Patents
Literature
420 results about "Security rule" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
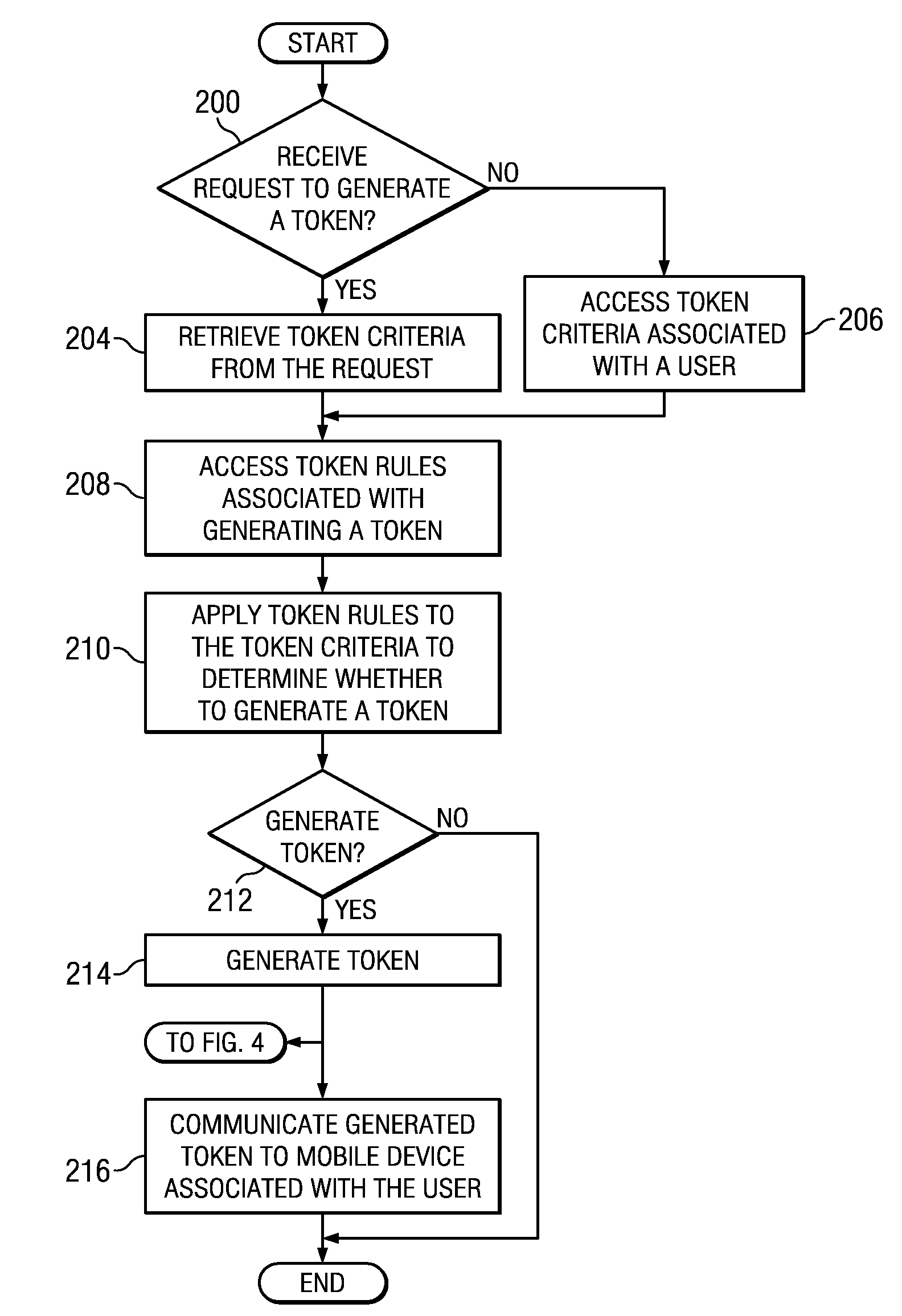
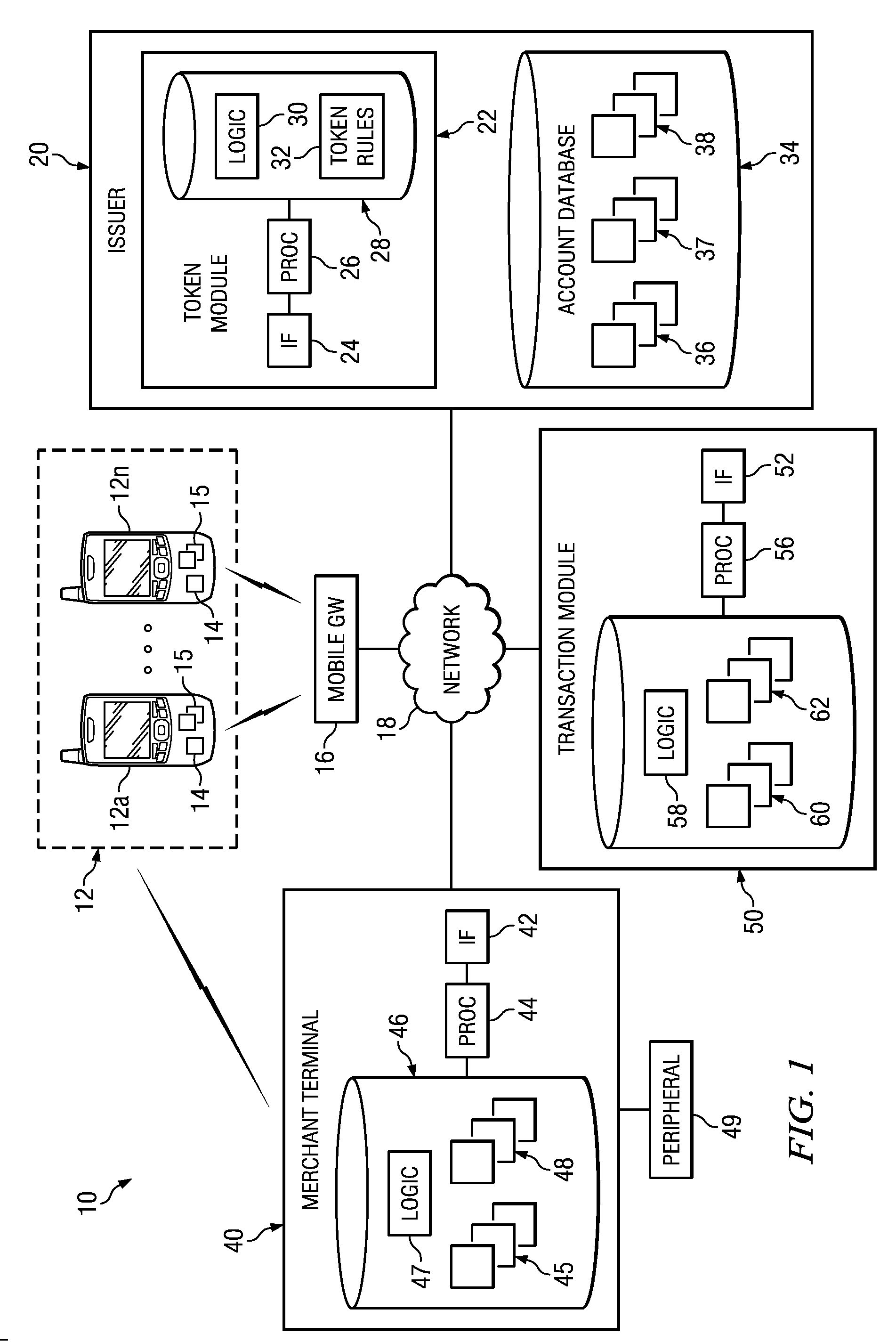
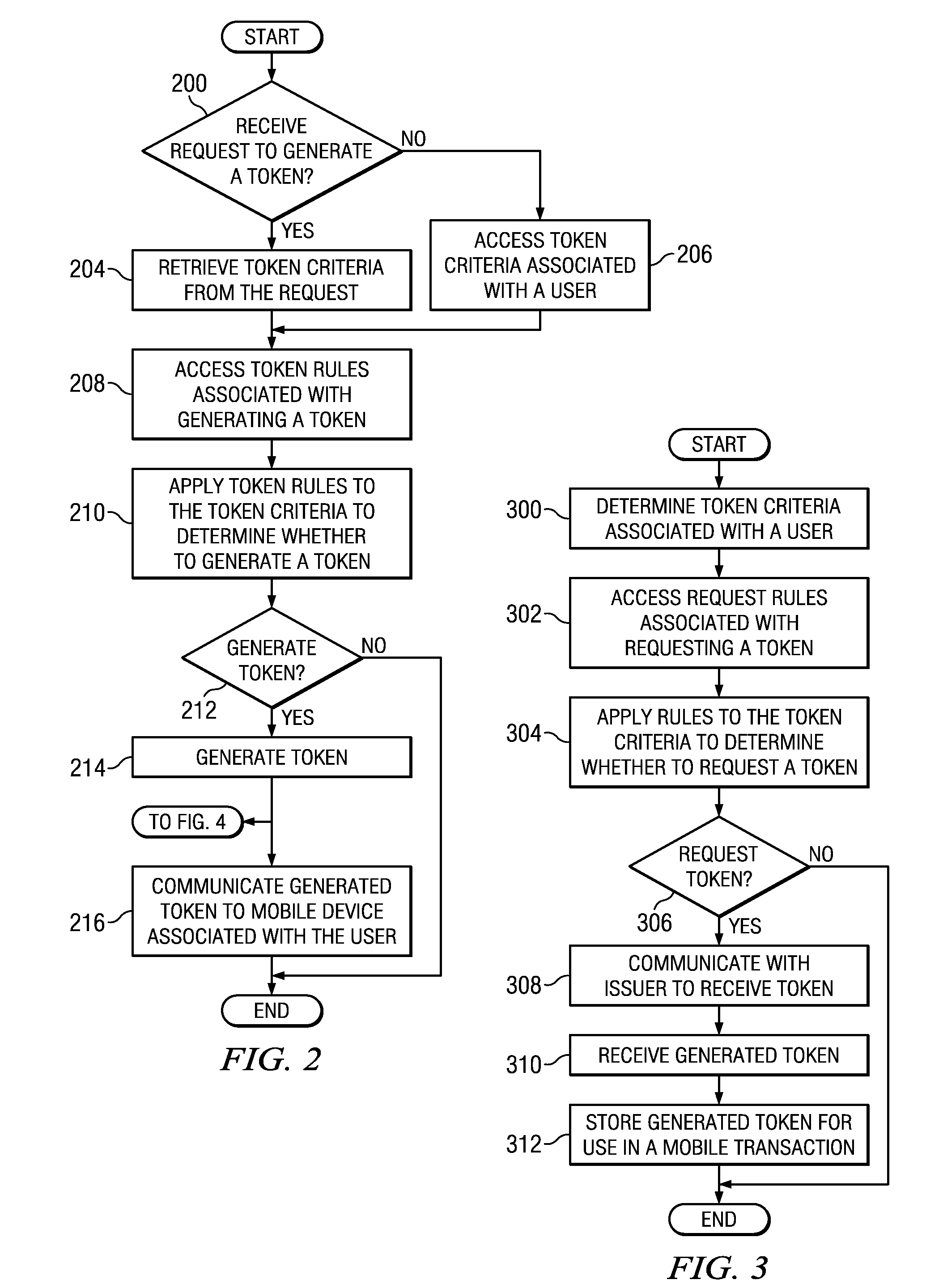
Implementing security measures for authorized tokens used in mobile transactions
ActiveUS20140025958A1Disadvantages can be reduced eliminatedTransactions be reduced eliminatedUnauthorized memory use protectionHardware monitoringSecurity MeasureMobile transaction
Security measures for tokens comprise storing security rules associated with a generated token in a memory. A processor, communicatively coupled to the memory, accesses the security rules associated with the generated token and determines whether to encrypt the generated token by applying at least a portion of the security rules to the generated token. The processor encrypts the generated token. An interface, communicatively coupled to the processor, communicates the encrypted token to a mobile device associated with a user.
Owner:BANK OF AMERICA CORP
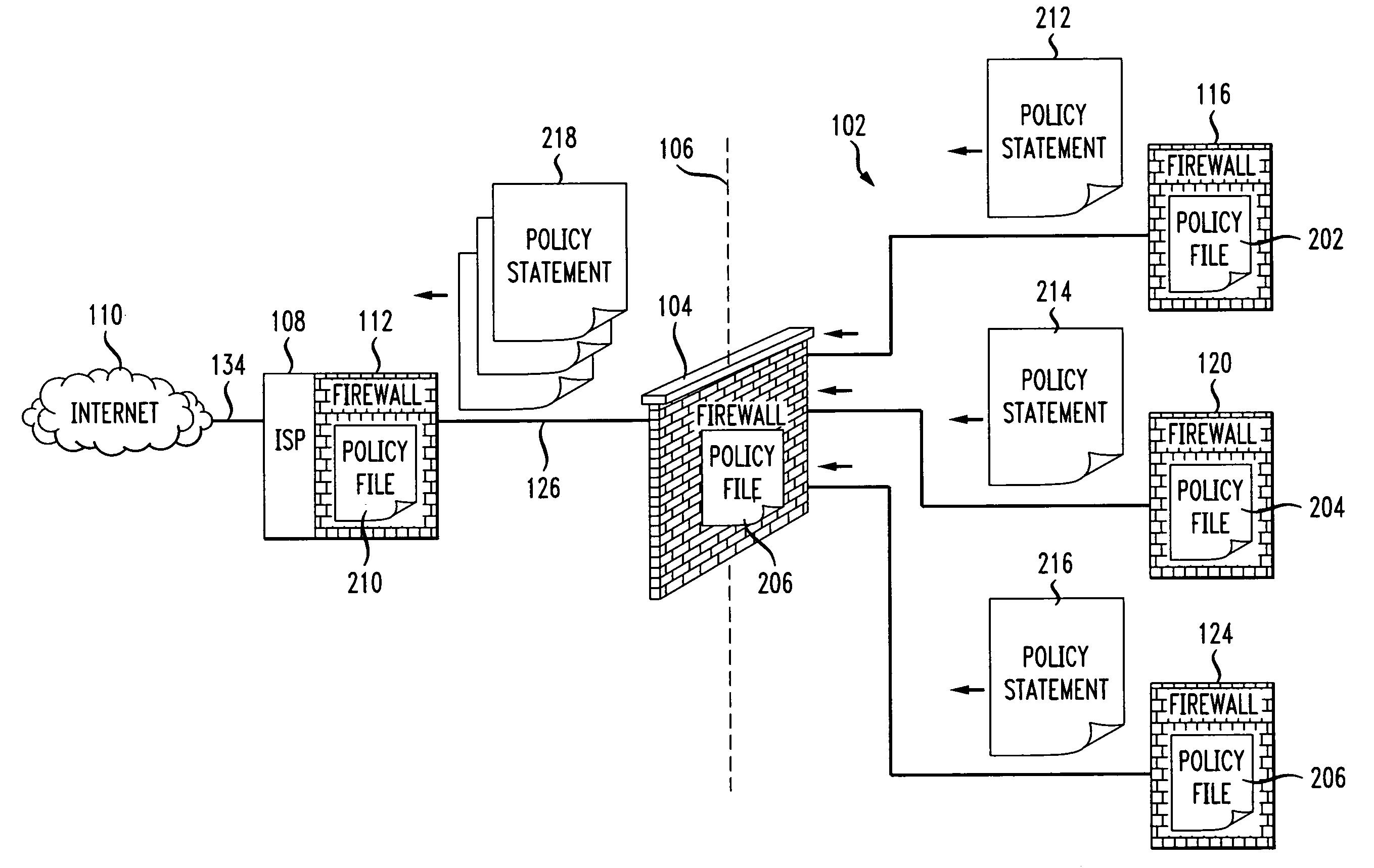
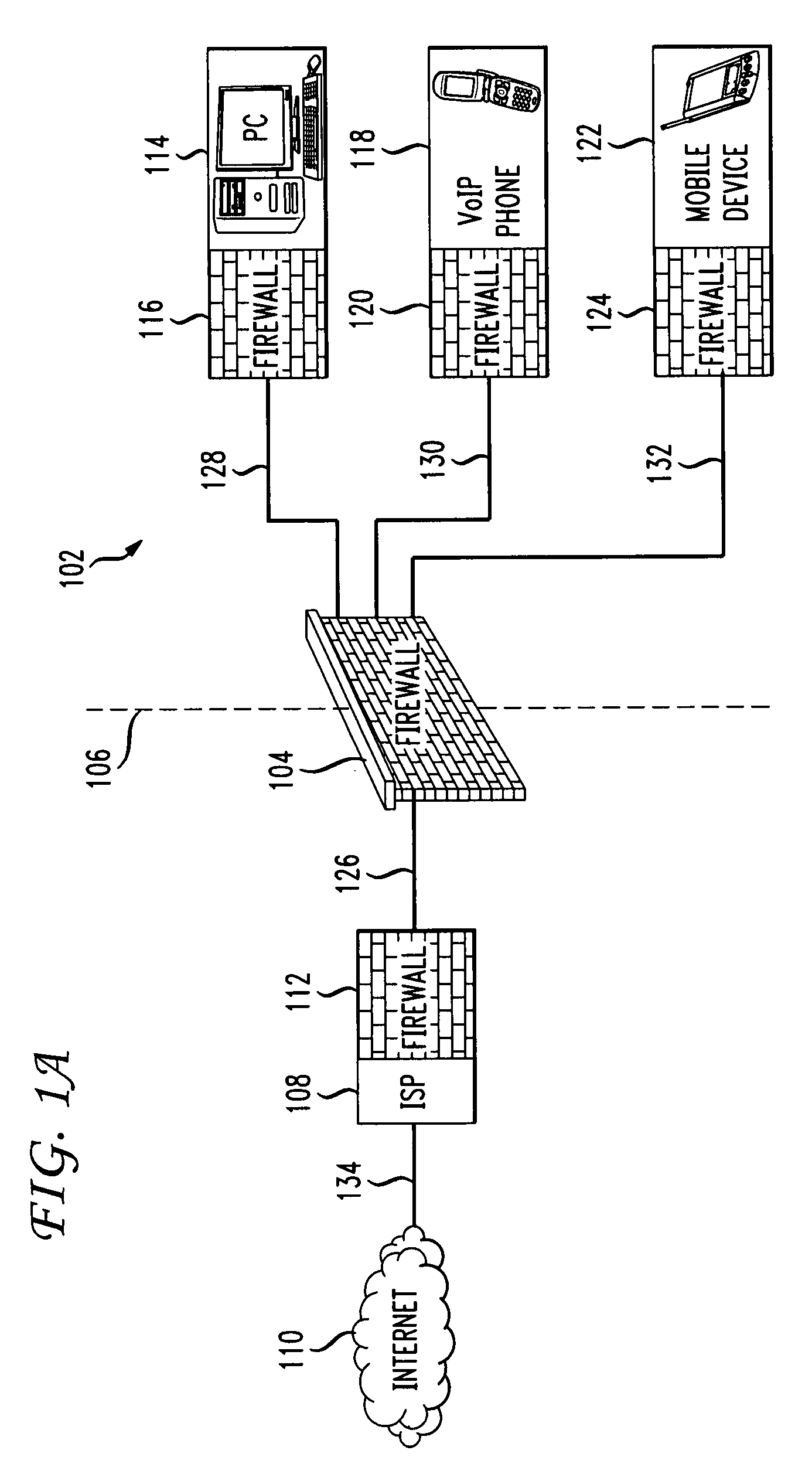
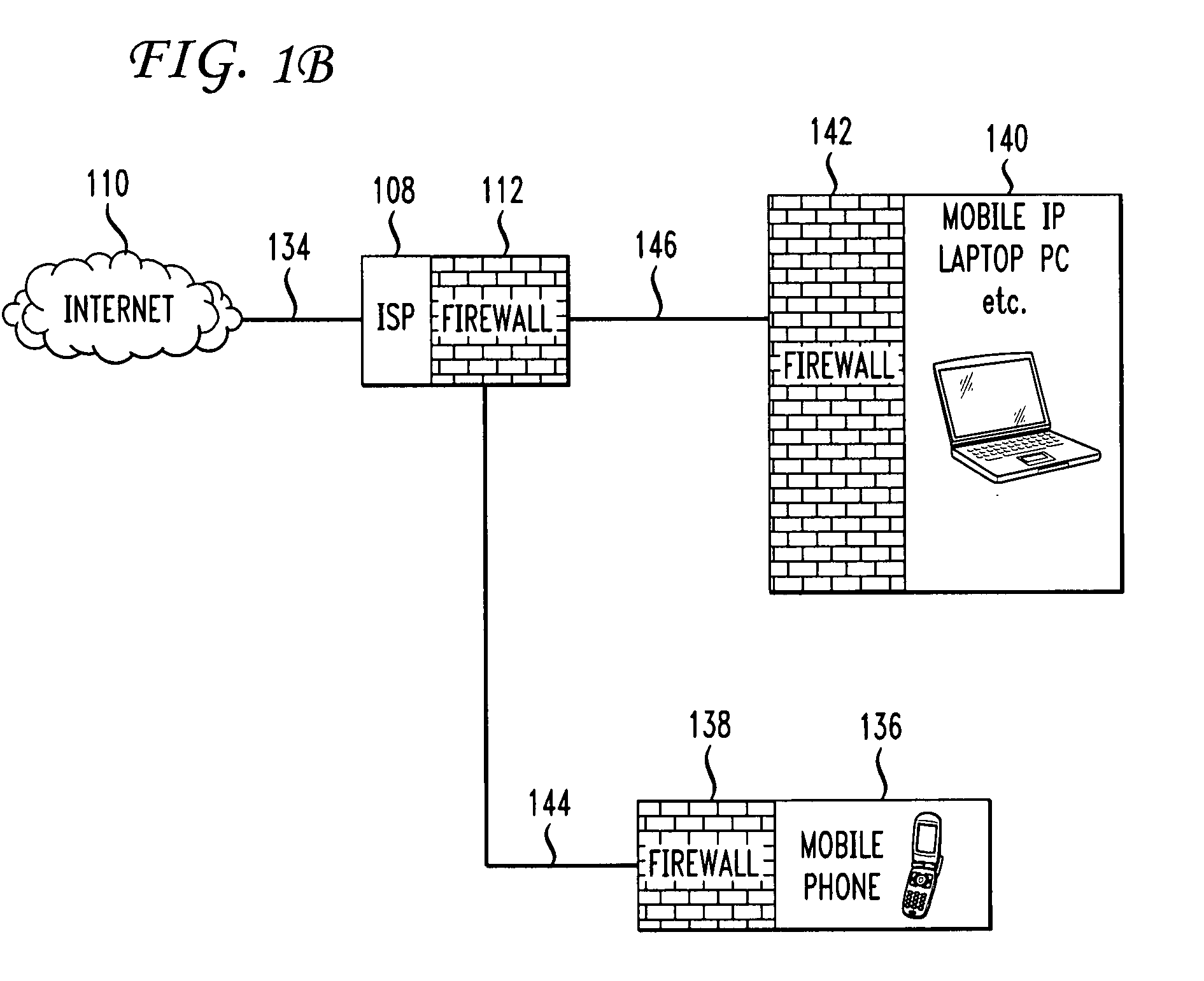
Firewall propagation
InactiveUS20080235755A1Unauthorized memory use protectionHardware monitoringSecurity ruleSecurity policy
Methods and systems for propagating data security policies and rules up a chain of network components, for example, from an end-user device having a firewall, to a network component at the “edge” of the network, such as a so-called “edge” firewall server, from where a policy statement can be transmitted to a service provider, such as an ISP, are described. A device, such as a computer or mobile phone, has, as part of its firewall software, a policy propagation file, that communicates with pre-existing firewall software. The firewall software creates a policy statement upon detecting a triggering event, which is transmitted from the device to the next data security component up the chain, “upstream,” in the network. In some cases this device may be a firewall server or a firewall policy server. The firewall server may combine policy statements from numerous end-user type devices and transmit the policy statement to an external network component, such as an ISP firewall server or similar device. The ISP or other service provider may then use the policy statement to implement date security rules for the devices in the network. In this manner, the firewall operated by the ISP implements rules and policies of a network owner or the owner of a stand-alone device, thereby preventing unwanted traffic from entering the network.
Owner:DIGICERT
Location-based security rules
InactiveUS20050272445A1Unauthorised/fraudulent call preventionInformation formatSecurity ruleApplication software
Location based security rules are provided for preventing unauthorized access to a device, application, system, content, and / or network, etc. The location-based security rules enable a user, computing device, system, etc. to access the requested item or information when the user provides proper identification information. The proper identification information is based in part on the location of the user and / or the user's access request.
Owner:GOOGLE LLC
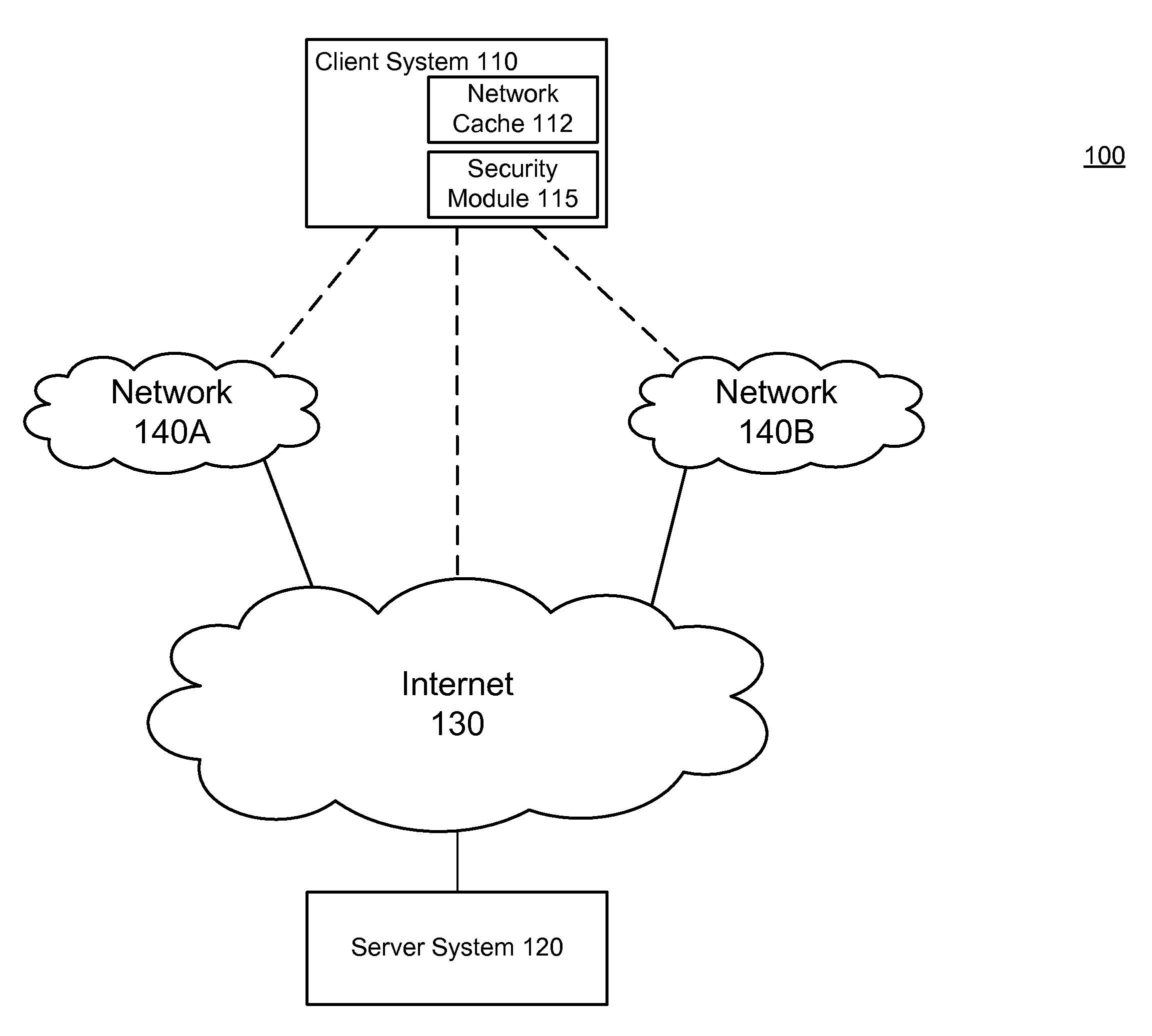
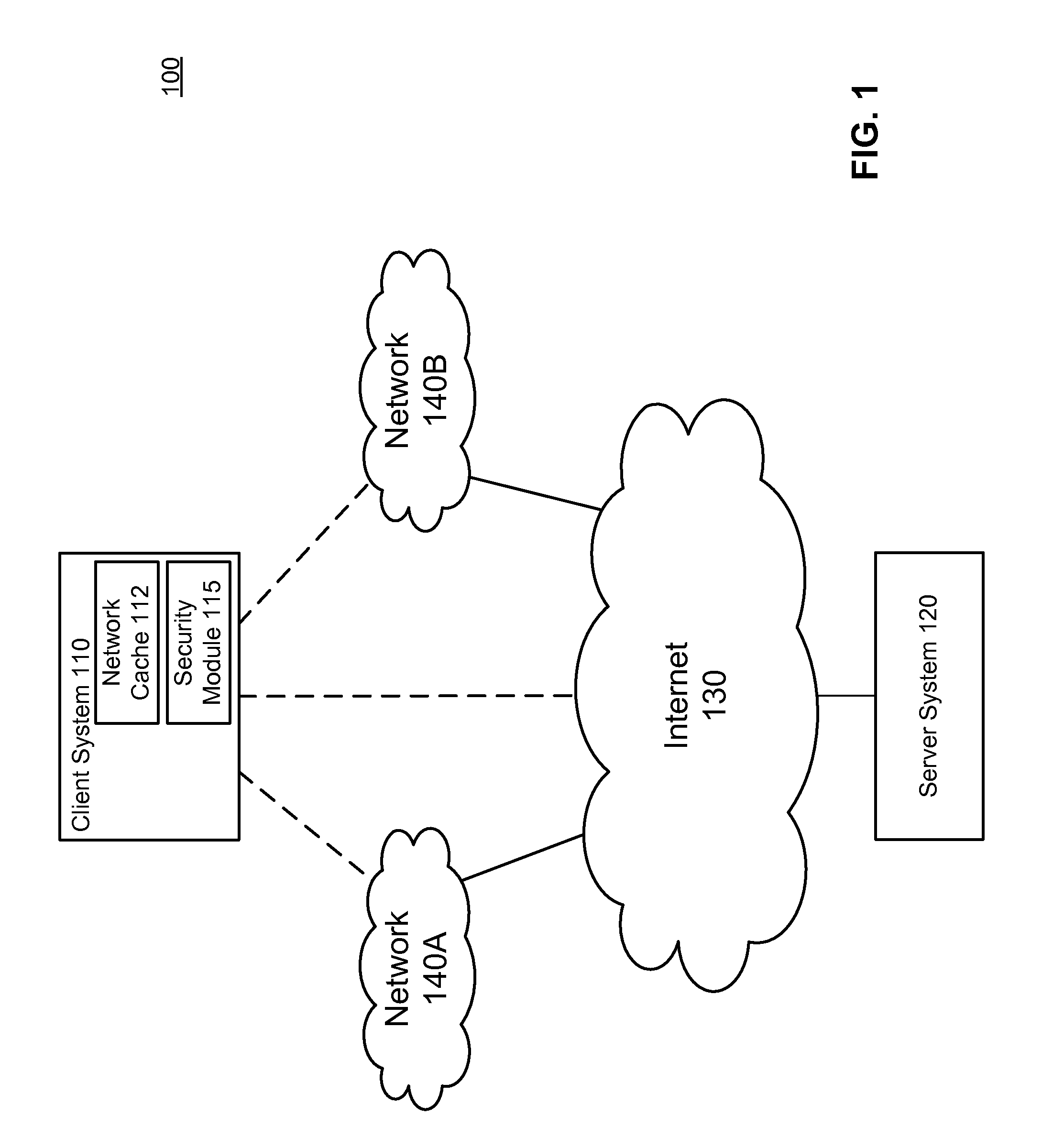
Secure network cache content
ActiveUS8584234B1Prevent malicious activityMemory loss protectionError detection/correctionAccess networkSecurity rule
A security module on a computing device applies security rules to examine content in a network cache and identify suspicious cache content. Cache content is identified as suspicious according to security rules, such as a rule determining whether the cache content is associated with modified-time set into the future, and a rule determining whether the cache content was created in a low-security environment. The security module may establish an out-of-band connection with the websites from which the cache content originated through a high security access network to receive responses from the websites, and use the responses to determine whether the cache content is suspicious cache content. Suspicious cache content is removed from the network cache to prevent the suspicious cache content from carrying out malicious activities.
