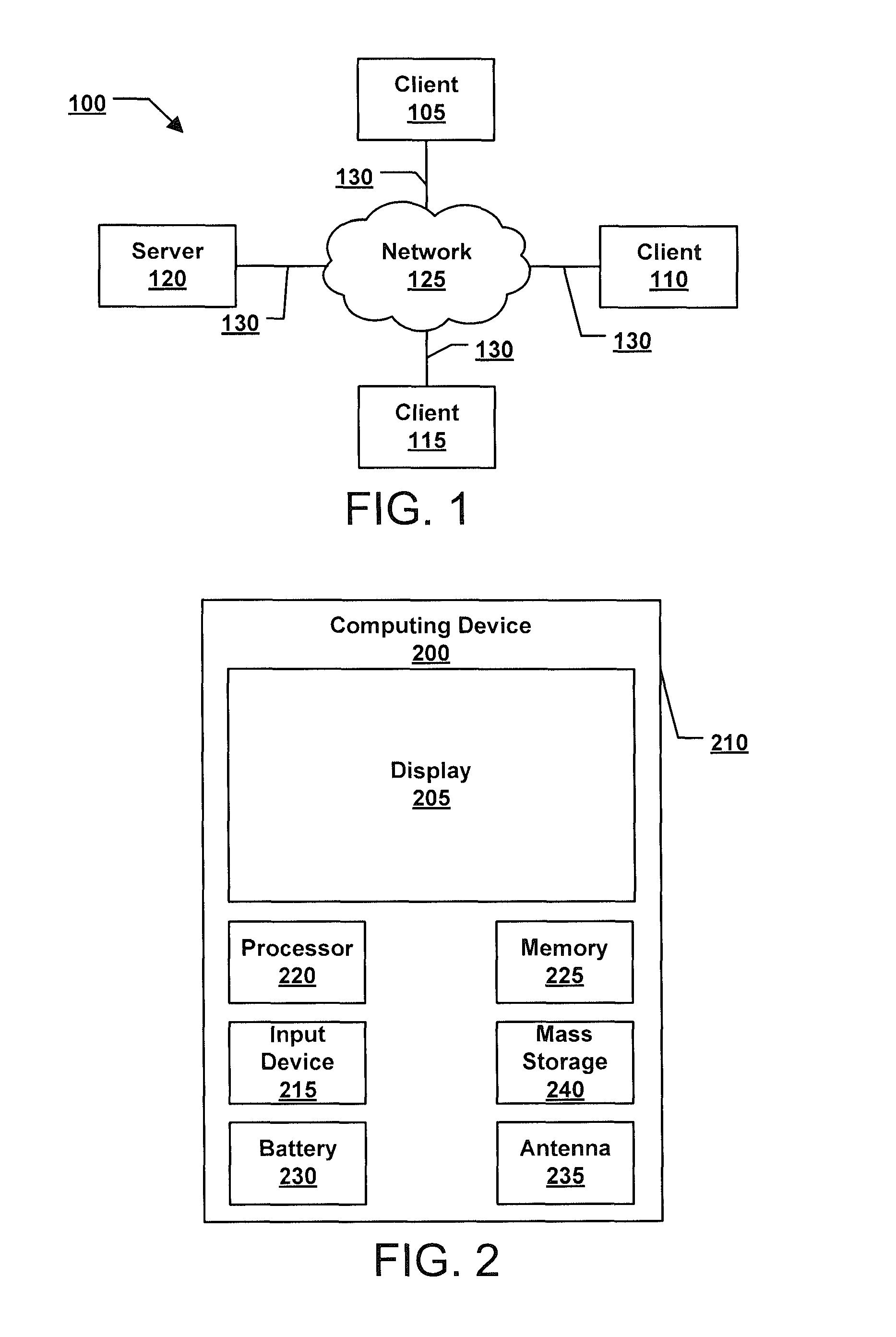
Patents
Literature
4618 results about "Resource use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term “resource use measures” is intended to broadly capture indicators of the cost and efficiency of health care provision. Health care resource use measures reflect the amount or cost of resources used to create a specific product of the health care system.
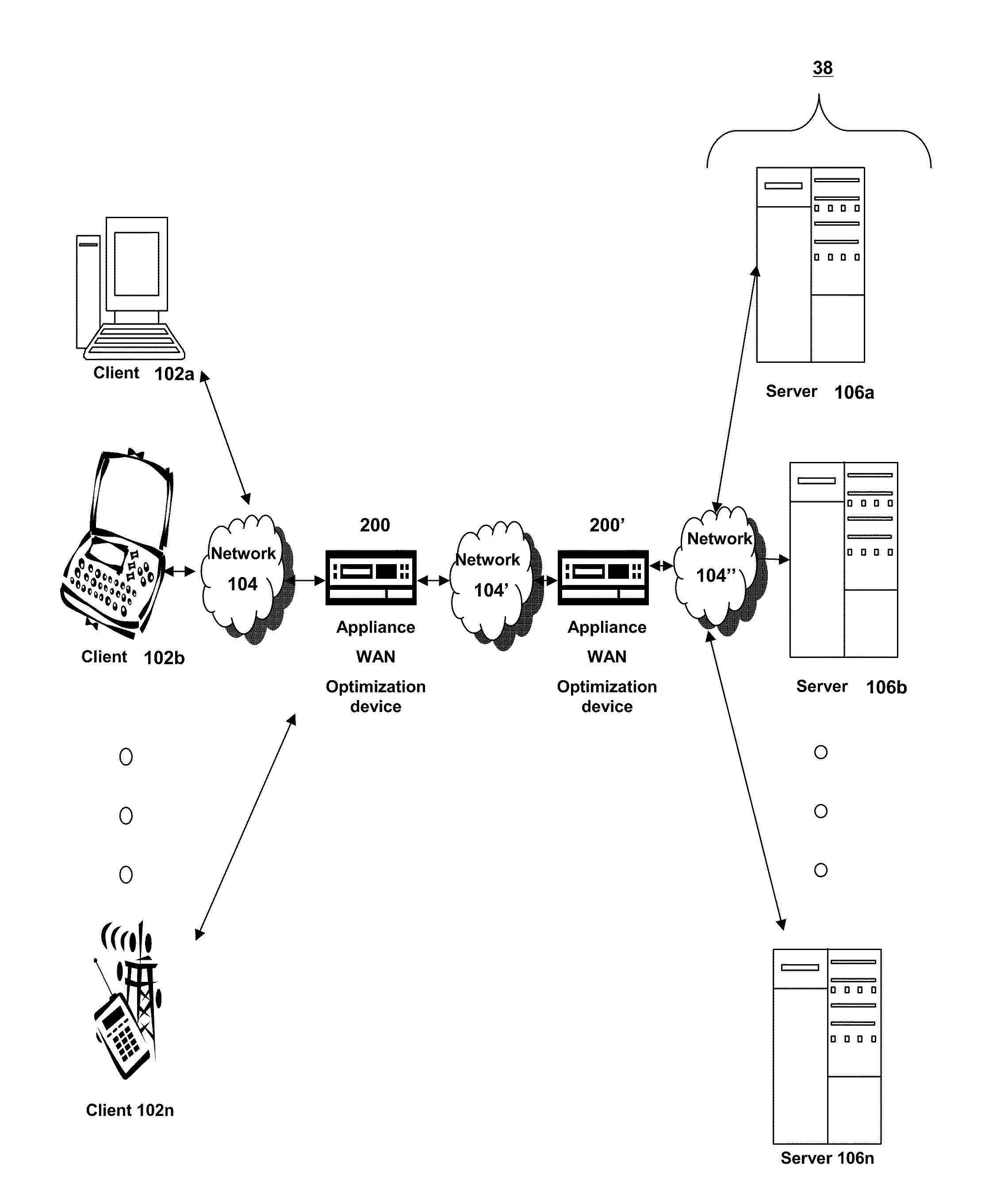
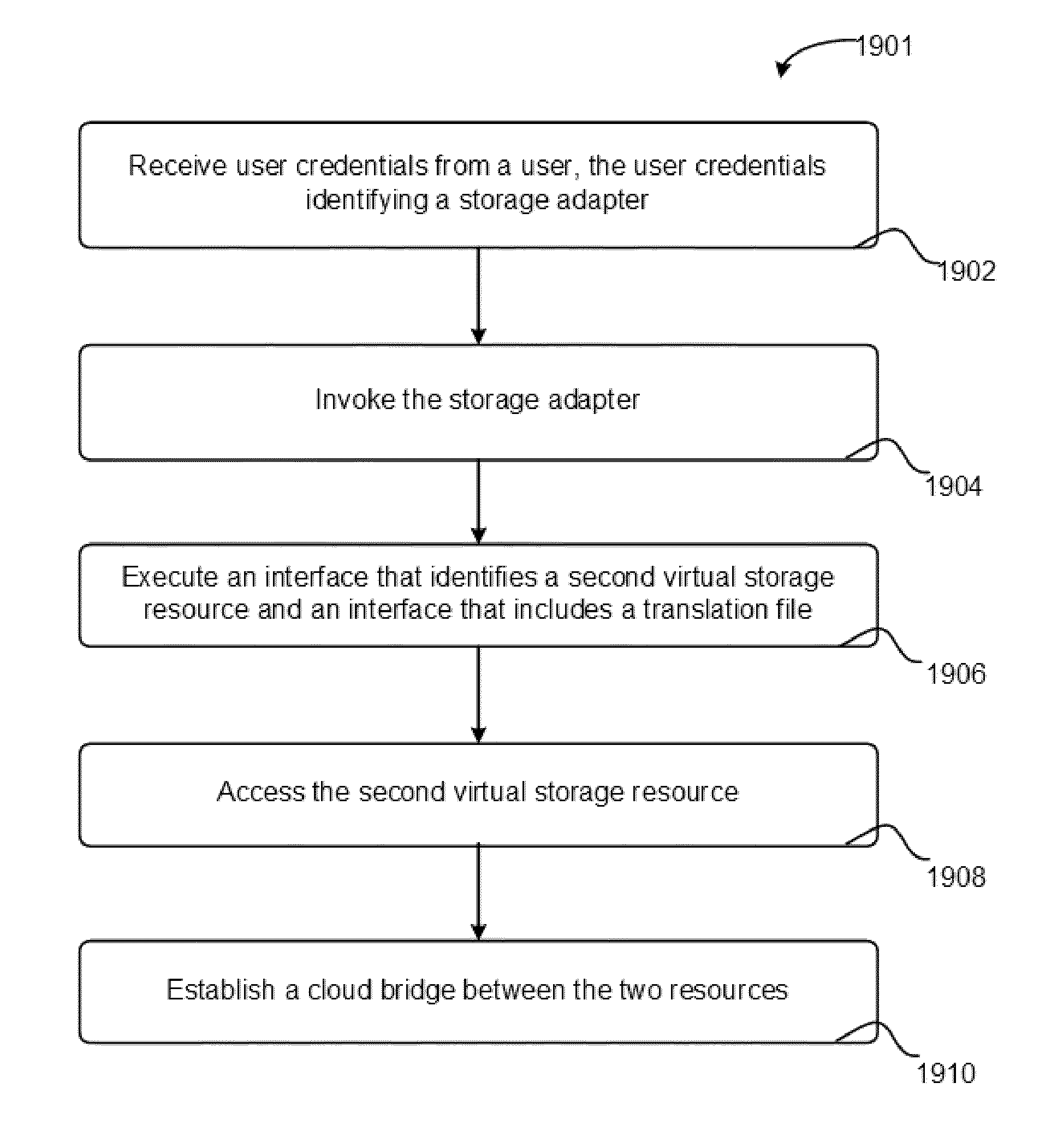
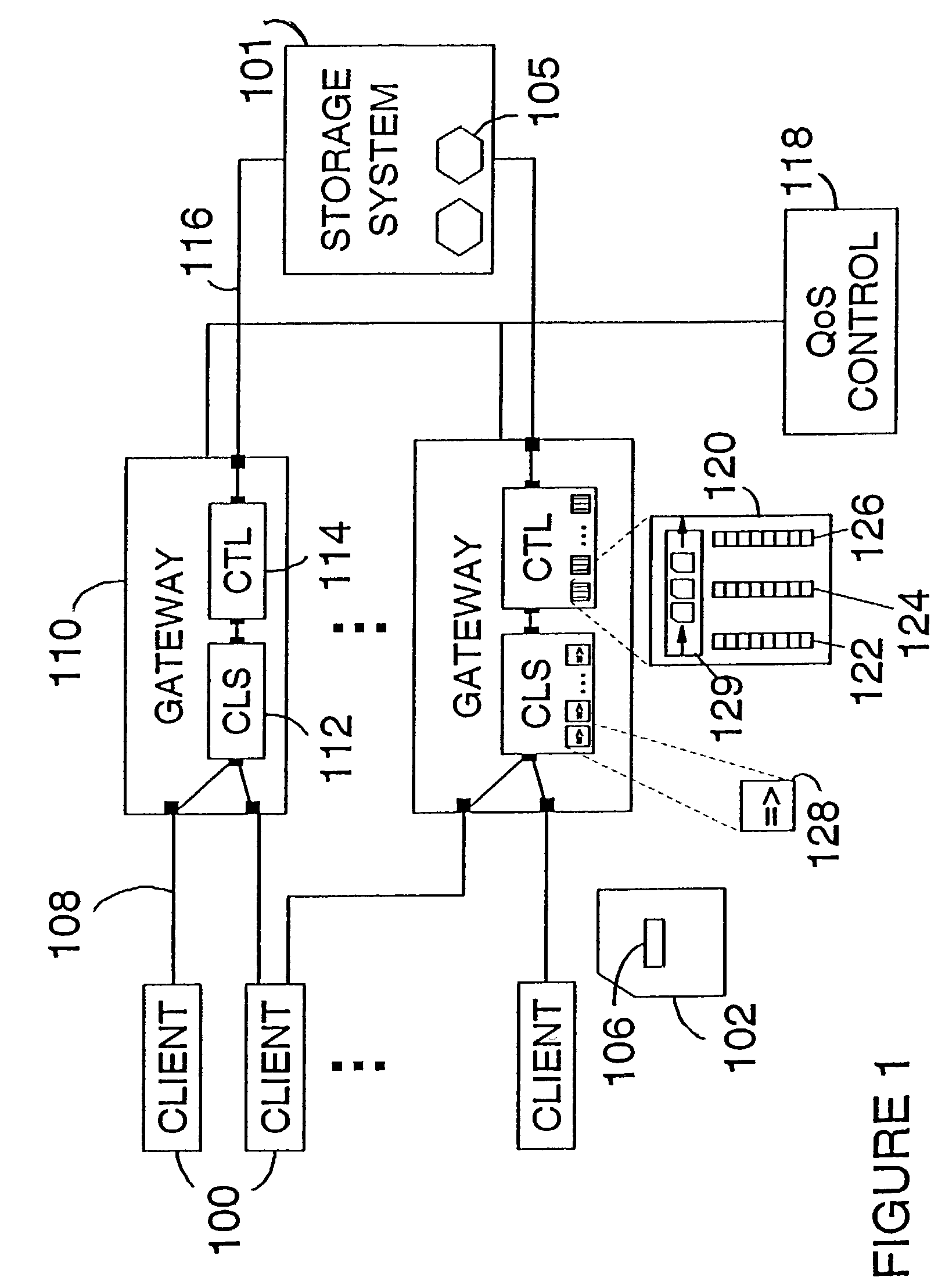
Systems and methods for establishing a cloud bridge between virtual storage resources
Methods and systems for establishing a cloud bridge between two virtual storage resources and for transmitting data from one first virtual storage resource to the other virtual storage resource. The system can include a first virtual storage resource or cloud, and a storage delivery management service that executes on a computer and within the first virtual storage resource. The storage delivery management service can receive user credentials of a user that identify a storage adapter. Upon receiving the user credentials, the storage delivery management service can invoke the storage adapter which executes an interface that identifies a second virtual storage resource and includes an interface translation file. The storage delivery management service accesses the second virtual storage resource and establishes a cloud bridge with the second virtual storage resource using information obtained from the second virtual storage resource and information translated by the storage adapter using the interface translation file.
Owner:CITRIX SYST INC
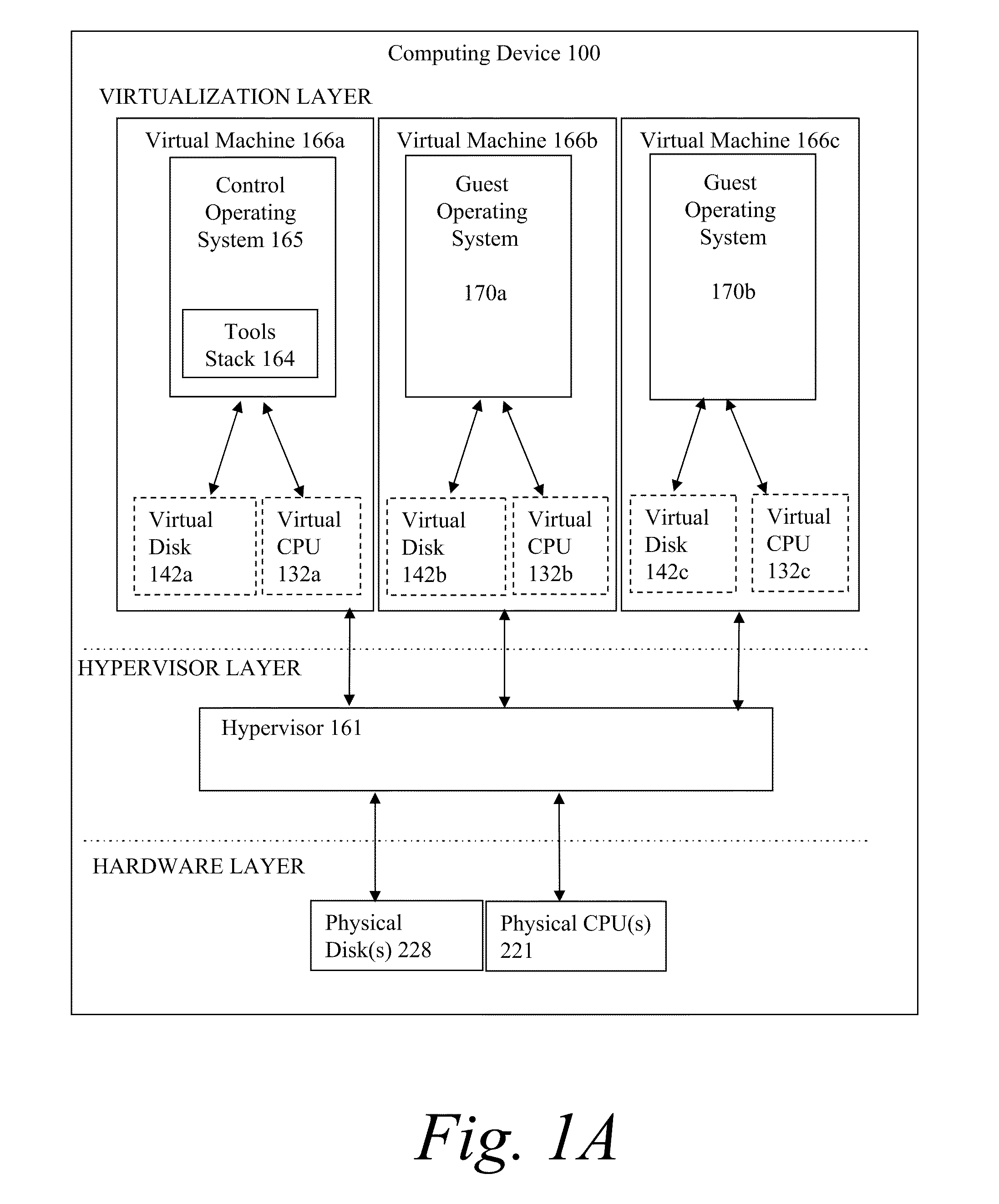
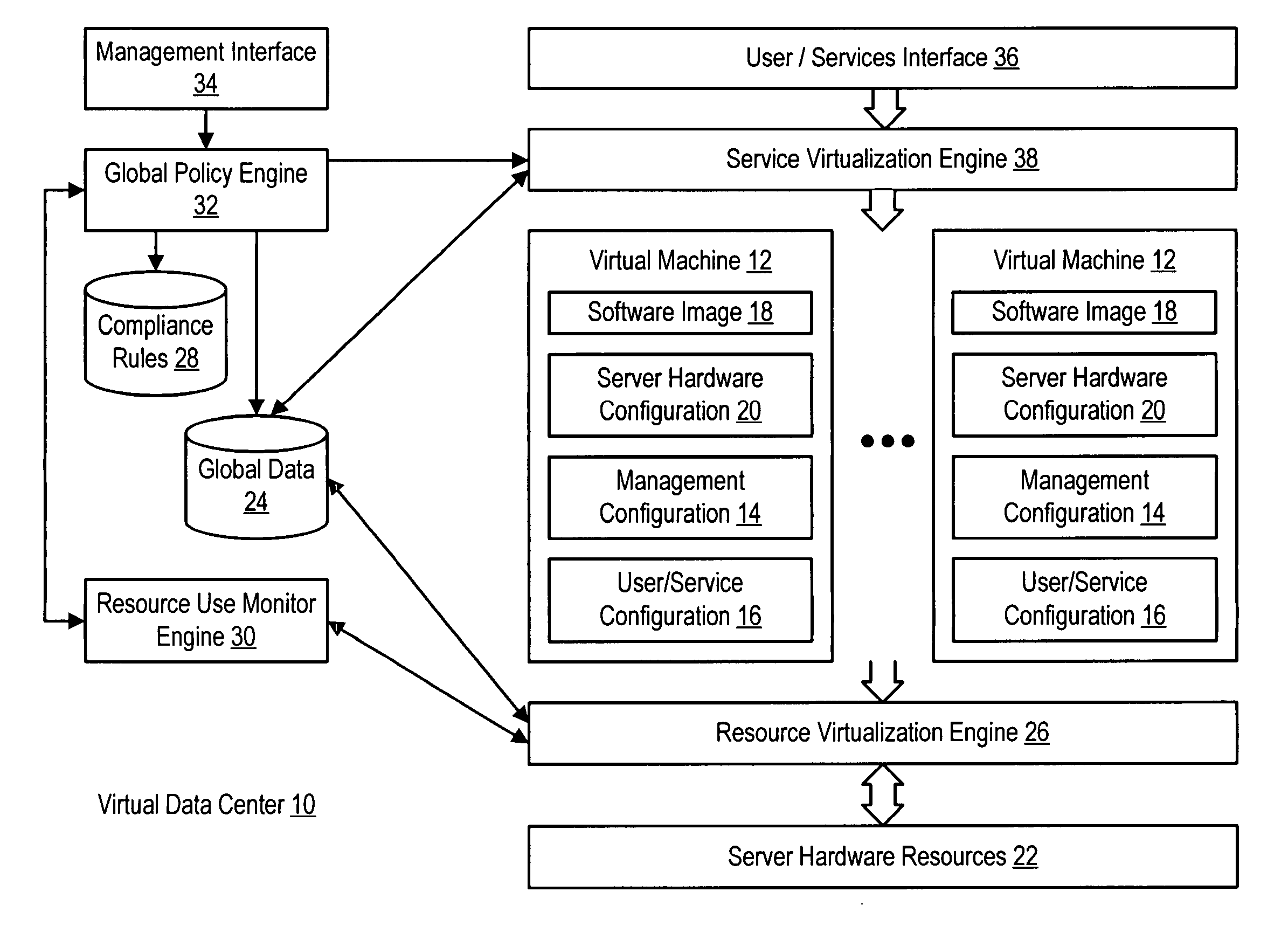
System and method for centralized software management in virtual machines
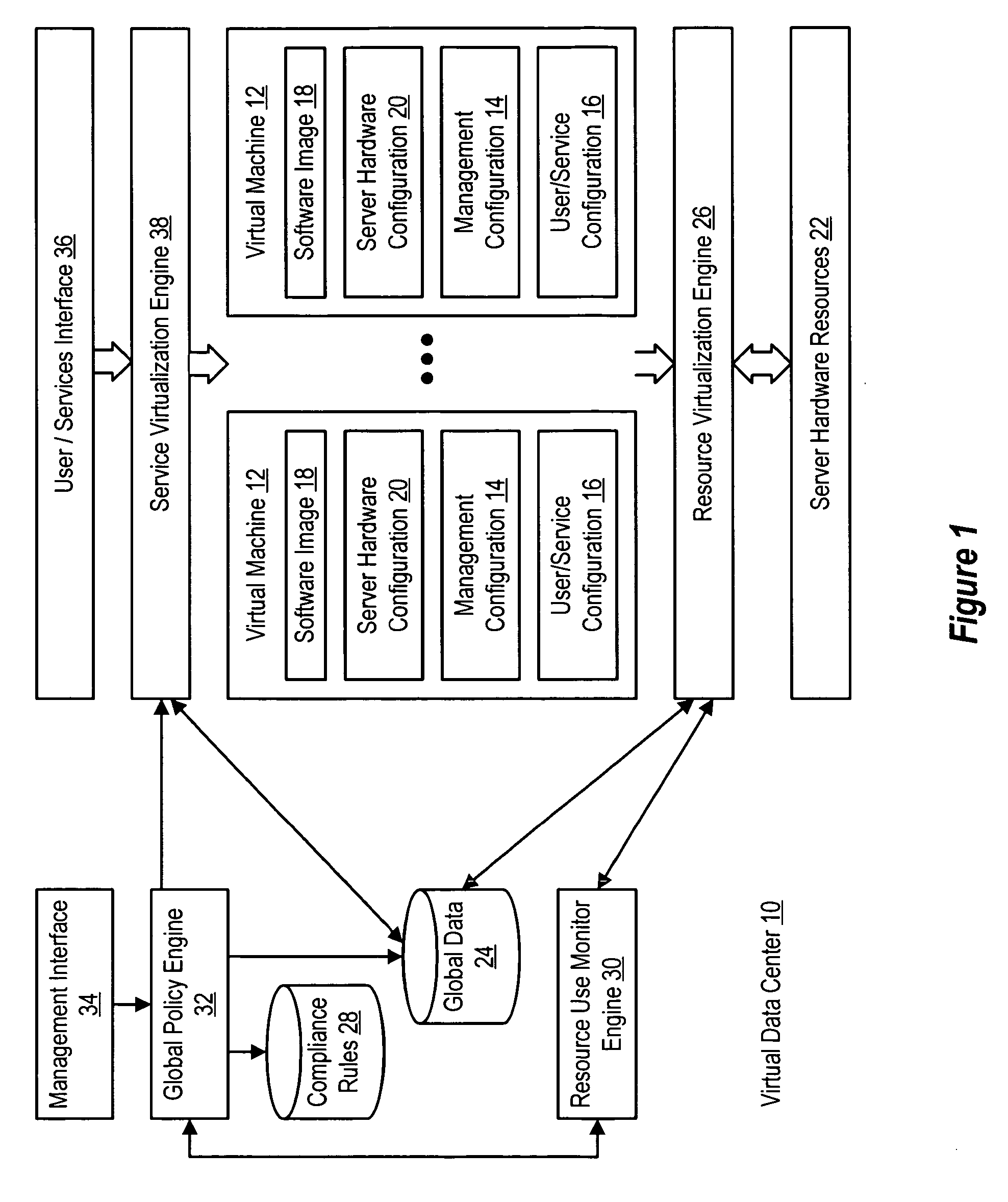
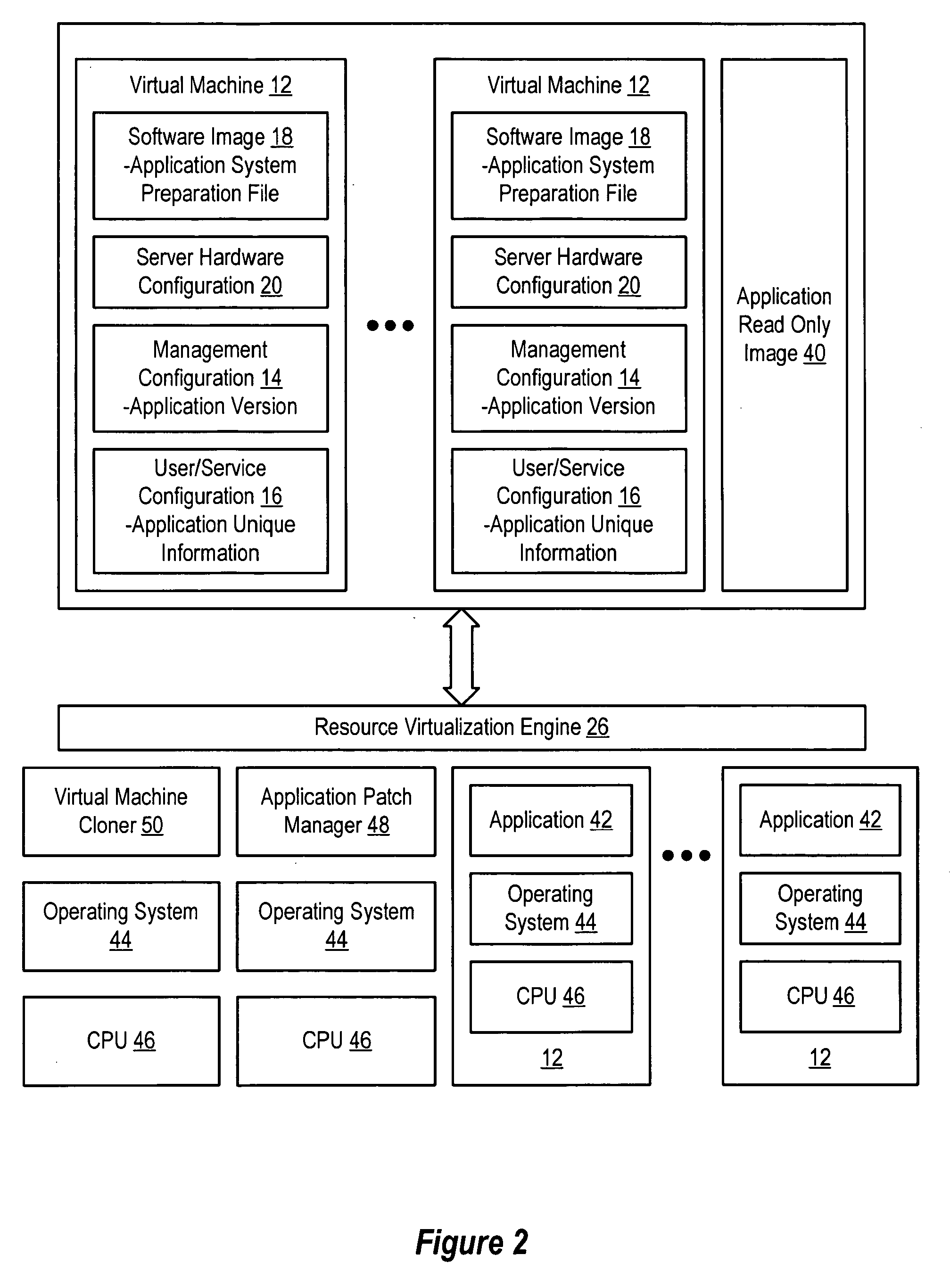
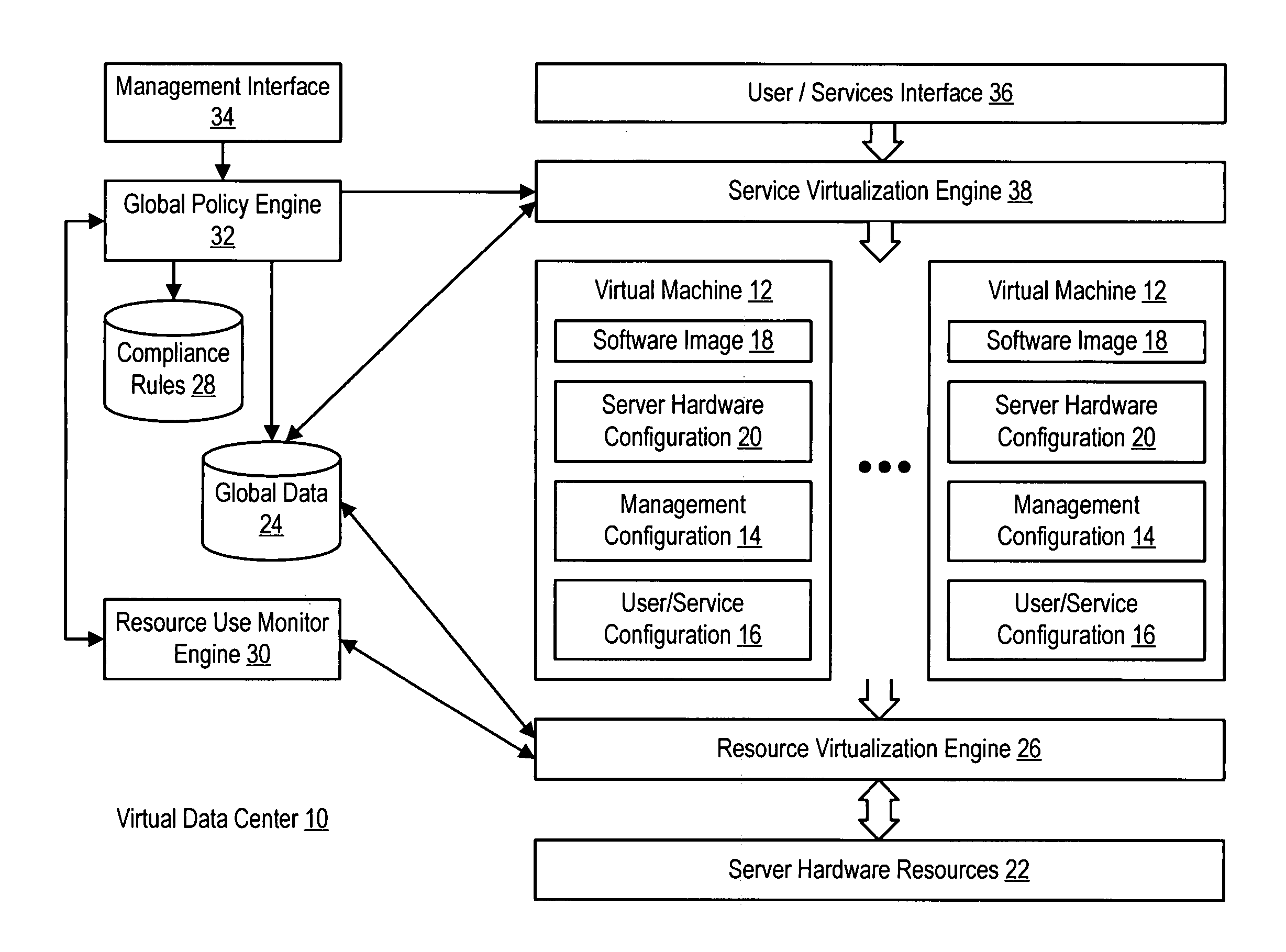
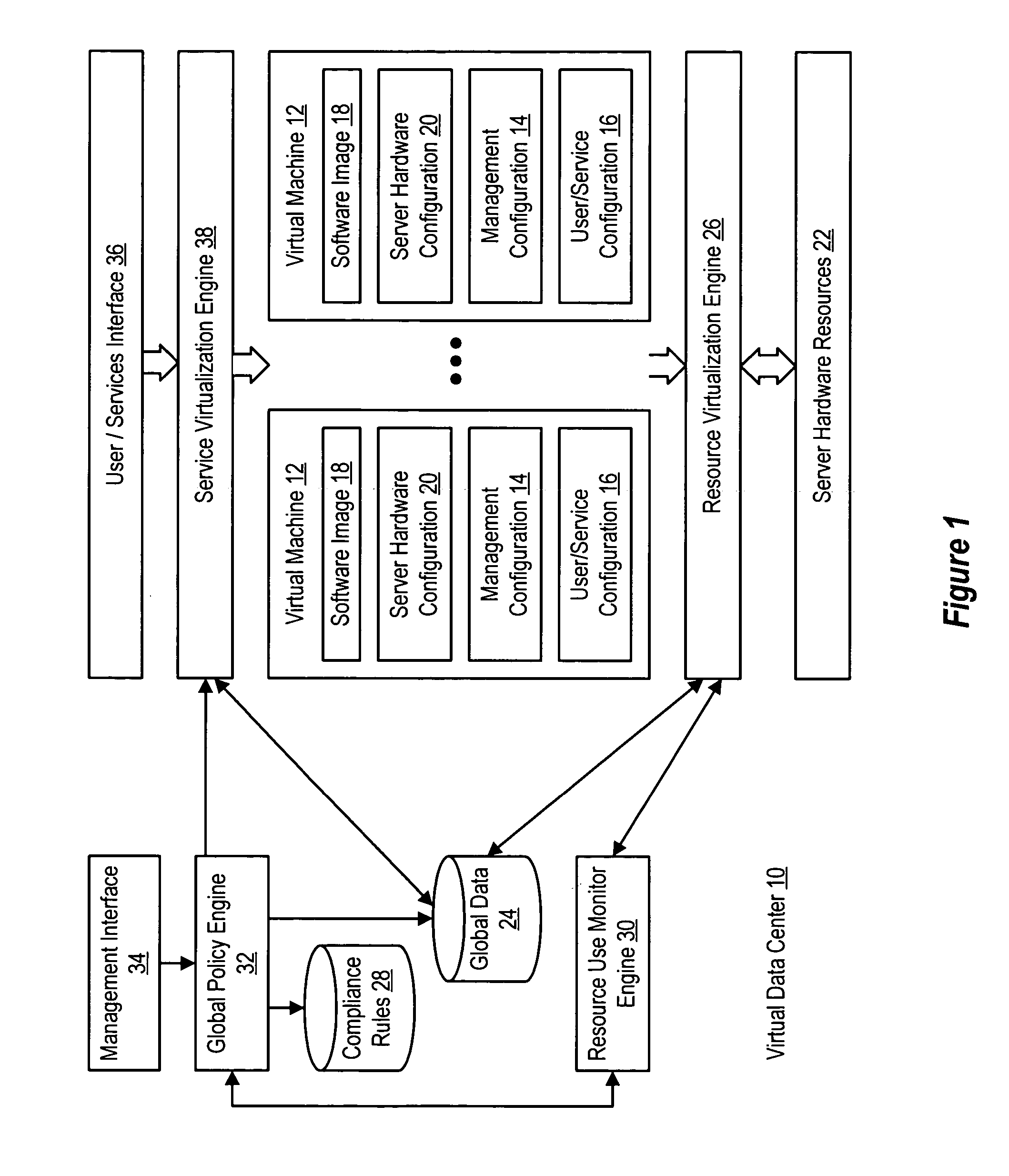
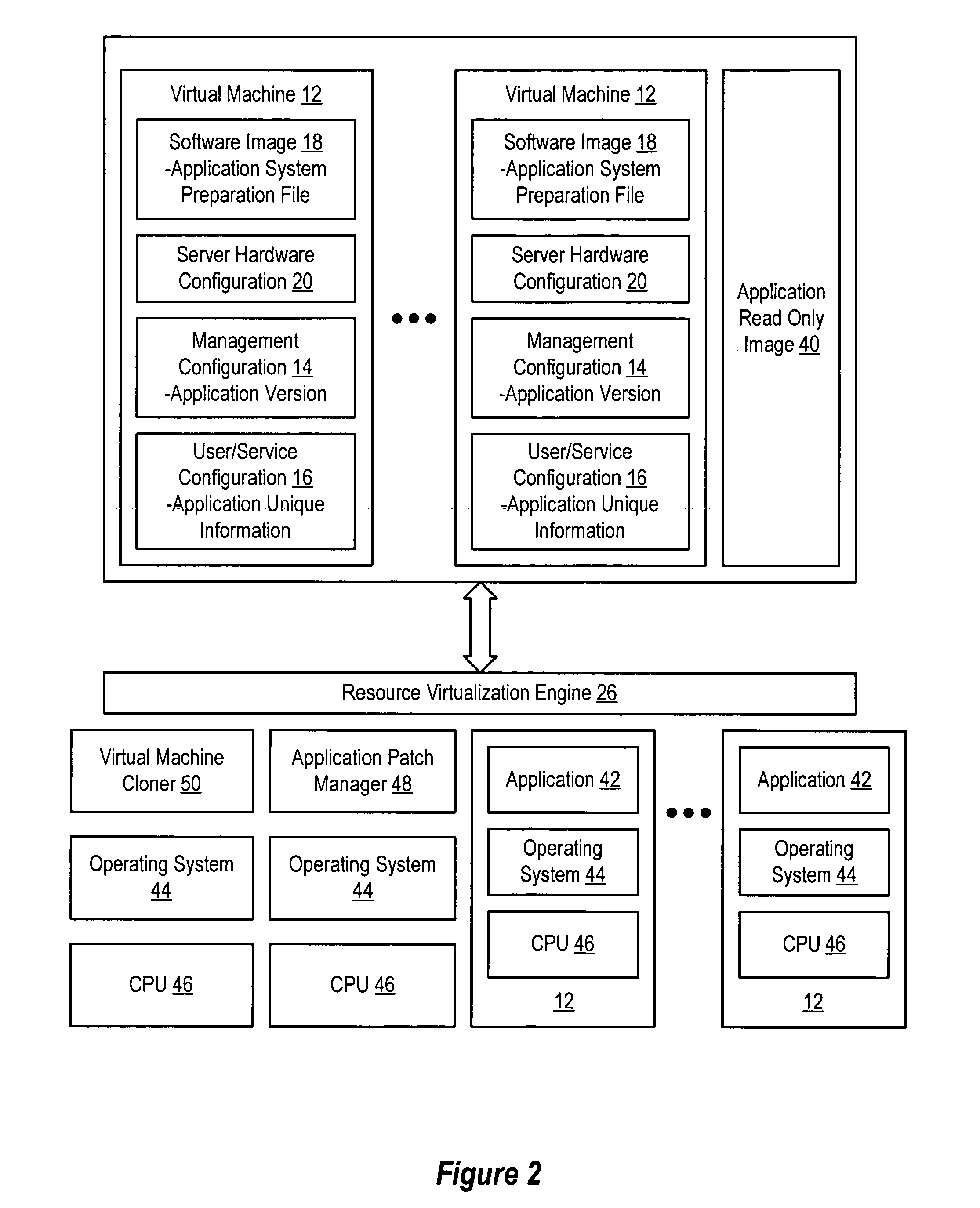
InactiveUS20060184937A1Simplifies management system updateSimple dataSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
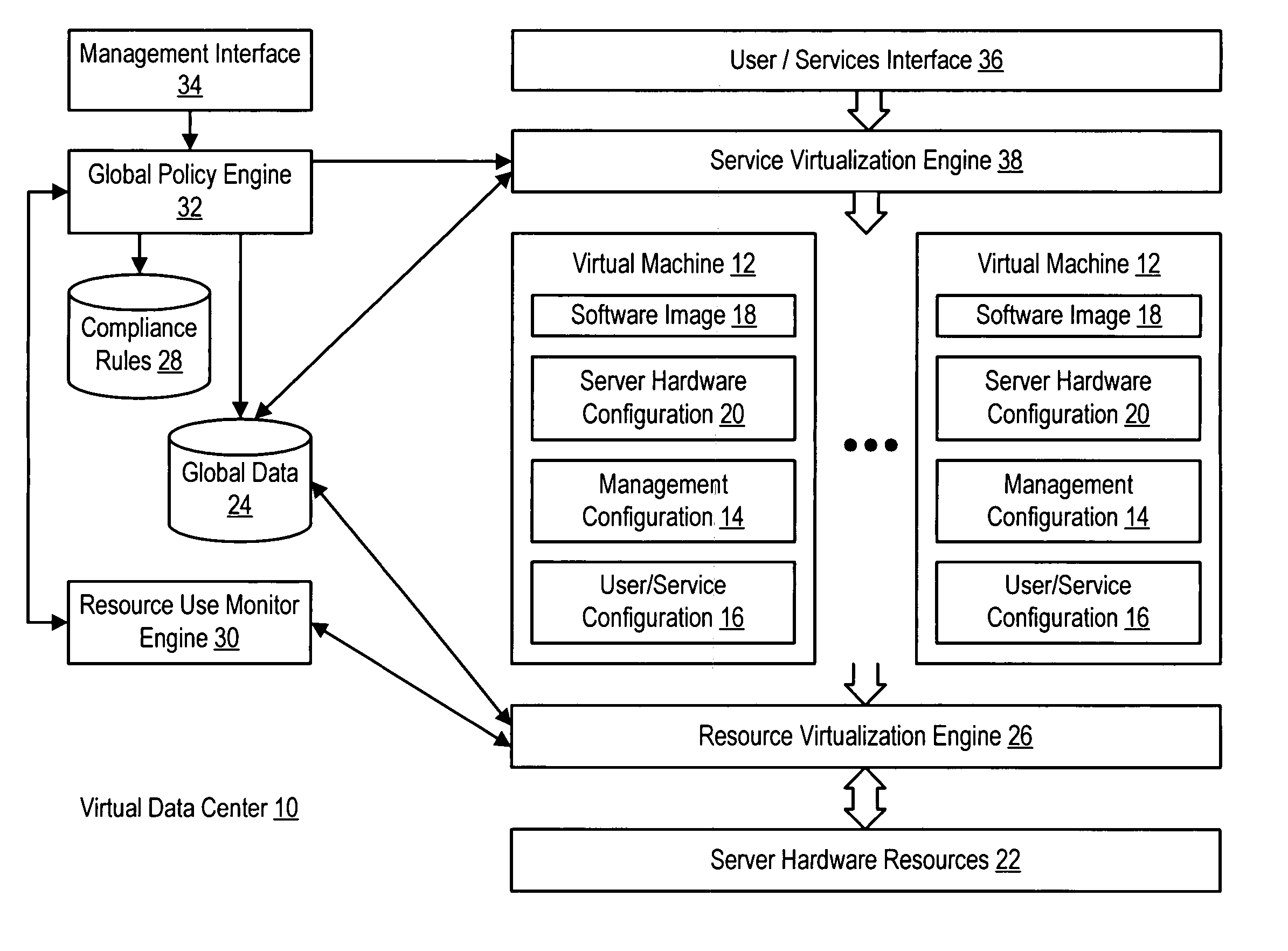
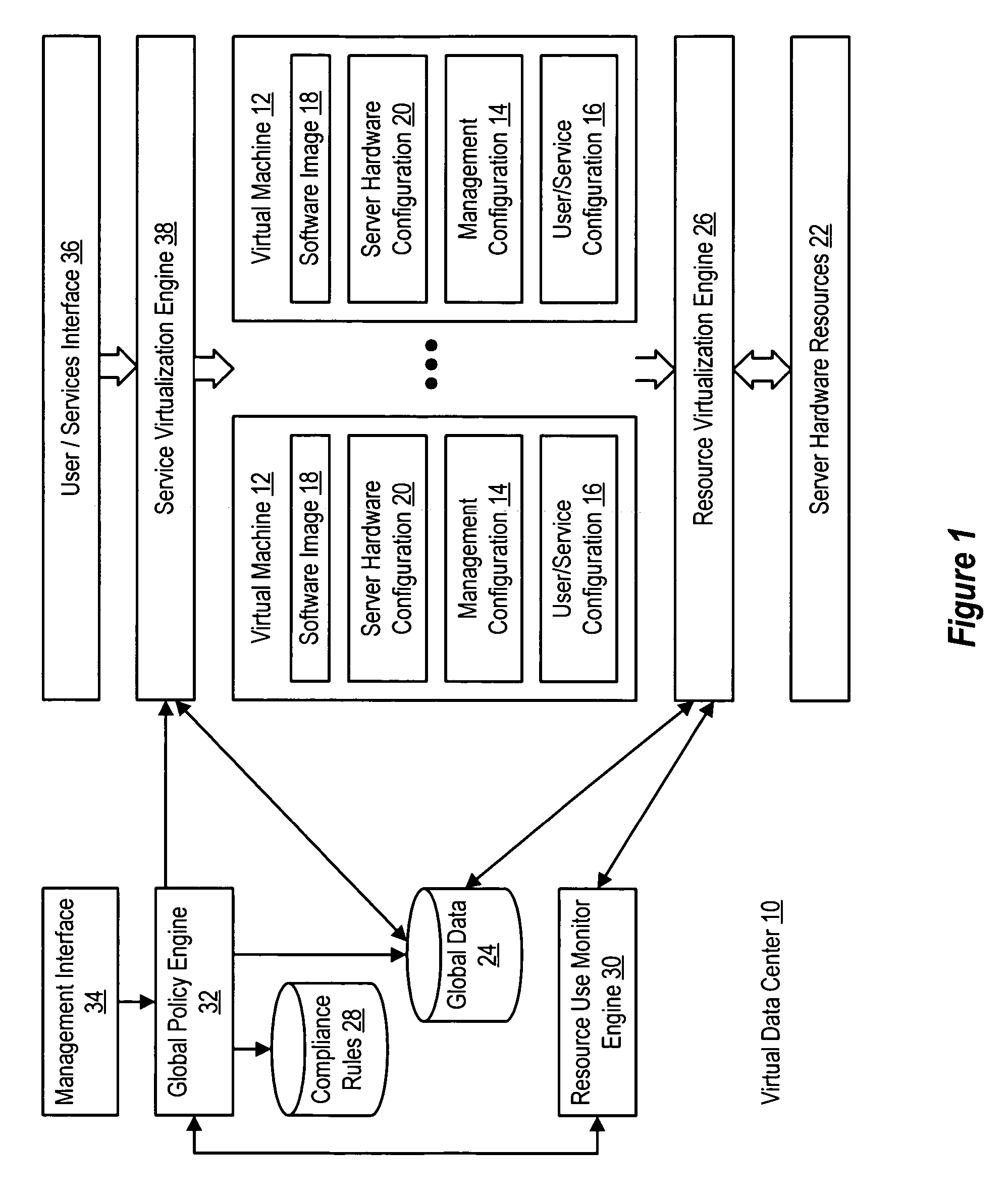
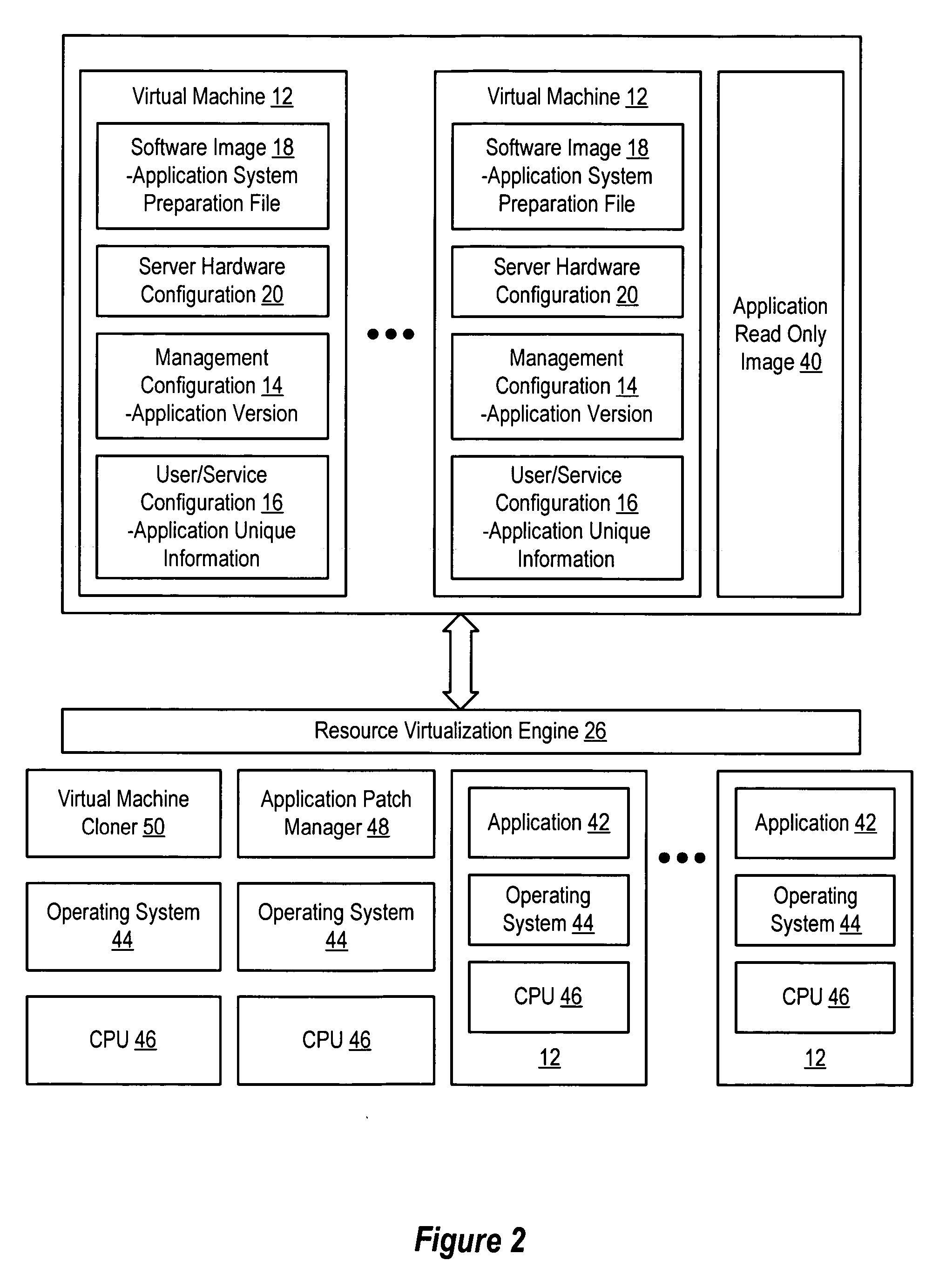
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
Systems and methods for monitoring data and bandwidth usage
