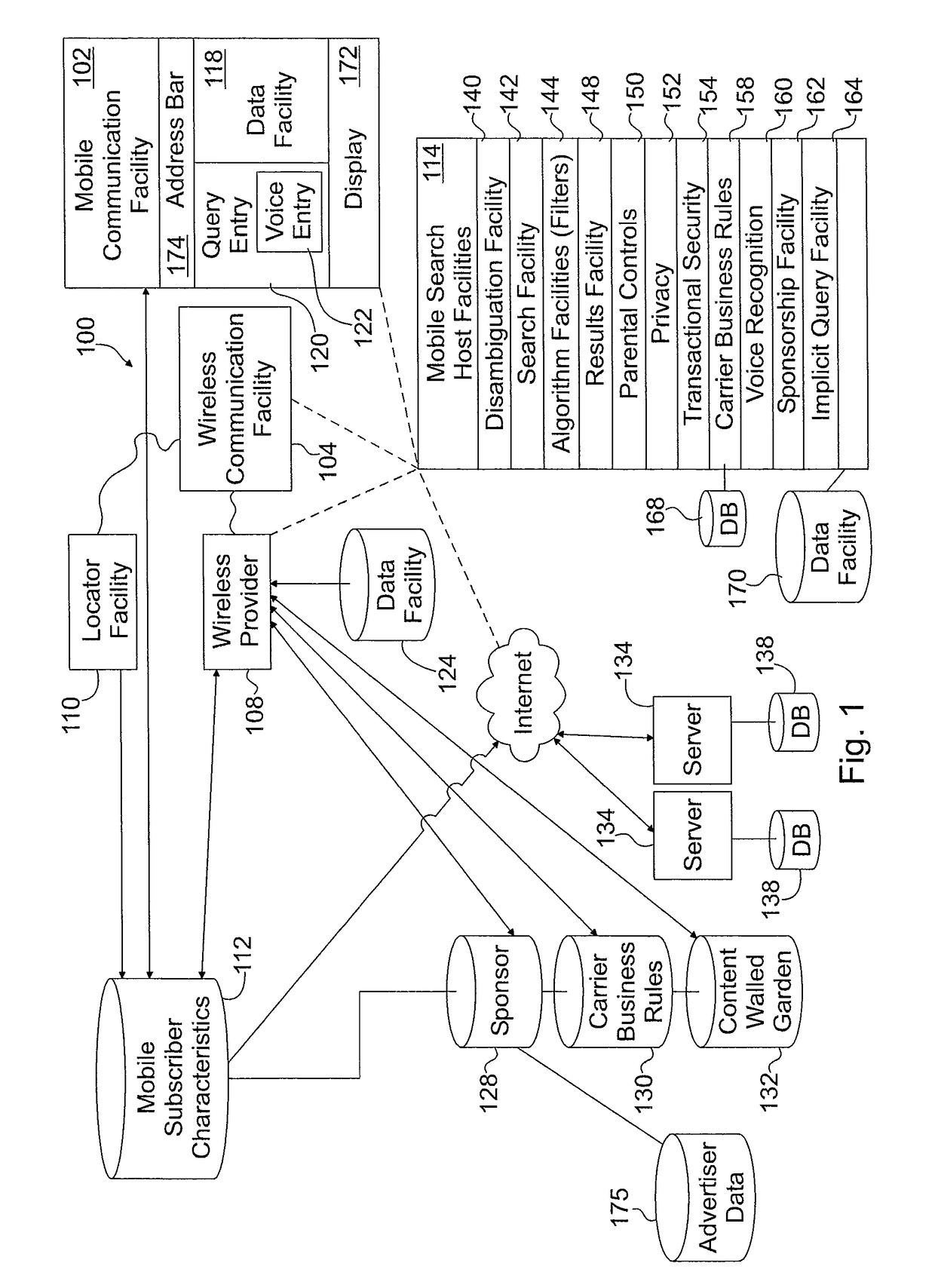
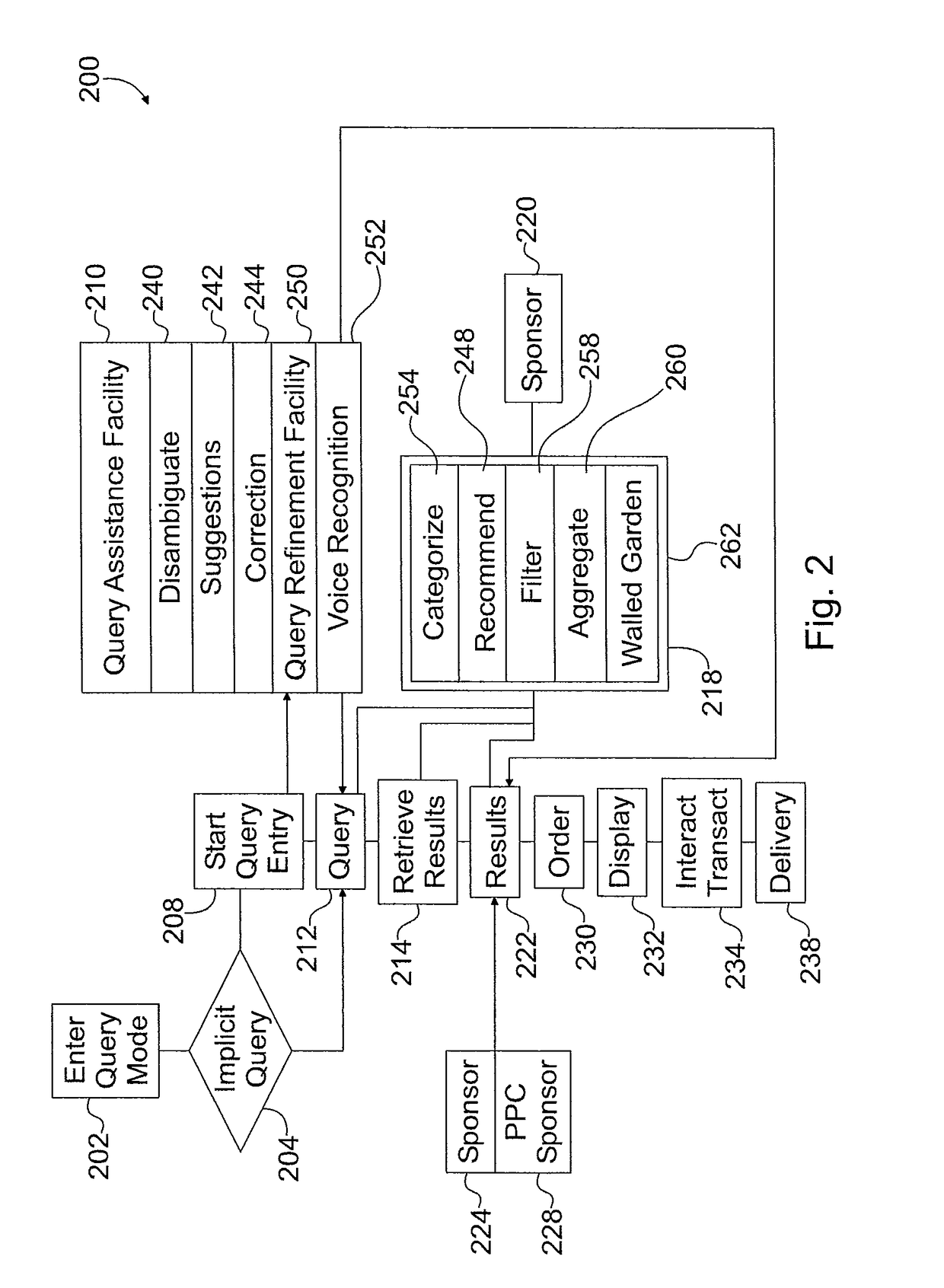
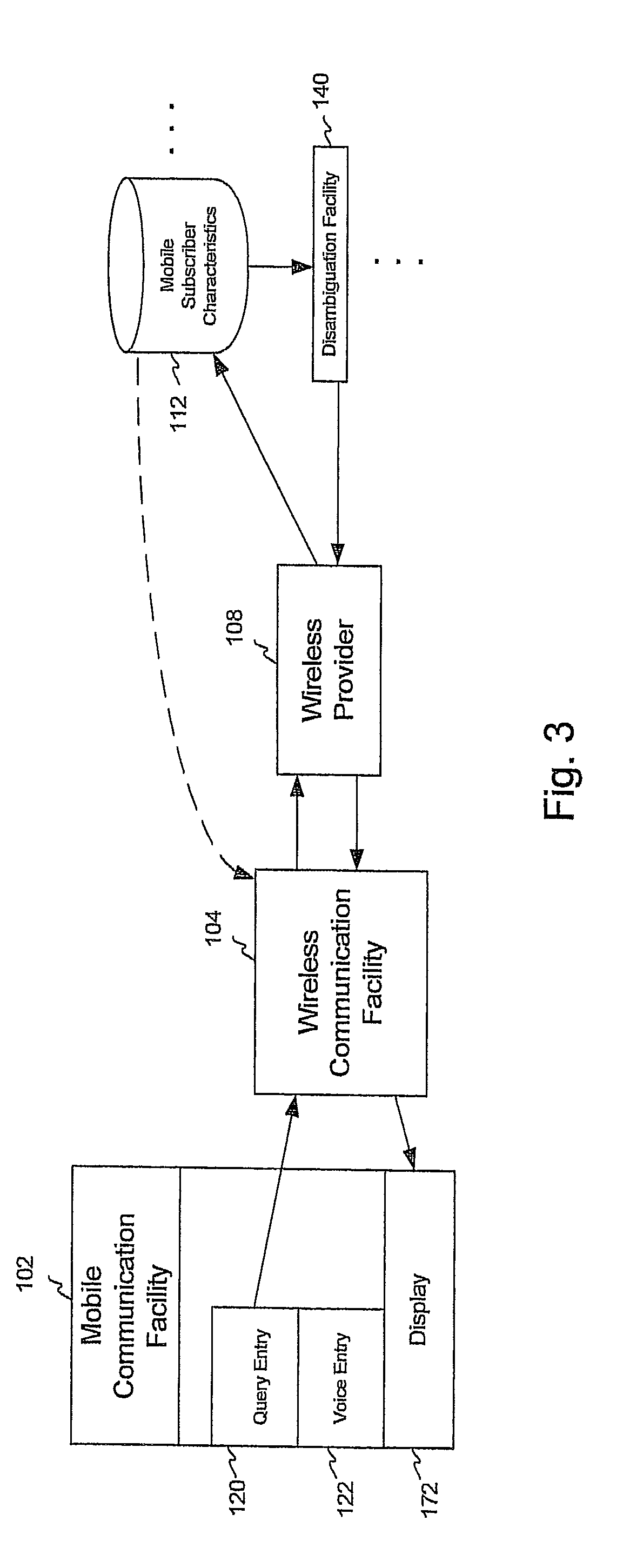
Patents
Literature
141 results about "Mobile transaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
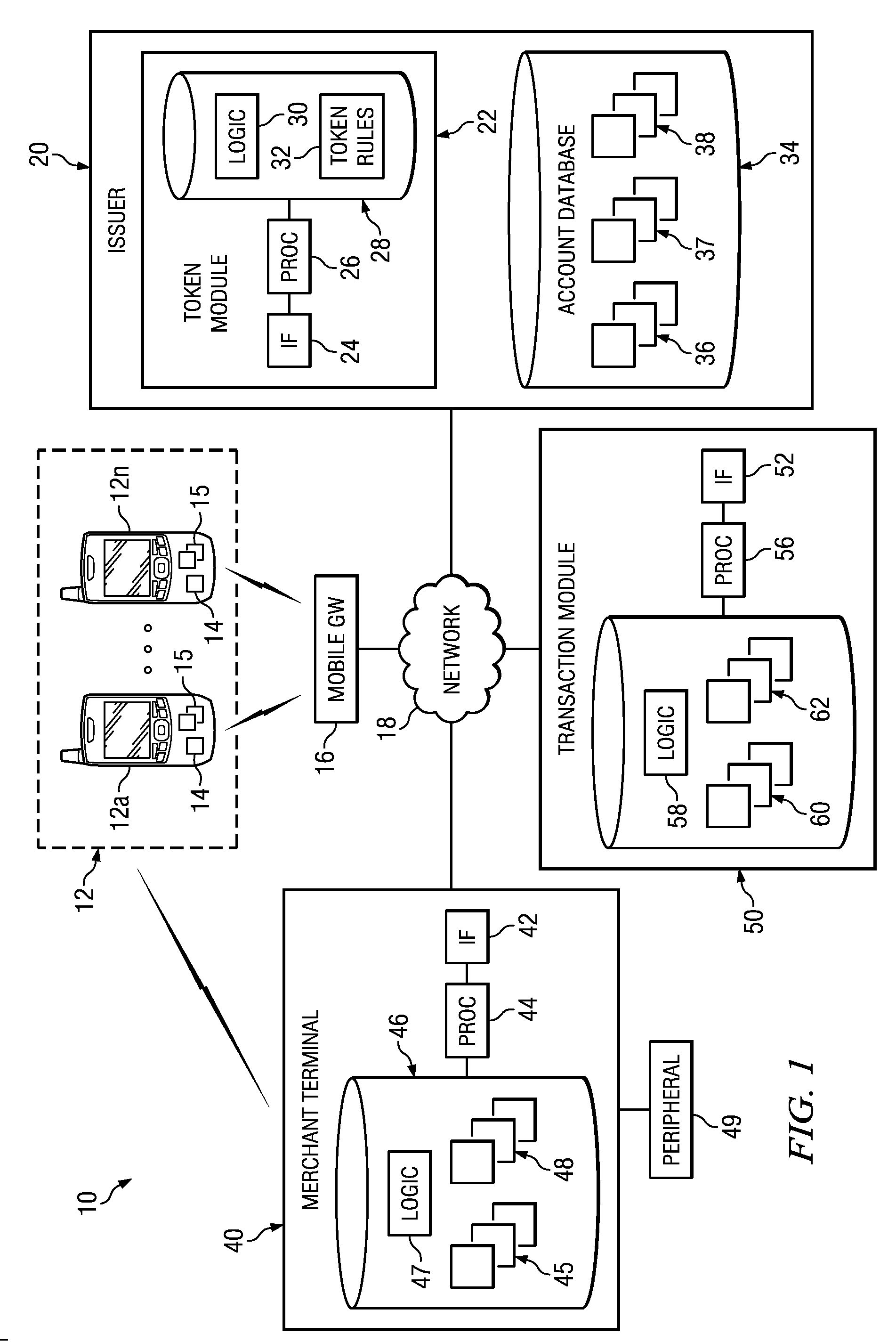
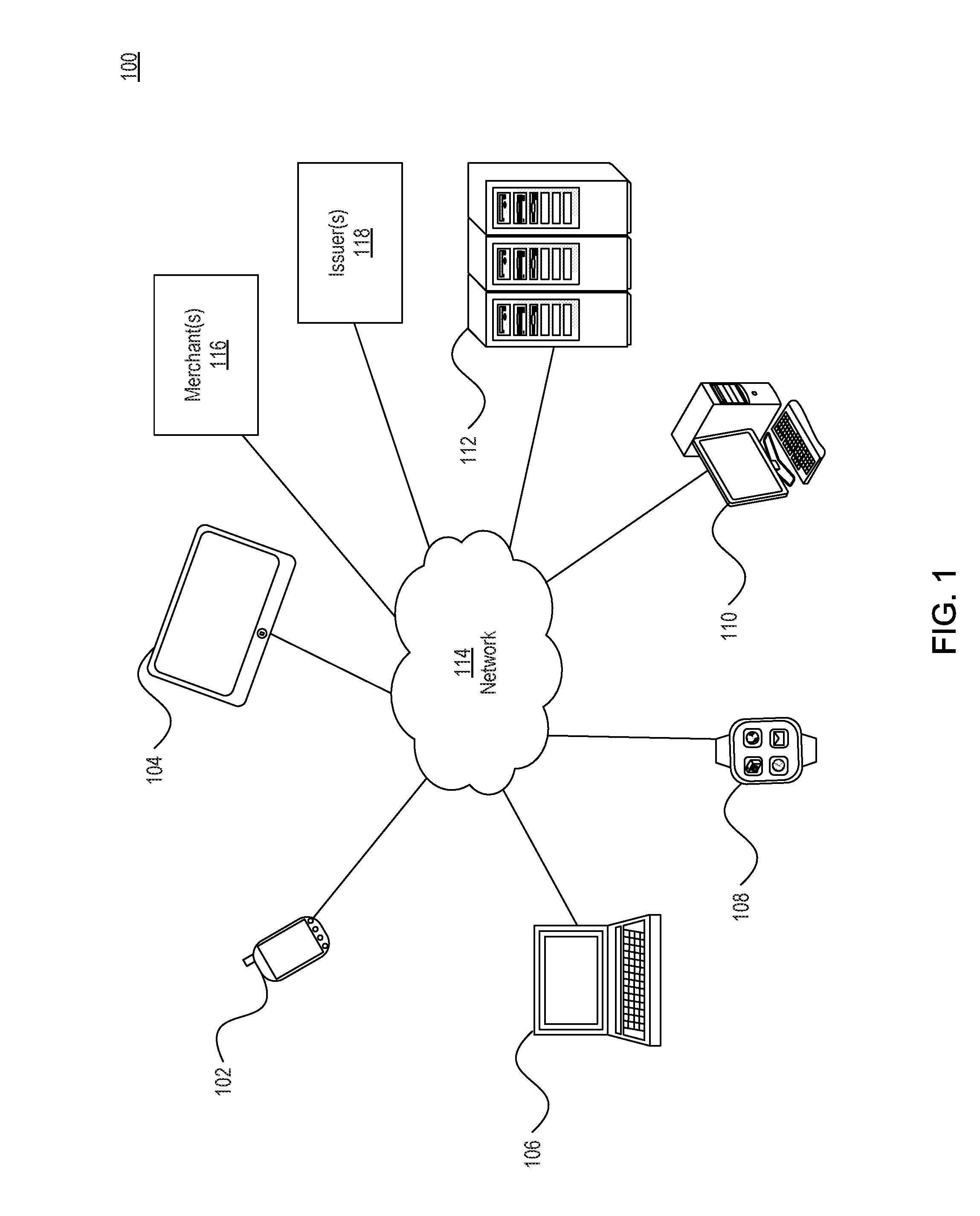
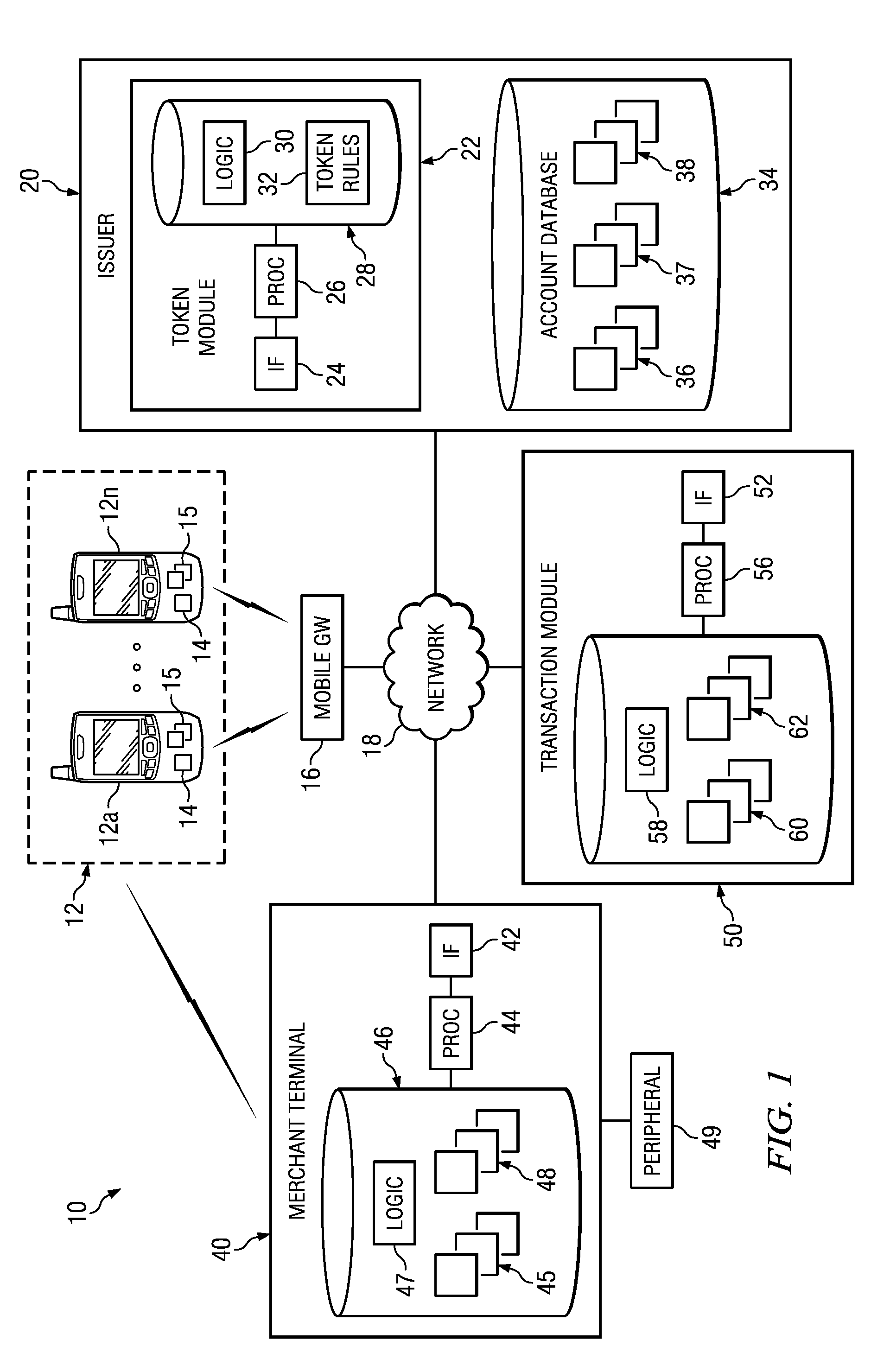
Implementing security measures for authorized tokens used in mobile transactions
ActiveUS20140025958A1Disadvantages can be reduced eliminatedTransactions be reduced eliminatedUnauthorized memory use protectionHardware monitoringSecurity MeasureMobile transaction
Security measures for tokens comprise storing security rules associated with a generated token in a memory. A processor, communicatively coupled to the memory, accesses the security rules associated with the generated token and determines whether to encrypt the generated token by applying at least a portion of the security rules to the generated token. The processor encrypts the generated token. An interface, communicatively coupled to the processor, communicates the encrypted token to a mobile device associated with a user.
Owner:BANK OF AMERICA CORP
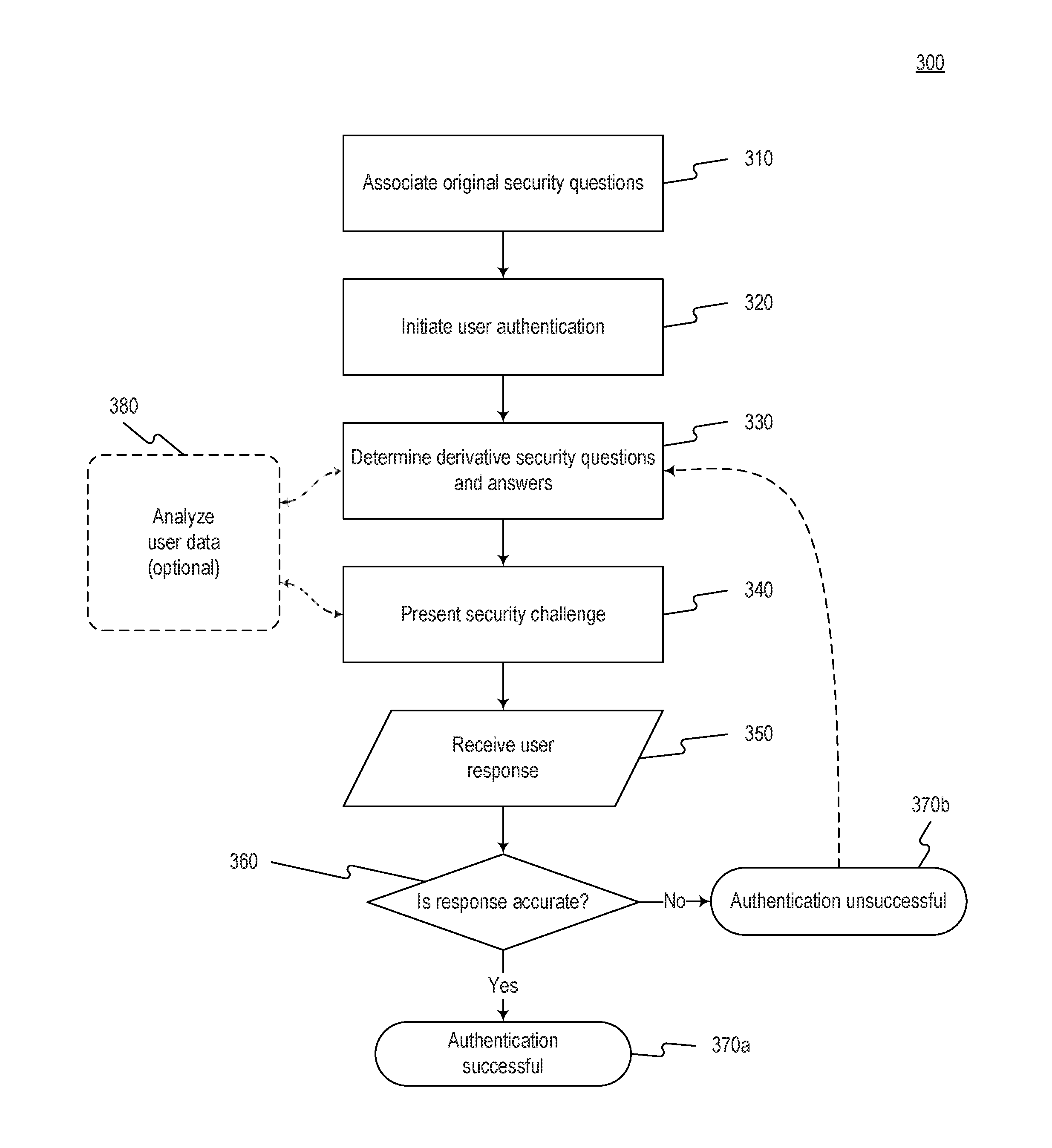
Systems and methods for derivative fraud detection challenges in mobile device transactions
InactiveUS20160381560A1Improve identification and verificationImprove experienceDigital data processing detailsMultiple digital computer combinationsInternet privacyMobile transaction
The disclosed embodiments include systems, methods, and computer-readable media configured to provide mobile device transaction security. The techniques described in the disclosed embodiments may be used to verify a mobile device user by providing derivative fraud protection challenges. Thus, the techniques may be used to improve identification and verification of users during mobile transactions. As a result, the disclosed embodiments improve mobile security and user experience as well as enhance access control.
