Patents
Literature
74 results about "Distributed firewall" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
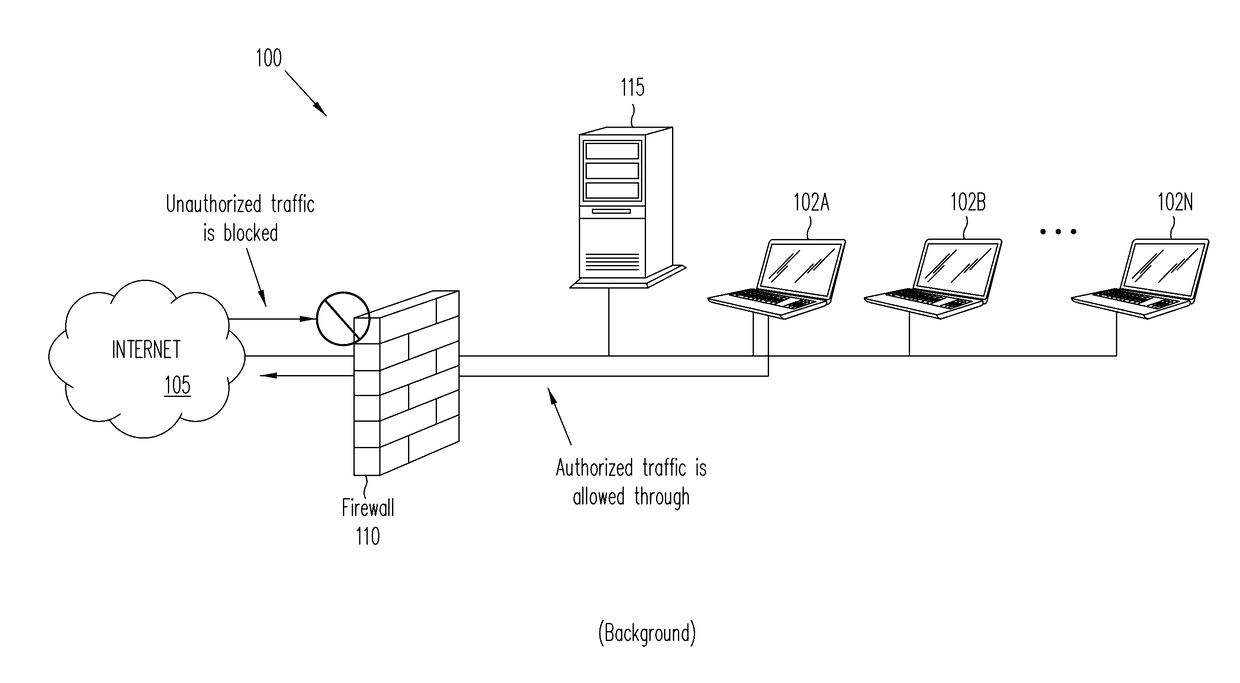
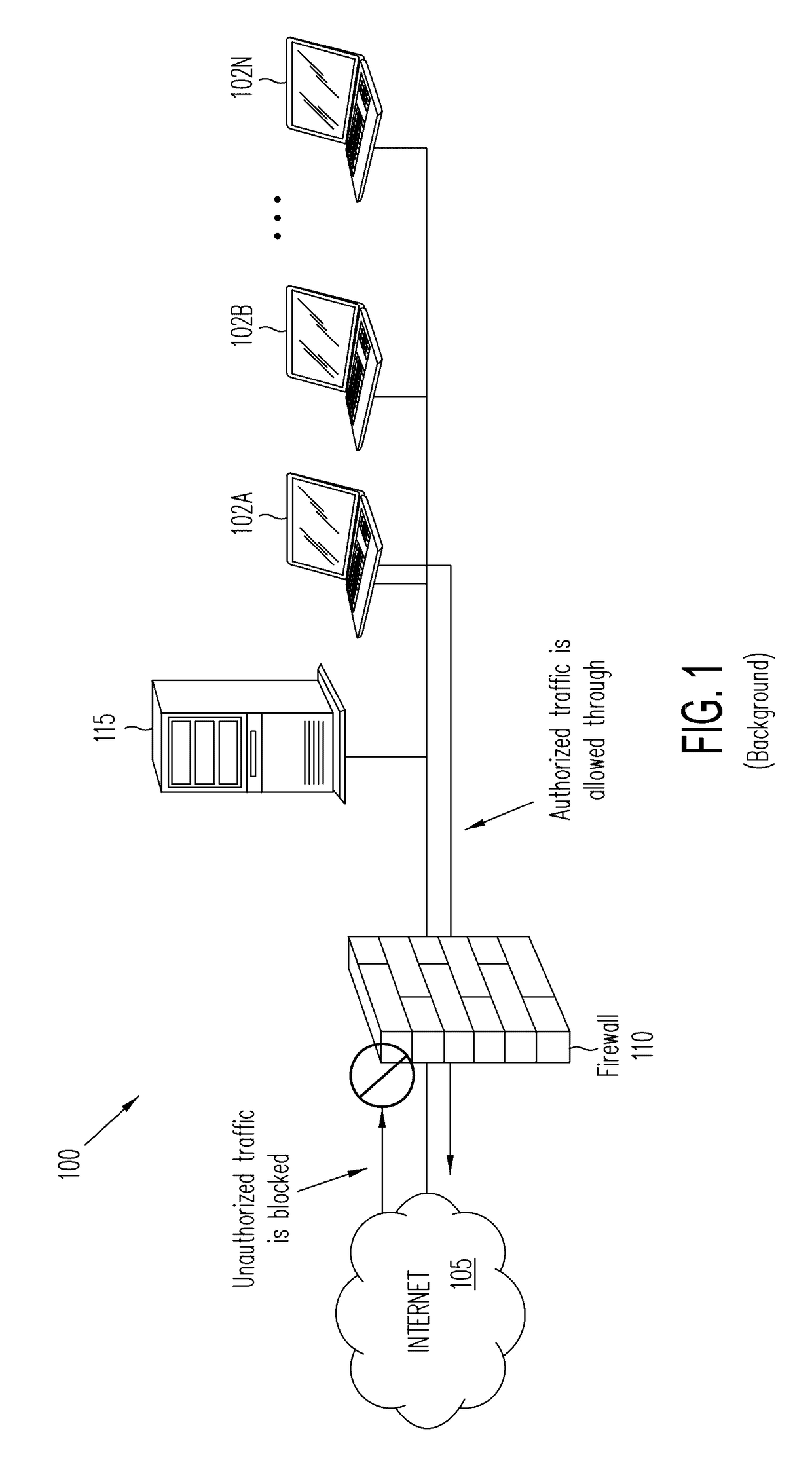
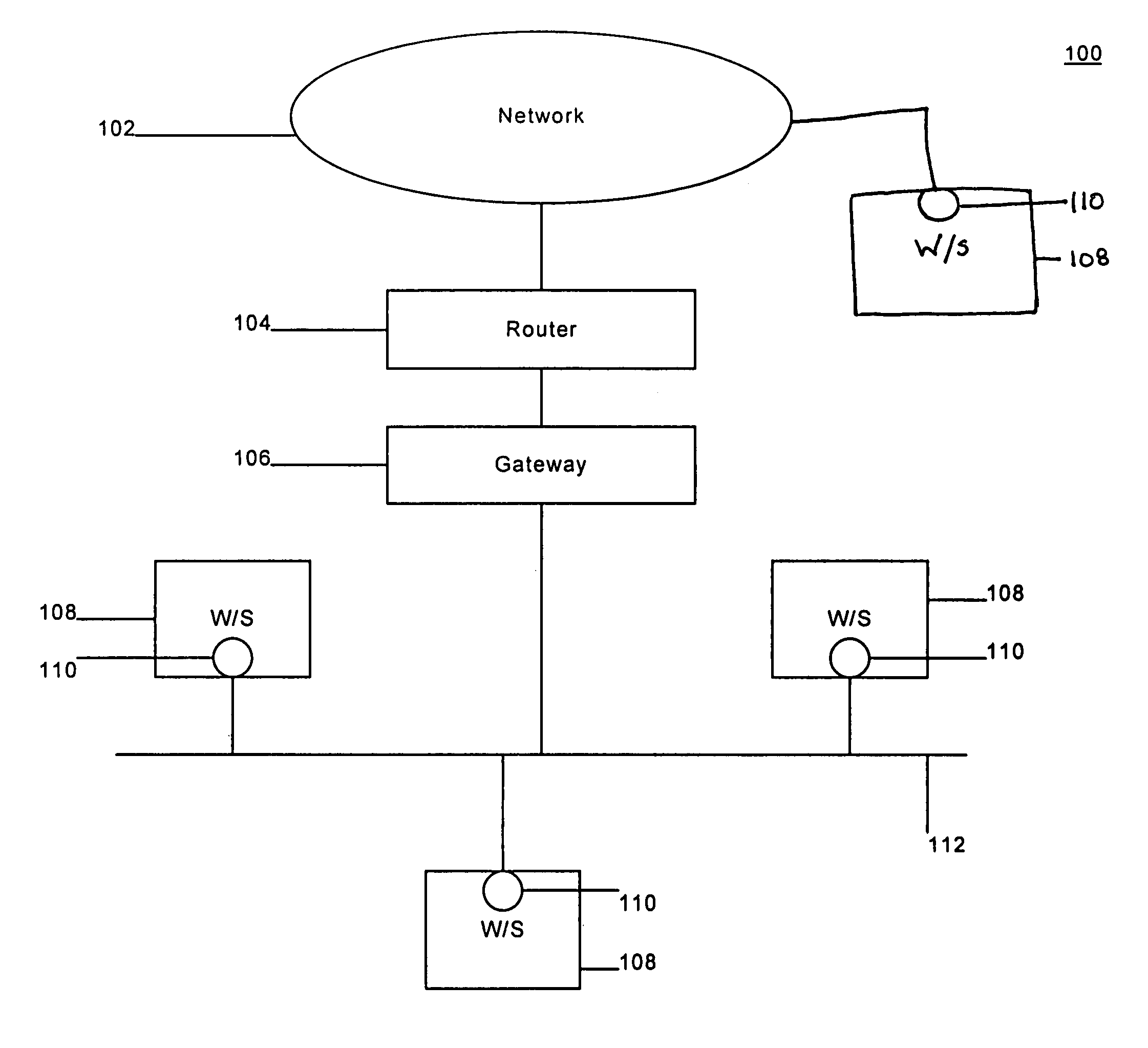
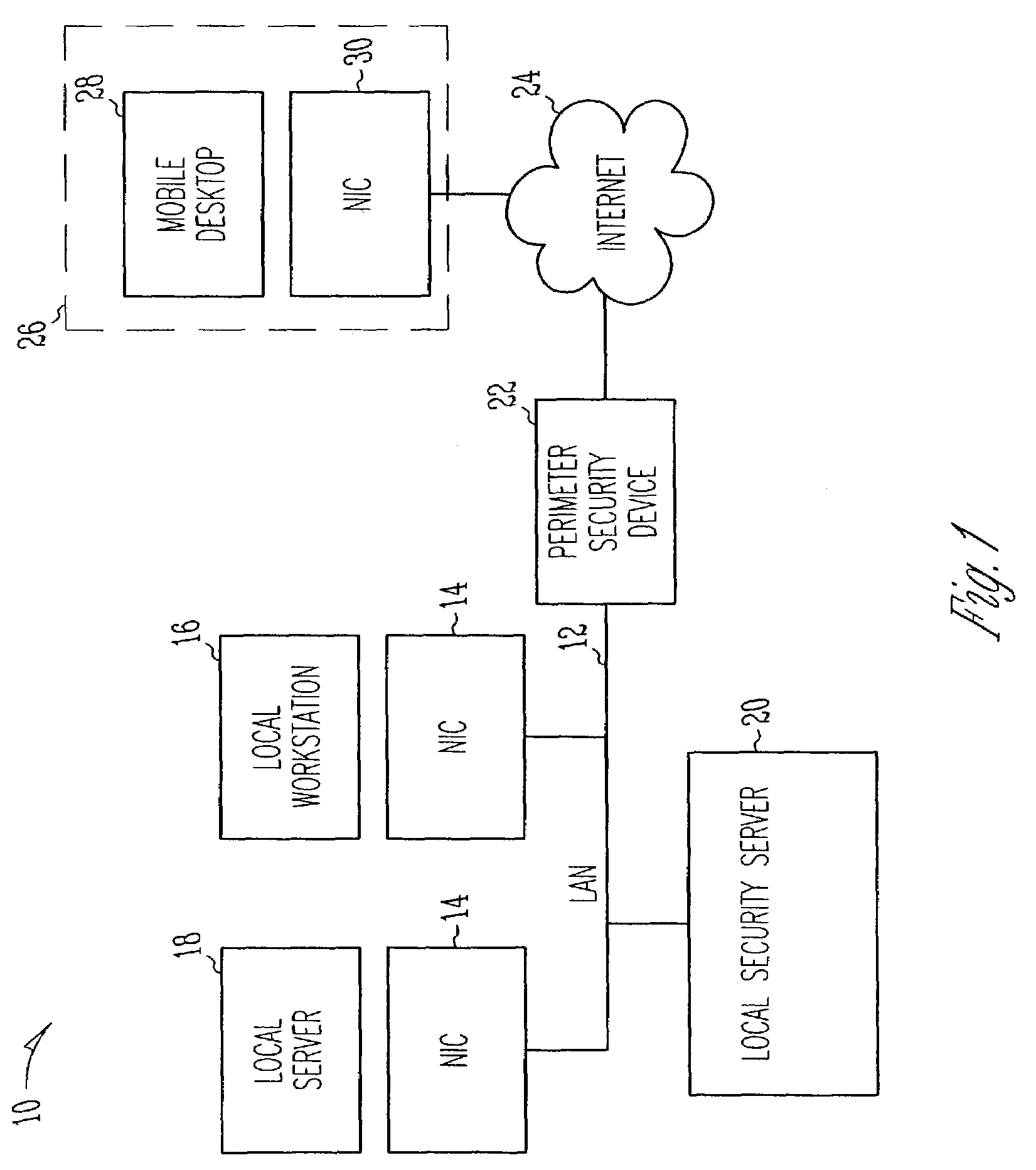
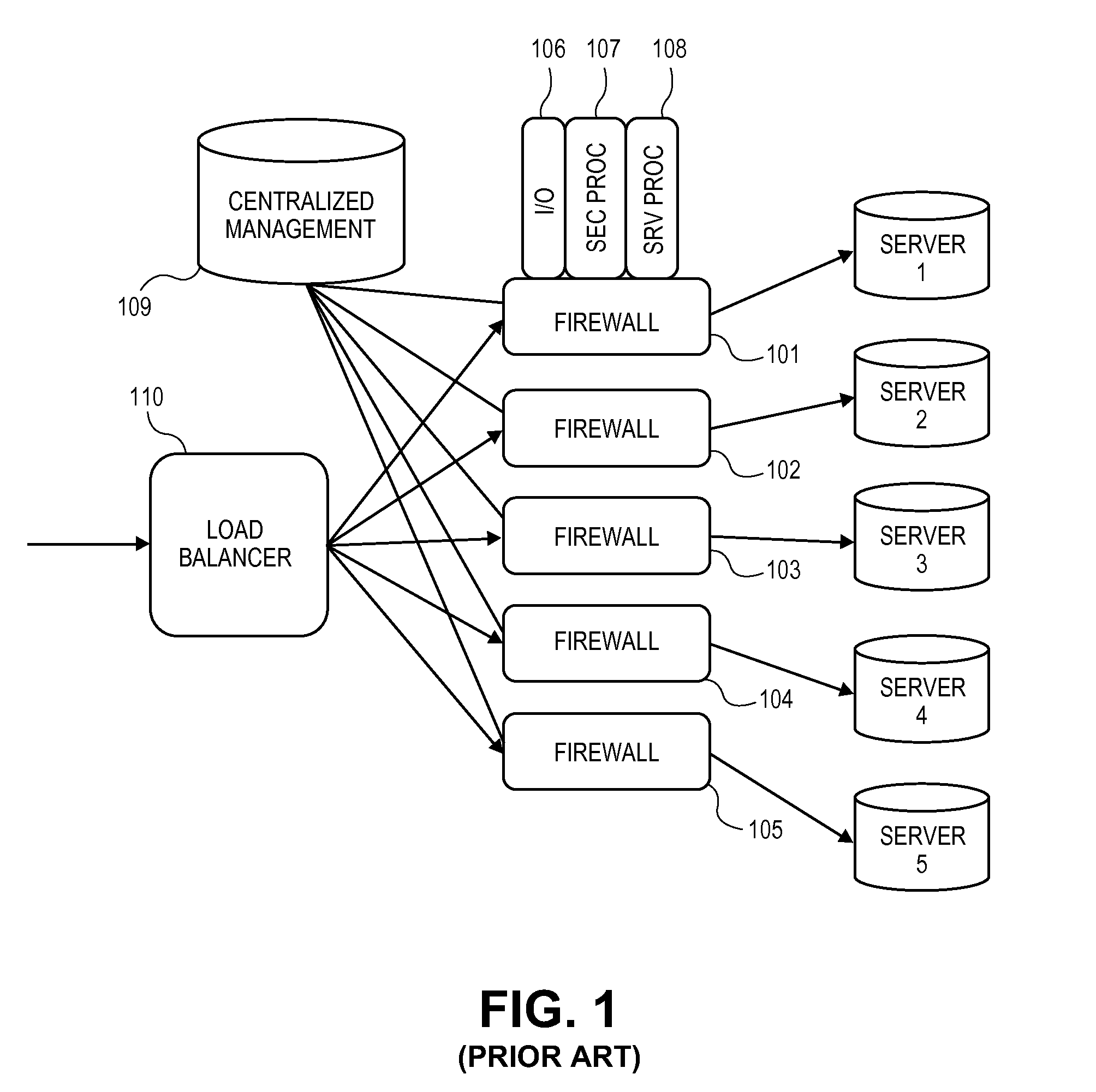
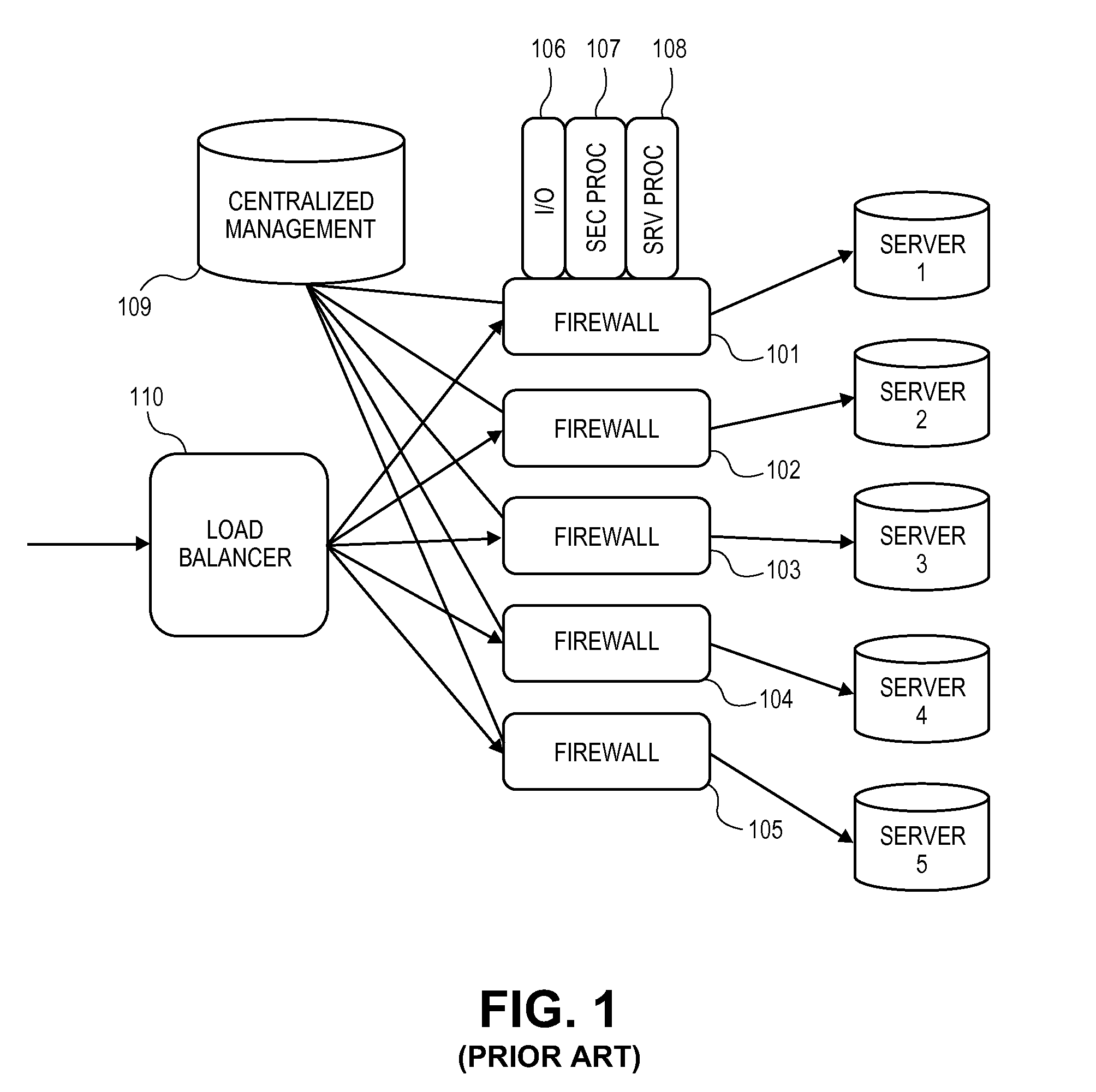
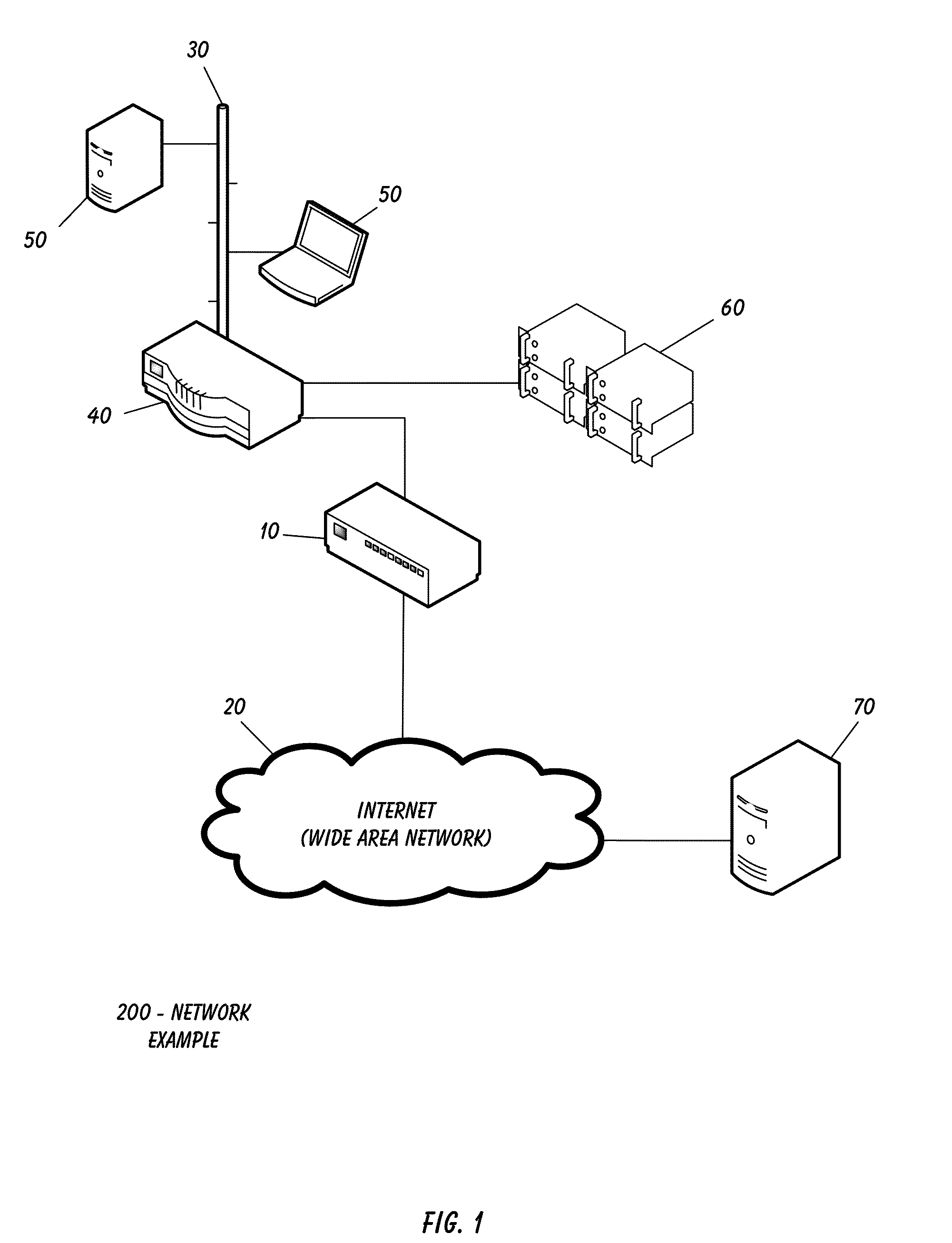
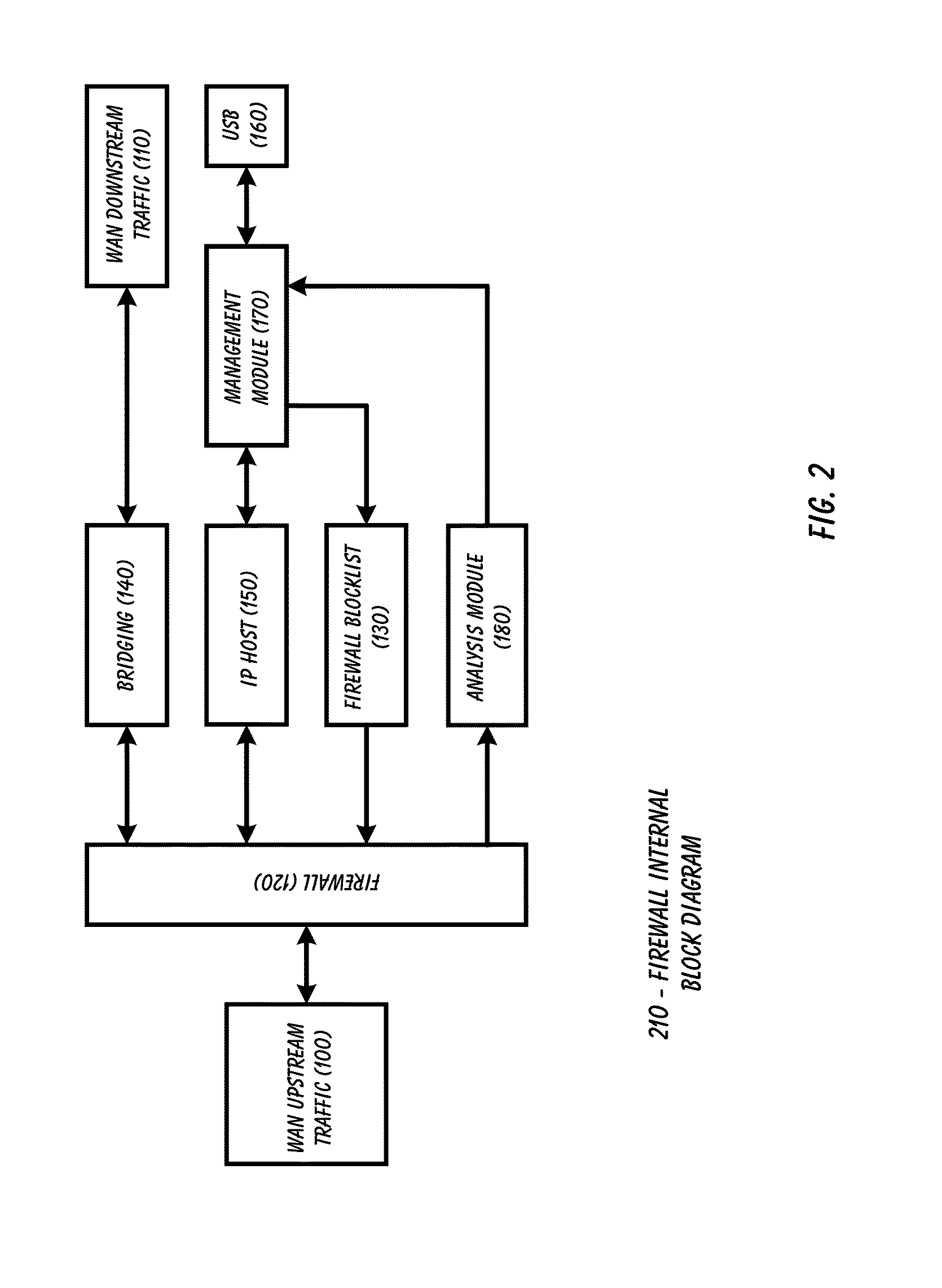
A firewall is a system or group of systems (router, proxy, or gateway) that implements a set of security rules to enforce access control between two networks to protect the "inside" network from the "outside" network. It may be a hardware device or a software program running on a secure host computer. In either case, it must have at least two network interfaces, one for the network it is intended to protect, and one for the network it is exposed to. A firewall sits at the junction point or gateway between the two networks, usually a private network and a public network such as the Internet.
