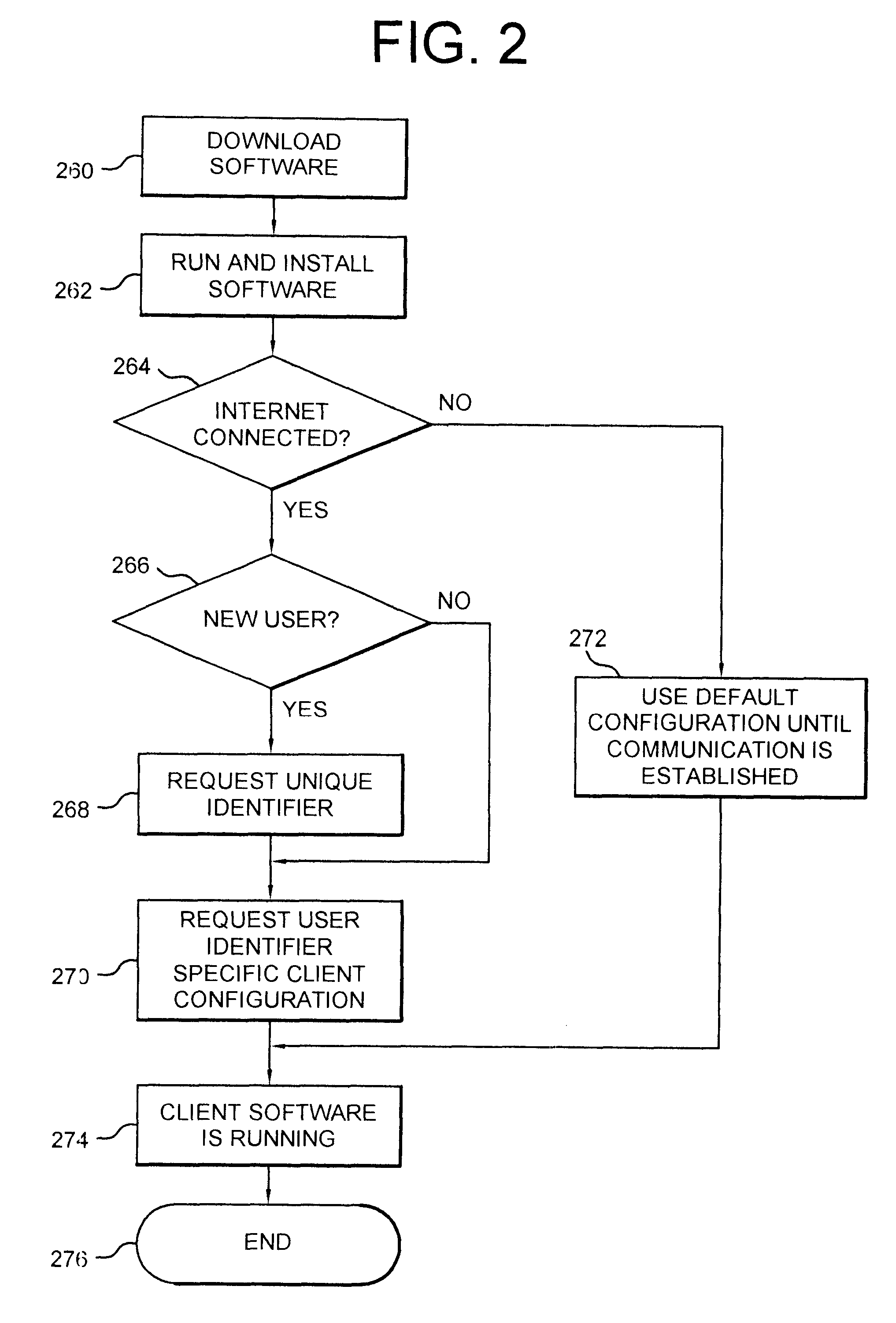
Patents
Literature
1408 results about "Application Identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An Application Identifier (AI) defines the purpose of the data in the symbol and how it is to be used. It is commonly used in GS1 barcodes. The GS1 Application Identifier (AI) appears after the Function Code 1 (FNC1) in Code 128, Data Matrix or DataBar Expanded barcodes.
User-convenient authentication method and apparatus using a mobile authentication application
ActiveUS20140040628A1Authentication process can be made convenientCost-effectiveDigital data authenticationCoding/ciphering apparatusUser authenticationApplication software
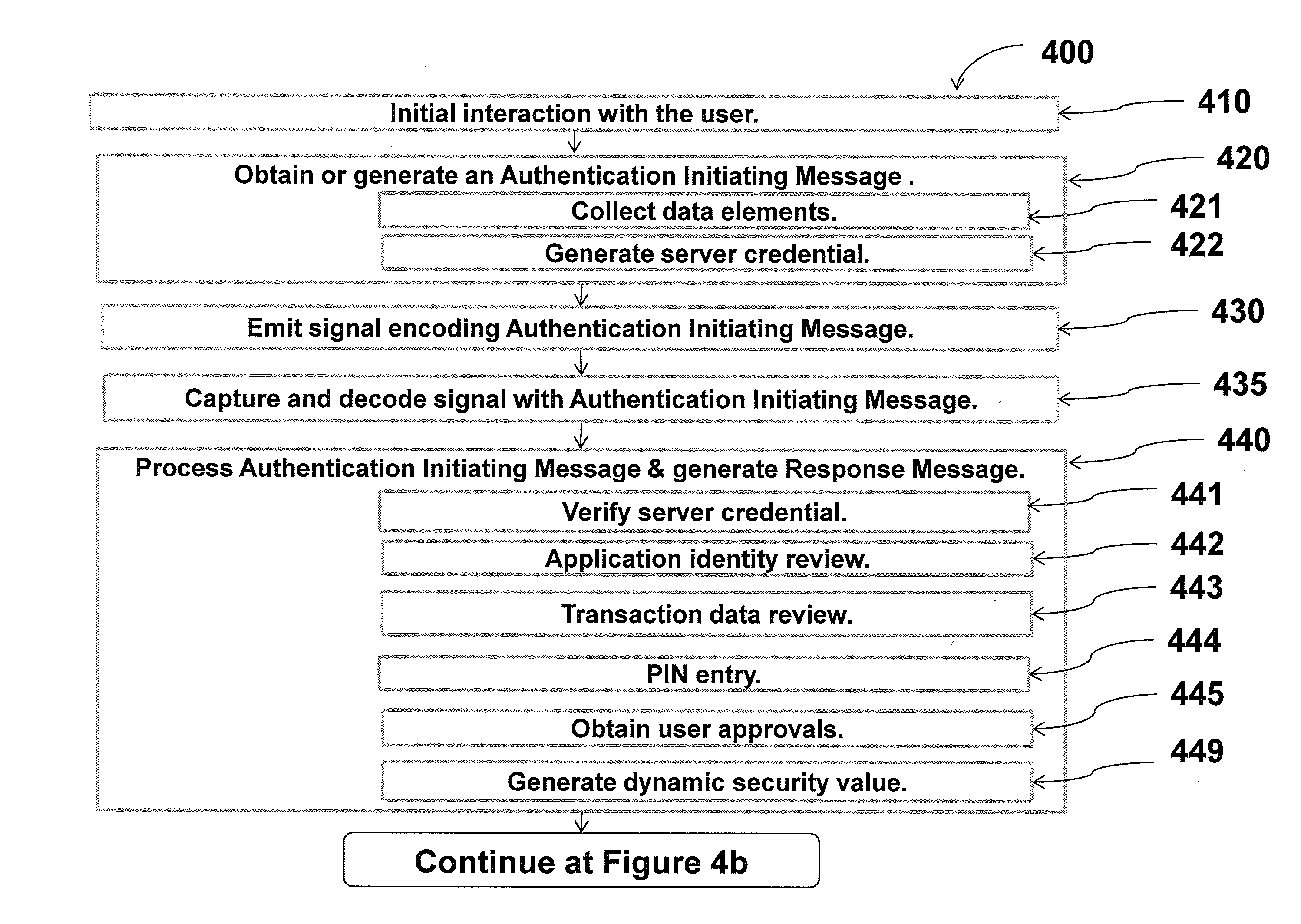
Methods, apparatus, and systems for securing application interactions are disclosed. Application interactions may be secured by, at a user authentication device, capturing a signal emitted by an access device encoded with an authentication initiating message including an application identifier, decoding the signal and obtaining the authentication initiating message, retrieving the application identifier, presenting a human interpretable representation of the application identity to the user, obtaining user approval to generate a response message available to a verification server, generating a dynamic security value using a cryptographic algorithm that is cryptographically linked to the application identity, and generating a response message including the generated dynamic security value; making the response message available to a verification server; and, at the verification server, receiving the response message, verifying the response message including verifying the validity of the dynamic security value, and communicating the result of the verification of the response message to the application.
Owner:ONESPAN NORTH AMERICA INC
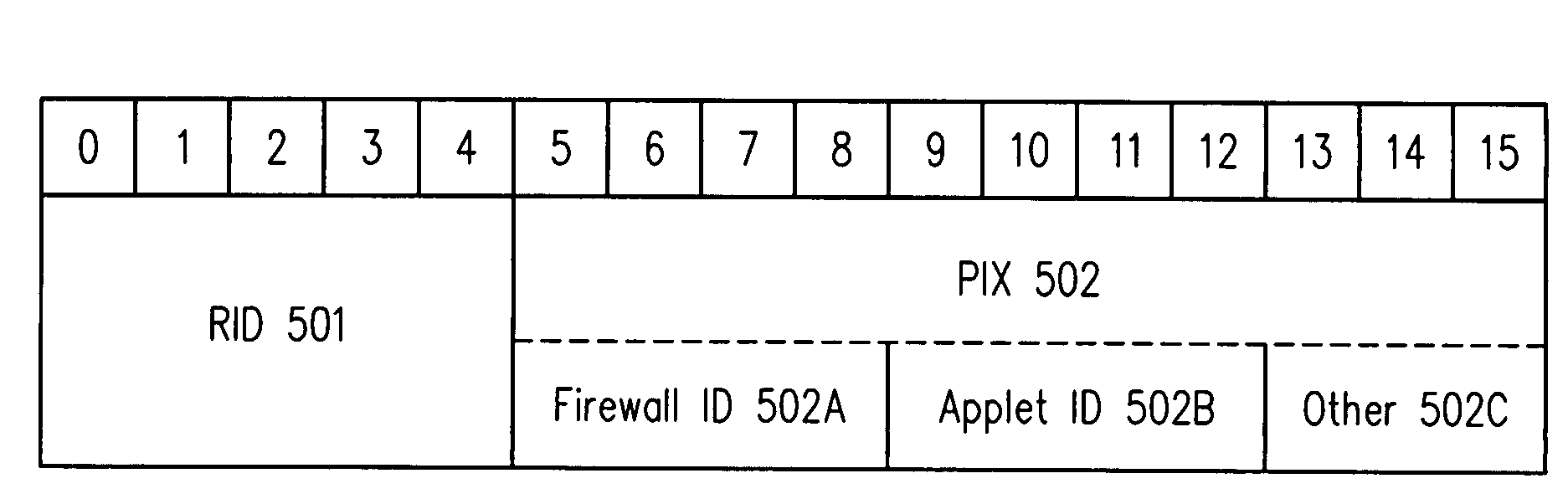
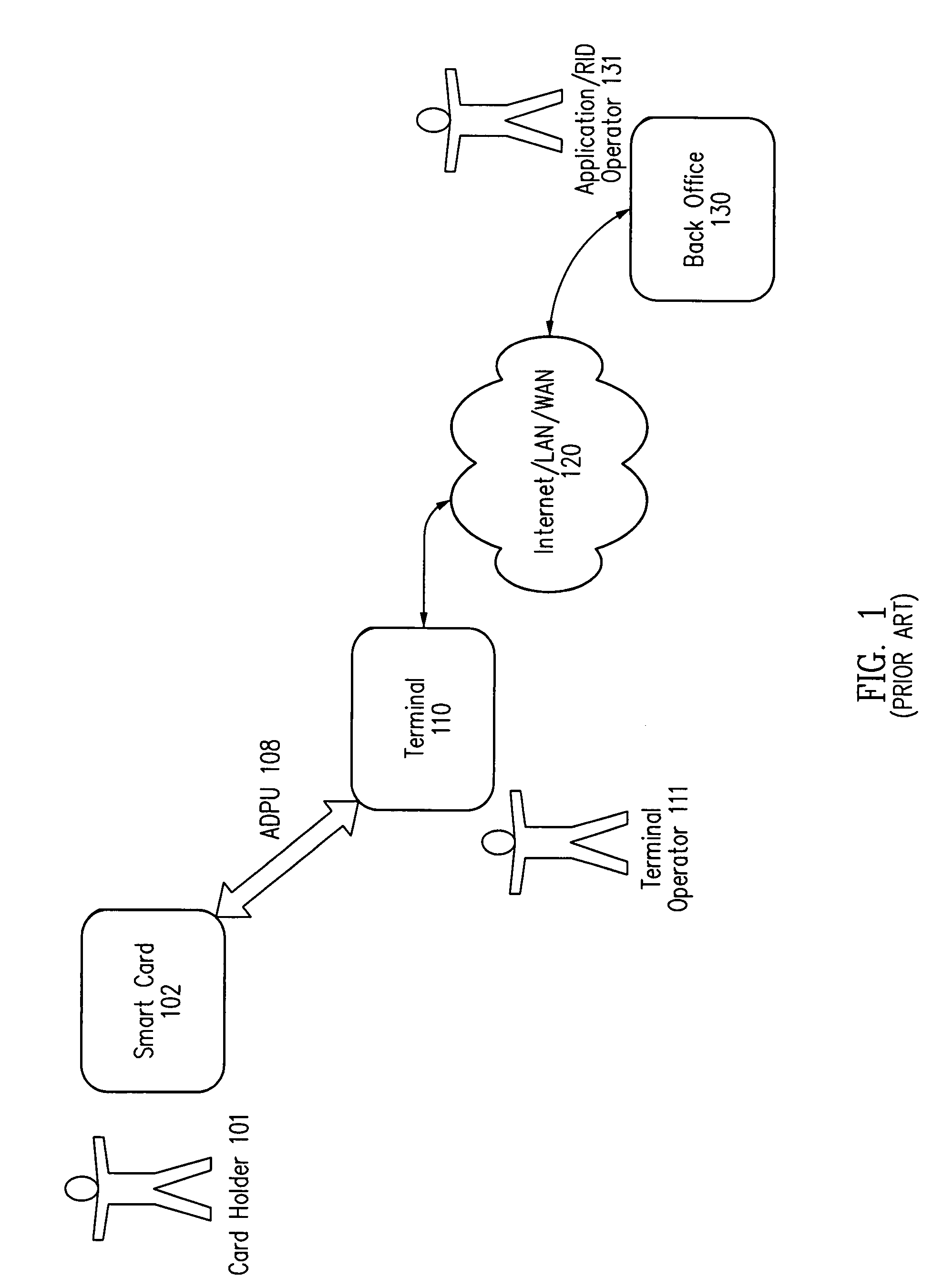
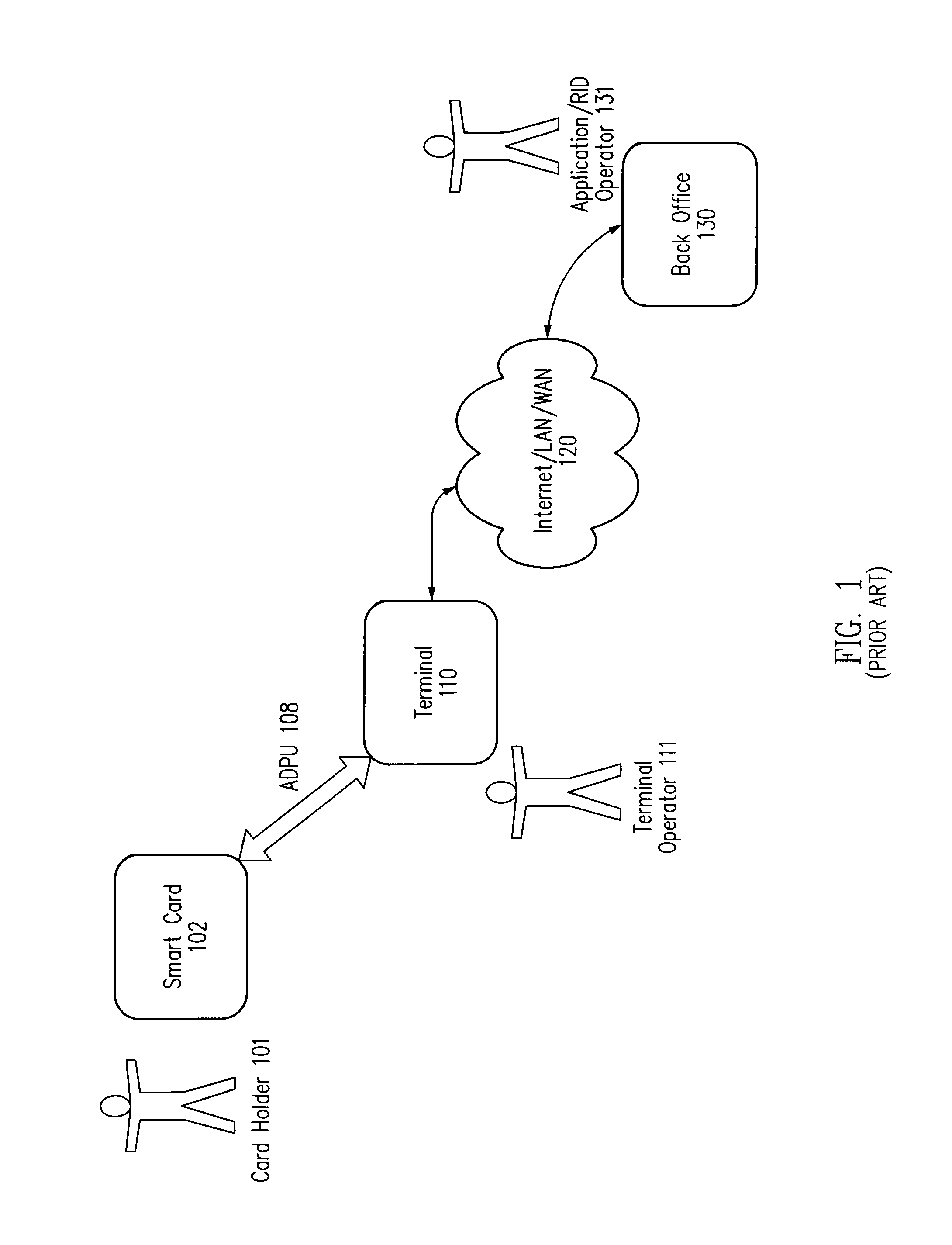
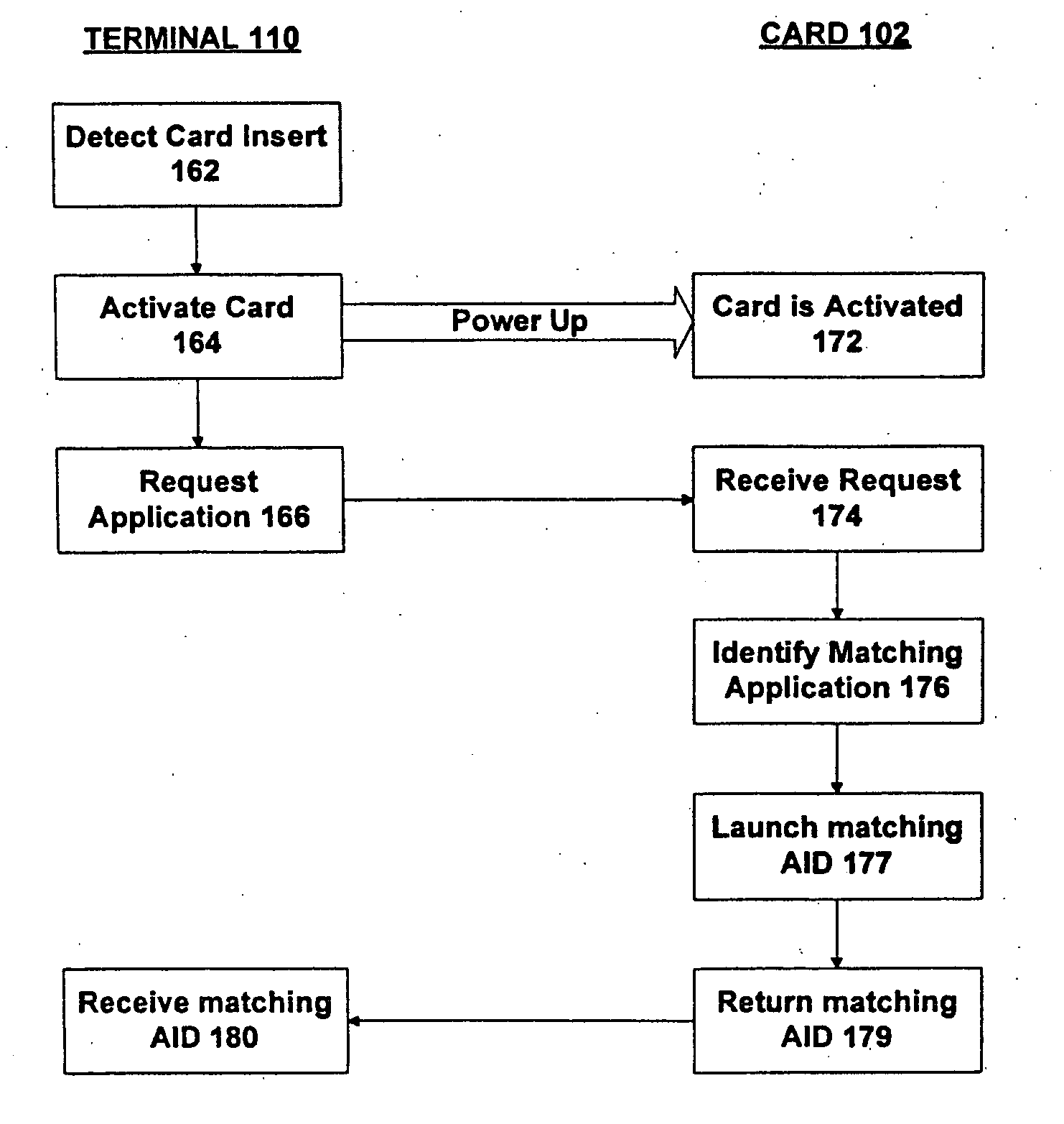
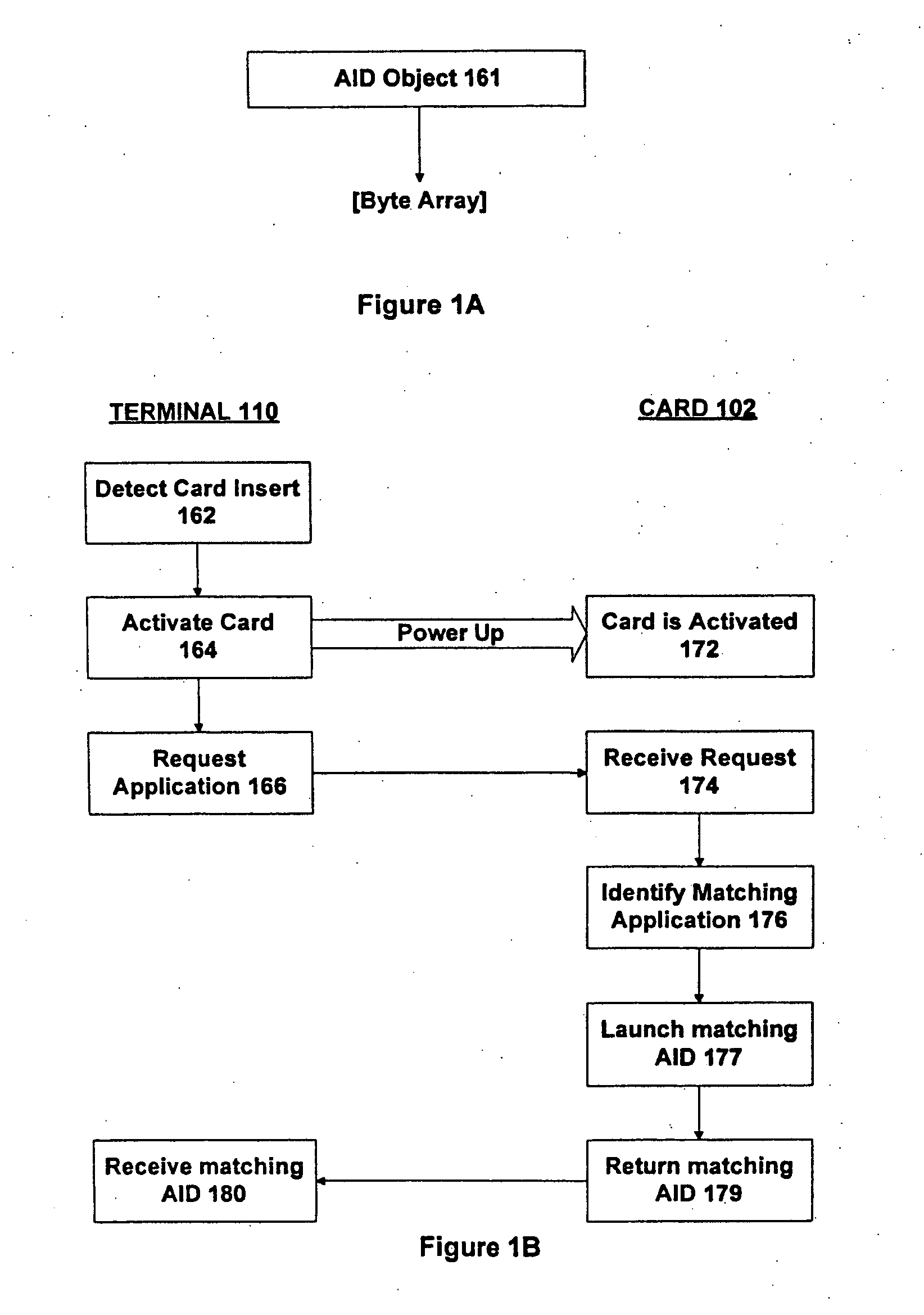
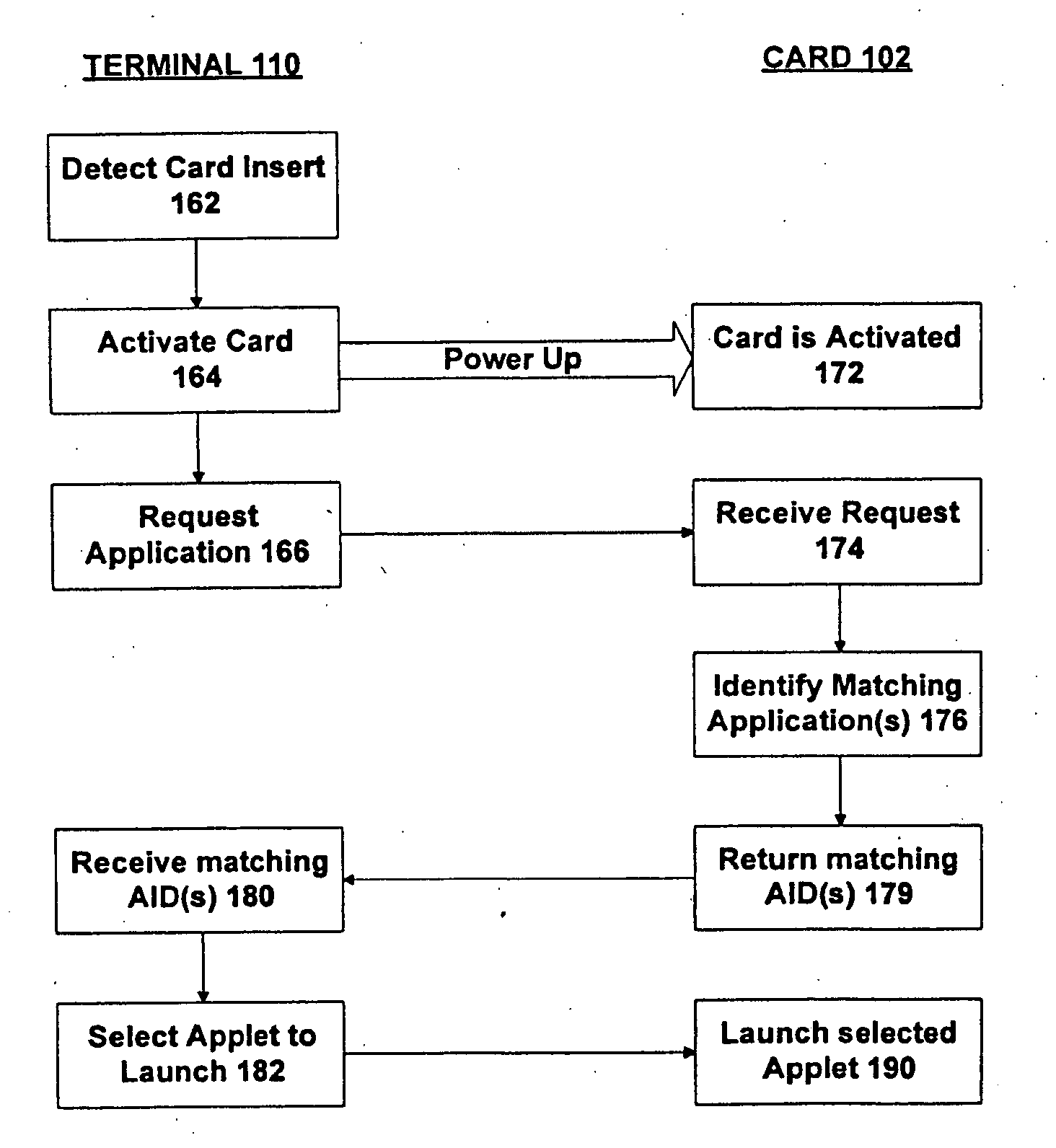
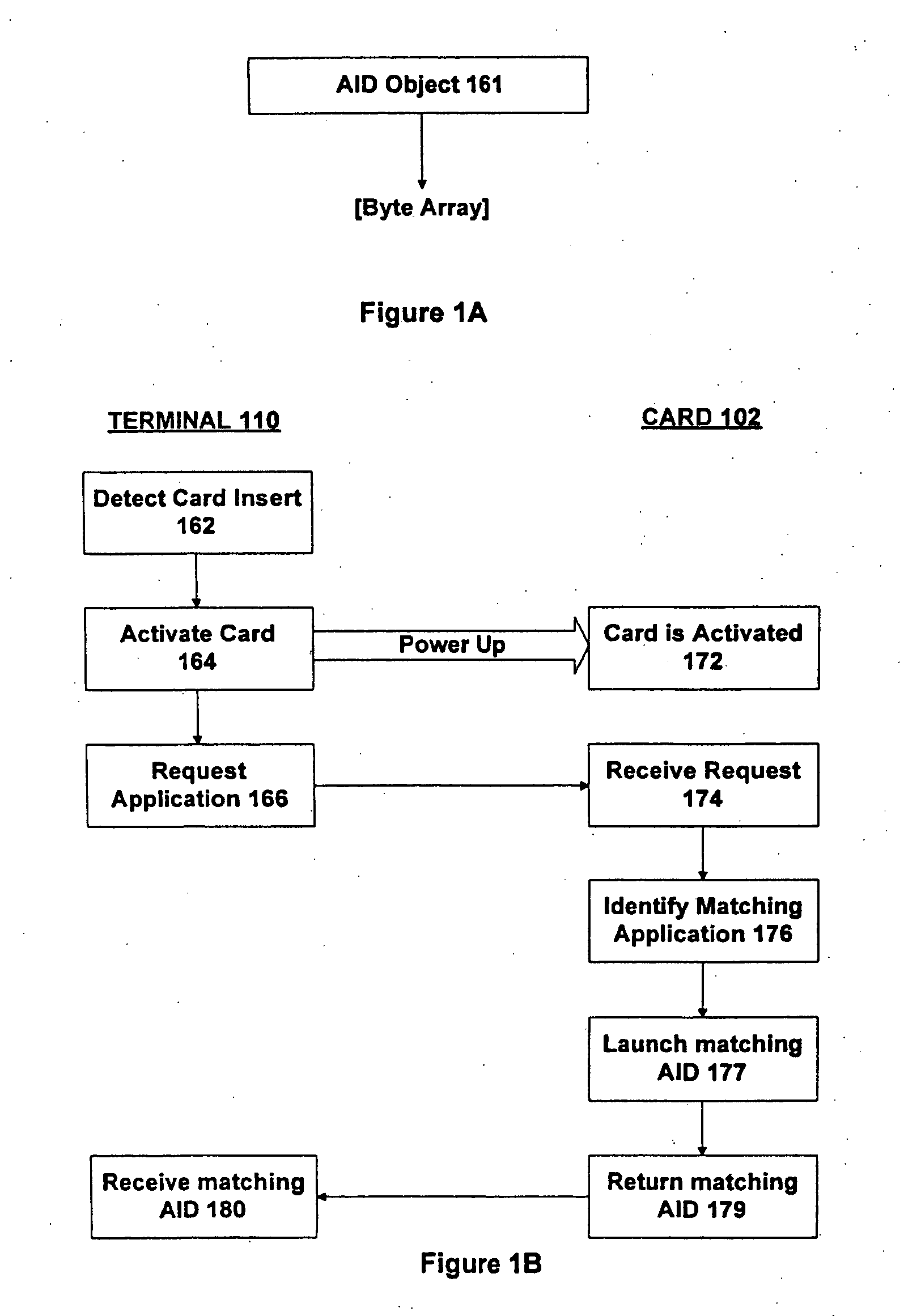
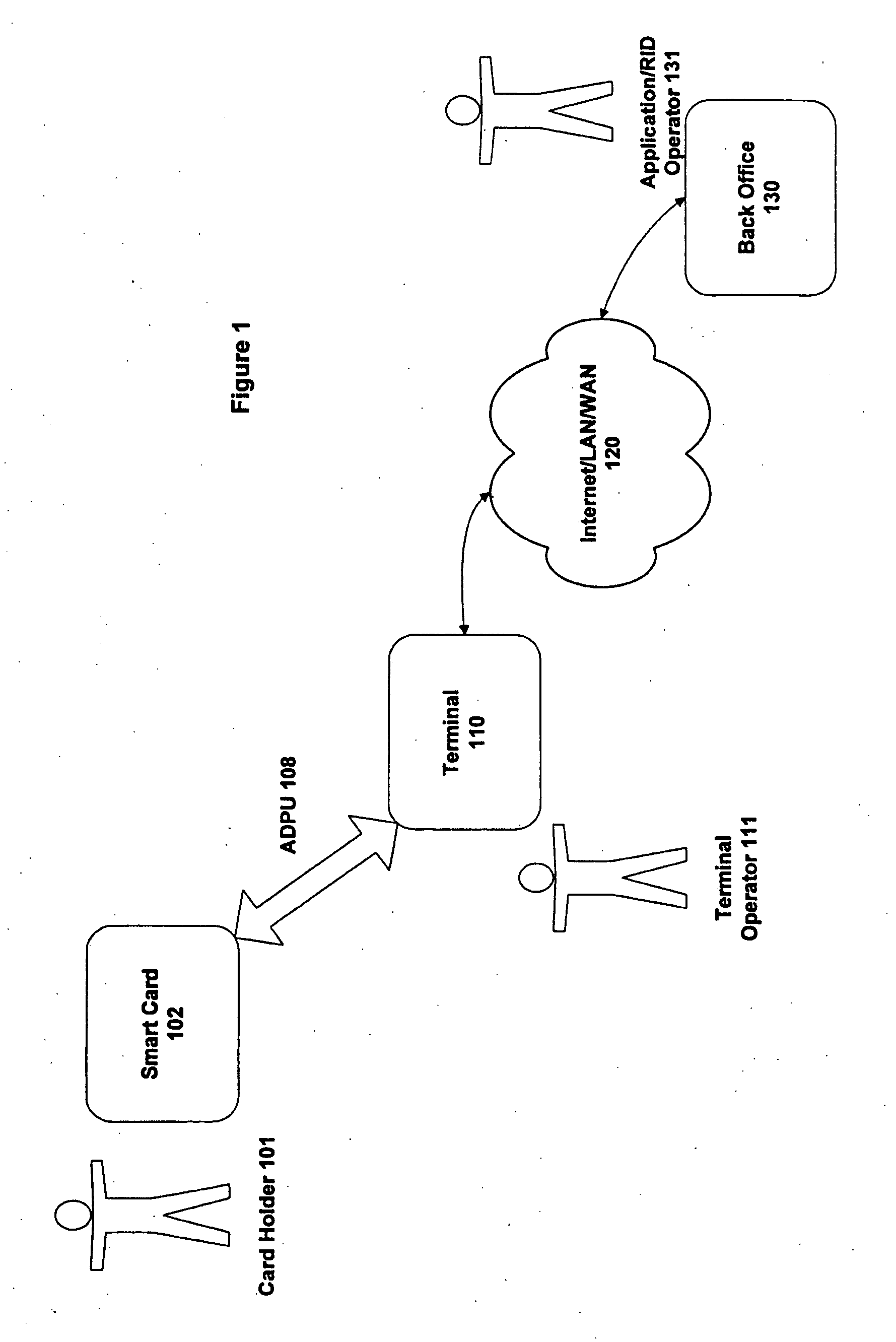
Method and apparatus for processing an application identifier from a smart card
An application identifier (AID) for an application installed on a smart card comprises a registered application provider identifier (RID). The AID may be processed by determining the RID for an application from the AID of the application, generating an identifier for a network resource from the RID, transmitting a request to the network resource using the identifier, and receiving a response to the request. The response comprises material for use in handling the application on the smart card.
