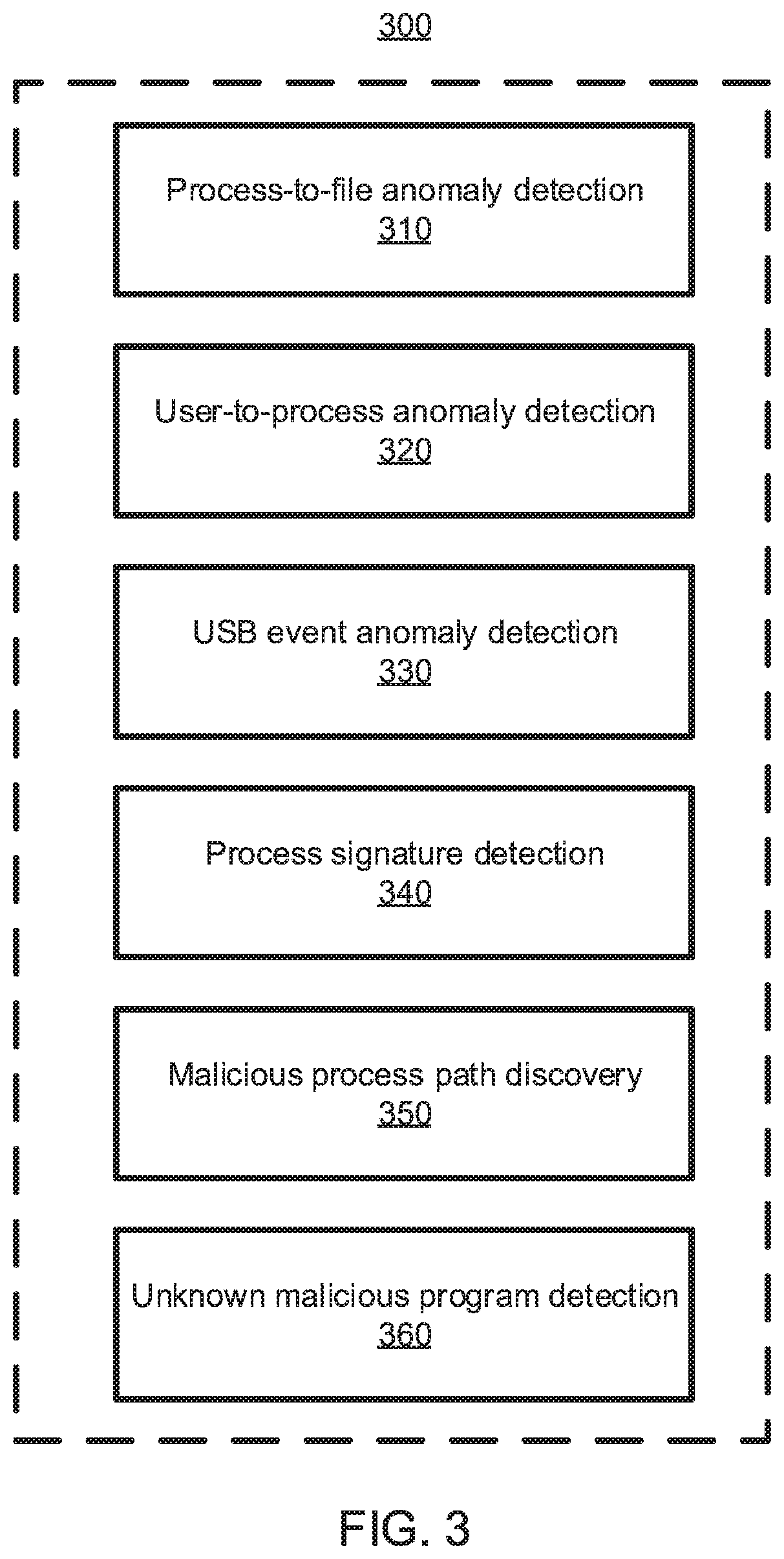
Unknown malicious program behavior detection using a graph neural network
ActiveUS20200137083A1Character and pattern recognitionComputer security arrangementsNerve networkProgram validation
A method for detecting malicious program behavior includes performing program verification based on system activity data, analyzing unverified program data identified from the program verification to detect abnormal events, including analyzing host-level events to detect abnormal host-level events by learning a program representation as a graph embedding through an attentional architecture based on an invariant graph between different system entities, generating detection results based on the analysis, and performing at least one corrective action based on the detection results.
Owner:NEC CORP
Information processing device, program verification method, and recording medium
InactiveUS20090138729A1Unauthorized memory use protectionHardware monitoringInformation processingProgram validation
A first storage unit stores a plurality of security functions each defining a first protection attribute requiring a storage of a value of an argument for input / output of data. A second storage unit stores a program list describing a second protection attribute of a variable indicating a storage area of the data and an executing procedure of a predetermined process. An identifying unit identifies a third protection attribute of an actual argument for input / output of a security function based on the second protection attribute. When a judging unit judges not all of third protection attributes match with first protection attributes, an output unit outputs error information indicating a mismatch of the protection attributes.
Owner:KK TOSHIBA
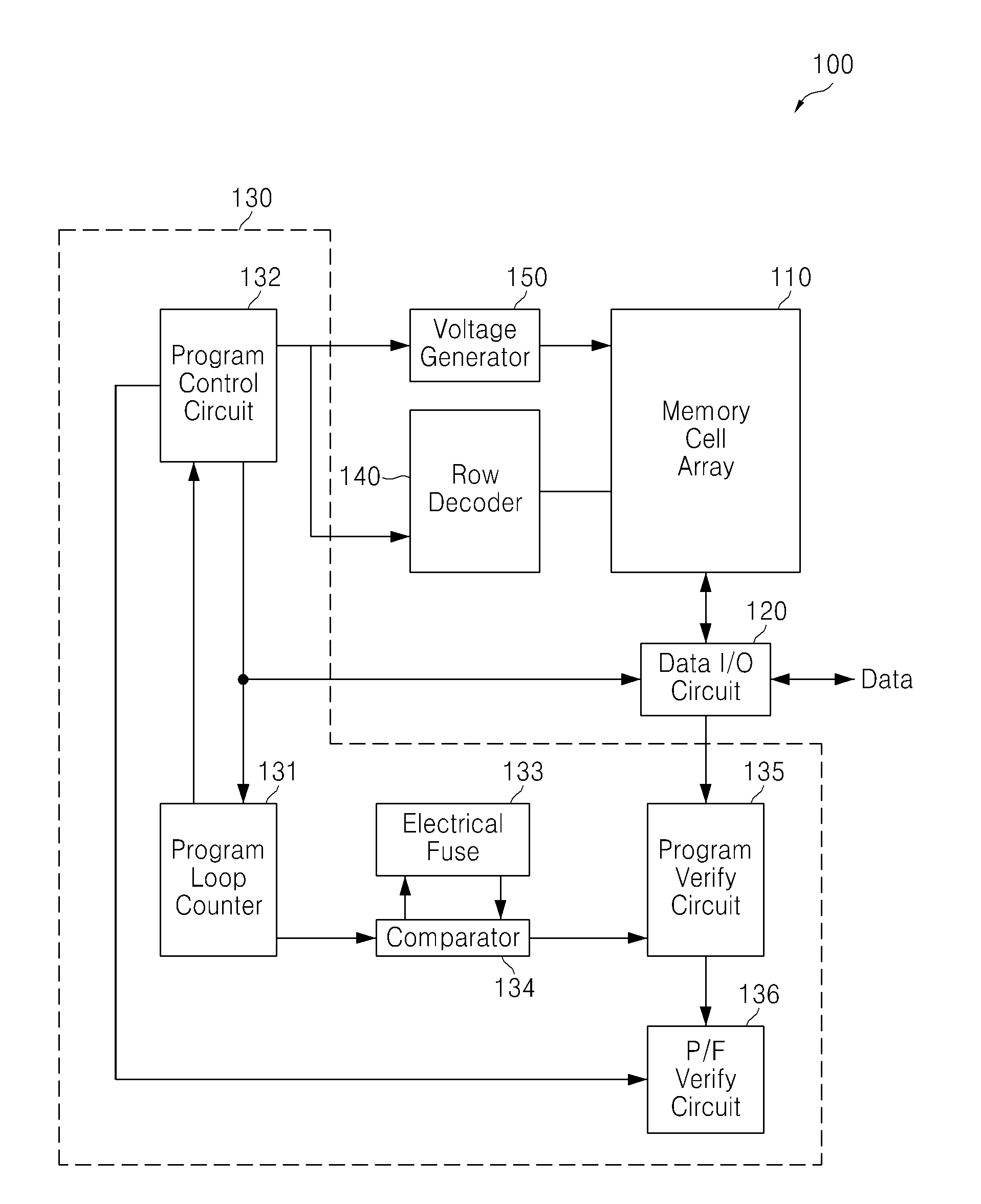
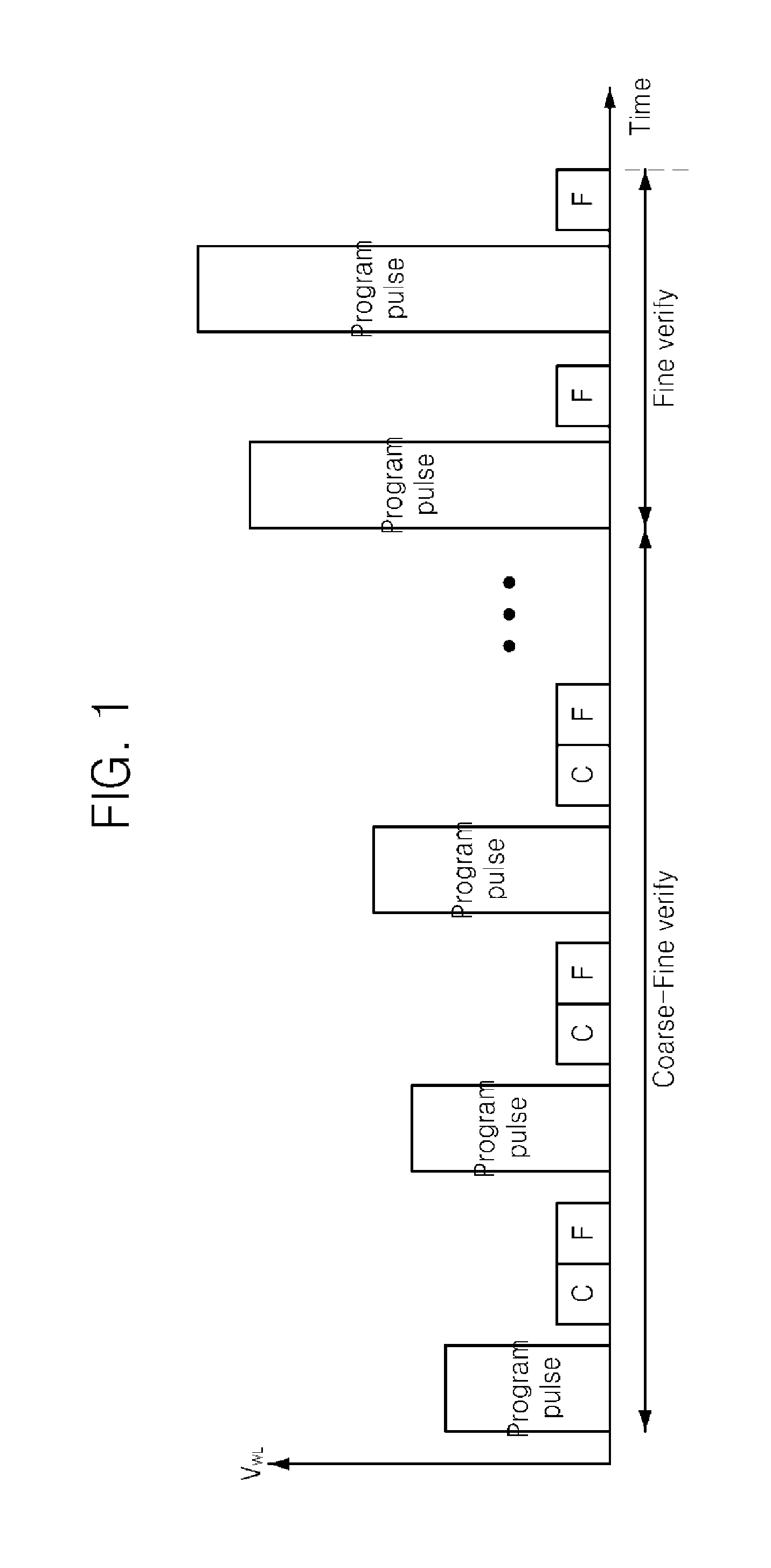
Flash memory device and related program verification method
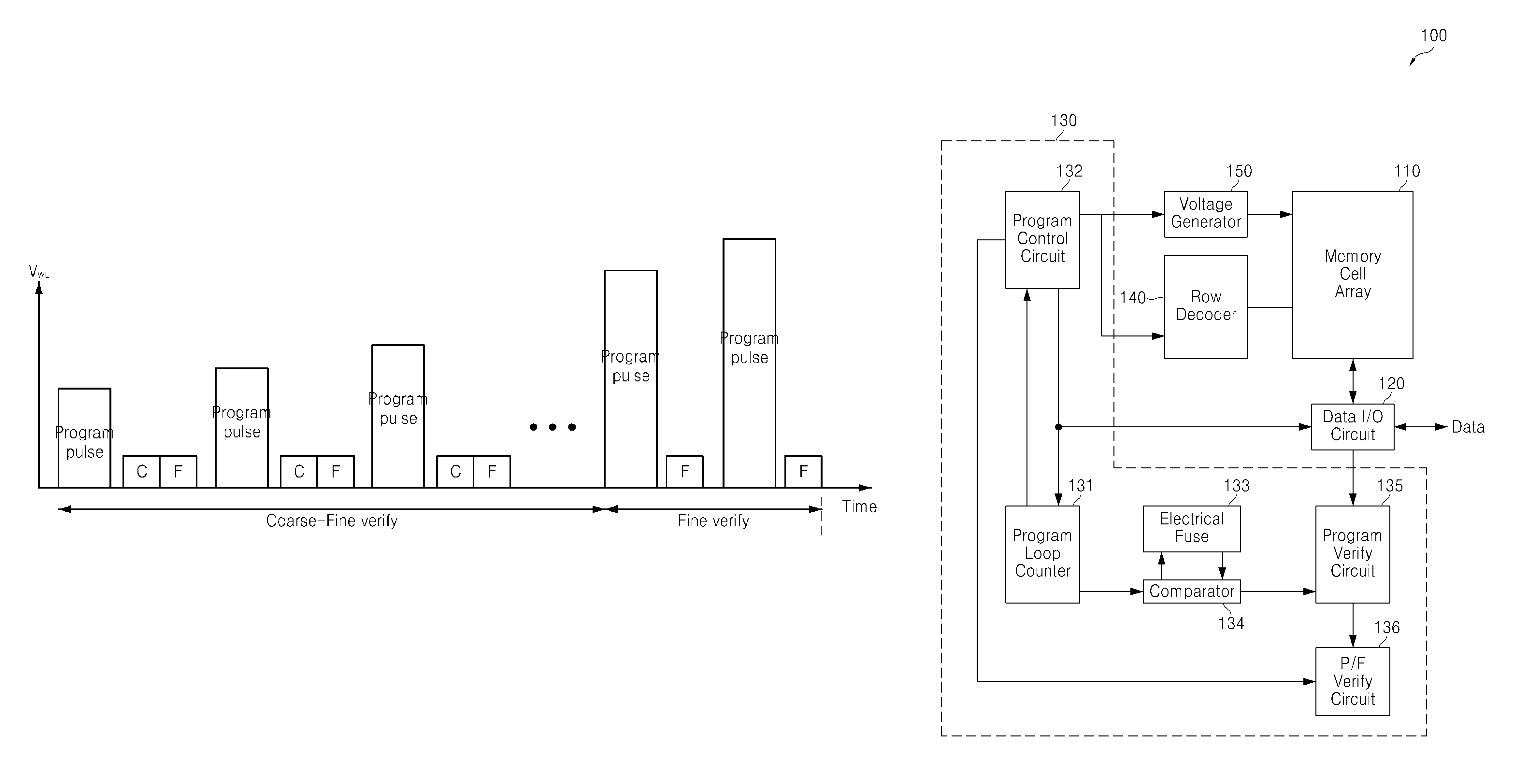
ActiveUS20120069674A1Improve reliabilityReducing common source line noiseRead-only memoriesDigital storageNon-volatile memoryLoop counter
A nonvolatile memory device performs a program operation using an incremental pulse programming (ISPP) scheme in which a plurality of program loops alternate between a coarse-fine verify operation, and a fine verify operation according to a value of a program loop counter.