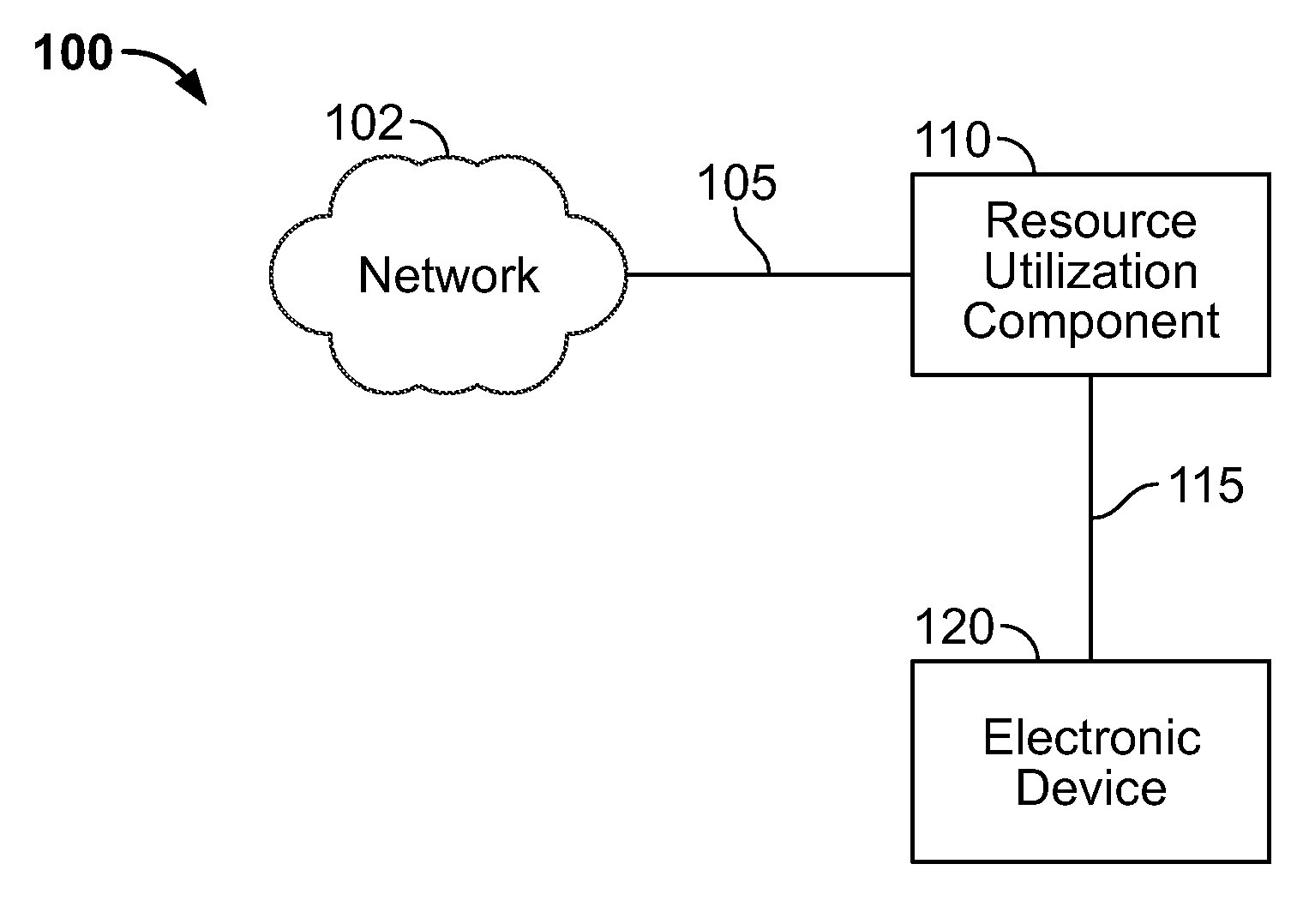
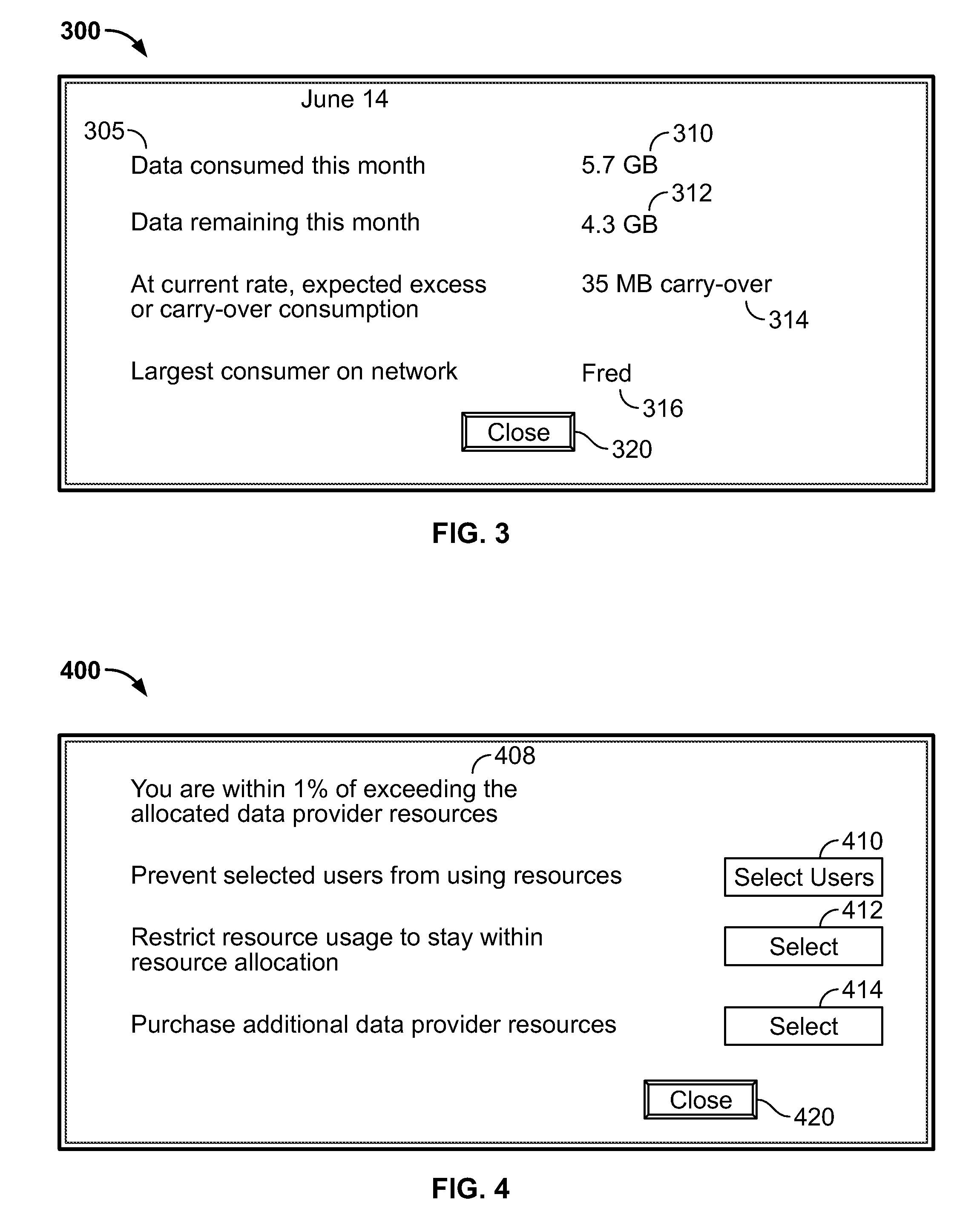
ActiveUS20100017506A1Assess restrictionMultiple digital computer combinationsResource consumptionResource utilization
Access to a communications network may be provided via a data provider that may charge for access. In some cases, the access fee may be related to the amount of network resources consumed (e.g., amount of data downloaded or bandwidth used). In some cases, a user may have access to a particular amount of data provider resources and be required to pay an additional fee for using resources in excess of the particular amount. To assist the user in managing his data resource consumption, a resource utilization component may provide different alerts and notices informing the user of current consumption, expected future consumption, and recommendations for reducing data provider resources consumed (e.g., stopping particular processes or data provider requests, such as downloading media). If several electronic devices in a network are connected to the same data provider resources, a network component may manage the data provider resource use among the several electronic devices (e.g., allow only particular users or devices access).
Owner:APPLE INC
Systems and methods for establishing a cloud bridge between virtual storage resources
Methods and systems for establishing a cloud bridge between two virtual storage resources and for transmitting data from one first virtual storage resource to the other virtual storage resource. The system can include a first virtual storage resource or cloud, and a storage delivery management service that executes on a computer and within the first virtual storage resource. The storage delivery management service can receive user credentials of a user that identify a storage adapter. Upon receiving the user credentials, the storage delivery management service can invoke the storage adapter which executes an interface that identifies a second virtual storage resource and includes an interface translation file. The storage delivery management service accesses the second virtual storage resource and establishes a cloud bridge with the second virtual storage resource using information obtained from the second virtual storage resource and information translated by the storage adapter using the interface translation file.