Owner:ORACLE INT CORP
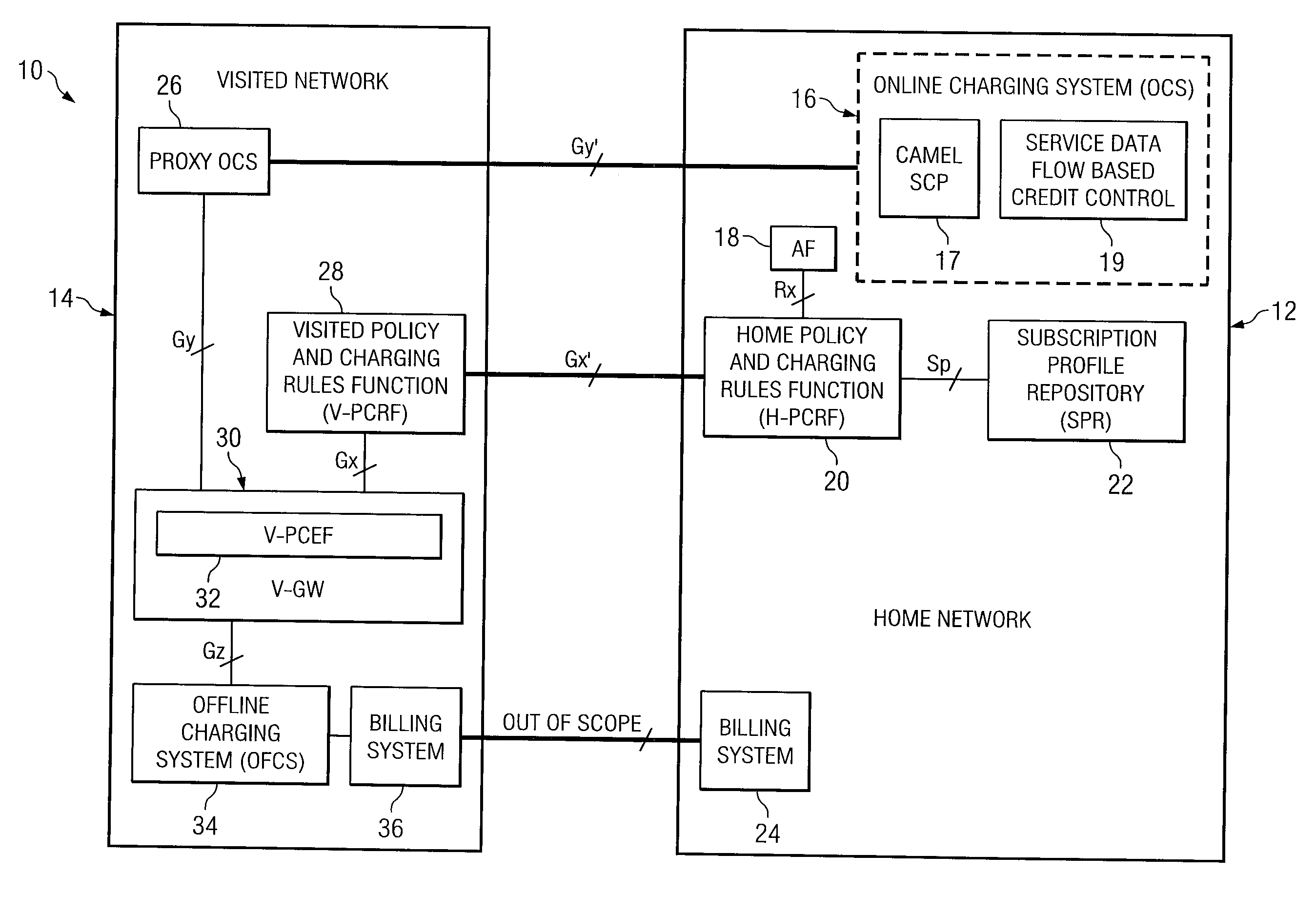
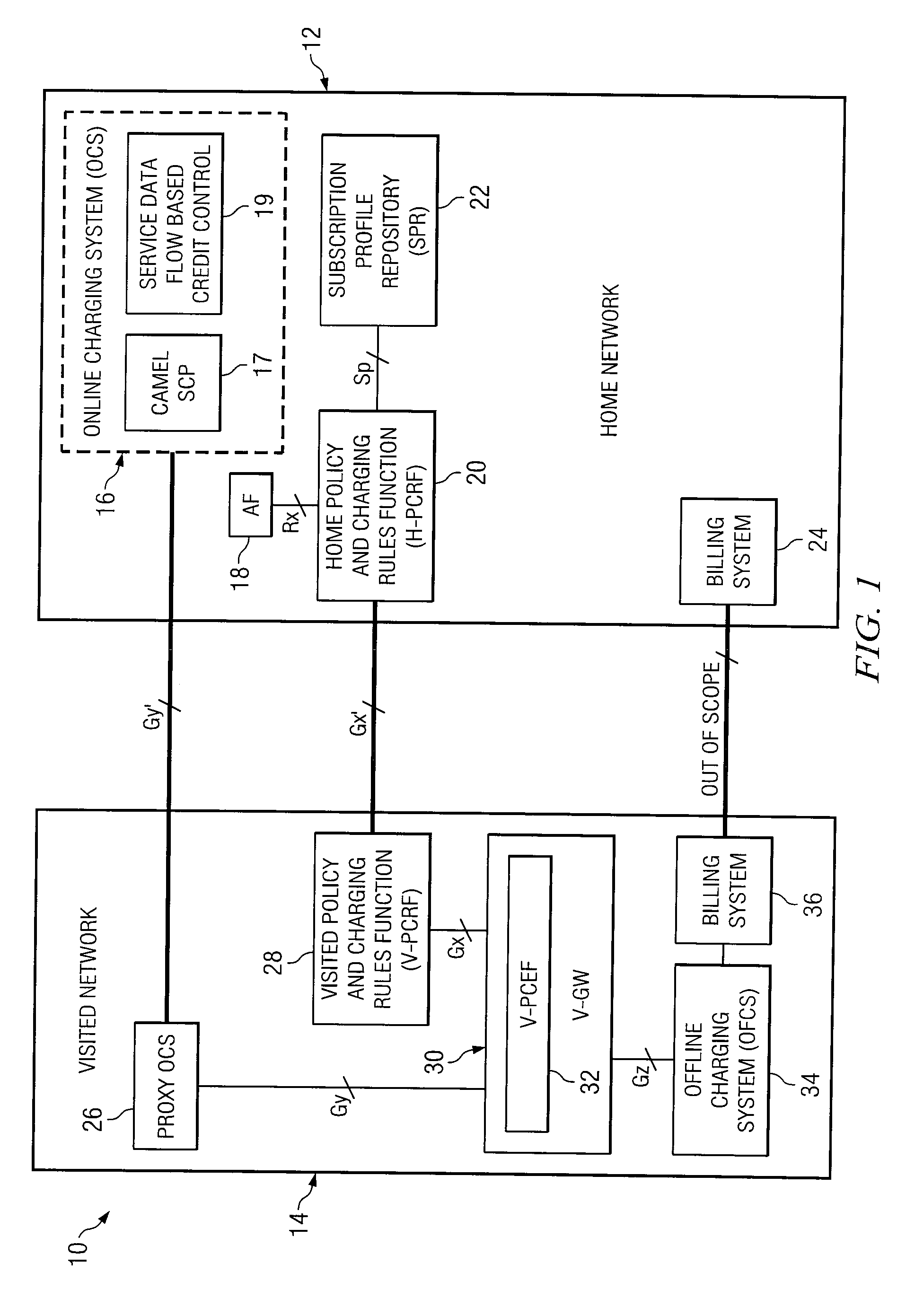
System and method for implementing policy server based application interaction manager
ActiveUS20080046963A1Network connectionsSpecial data processing applicationsApplication IdentifierOperating system
In one example embodiment, an apparatus includes a policy repository for storing a policy for application interaction. The policy defines, for a subscriber, a priority associated with a set of specific application identifiers. The priority further defines establishment priority and retention priority for an application identified by a selected application identifier. Another example embodiment includes an apparatus including a processor operable to evaluate a policy for application interaction. The policy defines, for a subscriber, a priority associated with a set of specific application identifiers. The priority further defines establishment priority and retention priority for an application identified by a selected application identifier. The processor is further operable to execute a decision for the subscriber based on the evaluation of the policy.
Owner:CISCO TECH INC
Method and apparatus for installing an application onto a smart card
Owner:ORACLE INT CORP
Control of interaction between client computer applications and network resources
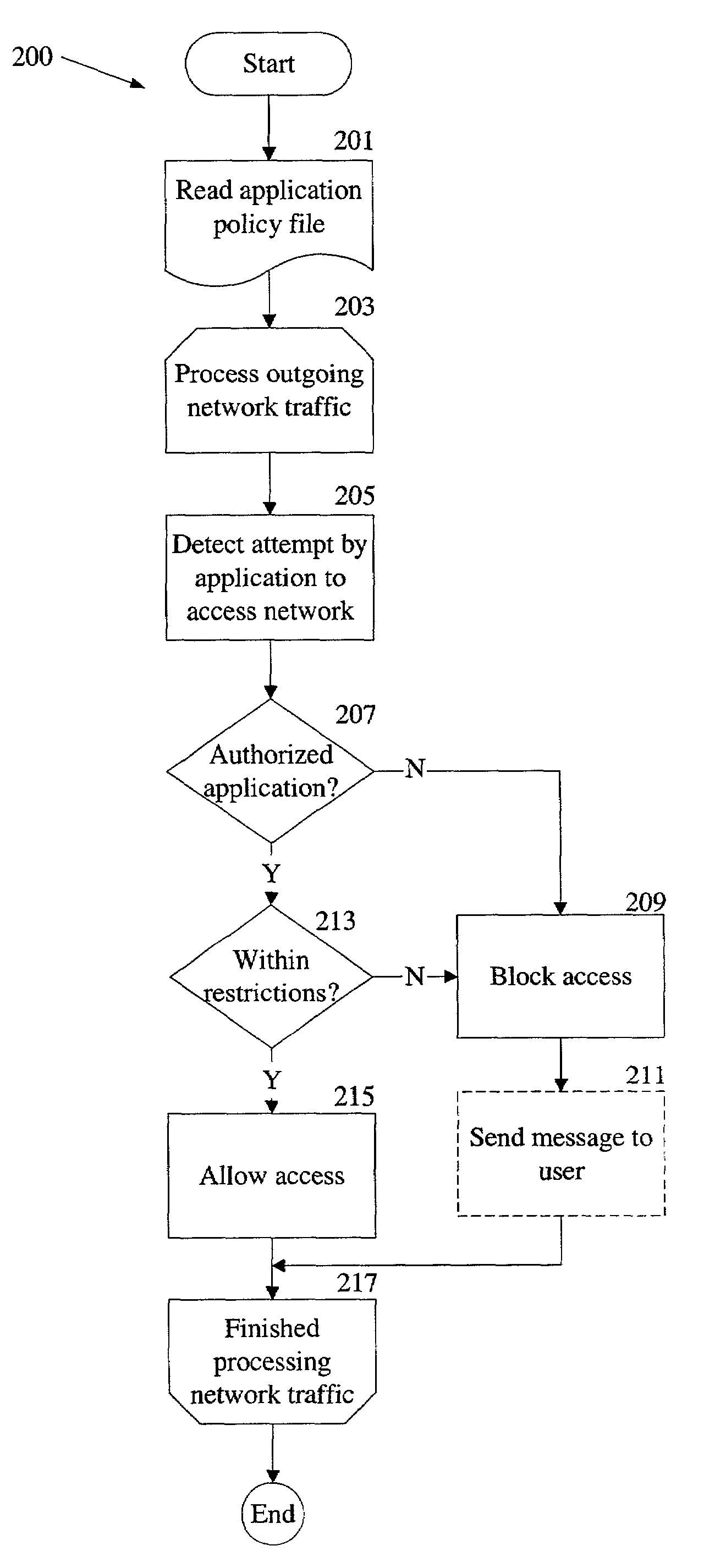
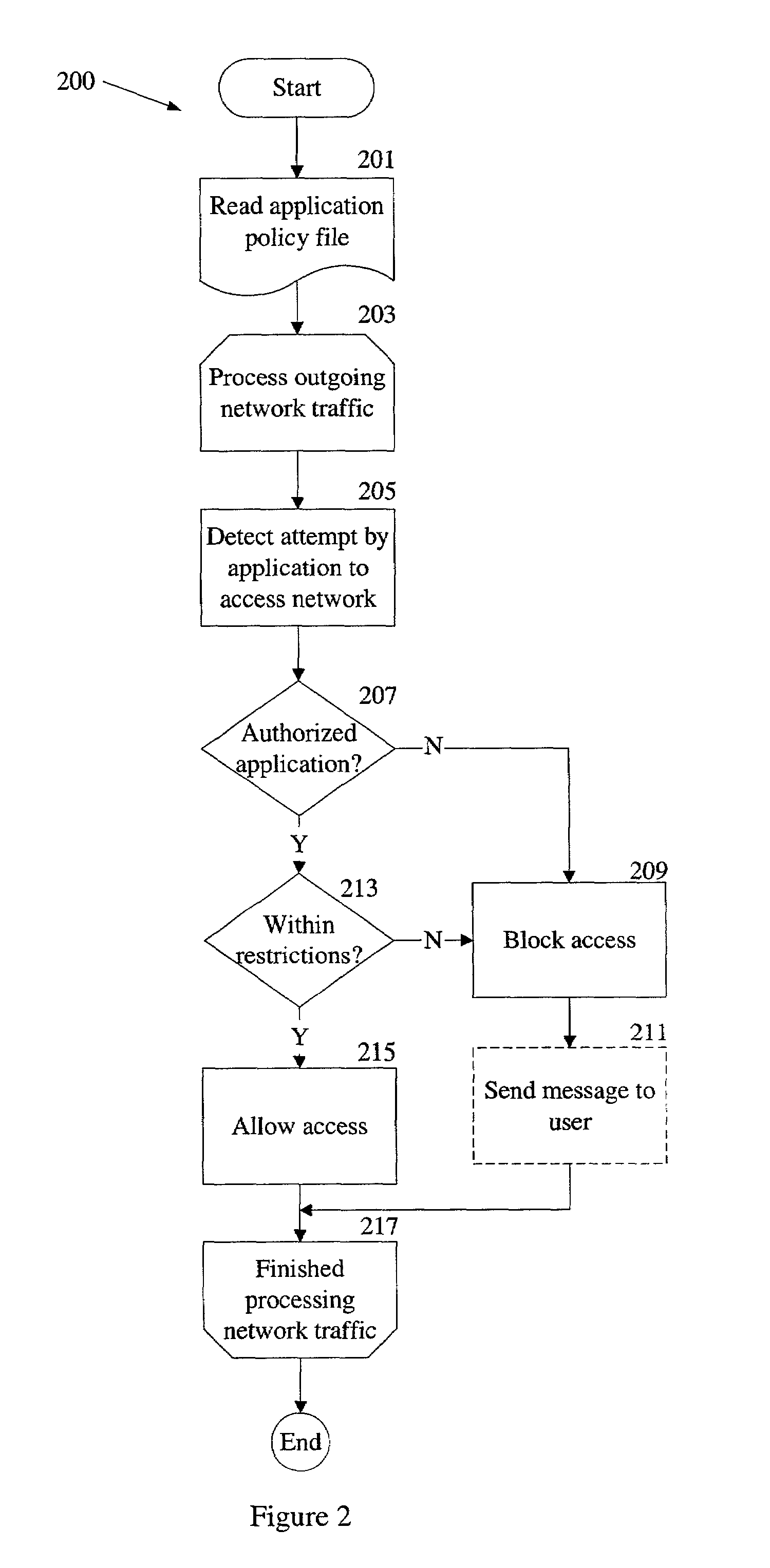
An application policy engine for a computer blocks access to network resources by applications executing on the computer that are not authorized for such access by an application policy file. The application policy engine monitors outgoing network traffic from the computer and compares an identifier for the application contained in a network access request with application identifiers stored in the application policy file. If the application identifier is associated with an unauthorized application, access to the network is blocked by the application policy engine. In another aspect, an unauthorized application is allowed access to certain resources on a network while being blocked from other resources on the same network. In still a further aspect, an authorized application may be permitted only certain types of access to a network or network resource.
Owner:MCAFEE LLC
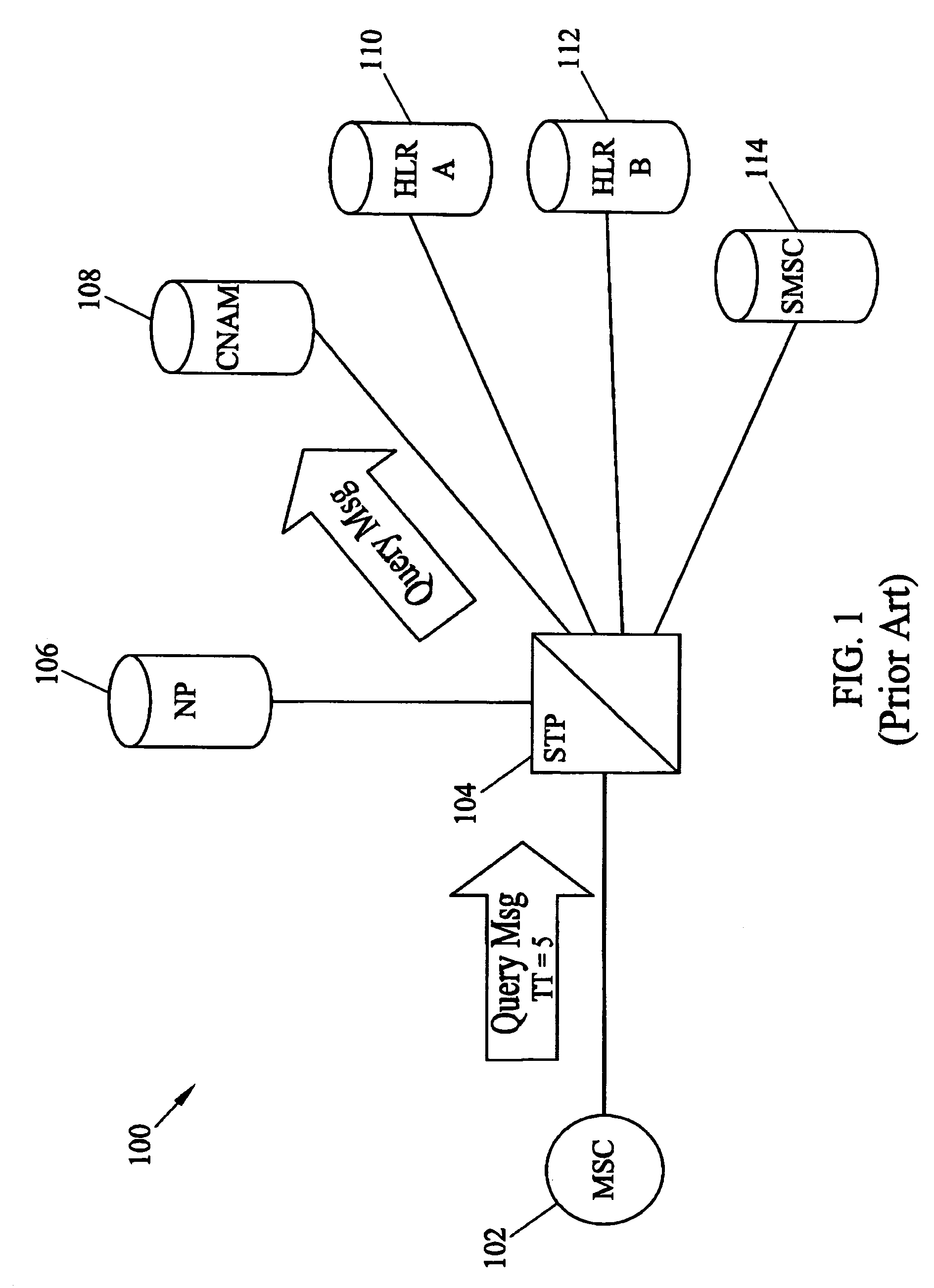
Methods and systems for universal, automatic service selection in a telecommunications signaling network
InactiveUS7092505B2Raise the possibilityRobust solutionInterconnection arrangementsTime-division multiplexMessage typeSignaling network
Methods and systems for universal, automatic service selection are disclosed. A method for universal, automatic service selection includes receiving signaling messages and identifying signaling connection control part (SCCP) messages from the signaling messages. The SCCP messages are decoded to extract SCCP parameters and application layer parameters from the messages. A routing address translation service is selected for each of the SCCP messages based on application identifiers that identify application layer message types alone or in combination with other parameters. Selecting the routing address translation service in this manner makes the service selection more robust and universally applicable, especially in networks where different or non-standard selector parameters are utilized.