Owner:SAMSUNG ELECTRONICS CO LTD
Method, system and computer program for automated hardware design debugging
InactiveUS20080127009A1Bulky designEasy to handleError detection/correctionComputer aided designComputer hardwareComputer architecture
The present invention provides a method, system and computer program for automated debugging for pre-fabricated digital synchronous hardware designs implemented in Hardware Description Language (HDL). Required information is captured by interacting with the verification environment after verification fails. This capture information is used to build a diagnosis problem where the solution is a set of logic level error sources. Using the HDL information, the error at the logic level is translated to gates, modules, statements, and signals in the HDL description. The diagnosis problem can be solved efficiently formulating a Quantified Boolean Formula (QBF) problem and also by using the hierarchical and modular nature of the HDL design during diagnosis.
Owner:VENERIS ANDREAS +3
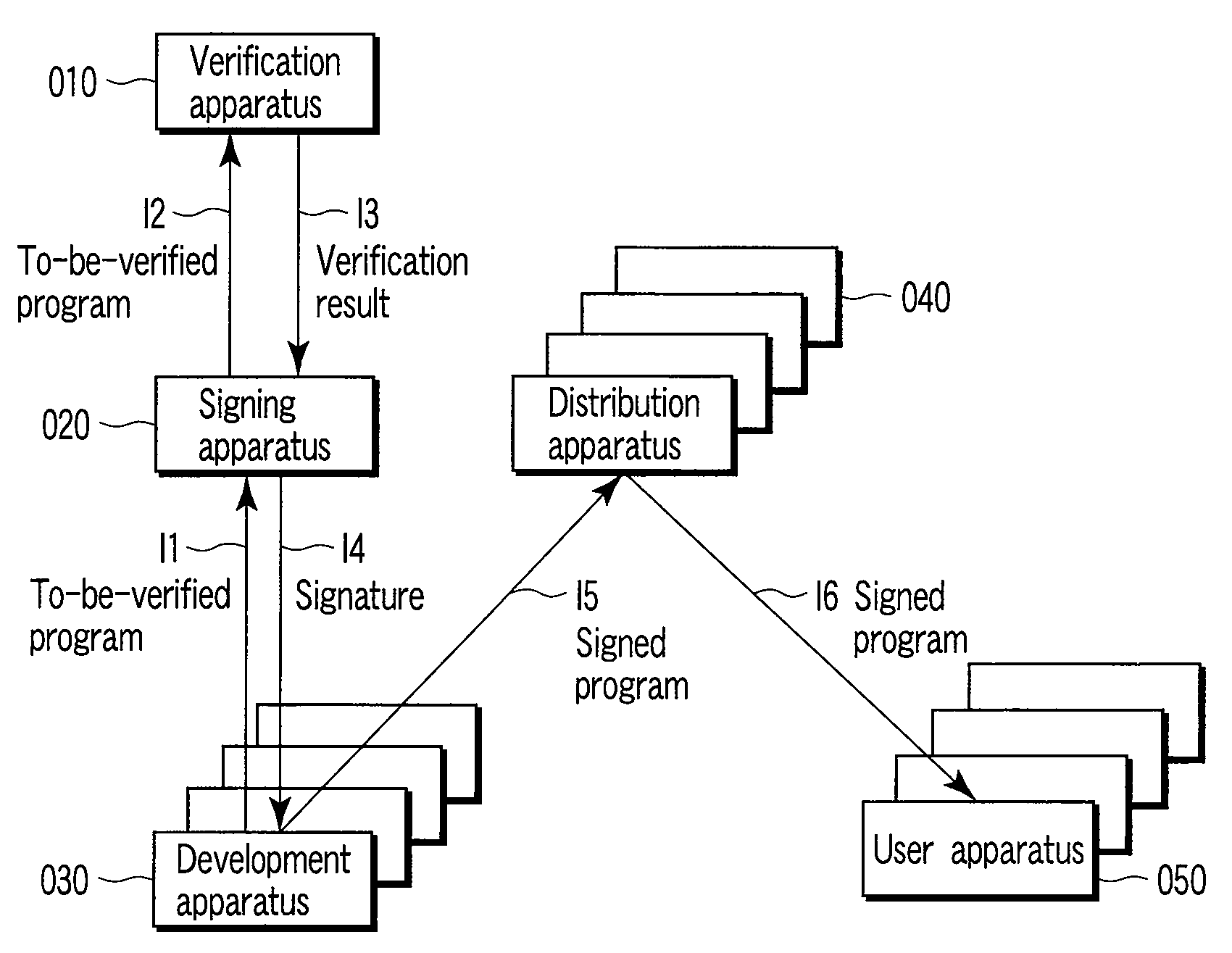
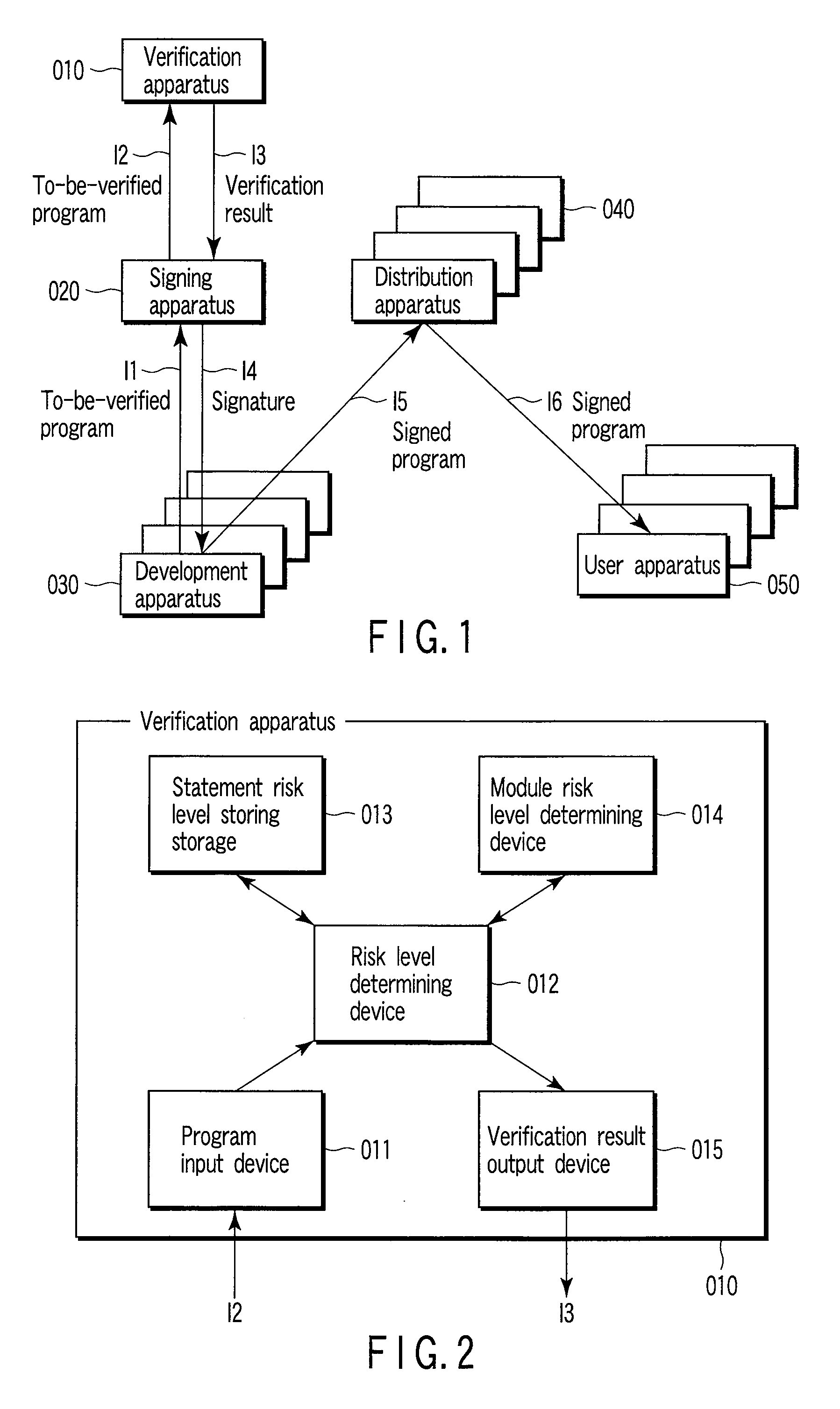
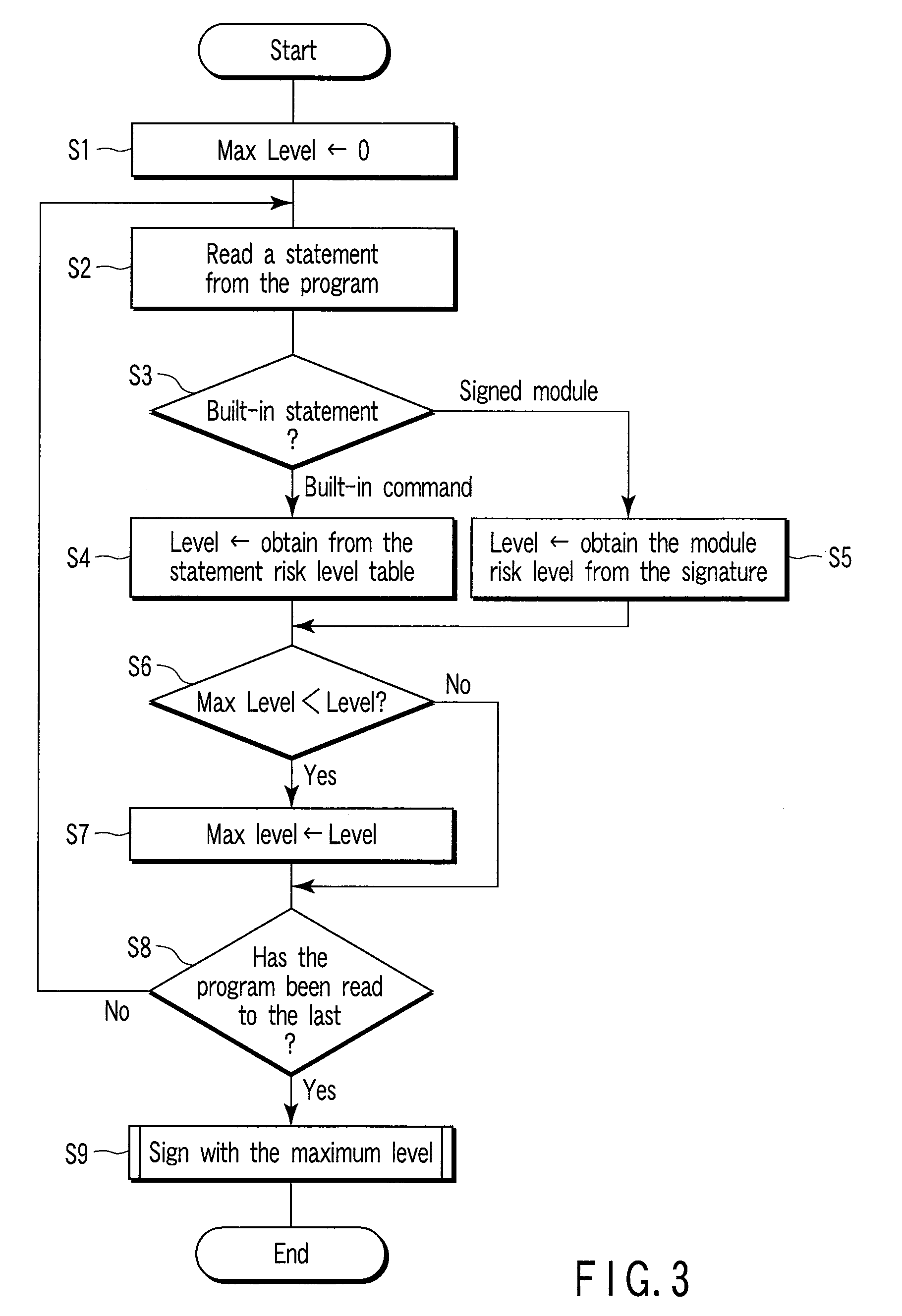
Program verification apparatus and method, and signature system based on program verification
InactiveUS20080168533A1TransmissionProgram/content distribution protectionRisk levelProgram validation
A program verification apparatus includes a storing which stores a plurality of statements in correspondence with values of respective risk levels of the statements. Referring to a signature included in a signed module, a value indicating a risk level of the signed module is obtained. A to-be-verified program including a plurality of statements or signed modules is input to the apparatus. Values of first risk levels of the statements included in the to-be-verified program are determined by referring to the storing device. Values of second risk levels of the signed modules included in the to-be-verified program are also determined. Then, a maximum value of a risk level of the to-be-verified program is calculated from the values of the first risk levels and the values of the second risk levels. A verification result including the maximum value of the risk level is outputted accordingly.