Owner:CITRIX SYST INC
System and method for resource management
InactiveUS20080172312A1Low costImprove efficiencyElectric signal transmission systemsLevel controlResource managementSystem usage
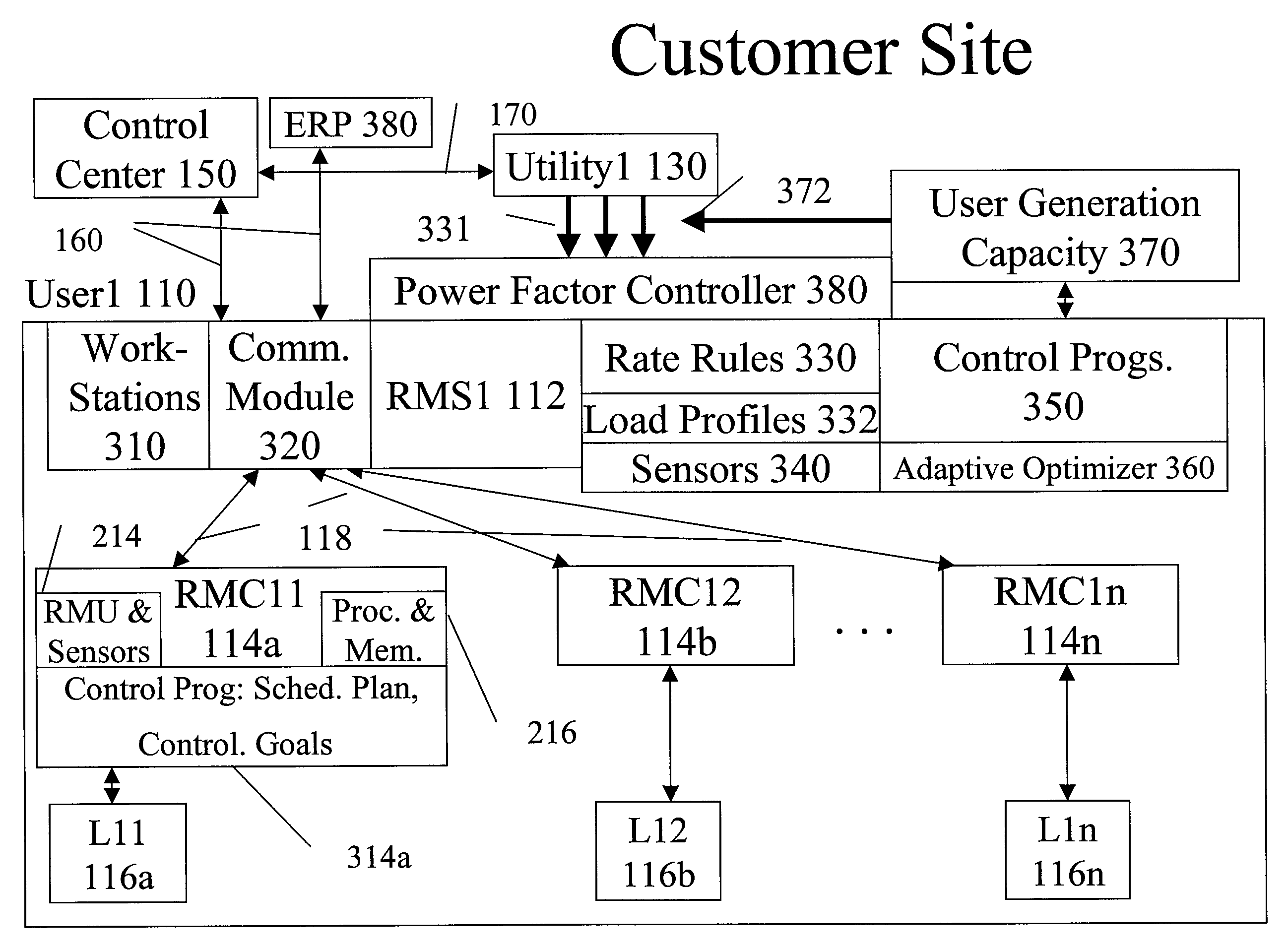
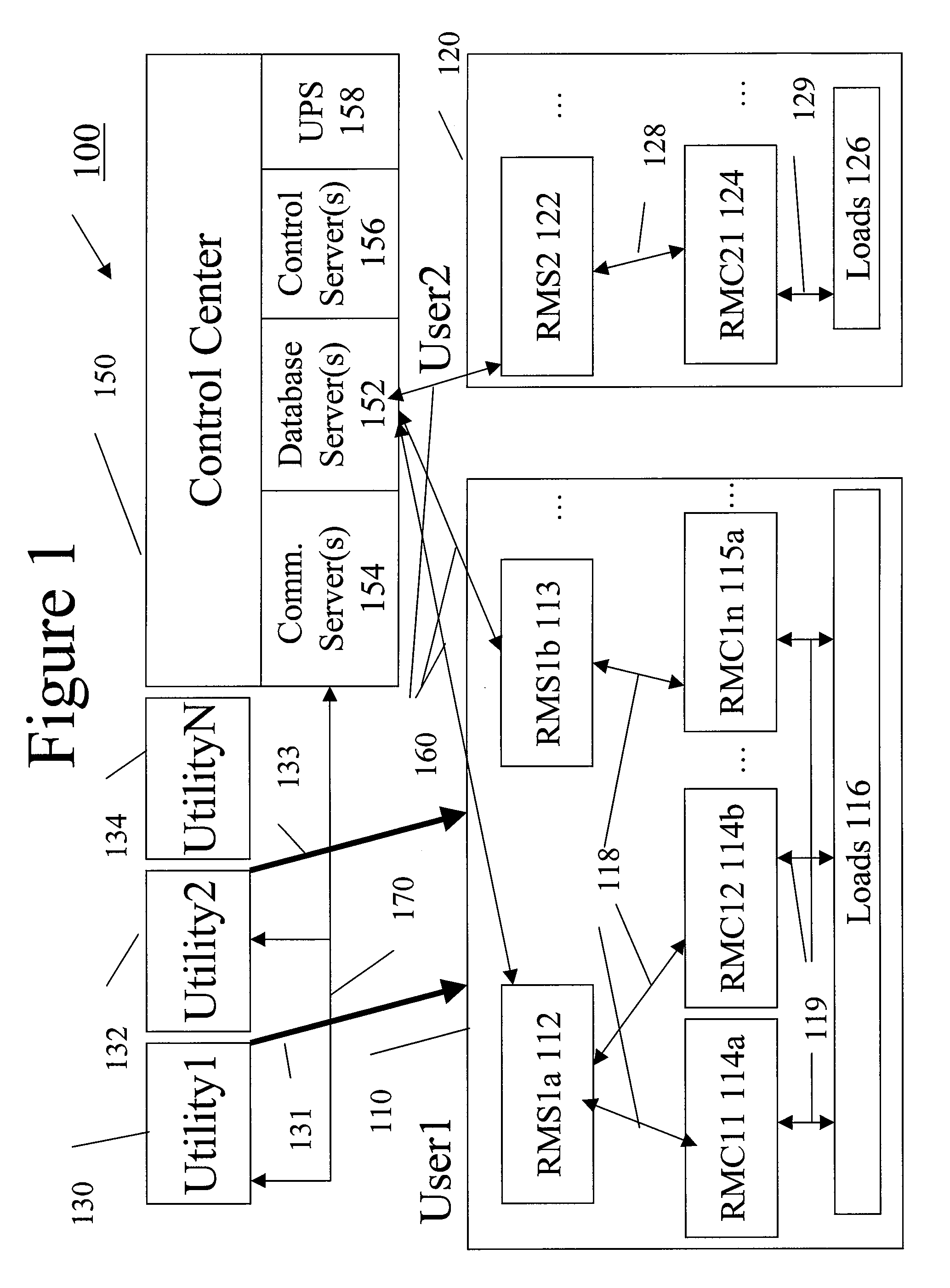
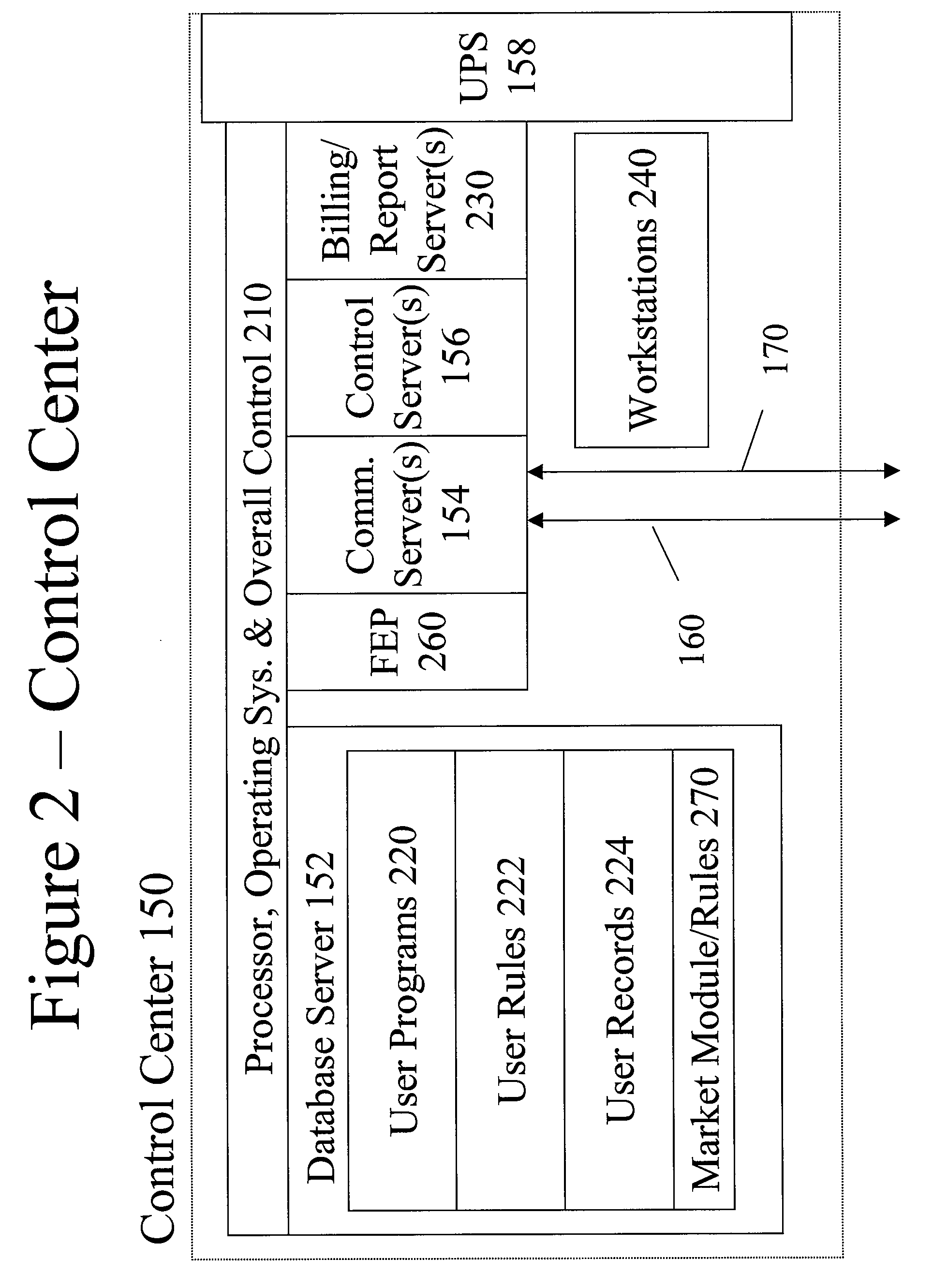
A system uses an intelligent load controller for managing use of a consumable resource at an associated load. The controller has a resource measuring component for measuring the rate of use of the resource by the associated load, including measuring at least one of an instantaneous usage rate and a usage rate over an integration period and a load status component for receiving load status data for the associated load. The controller also has a communication component for receiving control messages from and sending load status messages to other associated controllers; a memory for storing a load control goal set; and a load control computer program responsive to the resource measuring component, the load status component, the control messages from other associated controllers and the load control goal set, to determine a load operating level for, and provide control commands to, the associated load.
Owner:SYNESIOU ANDREAS JOANNI +1
System and method for automatic workload characterization
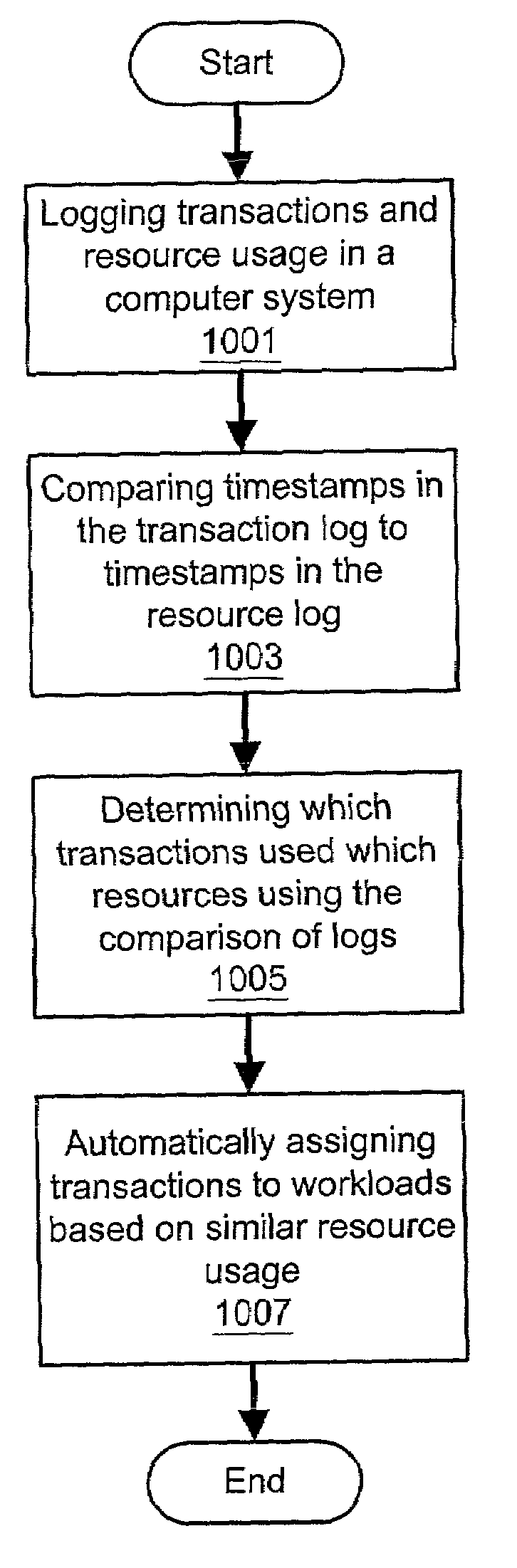
ActiveUS7028301B2Good precisionEasy accessResource allocationMemory systemsTimestampResource consumption
A system and method for automatic workload characterization are provided. Transactions performed in a computer system may be logged. The log of transactions comprises a timestamp for each transaction. Resource usage in the computer system may be logged. The log of resource usage comprises one or more periods of time during which each of a plurality of resources is used, and the log of resource usage comprises a plurality of system performance metrics which reflect resource consumption by one or more processes that performed the transactions. The timestamps in the log of transactions may be compared to the periods of time in the log of resource usage. It may be determined which transactions used which resources as a result of the comparing the timestamps in the log of transactions to the periods of time in the log of resource usage. One or more workloads may be determined using the determining which transactions used which resources. Heuristics may be used to group processes into workloads.
Owner:BMC SOFTWARE
Method for resource optimized network virtualization overlay transport in virtualized data center environments
ActiveUS20150195178A1Error preventionFrequency-division multiplex detailsTransport systemData center
A method for resource optimized network virtualization overlay transport in a virtualized data center environment includes an optimized virtualized transport mechanism based on MPLS-TP tunneling technology. The transport mechanism may include a usage monitoring and resource usage advertisement mechanism based on IGP-TE protocol extension. Also, the transport mechanism may include a path computation engine (PCE) based optimal path computation for a virtualized transport tunnel used to carry VM-to-VM traffic across the virtualized data center. Additionally, the transport mechanism may include a SDN controller for provisioning and control of virtualized machines and a virtualized transport system.
Owner:CIENA
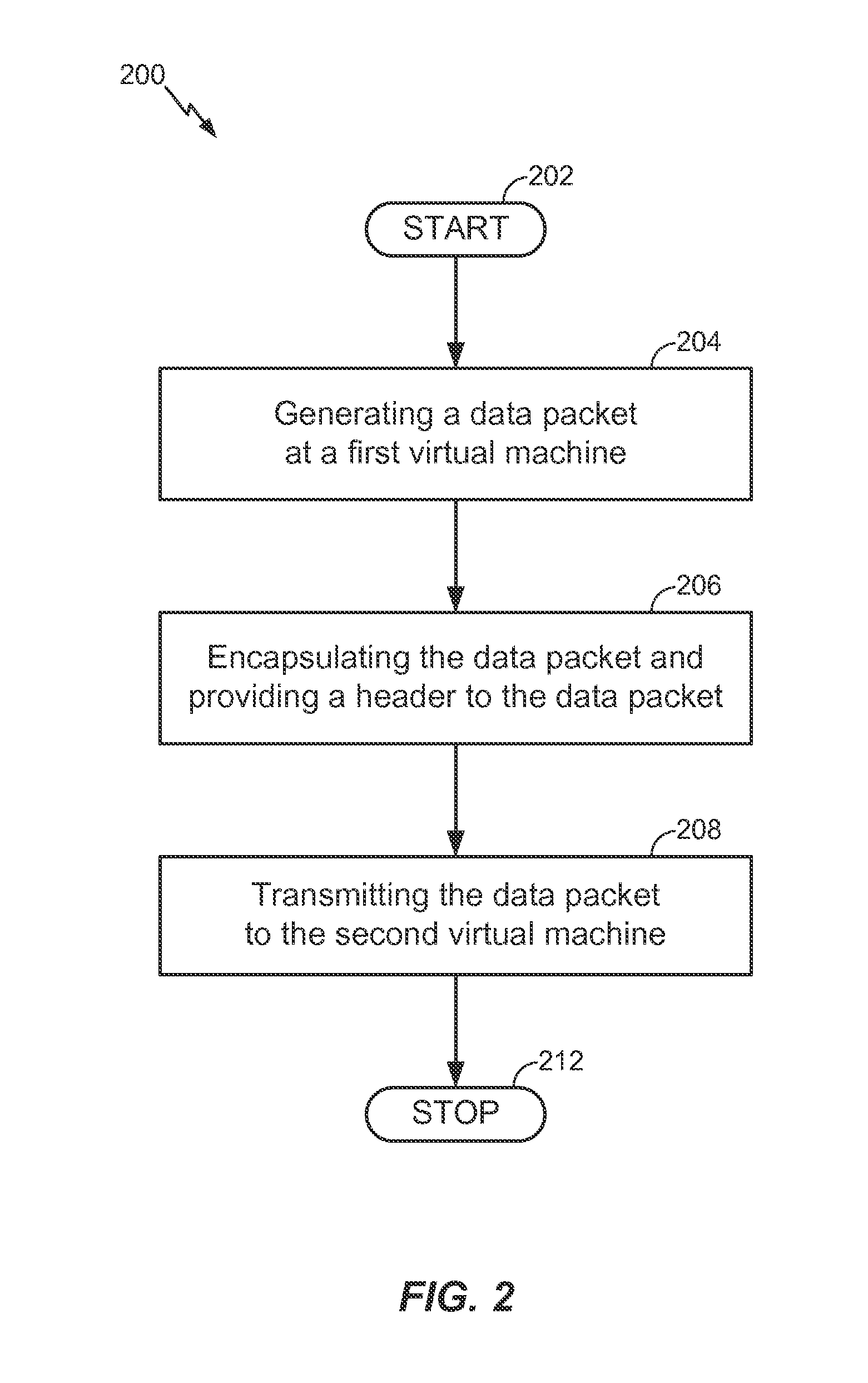
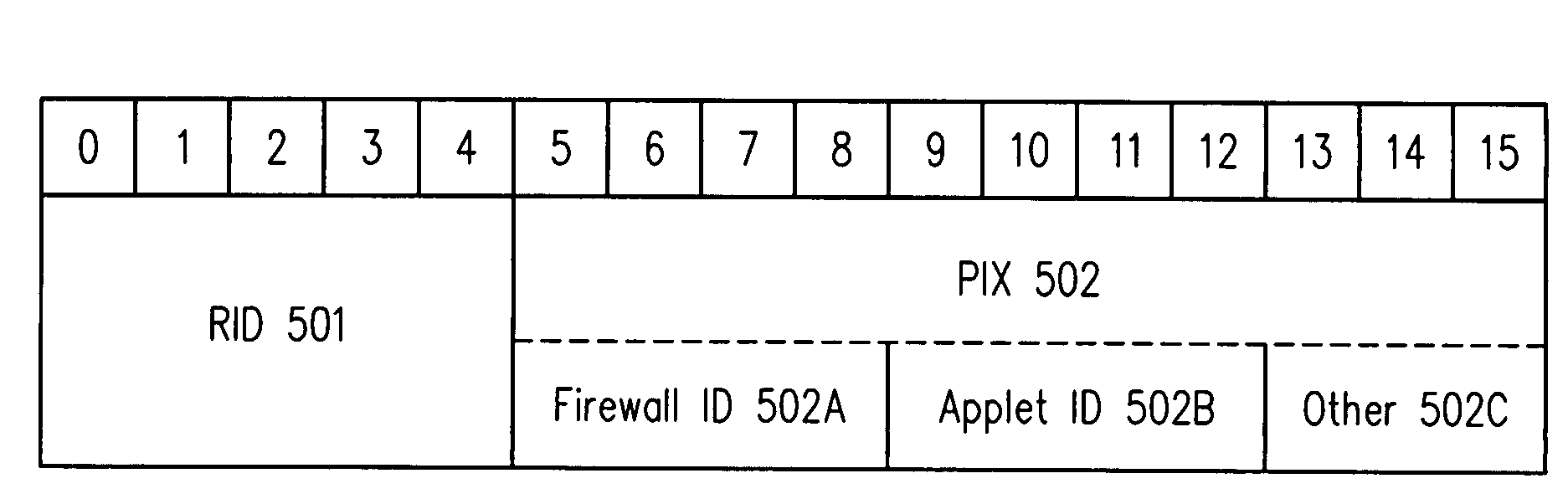
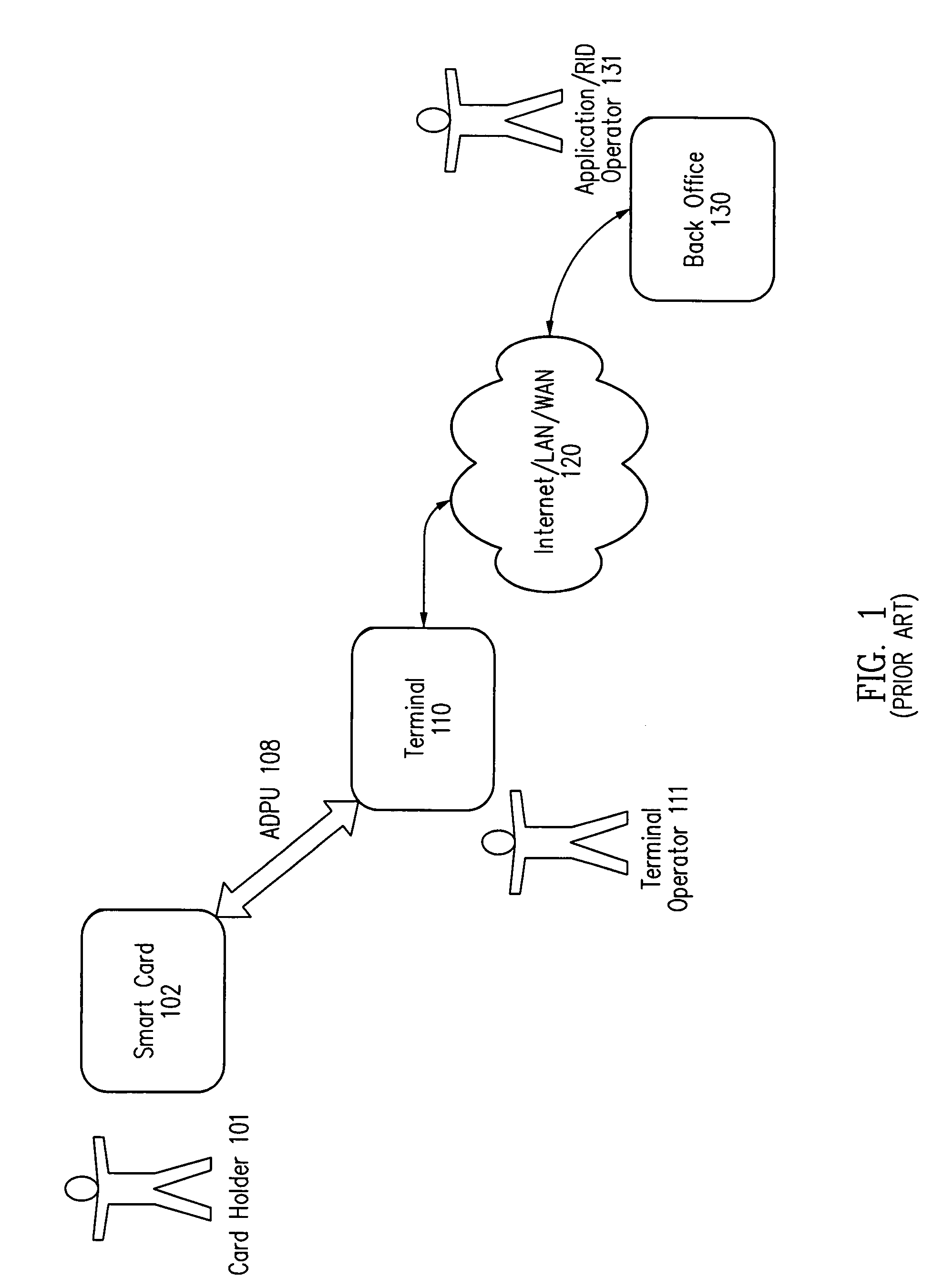
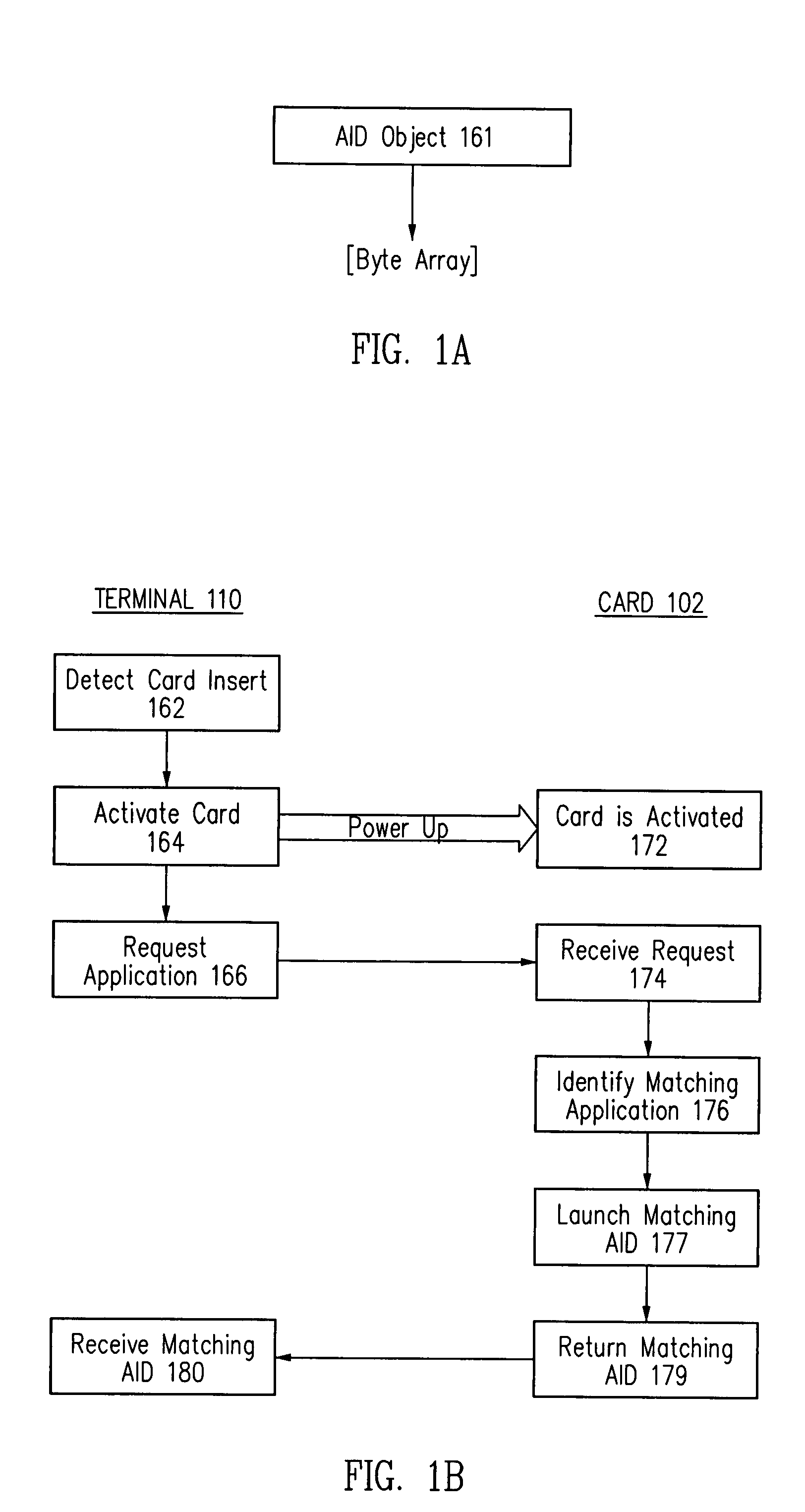
Method and apparatus for processing an application identifier from a smart card
An application identifier (AID) for an application installed on a smart card comprises a registered application provider identifier (RID). The AID may be processed by determining the RID for an application from the AID of the application, generating an identifier for a network resource from the RID, transmitting a request to the network resource using the identifier, and receiving a response to the request. The response comprises material for use in handling the application on the smart card.