Owner:CA TECH INC
Secure integrated media center
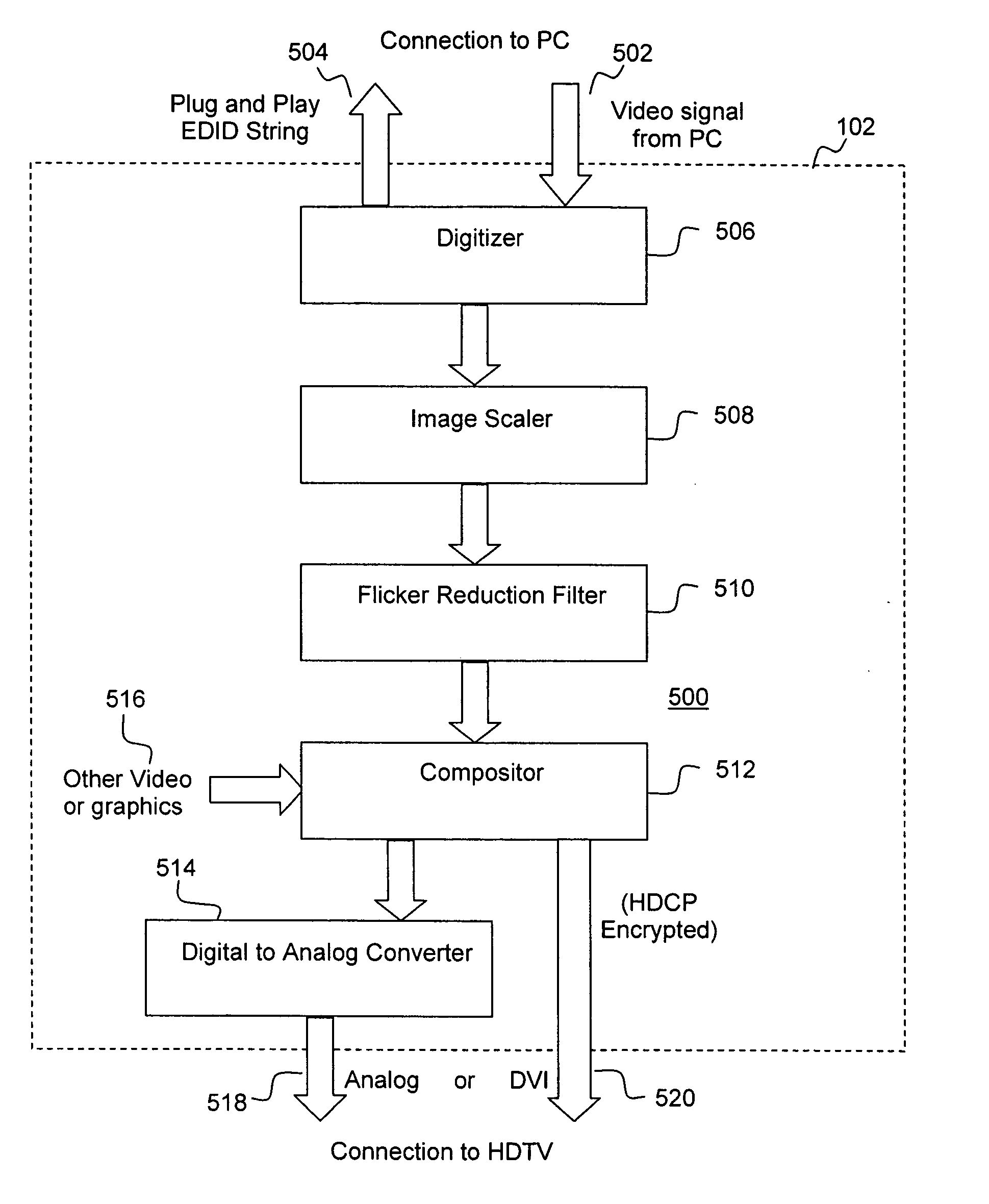
InactiveUS20050125357A1Safe storageTelevision system detailsUnauthorized memory use protectionHard disc driveHigh definition tv
A set-top media system is disclosed which can be combined with an open architecture personal computer (PC) to provide a feature-rich secure integrated media center while meeting security rules of most major conditional access and content protection industry rules such as Cable Labs DFAST and PHILA agreements; and DTLA agreements for 5C-DTCP for IEEE1394, USB, and IP. The set-top media center and PC share common resources such as high definition display, remote control, hard disk drive, and other external unsecure storage devices. All media content is available seamlessly using a PC user interface, including controlled-content media such as high definition TV, within a PC desktop window. All controlled-content media is manipulated and managed within the set-top media system in a seamless manner. A novel mechanism is disclosed to allow controlled-content media to be stored on unsecure devices in encrypted form while overcoming the disk cloning attack problem for move operations.
Owner:SAADAT ABBAS SASAN +1
Information record infrastructure, system and method
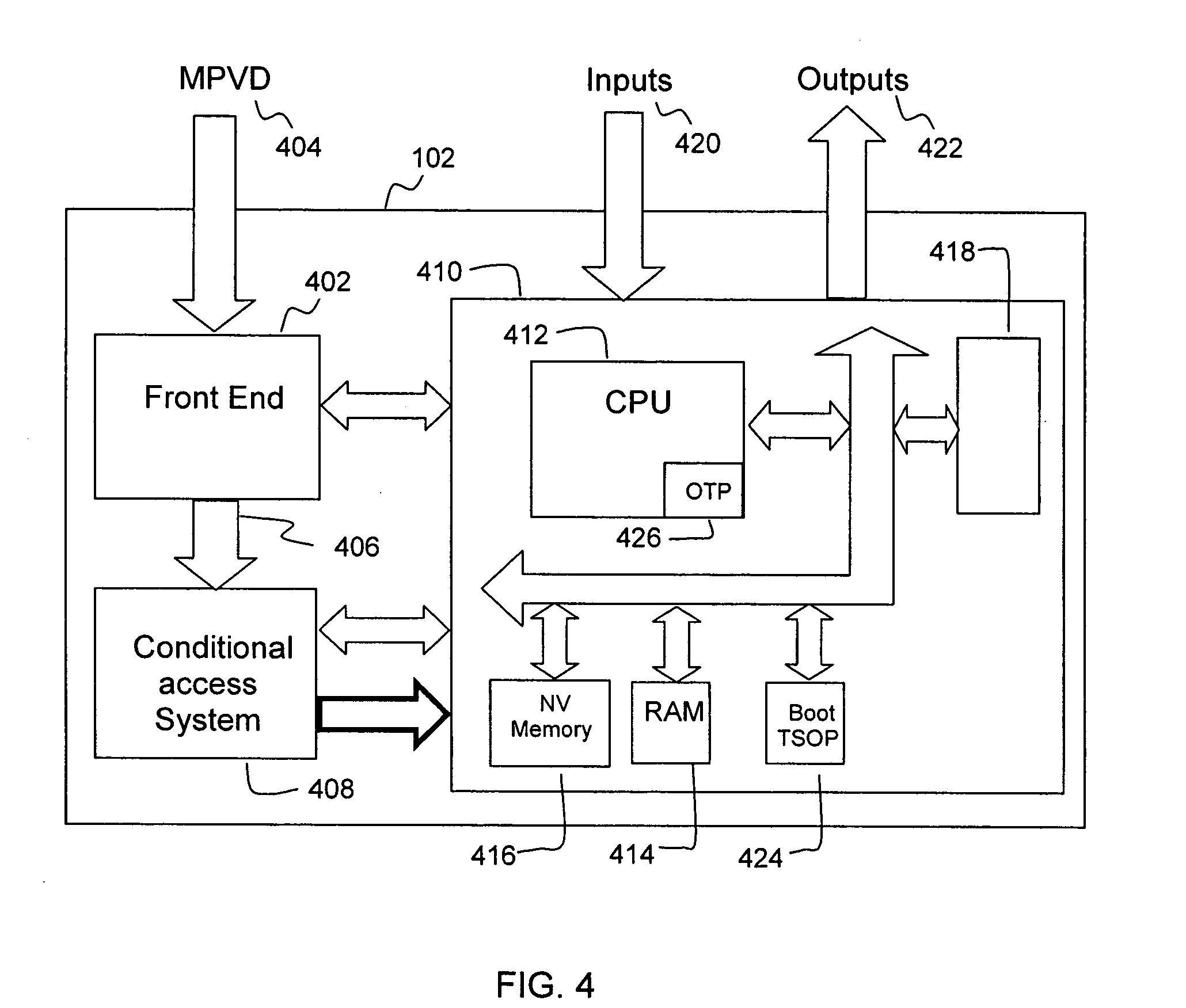
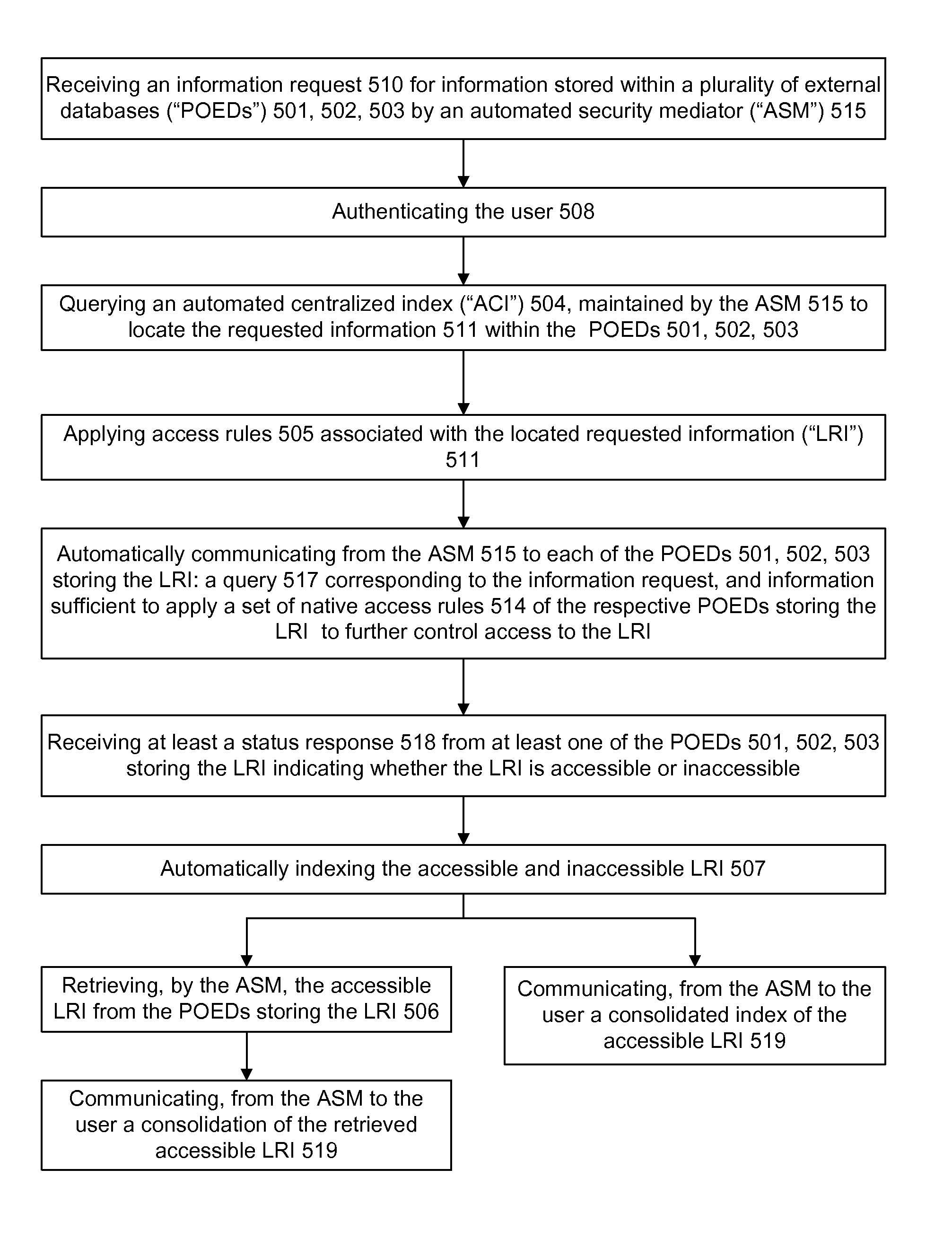
InactiveUS20100241595A1Low costIncrease the number ofDigital data processing detailsTelemedicineSecurity ruleInformation infrastructure
A security mediator, comprising an input configured to receive a user information request; an automated index, stored in a memory, configured to store information for determining which of a plurality of remote databases stores information responsive to the request; an automated security rule base, stored in a memory, containing rules applicable to information responsive to the request stored in the plurality of remote databases; a communication port configured to communicate to a plurality of remote databases which store information responsive to the request: security information, a query corresponding to the request and associated rules applicable to the information responsive to the request at the respective remote database; and at least one processor being configured to apply at least one security rule responsive to the query of the automated security rule base, and index information derived from a plurality of the remote databases, in a manner which permits application of the rules and which restricts insecure use of the index.
Owner:RPX CORP
Usage pattern based user authenticator
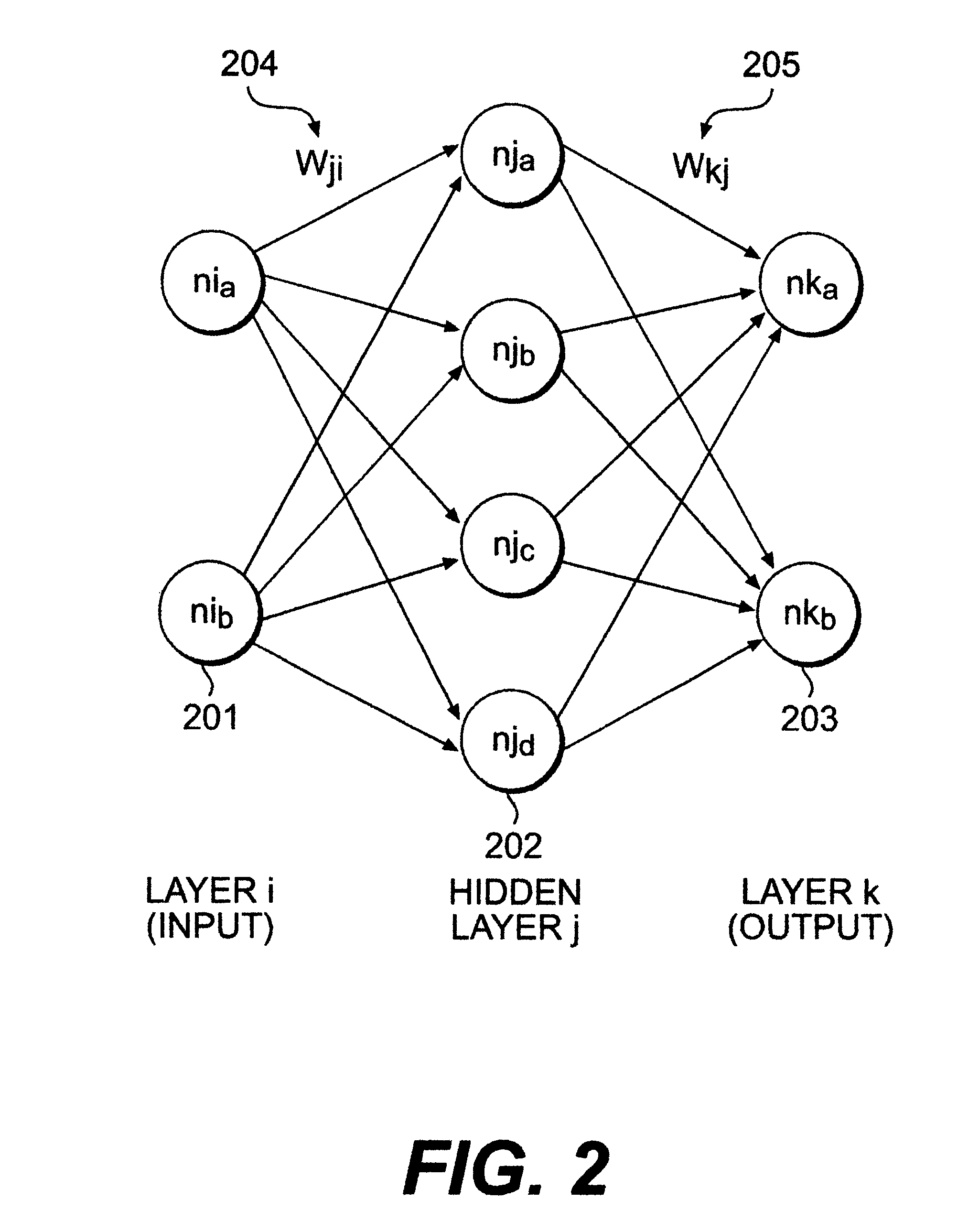
InactiveUS6334121B1Control damagePreventing executionDigital computer detailsComputer security arrangementsOperational systemOperating system level
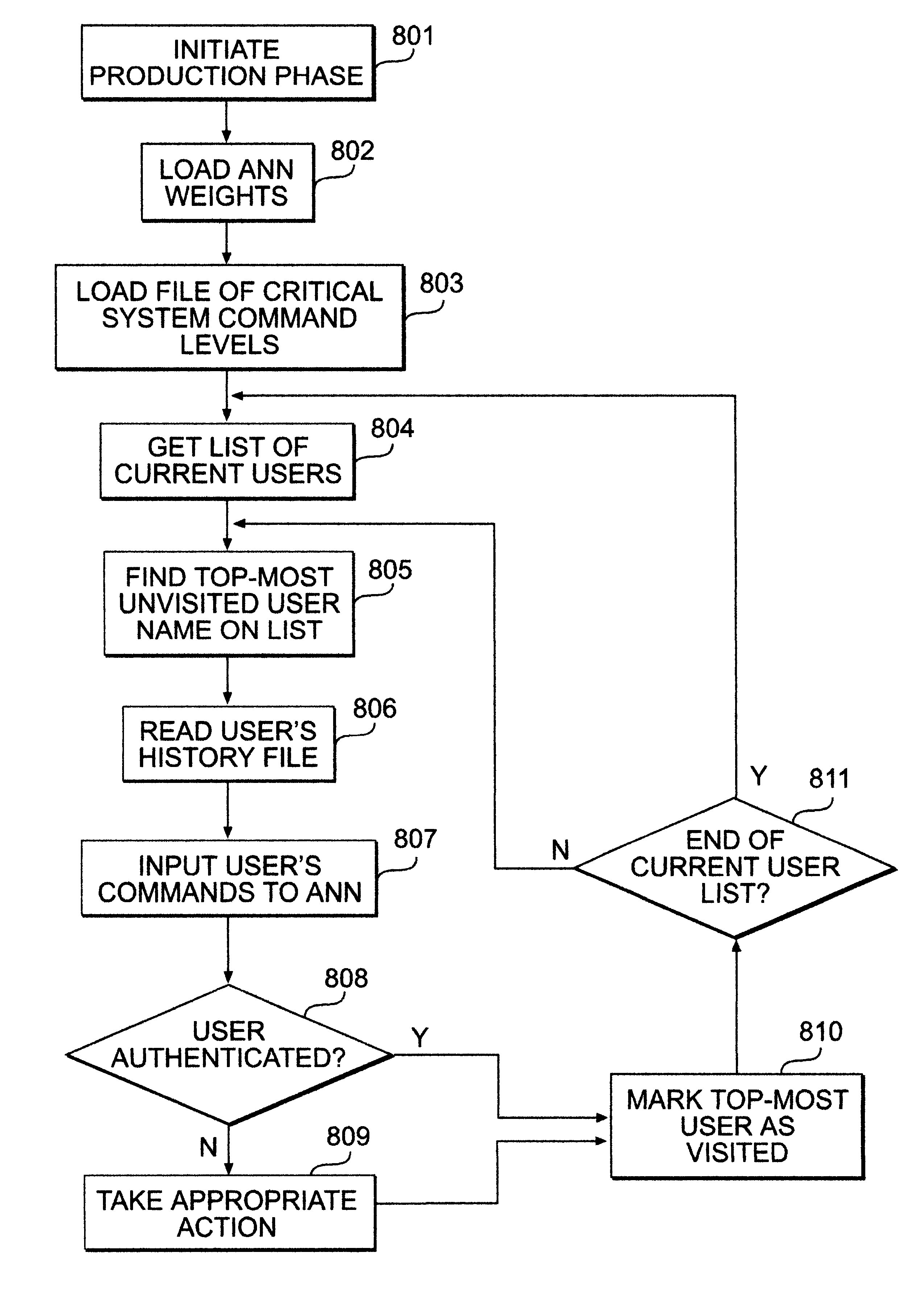
A usage based pattern authenticator for monitoring and reporting on user usage patterns in an operating system using a set of security rules and user usage patterns. This computer system security tool authenticates users at the operating system level in multi-user operating systems. It supports system administrators in limiting the ability of unauthorized users to disrupt system operations using a neural network and set of rules to track usage patterns and flag suspicious activity on the system. The data collection mode collects and stores usage patterns of authenticated users. The training mode trains an artificial neural network and sets the interconnection weights of the network. The production mode monitors and reports on usage patterns, and optionally performs automatic responses when confronted with non-authenticated users.