Owner:TEKELEC
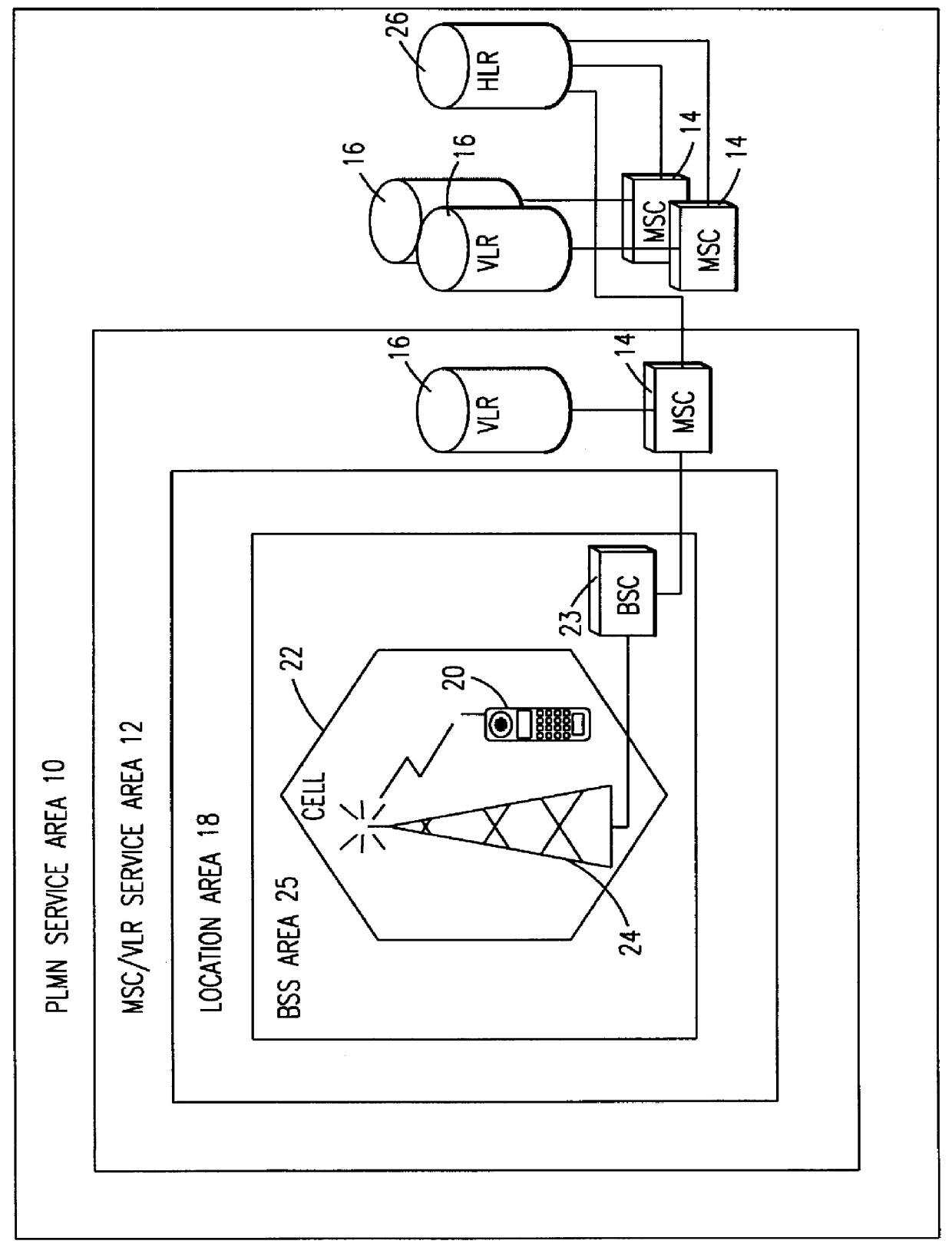
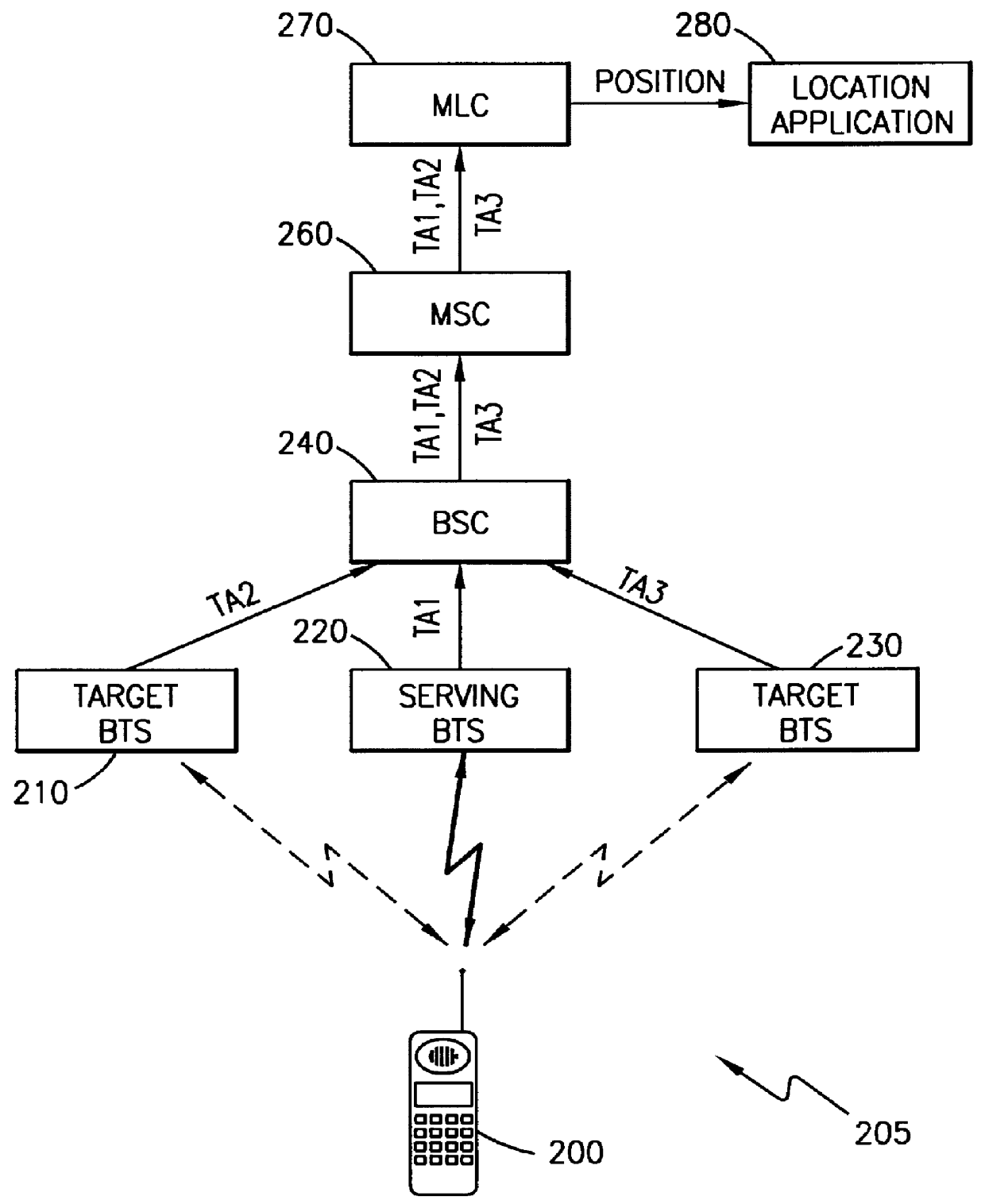
System and method for defining location services
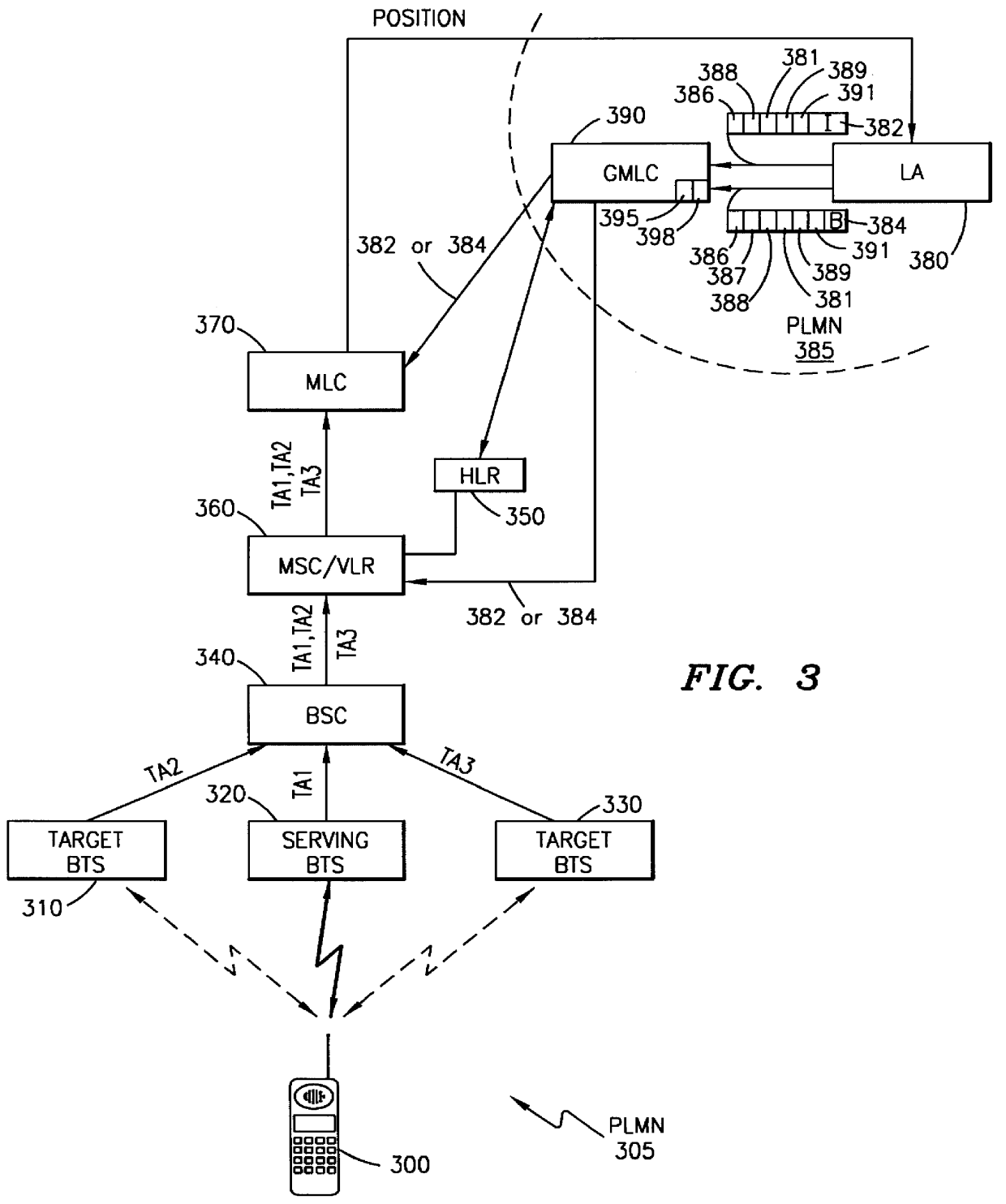
InactiveUS6104931ARadio/inductive link selection arrangementsWireless commuication servicesTelecommunicationsApplication Identifier
A telecommunications system and method is disclosed for defining location services in a simplified manner based upon whether the positioning request is an interactive request or a batch mode request. In order to initiate a positioning request, a Location Application (LA) must first register with at least one Mobile Location Center (MLC), define the service parameters specific for that LA and receive a Location Application Identifier Number (LAIN). Thereafter, the LA can send either an interactive or batch mode positioning request along with the LAIN. An interactive positioning request is a request to position a specific subscriber or group of subscribers immediately, while a batch mode positioning request is a request to position a subscriber or group of subscribers when a particular event defined by the LA occurs. Advantageously, the definition of location services is decoupled from issues, such as the point of origin of the request, the identity of the subscriber to be positioned and authorization options.
Owner:ERICSSON INC
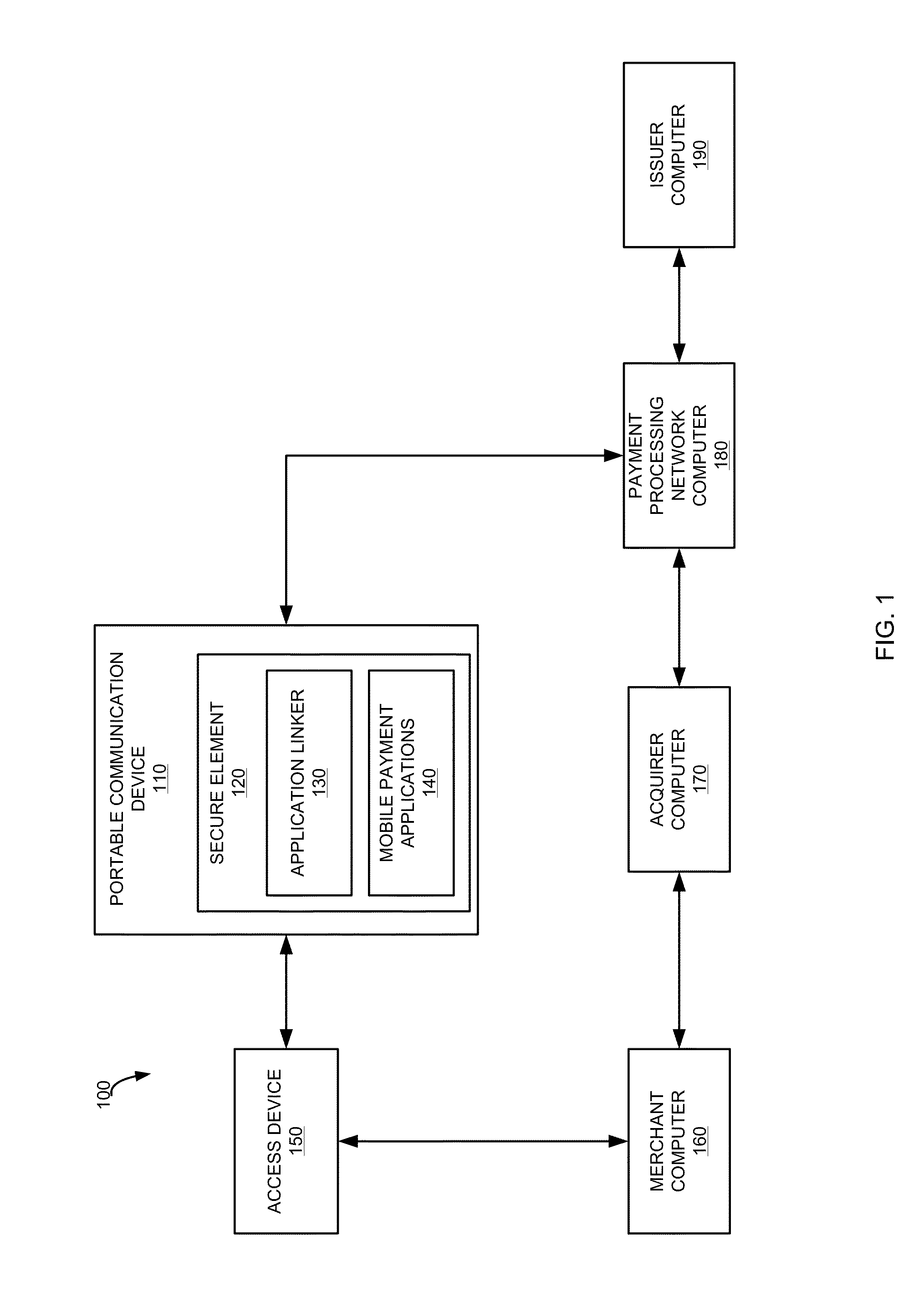
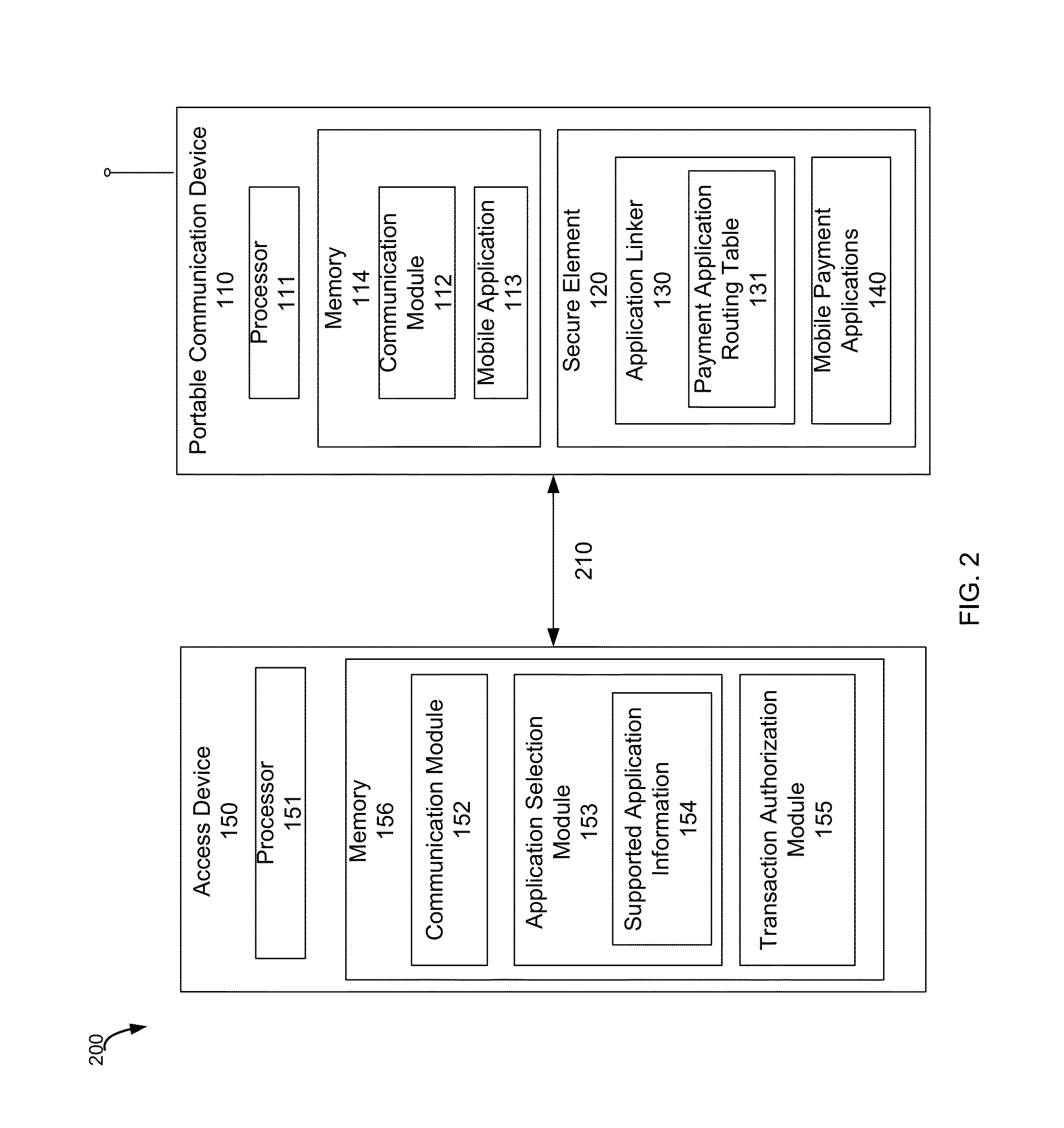
Methods and systems for mobile payment application selection and management using an application linker
An application linker system that manages a plurality of application identifiers associated with a plurality of payment applications present on a device is disclosed. The application linker may manage relationships between application identifiers and payment applications that are provisioned for secure storage on a device. For example, a transaction can be conducted between a portable communication device and an access device. The method includes receiving a request for available payment applications located on the portable communication device from the access device, determining application identifiers associated with payment applications on the device, and sending a list of available payment applications including the application identifiers to the access device. The payment applications store payment information associated with one or more consumer accounts. One of the application identifiers is associated with two or more payment applications.
Owner:VISA INT SERVICE ASSOC
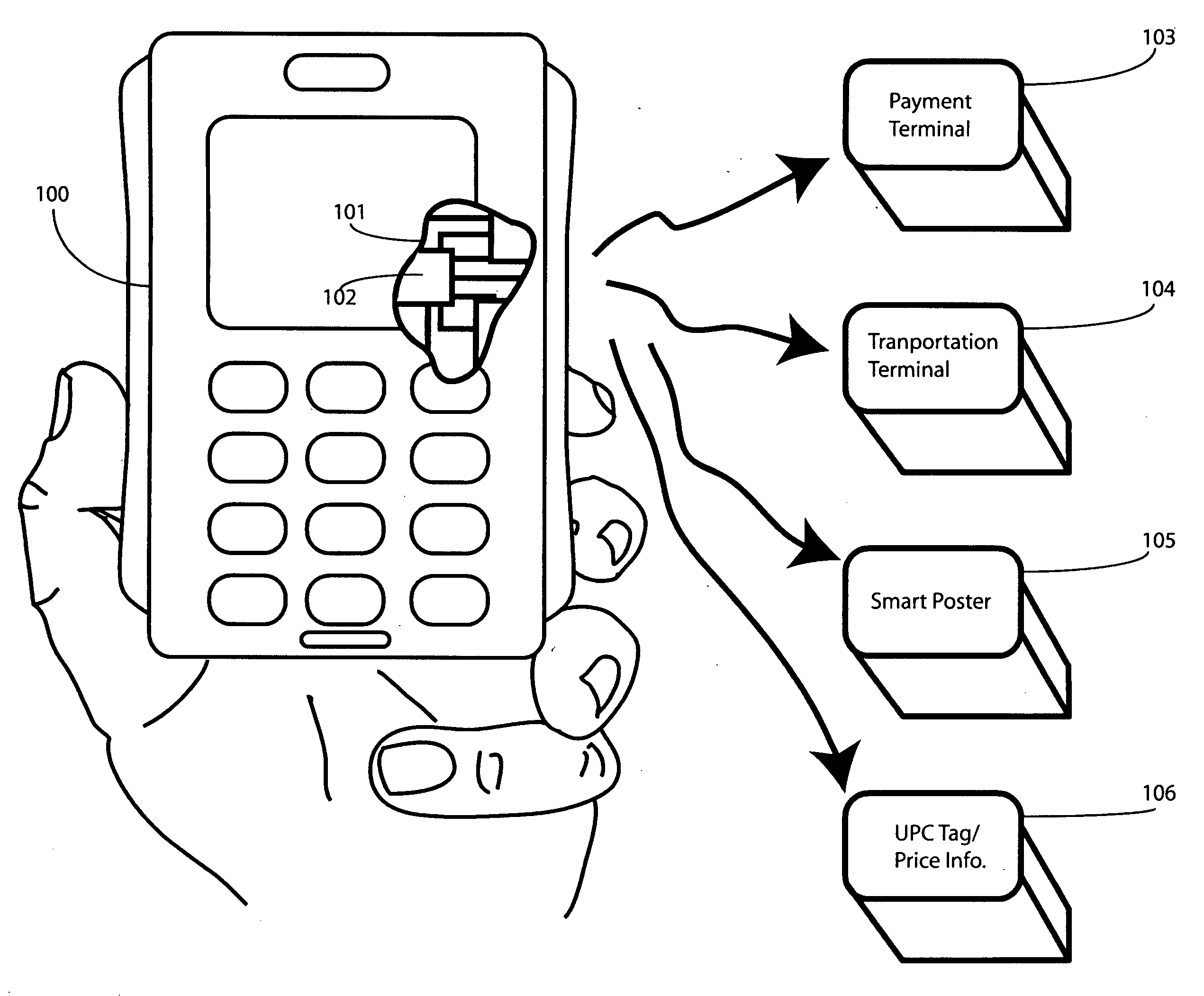
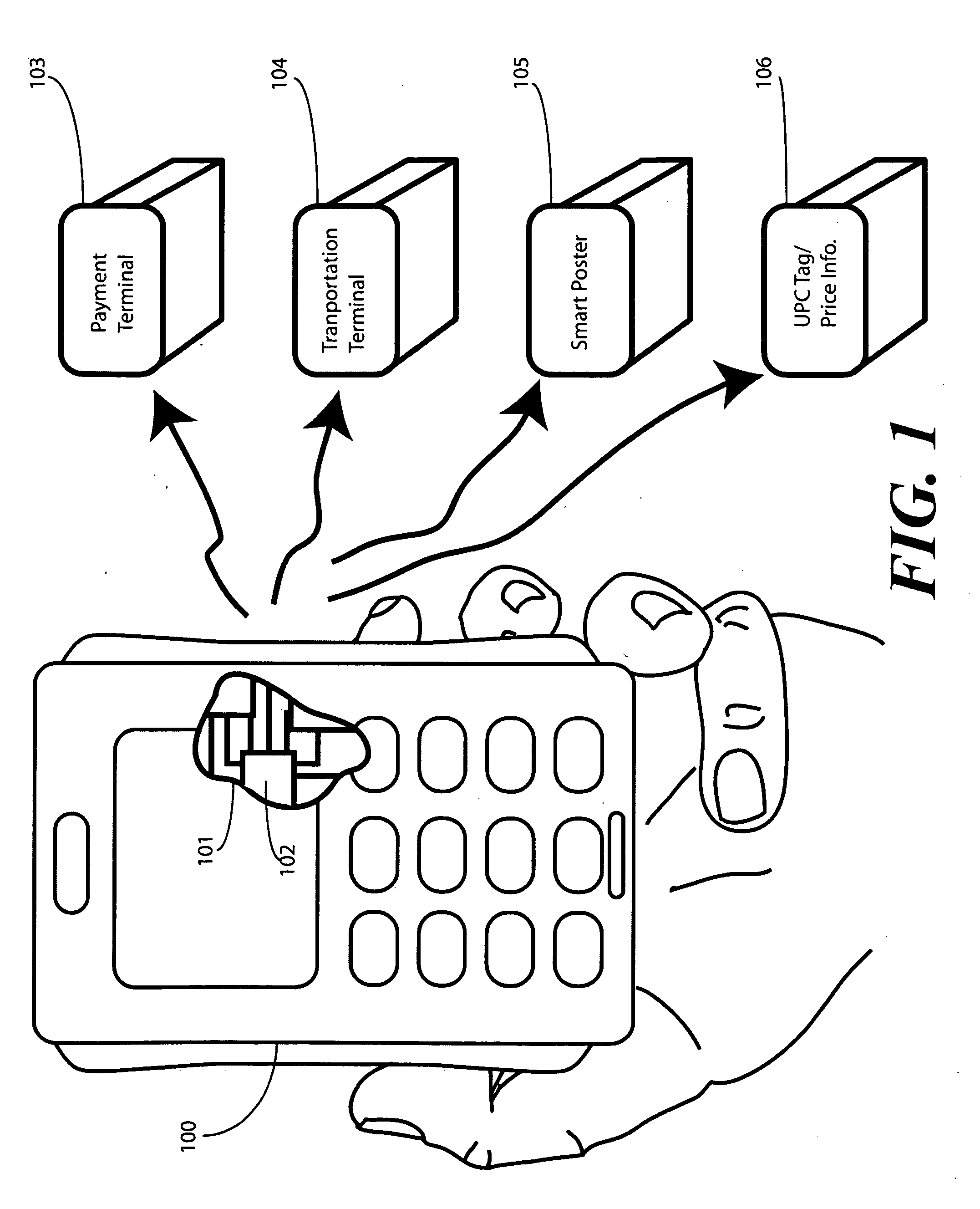
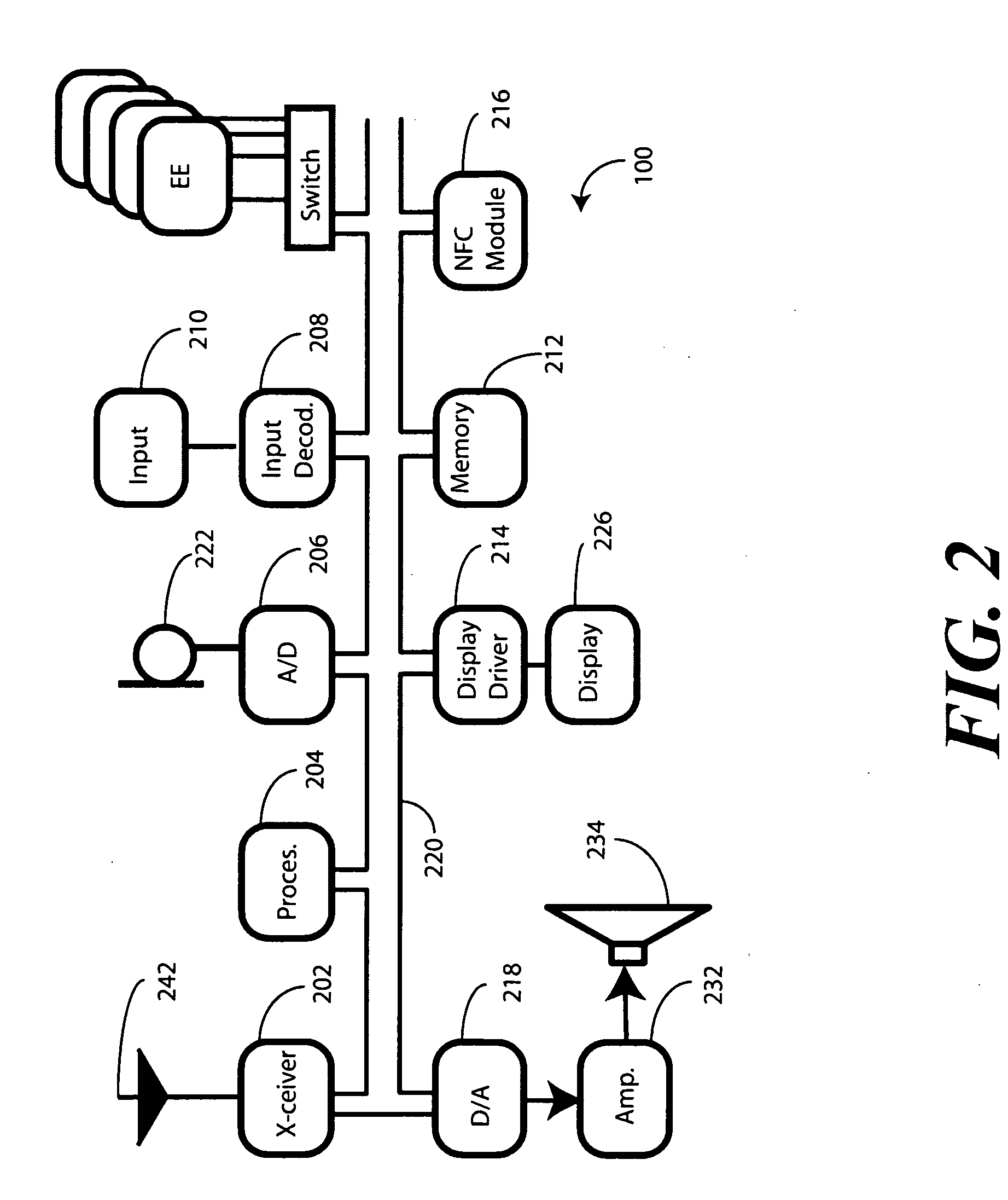
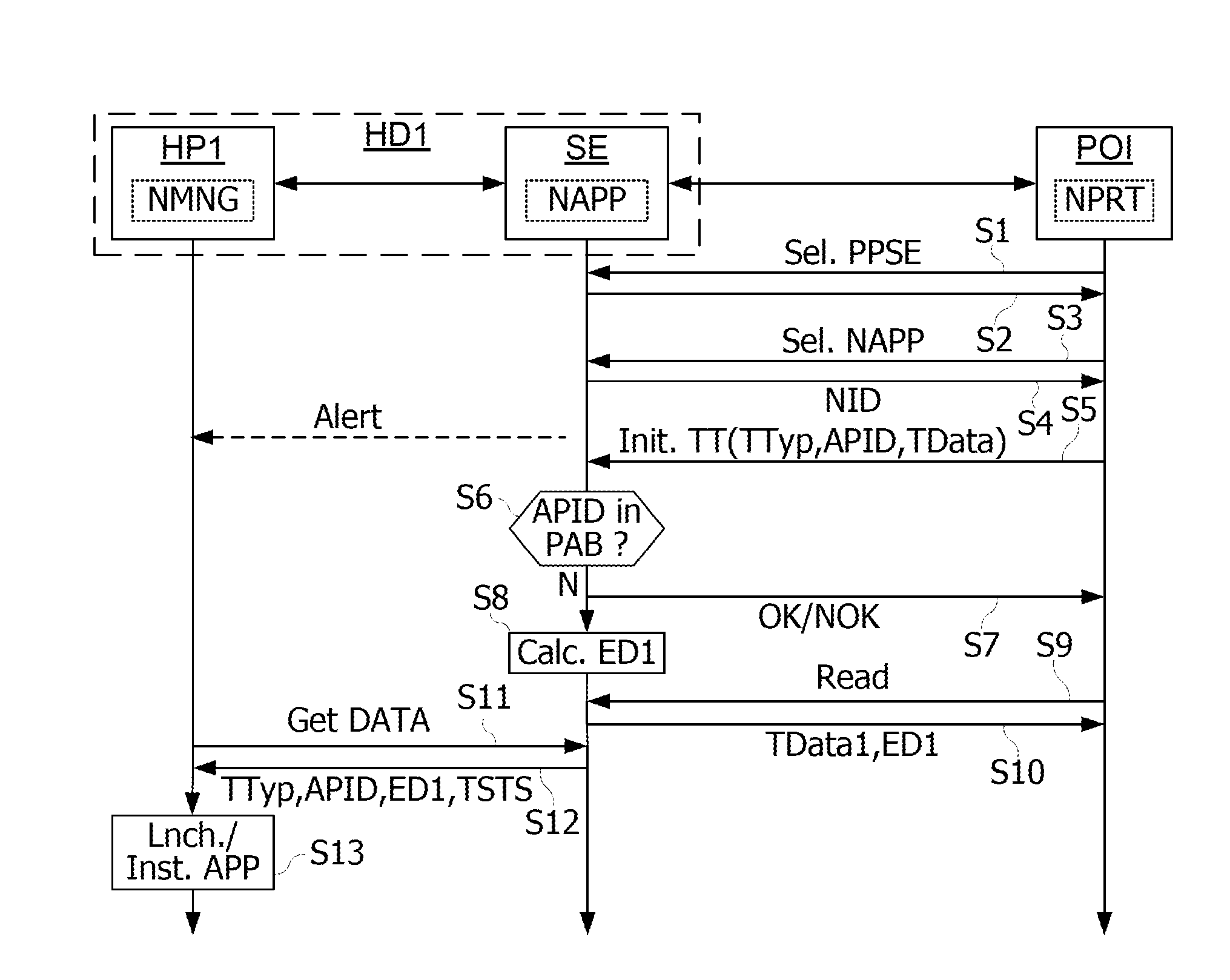
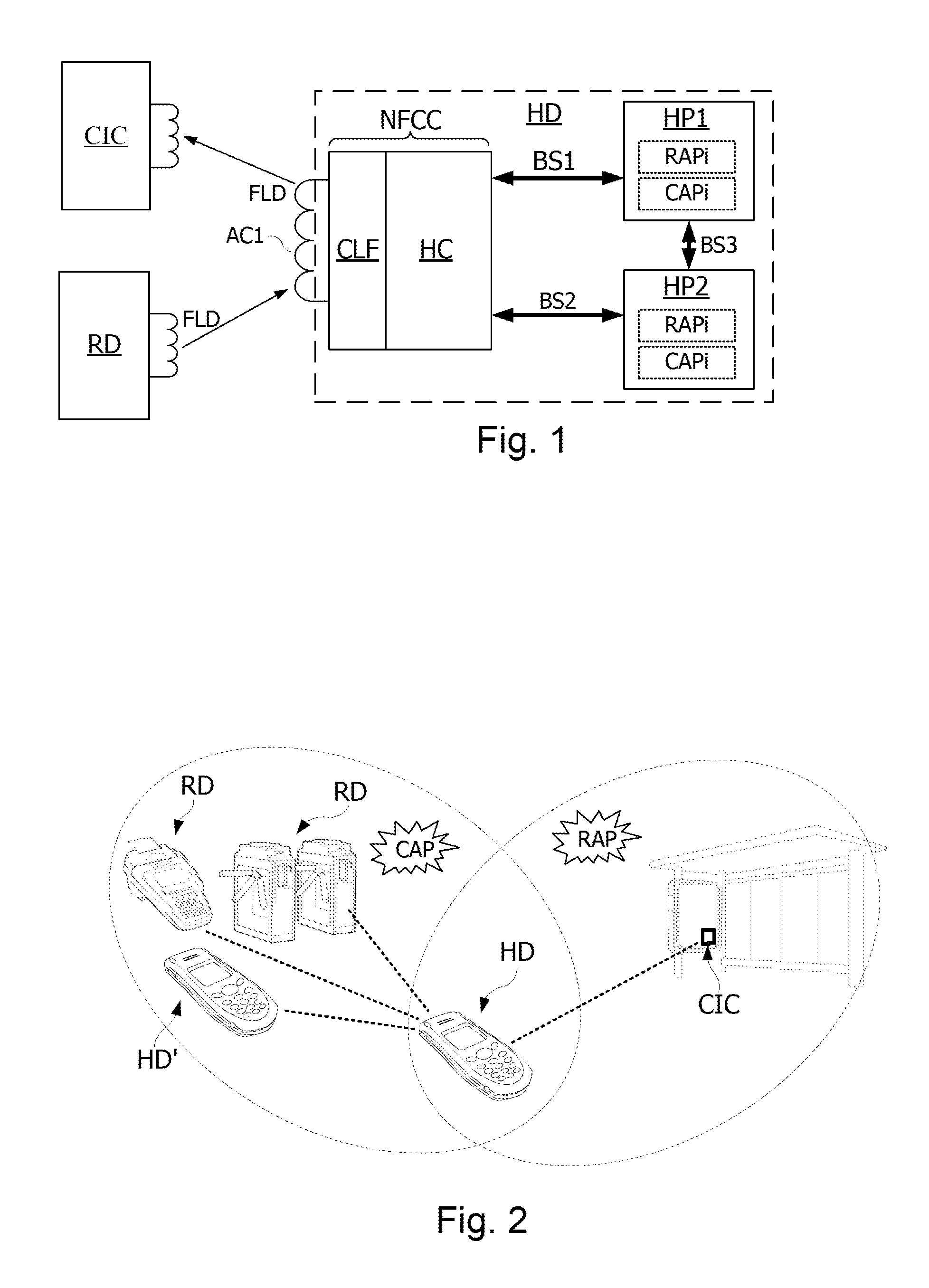
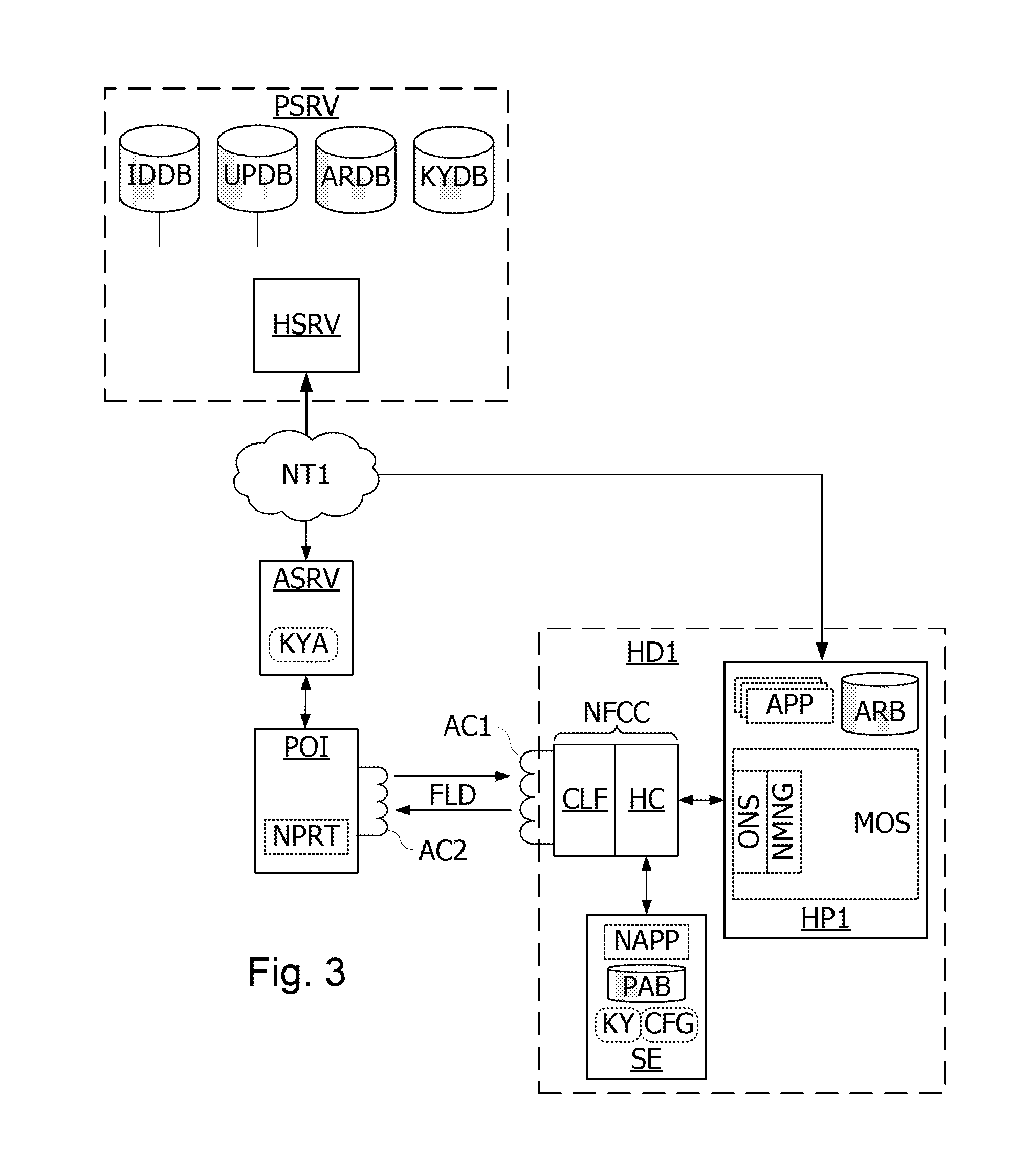
Method and apparatus for automatic near field communication application selection in an electronic device
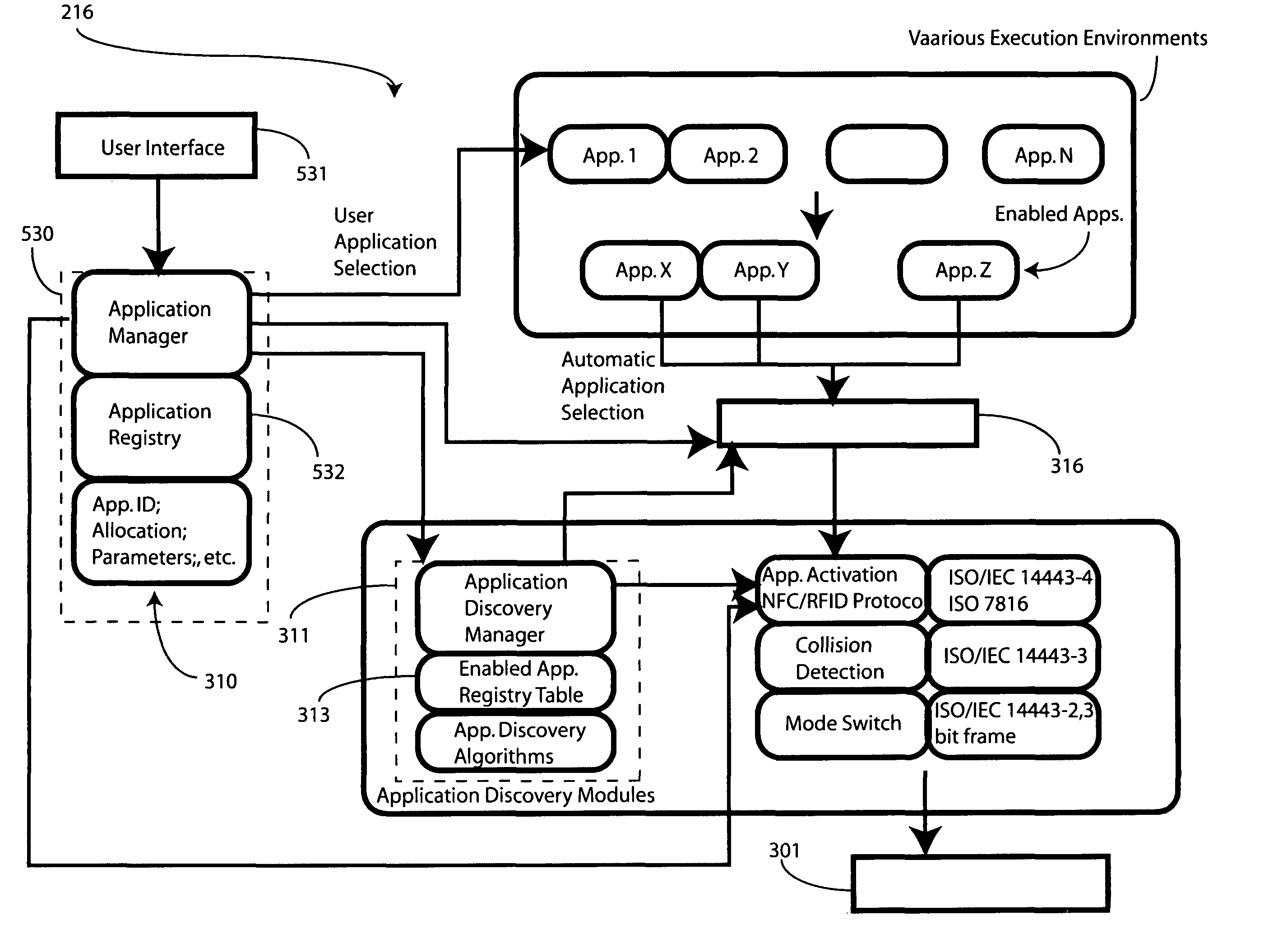
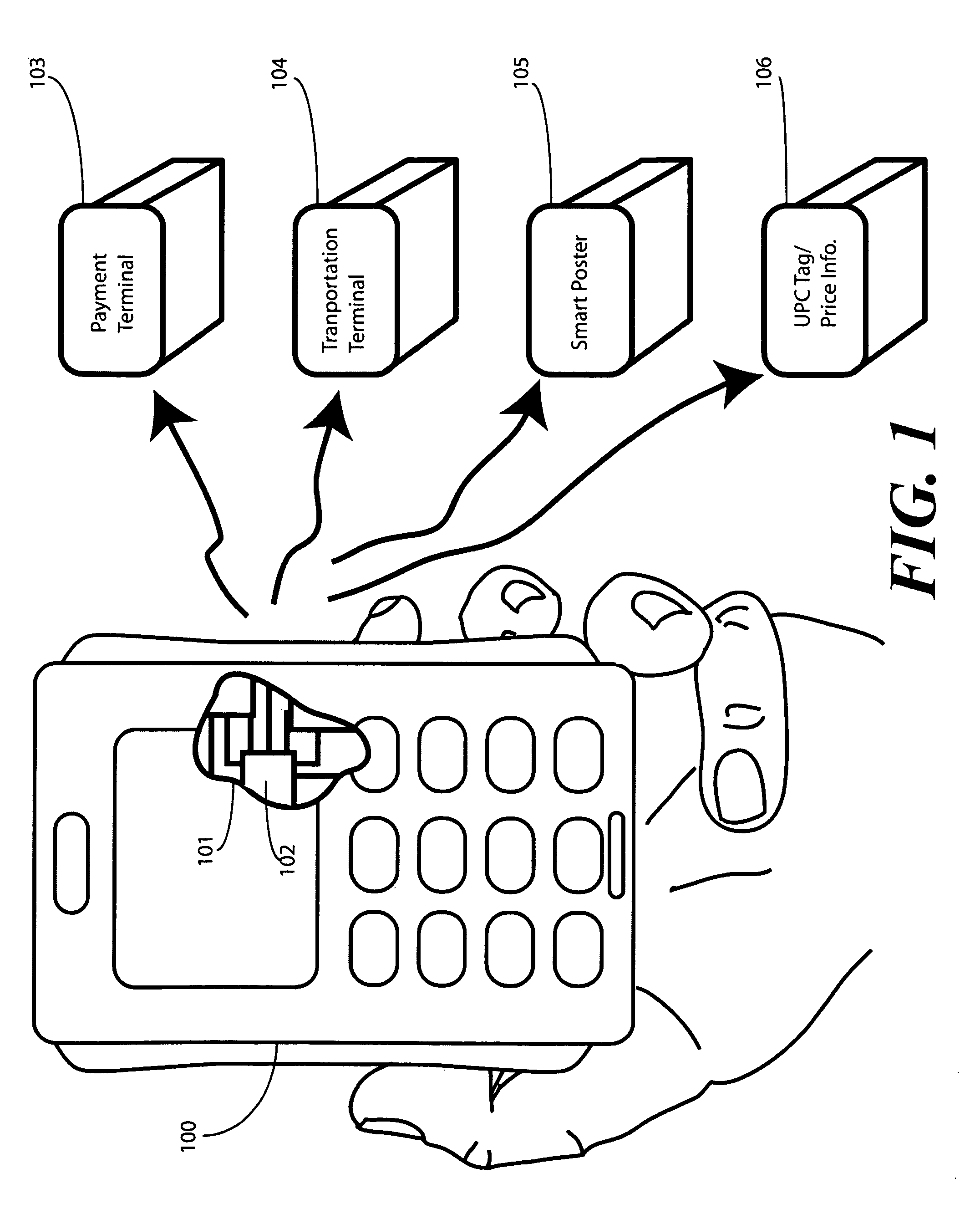
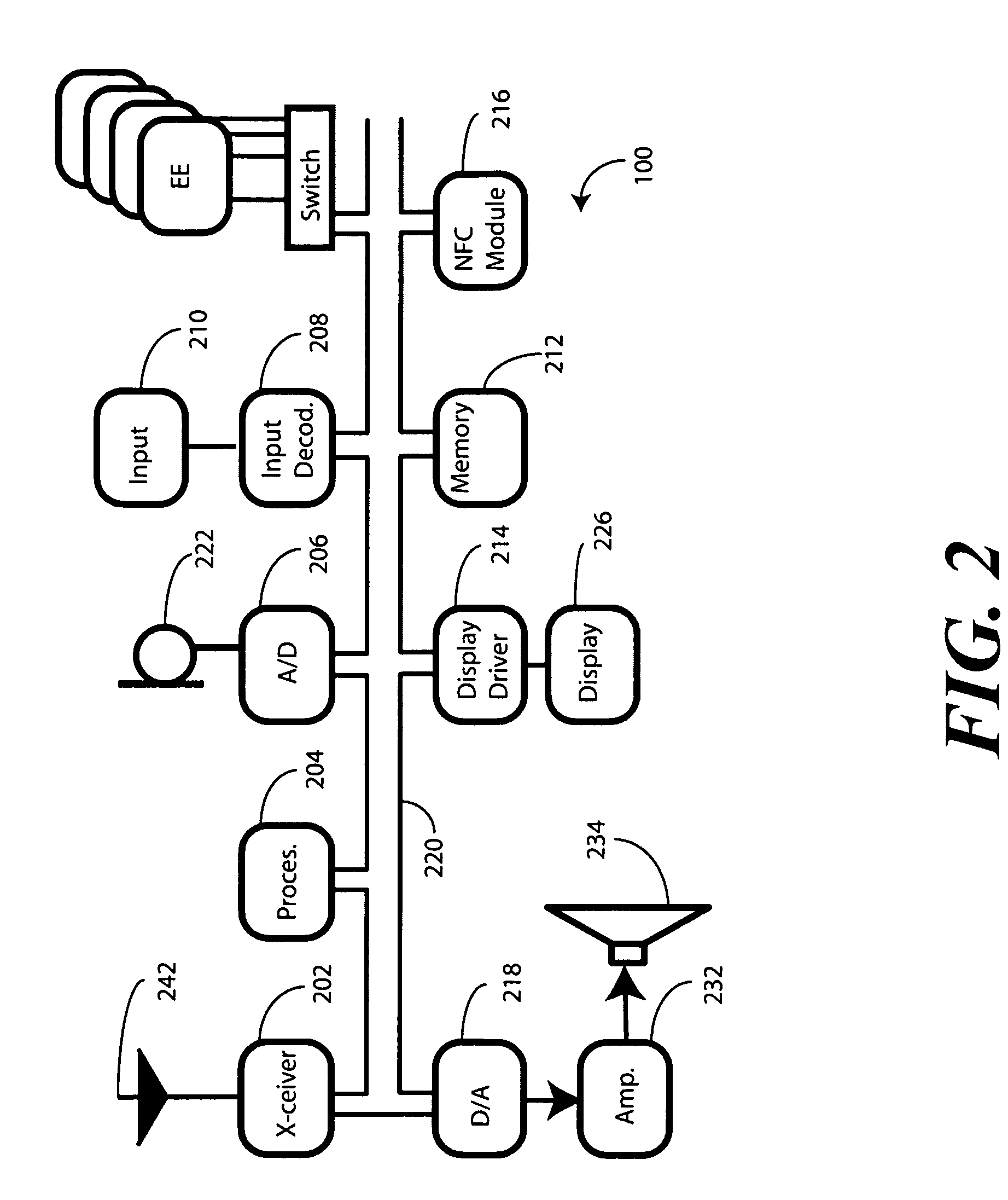