Owner:KK TOSHIBA
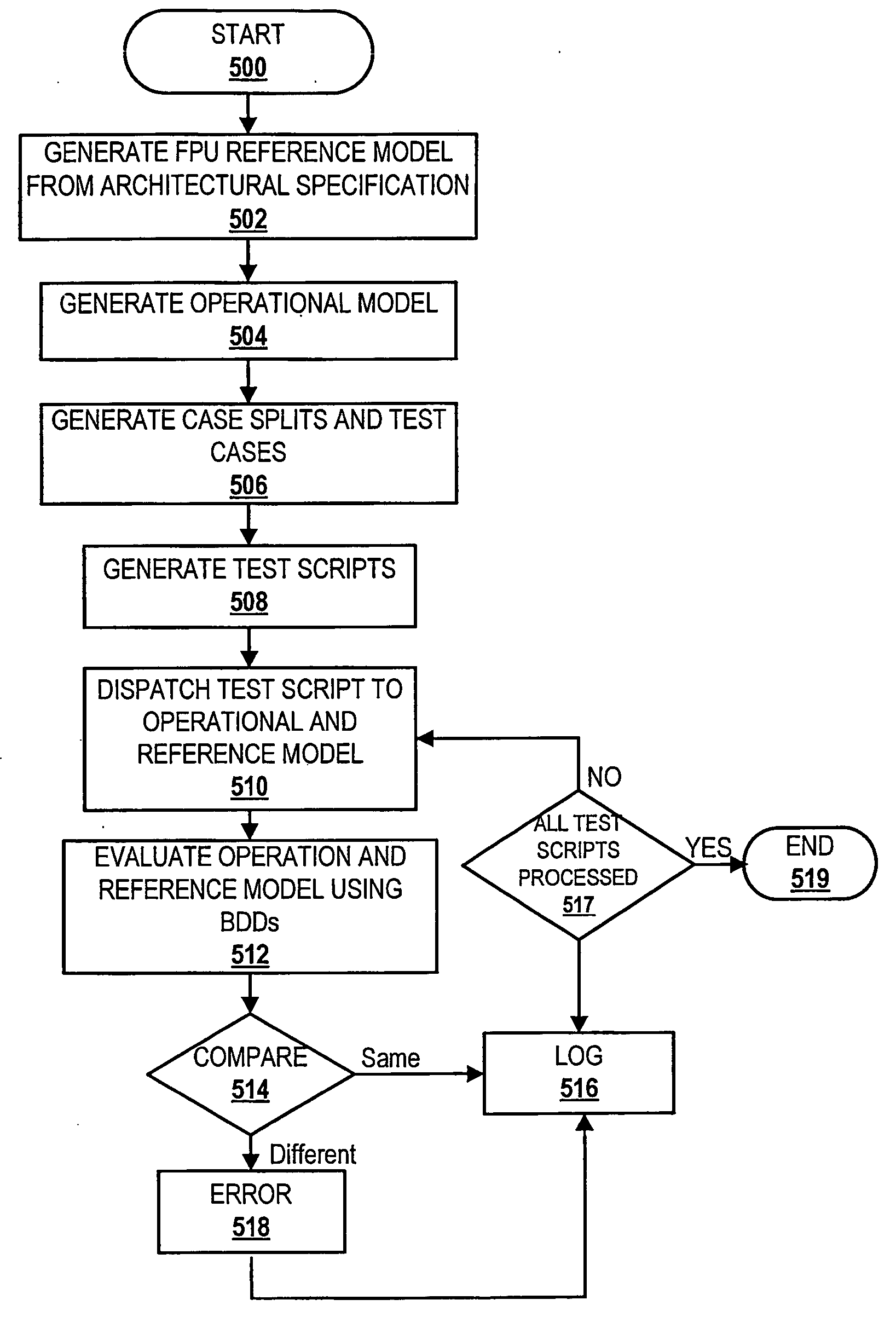
Method, system and computer program product for verification of digital designs using case-splitting via constrained internal signals
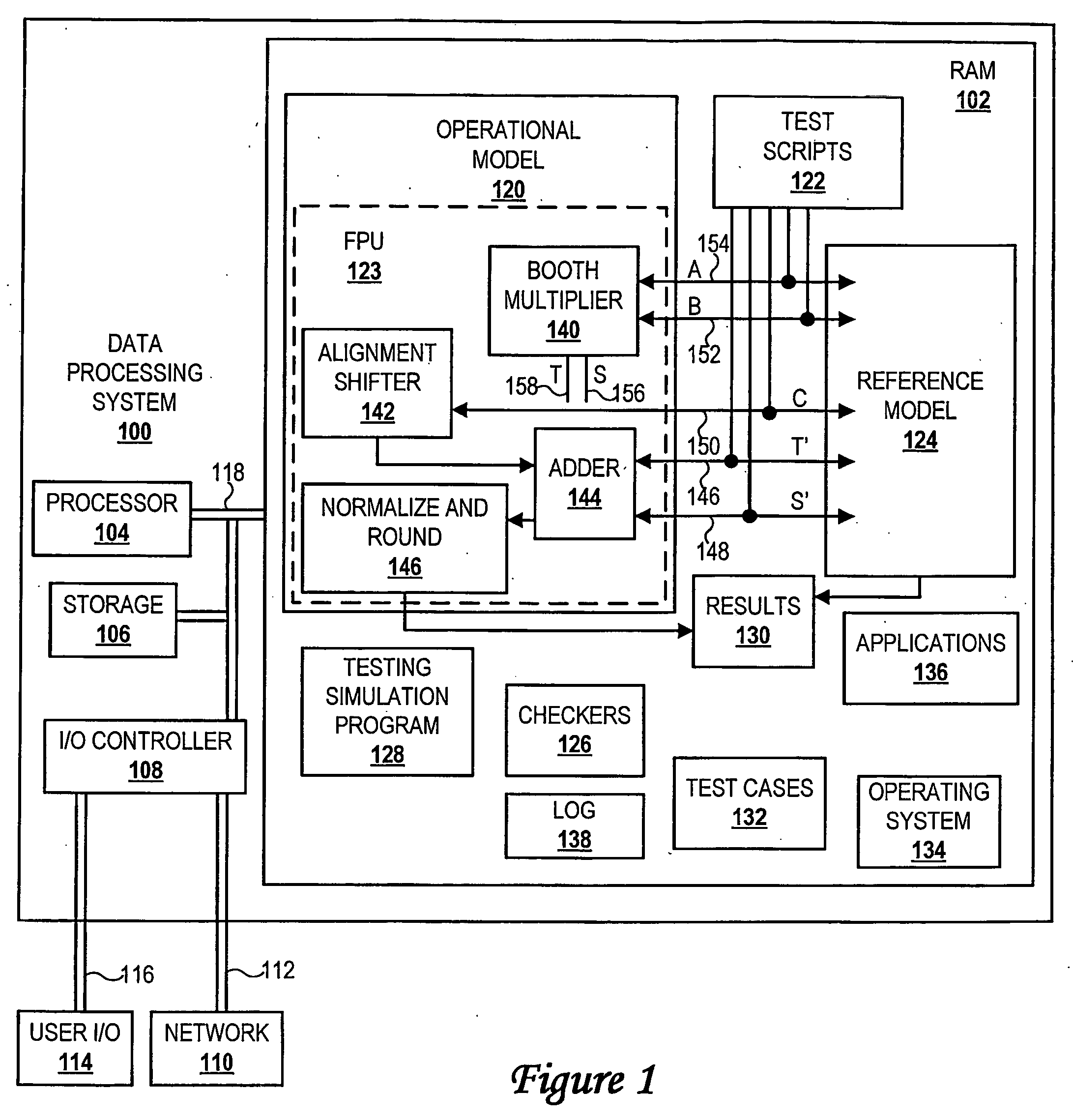
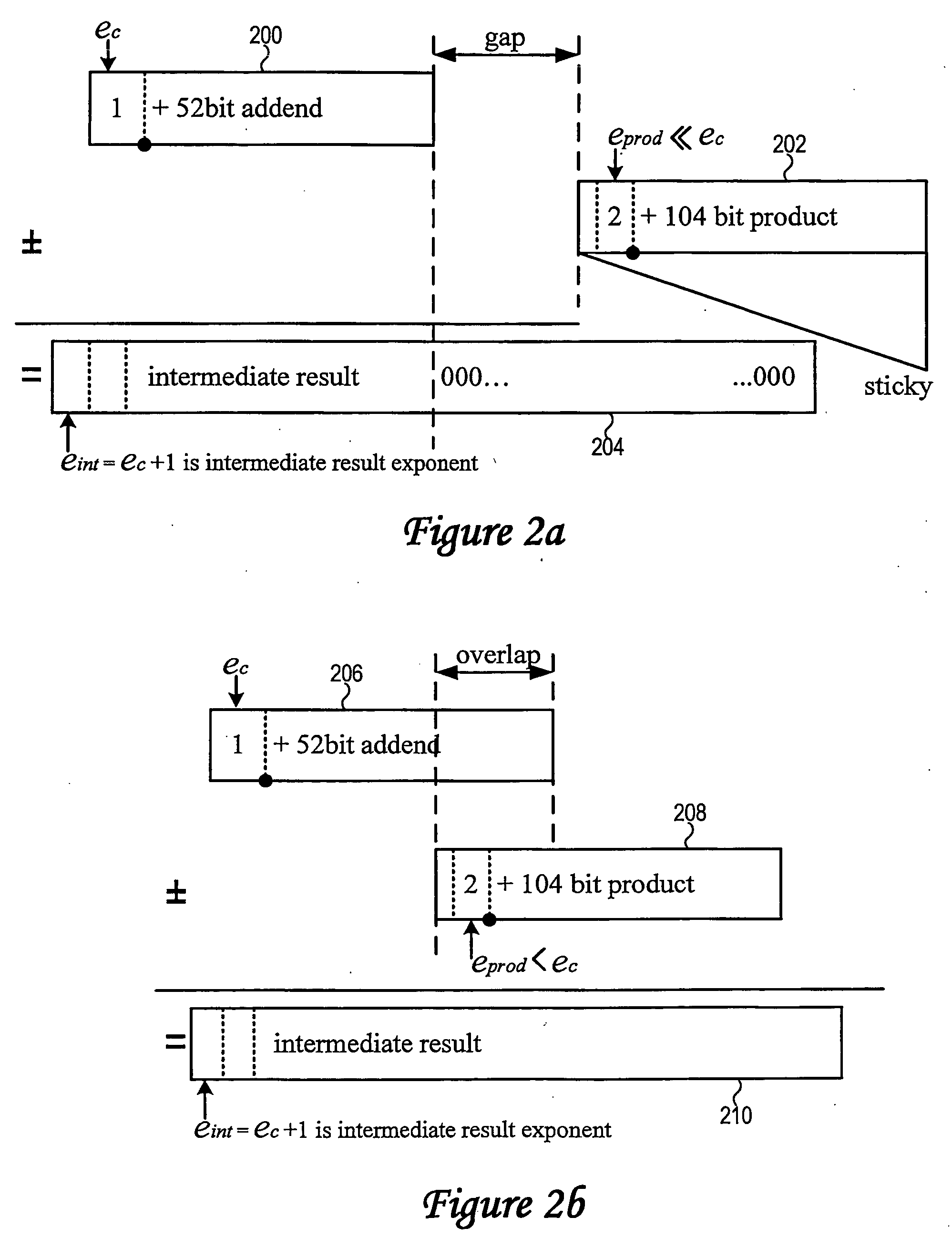
InactiveUS20060122817A1CAD circuit designSoftware simulation/interpretation/emulationReference modelTest script
A method of verifying a digital design is disclosed. The method comprises generating a reference model for a first digital design and creating an operational model for a second digital design, wherein the first digital design and the second digital design are intended to have a same logical function. A plurality of testcase types are then created by constraining one or more internal signals, and one or more test scripts representing the plurality of testcase types are produced. The method also includes verifying the second digital design with a testing simulation program by comparing results of the test scripts from the operational model and the reference model.