Owner:OFFLA SELFSAFE
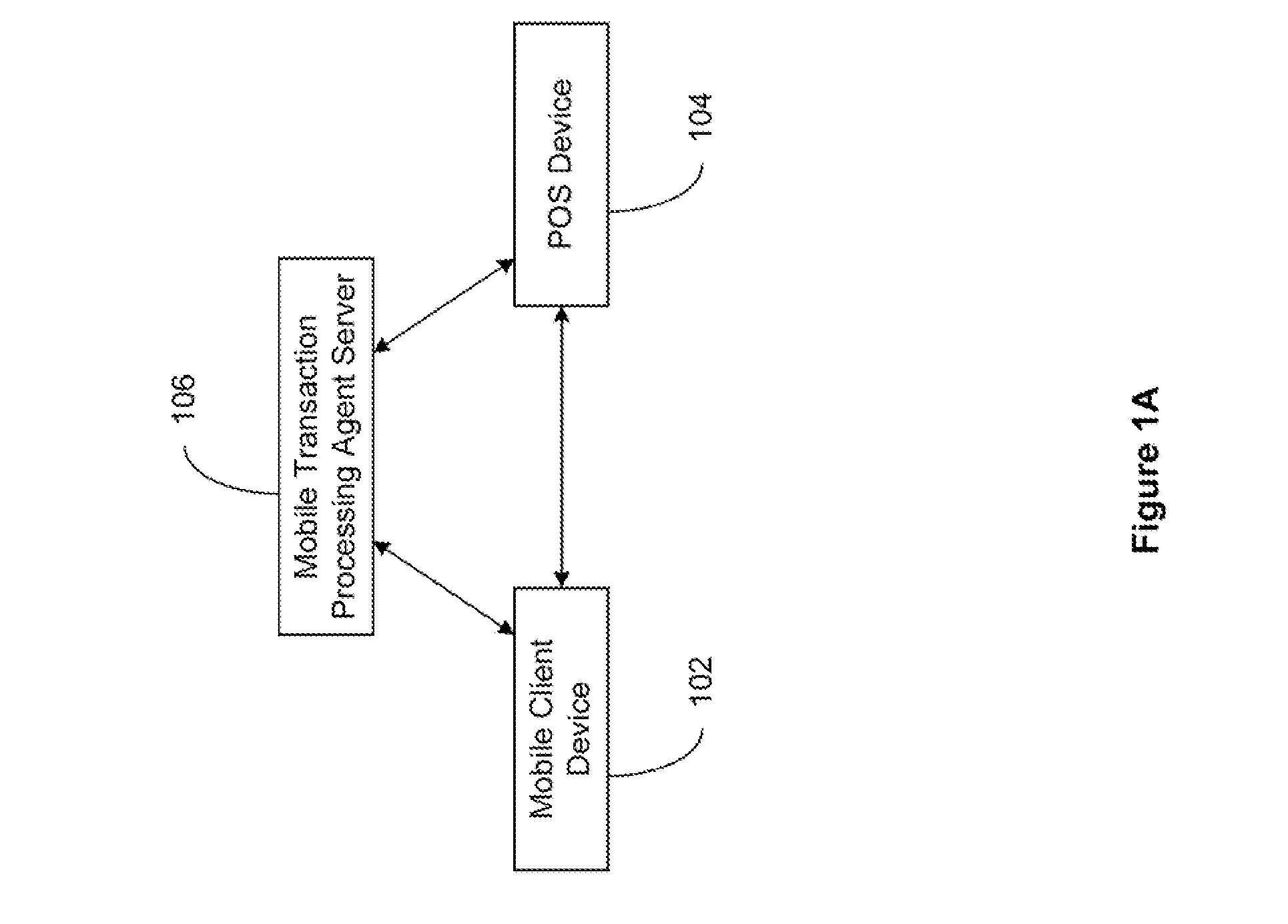
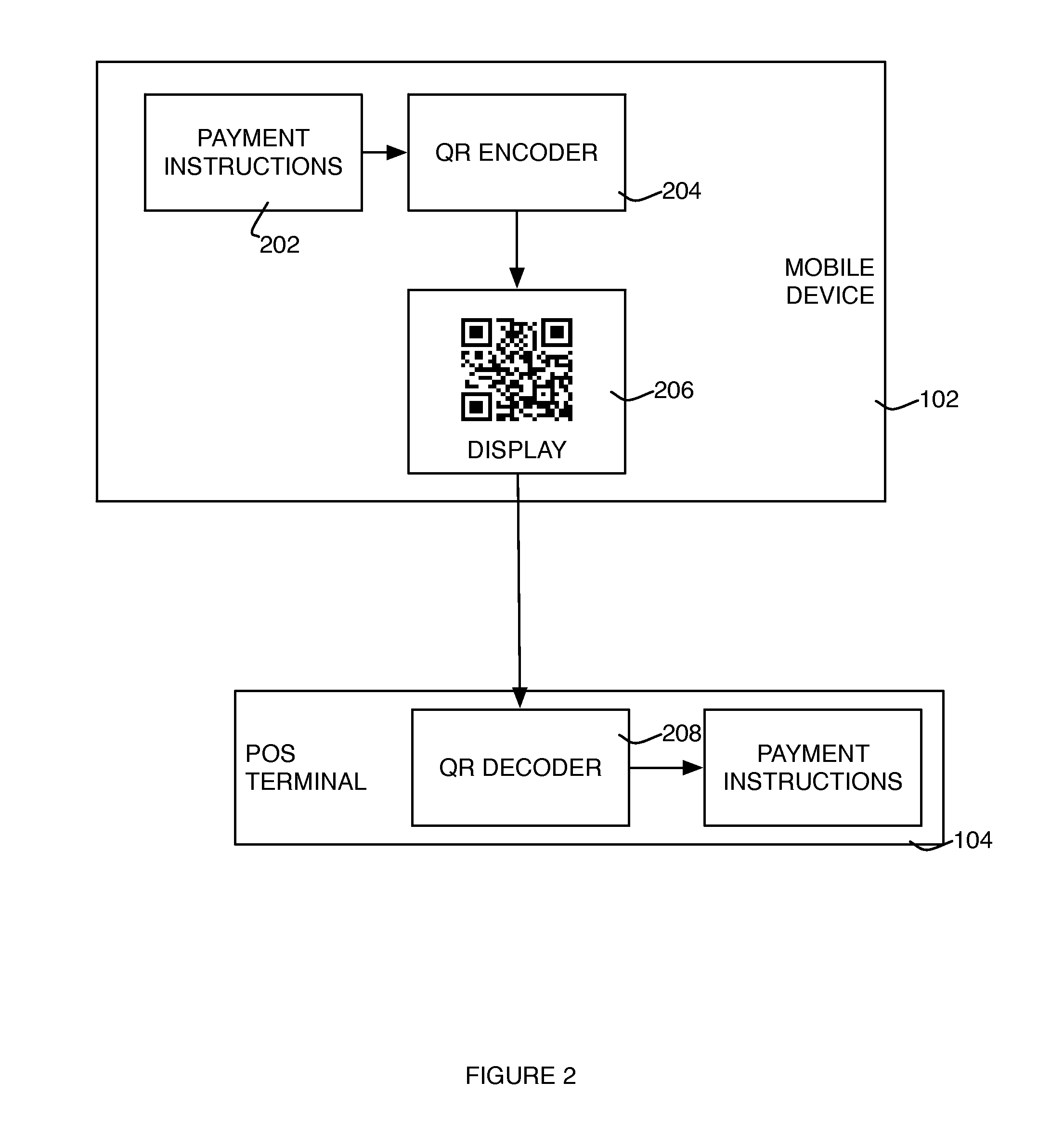
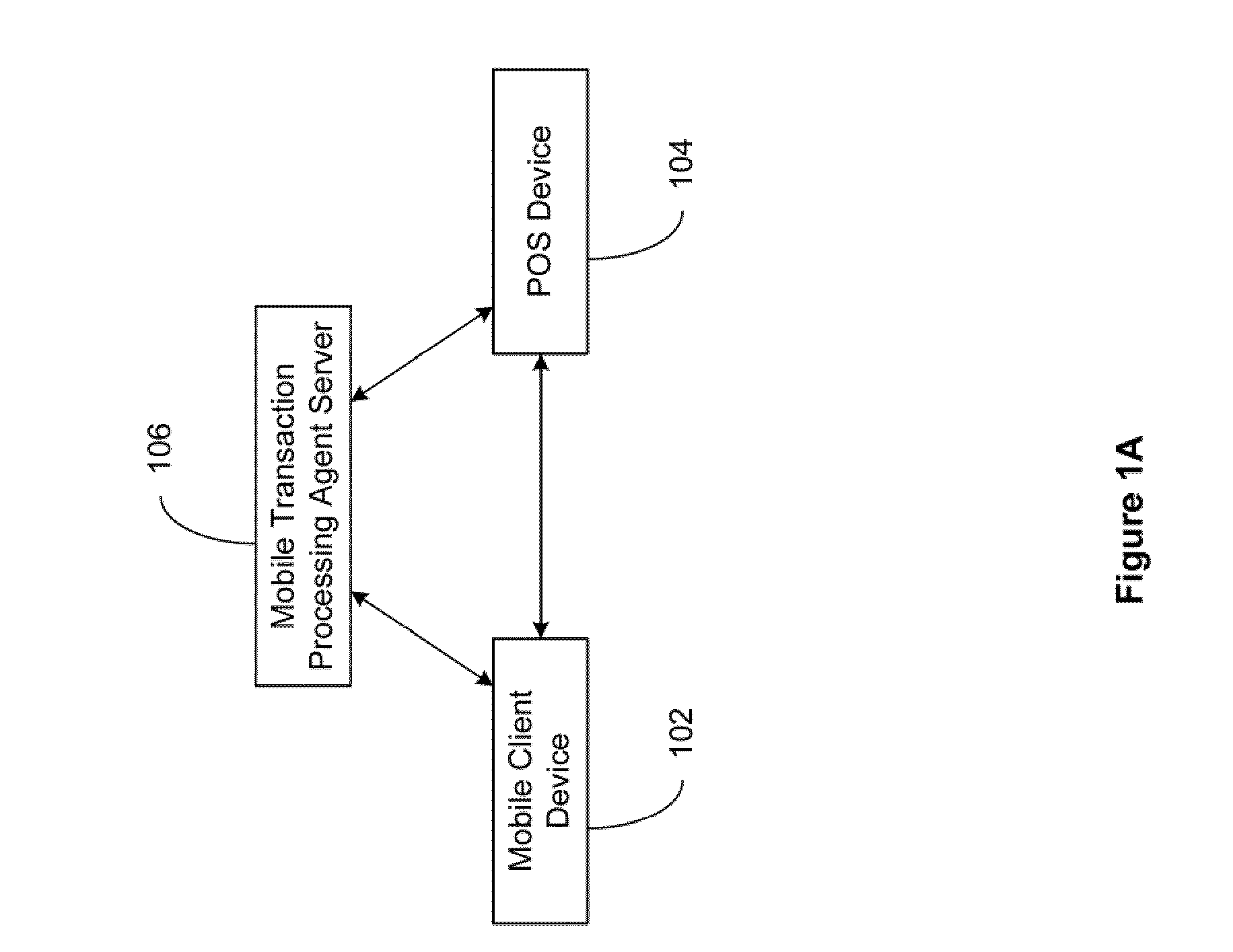
Secured Transaction System
The present invention relates to a secured transaction system. In one embodiment, a mobile transaction processing agent system includes a communication module configured to receive a secured transaction description from a mobile client device or an encrypted transaction description from a point-of-sale (POS) device, wherein the secured transaction description is in the form of a bar code generated by the mobile client device, an authentication module configured to decode the secured transaction description and verify the secured transaction description is valid based on the mobile client device or the point-of-sale device, and a transaction processing module configured to process the transaction in accordance with the secured transaction description.
Owner:DAI XIA
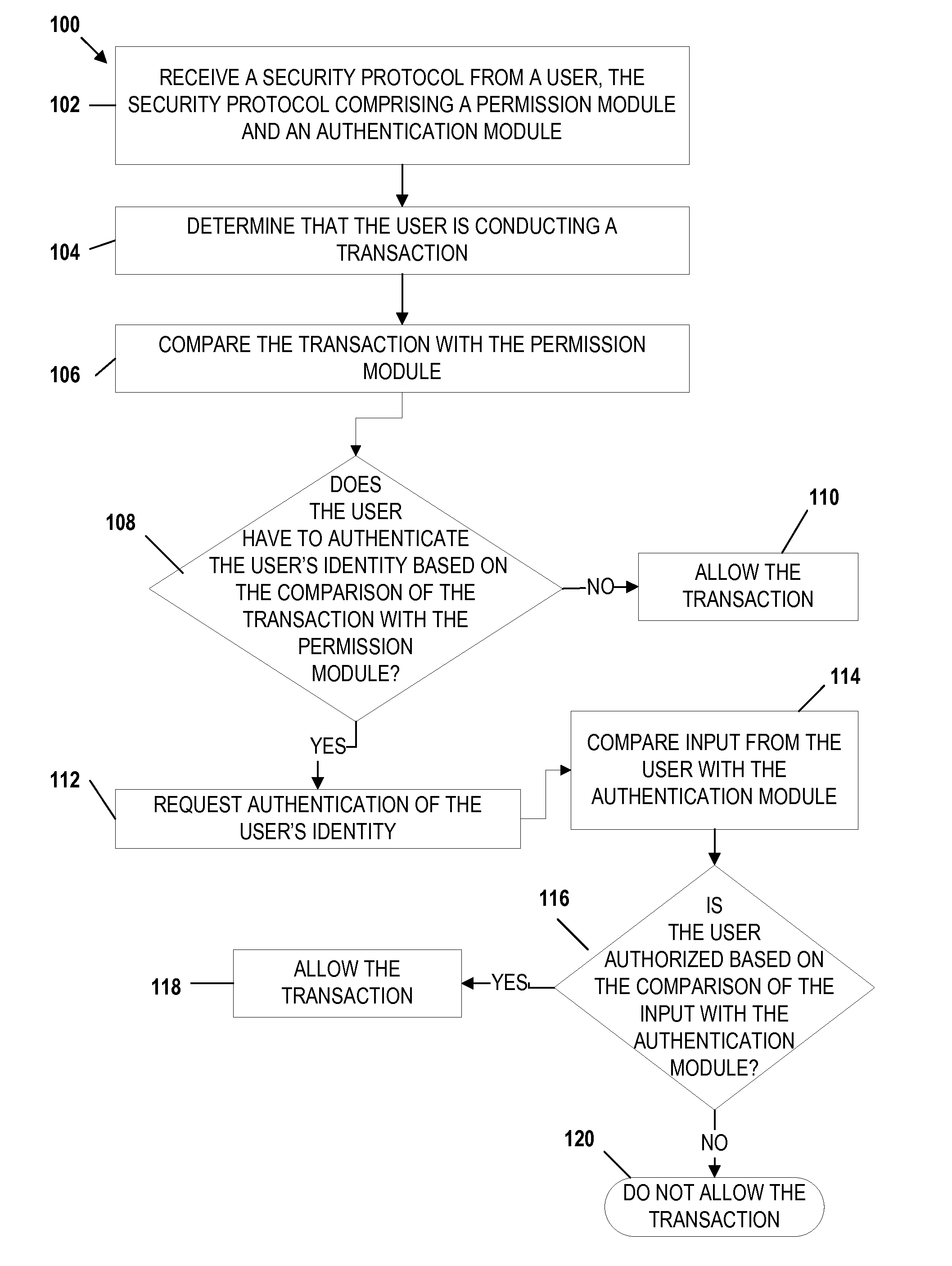
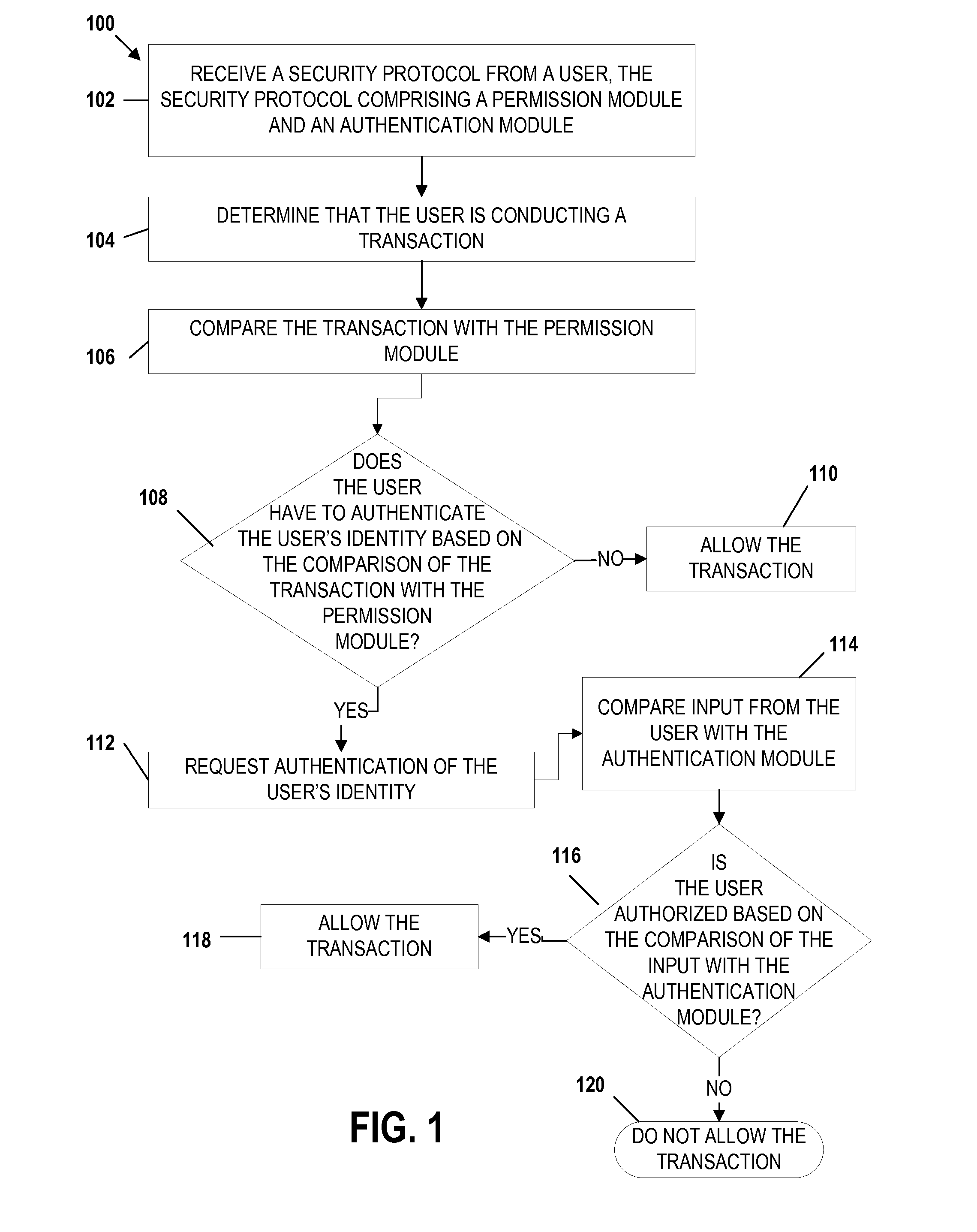
Mobile transaction device security system
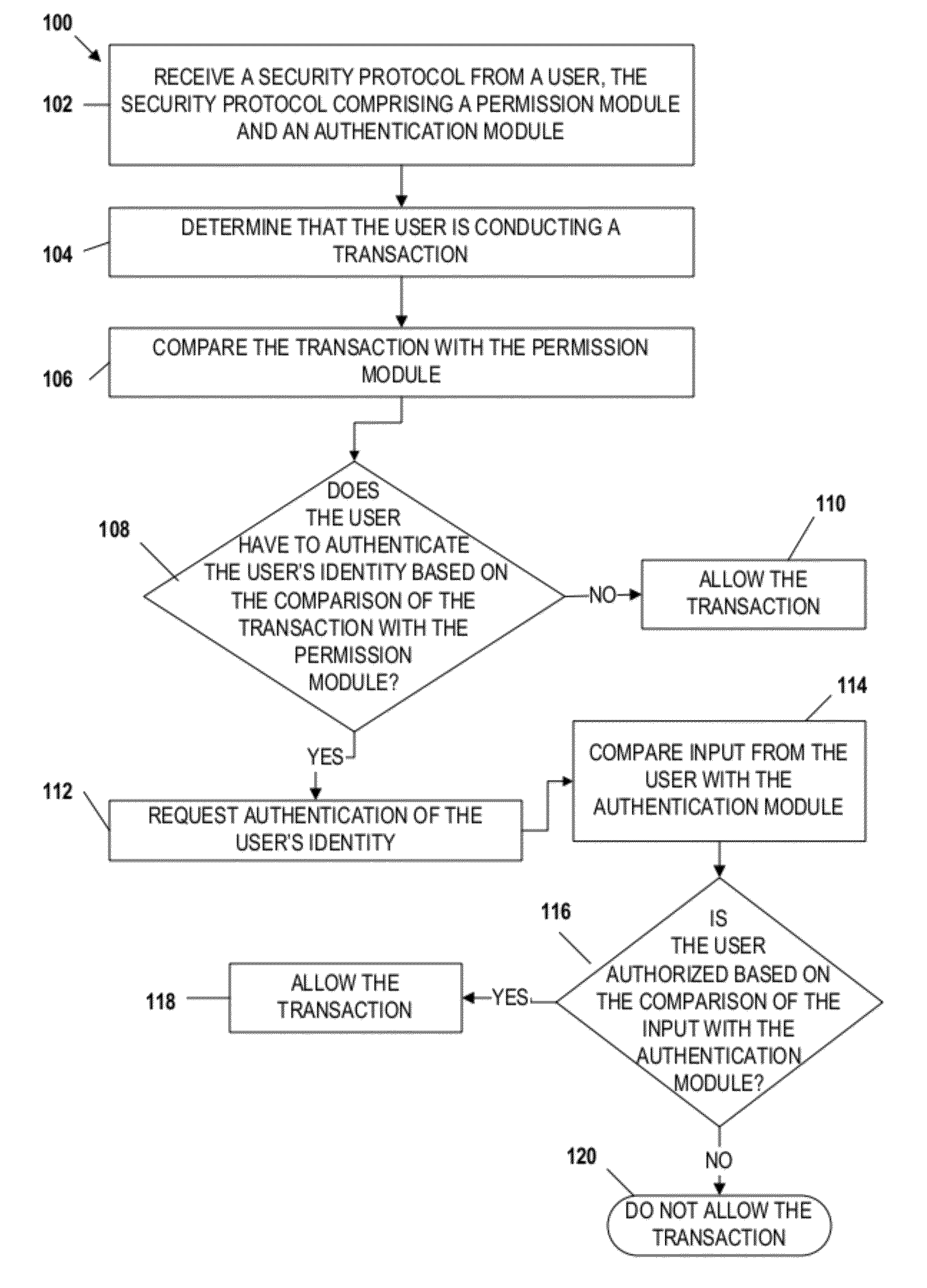
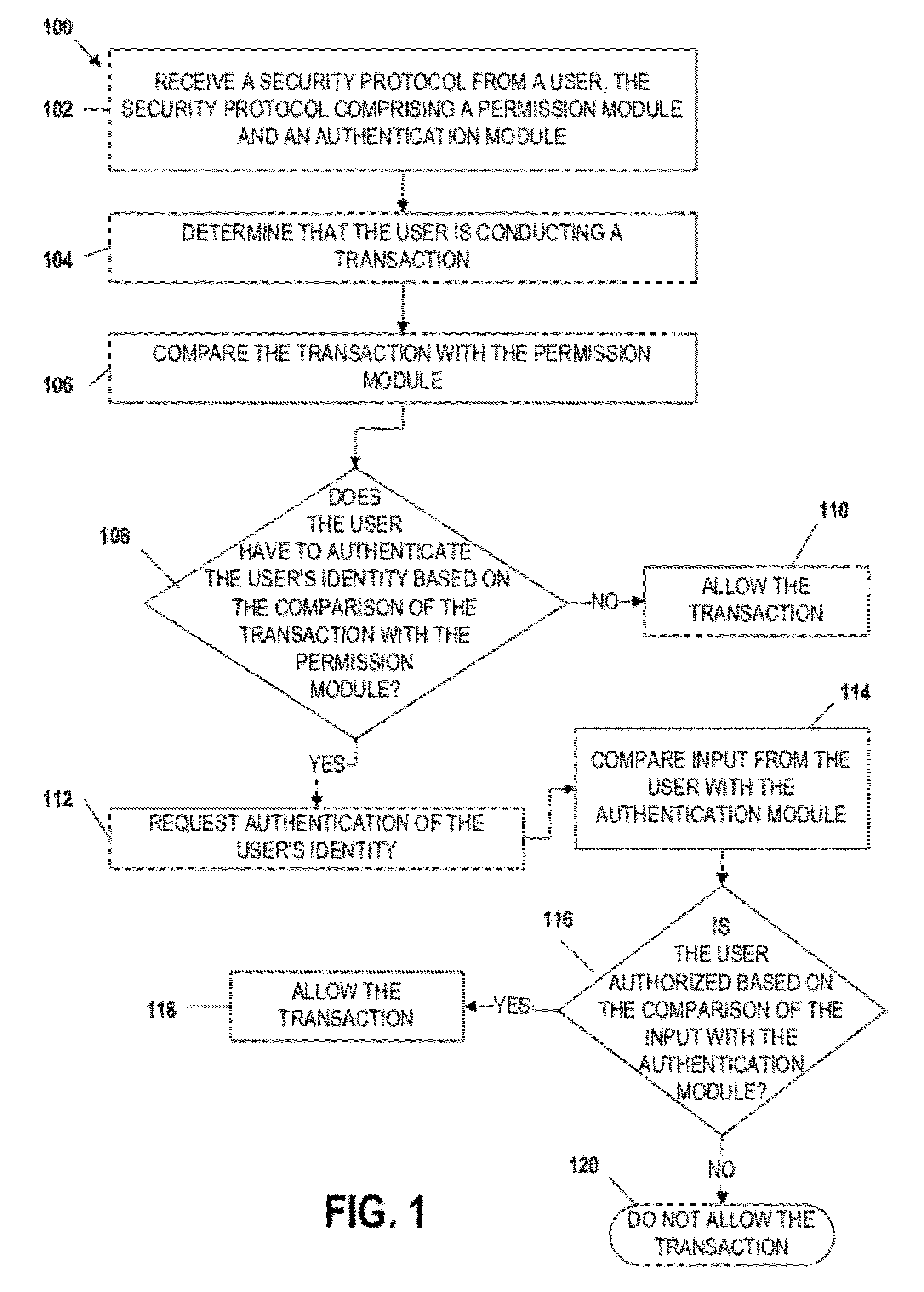
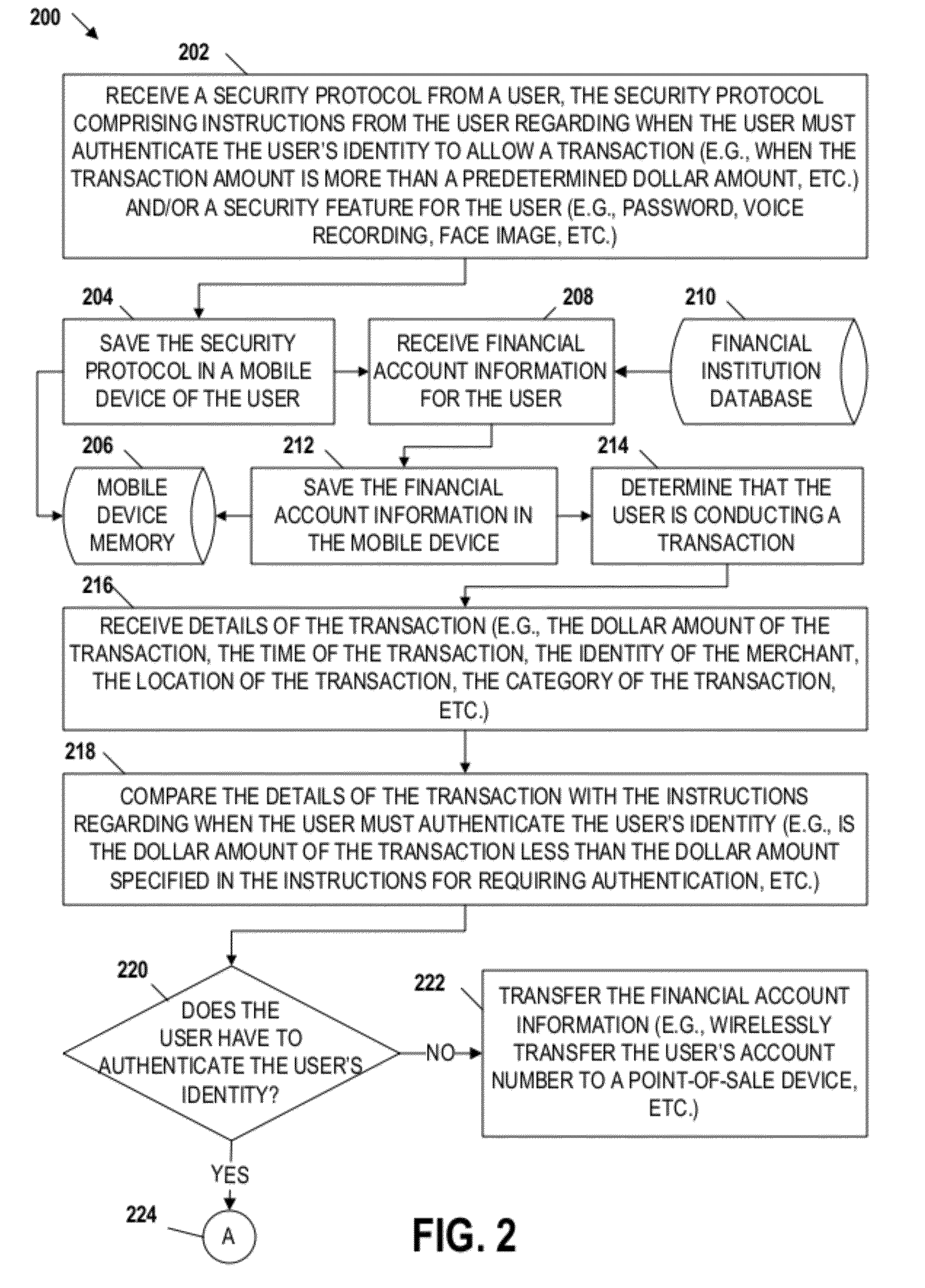
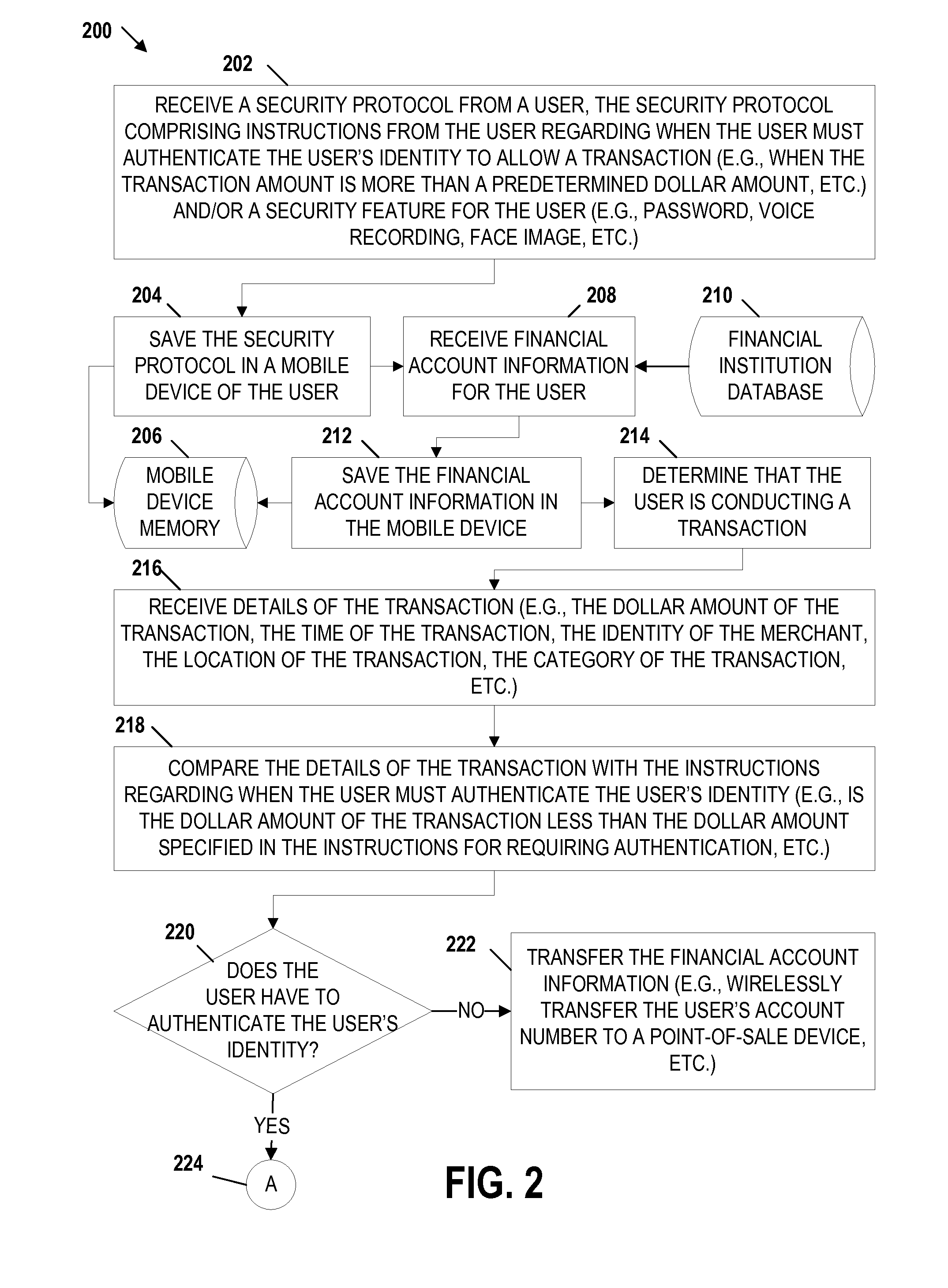
Embodiments of the invention include apparatuses, methods, and computer-program products that provide for a unique financial transaction security system. In one embodiment, the financial transaction security system receives a security protocol from a user. The security protocol includes instructions for allowing transactions without authentication and security features for the user if authentication is necessary. The system then determines that the user is conducting a transaction, compares the transaction to the instructions, and determines whether the transaction can occur without authentication. If the user is required to authenticate his identity, the system requests input from the user, compares the input to the security feature, and determines if the user is authenticated. The user is able to customize both the instructions and the security features to provide greater control over financial transaction security.