Owner:VIRGINIA COMMONWEALTH UNIV
Database cloning and migration for quality assurance
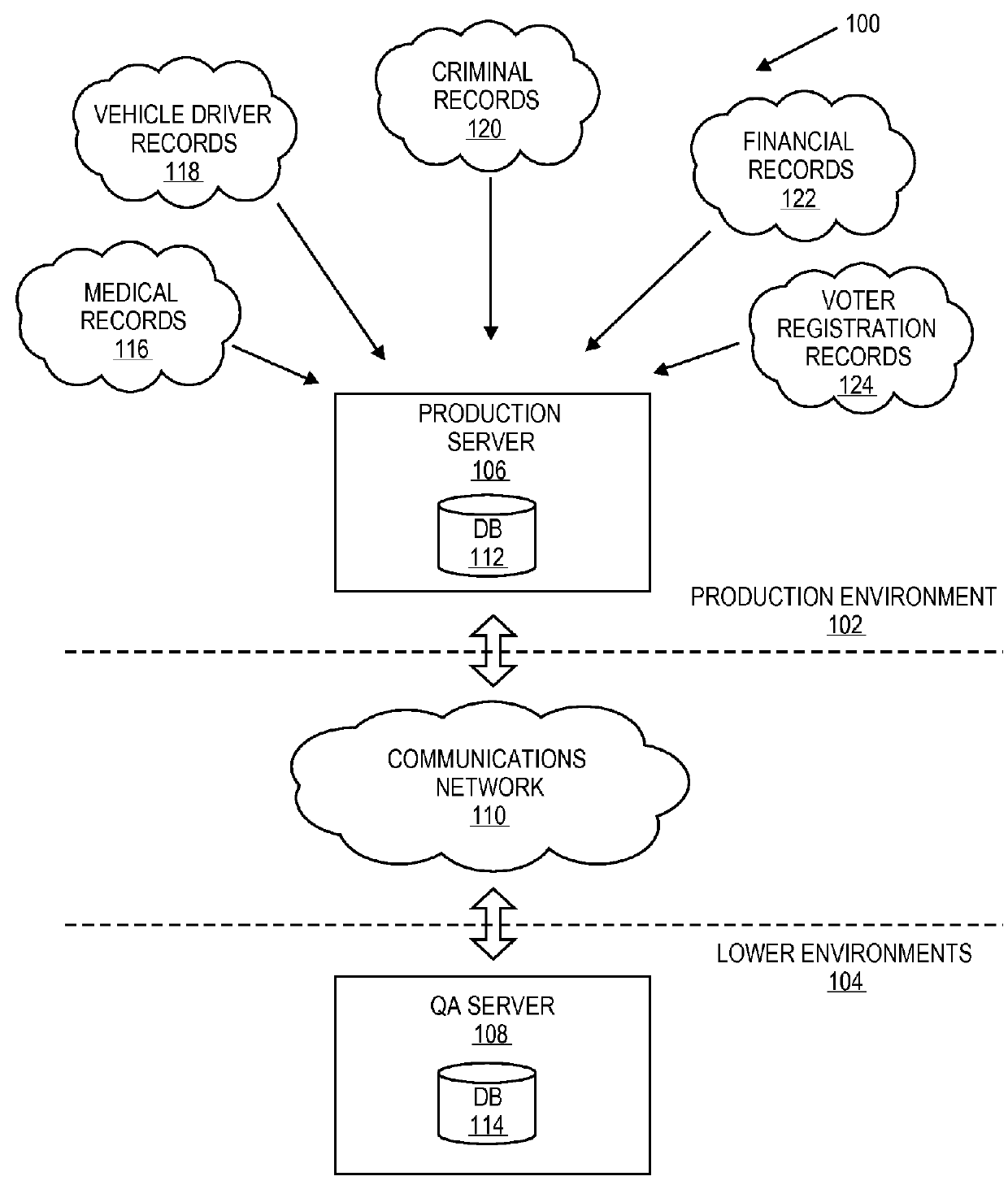
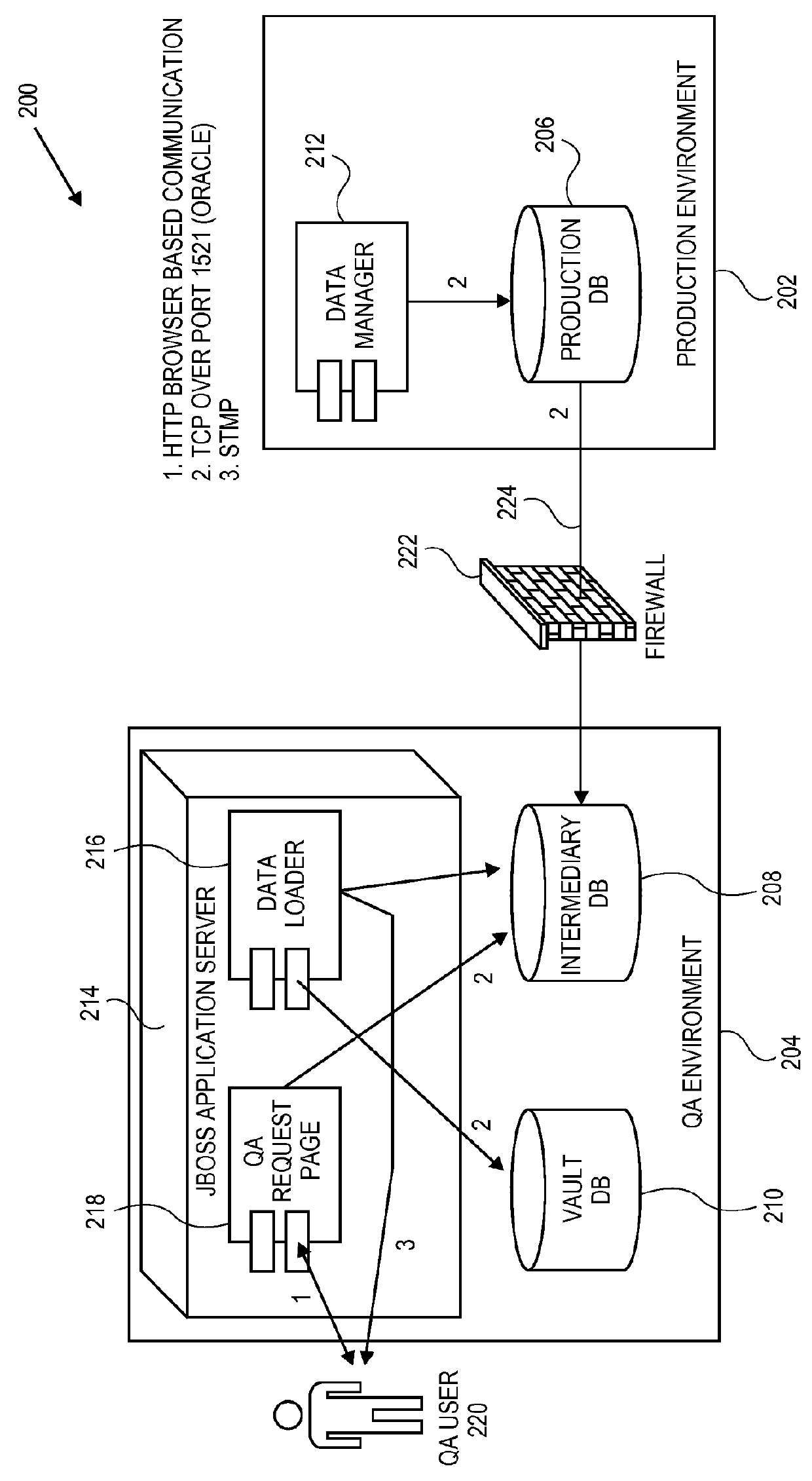
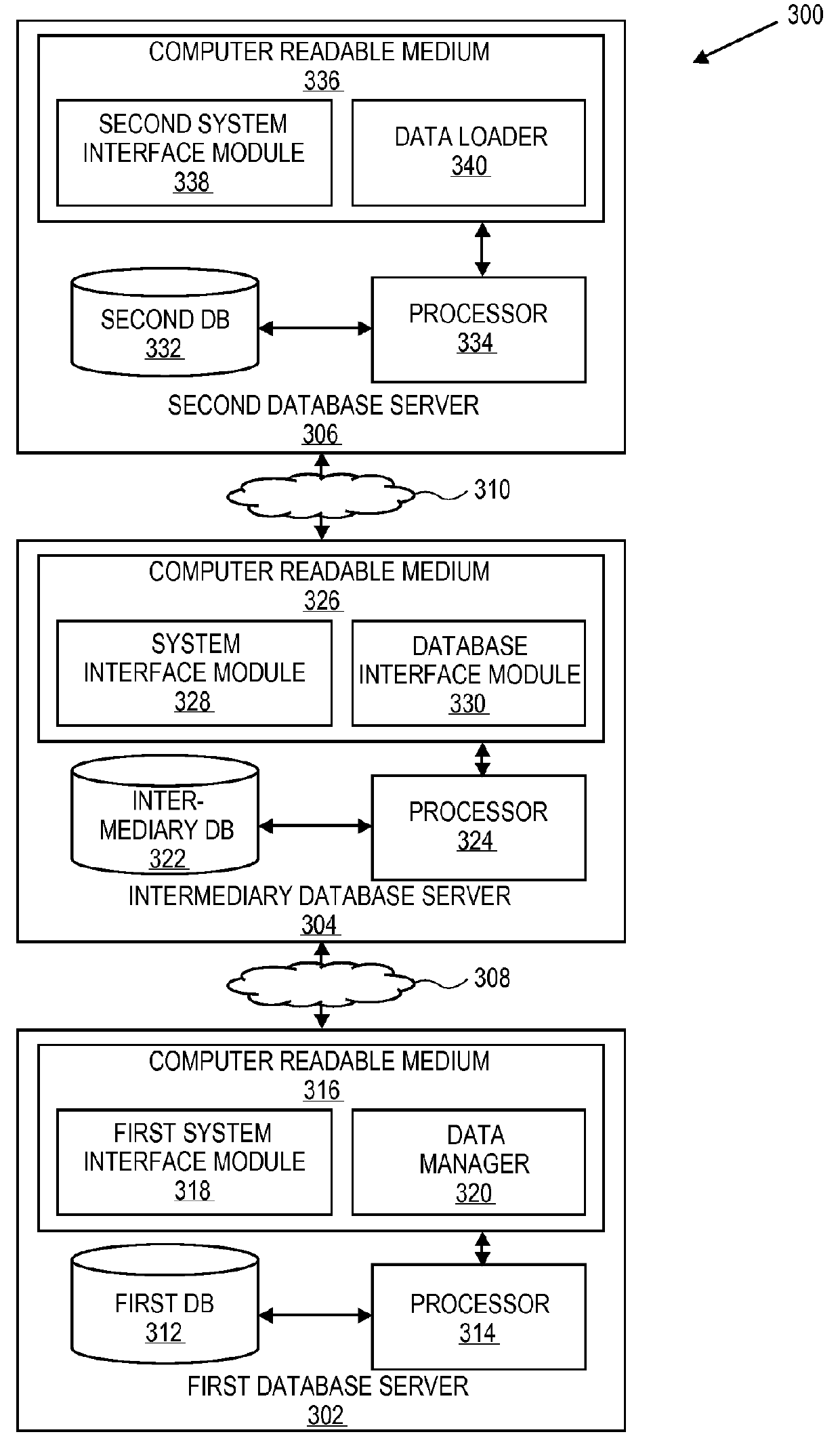
ActiveUS9229964B2Data processing applicationsDigital data information retrievalPaymentQuality assurance
Embodiments of the invention relate to systems and methods for cloning a production database for quality assurance (QA) by the merchant users. A QA user may request tokens, card types and other data associated with a payment device for quality assurance purposes. The payment network redirects the QA request to a go-between database that is present between the QA user and the production environment of the payment network rather than pull the information directly from the production environment. As a result, the merchant is able to use tokens for testing, without violating consumer privacy and security rules and regulations (e.g., PCI rules). The QA user does not have to create a customized testing solution.
Owner:VISA INT SERVICE ASSOC
Information record infrastructure, system and method
InactiveUS8380630B2Low costIncrease the number ofDigital data processing detailsTelemedicineSecurity ruleInformation infrastructure
A security mediator, comprising an input configured to receive a user information request; an automated index, stored in a memory, configured to store information for determining which of a plurality of remote databases stores information responsive to the request; an automated security rule base, stored in a memory, containing rules applicable to information responsive to the request stored in the plurality of remote databases; a communication port configured to communicate to a plurality of remote databases which store information responsive to the request: security information, a query corresponding to the request and associated rules applicable to the information responsive to the request at the respective remote database; and at least one processor being configured to apply at least one security rule responsive to the query of the automated security rule base, and index information derived from a plurality of the remote databases, in a manner which permits application of the rules and which restricts insecure use of the index.
Owner:RPX CORP
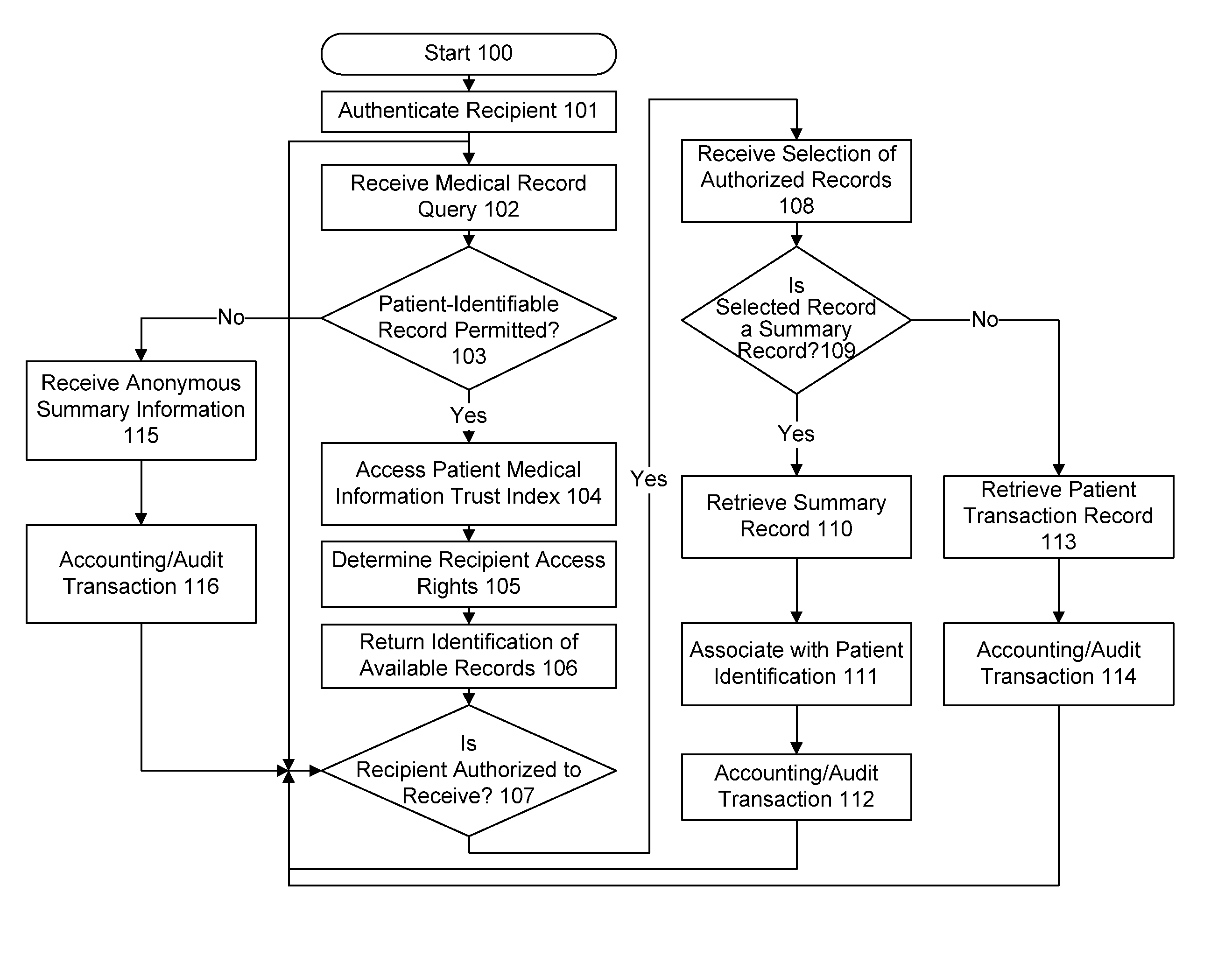
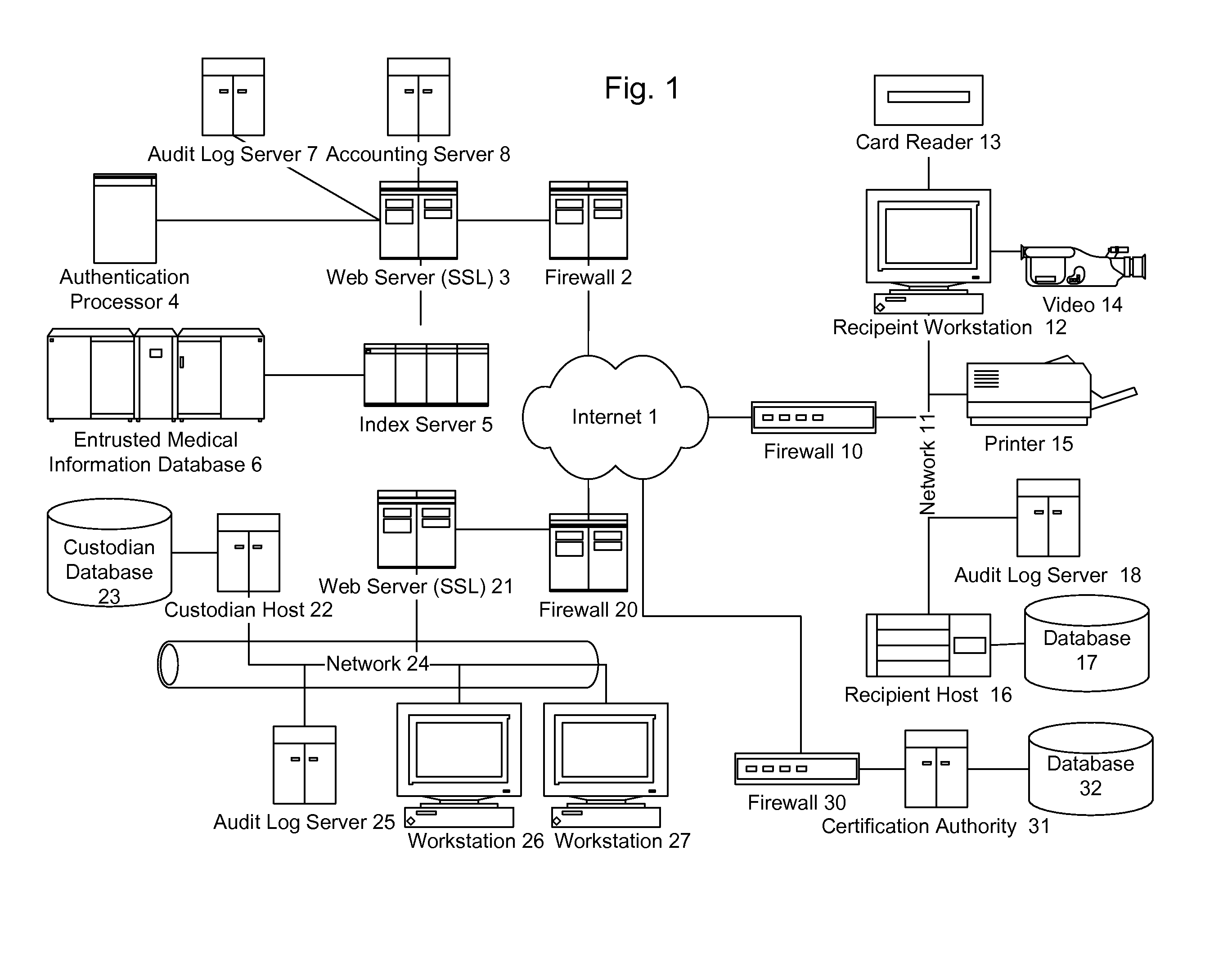
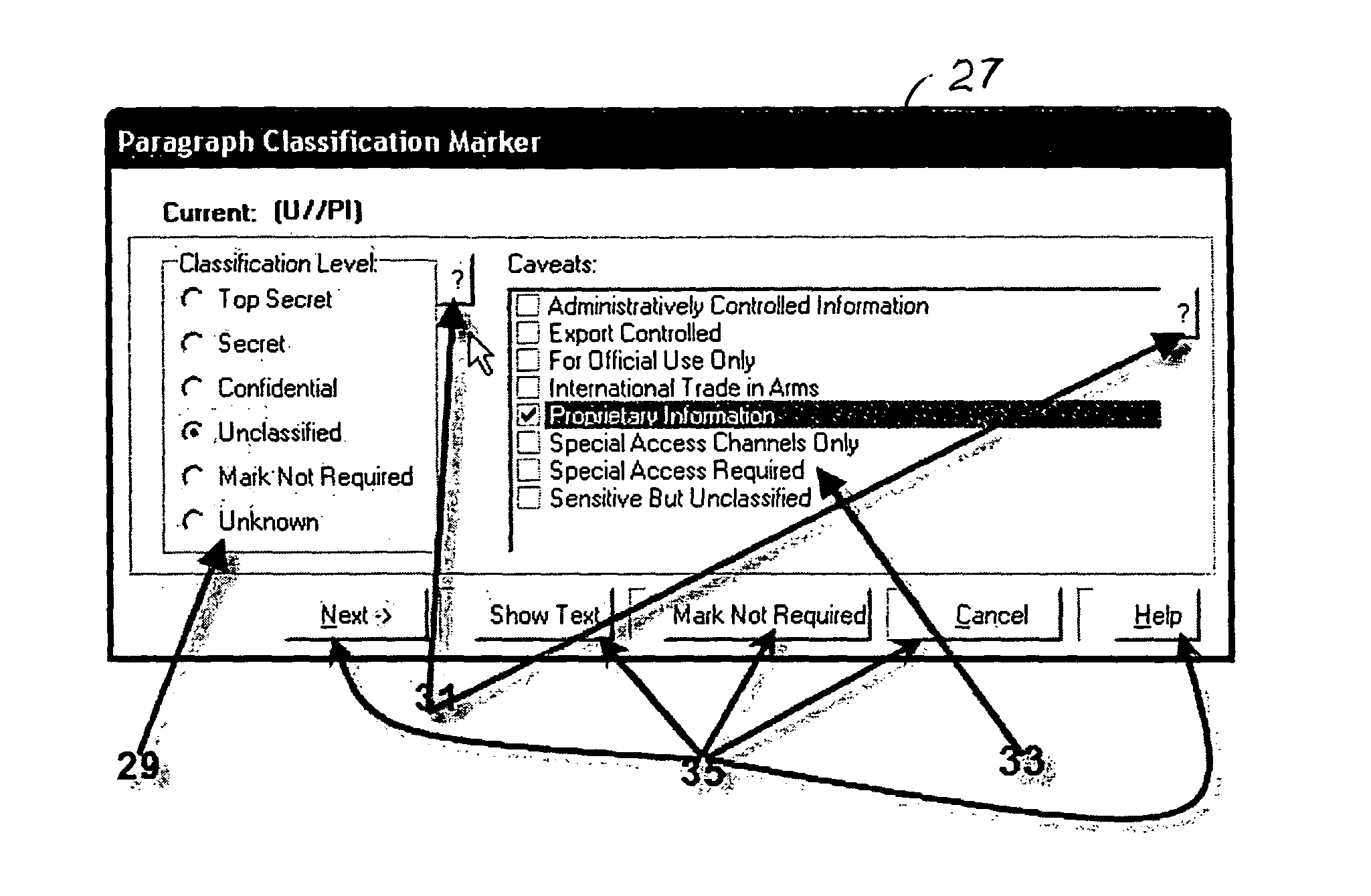
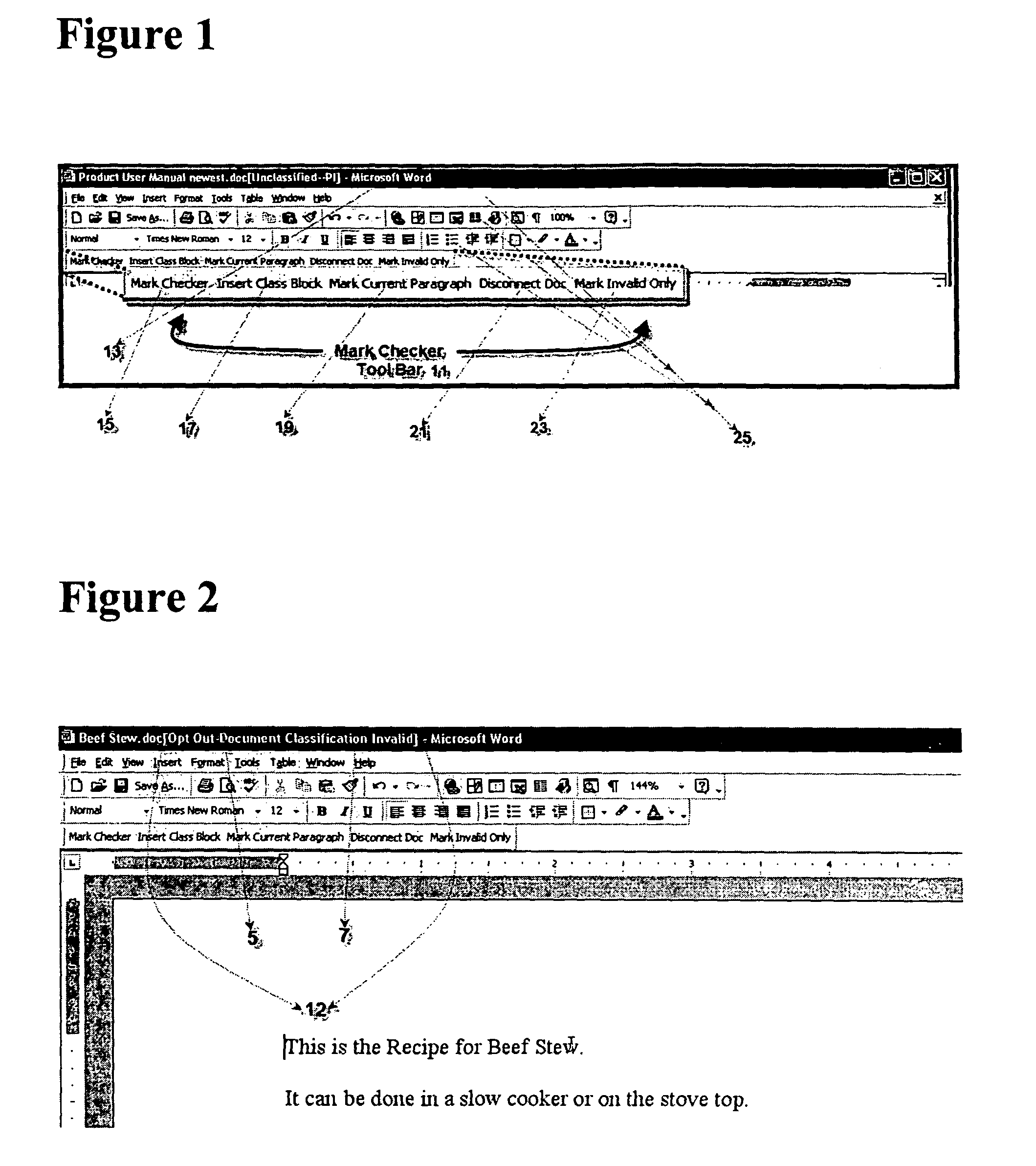
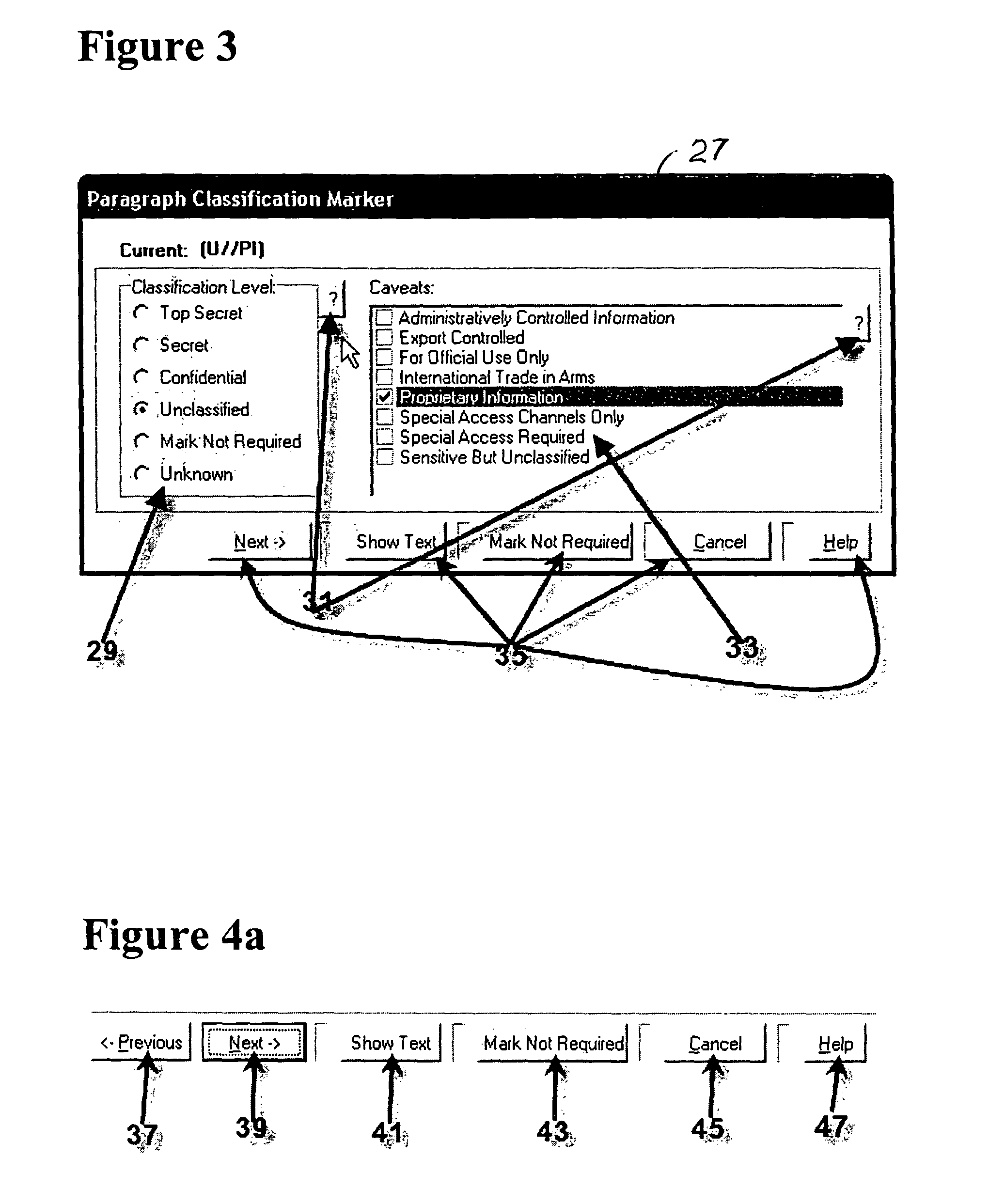
Method for providing customized and automated security assistance, a document marking regime, and central tracking and control for sensitive or classified documents in electronic format
ActiveUS7958147B1Guarantee capacityPositive determinationDigital data information retrievalDigital data processing detailsOff the shelfDocumentation procedure
A software engine runs in a compatible mode with off-the-shelf word processors, e-mail programs and presentation development software and other document development software. The software engine is used for the security classification of sensitive or national security classified information in electronic and resultant hard copy document formats. The software engine ensures that the individual considers all informational portions of a document, that appropriate document marks are employed, that document marks in their electronic format are persistent and that all necessary information, such as classification guides, standards and security regulations, provided by the organization to classify information is at hand and immediately available. In addition to the document sensitivity or classification determination and marking support, the software engine tracks and controls documents and the electronic media storing documents. It also provides warnings and alarms, ad hoc document security analysis and reporting capability to system security administrators with respect to document or network events or captured information that may be indicative of risk to the information requiring protection. The software also provides the ability for an organization to centrally establish and control a security classification or sensitivity marking hierarchy for automated security classification support.