Owner:GLOBALFOUNDRIES INC
Method and system for monitoring and verifying software drivers
InactiveUS20060248542A1Error detection/correctionMultiprogramming arrangementsProgram validationComputerized system
A method and system for verifying computer system drivers such as kernel mode drivers. A driver verifier sets up tests for specified drivers and monitors the driver's behavior for selected violations that cause system crashes. In one test, the driver verifier allocates a driver's memory pool allocations from a special pool bounded by inaccessible memory space to test for the driver's accessing memory outside of the allocation. The driver verifier also marks the space as inaccessible when it is deallocated, detecting a driver that accesses deallocated space. The driver verifier may also provide extreme memory pressure on a specific driver, or randomly fail requests for pool memory. The driver verifier also checks call parameters for violations, performs checks to ensure a driver cleans up timers when deallocating memory and cleans up memory and other resources when unloaded. An I / O verifier is also described for verifying drivers use of I / O request packets.
Owner:ZHIGU HLDG
Data structure, recording medium, authoring apparatus, method, and program, recording apparatus, method, and program, verification apparatus, method, and program, and manufacturing apparatus and method for recording medium
InactiveUS20070280641A1Television system detailsElectronic editing digitised analogue information signalsTime informationProgram validation
A data structure includes content data and accompanying data which is formed on the basis of a plurality of first units, the accompanying data being used for displaying information accompanying the content data. Among the first units in which time information is defined, the time of a target first unit based on the order of the first units is set to be later than the decoding time defined in the first unit arranged in the order earlier than the target first unit by an amount equal to N first units where N indicates the upper limit of the number of first units that can be stored in a buffer provided for a decoder for decoding the first units.
Owner:SONY CORP
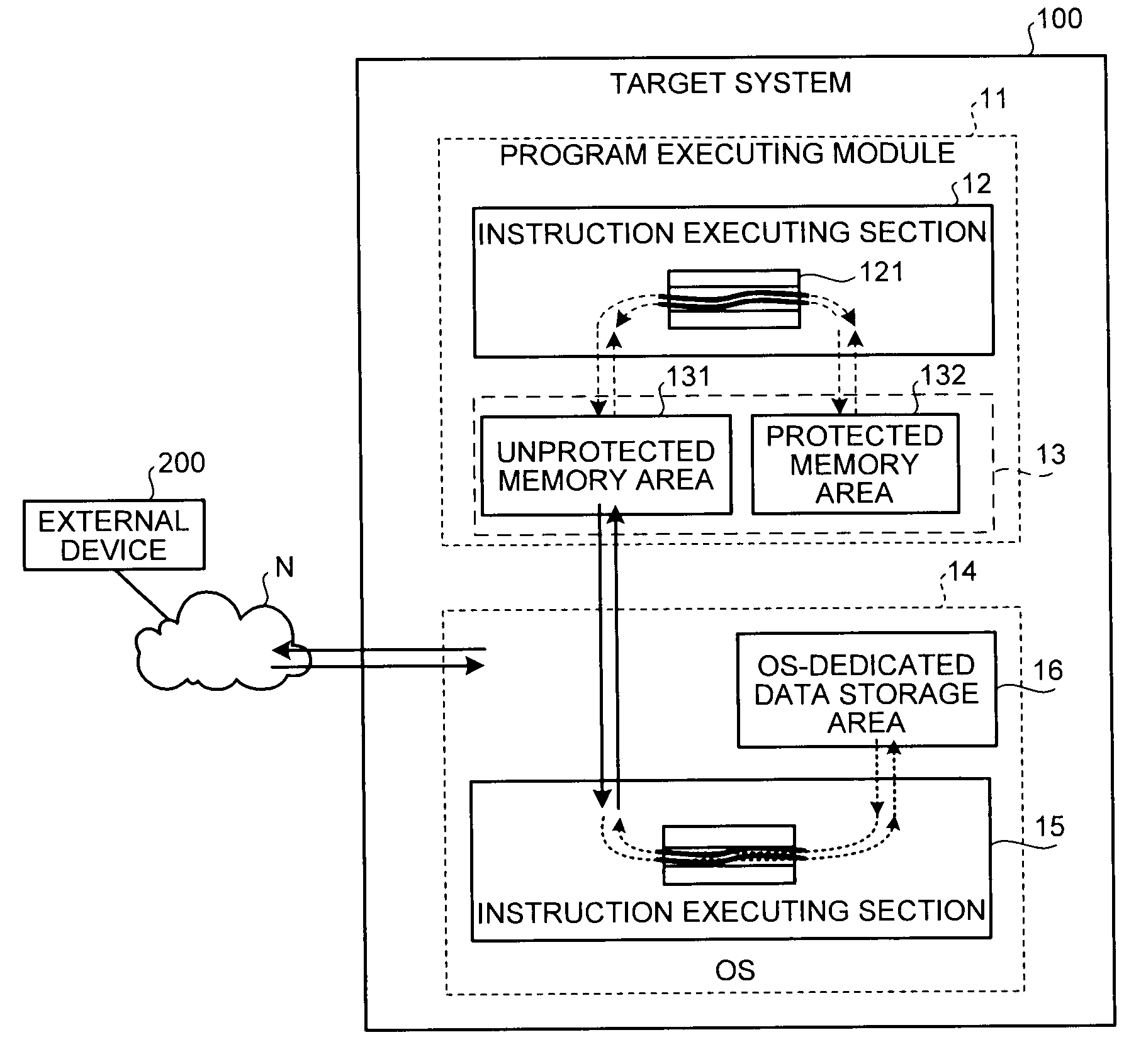
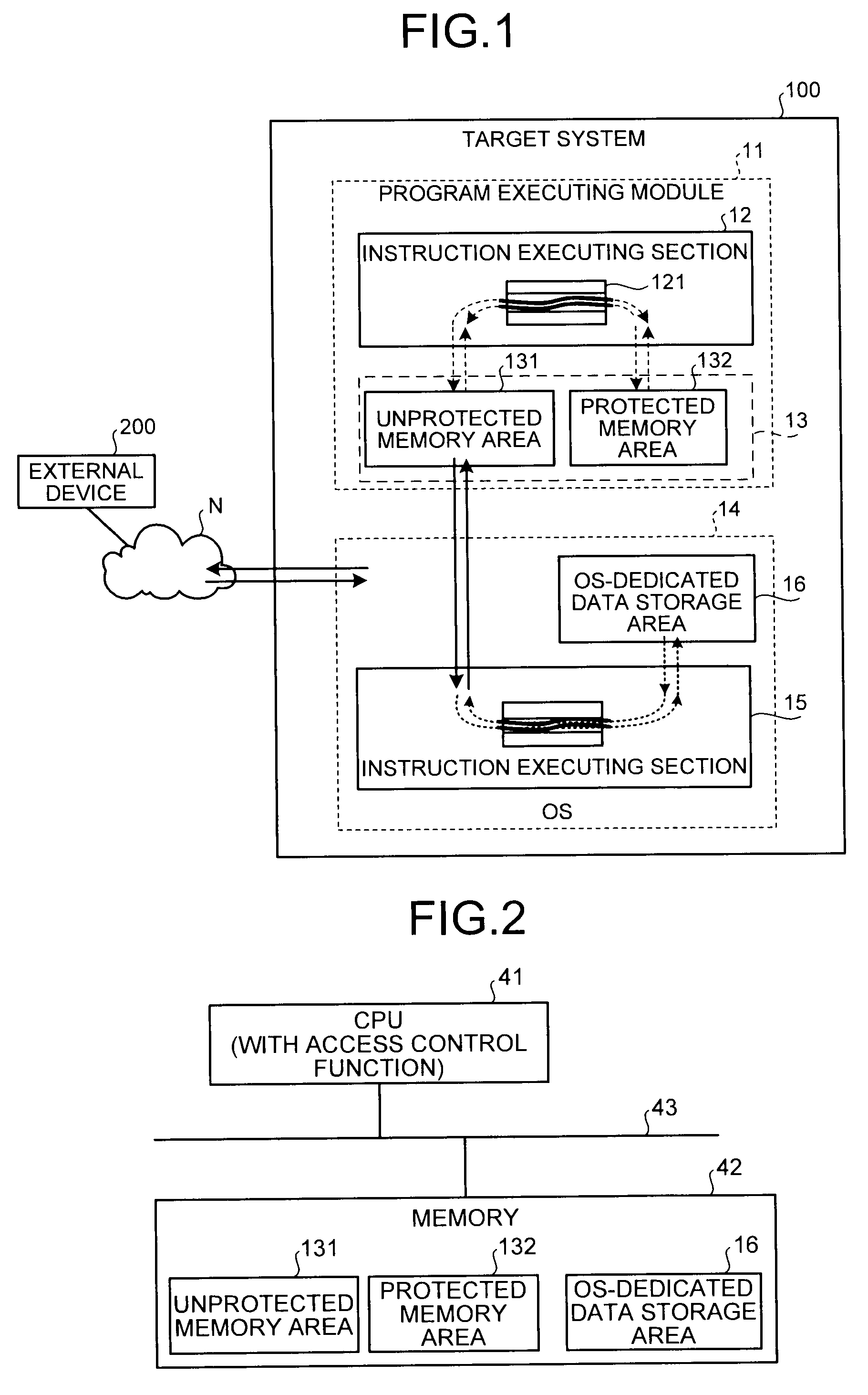
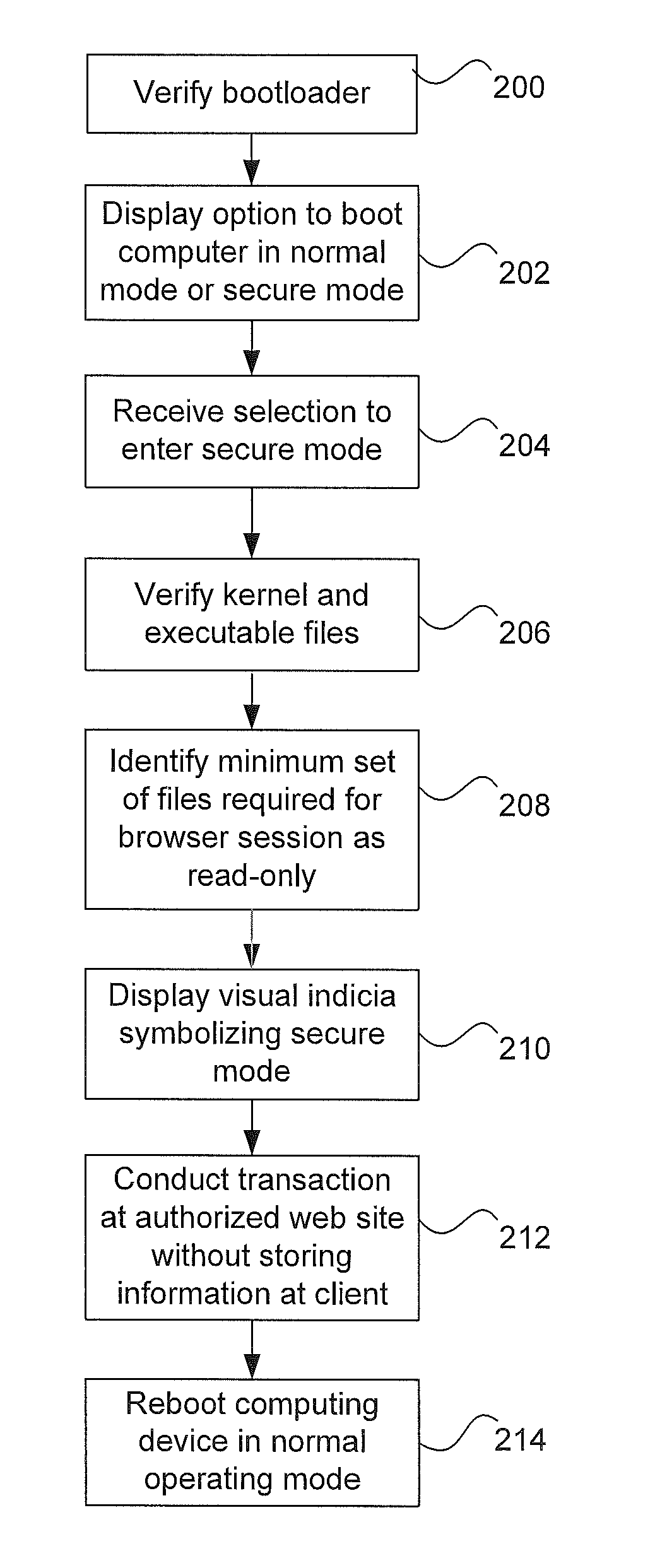
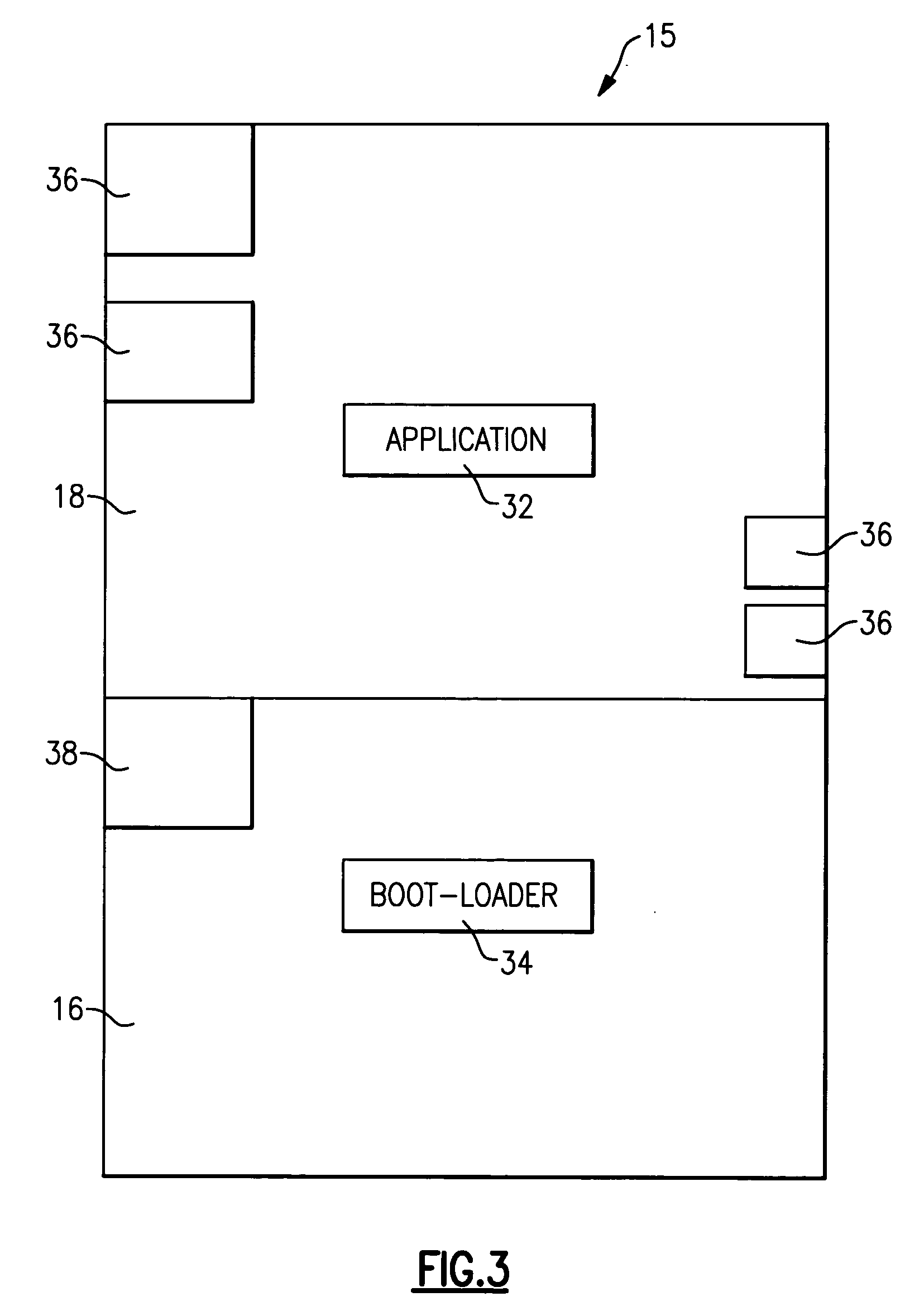
System and method for operating a computing device in a secure mode
ActiveUS8700895B1Memory loss protectionDigital data processing detailsOperational systemProgram validation
A computing device operates in a secure operating mode in response to user selection. Computer hardware is initialized to verify a bootloader of an operating system, and the bootloader verifies the operating system kernel. The kernel then verifies operating-system level executable files. After verification, a limited set of the verified files is loaded into a portion of the memory that is subsequently marked by the kernel as read-only. These files are executed to provide a basic Internet browser session; all other files are identified as non-executable. When the user accesses an authorized website and conducts a transaction that requires a user to provide information, the information is encrypted during transmission of the network. In addition, such information cannot be accessed by other parties since the information provided is not persisted at the computing device.