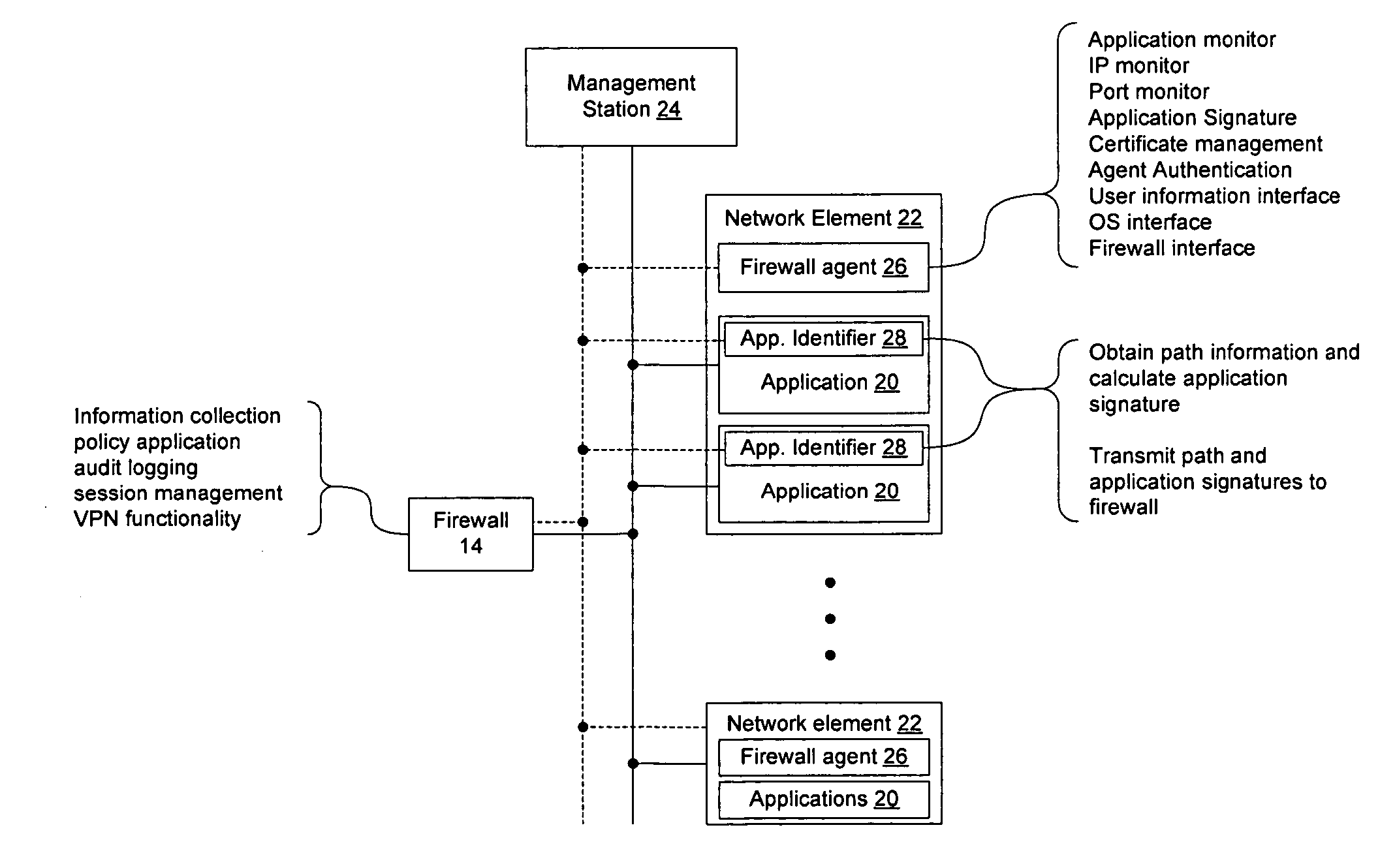
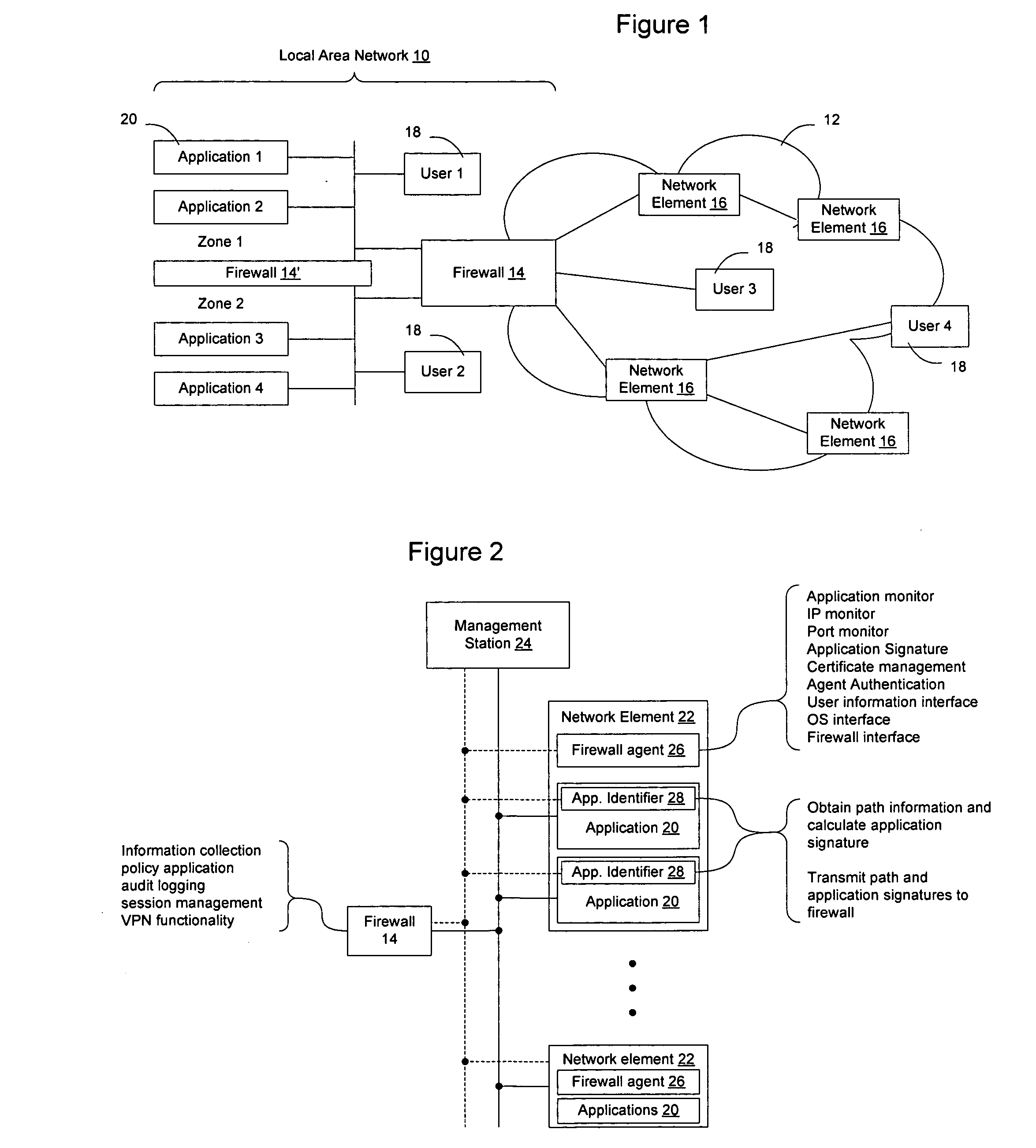
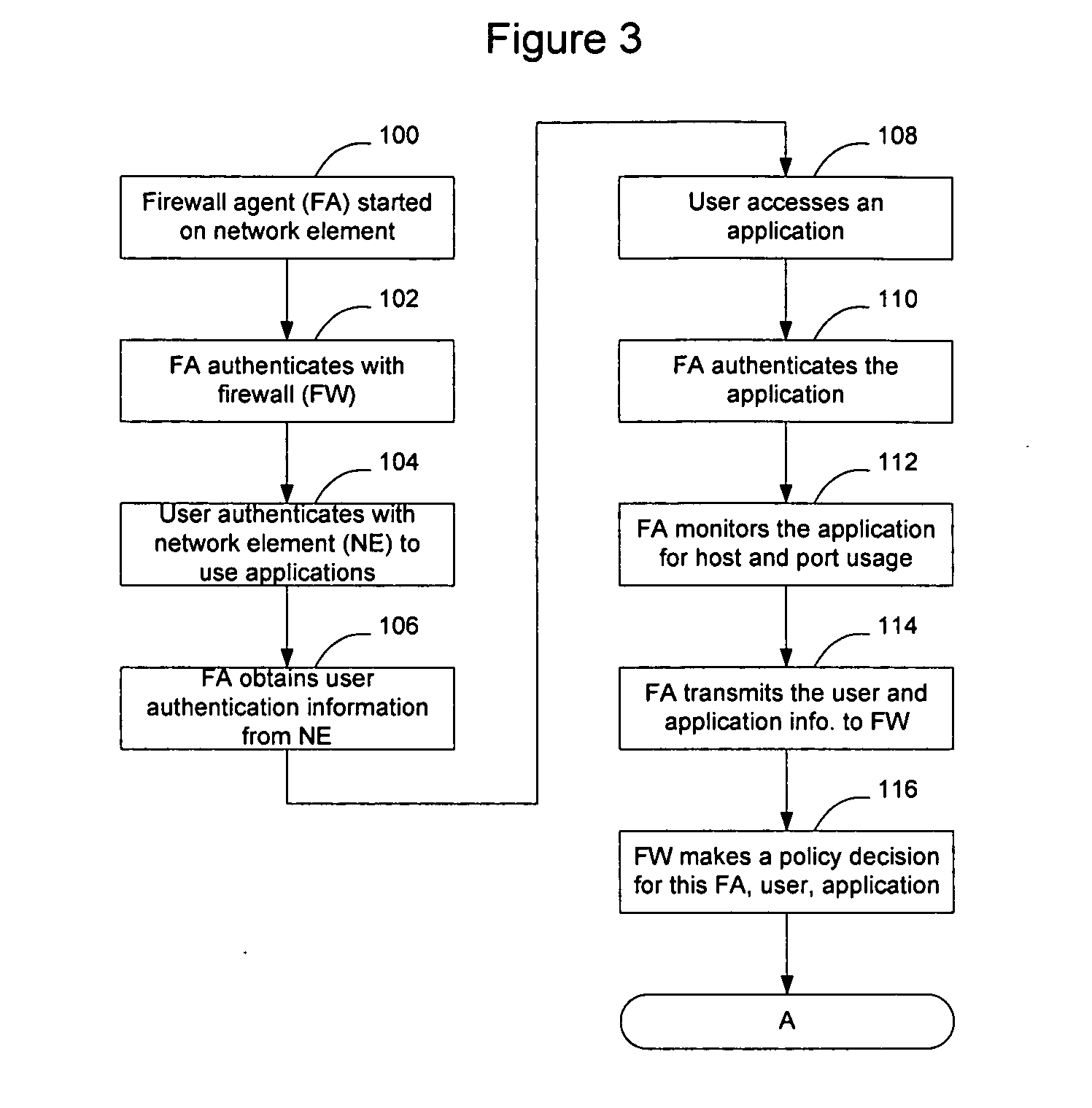
Method and apparatus for enabling enhanced control of traffic propagation through a network firewall
InactiveUS20060075478A1Easy to controlImprove abilitiesMultiple digital computer combinationsProgram controlInternet trafficApplication Identifier
A distributed firewall system is used to implement a network firewall with enhanced control over network traffic to allow policy to be implemented on a per-user basis, a per-application basis, a per-user and application basis, and to allow ports to be dynamically opened and closed as needed by the applications. The distributed firewall system may include application identifiers associated with applications running on a network element, one or more firewall agents instantiated on the network element hosting the applications, and a firewall configured to interface with the firewall agents. Communications between the distributed components are secured to allow the firewall to detect if an agent has been compromised, and to allow the firewall agent to determine if the application has been compromised. The distributed firewall system may work in a VPN environment, such as in connection with a VPN server, to implement firewall policy at the point where VPN traffic enters the protected network.
Owner:RPX CLEARINGHOUSE
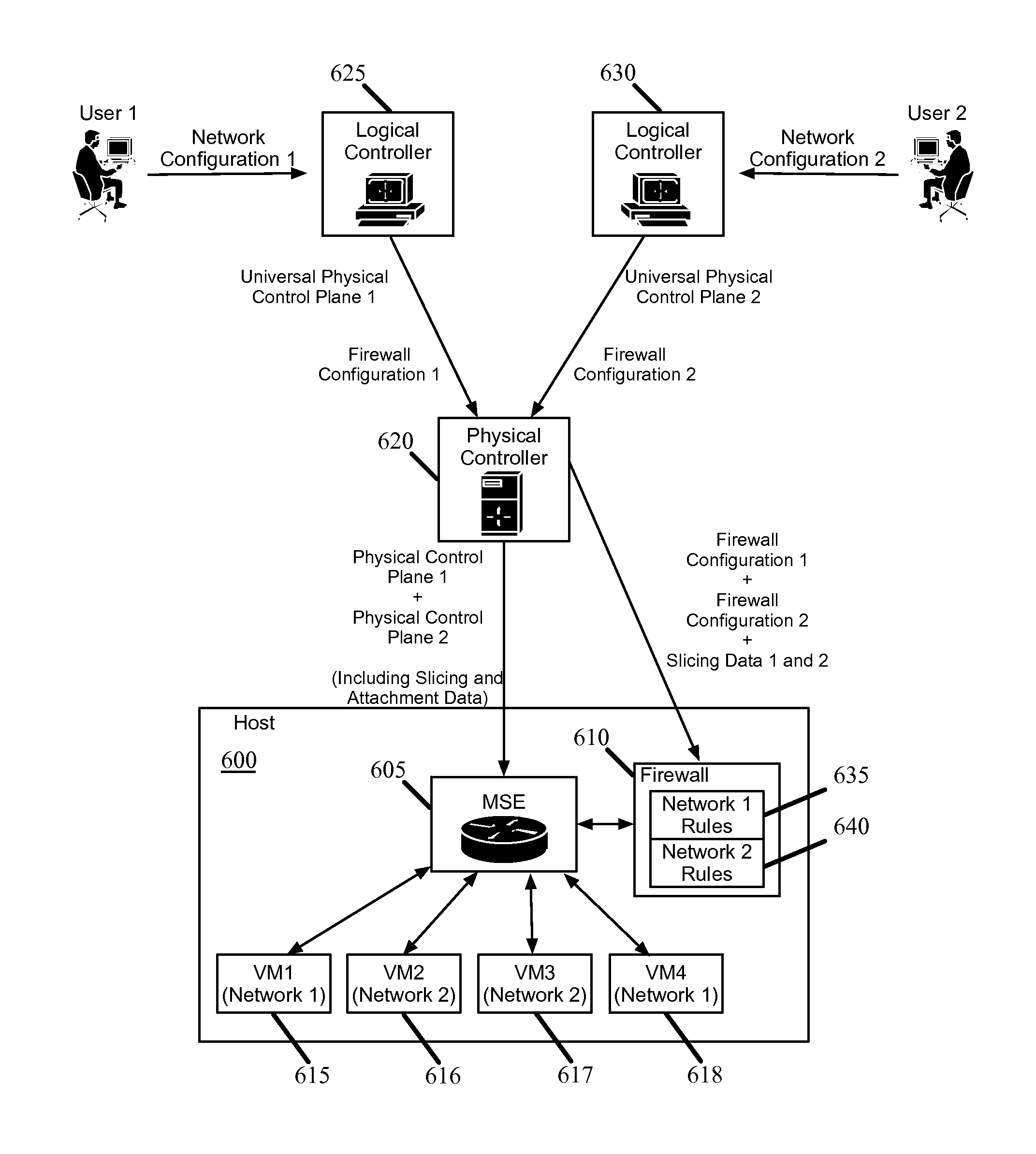
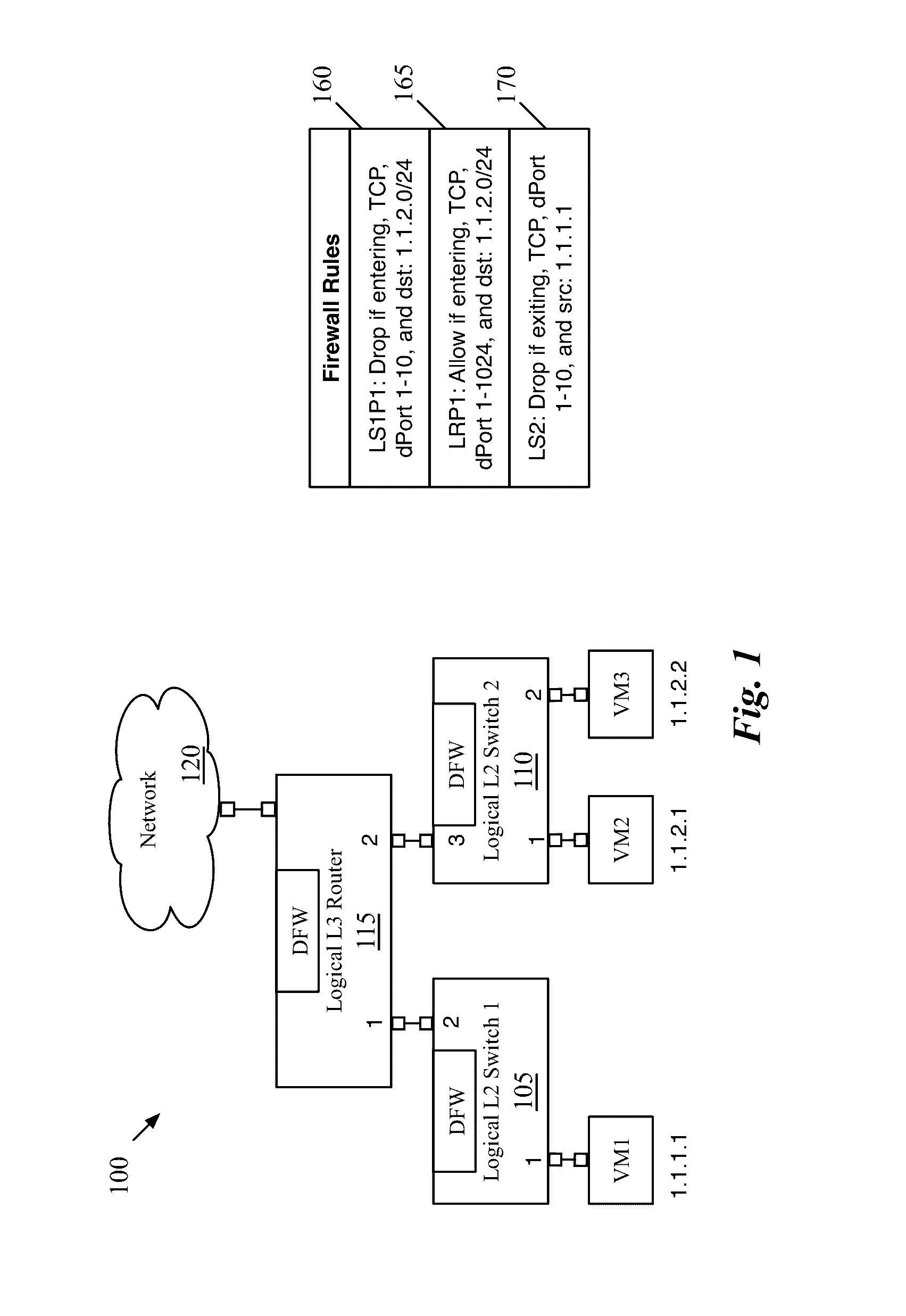
Firewalls in logical networks
ActiveUS20130125230A1Faster packet processing decisionEasy to handleMultiple digital computer combinationsData switching networksLogical networkSoftware
Some embodiments provide a method for configuring a logical firewall in a hosting system that includes a set of nodes. The logical firewall is part of a logical network that includes a set of logical forwarding elements. The method receives a configuration for the firewall that specifies packet processing rules for the firewall. The method identifies several of the nodes on which to implement the logical forwarding elements. The method distributes the firewall configuration for implementation on the identified nodes. At a node, the firewall of some embodiments receives a packet, from a managed switching element within the node, through a software port between the managed switching element and the distributed firewall application. The firewall determines whether to allow the packet based on the received configuration. When the packet is allowed, the firewall the packet back to the managed switching element through the software port.
Owner:NICIRA
Distributed firewalls and virtual network services using network packets with security tags
A method, system, and apparatus are provided for a distributed firewall and virtual network services on a network. In one example, the method includes storing a plurality of predefined security groups, wherein each predefined security group has a set of predefined security rules for network packets configured to be transmitted between virtual machines (VMs) within the network; associating each virtual machine (VM) within the network with one or more predefined security groups (SGs); filtering an outgoing network packet from a sending VM to a receiving VM in response to the predefined security rules associated with the predefined SGs associated with the sending VM to validate the communication desired in the outgoing network packet; forming a secured network packet by encapsulating a header, a security tag, and the outgoing network packet together; and transmitting the secured network packet into the network for delivery to the receiving VM.
Owner:ATTALA SYST LLC
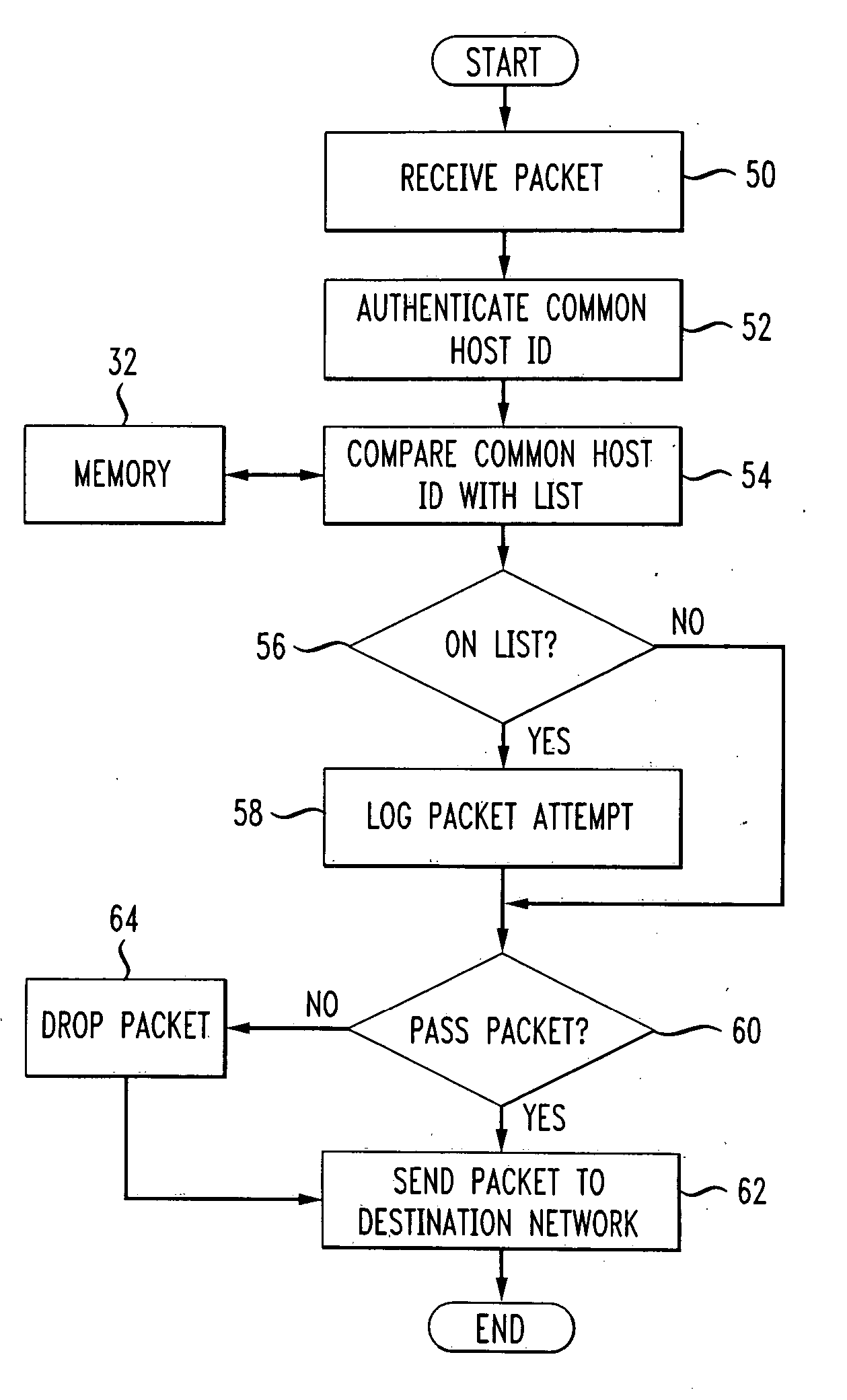
Method and apparatus for a distributed firewall
InactiveUS20060070122A1Multiple digital computer combinationsProgram controlAuthenticationDistributed firewall
A method and apparatus for implementing a distributed firewall is described. A packet filter processor receives a packet sent from a first device to a second device. The packet filter processor authenticates an identifier for the packet. For example, authentication could be performed using a cryptographically-verifiable identifier. The packet filter processor determines whether to send the packet to the second device, based on the authentication and a set of policy rules. The packet filter processor sends the packet to the second device in accordance with the determination
Owner:RPX CORP
Method and apparatus for a distributed firewall
InactiveUS7051365B1Multiple digital computer combinationsProgram controlAuthenticationDistributed firewall
Owner:RPX CORP
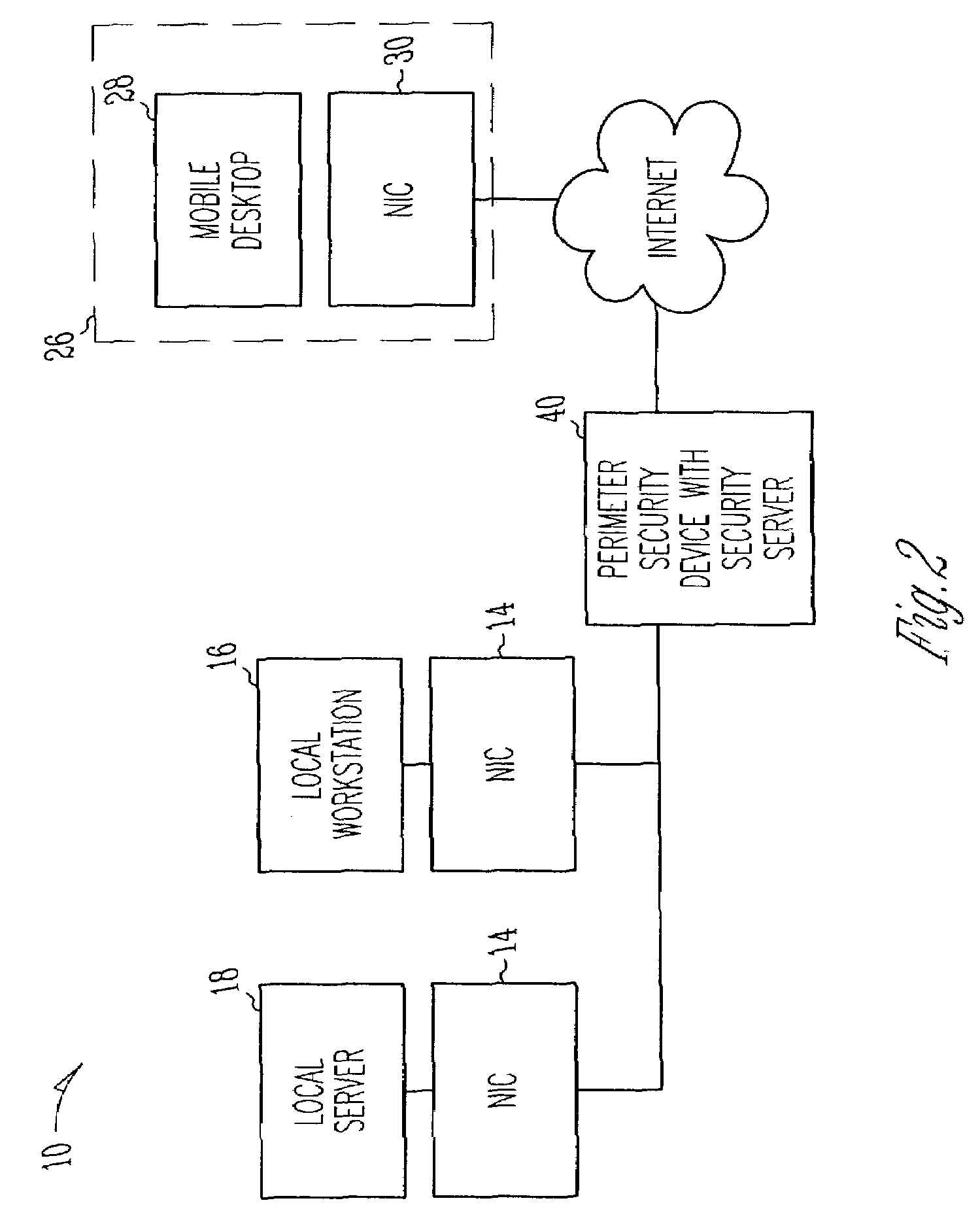
Distributed firewall system and method
InactiveUS7536715B2Limitation for transferData switching by path configurationMultiple digital computer combinationsComputer networkNetwork interface device
A system and method for restricting packet transfer to a computer across a network, wherein the computer includes a network interface device coupled to the network and wherein the network interface device includes a packet filter. A security server is connected to the network. A packet is received at the network interface device and the network interface device determines if the packet is an authorized transaction. If the packet is not an authorized transaction, the packet is routed to the security server, where the security server determines whether the packet is an authorized transaction. If the security server determines that the packet is an authorized transaction, the network interface device is configured to accept similar transactions.
Owner:MCAFEE LLC
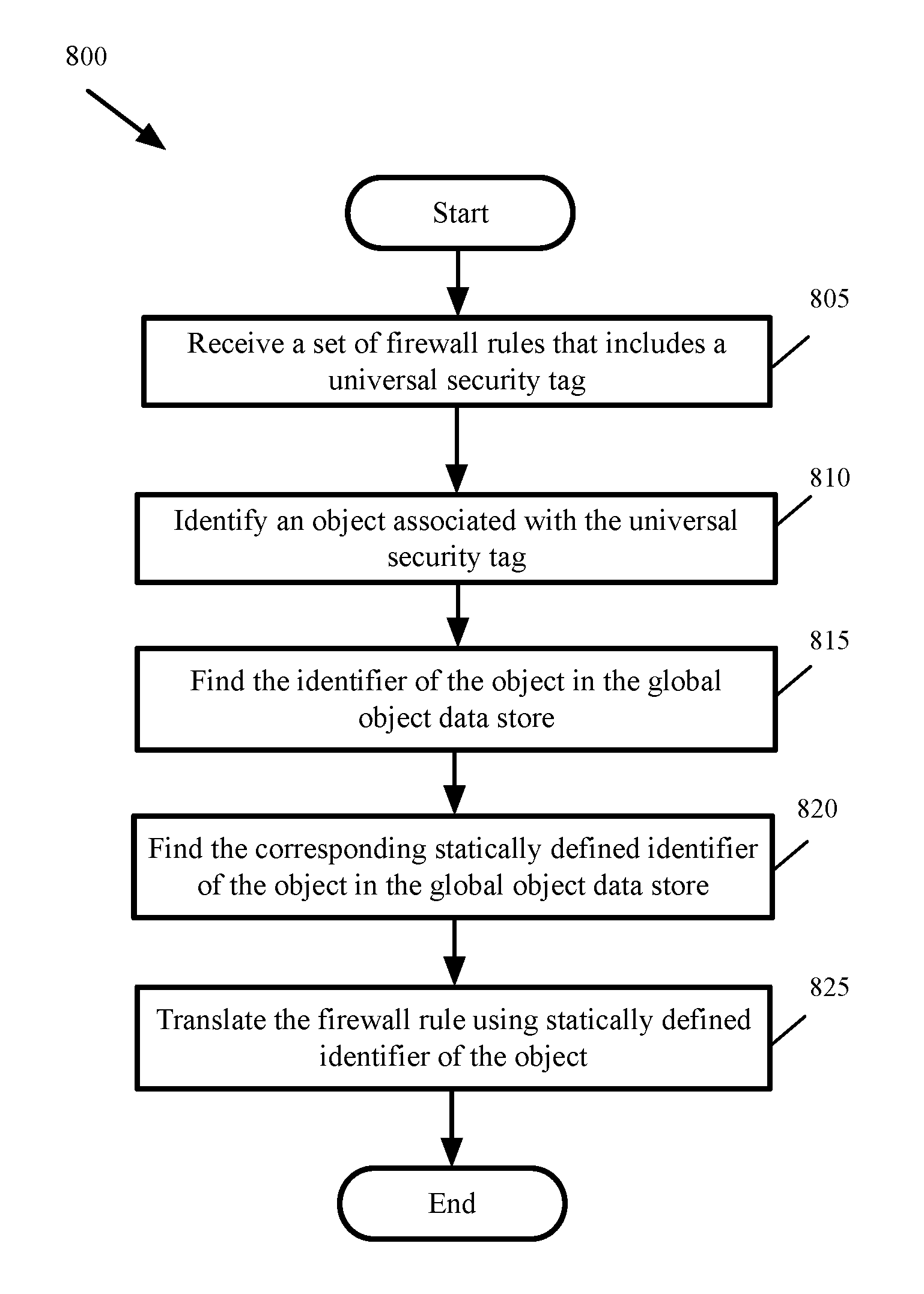
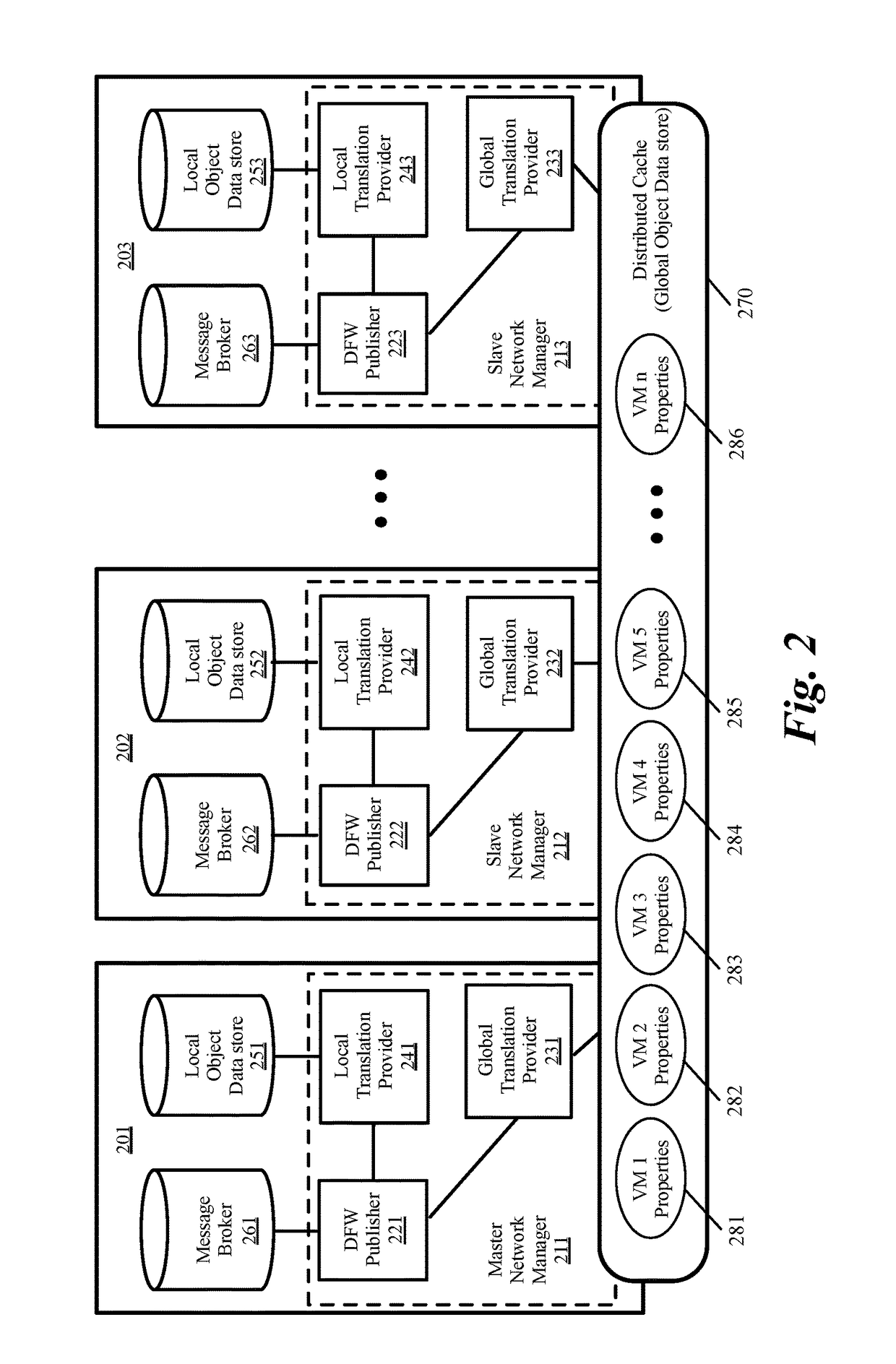
Global objects for federated firewall rule management
ActiveUS20170005988A1Memory architecture accessing/allocationDatabase management systemsComputer networkUnique identifier
A method of defining distributed firewall rules in a group of datacenters is provided. Each datacenter includes a group of data compute nodes (DCNs). The method sends a set of security tags from a particular datacenter to other datacenters. The method, at each datacenter, associates a unique identifier of one or more DCNs of the datacenter to each security tag. The method associates one or more security tags to each of a set of security group at the particular datacenter and defines a set of distributed firewall rules at the particular datacenter based on the security tags. The method sends the set of distributed firewall rules from the particular datacenter to other datacenters. The method, at each datacenter, translates the firewall rules by mapping the unique identifier of each DCN in a distributed firewall rule to a corresponding static address associated with the DCN.