In a portable electronic device (100) having a plurality of near field communication applications stored within a plurality of execution environments, an application discovery manager (311) is configured to automatically select and launch one or more of the near field communication applications. A near field communication circuit (300) receives a near field communication request from an external near field communication device (700). The application discovery manager (311) identifies a near field communication technology, a protocol, and an application identifier and then references a registry table (313) to determine identification parameters corresponding with the identified information. The application discovery manager (311) then selects a near field communication application and launches it. The application discovery manager (311) further configures a routing switch (316) to direct data between the near field communication circuit controller (301) and the appropriate execution environment.
Owner:GOOGLE TECH HLDG LLC
Method and apparatus for routing confidential information
InactiveUS6363525B1User identity/authority verificationMultiple digital computer combinationsAs DirectedInternet privacy
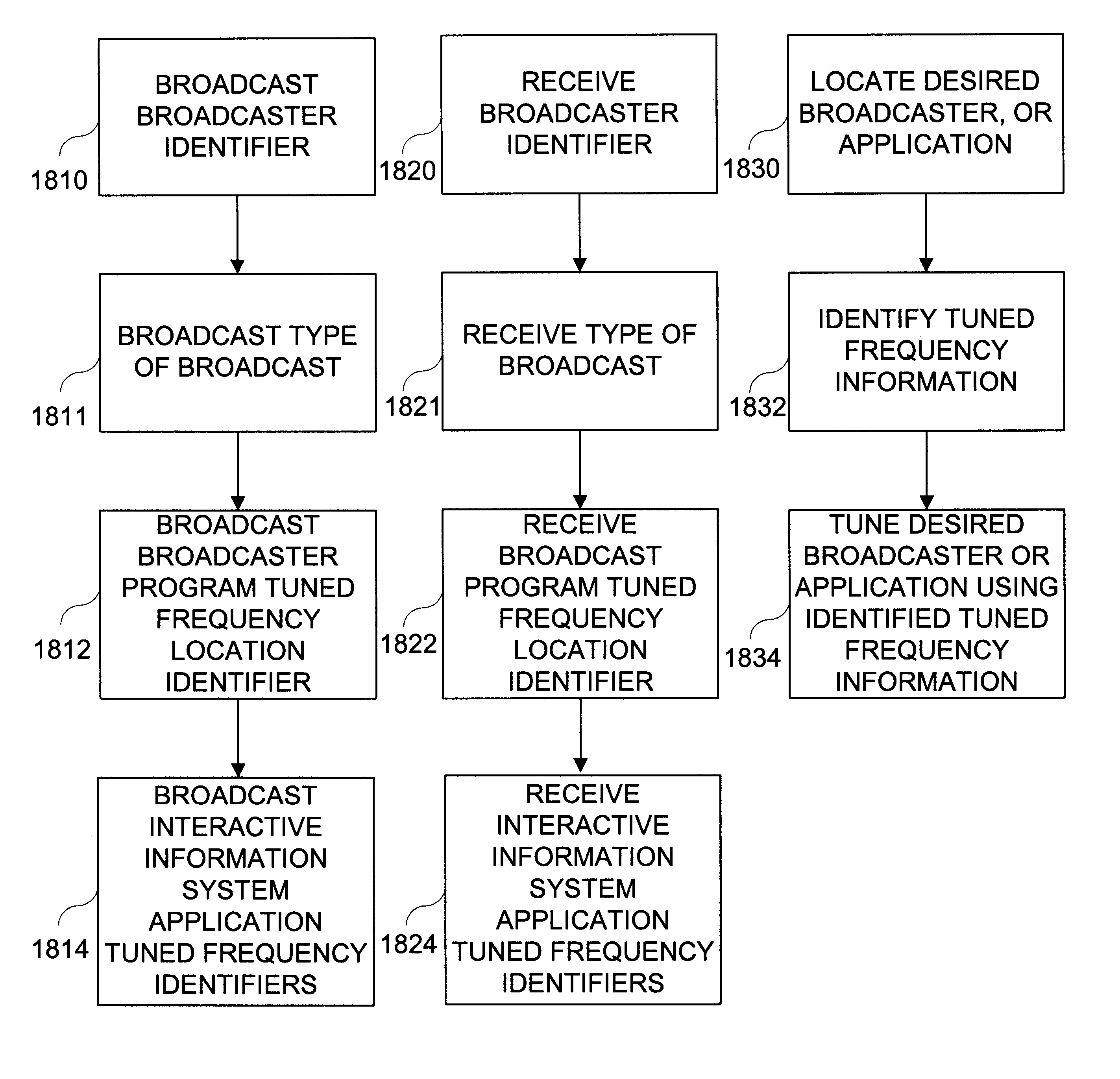
A method and apparatus routes user information including confidential information and other information to a vendor in a secure manner without requiring the user to transmit information in a secure manner. The user provides a user identifier and information including confidential information to a response collector, who relates the user identifier to the user information. The response collector may verify the information to protect against fraud. An information provider provides an application identifier and vendor routing information to a response collector, who relates the vendor routing information to the application identifier. The application identifier corresponding to the vendor is broadcast to the user via an interactive information system application, and the interactive information system sends the application identifier, a user identifier and other response information to a response collector as directed by the user and the interactive information system application. The response collector may then route the user's information and other response information to the vendor according to the vendor routing information. The user may send anonymous responses in the same manner without sending the user identifier to the response collector.
Owner:OPEN TV INC
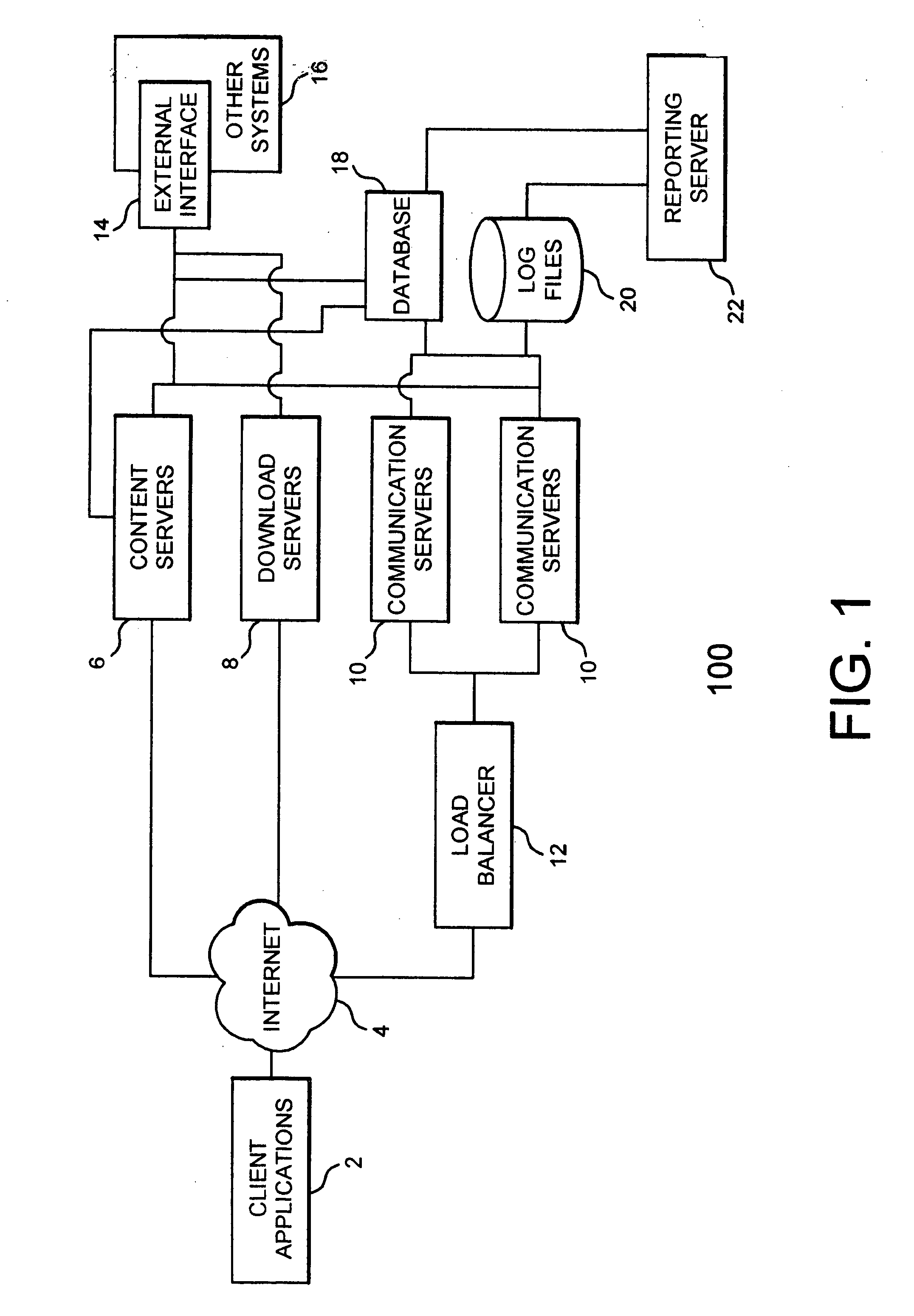
Method and apparatus for providing dynamic information to a user via a visual display
A client-server system for recording web site activity by web users and dynamically customizing web display apparatuses for optimal information presentation based on the users' prior activity history. The system assigns each user a user identifier that allows the system to track the user's web sessions. The system also assigns every web site an application identifier that allows the system to track the user's activities at a particular web site. The system then records the user's activities as they visit different web sites via the user and application identifiers. The system determines how the user prefers to view each web site based on their prior activity, their preferences, the web site, and various other factors. As the user surfs from web site to web site, the system dynamically configures the user's web browser and the web page information for optimum presentation based on how the user prefers to view the web site.