Owner:TURNER JAMES LUKE +1
Location-Based Security Rules
InactiveUS20080096529A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecurity ruleApplication software
Location based security rules are provided for preventing unauthorized access to a device, application, system, content, and / or network, etc. The location-based security rules enable a user, computing device, system, etc. to access the requested item or information when the user provides proper identification information. The proper identification information is based in part on the location of the user and / or the user's access request.
Owner:GOOGLE LLC
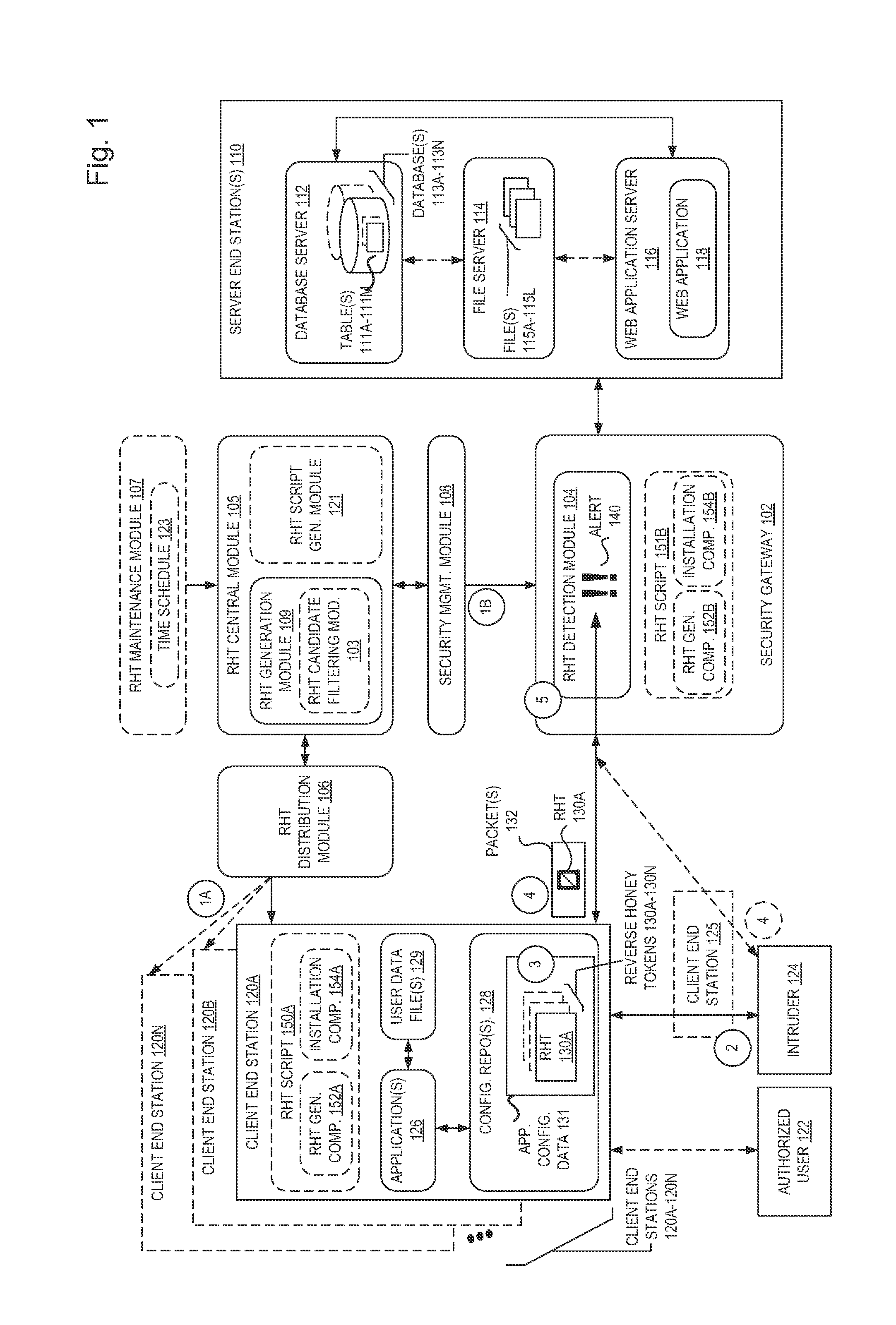
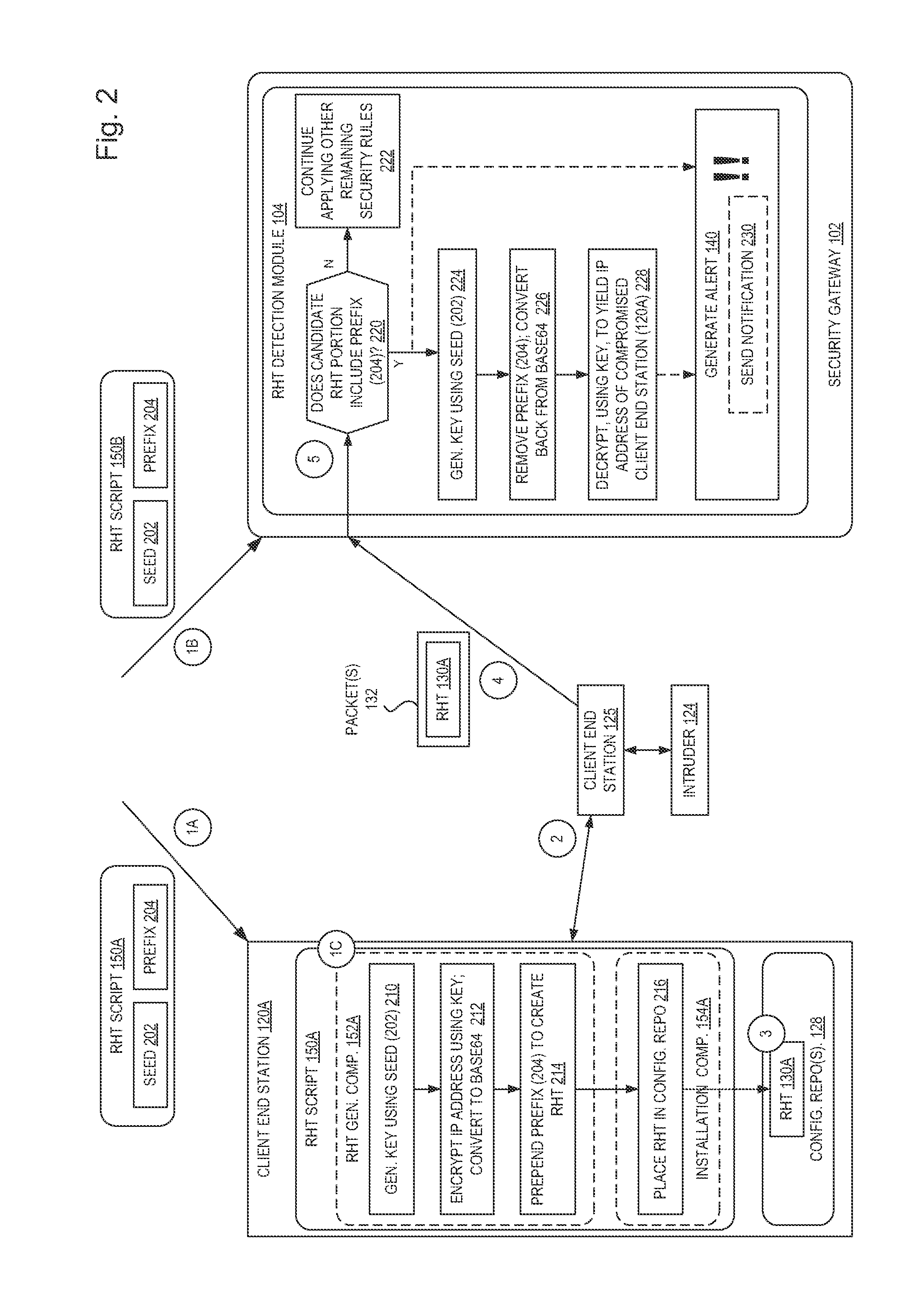
Compromised insider honey pots using reverse honey tokens
According to one embodiment, a method for setting a trap to detect that an intruder has compromised a client end station (CES) in an attempt to gain unauthorized access to enterprise data provided by a server is described. The method includes causing a honey token to be placed on the CES secluded within a configuration repository, wherein the honey token is metadata and / or instructions indicating how applications can seemingly access the enterprise data but that is actually invalid, and the honey token is placed on the CES and not on the server. The method also includes causing attribute values to be installed on a security gateway for a security rule causing the security gateway to monitor network traffic for attempted use of the honey token, and to generate an alert when a set of one or more packets that include the honey token are received.
Owner:IMPERVA
Rule-driven specification of web service policy
ActiveUS7661124B2Computer security arrangementsMultiple digital computer combinationsWeb serviceUser input
Example embodiments provide for a rule-based wizard type tool for generating secure policy documents. Wizard pages present a user with general Web Service security options or questions at a user interface, which abstracts the user from any specific code, e.g., XML code, used for creating a Web Service policy document. Based on user input selecting general criteria, security rules are accessed and evaluated for automatically making choices on behalf of the user for creating a secure policy document. Other embodiments also provide for presenting the user with an easily understandable visual representation of selected criteria of a policy document in, e.g., a tree like structure that shows relationships between various elements of the criteria.
Owner:MICROSOFT TECH LICENSING LLC
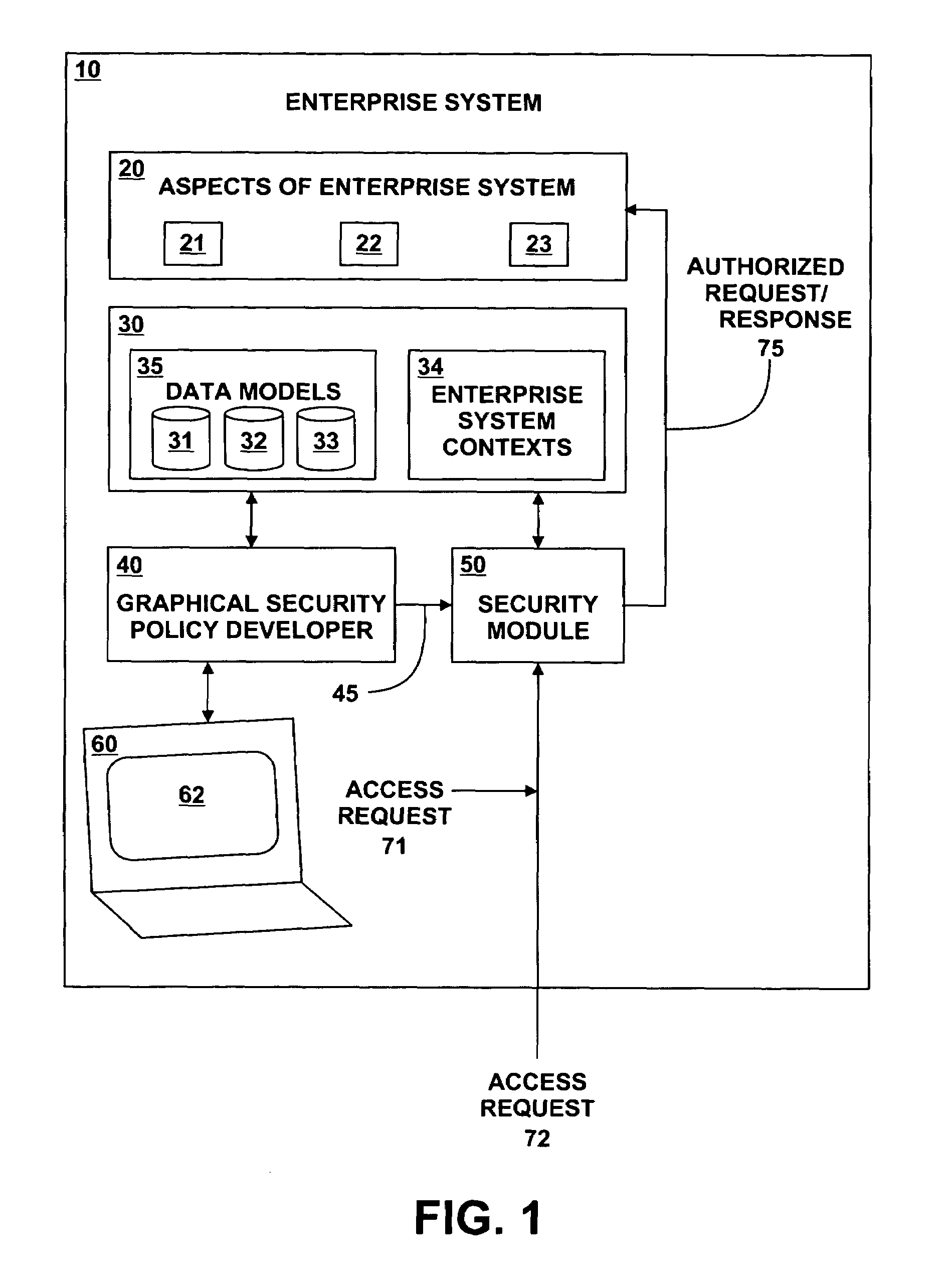
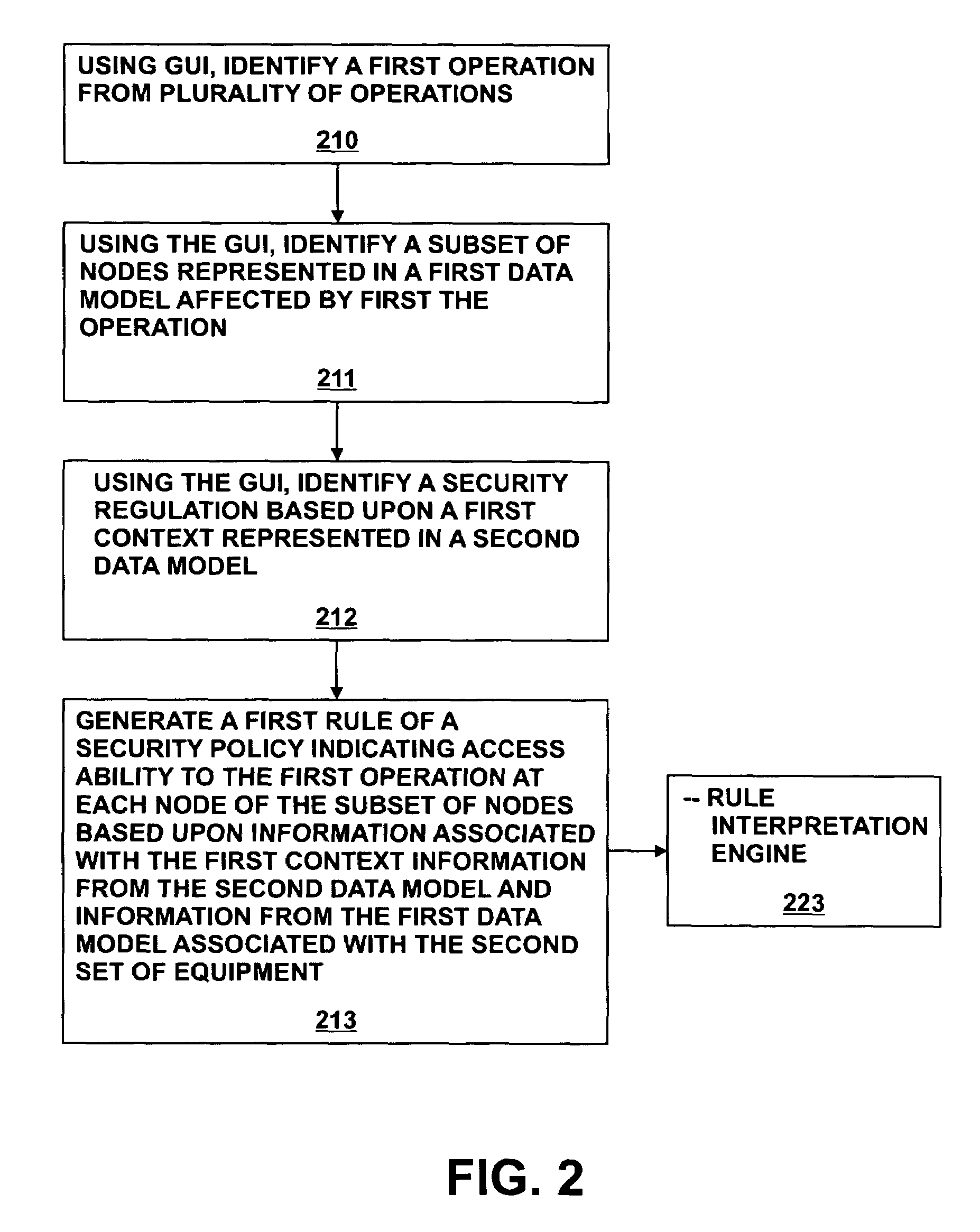
Method and system for generating access policies
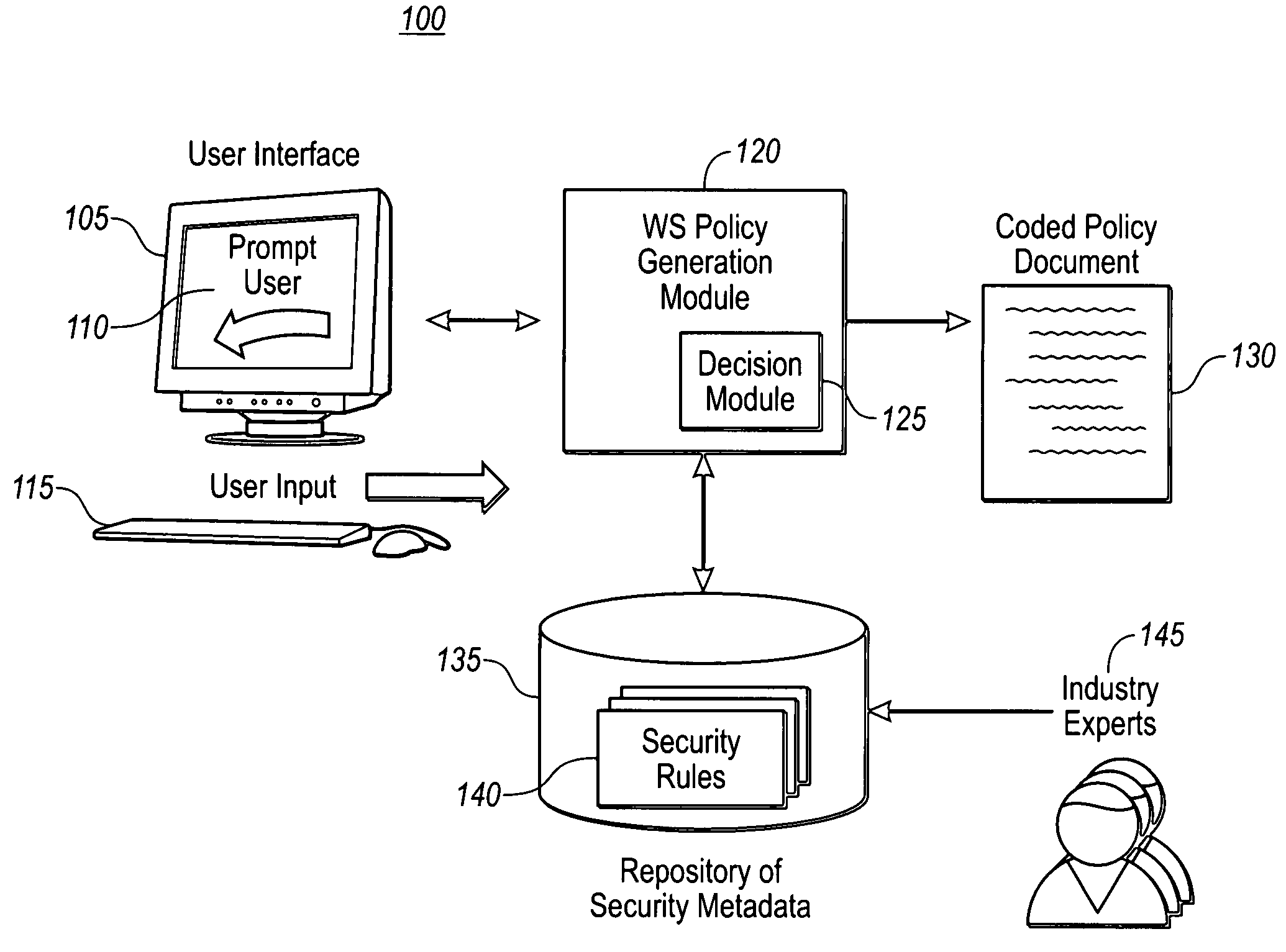
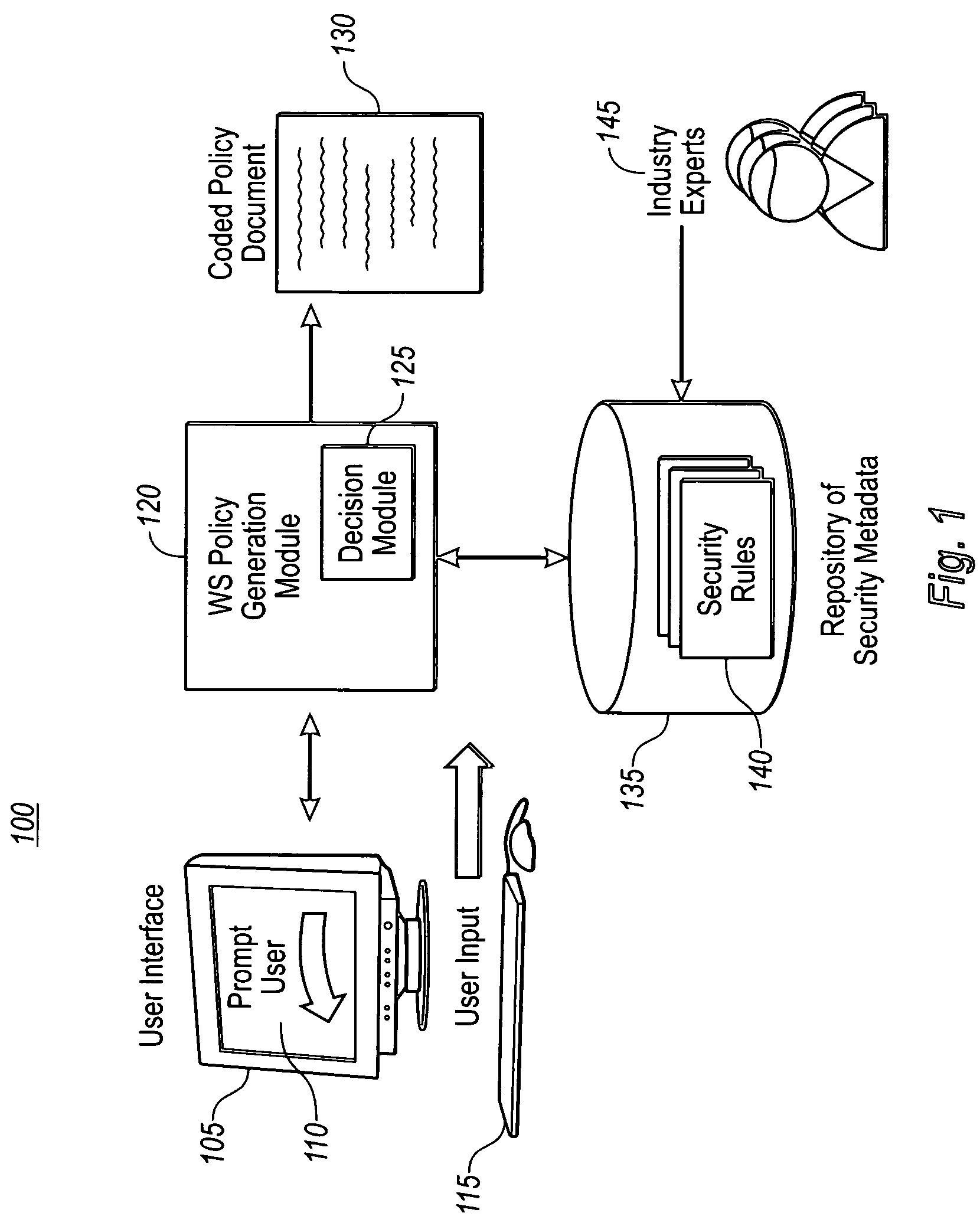
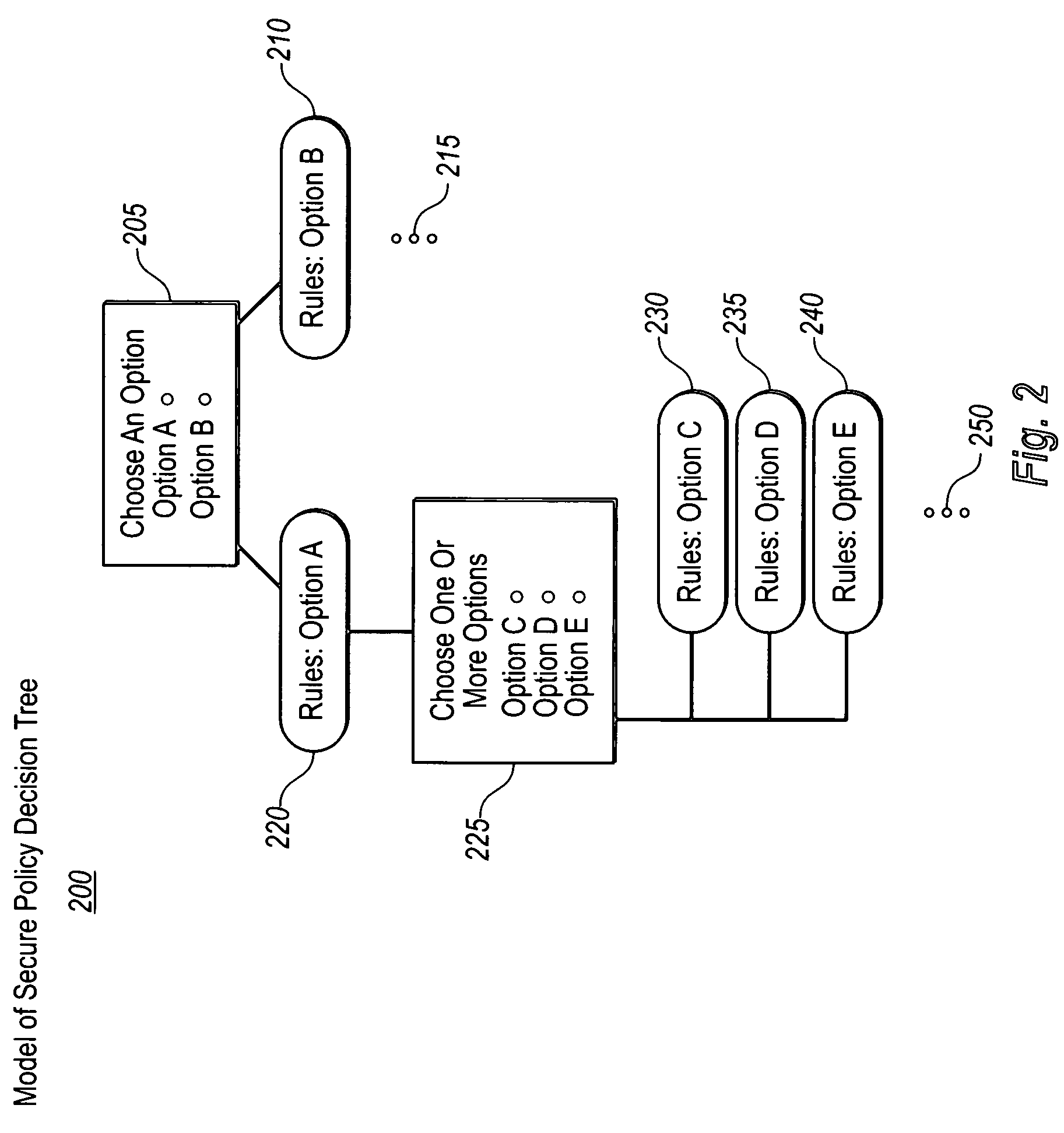
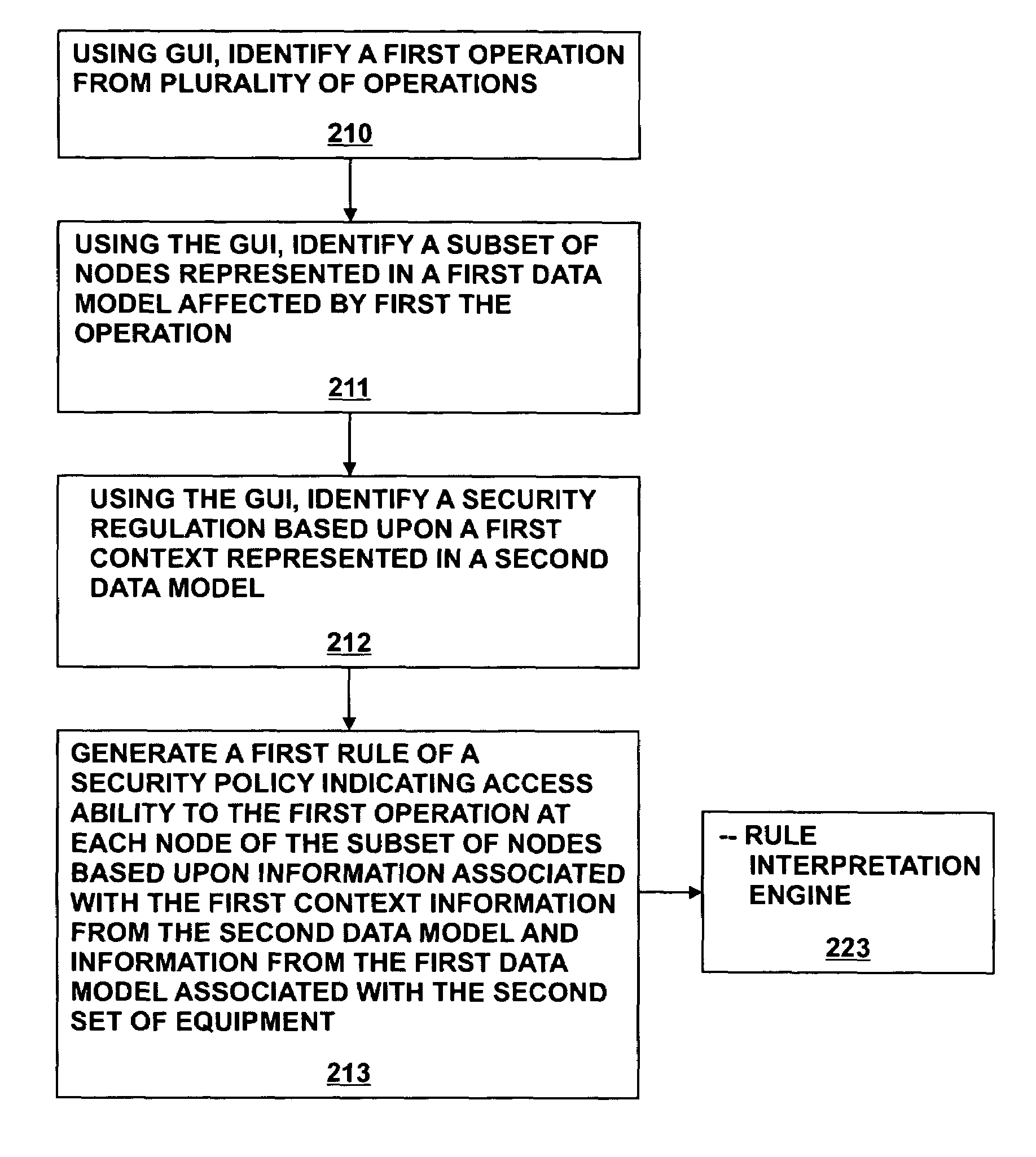
A method and system for generating security rules for implementation by a rule interpretation engine to define accessibility to one or more aspects of an Enterprise System is described. The method and system allow a security officer to graphically indicate an operation to be affected by the security rule being defined; a specific aspect of the system affected by the rule; a security regulation to be implemented by the rule; and an access type to be permitted by the rule.