Owner:NICIRA
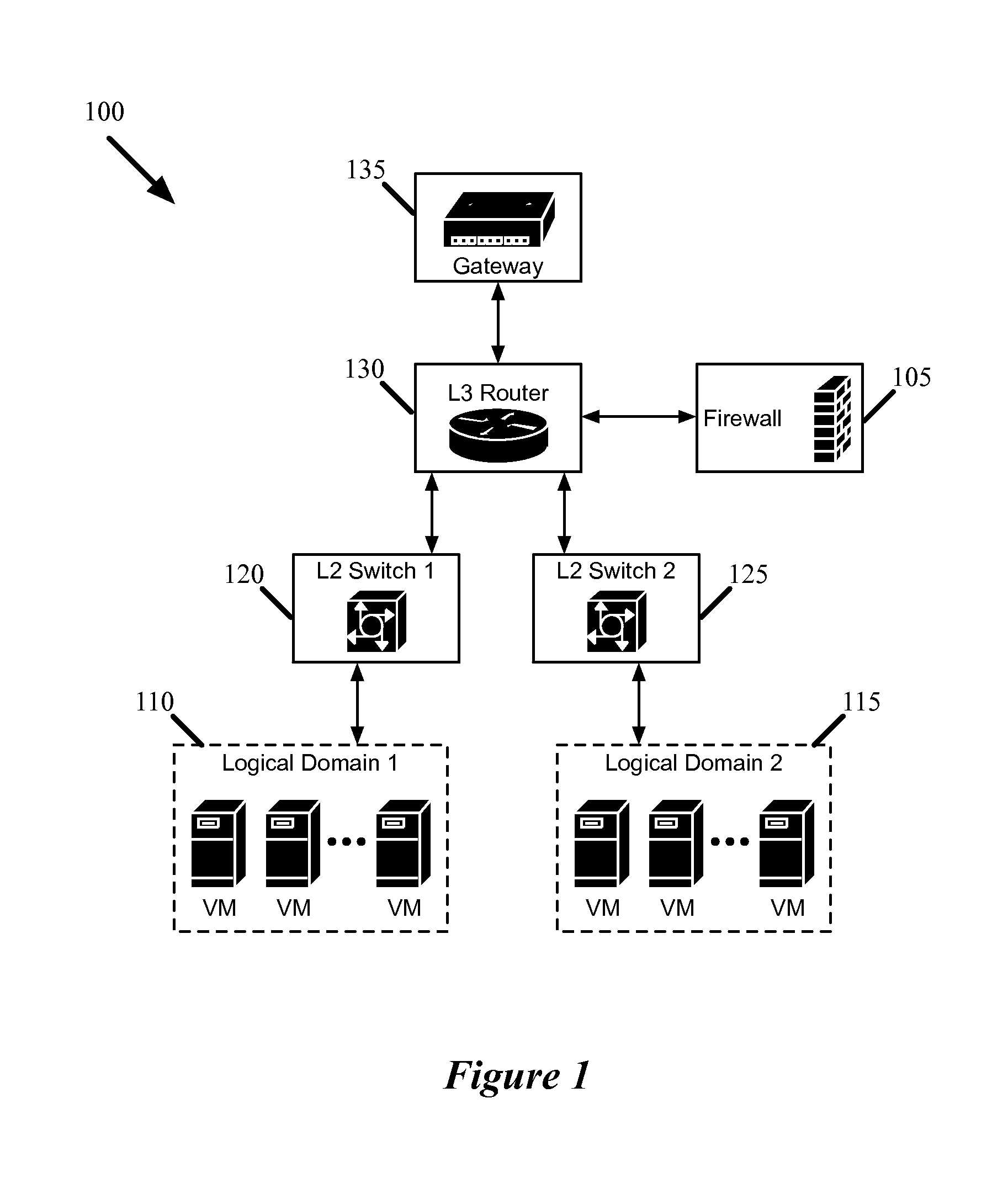
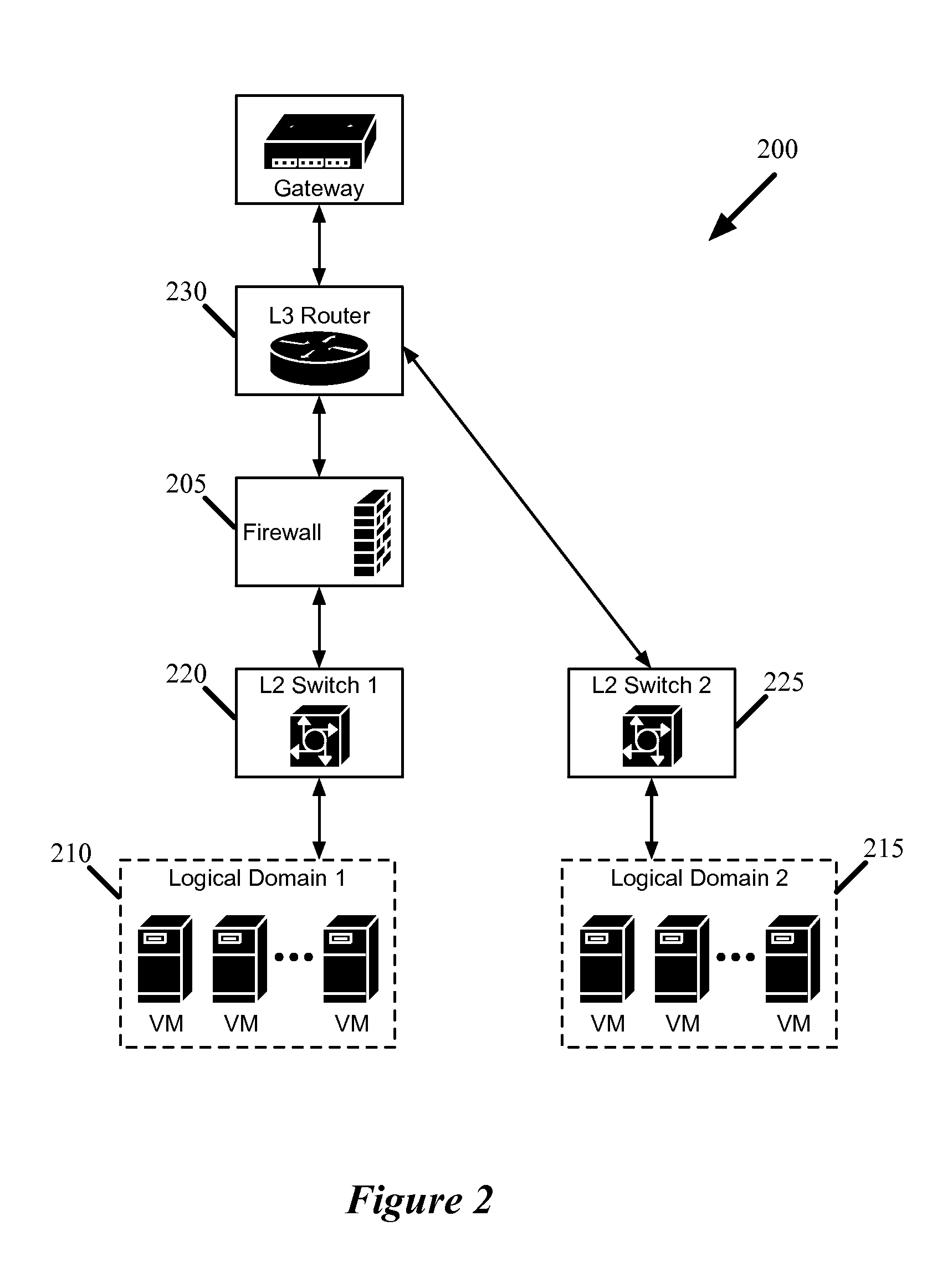
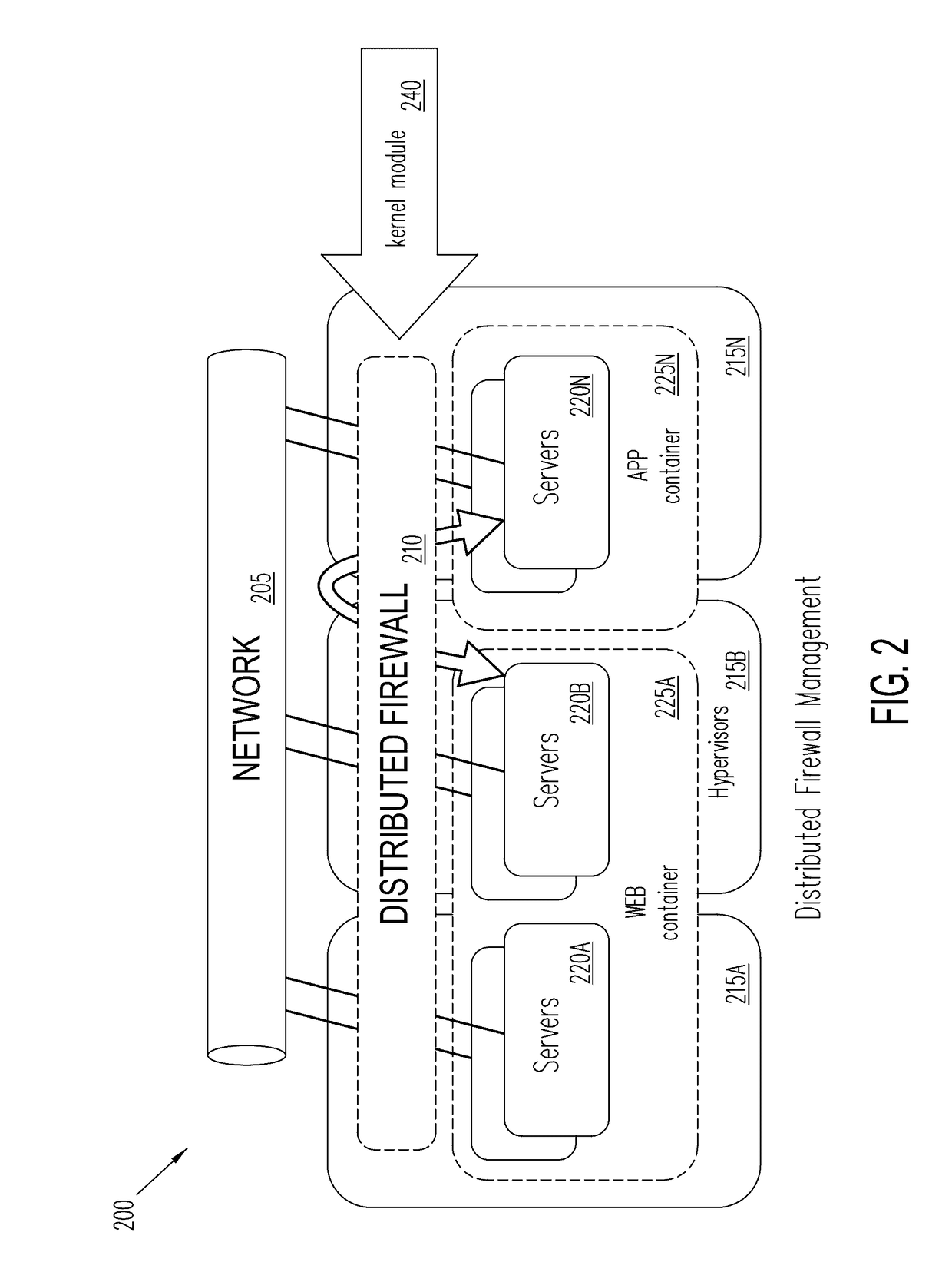
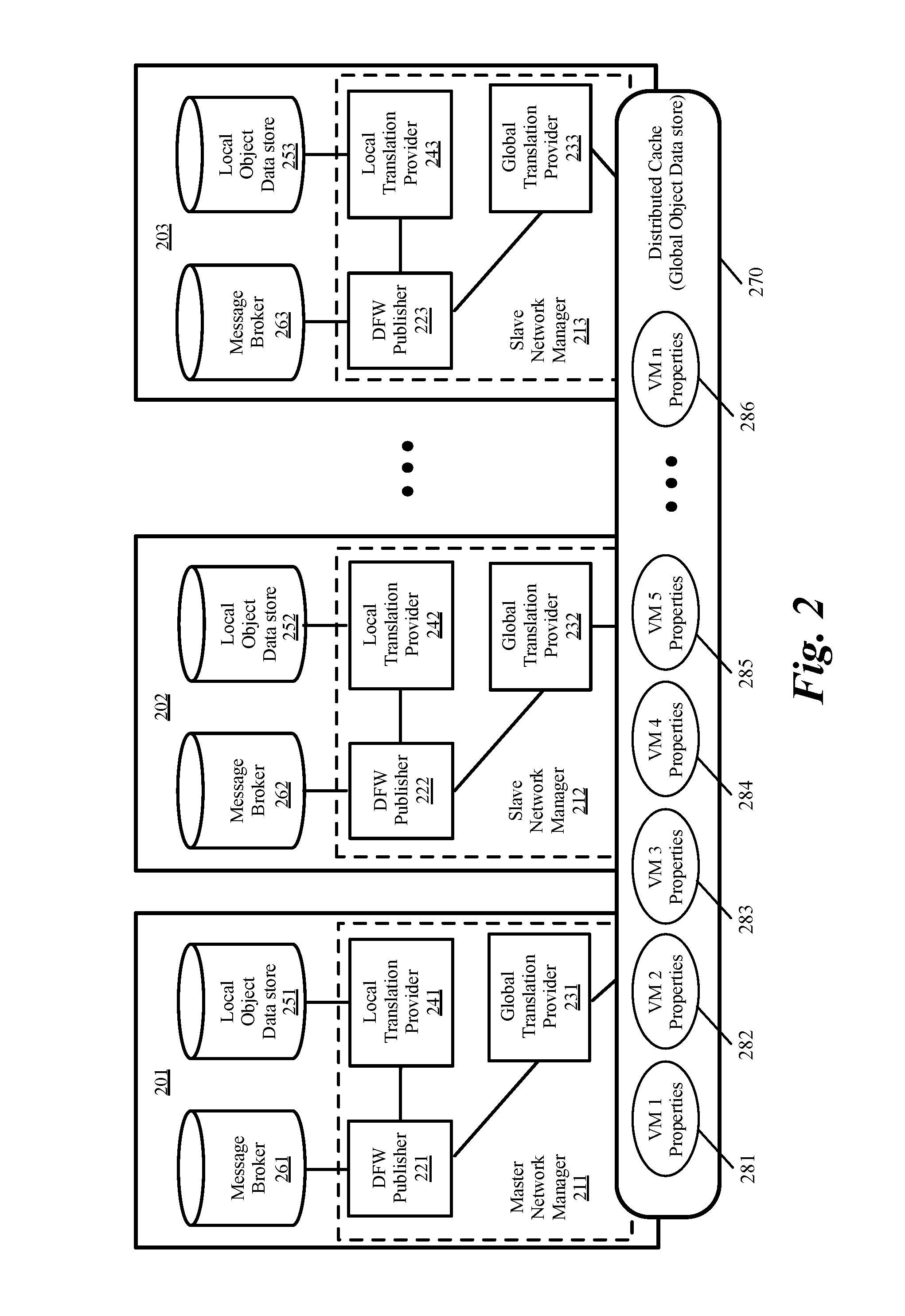
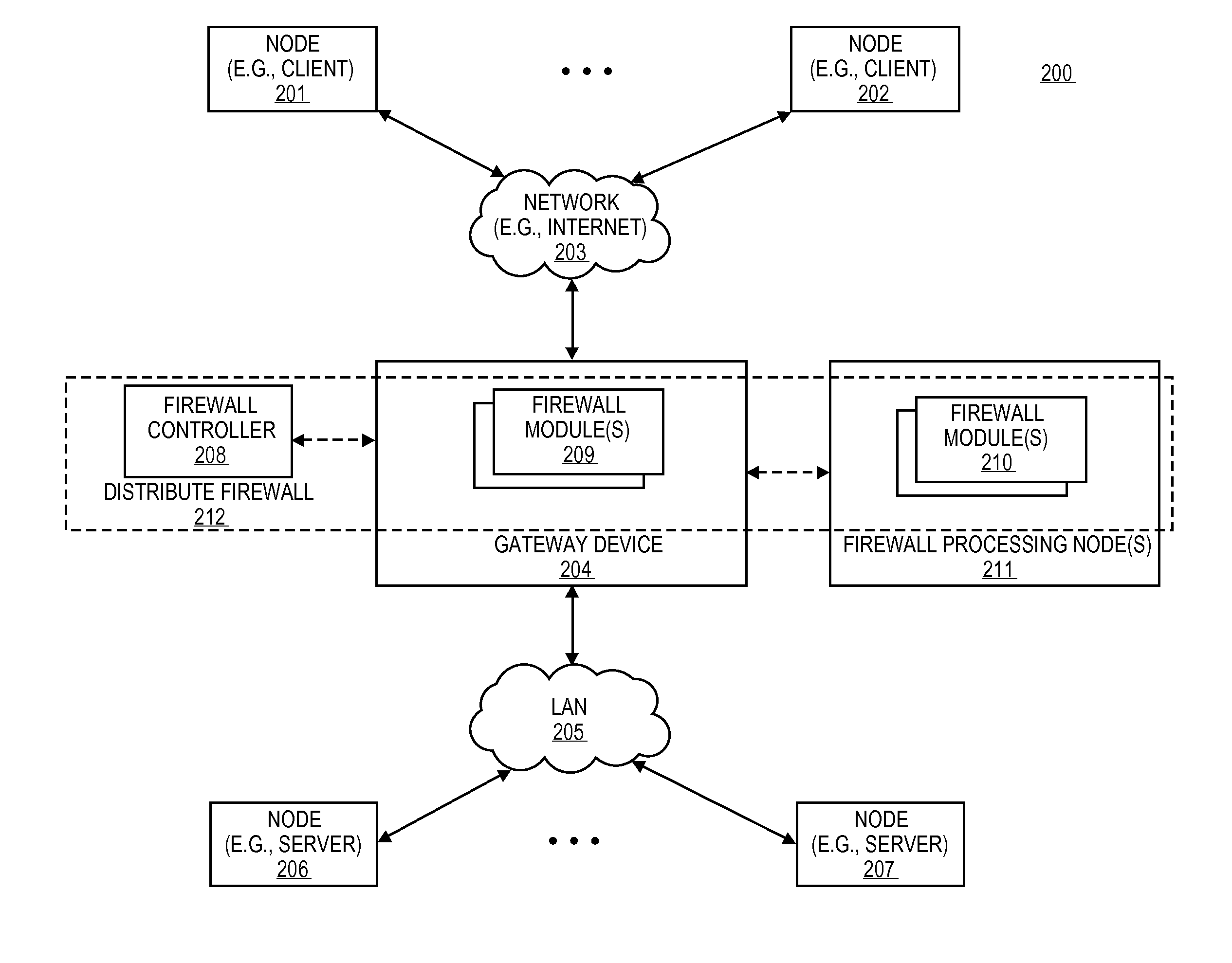
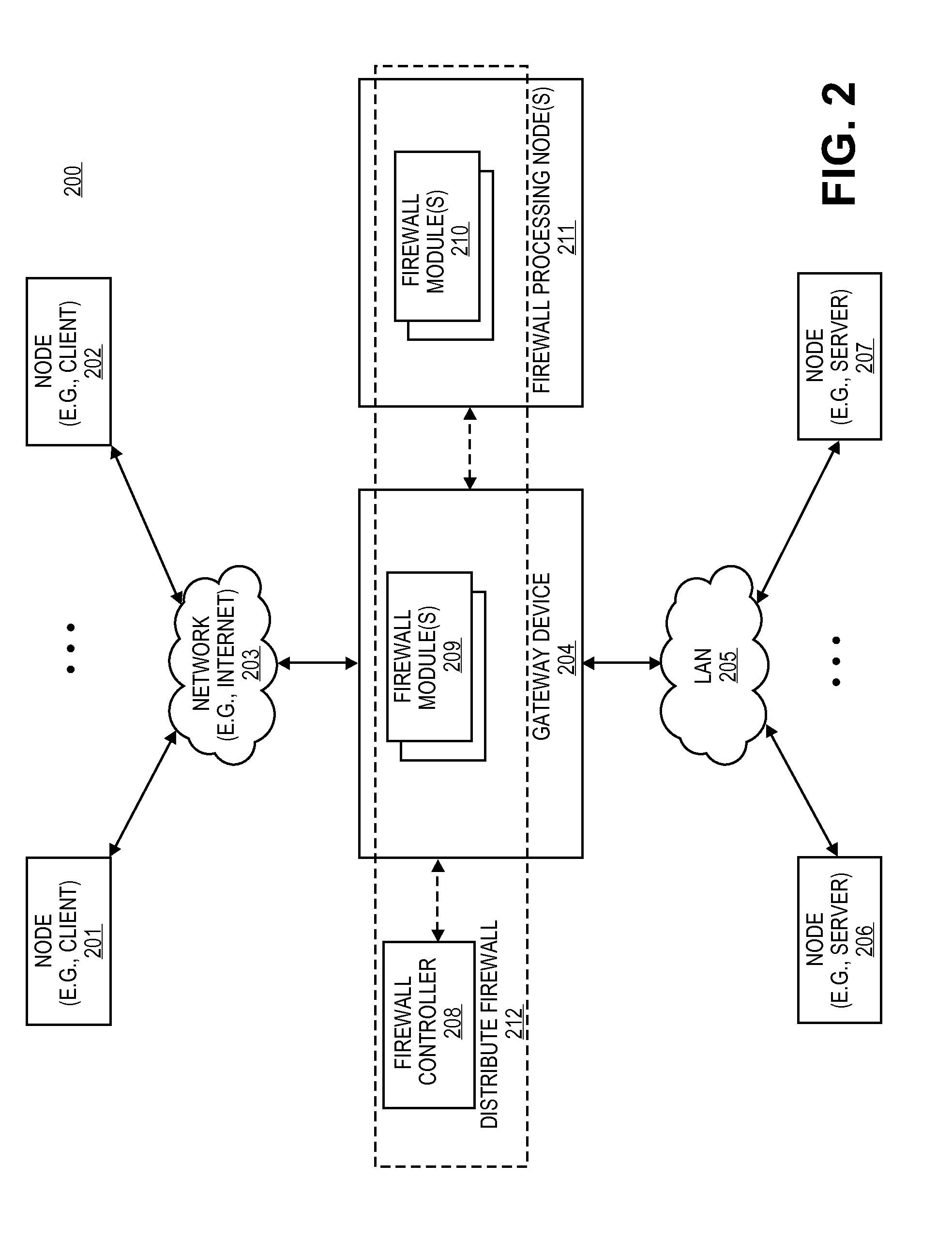
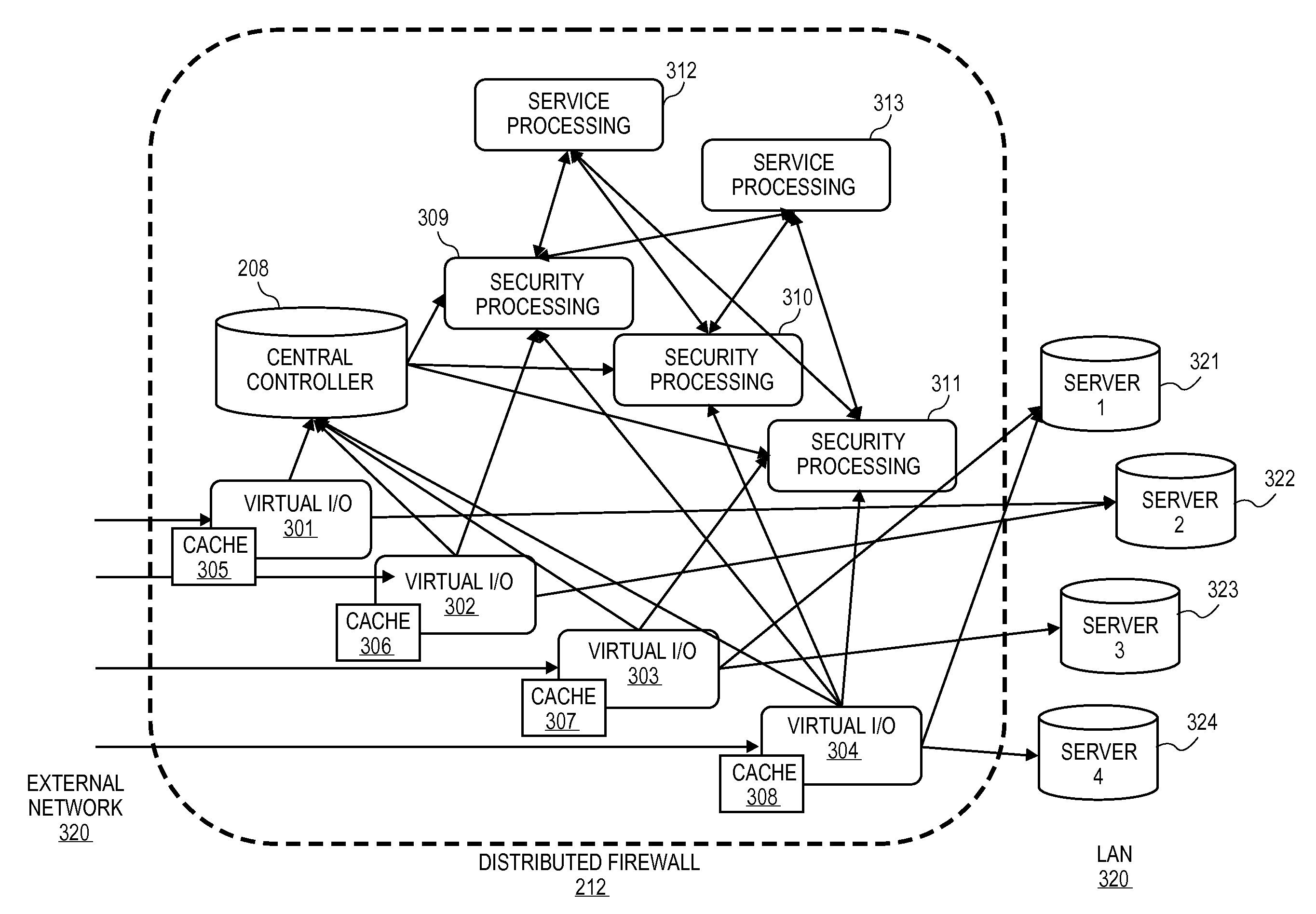
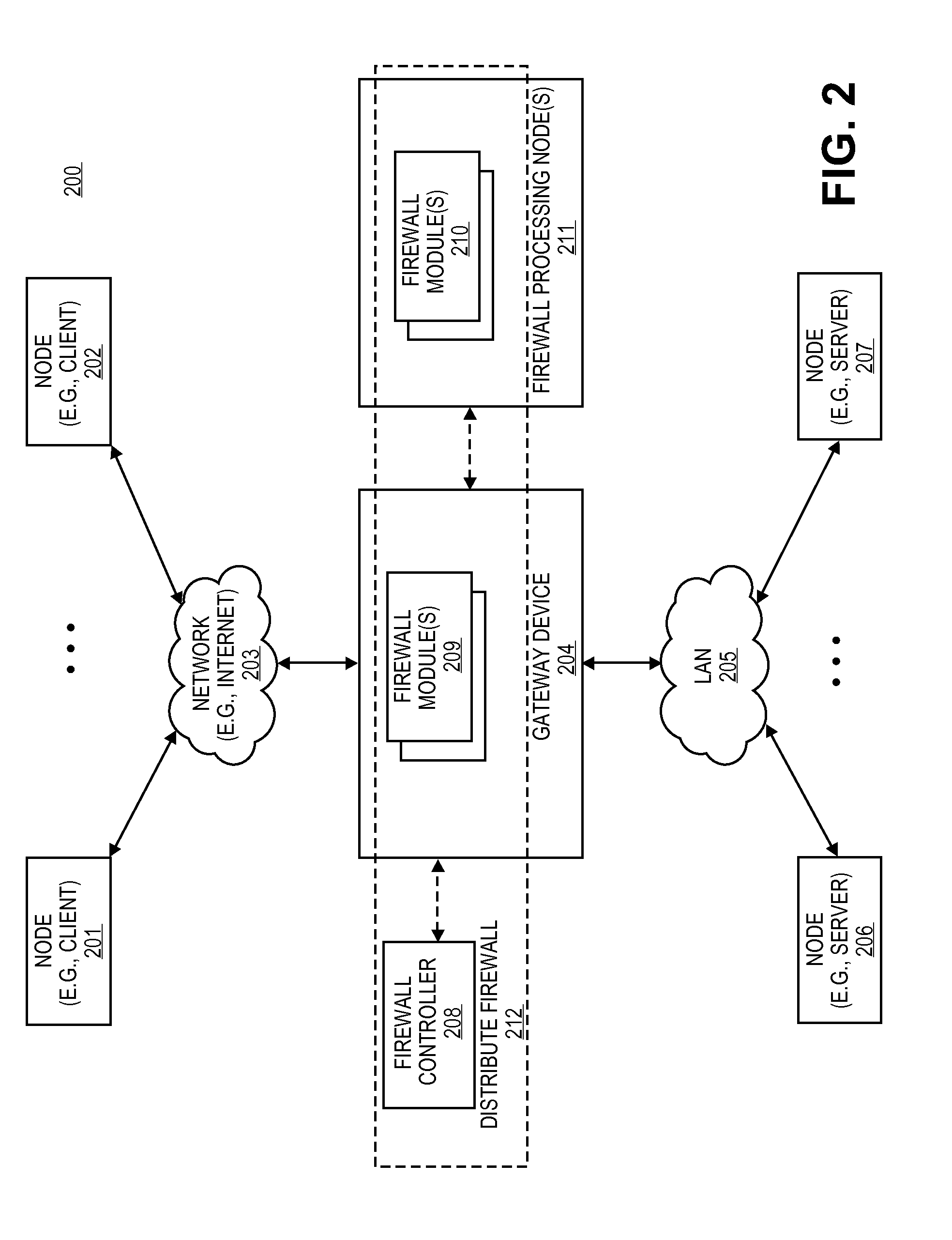
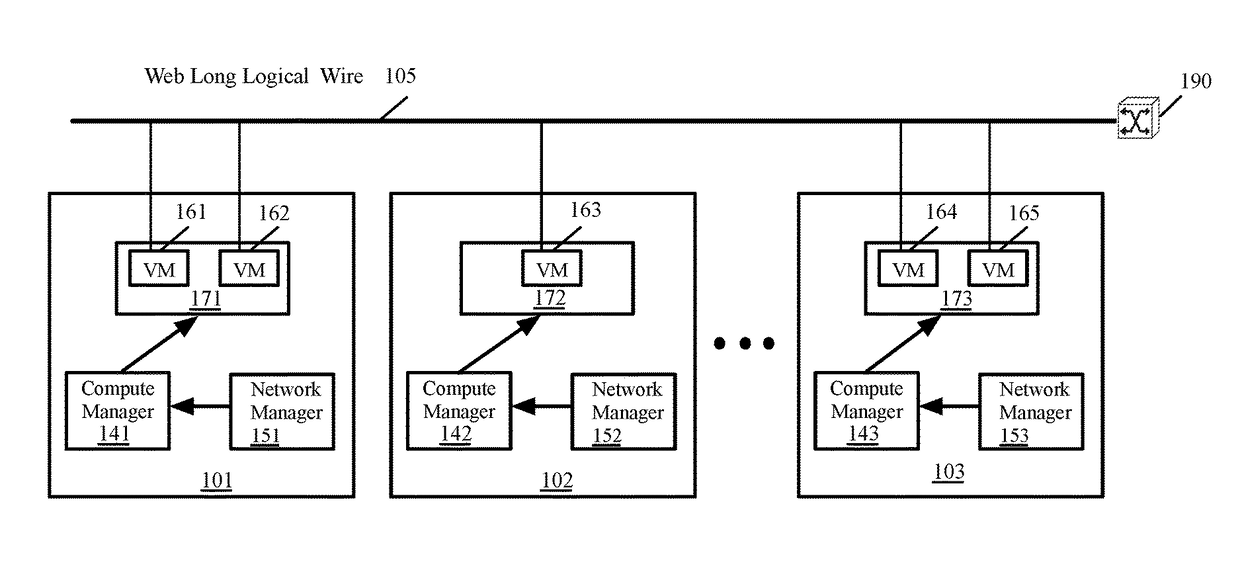
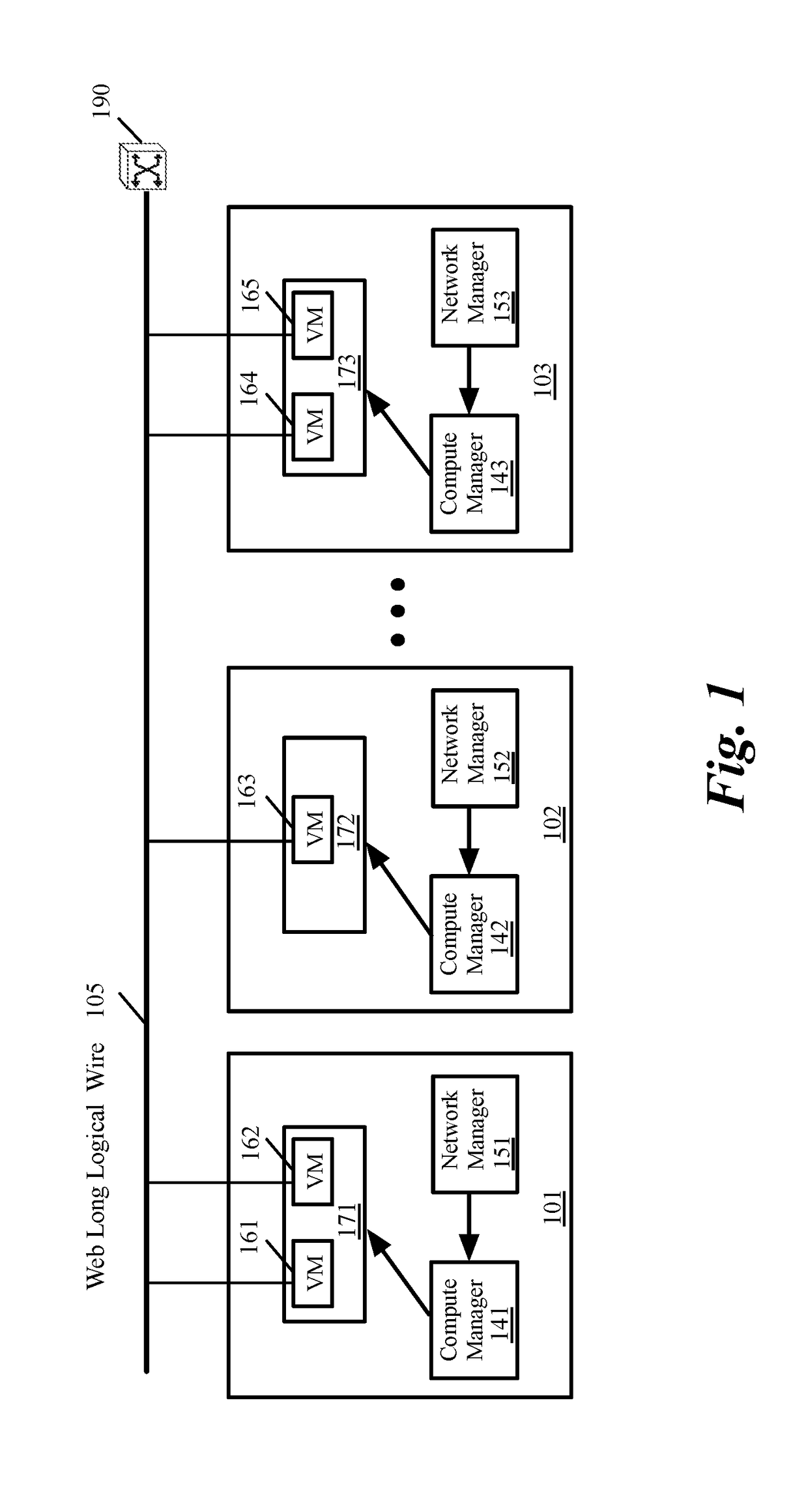
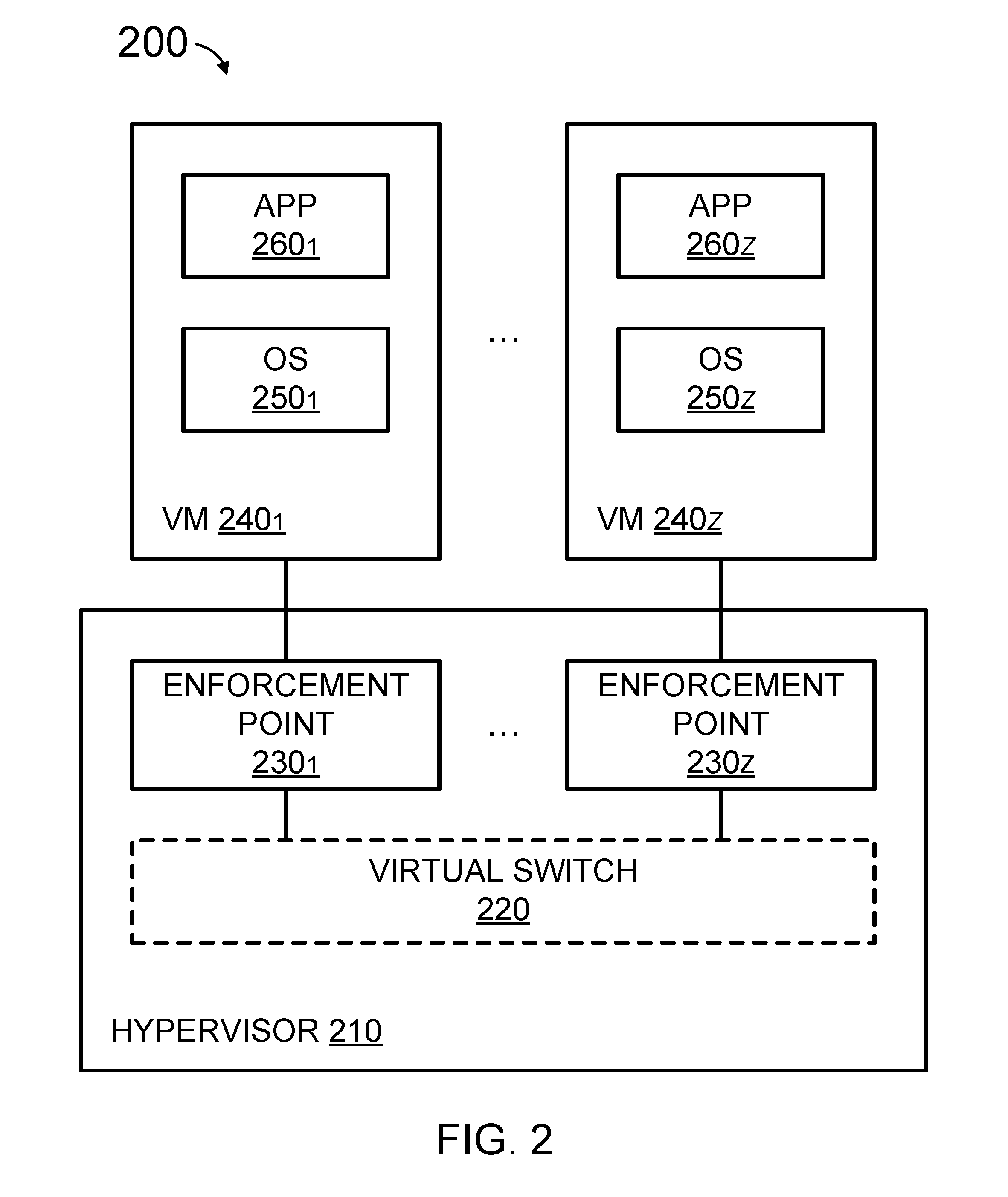
Distributed firewall architecture using virtual machines
ActiveUS20120210417A1Computer security arrangementsMultiple digital computer combinationsSafe handlingVirtual machine
A distributed firewall of a gateway device includes at least one IO module for performing IO functionality of the distributed firewall, at least one security processing module for performing security functionality of the distributed firewall and a firewall controller for managing the IO module and the security processing module. Each of the at least one IO and security processing modules is executed within a virtual machine. In response to a packet received from an ingress interface, the at least one IO module is to identify a security processing module corresponding to a connections session associated with the packet, to transmit the packet to the identified security processing module to perform a security process on the packet, and in response to a signal received from the identified security processing module indicating that the security process has been completed, to transmit the packet to the egress interface.
Owner:VARMOR NETWORKS
Distributed firewall security system that extends across different cloud computing networks