Owner:GOOGLE LLC
System and method for providing graphical representation and development of a processing application
ActiveUS7512840B2Good serviceError detection/correctionNatural language data processingChange managementWeb service
A system and methods are provided for operating and building graphically XML processing programs, guiding the user in development of the program, preventing and detecting development errors as the program is being designed, ensuring that the program is valid, i.e. satisfies required input and output constraints at all times, i.e. from the time it is developed to when it is deployed in a production environment, ensuring the automated change management if the internal logic of the Web service, or data sources called by the service or the schema that underlies the Web service are modified. The system includes a graphical XML Programming system where XML processing programs are built and represented in a graphical fashion, a real-time metadata computation and visualization method for each selected execution point in the visual program that provides guided programming, error prevention and detection, and change impact analysis and change management, and, an automated execution path exploration method that enables overall program validation and error identification. The system and methods allow a user to reduce by at least a factor of 2 the costs of development and maintenance of reliable XML processing programs such as Web Services.
Owner:DIEBOLD NIXDORF
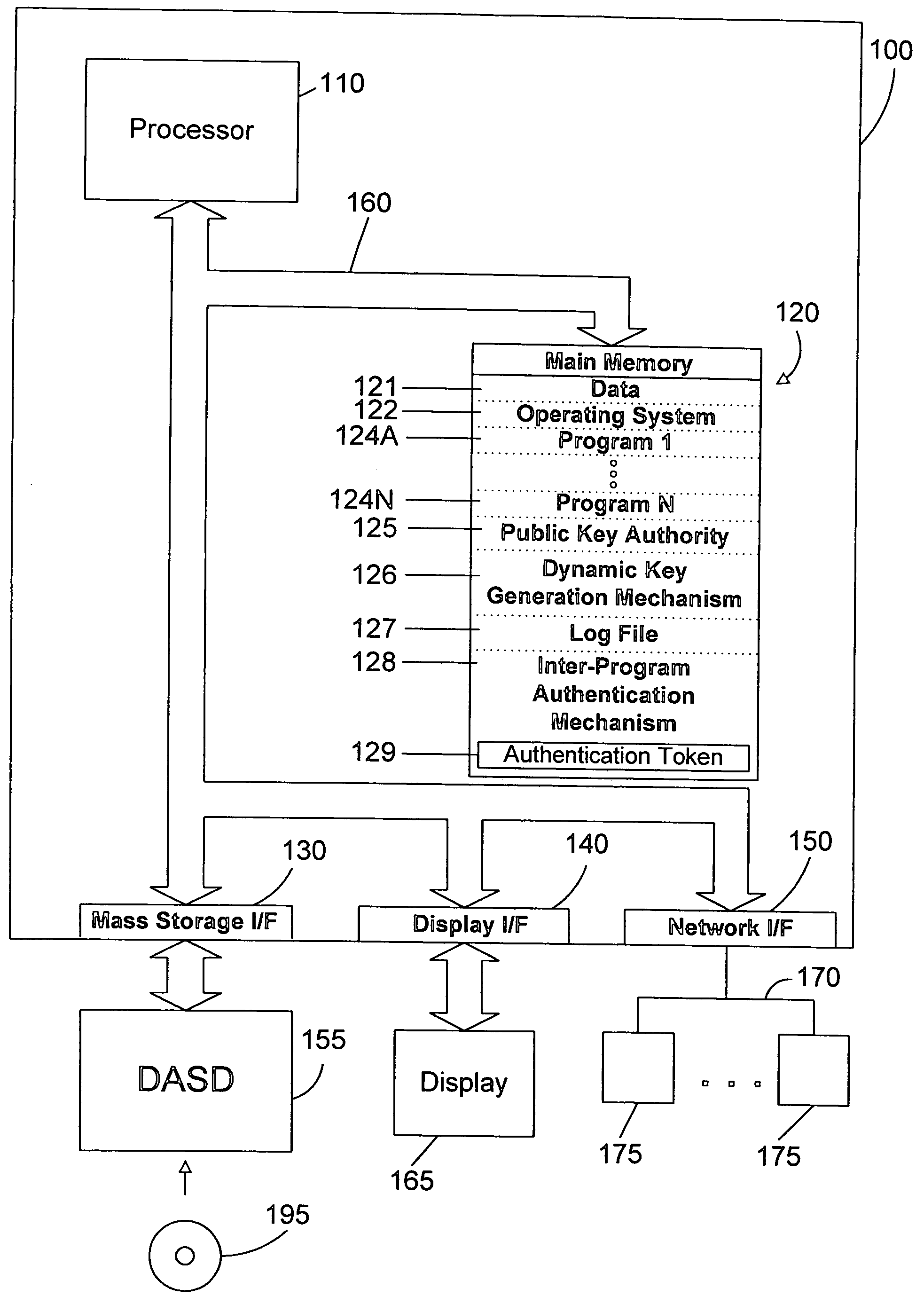
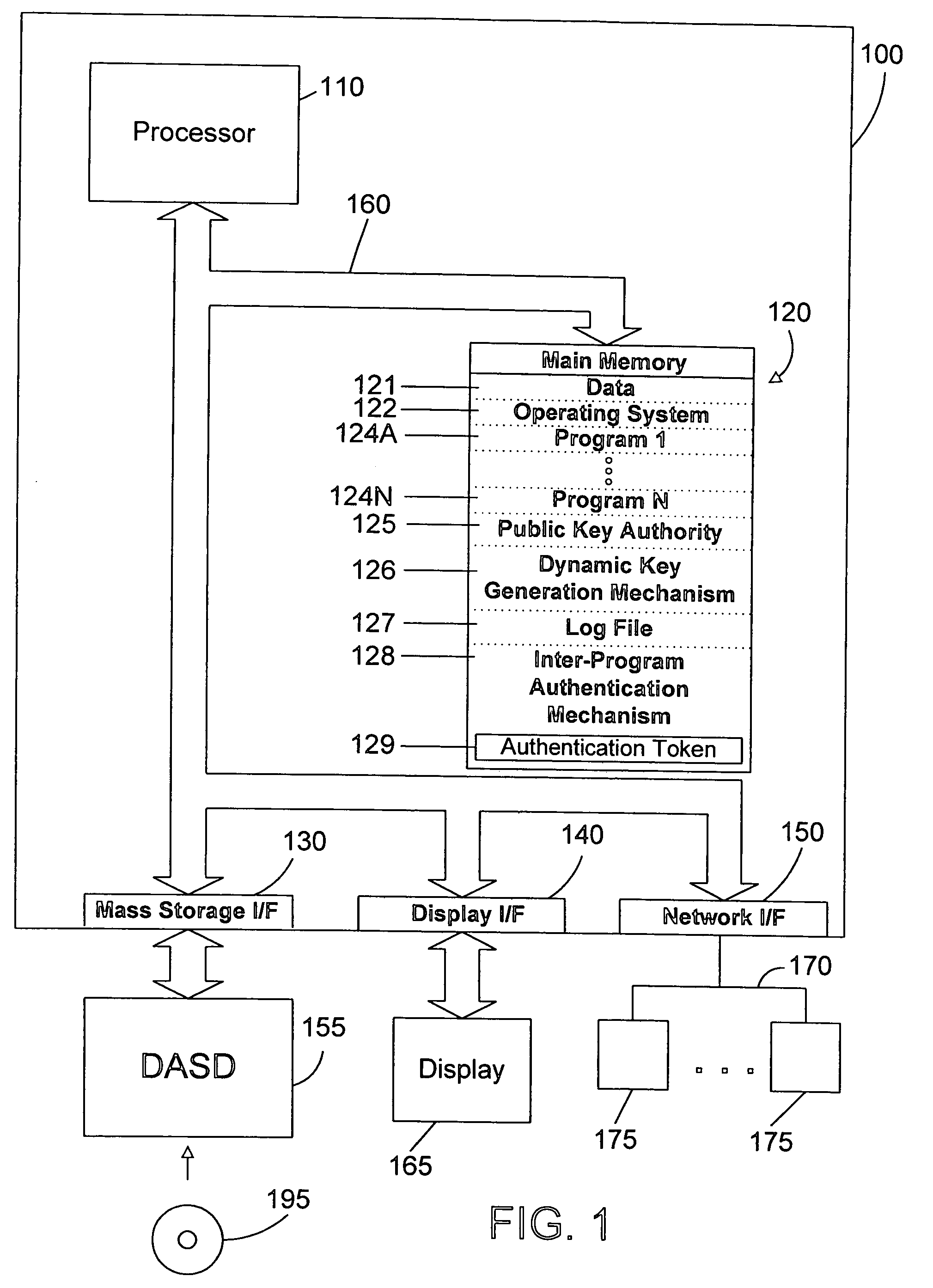
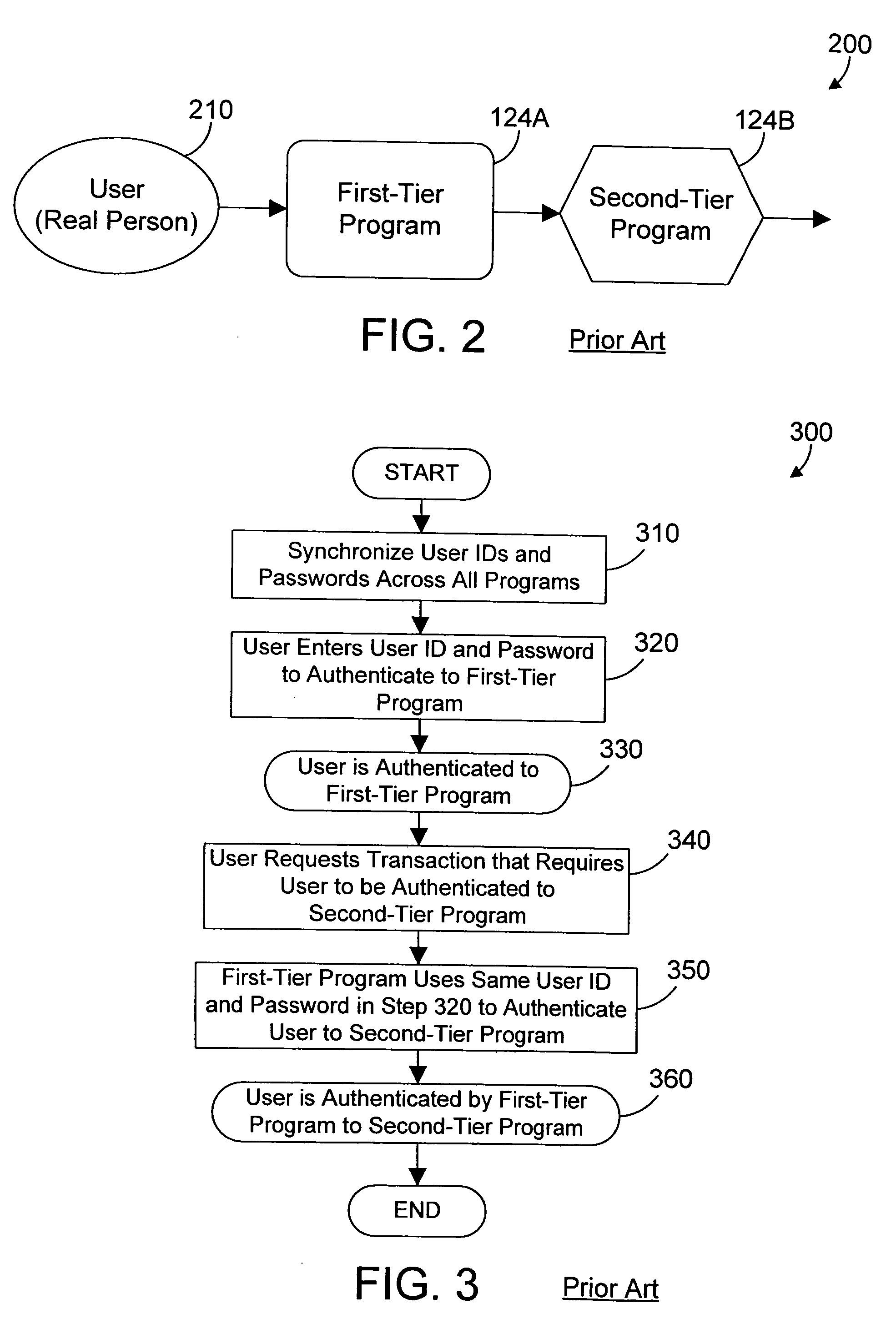
Apparatus and method for inter-program authentication using dynamically-generated public/private key pairs
ActiveUS20050125668A1Digital data processing detailsUser identity/authority verificationProgram validationDigital signature
In a multi-tiered computing environment, a first program may authenticate with a second program using dynamically-generated public / private key pairs. An authentication token is constructed that includes user information and information about the first program and the second program. The first program then digitally signs the authentication token using the dynamically-generated private key, and sends the authentication token to the second program. The second program then verifies the authentication token using the public key corresponding to the first program. Once verified, the first program is authenticated to the second program. The second program may then authenticate to a next-tier program by constructing an authentication token that includes the information in the authentication token received from the first program. This may continue to any suitable number of tiers, using dynamically-generated public / private key pairs to allow authentication between programs without requiring any user interaction or input from a system administrator.