Owner:MEDIACOM NET
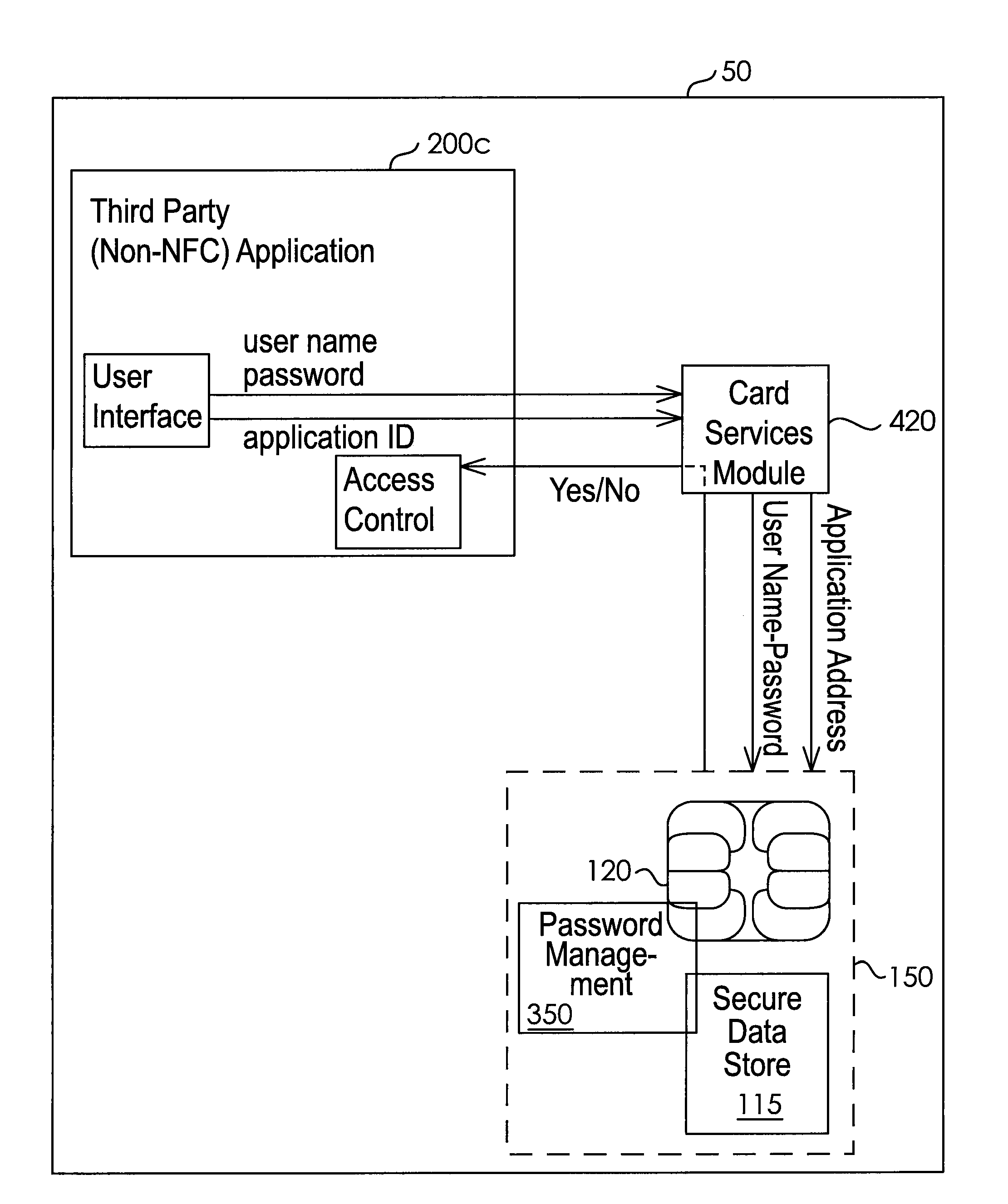
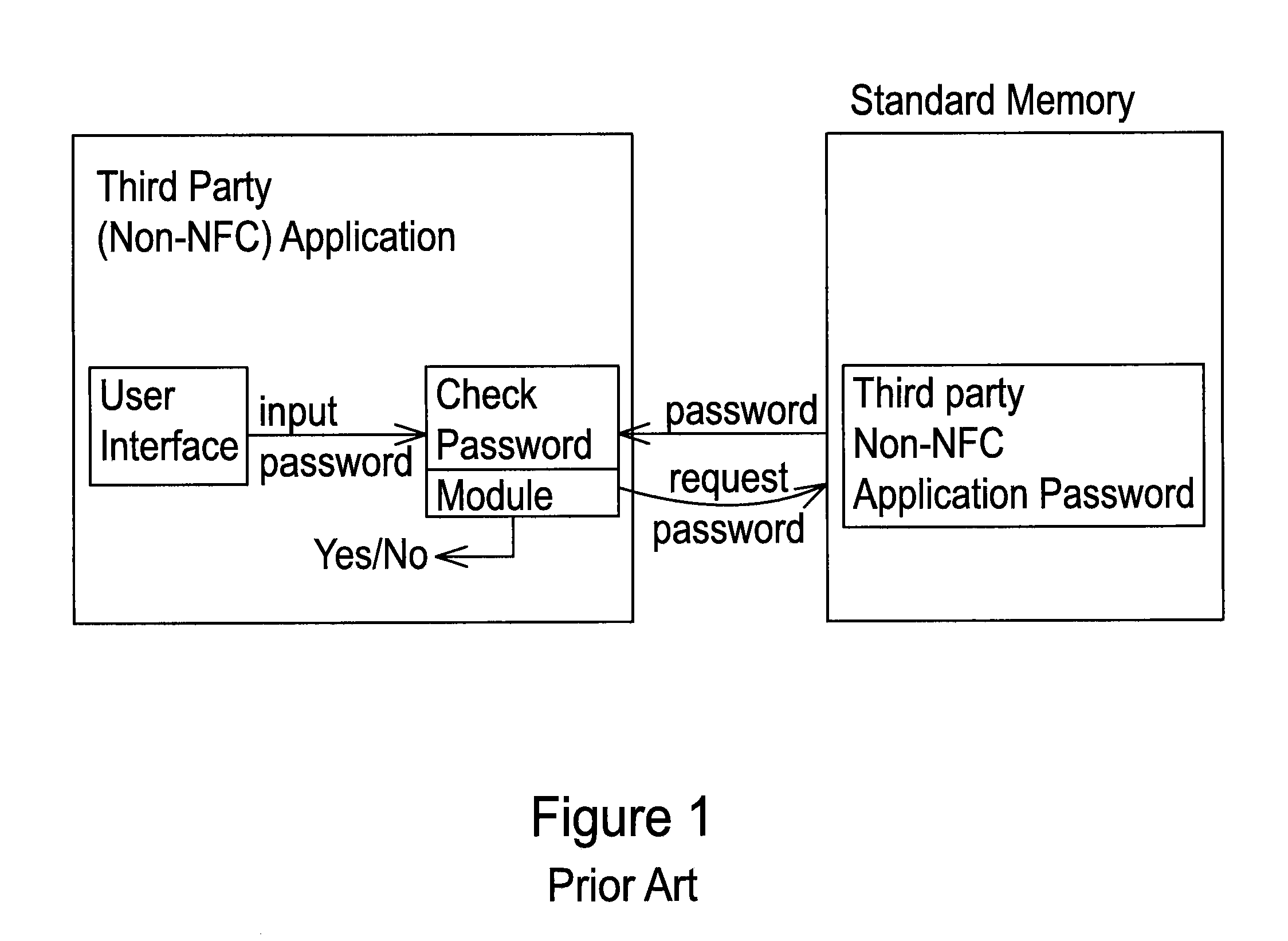
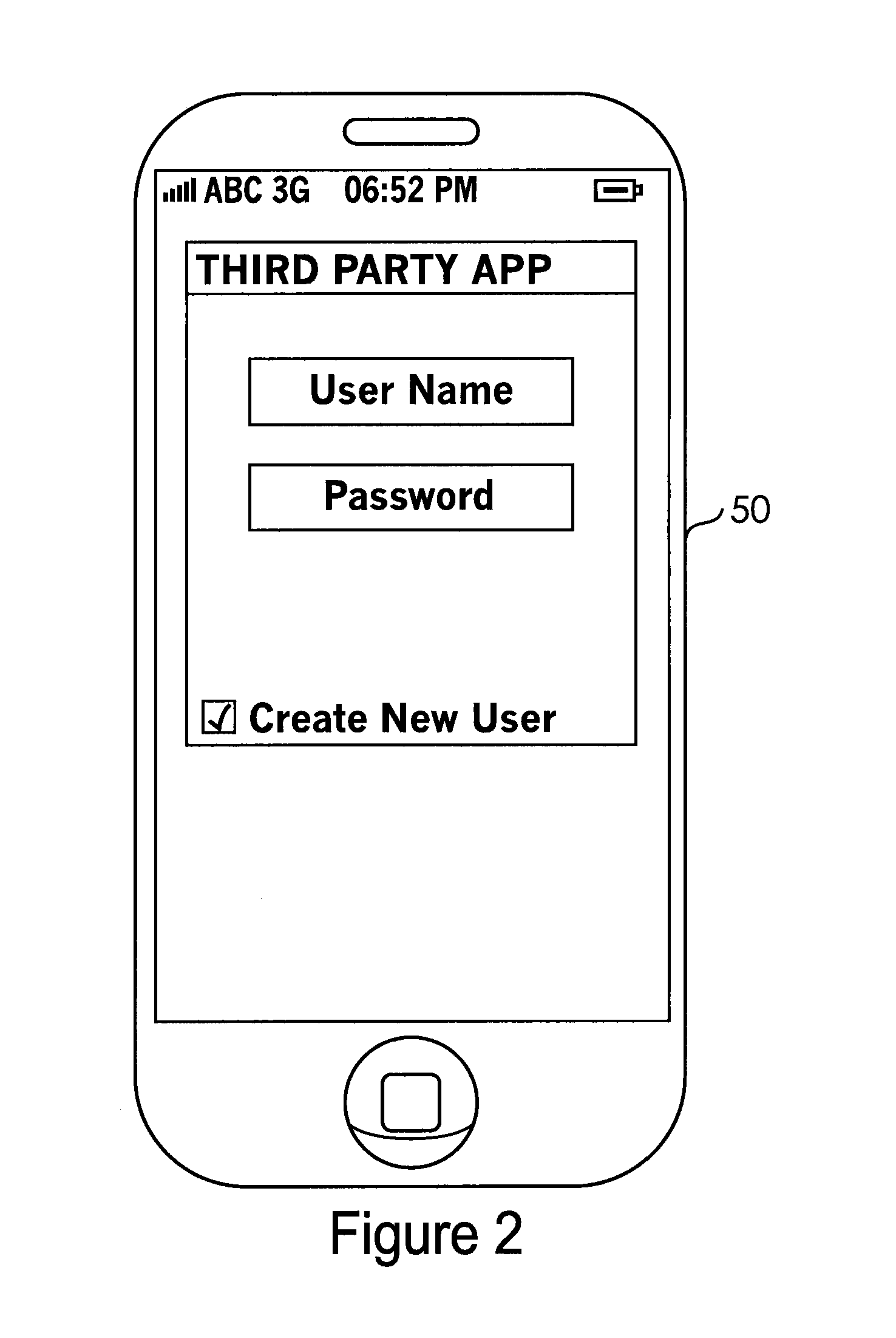
System and Method for Controlling Access to a Third-Party Application with Passwords Stored in a Secure Element
InactiveUS20120266220A1Easy to writeDigital data processing detailsMultiple digital computer combinationsThird partyApplication Identifier
A system for controlling access to an application on a portable communication device having a secured element and a user interface comprises memory associated with the secure element; a card management module operably associated with the portable communication device and with the secure element capable of controlling the secured element to facilitate writing to and reading from the memory; and a password management module operably associated with the card management module, the portable communication device user interface, and the application, the password management module receiving an application identifier associated with the application, a user name, and a password from the user interface, and providing an access command to the application based on whether the received user name and password match information stored in the memory.
Owner:T I S
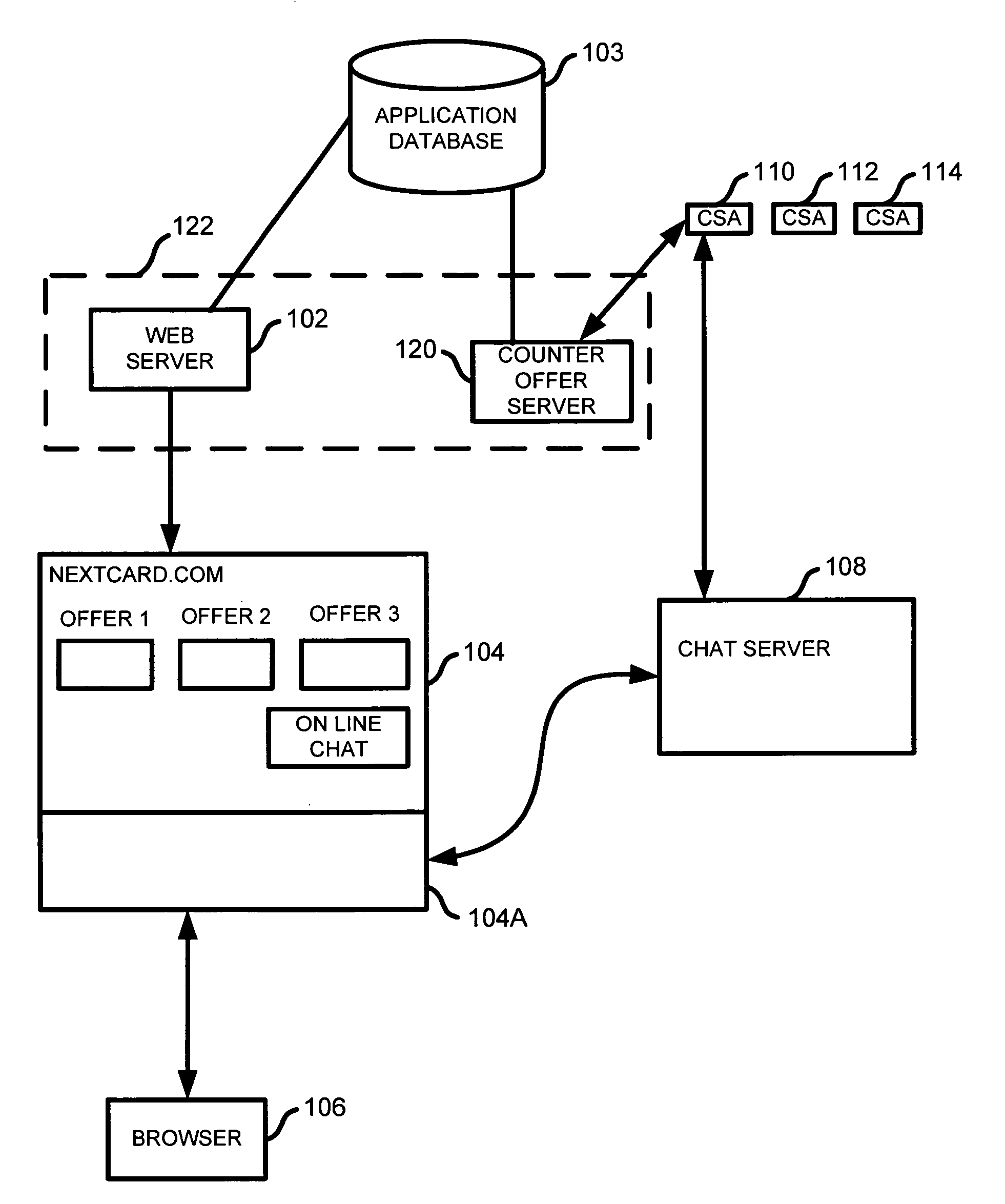
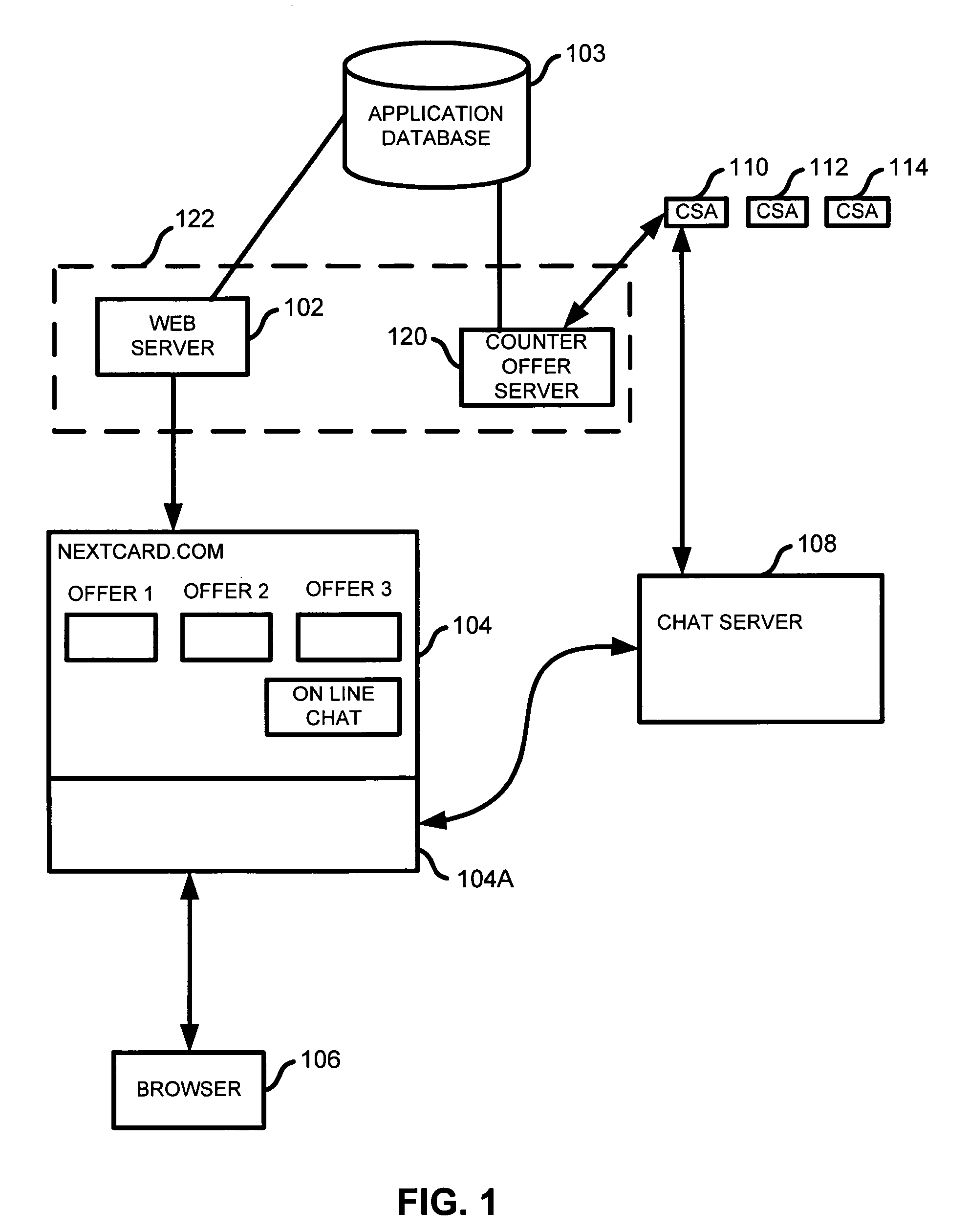
Integrating live chat into an online credit card application
A system and method are described for providing on line chat help to an applicant. An application identifier and a chat applet are inserted into a web page. The web page is sent to the applicant. The chat applet is configured to determine based on an event that the applicant could benefit from online chat and, upon such determination, to send a request to a chat server for a connection and to include the application identifier with the request.
Owner:LIVEPERSON
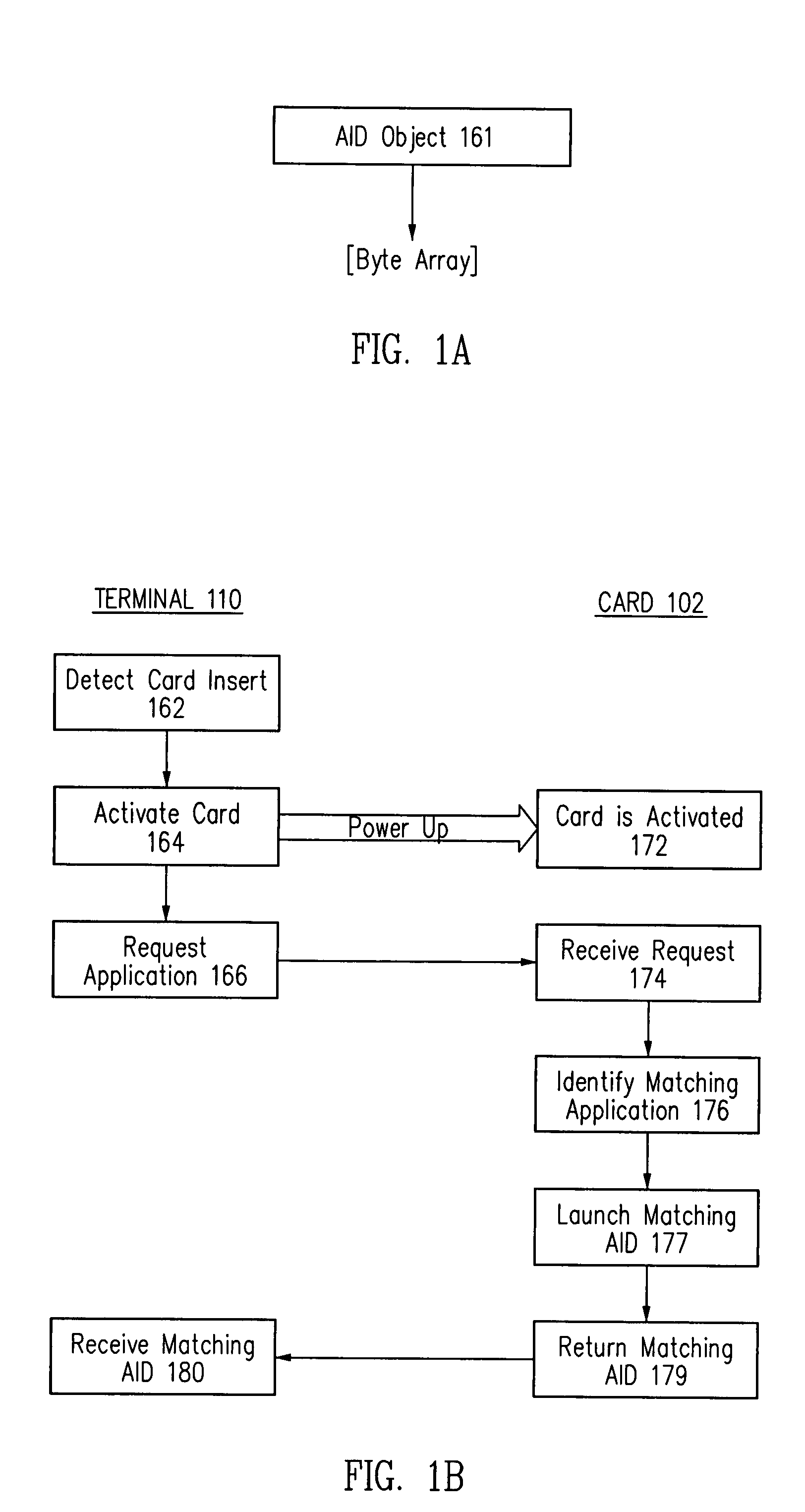
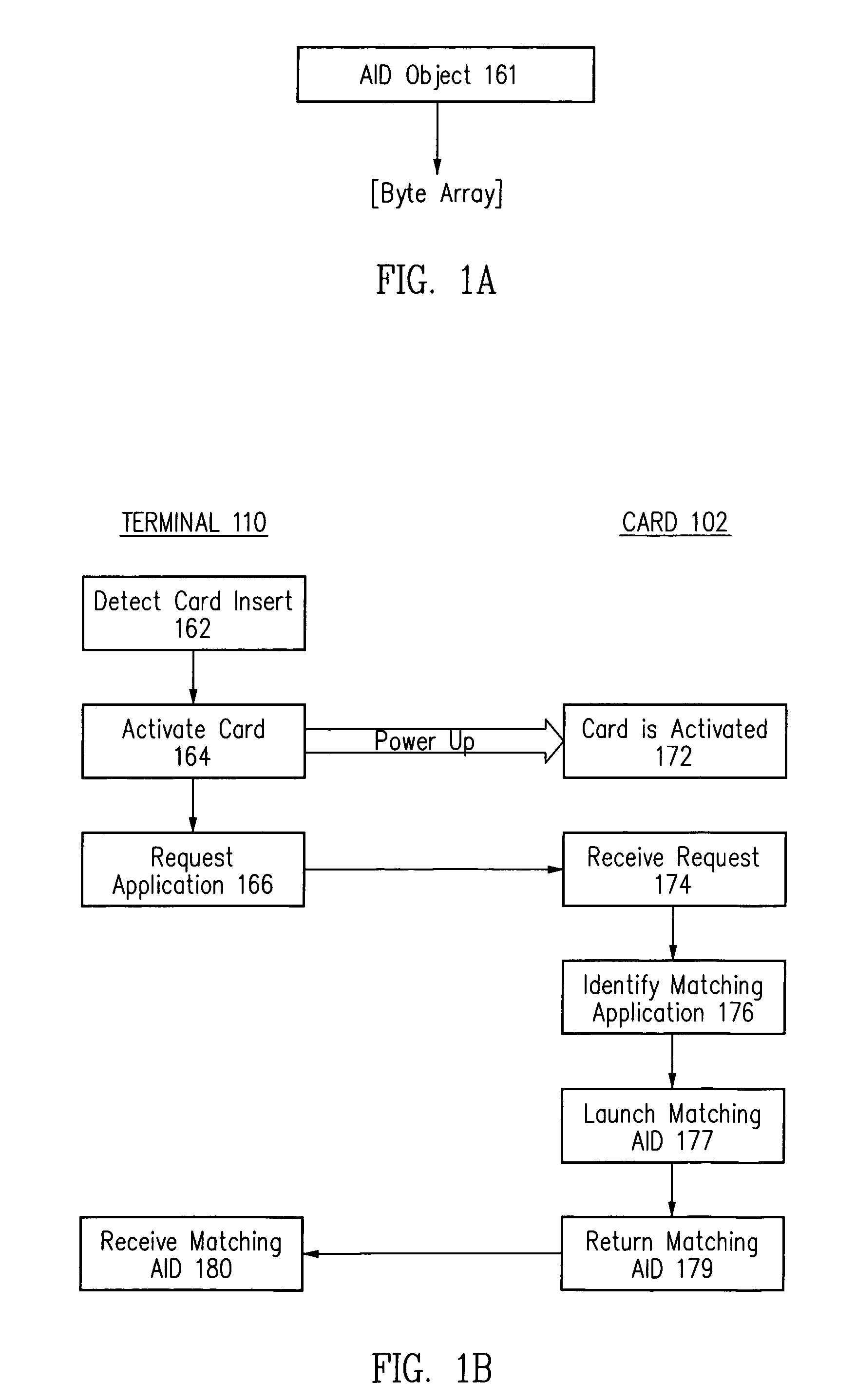
Method and apparatus for selecting a desired application on a smart card
Owner:ORACLE INT CORP
Method and Apparatus for Automatic Near Field Communication Application Selection in an Electronic Device
ActiveUS20090247077A1Near-field transmissionSubstation equipmentComputer hardwareApplication Identifier
In a portable electronic device (100) having a plurality of near field communication applications stored within a plurality of execution environments, an application discovery manager (311) is configured to automatically select and launch one or more of the near field communication applications. A near field communication circuit (300) receives a near field communication request from an external near field communication device (700). The application discovery manager (311) identifies a near field communication technology, a protocol, and an application identifier and then references a registry table (313) to determine identification parameters corresponding with the identified information. The application discovery manager (311) then selects a near field communication application and launches it. The application discovery manager (311) further configures a routing switch (316) to direct data between the near field communication circuit controller (301) and the appropriate execution environment.