An application profile is provided to manage security of an application deployed across two or more cloud computing networks. A user can define in the application profile first and second server groups, a cloud chamber as including the first and second server groups, and a computing flow to the cloud chamber. A firewall rule is generated based on the computing flow. The firewall rule is distributed to the first server group of the cloud chamber. A copy of the firewall rule is distributed to the second server group of the cloud chamber. The first server group is in a first cloud computing network that is provided by a first cloud provider. The second server group is in a second cloud computing network that is provided by a second cloud provider, different from the first cloud provider.
Owner:ZENTERA SYST
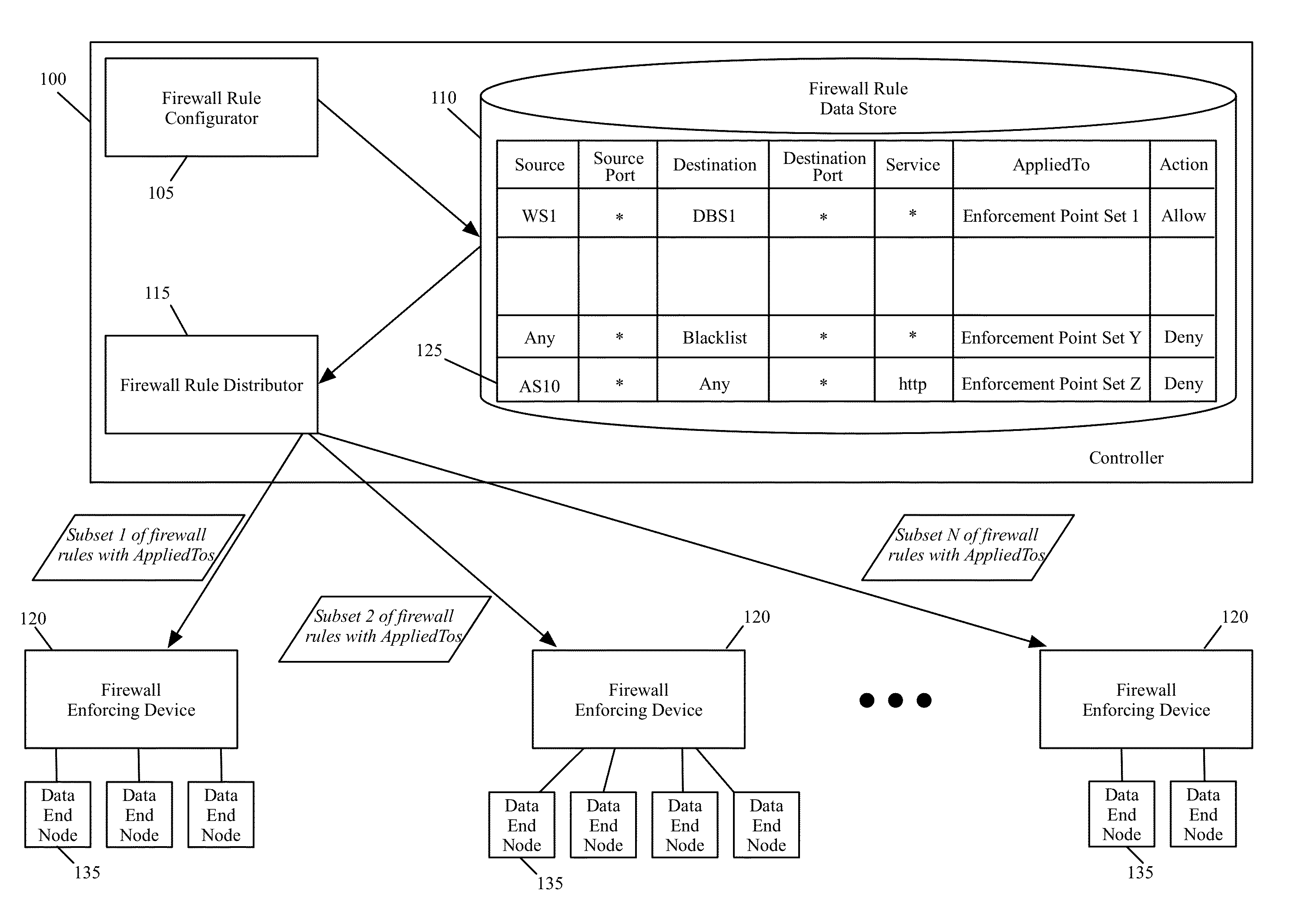
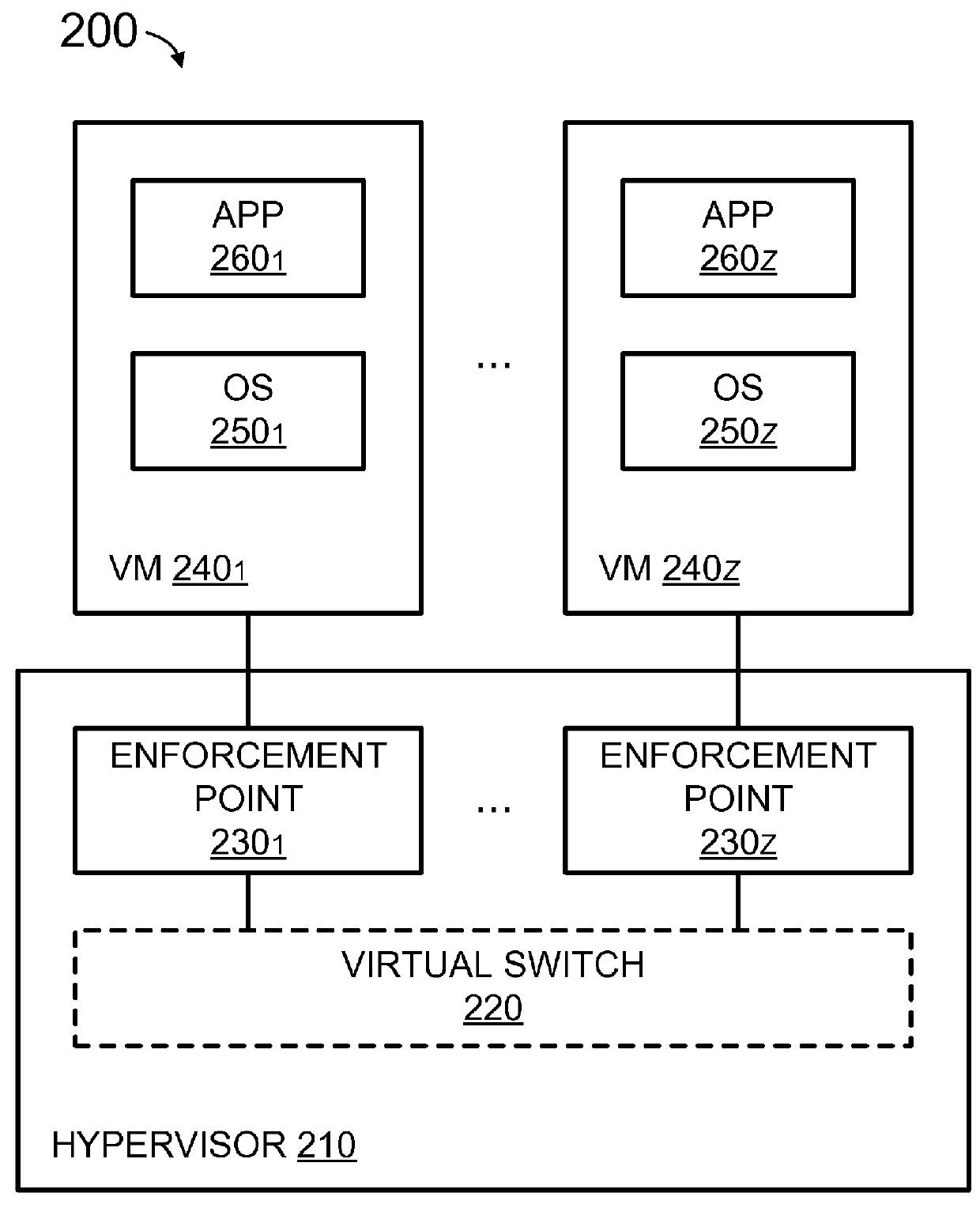
Method and apparatus for distributing firewall rules
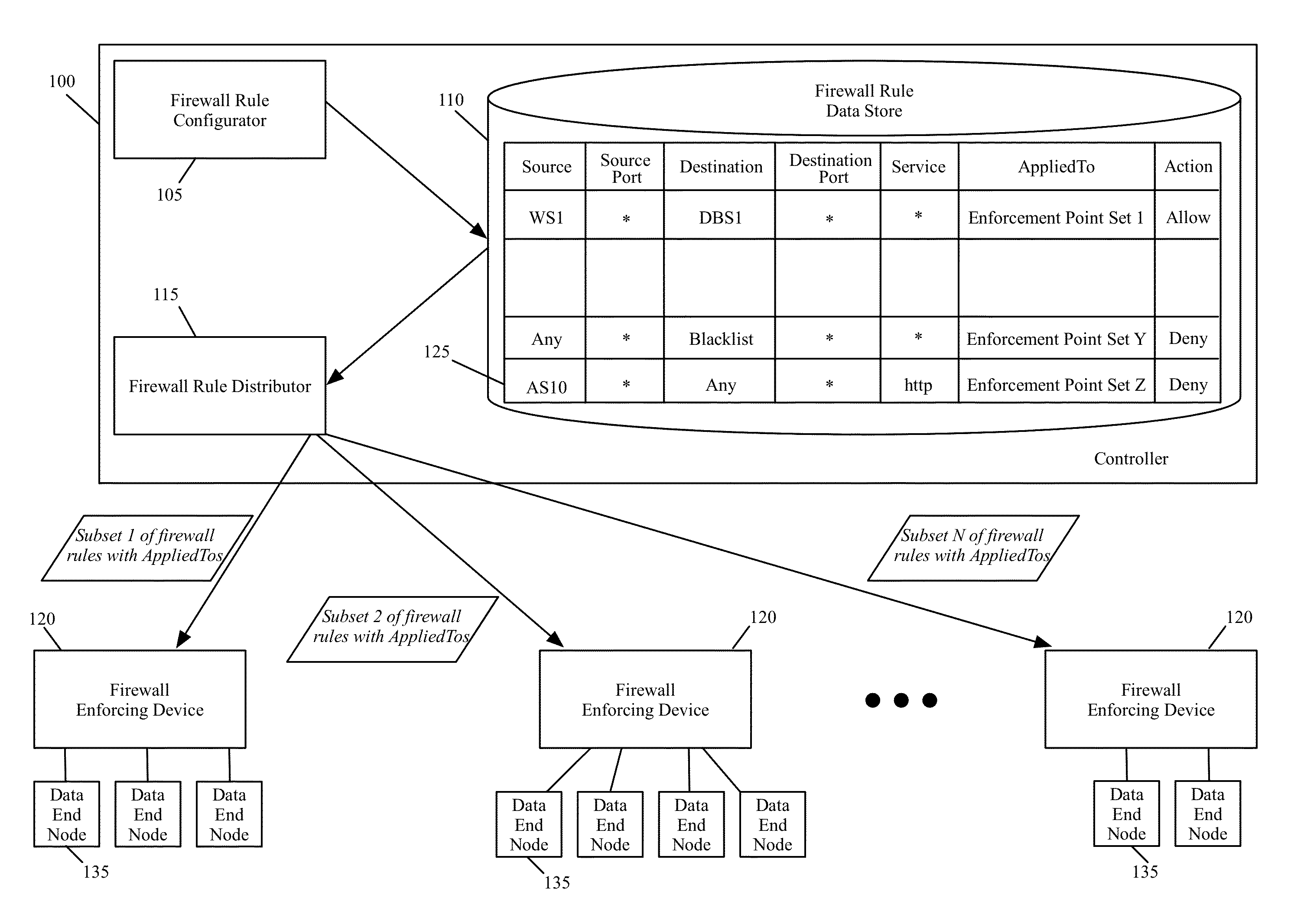
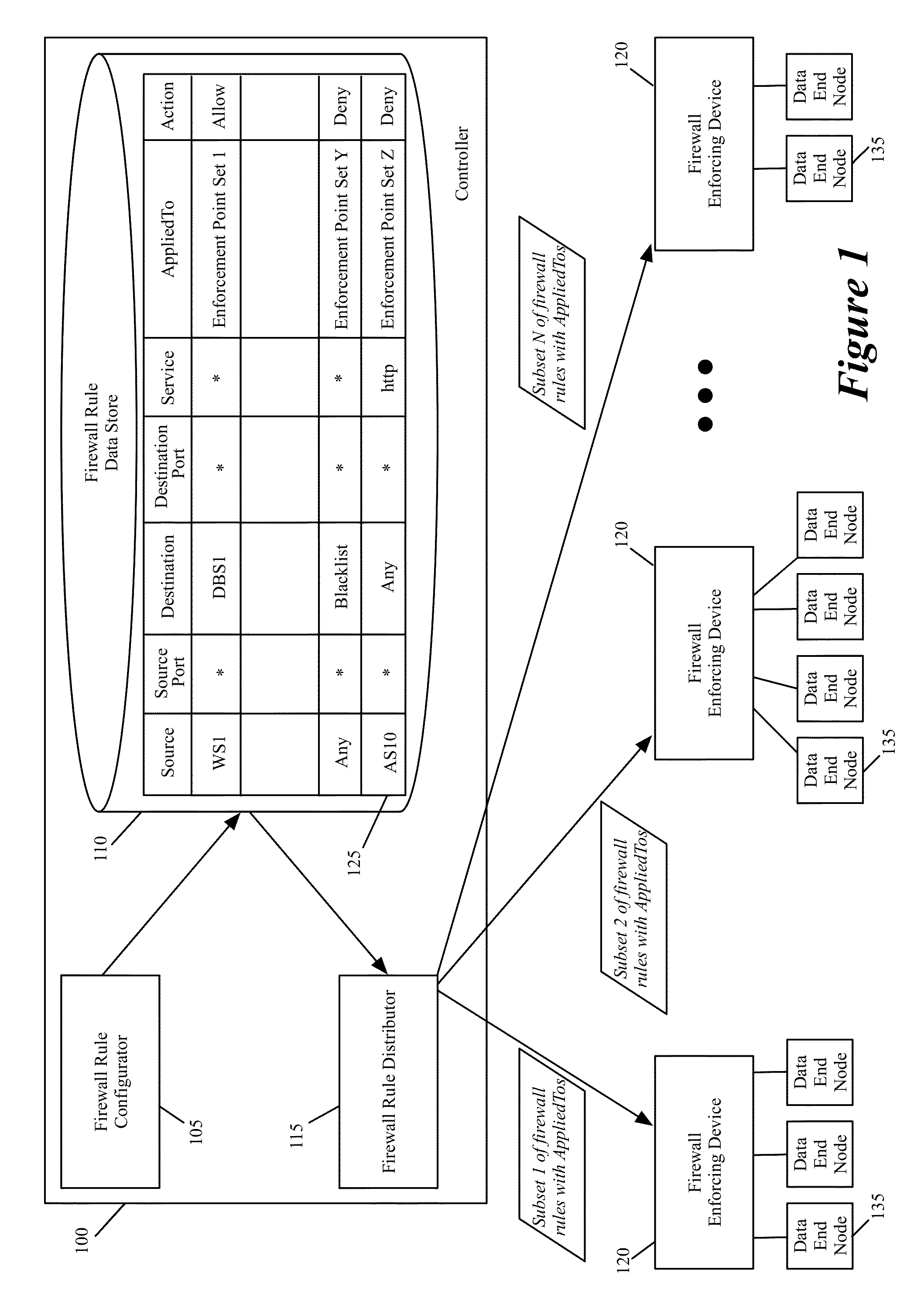
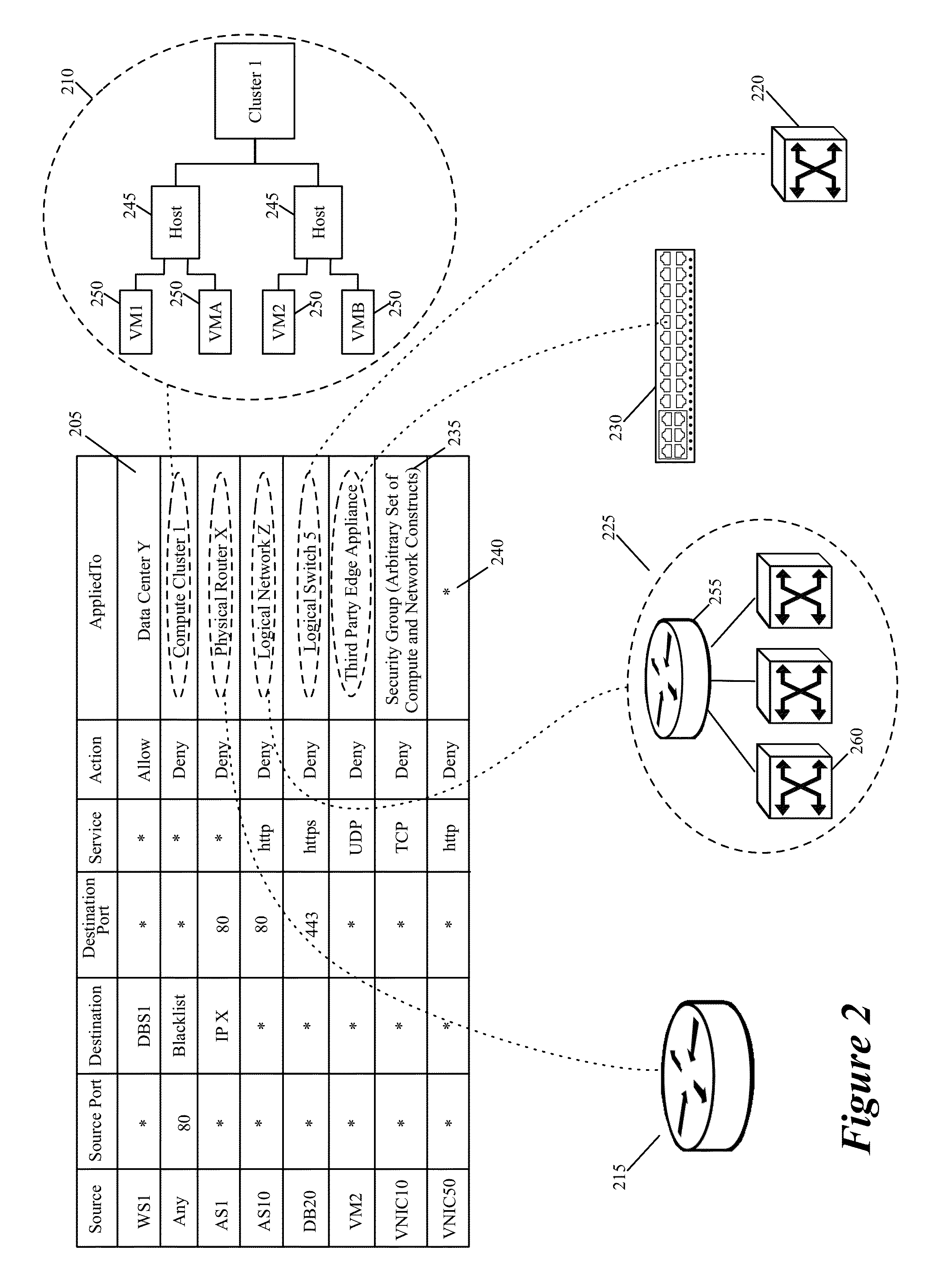
ActiveUS9215213B2Quick searchSmall sizeInternal/peripheral component protectionData switching networksComputer networkDistributed firewall
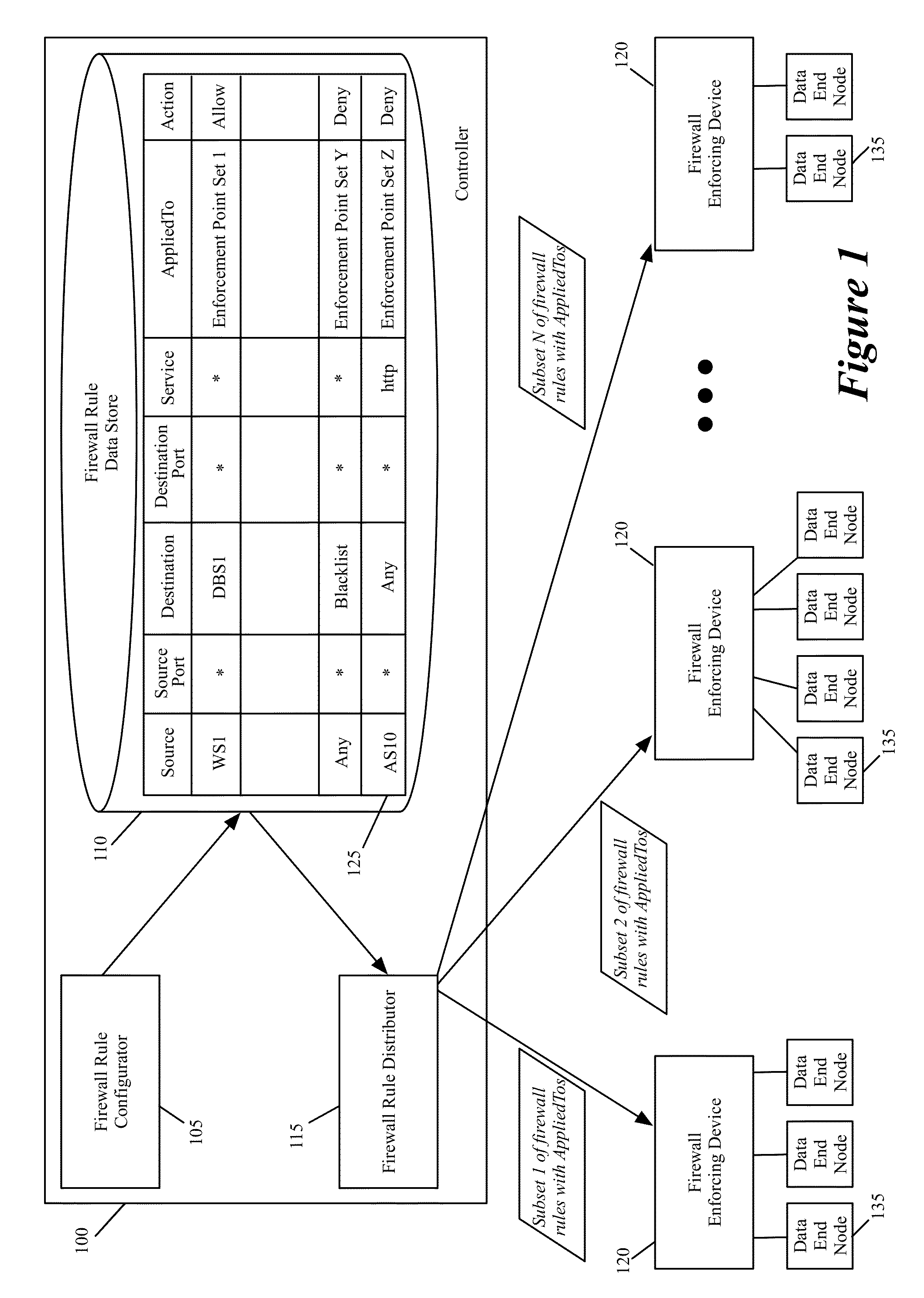
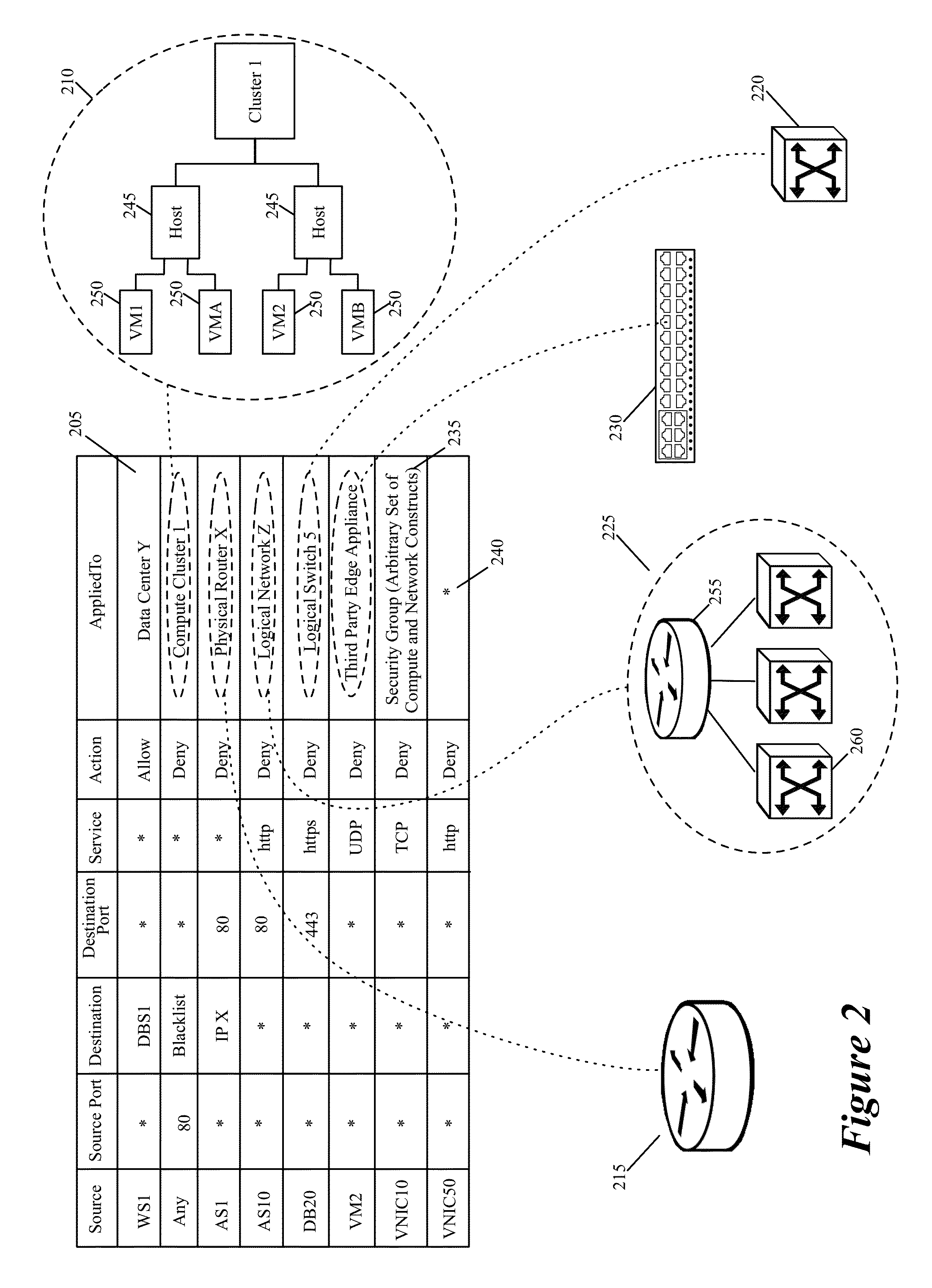
Some embodiments of the invention provide a novel method for specifying firewall rules. In some embodiments, the method provides the ability to specify for a particular firewall rule, a set of network nodes (also called a set of enforcement points below) at which the particular firewall should be enforced. To provide this ability, the method of some embodiments adds an extra tuple (referred to below as the AppliedTo tuple) to a firewall rule. This added AppliedTo tuple lists the set of enforcement points at which the firewall rule has to be applied (i.e., enforced).