Owner:BANK OF AMERICA CORP
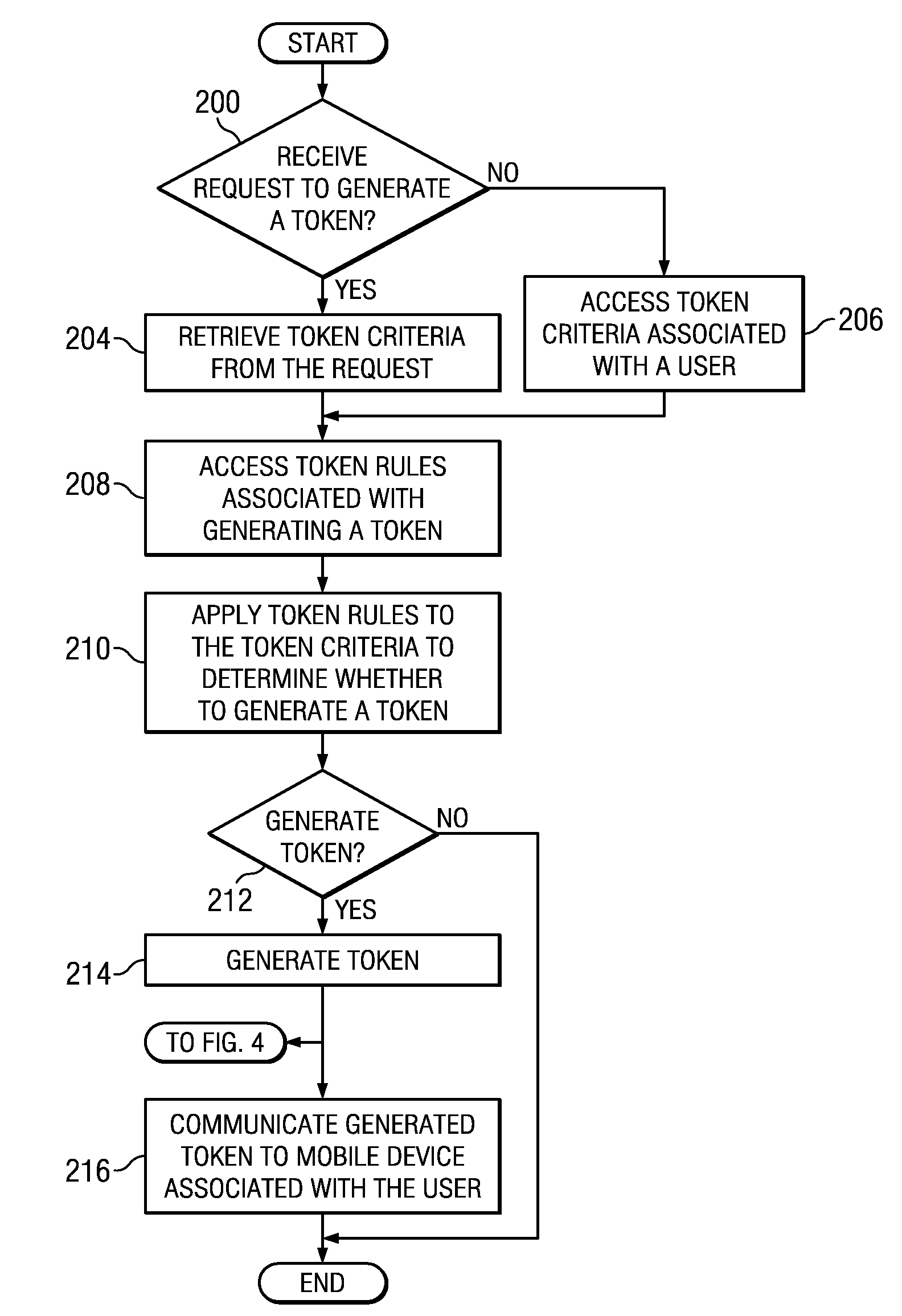
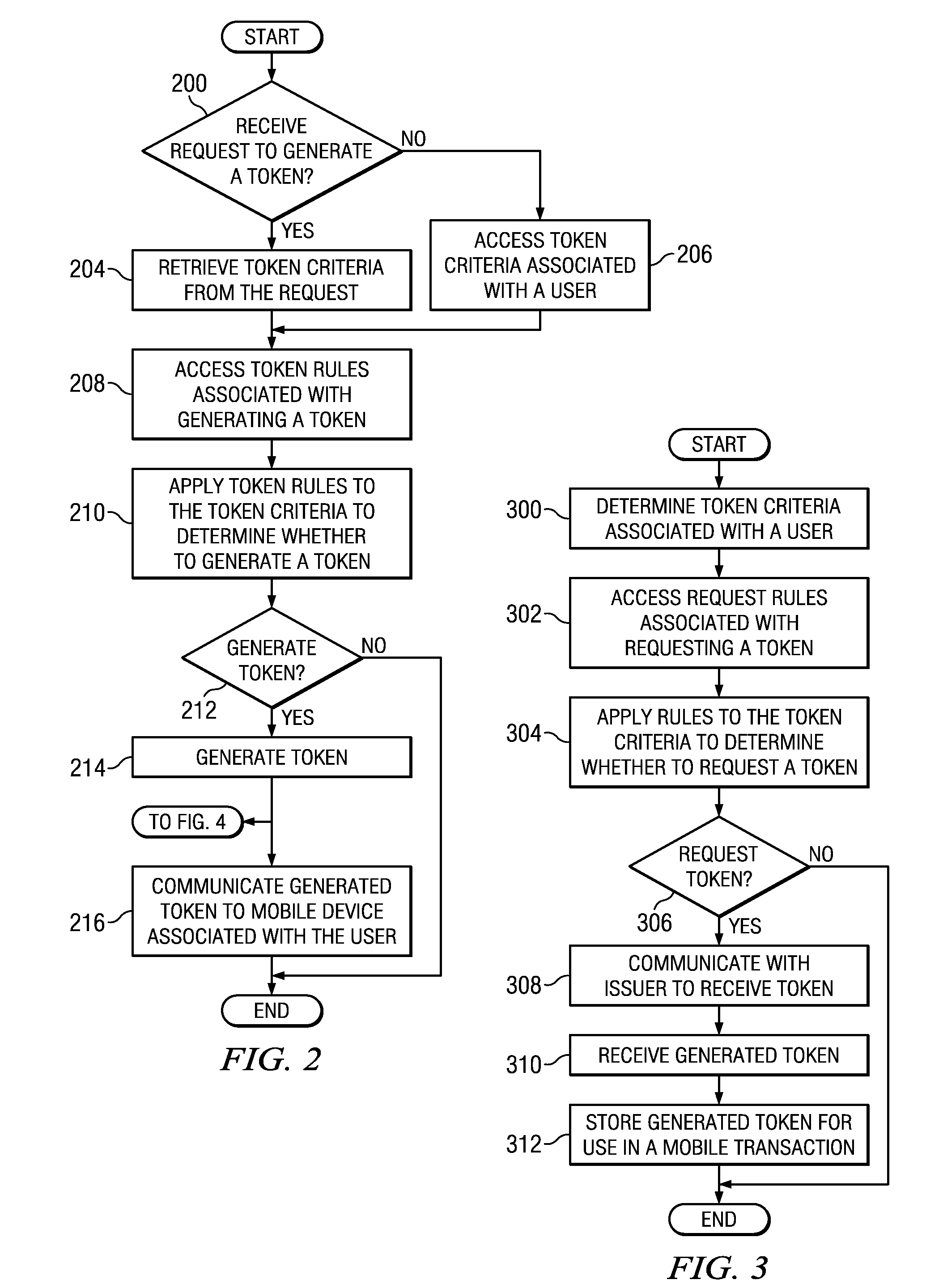
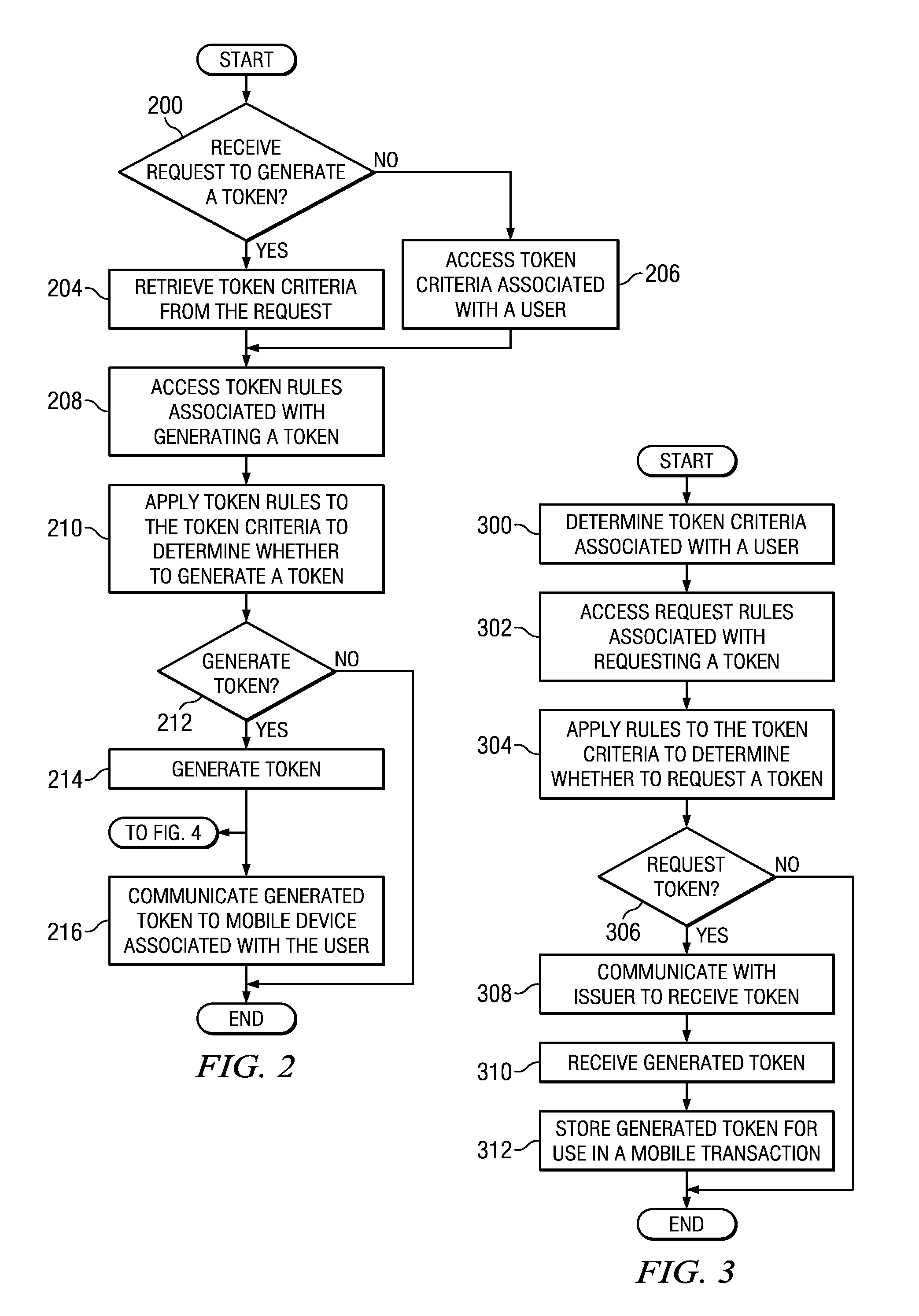
Distributing authorized tokens to conduct mobile transactions
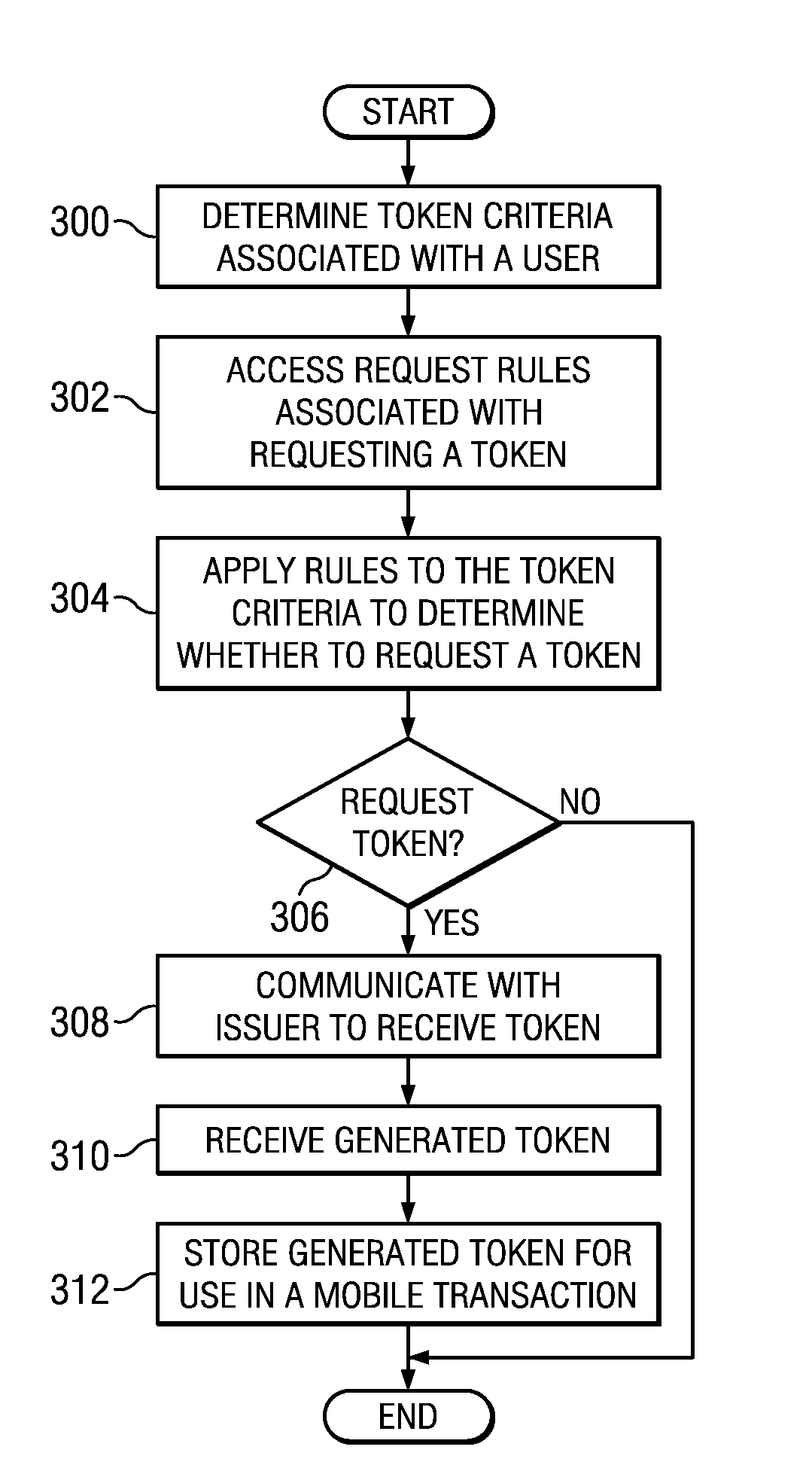
Token rules that facilitate determining whether to generate a token for use in a mobile transaction are stored in a memory. The memory also stores token criteria associated with a user. A processor, communicatively coupled to the memory, accesses the token rules and determines whether to generate the token by applying at least a portion of the token rules to the token criteria associated with the user. The token is generated upon a determination to generate the authorized token, and the token is generated before the mobile transaction begins. An interface, communicatively coupled to the processor, communicates the token to a mobile device associated with the user.
Owner:BANK OF AMERICA CORP
Method, system and device for executing a mobile transaction
InactiveUS20120253913A1Promote quick completionQuick and efficient and robustPoint-of-sale network systemsMarketingPaymentMobile transaction
A method of and system for a user executing a mobile transaction. A virtual wallet is generated on a mobile device, the mobile wallet including a reward value component. Information about an item desired to be purchased by the user is input to the mobile device. A proposed payment solution is generated from the virtual wallet that is sufficient to pay for the item and then presented to a point of sale terminal. The point of sale terminal then executes instructions from the proposed payment solution sufficient to execute payment for the item.
Owner:RICHARD POSTREL
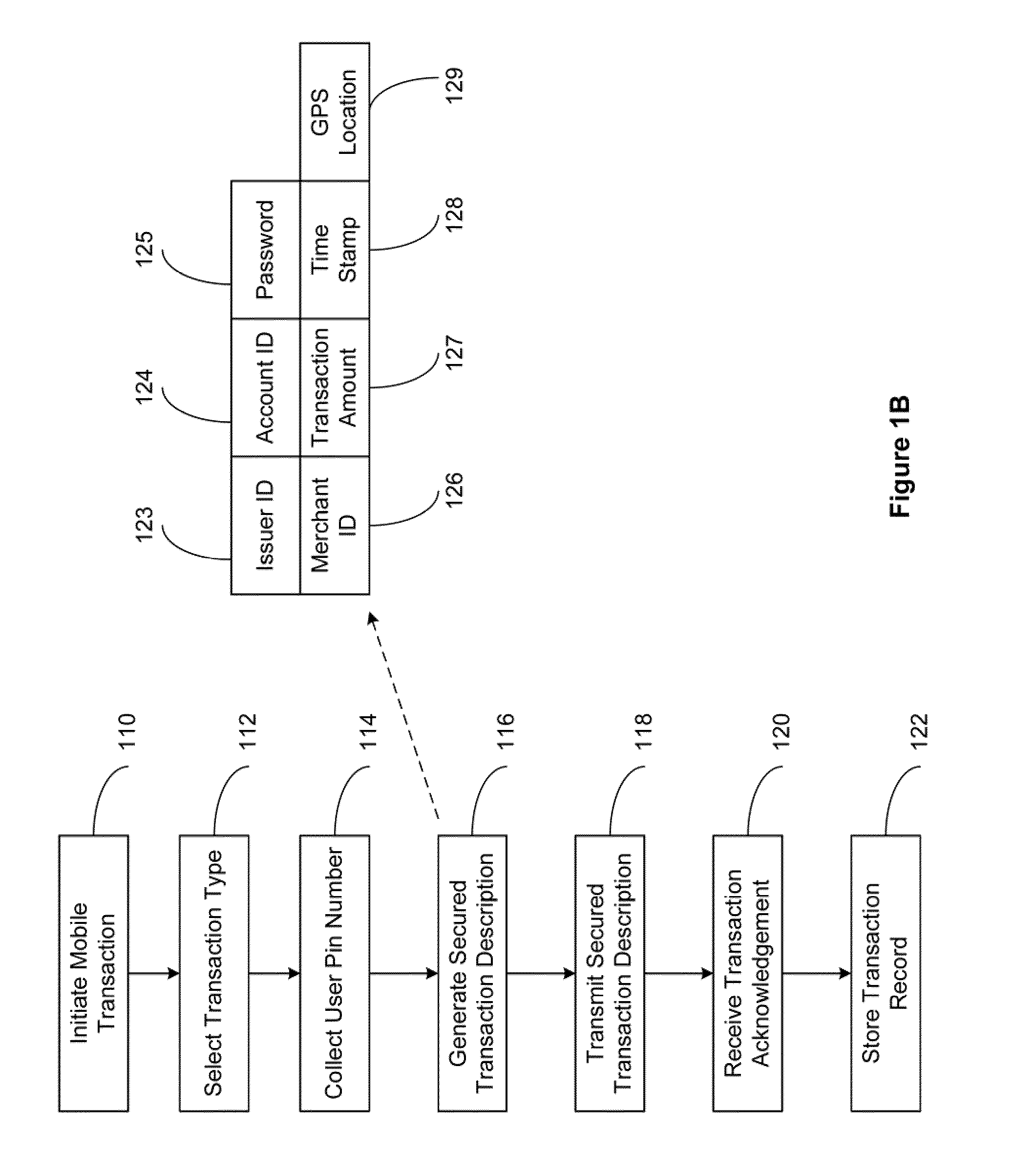
Secured Mobile Transaction Device
InactiveUS20110191161A1Improve securityFinanceBuying/selling/leasing transactionsPasswordMobile transaction
The present invention relates to a secured transaction system. In one embodiment, a mobile client device includes a user interface configured to enable a user to select a transaction type and collect a user pin number, a processor configured to generate a secured transaction description using the transaction type and the user pin number, wherein the secured transaction description includes issuer ID, account ID, merchant ID, password, transaction amount, and transaction time stamp, and the processor is further configured to transmit the secured transaction description to a mobile processing agent for processing, and receive a transaction record from the mobile transaction processing agent, and a memory configured to store the transaction record in the mobile client device.
Owner:DAI XIA
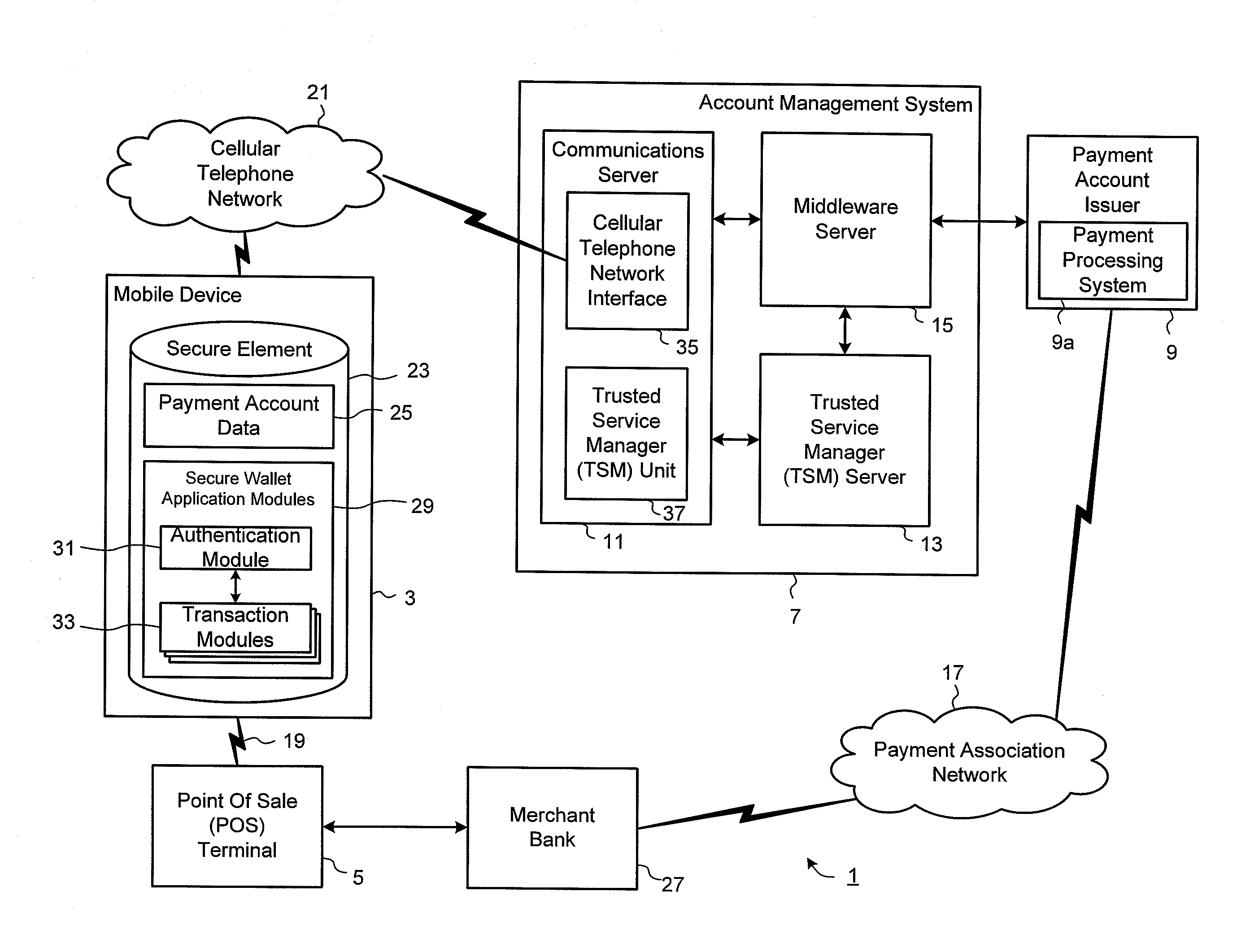
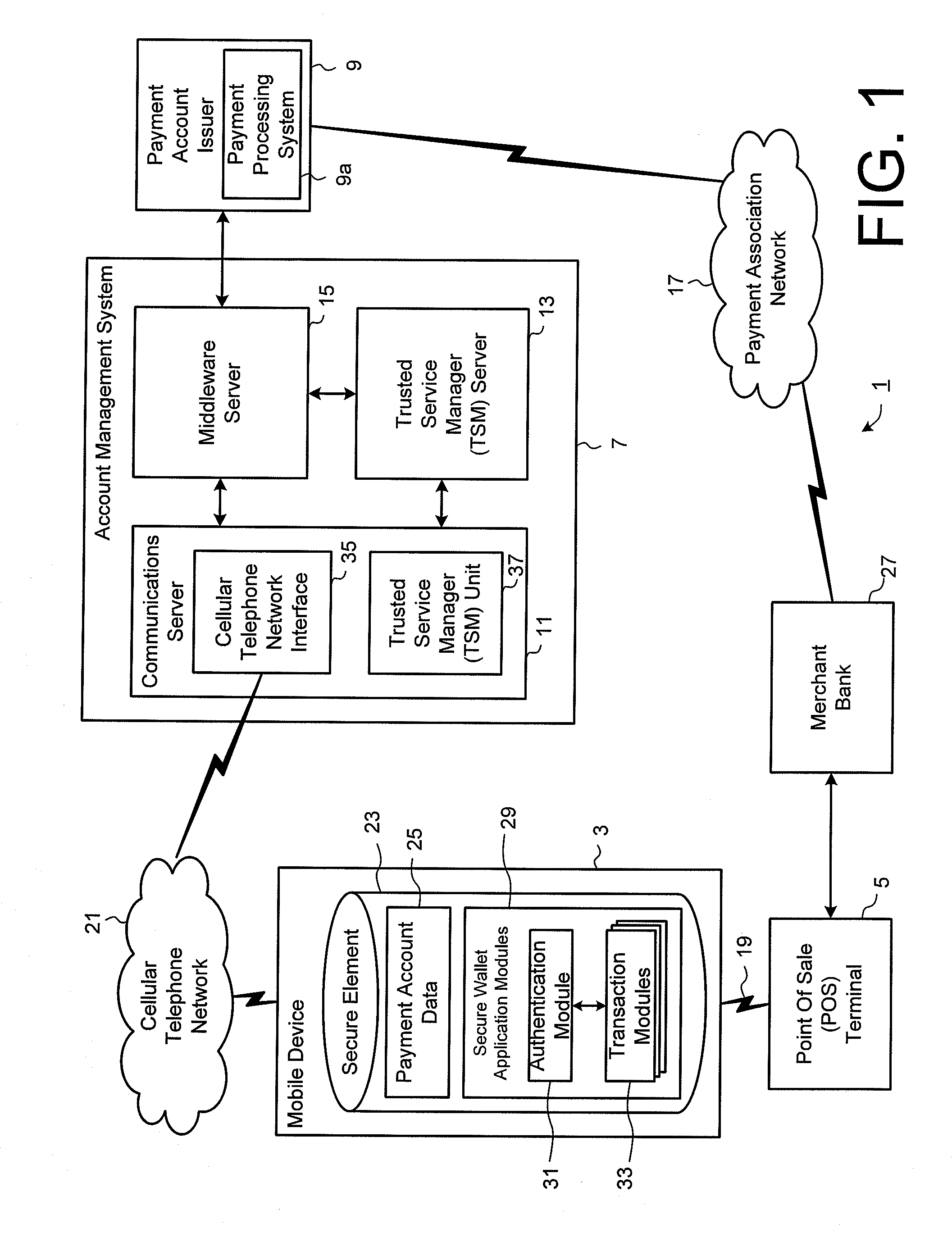
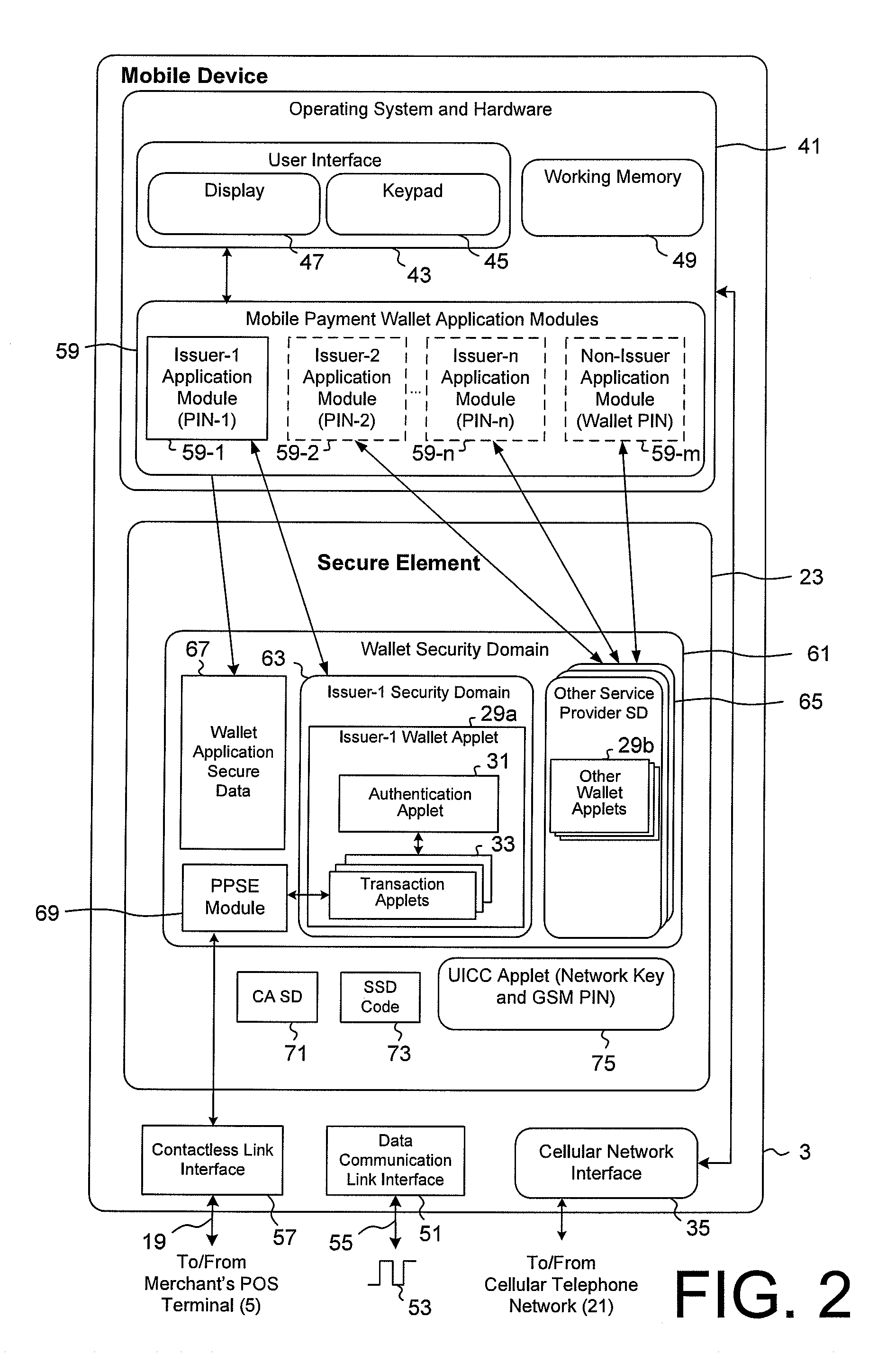
Method and System for Electronic Wallet Access
ActiveUS20130060618A1Facilitate user authenticationGood flexibilityPayment architectureBuying/selling/leasing transactionsTelecommunications linkPayment transaction
A mobile payment system is described that facilitates efficient and secured payment transactions from an electronic wallet on a user portable electronic device with a merchant point of sale terminal over a communication link. In one aspect, a mobile device is configured for transaction operations from a plurality of mobile transaction accounts in an electronic wallet. The mobile device includes a plurality of transaction modules operable to process transaction operations with a respective mobile transaction account, each transaction module configured for transaction operations to be completed after an authentication process using a central authentication module coupled to the plurality of transaction modules, operable to verify a user input passcode and to respond to authentication requests from the plurality of transaction module after the user input passcode is verified. Preferably, at least one of the transaction modules is configured for contactless transaction operations over a contactless communication link.