Owner:ADVANCED MICRO DEVICES INC +2
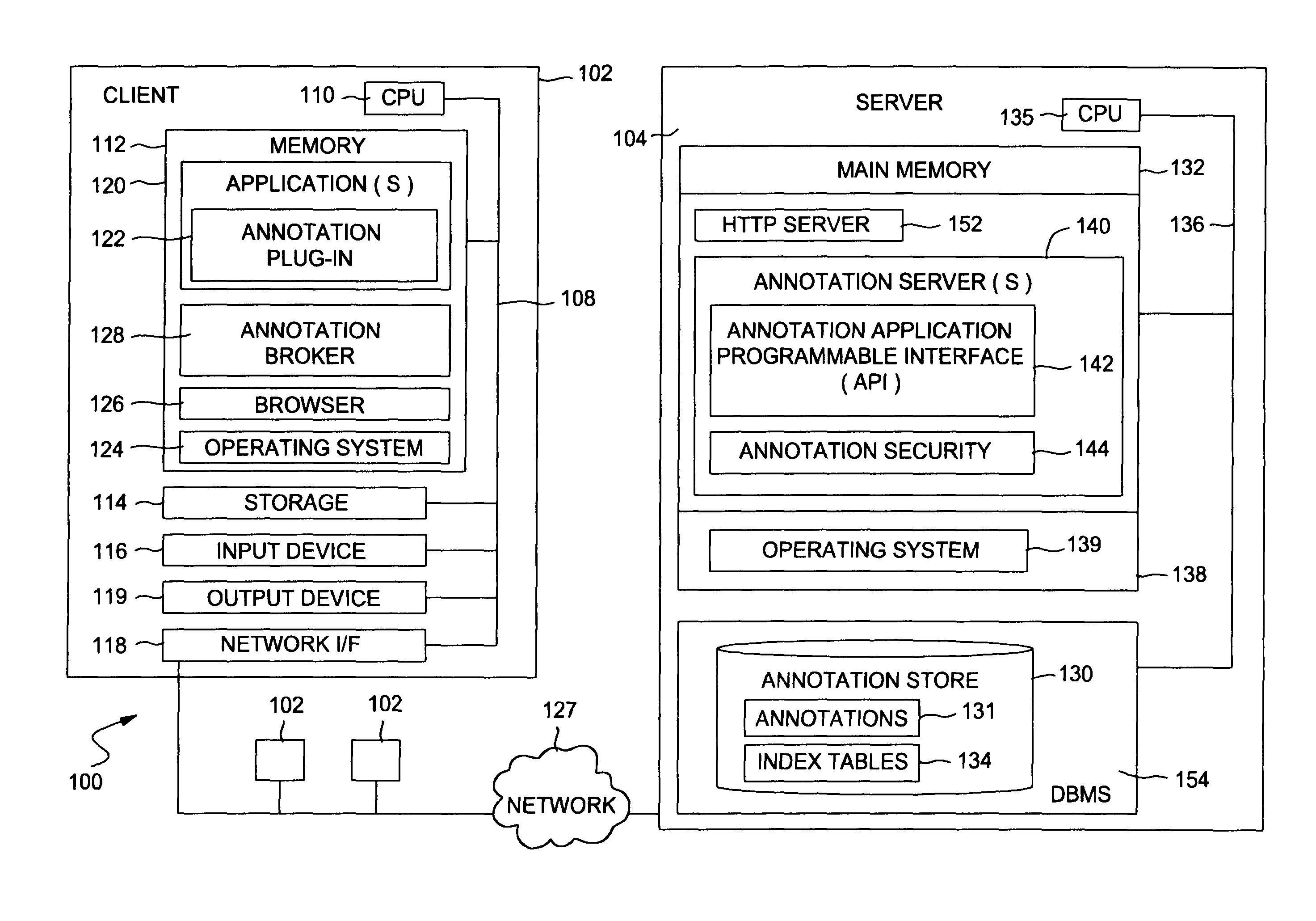
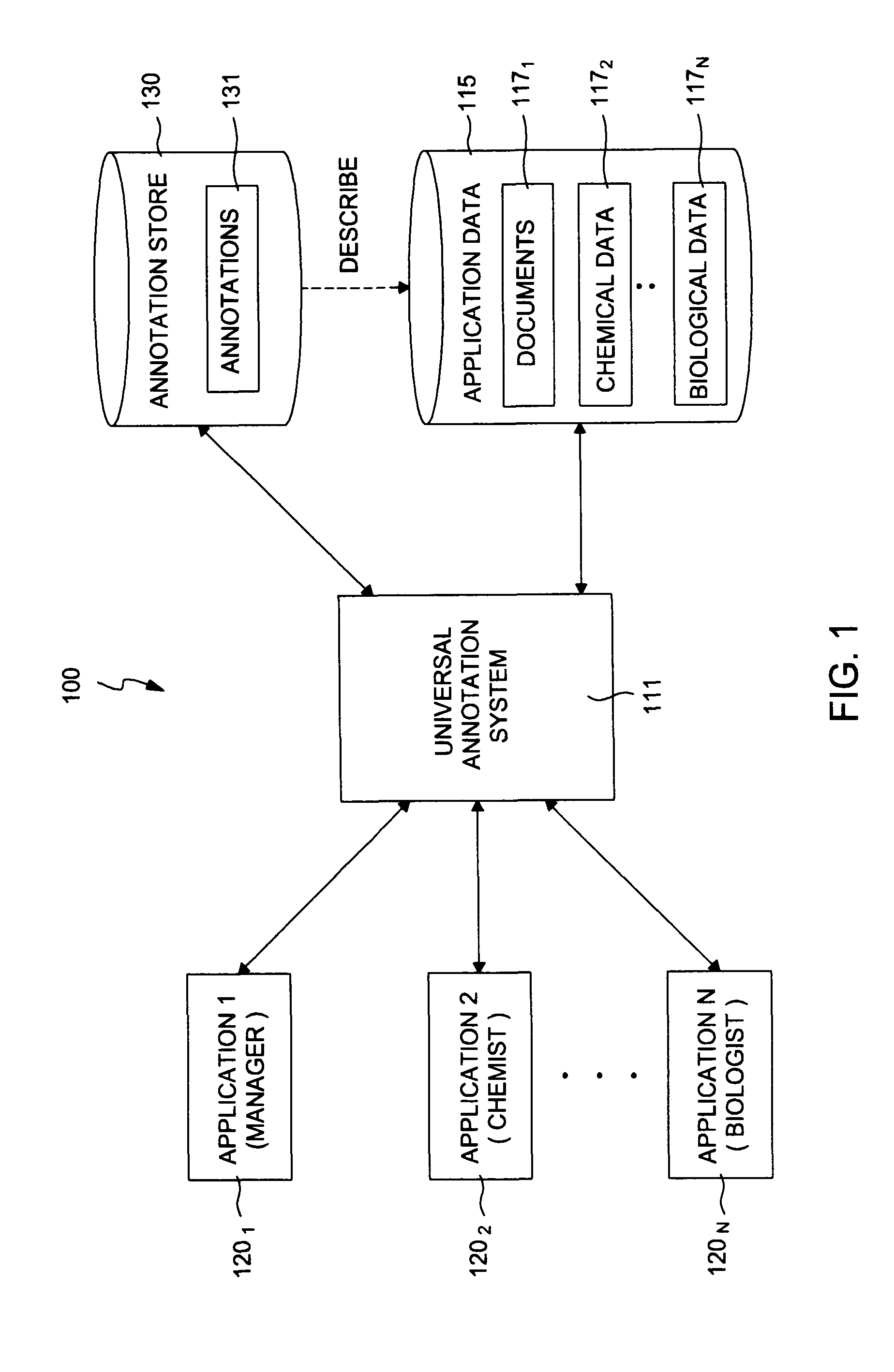
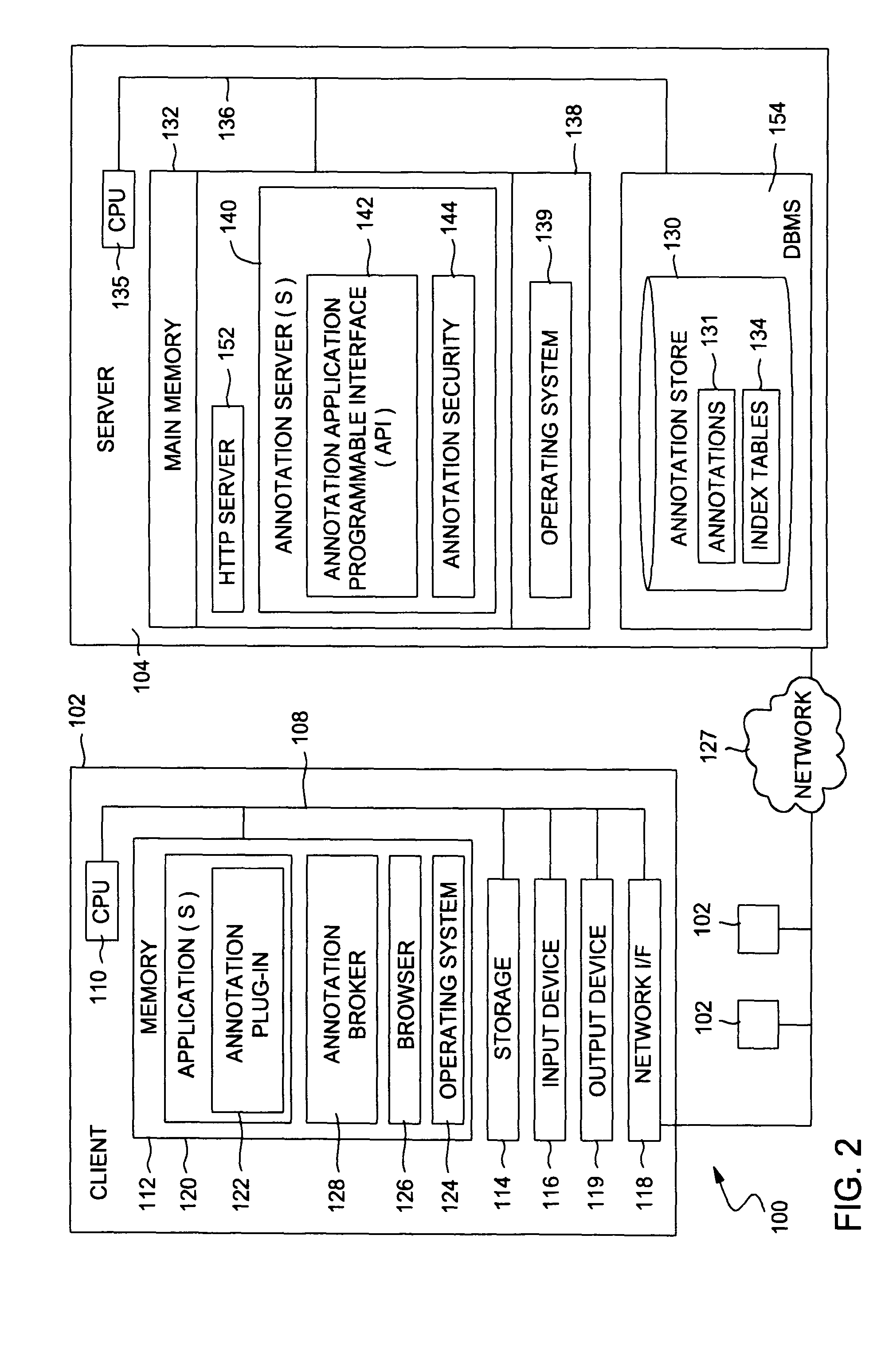
Annotation security to prevent the divulgence of sensitive information
InactiveUS20050038788A1Preventing divulgence of sensitive informationAvoid problemsComputer security arrangementsSpecial data processing applicationsInternet privacySecurity Measure
Methods, systems, and articles of manufacture that may be used to prevent sensitive information from being divulged in an annotation are provided. Upon creation, modification and / or retrieval of an annotation, a set of predefined security rules may be applied to the annotation, in an effort to detect sensitive information contained therein. Upon detecting sensitive information in an annotation, appropriate security measures may be taken, such as notifying a user creating, modifying, or retrieving the annotation (e.g., prompting the user to modify annotation to remove the sensitive information), preventing entry of the annotation, and / or notifying appropriate personnel in charge of security, such as a system administrator.
Owner:IBM CORP
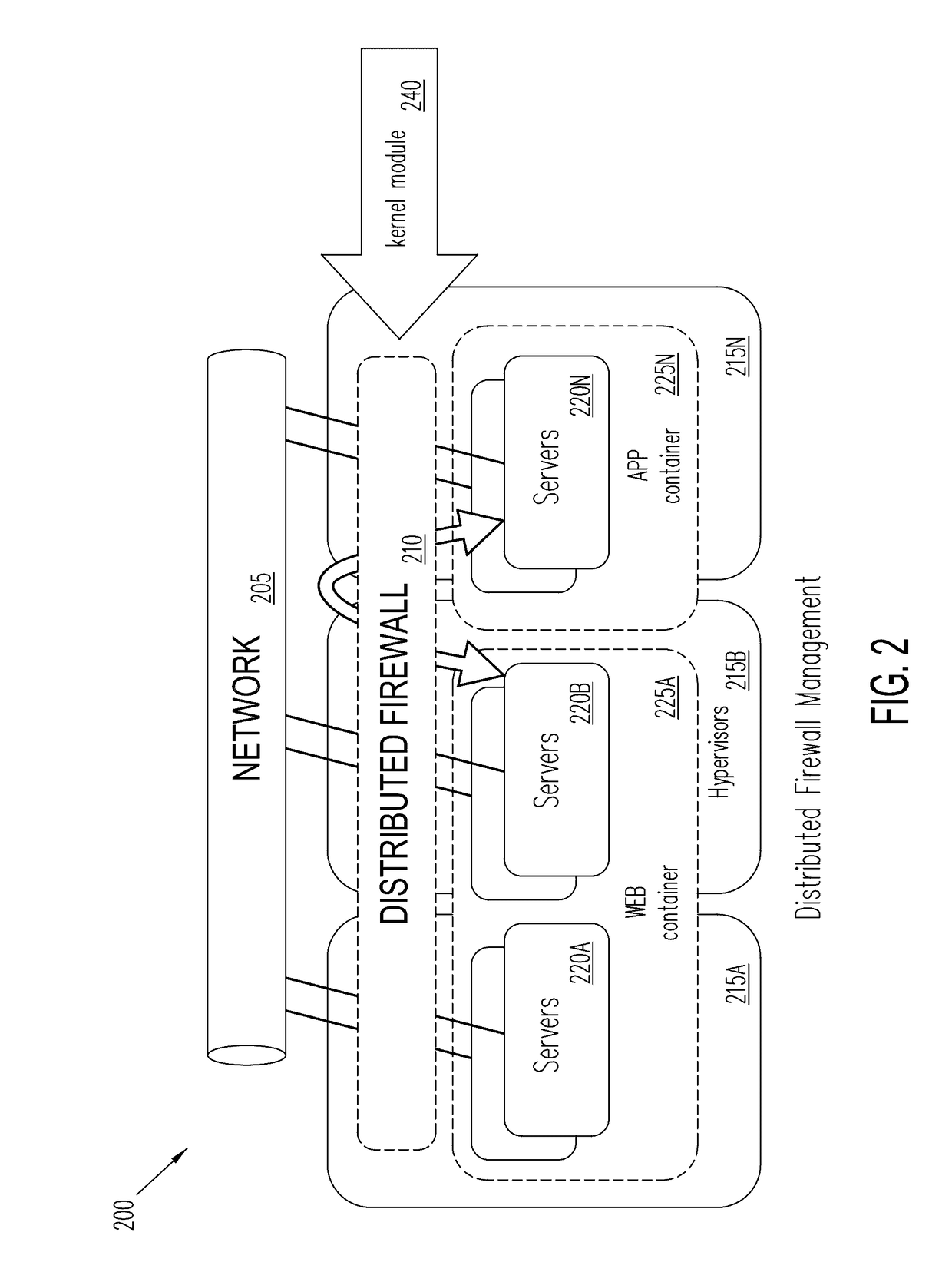
Distributed firewalls and virtual network services using network packets with security tags
A method, system, and apparatus are provided for a distributed firewall and virtual network services on a network. In one example, the method includes storing a plurality of predefined security groups, wherein each predefined security group has a set of predefined security rules for network packets configured to be transmitted between virtual machines (VMs) within the network; associating each virtual machine (VM) within the network with one or more predefined security groups (SGs); filtering an outgoing network packet from a sending VM to a receiving VM in response to the predefined security rules associated with the predefined SGs associated with the sending VM to validate the communication desired in the outgoing network packet; forming a secured network packet by encapsulating a header, a security tag, and the outgoing network packet together; and transmitting the secured network packet into the network for delivery to the receiving VM.
Owner:ATTALA SYST LLC
Enforcing security policies across heterogeneous systems
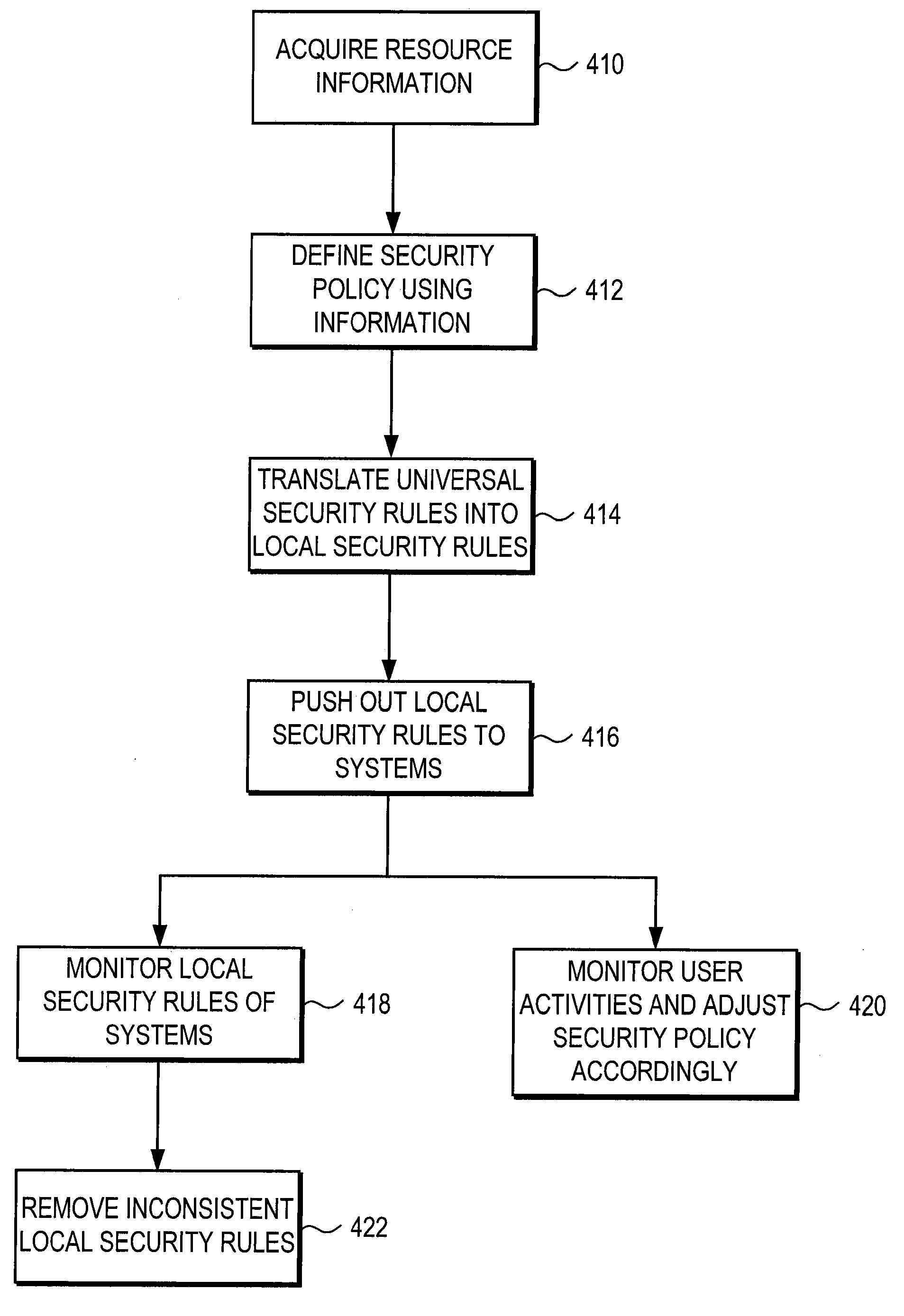
ActiveUS8490163B1Flexible and robustDigital data processing detailsComputer security arrangementsSecurity ruleSecurity policy
A system, method, and computer program product enforce a universal security policy across several systems. In one embodiment, the system comprises a translation module that translates the universal security policy into local security rules enforceable by the security components of the several systems. The system also comprises a policy pushing module that transmits the translated local security rules to each of the several systems. Further, the system can include an analysis module for detecting local security rules in the several systems that are inconsistent with the universal security policy.
Owner:INTAPP US INC
Computer system for performing reusable software application development from a set of declarative executable specifications
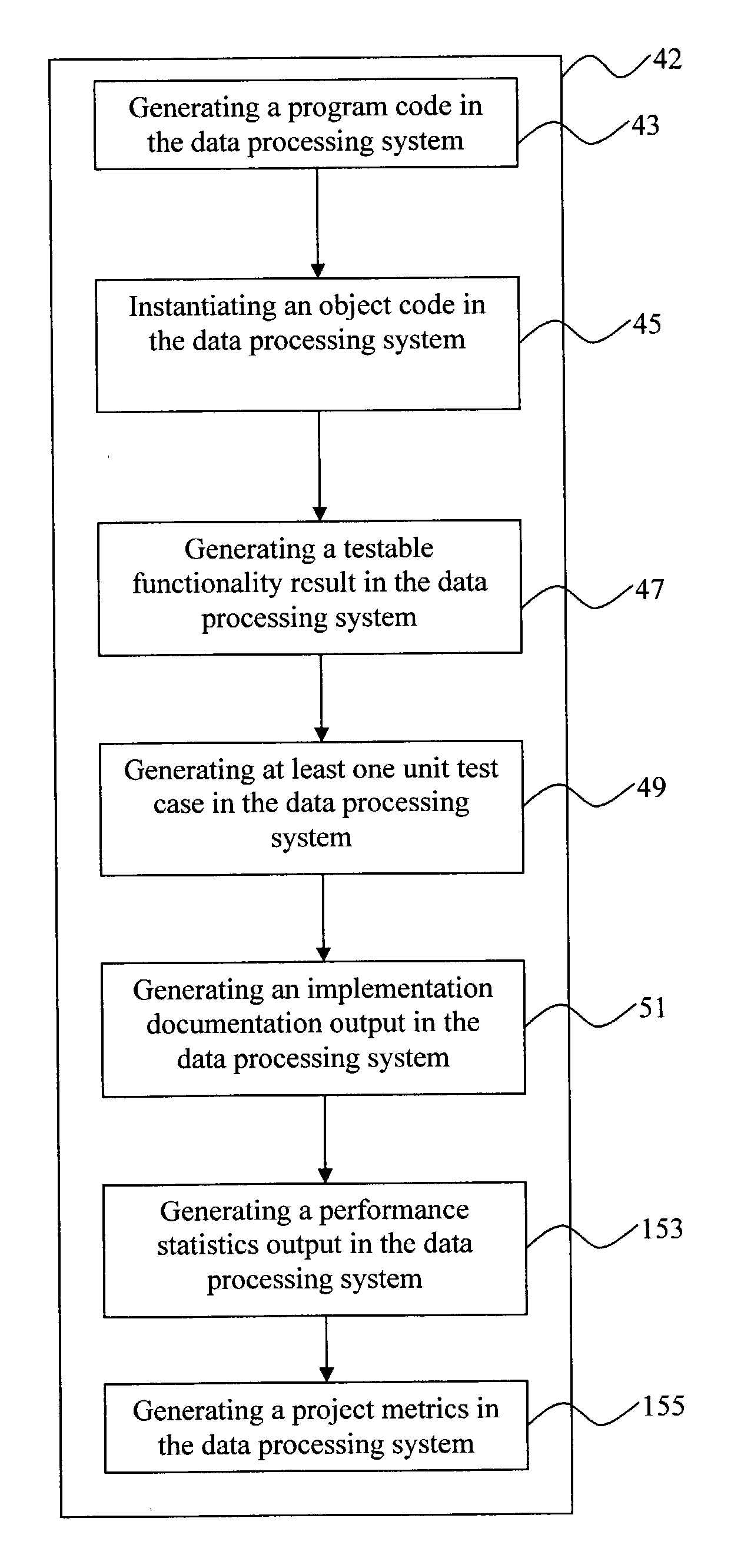
InactiveUS20040010776A1Time can be spentEasy to manageSoftware testing/debuggingSpecific program execution arrangementsDocumentation procedureProject metrics
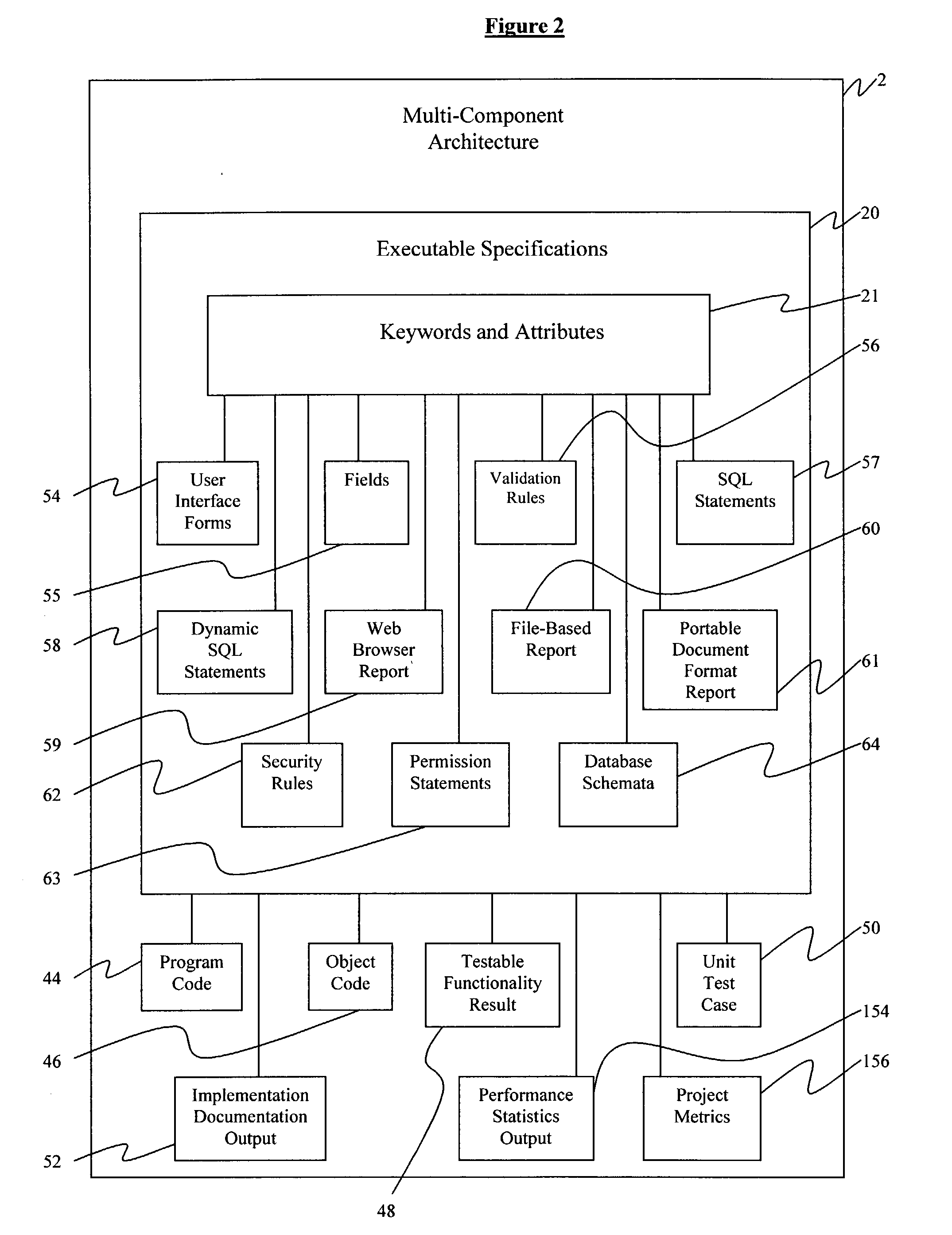
A computer system executing a method for performing reusable software application development comprises integrating a data processing system, providing a set of keywords and attributes, and declaring a set of executable specifications using the keywords and attributes, further comprising generating a program code, instantiating an object code, generating a testable functionality result, generating at least one unit test, generating an implementation documentation output, generating a performance statistics output, and generating a project metrics in the data processing system. The step of providing a set of keywords and attributes comprises generating a set of user interface forms, fields, and validation rules, generating a library of structured query language statements, generating a library of rules for generating dynamic structured query language statements, generating one of a web browser report, a file-based report, and a portable document format report, generating a library of security rules and permission statements, and generating database schemata.