Owner:NICIRA
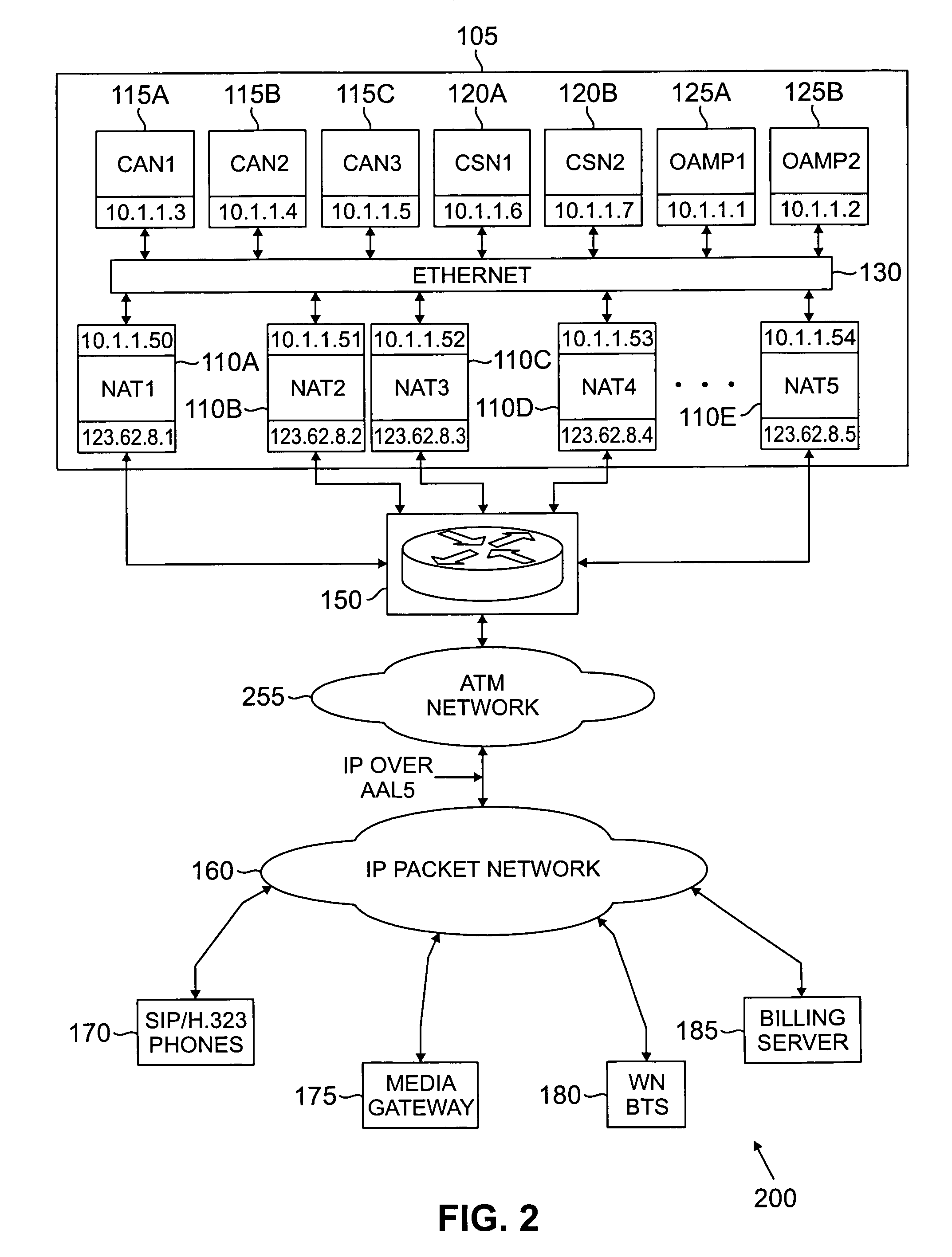
Soft switch using distributed firewalls for load sharing voice-over-IP traffic in an IP network
InactiveUS7072332B2Interconnection arrangementsData switching by path configurationVoice trafficVoice over IP
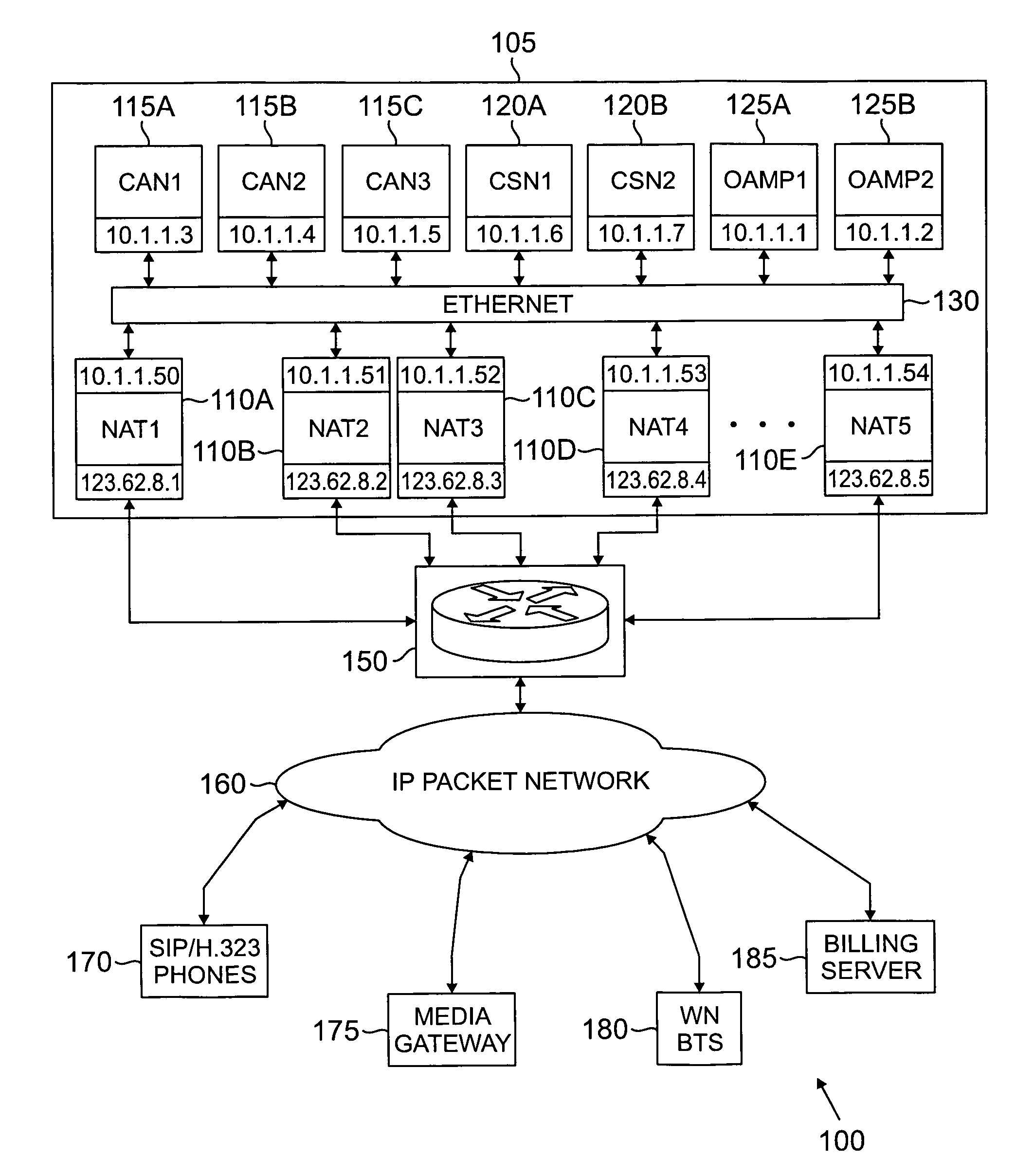
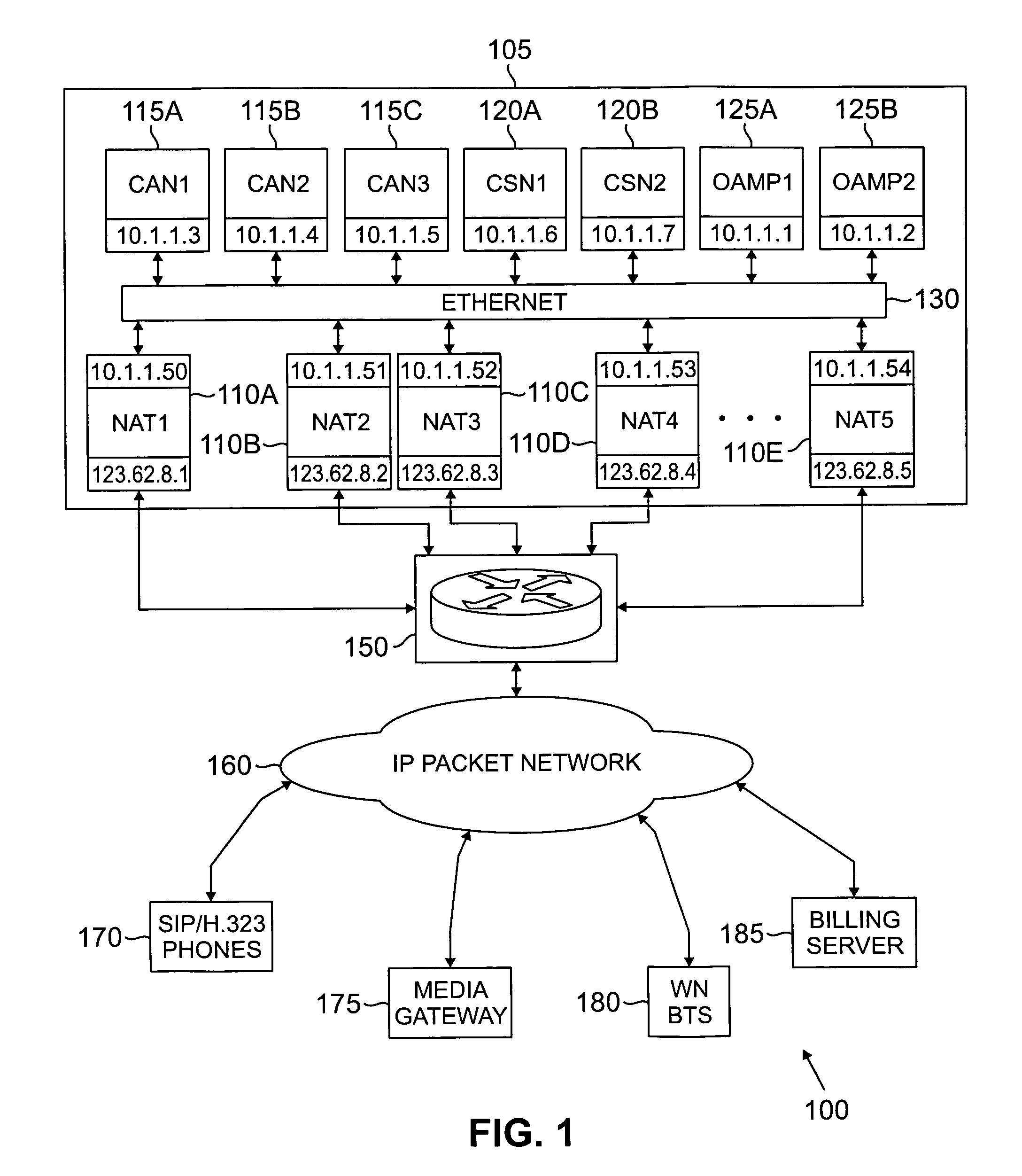
A switch capable of handling voice-over-IP (VoIP) traffic between calling devices and called devices. The switch comprises: 1) call application nodes for executing call process server applications, wherein a first call process server application and a similar second call process server application form a first load sharing group server application; and 2) network address translation nodes for executing firewall server applications. A first firewall server application executed on a first network address translation node is associated with a similar second firewall server application executed on a second network address translation nodes separate from the first network address translation node. The first and second firewall server applications form a second load sharing group server application. The second load sharing group server application receives VoIP traffic and selects one of the first and second firewall server applications to verify that the VoIP traffic is authorized to access at least one of the call process server applications in the call application nodes according to a load distribution algorithm.
Owner:SAMSUNG ELECTRONICS CO LTD
Distributed firewall architecture using virtual machines
ActiveUS8612744B2Computer security arrangementsMultiple digital computer combinationsVirtual machineSecurity function
A distributed firewall of a gateway device includes at least one IO module for performing IO functionality of the distributed firewall, at least one security processing module for performing security functionality of the distributed firewall and a firewall controller for managing the IO module and the security processing module. Each of the at least one IO and security processing modules is executed within a virtual machine. In response to a packet received from an ingress interface, the at least one IO module is to identify a security processing module corresponding to a connections session associated with the packet, to transmit the packet to the identified security processing module to perform a security process on the packet, and in response to a signal received from the identified security processing module indicating that the security process has been completed, to transmit the packet to the egress interface.
Owner:VARMOR NETWORKS
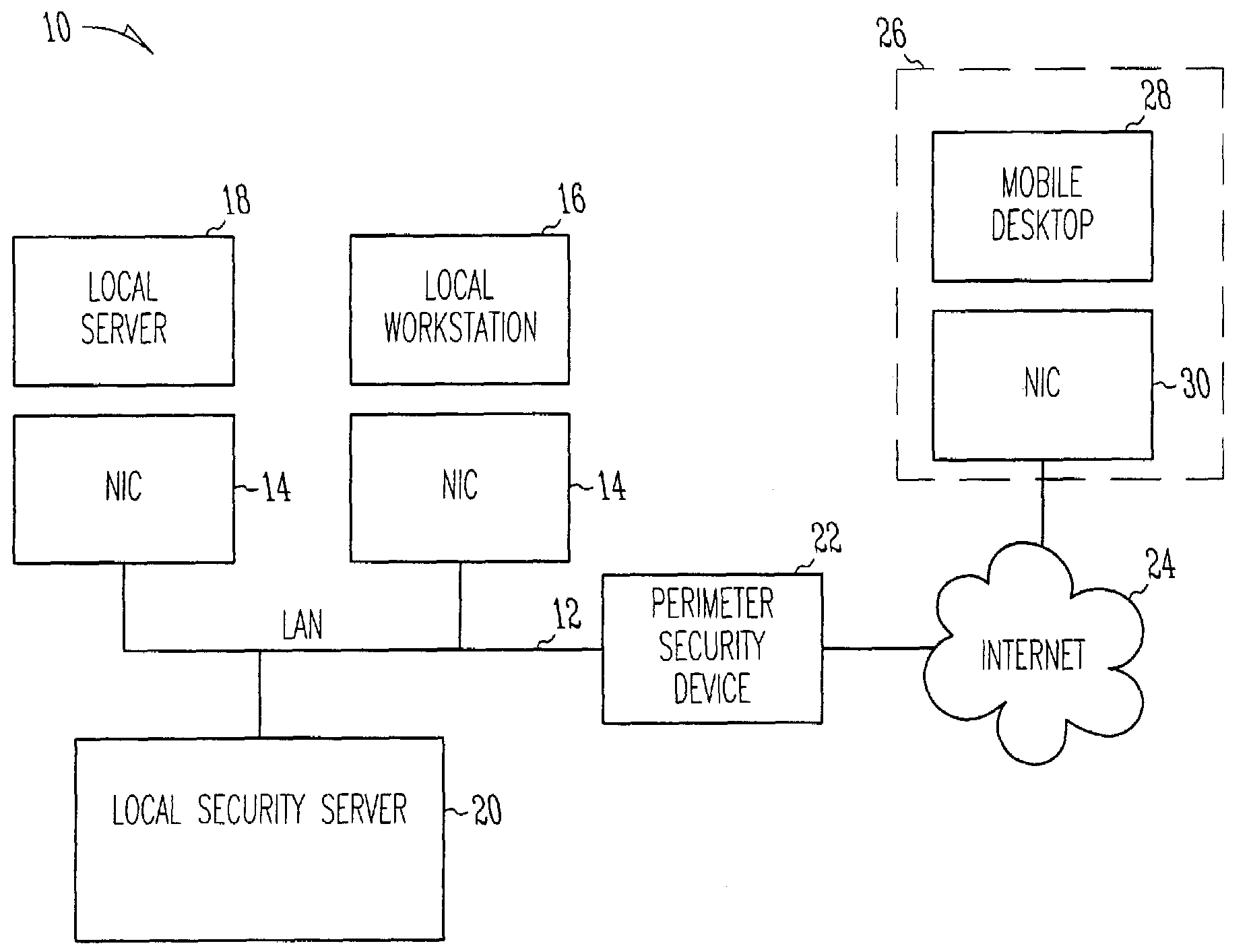
Storage area network system using internet protocol, security system, security management program and storage device
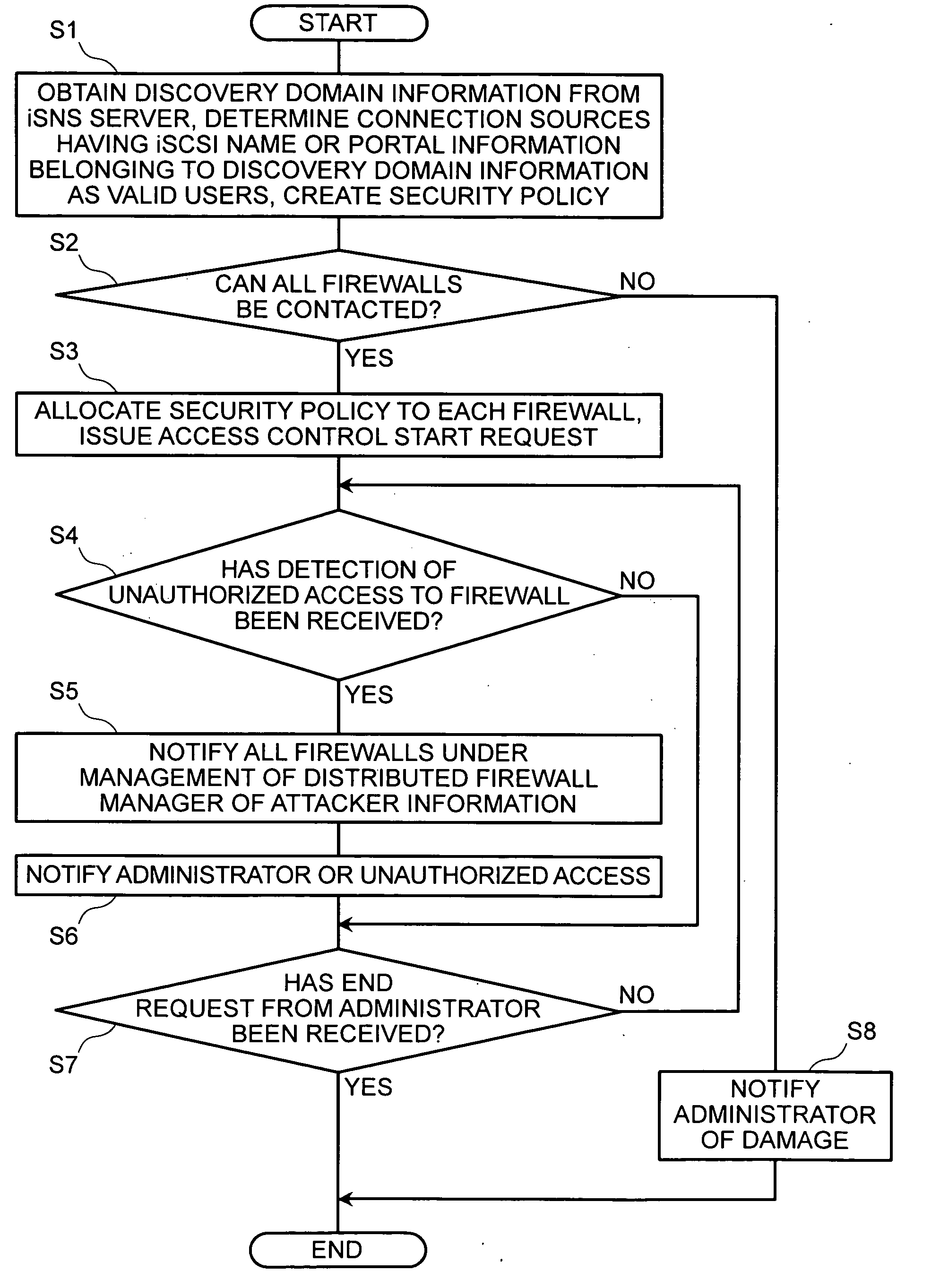
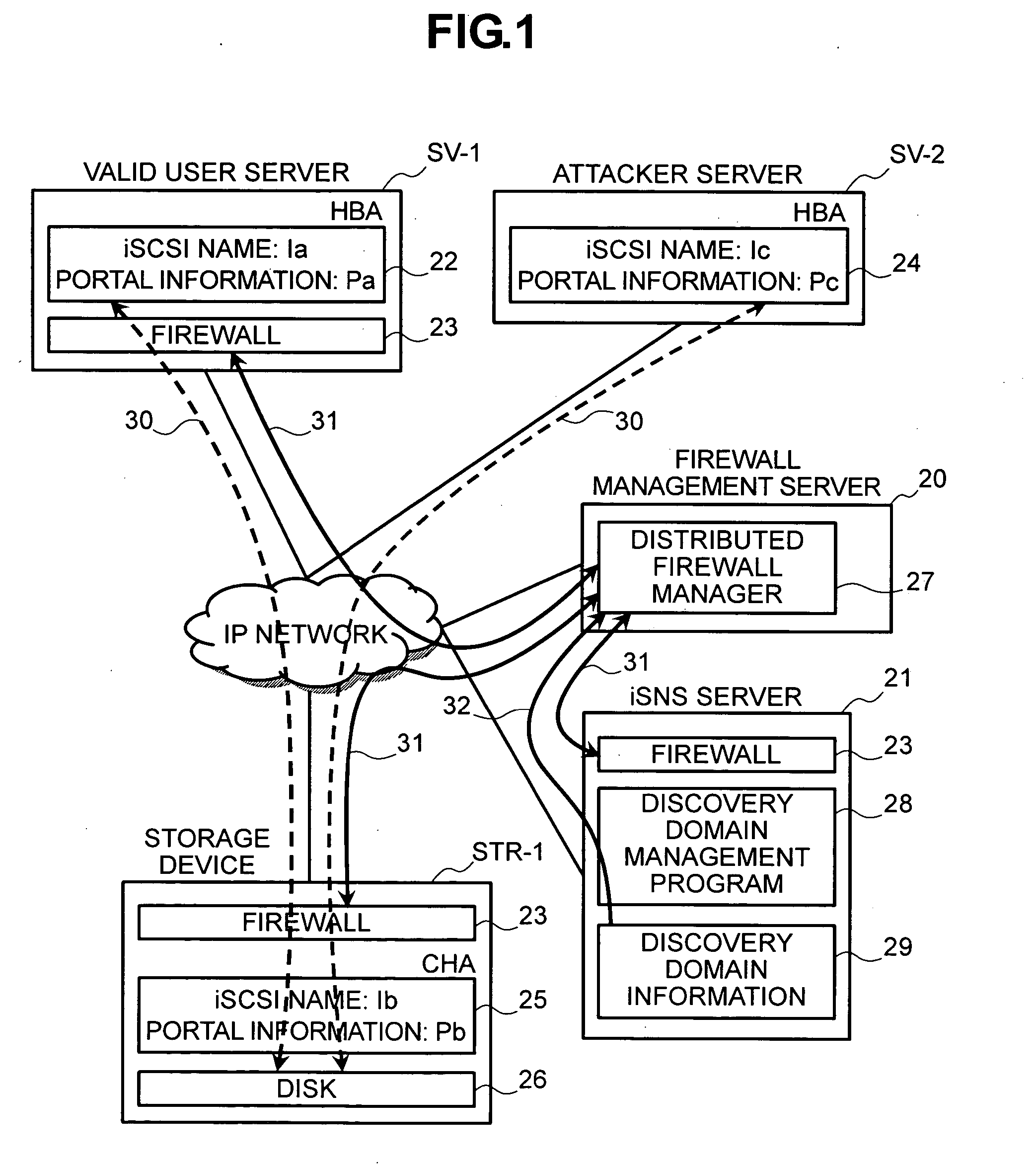
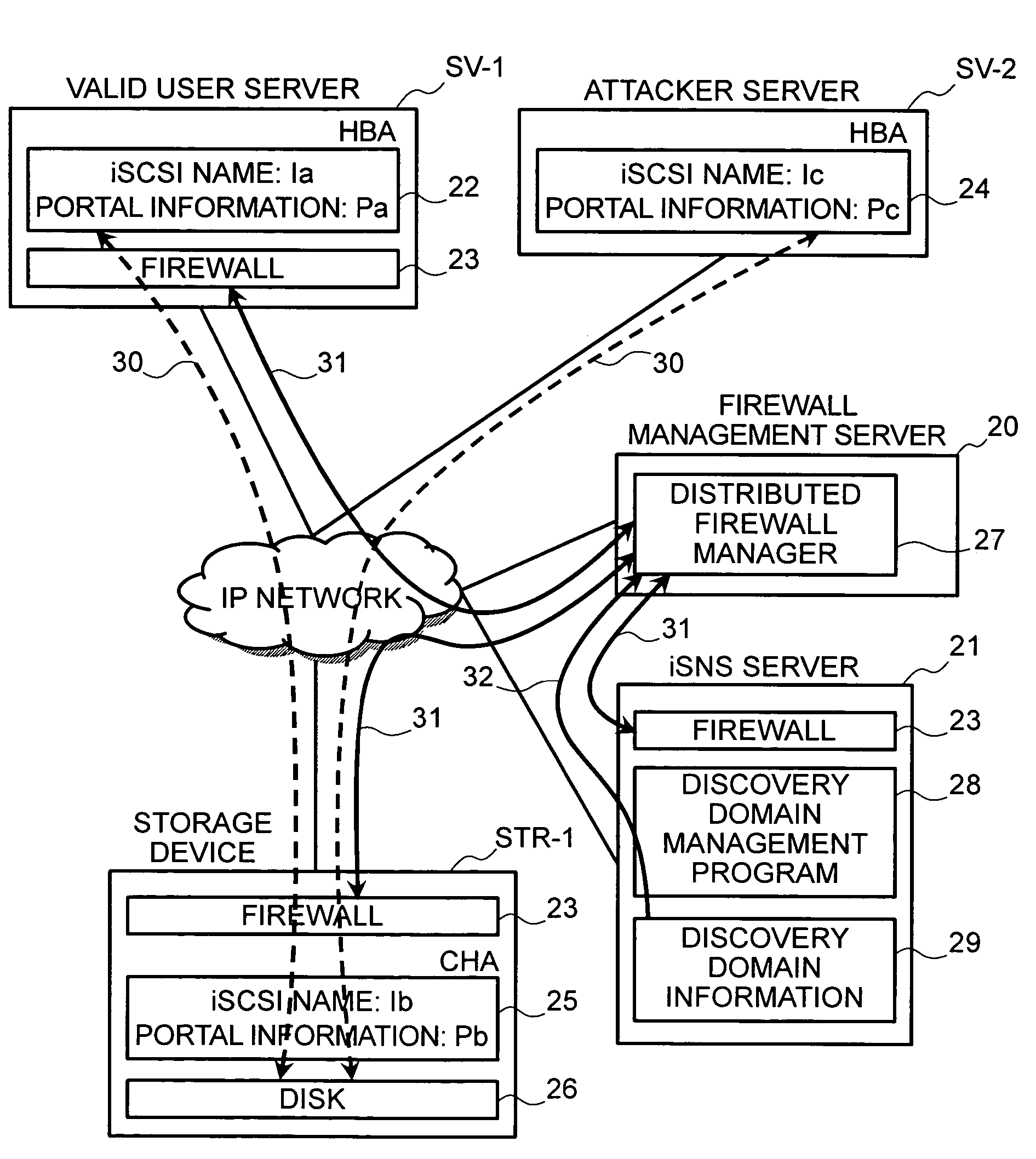
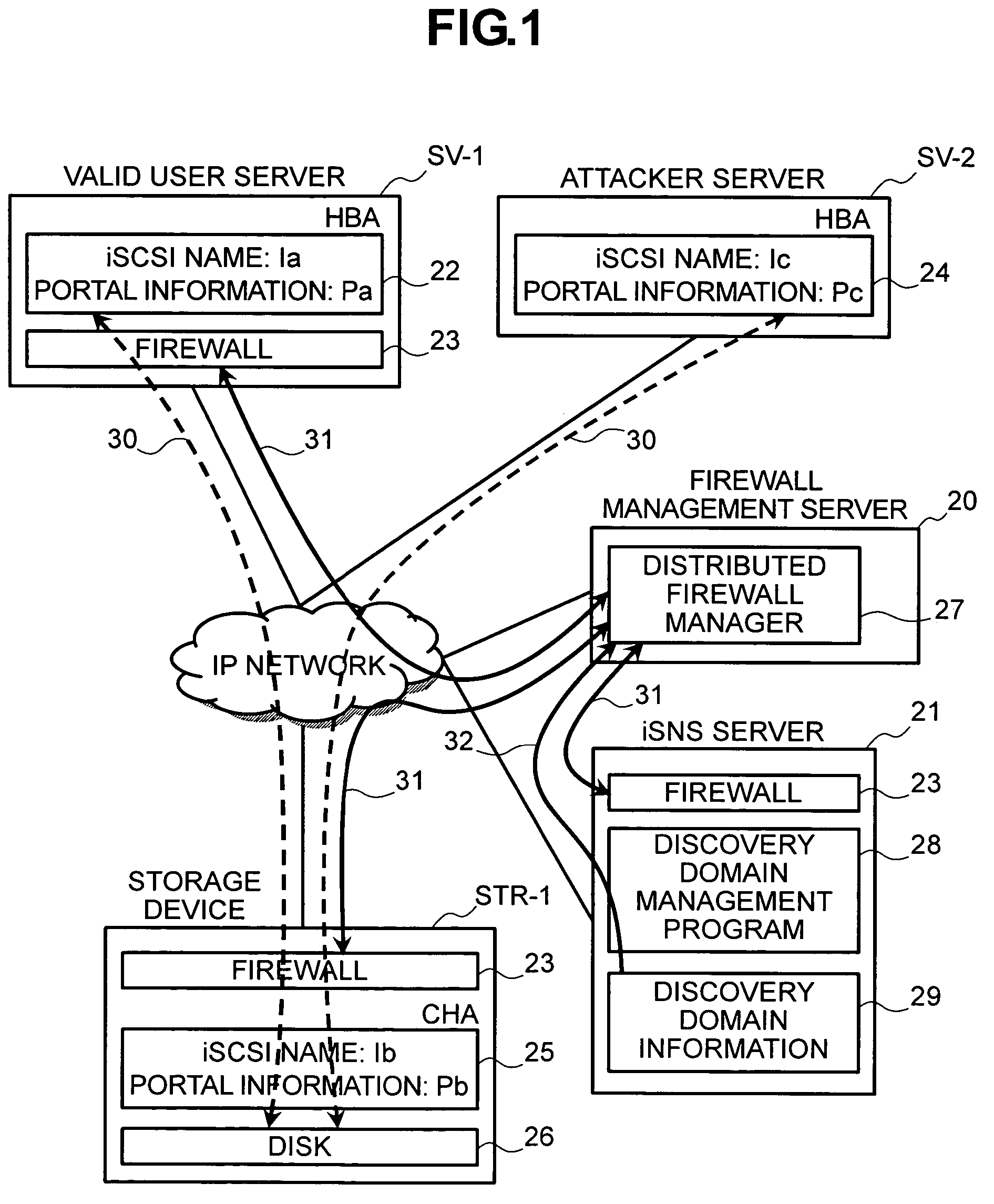
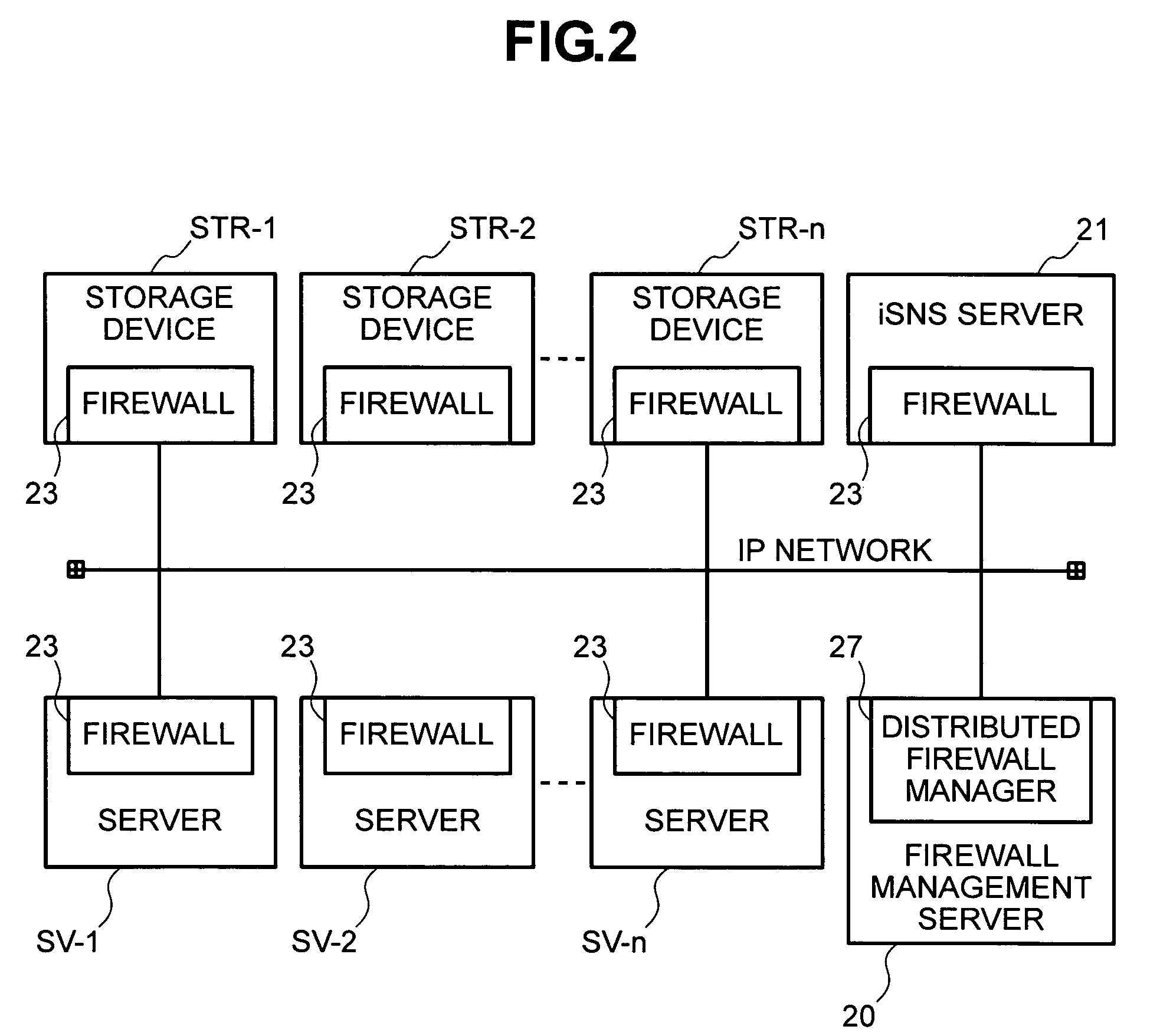
InactiveUS20050210291A1Input/output to record carriersDigital data processing detailsStorage area networkSecurity policy
In order to remove security vulnerability in an IP-SAN and eliminate unauthorized access by spoofing firewalls are installed in valid user servers and storage devices, and a distributed firewall manager for managing the firewalls integrally is provided in the IP-SAN. The distributed firewall manager obtains discovery domain information from an iSNS server, determines nodes registered in the iSNS server as the nodes of valid users, and autocreates a security policy according to sets consisting of an iSCSI name and portal information. This security policy is distributed to all of the firewalls as a common policy, whereupon access control is executed to deny TCP connection requests from unauthorized access sources.
Owner:GOOGLE LLC
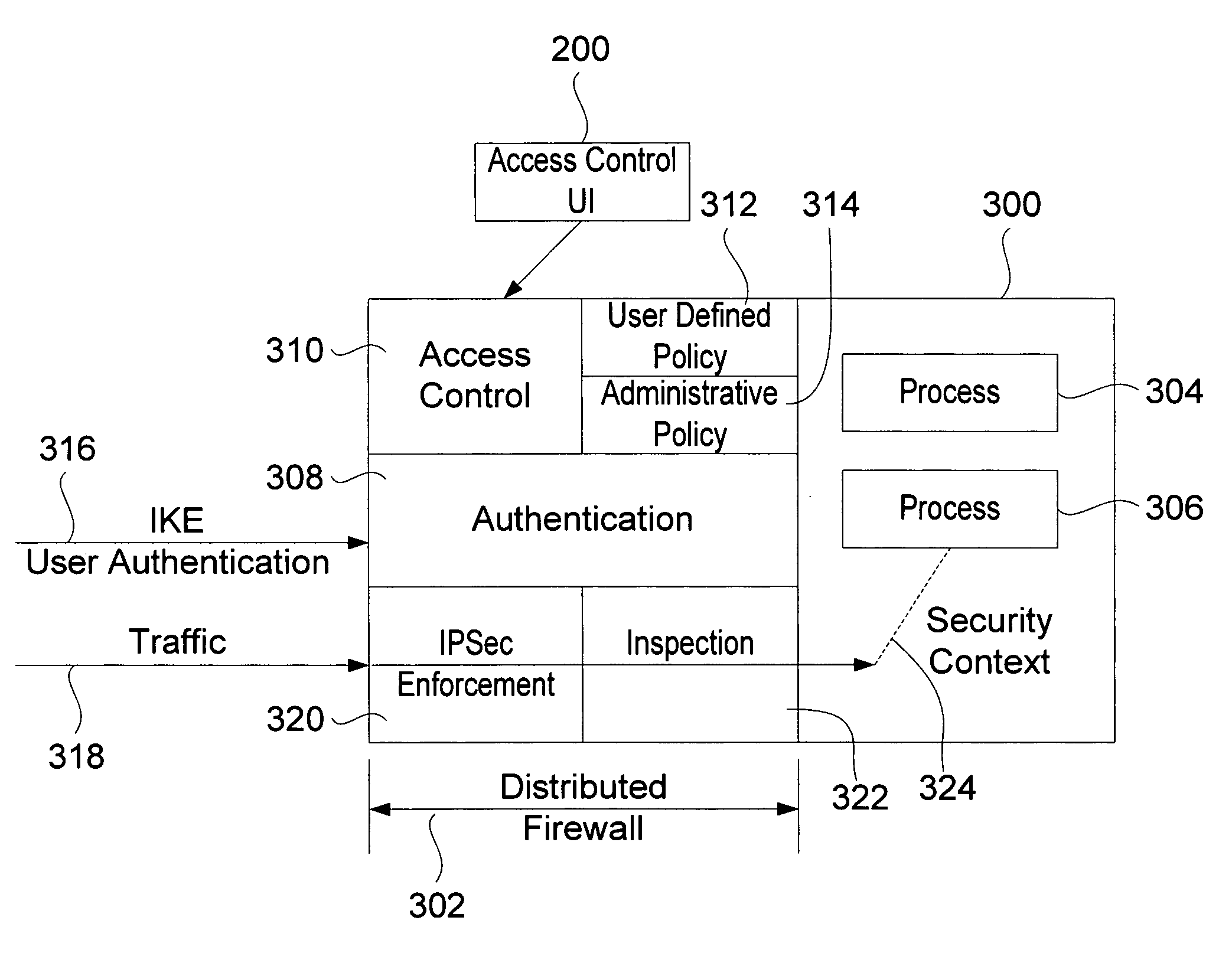