Owner:GOOGLE TECH HLDG LLC
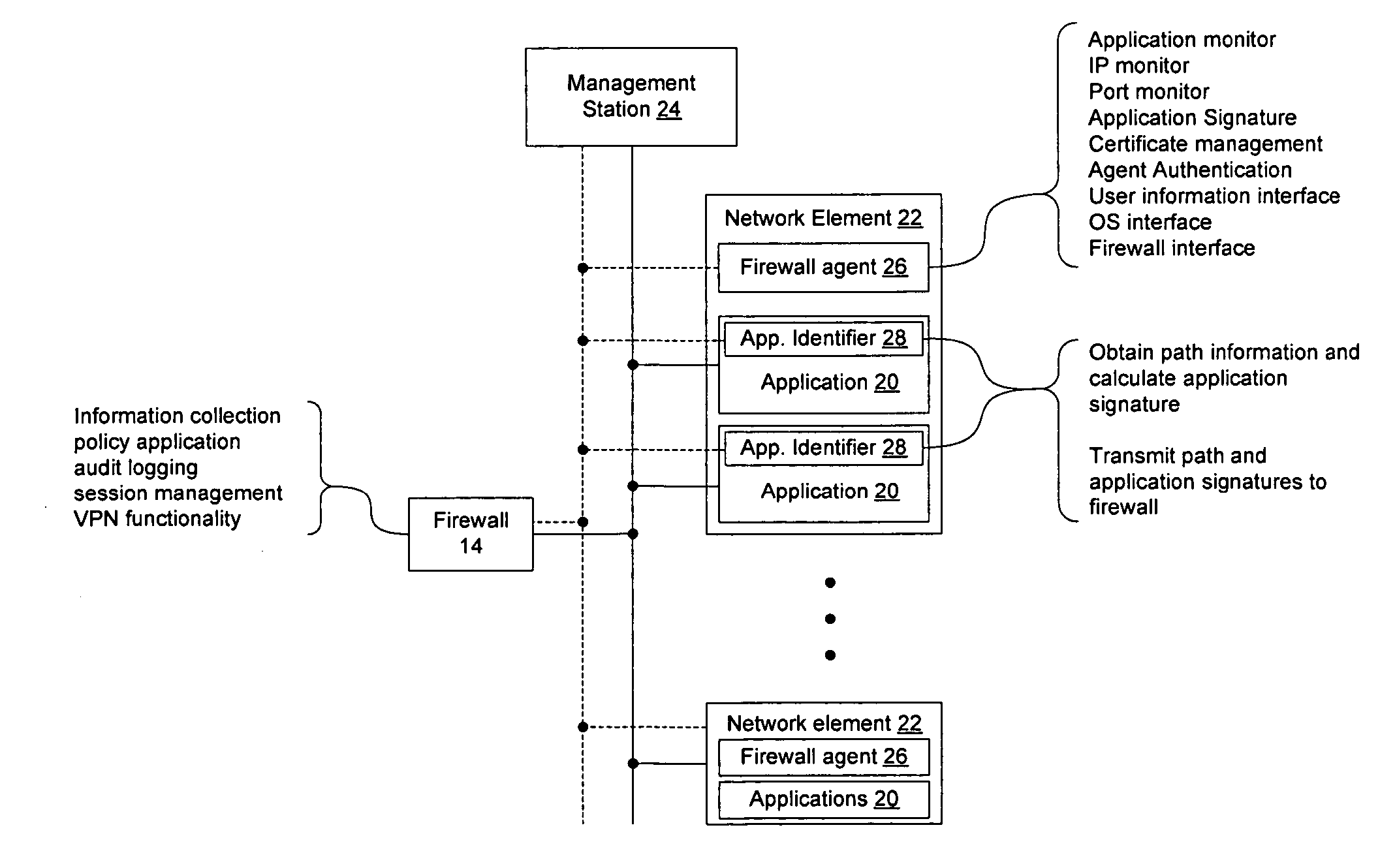
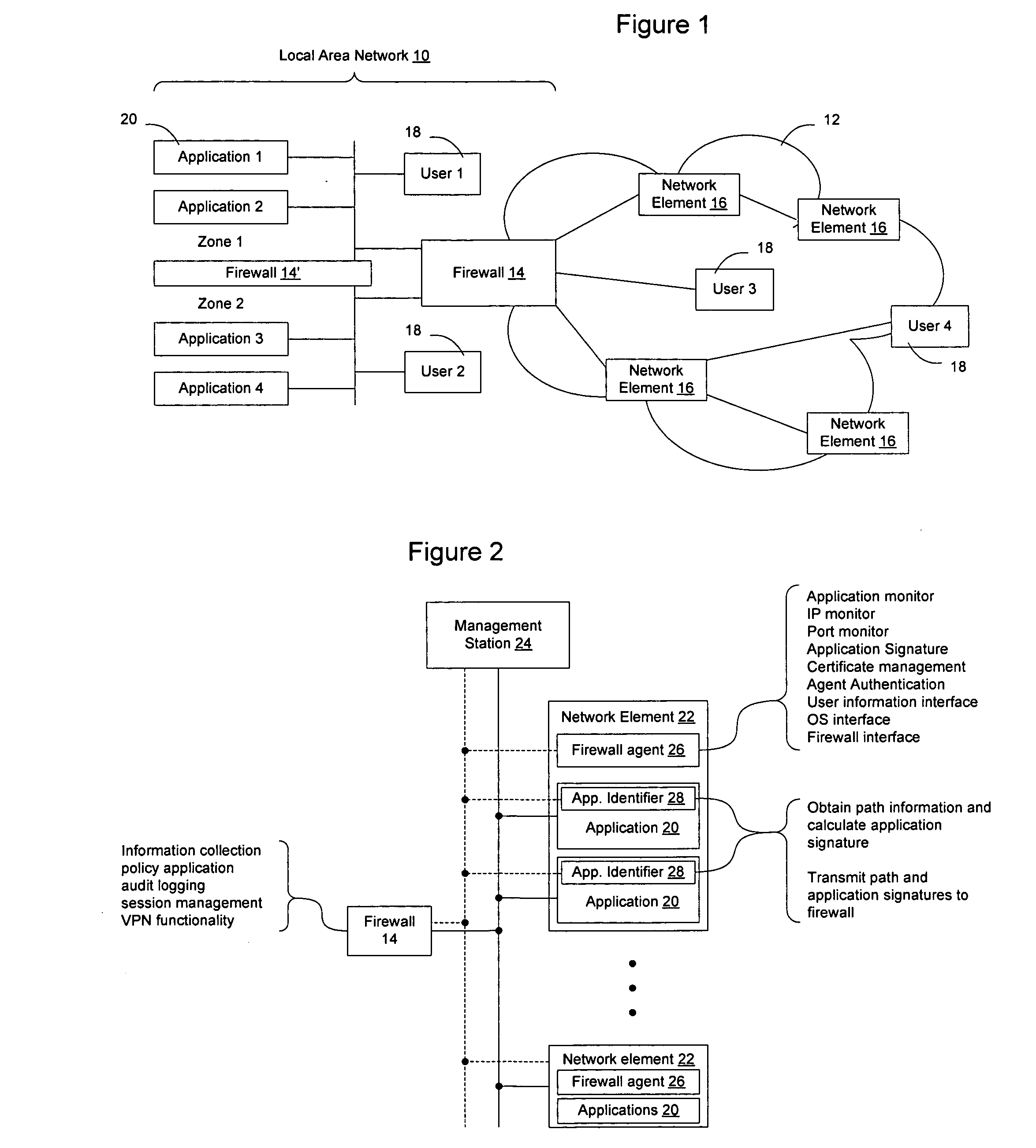
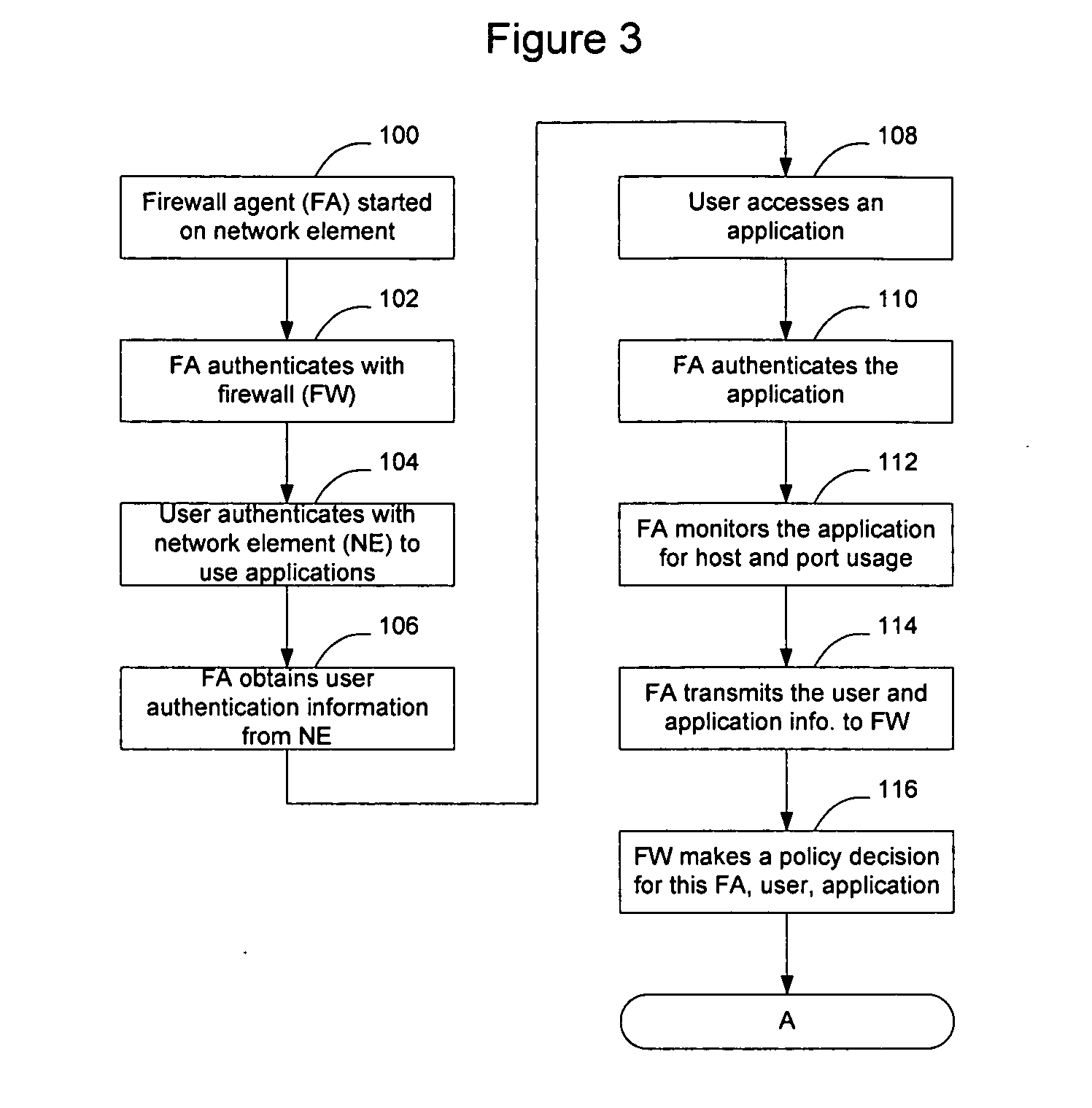
Method and apparatus for enabling enhanced control of traffic propagation through a network firewall
InactiveUS20060075478A1Easy to controlImprove abilitiesMultiple digital computer combinationsProgram controlInternet trafficApplication Identifier
A distributed firewall system is used to implement a network firewall with enhanced control over network traffic to allow policy to be implemented on a per-user basis, a per-application basis, a per-user and application basis, and to allow ports to be dynamically opened and closed as needed by the applications. The distributed firewall system may include application identifiers associated with applications running on a network element, one or more firewall agents instantiated on the network element hosting the applications, and a firewall configured to interface with the firewall agents. Communications between the distributed components are secured to allow the firewall to detect if an agent has been compromised, and to allow the firewall agent to determine if the application has been compromised. The distributed firewall system may work in a VPN environment, such as in connection with a VPN server, to implement firewall policy at the point where VPN traffic enters the protected network.
Owner:RPX CLEARINGHOUSE
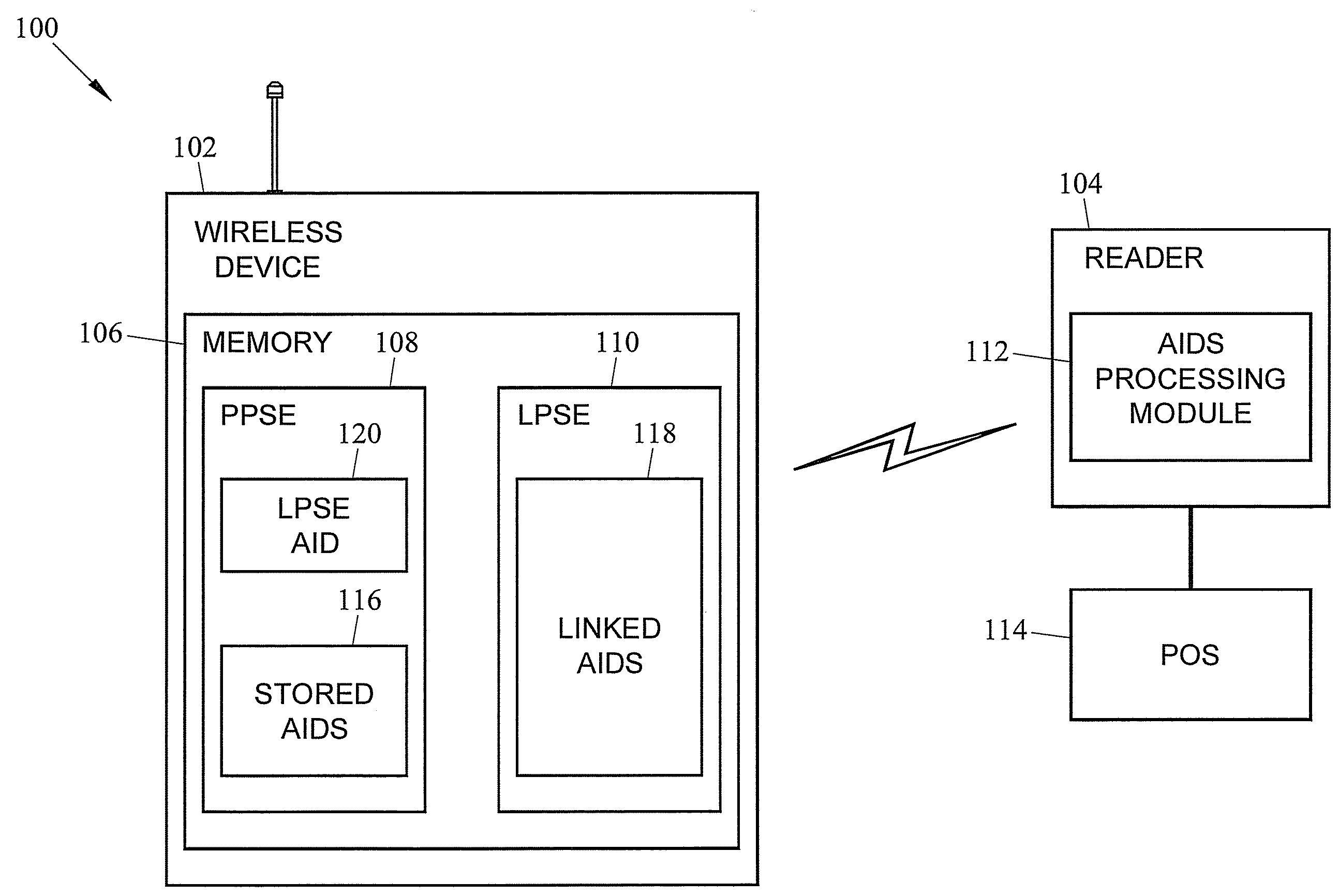
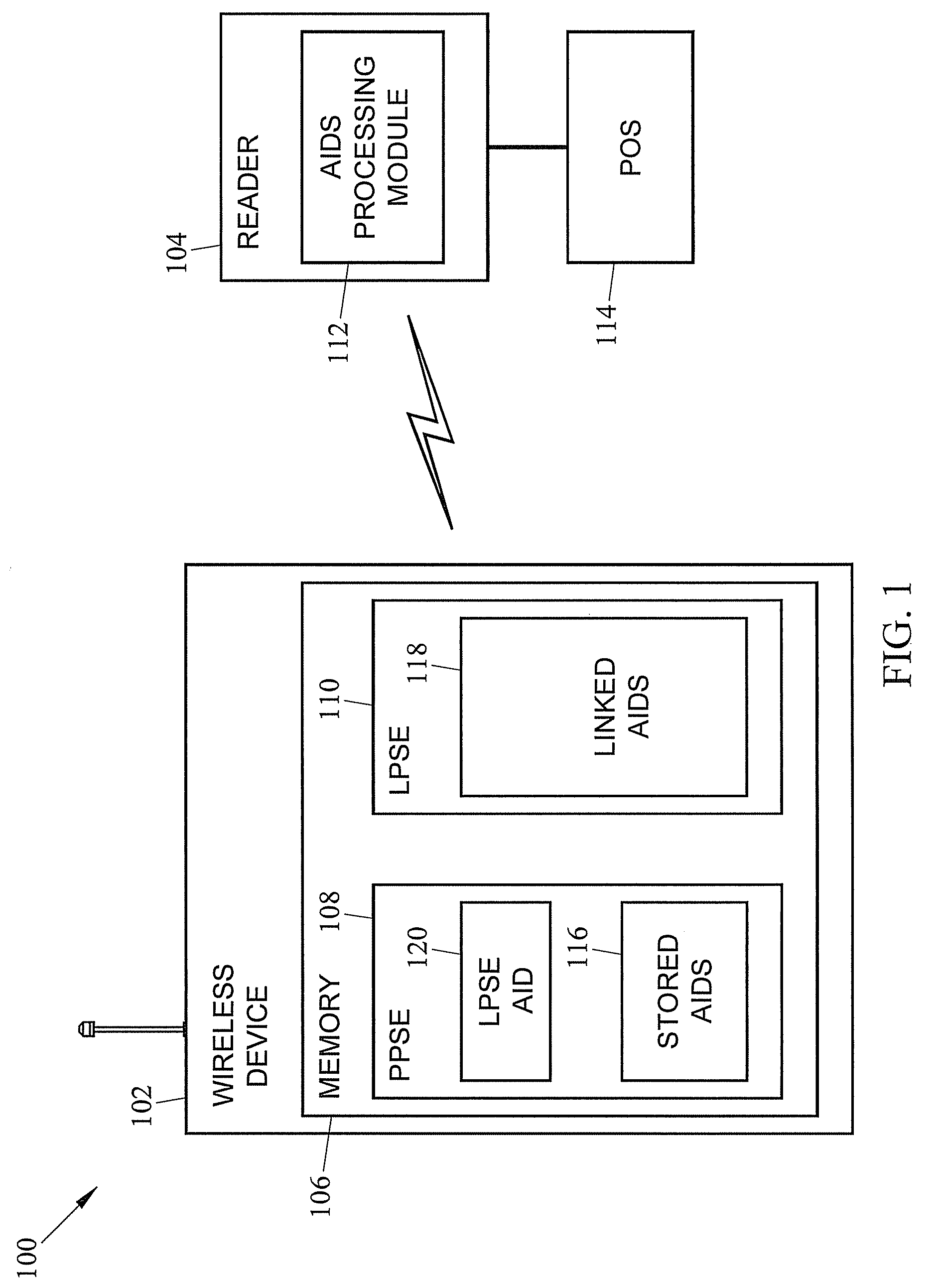
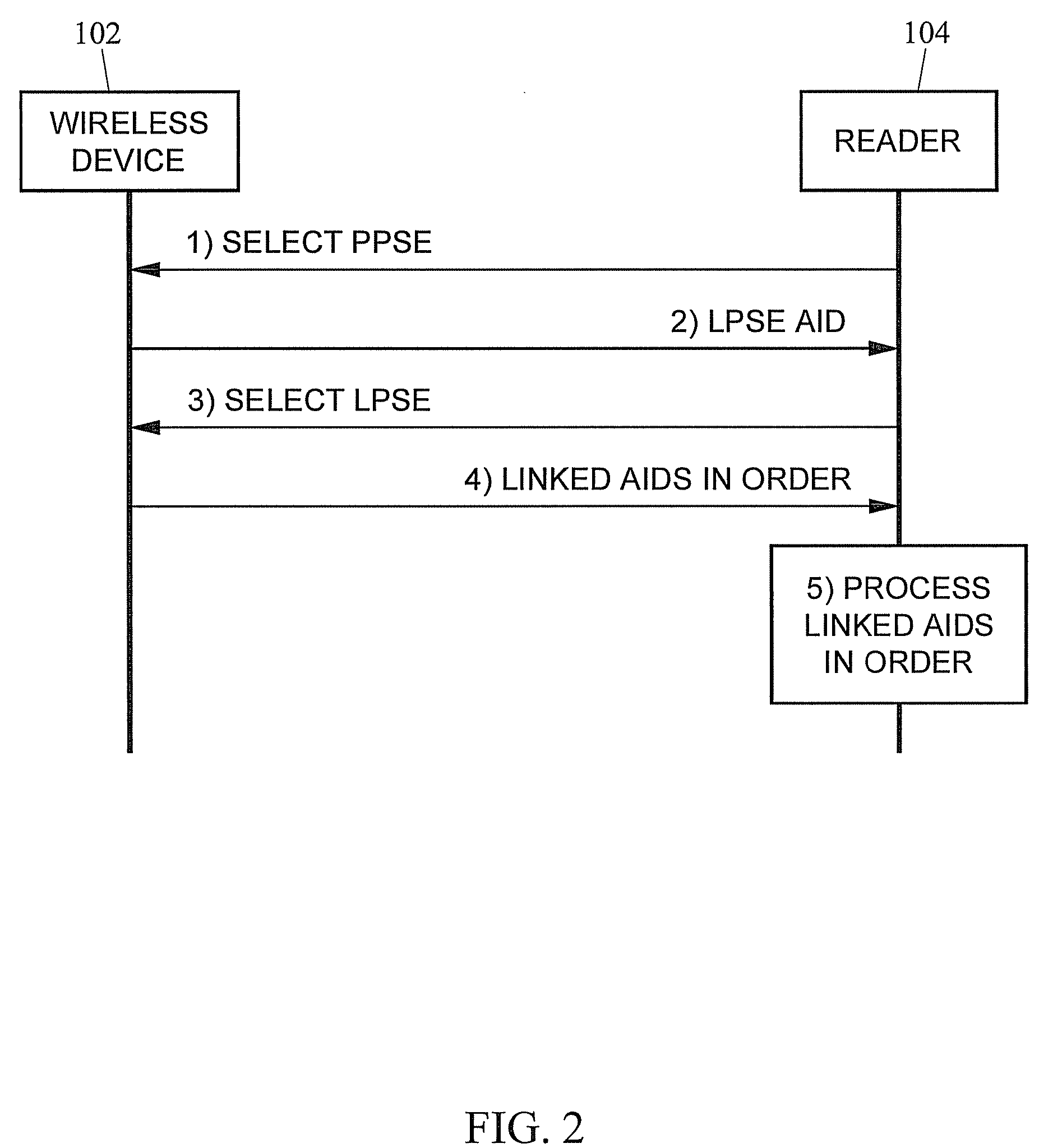
Systems, methods, and computer readable media for performing multiple transactions through a single near field communication (NFC) tap
The subject matter described herein includes a method of performing multiple transactions through a single near field communication (NFC) tap. The method includes storing, at a linking application in a wireless device, a plurality of application identifiers (AIDs) that identify a plurality of applications to be processed in a single NFC tap. The method can further include detecting, by a wireless device reader, a linking application AID in the wireless device that identifies the linking application upon interfacing the wireless device with the wireless device reader through the single NFC tap. The method can include accessing, by the wireless device reader, the plurality of AIDs using the linking application. The method can further include processing the plurality of applications associated with the plurality of AIDs through the single NFC tap.
Owner:MASTERCARD INT INC
Method and apparatus for providing dynamic information to a user via a visual display
A client-server system for recording web site activity by web users and dynamically customizing web display apparatuses for optimal information presentation based on the users'prior activity history. The system assigns each user a user identifier that allows the system to track the user's web sessions. The system also assigns every web site an application identifier that allows the system to track the user's activities at a particular web site. The system then records the user's activities as they visit different web sites via the user and application identifiers. The system determines how the user prefers to view each web site based on their prior activity, their preferences, the web site, and various other factors. As the user surfs from web site to web site, the system dynamically configures the user's web browser and the web page information for optimum presentation based on how the user prefers to view the web site.
Owner:MEDIACOM NET
Method of performing a secure application in an NFC device
InactiveUS20120011572A1Digital data processing detailsUser identity/authority verificationComputer hardwareApplication server
The invention relates to a method of executing a secure application in an NFC device, the method comprising steps during which: a contactless link is established between first and second NFC devices, the first NFC device transmits by the contactless link an identifier of a secure processor of the first NFC device, the second NFC device transmits by the contactless link an application identifier, the secure processor transmits by the contactless link first authentication data allowing the authentication of the secure processor of the first NFC device, the second NFC device transmits to an application server the first authentication data, the application server transmits to an authentication server the first authentication data and second authentication data) to authenticate the application and authorizes the two NFC devices to execute the application only if the secure processor and the application are authenticated.
Owner:VERIMATRIX INC
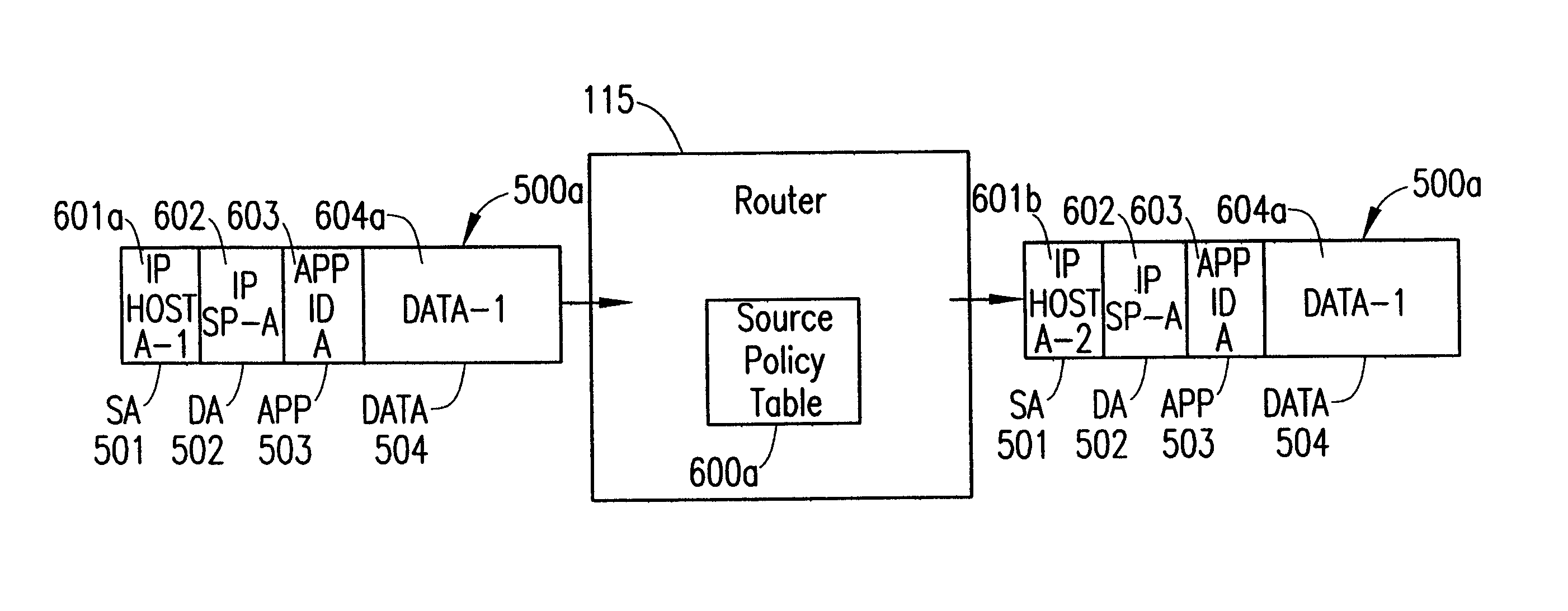
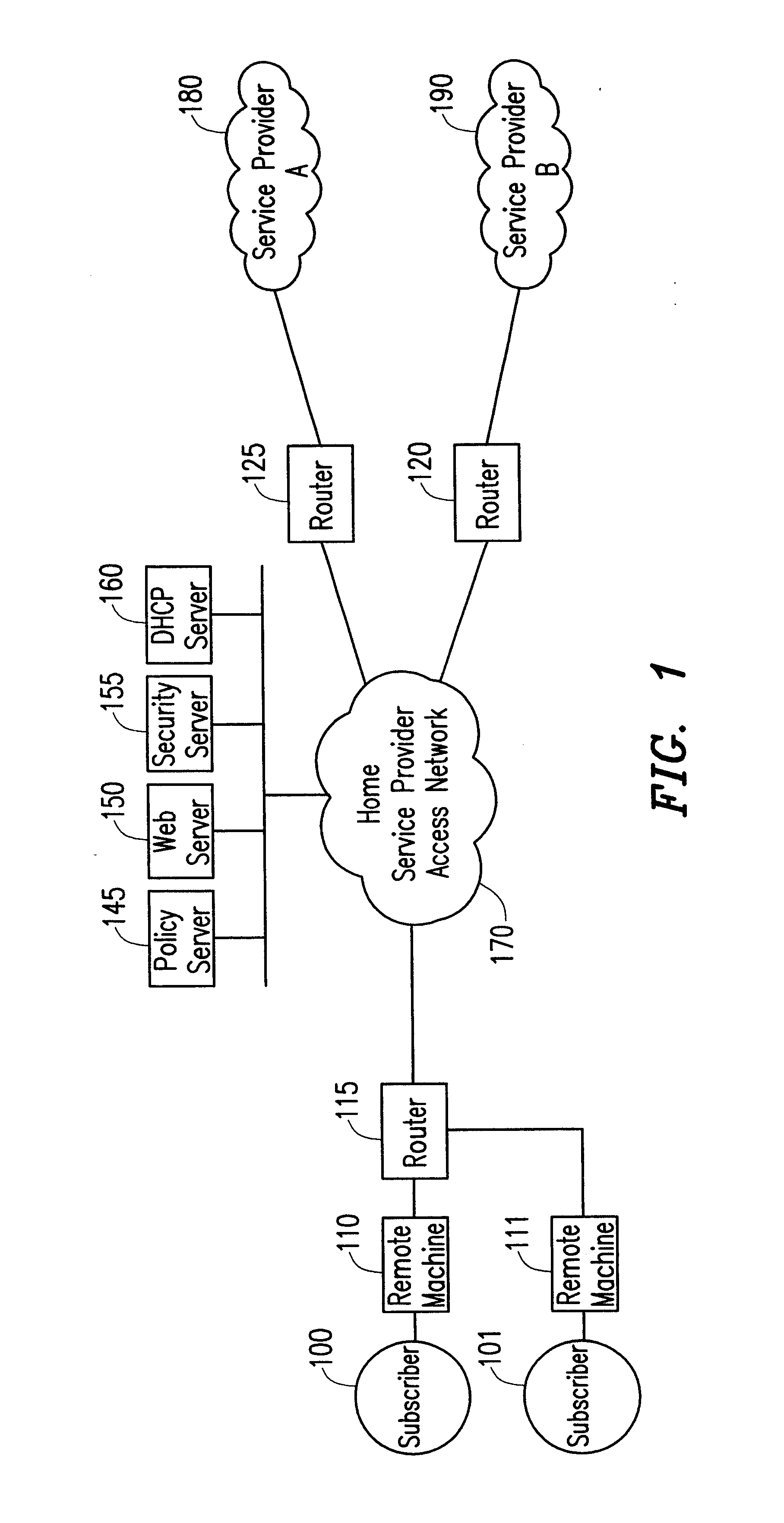
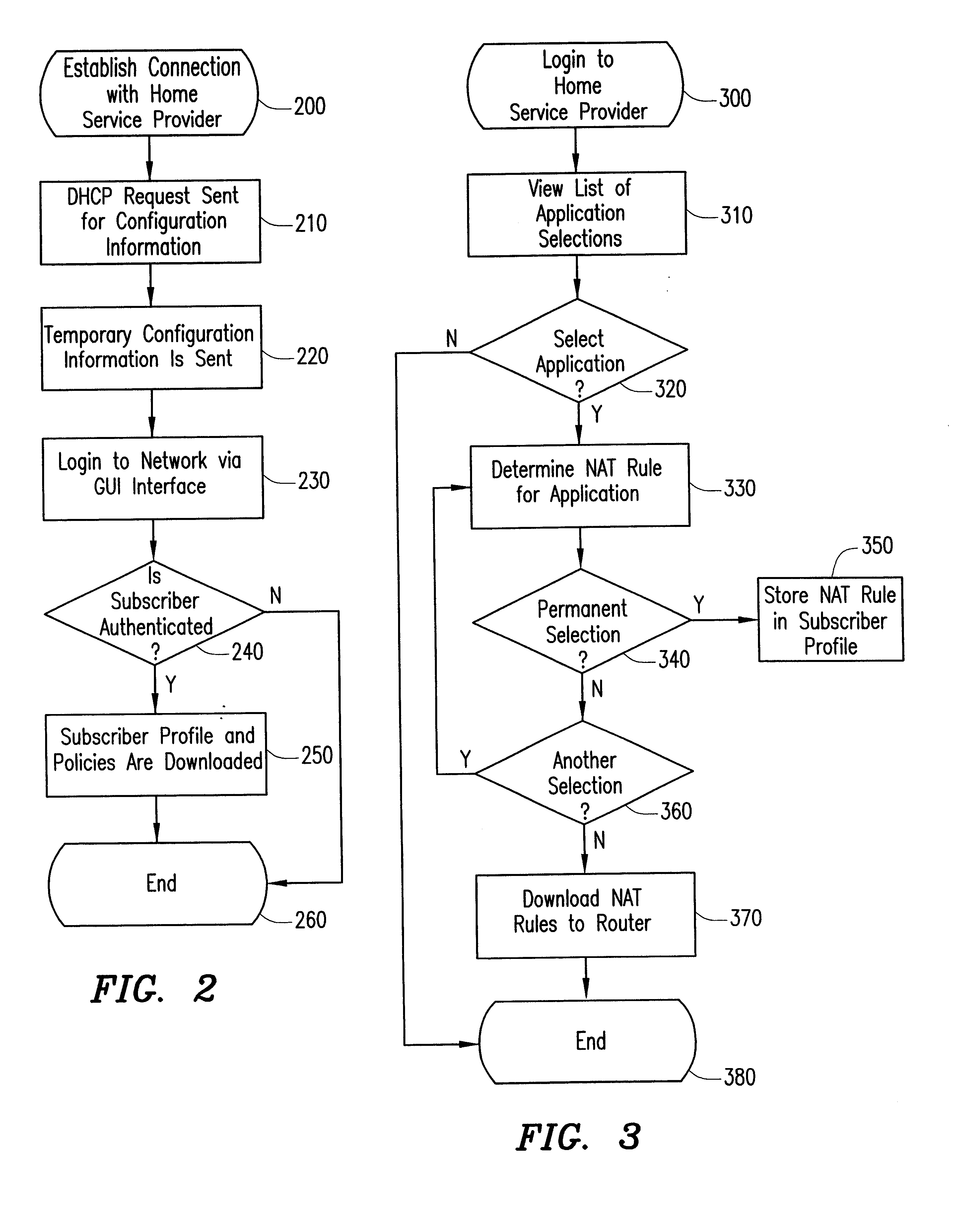
System and method for dynamic simultaneous connection to multiple service providers
InactiveUS6801528B2Data switching by path configurationMultiple digital computer combinationsAccess networkNetwork address translation
A policy enables a subscriber to connect to multiple service providers simultaneously using a network address translation technique that translates an address identifying the subscriber and associated with a first service provider into an address identifying the subscriber and associated with a second service provider for a particular application. The subscriber registers with a single home service provider and connects to that single home service provider for a packet session. To connect to additional service providers that provide additional applications during the packet session, the NAT rule is downloaded from the home service provider to a router at the border between the subscriber and the access network of the home service provider. Each IP packet received at the router to or from the subscriber is filtered to determine the subscriber's address and an application identifier. Based on the combination of both the subscriber's address and the application identifier, the router translates the subscriber's address into a new address, using the NAT rule. The new address is used to connect the subscriber to an additional service provider for a particular application during the packet session with the home service provider.