Owner:RPX CORP
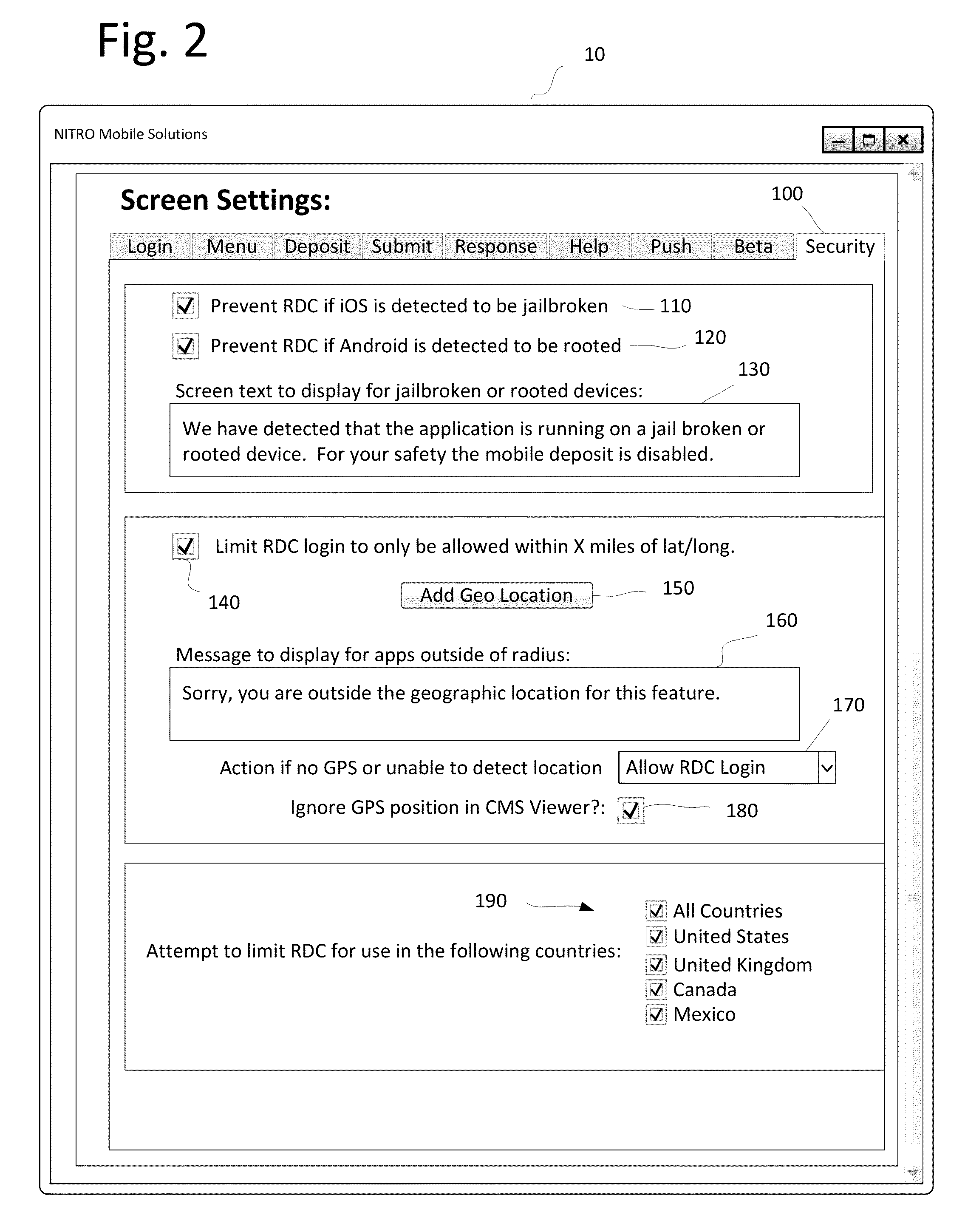
Location based mobile deposit security feature
InactiveUS20150120572A1Reduce the risk of fraudIncrease depositionFinancePayment architectureGeolocationApplication software
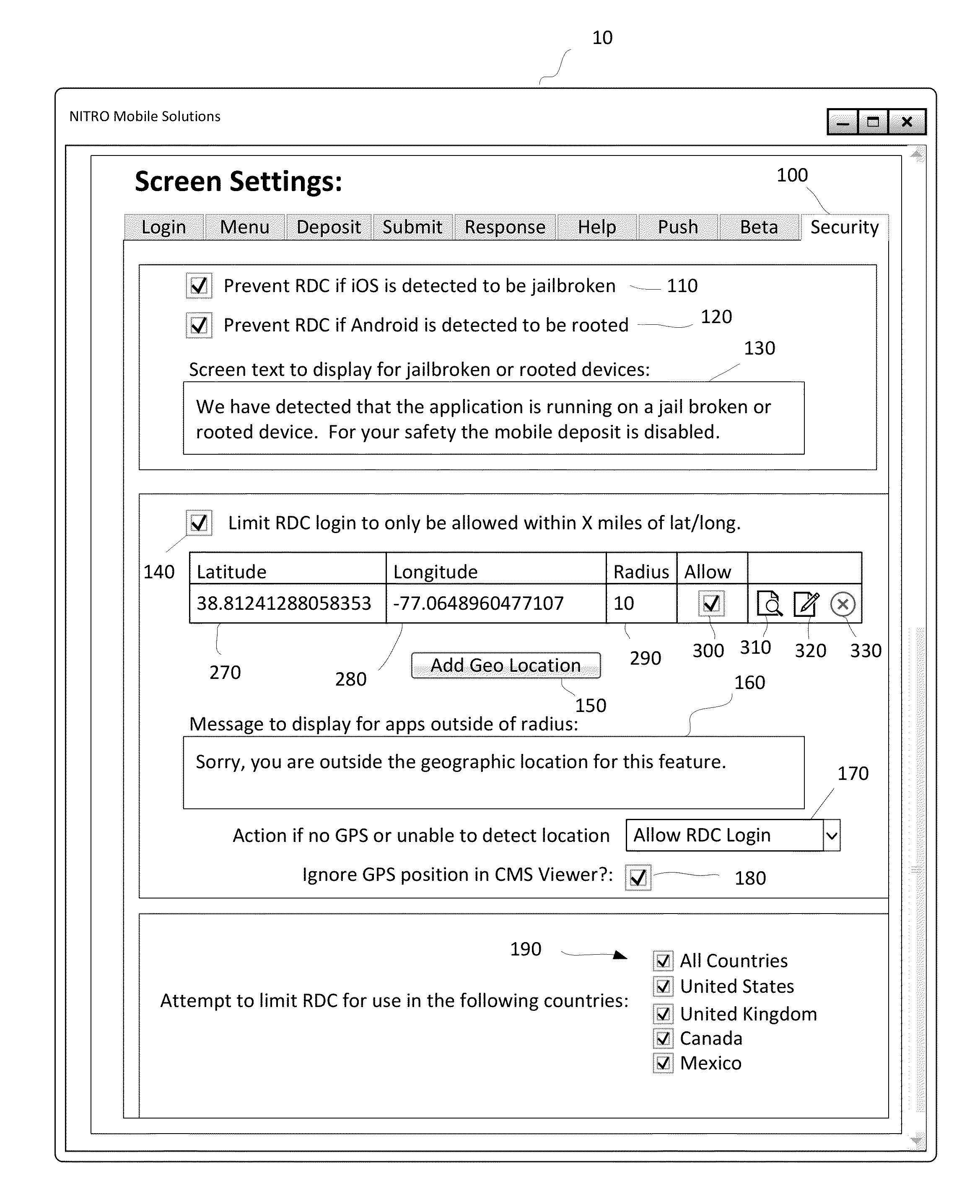
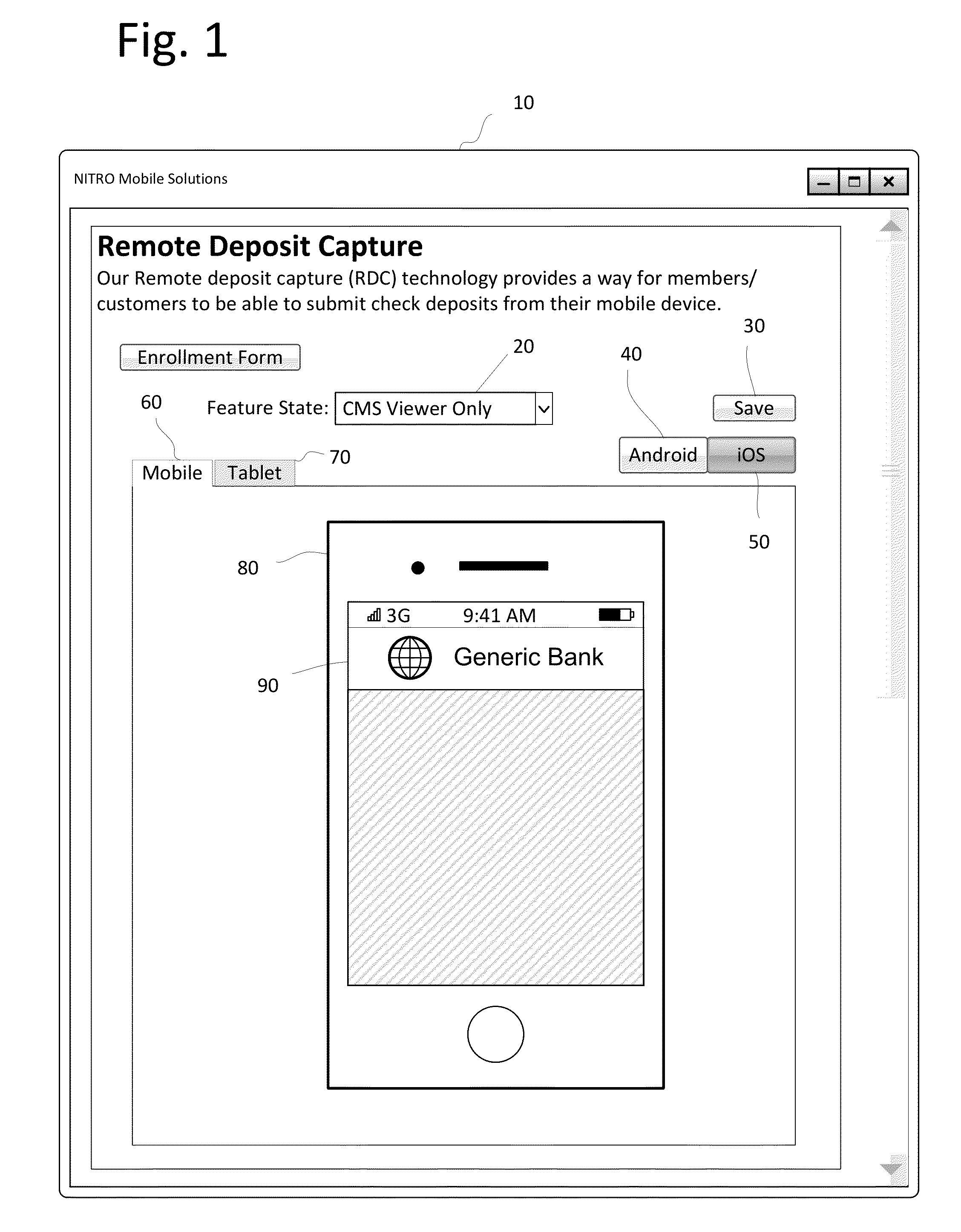
A mobile deposit application including a remotely accessible bank administrative interface module for setting a plurality of geographic-based security rules, a rules module communicative coupled to the bank administrative interface module, the rules module comprising bank-definable location parameters for enabling mobile deposit based on the geographic location of a mobile device, a geolocation module communicatively coupled to the rules module, the geolocation module receives coordinates of the mobile device and applies said coordinates to the rules module to determine if mobile deposit features are enabled or disabled and an exception presentation module communicatively coupled to the rules module, the exception presentation module displaying notifications to the mobile device responsive to a disabling of the mobile deposit features responsive to the geolocation module reporting the mobile device falls outside the bank-definable location parameters.
Owner:NITRO MOBILE SOLUTIONS
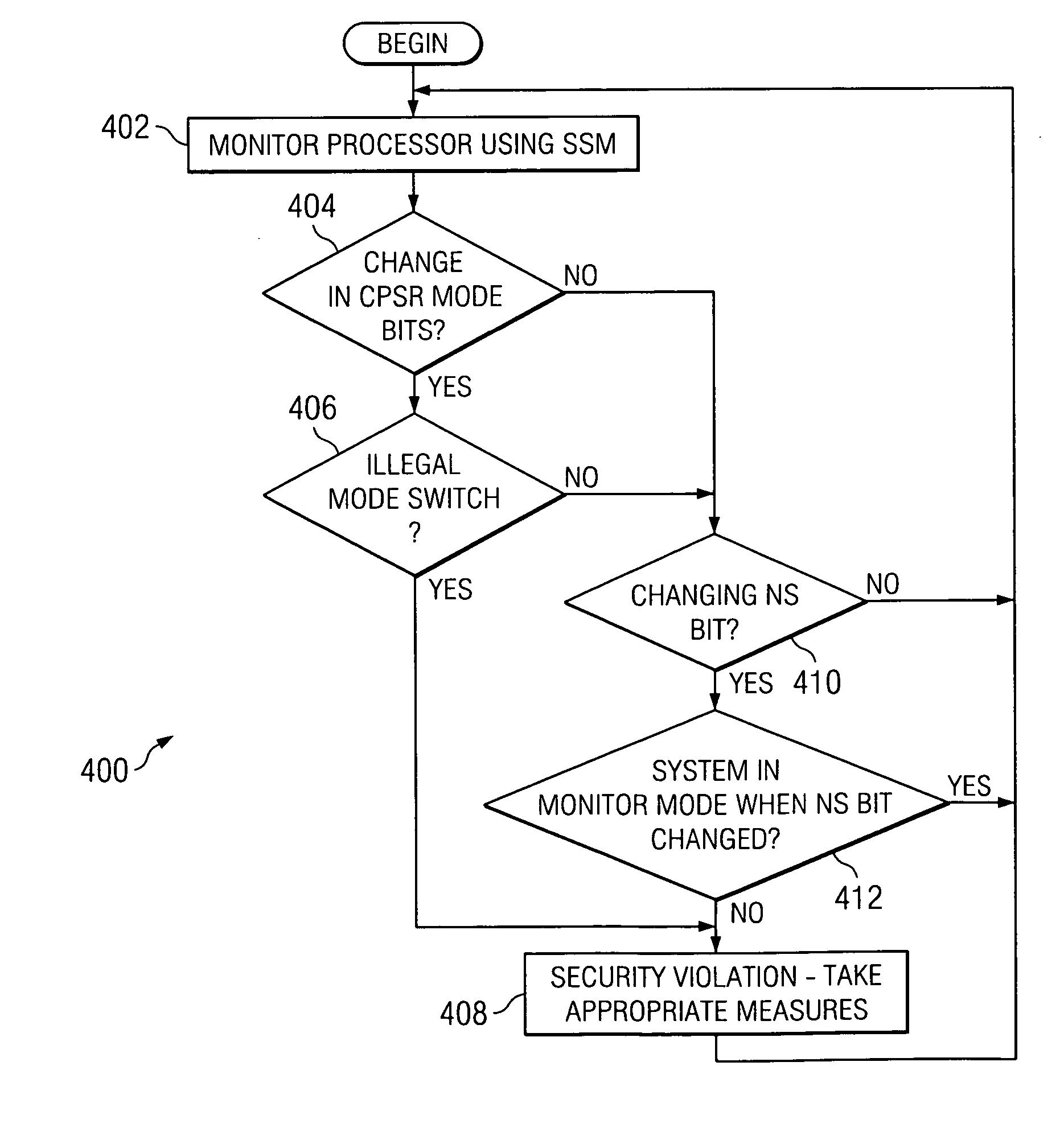
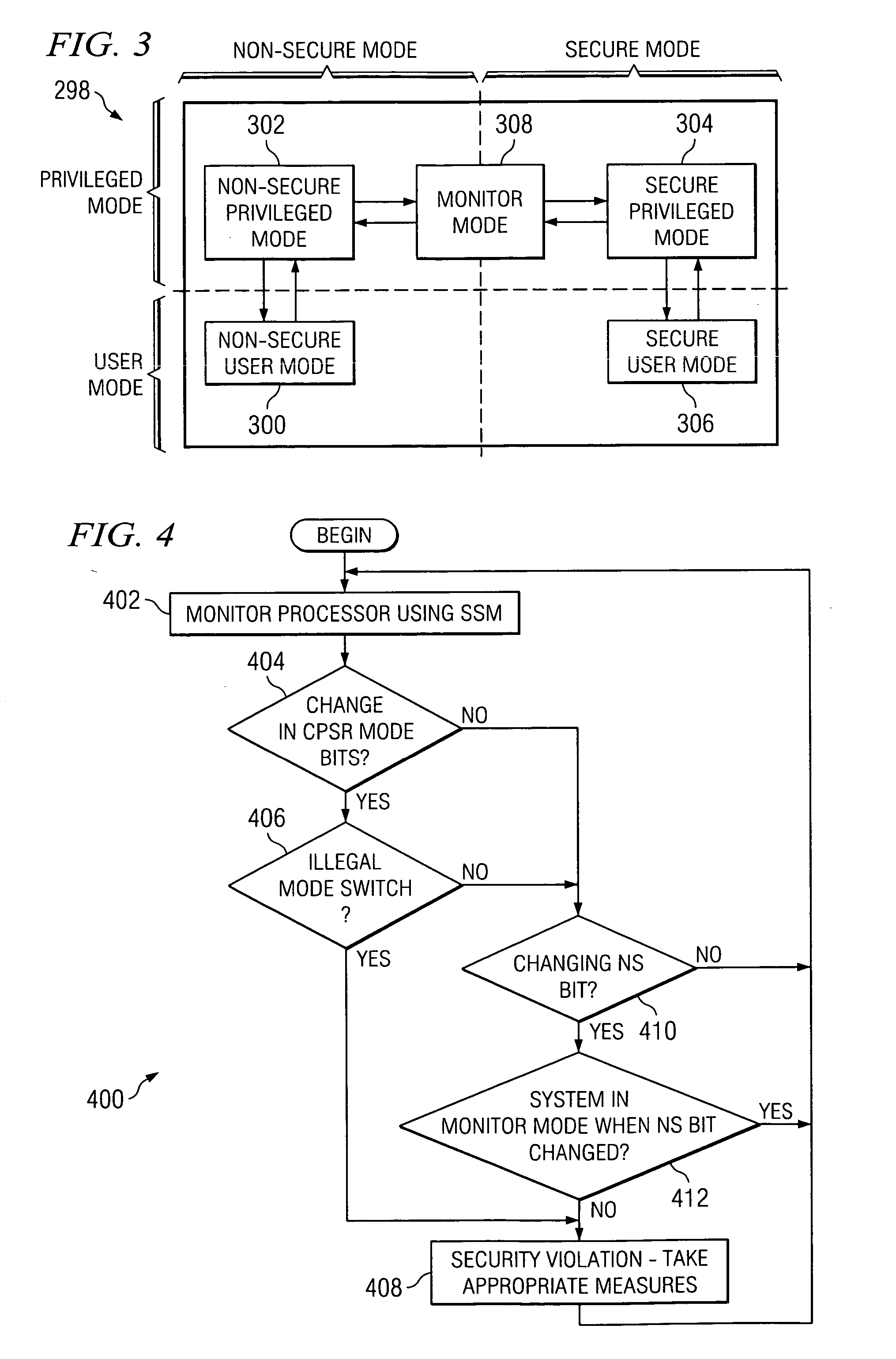
Method and system for preventing unauthorized processor mode switches
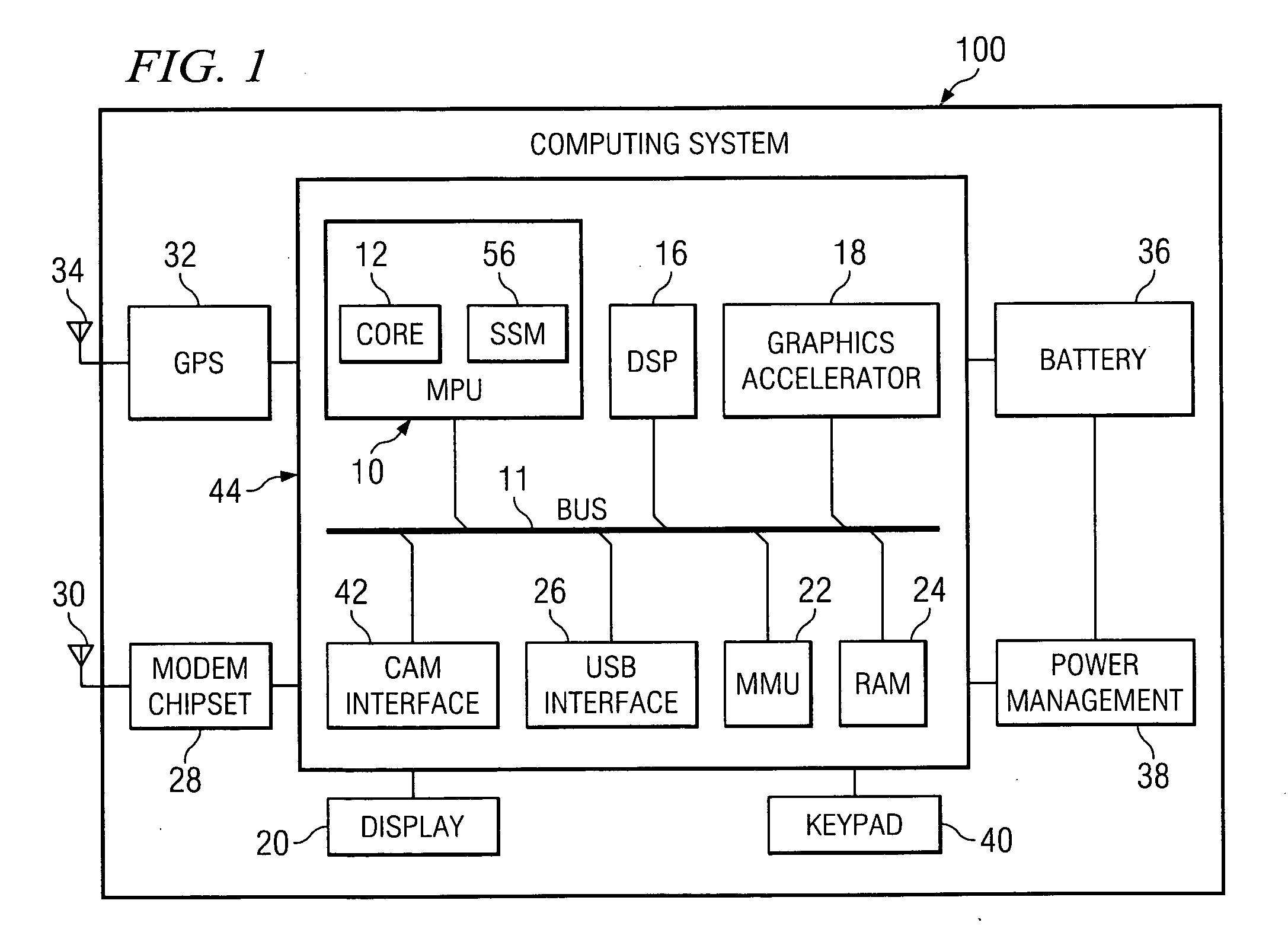
ActiveUS20070150730A1Prevent unauthorizedReduce usageData resettingInternal/peripheral component protectionSecurity ruleMonitor equipment
A system comprising a processor adapted to activate multiple security levels for the system and a monitoring device coupled to the processor and employing security rules pertaining to the multiple security levels. The monitoring device restricts usage of the system if the processor activates the security levels in a sequence contrary to the security rules.