Owner:ORACLE INT CORP
System and method using virtual machines for decoupling software from management and control systems
InactiveUS20060184936A1Simplifies management system updateSimple dataSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
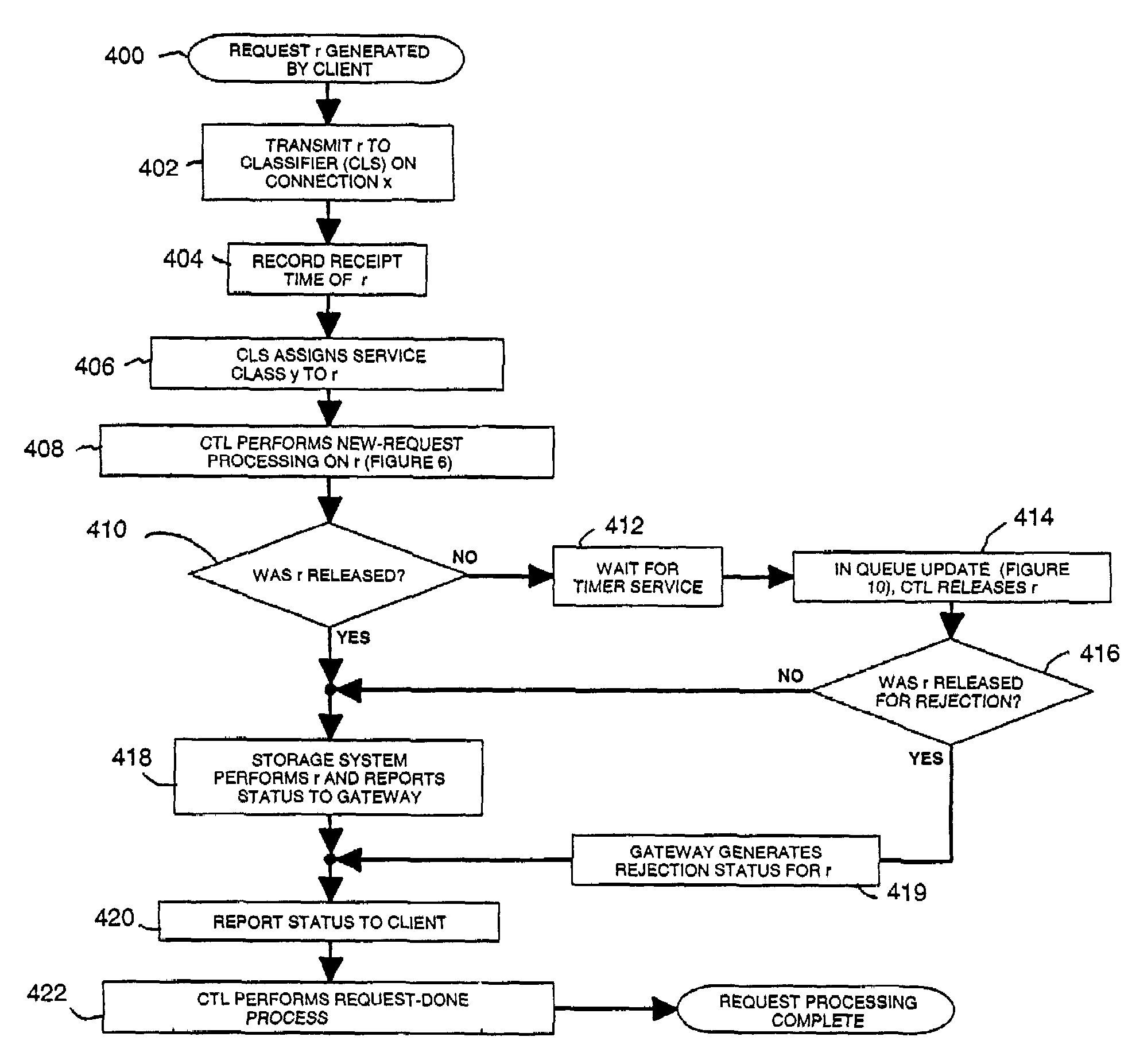
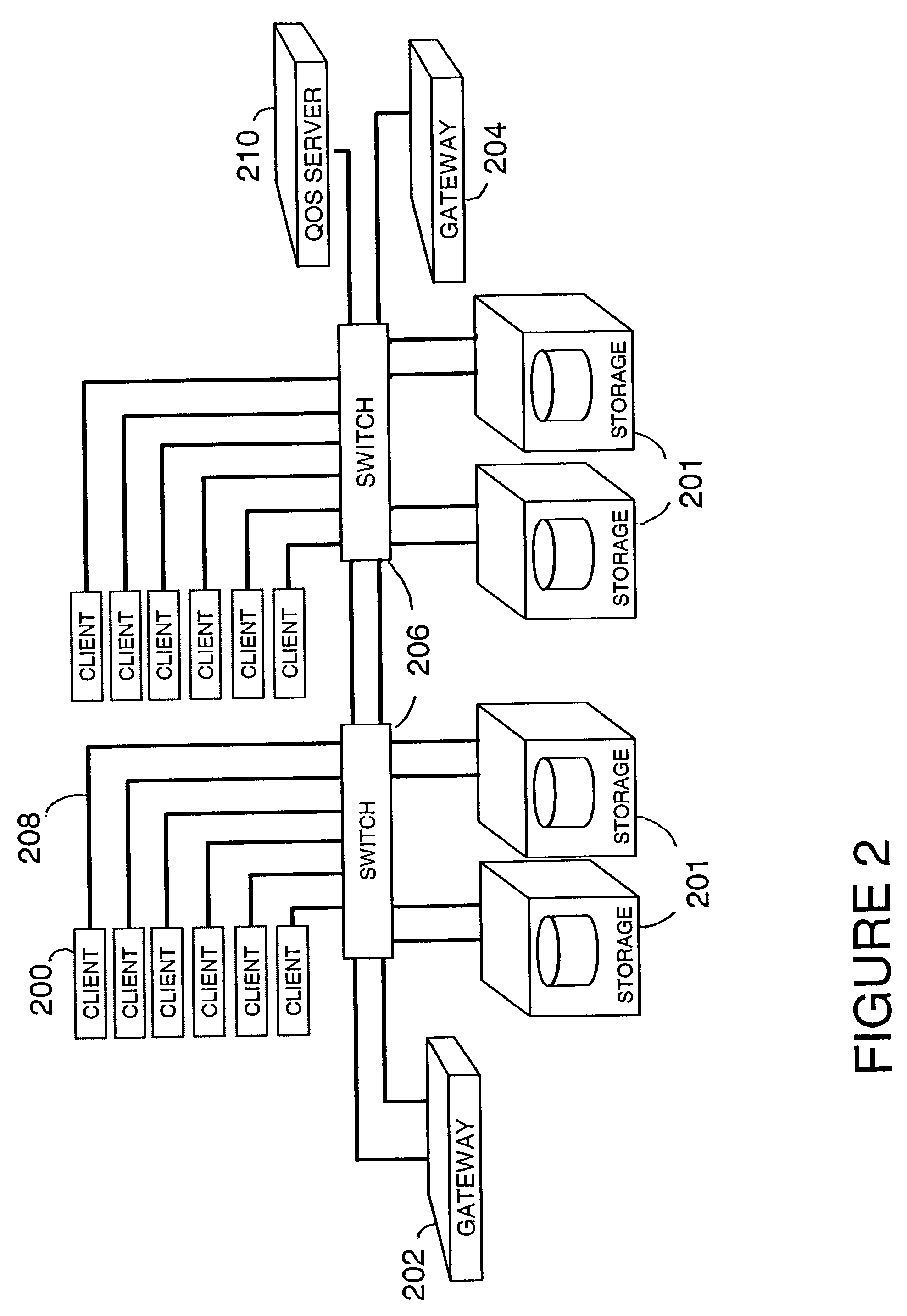
Method for improving performance in a computer storage system by regulating resource requests from clients
InactiveUS7228354B2Improve performanceTotal system performance requirements can be achieved and guaranteedError detection/correctionMultiprogramming arrangementsResource basedClient-side
Owner:IBM CORP
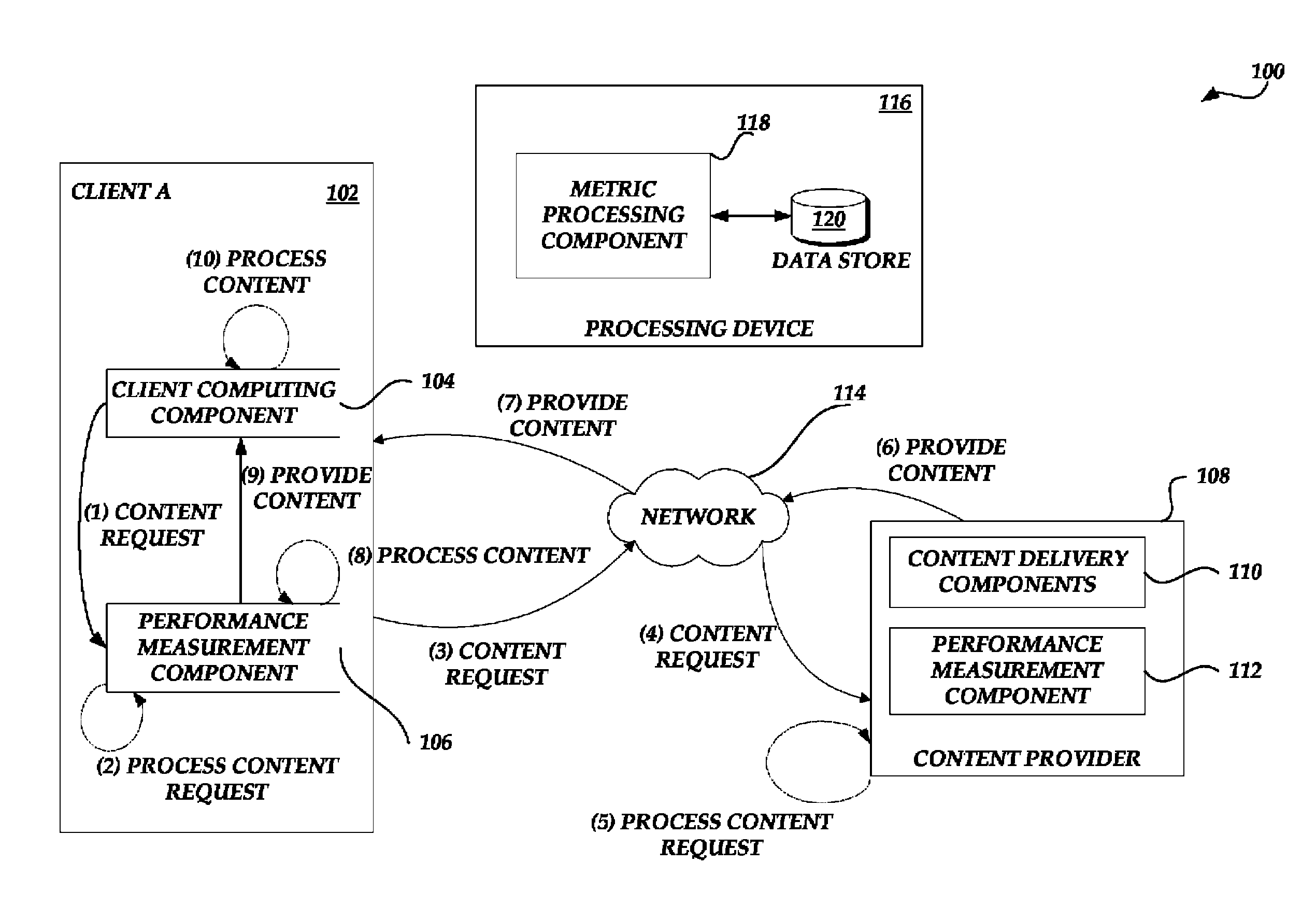
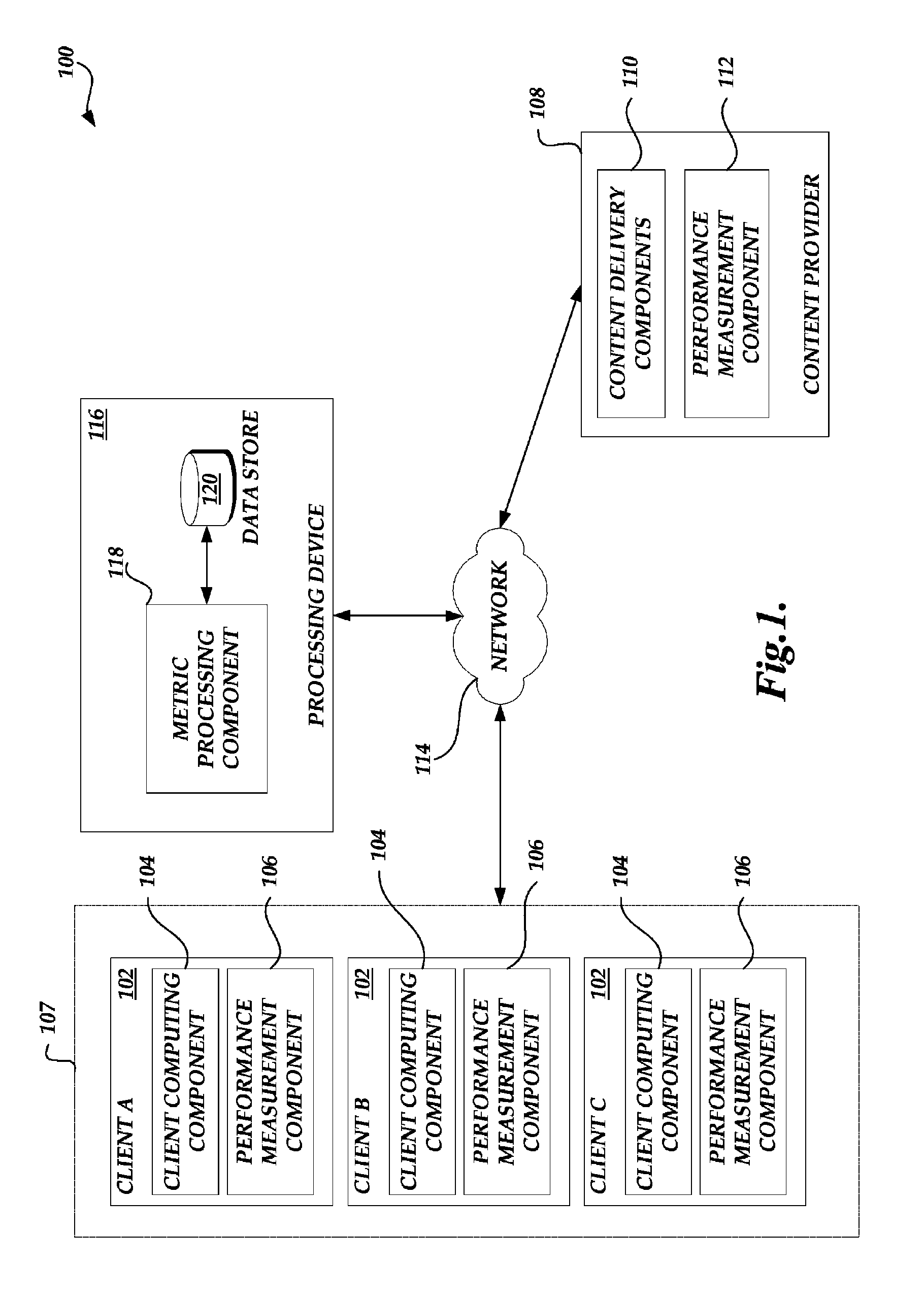
Monitoring domain allocation performance
ActiveUS7930393B1Error detection/correctionDigital computer detailsSelection criterionDistributed computing
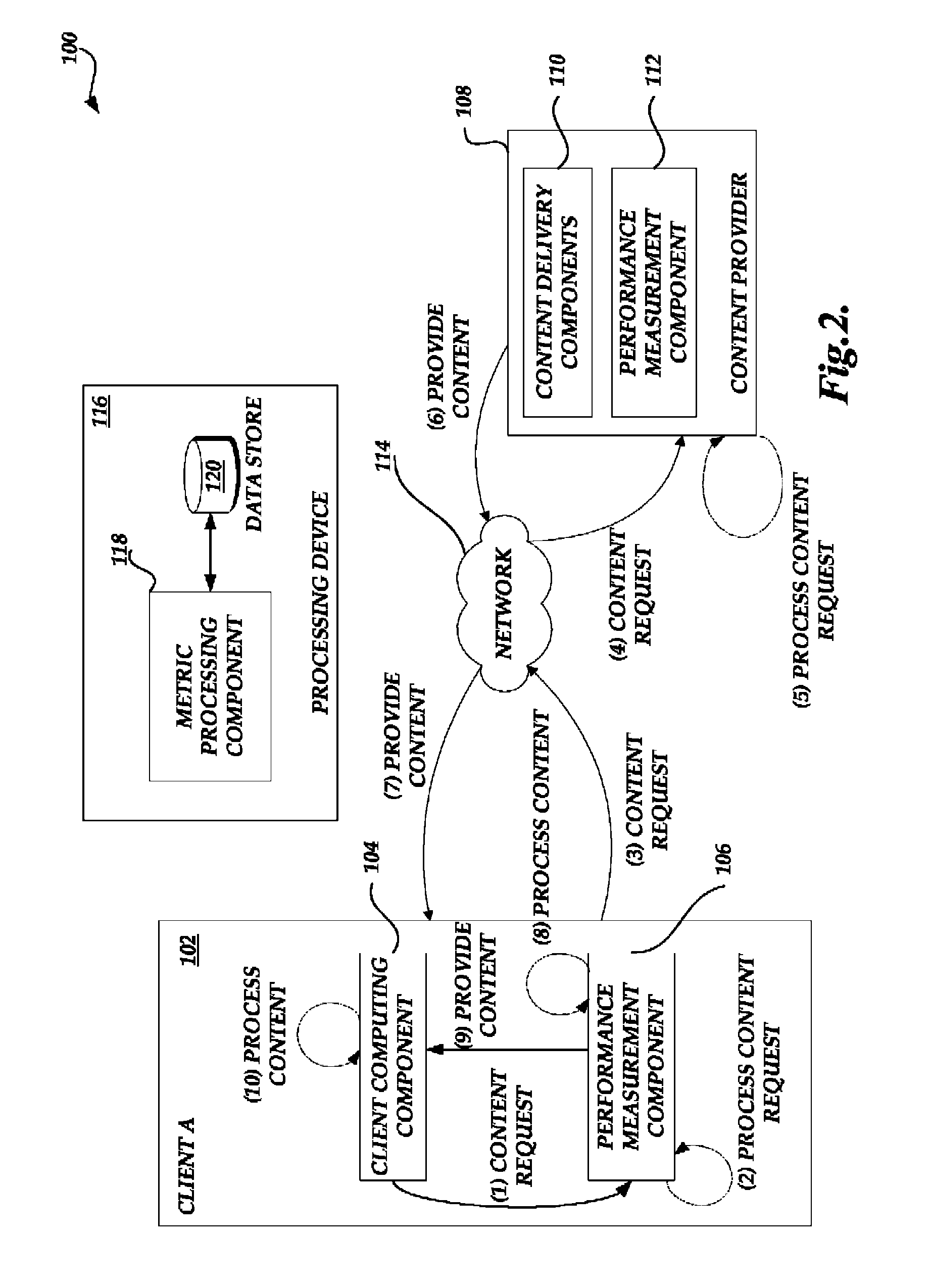
Systems and methods for monitoring the performance associated with fulfilling resource requests and determining optimizations for improving such performance are provided. A processing device obtains and processes performance metric information associated with processing a request corresponding to two or more embedded resources. The processing device uses the processed performance metric information to determine an allocation of one or more domains to be associated with the two or more embedded resources. In some embodiments, in making such a determination, the processing device assesses performance metric information collected and associated with subsequent requests for the two or more embedded resources using each of a variety of alternative allocations of domains associated with the two or more embedded resources. The processing device may also consider a number of factors, including domain selection criteria obtained from an original content provider. Aspects of systems and methods for generating recommendations to use a particular allocation of domains to process a subsequent request corresponding to the two or more embedded resources are also provided.
Owner:AMAZON TECH INC
Interference Control, SINR Optimization and Signaling Enhancements to Improve the Performance of OTDOA Measurements
ActiveUS20100317343A1Modulated-carrier systemsPosition fixationBase station identity codeCell carrier
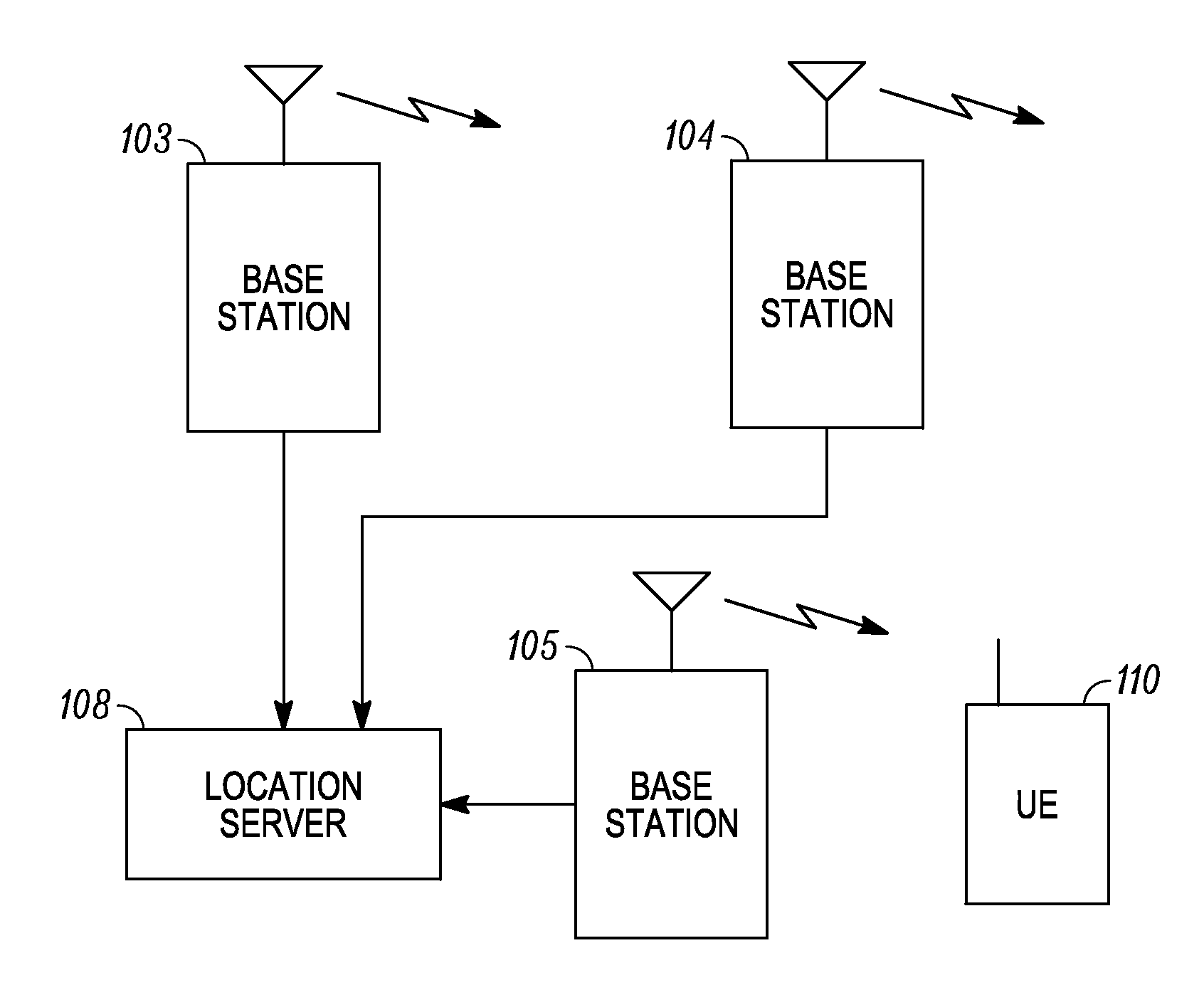
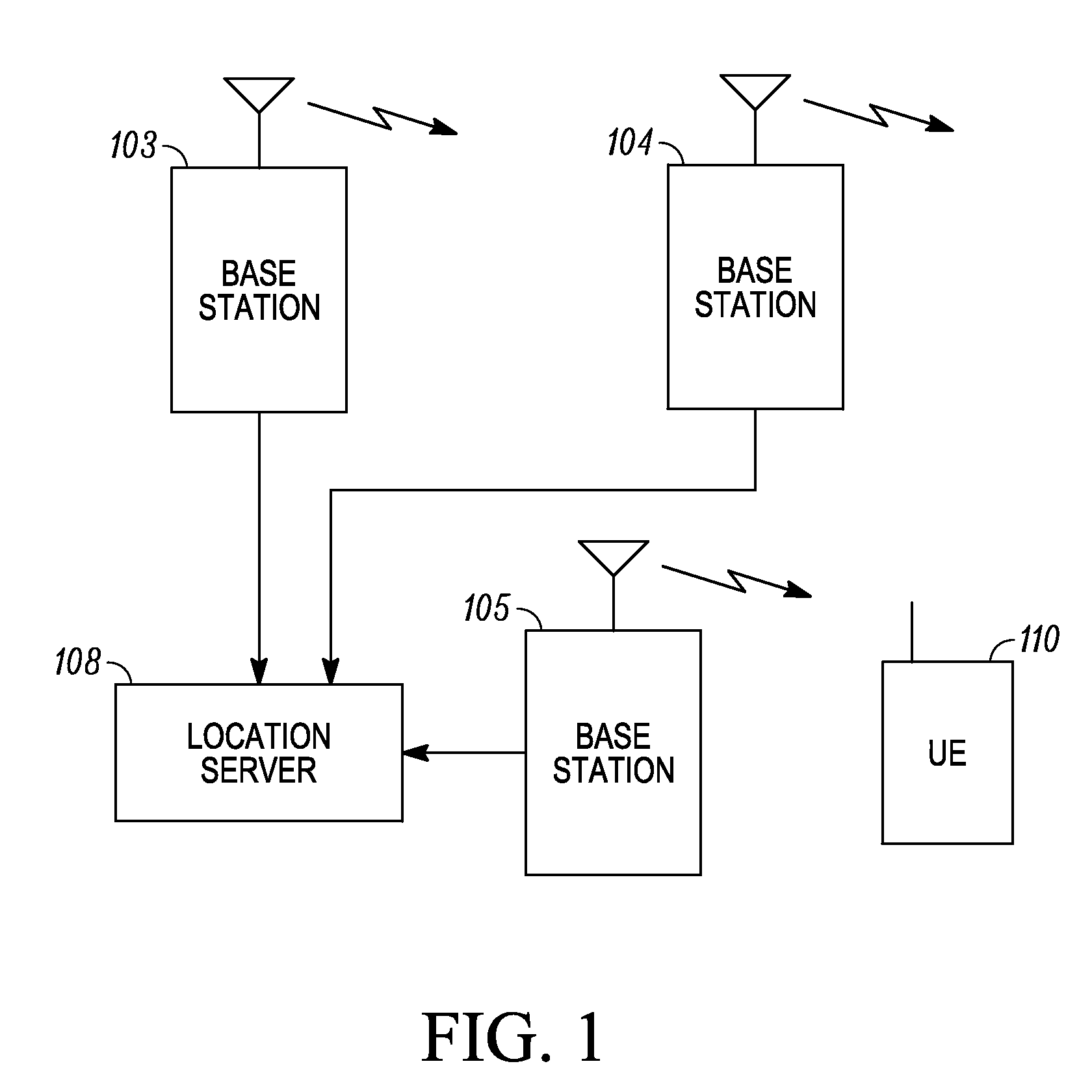
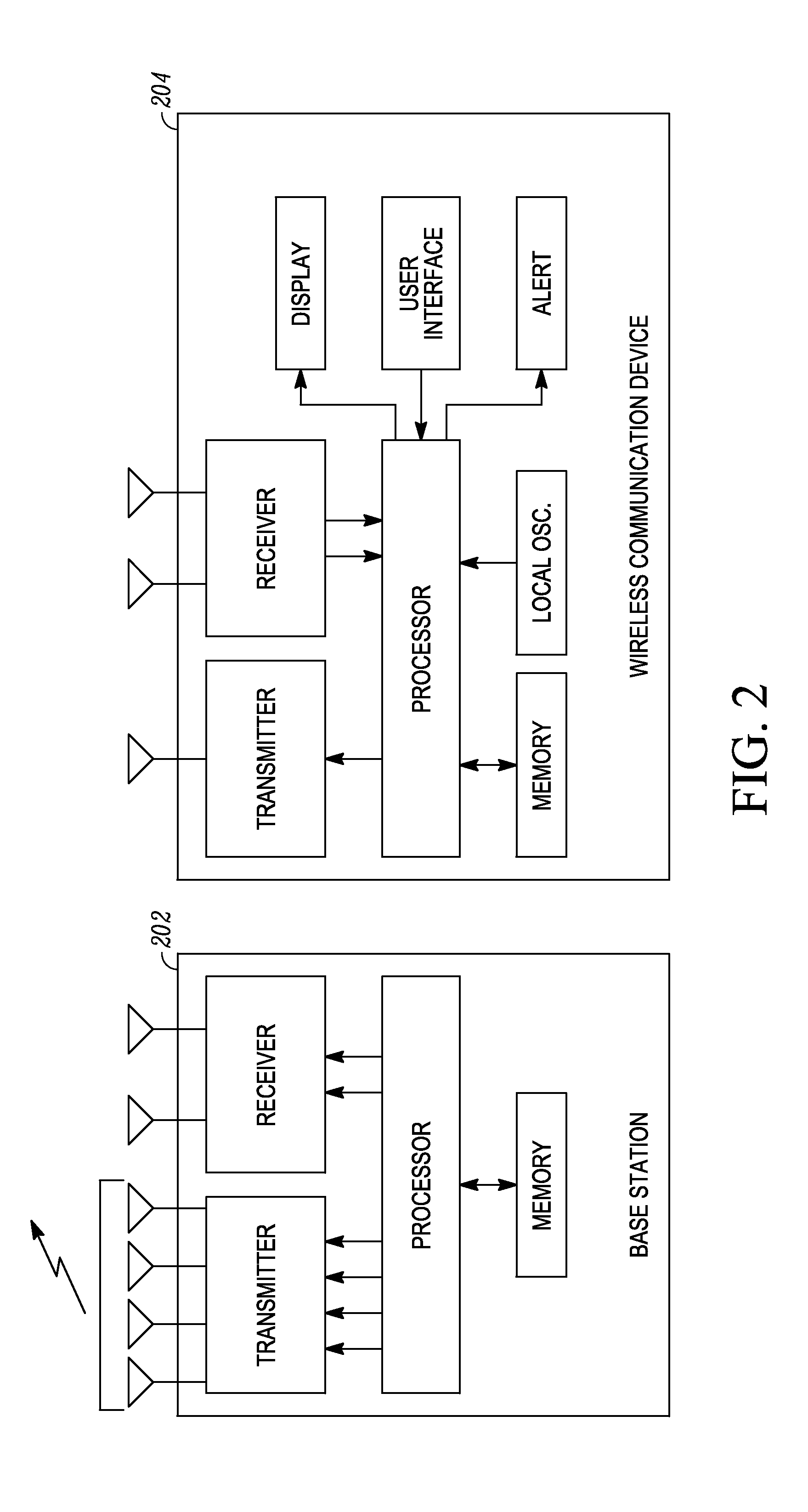
A wireless terminal receives signaling information, pertaining to a reference signal transmission in at least one specifically designated sub frame, the signaling information including a list, the list including base station identities. The terminal determines, from at least one of the base station identities in the list, the time-frequency resources associated with a reference signal transmission intended for observed time difference of arrival (OTDOA) measurements from a transmitting base station associated with said one base station identity. The time of arrival of a transmission from the transmitting base station, relative to reference timing, is measured. The wireless terminal can receive a command from a serving cell to start performing inter-frequency OTDOA measurement on a frequency layer containing reference signals, the frequency layer distinct from the serving frequency layer, the serving frequency layer not containing positioning reference signals. The wireless terminal can perform OTDOA measurements subsequent to the reception of the command on a carrier frequency different from the serving cell carrier frequency. A base station transmitter can jointly schedule a reference signal transmission from a plurality of base station transmitters for the purpose of OTD estimation enhancement, and transmit identical reference signals from the plurality of base station transmitters, the reference signals being identical both in the signal sequence and time-frequency resources used for transmission.
Owner:GOOGLE TECH HLDG LLC
System and method for application performance management
InactiveUS7350209B2General purpose stored program computerHardware monitoringComputer resourcesUser interface
Owner:BMC SOFTWARE
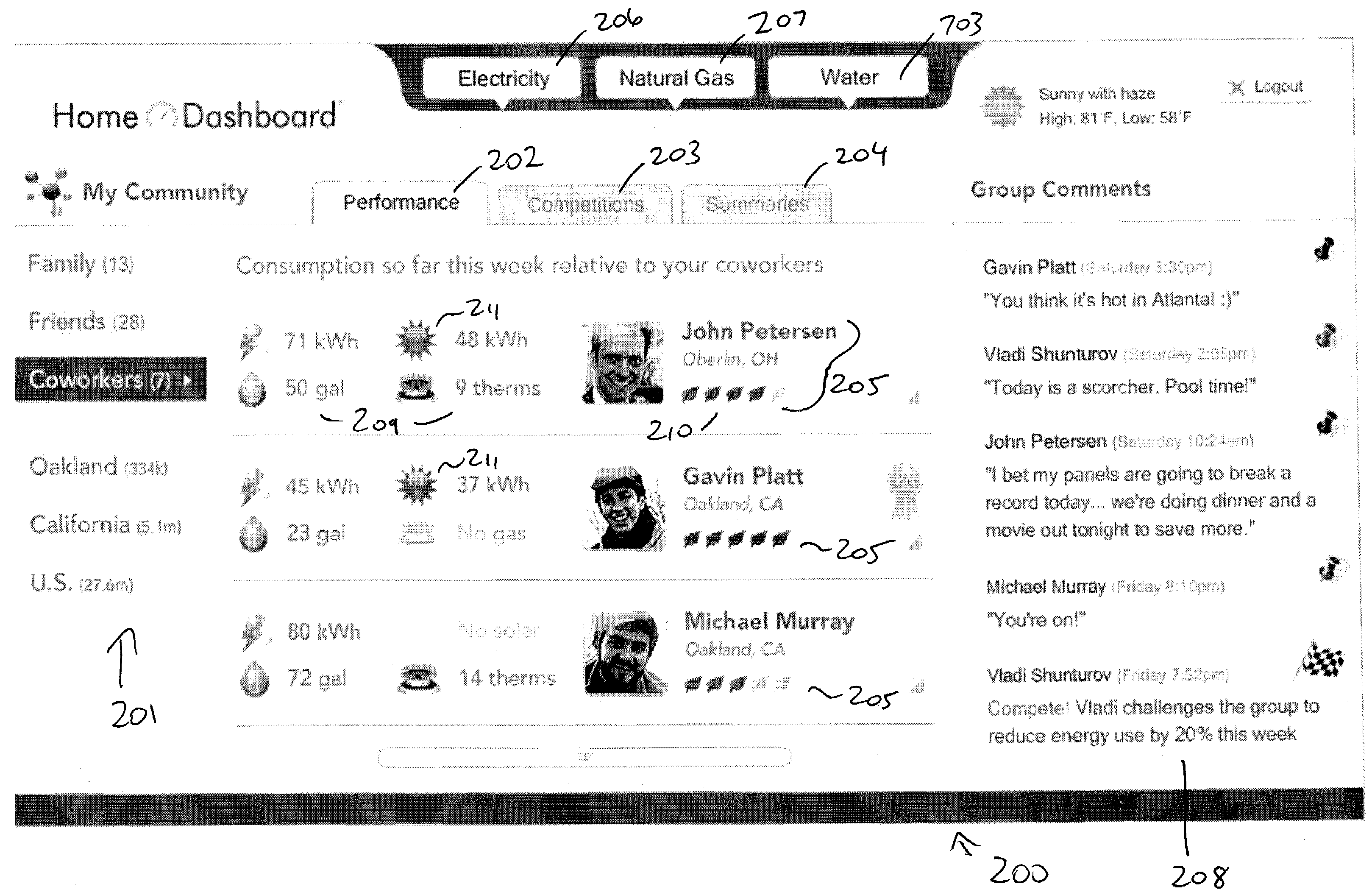
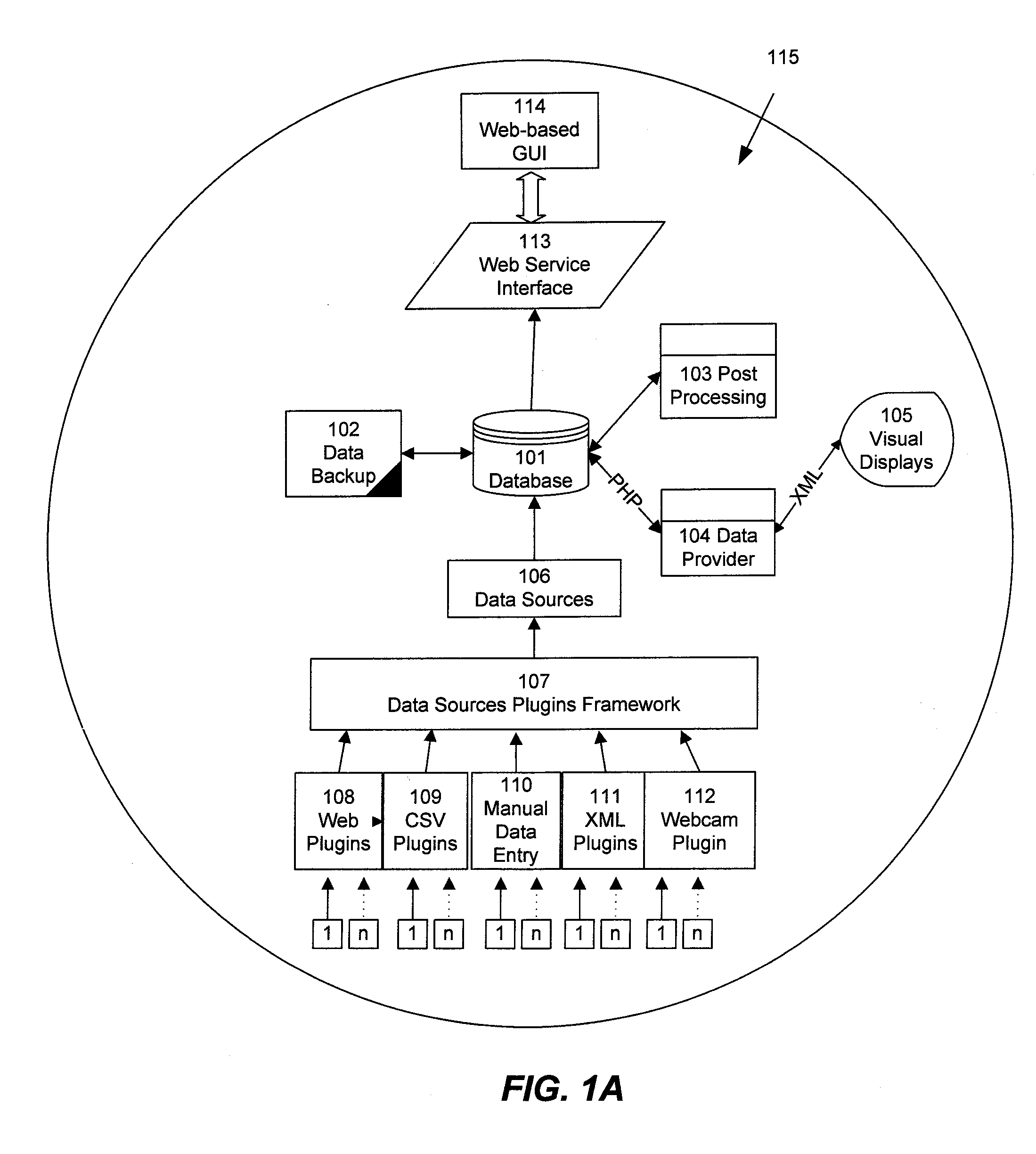
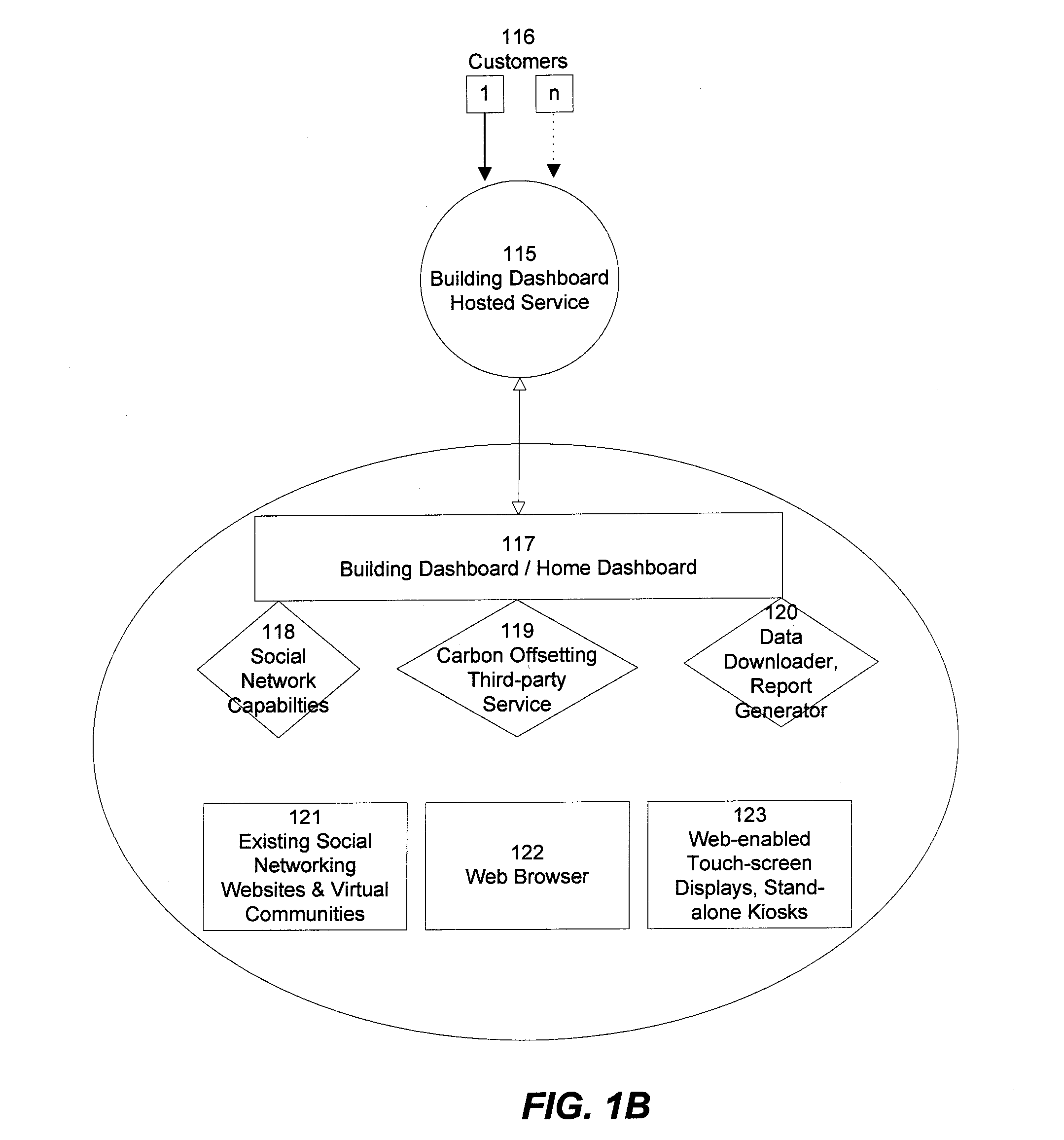
Collecting, sharing, comparing, and displaying resource usage data
ActiveUS20080306985A1Easy to compareThe effect is highlightedOffice automationCommerceGraphicsInteractive displays
Resource usage data is automatically collected for an individual, house-hold, family, organization, or other entity. The collected data is transmitted to a central repository, where it is stored and compared with real-time and / or historical usage data by that same entity and / or with data from other sources. Graphical, interactive displays and reports of resource usage data are then made available. These displays can include comparisons with data representing any or all of community averages, specific entities, historical use, representative similarly-situated entities, and the like. Resource usage data can be made available within a social networking context, published, and / or selectively shared with other entities.