Owner:ERICSSON INC
Load balancing of server clusters
InactiveUS7512707B1Flexible handlingEffective balanceDigital computer detailsTransmissionClient-sideApplication software
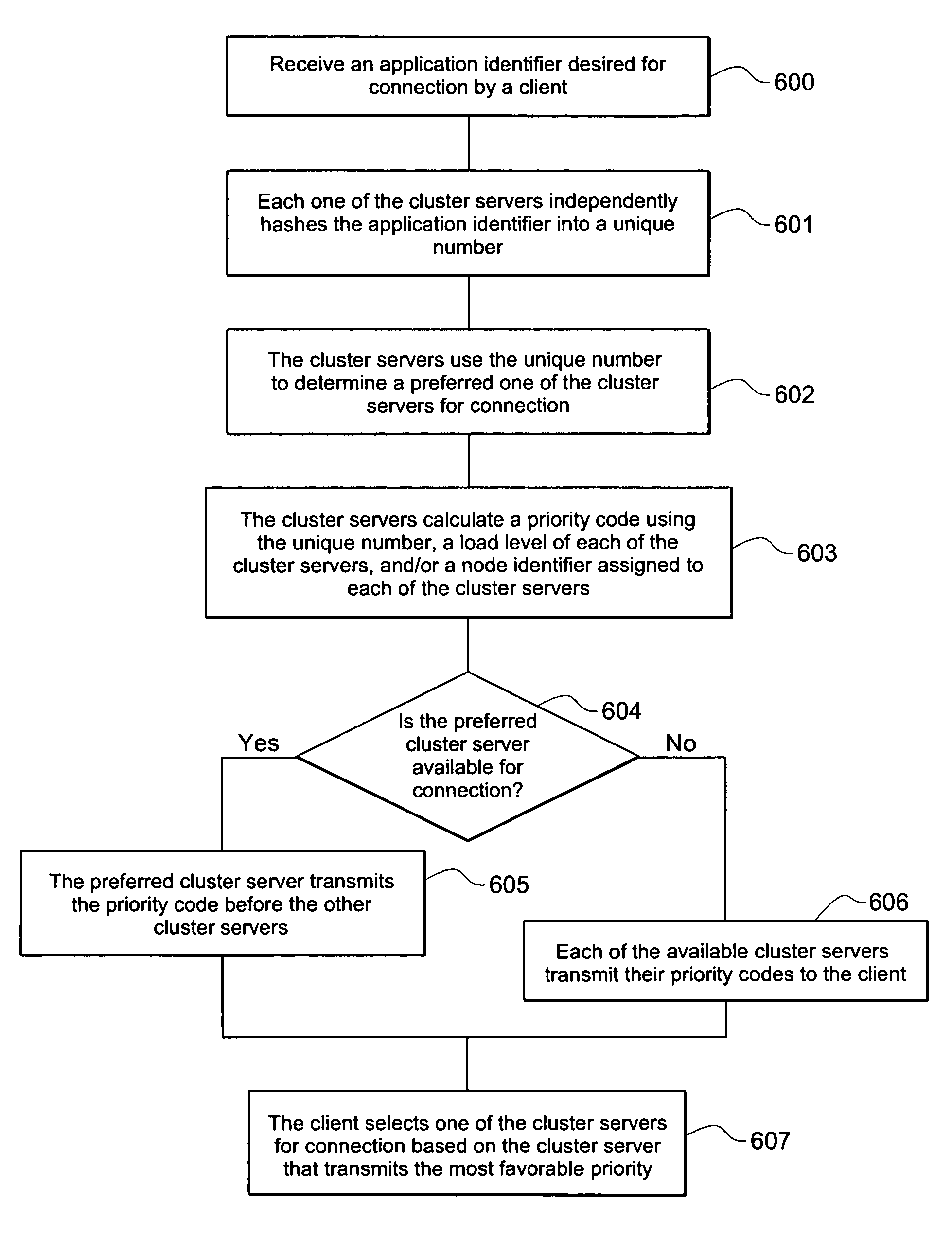
A load balancing scheme is described for a server cluster. An application identifier is received by the cluster from a client desiring to connect to the application. Each one of the servers in the cluster independently hashes the application identifier into a unique number. This unique number is used to determine a preferred one of the servers for the connection. The servers then each calculate a priority code using the unique number, a load level for each server, and / or a node identifier assigned to the servers in the cluster. If the preferred cluster server is available, it transmits its priority code to the client before the other servers transmit their priority codes. Otherwise, each of the available cluster servers transmits their priority codes to the client. The client selects the cluster server with the most favorable priority for making the connection.
Owner:ADOBE INC
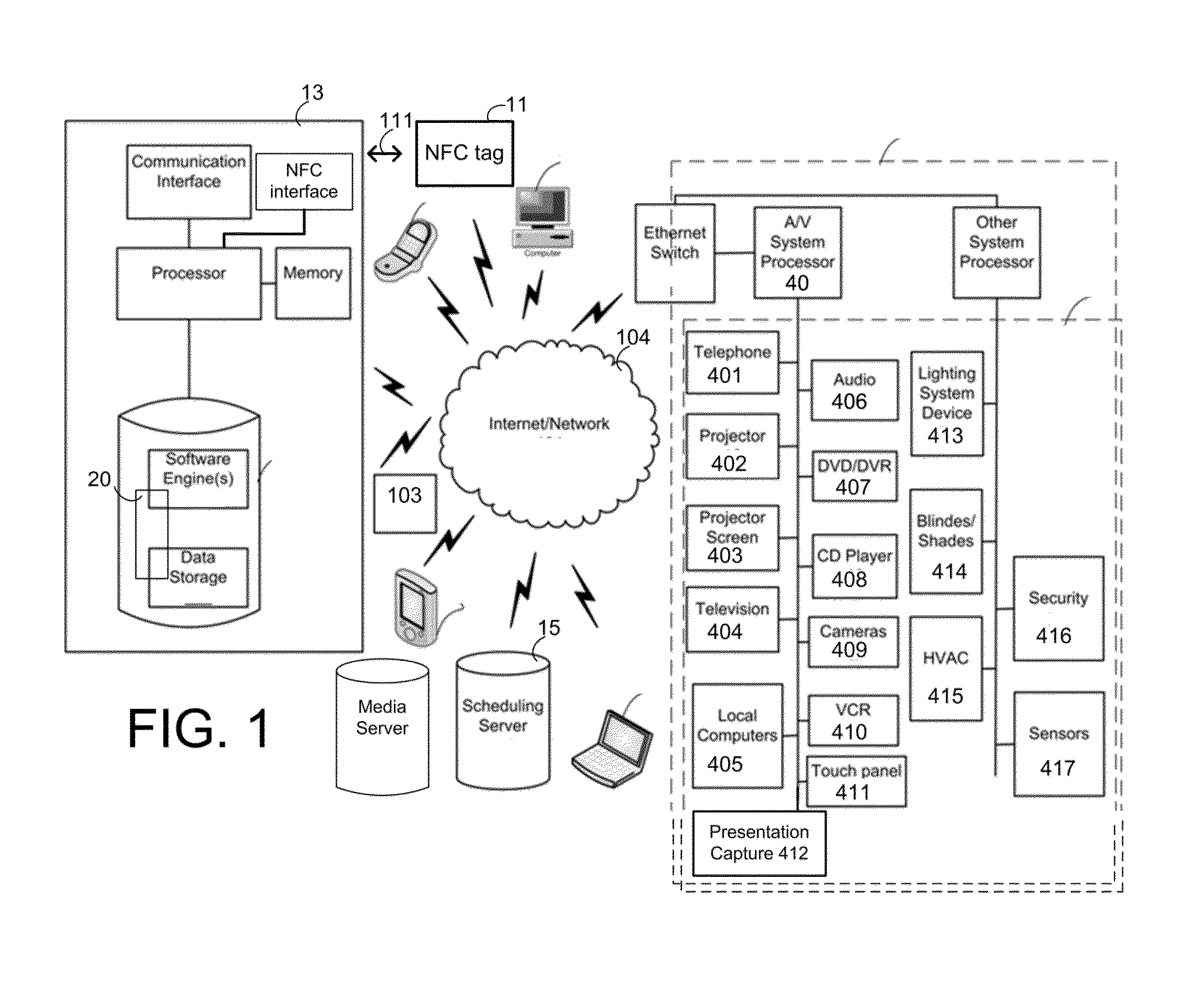
Initiating Schedule Management Via Radio Frequency Beacons
A portable electronic device receives broadcasts from one or more RF beacons to determine a location of a user and communicates with a scheduling server to manage the schedule of a conference room. The portable electronic device receives an address and an application identifier from each RF beacon and opens a scheduling application in response. The portable electronic device then communicates with a scheduling server to receive the schedule of the location determined from the beacon broadcasts. The user may reserve the location and set a number of presets through the scheduling application. Updates to the schedule are communicated to the scheduling server from the portable electronic device.
Owner:CRESTRON ELECTRONICS
Method and apparatus for processing an application identifier from a smart card
An application identifier (AID) for an application installed on a smart card comprises a registered application provider identifier (RID). The AID may be processed by determining the RID for an application from the AID of the application, generating an identifier for a network resource from the RID, transmitting a request to the network resource using the identifier, and receiving a response to the request. The response comprises material for use in handling the application on the smart card.
Owner:ORACLE INT CORP
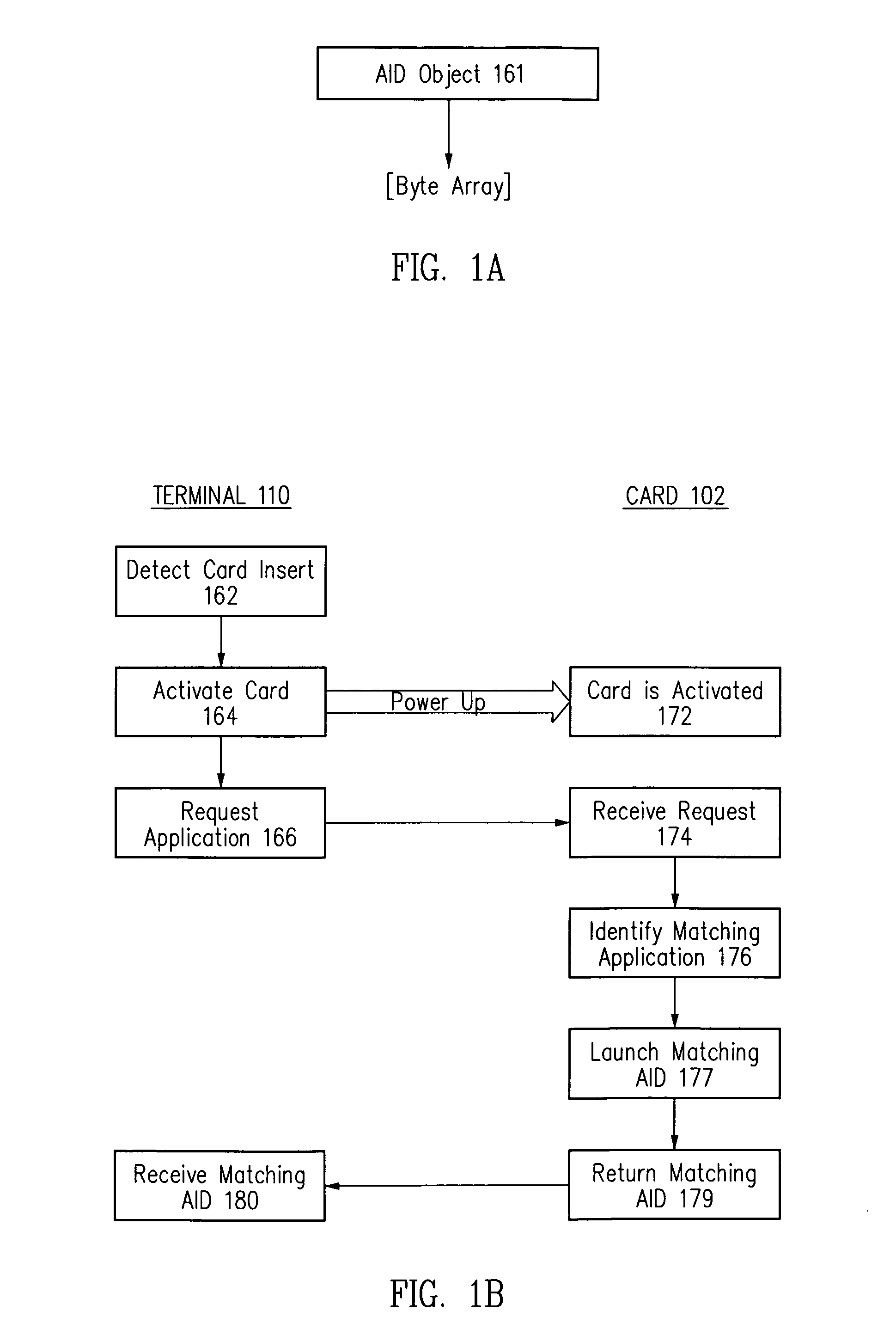
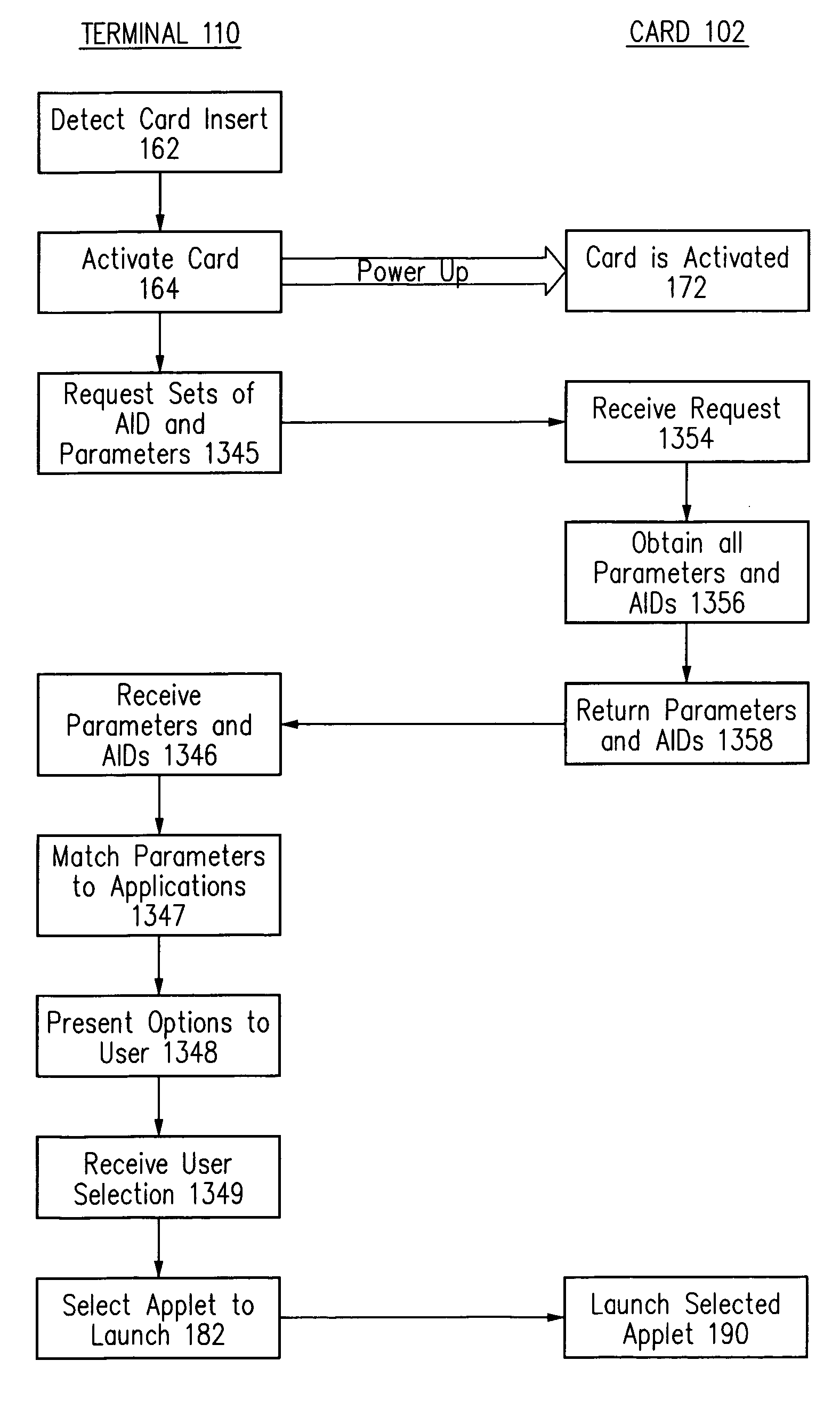
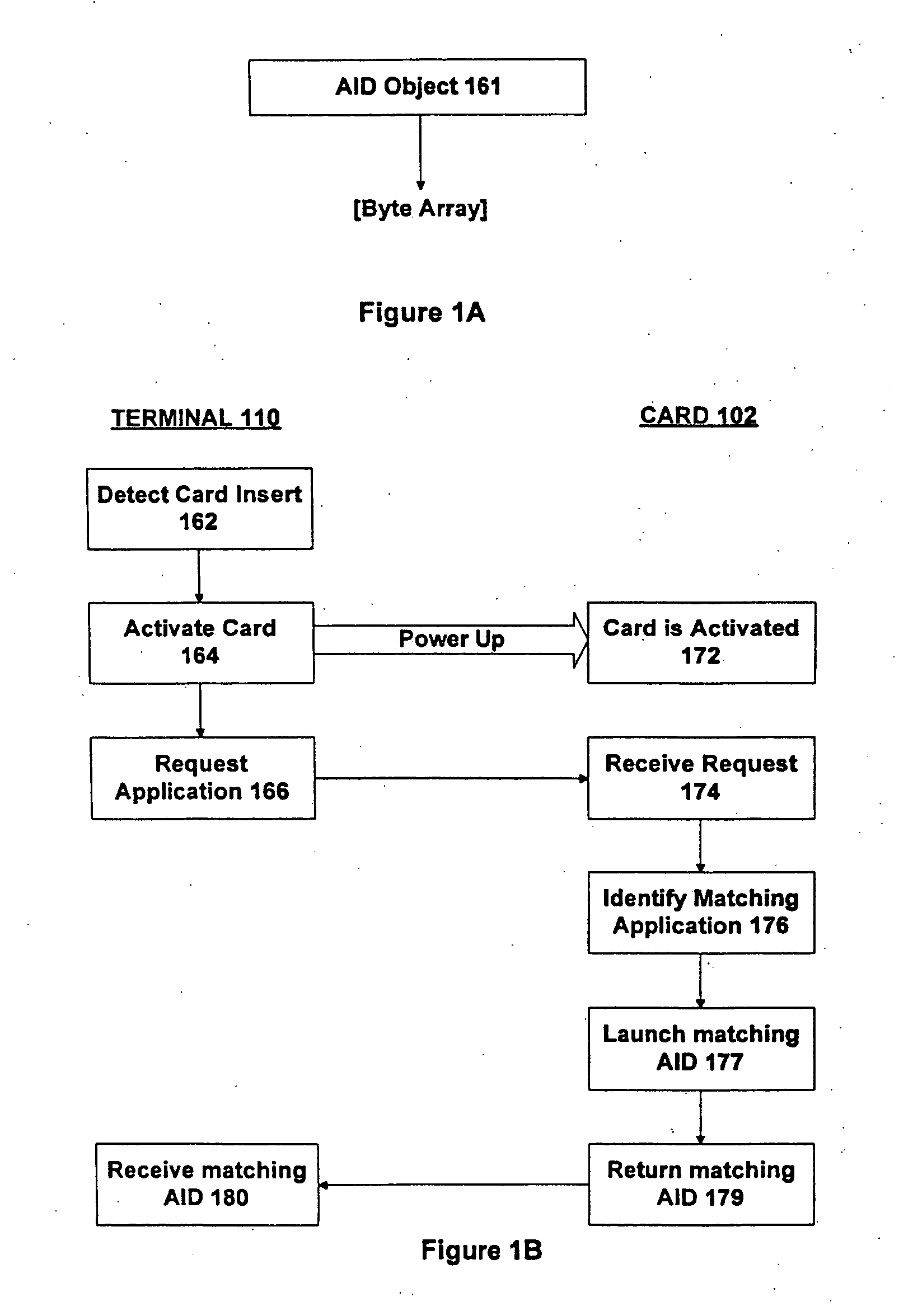
Method and appatatus for selecting a desired application on a smart card
Where there are potentially two or more applications installed on a smart card, with each application having a stored application identifier (AID), a desired application may be selected by specifying a desired application in terms of multiple parameters, retrieving multiple parameters from a stored AID for an application on the smart card, and comparing the specified multiple parameters with the retrieved multiple parameters to determine whether there is a match.