Method for providing user authentication/authorization and distributed firewall utilizing same
InactiveUS20060015935A1Multiple digital computer combinationsProgram controlKey exchangeThe Internet
The distributed firewall performs user authentication at a first level to establish a user security context for traffic from that user, and an authority context provides authorization for subsequent traffic. This authority context may be based on an underlying policy for particular types of traffic, access to particular applications, etc. Additionally, the system includes the ability to allow a user / process / application to define its own access control. The linking of the user security context from the traffic to the application is accomplished by enabling IPSec on a socket and forcing the socket to be bound in exclusive mode. The most common policy definitions may be included by default. Extensions of the Internet key exchange protocol (IKE) to provide the desired user authentication plus application / purpose are also provided. The architecture includes pluggable authorization module(s) that are called after IKE has successfully authenticated the peer, but before the connection is allowed to complete.
Owner:MICROSOFT TECH LICENSING LLC
Global object definition and management for distributed firewalls
ActiveUS20170104720A1Memory architecture accessing/allocationDatabase management systemsComputer networkObject definition
A method of defining distributed firewall rules in a group of datacenters is provided. Each datacenter includes a group of data compute nodes (DCNs). The method sends a set of security tags from a particular datacenter to other datacenters. The method, at each datacenter, associates a unique identifier of one or more DCNs of the datacenter to each security tag. The method associates one or more security tags to each of a set of security group at the particular datacenter and defines a set of distributed firewall rules at the particular datacenter based on the security tags. The method sends the set of distributed firewall rules from the particular datacenter to other datacenters. The method, at each datacenter, translates the firewall rules by mapping the unique identifier of each DCN in a distributed firewall rule to a corresponding static address associated with the DCN.
Owner:NICIRA
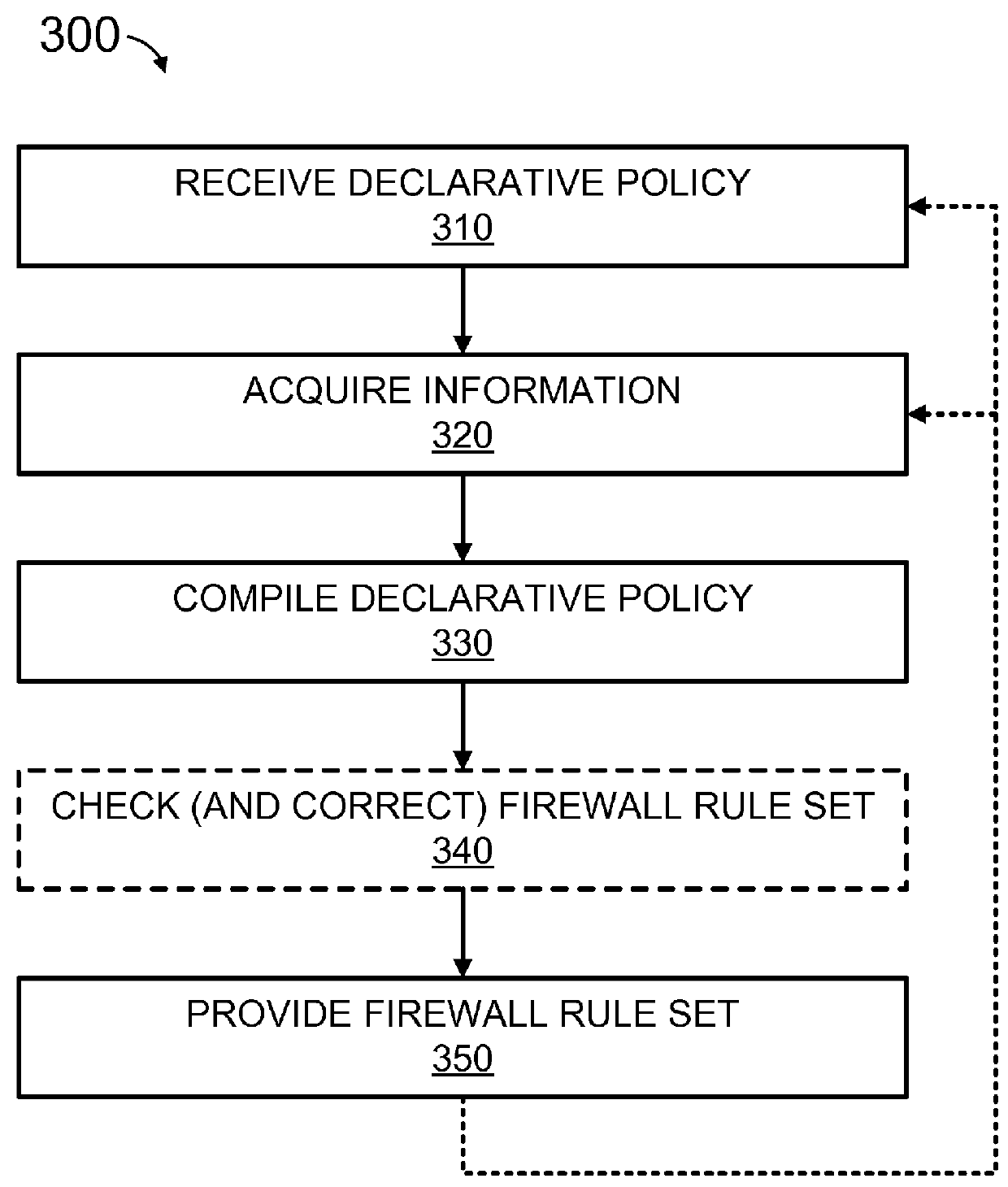
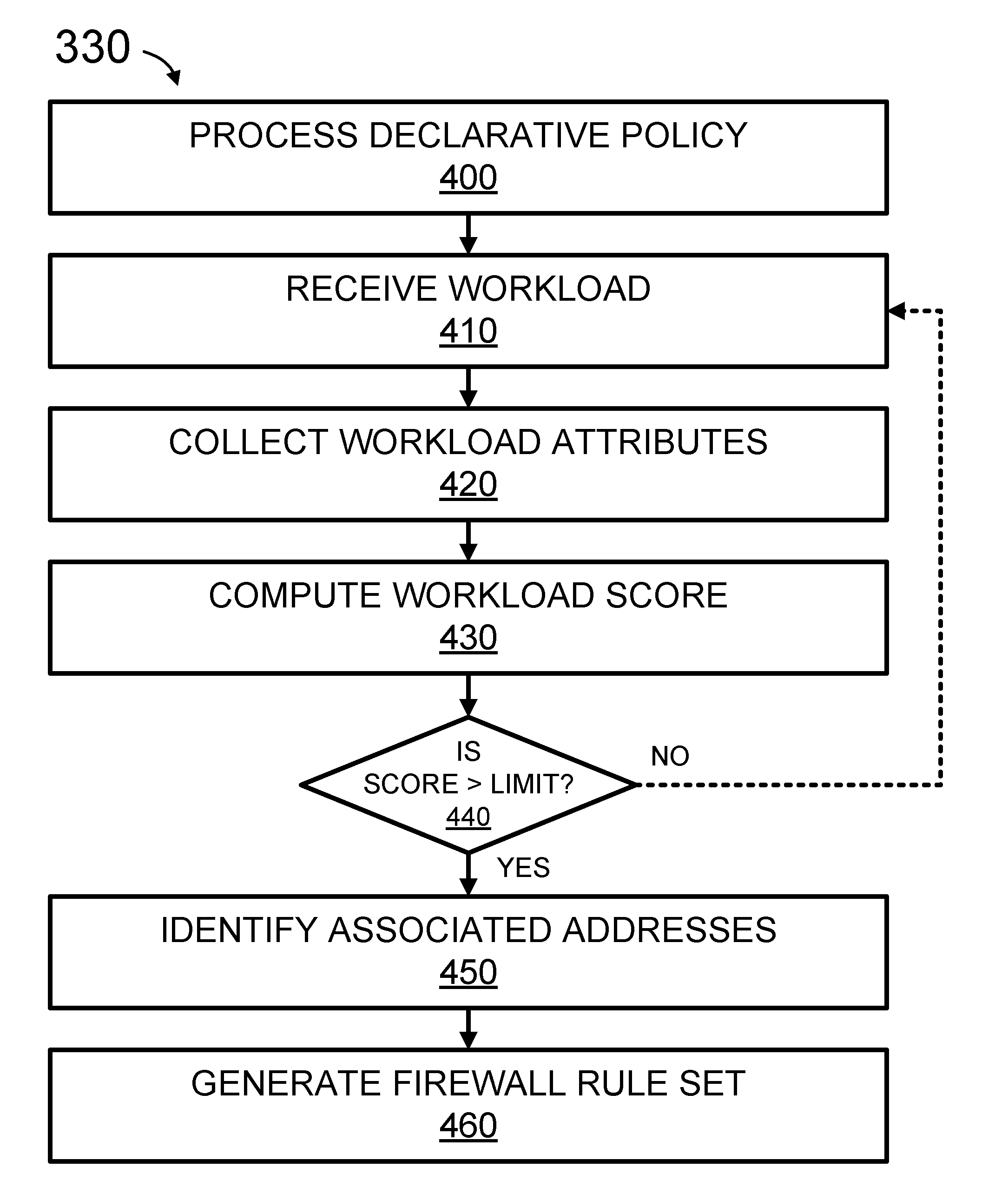
Conditional declarative policies
Methods, systems, and media for producing a firewall rule set are provided herein. Exemplary methods may include receiving a declarative policy associated with a computer network security policy; collecting information from at least one external system of record; generating a firewall rule set using the declarative policy and information, the firewall rule set including addresses to or from which network communications are permitted, denied, redirected or logged, the firewall rule set being at a lower level of abstraction than the declarative policy; and provisioning the firewall rule set to a plurality of enforcement points of a distributed firewall, the firewall selectively policing network communications among workloads using the firewall rule set.
Owner:VARMOR NETWORKS
Hybrid distributed firewall apparatus, systems, and methods
InactiveUS20060282887A1Multiple digital computer combinationsProgram controlData packNetwork control
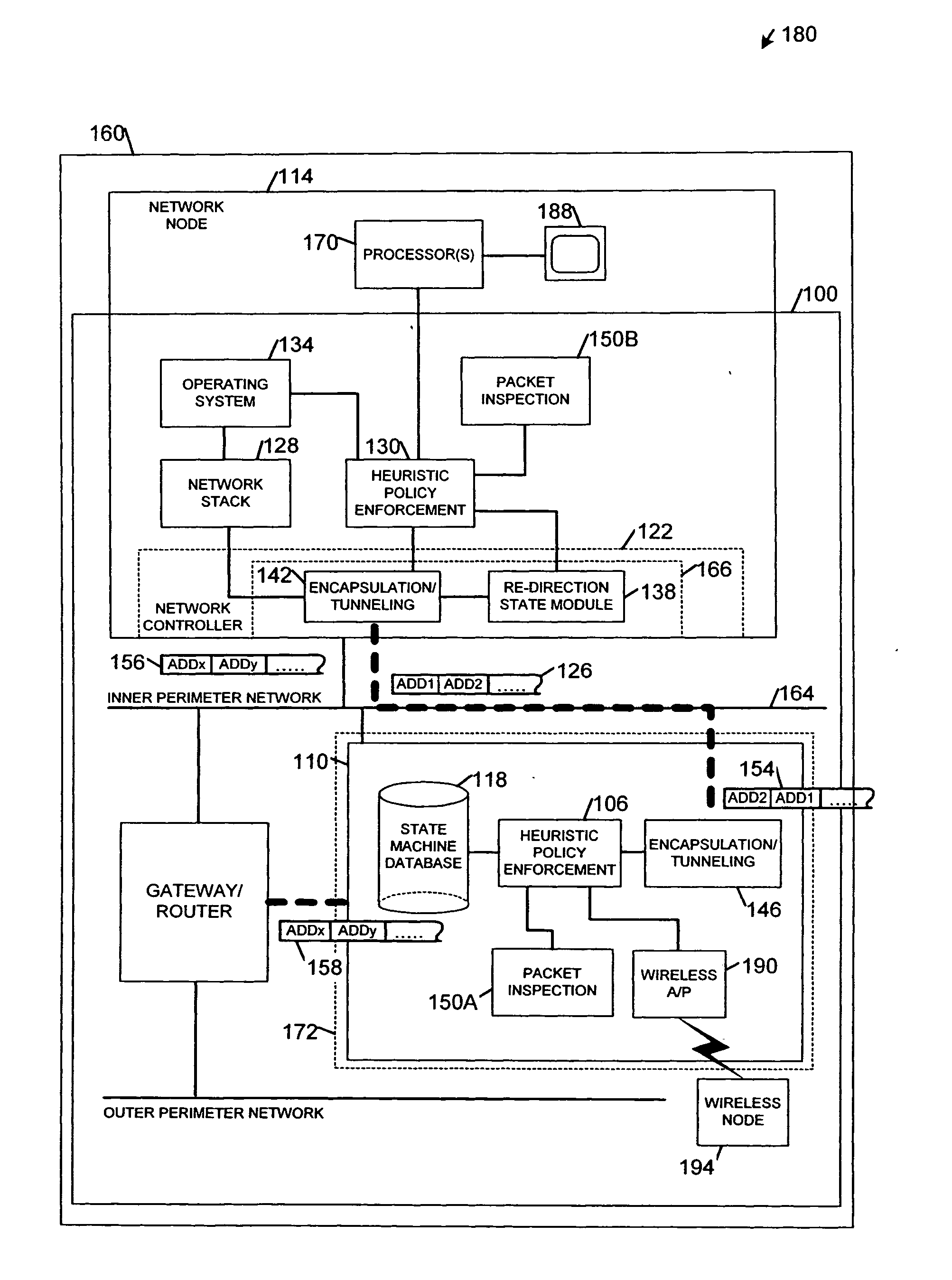
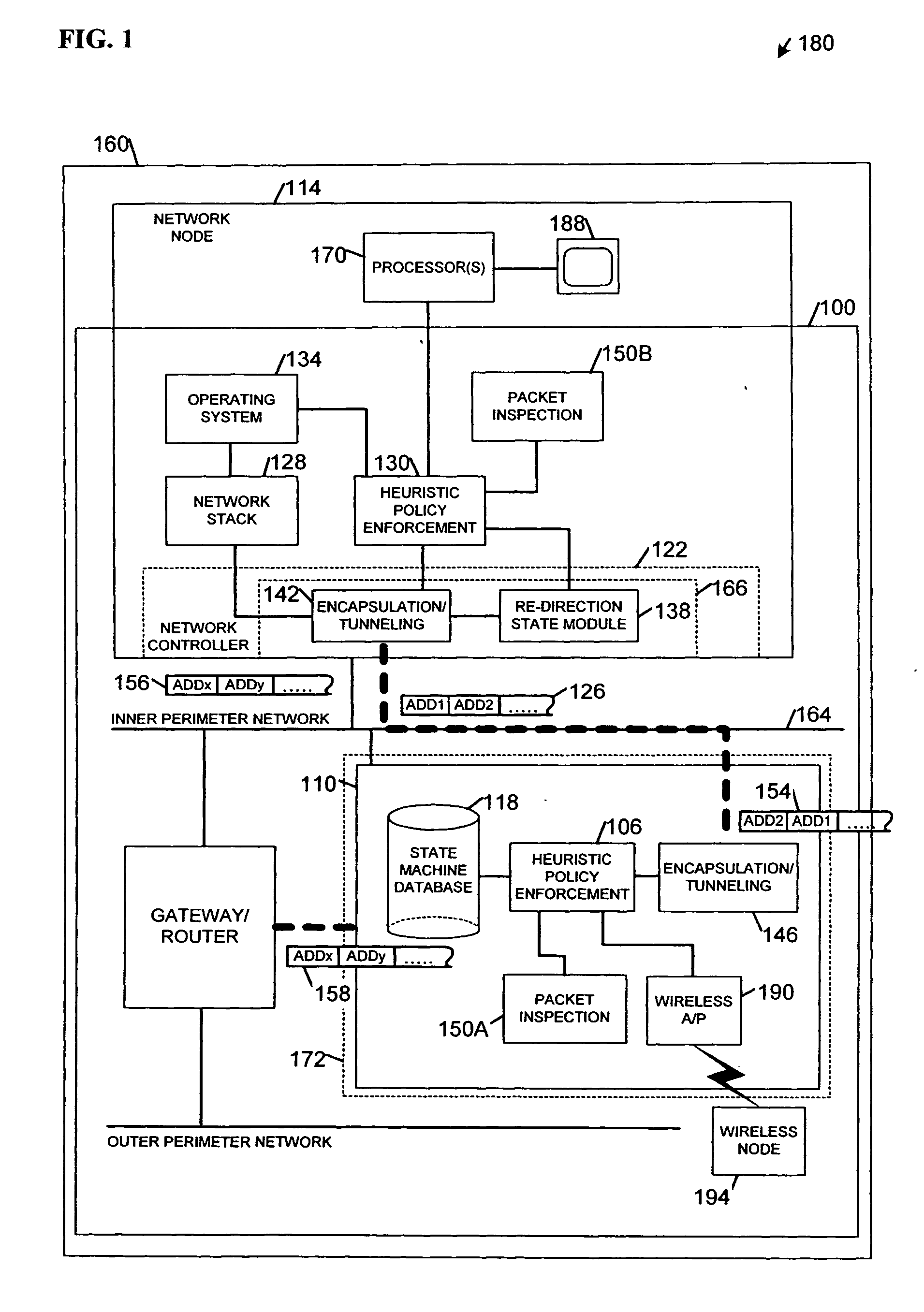
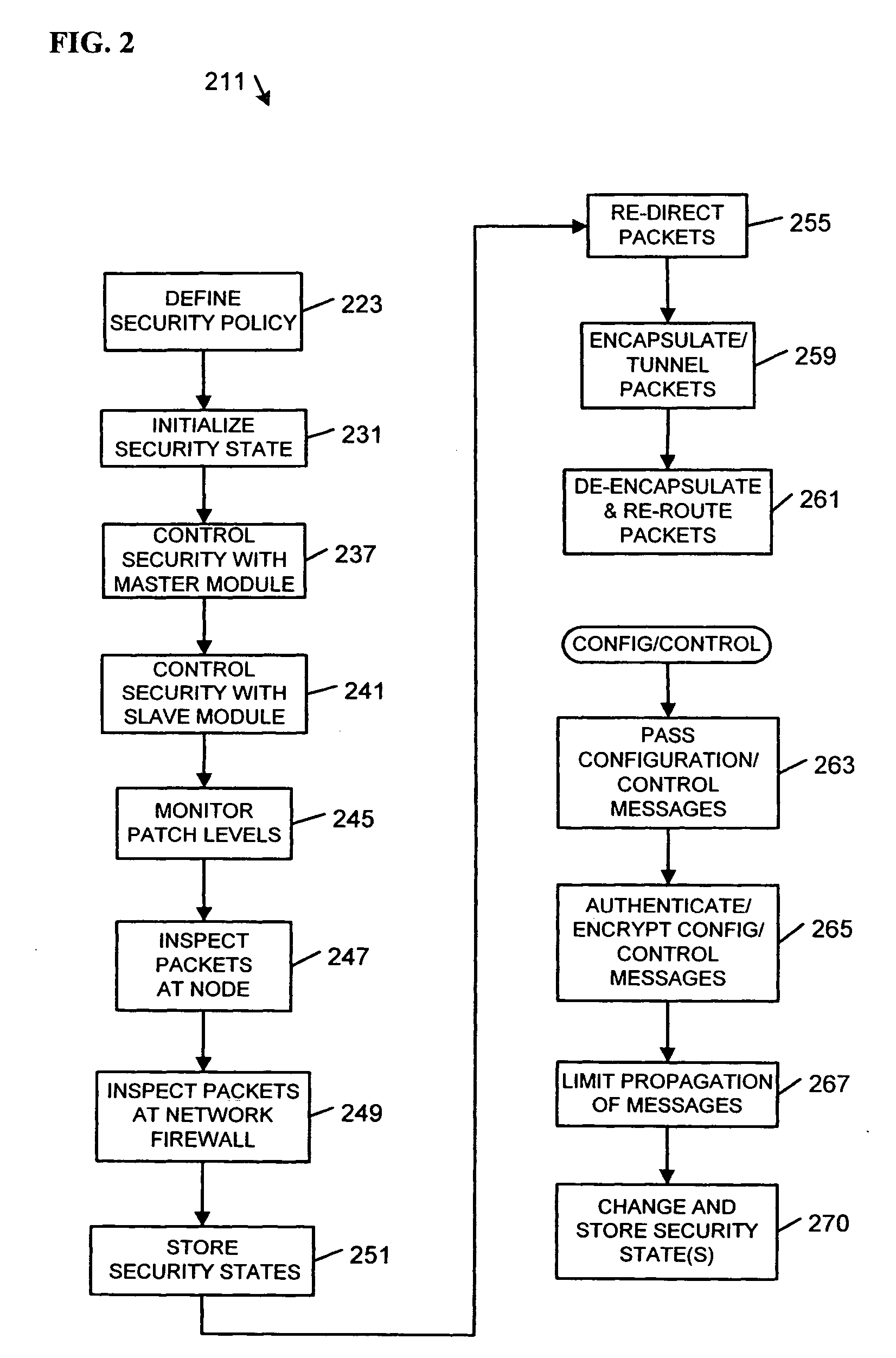
Apparatus and systems, as well as methods and articles, may operate to control a security state associated with one or more network node(s) using a master heuristic policy enforcement module associated with a network firewall, and to selectively re-direct first packets to the network firewall from a remotely manageable network controller located within the network node(s) based upon the security state.