Owner:IBM CORP
System and method for generating error traces for concurrency bugs
ActiveUS8527976B2Error detection/correctionSpecific program execution arrangementsProgram validationData stream
A system and method for program verification includes generating a product transaction graph for a concurrent program, which captures warnings for potential errors. The warnings are filtered to remove bogus warnings, by using constraints from synchronization primitives and invariants that are derived by performing one or more dataflow analysis methods for concurrent programs. The dataflow analysis methods are applied in order of overhead expense. Concrete execution traces are generated for remaining warnings using model checking.
Owner:NEC CORP
Information providing apparatus and method, information processing apparatus and method, and program storage medium
InactiveUS6990580B2Key distribution for secure communicationUser identity/authority verificationInformation processingProgram validation
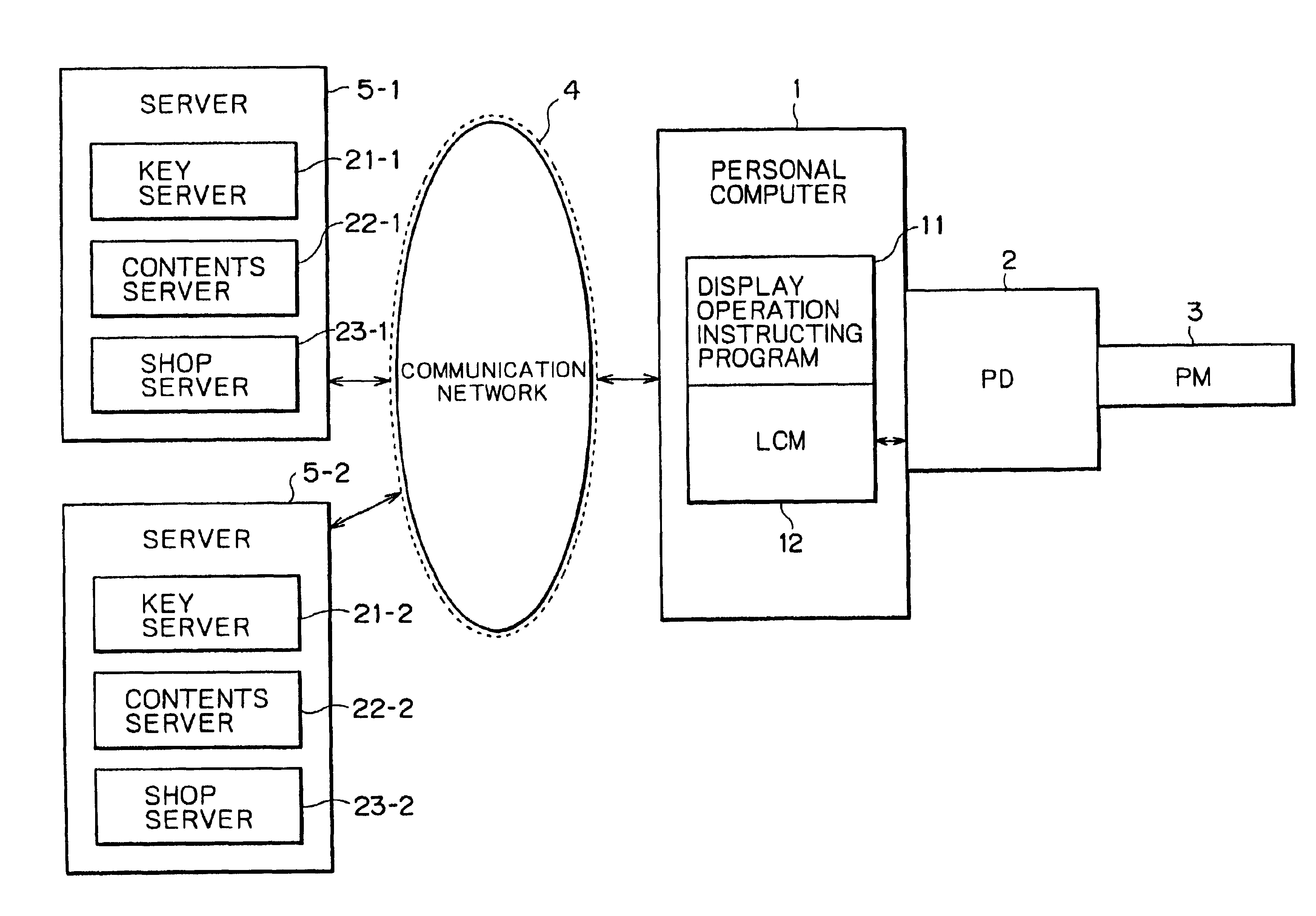
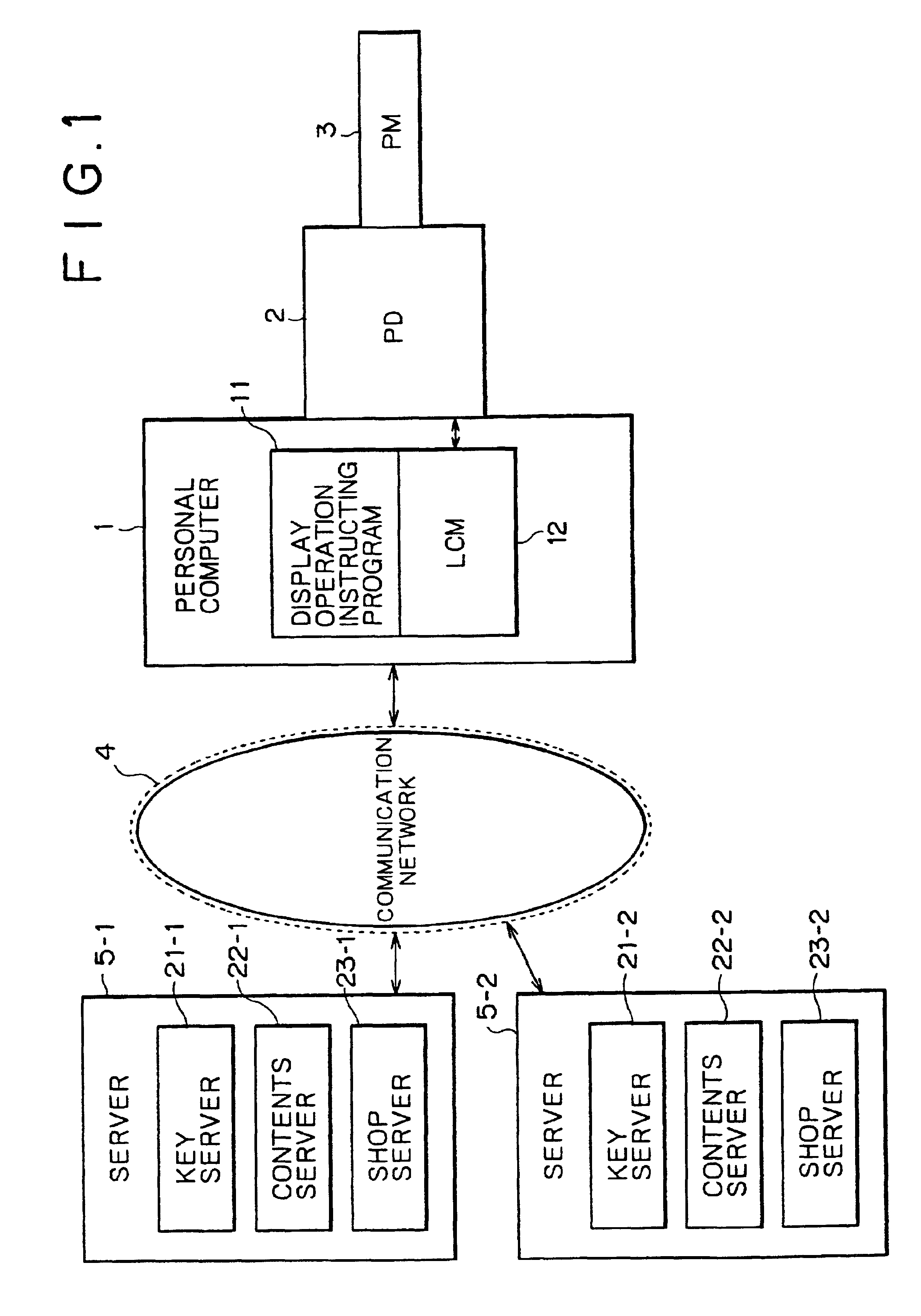
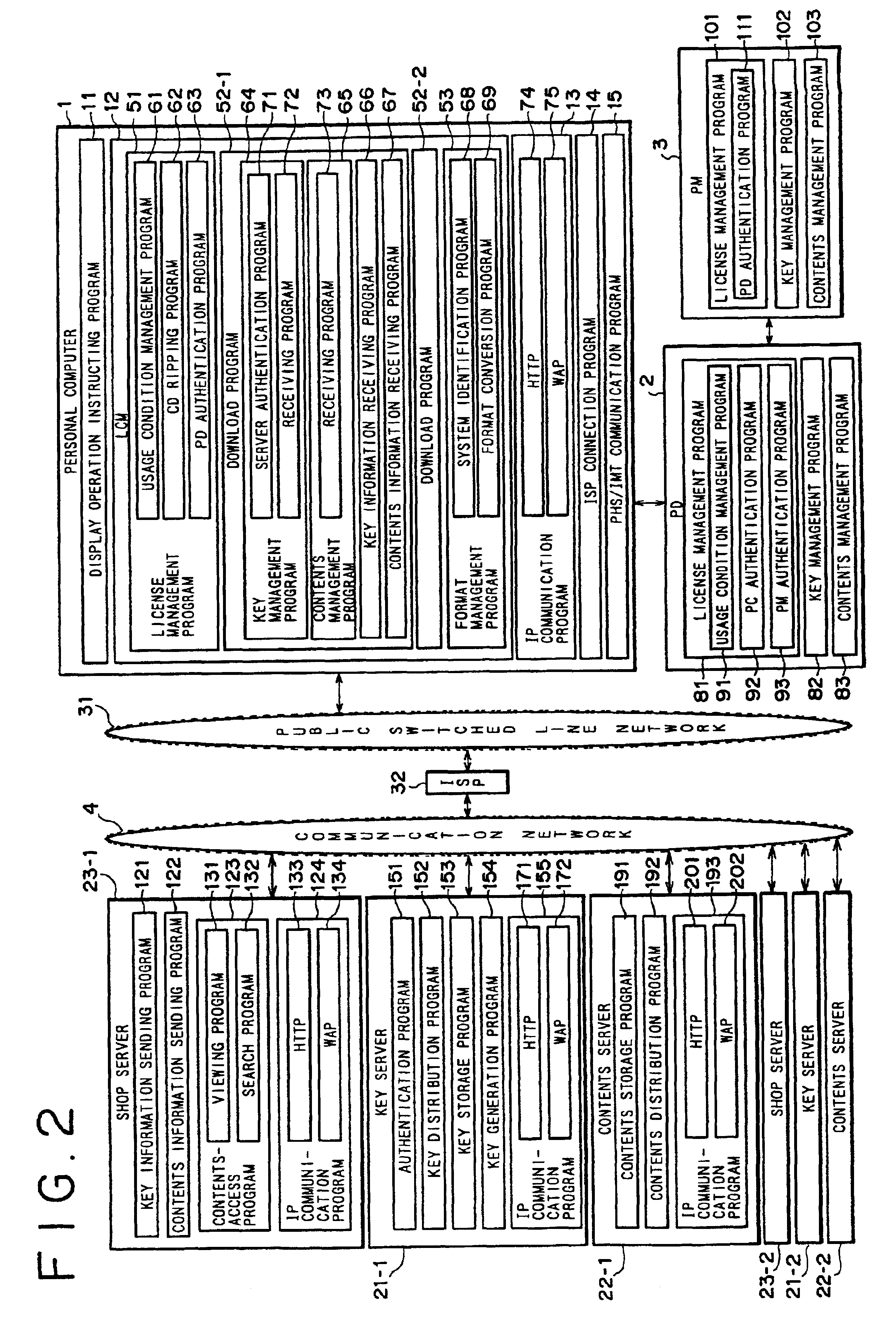
Contents and its key are supplied in different procedures. License management program authenticates telephone-integrated terminal device and authenticates first server or second server. Server LCM controls the reception of contents and key transmission requests and of data for identifying first server or second server. If data for identifying first server are received, contents and its key are received from first server in a procedure corresponding to first server. If data for identifying second server are received, contents and its key are received from second server in a procedure corresponding to second server. Server LCM controls the transmission of contents and its key to telephone-integrated terminal device.