Owner:ORACLE INT CORP
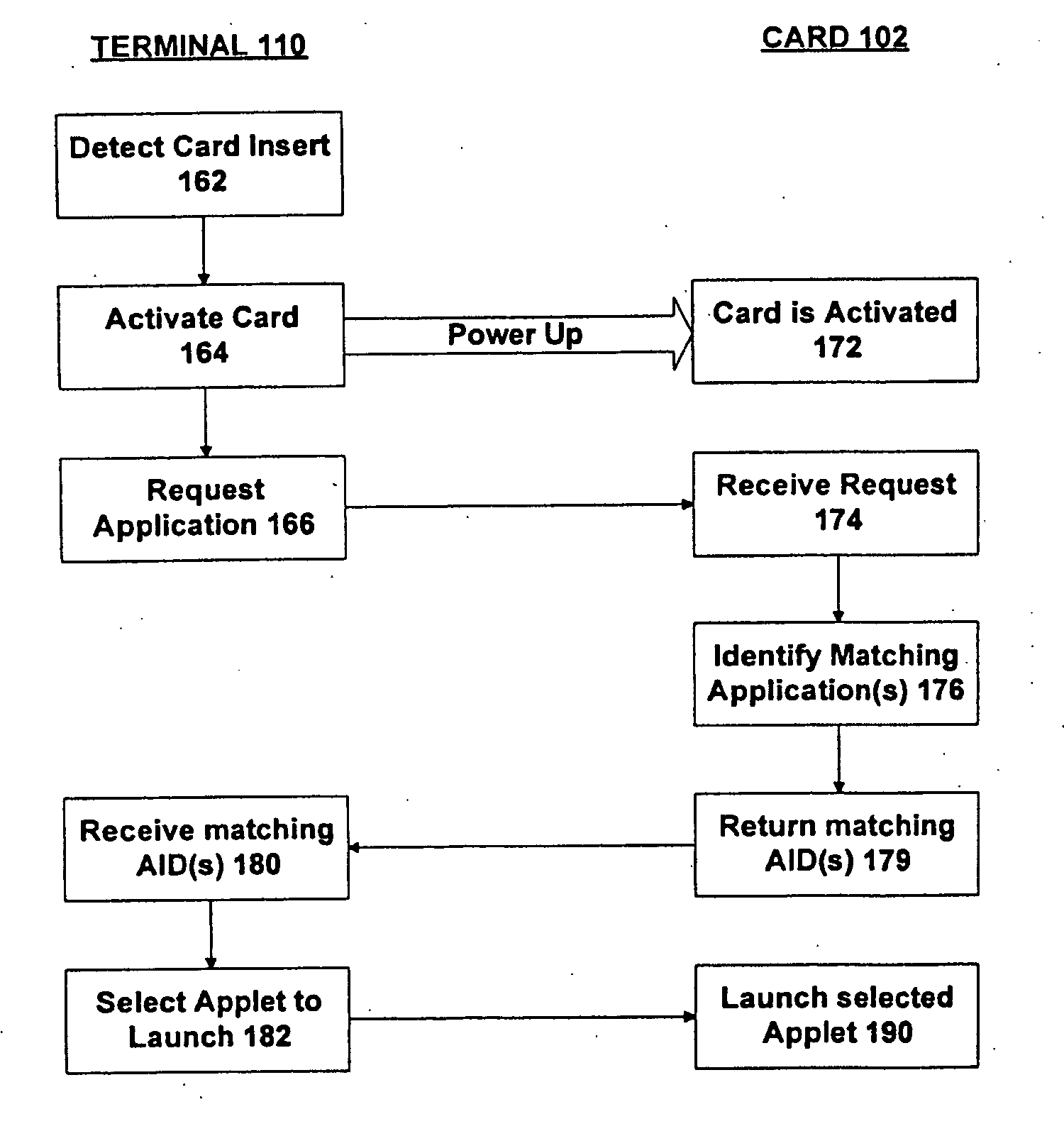
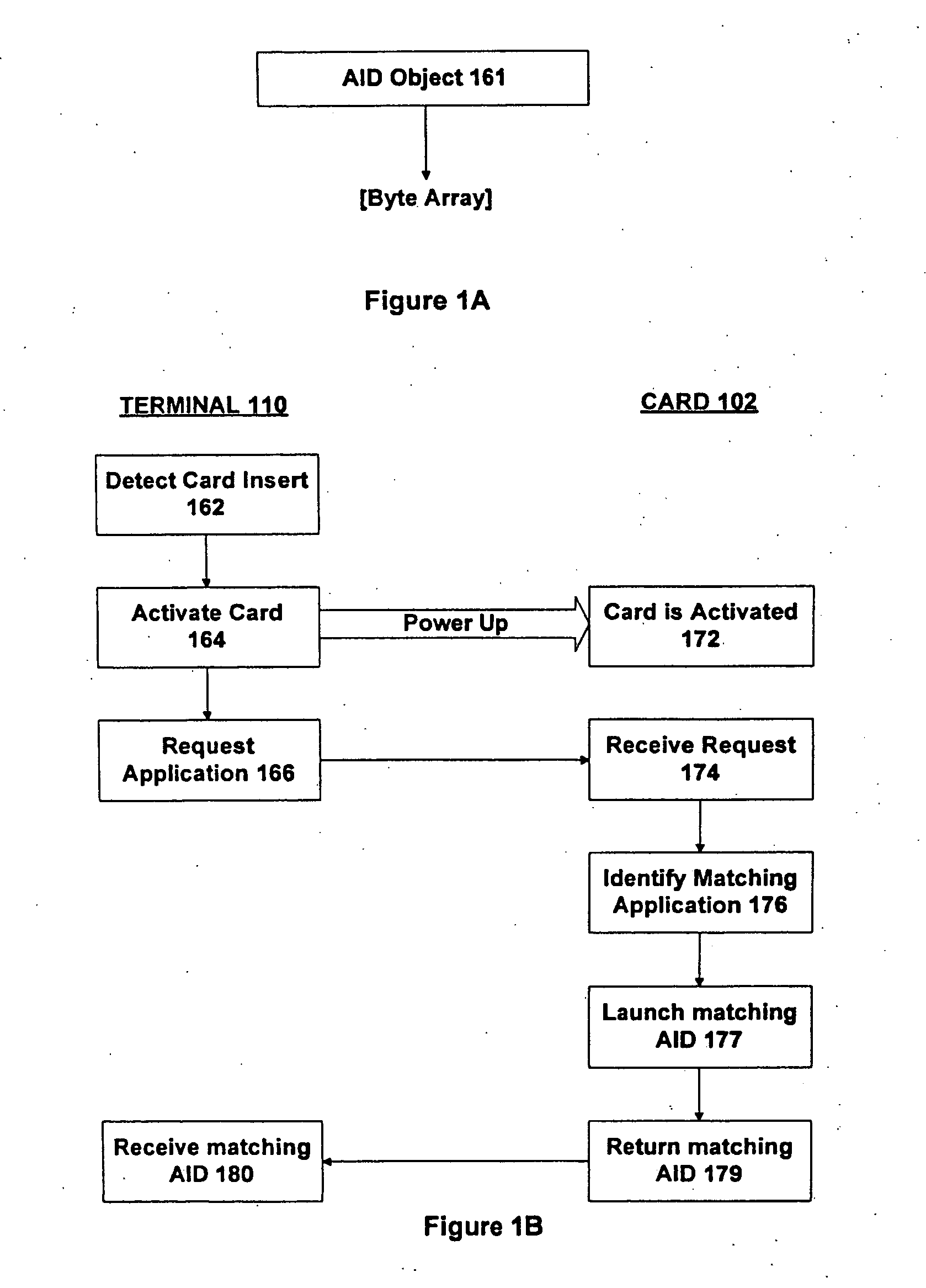
Method and apparatus for providing an application on a smart card
A smart card contains potentially multiple applications, each containing an application identifier (AID). Each application also incorporates an AID interpreter for providing access to the AID. This is achieved by making a request to the AID interpreter to provide the AID for the application. In response, the AID interpreter retrieves a first component of the AID. This first component is logically internal to the AID interpreter. The AID interpreter also retrieves a second component of the AID. This second component is logically external to the AID interpreter and is indicative of a state relevant to the application, such as a current balance in the card. The first and second components of the AID are then combined in order to generate the AID for providing in response to the request.
Owner:ORACLE INT CORP
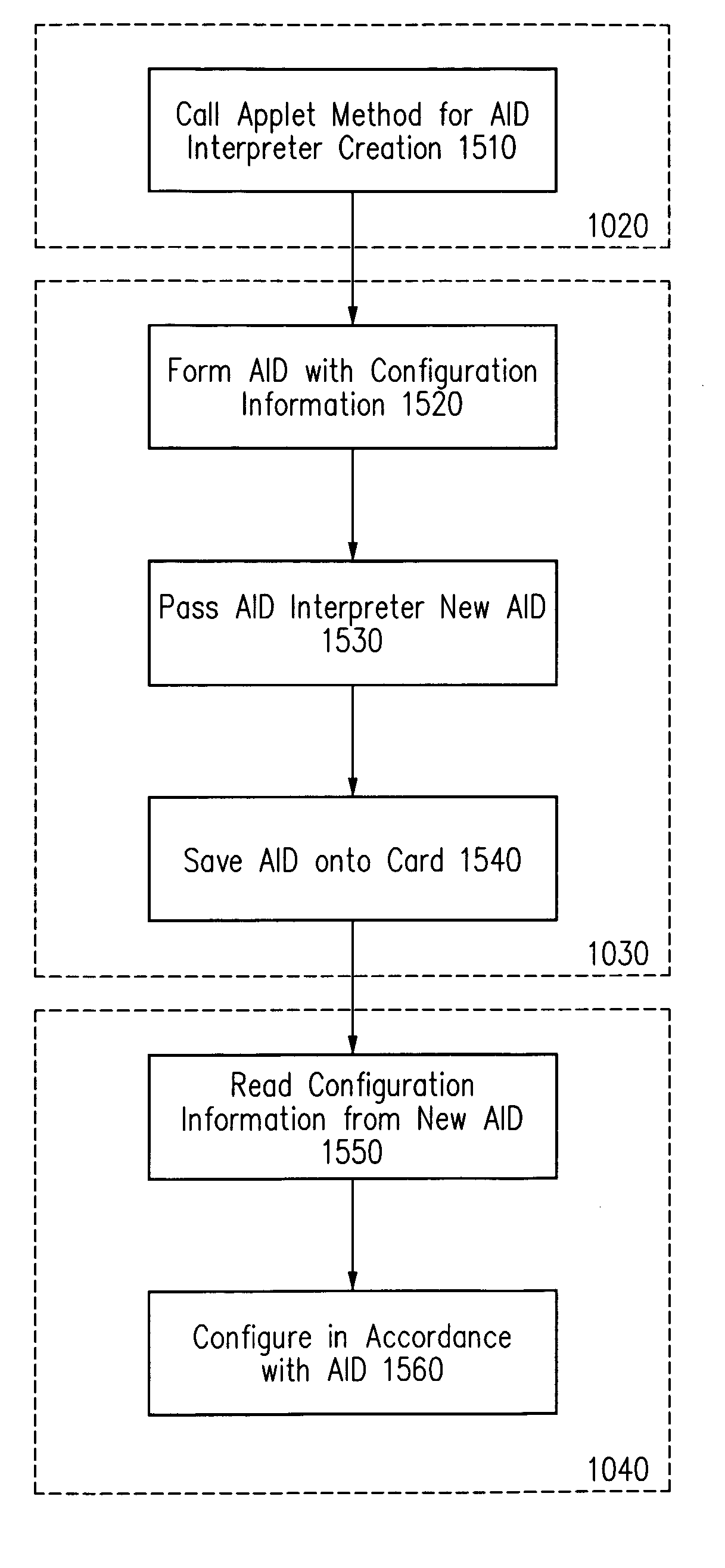
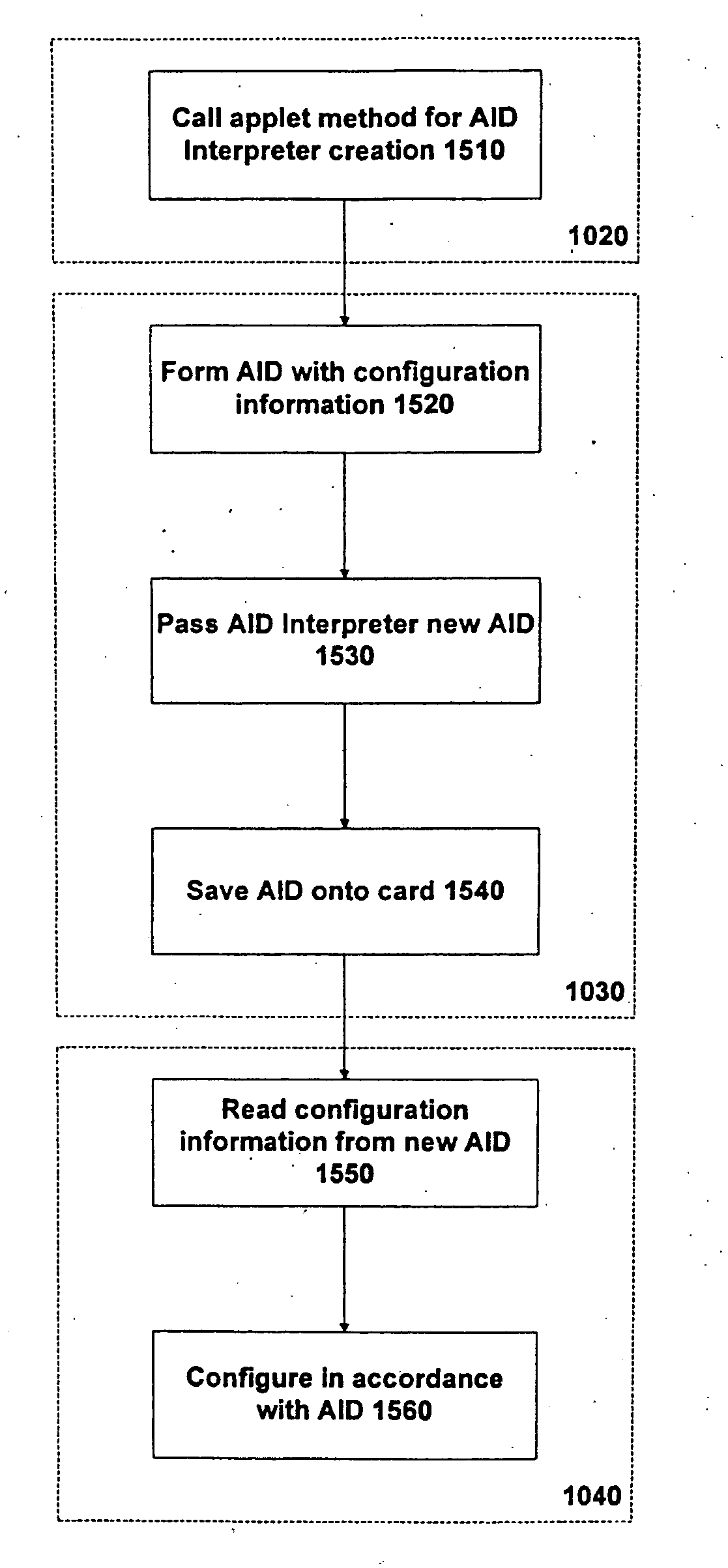
Method and apparatus for installing an application onto a smart card
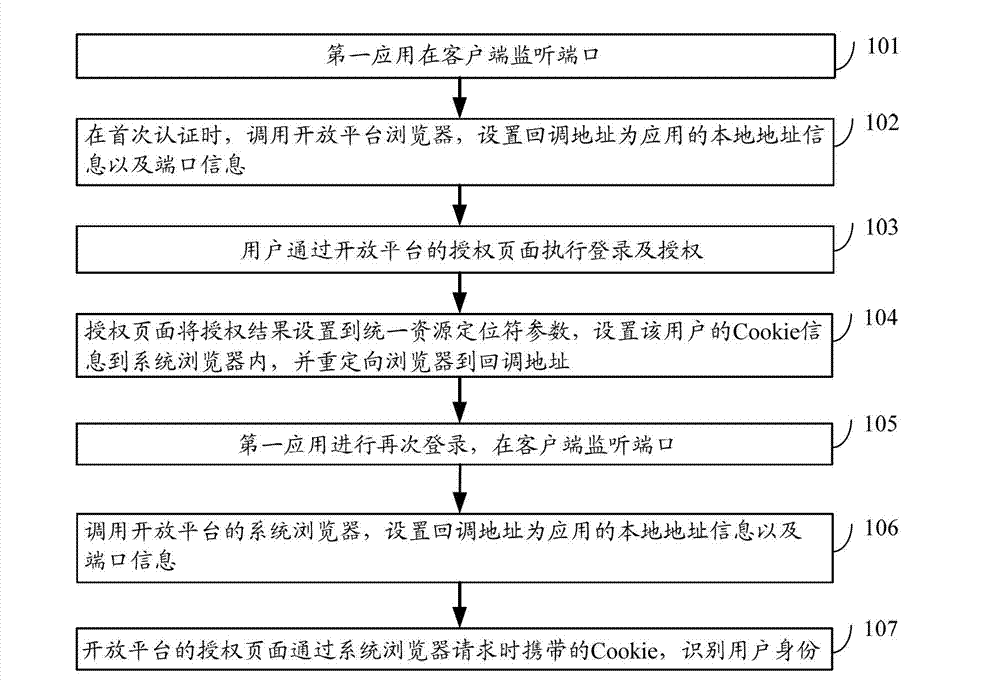
An application identifier (AID) comprises at least one customization parameter for an application to be installed onto a smart card. The application may be installed onto the smart card by providing the AID, instantiating the application onto the smart card, storing the AID onto the card, and configuring the application in accordance with the stored AID, wherein the application is configured in accordance with the at least one customization parameter.
Owner:ORACLE INT CORP
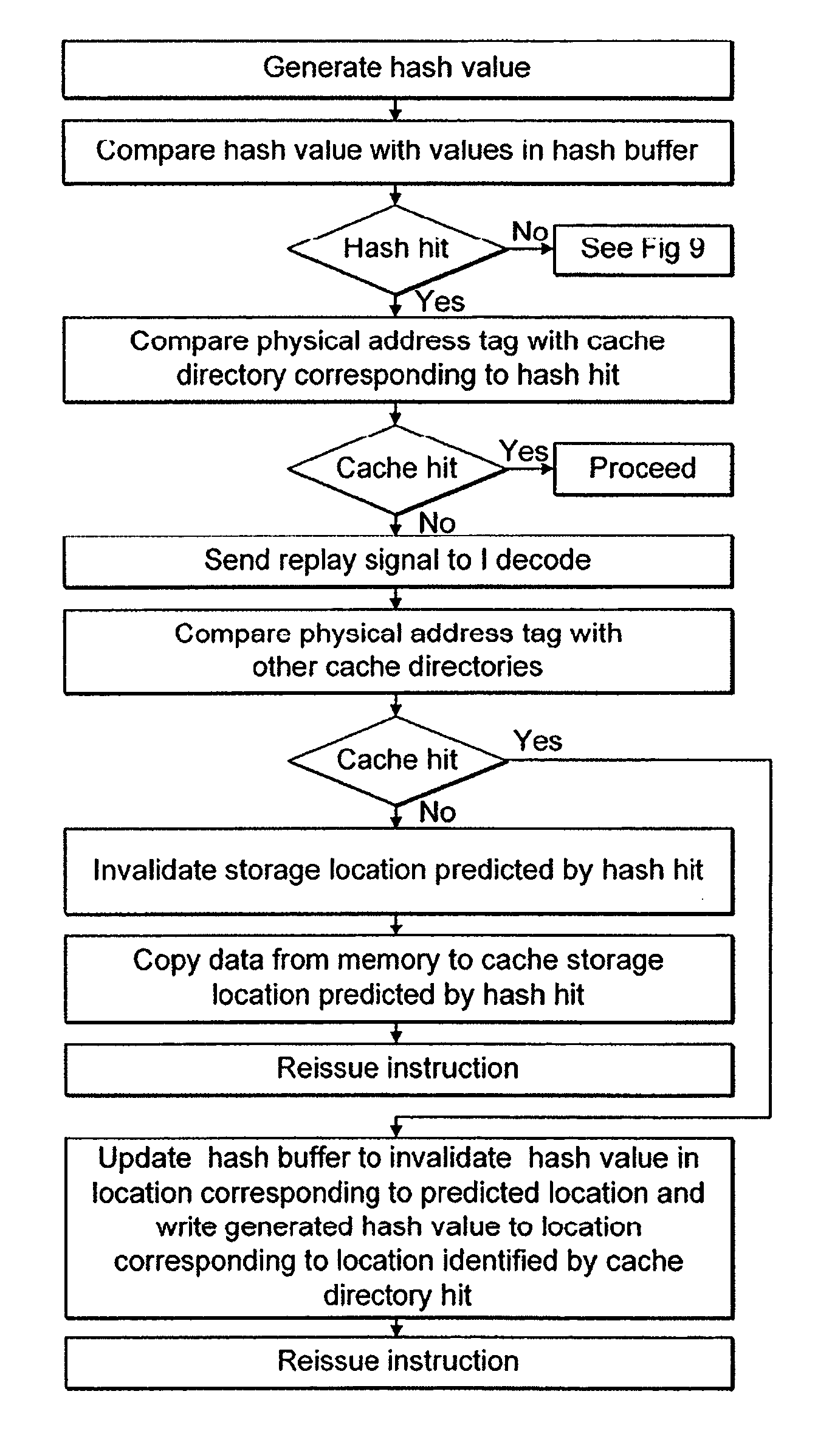
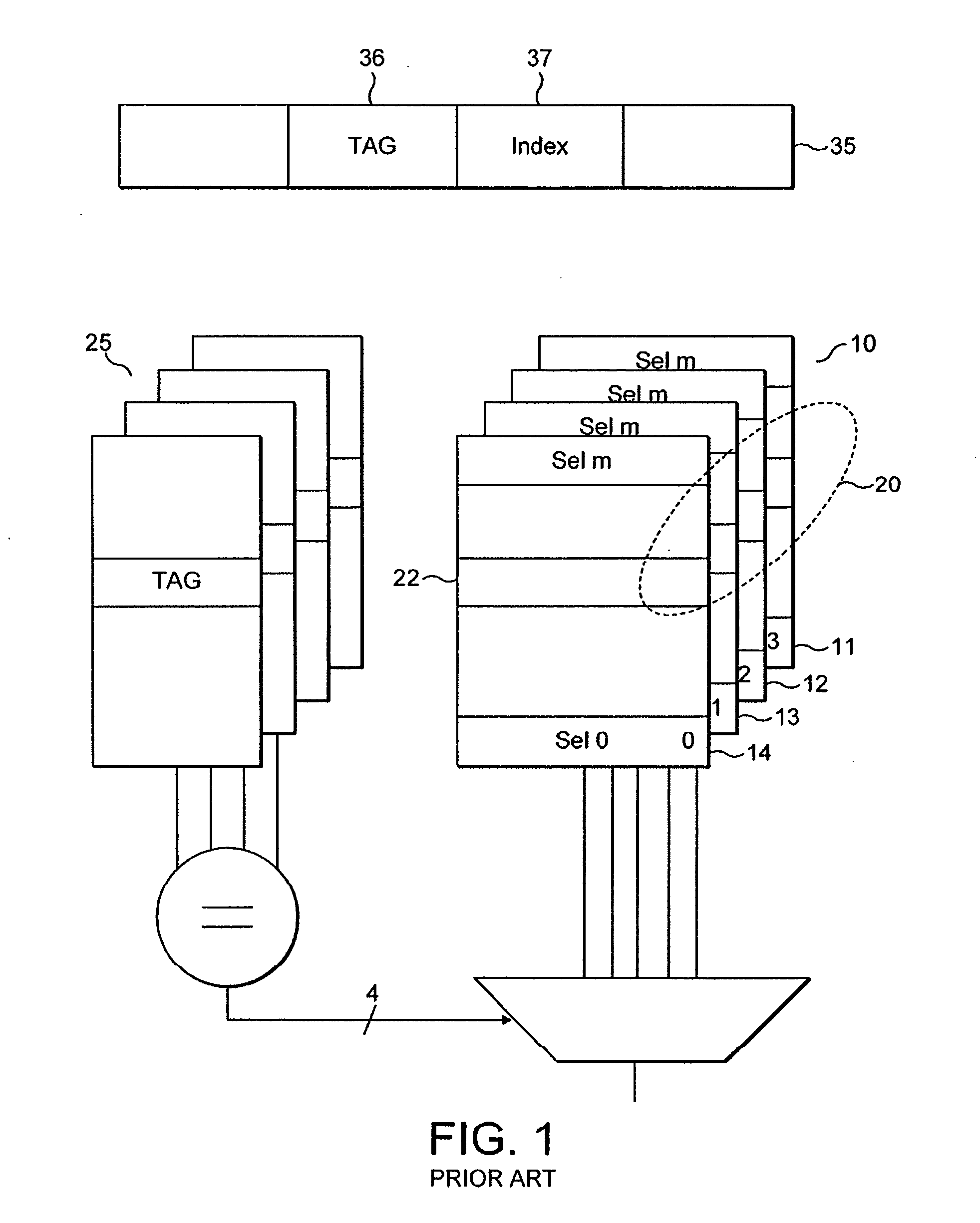
Indicating storage locations within caches
InactiveUS20060236074A1Reduce the number of stepsAccurately indicatedMemory systemsMicro-instruction address formationApplication IdentifierMultiple applications
A data processor operable to process data said data processor being operable to perform a plurality of processes or a plurality of applications on said data, said data processor comprising: a cache; a data storage unit operable to store a process or application identifier defining a process or application that is currently executing on said data processor on said data; wherein a data item storage location within said cache is indicated by an address, and said data processor further comprises: a hash value generator operable to generate a hash value from at least some of said bits of said address and at least some bits of said process or application identifier, said hash value having fewer bits than said address.
Owner:ARM LTD
Systems and methods for analyzing network metrics
ActiveUS20120317276A1Facilitate transmissionRemove networkDigital computer detailsTransmissionTraffic capacityNetwork packet
The present solution is directed to systems and methods for providing, by a device intermediary to a plurality of clients and one or more servers, analytics on a stream of network packets traversing the device. The systems and methods include the device identifying, while the device manages network traffic between the plurality of clients and the one or more servers, a stream of network packets, from a plurality of streams of network packets of the network traffic traversing the device, corresponding to a flow identifier, e.g., a selected one of an internet protocol address, a uniform resource locator or an application identifier. The systems and methods may include a collector of the analytics engine collecting, while the device manages network traffic, metrics on the identified stream of network packets and generating one or more stream objects that comprise the collected metrics.
Owner:CITRIX SYST INC
Method, device and system for implementing authorization of third-party application based on open platform
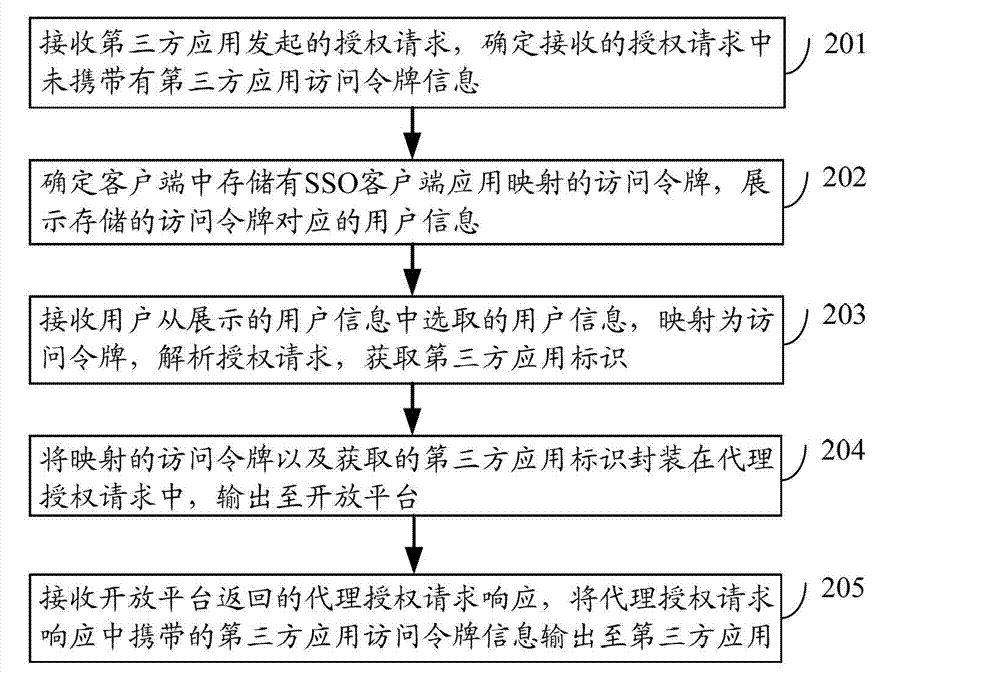
ActiveCN103051630AShorten the timeEasy to operateUser identity/authority verificationThird partyOpen platform
The invention discloses a method, a device and a system for implementing the authorization of a third-party application based on an open platform. The method comprises the following steps of: receiving an authorization request initiated by the third-party application, and determining that the received authorization request does not carry third-party application access token information; determining that an access token for single sign-on (SSO) client application mapping is stored in a client, and displaying user information corresponding to the stored access token; receiving user information which is selected from the displayed user information by a user, mapping the user information into the access token, analyzing the authorization request, and acquiring a third-party application identifier; packaging the mapped access token and the acquired third-party application identifier into an agent authorization request, and outputting the agent authorization request to the open platform; and receiving an agent authorization request response returned by the open platform, and outputting the third-party application access token information carried in the agent authorization request response to the third-party application. By the invention, application authorization efficiency can be improved.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
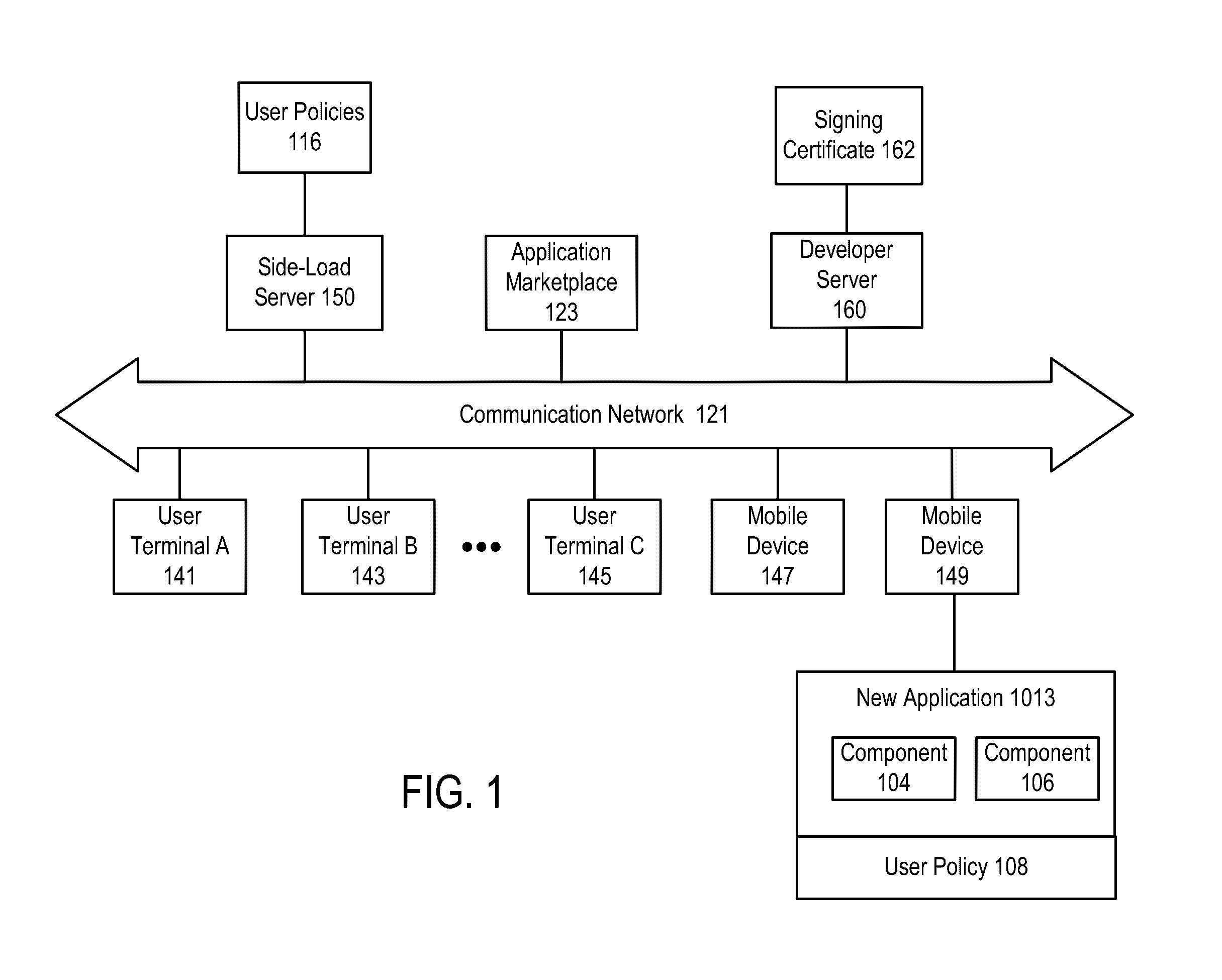
Determining source of side-loaded software
ActiveUS20160321452A1Digital data authenticationPlatform integrity maintainanceApplication softwareWhitelist
A source of side-loaded software is determined. An action may be performed in response to the determination of the source. In one case, the handling of an application on a mobile device may be based on whether the source of the application is trusted or untrusted. If a software application being newly-installed on a mobile device of a user is determined to be untrusted, installation or execution is blocked. In one approach, the determination of the source includes: determining whether a first source identifier of a first application matches a white list of source identifiers or a black list of source identifiers; and sending the first source identifier and a first application identifier for the first application to a different computing device.
Owner:LOOKOUT MOBILE SECURITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com