Owner:TEXAS INSTR INC
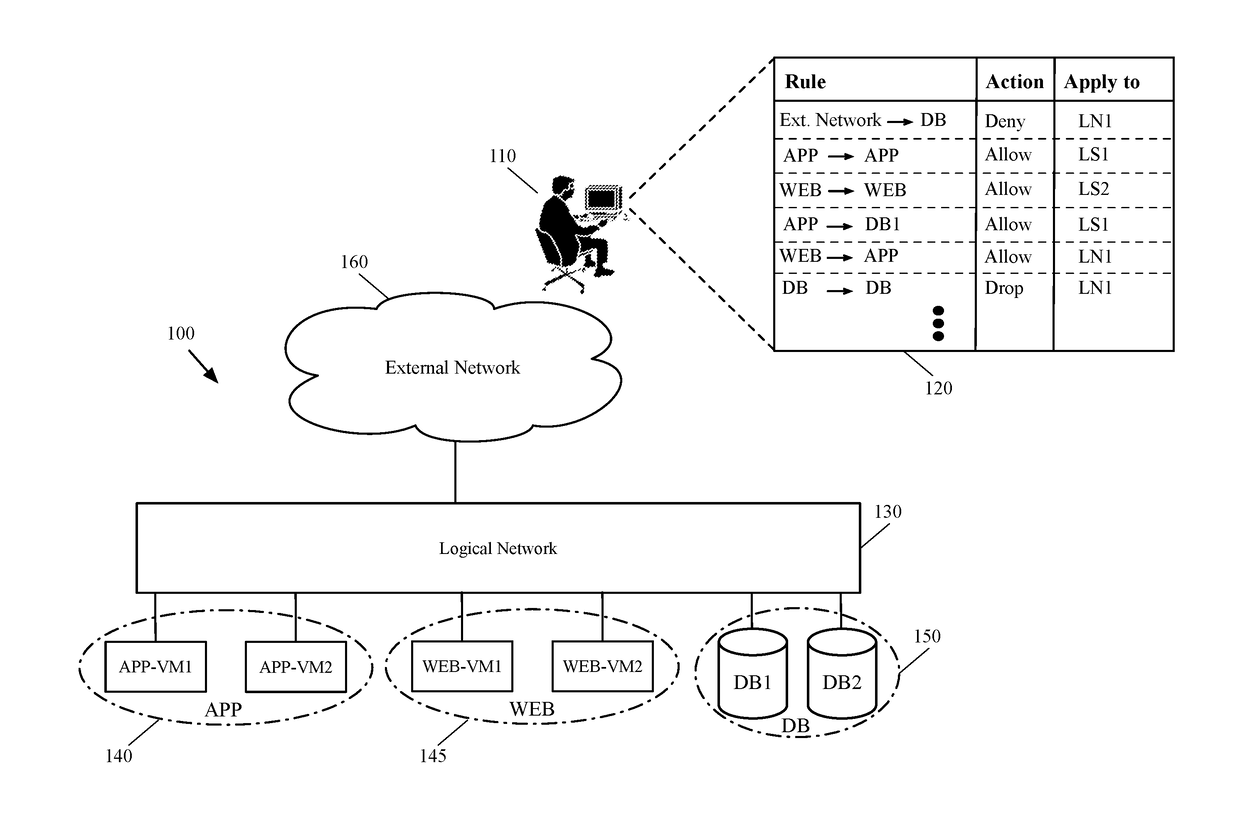
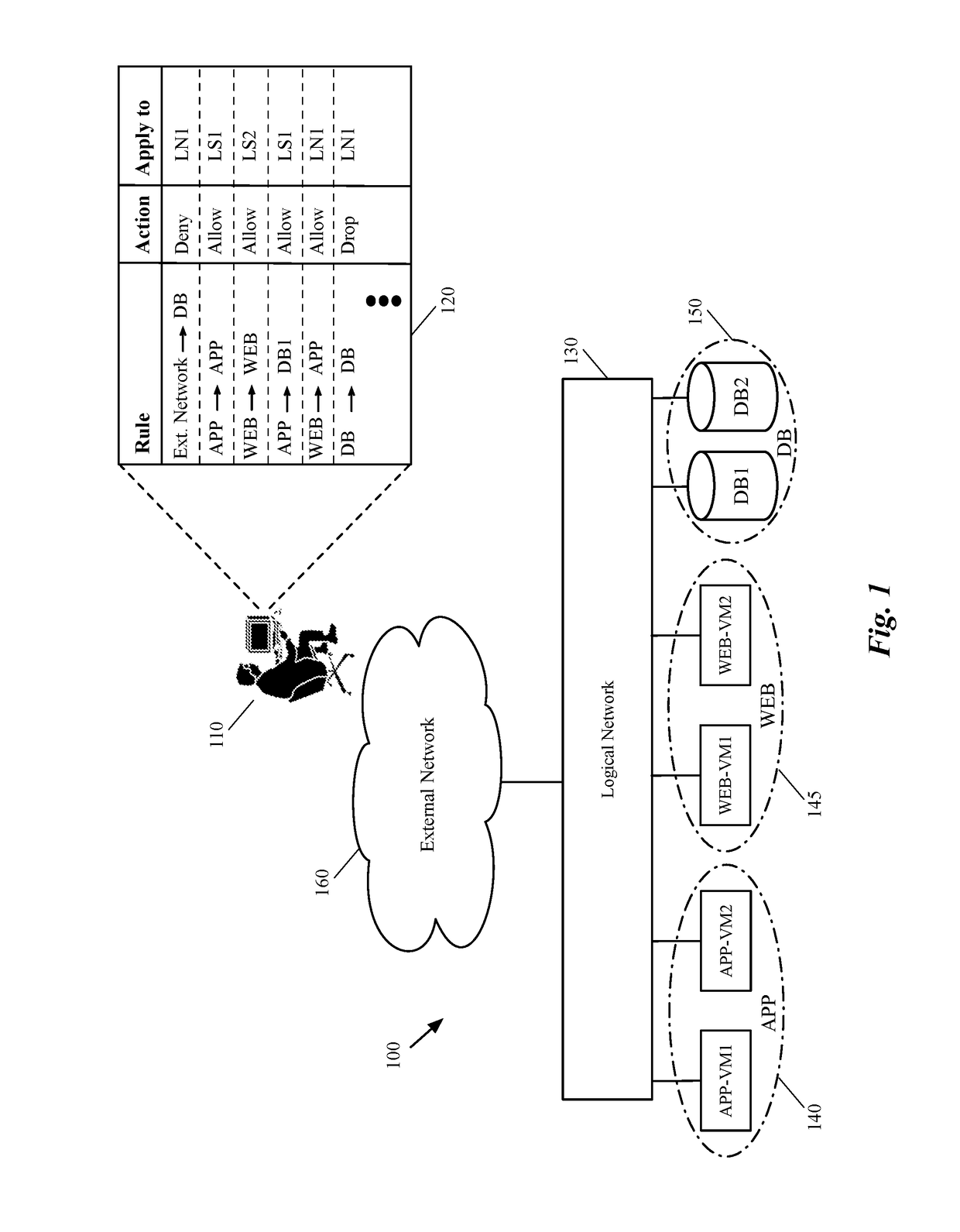
Implementing logical network security on a hardware switch
Some embodiments provide a method for configuring a hardware switch to implement a security policy associated with a logical router of a logical network. The method receives a logical router definition. The logical router logically connects a physical machine, connected to a physical port of the hardware switch, to several VMs that execute on a set of host machines. The method defines a set of routing components for the logical router, each of which, has several interfaces. The method receives a security policy that includes a set of security rules for the physical machine and populates an ACL table with ACL rules data generated based on the received set of security rules. The method then for at least one interface of one of the routing components, generates linking data that links a set of one or more ACL rules in the ACL table to the interface of the routing component.
Owner:NICIRA
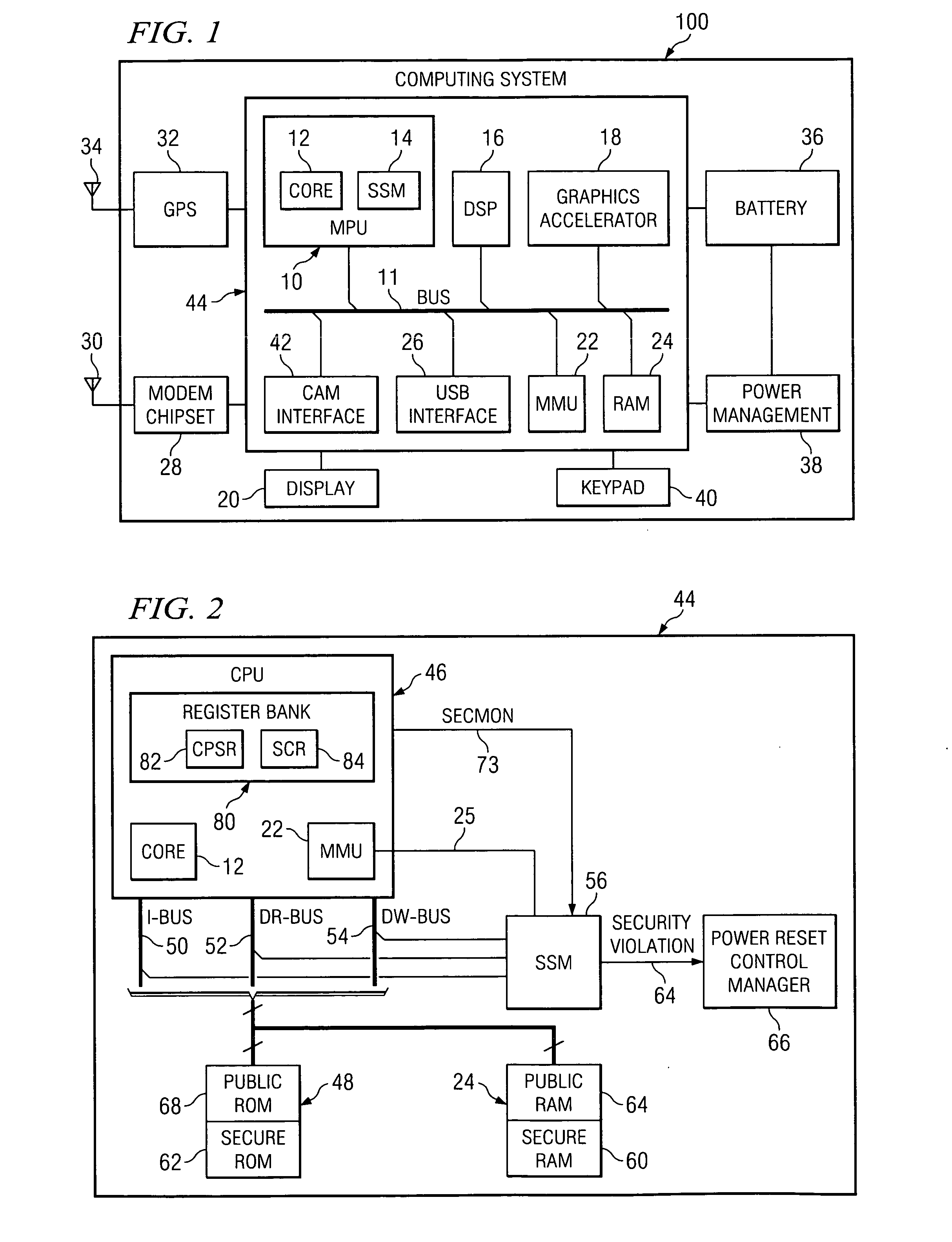
Method and system for preventing unsecure memory accesses
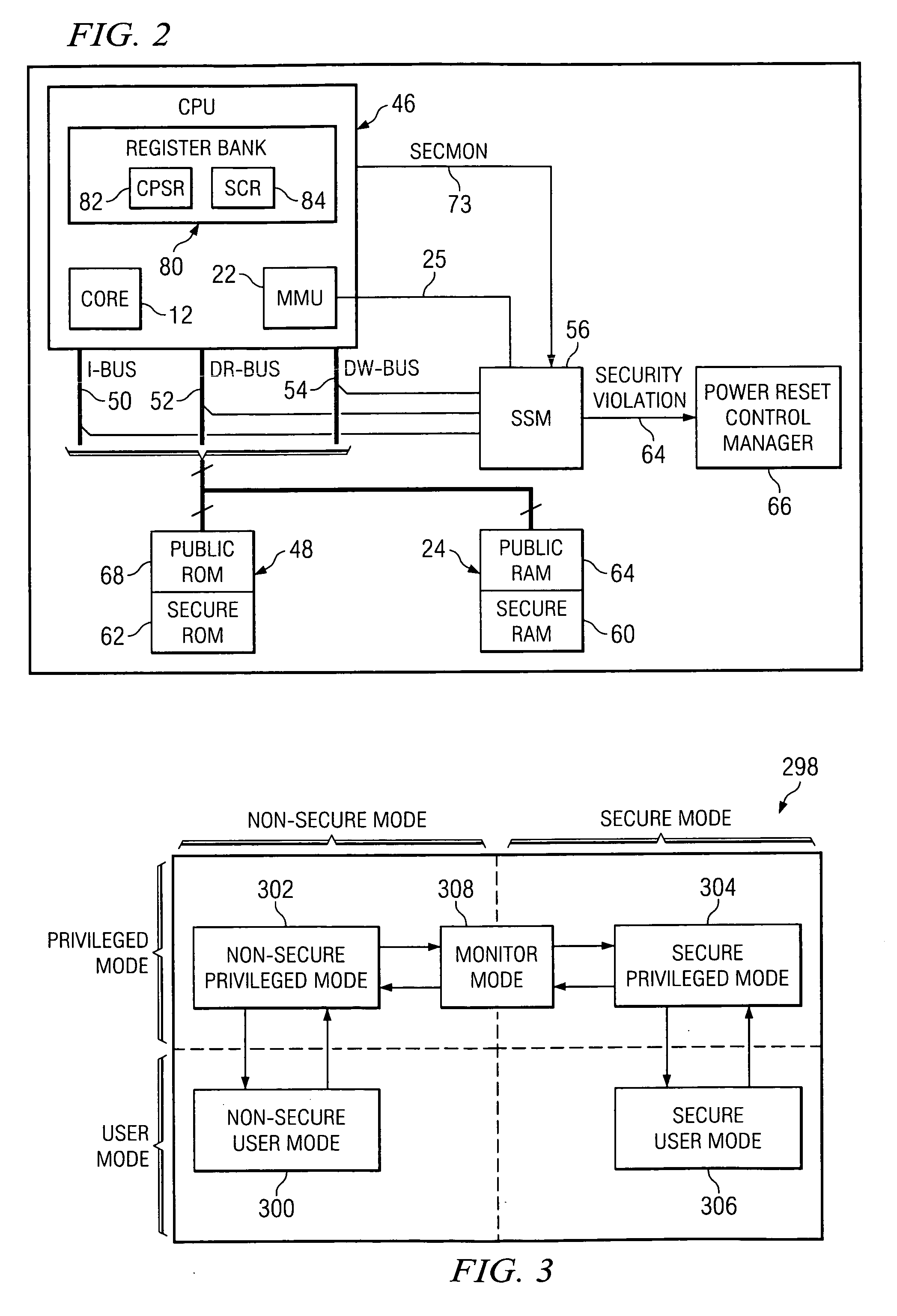
InactiveUS20070067826A1Avoid problemsReduce usageDigital data processing detailsUser identity/authority verificationSecurity ruleMemory management unit
A system comprising a processor adapted to activate multiple privilege levels for the system, a monitoring unit coupled to the processor and employing security rules pertaining to the multiple privilege levels, and a memory management unit (MMU) coupled to the monitoring unit and adapted to partition memory into public and secure memories. If the processor switches privilege levels while the MMU is disabled, the monitoring unit restricts usage of the system. If the processor accesses the public memory while in a privilege level not authorized by the security rules, the monitoring unit restricts usage of the system.
Owner:TEXAS INSTR INC
System and method for intelligence based security
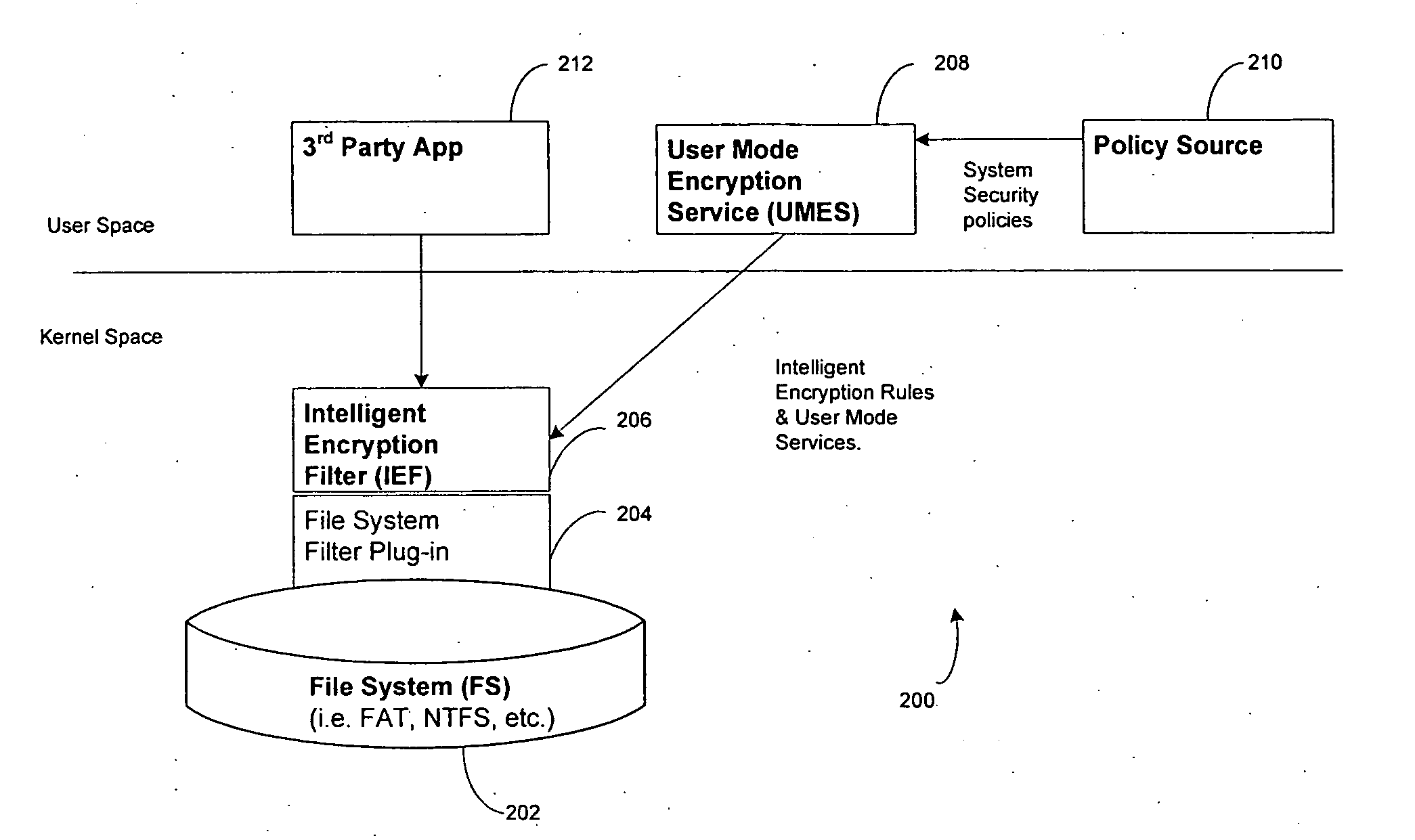
ActiveUS20070174909A1Safe storageSlow performanceRandom number generatorsUser identity/authority verificationInformation processingOperational system
Included in the present disclosure are a system, method and program of instructions operable to protect vital information by combining information about a user and what they are allowed to see with information about essential files that need to be protected on an information handling system. Using intelligent security rules, essential information may be encrypted without encrypting the entire operating system or application files. According to aspects of the present disclosure, shared data, user data, temporary files, paging files, the password hash that is stored in the registry, and data stored on removable media may be protected.
Owner:DELL MARKETING
System and method for lost data destruction of electronic data stored on portable electronic devices
ActiveUS20060021007A1Reduces and eliminates riskReduce dataDigital data processing detailsUser identity/authority verificationBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. Rules relating to encryption, as well as other security procedures, can be defined and entered by an administrator with access to the server, and then disseminated to each of a plurality of clients that access the server.
Owner:BEACHHEAD SOLUTIONS
System and method for lost data destruction of electronic data stored on a portable electronic device which communicates with servers that are inside of and outside of a firewall
ActiveUS20060021006A1Reduces and eliminates riskReduce riskDigital data processing detailsUser identity/authority verificationBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. The server with which the client computer device communicates includes one server located inside the firewall of a particular organization, or a mirror server located outside the firewall, and thereby allow for the re-setting of the activation interval when the client is properly outside of the firewall through communication with the mirror server, as well as the to provide command an control over a lost or stolen client by pushing updated rules if communication is subsequently attempted with the mirror server.
Owner:BEACHHEAD SOLUTIONS
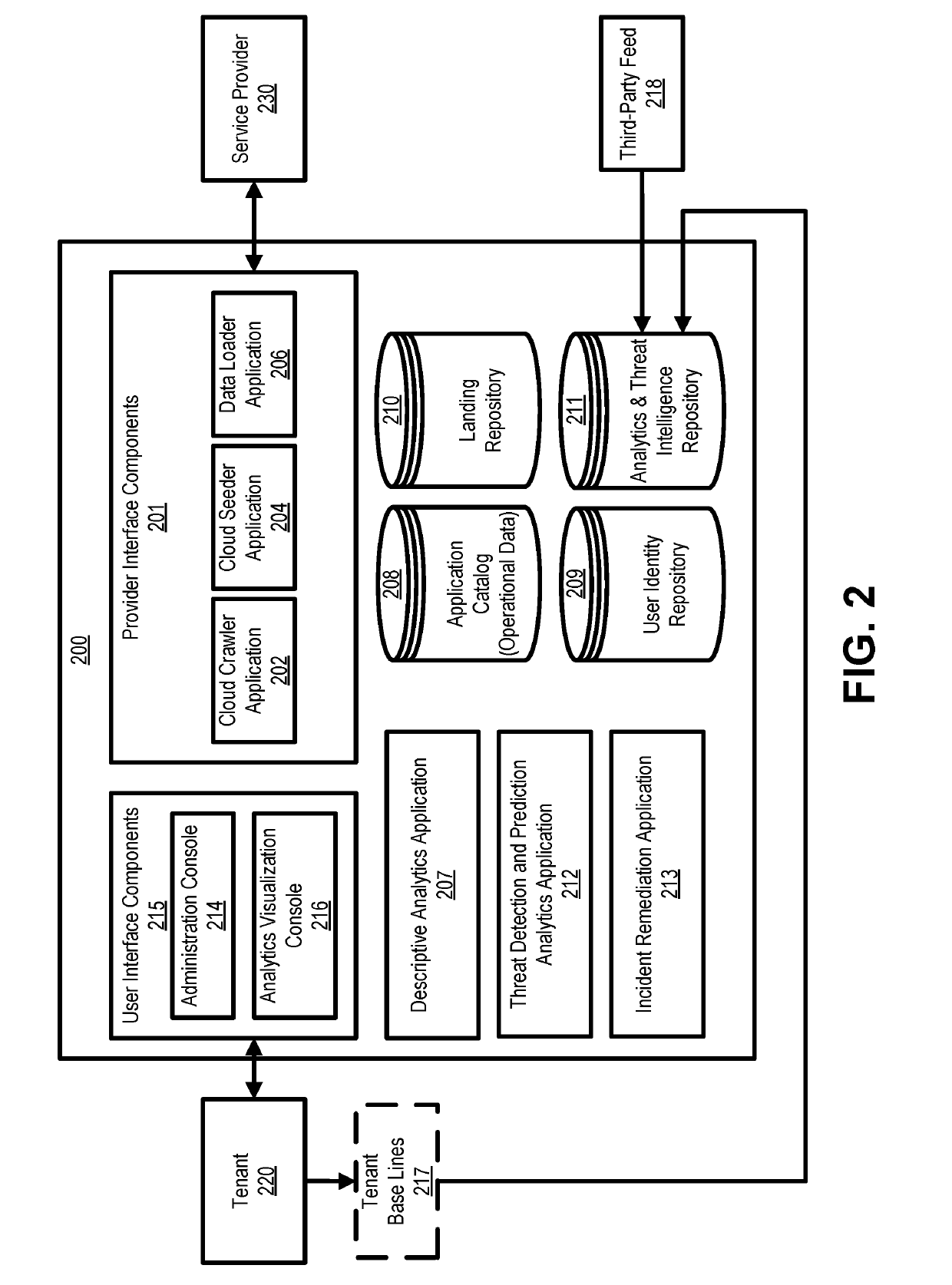
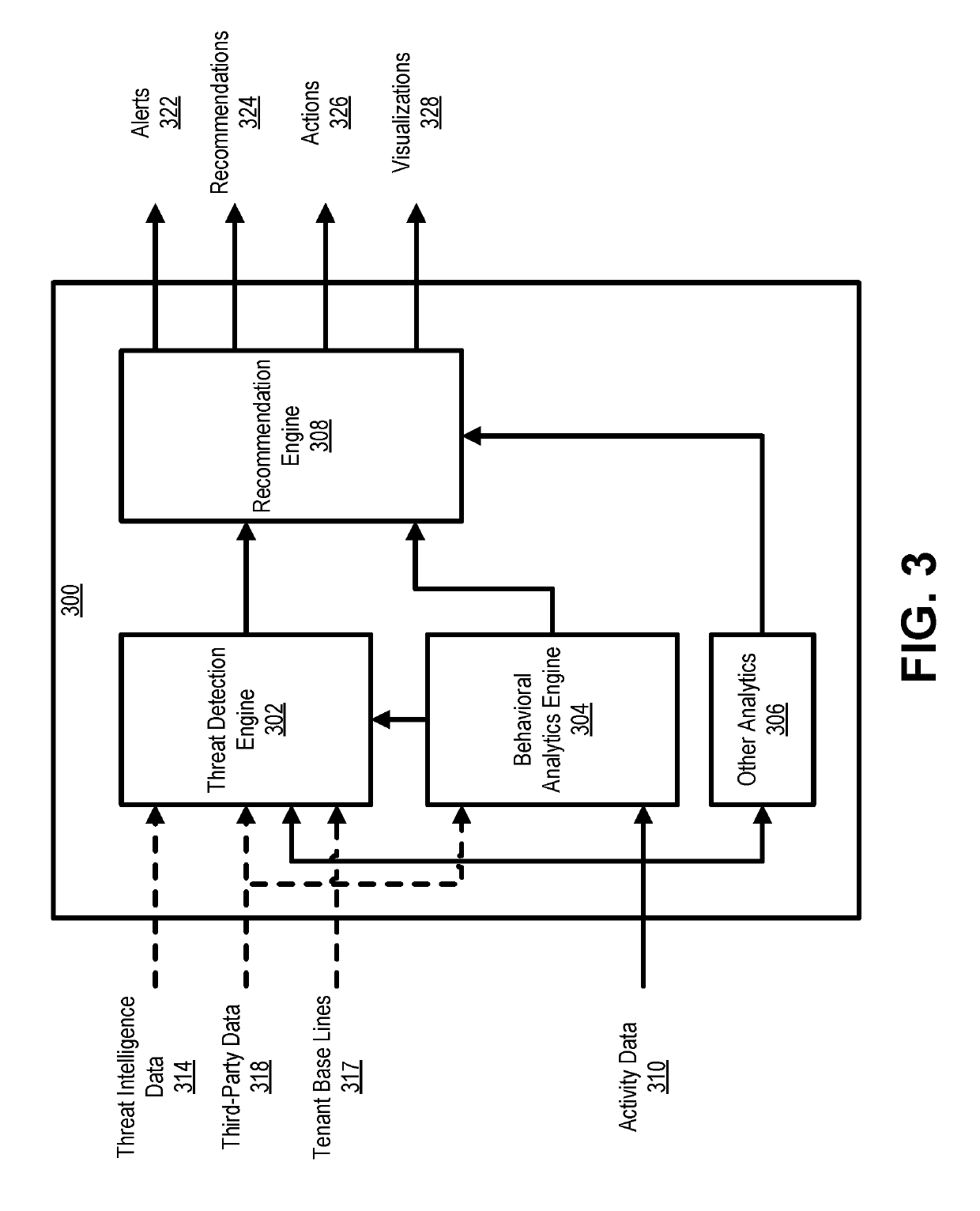
Cloud-based threat detection
In certain embodiments, a security system is provided to receive activity data associated with a first source. The security system may scan the activity data to determine if there are one or more actions of interest associated with a first user account in the activity data. The security system may retrieve, from memory, security rules associated with the first cloud-based service and / or an organization associated the first user account. The security system may compare the actions of interest associated with the first user account to the security rules to determine if there are one or more security violations. In certain embodiments, the security system may retrieve additional activity data from a second source. The security system may scan the additional activity data to determine if there are one or more actions of interest associated with the second user account in the additional activity data.