Owner:BARCLAYS EXECUTION SERVICES LTD
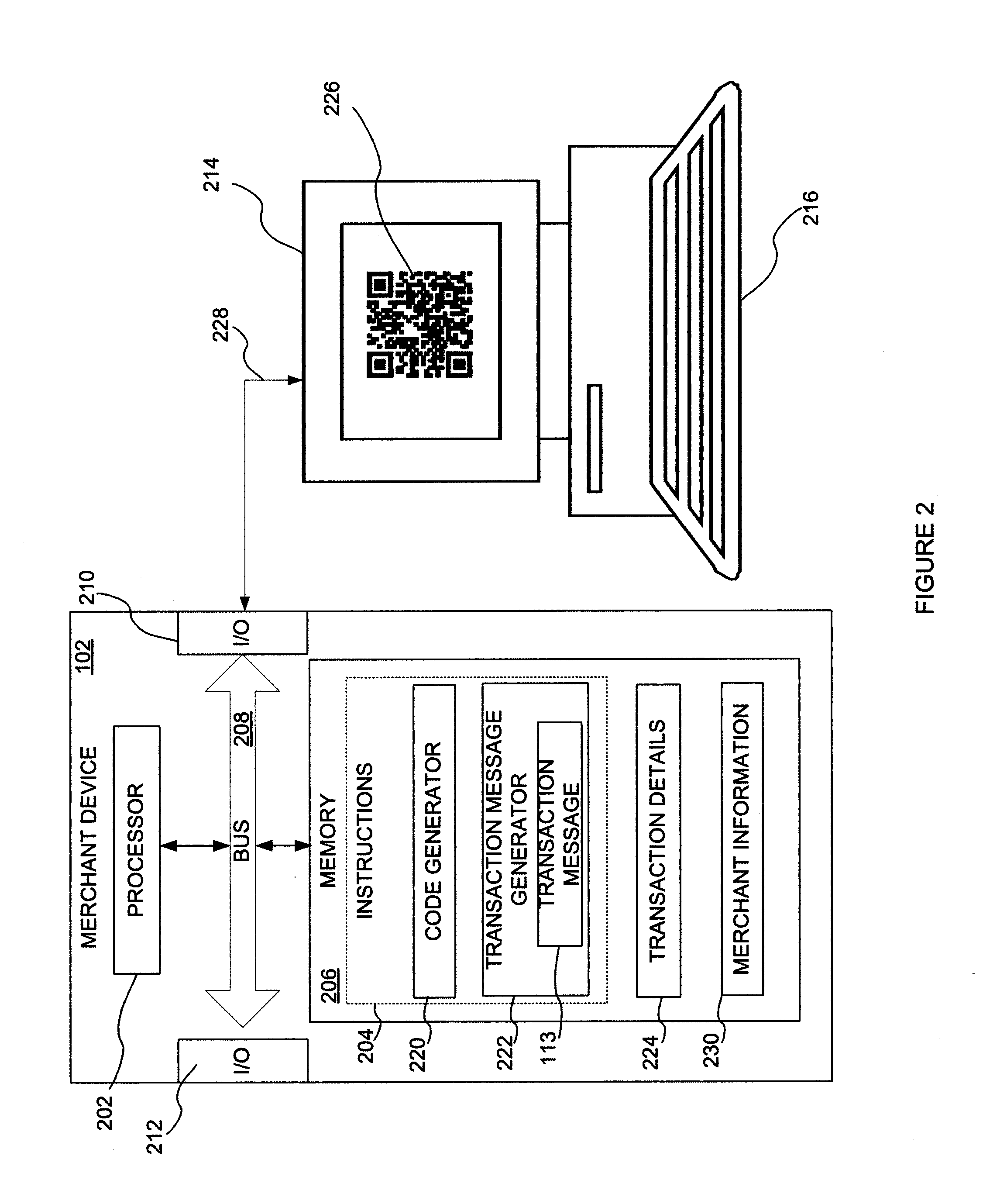
Point of Sale for Mobile Transactions
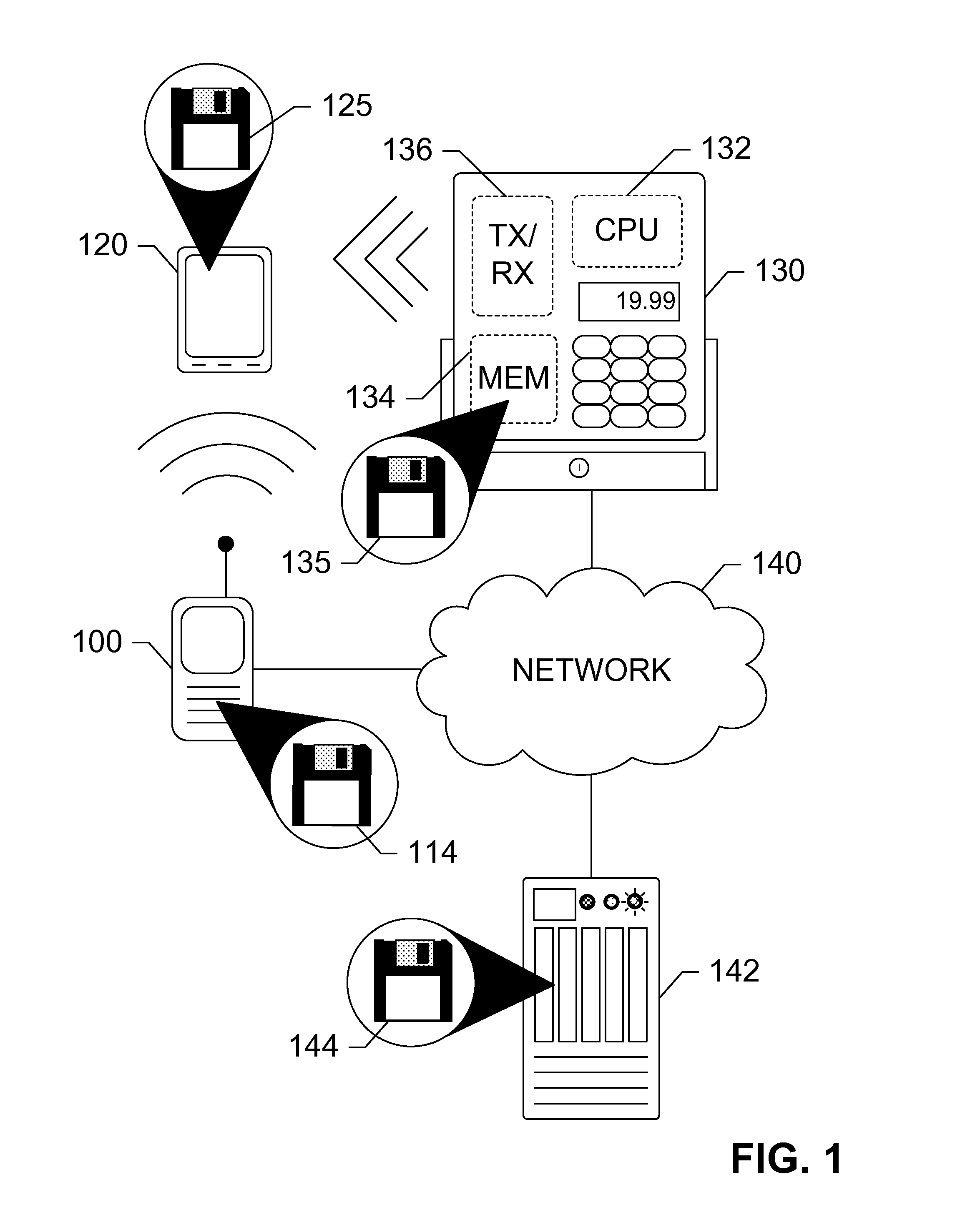
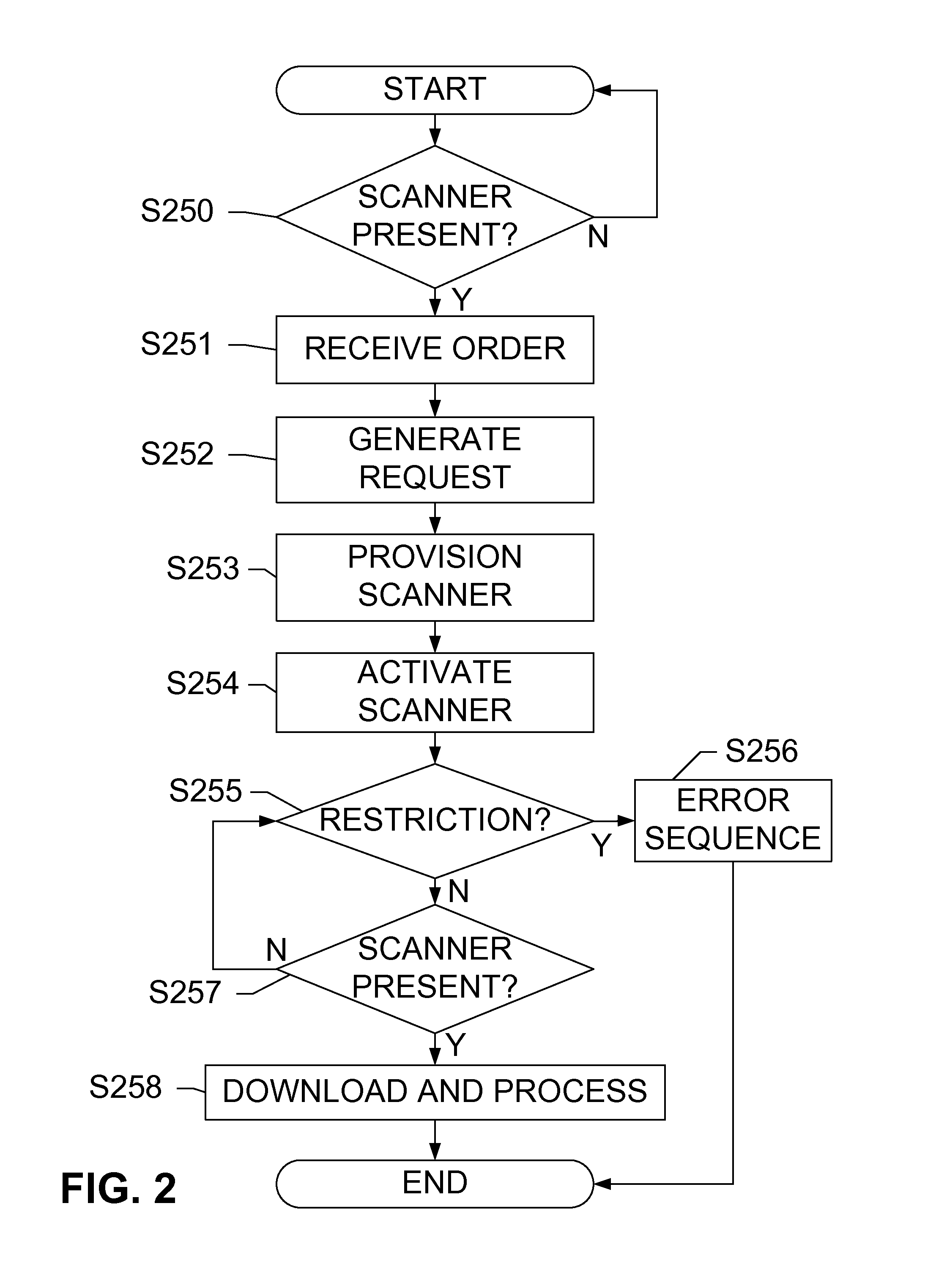
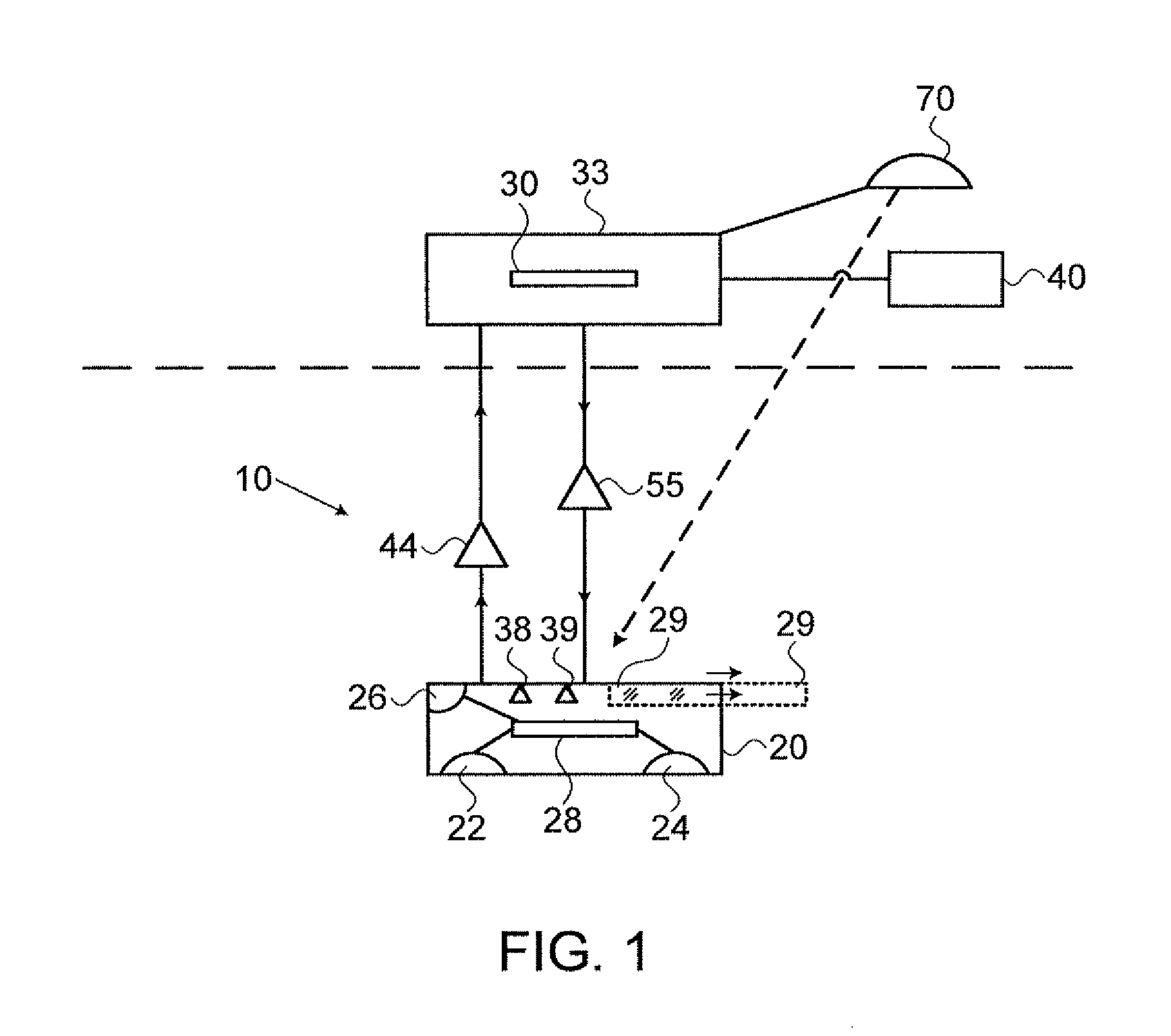
ActiveUS20130144731A1Buying/selling/leasing transactionsPoint-of-sale network systemsMobile transactionMobile device
Devices, systems, and methods are disclosed which relate to using a remote scanner for mobile transactions. A point of sale (POS) terminal communicates with a remote scanner that is removably coupled to the POS terminal. Logic on the POS terminal generates a request for a transaction information and transmits the request along with a restriction to the remote scanner. Logic on the remote scanner receives the request and the restriction, transmits the request to a mobile device, receives the transaction information while monitoring the restriction, and transmits the transaction information to the POS terminal for processing. The transaction information may be provided subject to the restriction.
Owner:AT&T INTPROP I L P
Variable fractions of multiple biometrics with multi-layer authentication of mobile transactions
Virtually fraud-proof authentication for wireless mobile financial transactions. A mobile telephone, genius card or dongle may capture multiple biometrics, such as fingerprint, voiceprint, retinal recognition data, facial biometric data, ear biometric data and bio print, iris scanning data, pupil movement recognition data, and send segments of each of them to a server computer that re-constitutes them and stores them for matching during an attempted financial transaction. A purchasing individual has multiple biometrics read by separate readers integrated into a single hand-held device. An automatic process of the server computer has previously sent a command packet to the hand-held device defining percentage and portion of each biometric to select and the sequence and channel of transmission for matching along with other out of band security data. During the charging phase, the hand-held device may utilize a slidable antenna for swiping a magnetic strip of a charge card reader or may display credit card data for a limited amount of time.
Owner:LEVOVITZ YERUCHAM
Secure mobile transactions
InactiveUS20130246272A1Reduce the possibilityReduce errorsFinanceElectronic credentialsInternet privacyMobile transaction
Owner:NEUSTAR
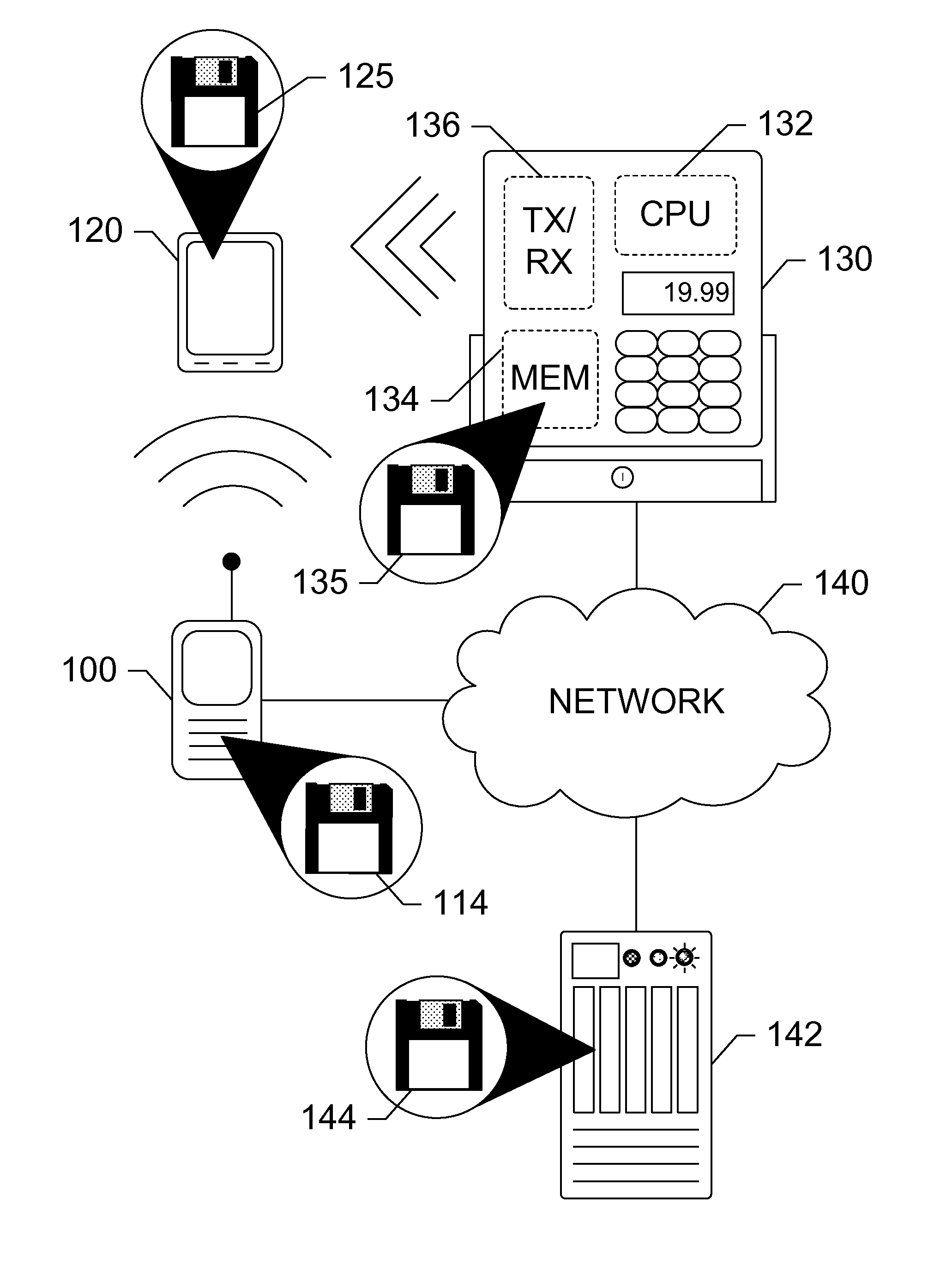
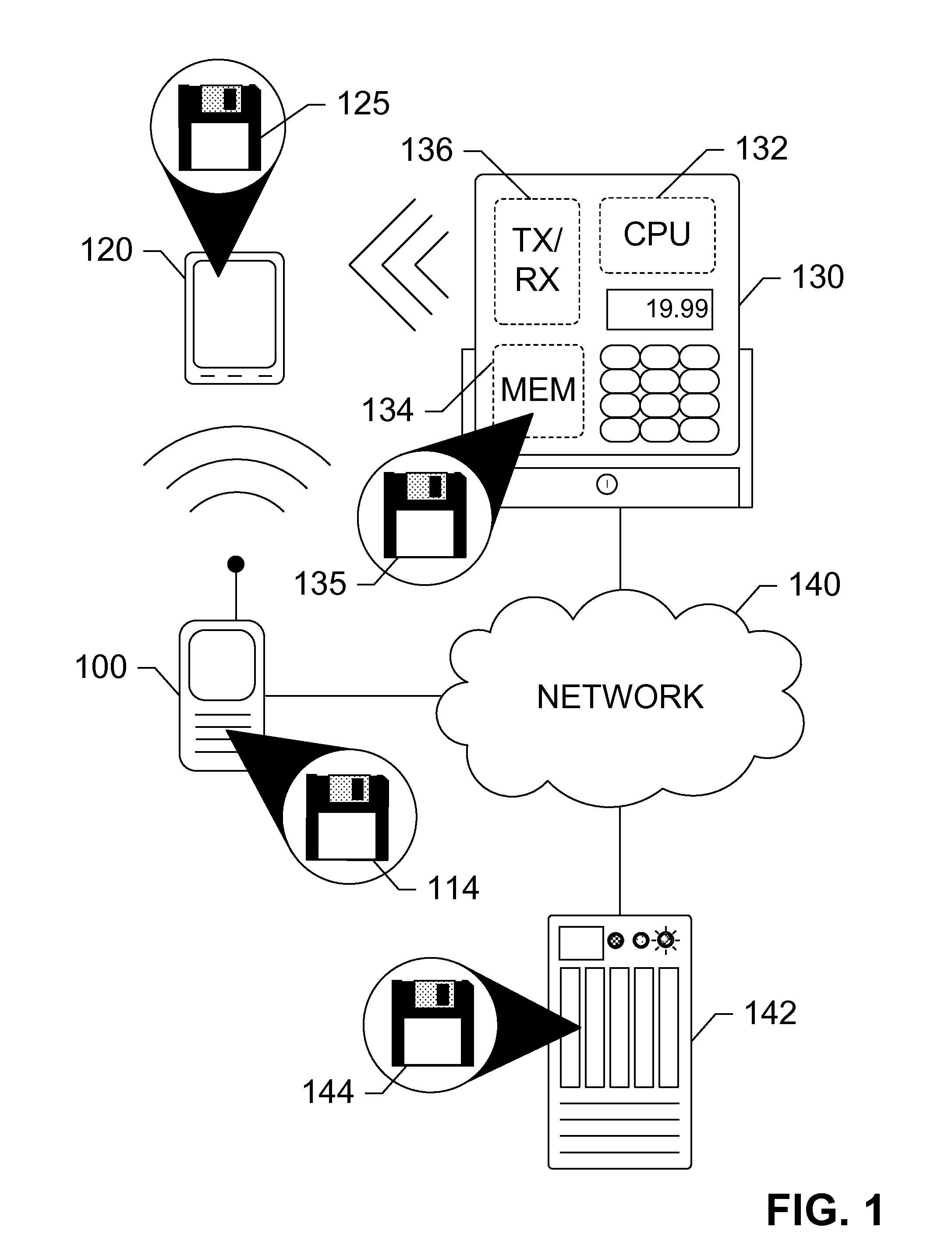
Method and system to enable mobile transactions
ActiveUS7424303B2Easy mobile monitoringNo longer be usedFinanceCash registersInterface layerMobile transaction
Owner:CHEMTRON RES
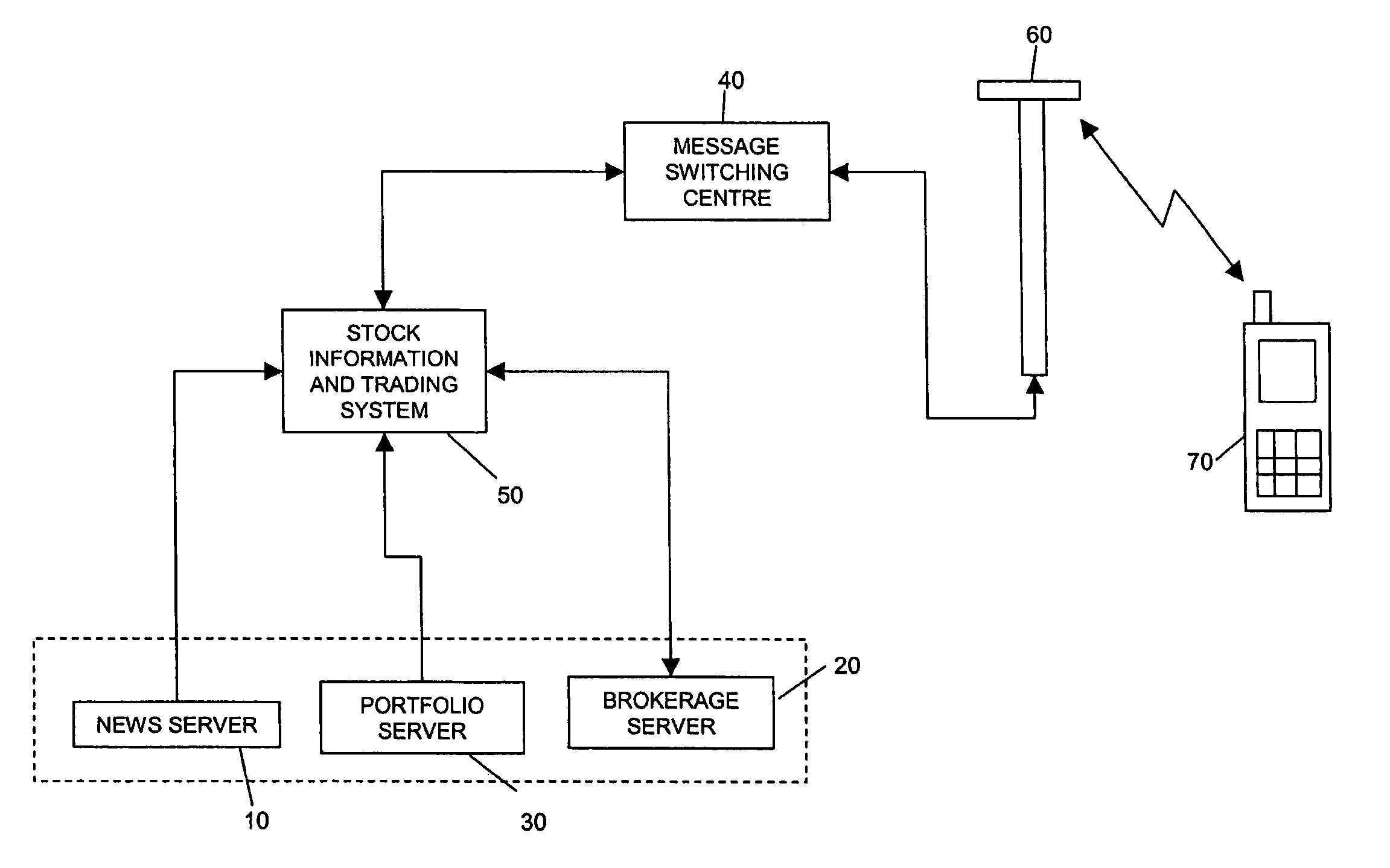
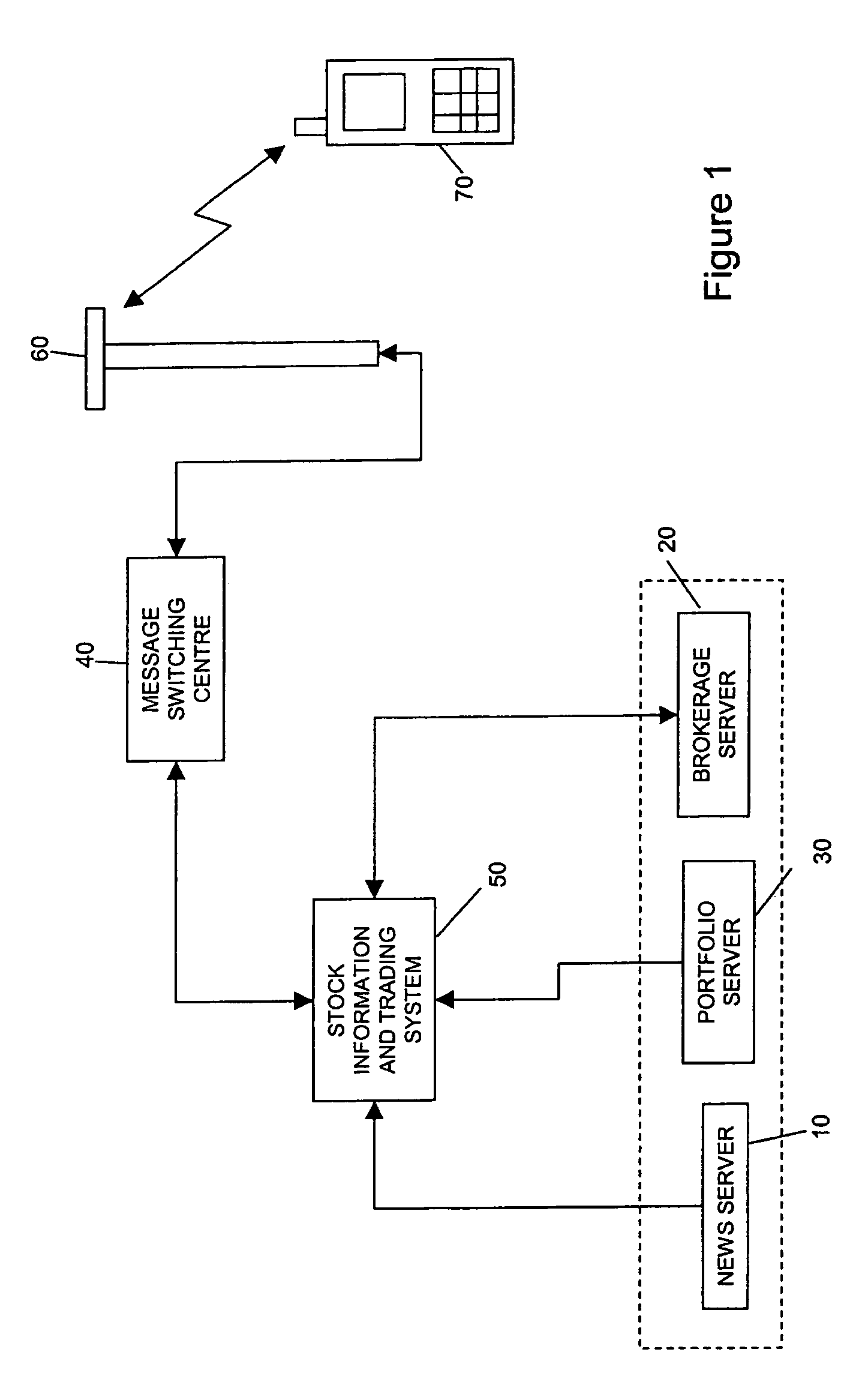
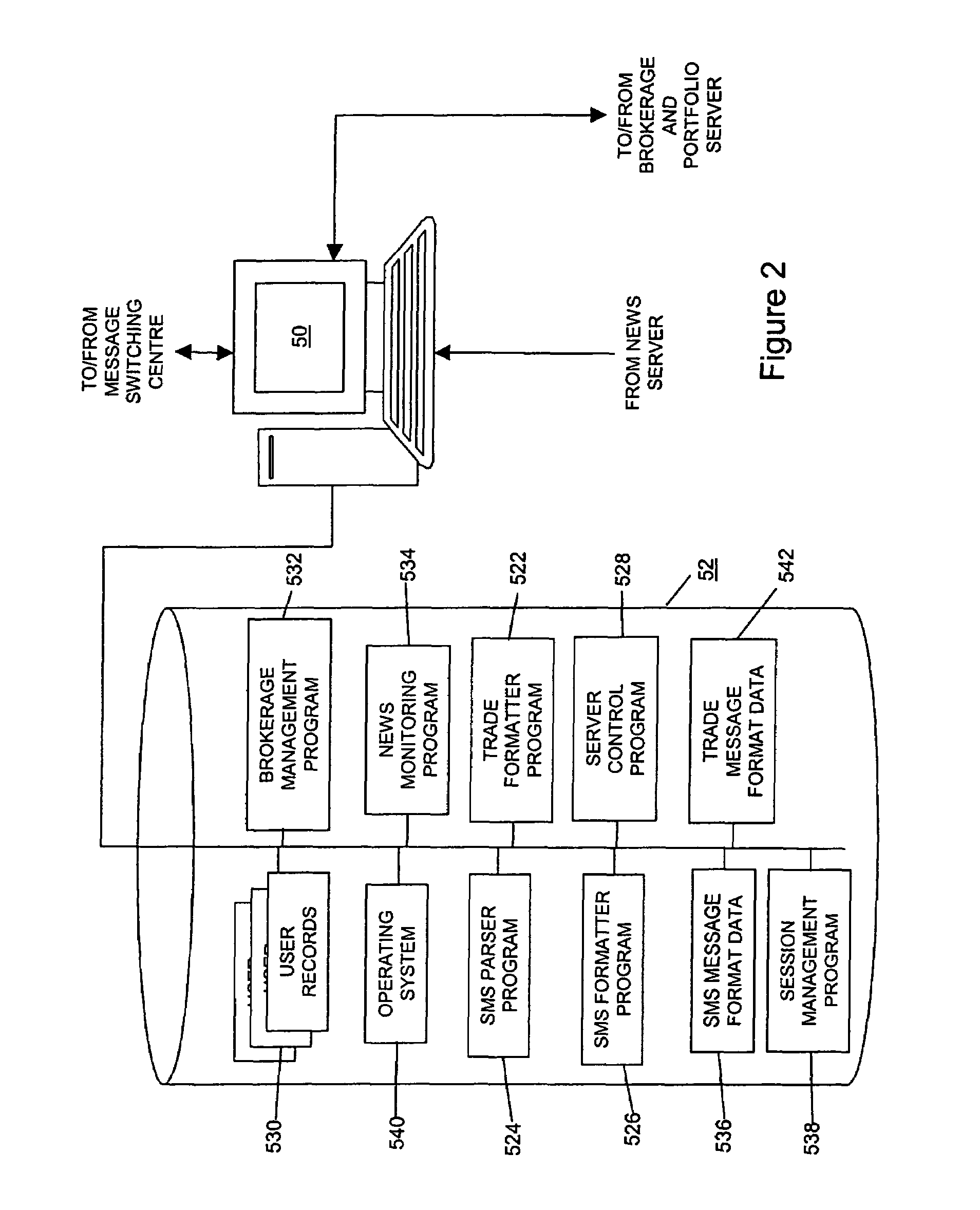
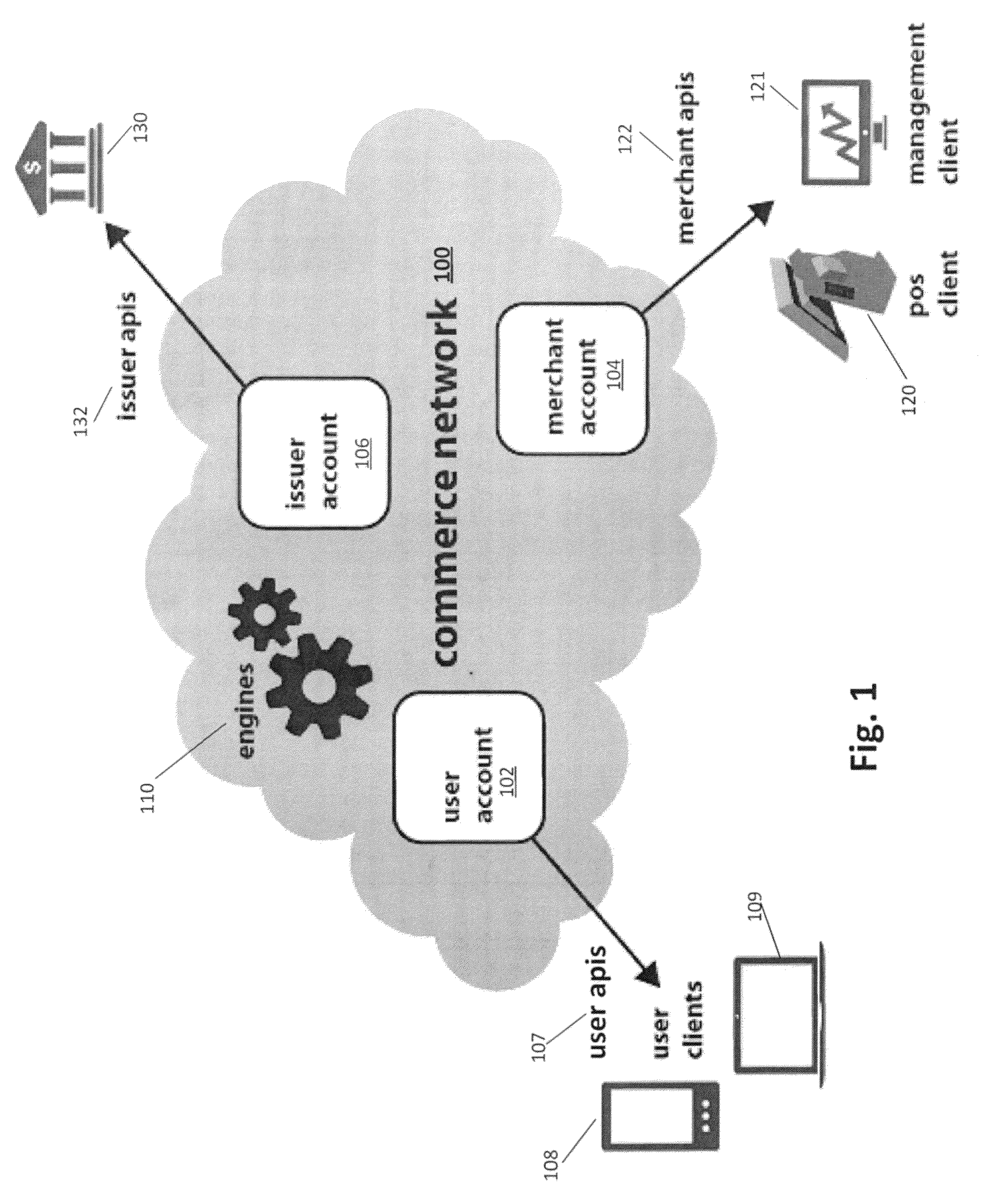
Electronic commerce network with mobile transactions
InactiveUS20140012701A1Point-of-sale network systemsAnonymous user systemsPaymentPersonal identification number
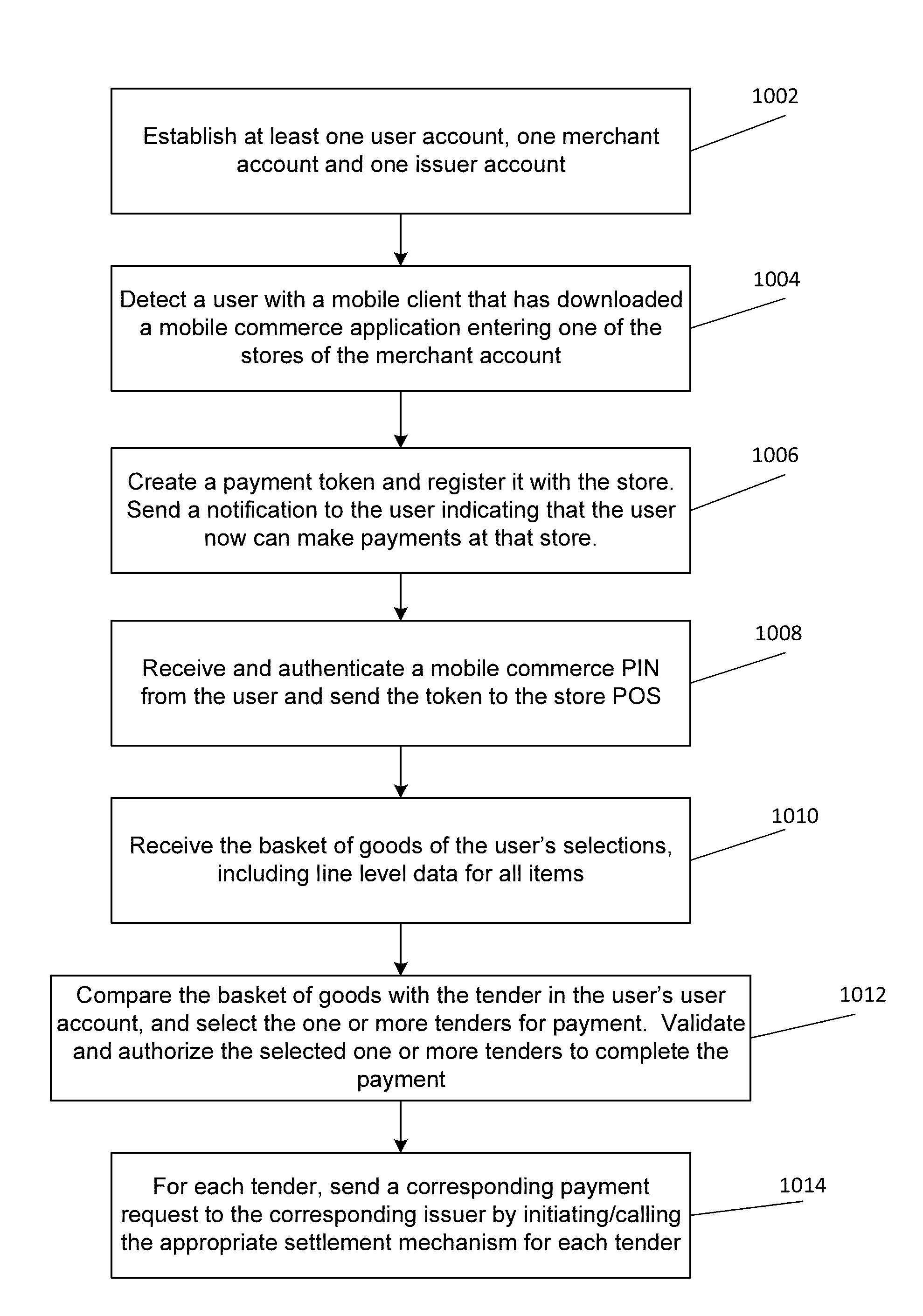
A commerce network that processes a mobile transaction detects a mobile device of a user entering a store, the user having a corresponding user account that includes one or more tenders. The network creates a payment token corresponding to the detecting and registers it with the store. The network receives a personal identification number (“PIN”) from the user and authenticates the PIN. The network receives a basket of goods of one or more items selected by the user for purchase, the basket of goods including line level data for the items. The network then selects one or more payment tenders from the one or more tenders based at least on the line level data and validates and authorizes the selected payment tenders.