Owner:SONY CORP
Flash memory device and related program verification method
ActiveUS8675416B2Improve reliabilityReduce noiseRead-only memoriesDigital storageVolatile memoryLoop counter
Owner:SAMSUNG ELECTRONICS CO LTD
Method and device for determining flash software compatibility with hardware
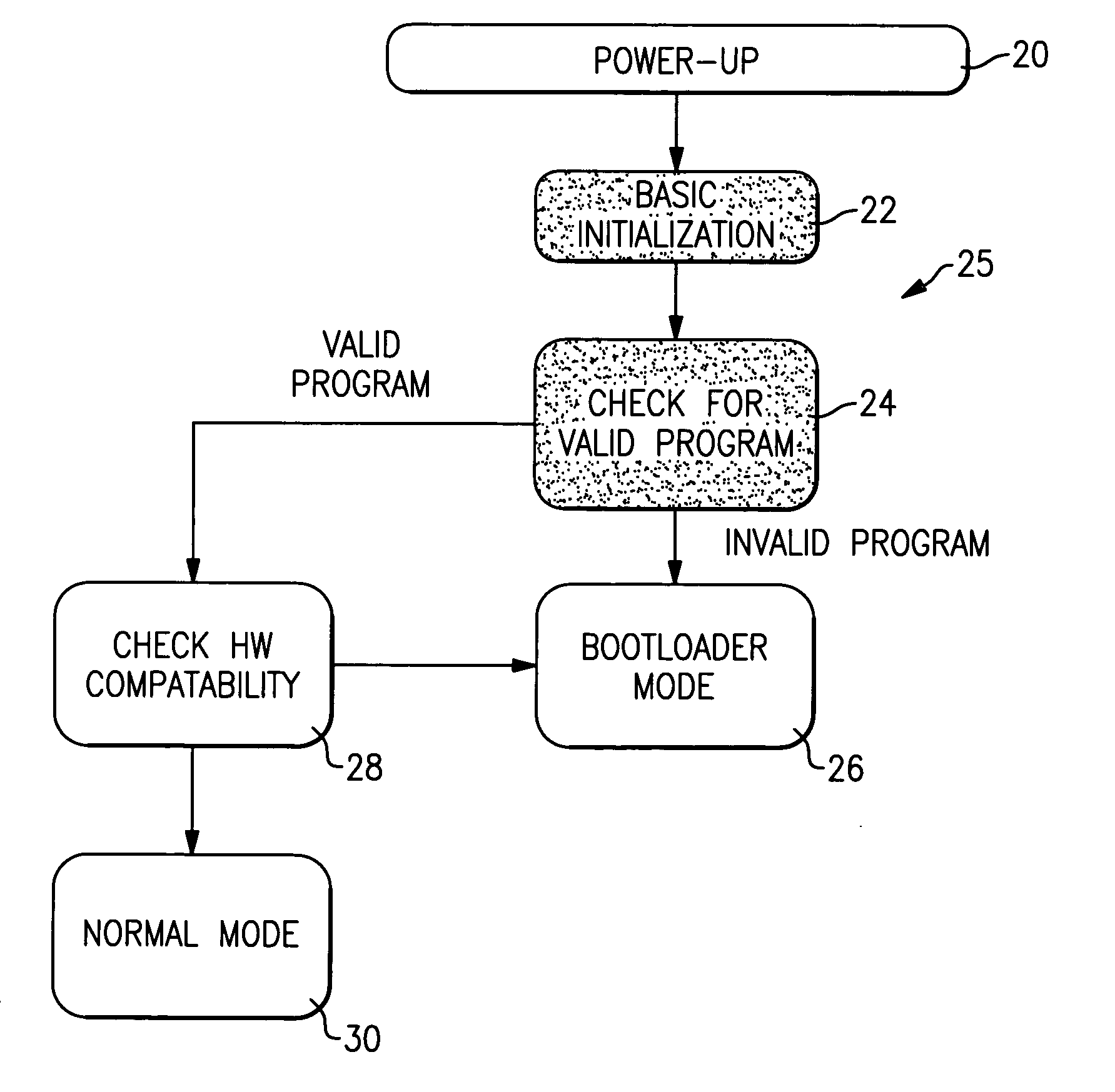
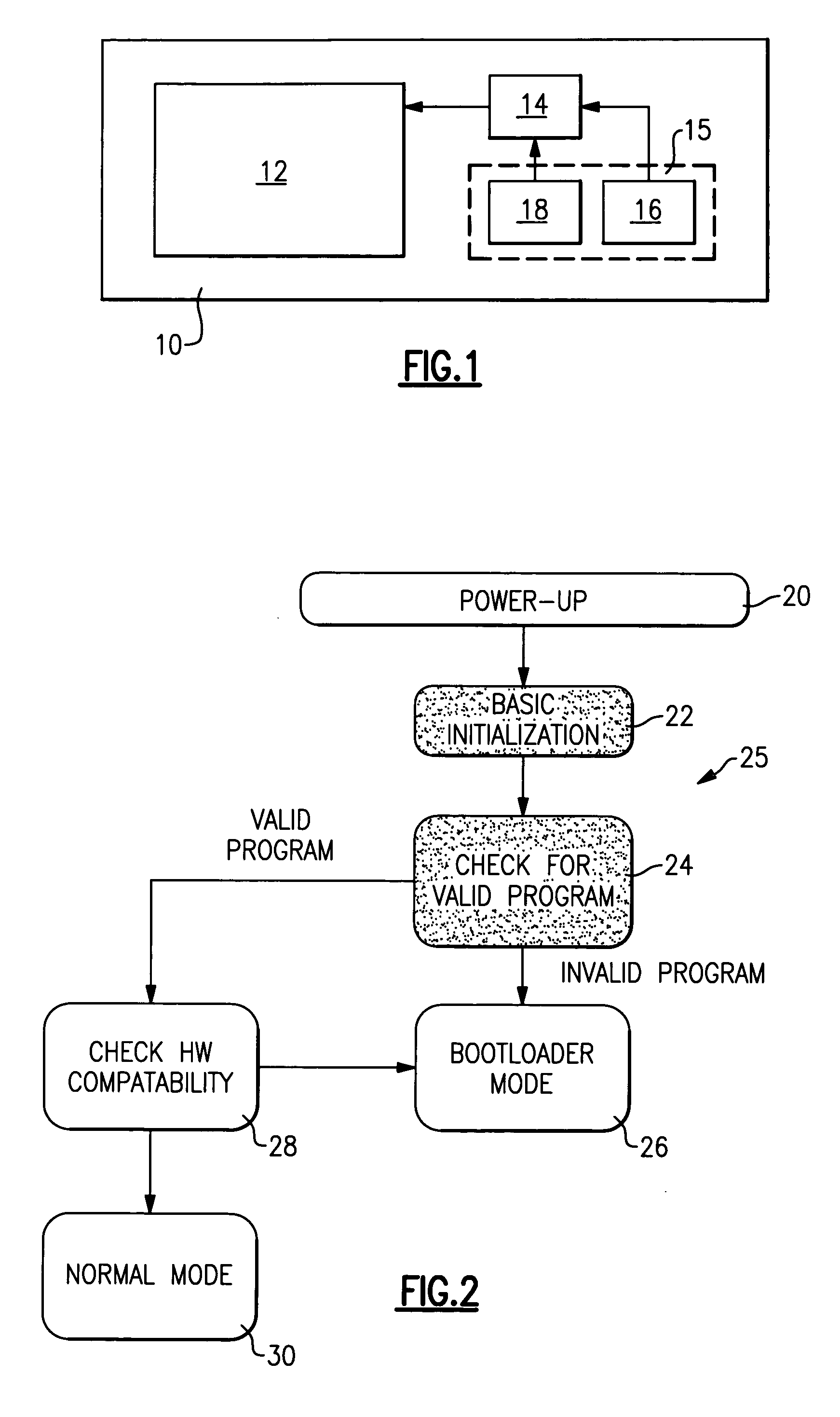
InactiveUS20050262337A1Version controlDigital computer detailsProgram validationComputer compatibility
A method of determining compatibility between a hardware device and a software application includes the step of initializing a boot loader application. Initialization of the boot loader application includes verifying the presence and validity of a software application. Once the software application has been validated by the boot loader application, control is transferred to the software application. The software application determines compatibility by checking a hardware identifier stored in a substantially permanent memory location. If the hardware identifier matches the software application, the software application operates normally. If the hardware identifier does not match the software application, control of the hardware device is transferred back to the boot loader application for reprogramming with a compatible program.