Owner:ABL IP HLDG
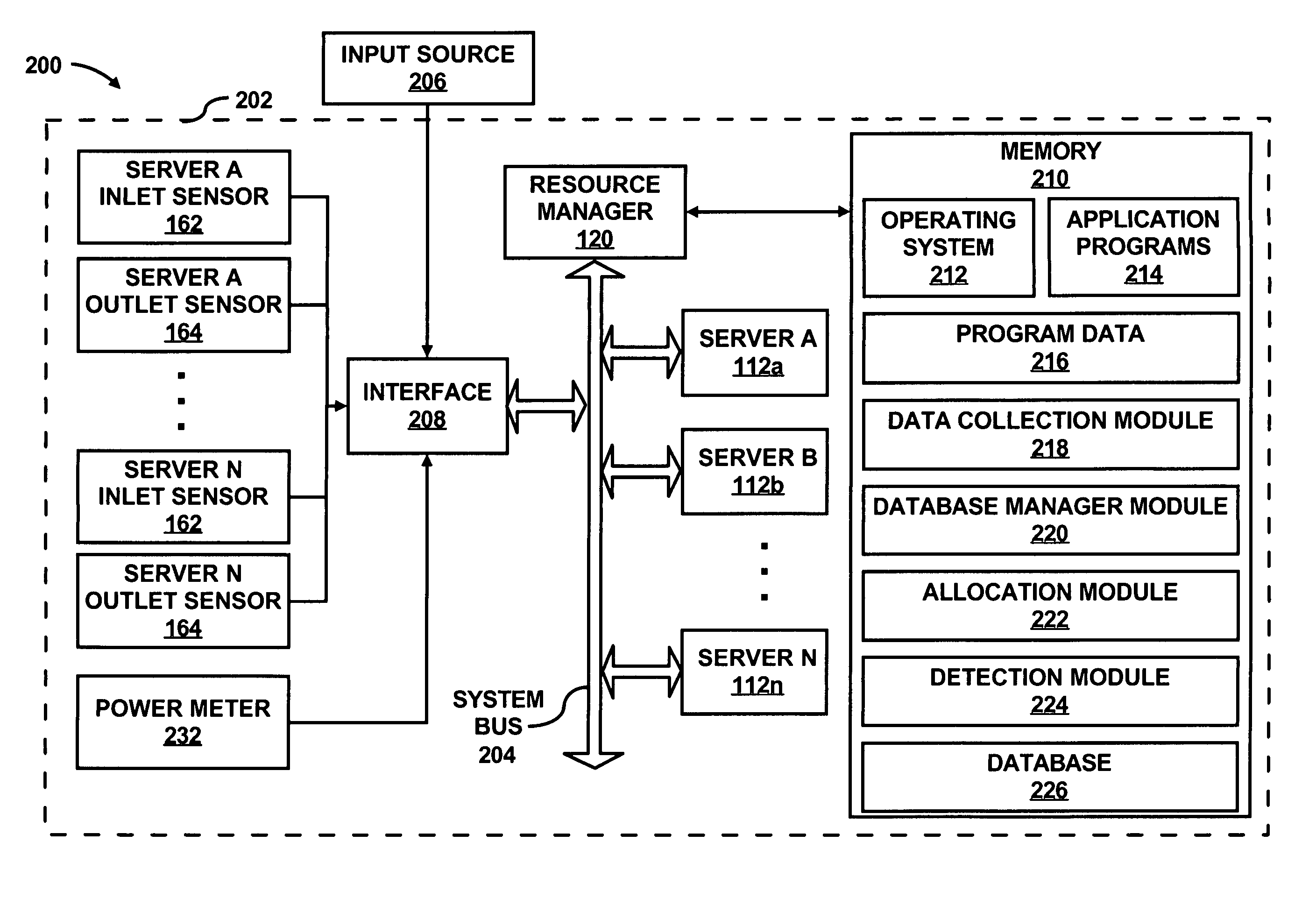
Historical data based workload allocation
ActiveUS20060259621A1Minimizing resource usageMinimize powerEnergy efficient ICTDigital data processing detailsWorkload profilingWorkload
In a method of allocating workload among servers based upon historical data, a requested workload profile is received and is compared with a plurality of historical workload profiles. A historical workload profile that is within a predefined range of the requested workload profile and that corresponds to a substantially minimized resource usage for power and cooling is selected. In addition, workload among the servers is allocated according to the selected historical workload profile to thereby substantially minimize resource usage for power and cooling.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
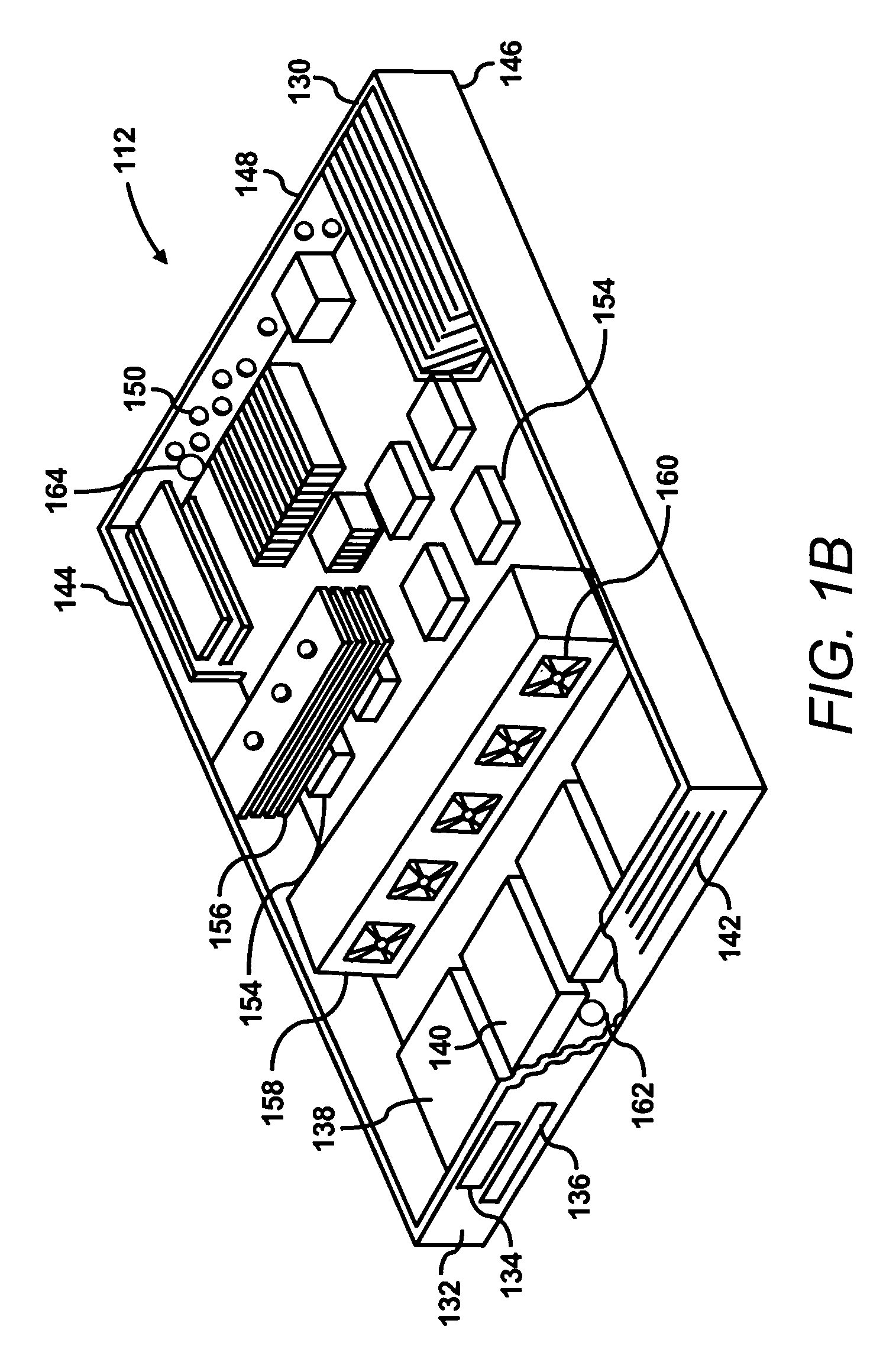
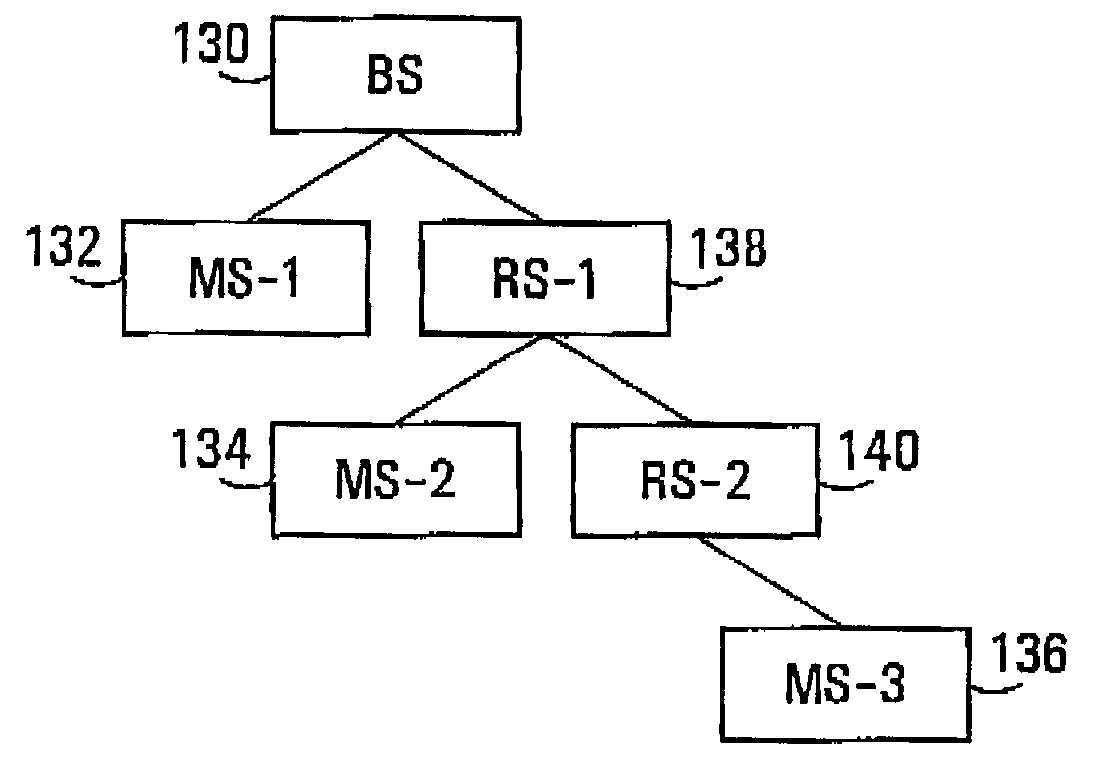
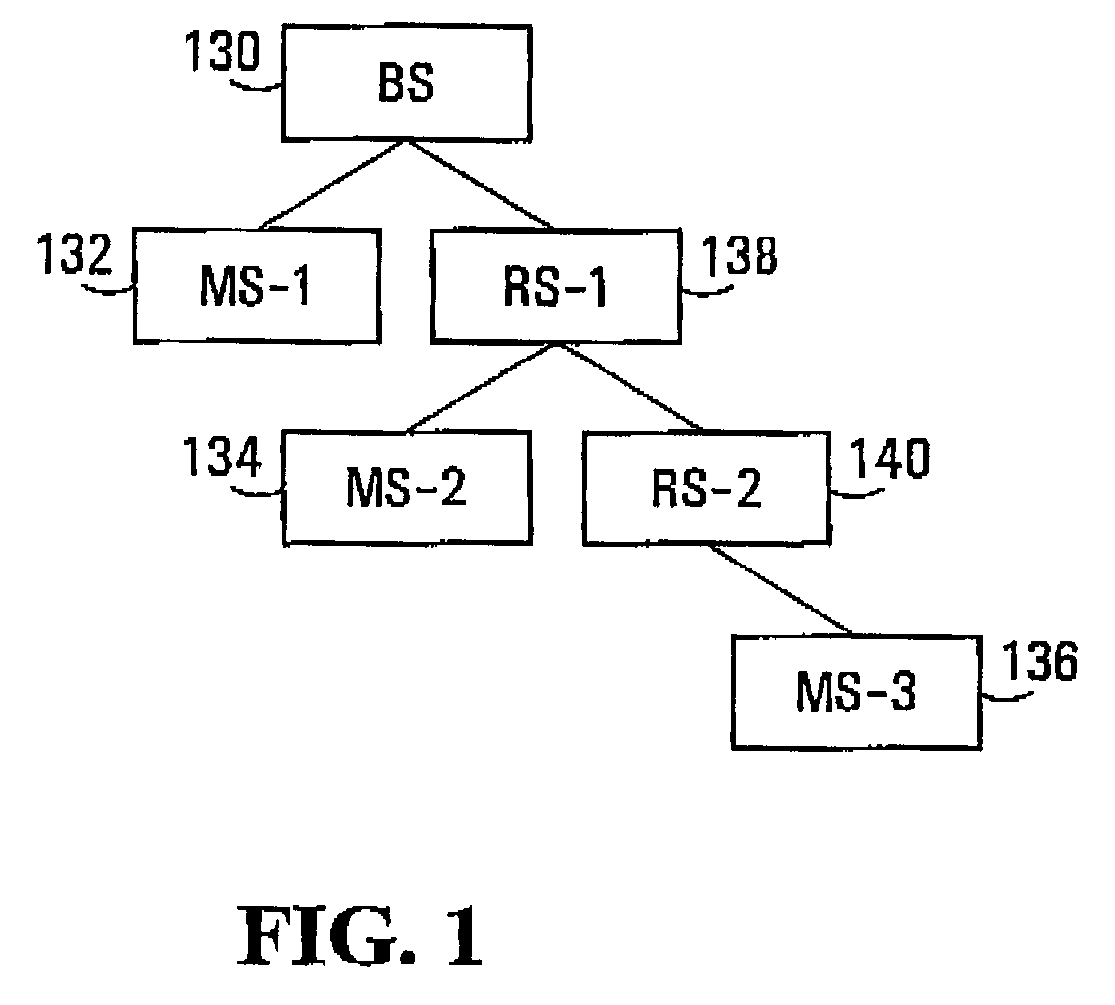
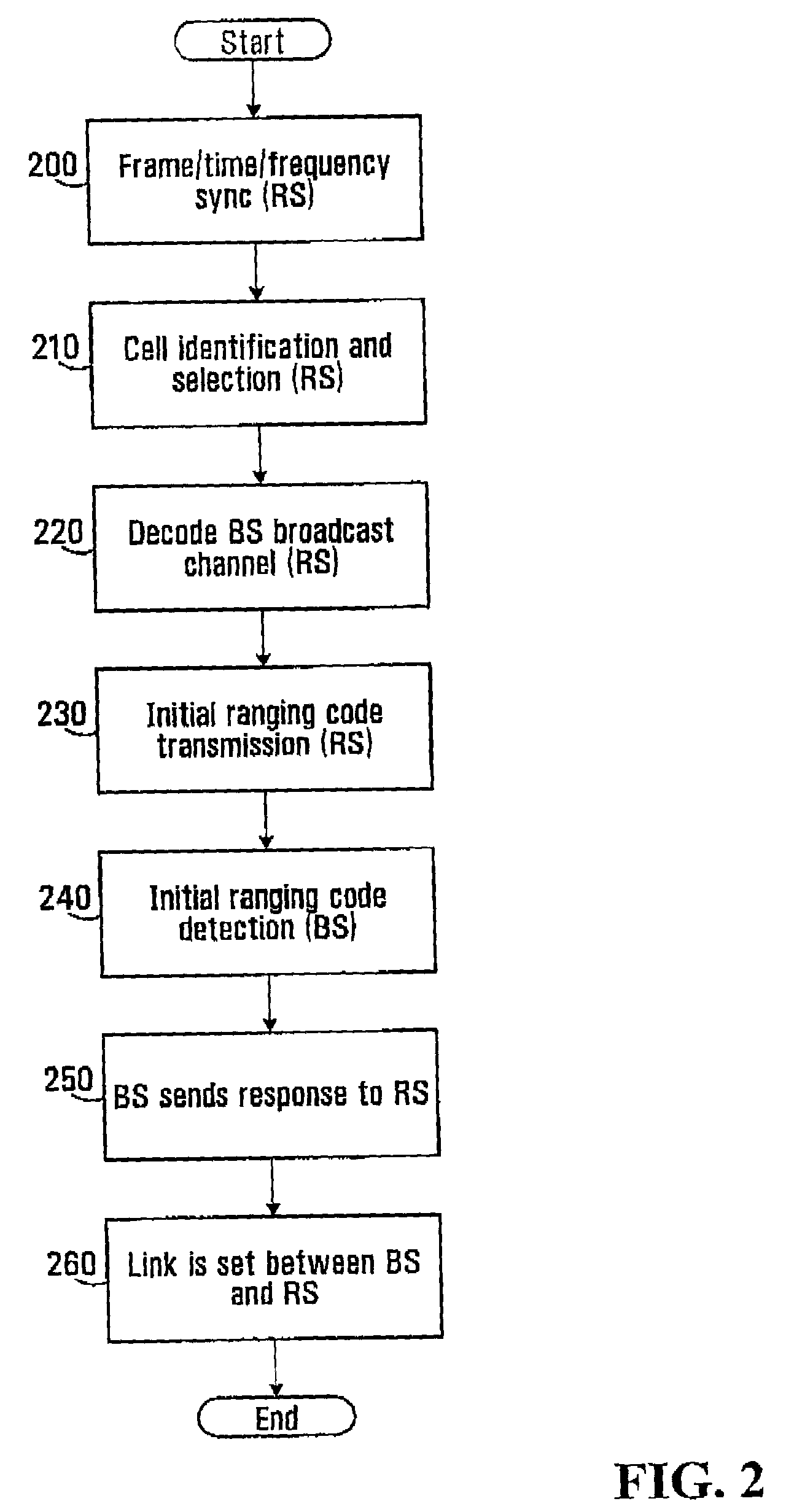
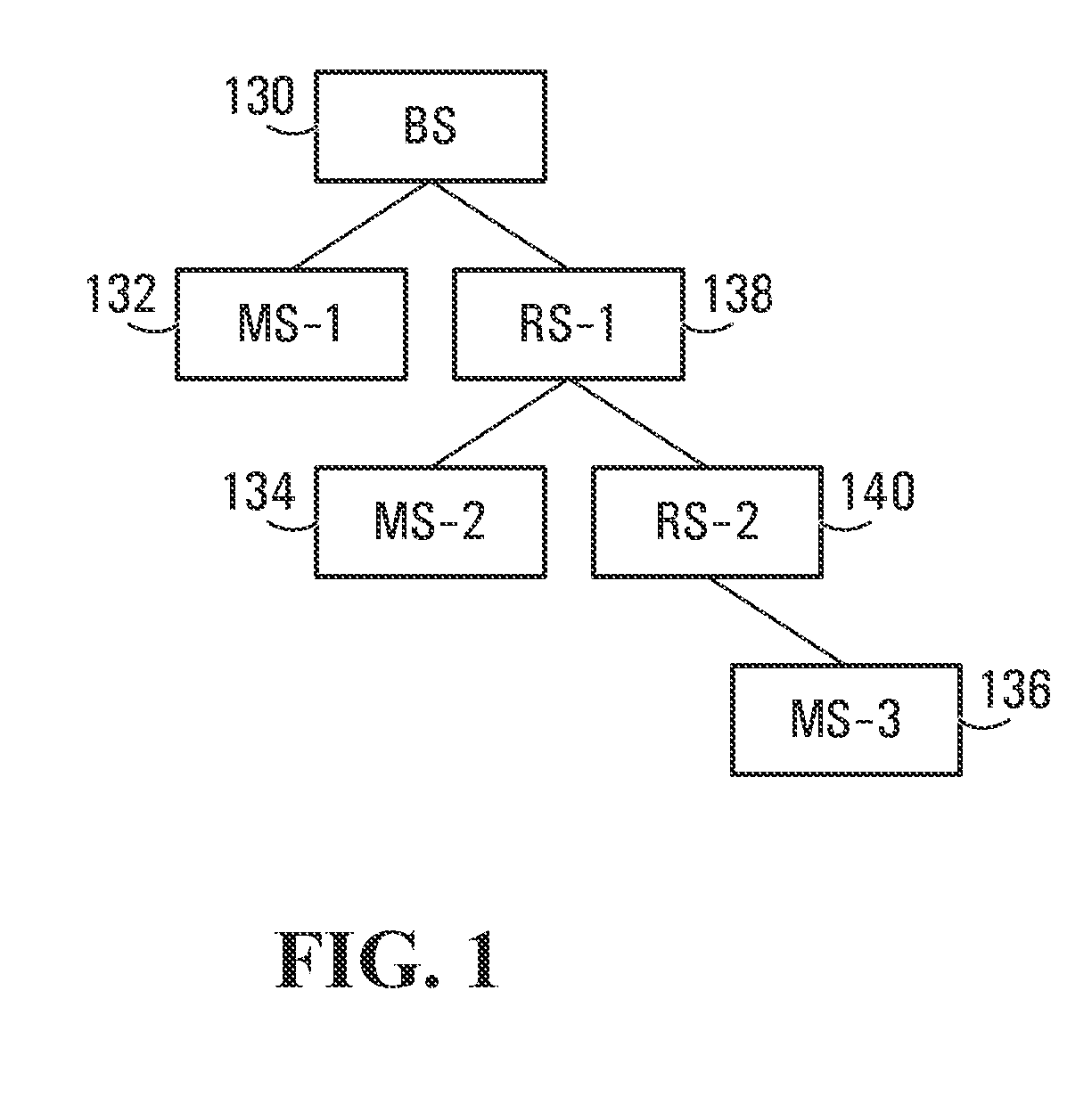
Zones for wireless networks with relays
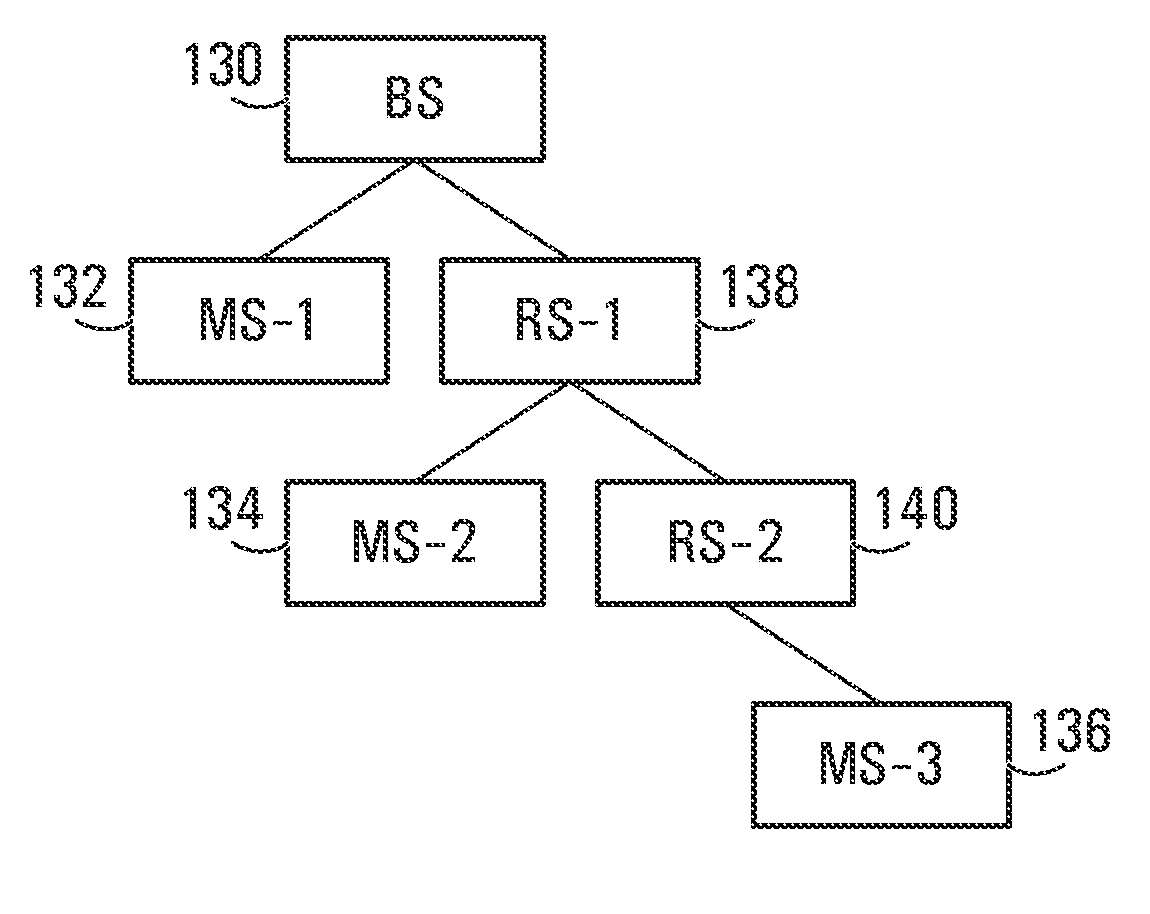
ActiveUS20090303918A1Easy to detectAvoid collisionFrequency-division multiplex detailsModulated-carrier systemsDistribution methodMobile station
Methods and systems are provided for use with wireless networks having once or more cell in which each cell includes a base station (BS), at least one relay station (RS) and at least one mobile station (MS). The at least one relay station can be used as an intermediate station for providing communication between the BS and MS. Methods are provided for an RS to initially access the network, access of the RS by MSs initially accessing the network, methods of allocating OFDM resources for communicating between the BS, RS and / or MS for example dividing transmission resources into uplink and downlink transmissions, and methods of inserting pilot symbols into transmission resources used by the RS. In some embodiments on the invention, the methods are consistent and / or can be used in conjunction with existing standards such as 802.16e.