Owner:INDEX SYST
Mobile transaction system and method
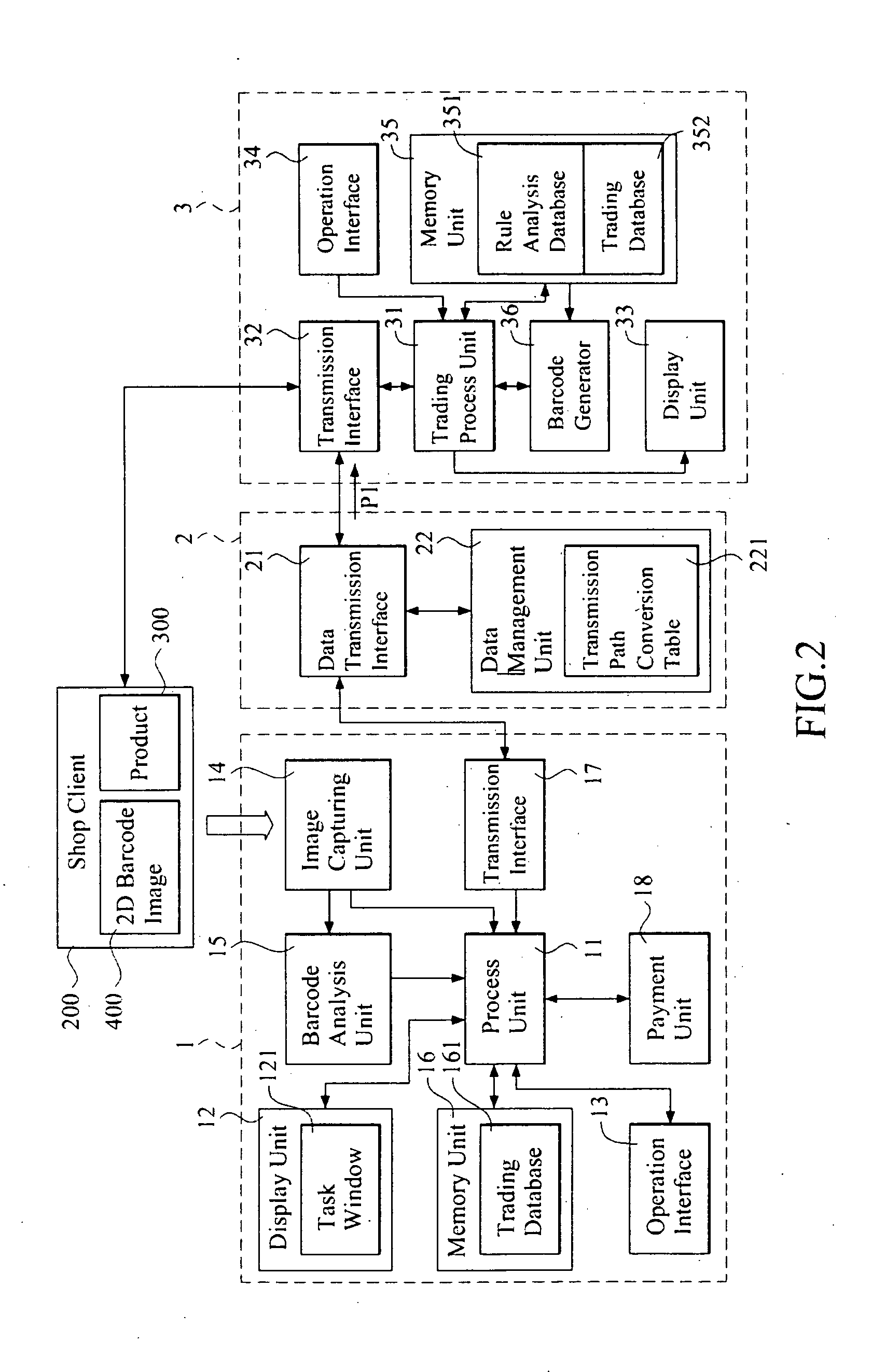
InactiveUS20100211506A1Reduce investmentImprove securityDigital data processing detailsPayment architecturePaymentTransaction service
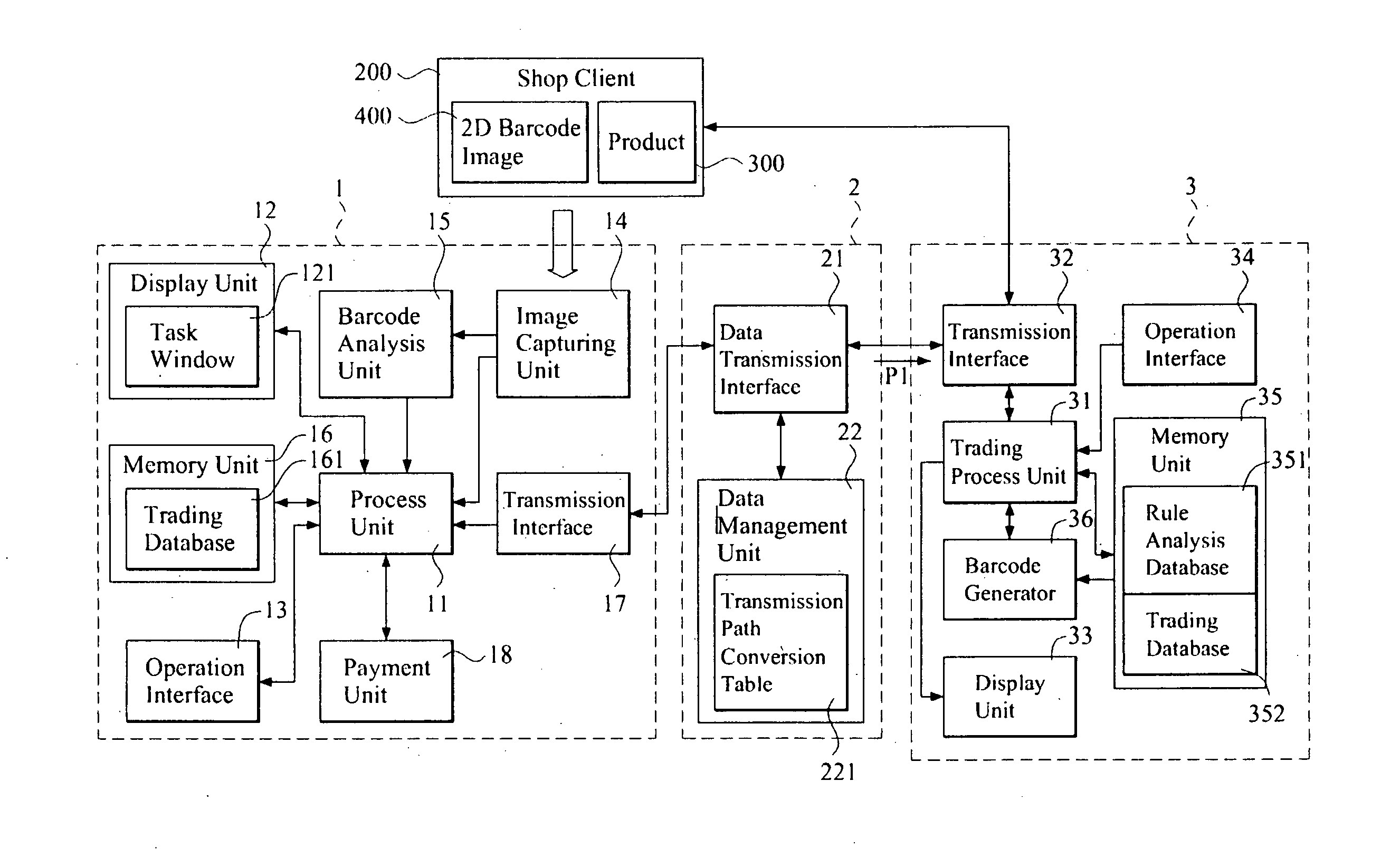
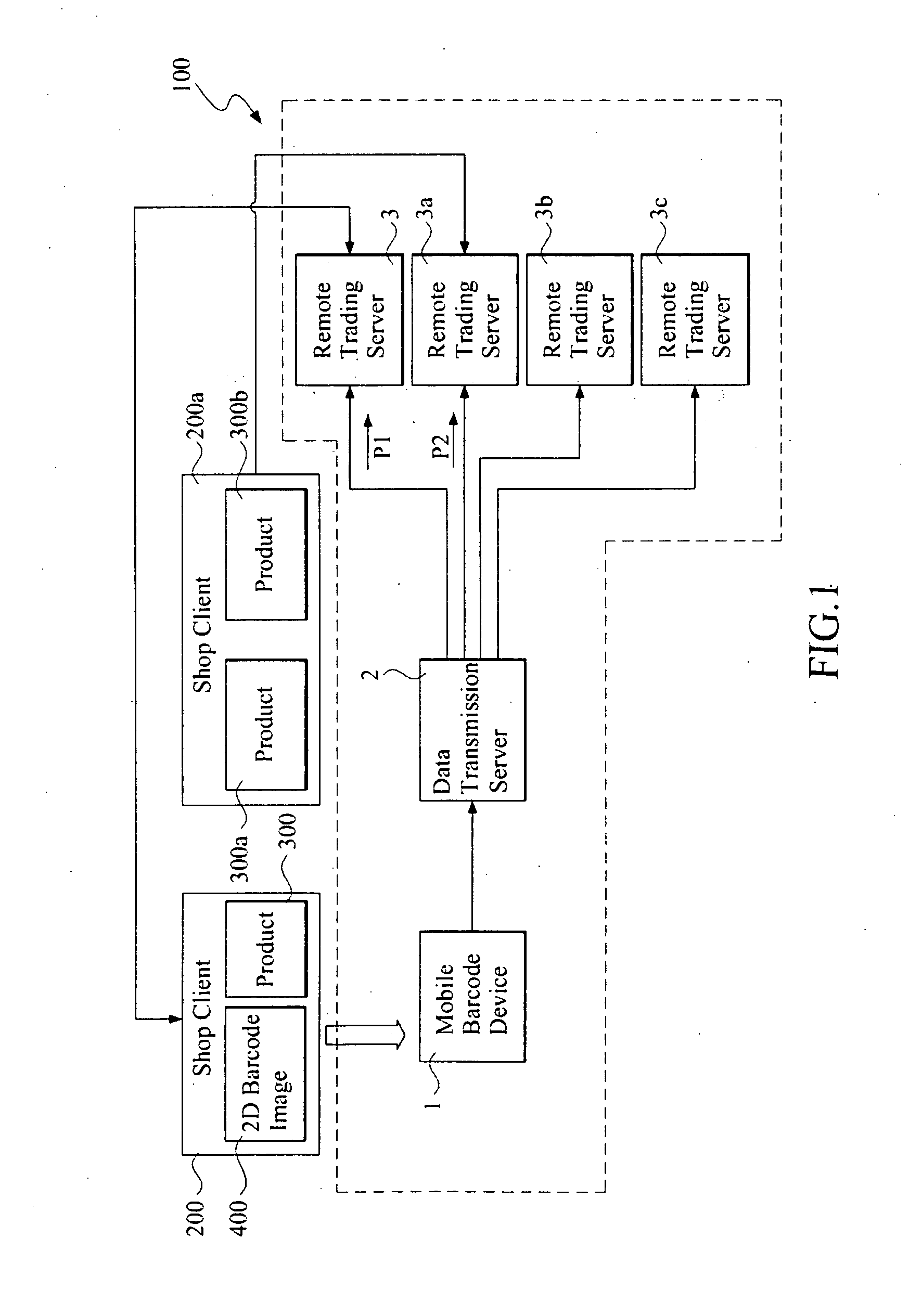
A mobile transaction system and method are carried out by a plurality of remote trading servers, a mobile barcode trading device and a data transmission server. The remote trading server generates and transmits a two-dimensional barcode image to at least one store client to display thereon after a user selects at least one product from the store client. The mobile barcode trading device captures the two-dimensional barcode image, analyzes the two-dimensional barcode image to obtain an encrypted key data and a trade data, and generates an encrypted payment data by the encrypted key data after the user input a payment data. The encrypted payment data and the trade data are combined to generate an encrypted trade data being transmitted to at least one of a plurality of the remote trading servers via a data transmission server, so as to carry out a mobile transaction.
Owner:SIMPLEACT
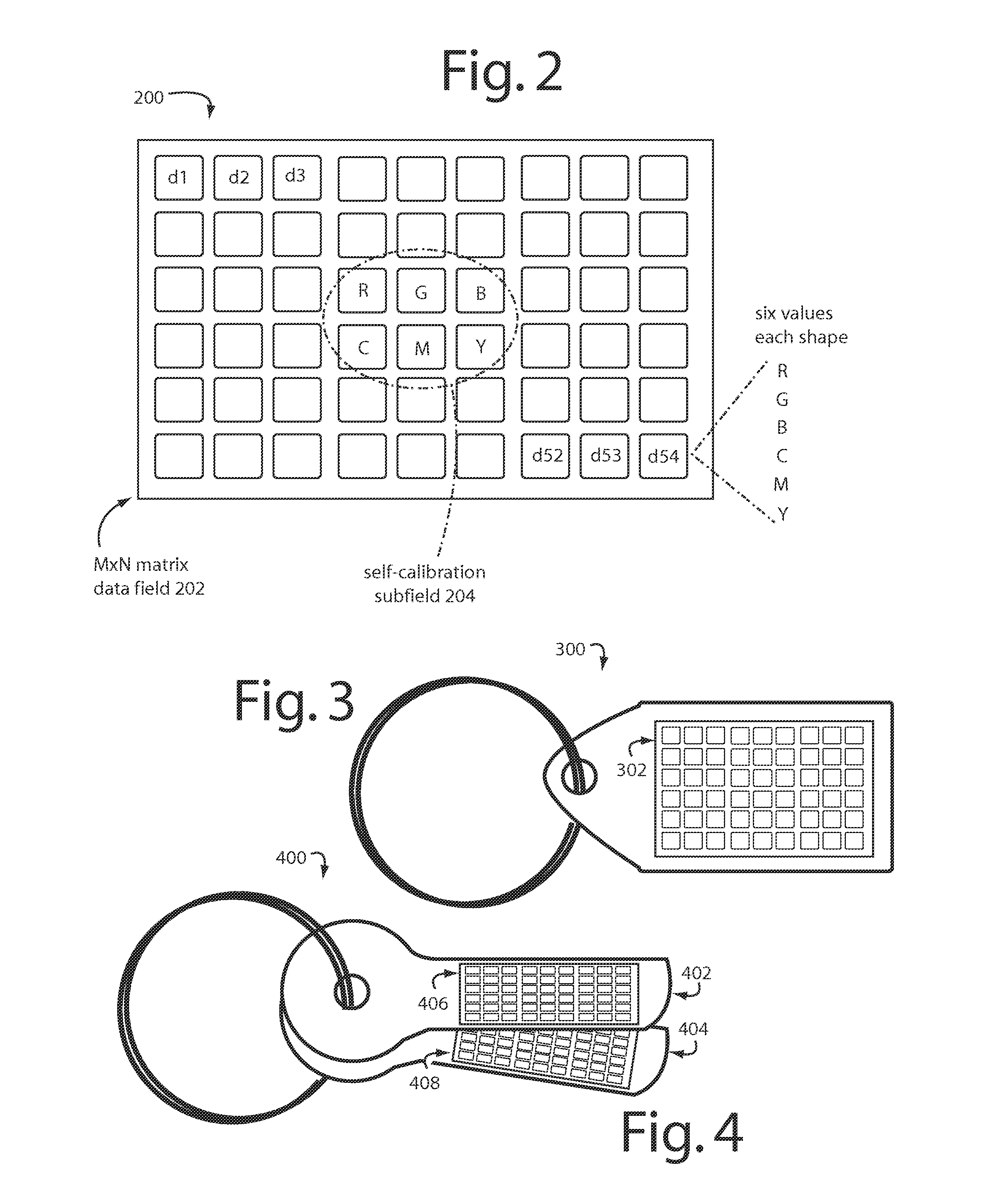
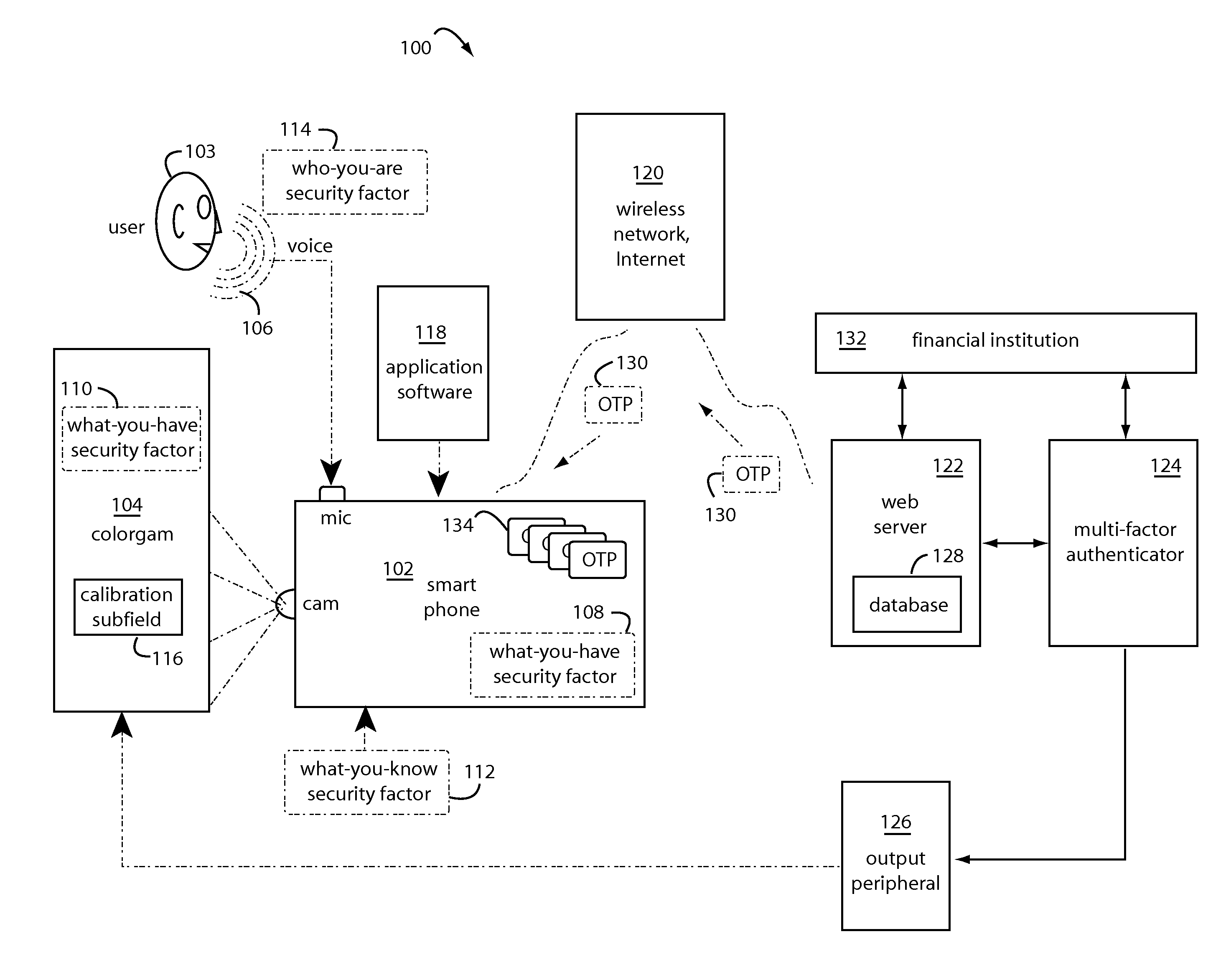
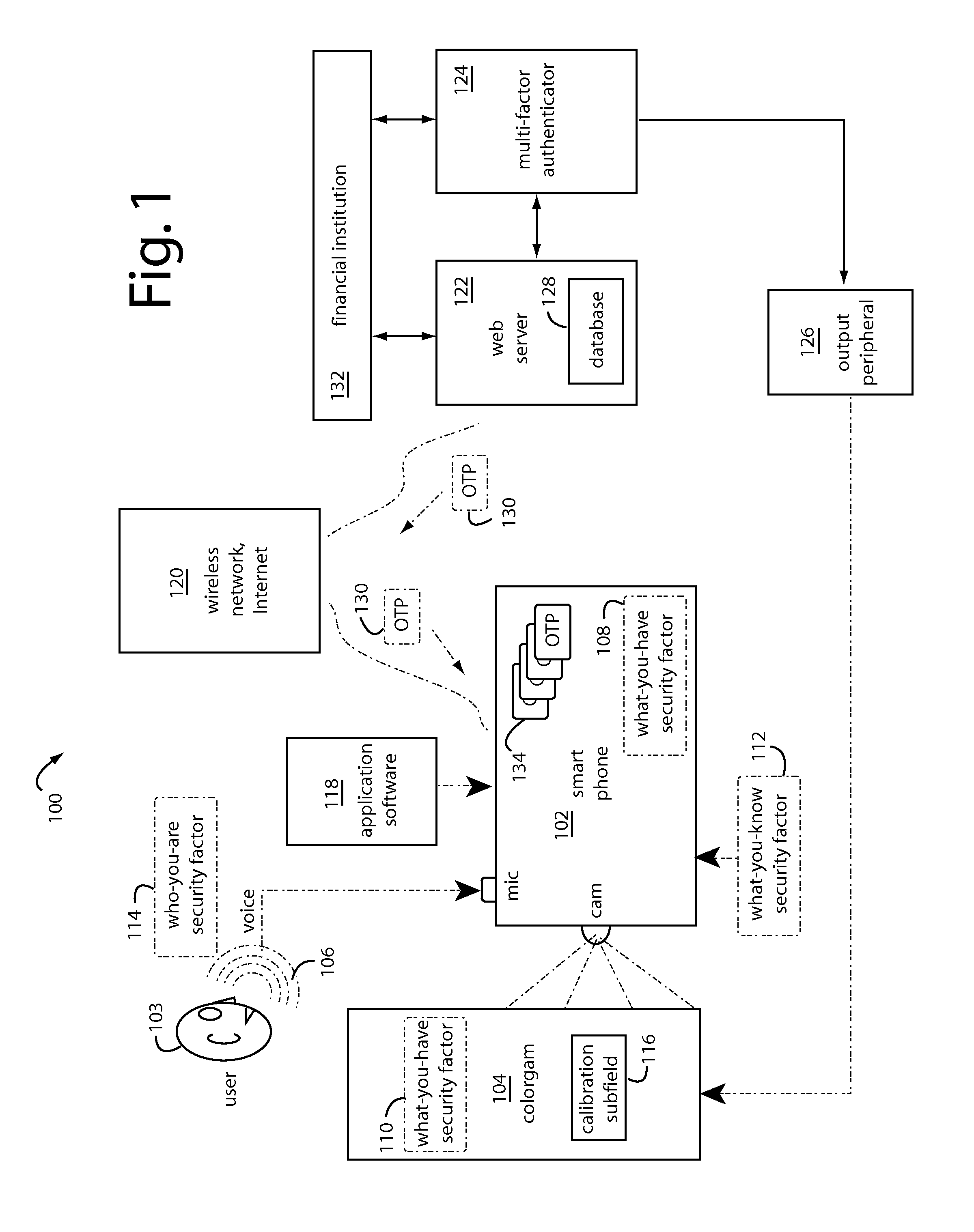
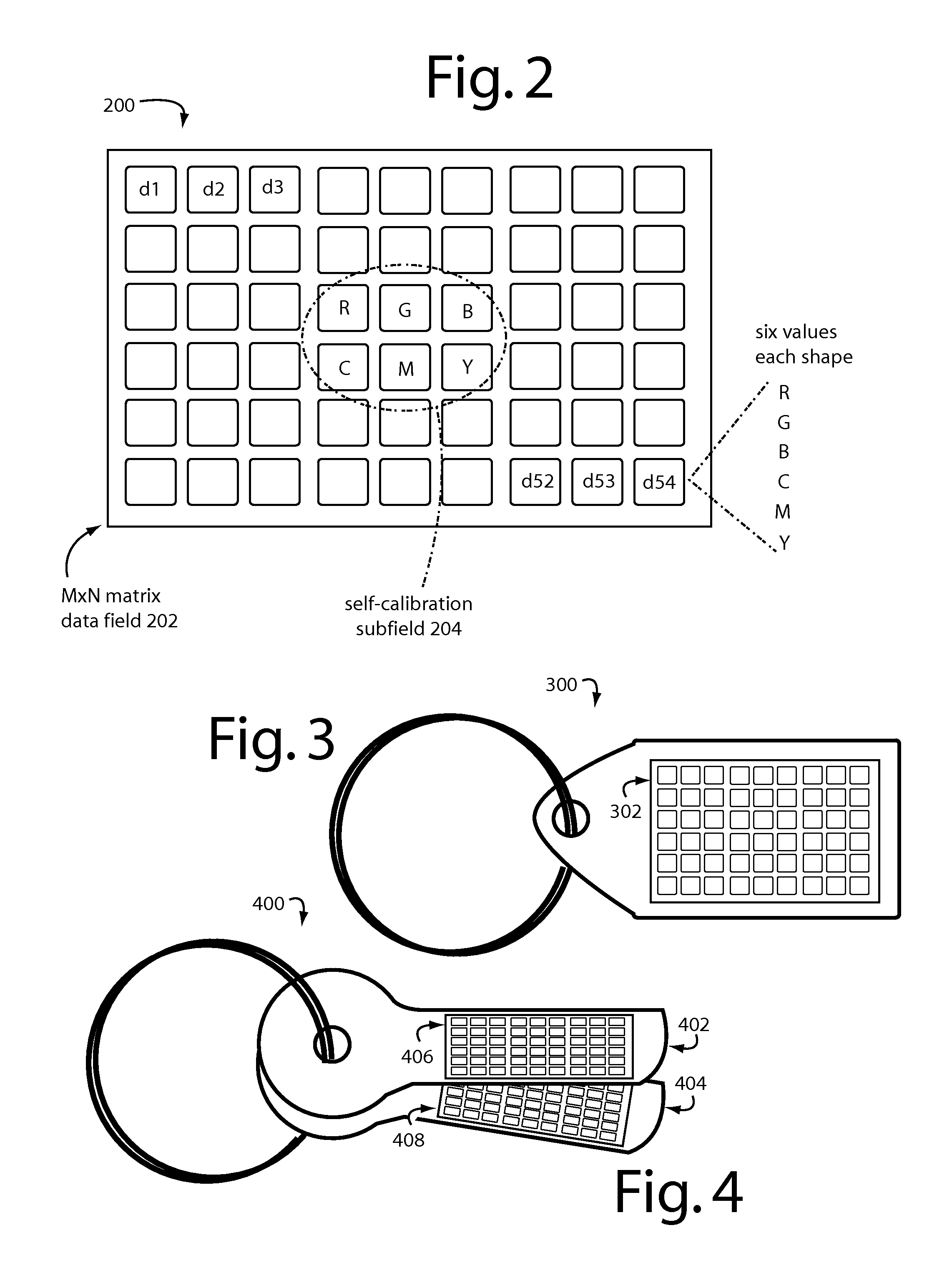
Mobile Transaction Methods and Devices With Three-Dimensional Colorgram Tokens
ActiveUS20120311320A1User identity/authority verificationComputer security arrangementsUser authenticationMobile transaction
A transaction security process includes authentication and identification parts for pushing an encrypted colorgram for user authentication and persona descriptors for user identification from a transaction server to a first personal trusted device. A decryption of the colorgram is displayed on the first personal trusted device. An image is captured by a second personal trusted device. An encryption of the image captured from the second personal trusted device is uploaded to the transaction server. The persona descriptors are used to build a composite rendering for identification of the first user to the second user. The second user clicks “OK” if they recognize the composite drawing as a reasonable persona of the first user.