Owner:INTEL CORP
Method And Technique for Automated Collection, Analysis, and Distribution of Network Security Threat Information
InactiveUS20150281176A1Improve scalabilityImprove securityMultiple digital computer combinationsProgram controlAnalysis dataDistribution system
A Method and Technique for Automated Collection, Analysis, and Distribution of Network Security Threat Information. A new and modern threat distribution system be able to update a large number of distributed firewall devices with threat information without impacting performance. The network of firewall devices collects analysis data from all firewall devices in the network, and transmits it to a central server system. The central server system will continually distribute new threat and update information to the networked firewall devices. This feedback and update operation within the network is automated in order to result in drastic improvements in the performance, scalability and security of a modern network infrastructure.
Owner:SPECTRANETIX
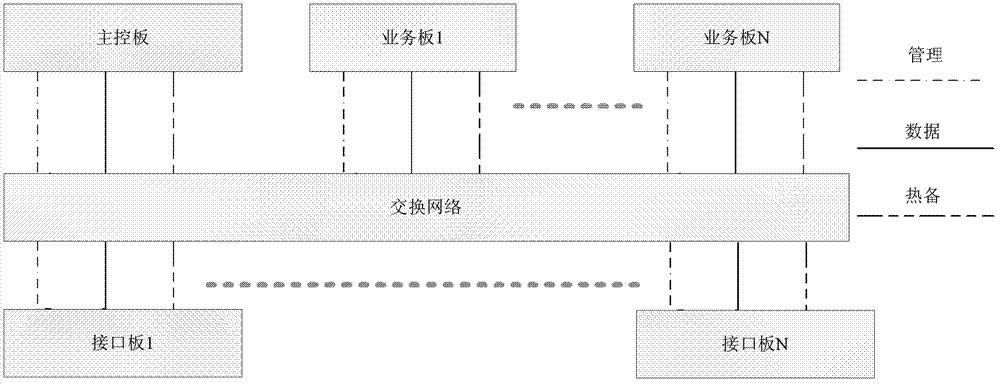
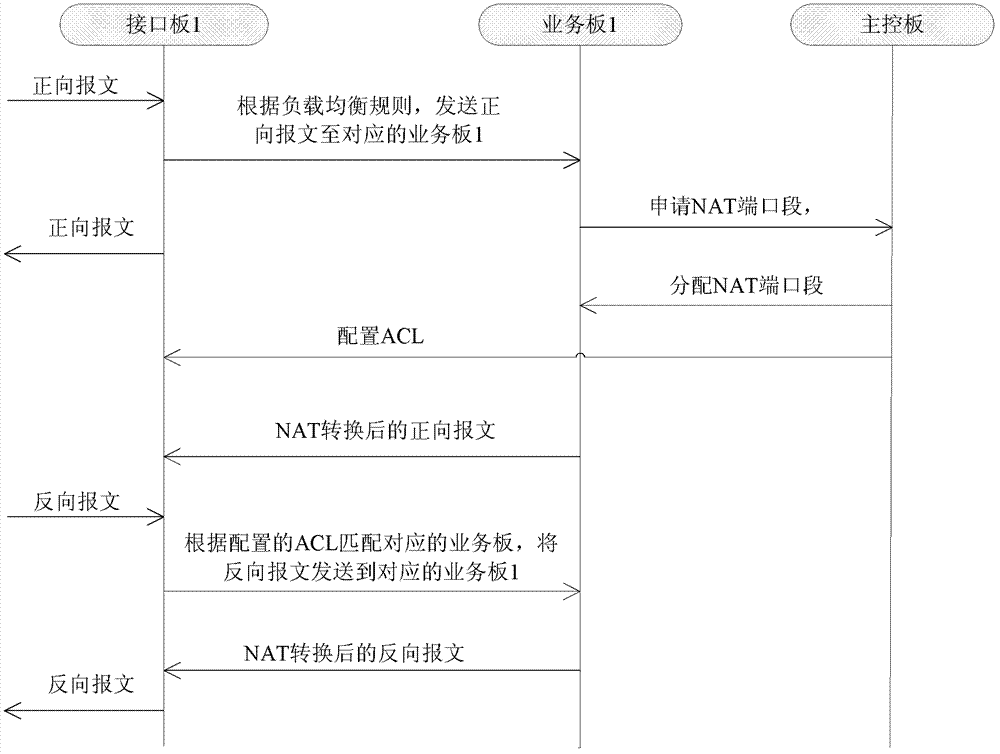
Method and device for achieving packet forwarding
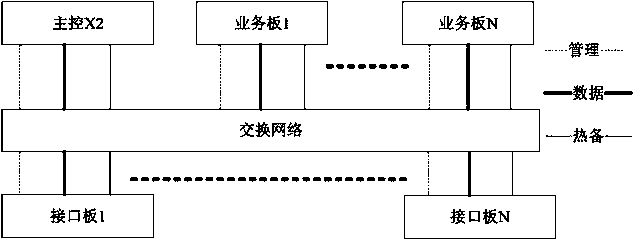
The invention provides a method and a device for achieving packet forwarding. The method is applied to a distributed firewall device which is at least composed of a plurality of interface boards, a plurality of business boards and a main control board. The method at least includes that each interface board receives a forward message in a private network and sends the forward message to a corresponding business board, each business board receives the forward message, a source internet protocol (IP) address of the forward message is modified to a preset public network IP address of the local business board, a source port of the forward message is modified to any network address translation port of a network address translation port section distributed by the main control board, a network address translation session is established, the converted forward message is sent to a corresponding interface board, and the interface boards send the converted forward message in a public network. According to the method and the device, the main control board of a distributed firewall distributes ports used for network address translation (NAT) based on a request of each business board, and thereby the NAT is performed for the forward message, a corresponding NAT is established, and the new establishing and concurrence of the NAT session can increase with the increasing of the business boards.
Owner:NEW H3C TECH CO LTD
Method and apparatus for distributing firewall rules
ActiveUS20150237014A1Quick searchSmall sizeMultiple digital computer combinationsProgram controlComputer networkDistributed firewall
Some embodiments of the invention provide a novel method for specifying firewall rules. In some embodiments, the method provides the ability to specify for a particular firewall rule, a set of network nodes (also called a set of enforcement points below) at which the particular firewall should be enforced. To provide this ability, the method of some embodiments adds an extra tuple (referred to below as the AppliedTo tuple) to a firewall rule. This added AppliedTo tuple lists the set of enforcement points at which the firewall rule has to be applied (i.e., enforced).
Owner:NICIRA
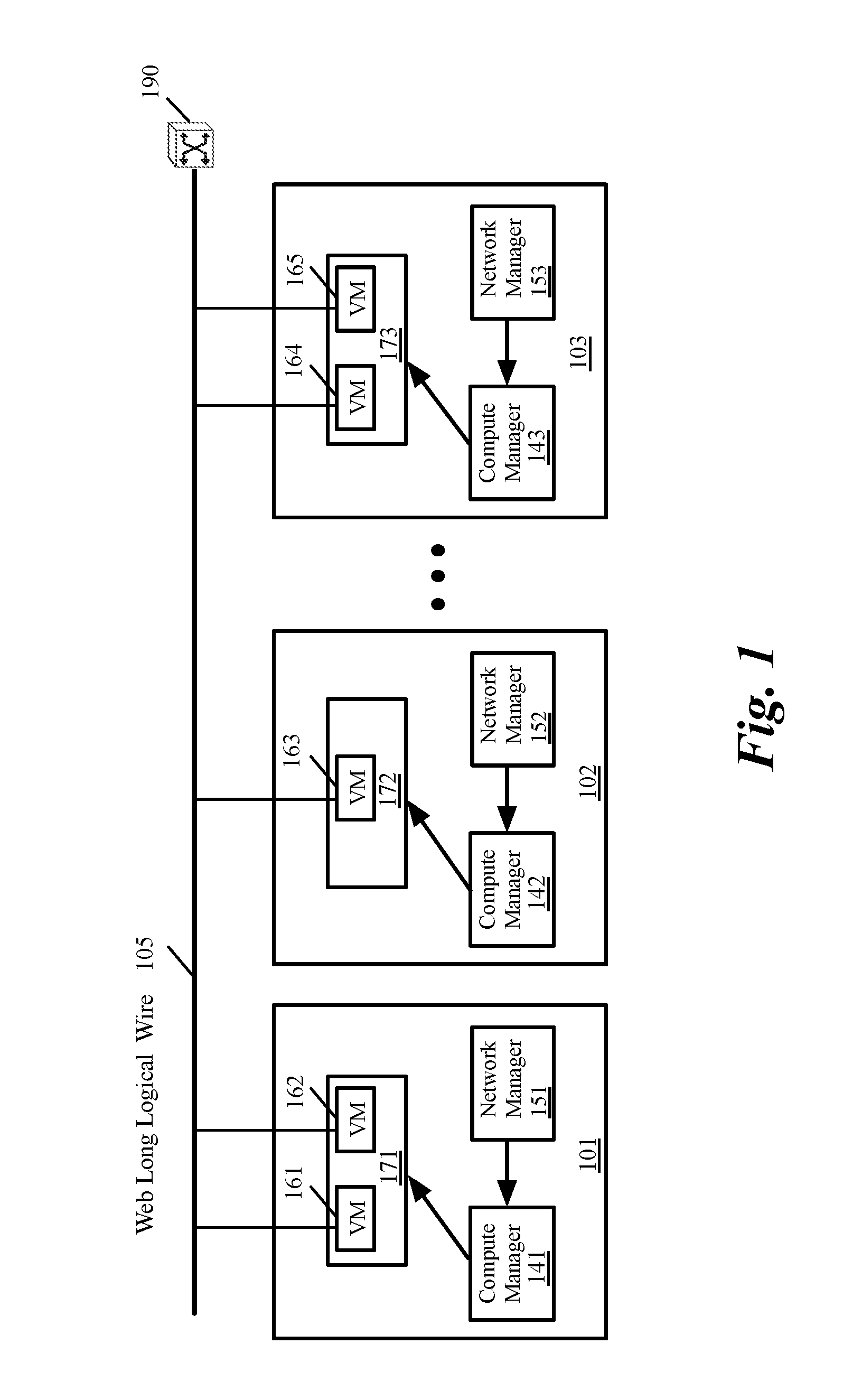
Distributed traffic management system and techniques
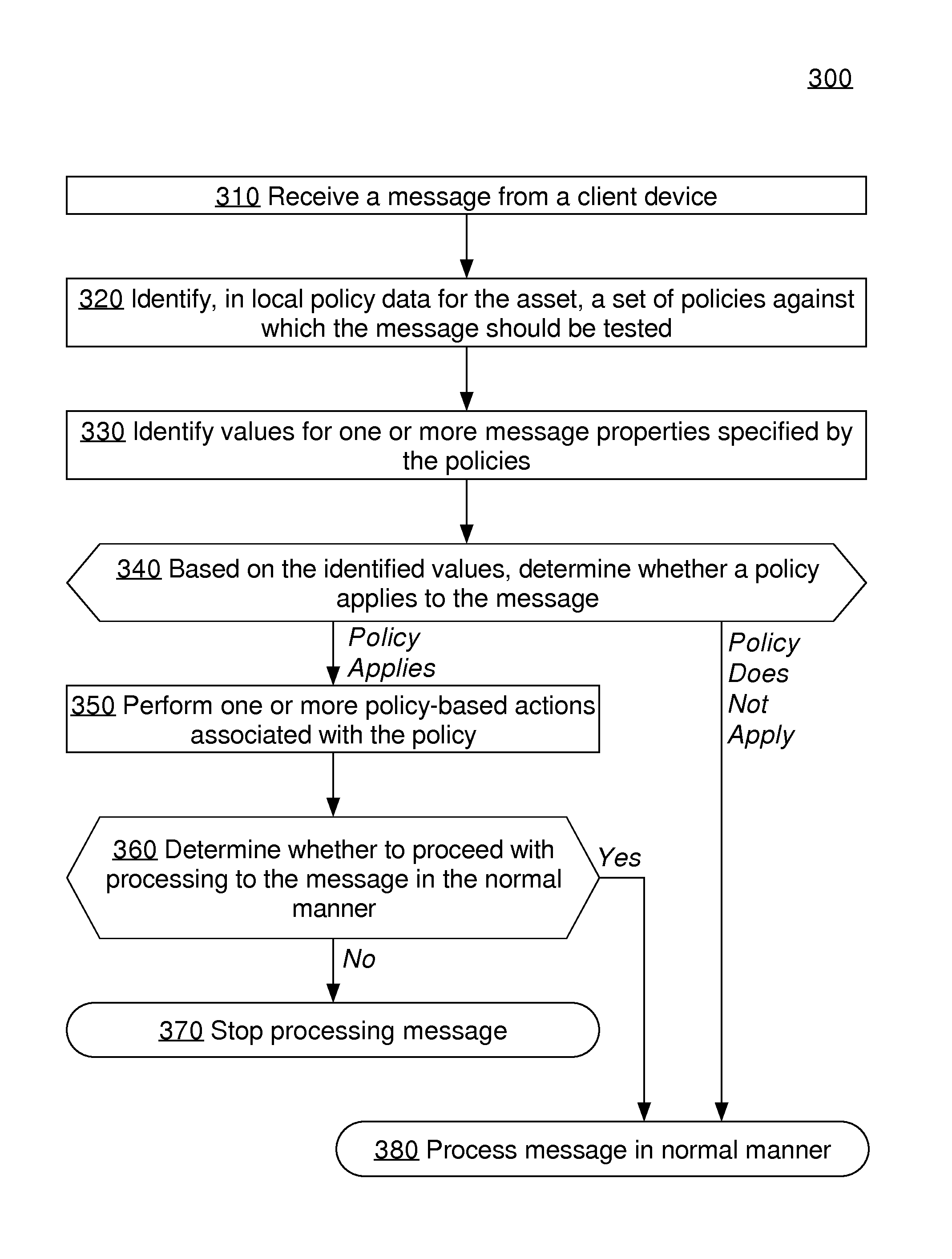
ActiveUS20160088020A1TransmissionSpecial data processing applicationsData synchronizationDecision taking
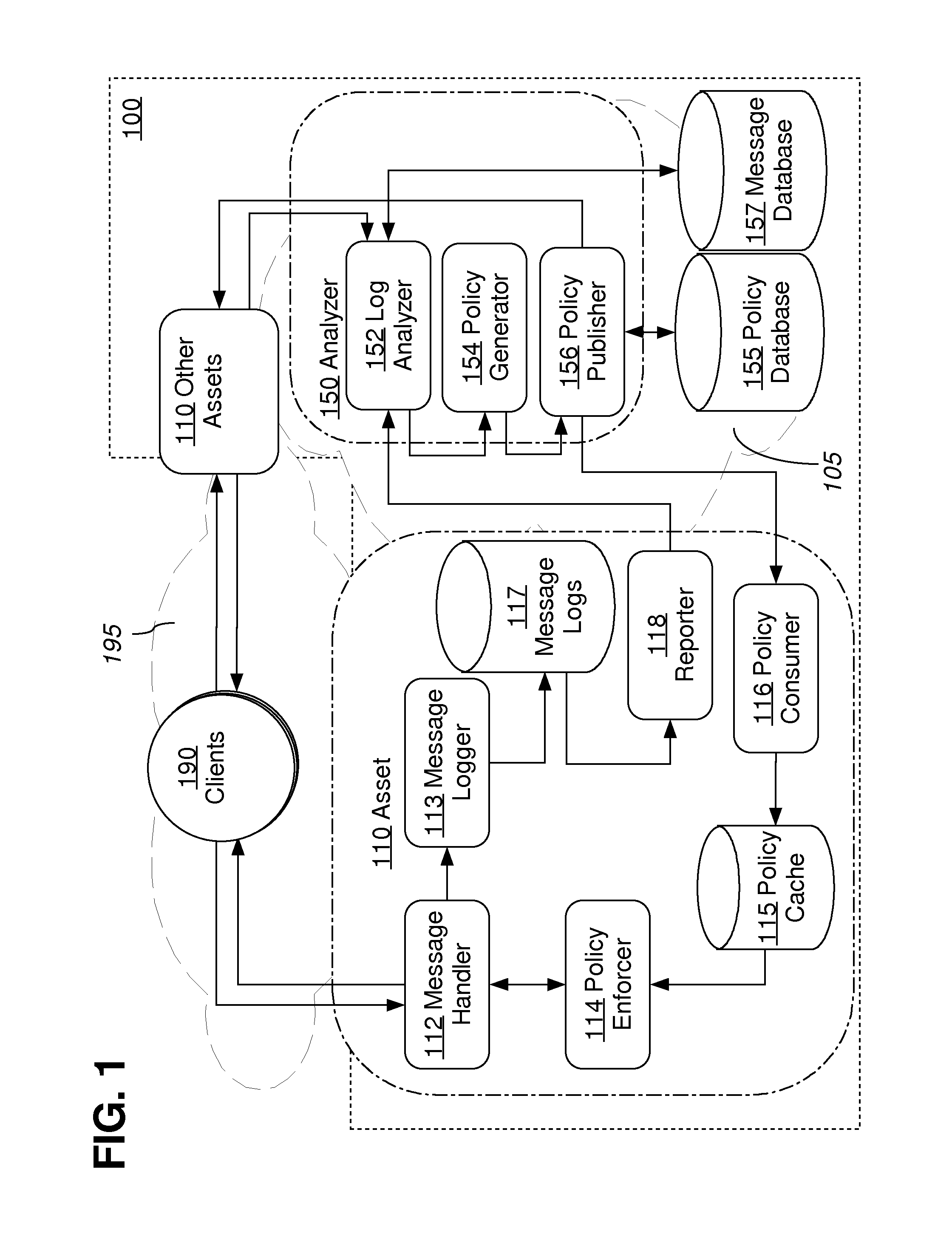
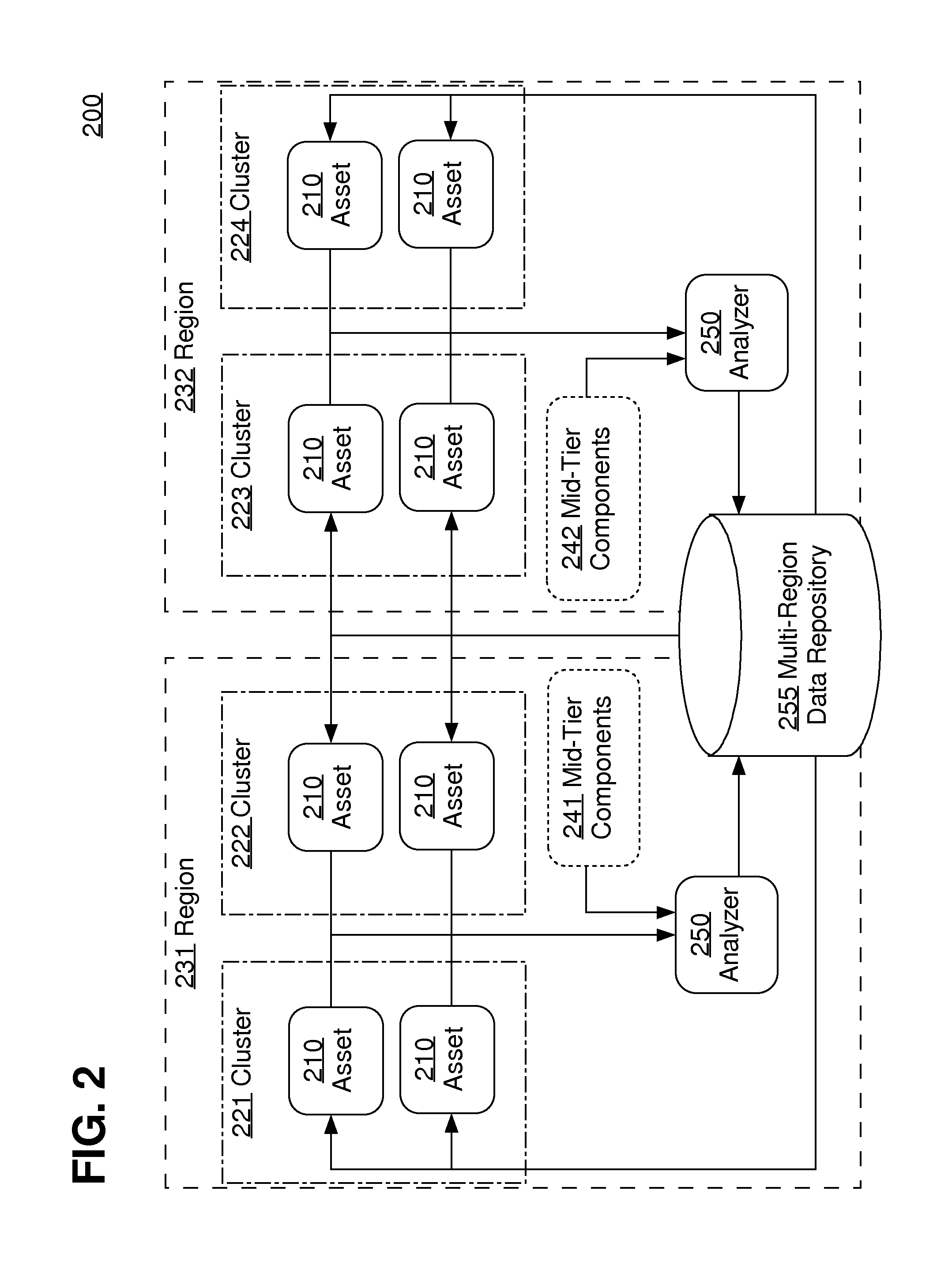
Approaches, techniques, and mechanisms are disclosed for implementing a distributed firewall. In an embodiment, many different computer assets police incoming messages based on local policy data. This local policy data is synchronized with global policy data. The global policy data is generated by one or more separate analyzers. Each analyzer has access to message logs, or information derived therefrom, for groups of computer assets, and is thus able to generate policies based on intelligence from an entire group as opposed to an isolated asset. Among other effects, some of the approaches, techniques, and mechanisms may be effective even in computing environments with limited supervision over the attack surface, and / or computing environments in which assets may need to make independent decisions with respect to how incoming messages should be handled, on account of latency and / or unreliability in connections to other system components.
Owner:NETFLIX
Firewall service system and method based on virtual network
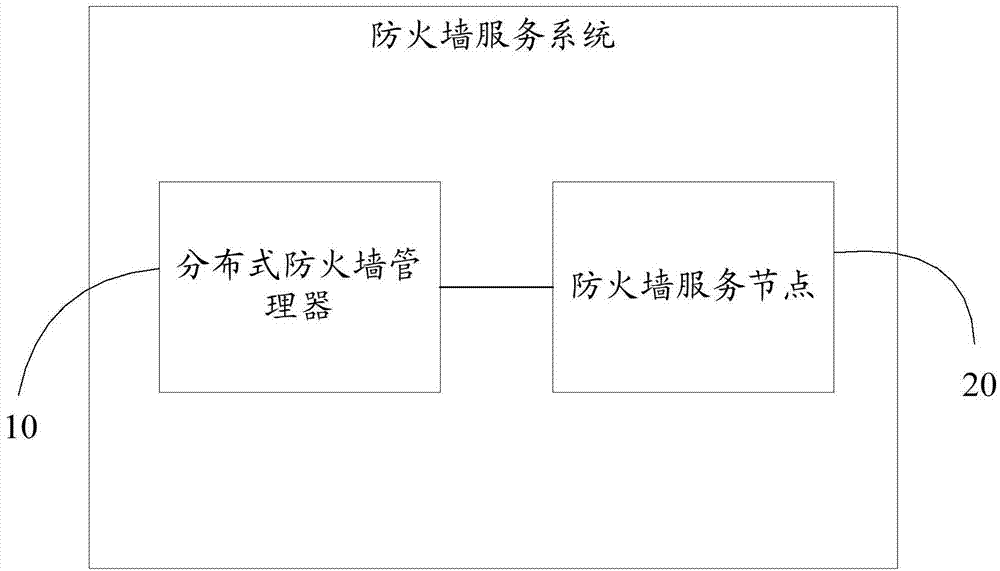
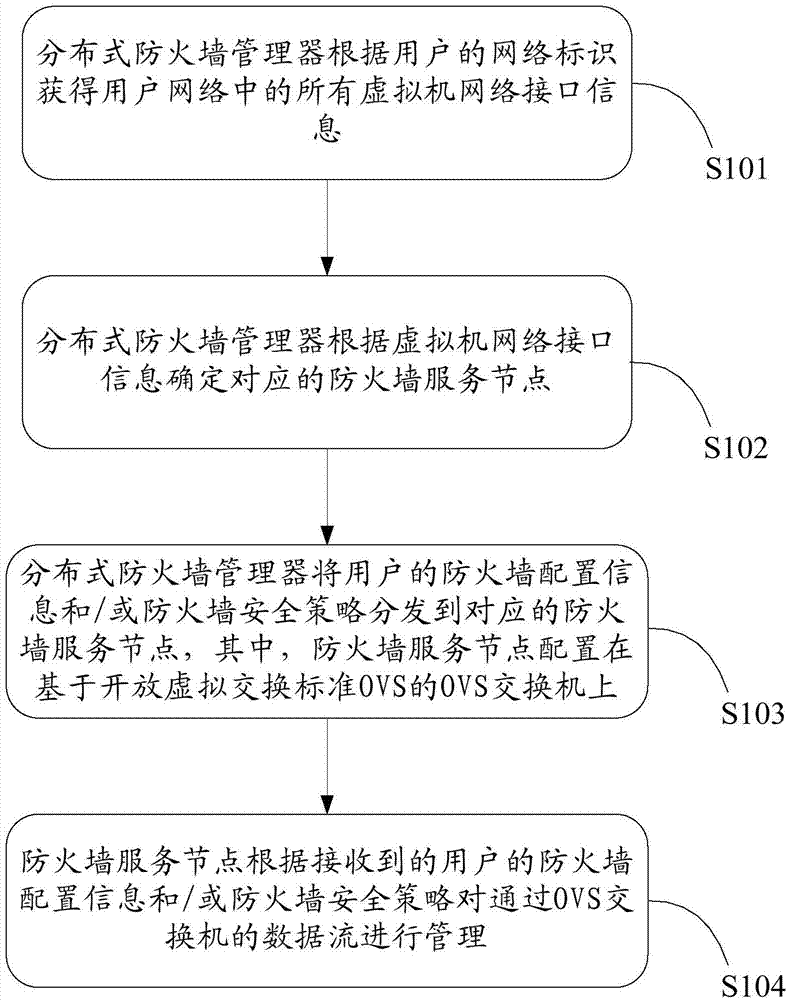
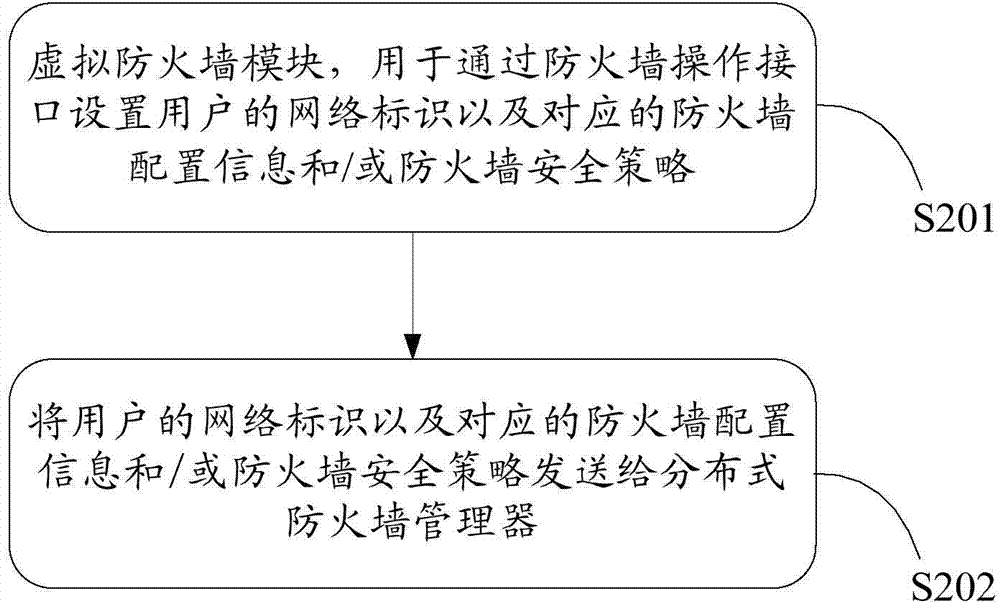
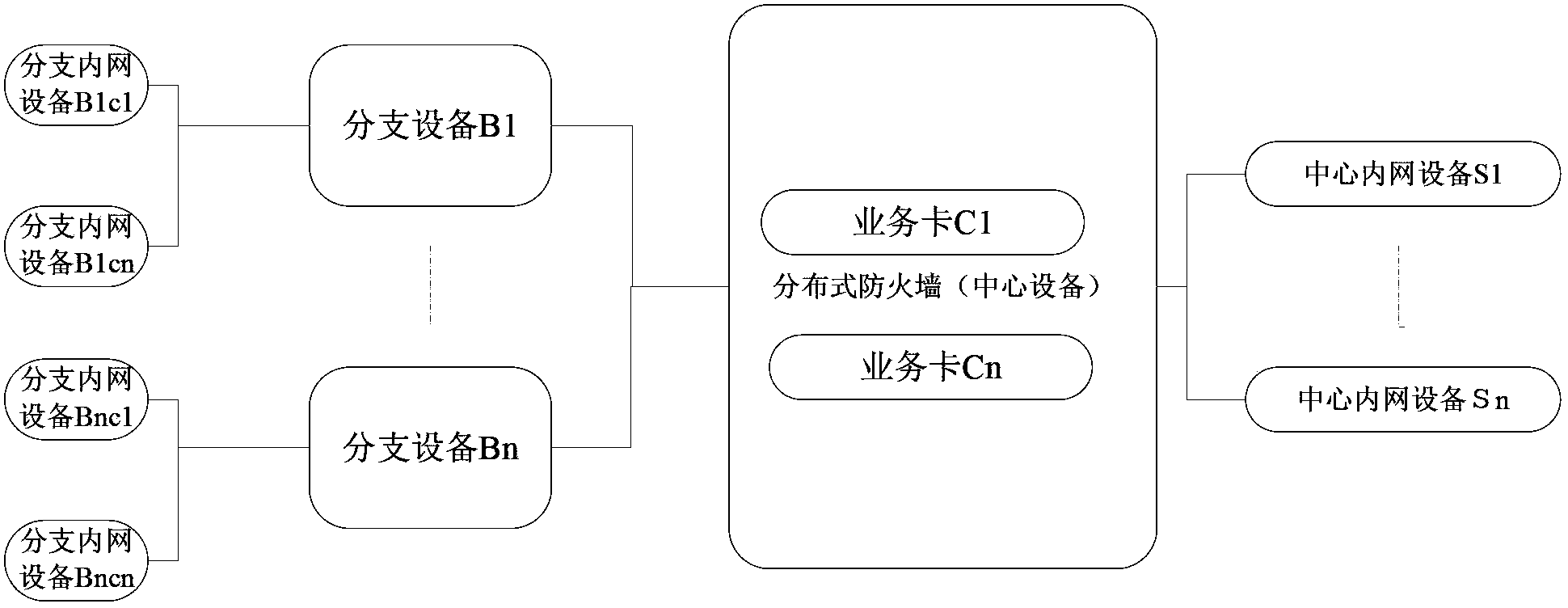
The invention provides a firewall service system based on a virtual network. The firewall service system based on the virtual network comprises a distributed type firewall manager and firewall service nodes, wherein the distributed type firewall manager is used for obtaining information of all virtual machine network interfaces in a user network according to the network identity of a user, determining the corresponding firewall service nodes according to the information of the virtual machine network interfaces, and distributing firewall configuration information and / or firewall security strategies of the user to the corresponding firework service nodes; the firewall service nodes are configured on an OVS switch based on OVS and are used for managing data flow passing through the OVS switch according to the received firewall configuration information and / or the received firewall security strategies of the user. The invention further provides a method for obtaining a virtual network firewall. By the adoption of the firewall service system based on the virtual network and the method for obtaining the virtual network firewall, through the deployment and the distributed management of the firewall service nodes, establishment of the distributed virtual network firewall is achieved.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Conditional declarative policies
Methods, systems, and media for producing a firewall rule set are provided herein. Exemplary methods may include receiving a declarative policy associated with a computer network security policy; collecting information from at least one external system of record; generating a firewall rule set using the declarative policy and information, the firewall rule set including addresses to or from which network communications are permitted, denied, redirected or logged, the firewall rule set being at a lower level of abstraction than the declarative policy; and provisioning the firewall rule set to a plurality of enforcement points of a distributed firewall, the firewall selectively policing network communications among workloads using the firewall rule set.