Owner:APPLE INC
Methods and apparatus for managing network resources using a network topology view
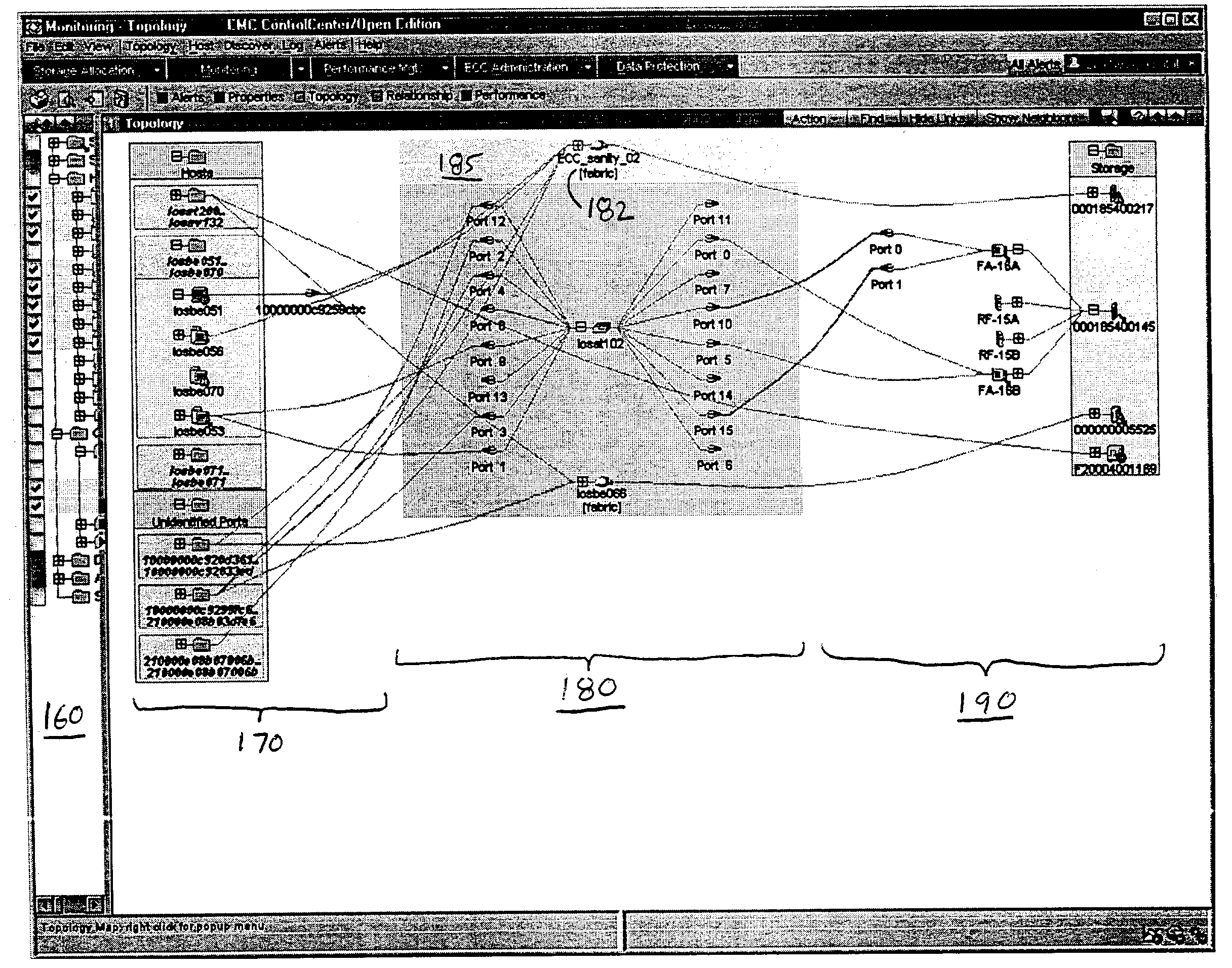
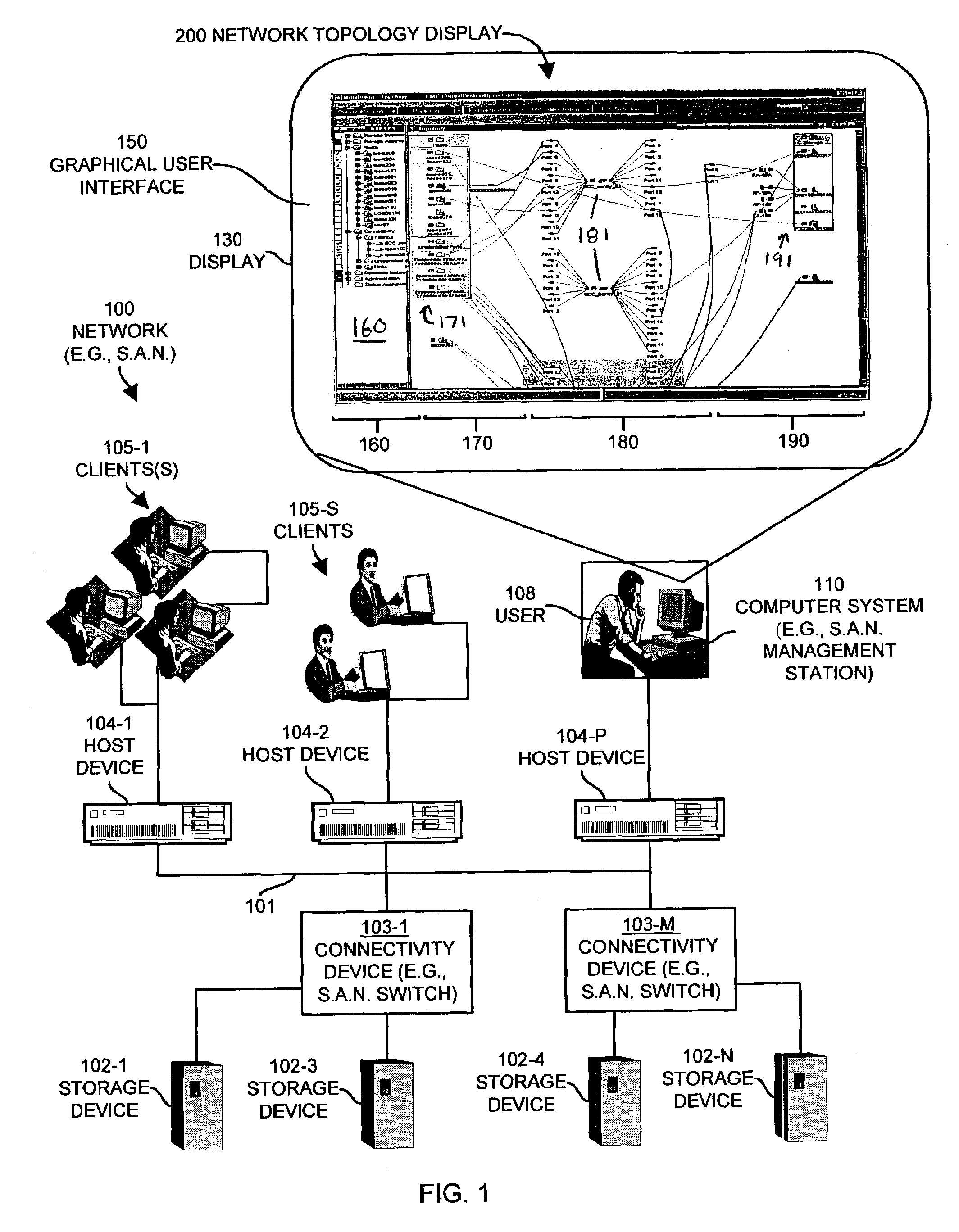
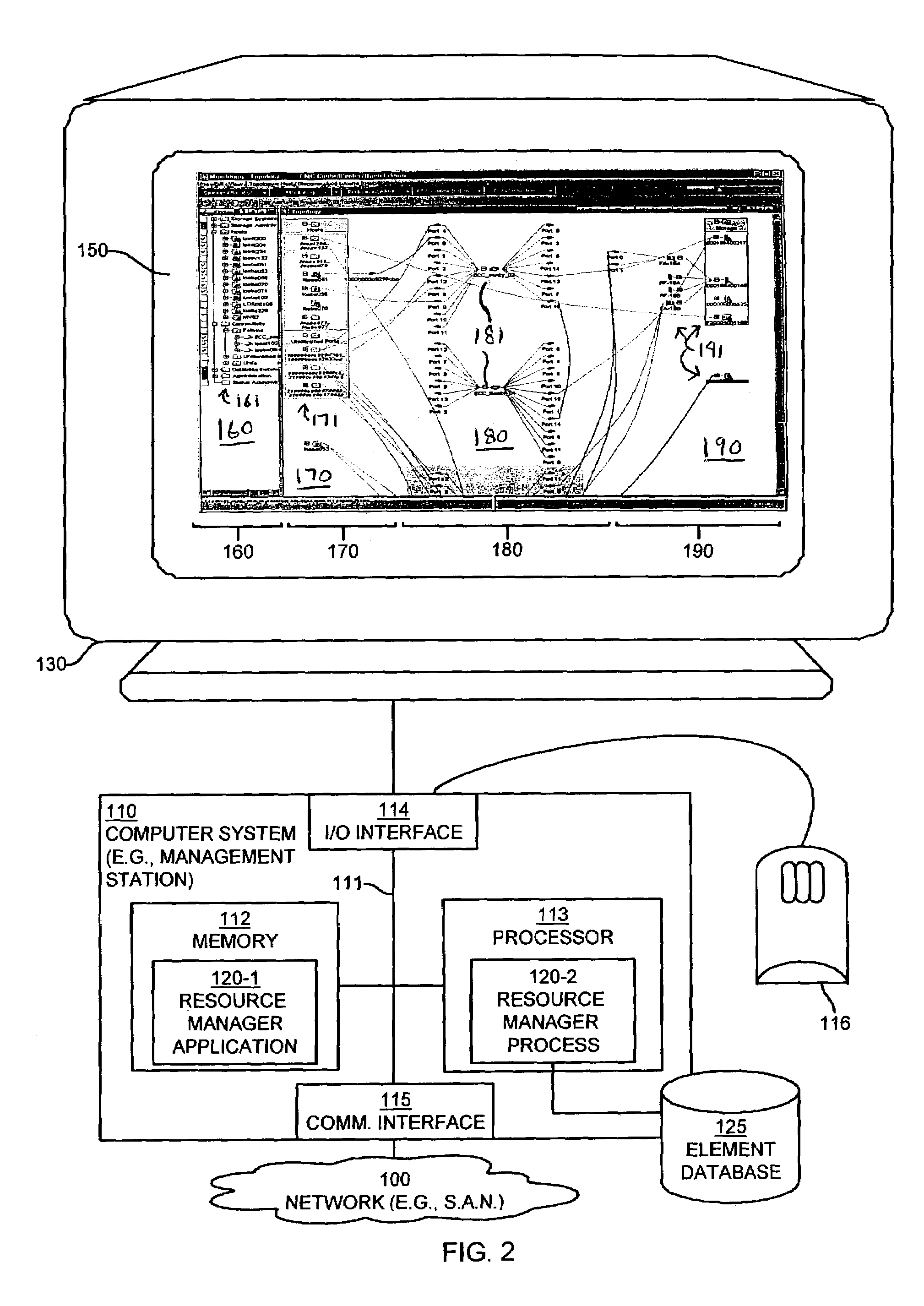
ActiveUS7315985B1Quick fixReduce usageDigital computer detailsProgram controlGraphicsGraphical user interface
Mechanisms and techniques provide a system for visualization of manageable network resources in a graphical user interface. The system displays a host element in a host display area, a storage element in a storage display area, and a connectivity element in a network display area of the network topology view on the display of the computerized device. The system displays the network display area in between the host display area and the storage display area. The system determines a coupling condition of the connectivity element in relation to at least one of the host element and the storage element and displays the coupling condition as a link on the display of the computerized device between the connectivity element and either or both of the host element and the storage element to which that coupling condition relates in order to visually convey the coupling condition to a user viewing the network topology view on the display of the computerized device.
Owner:EMC IP HLDG CO LLC
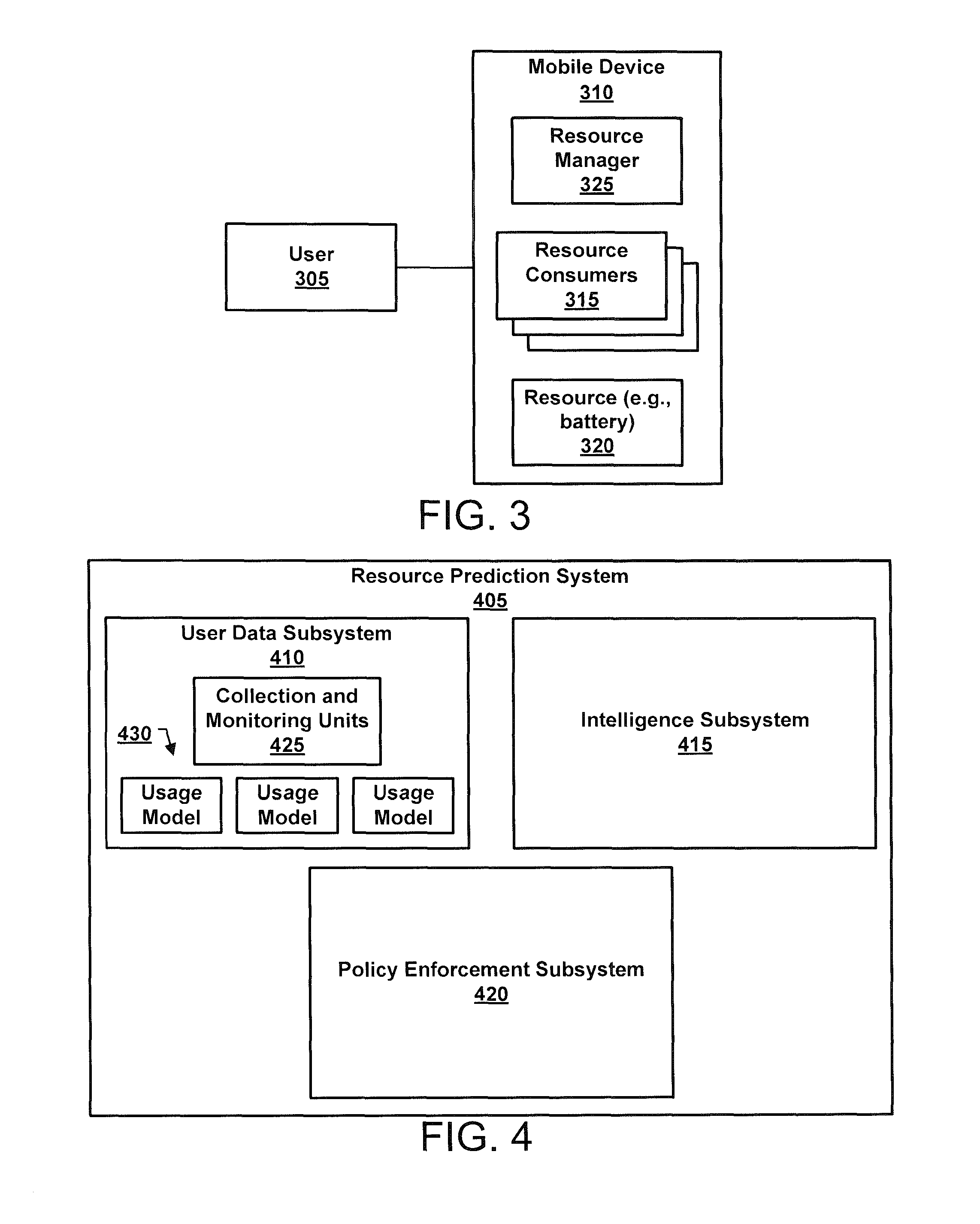
System and method for developing, updating, and using user device behavioral context models to modify user, device, and application state, settings and behavior for enhanced user security
ActiveUS8655307B1Reduce battery usageImprove battery usageEnergy efficient ICTPower managementUser deviceContext model
Security is enhanced for a user of a mobile device by monitoring and controlling resource usage. Usage information associated with a mobile device is collected. The collected information is used to build a usage model for a user of the mobile device that describes a set of contexts in which the mobile device is used. User activity on the device is monitored and the model is consulted to determine a first time after which it will be acceptable for a battery of the mobile device to fall below a threshold charge level. Based on the monitored activity, a prediction of a second time is made for when the battery will fall below the threshold charge level. If the second time is before or a predetermined amount of time before the first time, usage of the battery is reduced, else, usage of the battery is not reduced.
Owner:LOOKOUT MOBILE SECURITY
Multipath routing process
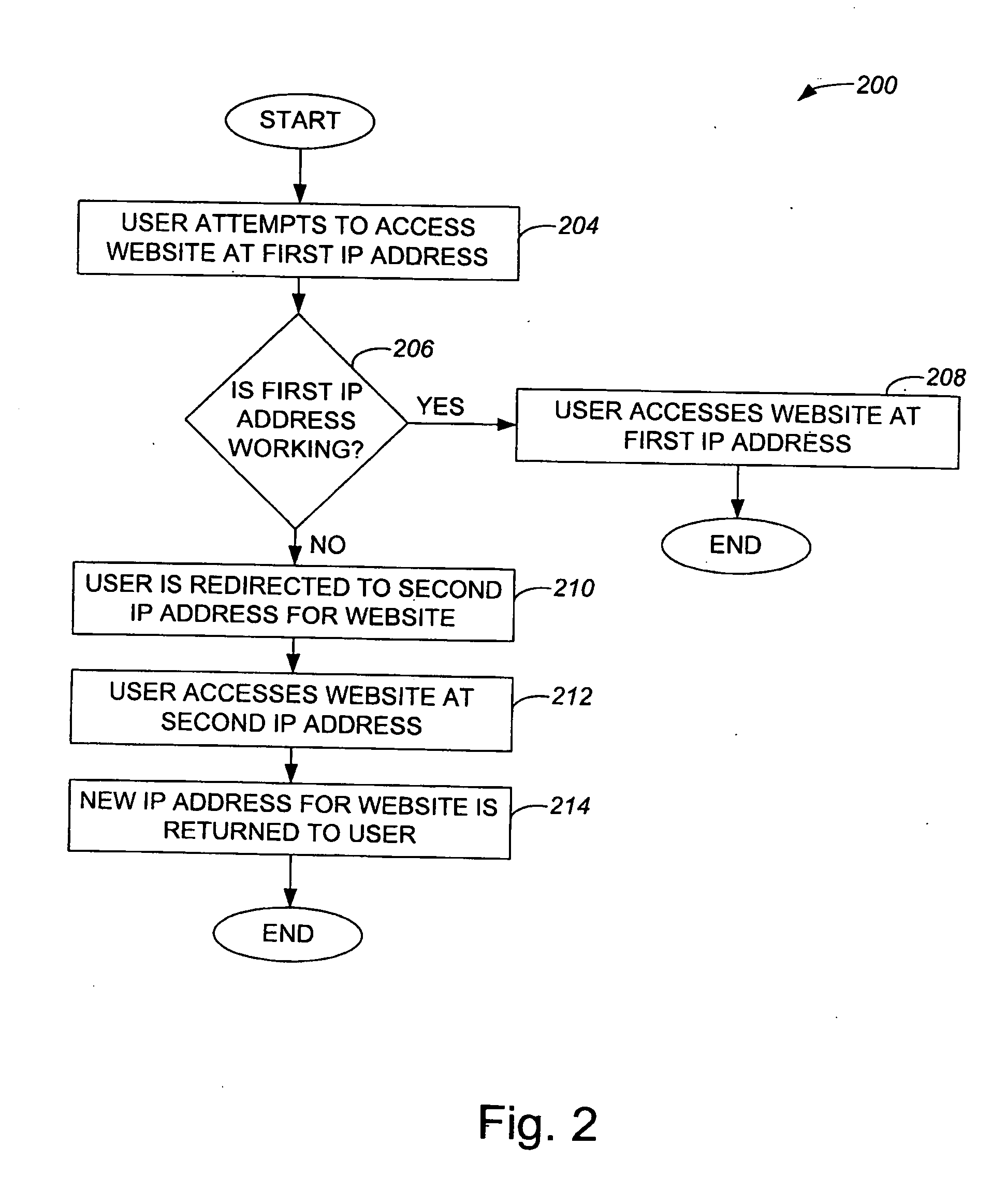
ActiveUS20070094361A1Reduce load effectShorten the timeError detection/correctionDigital computer detailsPathPingIp address
Methods and apparatus that enable more than one server to host a resource using a shared IP address such that a client may generally access the resource on any of the servers using the shared IP address are disclosed. According to one aspect of the present invention, a method for providing paths that allow a client to access a resource in a TCP / IP network includes obtaining an IP address, as well as associating the IP address to first and second servers. The first and second servers support the resource at the IP address, and a first path of the plurality of paths that allow the client to access the resource is between the client and the first server and a second path of the plurality of paths that allow the client to access the resource is between the client and the second server.
Owner:ORACLE INT CORP
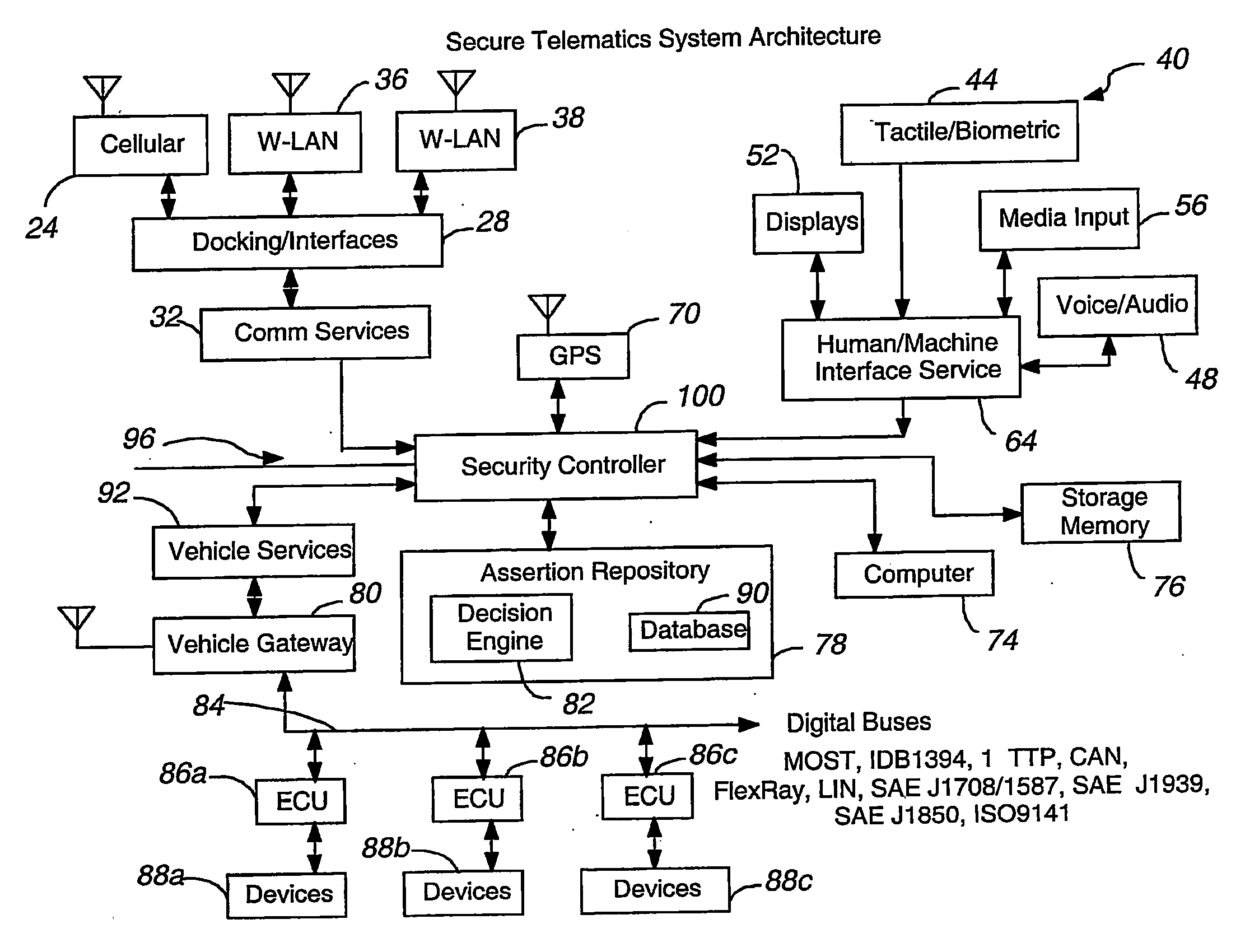
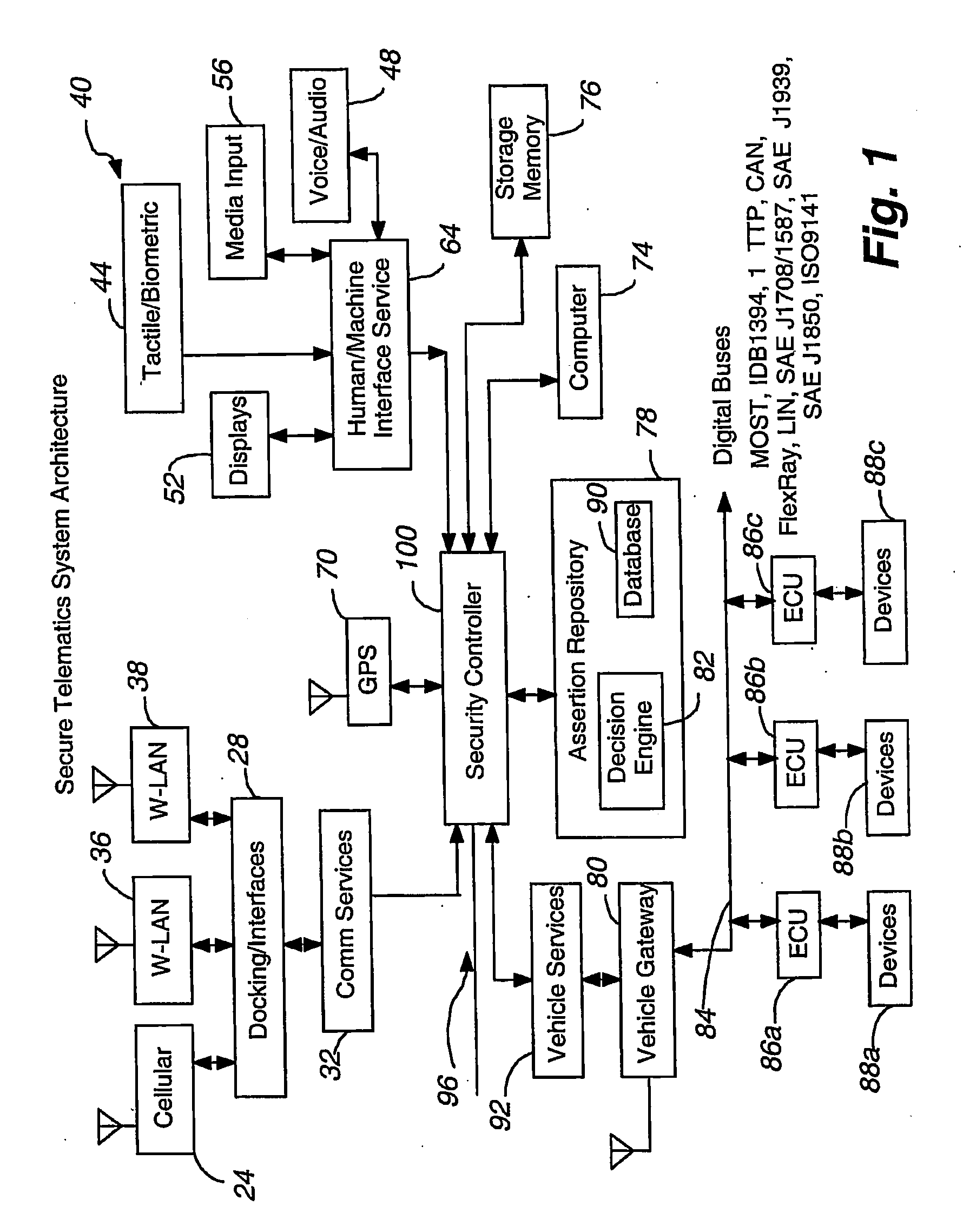
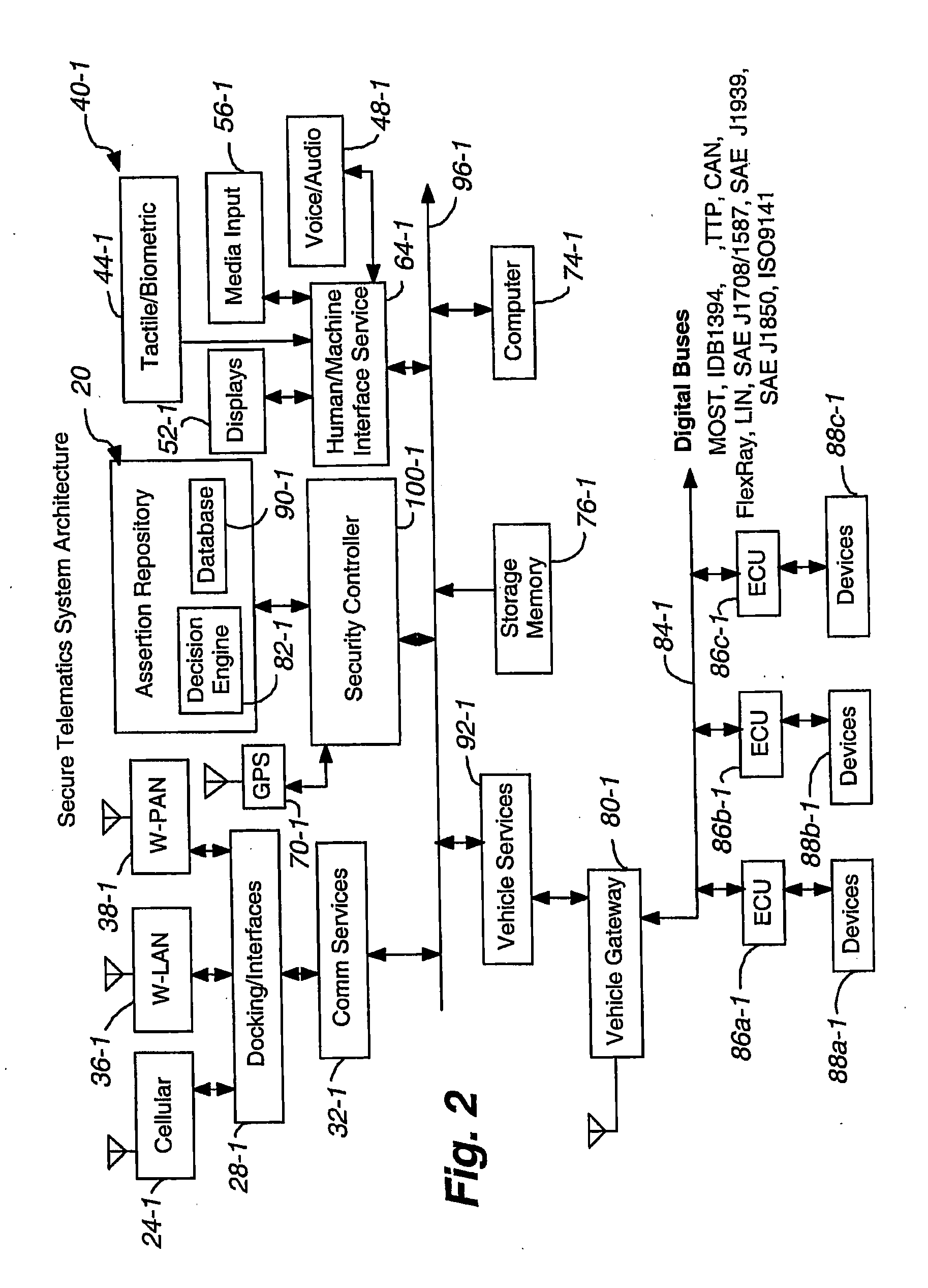
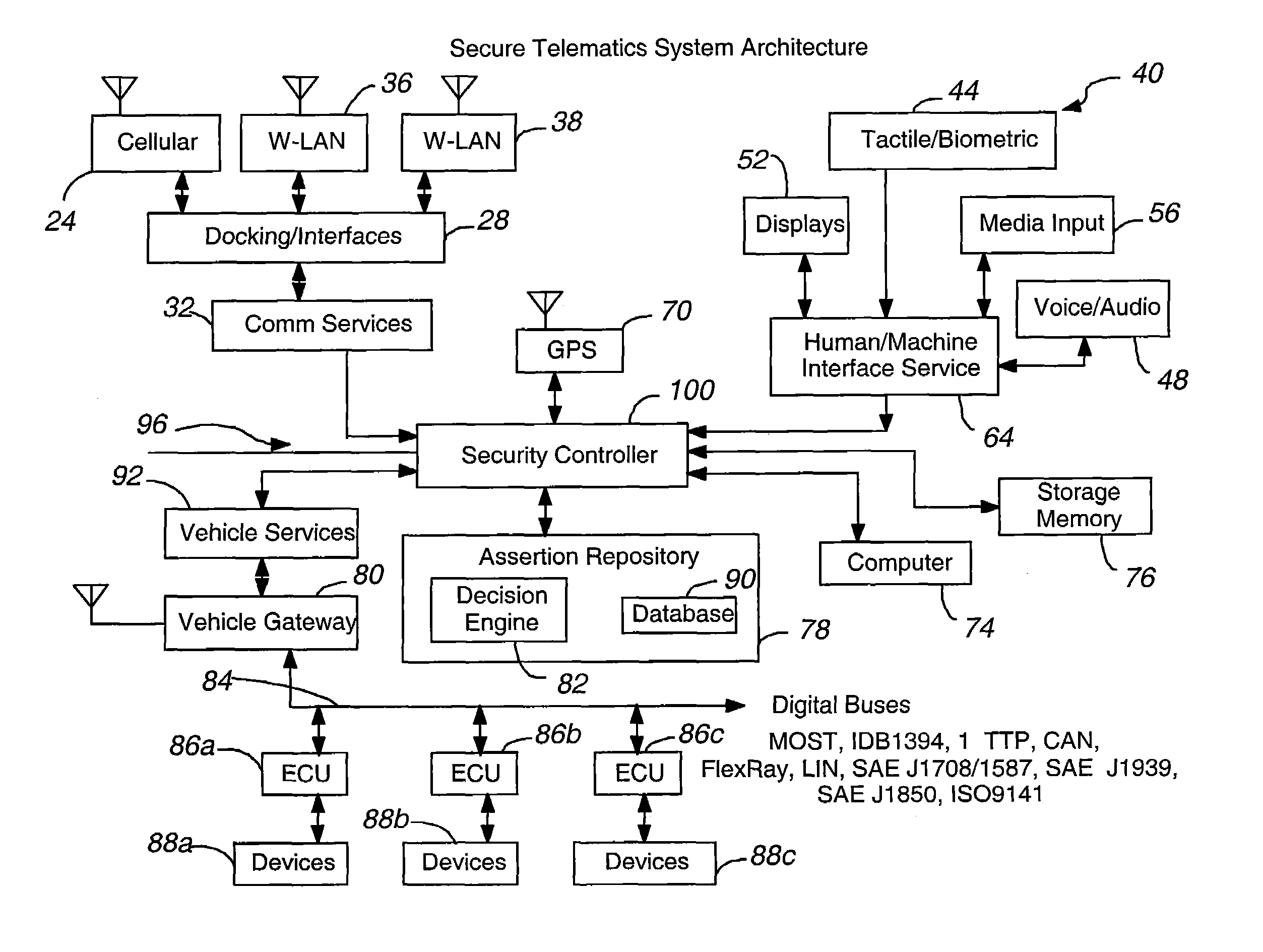
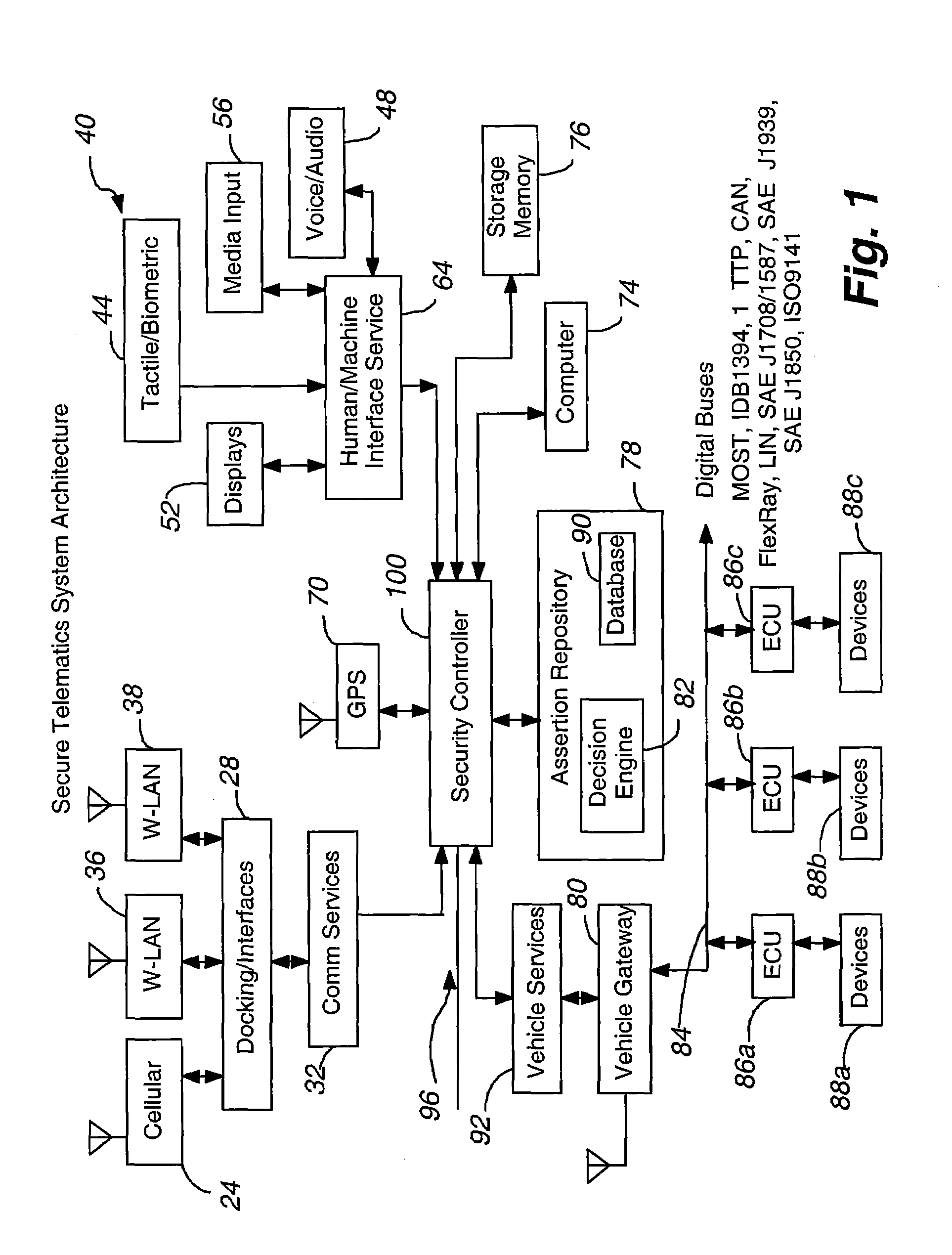