Owner:CRYPTITE LLC
Covers having RFID functionality for portable electronic devices
ActiveUS20120209745A1Acutation objectsBuying/selling/leasing transactionsTransceiverApplication server
A system for business wireless mobile transactions for electronic hand-held devices including a mobile electronic communication device including a dedicated communication component and a dedicated activatable component; a trigger, a good or service, and an application server; wherein the device and the dedicated communication component are operable for communication with RFID / NFC transceivers when the device is located within a predetermined proximity of a transceiver; and wherein the trigger activates the device to electronically initiate a business transaction for the good or service on the application server when the device detects activation of the dedicated activatable component by the trigger. The system can further include a financial transaction server. Methods of using the system for conducting business or social transactions are also included.
Owner:SMART CELLCO
Device Method & System For Facilitating Mobile Transactions
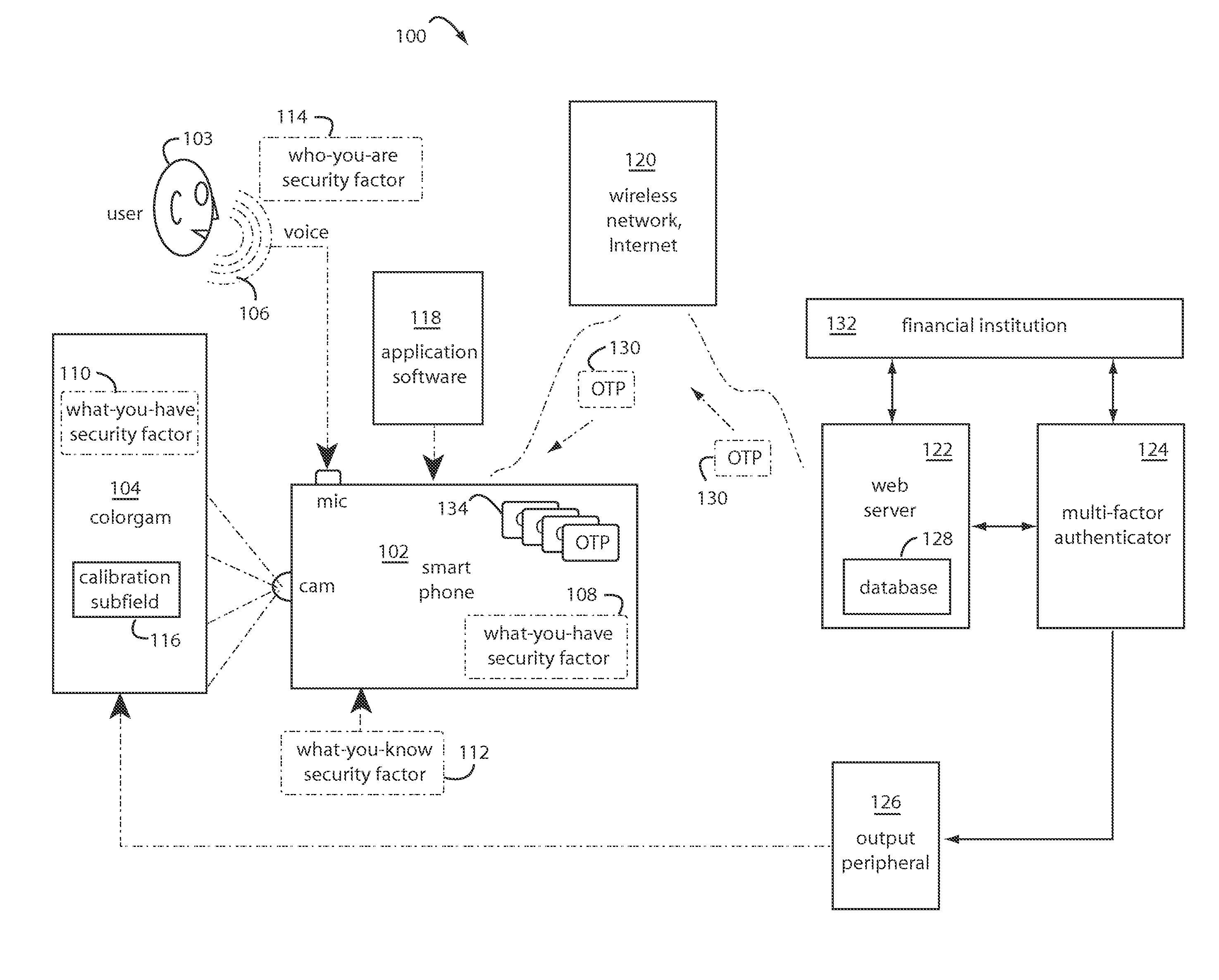
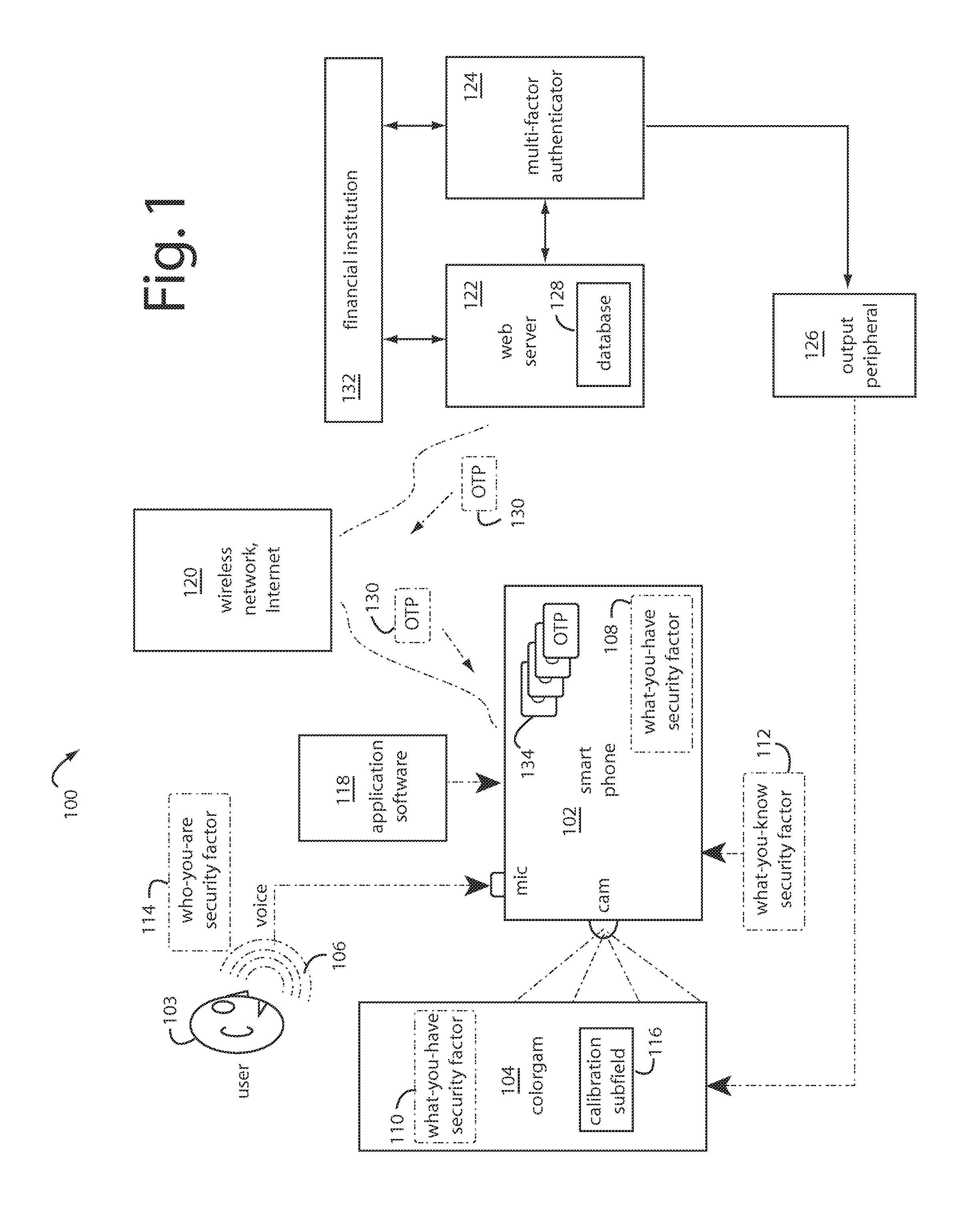
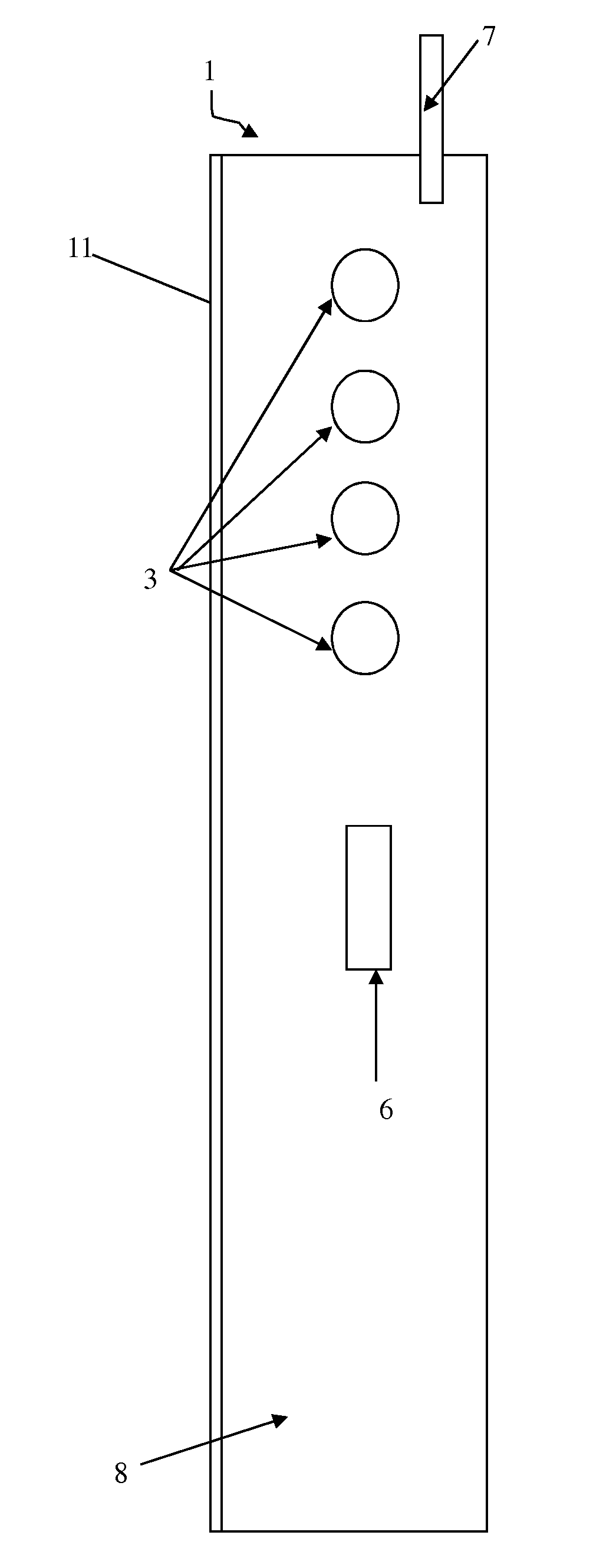
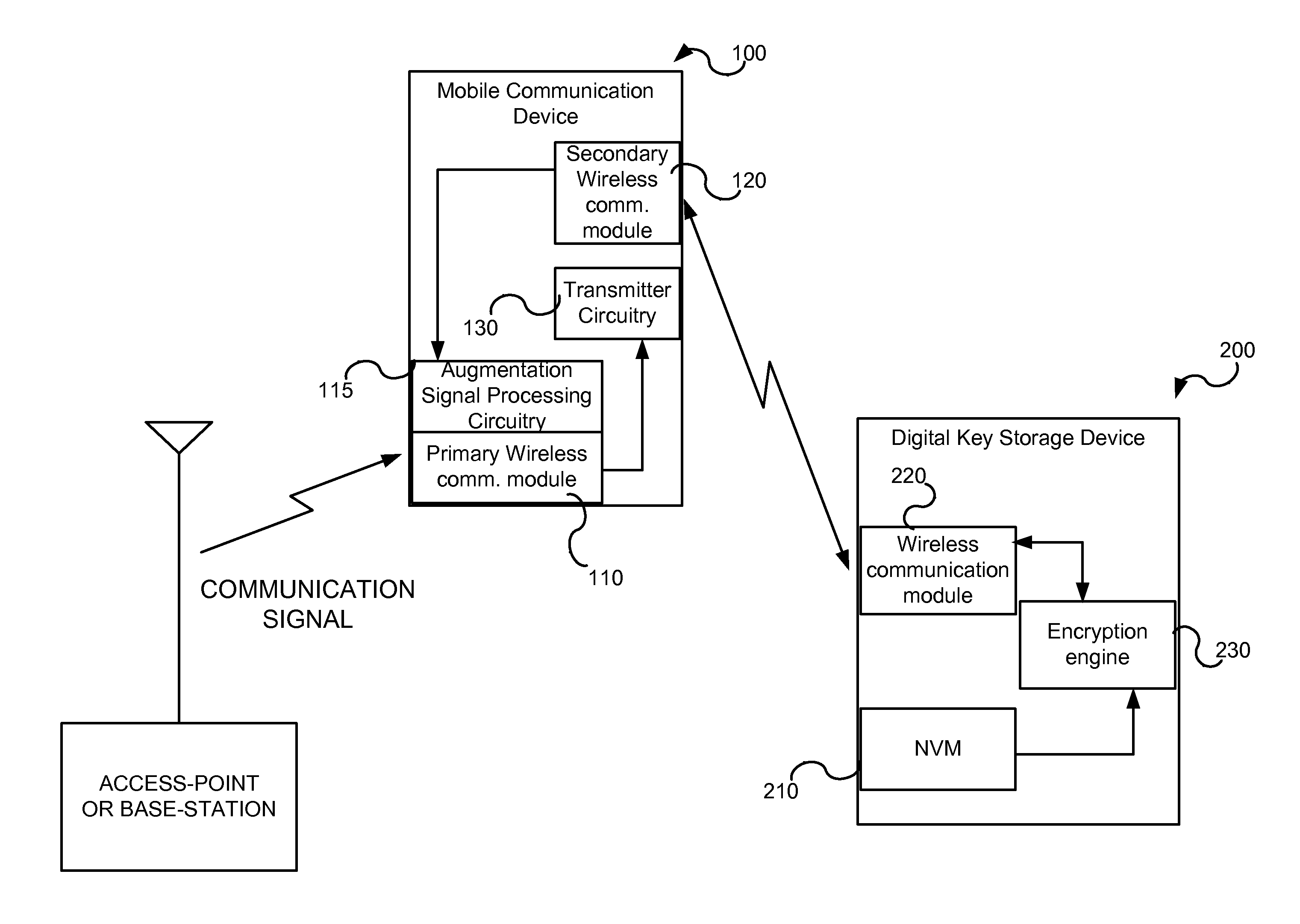
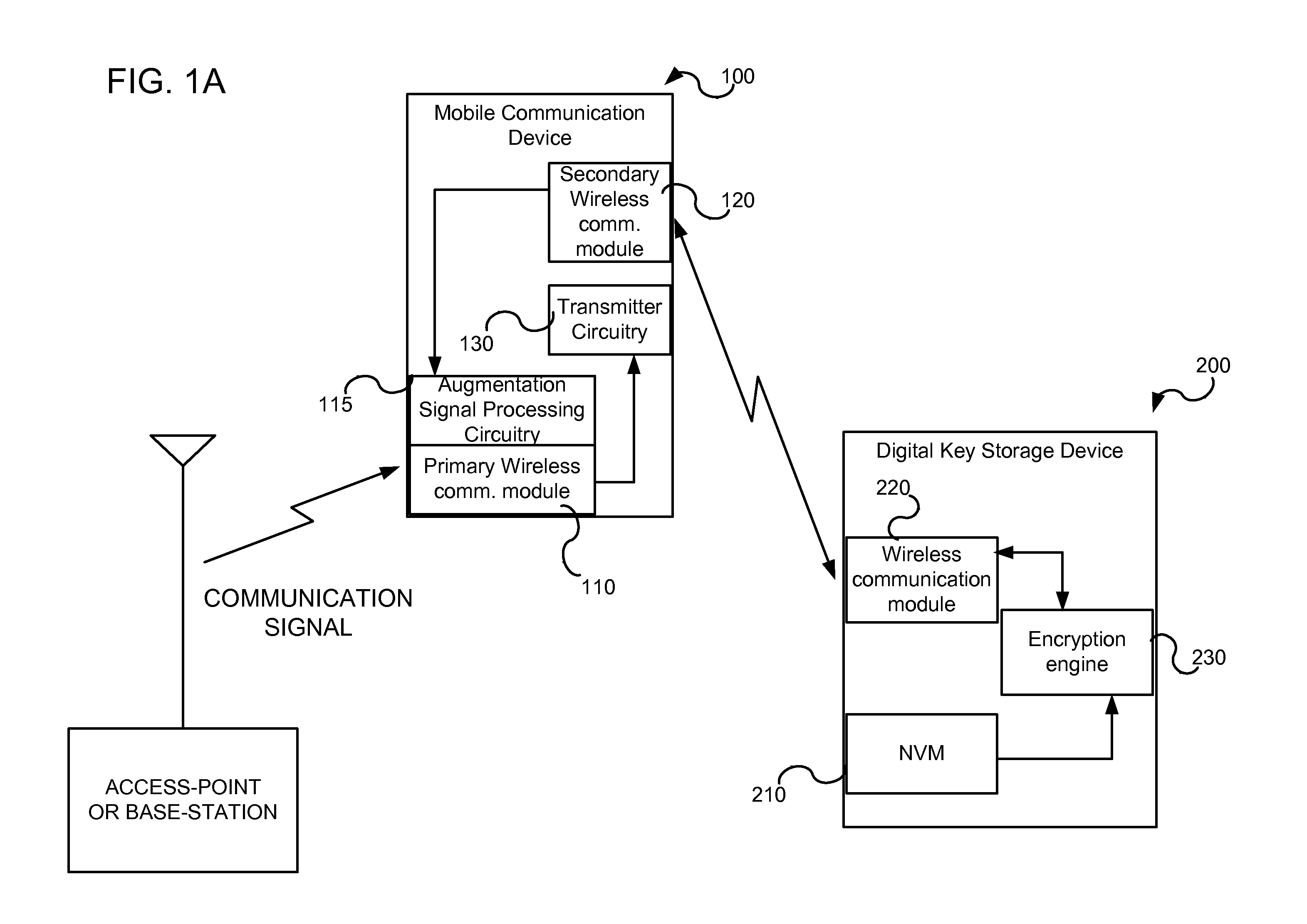
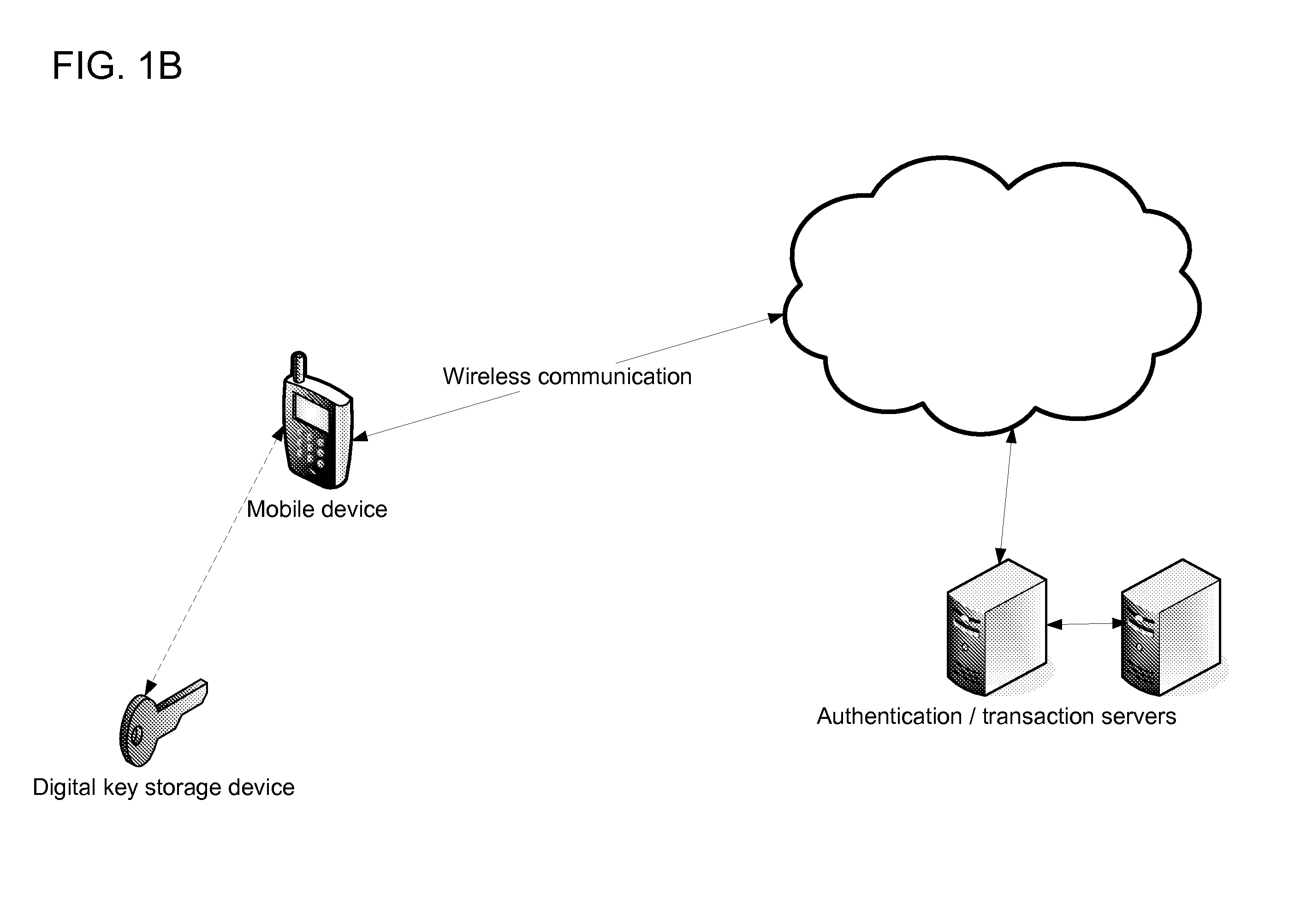
InactiveUS20080305769A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile transactionKey storage
Disclosed is a method and system for facilitating secure transactions via mobile devices such as cell-phones, smart-phones, person digital assistants (“PDA”) and the like. According to some embodiments of the present invention, there is provided a system and method for authenticating a user via multi-factor authentication. According to further embodiments of the present invention, a user engaging in a transaction associated with a given transaction system (e.g. banking network, etc.) and requiring authentication may be authenticated using a combination of two or more keys, where a first key may be stored on a mobile device used as an interface to the transaction system, and where a second key may be stored on a digital key storage device functionally associated with the mobile device.
Owner:RUBINSTEIN NAHUM
Mobile transaction device security system
InactiveUS20120221475A1Point-of-sale network systemsProtocol authorisationUser verificationInternet privacy
Embodiments of the invention include apparatuses, methods, and computer-program products that provide for a unique financial transaction security system. In one embodiment, the financial transaction security system receives a security protocol from a user. The security protocol includes instructions for allowing transactions without authentication and security features for the user if authentication is necessary. The system then determines that the user is conducting a transaction, evaluates the instructions, and determines whether the transaction can occur without authentication. If the user is required to authenticate his identity, the system requests input from the user, compares the input to the security feature, and determines if the user is authenticated. The user is able to customize both the instructions and the security features to provide greater control over financial transaction security.