Owner:VARMOR NETWORKS
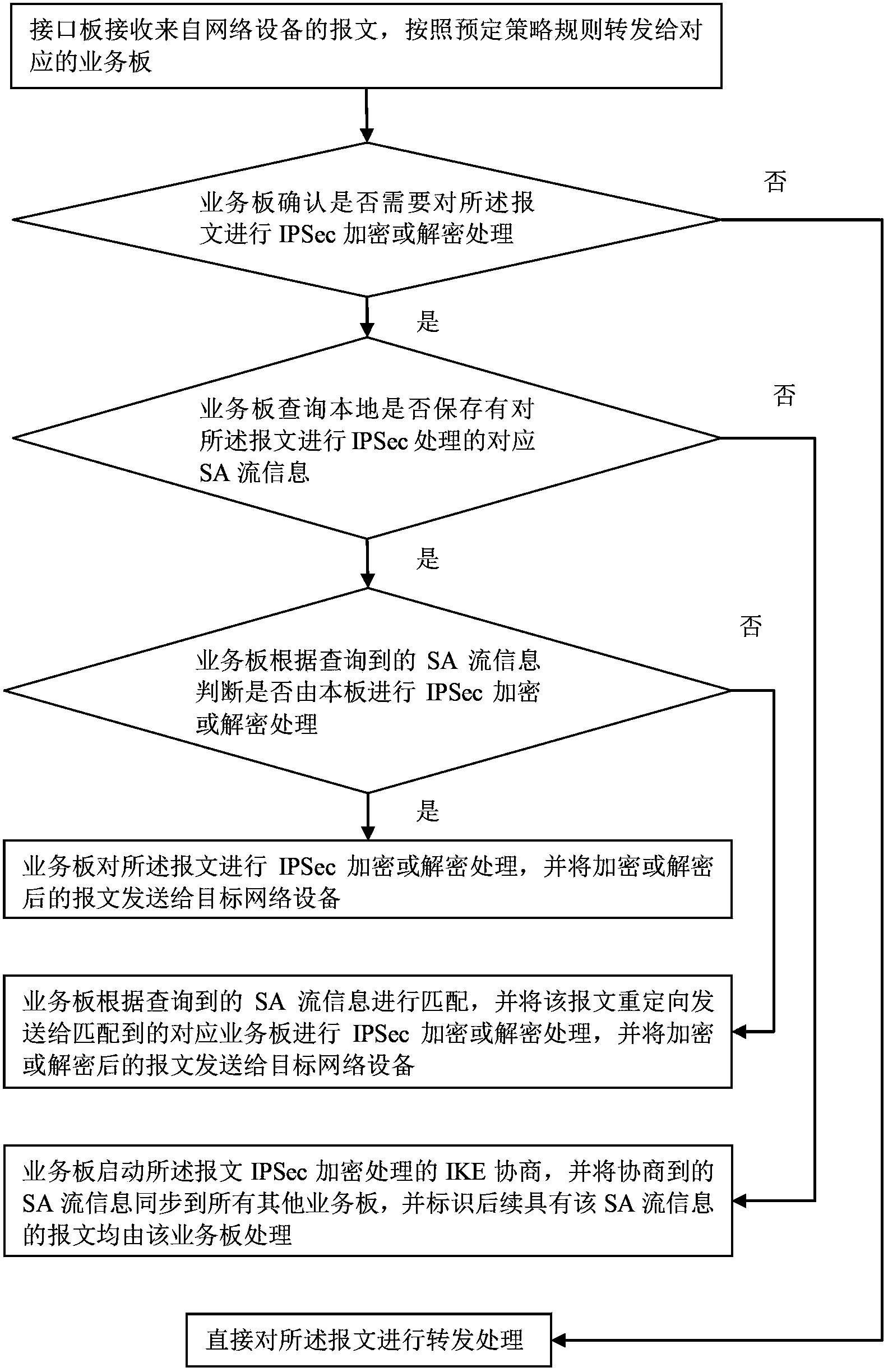
Method and device for distributed firewall IPSec (internet protocol security) business load sharing
ActiveCN103546497ARealize load sharingData switching networksDistributed computingAccess control list
The invention relates to a method and a device for distributed firewall IPSec (internet protocol security) business load sharing. A master control board timely issues ACL (access control list) strategy information to all interface boards so as to guarantee that messages from specific network equipment are all sent to the corresponding interface boards; SA stream information is synchronized to all business boards, and when the business boards discover that the received messages thereof do not belong to themselves for processing according to the SA stream information, the messages are further redirected to the business boards matched with the SA stream information. By the means, the messages of the same stream can be enabled to be sent to the same business board to be processed, so that load sharing of IPSec business on a distributed firewall is realized.
Owner:NEW H3C SECURITY TECH CO LTD
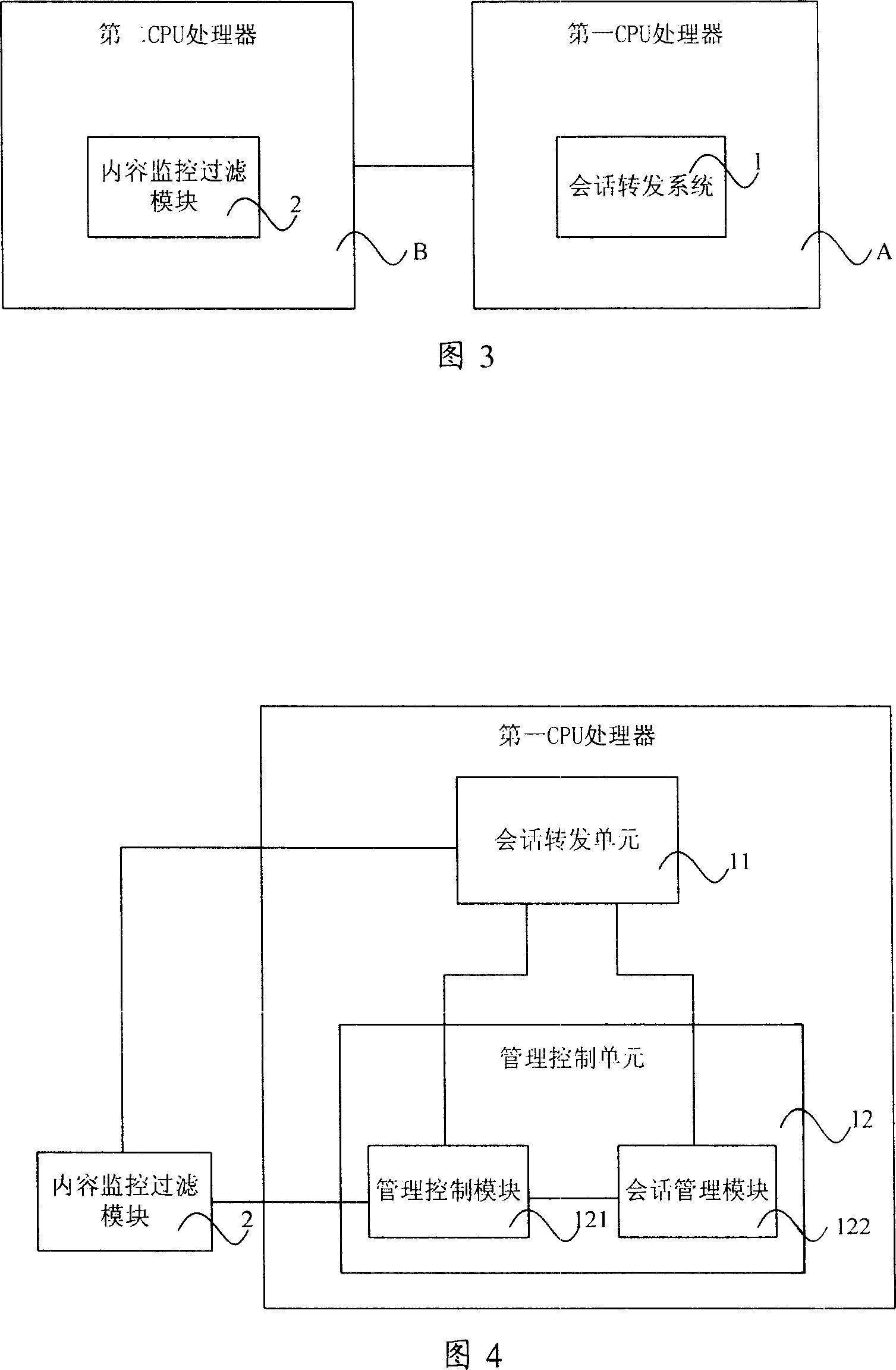
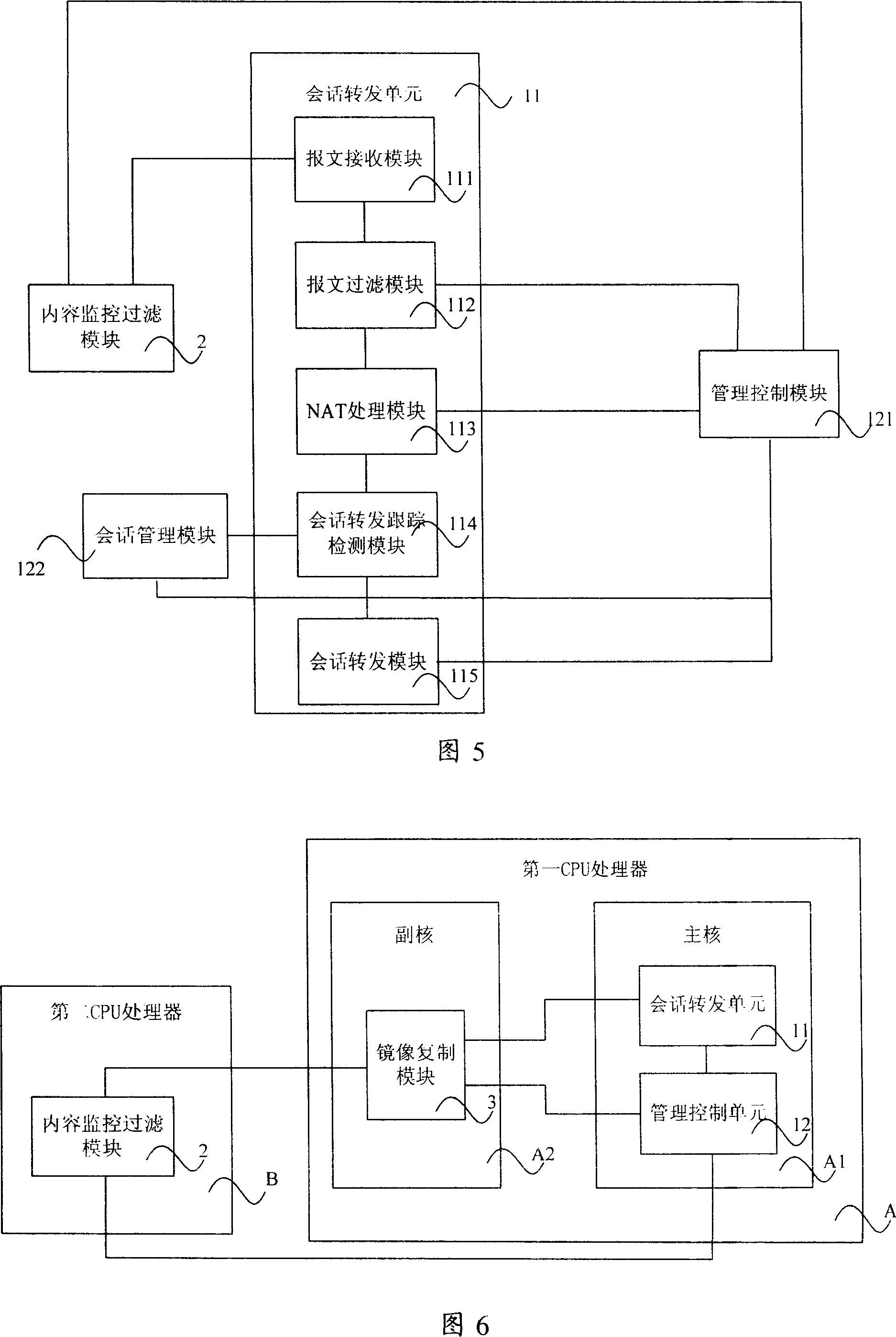
Distributed firewall system and method for realizing content diction of firewall
InactiveCN101014048AImprove throughputImprove stabilityData switching networksTransfer systemMonitor filter
The invention discloses one distribution firewall system, which comprises dialogue transfer system and connected content monitor filter module, wherein, the content monitor filter module is to monitor filter condition according to preset content and to filter on the message content and to send the filter result to the dialogue transfer system; the content monitor filter module and dialogue transfer system are operated in first and second processors. The invention also discloses one method to realize firewall content test.
Owner:NEW H3C TECH CO LTD
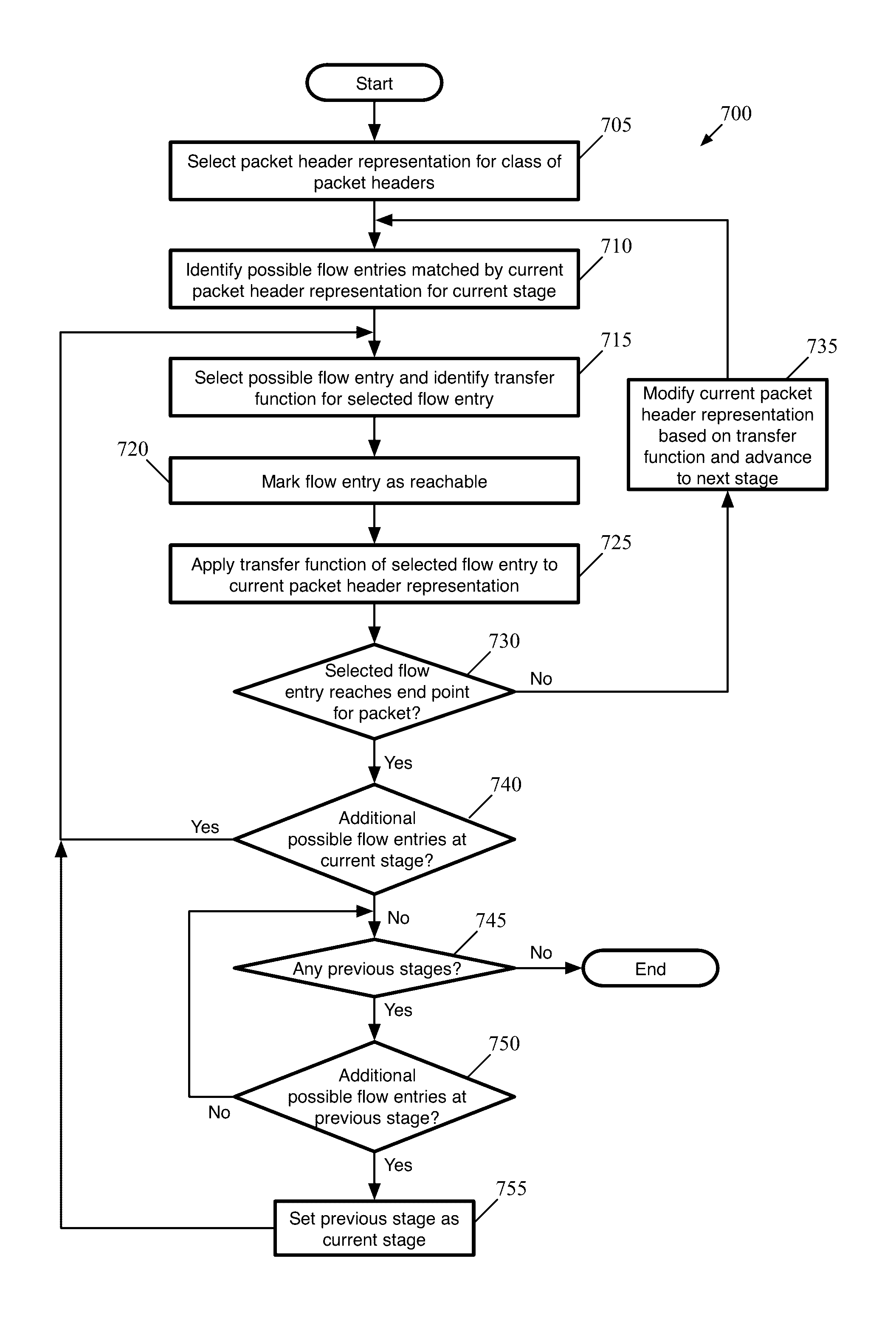
Using headerspace analysis to identify unneeded distributed firewall rules
Some embodiments provide a method for identifying unnecessary firewall rules for a distributed firewall of a logical network. The method identifies a firewall policy for network traffic of the logical network. The firewall policy includes a set of firewall rules. The method generates a set of data for implementing the firewall policy on a set of managed forwarding elements that implement the logical network. The method analyzes potential network traffic based on the generated set of data to identify a subset of unnecessary data. The method identifies a subset of unnecessary firewall rules of the set of firewall rules that corresponds to the subset of unnecessary data.
Owner:NICIRA
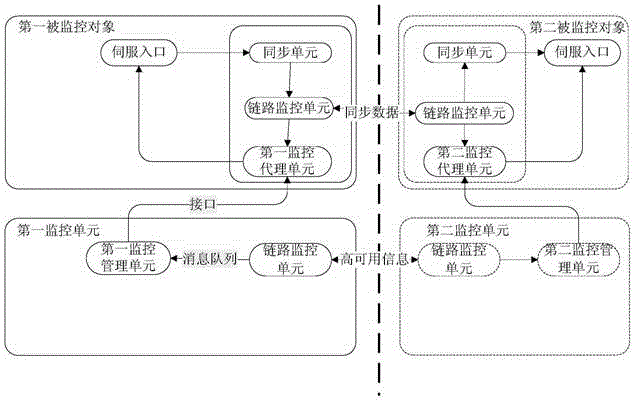
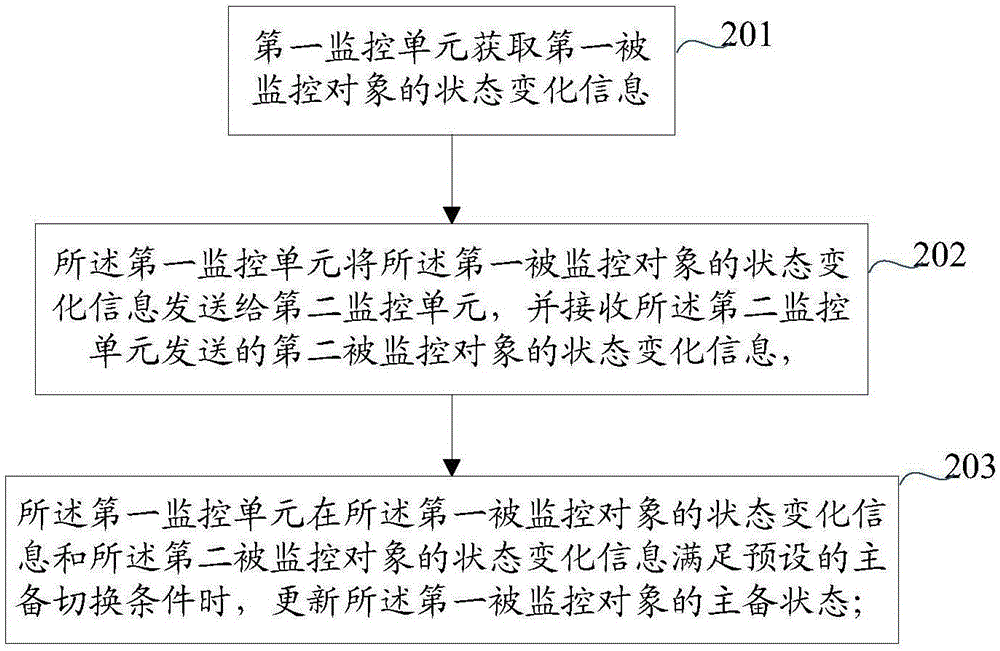
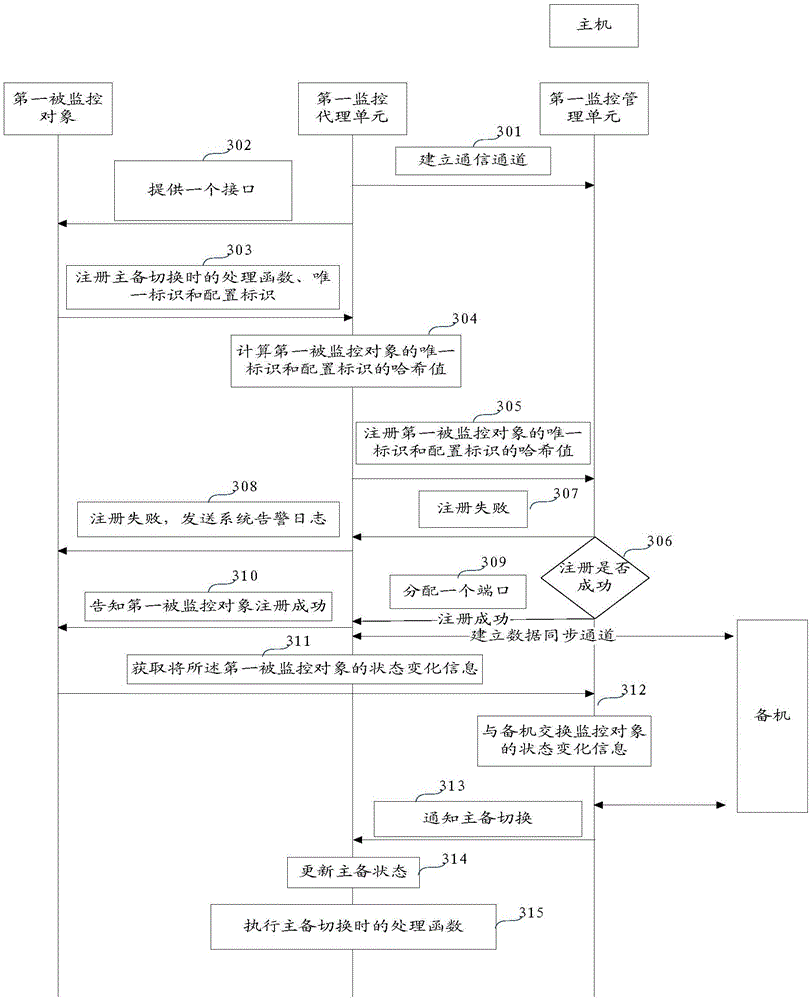
Method and apparatus for realizing high availability
InactiveCN106411589ALow running costImprove work efficiencyData switching networksState variationVirtual firewall
The embodiment of the invention relates to the field of network security, and particularly relates to a method and apparatus for realizing high availability. The method and apparatus is used for realizing the high availability of a plurality of network security devices. The method comprises the following steps: a first monitoring unit acquires state change information of a first monitored object and receives the state change information of a second monitored object sent by a second monitoring unit, wherein the second monitored object is a master device or a slave device of the first monitored object; the first monitoring unit updates an active / standby state of the first monitored object when the state change information of the first monitored object and the state change information of the second monitored object satisfy a preset active / standby switching condition; a next generation firewall / intrusion prevention system and an ATCA distributed firewall and virtual firewall under the ''parallel forwarding engine'' architecture are compatible at the same time; and when the network security device needs to be changed, the device or the system of the device does not need to be changed or replaced, thereby reducing the operation cost and improving the working efficiency.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Storage area network system using internet protocol, security system, security management program and storage device
InactiveUS7346924B2Input/output to record carriersDigital data processing detailsStorage area networkSecurity policy
In order to remove security vulnerability in an IP-SAN and eliminate unauthorized access by spoofing, firewalls are installed in valid user servers and storage devices, and a distributed firewall manager for managing the firewalls integrally is provided in the IP-SAN. The distributed firewall manager obtains discovery domain information from an iSNS server, determines nodes registered in the iSNS server as the nodes of valid users, and autocreates a security policy according to sets consisting of an iSCSI name and portal information. This security policy is distributed to all of the firewalls as a common policy, whereupon access control is executed to deny TCP connection requests from unauthorized access sources.
Owner:GOOGLE LLC
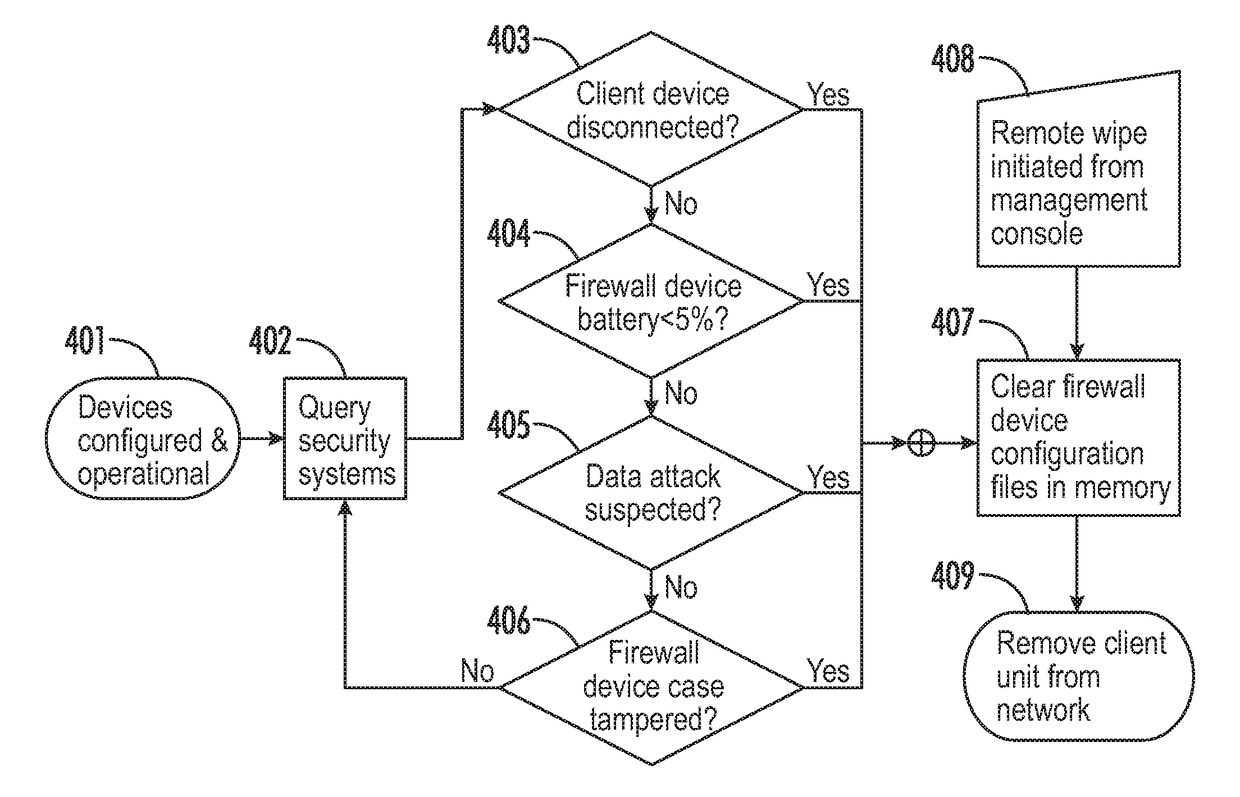
Distributed firewall device and system
InactiveUS20180013722A1Data processing applicationsHealthcare resources and facilitiesWireless mesh networkComputer network
A distributed firewall device that can be hardwired to a client device and securely connect the client device to a wireless network. The client device can be a medical device connected to a healthcare facility network. The distributed firewall device transmits allowed data packets received from the client device to the wireless network and transmits allowed data packets received from the wireless network to the client device using firewall and routing configurations stored in volatile memory. A wipe module in the firewall device clears firewall and routing configurations from volatile memory upon detecting a security threat. A reload device is used to load configurations onto new or wiped firewall devices and initially connect the loaded firewall devices to the wireless network.
Owner:ENOS ERIC
Method for solving consistent update of distributed firewall network through utilization of SDN (Software Defined Network) technology
ActiveCN106850616AAchieve consistent updatesSave complicated stepsData switching networksAuto-configurationComputer science
The invention discloses a method for solving consistent update of a distributed firewall network through utilization of an SDN (Software Defined Network) technology. According to the method, through utilization of an SDN, a user is supported to define development according to own practical demand; a controller is enabled to issue different flow tables to online switches in a mode of carrying out programming through an API (Application Program Interface), so a step of configuring each switch one by one is removed, influences of update of the configuration in the switches on transmitted data messages and original network security rules are no longer taken into consideration, and the configuration difficulty of distributed firewalls is solved. According to the method, the switches are automatically configured by issuing the flow tables through programming, and the consistent update of the distributed firewalls can be finished.
Owner:NANJING UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com