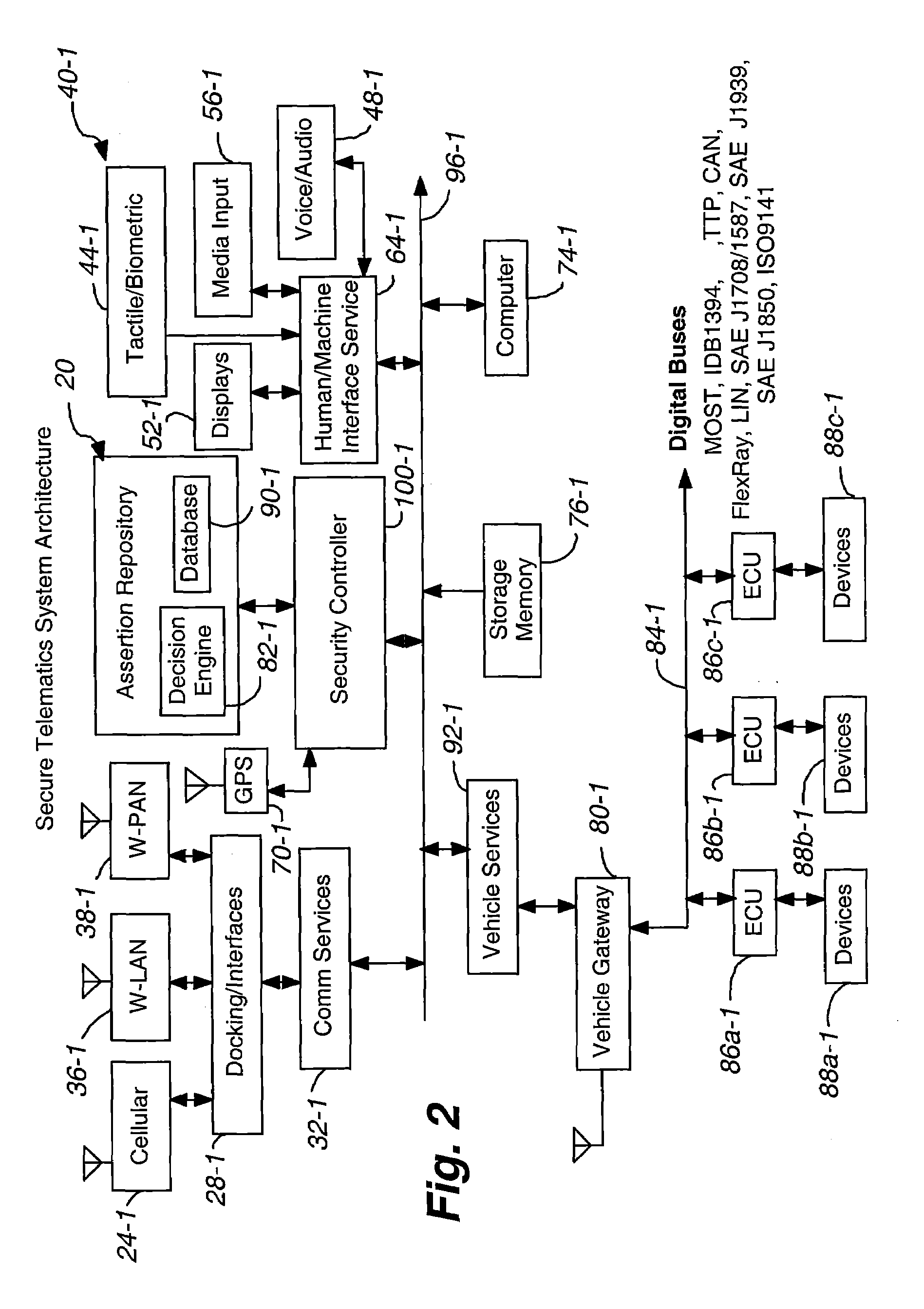
Secure telematics
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Secure telematics
ActiveUS7366892B2Expands telematics usageLow costUnauthorised/fraudulent call preventionRegistering/indicating working of vehiclesService provisionSecurity Measure
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resource'0 security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
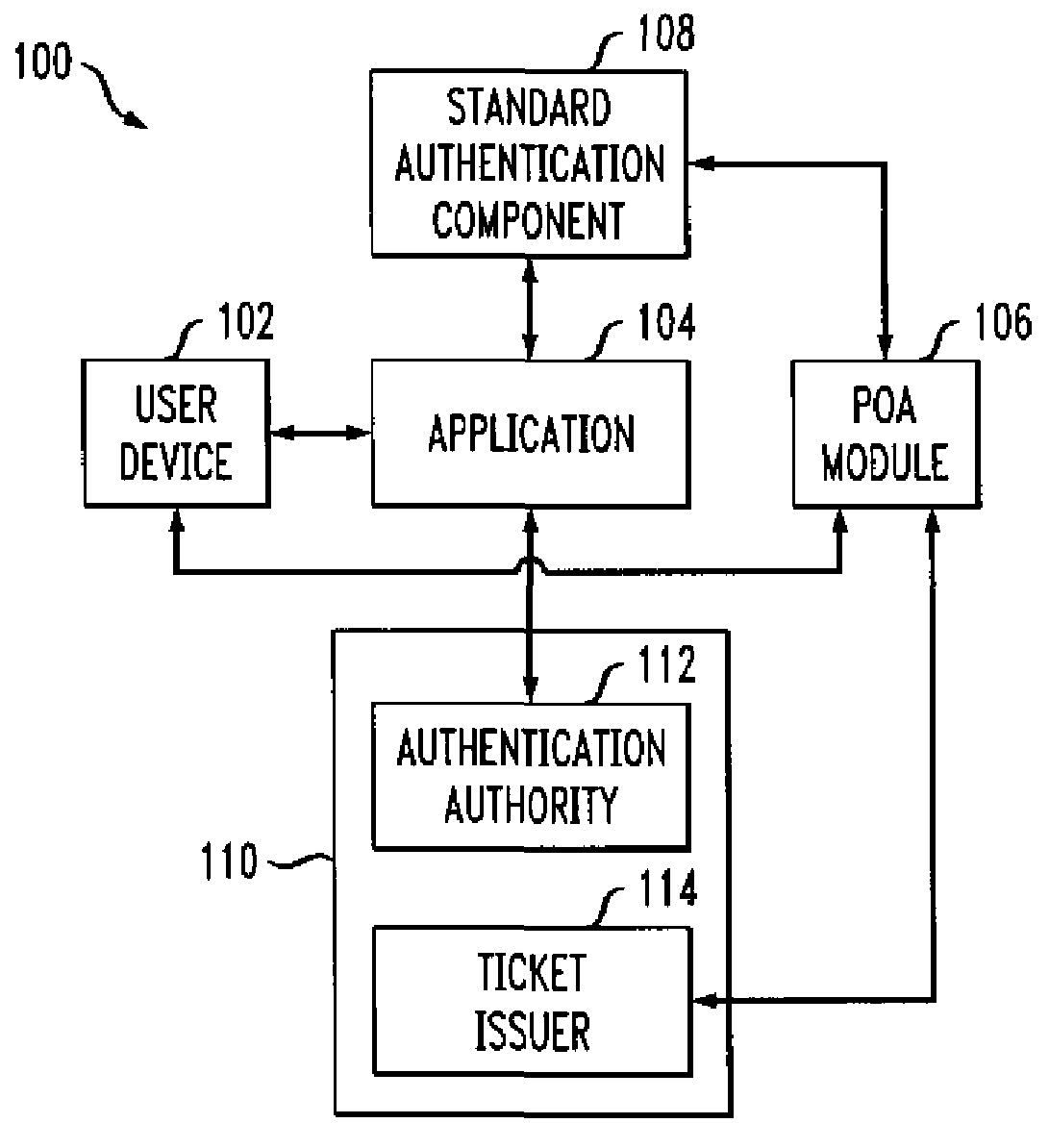
Authentication method and apparatus utilizing proof-of-authentication module
ActiveUS7562221B2Unauthorised/fraudulent call preventionDigital data processing detailsComputer hardwareValidation methods
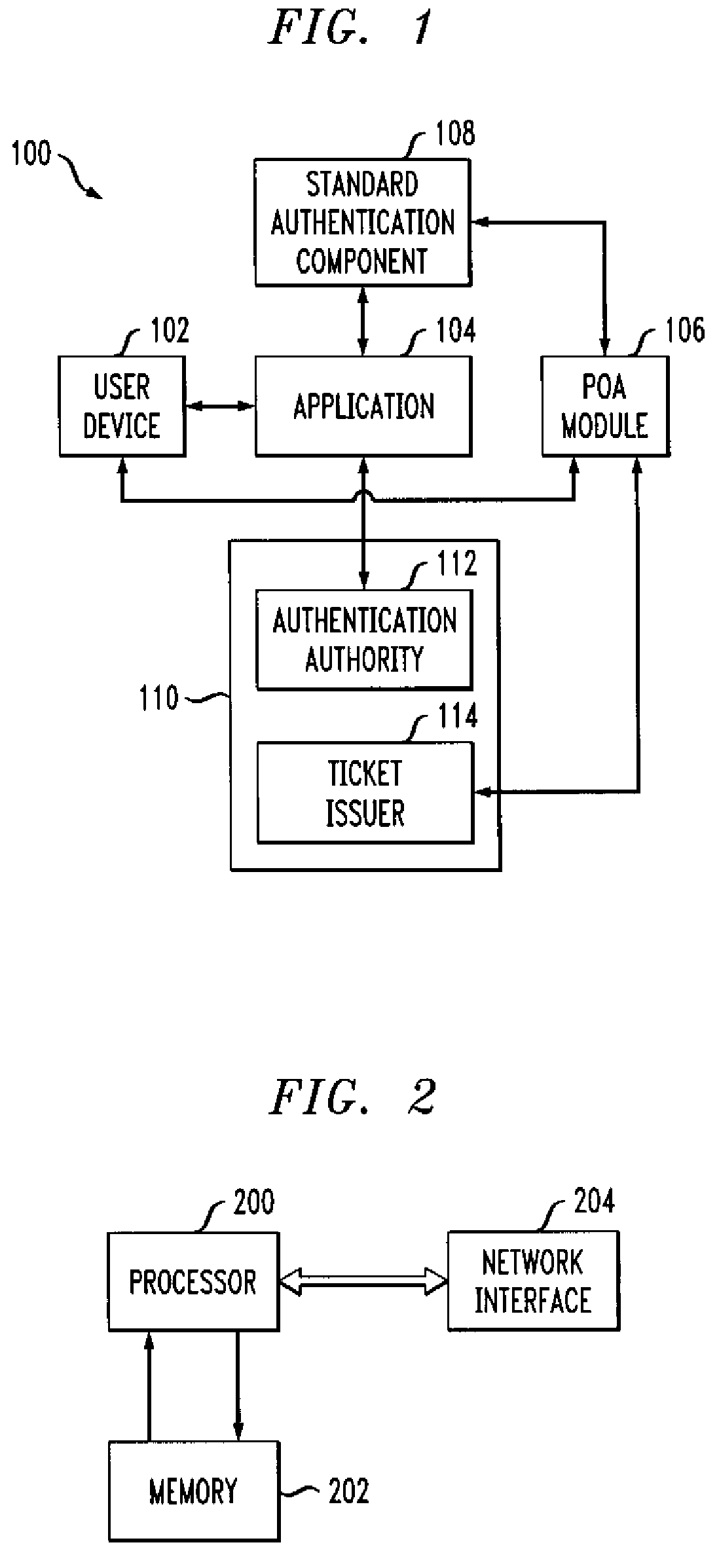
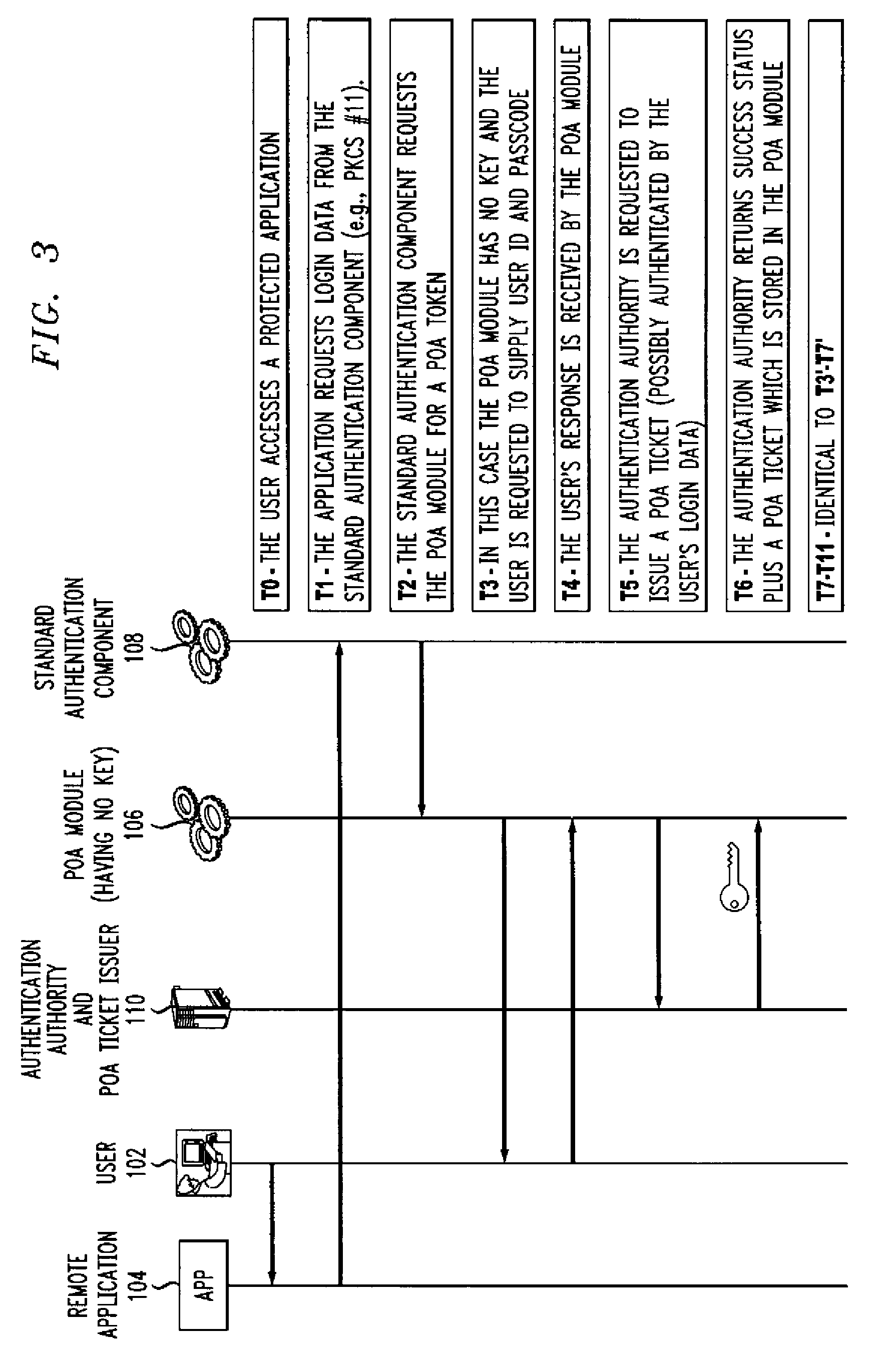
A single sign-on technique allows multiple accesses to one or more applications or other resources using a proof-of-authentication module operating in conjunction with a standard authentication component. The application or other resource issues an authentication information request to the standard authentication component responsive to an access request from the user. The application or other resource receives, responsive to the authentication information request, a proof-of-authentication value from the standard authentication component, and authenticates the user based on the proof-of-authentication value. The standard authentication component interacts with the proof-of-authentication module to obtain the proof-of-authentication value. The proof-of-authentication module is configured to generate multiple proof-of-authentication values for authentication of respective access requests of the user.
Owner:EMC IP HLDG CO LLC
Methods, systems, and media to expand resources available to a logical partition
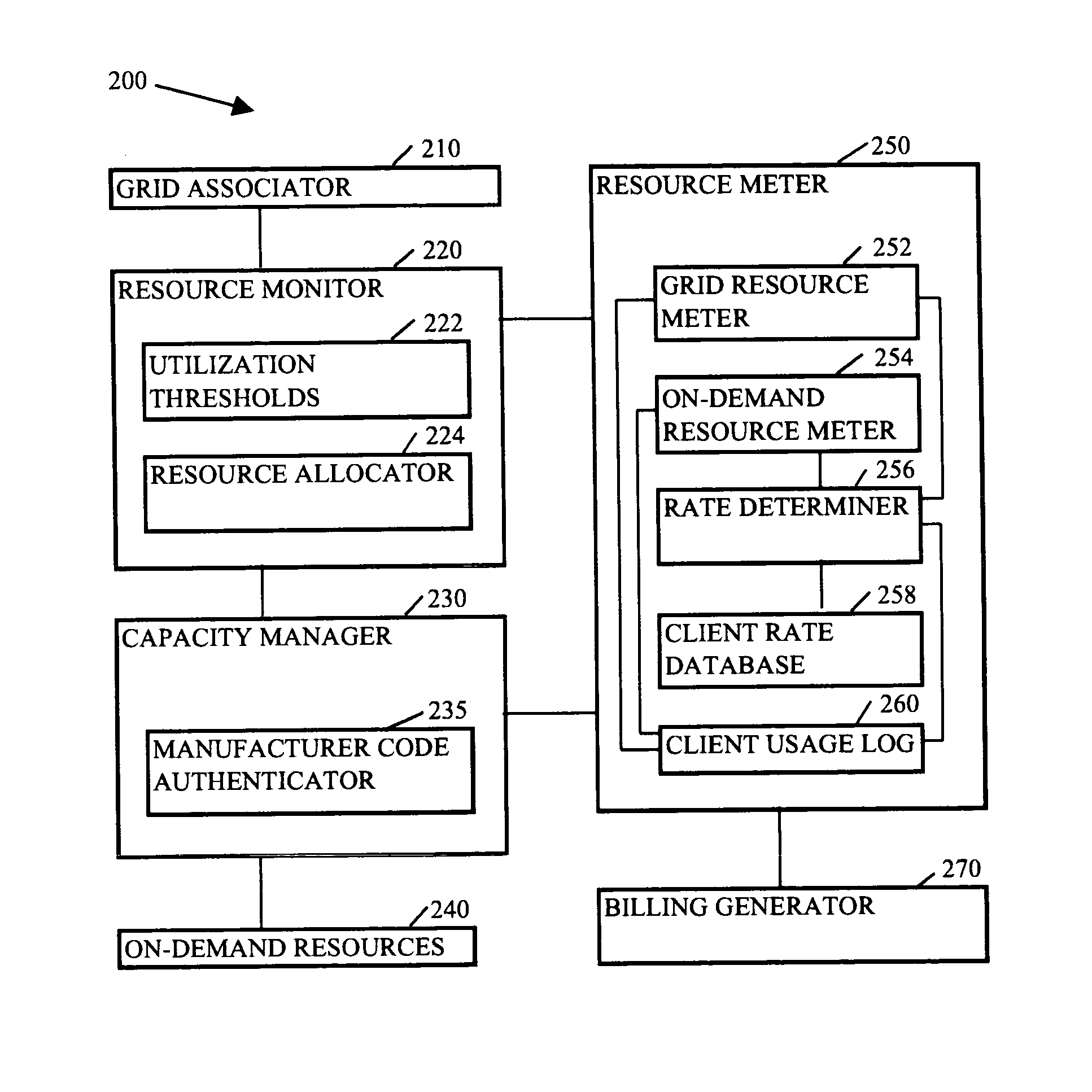
InactiveUS20050044228A1Digital computer detailsMultiprogramming arrangementsGrid resourcesService provision
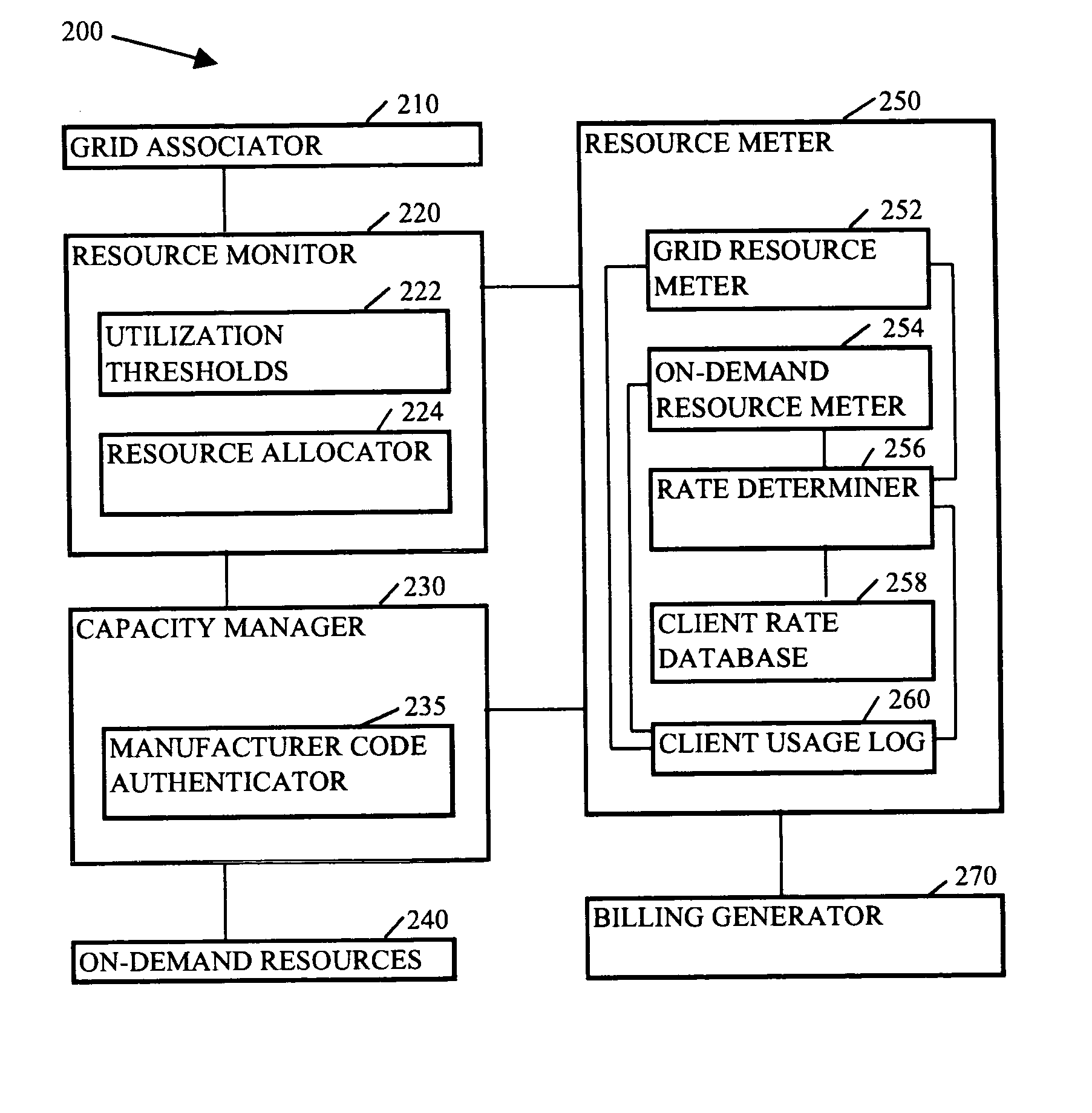
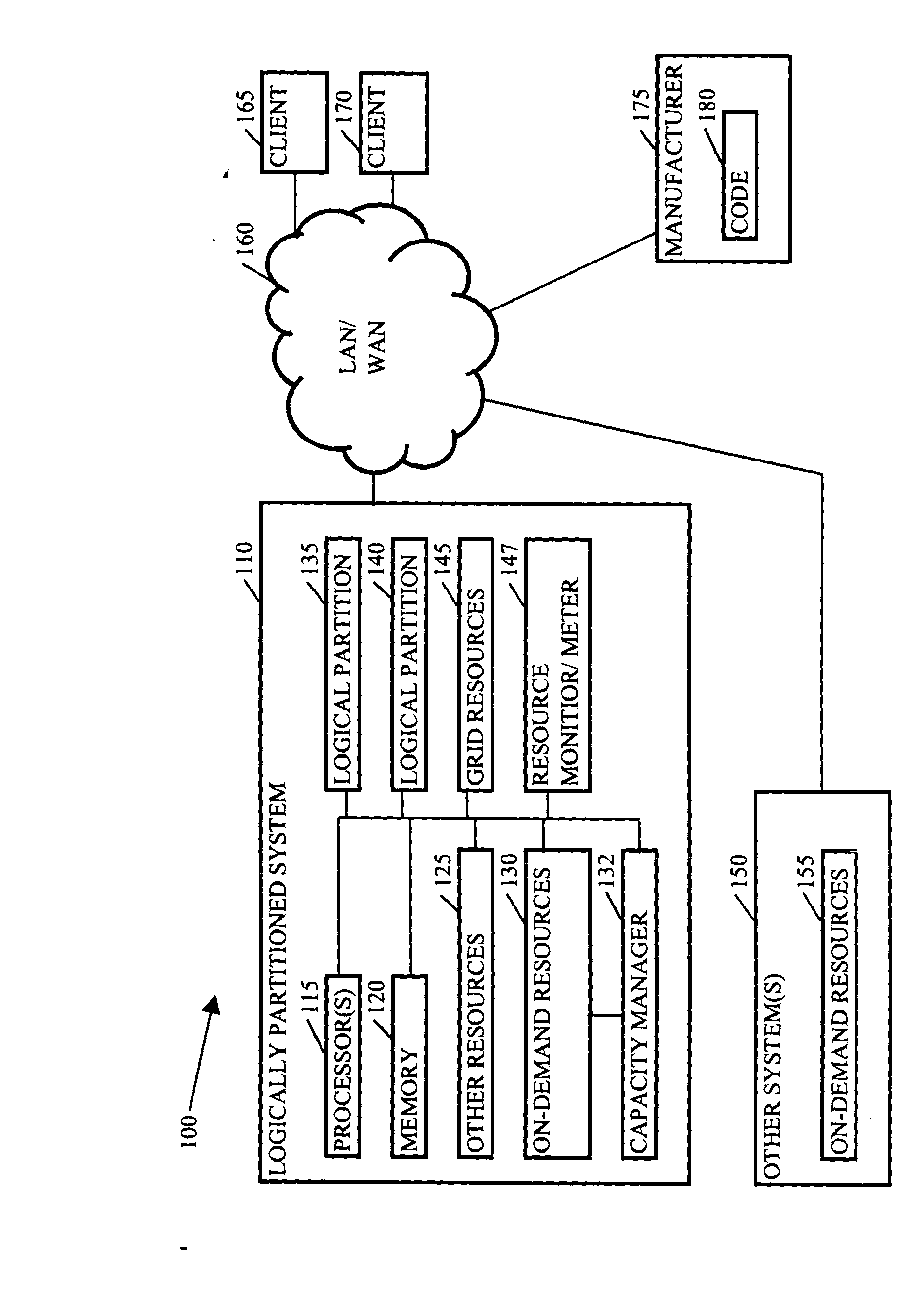
Methods, systems, and media to expand resources available to logical partition associated with a client are contemplated. Embodiments may associate the logical partition with a grid that retains a list of resources, referred to as grid resources, available for allocation to logical partitions. The grid resources may include resources from, e.g., other logical partitions within the logically partitioned system, logical partitions from other logically partitioned systems, another type of system, a cluster, and the like. Further, one or more of the systems associated with the grid may include on-demand resources that are also available to supplement resources based upon the demands of the client. Embodiments may also monitor resource usage by the client and meter billable usage of the grid resources and / or on-demand resources based upon agreements between service providers and clients.
Owner:IBM CORP
Provisioning aggregated services in a distributed computing environment
ActiveUS20030135628A1Multiple digital computer combinationsDigital data authenticationDistributed Computing EnvironmentDistributed services
Methods, systems, and computer program products are disclosed for provisioning software resources used with aggregated web services. The disclosed techniques enable heterogeneous identity systems to be joined in the dynamic, run-time web services integration environment. Authentication and authorization may now be performed for the aggregated service, as well as for its sub-services. SOAP ("Simple Object Access Protocol") messages, as an example, may be used to relay identity information among distributed services, whereby credentials may be specified in the SOAP message header to accompany a service request specified in the SOAP message body.