Owner:ORACLE INT CORP
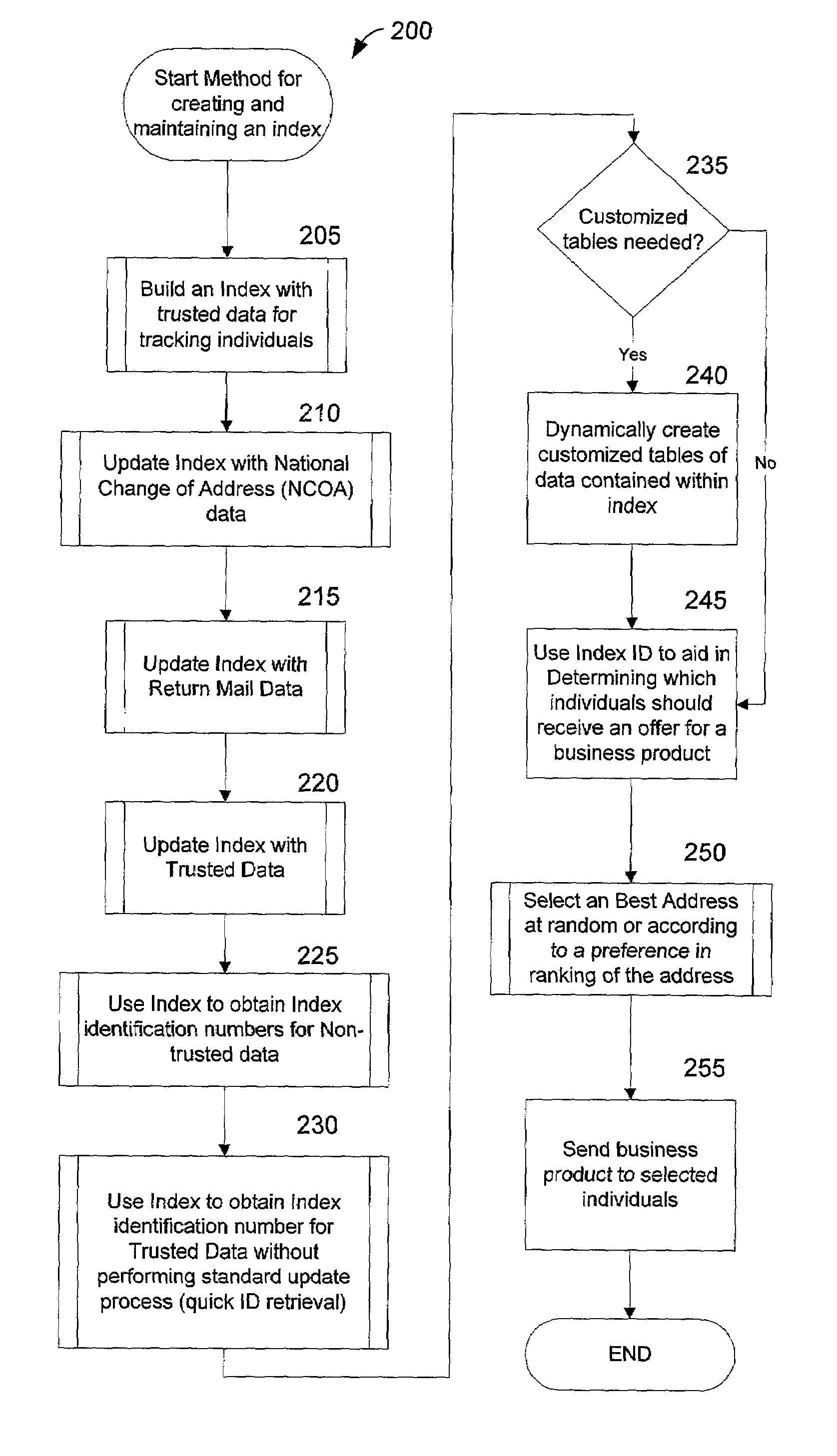
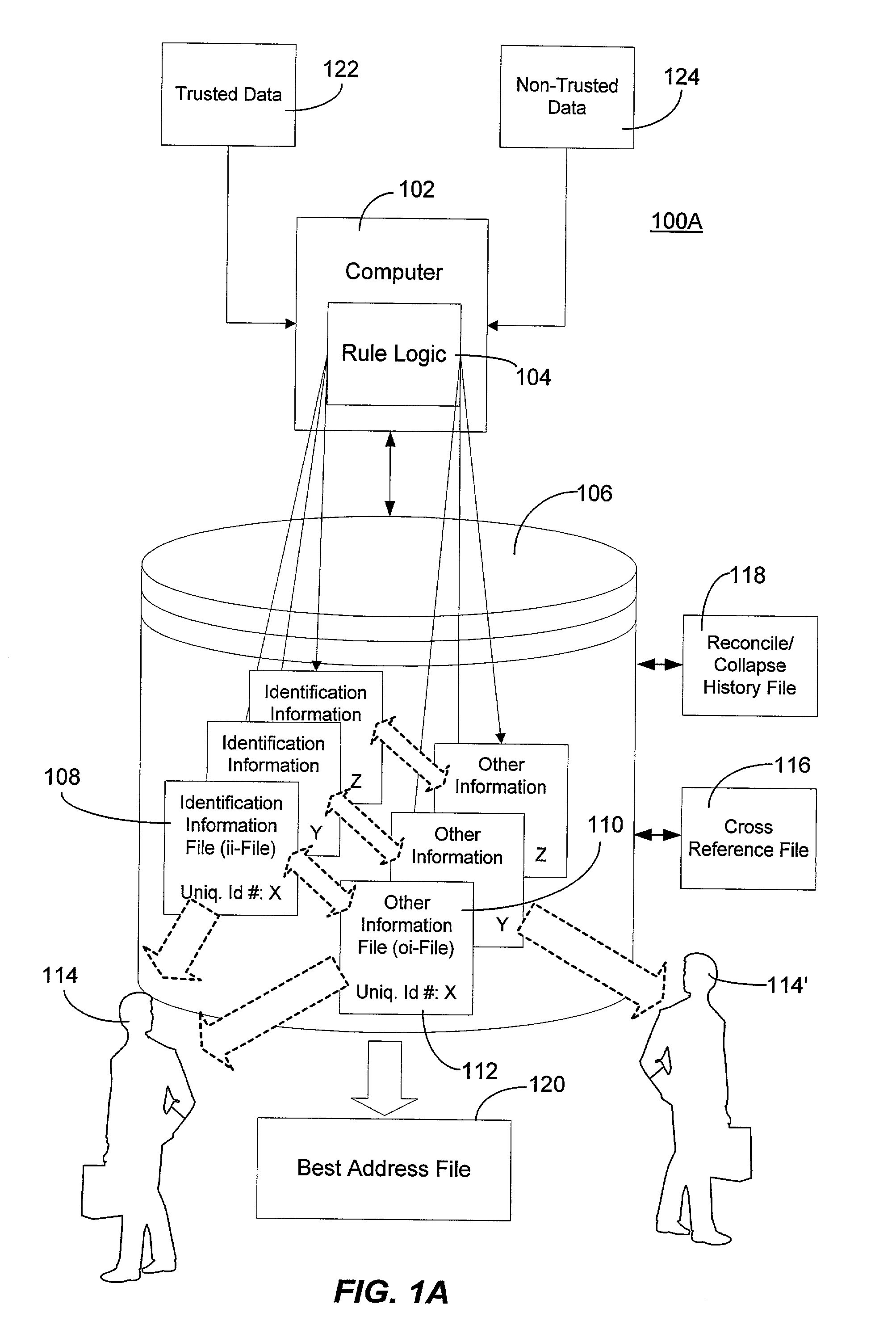
Method and system for creating and maintaining an index for tracking files relating to people
InactiveUS6968348B1Easy accessEasy to manufactureFinanceDigital data processing detailsFile allocationSocial Security number
A computer system creates and maintains an index for tracking information relating to individuals. Such information can include, but is not limited to, social security numbers, names, address information, credit bureau identification numbers, and credit history information on individuals. The invention employs logical rules to this information in order to create and maintain a set of files for each individual. The logical rules can include social security rules, geography rules, and address ranking rules. The invention is designed to evaluate slight variations in information very carefully in order to insure that appropriate files are assigned the same index identification number or that appropriate records are assigned separate and different index identification numbers as a situation warrants. The present invention is designed to maintain numerous files for each individual being tracked instead of merging and purging files as is done in the conventional art.
Owner:PROVIDIAN FINANCIAL CORP +1
Zoned based security administration for data items
InactiveUS20050039001A1Digital computer detailsUnauthorized memory use protectionComputerized systemSecurity rule
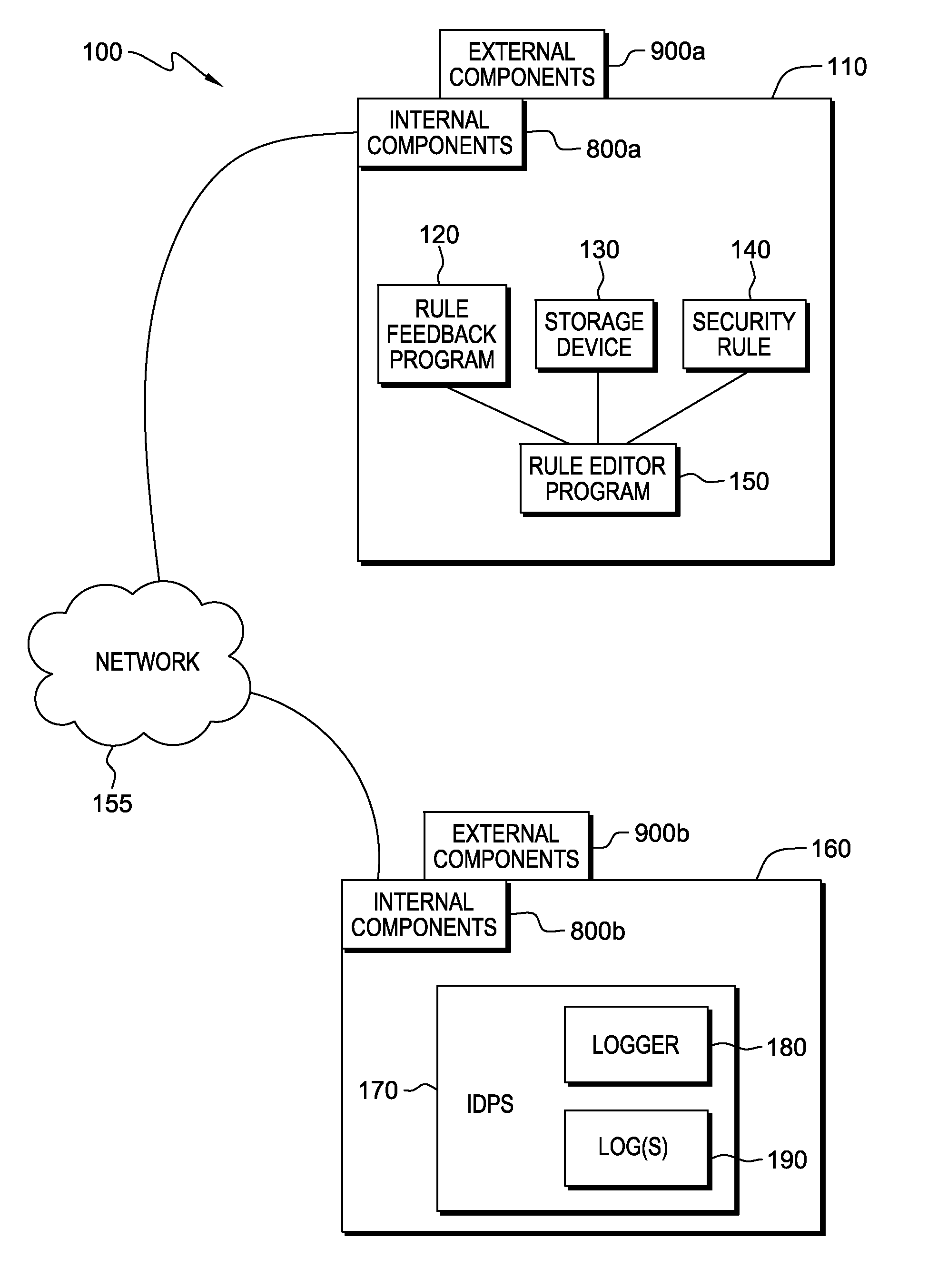
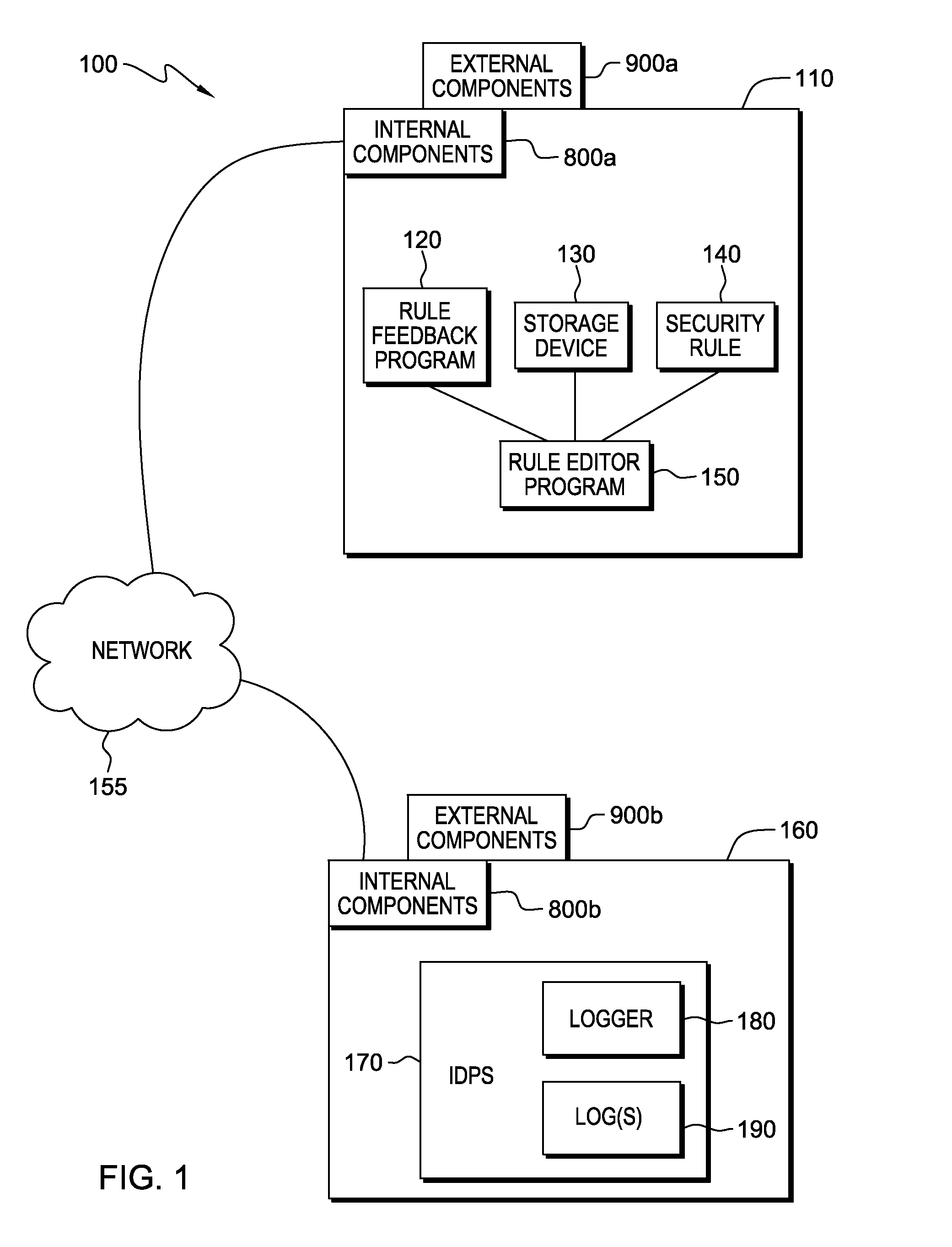
Administering digital security is disclosed. Data and method items are stored on a computer system in a volume. The volume is divided up into non-overlapping security zones. Each item exists in a security zone. Security rules are granted to principals where the security rules apply to items in a particular zone. The security rules specify what principals have what rights; such as read, write delete and execute; to what items. Administrative rights can be delegated by principals by splitting a security zone to form two security zones. Principals who have administrative rights to the security zone assign additional principals to one of the security zones while maintaining all administrative rights to the other zone. Thus principals can retain certain administrative rights to certain items exclusively to themselves while delegating administrative rights to other items to other principals.
Owner:MICROSOFT TECH LICENSING LLC
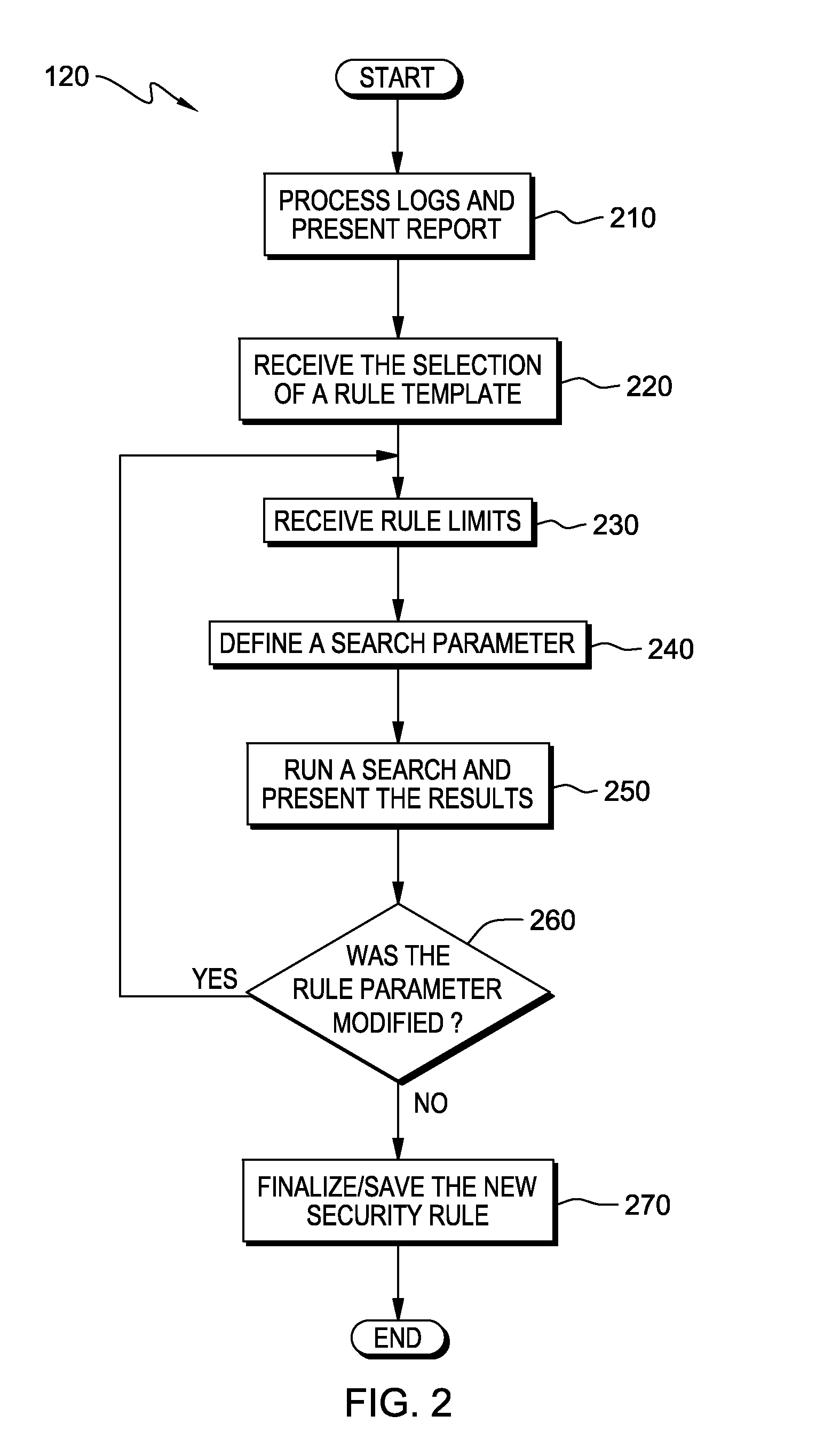
Automated feedback for proposed security rules
InactiveUS20140059641A1Desirable performanceComputer security arrangementsTransmissionEngineeringPredicting performance
A computer receives entry of a proposed security rule during a security rule entry or editing session and determines that the proposed security rule requires review of a type of security data. The number of matches of the proposed security rule to the logged security data is determined and a user is notified as to the number of matches. The computer searches the security data and applies the proposed security rule to the security data to determine the predicted performance of the proposed security rule. The computer generates a report that may include warnings, recommendations, and information correlated to the security data. The report is presented to a user during the rule editing session, and based on the report a modification to the proposed security rule can be made.
Owner:KYNDRYL INC
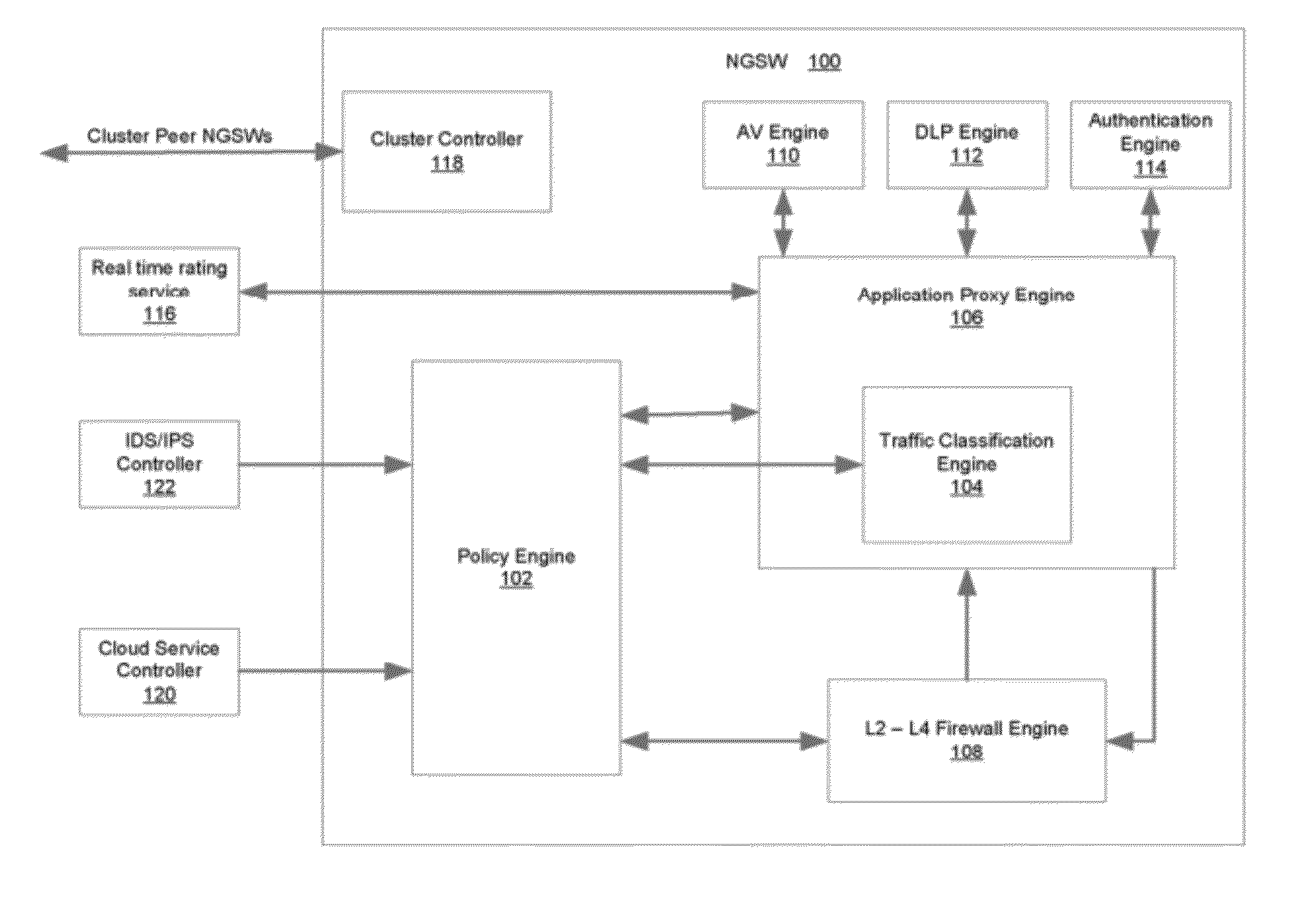
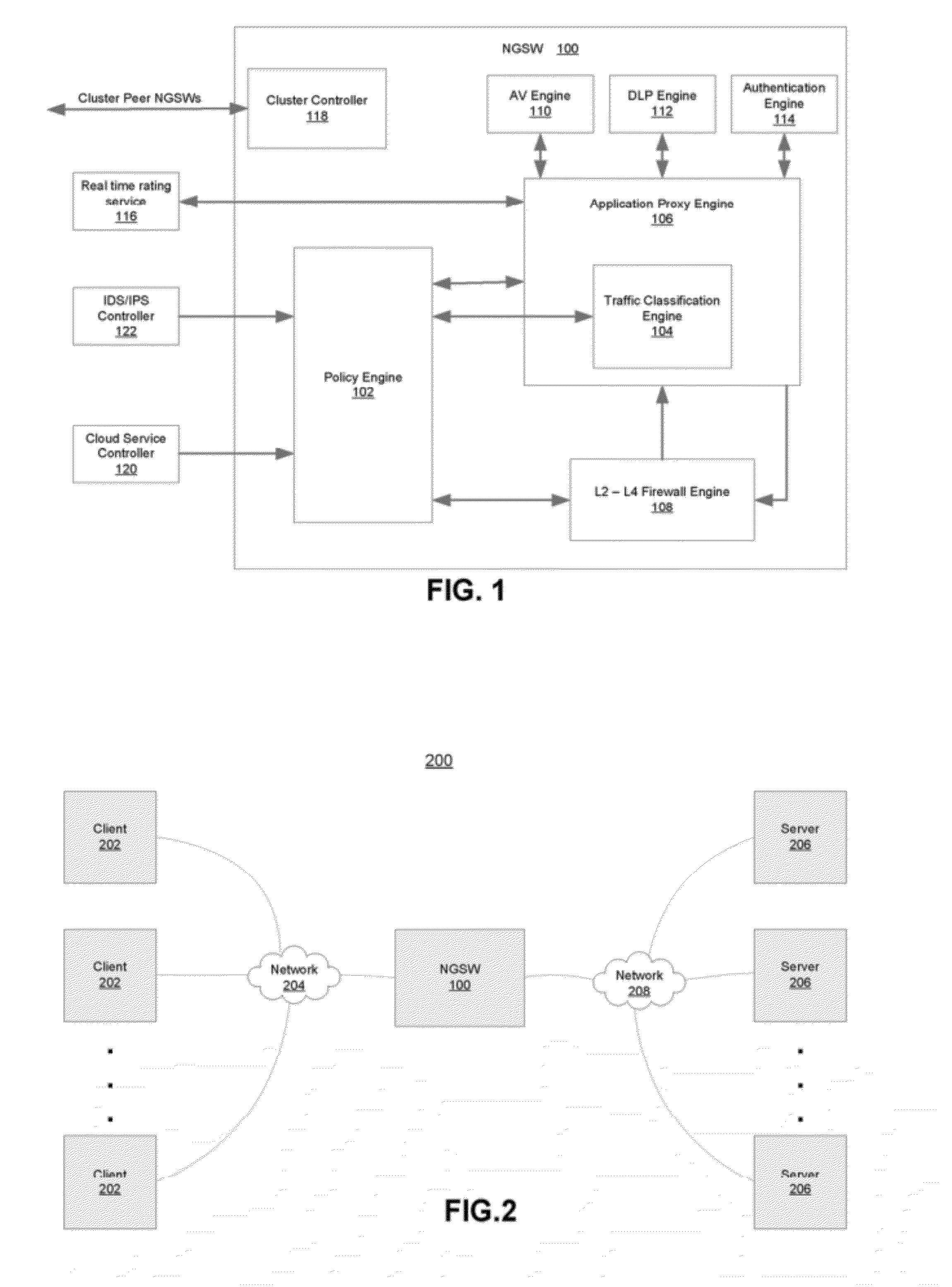
System and Method for Building Intelligent and Distributed L2 - L7 Unified Threat Management Infrastructure for IPv4 and IPv6 Environments
ActiveUS20120304277A1Easy to handleQuality of serviceComputer security arrangementsMultiple digital computer combinationsAnti virusApplication software
A security gateway appliance is configured to evaluate network traffic according to security rules that classify traffic flows according to specifically identified application programs responsible for producing and / or consuming the network traffic and to enforce policies in accordance with network traffic classifications. The appliance includes an on-box anti-virus / anti-malware engine, on-box data loss prevention engine and on-box authentication engine. One or more of these engines is informed by an on-box dynamic real tie rating system that allows for determined levels of scrutiny to be paid to the network traffic. Security gateways of this type can be clustered together to provide a set of resources for one or more networks, and in some instances as the backbone of a cloud-based service.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com