Owner:SIEMENS VDO AUTOMOTIVE CORP
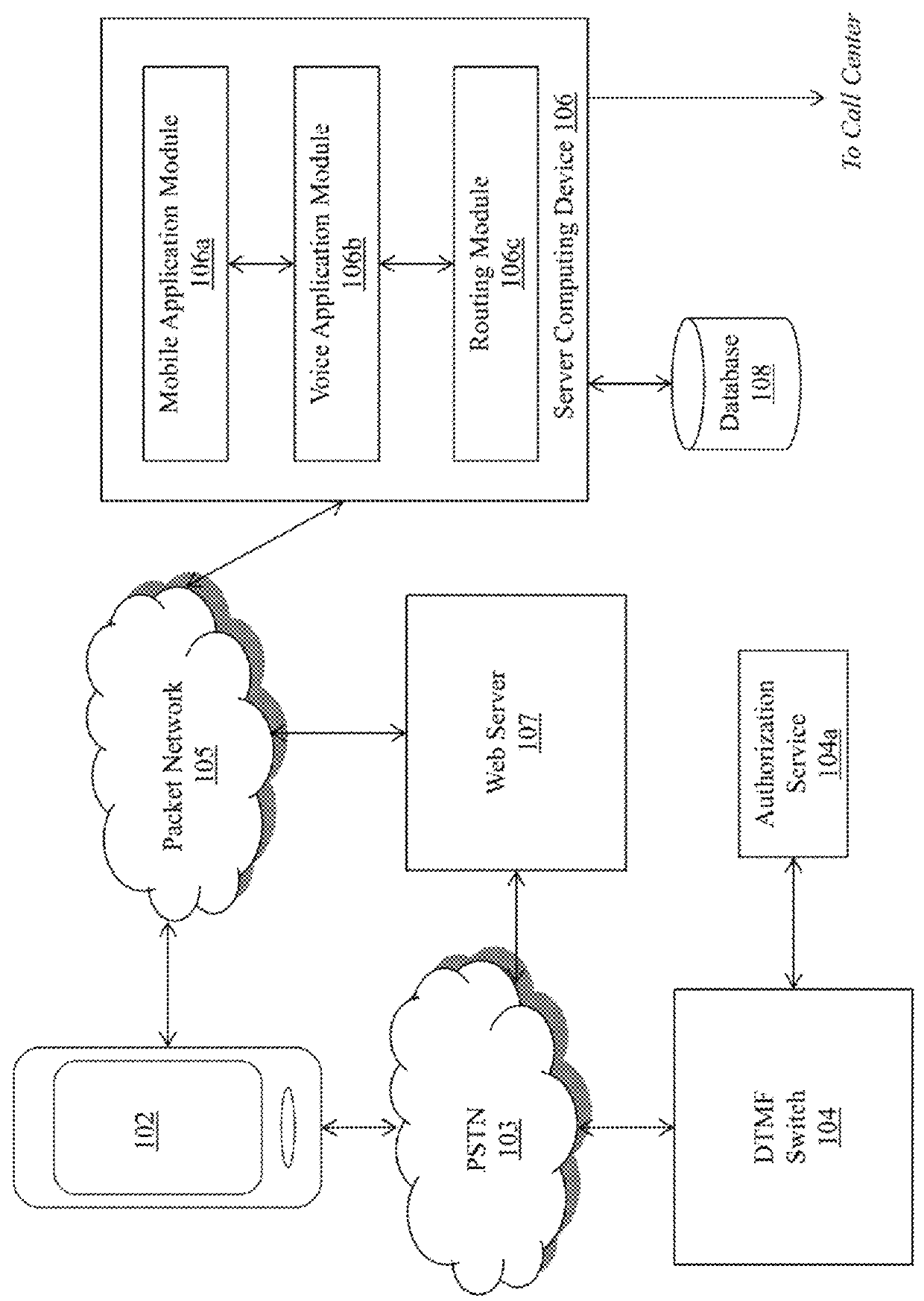
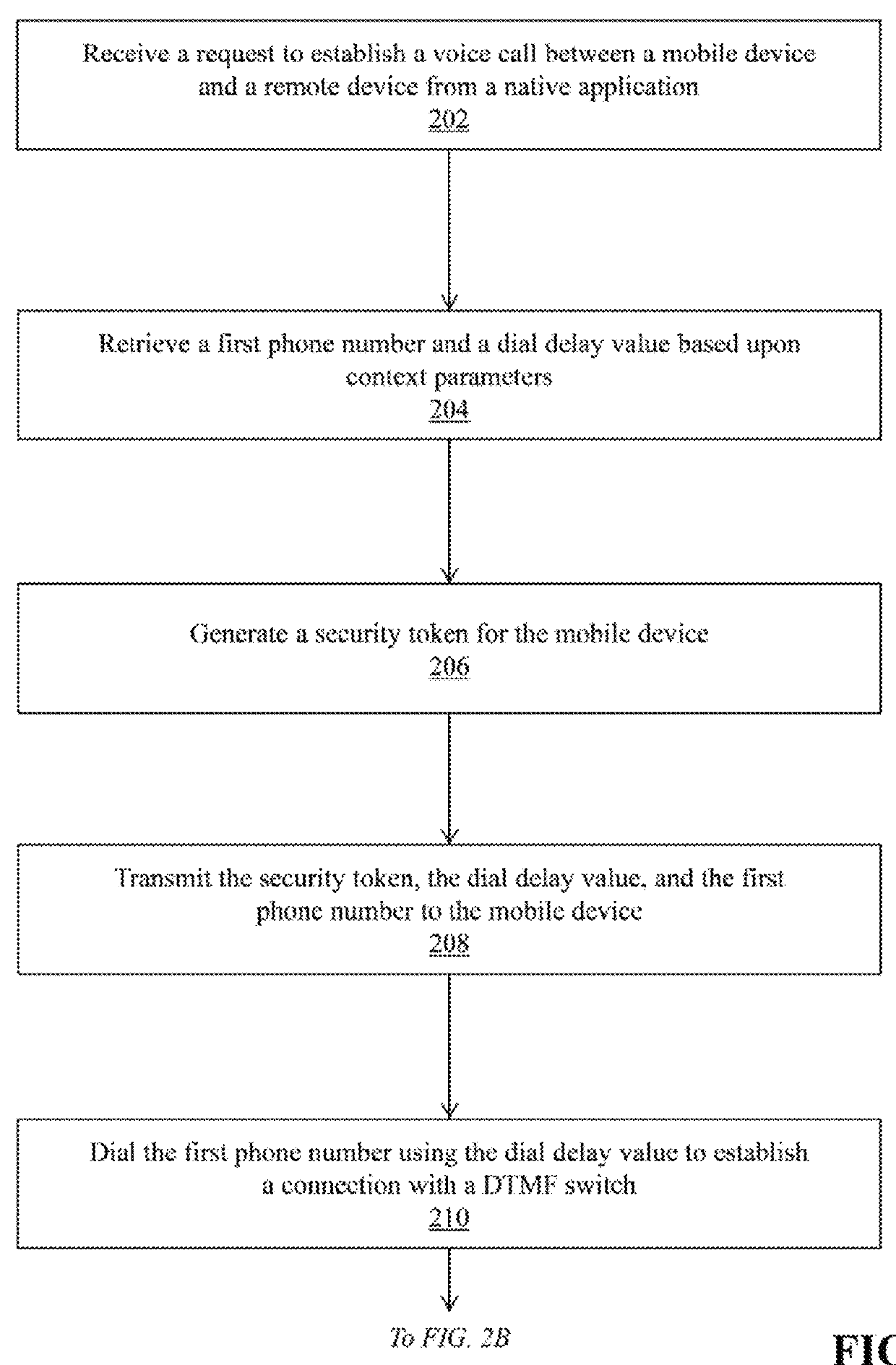
Mobile device authentication and call routing using dual-tone multi-frequency signaling
Methods and apparatuses are described for mobile device authentication and call routing using dual-tone multi-frequency signaling. A server computing device receives a request to establish a call between a mobile device and a remote device, the request including context parameters and automatic number identification data. The server retrieves a first phone number and a dial delay value based upon the context parameters, generates a security token and a request token, and stores the security token, the request token, the context parameters, and the ANI data in a database record. The mobile device dials the first phone number to establish a connection with a telephony application. The mobile device generates DTMF tones based upon the request token and transmits the DTMF tones to the telephony application. The telephony application validates the request token and requests a second phone number to connect the mobile device and the remote device.
Owner:FMR CORP
Correctness verifying method of cache consistency protocol
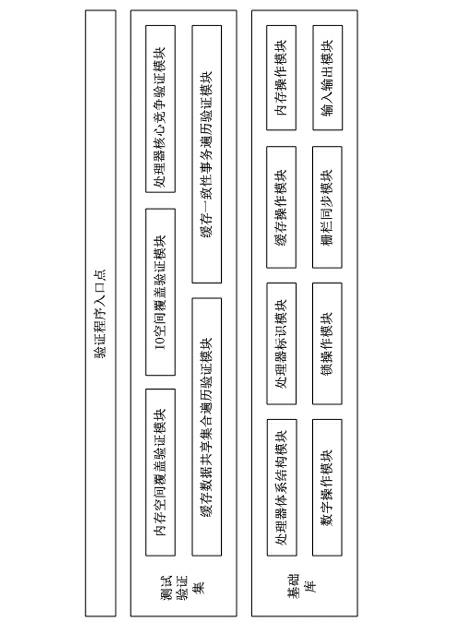
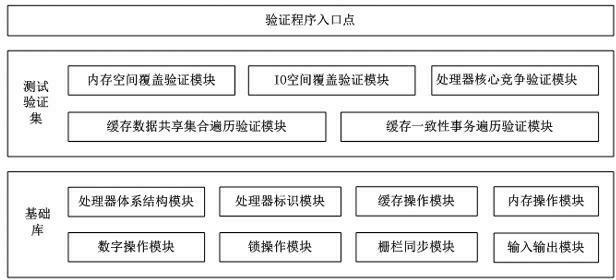
ActiveCN102681937AMake up for efficiencyMake up for poor verification coverageDigital computer detailsMultiprogramming arrangementsOperational systemTerm memory
The invention provides a correctness verifying method of a cache consistency protocol. After a computer enters an operating system, the complexity of a core and the application of the operating system is higher; the action of a processor is not easy to control accurately; therefore, in order to keep verification correctness, a verifying program for the cache consistency protocol is necessary to embed in a systematic procedure; the program is embedded in a BIOS (basic input / output system) code; after the initialization of a memory subsystem is completed at the initialization initial stage of the system, the verifying program is started to be executed; the verifying program needs to be capable of accurately controlling actions of each processor of the system, supports a user to select a verification item to be particularly executed, and feeds back a verification result to the user; by using the method, the verification of the correctness of the cache consistency protocol is realized at a system level; all application scenes of a real system can be completely covered; the disadvantages that a conventional verifying method based on an analog way is low in efficiency and poor in verification coverage rate are made up; the design period and the verifying period of an inter-domain cache consistency chip of the processor can be shortened; the one-time taping-out mission success rate of the chip can be guaranteed effectively; and therefore, the correctness verifying method has an extremely wide development prospect and an extremely high technical value.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
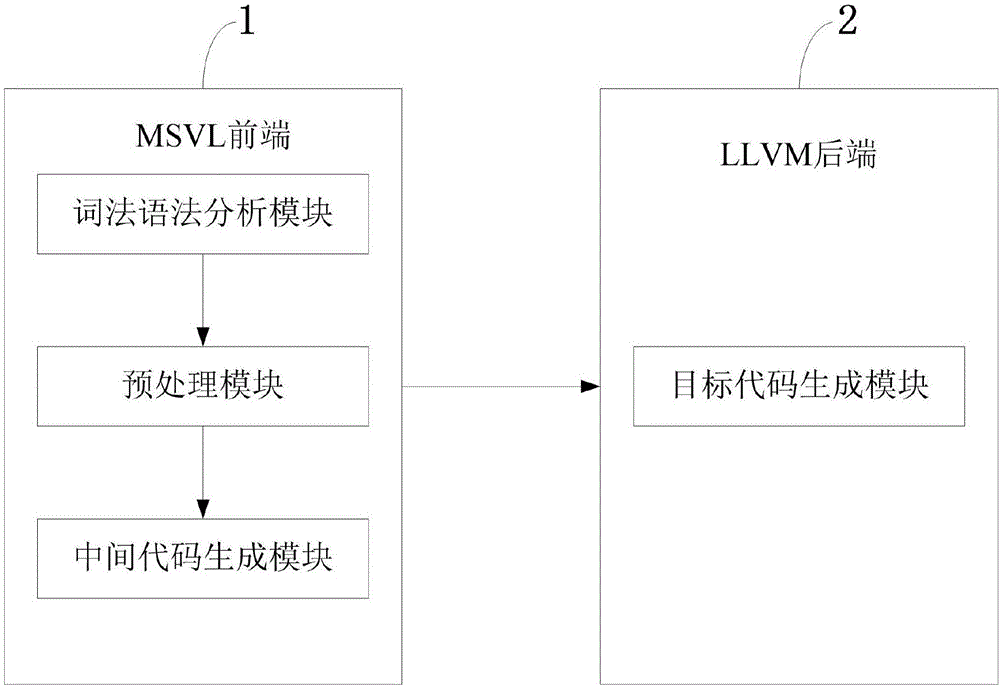
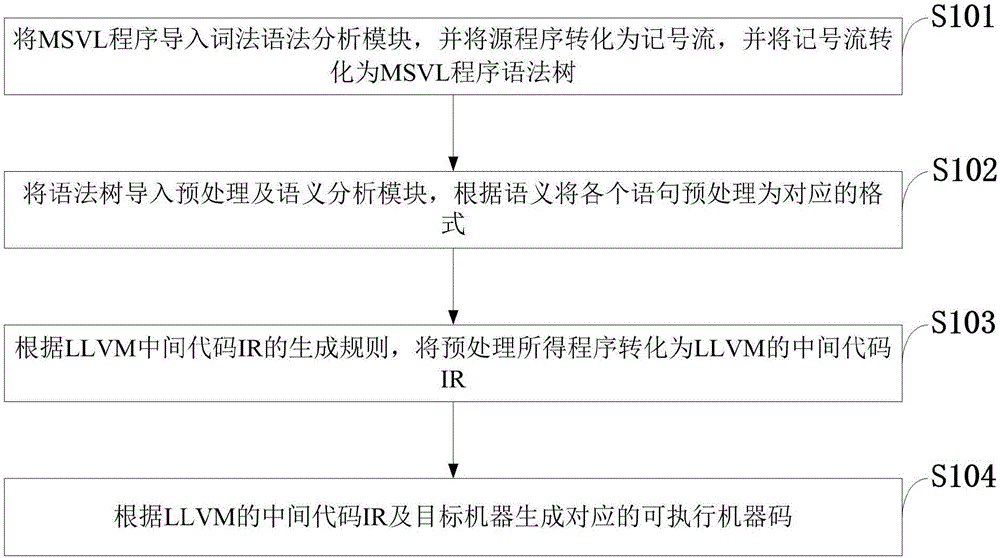
System and method for MSVL compiling
ActiveCN106371887AImprove Execution and Validation EfficiencyImprove execution efficiencyProgram controlMemory systemsA-normal formVirtual machine
The invention discloses a system and method for MSVL compiling. The system comprises an MSVL leading end and a bottom layer virtual machine rear end. The MSVL leading end comprises a morphology grammatical analysis module, a preprocessing module and an intermediate code generating module. An LLVM rear end comprises a target code generation module. A method for MSVL compiling comprises the steps of using a normal form method to preprocess simple statements in MSVL, respectively preprocessing each concurrent component for complex statements, and creating a thread for each concurrent component. According to the system and method for MSVL compiling, problems that in the prior art, efficiency of executing an MSVL program and the efficiency of program verification and execution is affected are solved well, and MSVL program execution and verification efficiency is improved. According to differences of the complexity of a program, the program execution speed can be improved by tens of times or even up to a hundred times; and the program can be repeatedly executed after being compiled successfully in one time and does not need to be compiled again.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com