Owner:IBM CORP
System and method using virtual machines for decoupling software from users and services
InactiveUS20060184935A1Reduce disadvantagesReduce problemsSoftware simulation/interpretation/emulationMemory systemsMaintenance releaseData center
Virtual machines of a virtual data center generate runtime instances with a software image, hardware configuration, management configuration and user / service configuration. Virtual data center resource use is monitored by reference to the management configuration of runtime instances, such as for environmental controls like power, cooling and balancing, or for policy limitations on users, software or hardware. Users or services generate runtime instances of stored virtual machines by reference to the user / service configuration, such as pricing or priority. In one example embodiment, the virtual machine software image comprises an application system preparation file that populates a read only application image common to plural virtual machines. Information unique to each virtual machine with respect to the application is maintained in the user / service configuration of the virtual machine and version information is maintained in the management configuration of the virtual machine. Updates to the application across each virtual machine are performed by updating the read only image or any of its configuration information for hardware configuration, management configuration or user / service configuration.
Owner:DELL PROD LP
Methods and systems for wireless networks with relays
ActiveUS20130010679A1Avoid collisionPower managementModulated-carrier systemsMobile stationDownlink transmission
Methods and systems are provided for use with wireless networks having one or more cell in which each cell includes a base station (BS), at least one relay station (RS) and at least one mobile station (MS). The at least one relay station can be used as an intermediate station for providing communication between the BS and MS. Methods are provided for an RS to initially access the network, access of the RS by MSs initially accessing the network, methods of allocating OFDM resources for communicating between the BS, RS and / or MS for example dividing transmission resources into uplink and downlink transmissions, and methods of inserting pilot symbols into transmission resources used by the RS. In some embodiments on the invention, the methods are consistent and / or can be used in conjunction with existing standards such as 802.16e.
Owner:APPLE INC
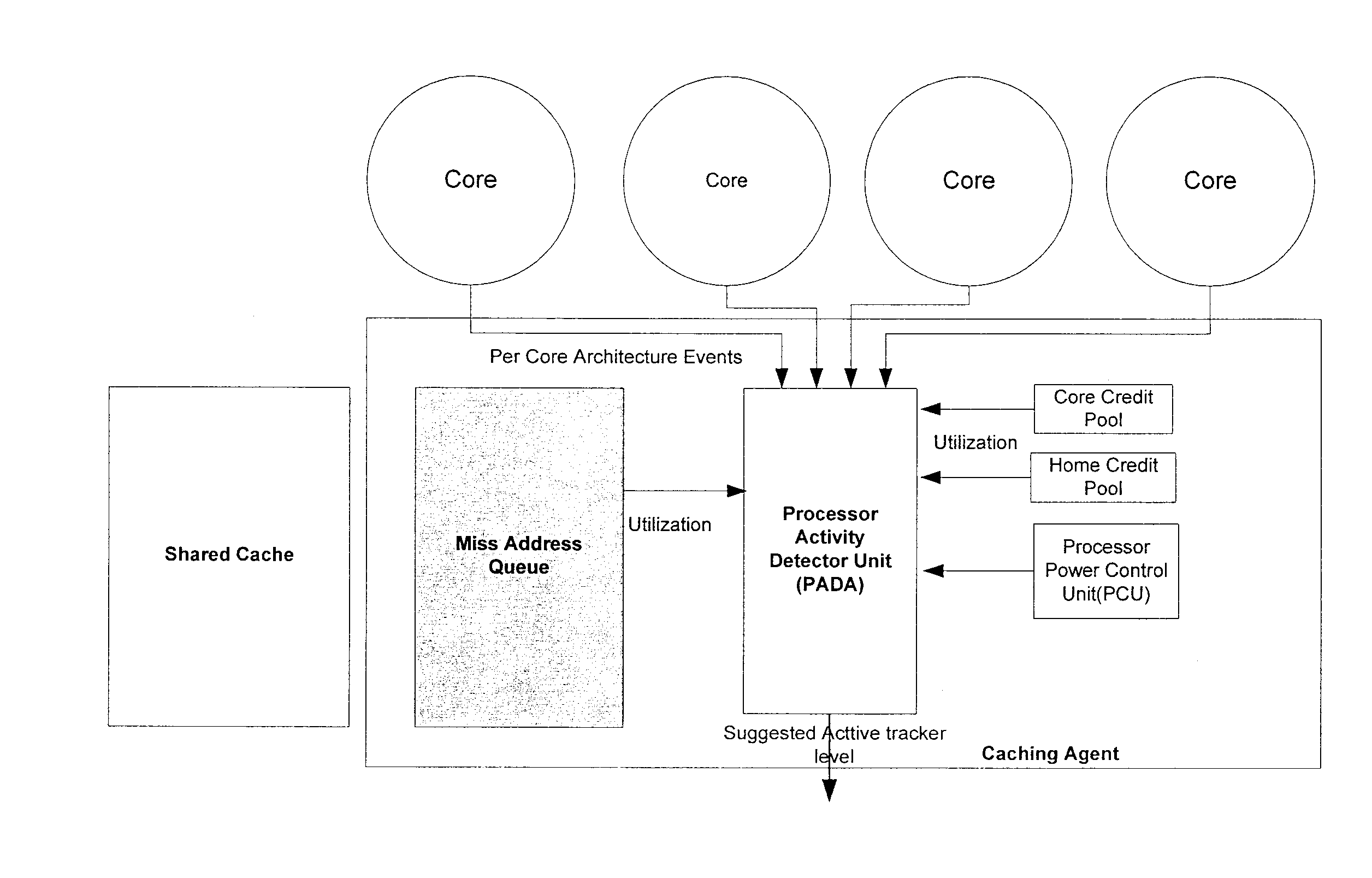
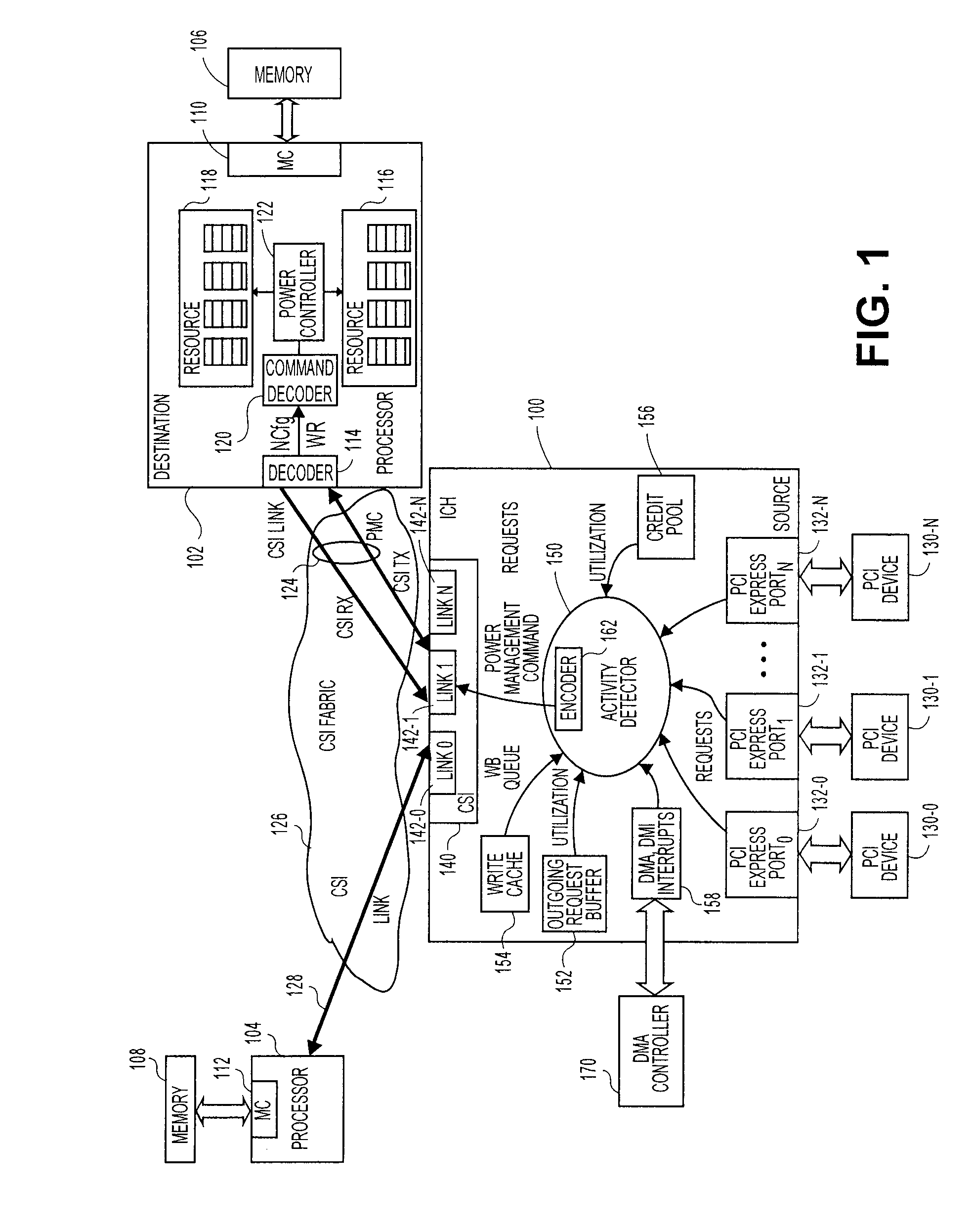
Method, system, and apparatus for a core activity detector to facilitate dynamic power management in a distributed system
A system and method to provide source controlled dynamic power management. An activity detector in a source determines expected future resource usage. Based on that expected usage, the source generates a power management command and sends that command to a destination. The destination then adjusts the power level of the resource based in the command.
Owner:INTEL CORP
Systems and methods for establishing a cloud bridge between virtual storage resources
Owner:CITRIX SYST INC
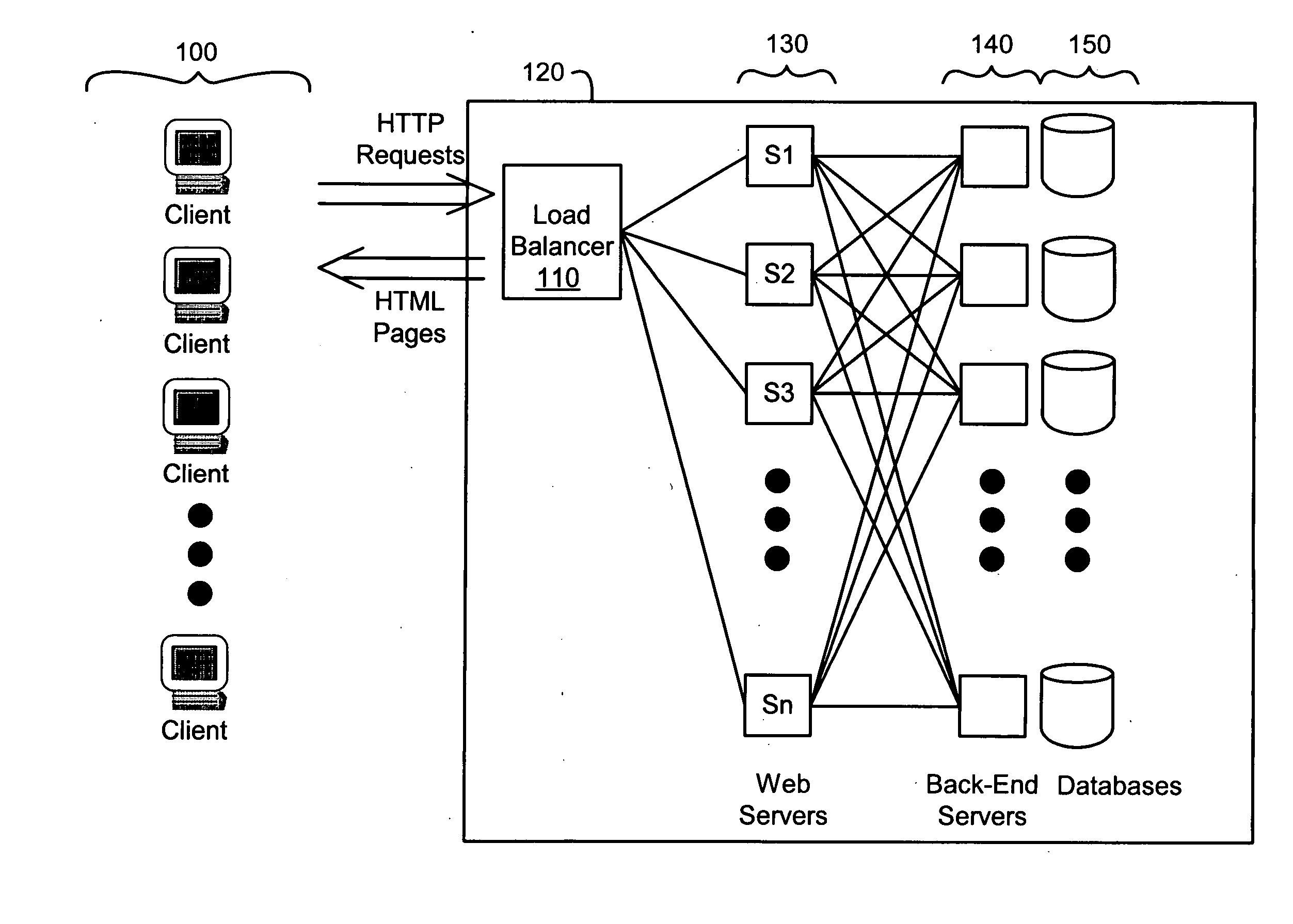
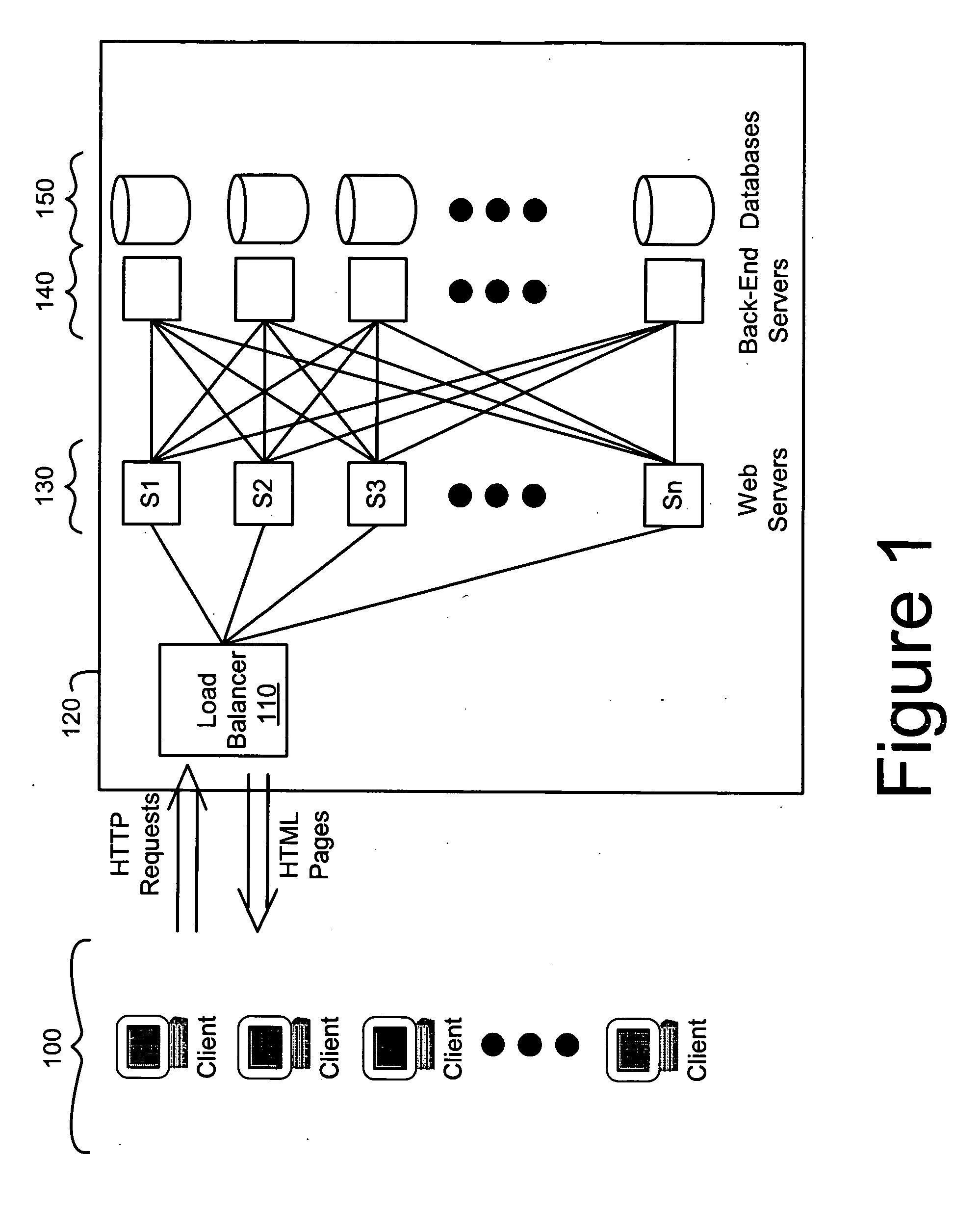
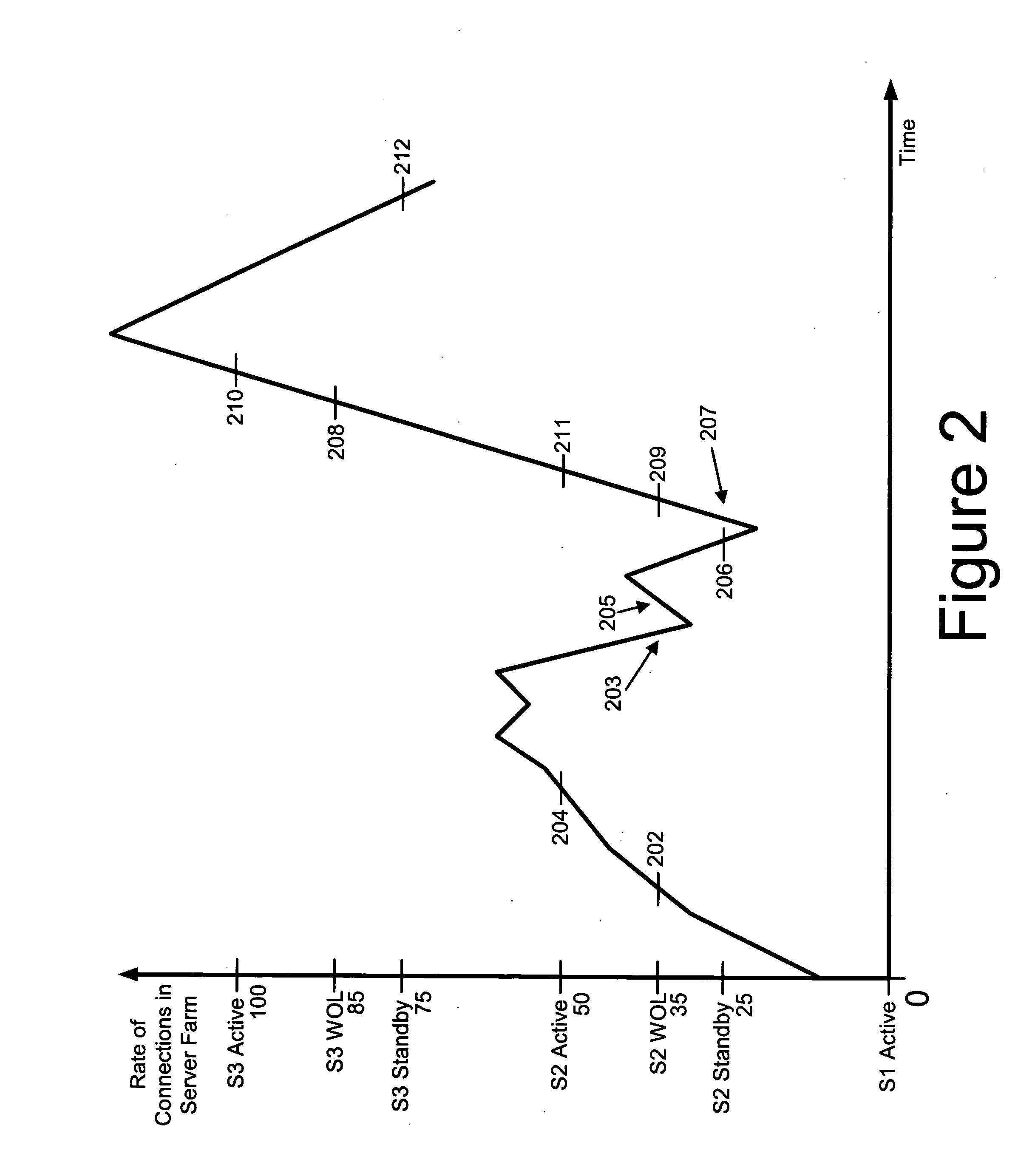
System for power savings in server farms
ActiveUS20070130341A1Energy efficient ICTMultiple digital computer combinationsBiological activationPower management
A threshold-based approach is used to assign tasks to servers in a server farm. A “number of connections” count or “connection rate” is maintained for an active server and when the count achieves a first value a wake up signal is sent to a next (inactive) server to alert the inactive server to become active and periodic keep alive signals are initiated. When the number of connections next reaches a second, higher value, subsequent requests for connections are sent to the newly active server. Variations of this approach allow for servers and their associated processes and devices to be handled in clusters for power management scaling efficiency. Servers can be placed in the inactive mode when the number of connections reaches a lower threshold. Other criteria can be used to determine activation of servers, processors or other devices or processes. Other types of resource use monitoring can also be used with this invention.
Owner:CISCO TECH INC
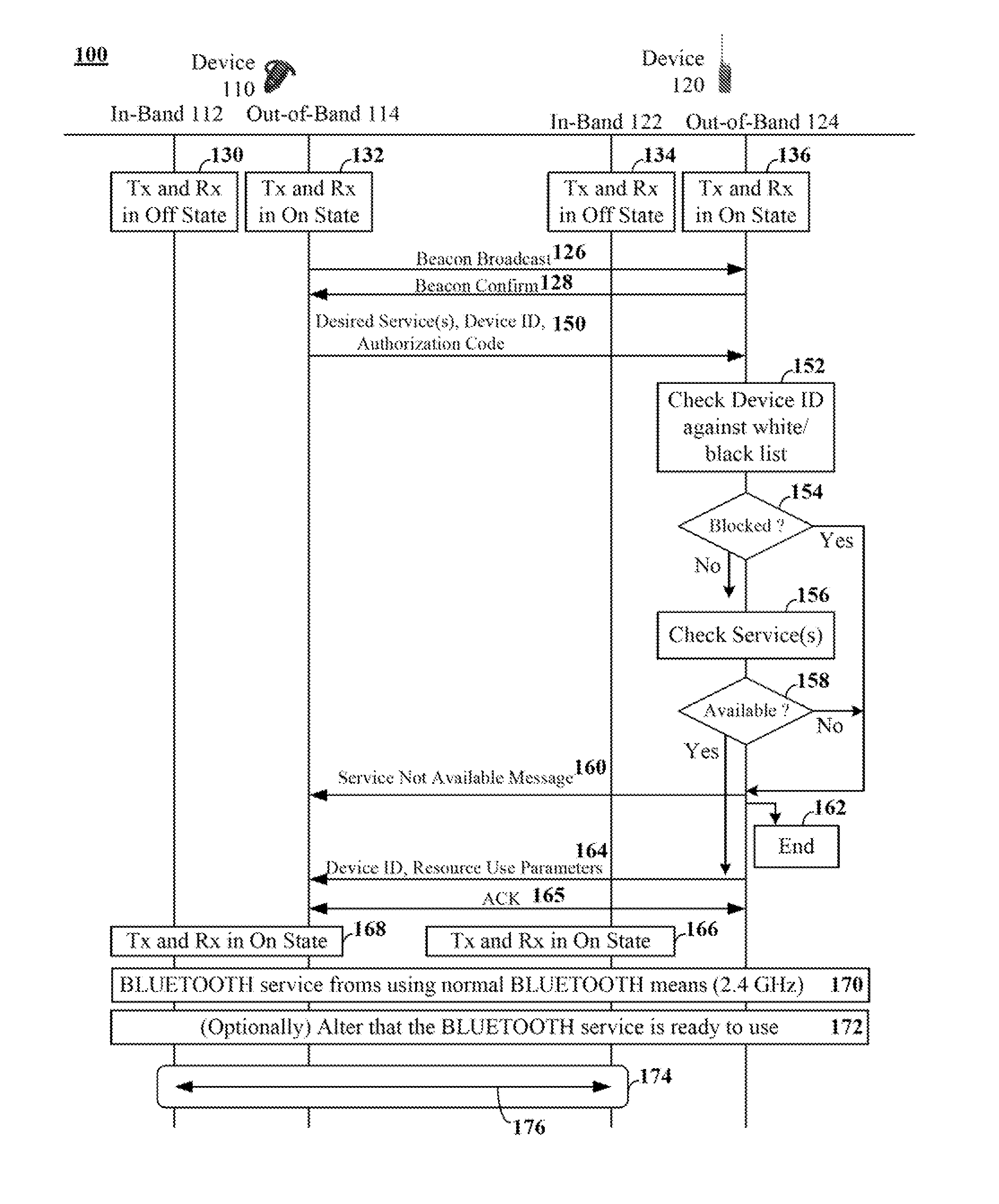
Pairing devices using data exchanged in an out-of-band channel
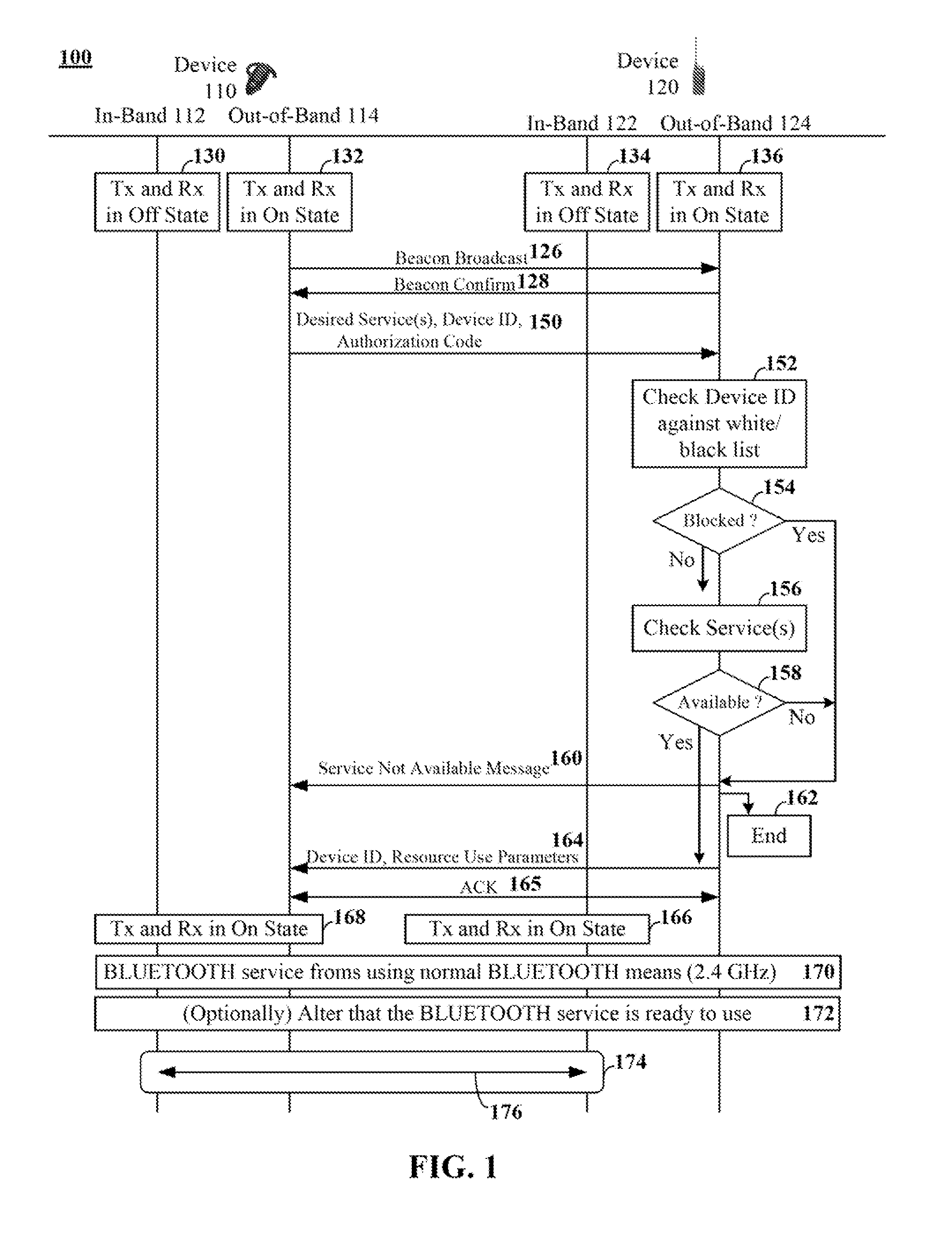
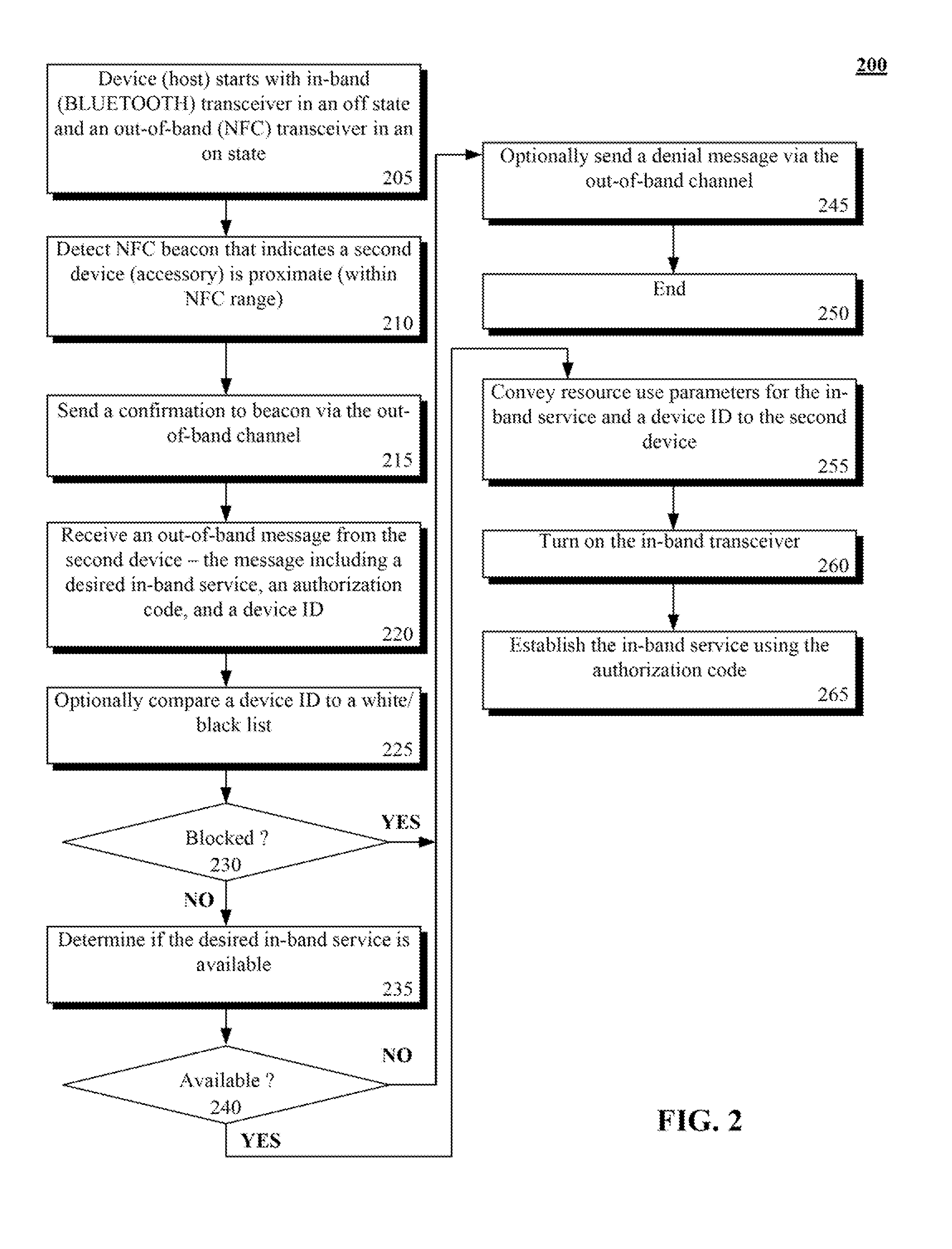
Two devices (110, 120) can be determined to be within near field communication (NFC) range of each other. Pairing information for a service can be conveyed over an out-of-band channel (114, 124). The out-of-band channel can be a near field communication (NFC) channel. The service can be a BLUETOOTH service provided via an in-band (e.g., BLUETOOTH) channel (112, 122). The conveying of the pairing information can require the first device (110) to request at least one desired service, to provide a device ID, and to provide an authorization code in a single message (150). In response to the single message (150), the second device (120) can either deny the request (160, 162) or can convey resource use parameters for the desired service and an ID for the second device within a second single message (164). Pairing the two devices (110, 120) can require use of the authorization code and the resource use parameters.
Owner:MOTOROLA SOLUTIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com