Owner:BANK OF AMERICA CORP
Mobile Transactions and Payments
Owner:MUELLER MICHAEL
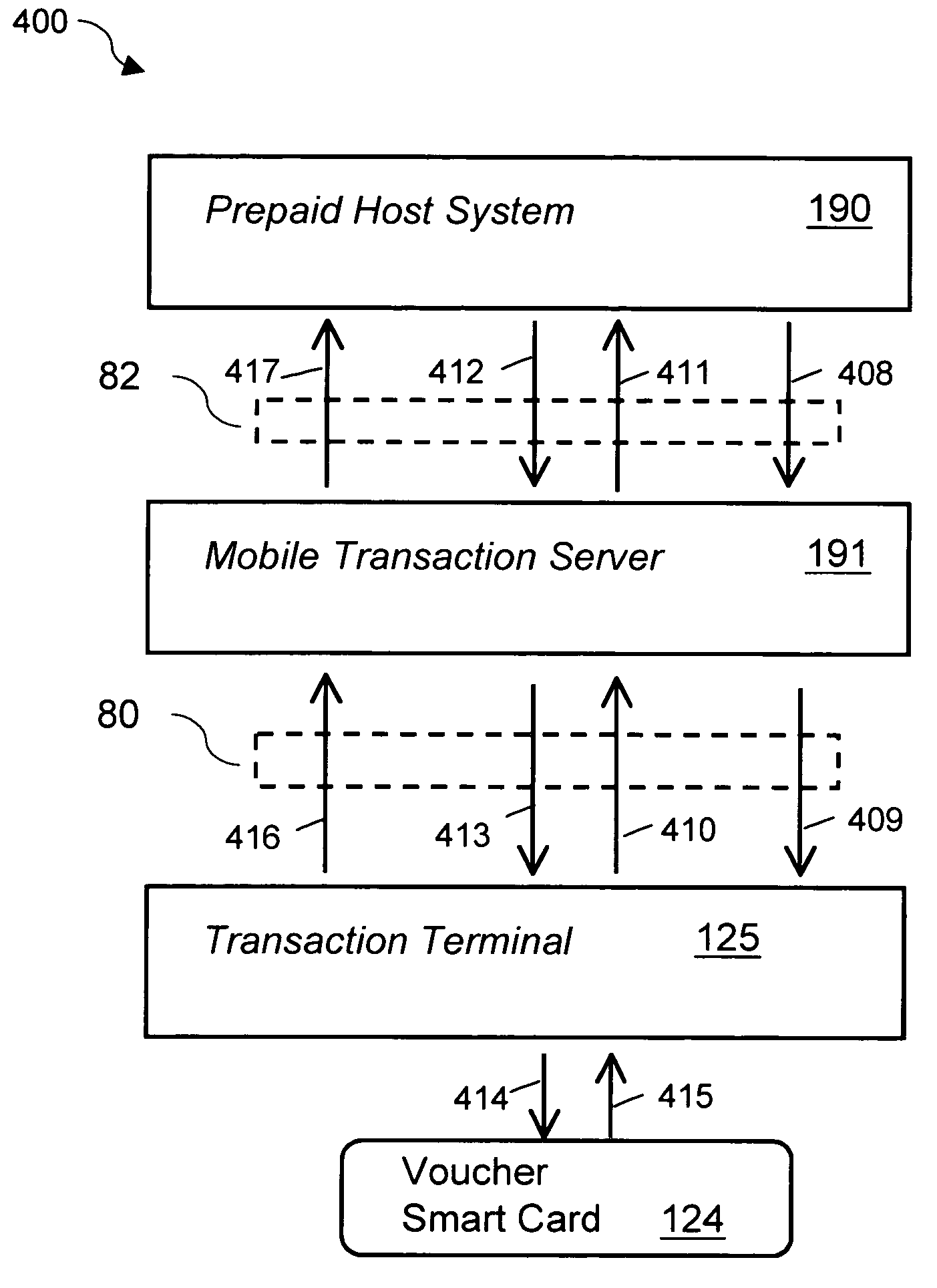
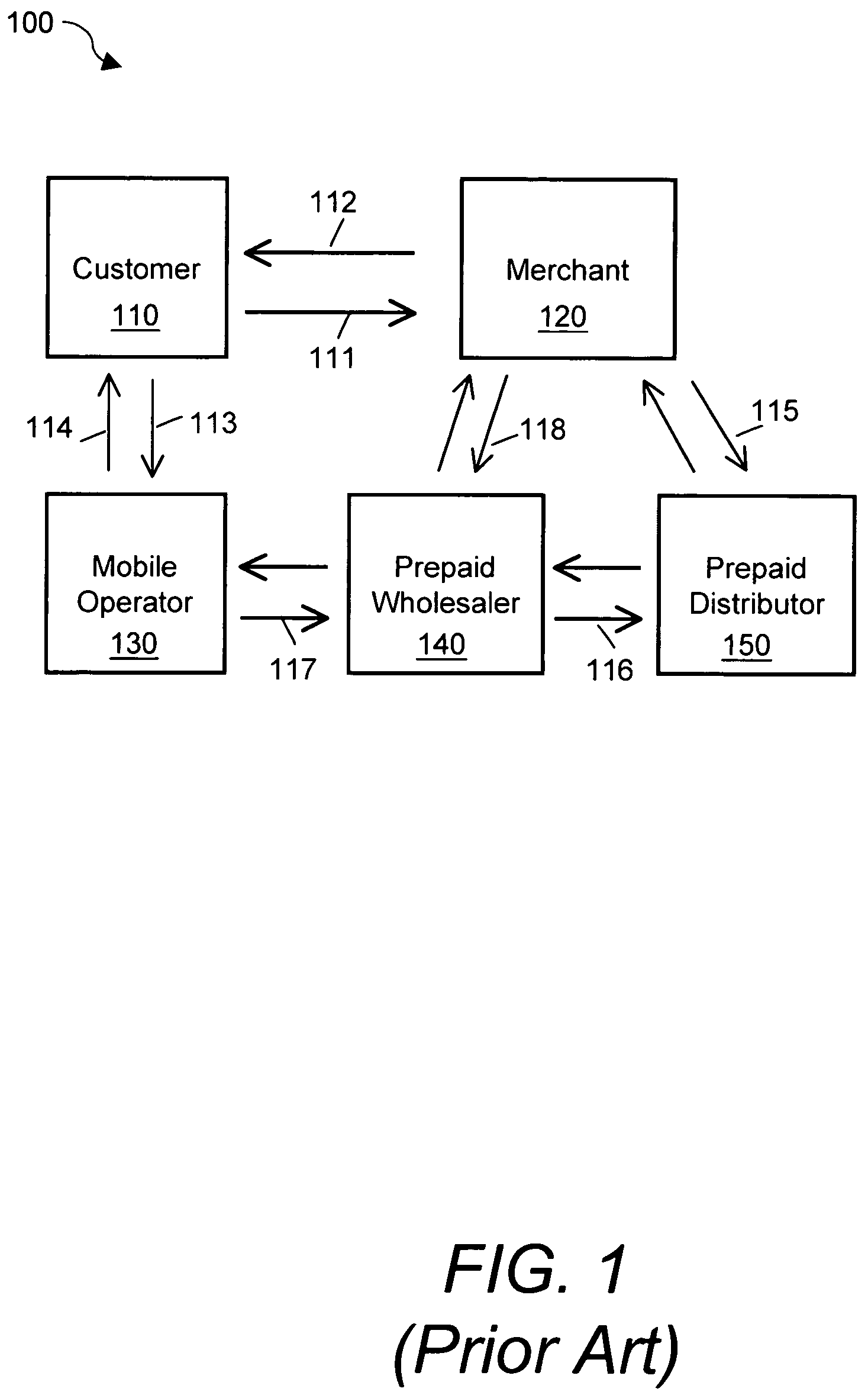
System and method for securely storing, generating, transferring and printing electronic prepaid vouchers
InactiveUS7188089B2Security is importantTimelyCredit registering devices actuationDevices with card reading facilityHardware security moduleMobile transaction
A system and a method that utilizes transaction terminals equipped with smart card readers to download and store a batch of multiple prepaid electronic vouchers to a smart card, retrieve and decrypt individual prepaid vouchers from the smart card and print a voucher receipt with a printer in connection with the transaction terminal. The transaction terminals are in connection with a mobile transaction server that acts as a gateway to a prepaid system and routes transactions between transaction terminals and the prepaid system and between transaction terminals. A method for storing a voucher encryption key on a second smart card or hardware security module. The voucher encryption key is utilized to decrypt encrypted vouchers on a voucher repository smart card. The transaction terminals are mobile devices communicating to the mobile transaction server over wireless networks.
Owner:VERIFONE INC
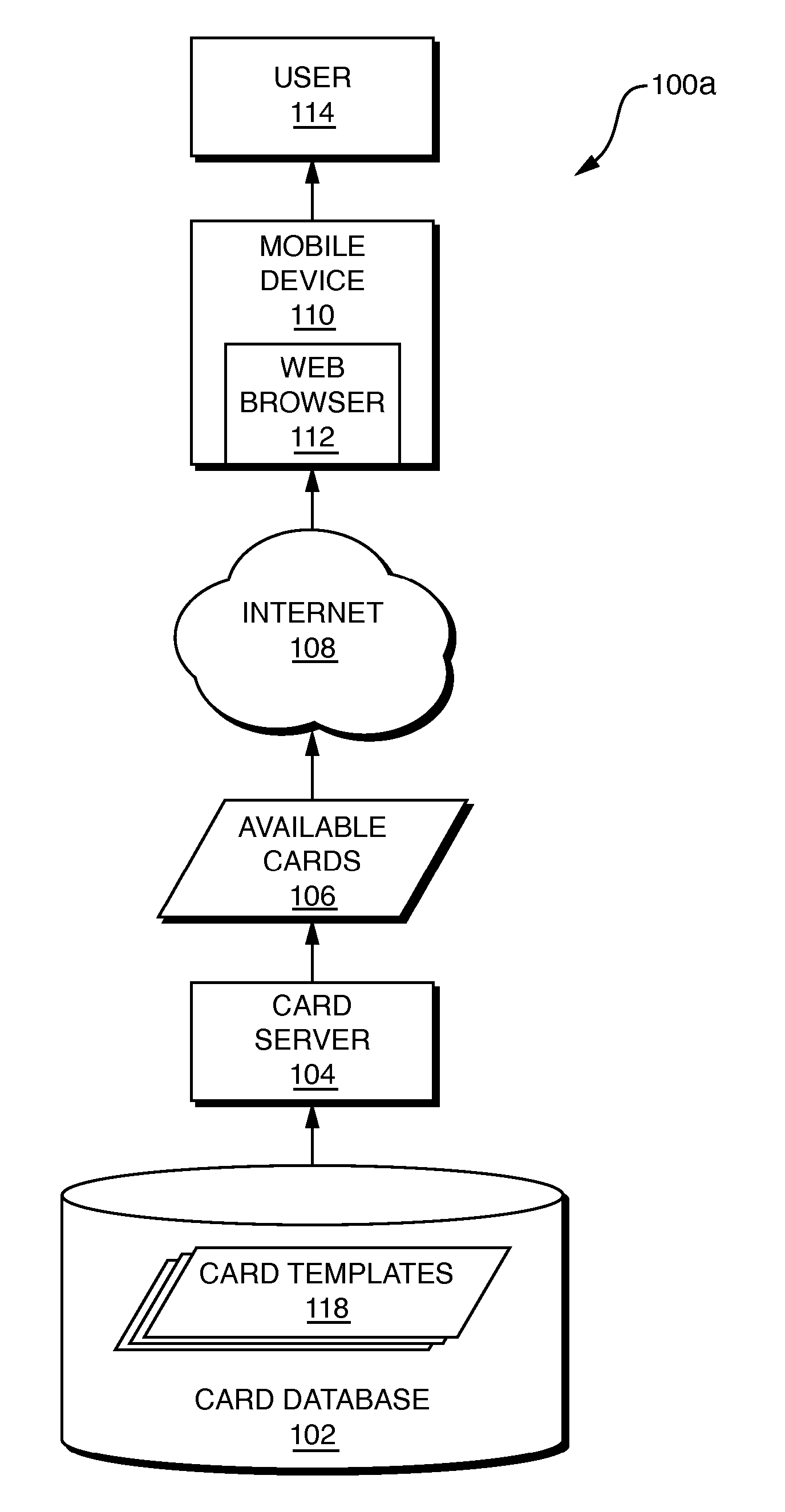
Mobile trading card generation and distribution
InactiveUS20070232399A1Video gamesSpecial data processing applicationsUnique identifierMobile transaction
A computer-implemented method for generating and distributing electronic trading cards, such as for use with mobile devices, generates instances of electronic trading cards and distributes the instances to users over a computer network. A finite number of instances of each electronic trading card may be generated. Electronic trading card instances may include an image and a digital watermark. Each instance of an electronic trading card may have a unique identifier. One instance of an electronic trading card may include content that is not included on all other instances of the same card. A randomly-generated “pack” of cards may be purchased by and distributed to the user. The contents of the pack may not be made visible to the user until completion of the purchase. Users may purchase additional features, such as a guarantee that the user will not be provided with duplicate instances of any trading card.
Owner:HOOK MOBILE
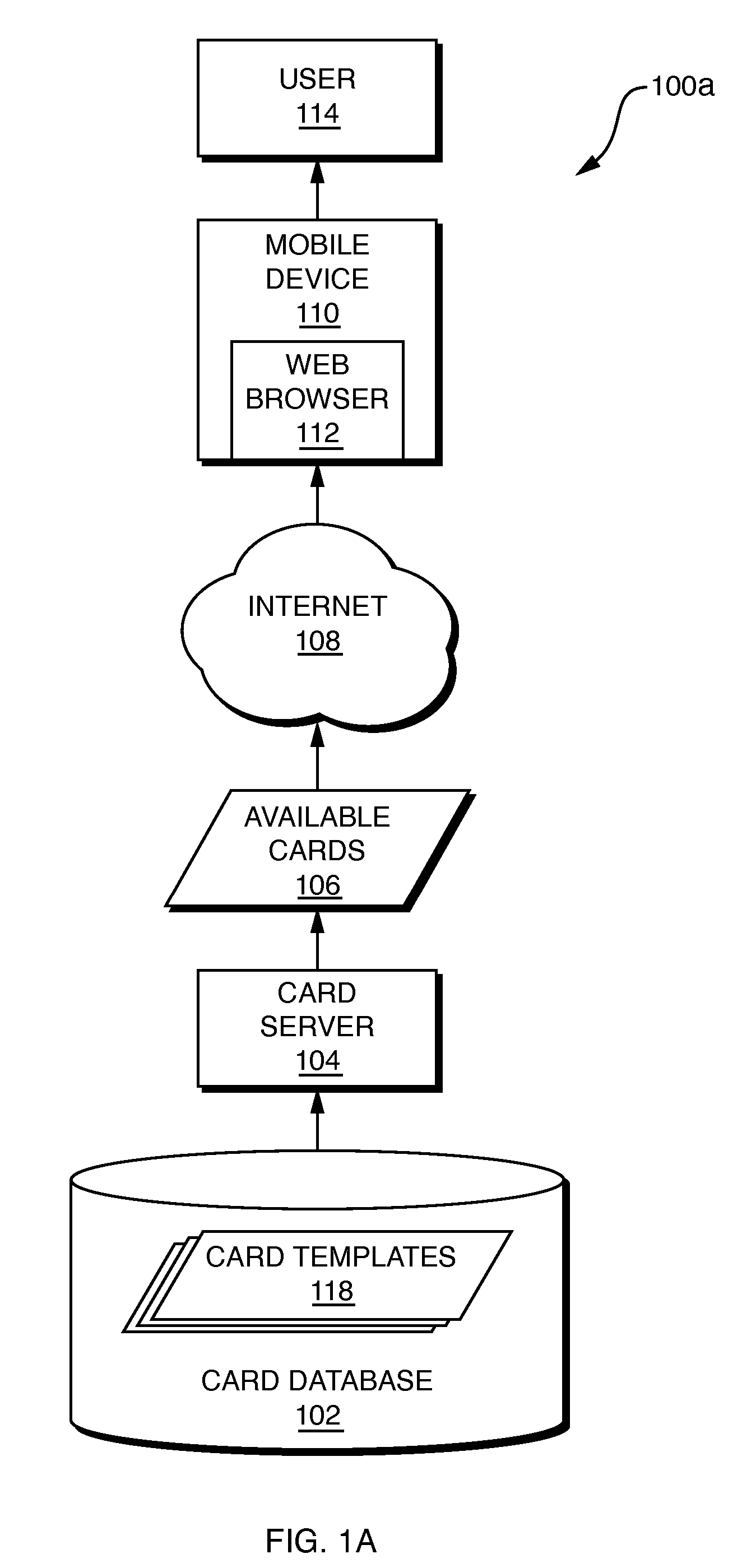
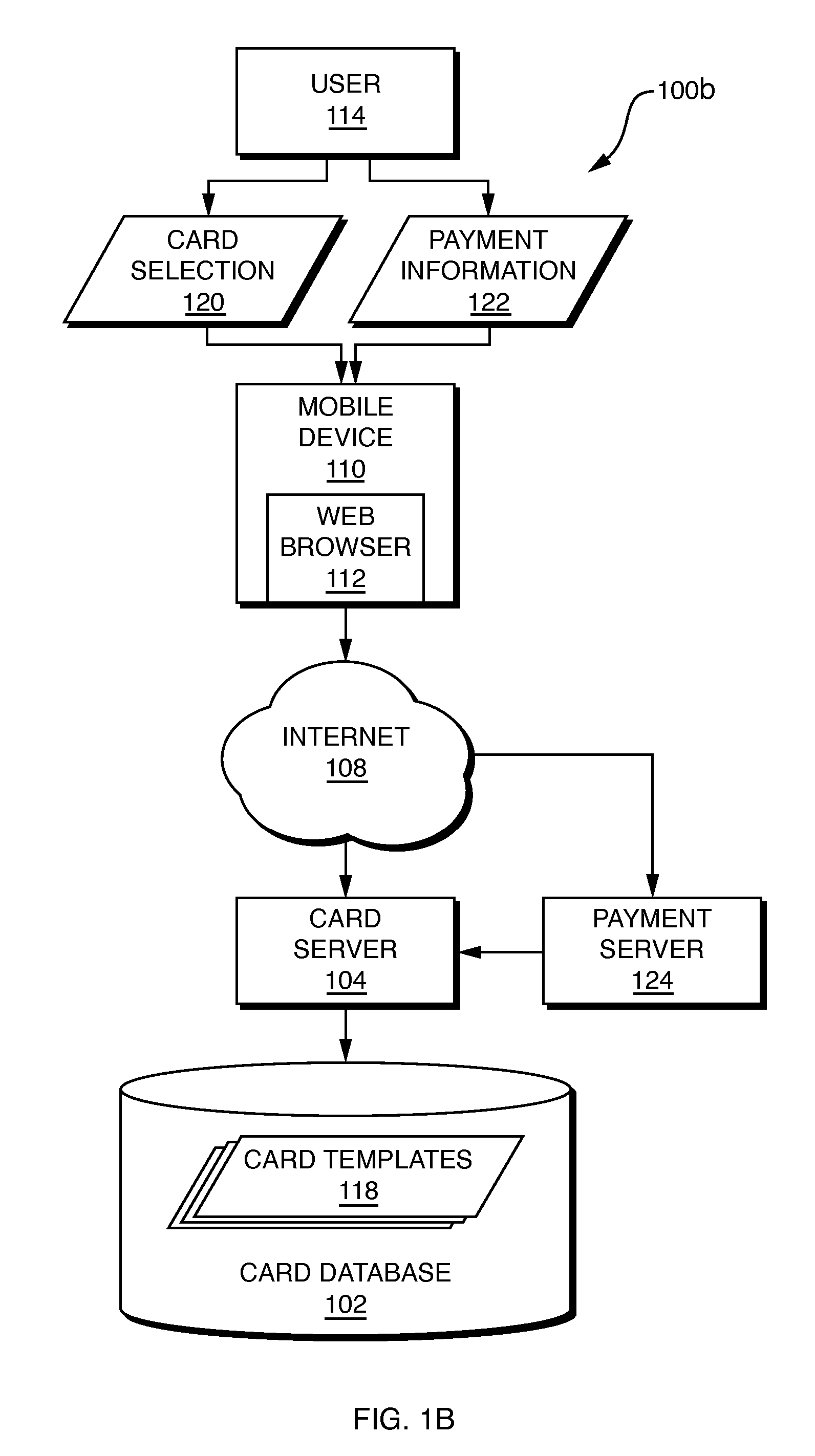
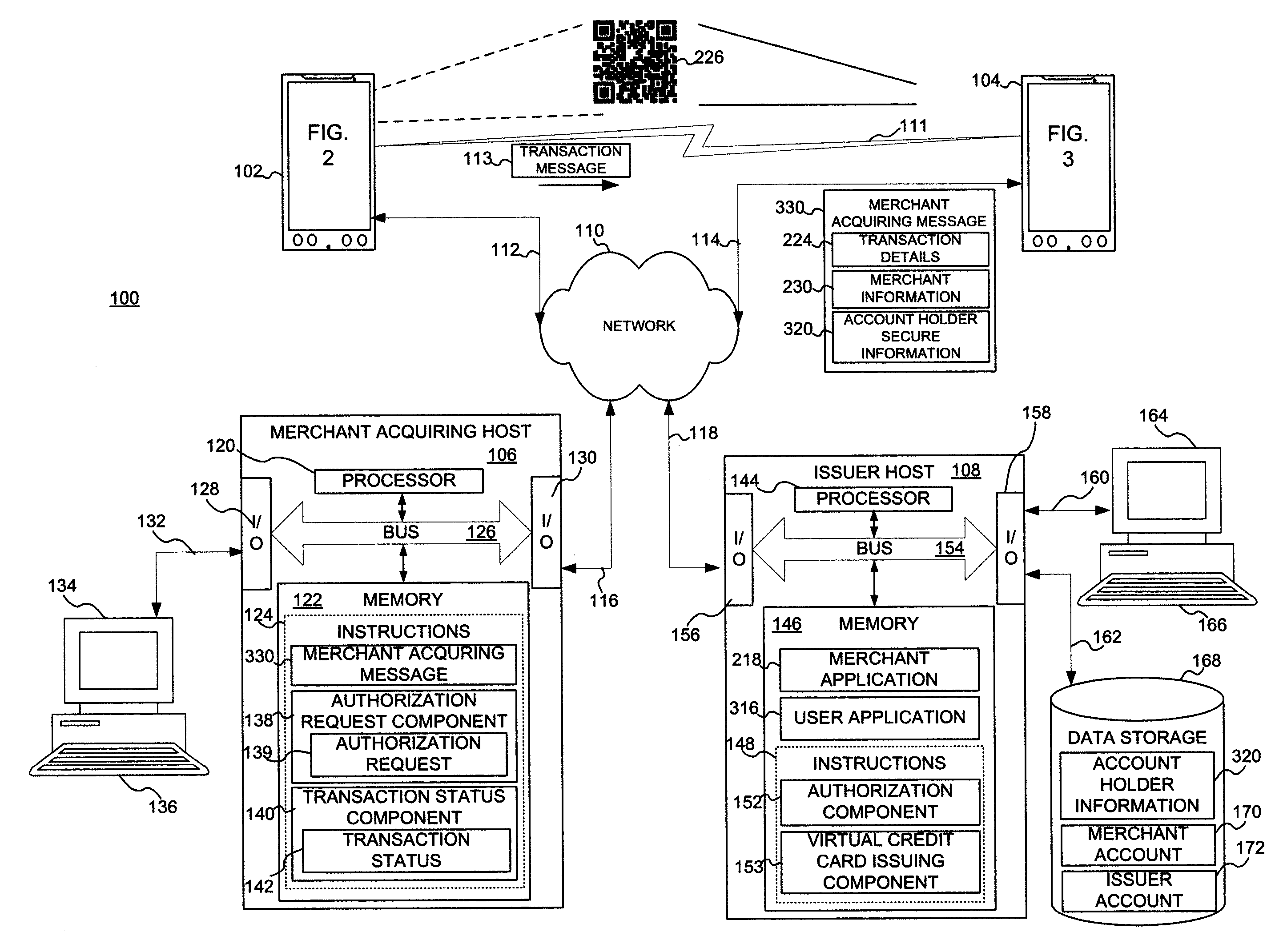
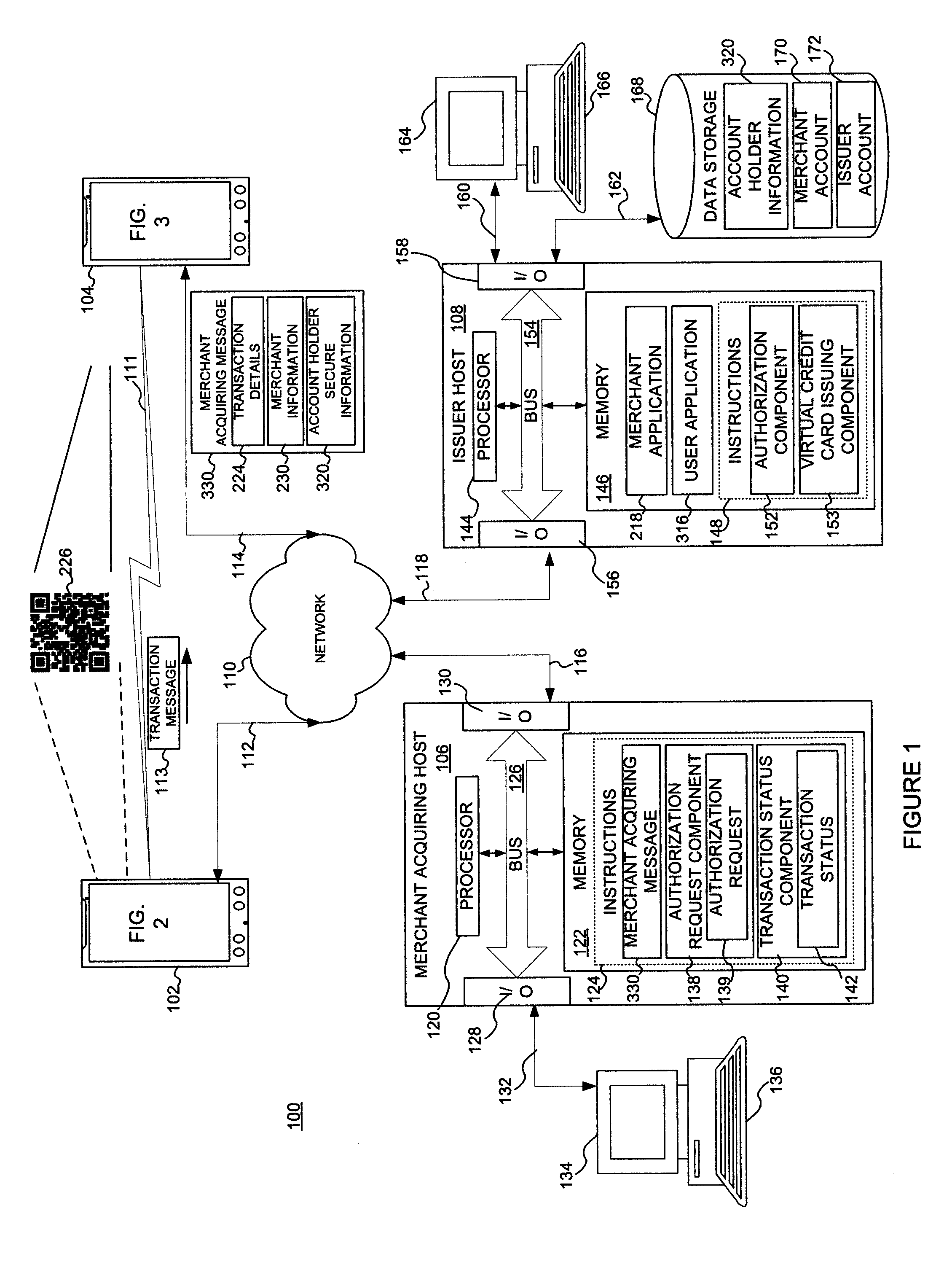
System and method for mobile transaction payments
A method and system are disclosed for mobile transaction payments. A merchant device generates a machine-readable code containing merchant information and details of a transaction and displays this to a user device. The user device scans the code, or receives a message via NFC from the merchant device, to retrieve the transaction details and the merchant information. The user device then communicates this information, along with secure account information containing a virtual credit card or other payment type, to a merchant acquiring host, which processes the payment in association with an issuer host. Upon receipt of authorization from the issuer host, the merchant acquiring host informs both the merchant and the use of the status of the transaction.
Owner:CARTA WORLDWIDE
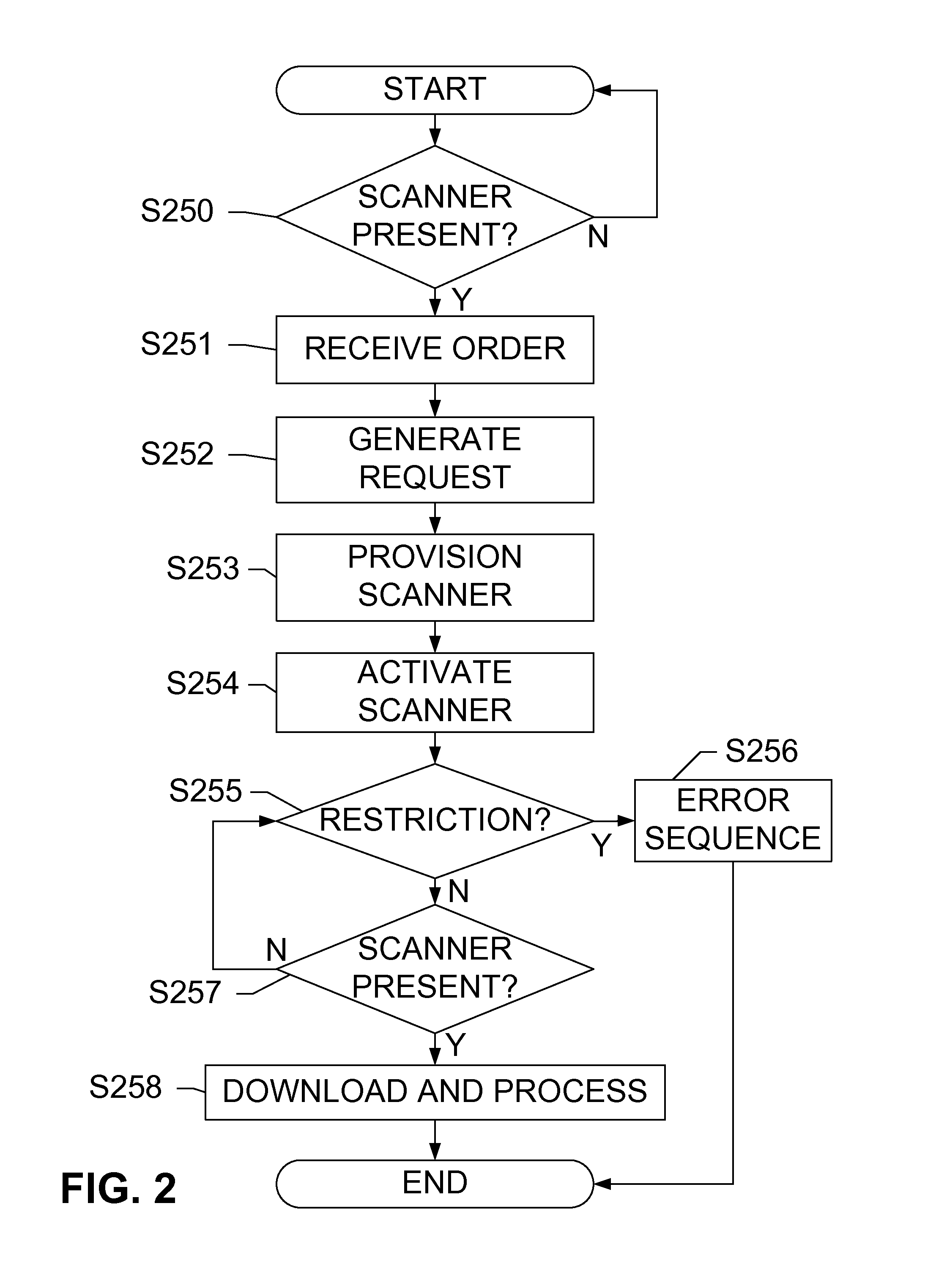
Point of sale for mobile transactions
ActiveUS9129273B2Complete banking machinesHand manipulated computer devicesMobile transactionMobile device
Devices, systems, and methods are disclosed which relate to using a remote scanner for mobile transactions. A point of sale (POS) terminal communicates with a remote scanner that is removably coupled to the POS terminal. Logic on the POS terminal generates a request for a transaction information and transmits the request along with a restriction to the remote scanner. Logic on the remote scanner receives the request and the restriction, transmits the request to a mobile device, receives the transaction information while monitoring the restriction, and transmits the transaction information to the POS terminal for processing. The transaction information may be provided subject to the restriction.
Owner:AT&T INTPROP I LP
Characteristically shaped colorgram tokens in mobile transactions
A transaction security process includes authentication and identification parts for pushing an encrypted colorgram for user authentication and persona descriptors for user identification from a transaction server to a first personal trusted device. A decryption of the colorgram is displayed on the first personal trusted device. An image is captured by a second personal trusted device. An encryption of the image captured from the second personal trusted device is uploaded to the transaction server. The persona descriptors are used to build a composite rendering for identification of the first user to the second user. The second user clicks “OK” if they recognize the composite drawing as a reasonable persona of the first user.
Owner:CRYPTITE LLC
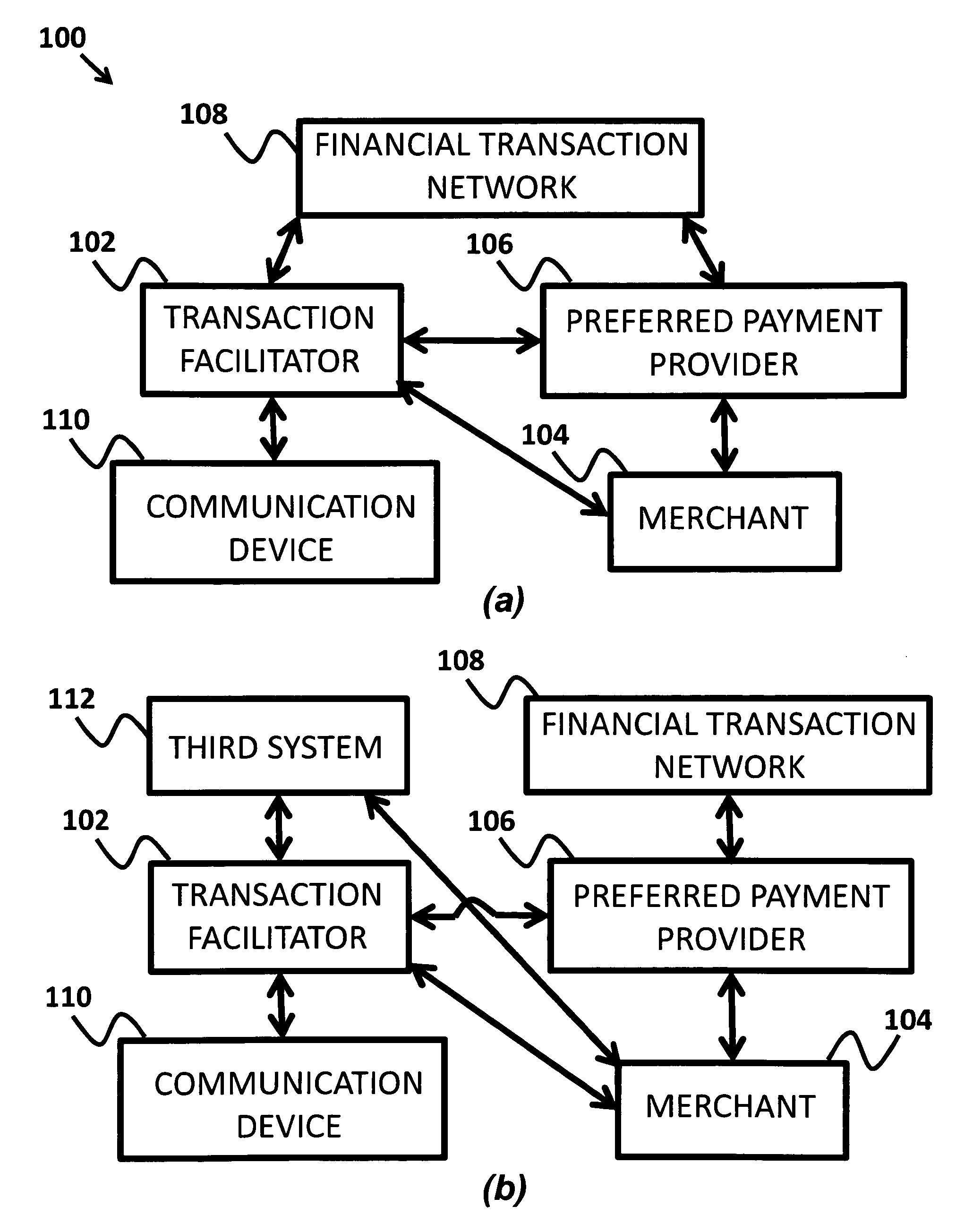
Facilitated mobile transactions
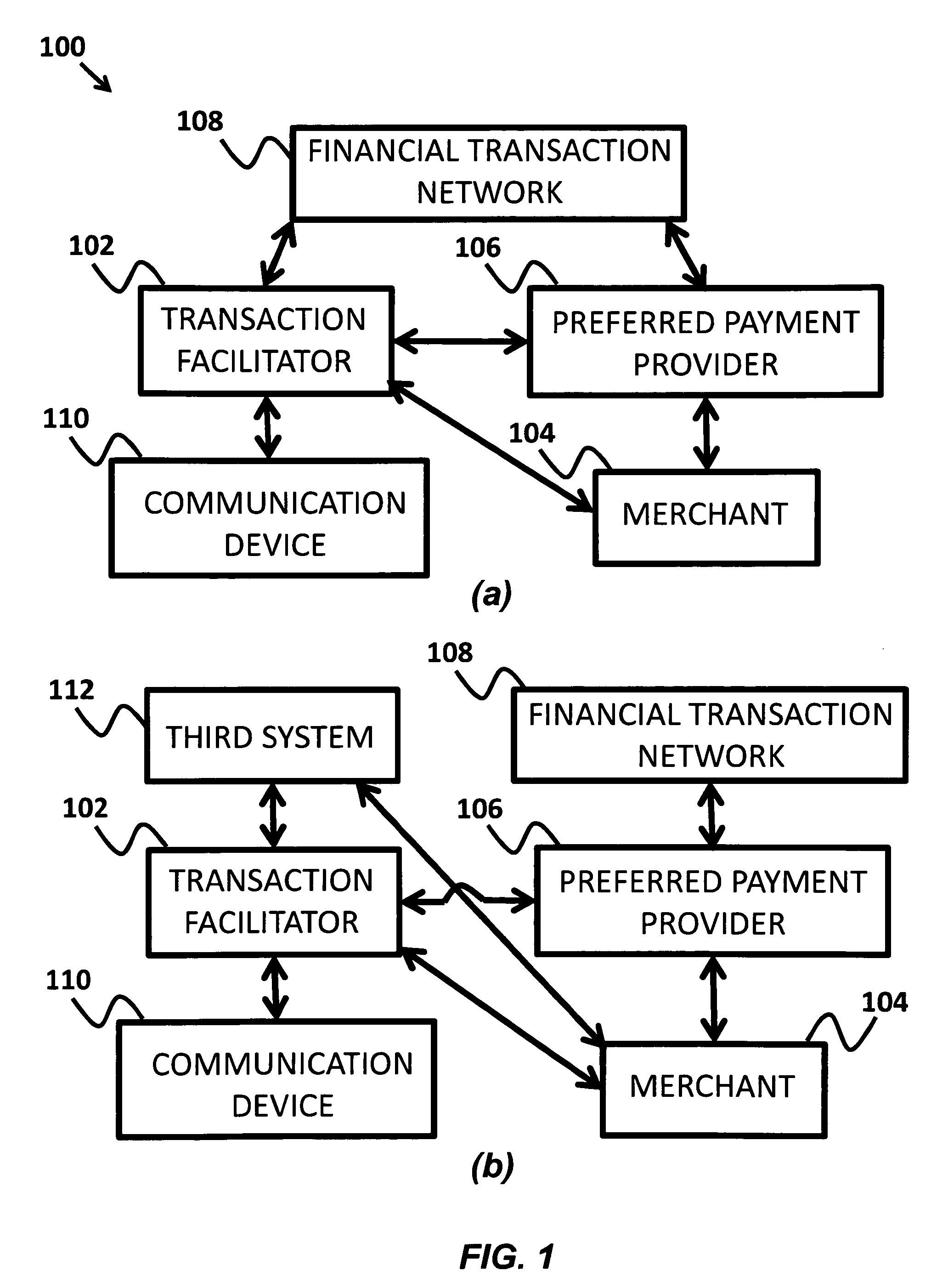
A stand-in payment and transaction facilitator system is provided. A merchant registers their details with a transaction facilitator and is assigned a merchant identifier. When a mobile user transacts with the merchant, the merchant identifier is communicated to the user's mobile device. At the payment step, the transaction facilitator uses the merchant's details referenced by their identifier to complete the payment portion of the transaction using any non-cash payment mechanism or service of the users choosing. The transaction facilitator offers for-purchase items from the merchants. The merchants use preferred payment providers. Communication devices are used to select for-purchase items from the transaction facilitator. The transaction facilitator communicates payment information received from the communication device to a financial transaction network for payment in the transaction to purchase the for-purchase item. On payment approval, the transaction facilitator communicates payment approval and a selected for-purchase item list to the merchant.
Owner:TAYLOR WILLIAM STUART ERVIN
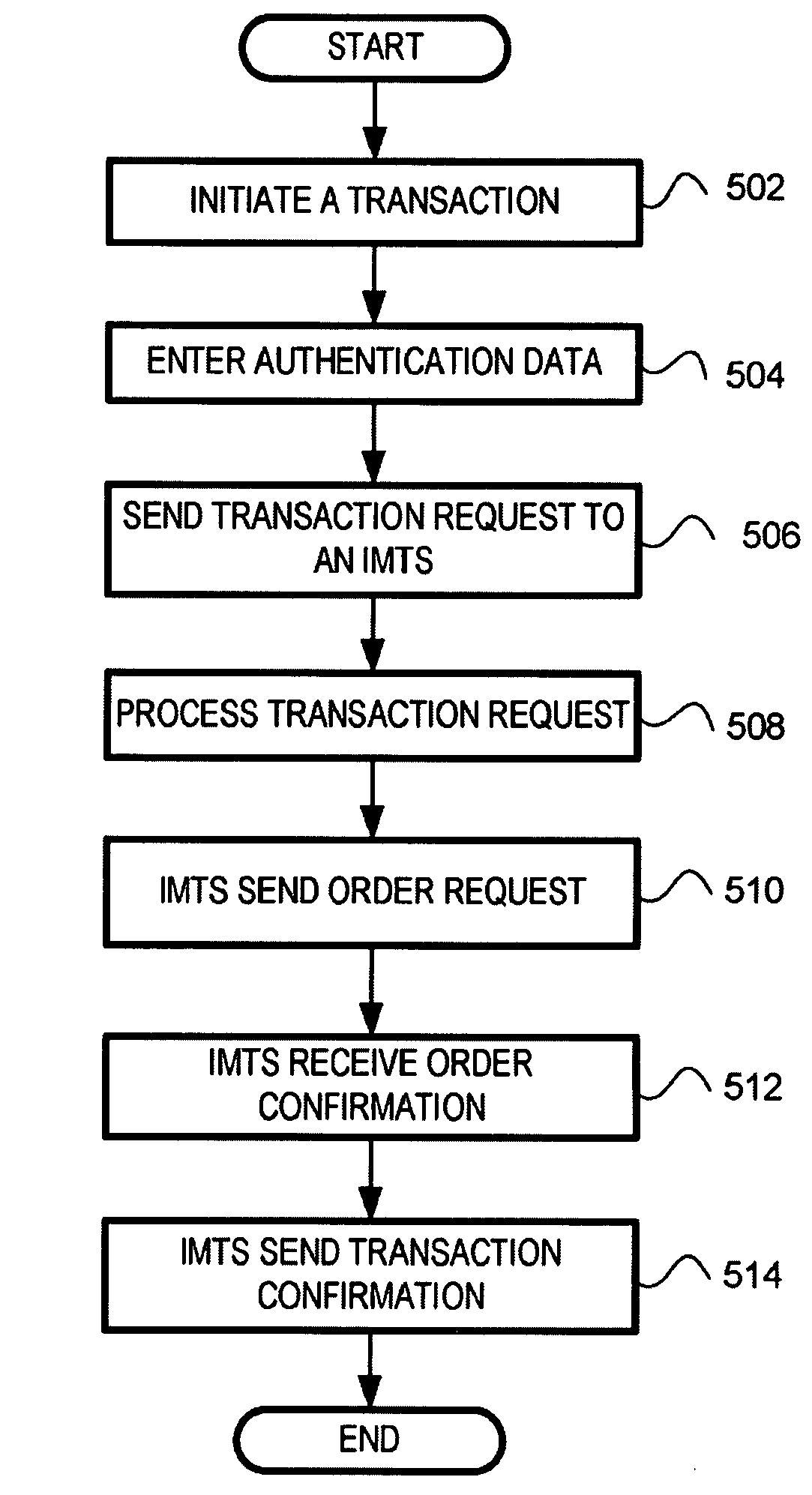
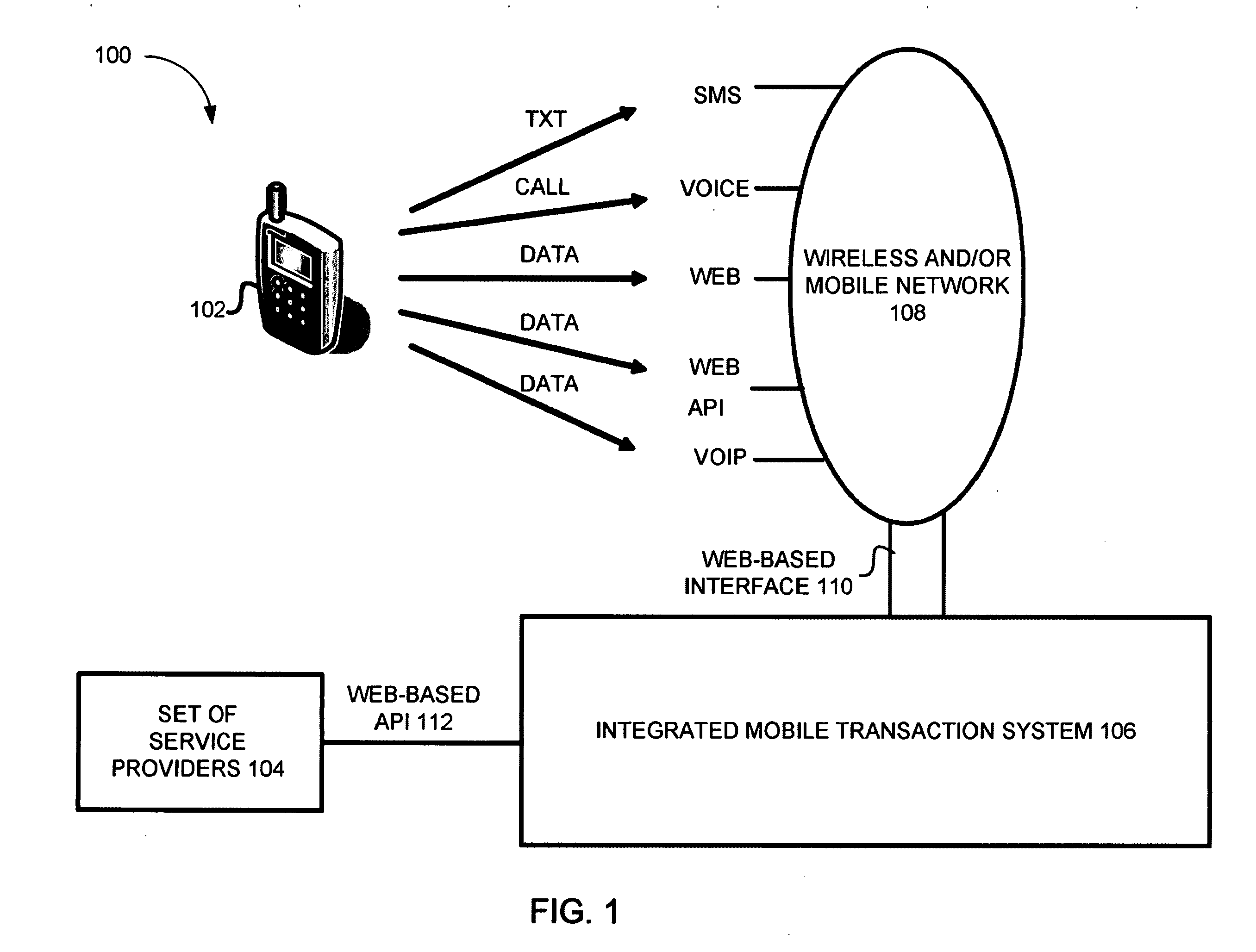
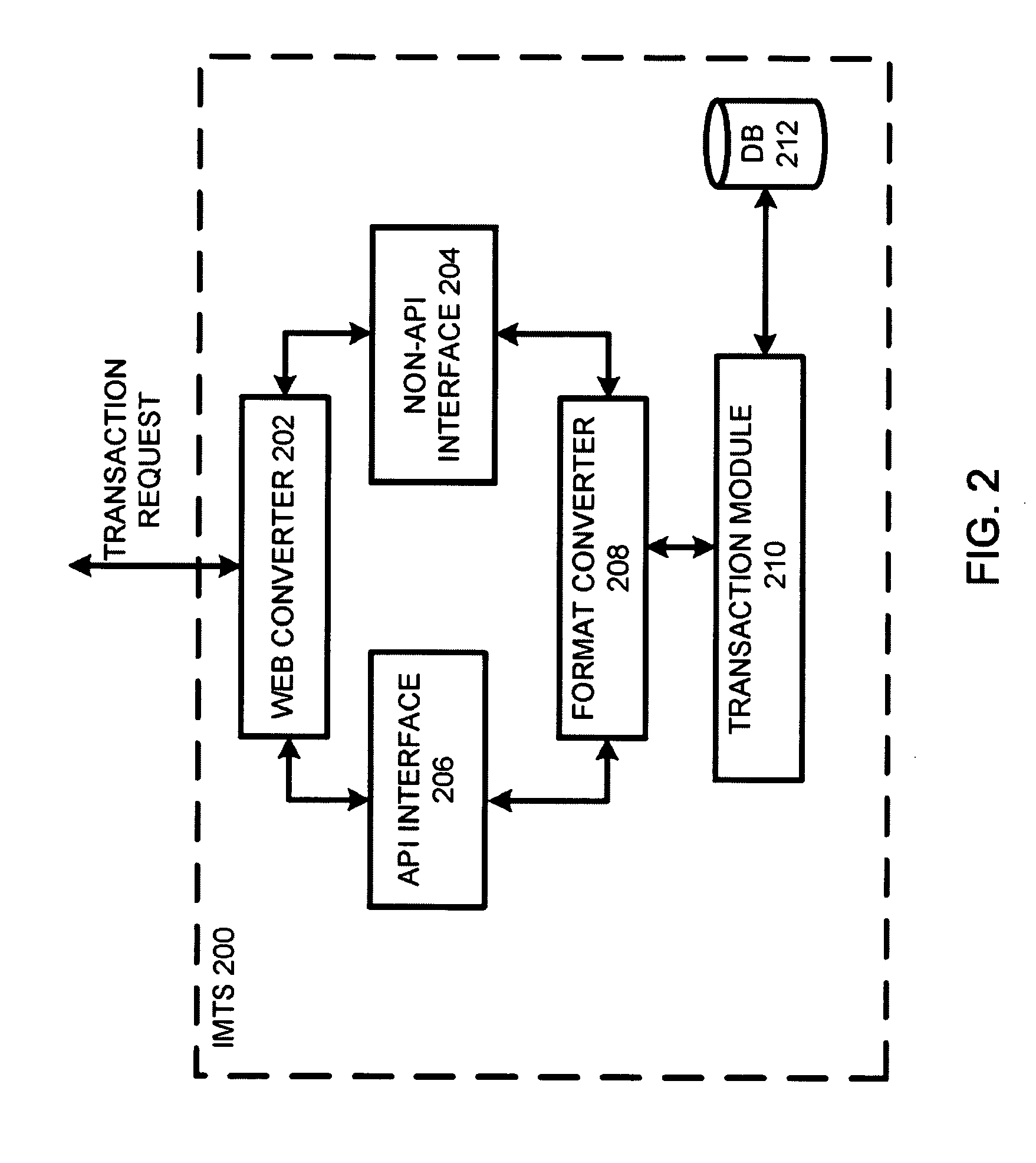
Integrated mobile transaction system and methods thereof
An architectural transaction arrangement for facilitating transactions is provided. The arrangement includes a set of transaction-enabled devices and an integrated mobile transaction system. The integrated mobile transaction system is configured to include at least a set of interfaces, which is configured for managing interaction between the set of transaction-enabled devices and the integrated mobile transaction system. The integrated mobile transaction system is also configured to include a format converter, which is configured to convert data packets into a format readable by at least one of the set of transaction-enabled devices and the integrated mobile transaction system. The integrated mobile transaction system is further configured to include a transaction module, which is configured to process the transactions (e.g., financial transactions, non-financial transactions, etc.) and a set of databases, which is configured for at least storing data about a set of in-system users of the integrated mobile transaction system.
Owner:MOBIDOUGH
Mobile transaction services
InactiveUS20120284101A1Payment architectureBuying/selling/leasing transactionsMobile transactionDatabase
A method may include receiving identification information associated with a user, where the identification information is used to store electronic receipts for the user. The method also includes receiving, from a point-of-sale device, transaction information for a transaction involving the user and generating an electronic receipt for the transaction. The method further includes storing the electronic receipt.
Owner:VERIZON PATENT & LICENSING INC
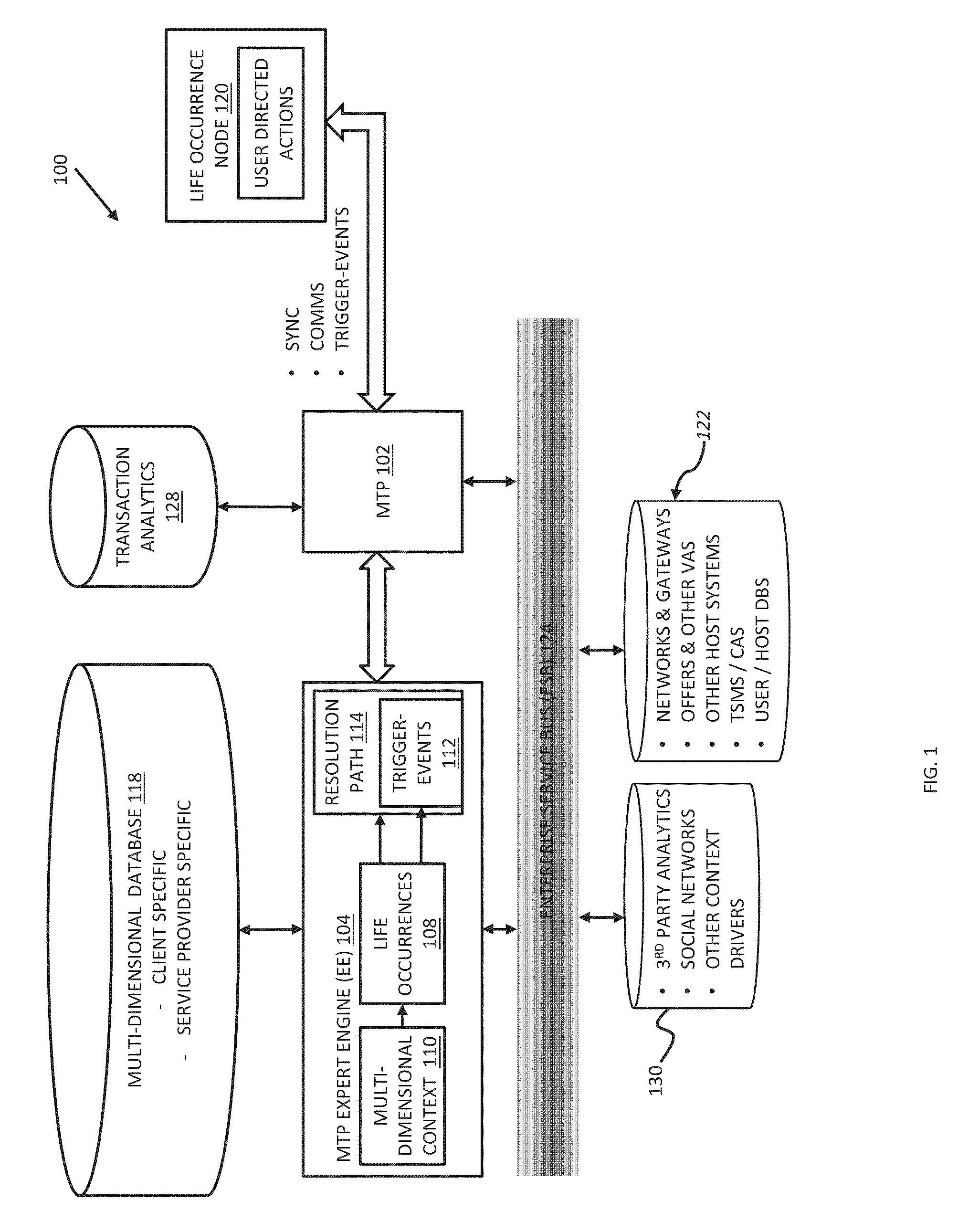
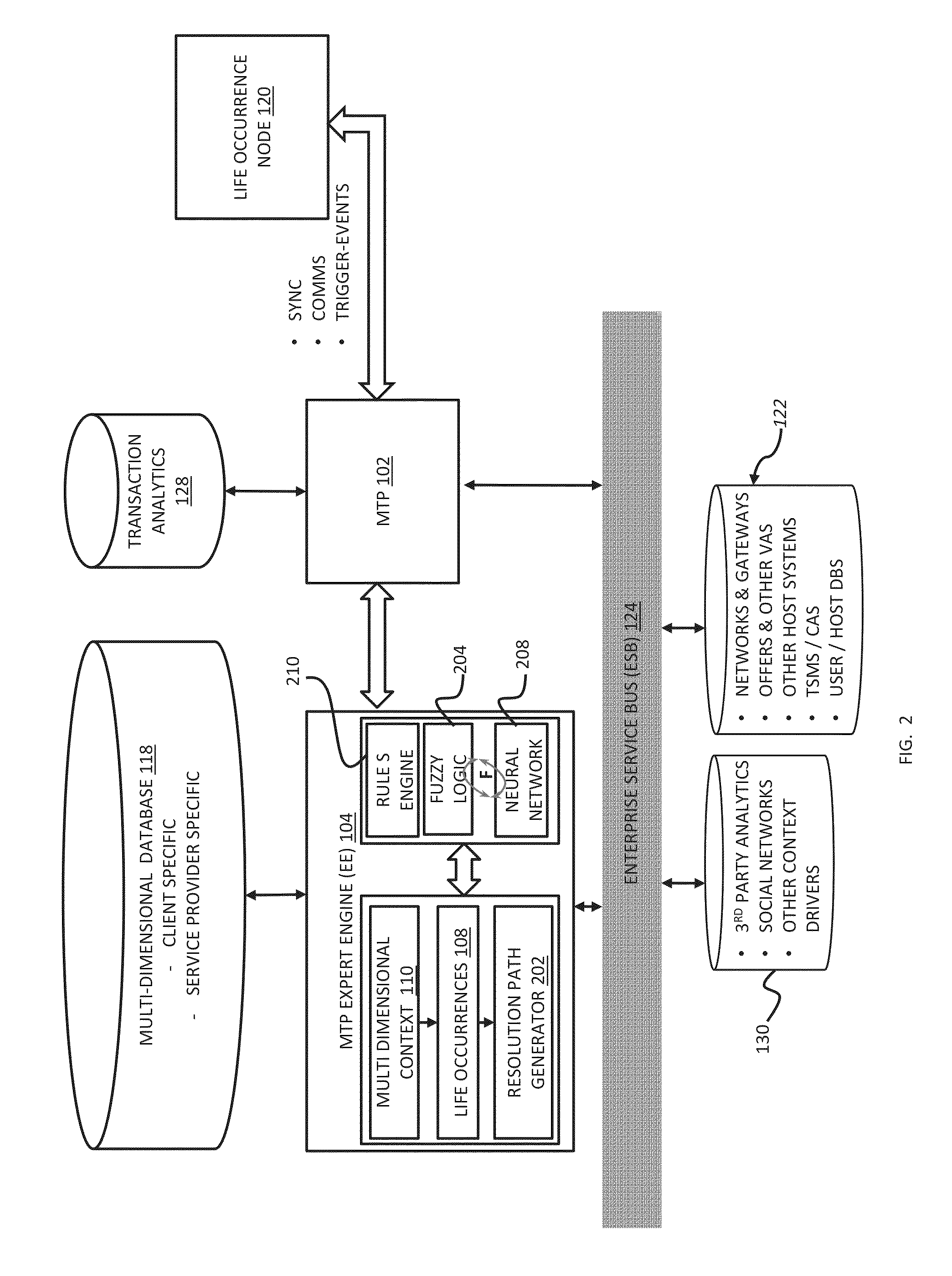
Life occurrence handling and resolution
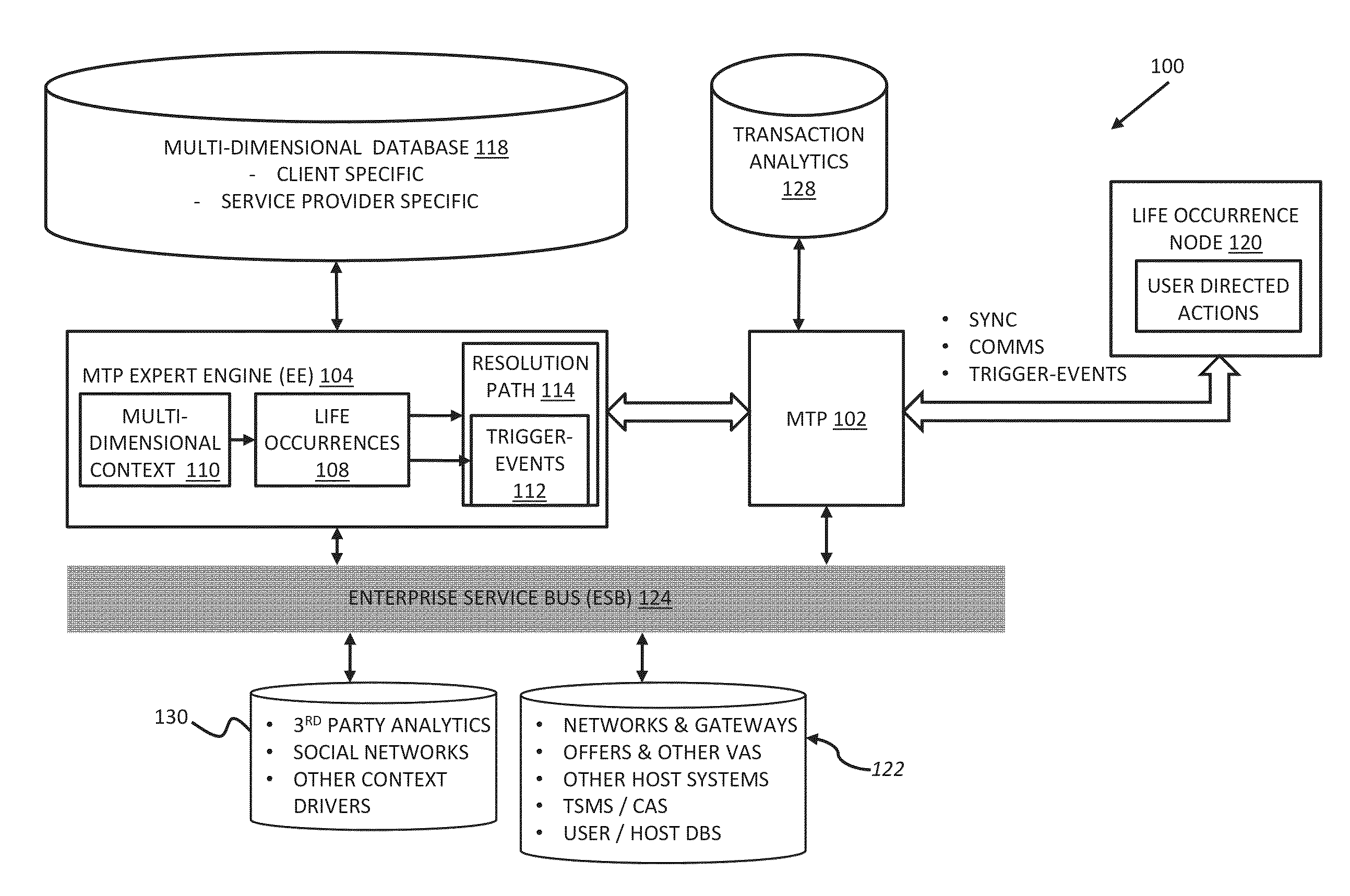
InactiveUS20150088739A1Reduce deliveryEasy to shareDiscounts/incentivesFinanceMobile transactionLife time
A method is disclosed herein in accordance with an embodiment of the present invention. The method may include deriving at a mobile transaction platform a multi-dimensional context from one or more user transactions and determining at least one life occurrence based, at least in part, on the multi-dimensional context. The one or more user transactions may be conducted through the mobile transaction platform. The one or more user transactions may be stored on a third-party source. In an aspect, the at least one life occurrence has yet to occur. In another aspect of the invention, the life occurrence has already occurred. The multi-dimensional context may include at least one of user location information and life occurrence location information. The multi-dimensional context may include at least one of a time of life occurrence and a current time.
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
Two-dimension code-based mobile terminal transaction encryption method
ActiveCN103714458ANot burdenedEnsure safetyUser identity/authority verificationBuying/selling/leasing transactionsPaymentRelevant information
The invention discloses a two-dimension code-based mobile terminal transaction encryption method and belongs to the network technical field. According to the two-dimension code-based mobile terminal transaction encryption method of the invention, based on the combination of a two-dimensional code technology and an existing mobile transaction protocol, related information can be encrypted through two-dimension codes in identity authentication of two transaction parties, order confirmation and payment, such that transaction security can be ensured. With the two-dimension code-based mobile terminal transaction encryption method of the invention adopted, safer and more reliable online transactions can be realized without too much burden brought to a mobile terminal device, and the safety, confidentiality and non-repudiation performance of the online transactions of the mobile terminal can be ensured.
Owner:JIANGSU UNIV
Presentation of sponsored content based on mobile transaction event
ActiveUS7907940B2Metadata audio data retrievalInformation formatDisplay deviceComputer compatibility
A system and computer-implemented method for positioning targeted sponsored content on a mobile communication facility includes the steps of: (a) receiving data corresponding to transaction events having occurred via the interaction of a user with the mobile communication facility, wherein the transaction events include transmission of data representative of a first set of products or services having been purchased by the user; (b) selecting advertising content based at least upon a relevance between an advertisement for a second product or a second service and the purchased first set of products or services in the transaction events, wherein the relevance is further based on information relating to compatibility of the advertising content, second product, or second service with the mobile communication facility; and (c) presenting the selected advertising content on a display of the mobile communication facility.
Owner:BLUE HILLS SERIES 95 OF ALLIED SECURITY TRUST I
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com